Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
71 results about "Misuse detection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Misuse detection actively works against potential insider threats to vulnerable computer data.
Insider threat detection
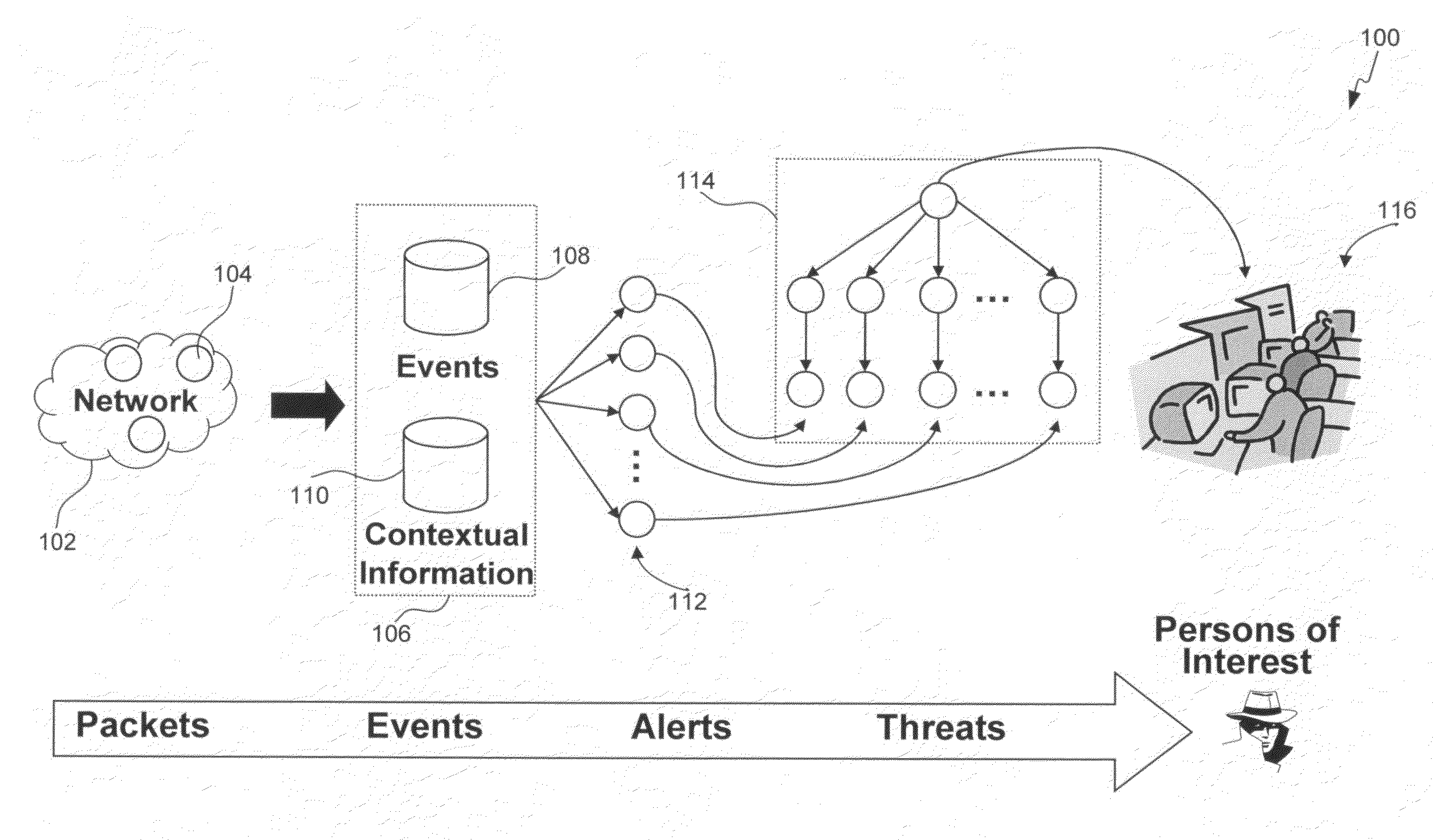
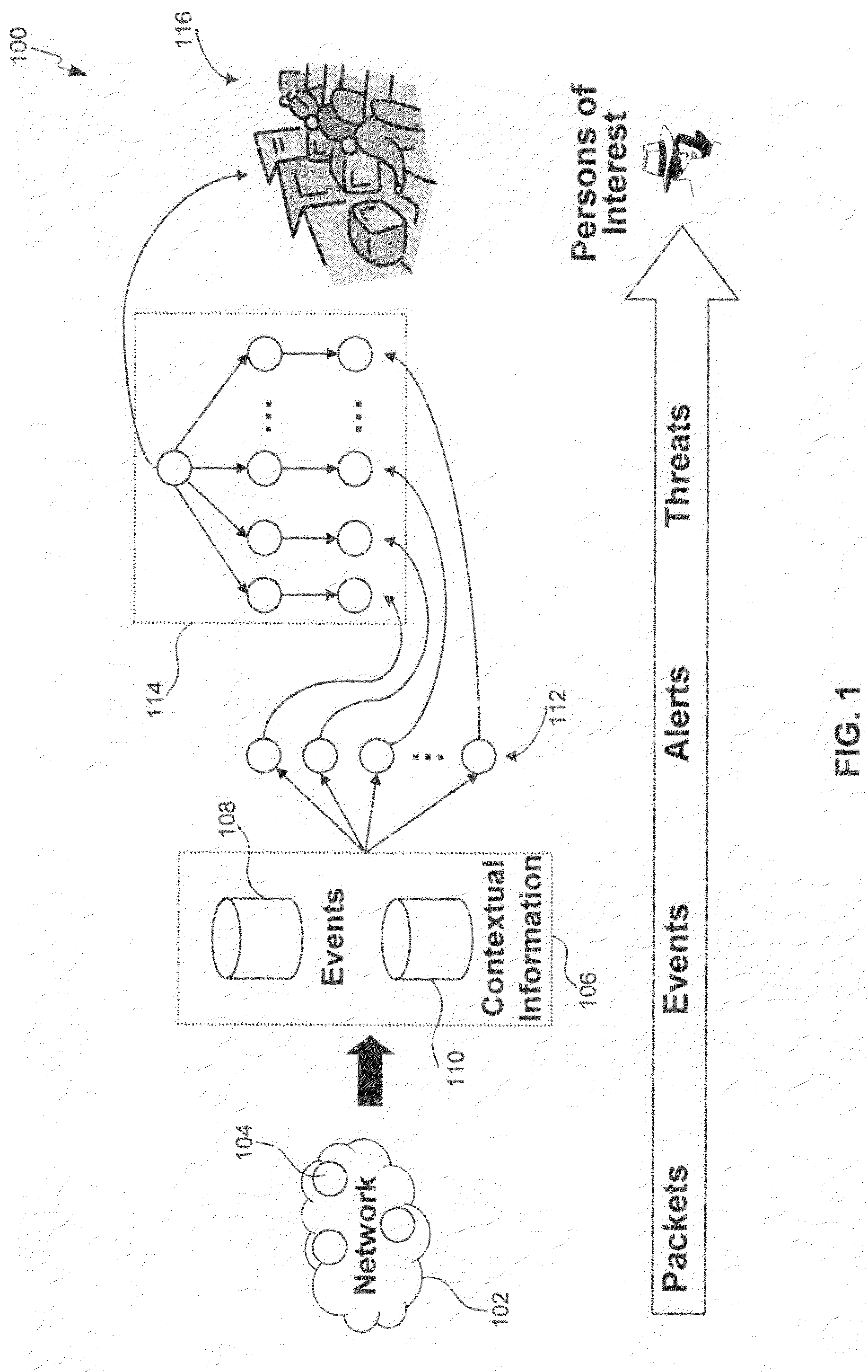
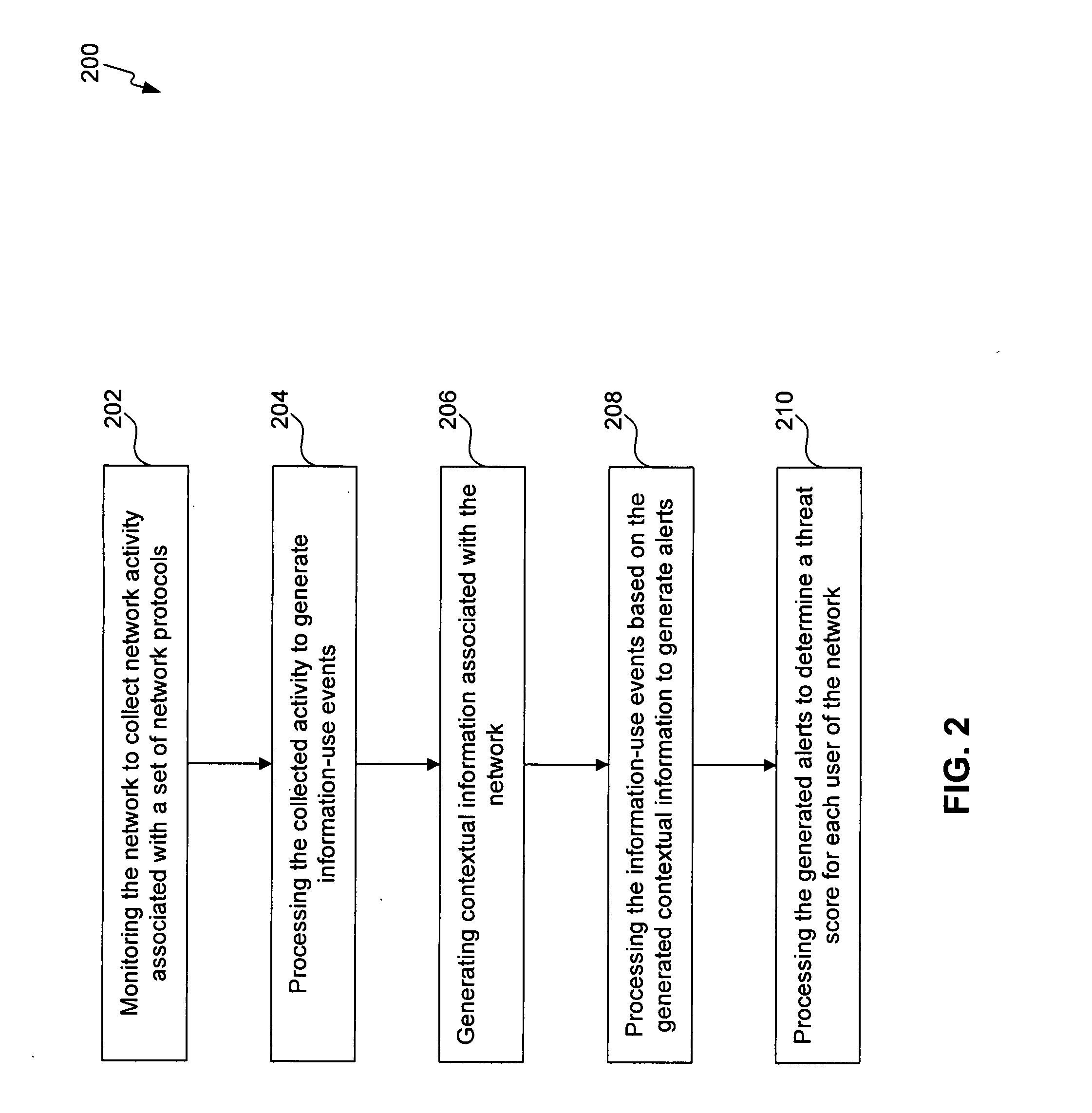
Methods, systems, and computer program products for insider threat detection are provided. Embodiments detect insiders who act on documents and / or files to which they have access but whose activity is inappropriate or uncharacteristic of them based on their identity, past activity, and / or organizational context. Embodiments work by monitoring the network to detect network activity associated with a set of network protocols; processing the detected activity to generate information-use events; generating contextual information associated with users of the network; and processing the information-use events based on the generated contextual information to generate alerts and threat scores for users of the network. Embodiments provide several information-misuse detectors that are used to examine generated information-use events in view of collected contextual information to detect volumetric anomalies, suspicious and / or evasive behavior. Embodiments provide a user threat ranking system and a user interface to examine user threat scores and analyze user activity.
Owner:MITRE SPORTS INT LTD
Fraud and abuse detection and entity profiling in hierarchical coded payment systems
Fraud and abuse detection in an entity's payment coding practices includes the ability to search for fraud at all levels of the hierarchical coded payment system within the context of an unsupervised model. The model uses variables derived and profiles created at any level or at all levels of the hierarchical coded payment system to create a comprehensive description of the payment coding activities submitted by the entity. That description is compared with other peer entities to determine unusual and potentially inappropriate activity. The profiles created may themselves be utilized for purposes other than the detection of fraud and abuse.
