Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
199 results about "Component object" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Component Object Model (COM) is a binary-interface standard for software components introduced by Microsoft in 1993. It is used to enable inter-process communication object creation in a large range of programming languages .
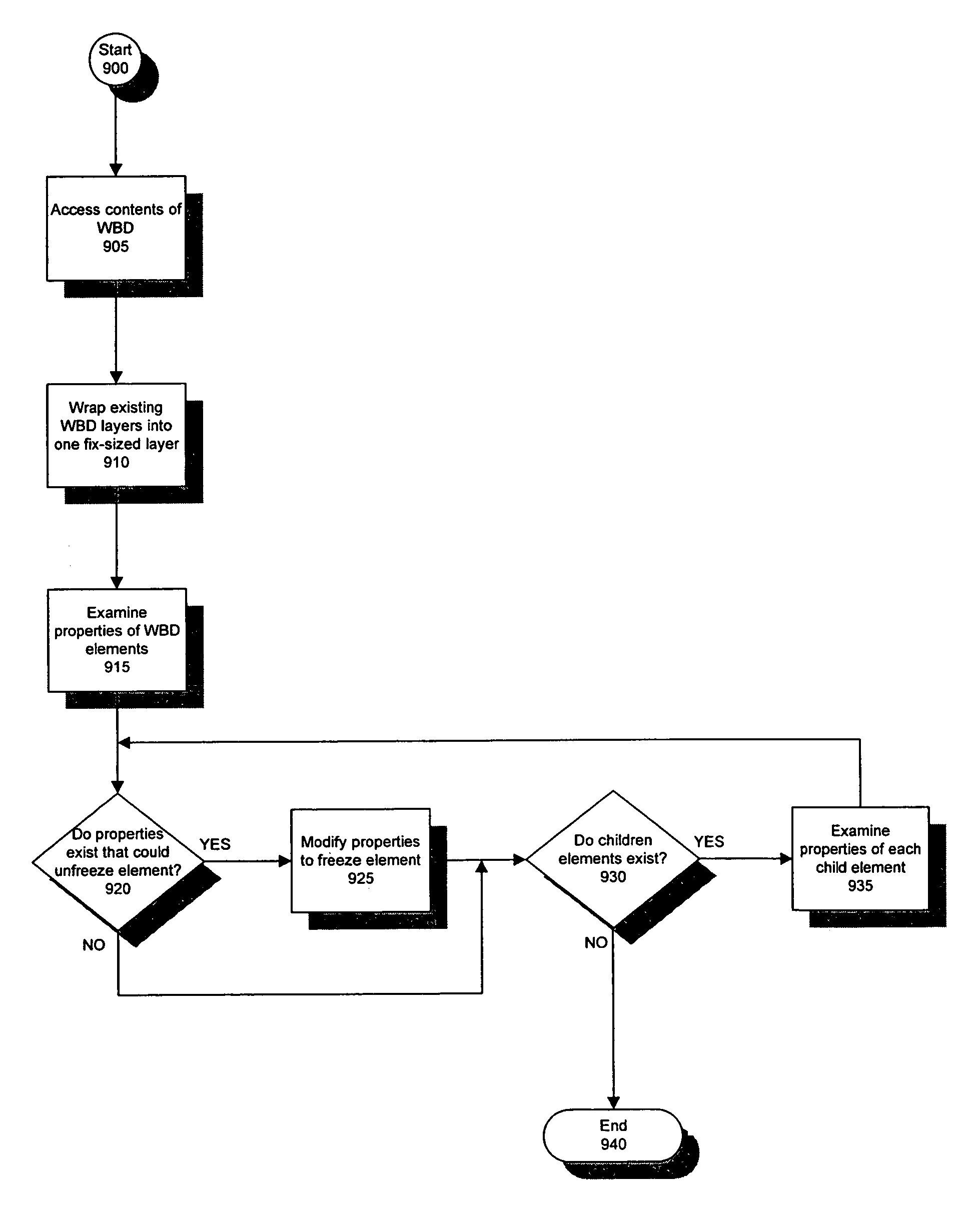
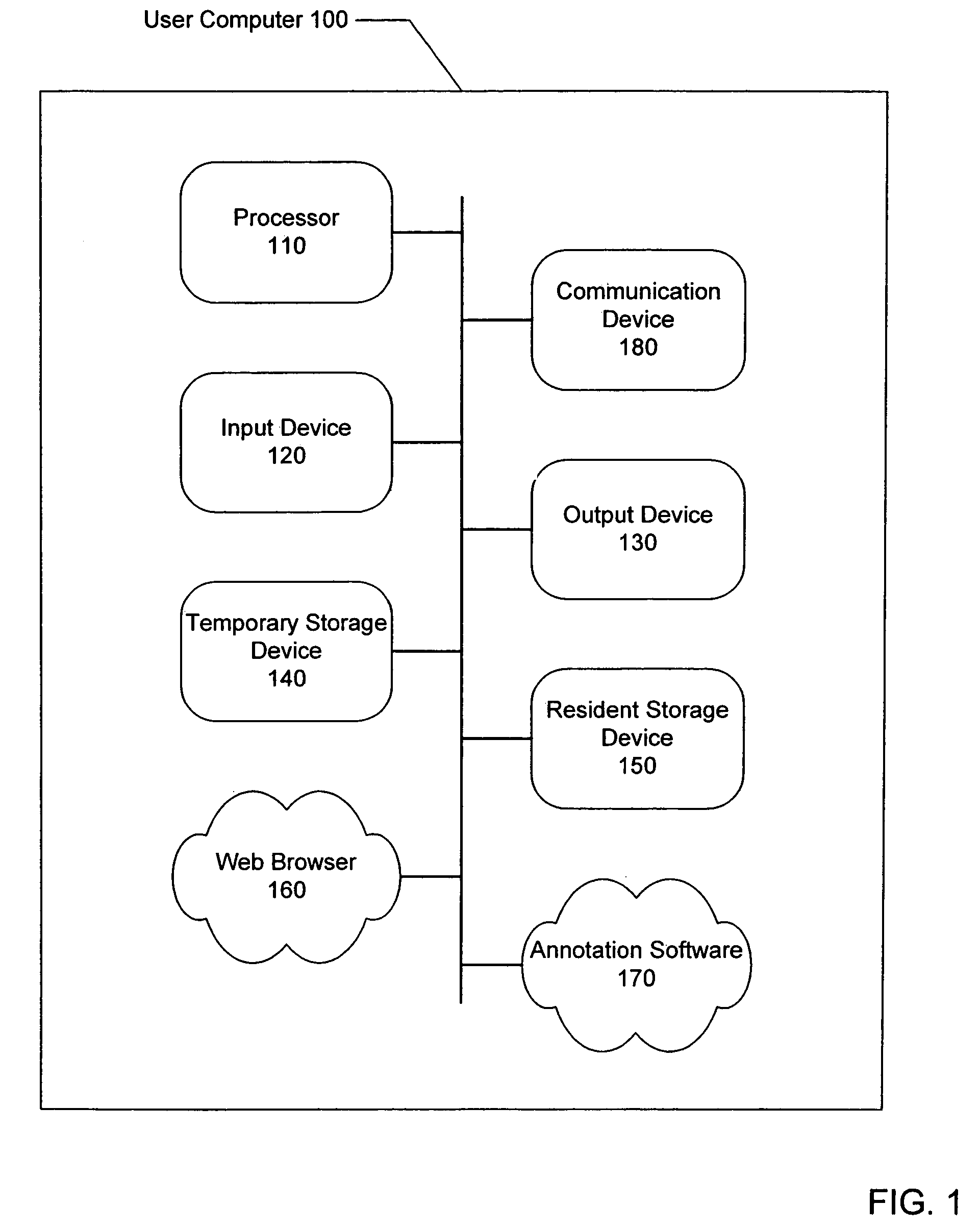
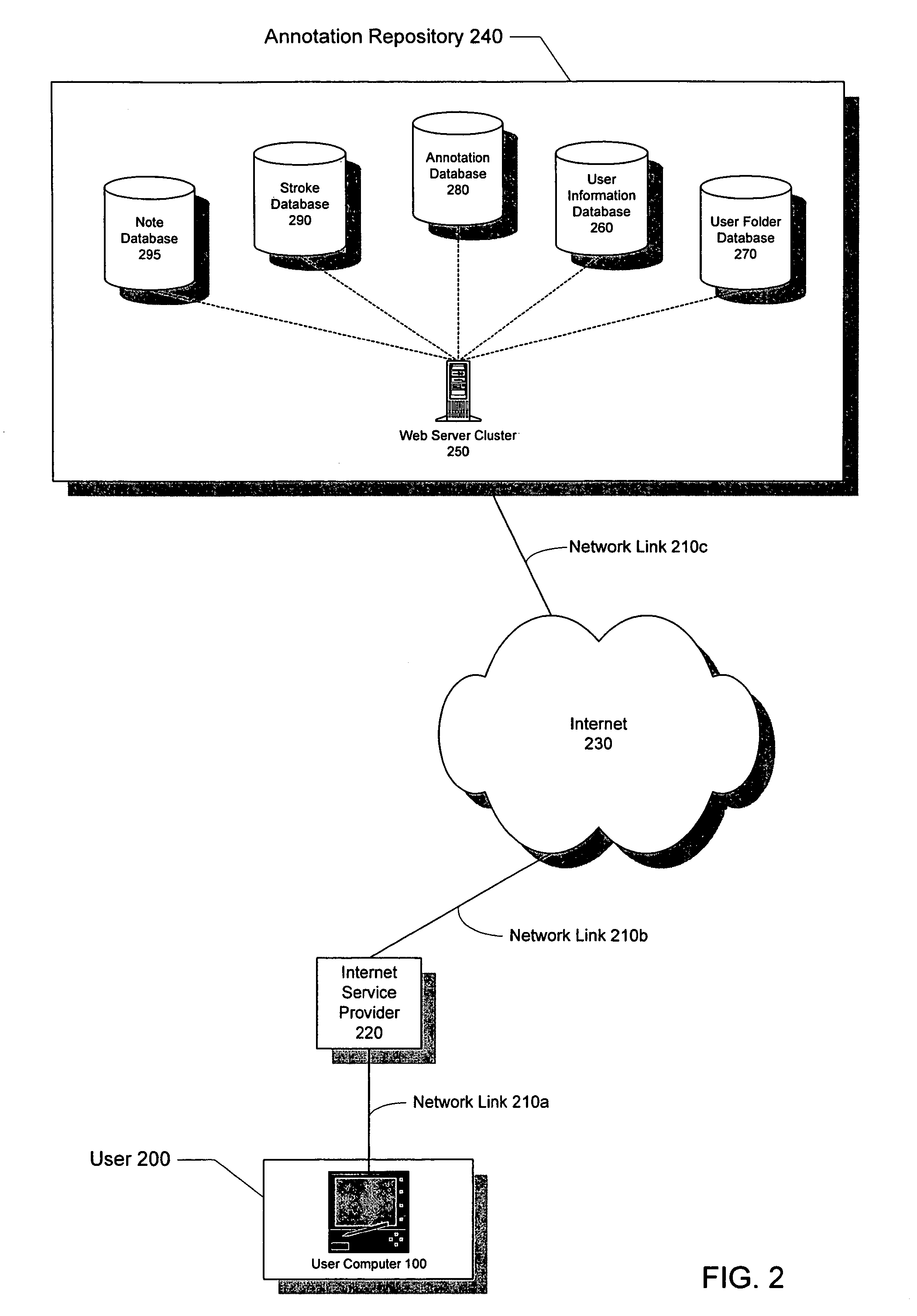
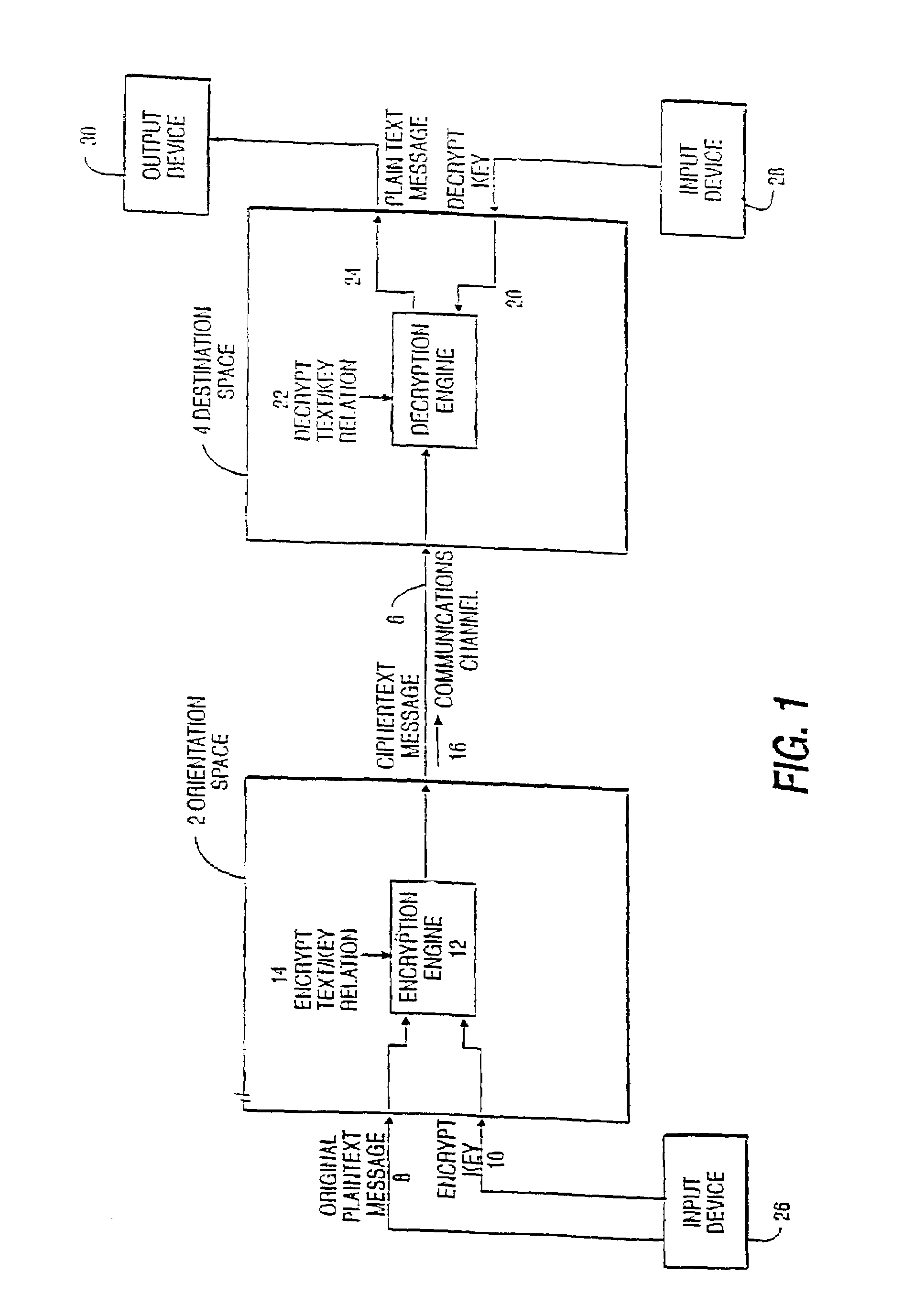
System and method for annotating web-based documents
InactiveUS6859909B1Simple interfaceEffectively converting their Web browsersDrawing from basic elementsDigital computer detailsPersonalizationComputer users
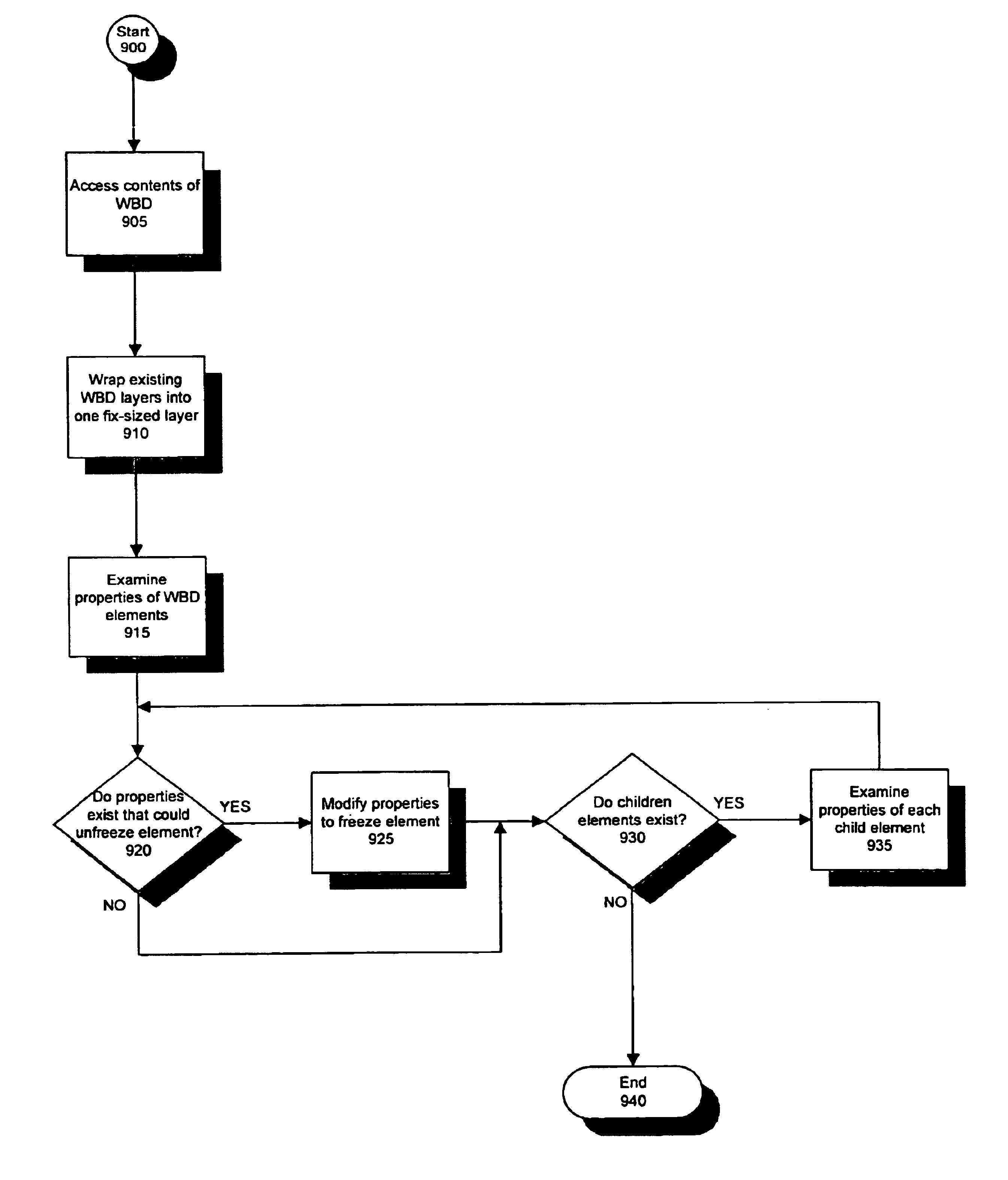
The present invention allows computer users to integrate any annotation, including ink, highlighter, text-based notes and audio, directly into a Web-based document (WBD) displayed by a Web browser. This integration enables others to view the personalized annotated WBD, which retains its original active links and properties, over the Internet without the need for specialized software. Annotations are integrated into WBDs by freezing the WBD, overlaying an image file containing the annotations onto the WBD, and enabling browser events to pass through the image layer. Annotations may also be integrated into WBDs by using component object technology. The present invention collects and organizes annotated WBDs, and provides users with an intuitive Web-based interface for accessing, viewing and searching the annotated WBDs. Users may annotate blank WBDs, effectively converting their Web browsers into online notebooks / scrapbooks. The present invention also provides users with many novel interface techniques, such as dog-ears and its associated navigation tools, splitting pages, turning pages, selecting and copying various portions of a WBD (including shaking out a copy), and marking menus suited for right-handed or left-handed users.
