Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
176 results about "Bit array" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A bit array (also known as bit map, bit set, bit string, or bit vector) is an array data structure that compactly stores bits. It can be used to implement a simple set data structure. A bit array is effective at exploiting bit-level parallelism in hardware to perform operations quickly. A typical bit array stores kw bits, where w is the number of bits in the unit of storage, such as a byte or word, and k is some nonnegative integer. If w does not divide the number of bits to be stored, some space is wasted due to internal fragmentation.
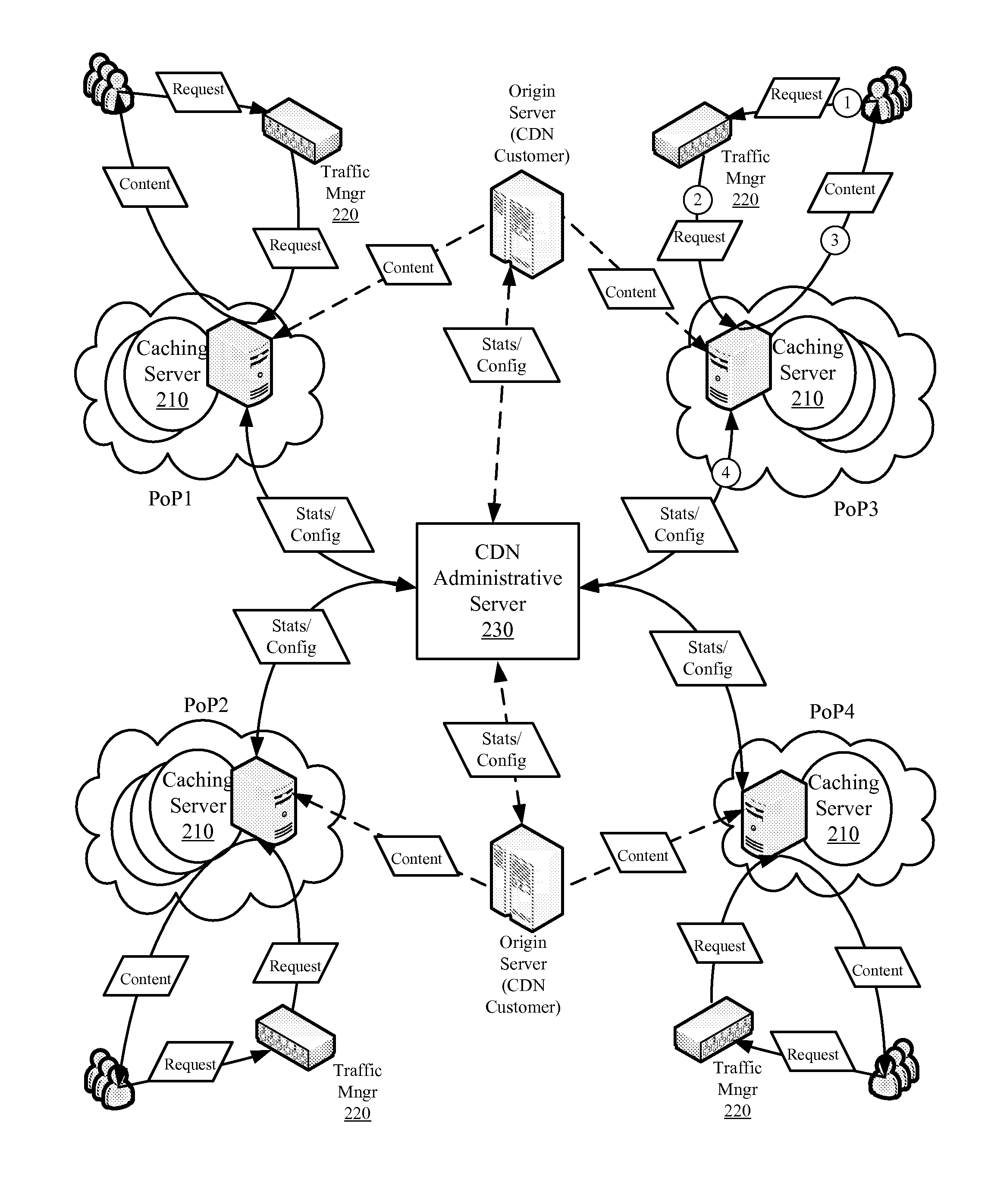
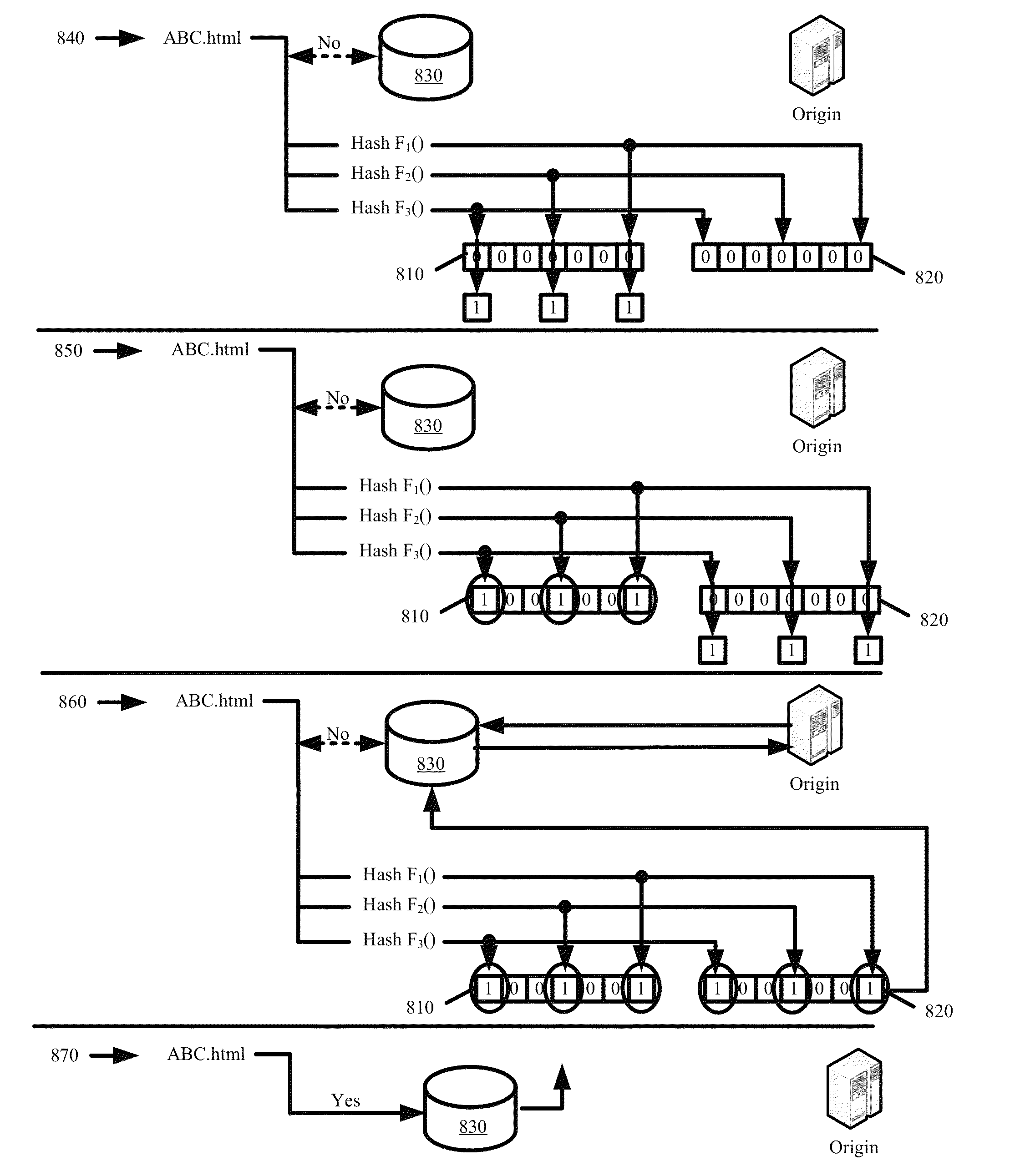
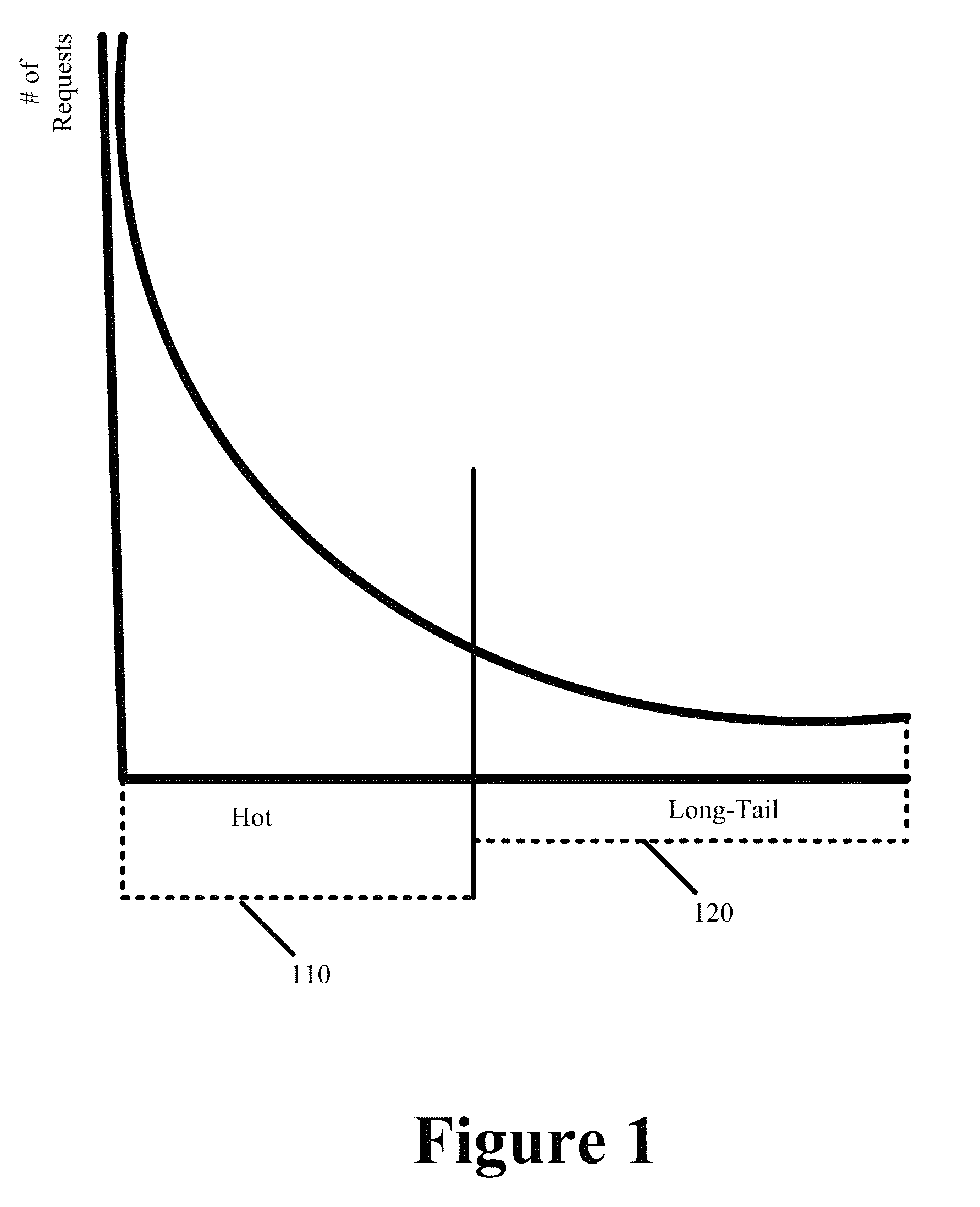
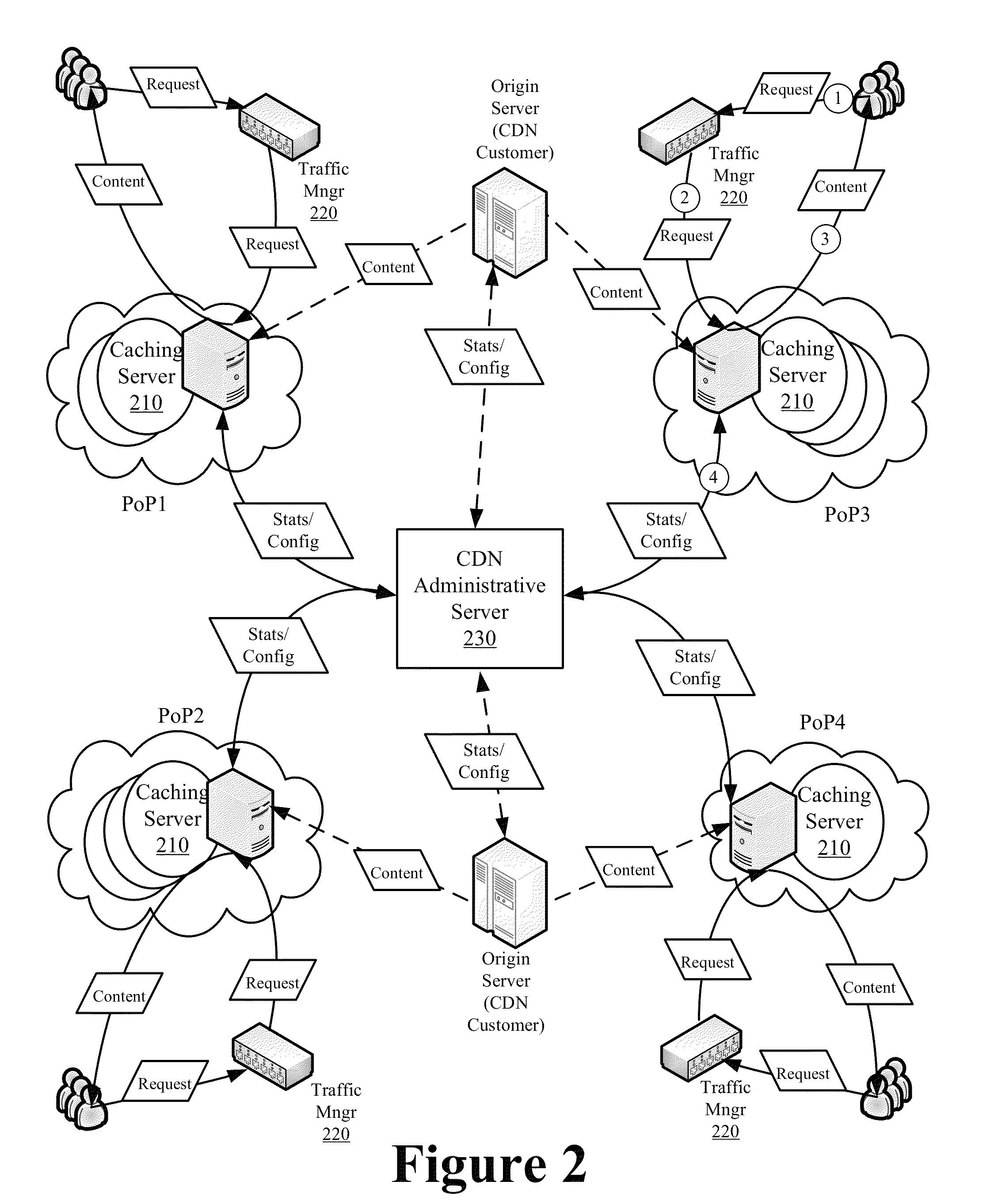
Multi-Layer Multi-Hit Caching for Long Tail Content
ActiveUS20130227051A1Easy to optimizeMinimize impactDigital computer detailsTransmissionBit arrayParallel computing
Owner:EDGIO INC
Efficient endpoint matching using a header-to-bit conversion table
ActiveUS20070078997A1Efficiently determinedEliminate duplicationMultiple digital computer combinationsTransmissionBit arrayComputer network
A header-to-bit conversion table is provided that includes a list of address headers for registered endpoints. Assigned to each address header within the list is a bit placement within a string of bits. As messages are received, select headers within a message are compared with the address headers within the list. Each intersection or match for headers sets a bit true within a bit array for the message corresponding to the bit assignment for the header within the header-to-bit conversion table. Such array may then be compared with bit masks for each endpoint, wherein those bits set true within the bit masks represent those headers needed to satisfy the criteria for a particular endpoint. If a match is found, the message (or portion(s) thereof) may be sent to the particular endpoint for processing.
