Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
425 results about "Software execution" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Execution in computer and software engineering is the process by which a computer or virtual machine executes the instructions of a computer program.
Method and apparatus for data communication
InactiveUS6094684AInterprogram communicationMultiple digital computer combinationsGraphicsGraphical user interface
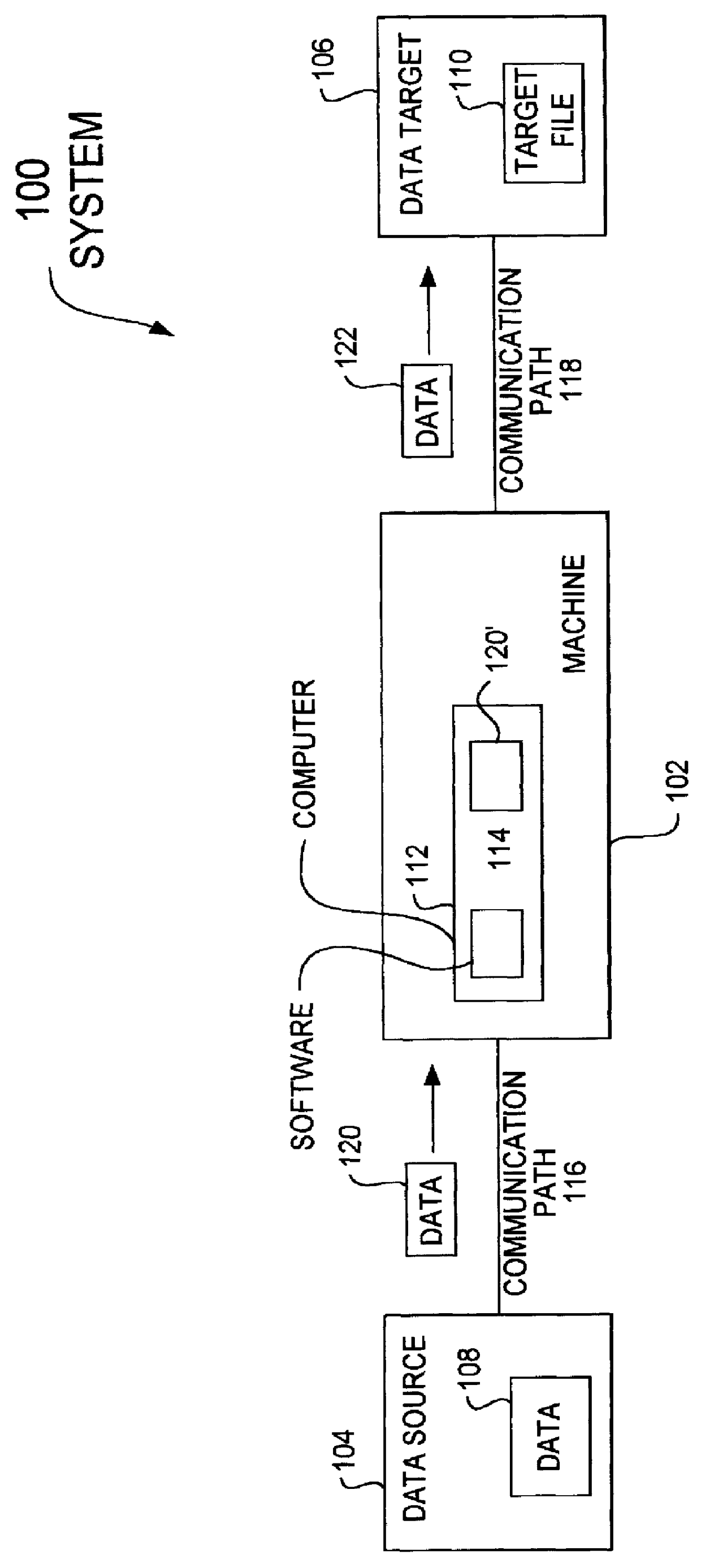
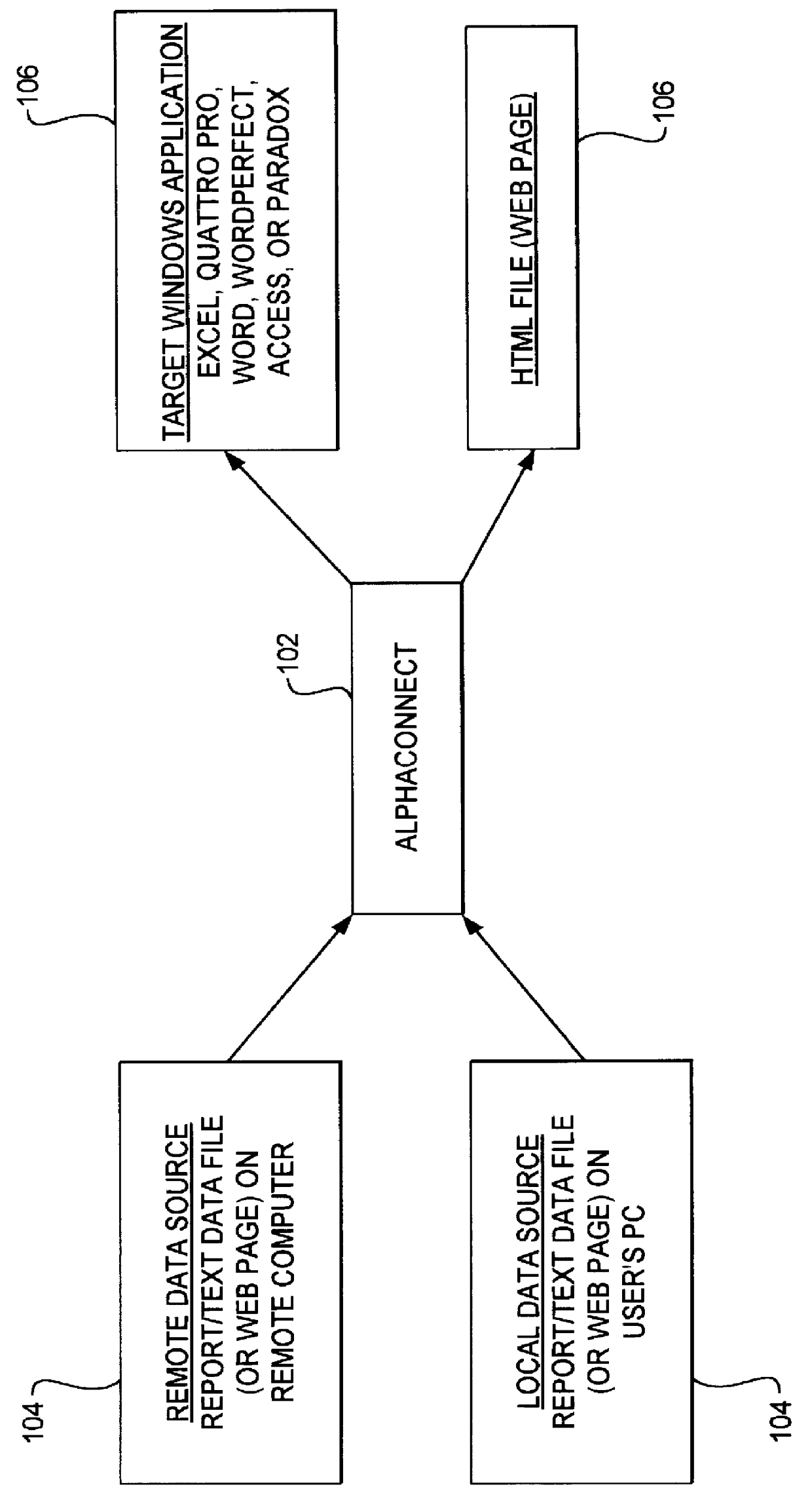
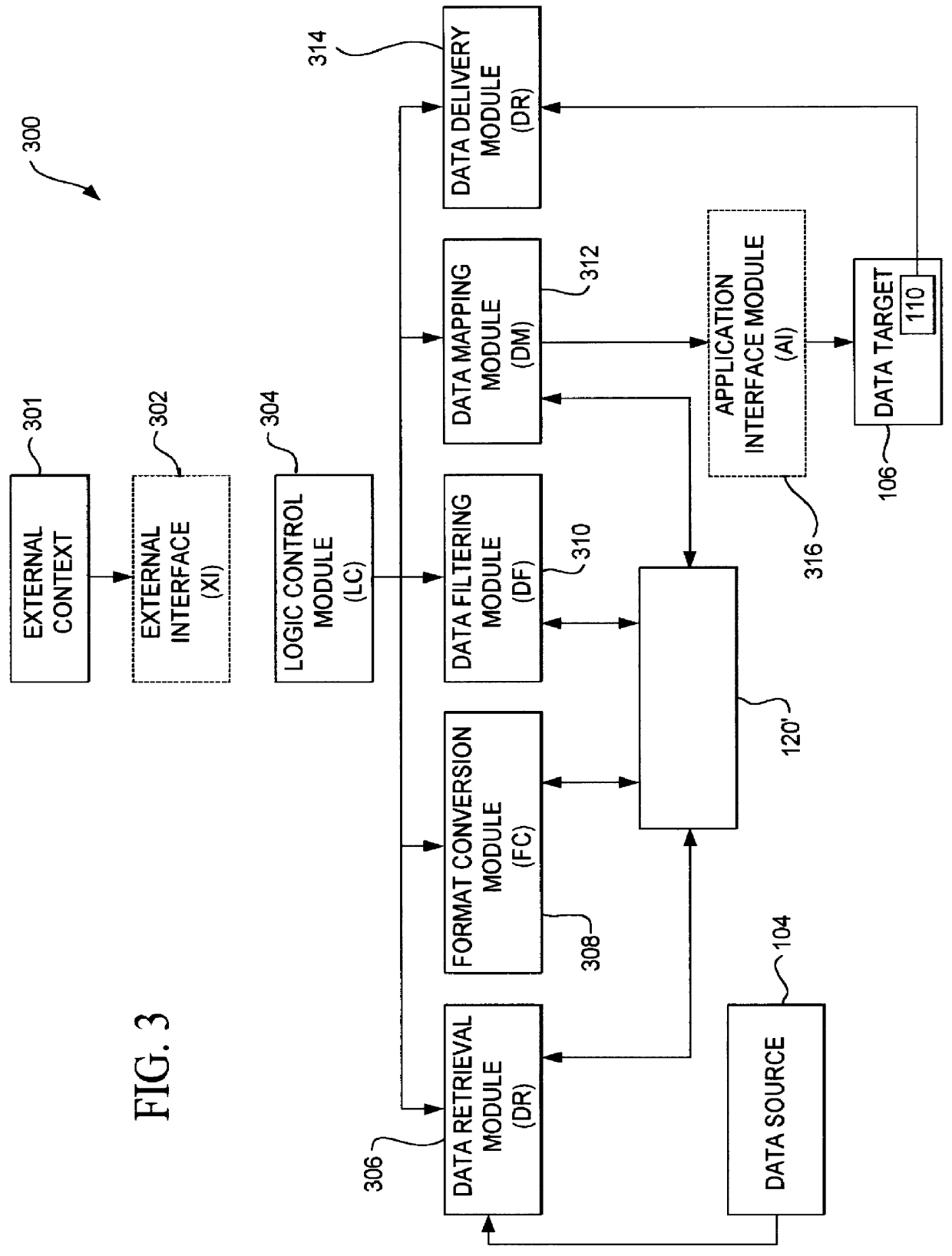
A data acquisition and delivery system for performing data delivery tasks is disclosed. This system uses a computer running software to acquire source data from a selected data source, to process (e.g. filter, format convert) the data, if desired, and to deliver the resulting delivered data to a data target. The system is designed to access remote and / or local data sources and to deliver data to remote and / or local data targets. The data target might be an application program that delivers the data to a file or the data target may simply be a file, for example. To obtain the delivered data, the software performs processing of the source data as appropriate for the particular type of data being retrieved, for the particular data target and as specified by a user, for example. The system can communicate directly with a target application program, telling the target application to place the delivered data in a particular location in a particular file. The system provides an external interface to an external context. If the external context is a human, the external interface may be a graphical user interface, for example. If the external context is another software application, the external interface may be an OLE interface, for example. Using the external interface, the external context is able to vary a variety of parameters to define data delivery tasks as desired. The system uses a unique notation that includes a plurality of predefined parameters to define the data delivery tasks and to communicate them to the software.
Owner:E BOTZ COM INC A DELAWARE +2
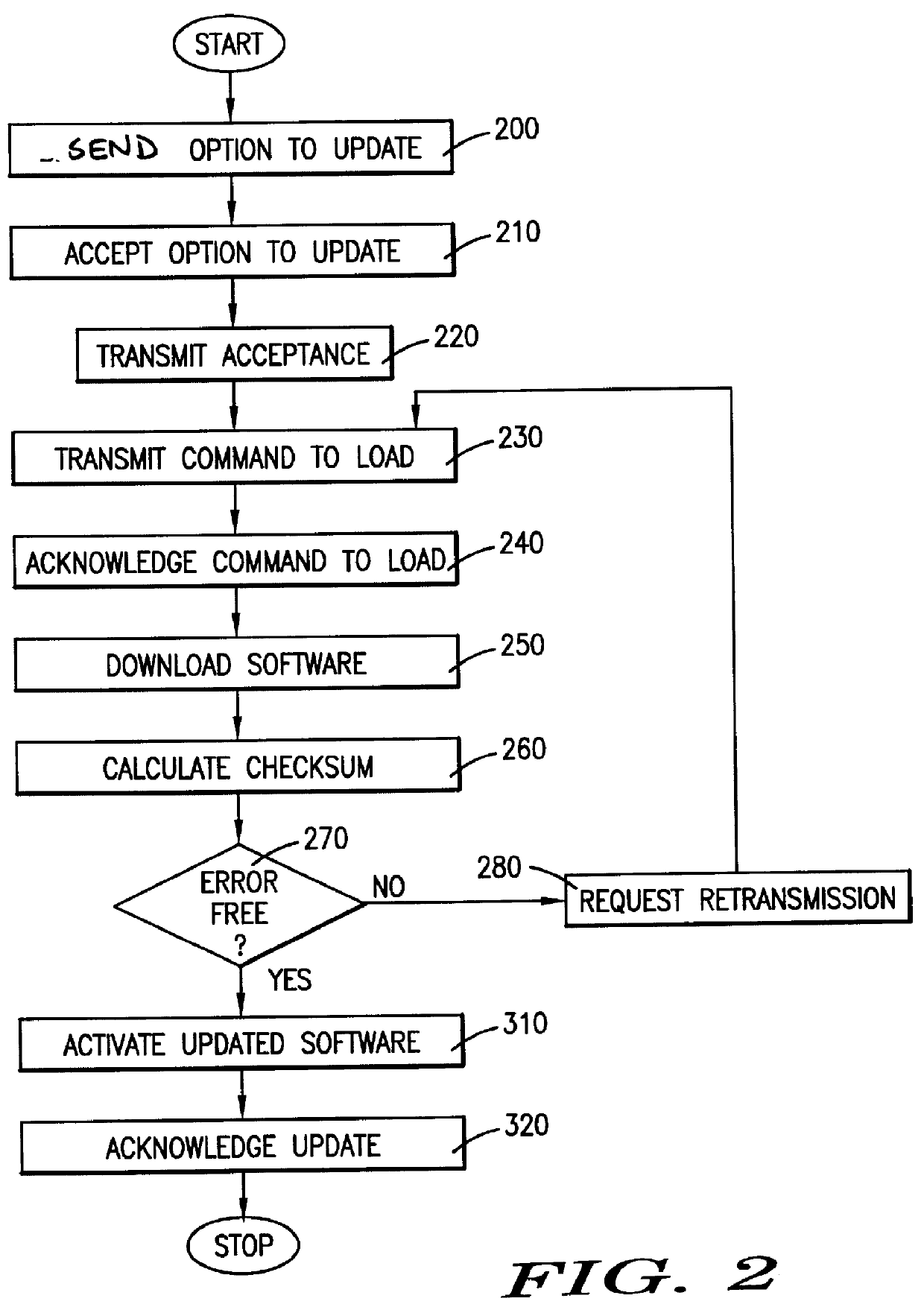
Method for downloading control software to a cellular telephone
InactiveUS6023620ACordless telephonesRadio/inductive link selection arrangementsChecksumControl software
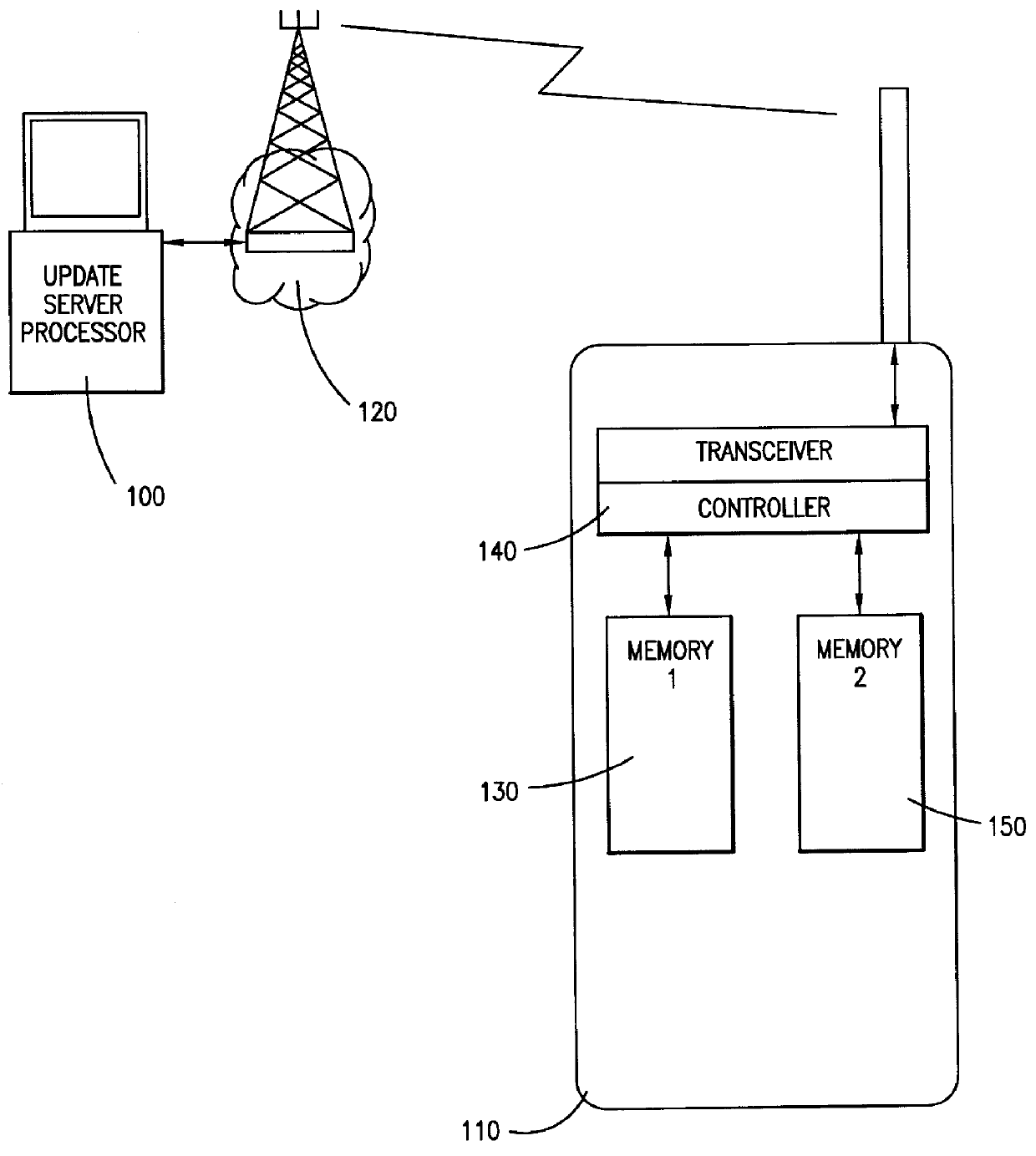
The present invention comprises a method and apparatus for downloading software into a remotely located cellular telephone via wireless communication. The cellular telephone includes two memories for storing software with one memory storing the current software and the second memory available for downloading new software. The present invention further includes a processor in communication with the cellular telephone via cellular telephone network. The processor contains the new software and controls the downloading of the software from the processor into the cellular telephone memory. The cellular telephone includes a controller for loading the received software into the cellular telephone memory and for performing a checksum on the new software.