Owner:MICROSOFT CORP
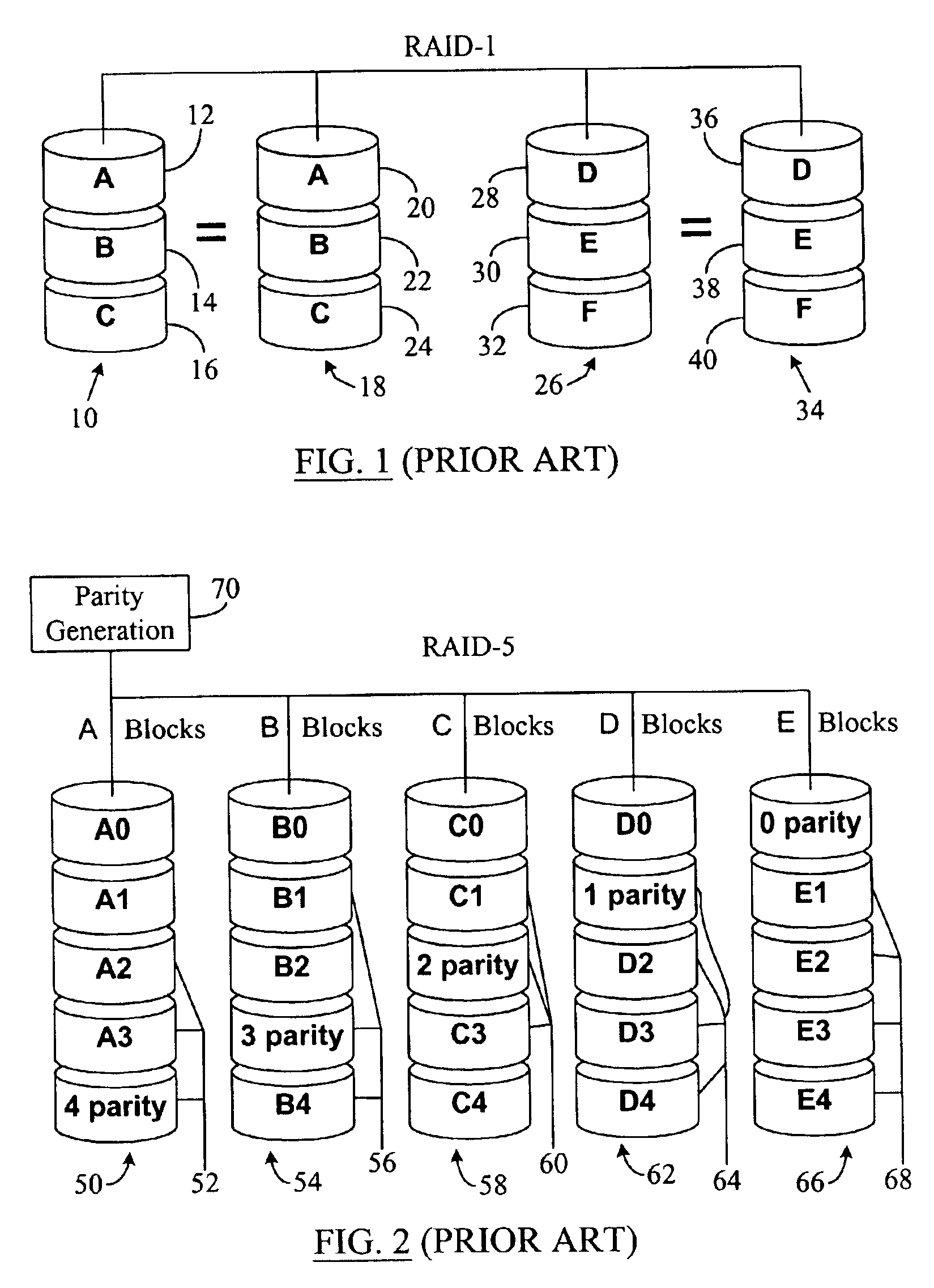
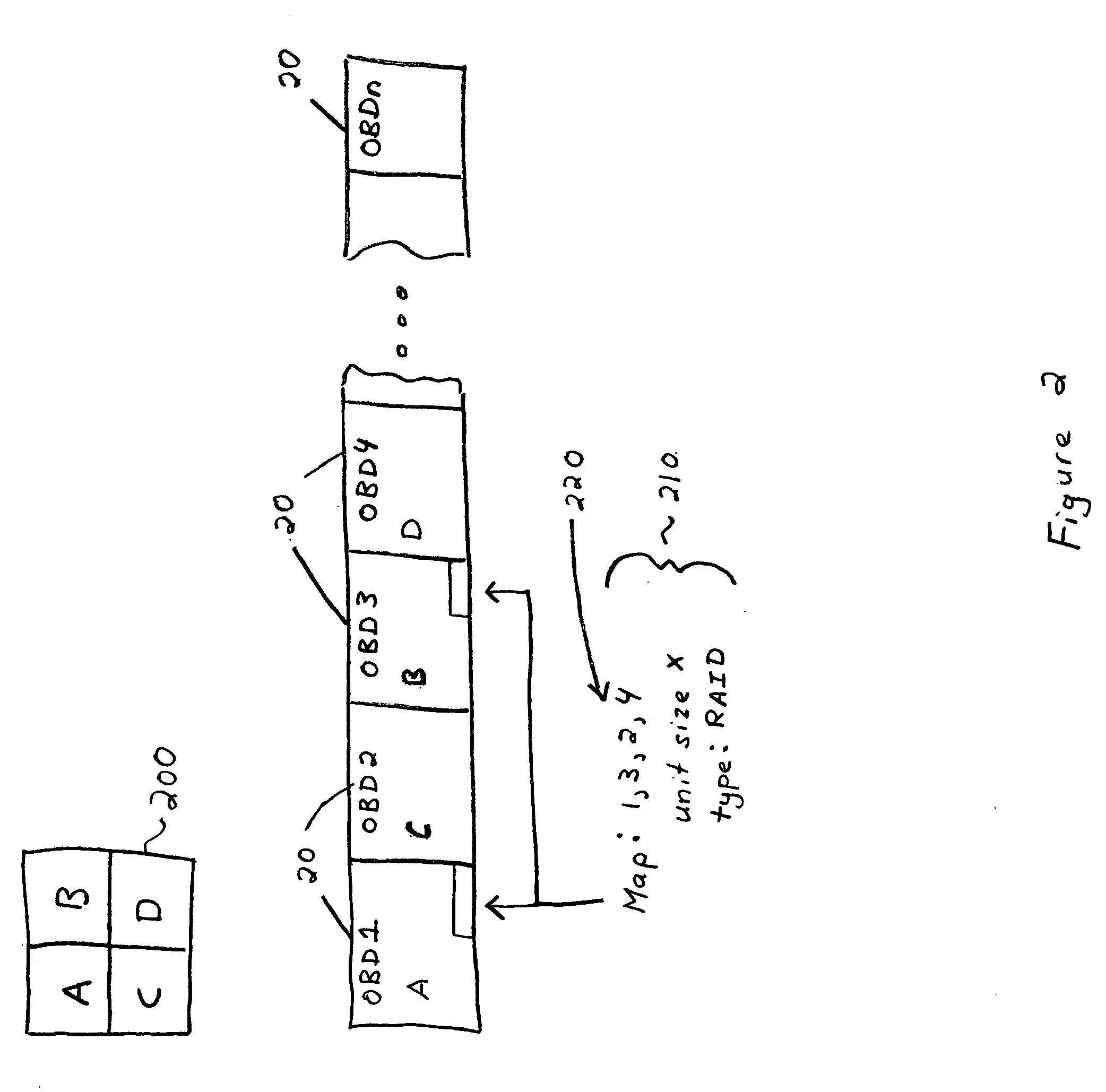
Data file migration from a mirrored RAID to a non-mirrored XOR-based RAID without rewriting the data
InactiveUS6985995B2Improve performanceImprove reliabilityData processing applicationsMemory loss protectionRAIDObject based
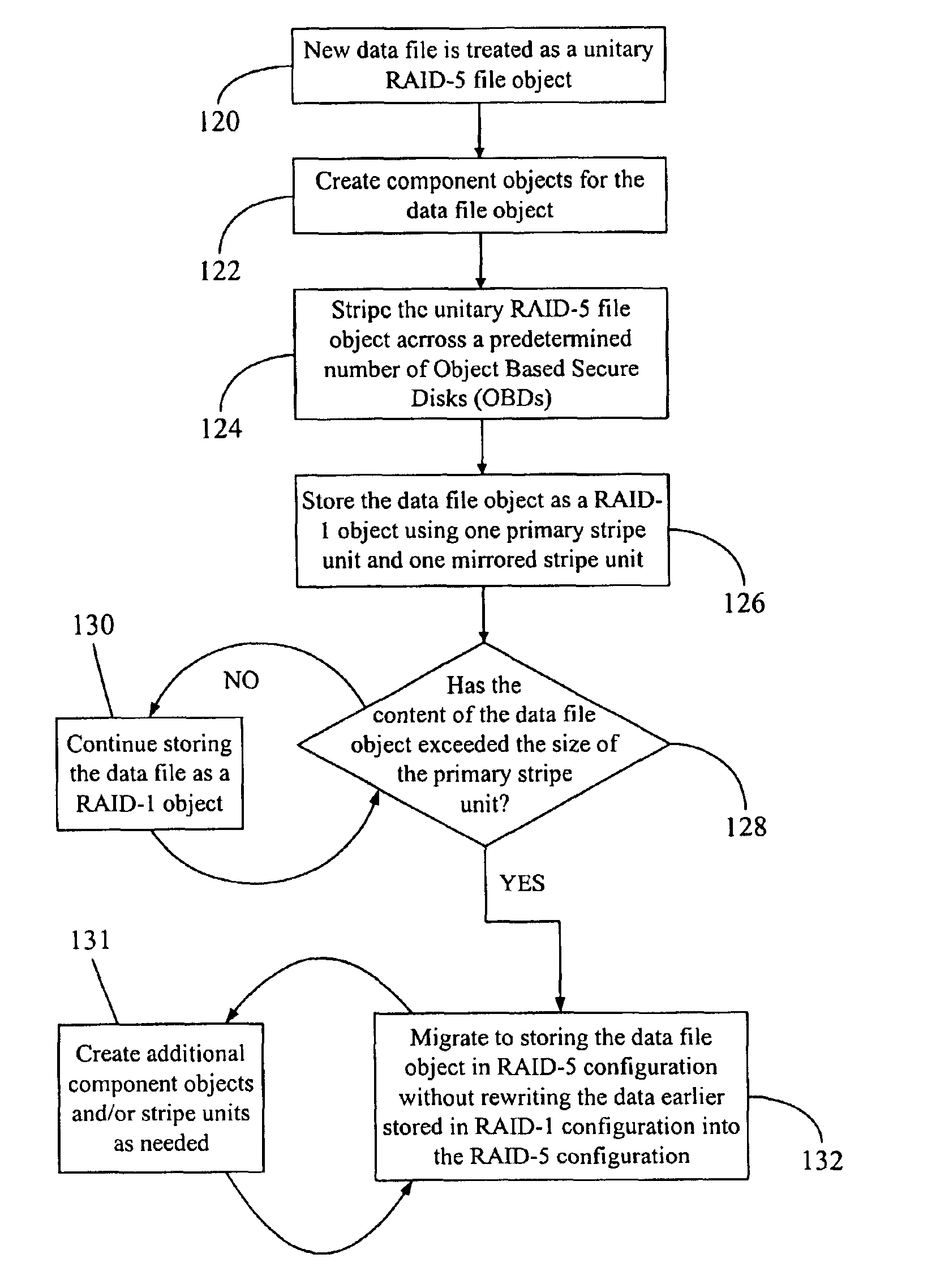
A data storage methodology wherein a data file is initially stored in a format consistent with RAID-1 and RAID-X and then migrated to a format consistent with RAID-X and inconsistent with RAID-1 when the data file grows in size beyond a certain threshold. Here, RAID-X refers to any non-mirrored storage scheme employing XOR-based error correction coding (e.g., a RAID-5 configuration). Each component object (including the data objects and the parity object) for the data file is configured to be stored in a different stripe unit per object-based secure disk. Each stripe unit may store, for example, 64 KB of data. So long as the data file does not grow beyond the size threshold of a stripe unit (e.g., 64 KB), the parity stripe unit contains a mirrored copy of the data stored in one of the data stripe units because of the exclusive-ORing of the input data with “all zeros” assumed to be contained in empty or partially-filled stripe units. When the file grows beyond the size threshold, the parity stripe unit starts storing parity information instead of a mirrored copy of the file data. Thus, the data file can be automatically migrated from a format consistent with RAID-1 and RAID-X to a format consistent with RAID-X and inconsistent with RAID-1 without the necessity to duplicate or rewrite the stored data.
Owner:PANASAS INC
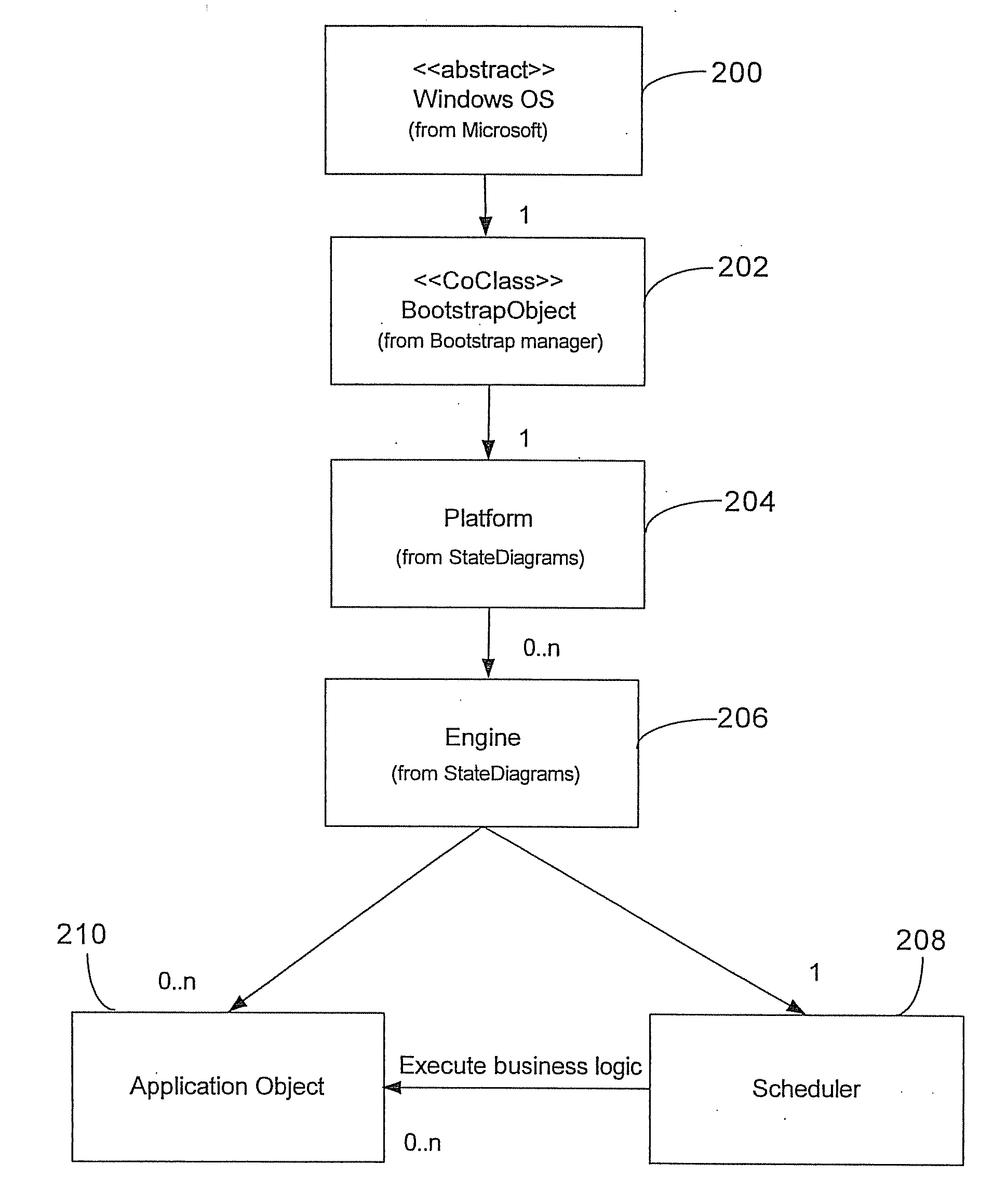
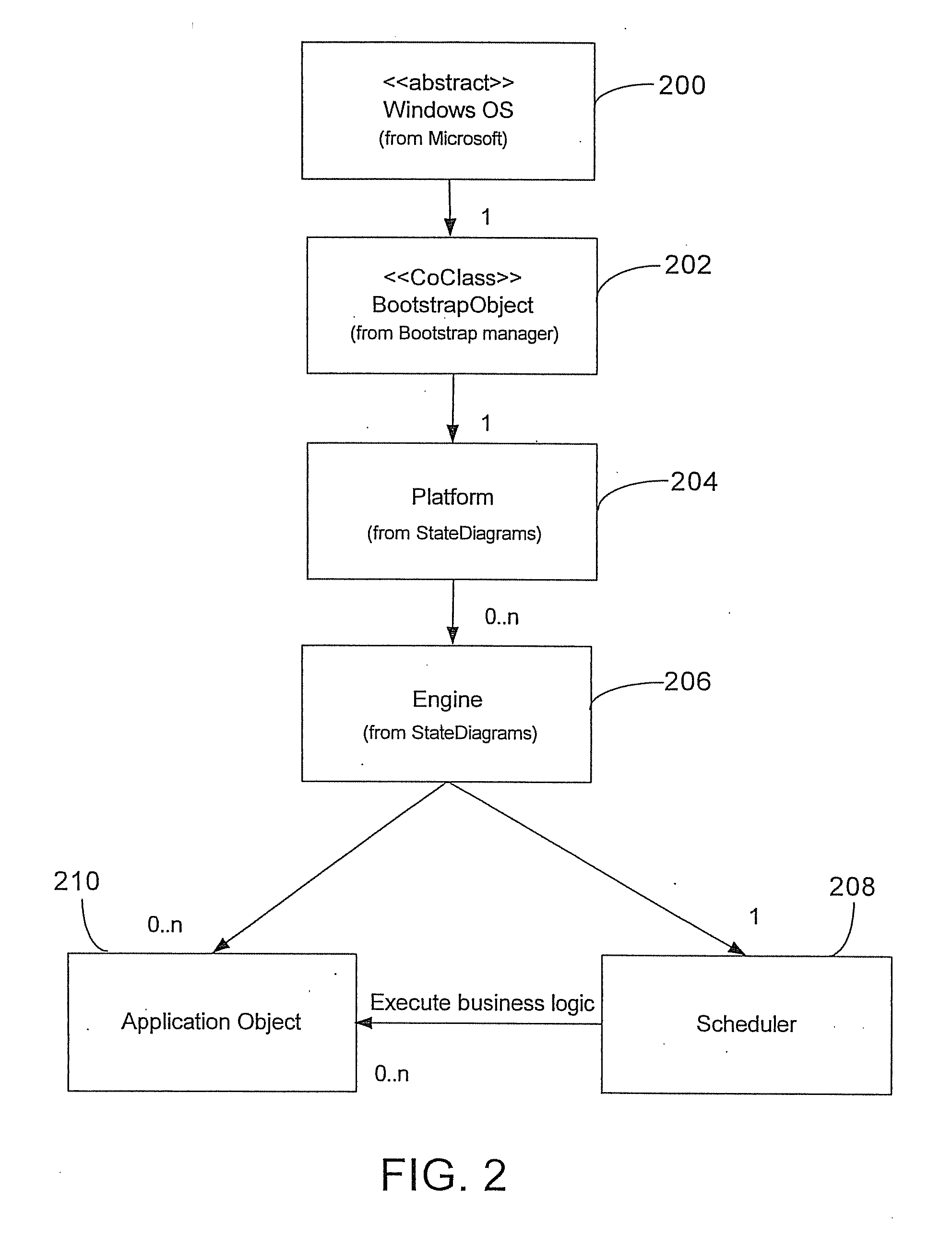
Customizable system for creating supervisory process control and manufacturing information applications
ActiveUS7086009B2Enhanced product offeringIntegration changesSoftware designSoftware simulation/interpretation/emulationThird partyDocumentation procedure
An extensible base process control and manufacturing information application development and execution software suite is disclosed that facilitates streamlined third party (e.g., OEM) development of derivative applications for particular vertical markets. The suite includes an object design toolkit that provides object template derivation tools for accessing and editing a set of base object templates. The objects derivable from the base templates include at least application objects deployed upon lower level hosting component objects of a supervisory process control and manufacturing information application. The toolkit also includes development tools for creating new base object templates that are added as extensions of the set of base object templates.In addition to the toolkit, the suite includes a set of marketing package customization tools facilitating seamlessly integrating changes by developers to the extensible base development and execution software suite. The marketing package customization tools include electronically editable base user documentation.
Owner:SCHNEIDER ELECTRIC SOFTWARE LLC
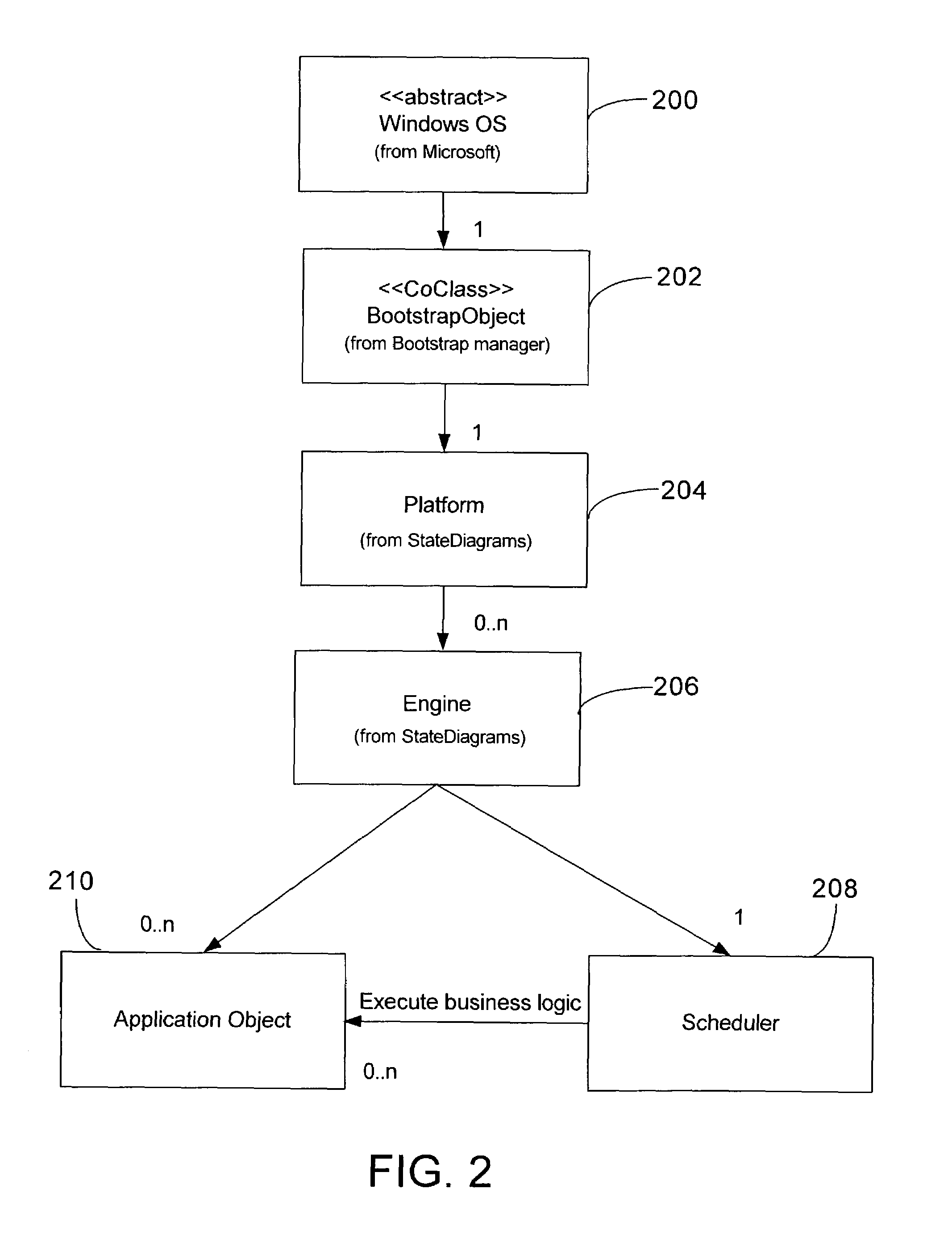
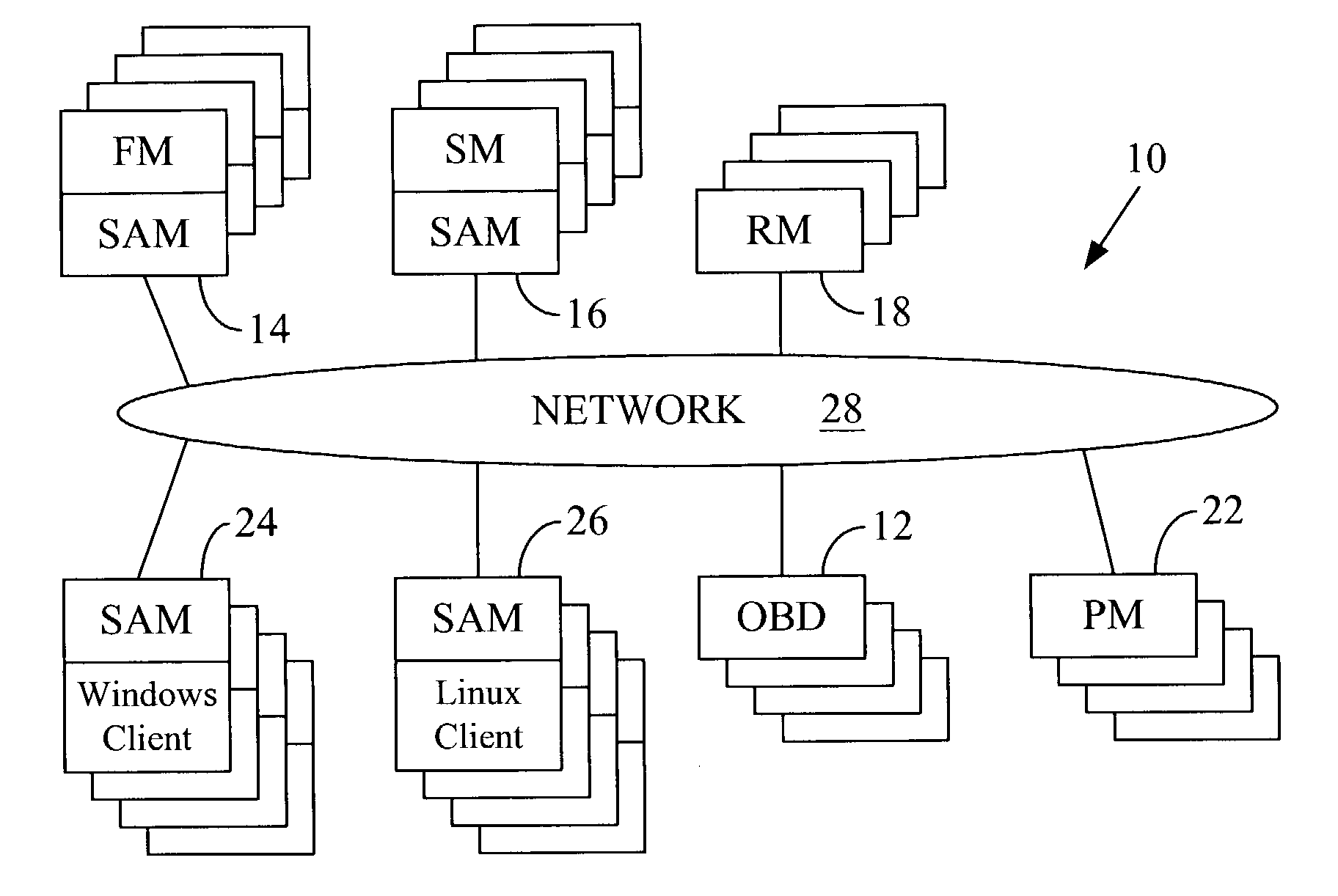
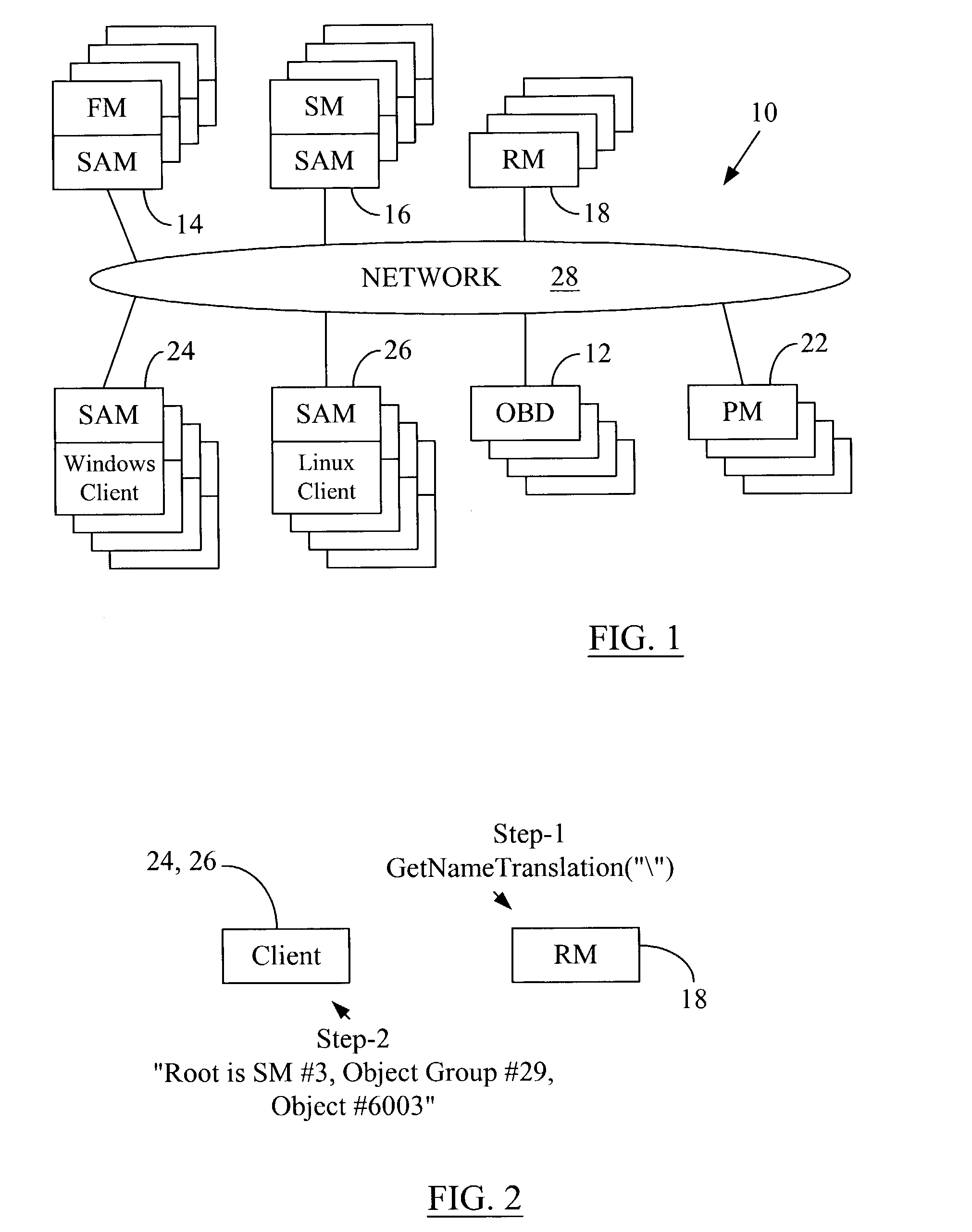
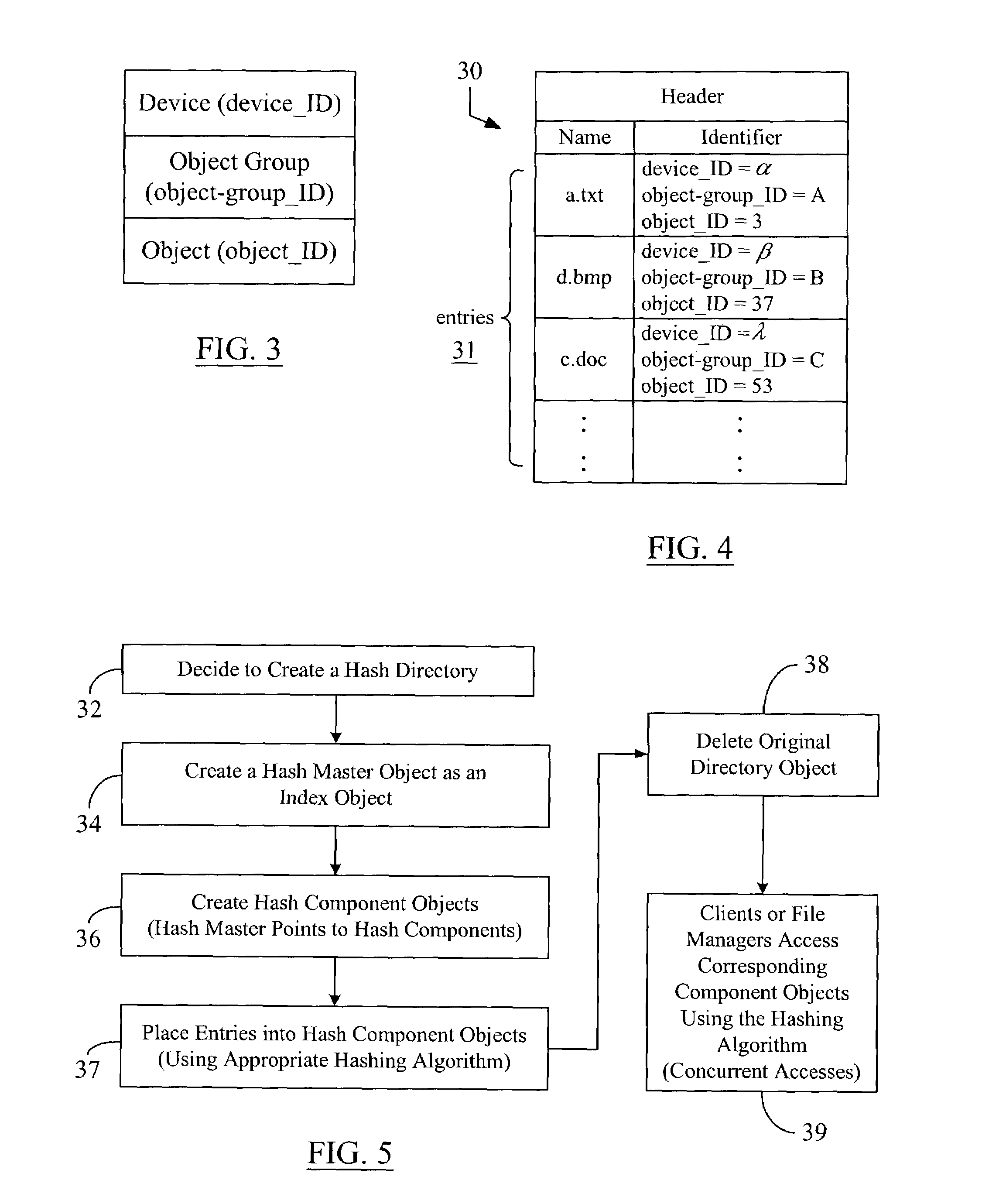
Hashing objects into multiple directories for better concurrency and manageability
ActiveUS7007024B2Decreases manageabilityReduce decreaseData processing applicationsDigital data processing detailsComputer hardwareClient-side
A data storage methodology wherein a hashing algorithm is applied to break a directory object experiencing frequent concurrent accesses from a number of client or manager applications into a predetermined number of hash component objects and a hash master object that manages the component objects. The hash master object and the hash components, together, constitute a hash directory, which replaces the original non-hashed directory object. Each hash component object contains a portion of the entries contained in the original directory object. Each hash component is managed by only one file manager. The entries in the original directory object are distributed among the hash component objects using a predefined hashing algorithm. The creation of hash components and the hash master allows more than one client application or file manager to concurrently write corresponding hash components without the need for access coordination on each access.
