Method for guarding against side channel attack virtual machine in cloud computing environment
A cloud computing environment and side-channel attack technology, applied in the field of cloud computing and network security, can solve problems such as failure to effectively prevent side-channel attacks, attacks, user privacy and data security hazards, and achieve simple detection and analysis algorithms Effective, safe and accurate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The technical solution of the present invention will be described in detail below in conjunction with the drawings.
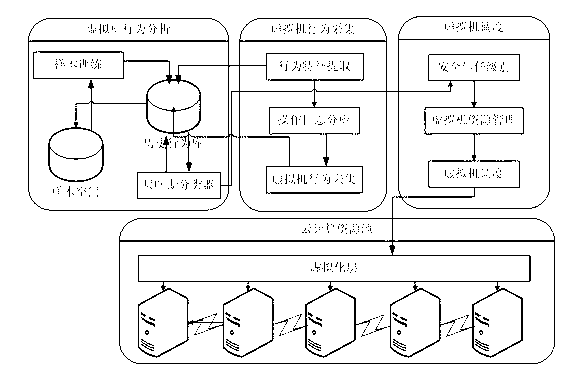
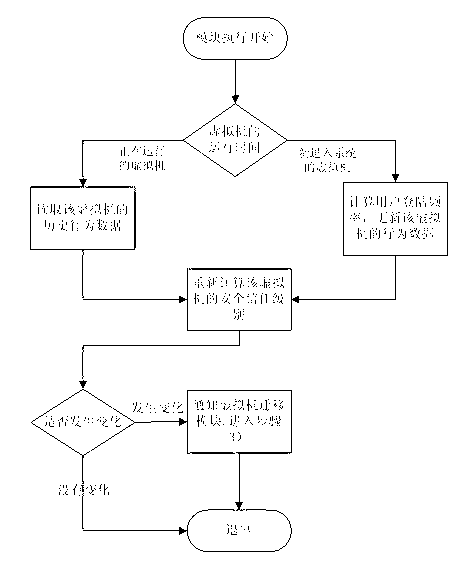
[0027] Such as Figure 2 to Figure 4 As shown, a method for preventing side-channel attacks on virtual machines in a cloud computing environment of the present invention includes the following steps:
[0028] Step 1) According to the behavior characteristics of the virtual machine performing the bypass attack and the behavior characteristics of the ordinary virtual machine, the behavior data of all virtual machines in the execution cycle of the data center is collected in real time.
[0029] In step 1), the behavior data of all virtual machines includes the resource usage characteristics of the virtual machine and the behavior characteristics of the user operating the virtual machine. The resource usage characteristics of the virtual machine include the peak usage rate of the virtual machine's CPU and the collection period. The average usage rate of the vir...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com