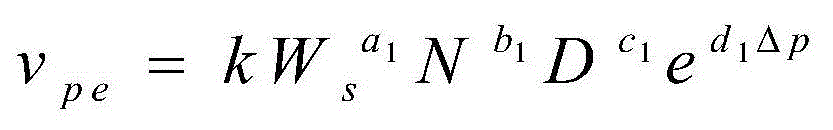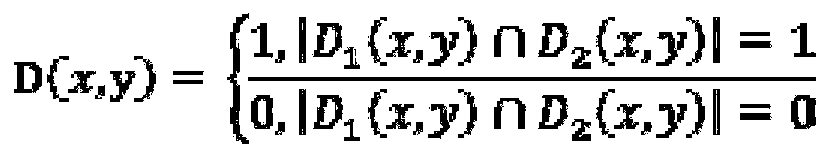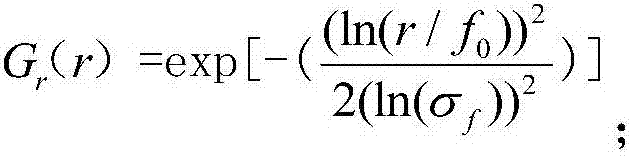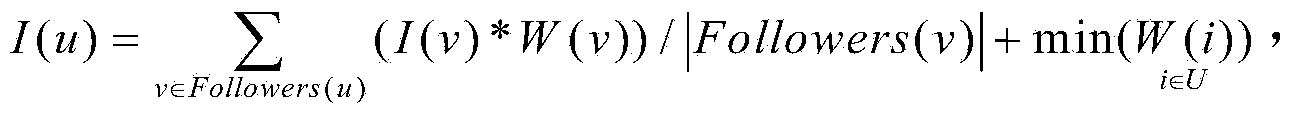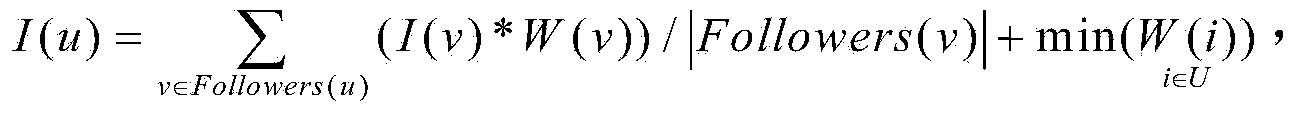Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
565results about How to "Accurate discovery" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
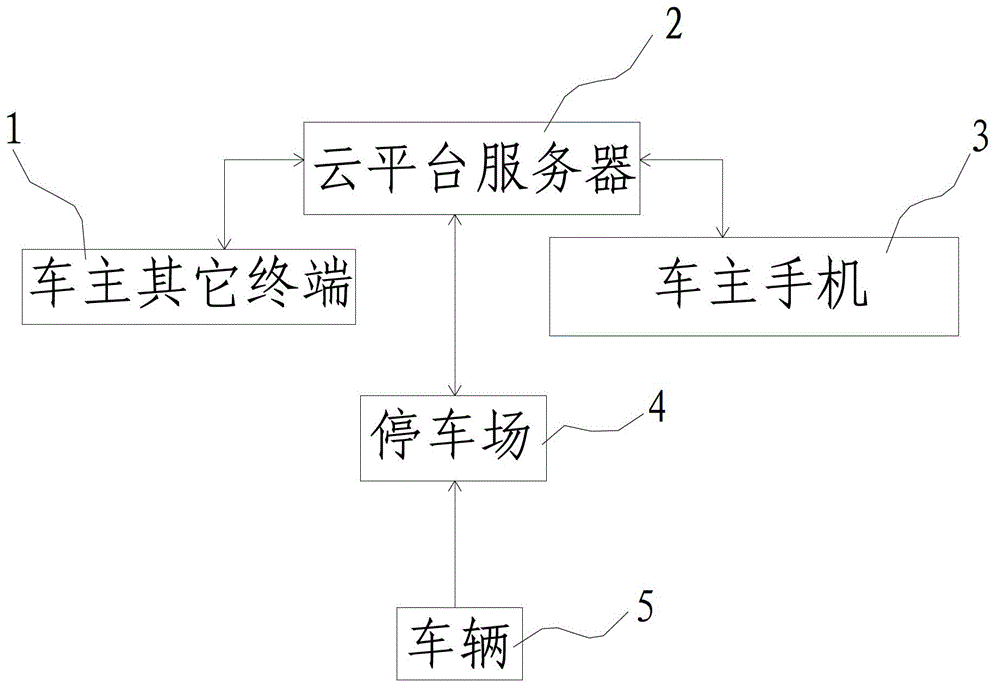
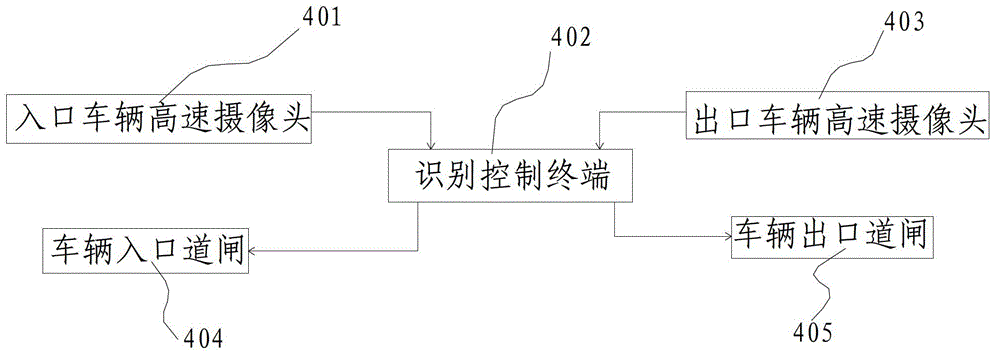
No-obstacle parking charging system and method thereof
InactiveCN102855671AShorten the timeImprove operational efficiencyTicket-issuing apparatusIntensive managementTerminal equipment
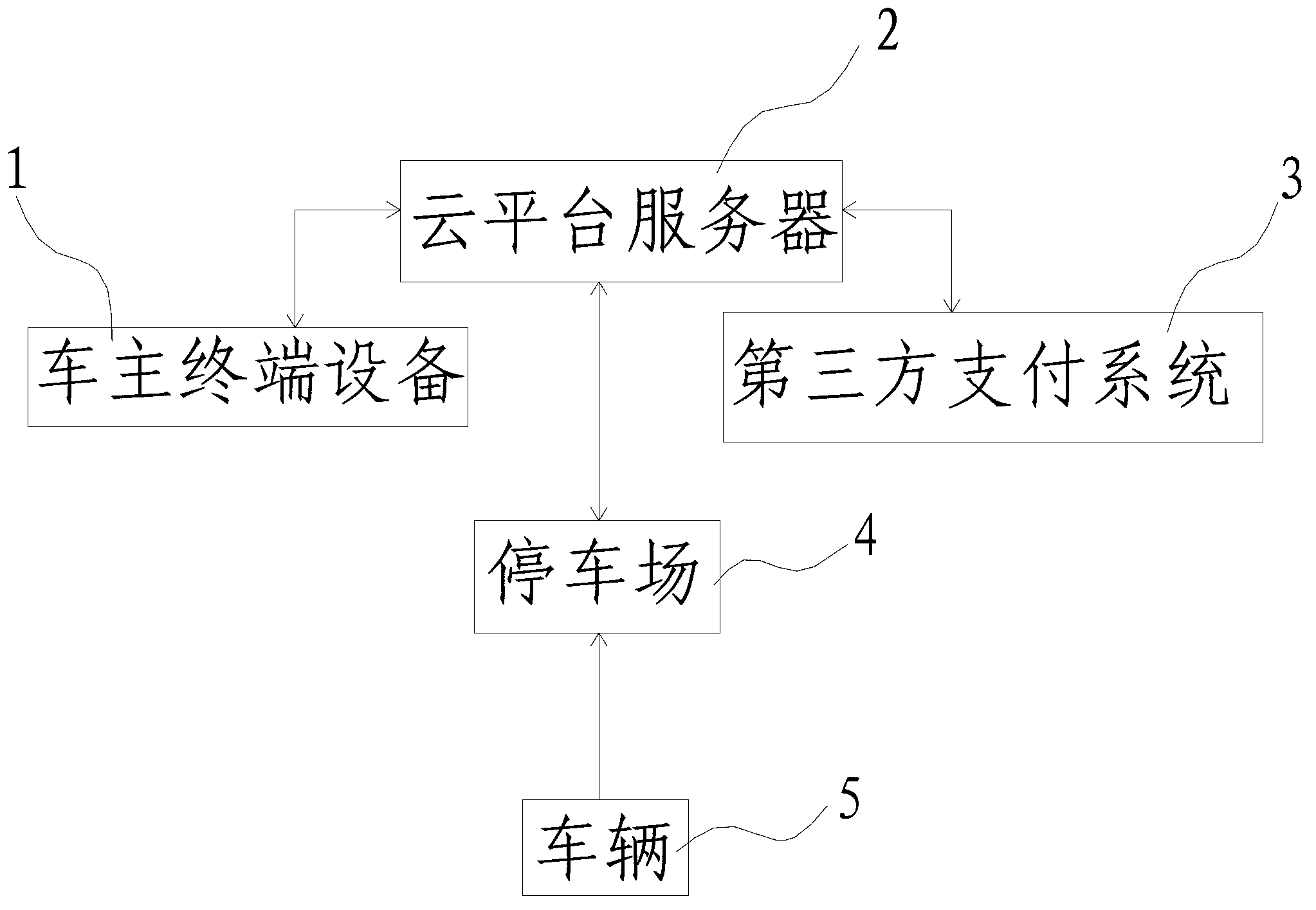
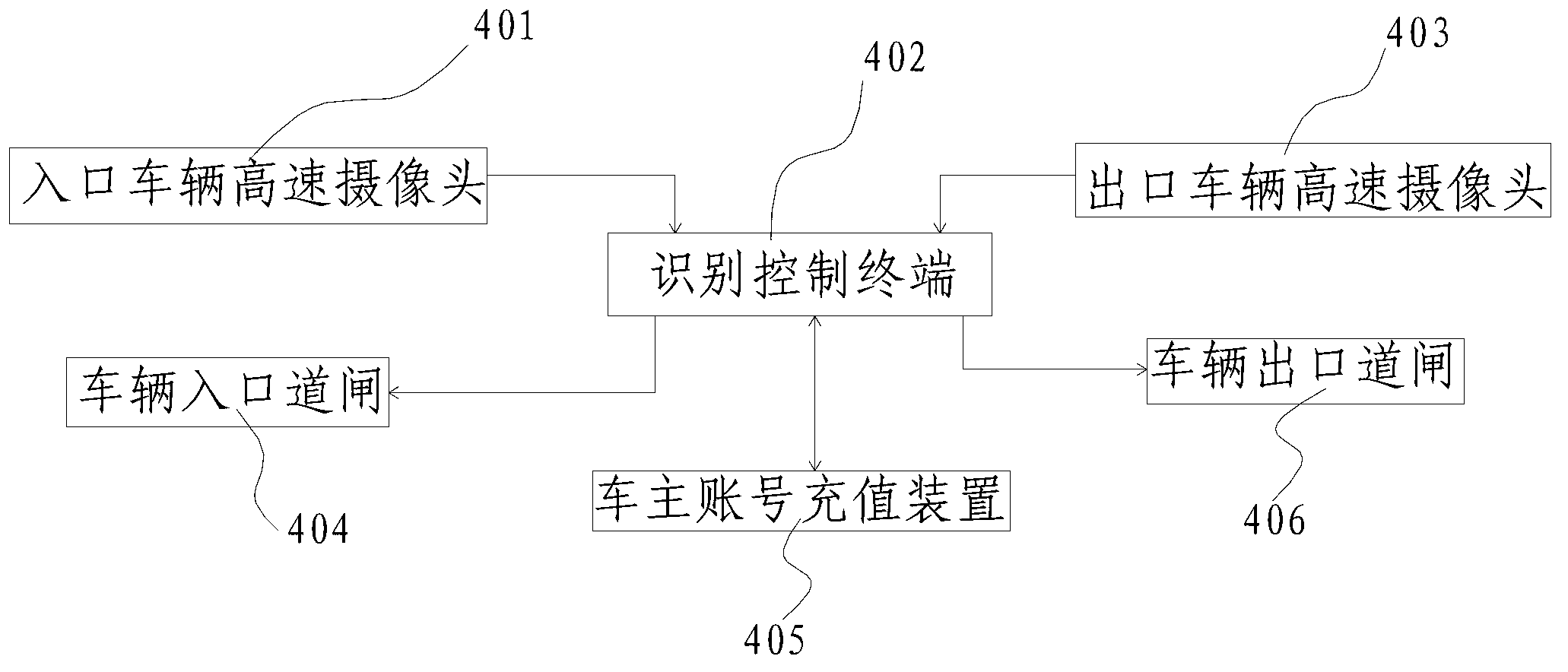
The invention relates to a charging system for automobiles and discloses a no-obstacle parking charging system, which comprises a cloud platform server, a plurality of parking lots being in data exchange with the cloud platform server through a network, a plurality of automobile owner terminal devices being in data exchange with the cloud platform server through the network, and a third-party payment system being in data exchange with the cloud platform server through the network. The invention also discloses a no-obstacle parking charging method, which comprises the following steps: S10, a member is registered; S30, an automobile enters the parking lot; and S40, the automobile is driven out of the parking lot. According to the system and the method disclosed by the invention, the time of passing through an entrance guard of the parking lot by the automobile is greatly saved, the