Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
106 results about "Dependency network" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
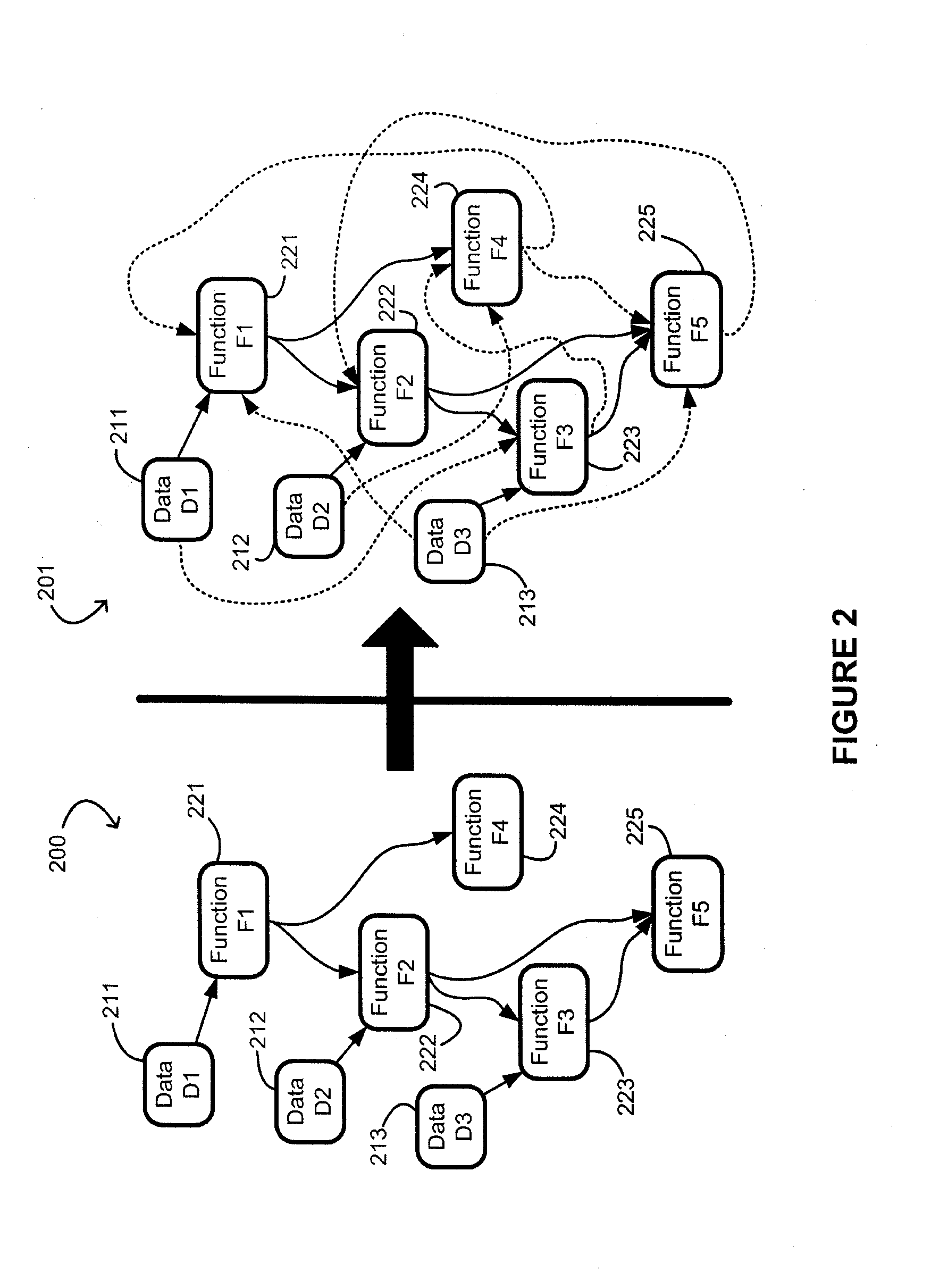
The dependency network approach provides a system level analysis of the activity and topology of directed networks. The approach extracts causal topological relations between the network's nodes (when the network structure is analyzed), and provides an important step towards [[inference of causal activity relations between the network nodes (when analyzing the network activity). This methodology has originally been introduced for the study of financial data, it has been extended and applied to other systems, such as the immune system, and semantic networks.
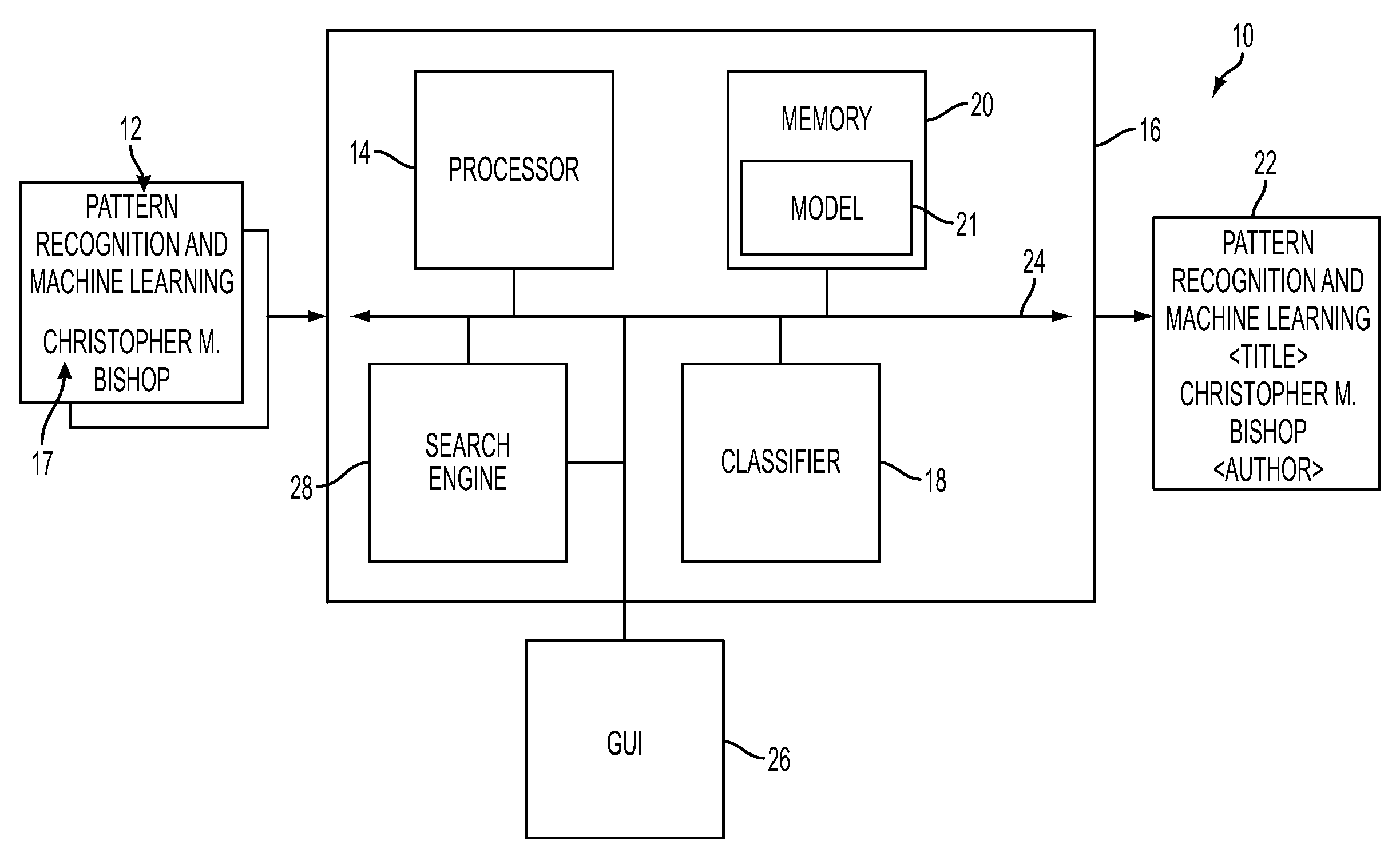
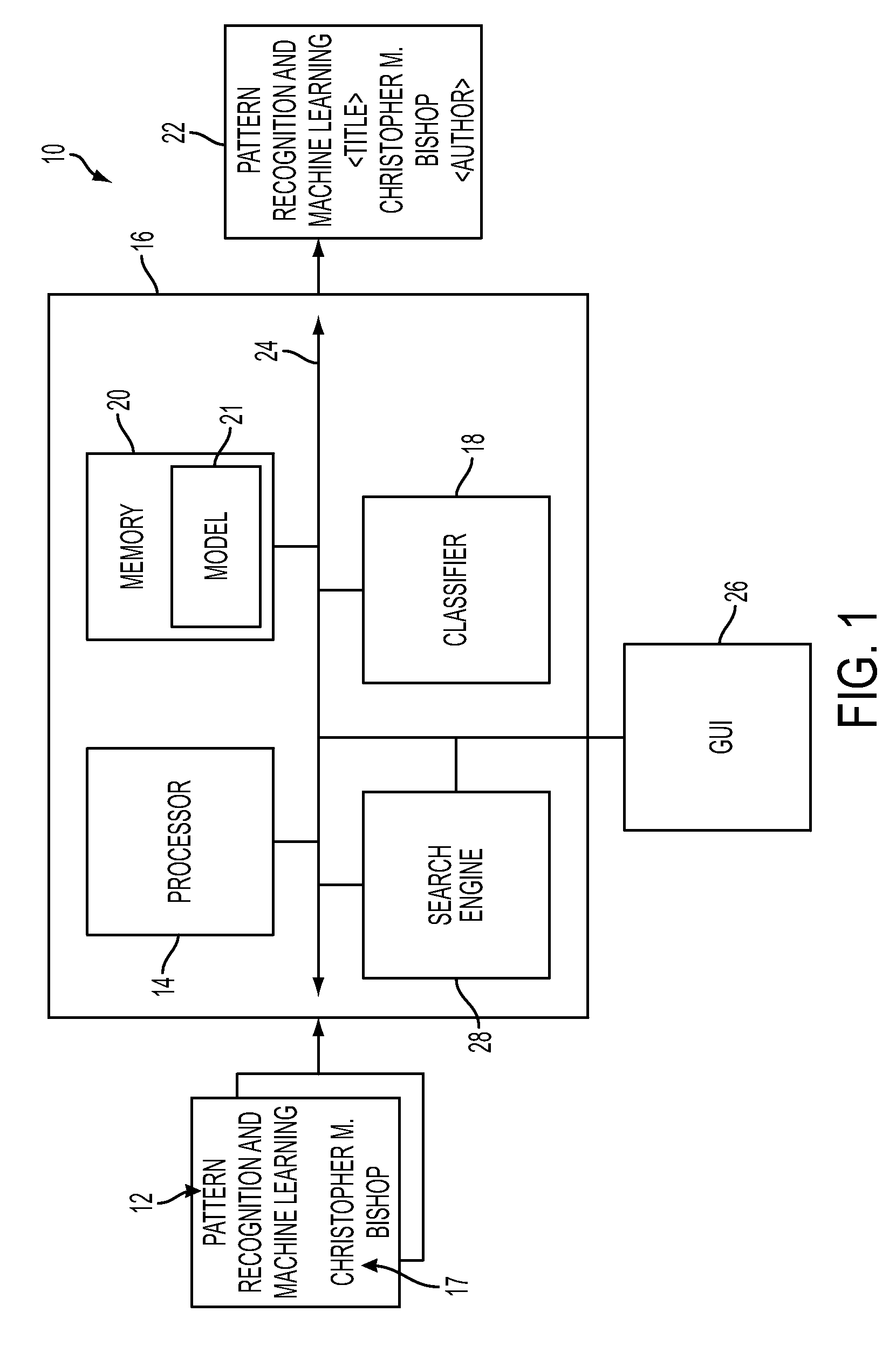
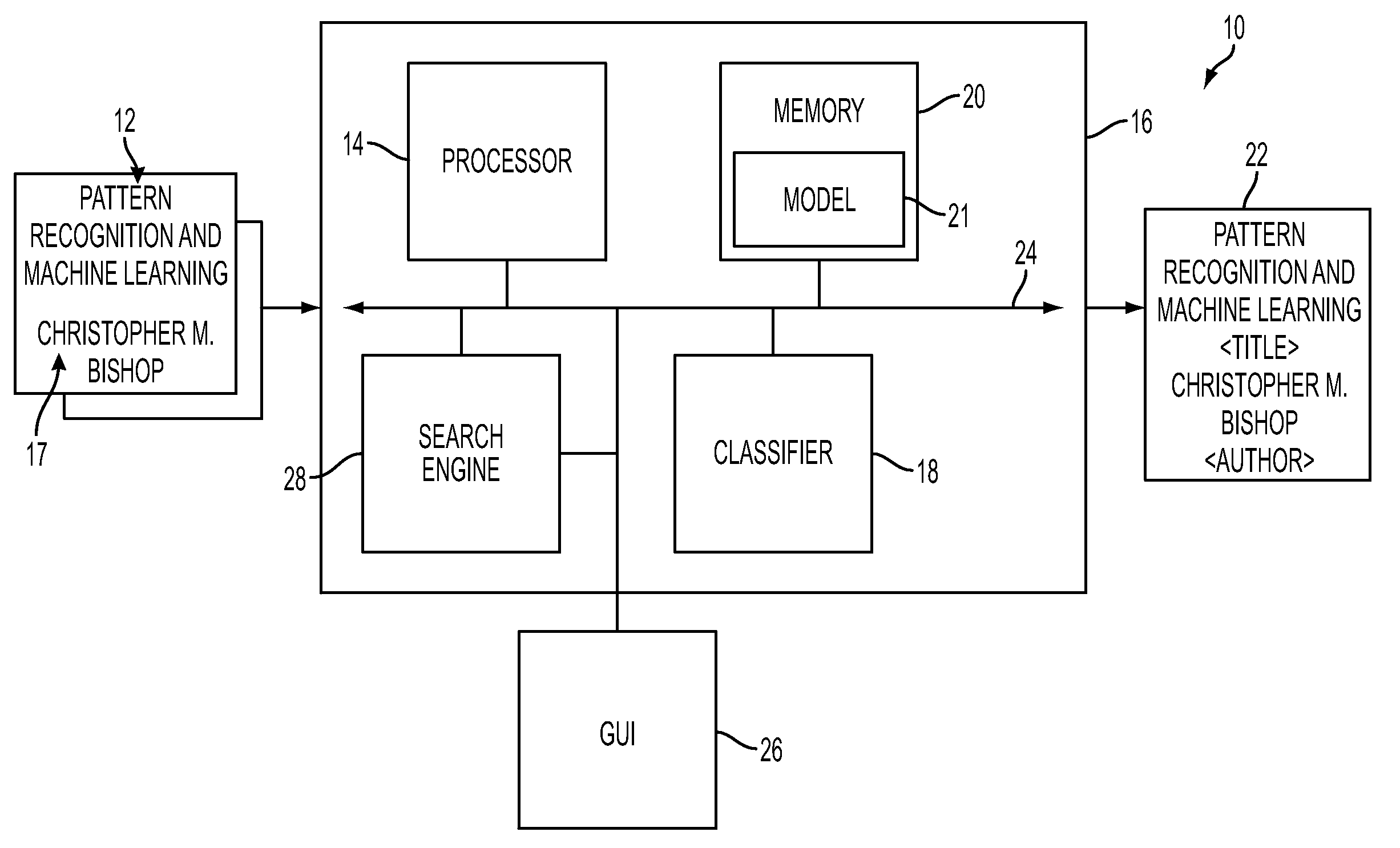
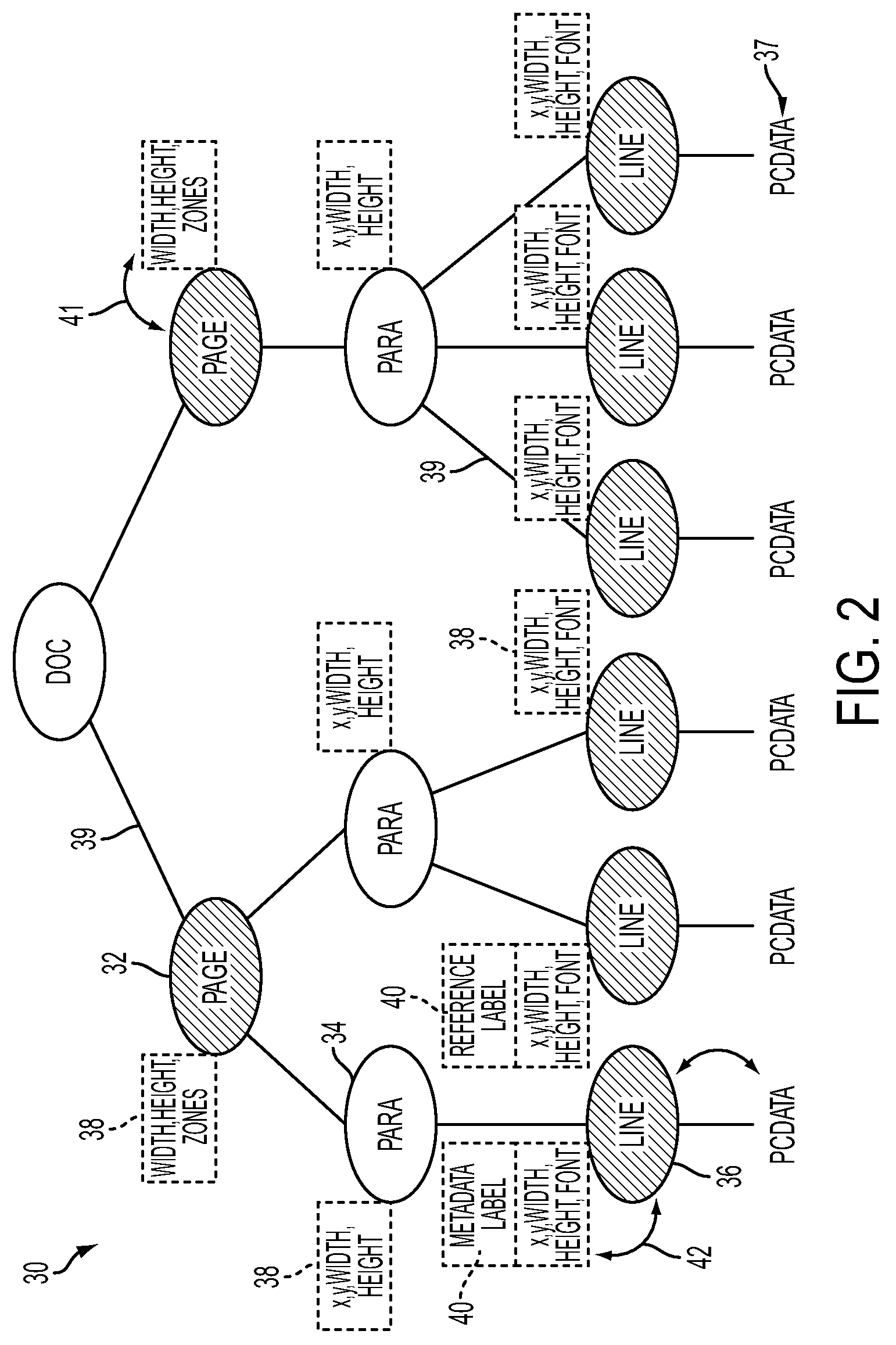
Stacked generalization learning for document annotation
A document annotation method includes modeling data elements of an input document and dependencies between the data elements as a dependency network. Static features of at least some of the data elements are defined, each expressing a relationship between a characteristic of the data element and its label. Dynamic features are defined which define links between an element and labels of the element and of a second element. Parameters of a collective probabilistic model for the document are learned, each expressing a conditional probability that a first data element should be labeled with information derived from a label of a neighbor data element linked to the first data element by a dynamic feature. The learning includes decomposing a globally trained model into a set of local learning models. The local learning models each employ static features to generate estimations of the neighbor element labels for at least one of the data elements.
