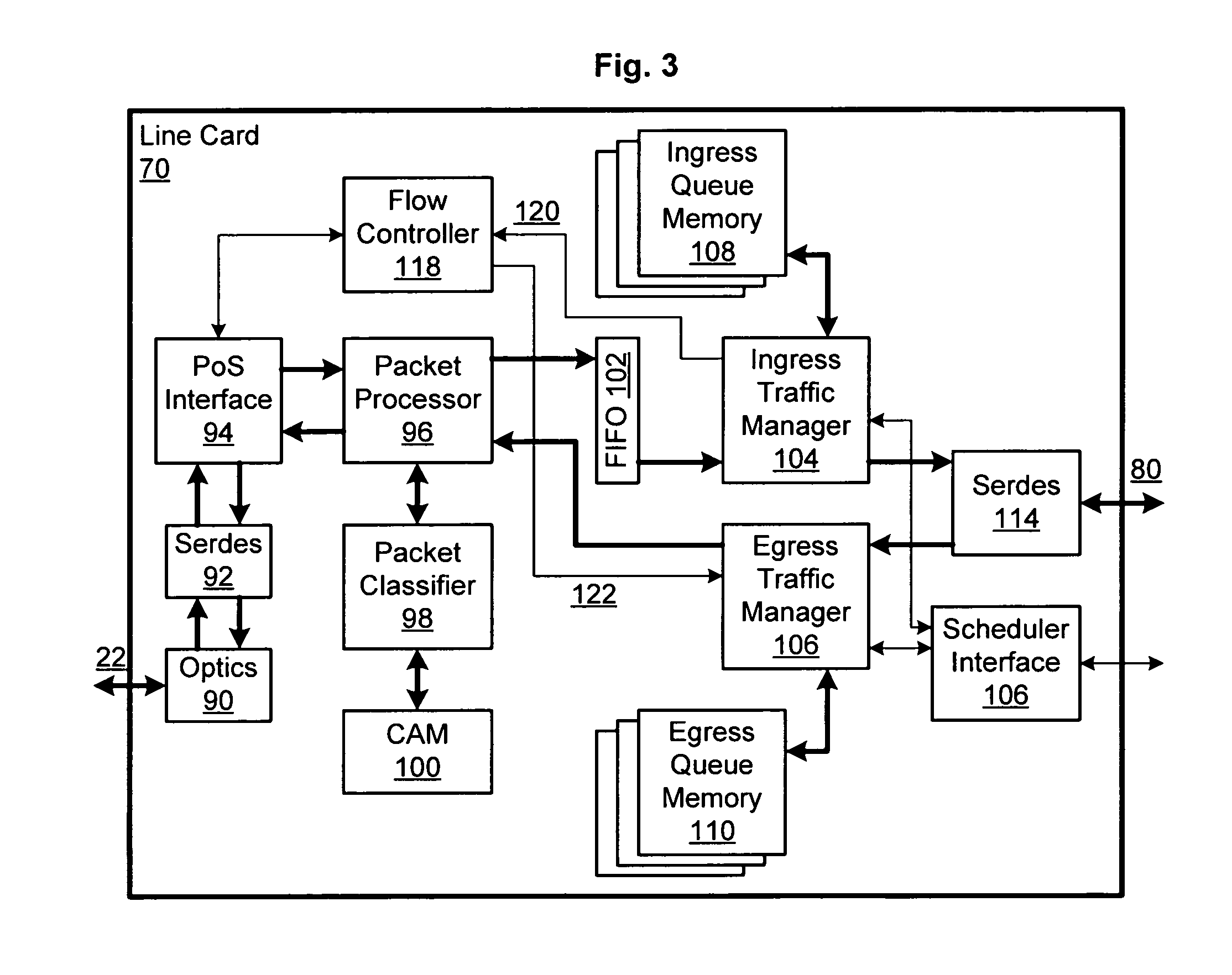
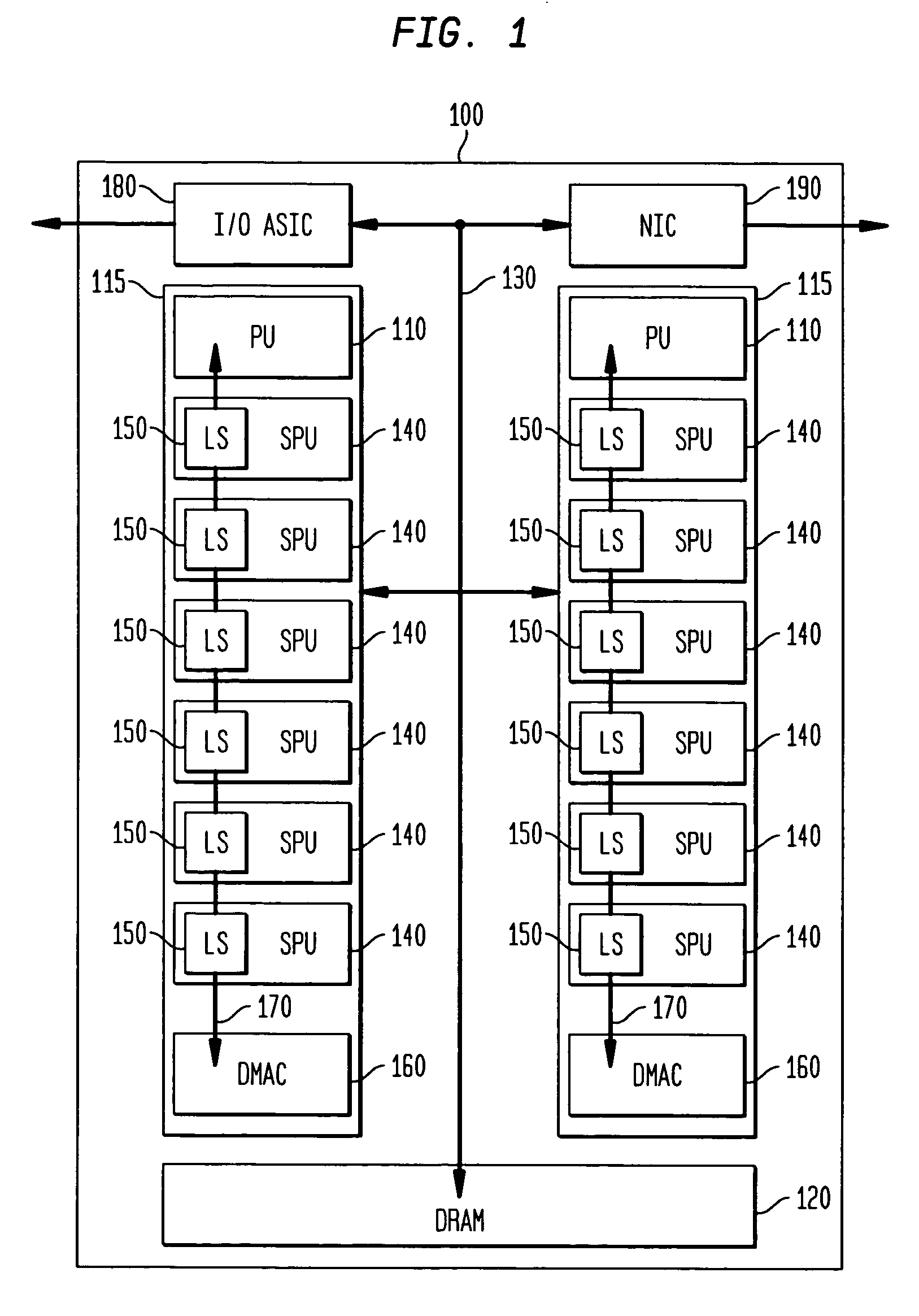
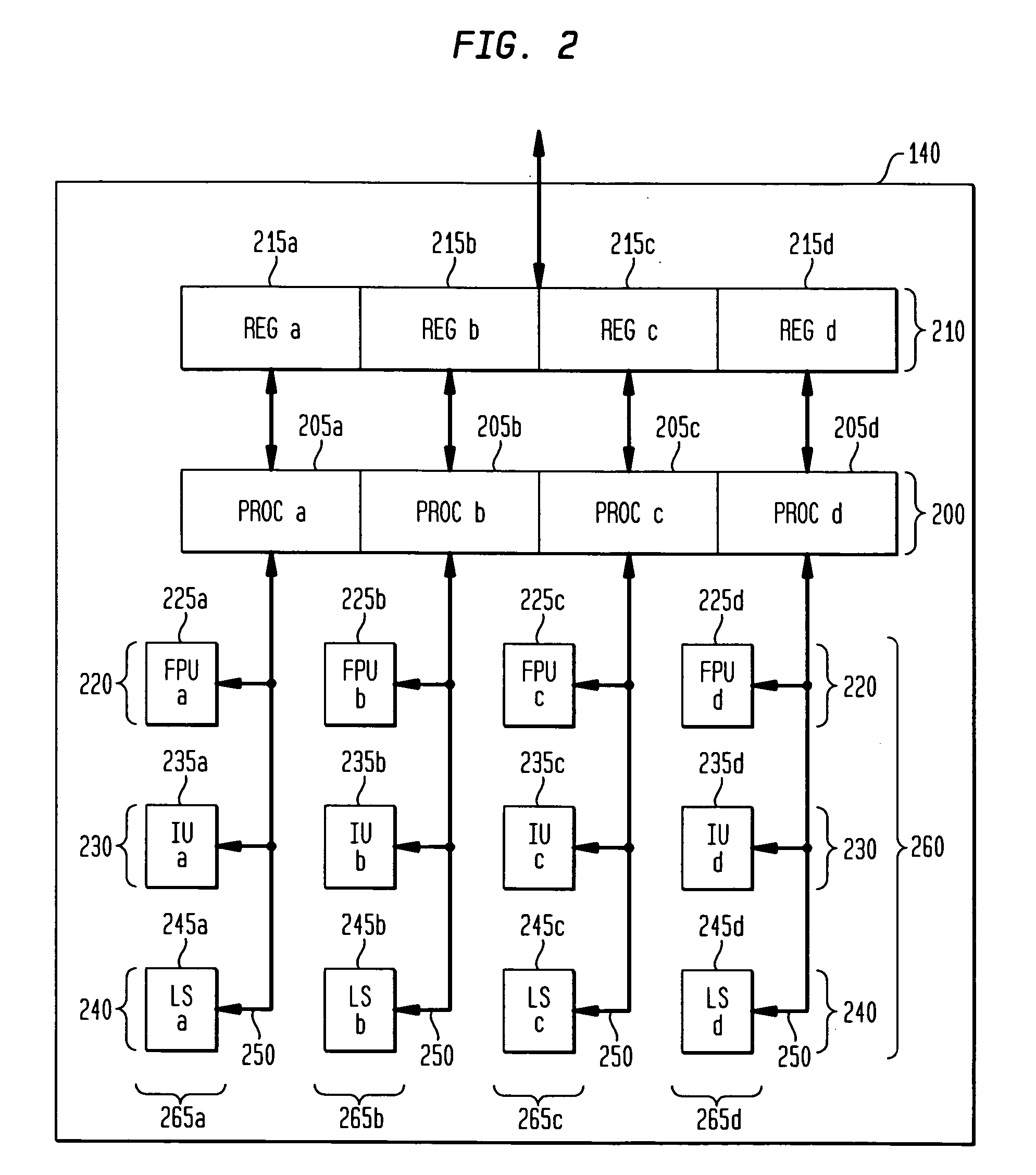
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1073 results about "Extension method" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
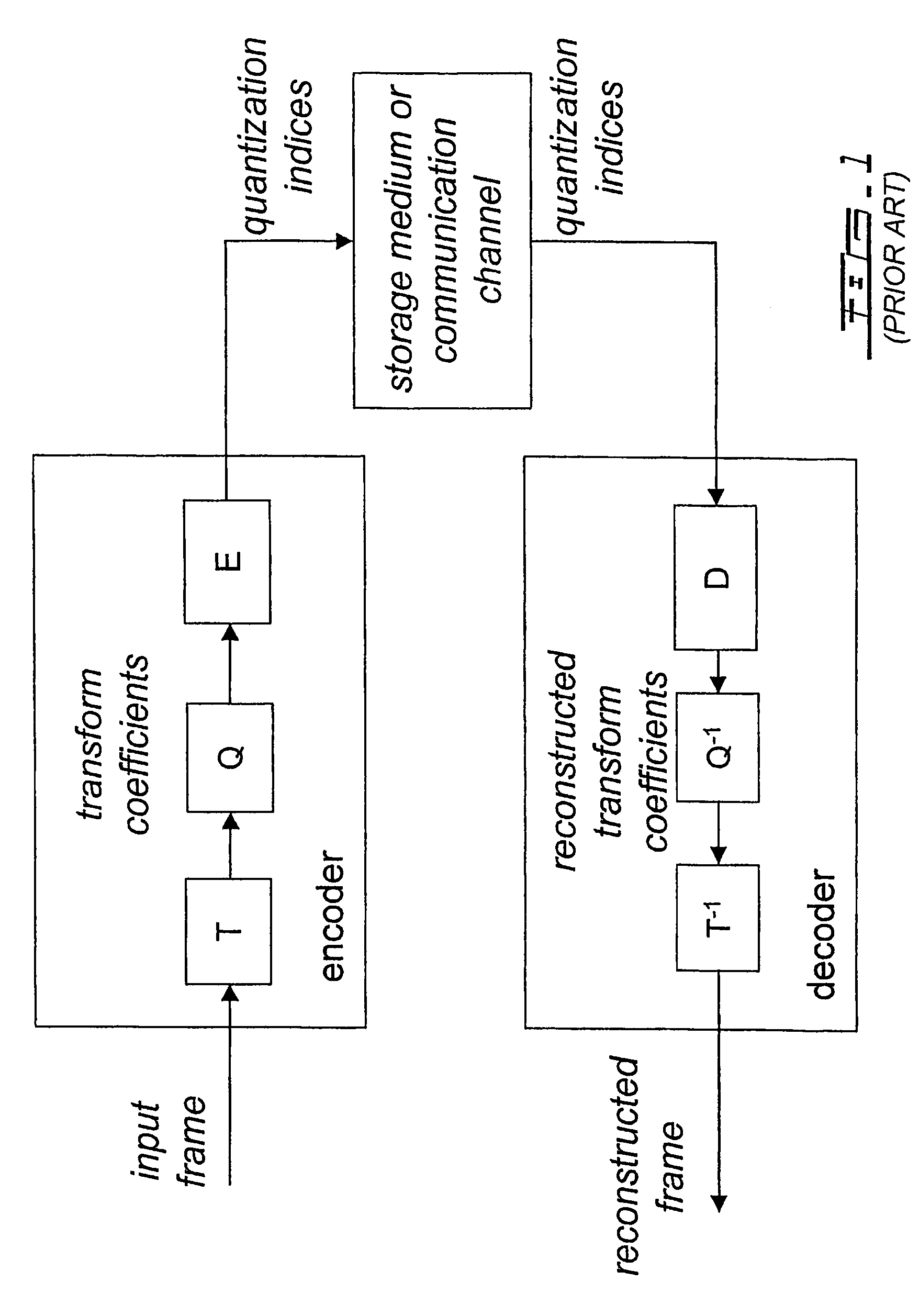
In object-oriented computer programming, an extension method is a method added to an object after the original object was compiled. The modified object is often a class, a prototype or a type. Extension methods are features of some object-oriented programming languages. There is no syntactic difference between calling an extension method and calling a method declared in the type definition.
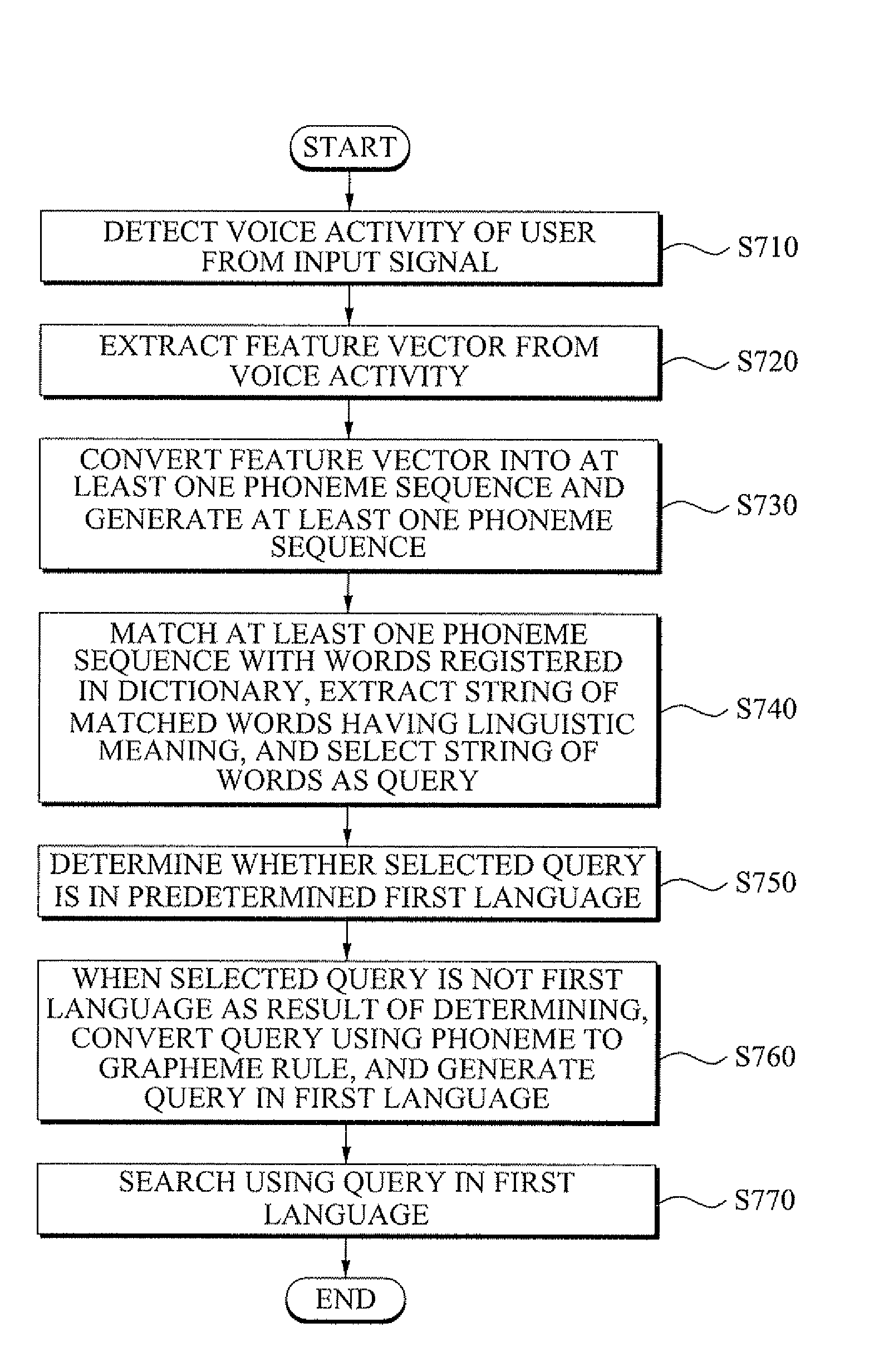
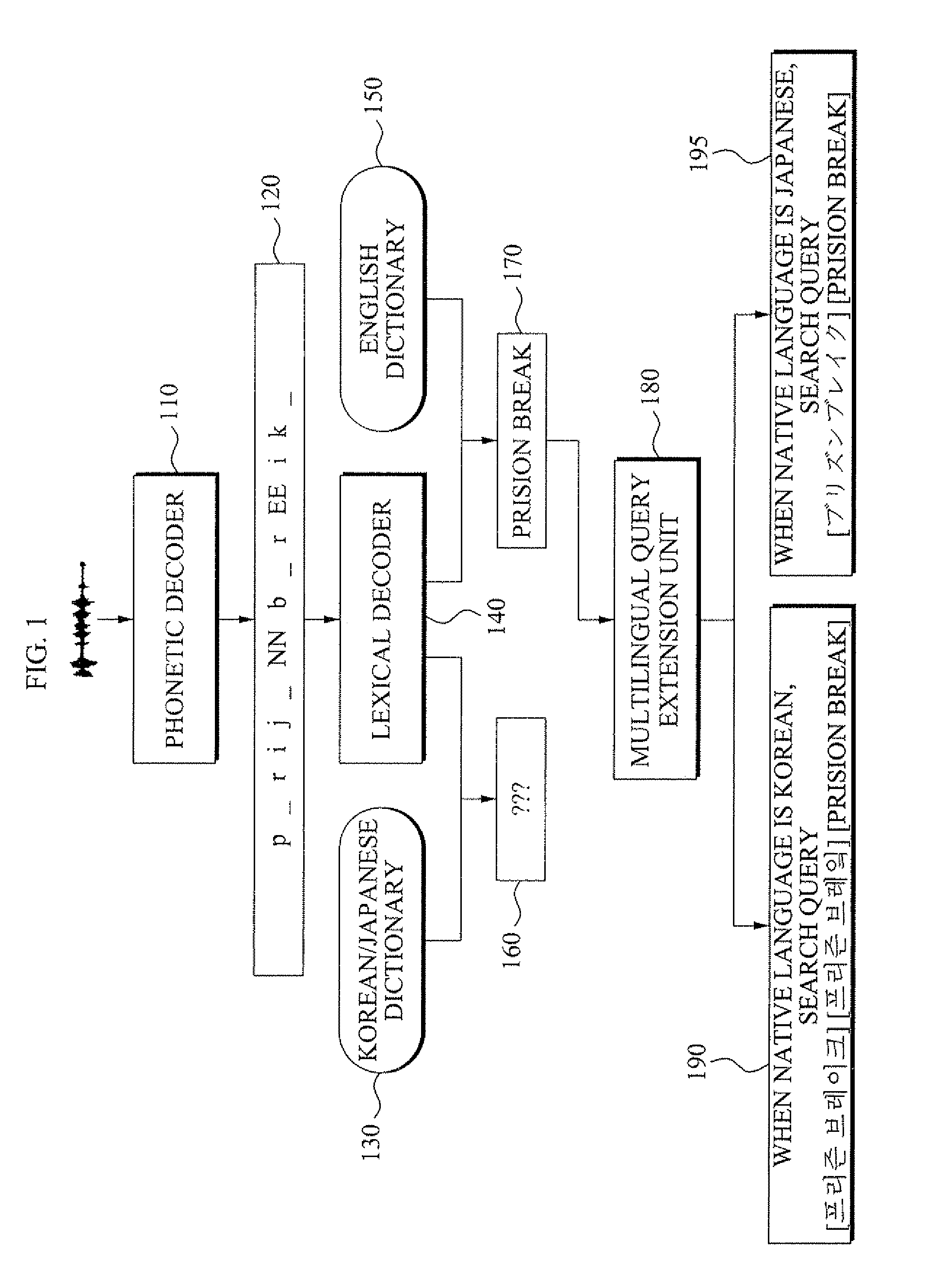
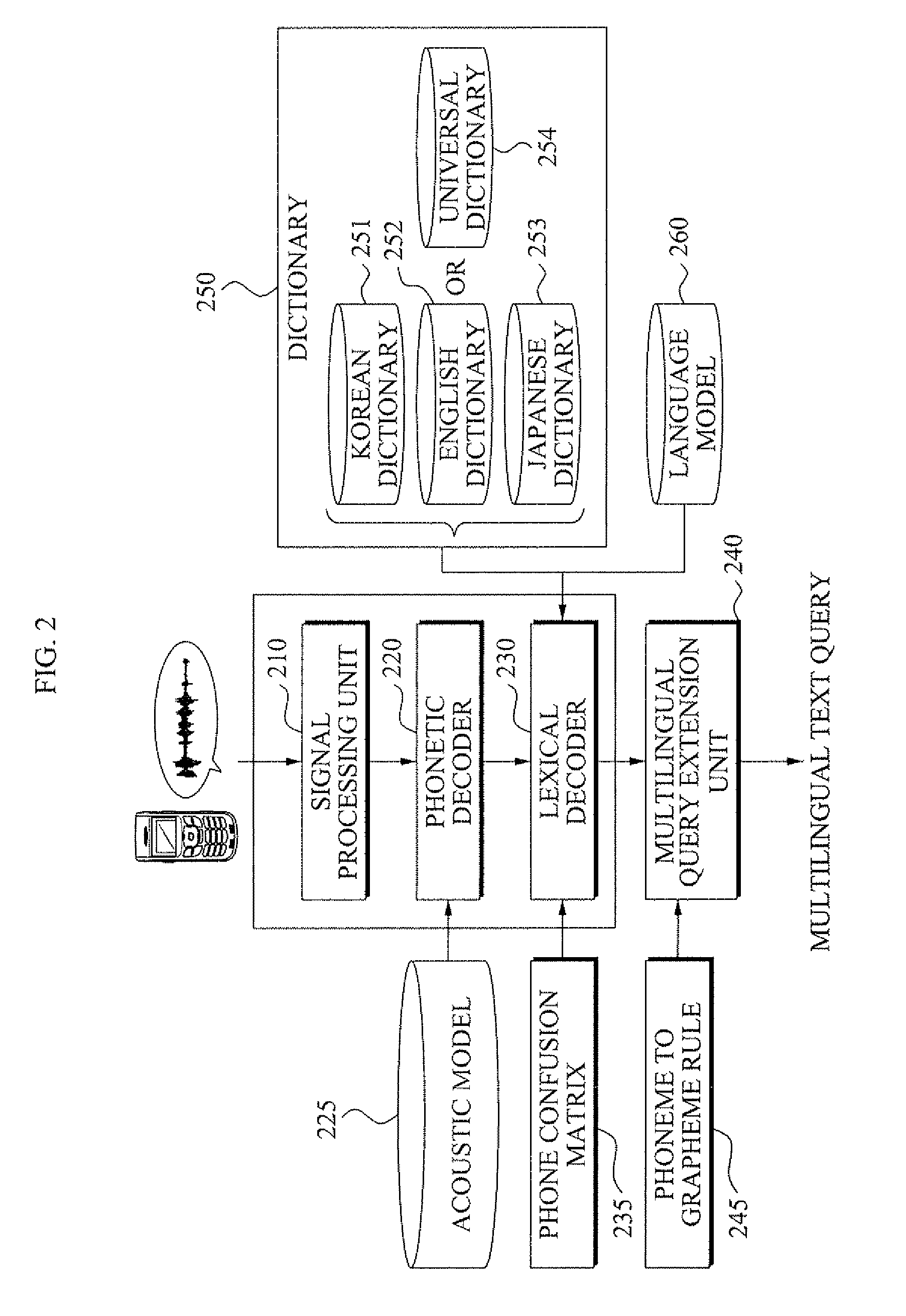
Voice query extension method and system
InactiveUS8155956B2Increase success rateDigital data information retrievalSpeech recognitionFeature vectorGlyph
A voice query extension method and system. The voice query extension method includes: detecting voice activity of a user from an input signal and extracting a feature vector from the voice activity; converting the feature vector into at least one phoneme sequence and generating the at least one phoneme sequence; matching the at least one phoneme sequence with words registered in a dictionary, extracting a string of the matched words with a linguistic meaning, and selecting the string of the matched words as a query; determining whether the query is in a predetermined first language, and when the query is not in the first language as a result of the determining, converting the query using a phoneme to grapheme rule, and generating a query in the first language; and searching using the query in the first language.