process of parking charging is simplified, the operation efficiency of the parking lots is improved, and the parking lots are managed intensively through the cloud platform server, so that great convenience is brought to automobile owners.
Owner:陈淼
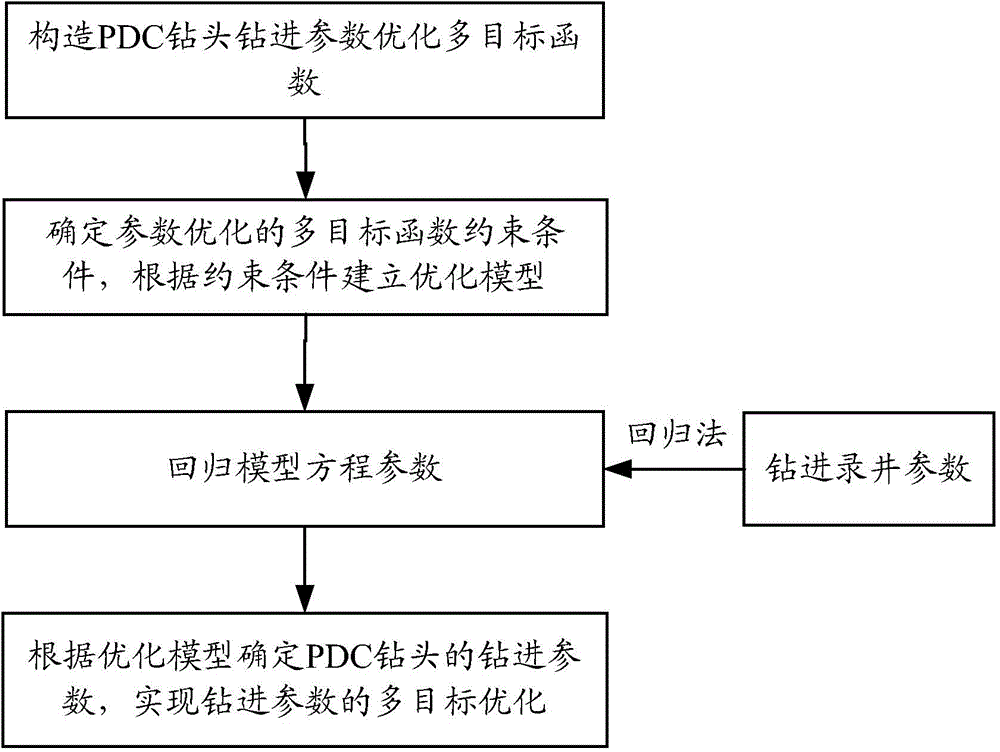
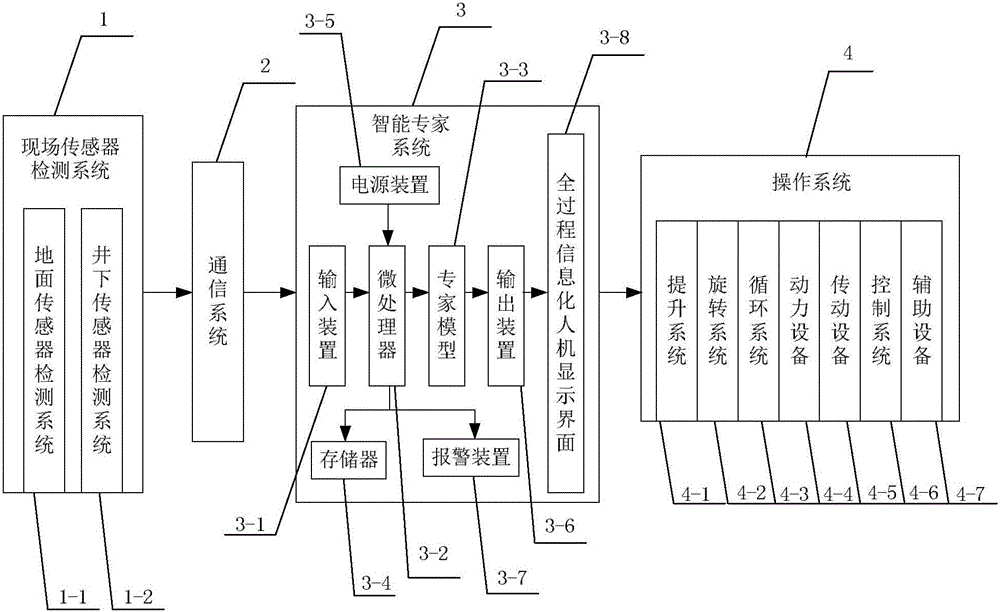
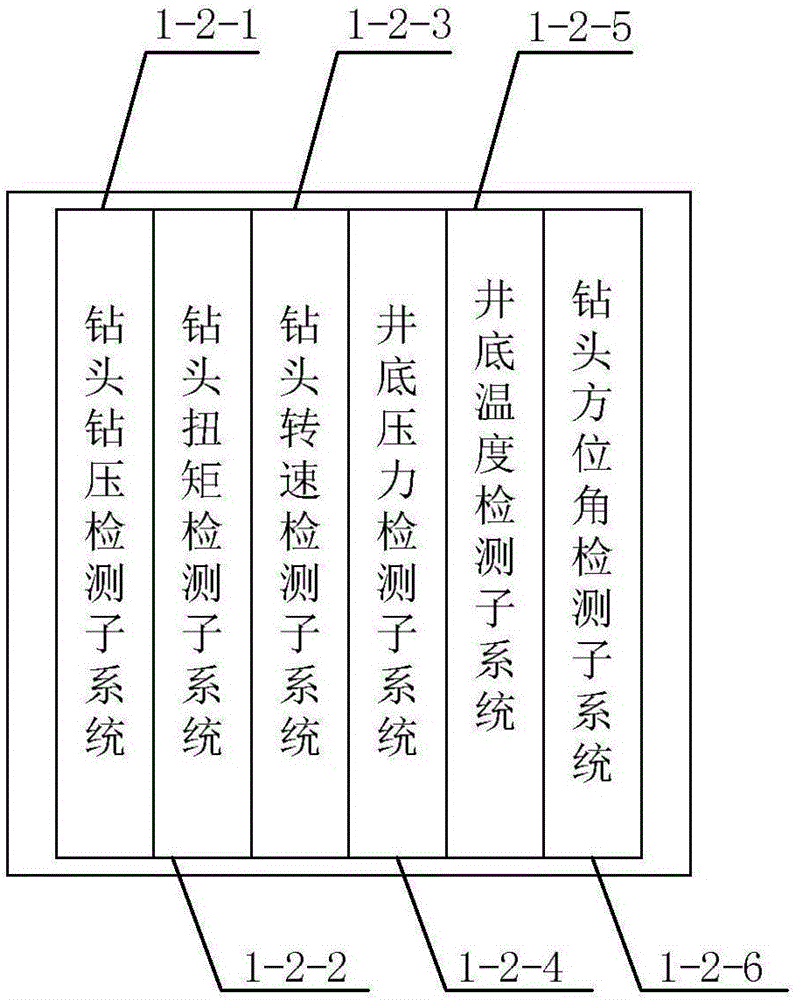
Intelligent drilling expert system
ActiveCN104806226AAccurate discoveryReal-timeAutomatic control for drillingEarly predictionAutomatic control
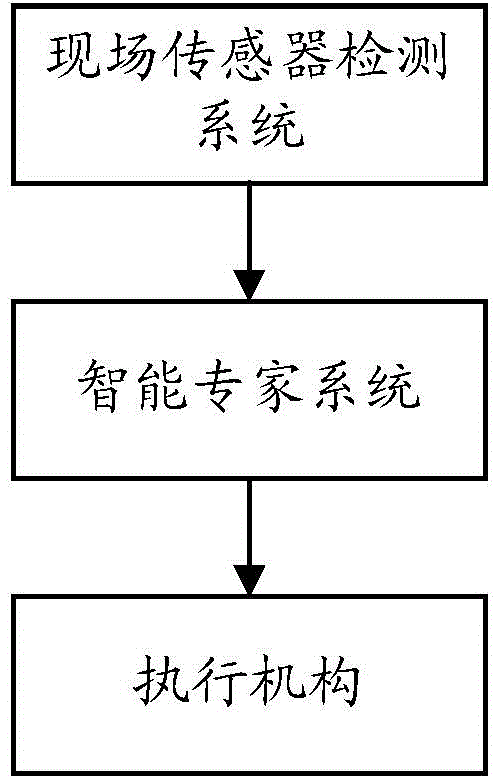
The invention provides an intelligent drilling expert system. The intelligent drilling expert system comprises a field sensor detection system, an intelligent expert system and an execution mechanism. An automatic closed-loop drilling regulation and control system is formed. Data in a whole drilling process are acquired through a field sensor; then, the acquired data are transmitted into a computer for processing, monitoring, prediction, analysis, explanation, control and the like. Most importantly, through the researched cross-specialty and cross-industry intelligent expert control models for drilling hydraulic control, well wall stability control, friction resistance and torque control, drilling speed and cost control, drilling complexity and accident control and the like, instantaneity, early discovery, early prediction, interpretation while drilling and an automatic control function can be realized, and accurate information is provided for drilling engineering; moreover, the intelligent drilling expert system has the advantages of reducing the drilling cost, increasing the drilling speed, avoiding sudden accidents and discovering oil and gas accurately.
