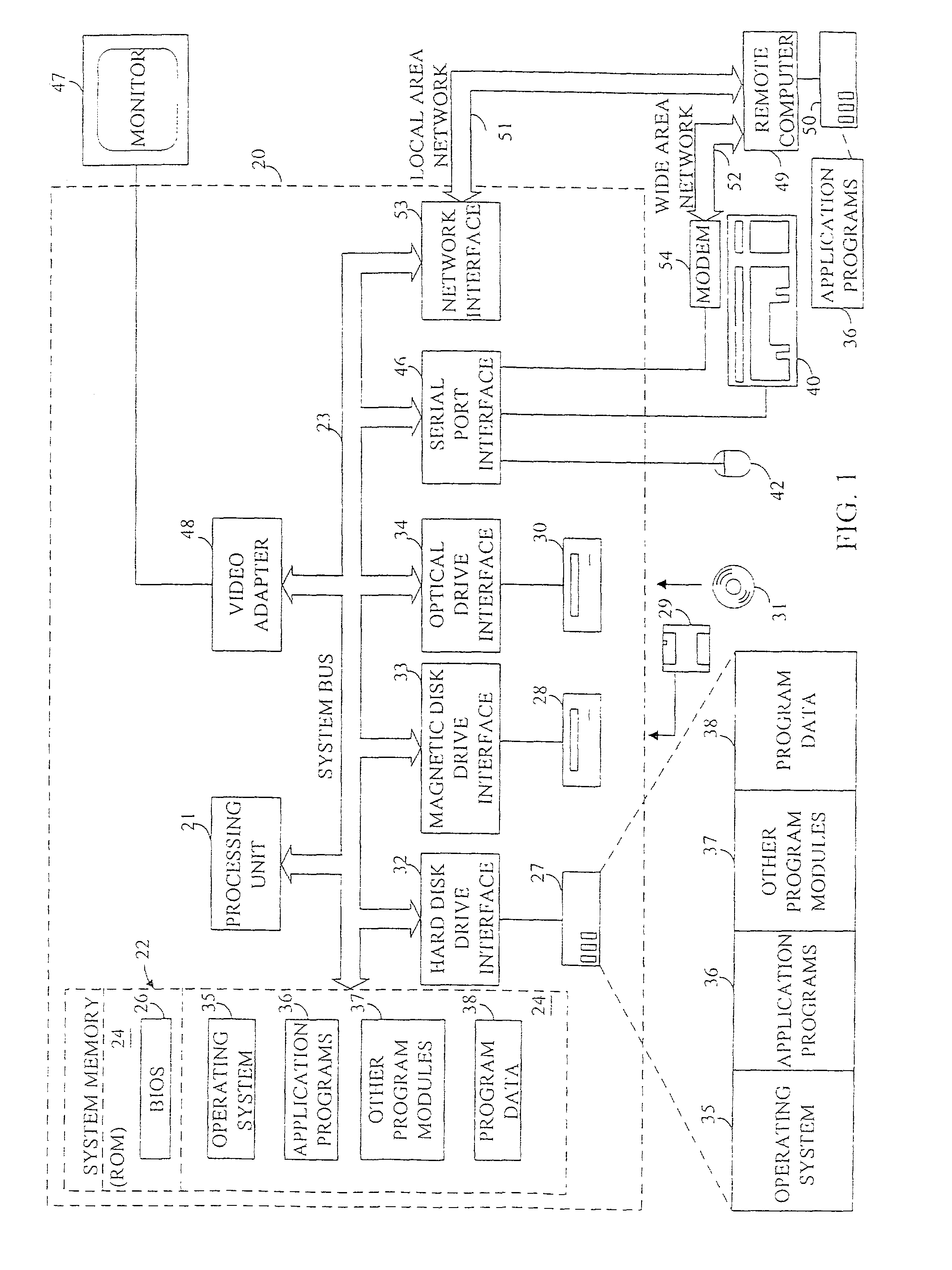
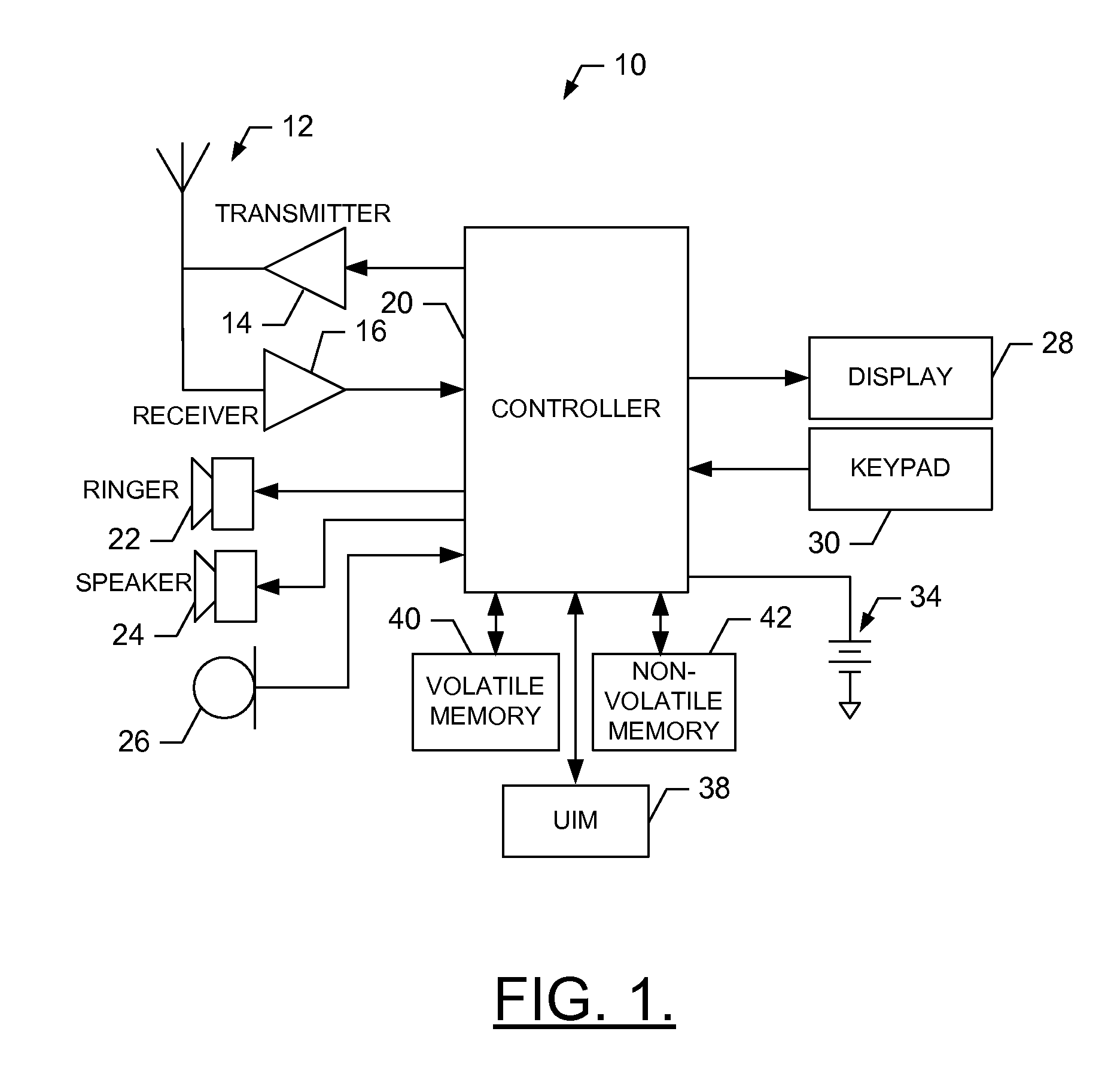
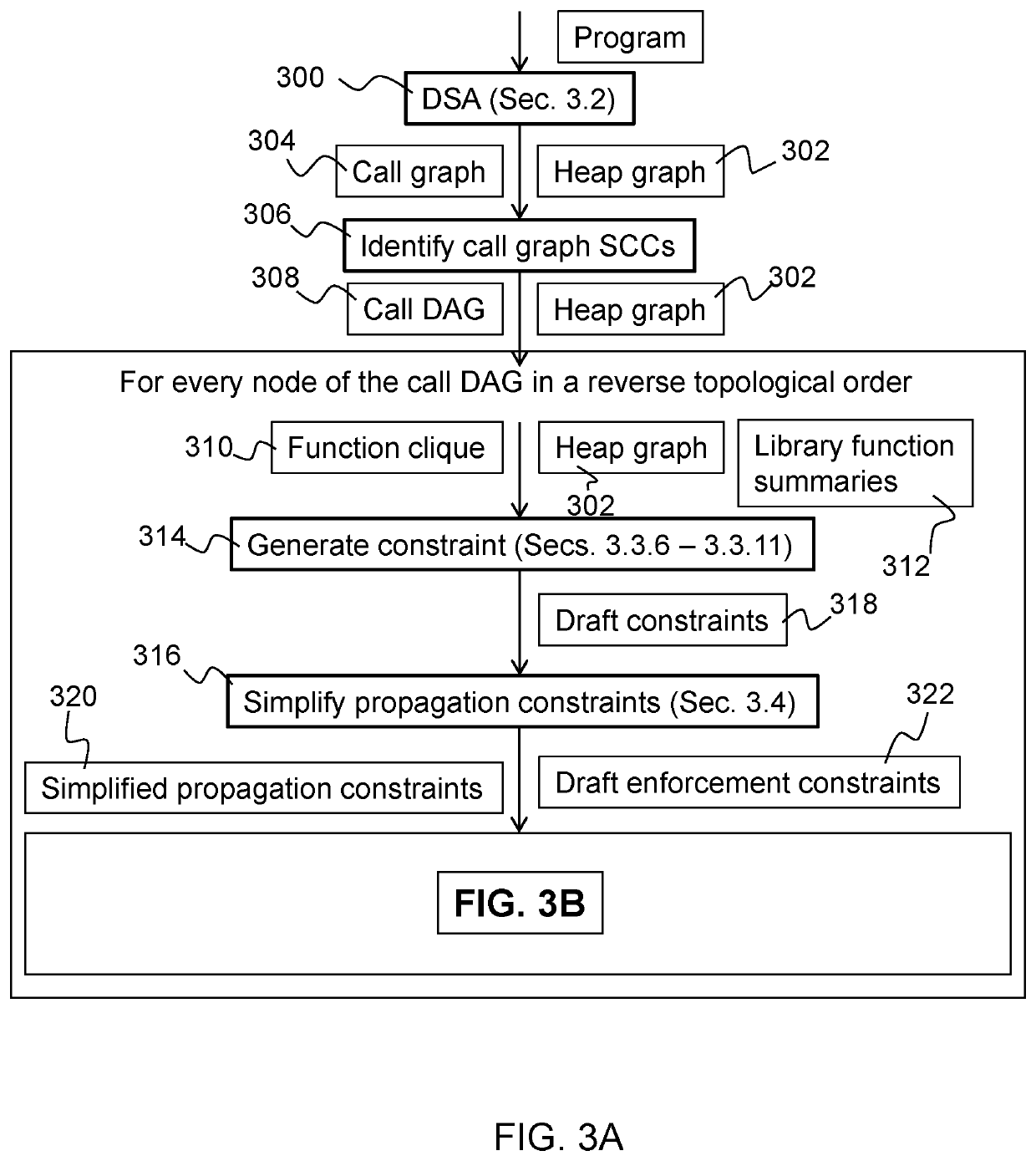
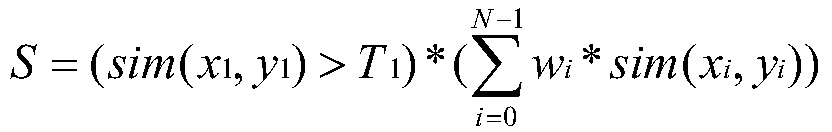Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
76 results about "Software dependencies" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
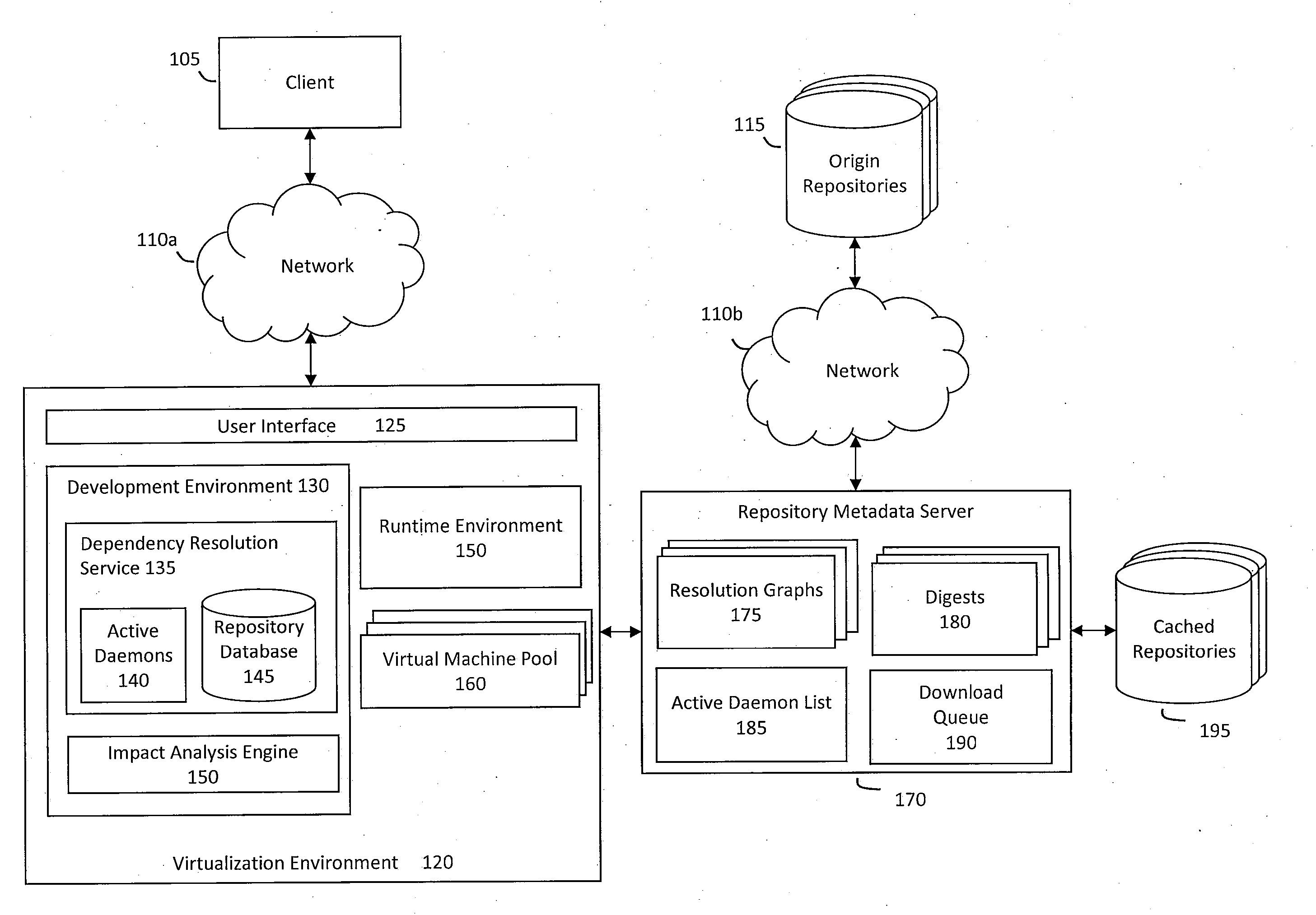
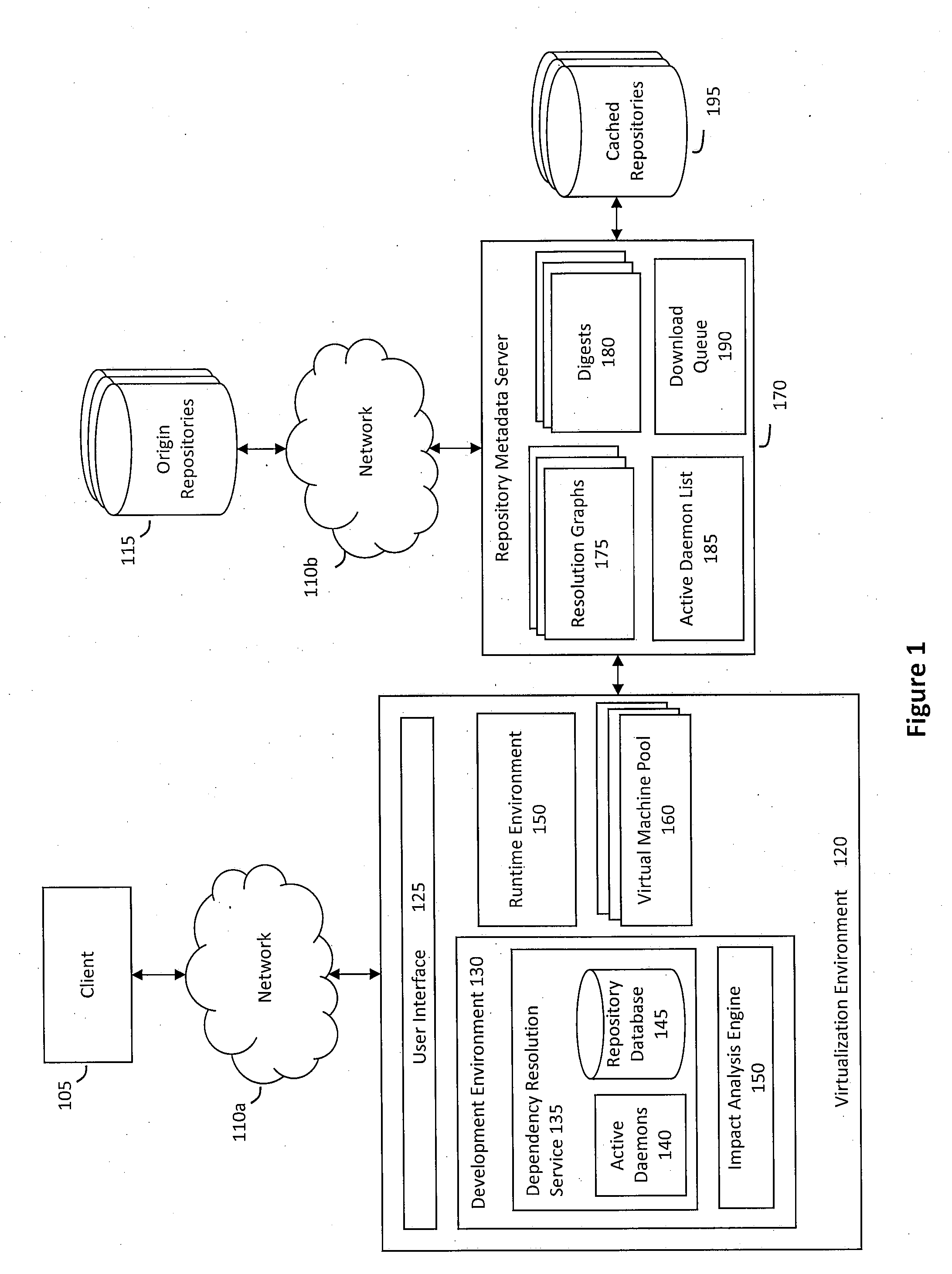
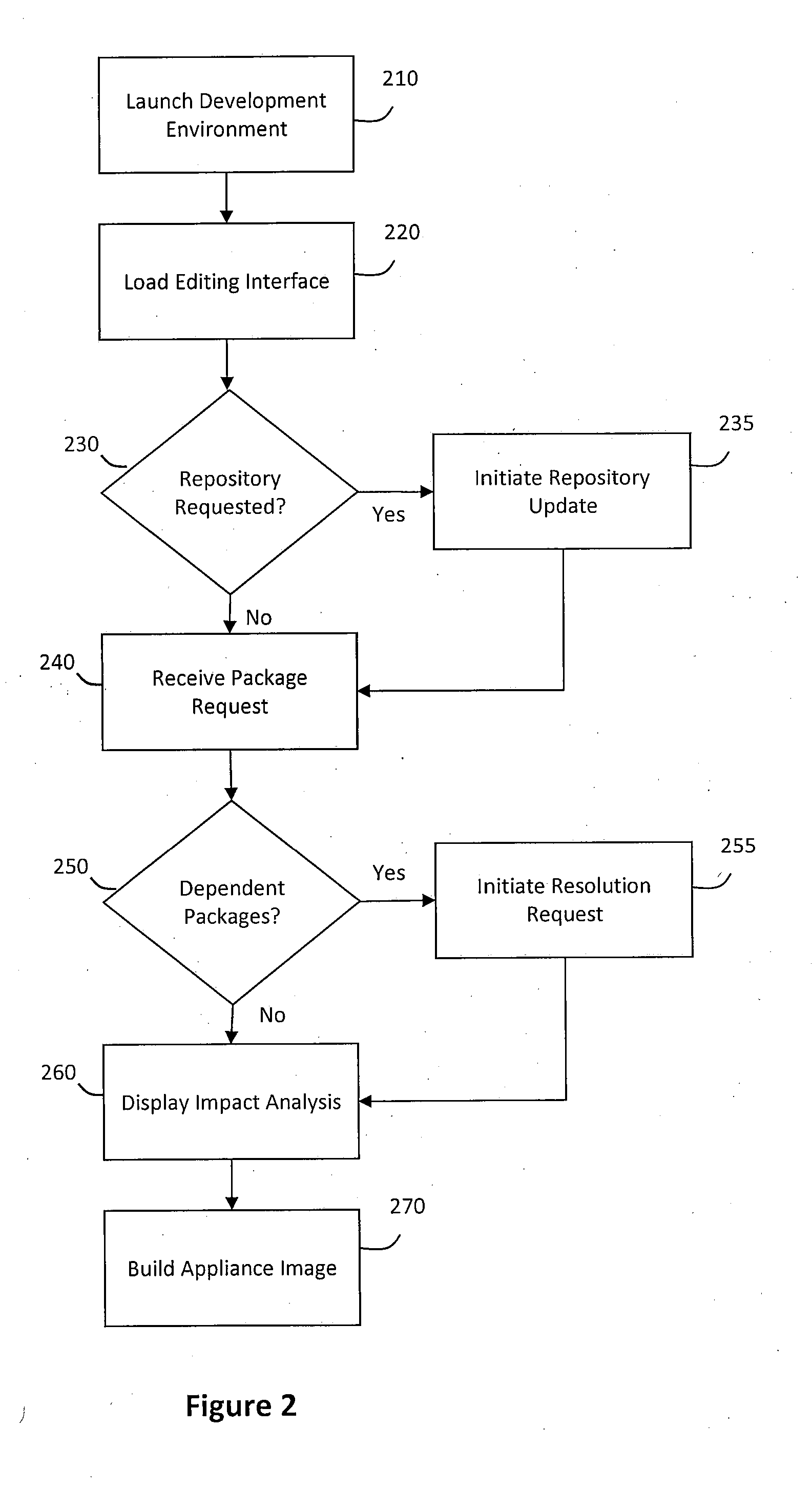
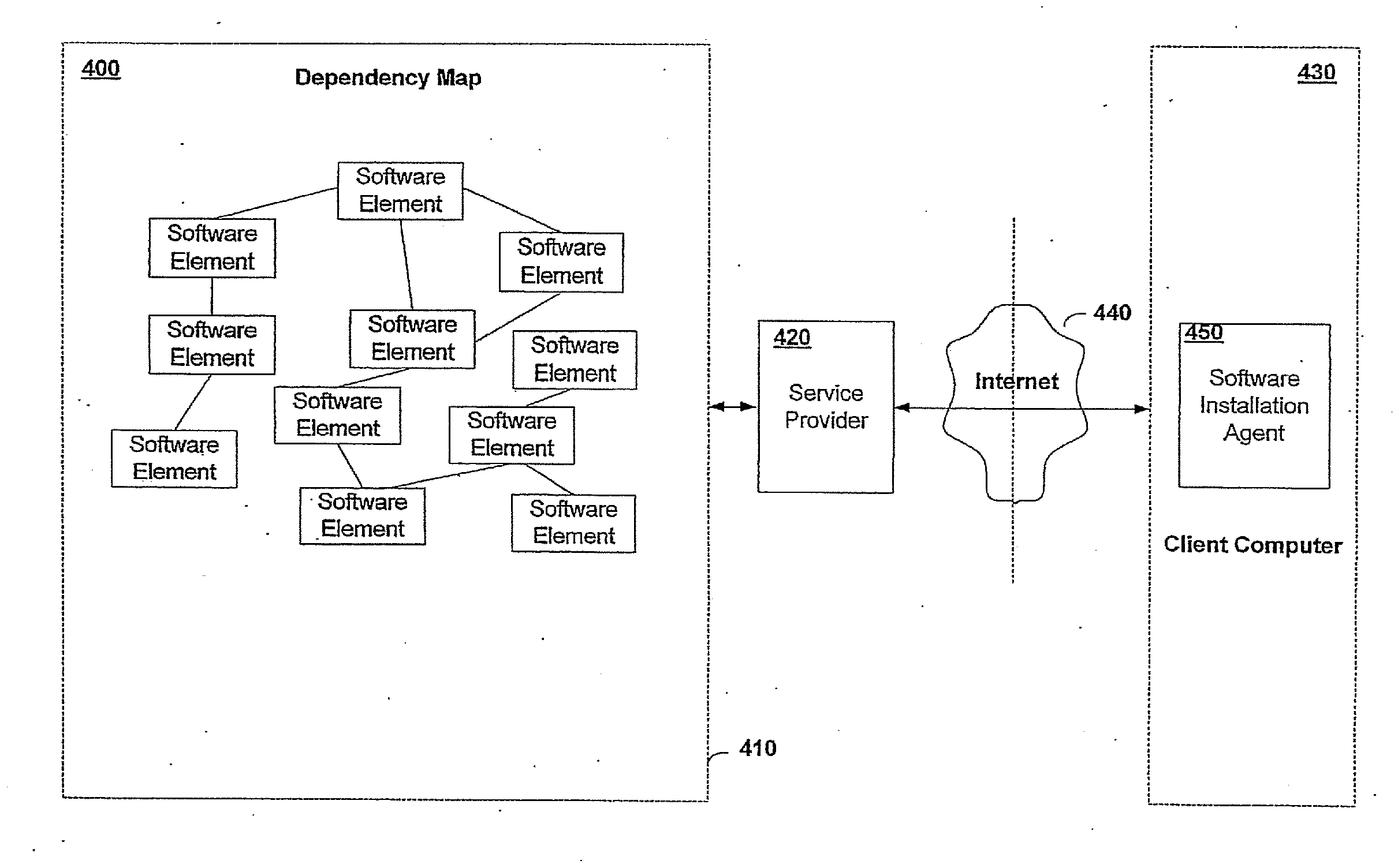
System and method for building virtual appliances using a repository metadata server and a dependency resolution service
ActiveUS20090300604A1Easy to buildEasy to configureError detection/correctionProgram loading/initiatingWeb serviceImage resolution
A system and method for building virtual appliances using a repository metadata server and a dependency resolution service is provided. In particular, a hosted web service may provide a collaborative environment for managing origin repositories and software dependencies, whereby remote clients may follow a simple and repeatable process for creating virtual appliances. For example, the repository metadata server may cache and parse metadata associated with an origin repository, download software from the origin repository, and generate resolution data that can be used by the dependency resolution service. The dependency resolution service may then use the resolution data to resolve dependencies for a package selected for an appliance, wherein the dependencies may include packages that are required, recommended, suggested, banned, or otherwise a dependency for the selected package.