Owner:SAMSUNG ELECTRONICS CO LTD
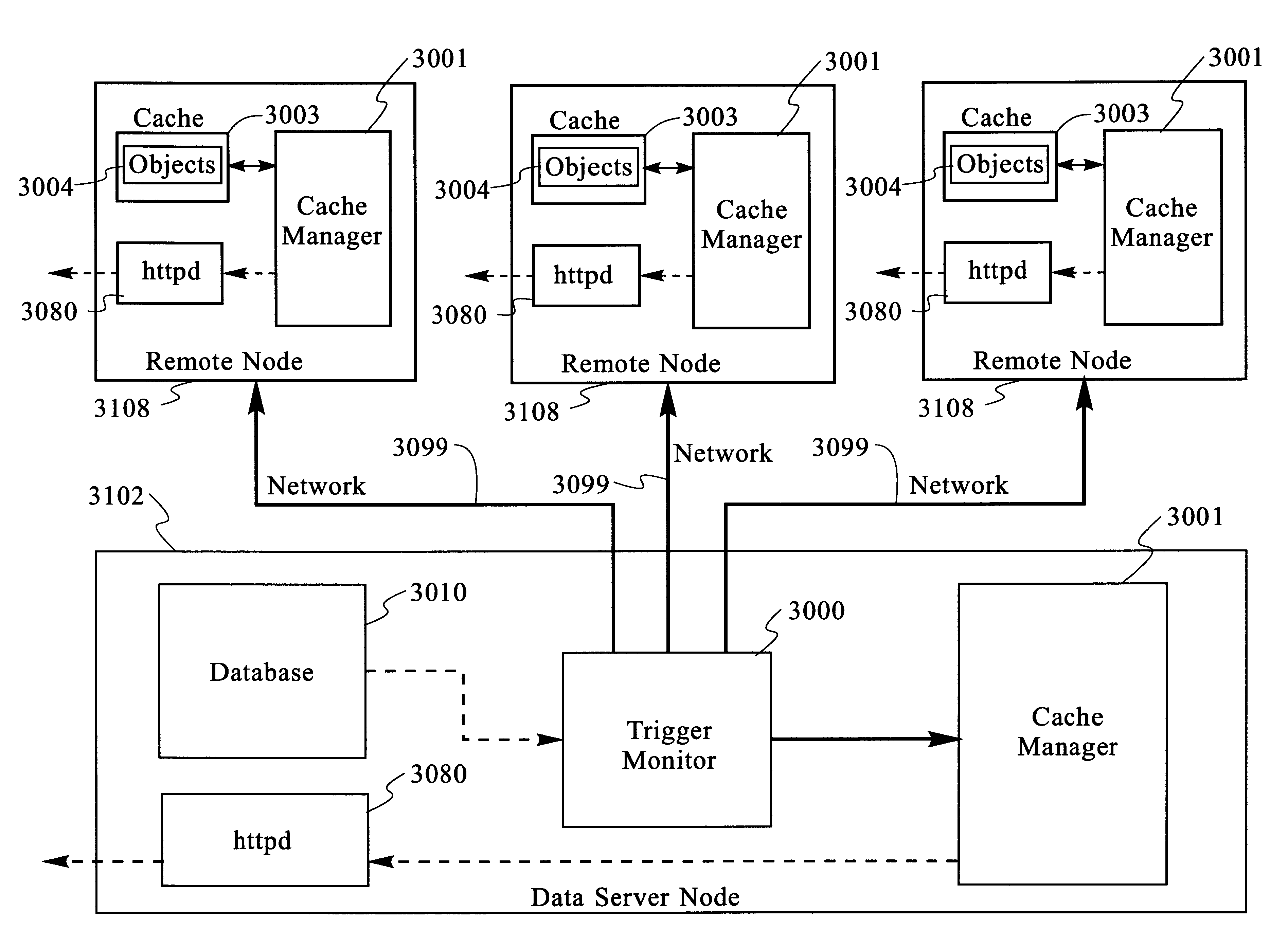
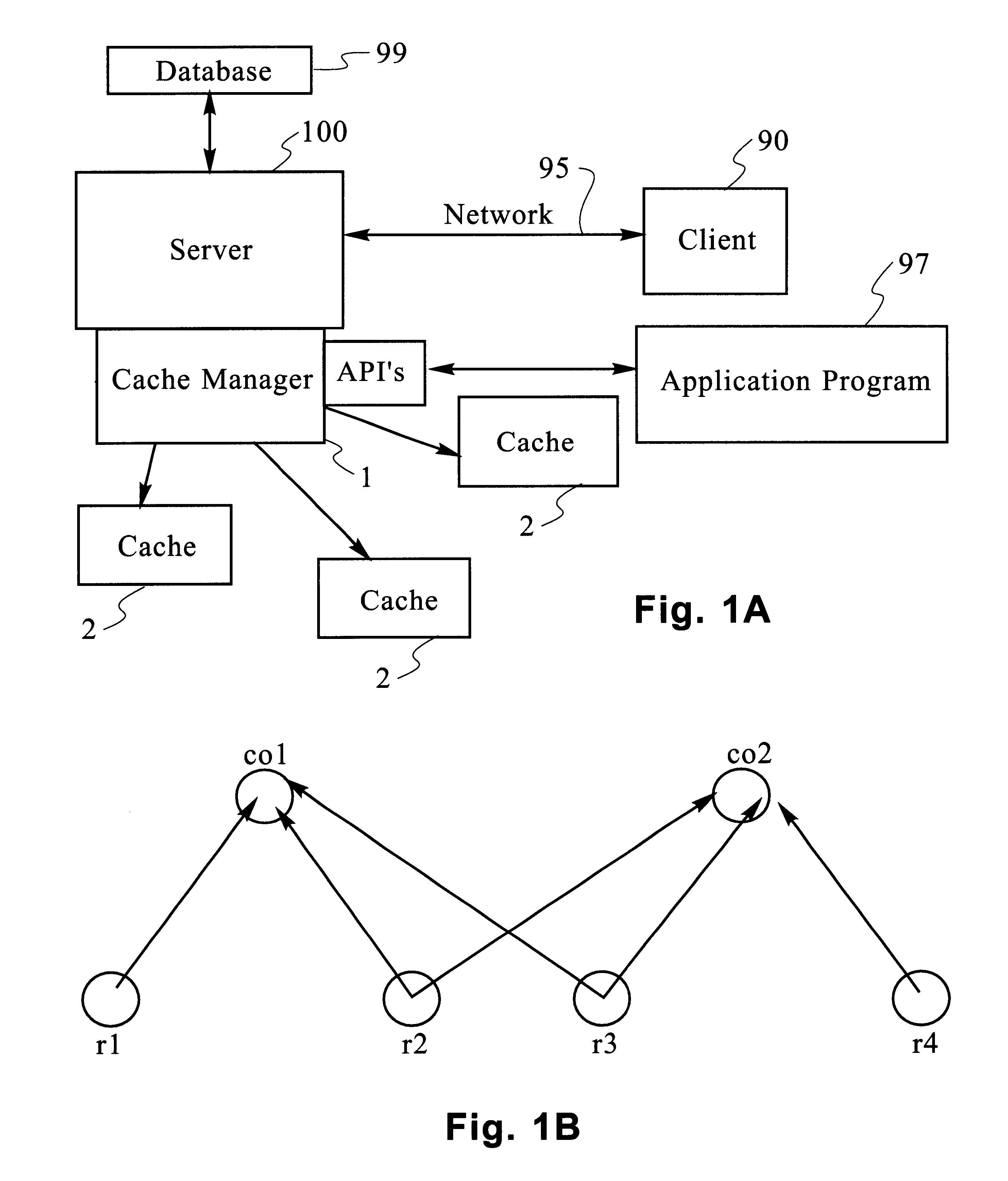
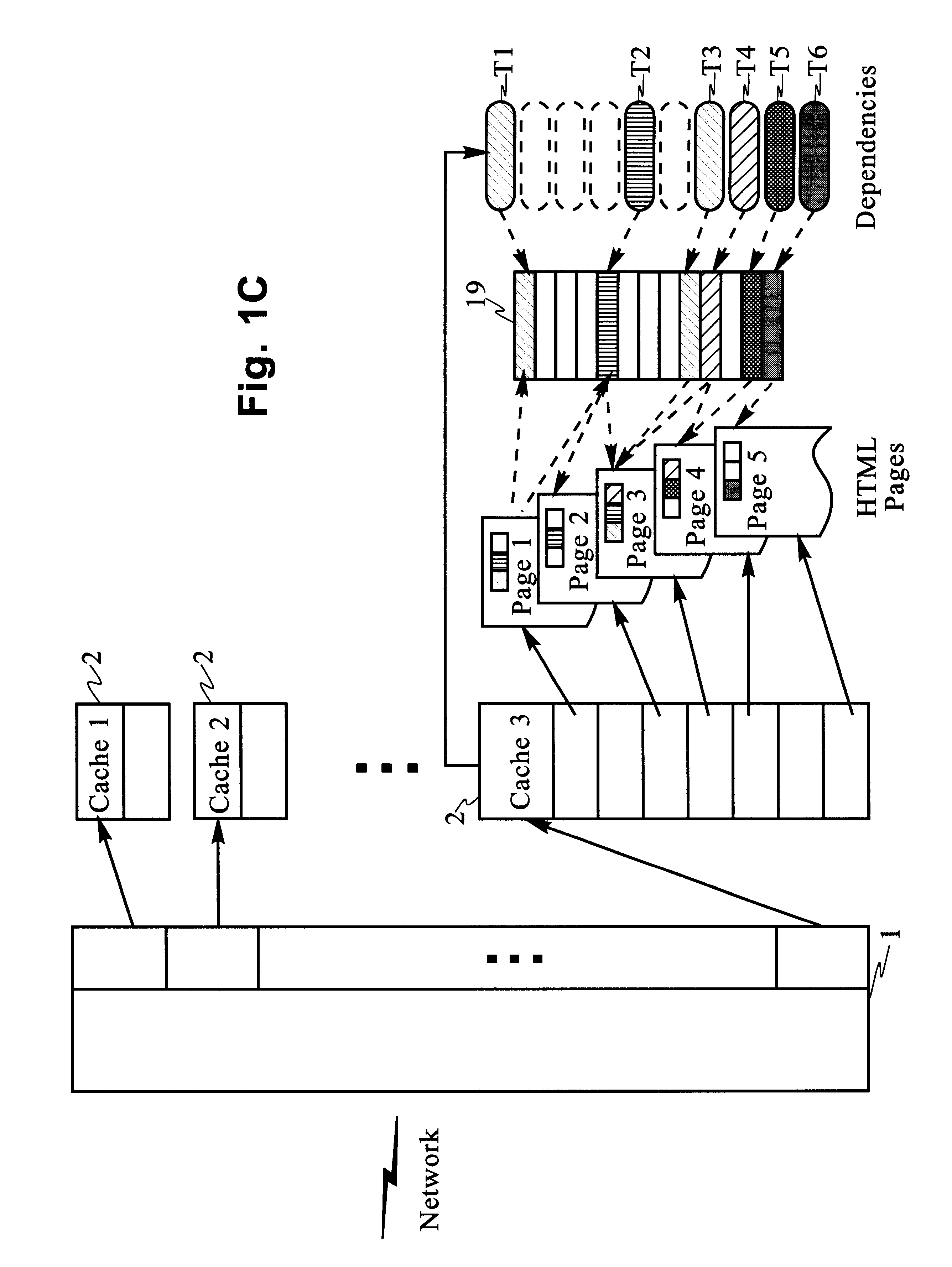
Scaleable method for maintaining and making consistent updates to caches
InactiveUS6256712B1High degreeData processing applicationsDigital data information retrievalData synchronizationExtensibility
A determination can be made of how changes to underlying data affect the value of objects. Examples of applications are: caching dynamic Web pages; client-server applications whereby a server sending objects (which are changing all the time) to multiple clients can track which versions are sent to which clients and how obsolete the versions are; and any situation where it is necessary to maintain and uniquely identify several versions of objects, update obsolete objects, quantitatively assess how different two versions of the same object are, and / or maintain consistency among a set of objects. A directed graph called an object dependence graph, may be used to represent the data dependencies between objects. Another aspect is constructing and maintaining objects to associate changes in remote data with cached objects. If data in a remote data source changes, database change notifications are used to "trigger" a dynamic rebuild of associated objects. Thus, obsolete objects can be dynamically replaced with fresh objects. The objects can be complex objects, such as dynamic Web pages or compound-complex objects, and the data can be underlying data in a database. The update can include either: storing a new version of the object in the cache; or deleting an object from the cache. Caches on multiple servers can also be synchronized with the data in a single common database. Updated information, whether new pages or delete orders, can be broadcast to a set of server nodes, permitting many systems to simultaneously benefit from the advantages of prefetching and providing a high degree of scaleability.
Owner:IBM CORP
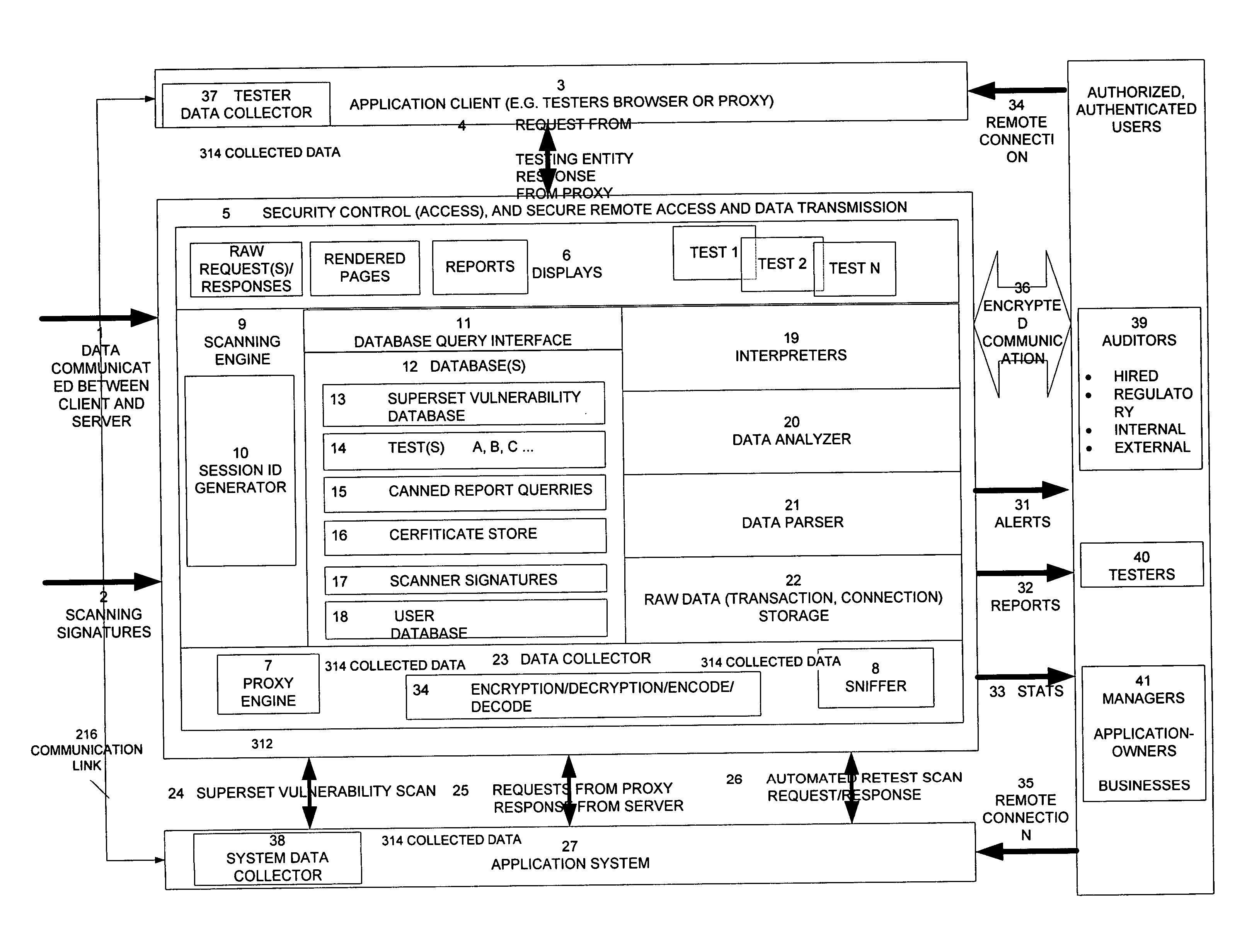
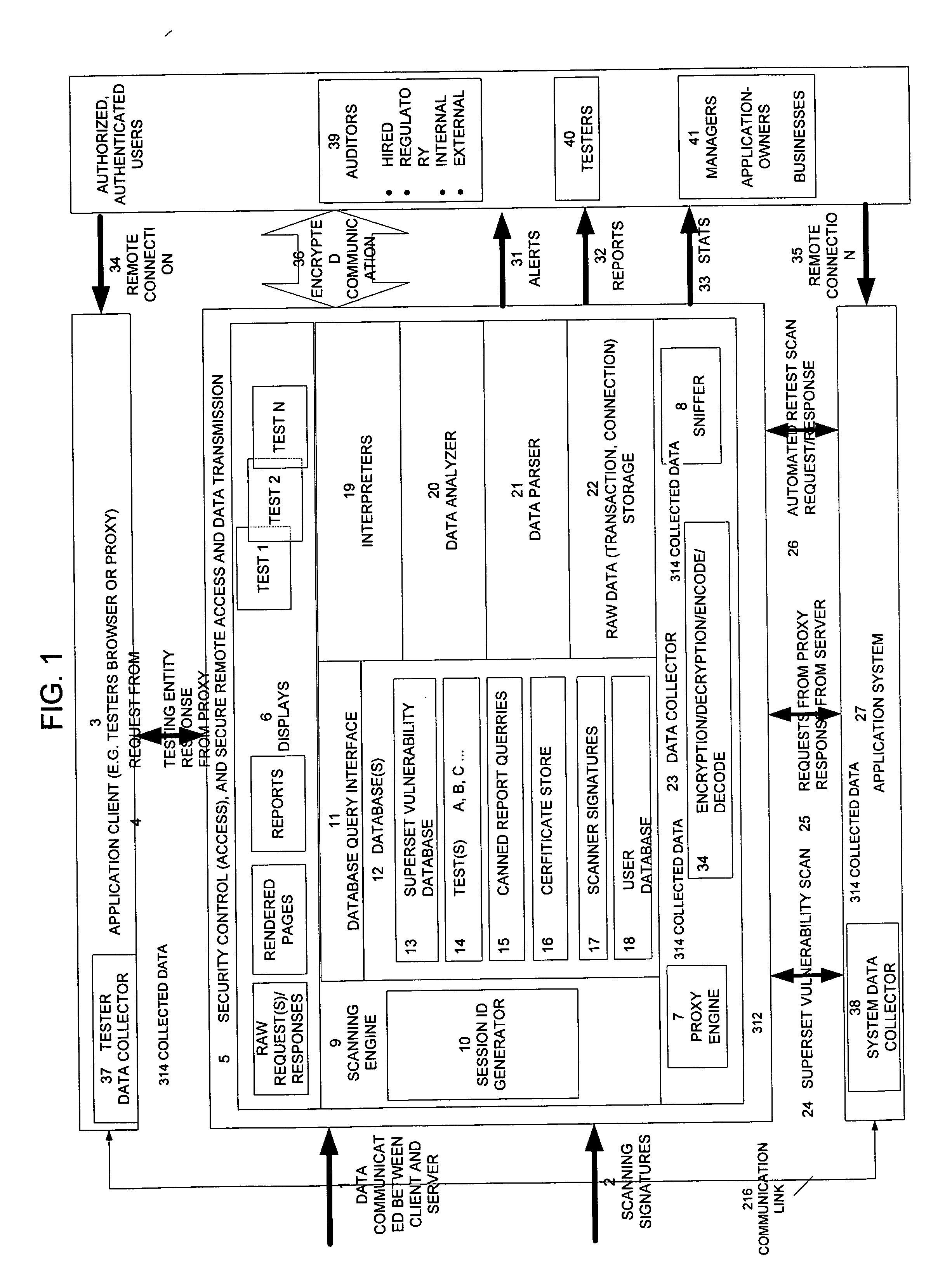
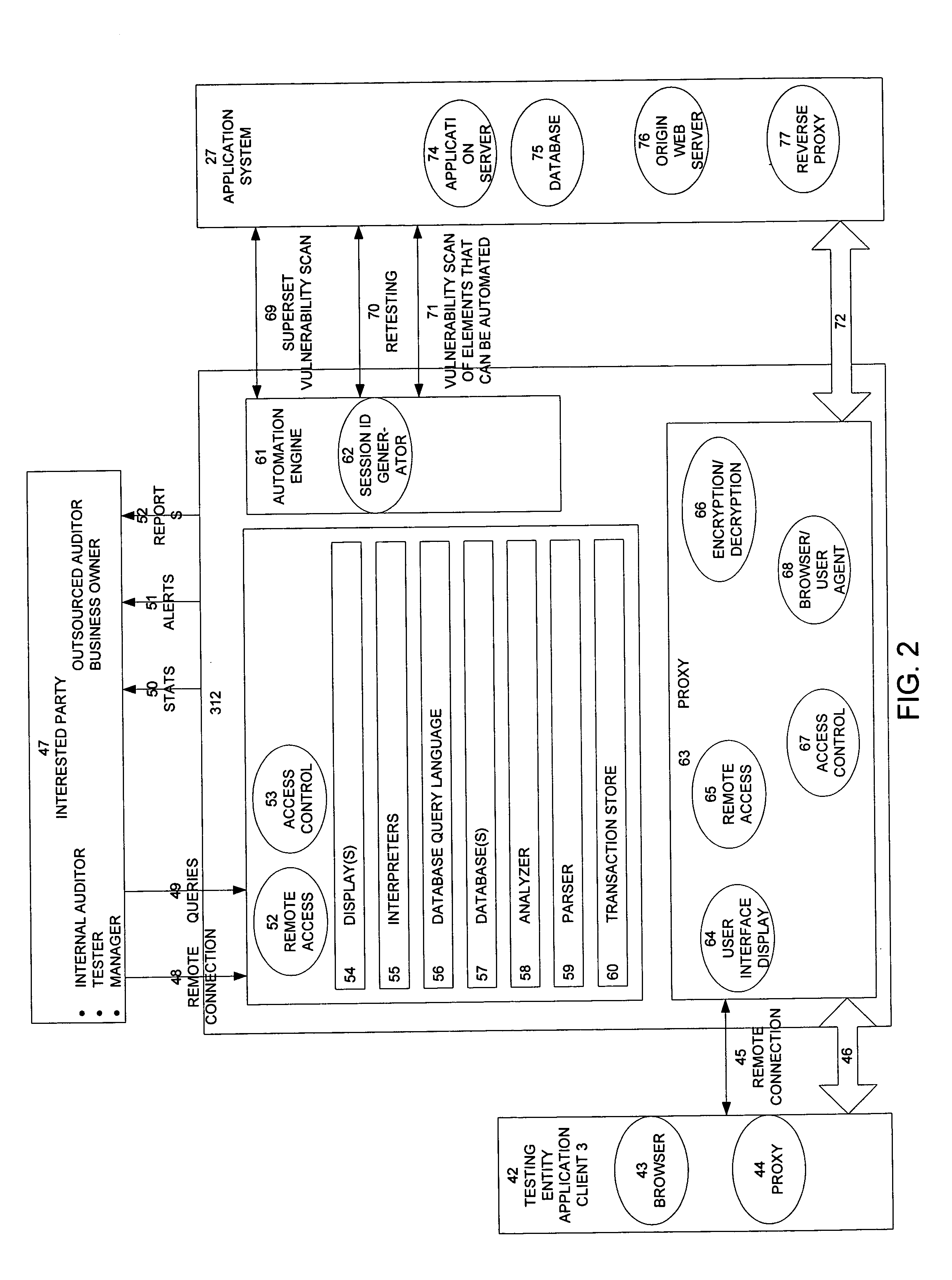
Method, system, and apparatus for managing, monitoring, auditing, cataloging, scoring, and improving vulnerability assessment tests, as well as automating retesting efforts and elements of tests
InactiveUS20050138426A1Streamline and improve test effortImprove consistencyDigital data processing detailsHardware monitoringAnalysis dataWeb application
A scalable method, system, and apparatus for non-intrusively auditing and improving security assessments includes capturing, storing, presenting, displaying, inspecting, monitoring, and analyzing data flow in client-server security assessments and / or network / infrastructure security assessments. The invention provides interested parties with a mechanism to non-intrusively audit in real-time the vulnerability test effort, as well as review, replay, and analyze all aspects of the security assessment during and after the test. For web application assessments, the data capture includes one of the following or some combination: an intermediary with all data passing through the intermediary; a sniffer that can passively extract all data being communicated between the application and tester; and a plurality of computing modules (e.g., software, appliances, etc.) installed in the tester environment or within the application system environment (e.g., software installed on the tester's computer, or on the computer where the intermediary is running, or software installed on the application systems proxy or web server, or an appliance in either environment) for storing, processing, analyzing, reporting, and displaying the data.
