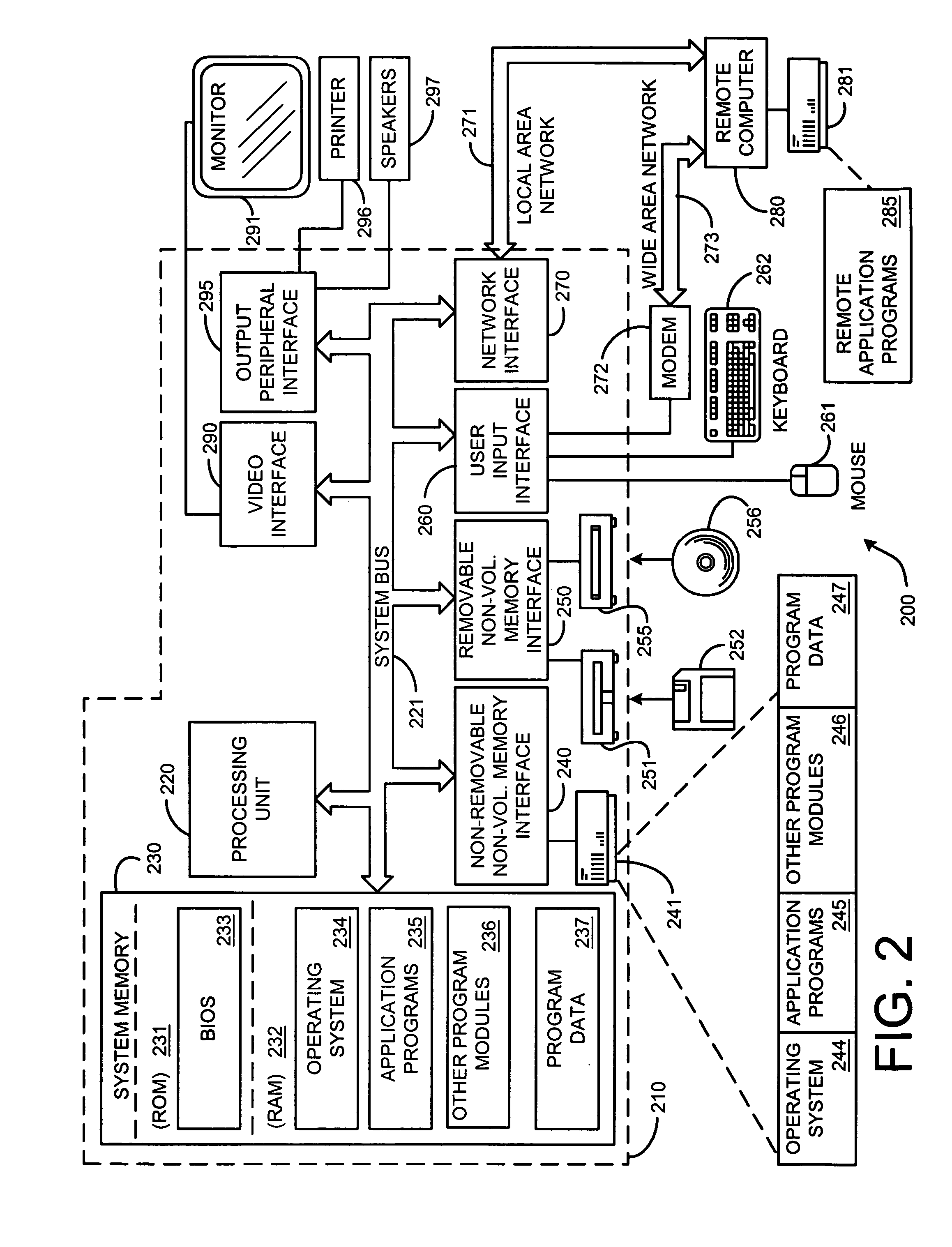
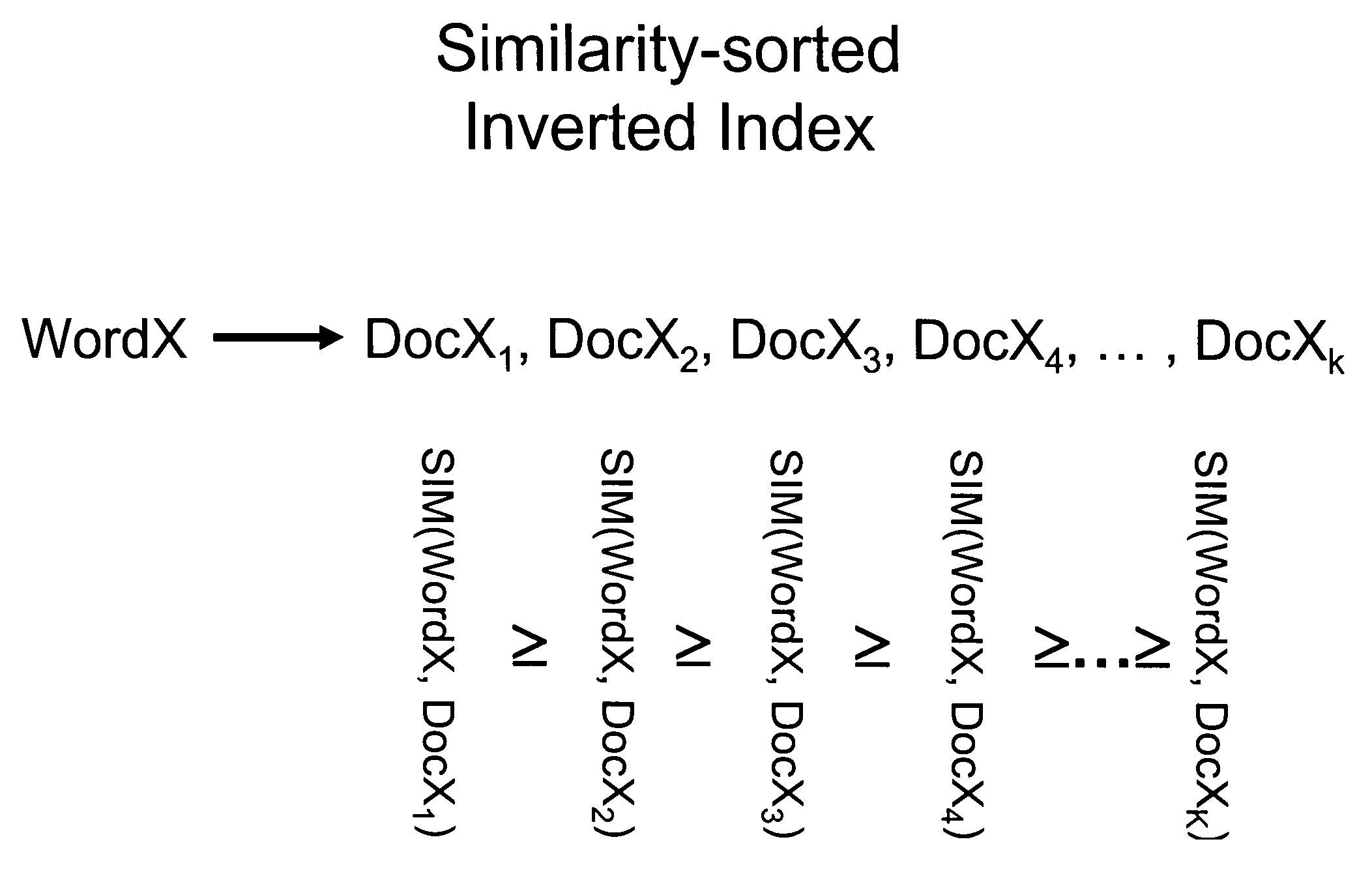
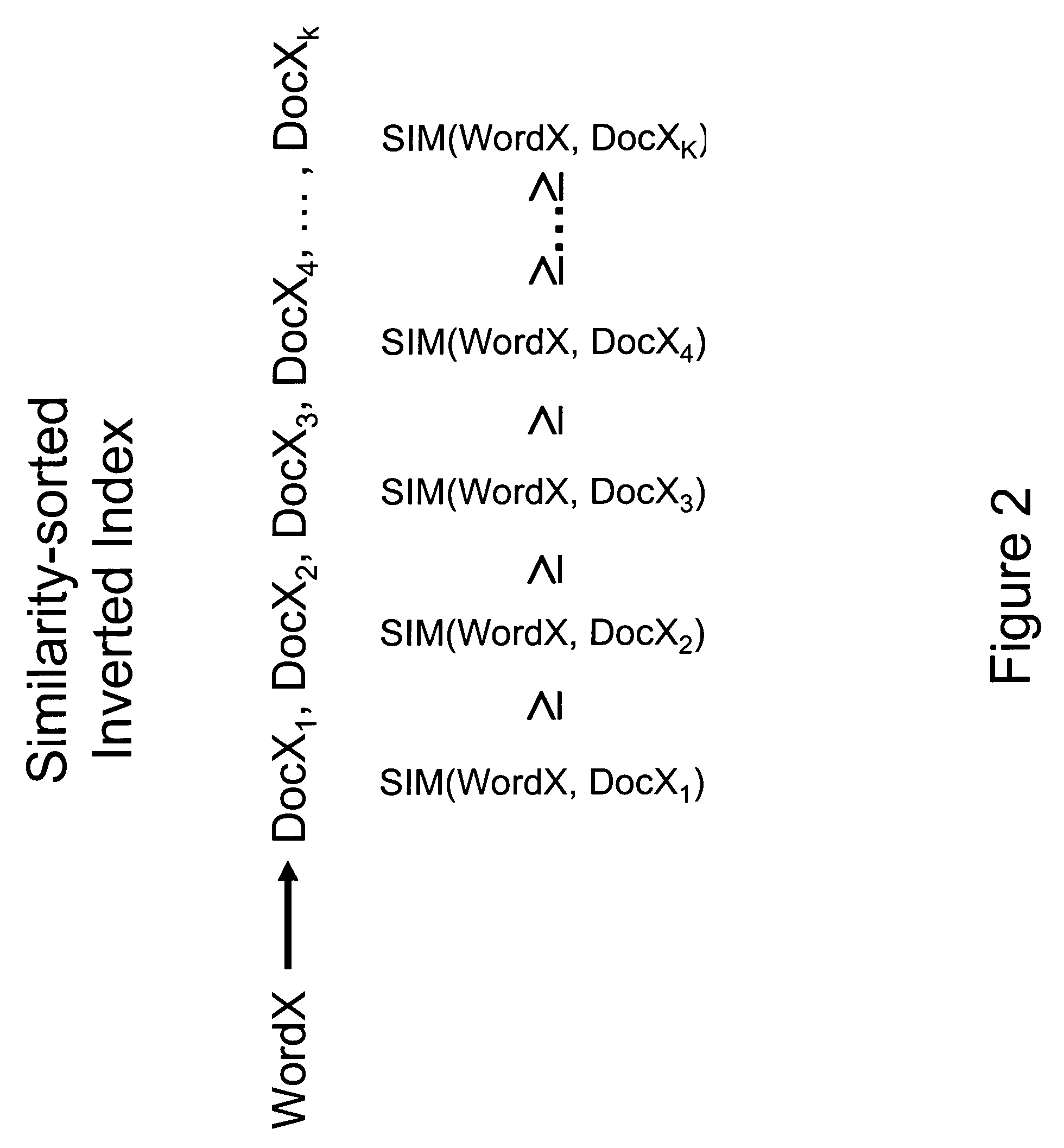
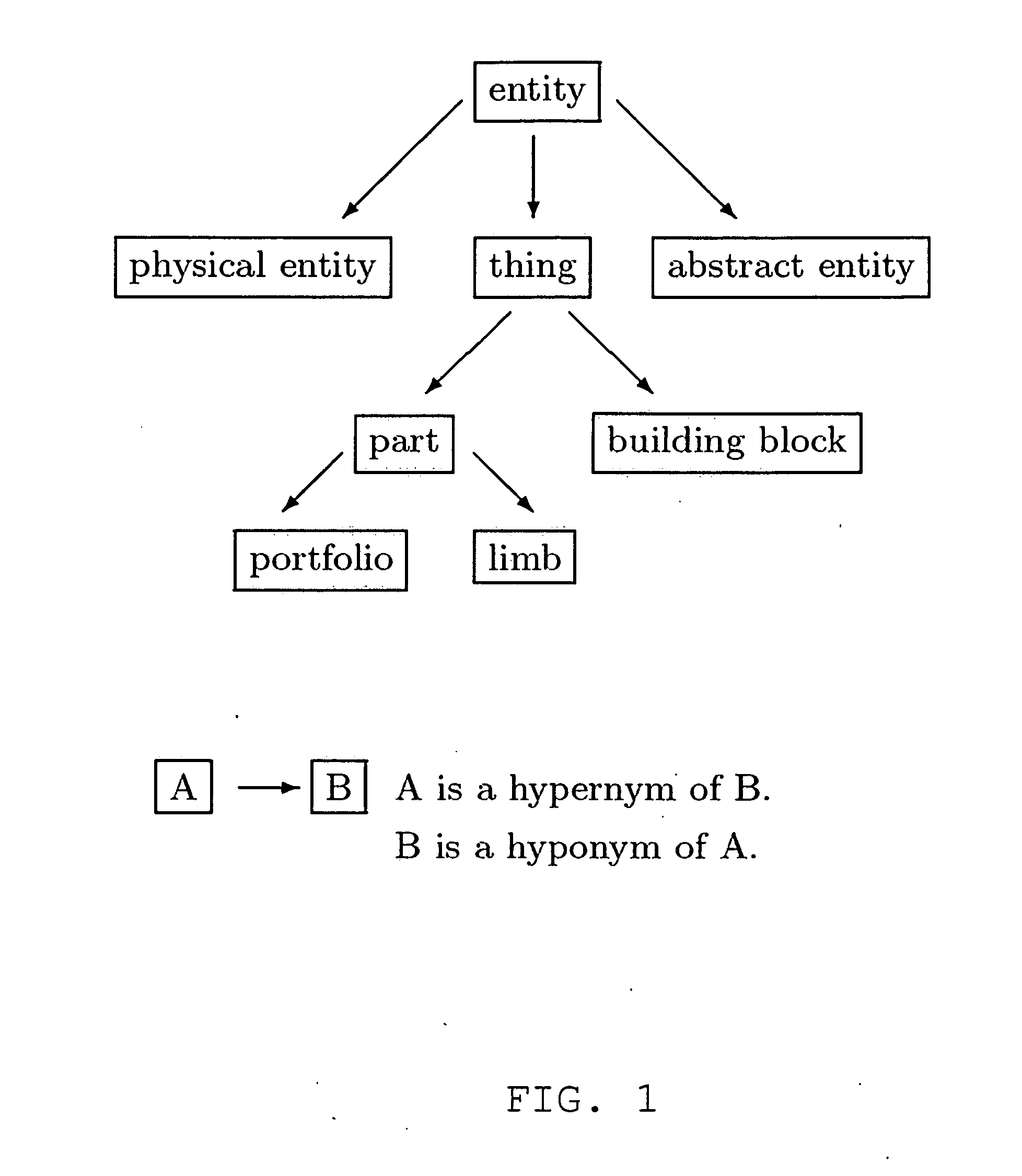
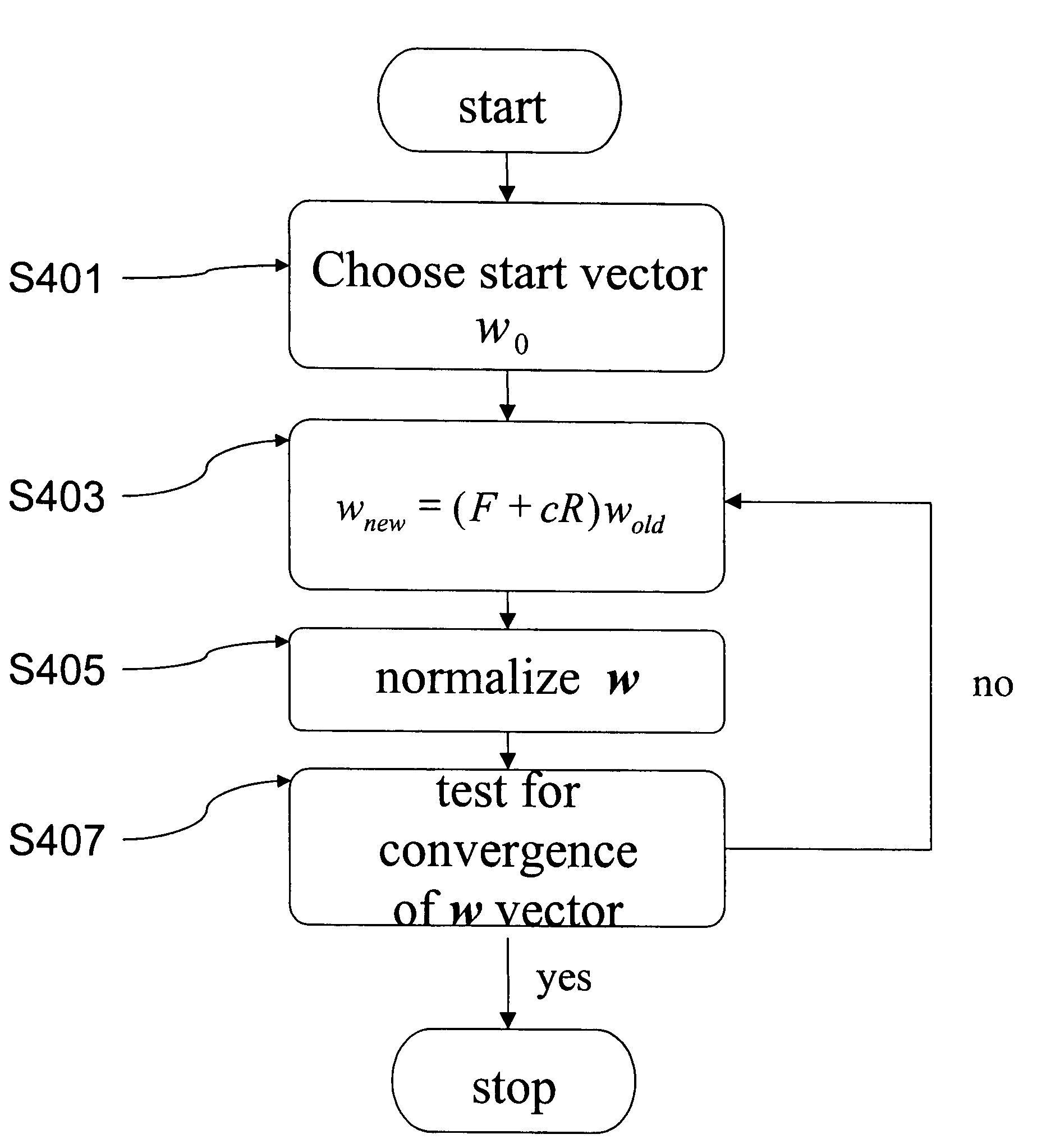
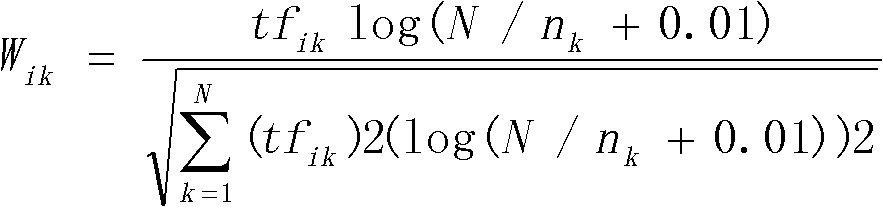Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
239 results about "Link analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
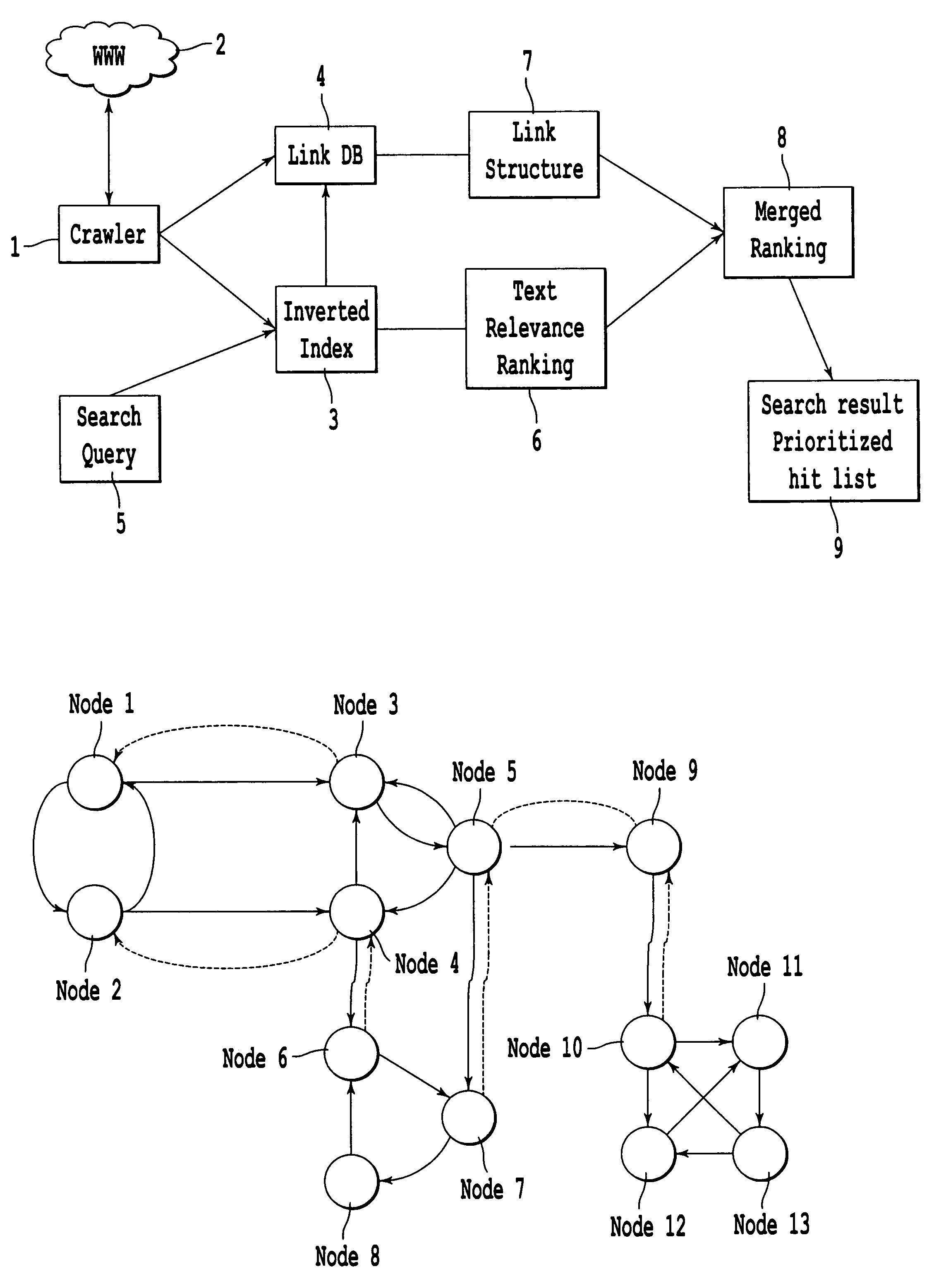
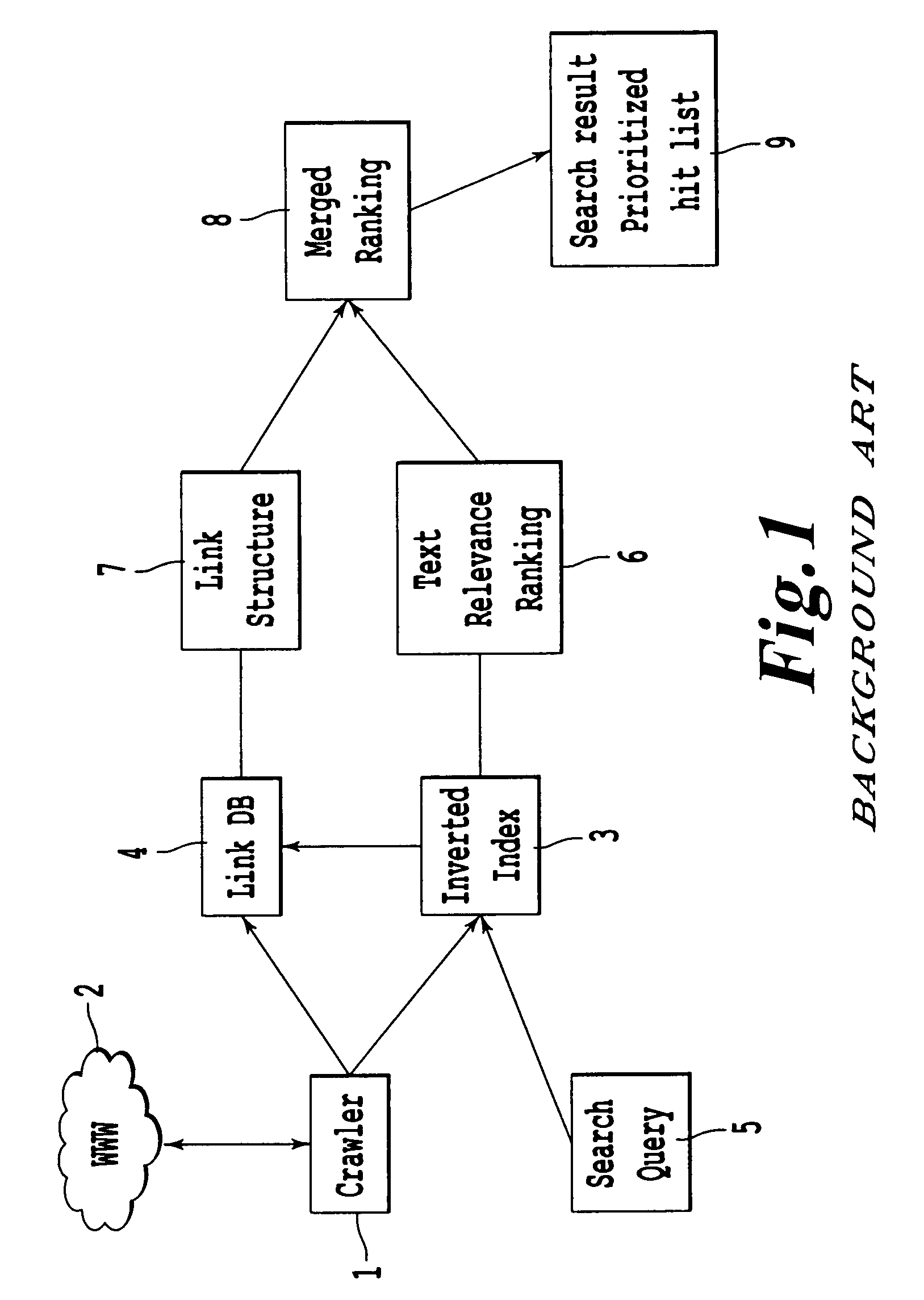
In network theory, link analysis is a data-analysis technique used to evaluate relationships (connections) between nodes. Relationships may be identified among various types of nodes (objects), including organizations, people and transactions. Link analysis has been used for investigation of criminal activity (fraud detection, counterterrorism, and intelligence), computer security analysis, search engine optimization, market research, medical research, and art.