Owner:ORACLE INT CORP
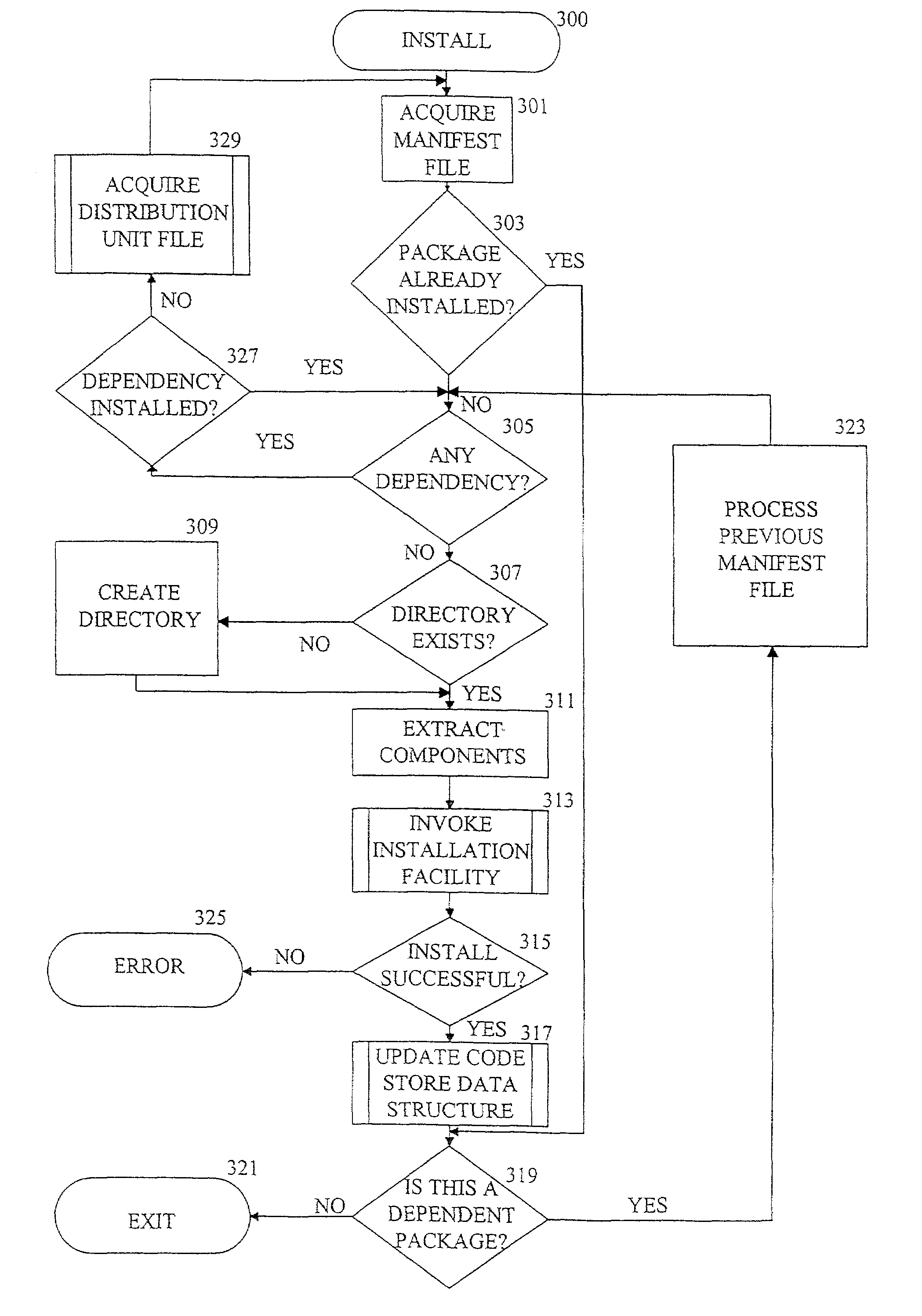
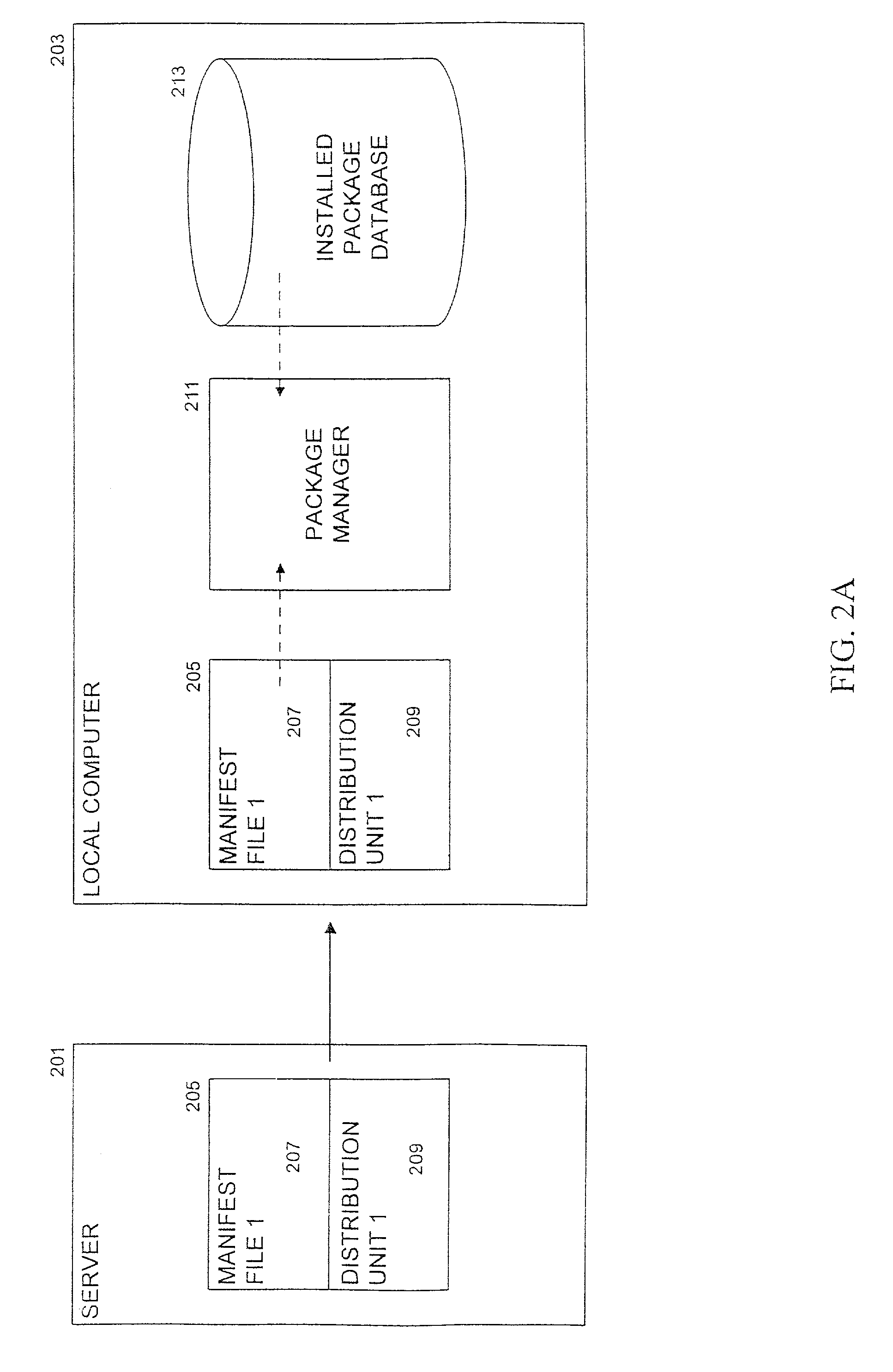
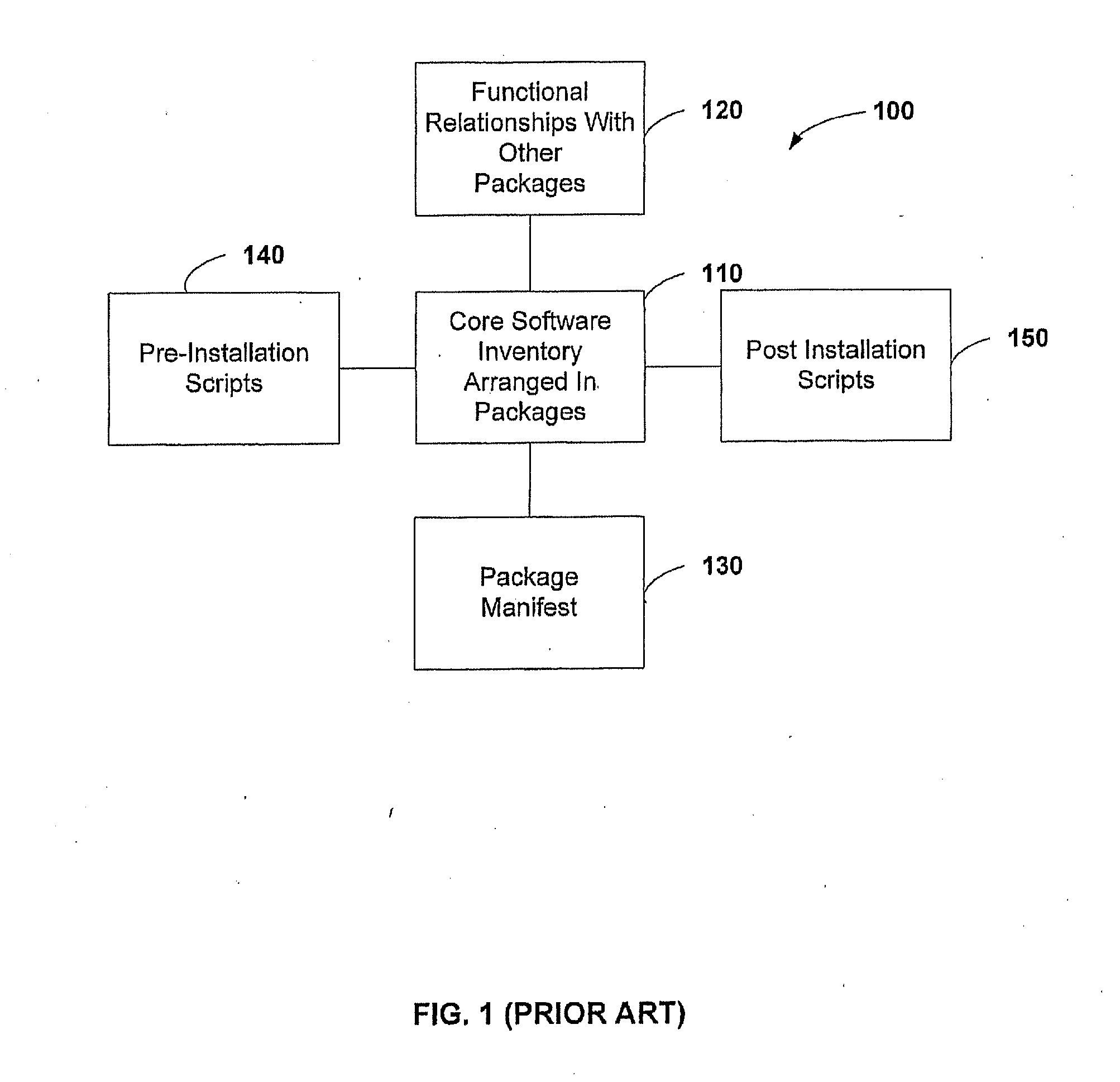
Method and system for processing software dependencies in management of software packages
InactiveUS7222341B2Easy to shareEases uninstallation processData processing applicationsProgram loading/initiatingManifest fileSoftware engineering
A software package manager uses a distribution unit containing components for a software package and a manifest file that describes the distribution unit to manage the installation, execution, and uninstallation of software packages on a computer. Information in the manifest file pertaining to a software package is stored in a code store data structure upon installation of the package. The manifest file also contains information that permits the software package manager to resolve any software dependencies upon installation. The software package manager uses the code store data structure to locate the required components when the software is executed and to remove the components appropriately when the software is uninstalled.
Owner:MICROSOFT TECH LICENSING LLC
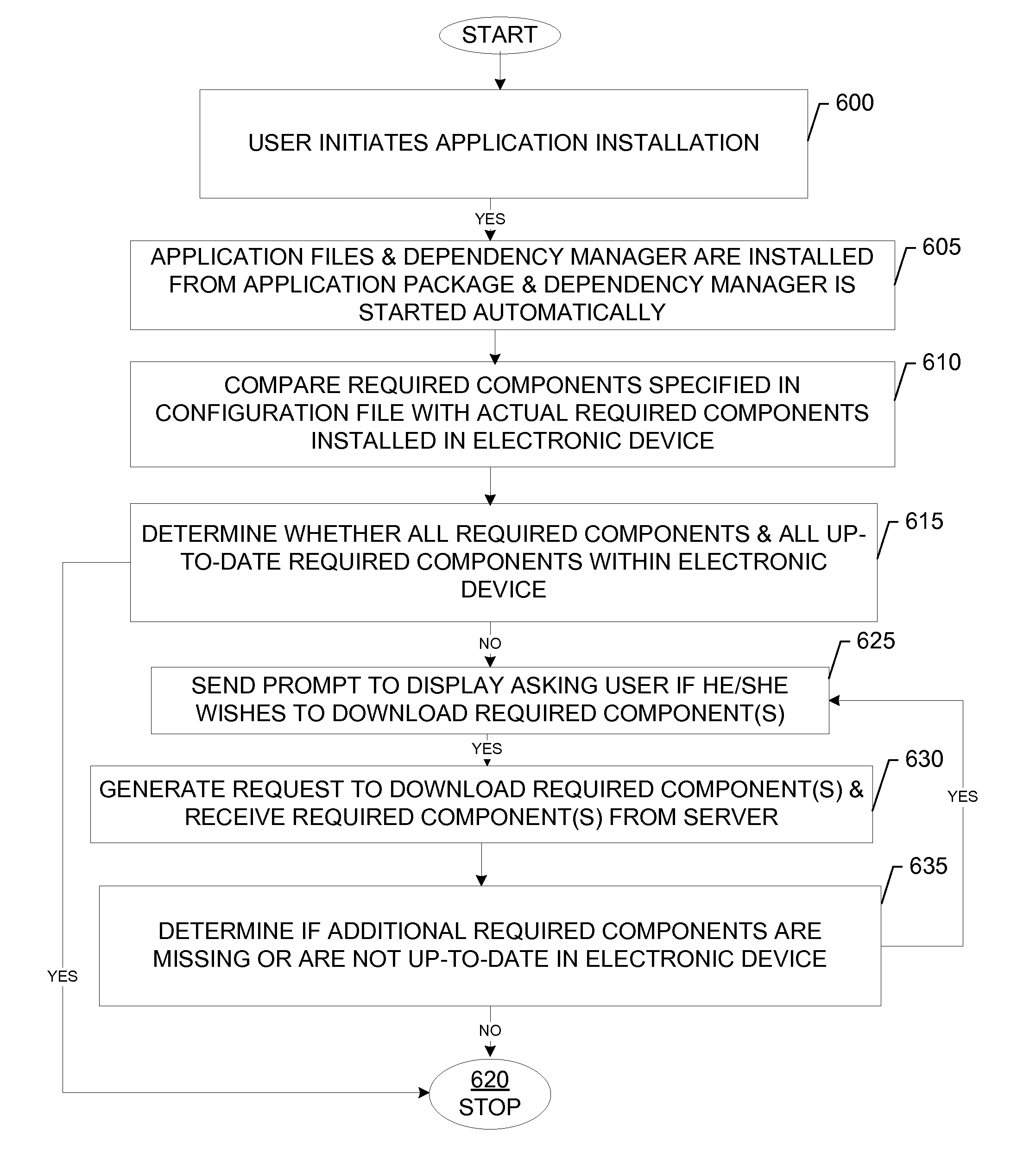
Methods, apparatuses and computer program product for automatic download of software dependencies on installation
InactiveUS20090133014A1Program loading/initiatingMemory systemsApplication softwareSoftware dependencies
A device for automatically downloading an application package is provided. The application package that is downloaded contains a dependency manager, a configuration file and other application files. During installation of the application package the dependency manager is started automatically and is capable of reading data in the configuration file contained within the application package. The dependency manager is further capable of comparing information relating to required components in the file with required components in the device and determining if any required components are missing or whether a newer version of the required components in the device are required. In this regard, the dependency manager is further capable of generating a request for a required component(s) that is missing or is not up-to-date and downloading the missing or outdated required component(s) from a server. The dependency manager is further capable of installing the downloaded required component(s) in the device.
Owner:NOKIA CORP
Efficient extraction of software dependencies from program code
InactiveUS20110029946A1Efficient extractionError detection/correctionSoftware maintainance/managementSoftware dependenciesProgram code
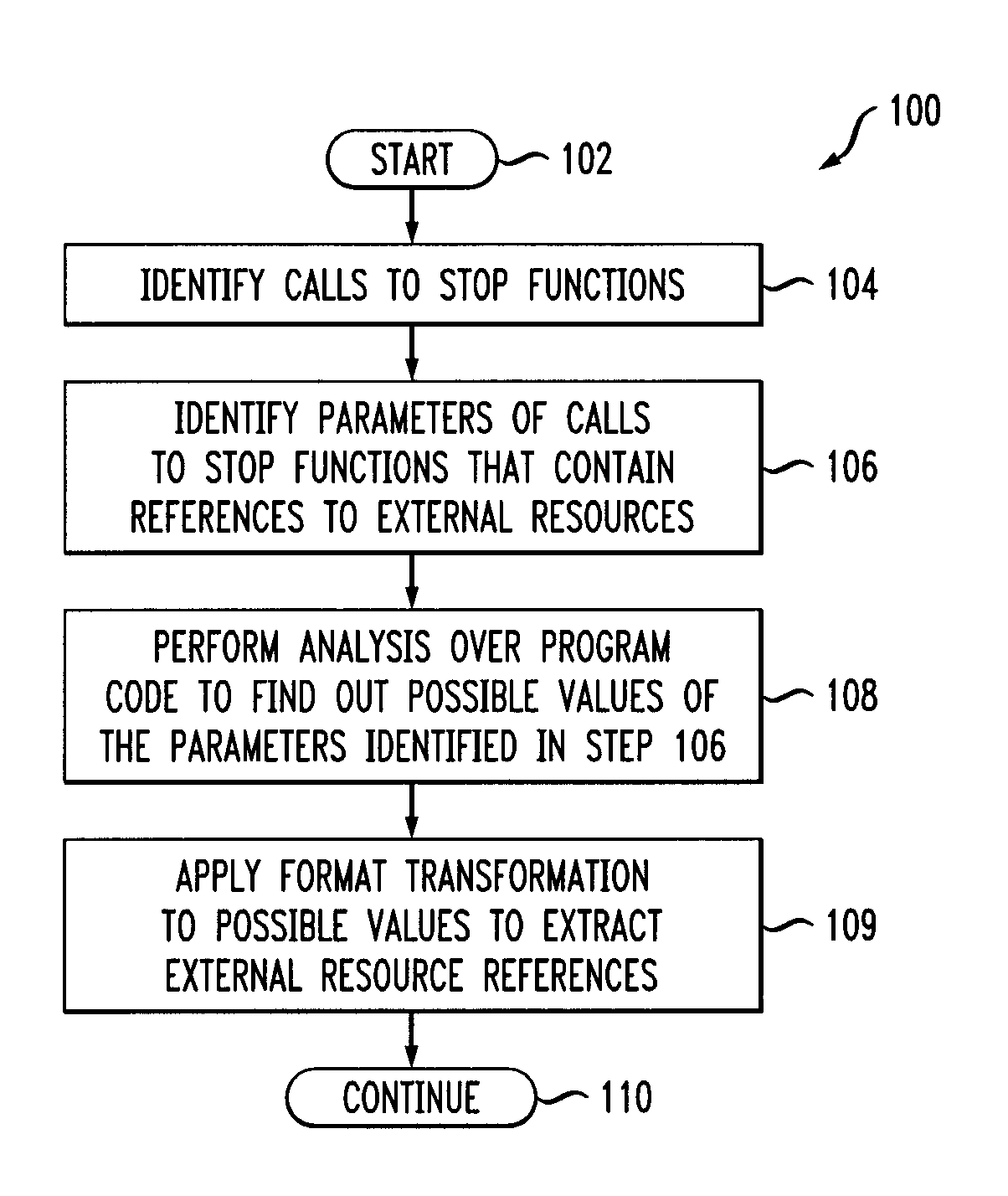
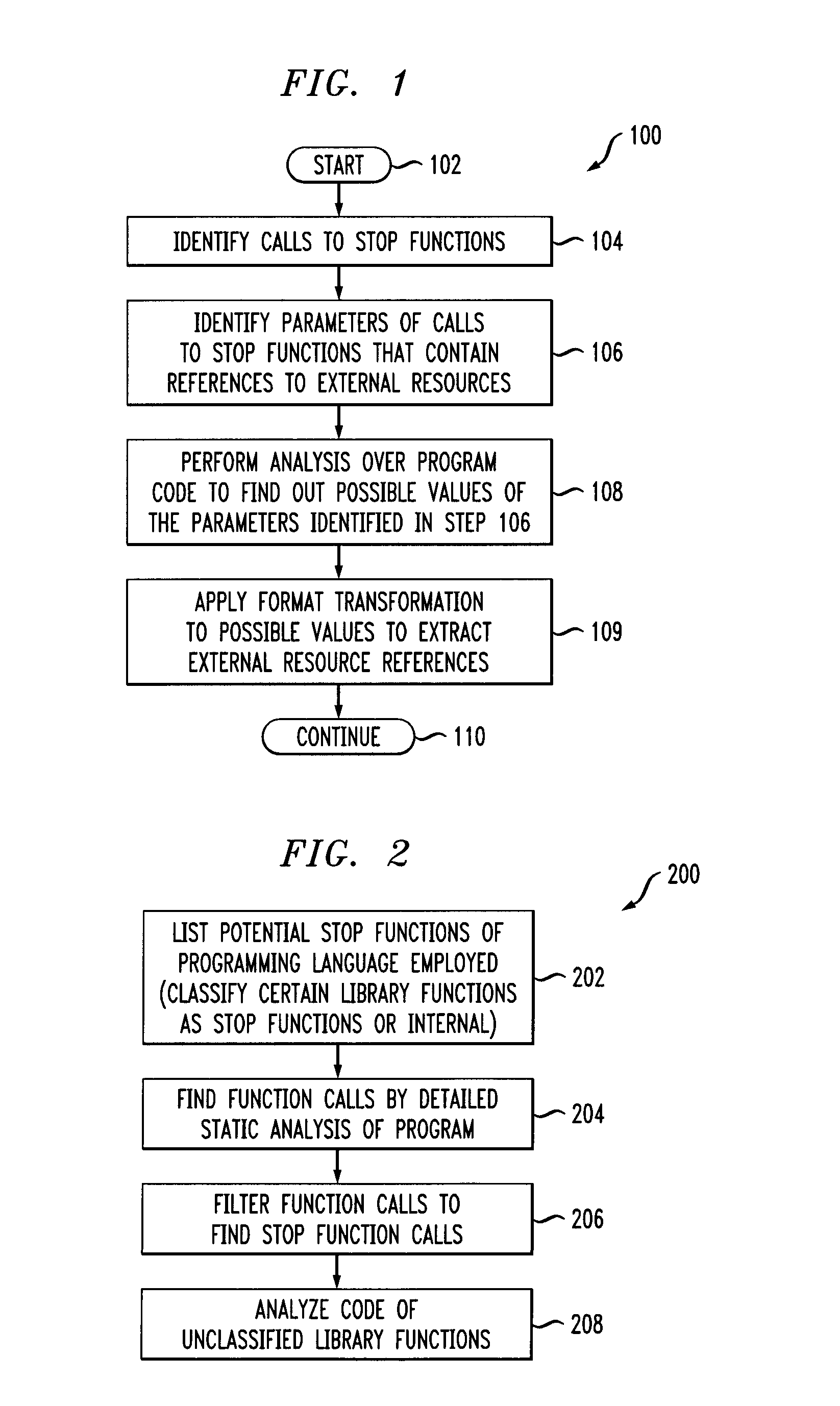
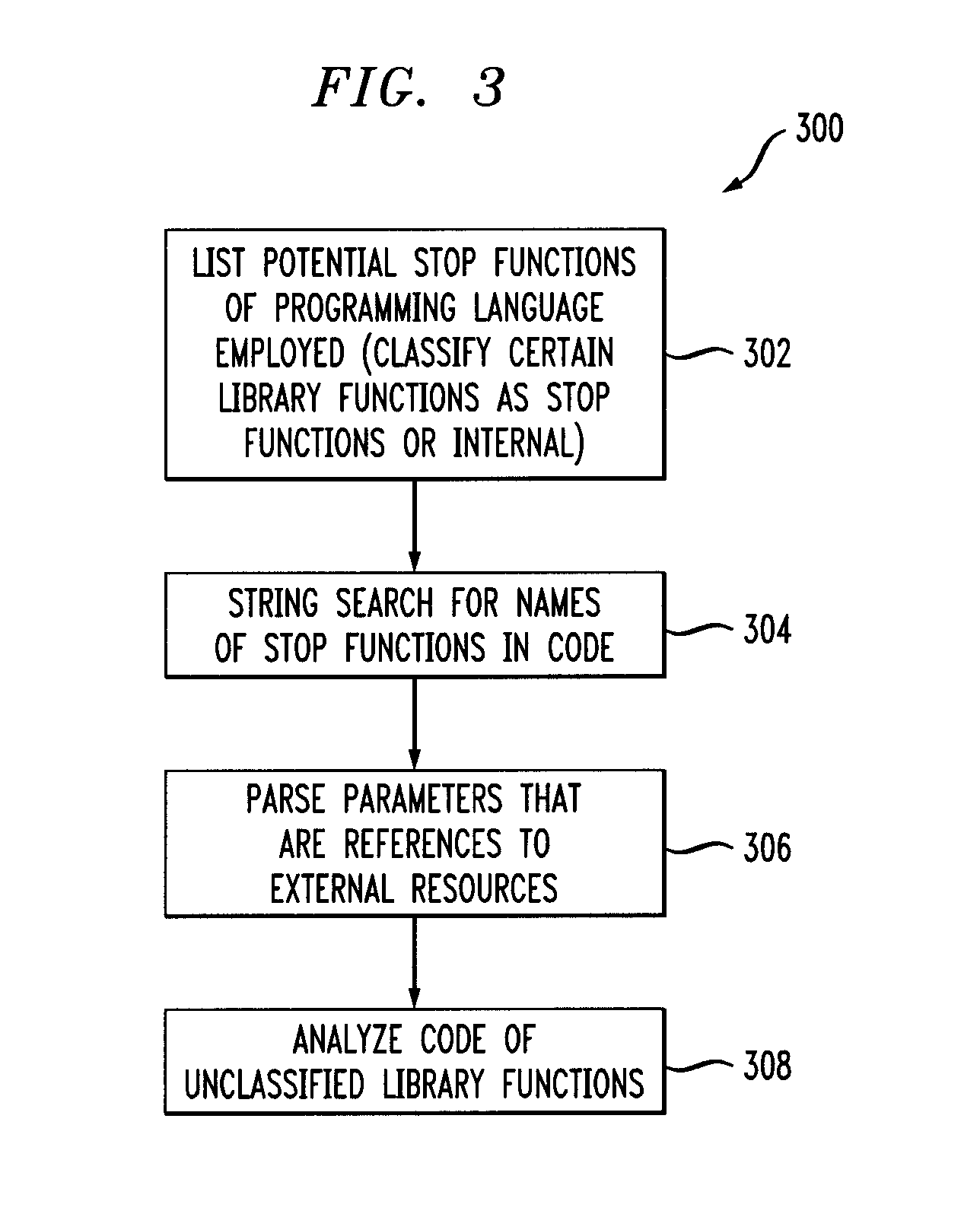
Calls to stop functions are identified in a computer program file. The stop functions are functions that interact with external resources. Parameters of the calls to the stop functions that are references to the external resources are identified. An analysis is performed over the computer program file to find out possible values of the parameters of the calls.
Owner:IBM CORP
Large-scale network monitoring oriented virtual deployment system and method
InactiveCN102437938AImprove work efficiencyImprove scalabilityData switching networksVirtualizationMatch rule
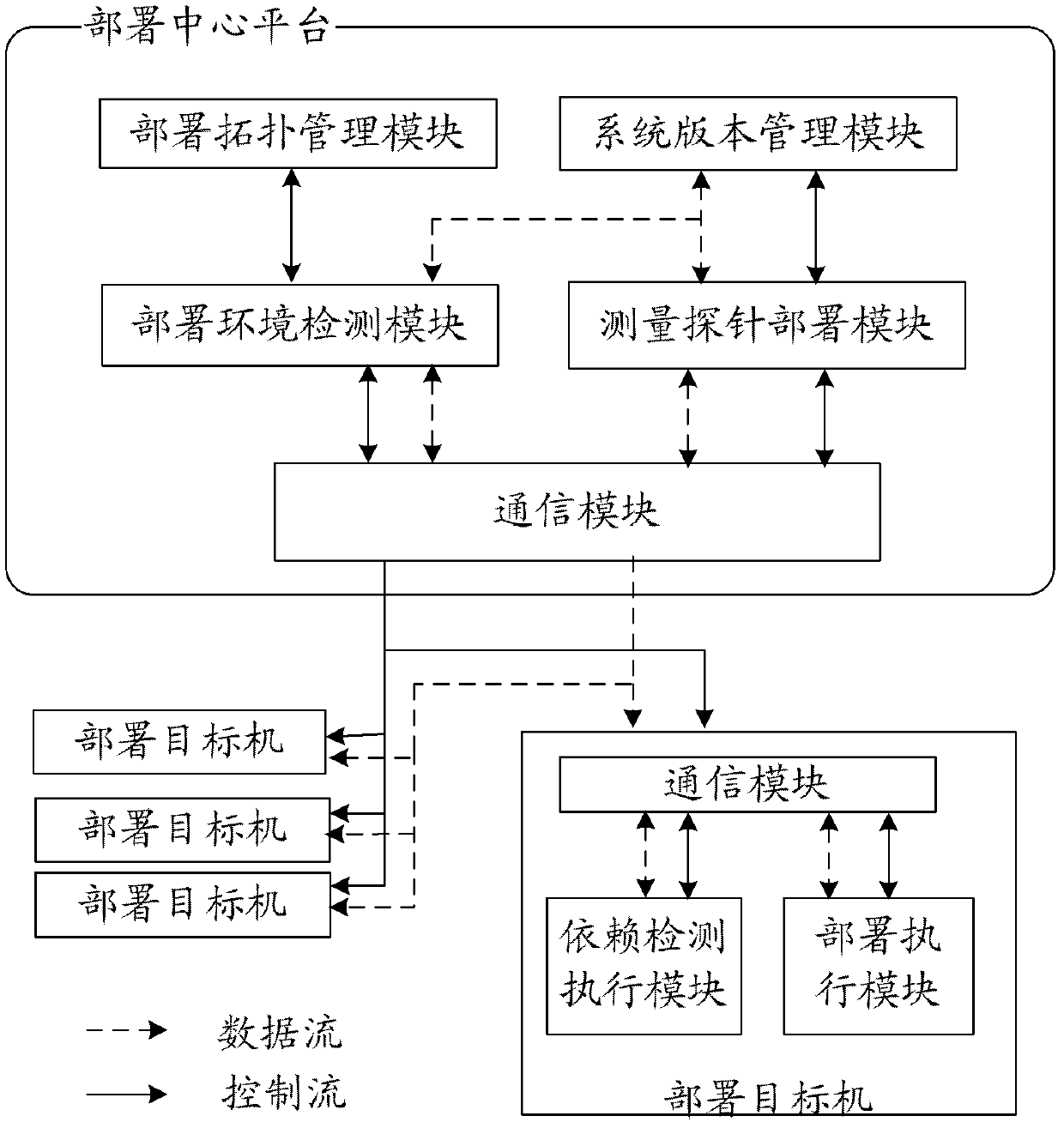
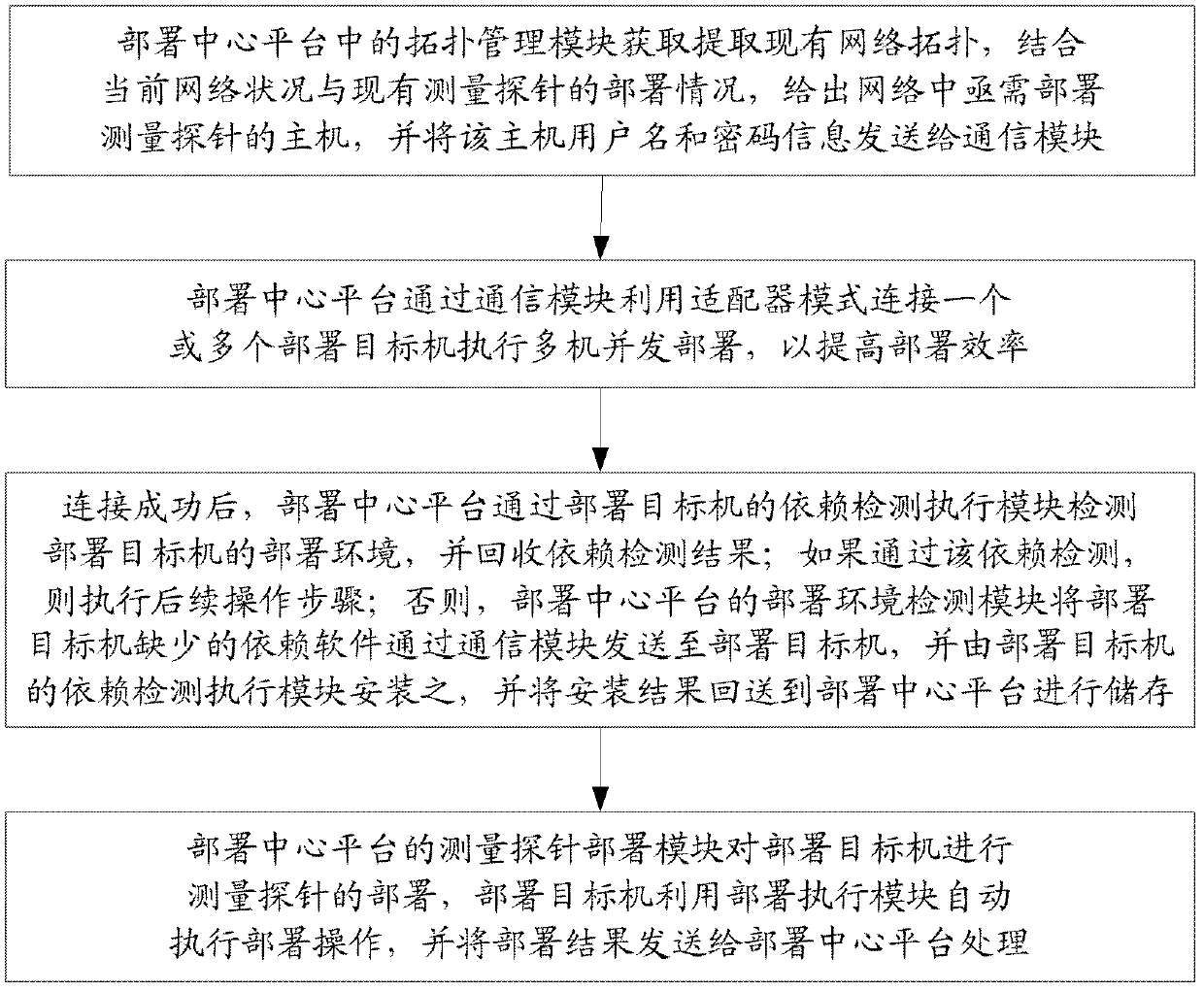
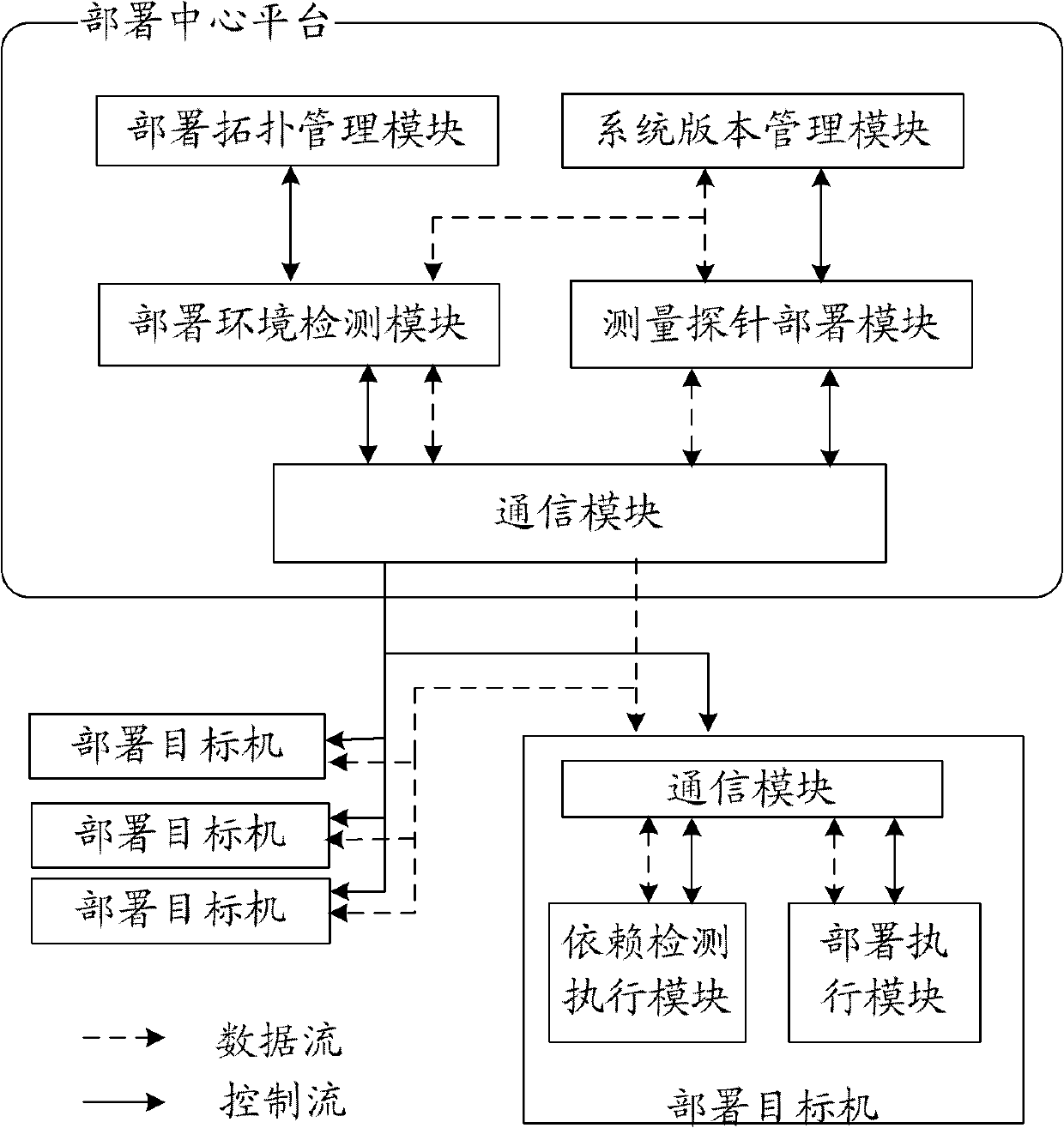
The invention discloses a large-scale network monitoring oriented virtual deployment system and method. The system is provided with a deployment center platform and a plurality of deployment target machines communicated with the deployment center platform via a network. The deployment center platform is responsible for uniformly planning and managing a topology structure of measurement probe deployment in an entire computer network, issuing a deployment task according to the existing measurement probe deployment condition and network congestion condition, and executing management and version control on the deployed measurement probes. The deployment target machines receive and execute commands from the deployment center platform, and automatically execute corresponding operations so as to enable the measurement probes to be usable in the network; and a software dependency detection mechanism and a process matching rule are respectively used for realizing the platform independency of deployment and verifying the achievement of deployment. The system and the method can be used for solving a plurality of problems, such as dependency detection for deployment environment of the target machines, upgrading and maintaining of a management system version, concurrent deployment, automatic installation and detection of the plurality of target machines, dynamic scheduling and the like, in the prior art, and have better promotion and application prospects.