Owner:STYSLINGER BRIAN
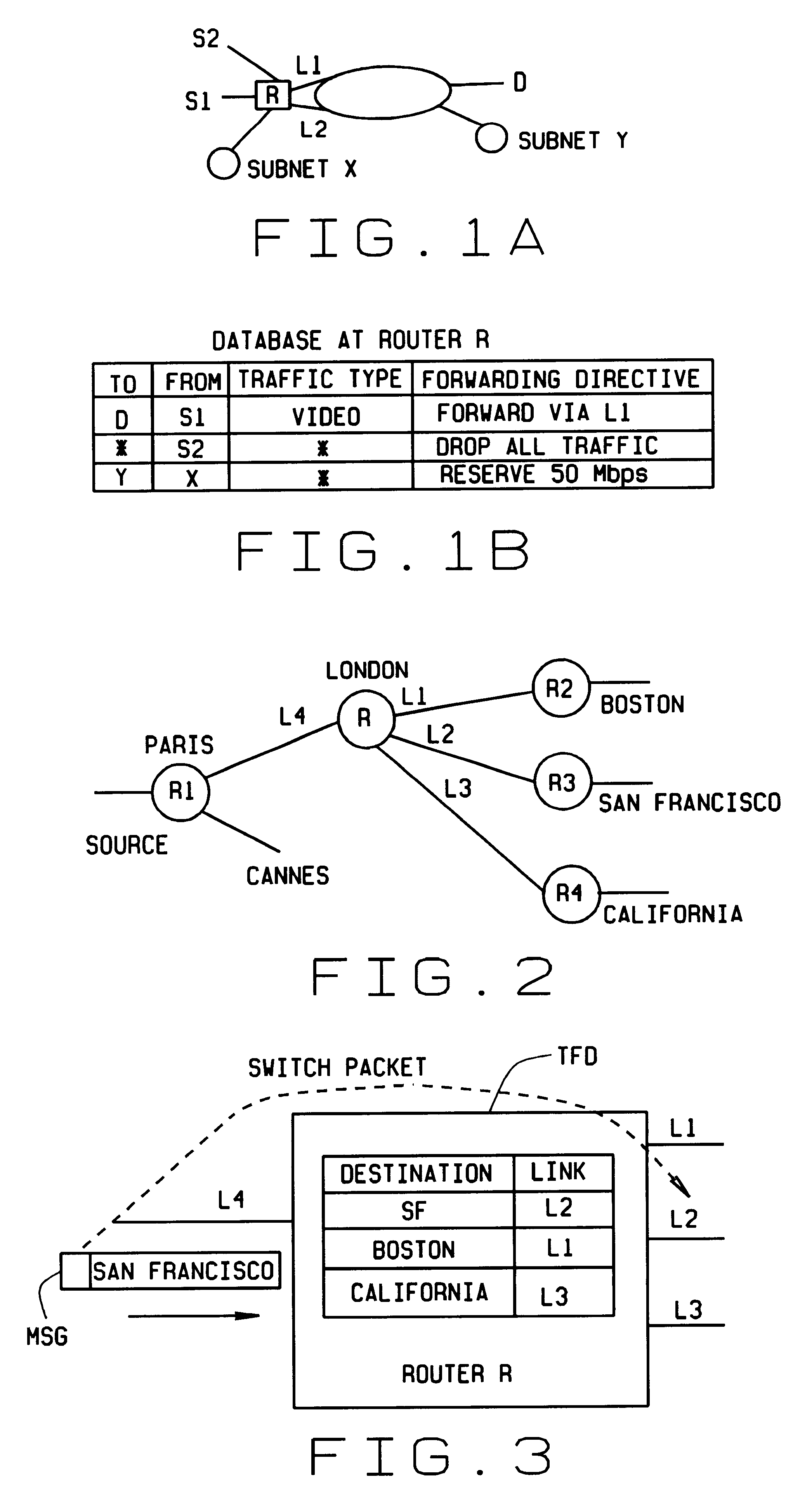
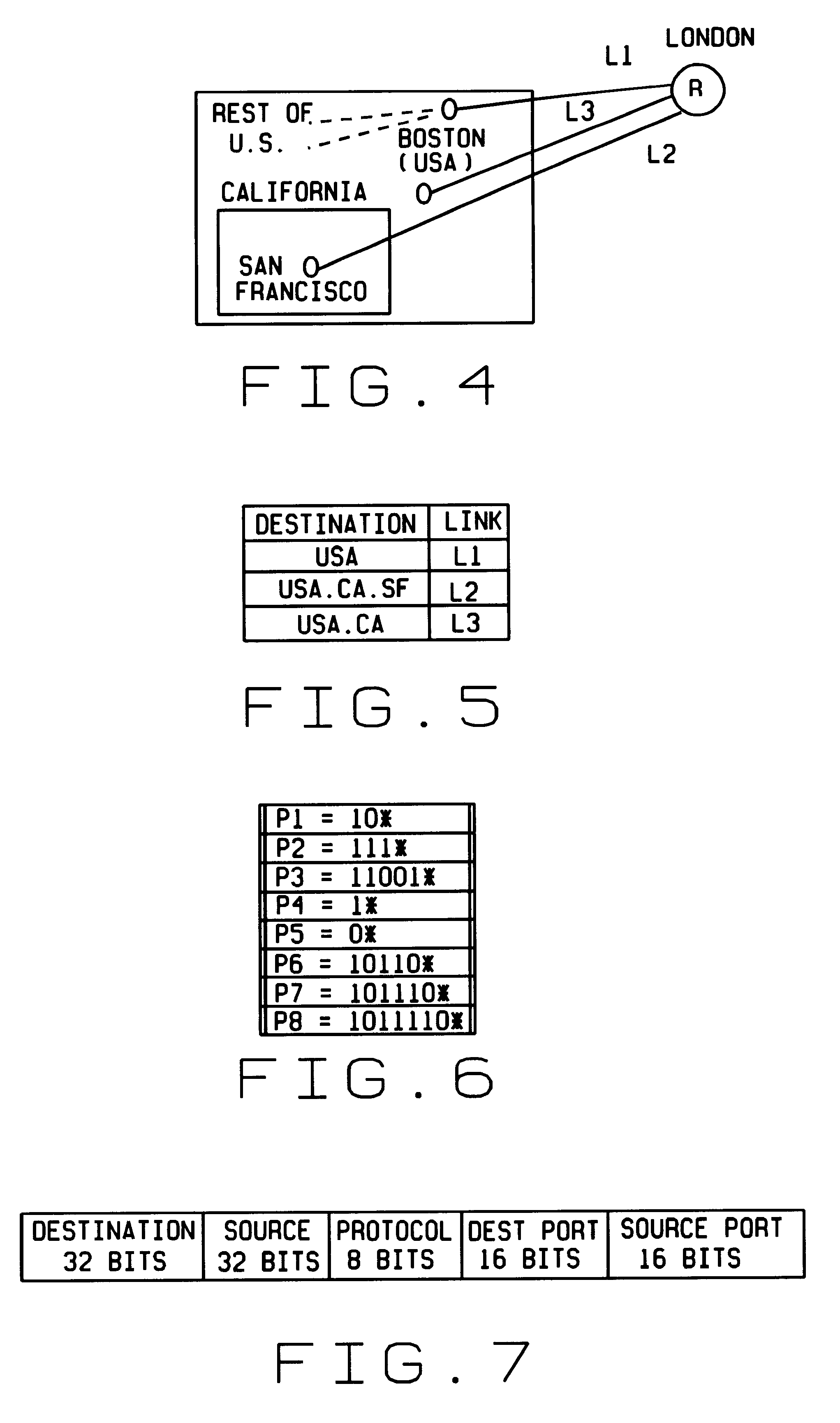
Fast scaleable methods and devices for layer four switching
InactiveUS6212184B1Enormous saving in table sizeAvoid the needError preventionTransmission systemsPrecomputationRoute filtering
Fast, scalable methods and devices are provided for layer four switching in a router as might be found in the Internet. In a first method, a grid of tries, which are binary branching trees, is constructed from the set of routing filters. The grid includes a dest-trie and a number of source tries. To avoid memory blowup, each filter is stored in exactly one trie. The tries are traversed to find the lowest cost routing. Switch pointers are used to improve the search cost. In an extension of this method, hash tables may be constructed that point to grid-of-tries structures. The hash tables may be used to handle combinations of port fields and protocol fields. Another method is based on hashing, in which searches for lowest cost matching filters take place in bit length tuple space. Rectangle searching with precomputation and markers are used to eliminate a whole column of tuple space when a match occurs, and to eliminate the rest of a row when no match is found. Various optimizations of these methods are also provided. A router incorporating memory and processors implementing these methods is capable of rapid, selective switching of data packets on various types of networks, and is particularly suited to switching on Internet Protocol networks.
Owner:WASHINGTON UNIV IN SAINT LOUIS
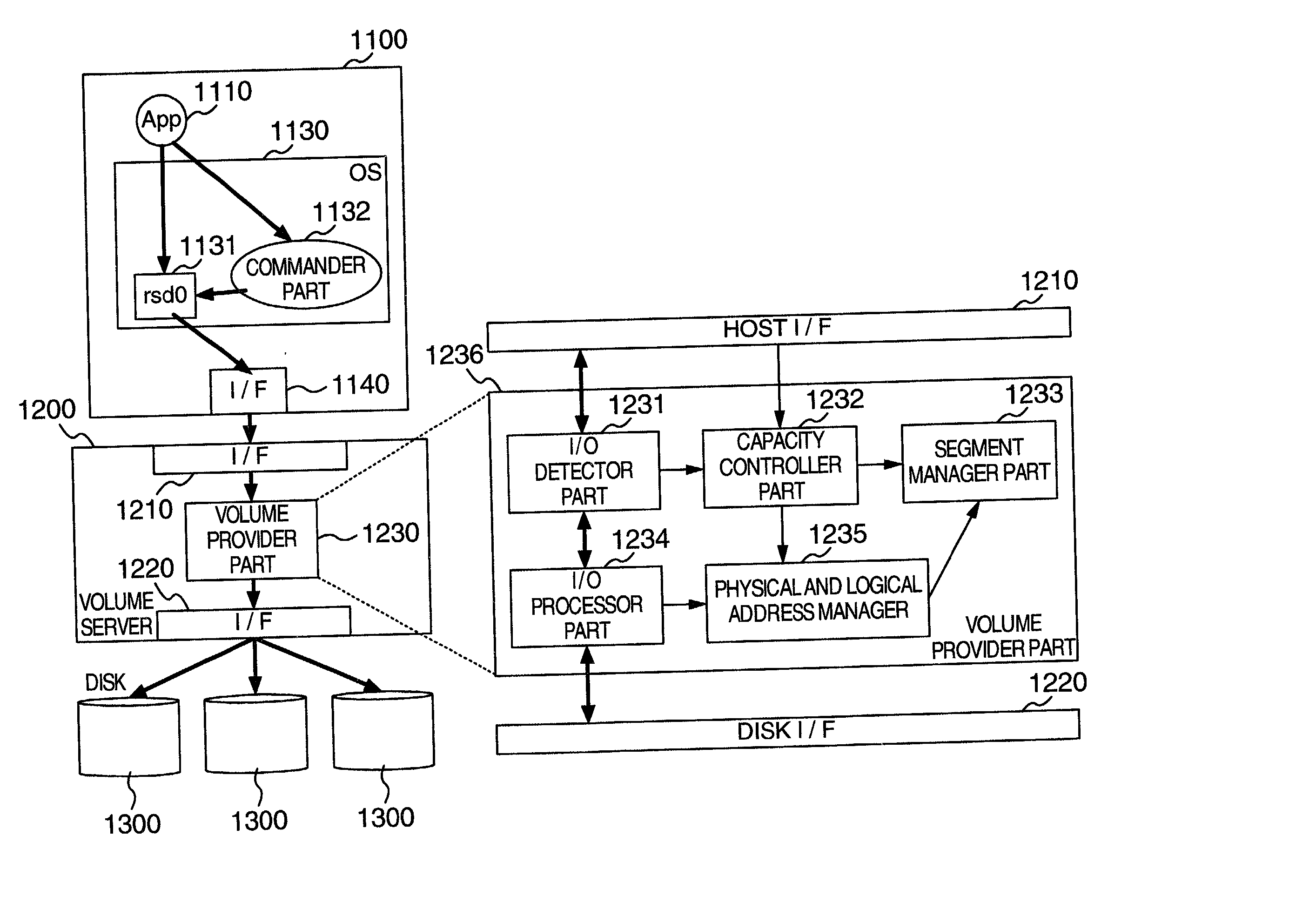
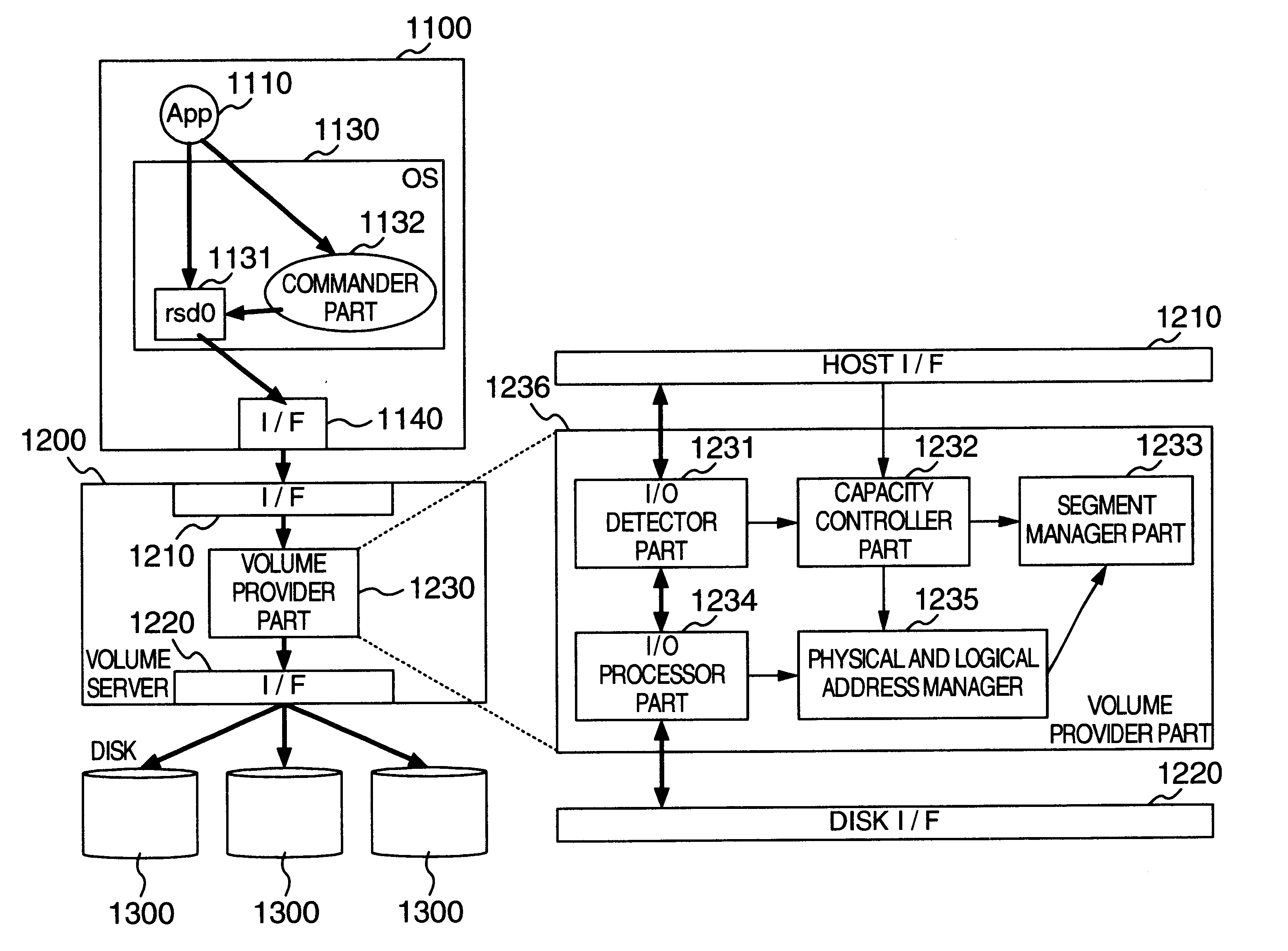
Automated on-line capacity expansion method for storage device
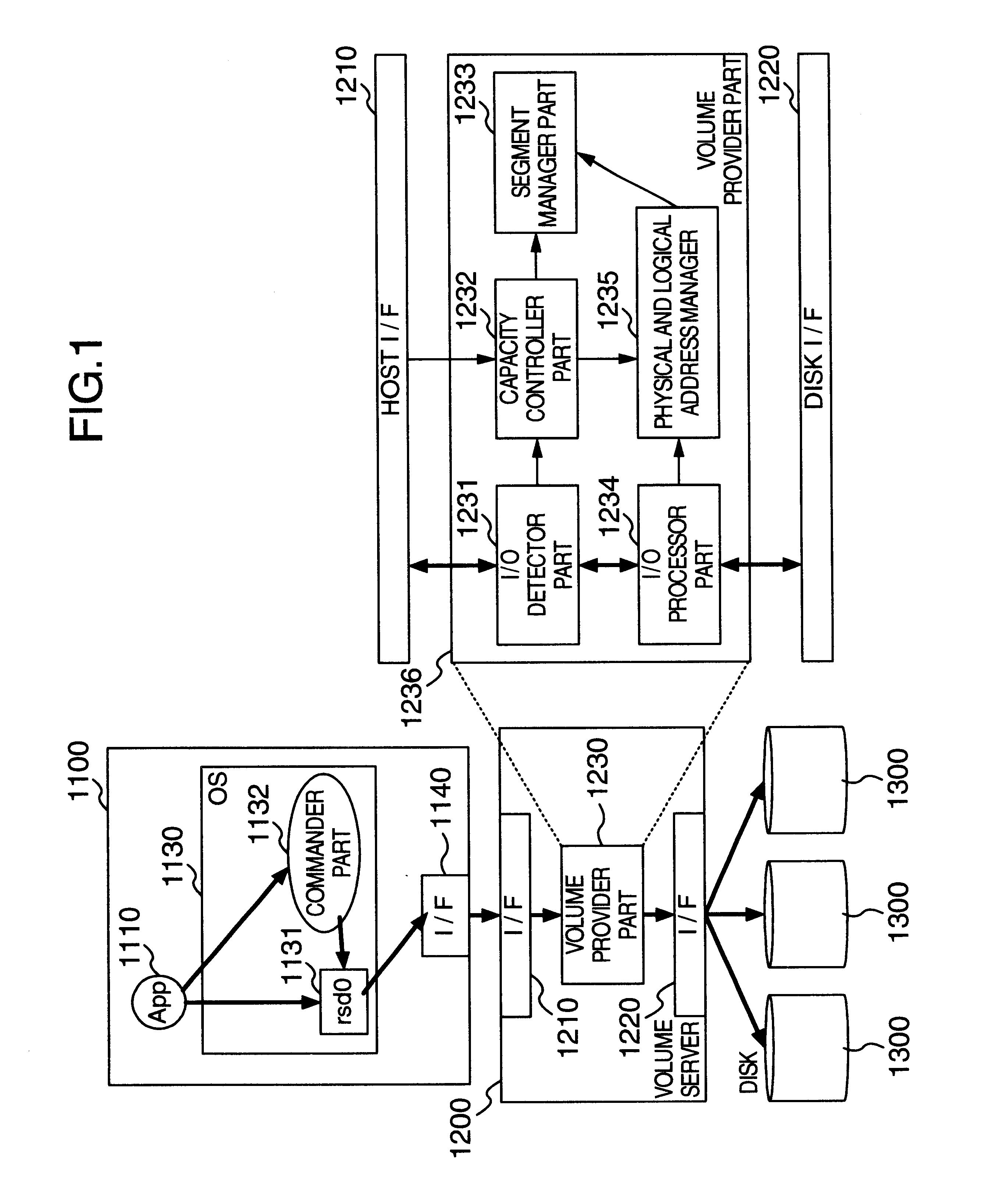
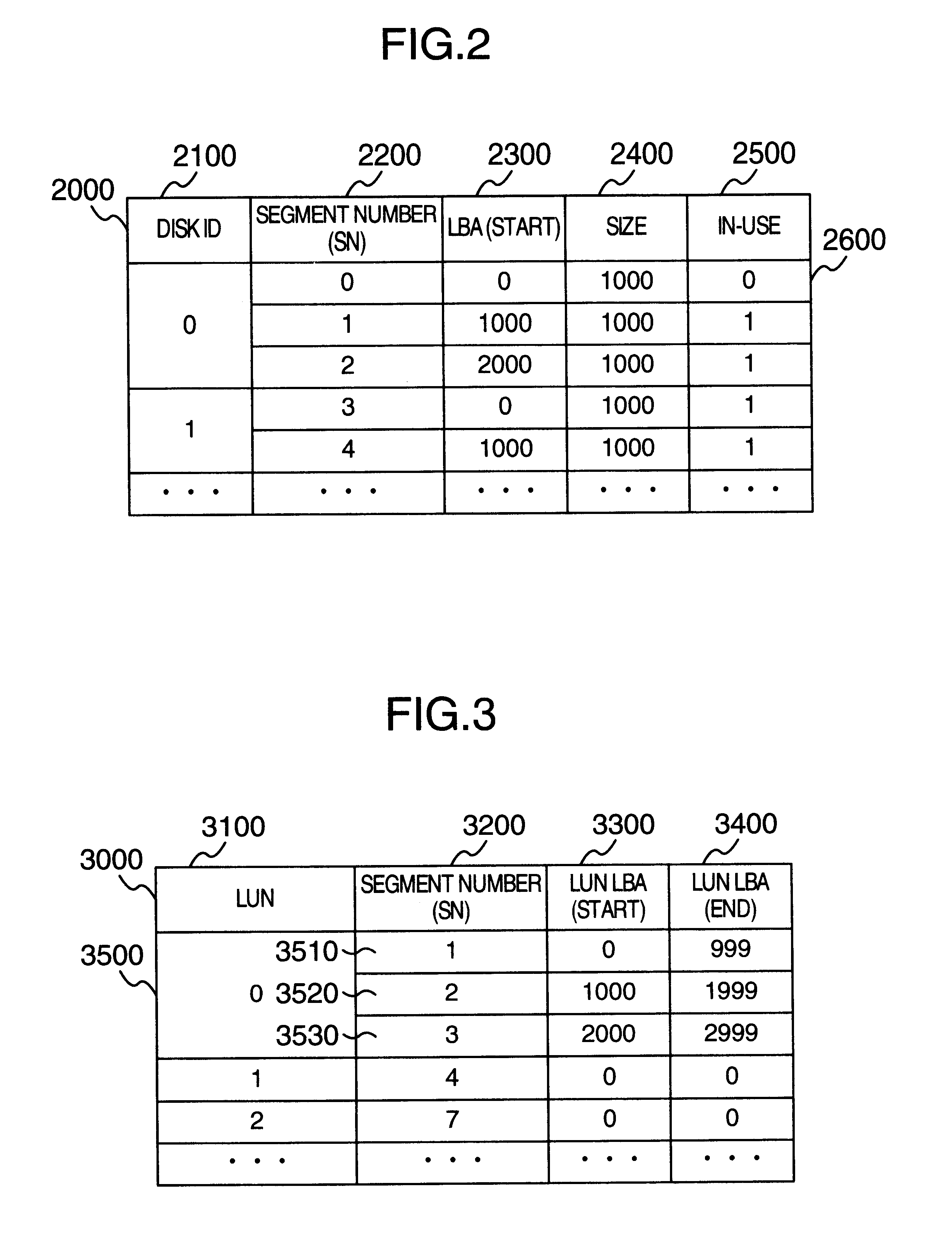
InactiveUS20030009619A1Input/output to record carriersMemory adressing/allocation/relocationLogical block addressingComputerized system
A volume provider unit in a computer system detects a logical block address of a read or write I / O accessing a logical volume of a storage device from a host. According to the logical block address fetched, a storage domain of the logical volume is dynamically expanded. Moreover, the storage domain of the logical volume is reduced or expanded according to an instruction of a logical volume capacity reduction or expansion from a host commander part to a volume server.
Owner:HITACHI LTD
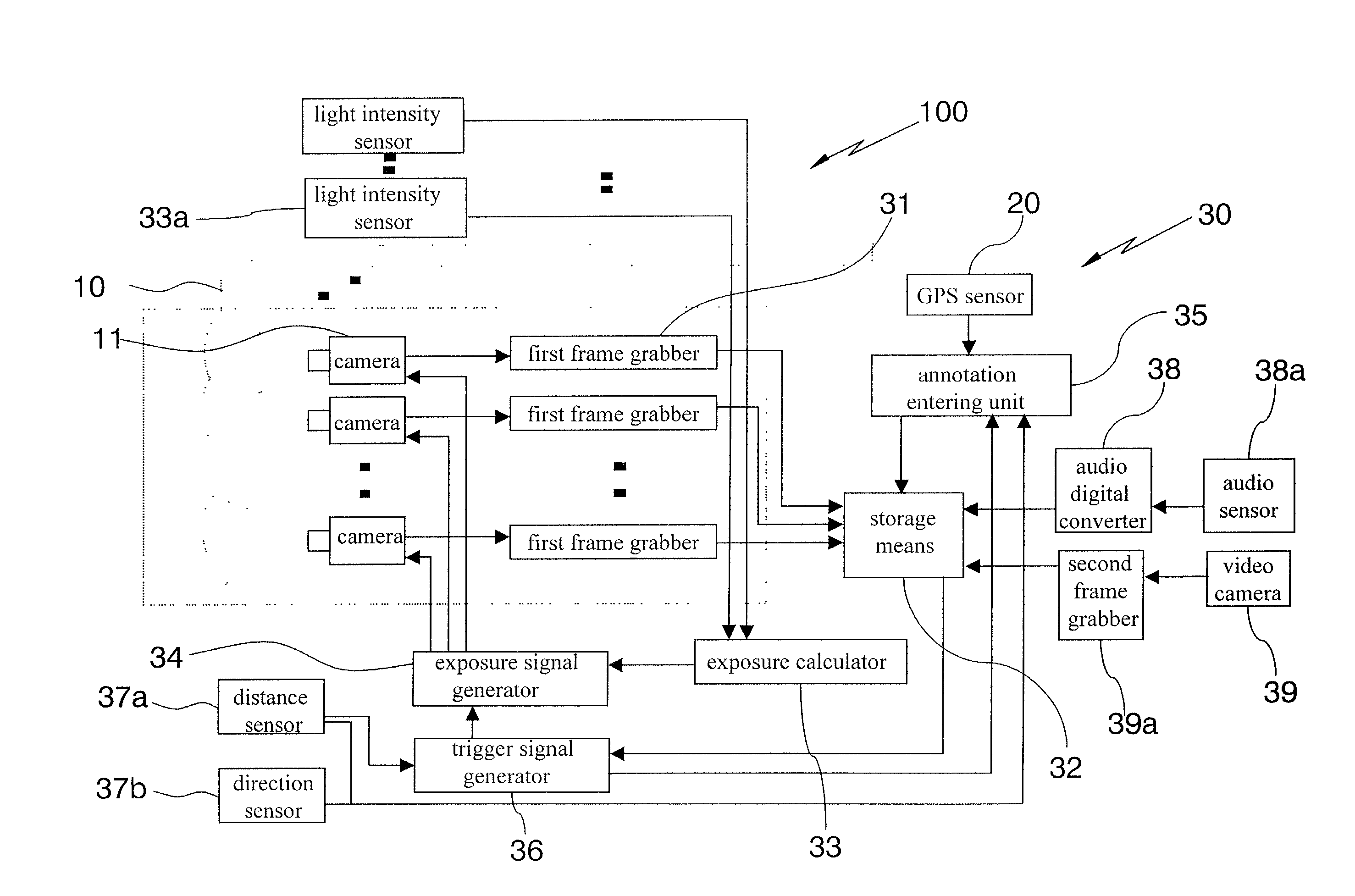
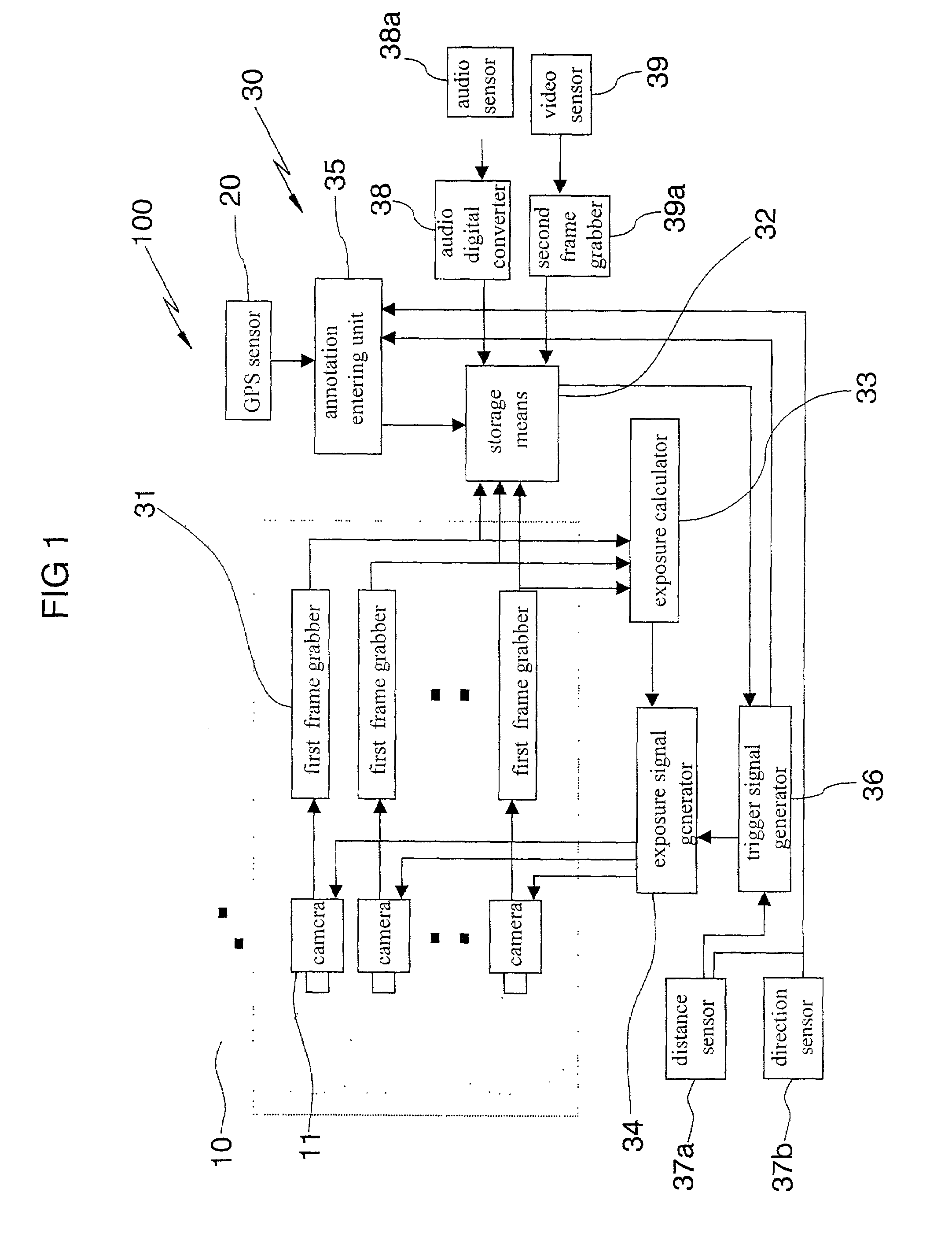
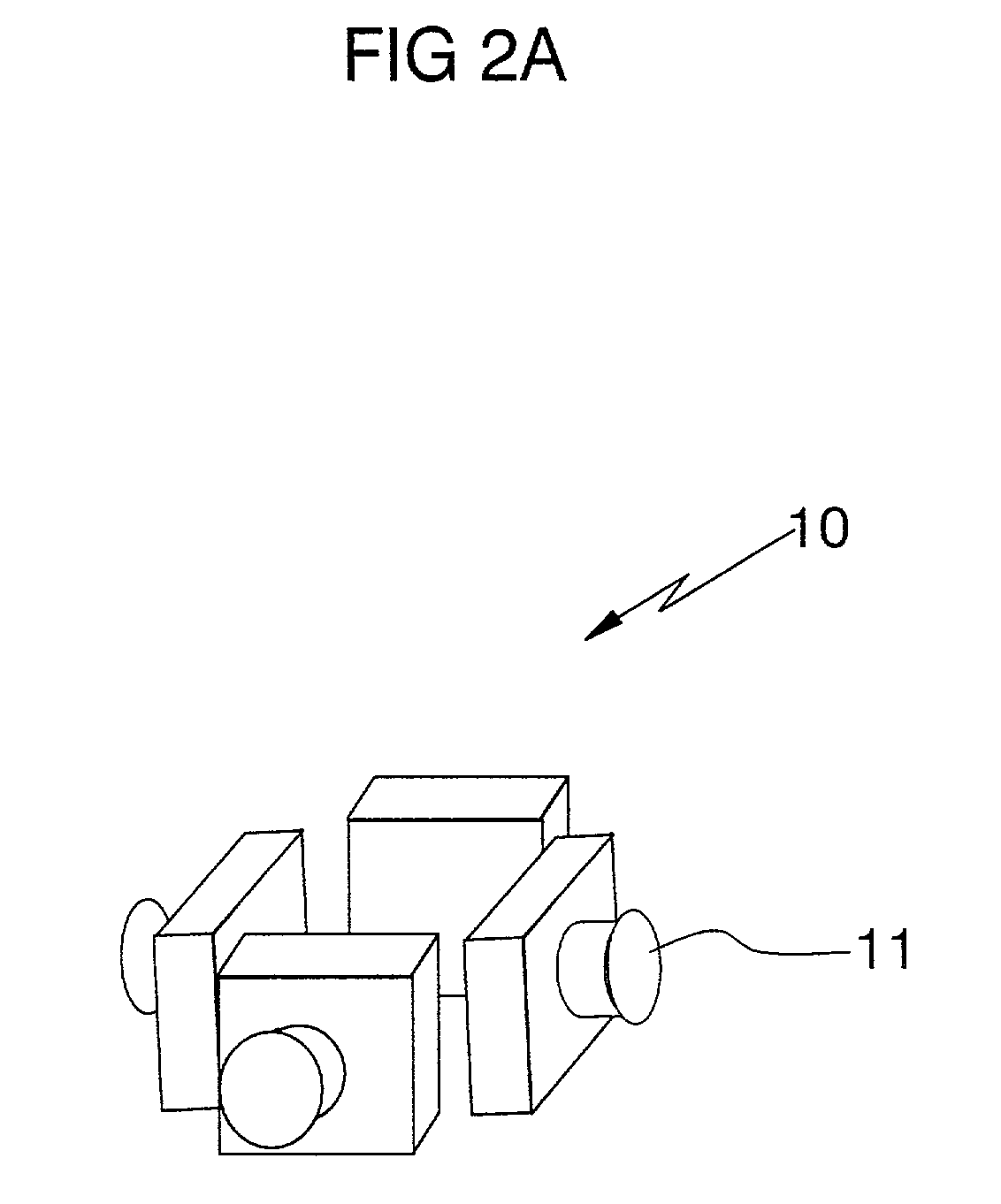
Method and apparatus for omni-directional image and 3-dimensional data acquisition with data annotation and dynamic range extension method
InactiveUS7126630B1Accurate signalIncrease exposureTelevision system detailsColor television detailsMulti cameraData acquisition
A method and apparatus for omni-directional image and 3-dimensional data acquisition with data annotation and dynamic rage extension method is capable of omni-directionally photographing, acquiring 3-dimensional images photographed by cameras having each different exposure amount in connection with the direction of height of an object, extending dynamic range, and generating an geographical information by entering an annotation such as photographing location and time into the photographed images, which can be connected with other geographical information system database. The apparatus includes one or more multi camera module(s) which are stacked and formed multi layers in the direction of height for acquiring 3-dimensional images and extending dynamic range of the 3-dimensional images, wherein each multi camera module includes a plurality of cameras symmetrically arranged with a specific point in a plane.