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for encoding a plurality of pre-defined codes into a search key and for locating a longest matching pre-defined code
InactiveUS20050157724A1Precise positioningEliminate needData processing applicationsCode conversionBit arrayTheoretical computer science
A method and apparatus for locating in a list of pre-defined codes, a longest code matching a given code. The method and apparatus involve producing a search mask encoding at least one portion of said given code and comparing the search mask to a search key having a Prefix Node Bit Array (PNBA) in which a bit is set active in at least one of a plurality of bit positions corresponding to possible bit combinations of bits in a bit string having a length equal to or less than the longest predefined code in the plurality of pre-defined codes and arranged by the lengths of possible bit combinations and by numeric values of the bit combinations, to identify a common active bit position in the search key and the search mask corresponding to one of the pre-defined codes having a length greater than all others of said pre-defined codes which correspond to common active bit positions.
Owner:RPX CLEARINGHOUSE
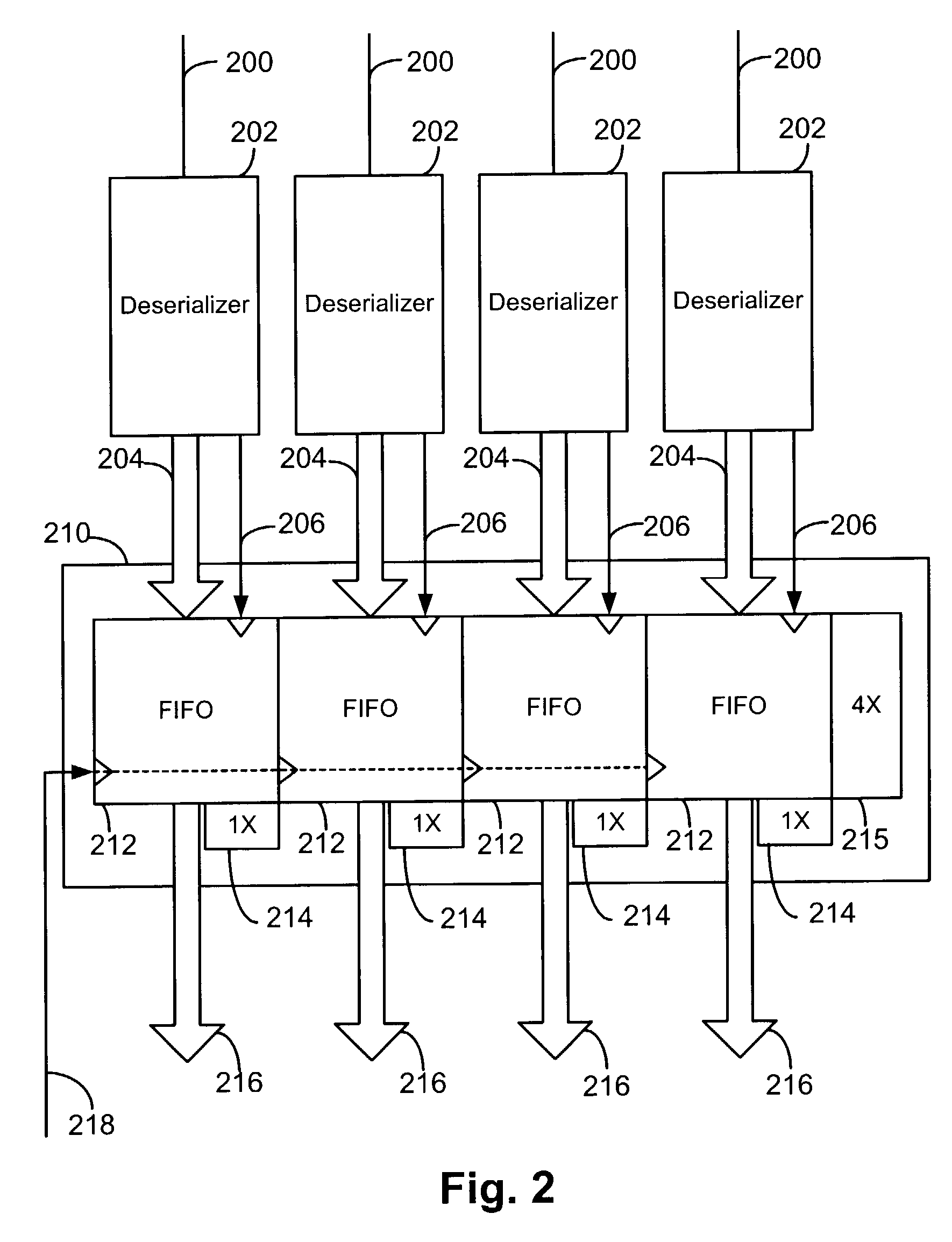
Method and apparatus for asynchronous read control
A method and apparatus for operating a memory is presented. Information is stored in the memory based on a first time domain and information is read from the memory based on a second time domain. A cooperative relationship is maintained between a write pointer which points to memory locations, where data will be stored and a read pointer which points to memory locations, from which data will be read. A FIFO memory is presented which has memory locations and a register array is presented which stores a bit array that has bit locations. Each bit location in the bit array corresponds to a memory location in the memory. As the write pointer points to a memory location and data is stored in the memory location, a bit (e.g. flag) is set in the bit array. The Flag designates whether the data stored in the memory location is available for reading. Prior to reading information from the memory location, a test is made of the bit location that corresponds to the memory location. The bit value denotes whether the data stored in the memory location is valid data and available for reading.
Owner:AVAGO TECH INT SALES PTE LTD
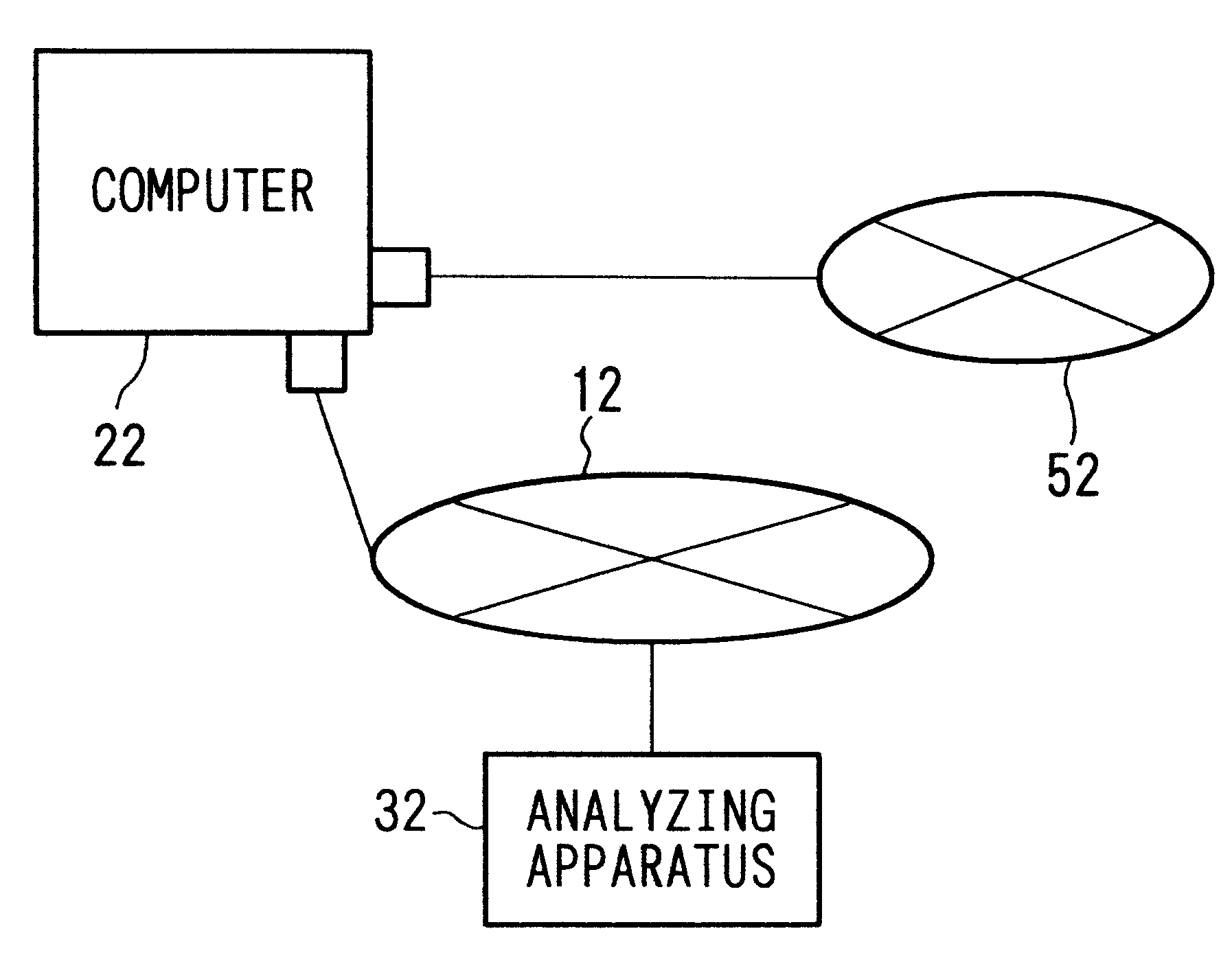
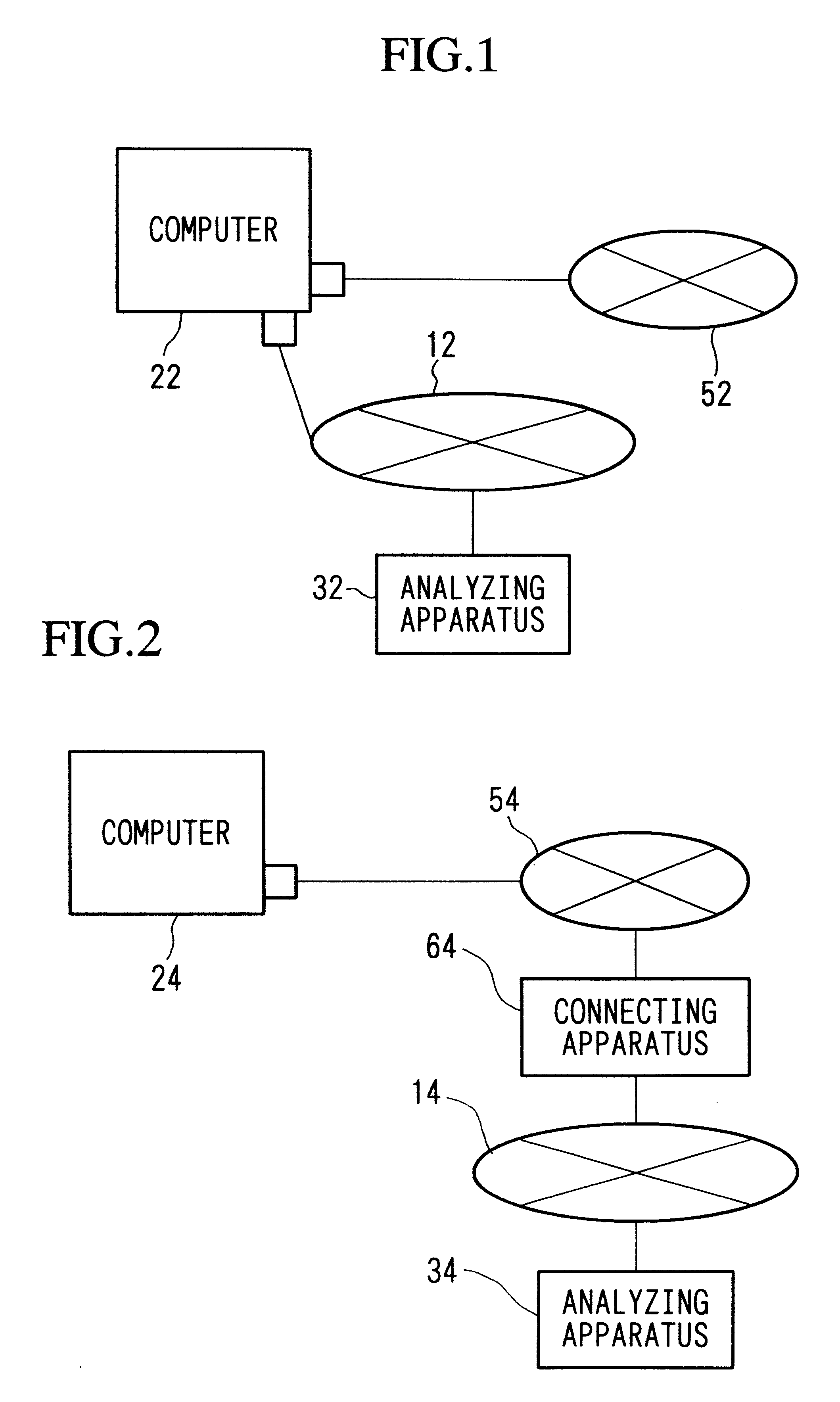
Communication monitoring apparatus
The present invention has the objective of offering an apparatus which comprehensively monitors networks which include small-scale computers and small-scale management protocols which are to be installed. In order to achieve the above objective, with respect to a system formed by a computer 22 and an analyzing apparatus 32 which are connected to a network 12, the present invention has the computer 22 connected to a network 52, and the computer 22 transmits a bit array received via the network 52 to the analyzing apparatus 32 as data. And the analyzing apparatus 32 analyzes the bit array, transmits the analysis result to the computer 22, and aides in the communication of the computer 22.