Owner:北京四利通控制技术股份有限公司
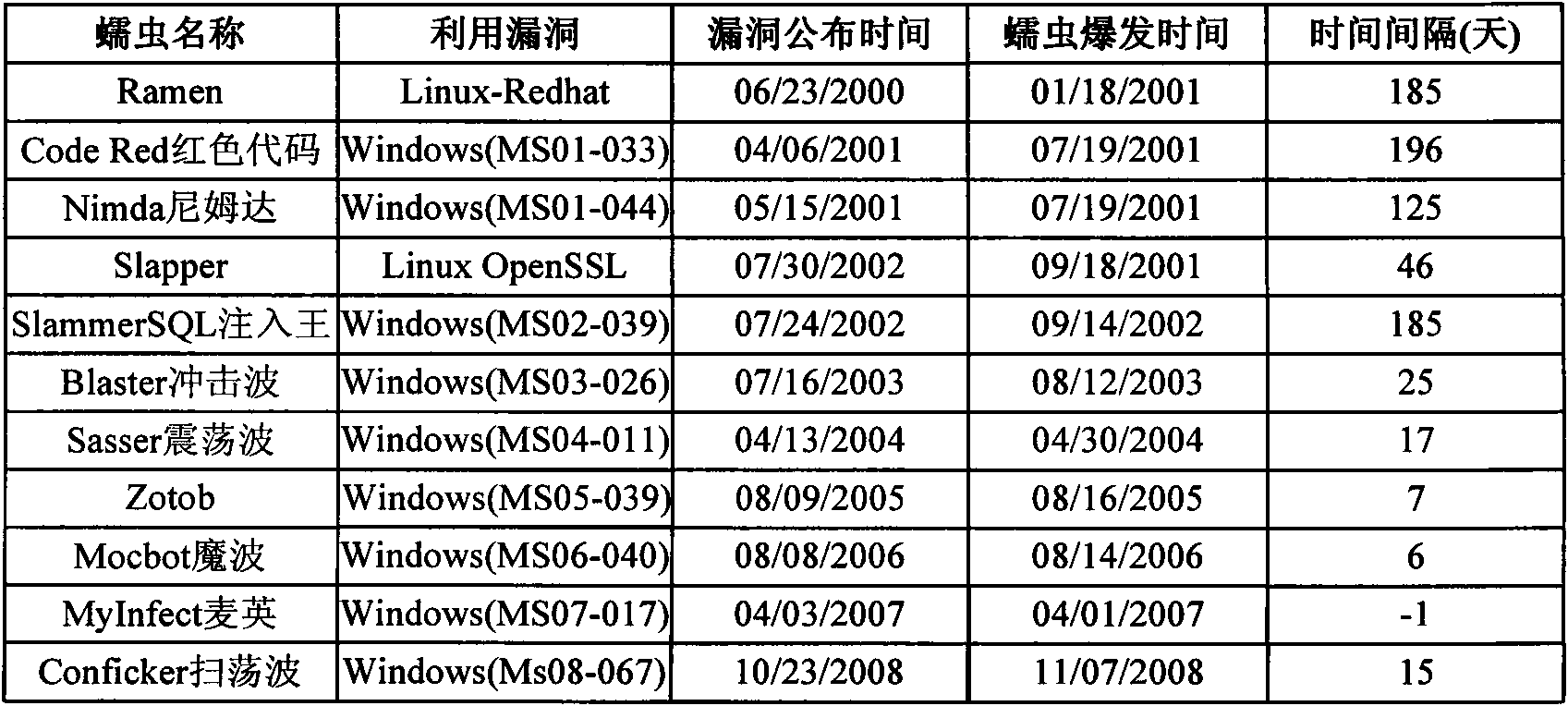
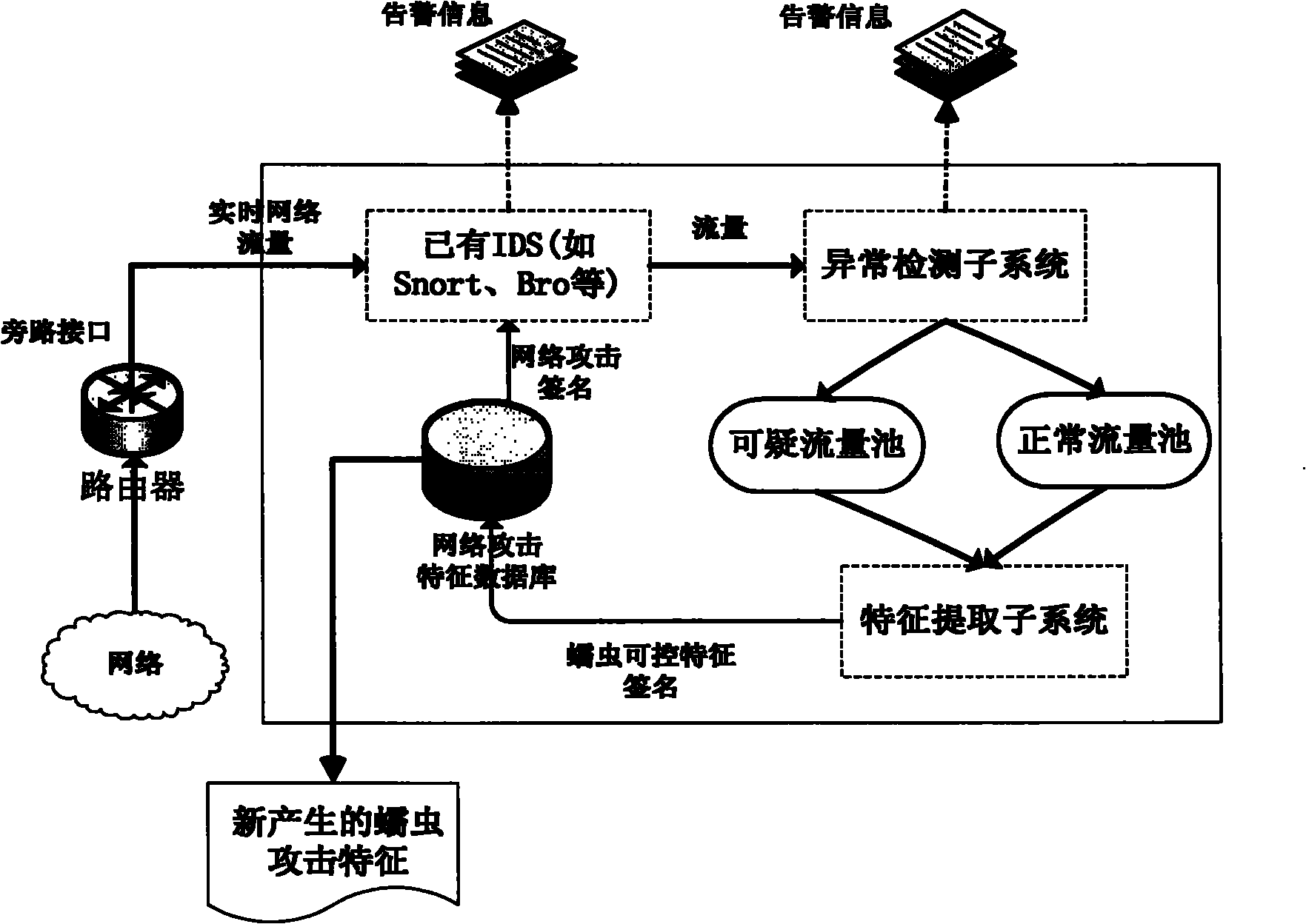
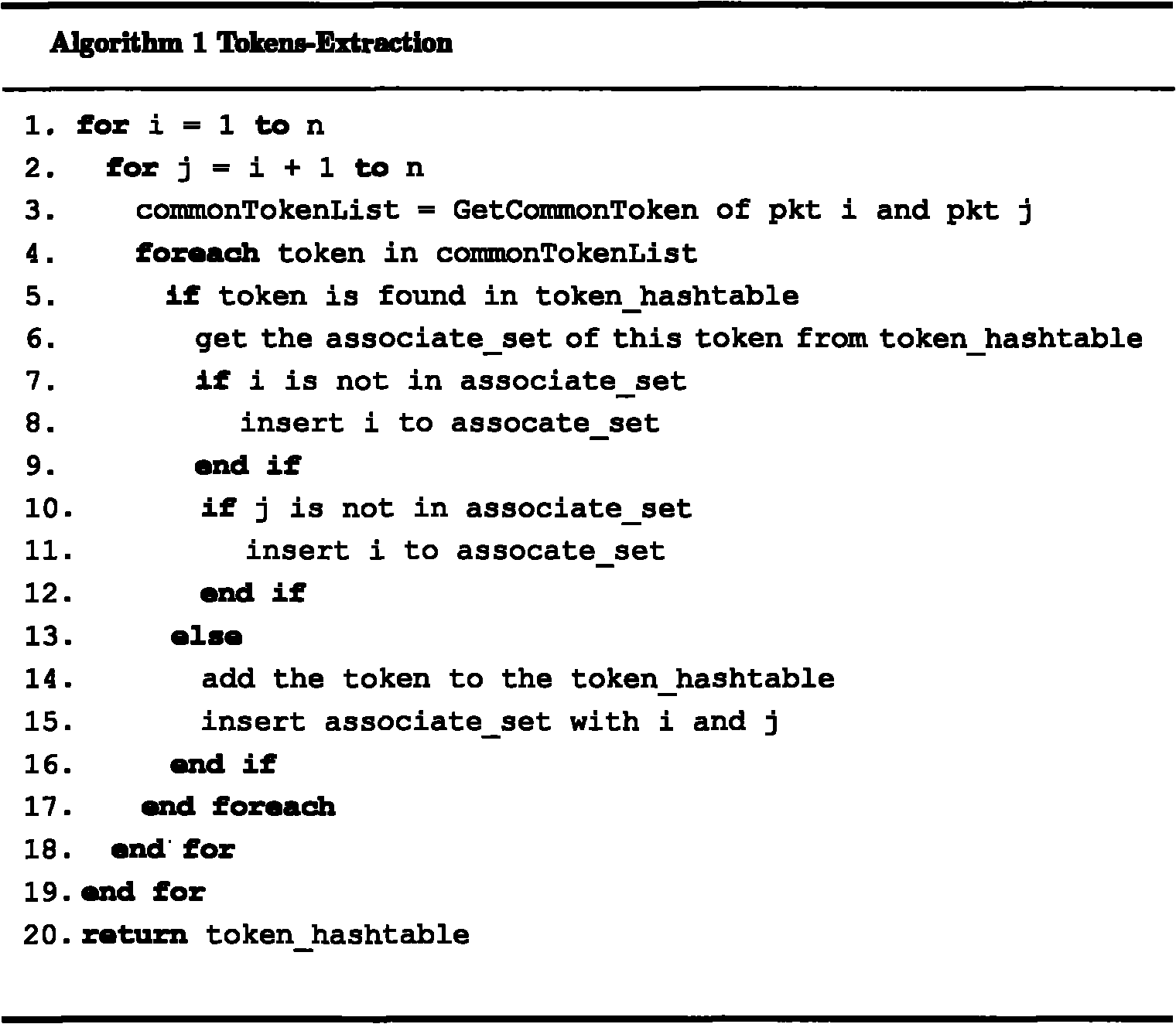
Network worm detection and characteristic automatic extraction method and system
InactiveCN101895521AStop the spreadAccurate discoveryData switching networksFeature extractionAnomaly detection
The invention discloses a network worm detection and characteristic automatic extraction method and a network worm detection and characteristic automatic extraction system and belongs to the technical field of network safety. The method comprises the following steps of: 1) performing abnormal detection on captured network data packets, and dividing the data packets into suspicious network flow and normal network flow according to detection results; 2) storing the suspicious network flow in a suspicious flow pool, and storing the normal network flow in a normal flow pool; 3) clustering the network flow in the suspicious flow pool and the normal flow pool, and extracting a characteristic signature; and 4) updating the extracted characteristic signature in a network attack database, and detecting the network worm. The system comprises an abnormal detection subsystem, a characteristic extraction subsystem, a network attack characteristic database, and a misuse detection system. The methodand the system can more accurately and timely discover the network worm, can automatically extract the worm characteristics and update the attack characteristic database of the existing misuse detection system. Therefore, the aim of suppressing worm propagation is really fulfilled.
Owner:GRADUATE SCHOOL OF THE CHINESE ACAD OF SCI GSCAS
Method for discovering network topology and related equipment
ActiveCN101330405AAvoid the problem of incomplete topology discoveryAccurate discoveryStar/tree networksInformation processingTelecommunications
The invention discloses a network topology discovery method and related equipment thereof. The method comprises the following steps: acquiring a spanning tree protocol (STP) result of a switch; processing the STP result of the switch to obtain the topological connection relationships of uplink ports of the switch; judging whether a switch uplink port with an undetermined topological connection relationship exists, and, if yes, obtaining the topological connection relationship of the switch uplink port with the undetermined topological connection relationship according to the MAC address forward table of the switch uplink port with the undetermined topological connection relationship. The invention further discloses a network information processing device with a network topology discovery function. In the method, the link layer topological connection relationship discovered by the STP result and the link layer topological connection relationship discovered by the MAC address forward table are closely related, so that the method can accurately discover and obtain various types of topological connection relationships of the switch uplink ports.
