Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
212 results about "Precomputation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In algorithms, precomputation is the act of performing an initial computation before run time to generate a lookup table that can be used by an algorithm to avoid repeated computation each time it is executed. Precomputation is often used in algorithms that depend on the results of expensive computations that don't depend on the input of the algorithm. A trivial example of precomputation is the use of hardcoded mathematical constants, such as π and e, rather than computing their approximations to the necessary precision at run time.
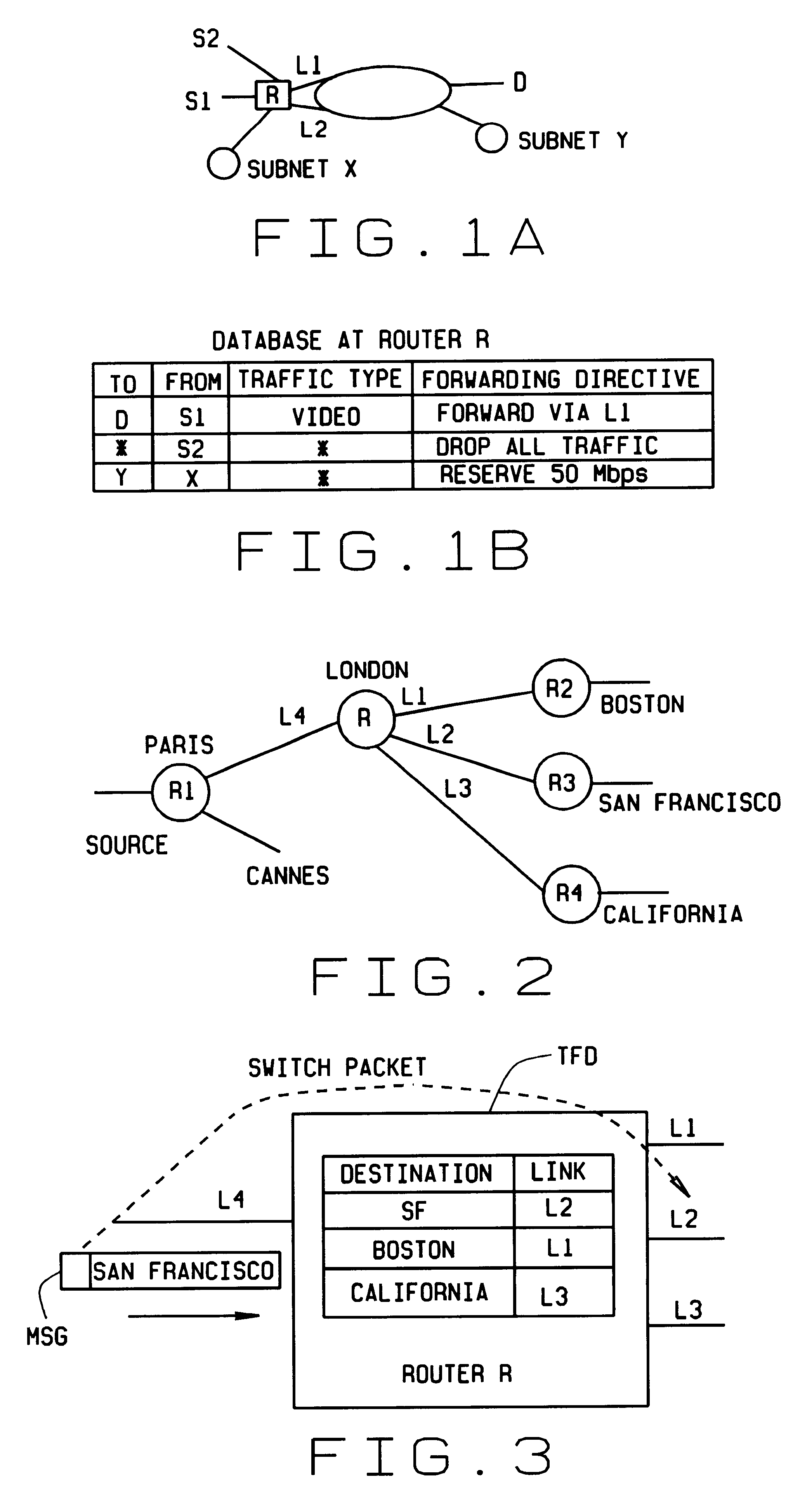
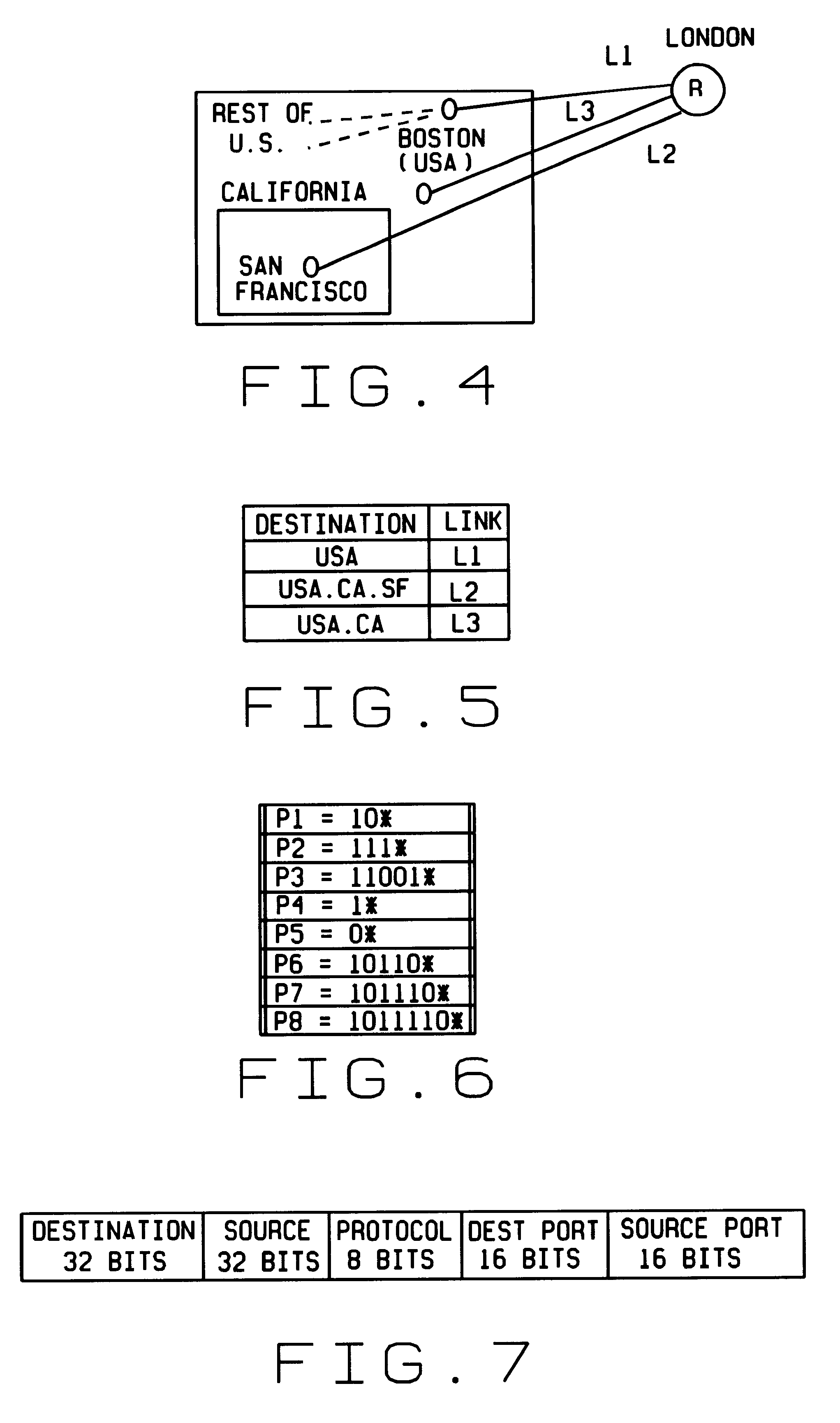
Fast scaleable methods and devices for layer four switching
InactiveUS6212184B1Enormous saving in table sizeAvoid the needError preventionTransmission systemsPrecomputationRoute filtering
Fast, scalable methods and devices are provided for layer four switching in a router as might be found in the Internet. In a first method, a grid of tries, which are binary branching trees, is constructed from the set of routing filters. The grid includes a dest-trie and a number of source tries. To avoid memory blowup, each filter is stored in exactly one trie. The tries are traversed to find the lowest cost routing. Switch pointers are used to improve the search cost. In an extension of this method, hash tables may be constructed that point to grid-of-tries structures. The hash tables may be used to handle combinations of port fields and protocol fields. Another method is based on hashing, in which searches for lowest cost matching filters take place in bit length tuple space. Rectangle searching with precomputation and markers are used to eliminate a whole column of tuple space when a match occurs, and to eliminate the rest of a row when no match is found. Various optimizations of these methods are also provided. A router incorporating memory and processors implementing these methods is capable of rapid, selective switching of data packets on various types of networks, and is particularly suited to switching on Internet Protocol networks.
Owner:WASHINGTON UNIV IN SAINT LOUIS
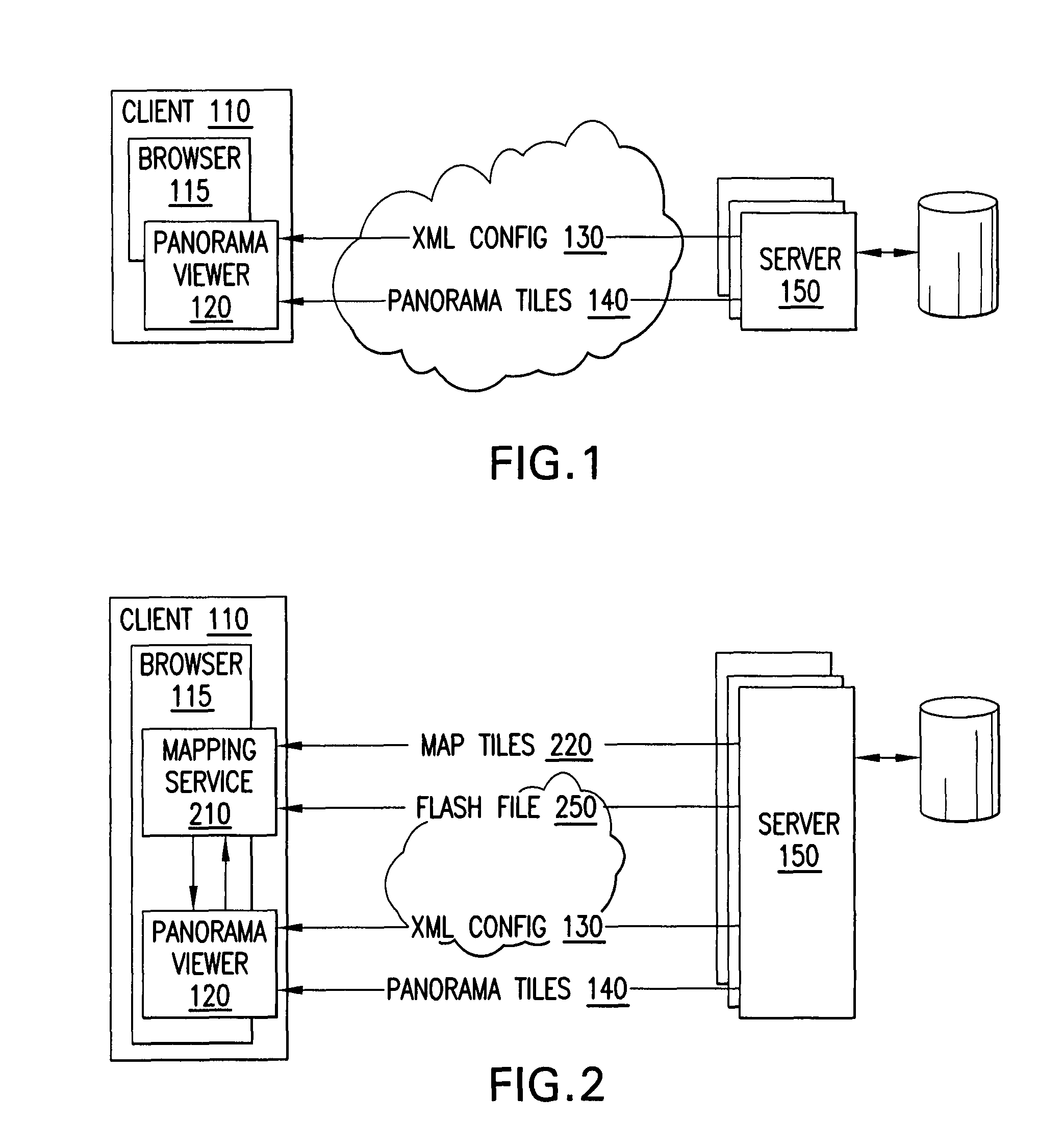
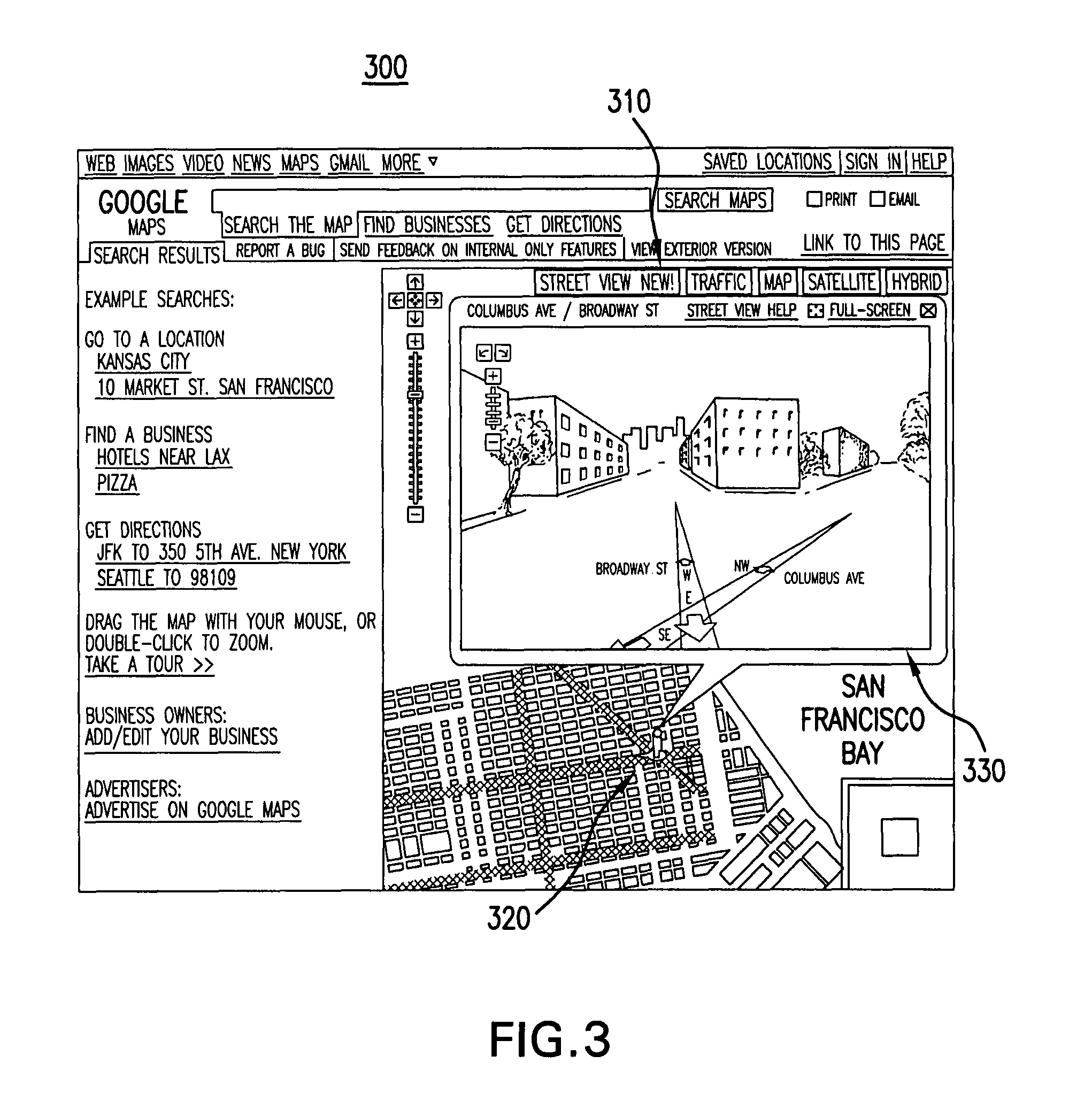
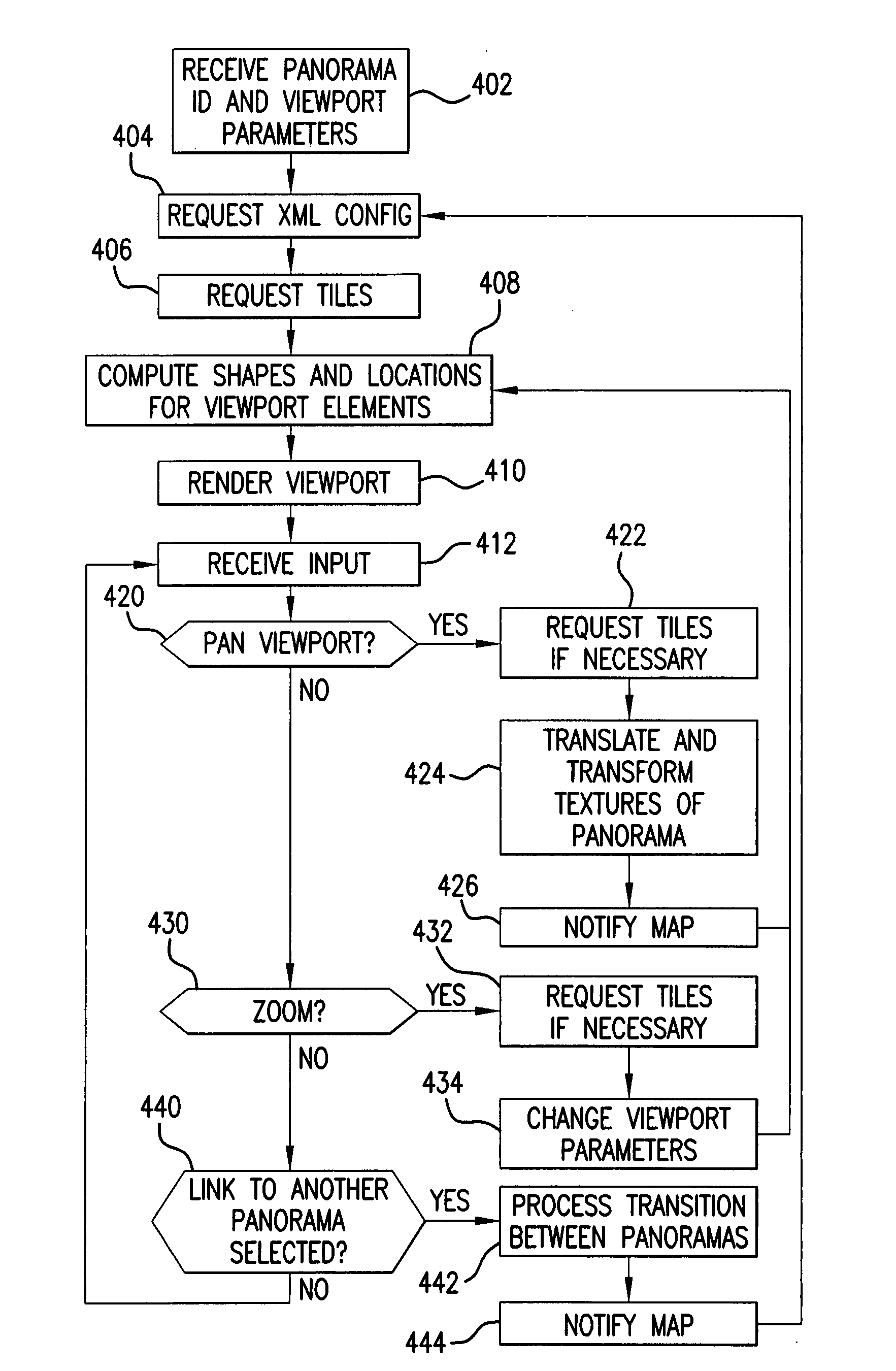
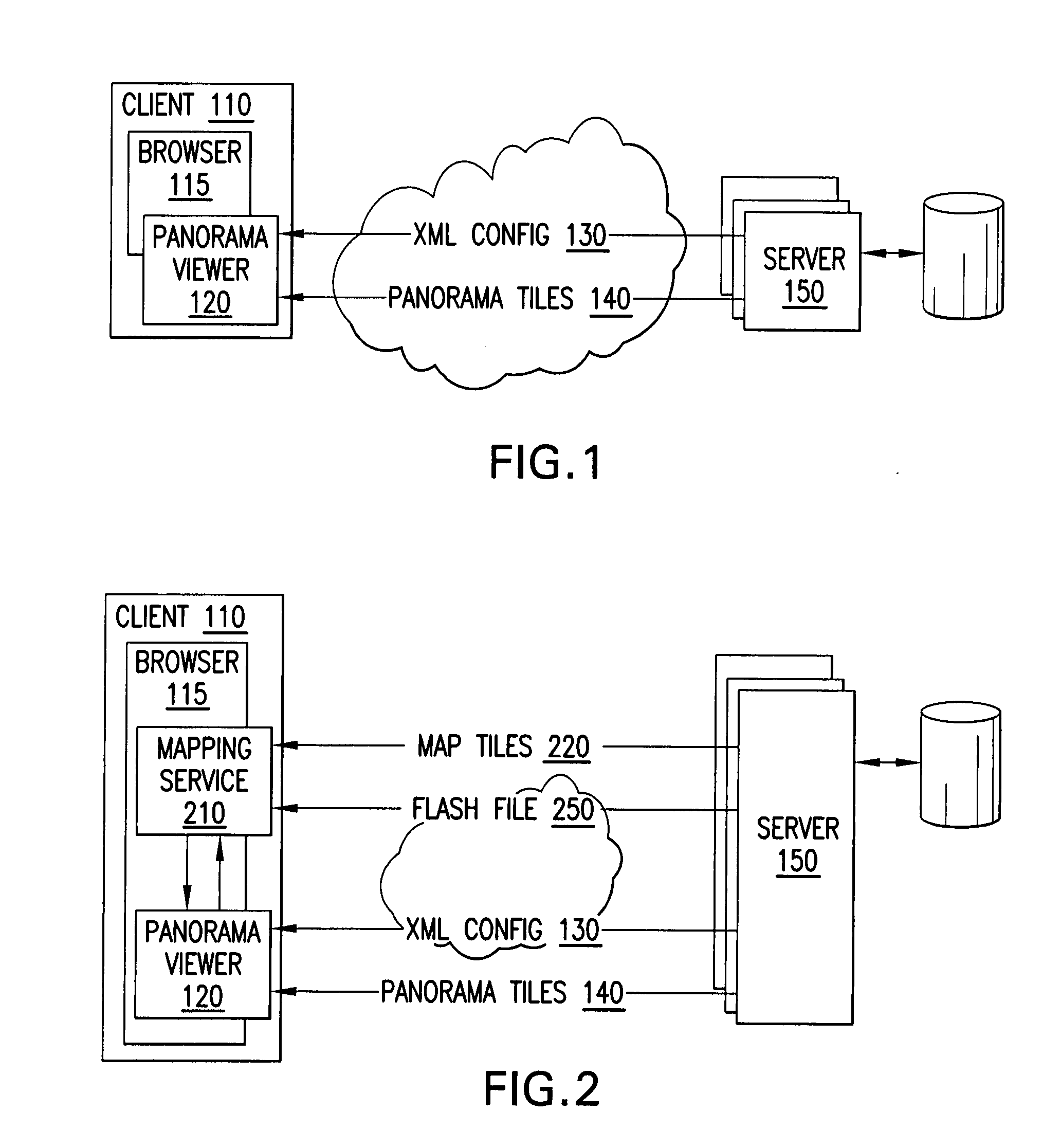
Efficient rendering of panoramic images, and applications thereof
ActiveUS7843451B2Easy to handleQuickly renderedCharacter and pattern recognitionCathode-ray tube indicatorsPrecomputationViewport
A fast renderer for panoramic images is herein disclosed. In an embodiment, a precomputation is made of (a) a region on a surface defined by a first transformation from a viewport to the surface and (b) a second transformation that maps from the precomputed region to the viewport. In order to render the surface on the viewport, the renderer determines what portion of the image intersects with the precomputed region and proceeds to apply the precomputed second transformation to the portion of the image, thereby resulting in a transformed image which can be rendered in the viewport for display.