Owner:TELEFON AB LM ERICSSON (PUBL)
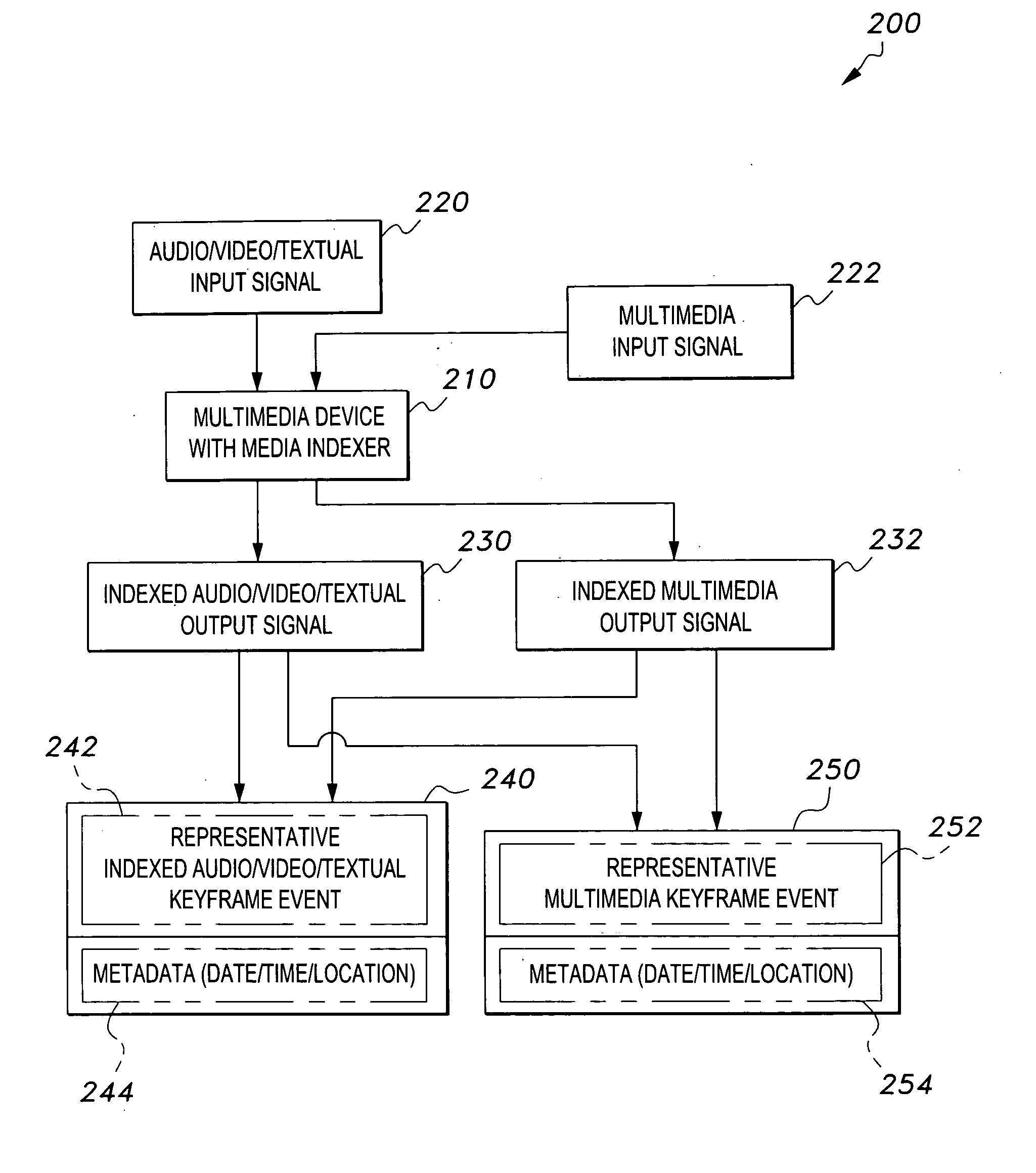
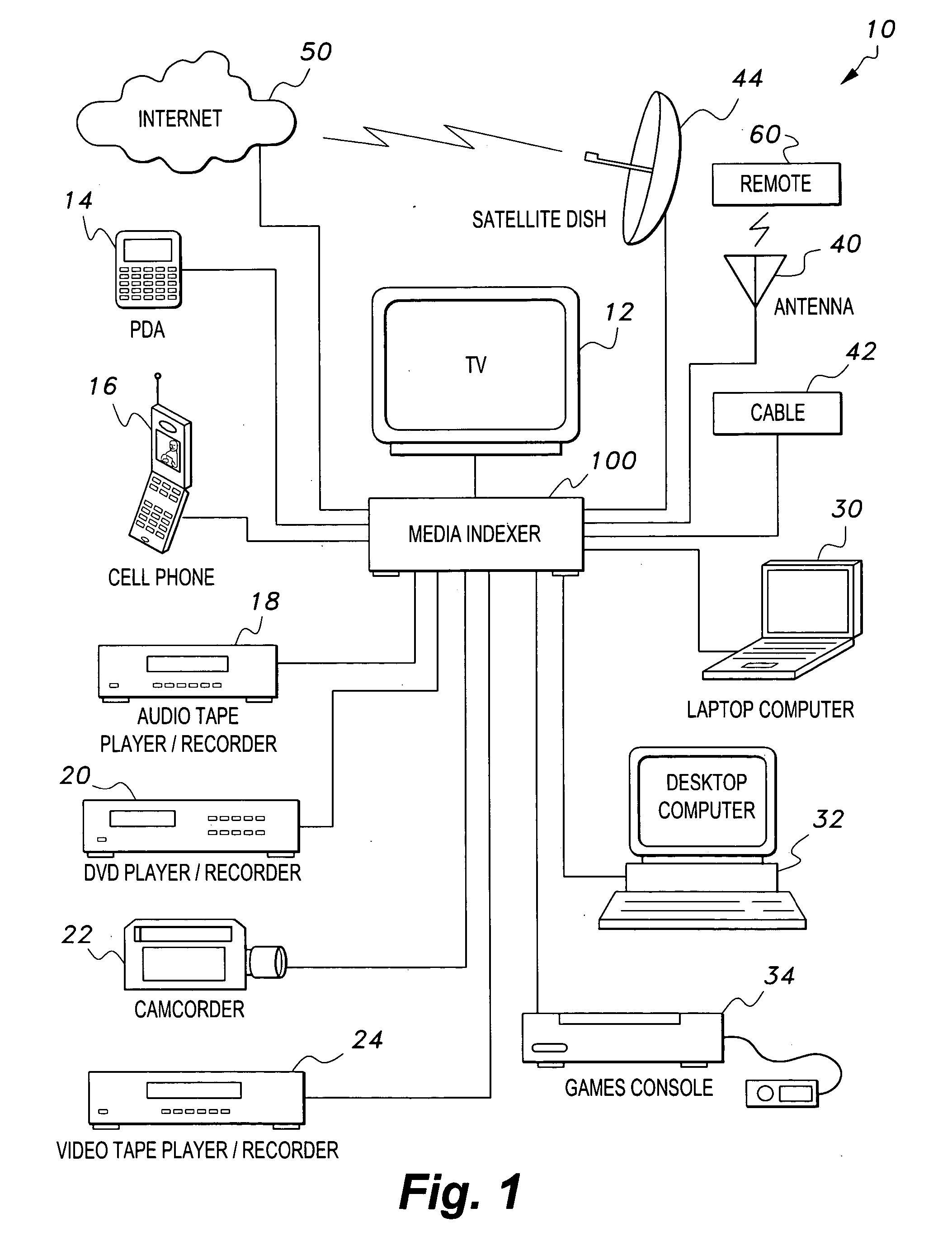
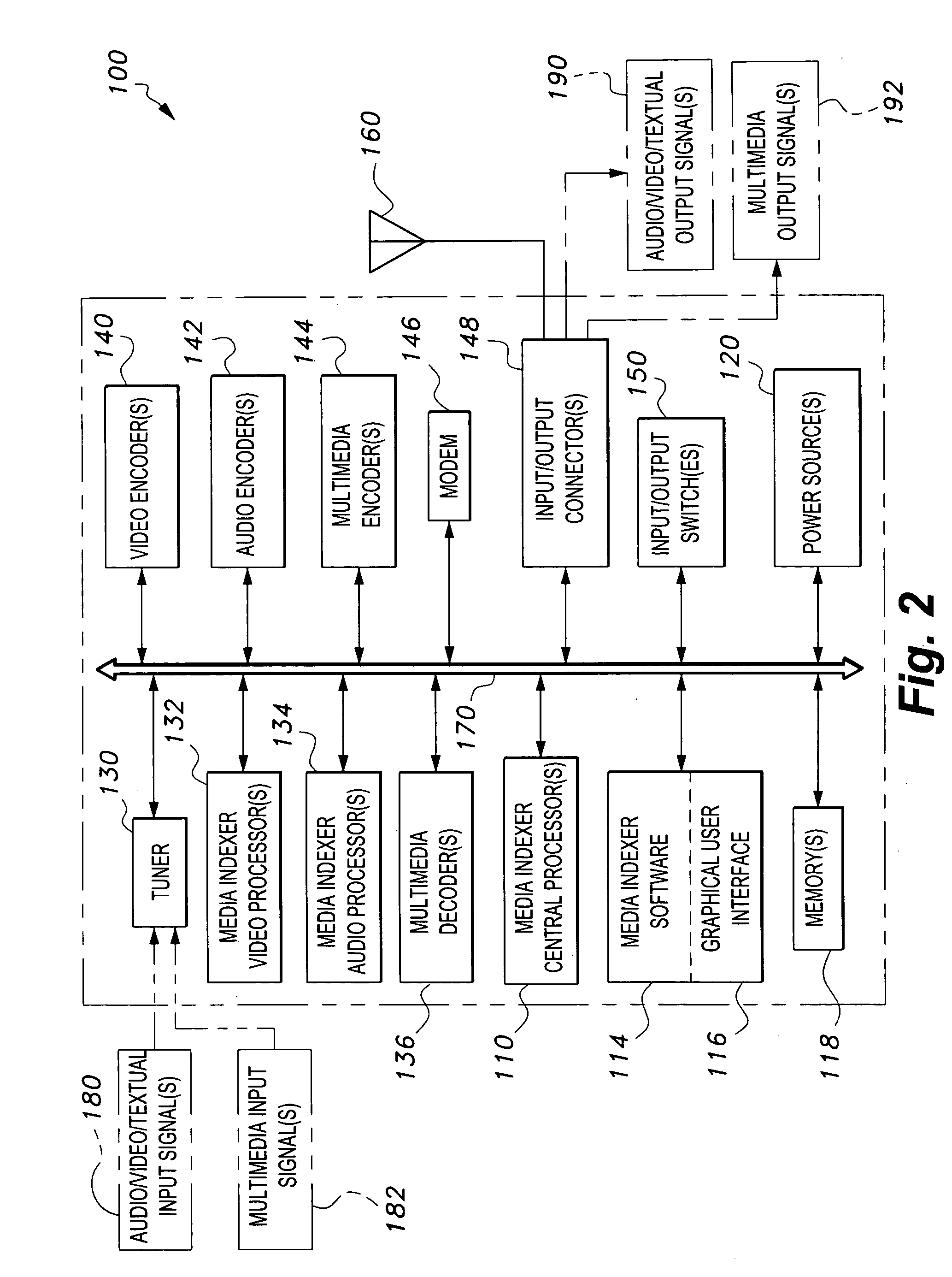
Media indexer
InactiveUS20050033758A1Inexpensive and dependable and fully effectiveTelevision system detailsPeptide/protein ingredientsData operationsFile sharing
A media indexer method, a media indexer, and / or a media indexer computer useable medium. The media indexer includes a central processor and a memory carrying thereon media indexer software which carries out steps including receiving a media signal, identifying keyframes of the media signal, establishing metadata for each identified keyframe, tagging each identified keyframe with metadata established for the associated keyframe, and outputting the media signal in a form unchanged from the received media signal, and / or a form including identified keyframes of the received media signal, each identified keyframe including a representative media keyframe event with metadata associated with the corresponding media keyframe event. The media indexer can generate parallel index signals that are synchronized to the time rate of the received media signal, and can input and output data using standard compatible file formats for file sharing and data manipulations with other compatible files and software.
Owner:BAXTER BRENT A
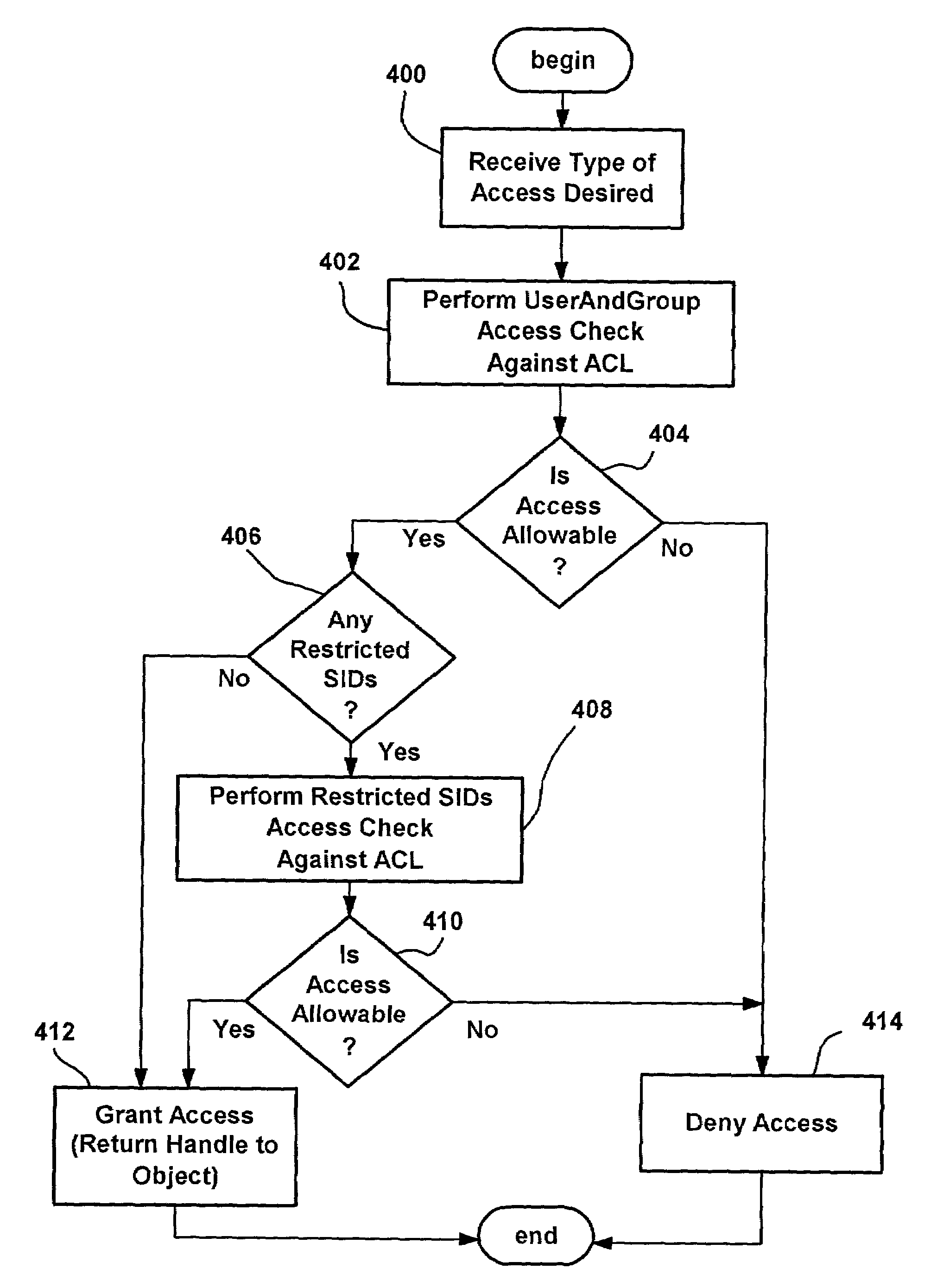
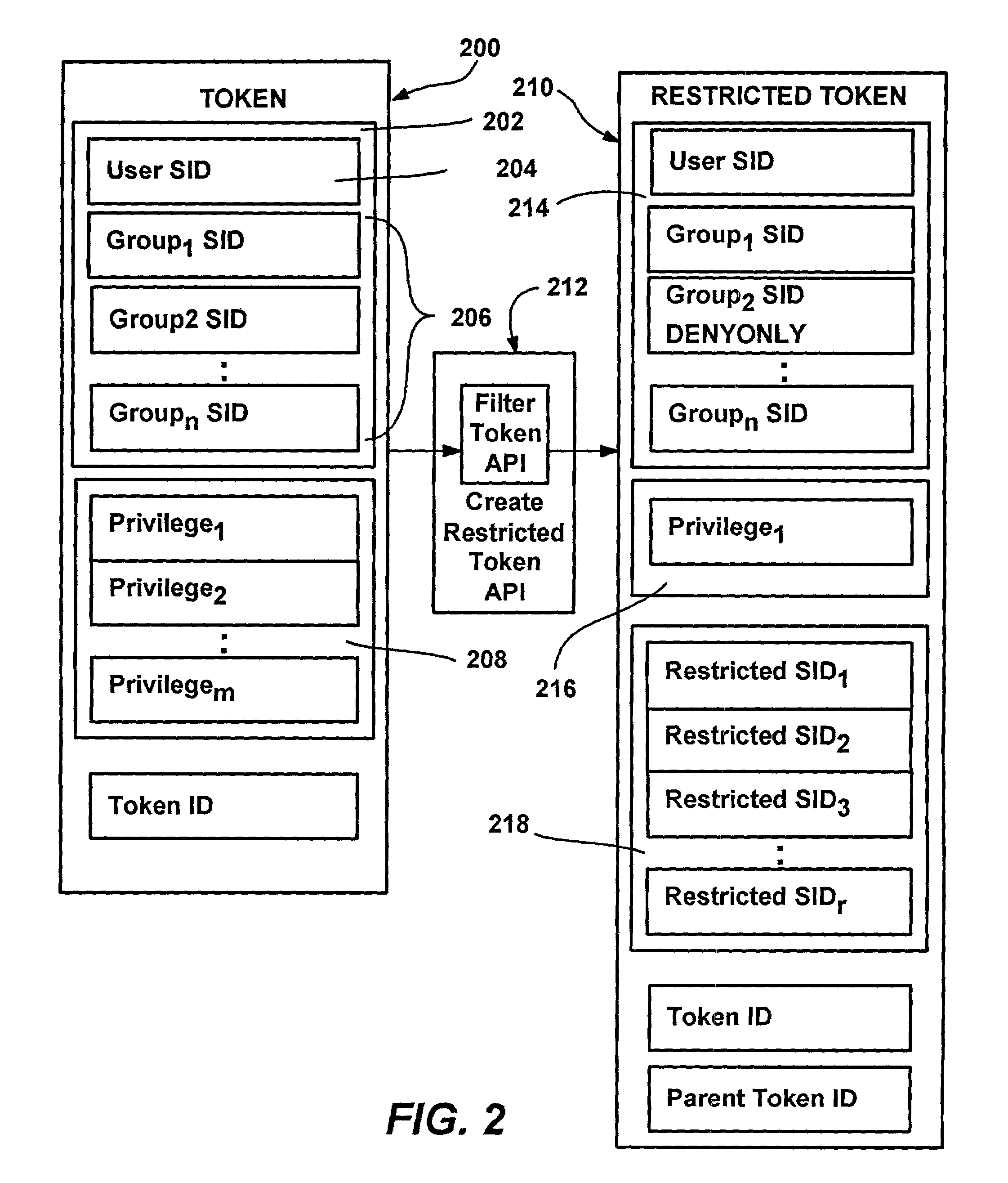
Policies for secure software execution
InactiveUS7350204B2Efficiently constrain (or prevent from running) everything on a machineDigital data processing detailsUnauthorized memory use protectionFile systemDigital signature
A system and method that automatically, transparently and securely controls software execution by identifying and classifying software, and locating a rule and associated security level for executing executable software. The security level may disallow the software's execution, restrict the execution to some extent, or allow unrestricted execution. To restrict software, a restricted access token may be computed that reduces software's access to resources, and / or removes privileges, relative to a user's normal access token. The rules that control execution for a given machine or user may be maintained in a restriction policy, e.g., locally maintained and / or in a group policy object distributable over a network. Software may be identified / classified by a hash of its content, by a digital signature, by its file system or network path, and / or by its URL zone. For software having multiple classifications, a precedence mechanism is provided to establish the applicable rule / security level.