Owner:YOKOGAWA ELECTRIC CORP
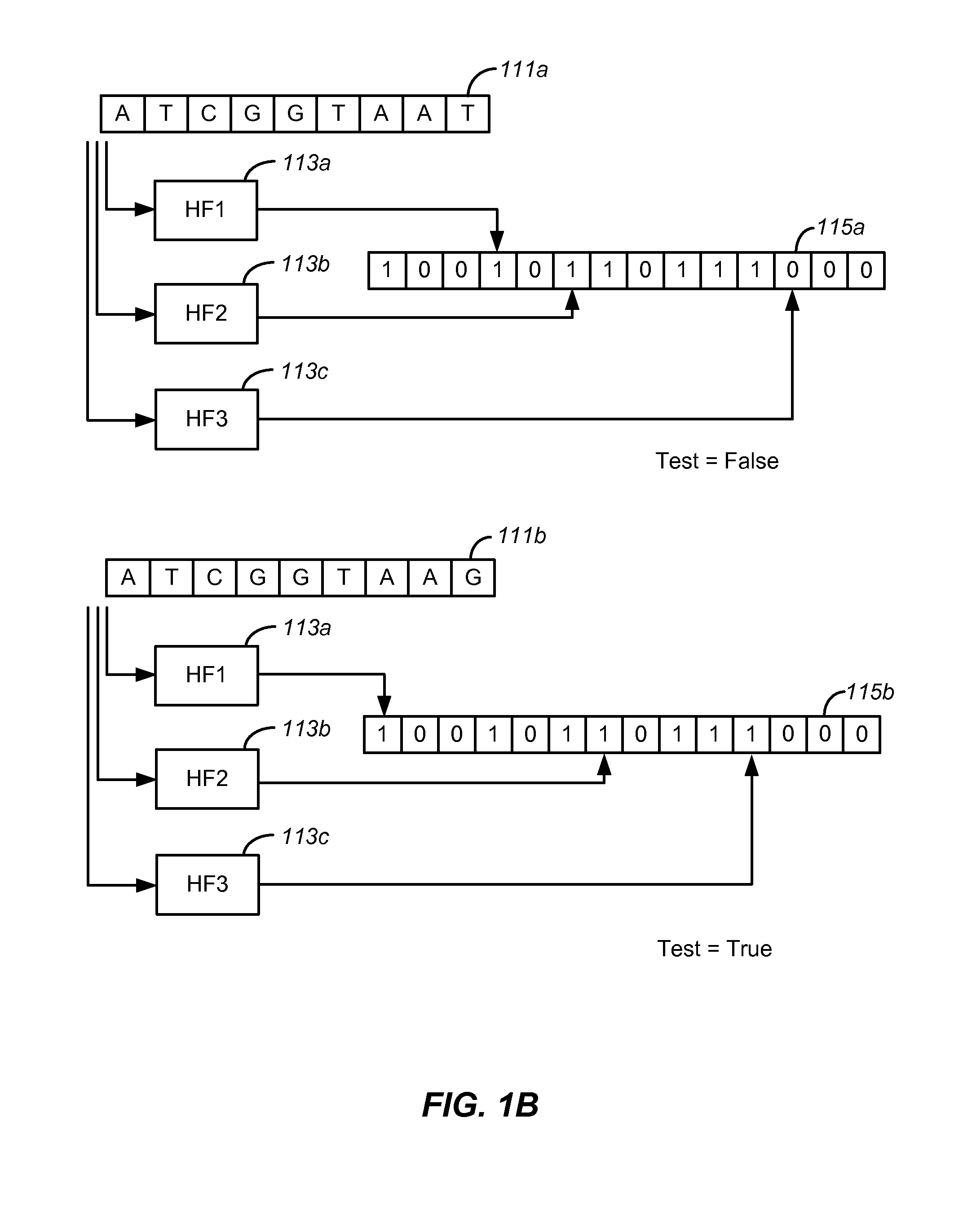
Set membership testers for aligning nucleic acid samples
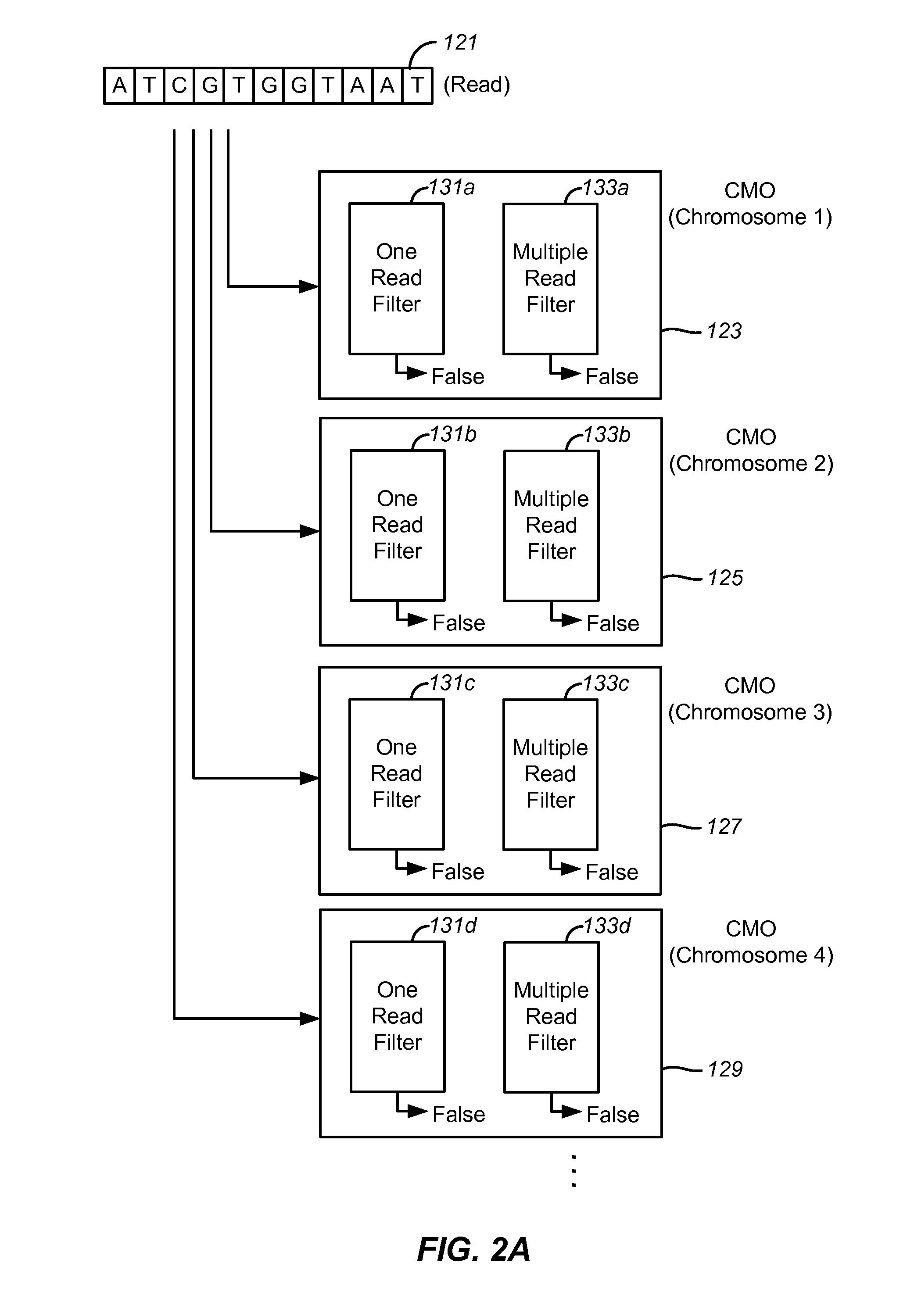
Disclosed are methods and tools for rapidly aligning reads to a reference sequence. These methods and tools employ Bloom filters or similar set membership testers to perform the alignment. The reads may be short sequences of nucleic acids or other biological molecules and the reference sequences may be sequences of genomes, chromosomes, etc. The Bloom filters include a collection of hash functions, a bit array, and associated logic for applying reads to the filter. Each filter, and there may be multiple of these used in a particular application, is used to determine whether an applied read is present in a reference sequence. Each Bloom filter is associated with a single reference sequence such as the sequence of a particular chromosome. In one example, chromosomal abundance is determined by aligning reads from a sequencer to multiple chromosomes, each having an associated Bloom filter or other set membership tester.