Systems and methods for fraud detection via interactive link analysis
ActiveUS20090044279A1Facilitate fraud detectionFinanceDigital data processing detailsHigh probabilitySystem identification
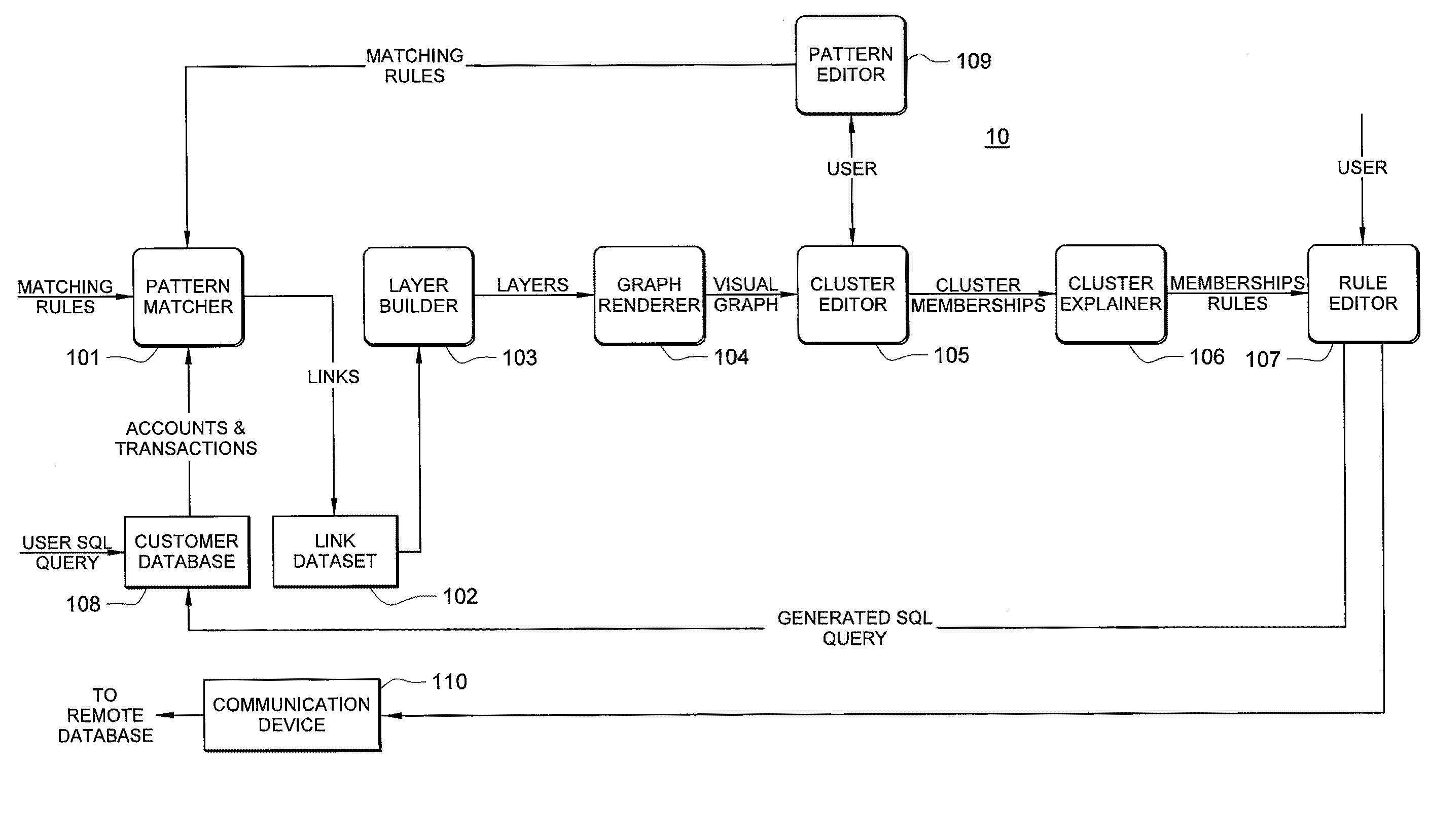
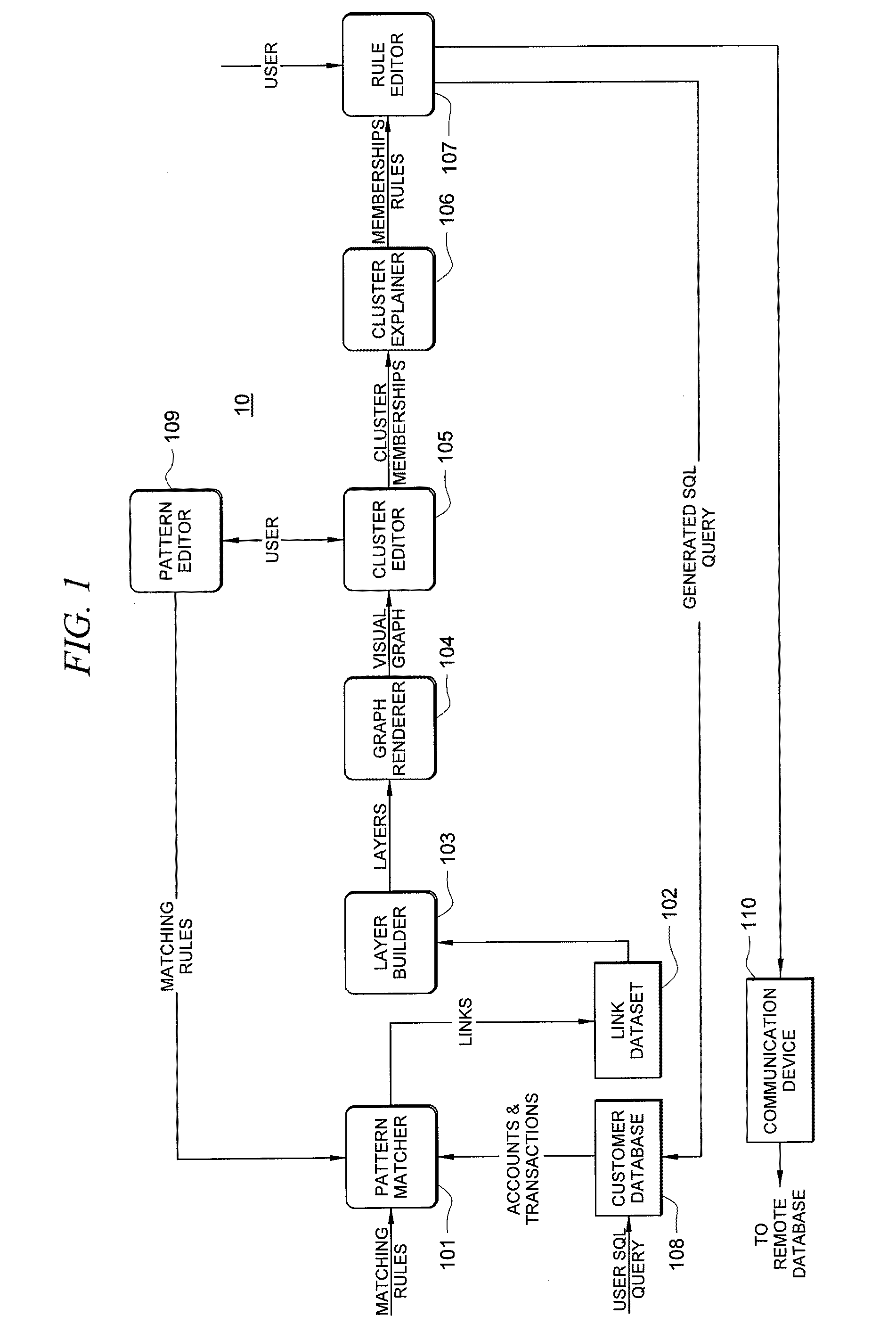
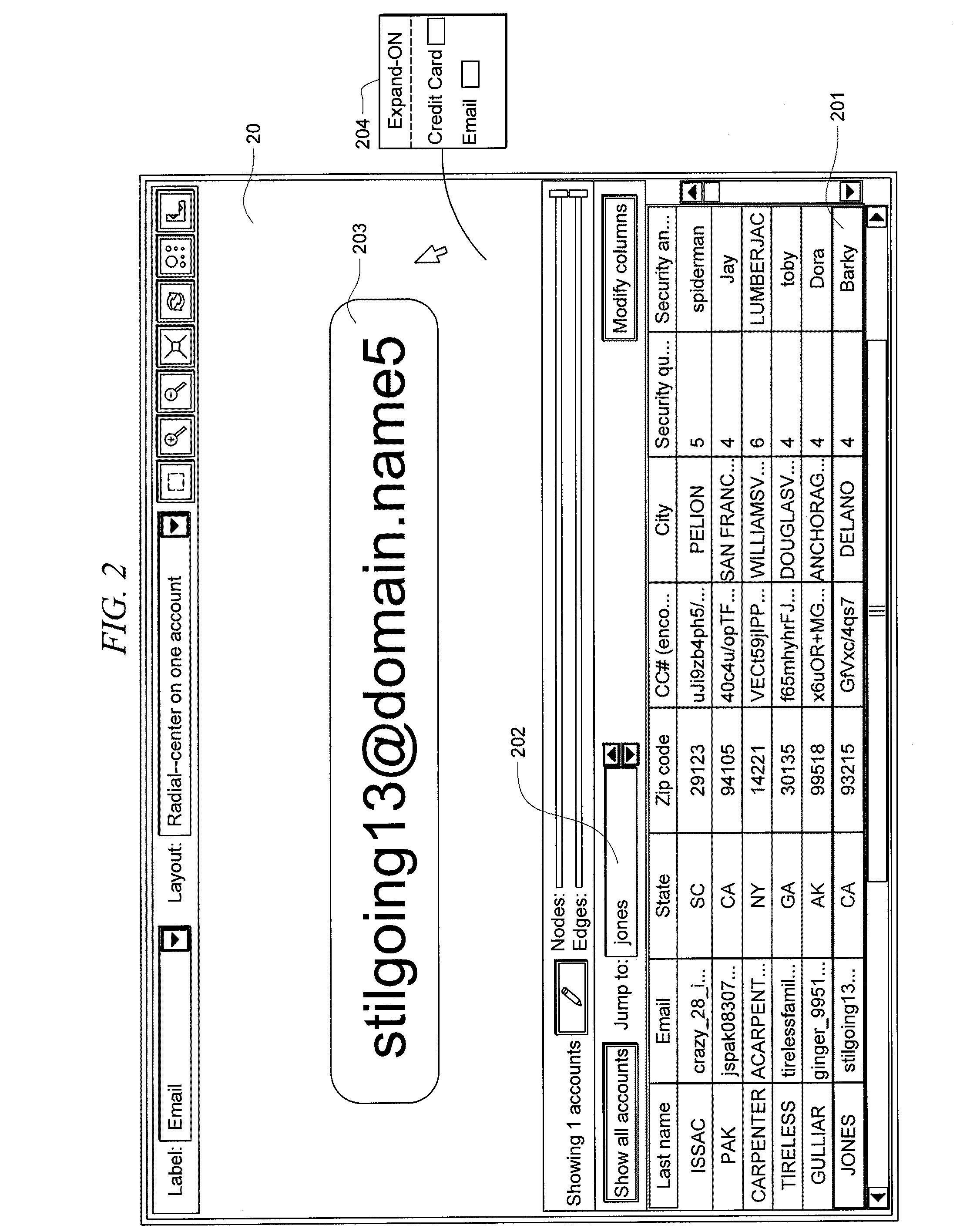
Fraud detection is facilitated by developing account cluster membership rules and converting them to database queries via an examination of clusters of linked accounts abstracted from the customer database. The cluster membership rules are based upon certain observed data patterns associated with potentially fraudulent activity. In one embodiment, account clusters are grouped around behavior patterns exhibited by imposters. The system then identifies those clusters exhibiting a high probability of fraud and builds cluster membership rules for identifying subsequent accounts that match those rules. The rules are designed to define the parameters of the identified clusters. When the rules are deployed in a transaction blocking system, when a rule pertaining to an identified fraudulent cluster is triggered, the transaction blocking system blocks the transaction with respect to new users who enter the website.
Owner:FAIR ISAAC & CO INC
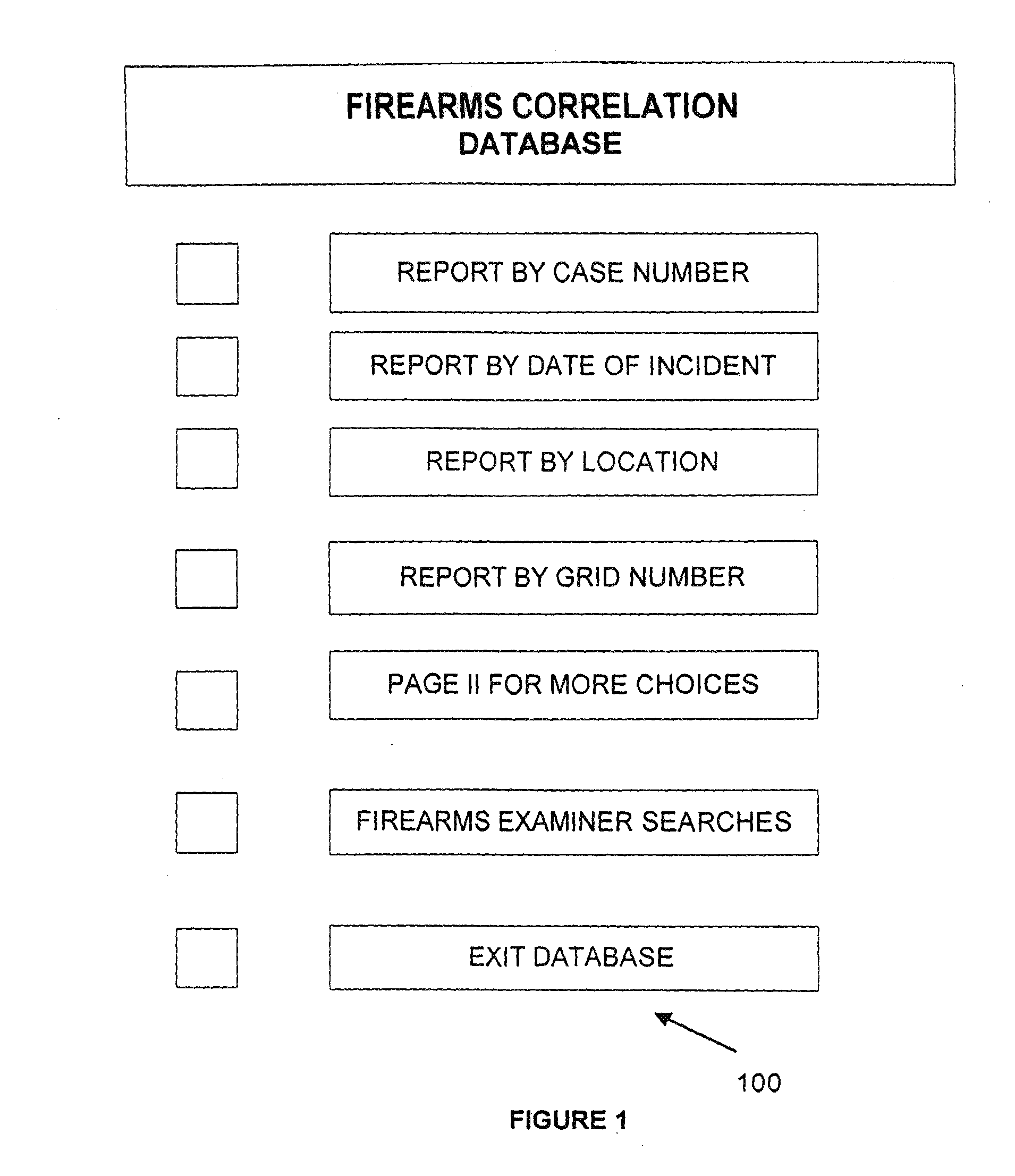
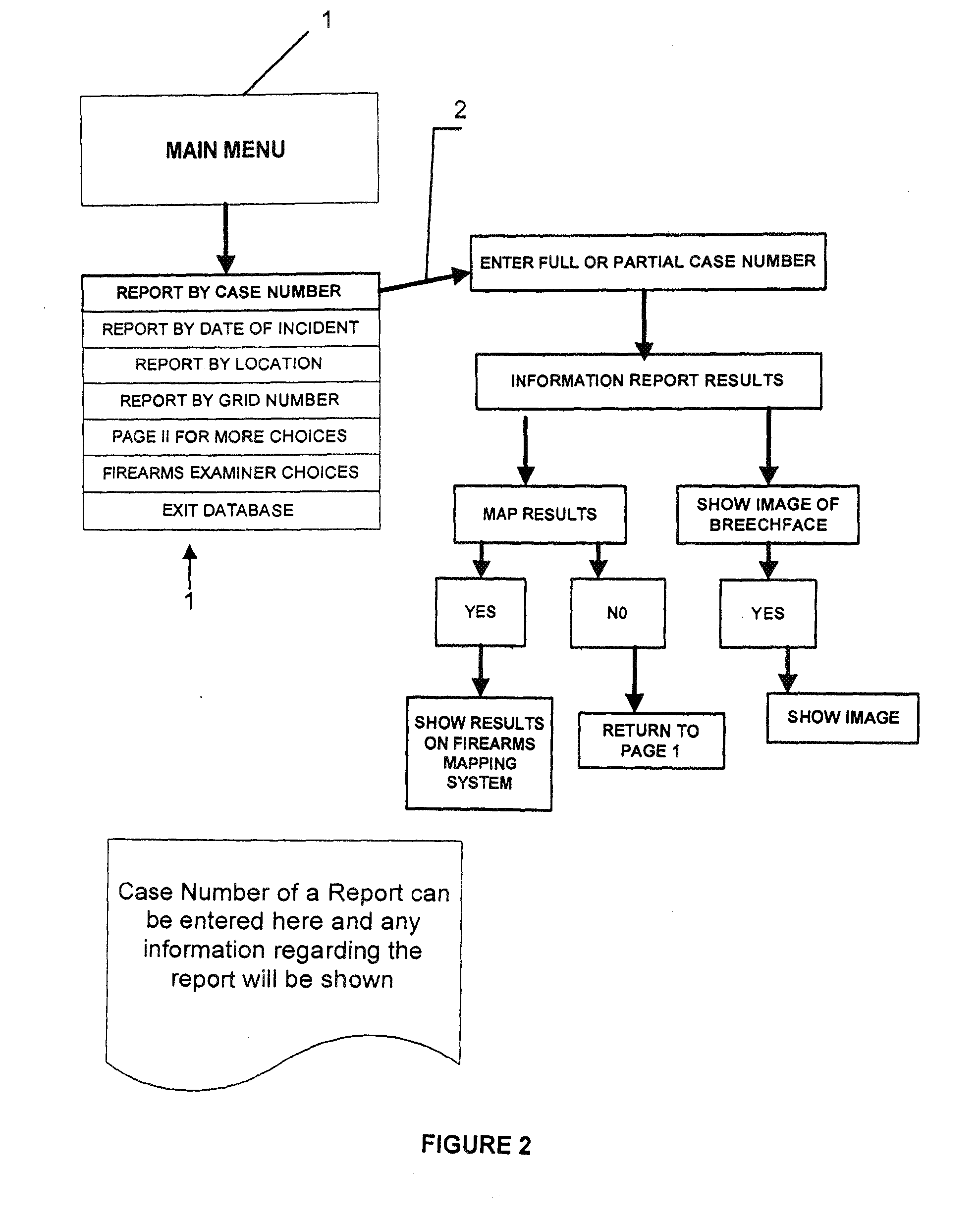
System and Methods for Linking Multiple Events Involving Firearms and Gang Related Activities
InactiveUS20110225198A1Data processing applicationsDigital data processing detailsEvent typeGeolocation
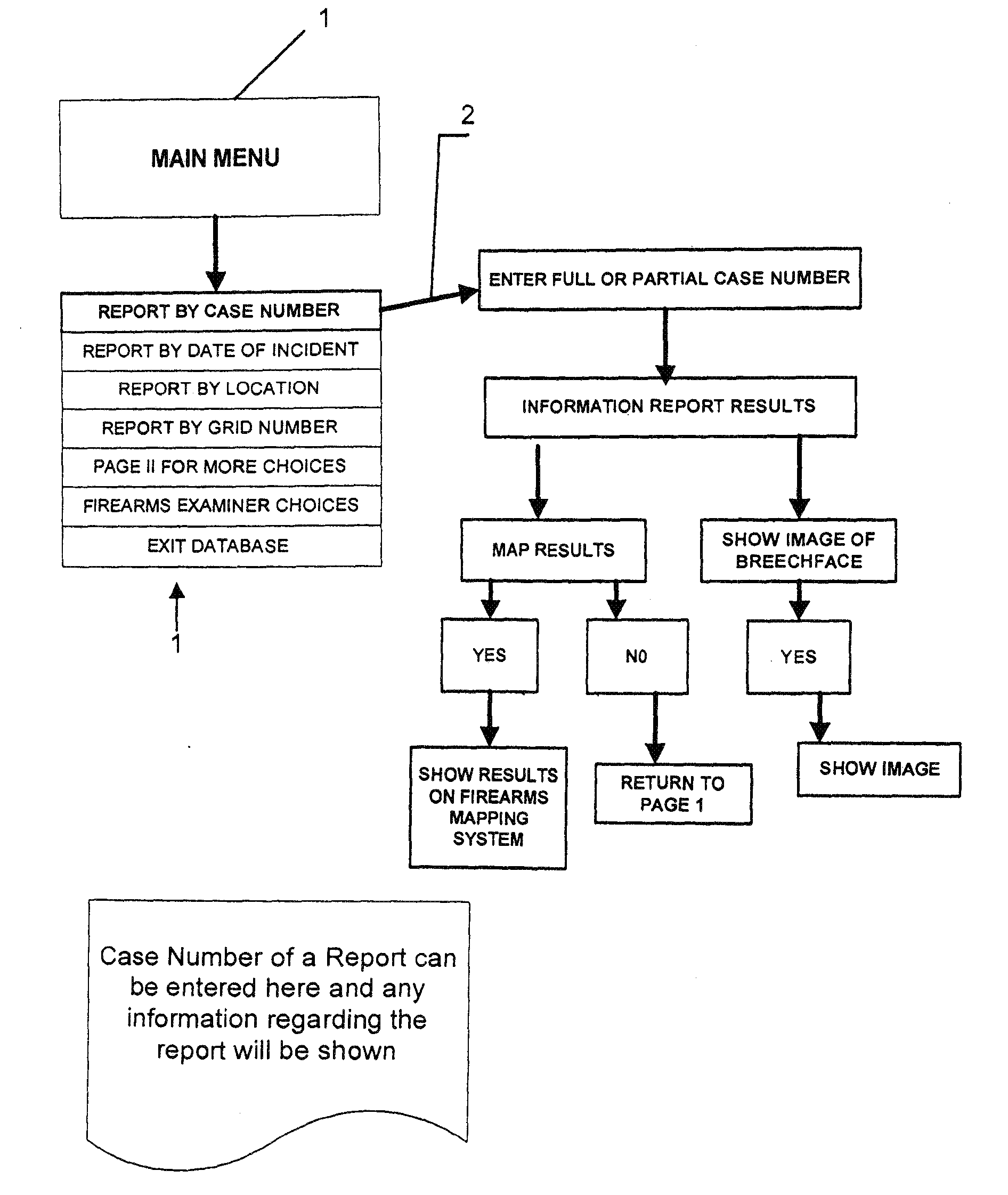
Methods for linking multiple events involving firearms submit event information data and firearms information data to a system that includes a database for multiple firearms events and generate a query map that correlates data in the system database with a preselected geographical grid based upon one or more preselected matching criteria to one or more data entries for a selected event. The map is used to generate a request for a possible link analysis which may be initiated by a firearms examiner and is then performed to determine if there is a link. The event information data can include a case number, a geographical location data entry, a date entry, a crime type, a weapon involved and a suspect information data field based upon input from an investigating officer while the firearms information data can include a weapon data entry and a bullet data entry based upon input from a person with firearms examiner training. The methodology can be used to prioritize multiple requests for a possible link analysis based upon information obtained in one or more query responses and the query response can display at least some of its information in a query map that correlates data in the system database with a preselected geographical grid. One or more gang database modules allow users to execute searches of a gang database and plot incidents on a geographic grid with each incident being represented by a unique icon related to a class of crime or type of incident.