Owner:GOOGLE LLC
Systems and methods for all-frequency relighting using spherical harmonics and point light distributions
InactiveUS20050080602A1Efficient lighting sourceEffective lightingComputation using non-denominational number representationComplex mathematical operationsPoint lightDecomposition
The present invention is directed to systems and methods for all-frequency relighting by representing low frequencies of lighting with spherical harmonics and approximate the residual high-frequency energy with point lights. One such embodiment renders low-frequencies with a precomputed radiance transfer (PRT) technique (which requires only a moderate amount of precomputation and storage), while the higher-frequencies are rendered with on-the-fly techniques such as shadow maps and shadow volumes. In addition, various embodiments are directed to a systems and methods for decomposing the lighting into harmonics and sets of point lights. Various alternative embodiments are directed to systems and methods for characterizing the types of environments for which the described decomposition is a viable technique in terms of speed (efficiency) versus quality (realism).
Owner:MICROSOFT TECH LICENSING LLC
Efficient rendering of panoramic images, and applications thereof
ActiveUS20080291201A1Easy to handleQuickly renderedCharacter and pattern recognitionCathode-ray tube indicatorsPrecomputationComputer science
A fast renderer for panoramic images is herein disclosed. In an embodiment, a precomputation is made of (a) a region on a surface defined by a first transformation from a viewport to the surface and (b) a second transformation that maps from the precomputed region to the viewport. In order to render the surface on the viewport, the renderer determines what portion of the image intersects with the precomputed region and proceeds to apply the precomputed second transformation to the portion of the image, thereby resulting in a transformed image which can be rendered in the viewport for display.
Owner:GOOGLE LLC
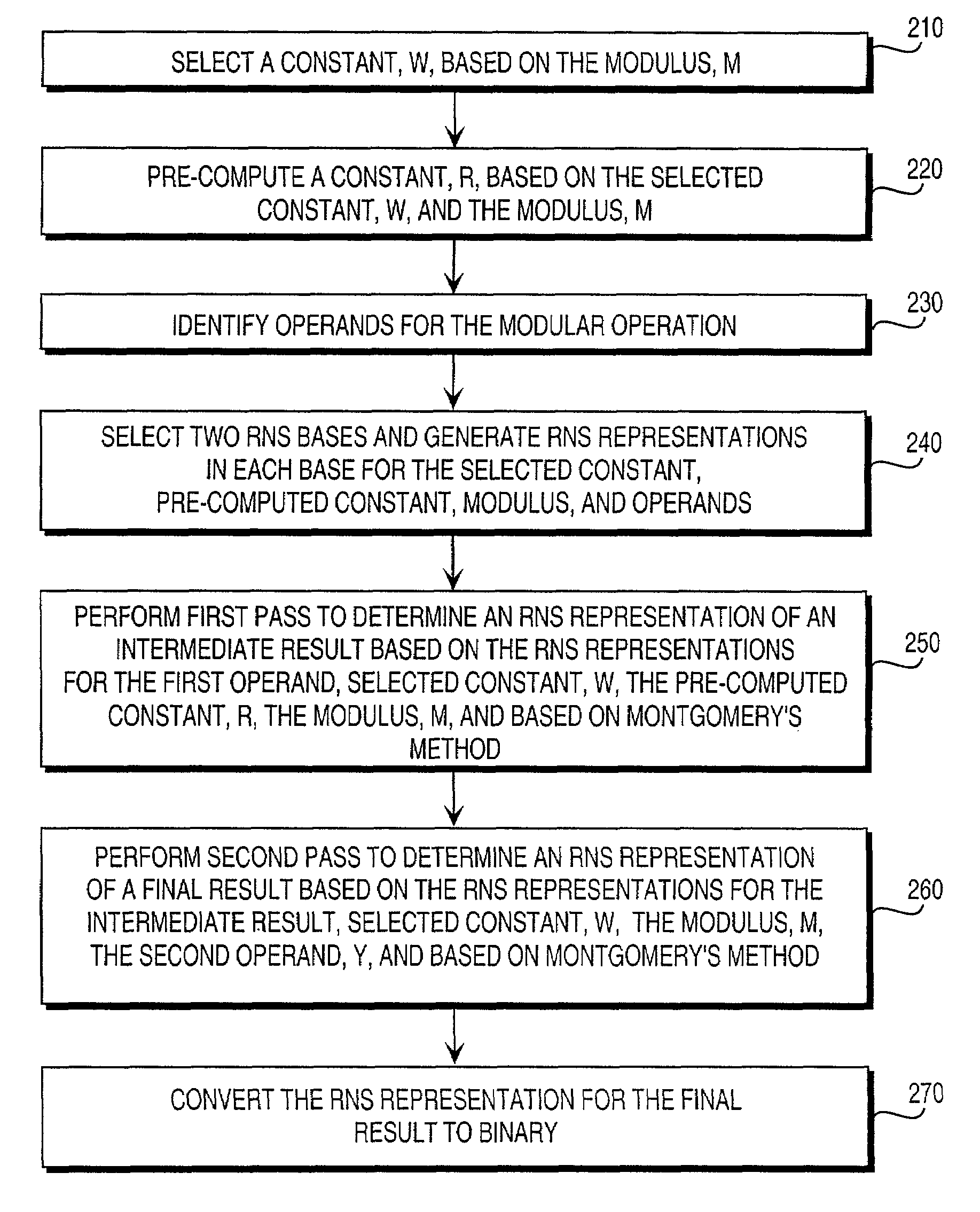
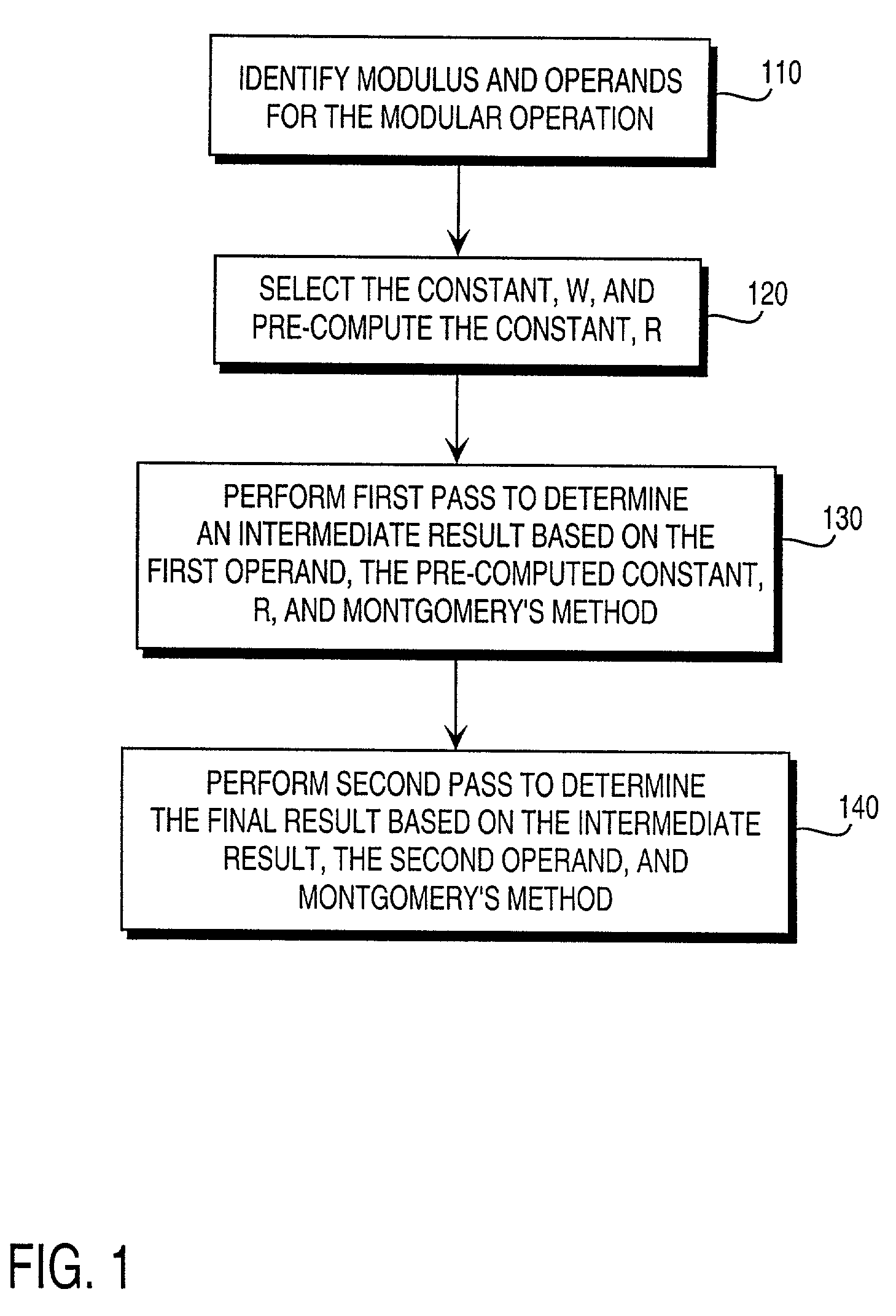
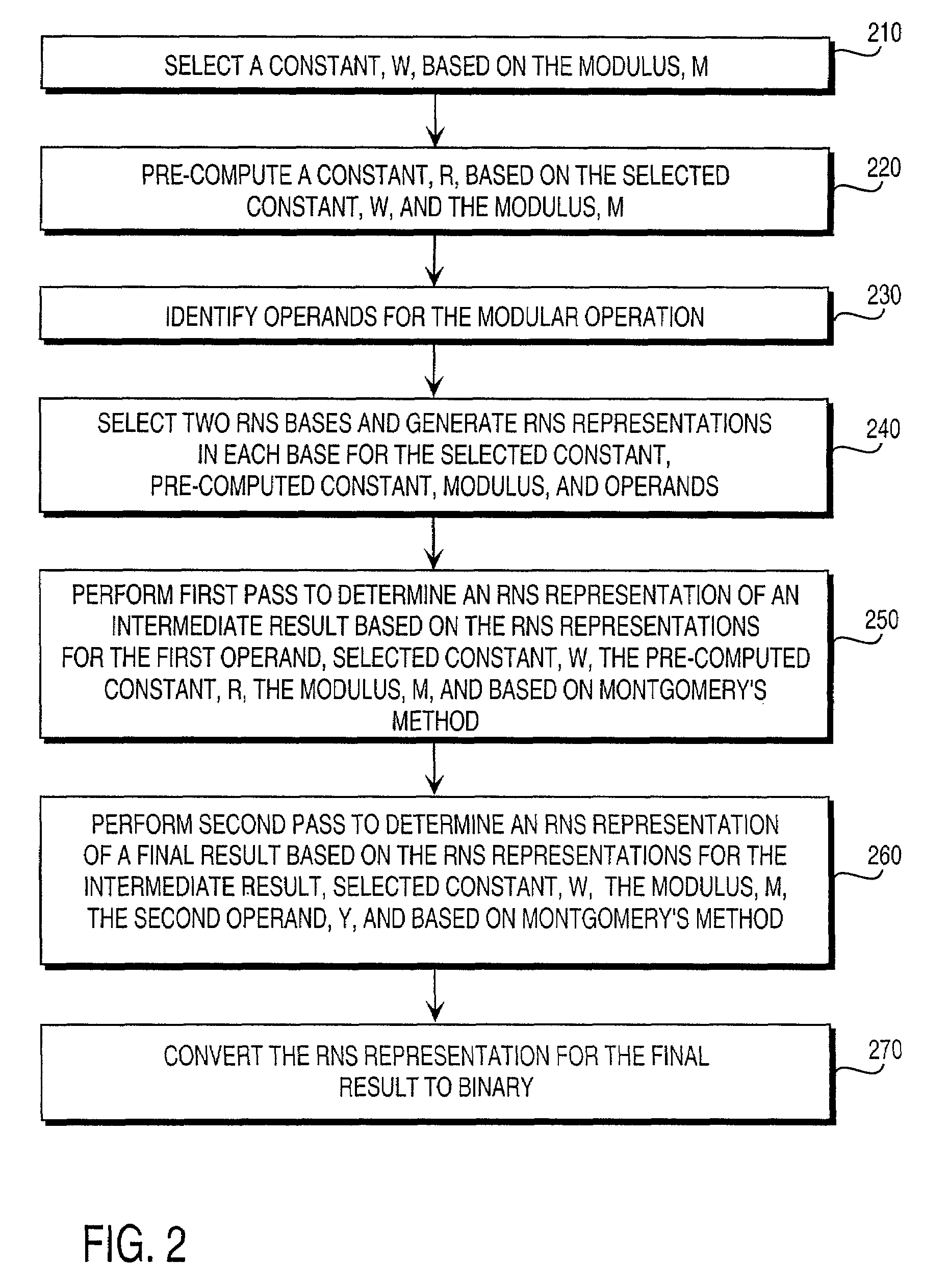
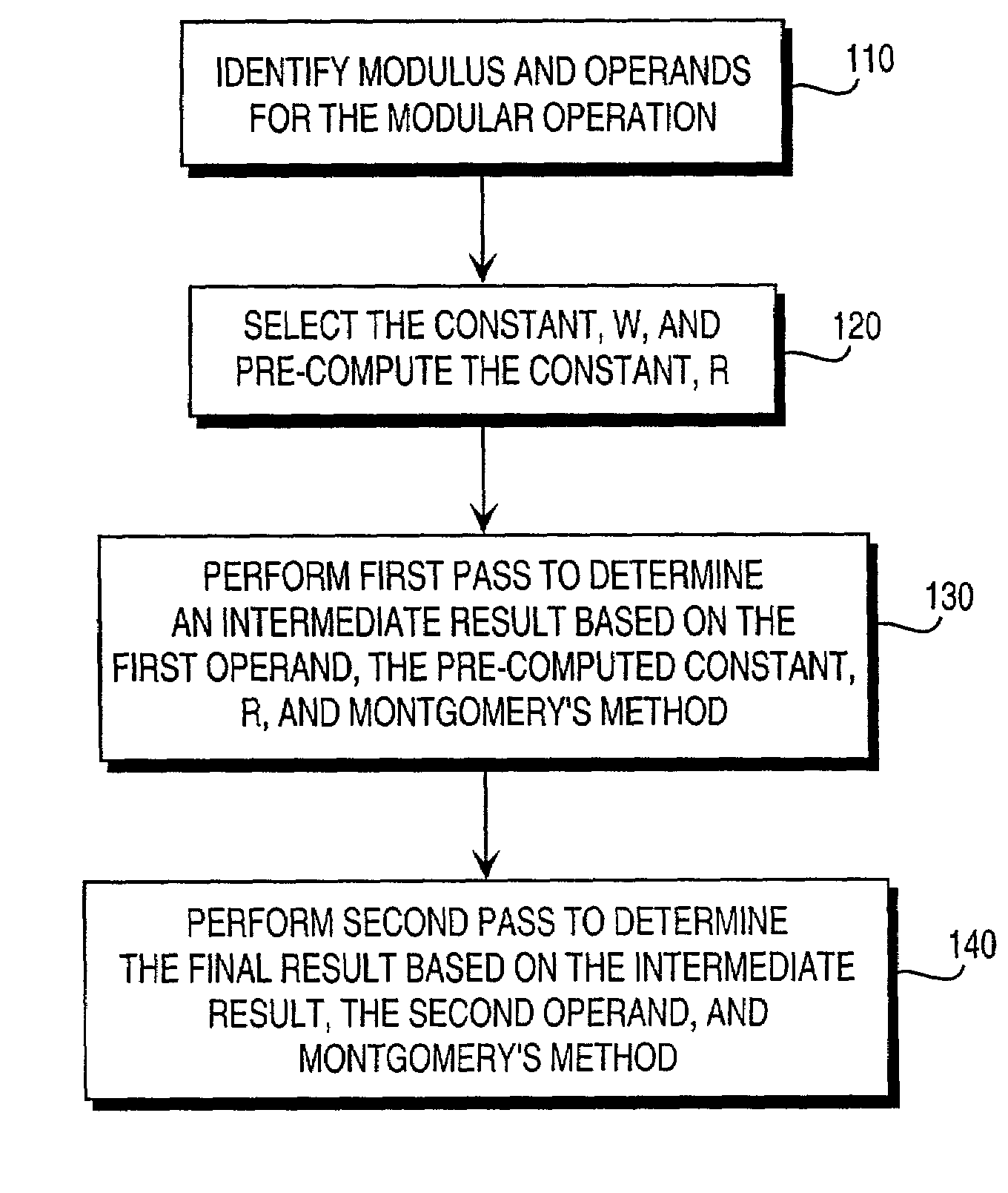
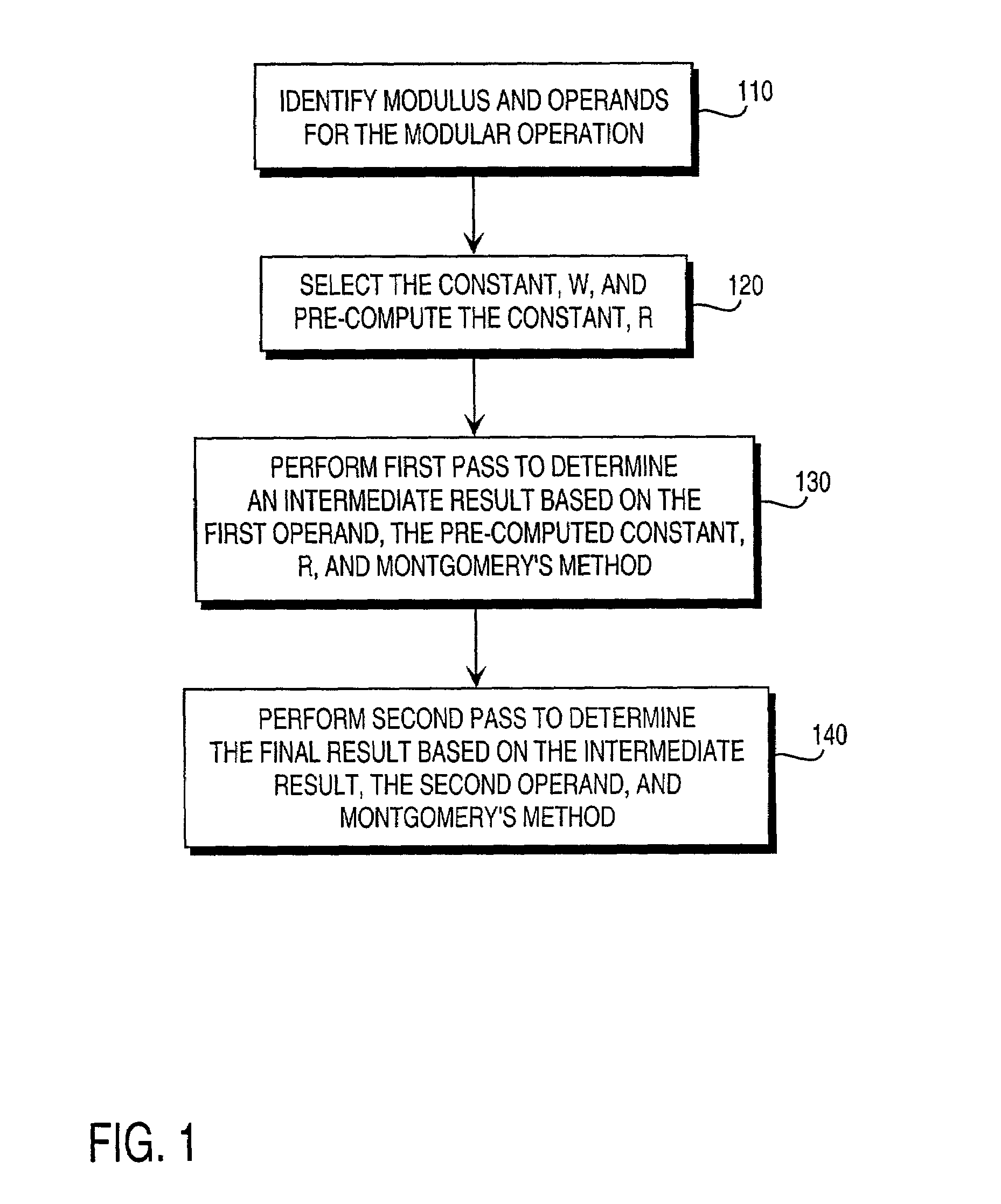
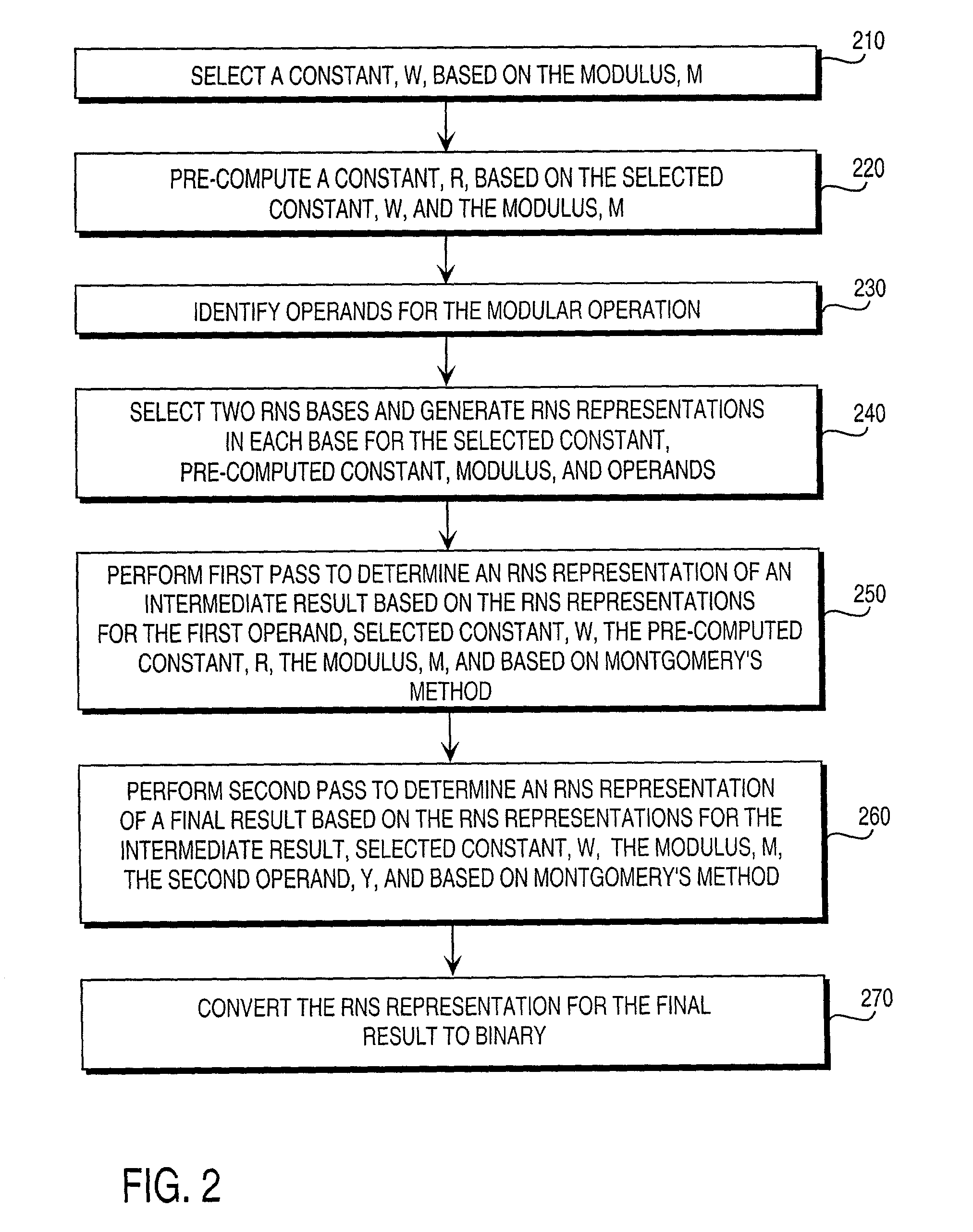
Residue number system based pre-computation and dual-pass arithmetic modular operation approach to implement encryption protocols efficiently in electronic integrated circuits
InactiveUS7027598B1Computations using contact-making devicesComputation using non-contact making devicesProcessor registerModularity
A pre-computation and dual-pass modular operation approach to implement encryption protocols efficiently in electronic integrated circuits is disclosed. An encrypted electronic message is received and another electronic message generated based on the encryption protocol. Two passes of Montgomery's method are used for a modular operation that is associated with the encryption protocol along with pre-computation of a constant based on a modulus. The modular operation may be a modular multiplication or a modular exponentiation. Modular arithmetic may be performed using the residue number system (RNS) and two RNS bases with conversions between the two RNS bases. A minimal number of register files are used for the computations along with an array of multiplier circuits and an array of modular reduction circuits. The approach described allows for high throughput for large encryption keys with a relatively small number of logical gates.