Owner:VERINATA HEALTH INC
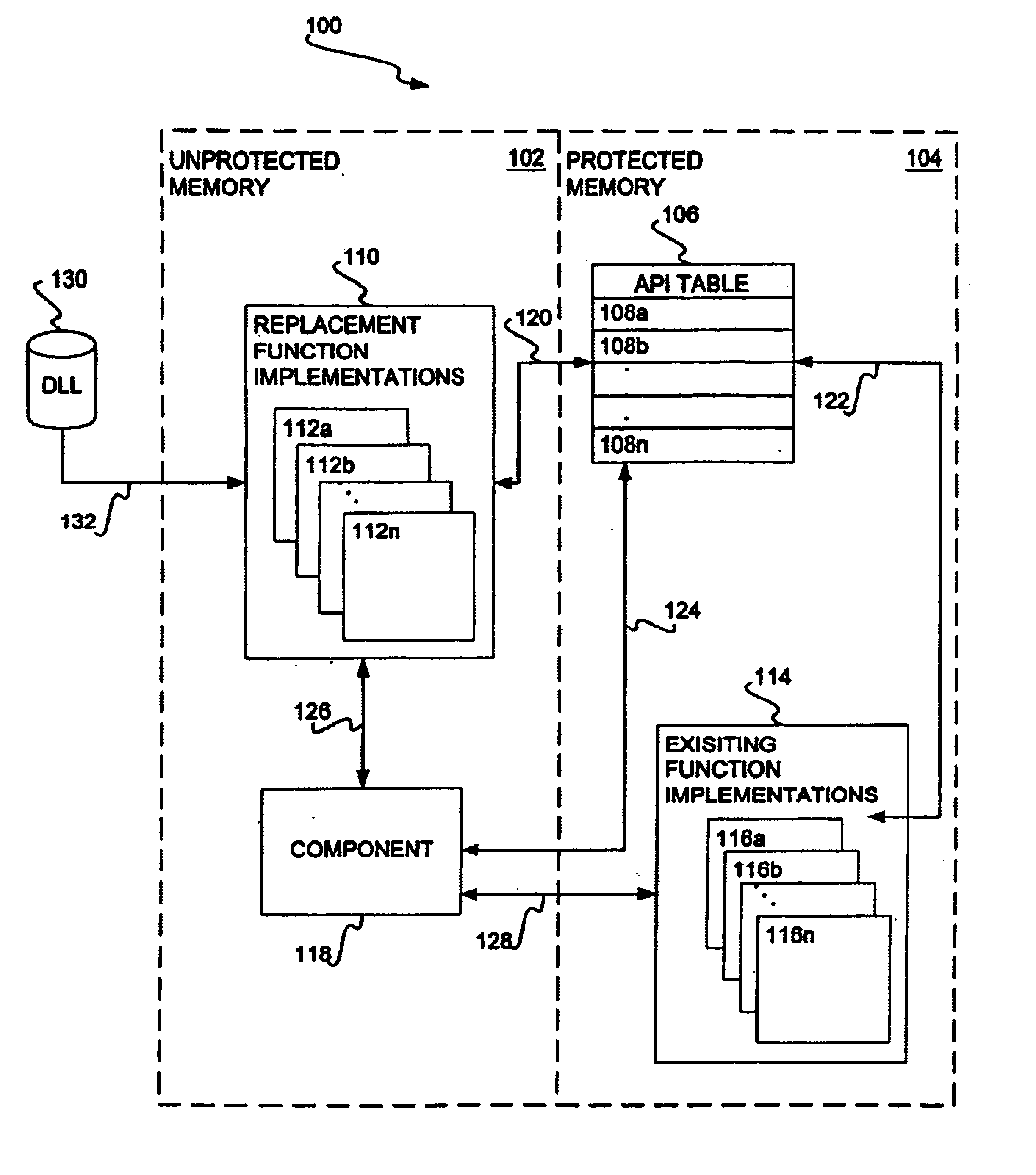
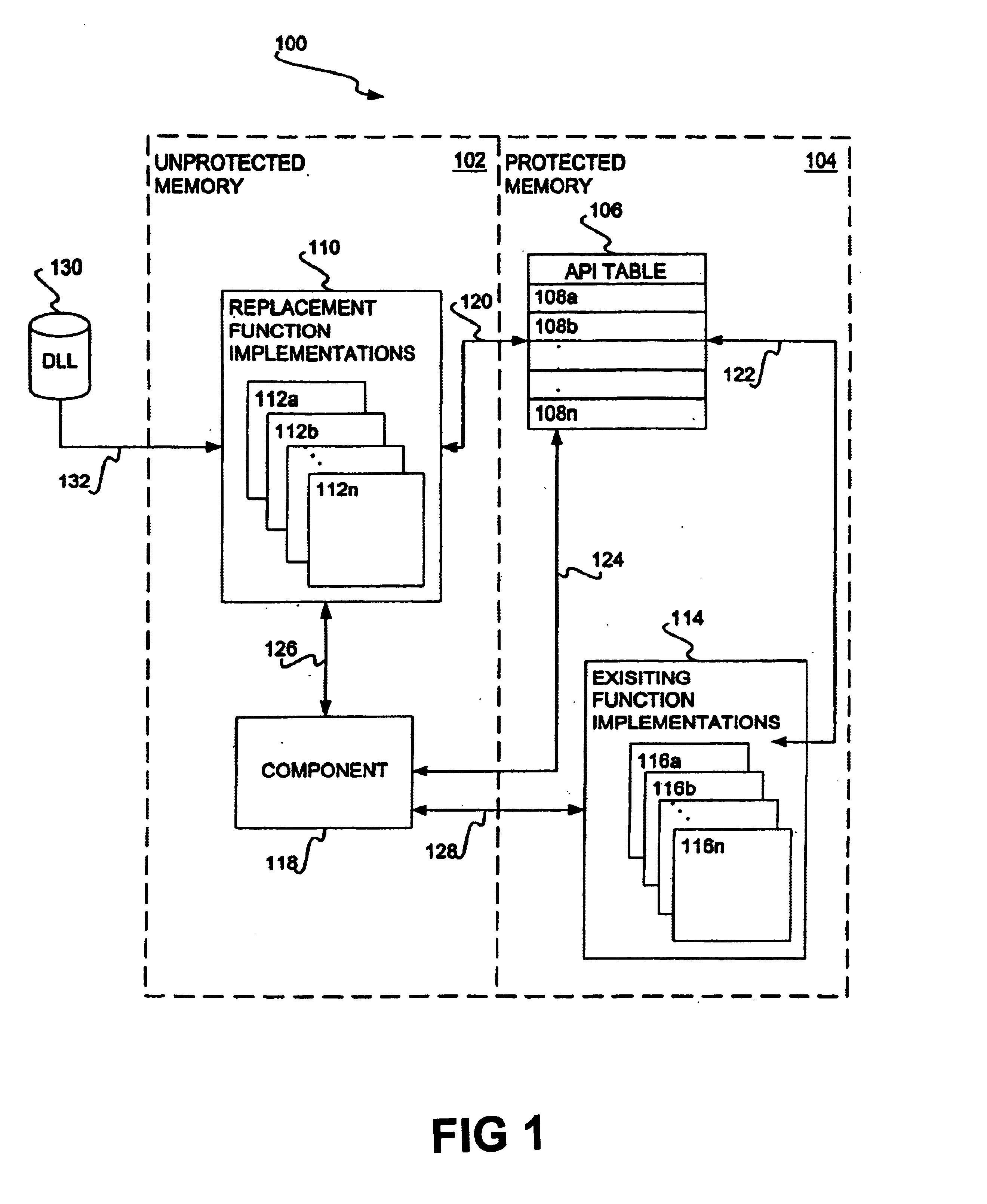
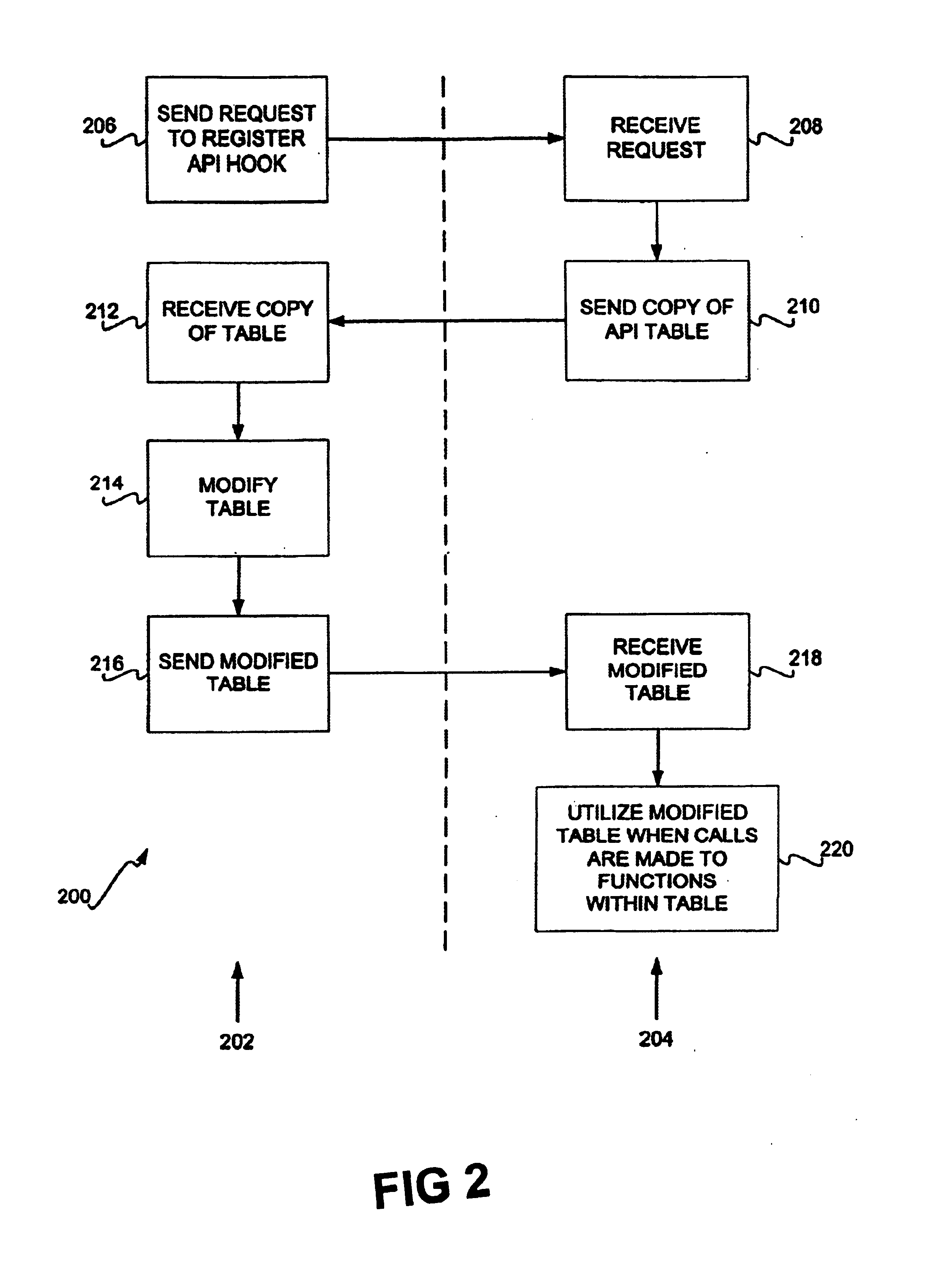
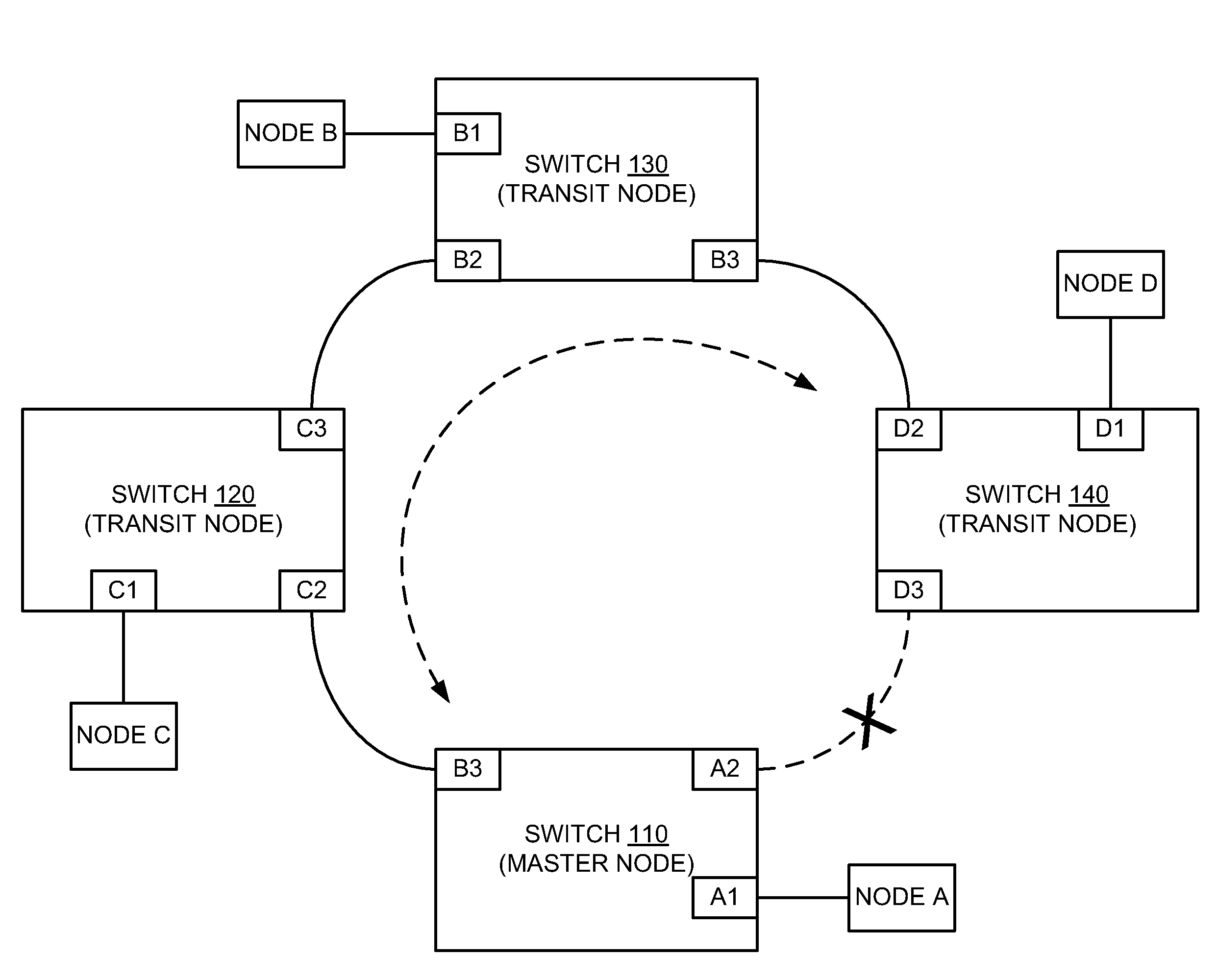
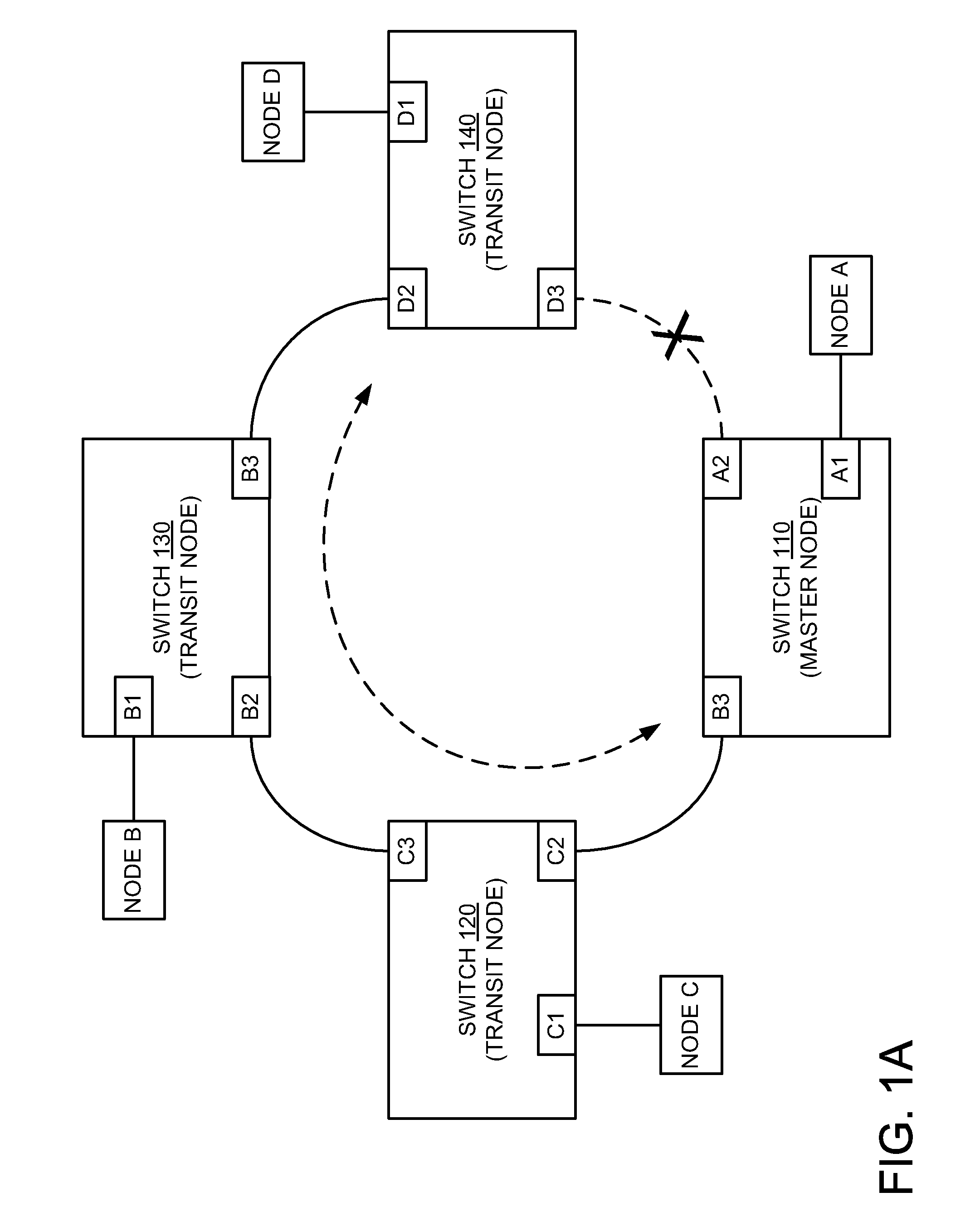
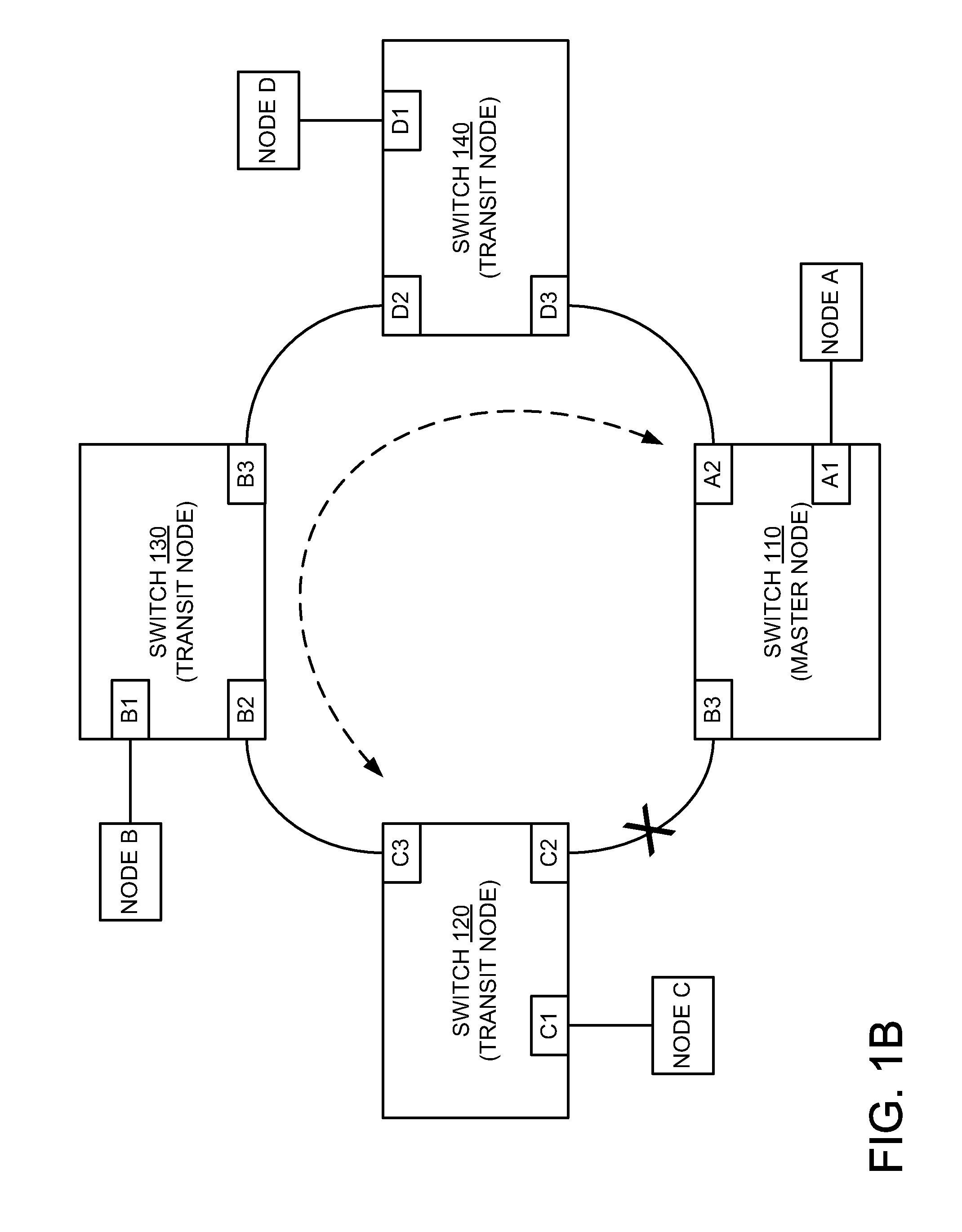
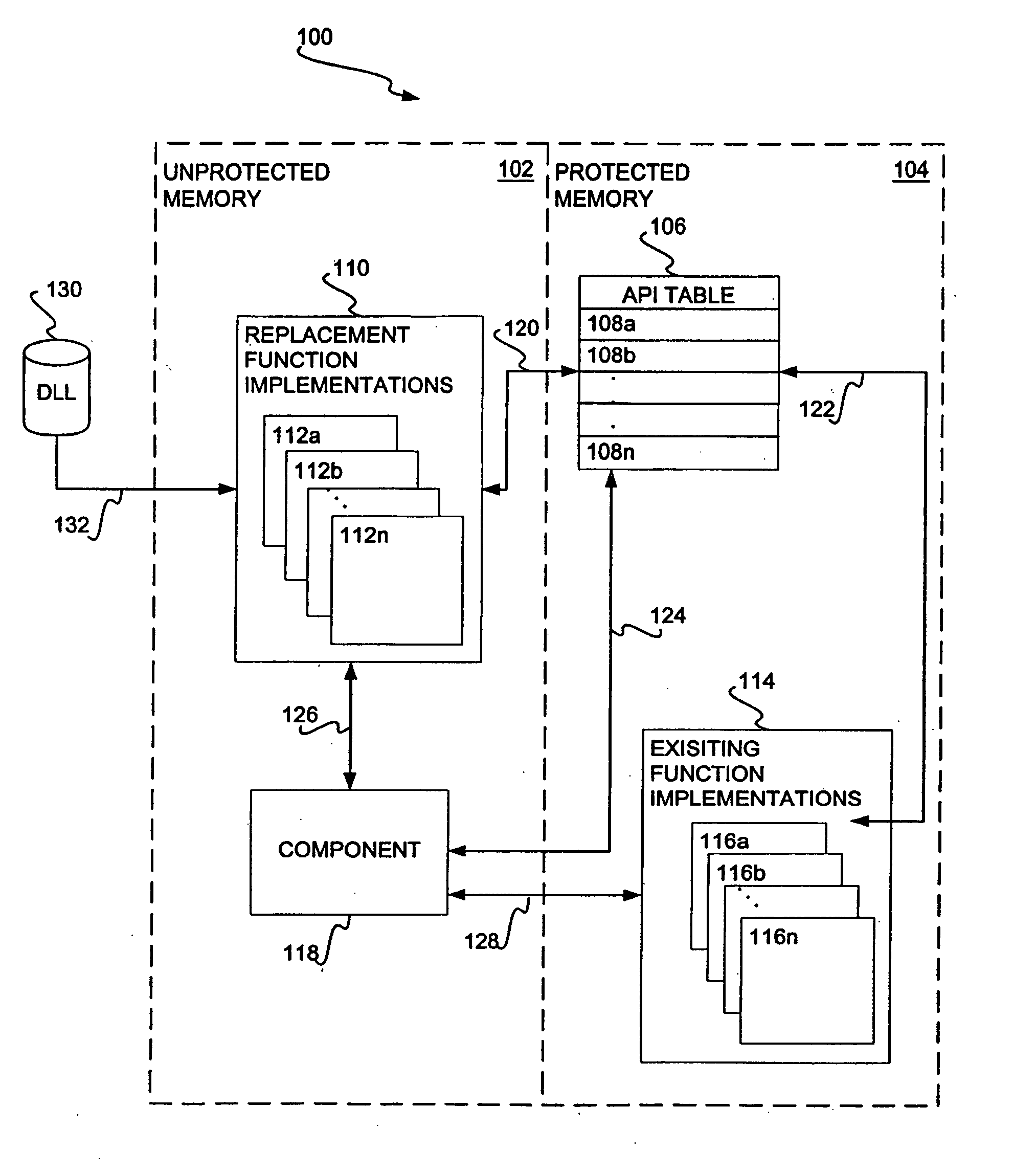
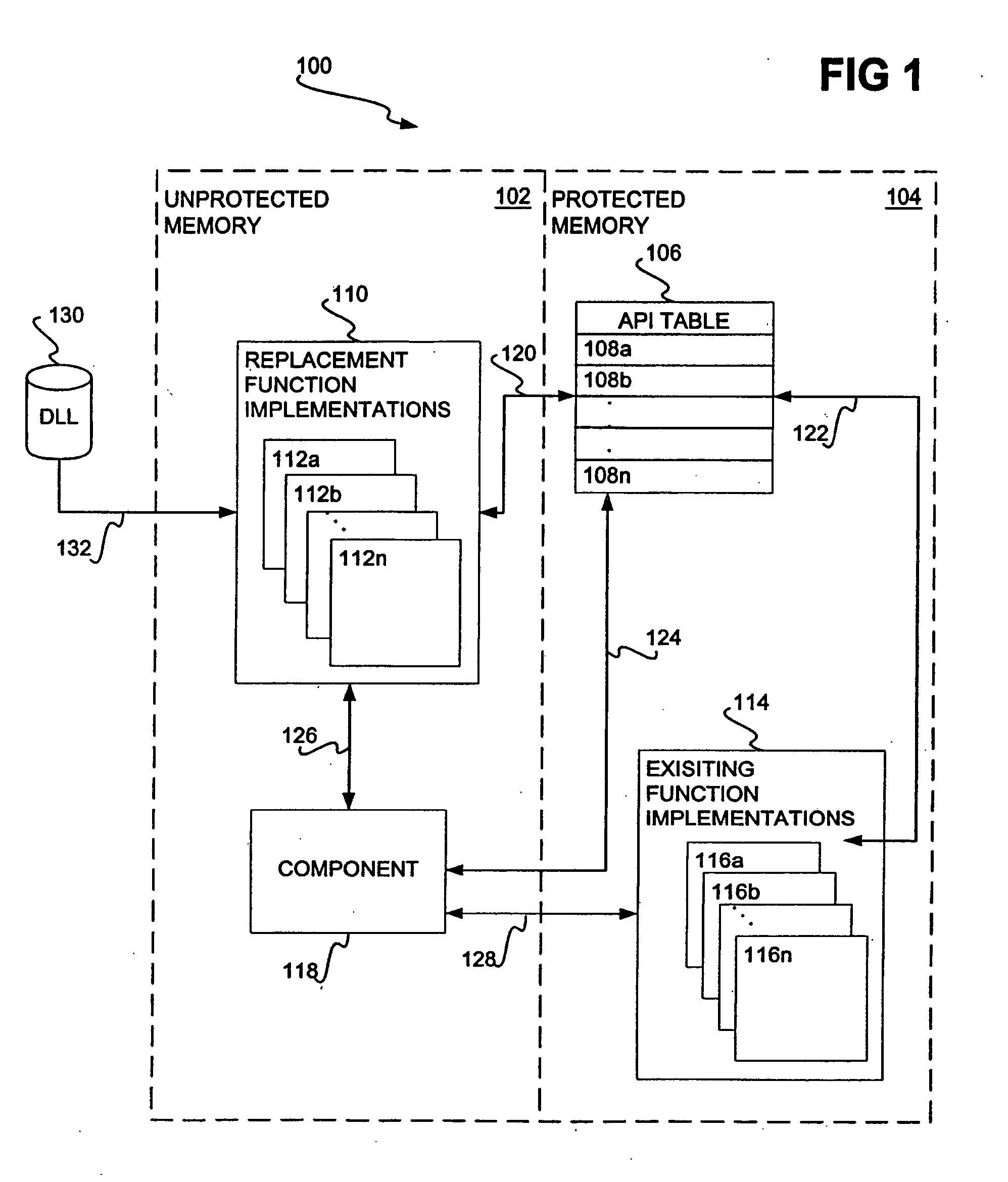
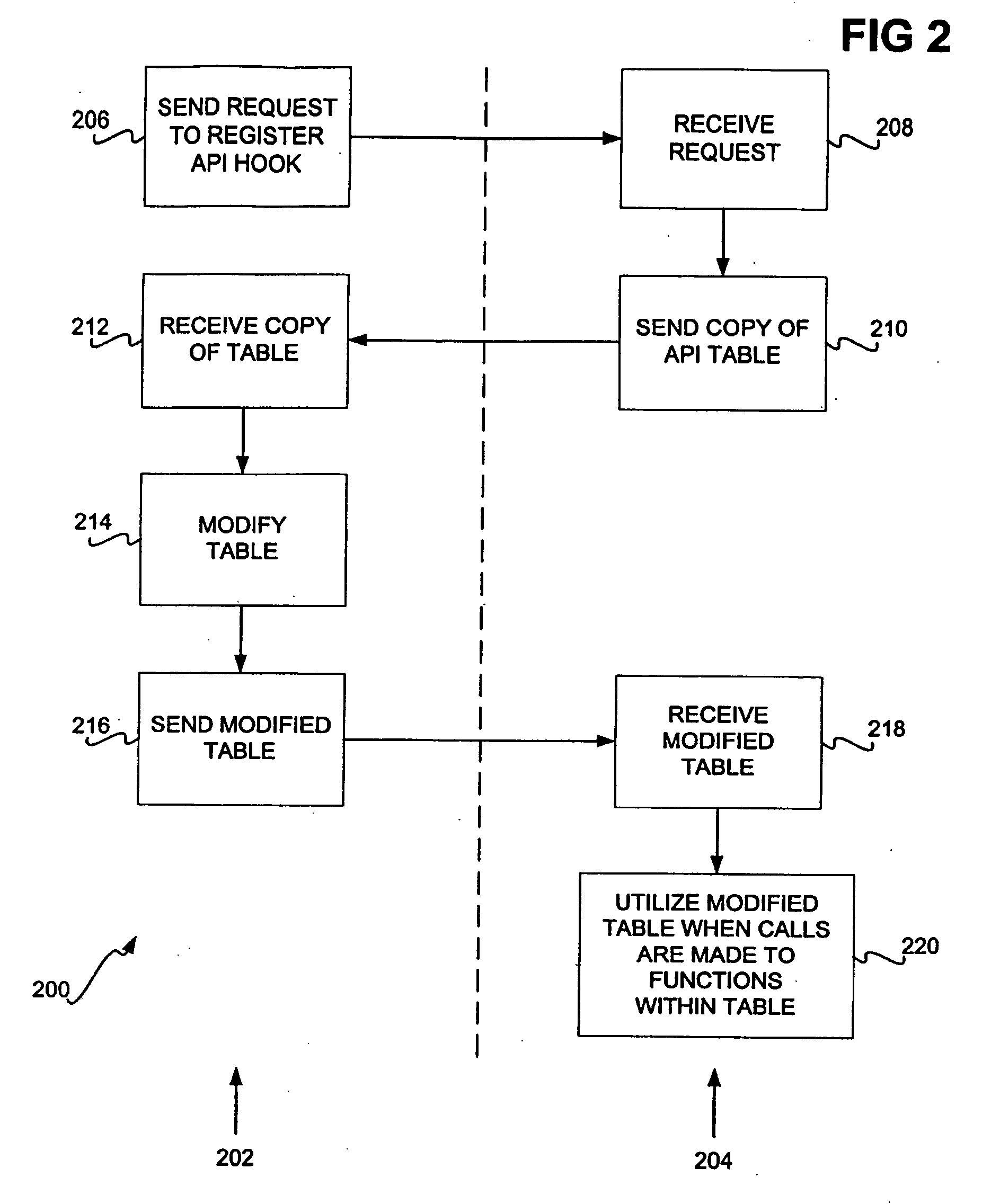
Hooking of replacement and augmented API functions
Hooking replacement and augmented API functions is disclosed. In one embodiment, an alternative implementation of one or more API functions is hooked into the operating system through utilization of a replacement API table. The functions that have been replaced, augmented, or otherwise modified have entries in the table pointing to their new implementation. The entries for functions that have not been change continue to point to their existing implementation. A bit array is also