Owner:EDWARDS ROCKY L +1
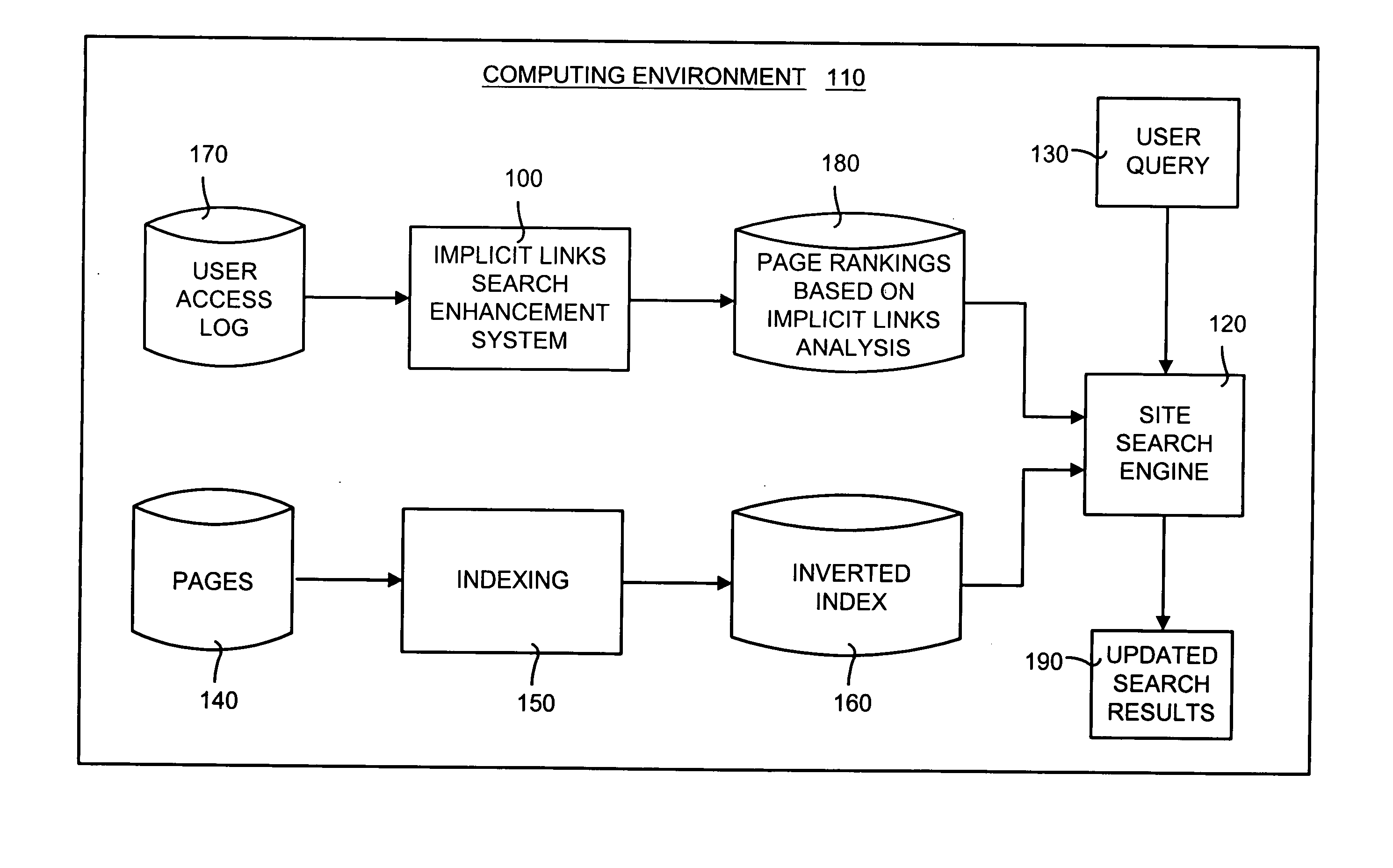
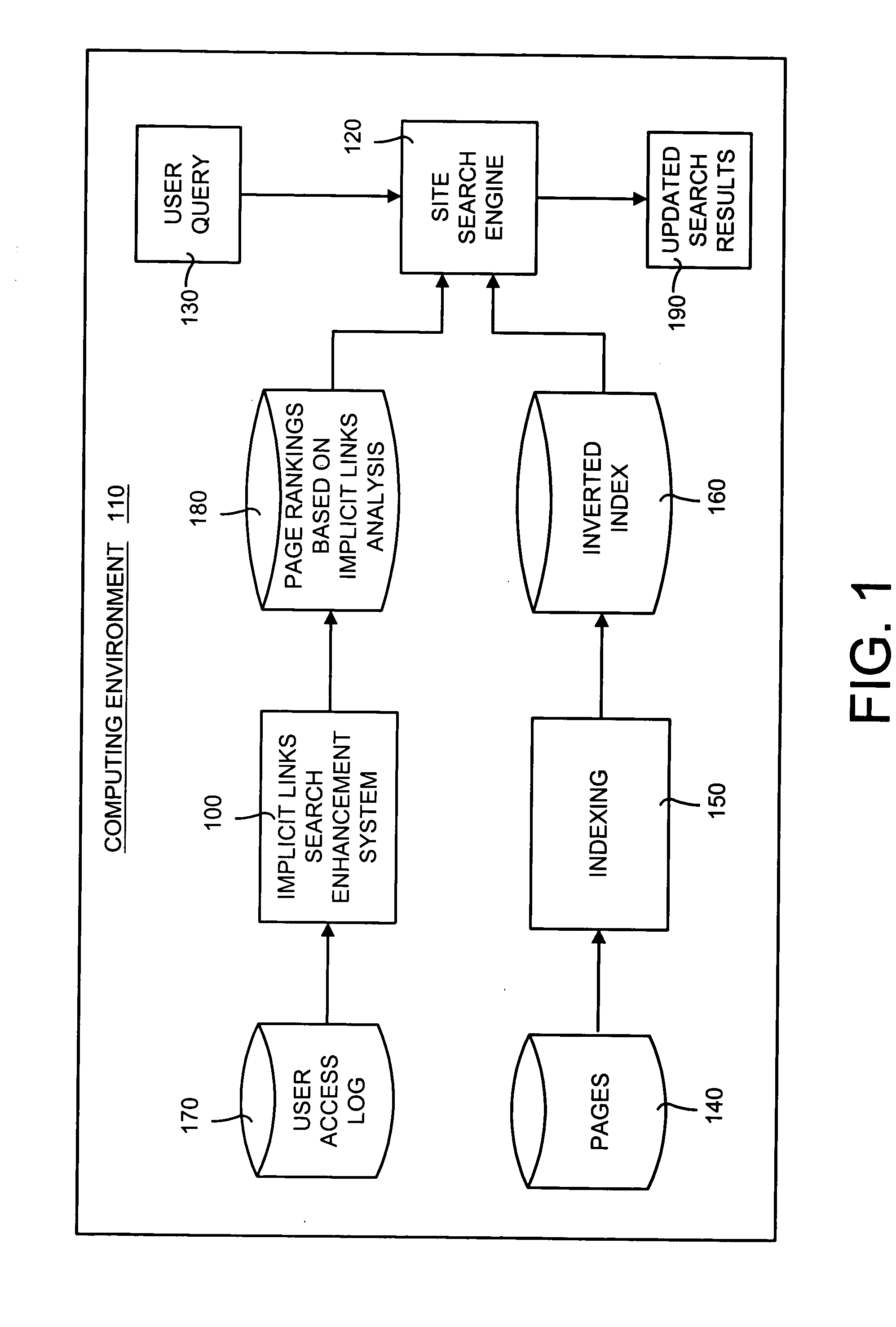
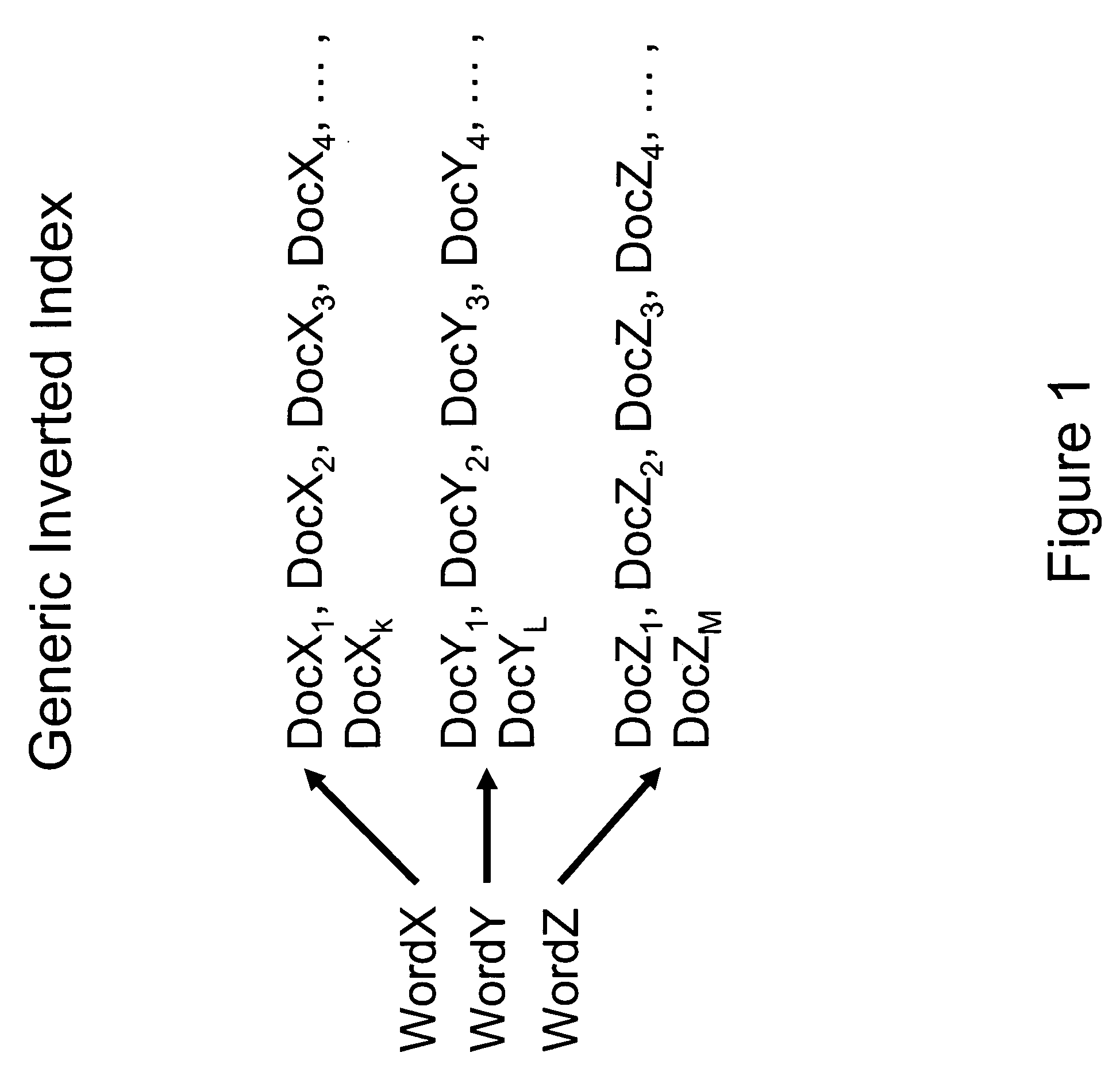
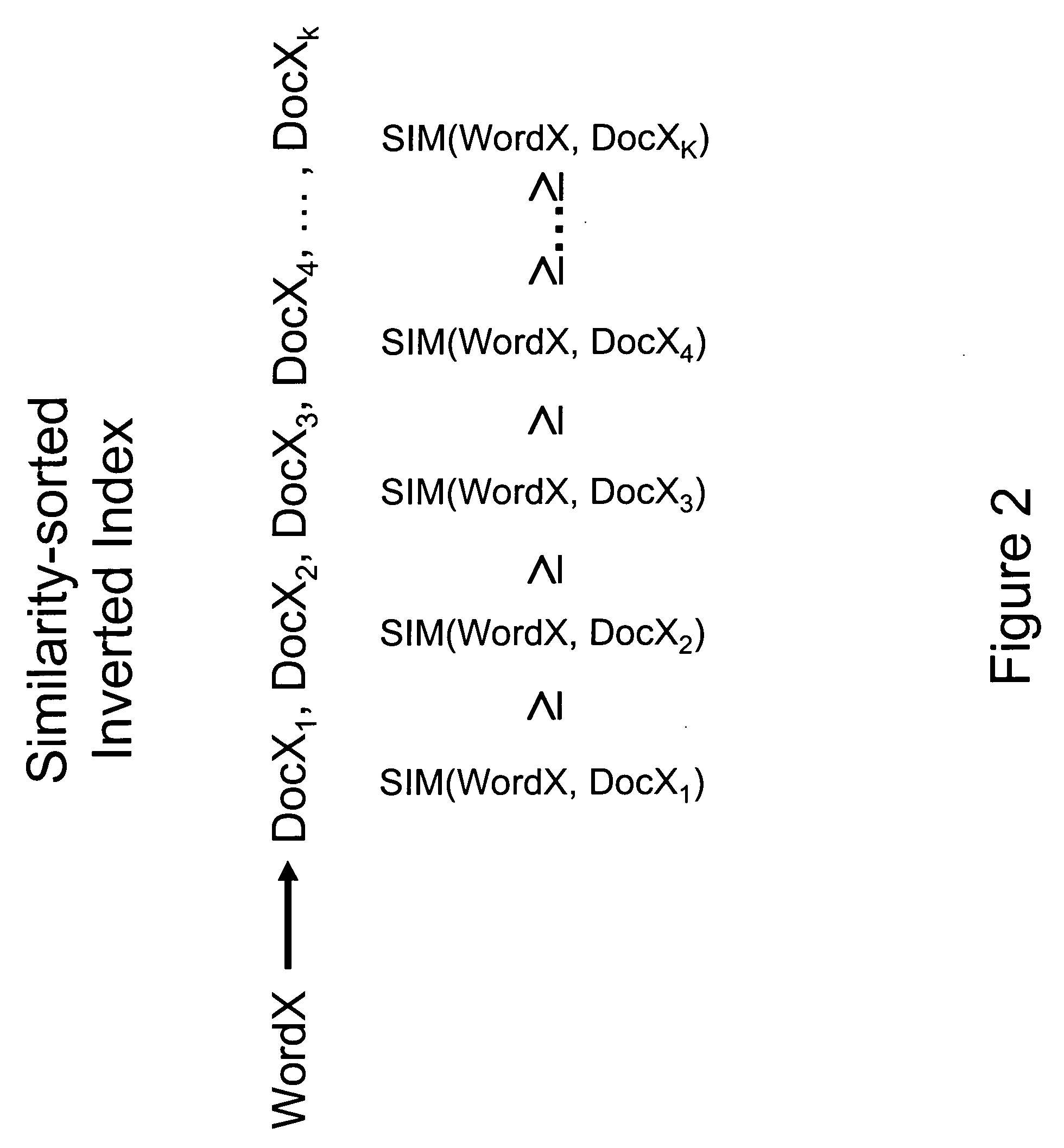
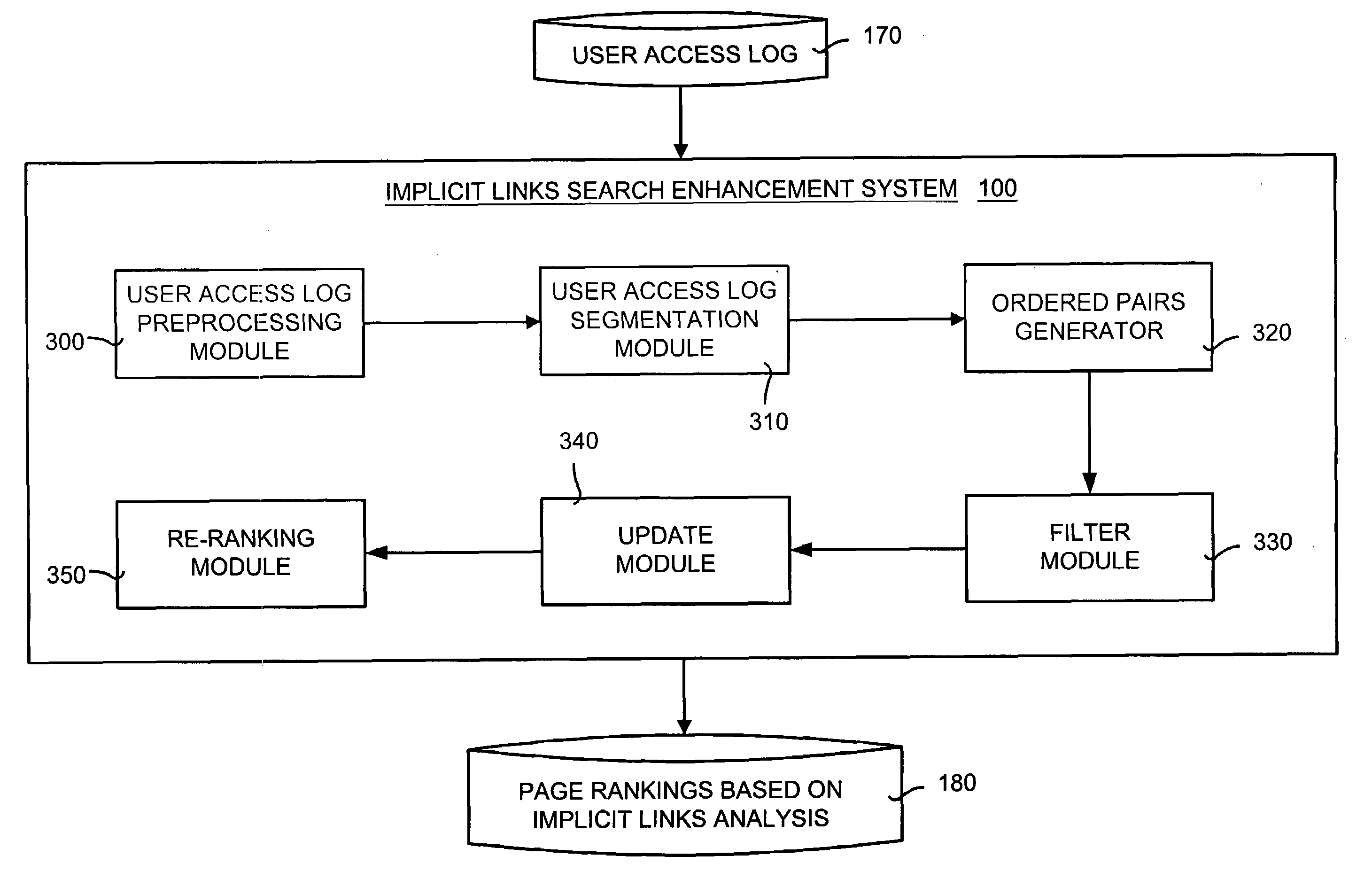
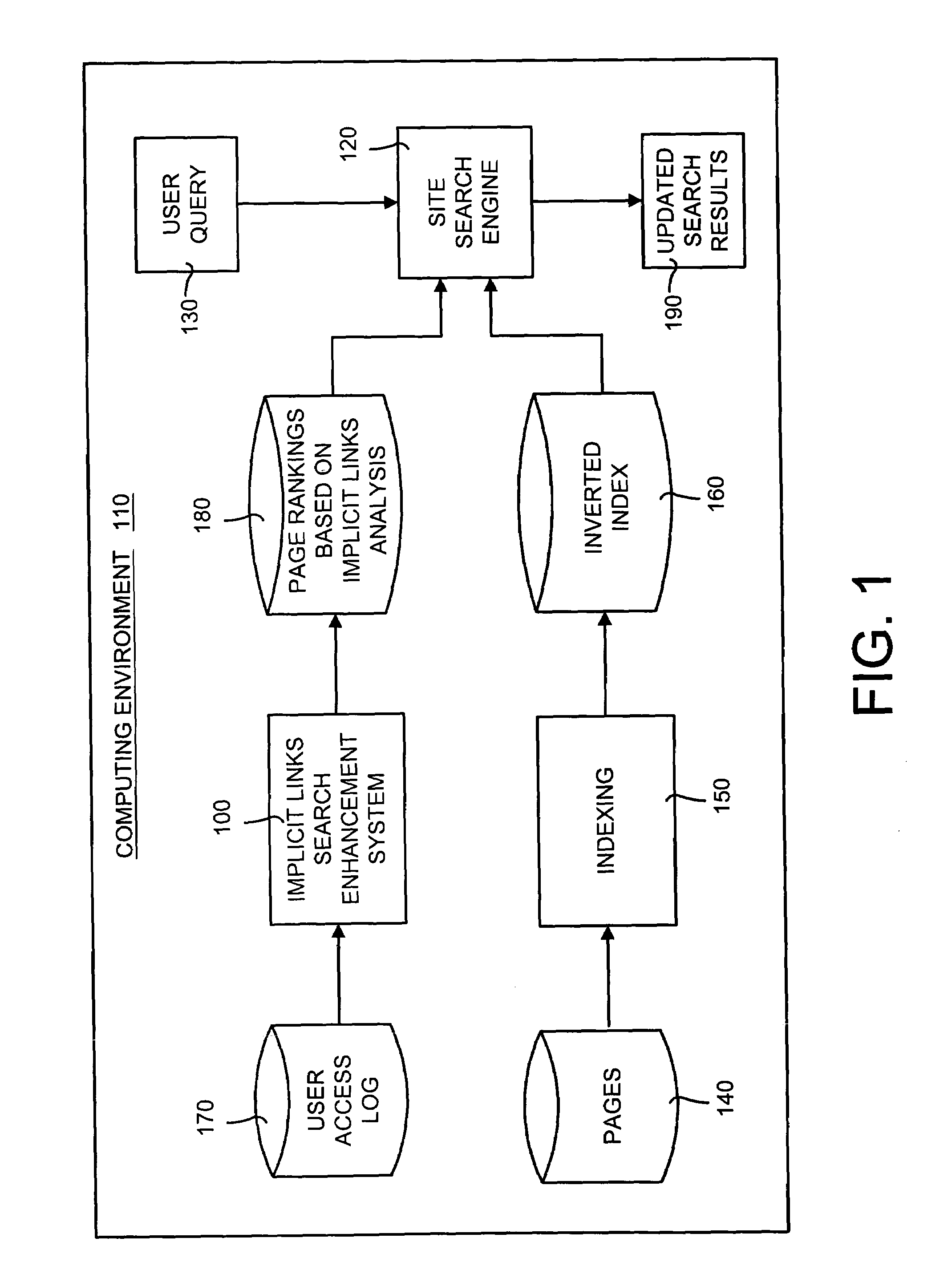
Implicit links search enhancement system and method for search engines using implicit links generated by mining user access patterns
InactiveUS20050071465A1Handy search resultsSearch results are accurateData processing applicationsDigital data information retrievalWeb sitePattern generation
An implicit links enhancement system and method for search engines that generates implicit links obtained from mining user access logs to facilitate enhanced local searching of web sites and intranets. The implicit links search enhancement system and method includes extracting implicit links by mining users' access patterns and then using a modified link analysis algorithm to re-rank search results obtained from traditional search engines. More specifically, the implicit links search enhancement method includes extracting implicit links from a user access log, generating an implicit links graph from the extracted implicit links, and computing page rankings using the implicit links graph. The implicit links are extracted from the log using a two-item sequential pattern mining technique. Search results obtained from a search engine are re-ranked based on an implicit links analysis performed using an updated implicit links graph, a modified re-ranking formula, and at least one re-ranking technique.
Owner:MICROSOFT TECH LICENSING LLC
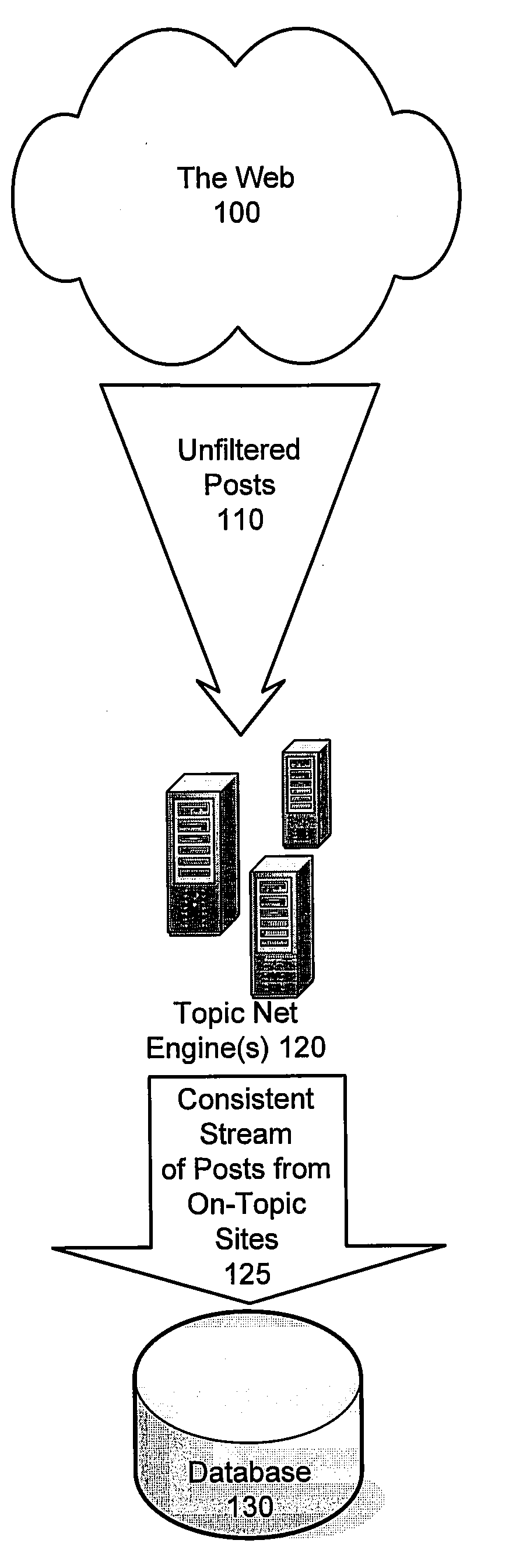
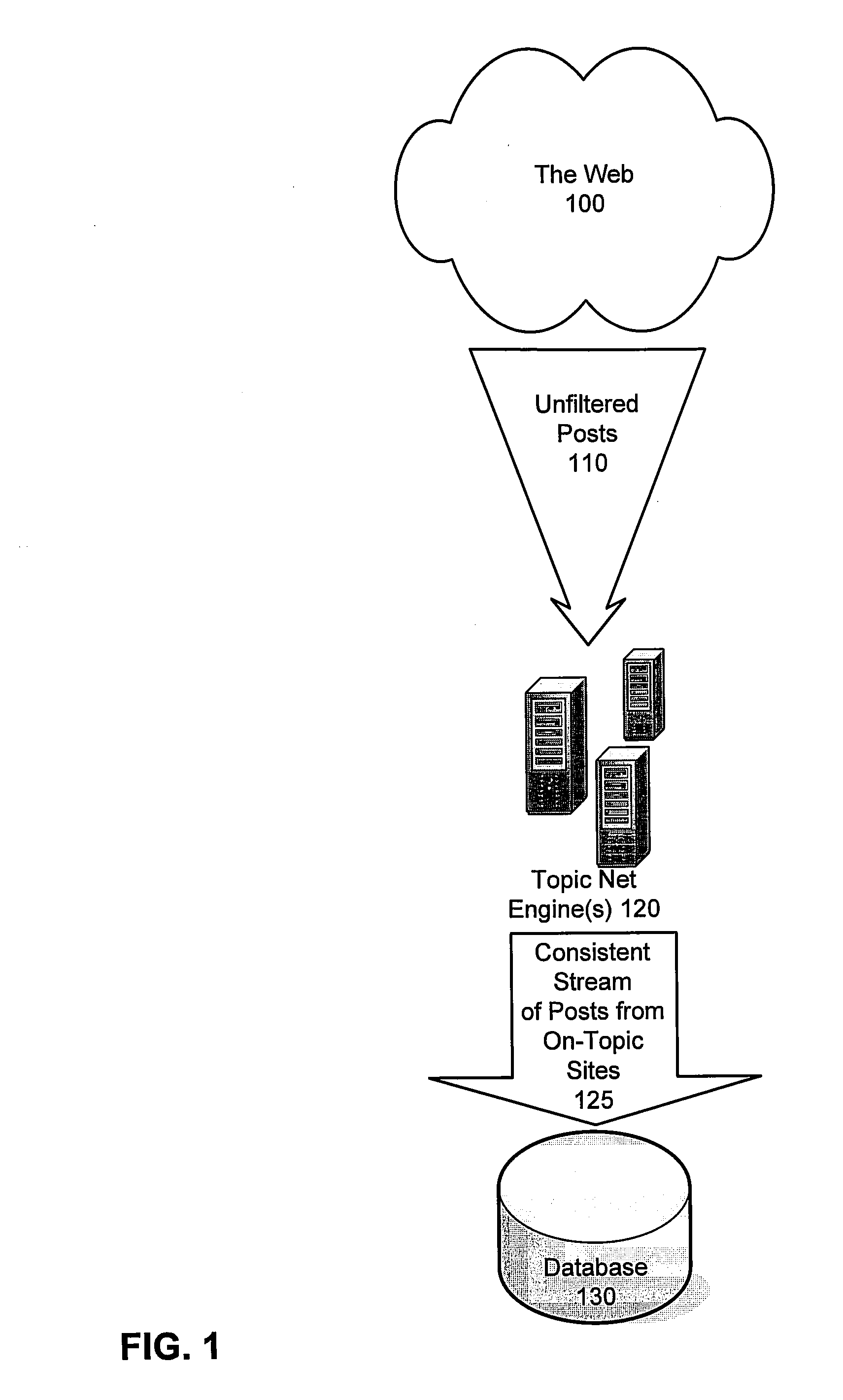
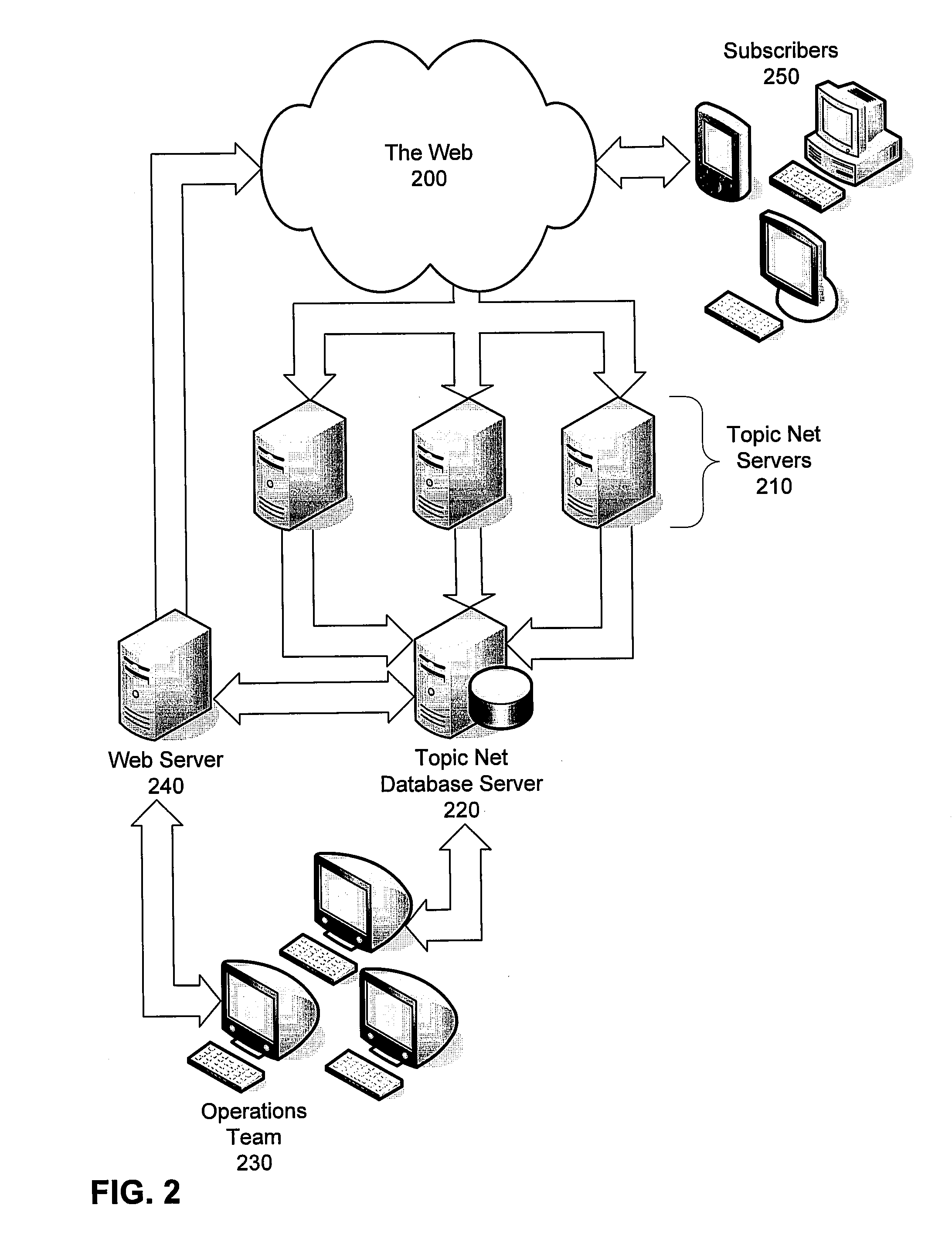
Identifying sources of media content having a high likelihood of producing on-topic content
InactiveUS20080114755A1Web data navigationSpecial data processing applicationsTopic areasSubject matter
Methods and systems are provided for identifying on-topic sources of media content. According to one embodiment, candidate seed sites are identified from which current seeds are selected for deep crawling. The current seeds are identified by correlating relevancy scores or key-word search results from multiple search engines; and selecting the current seeds based on on-topic scores of the candidate seeds. Periodically, a topic net associated with the topic area of interest is executed to locate relevant sources of media content by (i) building a graph in which nodes represent pages and edges represent links among pages by performing an iterative 360 crawl starting from the seeds; (ii) assigning initial node graph scores; (iii) computing final node graph scores by performing link analysis; (iv) computing a site graph scores by aggregating and averaging corresponding node graph scores; and (v) configuring sites with the highest site graph scores to be scraped.