Owner:PANASAS INC
Customizable system for creating supervisory process control and manufacturing information applications
ActiveUS20070006149A1Enhanced product offeringIntegration changesSoftware designSoftware simulation/interpretation/emulationThird partyDocumentation procedure
An extensible base process control and manufacturing information application development and execution software suite is disclosed that facilitates streamlined third party (e.g., OEM) development of derivative applications for particular vertical markets. The suite includes an object design toolkit that provides object template derivation tools for accessing and editing a set of base object templates. The objects derivable from the base templates include at least application objects deployed upon lower level hosting component objects of a supervisory process control and manufacturing information application. The toolkit also includes development tools for creating new base object templates that are added as extensions of the set of base object templates. In addition to the toolkit, the suite includes a set of marketing package customization tools facilitating seamlessly integrating changes by developers to the extensible base development and execution software suite. The marketing package customization tools include electronically editable base user documentation.
Owner:SCHNEIDER ELECTRIC SOFTWARE LLC
System and method for annotating web-based document
InactiveUS7409633B2Effectively converting their Web browsersSimple interfaceNatural language data processingSpecial data processing applicationsPersonalizationDocumentation procedure
Computer users may integrate any annotation, including ink, highlighter, text-based notes and audio, directly into a Web-based document (WBD) displayed by a Web browser. This integration enables others to view the personalized annotated WBD, which retains its original active links and properties, over the Internet without the need for specialized software. Annotations are integrated into WBDs by freezing the WBD, overlaying an image file containing the annotations onto the WBD, and enabling browser events to pass through the image layer. Annotations may also be integrated into WBDs by using component object technology. By collecting and organizing annotated WBDs, users can be provided with an intuitive Web-based interface for accessing, viewing and searching the annotated WBDs. Users may annotate blank WBDs, effectively converting their Web browsers into online notebooks / scrapbooks. Users may also be provided with many interface techniques, such as dog-ears and its associated navigation tools, splitting pages, turning pages, selecting and copying various portions of a WBD (including shaking out a copy), and marking menus suited for right-handed or left-handed users.
Owner:MICROSOFT CORP
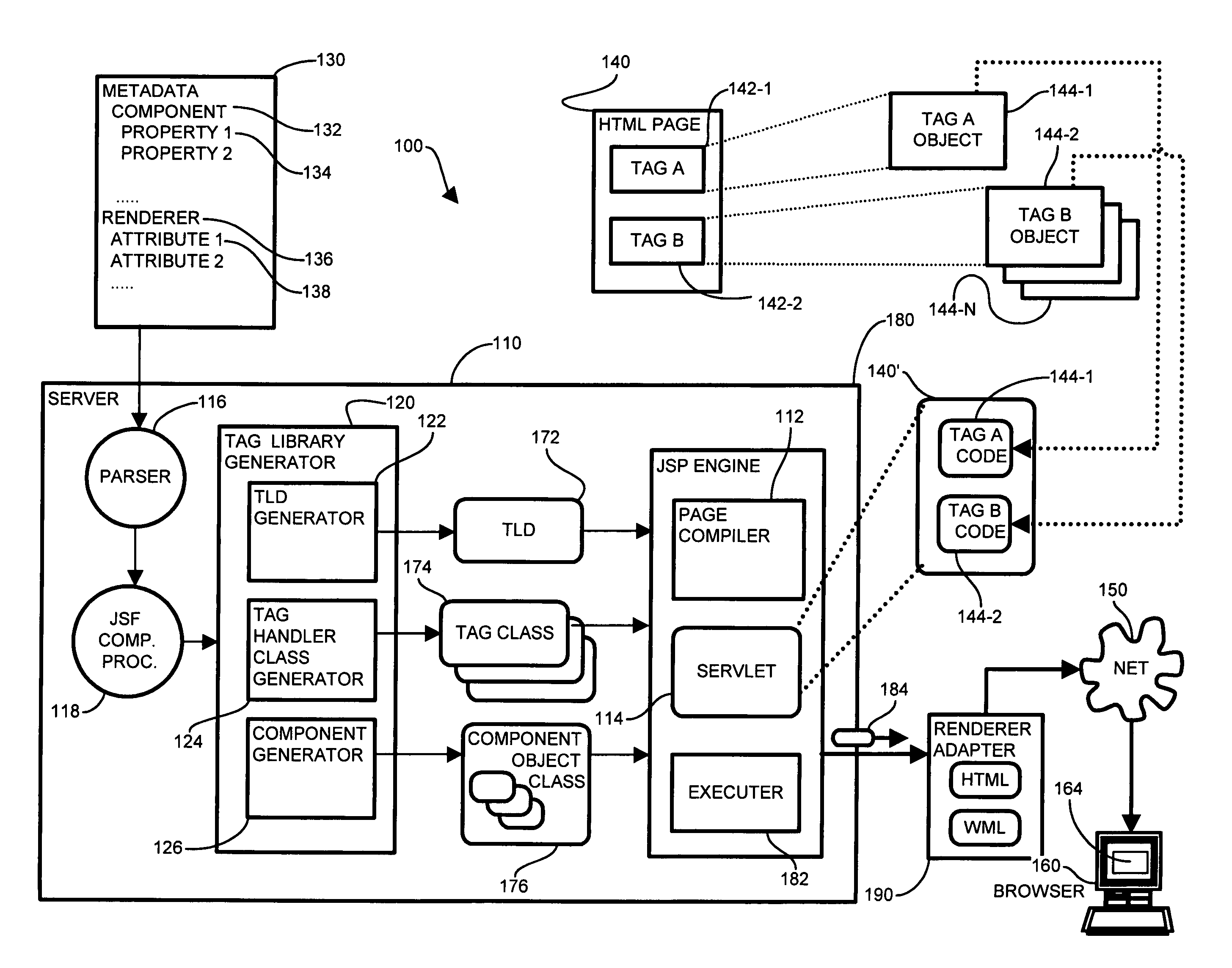
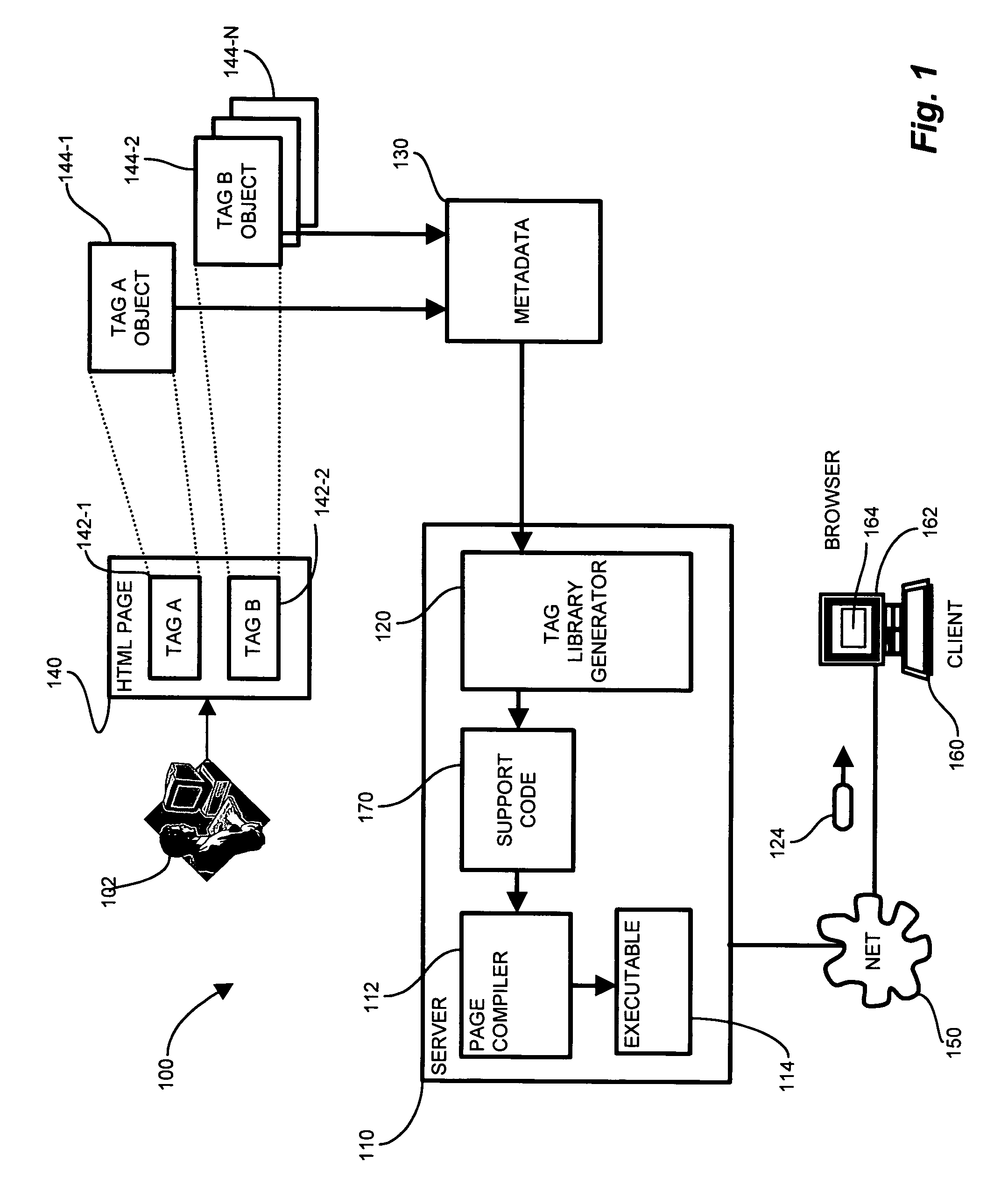
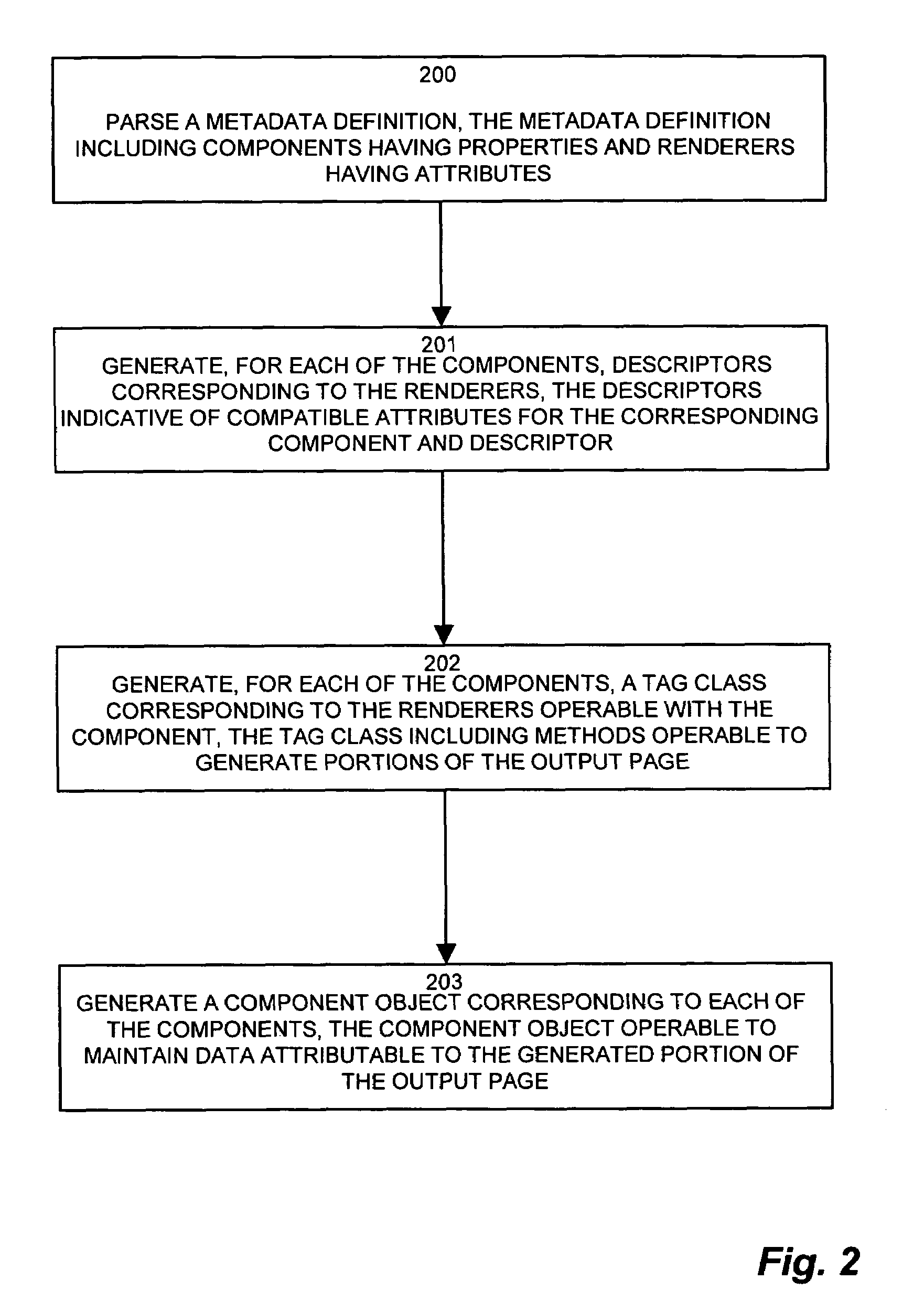
System and methods for tag library generation
ActiveUS7246134B1Easy to buildQuickly and easily buildData processing applicationsDigital data processing detailsProgramming languageComponent object
Conventional tag libraries facilitate web page development by referencing external code from within an HTML page via a mnemonic tag, however such conventional tag libraries typically rely on a manually generated set of supporting code. Such supporting code typically requires a thorough knowledge of the underlying code language, such as Java, C++ and Java Server Pages (JSP). A tag library generator for generating the supporting code corresponding to a tag library mitigates the shortcomings of manually generated support code by parsing a metadata file defining the operations and functions provided by the supporting code. The parser extracts components and renderers corresponding to the supporting code. Each of the components may have corresponding properties, and each of the renderers may have corresponding attributes, which the parser also extracts. The tag library generator receives the parsed items, and processes each of the components with corresponding renderers to generate the applicable support code. The support code includes a tag library descriptor defining the tags whose attributes are a combination of component properties and renderer attributes, a tag handler class definition, in which each tag handler class corresponds to a “tag” entry in the TLD file, and component objects for maintaining the state of web output pages.
Owner:ORACLE INT CORP
Distributed object-based storage system that stores virtualization maps in object attributes
InactiveUS20060036602A1No lossSpecial data processing applicationsFile systemsVirtualizationObject based
A distributed object-based storage system and method includes a plurality of object storage devices for storing object components, a metadata server coupled to each of the object storage devices, and one or more clients that access distributed, object-based files on the object storage devices. A file object having multiple components on different object storage devices is accessed by issuing a file access request from a client to an object storage device for a file object. In response to the file access request, a map is located that includes a list of object storage devices where components of the requested file object reside. The map is stored as at least one component object attribute on an object storage device. The map is sent to the client which retrieves the components of the requested file object by issuing access requests to each of the object storage devices on the list.
Owner:PANASAS INC
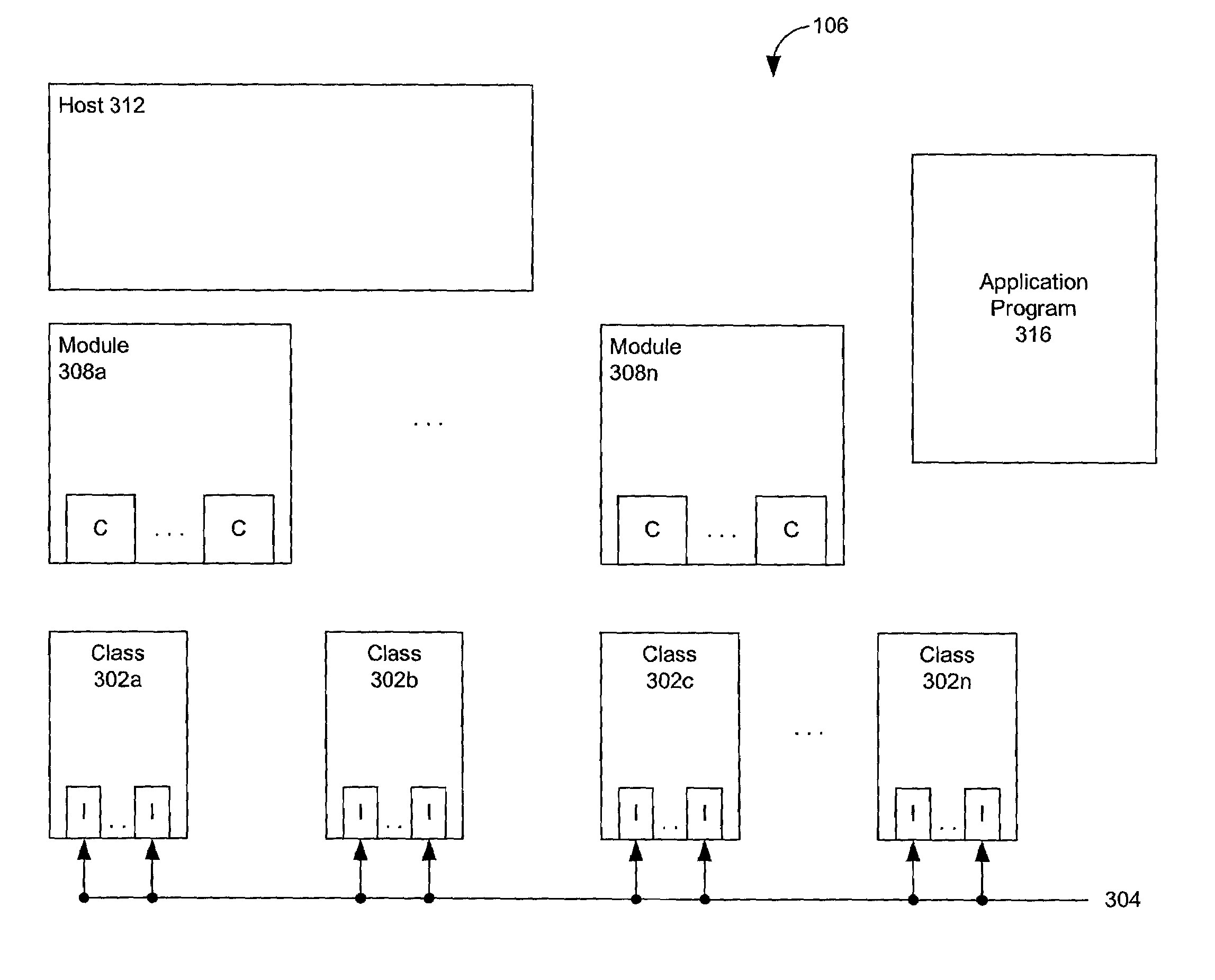
Methods and systems for providing platform-independent shared software components for mobile devices
InactiveUS6986148B2Increase flexibilityEasy to handleData processing applicationsInterprogram communicationApplication softwareRunning time
Systems and methods integrate and provide platform independence to shared component objects. A host is targeted for a mobile device and registers software components. Upon a request for services by an application program, the host finds and facilitates the creation of instances requested by the application program, thereby providing platform independence to the application program and the developer thereof. A module, deployable unit of software components, is also an addressable and programmable object during a run time, thereby facilitating implicit registry of software components on the target device and reducing storage space required on a target device, as well as the CPU processing power. The module also provides module-wide variables, thereby enabling distinct instances constructed from classes contained within the module to share common variables.