Owner:KUJIN LEE
Automated on-line capacity expansion method for storage device
InactiveUS6725328B2Input/output to record carriersMemory adressing/allocation/relocationLogical block addressingComputerized system
A volume provider unit in a computer system detects a logical block address of a read or write I / O accessing a logical volume of a storage device from a host. According to the logical block address fetched, a storage domain of the logical volume is dynamically expanded. Moreover, the storage domain of the logical volume is reduced or expanded according to an instruction of a logical volume capacity reduction or expansion from a host commander part to a volume server.
Owner:HITACHI LTD
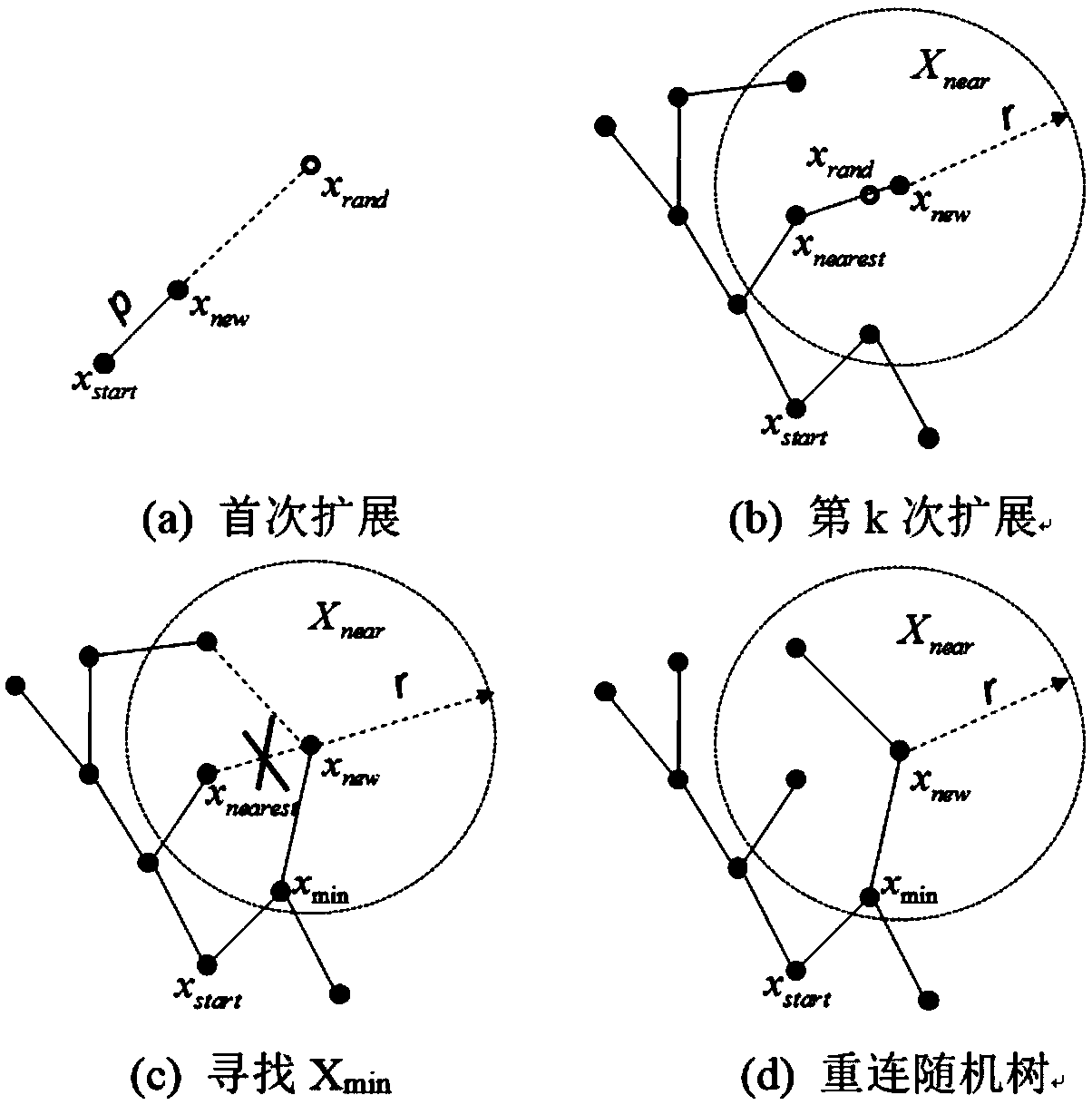
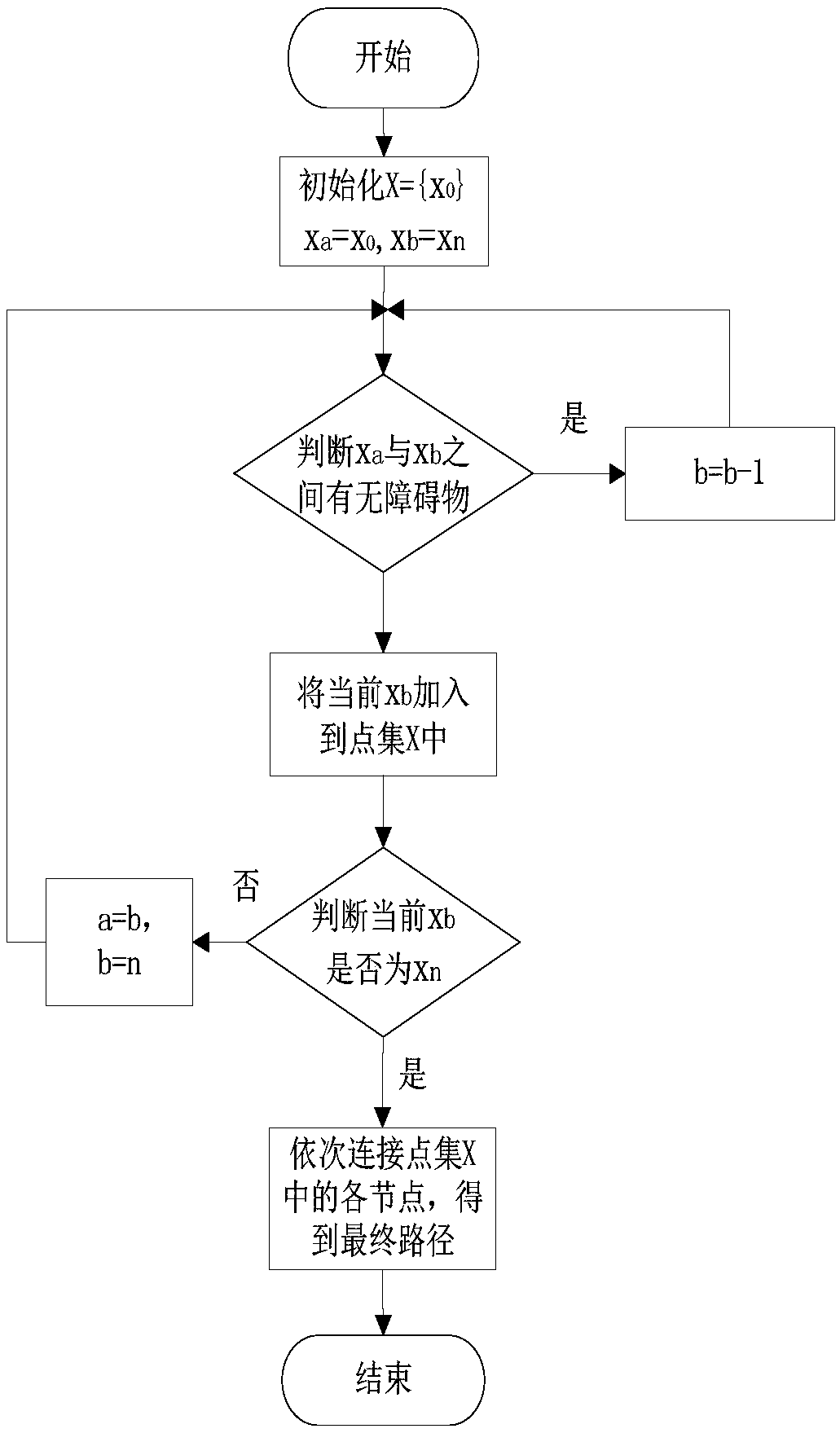
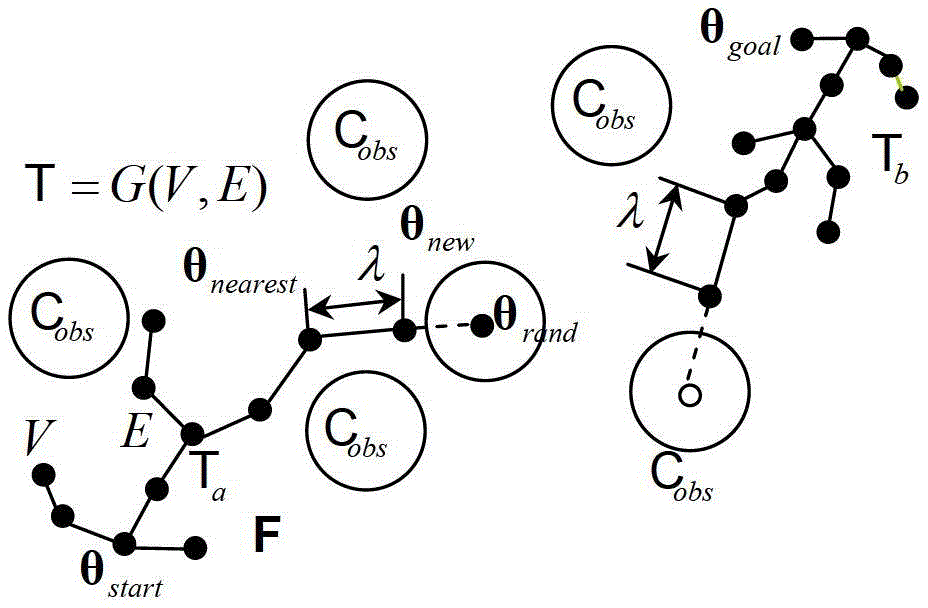
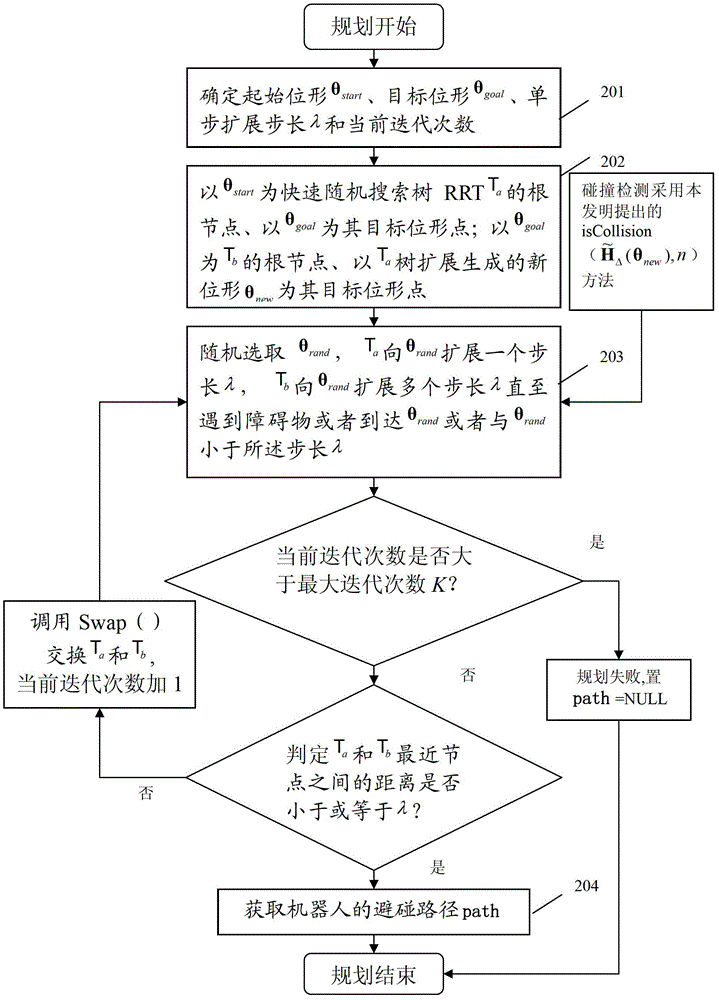
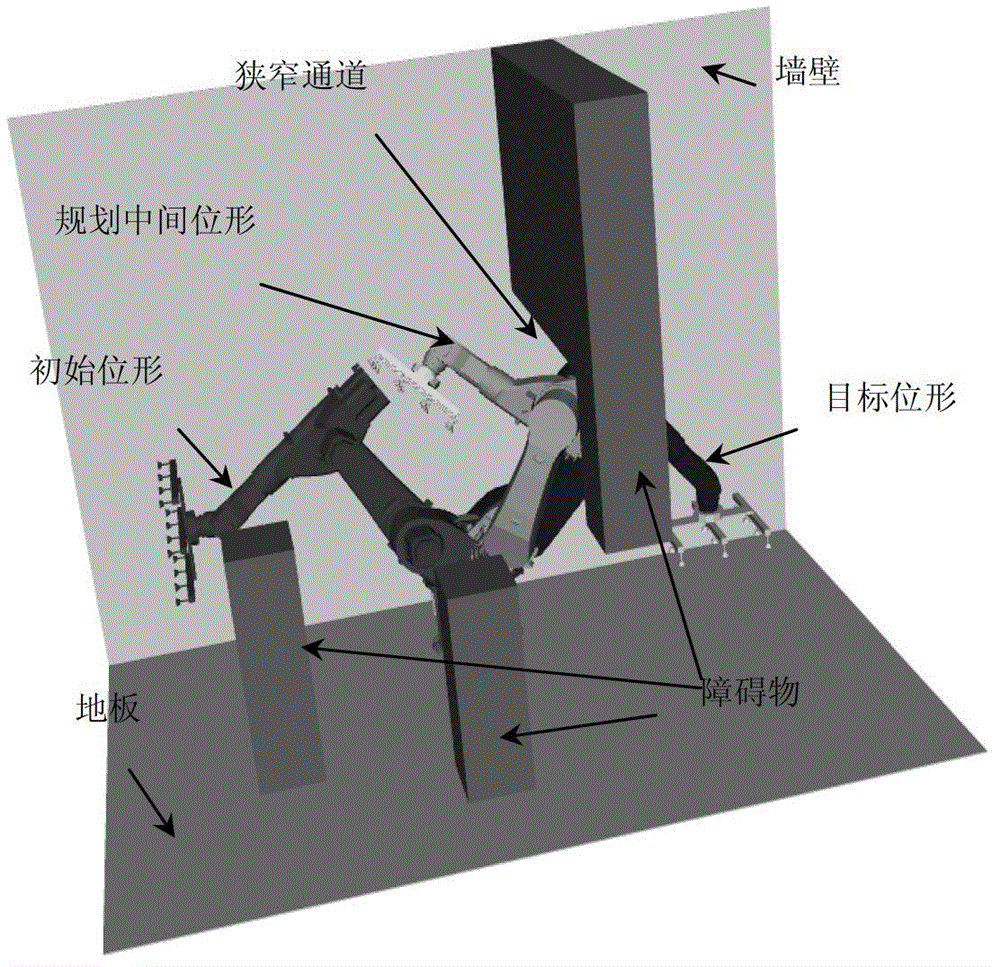
Mobile robot path planning method based on improved RRT* algorithm
InactiveCN108983780AReduce randomnessImprove search efficiencyInstruments for road network navigationPosition/course control in two dimensionsAlgorithmMobile robots path planning
The invention discloses a mobile robot path planning method based on an improved RRT* algorithm. The method introduces a target biasing strategy into a standard RRT* algorithm so as to reduce the randomness of sampling points; provides an avoidance step length extension method in order that a random tree can reasonably stay away from an obstacle area and avoids falling into a local minimum; and smoothes a path obtained by the improved RRT* algorithm by using a reverse sequence connection method smoothing strategy, so as to reduce the direction-changing operations of the robot and achieve the stable movement of the robot. Compared with an original standard RRT* algorithm, the improved RRT* algorithm has a better planned path and takes less time.
Owner:WUHAN UNIV OF TECH
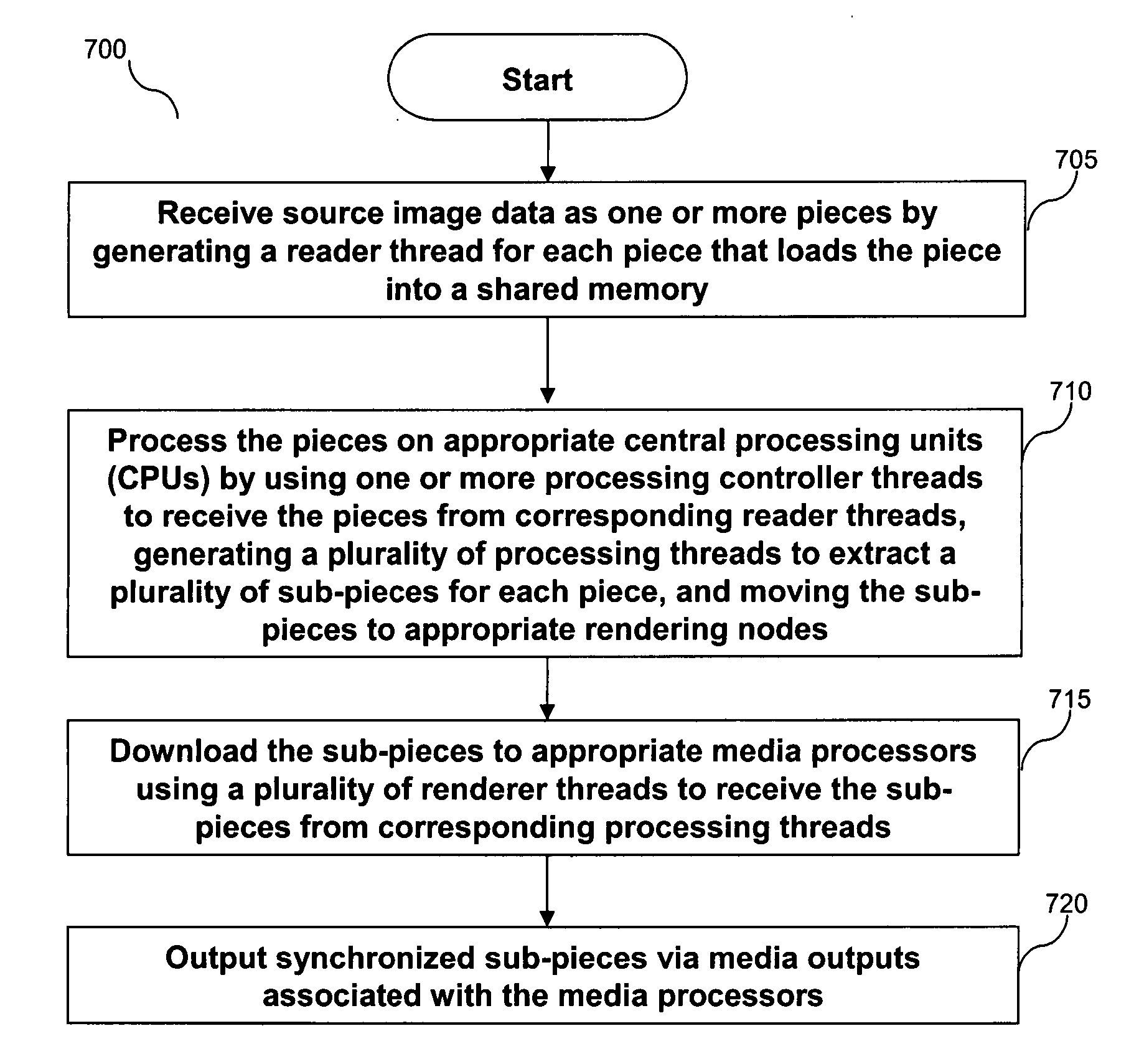
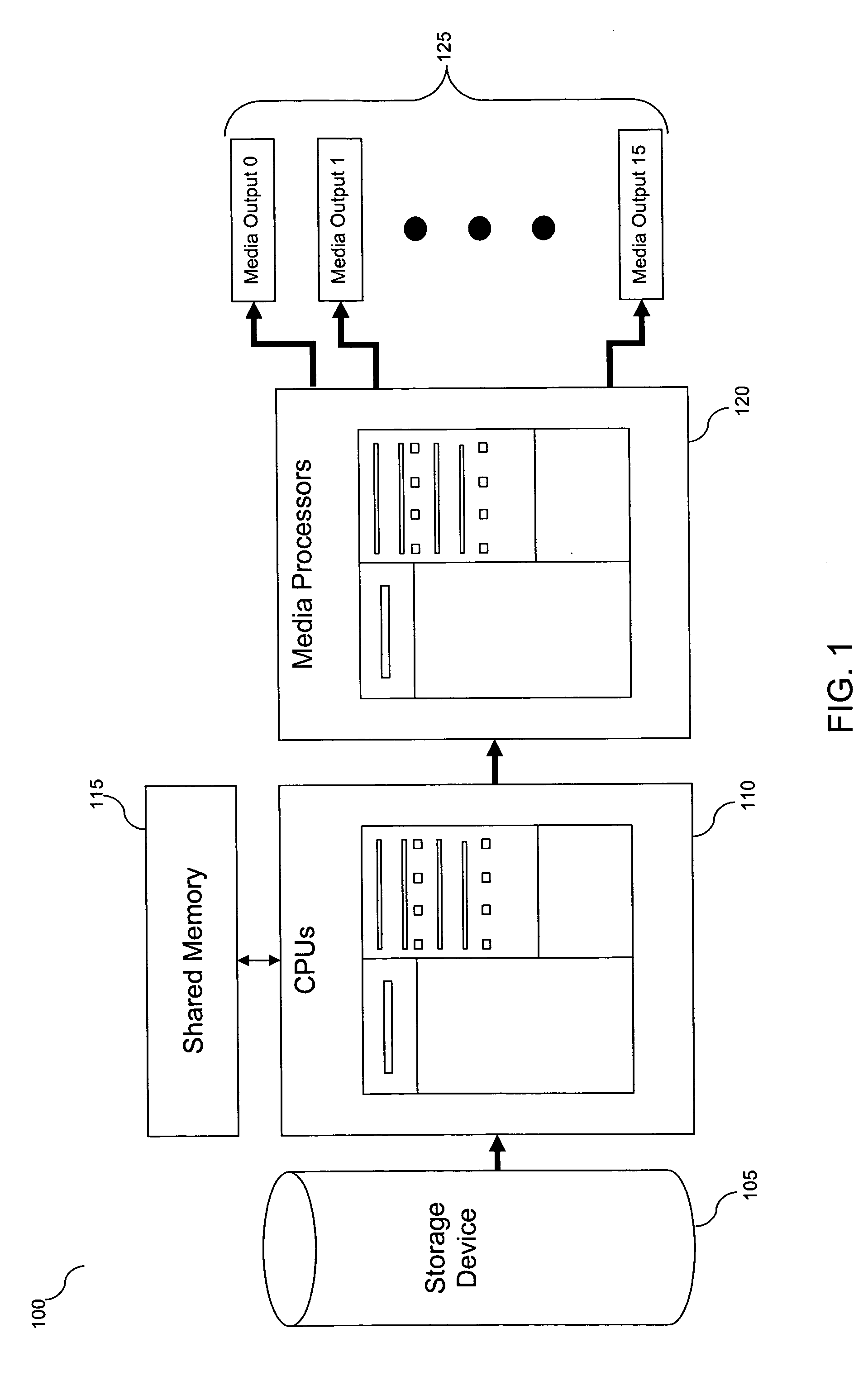
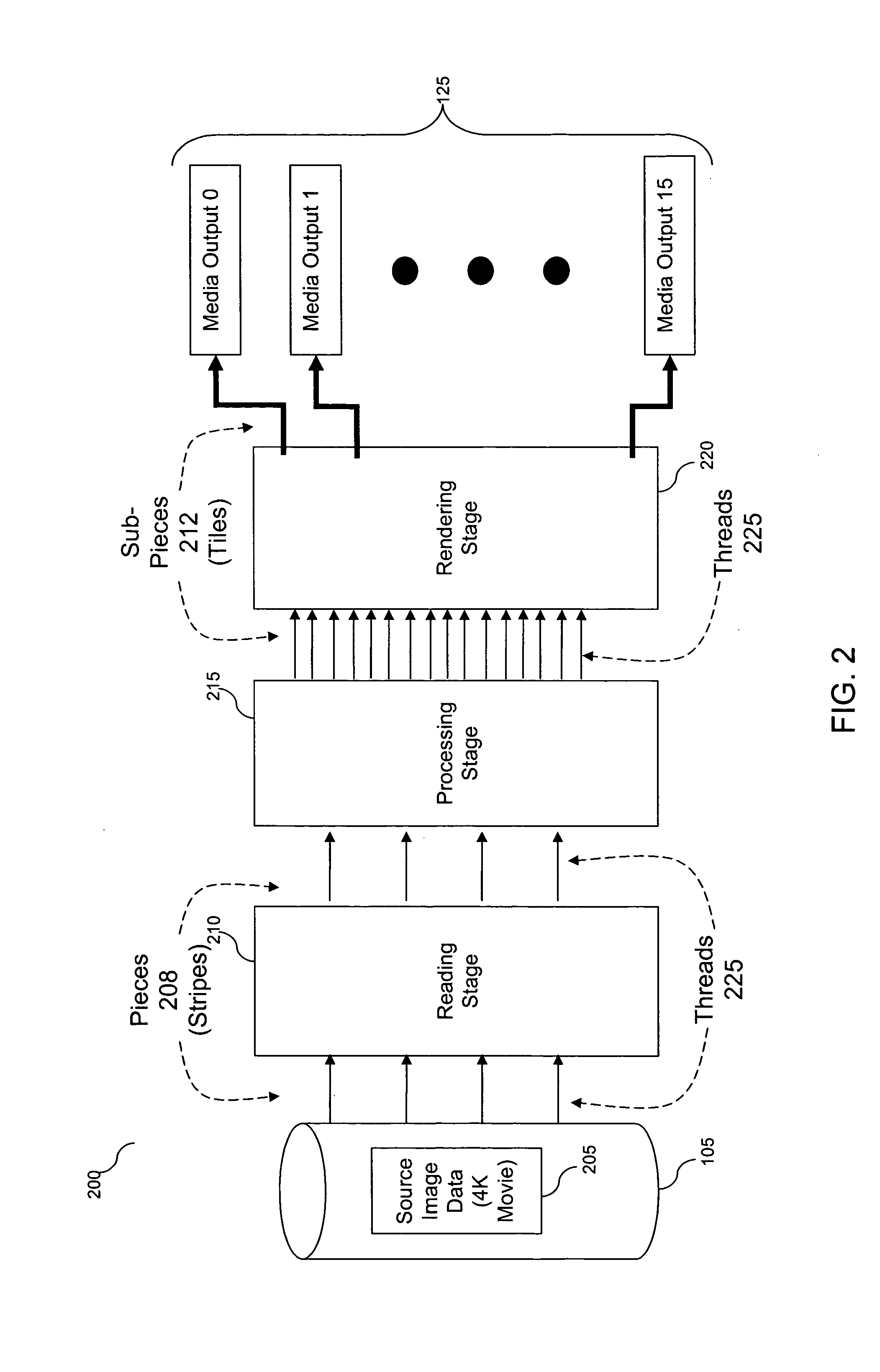
Scalable method and system for streaming high-resolution media
ActiveUS20060093044A1Television system detailsPicture reproducers using cathode ray tubesGraphicsData source
A system and method for distributing data (e.g., imaging data such as pixels, or 3D graphics data such as points, lines, or polygons) from a single or a small number of data sources to a plurality of graphical processing units (graphics processors) for processing and display is presented. The system and method provide a pipelined and multithreaded approach that prioritizes movement of the data through a high-speed multiprocessor system (or a high-speed system of networked computers), according to the system topology. Multiple threads running on multiple processors in shared memory move the data from a storage device (e.g., a disk array), through the high-speed multiprocessor system, to graphics processor memory for display and optional processing through fragment programming. The data can also be moved in the reverse direction, back through the high-speed multiprocessor system, for storage on the disk array.