Owner:MICROSOFT TECH LICENSING LLC
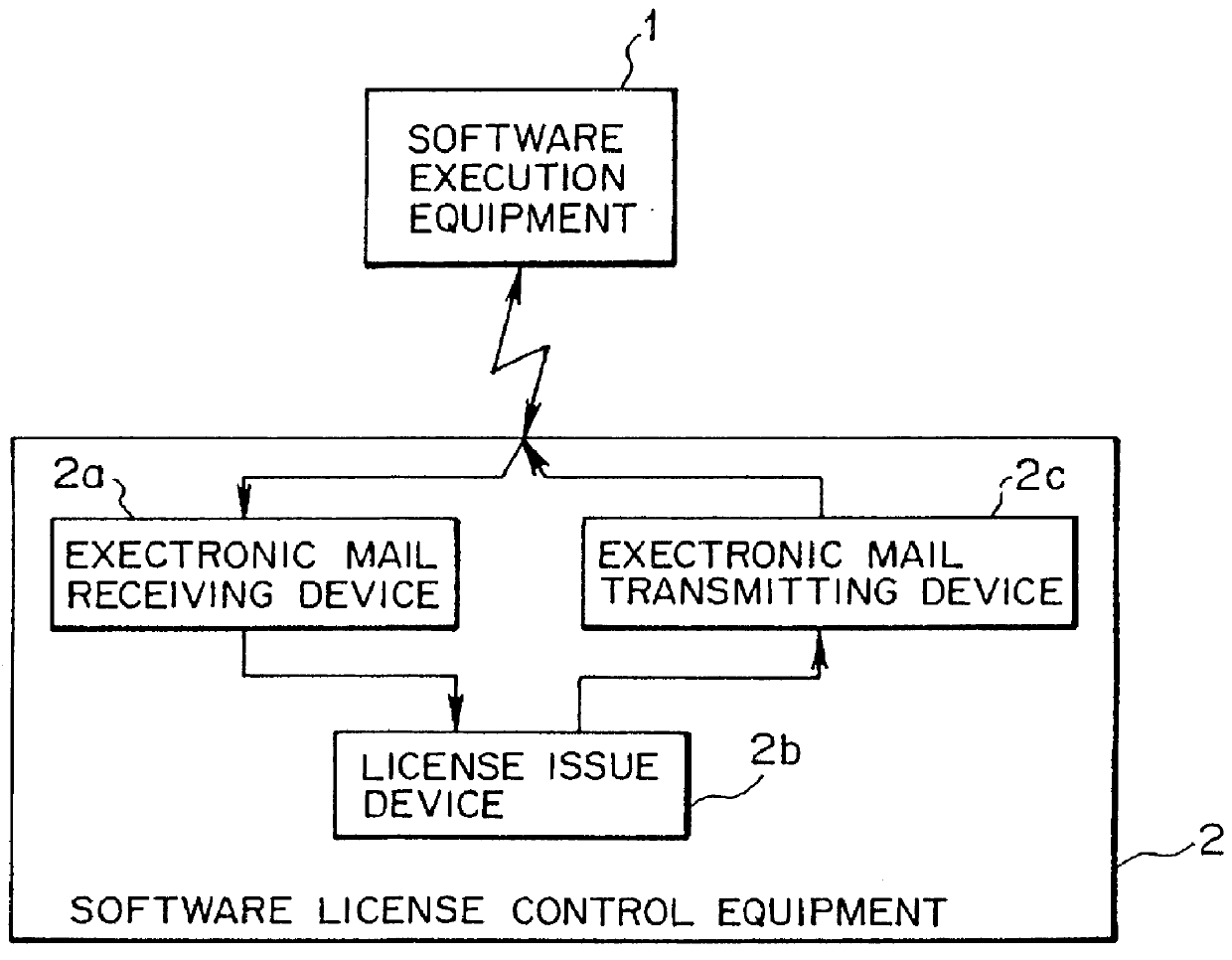
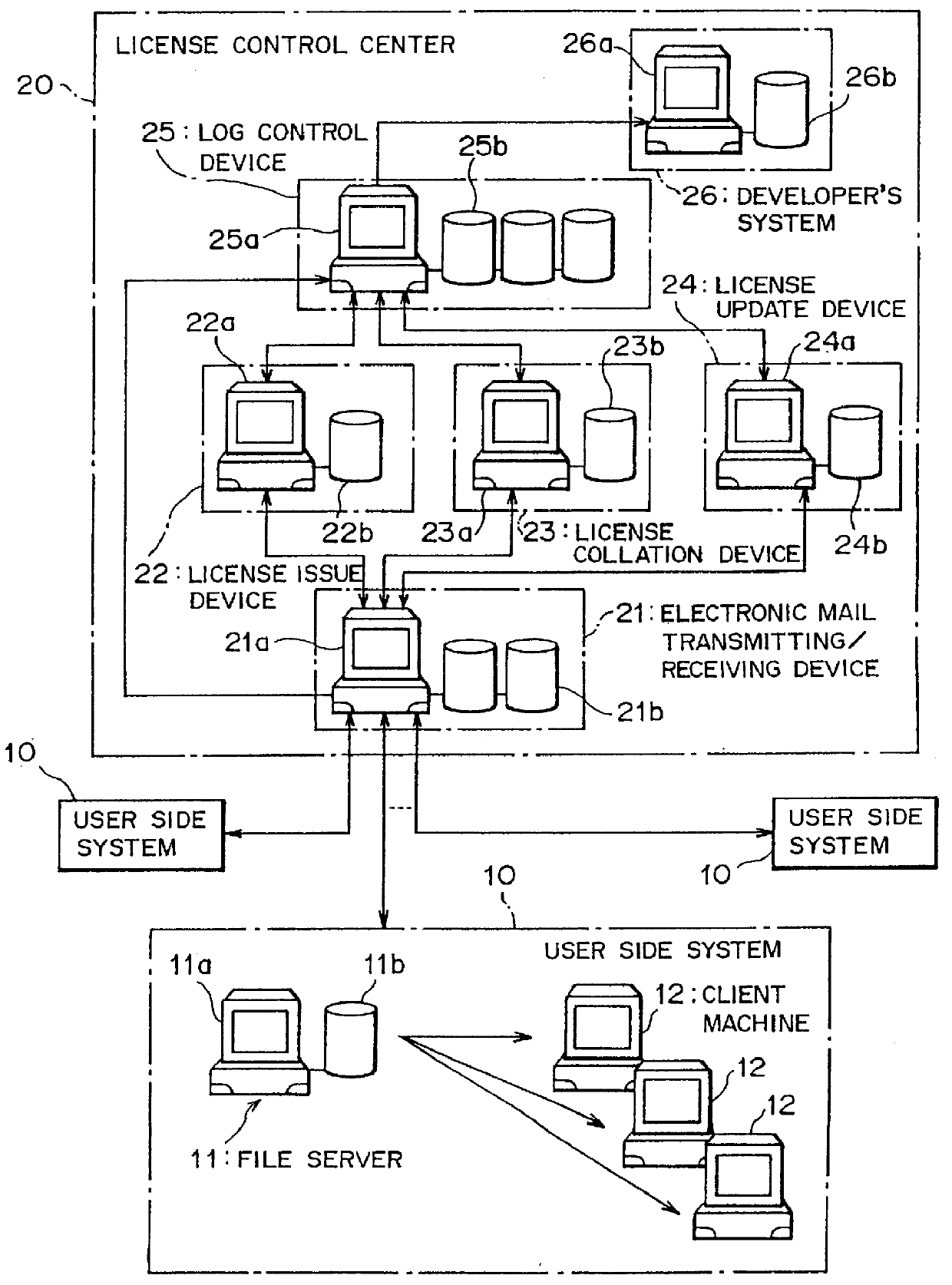
Software license control system and software license control equipment
InactiveUS6023766AImprove reliabilityEasy to operate and controlDigital data processing detailsUnauthorized memory use protectionSoftware licenseLicense control
The invention provides a software license control system and a software license control equipment that control a license for a software (application program) used in a computer, that realizes to make the license control of the software efficient, to enhance reliability of the license, and to simplify control operations by users. In order to achieve the object, the system according to the invention is provided with a software execution equipment that executes the software on which a license control software is added and a software license control equipment that controls the license for the software. The system is so designed as to interchange information relating to the license for the software between the software execution equipment and the software license control equipment by means of an electronic mail.
Owner:SOCIONEXT INC
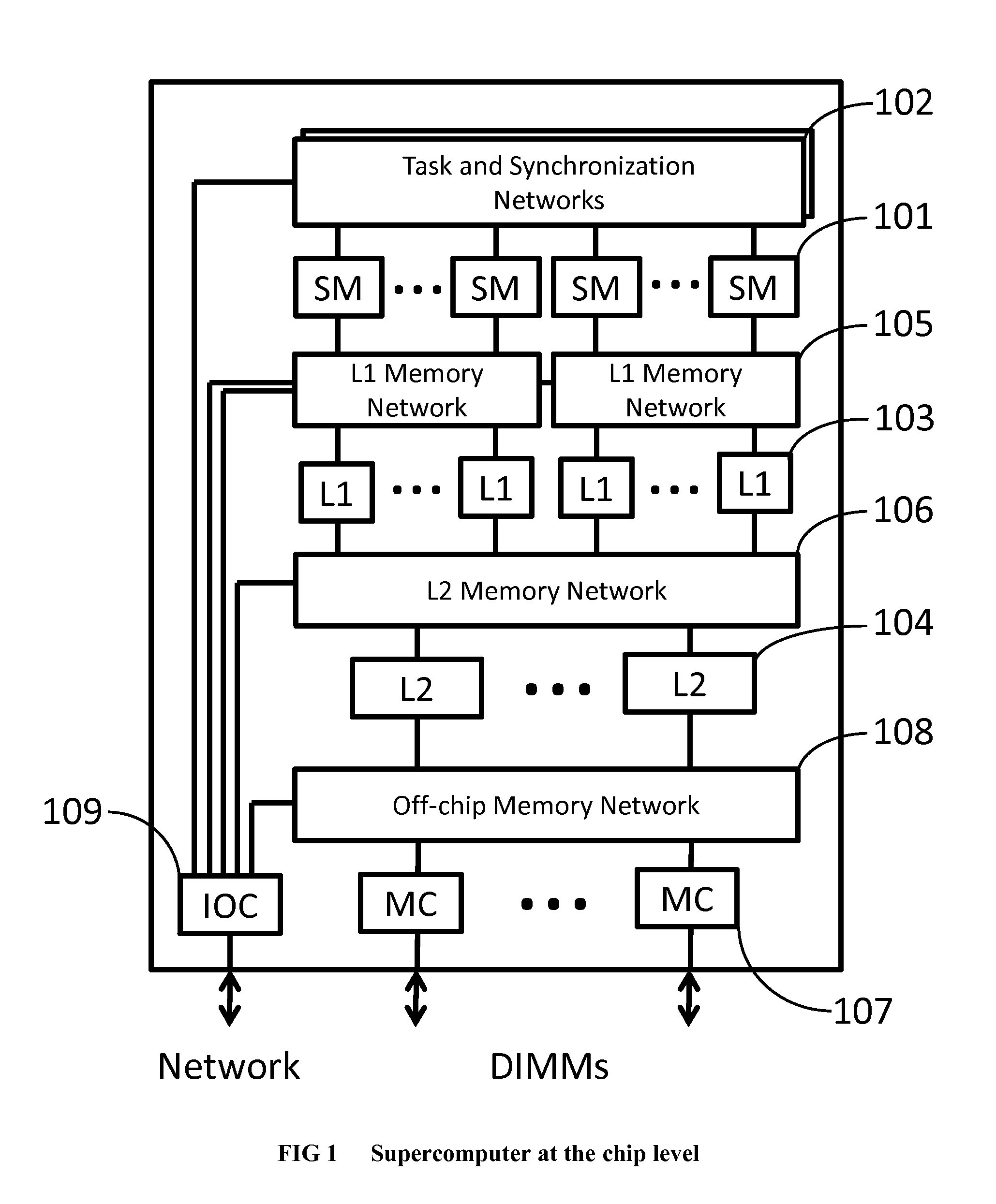
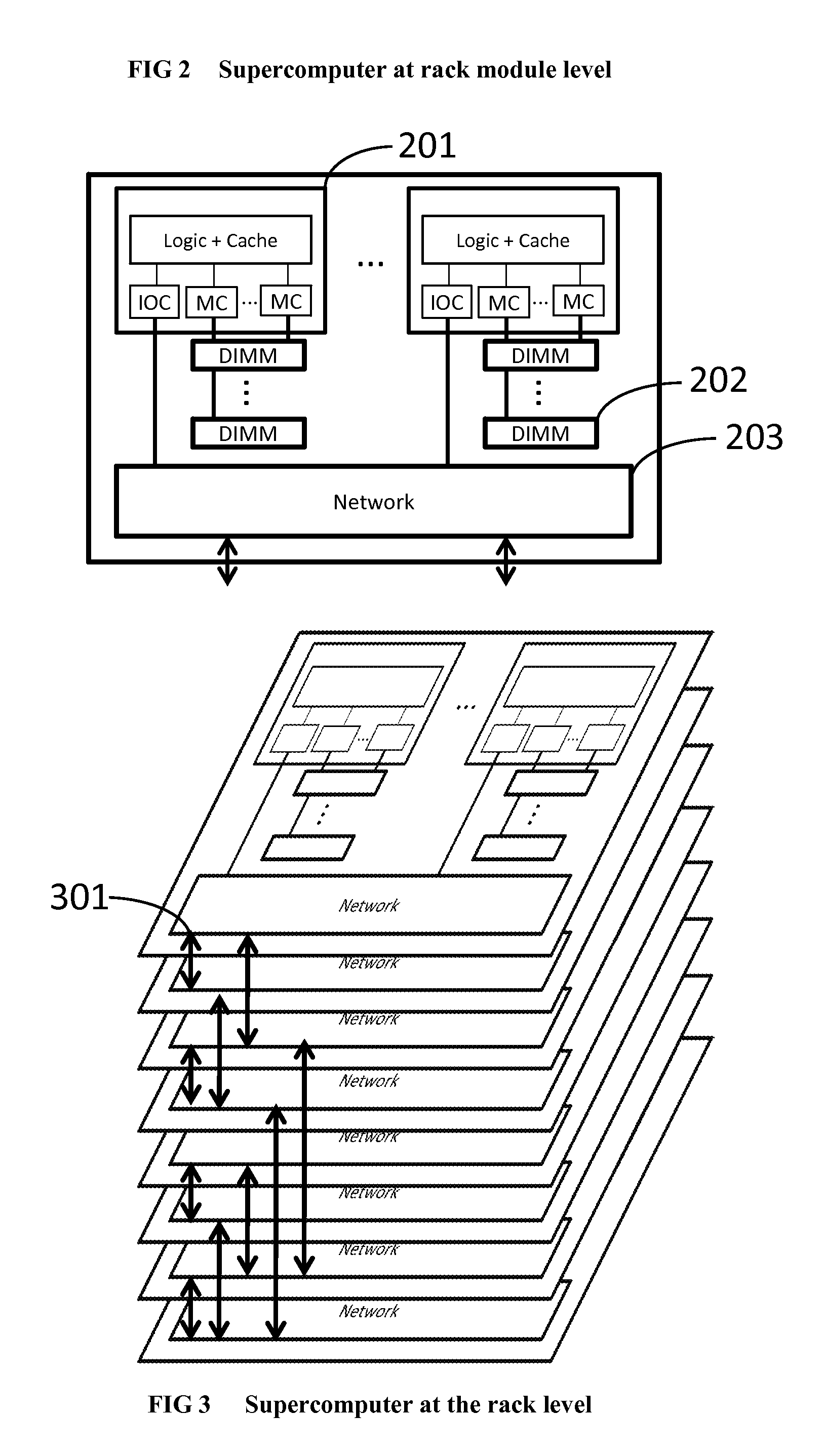
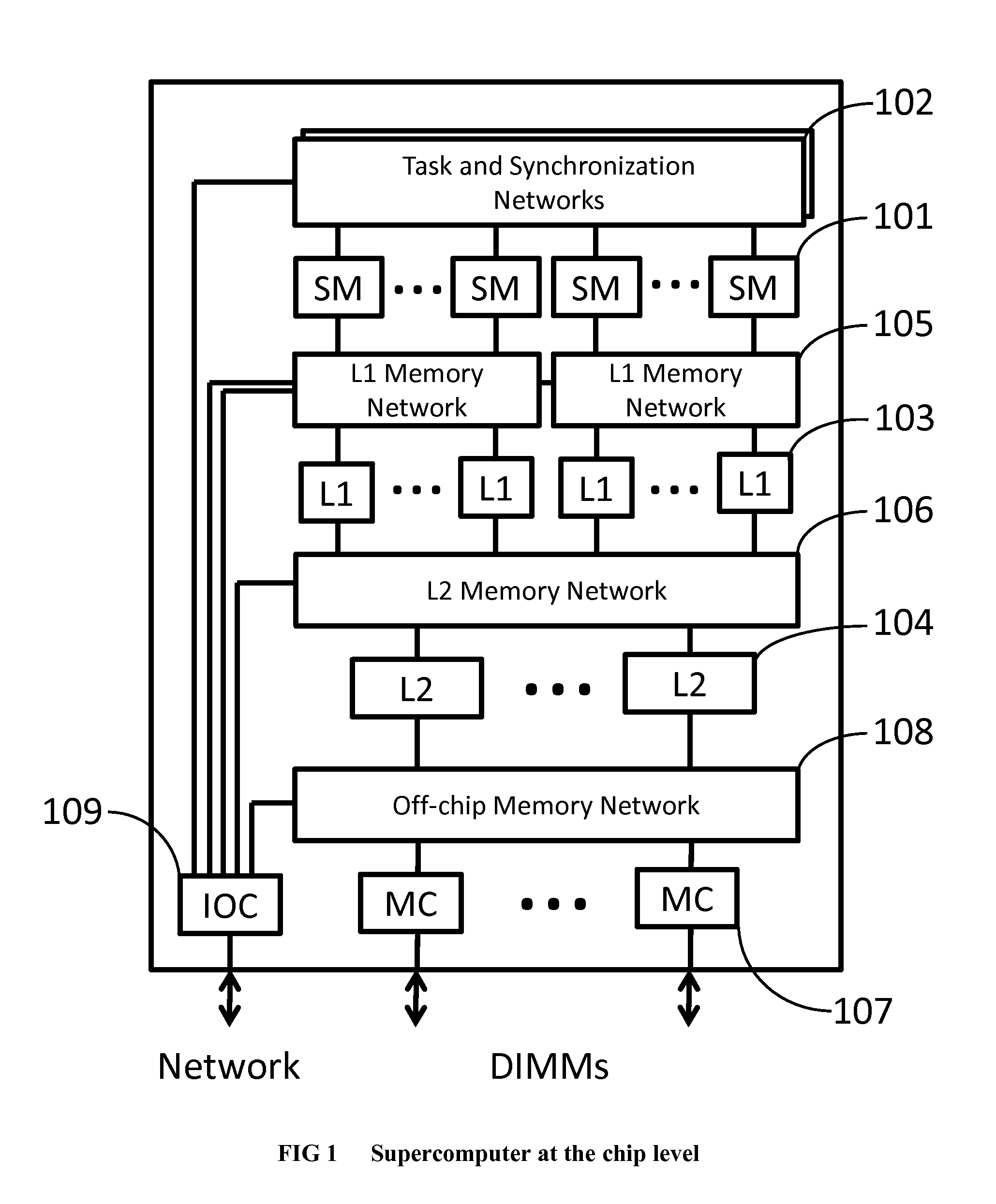
Method and system for converting a single-threaded software program into an application-specific supercomputer
ActiveUS20130125097A1Improve efficiencyLow overhead implementationMemory architecture accessing/allocationTransformation of program codeSupercomputerComputer architecture
The invention comprises (i) a compilation method for automatically converting a single-threaded software program into an application-specific supercomputer, and (ii) the supercomputer system structure generated as a result of applying this method. The compilation method comprises: (a) Converting an arbitrary code fragment from the application into customized hardware whose execution is functionally equivalent to the software execution of the code fragment; and (b) Generating interfaces on the hardware and software parts of the application, which (i) Perform a software-to-hardware program state transfer at the entries of the code fragment; (ii) Perform a hardware-to-software program state transfer at the exits of the code fragment; and (iii) Maintain memory coherence between the software and hardware memories. If the resulting hardware design is large, it is divided into partitions such that each partition can fit into a single chip. Then, a single union chip is created which can realize any of the partitions.