disclosed to track desired messages, as compared to undesired messages, where each bit of the array corresponds to a type of message. The table can be variably sized, and can support nested and re-entrant calls.
Owner:MICROSOFT TECH LICENSING LLC
Serializing event handling in a threaded system with no wait states
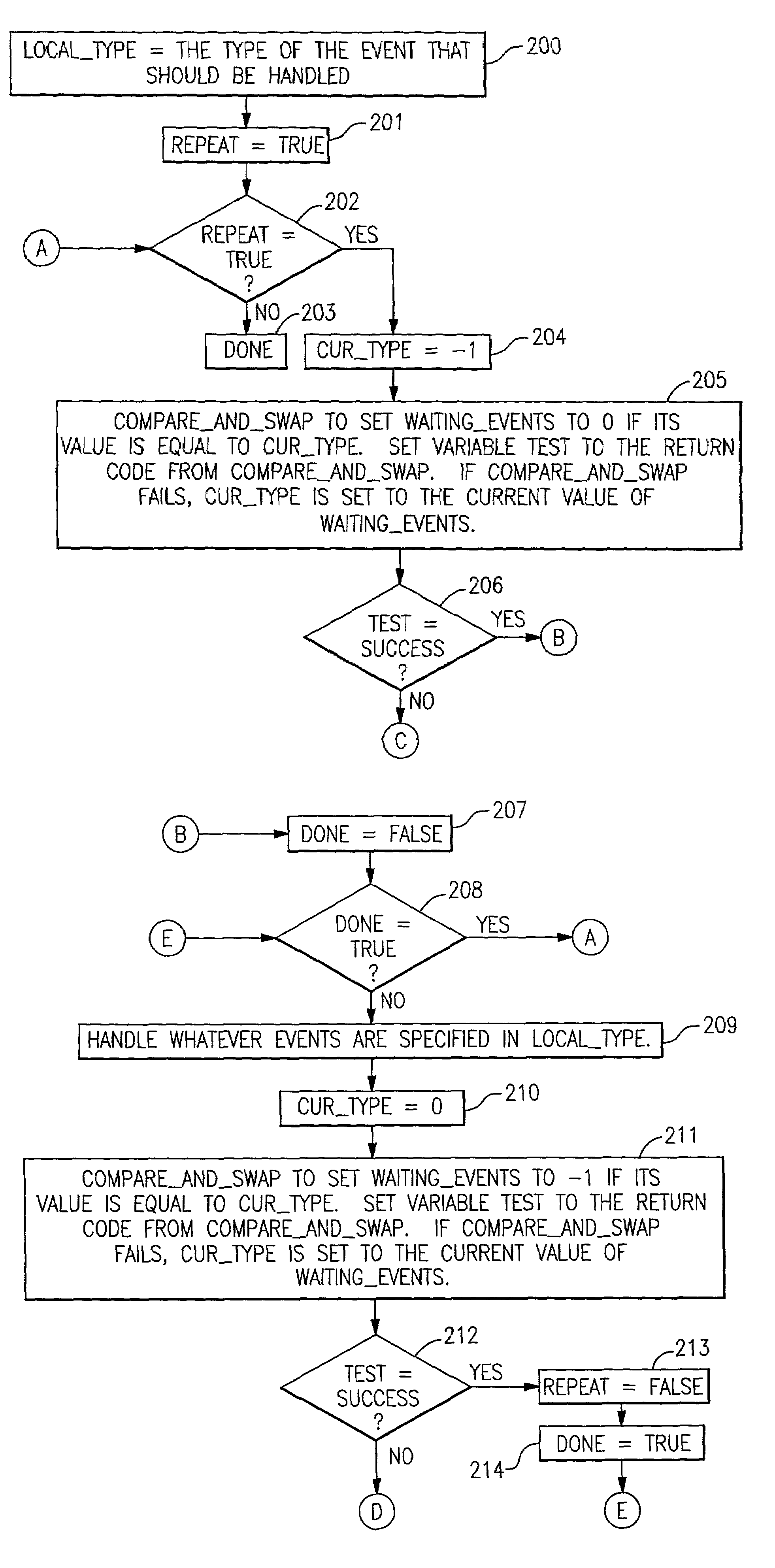
InactiveUS7065765B2Increase speed and efficiencyDigital data processing detailsMultiprogramming arrangementsArray data structureBit array
Event handling in multinode data processing networks, in which data structures are shared between nodes and are subject to concurrent requests for access, is facilitated through the use of a separate small data structure (bit array or linked list) which permits an event handler to hand off the task of accessing the data structure to an event handler which is already accessing data from the same data structure. This eliminates the need for locking arrangements and / or the use of special coordinating event handlers.