Owner:FAIR ISAAC & CO INC
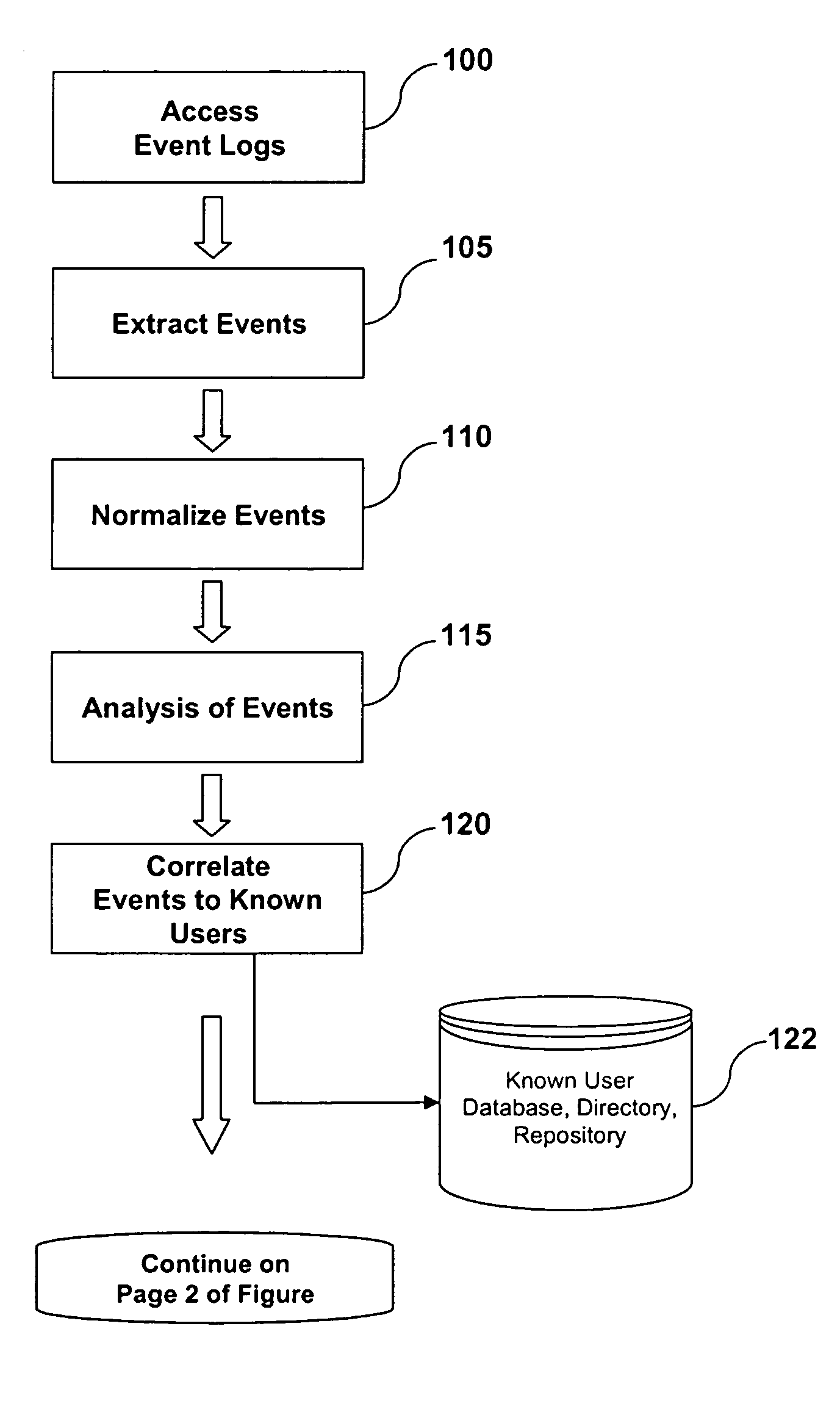
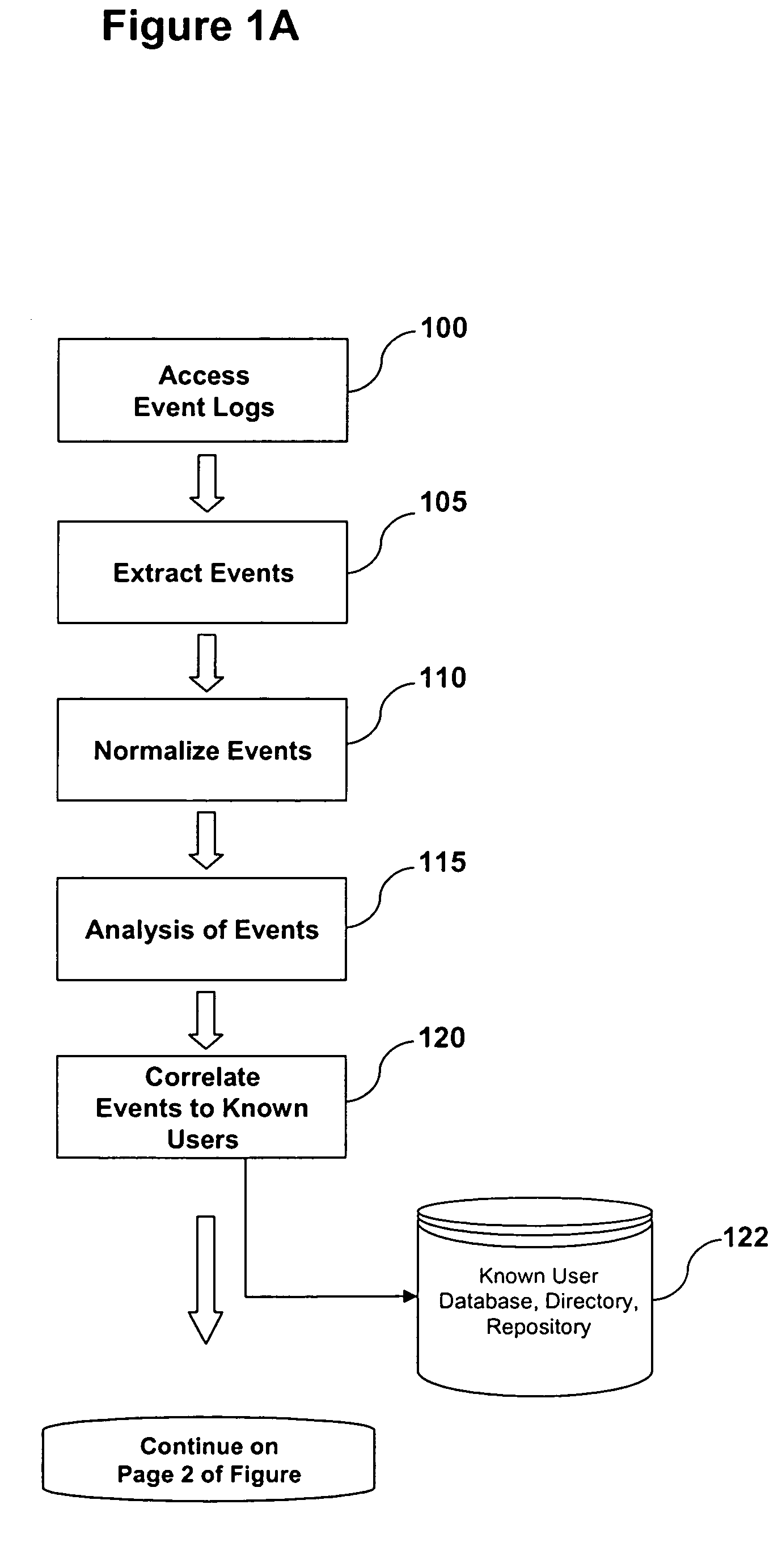
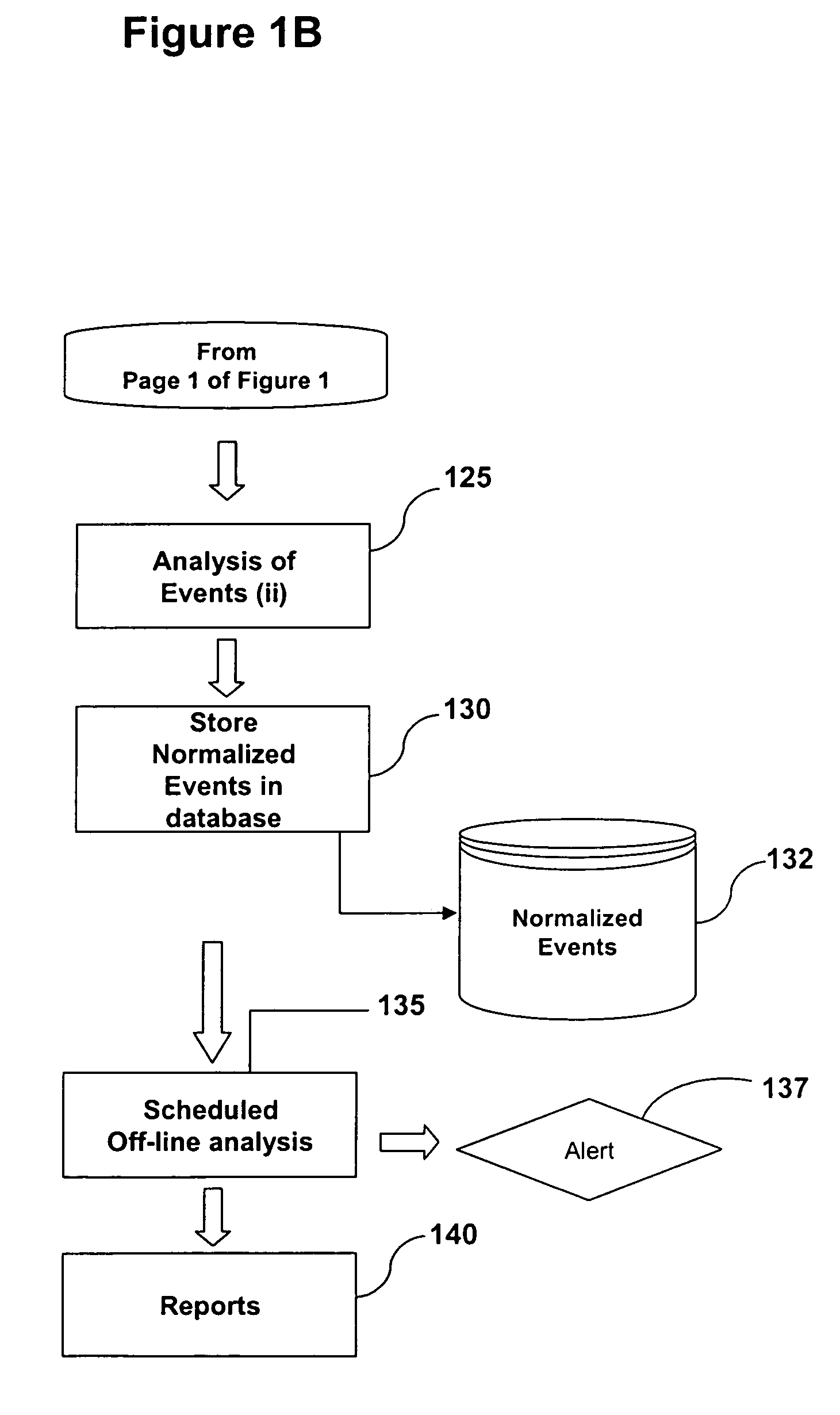
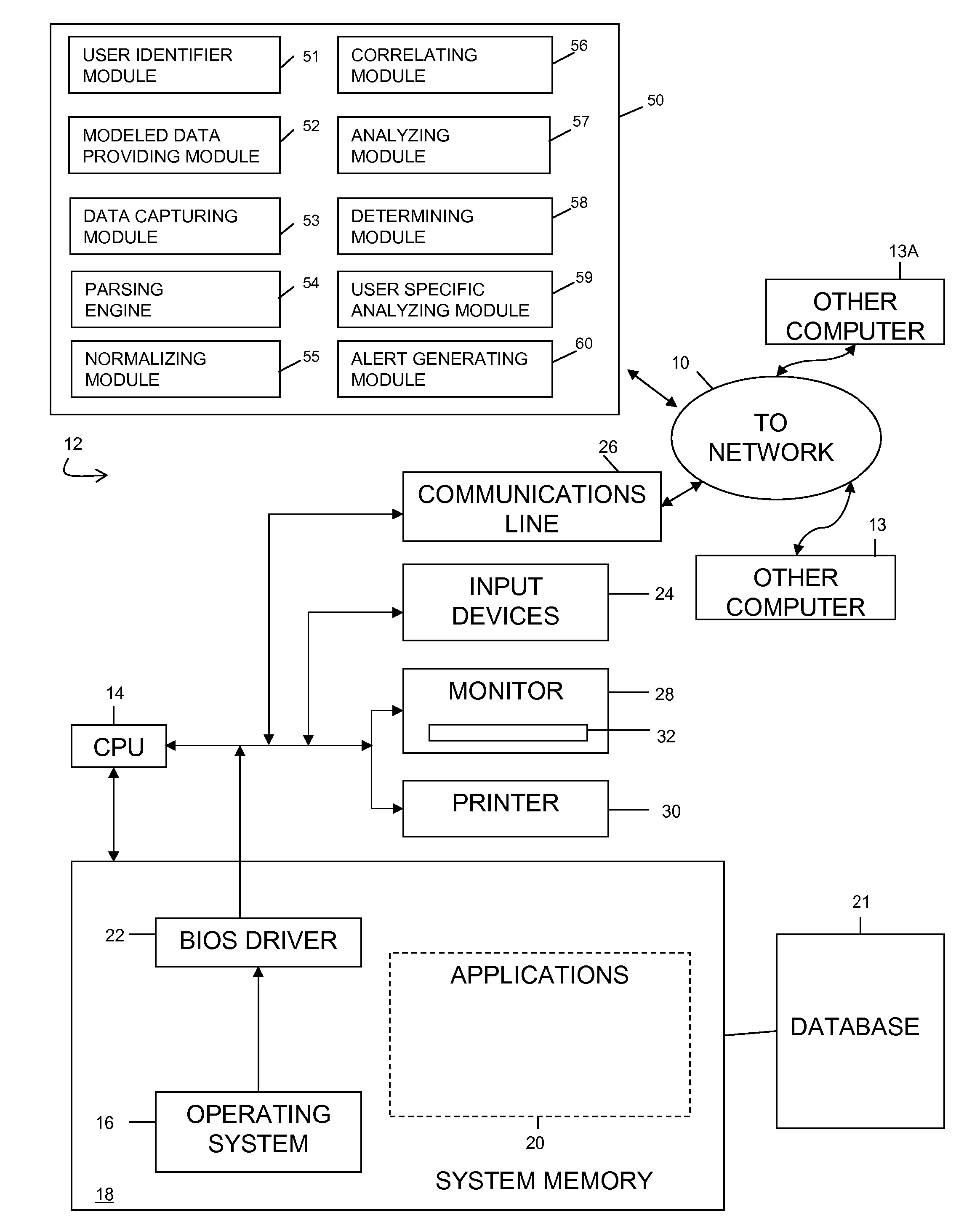
System and Method of Fraud and Misuse Detection Using Event Logs
InactiveUS20070073519A1Nuclear monitoringDigital computer detailsRelevant informationMisuse detection
A system and method are provided for detecting fraud and / or misuse in a computer environment through tracking users activities at the application layer for known users. Application layer data and other data are normalized and records are created. The normalized data is correlated to user identities to produce correlated information that is analyzed against modeling information. The modeling information is generated using rules, algorithms, and / or database queries to define fraud scenarios and misuse scenarios. Reports and / or alerts may be generated if fraud and / or misuse are detected.
Owner:LONG KURT
System and Method of Fraud and Misuse Detection
ActiveUS20070220604A1Memory loss protectionDigital data processing detailsMisuse detectionData mining
A system and method are provided for detecting fraud and / or misuse of data in a computer environment through generating a rule for monitoring at least one of transactions and activities that are associated with the data. The rule can be generated based on one or more criteria related to the at least one of the transactions and the activities that is indicative of fraud or misuse of the data. The rule can be applied to the at least one of the transactions and the activities to determine if an event has occurred, where the event occurs if the at least one criteria has been met. A hit is stored if the event has occurred and a notification can be provided if the event has occurred. A compilation of hits related to the rule can be provided.
Owner:FAIRWARNING IP
System and method of fraud and misuse detection
Owner:FAIRWARNING IP
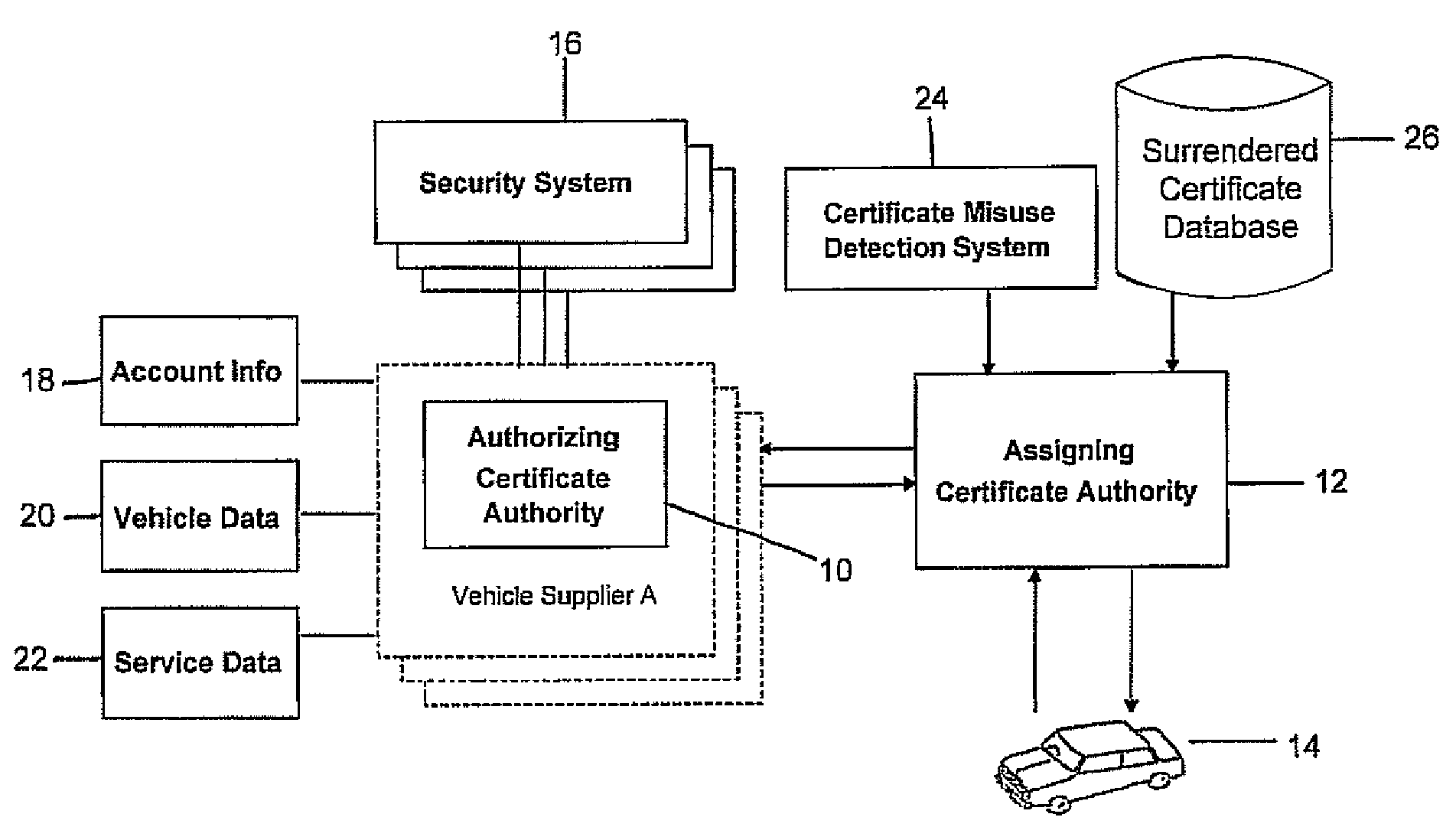
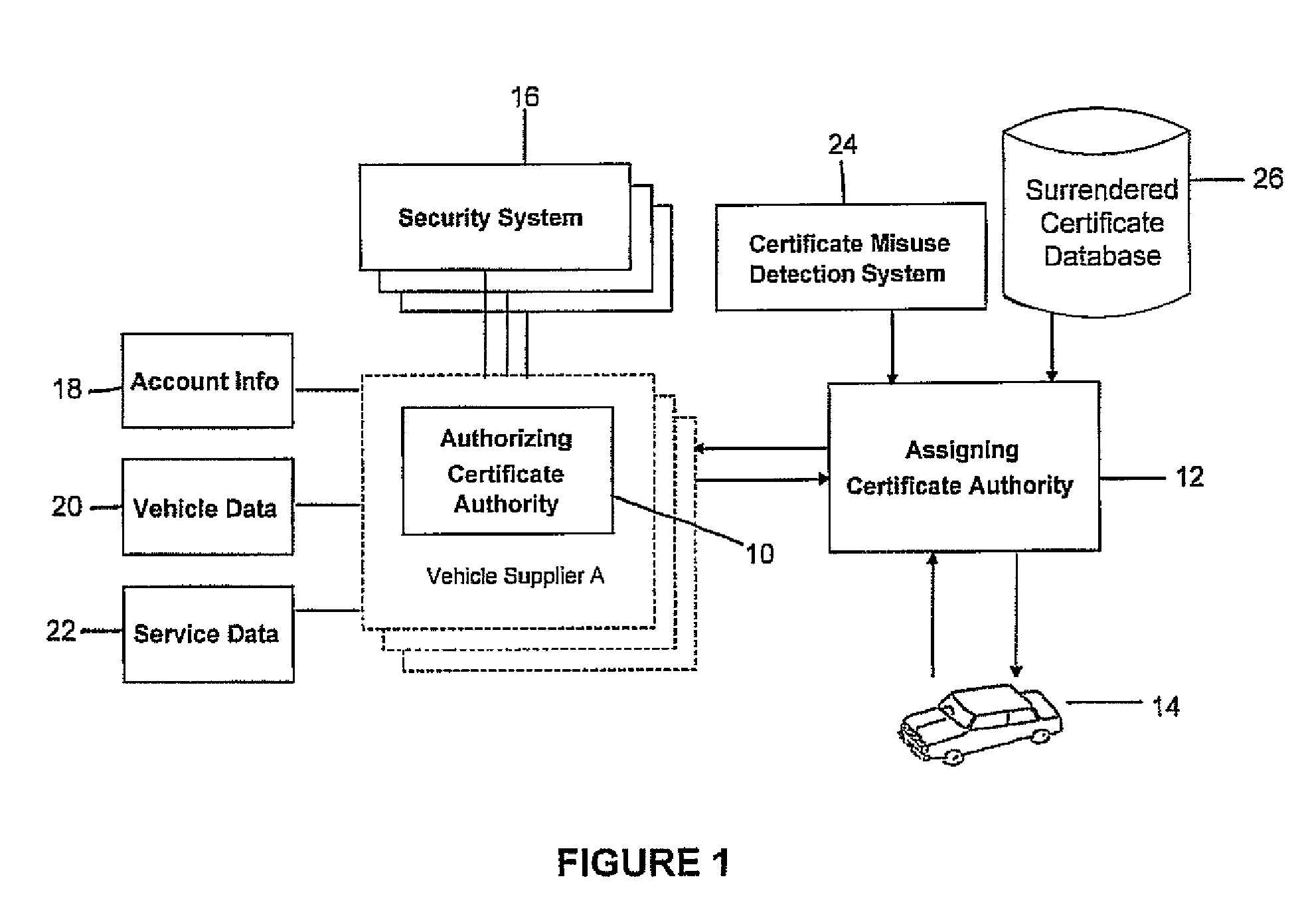
Vehicle Segment Certificate Management Using Short-Lived, Unlinked Certificate Schemes
ActiveUS20080232595A1Avoid cumulative effectsKey distribution for secure communicationMultiple keys/algorithms usageMisuse detectionTime distribution
The present invention advantageously provides a system and method for management of cryptographic keys and certificates for a plurality of vehicles. Each vehicle of the plurality of vehicles generates public / private key pairs, requests multiple time-distributed certificates, creates an encrypted identity, and surrenders expired certificates. An assigning authority receives the public / private key pairs, the request for multiple time-distributed certificates, the encrypted identity, and the expired certificates from said vehicle. The assigning authority authorizes the vehicle with an authorizing authority, validates the expired certificates, proves ownership, and distributes the requested time-distributed certificates to said vehicle. Validation can comprise checking expired certificates against misused, compromised and / or previously surrendered certificates. Time-distributed certificates can have lifetimes adjustable based on certificate misuse detection system algorithms, amount of malicious activity detected, and / or certificate authority capacity.