Owner:COLLECTIVE INTELLECT
Method, system, and computer program product for searching for, navigating among, and ranking of documents in a personal web
InactiveUS20060059144A1Least labor-intensiveScale be relatively lowData processing applicationsText database indexingHyperlinkRanking
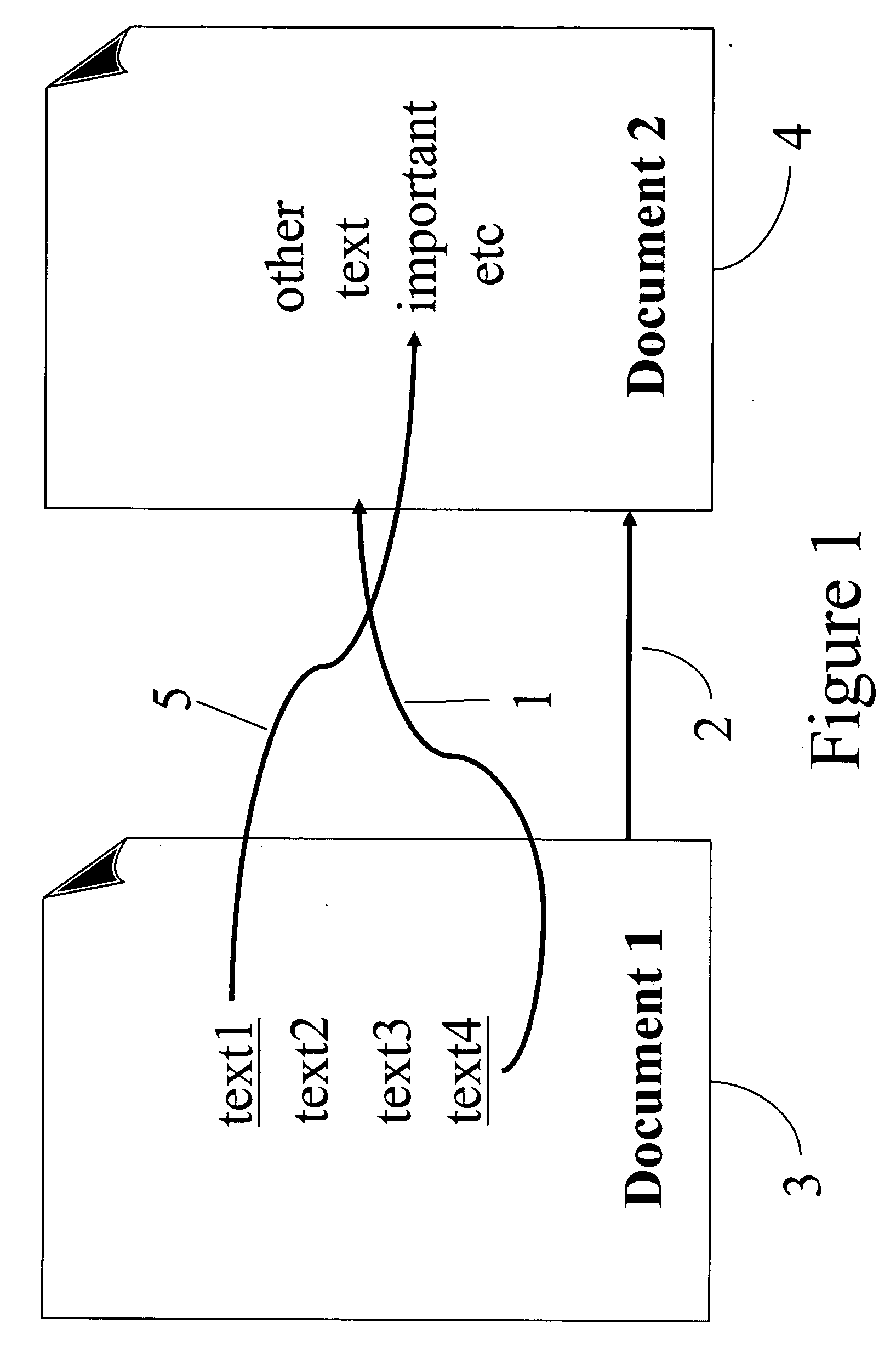
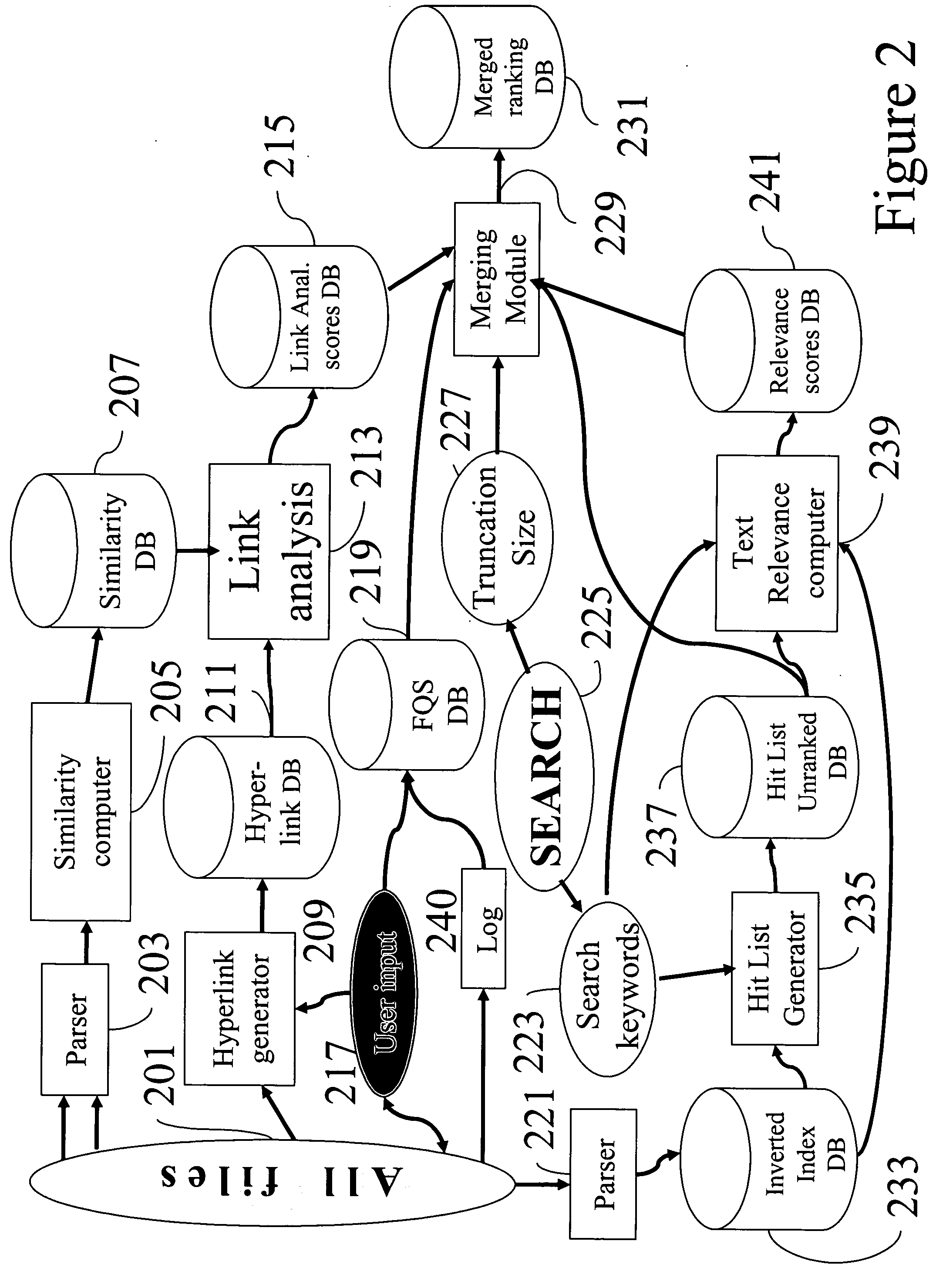
A method, apparatus, and computer program product for a personal search engine that includes a hybrid web composed of: the similarity web, and directed hyperlinks. Components include a parser (extracting words from documents); a text relevance analyzer; a link analysis method; the similarity web; a similarity analyzer; and hyperlinks. Other components include a navigation window; and FQSs. The combination of all the above may be incorporated into a working personal search engine.
Owner:TELENOR AS
Method and system for analysis of a system for matching data records
InactiveUS20090089630A1Ensure performanceDigital data information retrievalError detection/correctionGraphicsReal time analysis
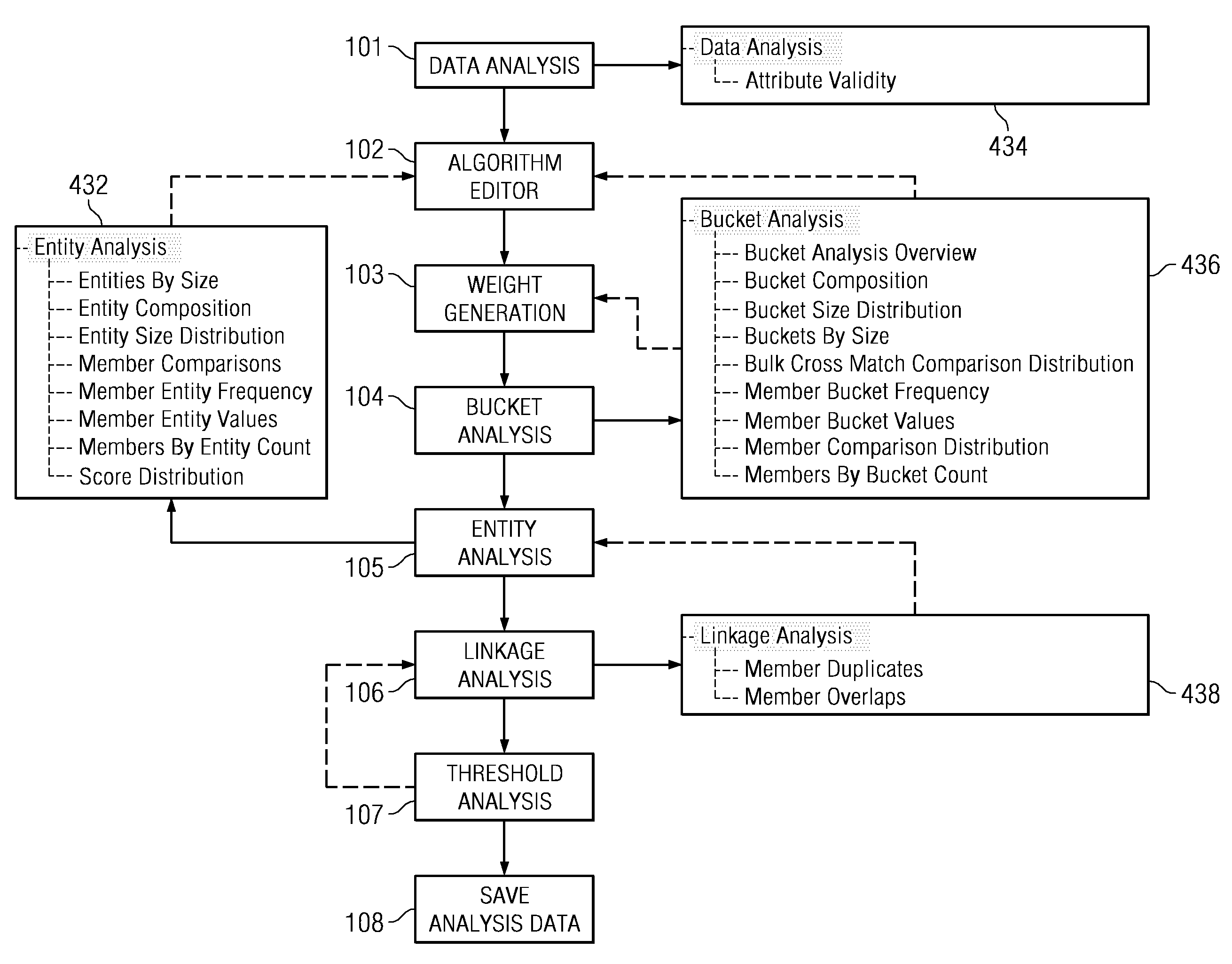
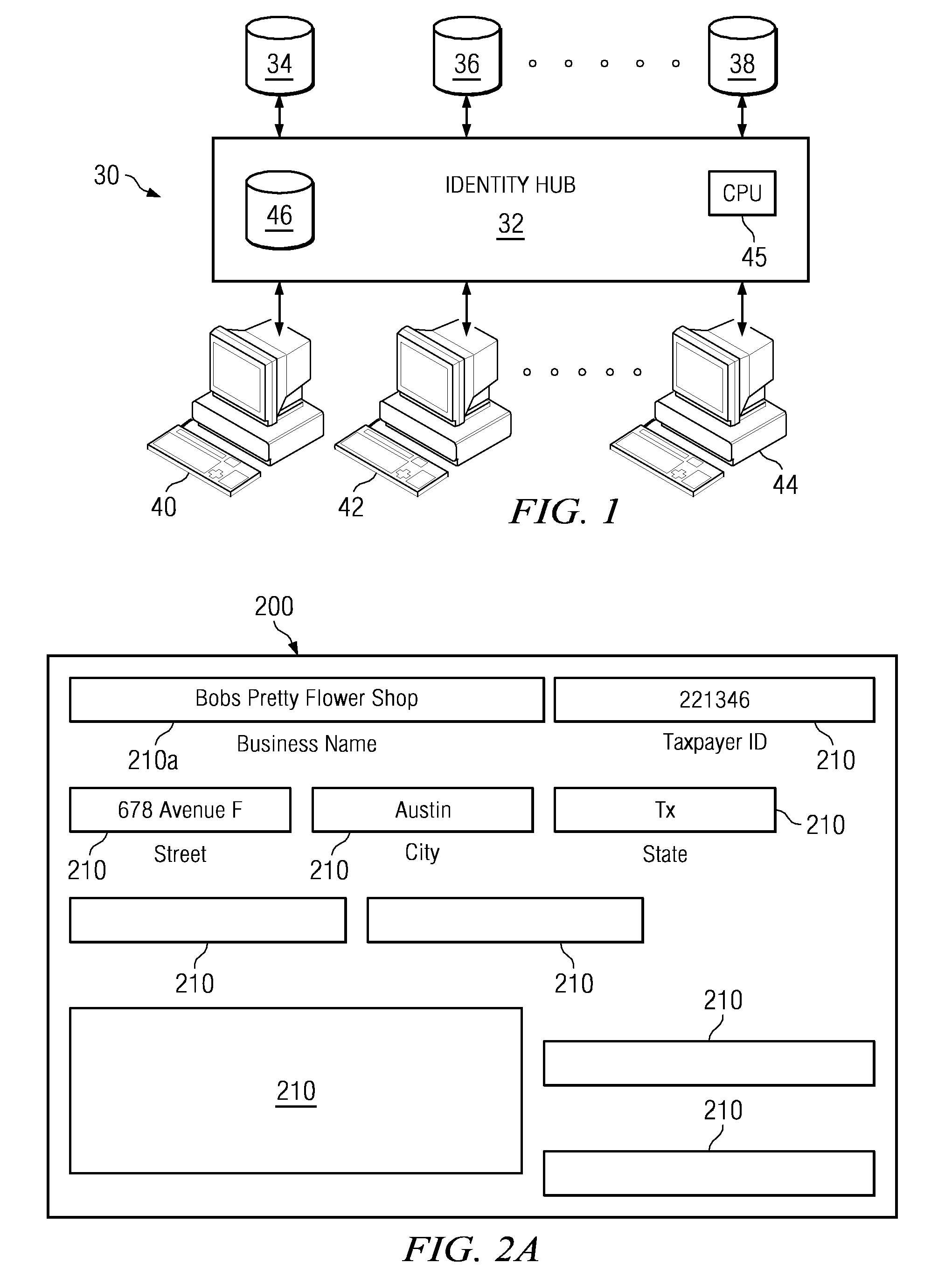
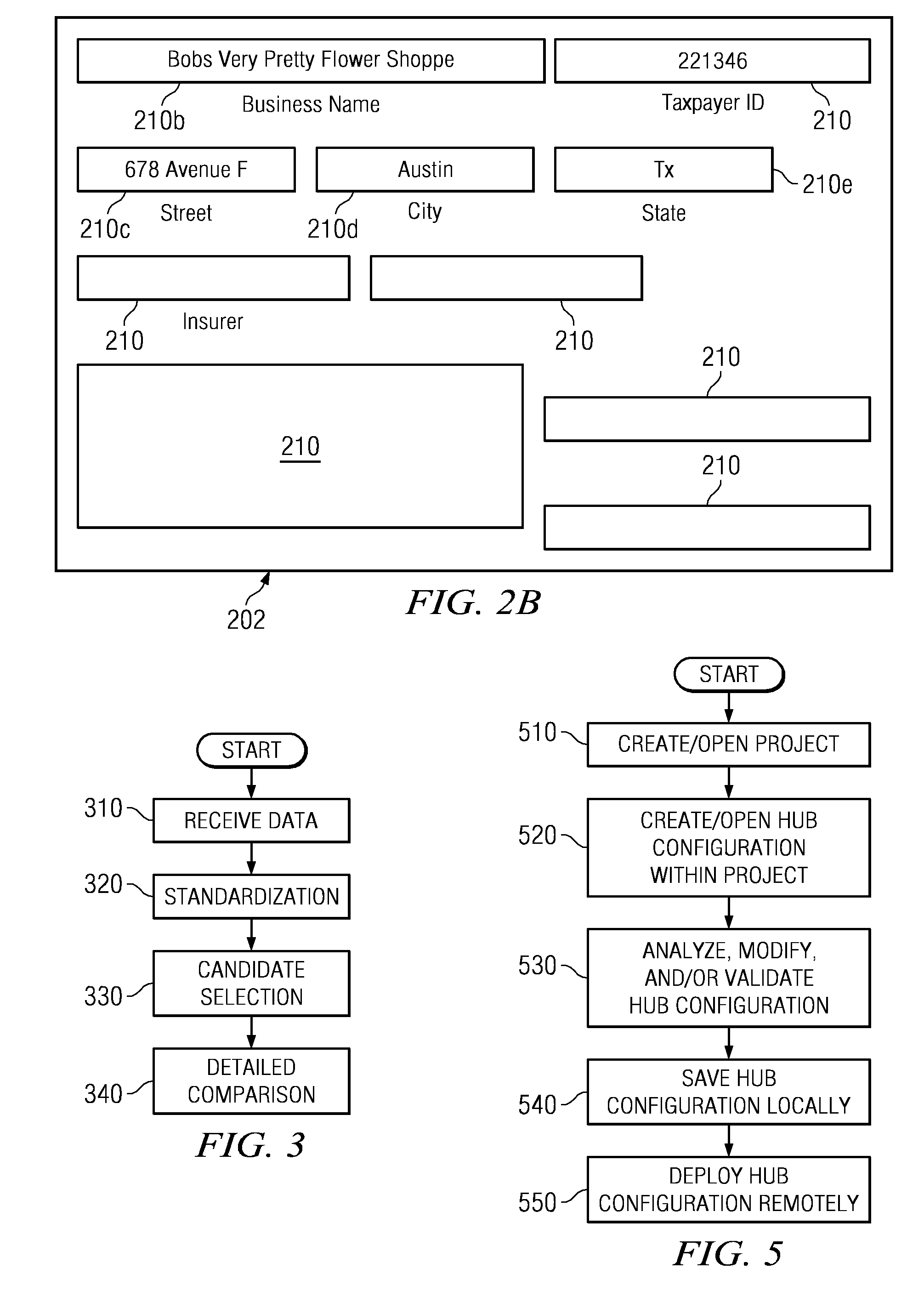
Embodiments disclosed herein provide a system and method for analyzing an identity hub. Particularly, a user can connect to the identity hub, load an initial set of data records, create and / or edit an identity hub configuration locally, analyze and / or validate the configuration via a set of analysis tools, including an entity analysis tool, a data analysis tool, a bucket analysis tool, and a linkage analysis tool, and remotely deploy the validated configuration to an identity hub instance. In some embodiments, through a graphical user interface, these analysis tools enable the user to analyze and modify the configuration of the identity hub in real time while the identity hub is operating to ensure data quality and enhance system performance.