Owner:BEIJING BOCO COMM TECH +1
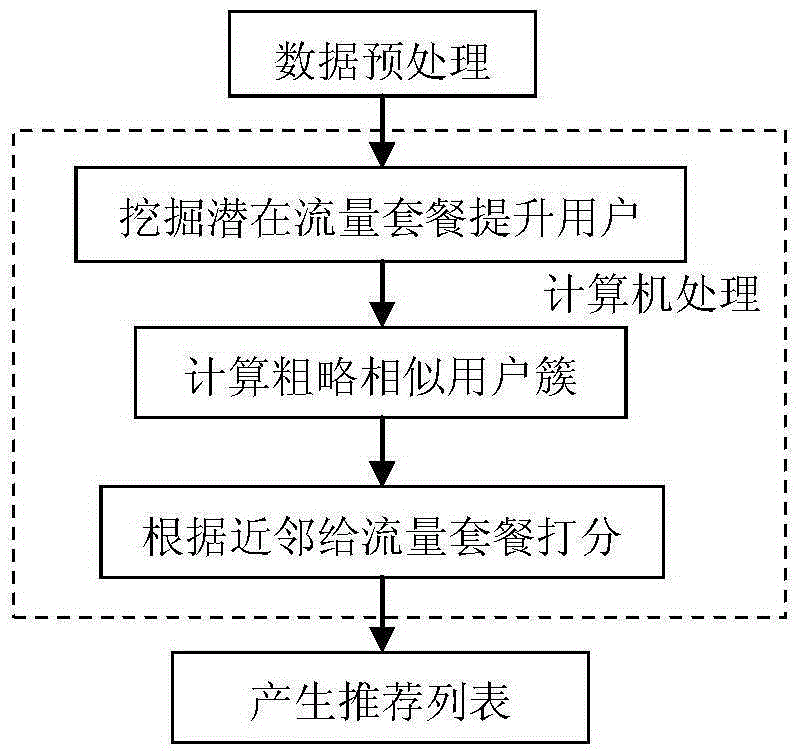
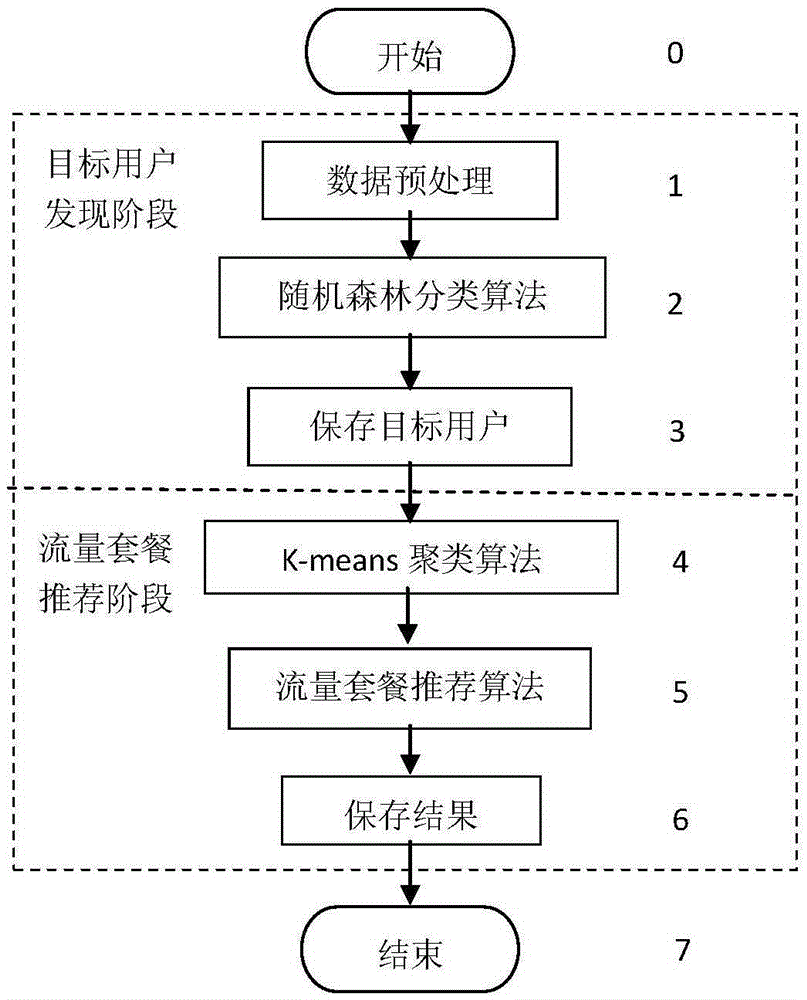
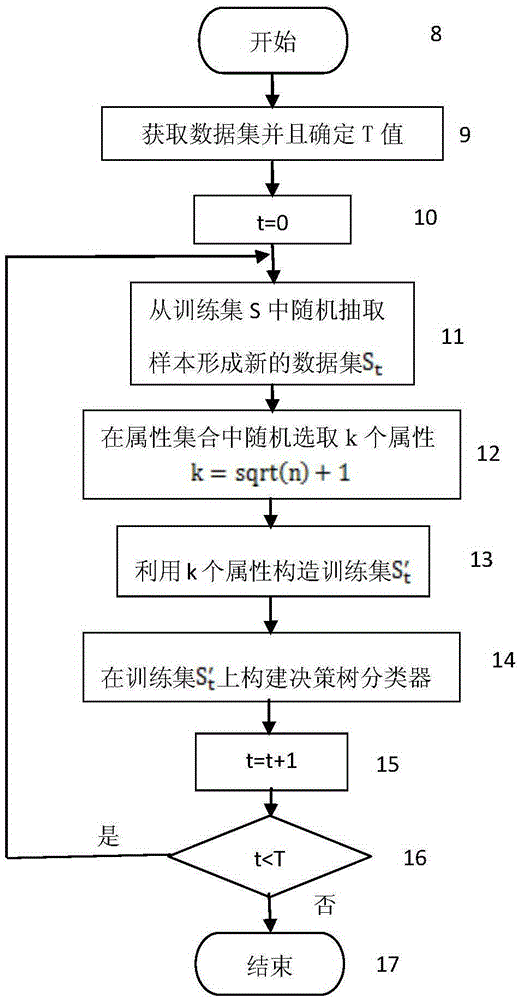
Mobile data traffic package recommendation algorithm based on user historical data
InactiveCN105389713AAccurate discoveryReduce computational complexityCharacter and pattern recognitionMarketingData dredgingData set
The invention provides a mobile data traffic package recommendation algorithm based on user historical data according to data mining analysis technology. The mobile data traffic package recommendation algorithm comprises the following steps of: 1) a target user finding period comprising the processes of a, acquiring a processed generated data set which comprises a training set and a prediction set, b, executing a random forest classification algorithm for finding a latent data traffic package improving user as a target user, and c, ending; 2), a data traffic package recommendation period comprising the process of a, acquiring a processed generated prediction set, b, executing a K-means clustering algorithm for obtaining a slightly similar user cluster, c, obtaining the target user obtained in the process 1)-b, d, executing a TopN recommendation algorithm on the target user in a same cluster according to a similarity function of the user, and e, ending. The mobile data traffic package recommendation algorithm is used for finding the latent user with a latent data traffic improvement requirement according to data mining technology and executing a recommended plan on the user. Compared with a traditional method, the mobile data traffic package recommendation algorithm has advantages of higher accuracy, higher efficiency, simple realization, low cost, etc.
Owner:NANJING UNIV
Intelligent well drilling expert system
InactiveCN106121621AAccurate discoveryReal-timeAutomatic control for drillingCommunications systemAutomatic control
The invention discloses an intelligent well drilling expert system. The intelligent well drilling expert system comprises an on-site sensor detection system, a communication system, an intelligent expert system and an operation system. The on-site sensor detection system is connected with the intelligent expert system through the communication system, the intelligent expert system is connected with the operation system, and thus the automatic closed loop well drilling adjusting and controlling system is formed. The on-site sensor detection system acquires data of the whole well drilling process. The acquired data are transmitted to the intelligent expert system through the communication system, so that processing monitoring, forecasting, analyzing, controlling and processing are conducted, and finally the operation system executes an operation instruction sent by the intelligent expert system after analyzing. The intelligent well drilling expert system can achieve real-time performance and the functions of early finding, early forecasting, explanation at any time and automatic control, and not only provides accurate information for well drilling engineering but also has the advantages of reducing well drilling cost, increasing well drilling speed, completely preventing accidents, and finding oil and gas accurately.