Owner:TELCORDIA TECHNOLOGIES INC
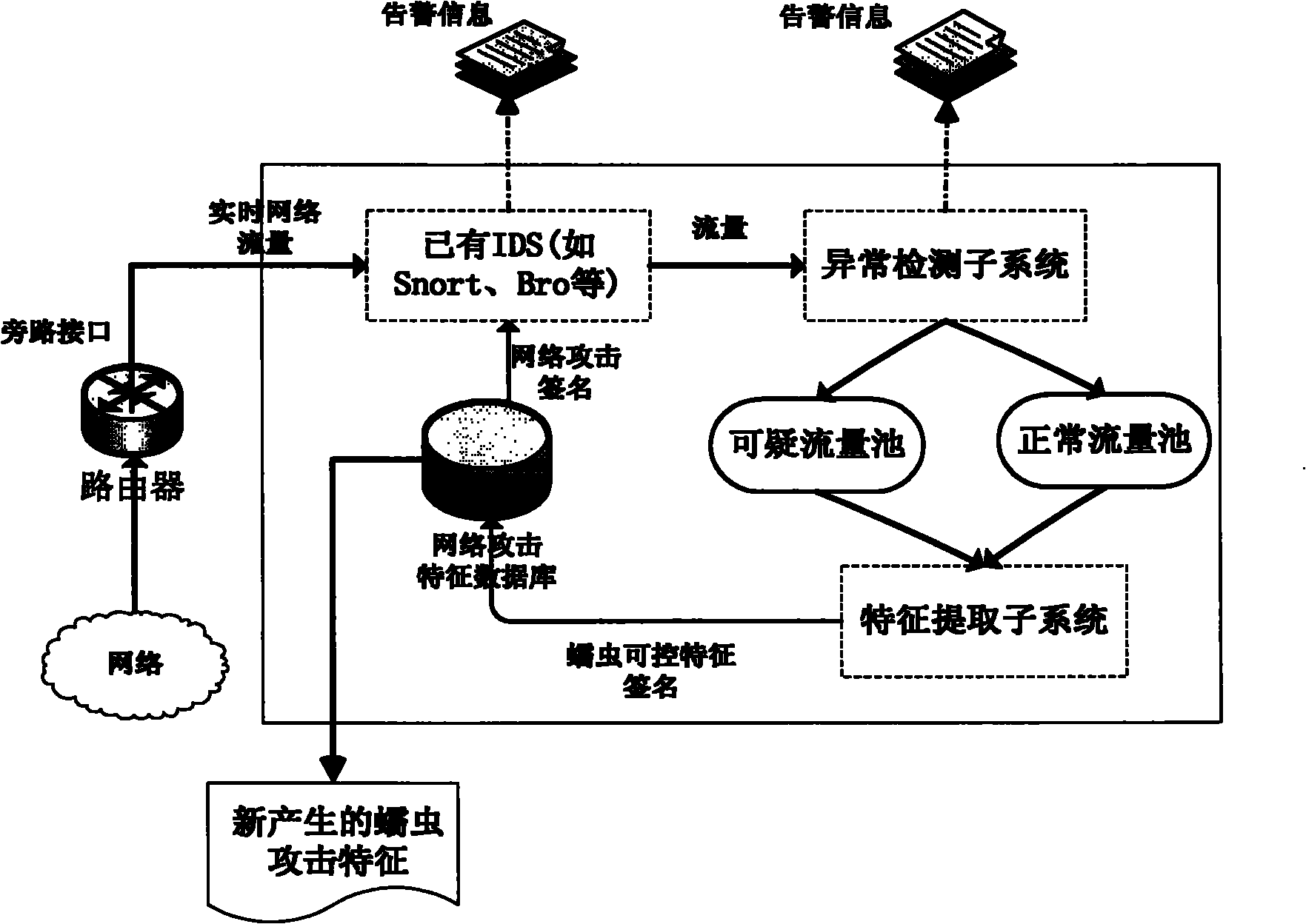
Network worm detection and characteristic automatic extraction method and system
InactiveCN101895521AStop the spreadAccurate discoveryData switching networksFeature extractionAnomaly detection
The invention discloses a network worm detection and characteristic automatic extraction method and a network worm detection and characteristic automatic extraction system and belongs to the technical field of network safety. The method comprises the following steps of: 1) performing abnormal detection on captured network data packets, and dividing the data packets into suspicious network flow and normal network flow according to detection results; 2) storing the suspicious network flow in a suspicious flow pool, and storing the normal network flow in a normal flow pool; 3) clustering the network flow in the suspicious flow pool and the normal flow pool, and extracting a characteristic signature; and 4) updating the extracted characteristic signature in a network attack database, and detecting the network worm. The system comprises an abnormal detection subsystem, a characteristic extraction subsystem, a network attack characteristic database, and a misuse detection system. The methodand the system can more accurately and timely discover the network worm, can automatically extract the worm characteristics and update the attack characteristic database of the existing misuse detection system. Therefore, the aim of suppressing worm propagation is really fulfilled.
Owner:GRADUATE SCHOOL OF THE CHINESE ACAD OF SCI GSCAS
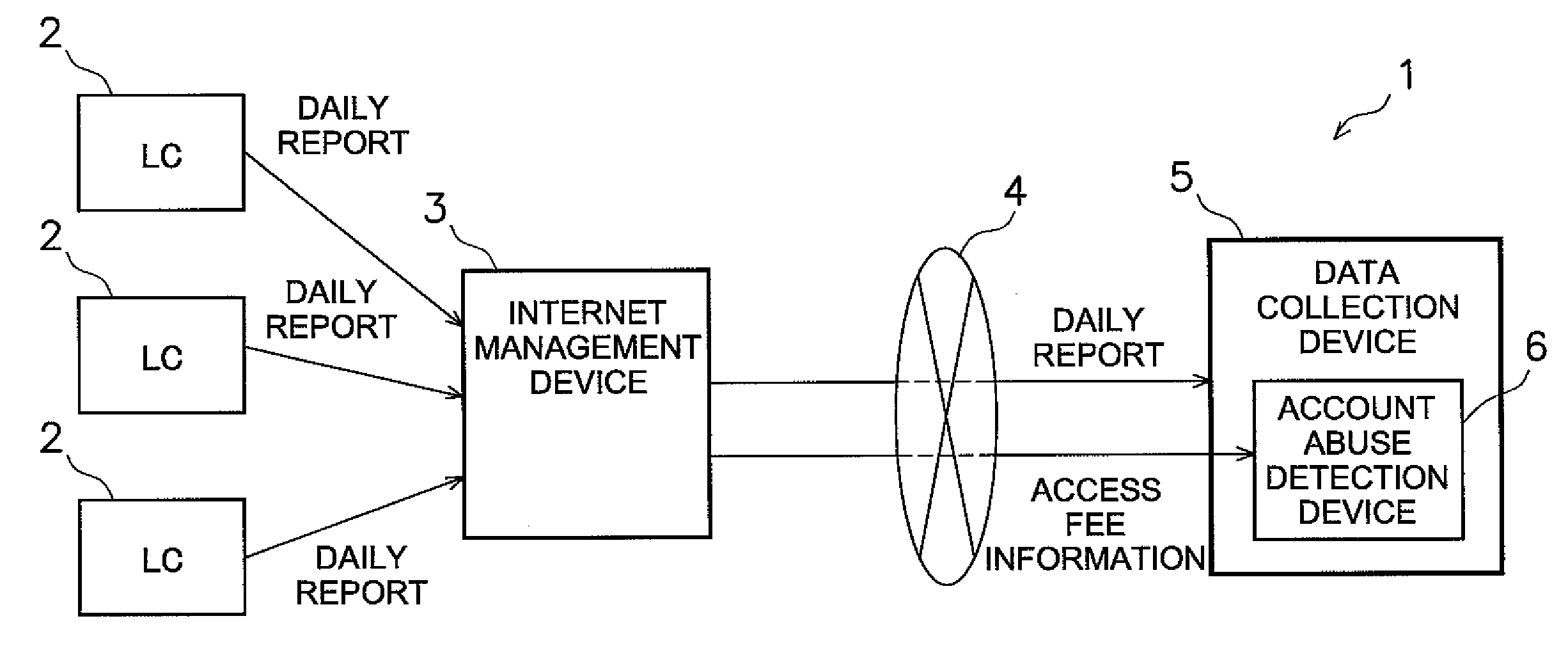
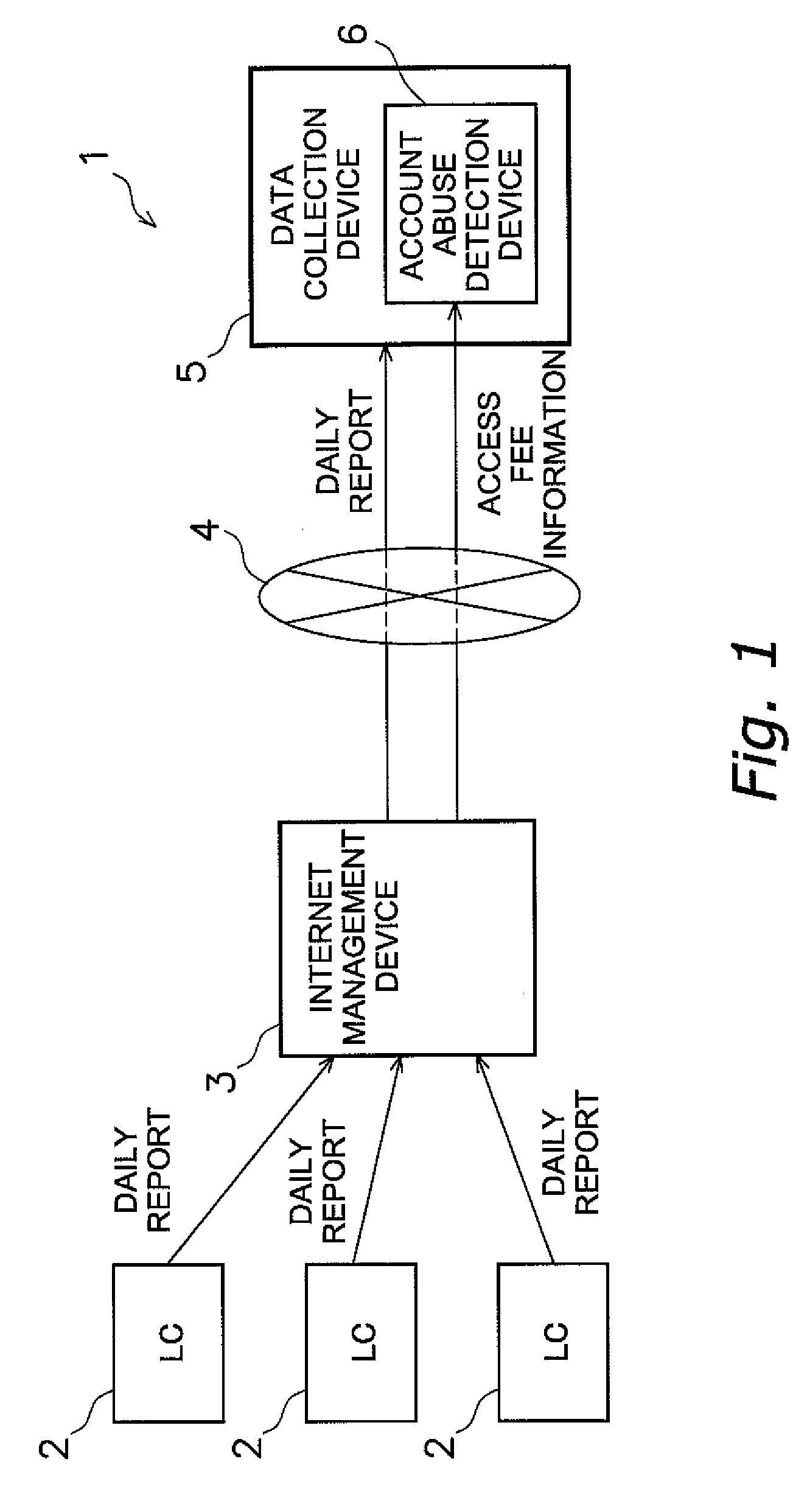
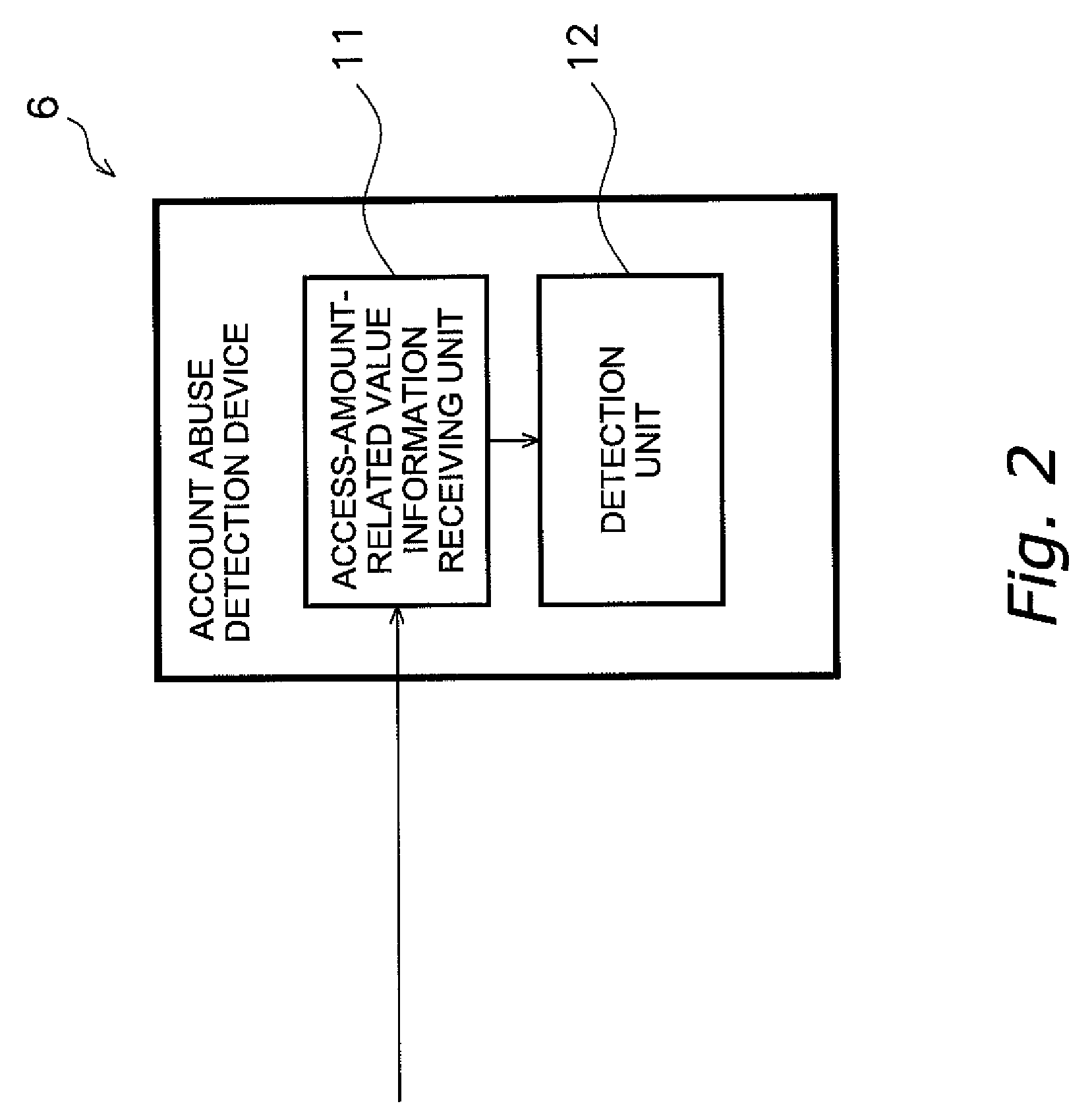
Account abuse detection or prevention device, data collection device, and account abuse detection or prevention program
InactiveUS20090281816A1Easy to detectMemory loss protectionError detection/correctionMisuse detectionPublic network
An account abuse detection or prevention device, a data collection device, and an account abuse detection or prevention program, which are capable of promptly detecting or preventing abuse of an account.An account abuse detection device (6) includes an access-amount-related value information receiving unit (11) and a detection unit (12). The access-amount-related value information receiving unit (11) receives access-amount-related value information from a management device (3). The management device (3) manages a specific account. The specific account is used when transmitting data from a plurality of data transmission devices (2) to a data collection device (5) via a public network. Access-amount-related value information is related to an access-amount-related value. The access-amount-related value is related to the amount of access by the public network (4) through the account. The detection unit (12) compares the access-amount-related value to a predetermined threshold value to detect abuse of the account.
