Data flow analysis based hostile attack detecting method
A data flow analysis, malicious attack technology, applied in data exchange network, digital transmission system, electrical components, etc., can solve the problem of high probability of false alarm
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings.
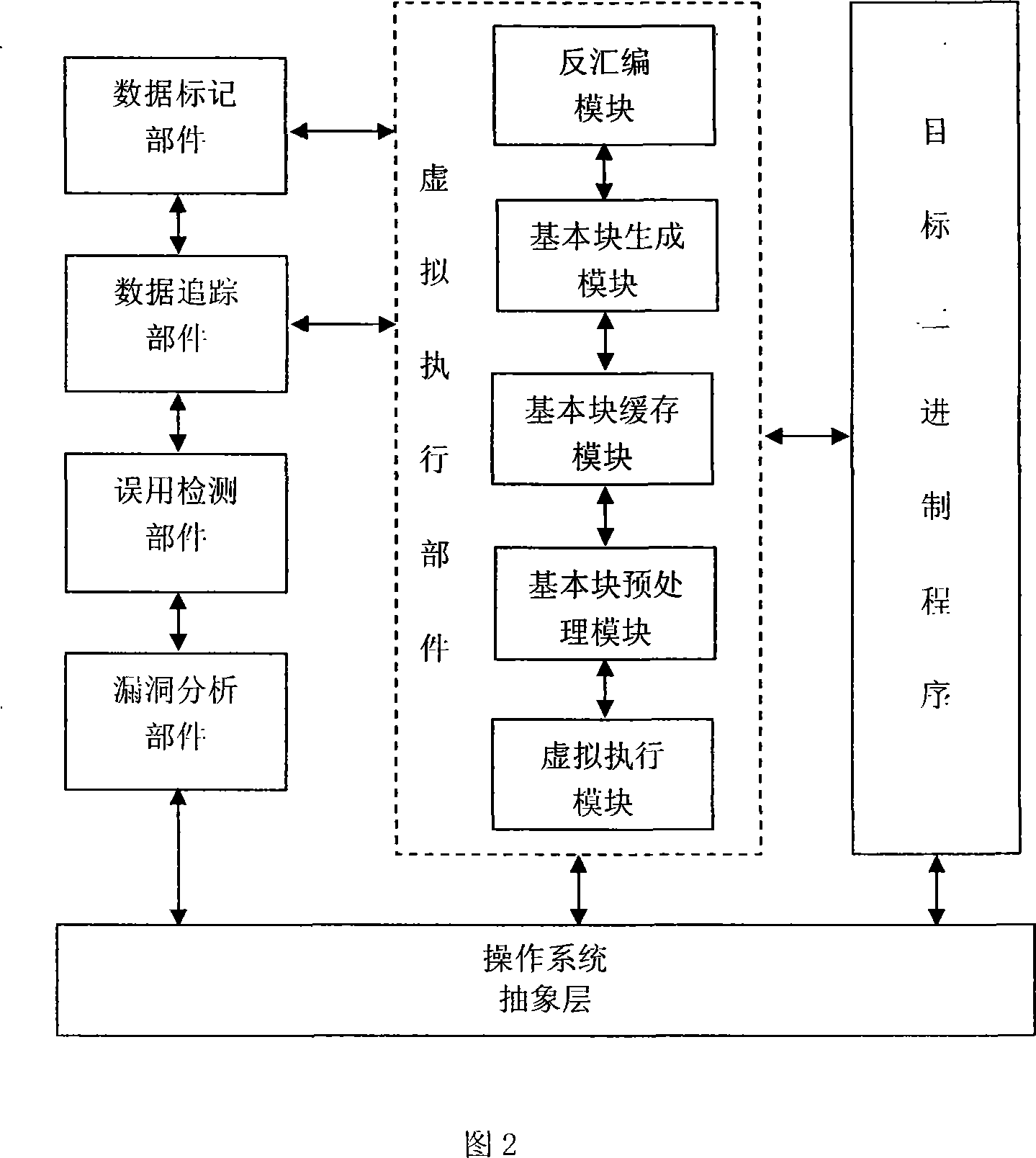
[0022] Referring to Fig. 1, the virtual execution unit loads the monitored program, and obtains the code flow of the target program after mastering the control right of the target binary program. The disassembly module is used to obtain the assembly instructions of the target code flow, and the basic blocks are obtained by analyzing these instructions. A basic block is an instruction sequence that does not contain a control flow transfer instruction, and then each instruction of each basic block is instructed separately.
[0023] When the target program receives external input data, the data marking component records the input data as infected data. During subsequent command execution, all operations on the infected data will be monitored, and the data tracking c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com