Owner:CISCO TECH INC
Method and system for resilient routing reconfiguration
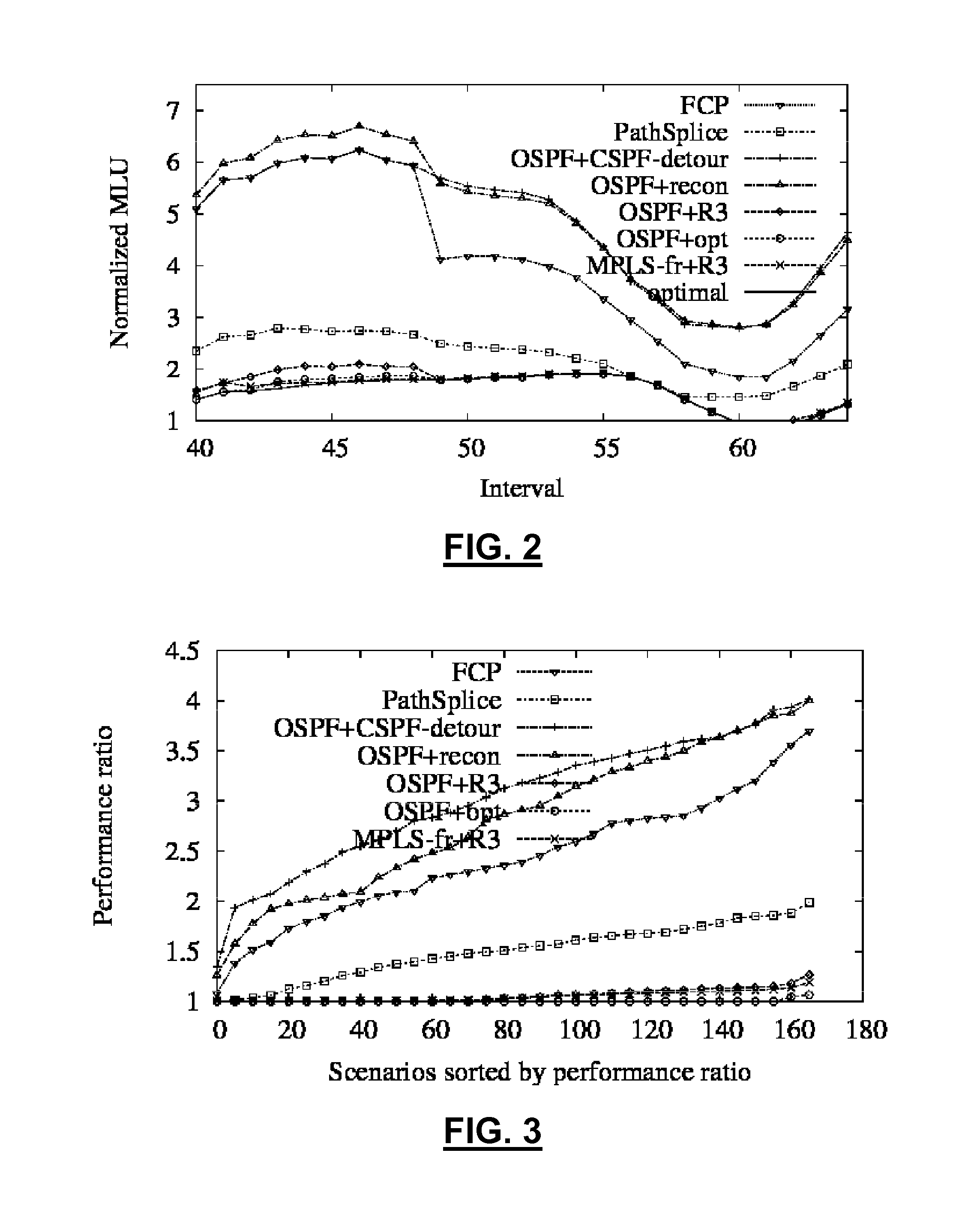
InactiveUS20100302935A1Improve efficiencyEasy to takeError preventionTransmission systemsPrecomputationTrade offs
A method and system for resilient routing reconfiguration, which provides provably congestion-free rerouting under a large number of failure scenarios and achieves efficiency and flexibility in accommodating different performance requirements, is disclosed. The method of embodiments comprises an offline precomputation phase and an online reconfiguration phase. Embodiments of the present invention also provide a number of useful functionalities, including (i) coping with traffic variations, (ii) supporting realistic failure scenarios, (iii) accommodating prioritized traffic with different protection levels, and (iv) balancing the trade-off between performance and resilience.
Owner:ZHANG YIN +1
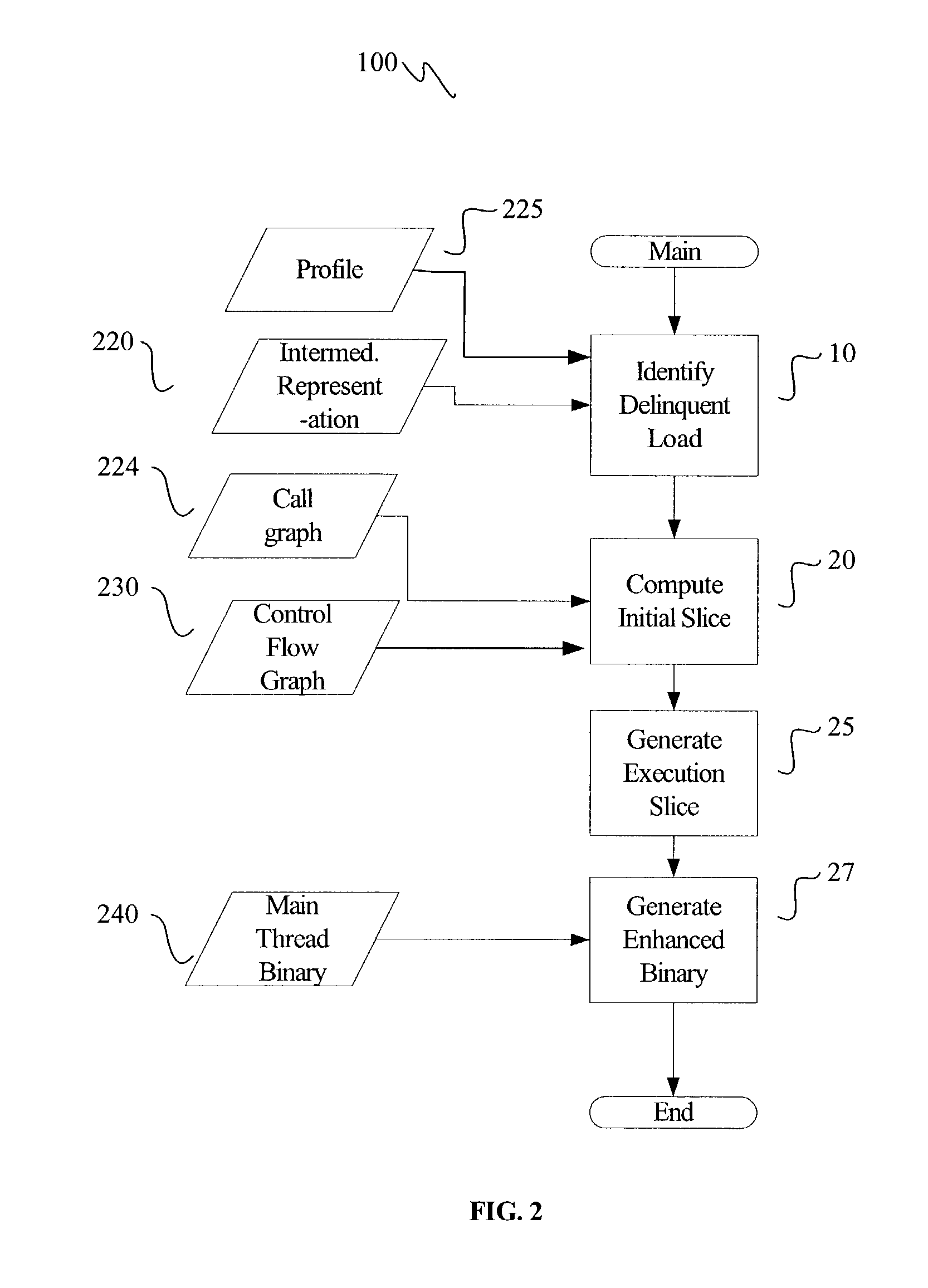
Post-pass binary adaptation for software-based speculative precomputation
ActiveUS20040054990A1Software engineeringSpecific program execution arrangementsLong latencyPrecomputation
The latencies associated with cache misses or other long-latency instructions in a main thread are decreased through the use of a simultaneous helper thread. The helper thread is a speculative prefetch thread to perform a memory prefetch for the main thread. The instructions for the helper thread are dynamically incorporated into the main thread binary during post-pass operation of a compiler.
Owner:INTEL CORP
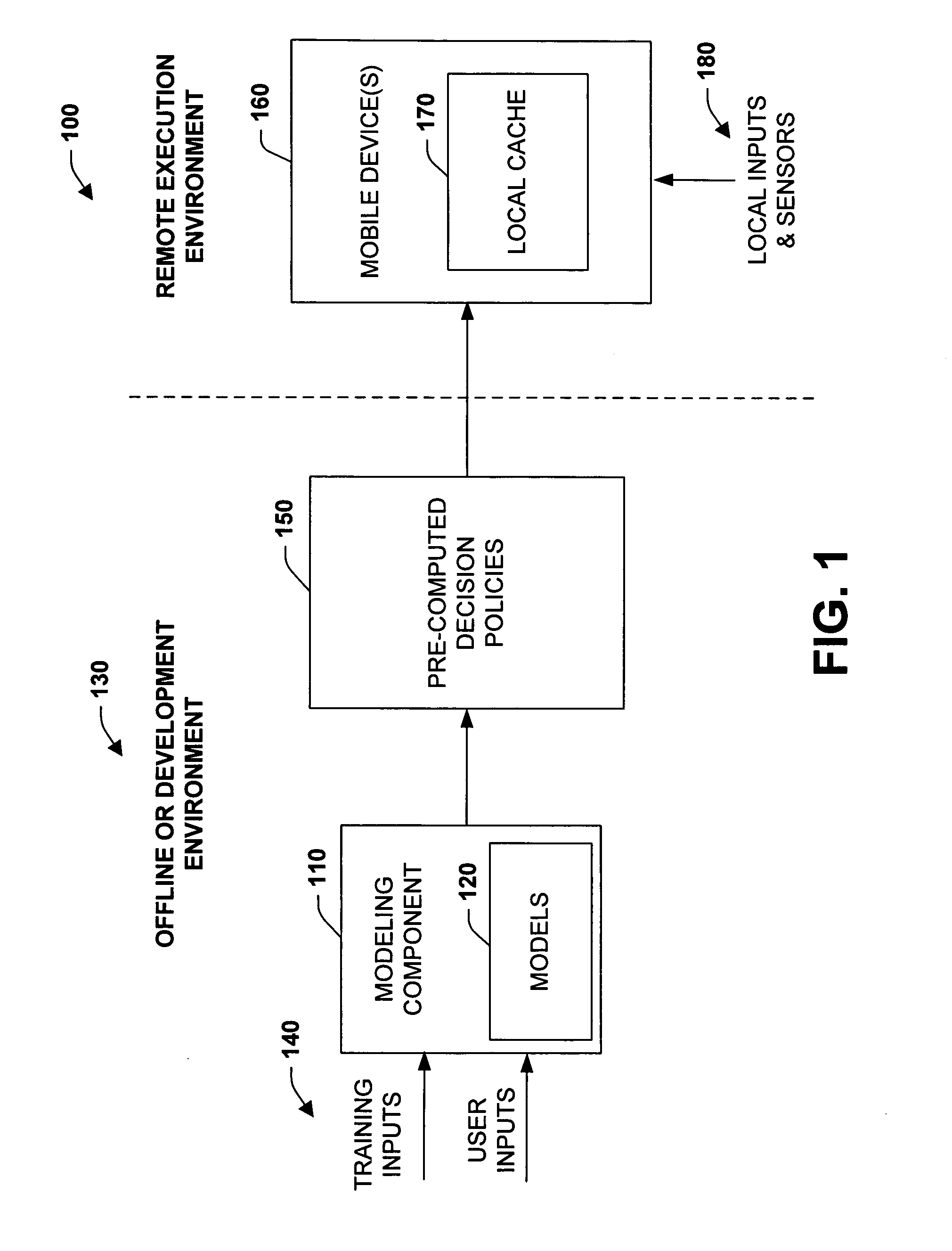
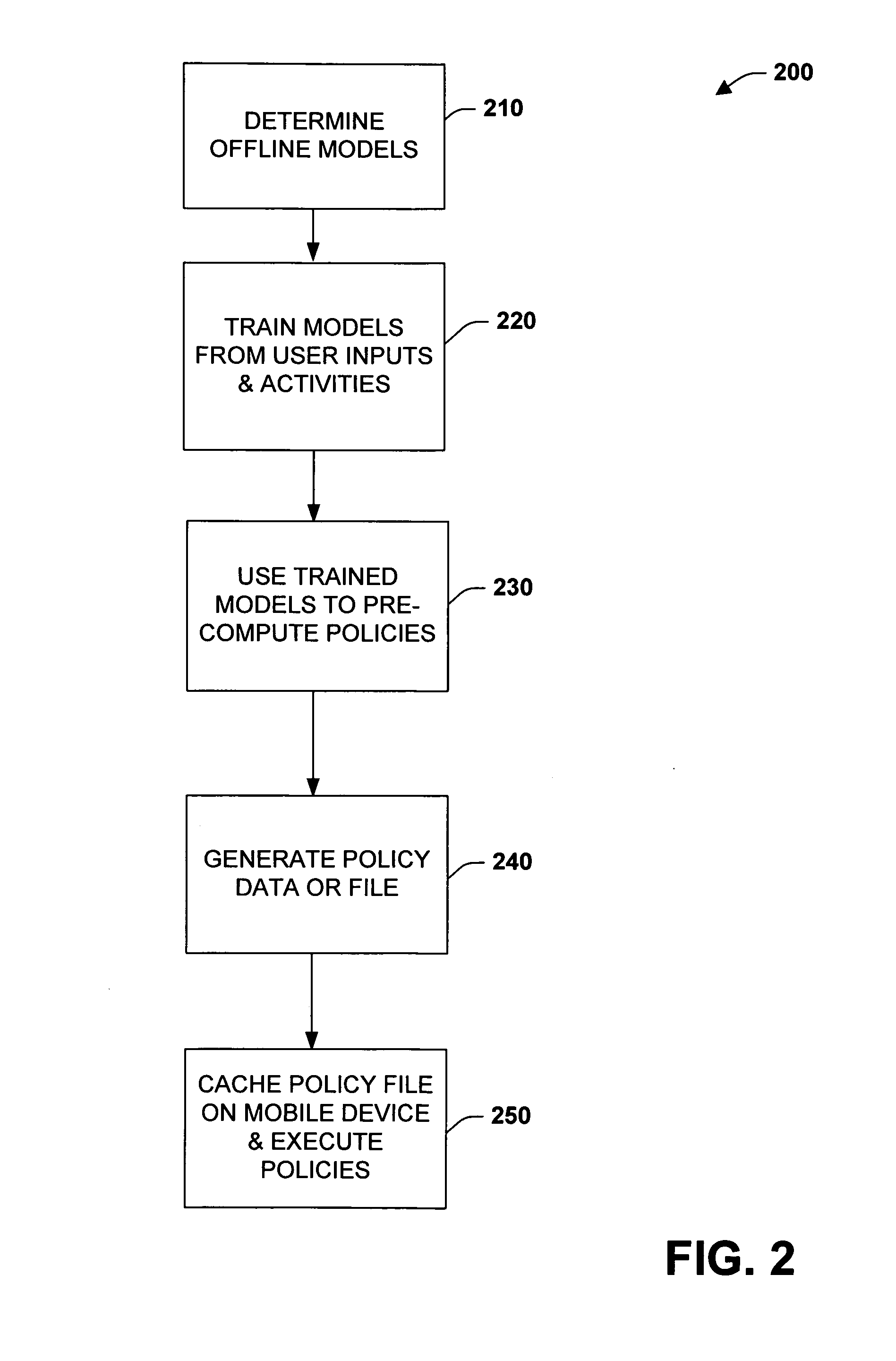
Precomputation of context-sensitive policies for automated inquiry and action under uncertainty
InactiveUS20070022075A1Enhance decision-making capability of deviceImprove device performanceProbabilistic networksFuzzy logic based systemsPrecomputationContext sensitivity
Learning, inference, and decision making with probabilistic user models, including considerations of preferences about outcomes under uncertainty, may be infeasible on portable devices. The subject invention provides systems and methods for pre-computing and storing policies based on offline preference assessment, learning, and reasoning about ideal actions and interactions, given a consideration of uncertainties, preferences, and / or future states of the world. Actions include ideal real-time inquiries about a state, using pre-computed value-of-information analyses. In one specific example, such pre-computation can be applied to automatically generate and distribute call-handling policies for cell phones. The methods can employ learning of Bayesian network user models for predicting whether users will attend meetings on their calendar and the cost of being interrupted by incoming calls should a meeting be attended.