Owner:DAIKIN IND LTD
Automated forensic document signatures
ActiveUS20090164517A1Facilitate methodDigital data processing detailsUser identity/authority verificationDigital signatureMisuse detection
Methods and systems are provided for a proactive approach for computer forensic investigations. The invention allows organizations anticipating the need for forensic analysis to prepare in advance. Digital signatures are generated proactively for a specified target. The digital signature represents a digest of the content of the target, and can be readily stored. Searching and comparing digital signatures allows quick and accurate identification of targets having identical or similar content. Computational and storage costs are expended in advance, which allow more efficient computer forensic investigations. The present invention can be applied to numerous applications, such as computer forensic evidence gathering, misuse detection, network intrusion detection, and unauthorized network traffic detection and prevention.
Owner:GEORGETOWN UNIV
Method for detecting and dealing with unauthorized frames in vehicle network system
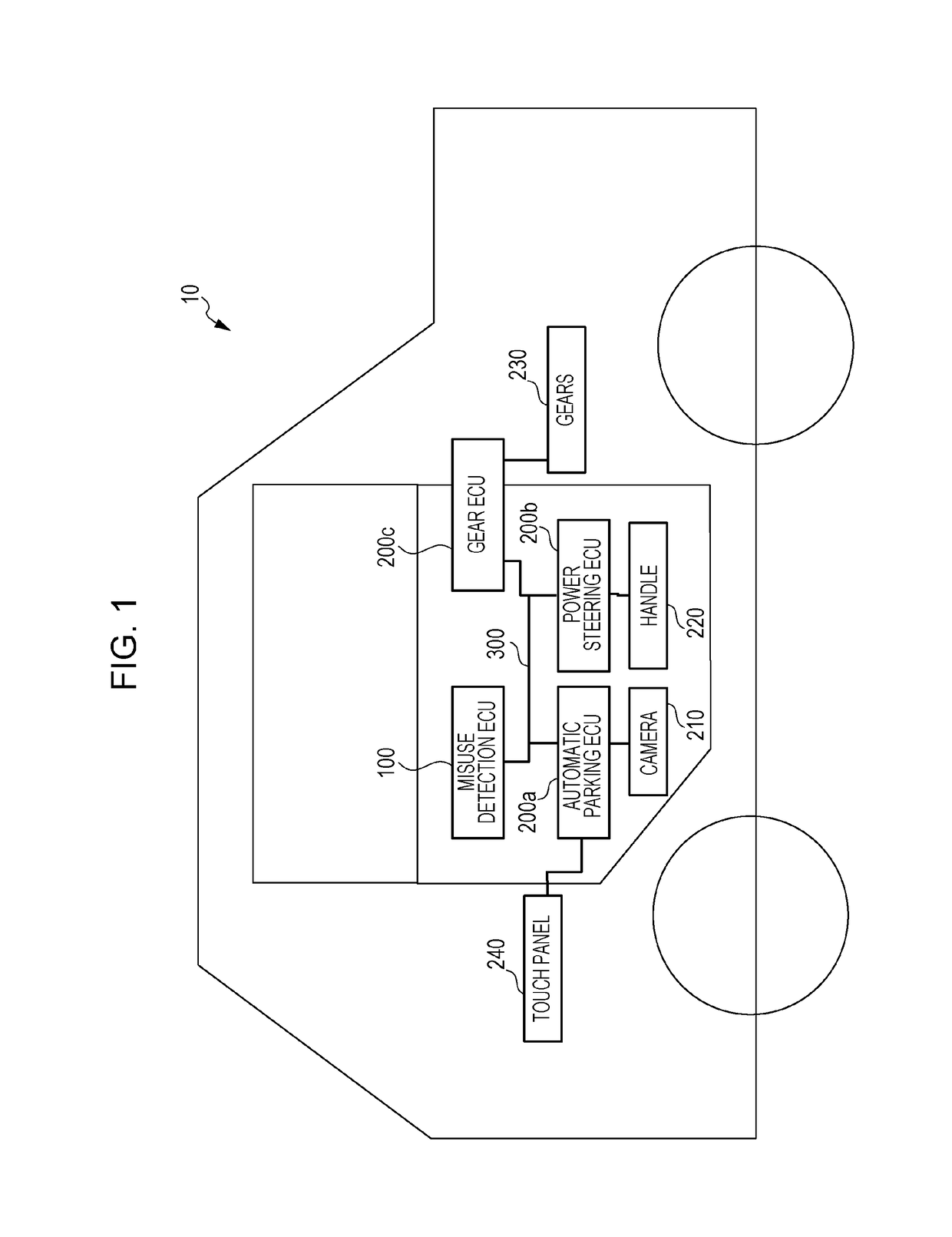
ActiveUS20160323287A1Effect be problematicLocation information based serviceElectric/fluid circuitIn vehicleMisuse detection
A method for dealing with unauthorized frames that makes it possible to take appropriate measures when an unauthorized data frame is detected in a vehicle network system is provided. A plurality of ECUs in the vehicle network system are connected to a bus used for communicating frames. In the method for dealing with unauthorized frames, if a misuse detection ECU that checks a frame appearing in the bus detects an unauthorized frame that does not comply with a certain rule and a certain prevention condition is satisfied, a process for preventing the plurality of ECUs from performing a process corresponding to the unauthorized frame is performed (an error frame is transmitted) or, if the certain prevention condition is not satisfied, the process is not performed.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
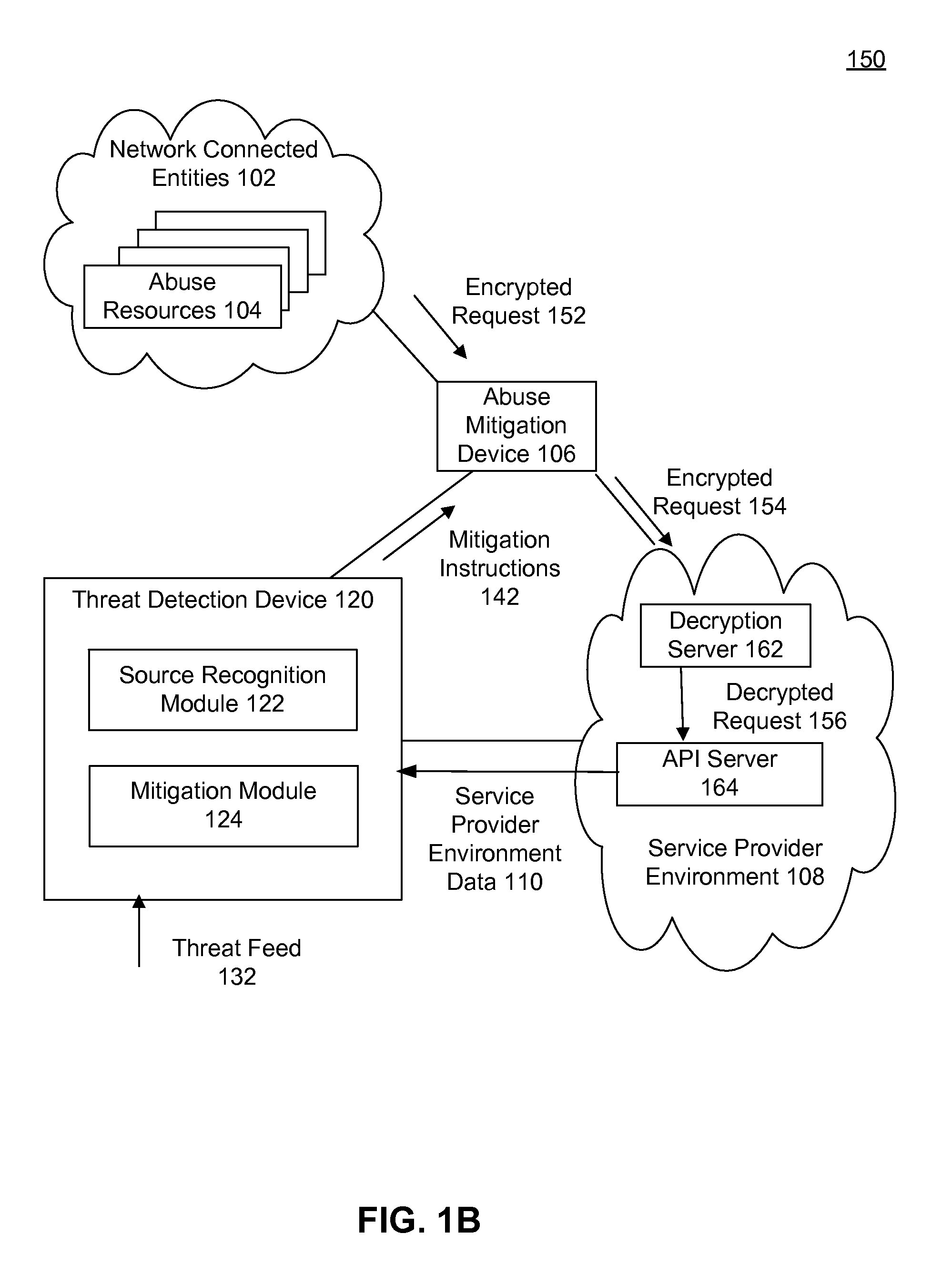
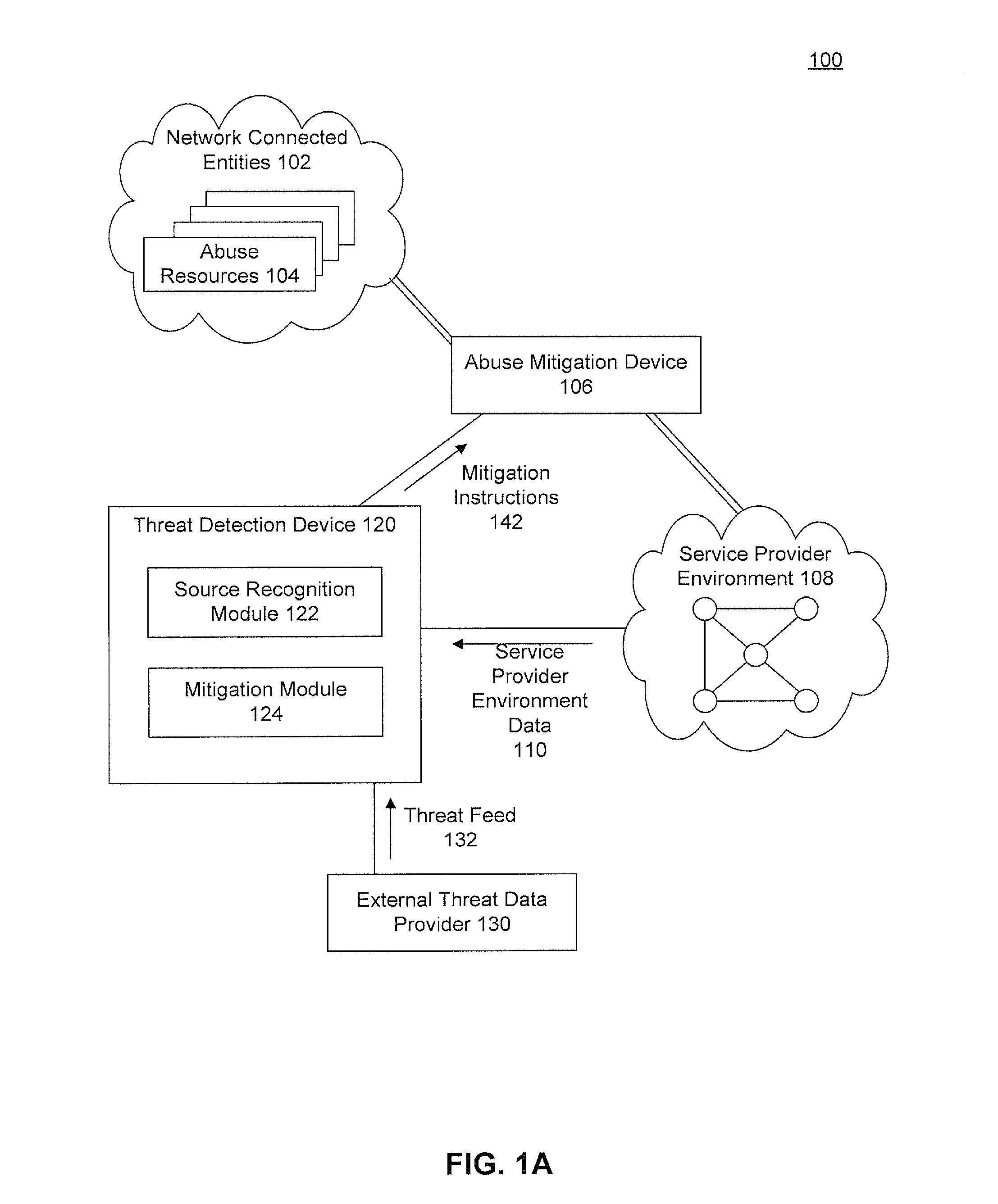
Application and network abuse detection with adaptive mitigation utilizing multi-modal intelligence data
In an embodiment, a computer-implemented method detects a network or application abuse to a service provider environment. In the method, data is collected describing incoming requests from plurality of different external source addresses to the service provider environment. The collected data is used to compare the incoming requests against a heuristic. When the incoming requests are determined to match the heuristic, the requests, having the plurality of different external source addresses, are from a common abuse entity. Finally, the collected data is evaluated to determine that the common abuse entity is a potential network abuser of the service provider environment.