Owner:MEDIATEK INC
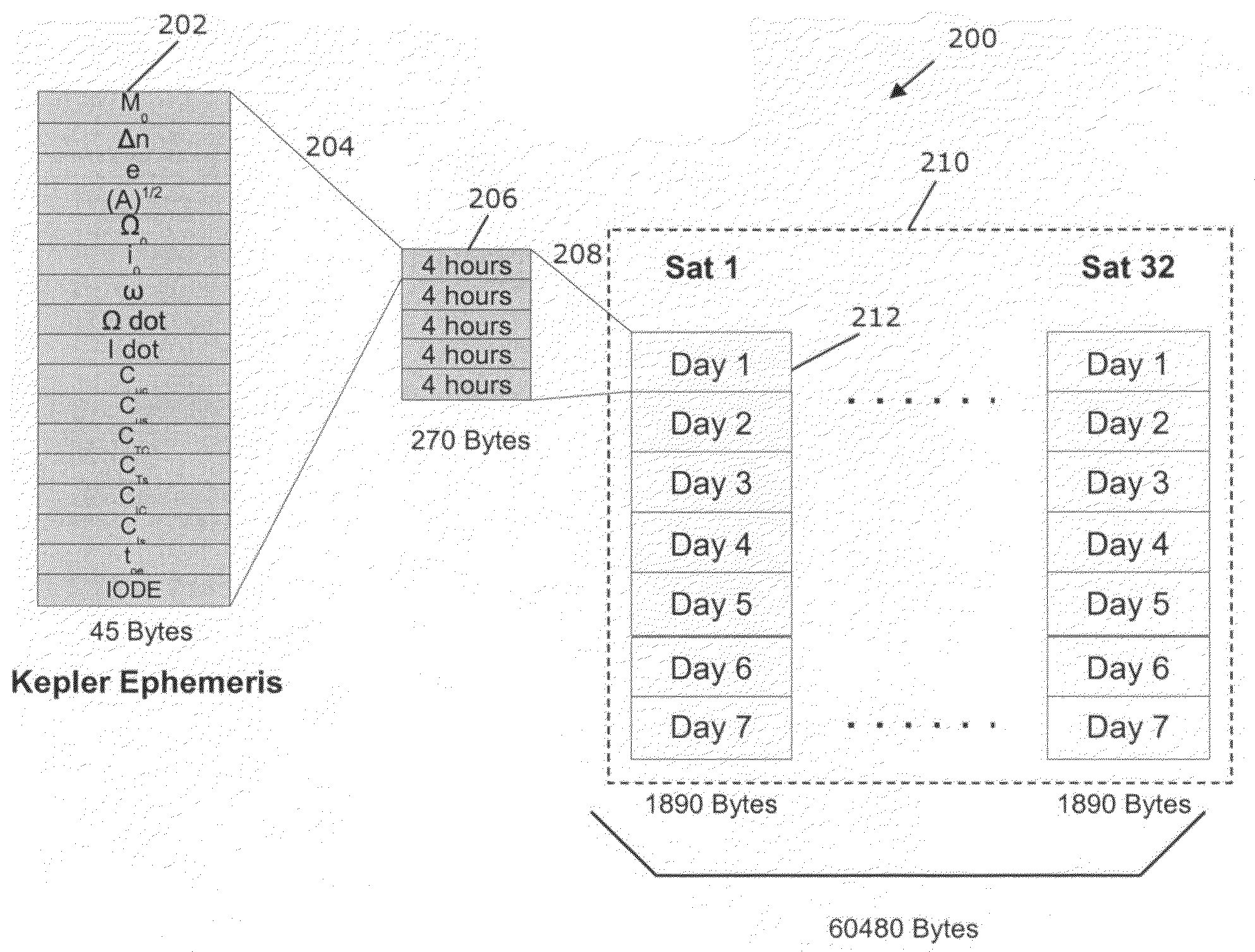
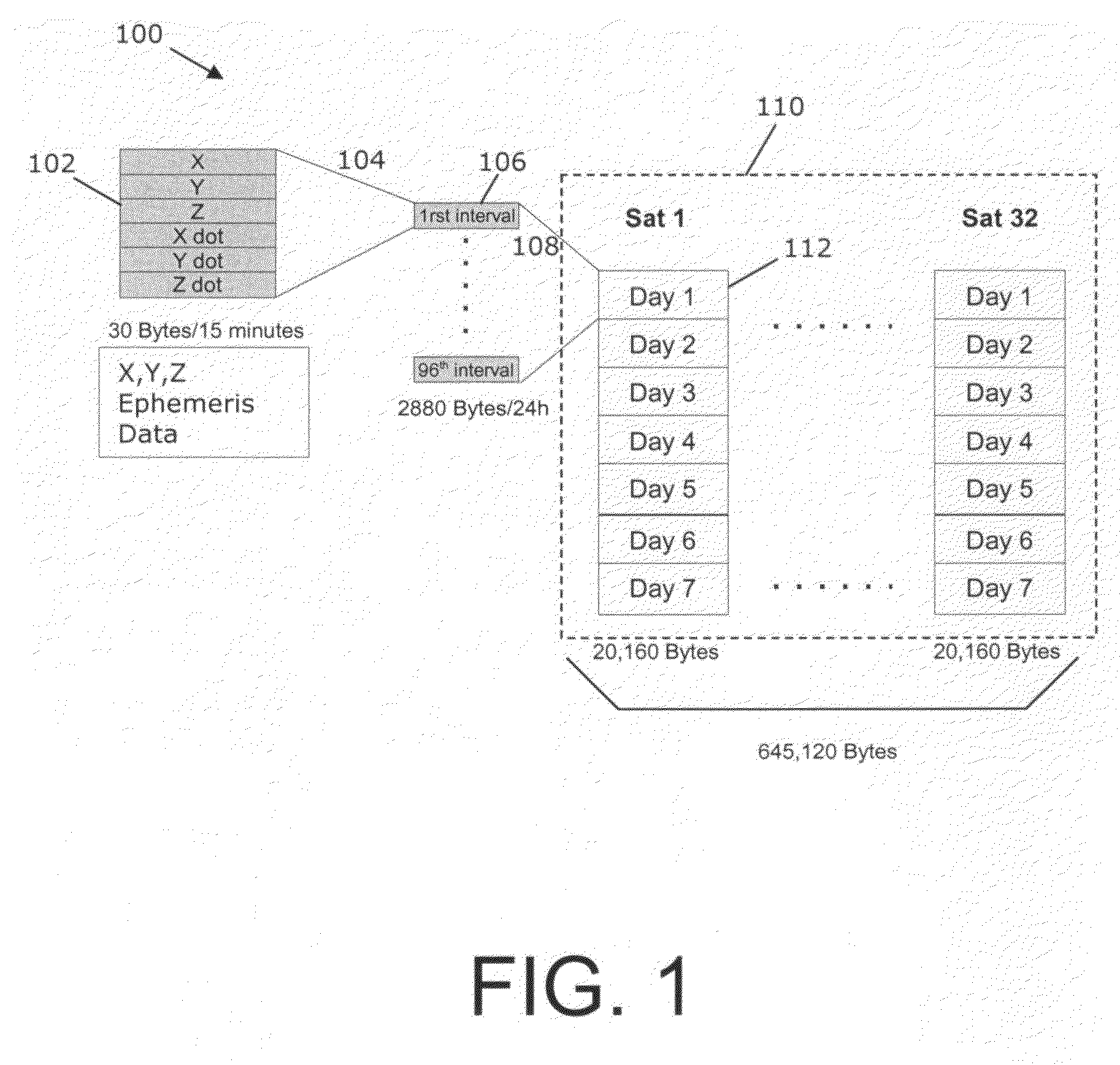
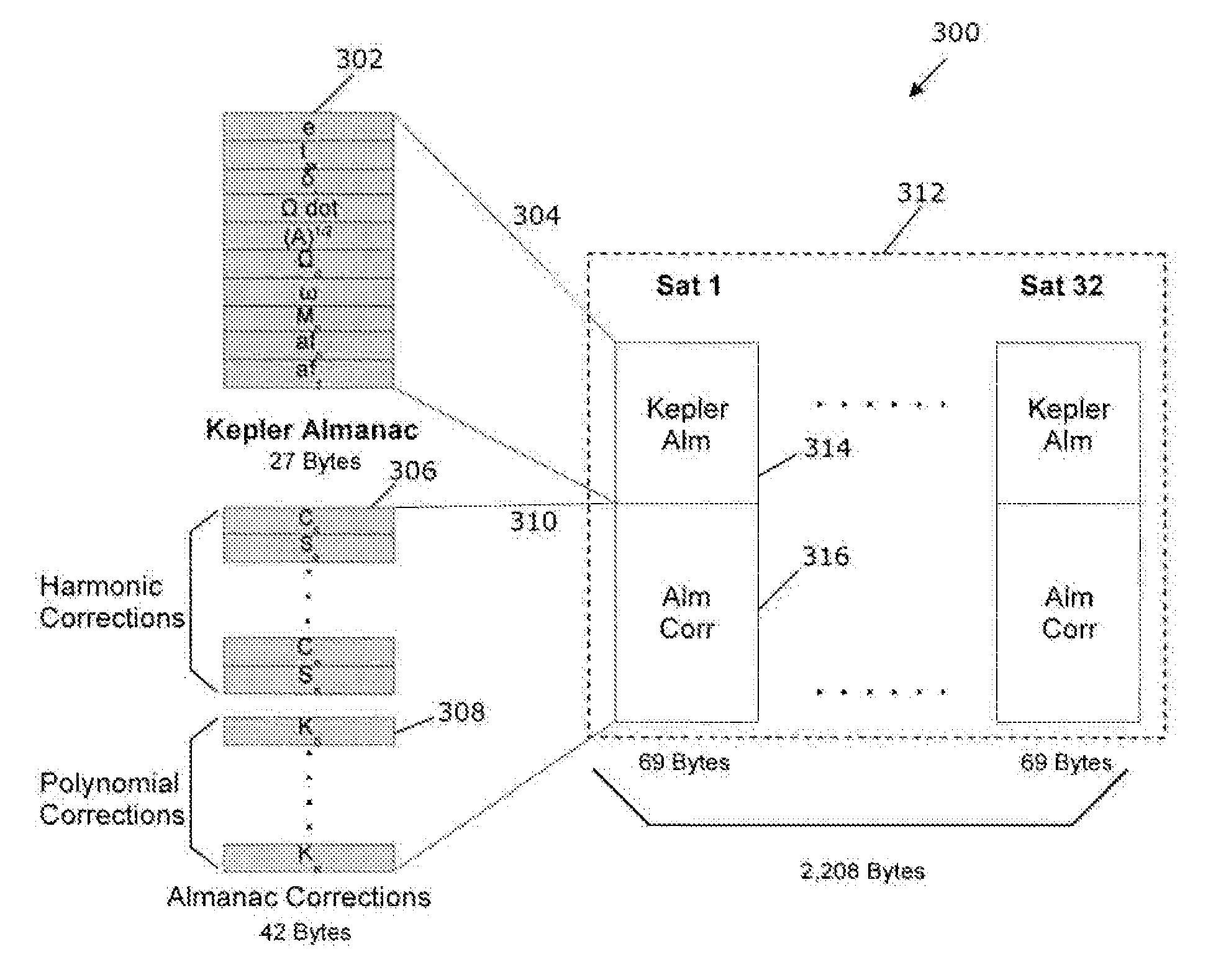
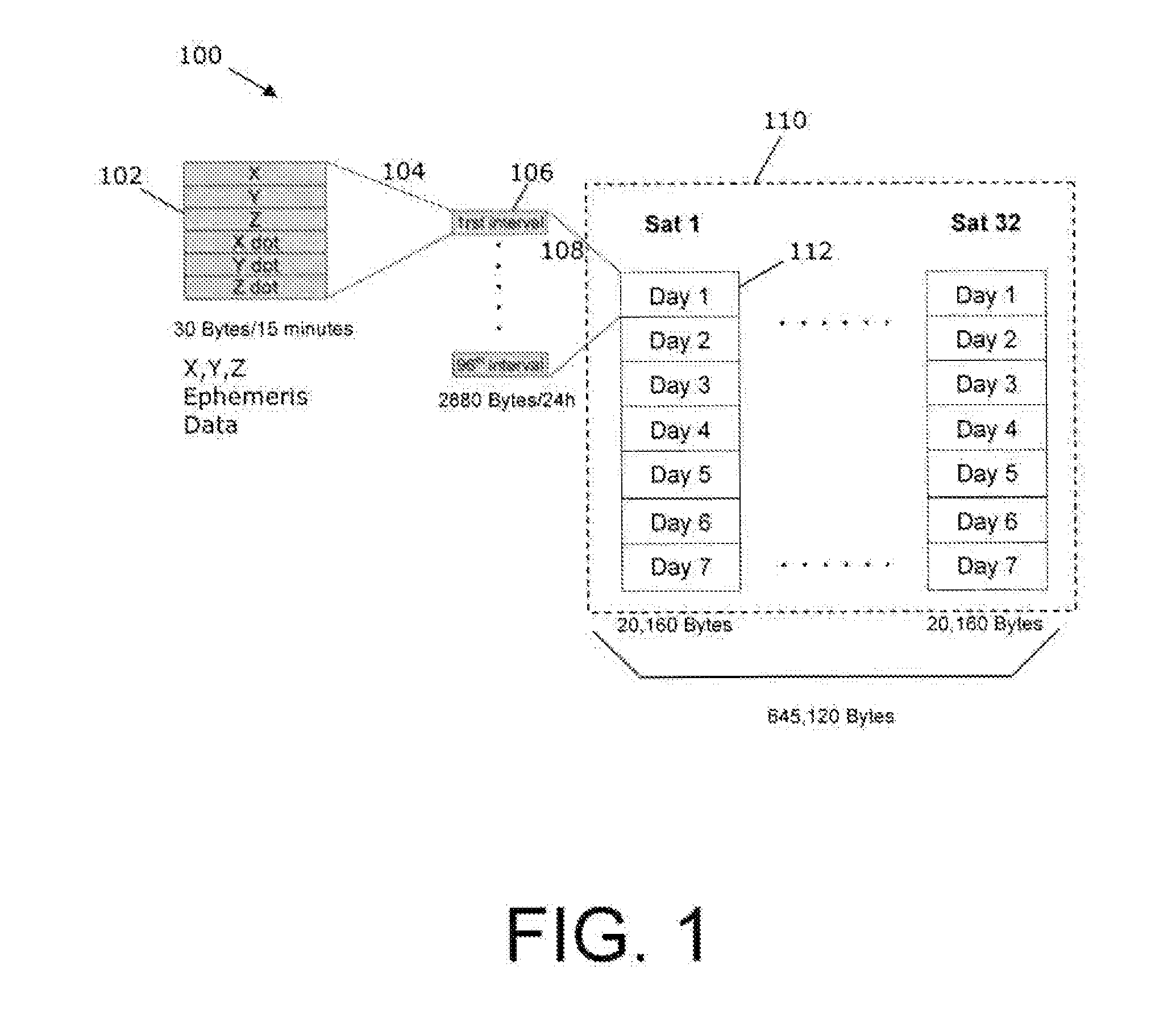
Ephemeris extension method for GNSS applications
Systems, methods and devices for improving the performance of Global Navigation Satellite System (GNSS) receivers are disclosed. In particular, the improvement of the ability to calculate a satellite position or a receiver position where a receiver has degraded ability to receive broadcast ephemeris data directly from a GNSS satellite is disclosed. Correction terms can be applied to an approximate long-term satellite position model such as the broadcast almanac.
Owner:QUALCOMM INC
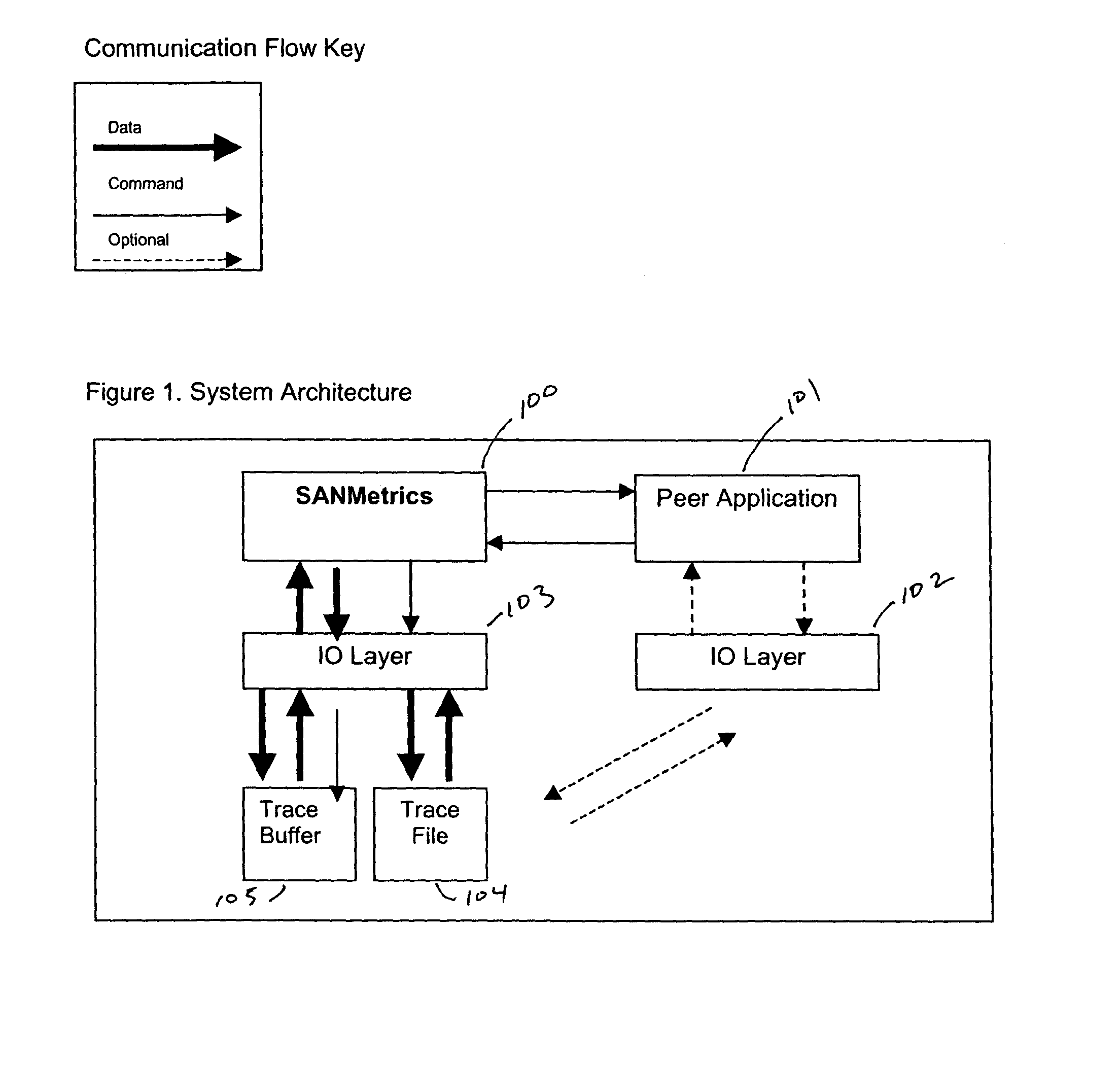
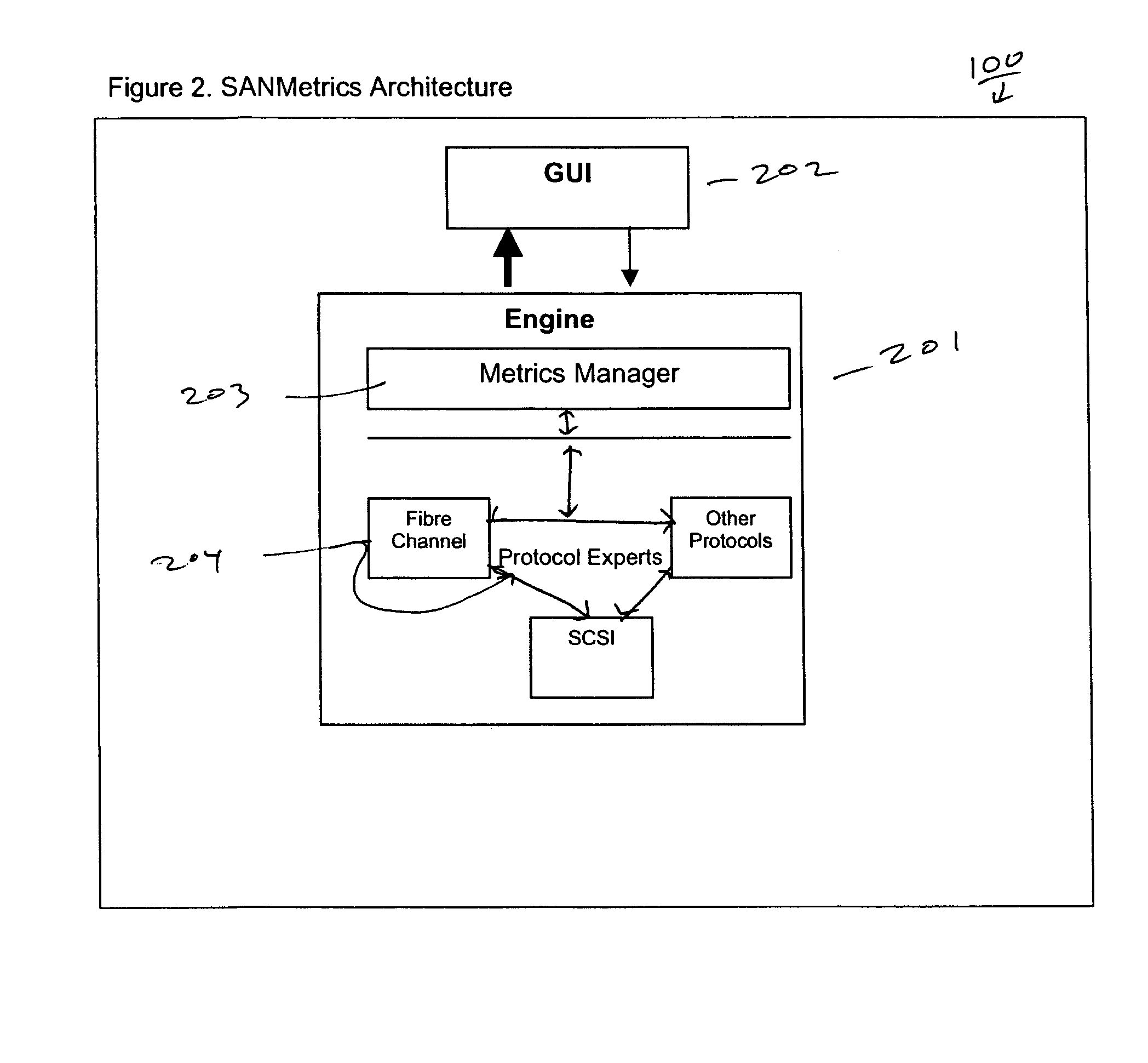
Network analysis scalable analysis tool for multiple protocols
ActiveUS7352706B2Efficient analysisError preventionFrequency-division multiplex detailsAnalysis dataAnalysis tools
Embodiments of the invention provide a scalable method for analyzing a network. The method includes generating a data trace representative of the network, determining a topology for the network from the data trace, and sequentially analyzing each frame in the data trace to determine at least one of network errors, warnings, and metrics. The analysis of each frame generally includes analyzing a first protocol layer of the frame with a first expert engine, determining if a second protocol layer is present in the frame, passing the frame to a second expert engine, and passing the frame to additional expert engines if the frame contains additional protocol layers.
