Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1520results about How to "Reduce computing load" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
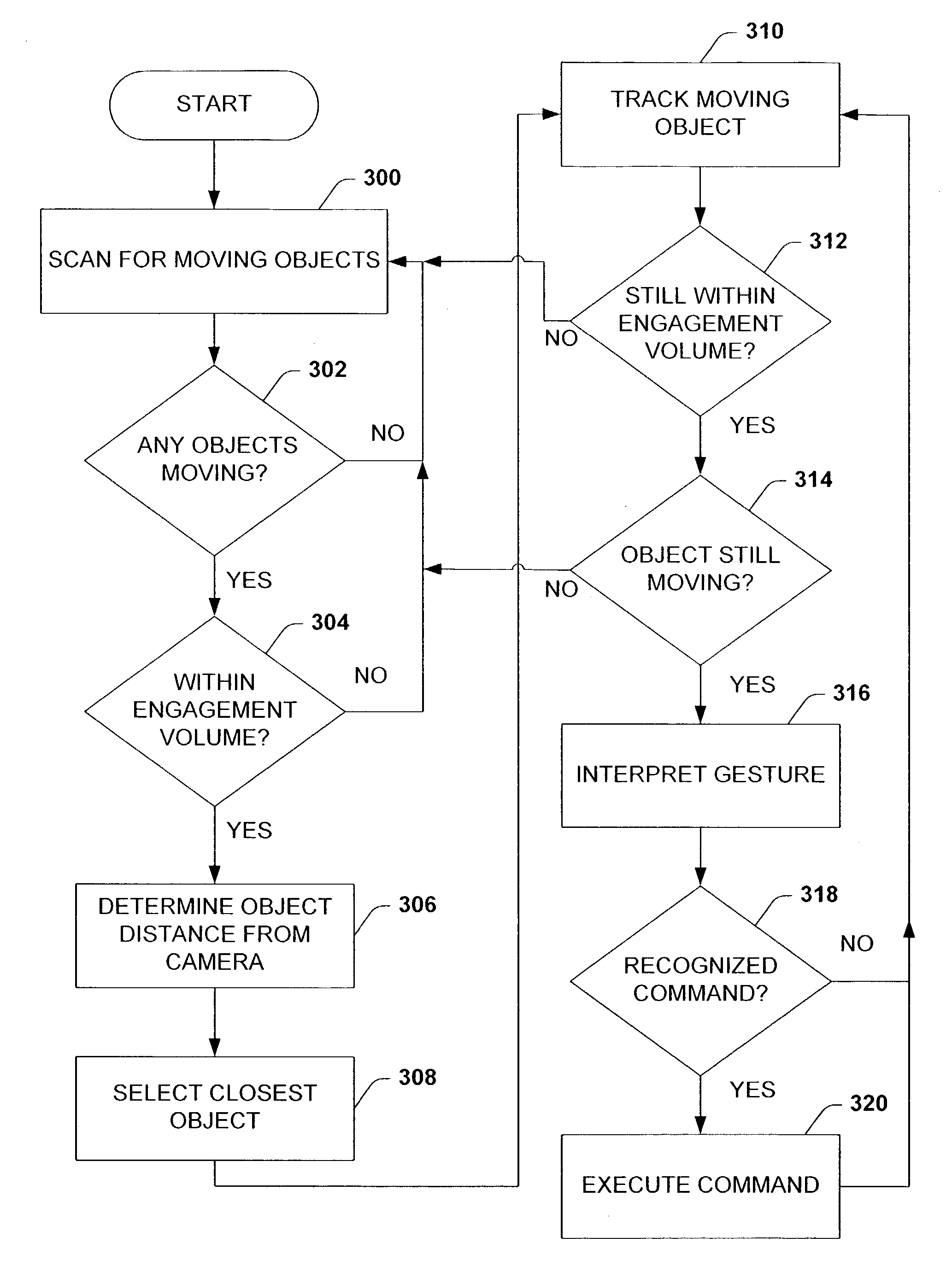
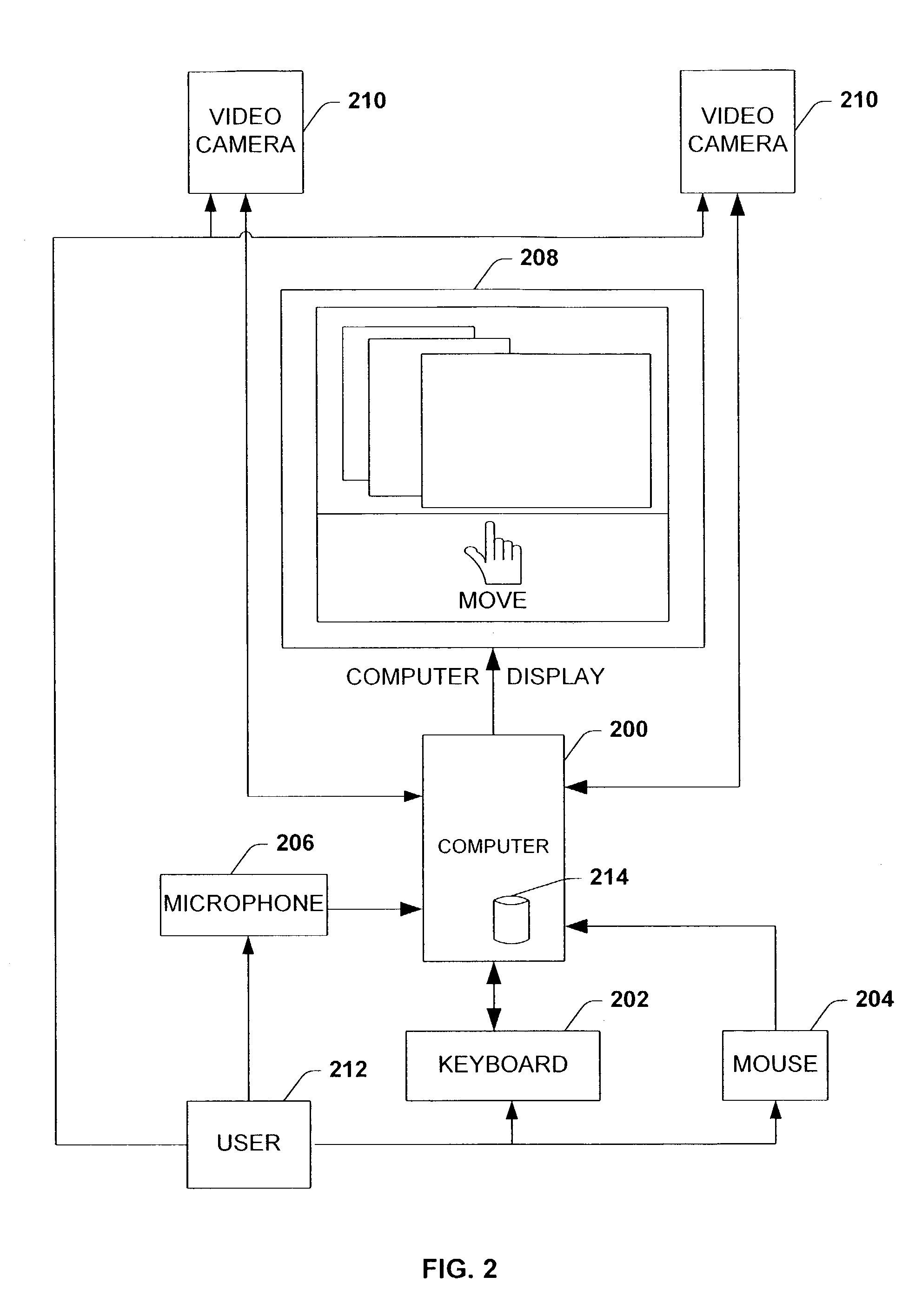
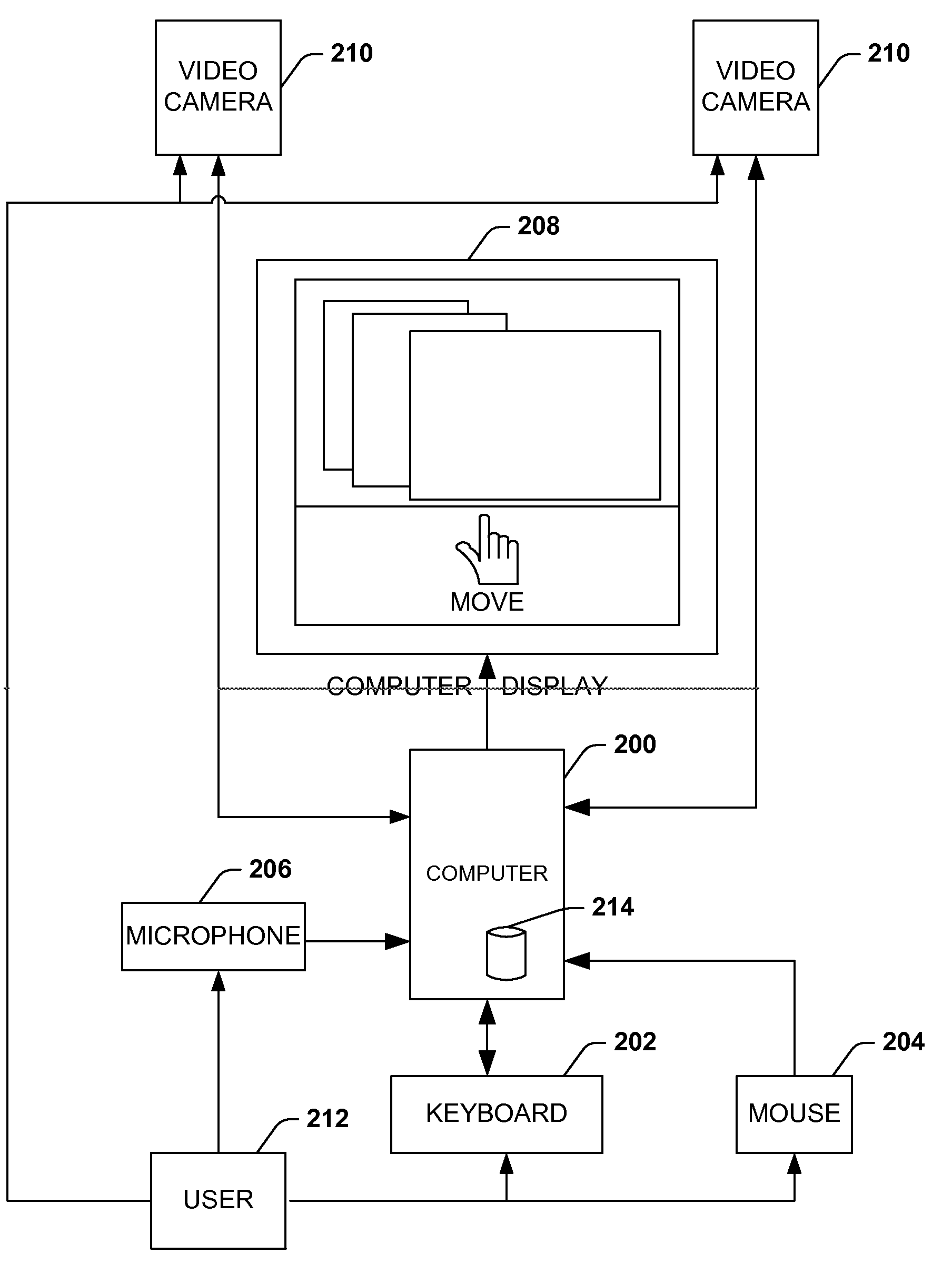
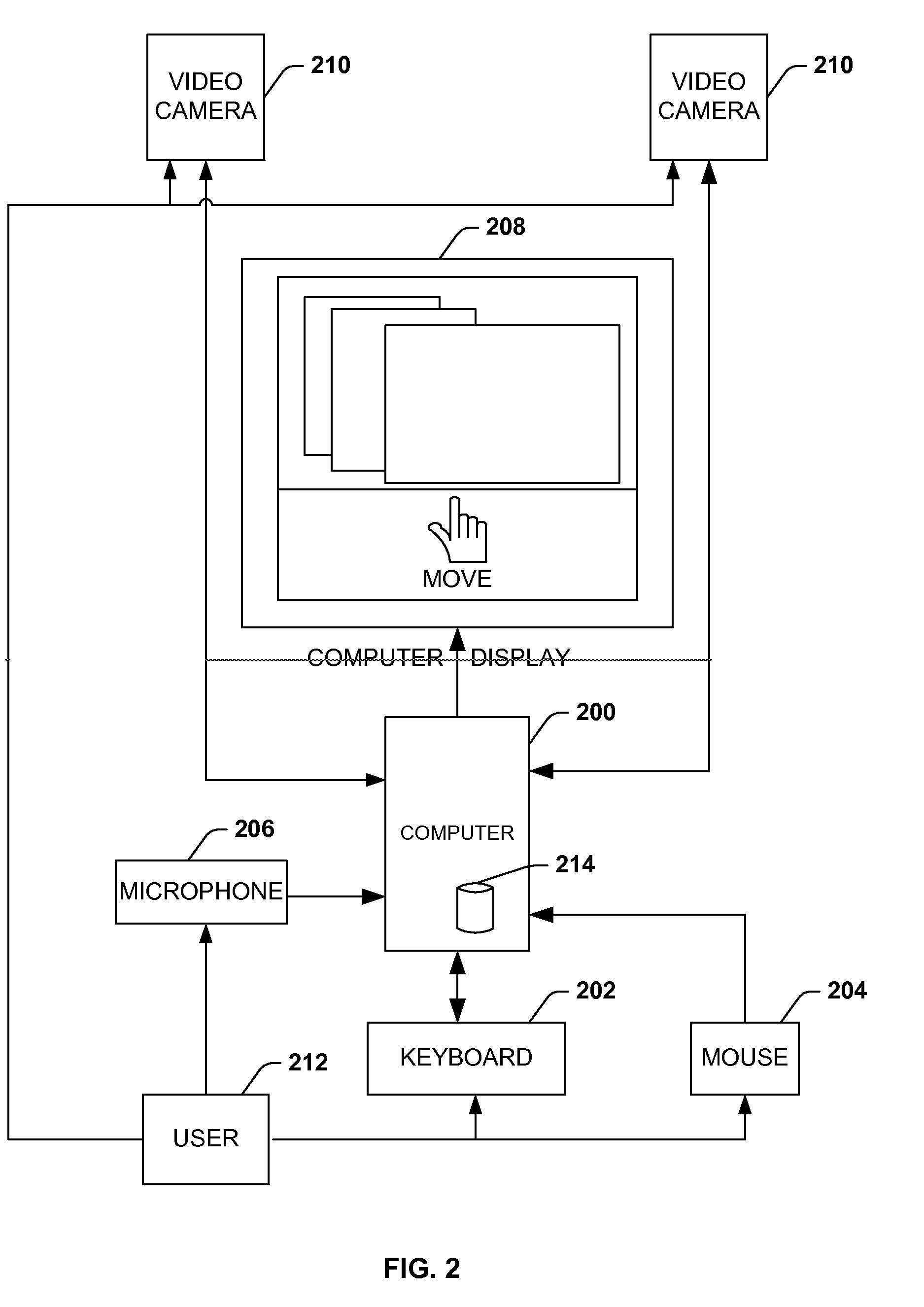
Architecture for controlling a computer using hand gestures
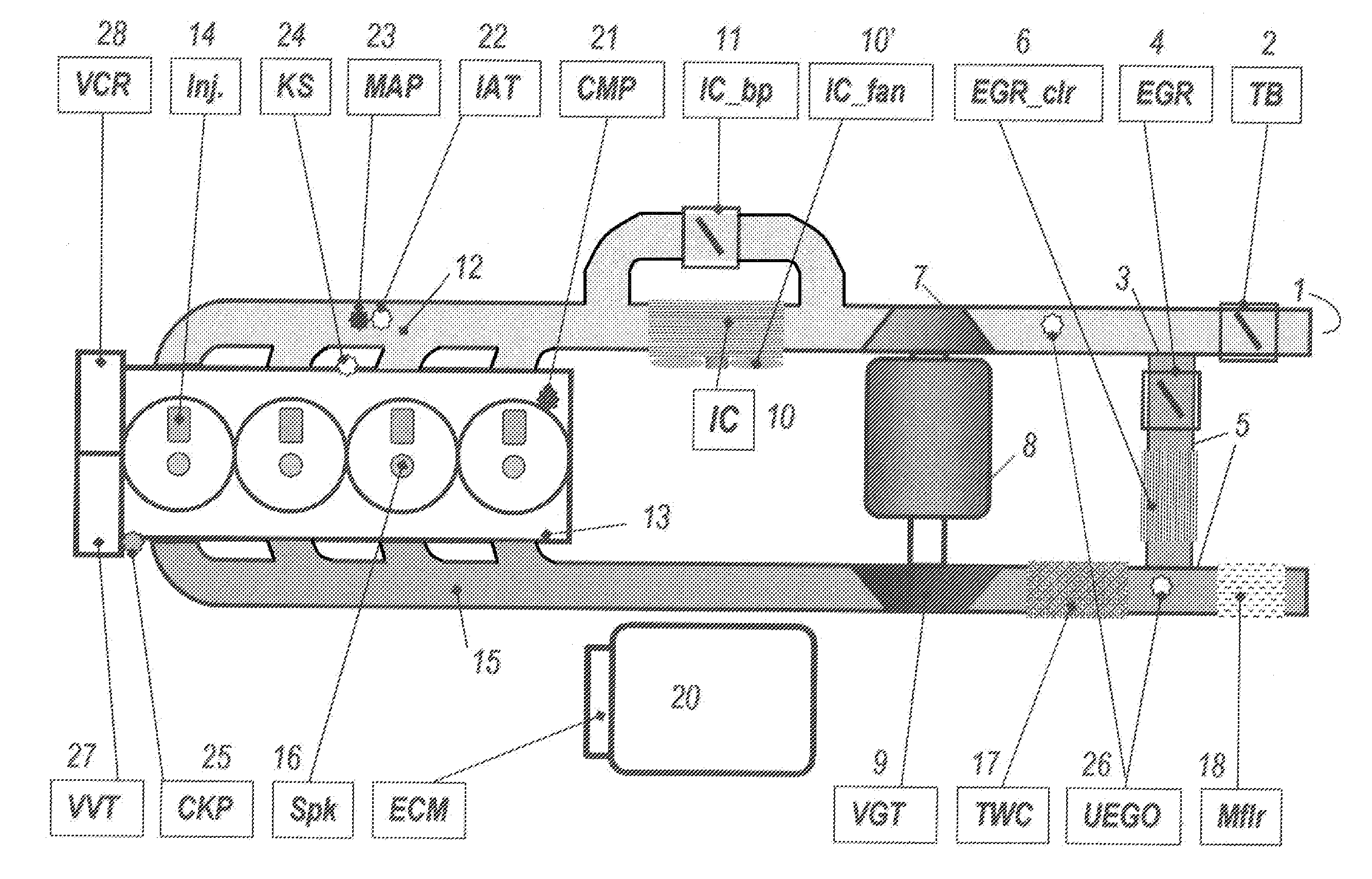
InactiveUS7665041B2Reduce computing loadReduced representation of imageInput/output for user-computer interactionCharacter and pattern recognitionPattern recognitionObject based
Owner:MICROSOFT TECH LICENSING LLC
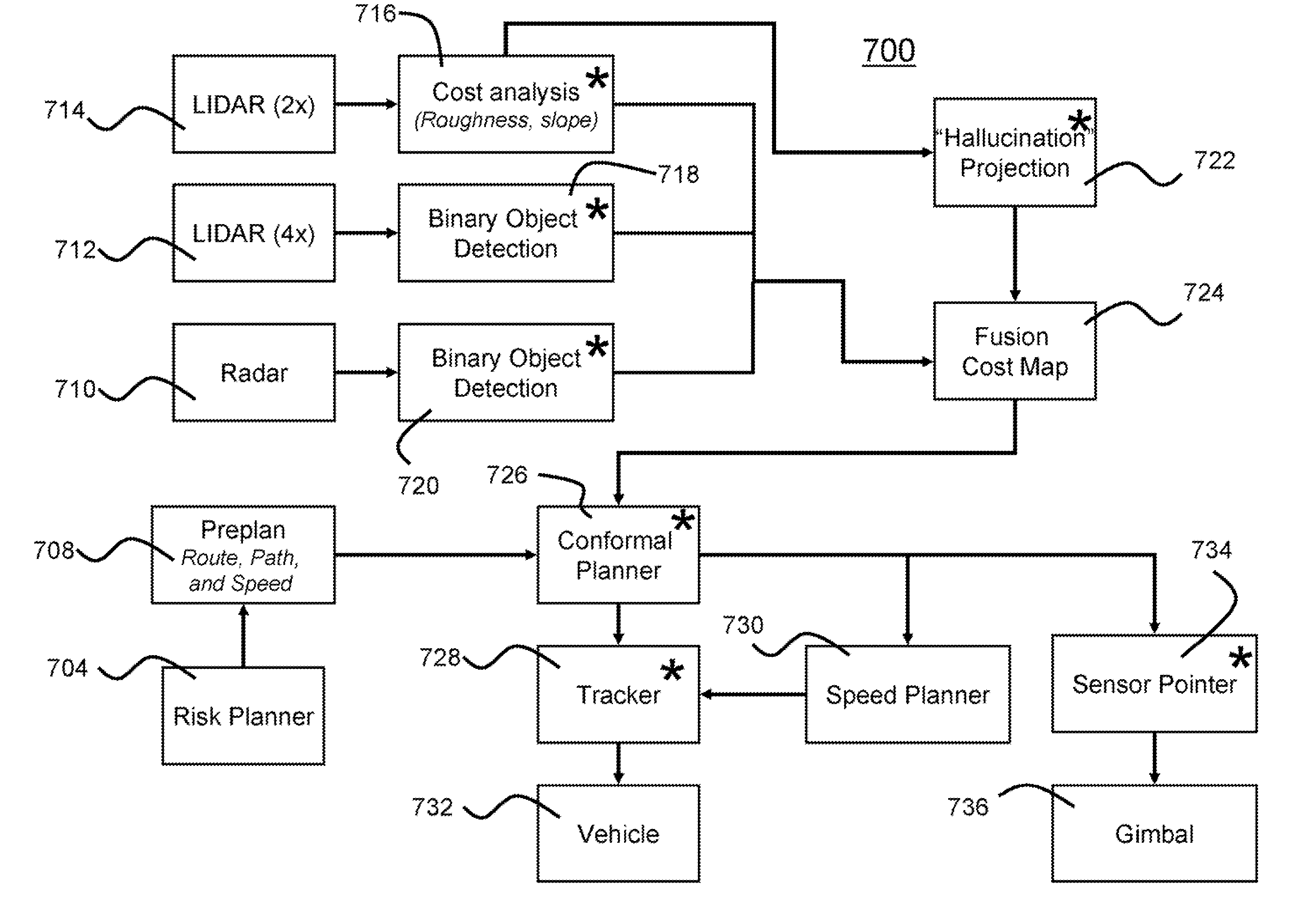
Software architecture for high-speed traversal of prescribed routes
InactiveUS20080059015A1Reduce computing loadImprove abilitiesPlatooningVehicle position/course/altitude controlTerrainLocal environment
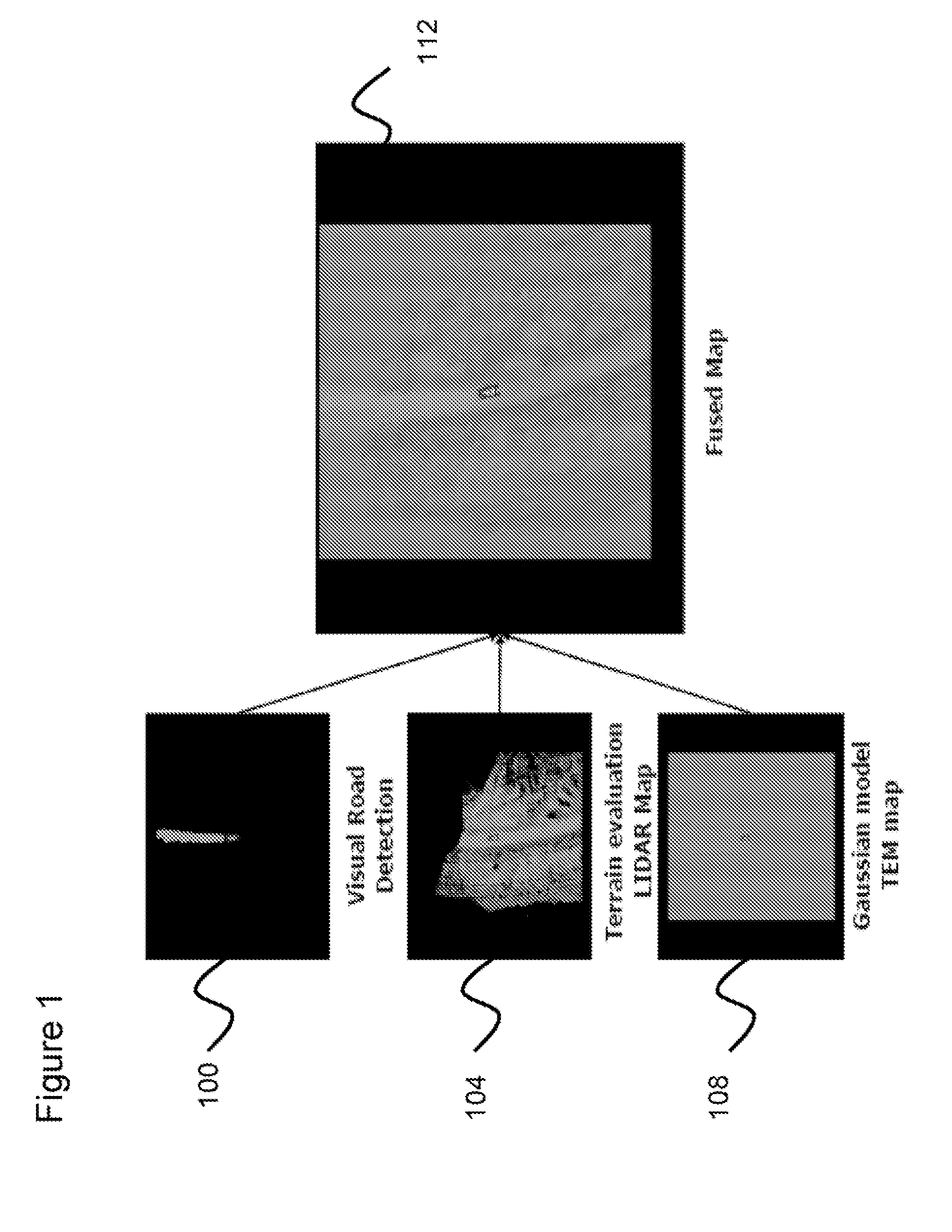
Systems, methods, and apparatuses for high-speed navigation. The present invention preferably encompasses systems, methods, and apparatuses that provide for autonomous high-speed navigation of terrain by an un-manned robot. By preferably employing a pre-planned route, path, and speed; extensive sensor-based information collection about the local environment; and information about vehicle pose, the robots of the present invention evaluate the relative cost of various potential paths and thus arrive at a path to traverse the environment. The information collection about the local environment allows the robot to evaluate terrain and to identify any obstacles that may be encountered. The robots of the present invention thus employ map-based data fusion in which sensor information is incorporated into a cost map, which is preferably a rectilinear grid aligned with the world coordinate system and is centered on the vehicle. The cost map is a specific map type that represents the traversability of a particular environmental area using a numeric value. The planned path and route provide information that further allows the robot to orient sensors to preferentially scan the areas of the environment where the robot will likely travel, thereby reducing the computational load placed onto the system. The computational ability of the system is further improved by using map-based syntax between various data processing modules of the present invention. By using a common set of carefully defined data types as syntax for communication, it is possible to identify new features for either path or map processing quickly and efficiently.
Owner:CARNEGIE MELLON UNIV
Omnidirectional sensor array system
InactiveUS20140146132A1Simple and efficientIncrease capacityTelevision system detailsColor television detailsSensor arrayIntegrated electronics
An omnidirectional sensor array system, for example a panoptic camera, comprising a plurality of sensors arranged on a support of predetermined shape to acquire data, wherein said sensors are directional and wherein each sensor is attached to a processing node which comprises integrated electronics that carries out at least a portion of the signal processing algorithms locally in order to reduce the computational load of a central hardware unit.