Owner:CISCO TECH INC
Detection method and system for protocol format exception
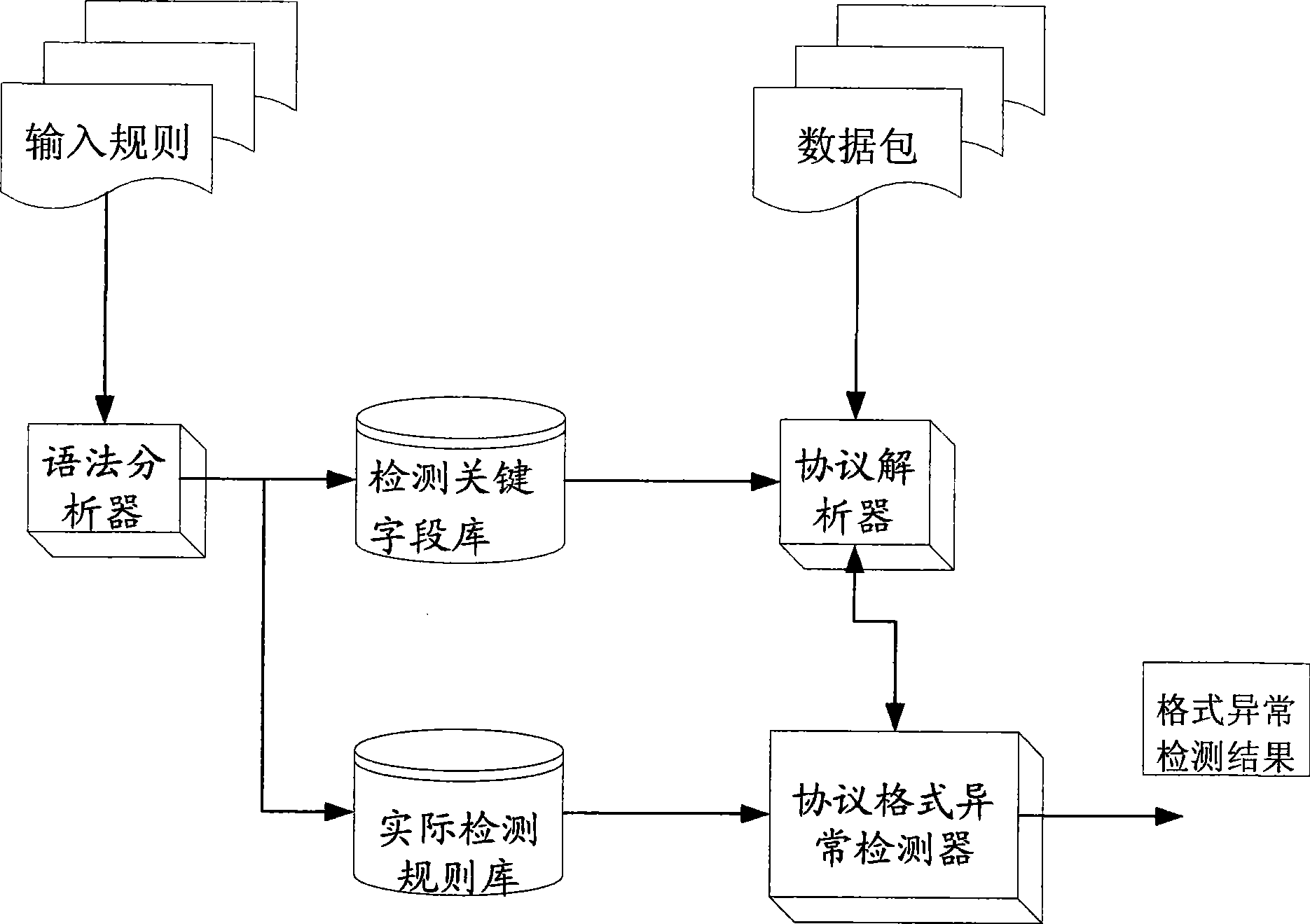
InactiveCN101399710AImprove accuracyImprove scalabilityError preventionData switching networksNetwork packetAnomaly detection
The invention relates to a method used for detecting the anomalies of protocol format and a system thereof; the system comprises a detection key field library, a practical detection rule library, a grammar analyzer, a protocol analyzer and a protocol format anomalies detector; the method comprises the steps as follows: establishing of the detection key field library, establishing of the practical detection rule library, data extraction and deep detection. The method and the system solve the performance problem that only misused detection is used for carrying out mode matching on the load part of all data packets in the prior art. The method and the system adopt the grammar analyzer which has powerful function so as to lead the extension of the system to be extremely convenient, can automatically generate the practical detection rule and corresponding processing function correlation, have the advantages of fast detection speed for protocol format anomalies, high exactness and the like, and have wide application prospect.
Owner:BEIJING VENUS INFORMATION TECH
Methods of identifying activex control distribution site, detecting security vulnerability in activex control and immunizing the same
InactiveUS20110219454A1Digital data information retrievalMemory loss protectionThe InternetMisuse detection
Provided is a method of identifying an ActiveX control distribution site, detecting a security vulnerability in an ActiveX control and immunizing the same. A security vulnerability existing in an ActiveX control may be automatically detected, effects brought on by the corresponding security vulnerability may be measured, and abuse of the detected security vulnerability in a user PC to be protected may be immediately prevented. Therefore, since the user PC may be protected regardless of a security patch, it is anticipated that security problems in the Internet environment caused by imprudent use of the ActiveX control may be significantly enhanced.
Owner:ELECTRONICS & TELECOMM RES INST
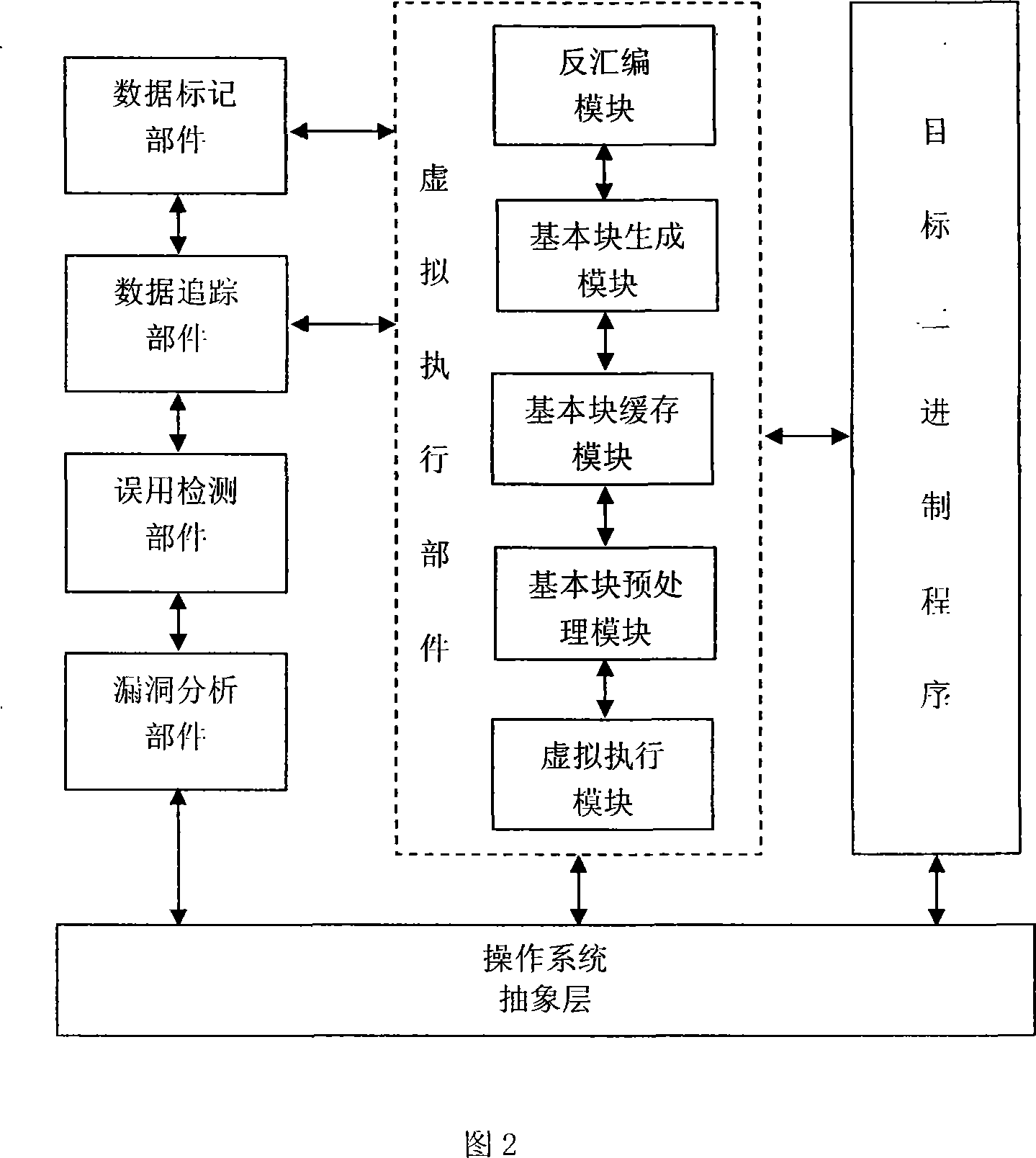
Data flow analysis based hostile attack detecting method
The invention relates to an attack detection method of computer security vulnerability. A detection system is composed of a dummy executing component, a data marking component, a data tracking component, a misuse detection component and a vulnerability analyzing component. The method comprises starting a program to be monitored by the dummy executing component, generating tainted data structure by the data marking component when an external input data is present, marking the propagated tainted data by the data tracking component, determining by the misuse detection component whether the use of the tainted data breaks the security rule and configuration, and collecting and analyzing information associated with the security vulnerability by the vulnerability analyzing component. The invention is suitable for hostile attack detection and analysis of security vulnerability during program running, thereby preventing the hostile attack behavior and providing the detailed information of the security vulnerability. The invention can detect most of the overflow security vulnerabilities without the need of source codes and with a zero misreport rate, and can provide sufficient information for automatically generating patches for the security vulnerability.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Method and device for detecting intrusion
The invention provides a method and a device for detecting intrusion, and relates to the field of information management. The problem that a misuse detection IDS (intrusion detection system) cannot detect unknown type aggression or trace report failure aggression is solved. The method includes the steps: loading a feature library including a plurality of intrusion behavior features; acquiring data stream to be analyzed; and analyzing the data stream to be analyzed according to the feature library and matching the data stream with an intrusion behavior conforming to the intrusion behavior features in the feature library from the data stream to be analyzed. The method and the device are applicable to the detection process of the IDS, and realize comprehensive and reliable intrusion detection.
Owner:BEIJING VENUS INFORMATION TECH +1
Vehicle segment certificate management using short-lived, unlinked certificate schemes
ActiveUS8171283B2Avoid cumulative effectsKey distribution for secure communicationDigital data processing detailsMisuse detectionTime distribution
The present invention advantageously provides a system and method for management of cryptographic keys and certificates for a plurality of vehicles. Each vehicle of the plurality of vehicles generates public / private key pairs, requests multiple time-distributed certificates, creates an encrypted identity, and surrenders expired certificates. An assigning authority receives the public / private key pairs, the request for multiple time-distributed certificates, the encrypted identity, and the expired certificates from said vehicle. The assigning authority authorizes the vehicle with an authorizing authority, validates the expired certificates, proves ownership, and distributes the requested time-distributed certificates to said vehicle. Validation can comprise checking expired certificates against misused, compromised and / or previously surrendered certificates. Time-distributed certificates can have lifetimes adjustable based on certificate misuse detection system algorithms, amount of malicious activity detected, and / or certificate authority capacity.
Owner:TELCORDIA TECHNOLOGIES INC
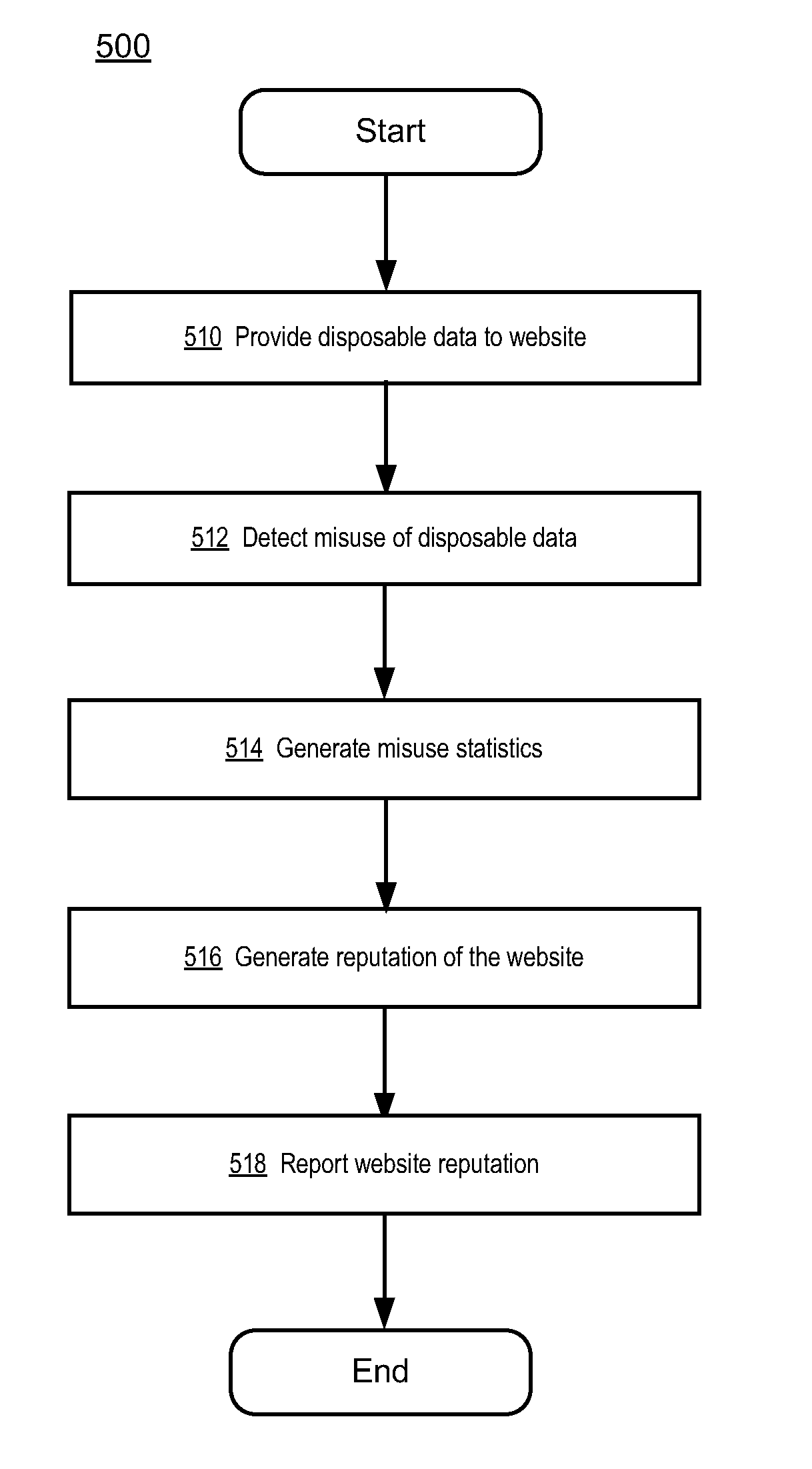
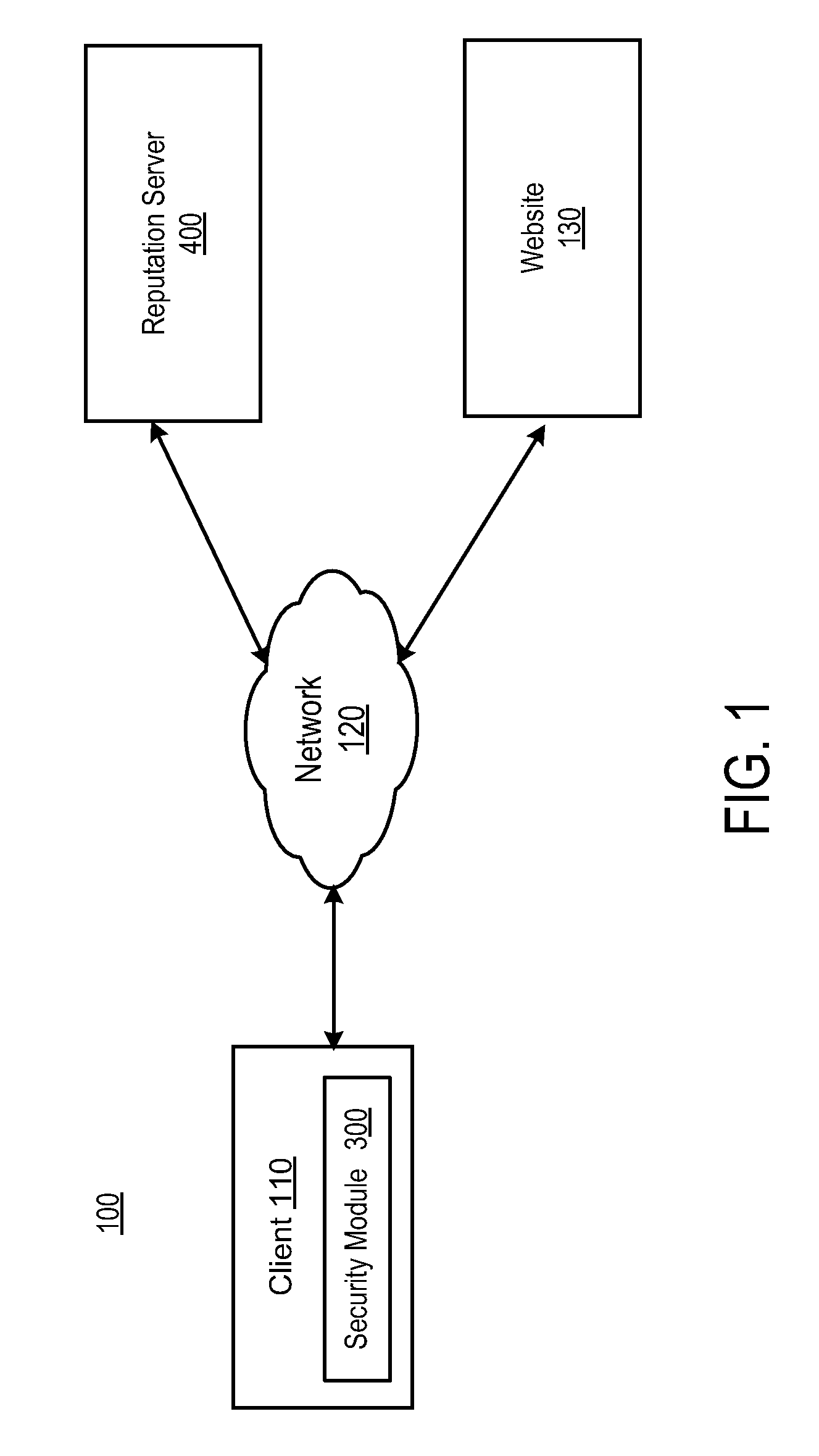
Using disposable data misuse to determine reputation
A reputation system generates reputation scores for websites based at least in part on analyses of disposable data misuse associated with the websites. The reputation system receives reports describing disposable data misuses detected by clients and / or other entities, such as credit card issuers. The reputation system also detects certain types of misuse itself by analyzing received disposable data involved in a misuse detection to determine the websites or other entities that misused the data. The reputation system generates misuse statistics describing the amount of data misuse performed by websites. The reputation system generates reputation scores for websites based on the disposable data misuse statistics and, optionally, other reputation information for the websites, such as malware distribution associated with the websites. The reputation system reports the reputations of the websites to the clients.
