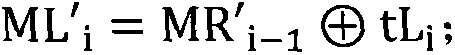DES masking method for resisting side-channel attack
A side-channel attack and mask technology, applied in the field of anti-side-channel attack, can solve the problems of poor mask effect, weak security strength, leakage, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
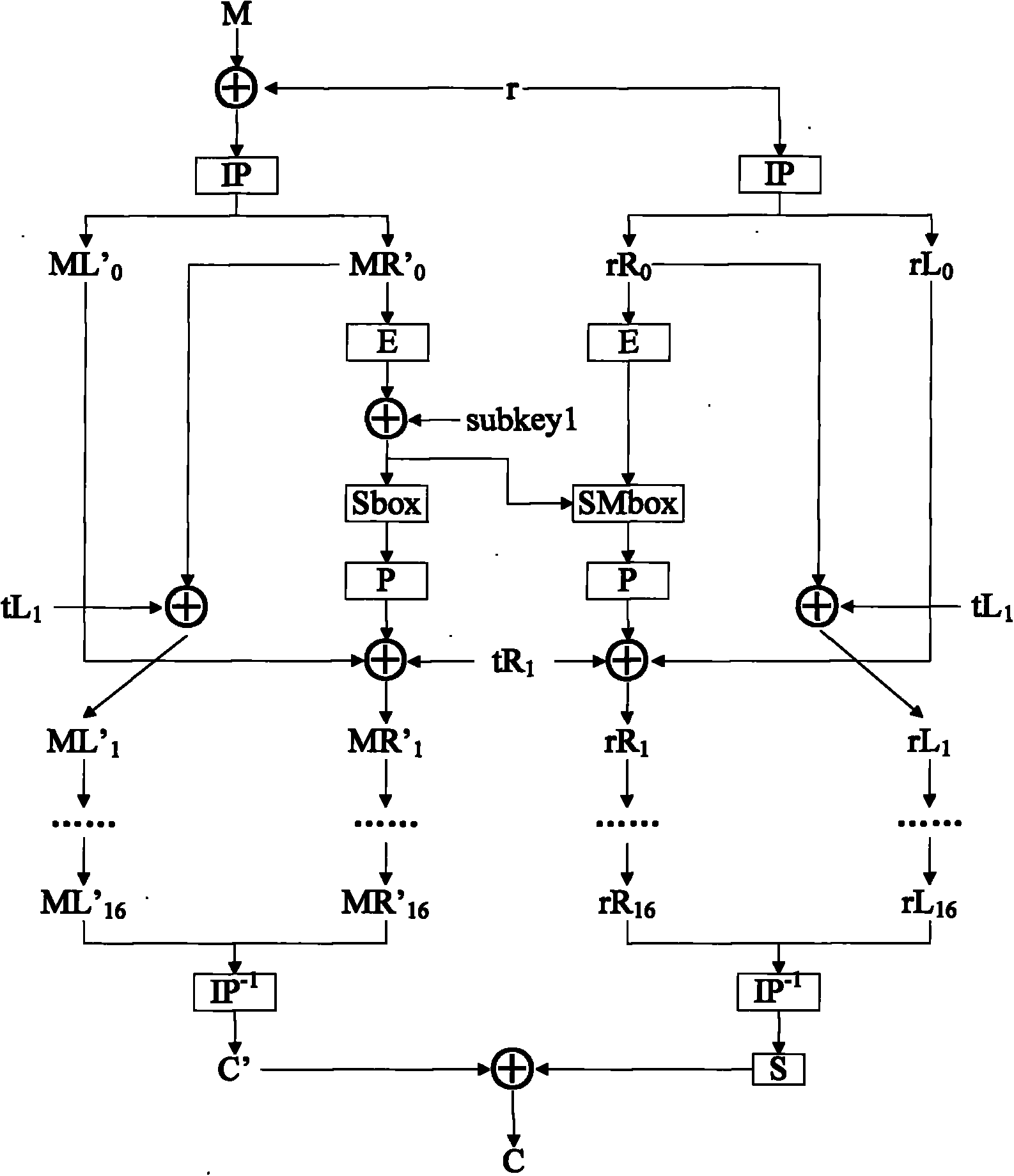
[0035] The method in the present invention can be implemented entirely by hardware, or by software, or by a combination of software and hardware. The specific implementation is introduced below.
[0036] This method needs two paths of DES computing paths, wherein one path is used for the calculation of plaintext encryption (ciphertext decryption) behind the mask, and the other path is used for the calculation of removing the mask. The two paths of DES are preferably calculated in parallel. In addition, the DES The wheel keys are still organized in the same way as the original DES.
[0037] 1) The external input data M, the module starts, first use the random number r to mask the bits Input M' into one DES module on the left, and input r to one DES module on the right for mask calculation.
[0038] 2) Perform initial IP permutation on the masked data M', and at the same time perform initial IP permutation on the random number r.
[0039] 3) On the left side, the intermediat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com