Owner:MICROSOFT TECH LICENSING LLC
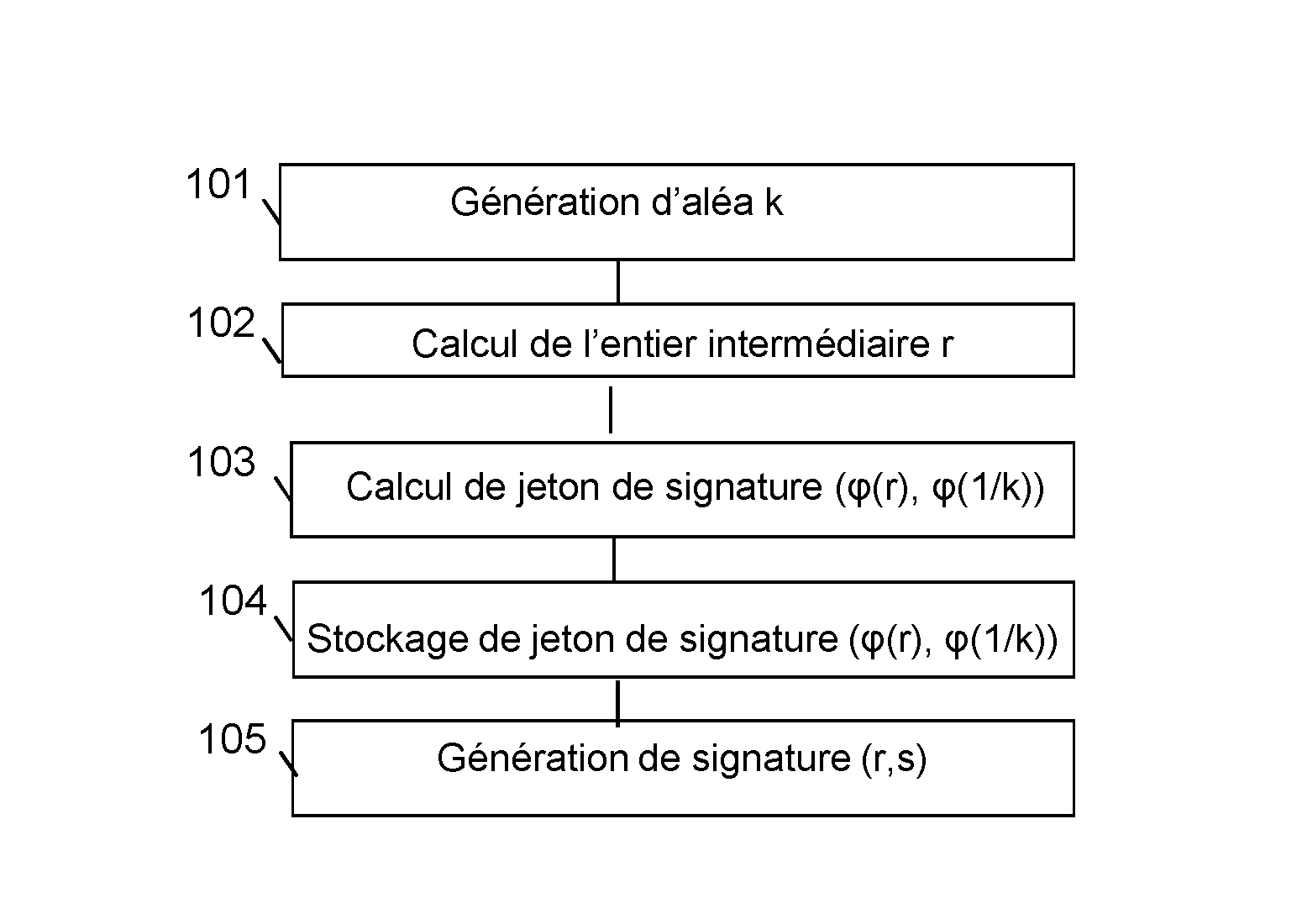
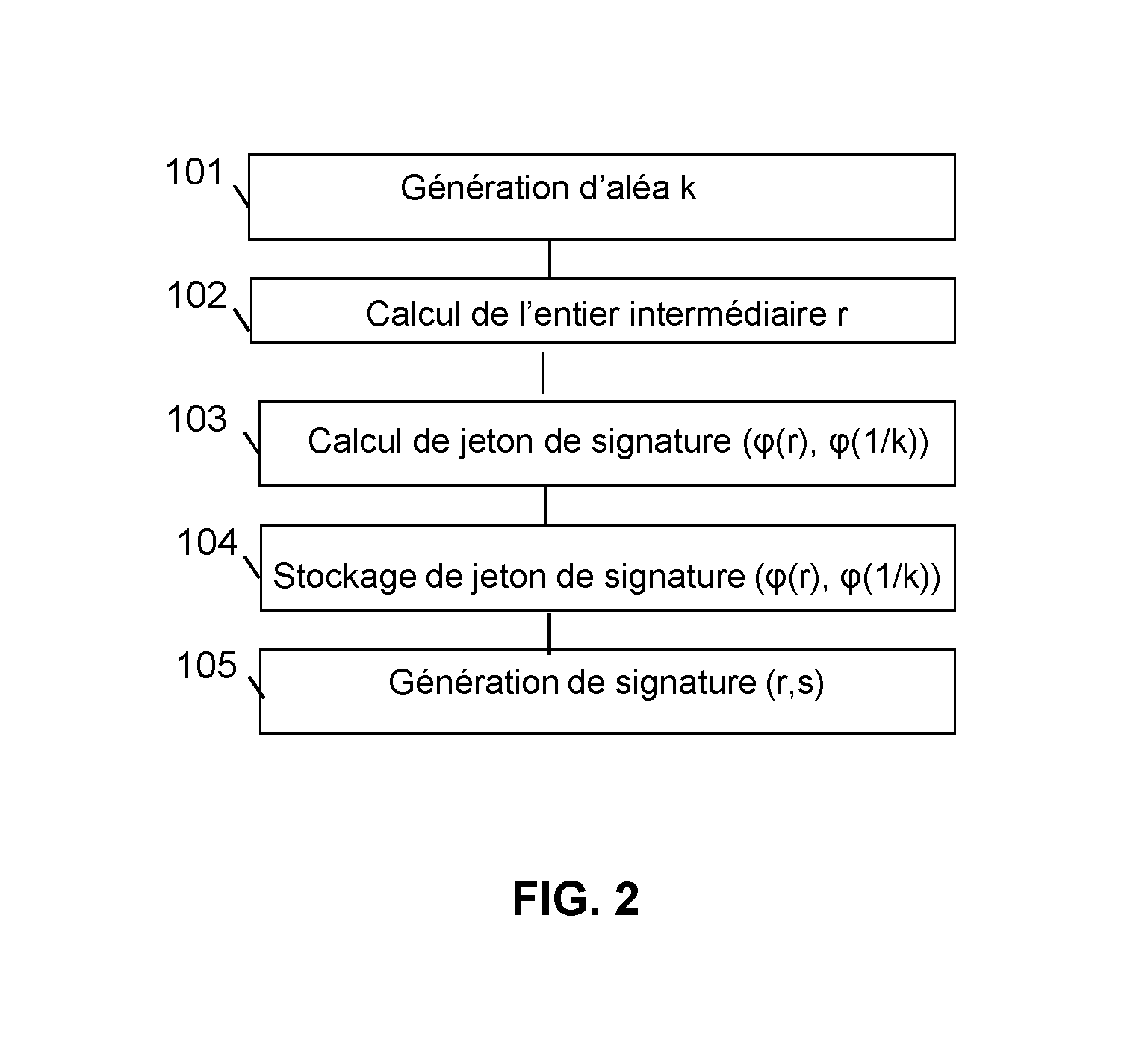
Method for generating a message signature from a signature token encrypted by means of a homomorphic encryption function
ActiveUS20160344557A1Not to endanger securityReduce power generation costsPublic key for secure communicationUser identity/authority verificationHardware security modulePrecomputation
The invention relates to a method for generating a message signature intended to be validated by a verifier server, a client device being configured to hold a private key and a corresponding public key and comprising steps of:offline precomputation (103) by a hardware security module of a signature token, a result of encryption by means of a homomorphic encryption function,storage (104) of said signature token;generation (105) of said signature of said encrypted message by means of said homomorphic encryption function from the result of the encryption by said homomorphic encryption function of the private key stored by the client device, of the signature token and of said message, said signature being intended to be validated by said verifier server by means of said public key.
Owner:IDEMIA IDENTITY & SECURITY FRANCE
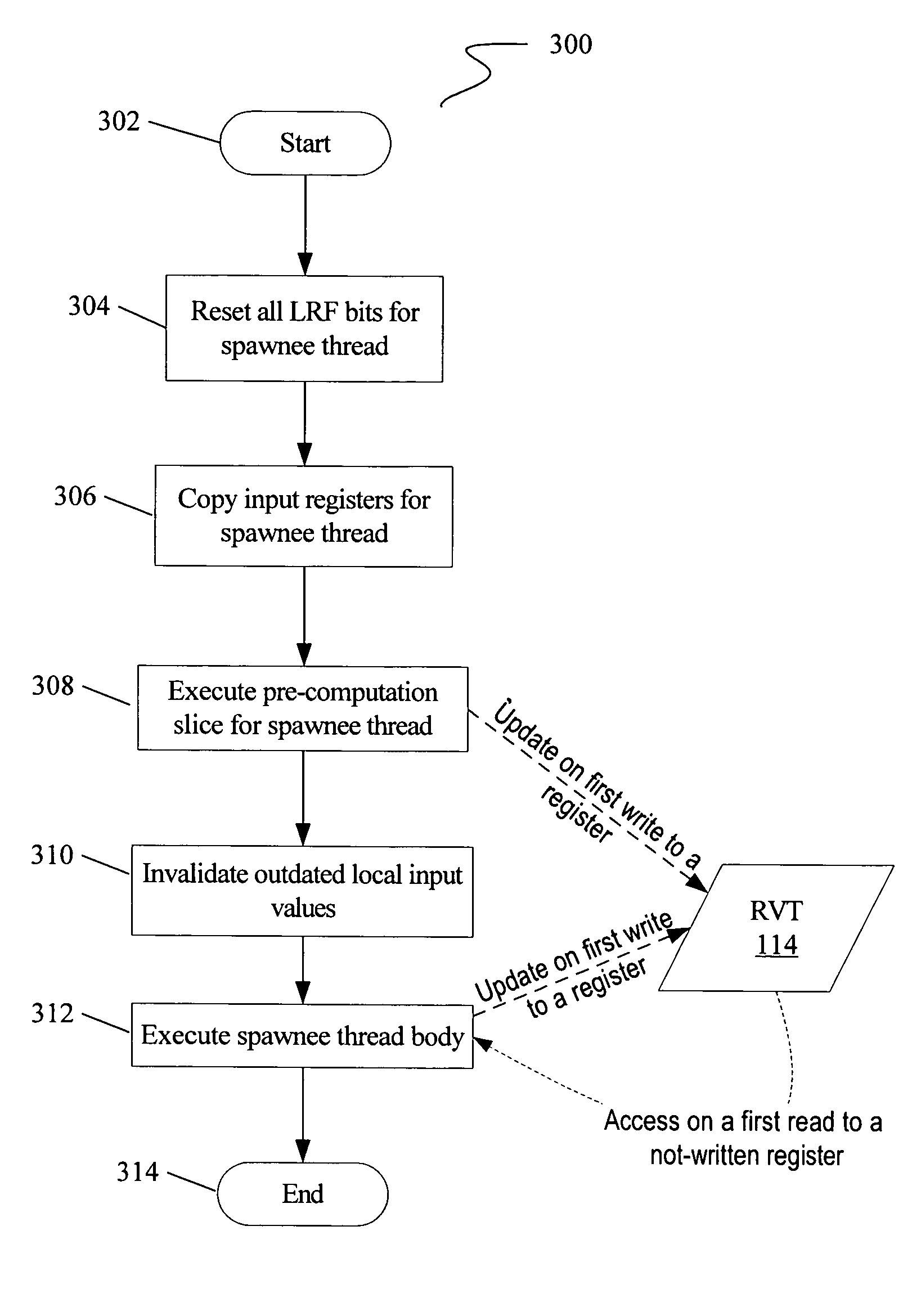
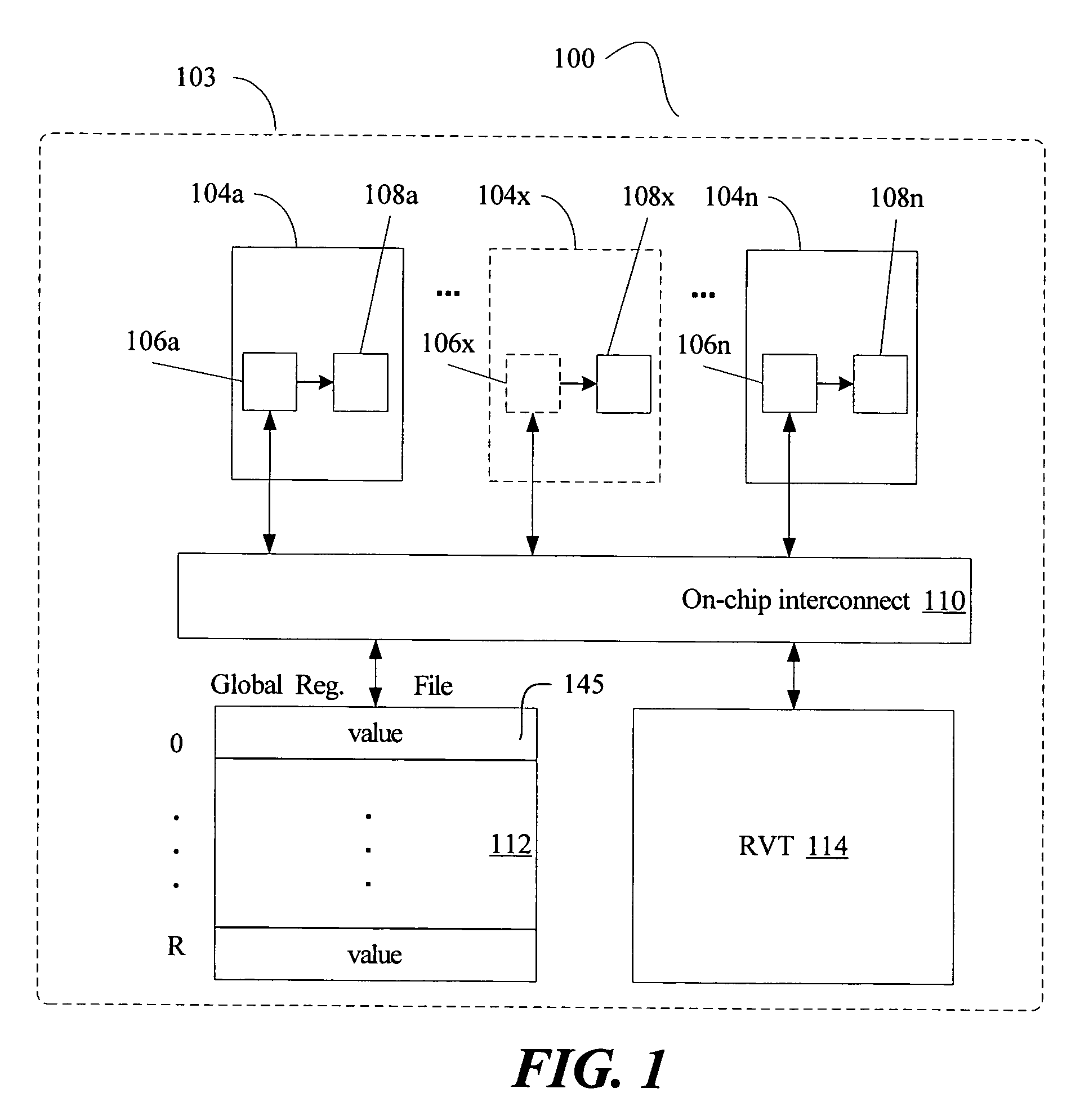
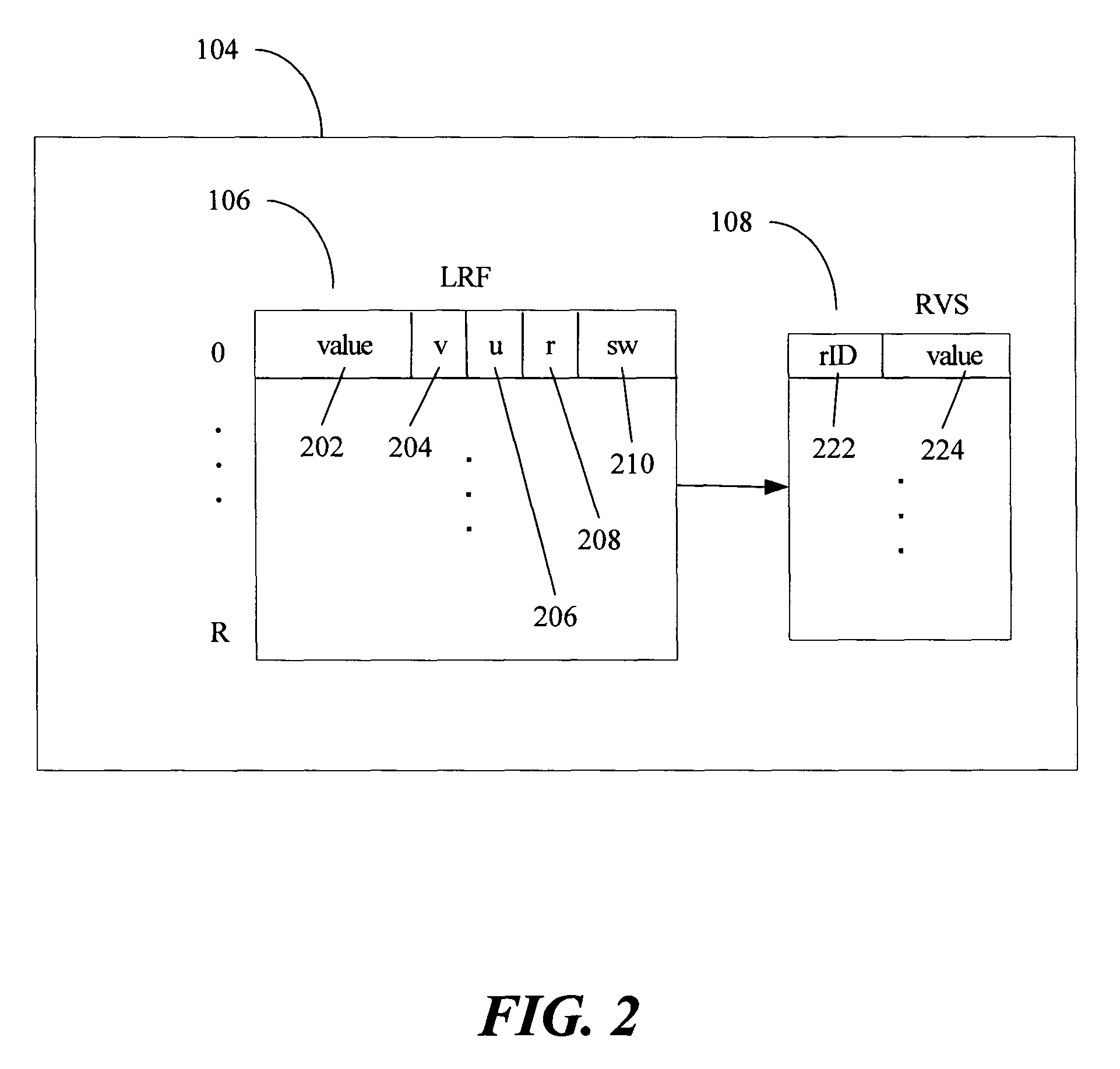
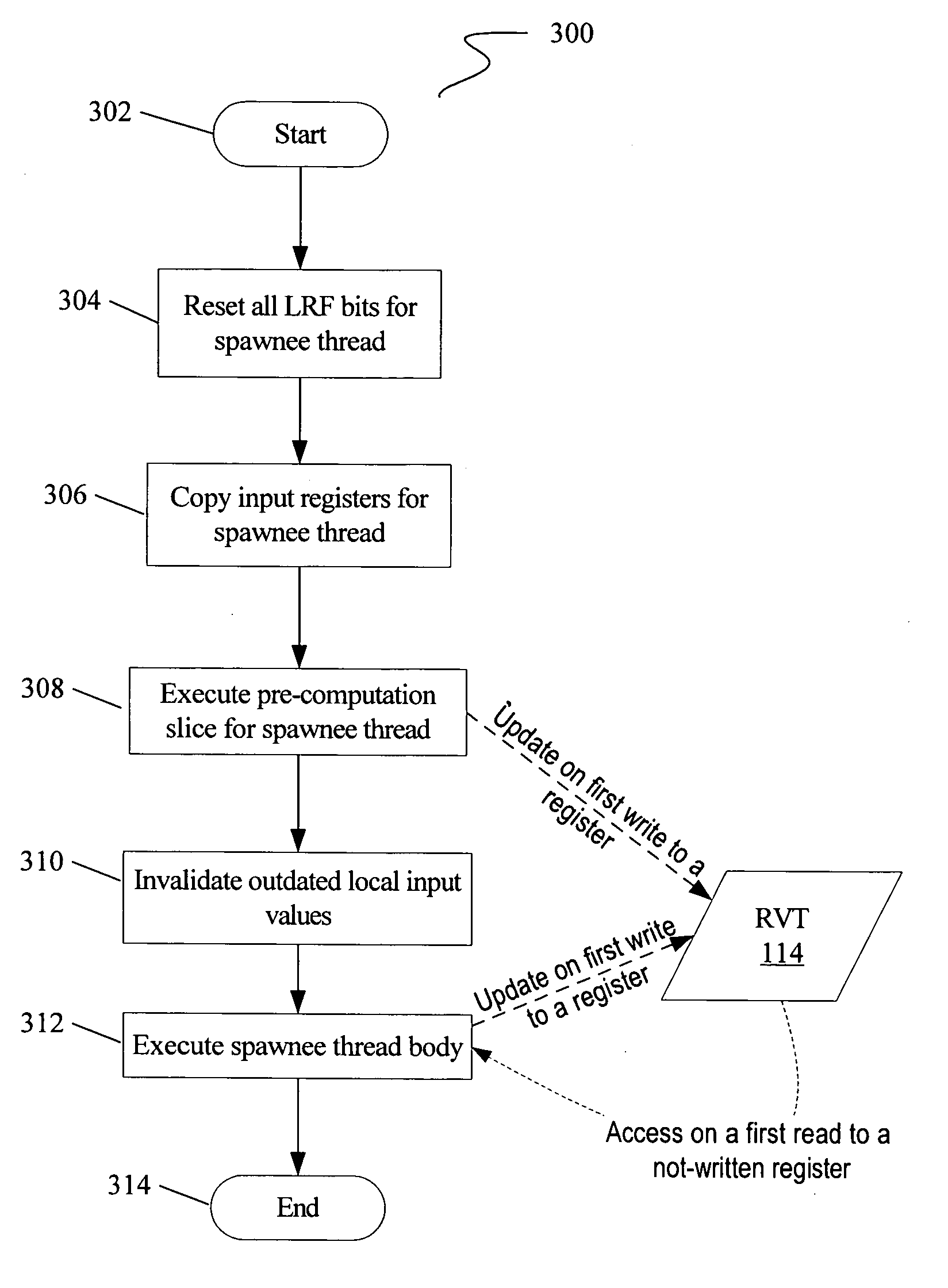
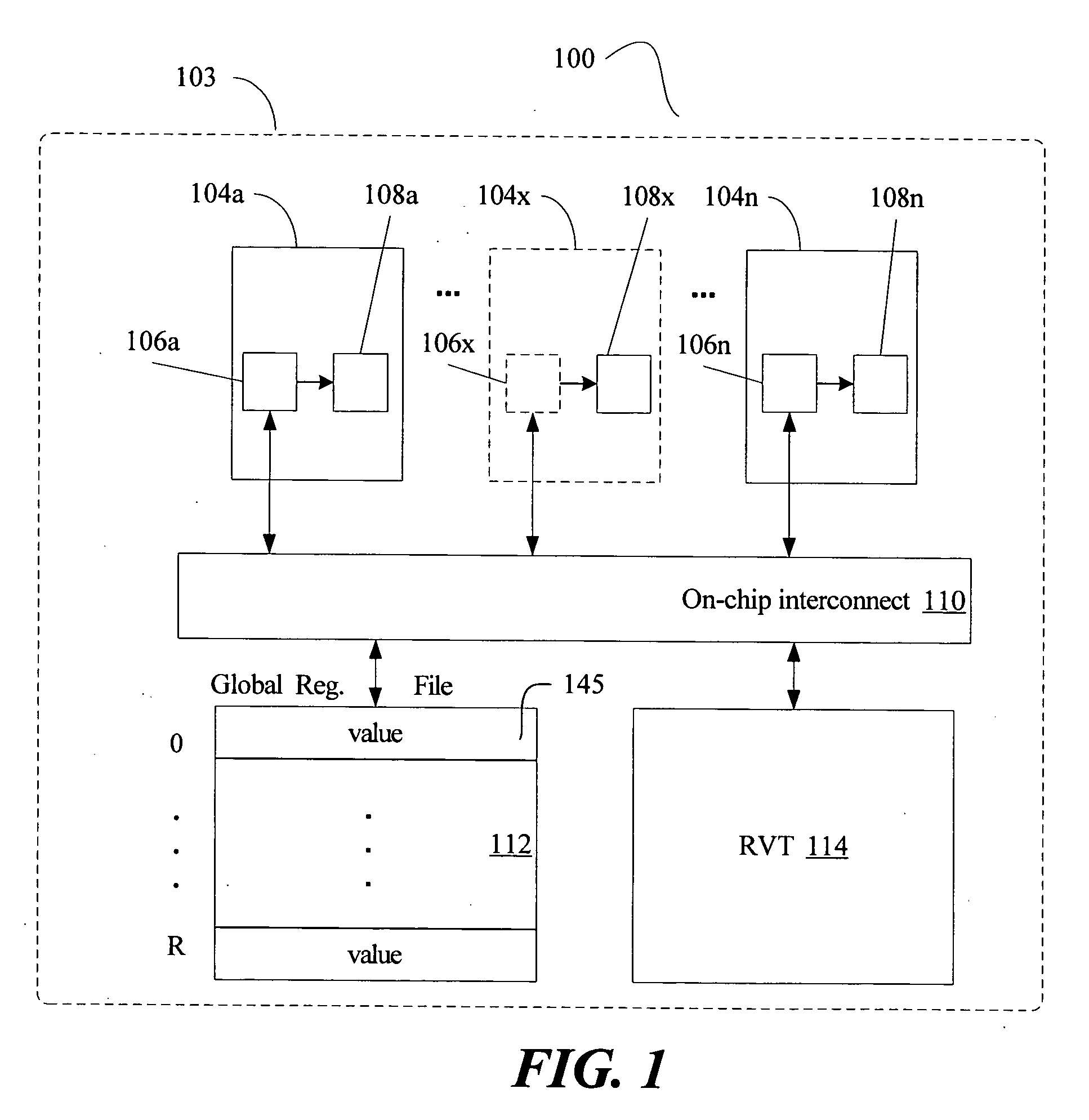
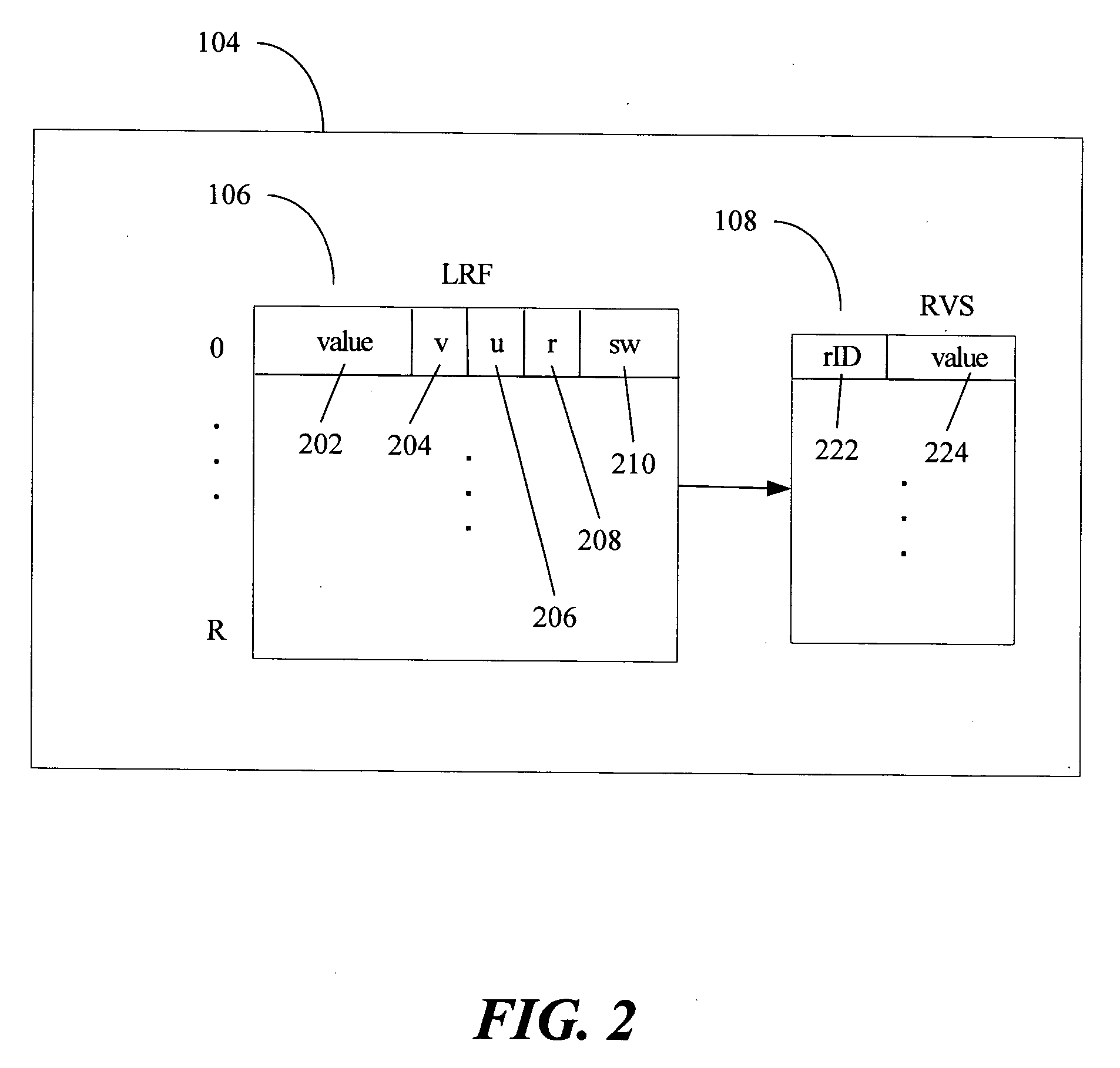
Multi-version register file for multithreading processors with live-in precomputation
Disclosed are selected embodiments of a processor that may include a plurality of thread units and a register file architecture to support speculative multithreading. For at least one embodiment, live-in values for a speculative thread are computed via execution of a precomputation slice and are stored in a validation buffer for later validation. A global register file holds the committed architecture state generated by a non-speculative thread. Each thread unit includes a local register file. A directory indicates, for each architectural register, which speculative thread(s) have generated a value for the architectural register. Other embodiments are also described and claimed.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
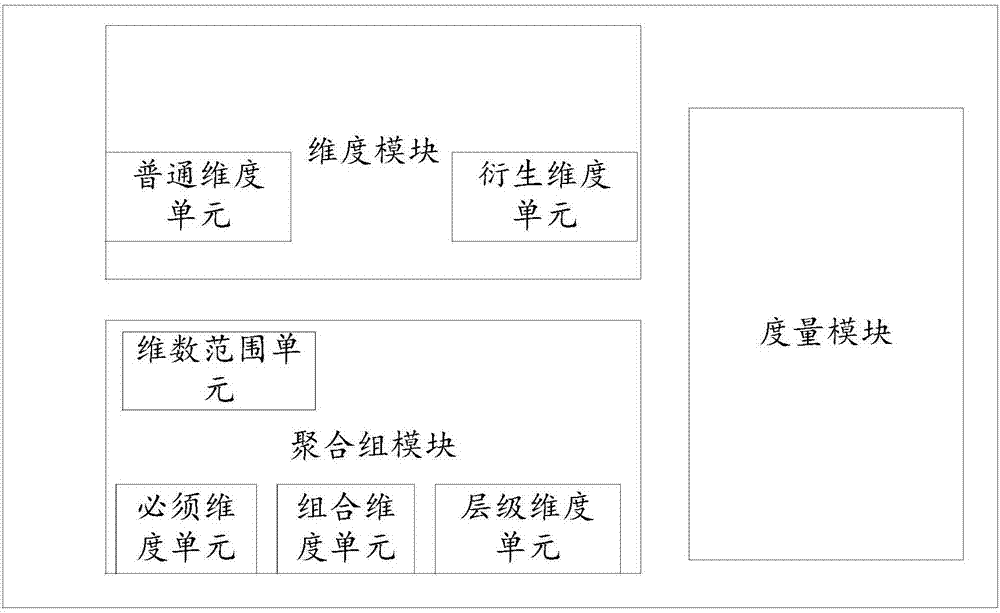
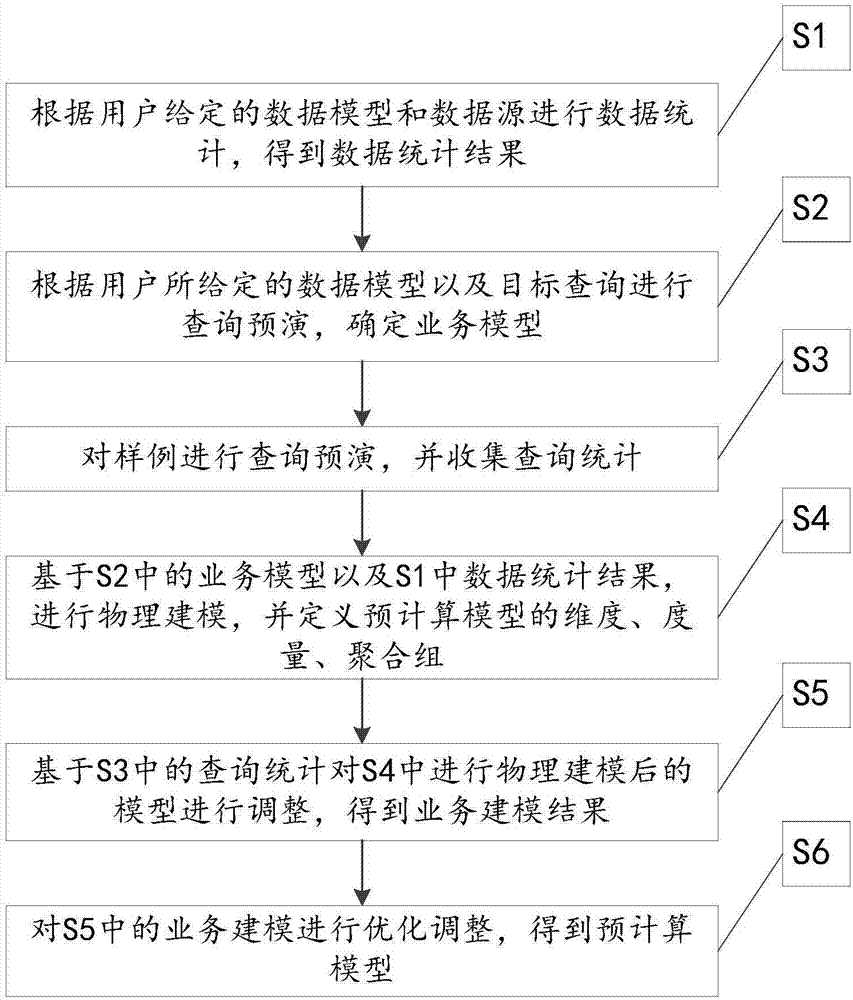
OLAP pre-calculation model, automatic modeling method and automatic modeling system
ActiveCN106997386AEfficient removalRemove Dimension CombinationsMulti-dimensional databasesSpecial data processing applicationsData sourceComputational model
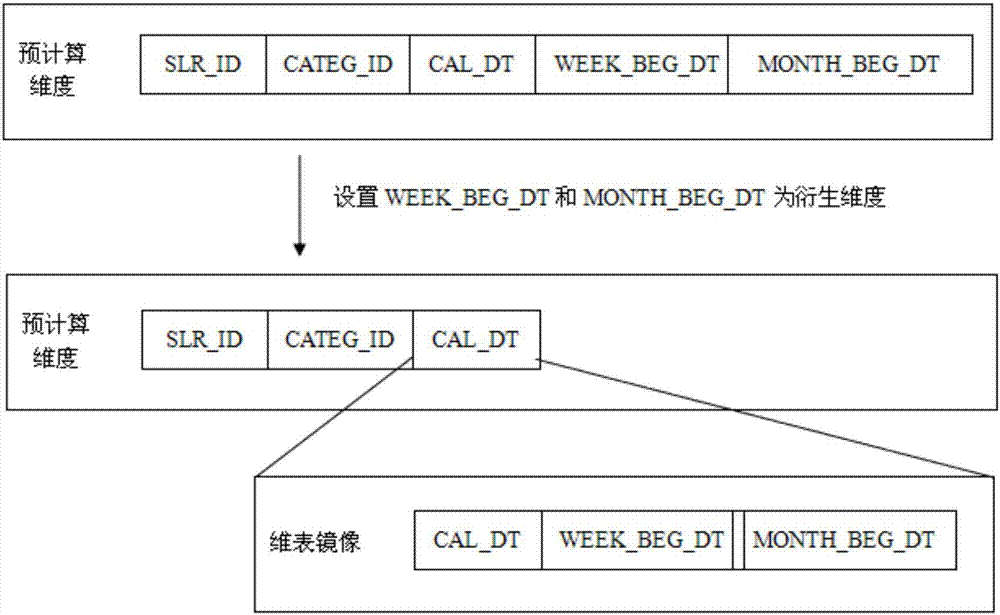
The invention relates to an OLAP pre-calculation model, an automatic modeling method and an automatic modeling system. The model comprises a dimension module, an aggregation group module and a measurement module. The method comprises the steps of performing data statistics on all data sources to obtain a data statistics result; according to a data model given by a user and operation of performing query rehearsal on a target query, determining a business model; performing query rehearsal on a sample, and collecting query statistics; performing physical modeling, and defining dimensions, measurement