Owner:ORACLE INT CORP
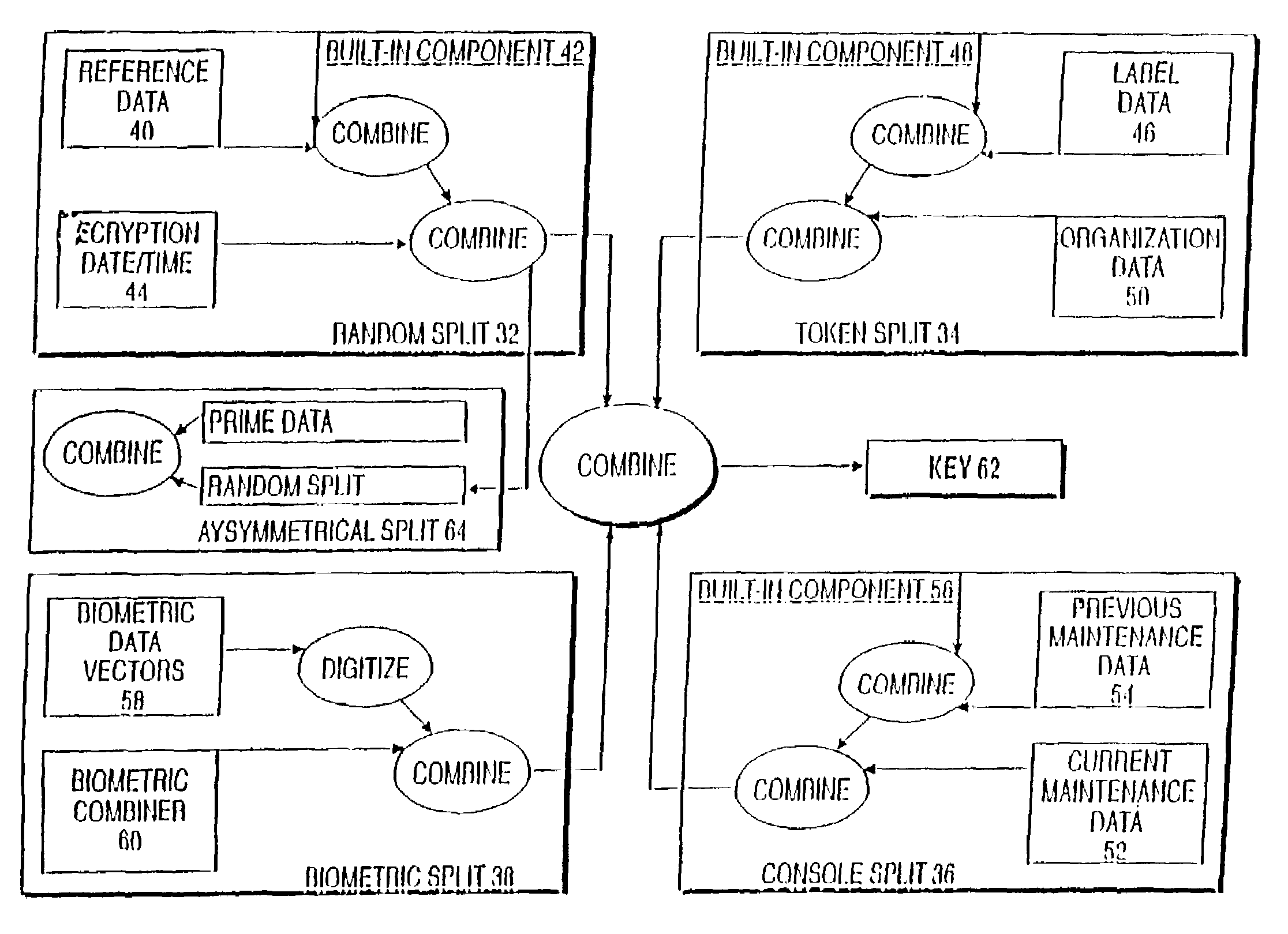
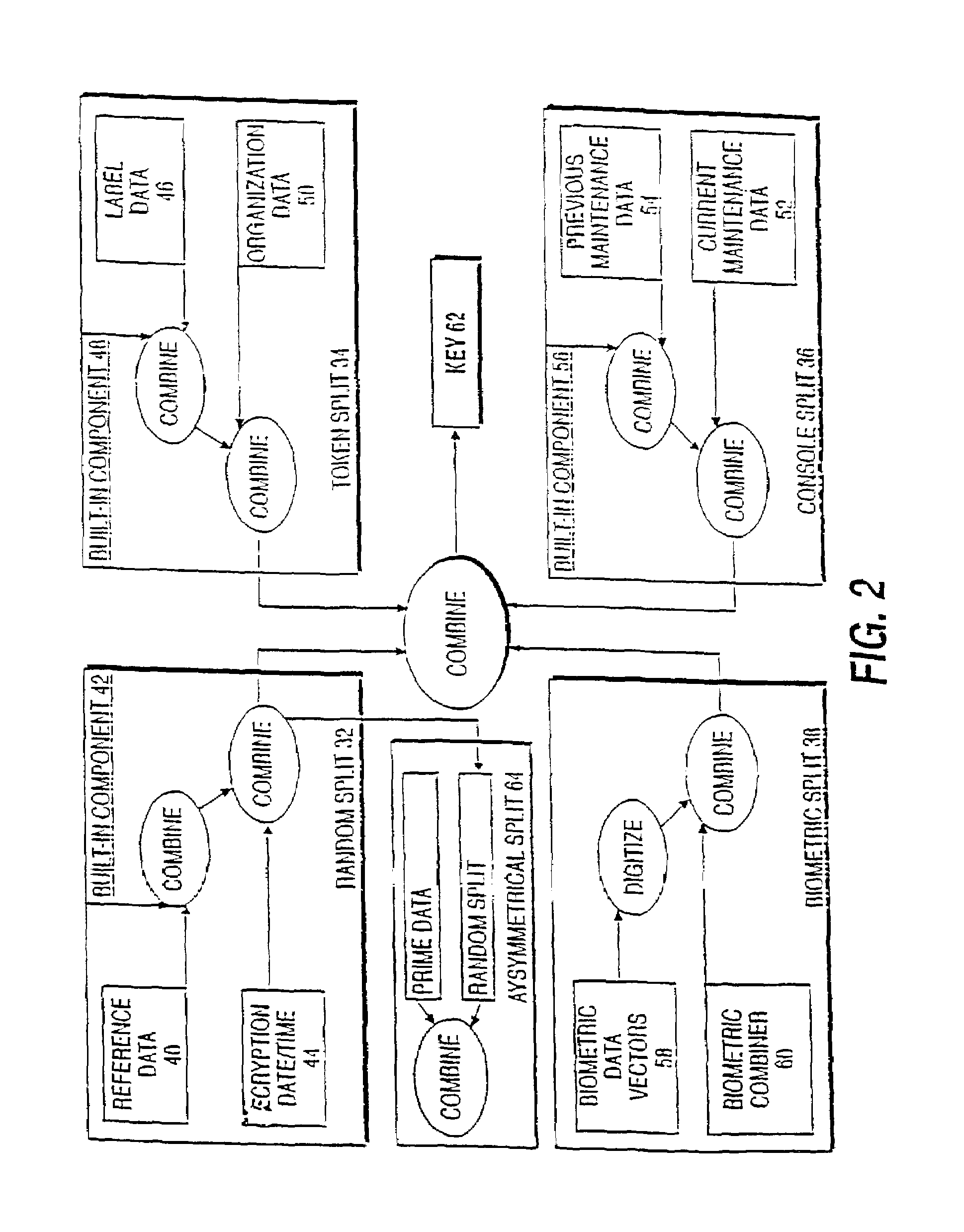
Voice and data encryption method using a cryptographic key split combiner
InactiveUS7095851B1Improve securityKey distribution for secure communicationUser identity/authority verificationMemory addressBiometric data
A cryptographic key split combiner, which includes a number of key split generators (42, 48, and 56) for generating cryptographic key splits (32, 34, 36, 38, and 64) and a key split randomizer for randomizing the cryptographic key splits to produce a cryptographic key (62), and a process for forming cryptographic keys. Each of the key split generators (42, 48 and 56) generates key splits (32, 34, 36, 38, and 64) from seed data (40, 44, 46, 50, 52, 54, 58, and 60). The key split generators may include a random split generator (42) for generating a random key split (32) based on reference data (40) and encryption date / time (44). Other key split generators may include a token split generator (48) for generating a token key split (34) based on label data (46) and organization data (50), a console split generator (56) for generating a console key split (36) based on current maintenance data (52) and previous maintenance data (54), and a biometric split generator for generating a biometric key split (38) based on biometric data (58). All splits may further be based on static data, which may be updated, for example by modifying a prime number divisor of the static data. The label data may be read from a storage medium, and may include user authorization data. The label data may be associated with label categories and subcategories of addresses, which are meaningful to a user who is specifying or determining the intended recipient(s) of the encrypted information or object. An array associated with a software component object may use key splits (32, 34, 36, 38, and 64) which determine which methods and properties are allowed and control access to the memory address for those allowed methods and properties. The resulting cryptographic key (62) may be, for example, a stream of symbols, at least one symbol block, or a key matrix.
Owner:TECSEC
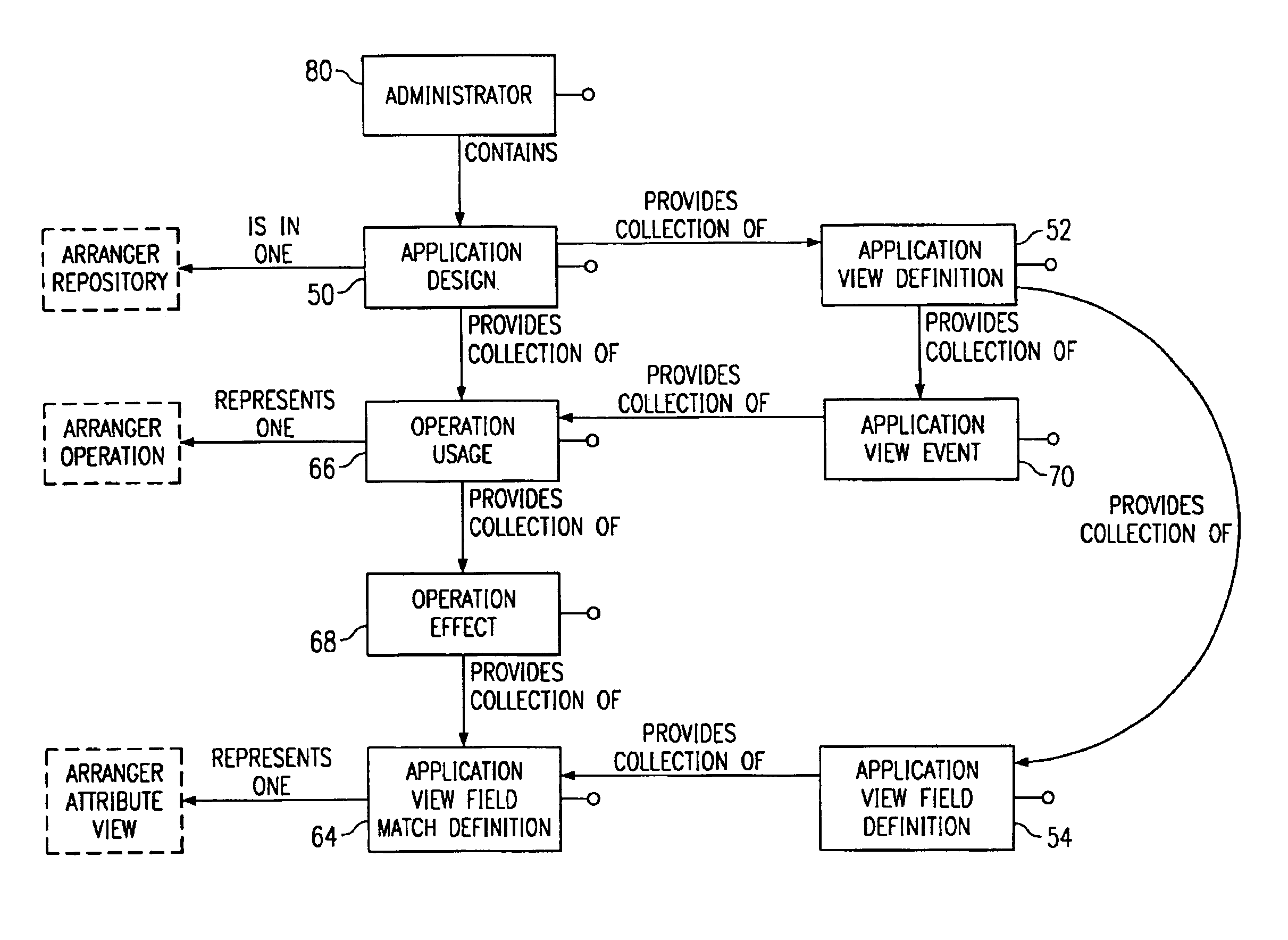
Apparatus and method for defining relationships between component objects in a business intelligence system
A computer readable memory includes a first data structure storing information characterizing a parent component object, a child component object, and a relationship object. The parent component object, the child component object, and the relationship object are associated to form a record of an edge in a graph that characterizes a business intelligence system. Executable instructions apply rules to the graph to alter the operation of the business intelligence system.
Owner:BUSINESS OBJECTS SOFTWARE
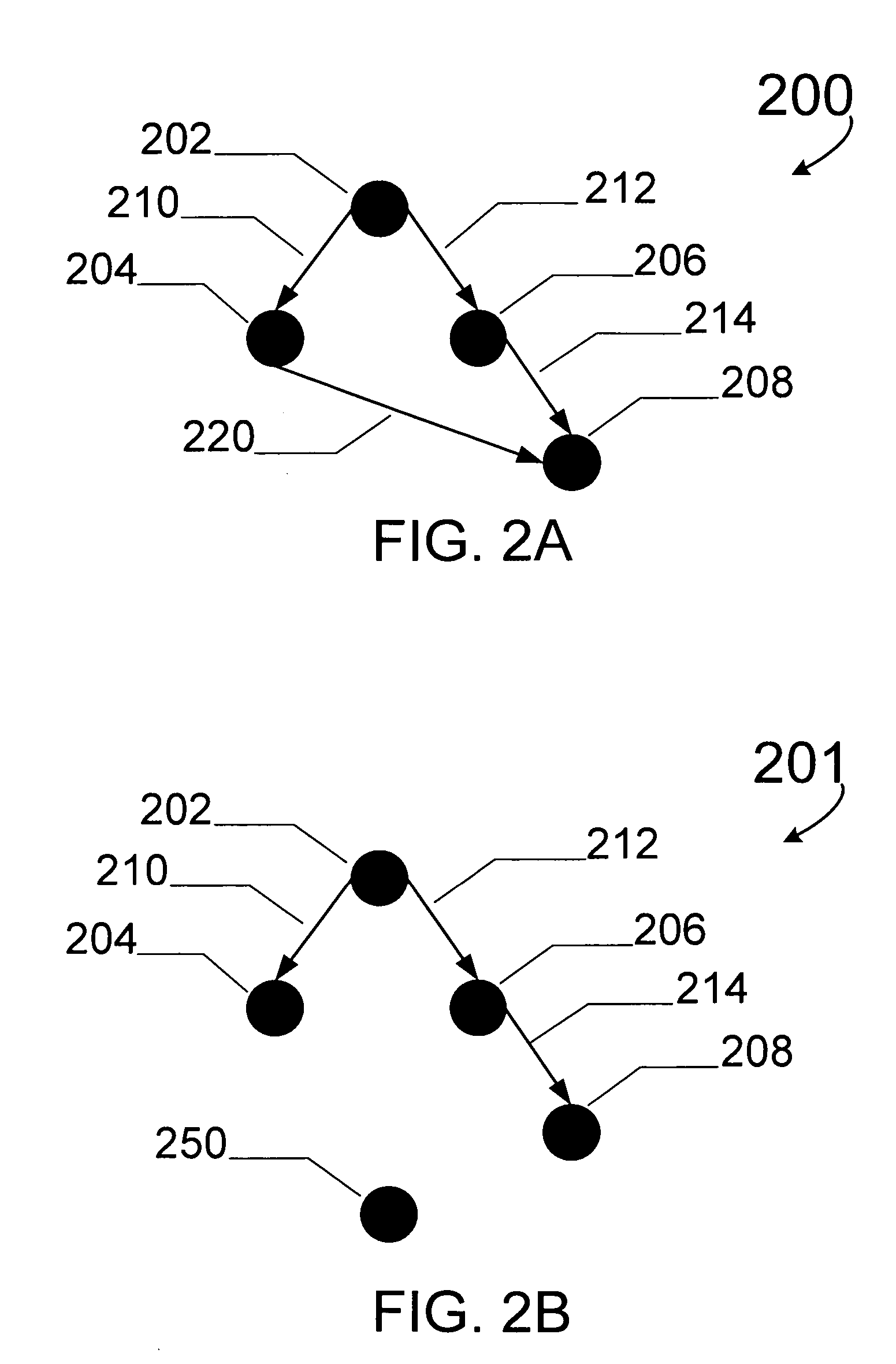
Method and system for managing component objects used in a plurality of composite objects
InactiveUS20110055289A1Avoids wasteful orderingAvoid wastingDigital data processing detailsResourcesComponent Object ModelComposite object
A composite physical object is formed of a plurality of component physical objects, which component physical objects can be used in a multiplicity of composite physical objects and a data management system and method is provided to manage the relationships. A user interface is provided to enable selection of component or composite objects for the addition or removal of component physical objects from the list. Because the relationship between component objects and composite objects is maintained, if a user selects to remove a component physical object from the list, its related component physical objects to be used in a composite object can be identified and also automatically removed. Similarly, operating the other way around, a user can select a composite object to be removed and this will result in the removal of all component physical objects in the list which are used in the composite object.
Owner:ENNIS RUSSEL
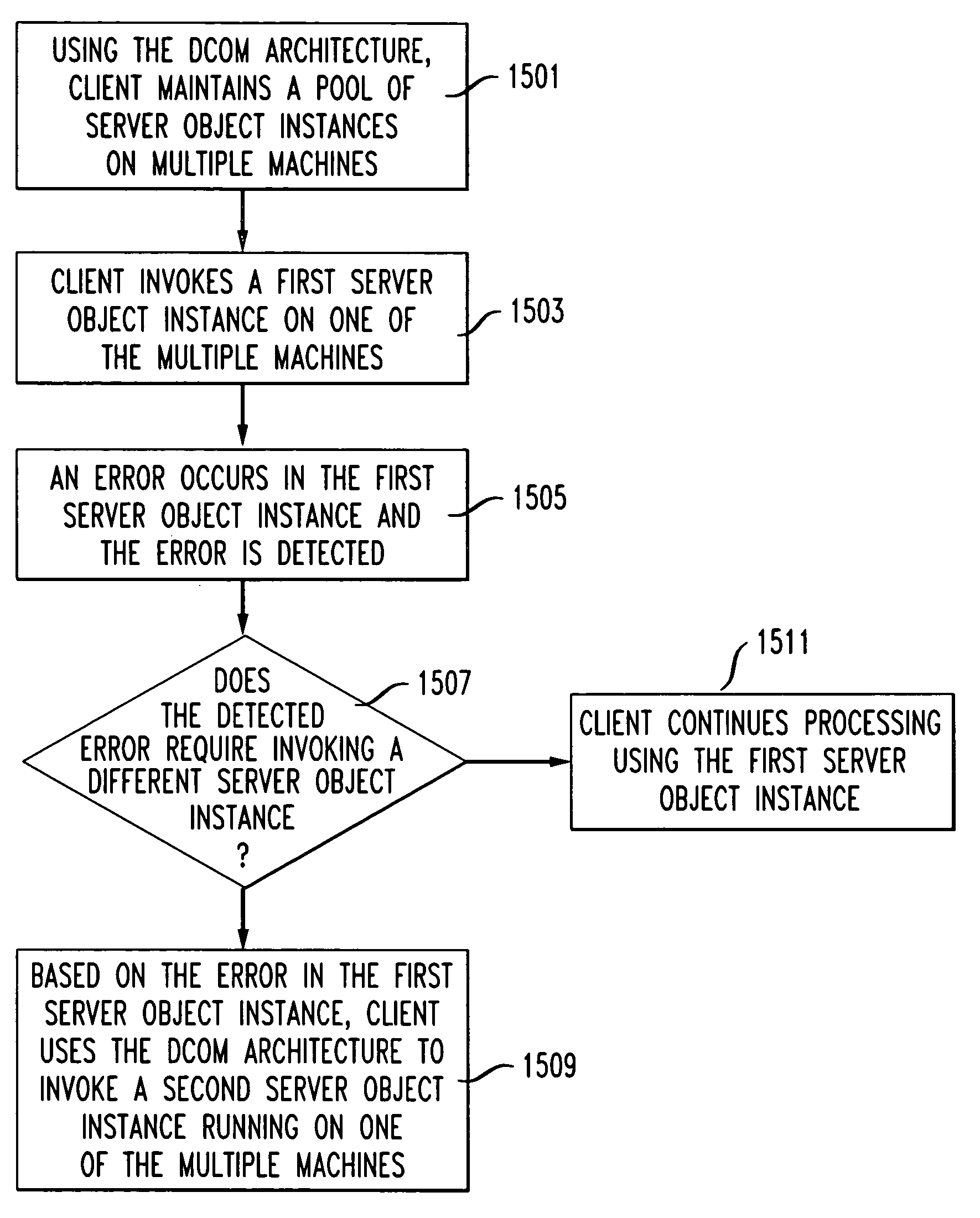
Method and system for providing reliability and availability in a distributed component object model (DCOM) object oriented system
InactiveUS7082553B1Improve reliabilityImprove availabilityError detection/correctionDistributed Component Object ModelFailover
A method and system for improving reliability and availability in distributed computer applications. The method and system may be used in the context of primary-backup, failover recovery. The method involves software-fault tolerance using technique of structured storage; referral components; and wrappers. The method and system exploit the platform and operating system independence of component object models to allow the dynamic linkage of different component objects, the objects being resident on different inter-linked machines, based on the application requirements at any given point in time.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
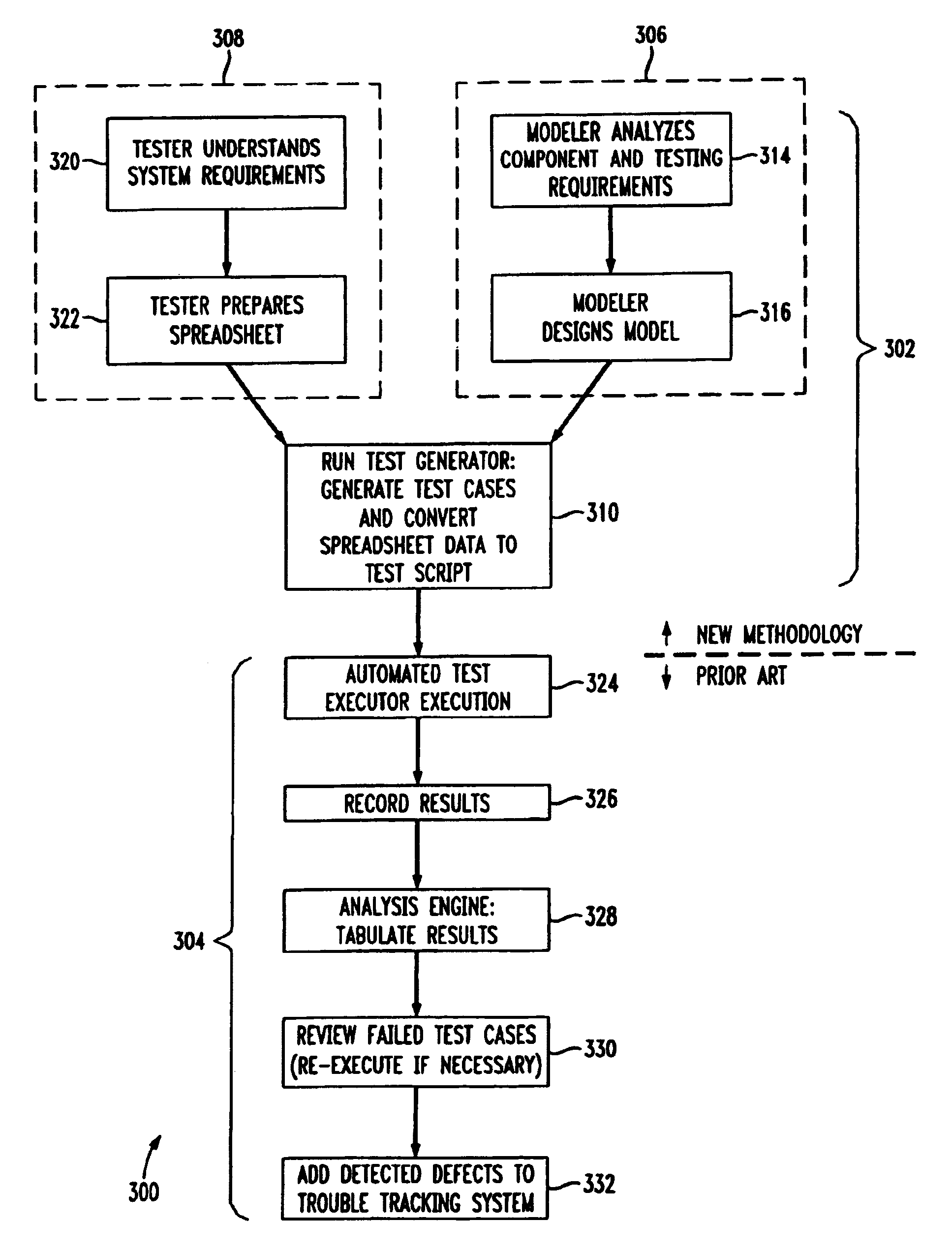
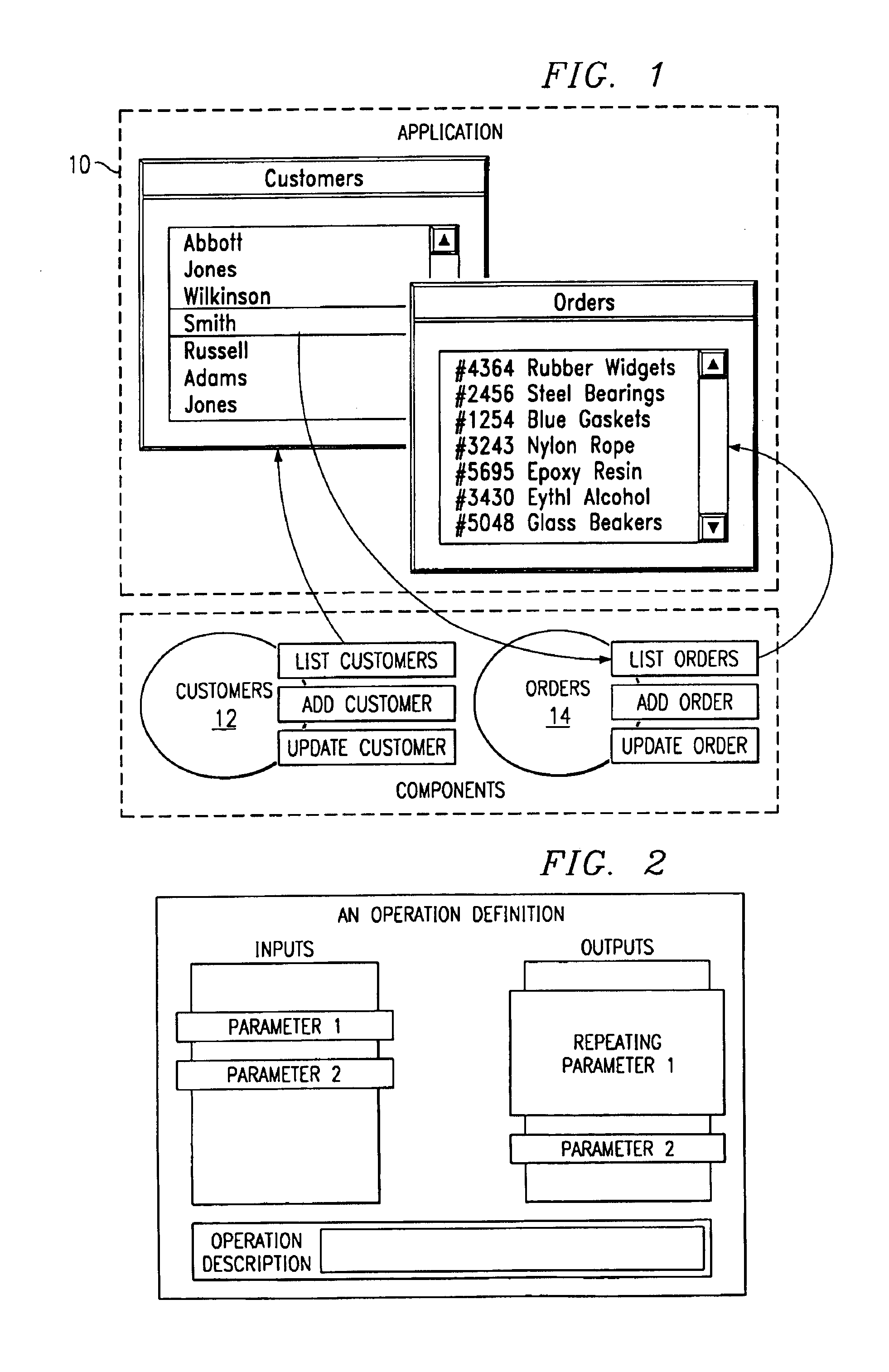
Test generator for converting a model of computer component object behavior and stimulus values to test script
InactiveUS7076713B1Electronic circuit testingError detection/correctionTest scriptTest vector generator
This invention relates to an apparatus and an associated method that tests the response of a computer component. The apparatus includes a modeler, a tester, and a test generator. The modeler provides a model of the computer component object behavior. The tester provides stimulus values to be applied to the computer component object. The test generator converts the model of the computer component object behavior and the stimulus values into test script. The test script can be executed by an automated test executor.