Owner:NORTONLIFELOCK INC
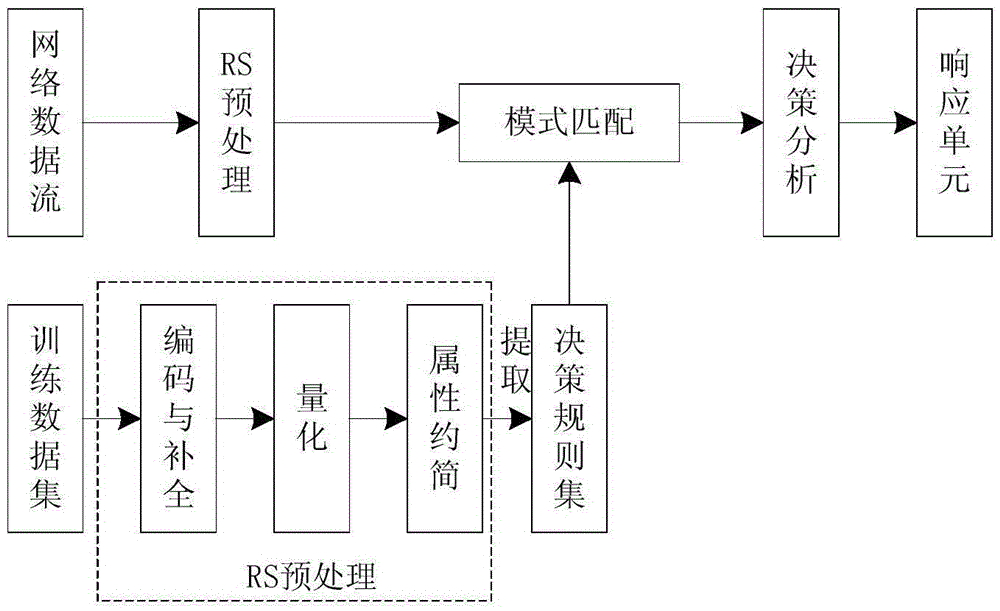
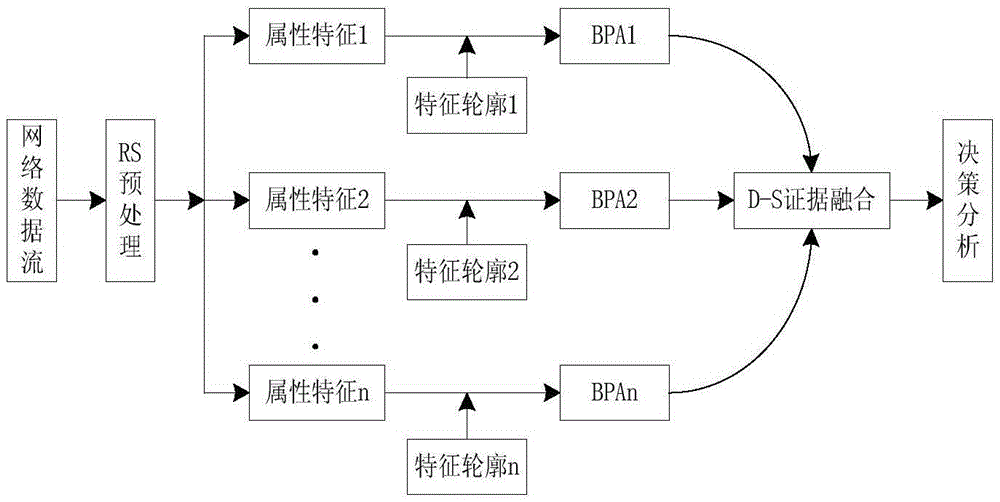
Incremental intrusion detection method fusing rough set theory and DS evidence theory
The invention relates to an incremental intrusion detection method fusing a rough set theory and a DS evidence theory, and belongs to the network information security field. Aiming at the problems that a detection system cannot satisfy a high speed network real-time detection demand and the detection precision is not high, the method uses a rough set theory to pre-treat a network data stream so as to reduce redundant data, and improves the detection speed. A misuse rule set is extracted from a reduced data set, most attack types are identified through a pattern matching mode, and furthermore the misuse detection is realized. The method employs a misuse detection module, an abnormal detection module, and an incremental unit. The abnormal detection module is realized based on the DS evidence theory and used for detecting attack types not included in a misuse rule base. The incremental unit is used for improving the misuse rule base and updating a built network normal behavior profile in real time. The incremental intrusion detection method fusing the rough set theory and the DS evidence theory improves the detection efficiency and the detection precision of the detection system, and especially for newly arisen attack types.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Misuse detection method, misuse detection electronic control unit, and misuse detection system
ActiveUS20180144119A1Reduce the possibilityInternal/peripheral component protectionDigital data authenticationTransceiverMisuse detection
A misuse detection electronic control unit in a vehicle network system including a plurality of electronic control units that communicate with one another through buses in accordance with a CAN protocol includes a transceiver unit that performs a reception step of receiving a target data frame and a reference data frame transmitted through the buses, wherein the target data frame is a data frame having a first identifier and wherein the reference data frame is a data frame having a second identifier different from the first identifier and a misuse detection process unit that performs a detection step of performing, as misuse detection for the target data frame, evaluation in accordance with a reception timing of the reference data frame and a reception timing of the target data frame on the basis of a certain rule specifying a reception interval between the reference data frame and the target data frame.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
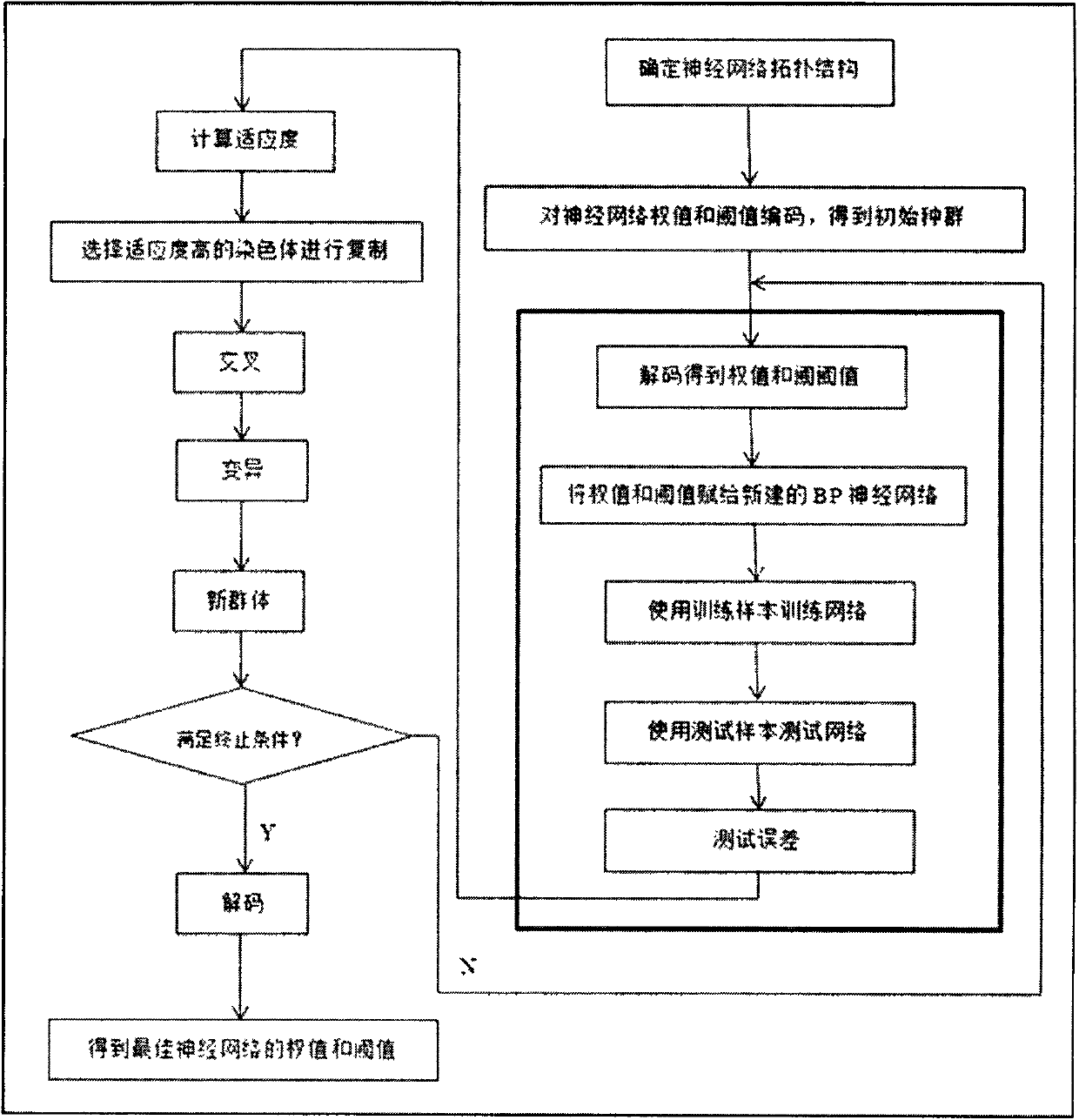
Neural network-based intrusion detection algorithm for wireless sensor network
The invention simply discloses an intrusion detection model by combining the existing network intrusion detection technology aiming at cluster heads (Cluster Head, CH for short) of a cluster-based wireless sensor network (Cluster-based Wireless Sensor Network, CWSN for short). The characteristics of low CH operating rate and limited energy are fully considered; the designed model is simple in structure, and composed of the following three modules: a misuse detection module, an abnormality detection module and a decision module, wherein the misuse detection module utilizes the neural network as a core. The existing neural network is various in variety and each neural network has advantages and defects, a back propagation (BP) neural network, a generalized regression neural network and a BP neural network optimized on the basis of a genetic algorithm are respectively selected to carry out an experiment to obtain the neural network which is more suitable for an intrusion detection system (IDS) aiming at a wireless sensor network (WSN). The experiment adopts a KDDCUP1999 data set, and a matrix laboratory (MATLAB) is utilized to carry out a simulation experiment.
Owner:TIANJIN POLYTECHNIC UNIV
Application and network abuse detection with adaptive mitigation utilizing multi-modal intelligence data
InactiveUS20150350240A1Memory loss protectionError detection/correctionService provisionApplication software
In an embodiment, a computer-implemented method detects a network or application abuse to a service provider environment. In the method, data is collected describing incoming requests from plurality of different external source addresses to the service provider environment. The collected data is used to compare the incoming requests against a heuristic. When the incoming requests are determined to match the heuristic, the requests, having the plurality of different external source addresses, are from a common abuse entity. Finally, the collected data is evaluated to determine that the common abuse entity is a potential network abuser of the service provider environment.
Owner:CISCO TECH INC
Self-adapting network intrusion detection system
InactiveCN101562539ALower deployment costsImprove adaptabilityData switching networksFeature vectorAdaptive learning
The invention provides a self-adapting network intrusion detection system, and the system comprises a message pre-processing and forwarding module, a misuse detection module, an abnormality responding module and an output device. The message pre-processing and forwarding module is used for extracting non-encrypted messages in network connecting objects and forwarding the messages to the misuse detection module which is used for forwarding the detected abnormal network connecting objects to the abnormality responding module. The system is characterized by also comprising a real-time database, a feature data arranging and storing module, a historical database, a semi-supervised self-adaptive learning module and an abnormality detection module which is used for analyzing the network connecting feature vectors in the real-time database and forwarding the detected abnormal network connection to the abnormality responding module. The beneficial effect of the system is as follows: the system uses the semi-supervised self-adaptive learning module to establish the rule of abnormality detection according to the data in the historical database, a lot of artificially-marked training data is not needed, thus reducing the deploying cost of the abnormality detection system.