Owner:XEROX CORP
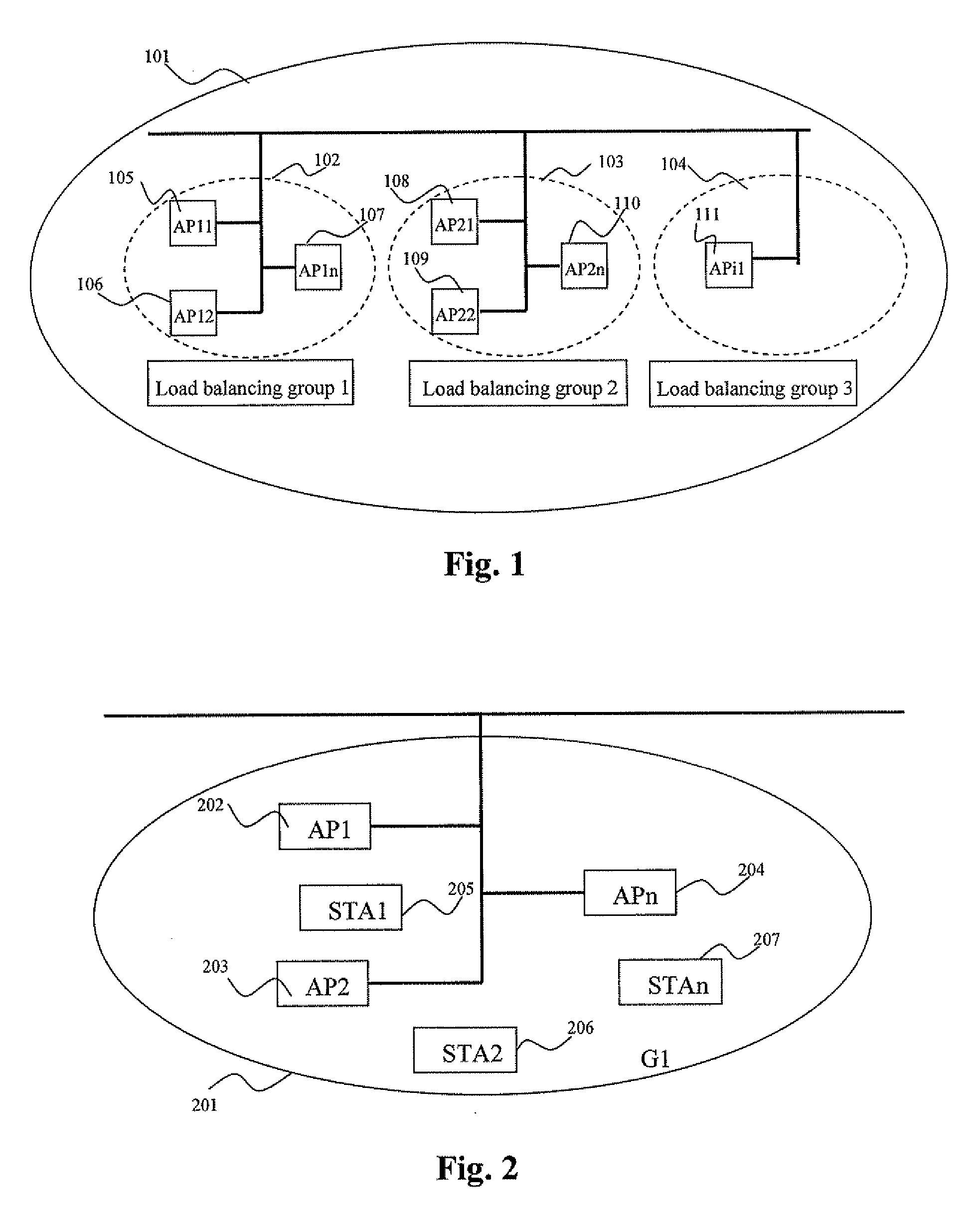
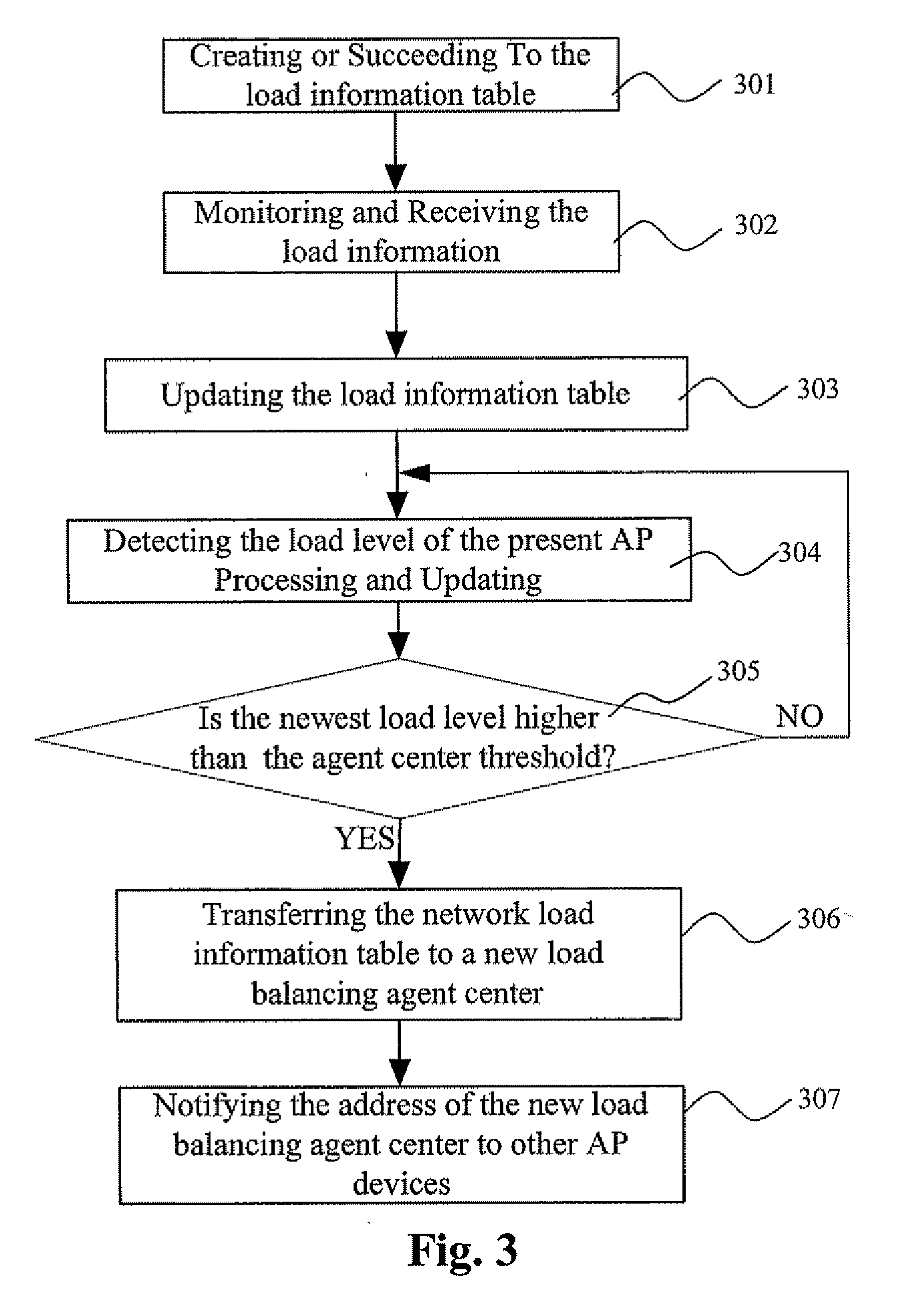
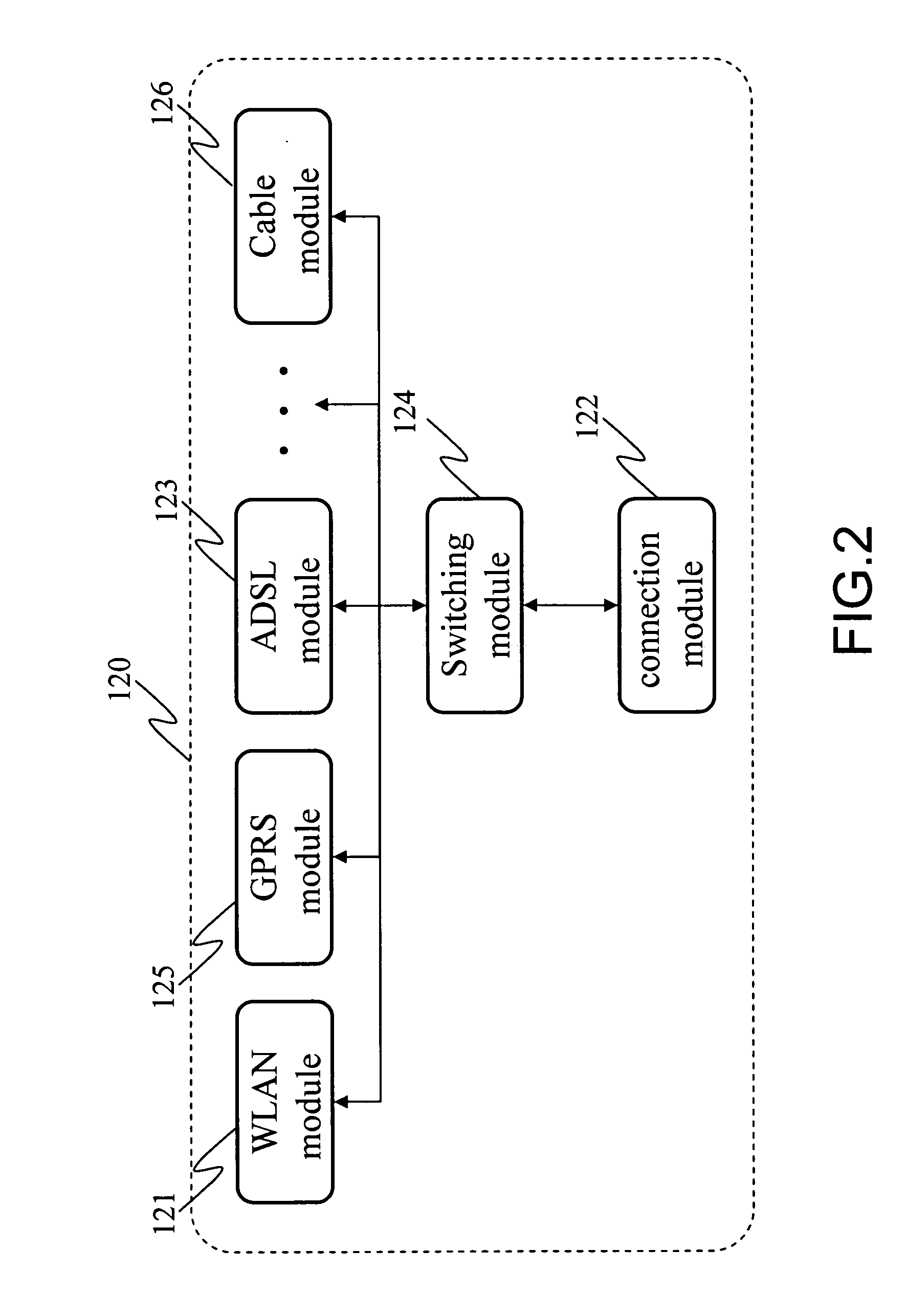
Load balancing method for a wireless area netowrk
InactiveUS20070115906A1Improve reliabilityReduce overheadNetwork traffic/resource managementAssess restrictionWireless lanDependability
The present invention relates to a load balancing method for a wireless local area network, which including the following steps: initializing the load balancing group, self-organizing to select an online access point from the load balancing group as a load balancing agent center, each access point of the said balancing group managing and processing the load balance in accordance with the load level and balance optimizing policy, therefore implements the network load balance. The method of the invention improves reliability of the network load information, prevents the load information from invalidly broadcasting in the wireless local area network, therefore reduces the additional overhead for managing the load balance of the wireless network, particularly in the network that having three layers switching equipment, self-organizing to select the agent center can utilize the network resource in effect, therefore managing the dynamic load balance information much more effect, reducing the dependence on the upper server, and managing the network much more flexible.
Owner:ZTE CORP
Alarm monitoring strategy analysis method based on data mining technology
InactiveCN106603317APerfect mining processImprove integrityData miningData switching networksData dredgingNetwork structure
The invention discloses an alarm monitoring strategy analysis method based on a data mining technology and belongs to the field of communication alarm monitoring. Through data mining, valuable knowledge can be extracted from enormous fuzzy data comprising noise, alarm data of a communication network is enormous and dynamic and is rich in knowledge, the alarm data of the communication network is mined without reliance on a network structure, and dynamic change of the network can be adapted. Data mining comprises the following steps: obtaining and preprocessing the alarm data; converting the obtained alarm data into a set of transaction items, and carrying out frequent item set data mining by use of a correlation algorithm; and through combination with actual application, performing compression, merging and classification processing on a result of a frequent item set. According to the invention, through merging and converting alarms, the multiple alarms are merged into one alarm with a larger information amount so as to replace the multiple alarms, and assistance is provided for network management personnel in analyzing fault information and rapidly positioning faults.
Owner:SHANDONG INSPUR COMML SYST CO LTD
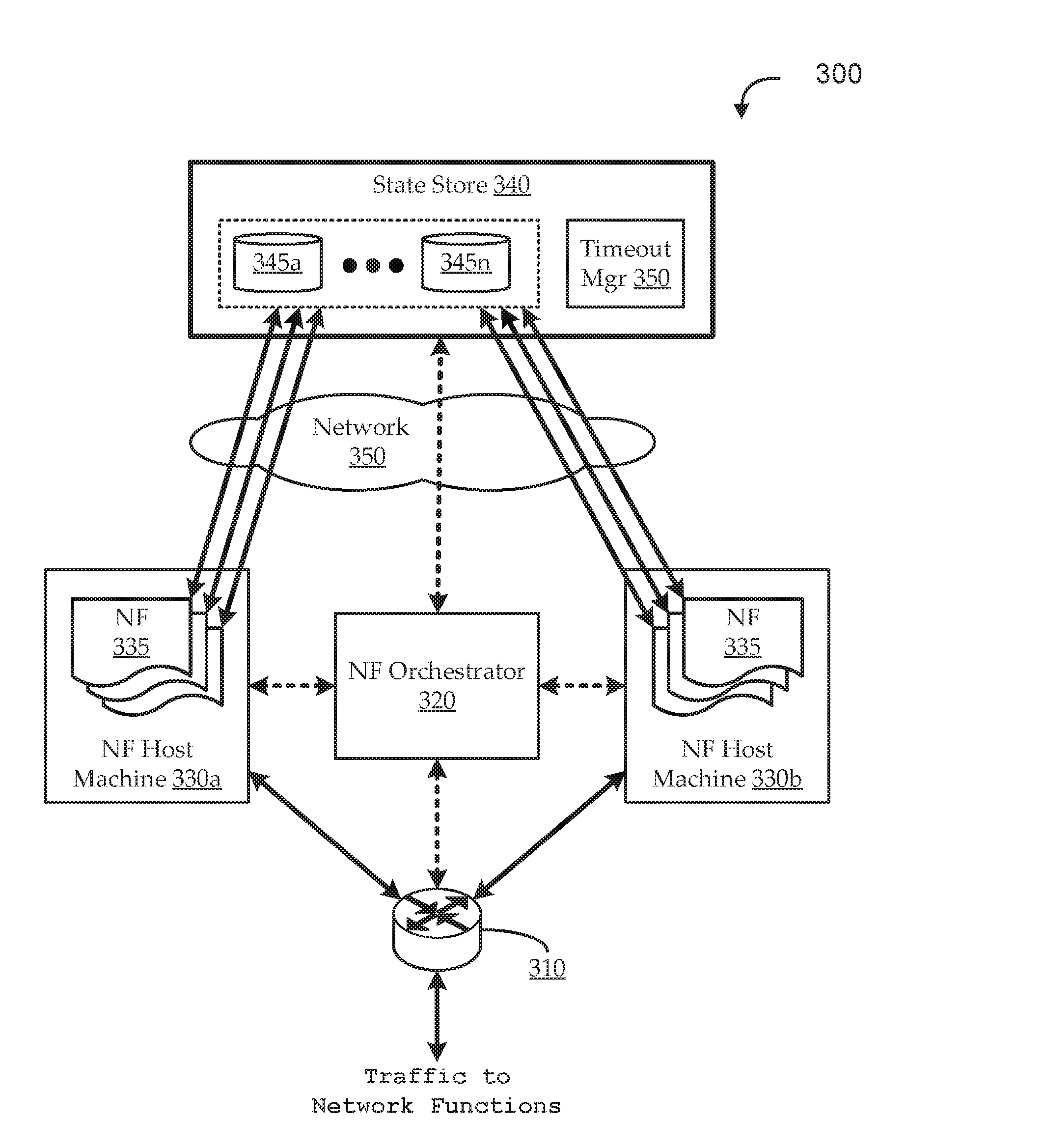
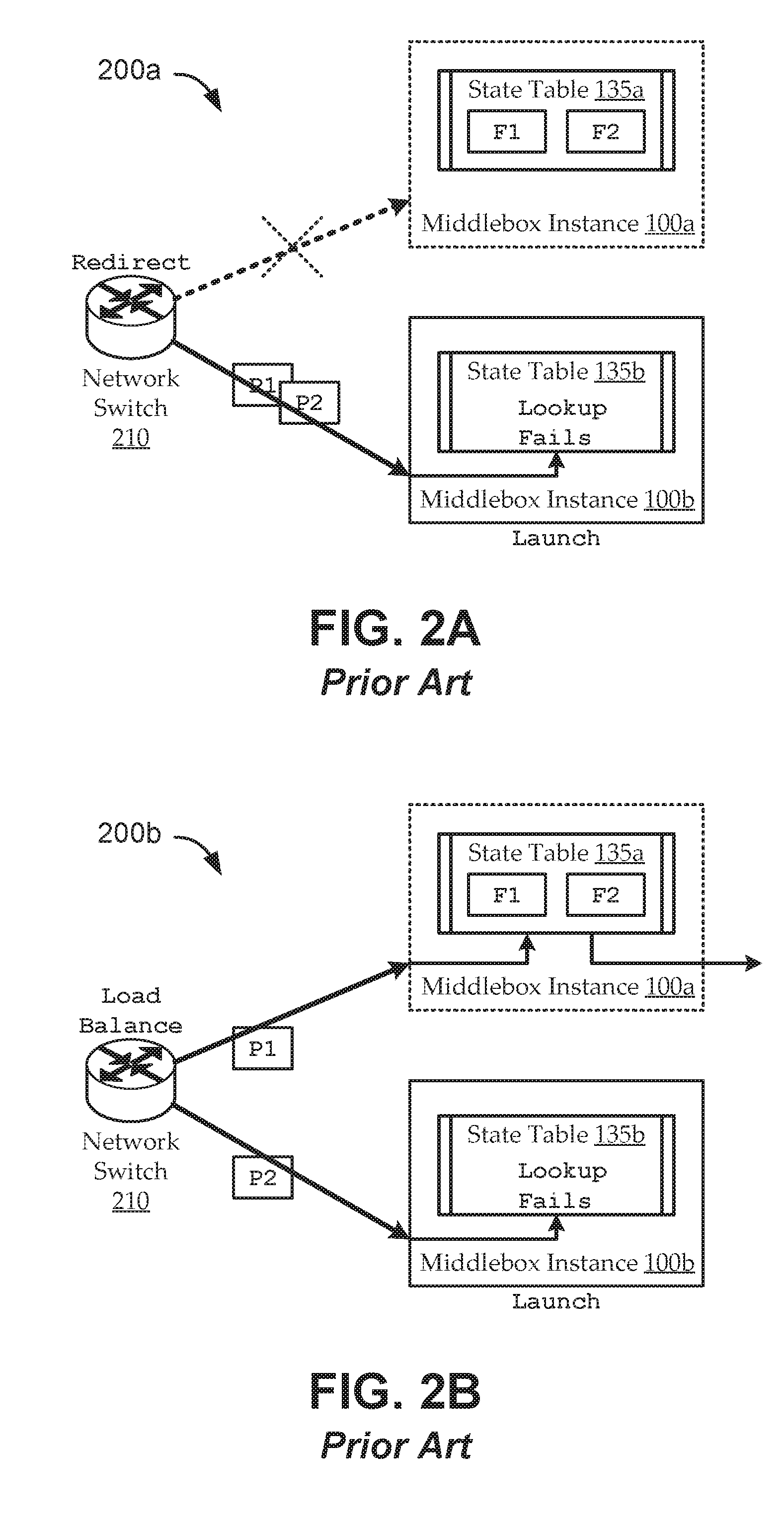
Stateless network functions
ActiveUS20170026301A1Improve fault toleranceImprove scalabilityProgram initiation/switchingData switching networksFault toleranceMiddleware
Systems and methods are described for stateless network function virtualization. Embodiments operate in context of a data network, in which network middleboxes are virtualized, for example, for added scalability and fault tolerance. The virtualized middleboxes can implement state-reliant network functions in a manner that decouples the state from the packet processing pipeline, while maintaining reliability and throughput even at very high data rates. Various embodiments include novel packet processing pipeline architectures, novel thread coordination structures (e.g., including batching and buffer pool sub-structures), novel remote state data store structures, and / or other novel features.
Owner:UNIV OF COLORADO THE REGENTS OF
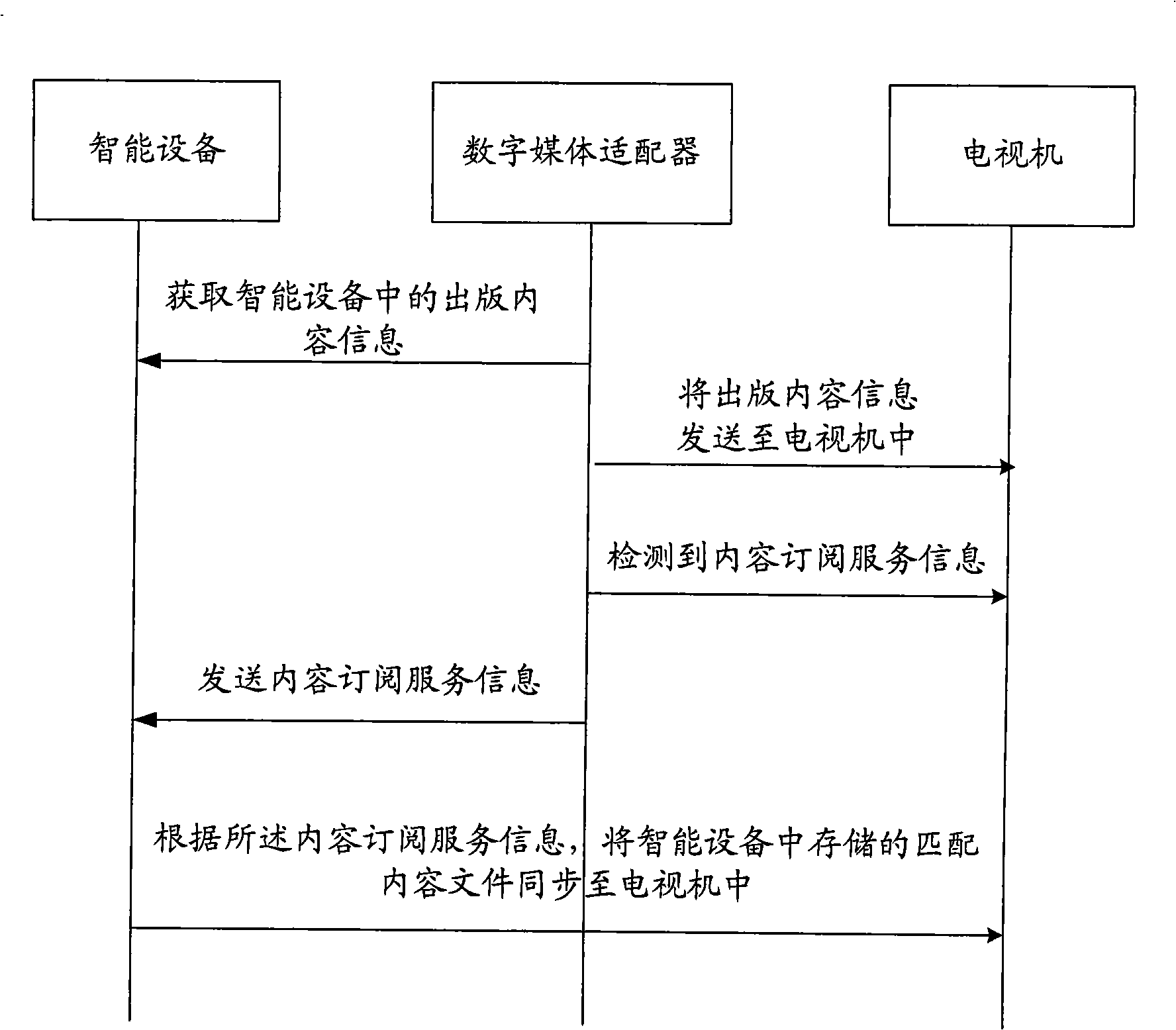
Content synchronizing method between television and intelligent apparatus
ActiveCN101340541AOnly involved in the experience effectTelevision system detailsColor television detailsFile synchronizationService information
The invention provides a content synchronization method used for a television and intelligent equipment, which is applicable to the field of communication technique. The method of the invention comprises the steps as follows: a digital media adapter detects content subscription information on the television; according to the content subscription information, match content file memorized in the intelligent equipment is synchronized into the television. The content synchronization of the invention only relates to the transmission of file and relates to no playing of code stream, thus relating to no experience effect of the subscriber; once the synchronization is completed, the network is not relied on, and the subscriber can watch the synchronized multimedia content off-line and is not needed to worry about that the signal of the wireless network affects the watching effect.