Owner:ECOLE POLYTECHNIQUE FEDERALE DE LAUSANNE (EPFL)
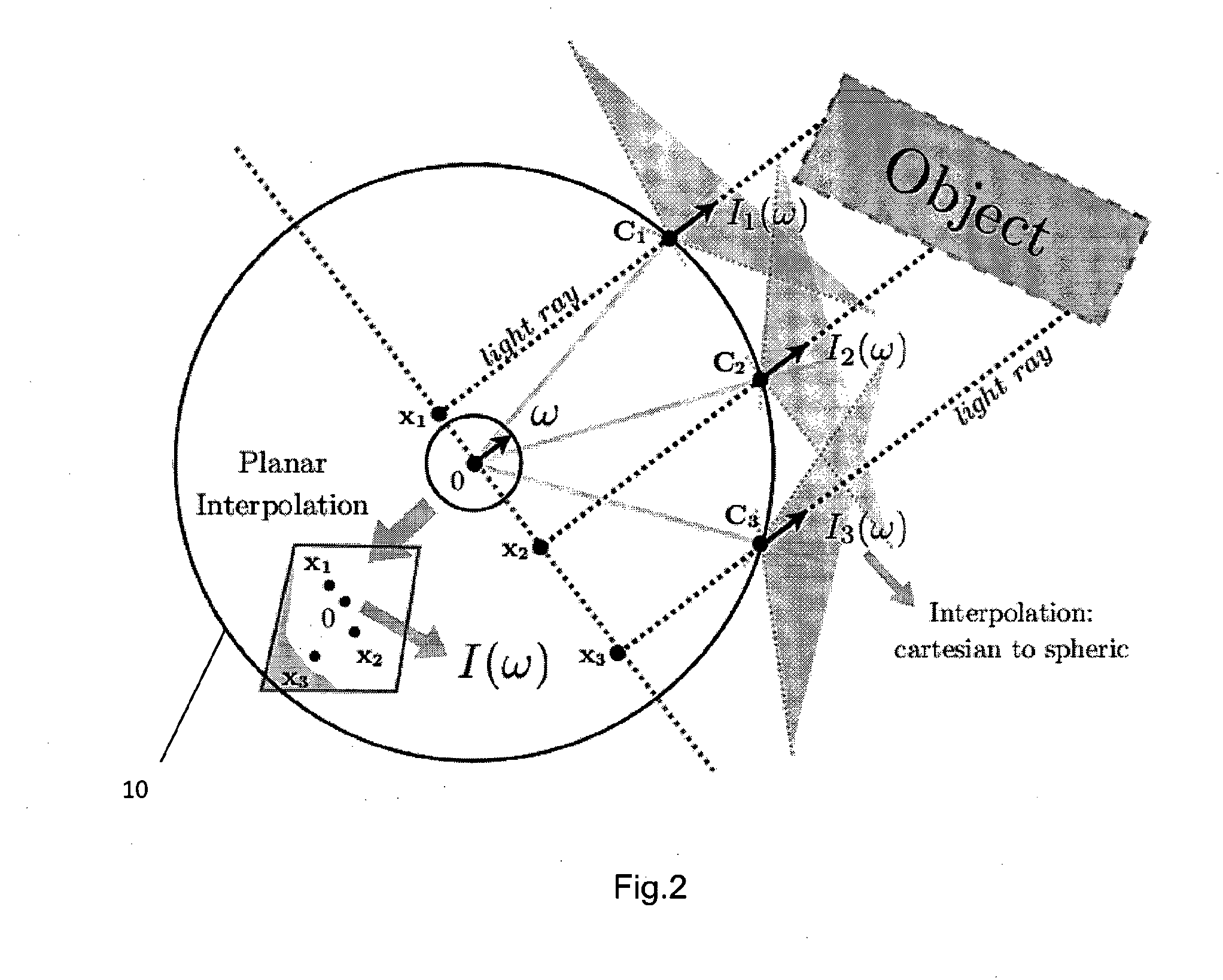
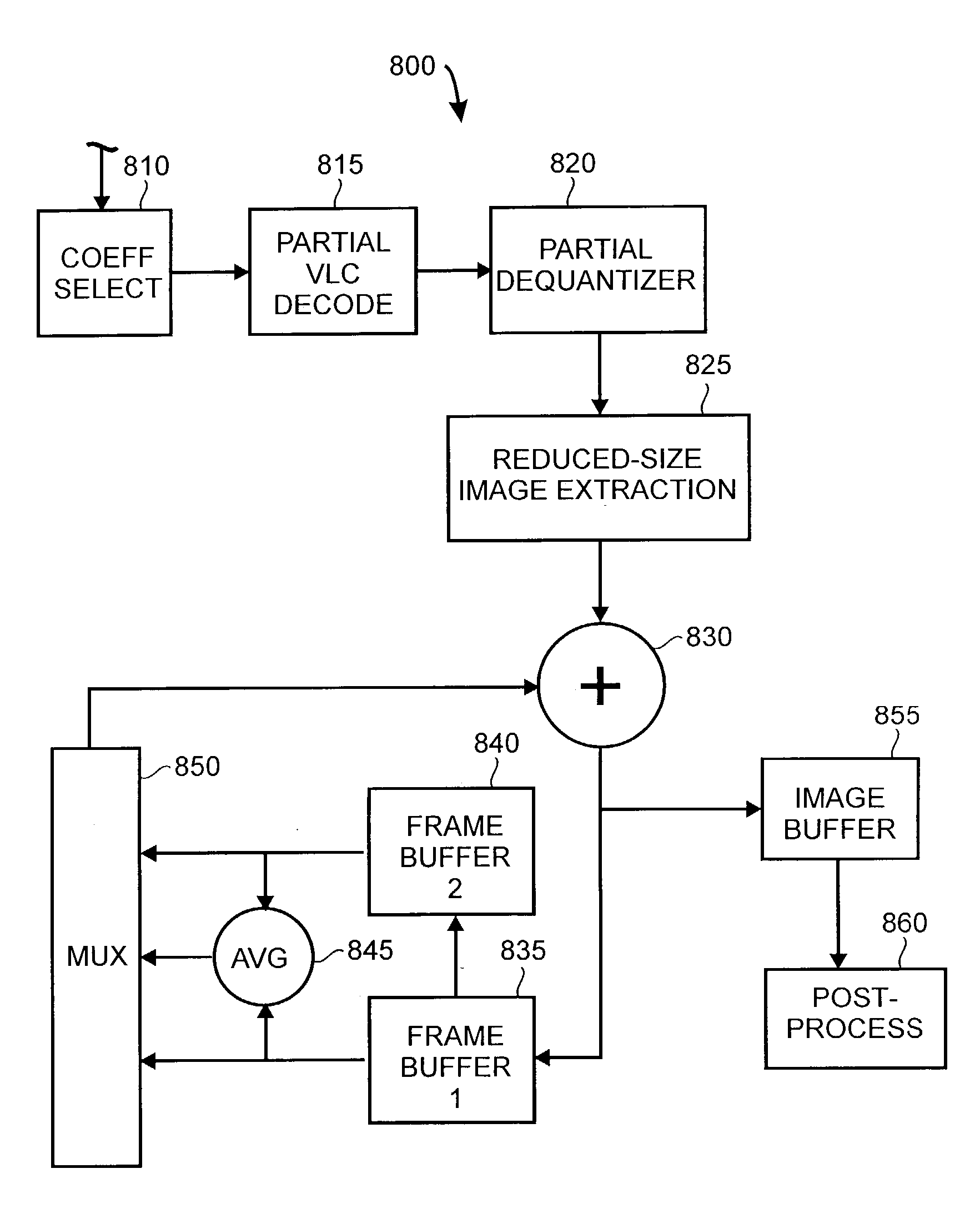
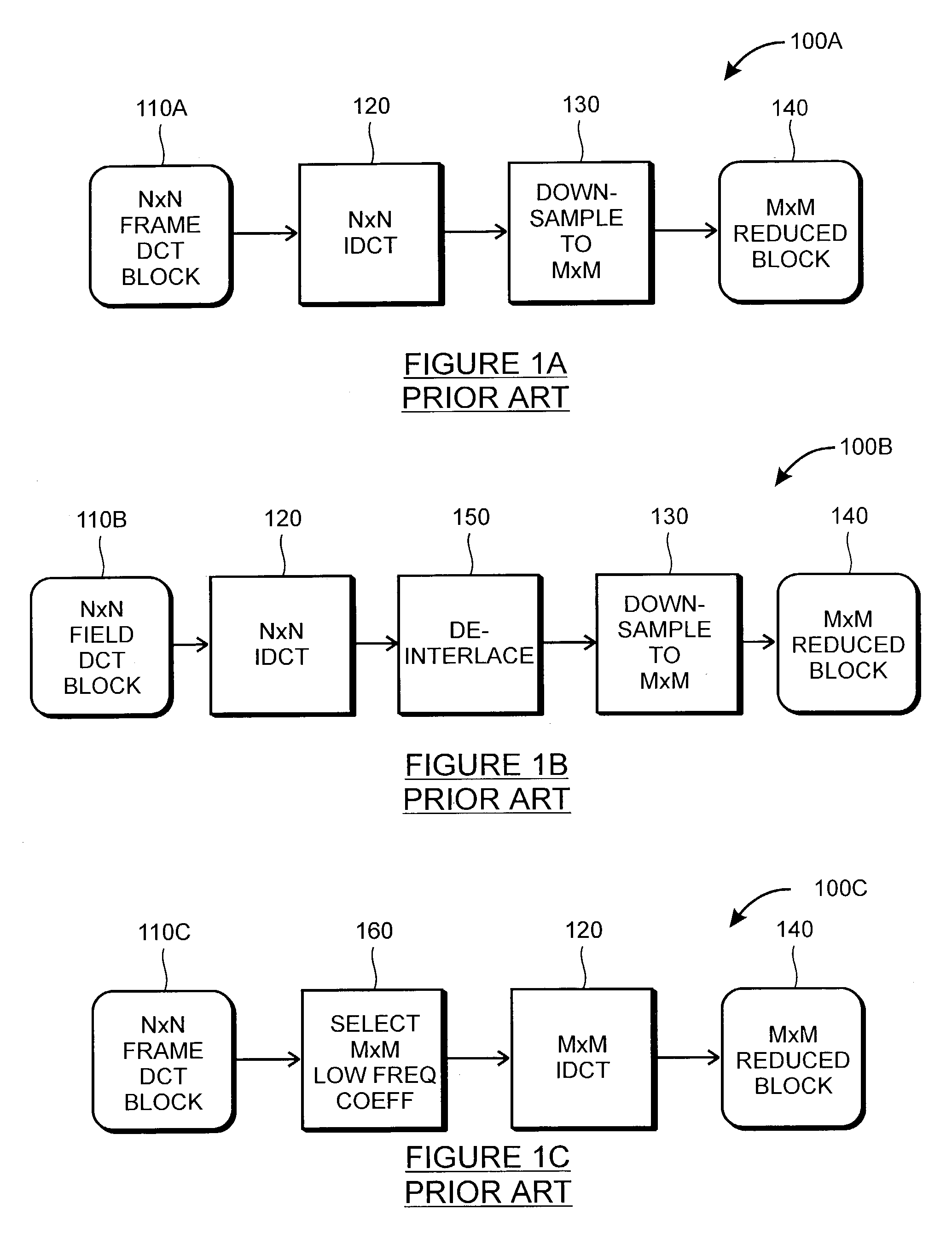
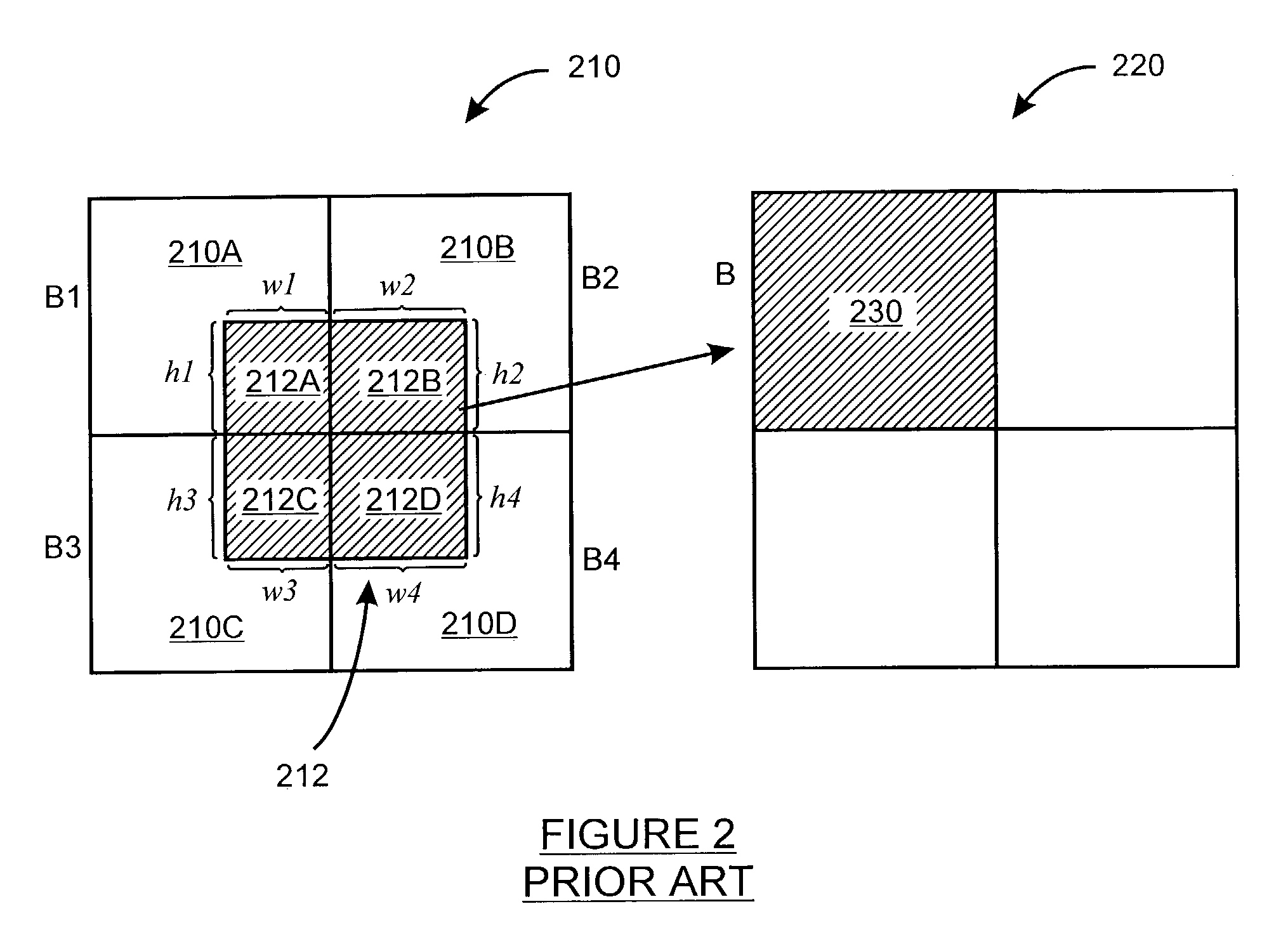
Rapid production of reduced-size images from compressed video streams
ActiveUS7471834B2Simple technologyRapid productionDisc-shaped record carriersFlat record carrier combinationsInterlaced videoReduced size
Methods for fast generating spatially reduced-size images directly from compressed video streams supporting the coding of interlaced frames through transform coding and motion compensation. A sequence of reduced-size images are rapidly generated from compressed video streams by efficiently combining the steps of inverse transform, down-sampling and construction of each field image. The construction of reduced-size field images also allows the efficient motion compensation. The fast generation of reduced-size images is applicable to a variety of low-cost applications such as video browsing, video summary, fast thumbnail playback and video indexing.
Owner:SCENERA INC
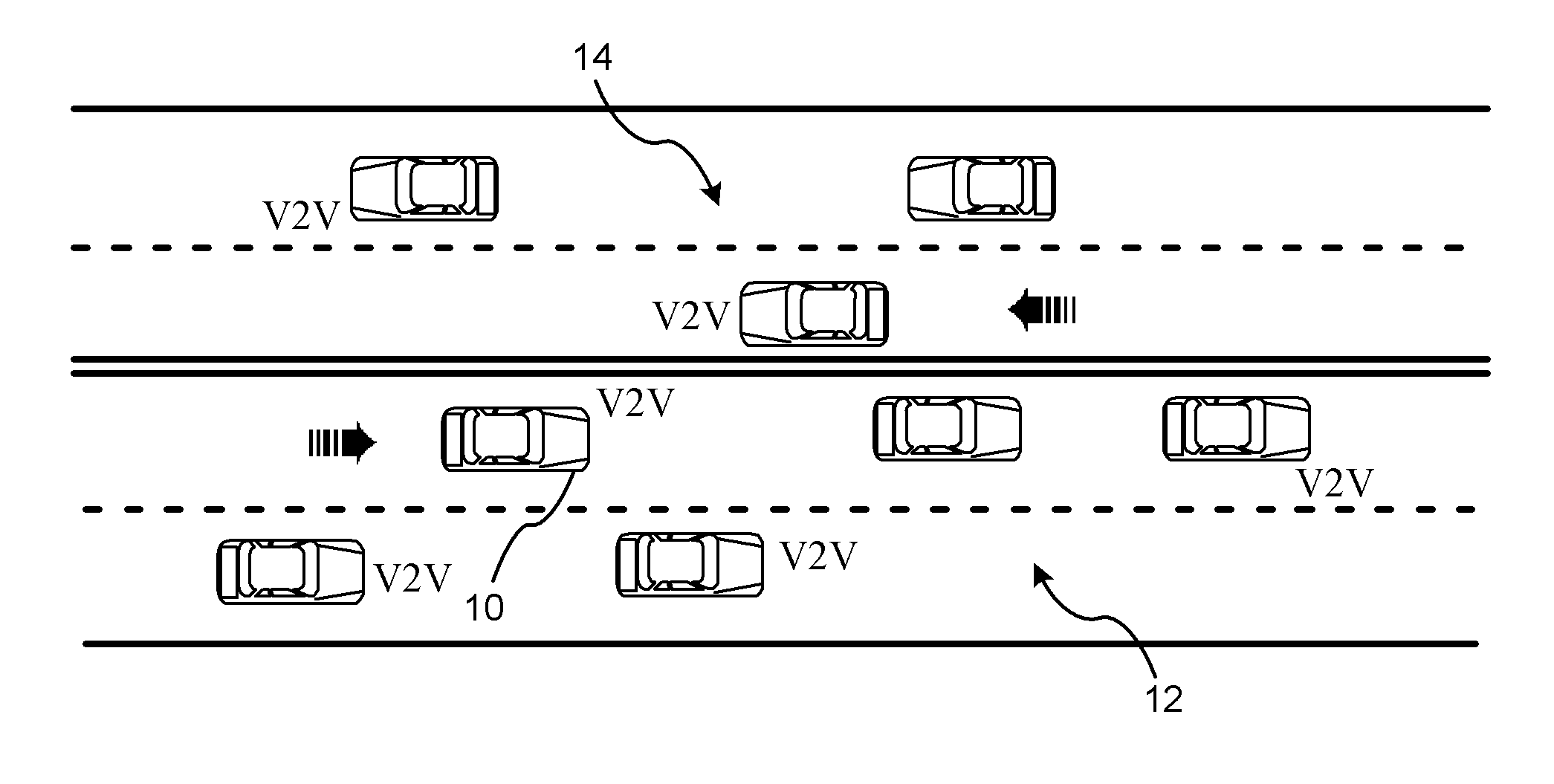
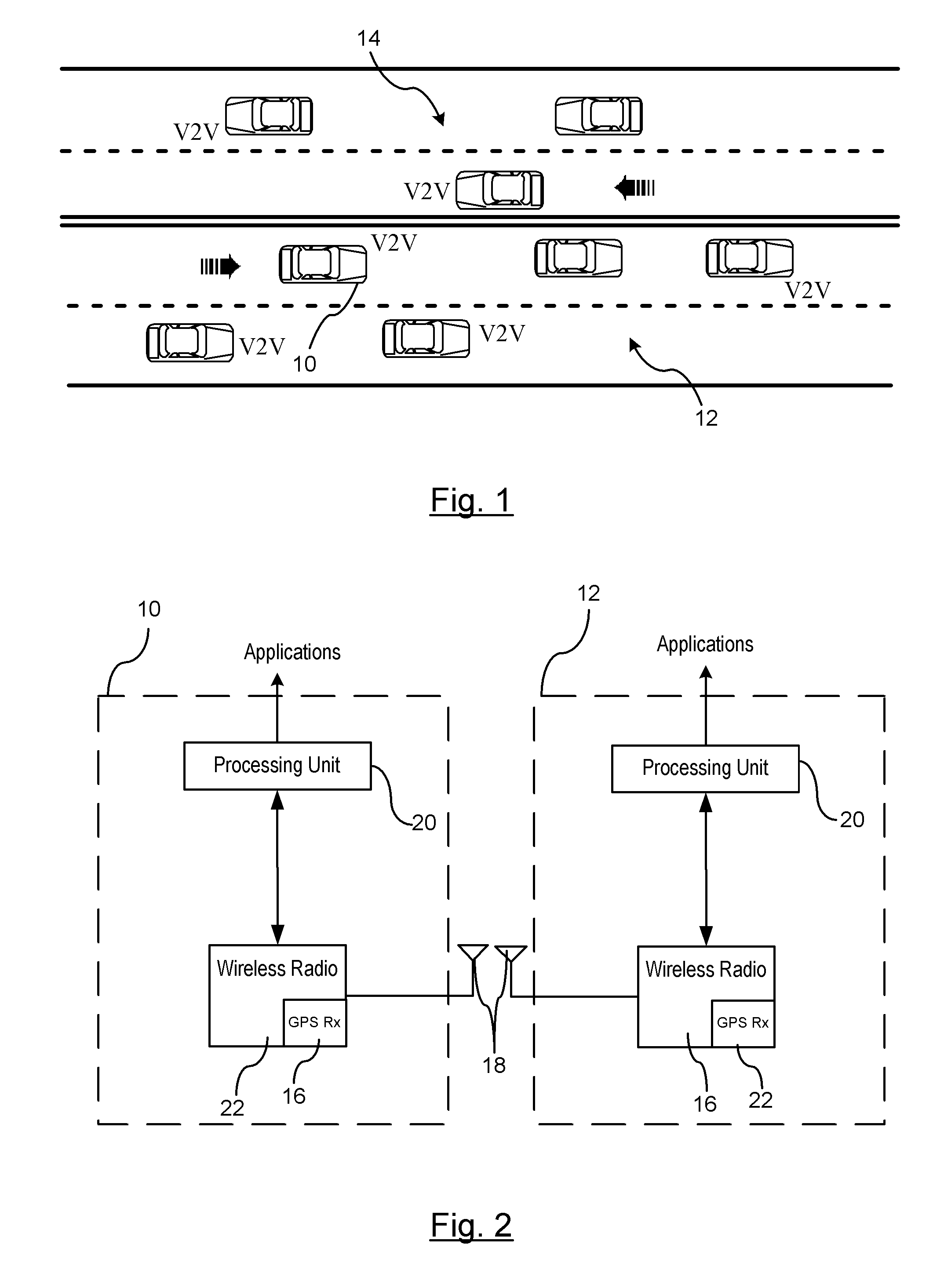
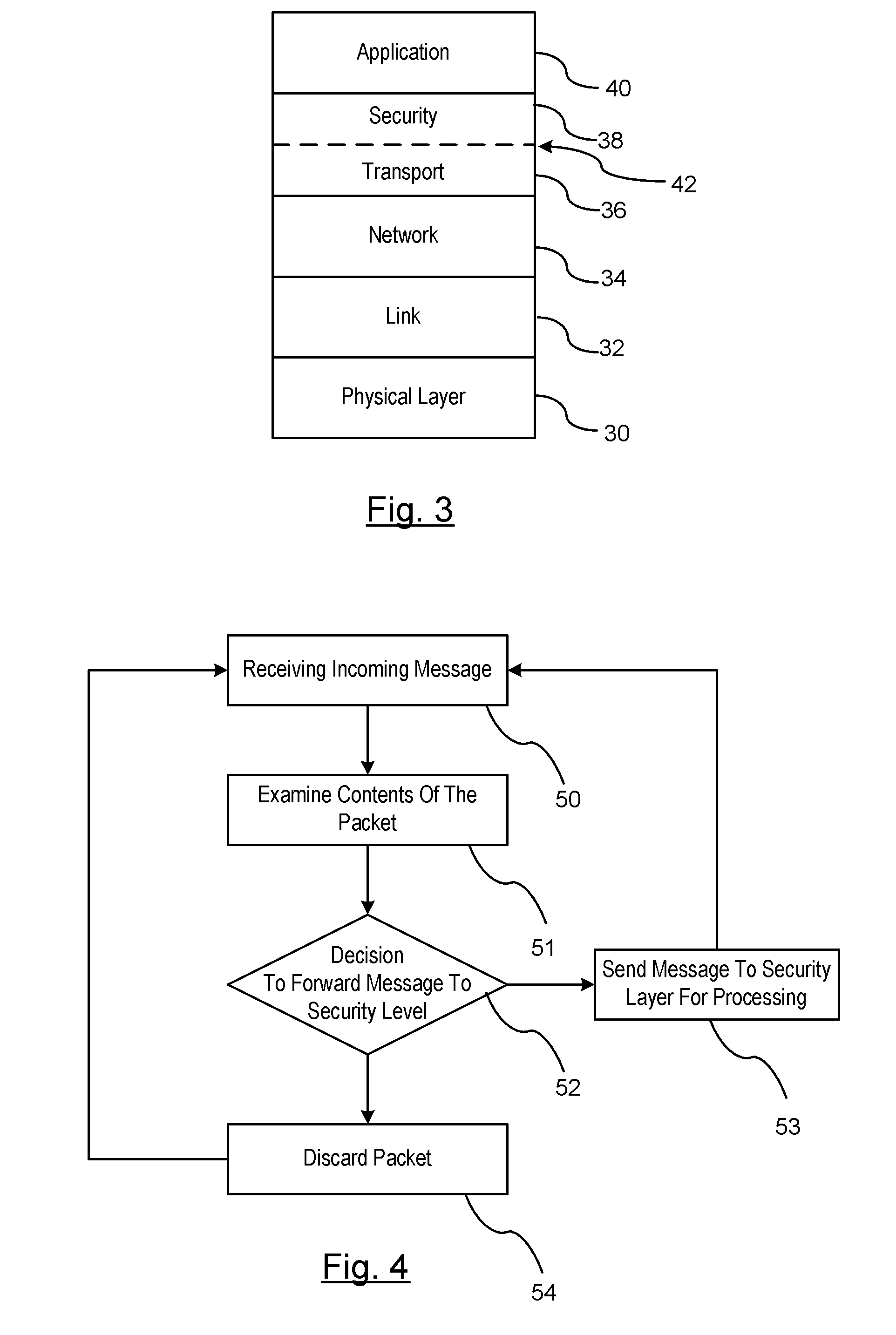
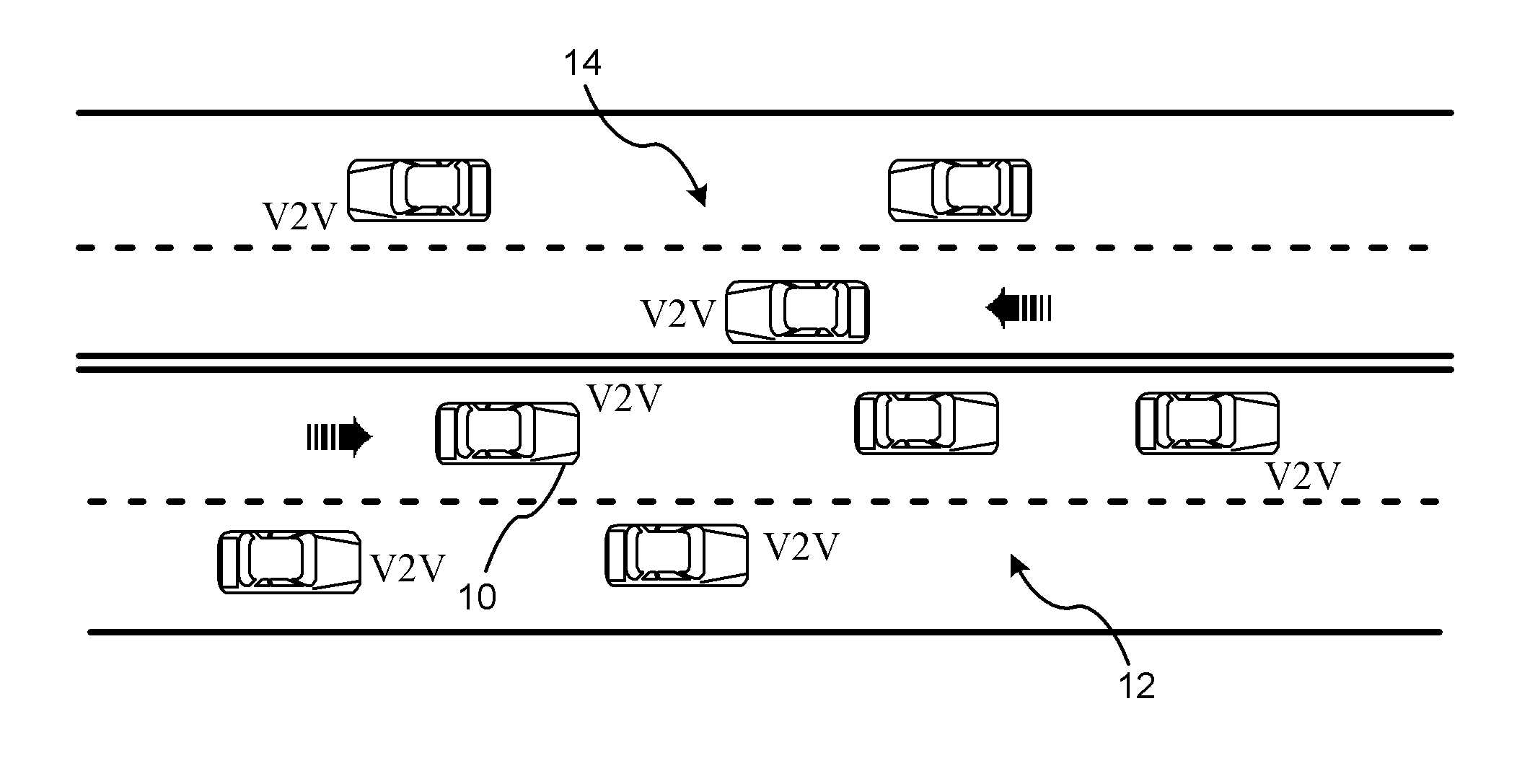
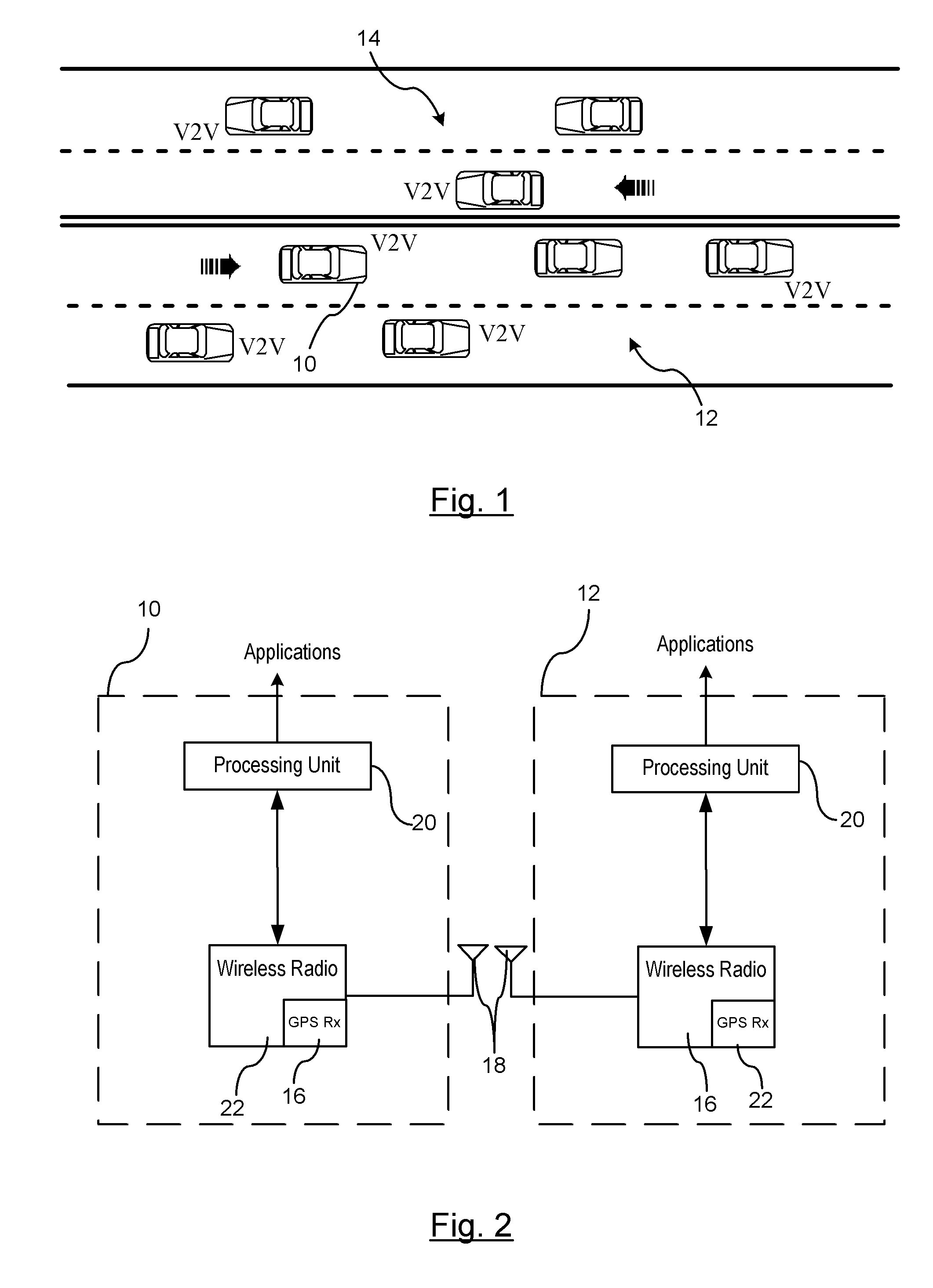
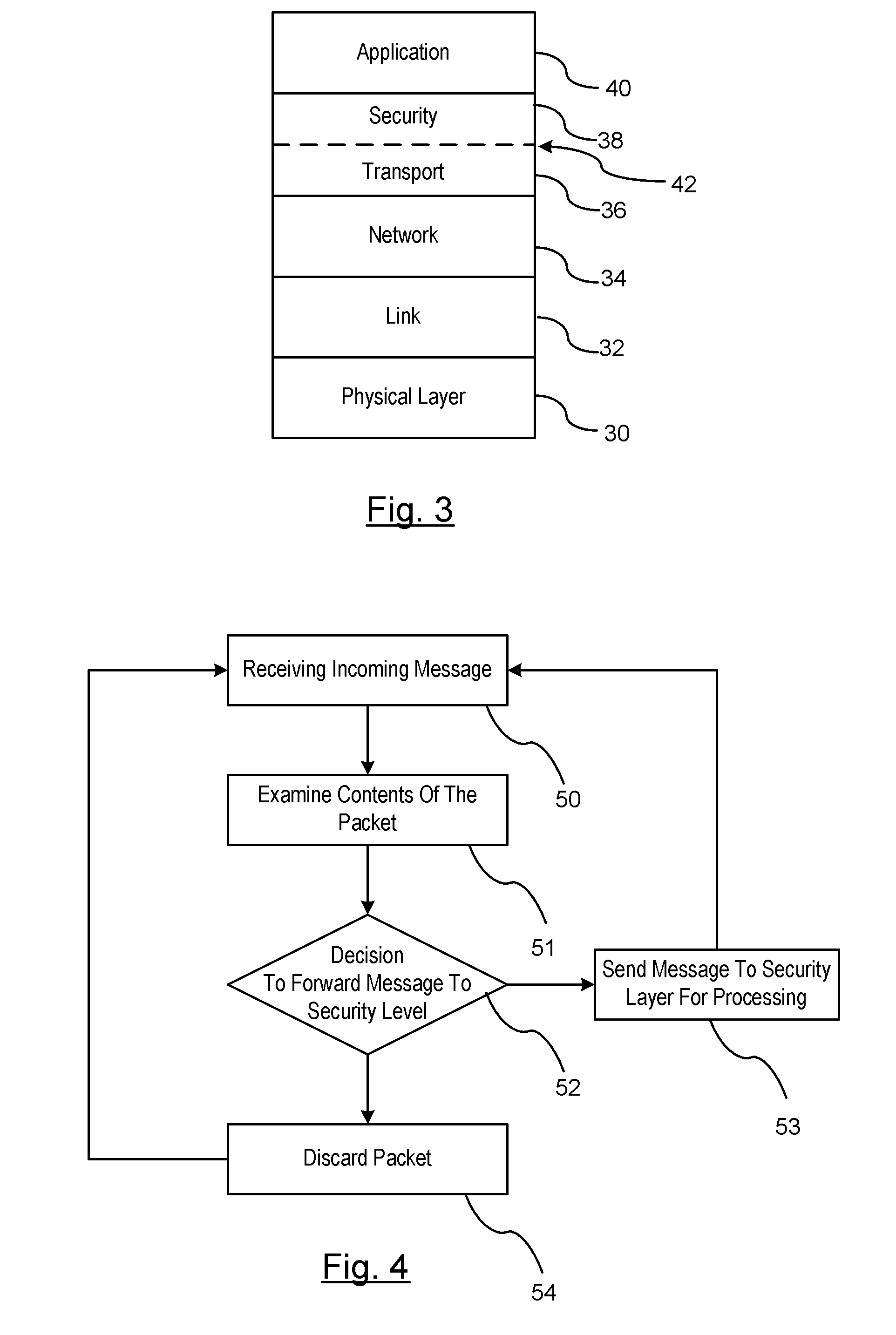
Reducing the Computational Load on Processors by Selectively Discarding Data in Vehicular Networks
ActiveUS20110080302A1Efficient processingReduce computing loadService provisioningParticular environment based servicesCommunications systemProtocol stack
A method is provided for efficiently processing messages staged for authentication in a security layer of a protocol stack in a wireless vehicle-to-vehicle communication system. The vehicle-to-vehicle communication system includes a host vehicle receiver for receiving messages transmitted by one or more remote vehicles. The host receiver is configured to authenticate received messages in a security layer of a protocol stack. A wireless message broadcast by a remote vehicle is received. The wireless message contains characteristic data of the remote vehicle. The characteristic data is analyzed for determining whether the wireless message is in compliance with a predetermined parameter of the host vehicle. The wireless message is discarded prior to a transfer of the wireless message to the security layer in response to a determination that the wireless message is not in compliance with the predetermined parameter of the host vehicle. Otherwise, the wireless message is transferred to the security layer.