Owner:IBM CORP
Techniques for providing protection against unsafe links on a social networking website
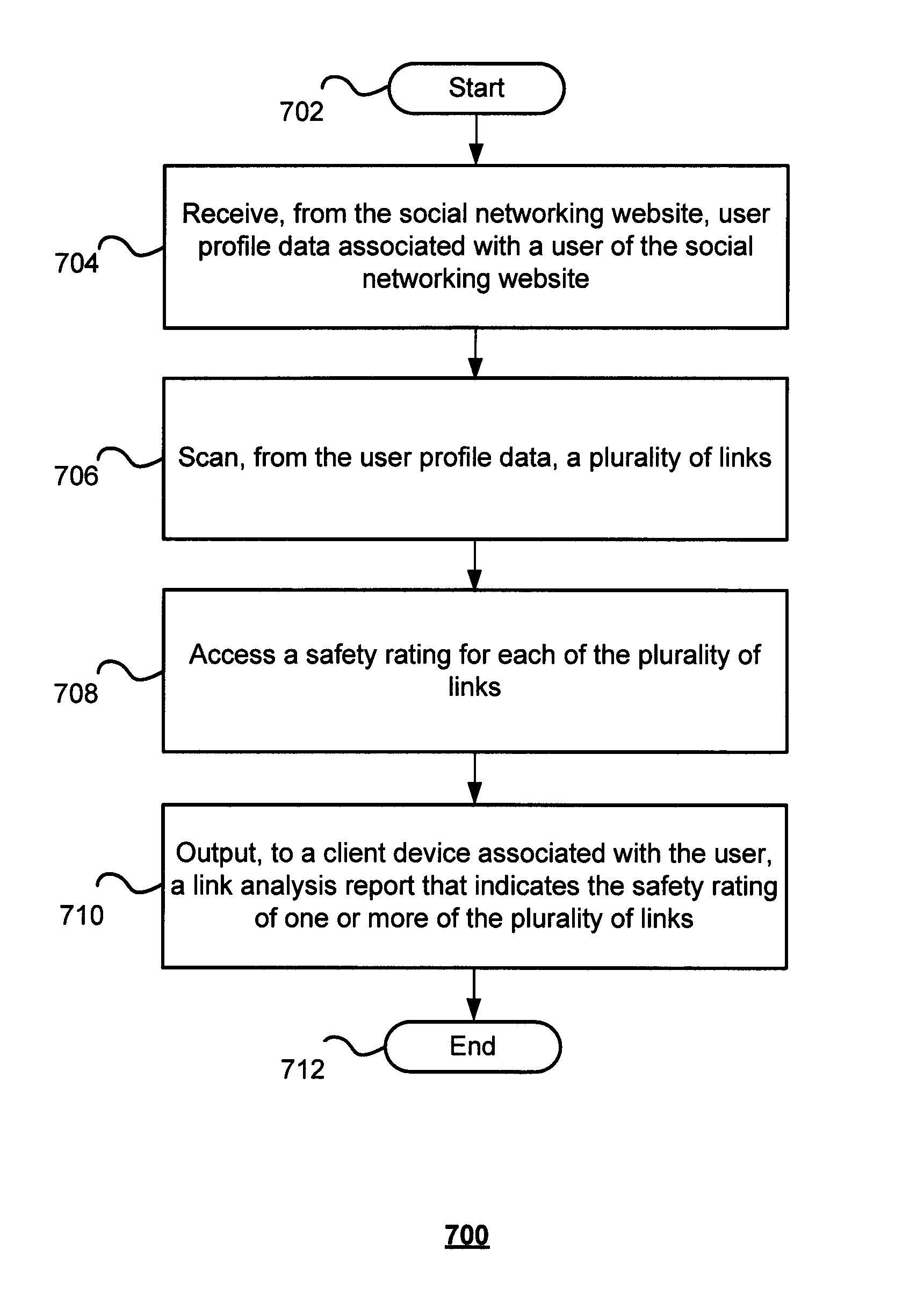
Techniques for providing protection against unsafe links on a social networking website are disclosed. In one particular exemplary embodiment, the techniques may be realized as a method for providing protection against unsafe links on a social networking website comprising: receiving, from the social networking website, user profile data associated with a user of the social networking website, scanning, from the user profile data, a plurality of links, accessing a safety rating for each of the plurality of links, and outputting, to a client device associated with the user, a link analysis report that indicates the safety rating of one or more of the plurality of links.
Owner:GEN DIGITAL INC
Document similarity scoring and ranking method, device and computer program product
InactiveUS7689559B2Avoids large and wasted effortSmall similarity scoreData processing applicationsWeb data indexingDocument similarityCollation
A device, computer program product and a method for searching, navigating or retrieving documents in a set of electronic documents, including performing a link analysis of the set of electronic documents. The link analysis includes one of analyzing at least two of the set of documents with at least a portion of a similarity graph constructed among the set of documents and analyzing the at least two of the set of documents with the at least a portion of the similarity graph and at least a portion of a hyperlink graph constructed from hyperlinks between the set of documents. Also described is a method for building a similarity matrix.
Owner:TELENOR AS
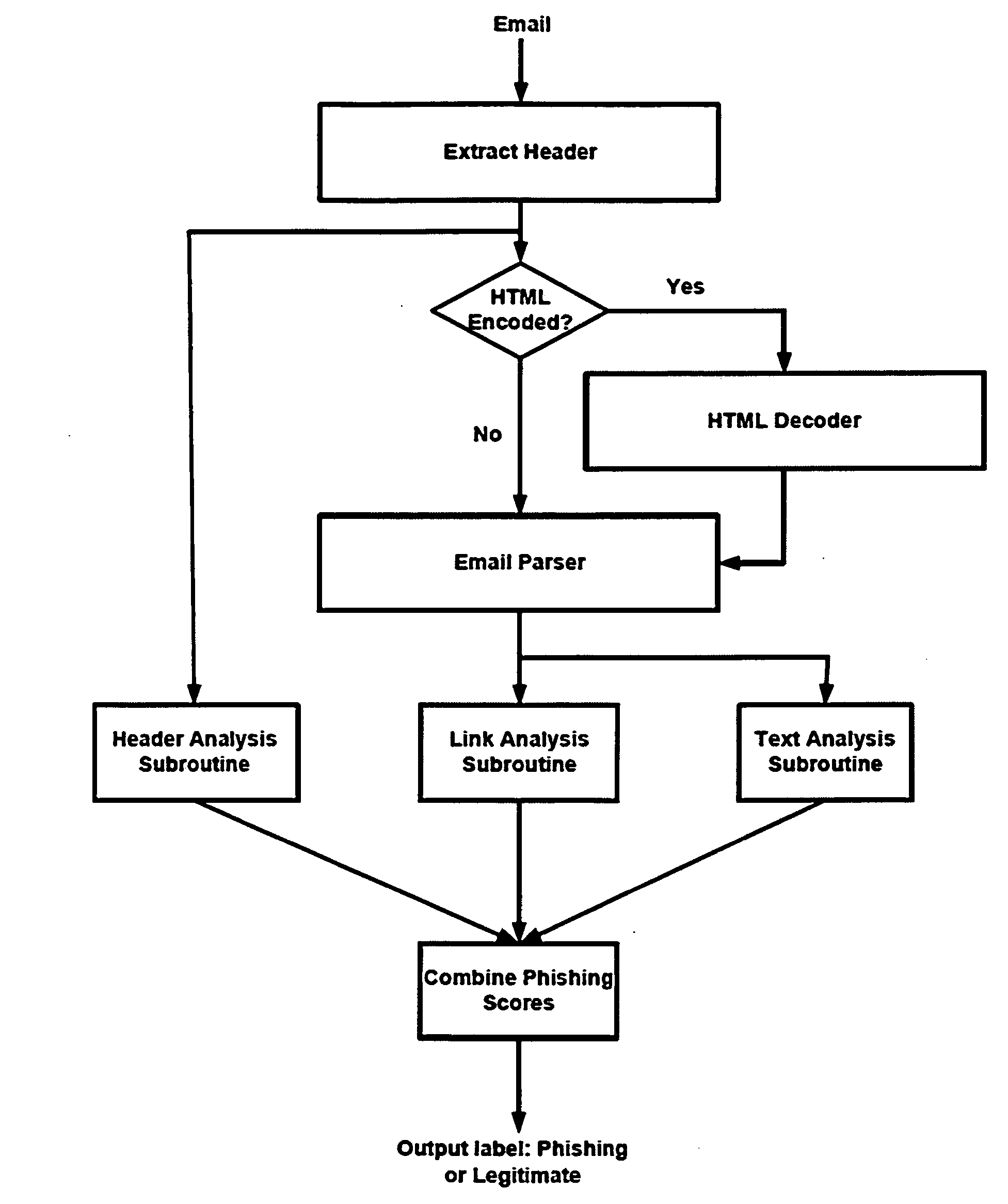
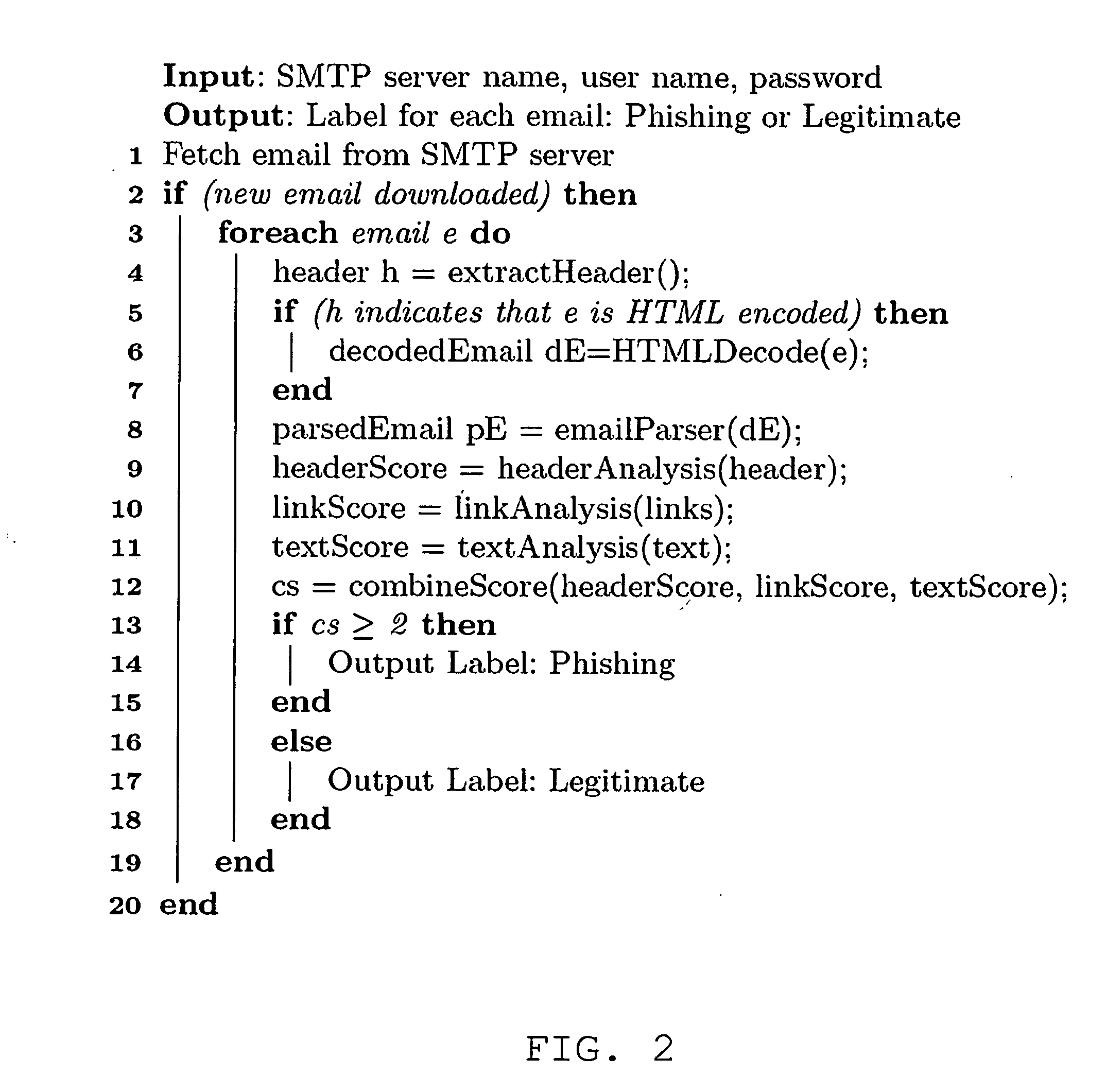
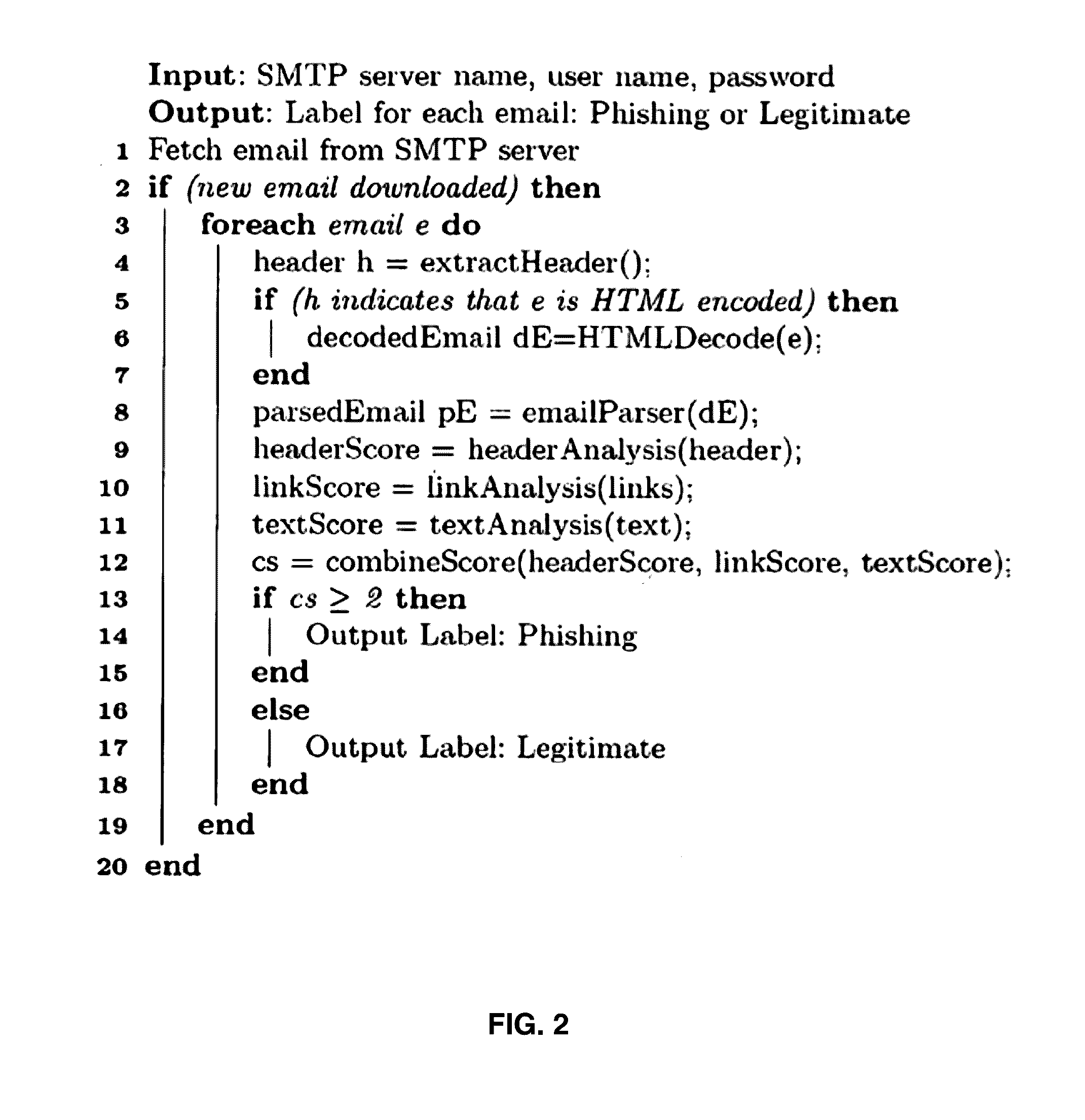
Automatic phishing email detection based on natural language processing techniques
InactiveUS20150067833A1Improve performanceMinimize timeMemory loss protectionError detection/correctionStatistical analysisPhishing
A comprehensive scheme to detect phishing emails using features that are invariant and fundamentally characterize phishing. Multiple embodiments are described herein based on combinations of text analysis, header analysis, and link analysis, and these embodiments operate between a user's mail transfer agent (MTA) and mail user agent (MUA). The inventive embodiment, PhishNet-NLP™, utilizes natural language techniques along with all information present in an email, namely the header, links, and text in the body. The inventive embodiment, PhishSnag™, uses information extracted form the embedded links in the email and the email headers to detect phishing. The inventive embodiment, Phish-Sem™ uses natural language processing and statistical analysis on the body of labeled phishing and non-phishing emails to design four variants of an email-body-text only classifier. The inventive scheme is designed to detect phishing at the email level.
Owner:SHASHIDHAR NARASIMHA +2
Automatic Phishing Email Detection Based on Natural Language Processing Techniques
ActiveUS20160344770A1Improve performanceMinimize detection timeEnsemble learningData switching networksPhishingLink analysis
A comprehensive scheme to detect phishing emails using features that are invariant and fundamentally characterize phishing. Multiple embodiments are described herein based on combinations of text analysis, header analysis, and link analysis, and these embodiments operate between a user's mail transfer agent (MTA) and mail user agent (MUA). The inventive embodiment, PhishNet-NLP™, utilizes natural language techniques along with all information present in an email, namely the header, links, and text in the body. The inventive embodiment, PhishSnag™, uses information extracted form the embedded links in the email and the email headers to detect phishing. The inventive embodiment, Phish-Sem™ uses natural language processing and statistical analysis on the body of labeled phishing and non-phishing emails to design four variants of an email-body-text only classifier. The inventive scheme is designed to detect phishing at the email level.
Owner:VERMA RAKESH +3
Automatic fact validation
InactiveUS20100306166A1Improve validityReduced effectivenessDigital data processing detailsChaos modelsLink analysisData mining
Owner:OATH INC
Document similarity scoring and ranking method, device and computer program product
InactiveUS20070185871A1Avoids largeAvoids wasted computational effortData processing applicationsWeb data indexingHyperlinkElectronic document
A device, computer program product and a method for searching, navigating or retrieving documents in a set of electronic documents, including performing a link analysis of the set of electronic documents. The link analysis includes one of analyzing at least two of the set of documents with at least a portion of a similarity graph constructed among the set of documents and analyzing the at least two of the set of documents with the at least a portion of the similarity graph and at least a portion of a hyperlink graph constructed from hyperlinks between the set of documents. Also described is a method for building a similarity matrix.
Owner:TELENOR AS
Implicit links search enhancement system and method for search engines using implicit links generated by mining user access patterns
InactiveUS7584181B2Handy search resultsSearch results are accurateData processing applicationsDigital data information retrievalWeb search engineWeb site
An implicit links enhancement system and method for search engines that generates implicit links obtained from mining user access logs to facilitate enhanced local searching of web sites and intranets. The implicit links search enhancement system and method includes extracting implicit links by mining users' access patterns and then using a modified link analysis algorithm to re-rank search results obtained from traditional search engines. More specifically, the implicit links search enhancement method includes extracting implicit links from a user access log, generating an implicit links graph from the extracted implicit links, and computing page rankings using the implicit links graph. The implicit links are extracted from the log using a two-item sequential pattern mining technique. Search results obtained from a search engine are re-ranked based on an implicit links analysis performed using an updated implicit links graph, a modified re-ranking formula, and at least one re-ranking technique.
Owner:MICROSOFT TECH LICENSING LLC
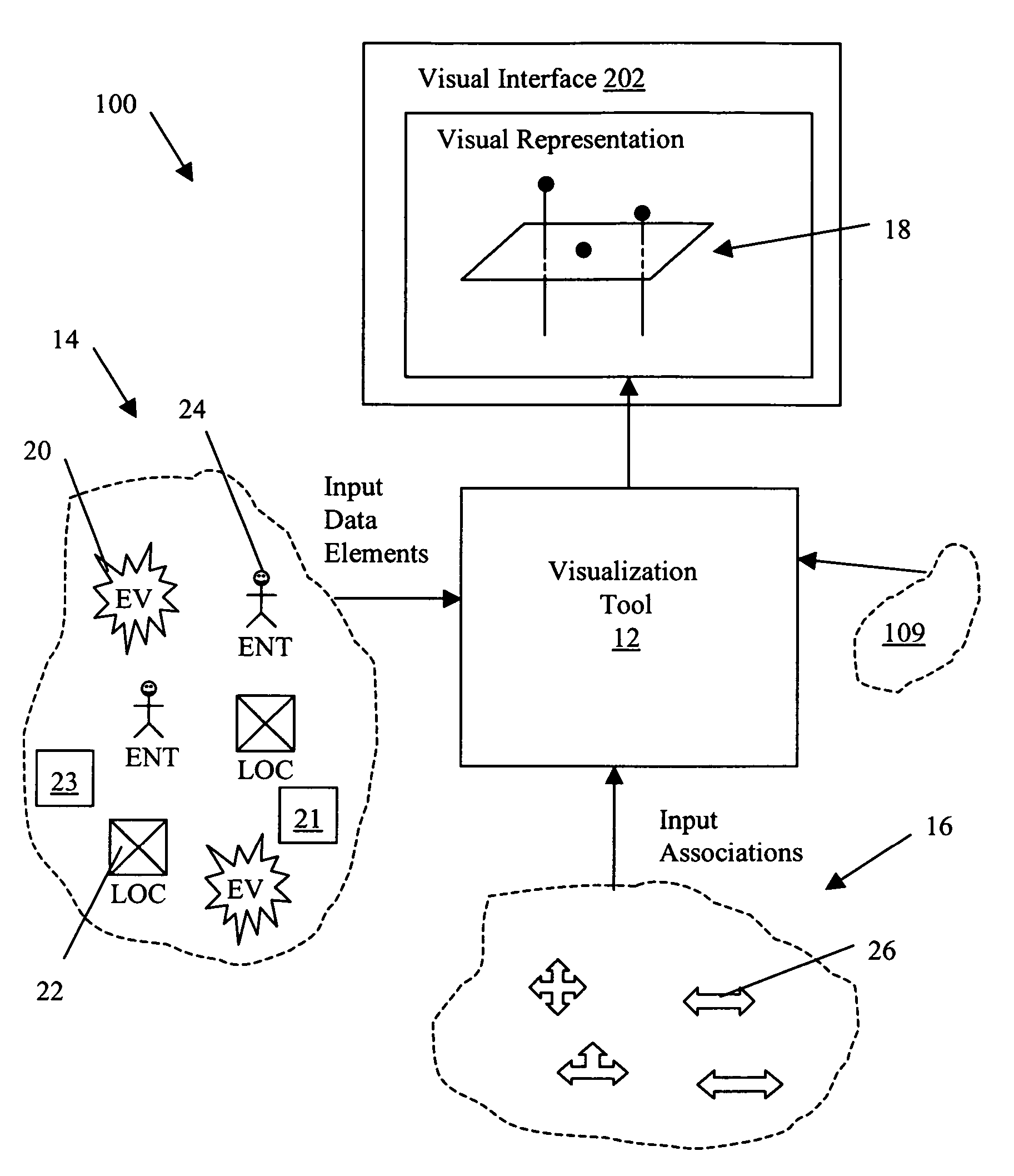
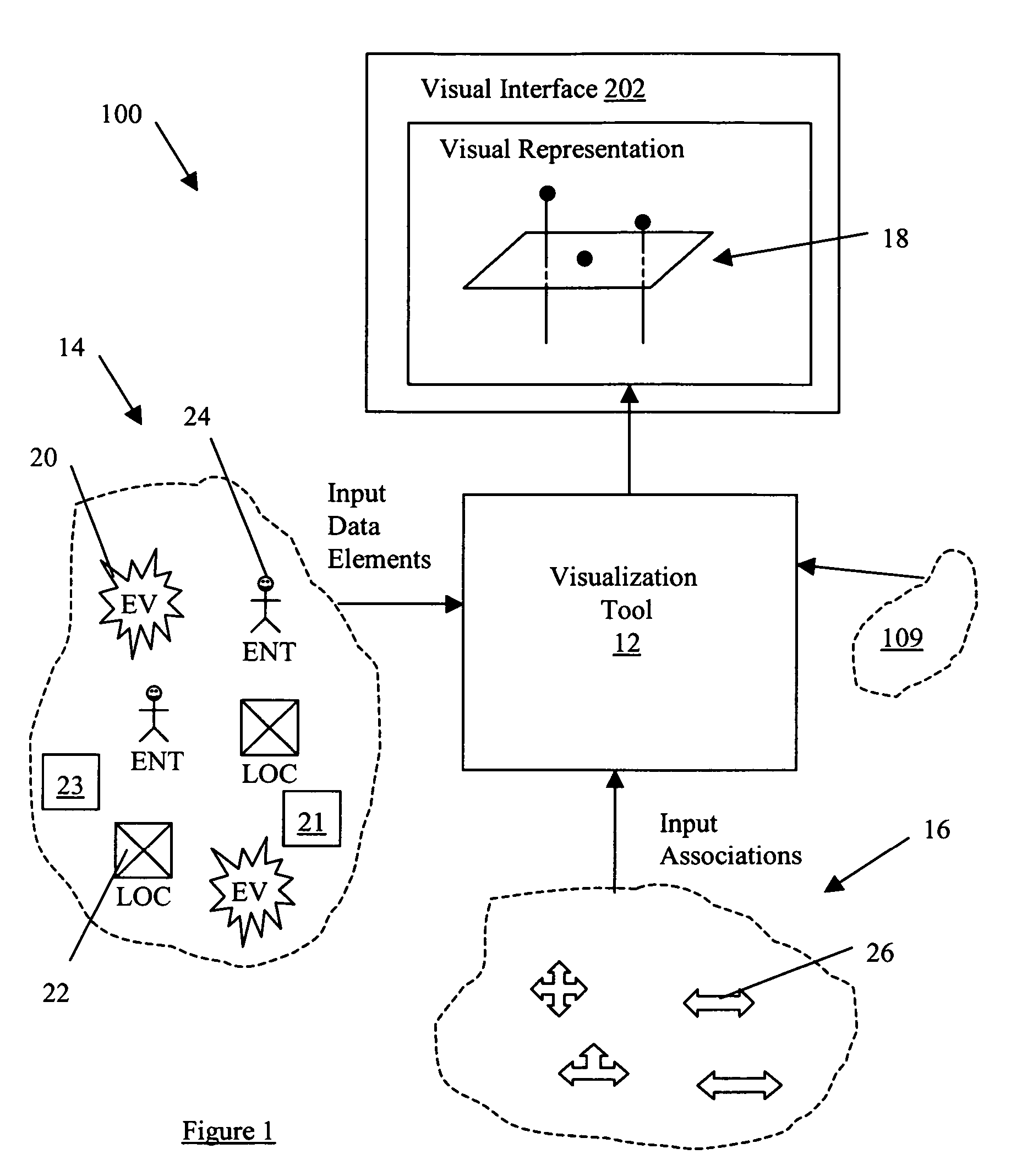
System and method for applying link analysis tools for visualizing connected temporal and spatial information on a user inferface
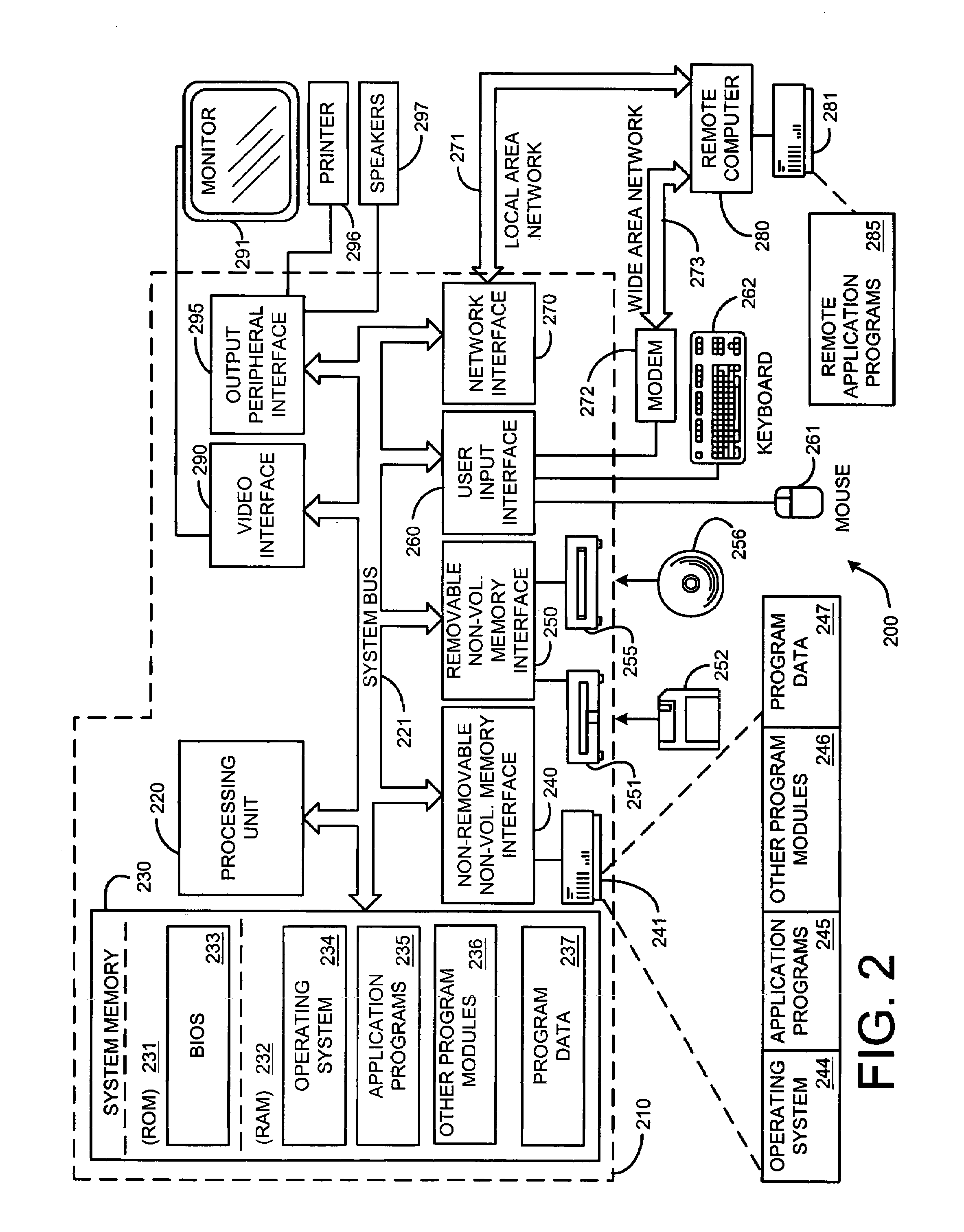
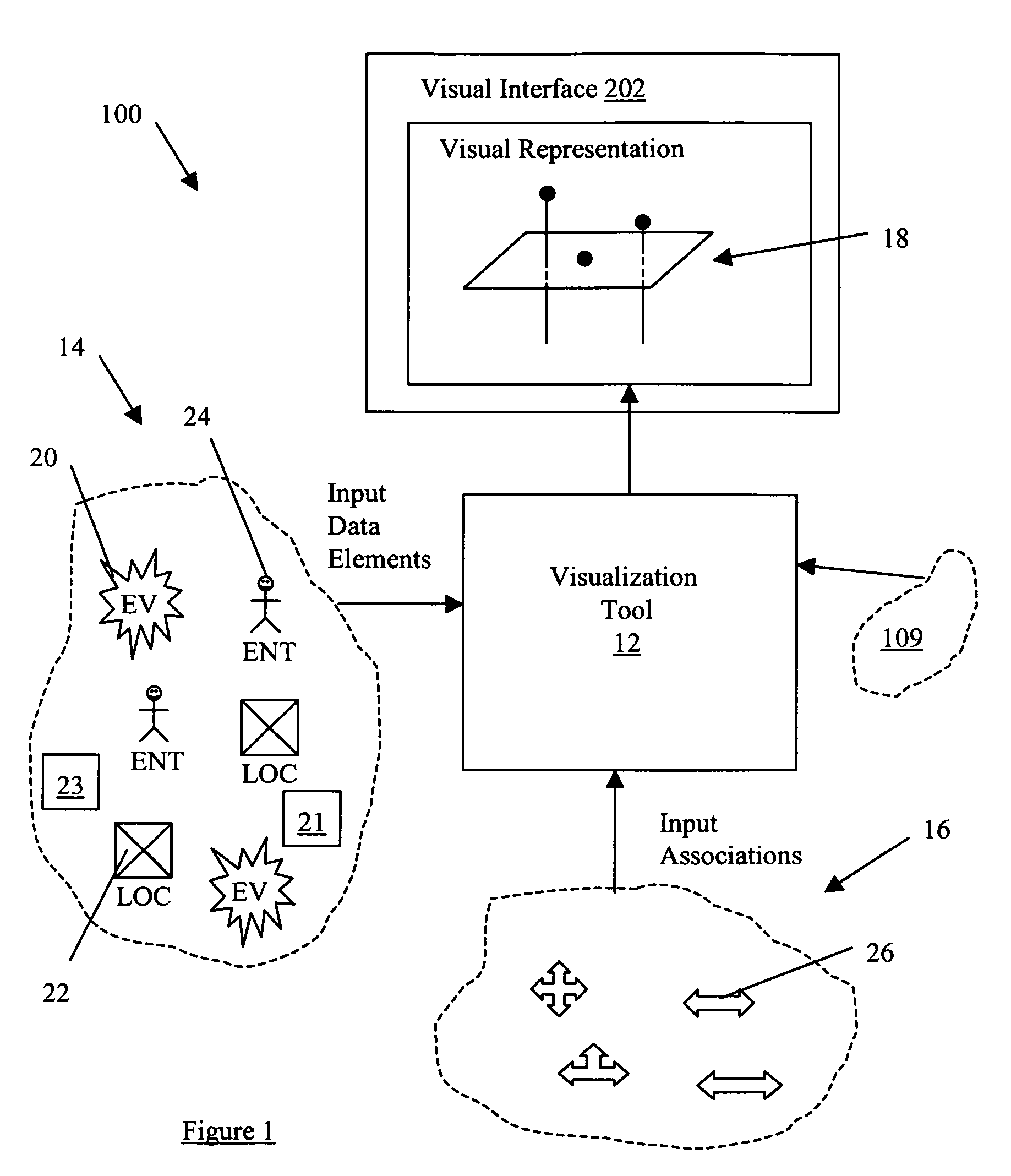
ActiveUS20070055782A1Drawing from basic elementsMultiple digital computer combinationsTime domainData element
A system and method for analyzing a plurality of data elements having both temporal and spatial properties, where a first data element and a second data element of the plurality of data elements are linked by at least one association element. The system and method include selecting the first data element from the plurality of data elements and providing at least one search criteria for use in analyzing the properties of the plurality of data elements with respect to at least one property of the first data element. An analysis module is used to apply the at least one search criteria to the properties of the plurality of data elements for identifying the second data element from the plurality of data elements and the corresponding at least one association element. The at least one association element is configured for representing a connection between the first data element and the second data element, such that the connection has a first property common to a property of the first data element and a second property common to a property of the second data element. A visualization module is used to generate a visual representation of the first and second data elements and the association element configured for display on a user interface for subsequent interaction with user events. The visual representation includes a spatial domain including a reference surface for providing a spatial reference frame having at least two spatial dimensions and a temporal domain operatively coupled to the spatial domain for providing a common temporal reference frame for locations of interest in the spatial domain.