Owner:SHENZHEN TCL IND RES INST
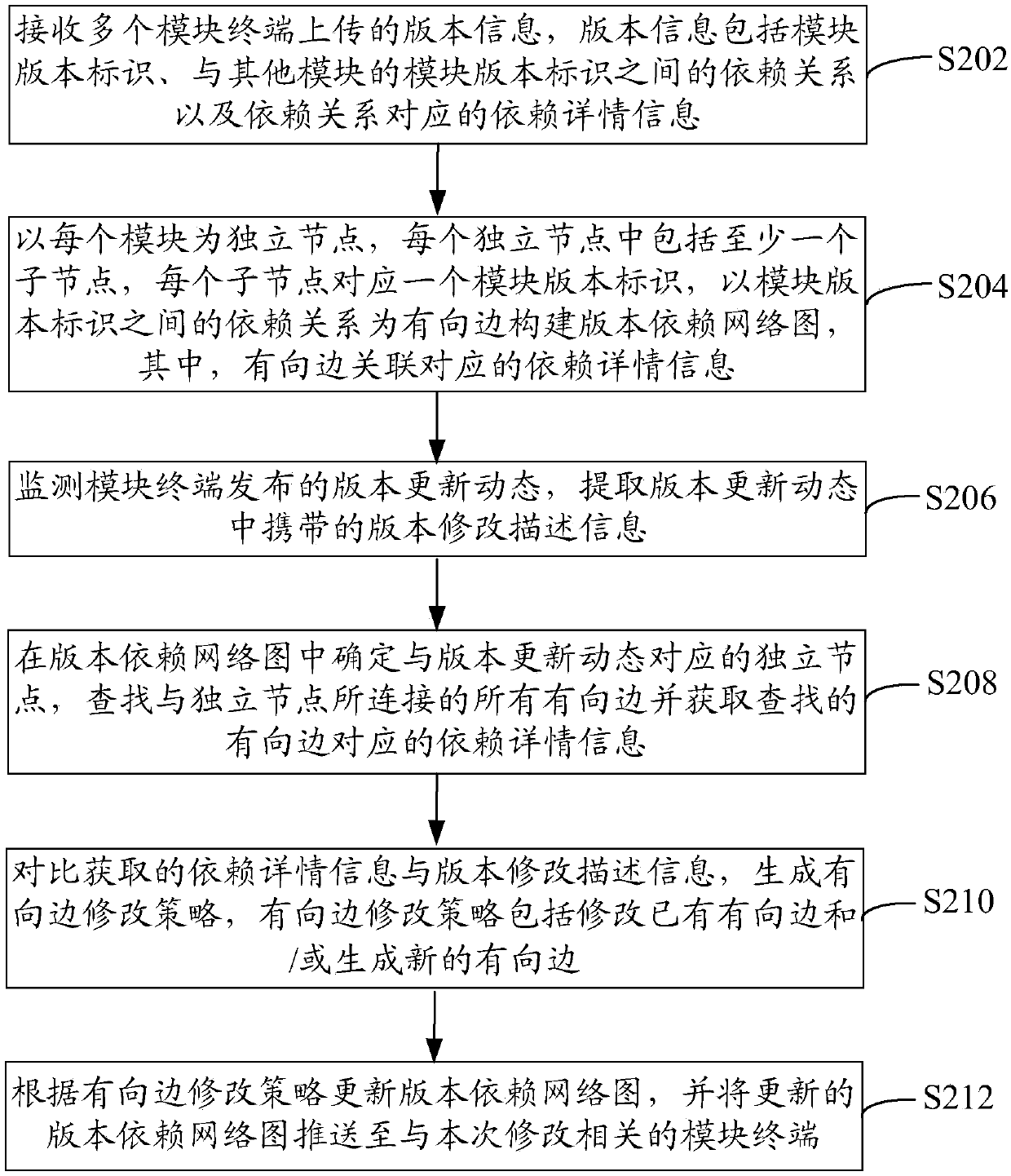
Multi-module version dependency relationship establishment method and apparatus, server and storage medium
The invention relates to a multi-module version dependency relationship establishment method. The method comprises the steps of receiving version information uploaded by multiple module terminals; bytaking each module as an independent node, and taking a dependency relationship between module version identifiers as a directed edge, establishing a version dependency network graph, wherein each independent node comprises at least one sub-node, and the directed edge is associated with corresponding dependency detail information; monitoring version update dynamics released by the module terminals, and extracting version modification description information; determining the independent nodes corresponding to the version update dynamics in the version dependency network graph, and searching forthe dependency detail information of all the directed edges connected with the independent nodes; comparing the obtained dependency detail information with the version modification description information, and generating a directed edge modification policy; and according to the directed edge modification policy, updating the version dependency network graph, and pushing the updated version dependency network graph to the module terminals. According to the method, related modules can be automatically located during visual display of the dependency relationship between the modules, and versionupgrading.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
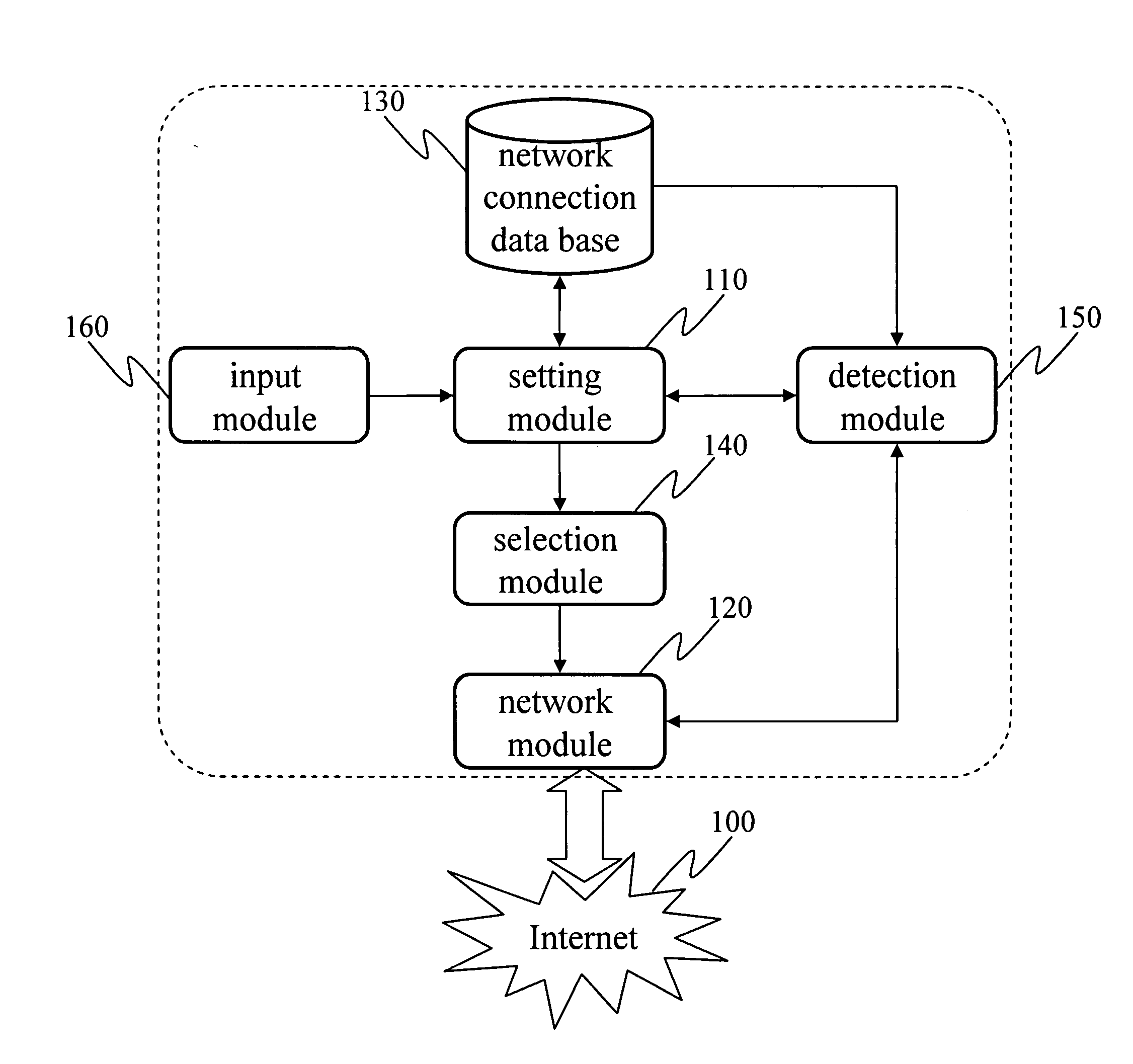
Environment dependent network connection switching setting system and method
An environment dependent network connection switching setting system and method thereof is provided, wherein the network connection is interrupted due to changes of the network environment of the user, the system is utilized to automatically detect a set of optimal current network setting parameters based on the network setting parameters previously set by the user, and proceed with network connection based on the optimal current network setting parameters, thus facilitating and expediting network connection in the changing network environments.
Owner:GETAC TECH CORP
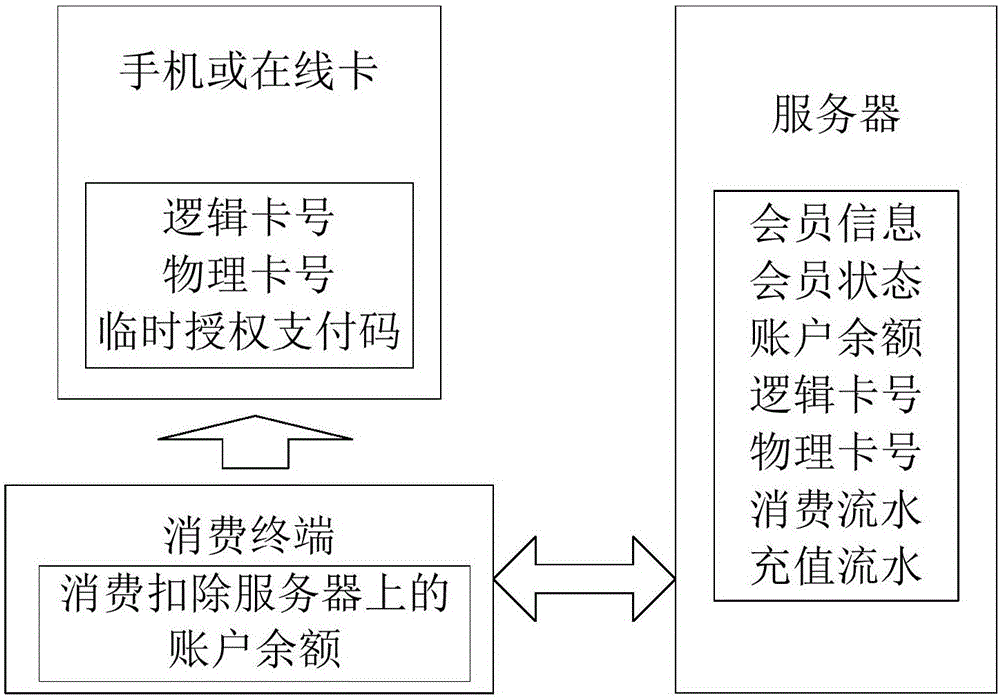
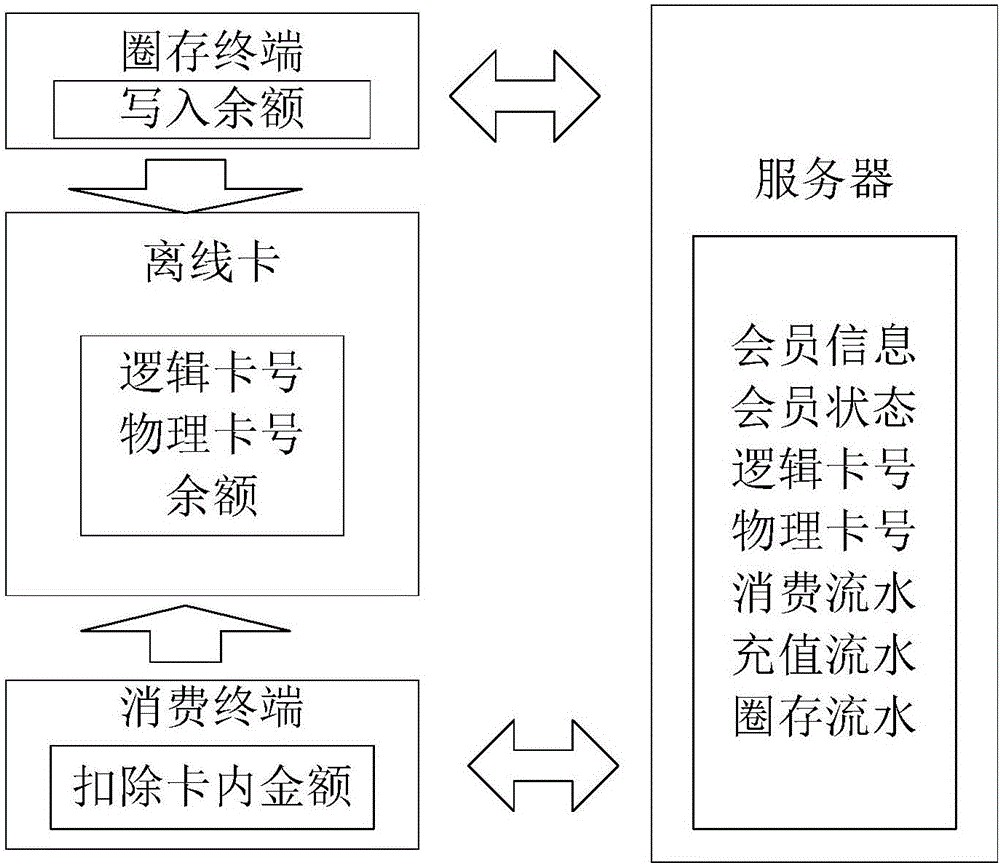
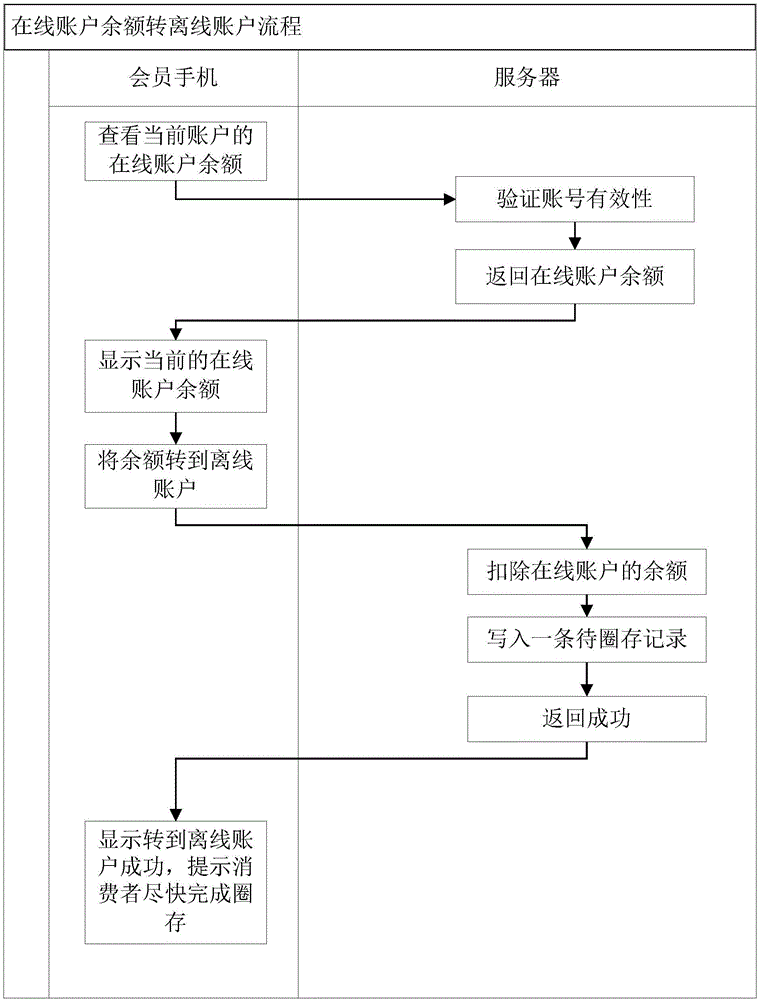
Off-line and on-line fused e-payment method and system
The invention discloses an off-line and on-line fused e-payment method and system. Two sub-accounts are established under one account, wherein one sub-account is used for off-line payment, and the other one is used for online payment, so that a member not only can carry out online payment through a mobile phone or a card, but also can finish off-line payment through the card; and after a payment terminal is reconstructed, the mobile phone can be utilized to realize online payment and a membership card can also be utilized to carry out offline payment. When the membership card is utilized for consumption, if the network is unobstructed, the consumption sum is deducted from the on-line account first by default; and if the online account balance is insufficient, the consumption sum is deducted from the balance of a recharge card. The method and system solve the problem that since online payment must depend on a network, and offline payment must depend on chip card encrypted storage balance information, cards cannot be integrated to the mobile phone, and are inconvenient to carry.
Owner:HUNAN KIMMA INTELLIGENT EQUIP MFR
Dependency network based model (or pattern)
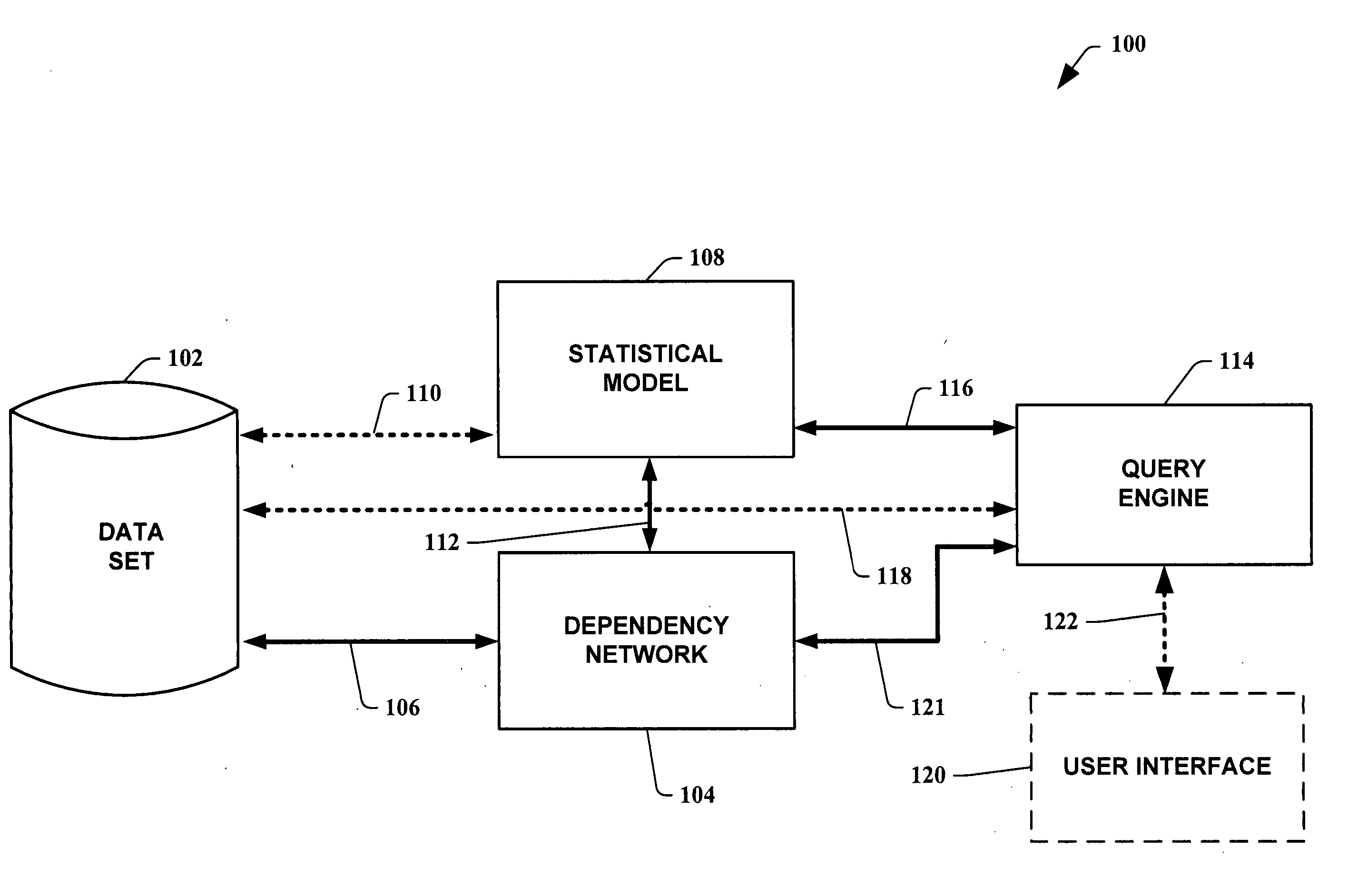
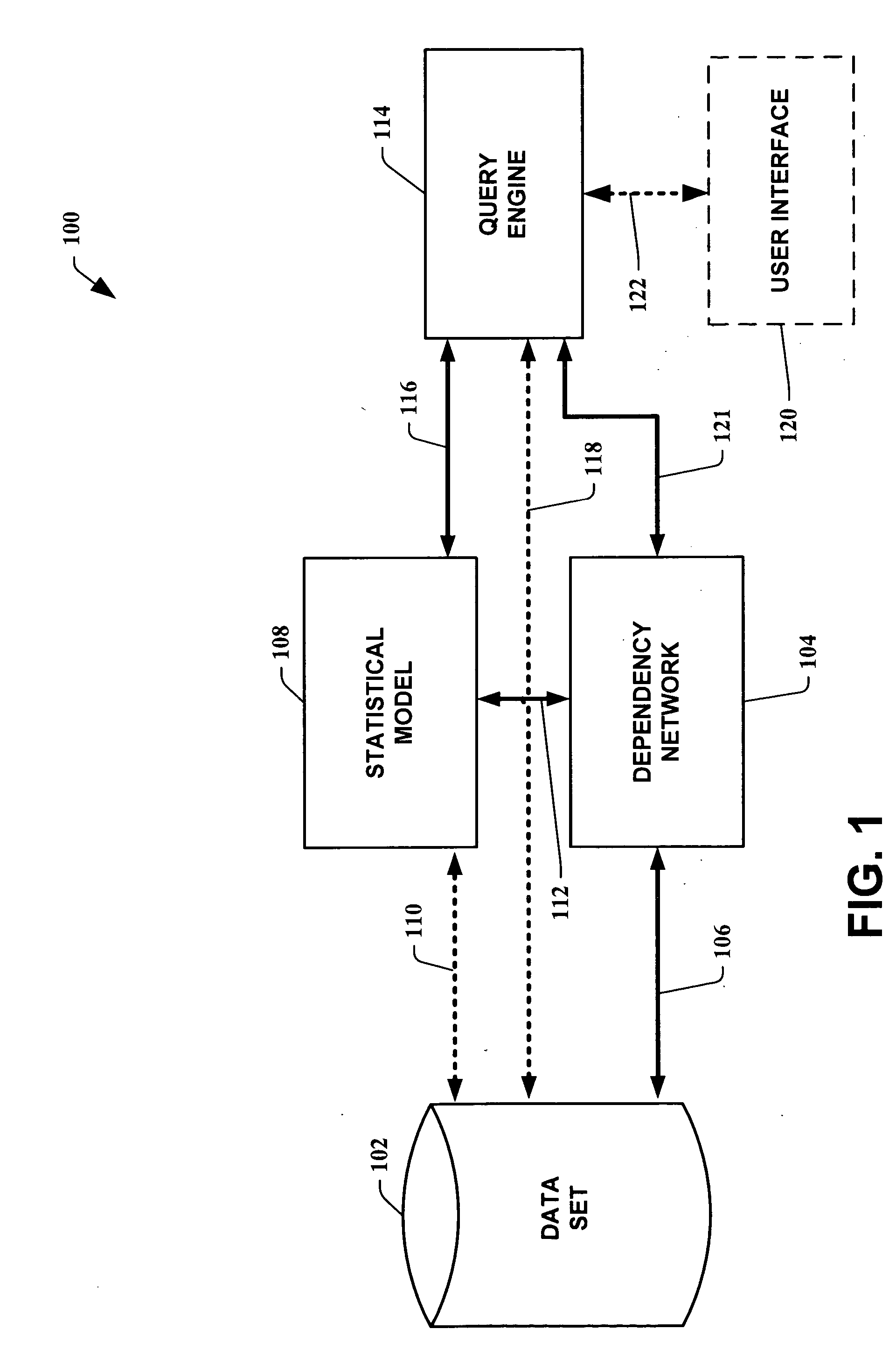
InactiveUS20060112190A1Valid conversionQuick and efficient analysisDigital data information retrievalDigital data processing detailsData setOriginal data
A dependency network is created from a training data set utilizing a scalable method. A statistical model (or pattern), such as for example a Bayesian network, is then constructed to allow more convenient inferencing. The model (or pattern) is employed in lieu of the training data set for data access. The computational complexity of the method that produces the model (or pattern) is independent of the size of the original data set. The dependency network directly returns explicitly encoded data in the conditional probability distributions of the dependency network. Non-explicitly encoded data is generated via Gibbs sampling, approximated, or ignored.