Owner:GM GLOBAL TECH OPERATIONS LLC
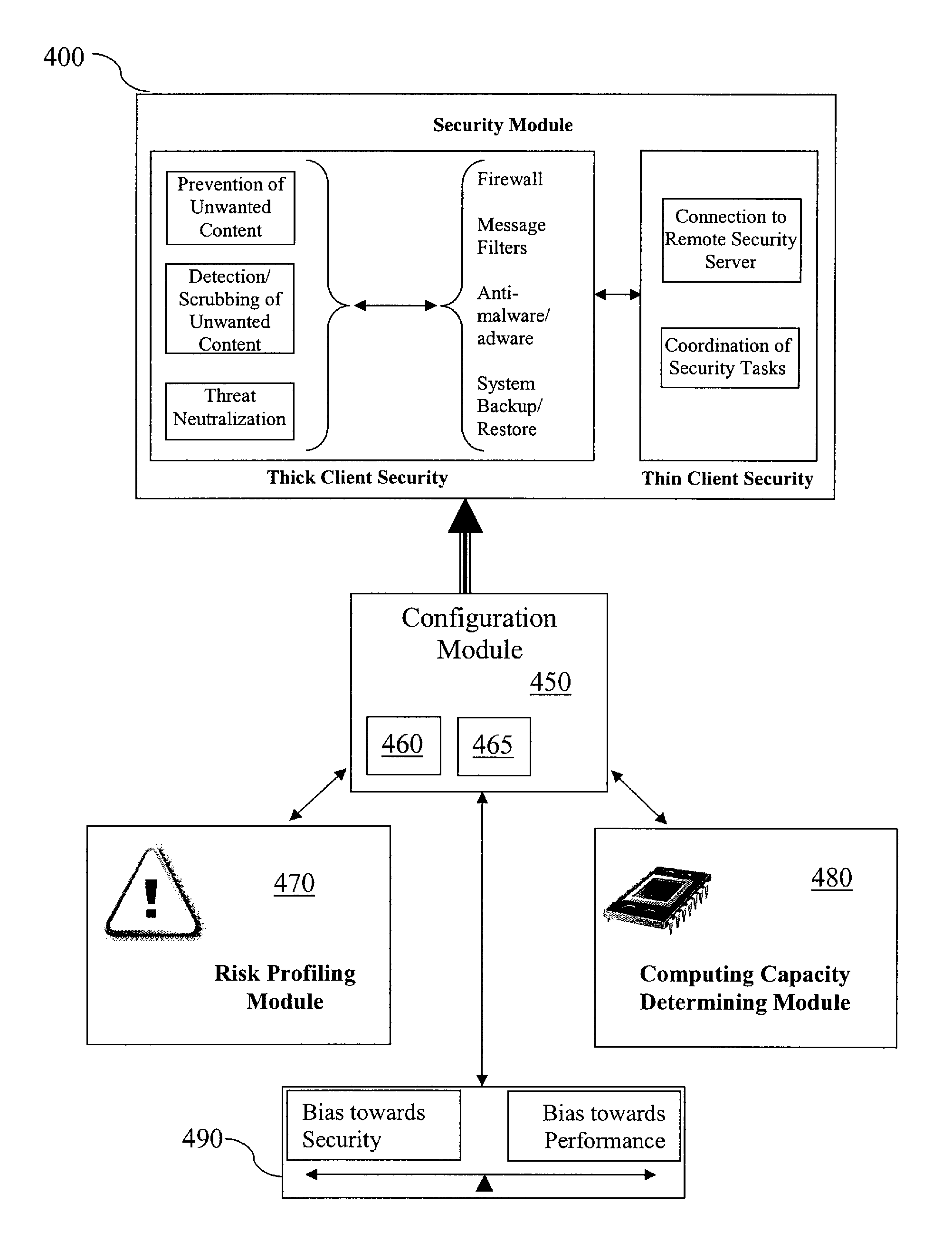
Adaptive security for information devices
ActiveUS7584508B1Improve usabilityReduce loadMemory loss protectionError detection/correctionRisk profilingInformation device
An information device includes a dynamically configurable security module in which operational settings are automatically and dynamically configured based on risk profile or computing capacity information, or both.
Owner:AO KASPERSKY LAB
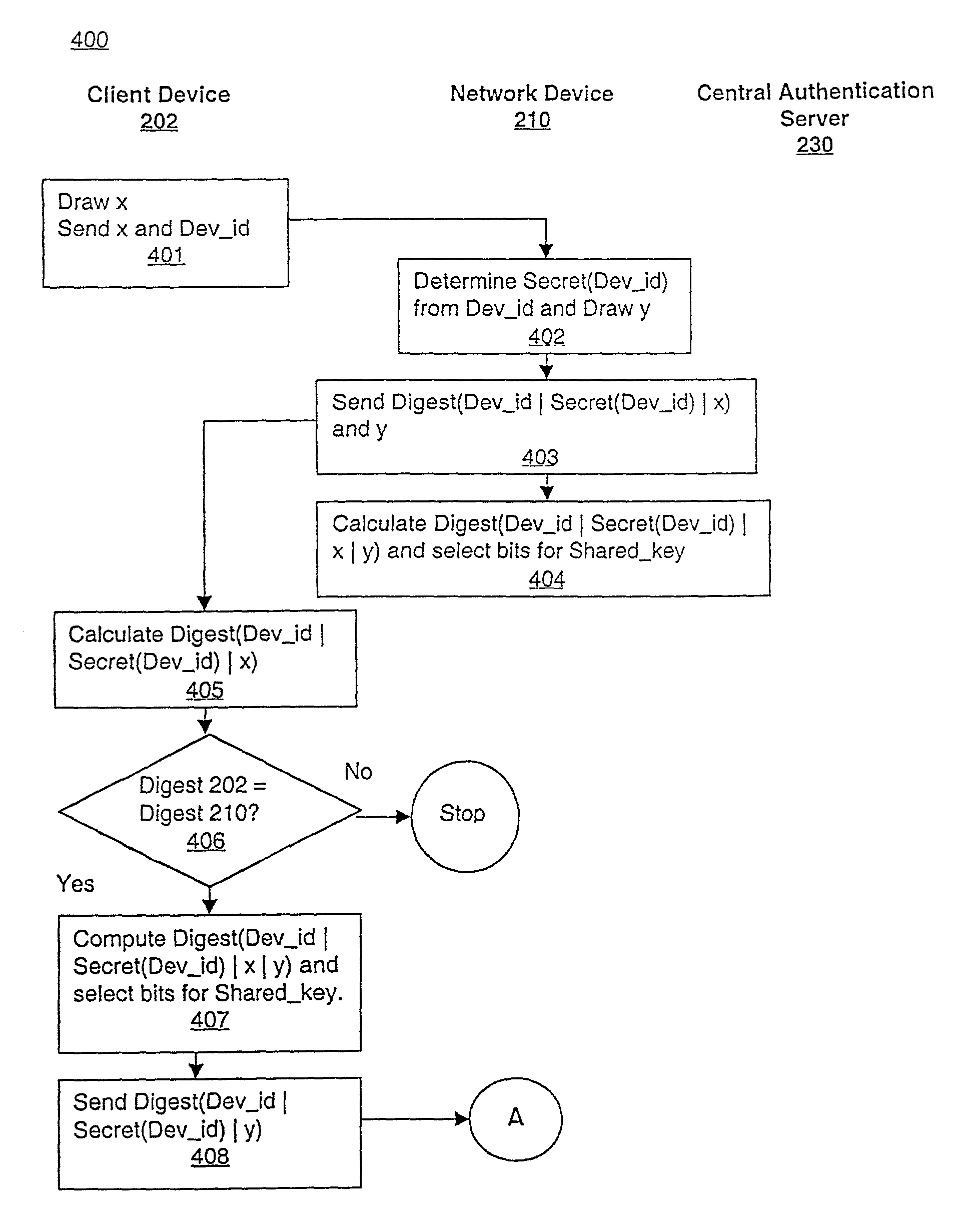
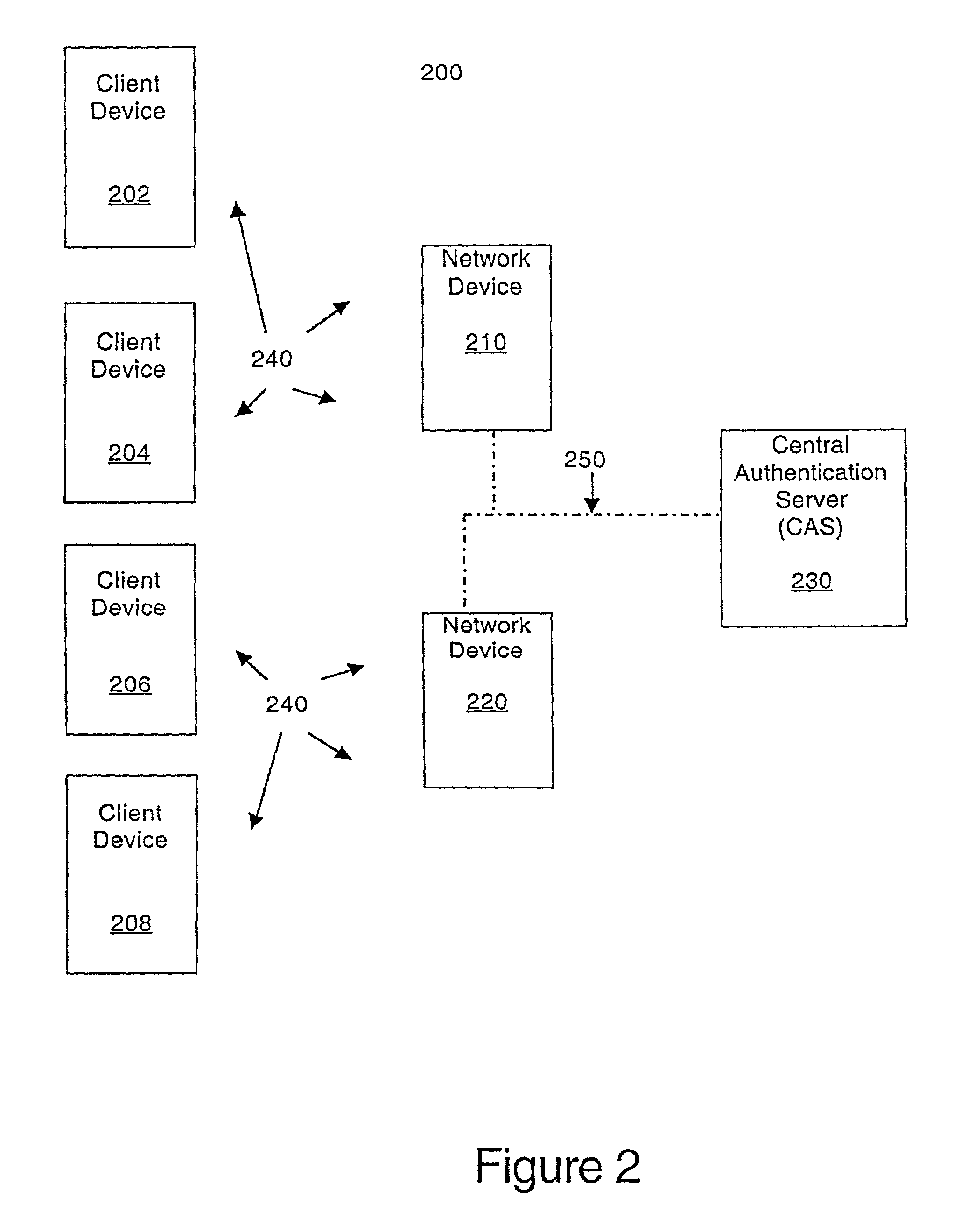
Scheme for device and user authentication with key distribution in a wireless network
ActiveUS7350076B1Reduction in marketLarge processing capabilityRandom number generatorsUser identity/authority verificationWeb authenticationSecret share
In a computer network, a method of mutually authenticating a client device and a network interface, authenticating a user to the network and exchanging encryption keys. In one embodiment, the method comprises authenticating the client device at the local network device point, with which the client device exchanges an encryption key and then the user is authenticated by a central authentication server. In another embodiment, the method comprises authenticating the client device at the central authentication server, with which the client device exchanges a key which is passed to the network device with a secret shared between the central authentication server and the network device. In this embodiment, the user is also authenticated at the central authentication server.
Owner:VALTRUS INNOVATIONS LTD +1
Systems and methods for operating and management of RFID network devices
InactiveUS20060280181A1Reduce network traffic loadReduce computational loadInformation formatNetwork topologiesCollections dataReal-time computing
Owner:RIPCORD TECH
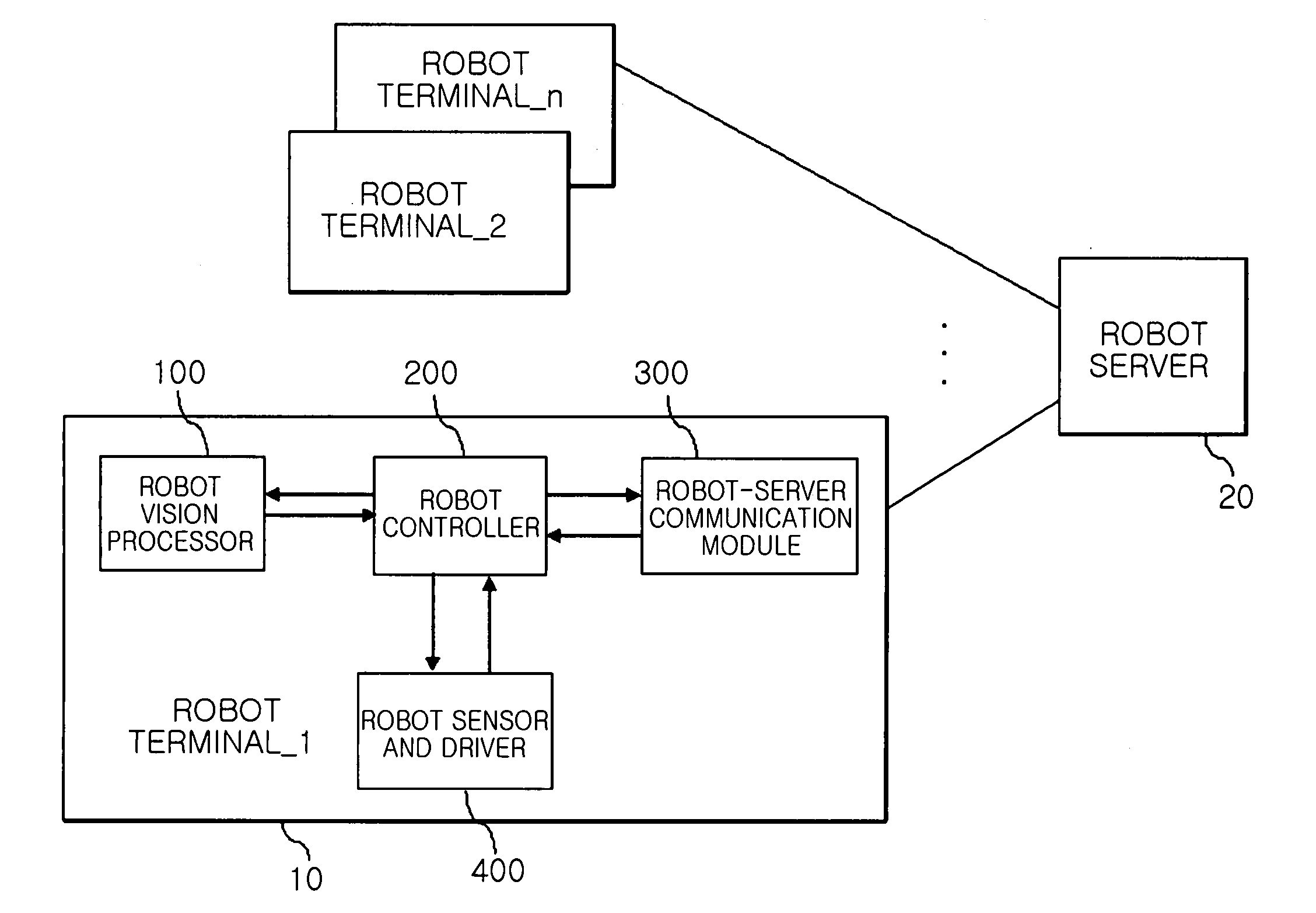
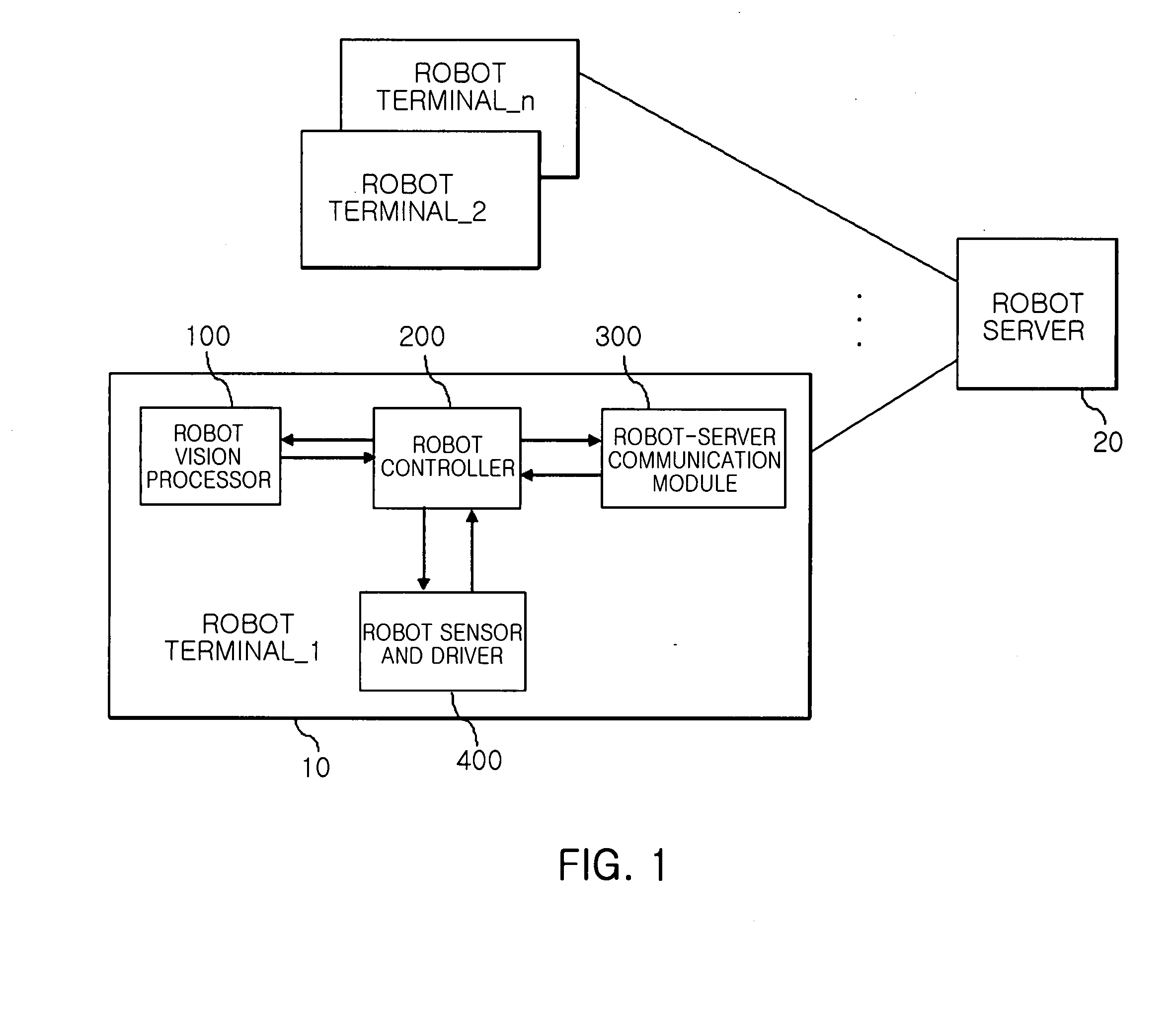
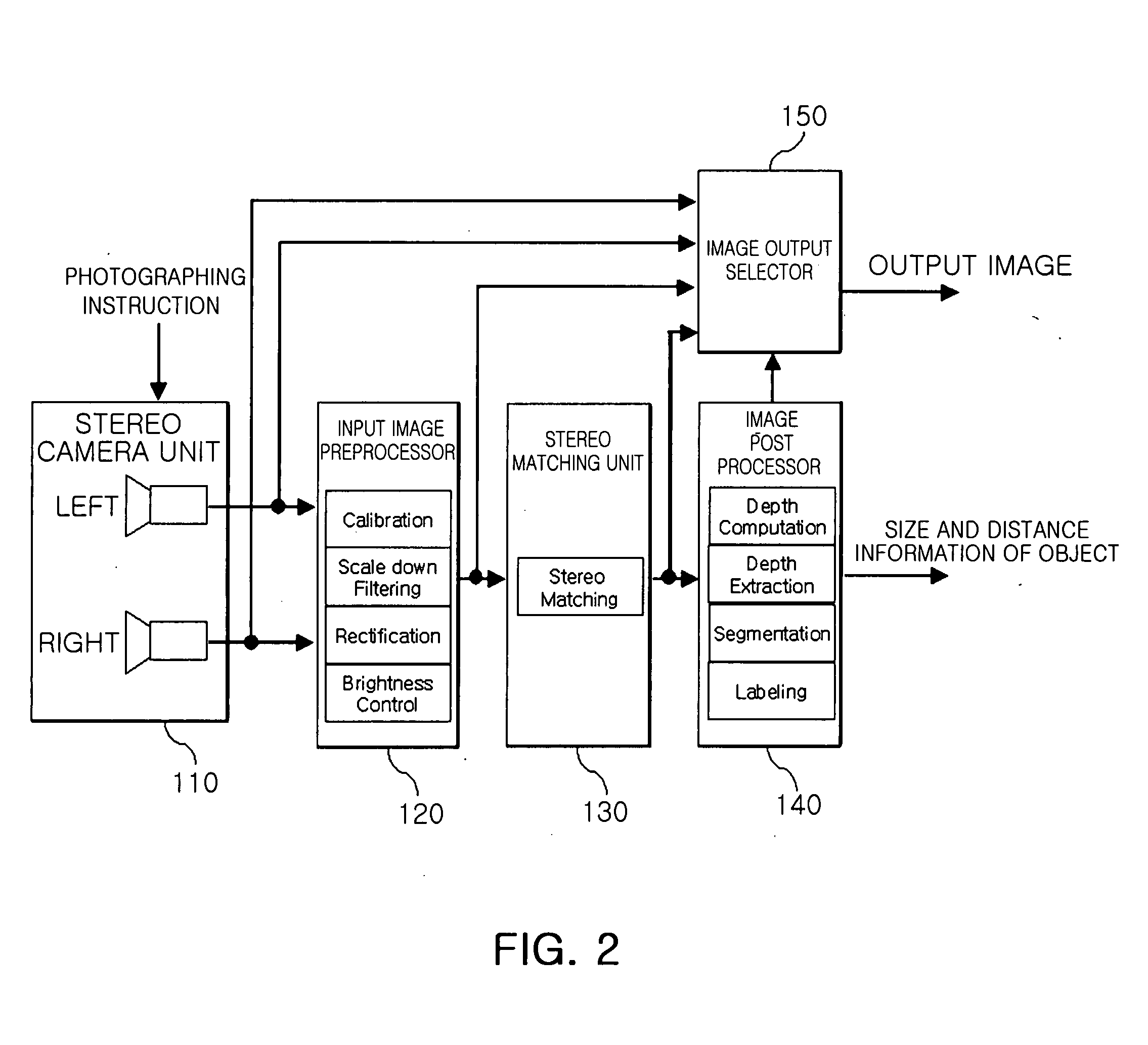
Method for searching target object and following motion thereof through stereo vision processing and home intelligent service robot using the same
InactiveUS20080215184A1Reduce computing loadReduce network trafficProgramme-controlled manipulatorComputer controlVision processingDriver/operator
A home intelligent service robot for recognizing a user and following the motion of a user and a method thereof are provided. The home intelligent service robot includes a driver, a vision processor, and a robot controller. The driver moves an intelligent service robot according to an input moving instruction. The vision processor captures images through at least two or more cameras in response to a capturing instruction for following a target object, minimizes the information amount of the captured image, and discriminates objects in the image into the target object and obstacles. The robot controller provides the capturing instruction for following the target object in a direction of collecting instruction information to the vision processor when the instruction information is collected from outside, and controls the intelligent service robot to follow and move the target object while avoiding obstacles based on the discriminating information from the vision processor.
Owner:ELECTRONICS & TELECOMM RES INST
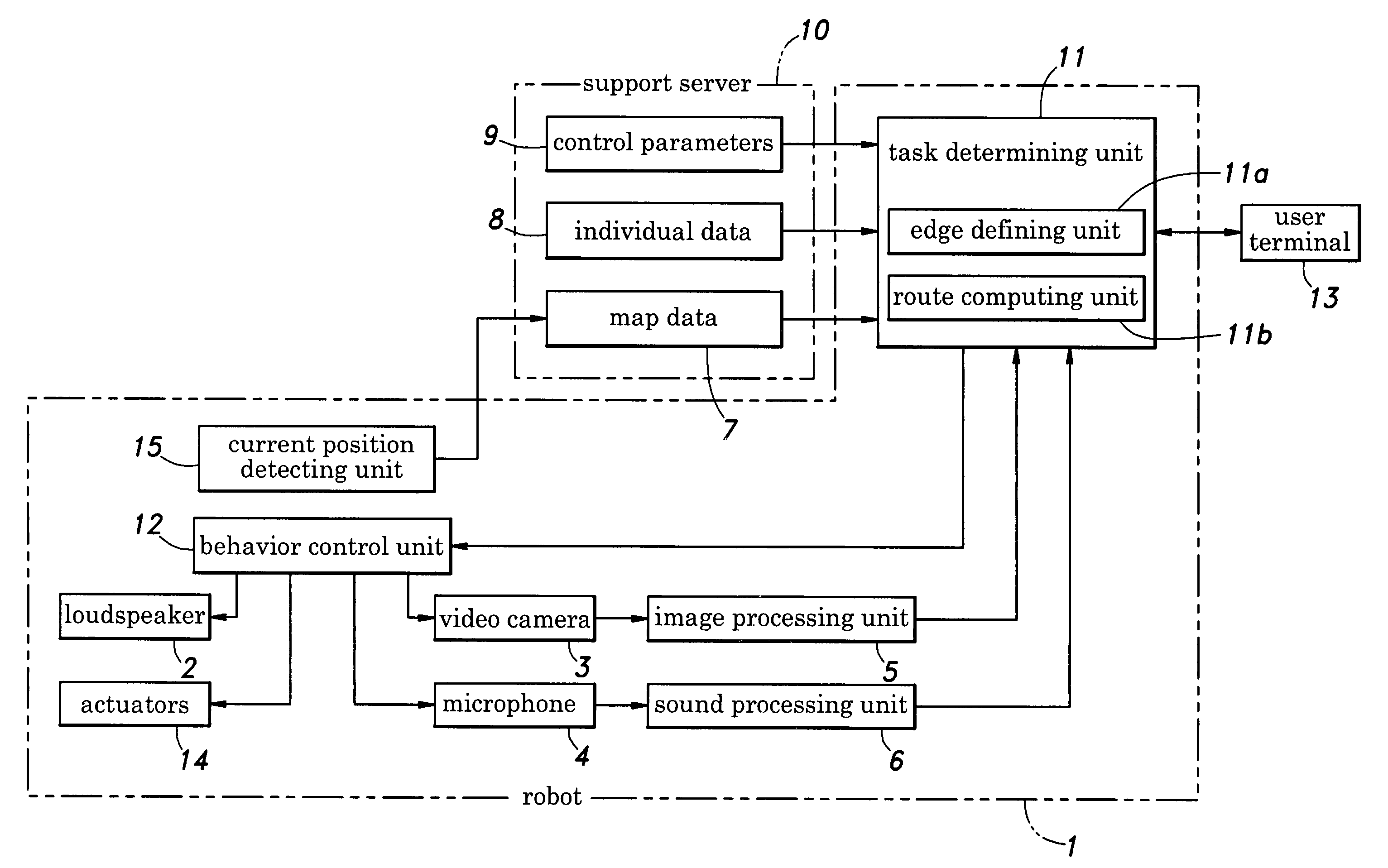
Route generating system for an autonomous mobile robot
ActiveUS7474945B2Easy programmingReduce computing loadAnti-collision systemsComplex mathematical operationsEngineeringRobot locomotion
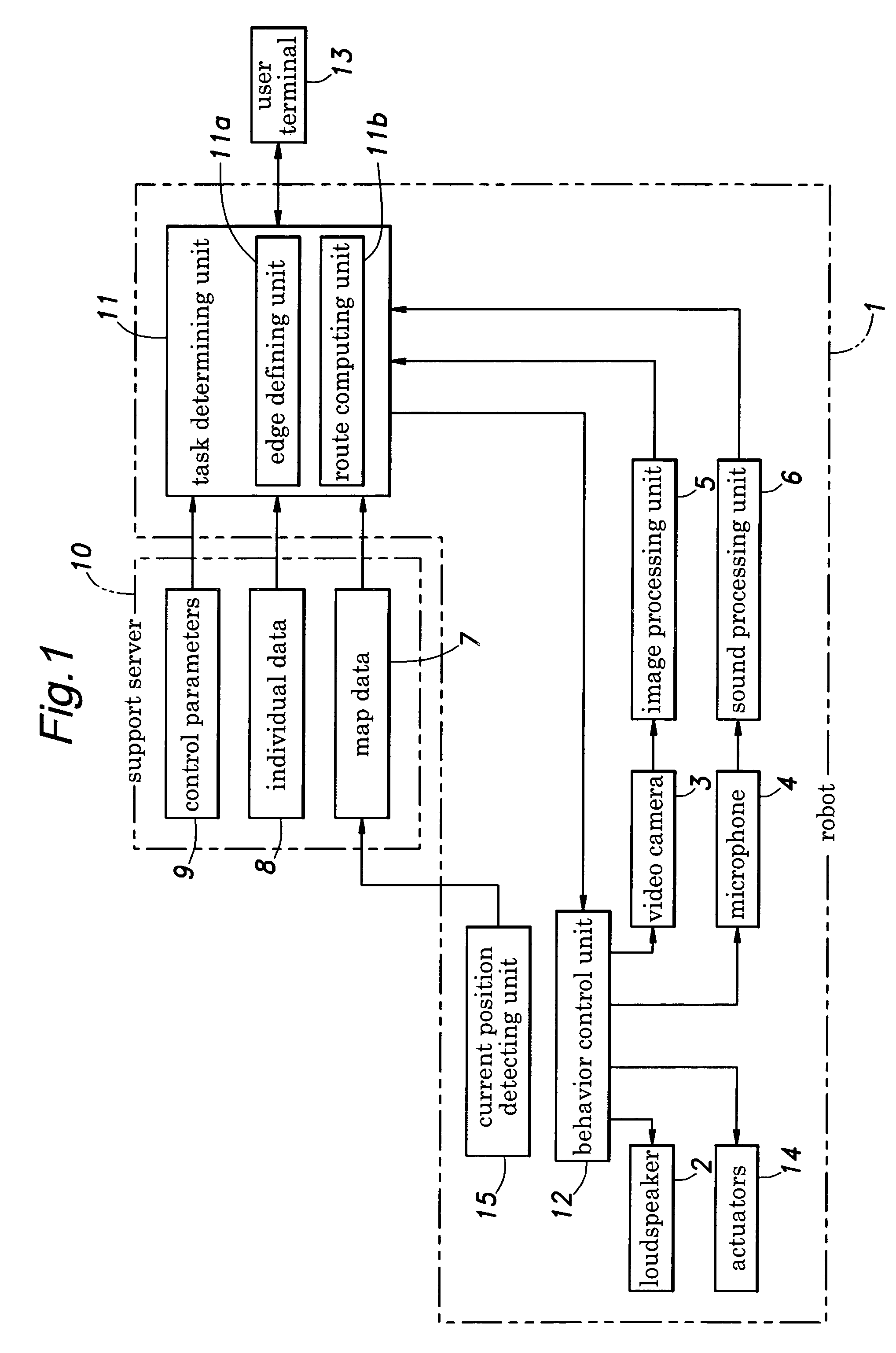
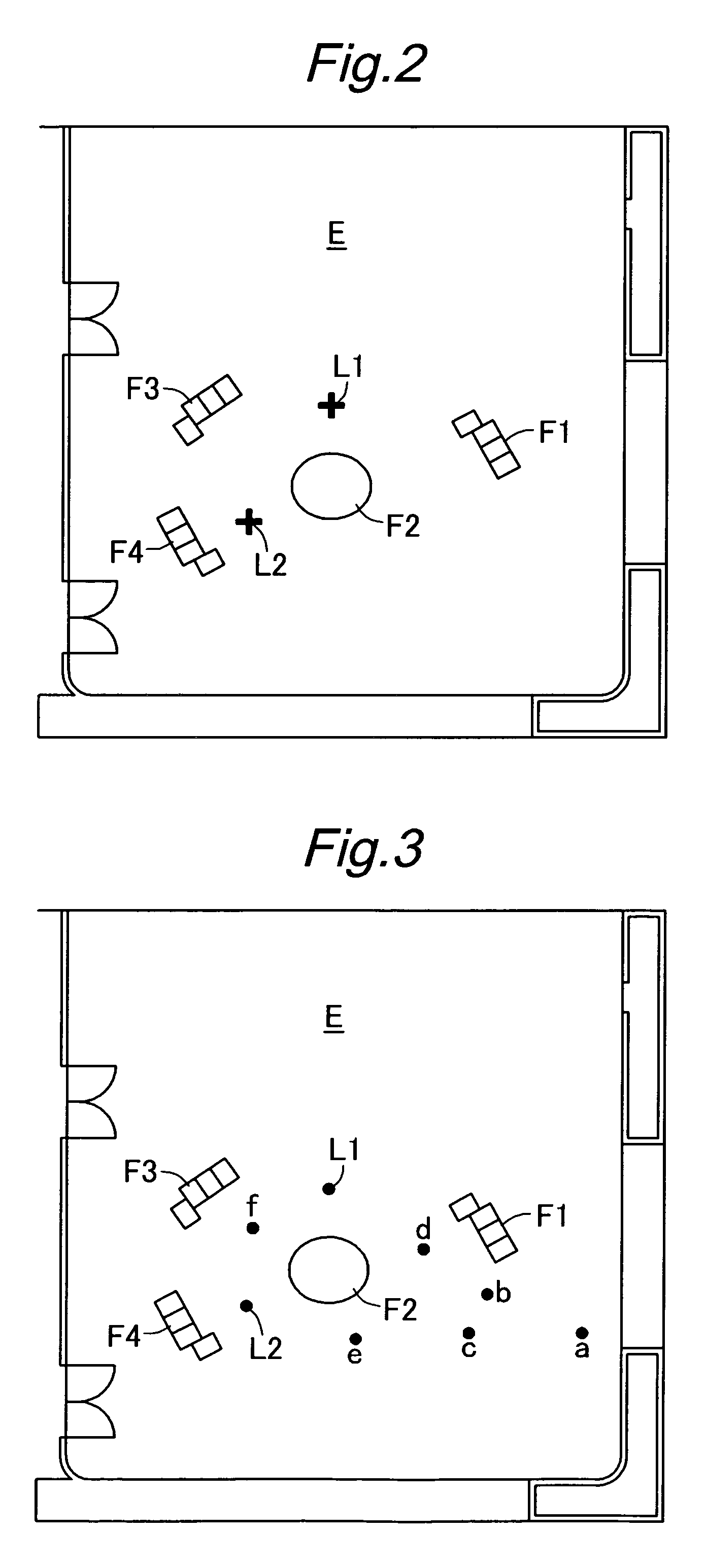
In a route generating system for an autonomous mobile robot, a plurality of nodes are designated within an area of movement of the robot and an edge is defined between a pair of nodes only if a distance from the one node to the other node is less than a threshold value and there is no obstacle on a line drawn between the one point and the other point. Because the route is generated from a collection of pre-defined edges which are free from obstacles and are selected so as to optimize the generated route, the robot is enabled to travel from the current position to the destination in a safe and optimum fashion. Furthermore, the edges are defined by connecting only those nodes that are relatively close to each other, the candidates of the edges for generating a route can be reduced to a small number and this reduces computational loads. Also, because the route can be selected in a relatively intelligent manner so as to optimize a certain criterion, a clumsy appearance in the movement of the robot can be avoided.