Owner:BEIJING UNIV OF POSTS & TELECOMM
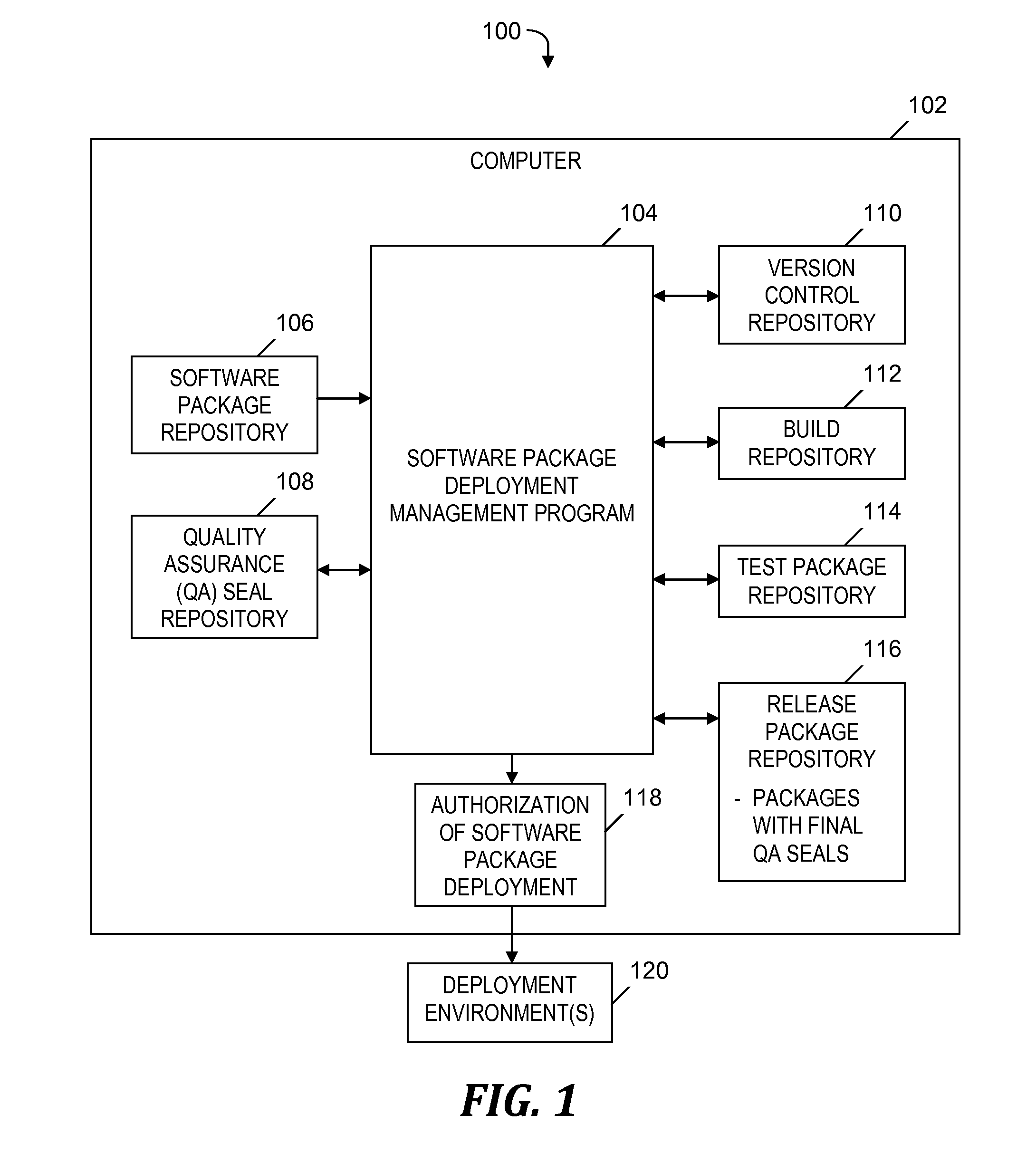
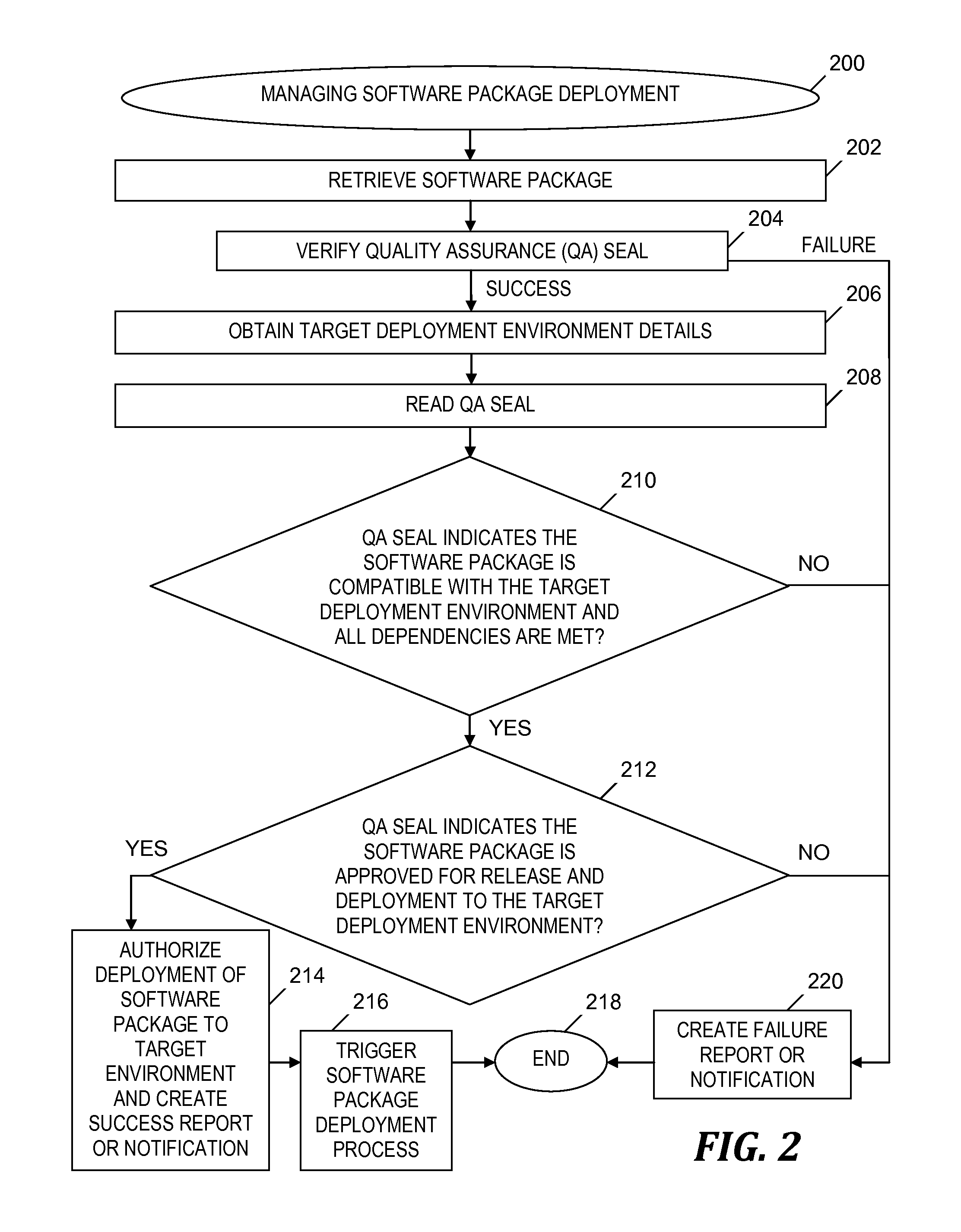
Seal-based regulation for software deployment management
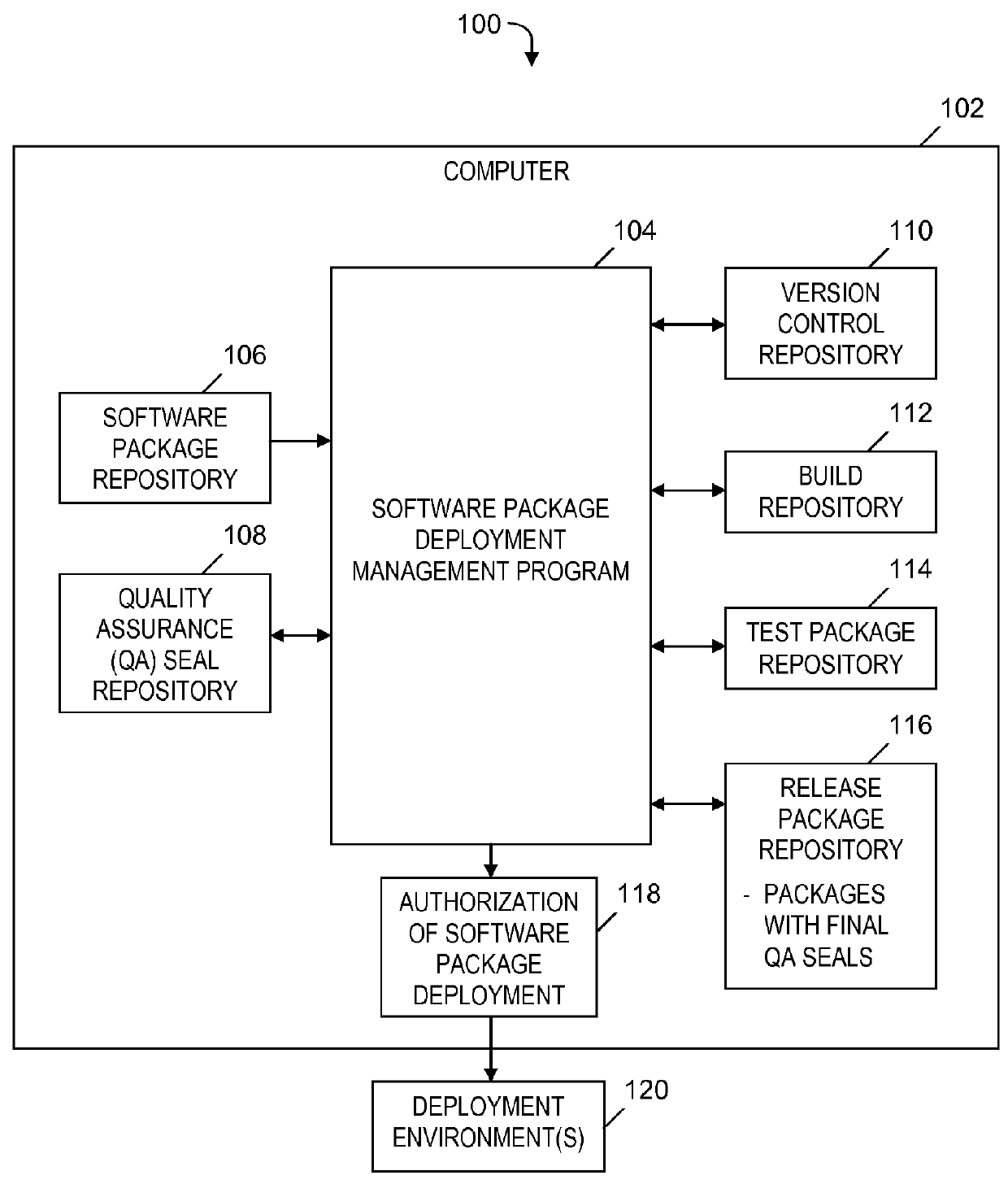
InactiveUS20150199188A1Easy to solveQuality improvementVersion controlComputer security arrangementsQuality assuranceSoftware dependencies
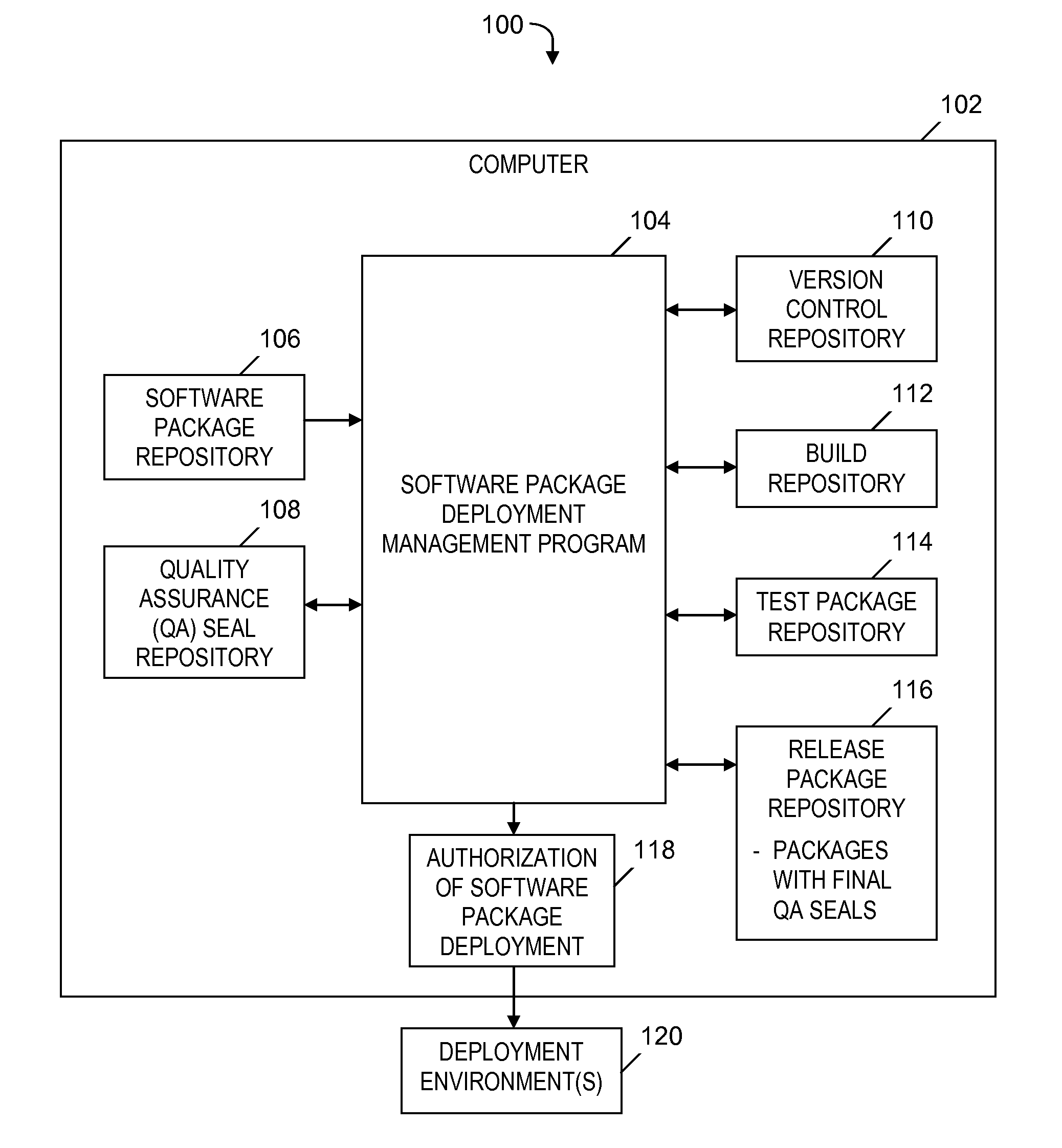
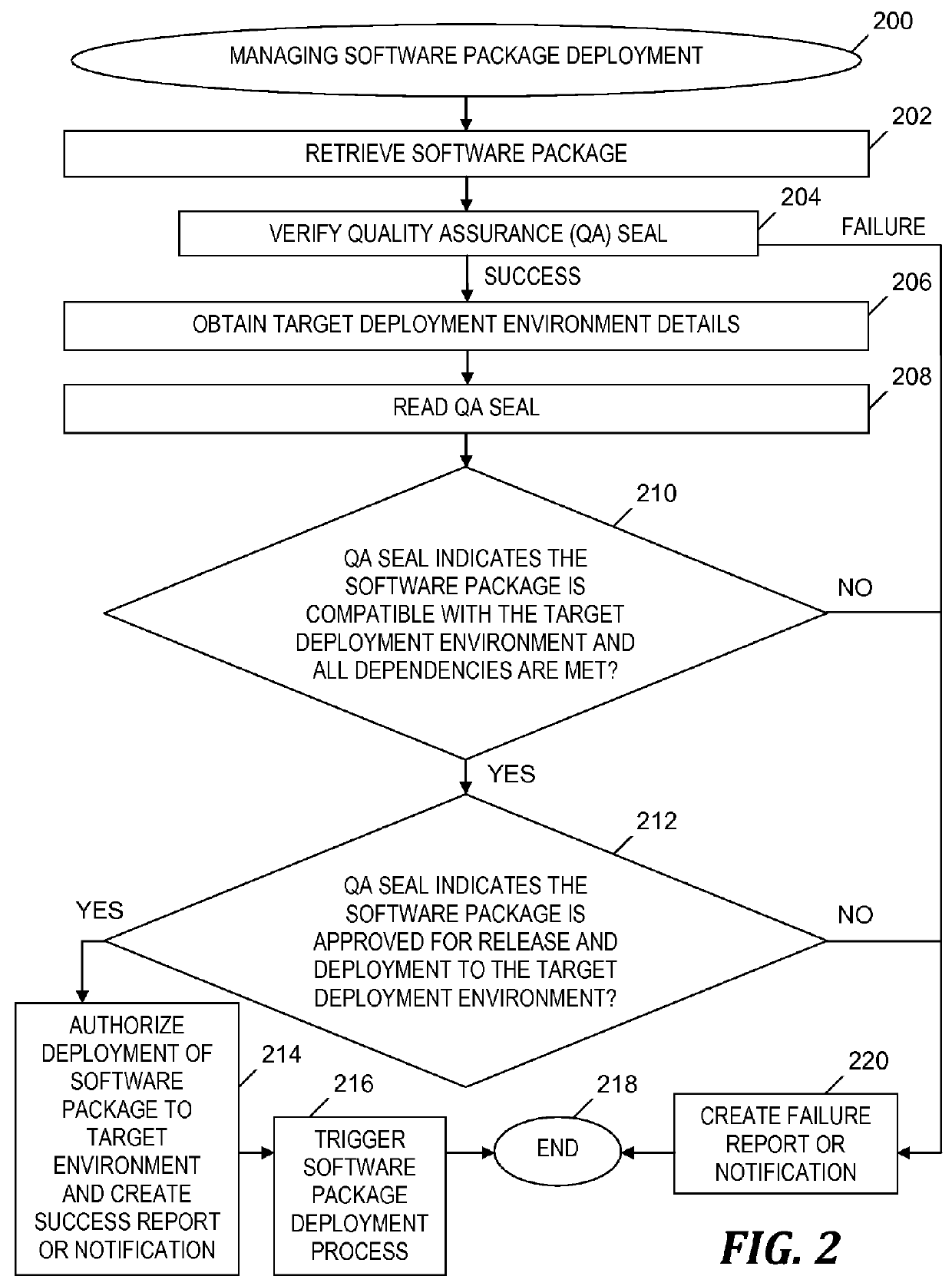
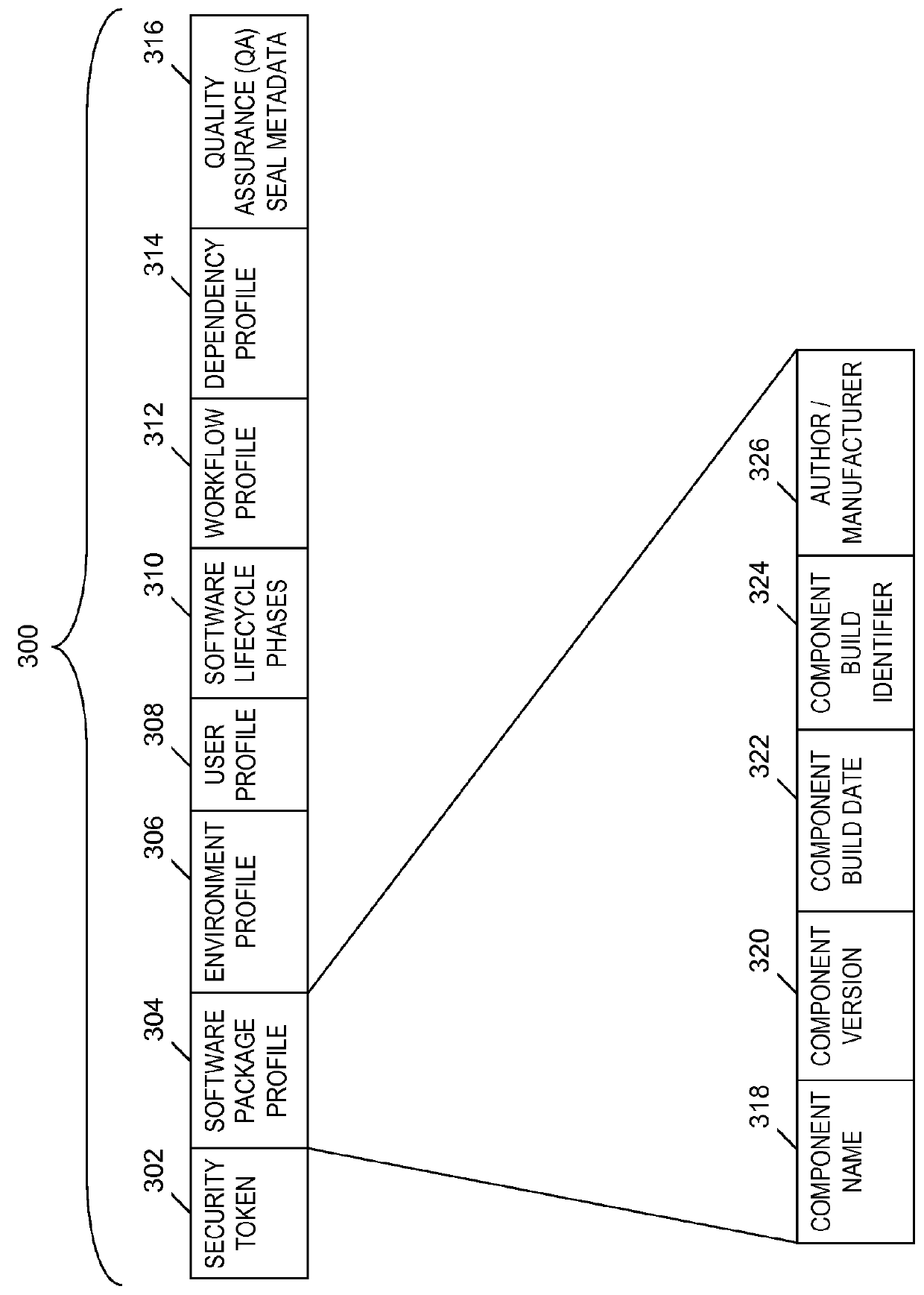
An approach is provided for managing a deployment of a software package. A retrieved quality assurance (QA) seal corresponding to a software package is verified. A target deployment environment (TDE) is obtained. The QA seal is read to obtain first and second profiles, and metadata, which specify a deployment environment, hardware and software dependencies required in the deployment, and an approval for a release of the software package to the specified deployment environment, respectively. Based on a determination that the TDE matches the specified deployment environment, the QA seal indicates the software package is compatible with the TDE. The dependencies are determined to be satisfied. Based on the software package being compatible with the TDE, the dependencies being satisfied, and the specified approval for the release of the software package, a notification of an authorization of the deployment of the software package to the TDE is generated.