Owner:WSOU INVESTMENTS LLC +1
Reactive polymer fused deposition manufacturing
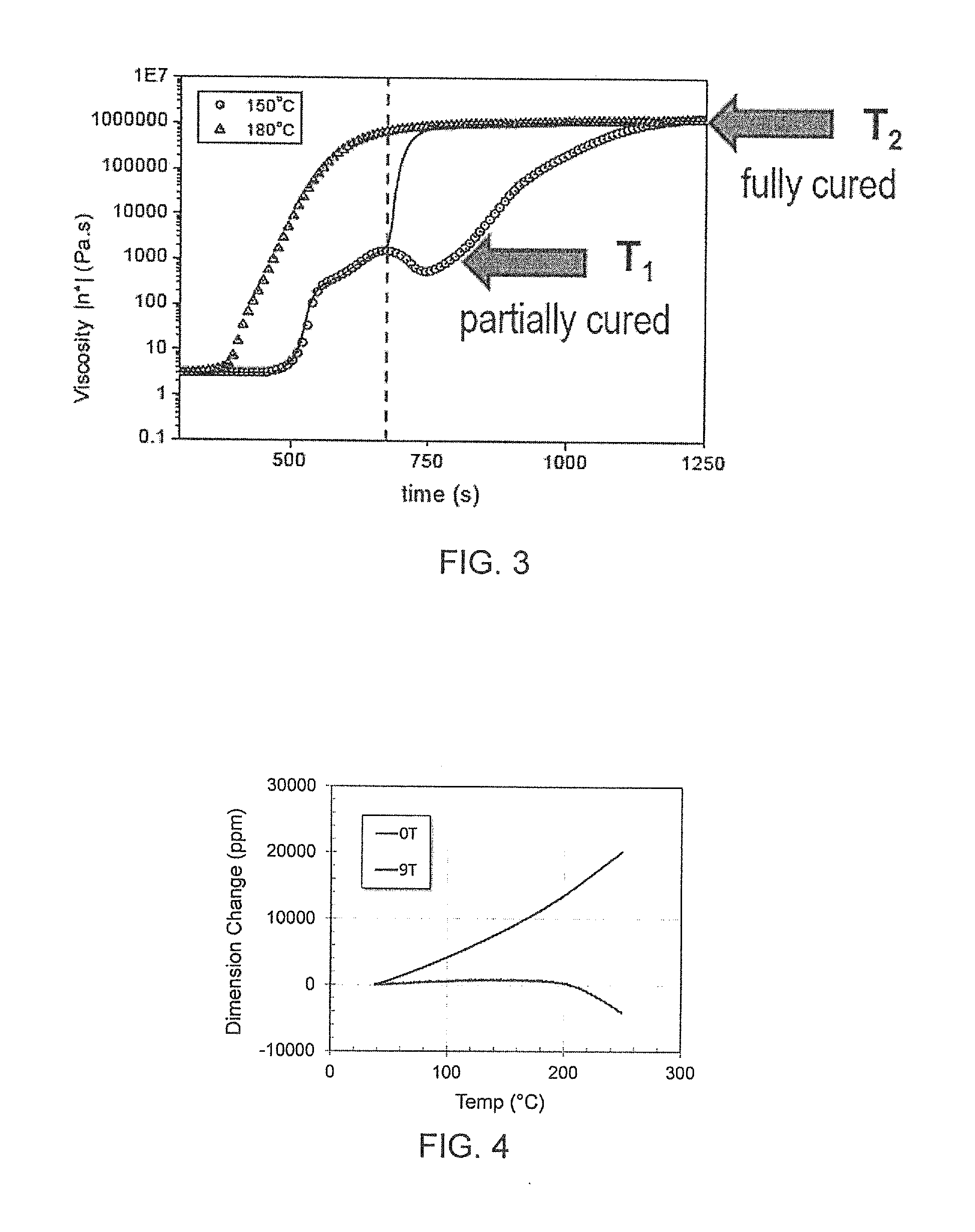
ActiveUS20150291833A1Improve bindingHigh mechanical strengthAdditive manufacturing apparatusElectric discharge heatingEpoxyCross-link
Methods and compositions for additive manufacturing that include reactive or thermosetting polymers, such as urethanes and epoxies. The polymers are melted, partially cross-linked prior to the depositing, deposited to form a component object, solidified, and fully cross-linked. These polymers form networks of chemical bonds that span the deposited layers. Application of a directional electromagnetic field can be applied to aromatic polymers after deposition to align the polymers for improved bonding between the deposited layers.
Owner:UT BATTELLE LLC
Software componentization for building a software product
ActiveUS7562346B2Easy to createLess laborLink editingProgram control using stored programsComponent Object ModelOperational system
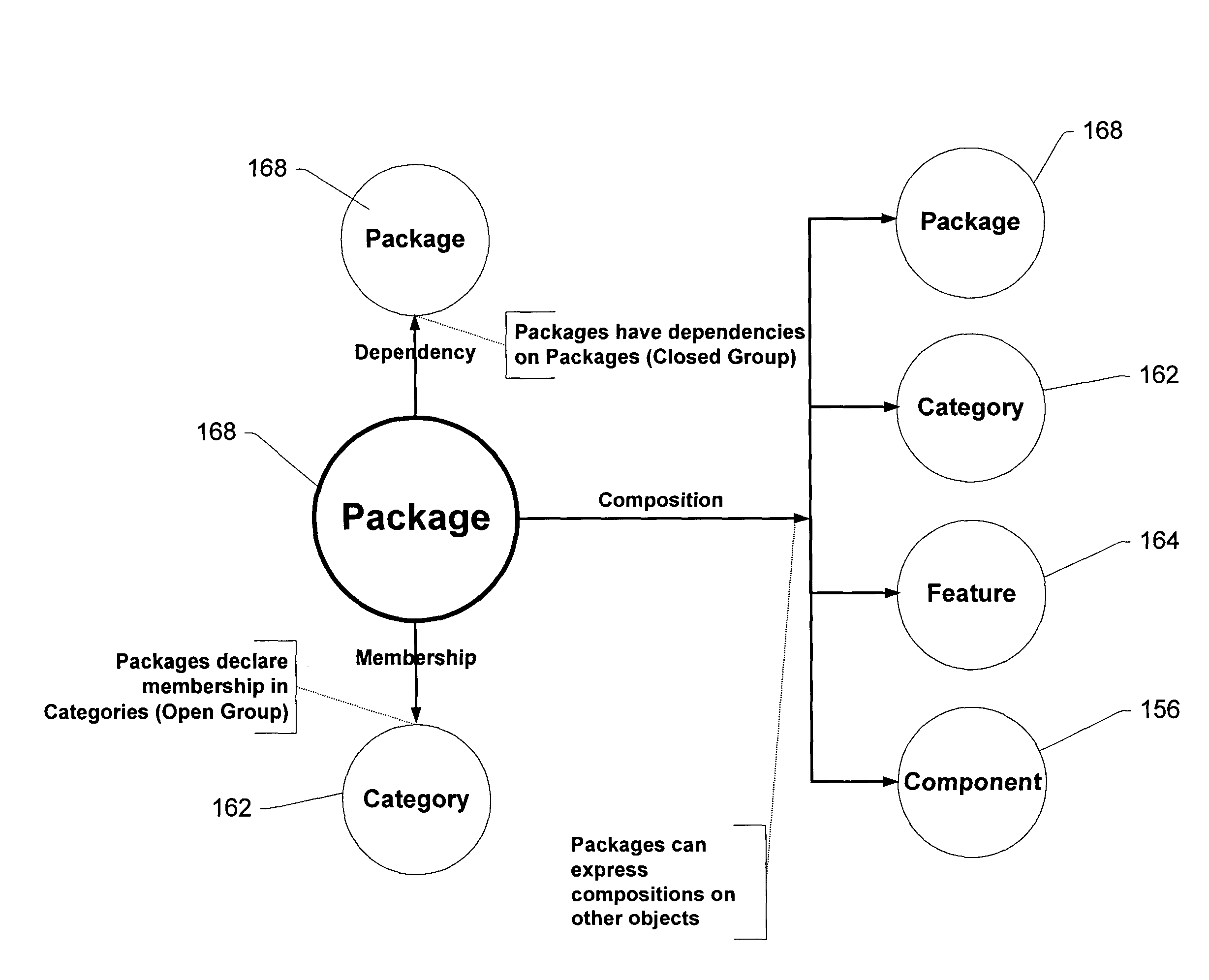
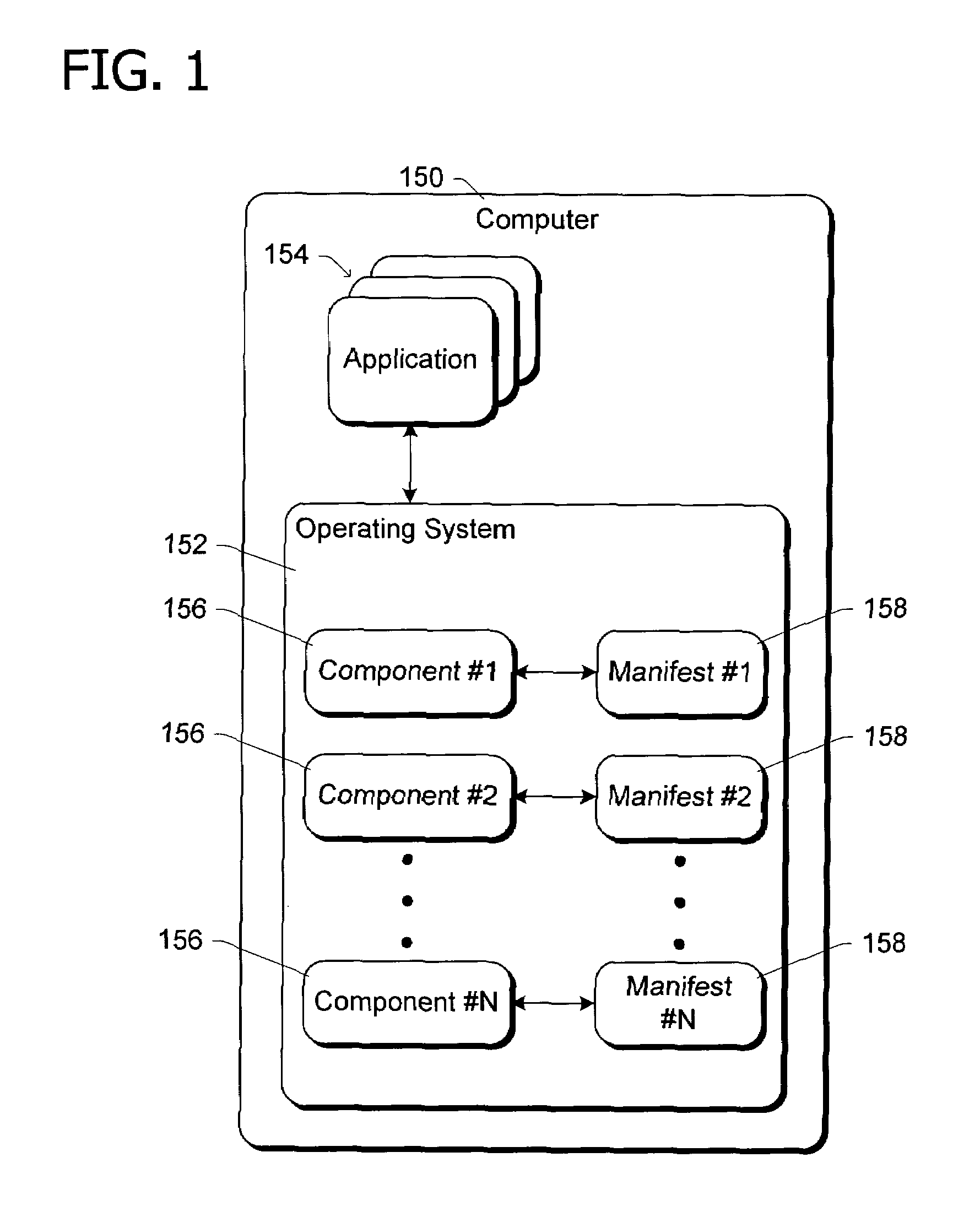
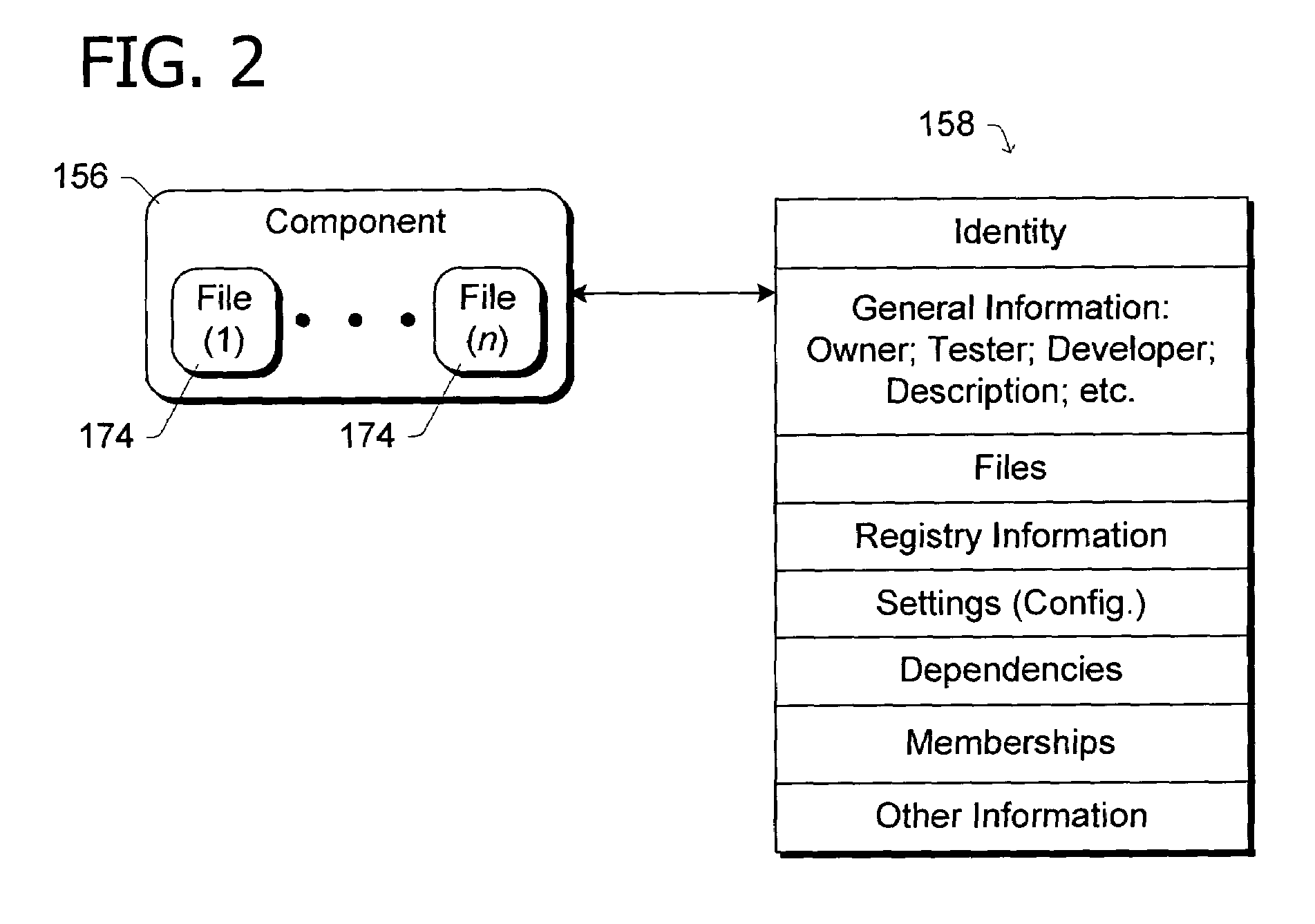
A componentization schema representing files from which an operating system or other software product is built. According to the schema, a component object represents one or more of the files. The component object has a manifest that identifies the component and specifies any dependencies between the component and other objects. Grouping objects according to the dependencies specified in manifests permits building the software product. A feature object defined by at least one component object represents a feature of the software product and a product object defined by at least one feature object represents the software product.
Owner:MICROSOFT TECH LICENSING LLC
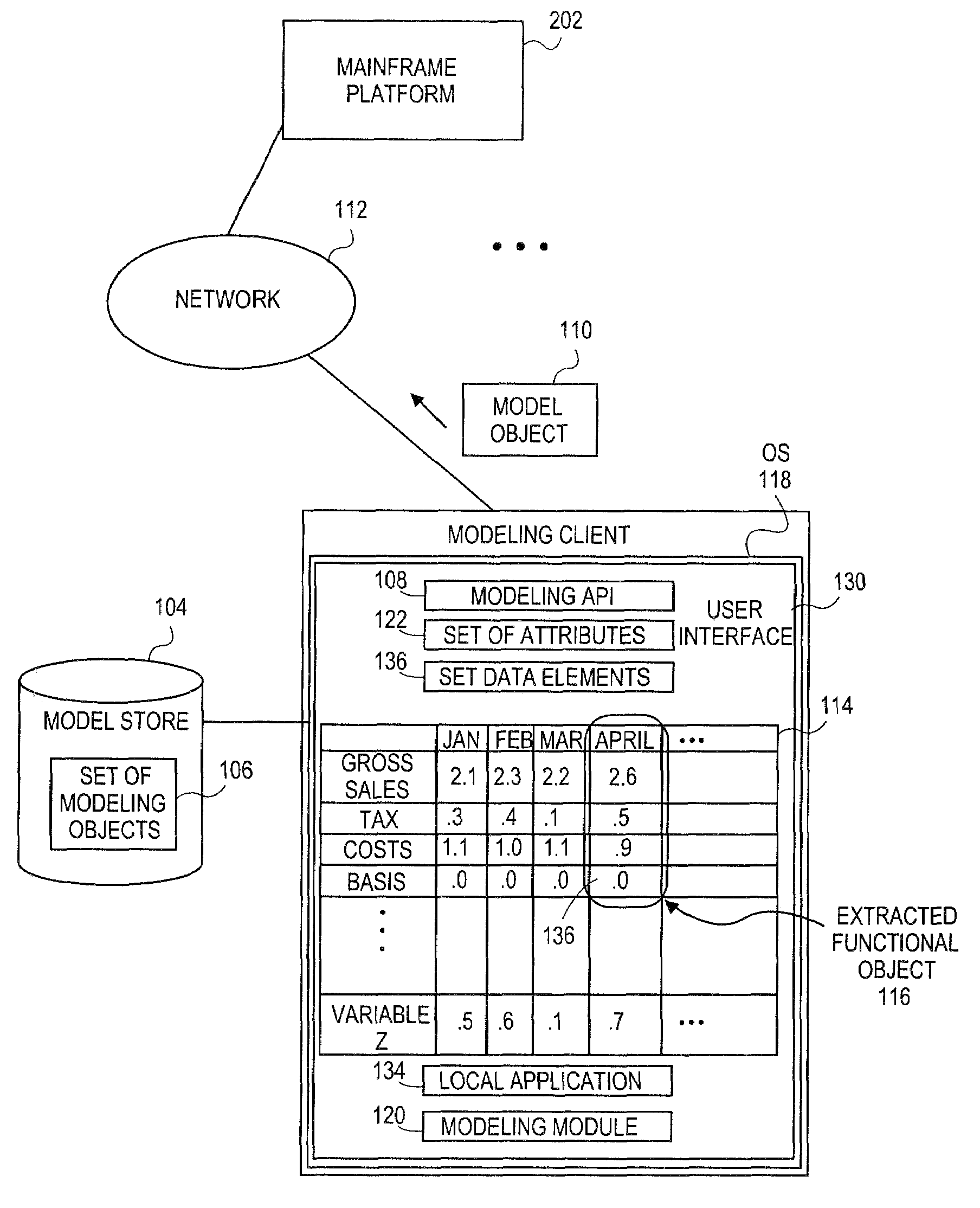
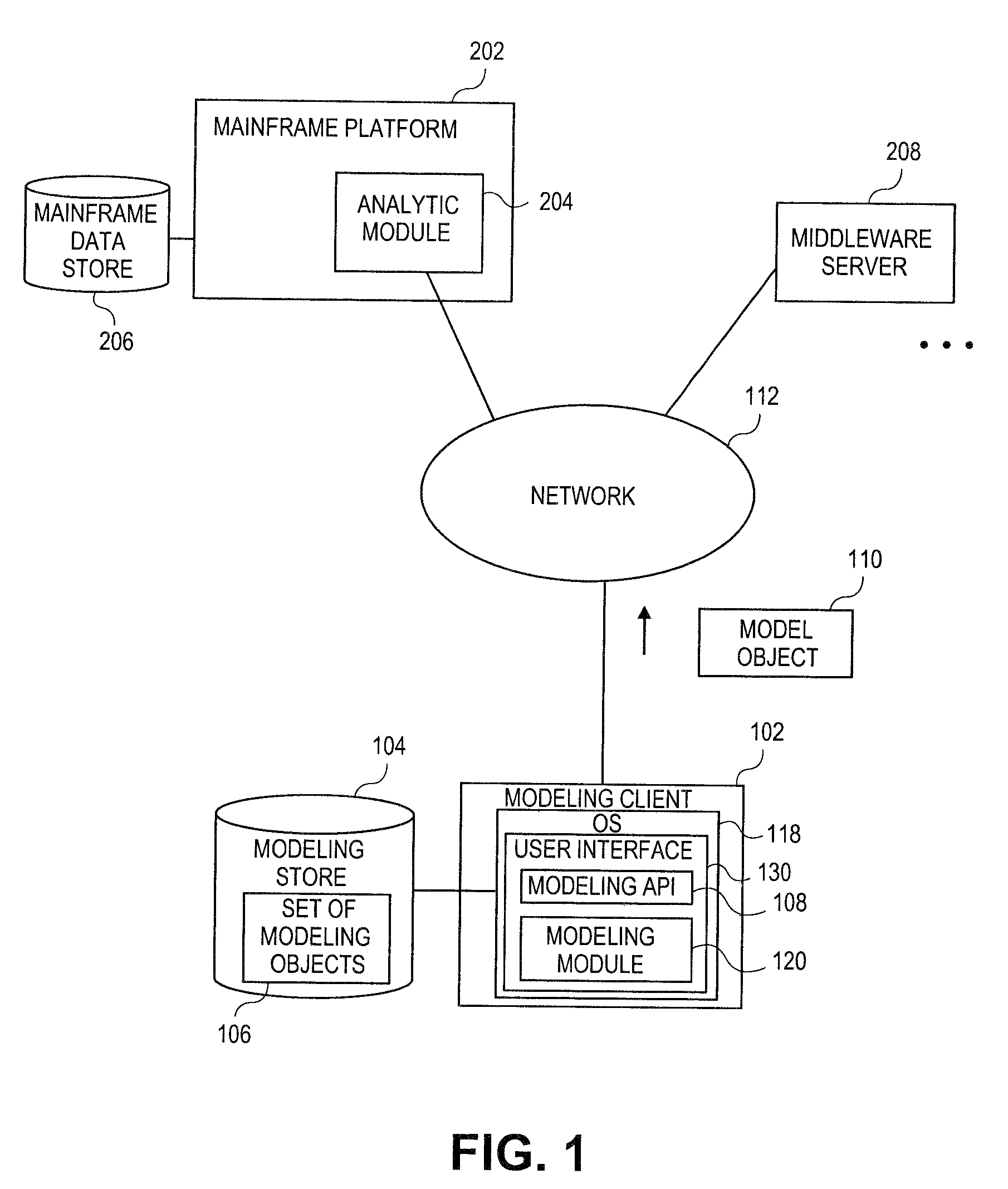
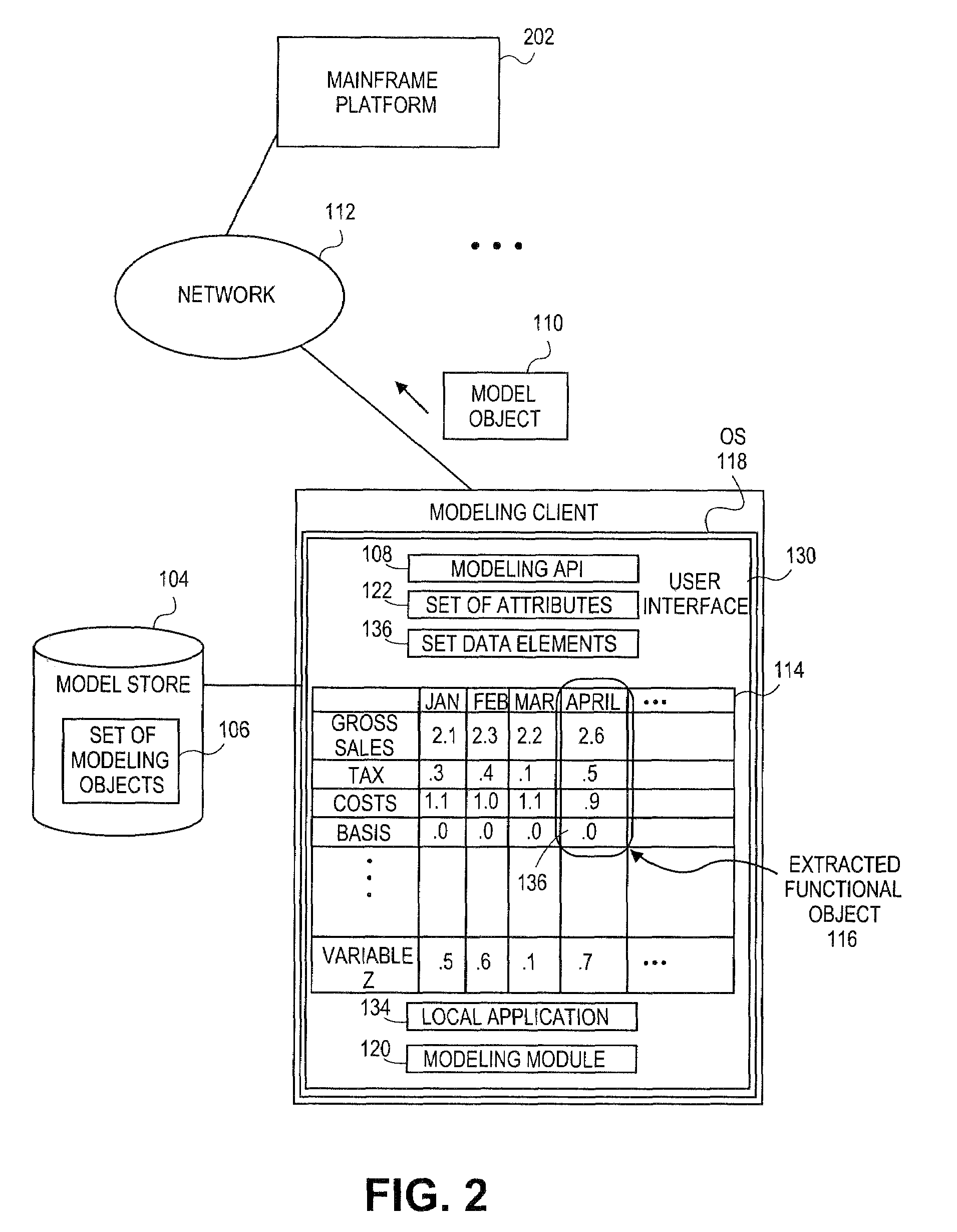
Systems and methods for object-based modeling using composite model object having independently updatable component objects
Embodiments relate to systems and methods for object-based modeling using a composite model object having independently updatable component objects. A modeling client can host modeling logic and an application programming interface (API) to create, access, manipulate, and import / export modeling objects used in modeling applications, such as engineering, medical, financial, and other modeling platforms. In aspects, the source data accepted into the modeling client can include consumer or business-level applications, whose spreadsheet, database or other content can be extracted and encapsulated in extensible markup language (XML) or other object-oriented format. Various model objects can be extracted from source data, and aggregated into a composite model object encapsulating the underlying set of component model objects. In aspects, each of the component model objects can be accessed, updated, and stored independently of the other constituent objects. The modeling client can exchange composite or other modeling objects with external platforms on a programmatic basis.