Owner:HONDA MOTOR CO LTD
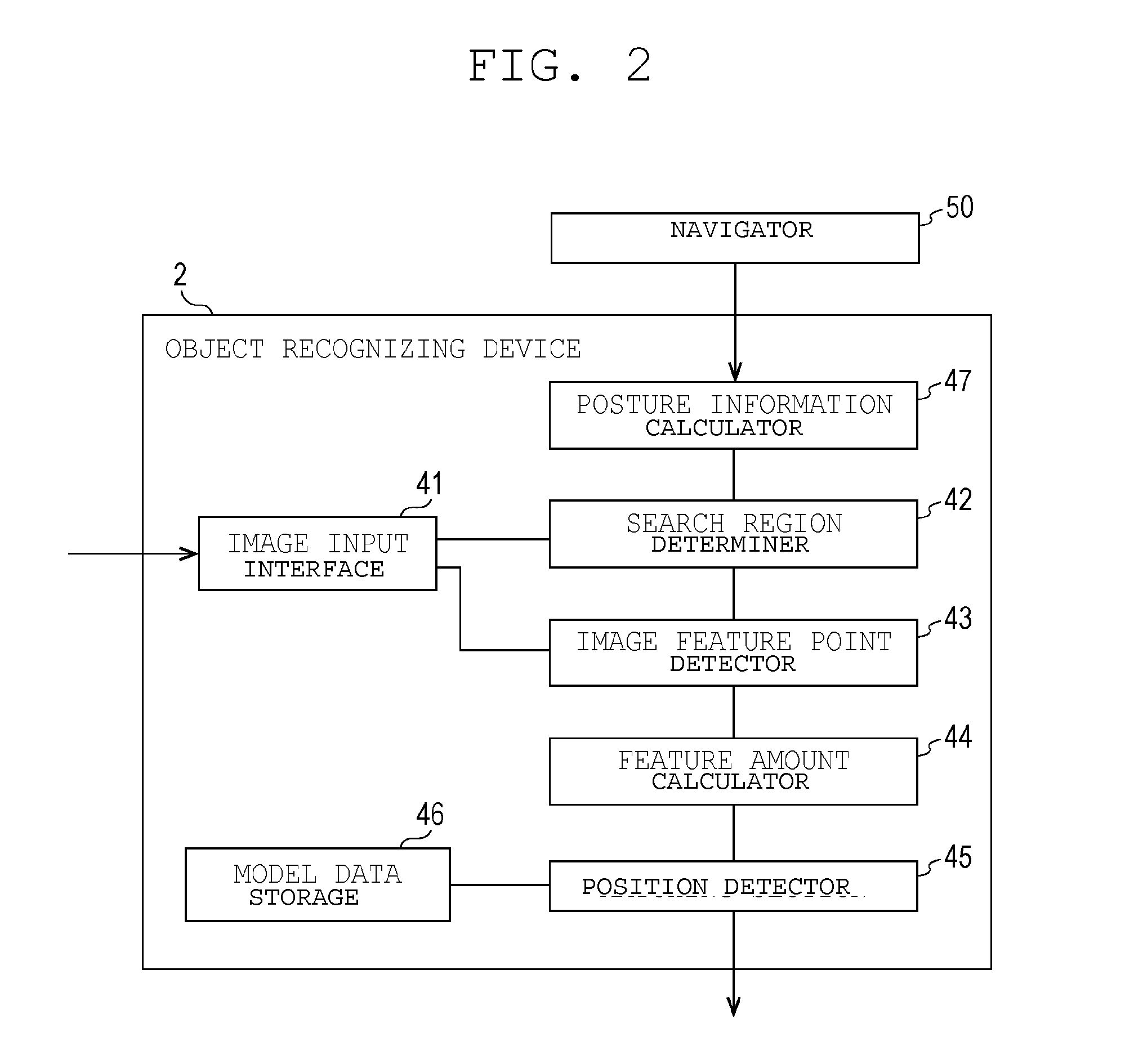
Autonomous vehicle, and object recognizing method in autonomous vehicle
ActiveUS20150347840A1Increase speedImprove recognition accuracyImage enhancementImage analysisPattern recognitionObject based
An autonomous vehicle includes a travel vehicle main body, a model data storage, a photographic device, a search region determiner, an image feature point detector, a feature amount calculator and a position detector. The travel vehicle main body autonomously travels to a target position. The model data storage stores model data related to a geometric feature of an object. The photographic device photographs a periphery of the travel vehicle main body at the target position to acquire image data. The search region determiner predicts a position of the object based on the image data, and determines a search region of a predetermined range including the predicted position of the object. The image feature point detector detects a feature point of the image data with respect to the search region. The feature amount calculator calculates a feature amount of a matching candidate point extracted from the feature point. The position detector matches the feature amount of the matching candidate point with the model data to recognize the position of the object based on the image data.
Owner:MURATA MASCH LTD
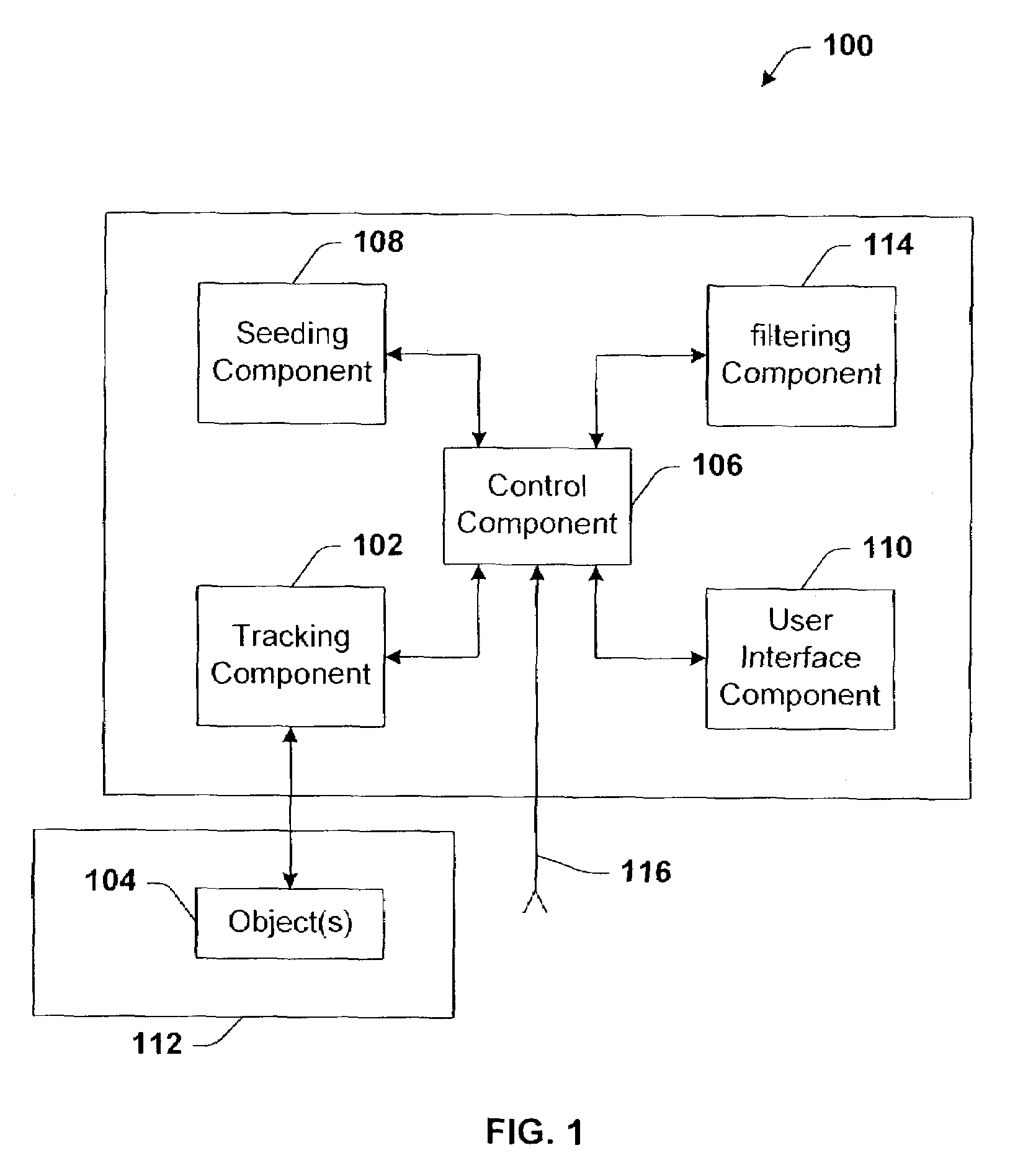
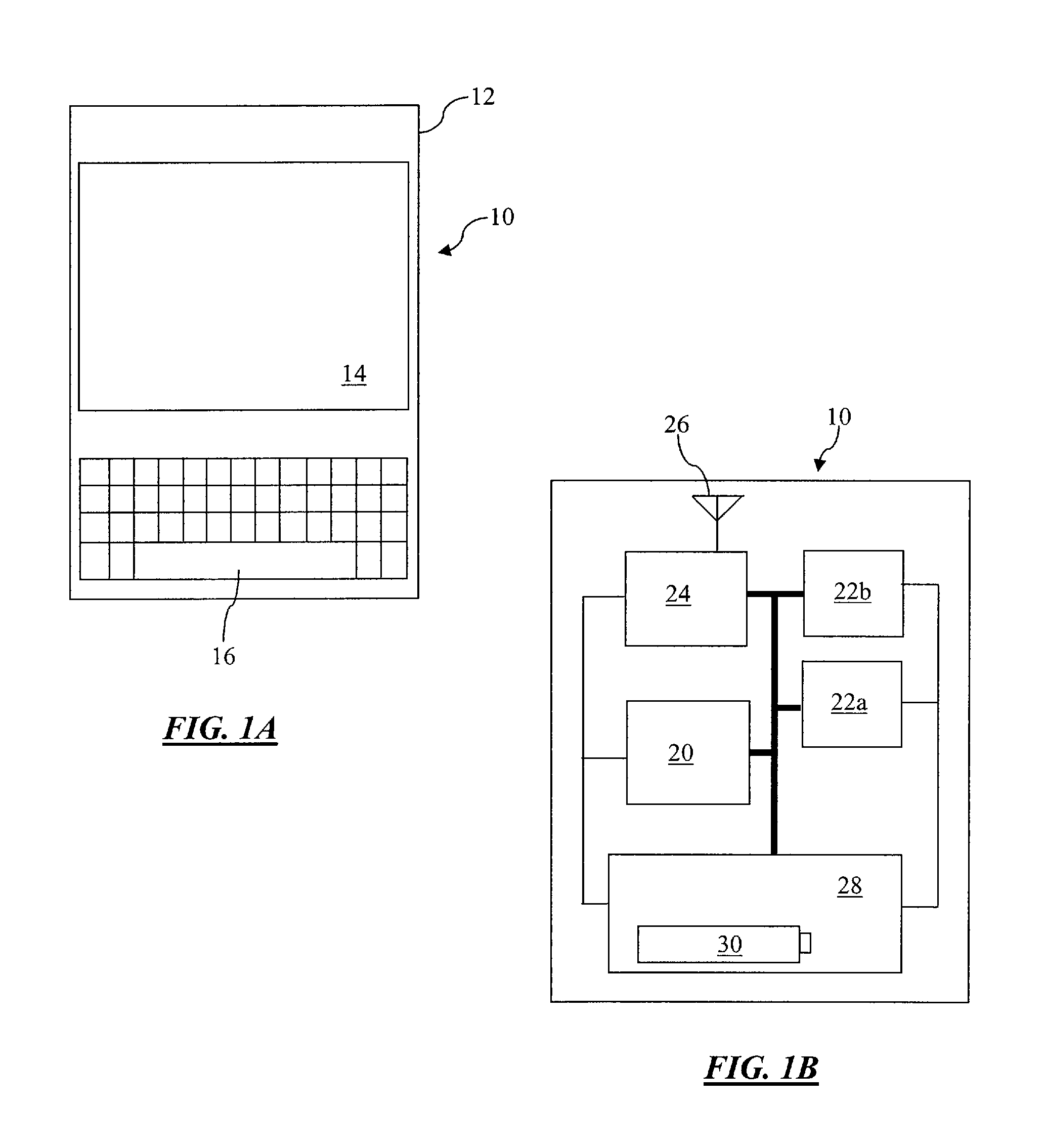
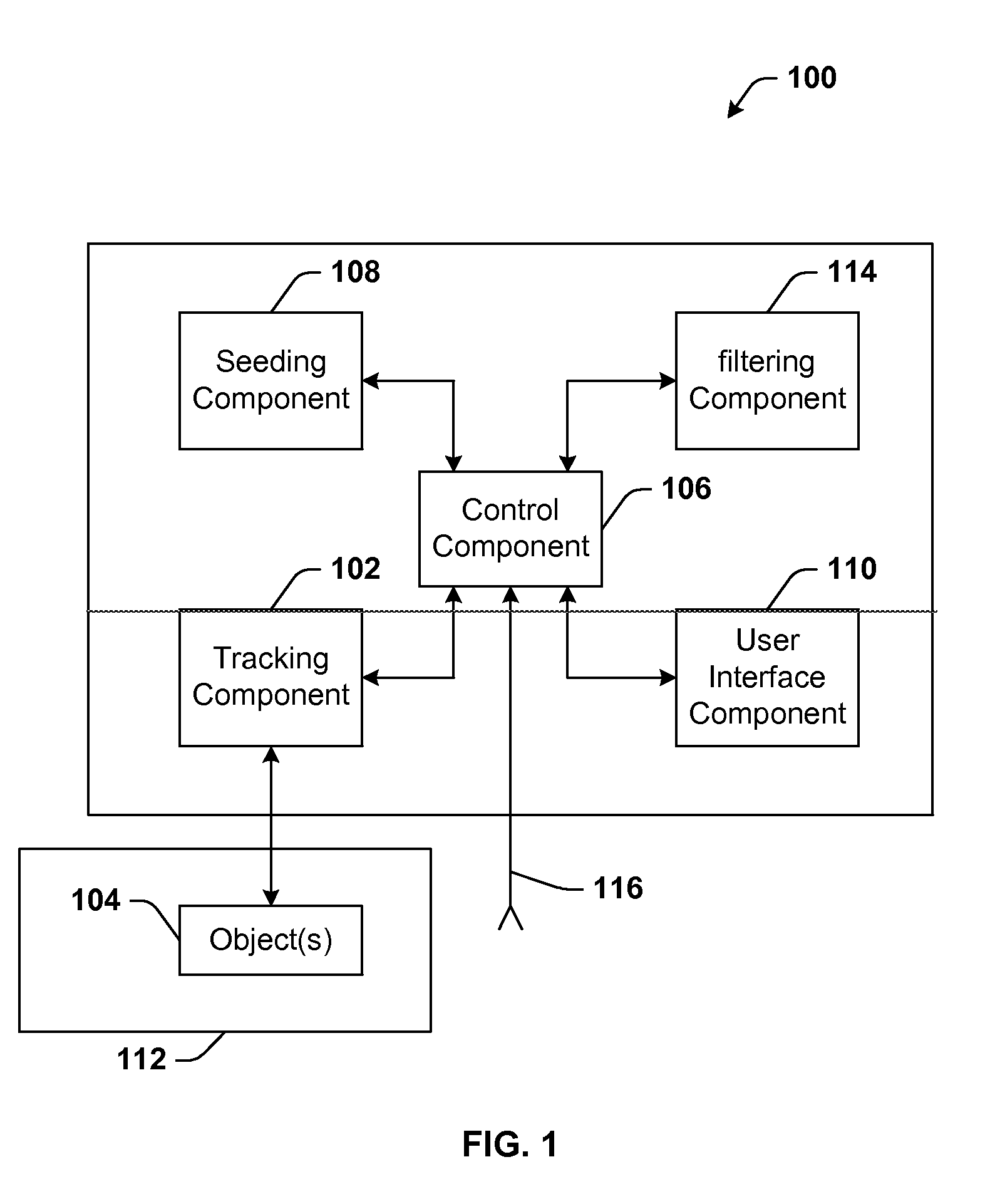
Architecture for controlling a computer using hand gestures
InactiveUS20090268945A1Reduce calculationReduce computing loadInput/output for user-computer interactionCharacter and pattern recognitionPattern recognitionObject based
Architecture for implementing a perceptual user interface. The architecture comprises alternative modalities for controlling computer application programs and manipulating on-screen objects through hand gestures or a combination of hand gestures and verbal commands. The perceptual user interface system includes a tracking component that detects object characteristics of at least one of a plurality of objects within a scene, and tracks the respective object. Detection of object characteristics is based at least in part upon image comparison of a plurality of images relative to a course mapping of the images. A seeding component iteratively seeds the tracking component with object hypotheses based upon the presence of the object characteristics and the image comparison. A filtering component selectively removes the tracked object from the object hypotheses and / or at least one object hypothesis from the set of object hypotheses based upon predetermined removal criteria.
Owner:MICROSOFT TECH LICENSING LLC
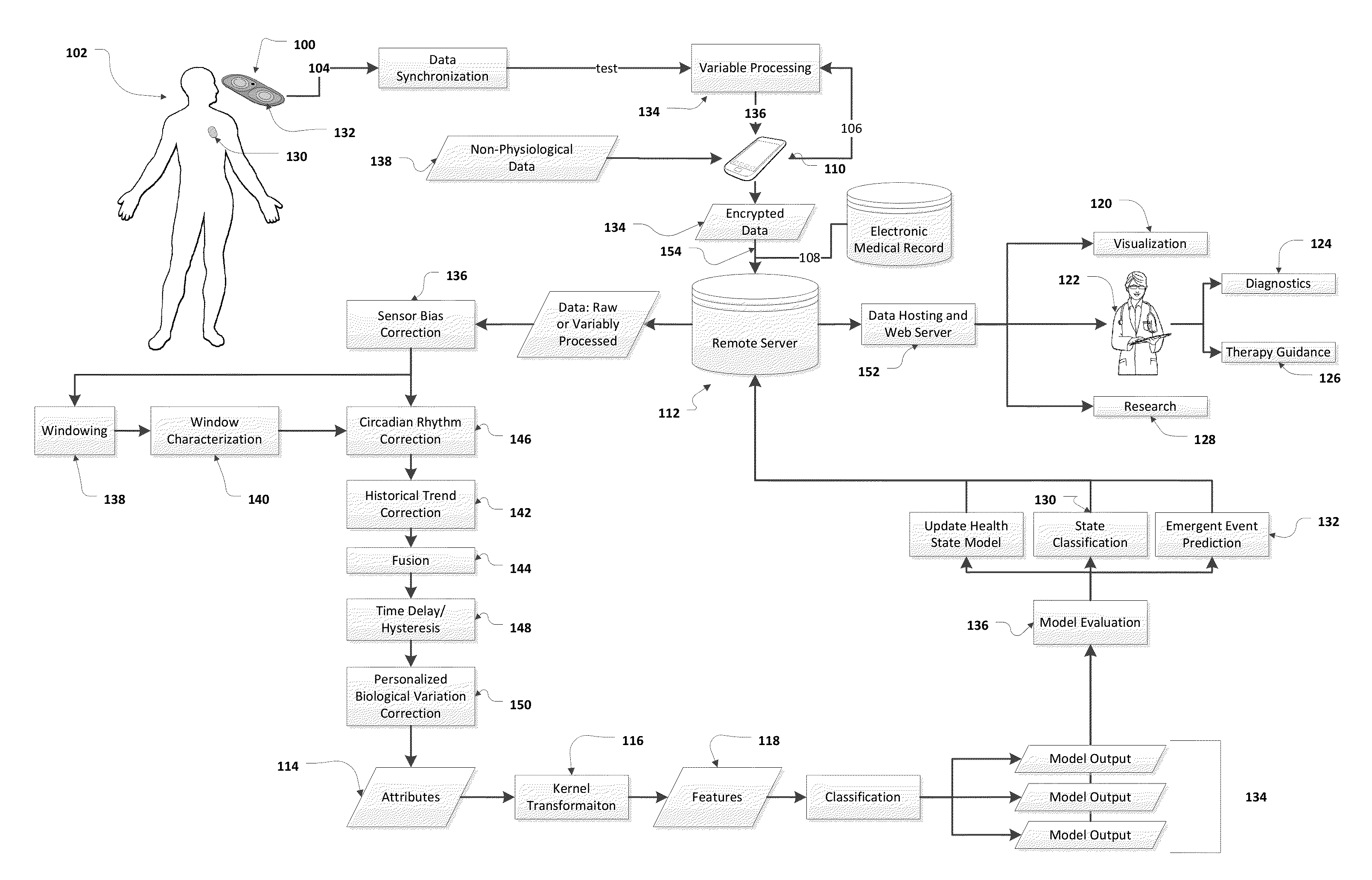
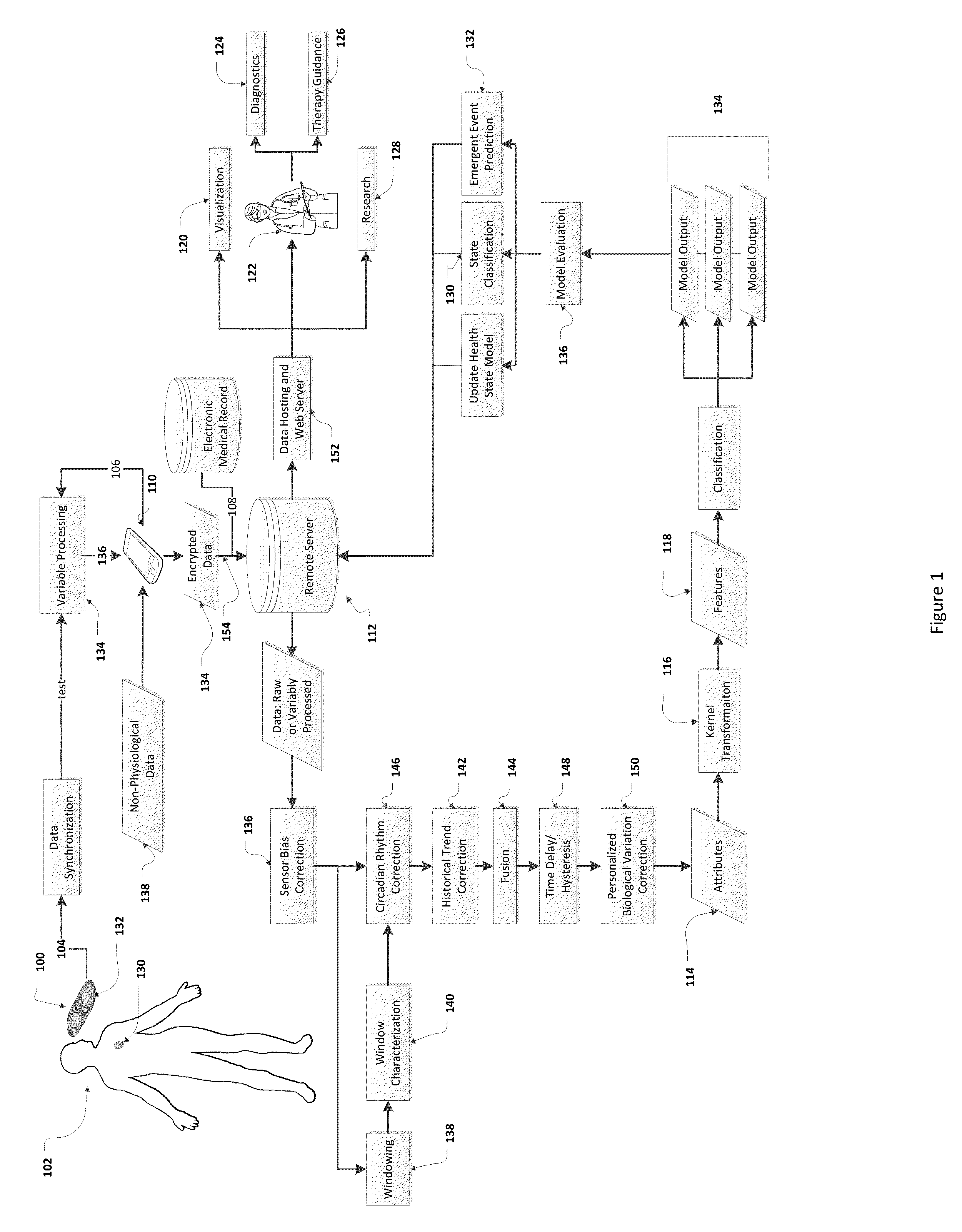
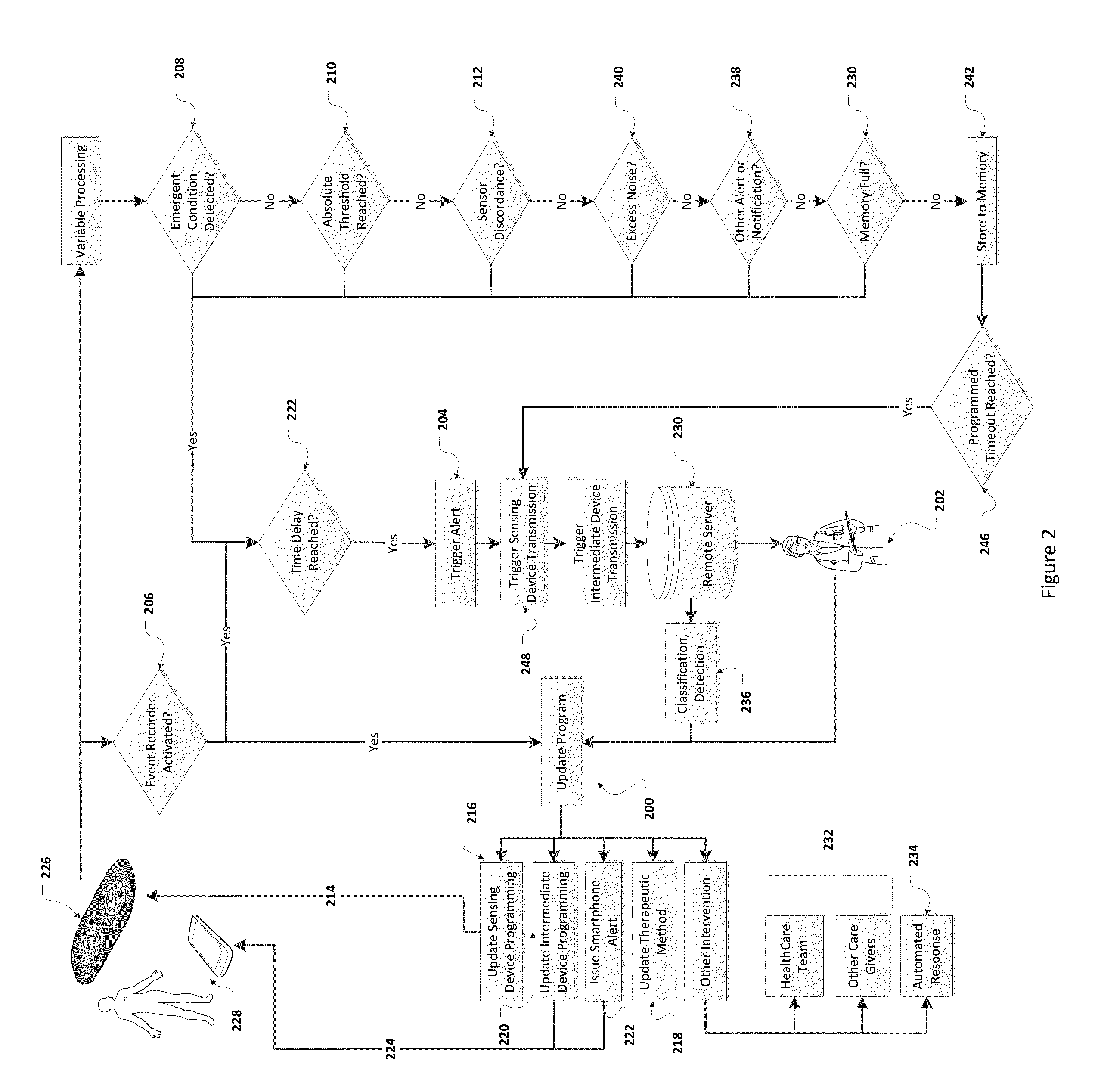
Method and Apparatus for Wireless Health Monitoring and Emergent Condition Prediction
ActiveUS20150106020A1Improve predictive performancePatient compliance is goodHealth-index calculationTelemedicinePersonalizationPredictive methods
The present invention relates generally to wireless, remote, physiological monitoring in the evaluation of health and disease state specifically with respect to cardiac and pulmonary pathologies, including heart failure and sleep apnea. Personalized thresholds are used to enhance performance of classification and prediction methods by utilizing patient clinical history and past empiric sensed data, such as through an initialization period, to learn the biological variation present in each sensed individual.Data from an adherent patch undergoes disseminated processing as data is securely sent from a sensing device ultimately to a remote server. Monitoring, classification, and prediction results are hosted and made accessible through an authenticated system to members of the individual's healthcare team, family, or other caregivers.Learning algorithms are used to characterize physiological attributes and to classify a health or disease state based on an aggregate of features. Classification models and feature selection are optimized with validation algorithms.