Owner:MICROSOFT TECH LICENSING LLC
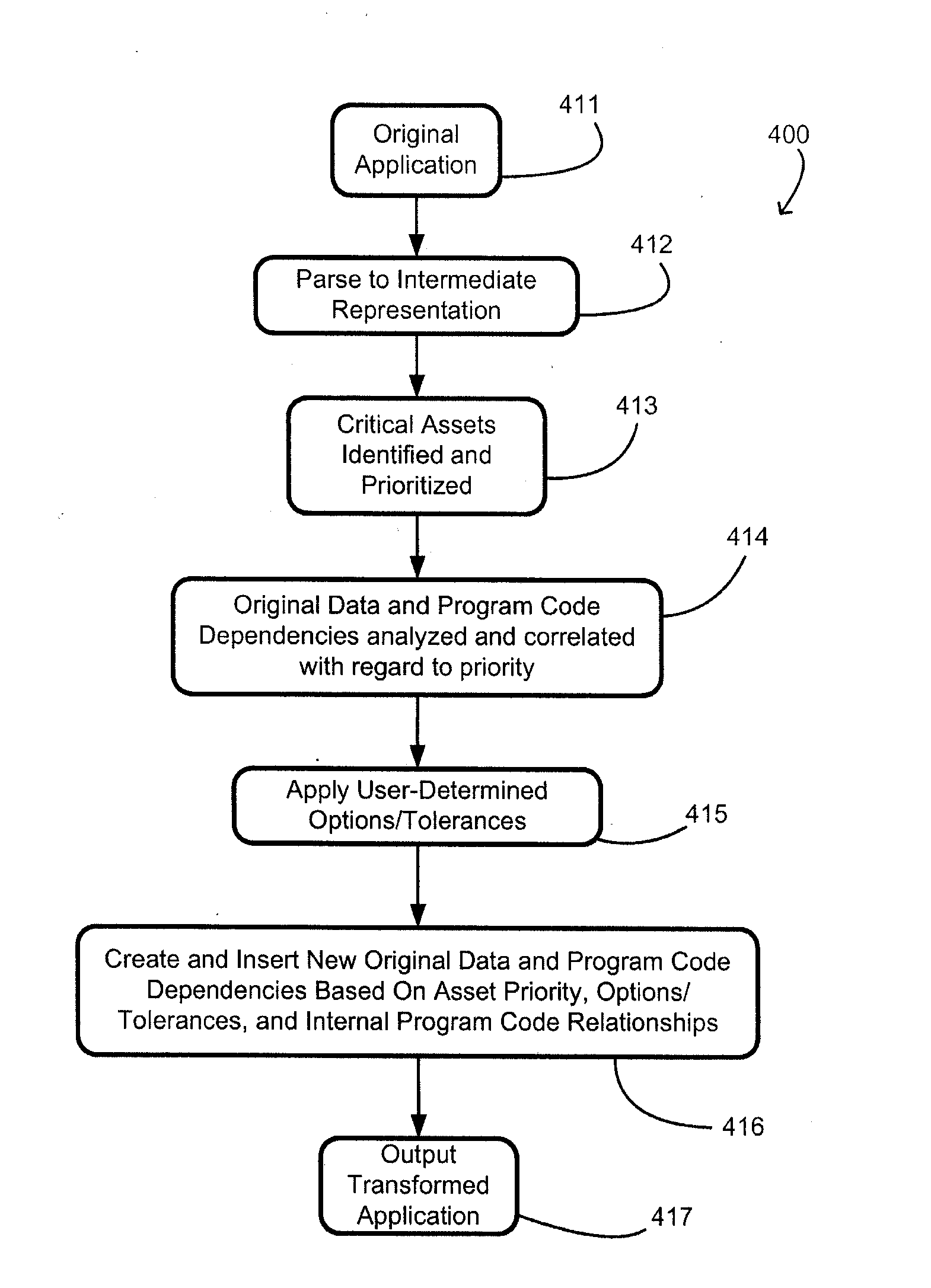
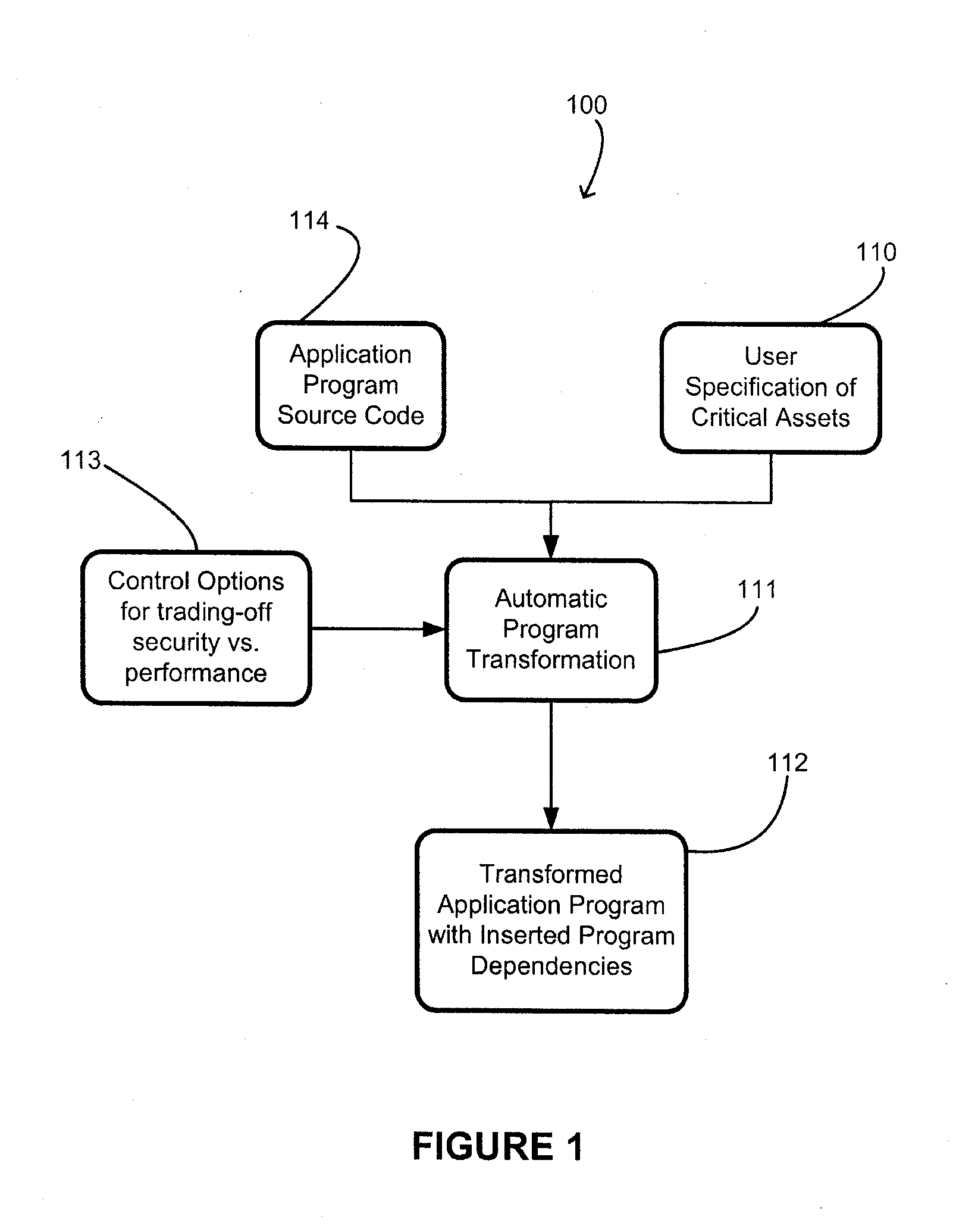
System And Method Providing Dependency Networks Throughout Applications For Attack Resistance
A method and system is provided to automatically propagate dependencies from one part of a software application to another previously unrelated part. Propagation of essential code functionality and data to other parts of the program serves to augment common arithmetic functions with Mixed Boolean Arithmetic (MBA) formulae that are bound to pre-existing parts of the program. A software application is first analyzed on a compiler level to determine the program properties which hold in the program. Thereafter, conditions are constructed based on these properties and encoded in formulae that encode the condition in data and operations. Real dependencies throughout the application are therefore created such that if a dependency is broken the program will no longer function correctly.
Owner:IRDETO ACCESS
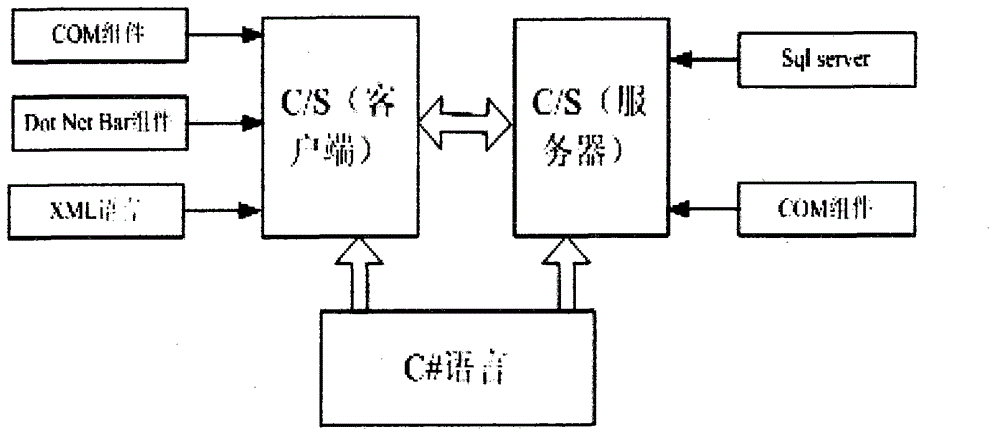
Multimedia long-distance family education system and equipment of system
InactiveCN102946390AImprove the environmentAbundant resourcesTransmissionElectrical appliancesComponent Object ModelNAT traversal
The invention discloses a multimedia long-distance family education system and equipment of the system. The multimedia long-distance family education system is based on a C / S model frame, uses a C # programming language, and combines an SQL (Structured Query Language) Server2012 database to realize data interaction; a COM (Component Object Model) control is used in the system and a third-party control such as DotNetBar is combined to realize teaching; and an NAT (Network Address Transfer) technique is used to realize the data interaction. The system mainly uses a hybrid P2P (peer-to-peer) network model, and is a novel network technique depending on the computing power and broadband of network users. The system is different from the traditional network structure, does not depend on a server for data transmission, establishes a virtual channel between the users for direct connection, and solves the problems that the safety of network data is imperfect in the traditional C / S system and the communication between two host machines requires a server for transfer, so that the privacy of the users is protected effectively; and the system has the characteristics of extendibility and load balancing.
Owner:孙霁
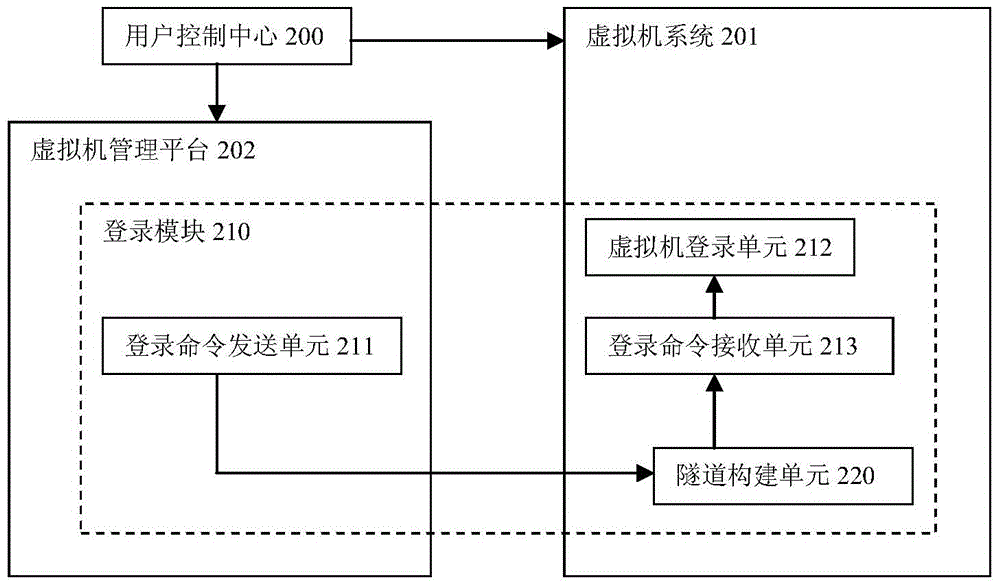
Virtual machine single sign-on method and system in cloud computing environment
ActiveCN104468587AImprove experienceImplement single sign-onTransmissionDependency networkCloud management
The invention discloses a virtual machine single sign-on method in the cloud computing environment. The method includes the steps of right allocation and single sign-on. The invention further discloses a virtual machine single sign-on system in the cloud computing environment. The system comprises a user control center used for allocating user rights and a sign-on module used for executing single sign-on. The virtual machine single sign-on method is simple in operation, free of modifying a virtual machine system kernel and free of depending on a network, and virtual machine single sign-on in the cloud computing environment can be simply and rapidly achieved. The virtual machine single sign-on system has the advantages that users with the single sign-on right can automatically sign onto a virtual machine system while signing on to a cloud management platform and being connected to a virtual machine, and user experiences are greatly improved.
Owner:CHINA STANDARD SOFTWARE
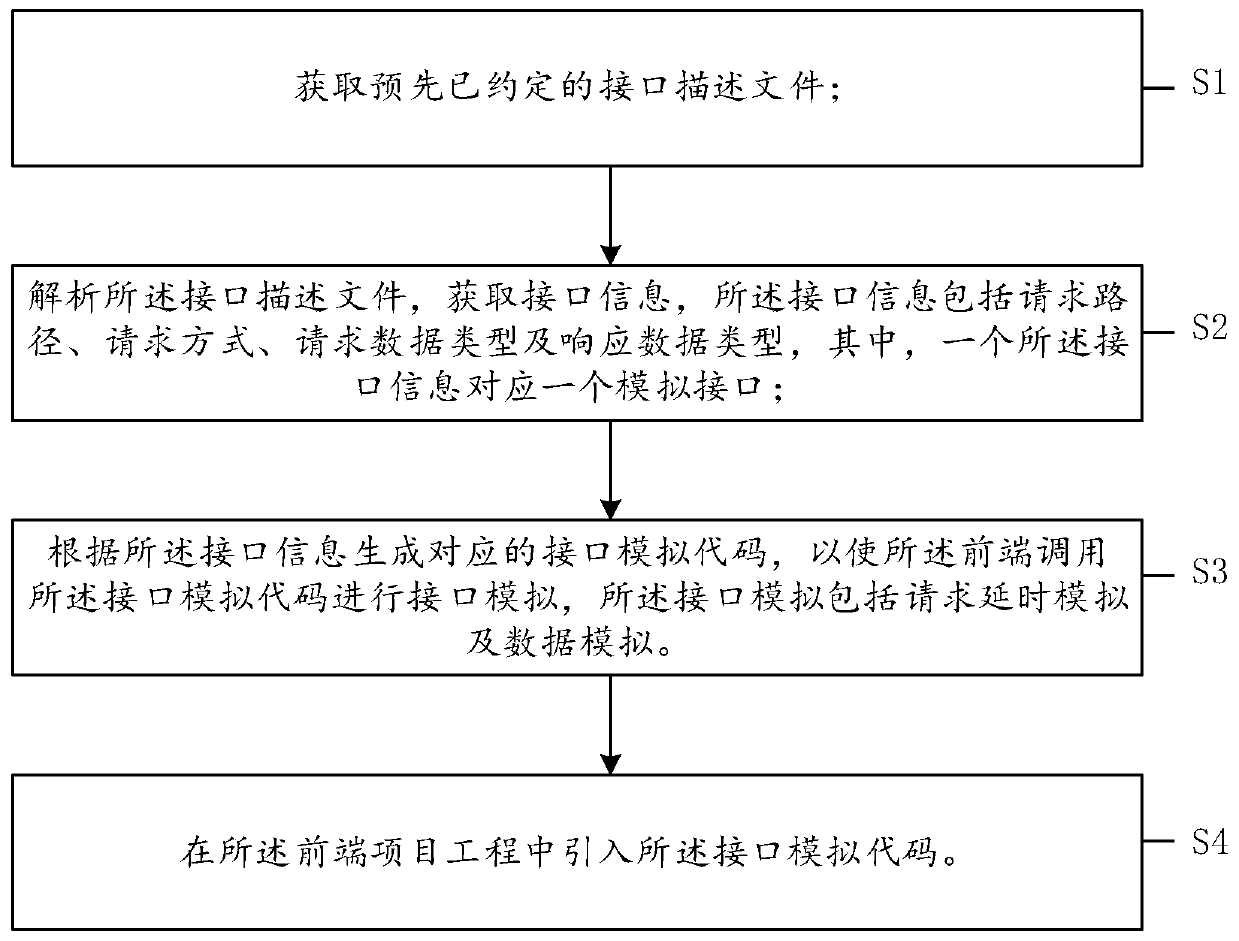
Interface simulation method and system, medium and electronic equipment
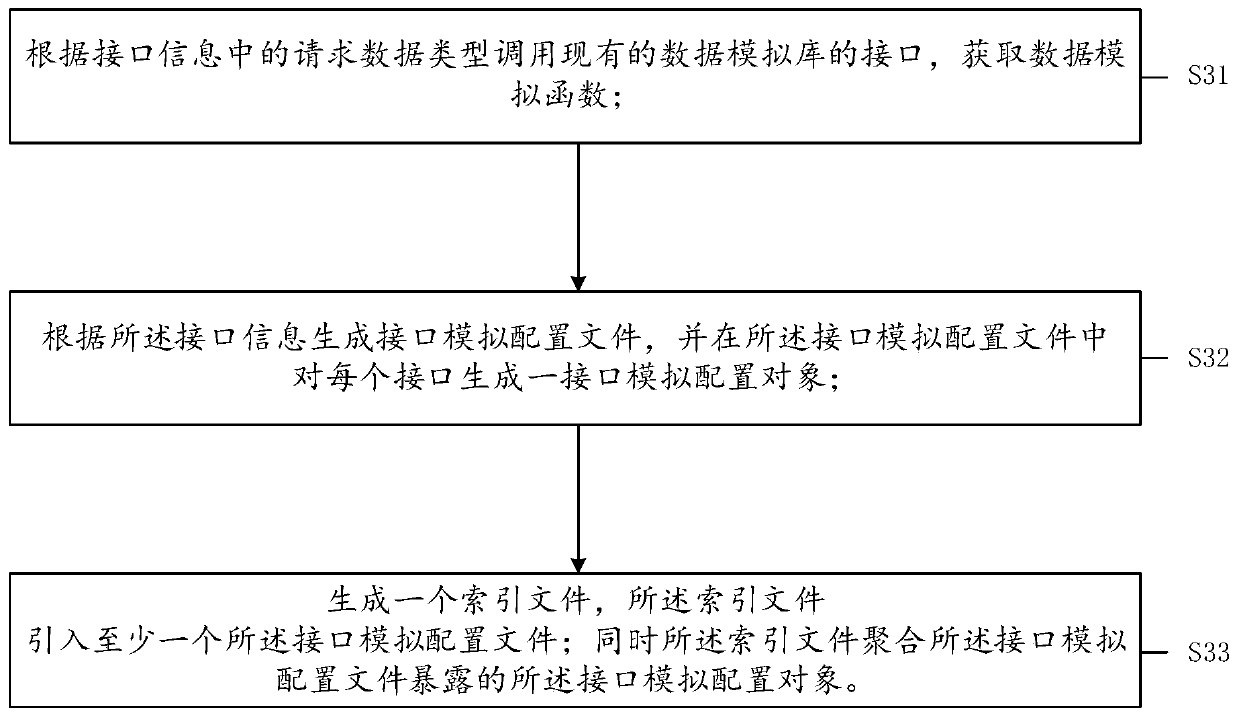
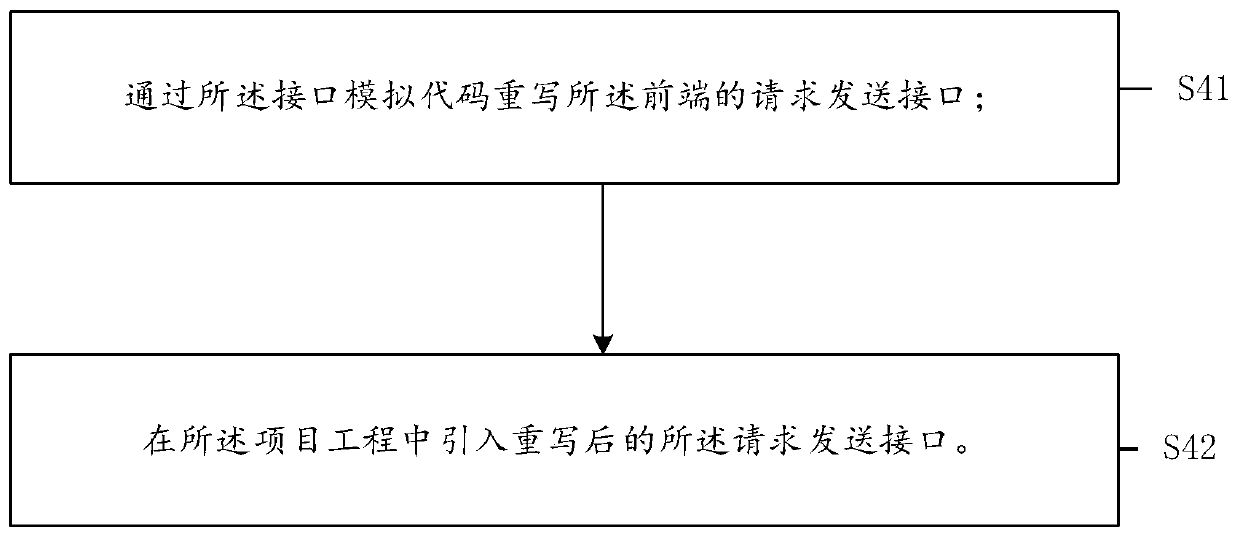
ActiveCN110489101AReduce management costsVersion controlProgram documentationData simulationData type
The invention provides an interface simulation method and system, a medium and electronic equipment. The method comprises the following steps: acquiring a pre-appointed interface description file; analyzing an interface description file to obtain interface information, with the interface information including a request path, a request mode, a request data type and a response data type, and one piece of interface information corresponding to one analog interface; and generating a corresponding interface simulation code according to the interface information, so that the front end calls the interface simulation code to perform interface simulation, and the interface simulation comprises request delay simulation and data simulation. The method is implemented locally and does not depend on a network. Meanwhile, analog data can be automatically generated, and manual configuration is not needed.