Owner:IBM CORP
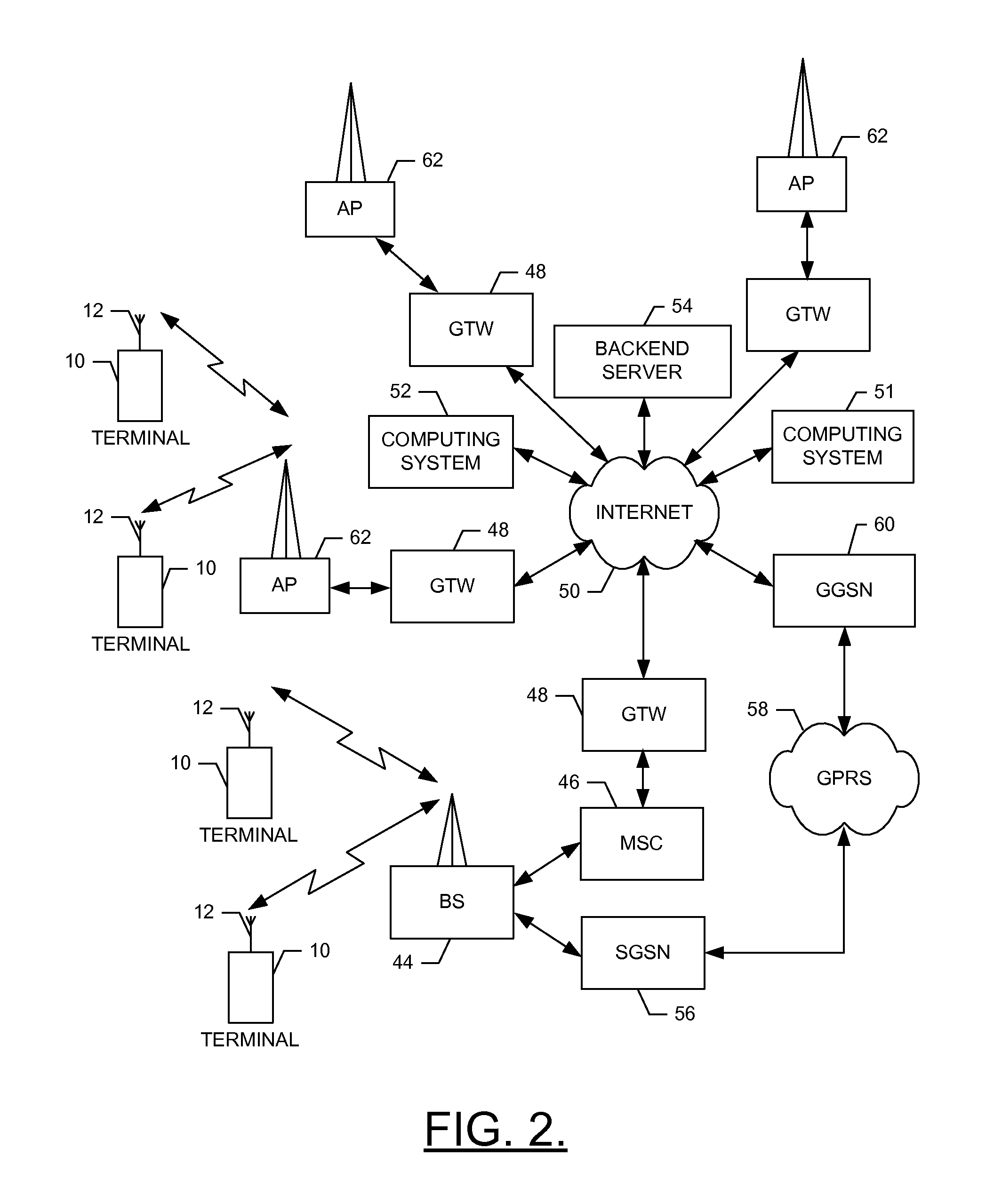
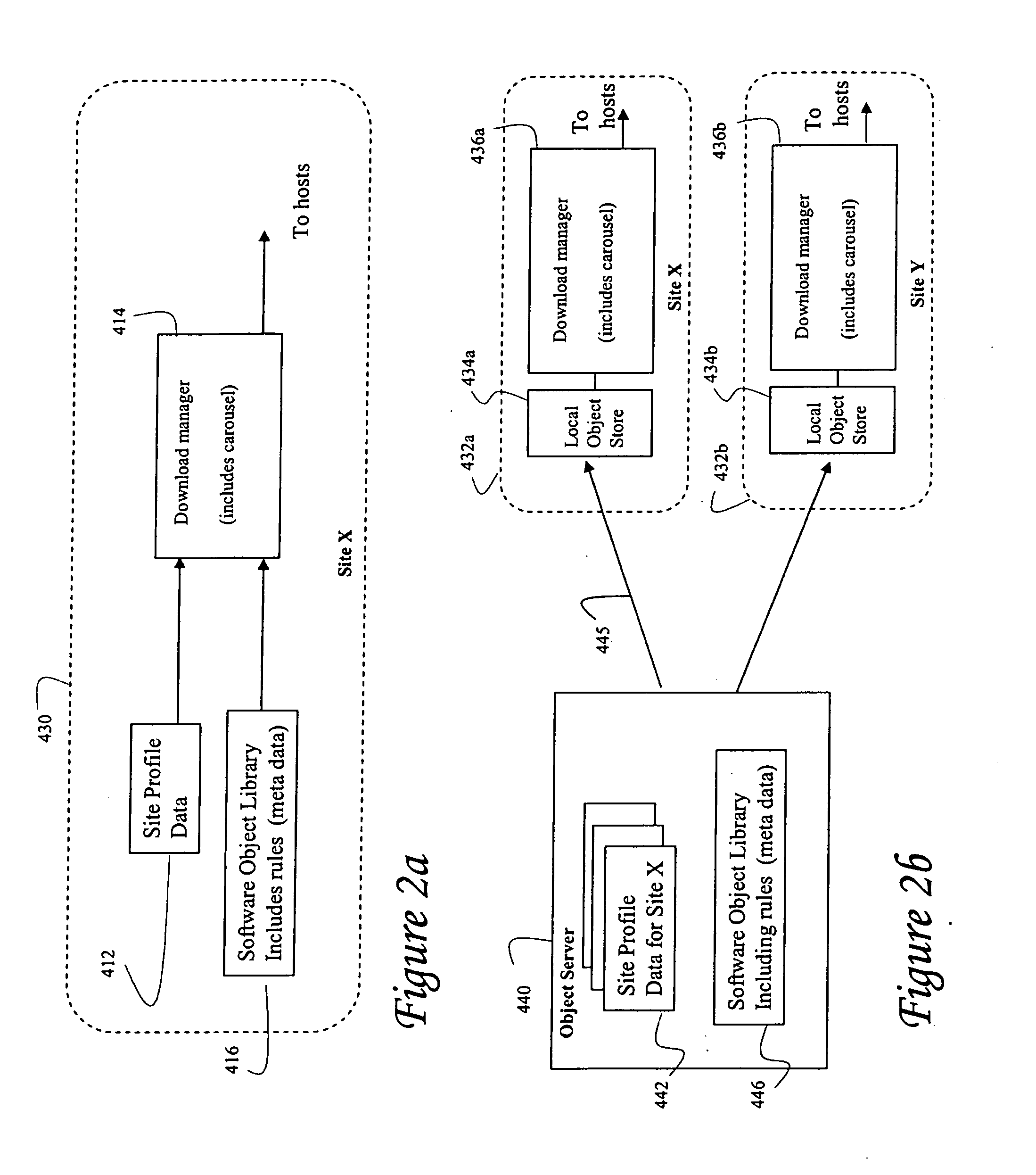
Systems and methods for distributing software to a host device in a cable system
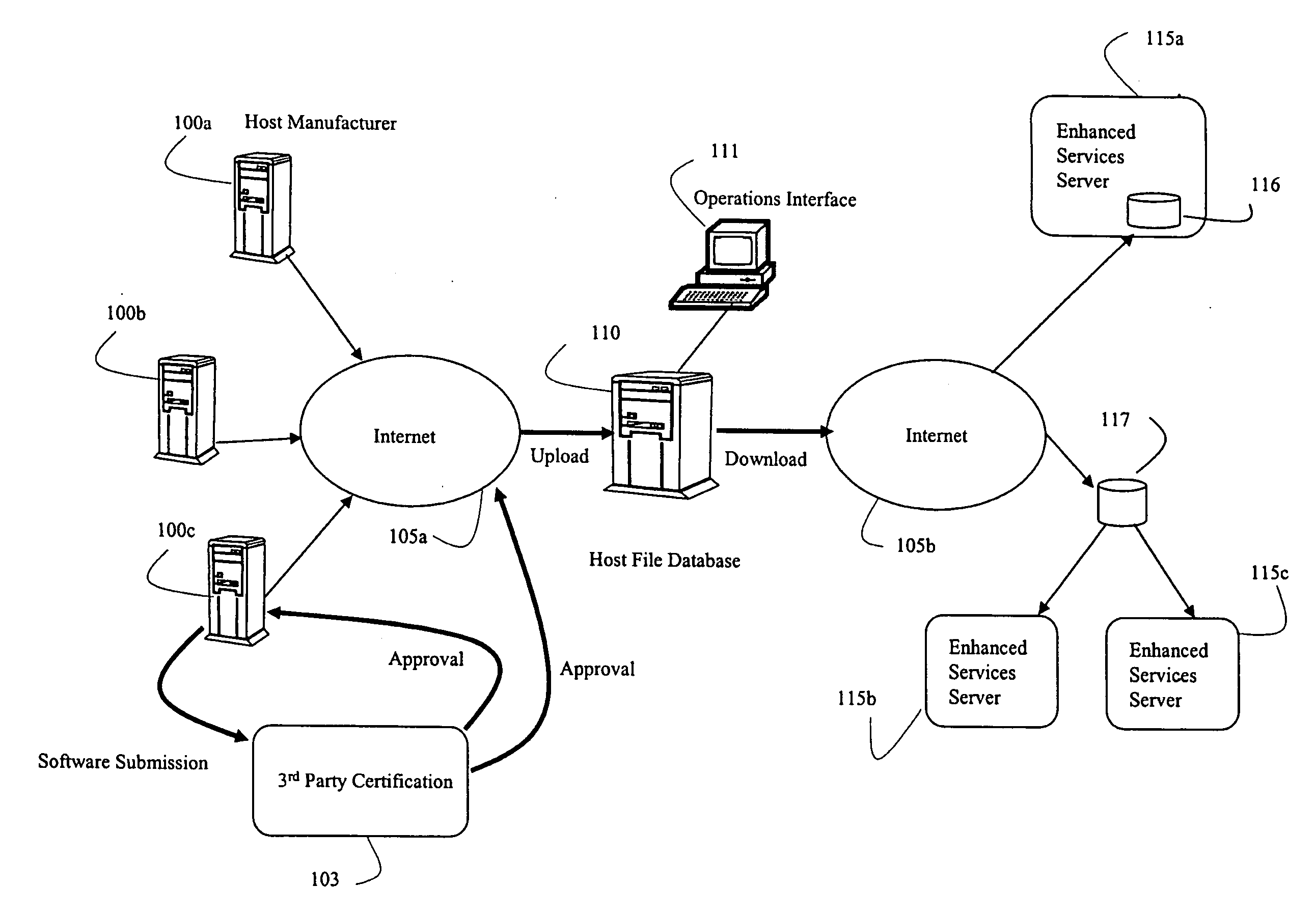
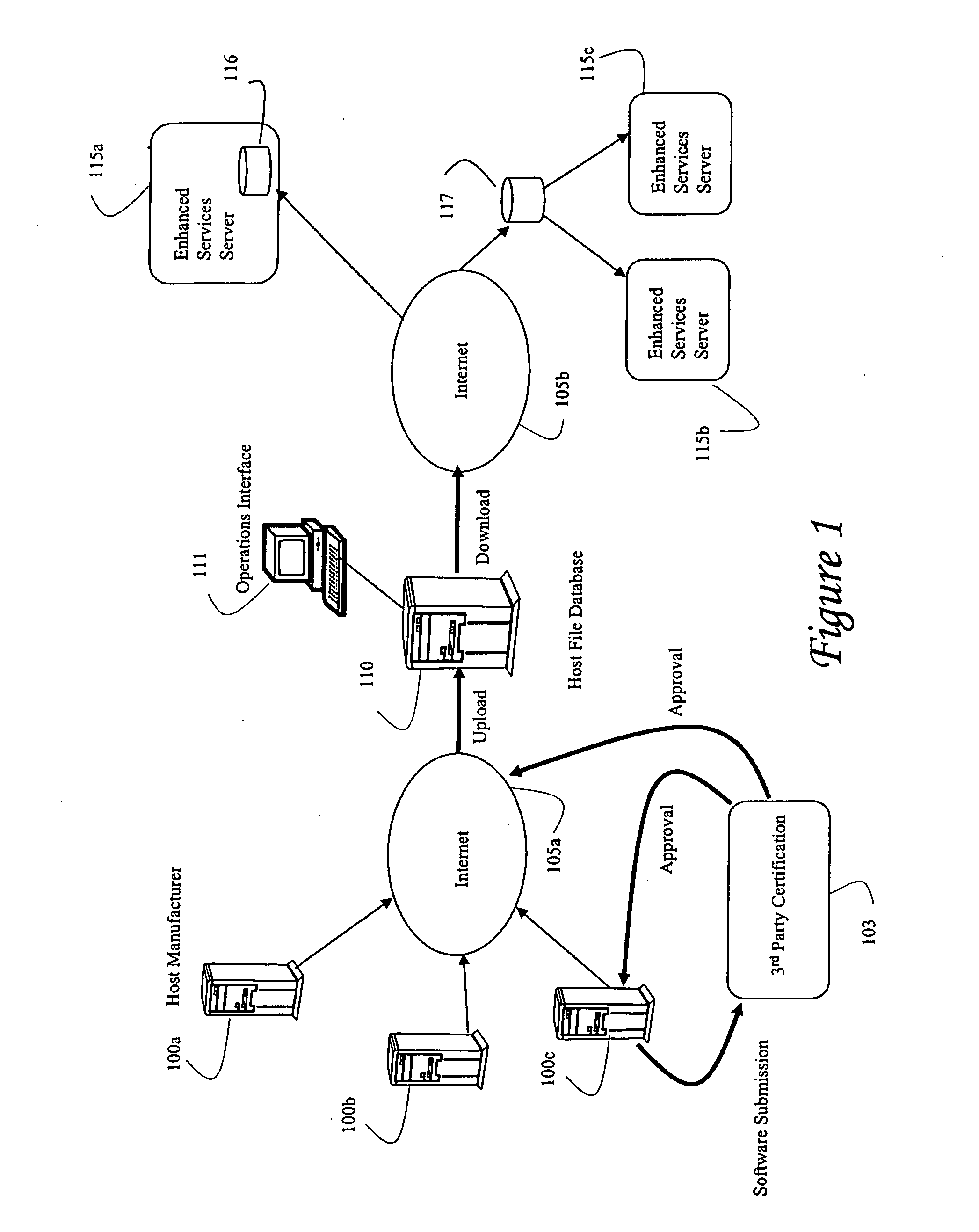
InactiveUS20070239841A1Multiple digital computer combinationsSelective content distributionComputer hardwareSoftware distribution
A system and method is disclosed for orderly distribution of software modules to various hosts in a cable system. A download manager ensures distribution of required and compatible software objects to various hosts in a cable system. The system abstracts various software dependencies and host-specific aspects from the network operator, allowing easy and efficient update of host software for a variety of host in an otherwise error prone process. The system allows a host to identify itself to the network for purposes of associating the host to a host profile, which ensures necessary and only compatible software modules are downloaded. The system also uses site profile data to determine appropriate software modules for distribution to the host.
Owner:TANDBERG TELEVISION +1
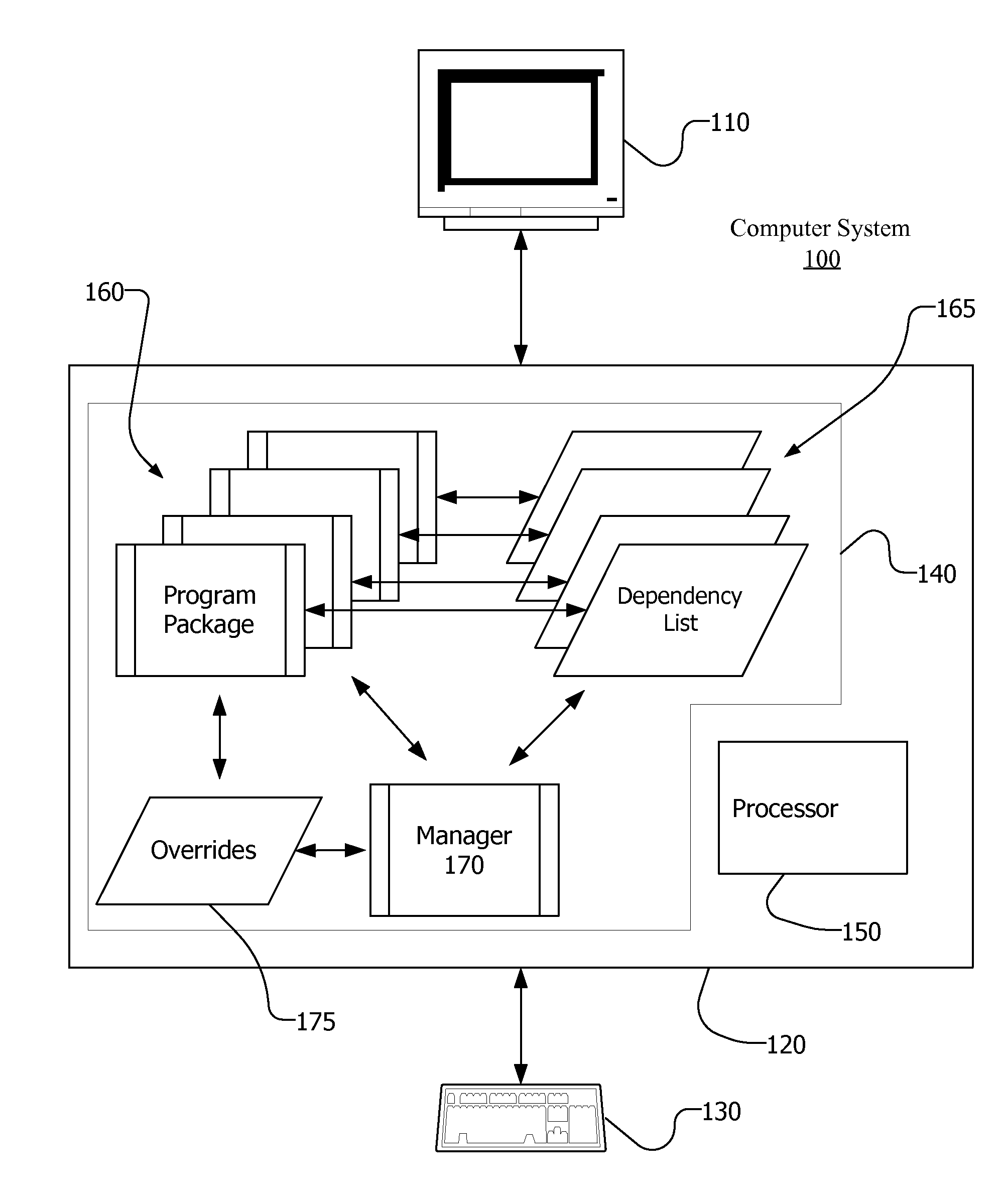
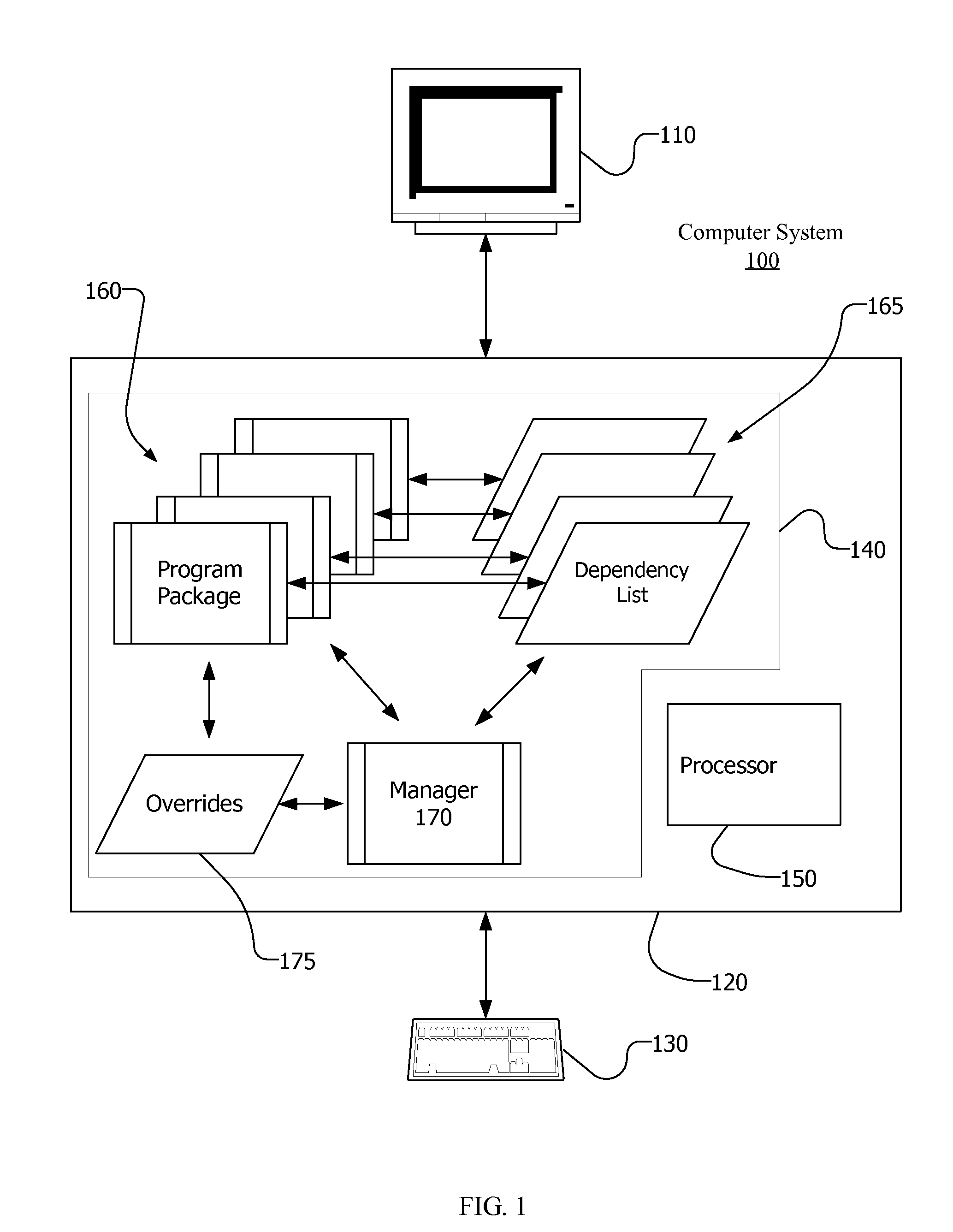
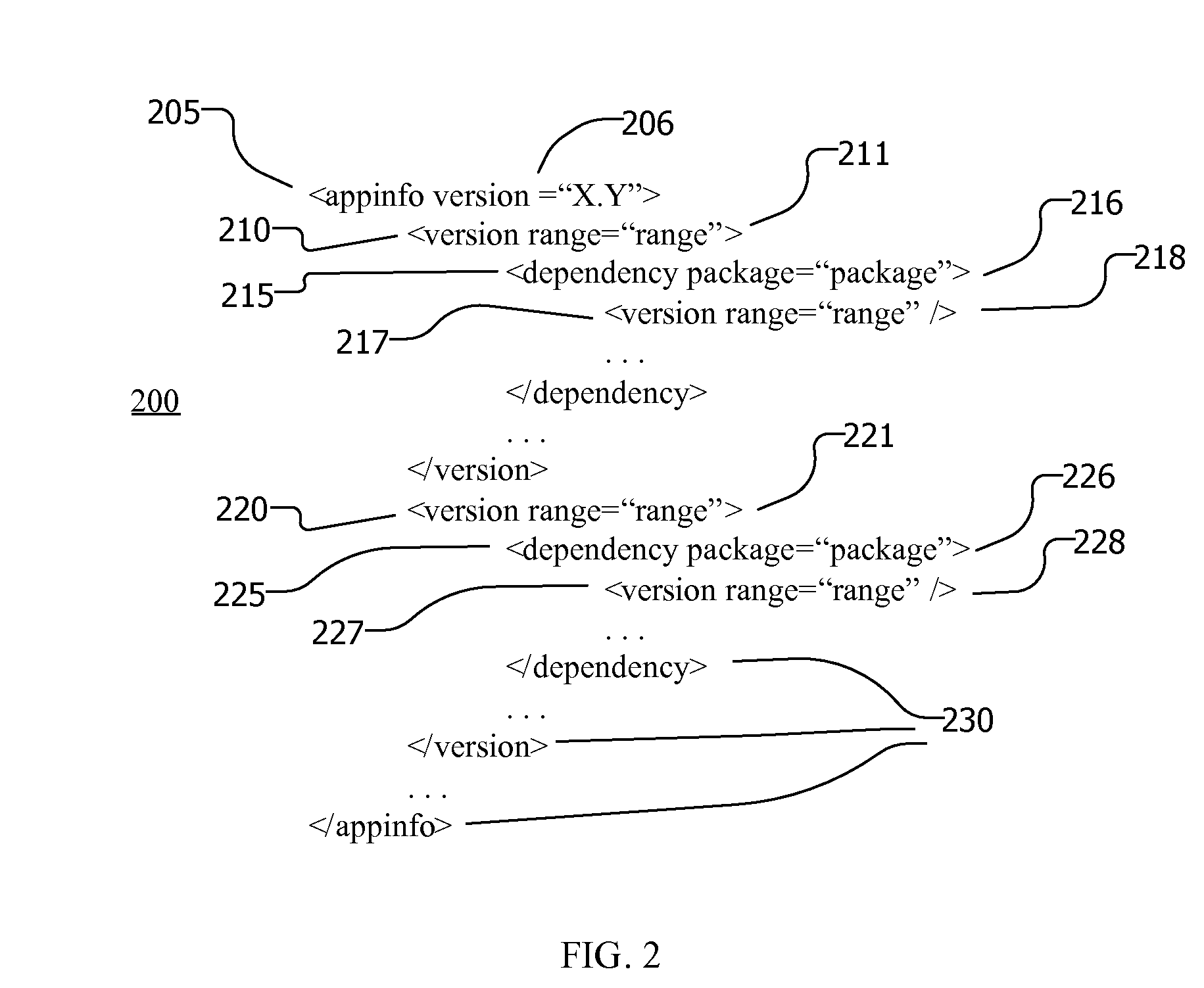
Specifying, Determining and Overriding Software Dependencies
InactiveUS20100125839A1Version controlSpecific program execution arrangementsSoftware dependenciesRunning time
Owner:IXIA
Plug-in type software deployment method and apparatus, and application server
ActiveCN105099739AEfficient managementEfficient life cycleProgram loading/initiatingData switching networksApplication serverMutual dependency
The invention provides a plug-in type software deployment method and an apparatus, and an application server. The method includes: receiving a request message of software deployment from a client; according to the request message, searching a plurality of plug-ins related to the request message of software deployment in a plug-in logic tree established according to the mutual dependency relation of the plug-ins; and sending scripts generated by the plurality of plug-ins obtained by searching to various to-be-deployed nodes, and feeding back results of software deployment of the to-be-deployed nodes to the client. In this way, the complicated software dependency relation is solved by employing the dependency relation between the software deployment plug-ins, and the convenience of the plug-in type software deployment is effectively improved.
Owner:CHINA MOBILE COMM GRP CO LTD
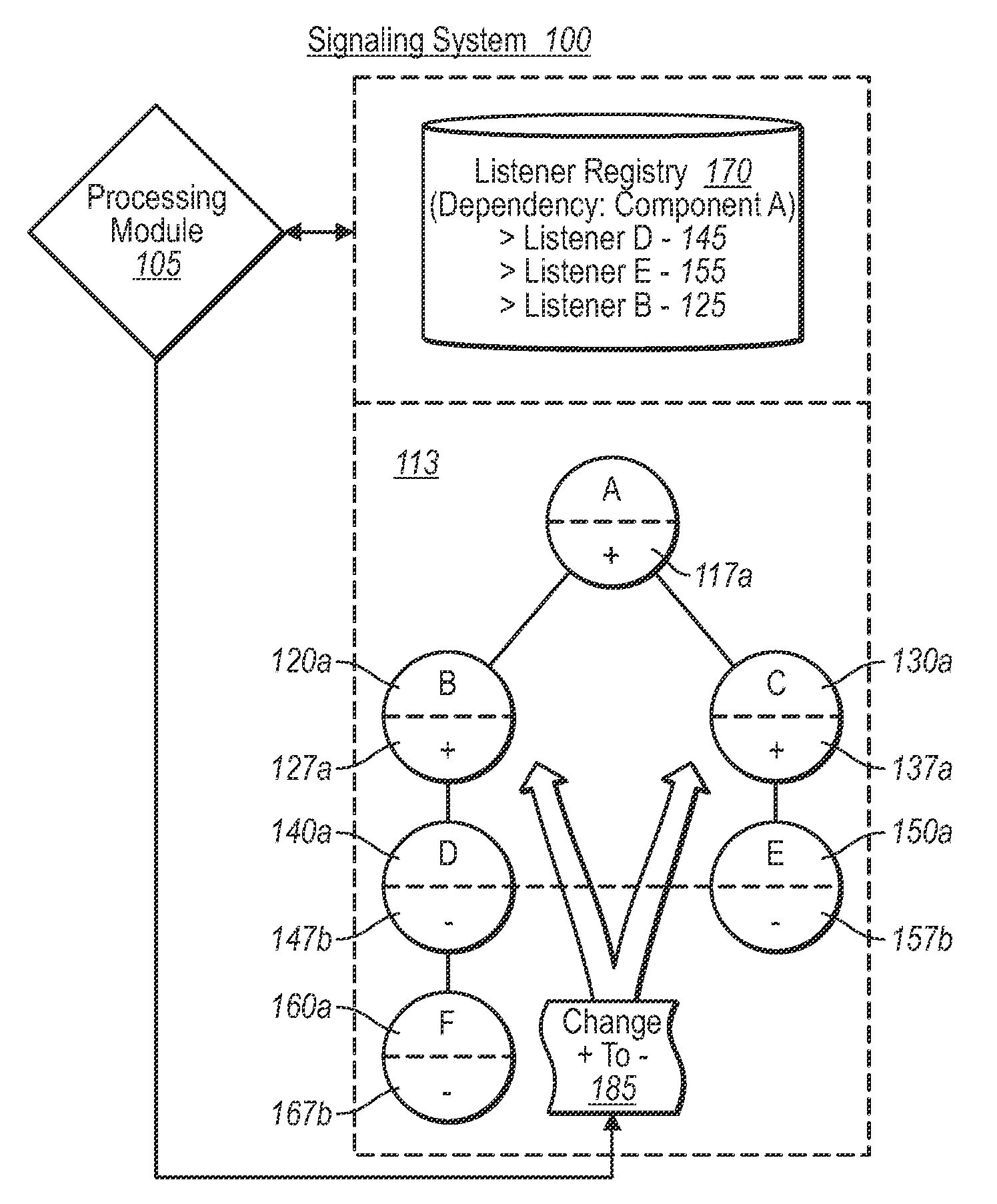
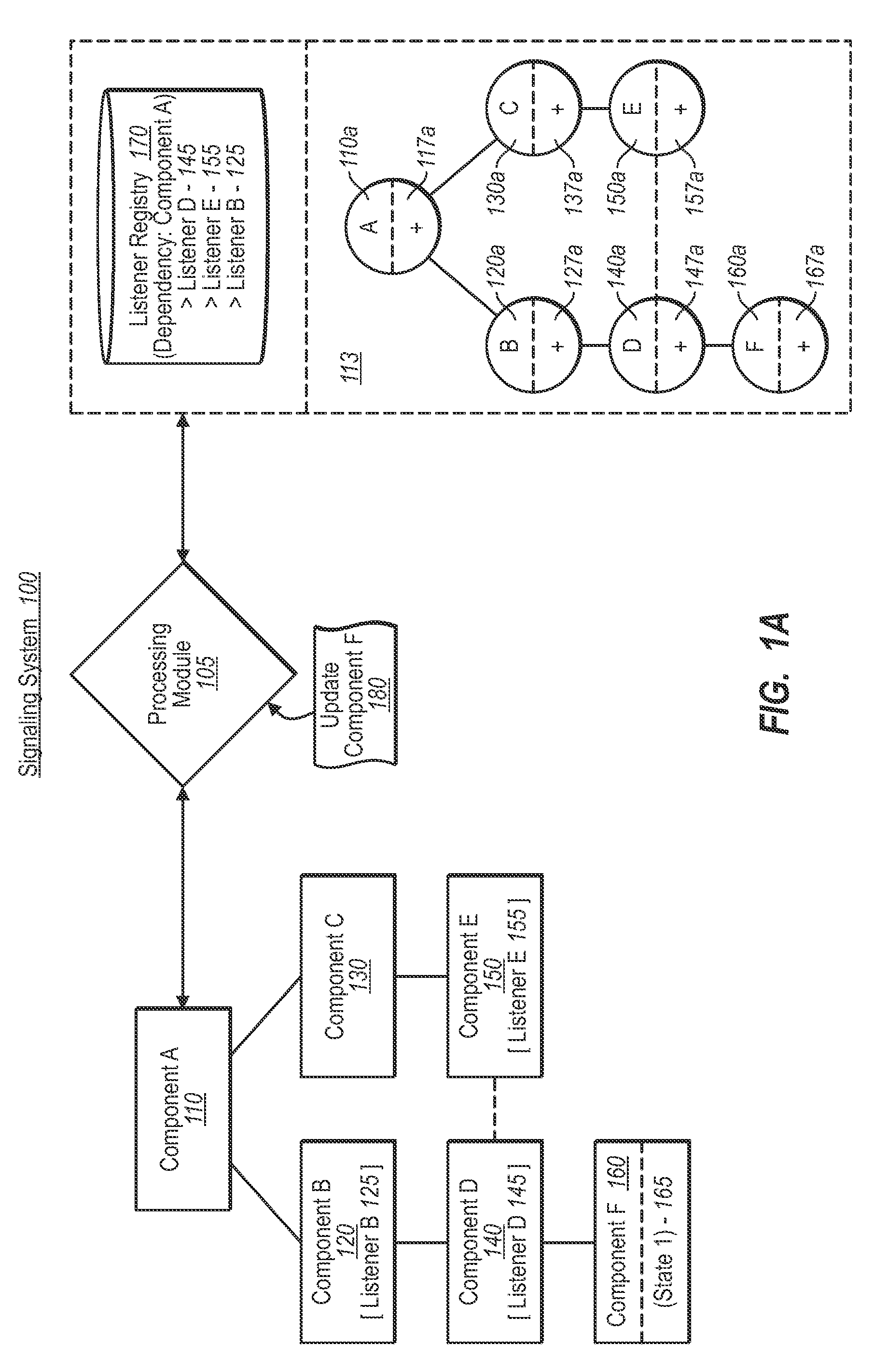
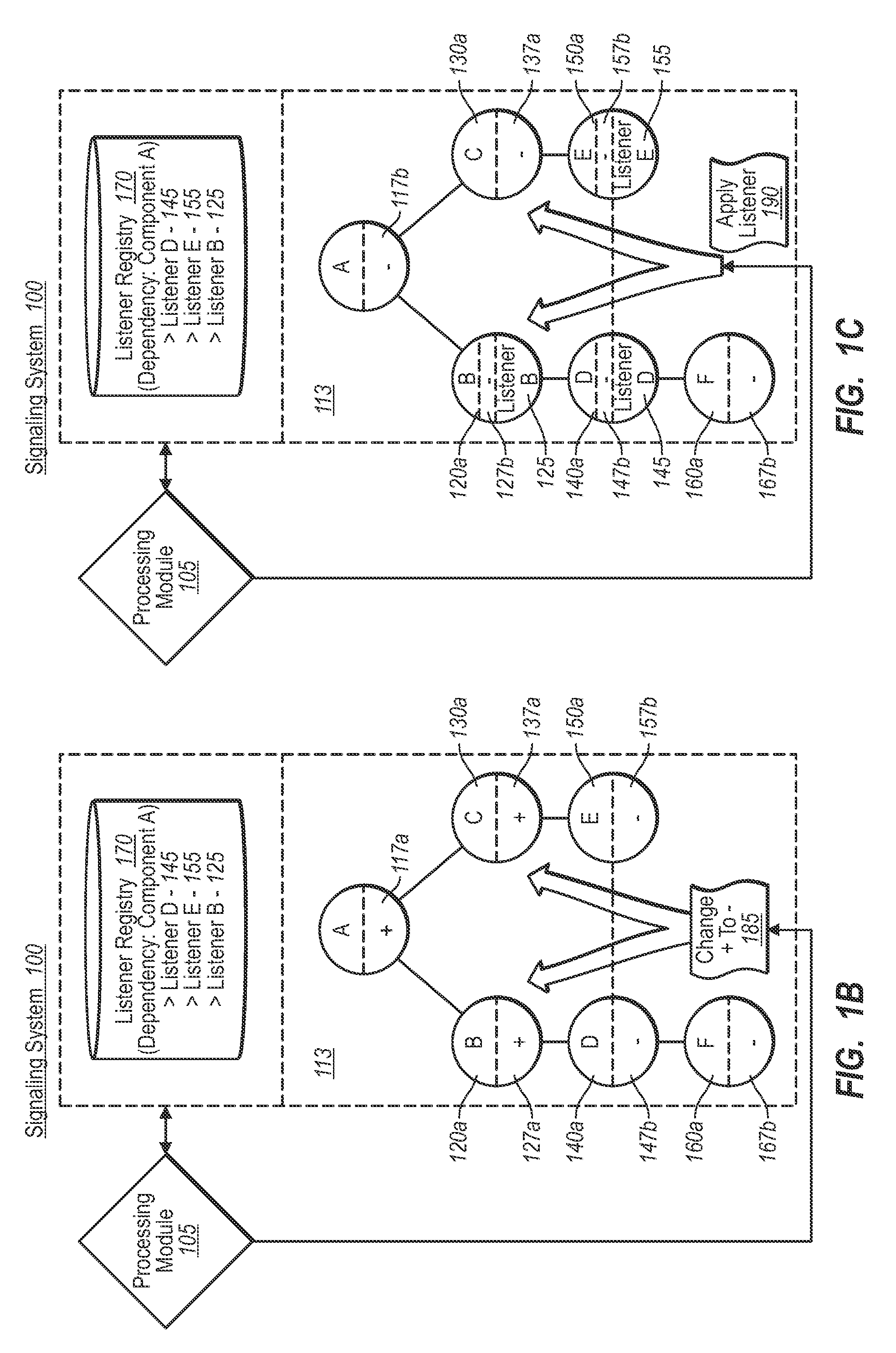
Consistently signaling state changes
ActiveUS20090216793A1Ensure consistencyDigital data processing detailsMultiprogramming arrangementsState variationSignaling system
A signaling system of the present invention provides a synchronized approach to delivering, reporting, and / or otherwise processing status changes in a software dependency chain. In a first phase, the signaling system identifies all dependencies between software components, and further sets a binary indicator of each node in a first representation. After identifying any changes in a source node, the system (e.g., a value is updated), the system updates each binary indicator to a second setting. In a second phase, the system initiates all listeners in the dependency chain in an essentially progressive order from source node, to intermediate node, and end-node, etc. Once all listeners have had a chance to perform one or more processes based on the updated value, the system can discard the dependency graph, allowing a new dependency graph to be built for subsequent value changes.