Owner:WIRELESS MEDICAL MONITORING
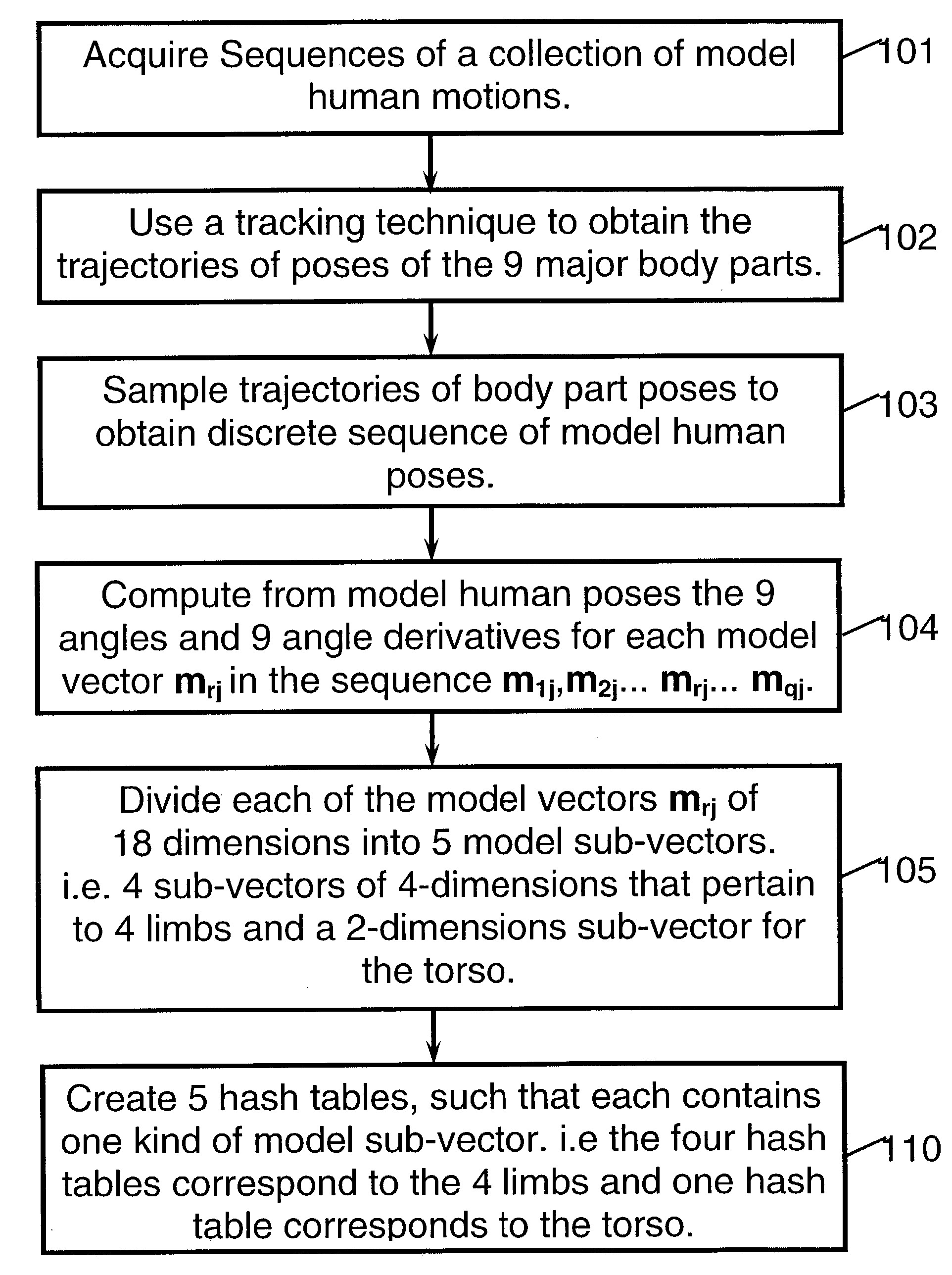
Method of recognition of human motion, vector sequences and speech
InactiveUS20030208289A1Robust recognitionReduce mistakesInput/output for user-computer interactionComputer controlPattern recognitionBody positions
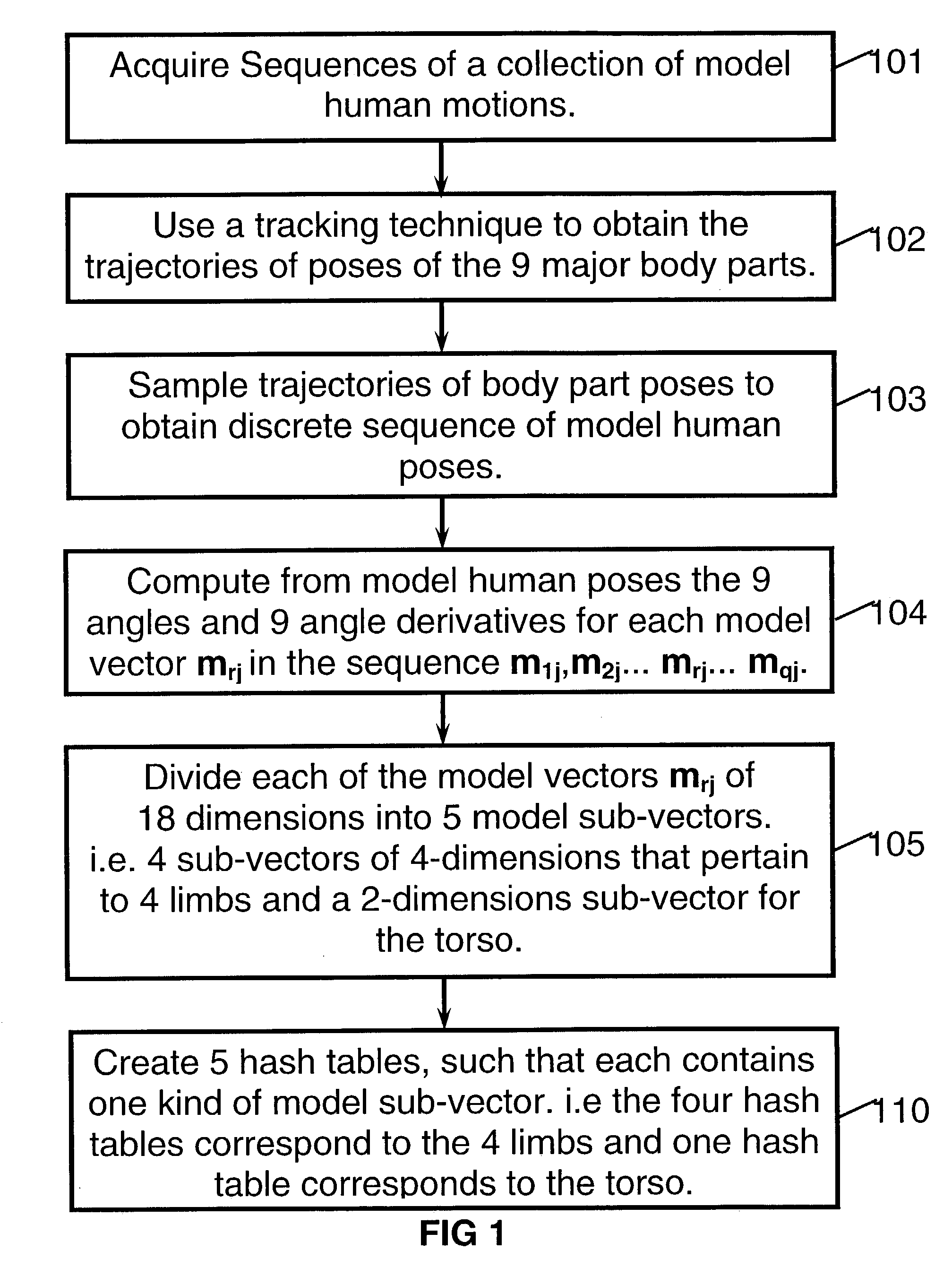
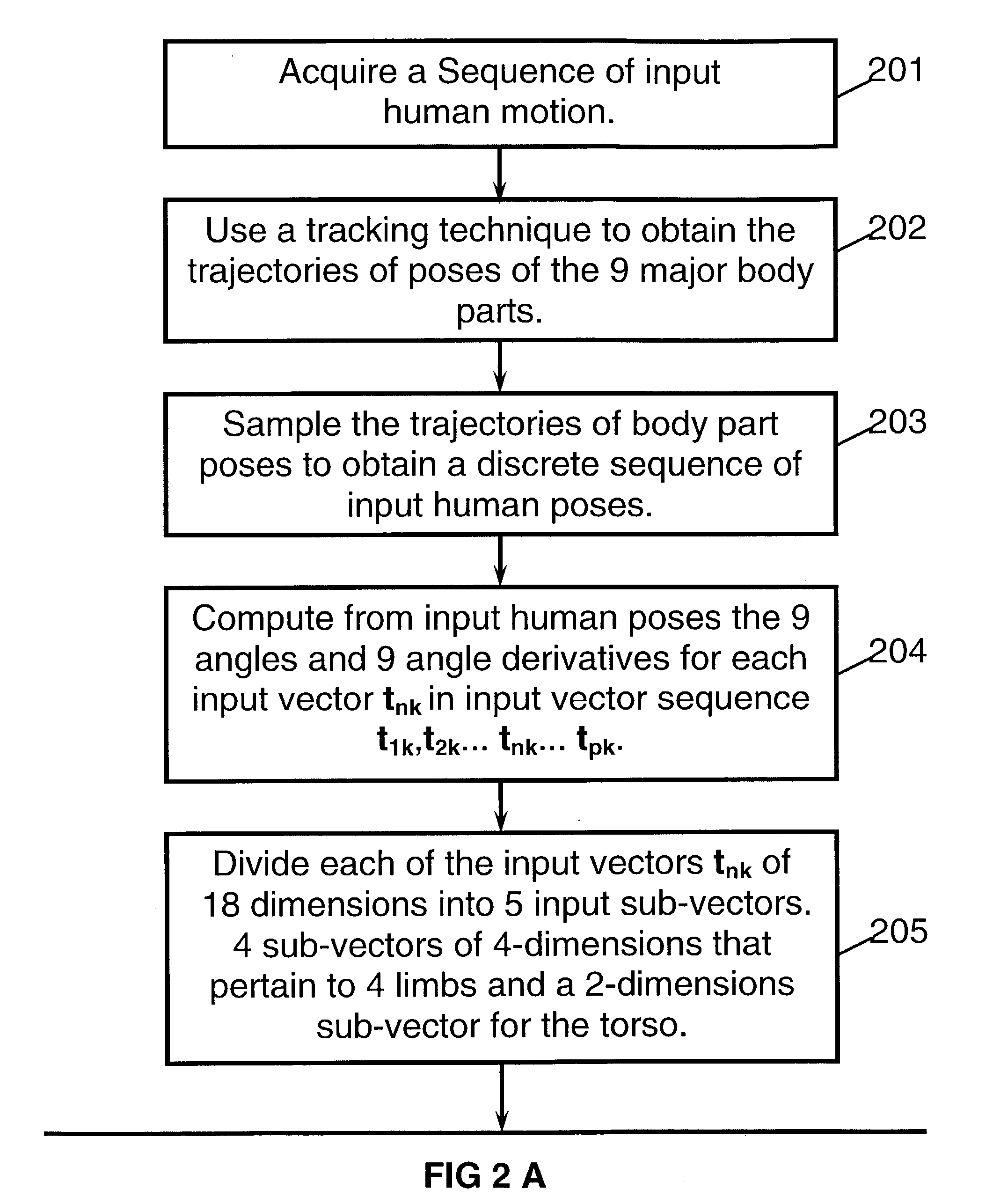
A method for recognition of an input human motion as being the most similar to one model human motion out of a collection of stored model human motions. In the preferred method, both the input and the model human motions are represented by vector sequences that are derived from samples of angular poses of body parts. The input and model motions are sampled at substantially different rates. A special optimization algorithm that employs sequencing constraints and dynamic programming, is used for finding the optimal input-model matching scores. When only partial body pose information is available, candidate matching vector pairs for the optimization are found by indexing into a set of hash tables, where each table pertains to a sub-set of body parts. The invention also includes methods for recognition of vector sequences and for speech recognition.
Owner:BEN ARIE JEZEKIEL
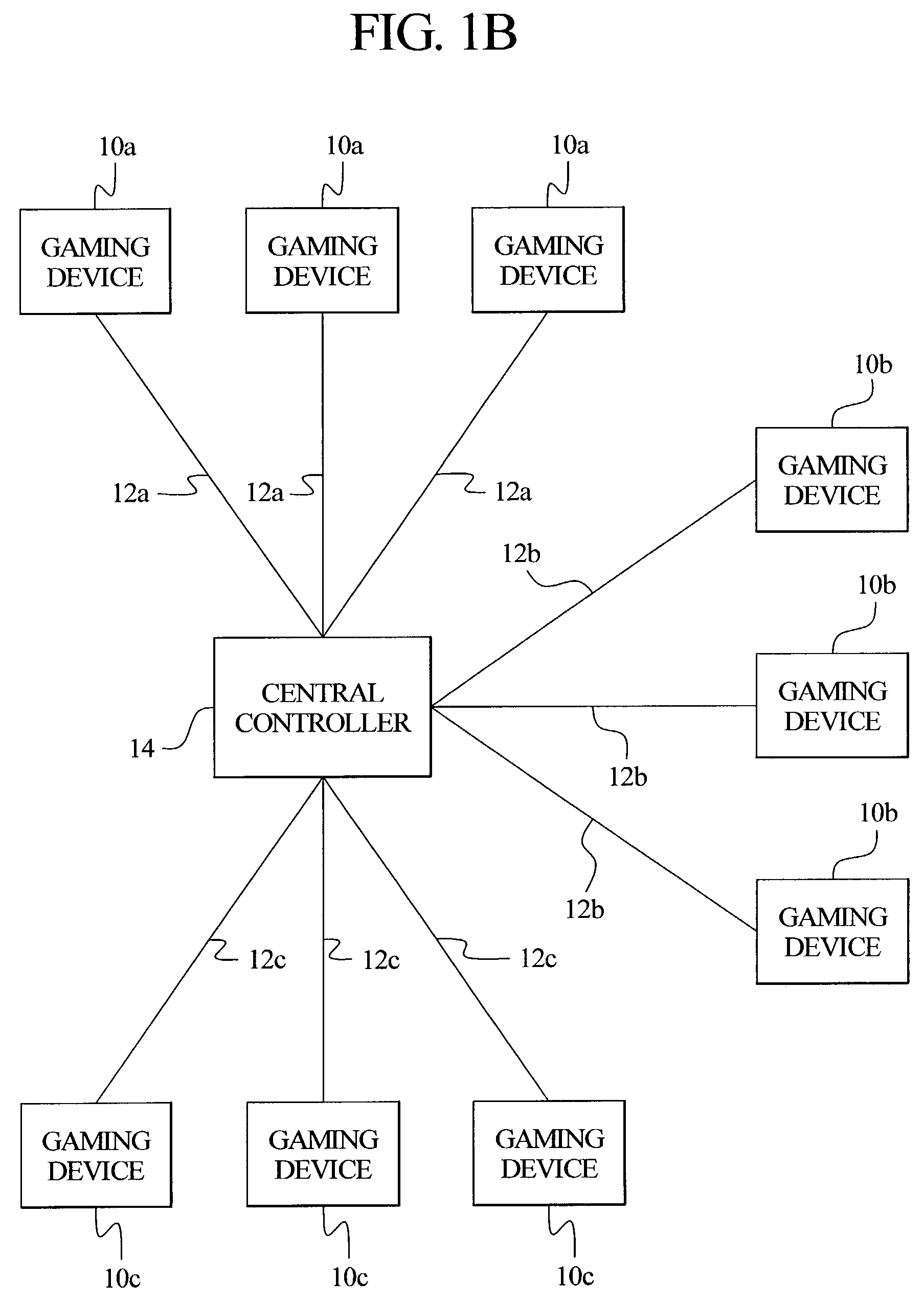
Central determination gaming system where the same seed is used to generate the outcomes for a primary game and a secondary game
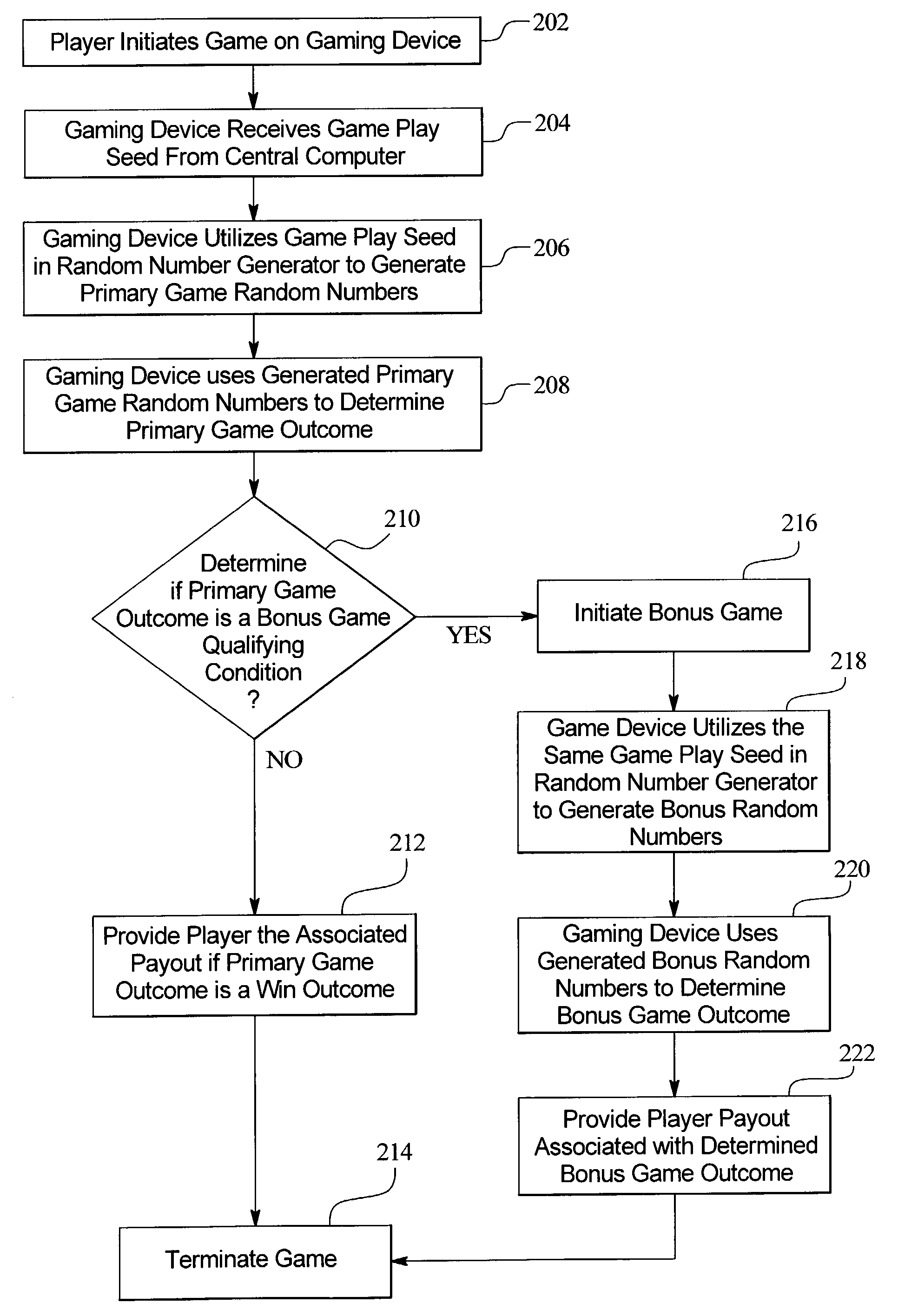
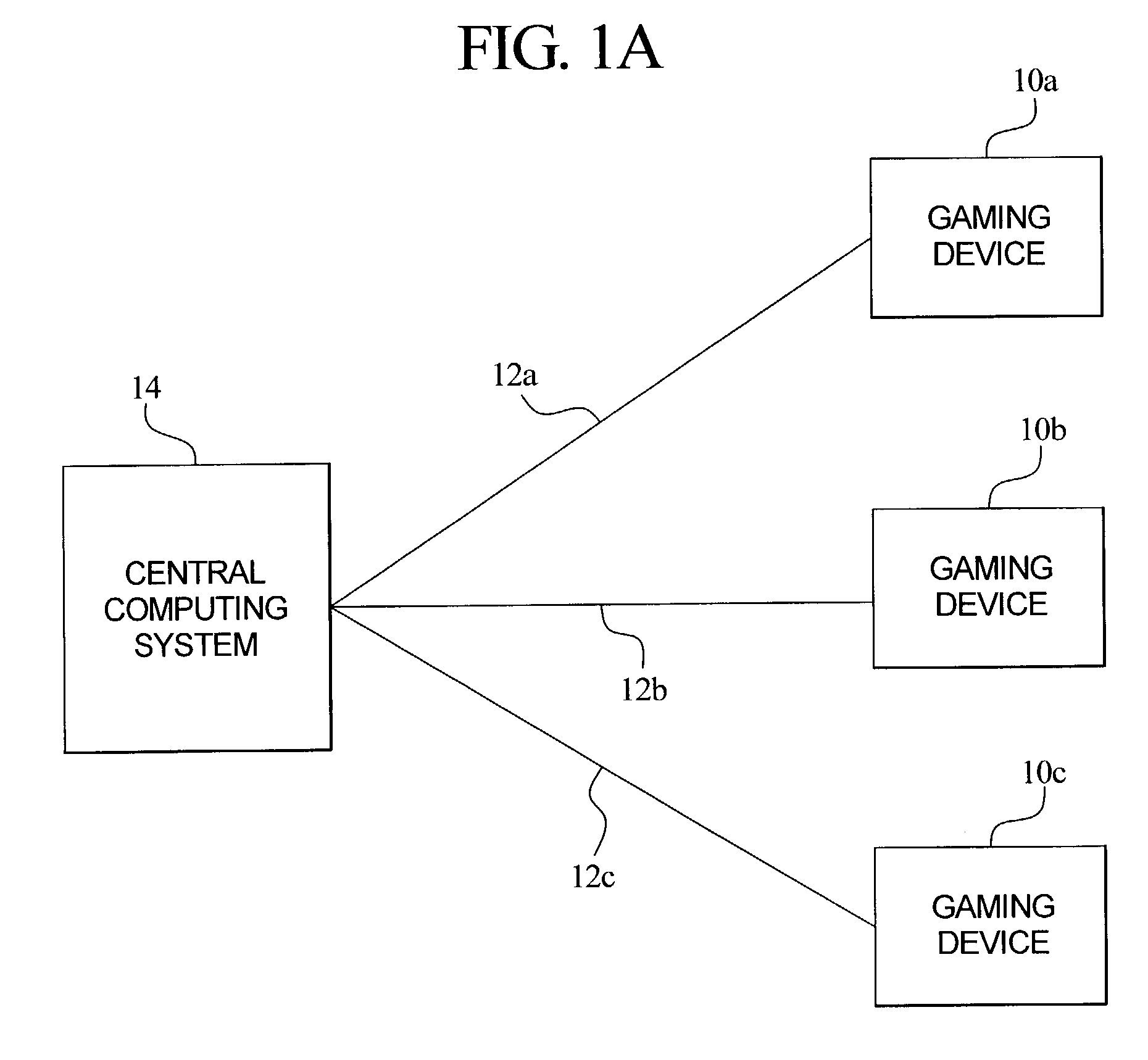
ActiveUS7329183B2Reduce computing loadLess game play seedsApparatus for meter-controlled dispensingVideo gamesComputing systemsGame play
A central determination gaming system wherein the same random number or game play seed is used to generate a primary or base game outcome and a secondary or bonus game outcome. The present invention includes a central computing system in communication with a plurality of gaming devices. The central computing system maintains one or more predetermined pools or sets of random number or game play seeds. In one embodiment, each game play seed is deterministic of a primary wagering game outcome and a secondary game outcome. That is, each gaming device is operable to utilize a game play seed to determine both the primary wagering game outcome and the secondary game outcome.
Owner:IGT
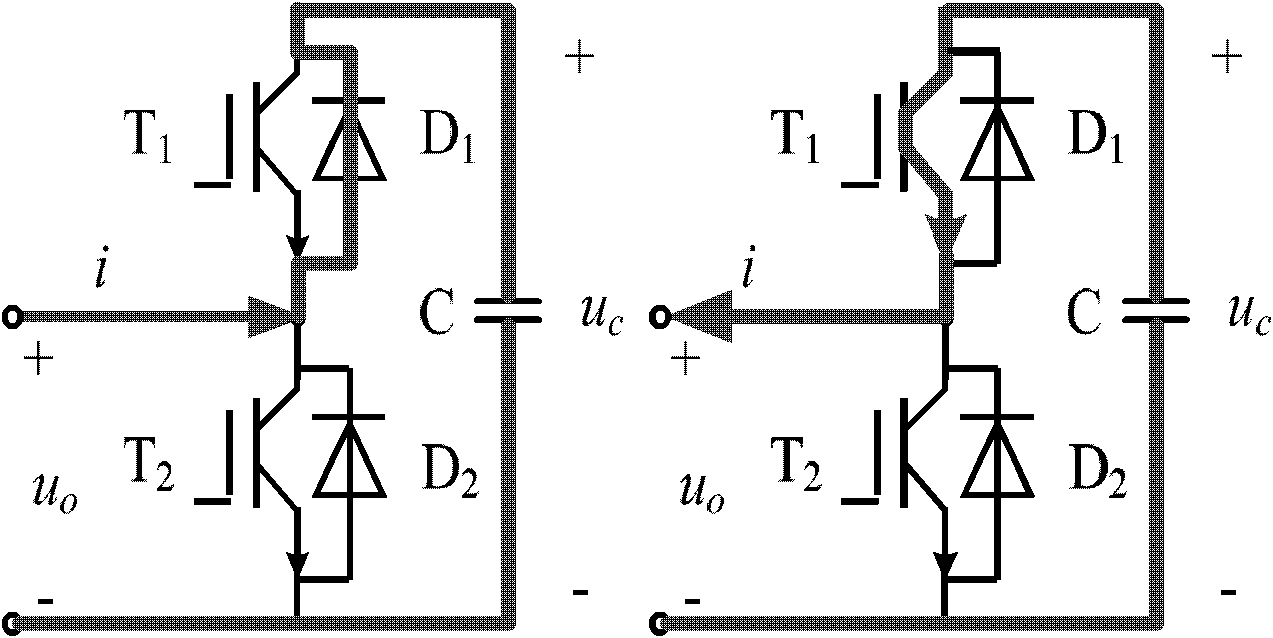
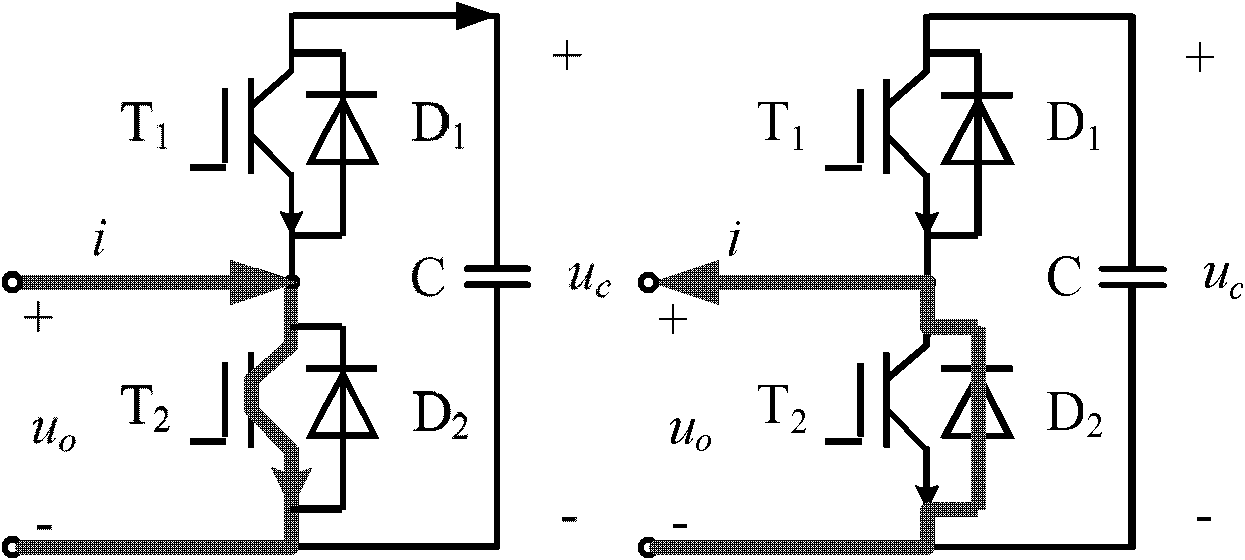
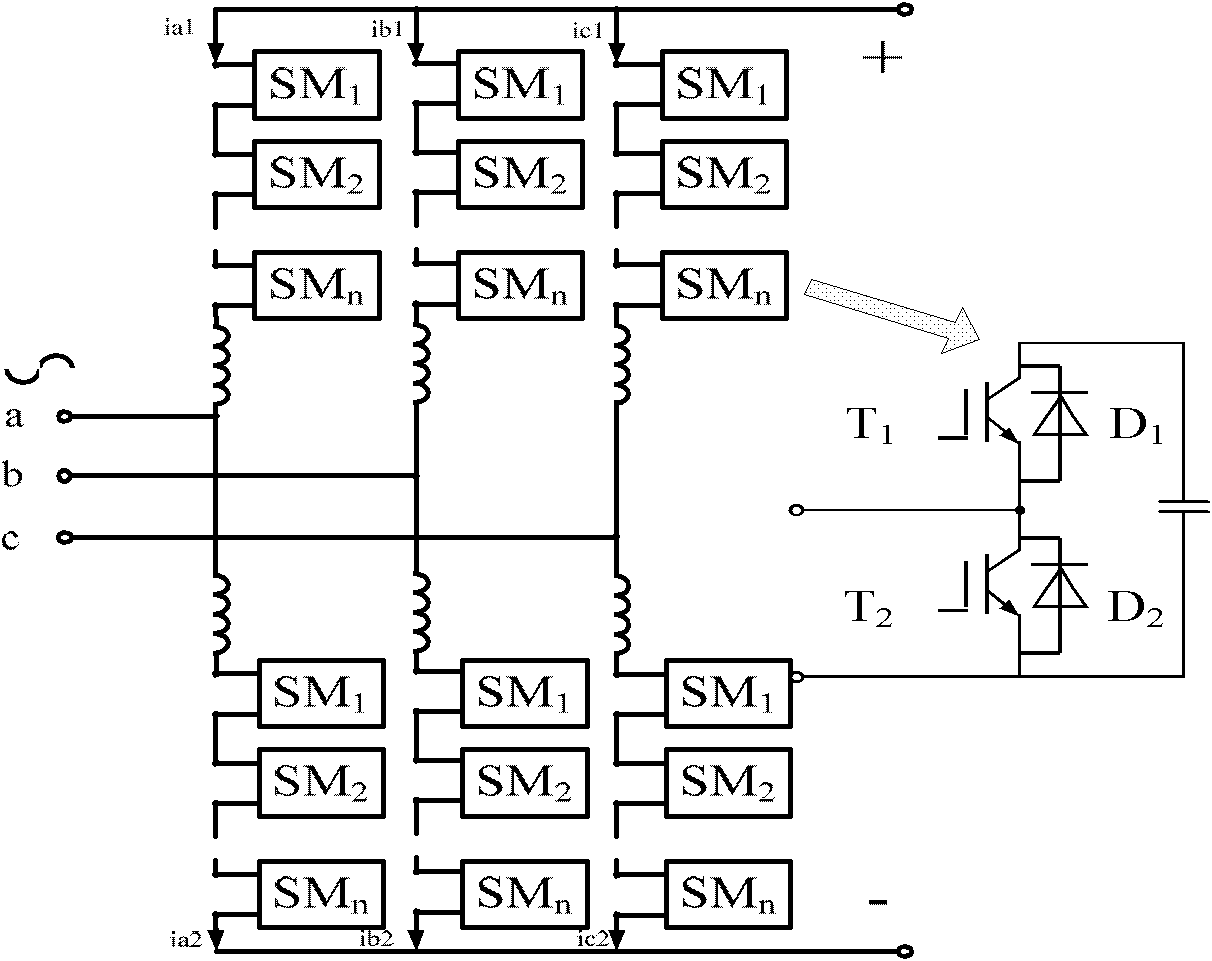
Voltage balancing control method for multi-level modular converter
ActiveCN102130619AAvoid randomnessReduce switching frequencyDc-ac conversion without reversalCapacitor voltageComputer module
The invention relates to a voltage balancing control method for a multi-level modular converter, which is characterized by comprising the following steps of: 1) judging whether the current direction of a bridge arm is a positive direction or a negative direction; 2) searching for a sub-module with the highest capacitor voltage amplitude value from the sub-modules in an output state, and simultaneously searching for the sub-module with the lowest capacitor voltage amplitude values from the sub-modules in a bypass state; and 3) judging whether to use or bypass the sub-modules or not. By the method, sub-module switching randomness is completely avoided, and the switching frequency of the sub-module is reduced; and the sub-module capacitor voltage balancing control method is more applicable in the field of high-voltage high-capacity converters with a great number of sub-modules.