Owner:SOUTHWEST PETROLEUM UNIV
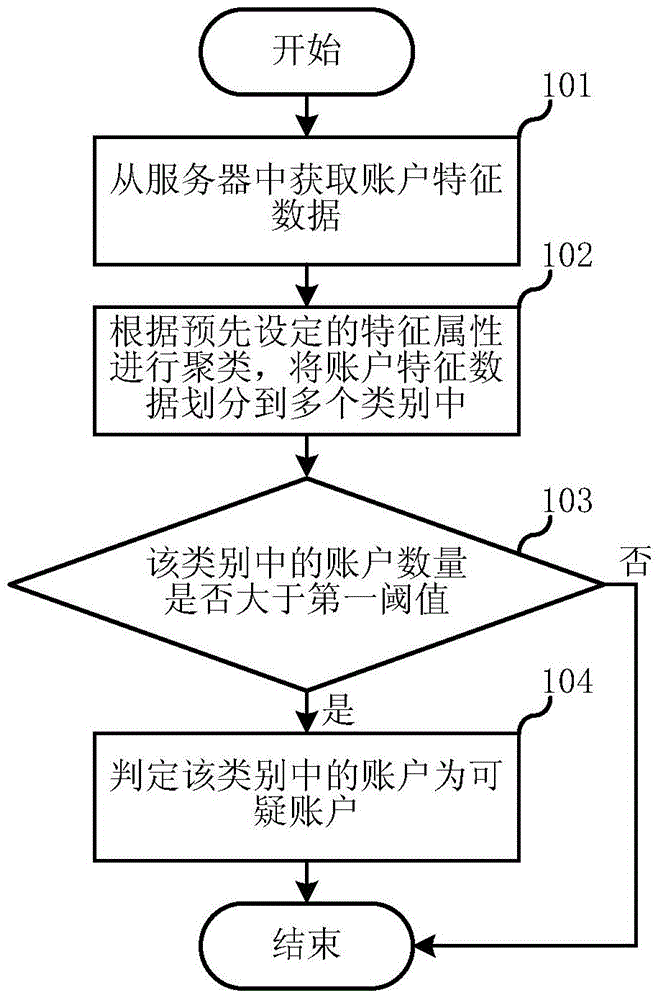
Method and system for identifying computer risks based on account clustering
ActiveCN105791255AReduce riskSpeed up online risk identificationTransmissionSpecial data processing applicationsRisk identificationMultiple category
The invention relates to an account security technology, and discloses a method and system for identifying computer risks based on account clustering. In the method disclosed by the invention, clustering is carried out according to a pre-set characteristic attribute; account characteristic data is divided into multiple categories; furthermore, whether the account number in various categories after division is greater than a first threshold value or not is judged, such that a potential batch suspicious account is identified; therefore, risks are avoided effectively; in addition, judgement of the suspicious account is completed through an offline server; furthermore, a service permission table is generated; an online server can find the suspicious account in time according to the service permission table and forbid the suspicious account to use corresponding services; therefore, the online risk identification speed is enhanced; and better services are provided.
Owner:ADVANCED NEW TECH CO LTD
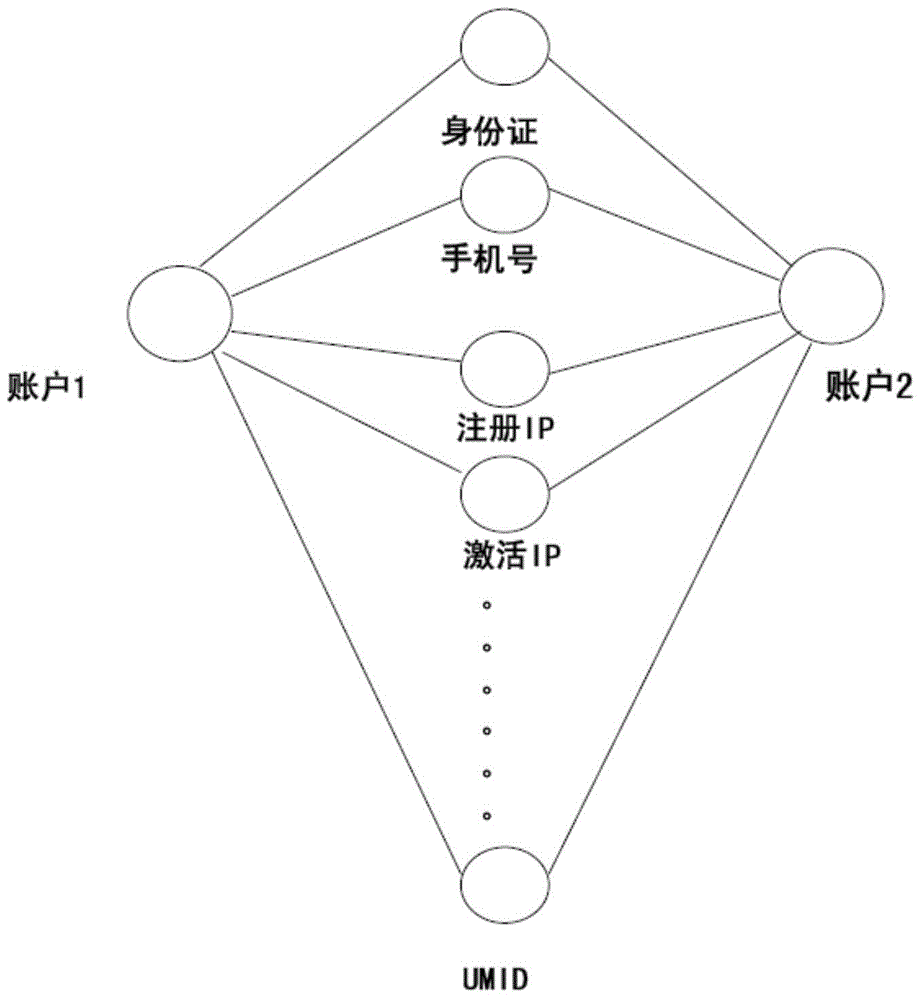
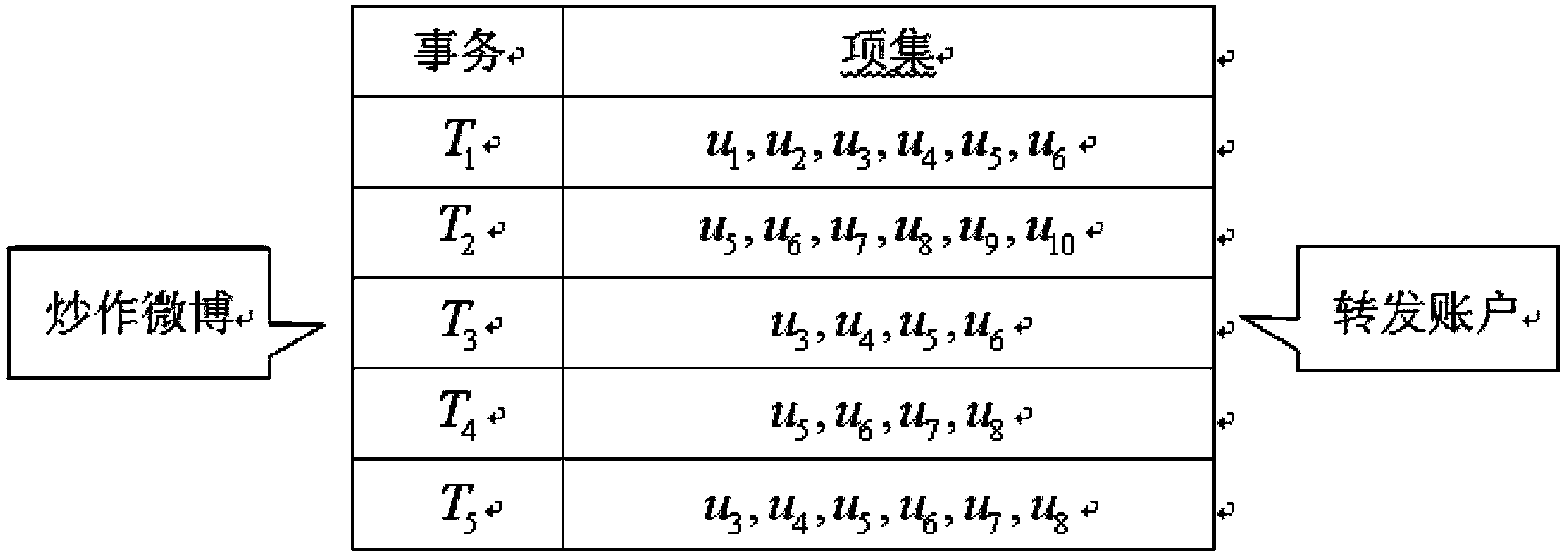
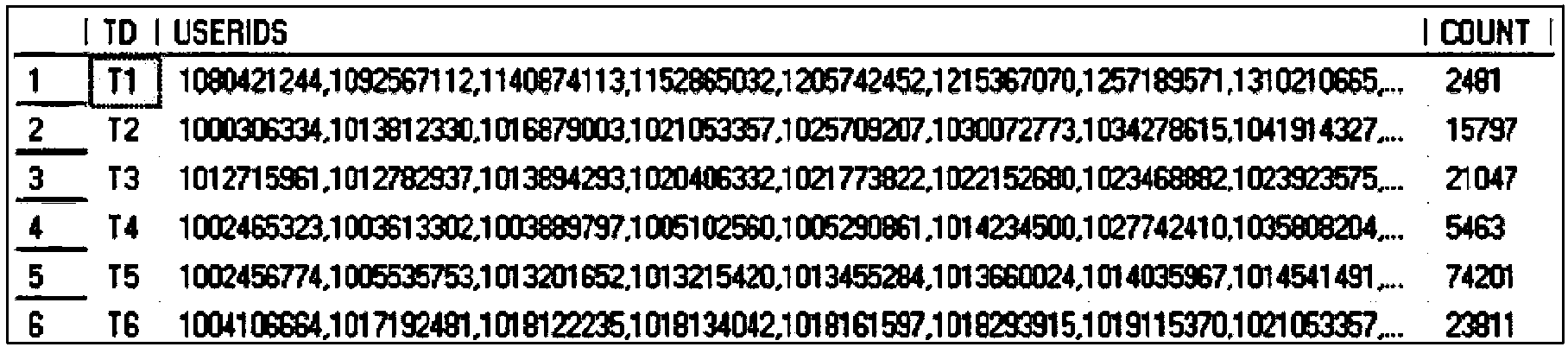
Microblog hype group discovering method based on maximum frequent item set mining
ActiveCN103927398ASmall scaleReduce the number of intersectionsWeb data indexingSpecial data processing applicationsFindings methodsData science
The invention relates to a microblog hype group discovering method based on maximum frequent item set mining. Microblog hype groups are effectively discovered, and false and malicious hype is avoided. The method comprises the steps that the correlation of a hype microblog is used as a clue, and an account set participating in hype microblog transmission is obtained based on the crawler technology or a microblog public open platform; single microblogs are used as transactions, accounts participating in microblog transmission are used as items, and a hype microblog transaction database is built; for transactions, corresponding to a microblog set to be detected, in the transaction database, the maximum frequent item sets contained in the transactions are found, the overlapping ratio of the maximum frequent item sets is calculated, small-scale item sets are merged into large item sets, the intersection frequency is reduced, whether the transactions comprise a certain item or not is judged through the binary search method when intersection is obtained between the transactions, the maximum frequent item set mining efficiency is improved, and microblog hype groups are discovered. The microblog hype group discovering method based on maximum frequent item set mining is simple, and can accurately discover malicious microblog hype groups and avoid negative influences on the society.