and an aggregation group of the pre-calculation model; obtaining a business modeling result; and obtaining the pre-calculation model. The system comprises a data statistics module, a business model module, a query statistics module and a model building module. By adding derived dimensions and the aggregation group, the pre-calculation dimensions are combined more effectively, so that redundancy calculation and data storage are reduced; and higher calculation efficiency and smaller storage occupation are achieved, so that a better effect is achieved in big data multidimensional analysis application.
Owner:SHANGHAI KYLIGENCE INFORMATION TECH CO LTD
Big data-based online analytical processing system and method
ActiveCN106372114AImprove acceleration performanceEfficiencySpecial data processing applicationsData setLow delay
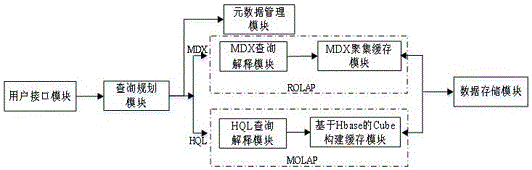
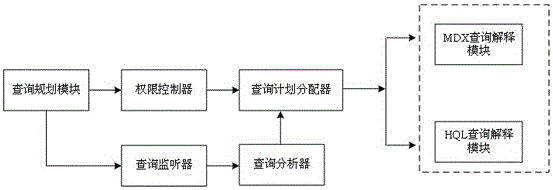
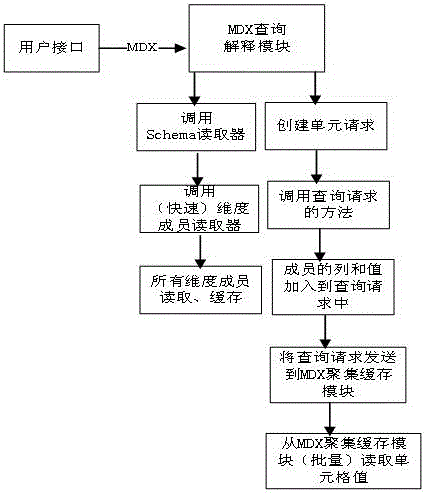
The invention discloses a big data-based online analytical processing system and method. The system can be used for carrying out quick multi-dimensional query and analysis on data sets with different scales and levels under a Hadoop environment. A query plan selected through query, planning and estimation comprises MDX query supporting Hive and Hbase precomputation cache mechanism-based multi-dimensional query. According to the system and method, optimization of the MDX query supporting Hive data warehouses on extensible cluster nodes and of the Hbase precomputation cache mechanism-based multi-dimensional query are realized, the low-delay multi-dimensional query requirements of the data sets with different scales and levels are satisfied, and the OLAP multi-dimensional query of different OLAP data organization models under a single data source background is solved. Aiming at the performance optimization problem of Hive multi-dimensional query on large-scale data sets, an Hbase cache-based segmented layered dimensionality-reduction aggregation algorithm is proposed, and the algorithm brings MOLAP for solving the multi-dimensional query calculation of large-scale data into a big data OLAP system, so that the extendibility and effectiveness of the multi-dimensional query of data with different scales and levels under a big data background are greatly enhanced.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Control-quasi-independent-points guided speculative multithreading
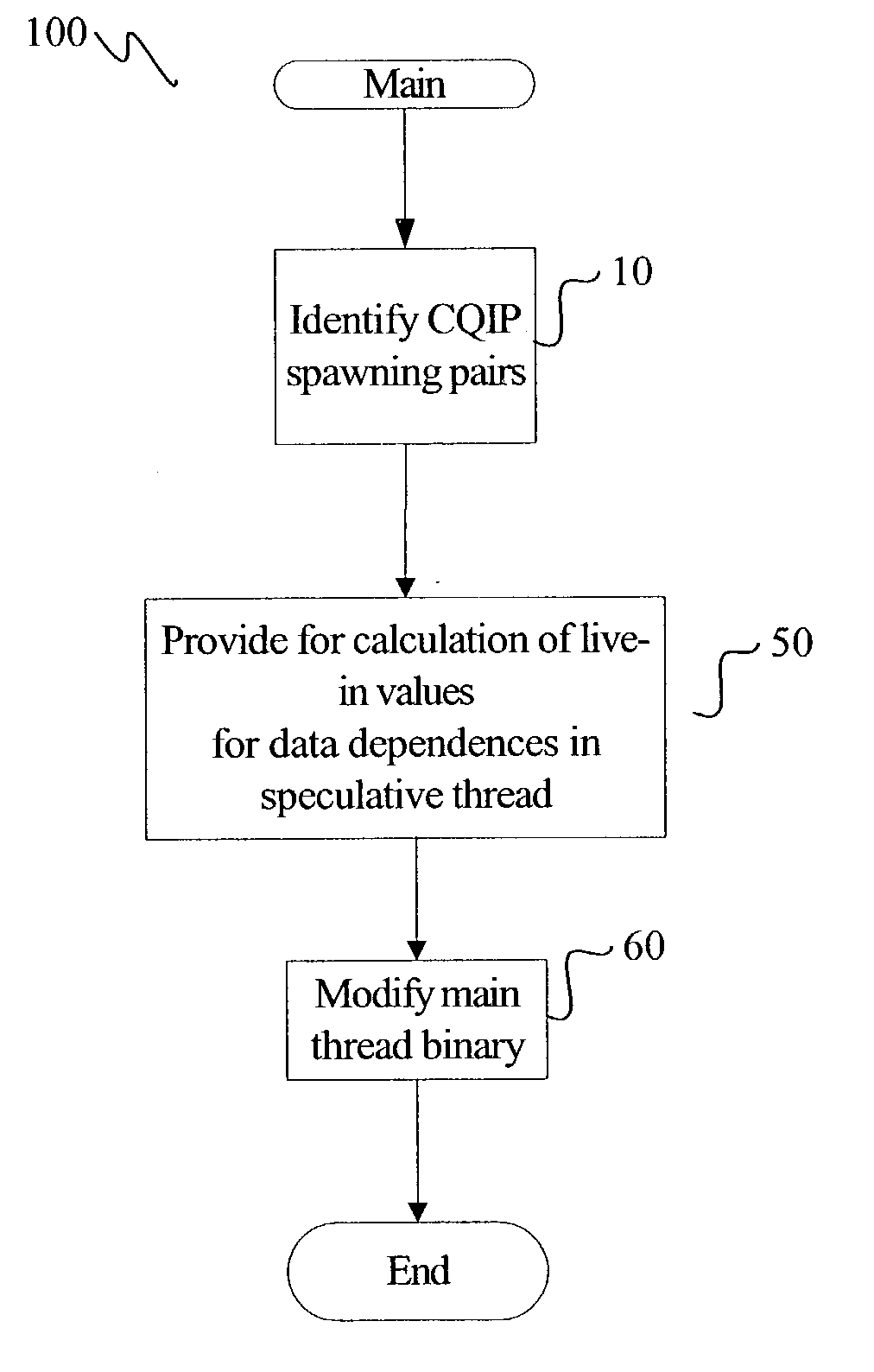
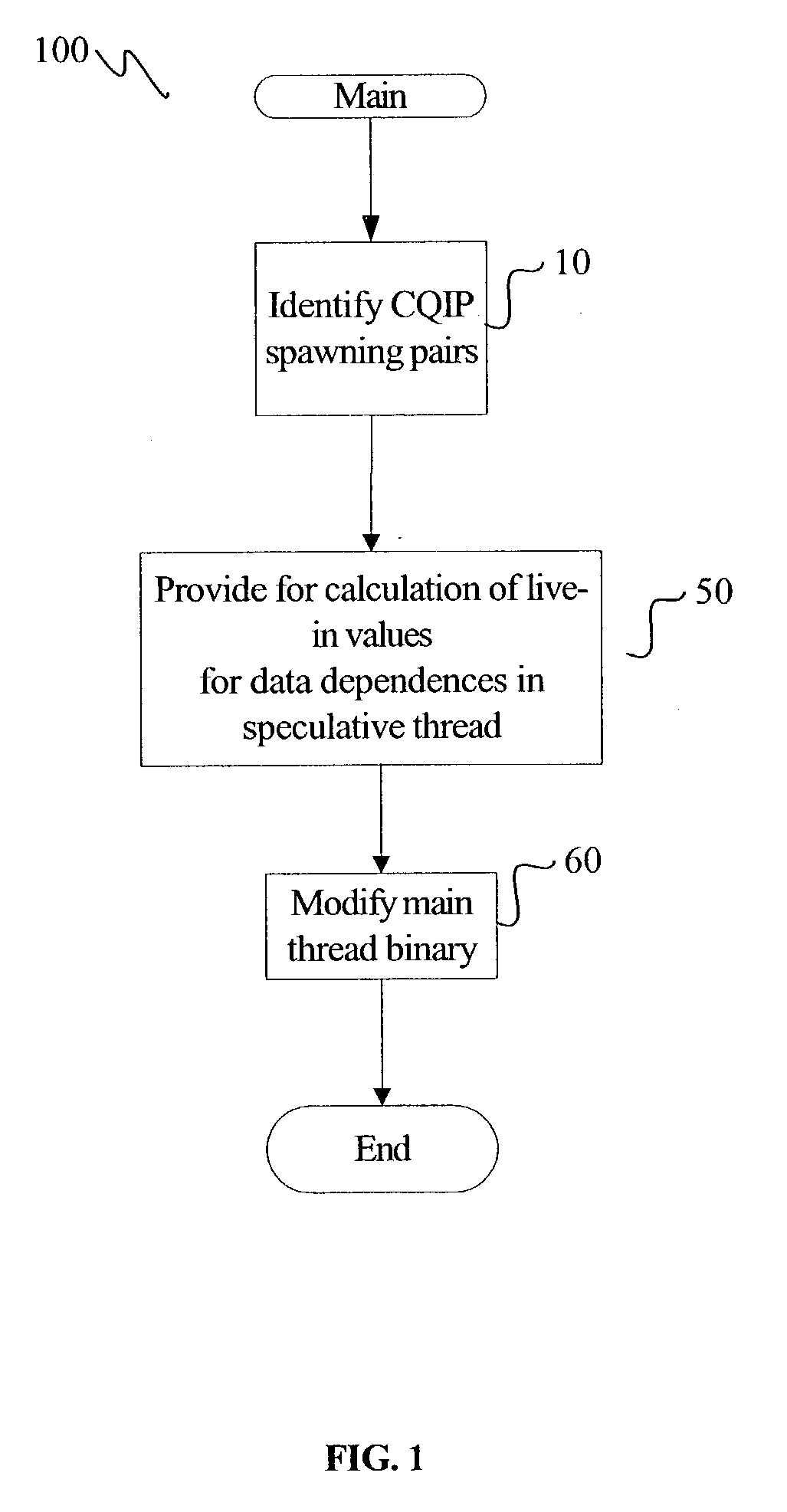
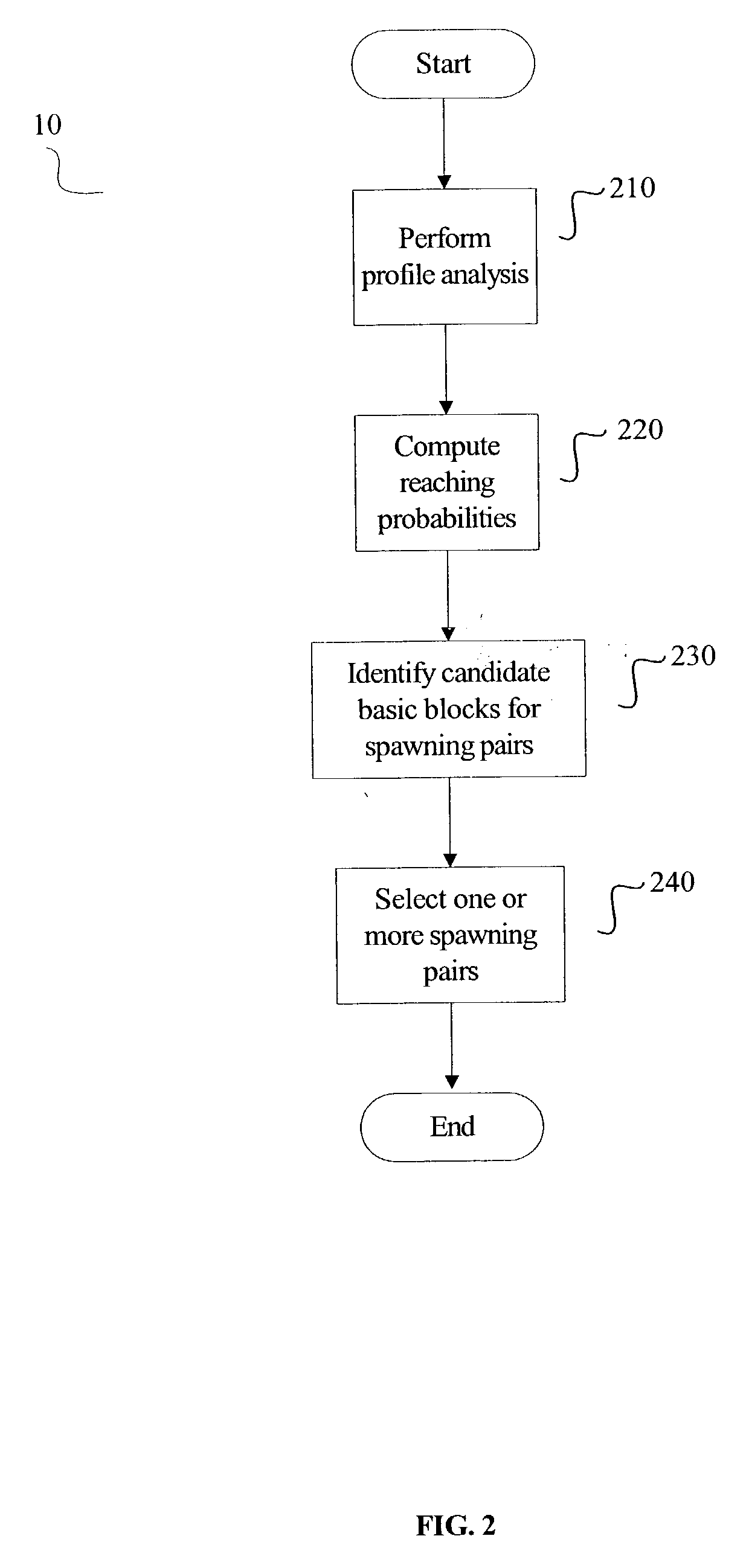
InactiveUS20040154010A1Program initiation/switchingSoftware engineeringPrecomputationExecution control
A method for generating instructions to facilitate control-quasi-independent-point multithreading is provided. A spawn point and control-quasi-independent-point are determined. An instruction stream is generated to partition a program so that portions of the program are parallelized by speculative threads. A method of performing control-quasi-independent-point guided speculative multithreading includes spawning a speculative thread when the spawn point is encountered. An embodiment of the method further includes performing speculative precomputation to determine a live-in value for the speculative thread.