Owner:CHINA ELECTRIC POWER RES INST +1
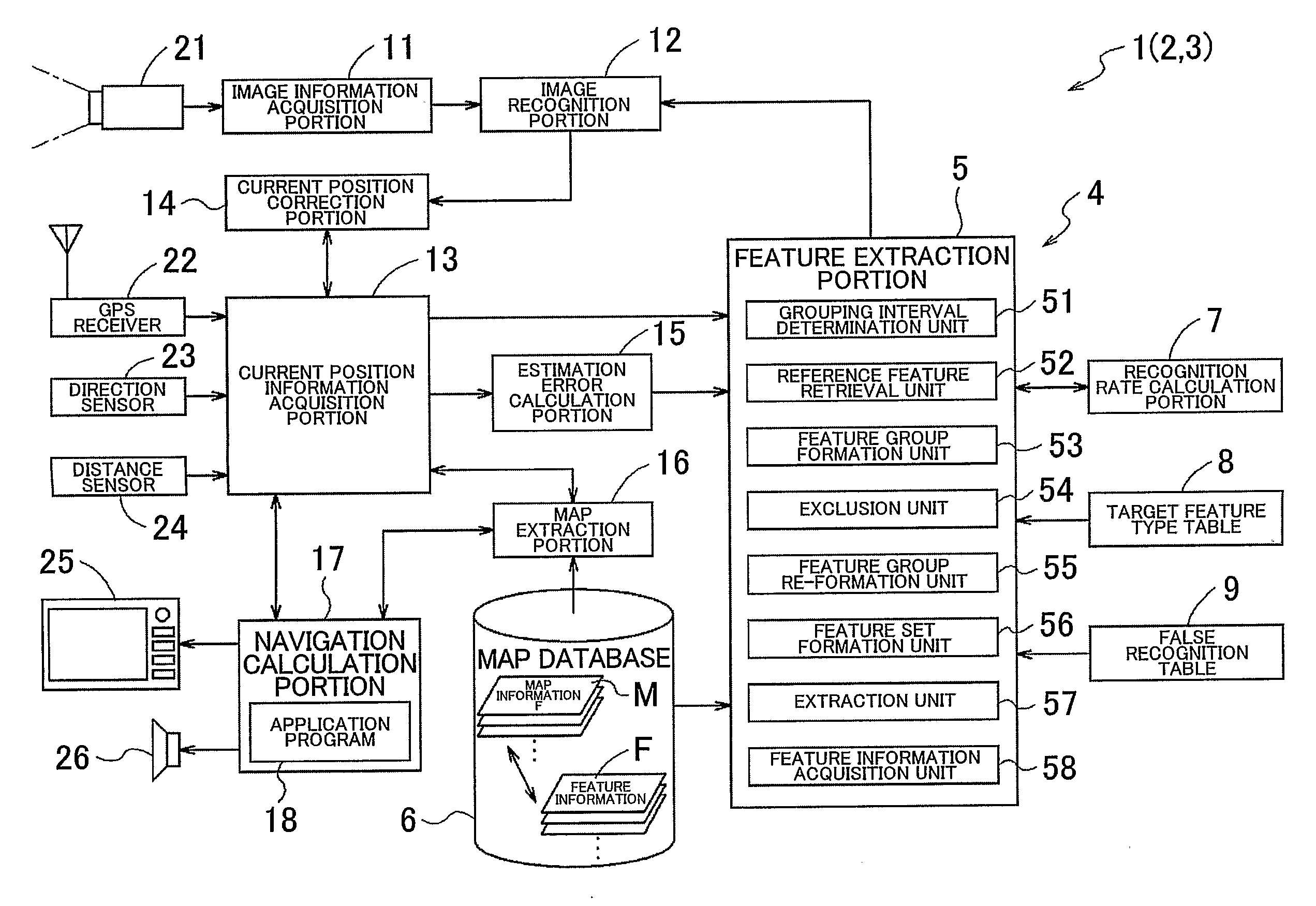
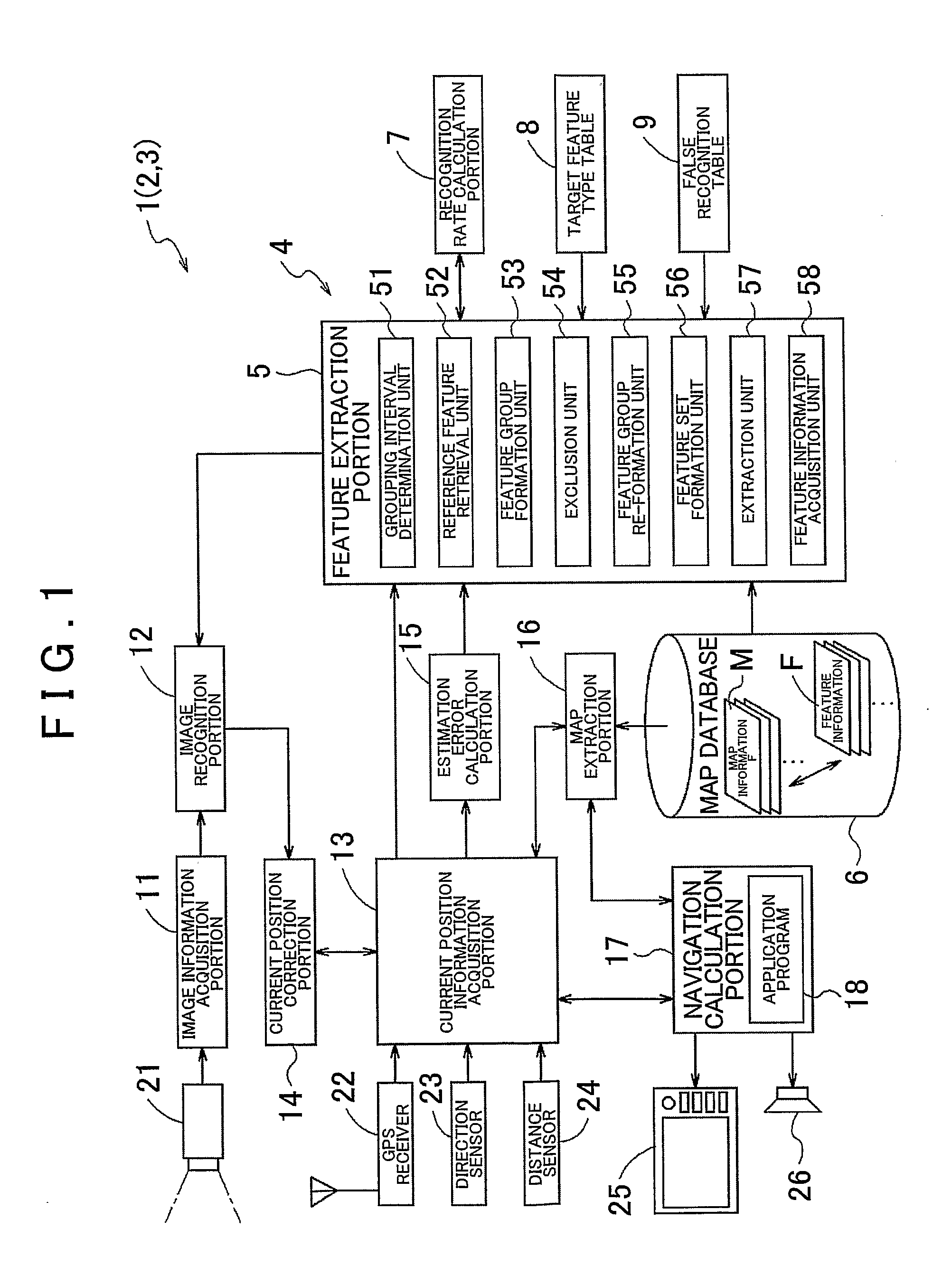
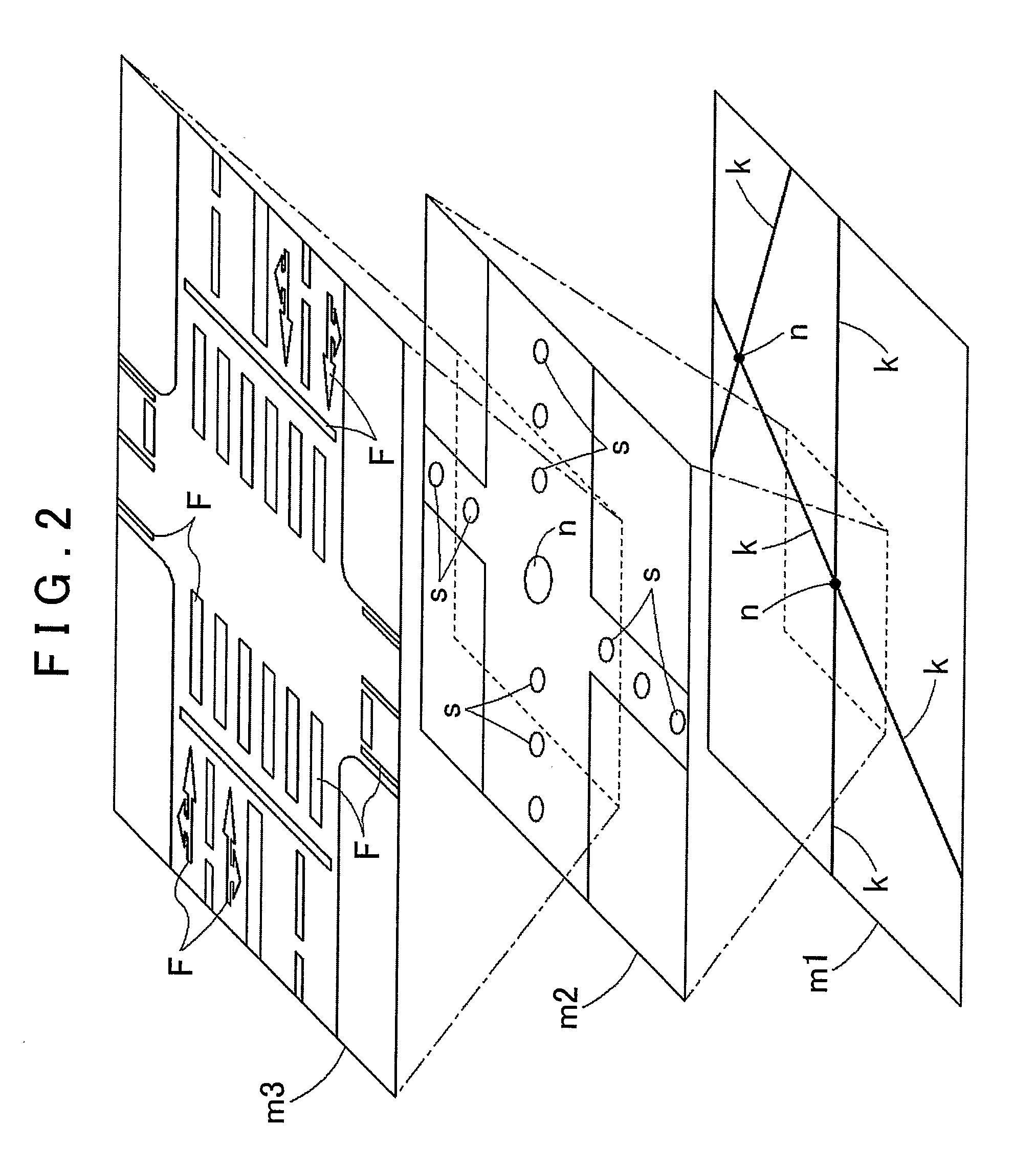
Feature extraction method, and image recognition method and feature database creation method using the same
InactiveUS20110044543A1Reduce generationReduce computing loadCharacter and pattern recognitionFeature extractionFeature data
A feature extraction method includes: the step of grouping a cluster of features, in which an internal of the respective features is less than or equal to a predetermined grouping interval, to form a feature group, for a plurality of features of which feature information including at least information of a position and a feature type is included in a predetermined feature information storage unit; the step of excluding the feature, not suitable for use in an image recognition process of the feature with respect to image information, from the cluster of the features within the feature group; and the step of extracting a part or all of one or more of the features within the feature group remaining as a result of the exclusion step as a target feature suitable for the use in the image recognition process.
Owner:AISIN AW CO LTD +1
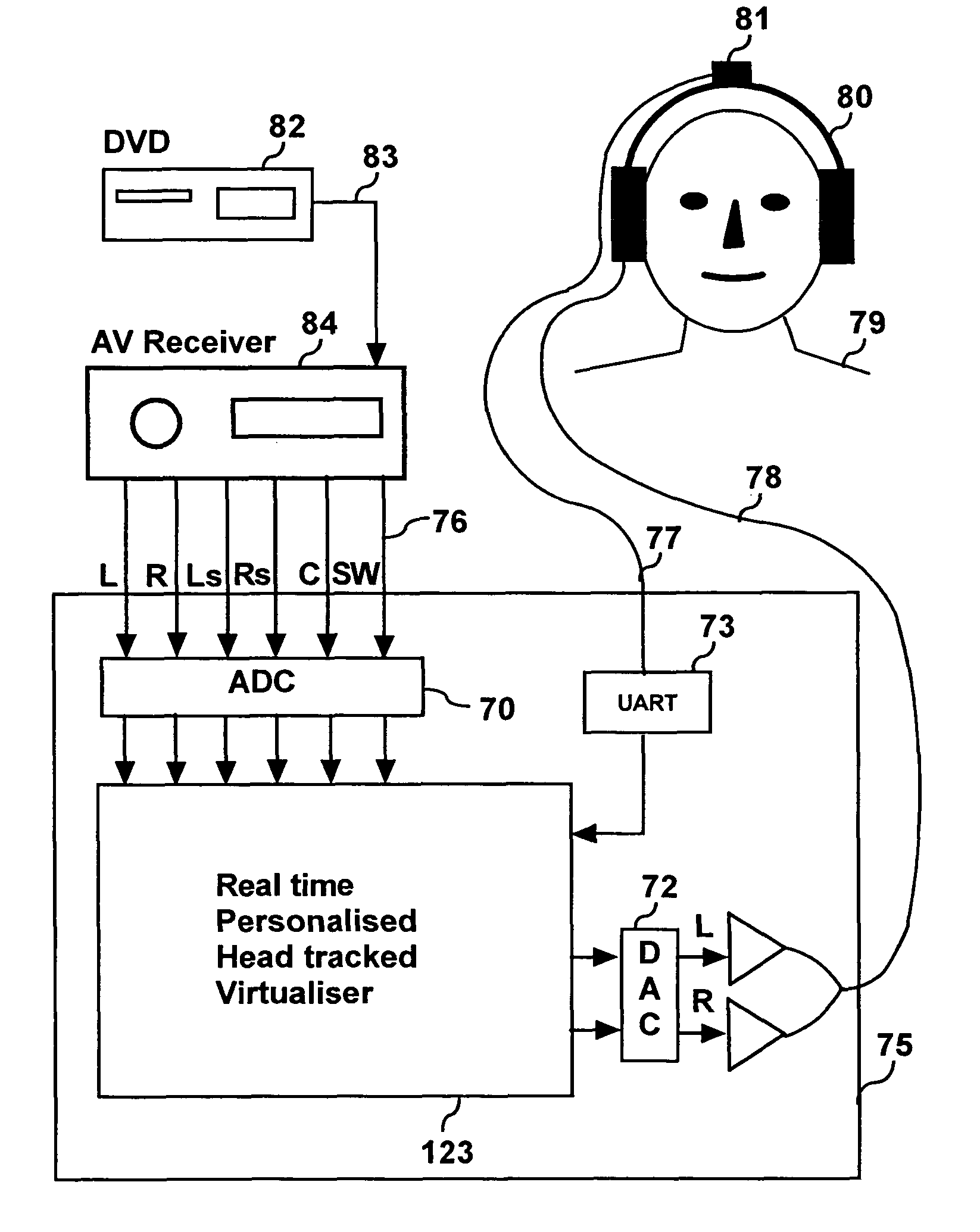
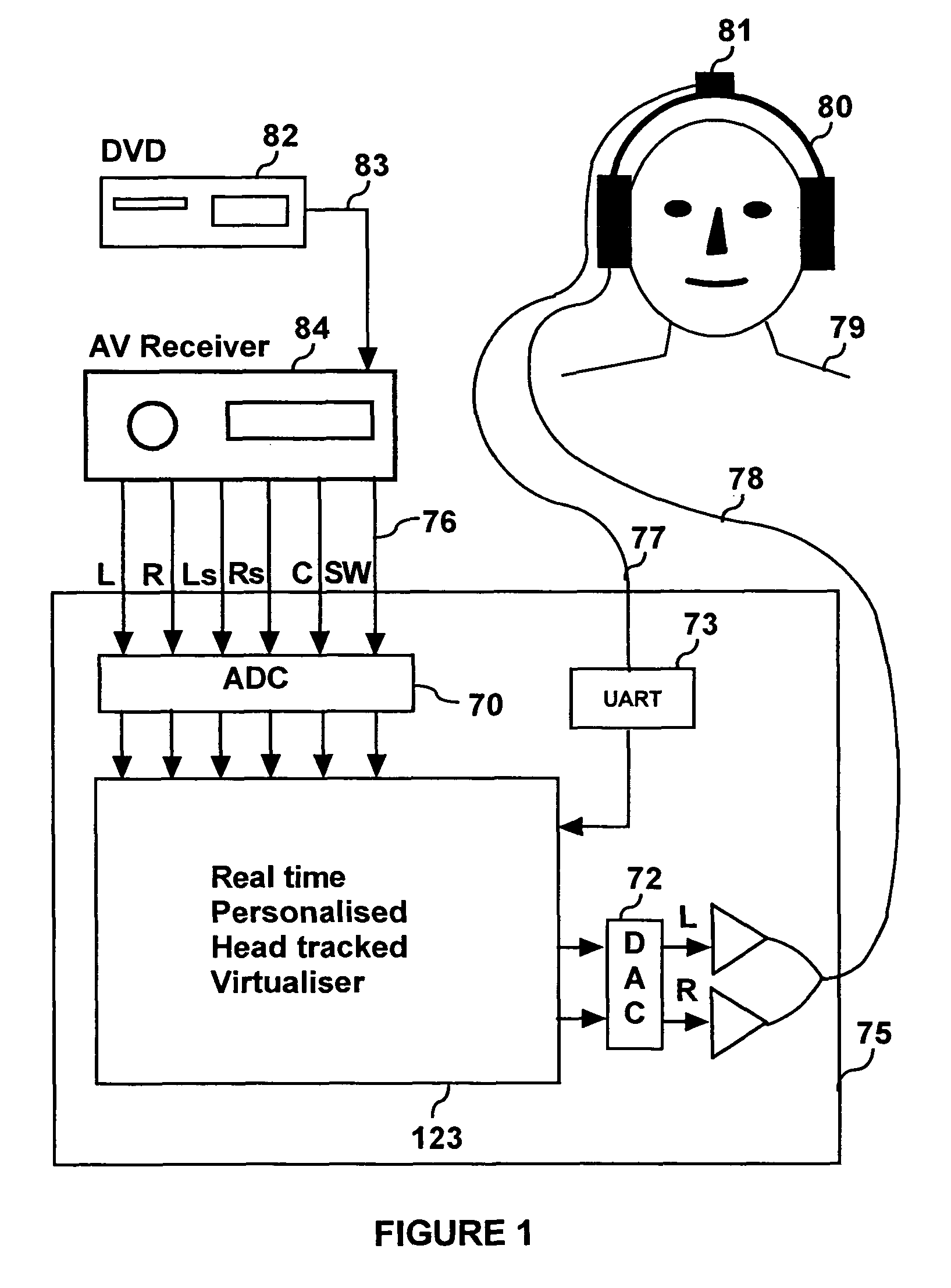
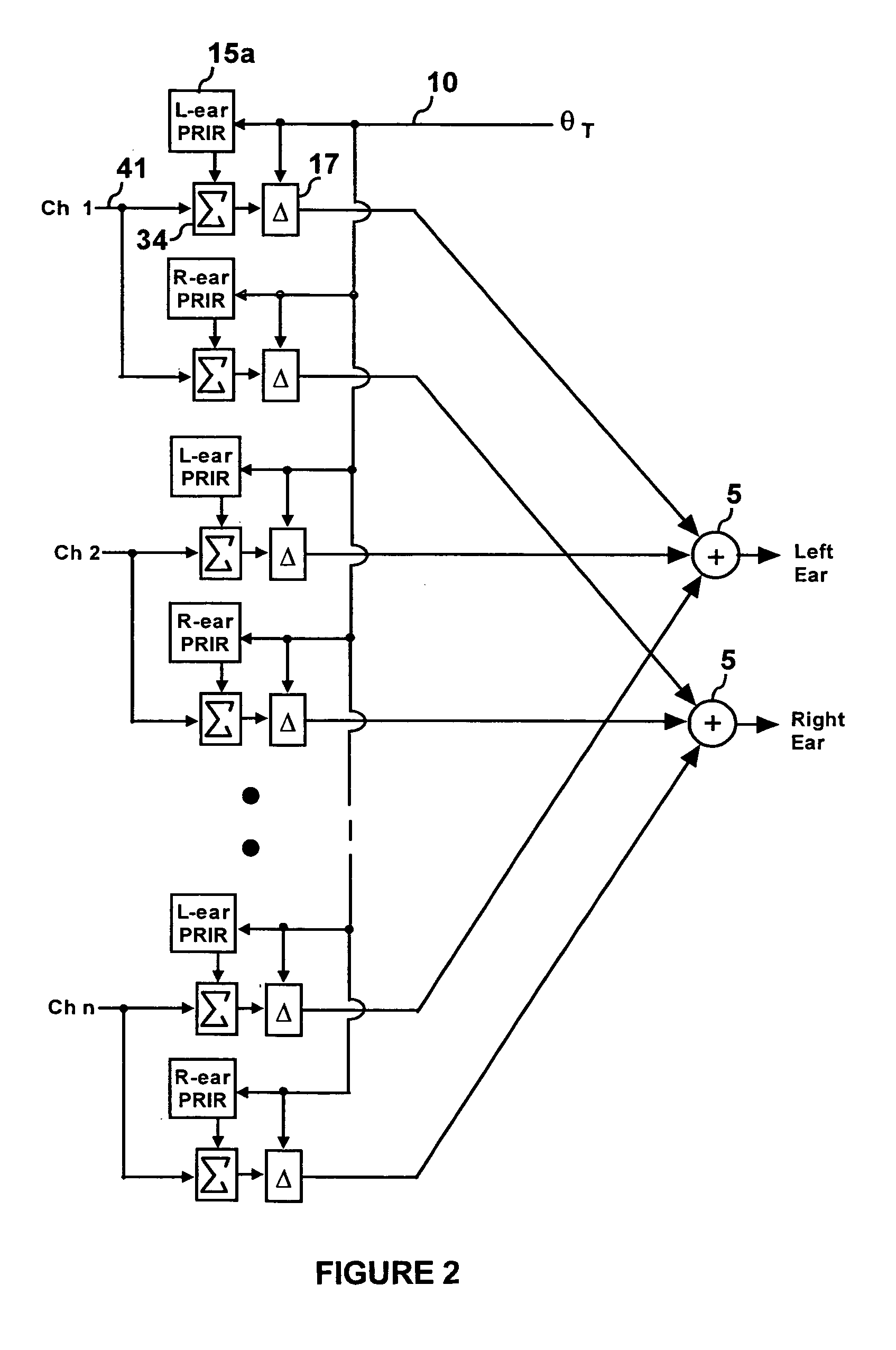
Personalized headphone virtualization
ActiveUS7936887B2Maximize signal qualityImprove accuracyHeadphones for stereophonic communicationEarpiece/earphone attachmentsPersonalizationVirtualization
A listener can experience the sound of virtual loudspeakers over headphones with a level of realism that is difficult to distinguish from the real loudspeaker experience. Sets of personalized room impulse responses (PRIRs) are acquired for the loudspeaker sound sources over a limited number of listener head positions. The PRIRs are then used to transform an audio signal for the loudspeakers into a virtualized output for the headphones. Basing the transformation on the listener's head position, the system can adjust the transformation so that the virtual loudspeakers appear not to move as the listener moves the head.
Owner:SMYTH RES
Method and apparatus for generating error correction data, and a computer-readable recording medium recording an error correction data generating program thereon
InactiveUS7320099B2Effective calculationEfficient errorError prevention/detection by using return channelData representation error detection/correctionComputer hardwareExclusive or
When error correction data, which is to be inserted into transmission data at specific intervals, is generated by calculating exclusive-OR of the transmission data, cumulative exclusive-OR of the transmission data is continuously calculated independent of the error correction data insertion intervals. Exclusive-OR between a calculation of the exclusive-OR at the time of the previous error correction data insertion and a calculation of the exclusive-OR at the time of the current error correction data insertion is calculated, thereby generating error correction data to be inserted at the present time. This provides efficient error correction data calculation.
Owner:FUJITSU LTD
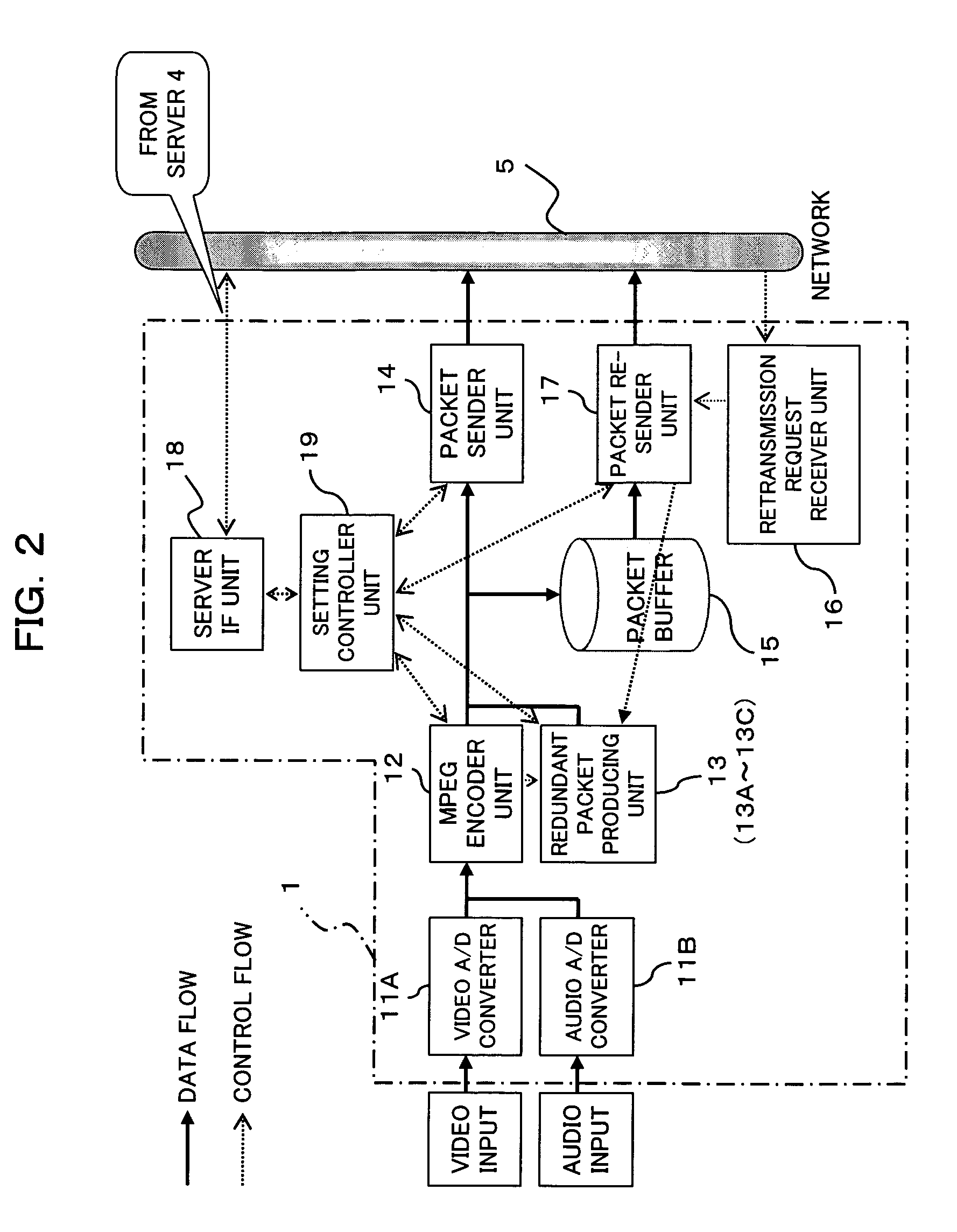
Data transfer system and data transfer method
InactiveUS20060085354A1Reduce loadReduce computing loadData processing applicationsDigital data processing detailsCryptographic key typesTransfer system
A transfer source gives a challenge key, own public key, an ID for identifying the target data, and an encryption key type to a transfer destination that is authenticated by a certificate. In accordance with the given key type, the transfer destination generates a first session key (and a second session key), encrypts the first session key and own public key (or second session key) with the transfer source's public key, encrypts the resulting encrypted data with the challenge key, and transmits the data encrypted with the challenge key to the transfer source. The transfer source encrypts the target data with the second session key (or the transfer destination's public key) that is derived from the received data, encrypts the resulting encrypted data with the first session key, and transmits the data encrypted with the first session key to the transfer destination. The transfer destination decrypts the received data with the first session key, and decrypts the resulting decrypted data with the second session key (or the own public key) to acquire the license.