Owner:THE PLA INFORMATION ENG UNIV
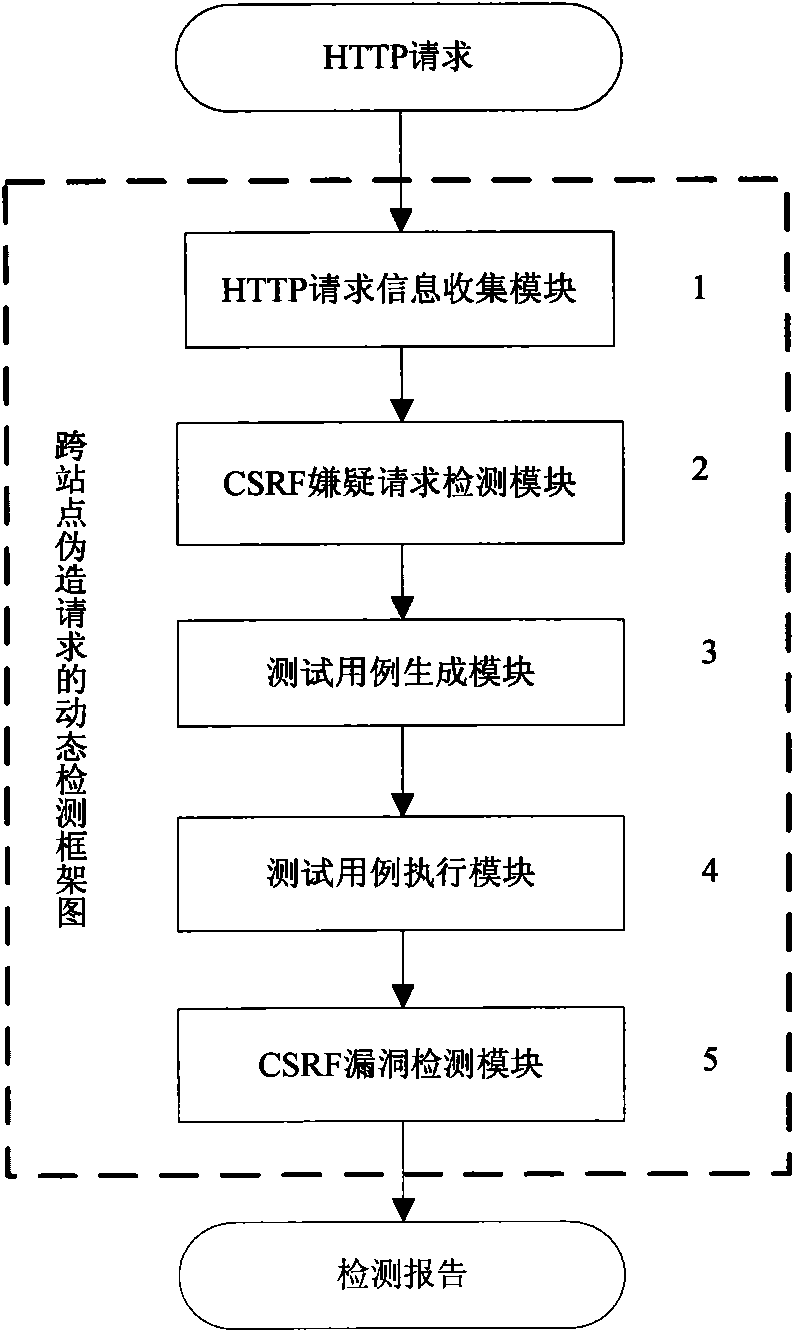
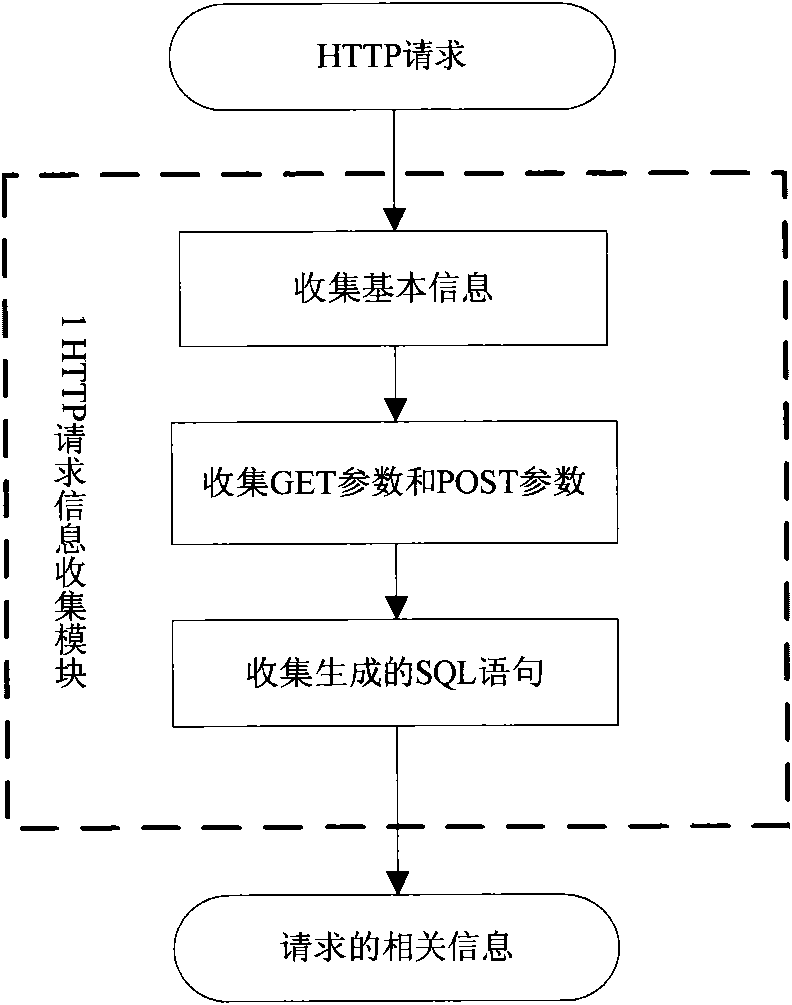
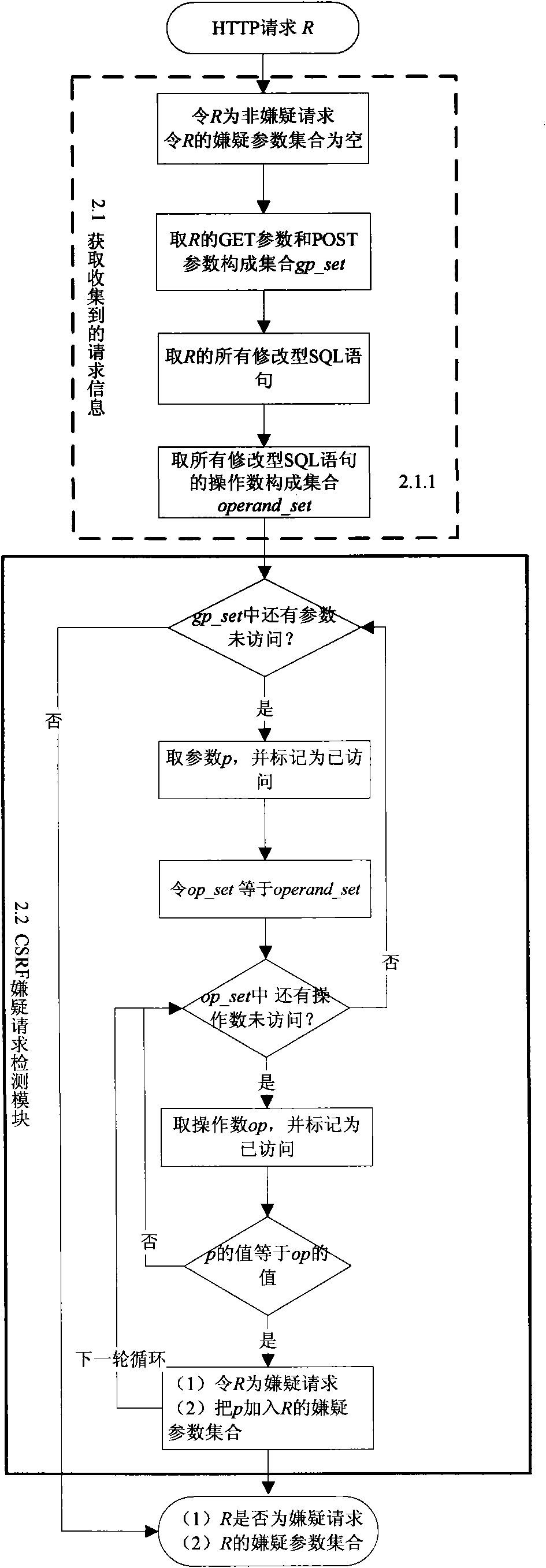
Dynamic detection method for cross-site forged request
InactiveCN101883024AQuick and accurate discoveryImprove test efficiencyData switching networksWeb applicationDynamic testing
The invention discloses a dynamic detection method for a cross-site forged request, which comprises the following steps: collecting HTTP request information; analyzing whether a request is a CSRF suspect request or not according to the collected information; generating a test case aiming at the suspect request and finding out all suspect parameters contained by the suspect request; using the suspect parameters to generate a plurality of forged requests and generating a test case for each forged request; when an environment in which the suspect request is generated recurs, executing the forged request corresponding to each test case; detecting CSRF vulnerabilities; and according to the suspect request, the execution information of the suspect request, the forged requests and the execution information of the forged requests, analyzing whether the forged requests find the CSRF vulnerabilities in Web application or not, forming a report and helping a Web application developer to repair the vulnerabilities. Since the dynamic detection method is used for detecting the CSRF vulnerabilities, the CSRF vulnerabilities in the Web application can be rapidly and accurately found out at low cost.