Owner:IBM CORP
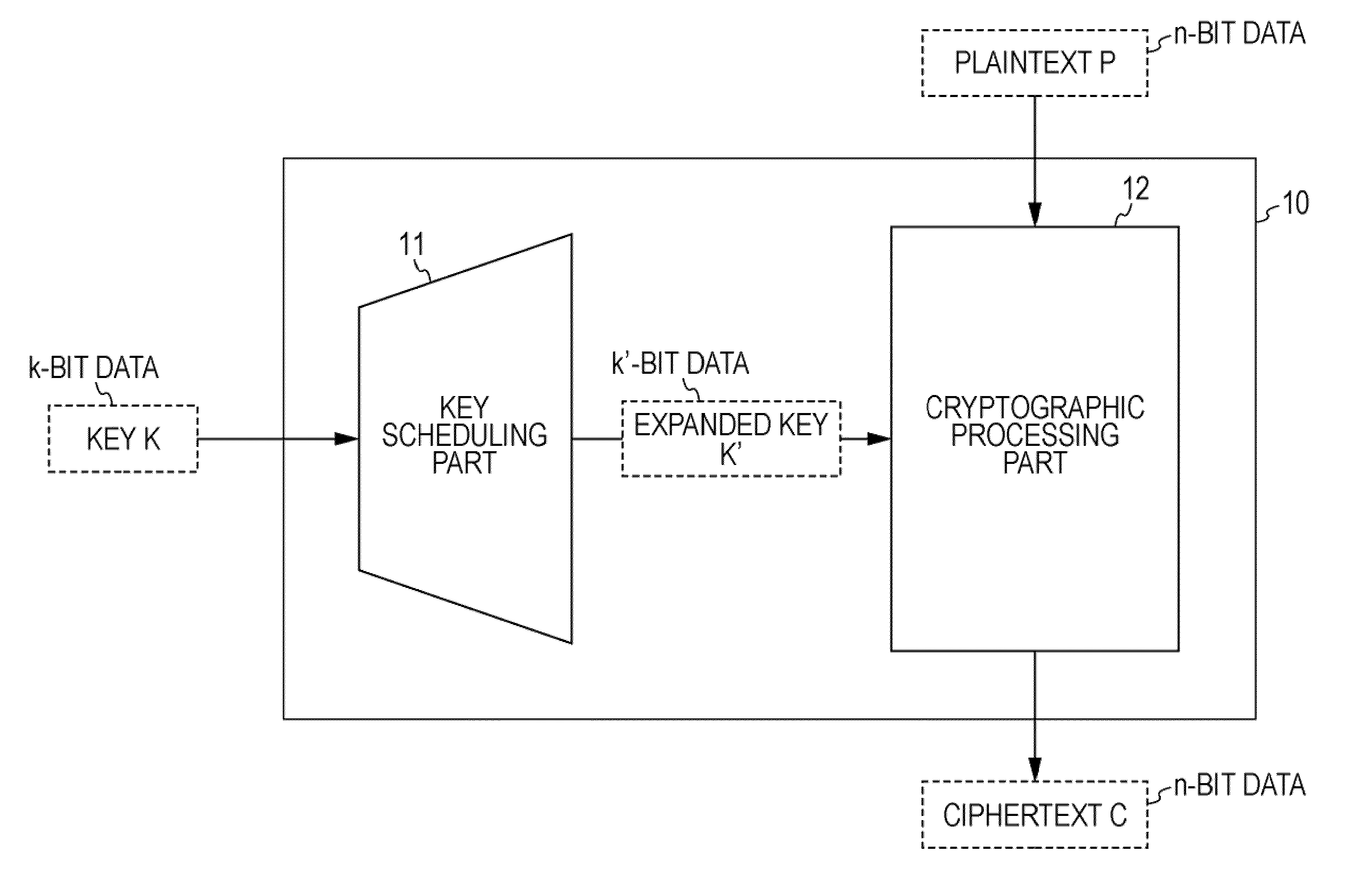
Cryptographic Processing Apparatus, Cryptographic Processing Method, and Computer Program
InactiveUS20100014664A1Increasingly difficultIncrease the difficultyMultiple keys/algorithms usagePublic key for secure communicationProcess configurationLow correlation
To realize a common-key block cipher process configuration with increased difficulty of key analysis and improved security. In a configuration for storing in a register an intermediate key generated by using a secret key transformation process and performing a transformation process on the register-stored data to generate a round key, a process of swapping (permuting) data segments constituting the register-stored data is executed to generate a round key. For example, four data segments are produced so that two sets of data segments having an equal number of bits are set, and a process of swapping the individual data segments is repeatedly executed to generate a plurality of different round keys. With this configuration, the bit array of each round key can be effectively permuted, and round keys with low relevance can be generated. A high-security cryptographic process with increased difficulty of key analysis can be realized.
Owner:SONY CORP
Method and System for Locating Update Operations in a Virtual Machine Disk Image
ActiveUS20110099187A1Digital data information retrievalDigital data processing detailsBit arrayBloom filter
A two dimensional bit array is maintained to keep track of the location of data records in a log file that is organized as a plurality of log segments, each comprising a plurality of data records. The data records are indexed in the log file according to randomized unique ids. Each column of the two dimensional bit array represents a Bloom filter corresponding to a log segment of the log file such that, given a particular randomized unique id, log segments that may contain the data record corresponding to the particular randomized unique id can be efficiently identified by utilizing Bloom filter techniques to analyze the columns of the two dimensional bit array.
Owner:VMWARE INC
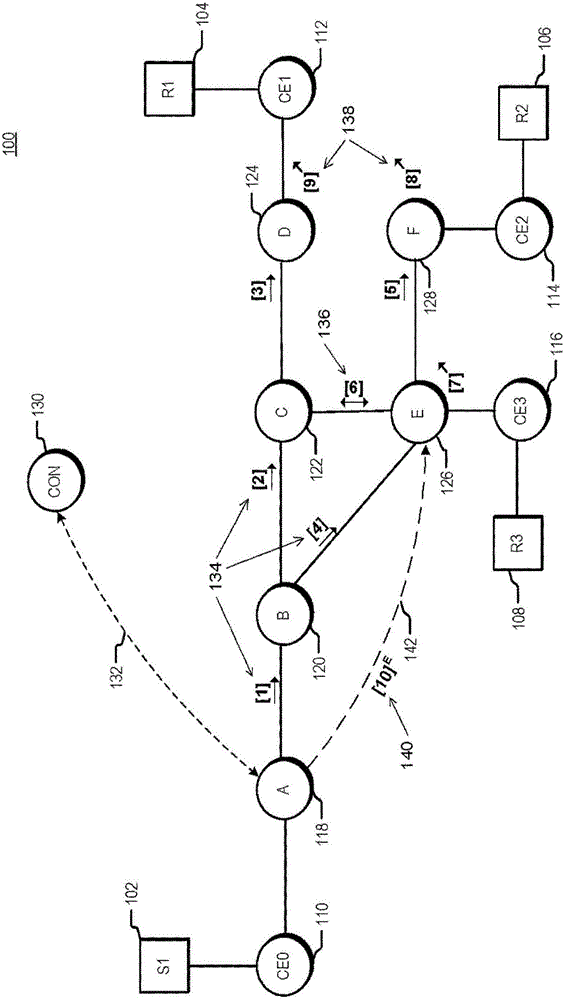
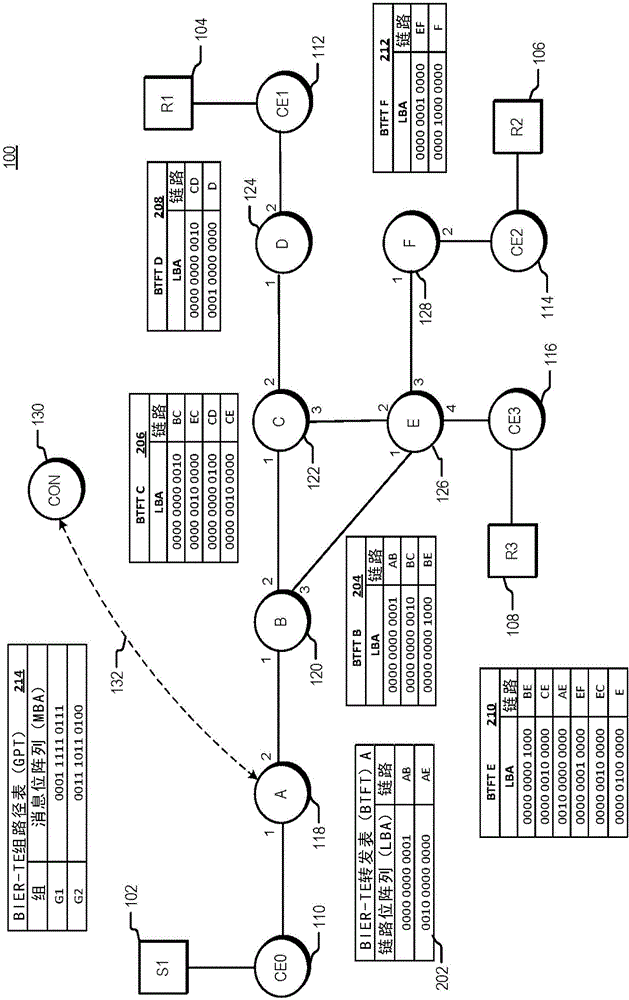
Traffic engineering for bit indexed explicit replication
The invention relates to a traffic engineering for bit indexed explicit replication. Methods and network devices are disclosed for traffic-engineered forwarding through a new form of bit indexed explicit replication. In one embodiment, a method includes receiving at a first node in a network a message comprising a message bit array, and comparing bit values at one or more bit positions in the message bit array to one or more entries in a forwarding table stored at the first node. The one or more bit positions correspond in this embodiment to links in the network. This embodiment of the method further includes forwarding the message over a link represented in the forwarding table if a result of the comparing indicates that the link is included in a path to be taken by the message. In a further embodiment of the method, the message is a multicast message and forwarding the message comprises forwarding a replica of the multicast message.
Owner:CISCO TECH INC
Using bit arrays in incremental scanning of content for sensitive data
A method for incremental scanning of documents may include identifying documents to be scanned for sensitive information according to at least one data loss prevention (DLP) policy, the documents being associated with a bit array. The method may further include generating a key of a documents and applying, for each document, a set of functions to the key of the document, where outputs of the functions map the key to positions in the bit array. The method further includes identifying a subset of the positions in the bit array that correspond to the outputs of the functions in the set of functions, the subset of the positions to indicate whether the document has been scanned.
Owner:CA TECH INC
Network convergence in response to a topology change
ActiveUS20100246387A1Reduce failover timeError preventionTransmission systemsNetwork ConvergenceFailover
In response to a network topology change, packets are initially flooded on ports of a network device. In addition, a bit array is cleared in response to the topology change. Each bit in the bit array is associated with a particular forwarding entry on the network device. In connection with the clearing of the bit array, the flooding of packets on ports of the network device is made conditional, reducing failover time of the network.
Owner:EXTREME NETWORKS INC
Hooking of replacement and augmented API functions
Hooking replacement and augmented API functions is disclosed. In one embodiment, an alternative implementation of one or more API functions is hooked into the operating system through utilization of a replacement API table. The functions that have been replaced, augmented, or otherwise modified have entries in the table pointing to their new implementation. The entries for functions that have not been change continue to point to their existing implementation. A bit array is also disclosed to track desired messages, as compared to undesired messages, where each bit of the array corresponds to a type of message. The table can be variably sized, and can support nested and re-entrant calls.
Owner:MICROSOFT TECH LICENSING LLC
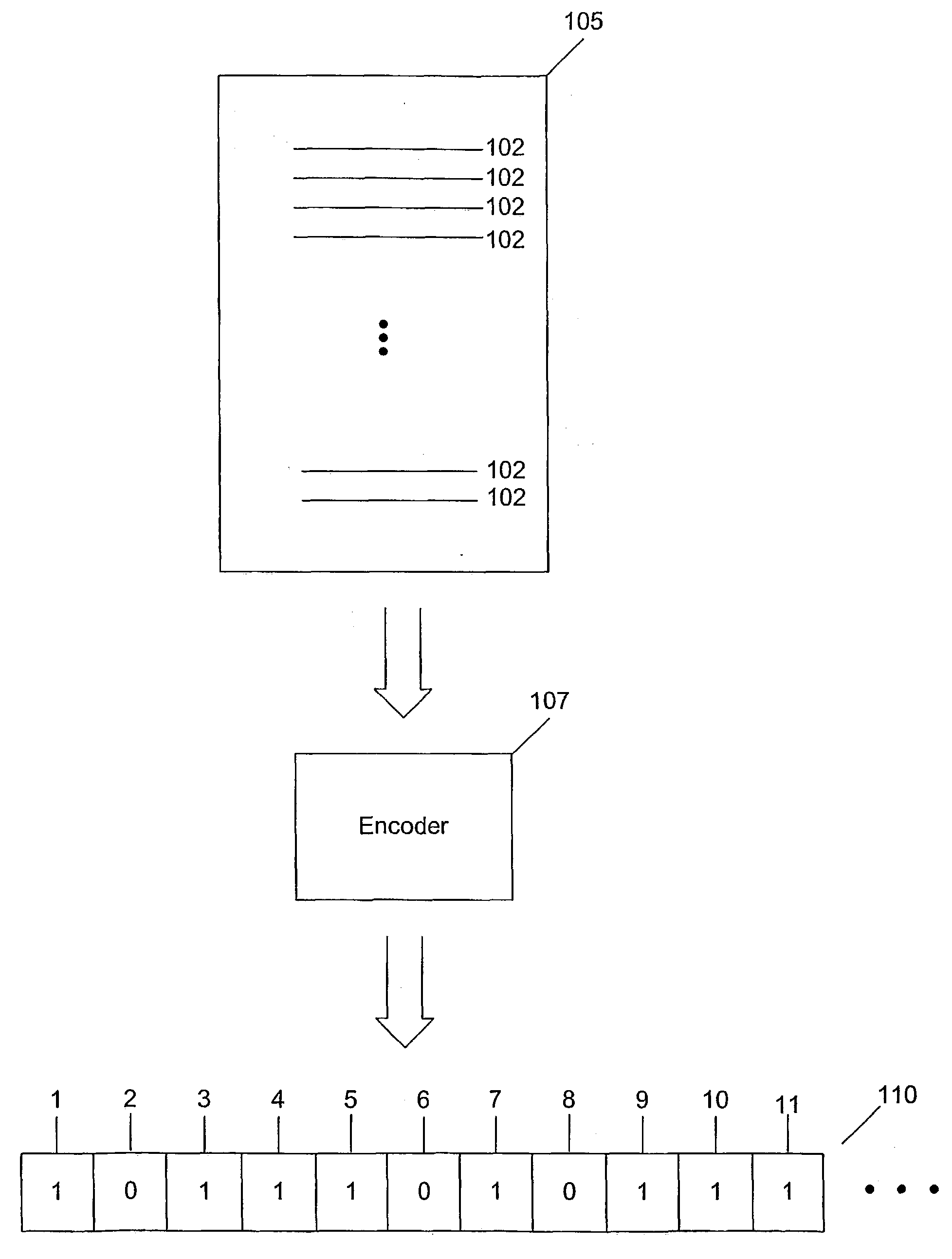
Delivery point validation system
InactiveUS20040128274A1Digital data processing detailsUser identity/authority verificationHash functionBit array
Systems and methods consistent with the present invention encode a list so users of the list may make inquires to the coded list without the entire content of the list being revealed to the users. Each item in the list turns on one or more bits in the array 110. Once each item in the list has been encoded by an encoder, a bit array with high and low values is used to represent the items in the list. The bit array may be embodied in a validation system for allowing users to query the list to determine whether an inquiry item is on the list 105. The validation system determines which bits to check by executing the same coding process executed by the encoder. If all the bits are high, then the inquiry item is determined to be part of the list, if at least one of the bits is low, then the inquiry item is determined not to be part of the original list. An exemplary encoder and validation system comprises a standardizer, a hashing function unit, an extraction circuit, and an offset circuit.
Owner:US POSTAL SERVICE
High speed operation method for twin MONOS metal bit array
ActiveUS20070047307A1Take setMemory cell area can be savedRead-only memoriesDigital storageBit lineDiffusion
The present invention provides a novel operational method of twin MONOS metal bit or diffusion bit structure for high-speed application. In a first embodiment of the present invention, the alternative control gates are set at the same voltage. In a second embodiment of the present invention, all the control gates are set at the operational voltage from the beginning. In both embodiments, the bit line and word gate are used to address the selected memory cell.
Owner:HALO LSI INC
Method and apparatus for rapid and scaleable directed advertisting service
A method and apparatus for selecting a subset of advertisements complying with an advertisement request from a set of advertisements is disclosed. Advertisements rules are specified according to a logical semantic simplifying search combinatorials yet allowing for flexible specification of advertising rules, and permitting significant precomputation of advertising rules to permit rapid identification of advertisements complying with advertisement requests. In one embodiment, advertisement rules and requests are represented as easily manipulable and computable bit arrays.