Owner:VIAVI SOLUTIONS INC
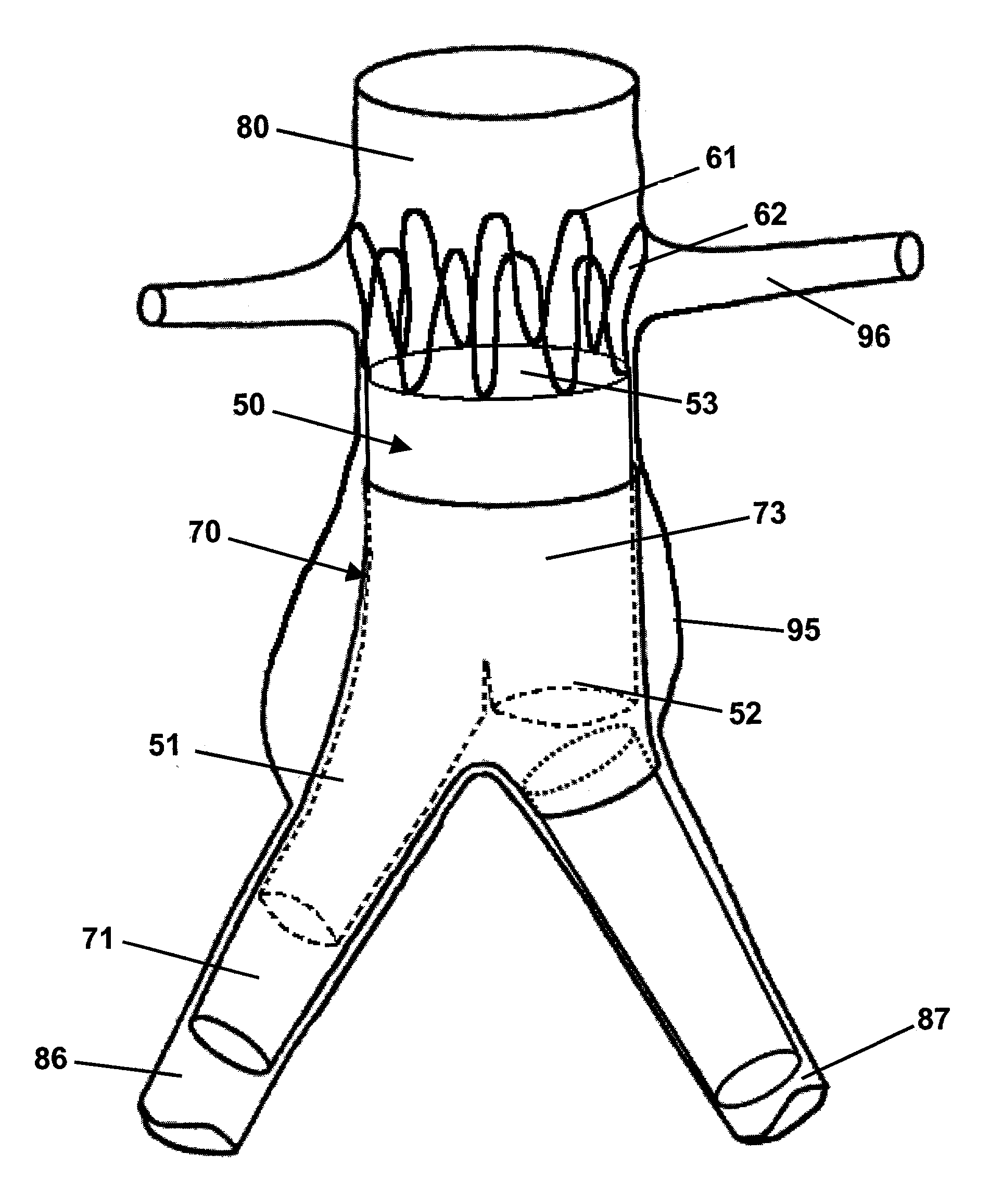
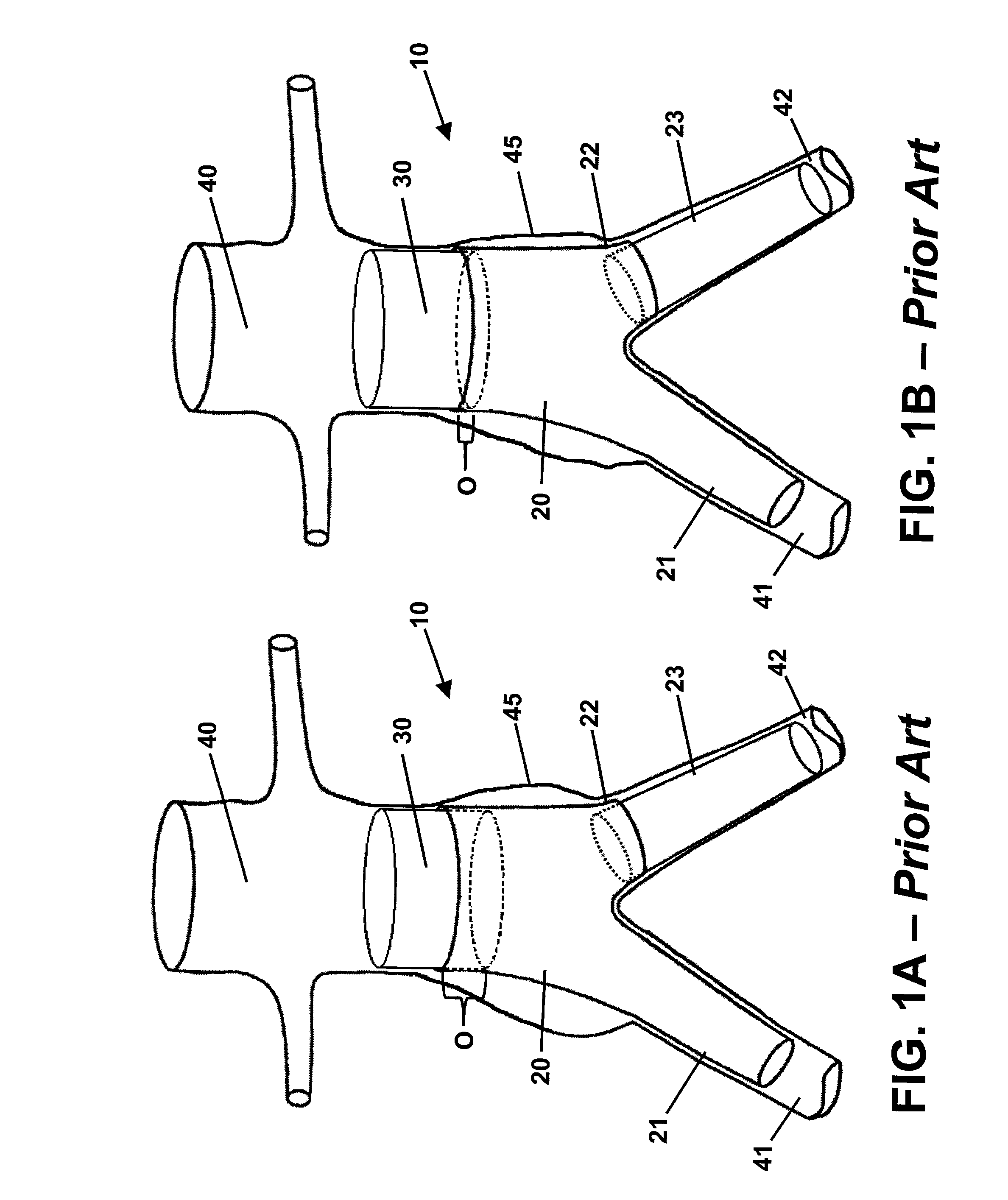
Endoluminal prosthetic assembly and extension method
An endoluminal prosthetic assembly includes a trunk body including first and second elongated branches. The trunk body and elongated branches include a bifurcated body lumen formed therein. The assembly further includes an extension cuff including a cuff branch and an access port. The extension cuff, cuff branch, and access port include a bifurcated cuff lumen formed therein. A portion of the extension cuff is retainably positioned within the trunk body. A portion of the cuff branch is retainably positioned within one of the elongated branches. The cuff lumen is in communication with the body lumen. A method of extending an endoluminal prosthetic assembly deployed in a bifurcated vessel is also provided. The assembly includes a trunk body including first and second elongated branches. A portion of a compressed extension cuff is positioned within the trunk body and the first elongated branch. The compressed extension cuff is expanded into operable engagement with the trunk body and the first elongated branch.
Owner:MEDTRONIC VASCULAR INC
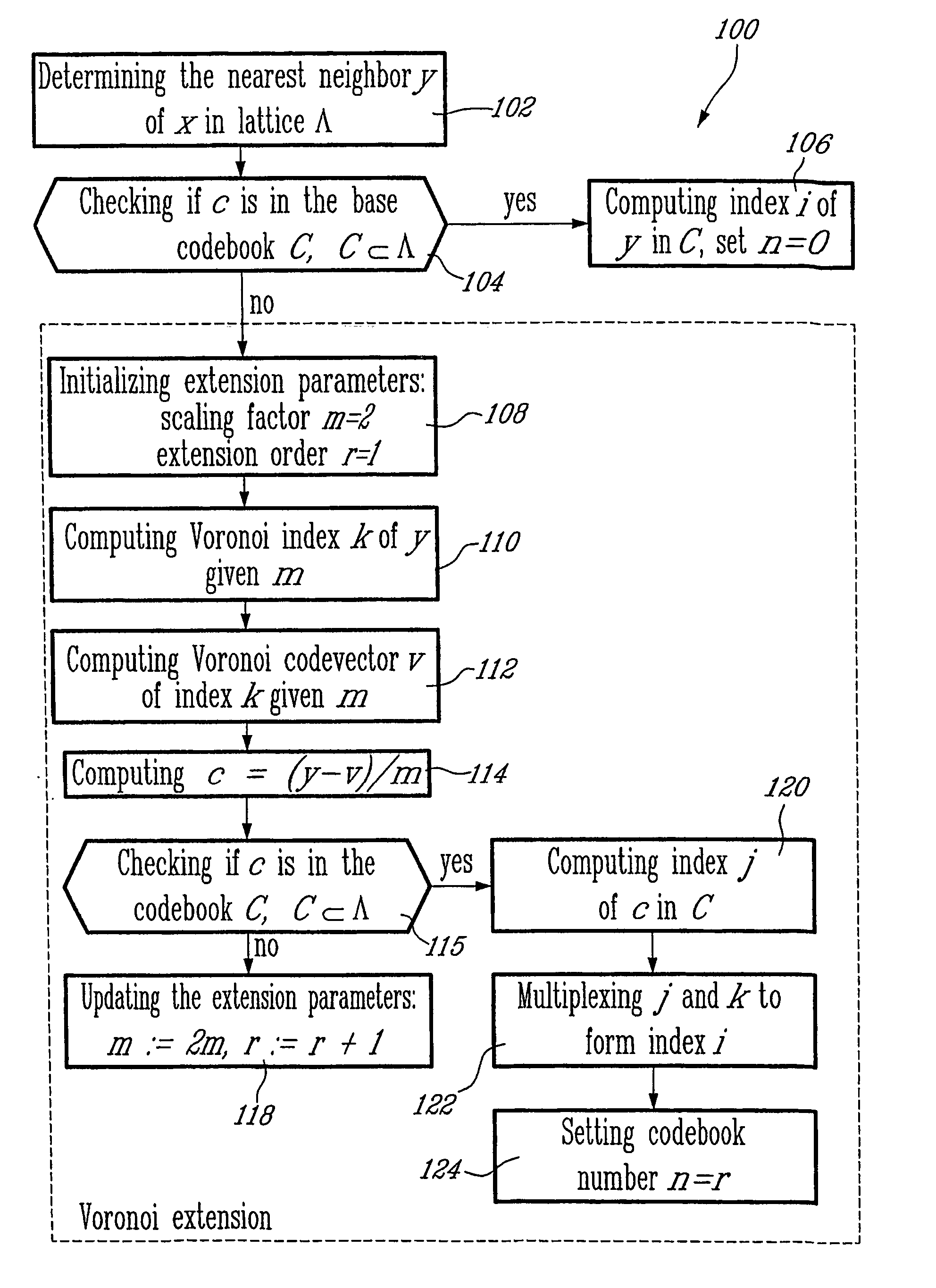
Method and system for multi-rate lattice vector quantization of a signal
InactiveUS7106228B2Increase bitrateAnalogue/digital conversionElectric signal transmission systemsDot matrixLattice vector quantization
The present invention relates to a method and system for multi-rate lattice vector quantization of a source vector x representing a frame from a source signal to be used, for example, in digital transmission and storage systems. The multi-rate lattice quantization encoding method comprises the steps of associating to x a lattice point y in a unbounded lattice Λ; verifying if y is included in a base codebook C derived from the lattice Λ; if it is the case then indexing y in C so as to yield quantization indices if not then extending the base codebook using, for example a Voronoi based extension method, yielding an extended codebook; associating to y a codevector c from the extended codebook, and indexing y in the extended codebook C. The extension technique allows to obtain higher bit rate codebooks from the base codebooks compared to quantization method and system from the prior art.
Owner:VOICEAGE CORP
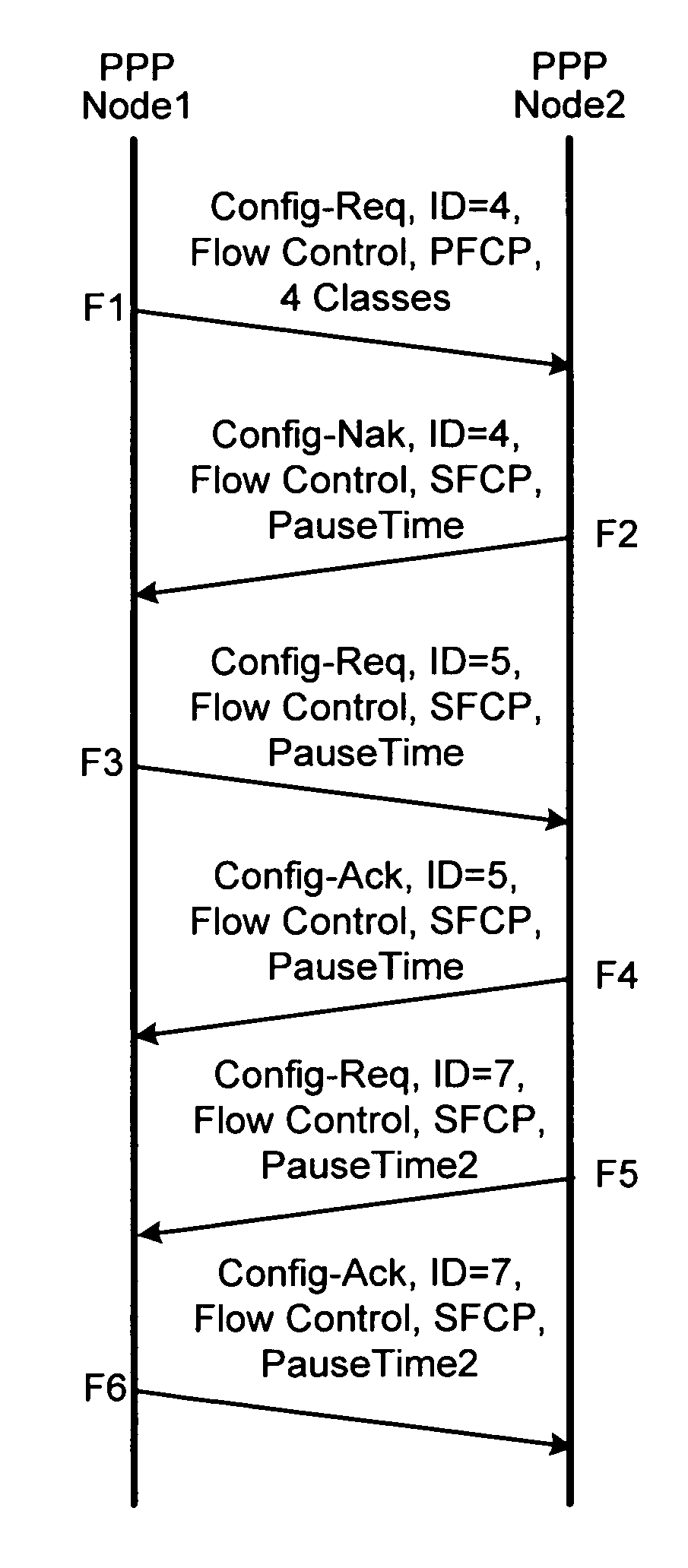
Point-to-point protocol flow control extension
ActiveUS7062568B1Less disruptiveEnergy efficient ICTError preventionPoint-to-Point ProtocolDistributed computing
Method and apparatus are disclosed for flow control over Point-to-Point Protocol (PPP) data links. A method of negotiating such flow control between two PPP peers is disclosed, along with methods for operating flow control across a PPP link. In one embodiment, flow control frames carry an IEEE802.3x MAC control frame payload—the PPP implementation repackages such frames as MAC control frames and passes them to a MAC, which performs flow control. In another embodiment, flow control frames allow flow control commands to be applied differently to different service classes such that PPP flow can be controlled on a per-class basis.
Owner:DELL MARKETING CORP
Automated on-line capacity expansion method for storage device
InactiveUS20040162958A1Input/output to record carriersMemory adressing/allocation/relocationLogical block addressingComputerized system
Owner:HITACHI LTD
Extensible method and apparatus for retrieving files having unique record identifiers as file names during program execution
InactiveUS6119133AData processing applicationsMultimedia data retrievalInformation processingUnique identifier
In an information processing system with a database for storing database records wherein each of said database records has a unique identifier, a method for naming data files comprising the steps of: (a) associating at least one of said database records with additional data specified by a data file name; and (b) naming at least part of said data file name to said unique record identifier for said one of said database records of step (a). In an alternate embodiment, an information processing system with a database for storing database records wherein each of said database records has a unique identifier; at least one data file name for specifying additional data wherein part of each data file name is composed of one of said unique identifiers for one of said database records, a method for locating data files comprising the steps of: retrieving one of said database records; determining said unique identifier for one of said database records; and retrieving any additional data using said data file name.
Owner:IBM CORP
Ephemeris extension method for GNSS applications
ActiveUS20070247354A1Improve accuracyPosition fixationSatellite radio beaconingEphemerisSystems approaches
Systems, methods and devices for improving the performance of Global Navigation Satellite System (GNSS) receivers are disclosed. In particular, the improvement of the ability to calculate a satellite position or a receiver position where a receiver has degraded ability to receive broadcast ephemeris data directly from a GNSS satellite is disclosed. Correction terms can be applied to an approximate long-term satellite position model such as the broadcast almanac.
Owner:QUALCOMM INC
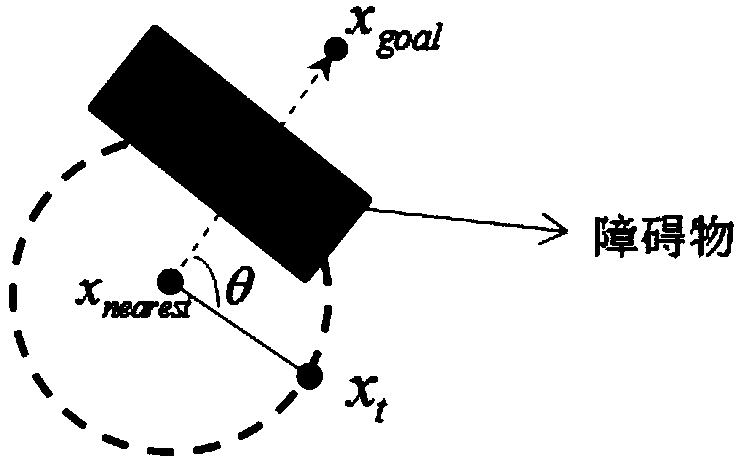
Path planning method and apparatus for robot fast collision avoidance
InactiveCN104155974AImprove execution efficiencyGuaranteed stabilityPosition/course control in two dimensionsCollision detectionSimulation
Owner:SHENZHEN INSTITUTE OF INFORMATION TECHNOLOGY
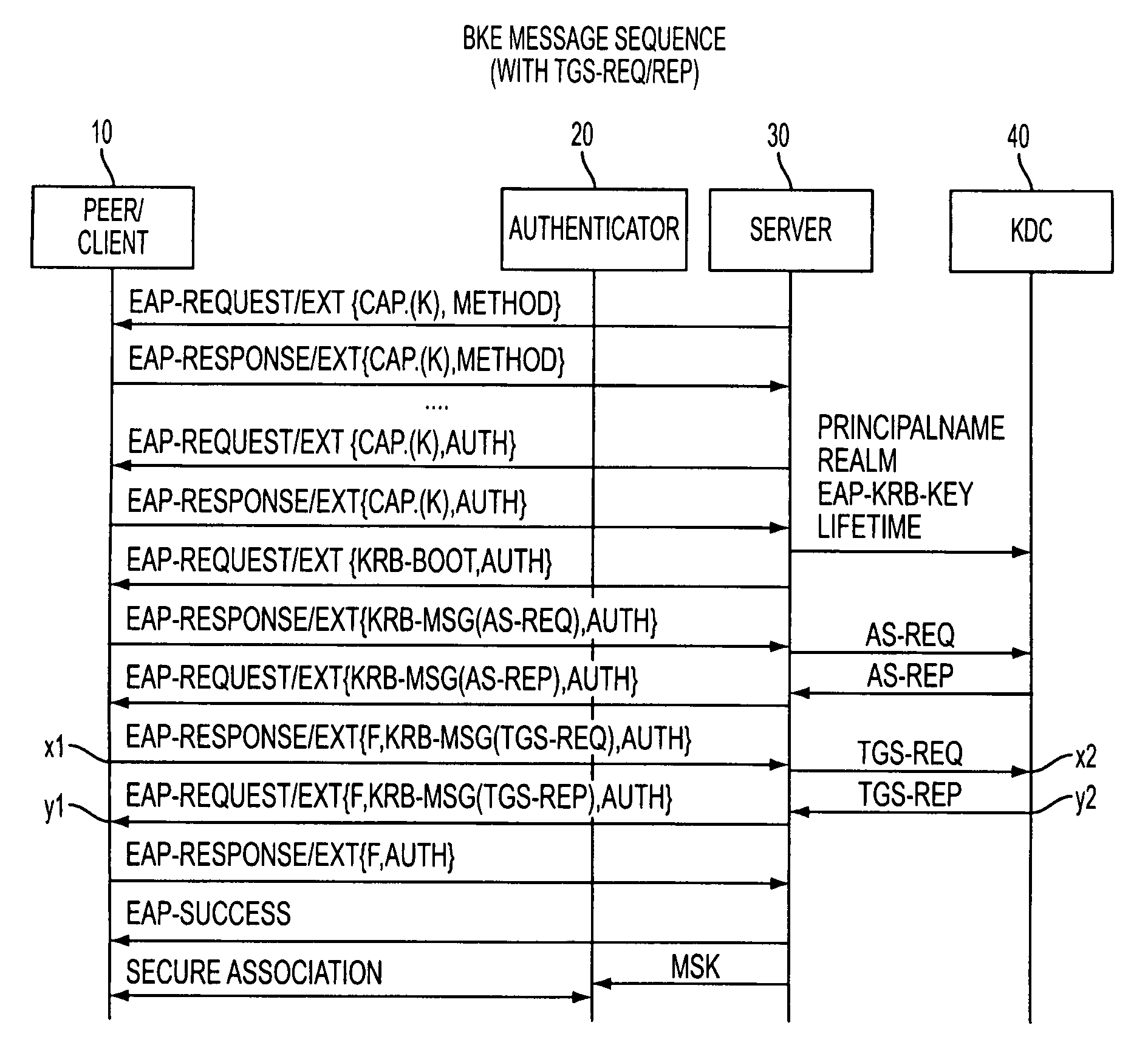
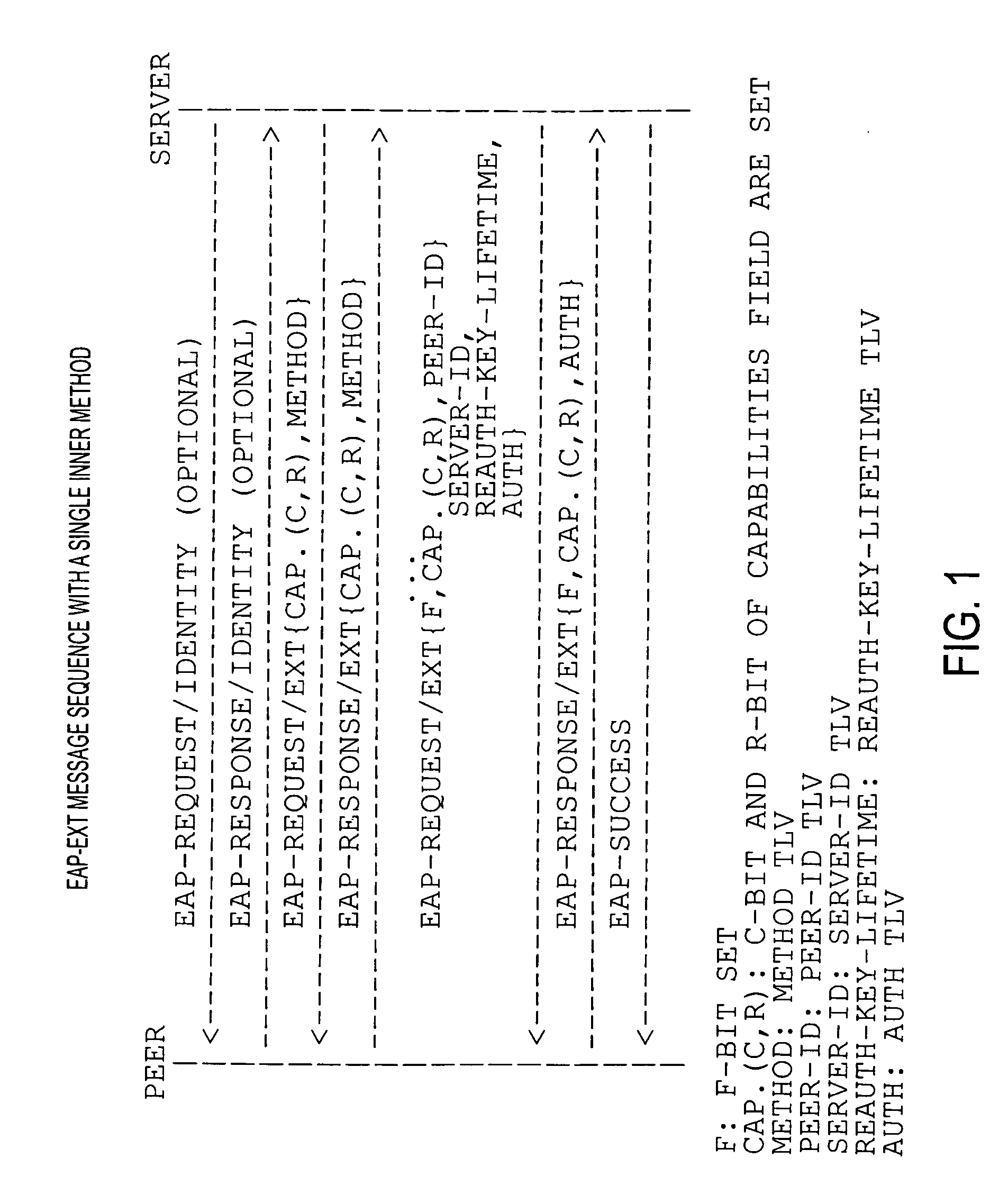
Bootstrapping Kerberos from EAP (BKE)
InactiveUS20080178277A1Improve performanceDigital data processing detailsComputer security arrangementsProtocol for Carrying Authentication for Network AccessSession key
The preferred embodiments involve a mechanism to bootstrap Kerberos from EAP in which EAP is used for initial network access authentication and Kerberos is used for provisioning session keys to multiple different protocols. The preferred embodiments make use of an EAP extension method (EAP-EXT) to realize the mechanism.