Owner:CHONGQING UNIV
Intrusion detection method of cosine time-variant PSO-SVM
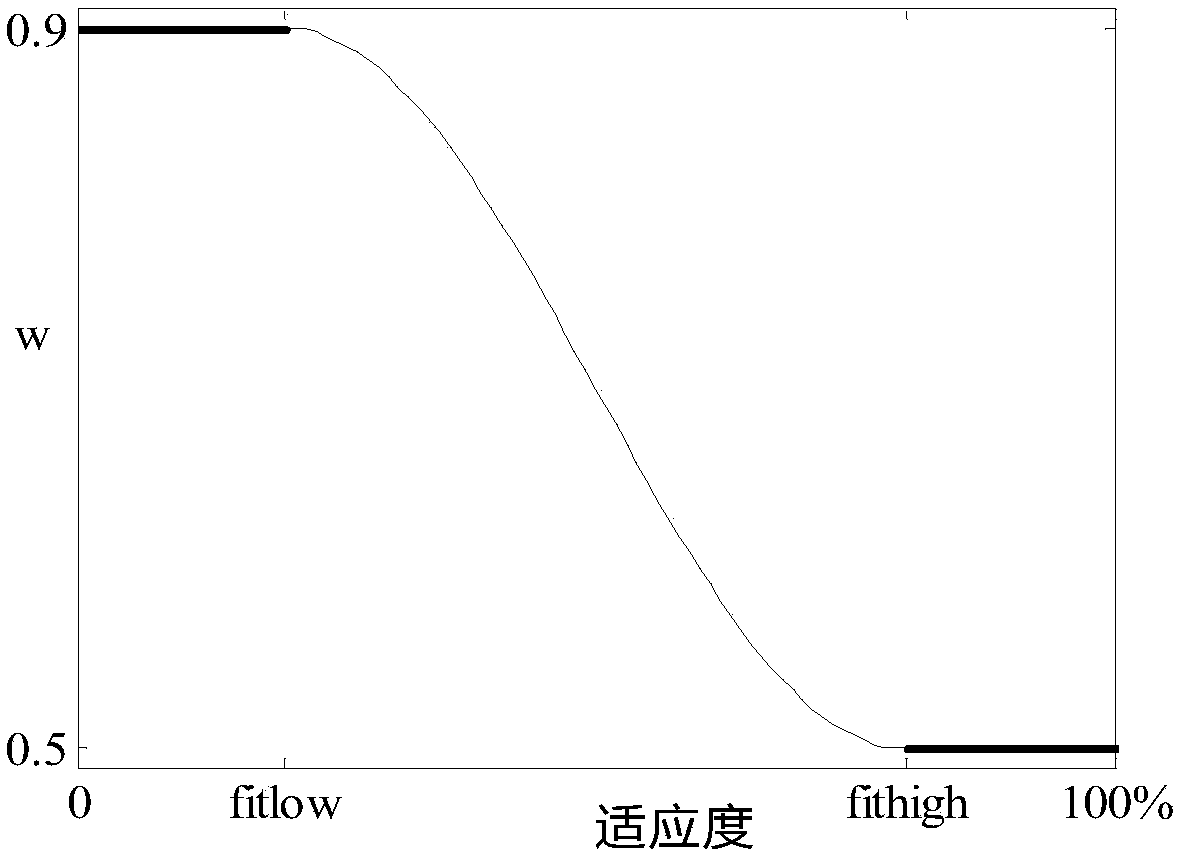
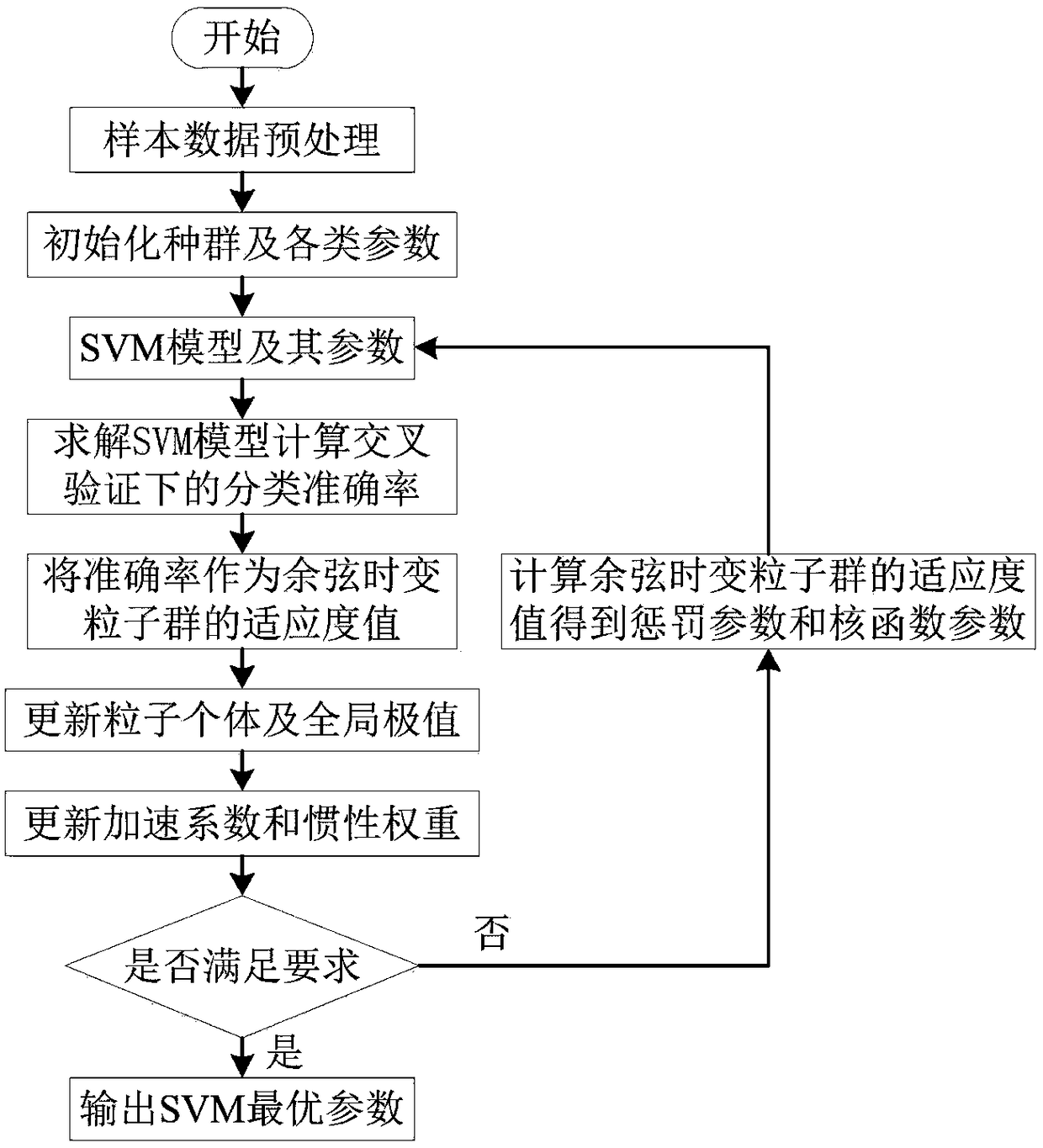
ActiveCN108462711AImprove learning effectBalanced Search CapabilitiesData switching networksData setAlgorithm
The invention discloses an intrusion detection method of a cosine time-variant PSO-SVW, and belongs to the technical field of the network information security. The method comprises the following steps: performing numeralization processing on all data in a NSL-KDD data set and an ADFA intrusion detection data set in a normal sample and an attack sample, and then performing cosine time-variant PSO optimization, and performing a misuse detection by applying the cosine time-variant PSO-SVM. Compared with the existing partial time-variant plasma swarm optimized SVW model, the learning capacity of the time-variant plasma swarm algorithm in the detection process is improved according to the cosine function nonlinearity, the cosine time-variant acceleration coefficient expression way is simplified, and a value policy of the inertia weight is improved, and the elaborate degree and the searching efficiency of the current optimal target region searching are improved, thereby accelerating the convergence speed of the time-variant PSO-SVW intrusion detection model, and effectively improving the detection rate of the time-variant PSO-SVW intrusion detection model.
Owner:JIANGNAN UNIV
Abusive traffic detection
ActiveUS20160366168A1Increase network bandwidth usageReduce performanceResourcesTransmissionGraphicsData set
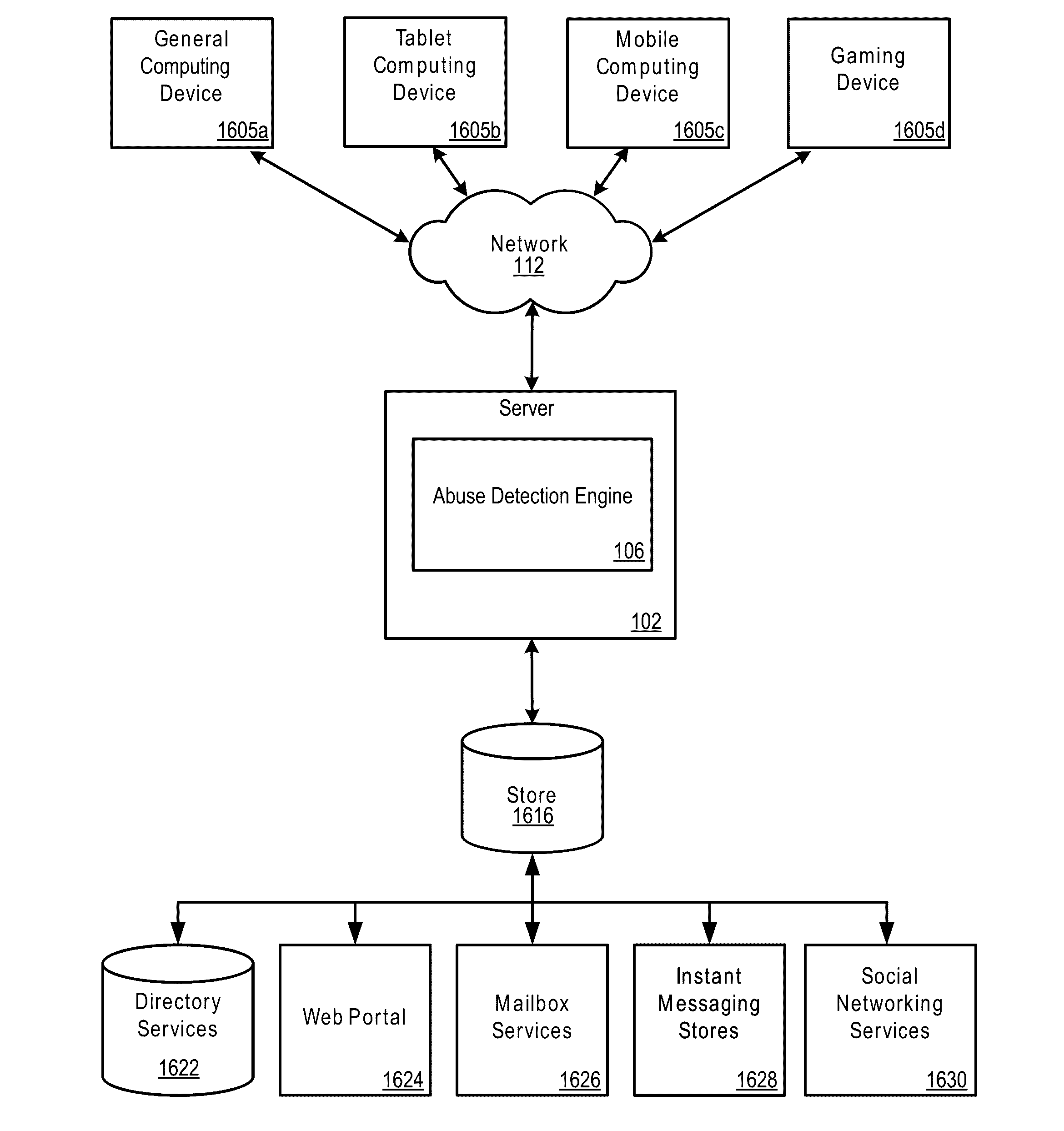
Aspects of an abuse detection system for a web service include an abuse detection engine executing on a server. The abuse detection engine includes a pre-processing module for aggregating a data set for processing and analysis; a suspiciousness test module for identifying suspicious content owners and suspicious users; a graphing module for finding connections between suspicious content owners and suspicious users; an analysis module for determining which groups are constituted of fraudulent or abusive accounts; and a notification generation and output module for generating a list of abusive entities and a notification for output to at least one of: the abusive entity, a digital content distribution company associated with the abusive entity, and a legal department or other entity for further investigation or action. Additionally, royalties for content consumptions associated with abusive accounts may be held. Aspects of an abusive traffic detection method enable multi-account and multi-content owner fraud detection.
Owner:MICROSOFT TECH LICENSING LLC
Wireless Mesh network intrusion detection system and detection method thereof
InactiveCN102006586ASolve the problem of inaccurate intrusion detectionReduce resource consumptionNetwork topologiesSecurity arrangementWireless mesh networkResource consumption
The invention discloses a wireless Mesh network intrusion detection system and a detection method thereof in the technical field of network safety. The system comprises a data acquisition module, a detection recording module, a node dummy management module, a characteristic detection module and a response module. The detection method comprises the following steps of: forming a finite-state machine according to a routing protocol of a wireless Mesh network; deploying the intrusion detection system and determining a node which performs intrusion detection; starting state machine-based intrusiondetection; and establishing an anomaly-misuse detection mapping table to realize the intrusion detection. A routing protocol state machine can be adequately applied to the intrusion detection by establishing a node dummy so as to provide a detection basis for the detection of a detection node; the problem of inaccurate intrusion detection in the wireless Mesh network is solved by adopting an intrusion detection system deployment strategy; and the resource consumption of the network by the overall intrusion detection can be reduced by starting the timing selection of the detection system.
Owner:SHANGHAI JIAO TONG UNIV
Automated forensic document signatures
ActiveUS8280905B2Facilitate methodDigital data processing detailsUser identity/authority verificationDigital signatureMisuse detection
Methods and systems are provided for a proactive approach for computer forensic investigations. The invention allows organizations anticipating the need for forensic analysis to prepare in advance. Digital signatures are generated proactively for a specified target. The digital signature represents a digest of the content of the target, and can be readily stored. Searching and comparing digital signatures allows quick and accurate identification of targets having identical or similar content. Computational and storage costs are expended in advance, which allow more efficient computer forensic investigations. The present invention can be applied to numerous applications, such as computer forensic evidence gathering, misuse detection, network intrusion detection, and unauthorized network traffic detection and prevention.