Owner:GLOBAL SUPERCOMPUTING CORP
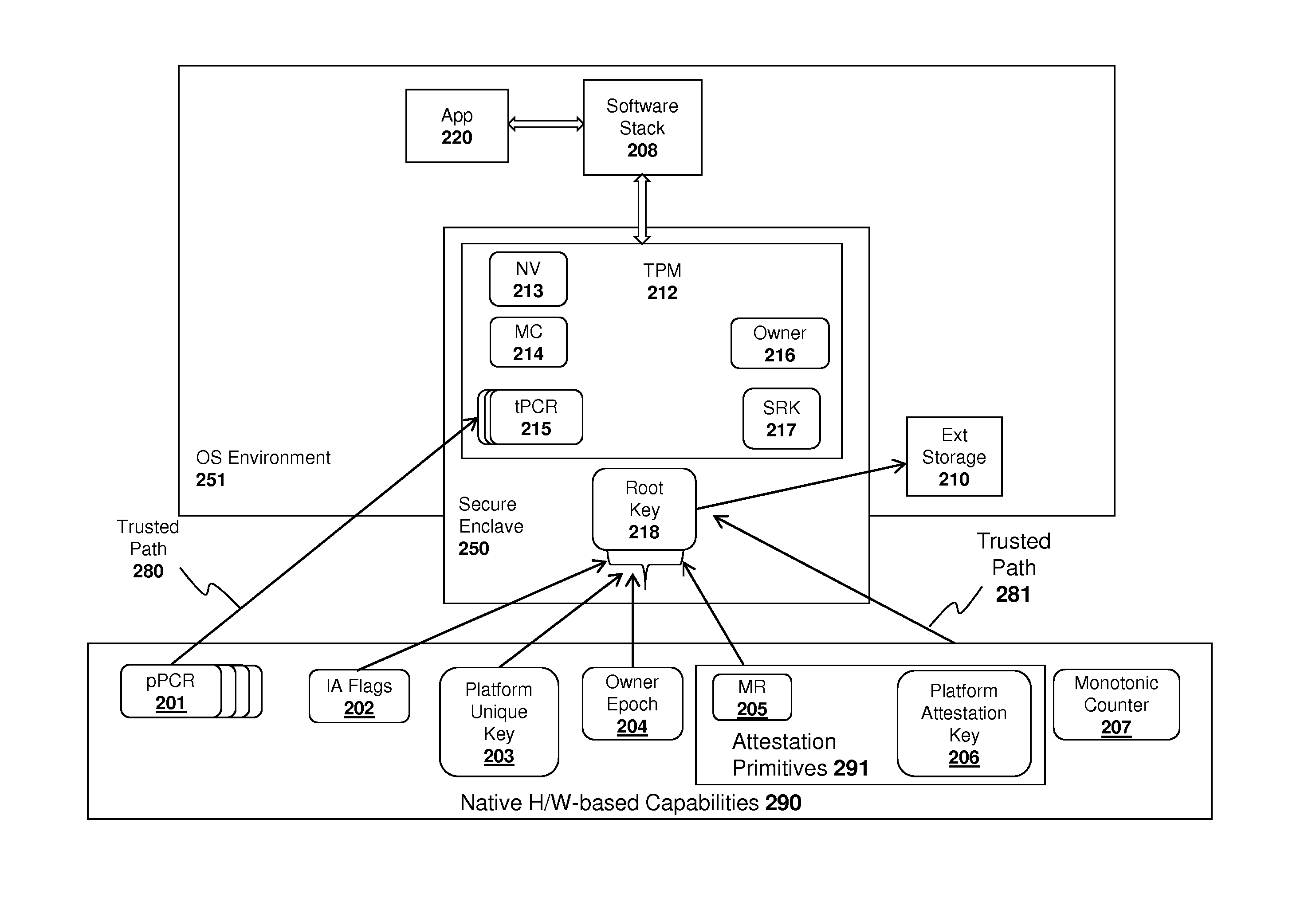
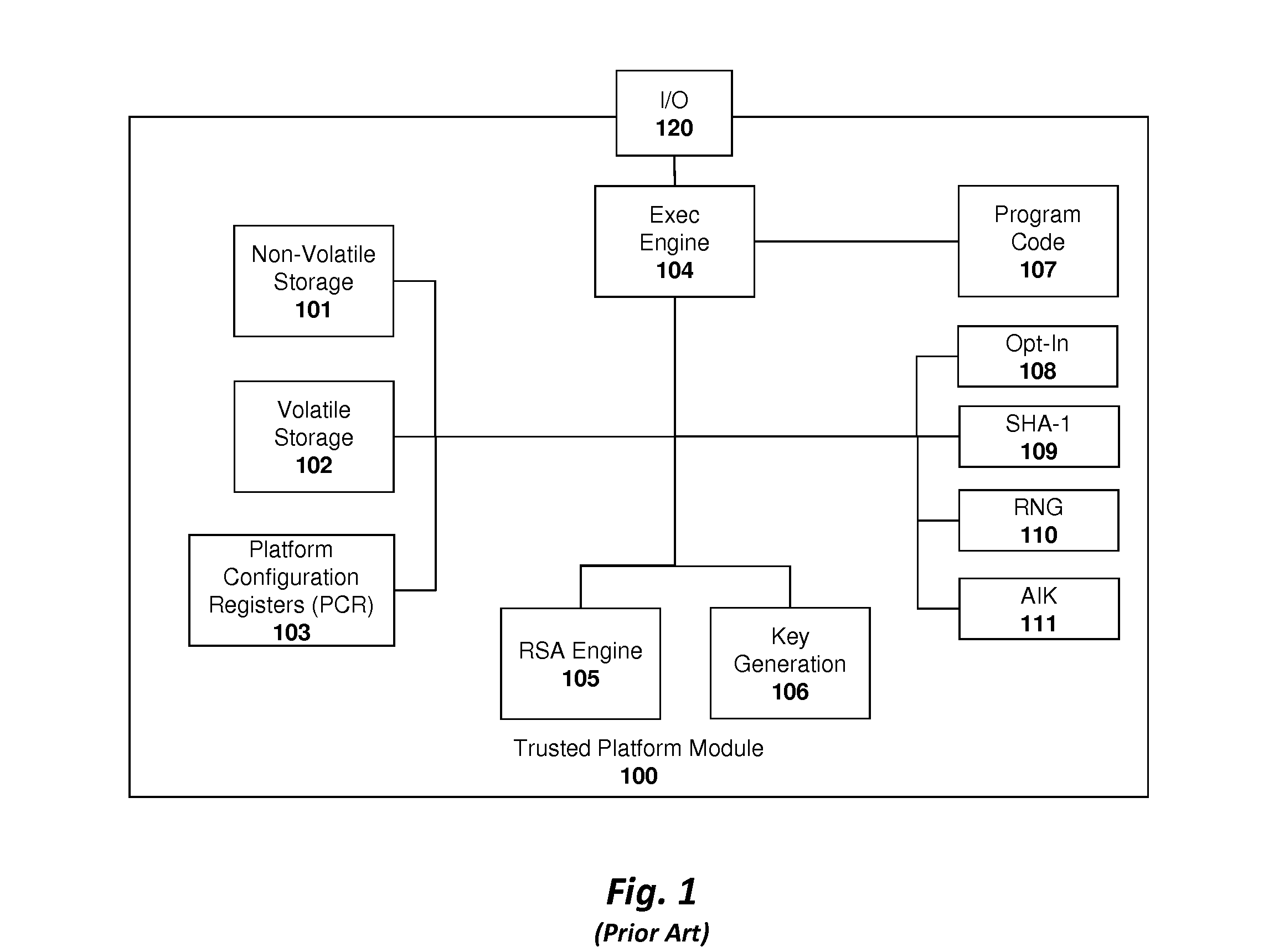
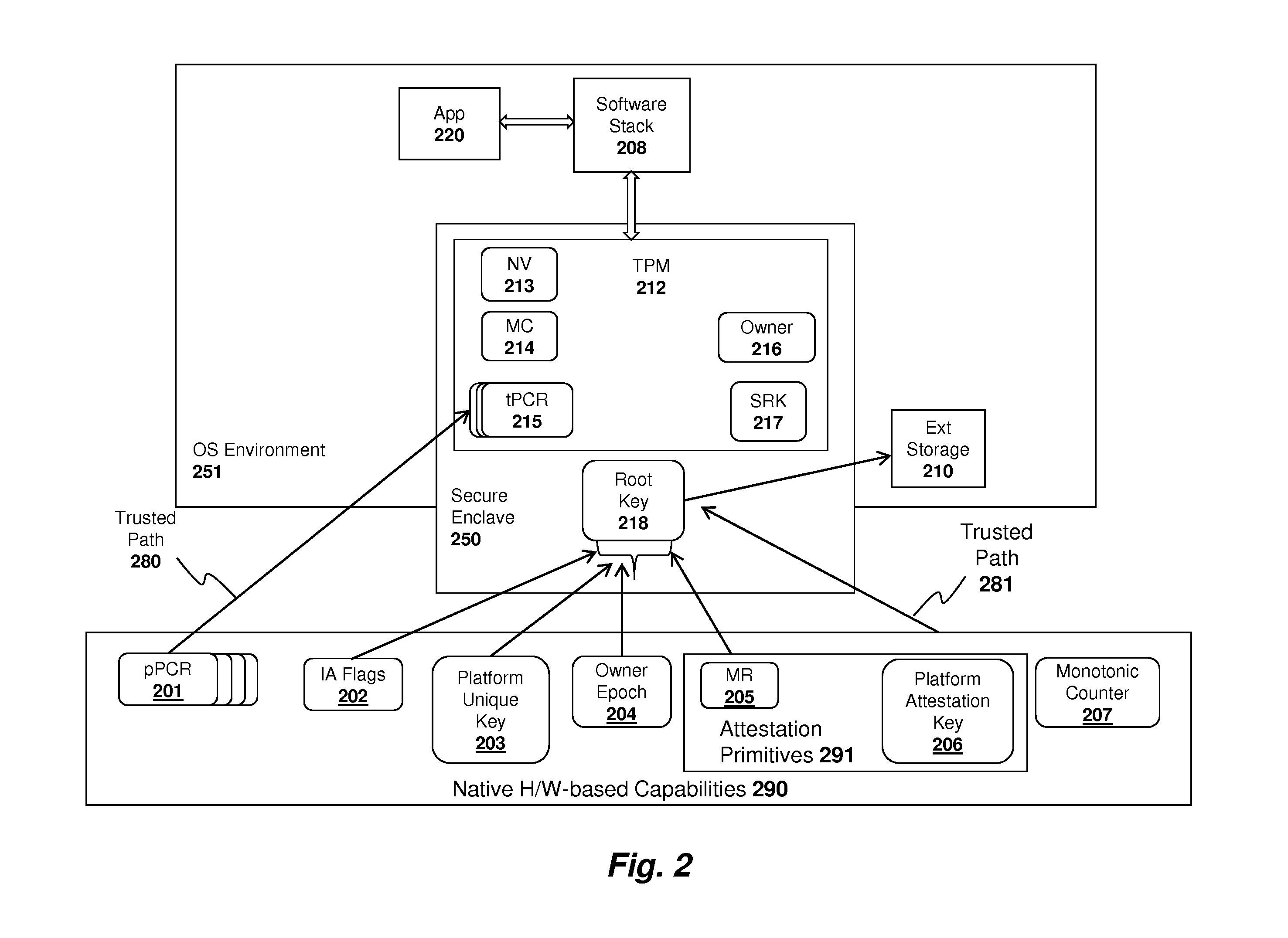
System and method for implementing a trusted dynamic launch and trusted platform module (TPM) using secure enclaves
ActiveUS20120163589A1Public key for secure communicationInternal/peripheral component protectionTrusted Platform ModuleControl register
An apparatus and method are described for implementing a trusted dynamic launch and trusted platform module (TPM) using a secure enclave. For example, a computer-implemented method according to one embodiment of the invention comprises: initializing a secure enclave in response to a first command, the secure enclave comprising a trusted software execution environment which prevents software executing outside the enclave from having access to software and data inside the enclave; and executing a trusted platform module (TPM) from within the secure enclave, the trusted platform module securely reading data from a set of platform control registers (PCR) in a processor or chipset component into a memory region allocated to the secure enclave.
Owner:INTEL CORP
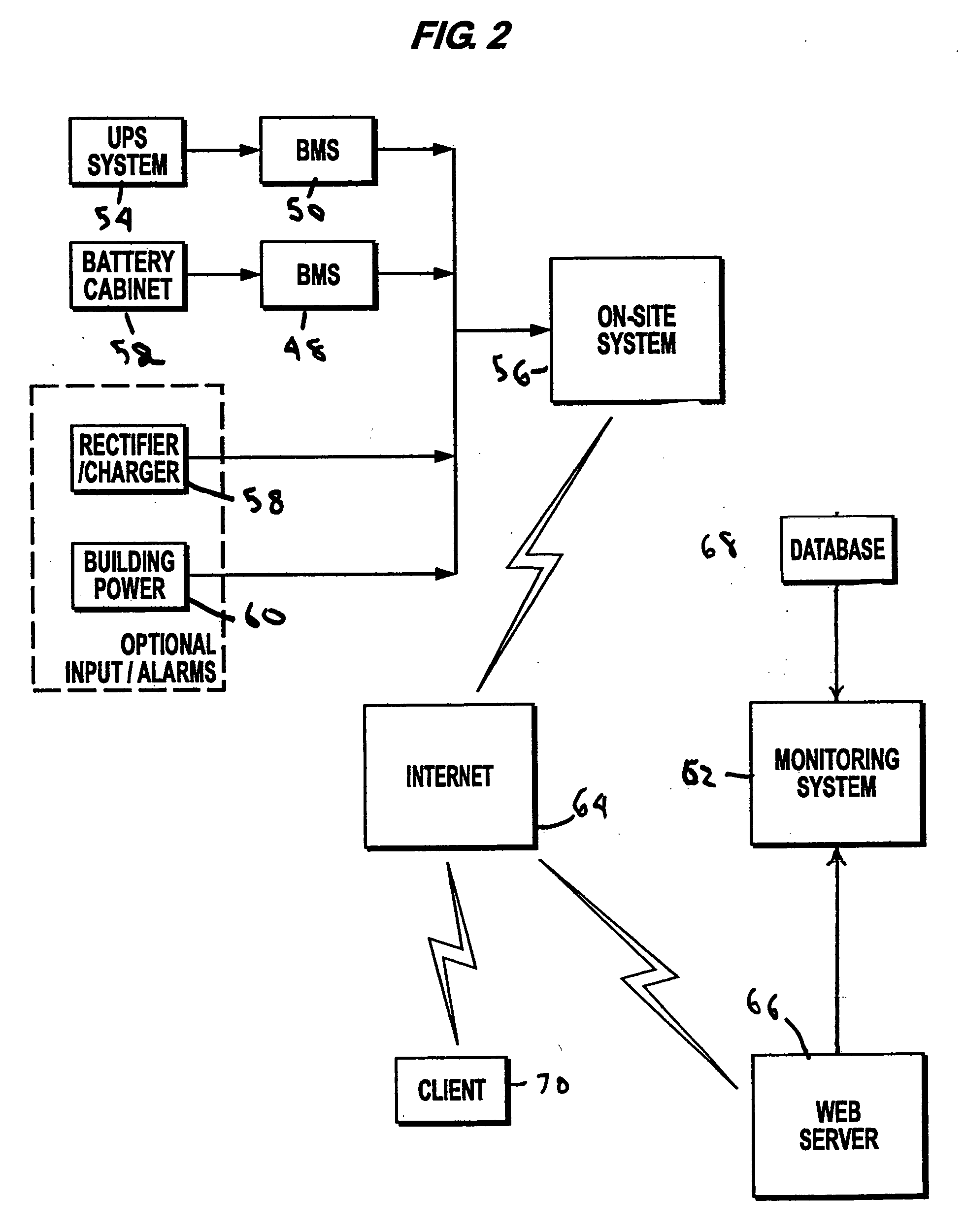
Method and system for monitoring power supplies
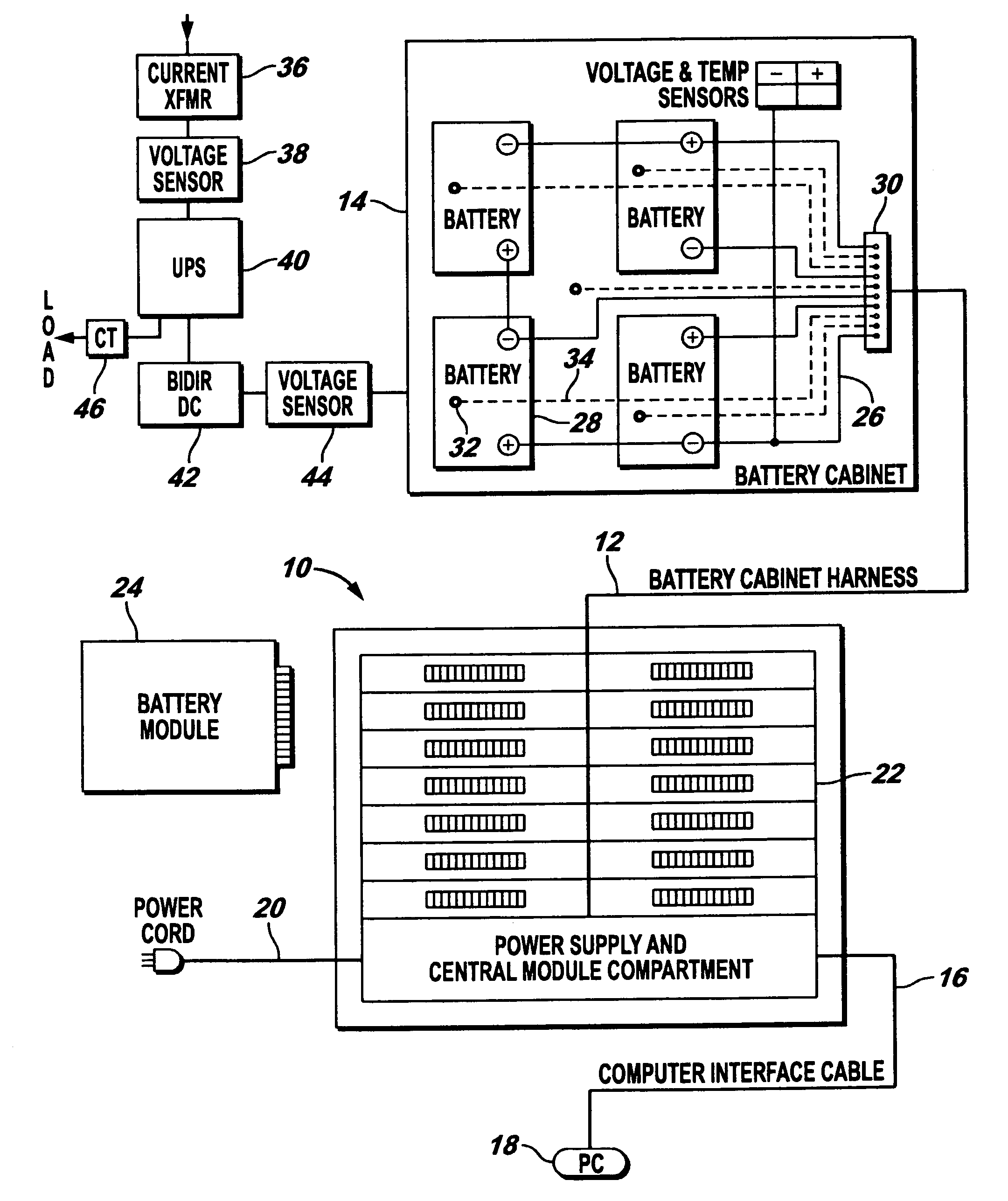
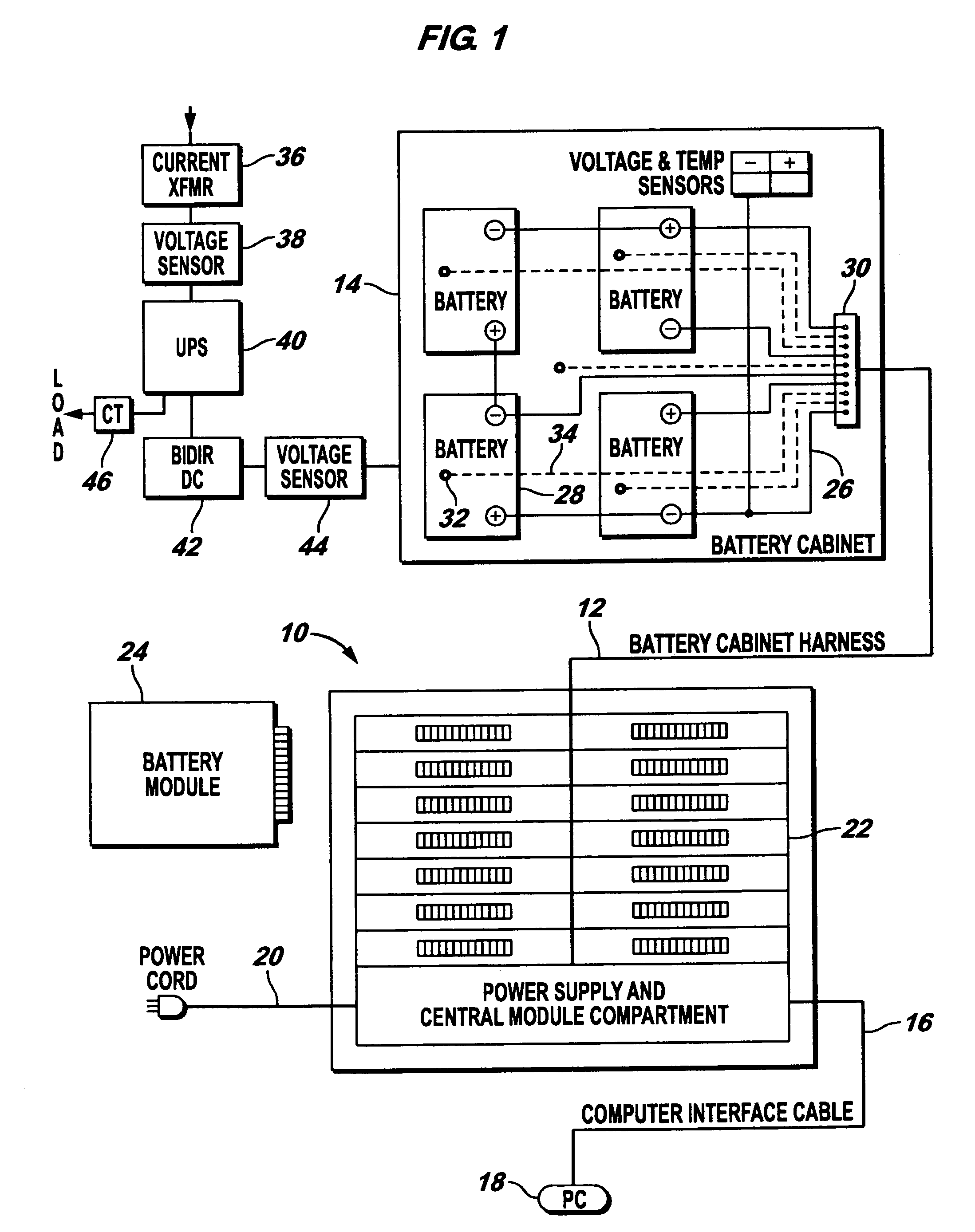
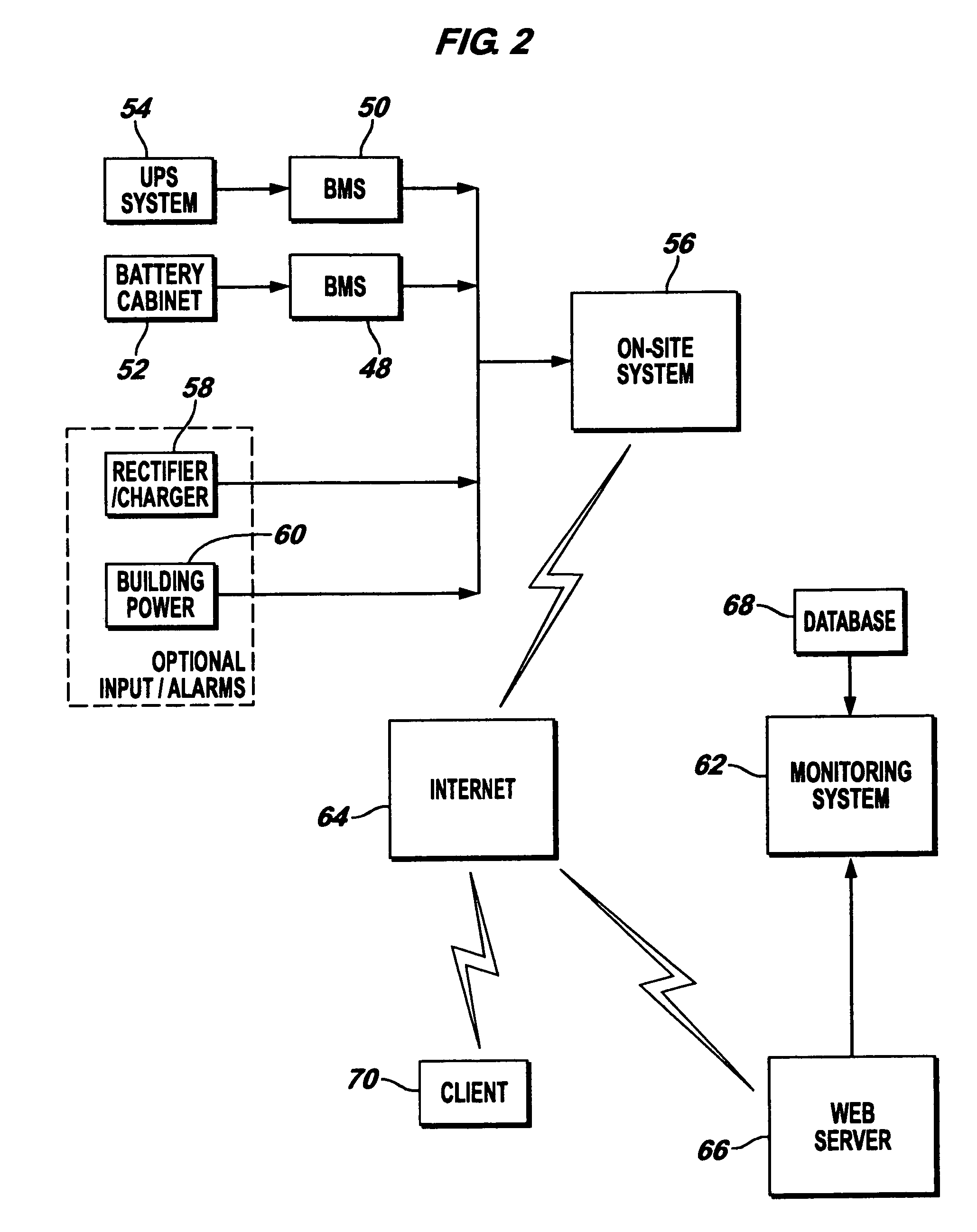
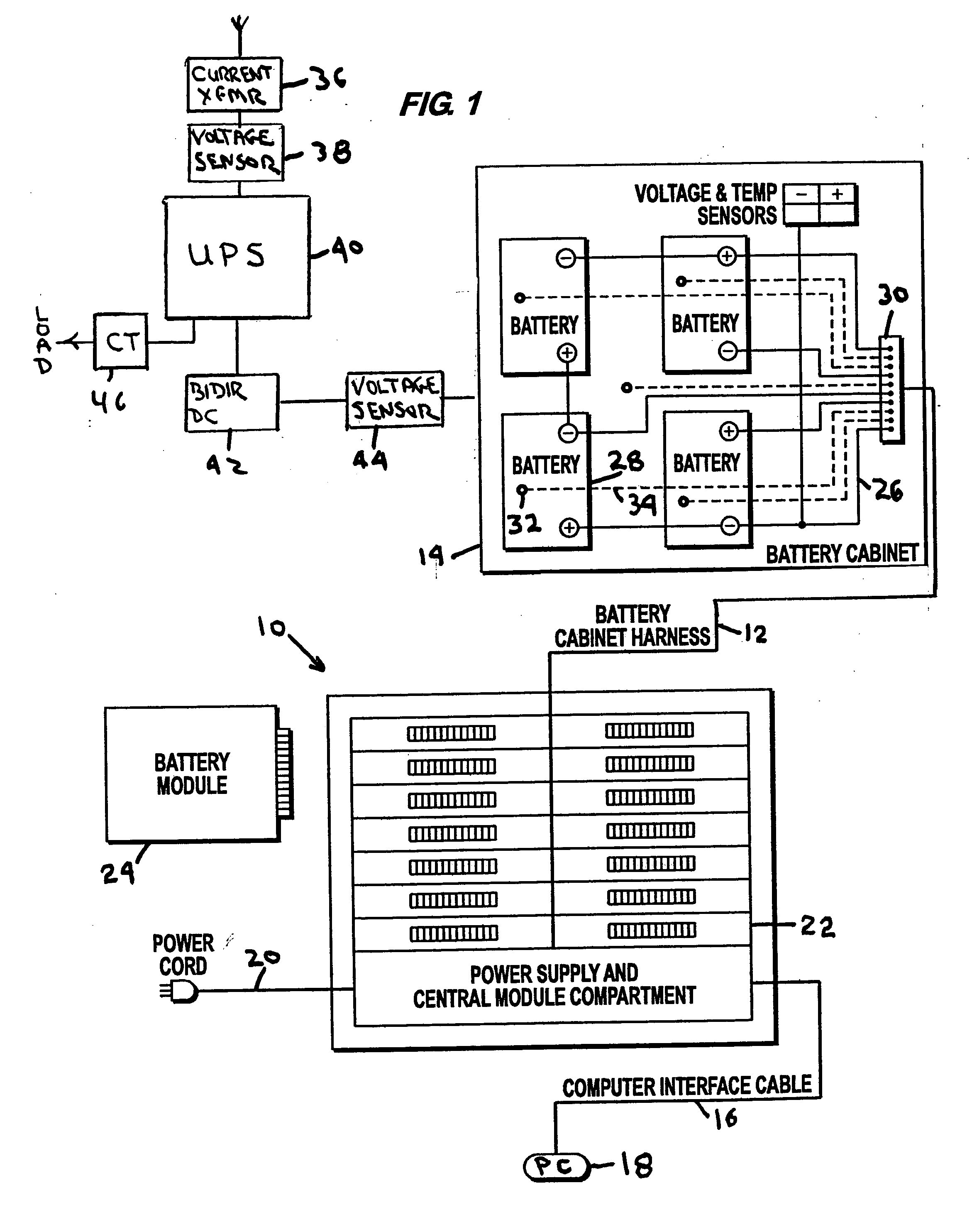
InactiveUS7184905B2Batteries circuit arrangementsElectric devicesElectrical batteryElectric power system
An electrical power (AC / DC) monitoring system remotely monitoring batteries and electrical power systems through a call center, providing continual monitoring, monthly reports, near real time viewing and service response. Modular by design, a plurality of individual input modules, which receive an analog voltage input, convert this signal to a digital format and send the digital signal to a central control which collects the data, then, at scheduled intervals, sends the collected data to a web server which contains the main software for the system. This software performs data comparisons, charts trends, predicts failures, plans and schedules service visits, then archives the data for future references. Alarm notifications are provided to the customer via Email, office phone (land line), cell phone (wireless), PDA, pager, etc. and can also be sent to a service provider to initiate the service response.