Owner:TAHOE RES LTD
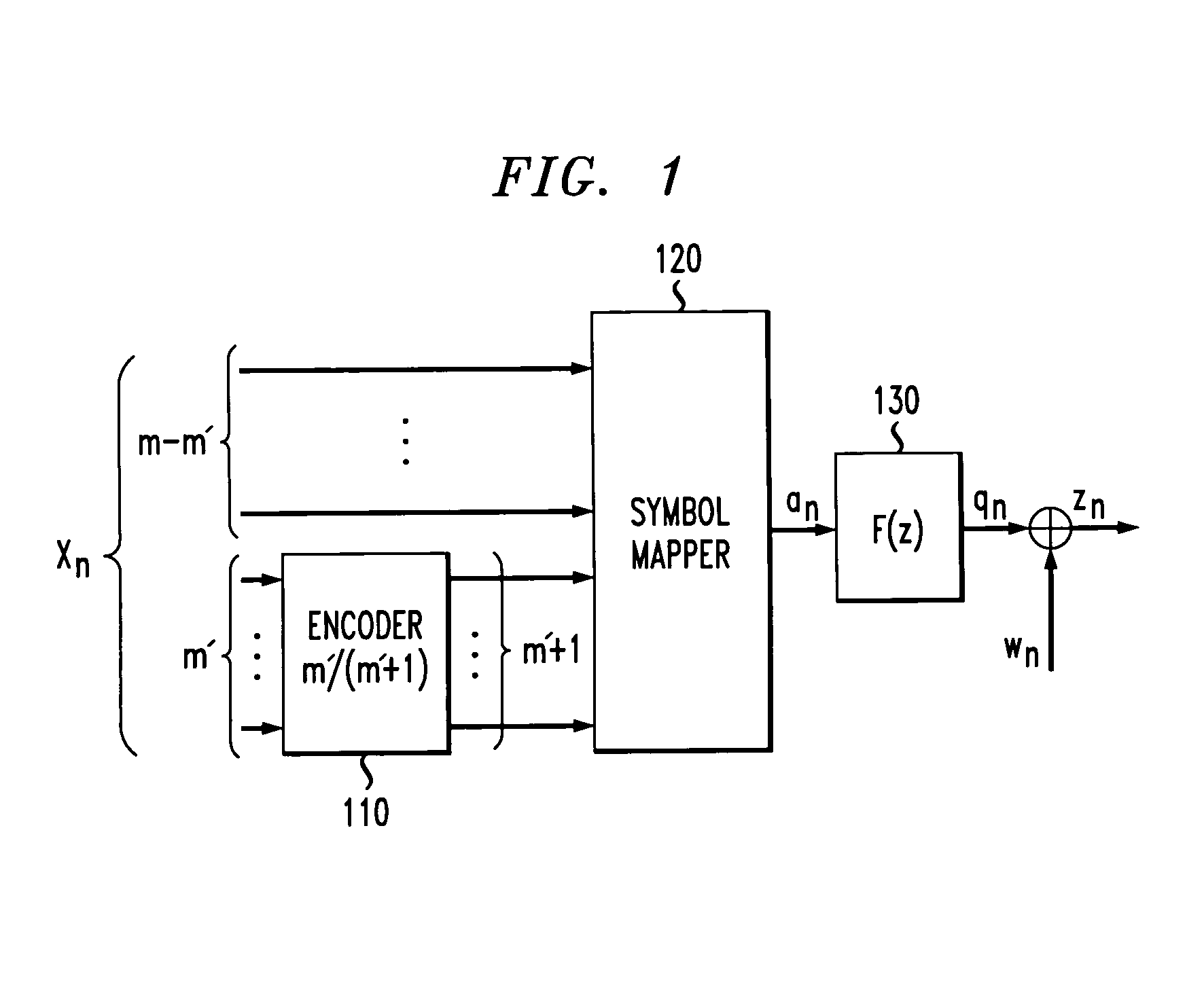
Method and apparatus for shortening the critical path of reduced complexity sequence estimation techniques
InactiveUS6999521B1Reduce computing loadReduce complexityData representation error detection/correctionOther decoding techniquesMultiplexerPrecomputation
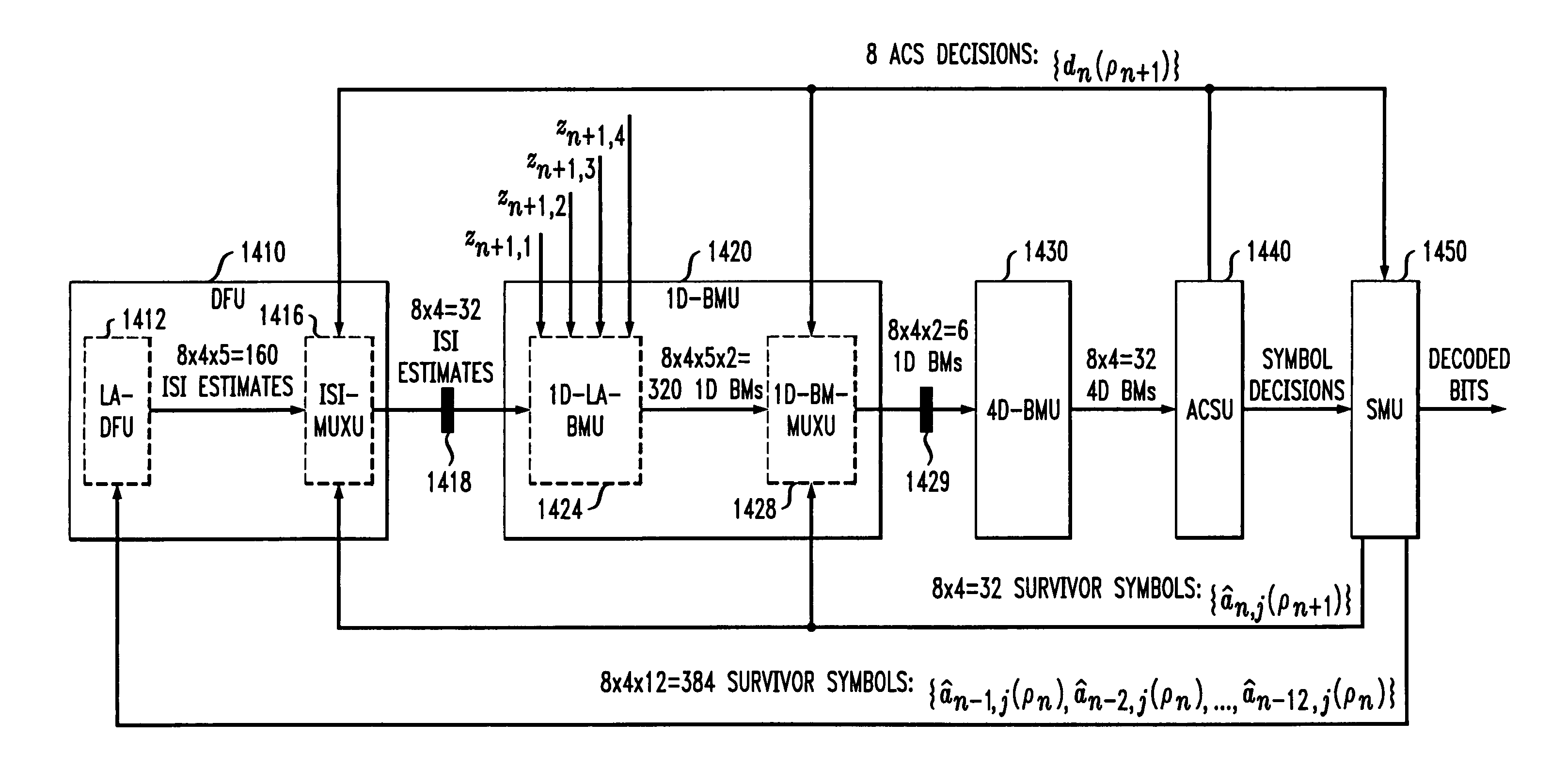
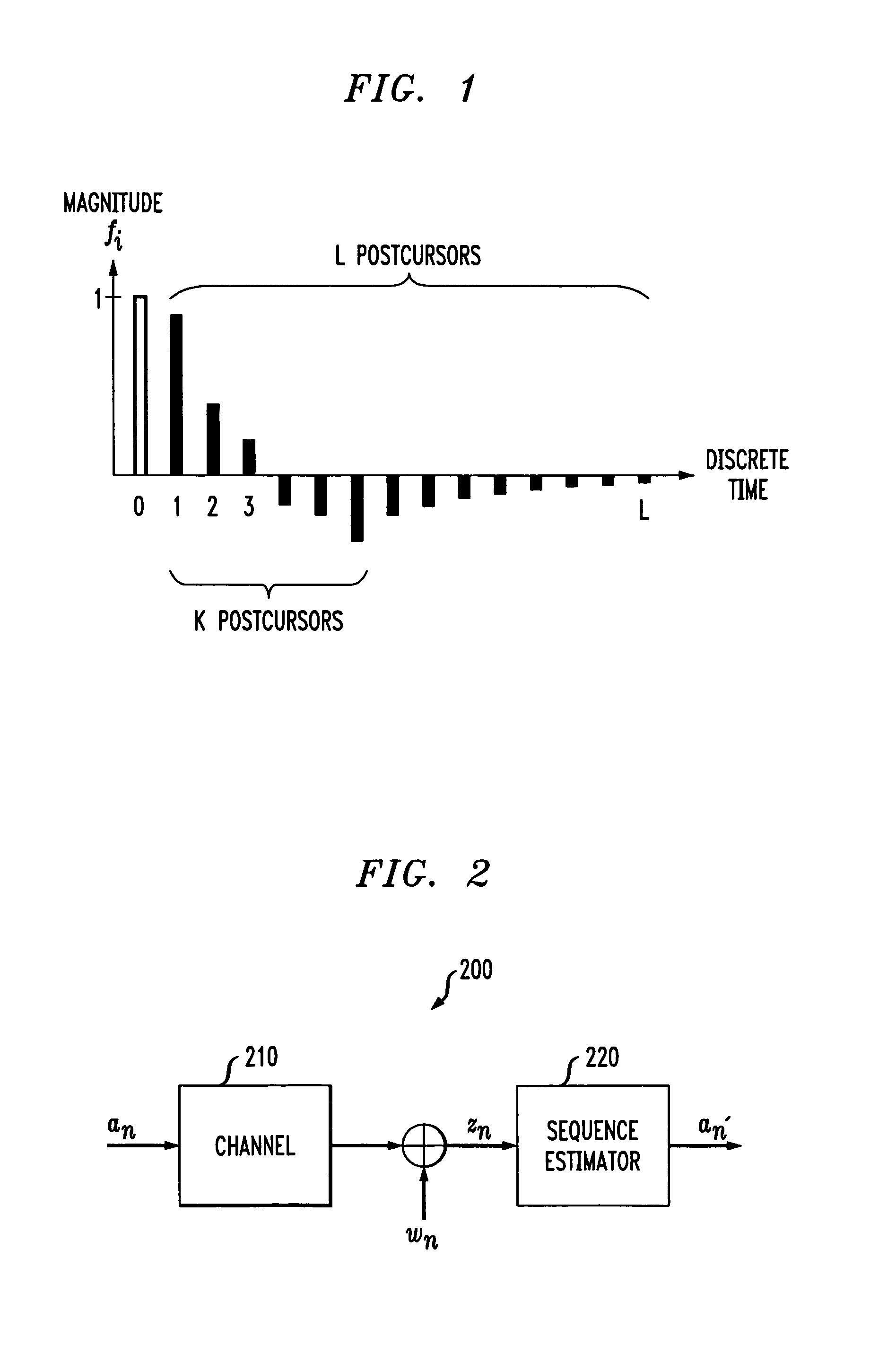
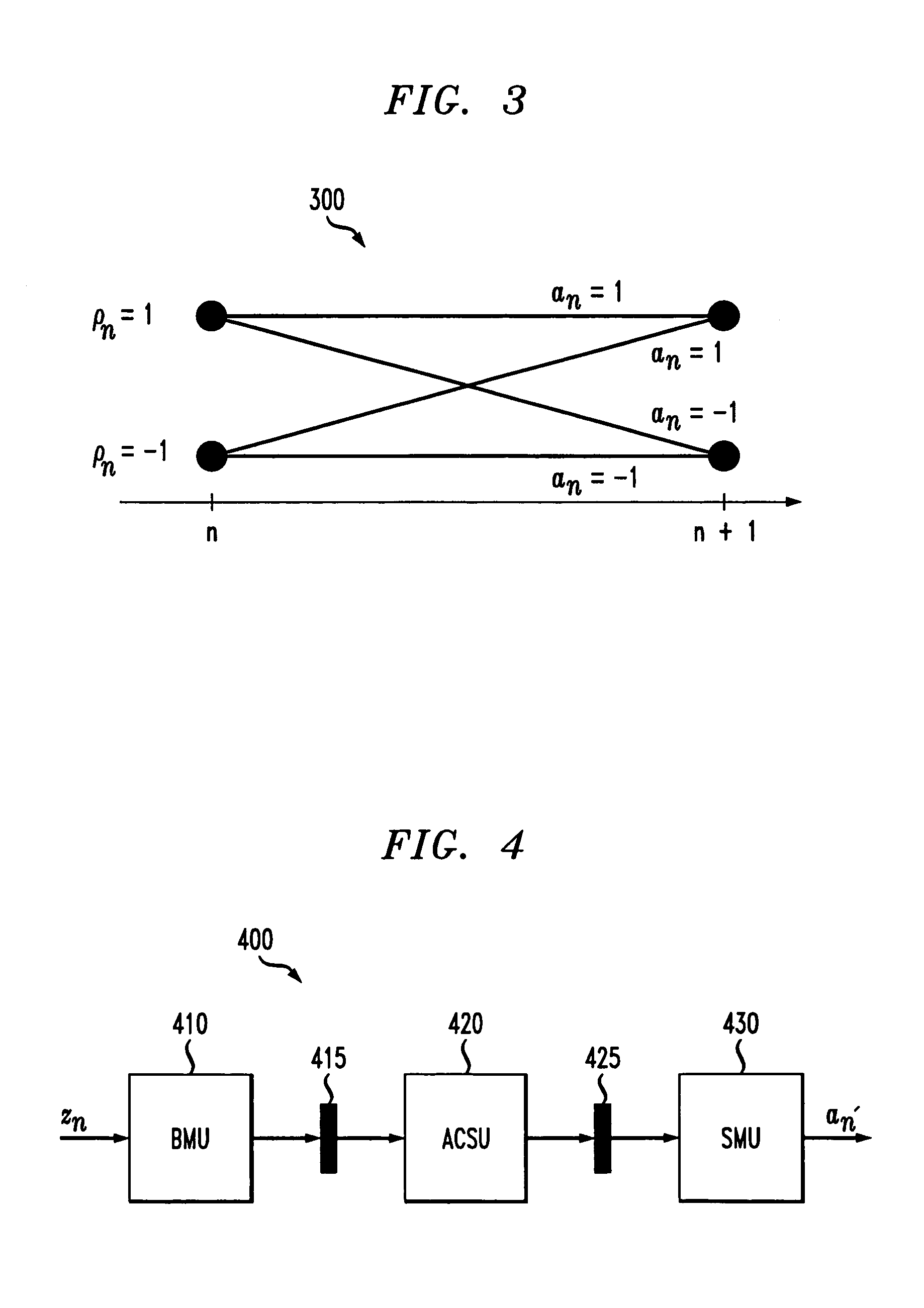
A method and apparatus are disclosed for improving the processing time of reduced complexity sequence estimation techniques, such as reduced state sequence estimation. Precomputing the branch metrics for all possible symbol combinations in the channel memory makes it possible to remove the branch metrics unit and decision-feedback unit from the feedback loop, thereby reducing the critical path. A set of multiplexers select the appropriate branch metrics based on the survivor symbols in the corresponding survivor path cells. The computational load of the precomputations is reduced for multi-dimensional trellis codes by precomputing each dimension of the multi-dimensional trellis code separately. A hybrid survivor memory architecture is also disclosed for a RSSE for a channel having a channel memory of length L, where the survivors corresponding to the L past decoding cycles are stored in a register exchange architecture (REA), and survivors corresponding to later decoding cycles are stored in a trace-back architecture (TBA) or REA.