Owner:RED HAT
Web based creation of printer instances on a workstation
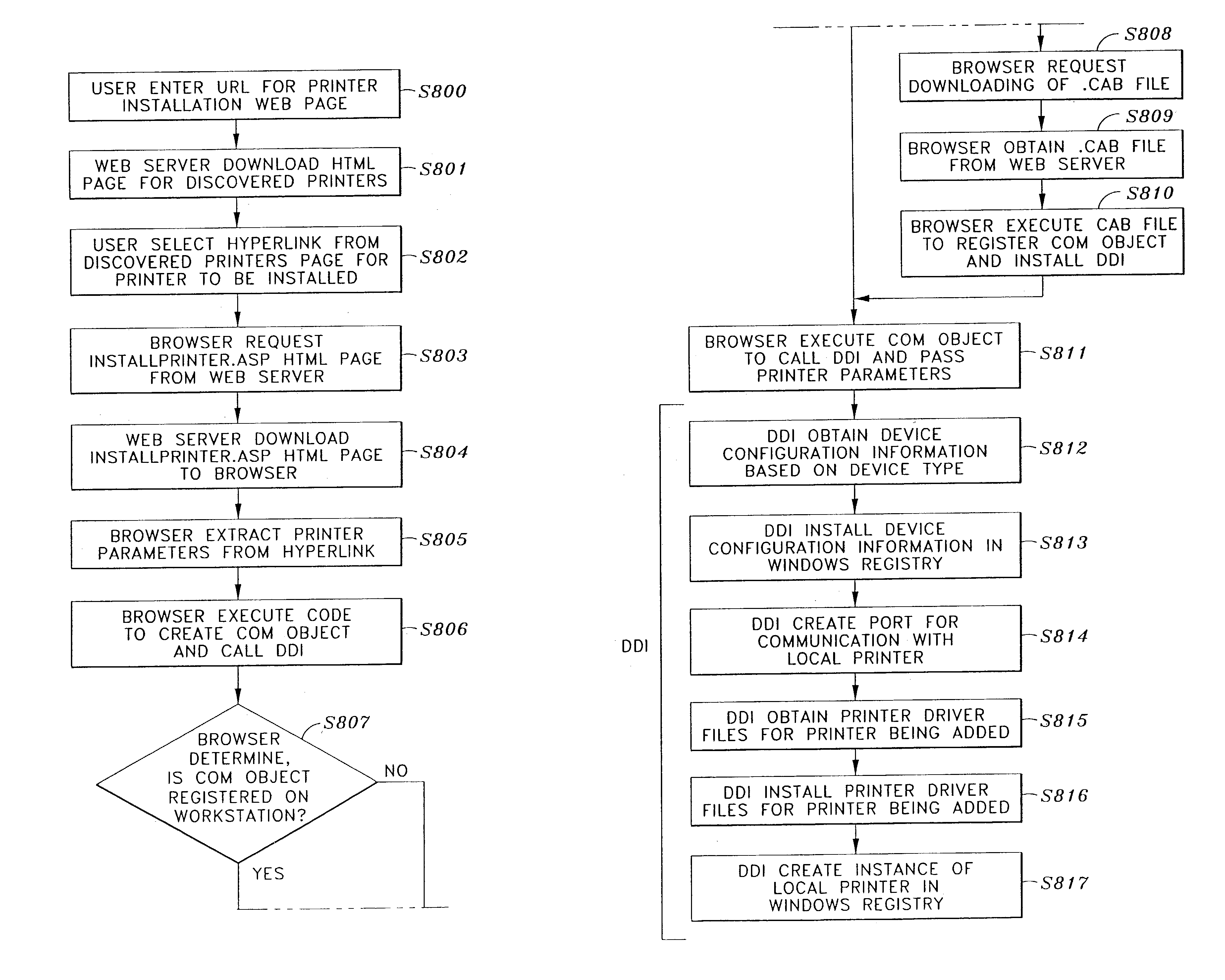
InactiveUS7213060B2Easy to createSimple processMultiple digital computer combinationsProgram loading/initiatingHyperlinkAuto-configuration
Web based installation of a printer in a printers folder on a workstation for peer-to-peer communication over a network between the workstation and the printer, by downloading a printers html page to the workstation, the printers html page providing hyperlinks of printers that can be added to the workstation, selecting a hyperlink for a printer to be added to the workstation, in response to the selecting step, extracting identification information of the selected printer from the selected hyperlink and executing a component object to install the printer, wherein, the component object calls a function that automatically obtains printer configuration information and print driver information based at least in part on the extracted identification information, automatically configures the printer and installs a print driver based on the obtained printer configuration information and print driver information, and creates a locally managed instance of the printer on the workstation. In a case where the component object is not installed on the workstation, an executable file (CAB) that includes the component object and the function (DDI) is downloaded such that, when the CAB file is executed, the DDI is installed and the component object is executed.
Owner:CANON KK
Framework for detecting a structured handwritten object
ActiveUS20070140566A1Well formedCharacter and pattern recognitionSpecial data processing applicationsPattern recognitionDocument preparation
Computer-readable media having computer-executable instructions and apparatuses detect a structured handwritten object is detected in a handwritten document. A primitive structure, which is associated with a set of component objects, is formed. A candidate handwritten object is identified by detecting a corresponding logical structure. A classifier for the candidate handwritten object is determined. Consequently, the candidate handwritten object is validated from the classifier.
Owner:MICROSOFT TECH LICENSING LLC
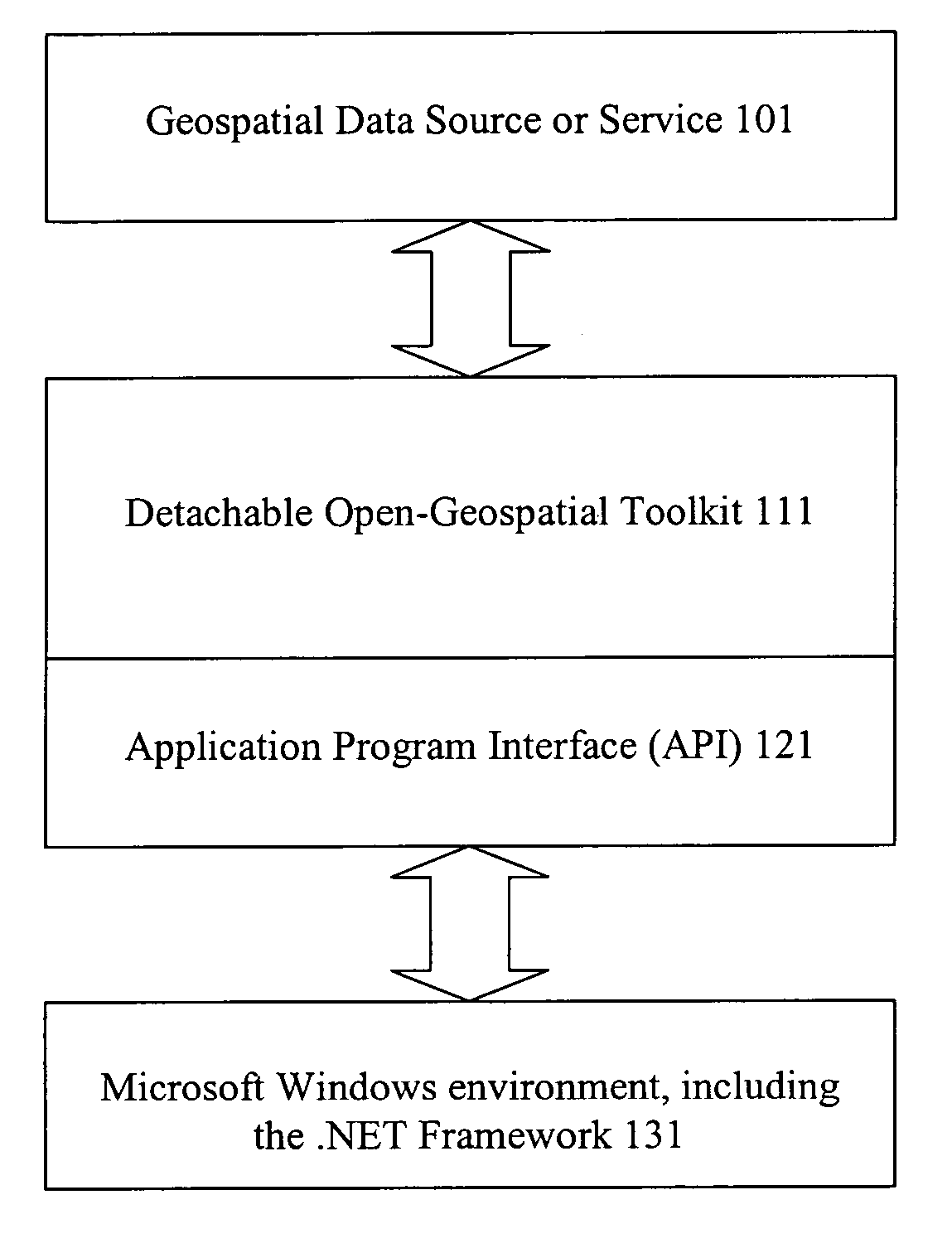
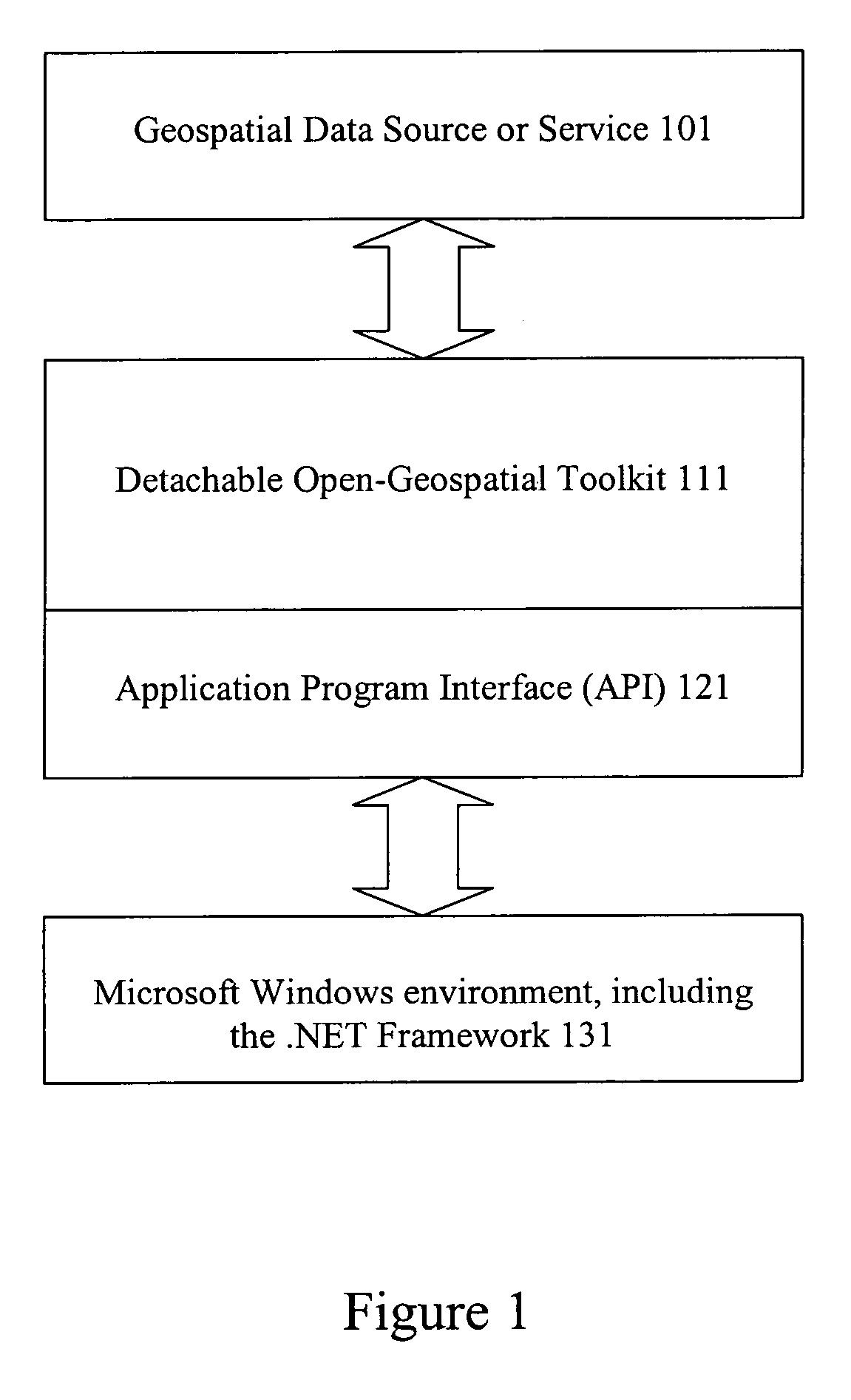
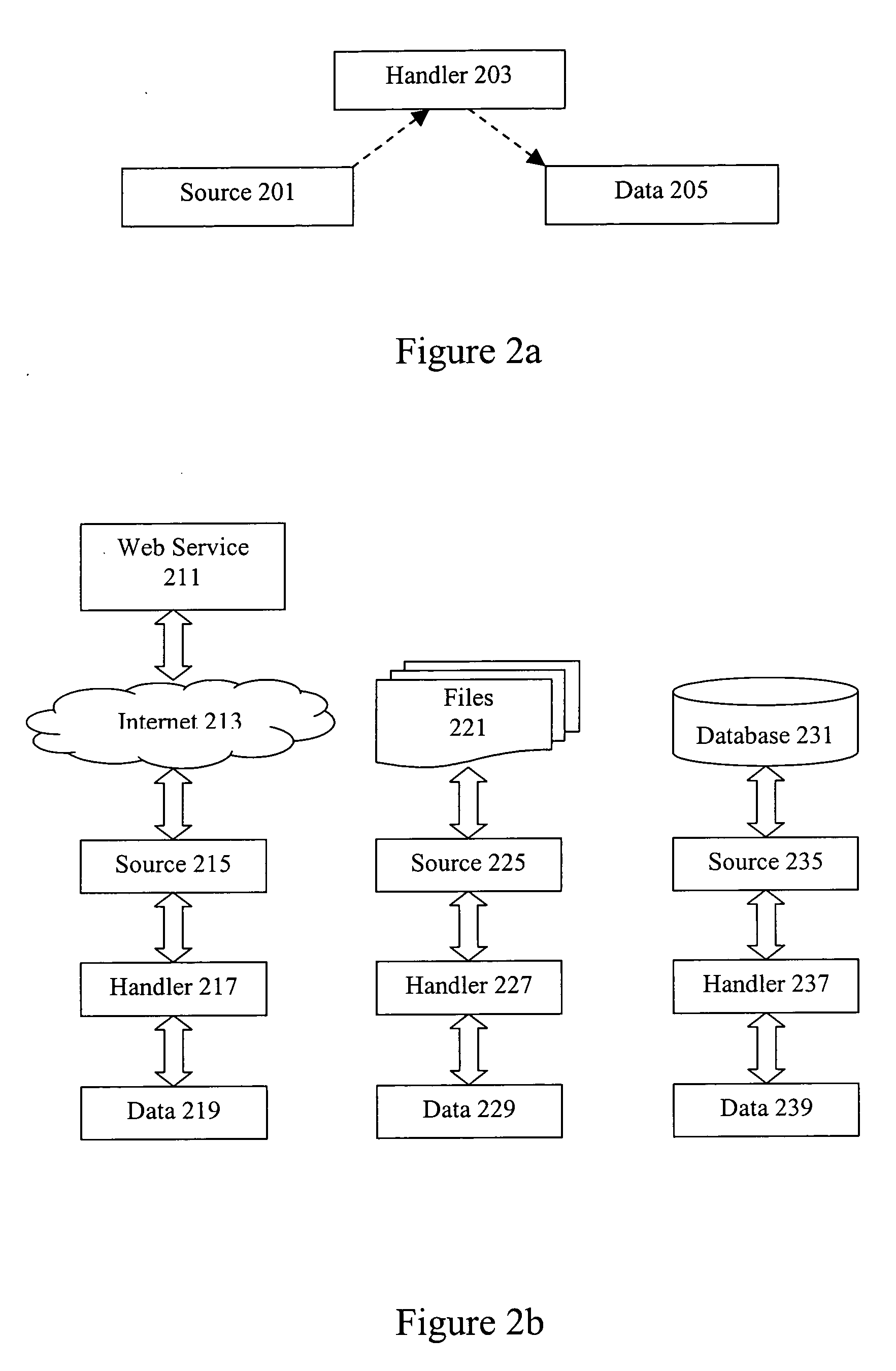
Methods and apparatus for accessing geospatial information
InactiveUS20060242111A1Facilitates open-geospatial developmentGeographical information databasesSpecial data processing applications.NET FrameworkComputer science
Methods and apparatus are provided for accessing geospatial information. A geospatial toolkit including source, handler, and data modules is configured to access geospatial data from a variety of sources, parse the geospatial data, and provide geospatial data in a unified format. Parameters including source, layer information, boundaries, query filters, etc. are set to allow retrieval of diverse geospatial data from different sources while providing a unified presentation on a system interface. The geospatial toolkit can be implemented in a framework such as the Component Object Module (COM) or .NET framework.
Owner:CARBON PROJECT
Method and device for XML document analysis
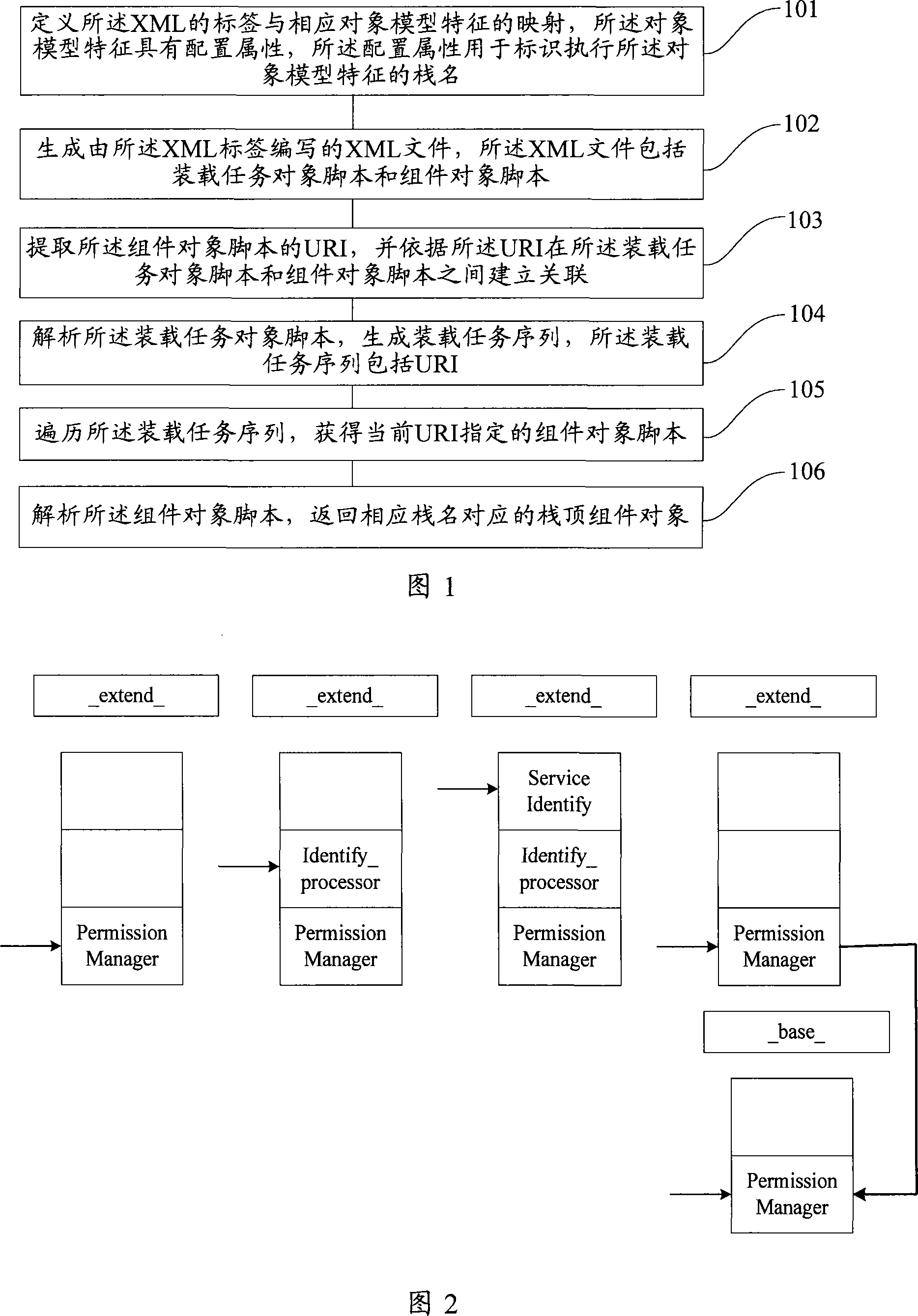
ActiveCN101221556ASimplify development workSimplify workSpecial data processing applicationsWeb document analysisDocument analysis
The invention provides an analytic method for an XML file which comprises a label used to define the XML and a mapping of the corresponding object model feature. The object model feature has a configuration attribute, the configuration attribute is used to identify a stack name for executing the object model feature; an XML file compiled by the XML label is produced and comprises a loading task object script and an assembly object script; a URI of the assembly object script is extracted, a correlation is established between the loading task object script and the assembly object script according to the URI; the loading task object script is analyzed to produce a loading task sequence, the loading task sequence comprises the URI; the loading task sequence is searched to obtain the assembly object script appointed by the current URI; the assembly object script is analyzed to return to a stack top assembly object corresponding to the corresponding stack name. The invention can simply and effectively realize the configuration and analysis of the XML file under the premise of saving system resources.
Owner:CHINA CONSTRUCTION BANK
Method and system for determining a volume of an object from two-dimensional images
The invention provides a method and a computer program stored in a tangible medium for automatically determining a volume of three-dimensional objects represented in two-dimensional images, by acquiring at two least two-dimensional digitized images, by analyzing the two-dimensional images to identify reference points and geometric patterns, by determining distances between the reference points and the component objects utilizing reference data provided for the three-dimensional object, and by calculating a volume for the three-dimensional object.