Owner:STEFAN DONALD A
Method and system for monitoring power supplies
An electrical power (AC / DC) monitoring system remotely monitoring batteries and electrical power systems through a call center, providing continual monitoring, monthly reports, near real time viewing and service response. Modular by design, a plurality of individual input modules, which receive an analog voltage input, convert this signal to a digital format and send the digital signal to a central control which collects the data, then, at scheduled intervals, sends the collected data to a web server which contains the main software for the system. This software performs data comparisons, charts trends, predicts failures, plans and schedules service visits, then archives the data for future references. Alarm notifications are provided to the customer via Email, office phone (land line), cell phone (wireless), PDA, pager, etc. and can also be sent to a service provider to initiate the service response.
Owner:STEFAN DONALD A
Workflow management system and method
InactiveUS20070208606A1Easy to editFacilitates economy of scale and processing efficiencyFinancePayment architectureStream managementSystems management
A computerized workflow management method and system to provide operational support for complex multi-step processes, having particular utility in supporting operations involving securitizations for which periodic valuation and distribution computations, disbursements and reporting must be set up and executed. The invention permits unification of manual operations and operations performed by legacy software, even if implemented with database structures different from the workflow management system, automated quality control, workflow status display and automatic updating of workflow status records. The method of workflow management involves creating an underlying database structure for recording the processing steps and other information required for each transaction, entering the necessary setup information by selection from lists of pre-stored information about processing functions, associated workflow events and milestones for the queues, mapping the data structures of the subsystem databases and the workflow management database to provide transparent interfacing and convenient manual entry of data were necessary, displaying for the user the workflow status of all transactions for which he or she is responsible, permitting menu driven initiation of required actions and automatically updating the database records for the universe of deals being managed by the system.
Owner:JPMORGAN CHASE BANK NA
Method and system for processing software dependencies in management of software packages
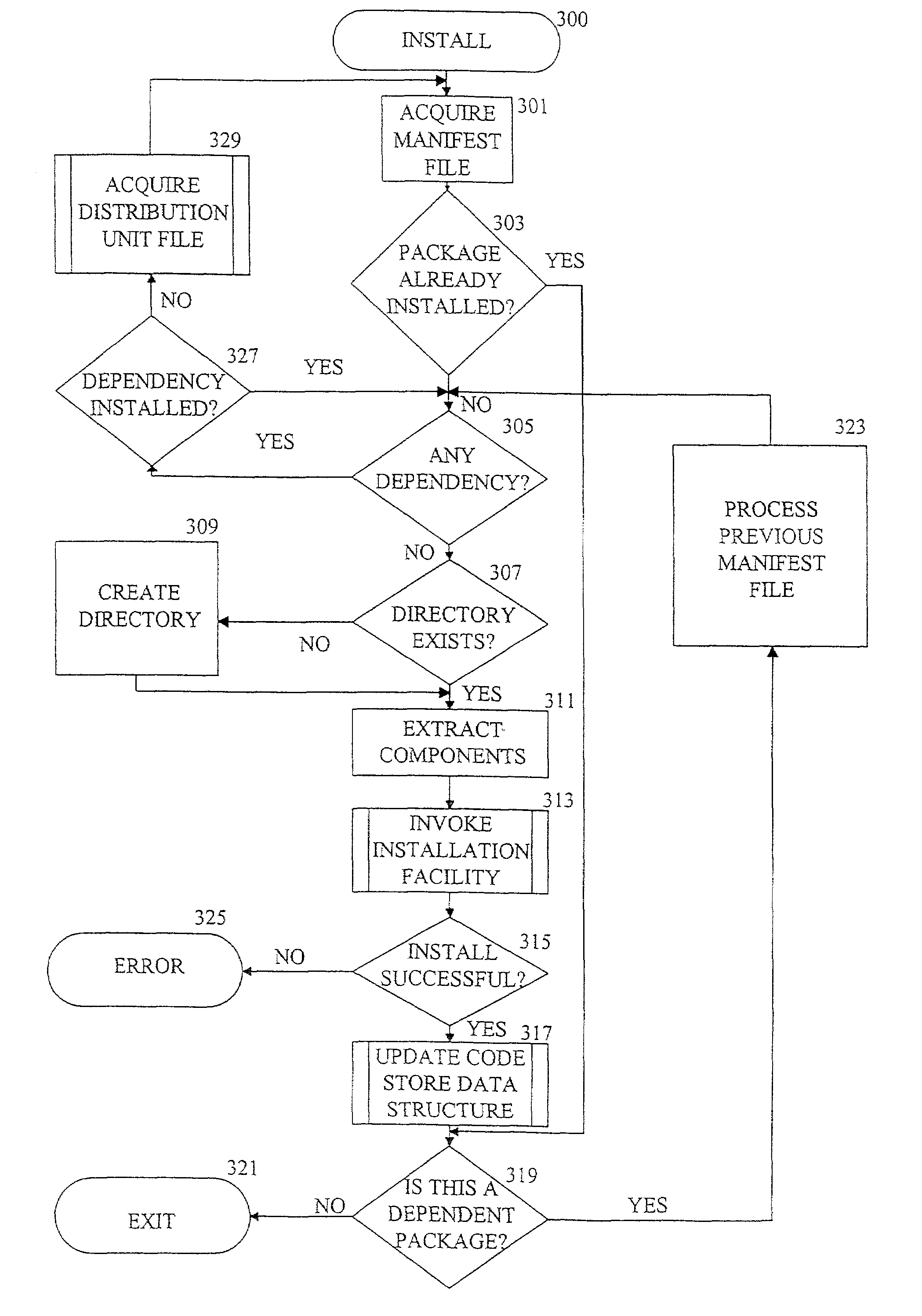
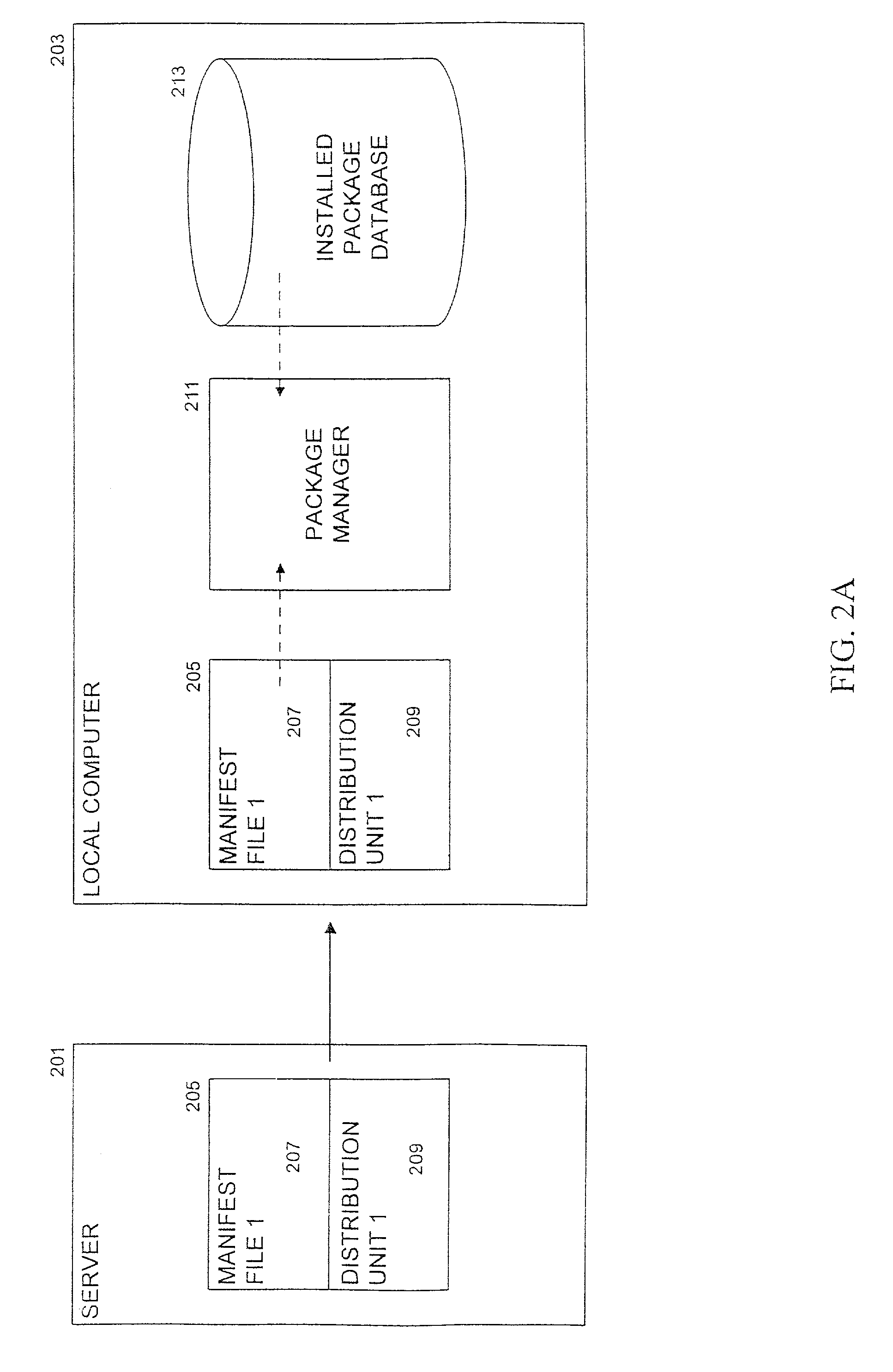
InactiveUS7222341B2Easy to shareEases uninstallation processData processing applicationsProgram loading/initiatingManifest fileSoftware engineering
A software package manager uses a distribution unit containing components for a software package and a manifest file that describes the distribution unit to manage the installation, execution, and uninstallation of software packages on a computer. Information in the manifest file pertaining to a software package is stored in a code store data structure upon installation of the package. The manifest file also contains information that permits the software package manager to resolve any software dependencies upon installation. The software package manager uses the code store data structure to locate the required components when the software is executed and to remove the components appropriately when the software is uninstalled.
Owner:MICROSOFT TECH LICENSING LLC
Software safety execution system
InactiveUS20050228990A1Digital data processing detailsUnauthorized memory use protectionFile systemData file
A secure software execution mechanism appropriate for software circulation is provided. At a sender site 312, an executable file 332 and a data file 334 processed by the executable file are encapsulated. The remaining two files 336 and 338 do not physically exist in a pot 320 at the sender site, and an archive file 320 is transferred to a receiver site 314. At the receiver site 314, intangible files 336 and 338 within a pot may be mapped to a file 354 in a local file system or a file 356 within another pot 350 and processed using a file 334 in a pot or the mapped file 354 or 356 by executing a program 332, in conformity with the specification of a security policy 340.
Owner:JAPAN SCI & TECH CORP
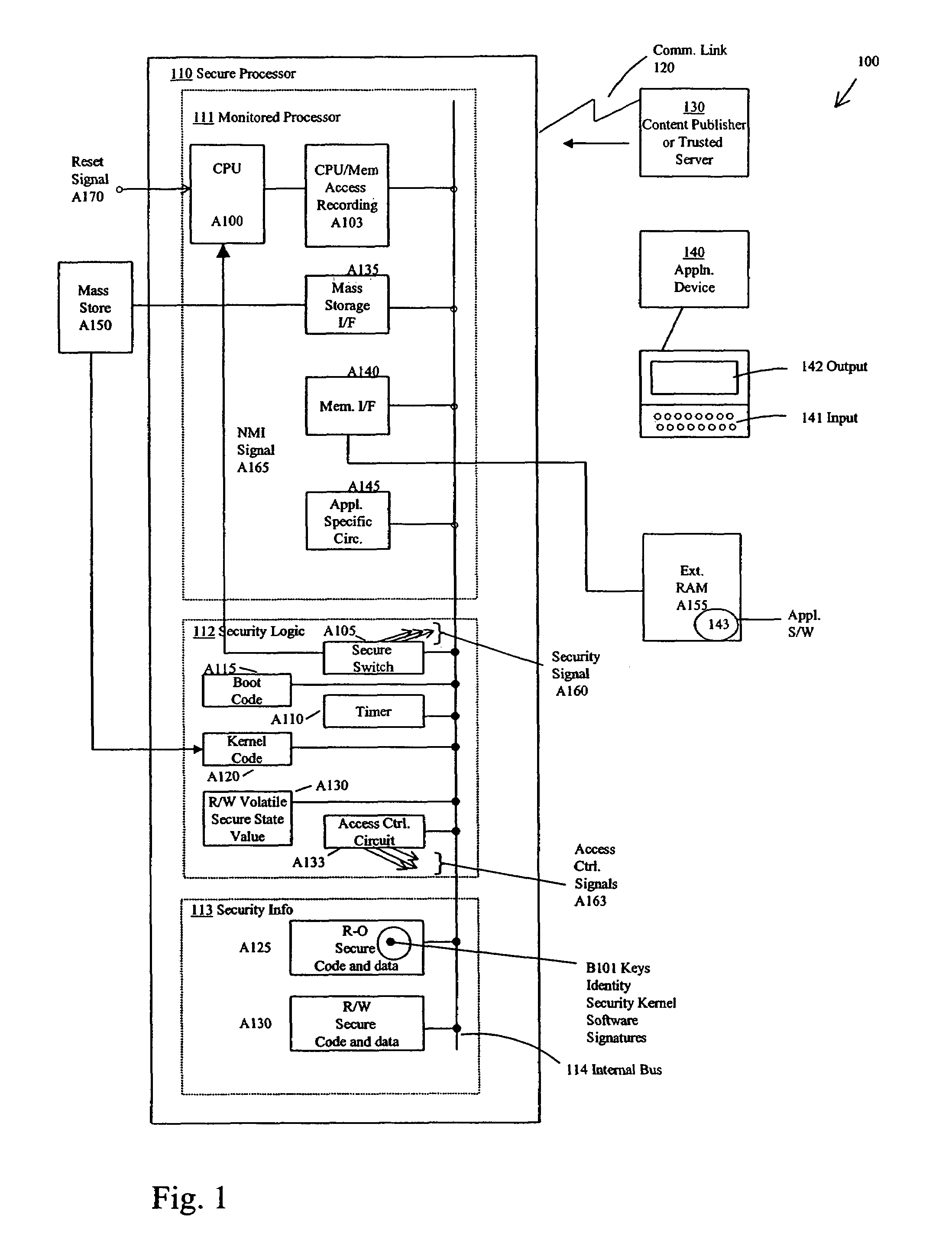
Using Power Fingerprinting (PFP) to Monitor the Integrity and Enhance Security of Computer Based Systems
ActiveUS20130318607A1Enhancing target system execution integrity assessmentImprove abilitiesMemory loss protectionDetecting faulty computer hardwareIntegrity assessmentComputerized system
Procedures are described for enhancing target system execution integrity determined by power fingerprinting (PFP): by integrating PFP into the detection phase of comprehensive defense-in-depth security; by deploying a network of PFP enabled nodes executing untrusted devices with predefined inputs forcing a specific state sequence and specific software execution; by embedding module identification information into synchronization signaling; by combining signals from different board elements; by using malware signatures to enhance PFP performance; by automatic characterization and signature extraction; by providing secure signature updates; by protecting against side-channel attacks; performing real-time integrity assessment in embedded platform by monitoring their dynamic power consumption and comparing it against signatures from trusted code, including pre-characterizing power consumption of the platform by concentrating on trace sections carrying the most information about the internal execution status; by using PFP from sequence of bit transitions to detect deviations from authorized execution of software in a digital processor.
Owner:VIRGINIA TECH INTPROP INC
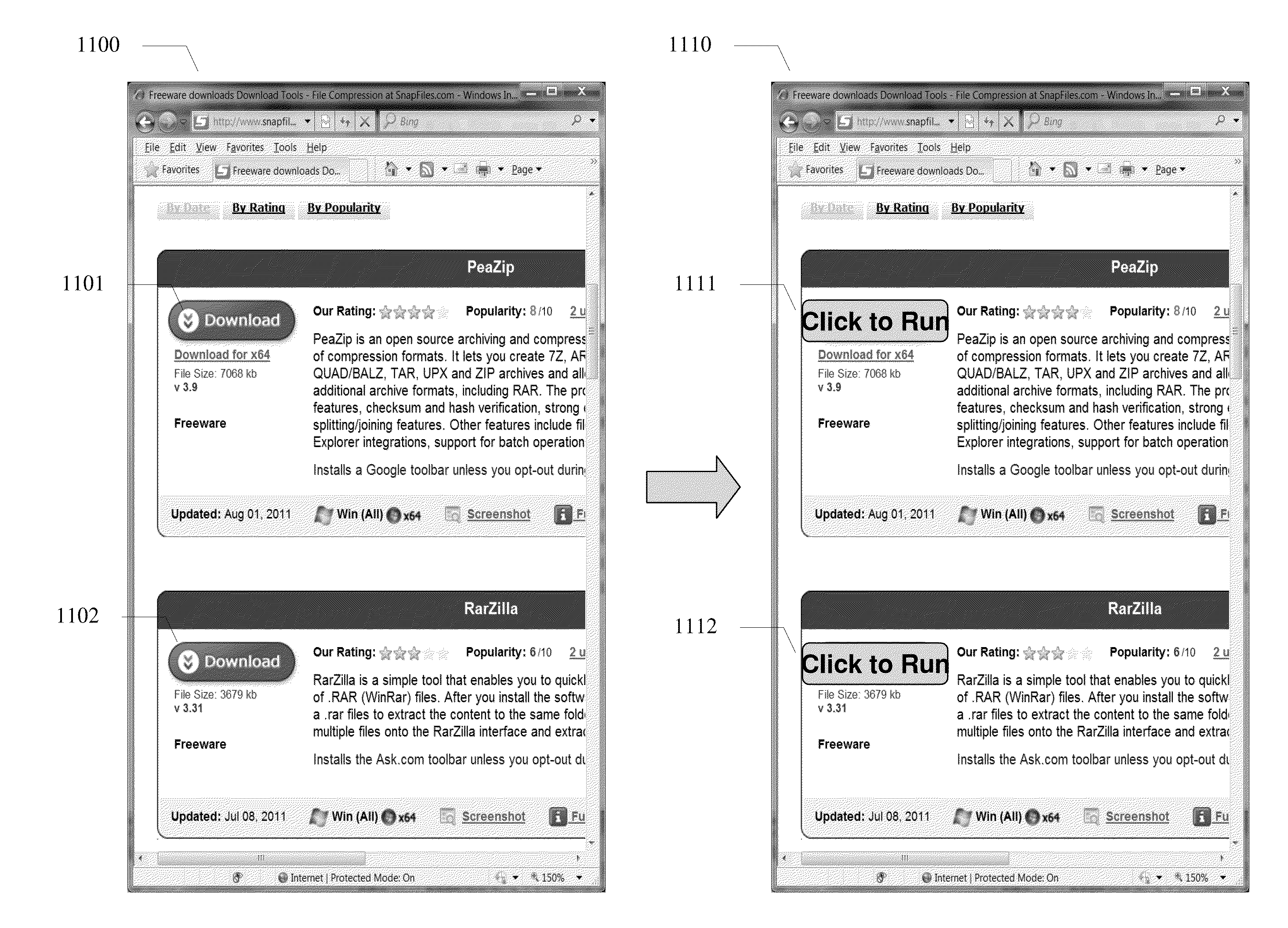
Online software execution platform
ActiveUS20130047149A1Reduce distractionsAccurate measurementText processingProgram code adaptionApplication softwareLocal environment
A system and method for a new type of software repository and remote execution solution where any native application can be run from within a web page is disclosed. Users now has a much easier way to launch, run or execute any software directly from within a server or server cloud without the need of manually download and installation. The system further allows software run inside an isolated environment to protect user's local environment.