Owner:BEIJING BYTEDANCE NETWORK TECH CO LTD
Software defect prediction method and system based on network embedding
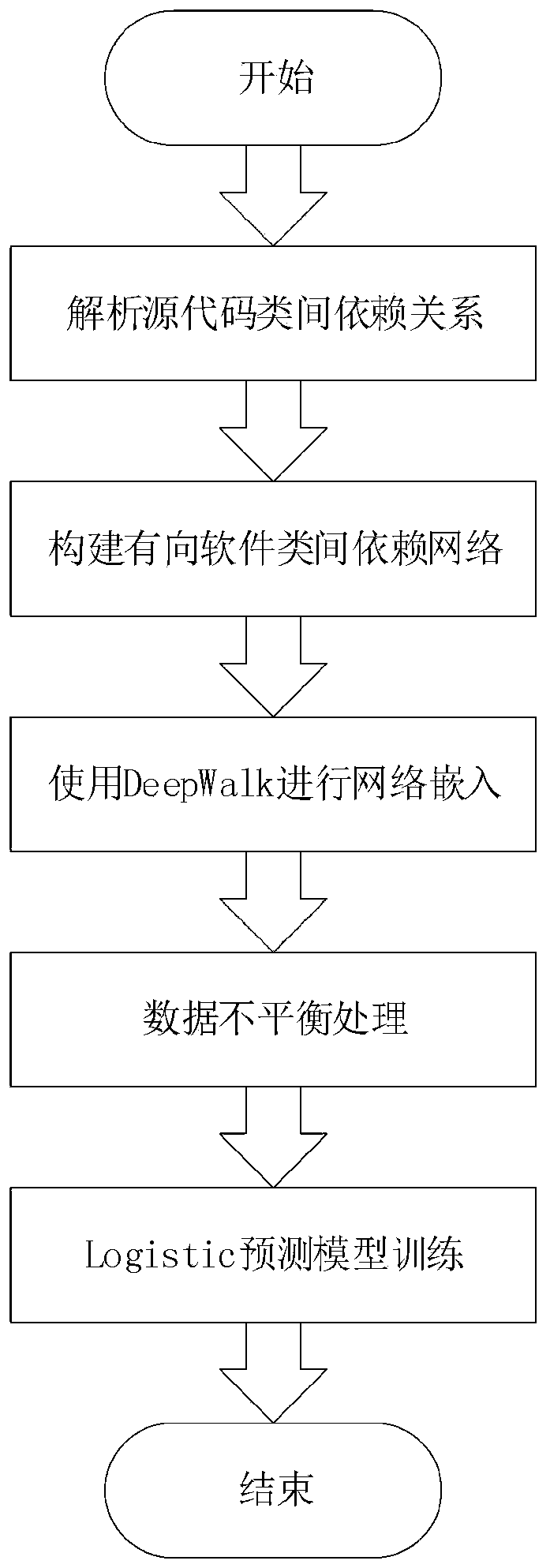
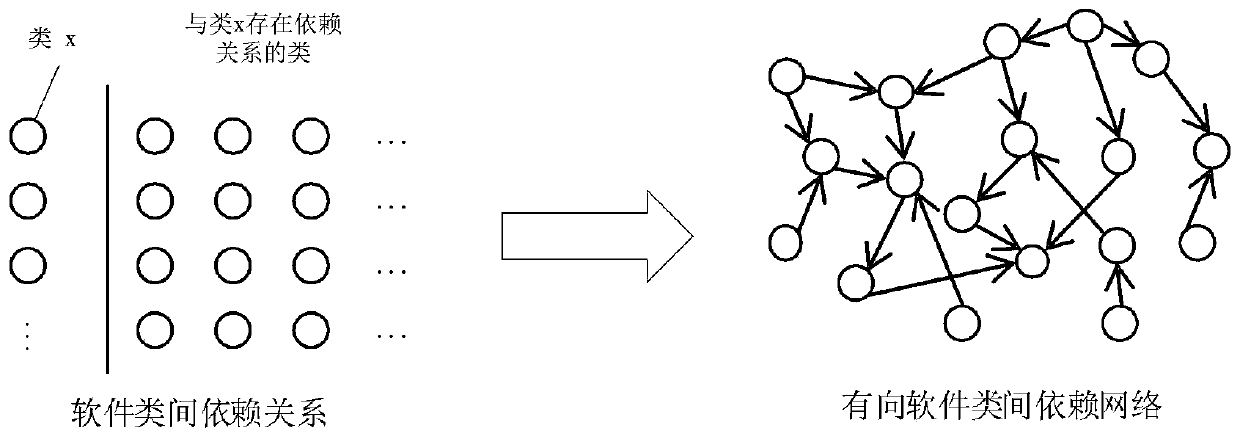
InactiveCN110825615AEffective predictionSolve the use problemSoftware testing/debuggingTheoretical computer scienceEngineering
The invention provides a software defect prediction method and a system based on network embedding. The method comprises the following steps: firstly, analyzing the inter-class dependency relationshipof source codes; establishing a directed software inter-class dependency network, performing network embedding on the established dependency network to obtain software structure feature data, and finally inputting the obtained software structure feature data into the software defect prediction model for evaluation to obtain software defect prediction in a software project. According to the method, potential structural features in software are automatically mined by using a network embedding method; therefore, the software defects can be more effectively predicted; the problem that structuralinformation in software is not utilized in an original defect prediction method is solved, the accuracy of a defect prediction model is improved, developers are helped to find possible defects in thesoftware in advance, test tasks are reasonably distributed, the test quantity is reduced, and the efficiency of the developers is improved.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Stacked generalization learning for document annotation
A document annotation method includes modeling data elements of an input document and dependencies between the data elements as a dependency network. Static features of at least some of the data elements are defined, each expressing a relationship between a characteristic of the data element and its label. Dynamic features are defined which define links between an element and labels of the element and of a second element. Parameters of a collective probabilistic model for the document are learned, each expressing a conditional probability that a first data element should be labeled with information derived from a label of a neighbor data element linked to the first data element by a dynamic feature. The learning includes decomposing a globally trained model into a set of local learning models. The local learning models each employ static features to generate estimations of the neighbor element labels for at least one of the data elements.
Owner:XEROX CORP
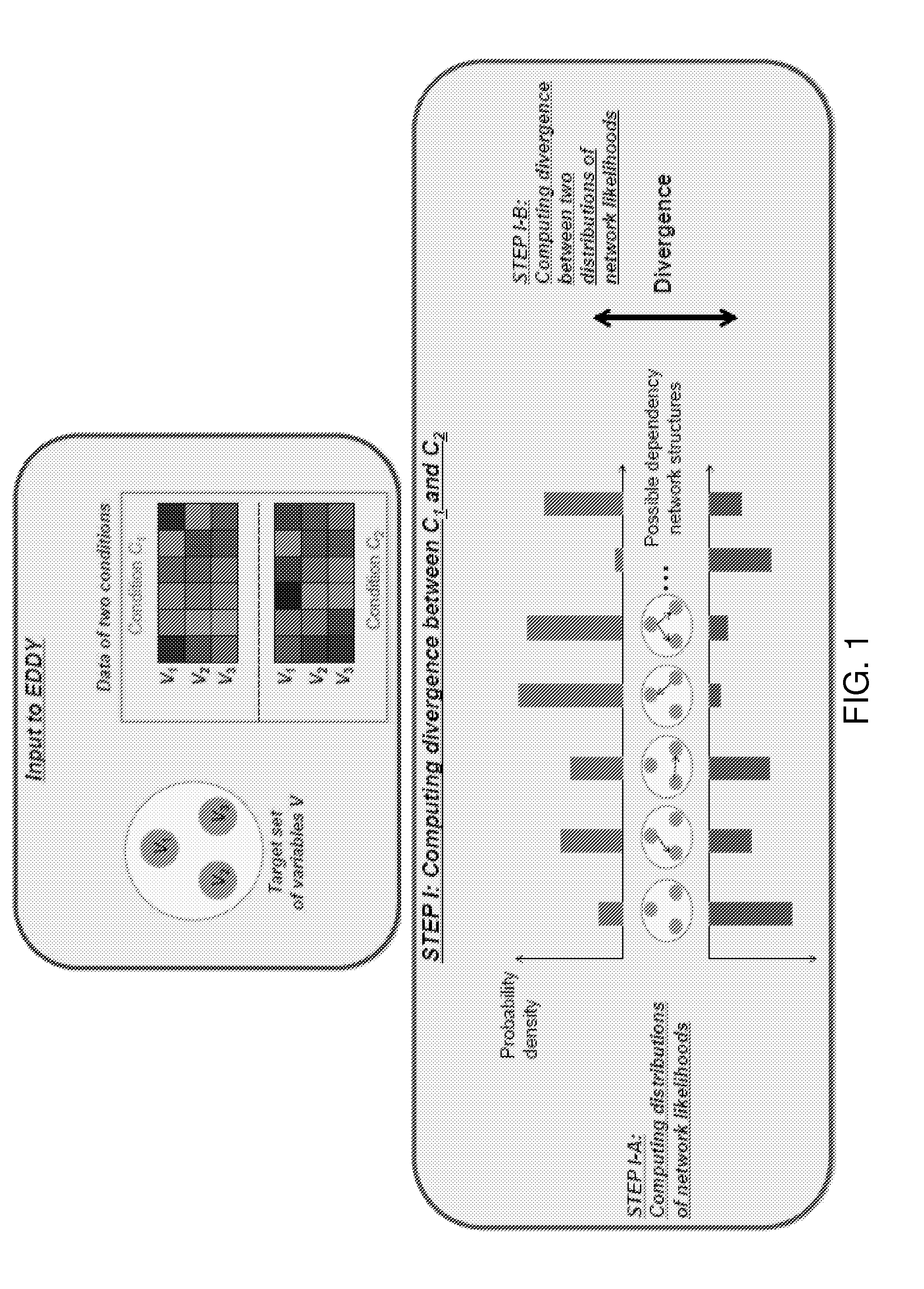
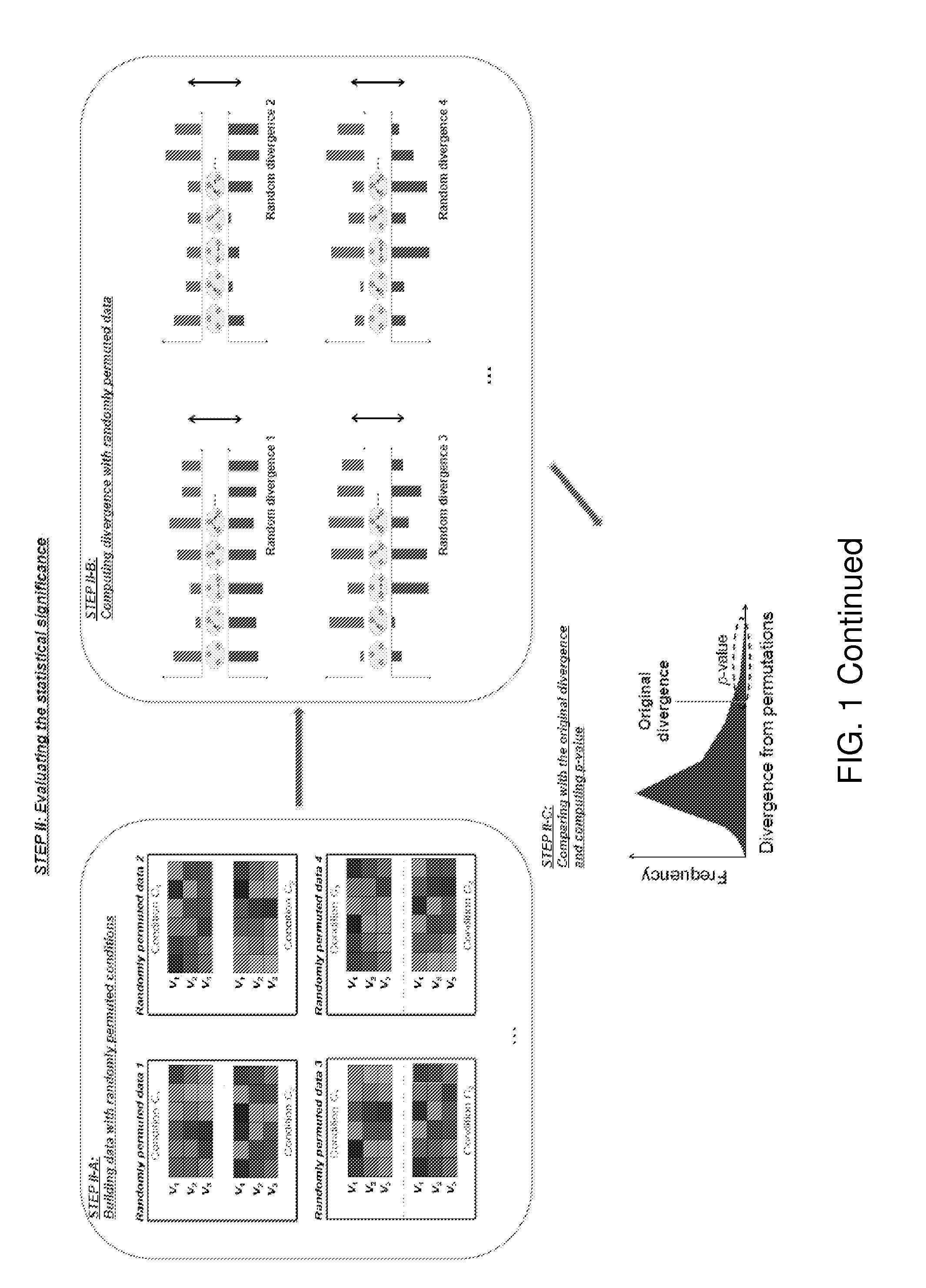
Systems and methods for identifying the relationships between a plurality of genes
The present invention relates to a method and system for the evaluation of differential dependencies of a set of discrete random variables between two conditions. In some embodiments, the system and method compares two conditions by evaluating the probability distributions of the likely dependency networks from random variables.
Owner:TRANSLATIONAL GENOMICS RESEARCH INSTITUTE
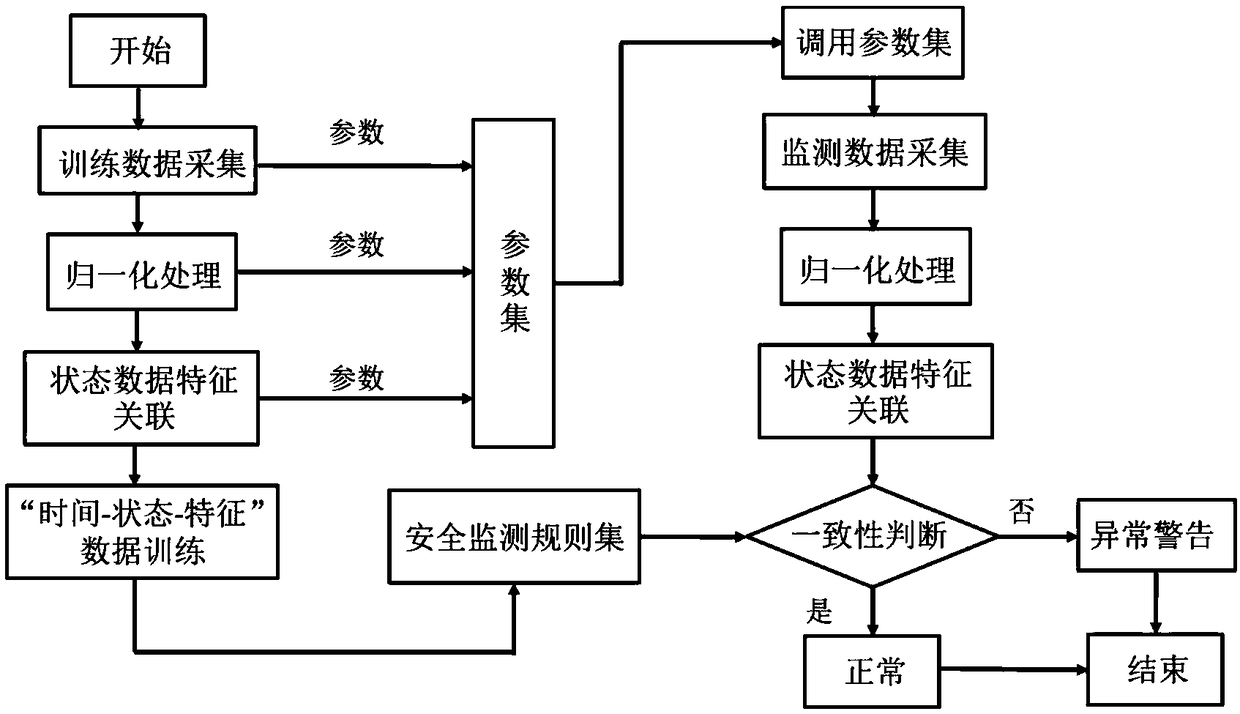
Safety monitoring method of electric power industrial control terminal based on service logic consistency
The invention discloses a safety monitoring method of electric power industrial control terminal based on service logic consistency, the invention aims at the safety problem of the electric power industrial control terminal equipment introduced by the diversified information in the 'Internet +' intelligent grid system, breaks through the existing attack detection method simply relying on the network space information, and puts forward a safety method of the electric power industrial control terminal based on the service logic consistency. By sampling the multi-modal data of physical world information and cyberspace information, normalized processing and temporal correlation, and through training, the safety monitoring set and parameter constraint set are obtained for safety monitoring andanomaly identification. From the business level, the method can effectively early-warn the state abnormality caused by equipment performance difference, equipment failure and hacker intrusion, and realize the 'time-state-service' trinity consistency safety monitoring of the electric power industrial control terminal based on equipment time logic, state logic and business logic.
Owner:HUANAN IND TECH RES INST OF ZHEJIANG UNIV
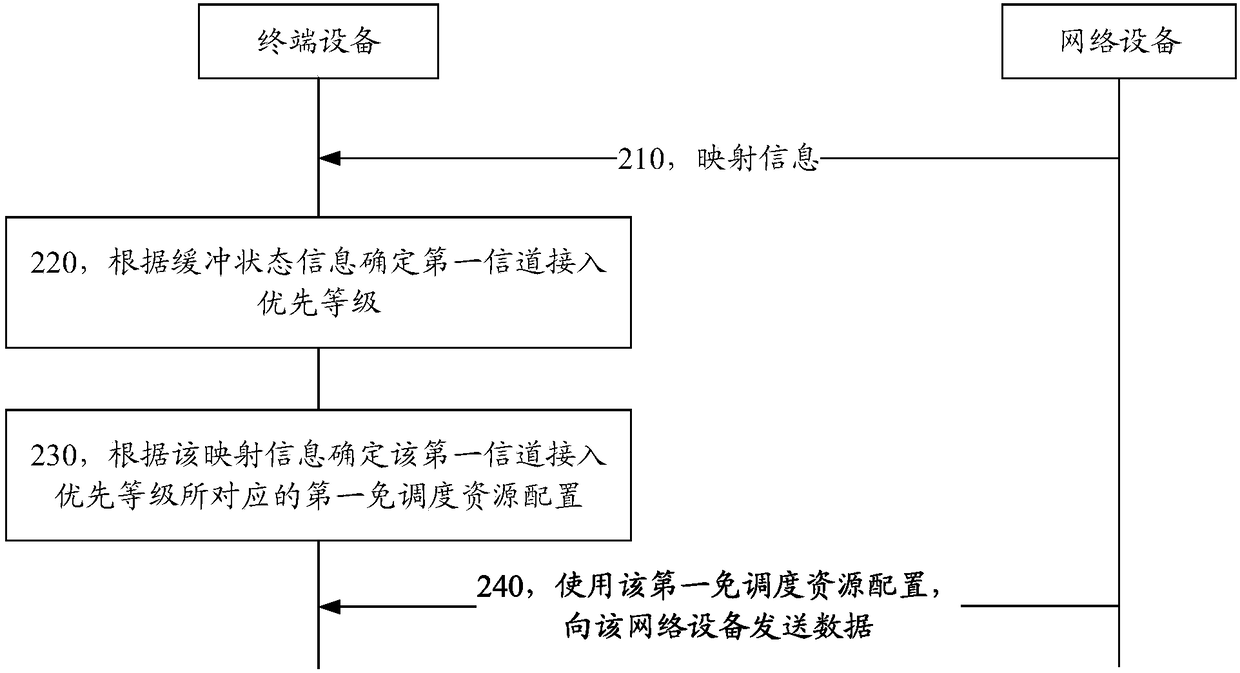
Communication method and equipment
ActiveCN109413744AReduce data transmission delayRealize scheduling-free transmissionSignal allocationWireless communicationTerminal equipmentData transmission
The application provides a communication method and equipment. The communication method includes the following steps that: terminal equipment receives mapping information from network equipment, wherein the mapping information includes a corresponding relationship between scheduling-free resource configurations and channel access priority levels; the terminal equipment determines a first channel access priority level according to buffer state information; the terminal equipment determines the first scheduling-free resource configuration corresponding to the first channel access priority levelaccording to the mapping information; and the terminal equipment uses the first scheduling-free resource configuration to send data to the network equipment. According to the scheme provided by the application, the data transmission on an unauthorized frequency band can be realized without depending on the scheduling of the network equipment, and the data transmission delay on the unauthorized frequency band can be reduced.