Owner:MICROSOFT TECH LICENSING LLC
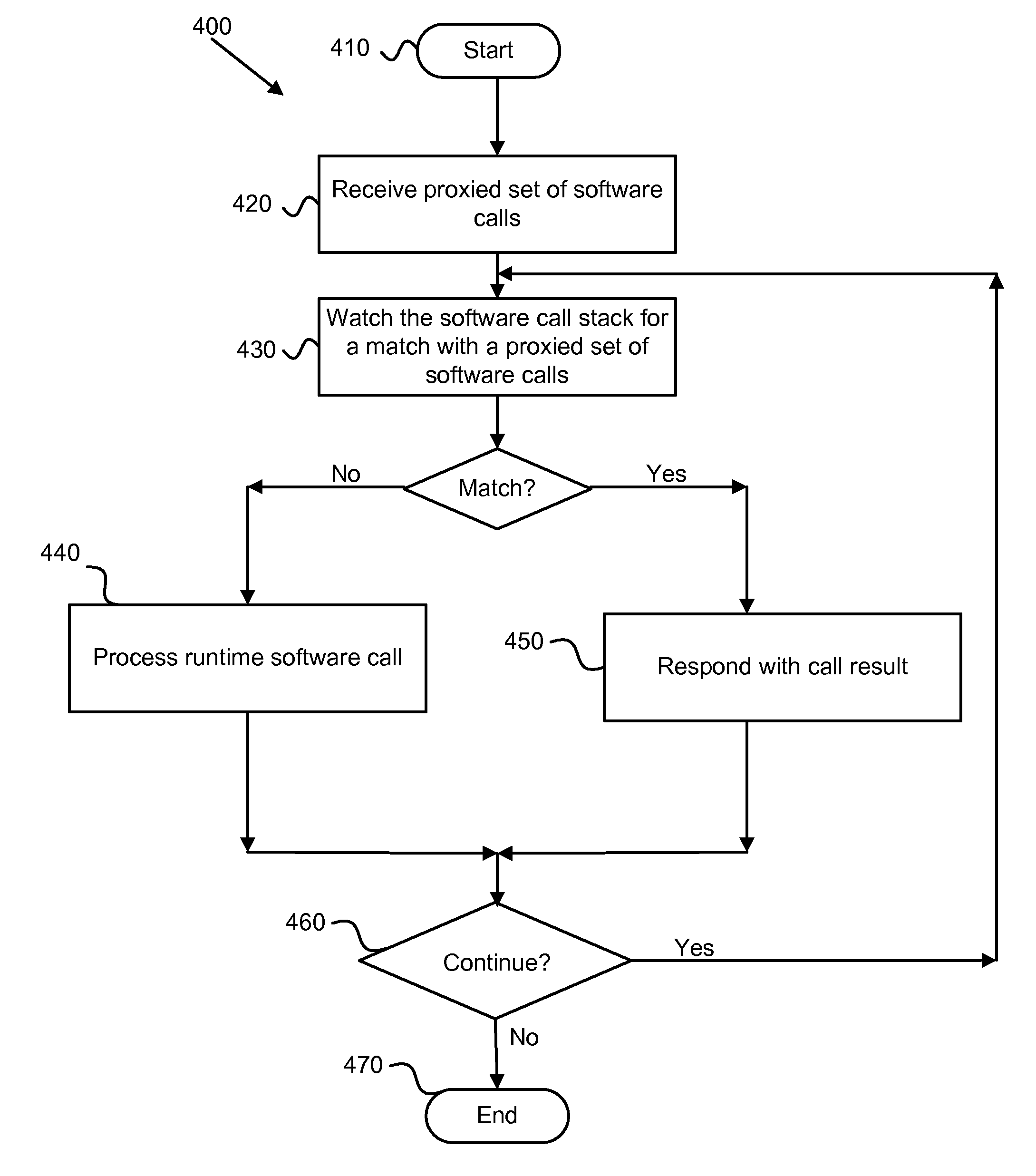
Managing software dependencies during software testing and debugging
InactiveUS20100005455A1Error detection/correctionInterprogram communicationCall stackSoftware engineering
A solution for managing software dependencies during software testing and debugging includes a capture module configured to capture a software call stack of a software execution environment, each software call of the software call stack including a call signature and a call result. The solution defines a set of proxied software calls within the software call stack suitable for simulating conversation responses to runtime software calls by a target application. Once a set of proxied software calls is defined, a playback module recognizes runtime software calls by the target application that are within the set of proxied software calls and responds to the recognized runtime software call with a captured call result corresponding to the recognized software call.
Owner:IBM CORP
Risk assessment method and apparatus for software system vulnerability
InactiveCN105046155AIntuitive and accurate comprehensive evaluationPlatform integrity maintainanceTransmissionSoftware systemSoftware engineering
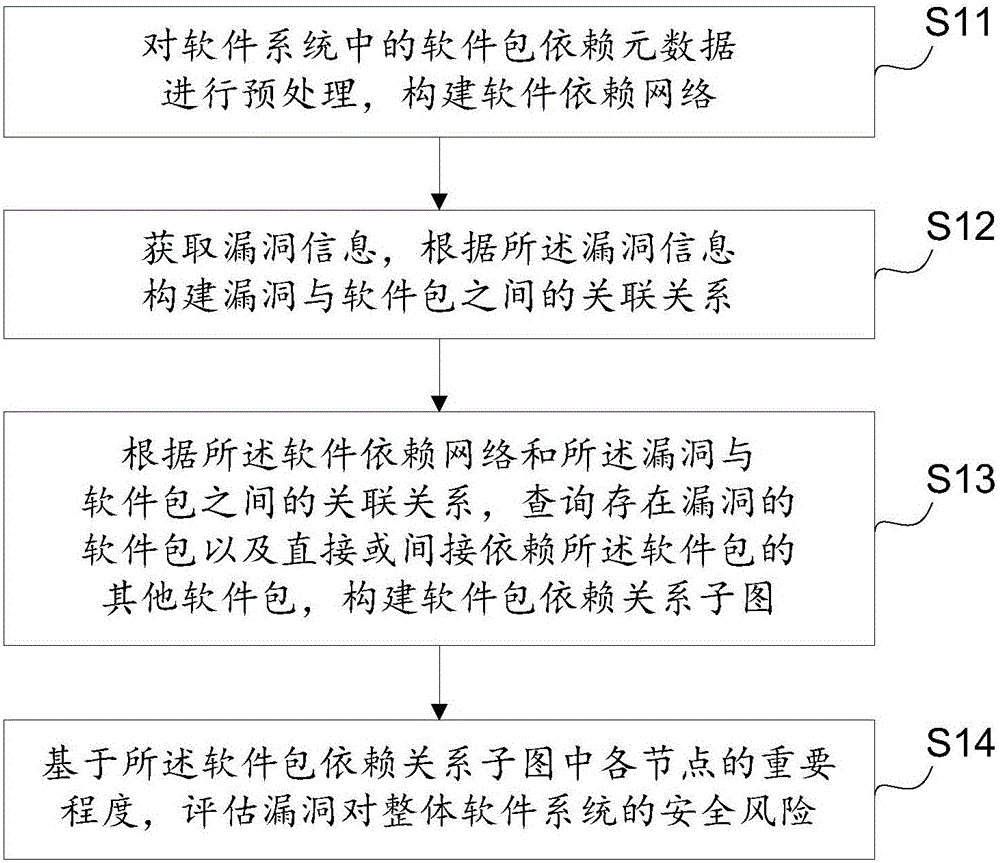
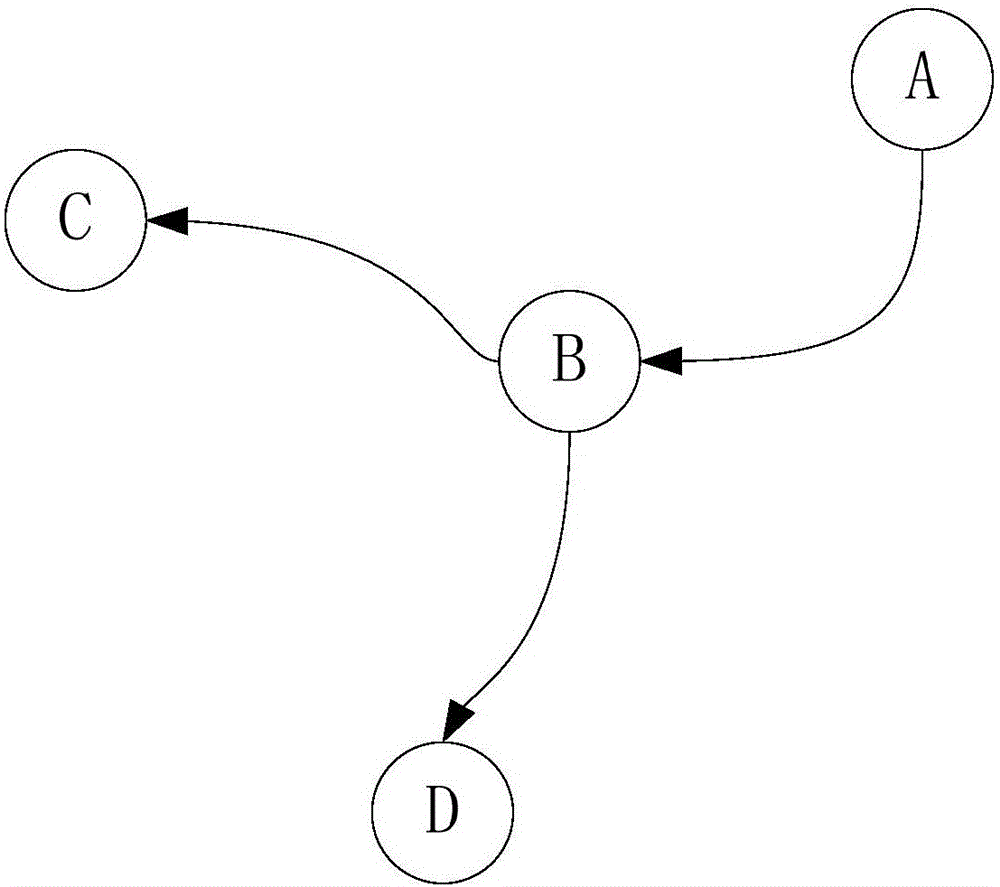
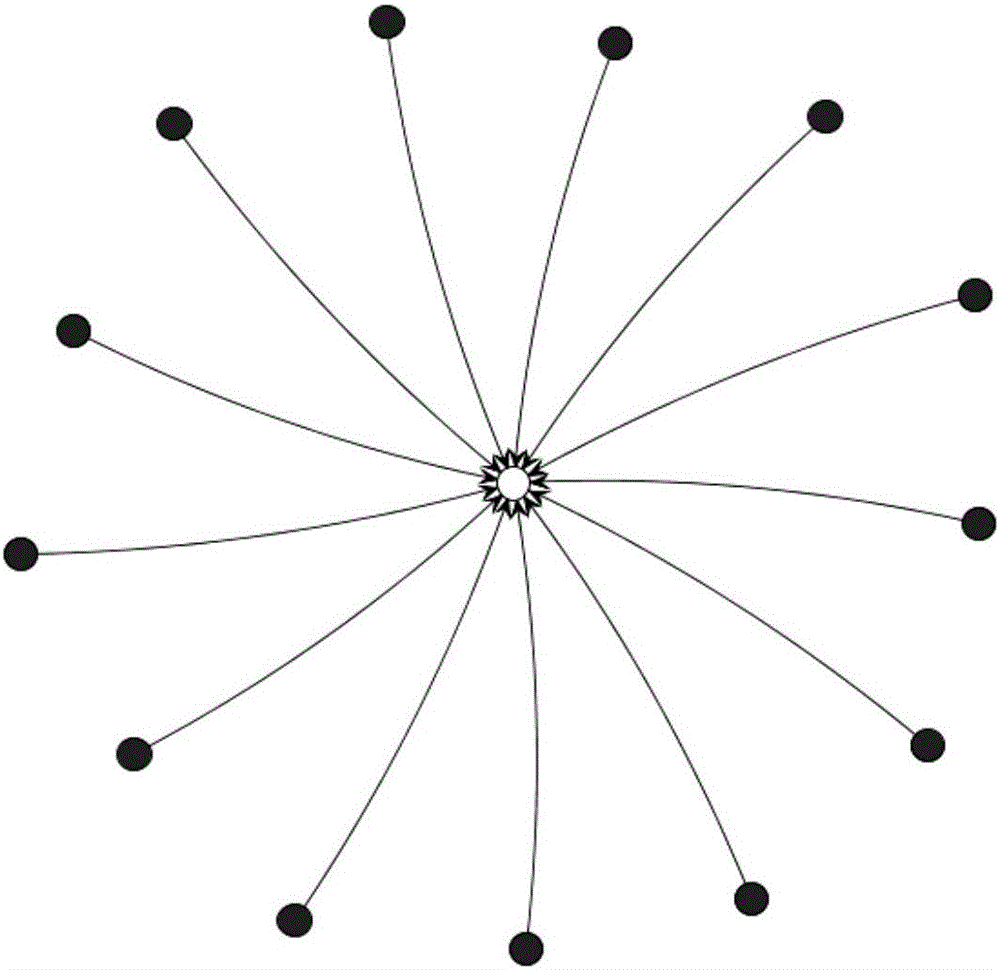
Embodiments of the present invention disclose a risk assessment method and apparatus for software system vulnerability, and relate to the technical field of information security, solving the problems in the prior art that comprehensive assessment on security risks in a software system cannot be performed visually and accurately. The risk assessment method for software system vulnerability comprises: preprocessing software package dependency metadata in a software system and establishing a software dependency network; obtaining vulnerability information, and according to the vulnerability information, constructing an association relationship between vulnerability and software packages; according to the software dependency network and the association relationship between vulnerability and software packages, searching for a software package with vulnerability and other software packages that directly or indirectly depend on the software package, and constructing a software package dependency relationship subgraph; based on importance of each node in the software package dependency relationship subgraph, assessing a security risk imposed by the vulnerability on the entire software system. The method and the apparatus provided by the embodiments of the present invention are mainly used for assessing a risk of vulnerability of a complex software system.
Owner:北京系统工程研究所
Seal-based regulation for software deployment management
InactiveUS9383984B2Improve quality and reliabilityEffective supervisionVersion controlSoftware testing/debuggingQuality assuranceSoftware dependencies
An approach is provided for managing a deployment of a software package. A retrieved quality assurance (QA) seal corresponding to a software package is verified. A target deployment environment (TDE) is obtained. The QA seal is read to obtain first and second profiles, and metadata, which specify a deployment environment, hardware and software dependencies required in the deployment, and an approval for a release of the software package to the specified deployment environment, respectively. Based on a determination that the TDE matches the specified deployment environment, the QA seal indicates the software package is compatible with the TDE. The dependencies are determined to be satisfied. Based on the software package being compatible with the TDE, the dependencies being satisfied, and the specified approval for the release of the software package, a notification of an authorization of the deployment of the software package to the TDE is generated.
Owner:INT BUSINESS MASCH CORP
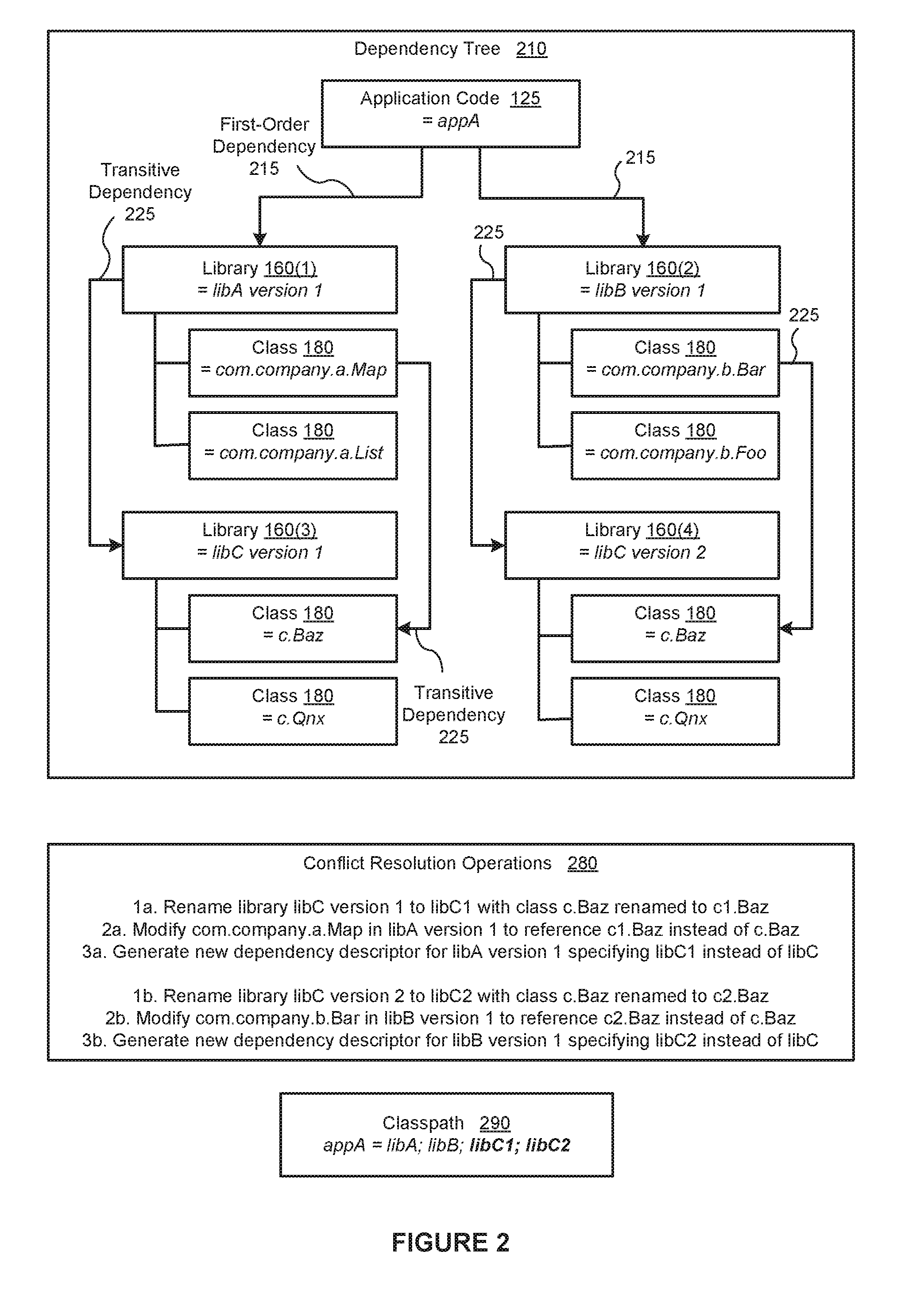
Software dependency shading
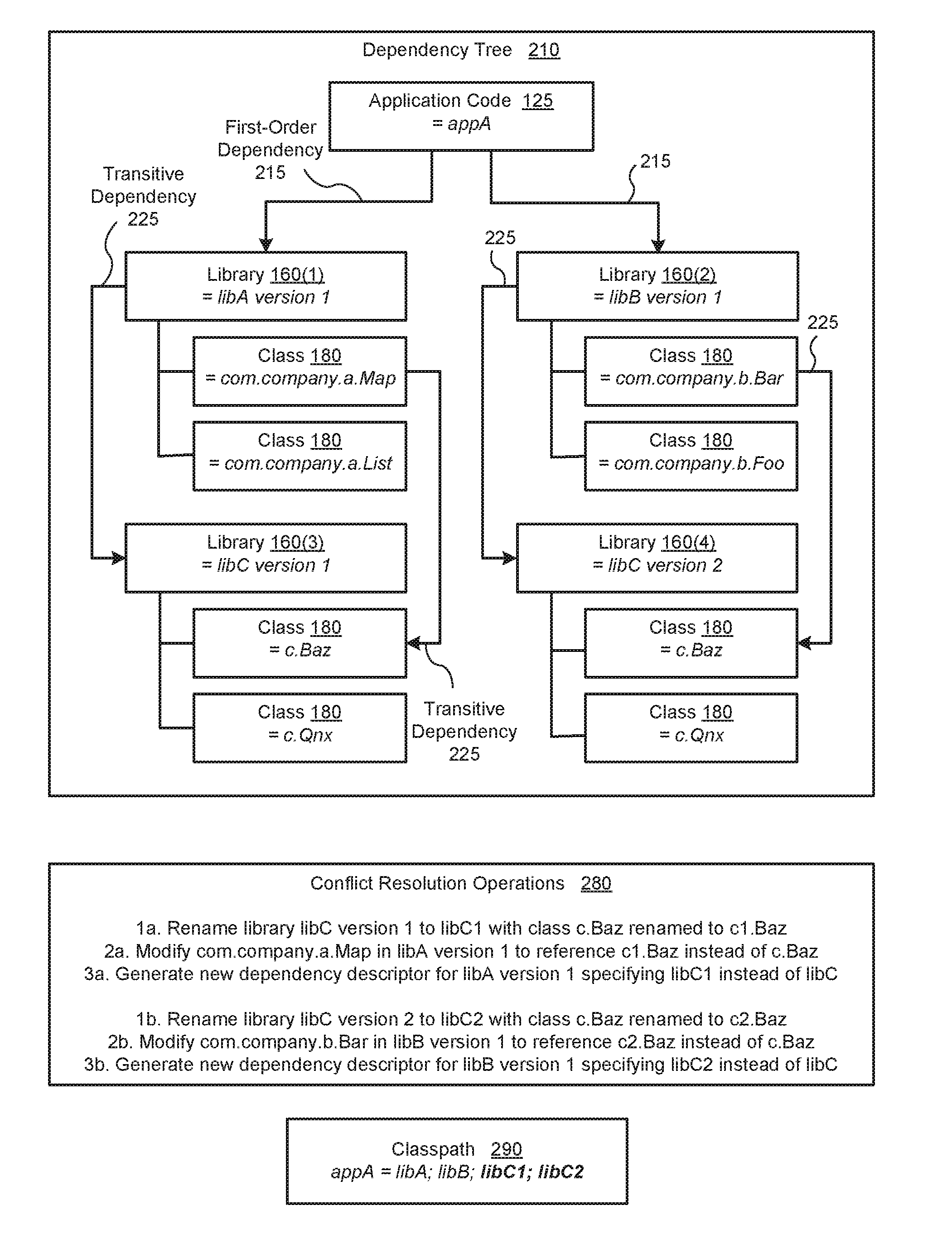
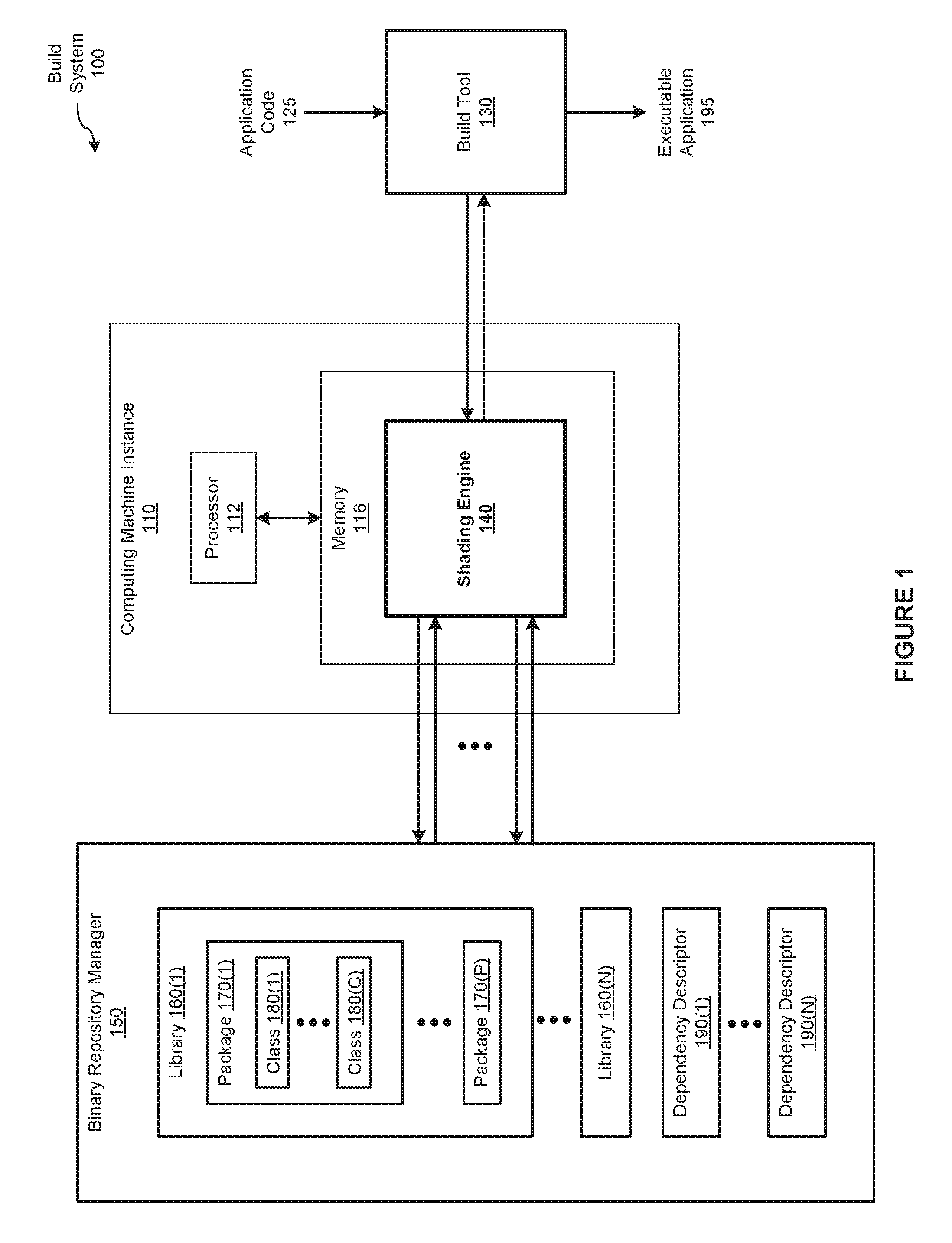
In one embodiment of the present invention, a shading engine enables multiple versions of dependencies to coexist in an executable software application. During the software build process, the shading engine dynamically renames transitive dependencies of the software application to disambiguated names. The shading engine performs this renaming at both the library and class level. Notably, the shading engine does not rename the first-order dependencies of the software application. Consequently, the code of the software application and interfaces between the software application and the first-order library dependencies of the software application are not modified. Notably, the shading engine efficiently and accurately shades the transitive dependencies without manual intervention. By contrast, primarily manually-based conventional approaches to dependency management are time consuming and susceptible to errors.