Owner:YONGYONG XU
Secure and backward-compatible processor and secure software execution thereon
ActiveUS7322042B2Substantial in resourcesSubstantial in speedDigital data processing detailsUnauthorized memory use protectionExternal storageApplication software
A secure processor assuring application software is executed securely, and assuring only authorized software is executed, monitored modes and secure modes of operation. The former executes application software transparently to that software. The latter verifies execution of the application software is authorized, performs any extraordinary services required by the application software, and verifies the processor has obtained rights to execute the content. The secure processor (1) appears hardware-identical to an ordinary processor, with the effect that application software written for ordinary processors can be executed on the secure processor without substantial change, (2) needs only a minimal degree of additional hardware over and above those portions appearing hardware-identical to an ordinary processor. The secure processor operates without substantial reduction in speed or other resources available to the application software. Functions operating in secure mode might reside in an on-chip non-volatile memory, or might be loaded from external storage with authentication.
Owner:SAMSUNG ELECTRONICS CO LTD
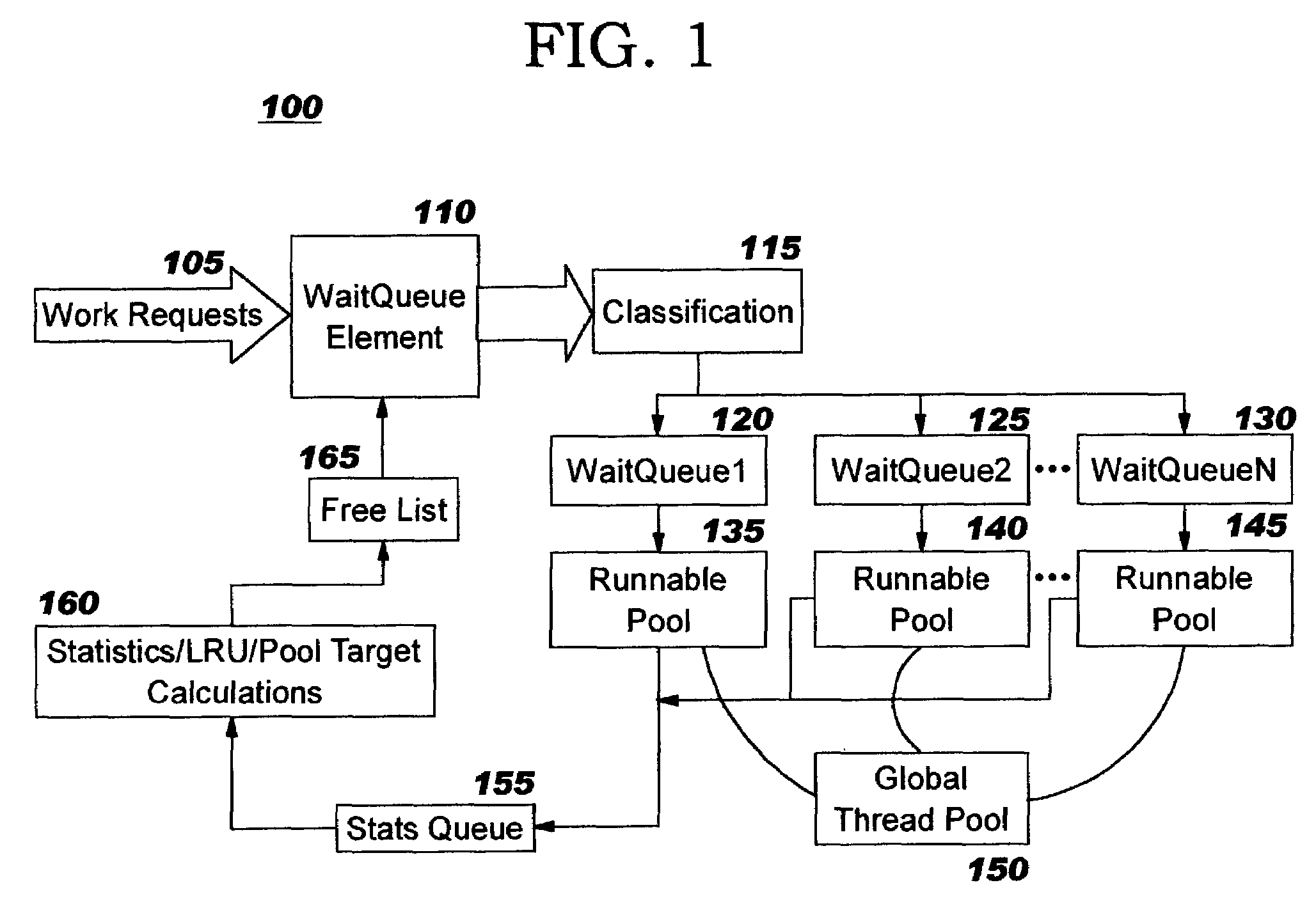
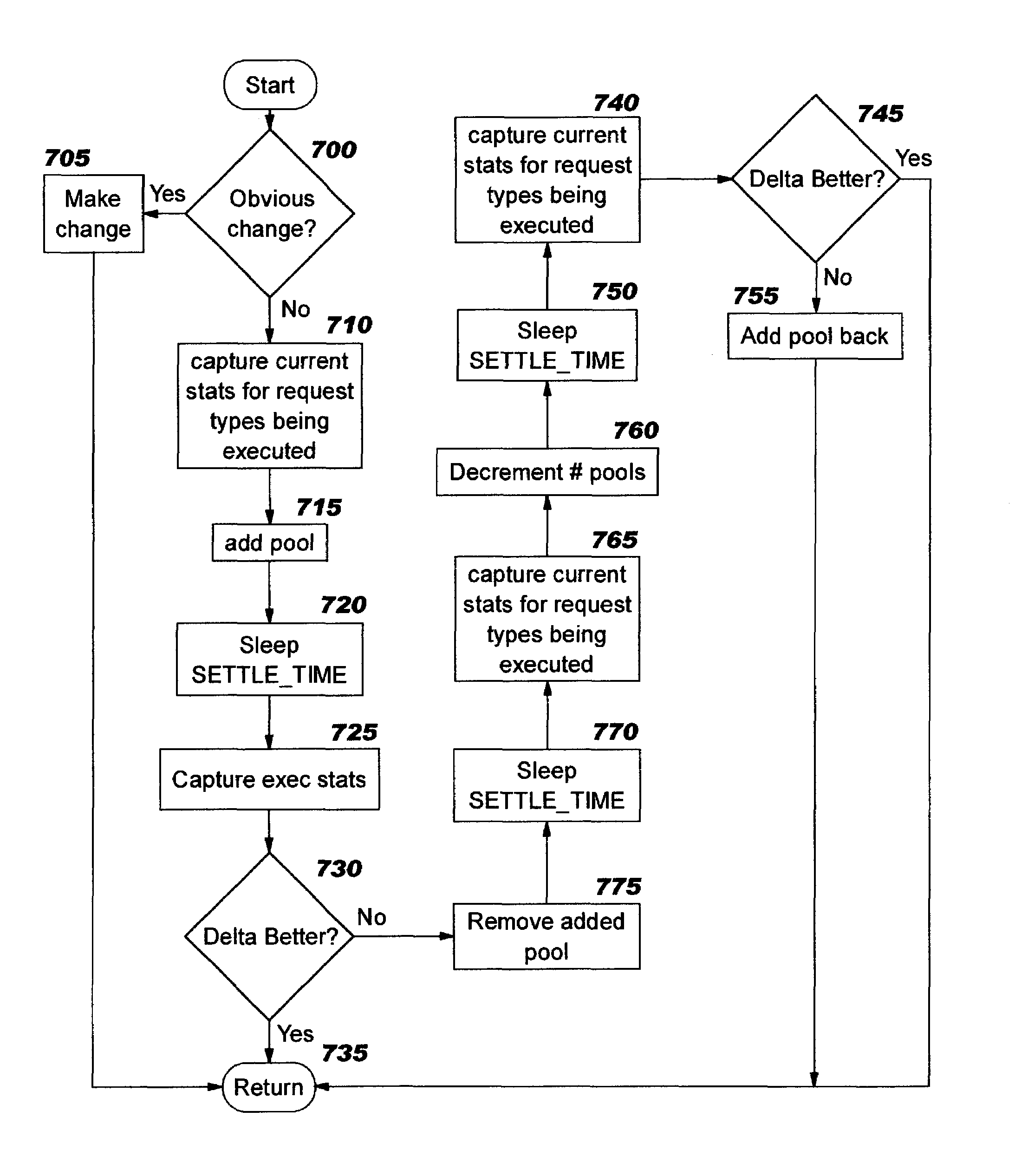
Dynamic thread pool tuning techniques
InactiveUS20040139434A1Improve performanceSimple technologyProgram initiation/switchingResource allocationParallel computingEngineering
Thread pools in a multithreaded server are programmatically adjusted, based on observed statistics from the server's inbound workload. In a multithreaded server environment, response time to end users is improved while increasing the efficiency of software execution and resource usage. Execution time and wait / queued time are tracked, for various types of requests being serviced by a server. Multiple logical pools of threads are used to service these requests, and inbound requests are directed to a selected one of these pools such that requests of similar execution-time requirements are serviced by the threads in that pool. The number and size of thread pools may be adjusted programmatically, and the distribution calculation (i.e., determining which inbound requests should be assigned to which pools) is a programmatic determination. In preferred embodiments, only one of these variables is adjusted at a time, and the results are monitored to determine whether the effect was positive or negative. The disclosed techniques also apply to tracking and classifying requests by method name (and, optionally, parameters).
Owner:IBM CORP
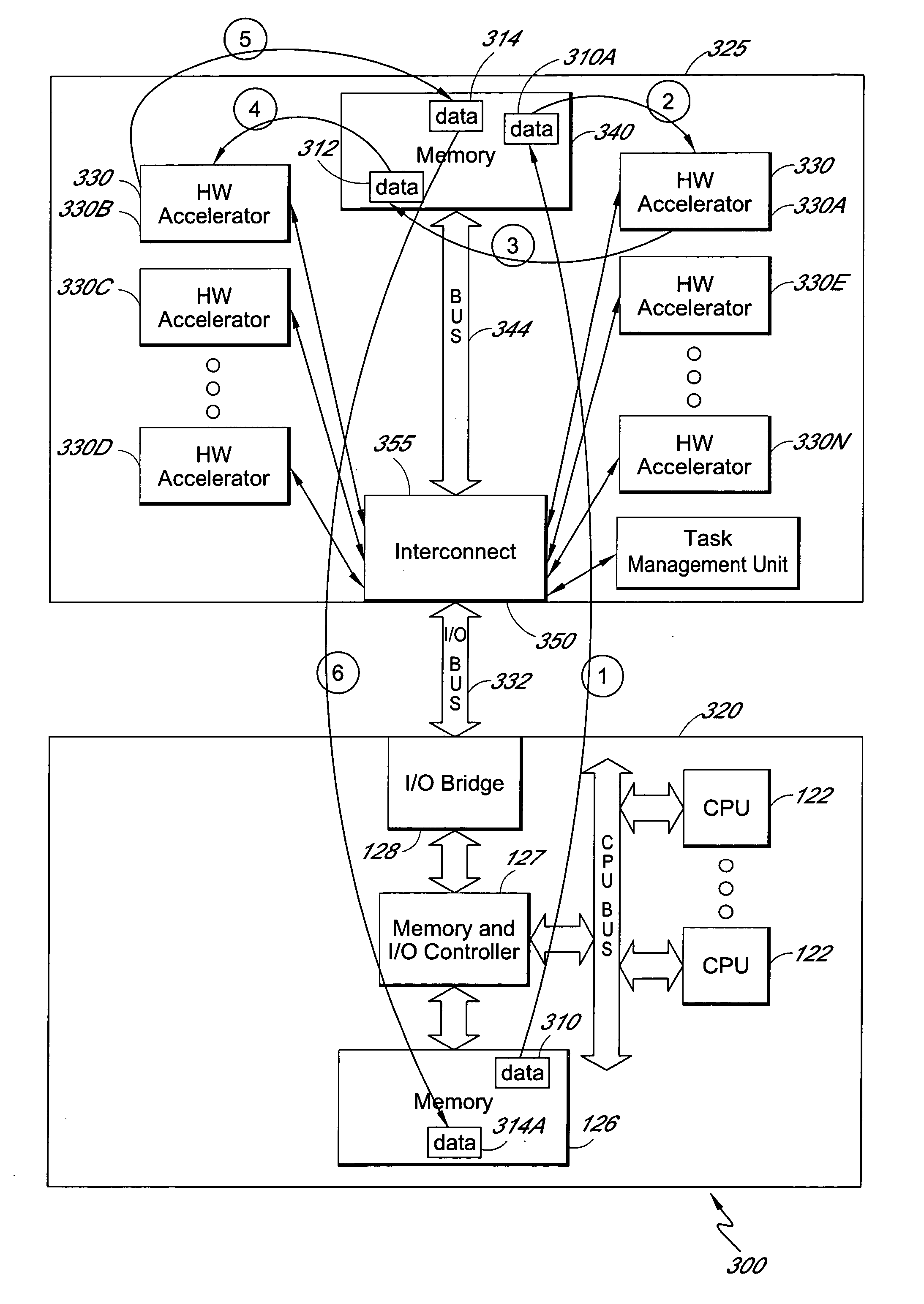
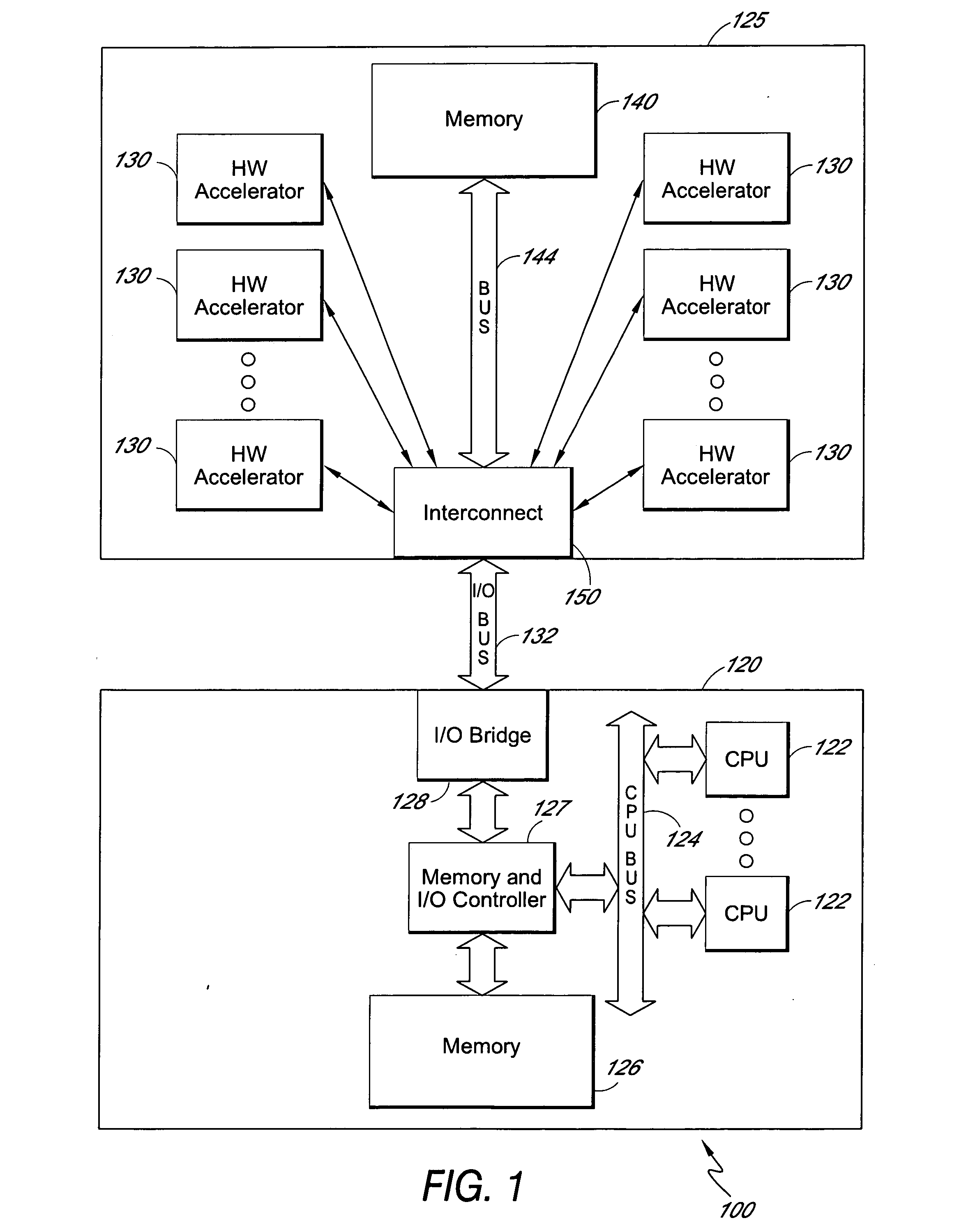
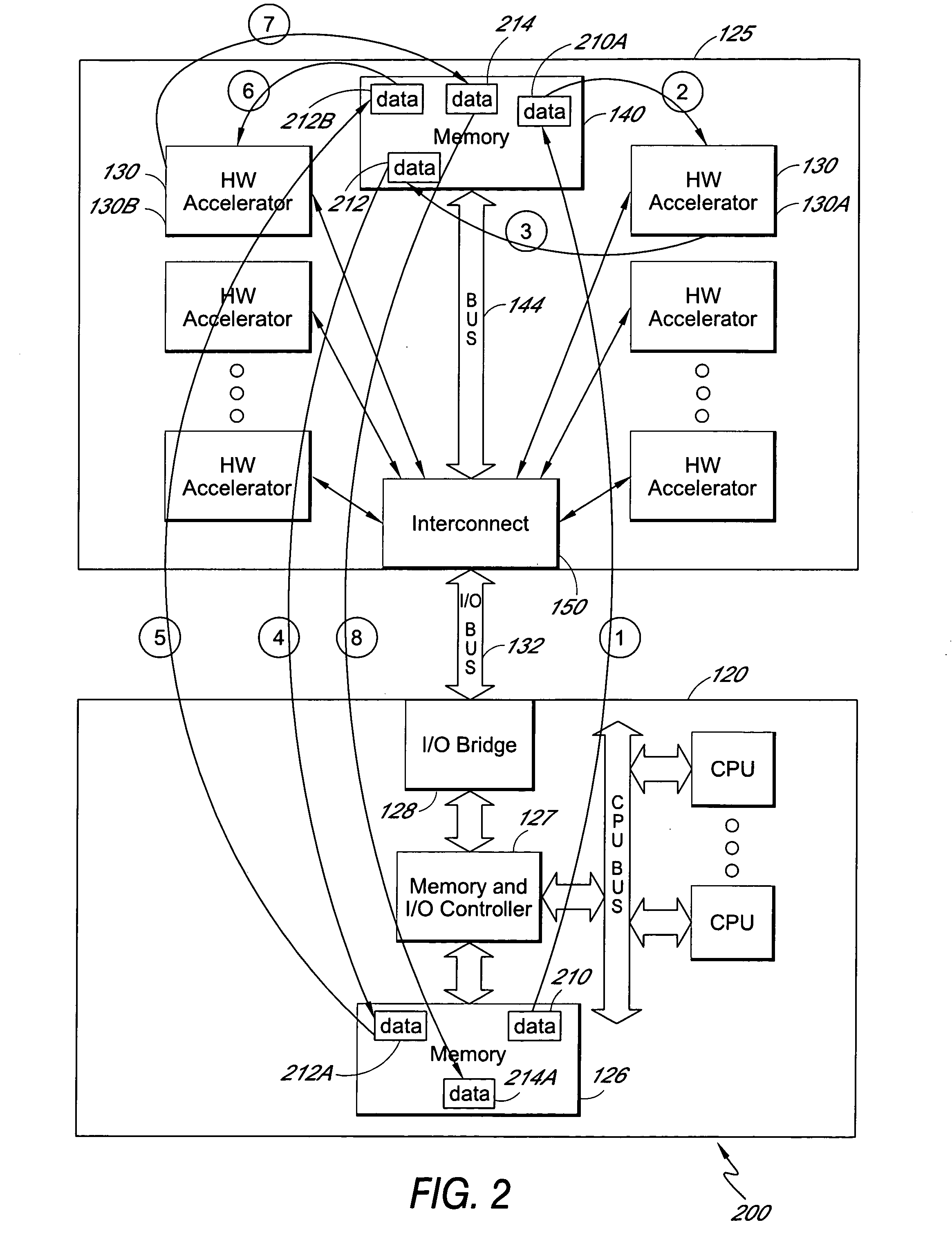
Method and apparatus for chaining multiple independent hardware acceleration operations
InactiveUS20050278502A1Reduce dataPreserving interconnect bandwidthProgram initiation/switchingGeneral purpose stored program computerComputer hardwareGeneral purpose
Multiple hardware accelerators can be used to efficiently perform processes that would otherwise be performed by general purpose hardware running software. The software overhead and bus bandwidth associated with running multiple hardware acceleration processes can be reduced by chaining multiple independent hardware acceleration operations within a circuit card assembly. Multiple independent hardware accelerators can be configured on a single circuit card assembly that is coupled to a computing device. The computing device can generate a playlist of hardware acceleration operations identifying hardware accelerators and associated accelerator options. A task management unit on the circuit card assembly receives the playlist and schedules the hardware acceleration operations such that multiple acceleration operations may be successively chained together without intervening data exchanges with the computing device.