Owner:WSOU INVESTMENTS LLC +1
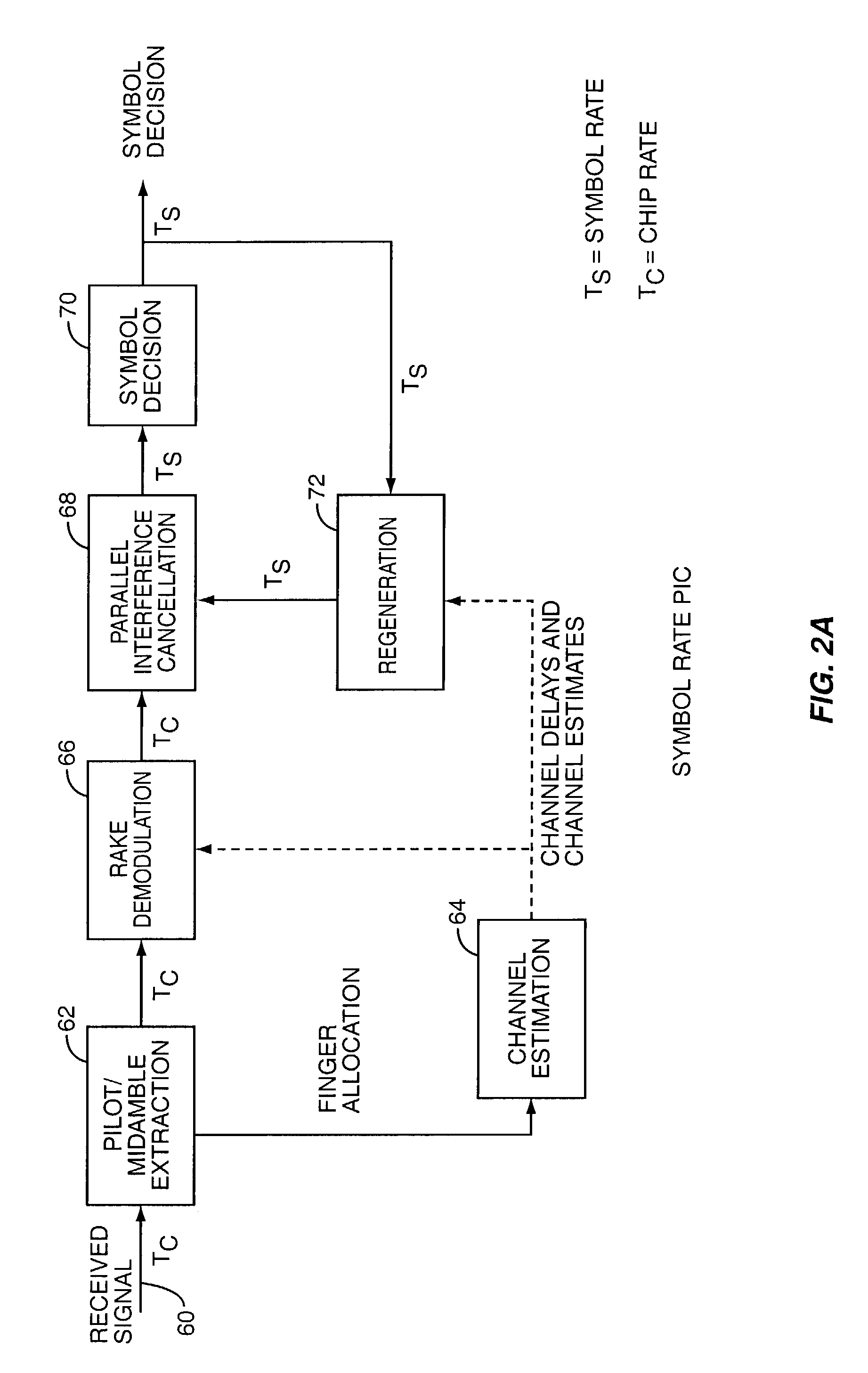
Low complexity interference cancellation
InactiveUS7324584B1Reduce processingReduce complexityTransmissionMultiuser detectionInterference cancelation
The present invention relates to a new parallel interference cancellation (PIC) configuration where the PIC is implemented after the rake reception and multipath combining. In the invention disclosed, the regenerated interference contributions (functions of signature sequence cross-correlations) for multiuser detection (MUD) in a multipath radio channel are explicitly filtered through the estimated multipath channels, and stored. These stored quantities already contain the effect of the channel, and only need updating according to the rate of change of channel dynamics, and not the symbol period. During each symbol period, interference is computed from each interfering user to each desired user using current estimates of symbol decisions and the aforementioned interference contributions. The precomputation of the interference contributions, which are valid for a sequence of symbols, allows for extremely low complexity baseband processing in the receiver.
Owner:APPLE INC
Method and apparatus for rapid and scaleable directed advertisting service
A method and apparatus for selecting a subset of advertisements complying with an advertisement request from a set of advertisements is disclosed. Advertisements rules are specified according to a logical semantic simplifying search combinatorials yet allowing for flexible specification of advertising rules, and permitting significant precomputation of advertising rules to permit rapid identification of advertisements complying with advertisement requests. In one embodiment, advertisement rules and requests are represented as easily manipulable and computable bit arrays.
Owner:HULU
Hybrid memory architecture for reduced state sequence estimation (RSSE) techniques
InactiveUS20060039492A1Extended processing timeShortening of the critical pathData representation error detection/correctionOther decoding techniquesComputation complexityPrecomputation
A method and apparatus are disclosed for improving the processing time of reduced complexity sequence estimation techniques, such as reduced state sequence estimation (RSSE). The possible values for the branch metrics in the RSSE are precomputed to permit pipelining and the shortening of the critical path. The computational load of the precomputations is reduced for multi-dimensional trellis codes by precomputing each dimension of the multi-dimensional trellis code separately. Prefiltering techniques are used to reduce the computational complexity by shortening the channel memory. A hybrid survivor memory architecture is disclosed for RSSE for a channel having a channel memory of length L, where the survivors corresponding to the L past decoding cycles are stored in a register exchange architecture, and survivors corresponding to later decoding cycles are stored in a trace-back architecture (TBA) or register exchange architecture (REA). Symbols are mapped to information bits to reduce the word size before being moved from the first register exchange architecture to the trace-back architecture (TBA) or the second register exchange architecture.
Owner:ALCATEL-LUCENT USA INC
Pre-computation and dual-pass modular arithmetic operation approach to implement encryption protocols efficiently in electronic integrated circuits
InactiveUS7027597B1Effective encryptionEfficient implementationComputations using contact-making devicesComputation using non-contact making devicesProcessor registerModularity
A pre-computation and dual-pass modular operation approach to implement encryption protocols efficiently in electronic integrated circuits is disclosed. An encrypted electronic message is received and another electronic message generated based on the encryption protocol. Two passes of Montgomery's method are used for a modular operation that is associated with the encryption protocol along with pre-computation of a constant based on a modulus. The modular operation may be a modular multiplication or a modular exponentiation. Modular arithmetic may be performed using the residue number system (RNS) and two RNS bases with conversions between the two RNS bases. A minimal number of register files are used for the computations along with an array of multiplier circuits and an array of modular reduction circuits. The approach described allows for high throughput for large encryption keys with a relatively small number of logical gates.
Owner:CISCO TECH INC
Method and apparatus for elliptic curve scalar multiplication
ActiveUS7215780B2Reducing a scalar modulo a truncatorKey distribution for secure communicationSecret communicationAlgorithmModularity
The applicants have recognized an alternate method of performing modular reduction that admits precomputation. The precomputation is enabled by approximating the inverse of the truncator T, which does not depend on the scalar.The applicants have also recognized that the representation of a scalar in a τ-adic representation may be optimized for each scalar that is needed.The applicants have further recognized that a standard rounding algorithm may be used to perform reduction modulo the truncator.In general terms, there is provided a method of reducing a scalar modulo a truncator, by pre-computing an inverse of the truncator. Each scalar multiplication then utilizes the pre-computed inverse to enable computation of the scalar multiplication without requiring a division by the truncator for each scalar multiplication.
Owner:MALIKIE INNOVATIONS LTD
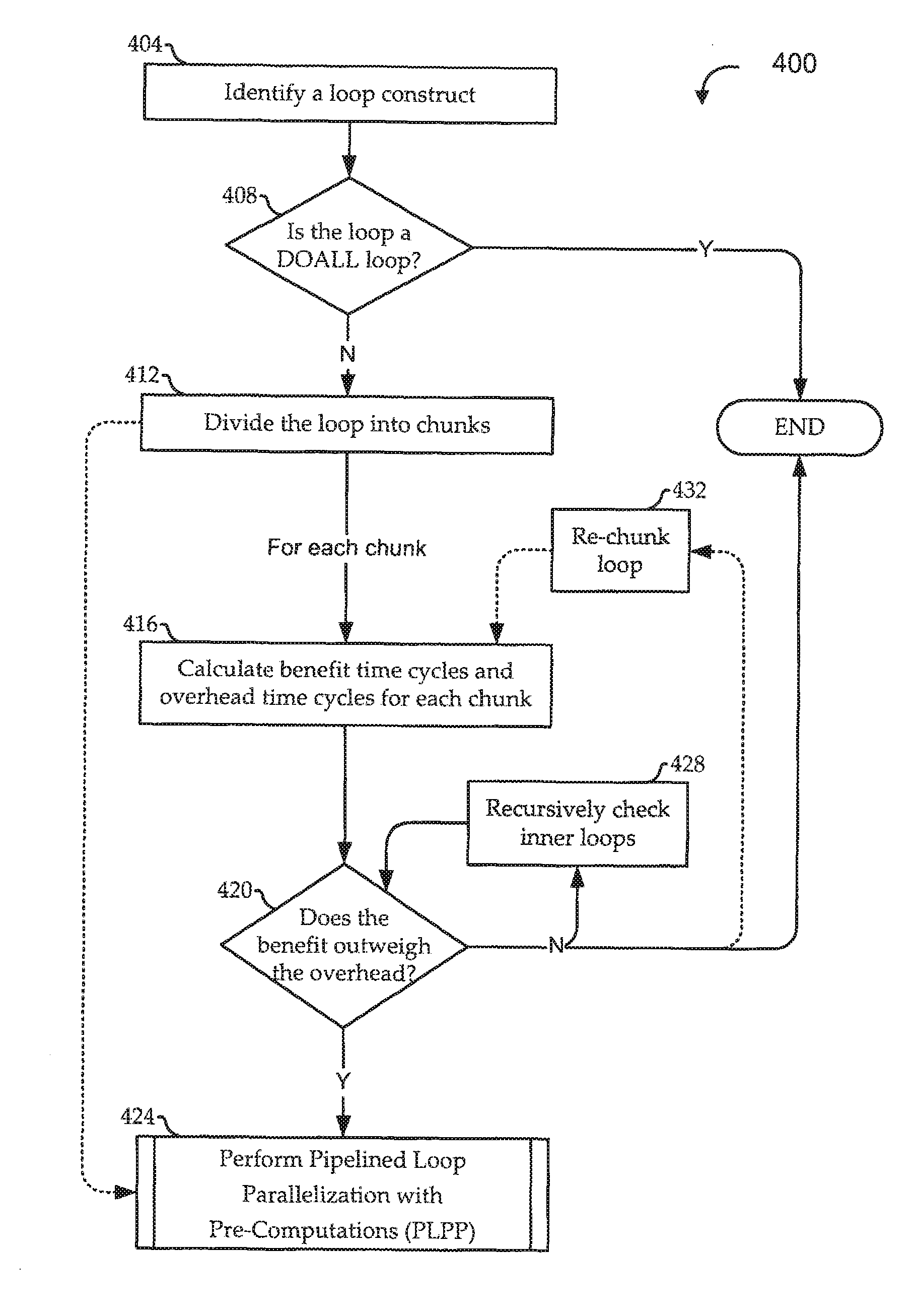
Pipelined loop parallelization with pre-computations
ActiveUS20120254888A1Easy to useMultiprogramming arrangementsMemory systemsComputational scienceHardware thread
Owner:ORACLE INT CORP
Large number multiplier based on secondary Booth coding
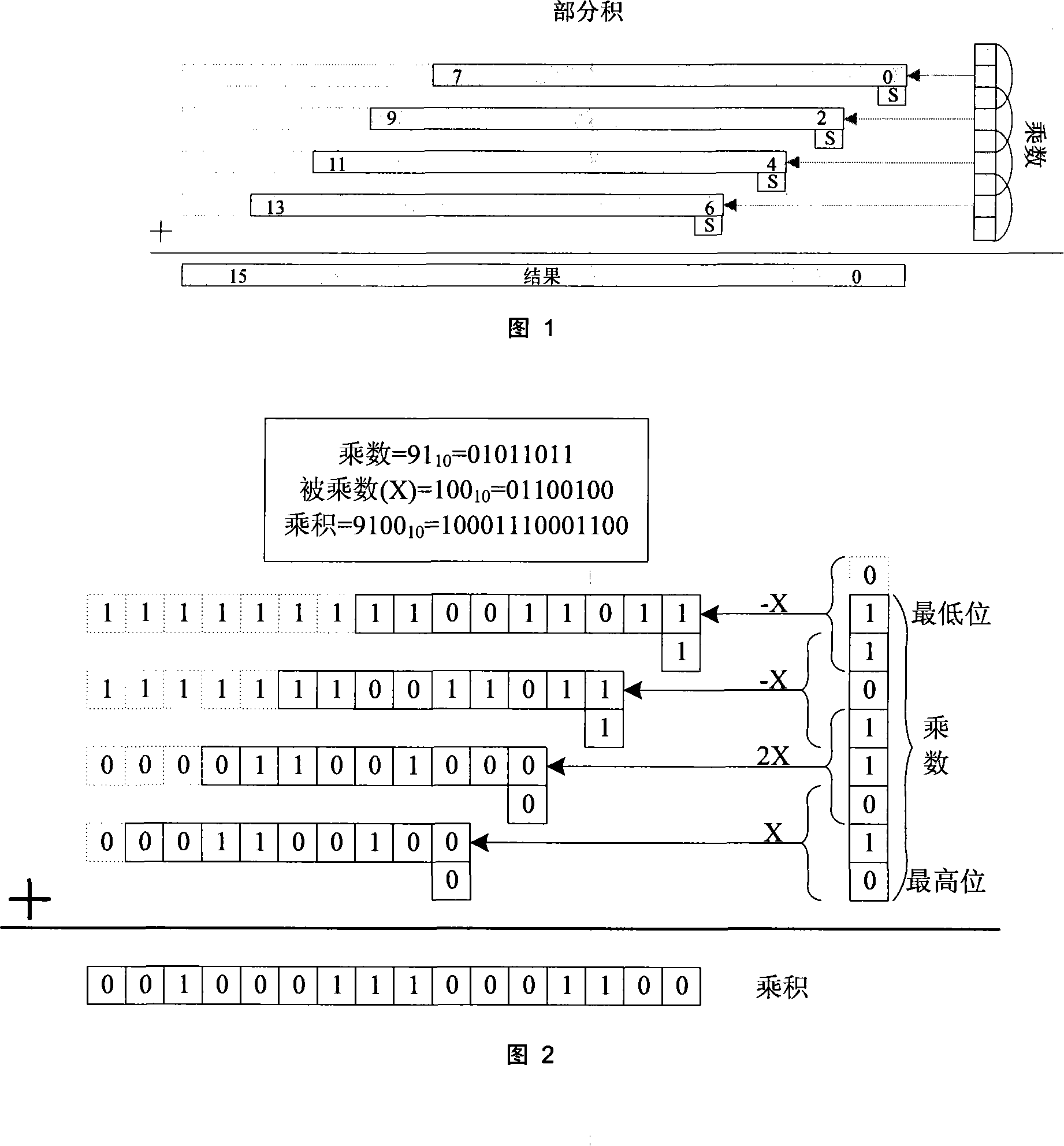
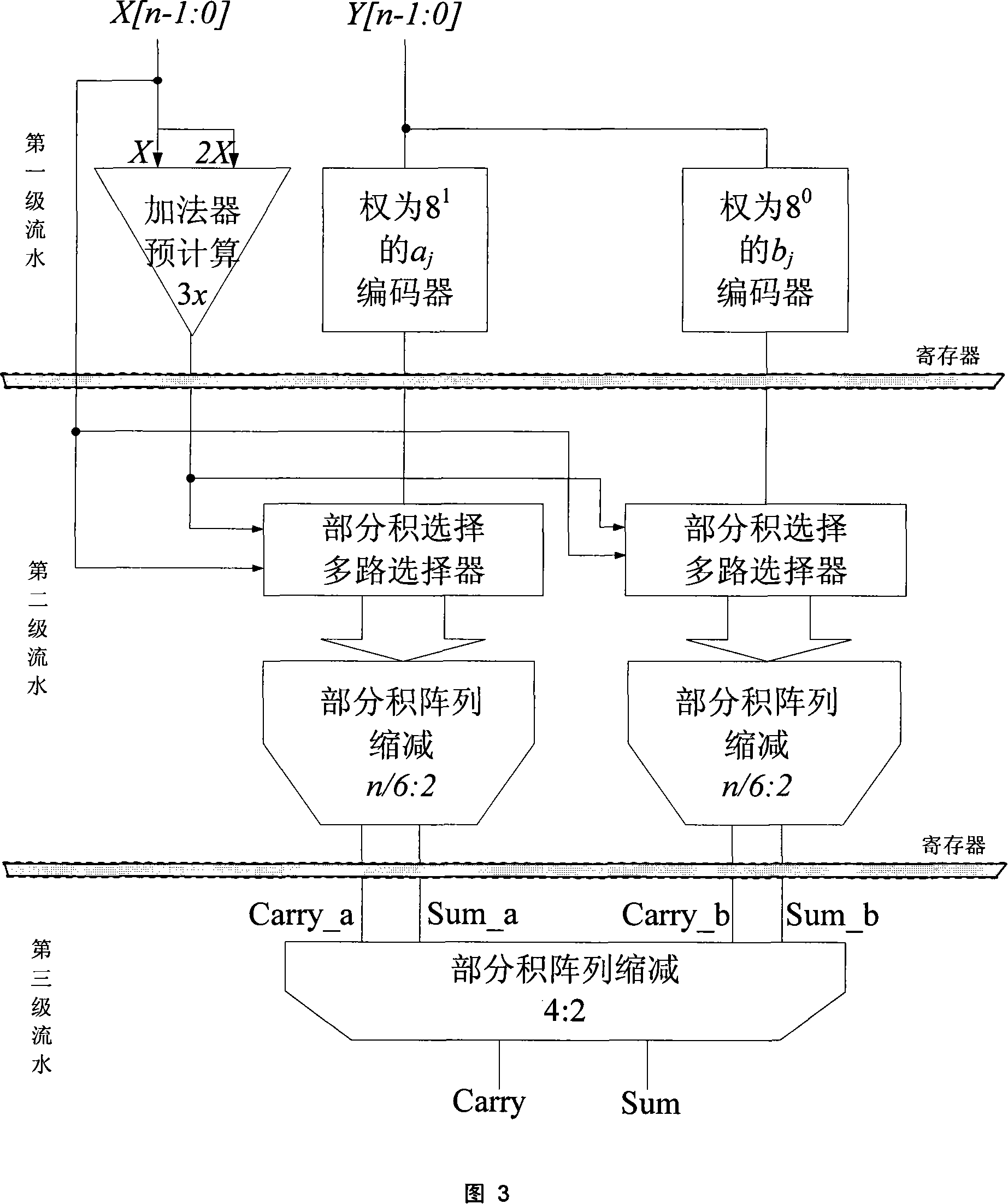
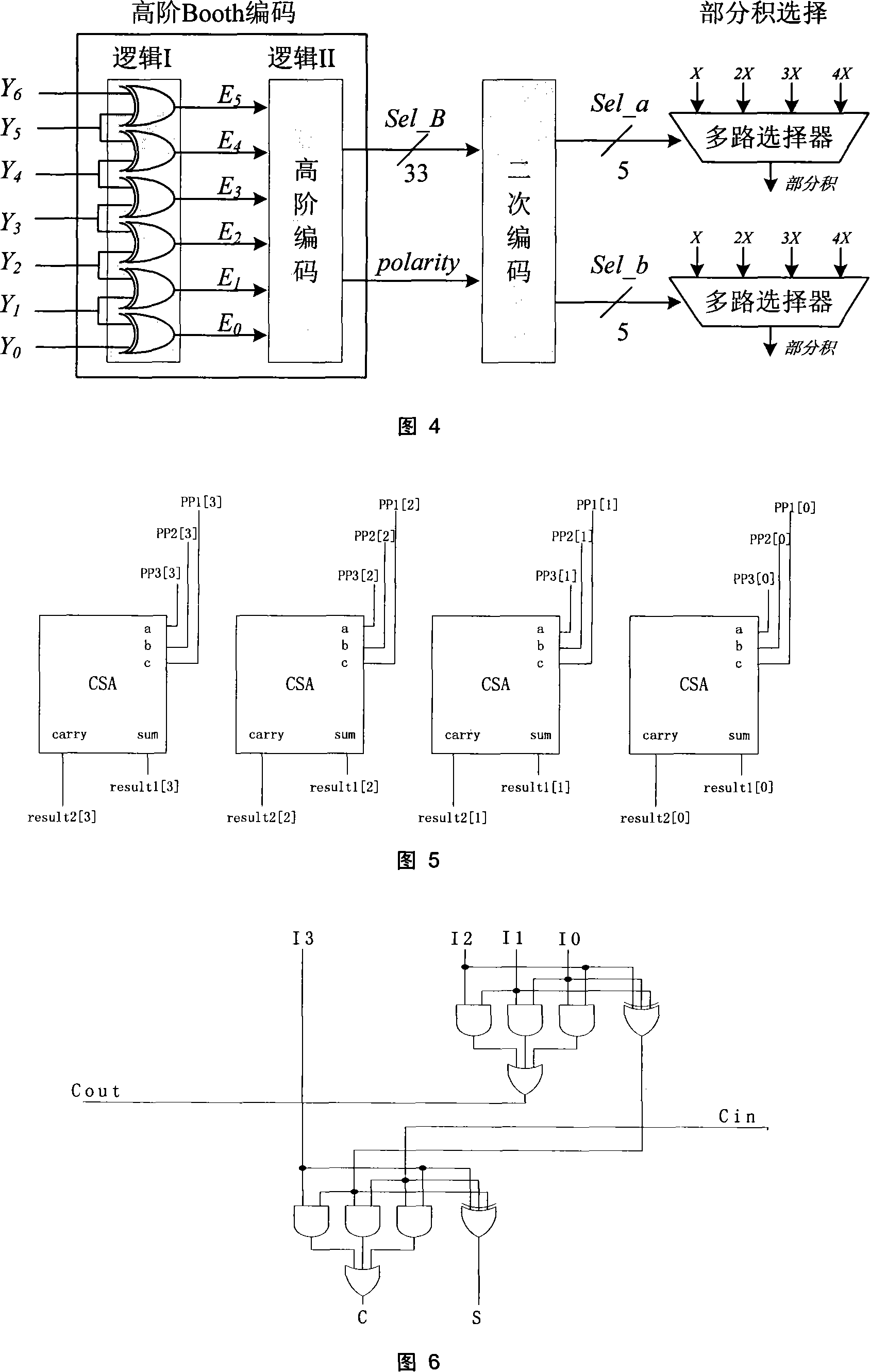
A secondary Booth-code-based large number multiplier belongs to the integrated circuit design technology field of the public key encryption algorithm. The present invention uses the linear transformation formula B=8a+b to do a secondary coding to the Booth 64 algorithm results generated by the partial product. The multiplier based on the secondary Booth 64code is divided into 3-level pipelining architectures. The first level architecture precomputes the multiplicands of three times with a carry look-ahead adder and at the same time does secondary Booth coding to aj with a weight of 81 and bj with a weight of 80. The second level architecture, consisting of two identical partial products selection and compression arrays, simplifies the partial products of aj and bi respectively. The third level architecture adds the partial products of the second level by an adder. The present invention improves the multiplication rate performance and can be applied to high performance RSA and ECC chips as well as large scale PKI system of servers.