Owner:TELCORDIA TECHNOLOGIES INC
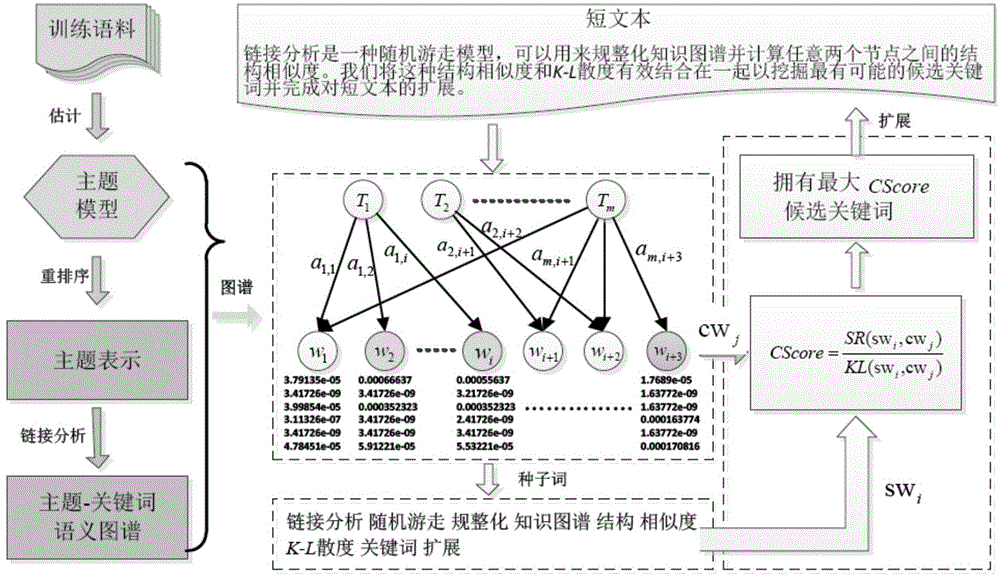
Short text characteristic expanding method based on semantic atlas
ActiveCN104391942AImprove classification performanceSolve the sparsity problemSemantic analysisSpecial data processing applicationsGraph spectraData set
The invention discloses a short text characteristic expanding method based on a semantic atlas. The method includes the steps: performing subject modeling by the aid of a training data set of a short text, and extracting subject term distribution; reordering the subject term distribution; building a candidate keyword dictionary and a subject-keyword semantic atlas; calculating comprehensive similarity degree evaluation of candidate keywords and seed keywords based on a link analysis method, and selecting the most similar candidate keywords to finish expanding the short text. Compared with a short text characteristic representation method based on a language model, the method is simple to operate and high in execution efficiency, and semantic correlation information between the keywords is sufficiently used. Compared with a traditional short text characteristic representation method based on a word bag model, the problems of data sparseness and semantic sensitivity are effectively relieved, and the method is independent of external large-scale auxiliary training corpus or a search engine.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
Point-to-point protocol flow control extension
InactiveUS7558872B1Less disruptiveEnergy efficient ICTError preventionPoint-to-Point ProtocolDistributed computing
Method and apparatus are disclosed for flow control over Point-to-Point Protocol (PPP) data links. A method of negotiating such flow control between two PPP peers is disclosed, along with methods for operating flow control across a PPP link. In one embodiment, flow control frames carry an IEEE802.3x MAC control frame payload—the PPP implementation repackages such frames as MAC control frames and passes them to a MAC, which performs flow control. In another embodiment, flow control frames allow flow control commands to be applied differently to different service classes such that PPP flow can be controlled on a per-class basis.
Owner:DELL MARKETING CORP
Methods and apparatus for address map optimization on a multi-scalar extension
InactiveUS20050251649A1Reduces memory conflictReduces thread delayMemory adressing/allocation/relocationConcurrent instruction executionData storingData store
Methods and systems are disclosed for staggered address mapping of memory regions in shared memory for use in multi-threaded processing of single instruction multiple data (SIMD) threads and multi-scalar threads without inter-thread memory region conflicts and permitting transition from SIMD mode to multi-scalar mode without the need for rearrangement of data stored in the memory regions.
Owner:SONY COMPUTER ENTERTAINMENT INC
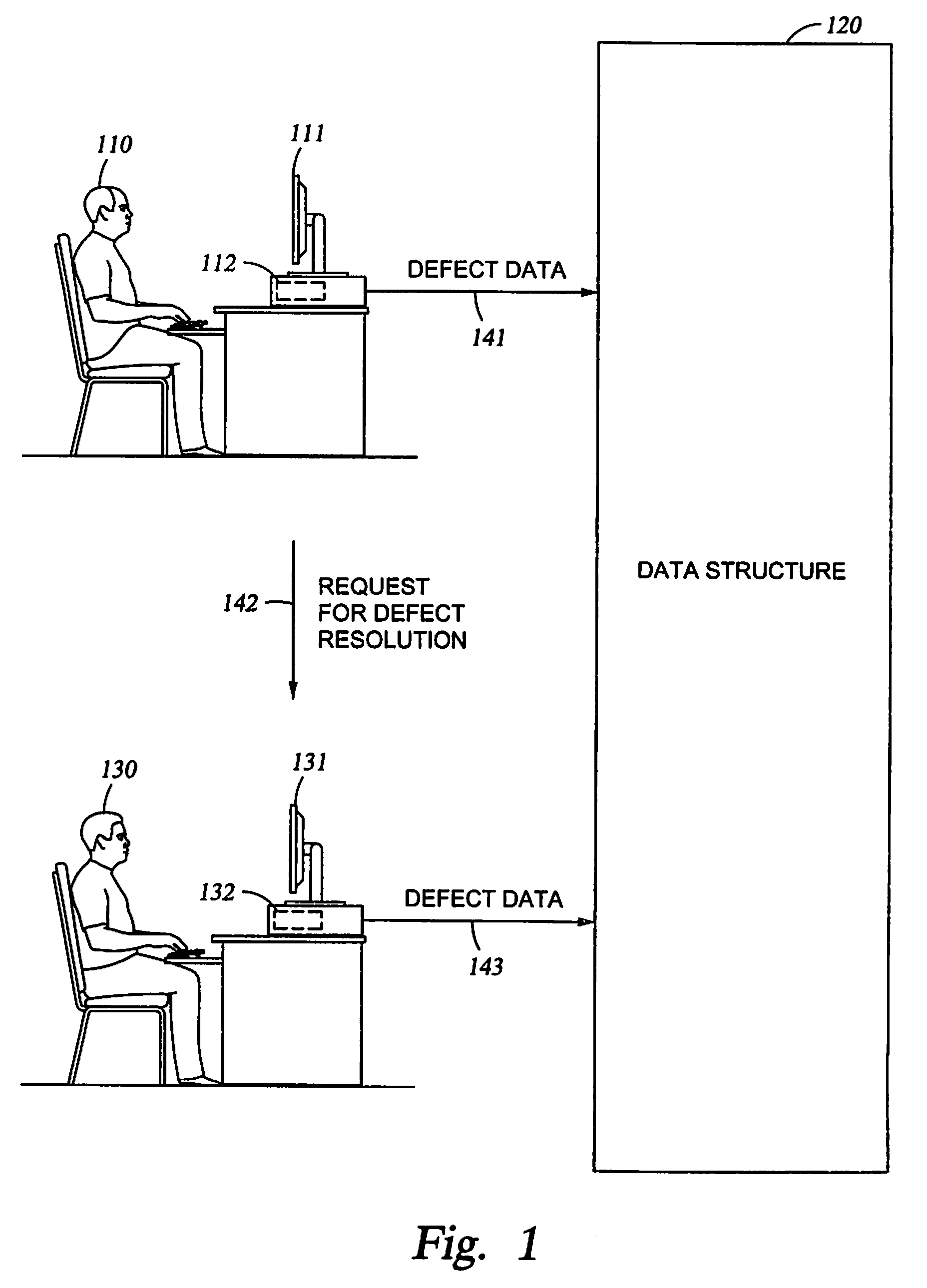
Defect Resolution Methodology and Data Defects Quality/Risk Metric Model Extension
InactiveUS20080201612A1Nuclear monitoringDigital computer detailsSoftware developmentExtension method
Methods, systems, and articles of manufacture for analyzing defects associated with a software development project. Descriptions of defects identified during the testing of a software product may be stored in a data structure. One or more of the defects may be identified as data defects. If data defects are determined to be the dominant class of defects in the data structure, the data defects may be analyzed to determine a cause for one or more data defects. For example, the focus areas affected by the defects, the trends over time of the defects, the particular types of the data defects, the stability of the system, etc. may be analyzed to determine a cause for the data defects. Therefore, corrective measures may be taken based on the identified cause of the one or more data defects.
Owner:IBM CORP
Non-destructive detection method of pulse-excited infrared thermal wave phase of fixed viewing field
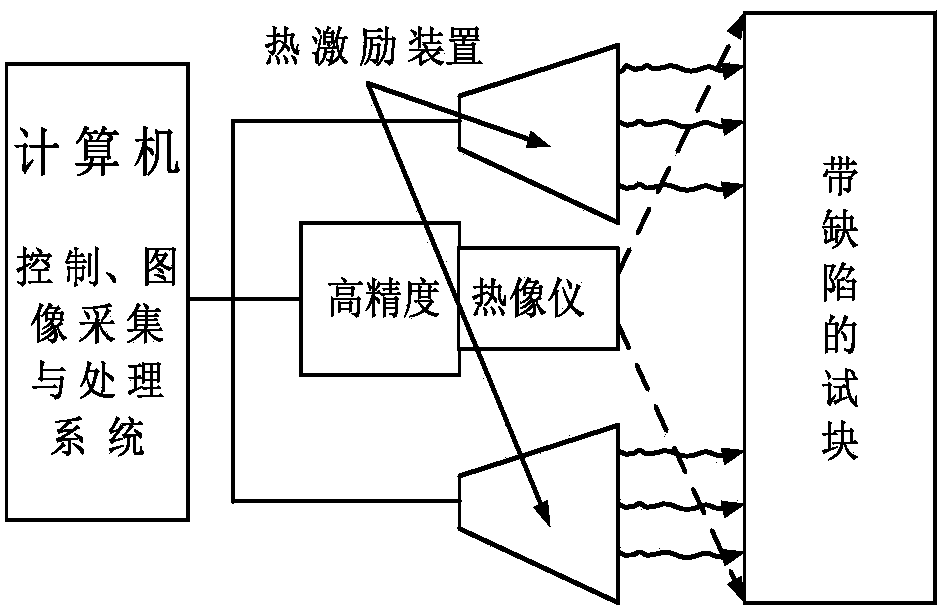
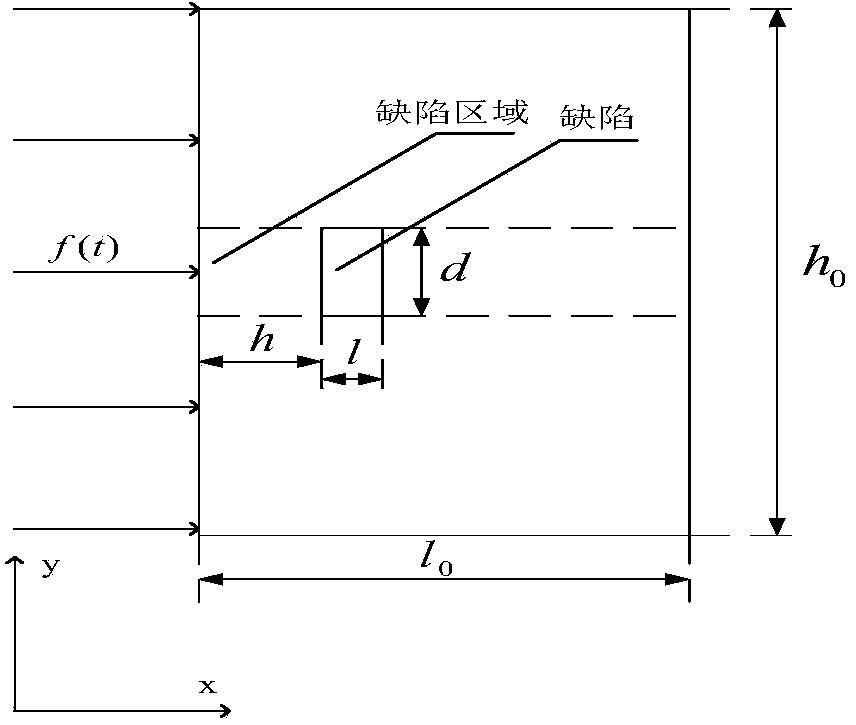
InactiveCN104359944AEasy to detectFlexible useMaterial flaws investigationFrequency spectrumImage sequence
The invention relates to a non-destructive detection method of pulse-excited infrared thermal wave phase of a fixed viewing field. The non-destructive detection method comprises the following steps: comprehensively applying a multiple-modulation Zoom-FFT refining spectrum method, a thermal-wave data fitting extension method and a zero-phase digital filter method, and carrying out high-accuracy spectral analysis on acquired continuous equally-spaced infrared thermal-wave image sequences before and after thermal excitation, thus quickly obtaining precise ultralow-frequency thermal-image phase diagram and amplitude diagram, and further realizing detection and recognition for defects or damages of equipment. Compared with the prior art, the non-destructive detection method has the beneficial effects that not only can the acquisition frequency, the acquisition time, the acquisition frame number and the refining degree of analysis of thermal images be flexibly set, but also the detection speed, the refining degree and the precision degree can be increased by ten times respectively, the multiplied increase of the detection effect and the detection depth of the defects also can be realized, simultaneously the requirement for computer hardware is also reduced, so that the method is flexible in use, is especially suitable for non-destructive detection of the infrared thermal wave on site and has a wide application prospect.
Owner:PLA SECOND ARTILLERY ENGINEERING UNIVERSITY
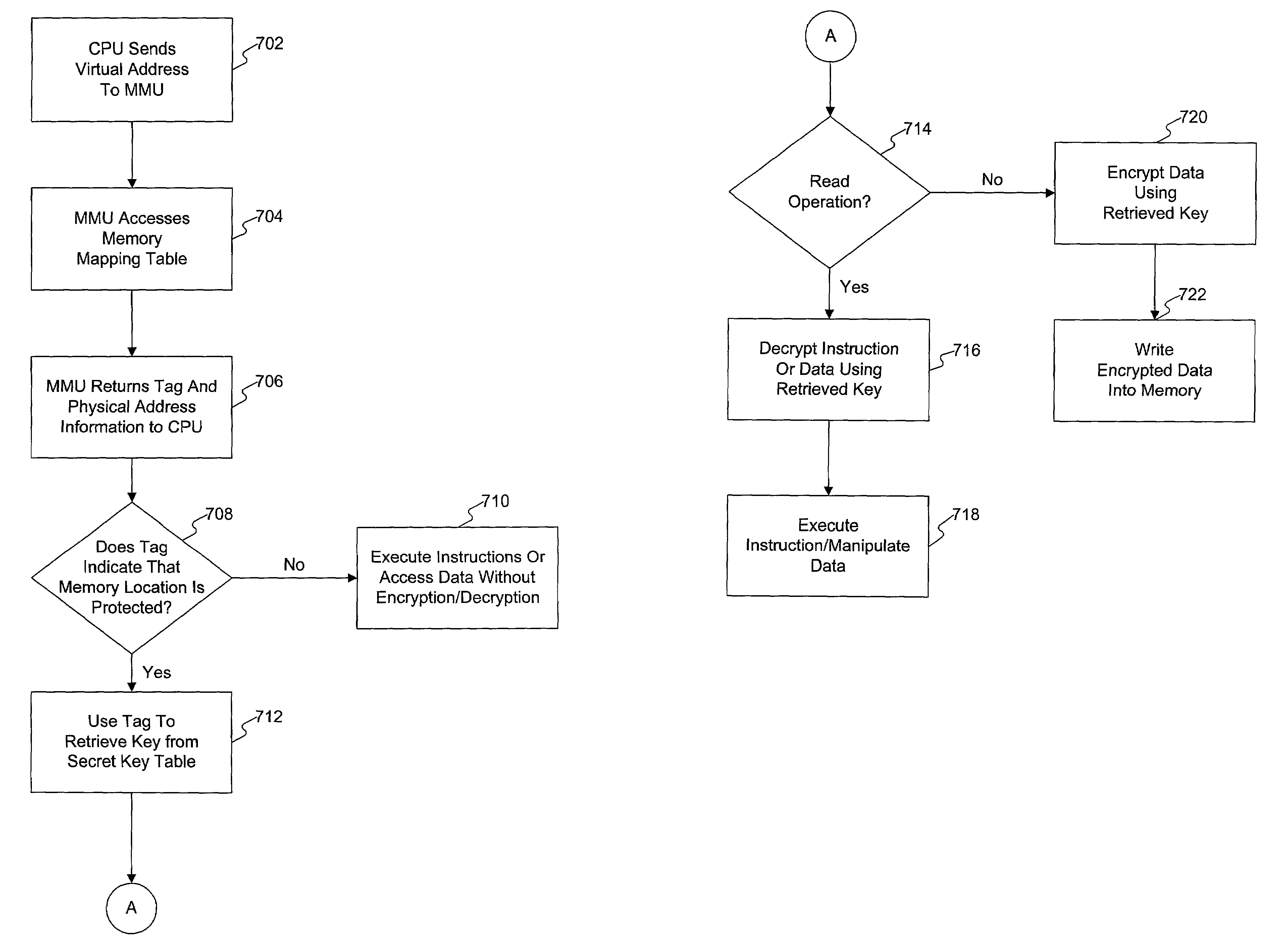
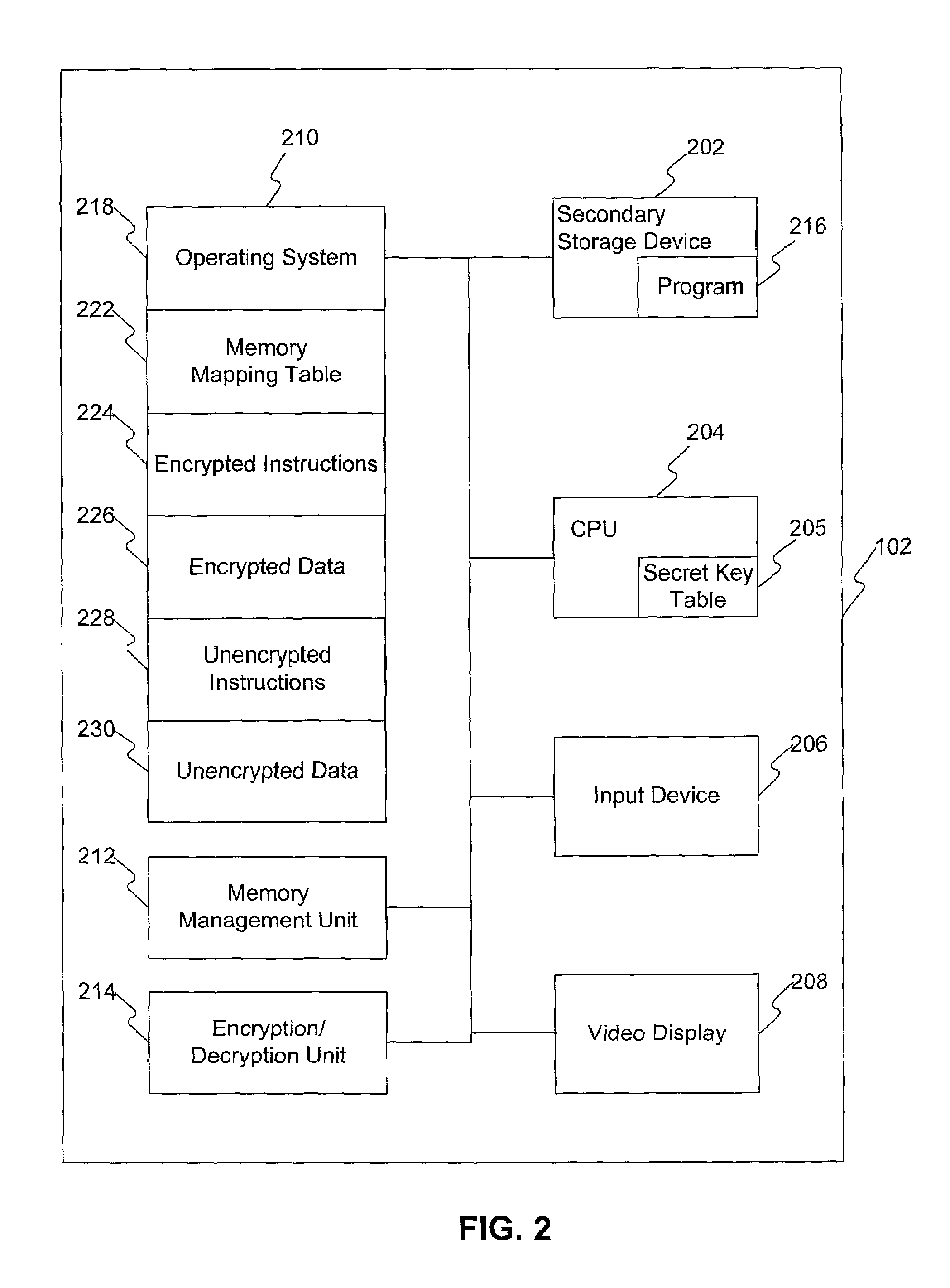
Secure CPU and memory management unit with cryptographic extensions
ActiveUS7107459B2Unauthorized memory use protectionHardware monitoringManagement unitMemory management unit
Methods and systems for accessing information in and loading encrypted information to memory. A processor provides virtual address information to a memory management unit. In response, the memory management unit retrieves a key tag and physical address information corresponding to the virtual address information. The memory management unit then sends the key tag and physical address information to the processor. The processor then determines whether a memory location corresponding to the physical address information is encrypted based on the key tag, and retrieves a secret key using the key tag based on the determining. Thereafter, information read from the memory location is decrypted using the secret key.
Owner:ORACLE INT CORP
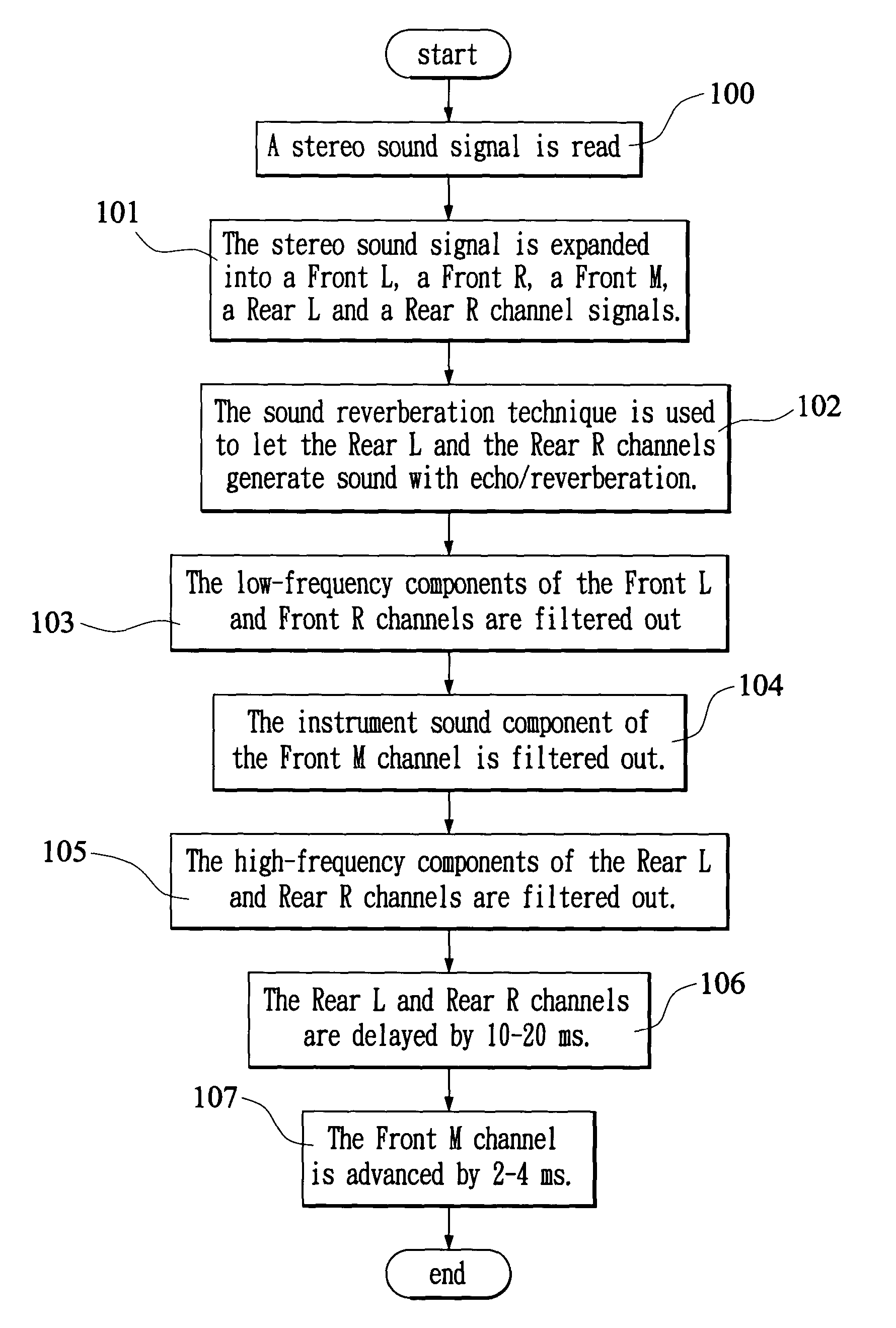
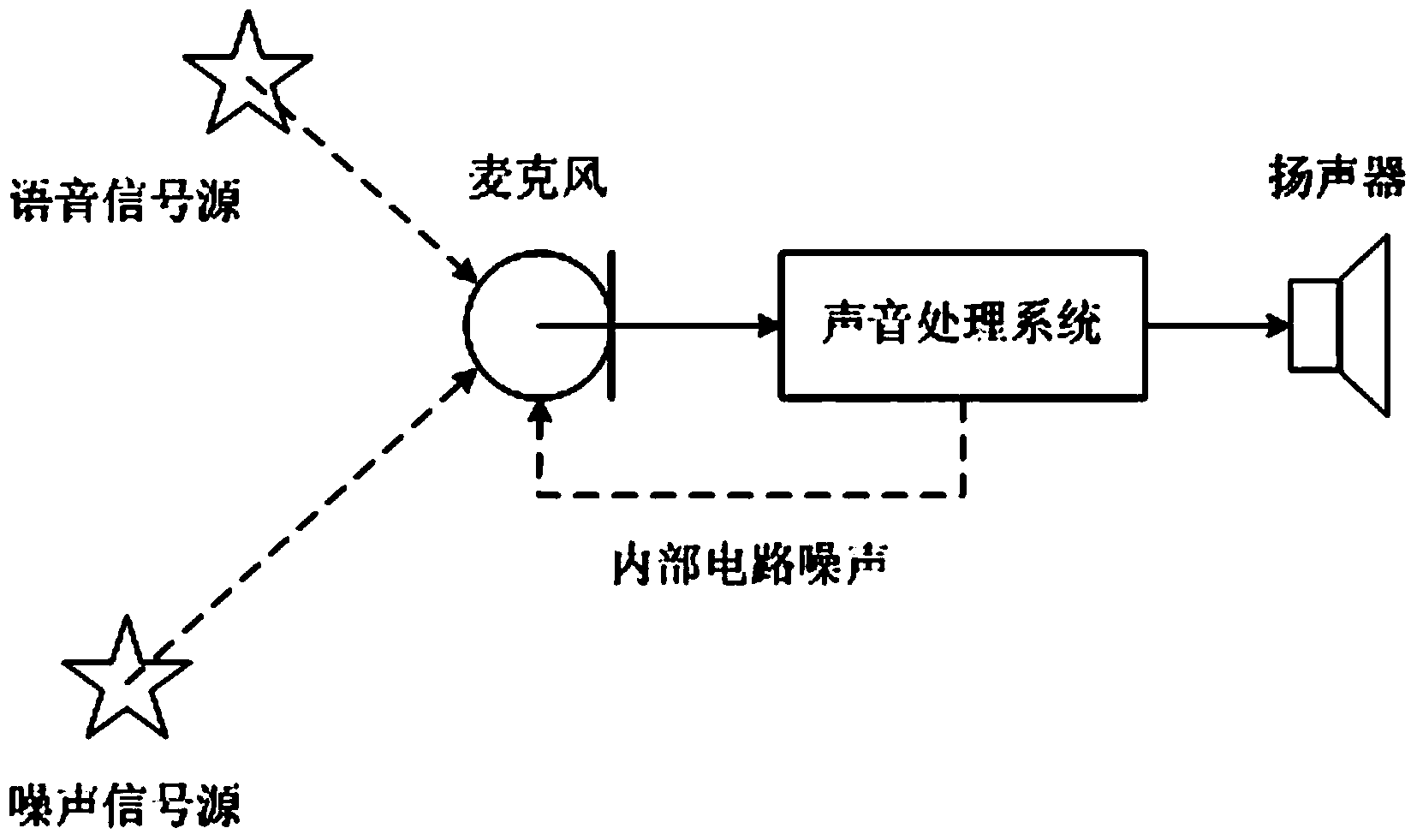
Multi-channel surround sound expansion method
InactiveUS20050063551A1Pseudo-stereo systemsLoudspeaker spatial/constructional arrangementsVocal tractEngineering
A multi-channel surround sound expansion method is proposed. First, a two-channel stereo sound is read and then expanded into a Front L channel, a Front R channel, a Front M channel, a Rear L channel and a Rear R channel sound signals by means of the Hafler technique. Next, the sound reverberation technique is used to let the Rear L channel and Rear R channel sound signals generate sound with echo / reverberation. Finally, the Rear L channel and Rear R channel sound signals are delayed by a first time value, and the Front M channel sound signal is advanced by a second time value to emphasize the front sound field and the human voices, thereby producing a 3D sound field surrounding a listener.