Owner:HULU
Optimized inequality join method
ActiveUS20170060944A1Readily apparentDigital data information retrievalSpecial data processing applicationsBit arrayBloom filter
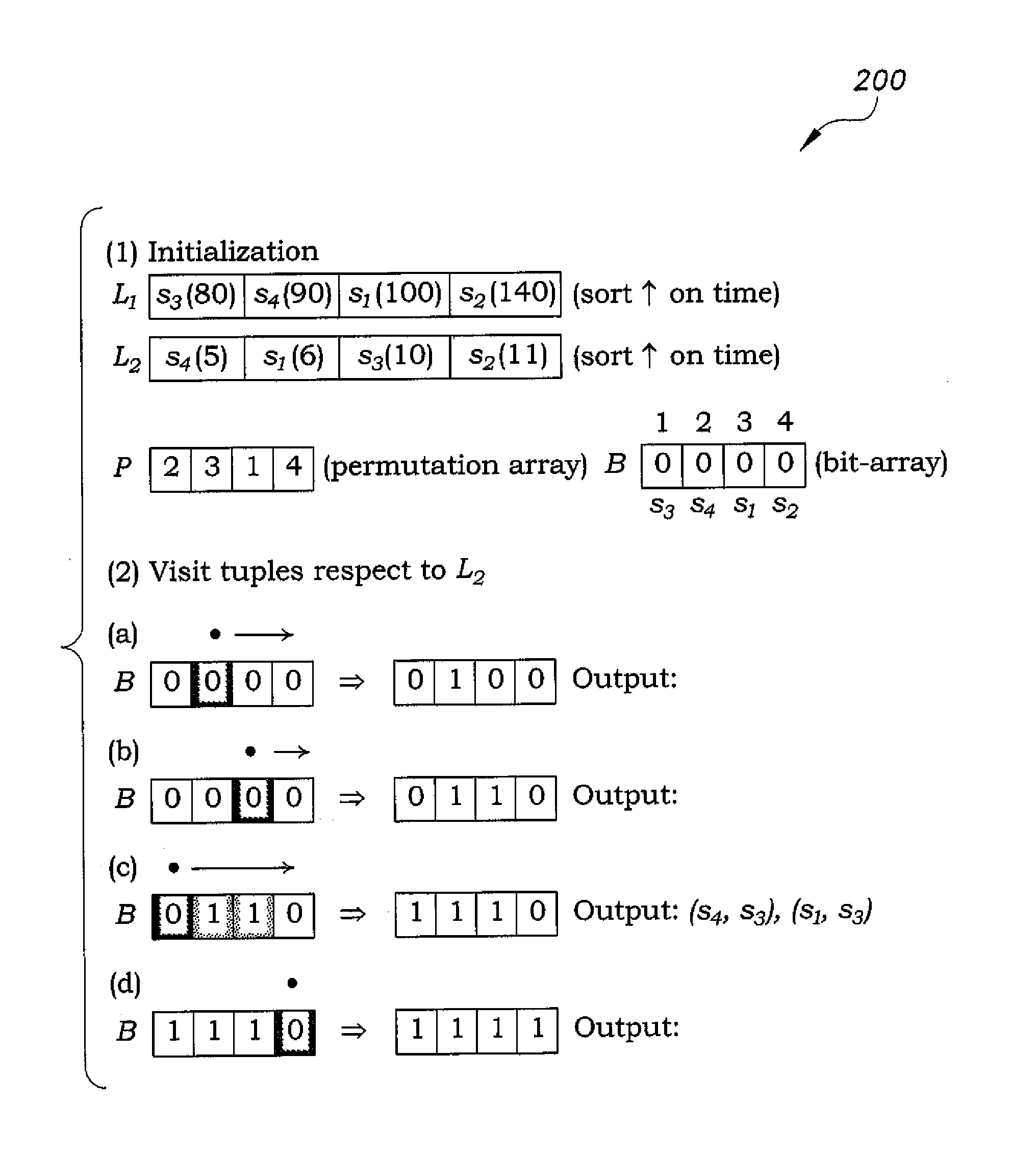
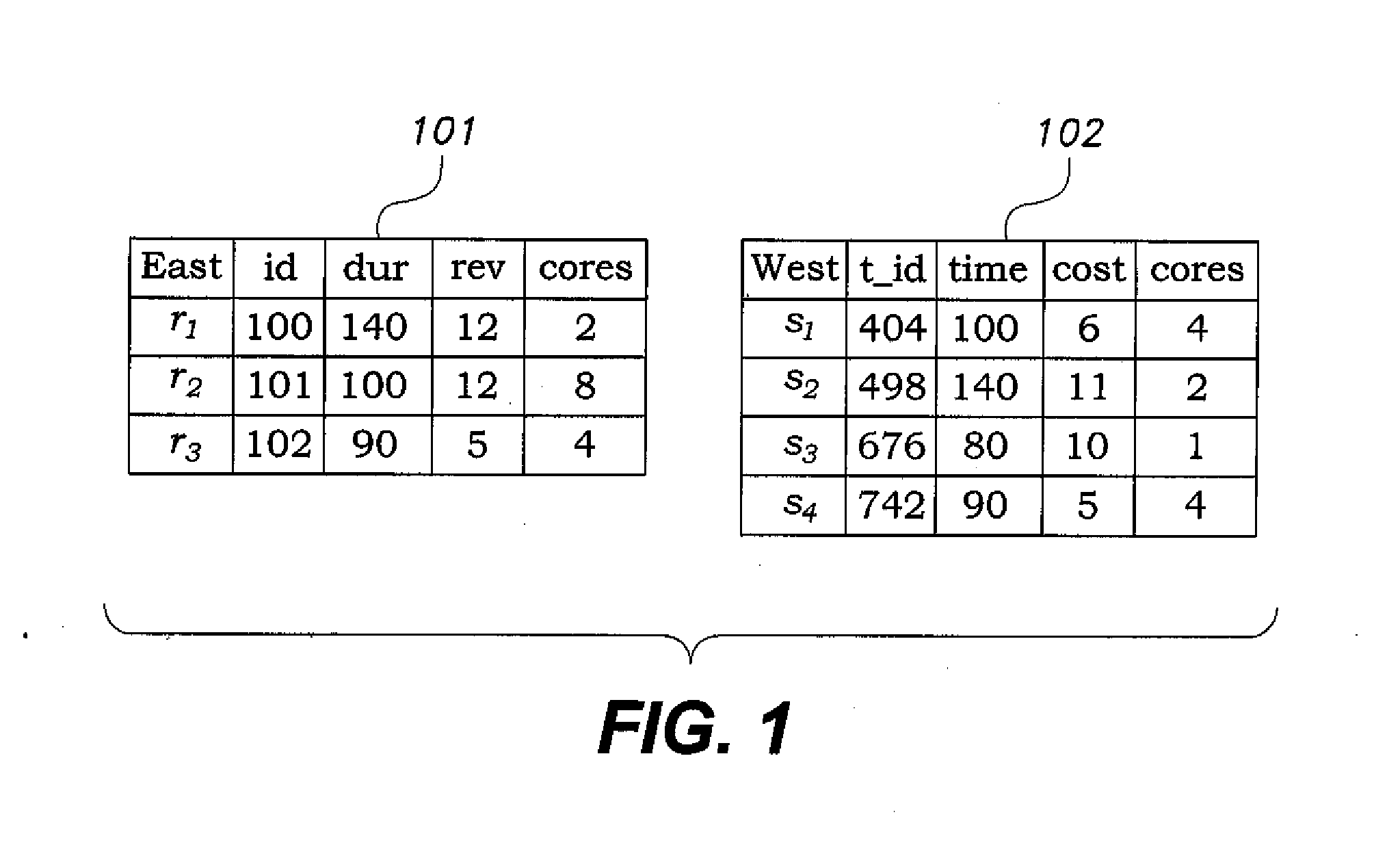
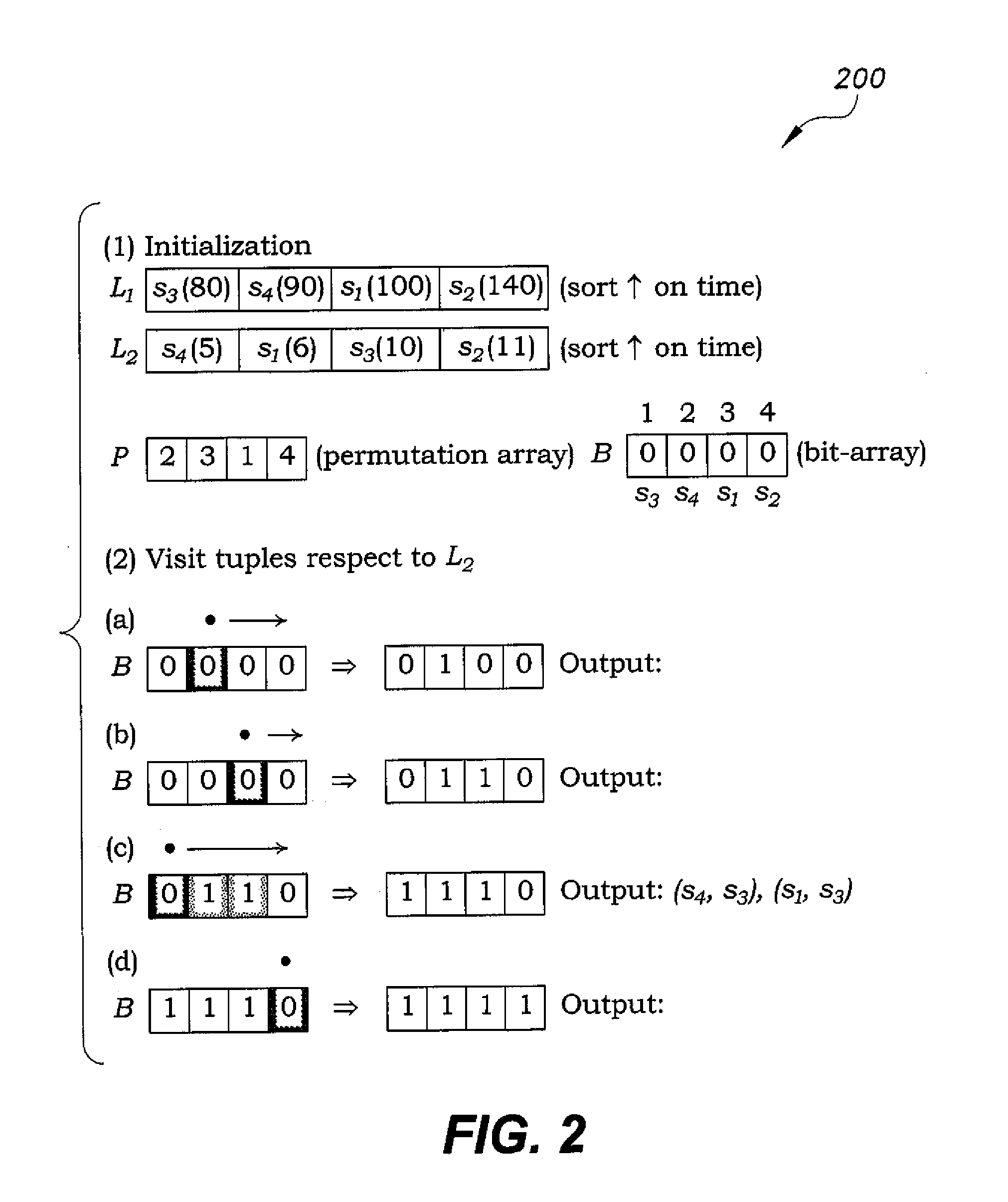
The optimized inequality join method is a method for joining relational tables on input inequality conditions. The optimized inequality join method is a relatively fast inequality join method using permutation arrays to store positional information for sorted attributed values. Additionally, space efficient bit arrays are used to enable optimization, such as Bloom filter indices, thus providing faster computation of the join results. The method may be used, for example, for joining various inequalities associated with a variety of measured environmental conditions for raising an alarm when certain conditions are met.
Owner:QATAR FOUND FOR EDUCATION SCI & COMMUNITY
Optimizing multi-hit caching for long tail content
ActiveUS8370460B1Efficient executionAvoid cachingMultiple digital computer combinationsTransmissionBit arrayParallel computing
Some embodiments provide an optimized multi-hit caching technique that minimizes the performance impact associated with caching of long-tail content while retaining much of the efficiency and minimal overhead associated with first hit caching in determining when to cache content. The optimized multi-hit caching utilizes a modified bloom filter implementation that performs flushing and state rolling to delete indices representing stale content from a bit array used to track hit counts without affecting identification of other content that may be represented with indices overlapping with those representing the stale content. Specifically, a copy of the bit array is stored prior to flushing the bit array so as to avoid losing track of previously requested and cached content when flushing the bit arrays and the flushing is performed to remove the bit indices representing stale content from the bit array and to minimize the possibility of a false positive.
Owner:EDGIO INC
Quantum chip, quantum processor and quantum computer
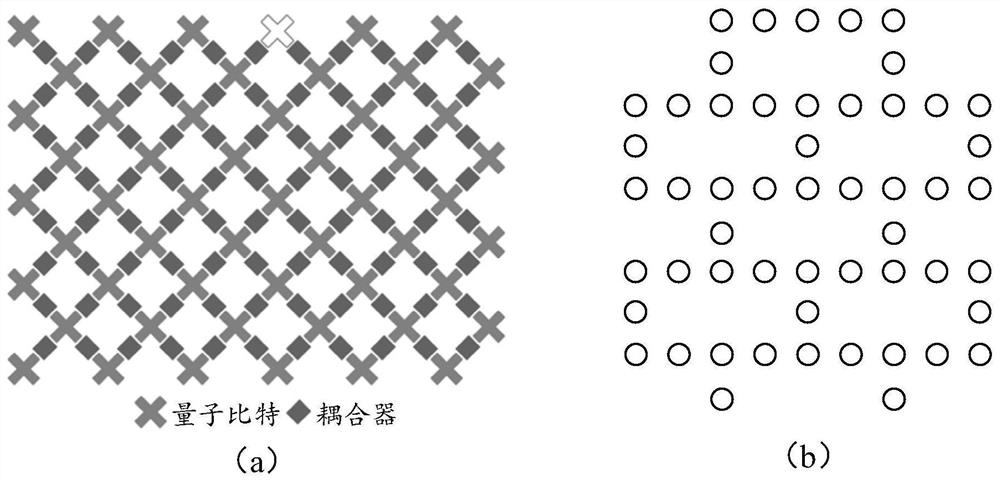
ActiveCN111967603AImprove adaptabilityImprove coherenceQuantum computersNanoinformaticsQuantum technologyBit array
Owner:TENCENT TECH (SHENZHEN) CO LTD
State-based jitter buffer and method of operation
InactiveUS7336678B2Hybrid switching systemsData switching by path configurationArray data structureWrite buffer
A buffer having an associated state array to store the current state of the buffer. The state array includes a bit array having a number of entries, each of the entries including a status bit to indicate storage of a corresponding packet in the buffer.