Owner:WESTERN DIGITAL TECH INC
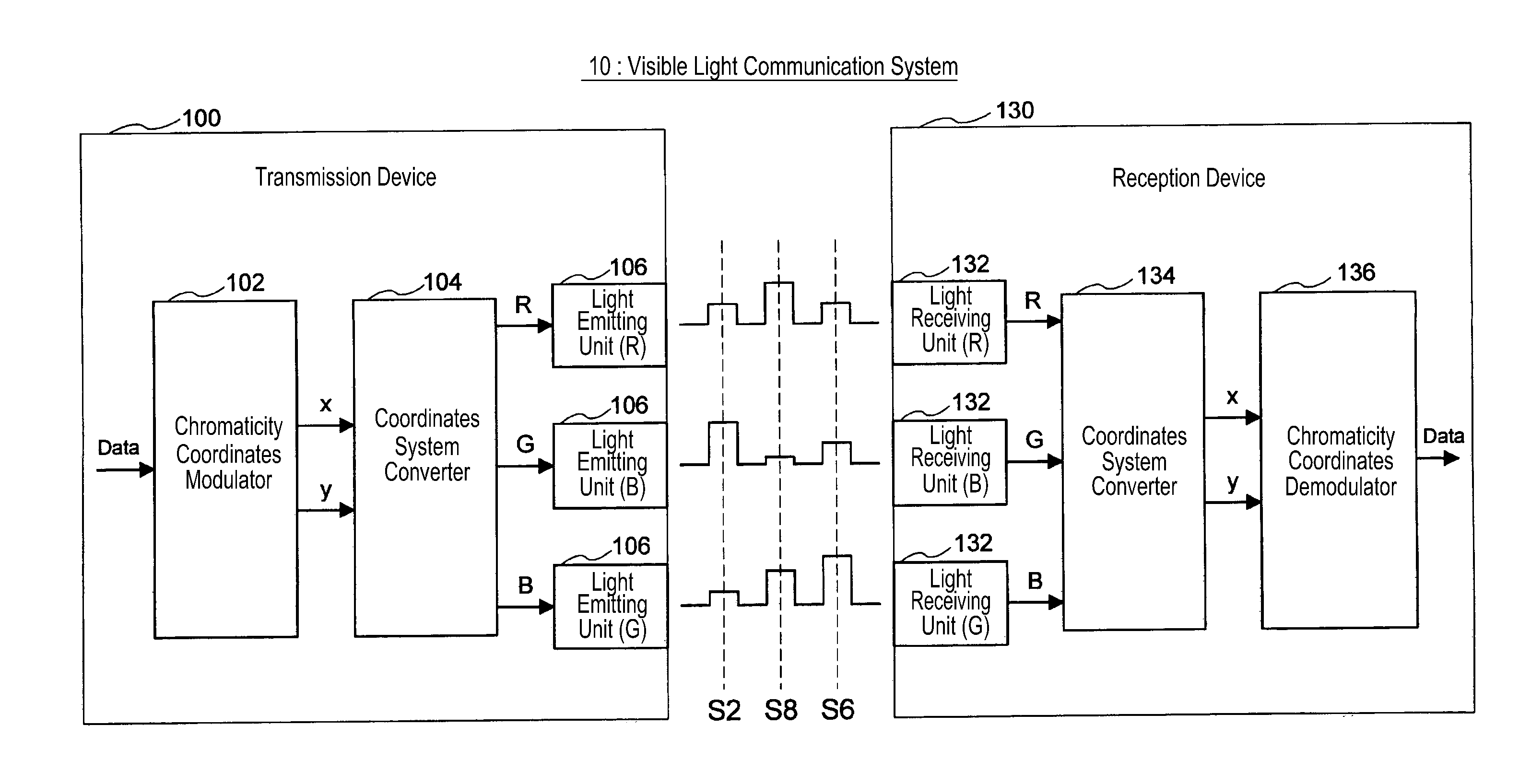
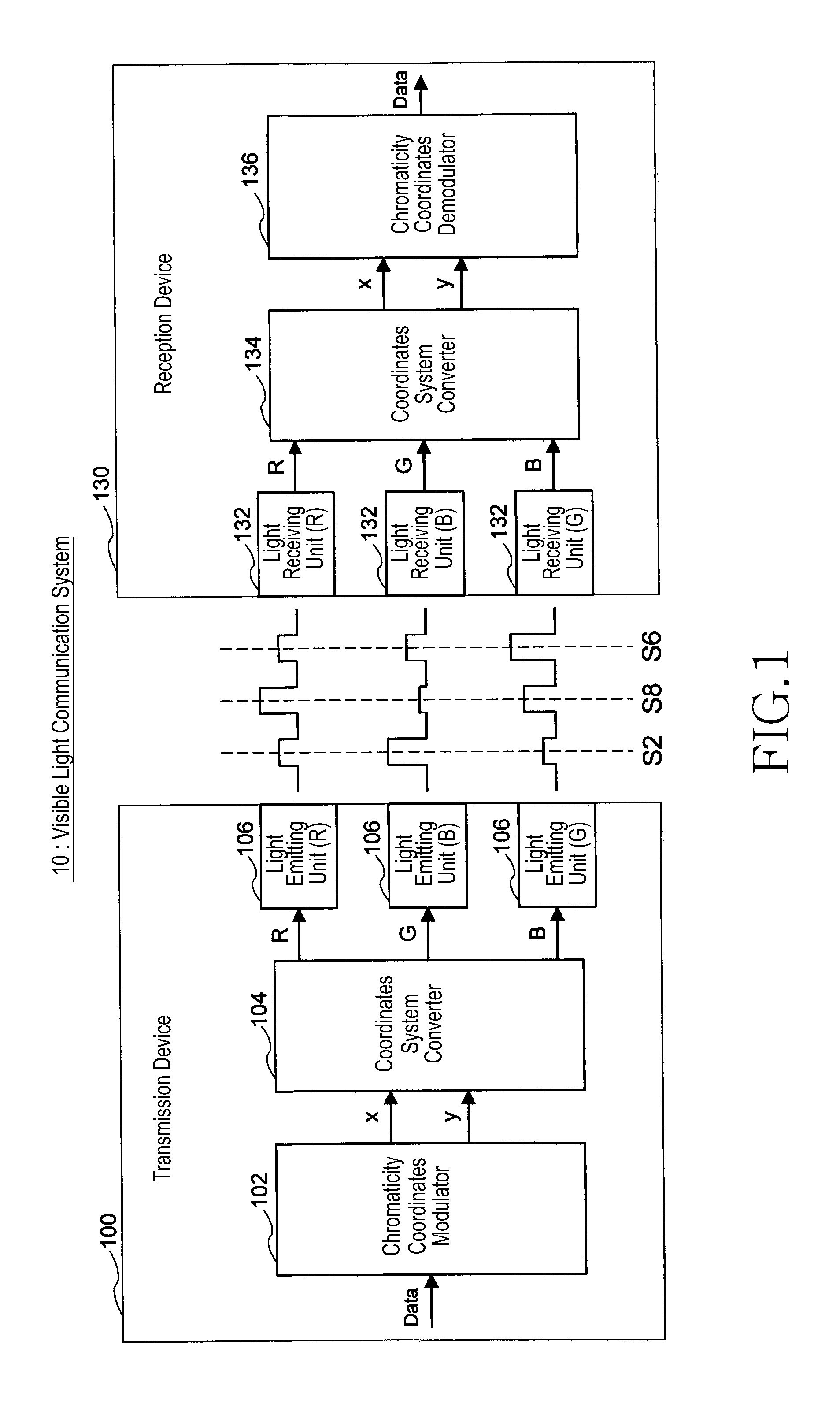
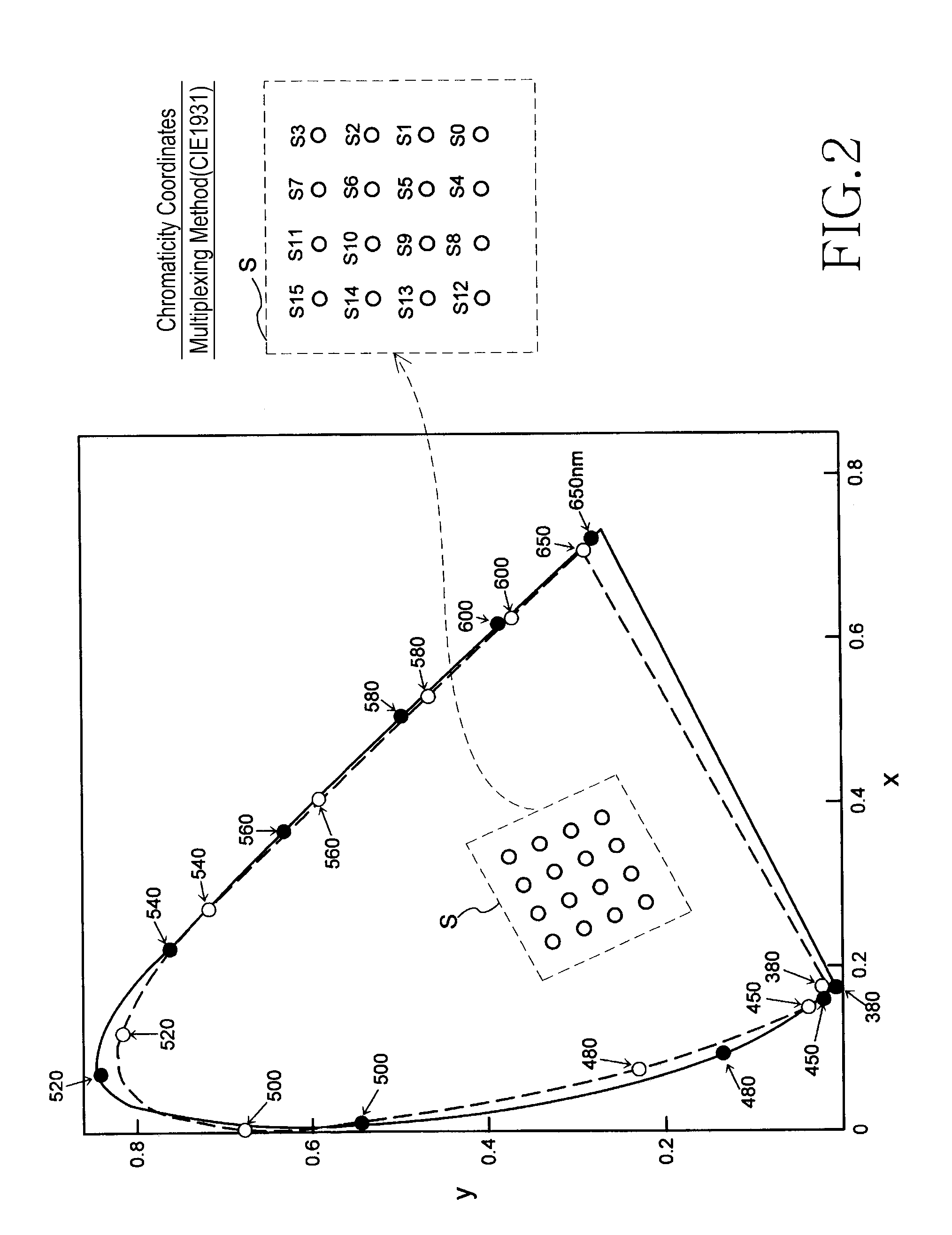
Visible-light communication system system and method
ActiveUS20110200338A1Deterioration of transmission qualityReduce computing loadWavelength-division multiplex systemsClose-range type systemsVisible light communicationLuminescence
Disclosed is a visible light communication system including a transmission device, including multiple light emitting units emitting light of different colors and mapping transmission data to a chromaticity point, calculating luminescence of each of the light emitting units, generating a preamble signal for channel matrix estimation, and emitting light based on the preamble signal and calculated luminescence amount. A reception device of the visible light communication system includes multiple light receiving units and estimates a channel matrix based on a corresponding optical signal when an optical signal corresponding to the preamble signal is received in each light receiving unit, compensates the optical signal corresponding to the chromaticity point for a propagation path based on the estimated channel matrix, detects a chromaticity point on the chromaticity coordinates based on a signal after the propagation path compensation, and demodulates the transmission data.
Owner:SAMSUNG ELECTRONICS CO LTD
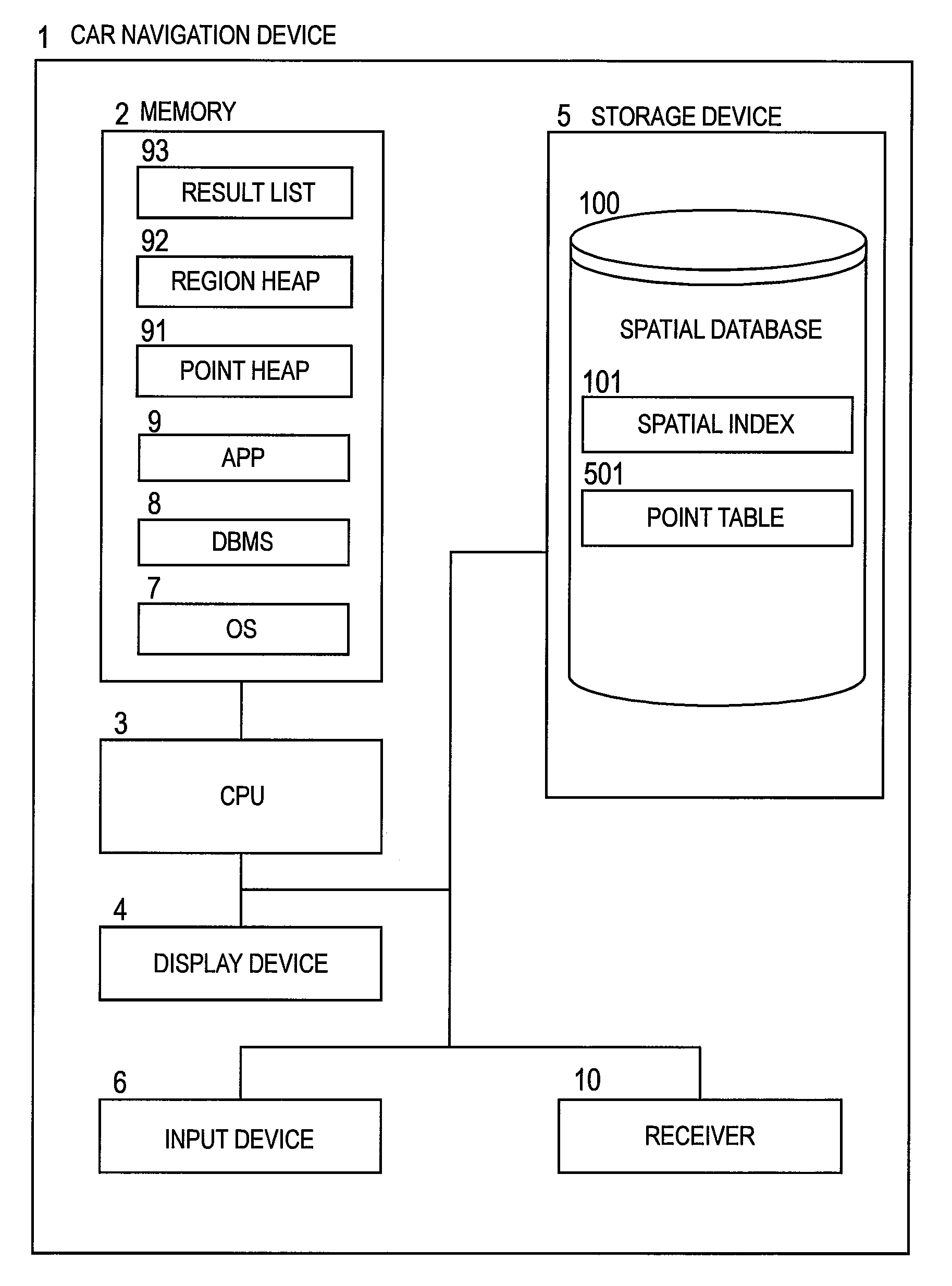
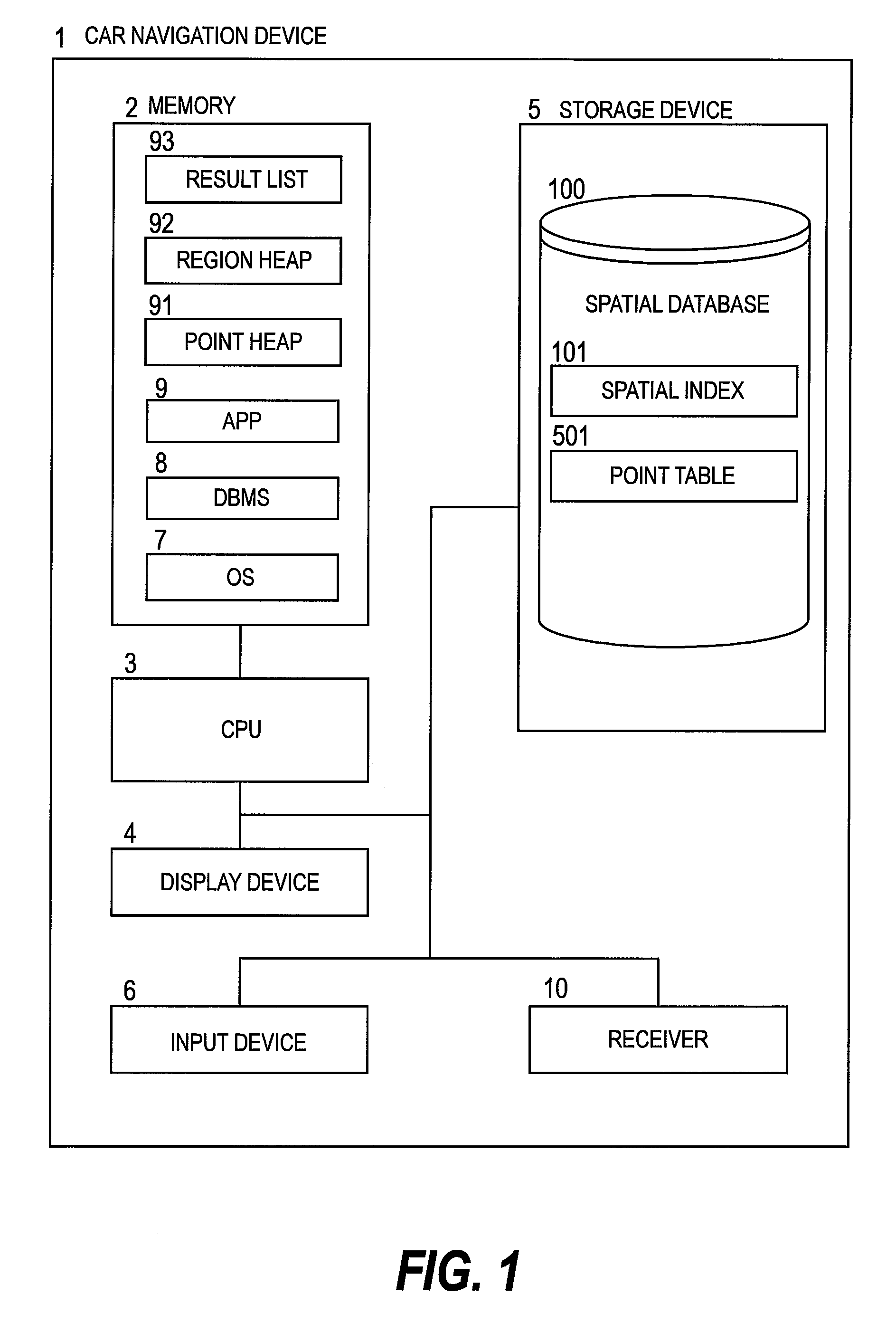
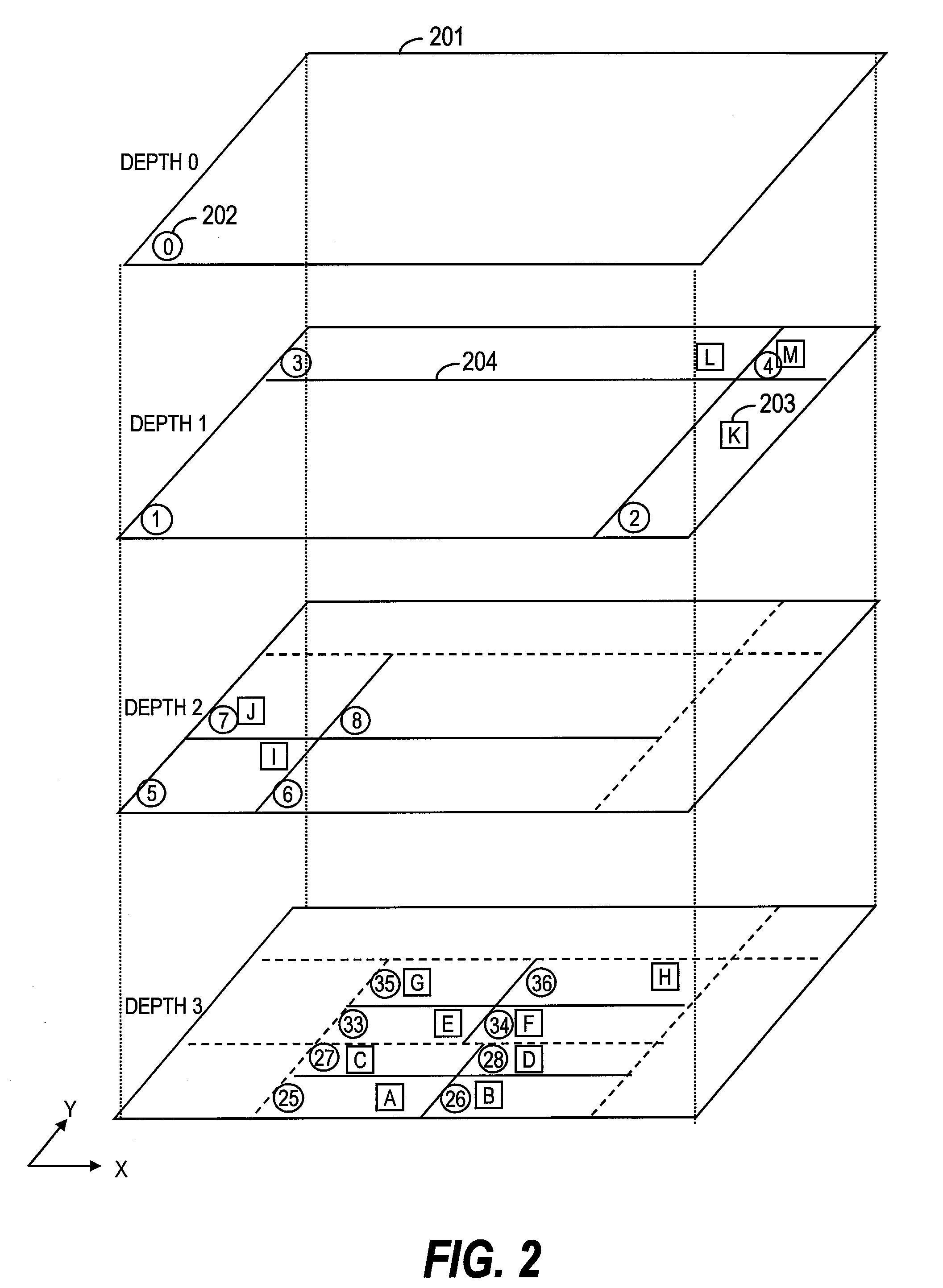
K-nearest neighbor search method, k-nearest neighbor search program, and k-nearest neighbor search device
ActiveUS20090210413A1Increase loadExtension of timeDigital data processing detailsCharacter and pattern recognitionNear neighborIntermediate region
Provided is a k-nearest neighbor search method of searching for a query number k of nearest points to an arbitrary point in a DBMS for creating a spatial index from multidimensional points, comprising setting a search conditions, judging which of a lowest branch and an intermediate branch of the spatial index a nearest region to the query point is, calculating, when the nearest region is judged to be the lowest branch, a distance between the query point and a child region of the nearest region, storing information of a divided region which has become a calculation target, calculating, when the nearest region is judged to be the intermediate region, a distance between the query point and a point included in the nearest region, storing information of the point which has become a calculation target, finishing search processing when the search conditions are satisfied, and obtaining a search result from the DBMS.
Owner:HITACHI SOFTWARE ENG +1
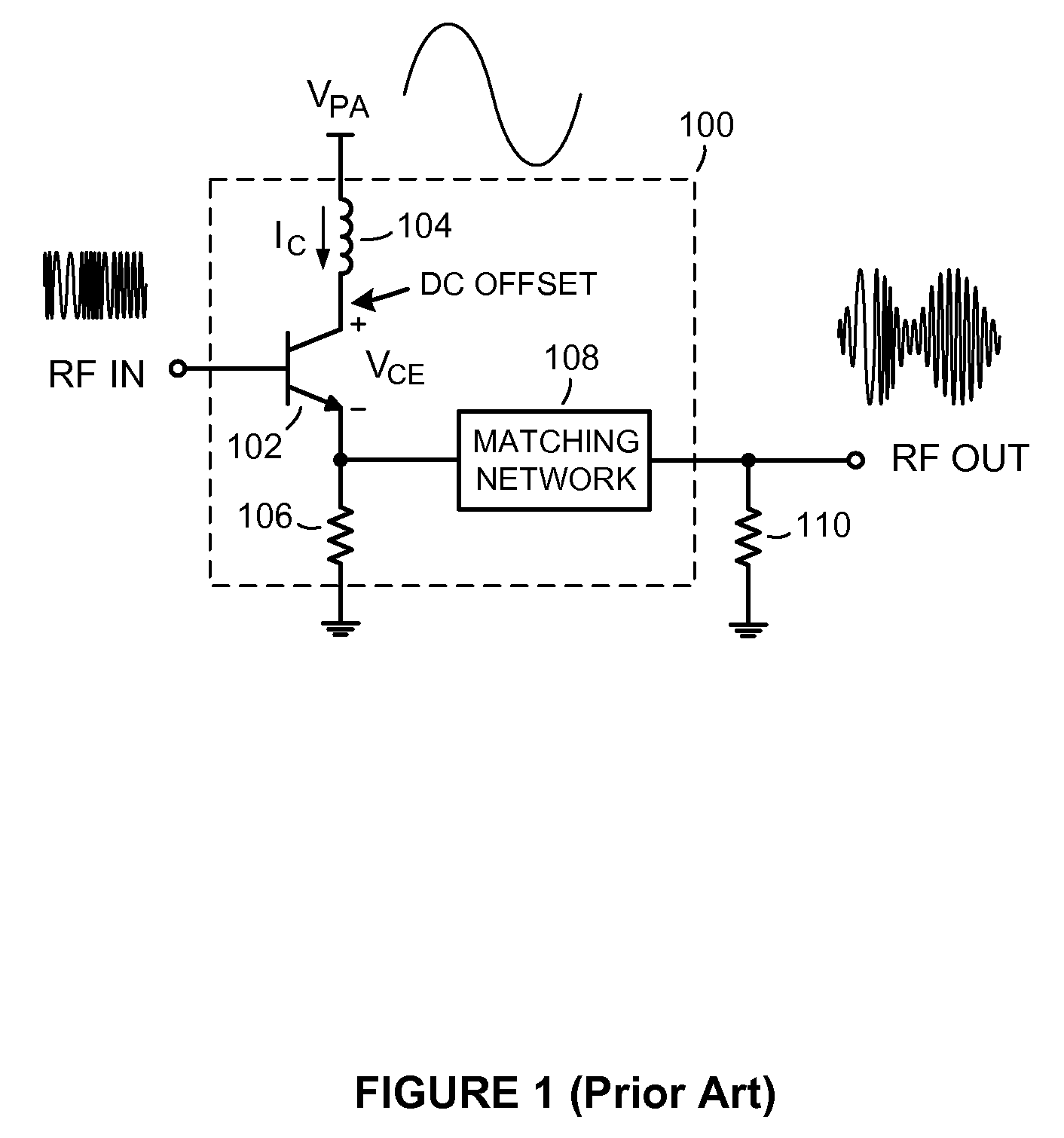
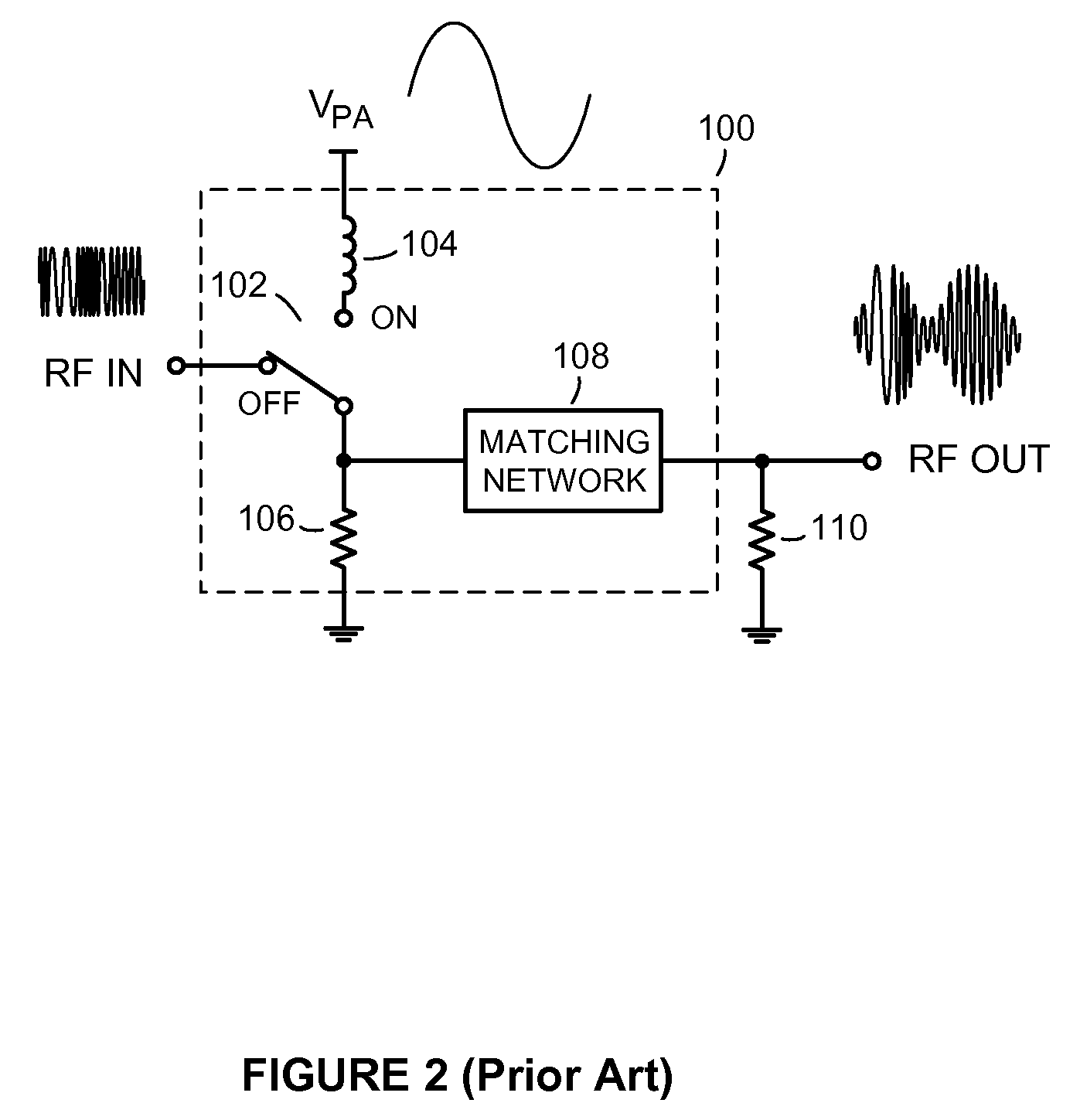
Methods and apparatus for dynamically compensating for DC offset drift and other pvt-related signal variations in polar transmitters
ActiveUS20100120384A1Reduce computing loadEasy CalibrationResonant long antennasModulated-carrier systemsPolar transmitterSignal characteristic
Methods and apparatus for dynamically compensating for signal variations in communications transmitters employing switch-mode PAs. An exemplary method includes first identifying a predetermined signal characteristic in an input signal applied to an input of a switch-mode PA. A modulated signal produced at the output of the switch-mode PA containing the identified signal characteristic is then sampled at approximately the same time the identified signal characteristic appears at the output of the switch-mode PA, to generate a digital sample representing an actual value of the identified signal characteristic. An error signal representing the extent to which the actual value deviates from an expected value is then generated. Finally, the DC level and / or gain of the input signal to the switch-mode PA is modified to reduce the error. By reducing the error in this manner, signal variations that adversely affect the accuracy of the switch-mode PA output signal are dynamically compensated for.
Owner:PANASONIC CORP
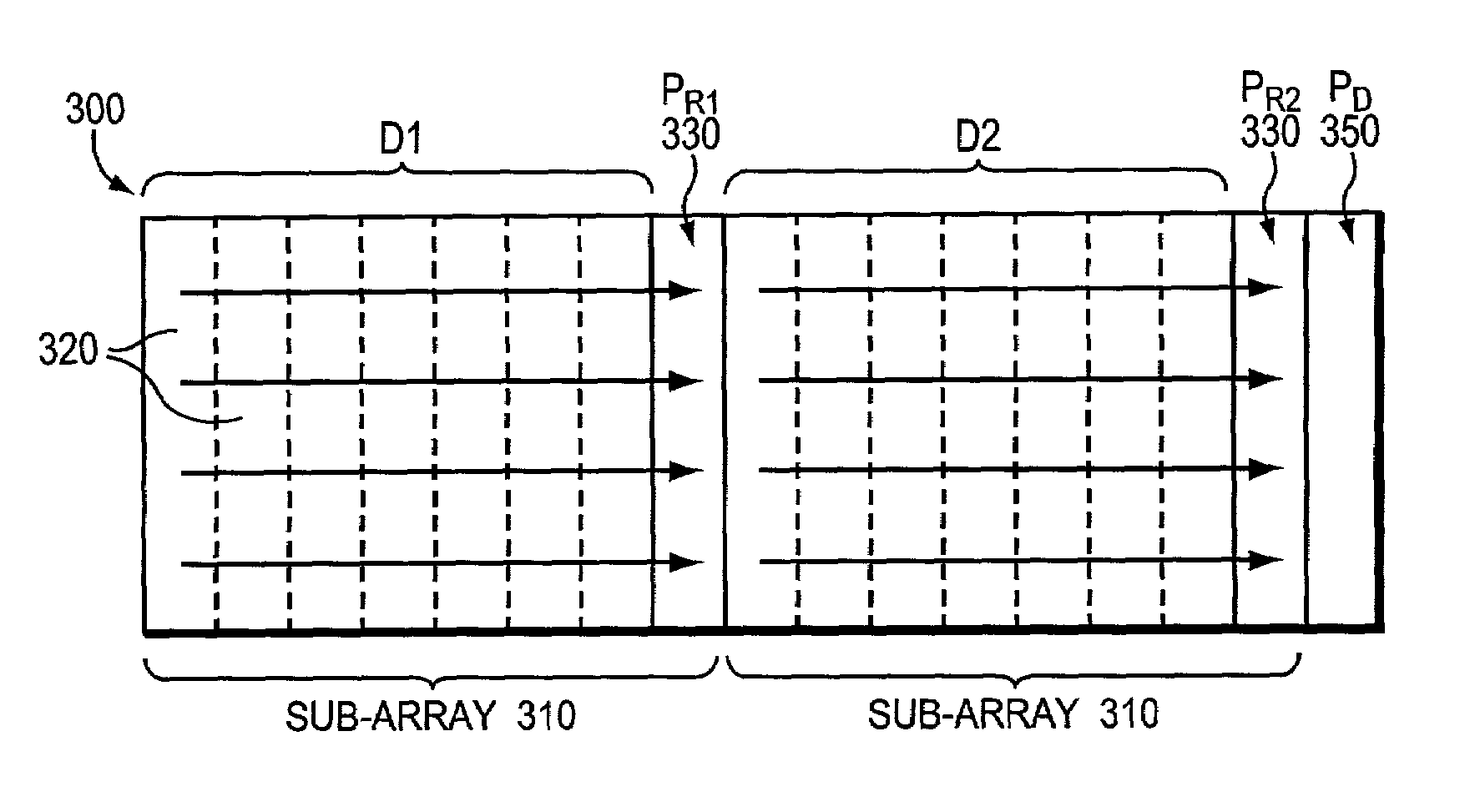
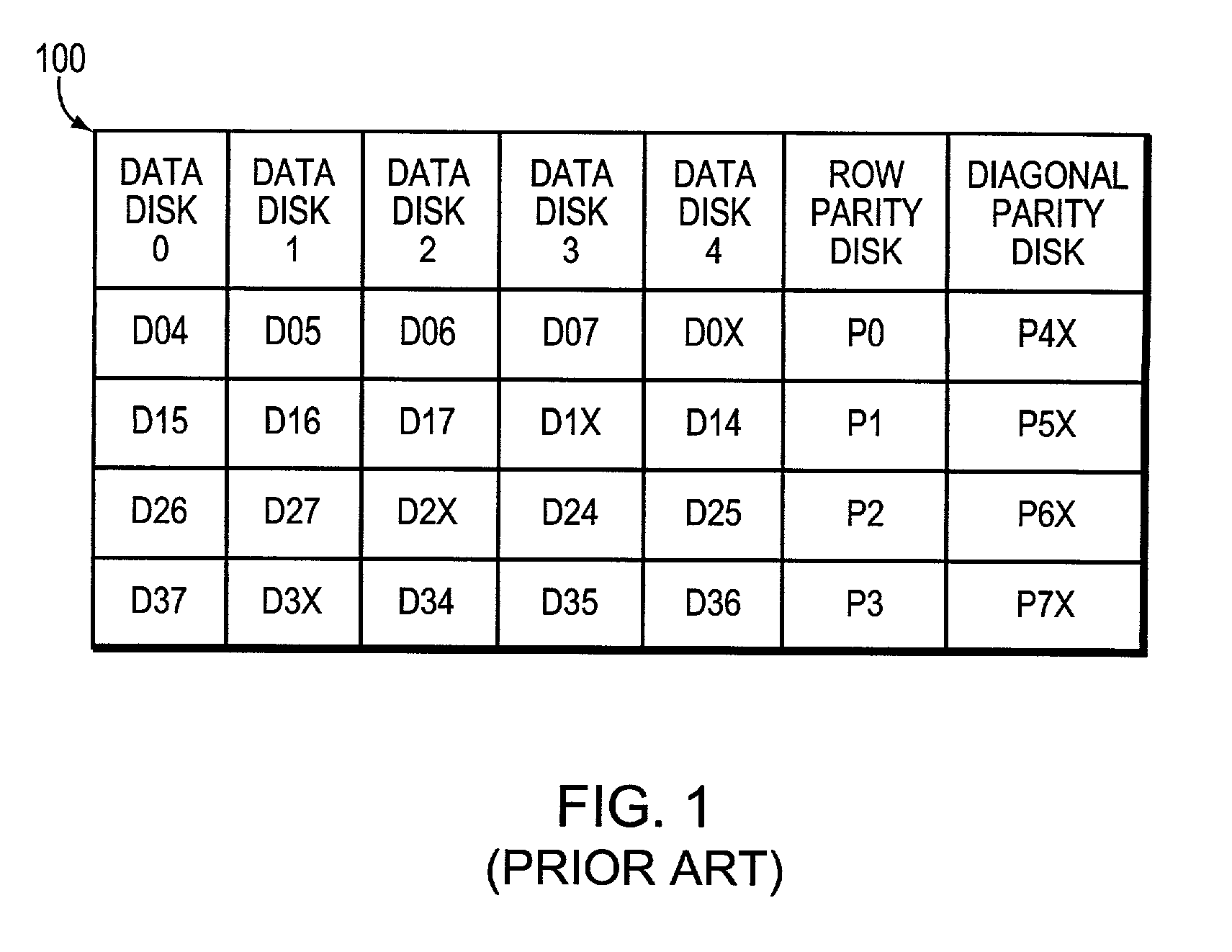
Technique for correcting multiple storage device failures in a storage array
InactiveUS7080278B1Effective correctionEffective recoveryInput/output to record carriersCode conversionComputer hardwareDiagonal
A technique efficiently corrects multiple storage device failures in a storage array. The storage array comprises a plurality of concatenated sub-arrays, wherein each sub-array includes a set of data storage devices and a local parity storage device that stores values used to correct a failure of a single device within a row of blocks, e.g., a row parity set, in the sub-array. Each sub-array is assigned diagonal parity sets identically, as if it were the only one present using a double failure protection encoding method. The array further includes a single, global parity storage device holding diagonal parity computed by logically adding together equivalent diagonal parity sets in each of the sub-arrays.
