Risk assessment method and apparatus for software system vulnerability
A software system and risk assessment technology, applied in the field of information security, can solve problems such as the inability to comprehensively assess the security risks of software systems, and achieve the effect of intuitive and accurate security risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
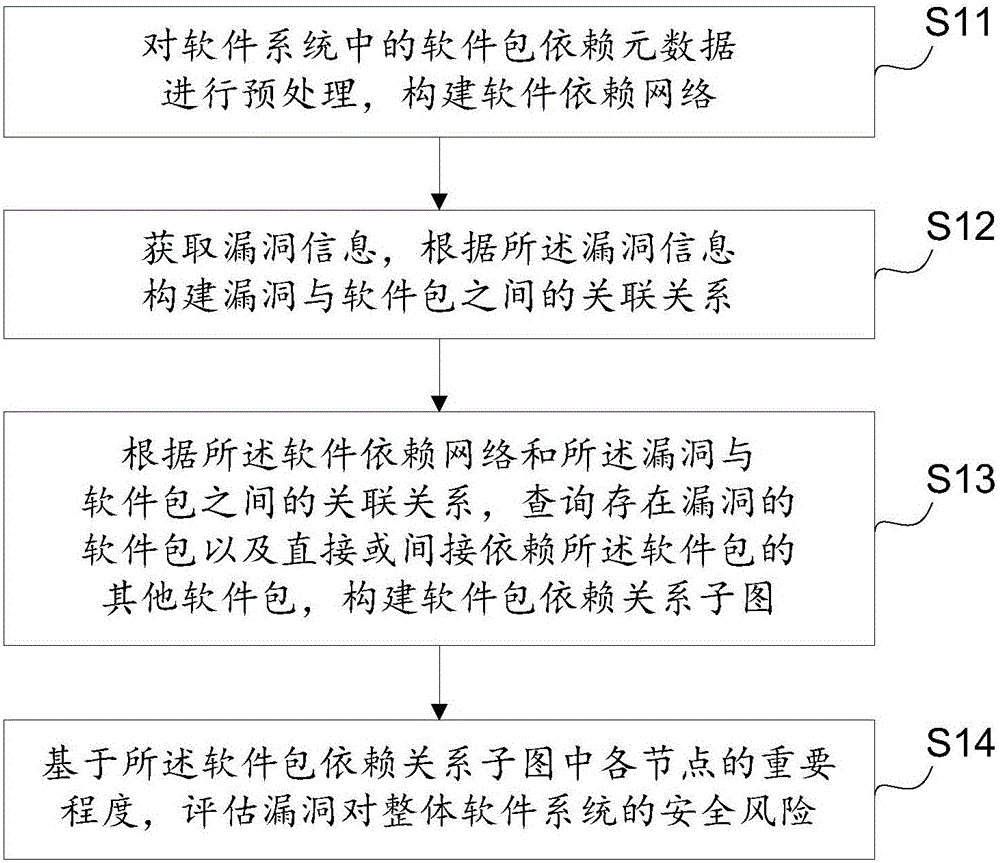
[0034] An embodiment of the present invention provides a software system vulnerability risk assessment method, such as figure 1 As shown, the software system vulnerability risk assessment method includes:
[0035] S11. Preprocessing the software package dependency metadata in the software system to construct a software dependency network, wherein the software package dependency metadata is a file recording information of all software packages in the software system.
[0036] For example: in the / dists / lucid / main / binary-i386 / packages.gz file in the Ubuntu system, the information of each software package in the system can be obtained from the metadata, including the package name, dependent software package, priority, etc.
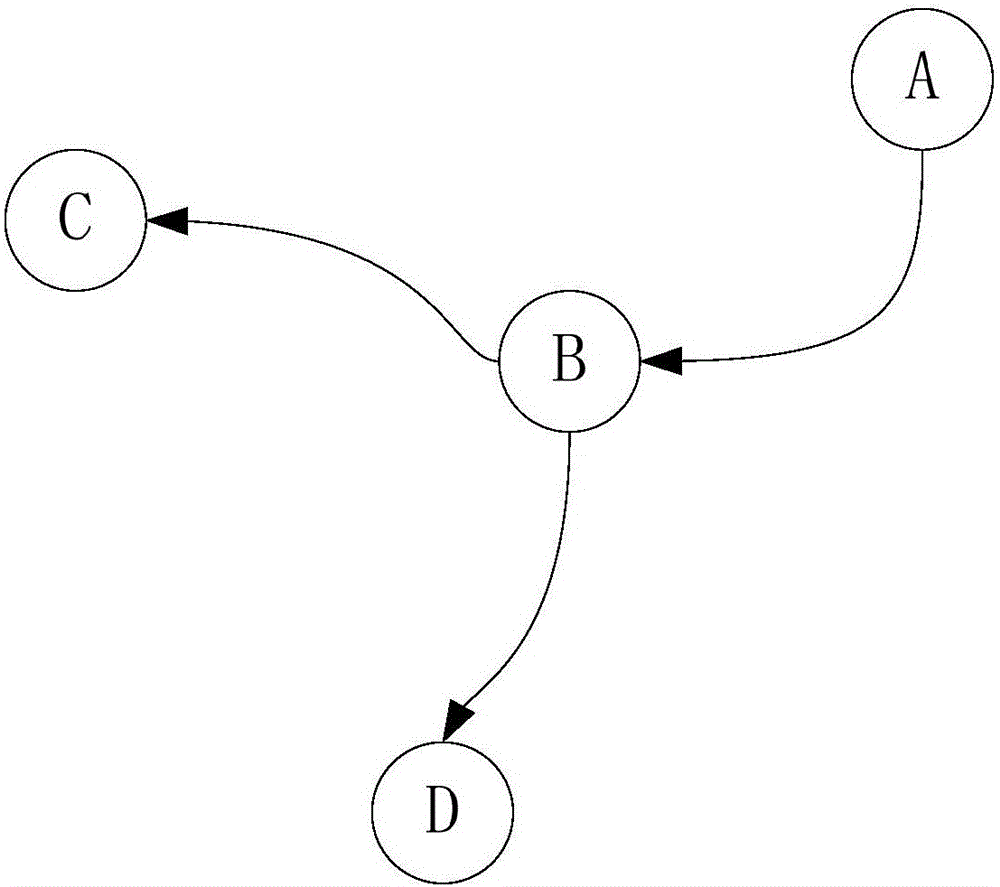
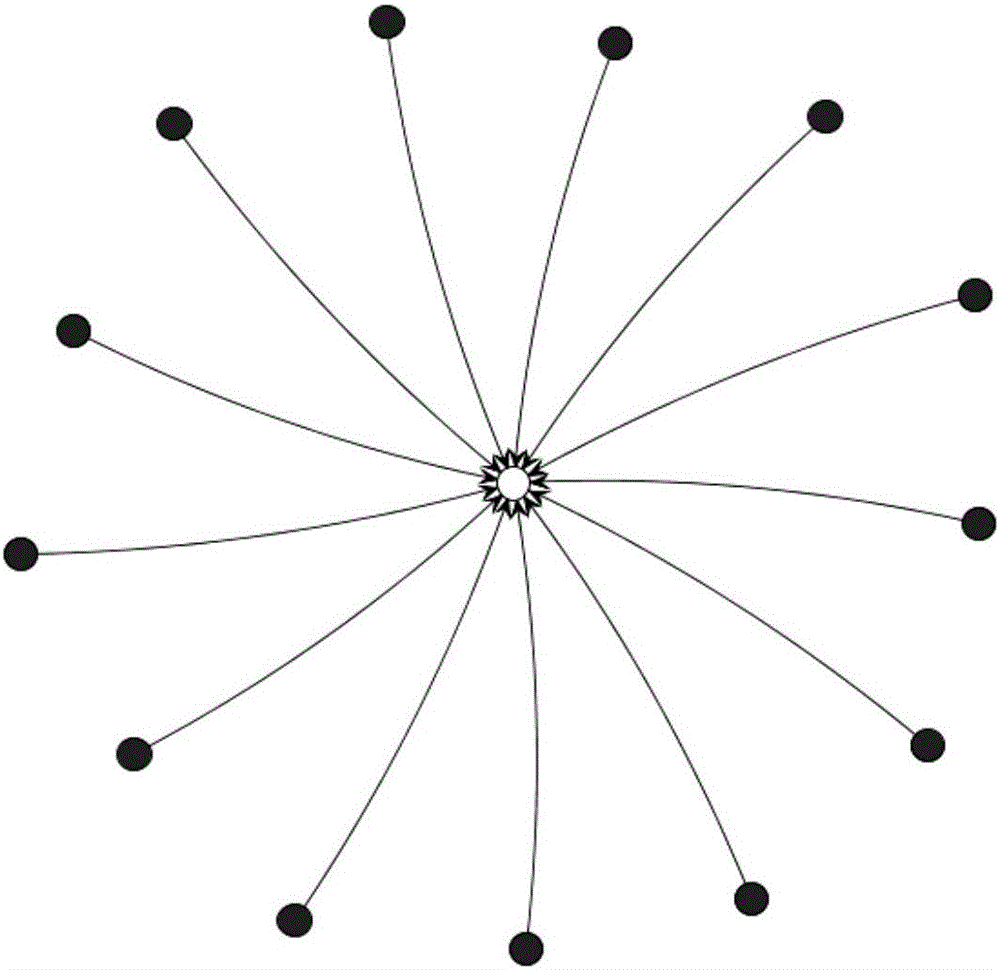
[0037] Construct the dependency network graph G(V, E) of all software packages in the system by relying on software package information, that is, the software dependency network, where V represents the set of all nodes in the graph, and E represents the set o...
Embodiment 2
[0066] This embodiment provides a software system vulnerability risk assessment device, such as Figure 7 As shown, the software system vulnerability risk assessment device includes:
[0067] Dependent network construction unit 11, used to preprocess the software package dependent metadata in the software system, and build a software dependent network, wherein the software package dependent metadata is a file recording all software package information in the software system;
[0068] An association relationship building unit 12, configured to acquire vulnerability information, and construct an association relationship between the vulnerability and the software package according to the vulnerability information;
[0069] The dependency subgraph construction unit 13 is used to query software packages with vulnerabilities and other software packages that directly or indirectly depend on the software packages according to the software dependency network and the association between...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com