Owner:CYBERLINK
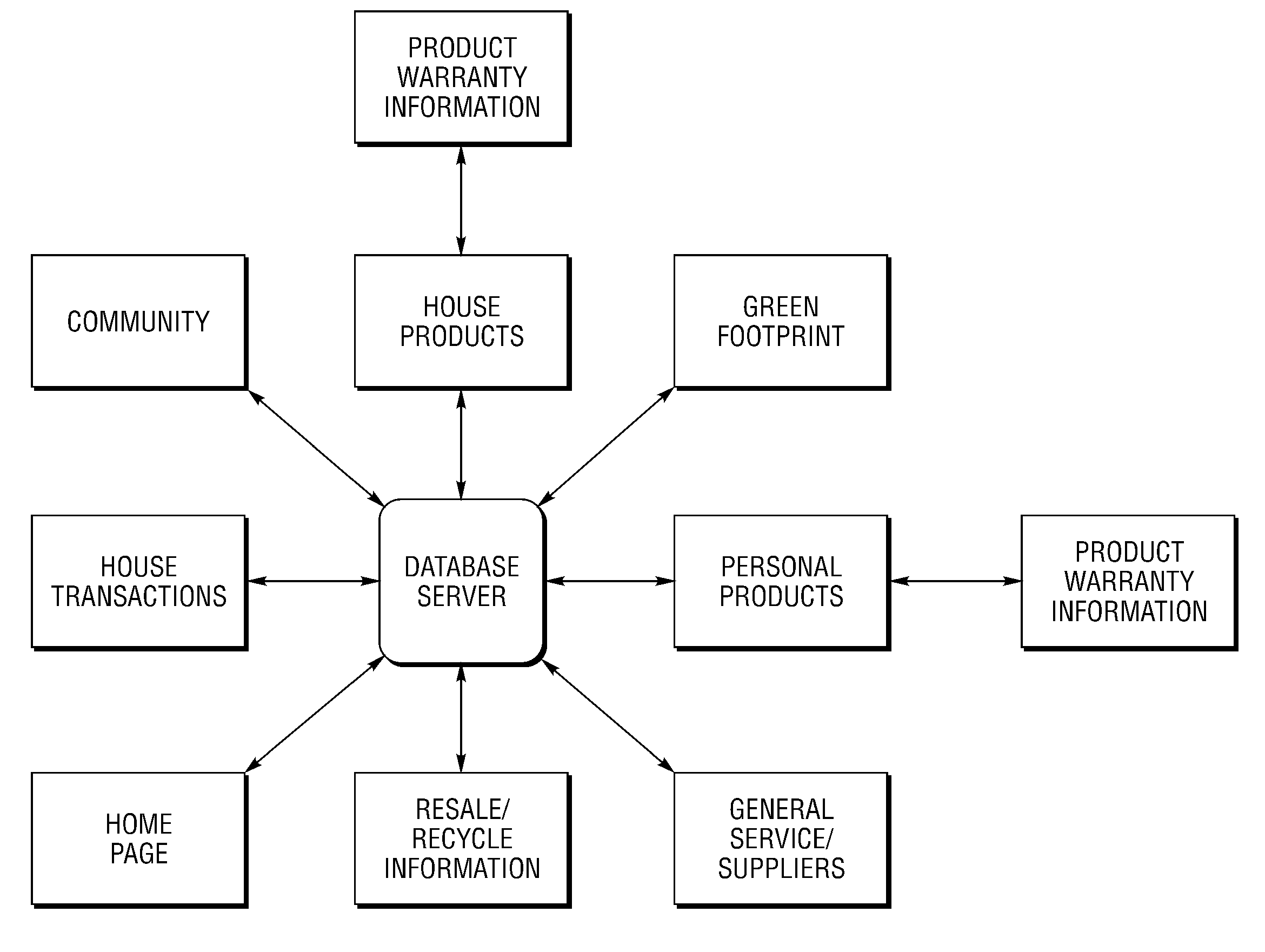
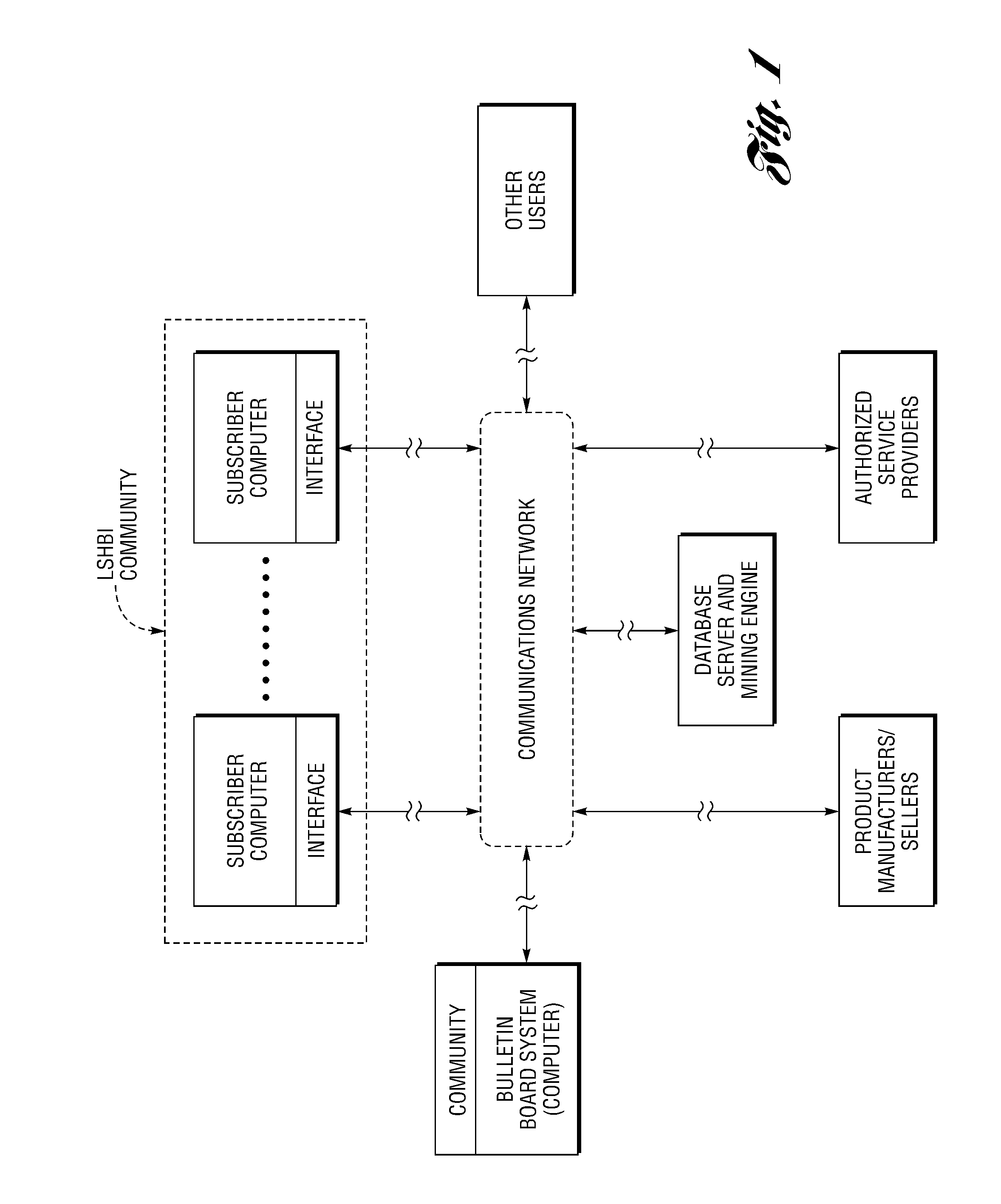
Scalable method and system for connecting, tracking and facilitating warranty, maintenance, service and replacement of products within a community of residential housing and/or commercial building inventories or units over a communications network
A scalable method and system are provided for connecting, tracking and facilitating warranties, recalls, maintenance, repair and upgrade / replacement and purchase of new products within a community of large-scale, homogeneous building inventories (LSHBI) or units over a communications network. The method includes providing a database of electronic data at a computer site. The data includes building product data that uniquely identifies building products common to and contained within each housing unit in a community of subscribing building units. The electronic data also includes service provider data that identifies service providers for the building products and warranty data that identifies warranties and warranty dates for at least one of the building products and services provided by the service providers. The method further includes analyzing the electronic data to determine whether an action to facilitate the maintenance, repair or replacement of at least one building product is to be performed.
Owner:MOSHER DOYLE W
Self-adaptive denoising method and system based on sub-band noise analysis
ActiveCN103871421ASignificant Gain DifferenceImprove signal-to-noise ratioSpeech analysisTarget signalAdaptive denoising
The invention relates to the field of voice technologies, in particular to a self-adaptive denoising method based on sub-band noise analysis. The method includes the steps that firstly, framing and short time frequency domain transformation are conducted on input time domain audio signals with noise, and then frequency domain audio signals with noise are generated; secondly, a noise energy spectrum of the frequency domain audio signals with noise is estimated through a minimum value tracking method; thirdly, the posterior signal to noise ratio and the prior signal to noise ratio of the noise energy spectrum are calculated; fourthly, through a nonlinear gain extension method, denoising gains of all time frequency units are calculated through the posterior signal to noise ratio and the prior signal to noise ratio; fifthly, smoothing filtering is conducted on the denoising gains of all the time frequency units to reduce tone quality distortion; sixthly, the denoising gains act on all the time frequency units of the audio signals with noise in the first step, and then denoised frequency domain audio signals are acquired; seventhly, short time frequency domain inverse transformation is conducted, and then the final denoised time frequency audio signals are acquired and output. According to the method and system, stable noise in target signals can be greatly lowered.
Owner:厦门莱亚特医疗器械有限公司
Method and device for enquire enquiry extending as well as related searching word stock
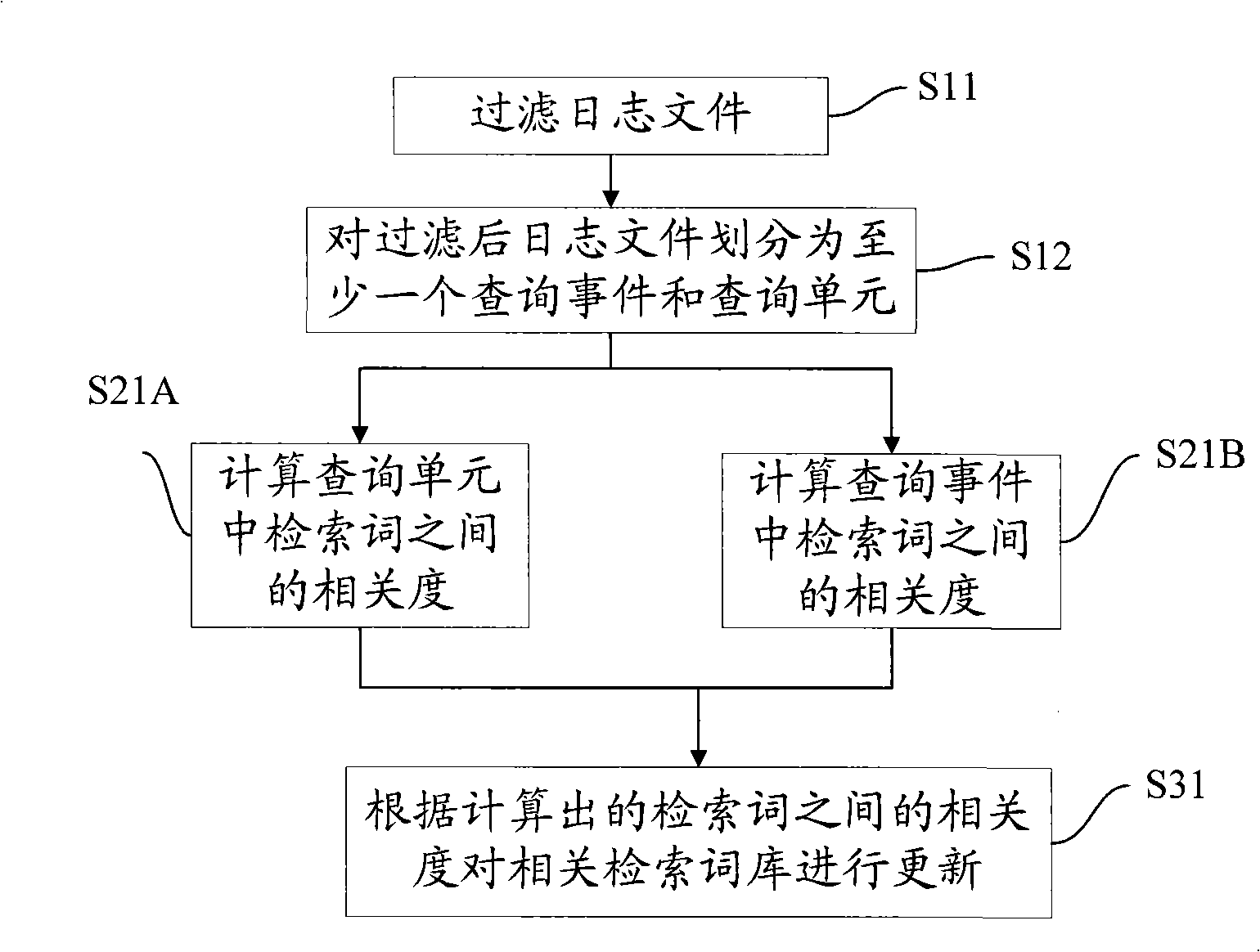
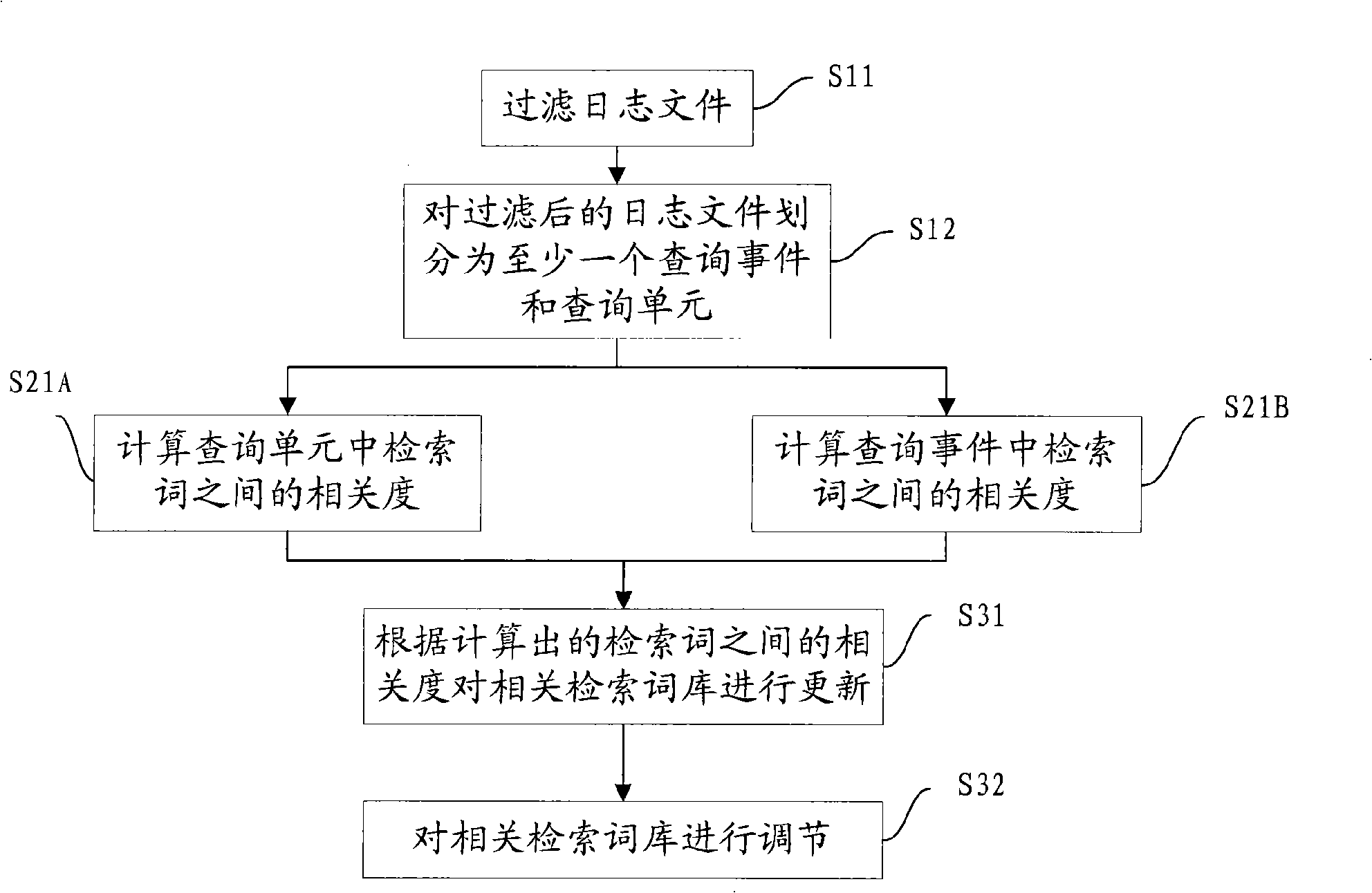
ActiveCN101281523AReduce query burdenImprove precisionSpecial data processing applicationsSearch wordsAccess time
The invention discloses a method and a device for query expansion and a correlation retrieval word library, which solves the problem that a current searching system can not automatically and effectively realize query expansion and provide effective support for retrieval behaviors of a user. The method comprises the steps of dividing the query behavior records of a user into at least a query event and query units according to the identity and access time of the user; calculating the correlation degrees between retrieval words in the query units and the query event periodically, and updating a correlation retrieval word library according to the calculated correlation degrees; and retrieving correlation retrieval words having a close correlation degree to the retrieval word inputted by the user in the correlation retrieval word library, thus forming a query expansion result. The invention can be applied to various searching systems, effectively assist users to query, reduce query load of the users, and improve the searching efficiency of the users.
Owner:NEW FOUNDER HLDG DEV LLC +2
Interface expanding method and device for tablet personal computer
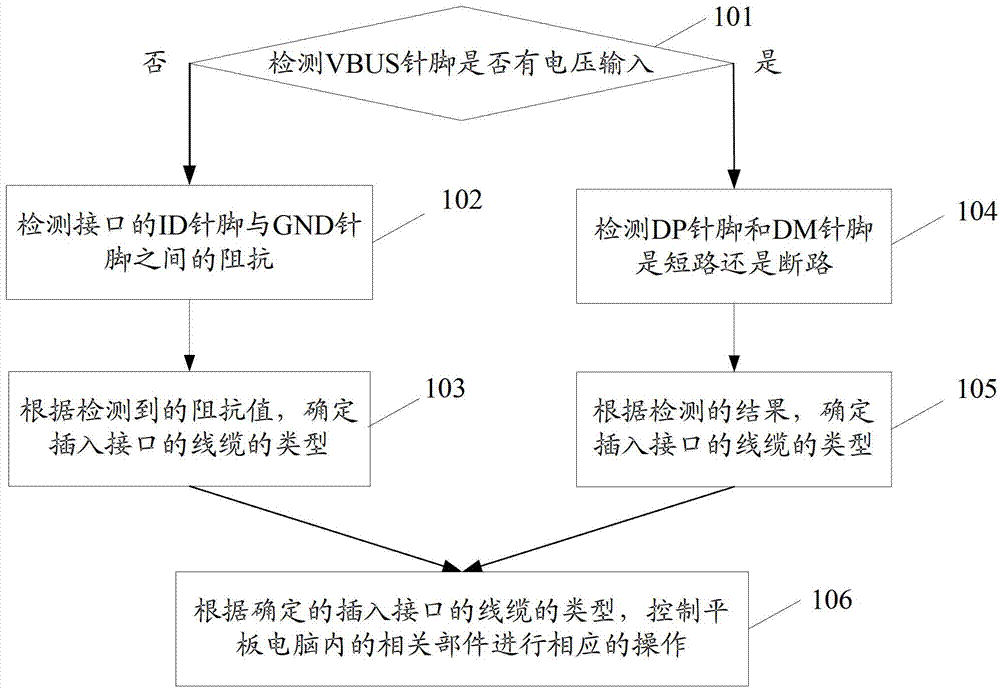
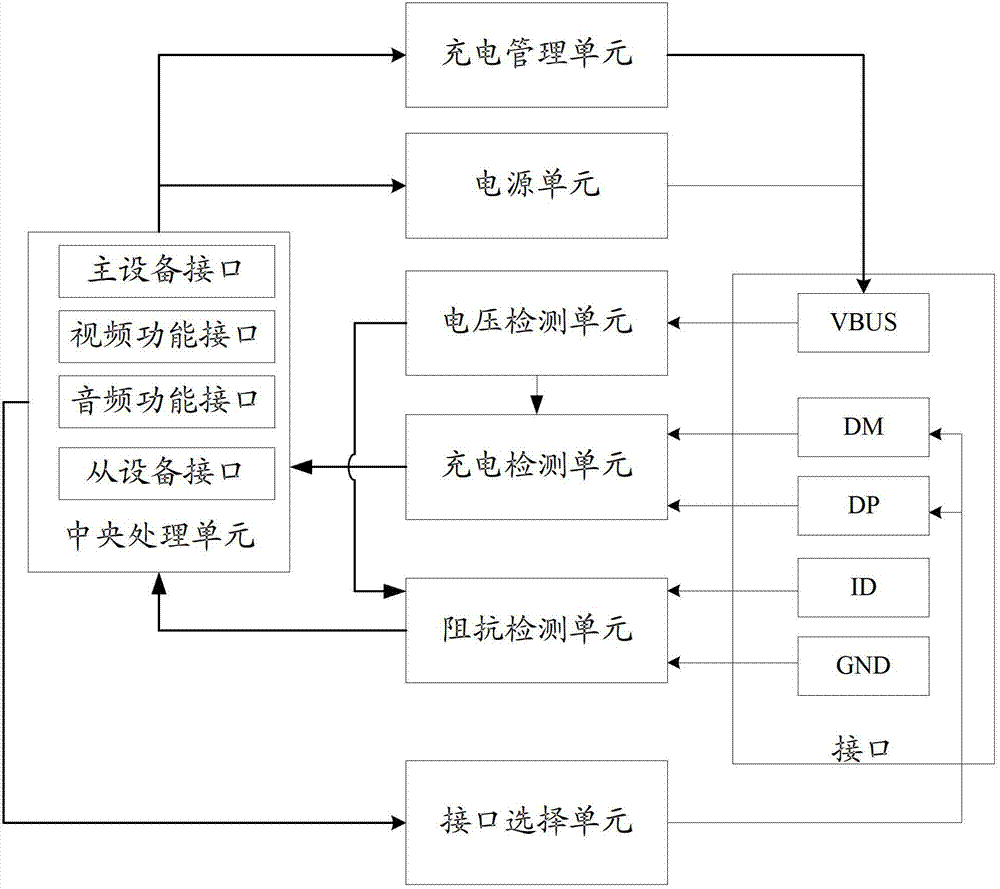
ActiveCN102880238AError detection/correctionDigital data processing detailsPersonal computerElectrical impedance
The invention provides an interface expanding method and device for a tablet personal computer. The device is embedded in a tablet personal computer, and comprises an interface, a voltage detecting unit, an impedance detecting unit, a charging detecting unit, and a central processing unit, wherein the interface is used for inserting a cable; the voltage detecting unit is used for detecting whether voltage is input in a power supply pin (VBUS), if not, informing the impedance detecting unit, if yes, informing the charging detecting unit; the impedance detecting unit is used for detecting the impedance between a signal identification pin (ID) and a grounded pin (GND) of the interface after the notice sent from the voltage detecting unit is detected; the charging detecting unit is used for detecting whether a digital positive pin (DP) and a digital minus (DM) pin are in a short circuit or open circuit; the central processing unit is used for determining the type of the cable inserted in the interface according to the impedance value detected by the impedance detecting unit or the result detected by the charging detecting unit, and controlling the associated parts in the tablet personal computer to perform corresponding operations. With the adoption of the method and the device provided by the invention, the cables in various types can be connected on micro USB (universal serial bus) interfaces or mini USB interfaces without using an external expanding apparatus.
Owner:高新兴物联科技股份有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com