Owner:UT BATTELLE LLC
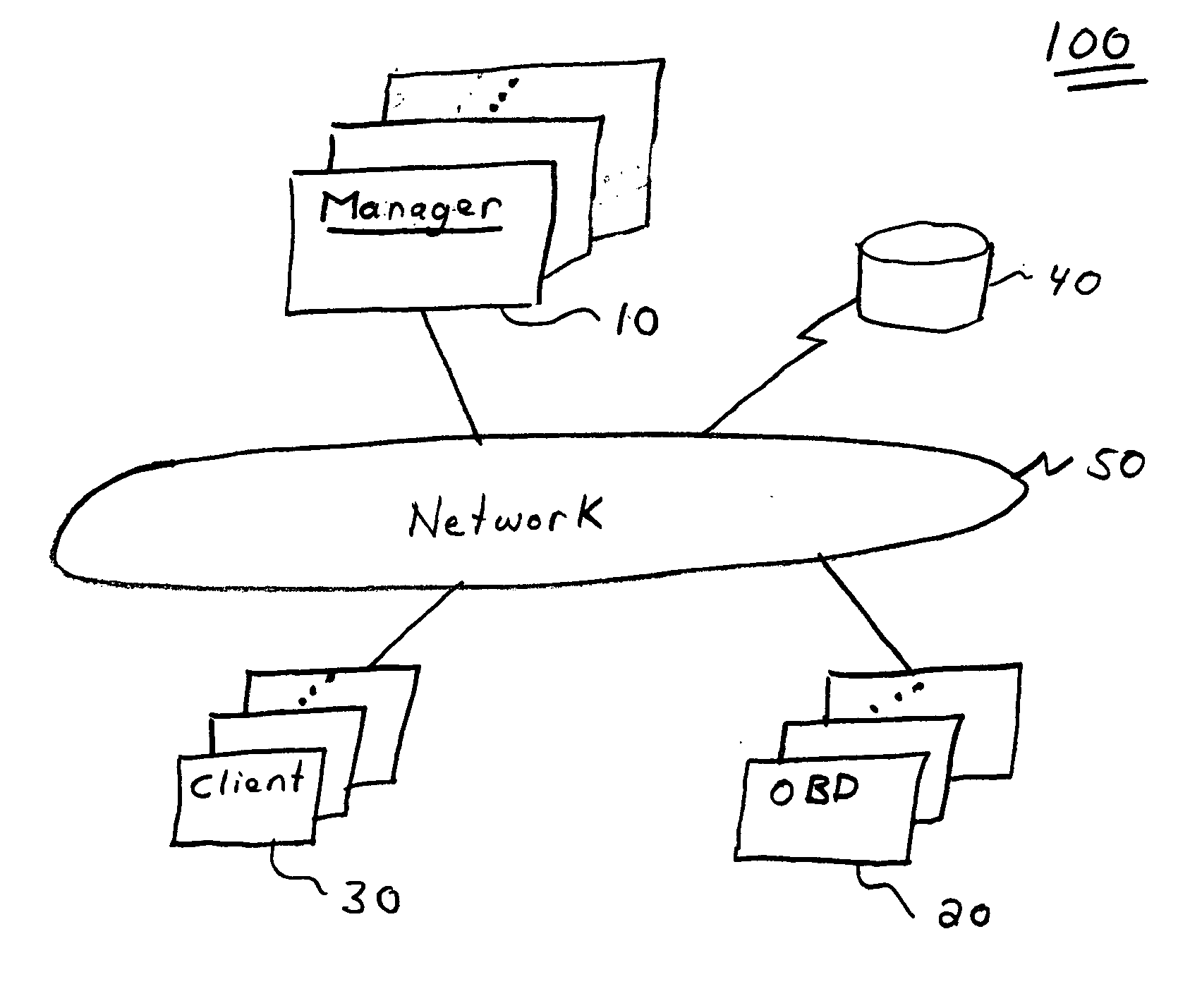
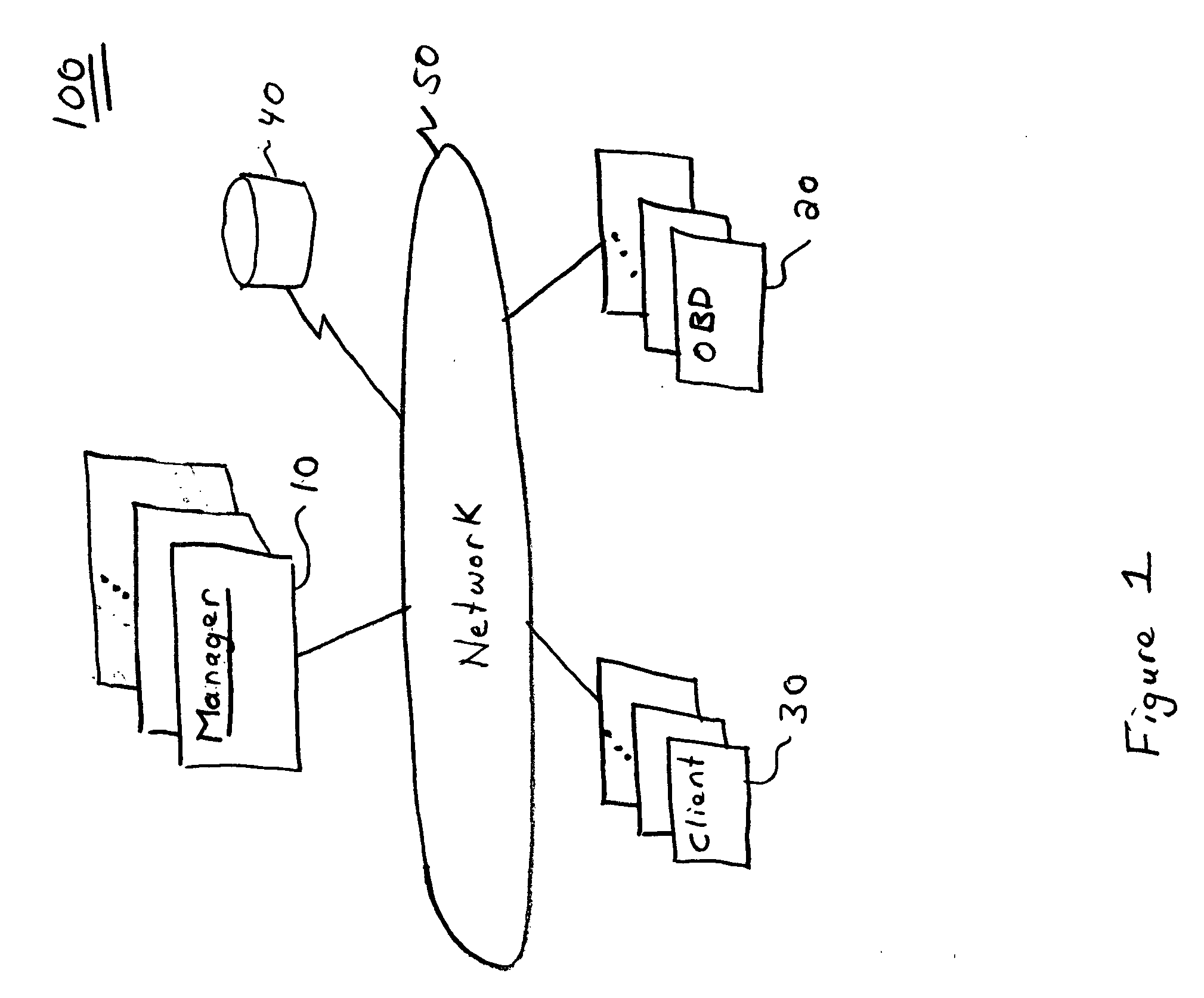
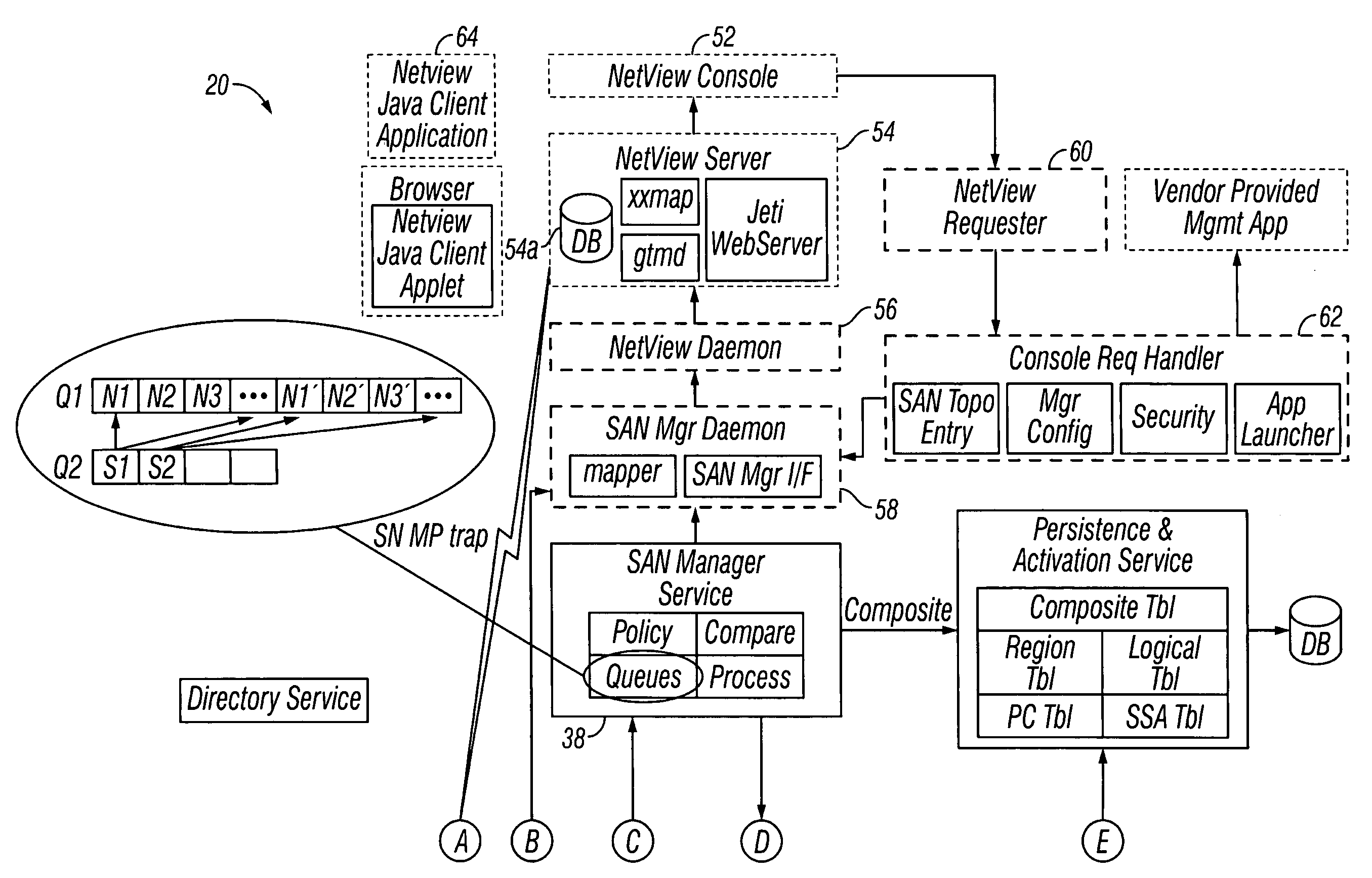
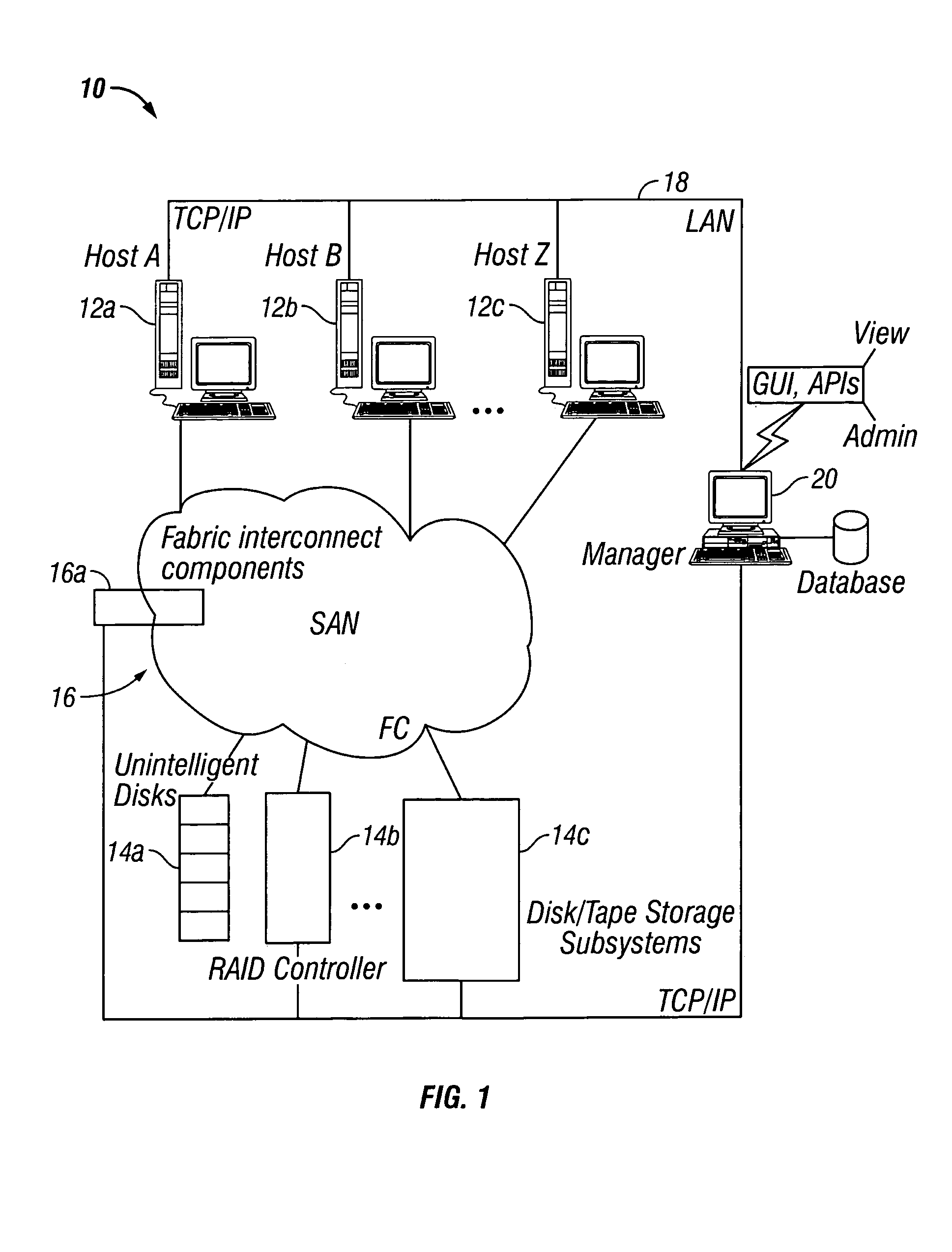
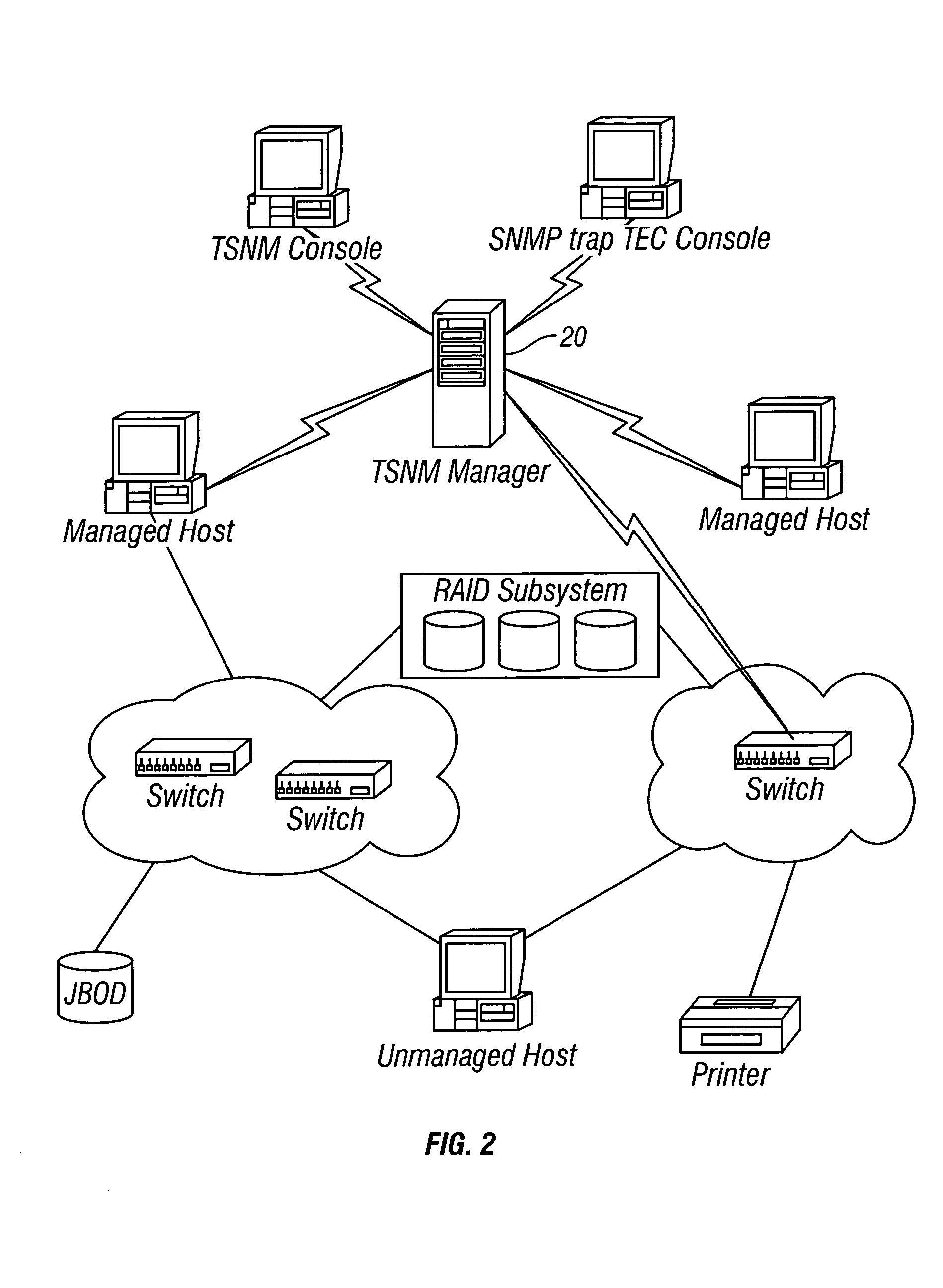
Storage area network methods and apparatus for validating data from multiple sources
InactiveUS7080140B2Easy accessWithout riskMultiple digital computer combinationsTransmissionDigital dataStorage area network
A storage area network has a plurality of components, such as host digital data processors and storage devices. A store, e.g., resident on a manager digital data processor, contains one or more objects (or other data constructs) that represent information gathered from the hosts, i.e., scans. Further such objects represent components in the SAN and / or relationships between and among those components. A discover engine or other functionality executing on the manager digital data processor validates information gathered from a selected host concerning a selected component or relationship based on a scan object, if any, that is associated with a component object or relationship object, respectively, corresponding to the selected component or relationship.
Owner:IBM CORP
Remote component and connection architecture
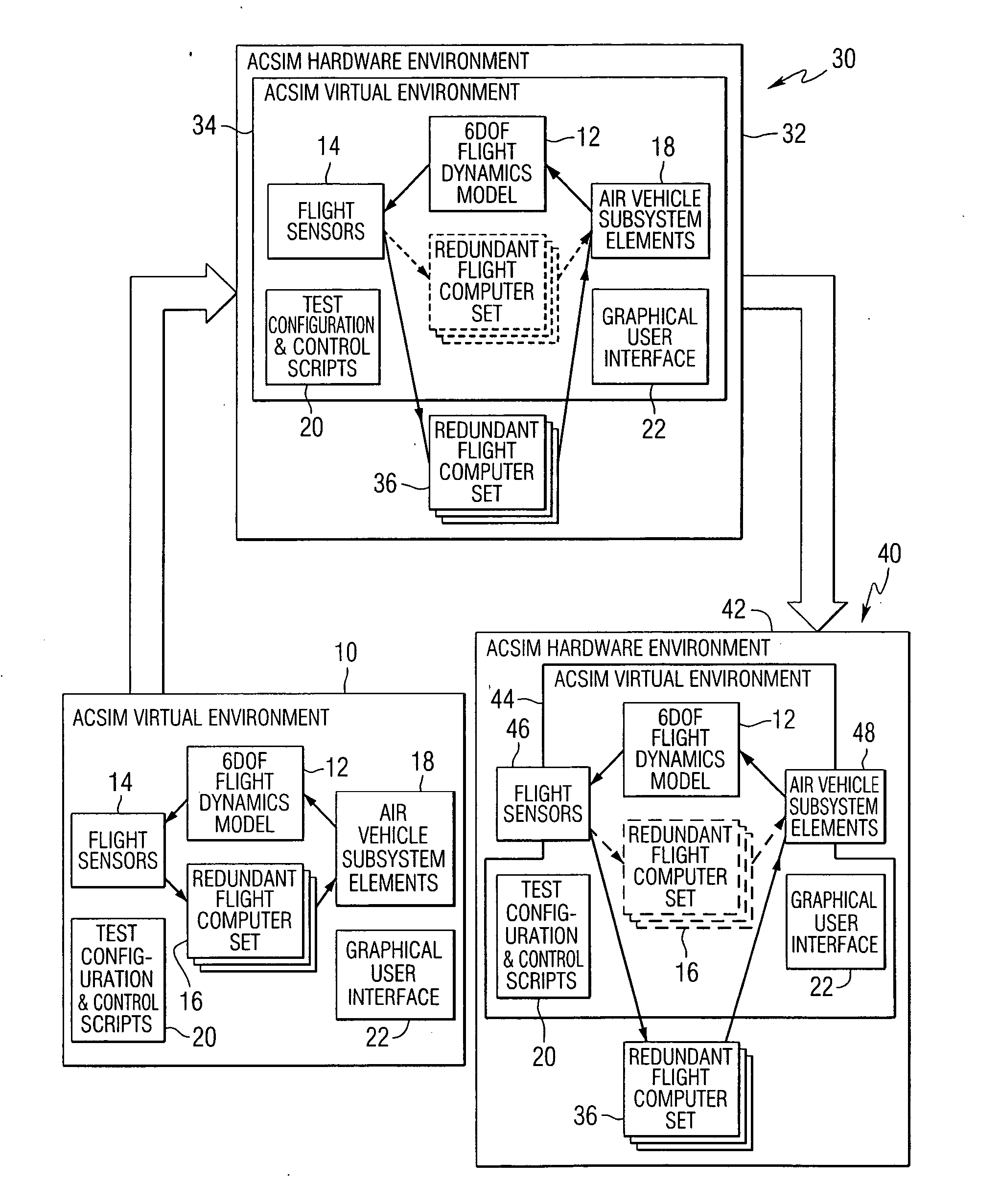
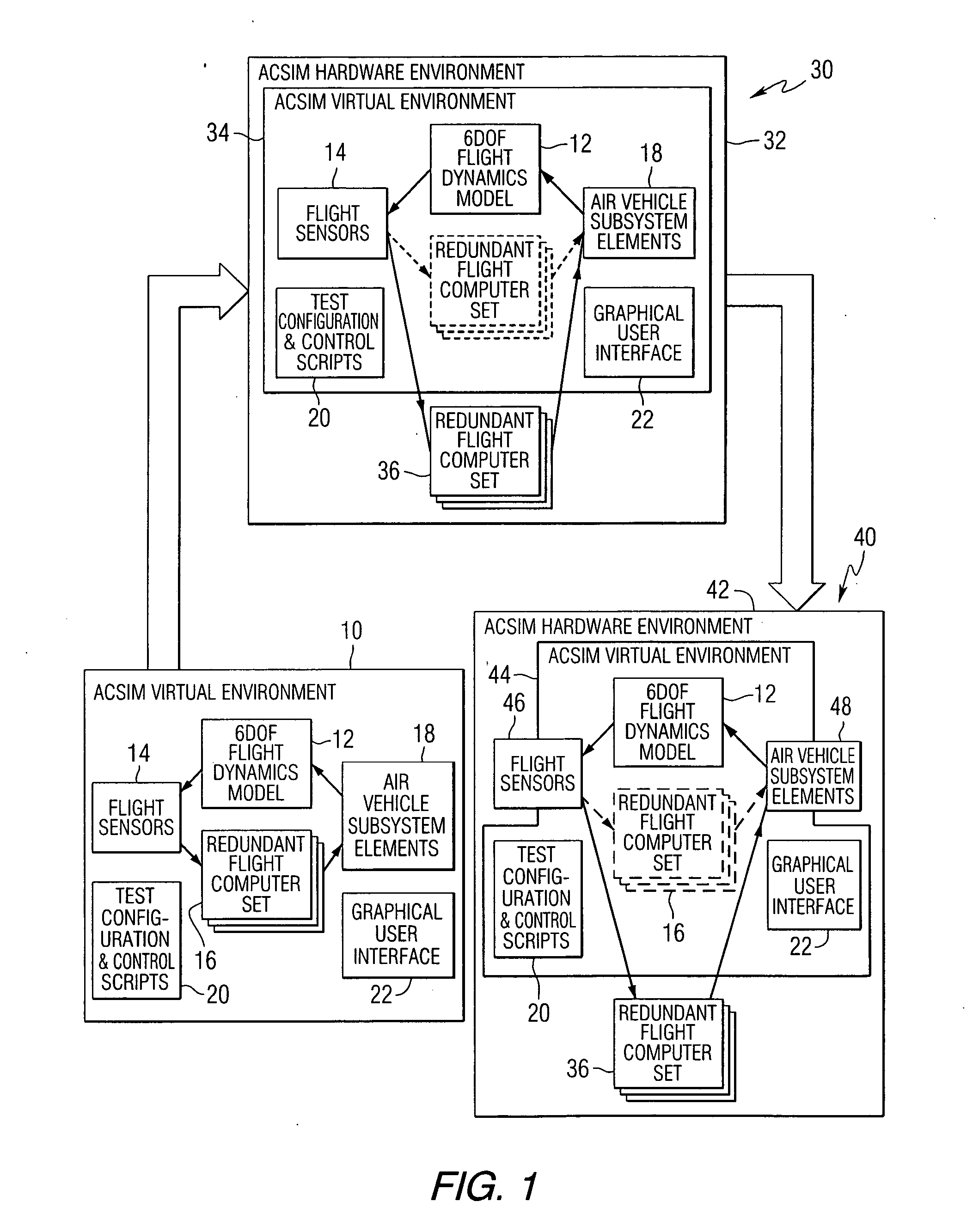
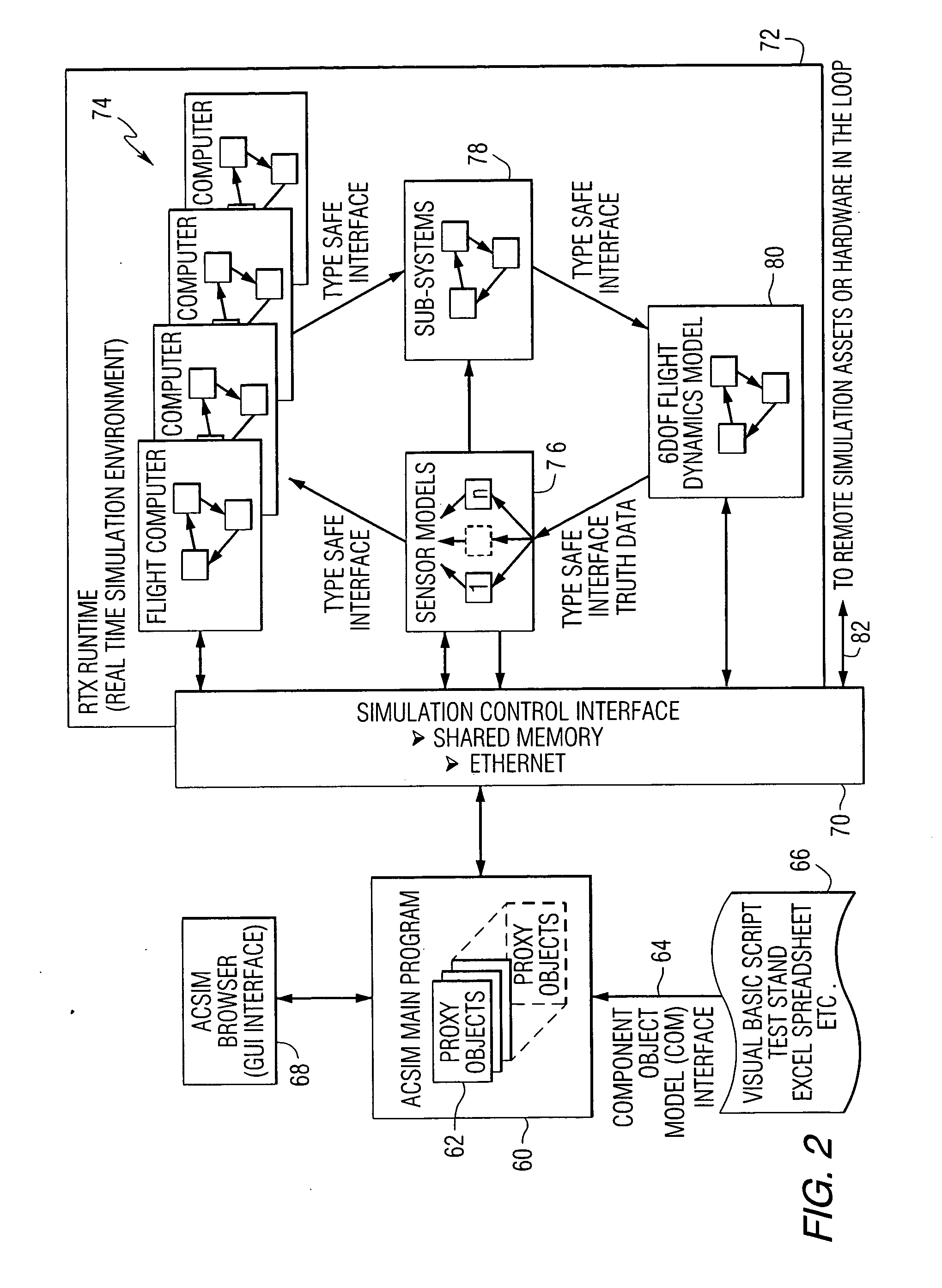
ActiveUS20060174221A1Software reuseSpecific program execution arrangementsSoftware engineeringSoftware development
A method of developing software comprises the steps of defining a plurality of component objects for receiving input data and producing output data, defining a plurality of connection objects for passing data between the component objects, and executing an initialization script to define a behavioral model for the system by defining relationships between the component objects and the connection objects. A software development system that performs the method is also provided.