Owner:INTEL CORP
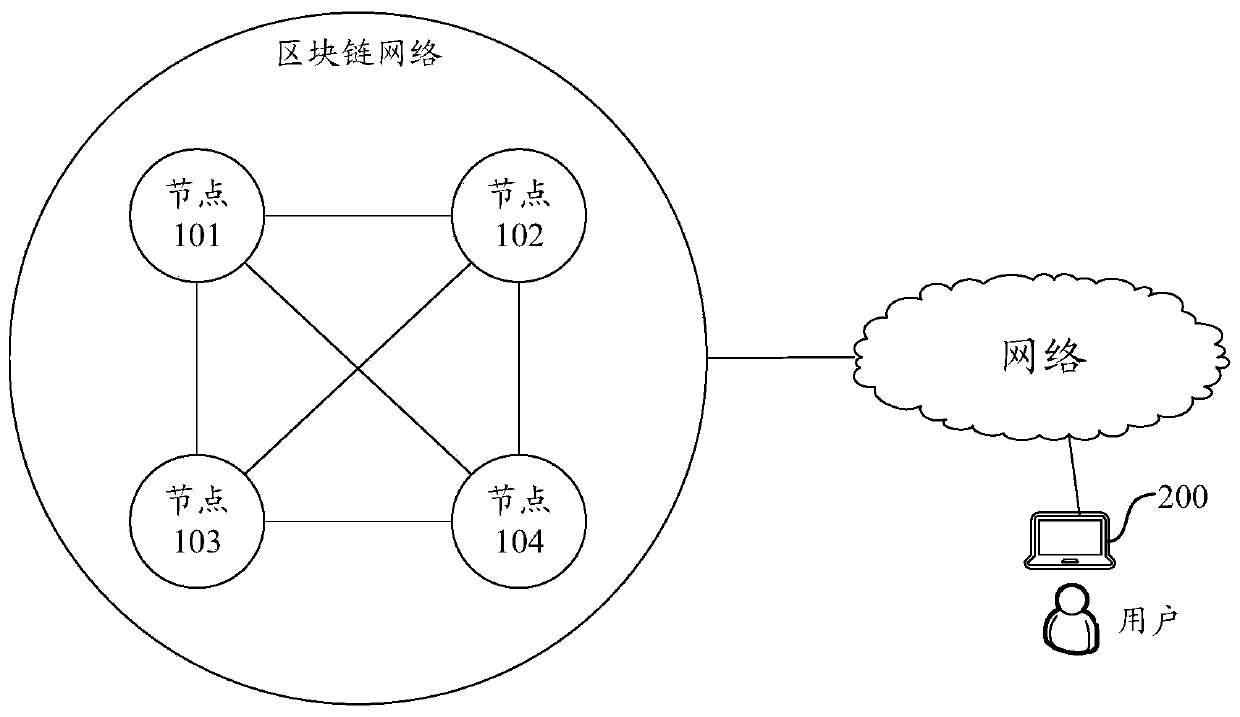
Processing method and device based on block chain system
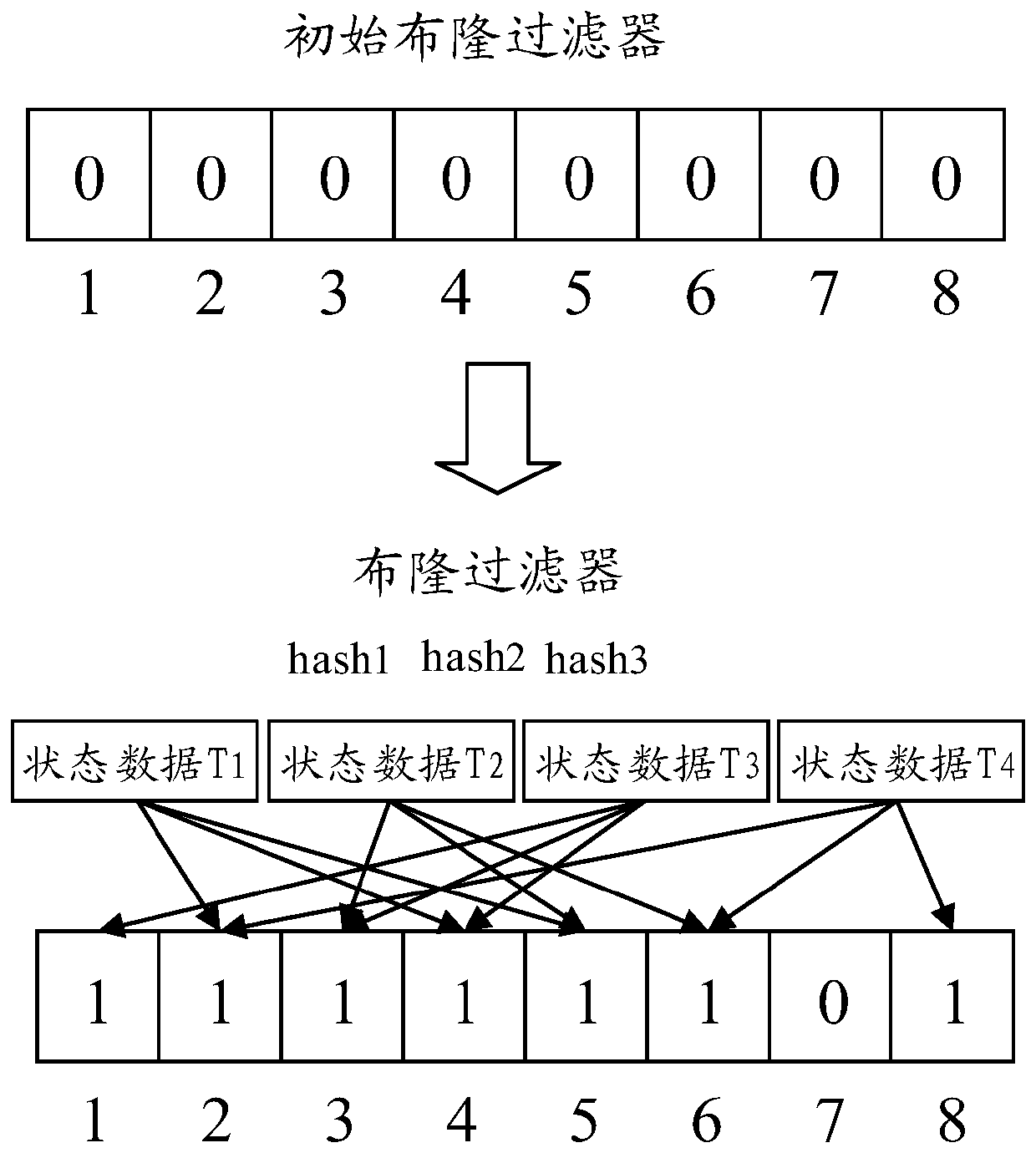
The embodiment of the invention discloses a processing method and device based on a block chain system. The method comprises the following steps: when a node executes a transaction in a to-be-consensus block, generating a plurality of pieces of state data corresponding to the transaction, constructing a Bloom filter corresponding to the block by using the plurality of pieces of state data, and updating a block head of the block by using a hash value of the Bloom filter corresponding to the block; thus, after the node determines that the block consensus succeeds, the block header of the block being linked, and using the Bloom filter corresponding to the block and the multiple pieces of state data for updating the preset database of the node. According to the embodiment of the invention, compared with a data structure of a Merkle tree, the Bloom filter can use a common bit array to store a plurality of pieces of state data, so that the storage space can be well saved and the query response speed can be improved by using the Bloom filter to store the state data corresponding to the transaction, thereby reducing the calculation overhead and cost of the blockchain system.
Owner:WEBANK (CHINA)
Shared physical memory protocol
A computer implemented method for receiving data to a targeted logical partition. A computer locates buffer element in reliance on a connection status bit array. The computer copies control information to the targeted logical partition's local storage. The computer updates a targeted logical partition's local producer cursor based on the control information. The computer copies data to an application receive buffer. The computer determines that an application completes a receive operation. Responsive to a determination that the application completed the receive operation, the computer a targeted logical partition's local consumer cursor to match the targeted logical partition's producer cursor.
Owner:IBM CORP
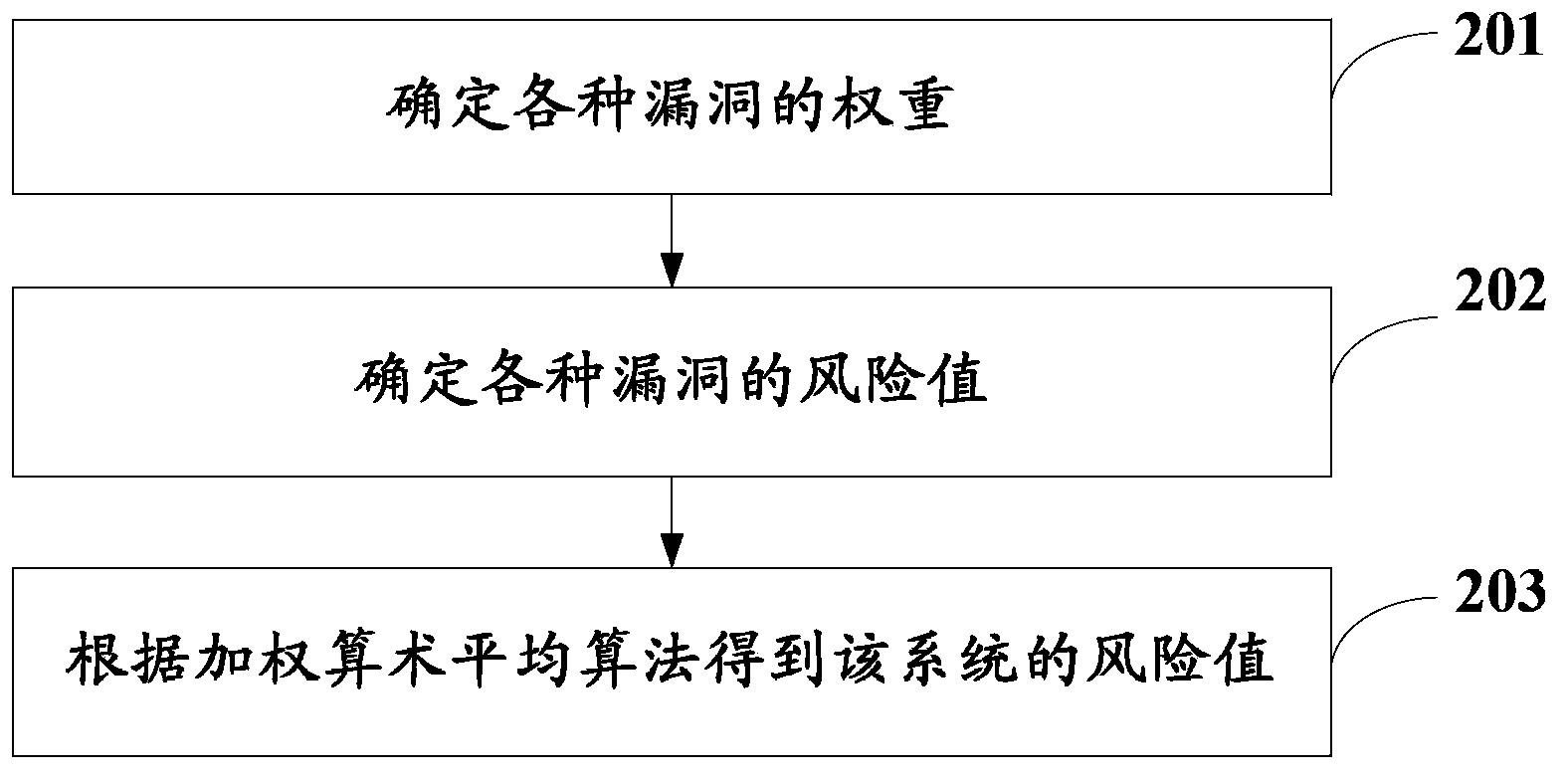
Vulnerability scanning method and server and risk assessment system
InactiveCN104144148ASave storage spaceFast matchingPlatform integrity maintainanceTransmissionBit arrayBloom filter
The invention discloses a vulnerability scanning method and server and a risk assessment system and relates to the technical field of information security. The method comprises the steps that the server receives a scanning parameter configuration file from a client side and scans a scanned target according to the scanning parameter configuration file; the server extracts keywords from a scanning result; based on a bloom filter algorithm, the server performs quick matching on the extracted keywords and vulnerability features, compressed based on the bloom filter algorithm, in a vulnerability library, and the server determines whether vulnerability exists in the scanning result according to a matching result. As the vulnerability features are compressed based on the bloom filter algorithm, the know vulnerability features can be compressed into an m-bit array, and then storage space is reduced. In addition, a Hash operation is performed on the scanned keywords based on the bloom filter algorithm, matching is performed on Hash operation results and the m-bit array of the known vulnerability features, in this way, it can be determined whether the vulnerability exists in the scanning result, and the matching speed is higher.
Owner:CHINA TELECOM CORP LTD
Method of multi-dimensional Packet Classification based on muti-bit segmentation
A multidimensional grouping classification method based on multi-bit division includes following steps: 1) establish a decision tree root node, and assign the full set of the rules set of classification algorithm to the root node; 2) recursively divide each node of decision tree with the corresponding rules set, and generate a number of sub-nodes, and each sub-node corresponds to a rules subset after the division; until the scale of all the rules sets of the nodes is smaller than a certain predetermined threshold; in which, the said division method including the following steps in turn: convert the rules table into two-dimensional bit array, and evaluate the performance when each bit generating decision tree, and according to the performance influence scale, select the bit to generate decision tree. This invention uses bit value as the basis of node separating, and based on the new view of bit division, to establish the decision tree, so the established tree is small in scale, and the comprehensive performance is very good in time / space.
Owner:HUAWEI TECH CO LTD +1
Ferroelectric Memories based on Arrays of Autonomous Memory Bits
A memory having a plurality of ferroelectric memory cells connected between first and second bit lines is disclosed. A read circuit is also connected between the first and second bit lines. A word select circuit selects one of the ferroelectric memory cells and generates a potential on the first hit line indicative of a value stored in the selected one of the plurality of ferroelectric memory cells. Each ferroelectric memory cell includes a ferroelectric capacitor and a variable impedance element having an impedance between first and second switch terminals that is determined by a signal on a control terminal. The ferroelectric capacitor is connected between the control terminal and the first switch terminal. First and second gates connect the ferroelectric memory cell to the bit lines in response to the word select circuit selecting that ferroelectric memory cell.
Owner:RADIANT TECH
Private database logging with minimal storage requirements
ActiveUS20120109893A1Minimal storage requirementDigital data information retrievalDigital data processing detailsTime informationBit field
An apparatus, system, and method are disclosed for logging operations for a database. An operation event module detects an operation on a record in a database table. A translation module creates a changed field bit field, one or more operation time bit fields, and a user bit field. The translation module creates the changed field bit field by encoding indicators of one or more fields of the record that the operation is configured to change, creates the one or more operation time bit fields by encoding time information for the operation, and creates the user bit field by encoding information of a user associated with the operation. A consolidation module packs at least the changed field bit field, the one or more operation time bit fields, and the user bit field into a single bit array. A log module stores the bit array in a change log.
Owner:IBM CORP
Method and Apparatus for Encoding/Decoding
InactiveUS20080288263A1Quality improvementEfficient use ofSpeech analysisCode conversionBit arrayData encoding
An encoding method and apparatus and a decoding method and apparatus are provided. The encoding method includes encoding data, generating a data bit array comprising the encoded data and encoding information, and generating an align bit array comprising one or more Is. According to the encoding method and apparatus and the decoding method and apparatus, it is possible to enhance the quality of decoded data by inserting various information into an align bit array that is included in a bitstream for aligning a plurality of encoded data bit arrays with one another. In addition, according to the encoding method and apparatus and the decoding method and apparatus, it is possible to efficiently utilize data bandwidths that are allocated for the encoding / decoding of data at low bitrates by enhancing the efficiency of data encoding.
Owner:LG ELECTRONICS INC
Apparatus and method for snoop access in a dual access, banked and pipelined data cache memory unit
ActiveUS20040158683A1Memory adressing/allocation/relocationGenerating/distributing signalsThree stageControl signal
In a data cache unit that exchanges data signal groups with at least two execution units, the operation of the data cache unit is implemented as a three-stage pipeline in order to access data at the speed of the system clock. The data cache unit has a plurality of storage cell banks. Each storage cell bank has valid bit array unit and a tag unit for each execution unit incorporated therein. Each valid bit array unit has a valid / invalid storage cell associated with each data group stored in the storage cell bank. The valid bit array units have a read / write address port and snoop address port. During a read operation, the associated valid / invalid signal is retrieved to determine whether the data signal group should be processed by the associated execution unit. In a write operation, a valid bit is set in the valid / invalid bit location(s) associated with the storage of a data signal group (or groups) during memory access. The valid bit array unit responds to a snoop address and a control signal from the tag unit to set an invalid bit in a valid / invalid bit address location associated with the snoop address. The tag unit can be divided into a plurality of tag subunits to expedite processing.
Owner:ORACLE INT CORP
High performance carry chain with reduced macrocell logic and fast carry lookahead
InactiveUS6990508B1Improve performanceReduced macrocell logicComputation using non-contact making devicesProgrammable logic deviceComputer science
A programmable logic block in an integrated circuit comprising a plurality of macrocells, an AND-array, an OR-array, and a logic circuit. The plurality of macrocells may comprise logic that may be configured to (i) generate and propagate an inverted carry-input signal and (ii) generate a sum bit. The AND-array may comprise at least two product terms per macrocell. The OR-array may be configured to generate a sum-of-products term for each macrocell in response to the two product terms. The logic circuit may be configured to (a) receive (i) the product terms and (ii) the carry-input signal generated by a first macrocell of the plurality of macrocells and (b) generate (i) a block carry-propagate signal, (ii) a block carry-generate signal, and (iii) a block carry-output signal.
Owner:MONTEREY RES LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com