Owner:PEN LINK LTD
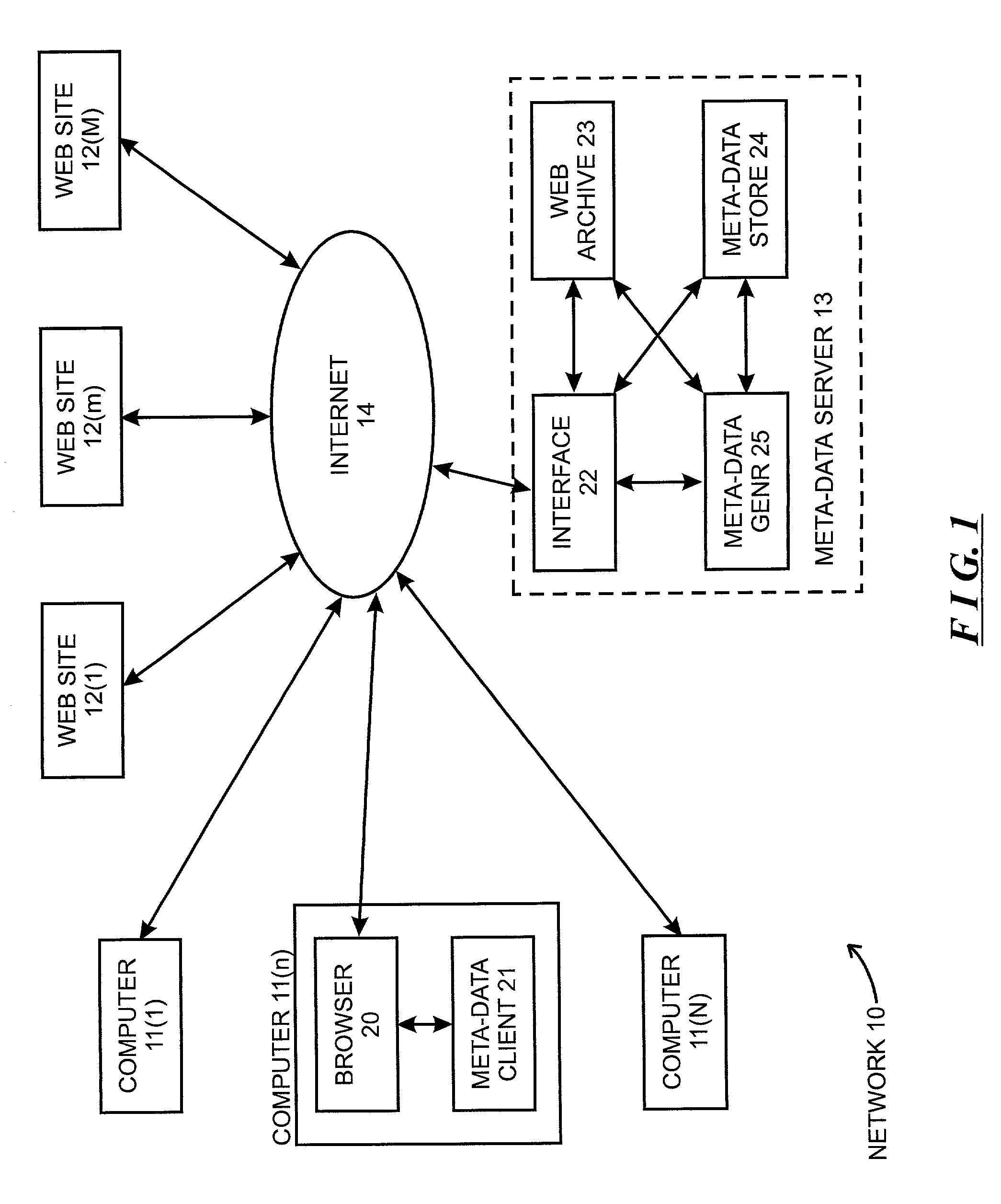
Analysis of search activities of users to identify related network sites
A meta-data generator is described for generating meta-data relating to at least one Web site, the meta-data identifying, for a Web site providing at least one Web page, identification of, for other Web sites, at least one Web page associated therewith having a selected relationship with the at least one Web site. The meta-data generator includes an information accumulation module, a meta-data generation module and a meta-data storage module. The information accumulation module accumulates Web page information associated with respective Web sites. The meta-data generation module uses the accumulated Web page information according to a selected meta-data generation methodology to generate said meta-data, and the meta-data storage module stores the meta-data generated by the meta-data generation module. Several meta-data generation methodologies are described, including a link (Web page identifier) analysis methodology, two Web page usage analysis methodologies; and a search results analysis methodology. In the link analysis methodology, meta-data is generated associated with Web pages based on the proximity of links to Web pages in each of a plurality of Web pages. In the Web page usage analysis methodologies, the meta-data generator 25 generates meta-data based on the sequence of Web sites which operators enable their computers to request Web pages during a session. In the search results analysis methodology, the meta-data generator generates meta-data based on activities of an operator after he or she receives results generated by a search engine in response to a search query.
Owner:ALEXA
Method and system for analyzing digital wireless network performance
InactiveUS7395058B1Accurate analysisAccurate performanceRadio/inductive link selection arrangementsAutomatic exchangesCode division multiple accessModularity
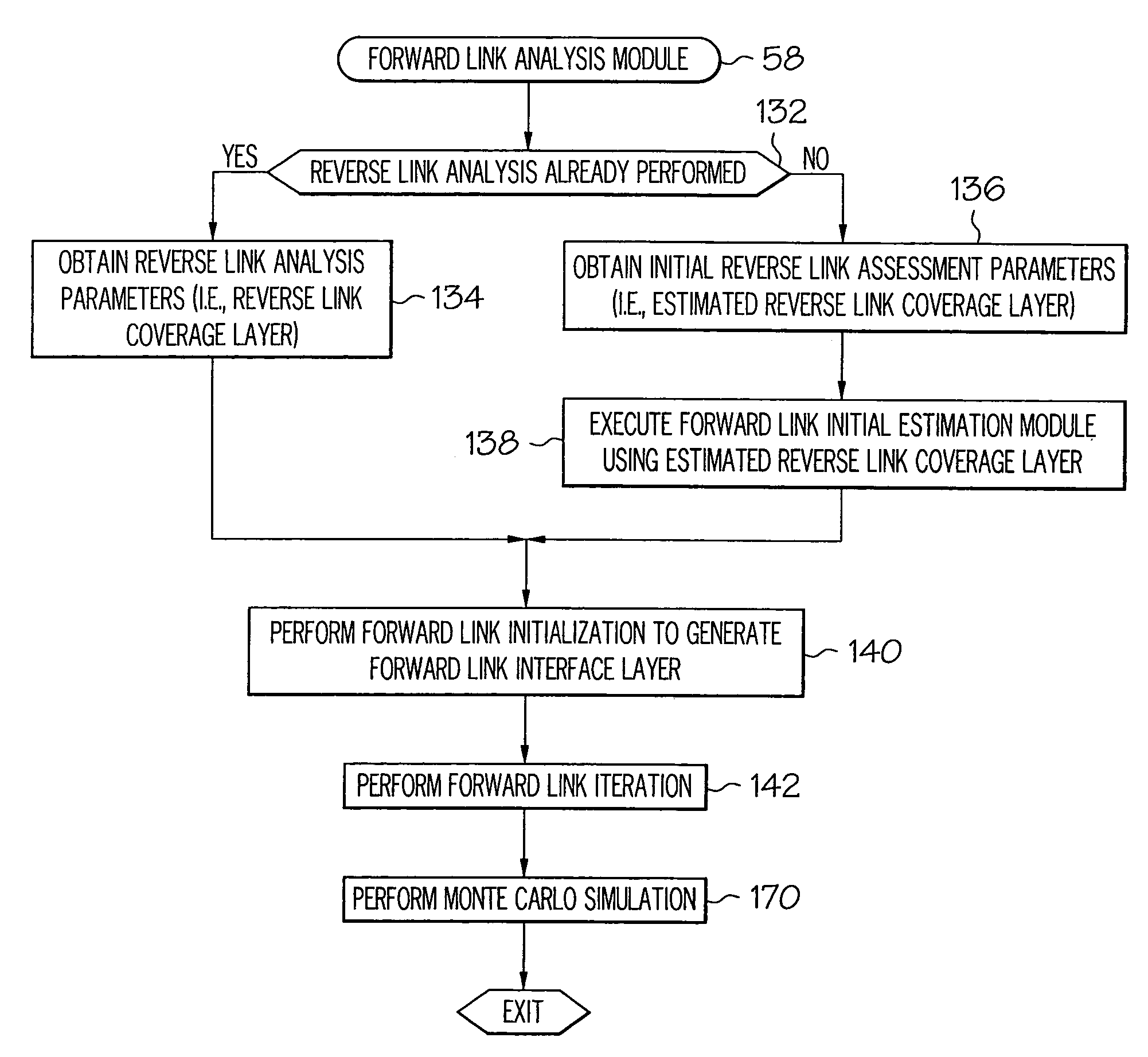
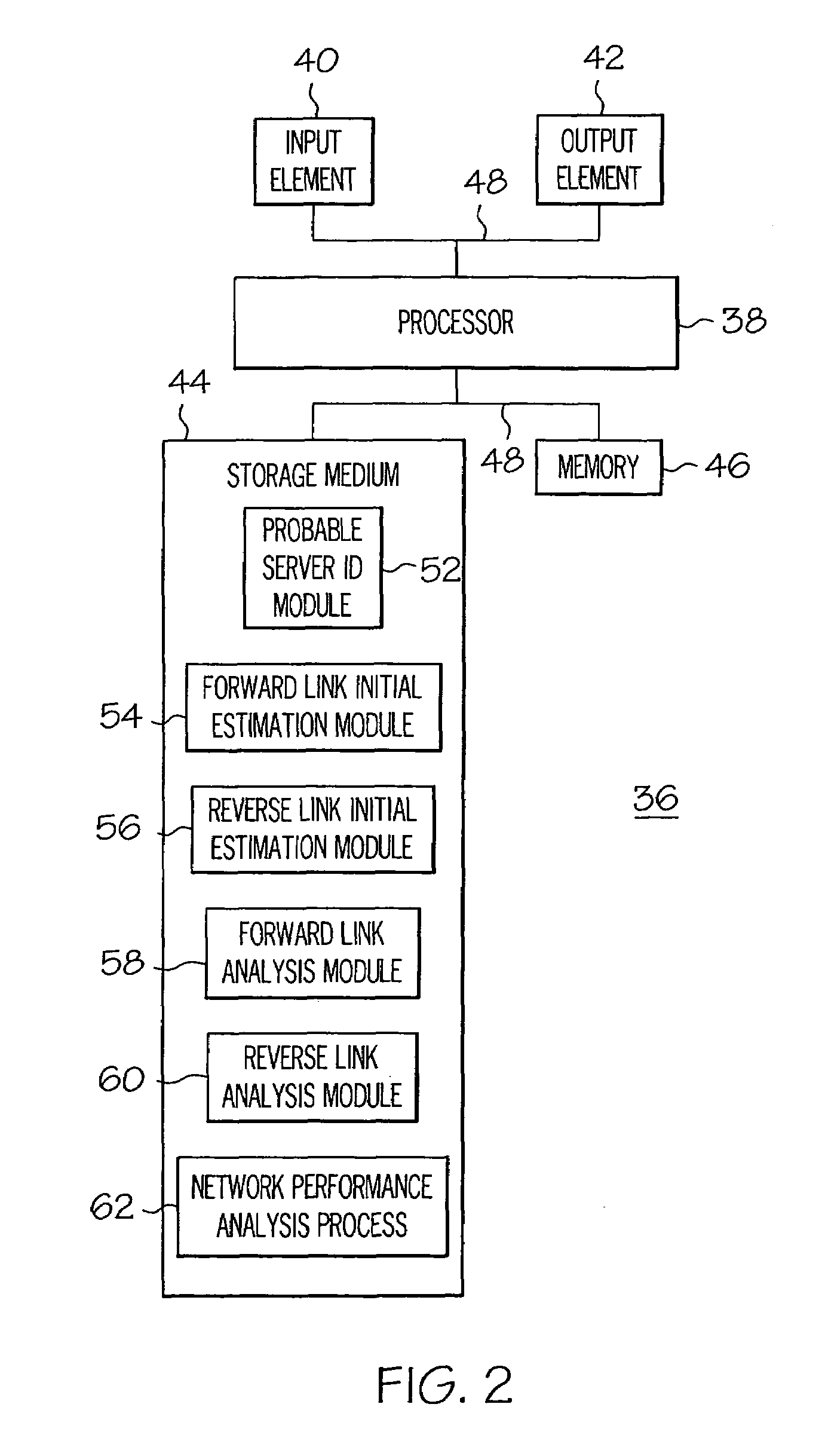
A system (36) provides a network designer with a mechanism for analyzing the performance of a code division multiple access wireless network (20). The system (36) includes executable code in the form of a probable server identification module (52), a forward link initial estimation module (54), a reverse link initial estimation module (56), a forward link analysis module (58), and a reverse link analysis (60). The modular architecture of the modules (52, 54, 56, 58, and 60) are appropriately configured and interconnected in order to form a network performance analysis process (62) that accurately analyzes both the reverse link performance and the forward link performance of the network (20).
Owner:VERIZON PATENT & LICENSING INC
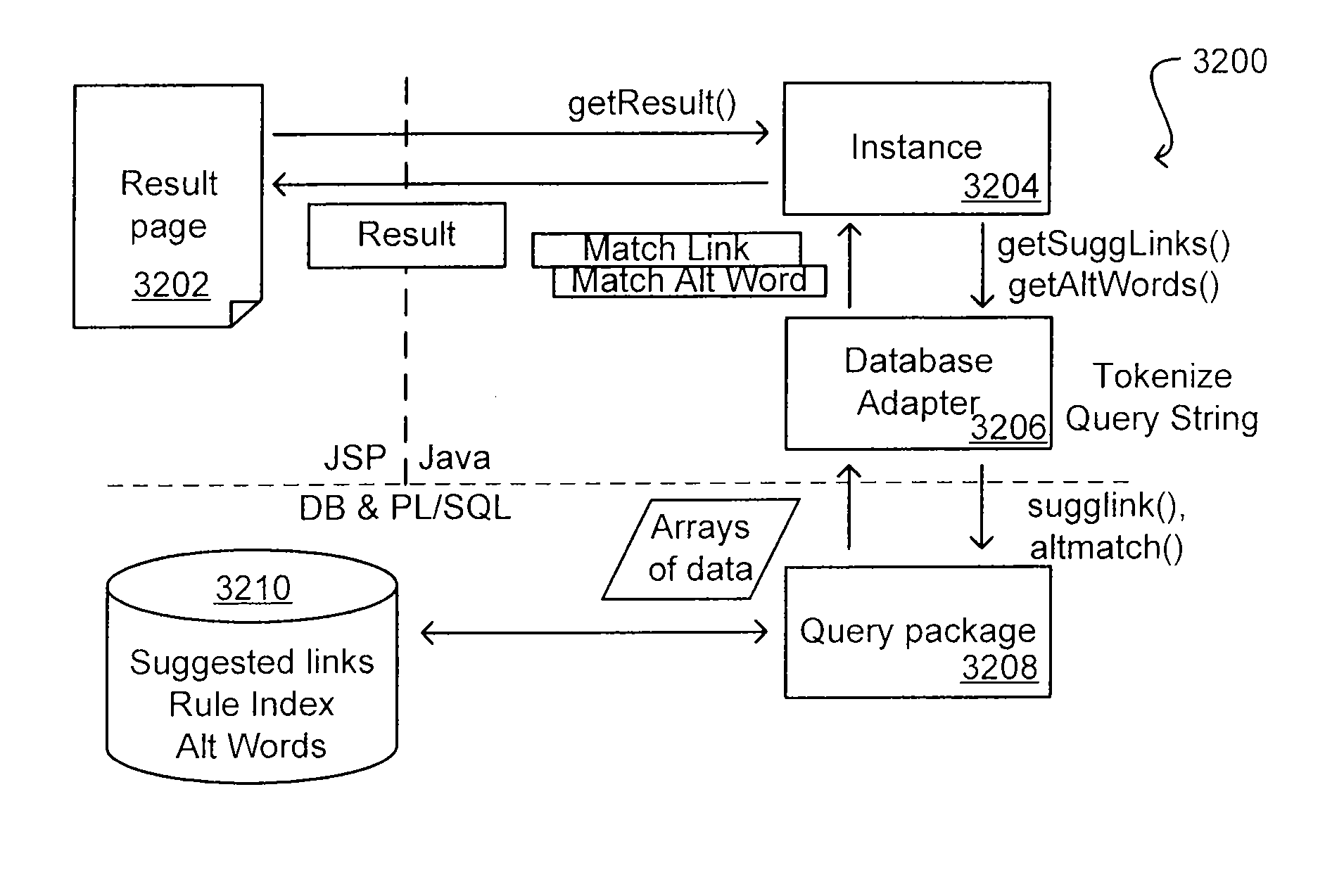
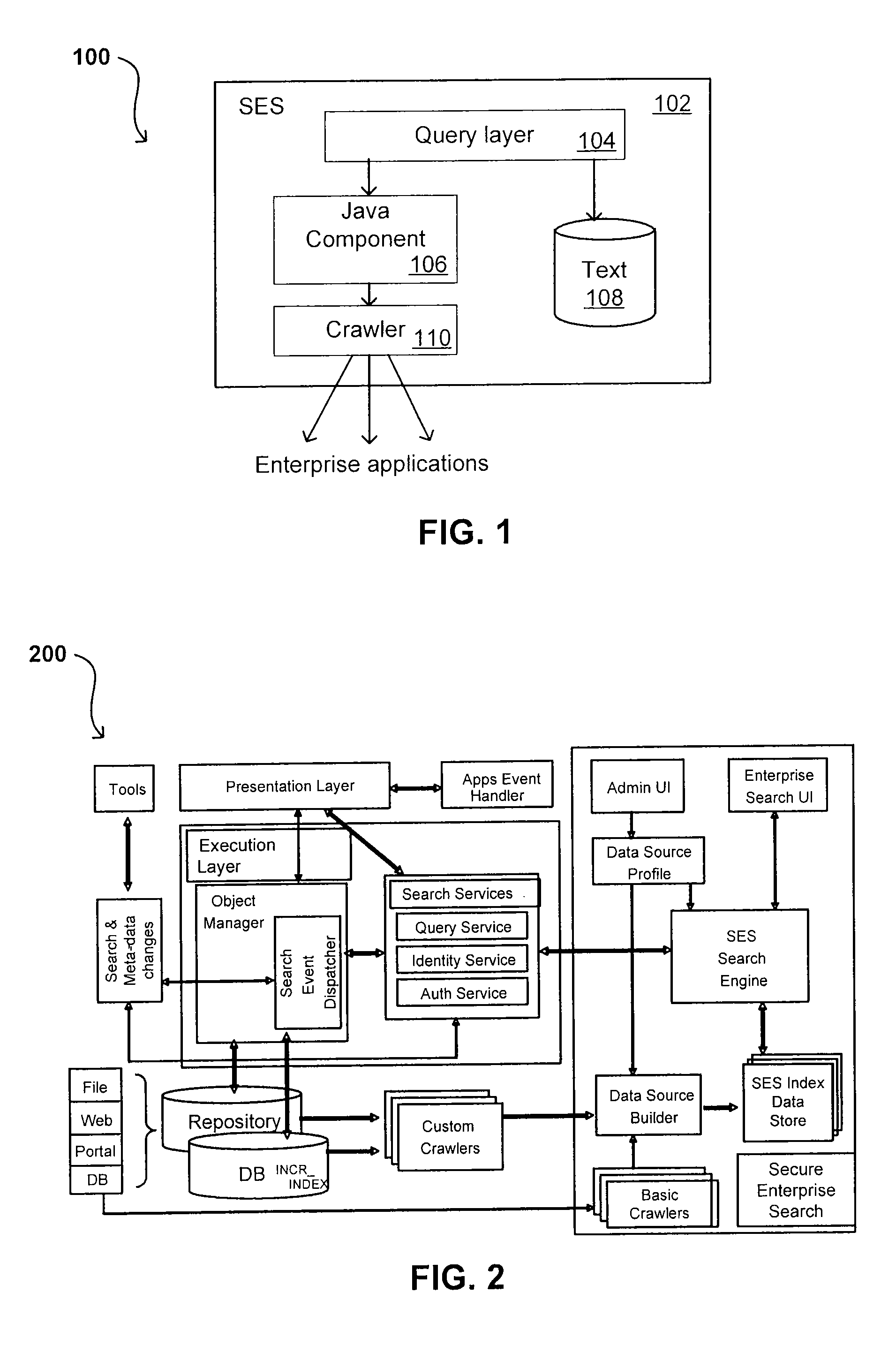
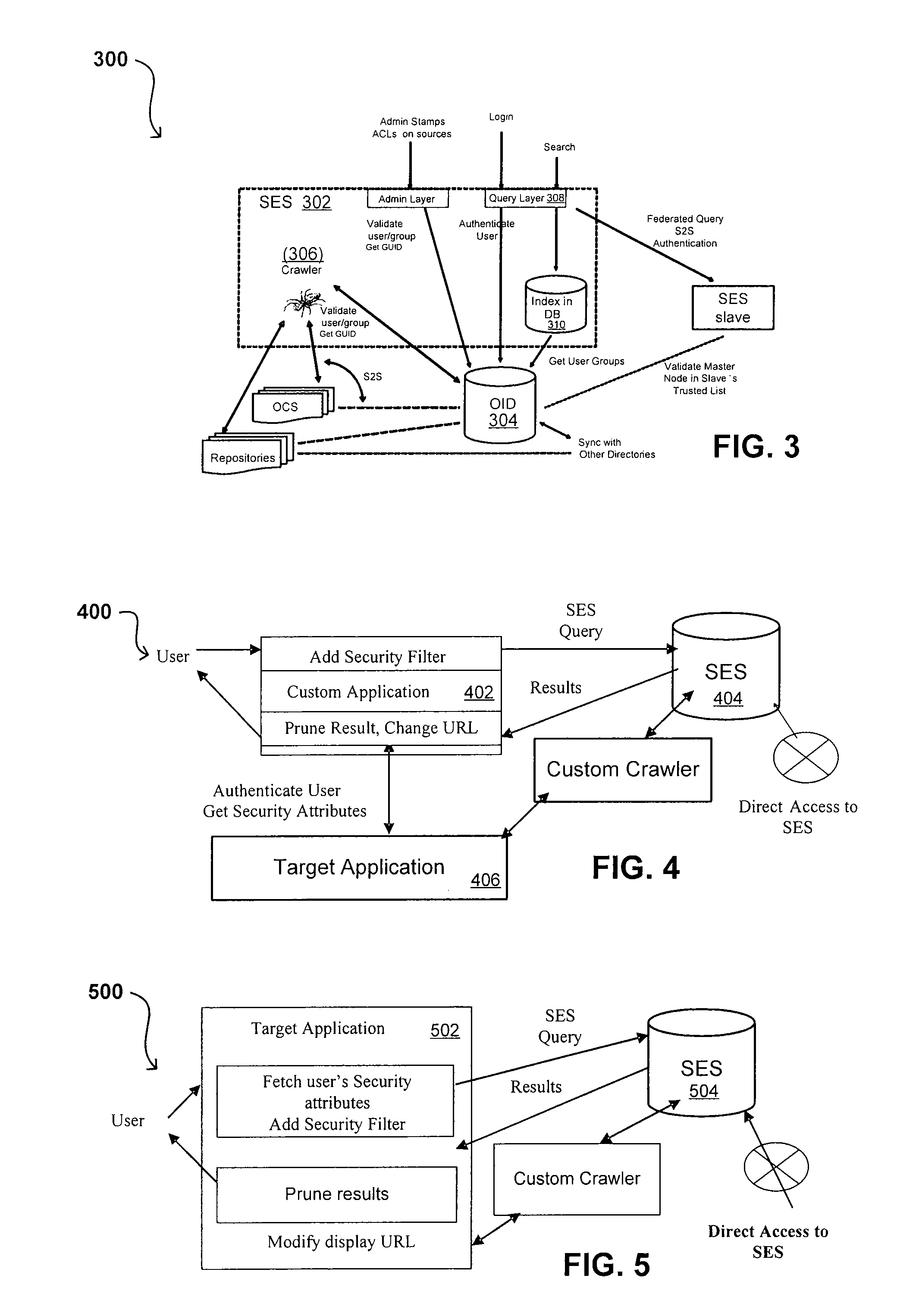
Link Analysis for Enterprise Environment
ActiveUS20070208734A1Limited lifetimeImprove performanceDigital data information retrievalDigital data processing detailsThe InternetExtensible architecture
A flexible and extensible architecture allows for secure searching across an enterprise. Such an architecture can provide a simple Internet-like search experience to users searching secure content inside (and outside) the enterprise. The architecture allows for the crawling and searching of a variety or sources across an enterprise, regardless of whether any of these sources conform to a conventional user role model. The architecture further allows for security attributes to be submitted at query time, for example, in order to provide real-time secure access to enterprise resources. The user query also can be transformed to provide for dynamic querying that provides for a more current result list than can be obtained for static queries.