Owner:NORTHROP GRUMMAN SYST CORP
Method and system for determining a volume of an object from two-dimensional images
The invention provides a method and a computer program stored in a tangible medium for automatically determining a volume of three-dimensional objects represented in two-dimensional images, by acquiring at two least two-dimensional digitized images, by analyzing the two-dimensional images to identify reference points and geometric patterns, by determining distances between the reference points and the component objects utilizing reference data provided for the three-dimensional object, and by calculating a volume for the three-dimensional object.
Owner:UT BATTELLE LLC
Method and system for assembling and utilizing components in component object systems
InactiveUS6957417B2Easy to assembleEasy maintenanceCargo handling apparatusDrilling rodsComponent Object ModelObject based
A design tool for assembling component objects to form an object-based computer system application includes a declarative user input interface mechanism and a design engine. The declarative user input interface mechanism provides an input structure for the input of user declarations specifying operative interactions between component objects. The design engine automatically generates, in response to input user declarations, an application design definition modeling an application infrastructure for managing component object interactions. The design engine automatically generates, in response to input user declarations, a match between an application view field definition and a parameter of an associated component object operations. A runtime tool includes an application engine which is responsive to an application design definition and is operative at runtime automatically to create application view instances from respective application view definitions for managing runtime component object interactions for the applications.
Owner:COMP ASSOC THINK INC
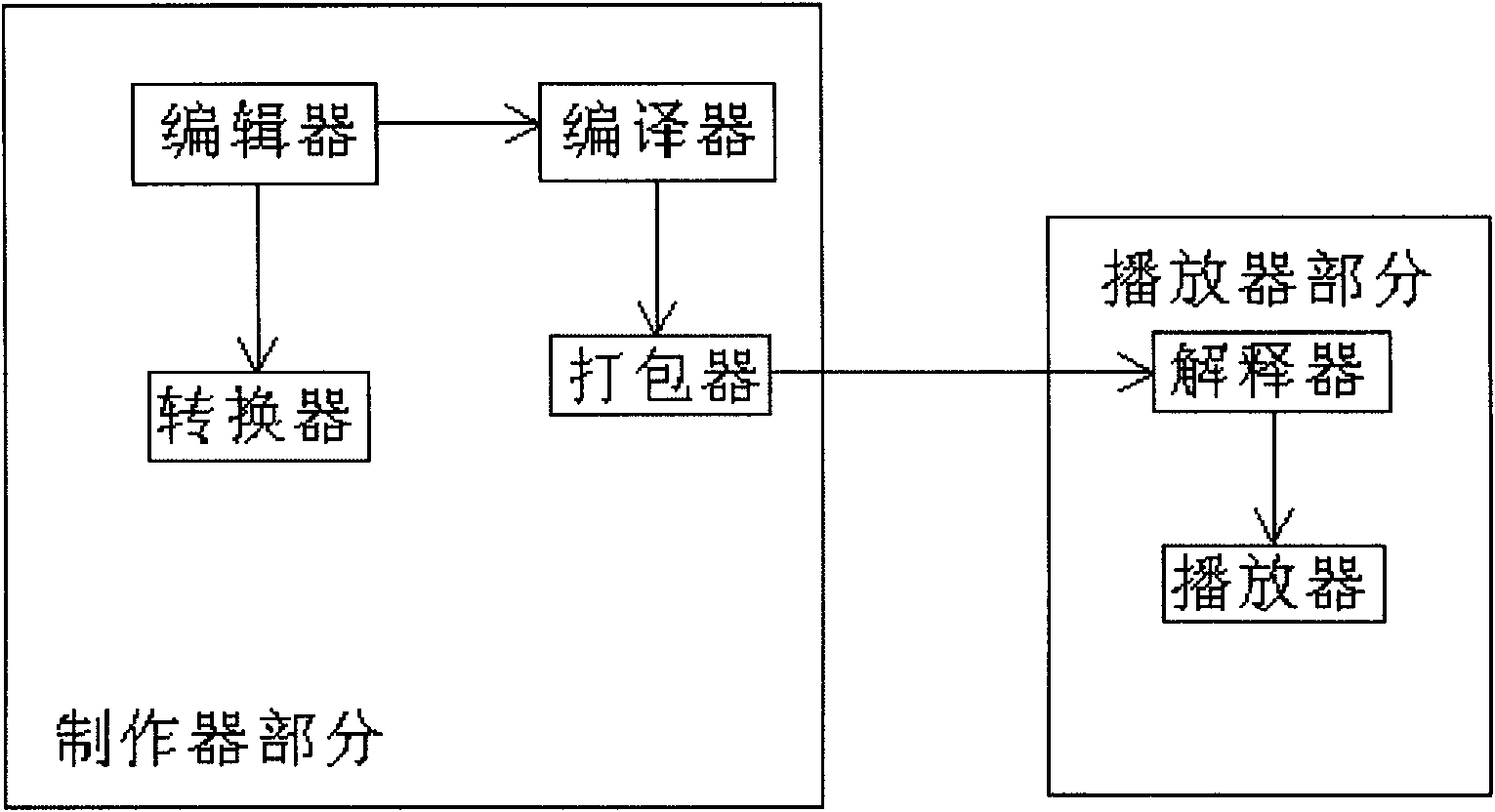
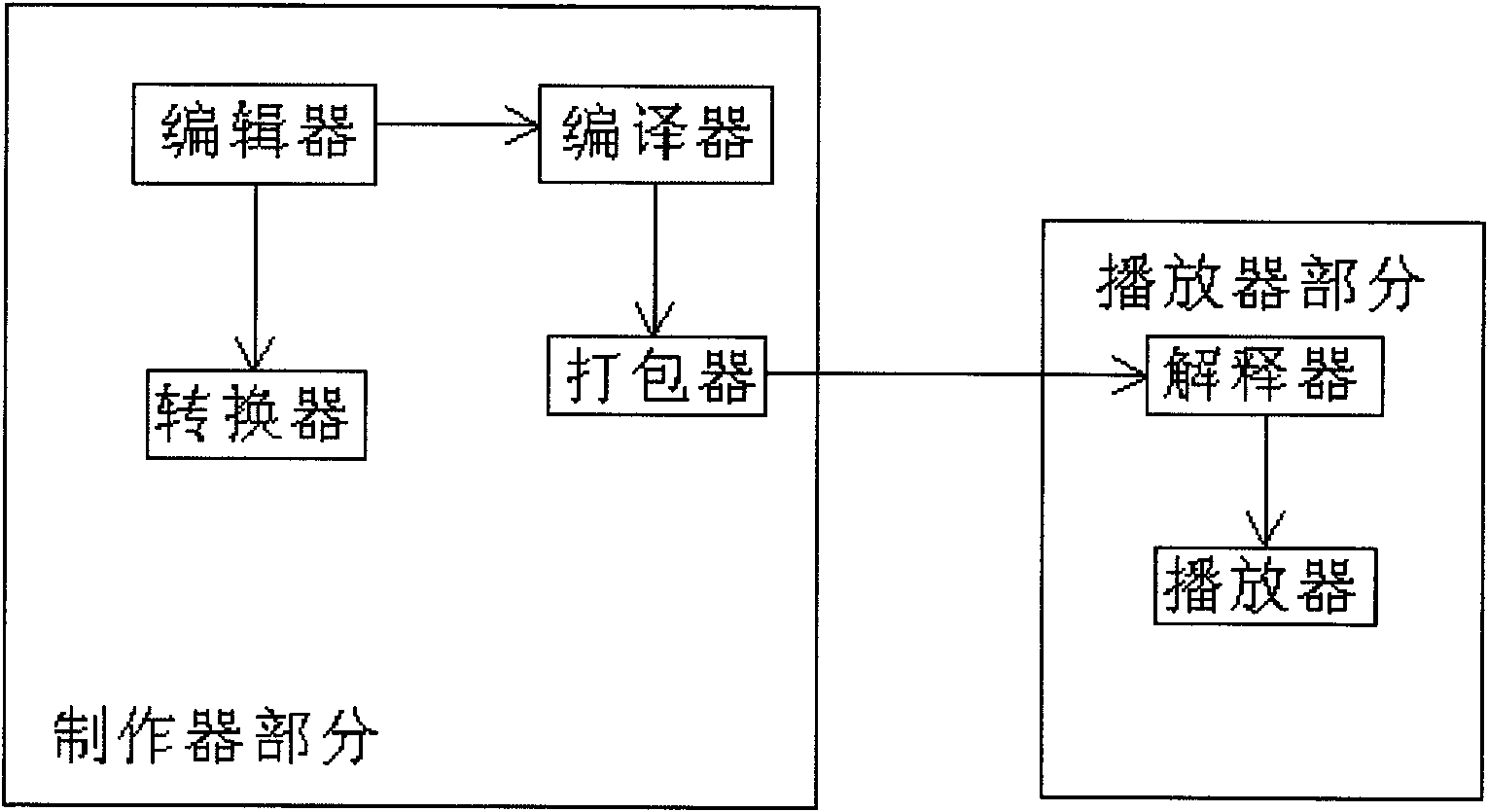
Logic cartoon platform system
InactiveCN101963899AEasy to makeSpecific program execution arrangementsComponent Object ModelAnimation
The invention discloses a logic cartoon platform system, which comprises a maker part and a player part. The maker part comprises an editor, a compiler and a packetizer, wherein the editor is used for importing an acquired and added material serving as a component into the editor, then processing and editing the component, and packaging the component into a component object; the compiler is used for compiling the component object into a vector; and the packetizer is used for packaging the vector into a project primary index file, then contacting the component object provided by the editor according to the project primary index file, and then classifying the file into a logic cartoon project file. The player part comprises an interpreter and a player, wherein the interpreter is used for interpreting functions of the component object, a corresponding event action and a logical relationship according to the project primary index file; and the player is used for restoring the component object, the corresponding event action and the logical relationship according to an interpretation result so as to run and play the logic cartoon. The logic cartoon platform system of the invention provides the function of making the logic cartoon, and can be used for making the logic cartoon, a puzzle game or a dynamic courseware.
Owner:HUAZHONG NORMAL UNIV
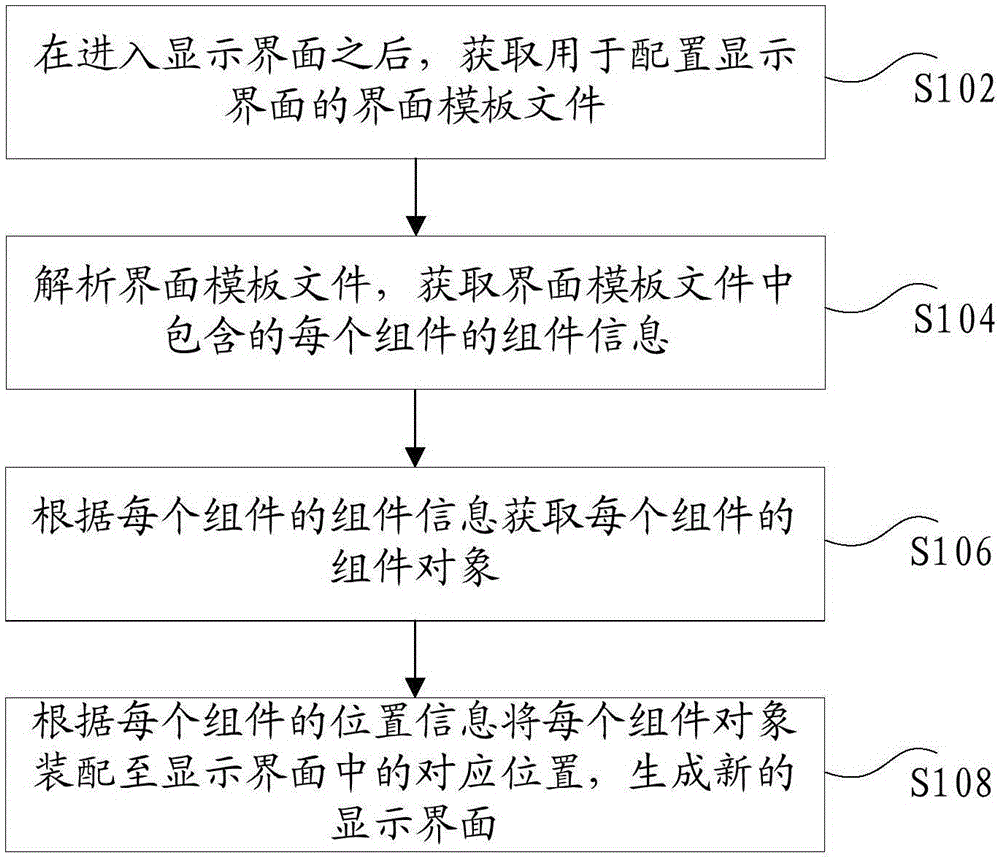
A display interface creating method and device
ActiveCN106406846AEasy to customize settingsTroubleshoot technical issues with frequent updatesSpecific program execution arrangementsSoftware engineeringComponent type
The invention provides a display interface creating method and device. The method comprises the steps of after entering a display interface, acquiring an interface template file used for configuring a display interface; analyzing the interface template file and acquiring the component information of each component contained in the interface template file, wherein the component information at least includes the component name, the component type, and the position information of the component in the display interface; acquiring a component object of each component according to the component information of each component; assembling each component object to a corresponding position in the display interface according to the position information of each component to generate a new display interface. The method and the device solve the technical problem that since a template used for controlling a display interface cannot be updated singly, a client is frequently updated because of the change of the display interface.
Owner:TENCENT TECH (SHENZHEN) CO LTD
System for the computed-aided design of technical devices
ActiveUS20100106466A1Simple and clear and individual productionSave inputGeometric CADComputation using non-denominational number representationComponent Object ModelComputer Aided Design
The invention concerns an apparatus and a computer software product for the conceptioneering, predesign and configuration of a machine object represented by an object data model. Component objects are stored in an object database, wherein a component object contains at least one parameter object. In addition the database contains functional objects. The modeling approach implemented by the separation according to the invention of component objects and functional objects permits a distinction to be drawn between constraints within a component object and constraints which exist between component objects. The former are embraced by the component objects themselves and the latter by the functional objects. That encapsulation has in particular the advantage that the modeling process can be substantially clearer. In addition encapsulation permits re-use of the component objects in various systems.
Owner:PACE AEROSPACE ENG & INFORMATION TECH
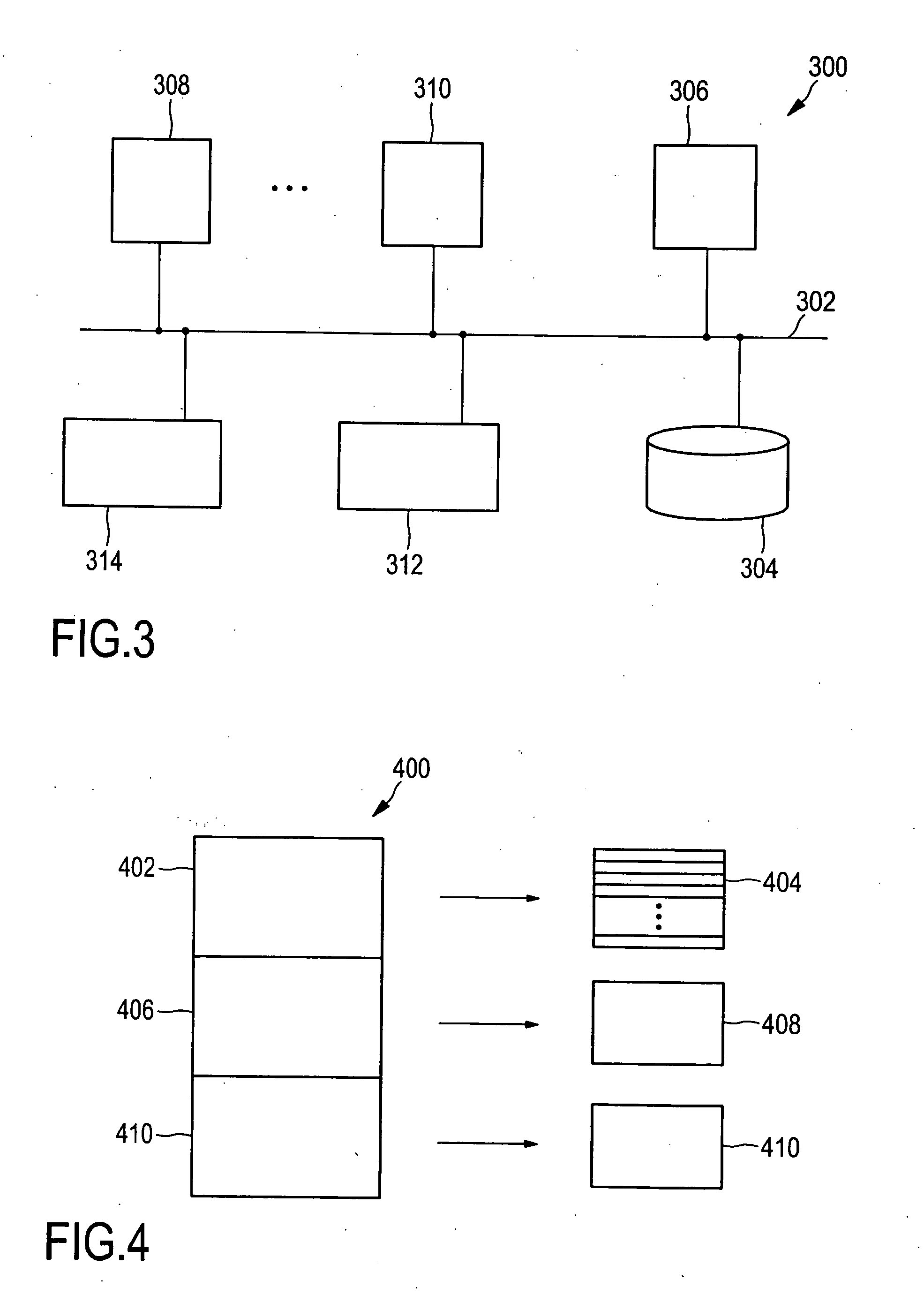
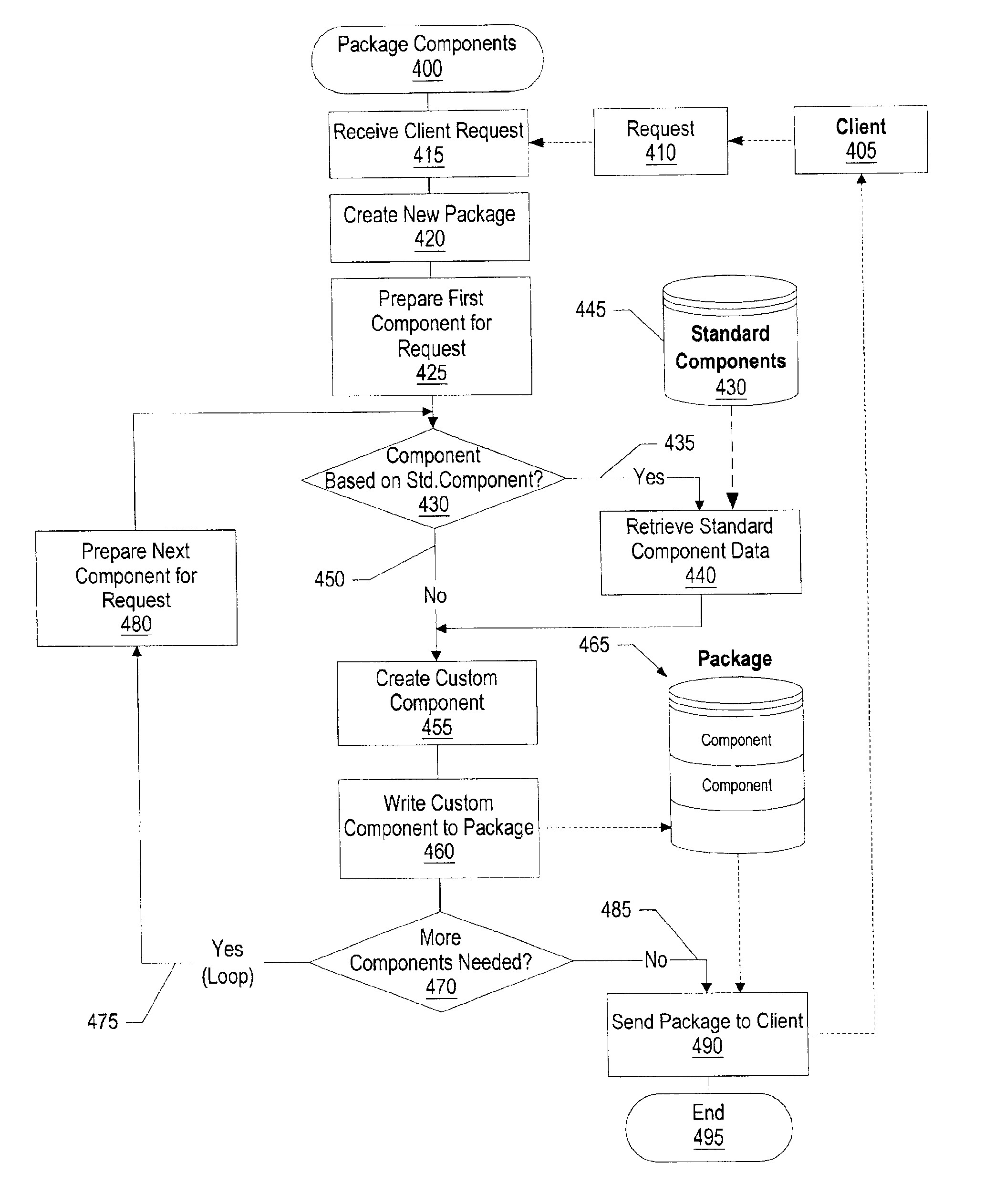
System and method for dynamic packaging of component objects
InactiveUS6948151B2Limited amountMultiple digital computer combinationsProgram loading/initiatingComponent Object ModelObject based
A system and method for dynamically packaging component objects. A server receives a request from a client. The server identifies one or more objects based on the request. The identified objects may be copied from the server's nonvolatile storage area, generated dynamically, or be a result of modifying objects stored on the server's nonvolatile storage area. The identified objects are written to a package file. The server downloads the package file to the client. A dialog may be sent to the client to determine whether the client wishes to download the package file. The package file is provided dynamically in response to the client's request. The package file may include objects that include generated code, such as Java tag handler files, Java tag extra info files, and Java tag library description information. Java definitions may be included with the package file to create a Java jar file.
Owner:INTELLECTUAL DISCOVERY INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com