Owner:INTEL CORP
Creating macro language files for executing structured query language (SQL) queries in a relational database via a network
InactiveUS6105043AData processing applicationsRelational databasesRelational database management systemQuery language
A method, apparatus, and article of manufacture for creating macro language files for executing SQL queries in a relational database management system via the World Wide Web of the Internet. In accordance with the present invention, Web users can request information from RDBMS software via HTML input forms, which request is then used to create an SQL statement for execution by the RDBMS software. The results output by the RDBMS software are themselves transformed into HTML format for presentation to the Web user.
Owner:IBM CORP
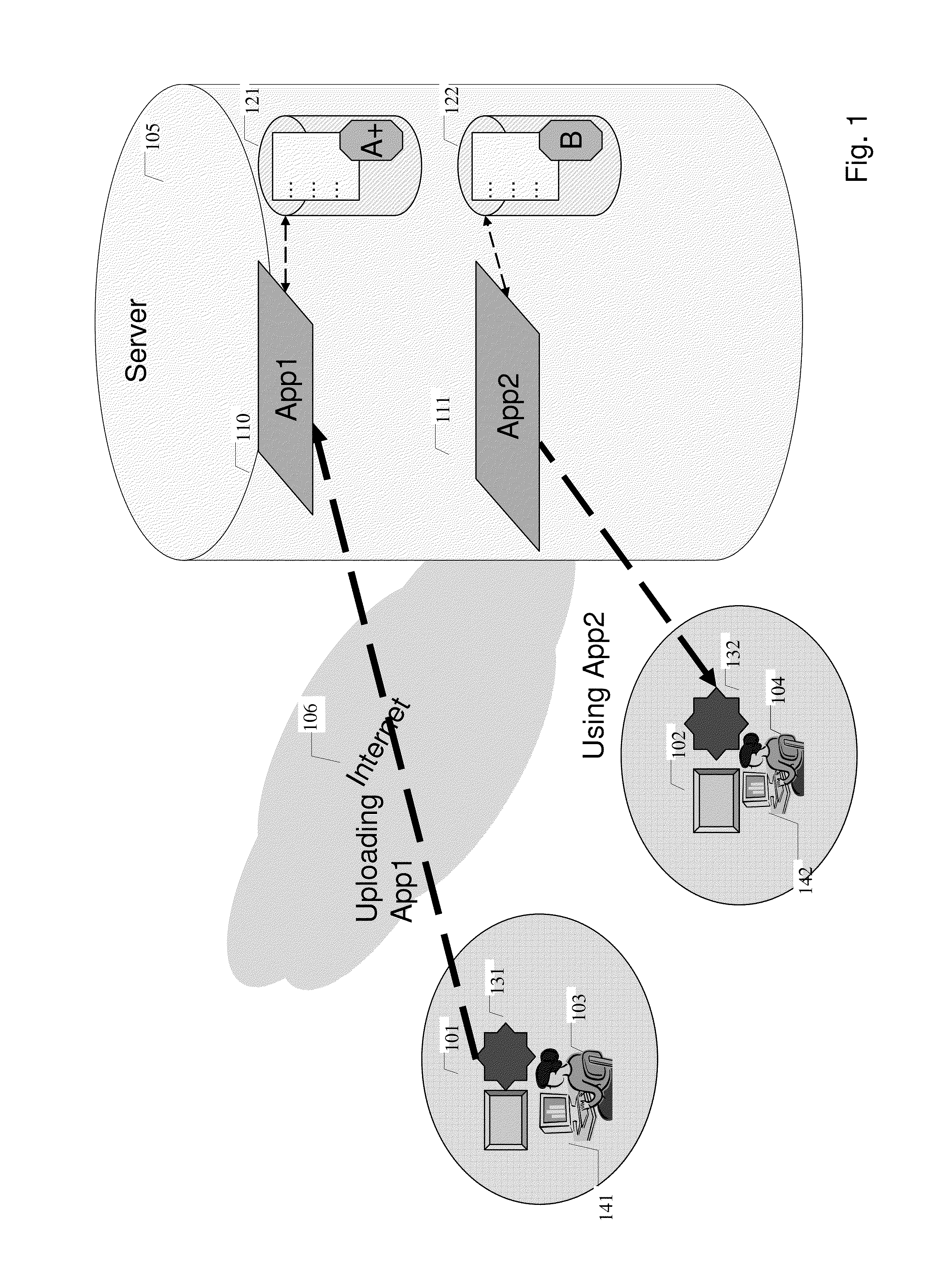
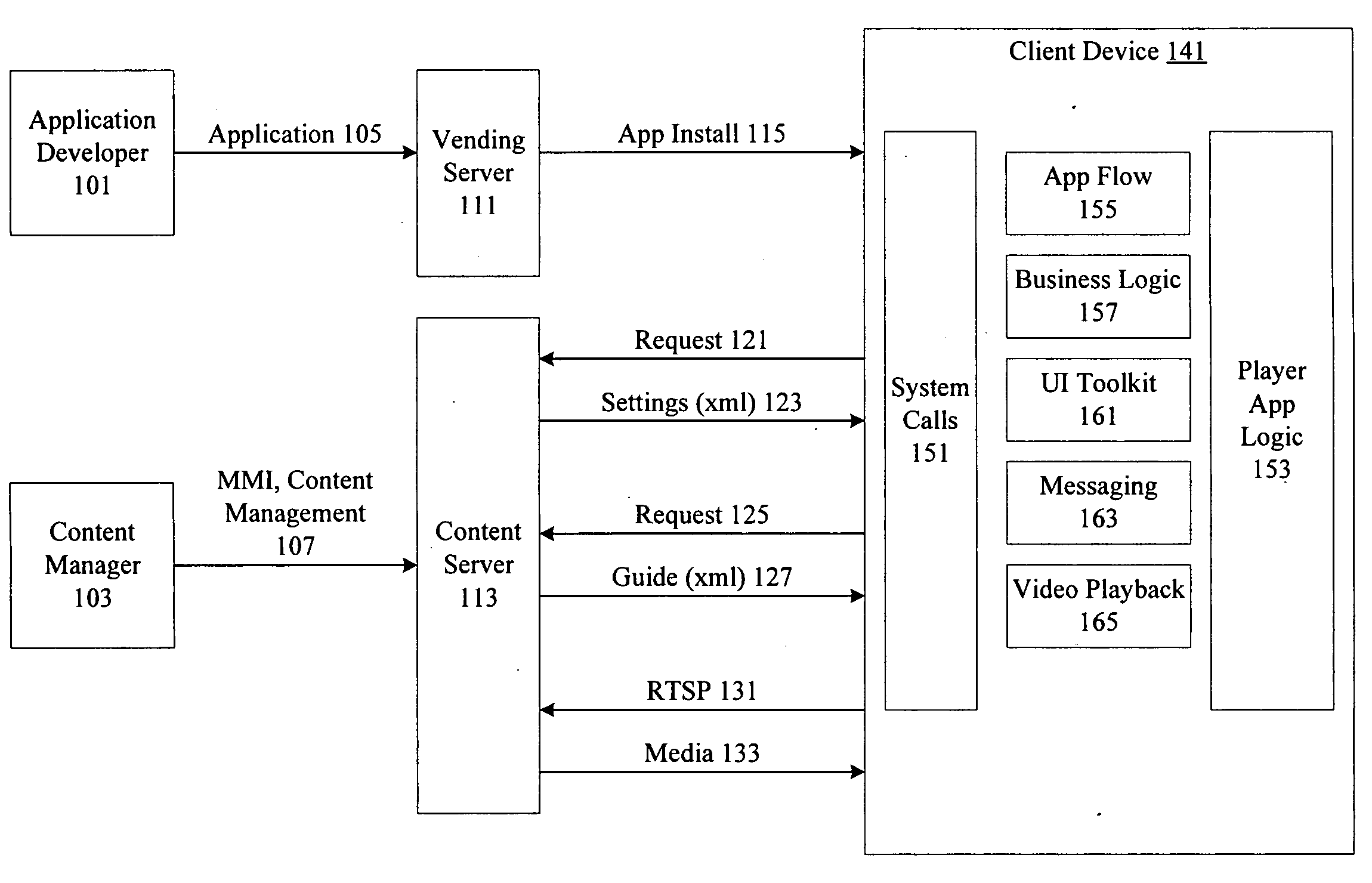
System for automatic management of applications on remote devices
Management of applications on remote devices is performed independently of managing platform software. A per platform player using a common protocol to communicate and receive applications is installed on a device. The player is developed and installed independently of applications which run using commands supported by the player. On player startup, the player obtains boot instructions, fetches an application manifest, and obtains player and application resources using the application manifest from a content and application server. The content and application server determines application resources to send to the player and tracks applications and application versions installed on a per user / per platform basis.
Owner:TIVO CORP
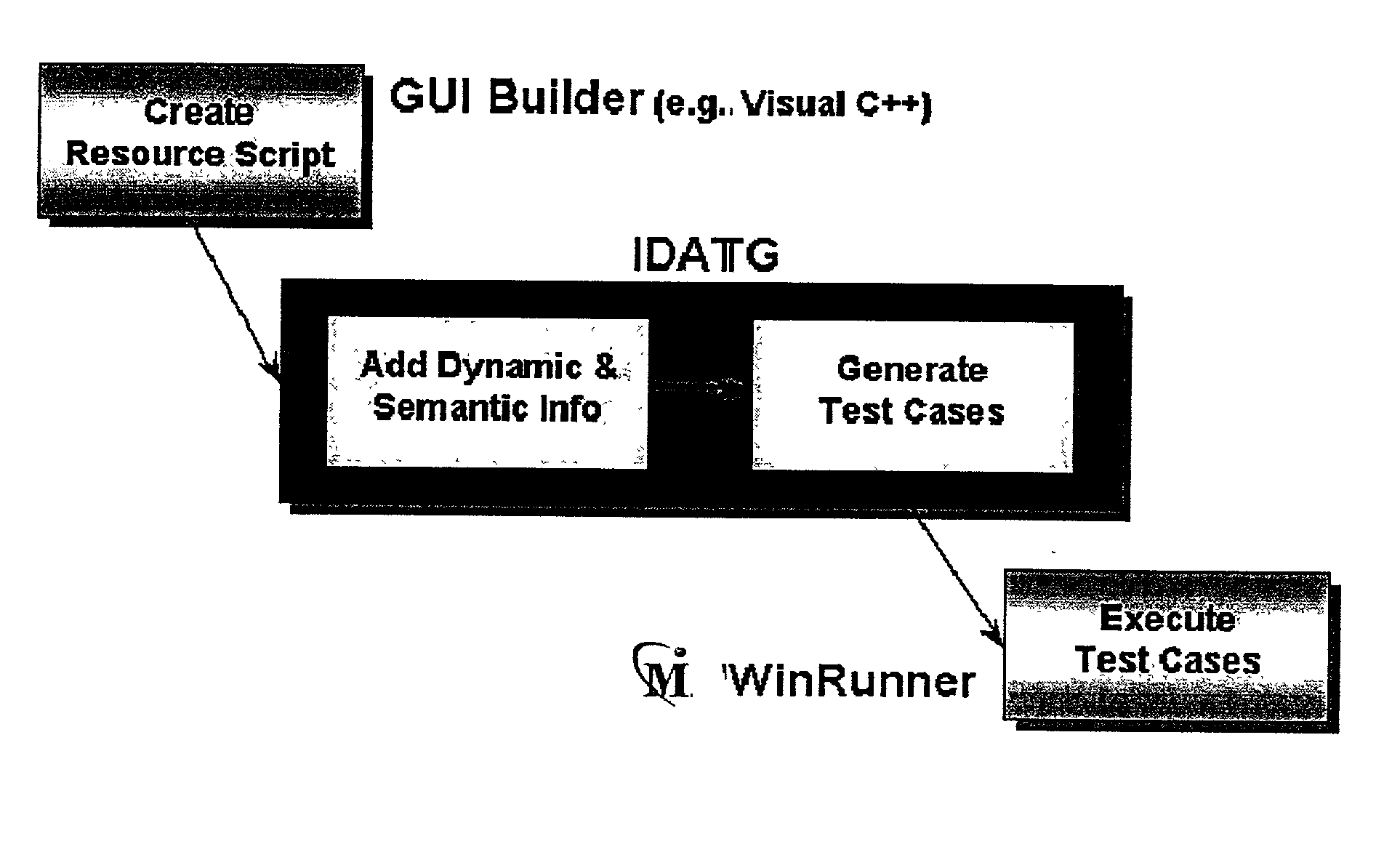
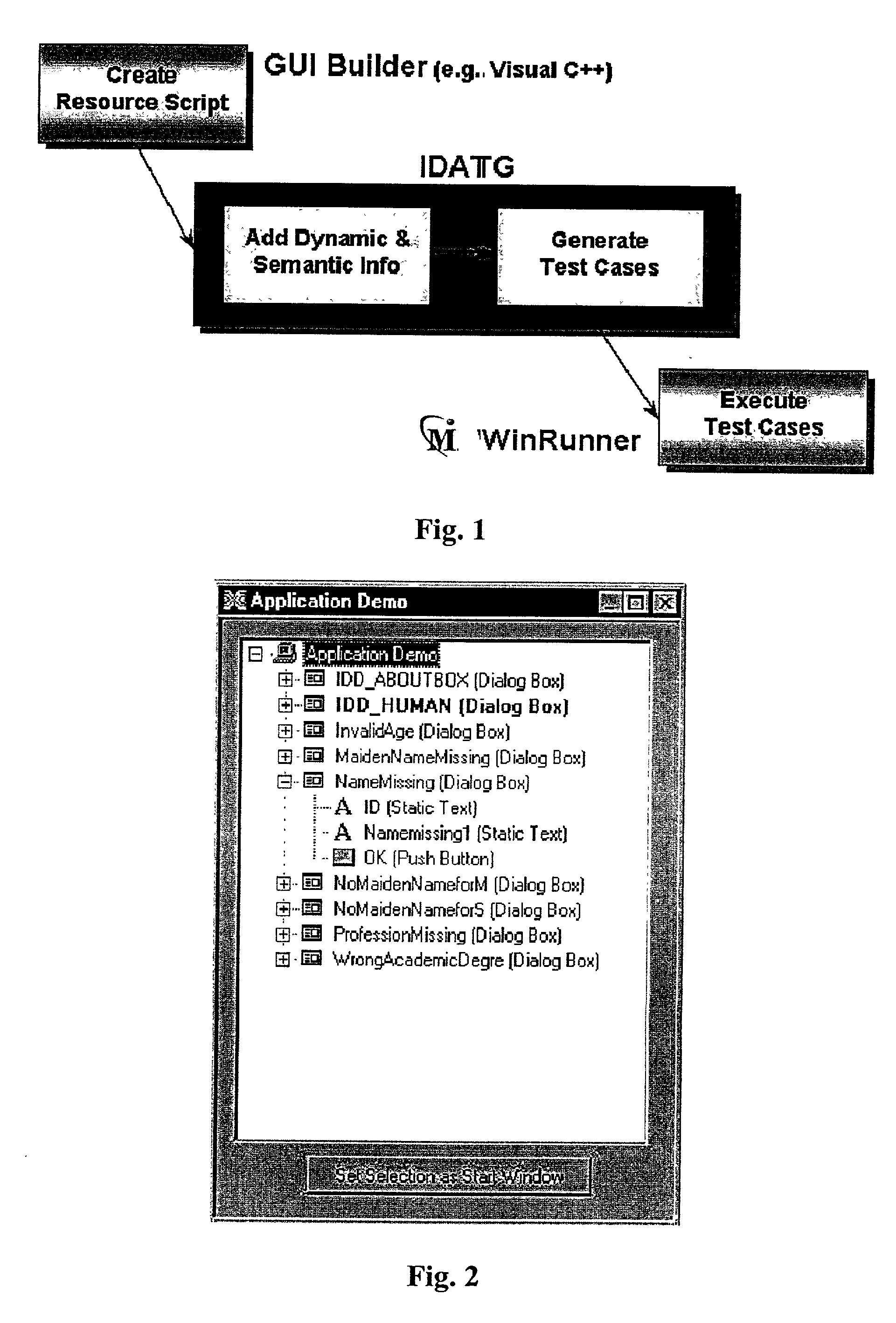
Method for testing of software
InactiveUS20030005413A1Enable designEnable processSoftware testing/debuggingSpecific program execution arrangementsComputer hardwareGraphics
There is provided a method for the automated testing of software, which has a graphic user interface. With at least one graphic editor, at least the dynamic and the semantic behavior of the user interface of the software is specified. Test cases are generated by a test case generator software using the thus specified behavior of the user interface, which are then executed by a software for automatic running test running either immediately or in a later step.
Owner:SIEMENS AG OESTERR
Secure and backward-compatible processor and secure software execution thereon
InactiveUS7380275B2Substantial in resourcesSubstantial in speedDigital data processing detailsUnauthorized memory use protectionExternal storageApplication software
A secure processor assuring application software is executed securely, and assuring only authorized software is executed, monitored modes and secure modes of operation. The former executes application software transparently to that software. The latter verifies execution of the application software is authorized, performs any extraordinary services required by the application software, and verifies the processor has obtained rights to execute the content. The secure processor (1) appears hardware-identical to an ordinary processor, with the effect that application software written for ordinary processors can be executed on the secure processor without substantial change, (2) needs only a minimal degree of additional hardware over and above those portions appearing hardware-identical to an ordinary processor. The secure processor operates without substantial reduction in speed or other resources available to the application software. Functions operating in secure mode might reside in an on-chip non-volatile memory, or might be loaded from external storage with authentication.
Owner:SAMSUNG ELECTRONICS CO LTD
Programmatic response-time based workload distribution techniques
InactiveUS7207043B2Improve performanceSimple technologyProgram initiation/switchingElectric devicesQueue timeWorkload
Workload is programmatically distributed across a set of execution resources. In a multithreaded server environment, response time to end users is improved while increasing the efficiency of software execution and resource usage. Execution time and wait / queued time are tracked, for various types of requests being serviced by a server. Multiple logical pools of threads are used to service these requests, and inbound requests are directed to a selected one of these pools such that requests of similar execution-time requirements are serviced by the threads in that pool. The number and size of thread pools may be adjusted programmatically, and the distribution calculation (i.e., determining which inbound requests should be assigned to which pools) is a programmatic determination. In preferred embodiments, only one of these variables is adjusted at a time, and the results are monitored to determine whether the effect was positive or negative. The disclosed techniques also apply to tracking and classifying requests by method name (and, optionally, parameters).
Owner:IBM CORP
Method and system for converting a single-threaded software program into an application-specific supercomputer
ActiveUS8966457B2Reduce expensesReduce overheadMemory architecture accessing/allocationTransformation of program codeSupercomputerComputer architecture
The invention comprises (i) a compilation method for automatically converting a single-threaded software program into an application-specific supercomputer, and (ii) the supercomputer system structure generated as a result of applying this method. The compilation method comprises: (a) Converting an arbitrary code fragment from the application into customized hardware whose execution is functionally equivalent to the software execution of the code fragment; and (b) Generating interfaces on the hardware and software parts of the application, which (i) Perform a software-to-hardware program state transfer at the entries of the code fragment; (ii) Perform a hardware-to-software program state transfer at the exits of the code fragment; and (iii) Maintain memory coherence between the software and hardware memories. If the resulting hardware design is large, it is divided into partitions such that each partition can fit into a single chip. Then, a single union chip is created which can realize any of the partitions.
Owner:GLOBAL SUPERCOMPUTING CORP
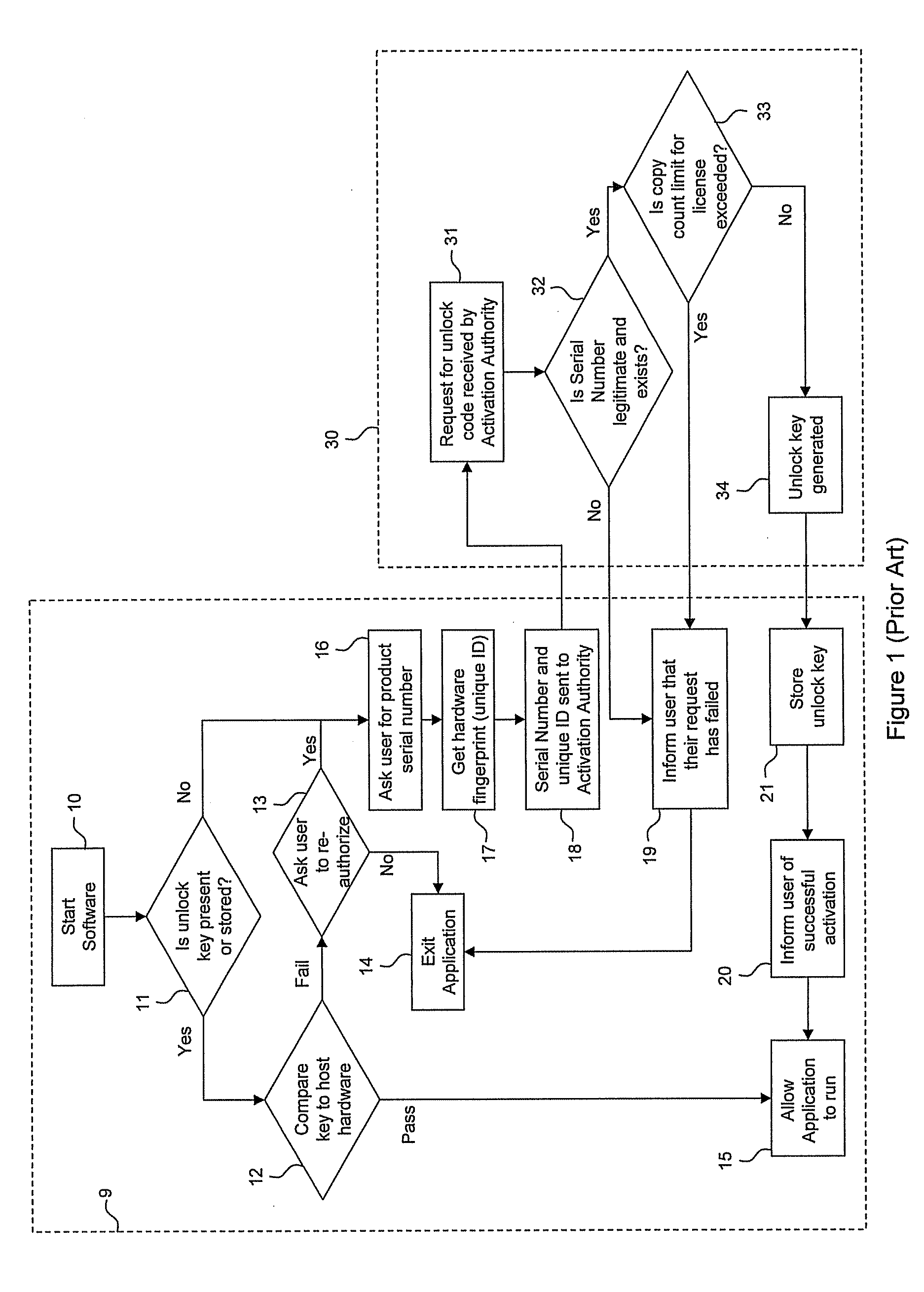
System and method for auditing software usage
ActiveUS20080320607A1Digital data processing detailsAnalogue secracy/subscription systemsSoftware executionSerial code
Systems and methods are provided for auditing and selectively restricting software usage based on, for example, software copy counts or execution counts. In one embodiment, the method comprises verifying whether the serial number for a software installed on a computing device corresponds to one of recognized serial numbers, and calculating a copy count (or software execution count) for the serial number. In response to the copy count exceeding a defined upper limit, a limited unlock key may be sent to the device. The limited unlock key may allow the software to be executed on the device for a defined time period, a defined number of executions, and / or with at least one feature of the software disabled.