Owner:ORACLE INT CORP
Vehicle data mining based on vehicle onboard analysis and cloud-based distributed data stream mining algorithm
The present invention relates to a system and method for performing vehicle onboard analysis on the data associated with the vehicle and implementing a cloud-based distributed data stream mining algorithm for detecting patterns from vehicle diagnostic and correlating the pattern with the contextual data. The system applies the distributed data mining algorithms for mining the results of the vehicle onboard analytics sent over the wireless network to the server and correlates the analyzed data with the contextual data of the vehicle. The system extracts performance patterns from data, builds predictive models from vehicle diagnostic, and correlates the predicted model with the business process using state of the art link analysis techniques.
Owner:AGNIK
Topic crawler system based on social labels
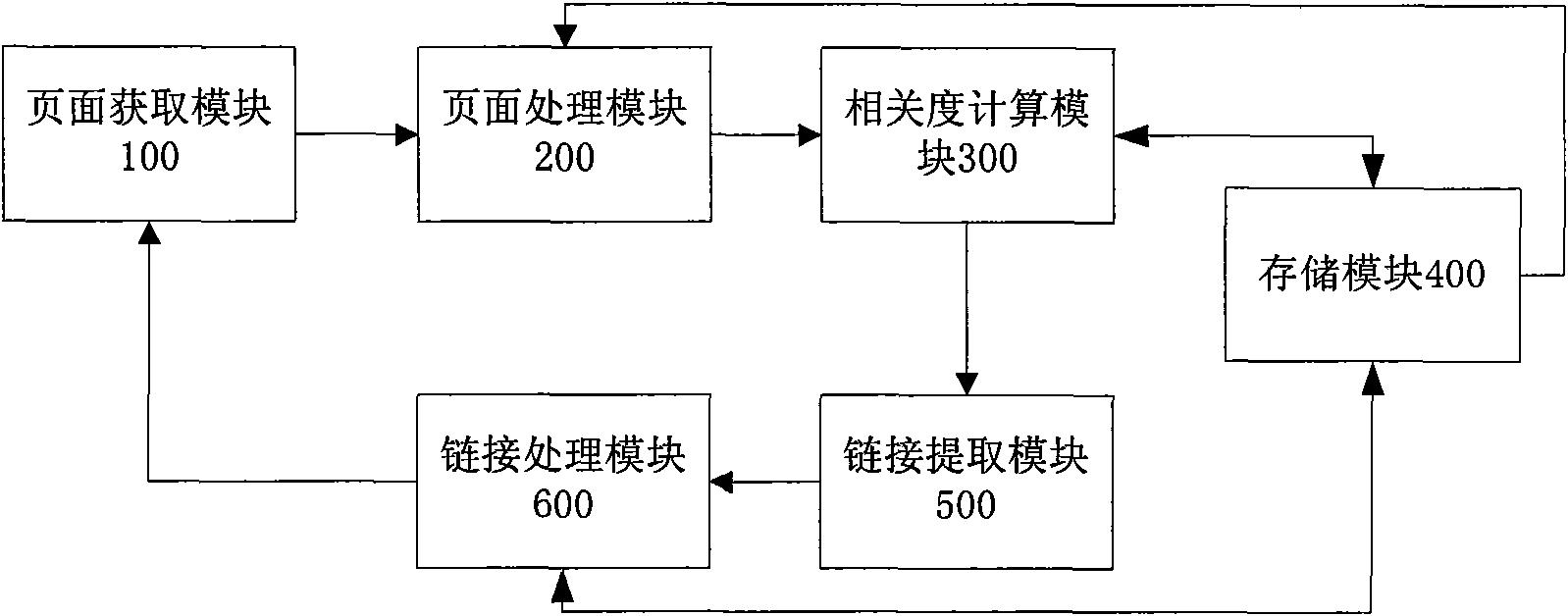
InactiveCN101561814ARealize functionImprove crawler efficiencySpecial data processing applicationsData setData content
The invention relates to a topic crawler system based on social labels, which comprises a page acquisition module, a page processing module, a correlation calculation module, a storage module, a link extraction module and a link analysis module. The system makes full use of the social labels of web pages, utilizes the properties that the social labels are the acknowledged description on page contents and are closer to actual contents described by the web pages to judge the correlation of the web pages, and applies the correlation to a network topic crawler to guide the crawling direction of the crawler and provide high-quality webpage data contents for a topic search engine. The system well uses the network bandwidth resources to reduce unnecessary expenditure during web page acquisition, adopts different storage modes aiming at different requirements to reduce the consumption of IO, and adopts a multi-level cache mechanism to reduce blockage and improve the efficiency of the crawler. Under the support of the social labels, the system optimizes a crawler framework, and provides an optimal webpage data set for subsequent other processing flows of the topic search engine.
Owner:HUAZHONG UNIV OF SCI & TECH
Short text characteristic expanding method based on semantic atlas
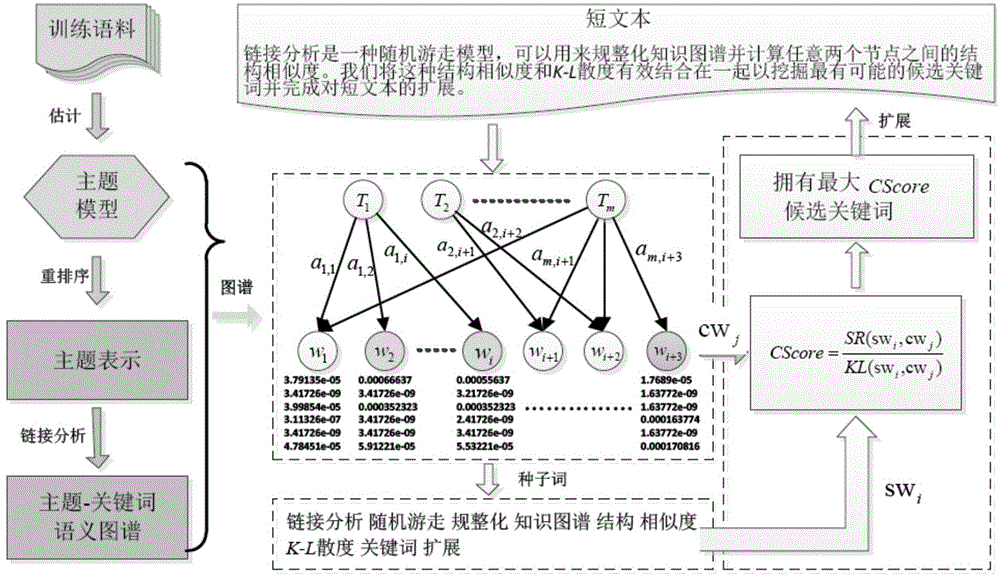
ActiveCN104391942AImprove classification performanceSolve the sparsity problemSemantic analysisSpecial data processing applicationsGraph spectraData set
The invention discloses a short text characteristic expanding method based on a semantic atlas. The method includes the steps: performing subject modeling by the aid of a training data set of a short text, and extracting subject term distribution; reordering the subject term distribution; building a candidate keyword dictionary and a subject-keyword semantic atlas; calculating comprehensive similarity degree evaluation of candidate keywords and seed keywords based on a link analysis method, and selecting the most similar candidate keywords to finish expanding the short text. Compared with a short text characteristic representation method based on a language model, the method is simple to operate and high in execution efficiency, and semantic correlation information between the keywords is sufficiently used. Compared with a traditional short text characteristic representation method based on a word bag model, the problems of data sparseness and semantic sensitivity are effectively relieved, and the method is independent of external large-scale auxiliary training corpus or a search engine.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
Backward and forward non-normalized link weight analysis method, system, and computer program product
A method, system, and computer program product for hypertext link analysis that includes independently employing non-normalized backward and forward operators to obtain two independent weights for each document in a hypertext-linked graph, for subsequent ranking and analysis.
Owner:TELENOR AS
Method for constructing topic web crawler system
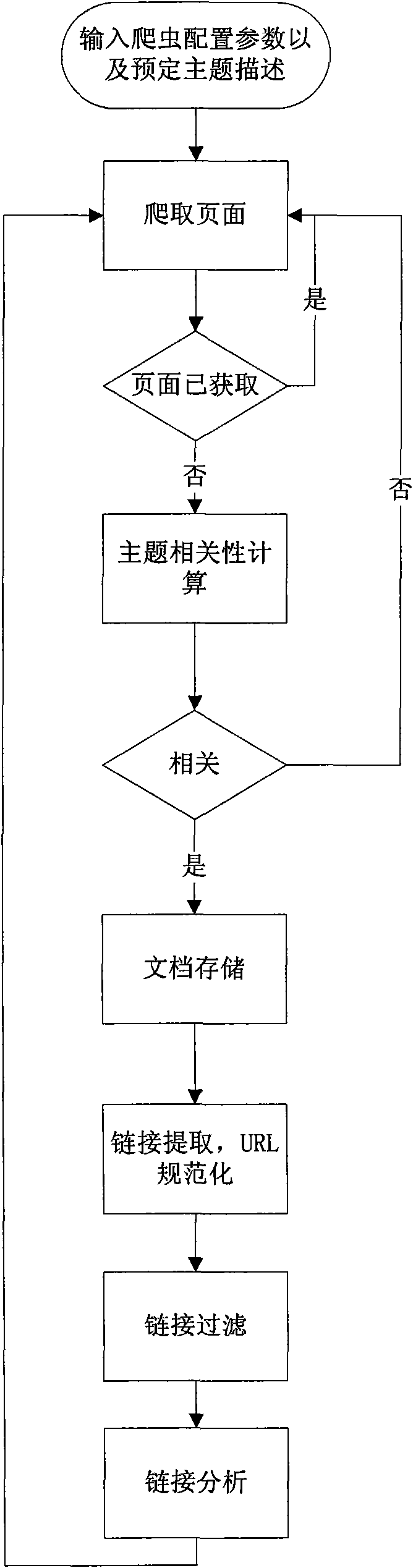
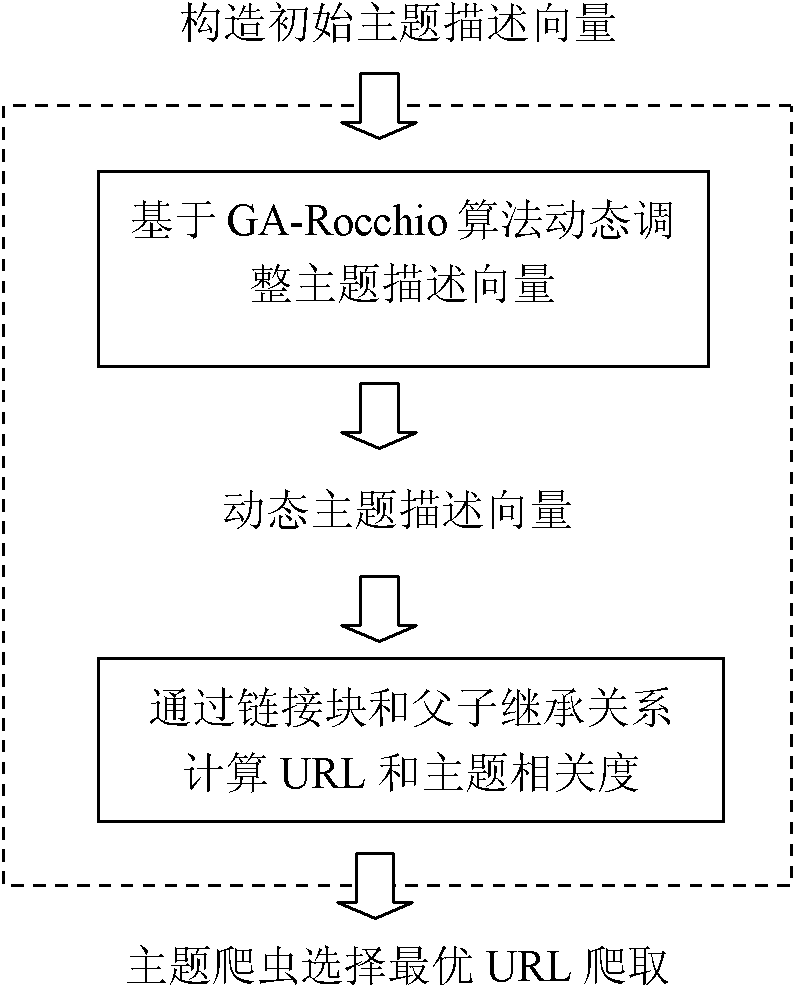
InactiveCN102073730AImprove relevanceSolve the small amount of wordsSpecial data processing applicationsAlgorithmGenetic algorithm
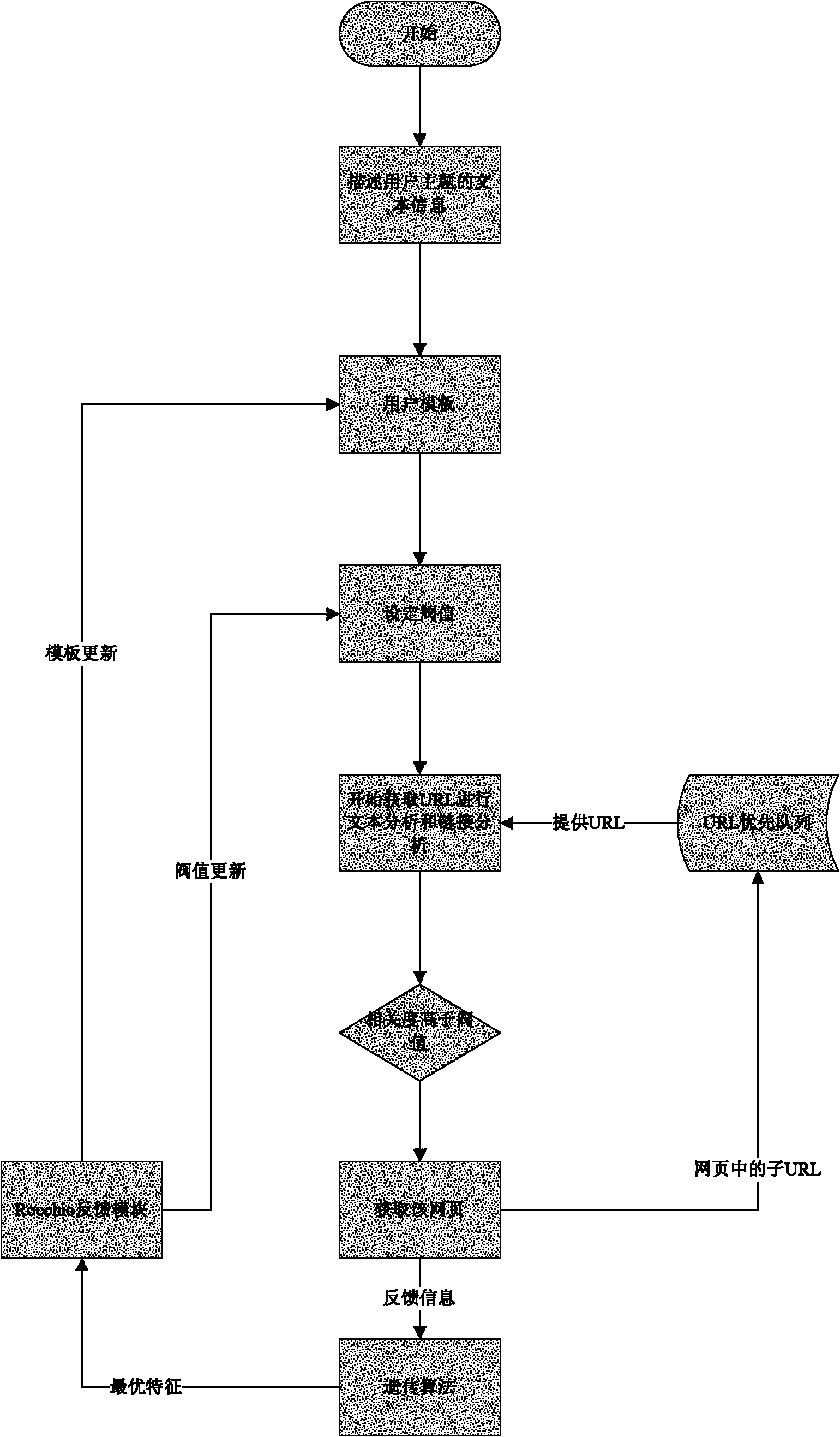
The invention provides a method for constructing a topic web crawler system, which comprises the following steps of: (1) defining an initial description vector of a topic, setting an initial threshold value of the correlation degree and initializing a URL (Uniform Resource Locator) queue; (2) sequentially acquiring URLs from the initial URL queue to carry out crawl; (3) carrying out text analysis on the URLs; (4) carrying out link analysis on the URLs; (5) calculating the correlation degrees of the URLs with the topic; (6) adding the URLs of which the correlation degrees are more than the threshold value of the correlation degree into an ordered URL queue, sorting the URLs according to the correlation degrees of the URLs with the topic vector, carrying out crawl sequentially until the queue is empty, extracting a sub URL in each crawled webpage, and returning the step (3); (7) carrying out optimization of a genetic algorithm by using the genetic algorithm; and (8) updating the topic vector by a Rocchio feedback module, dynamically regulating the threshold value of the correlaton degree and continously crawling the webpages. In the method, a great amount of training texts do not need to be prepared in advance. The method has high speed and is suitable for processing an immense amount of on-line webpage data.