Owner:TSINGHUA UNIV
Method and apparatus for pipelined joint equalization and decoding for gigabit communications
InactiveUS7000175B2Data representation error detection/correctionCode conversionGigabitPrecomputation
A method and apparatus for the implementation of reduced state sequence estimation is disclosed that uses precomputation (look-ahead) to increase throughput, with only a linear increase in hardware complexity with respect to the look-ahead depth. The present invention limits the increase in hardware complexity by taking advantage of past decisions (or survivor symbols). The critical path of a conventional RSSE implementation is broken up into at least two smaller critical paths using pipeline registers. Various reduced state sequence estimation implementations are disclosed that employ one-step or multiple-step look-ahead techniques to process a signal received from a dispersive channel having a channel memory.
Owner:AGERE SYST GUARDIAN +1
Pipelined loop parallelization with pre-computations
ActiveUS8726251B2Multiprogramming arrangementsConcurrent instruction executionHardware threadParallel computing
Owner:ORACLE INT CORP
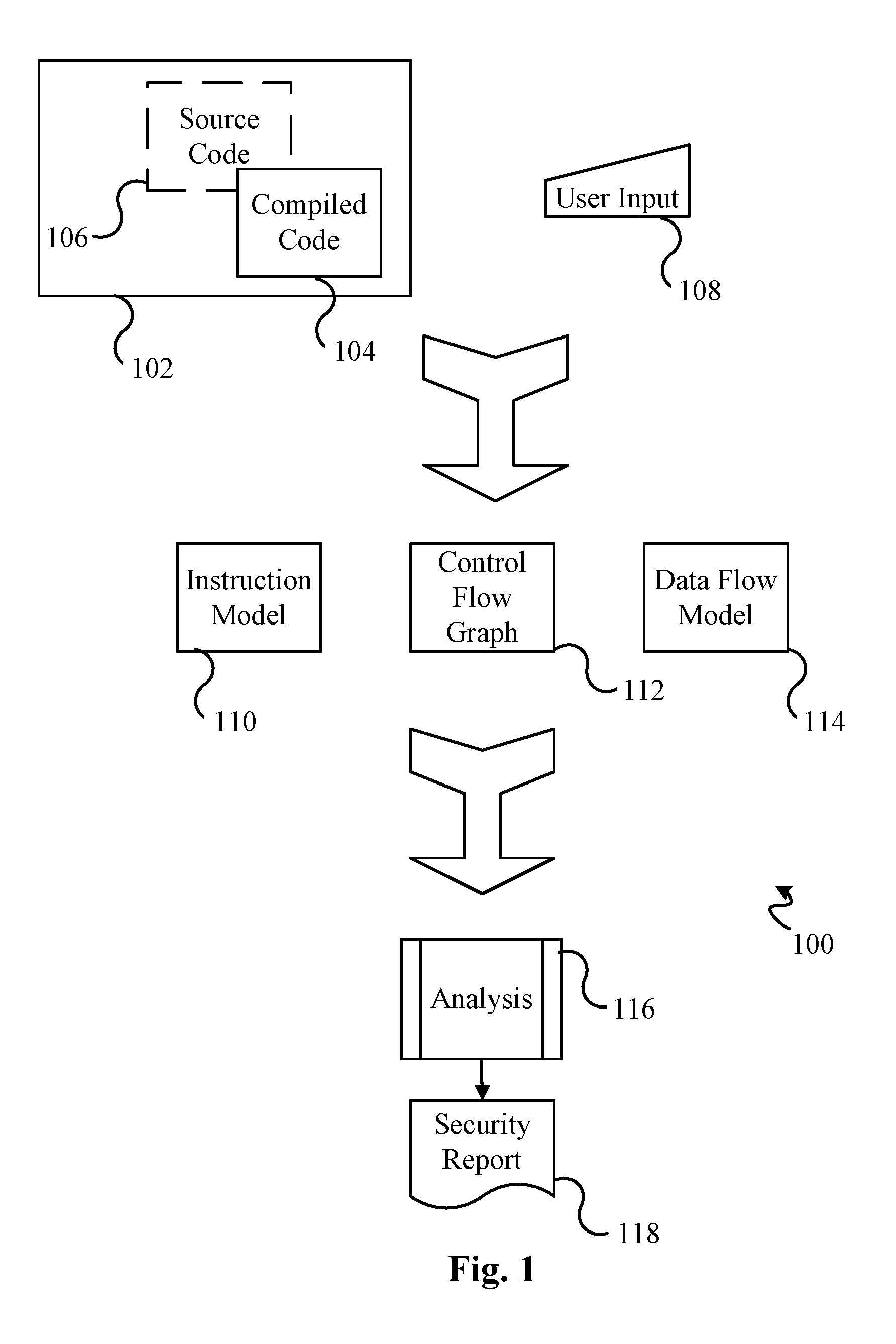
High Performance Software Vulnerabilities Detection System and Methods
ActiveUS20170017789A1Improve accuracyReduce consumptionSoftware testing/debuggingPlatform integrity maintainanceControl flowData stream
This invention teaches a system and methods of detecting software vulnerabilities in a computer program by analyzing the compiled code and optionally the source code of the computer program. The invention models compiled software to examine both control flow and data flow properties of the target program. A comprehensive instruction model is used for each instruction of the compiled code, and is complemented by a control flow graph that includes all potential control flow paths of the instruction. A data flow model is used to record the flow of unsafe data during the execution of the program. The system analyzes the data flow model and creates a security finding corresponding to each instruction that calls an unsafe function on unsafe data. The security findings are aggregated in a security report. The system further uses precomputation to improve performance by caching 1-to-many data flow mapping for each basic block in the code.
Owner:SECURISEA INC
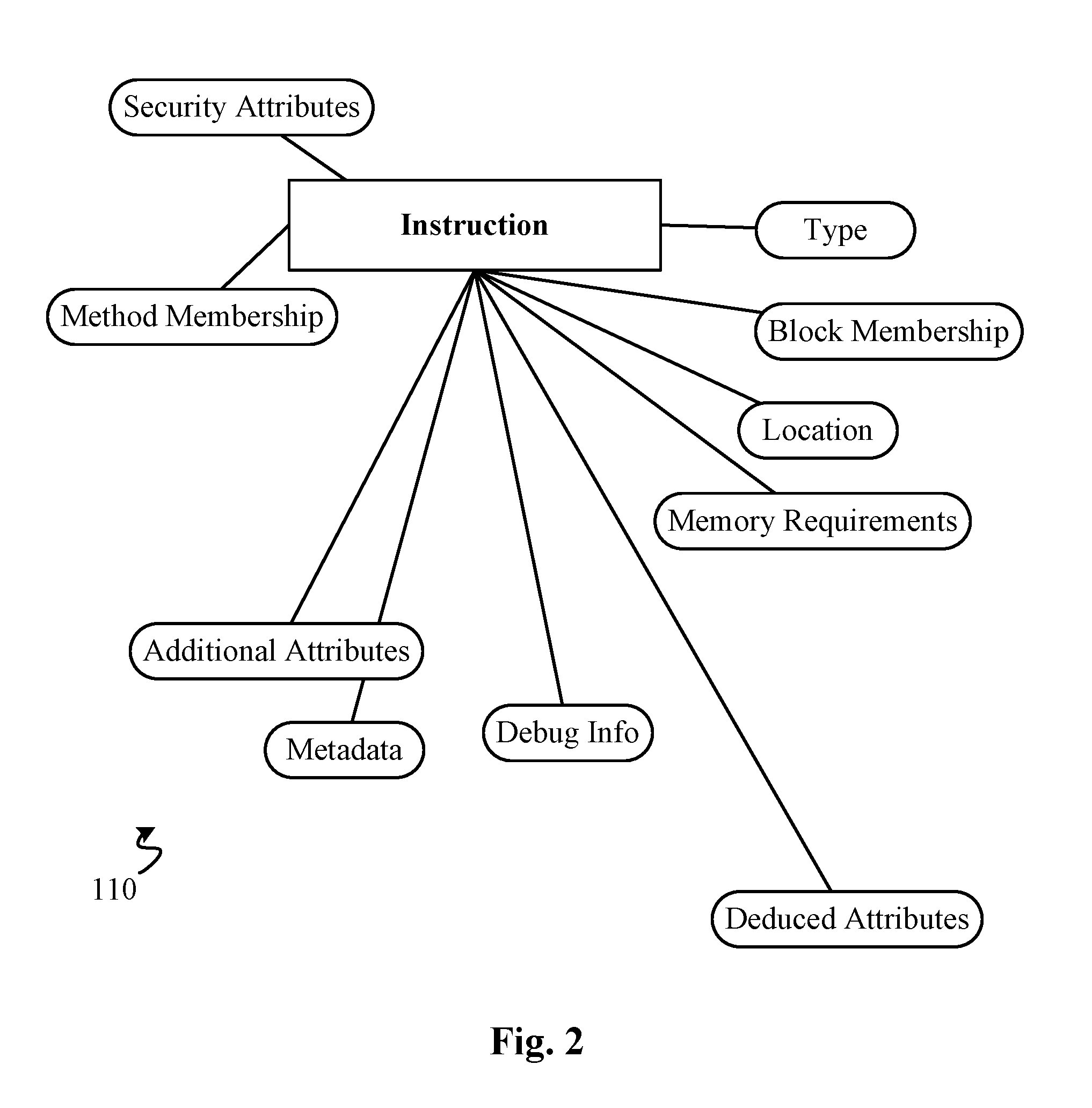
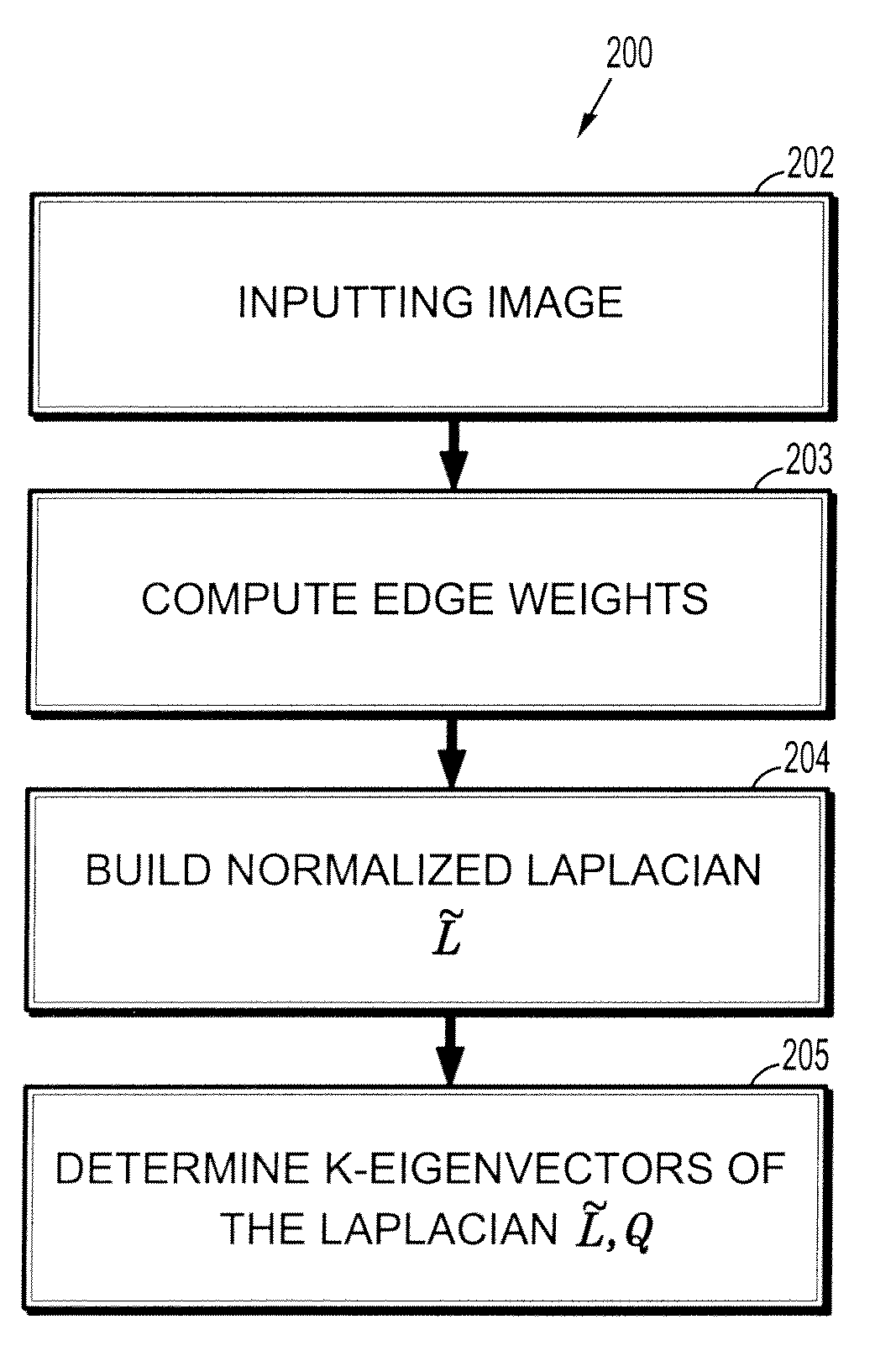
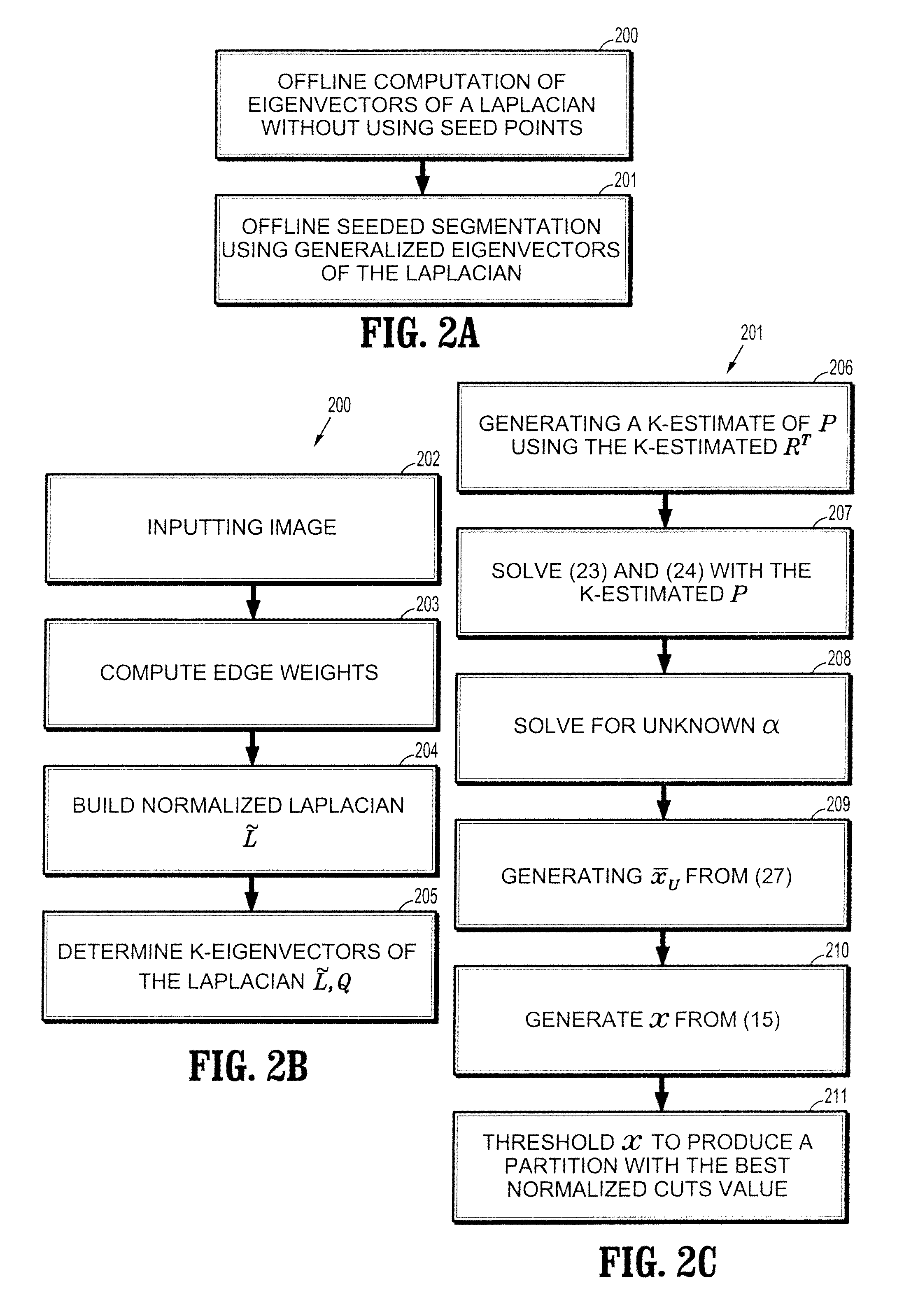
Interactive image segmentation by precomputation
A method for interactive image segmentation includes receiving an image to be segmented, performing an offline computation of eigenvectors of a Laplacian of the image without using seed points, receiving seed points, and performing an online segmentation taking the seed points and the eigenvectors of the Laplacian as input and outputting a partition of the image.
Owner:SIEMENS HEALTHCARE GMBH
Texture morphing process provided by the preferred embodiment of the present invention
InactiveUS6906732B1Simplify and reduce computationFast and efficientCathode-ray tube indicatorsAnimationMorphingComputational science
A fast, texture morphing algorithm for real-time computer simulation and video games dynamically generates objects “on the fly” by simplifying and reducing the computational load required for a texture morphing / blending process. Incremental interpolation techniques compute a morph parameter based on previous value and morph change rate. Precomputed initial and incremental morph parameter values for each texel component are applied during real-time morphing procedures using integer arithmetic. Approximation errors are reduced by incrementing / decrementing by an extra integer value when the number of morph iterations is a multiple of a frame counter. The frame counter avoids over-runs, and the morphing procedure is “snapped” the texel value to the precise texture target value to prevent under-runs and corresponding artifacts. Interlacing (applying interpolation to a subset of the texels each frame) significantly reduces computational load without introducing significant image artifacts. The morph texture buffer data structure is initially decomposed off-line to reduce the number of real-time calculations required to manipulate texel component data.
Owner:NINTENDO CO LTD
Iterative symmetric key ciphers with keyed s-boxes using modular exponentiation
InactiveUS20080232597A1Key distribution for secure communicationMultiple keys/algorithms usageComputer hardwareS-box
Disclosed is the design and development of a new cipher called the Dragonfire Cipher. The Dragon cipher includes message authentication code and keyed random number generator. Dragonfire cipher takes this transparent method of generating S-boxes and uses them to create a cipher with keyed S-boxes. This defeats most precomputations for cryptanalysis as the S-boxes are now different between sessions.
Owner:DE MARE MICHAEL
Method and system for navigating complex data sets
InactiveUS20140324882A1Facilitates pivoted faceted browsing of data setComplex data setDigital data information retrievalDigital data processing detailsData setPrecomputation
The present invention relates to systems and methods for storing, navigating and retrieving information. In particular, the present invention is concerned with systems and methods for storing data in, for retrieving data from, and for navigating large and / or complex datasets. The systems and methods of the present invention in particular are concerned with the materialization / denormalization of complex data sets comprising a plurality of large, interconnected but distinct data record collections. The materialization / denormalization of such data sets can be performed in a precomputation phase, prior to a browsing / searching operation.
Owner:GIOVANNI TUMMARELLO +1
Multiple-input multiple-output (MIMO) signal detection method based on breadth-first tree search
InactiveCN102006148AAvoid double countingSave complexitySpatial transmit diversityError prevention/detection by diversity receptionQR decompositionRound complexity
The invention relates to a multiple-input multiple-output (MIMO) signal detection method based on breadth-first tree search, mainly solving the problem of high complexity of the existing MIMO detection method. The method is implemented by the following steps: (1) preprocessing a system, wherein the step comprises QR decomposition of a channel matrix and precomputation of a path metric factor; (2)using the concept of breadth-first tree search to detect signals layer by layer: 2a) using survival paths of a previous layer to expand the paths of the current layer: using a Schnorr-Euchner enumeration method to sequentially determine path expansion sequence, expansion paths and path metrics; and 2b) using a merge sorting method to sort the path metrics of the expansion paths to determine survival paths; and (3) if the detection on all layer signals is finished, taking the survival path metric corresponding to the minimum path metric as the final detection output, otherwise, transmitting the survival path to the next layer to detect the signal of the next layer. The method of the invention has the advantages of low complexity and small performance loss, and can be applied to signal detection of an MIMO receiver of a next-generation broadband wireless communication system.
Owner:XIDIAN UNIV
Multi-version register file for multithreading processors with live-in precomputation
Disclosed are selected embodiments of a processor that may include a plurality of thread units and a register file architecture to support speculative multithreading. For at least one embodiment, live-in values for a speculative thread are computed via execution of a precomputation slice and are stored in a validation buffer for later validation. A global register file holds the committed architecture state generated by a non-speculative thread. Each thread unit includes a local register file. A directory indicates, for each architectural register, which speculative thread(s) have generated a value for the architectural register. Other embodiments are also described and claimed.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com