Owner:HUAWEI TECH CO LTD
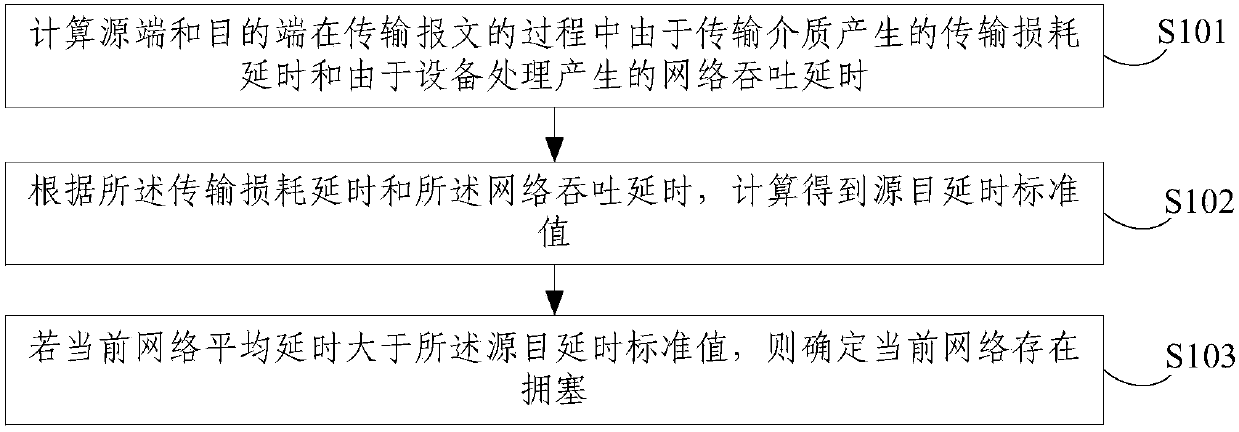
Network congestion determination method and device
ActiveCN108259364AQuickly judge congestionData switching networksTransmission lossDependency network
The embodiment of the invention discloses a network congestion determination method and device. The method comprises the following steps: calculating the transmission loss delay caused by a transmission medium and the network throughput delay caused by equipment processing during the transmission of messages by a source end and a destination end; calculating a source-destination delay standard value according to the transmission loss delay and the network throughput delay; and if the current network average delay is greater than the source-destination delay standard value, determining that thecurrent network is congested. The device comprises a delay calculation module, a delay standard value calculation module and a congestion determination module. According to the network congestion determination method and the device provided by the embodiment of the invention, the source-destination delay standard value is further calculated and obtained by calculating the transmission loss delayand the network throughput delay, and the source-destination delay standard value can be used to objectively and quickly determine whether a congestion condition exists between the source end and thedestination end, and there is no need to rely on the experience and capabilities of network engineers.
Owner:CHINA MOBILE GROUP ZHEJIANG +1
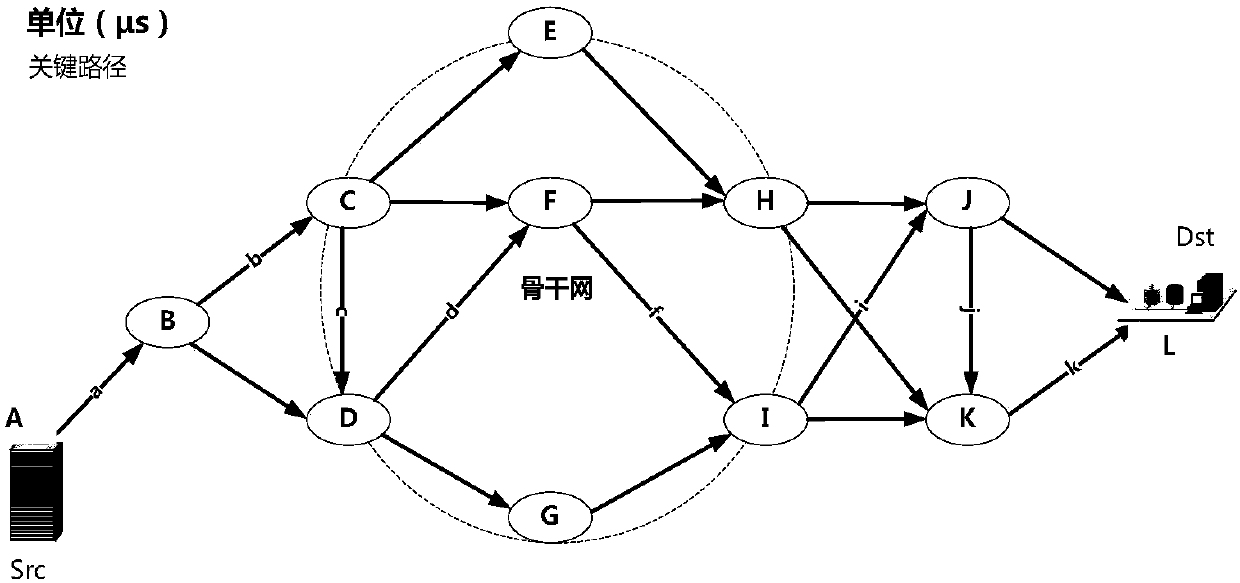
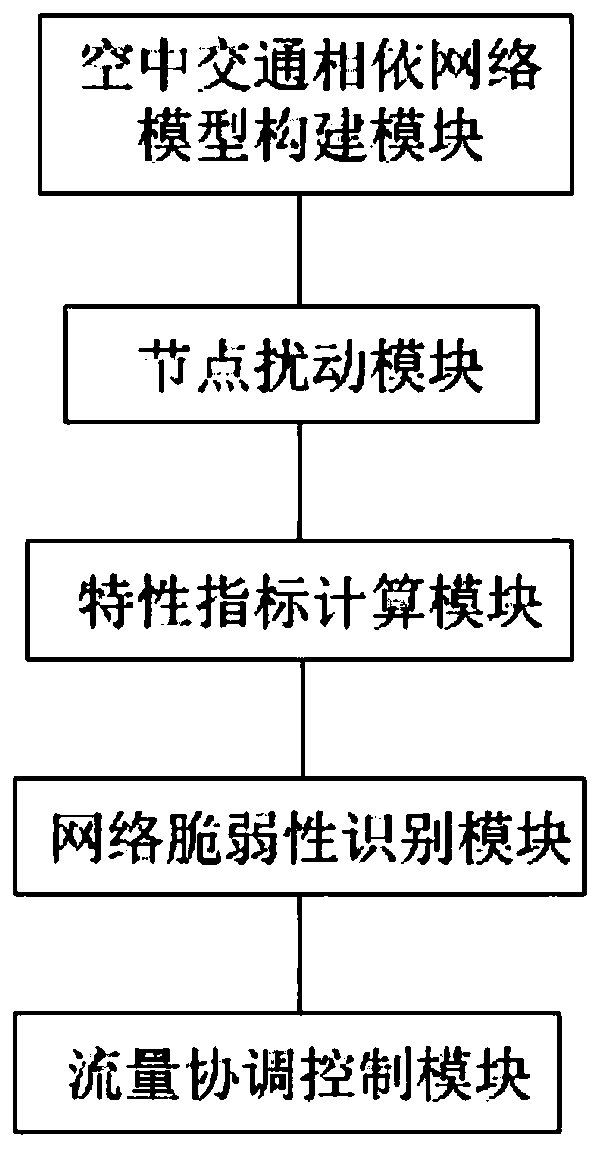
Air traffic dependent network vulnerability identification and control method and system
ActiveCN109768894AImprove securityEfficiencyData switching networksStructure of Management InformationTraffic flow
The invention provides an air traffic dependent network vulnerability identification and control method and system. According to the method and the system, firstly, an air traffic dependency network model connected by airport network, airway network and control sector network is established; disturbance strategies of random disturbance and deliberate disturbance are used for disturbing nodes of the air traffic dependent network; calculating a change rate of a structure vulnerability related characteristic index and a change rate of a function vulnerability related index of the dependent network; and identifying a change rule of the structure vulnerability and the function vulnerability of the dependent network, and finally, optimizing the vulnerability of the dependent network by performing flow coordination control on the dependent network according to an identification result. In combination with the vulnerability analysis result of the air traffic dependency network, the traffic flow of the network is subjected to coordination control again, so that the traffic flow of the air traffic dependency network tends to be ordered, and the vulnerability of the network is reduced.
Owner:CIVIL AVIATION UNIV OF CHINA
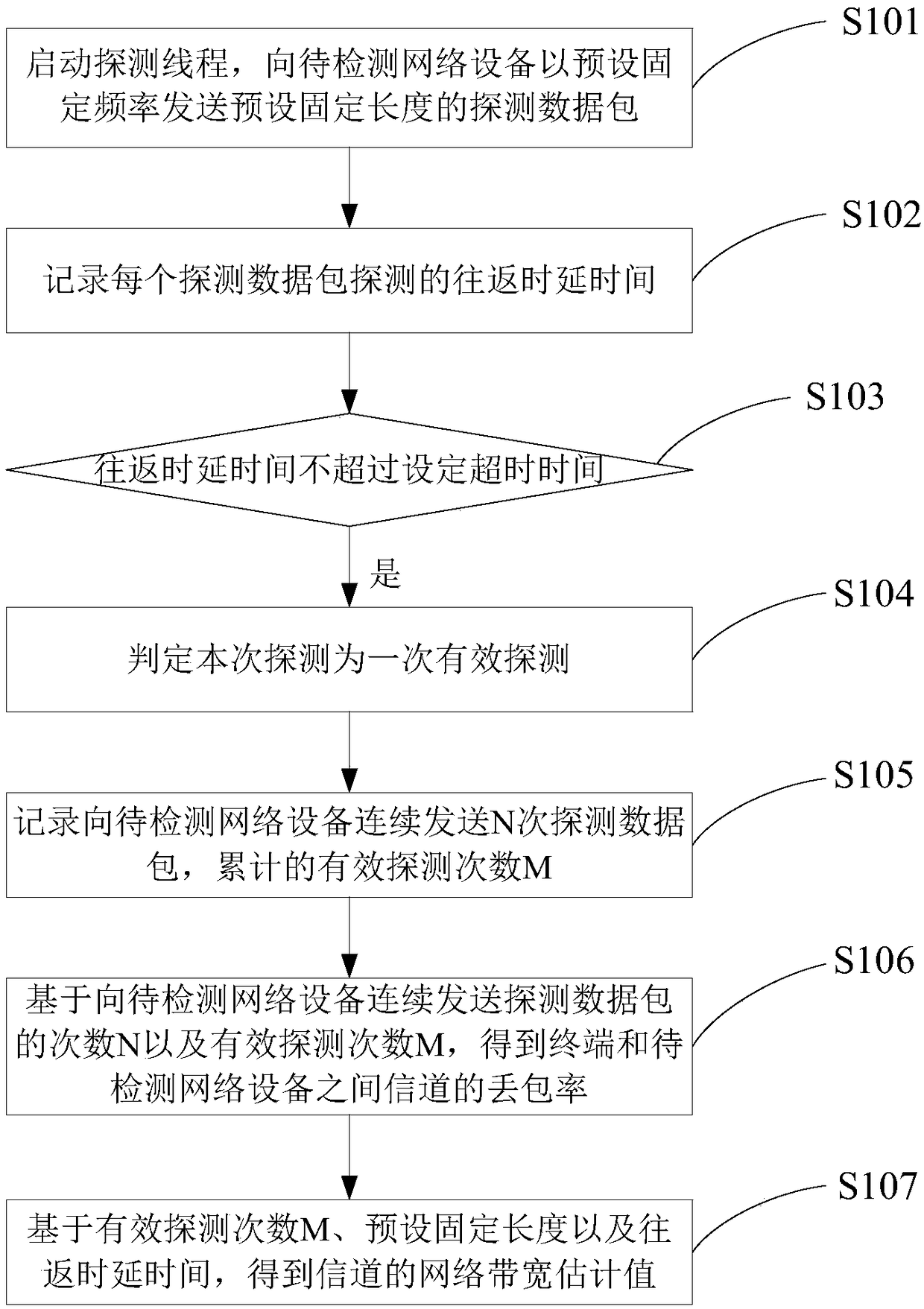
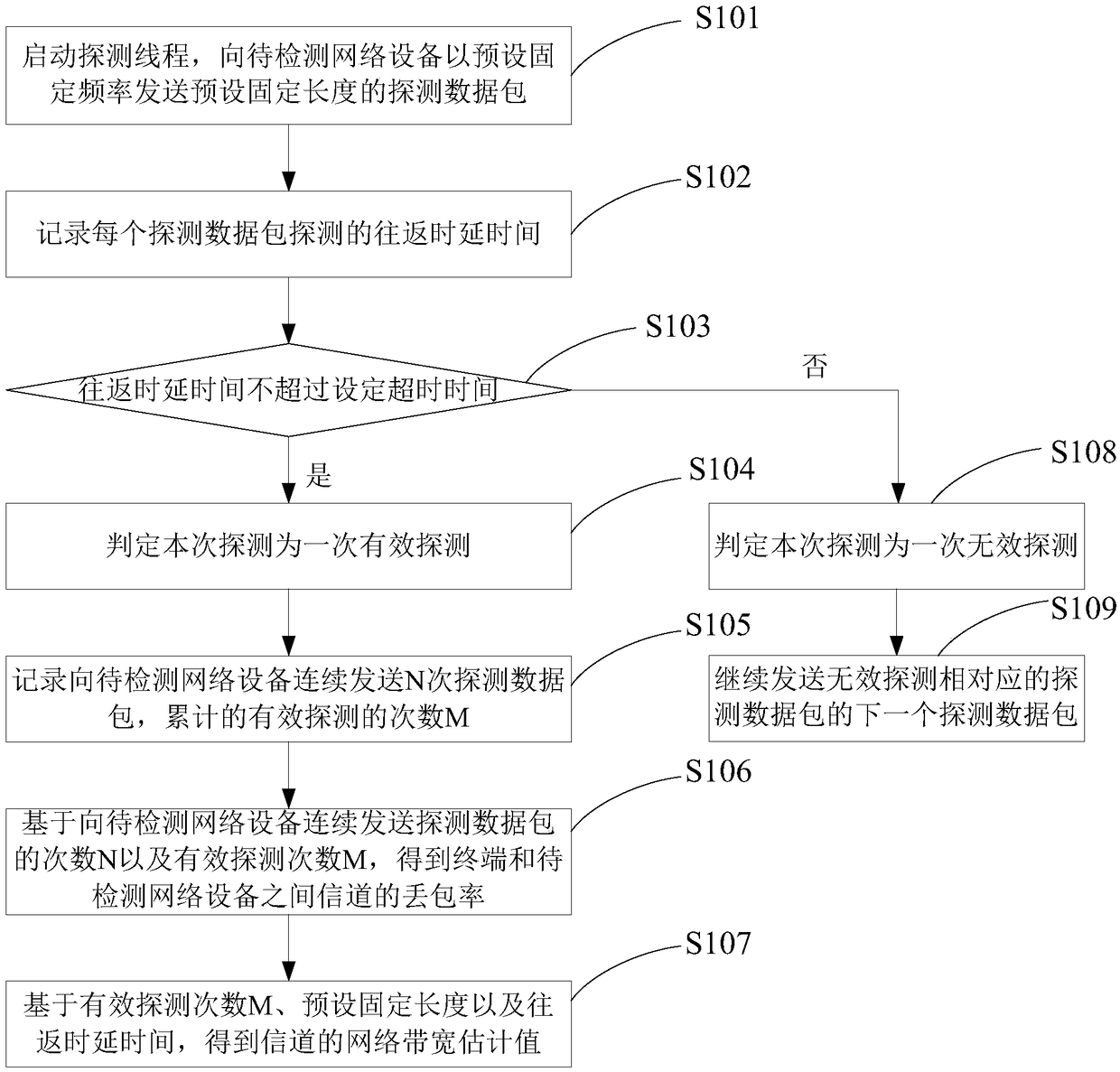
Terminal network performance detection method and system
The invention discloses a terminal network performance detection method and system. A terminal sends a preset fixed-length probe packet to a to-be-detected network device at a preset fixed frequency and calculates the round-trip time of each probe packet in each probe to obtain the packet drop rate and the network bandwidth estimated value of a channel between the terminal and the to-be-detected network device, so as to realize the network performance detection of the terminal. Compared with the traditional scheme, the present invention does not need to build web service at the to-be-detectednetwork device end, and because the packet sending frequency is fixed in the present invention, it effectively solves the problems of load increase of a network device on the terminal side and an impact on other features of the terminal that rely on network applications due to the use of a pressure test scheme that the packet sending frequency is continuously increased until the RTT value or the packet drop rate exceeds a certain threshold in the traditional scheme.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
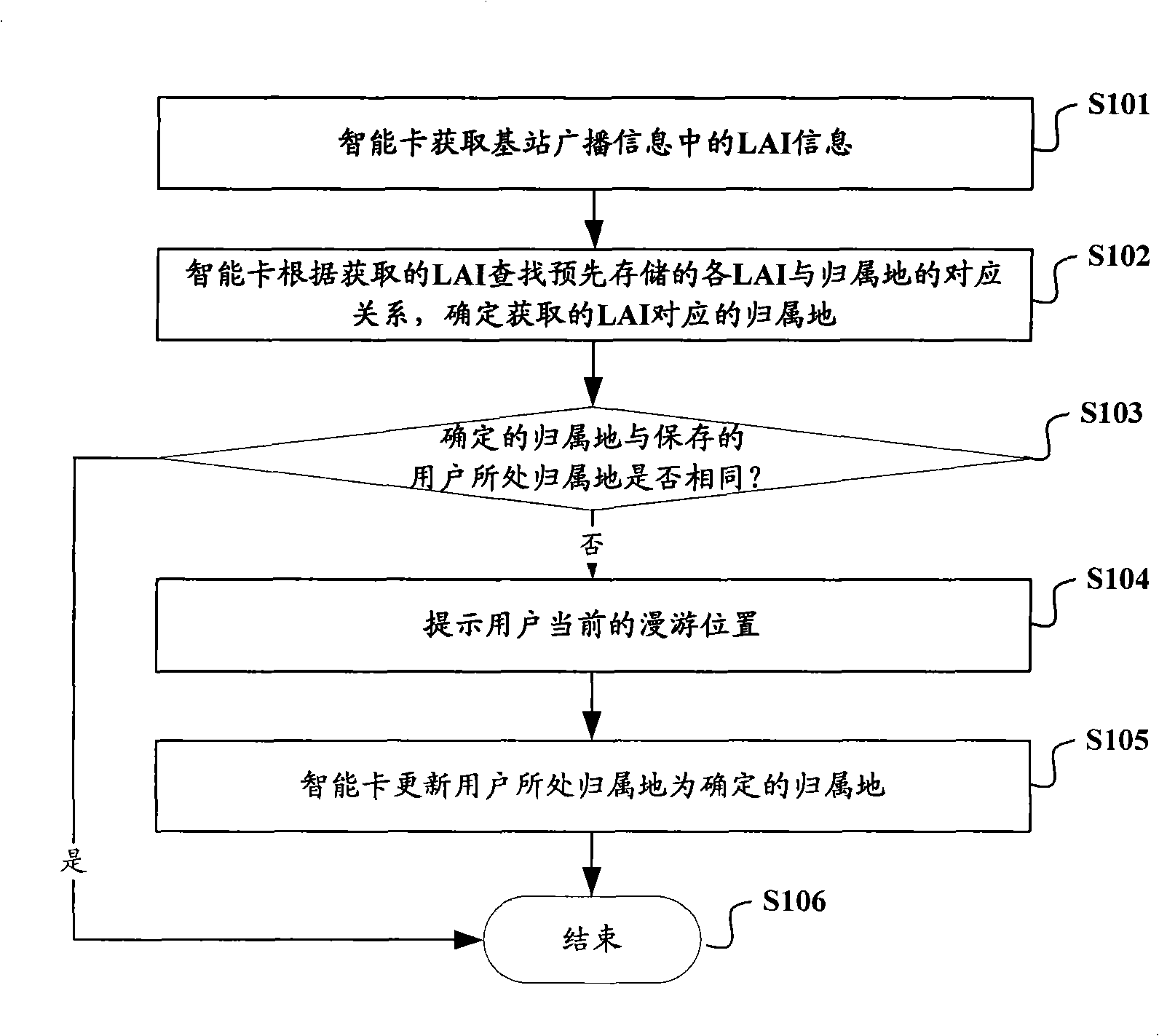
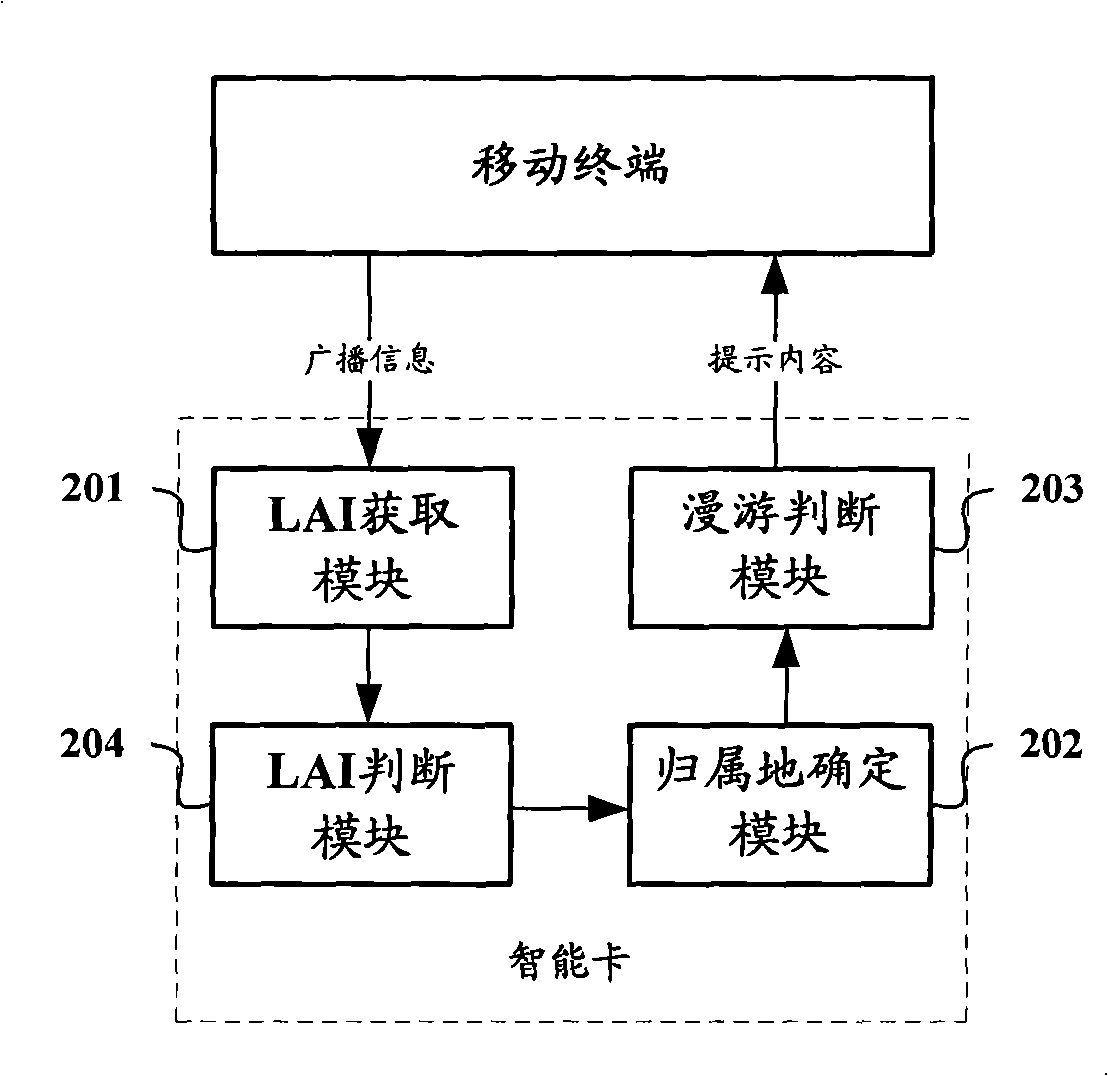
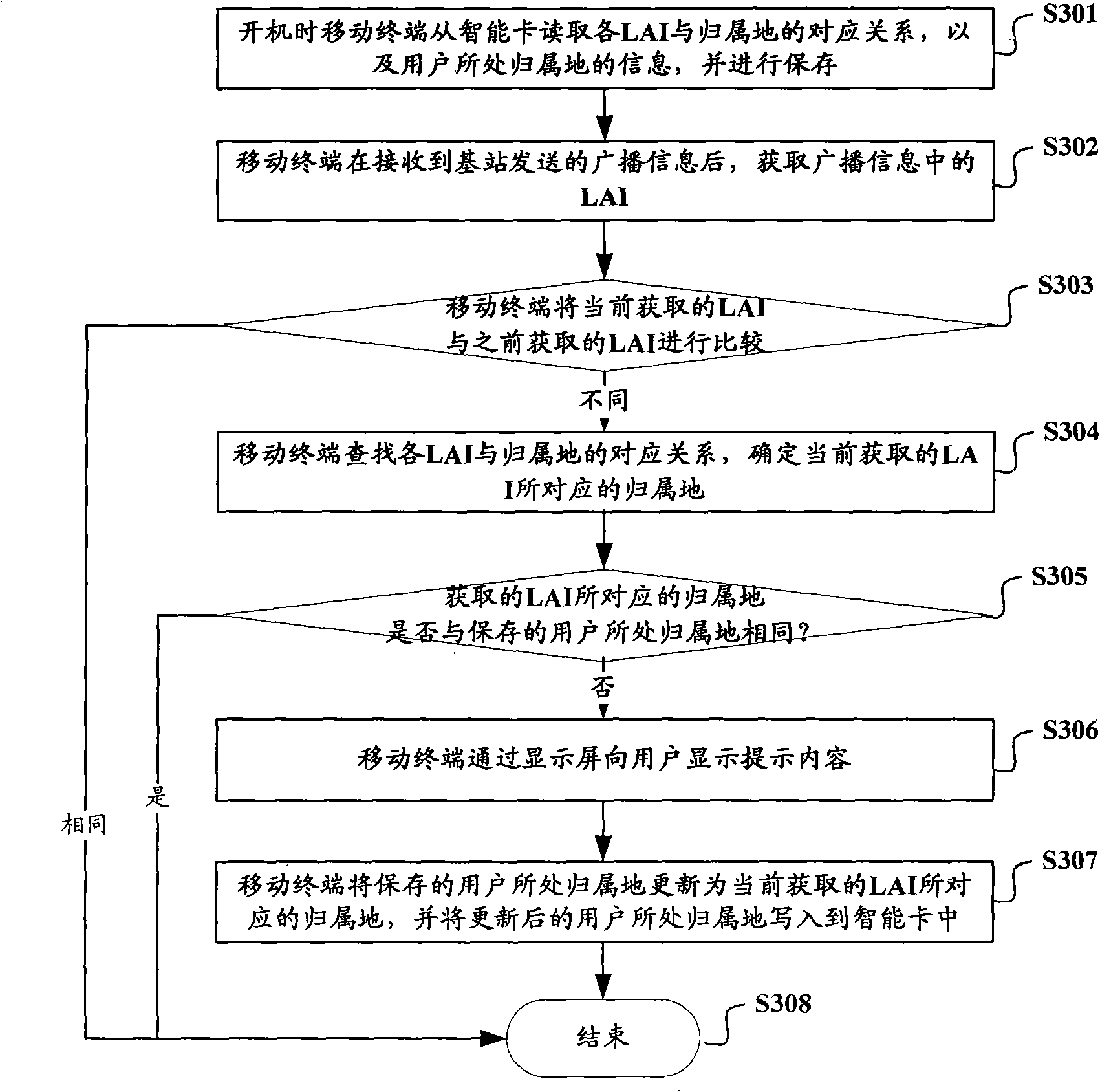
Method for prompting user of current roaming position, system, mobile terminal and intelligent card
ActiveCN101540949AAvoid judgmentReduce communication overheadBroadcast service distributionLocation information based serviceSmart cardDependency network