Owner:NETFLIX
Methods, apparatuses and computer program product for automatic download of software dependencies on installation
InactiveCN101861567AProgram loading/initiatingSoftware deploymentSoftware dependenciesComputer program
Owner:NOKIA CORP
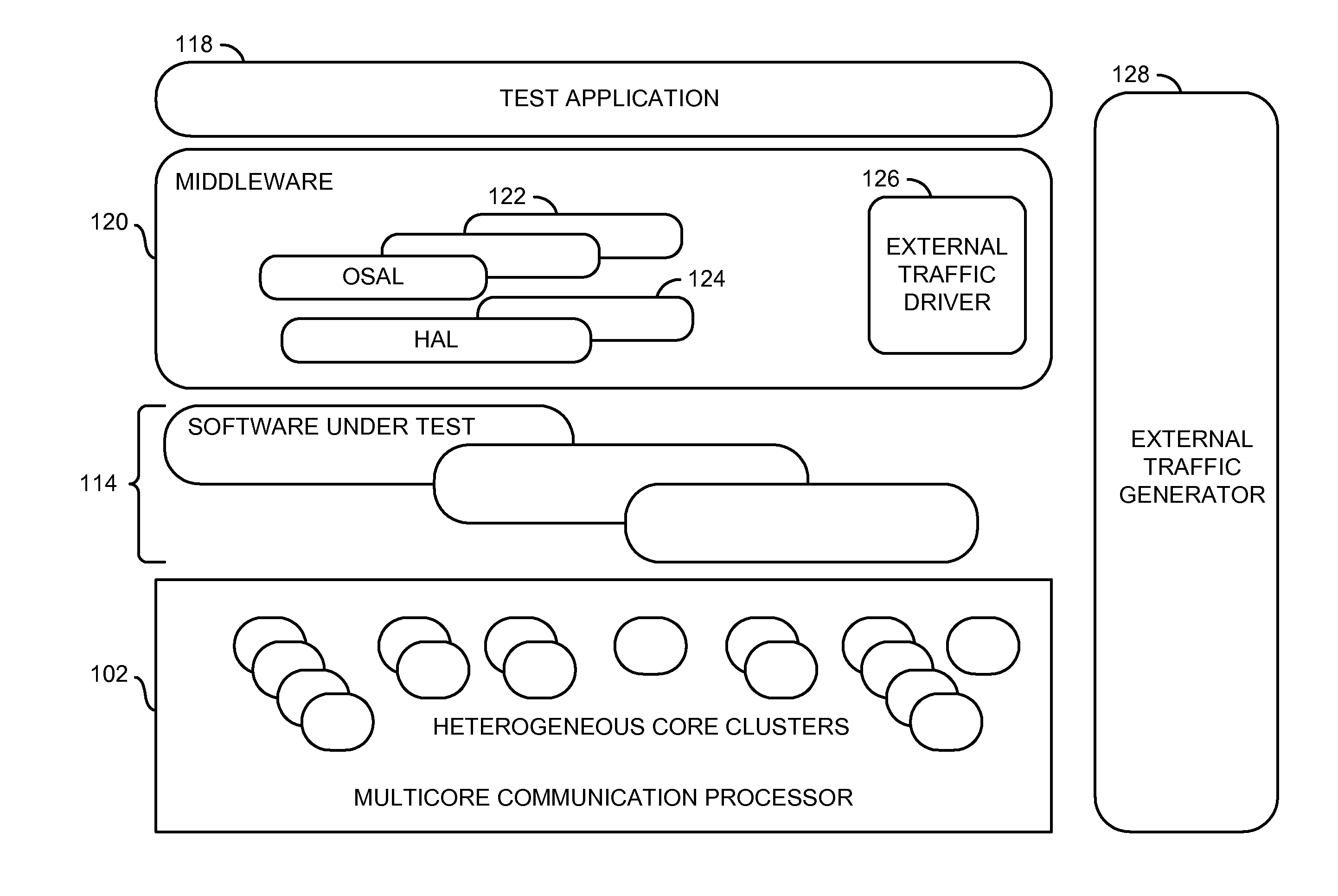
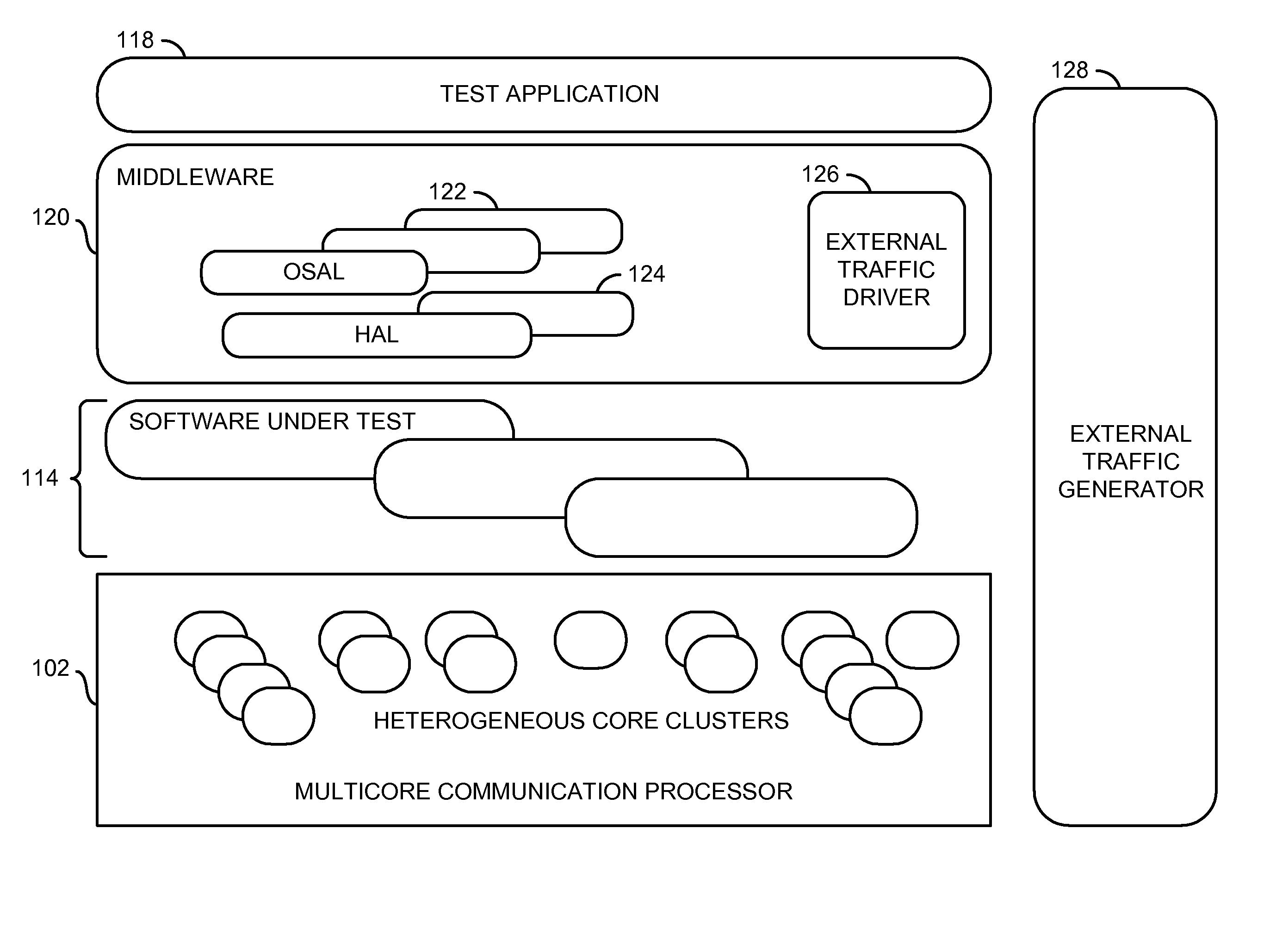
Middleware for multiprocessor software testing
InactiveUS20140040665A1Reduce turnaround timeSoftware testing/debuggingOperational systemMulti processor
An apparatus having a memory and multiple processors coupled to the memory is disclosed. The memory may be configured to store middleware. One or more processors may be configured to (a) generate initial test vectors to test one or more software modules executed on the processors and (b) generate modified test vectors by translating the initial test vectors in the middleware to a format that matches multiple hardware dependencies of the processors and multiple software dependencies of multiple operating systems. The test vectors generally have another format that is independent of (a) the hardware dependencies of the processors and (b) the software dependencies of the operating systems executed by the processors. The processors may be configured to generate a plurality of test results by exercising the software modules with the modified test vectors.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Middleware for multiprocessor software testing
An apparatus having a memory and multiple processors coupled to the memory is disclosed. The memory may be configured to store middleware. One or more processors may be configured to (a) generate initial test vectors to test one or more software modules executed on the processors and (b) generate modified test vectors by translating the initial test vectors in the middleware to a format that matches multiple hardware dependencies of the processors and multiple software dependencies of multiple operating systems. The test vectors generally have another format that is independent of (a) the hardware dependencies of the processors and (b) the software dependencies of the operating systems executed by the processors. The processors may be configured to generate a plurality of test results by exercising the software modules with the modified test vectors.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Linux basic software dependency relationship analysis method based on files
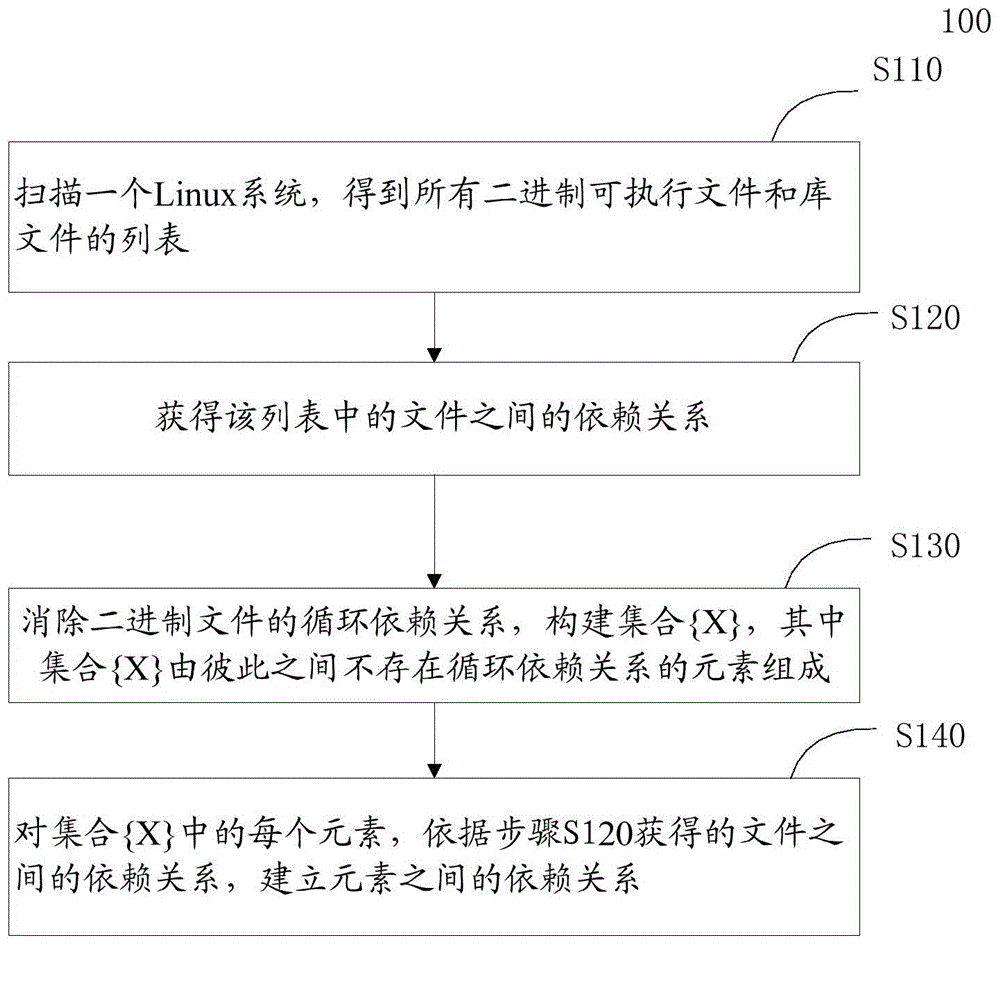
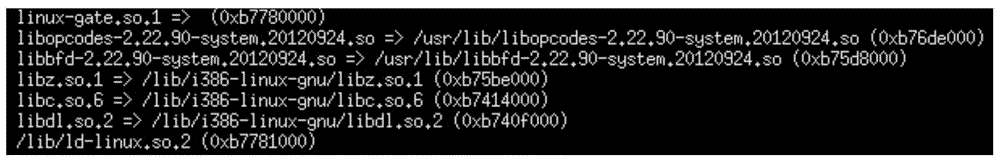
ActiveCN104063220ADependencies getSpecific program execution arrangementsSpecial data processing applicationsGNU/LinuxParallel computing
The invention provides a Linux basic software dependency relationship analysis method which can comprises the following steps: scanning a Linux system to obtain a list of all binary executable files and library files; obtaining dependency relationships among the files in the list; eliminating circular dependency relationships among the binary files, and creating a set {X}, wherein the set {X} is composed of elements without circular dependency relationships, and the elements X are a set of all files on a circular dependency chain or a set of single files which do not exist on any circular dependency chain; building dependency relationships among all the elements in the set {X} according to the dependency relationships among the files. Through the Linux basic software dependency relationship analysis method provided by the embodiment of the invention, the dependency relationships among the binary executable files and library files of all software on the inner core of the Linux system can be obtained directly without the need of software package description information.
Owner:TSINGHUA UNIV
Query-based software dependency analysis
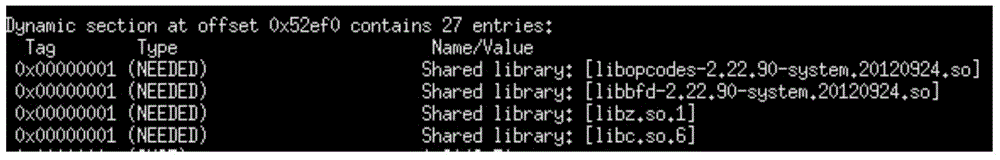
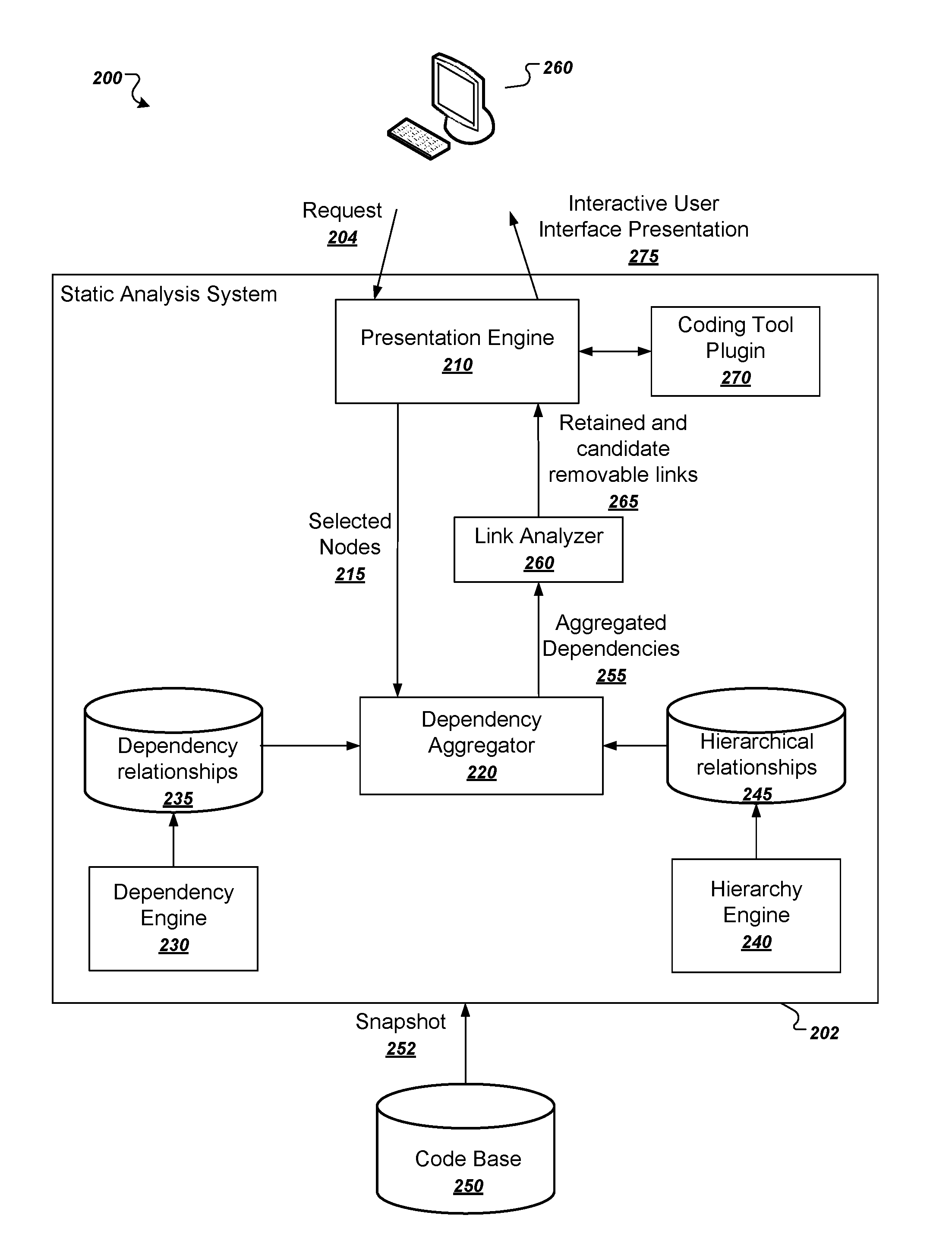
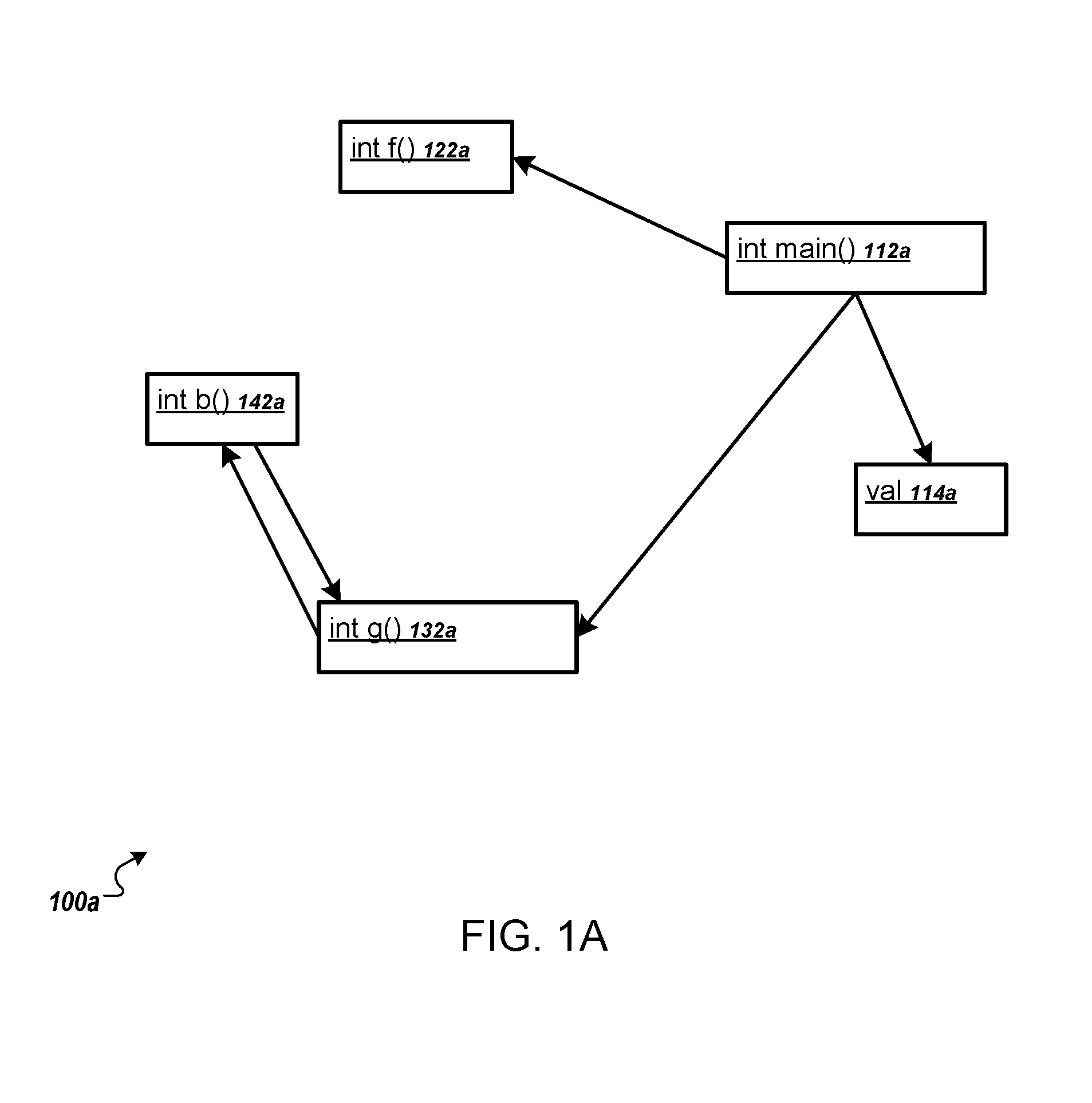
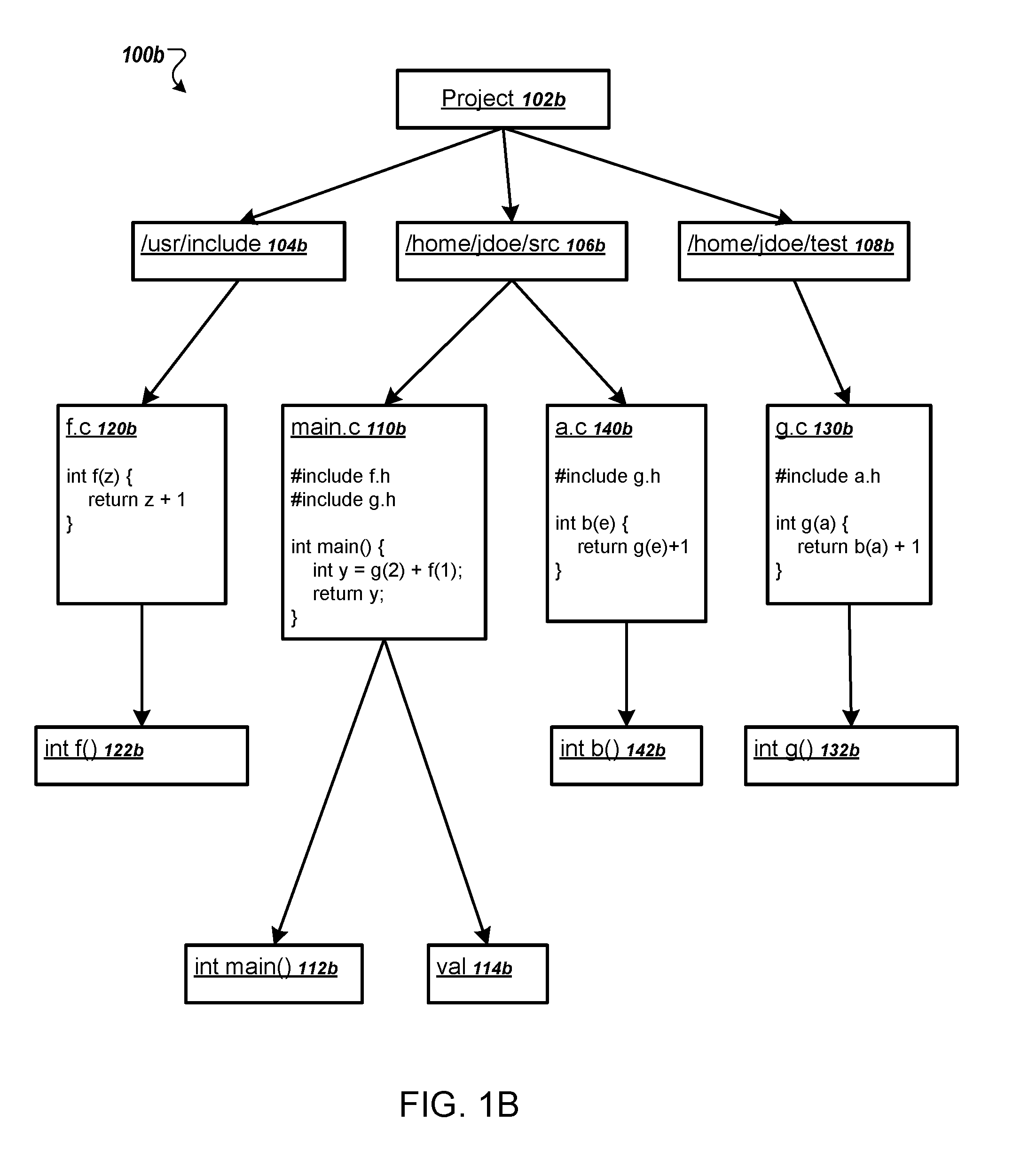
ActiveUS9552276B1Reduce complexityThe process is simple and easy to understandVersion control2D-image generationTheoretical computer scienceSoftware dependencies
Methods, systems, and apparatus, including computer programs encoded on computer storage media, for generated aggregated dependencies between software elements in a code base. One of the methods includes receiving a query that defines a dependency between the software elements in a project. Searching a database to identify matching source software elements having the one or more source attributes and target software elements having the one or more target attributes of the query. Identifying pairs of matching source software elements and matching target software elements having the specified relationship, and generating, for each pair of matching source software elements and matching target software elements having the specified relationship, a new dependency in a raw dependency graph, the new dependency being a dependency from a source software element of the pair to the target software element of the pair.