Owner:HARBIN ENG UNIV
Flow scheduling system and method based on SDN
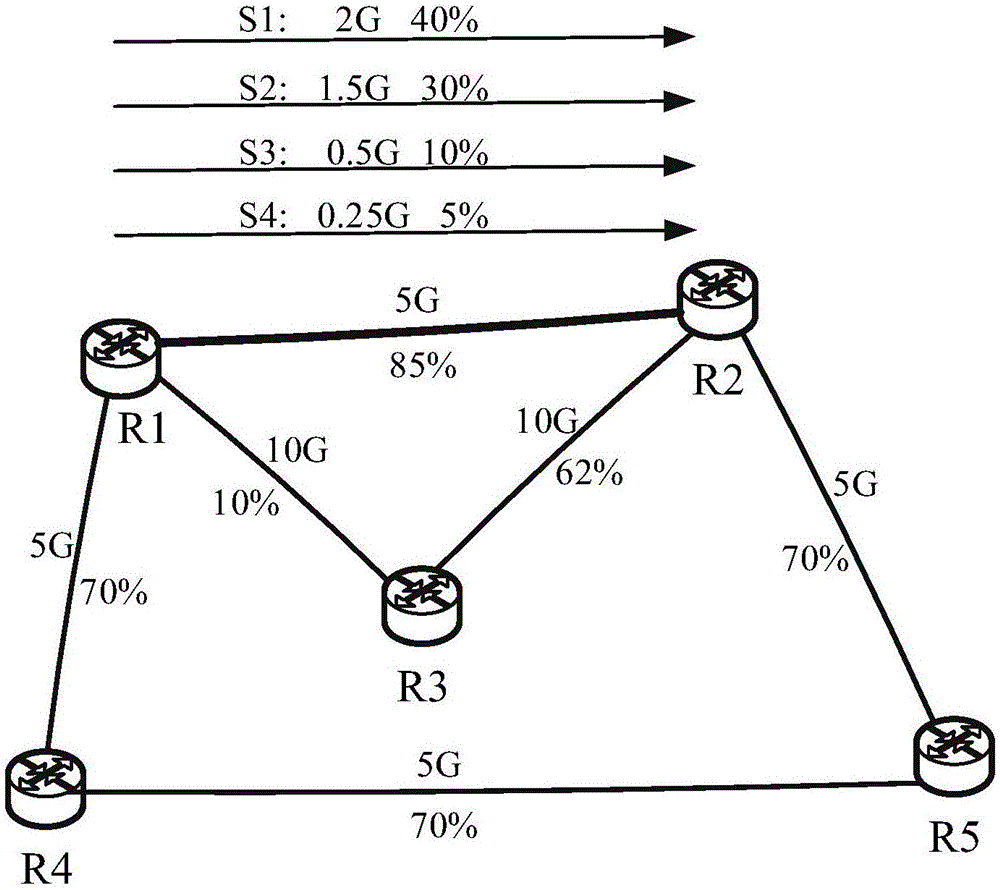
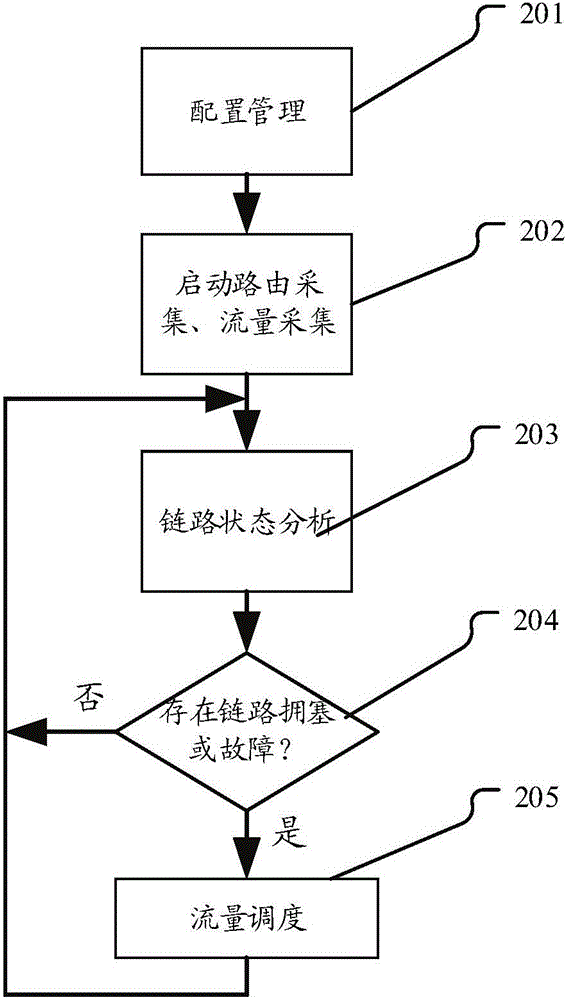
InactiveCN106411766AChoose accuratelyEliminate congestionData switching networksNetwork linkLink analysis
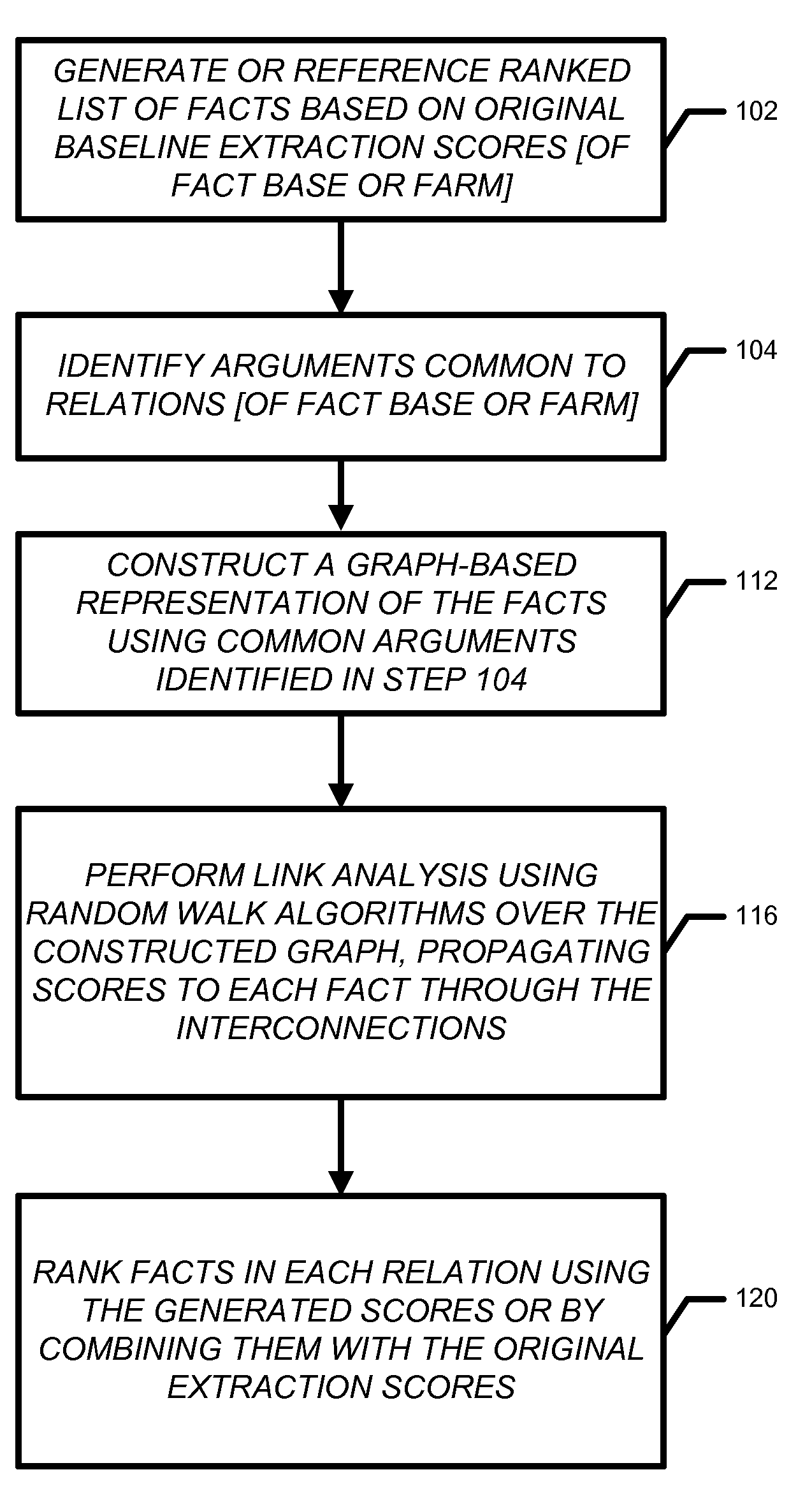
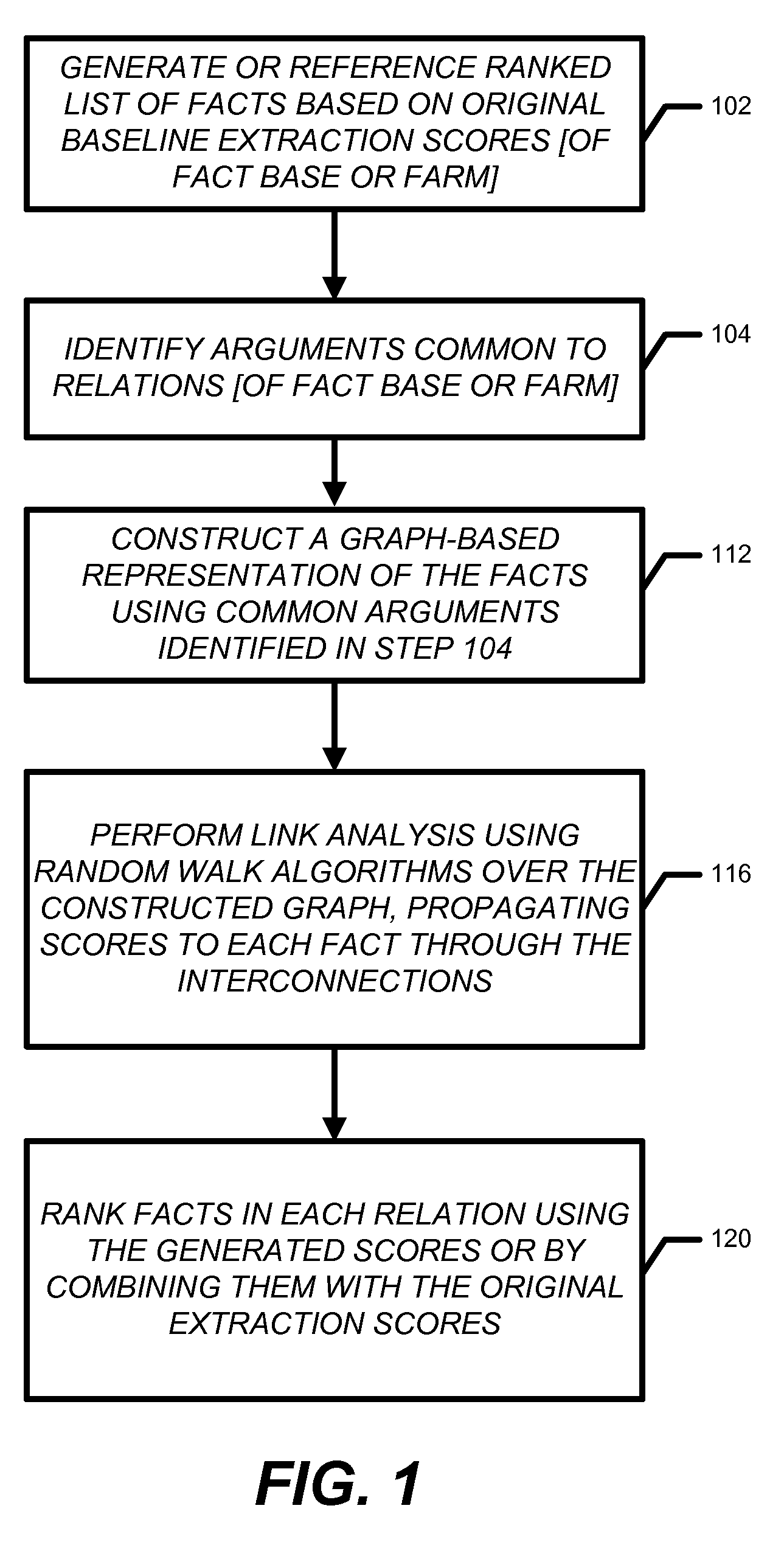
The invention relates to a flow scheduling system and method based on SDN. The method comprises the following steps: acquiring a network link parameter configured by a user; starting routing collection and flow collection processes; performing link analysis; judging whether a congested link exists, if so, scheduling the flow of the congested link to an idle link by a flow scheduling module, and otherwise, continuing to perform periodic link analysis. By adoption of the system and the method, being different from the system under distributed architecture, the flow scheduling method and system based on the SDN can comprehensively sense the link congestion or link faults; the network link heath condition updated in real time can be converted to a network link metric coefficient, and thus the selection of an optimal path is more accurate; and in the case of network link congestion, the flow scheduling method and system based on the SDN provided by the invention are started to quickly and effectively eliminate the link congestion, and the links are reasonably configured to maximize the bandwidth utilization rate, and flow load balance of the whole network can be realized.
Owner:CERTUS NETWORK TECHNANJING
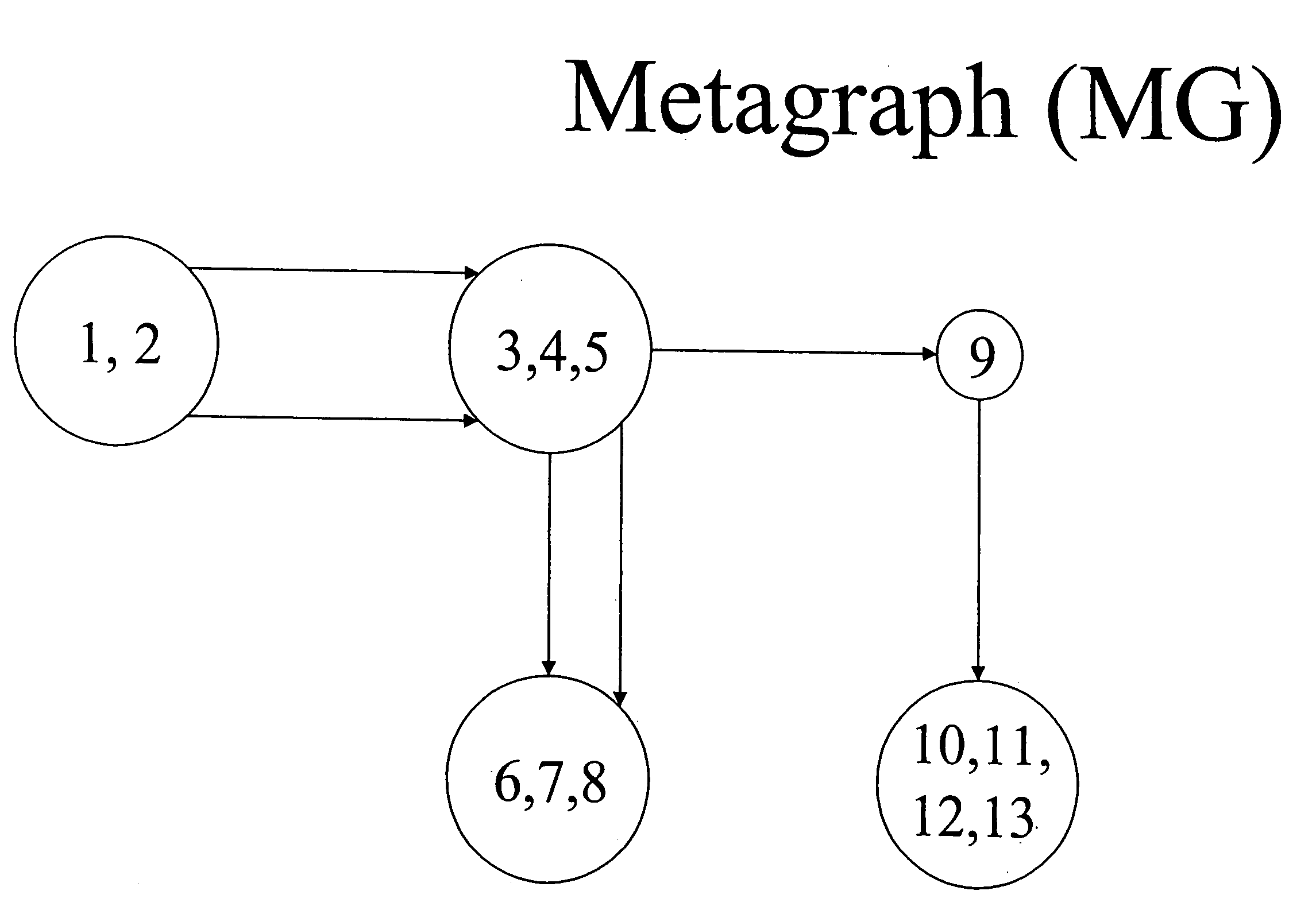
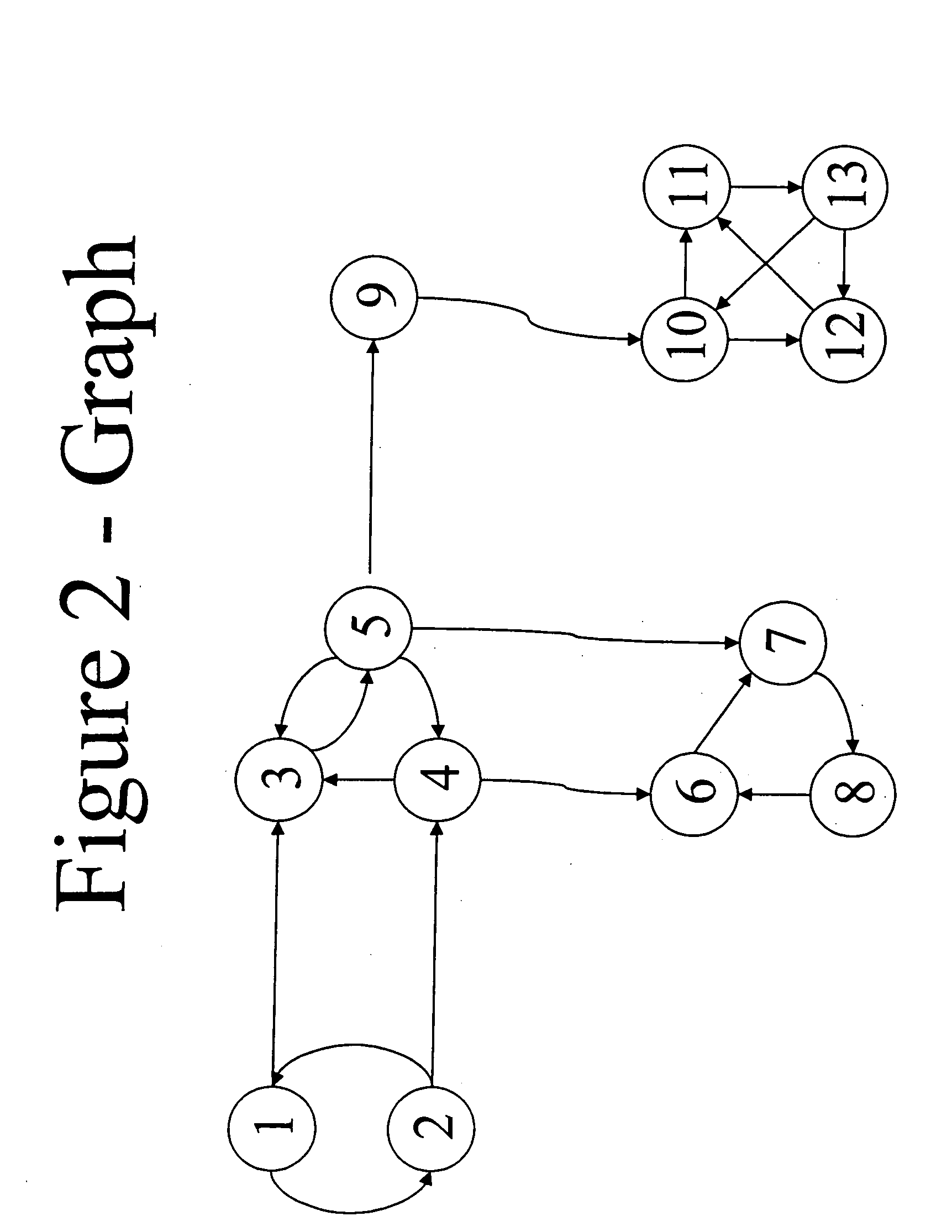
Method, system, and computer program product for ranking of documents using link analysis, with remedies for sinks
A method, device, and computer program product for ranking documents using link analysis, with remedies for sinks, including forming a metagraph from an original graph containing a link and a node; and one of reversing a link in the metagraph, and pumping a source in the metagraph.
Owner:TELENOR AS
Topic information acquisition method based on network topology
InactiveCN101441662ASave resourcesFull gatheringSpecial data processing applicationsTopic areasSubject matter
The invention relates to a topic information acquisition method based on network topology. An initial web page set is obtained from a search engine and is expressed as a vector set through purification, word division and removal of stop words, and a vector space model is used to calculate the text similarity. A network structure is utilized to perform linkage analysis to extracted URLs first, the linkage is filtered through directory hierarchies of the URLs, and then the weights of the URLs are modified according to the scaleless property of a network to perform the prior absorption selection. At the same time, unrelated topic areas are feedback, and the lengths of buffer areas of unrelated URLs are set through the distance between the URLs and a seed set. The heat of acquired topics is calculated to select one topic to obtain a new reply.
Owner:BEIJING JIAOTONG UNIV
Method for implementing topical crawler system based on learning URL string information
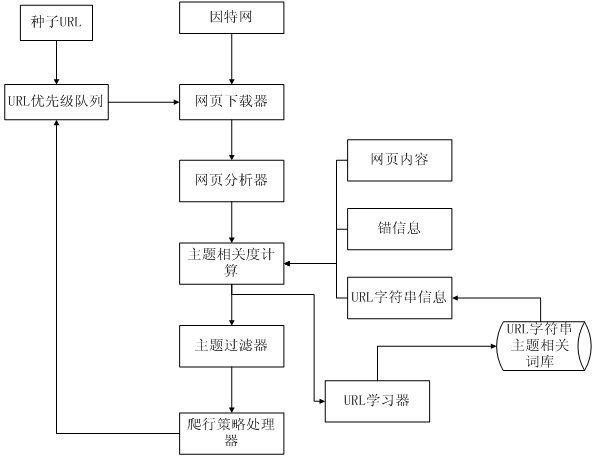
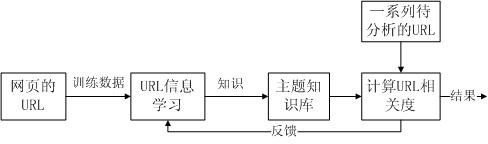
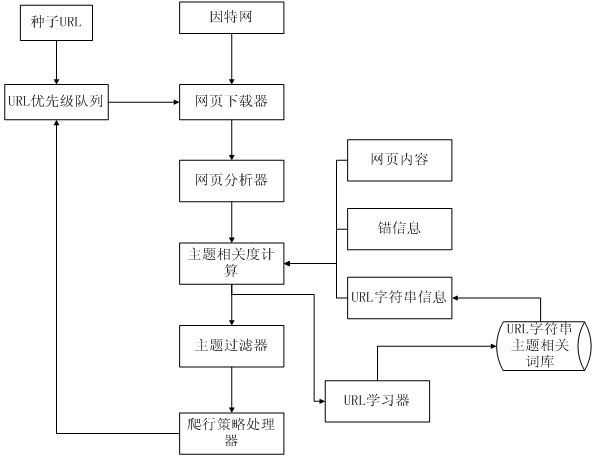
InactiveCN102662954AImprove accuracyCrawl moreSpecial data processing applicationsLocal optimumComputation complexity
The invention discloses a method for implementing a topical crawler system based on learning URL string information. First, a traditional correlation judgment method of the topical crawler is improved, and a method for judging the correlation between a target URL and a topic based on URL string information, web content, and anchor information is proposed. Information brought by the URL string is learned continuously by adopting a method of machine learning to update relevant vectors of the topic dynamically, and the judgment accuracy of correlation between the target URL and the topic is improved. Finally, a crawler strategy which combines content analysis and link analysis is adopted while computational complexity is not increased, which prevents the topical crawler from trapping in local optimum, improves overallness of the crawler when crawling, and improves efficiency of the crawler. The method of the invention can be used in a crawler module of a vertical search engine to crawl web pages of a particular field.
Owner:HANGZHOU DIANZI UNIV
Method, system, and computer program product for ranking of documents using link analysis, with remedies for sinks
A method, device, and computer program product for ranking documents using link analysis, with remedies for sinks, including forming a metagraph from an original graph containing a link and a node; and one of reversing a link in the metagraph, and pumping a source in the metagraph.
Owner:TELENOR AS
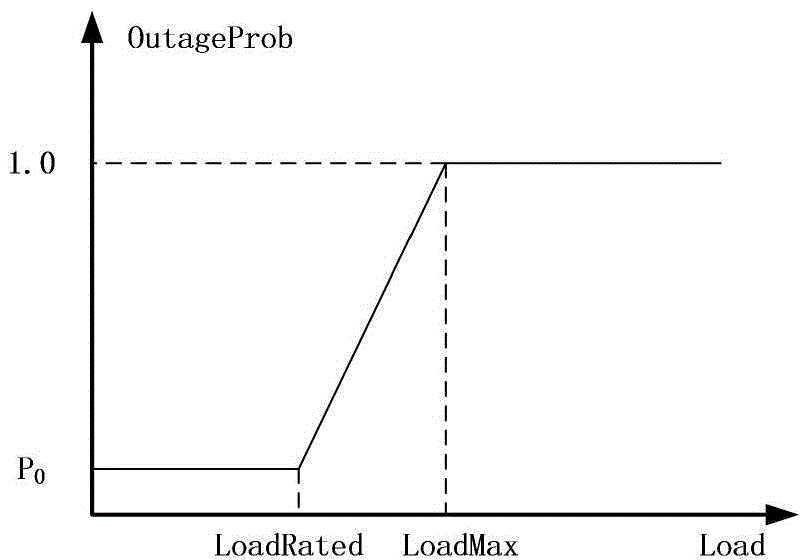
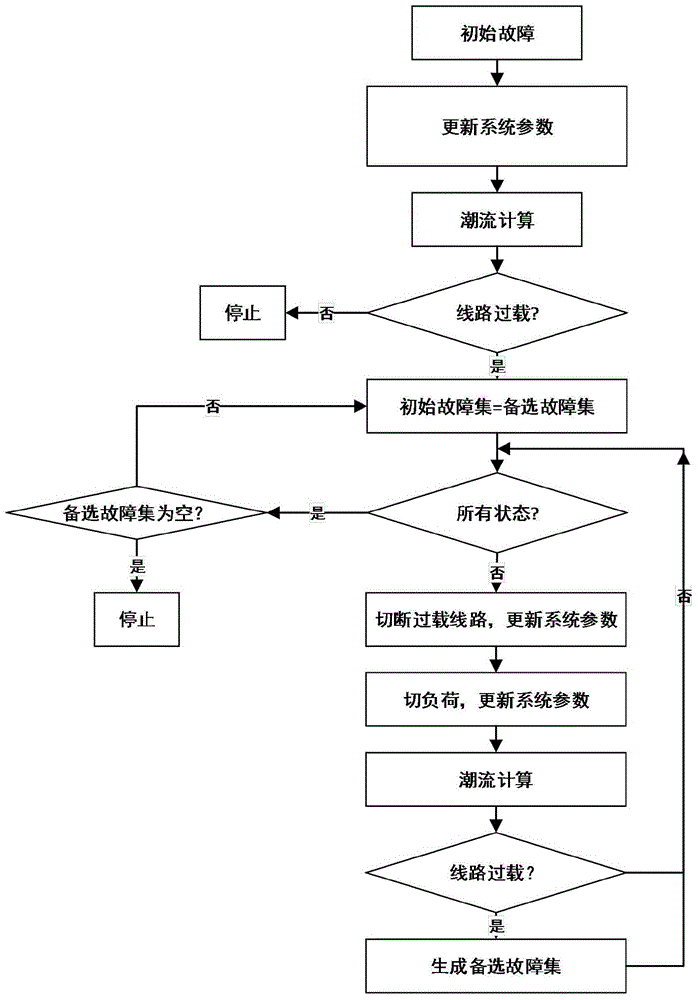
Cascading failure search and weak link analysis method based on operation reliability model
ActiveCN106327034ASimplify the difficulty of research questionsDifficulty of SimplificationResourcesCascading failurePower flow
The invention relates to a cascading failure search and weak link analysis method based on an operation reliability model. The method comprises steps: initial failure is generated randomly; a DC power flow is calculated, whether a load threshold-crossing line exists in a power system is judged, if yes, a next step is carried out, or otherwise, the operation is stopped; an initial failure set is generated, and through the operation reliability model, the threshold-crossing line outage probability is calculated; the power system state probability is calculated; if the power state probability is larger than a set threshold and the failure scale is smaller than a set threshold, the power state is added to an alternative failure set, and if no state meeting the condition exists, search is stopped; the initial failure set is taken as an alternative failure set, the current alternative failure set is emptied, and the above steps are repeated. Through searching a cascading failure event in different initial failure and analyzing a system weak link, a corresponding system reform scheme is provided, happening of the cascading failure is prevented, a subsequent event is found during an event development process, and further evolution of the cascading event can be prevented.
Owner:CHINA ELECTRIC POWER RES INST +3
System and method for applying link analysis tools for visualizing connected temporal and spatial information on a user interface
A system and method for analyzing a plurality of data elements having both temporal and spatial properties, where a first data element and a second data element of the plurality of data elements are linked by at least one association element. The system and method include selecting the first data element from the plurality of data elements and providing at least one search criteria for use in analyzing the properties of the plurality of data elements with respect to at least one property of the first data element. An analysis module is used to apply the at least one search criteria to the properties of the plurality of data elements for identifying the second data element from the plurality of data elements and the corresponding at least one association element. The at least one association element is configured for representing a connection between the first data element and the second data element, such that the connection has a first property common to a property of the first data element and a second property common to a property of the second data element. A visualization module is used to generate a visual representation of the first and second data elements and the association element configured for display on a user interface for subsequent interaction with user events. The visual representation includes a spatial domain including a reference surface for providing a spatial reference frame having at least two spatial dimensions and a temporal domain operatively coupled to the spatial domain for providing a common temporal reference frame for locations of interest in the spatial domain.
Owner:PEN LINK LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com