The invention relates to the mobile communication field, and in particular relates to a technology for carrying out roaming greeting on a user and informing the user of roaming positions in time. The invention provides a method for prompting the user of the current roaming position and a mobile terminal and an intelligent card. The method comprises the following steps of: acquiring LAI carried in broadcast messages of a base station by a terminal; searching corresponding relation of all pre-stored LAIs and attaching locations and determining the acquired attaching locations corresponding to the LAIs; prompting the user of the current roaming position when judging that the determined attaching location are different from the pre-stored attaching location of the user, and updating the attaching location of the user as determined attaching location. As the terminal judges that the attaching location of the user changes according to the broadcast of the base station, the user is prompted of the current roaming position, thus avoiding the dependence on a network side for realizing judgment on the roaming situation of the user, being capable of informing the user of roaming positions in time and saving the occupation to the network side resources.
Owner:CHINA MOBILE GRP BEIJING
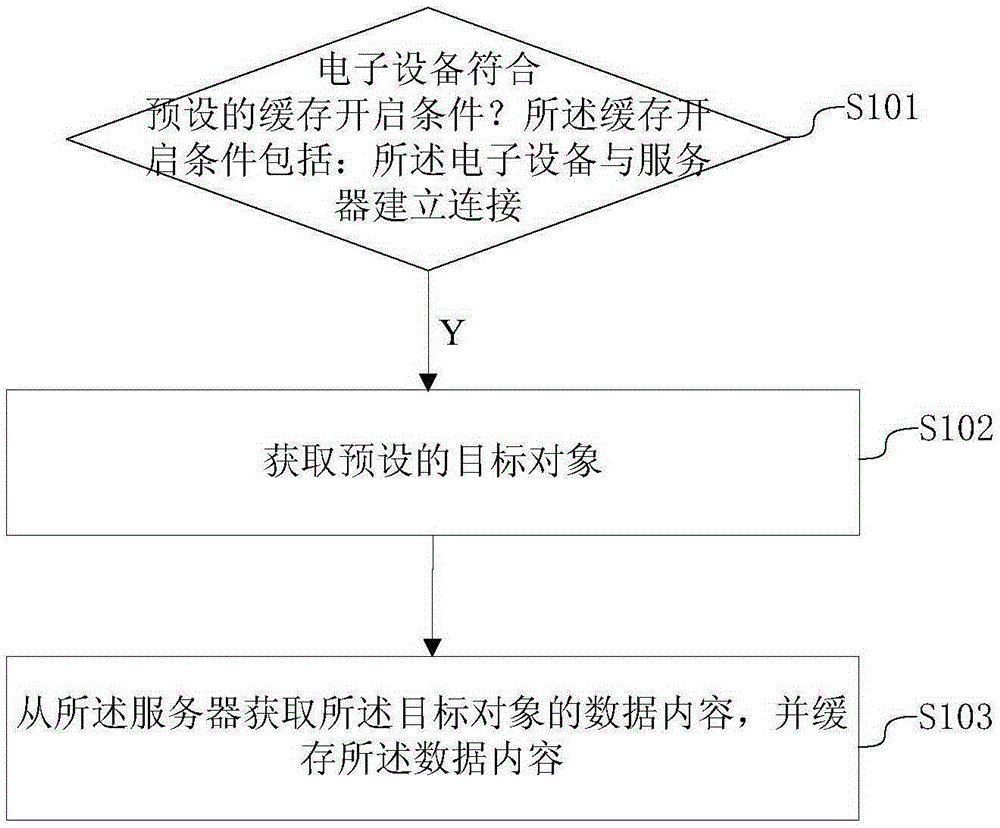
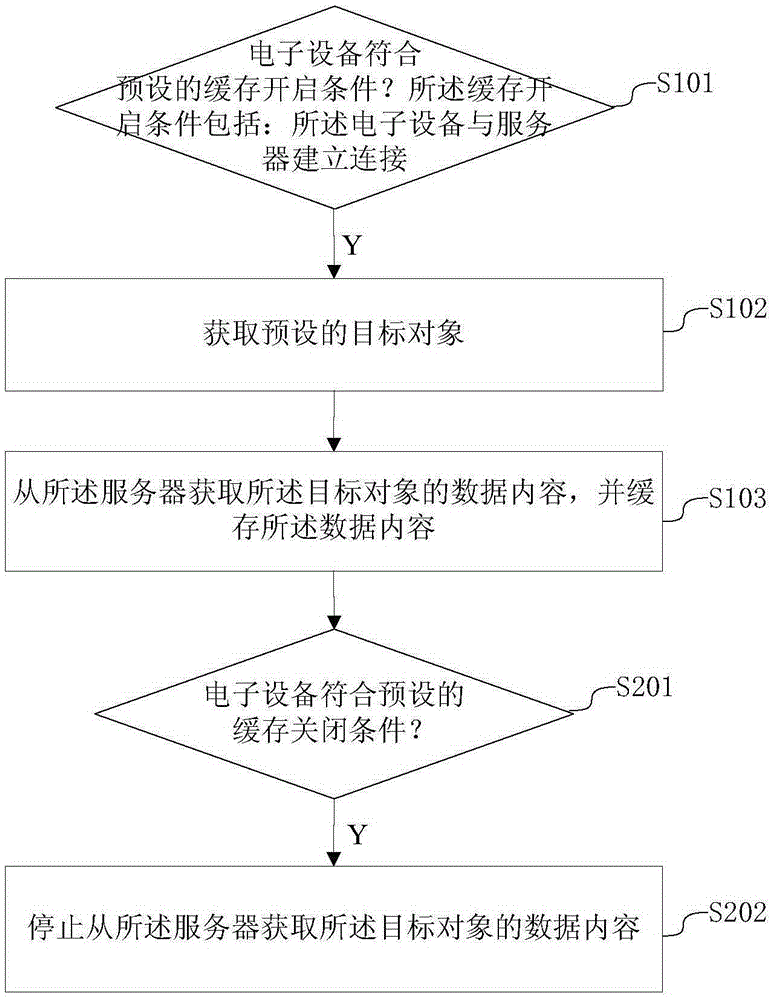
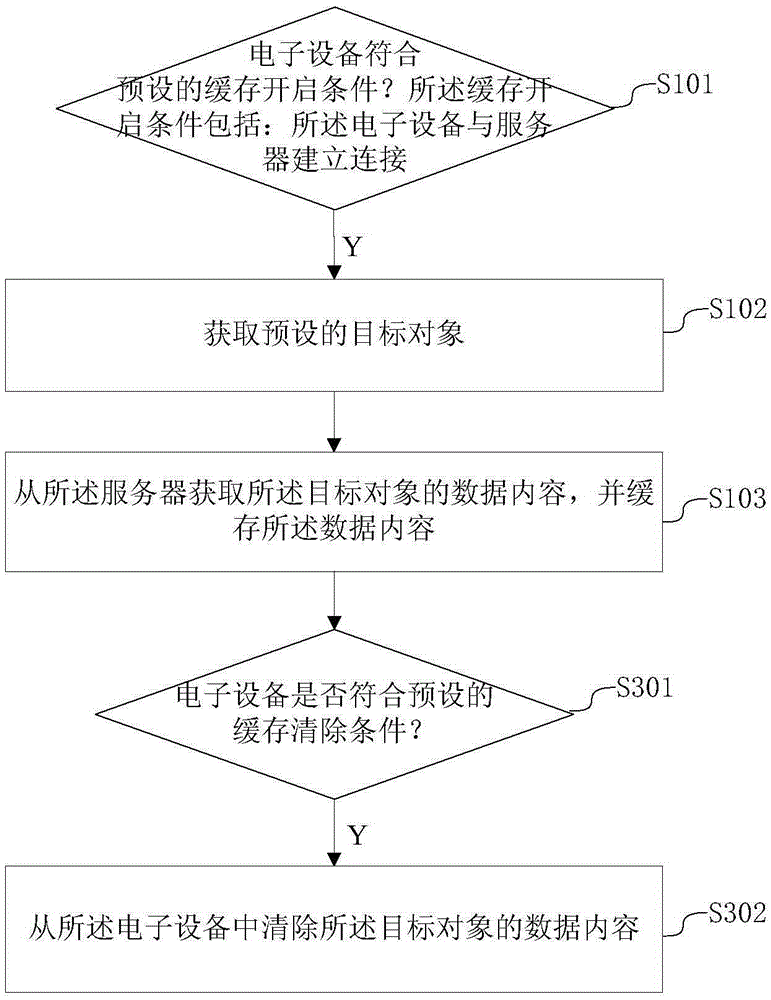
Data caching method and device
InactiveCN105279267AImprove dependencySpecial data processing applicationsService provisionMobile end
The invention discloses a data caching method and device, and the method and device can be applied to various mobile end electronic devices. The method comprises the following steps: firstly judging whether an electronic device accords with a preset caching starting condition, wherein the caching starting condition comprises that connection is established between the electronic device and a server; and obtaining the data content of a preset target object from the server and carrying out caching by utilizing the connection established between the electronic device and the server when the electronic device accords with the caching starting condition. According to the data caching method and device, the required network data is previously obtained and cached at the mobile end when the mobile end satisfies the preset condition (for example, connection is established between the mobile end and the network), so that support is provided for the experience of network end data service under network-free environment or relatively bad network environment; therefore, the data caching method and device has the advantages of improving the network dependency condition of the mobile end and the follow-up users can use the cached network data without depending on the network.
Owner:GUANGZHOU SHIRUI ELECTRONICS
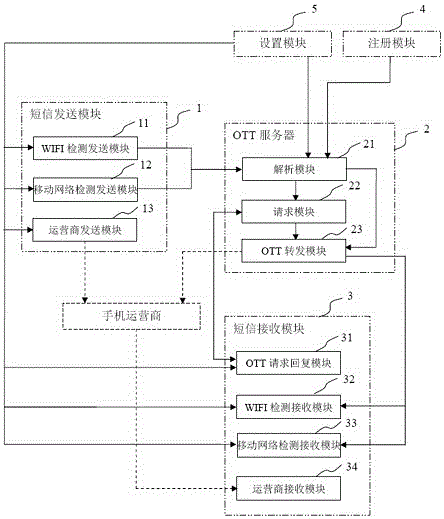
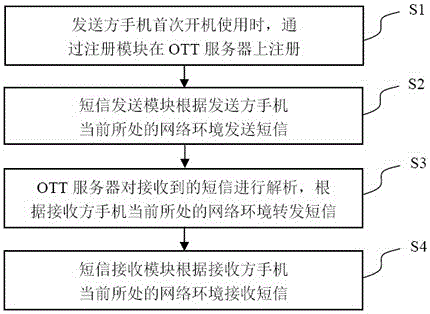
System of intelligently selecting network-service receiving-sending short message and method thereof
The invention discloses a system of intelligently selecting a network-service receiving-sending short message and a receiving-sending short message method by using the system. The method comprises the following steps that S1, when a mobile phone of a sender is firstly switched on and used, registration on an OTT server is performed through a registration module; S2, a short message sending module sends a short message according to a network environment where the mobile phone of the sender is located currently; S3, the OTT server analyzes the received short message and forwards the short message according to a network environment where a mobile phone of a receiver is located currently; S4, a short message receiving module receives the mobile phone of the sender according to the network environment where the mobile phone of the receiver is located currently. By using the system and the method of the invention, an OTT service and a service provider service are combined; when sending and receiving the short message, the most suitable and optimal network environment is selected; the user does not need to operate; on a basis of not relying on the network environment, flow consumption and cost can be saved maximumly.
Owner:PHICOMM (SHANGHAI) CO LTD
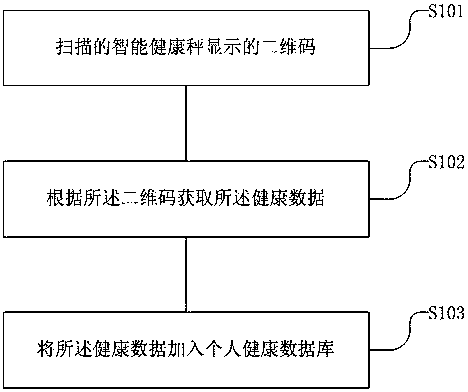
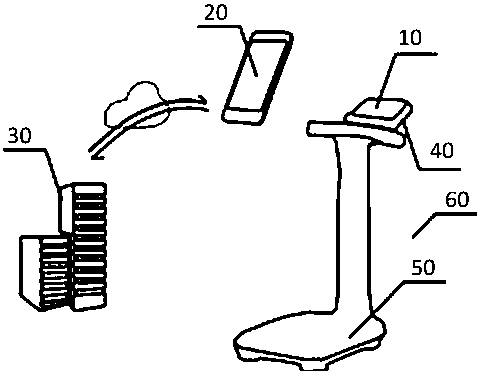
Smart body health scale, smart health management method, system and storage medium
InactiveCN107845418ALarge amount of informationEasy to operateData processing applicationsCo-operative working arrangementsDisplay deviceOperability
The invention discloses a smart body health scale, smart health management method, system and storage medium. The smart body health scale includes an acquisition device used for acquiring health data;a two-dimensional code generation device used for generating a two-dimensional code corresponding to the health data; a display device used for displaying the two-dimensional code. The smart body health scale acquires health data of a user after measuring, generates a corresponding two-dimensional code according to the health data without data transmission via any network modules, namely, generates one two-dimensional code after each measurement process, and then displays the two-dimensional code to the user. The user acquires health data according to the two-dimensional code. Currently, a plurality of mobile terminals has a function of two-dimensional code scanning. The health data can be acquired through scanning the two-dimensional code, so that convenience and quickness are achieved.Besides, high accuracy and large information volume are achieved. Immediate use of the smart body health scale is realized and dependence on factors including network and the like is removed, and theoperability is high.