Owner:MICROSOFT TECH LICENSING LLC
Observing and reporting changes in complex software dependencies
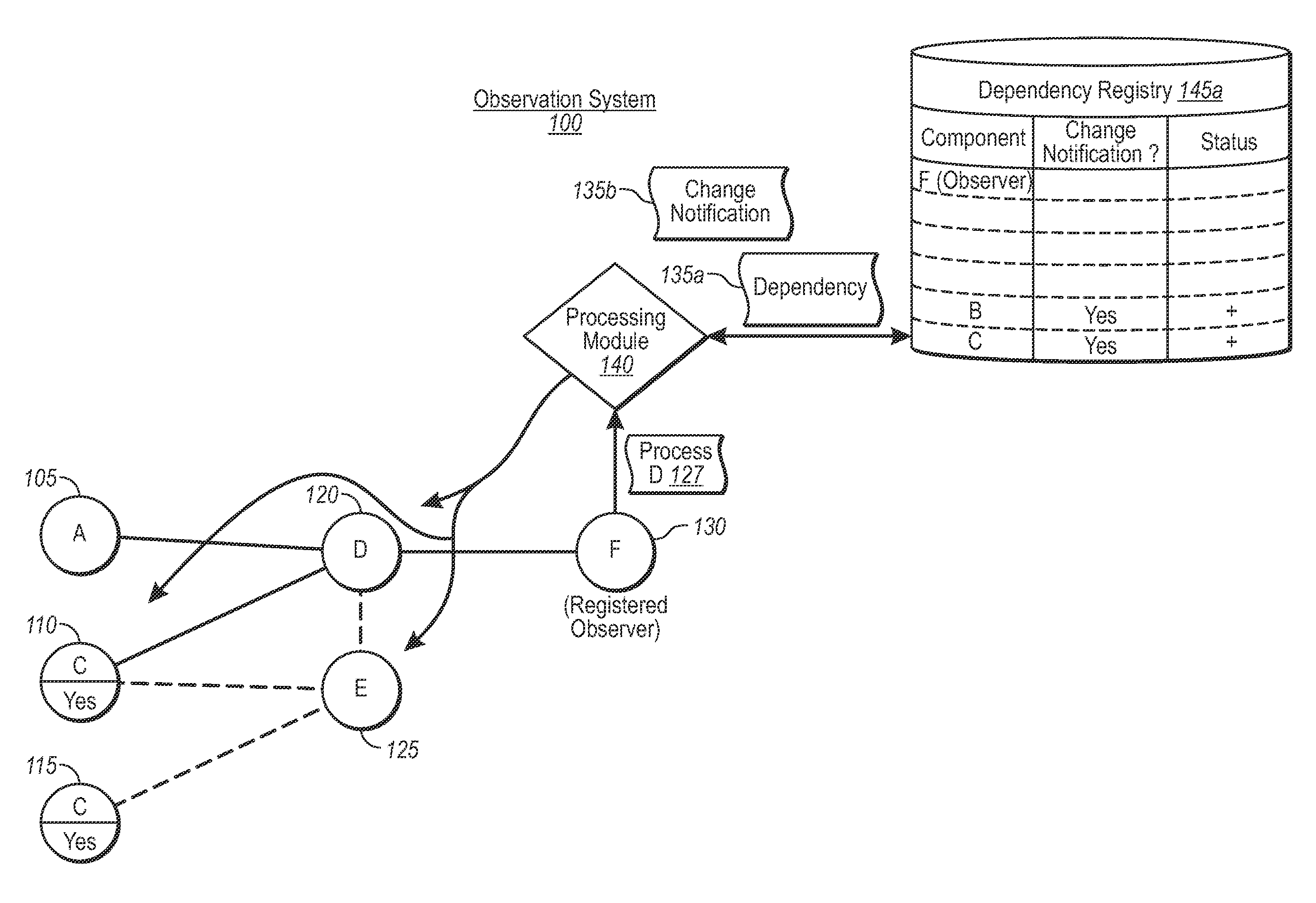
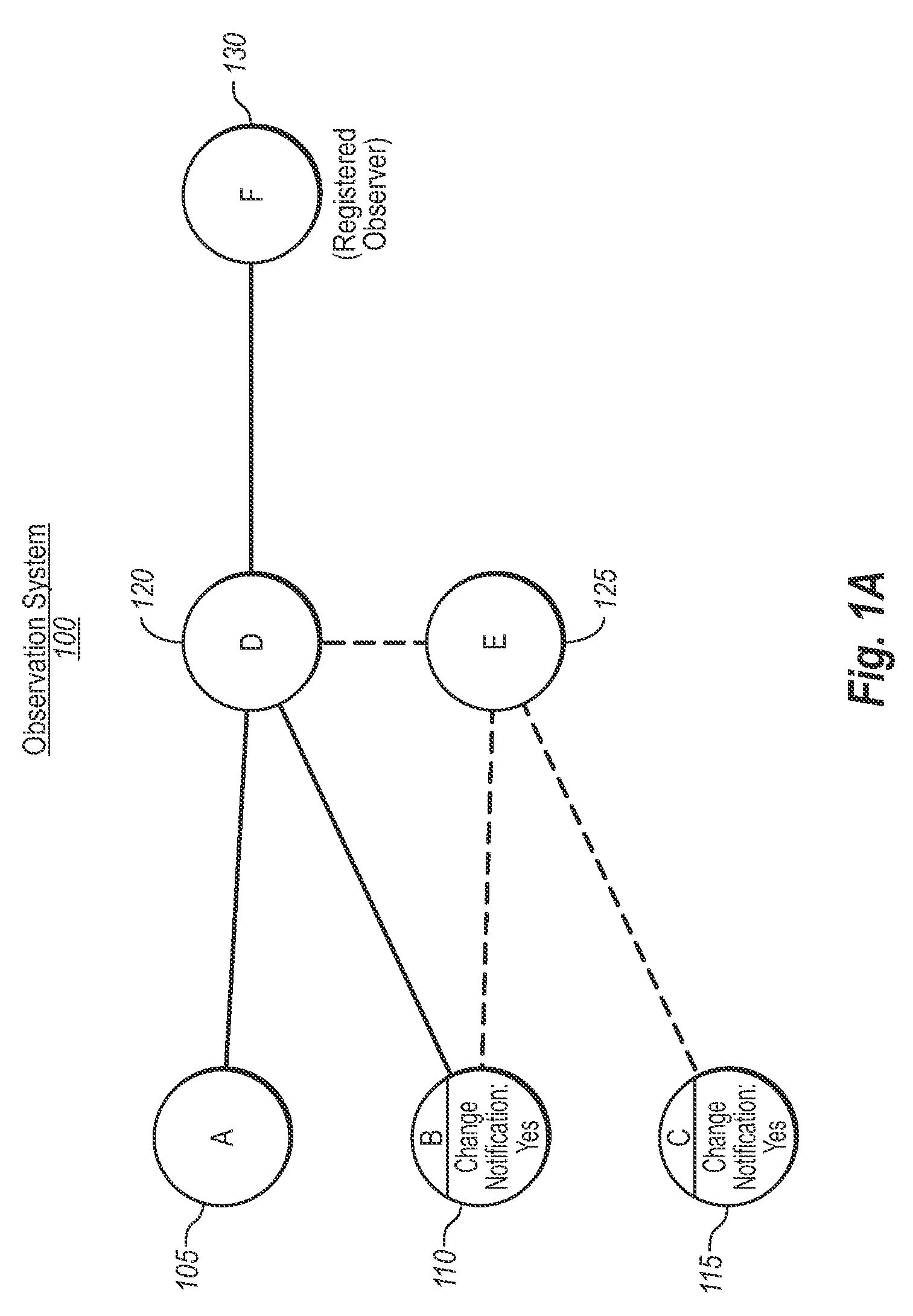
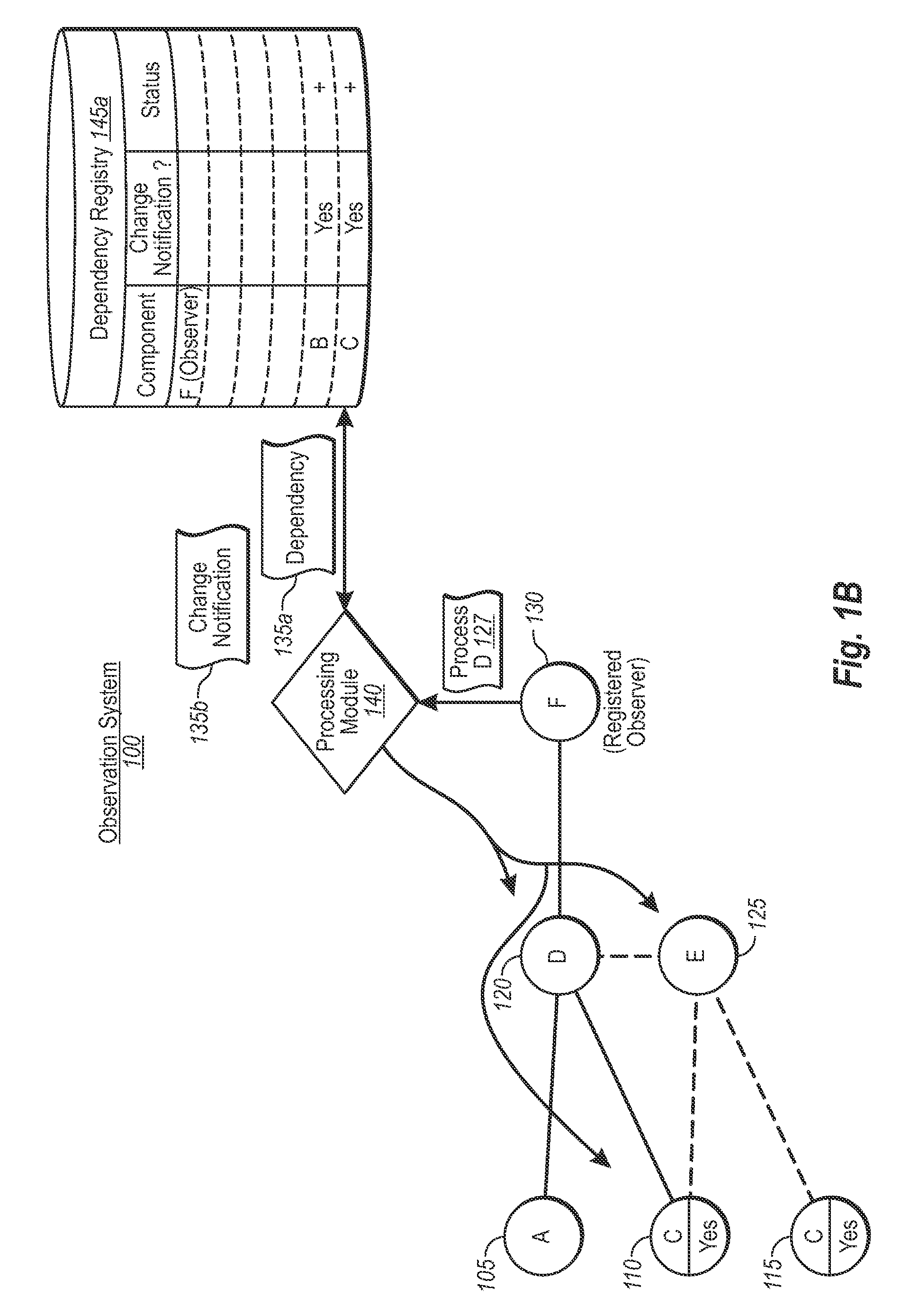
ActiveUS20090216782A1Efficiently report data freshnessDigital data processing detailsProgram controlSoftware dependenciesObservation system
An observation system includes mechanisms for efficiently tracking the state of source components, which include functions, arguments, or values, etc. In one implementation, an observing component requests that a source component processes a request. The observation system then identifies all possible components in a dependency chain for the request, and all such components that are configured for change notifications. A dependency registry stores a representation of each identified component that is configured for change notifications. Any time any component configured for change notifications changes, including indirectly related components, the observing component can be immediately notified of the change, without having to reprocess the entire set of component dependencies.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for assembling mirror image files
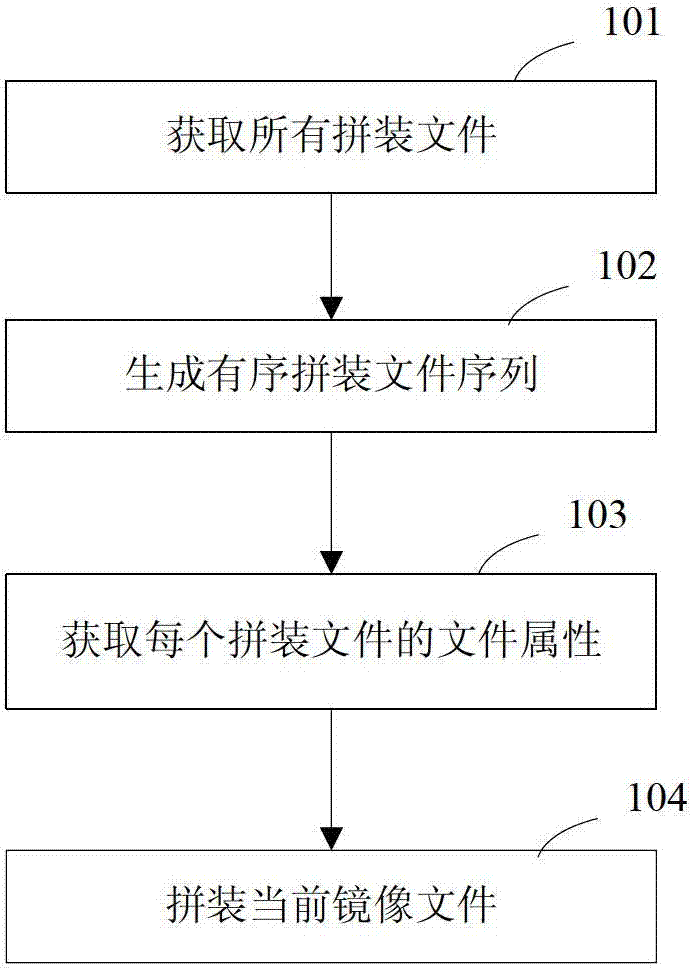
InactiveCN102902770ASave storage spaceSpecial data processing applicationsSoftware engineeringSoftware dependencies
The invention discloses a method and a system for assembling mirror image files, wherein the method comprises the following steps: acquiring all assembled files required by current mirror image files according to the assembling requests of the current mirror image files; generating all assembled files to be an orderly assembled file sequence according to preset software dependency relationship and software release dependency relationship; determining the file attribute of each assembled file in the orderly assembled file sequence according to the file layout of the assembled files recorded in the resource library of the assembled files; and assembling each assembled file according to an assembling path in sequence according to the determined file attribute to obtain the current mirror image files. According to the method and the system for assembling mirror image files, the storage of the software dependency relationship and the software release dependency relationship is used for replacing the storage of different mirror image files, and the space required for storing the software dependency relationship and the software release dependency relationship is smaller than the size of a mirror image file; and therefore, a large amount of storage space is saved.
Owner:NEUSOFT CORP
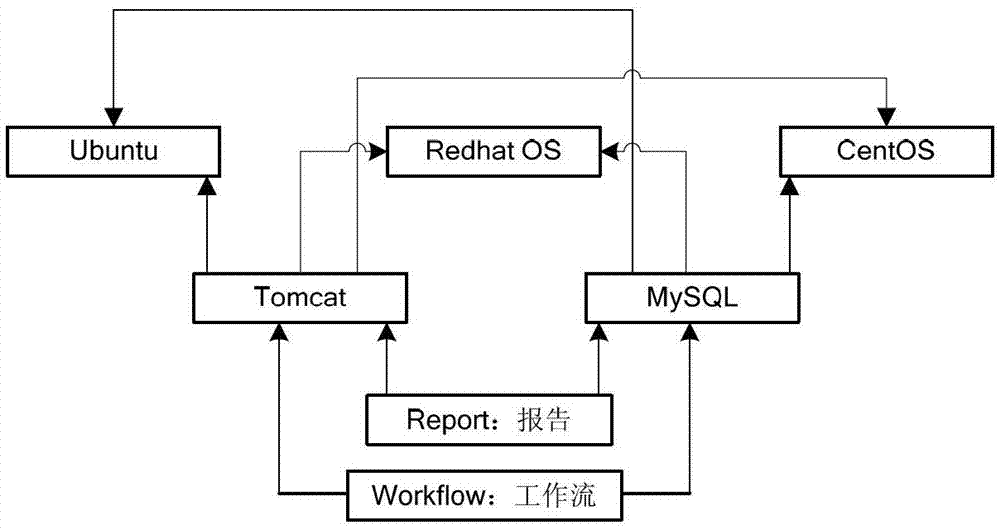
Apparatus and method for installing software using a software dependency map
ActiveUS20110231838A1Software engineeringProgram loading/initiatingSoftware engineeringSoftware dependencies
A virtual installation map, and method involving installing a software functionality using the same, the virtual installation map including a first software installation map including a plurality of software elements representative of a related software file, the software elements also including at least one dependency to another software element. The virtual installation map further including a second software installation map also including a second plurality of software elements representative of related software file along with related dependencies. The first and second software installation maps may be hosted in separate databases and may relate to software products provided by different vendors. One or both software installation maps may include a pointer or other reference to the other installation map thereby providing a virtual installation map, in one example.
Owner:ORACLE INT CORP
Software packaging method
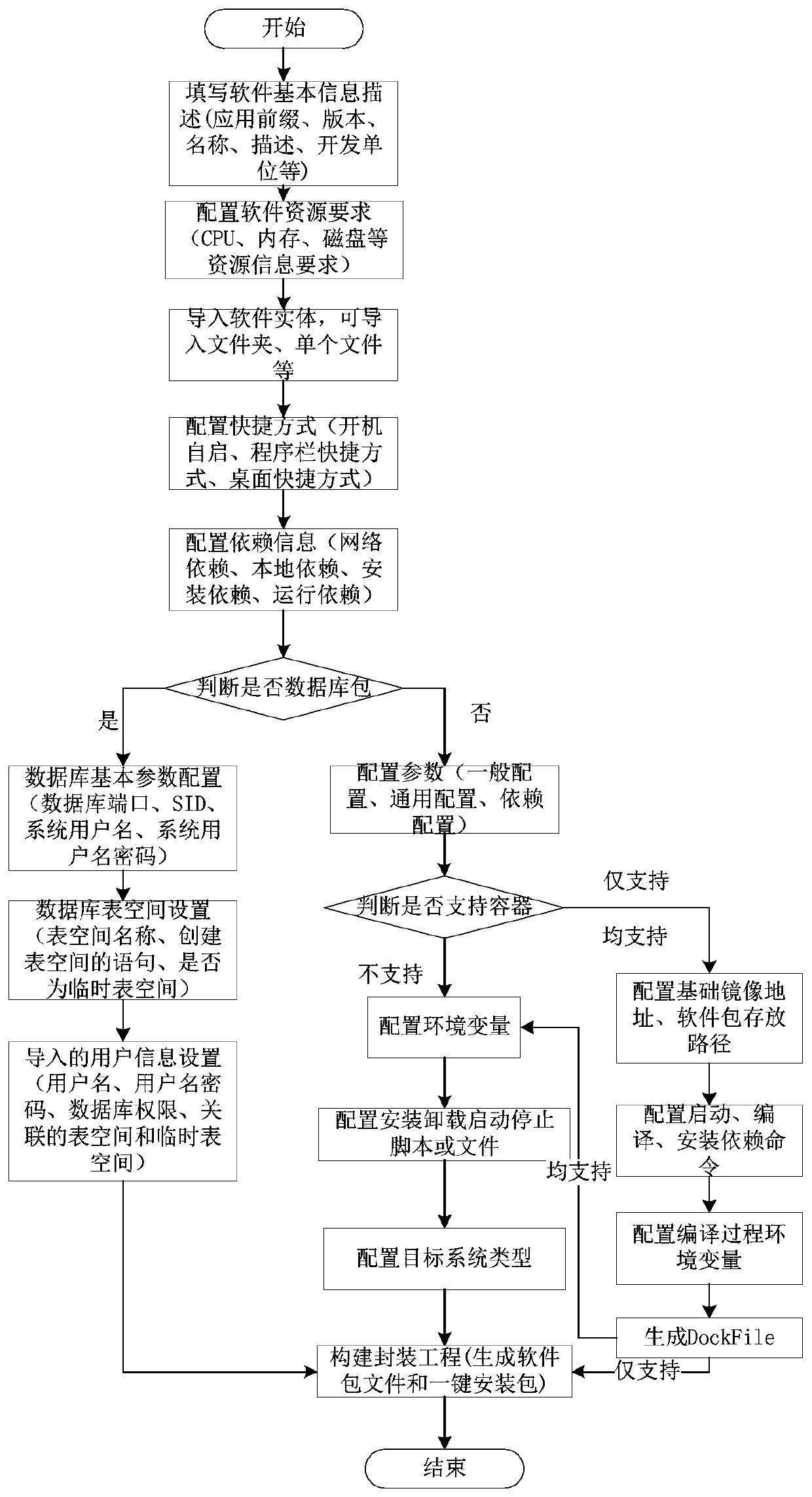
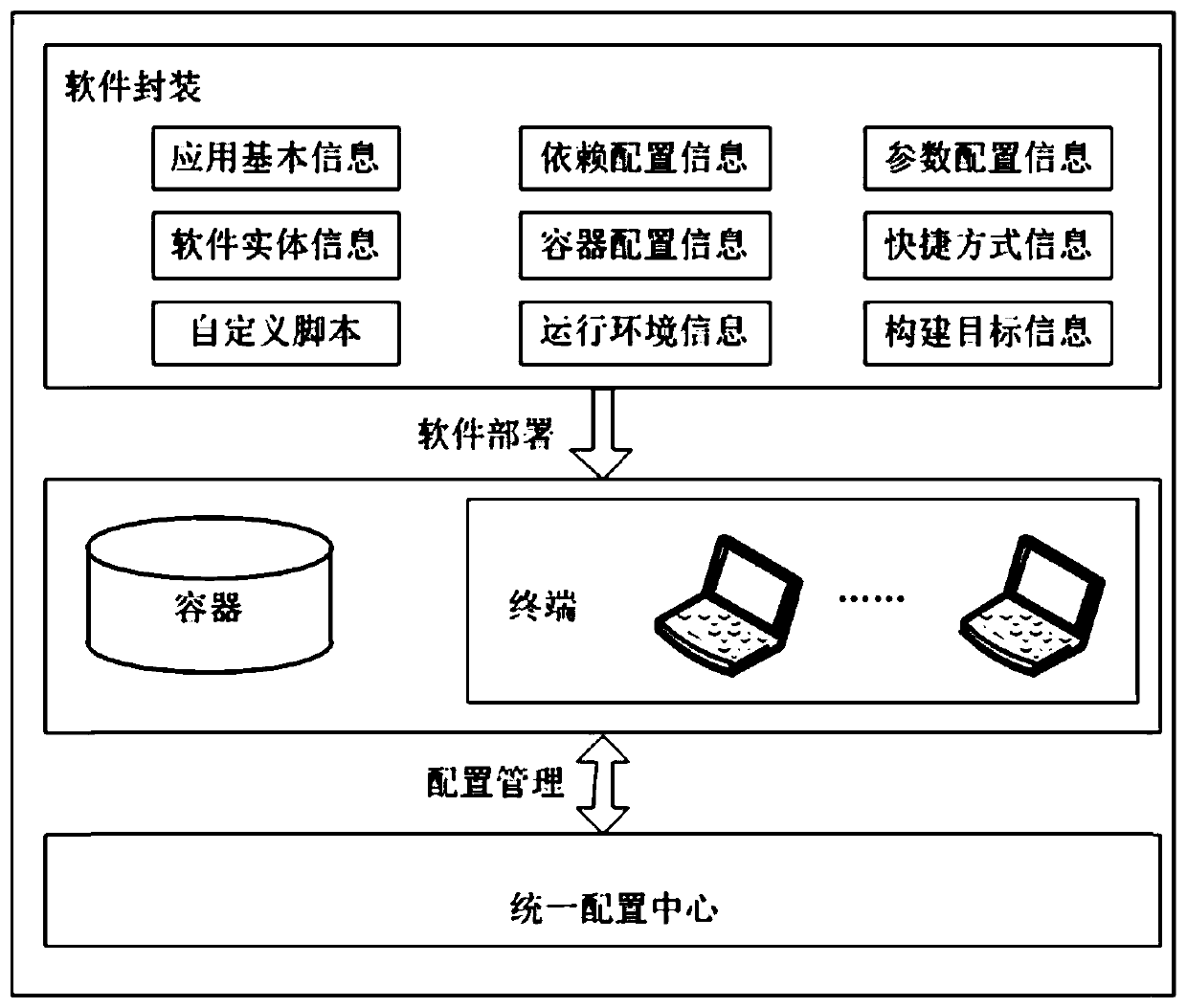
ActiveCN110727440ARealize unified packagingSupport dependency information descriptionSoftware deploymentSoftware engineeringSoftware dependencies
The invention discloses a software packaging method. The software packaging method comprises the following steps: 1, selecting a software type; 2, describing basic information of a software segment; 3, setting a software desktop shortcut, a program bar shortcut and startup self-starting; 4, describing a software dependency relationship; 5, setting the support of the software to the container; 6, configuring software parameter information; 7, setting scripts such as software installation, unloading, starting, stopping and the like; 8, setting software environment variables; 9, setting a software running environment; and 10, software packaging and one-key installation package generation. According to the method, through using general software packaging description, unified description and packaging of the software are realized through normative description of basic information, parameter information, dependency information, shortcuts, environment variables, user-defined running scripts,running environments and the like of the software, and unified management and maintenance of the software in two scenes of software independent installation and deployment and system integrated deployment can be supported.
Owner:THE 28TH RES INST OF CHINA ELECTRONICS TECH GROUP CORP
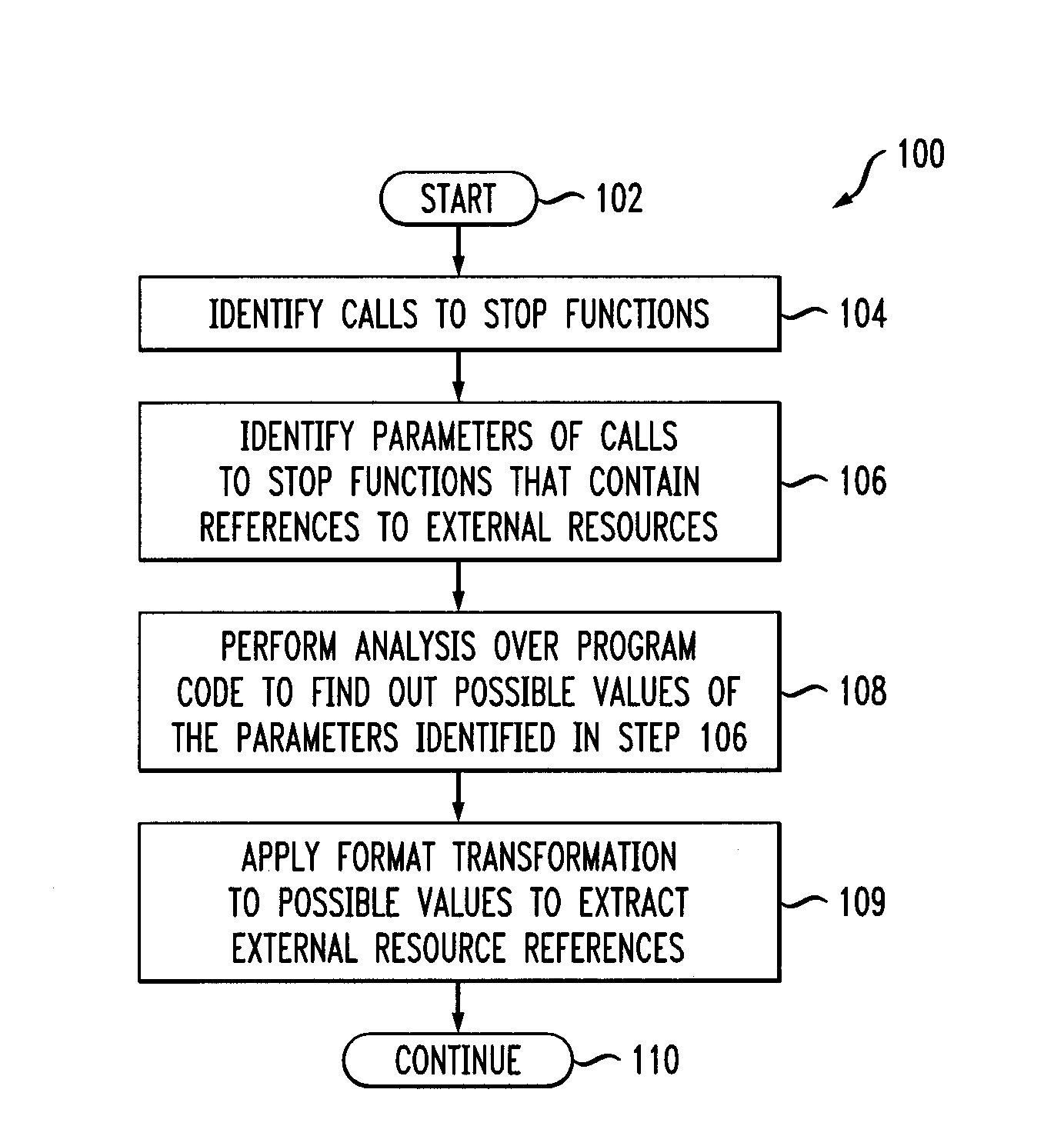
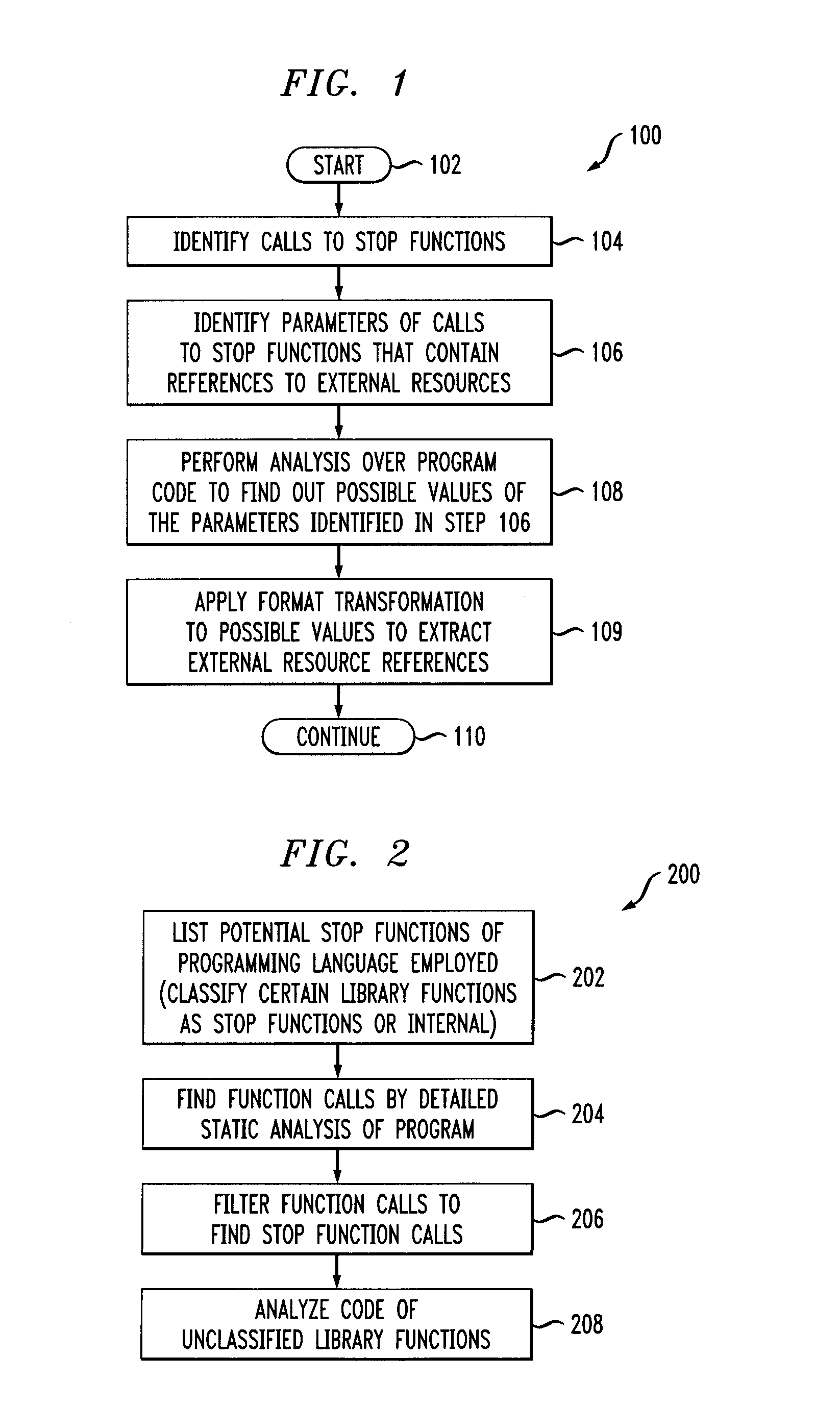
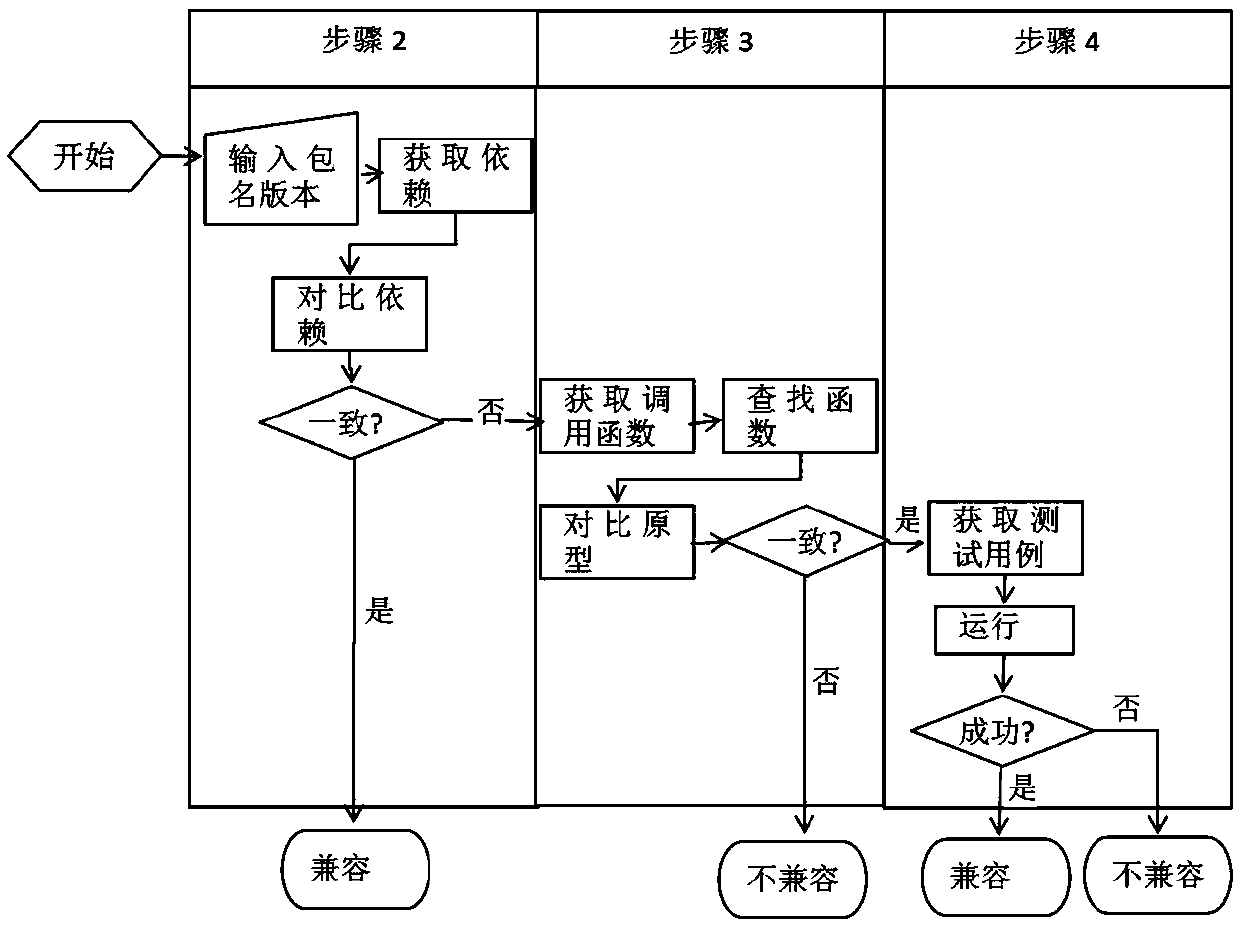
Software dependency package capacity detection method and system and medium
ActiveCN110543423AFix security issuesFix compatibility issuesSoftware testing/debuggingGoal systemSoftware dependencies
The invention discloses a software dependency package capability detection method and system and a medium. The method for judging whether the to-be-tested software is compatible with the target systemor not comprises: after the input to-be-tested software is obtained, judging whether the to-be-tested software is compatible with the target system or not through dependency library detection, library package calling function detection and external function test case execution detection, and outputting a compatibility detection report. The method for judging whether the interface provided by theto-be-tested software library is consistent with the expected function or not comprises: after input to-be-tested software is obtained, judging whether the interface provided by the to-be-tested software library is consistent with the expected function or not through library package calling function detection and external function test case execution detection, and outputting an expected functiondetection report. Whether the to-be-tested software is compatible with the target system or not is judged and is consistent with the expected function, so that the compatibility and safety problems ofthe software dependent package can be effectively solved.