Owner:GEORGETOWN UNIV
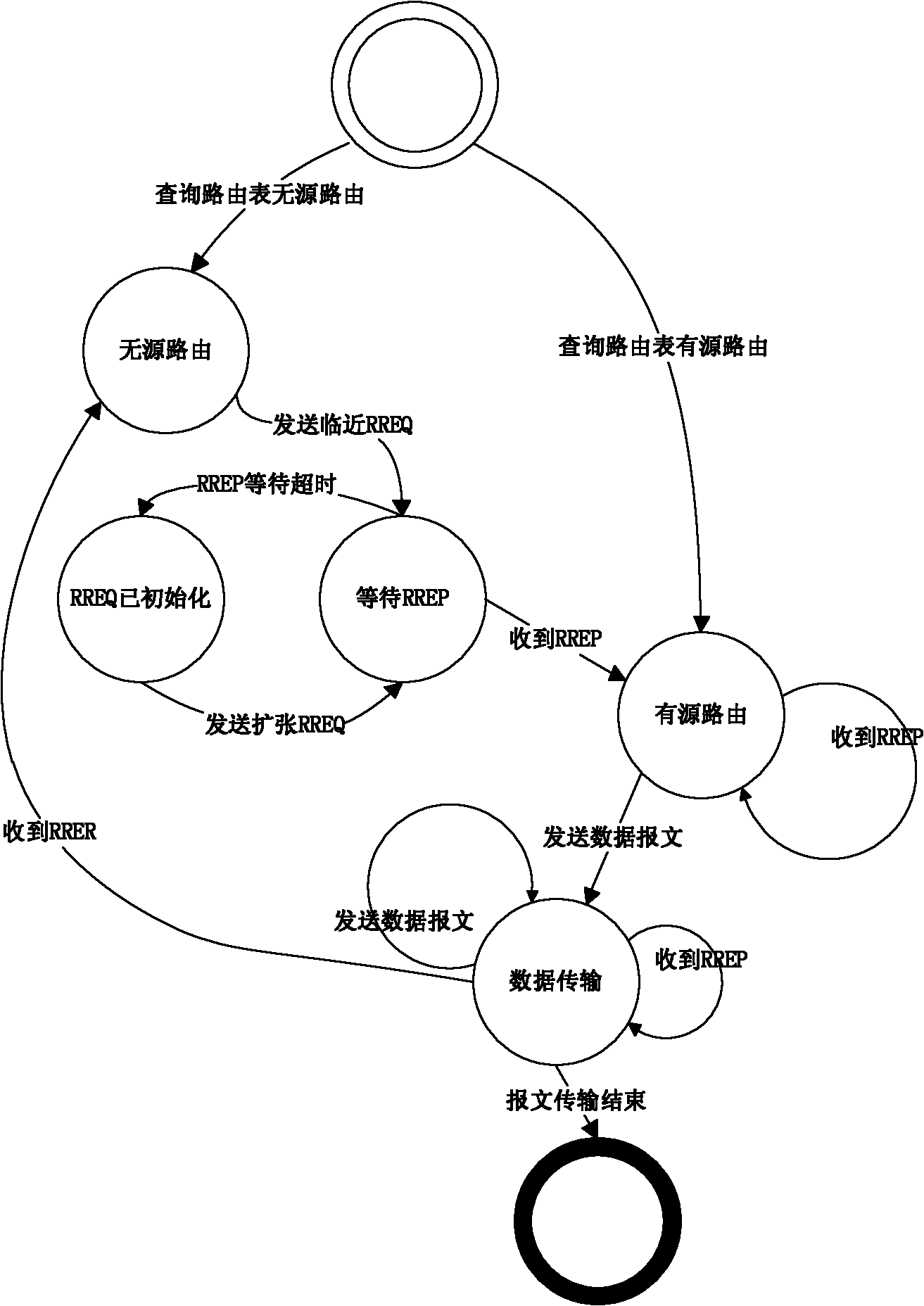
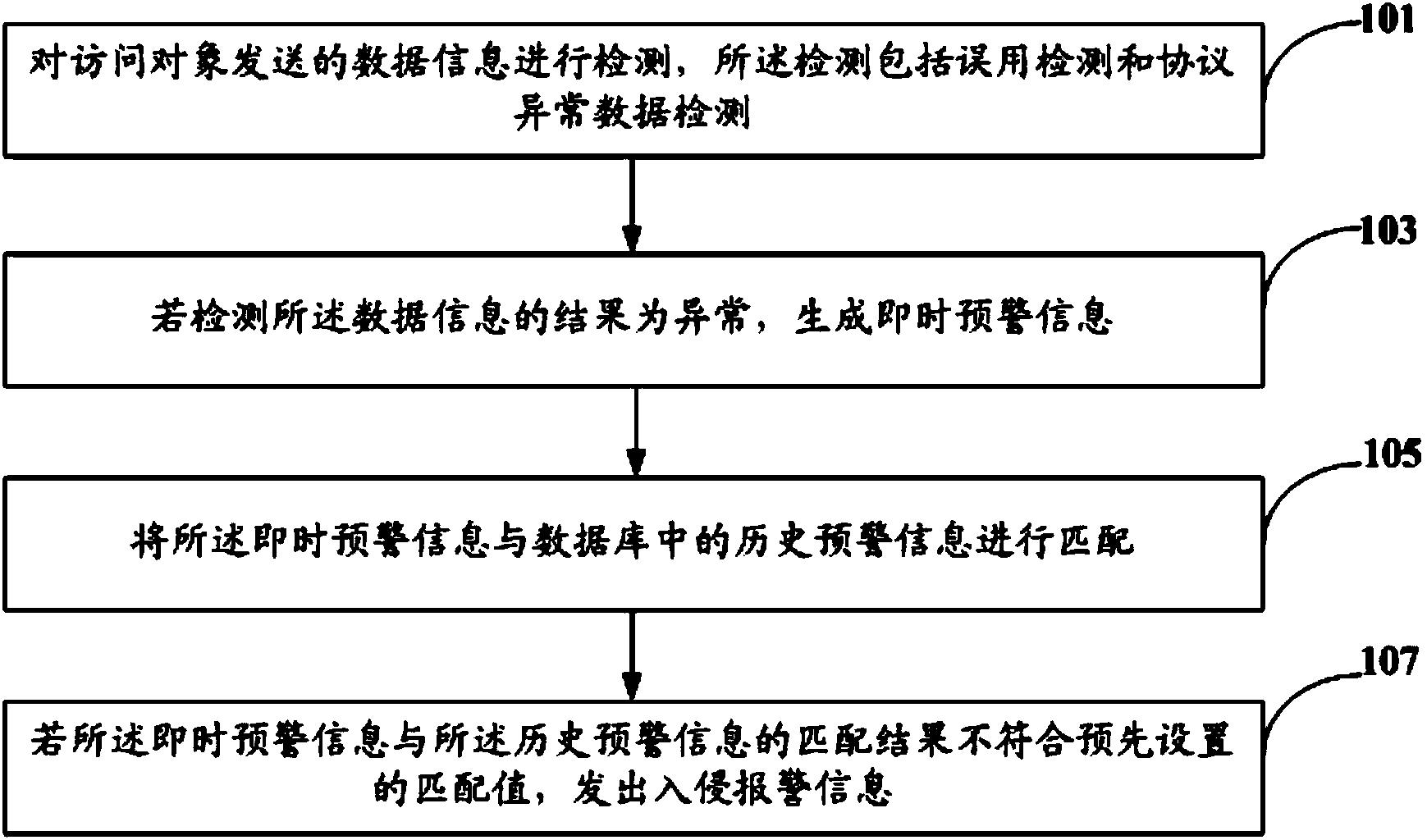
Network intrusion alarm method and system based on nuclear power plant
InactiveCN103888282AEasy to detectImprove the alarm mechanismData switching networksInformation technology support systemNuclear powerData information
The invention discloses a network intrusion alarm method based on a nuclear power plant. The method comprises the steps that data information sent by a visit object is detected, wherein the detection comprises misuse detection and protocol anomaly data detection; if the detection result of the data information is abnormal, real-time early warning information is generated; the real-time early warning information and historical early warning information in a database are matched; and if the matching result of the real-time early warning information and the historical early warning information does not accord with a preset matching value, intrusion alarm information is issued. The network intrusion alarm method based on the nuclear power plant, which is provided by the invention, can effectively meet the requirement of network security protection of an industrial network of the nuclear power plant. In addition, the invention further discloses a network intrusion alarm system based on the nuclear power station.
Owner:中广核工程有限公司 +2
Network intrusion detection method and device
The invention provides a network intrusion detection method and device. The method comprises the following steps of: according to a current intrusion feature database, performing misuse detection of network data acquired in real time; when the fact that the network data has an intrusion behavior is judged, processing feature value sequences of the network data according to a genetic algorithm, so that various current feature value sequences are obtained; and, calculating adaptation values of the various current feature value sequences, and storing the current feature value sequences, the adaptation values of which are greater than a threshold value, in the current intrusion feature database, wherein the threshold value is obtained by processing at least one training feature value sequence in the current intrusion feature database in advance. By means of the method disclosed by the invention, detection on network flow data is realized; furthermore, crossover and variation of the detected intrusion behavior can be carried out according to the genetic algorithm; furthermore, more intrusion behaviors can be obtained through comparison with the adaptation threshold value; therefore, the intrusion feature database can be continuously updated; and thus, the network intrusion detection accuracy rate can be continuously increased.
Owner:BEIJING AN XIN TIAN XING TECH CO LTD
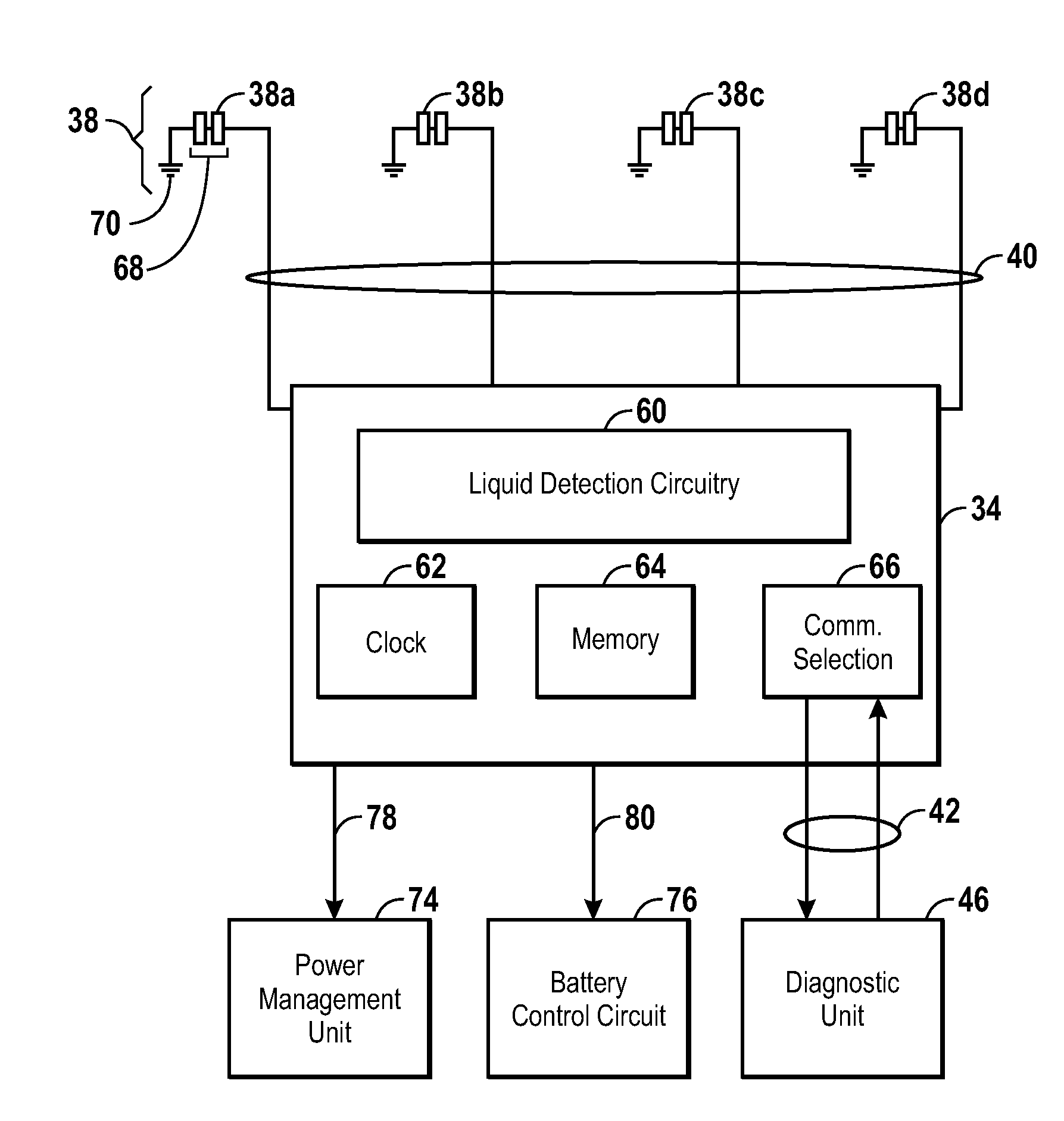
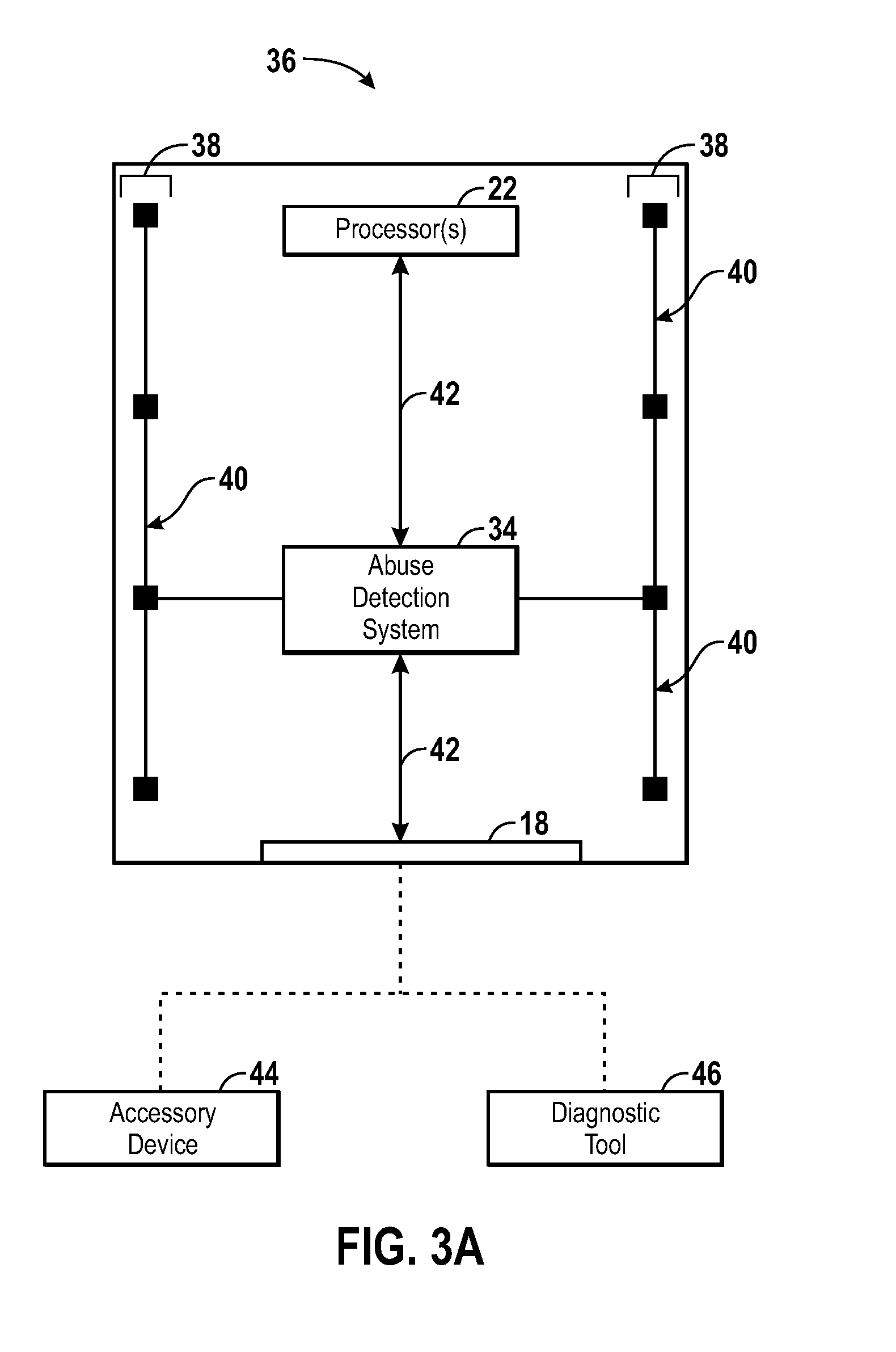
Consumer abuse detection system and method
ActiveUS20100312920A1Quickly and easily detectReduce risk of damageElectric signal transmission systemsElectrical testingCommunication interfaceEvent data
Embodiments disclosed herein provide systems, devices, and methods for detecting the occurrence of consumer abuse events in electronic devices. In one embodiment, a system includes one or more sensors coupled to an abuse detection sub-system for detecting the occurrence of an abuse event, wherein upon detecting an abuse event, a record of the abuse event is stored by the abuse detection sub-system. The system further provides a communication interface configured to provide a first mode of diagnostic communication and a second mode of non-diagnostic communication through a common input / output port. When using a diagnostic device, the diagnostic mode of communication may be enabled, thus allowing the diagnostic device to access consumer abuse event data stored by the abuse detection sub-system.
Owner:APPLE INC
Snort improvement method based on data mining algorithm
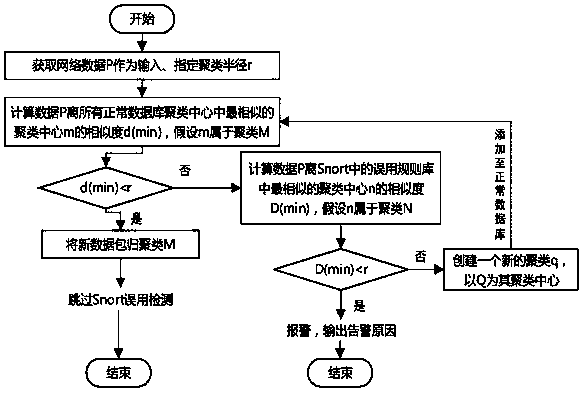
ActiveCN111224984AImprove detection efficiencyImproving detection efficiency means detection accuracyCharacter and pattern recognitionTransmissionAlgorithmNetwork on
The invention relates to a Snort improvement method based on a data mining algorithm. The method comprises the following steps that: acquiring, by an intrusion detection Snort system, data P on a network; carrying out similarity clustering on the P and a normal behavior database by utilizing an improved K-means algorithm, if the similarity is smaller than a clustering radius r, judging the P and the normal behavior database as normal data, and directly skipping a misuse detection process of Snort; otherwise, comparing the data with the abnormal database in the Snort again, calculating the similarity between the data and each abnormal behavior class, if the data can be clustered in the abnormal behavior classes, indicating that the data is of an abnormal data type, and sending out a corresponding alarm by the system; and if the abnormal class still cannot be clustered, adding the abnormal class to the normal database, and updating the normal behavior database again. Most of the data onthe network is normal data, the abnormal data only occupies a small part, the clustering accuracy of the improved K-means algorithm is high, and the data processed by misuse of a detection engine canbe greatly reduced through the above mode, so that the overall detection accuracy and efficiency of the Snort system are improved.
Owner:CHONGQING UNIV OF POSTS & TELECOMM +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com