Detecting method and device of Web attack
A technology of attack detection and anomaly detection, which is applied in the field of network security to achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
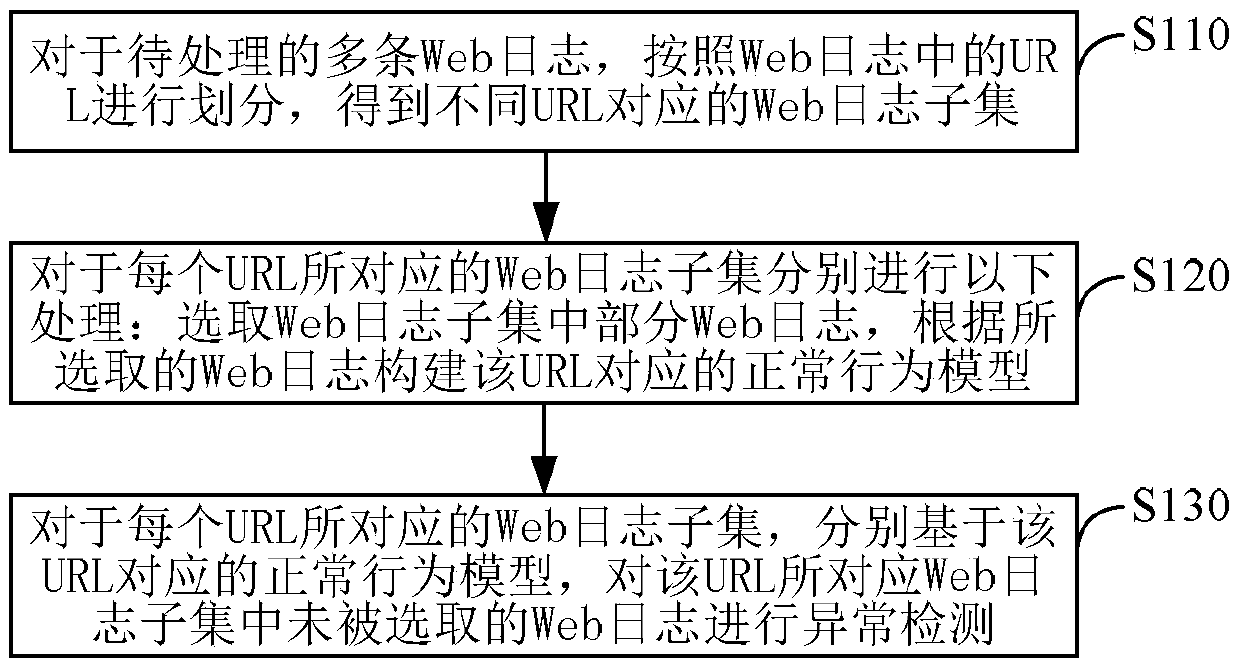
[0041] Embodiment 1. A method for detecting web attacks, such as figure 1 As shown, including steps S110-S130:
[0042]S110. For multiple Web logs to be processed, divide them according to URLs (UniformResourceLocator, uniform resource locator) in the Web logs, and obtain Web log subsets corresponding to different URLs.
[0043] This step may include: for multiple web logs to be processed, first extract URLs in each web log respectively, then divide the multiple web logs to be processed according to the URLs, and divide web logs containing the same URL into In the same Web log subset, the Web log subsets corresponding to different URLs are obtained; wherein, each of the Web log subsets may include one or more Web logs.
[0044] After this step, it may also include: pre-excluding the Web log subset whose number of Web log entries is less than the first predetermined threshold value, or only performing subsequent steps on the Web log subset whose Web log entry number reaches th...
Embodiment 2
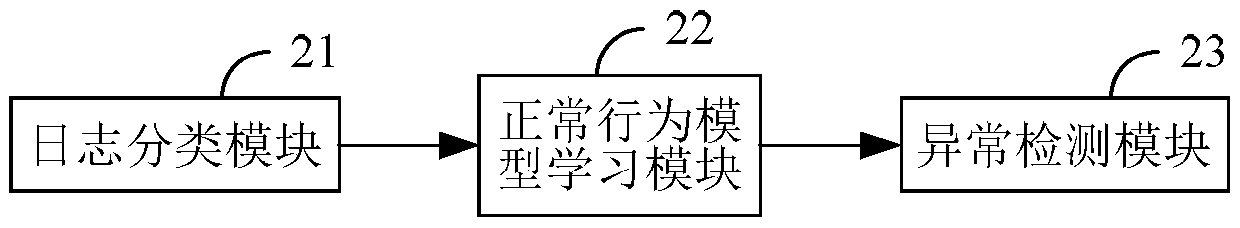
[0092] Embodiment 2, a kind of Web attack detection device based on Web log analysis, such as figure 2 shown, including:
[0093] The log classification module 21 is used for dividing a plurality of Web logs to be processed according to the Uniform Resource Locator URL in the Web logs, so as to obtain the corresponding Web log subsets of different URLs;
[0094] The normal behavior model learning module 22 is used to perform the following processing on the corresponding Web log subsets of each URL: select some Web logs in the Web log subset, and the selected Web logs account for the proportion of the selected Web log subsets. The proportion of is less than or equal to the predetermined upper limit of the proportion; according to the selected web log, the normal behavior model corresponding to the URL is constructed;
[0095] The anomaly detection module 23 is configured to perform anomaly detection on unselected web logs in the web log subset corresponding to each URL based ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com