Owner:NAT UNIV OF DEFENSE TECH
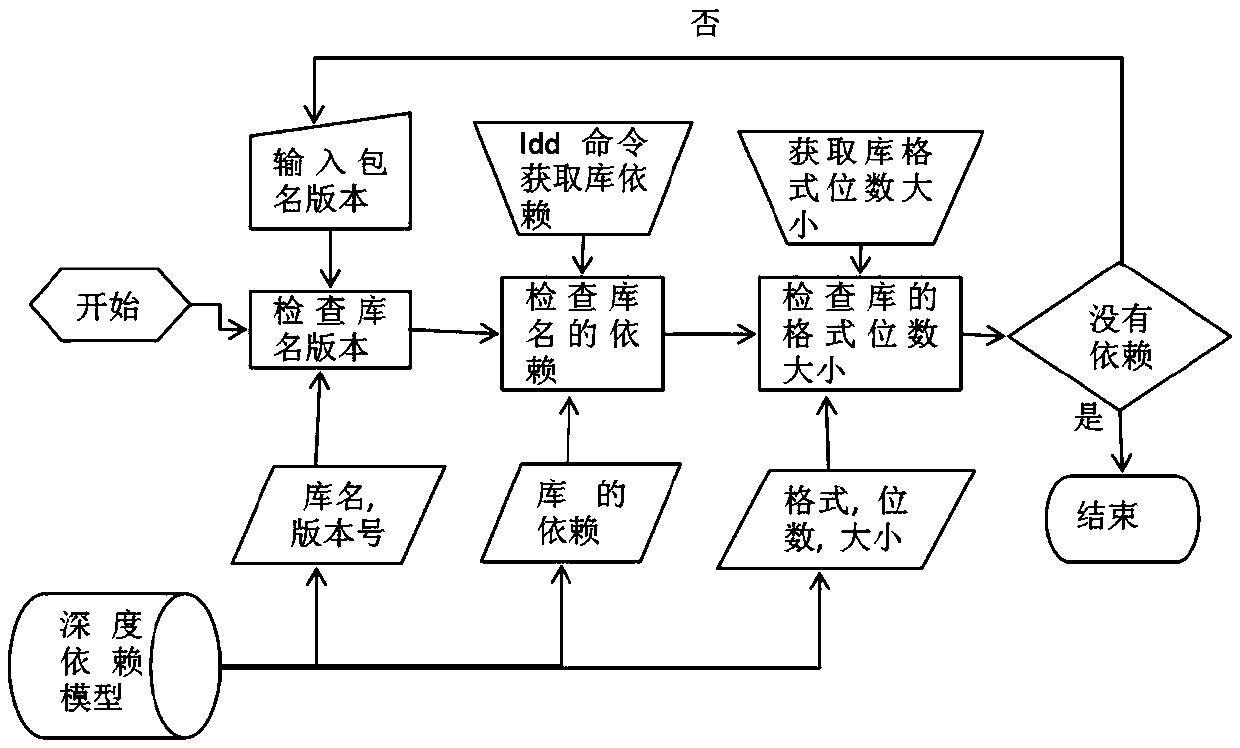
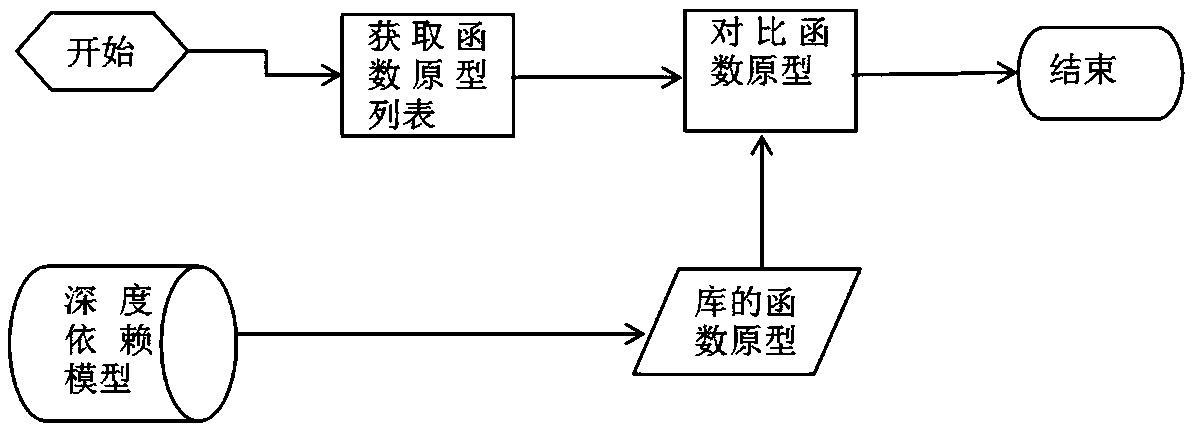
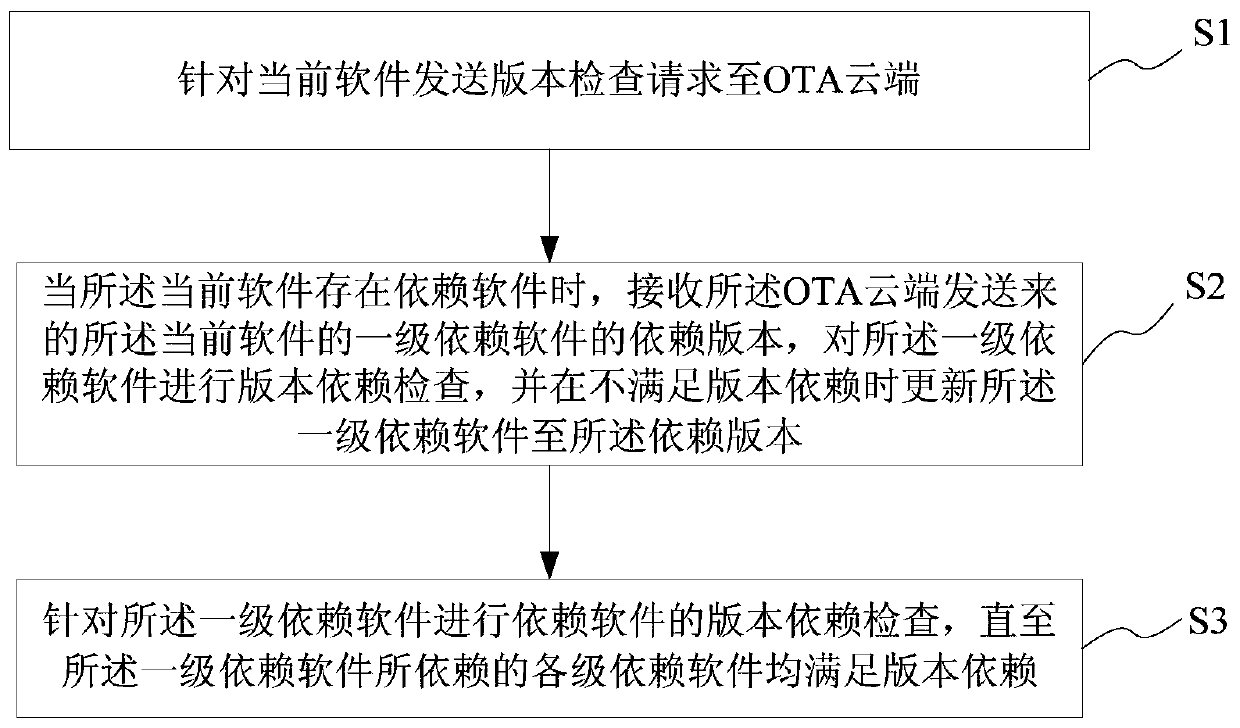
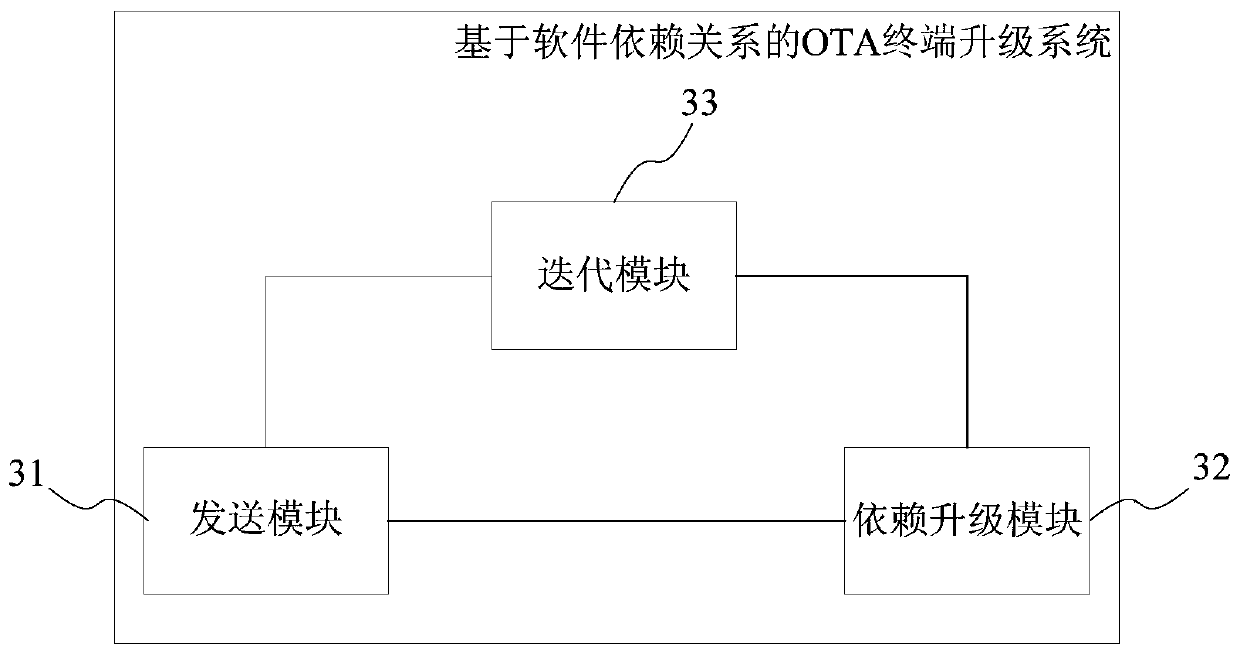
OTA terminal upgrading method and system based on software dependency relationship, medium and OTA terminal
PendingCN110377311AImplement automatic detectionGuaranteed normal upgradeVersion controlSoftware deploymentSoftware engineeringComputer terminal
The invention provides an OTA terminal upgrading method and system based on a software dependency relationship, a medium and an OTA terminal. The method comprises the following steps of sending a version checking request to an OTA cloud for current software; when the dependency software exists in the current software, receiving a dependency version, sent by the OTA cloud, of first-level dependencysoftware of the current software, performing version dependency check on the first-level dependency software, and updating the first-level dependency software to the dependency version when version dependency is not met; and performing version dependency check of the dependency software for the first-level dependency software until all levels of dependency software on which the first-level dependency software depends meet version dependency. According to the OTA terminal upgrading method and system based on the software dependence relation, the medium and the OTA terminal, automatic detectionof the software dependence relation can be achieved, OTA upgrading of all dependence software is automatically completed, and the user experience is greatly improved.
Owner:SHANGHAI QINGGAN INTELLIGENT TECH CO LTD
Management system and method for open software repository
ActiveCN106484458AOptimize management processSolve conflictsProgram loading/initiatingSoftware deploymentOperational systemApproaches of management
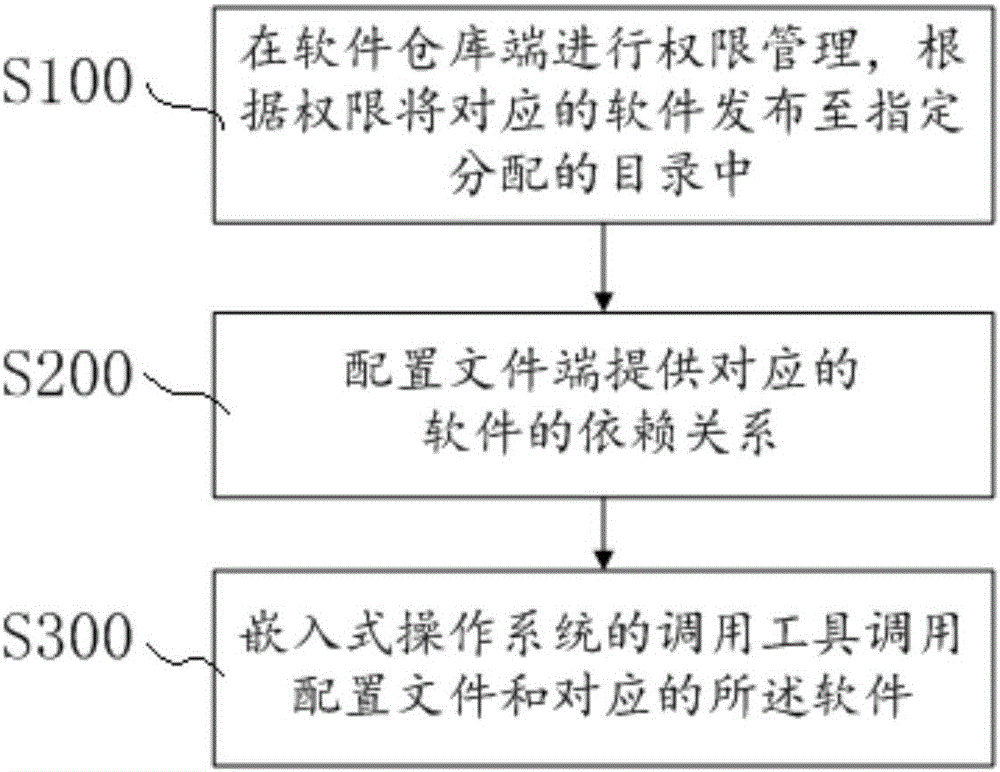
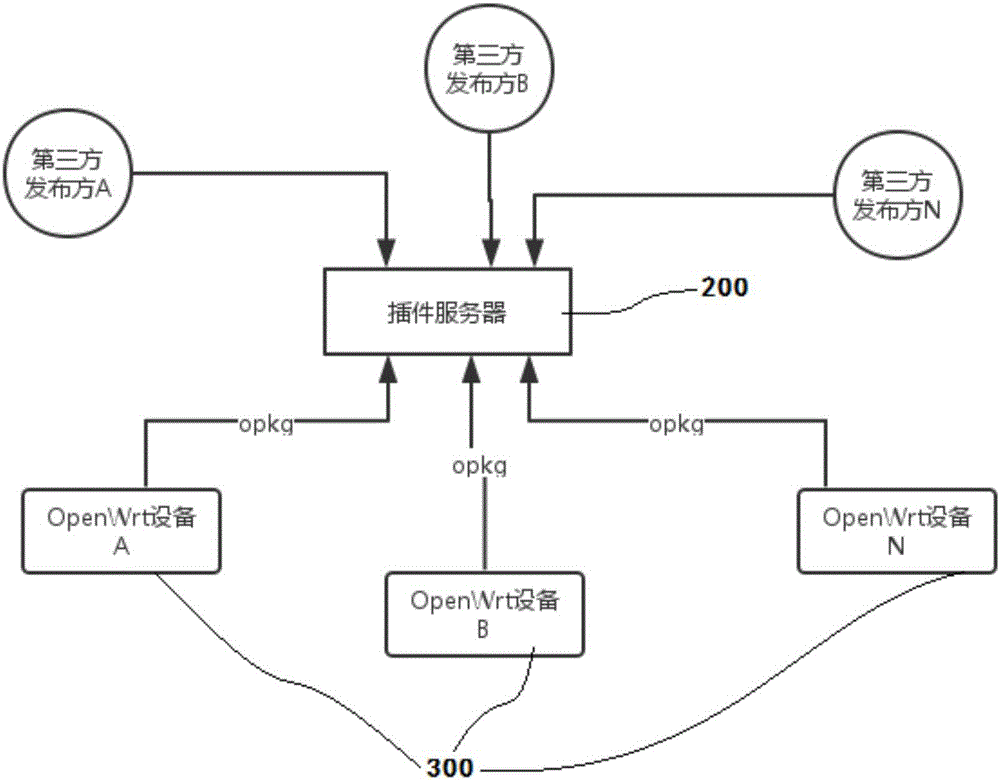
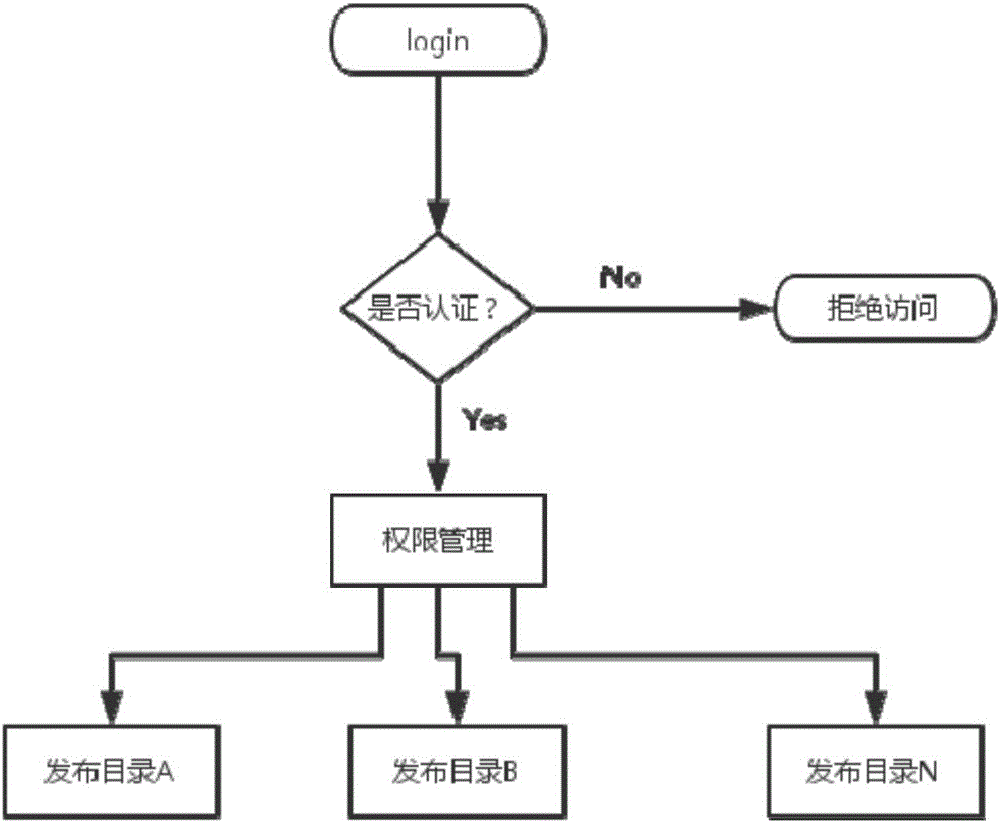
The invention relates to the technical field of network data access, particularly relates to the permission problem and the software dependency problem while a network device with embedded operating system accesses the network data. The invention discloses a management method for open software repository. The management method for open software repository comprises the following steps: S100, performing permission management in the software repository end, and releasing the corresponding software to the assigned directory according to the permissions; S200, providing dependency relationship of the corresponding software in the configuration file end; and S300, invoking the configuration file and the corresponding software by means of the invocation tool of the embedded operating system.
Owner:深圳德鲁克科技有限公司
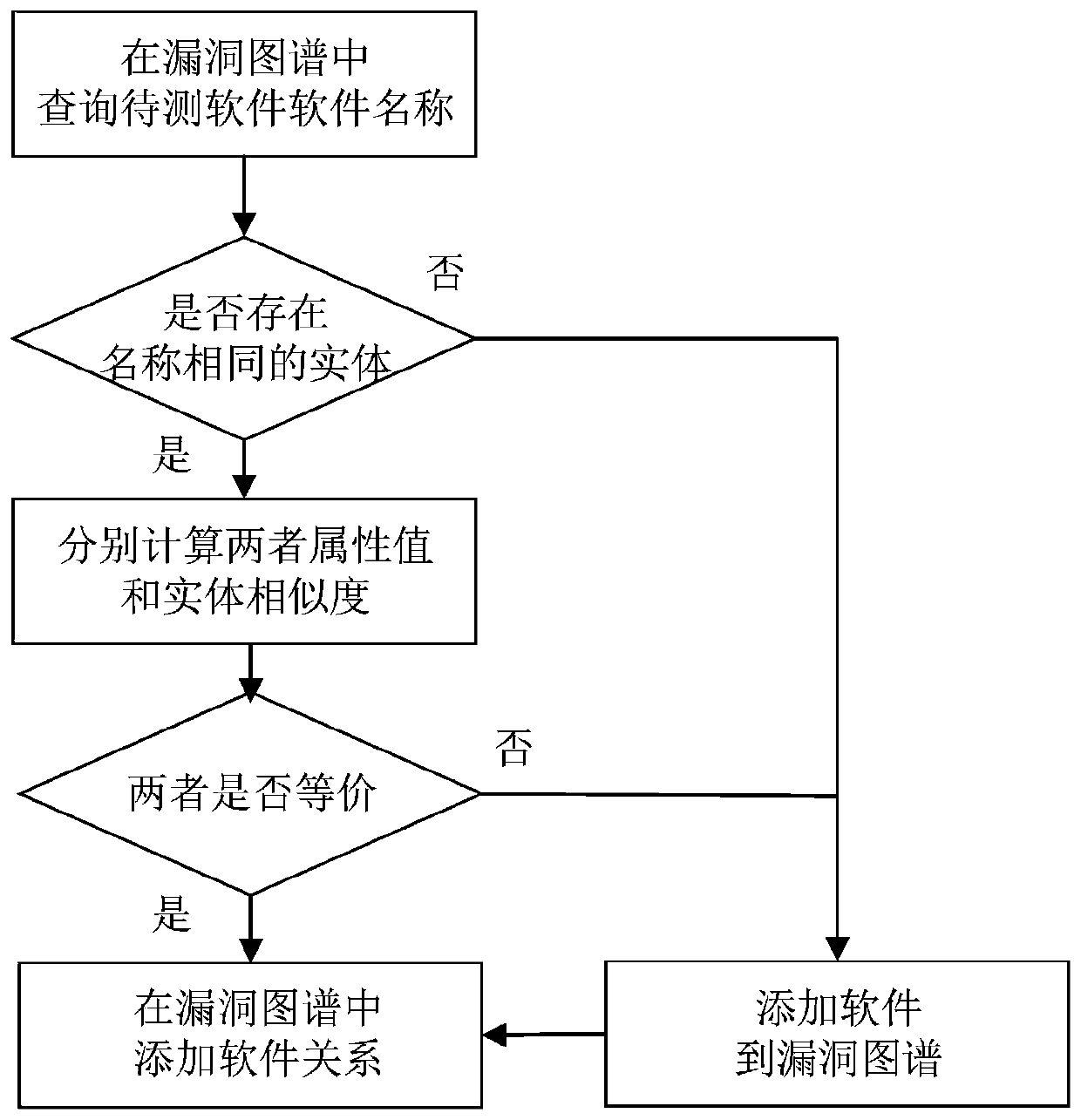
Vulnerability software dependency relationship construction method based on vulnerability map
ActiveCN110287704AReduce security risksHigh security riskPlatform integrity maintainanceSoftware engineeringSoftware dependencies
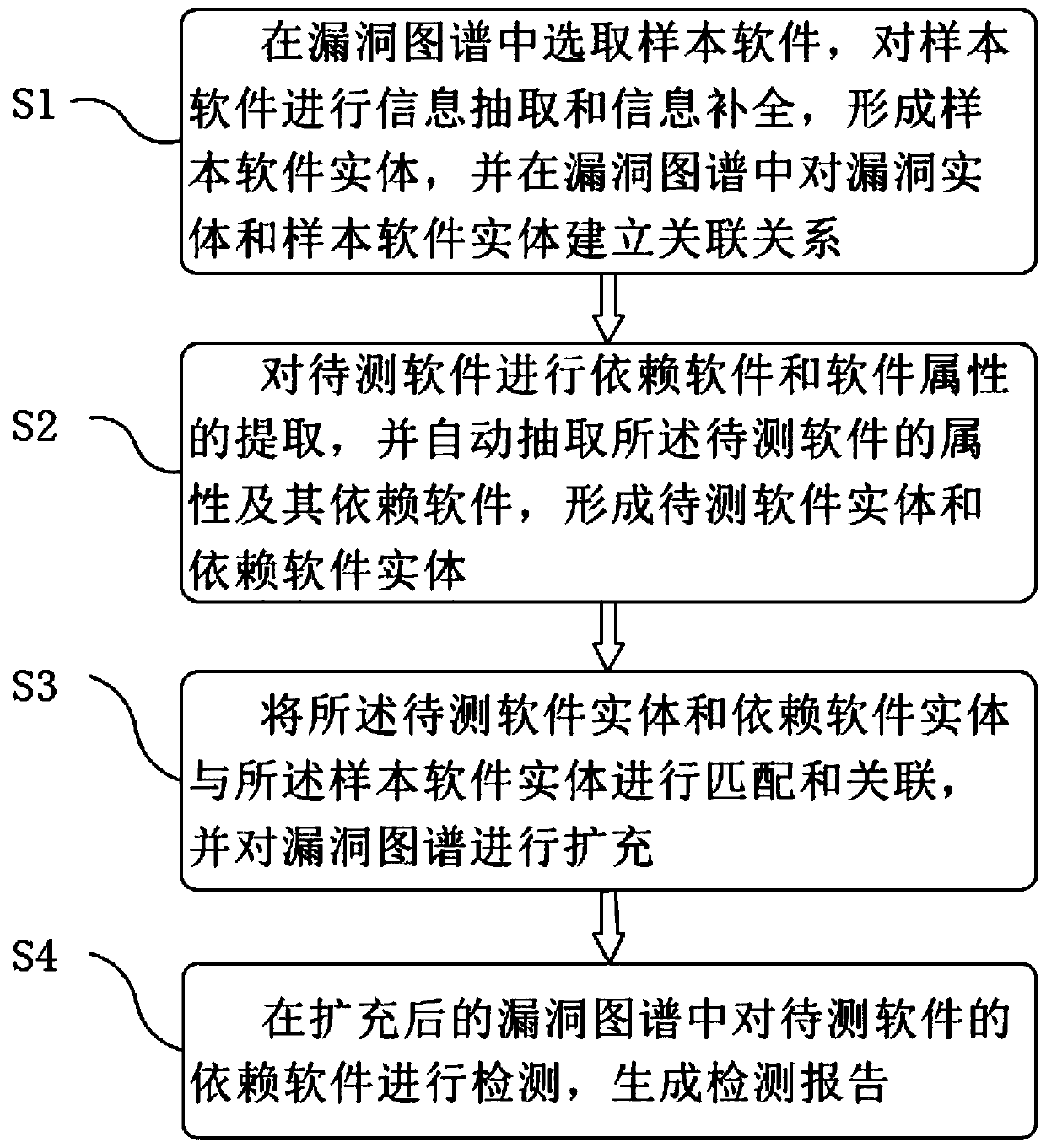
The embodiment of the invention discloses a vulnerability software dependency relationship construction method based on a vulnerability map, and relates to the technical field of information security. The method comprises the following steps: selecting sample software in a vulnerability map, performing information extraction and information completion on the sample software to form a sample software entity, and establishing an association relationship between the vulnerability entity and the sample software entity in the vulnerability map; extracting dependent software and software attributes of the to-be-tested software, and automatically extracting the attributes and the dependent software of the to-be-tested software to form a to-be-tested software entity and a dependent software entity; matching and associating the to-be-tested software entity and the dependent software entity with the sample software entity, and expanding the vulnerability map; and detecting the dependent software of the to-be-detected software in the expanded vulnerability map to generate a detection report. According to the embodiment of the invention, the problem of low software security caused by the fact that a vulnerability software dependency relationship construction method based on a vulnerability map does not exist in the prior art can be solved.
Owner:北京中科微澜科技有限公司
Low-overhead software transformation to enforce information security policies
ActiveUS10904291B1Reduce overheadAvoid passingTransformation of program codeSoftware testing/debuggingInformation transmissionSoftware analytics
Described is a system for enforcing software policies. The system transforms an original software by inserting additional instructions into the original software. The additional instructions have the effect of determining, at run-time, whether proceeding with execution of the original software is in accordance with a predefined policy. Transforming the original software relies on software analysis to determine whether any run-time checks normally inserted into the original software can be safely omitted. The transformed software prevents unauthorized information from passing to the network.
Owner:STEVENS INSTITUTE OF TECHNOLOGY +1
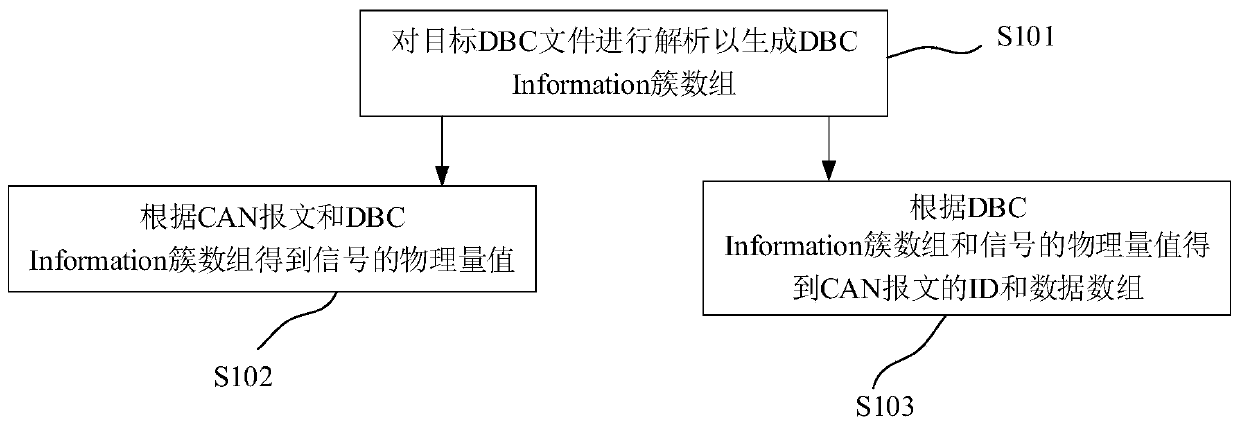
Message analysis method and system based on LabVIEW, electronic equipment and medium
The invention discloses a message analysis method and system based on LabVIEW, electronic equipment and a medium. The message analysis method based on LabVIEW comprises the following steps: analyzinga target DBC file to generate a DBC Information cluster array; obtaining a physical quantity value of the signal according to the CAN message and the DBC Information cluster array; and obtaining an IDand a data array of the CAN message according to the DBC Information cluster array and the physical quantity value of the signal. According to the method, the CAN network protocol DBC file is analyzed by using the XNET tool of the LabVIEW, calling and setting of any other control are not needed in the analysis process, the software dependence is low, and the analysis reliability is high. According to the method, the received CAN message and the sent CAN message are analyzed, and the analysis process is bidirectional.
Owner:SHANGHAI ELECTRICGROUP CORP
Efficient extraction of software dependencies from program code
InactiveUS8533659B2Error detection/correctionSoftware maintainance/managementSoftware dependenciesProgram code
Calls to stop functions are identified in a computer program file. The stop functions are functions that interact with external resources. Parameters of the calls to the stop functions that are references to the external resources are identified. An analysis is performed over the computer program file to find out possible values of the parameters of the calls.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com