Owner:上海臻十科技有限公司
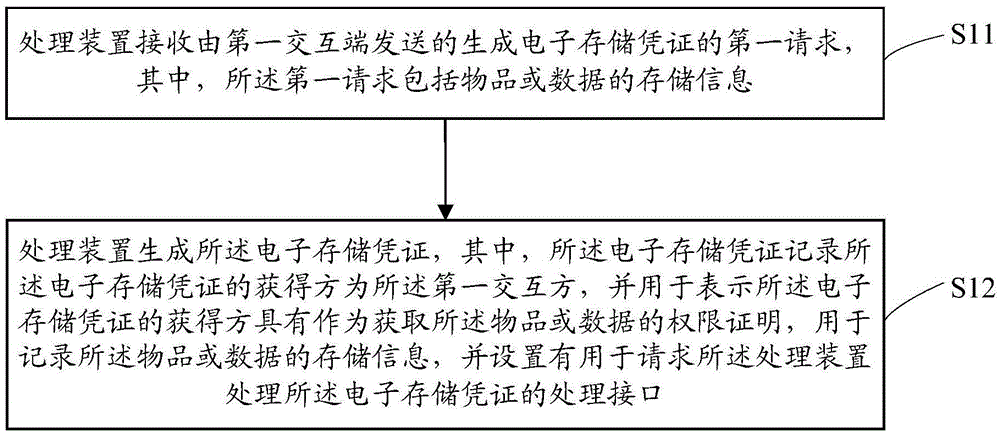
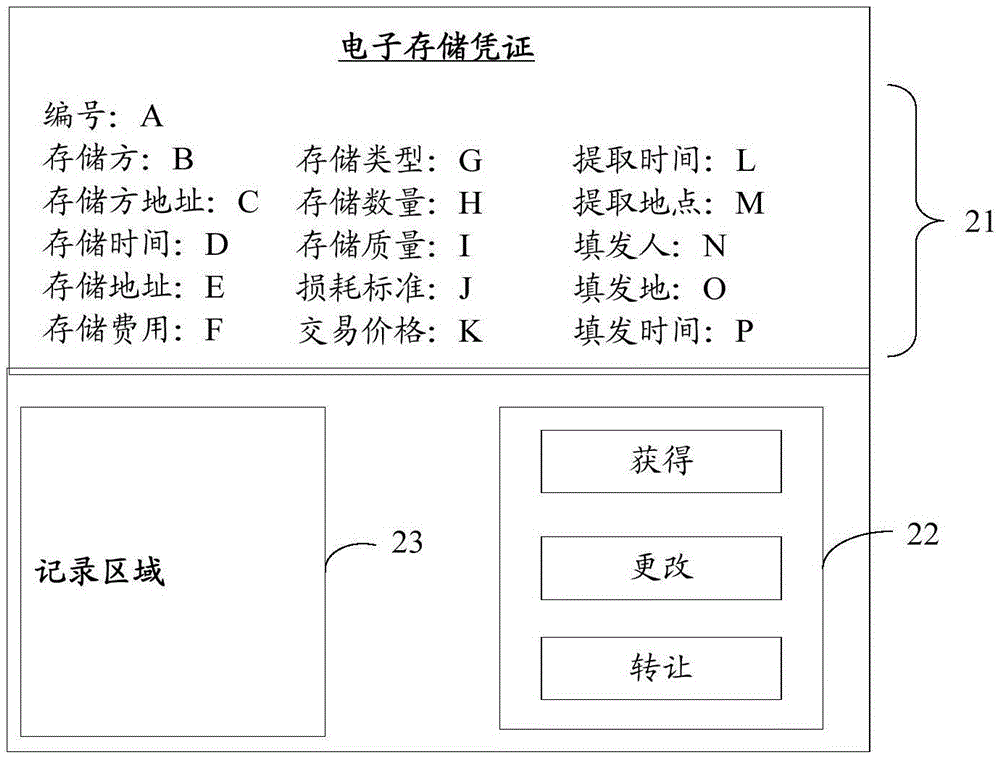
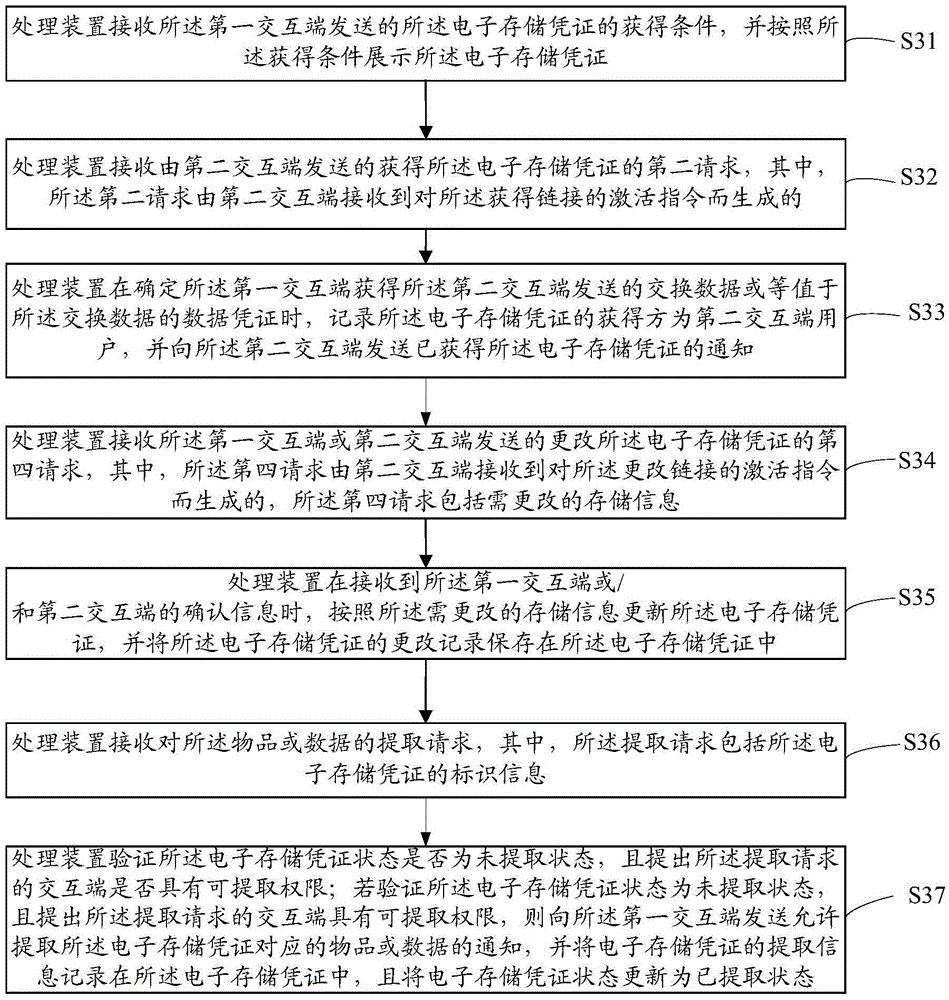
Processing method, apparatus and system of storage voucher
The invention discloses a processing method, apparatus and system of a storage voucher. The method comprises: the processing apparatus receives a first request transmitted by a first interaction terminal and used for generating an electronic storage voucher, wherein the first request comprises storage information of an article or data; responding to the first request, generating the electronic storage voucher, and setting a processing link used for generating a processing request of the electronic storage voucher, wherein the electronic storage voucher serves as a permission proof for obtaining the article or the data and is used for recording the storage information of the article or data. According to the method, apparatus and system, the processing of the storage voucher can be realized, the dependence on a network platform or a webpage is avoided, and the processing efficiency is improved.
Owner:SHENZHEN CIFPAY NETWORK BANK TECH
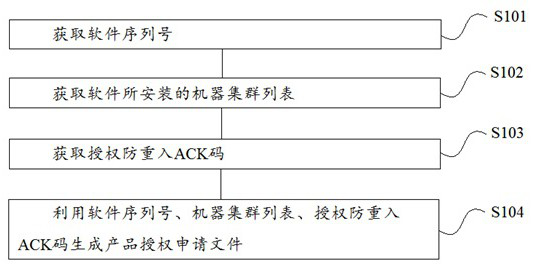
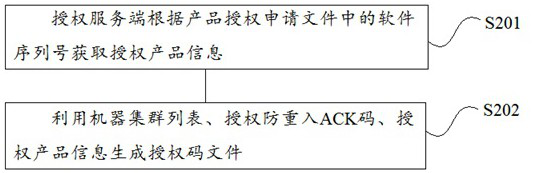
Offline authorization method for distributed software product
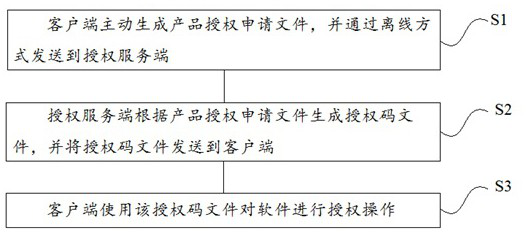
PendingCN112347428ADoes not affect authorized operationsEliminate the situation of infinite copy operationProgram/content distribution protectionEngineeringAuthorization
The invention relates to the technical field of software, in particular to an offline authorization method for a distributed software product, which comprises the following steps that: a client actively generates a product authorization application file and sends the product authorization application file to an authorization server in an offline mode; the authorization server generates an authorization code file according to the product authorization application file and sends the authorization code file to the client; and the client performs authorization operation on the software by using the authorization code file. The invention has the following beneficial effects: the method supports a distributed software system, the deployment number of the software system does not influence authorization operation, dynamic capacity expansion of the software system and offline authentication of some nodes of the system do not influence authentication, and re-authorization operation is not needed; the client and the authorization server communicate and are decoupled and are spatially independent, and the authorization operation is completely offline and does not depend on the network.
Owner:浙江百应科技有限公司
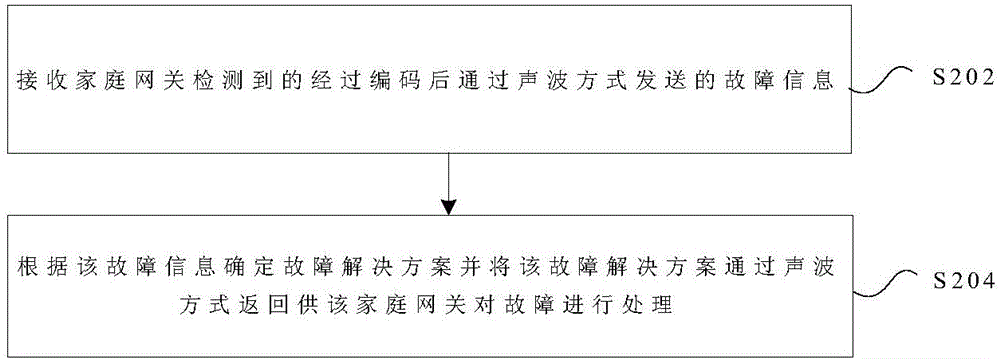
Fault handling method and device
ActiveCN106330491AReduce dependenceSonic/ultrasonic/infrasonic transmissionData switching networksAcoustic waveDependency network
The invention discloses a fault handling method and device. The method comprises the following steps: sending detected fault information to a server in a sound wave mode after being encoded; handling the fault according to a fault solution scheme returned by the server, wherein the fault solution scheme is the fault solution determined by the server according to the fault information and returned in the sound wave mode. Since the information is transmitted in the sound wave mode, the problem that the remote detection on the fault of a family gateway in the prior art is overly dependent on the network is solved, the dependence of the remote detection of the family gateway fault on the network environment is lowered.
Owner:ZTE CORP
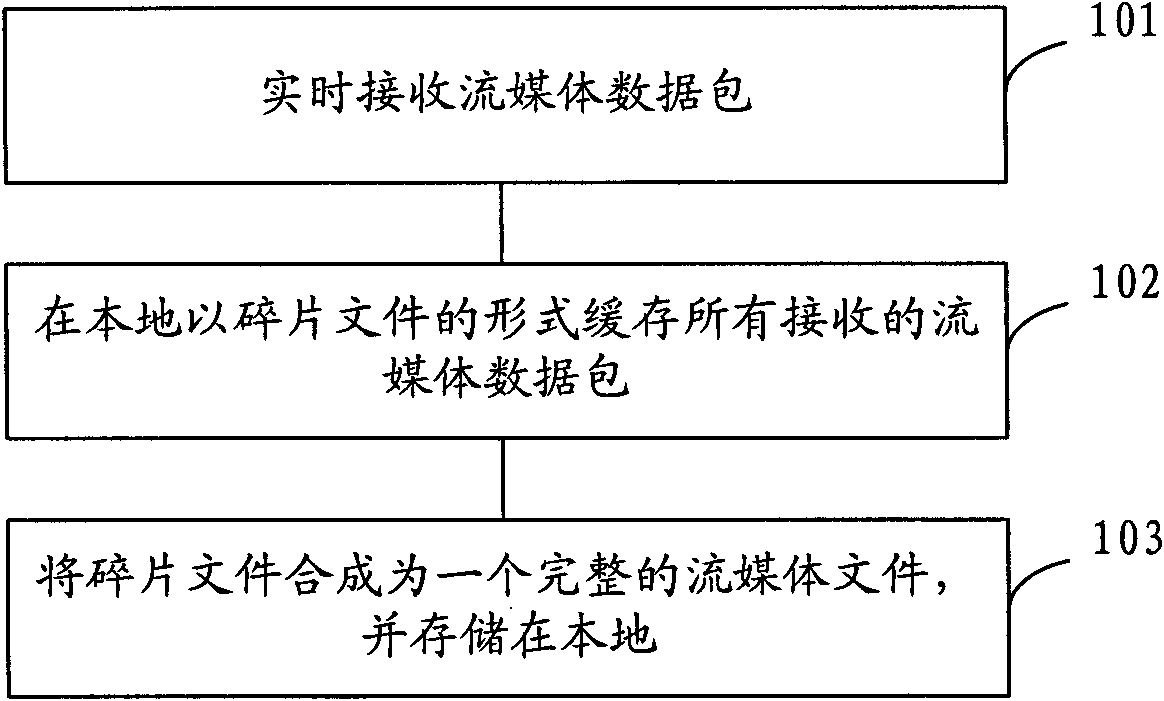
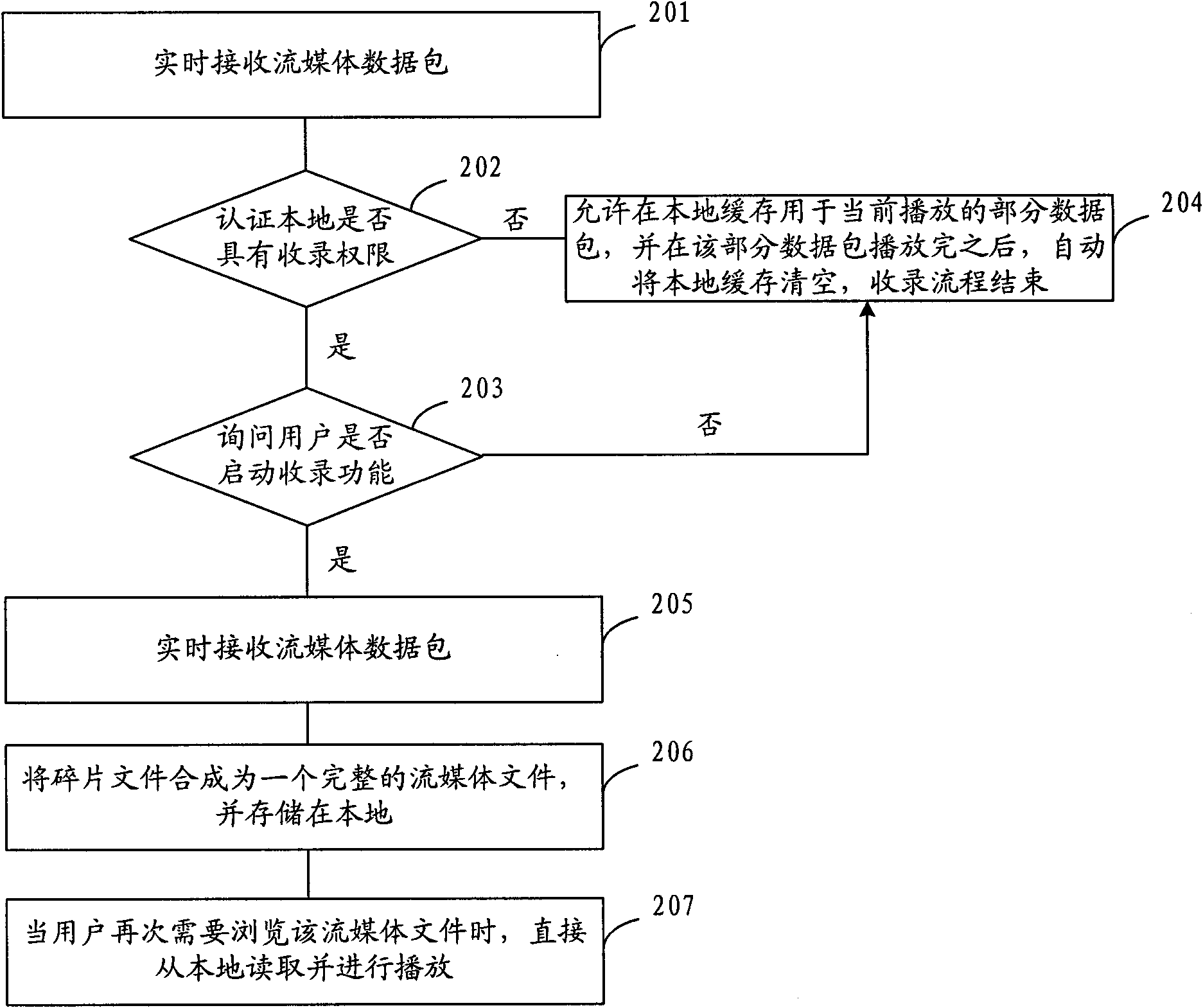
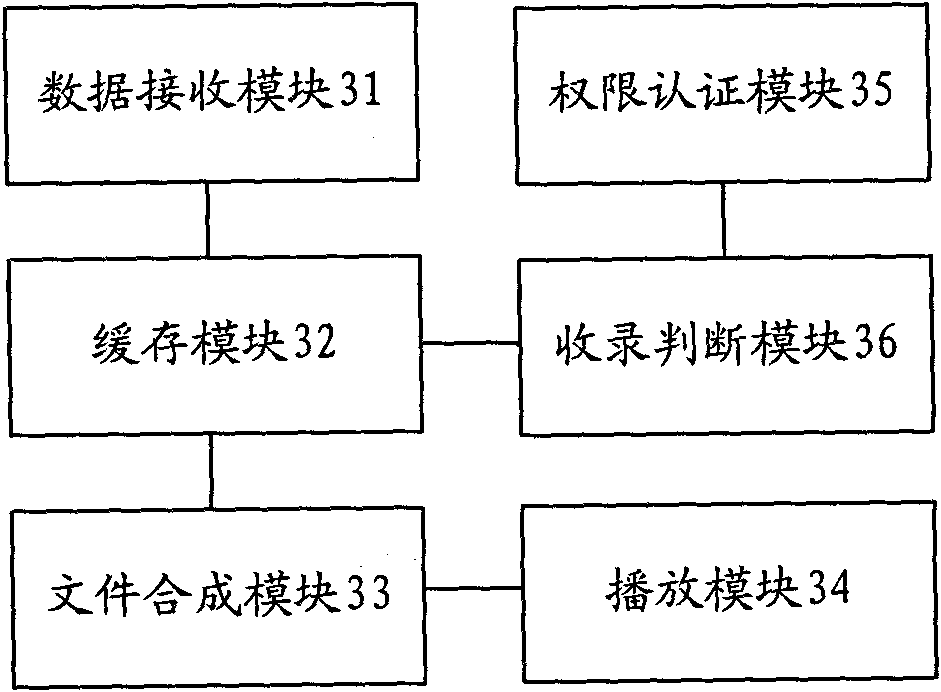
Streaming media recording method and player
InactiveCN101917327AEasy to managePulse modulation television signal transmissionData switching networksNetwork packetDependency network
Owner:CHINA DIGITAL VIDEO BEIJING
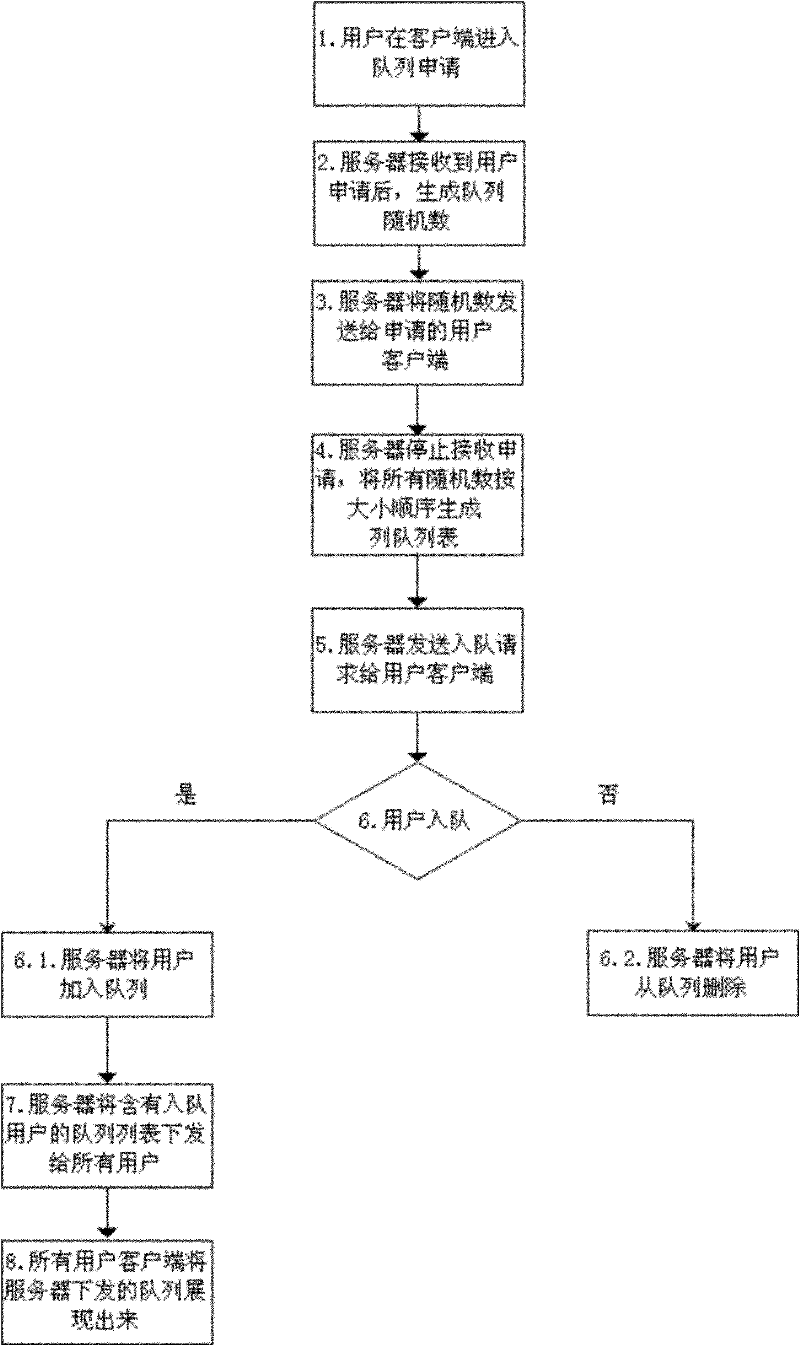
Method for allowing user to fairly enter into queue by random number
The invention discloses a method for allowing a user to fairly enter into a queue by a random number, comprising the steps as follows: 1), a user applies for entering into the queue at a client; 2), a server terminal generates a unique random number of the queue to the user after receiving application of the user; 3), the server terminal transmits the random number to a user client; 4), the server terminal stops receiving an enqueuing application, and generates a queue list from all random numbers according to the numerical order; 5), the server terminal transmits the queue list to the user according to the queue order and requests the user to enter into the queue; 6), the user confirms enqueuing and the server terminal adds the user into the queue; the user conceals enqueuing and the server terminal deletes the user from the queue; 7), the server terminal issues the queue list including the enqueuing user message to all users, and 8), all user clients display the queue message issued by the server terminal and communicate according to the queue order. The mode is fairer and more efficient than the mode of depending on network speed to enter into the queue by the method, so that the user experience is improved.
Owner:HANGZHOU BIANFENG NETWORK TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com