Owner:NETWORK APPLIANCE INC
Process for creating a media sequence by coherent groups of media files
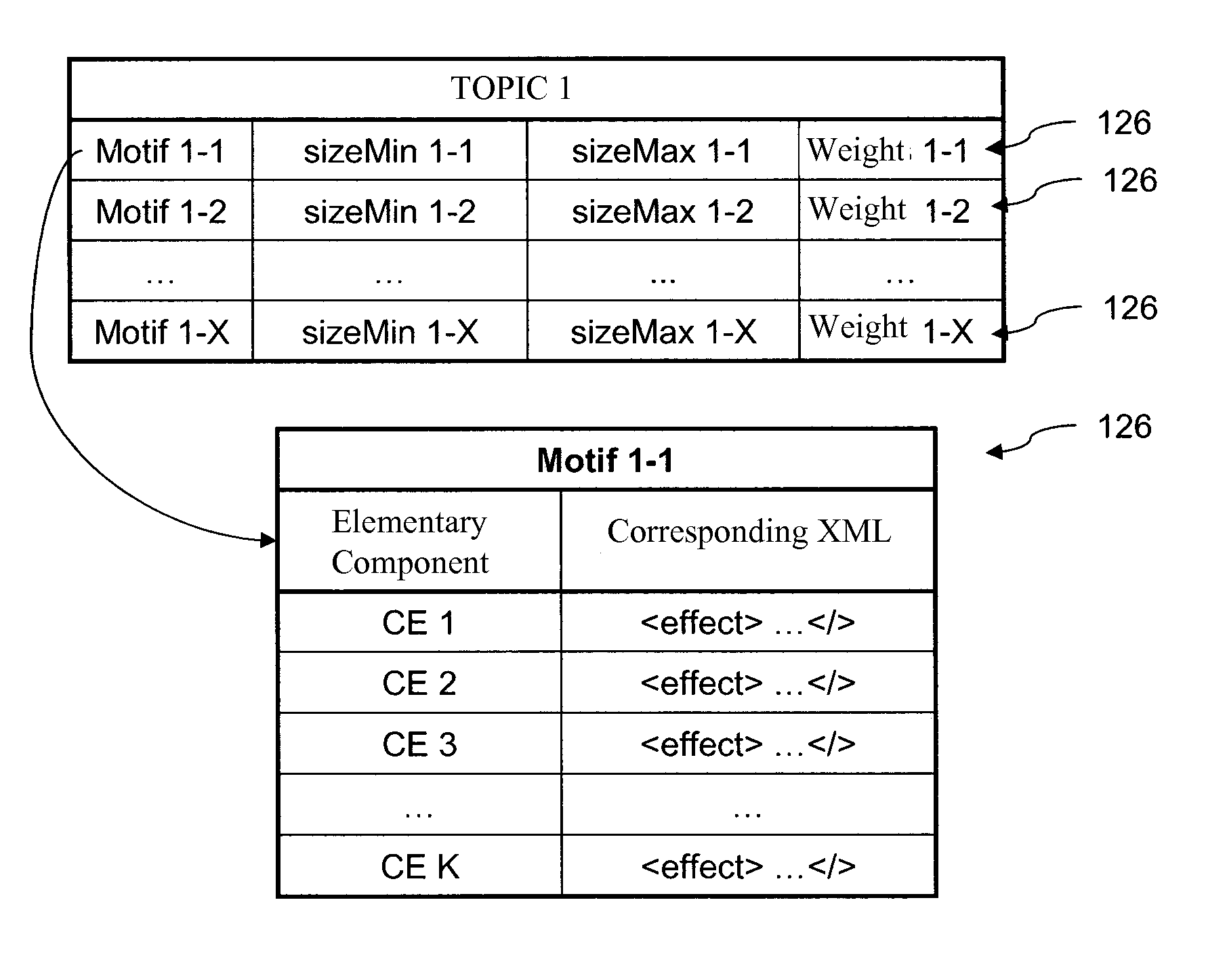
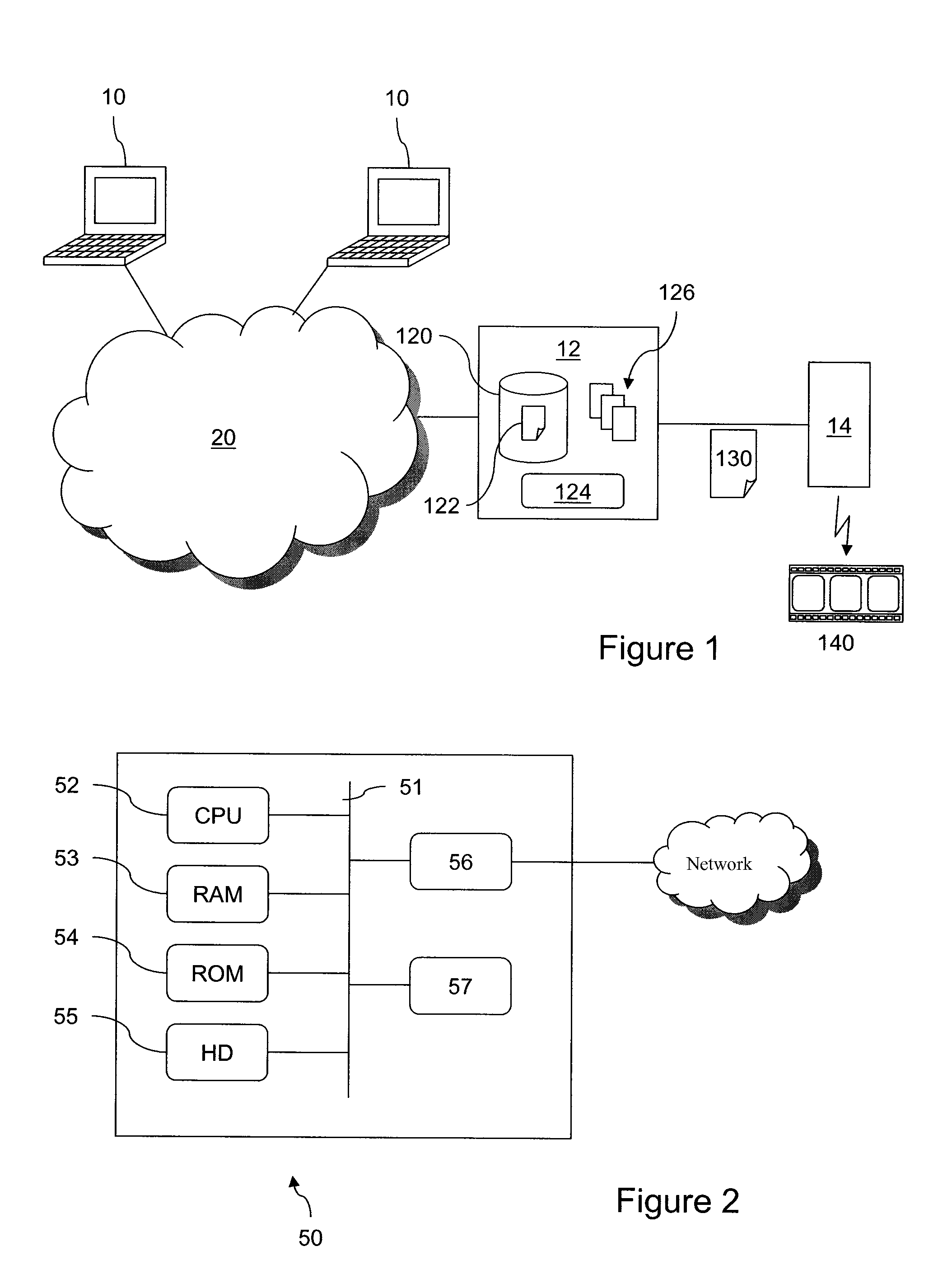
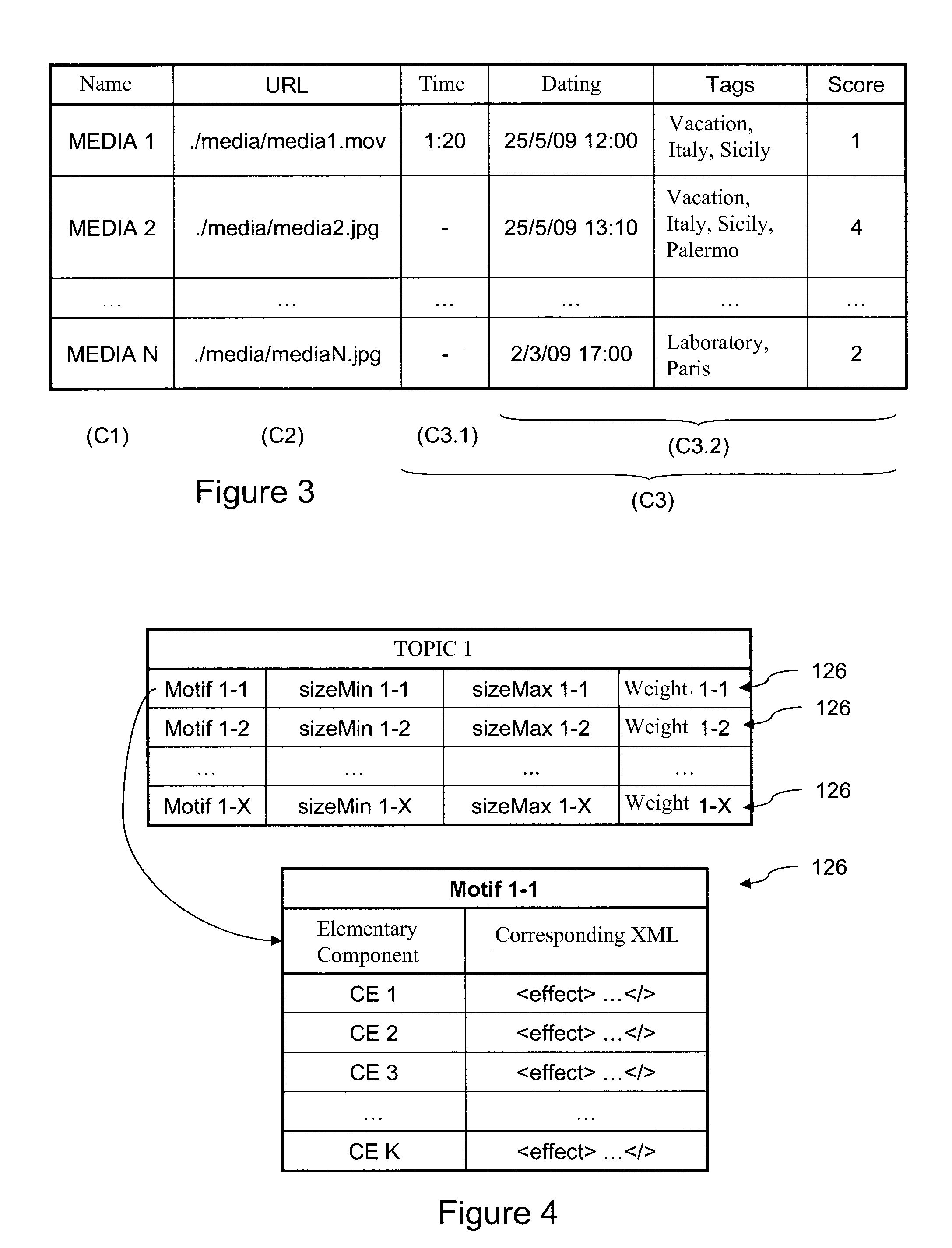
InactiveUS20110276864A1Volume andMedia file rendering of the group is reducedMultimedia data indexingMultimedia data queryingWeb serviceVideo editing
A process for creating a media sequence, for example video or audio, and an associated device includes the stages of:obtaining a selection of media files;regrouping the chosen media files into a plurality of groups according to at least one coherence criterion;selecting, for each group of media files assembled in this way, a media motif among a plurality of predefined media motifs, the chosen media motif being able to define a media rendering for the set of media files of the group; andassembling the media motifs selected in this way and their associated media files in such a way as to form at least one definition of the media sequence. The process can relate to automated video editing as implemented on Web servers.
Owner:ORANGE SA (FR)
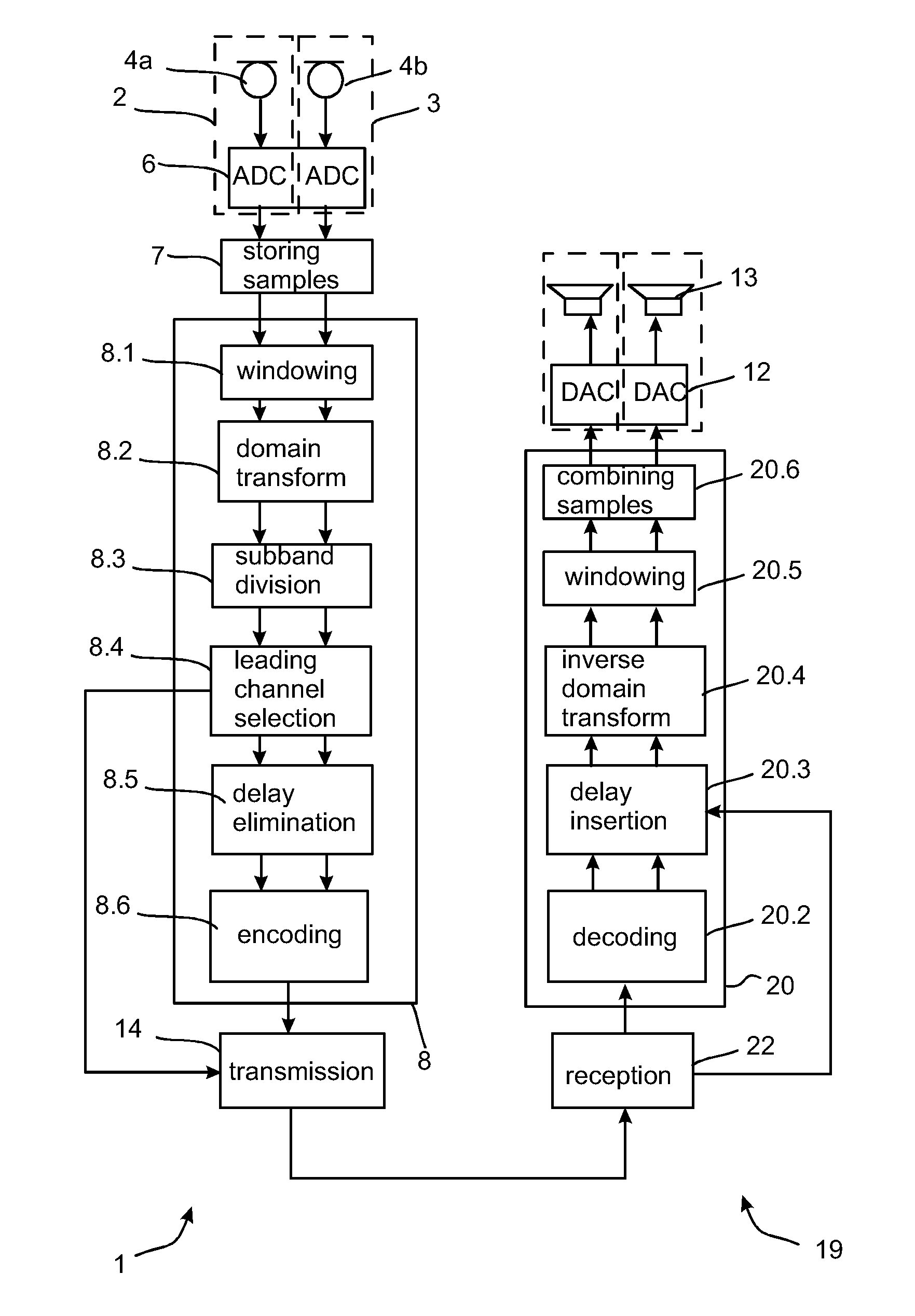
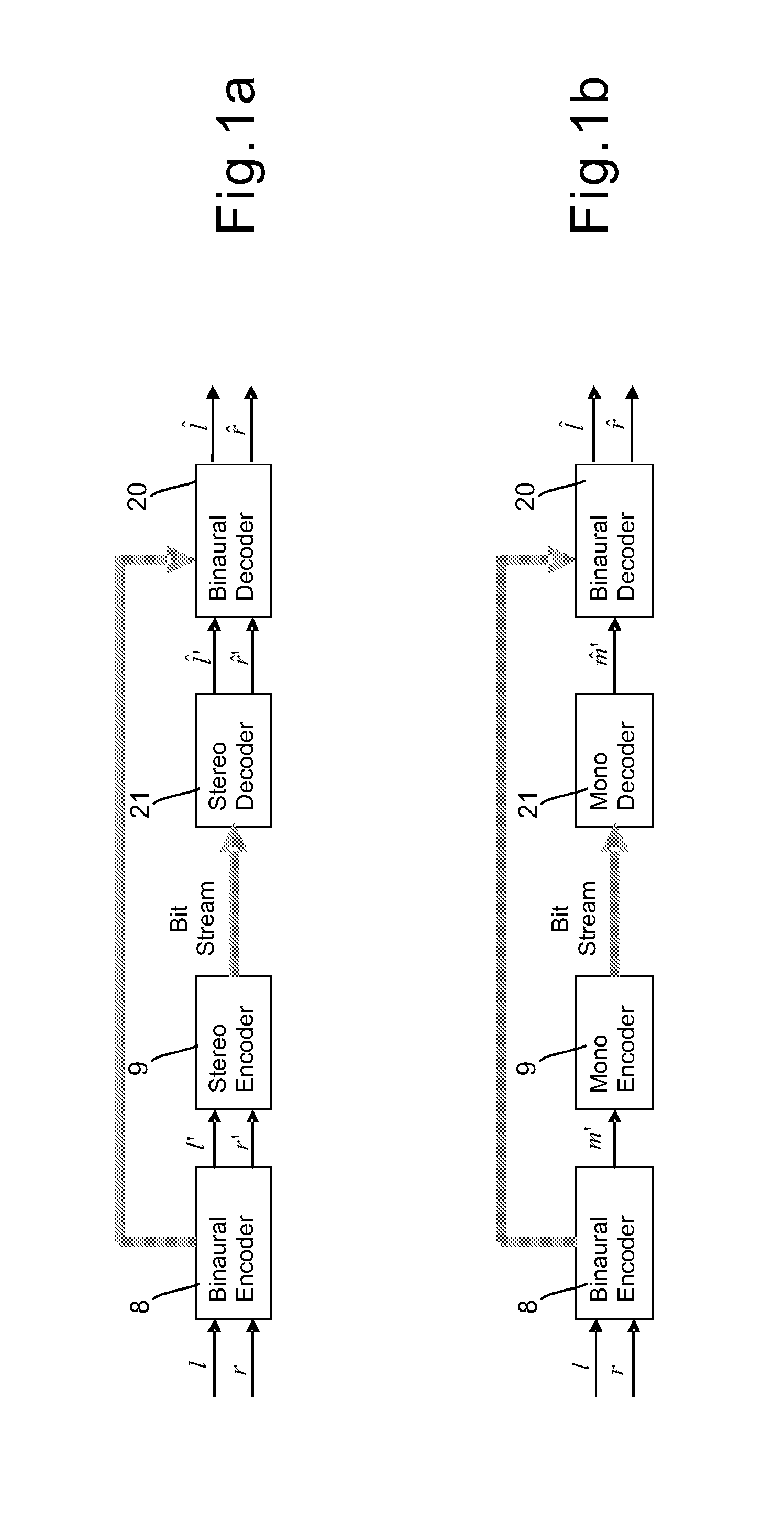
Method, Apparatus and Computer Program Product for Audio Coding
The invention relates to a method and an apparatus in which samples of at least a part of an audio signal of a first channel and a part of an audio signal of a second channel are used to estimate a time delay between said part of the audio signal of said first channel and said part of the audio signal of said second channel. The method includes windowing the samples; performing a time-to-frequency domain transform; and determining an inter-channel time delay between said part of the audio signal of the first channel and said part of the audio signal of said second channel on the basis of the frequency domain representations. There is also disclosed a method and an apparatus for decoding the encoded samples.
Owner:NOKIA TECHNOLOGLES OY
Method for fast locating decipherable pattern
ActiveUS20100163632A1Rapid positioningEasy to distinguishCharacter and pattern recognitionRecord carriers used with machinesPattern recognitionImage plane
A method for fast locating a decipherable pattern in an input image, which is characterized in utilizing an overly downscaled binary image to not only reduce computation time but also facilitate extraction of skeletons for fast and accurately locating pattern, is disclosed. First, a pre-process is applied to an input image to acquire a binary image downscaled n times, from which at least one skeleton corresponding to a decipherable pattern is extracted. Coordinate values of at least one pixel of each skeleton are respectively enlarged n1 / 2 times and used as the central points on the original image plane for establishing a plurality of detecting blocks with the identical size. Subsequently, a grading mechanism is employed to determine the corresponding detecting blocks of the decipherable pattern.
Owner:ARMORLINK +1
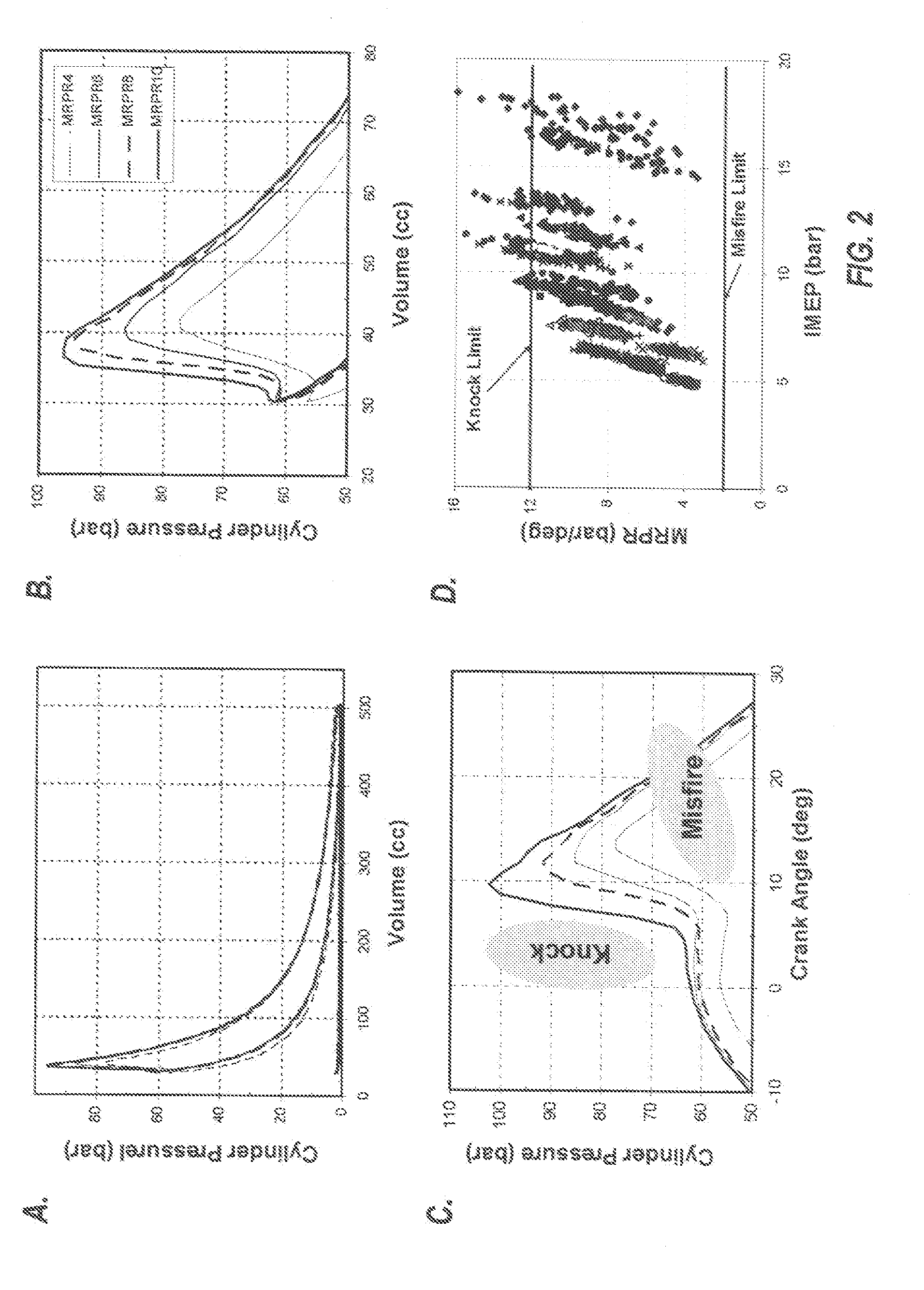
Method and system of transient control for homogeneous charge compression ignition (HCCI) engines
InactiveUS20100031924A1Reduce computing loadRobust engine controlElectrical controlInternal combustion piston enginesApplying knowledgeHcci combustion
A HCCI engine with a model reference adaptive feedback control system maintains stable HCCI combustion during speed / load transitions by: (1) estimating the maximum rate of pressure rise (MRPR), for each cycle, from an extra-cylinder sensor metric, such as a crankshaft dynamics or knock sensor metric, via statistical vector-to-vector correlation; (2) periodically self-tuning the vector-to-vector correlation; (3) applying knowledge base models to guide cycle-to-cycle adjustments of fuel quantity and other engine parameters, to maintain a target MRPR value.
Owner:U S ENVIRONMENTAL PROTECTION AGENCY UNITED STATES OF AMERICA AS REPRESENTED BY THE
Reducing the computational load on processors by selectively discarding data in vehicular networks
ActiveUS8314718B2Reduce computing loadReduce bottlenecksService provisioningParticular environment based servicesCommunications systemComputer science
Owner:GM GLOBAL TECH OPERATIONS LLC
System and Method for Wireless Communications
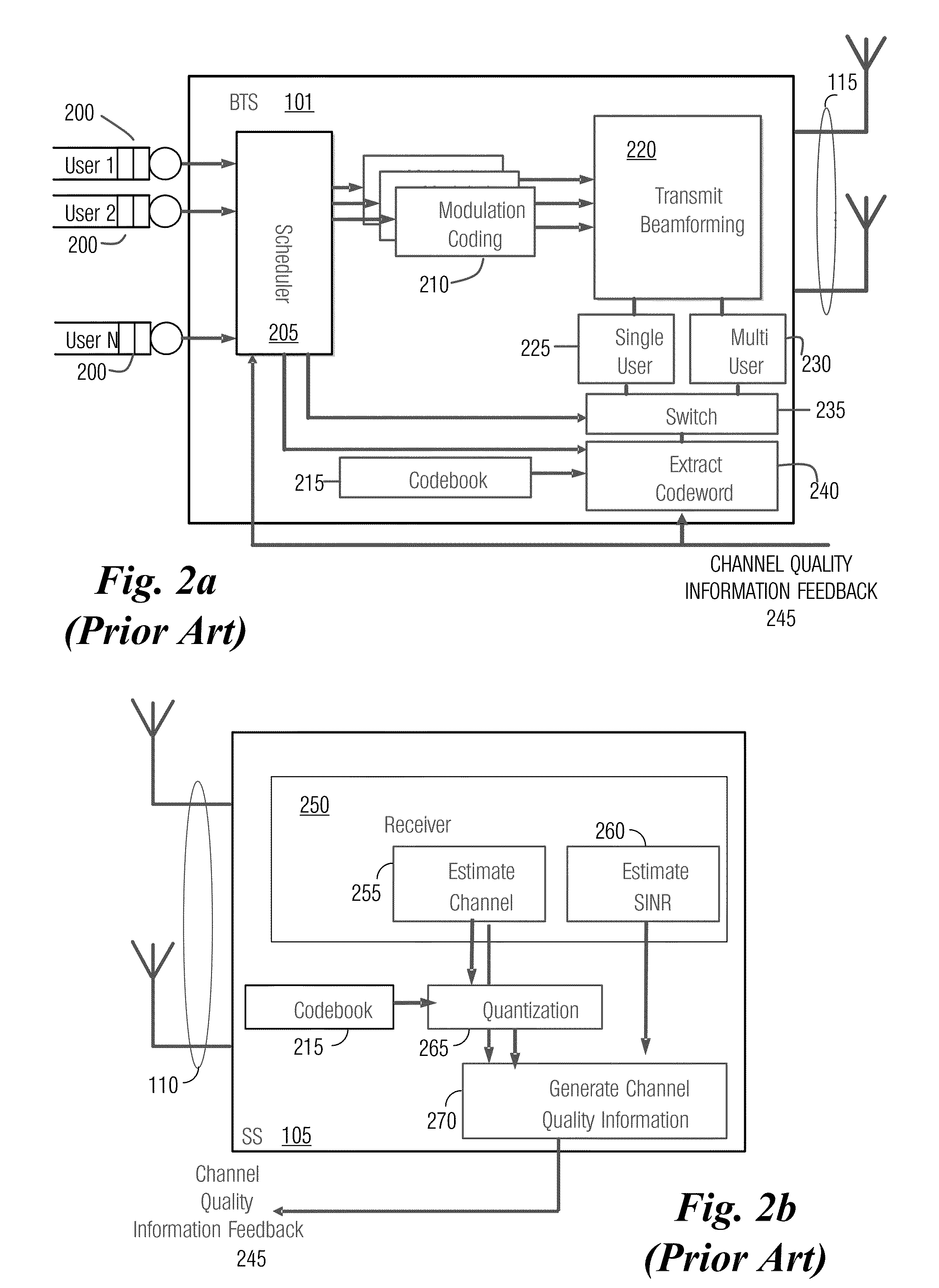
ActiveUS20100054212A1Avoid transmit power imbalanceReduce computational complexityMultiplex communicationSecret communicationComputer hardwareCommunication device
A system and method for wireless communications is provided. A method for operating in a communications network includes receiving a codebook, the codebook includes a plurality of codewords, and determining if the codebook satisfies a constant modulus property. The method also includes in response to determining that the codebook does not satisfy the constant modulus property, converting the codebook into a codebook satisfying the constant modulus property, and storing the codebook satisfying the constant modulus property. The method further includes storing the codebook in response to determining that the codebook does satisfy the constant modulus property, and causing to transmit a transmission to a communications device, wherein the transmission is encoded using a codeword in the stored codebook.
Owner:FUTUREWEI TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com