Owner:UNILOC 2017 LLC
Programmatic response-time based workload distribution techniques
InactiveUS20040139433A1Improve performanceSimple technologyProgram initiation/switchingElectric devicesQueue timeWorkload
Workload is programmatically distributed across a set of execution resources. In a multithreaded server environment, response time to end users is improved while increasing the efficiency of software execution and resource usage. Execution time and wait / queued time are tracked, for various types of requests being serviced by a server. Multiple logical pools of threads are used to service these requests, and inbound requests are directed to a selected one of these pools such that requests of similar execution-time requirements are serviced by the threads in that pool. The number and size of thread pools may be adjusted programmatically, and the distribution calculation (i.e., determining which inbound requests should be assigned to which pools) is a programmatic determination. In preferred embodiments, only one of these variables is adjusted at a time, and the results are monitored to determine whether the effect was positive or negative. The disclosed techniques also apply to tracking and classifying requests by method name (and, optionally, parameters).
Owner:IBM CORP
Dynamic configuration of a gaming system
ActiveUS20050172336A1Digital data processing detailsUser identity/authority verificationSubject NameData file
A method to enable dynamic configuration of gaming terminals installed in one or a plurality of gaming premises whereby certified games, certified data files and certified support software components are activated in accordance with a predetermined schedule or automatically in response to the observed gaming activity. The method may include allocating an individual PKI certificate to each executable software component and each of its versions, binding the PKI certificate to the executable software, associating a distinctive policy for each certificate and then enforcing the software execution policies in accordance with the desired authorized game configuration and schedule. The PKI certificate's “Subject Name” (or “Issued to” field or “CommonName” field) may be a concatenation of the software component identification, its version number and optionally other identification characters. The method applies equally to other network connected gaming subsystems. The method enables a fine-grained and secure control of the authorized software components and thus the flexibility to securely configure the gaming system in accordance with a schedule or in a close-loop fashion in order to meet business objectives. In addition, a method to enable the certification authority to bind the certificates to the tested code is described.
Owner:IGT
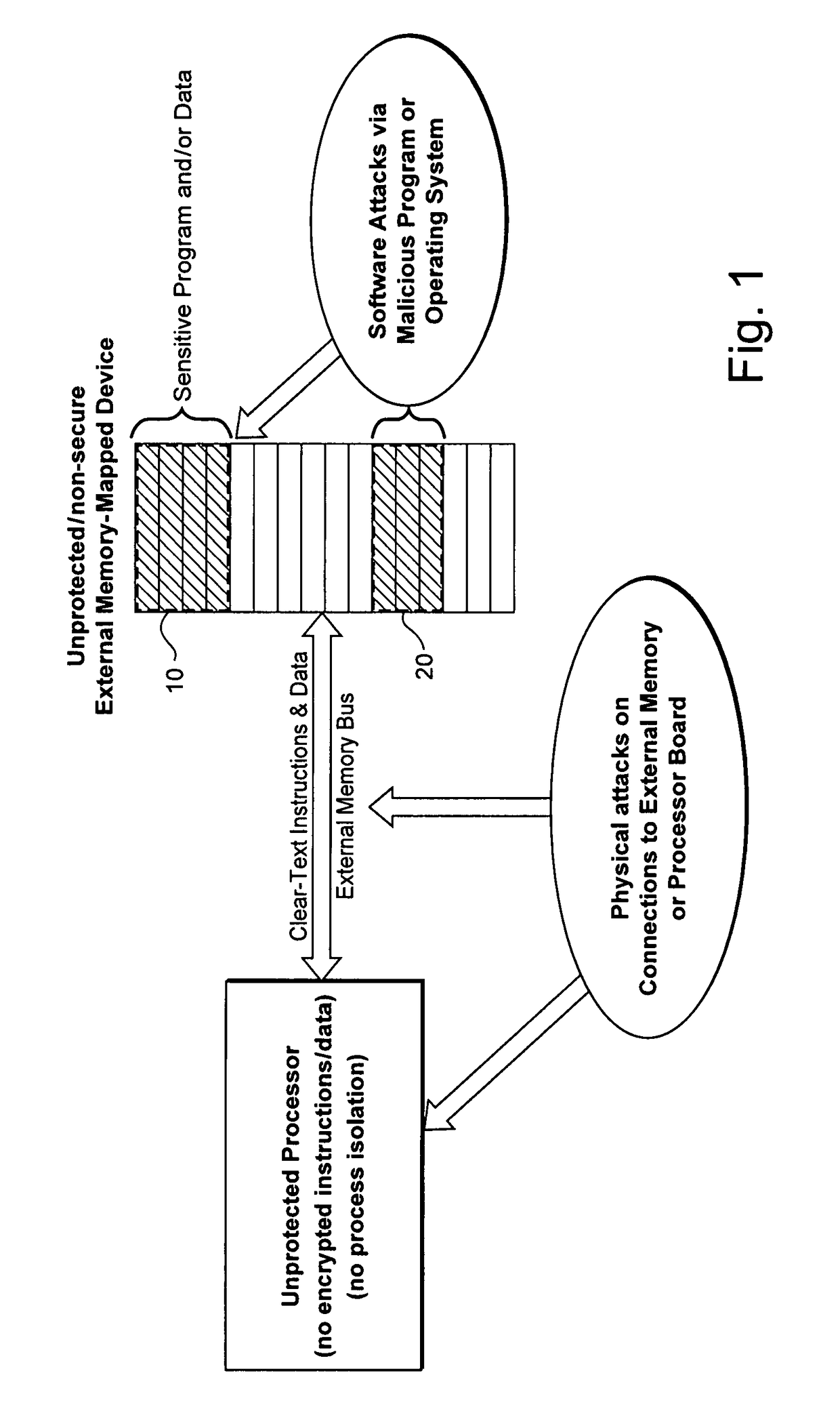
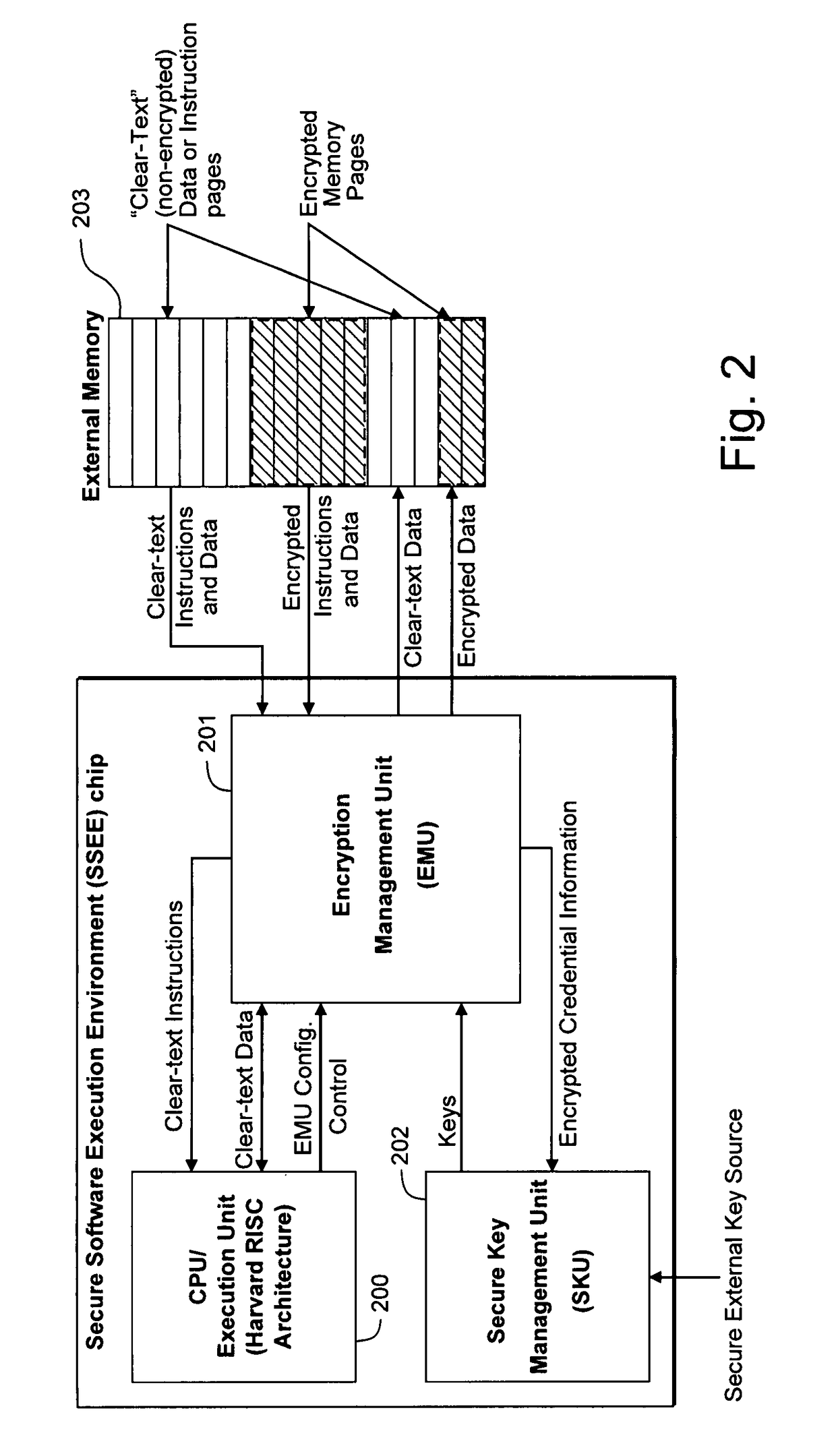
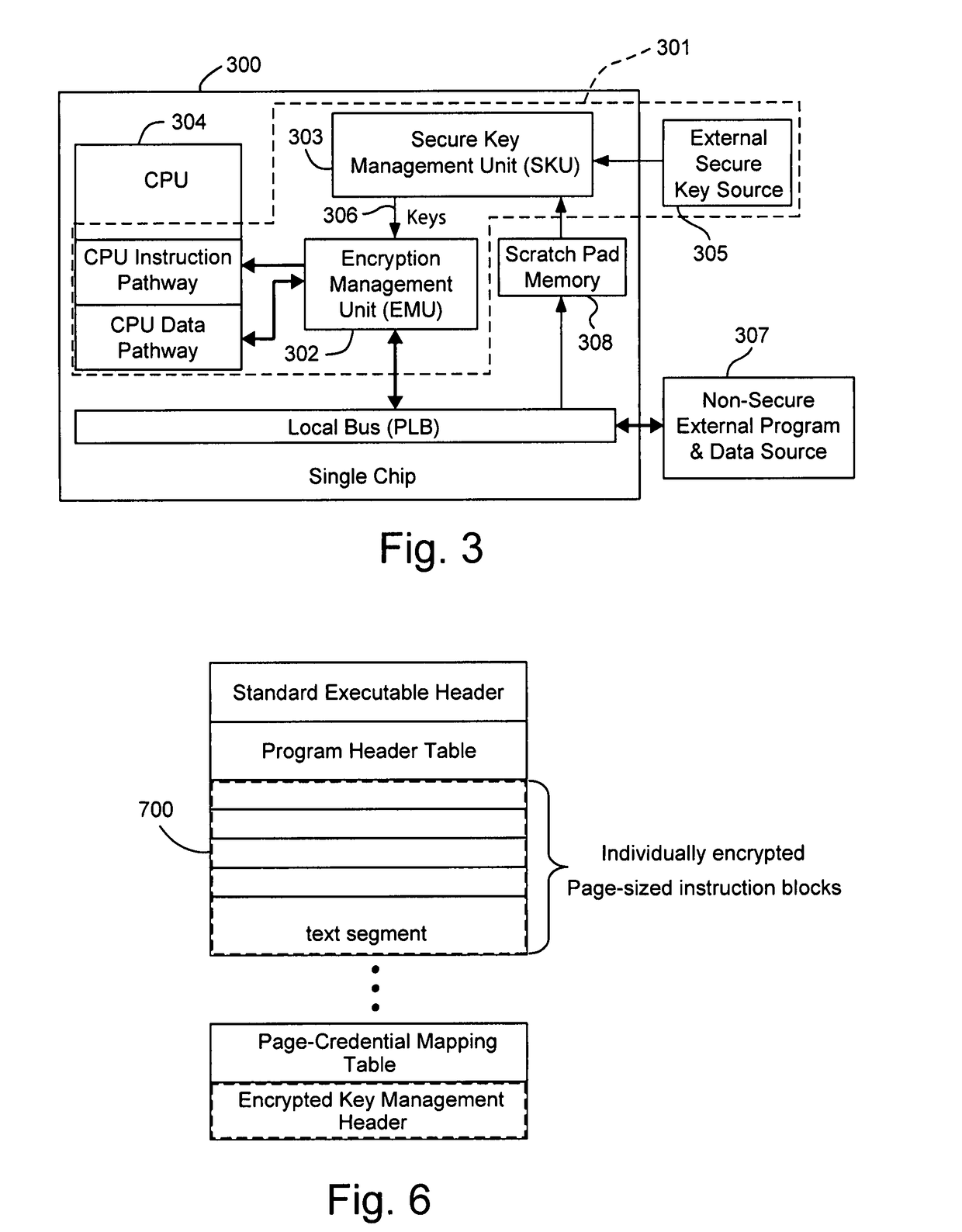
Hardware-facilitated secure software execution environment
InactiveUS8473754B2Avoid unwanted disclosureProvide confidentialityUser identity/authority verificationUnauthorized memory use protectionConfidentialityKey management
A hardware-facilitated secure software execution environment provides protection of both program instructions and data against unauthorized access and / or execution to maintain confidentiality and integrity of the software or the data during distribution, in external memories, and during execution. The secure computing environment is achieved by using a hardware-based security method and apparatus to provide protection against software privacy and tampering. A Harvard architecture CPU core is instantiated on the same silicon chip along with encryption management unit (EMU) circuitry and secure key management unit (SKU) circuitry. Credential information acquired from one or more sources is combined by the SKU circuitry to generate one or more security keys provided to the EMU for use in decrypting encrypted program instructions and / or data that is obtained from a non-secure, off-chip source such as an external RAM, an information storage device or other network source. In a non-limiting illustrative example implementation, the EMU decrypts a single memory page of encrypted instructions or data per a corresponding encryption key provided by the SKU. Although instantiated on the same chip, the CPU core does not have direct access to the SKU circuitry or to encryption key information generated by the SKU.
Owner:MACAULAY BROWN +1
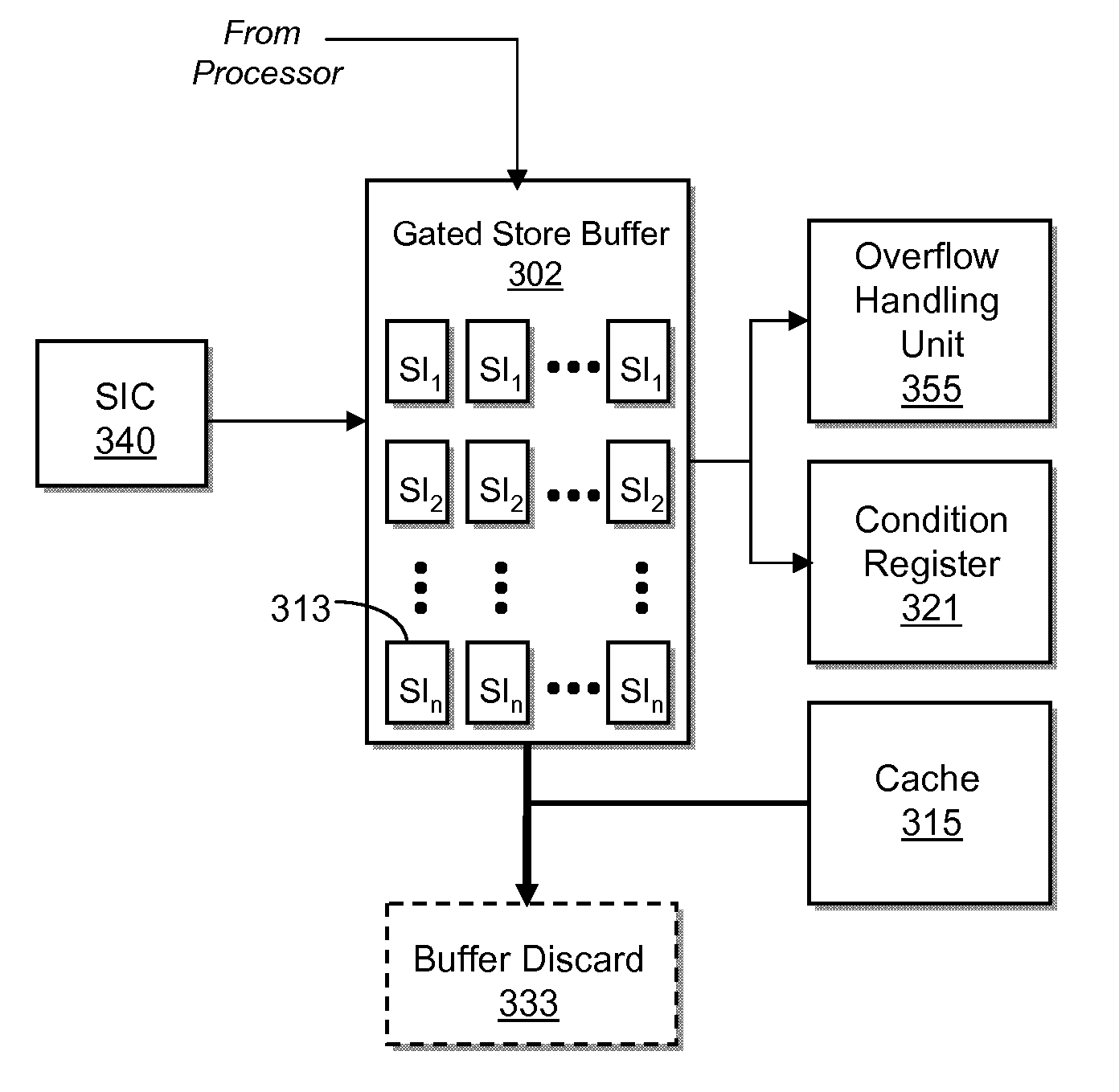
System and method for software initiated checkpoint operations
InactiveUS20110066831A1Pointing accuratelyError detection/correctionDigital computer detailsProcessor registerCondition Code
A method, system and computer program product for issuing one or more software initiated operations for creating a checkpoint of a register file and memory, and for restoring a register file and memory to the checkpointed state. At the execution of a checkpoint operation, the system returns a condition code indicating success or failure. When the condition code is set equal to one, one or more checkpoints are initiated. Contents of the register file and gated store buffer are stored each time the one or more checkpoints are initiated. When the checkpoint is created, the system notifies software when a hardware checkpoint capacity has been reached. One or more of the software checkpoint, hardware checkpoint, and handler checkpoint are utilized to provide a more precise point of restoration. During software execution, the register file and gated store buffer can be restored as defined by the one or more previous checkpoints.
Owner:IBM CORP
Method and system to determine the geographic location of a network user
InactiveUS20060212601A1Multiple digital computer combinationsTransmissionNetwork addressingNetwork address
A system and method to determine the geographic location of a network user based on a plurality of network addresses and a plurality of mapping request information. The method involves receiving a plurality of mapping requests from a plurality of network users identified by a plurality of network addresses. A geographic location of a network user associated with a network address is then derived based on the plurality of network addresses and the plurality of mapping requests. In one embodiment, the network address is an Internet Protocol (IP) address. The method may be implemented, in one embodiment, as part of a system that executes as software on a computer.
Owner:MICROSOFT TECH LICENSING LLC
Dynamic thread pool tuning techniques
InactiveUS7237242B2Improve performanceSimple technologyProgram initiation/switchingResource allocationQueue timeWorkload
Thread pools in a multithreaded server are programmatically adjusted, based on observed statistics from the server's inbound workload. In a multithreaded server environment, response time to end users is improved while increasing the efficiency of software execution and resource usage. Execution time and wait / queued time are tracked, for various types of requests being serviced by a server. Multiple logical pools of threads are used to service these requests, and inbound requests are directed to a selected one of these pools such that requests of similar execution-time requirements are serviced by the threads in that pool. The number and size of thread pools may be adjusted programmatically, and the distribution calculation (i.e., determining which inbound requests should be assigned to which pools) is a programmatic determination. In preferred embodiments, only one of these variables is adjusted at a time, and the results are monitored to determine whether the effect was positive or negative. The disclosed techniques also apply to tracking and classifying requests by method name (and, optionally, parameters).
Owner:INT BUSINESS MASCH CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com