Owner:NANJING UNIV
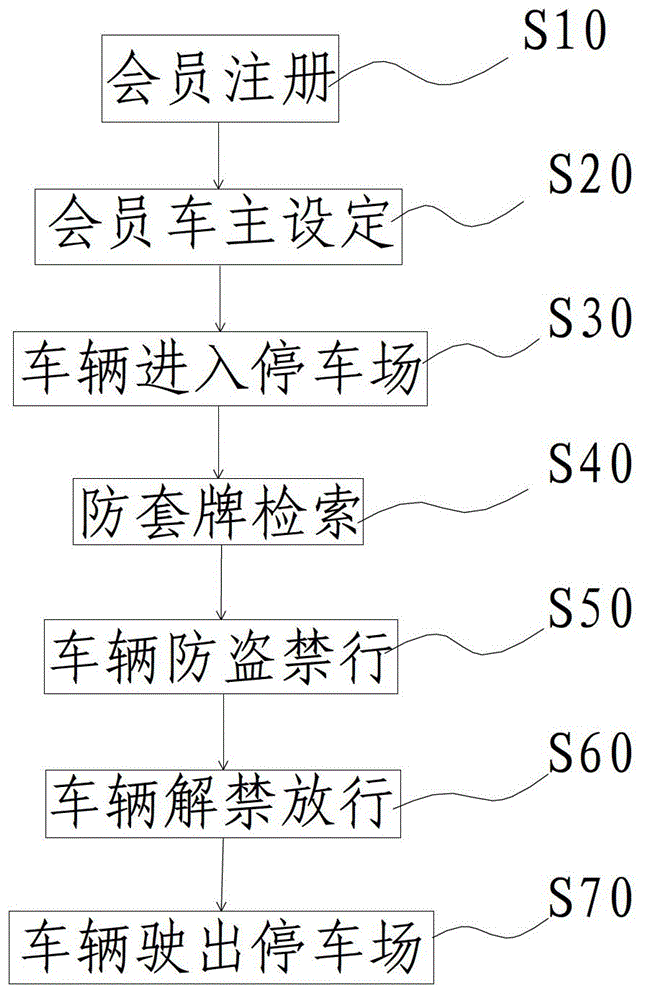
Anti-theft system and anti-theft method for automobiles in parking lots
InactiveCN102881170AAccurate discoveryAchieve anti-theft effectRoad vehicles traffic controlBurglar alarmAnti theftReal-time computing
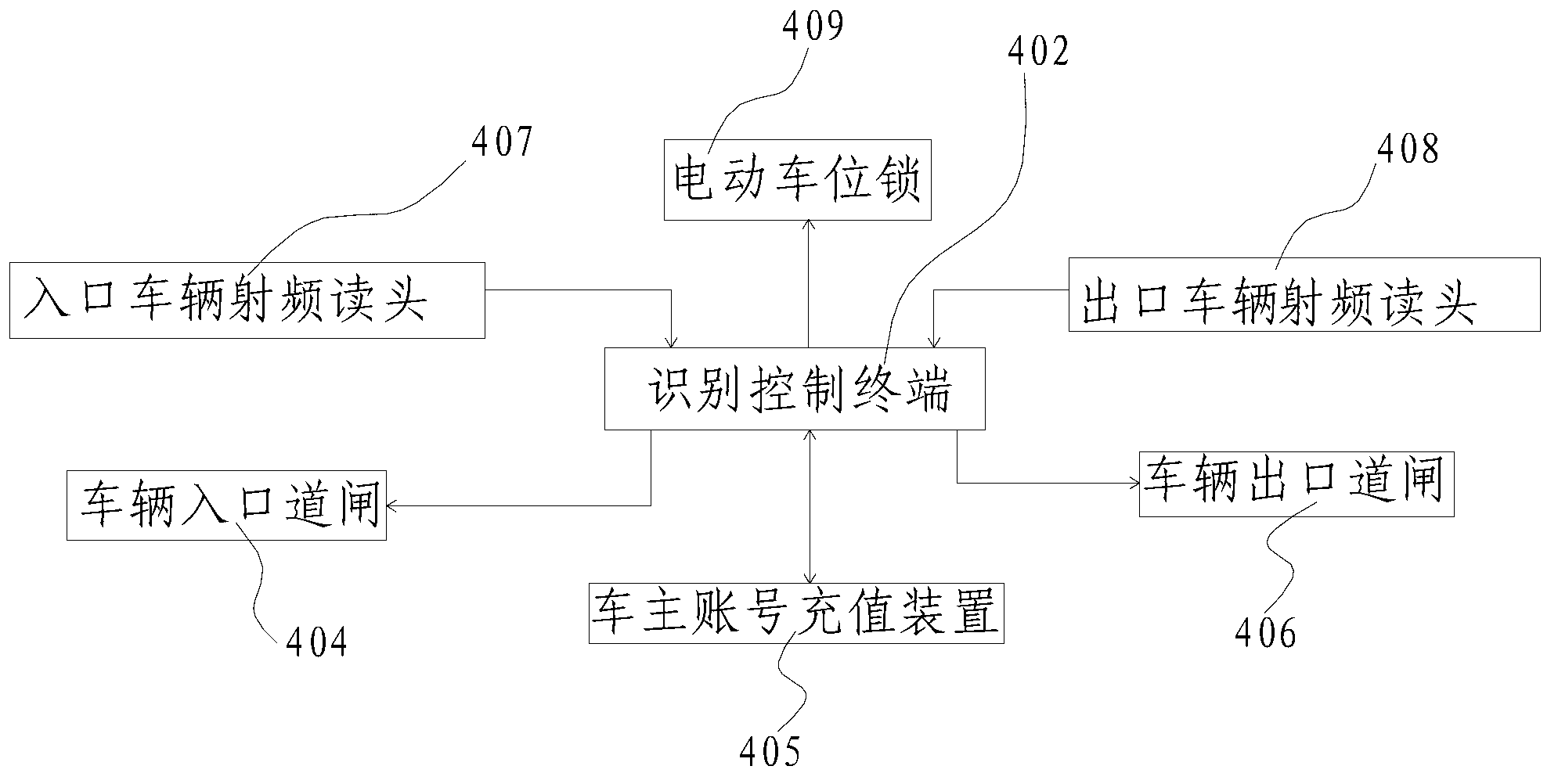
The invention relates to an anti-theft system for automobiles and discloses an anti-theft system for automobiles in parking lots. The anti-theft system comprises a cloud platform server, a plurality of parking lots and a plurality of automobile owner terminal devices, wherein the parking lots and the automobile owner terminal devices are in data exchange with the cloud platform server via the network, and each automobile owner terminal device at least comprises a cellphone. The invention further discloses an anti-theft method for automobiles in the parking lots. The anti-theft method includes S10, registering members; S20, setting member owners; S30, automobiles entering the parking lots; S40, checking for preventing fake license plates; S50, banning for anti-theft of the automobiles; S60, unbanning and letting the automobiles go; and S70, letting the automobiles driven out of the parking lots. By the anti-theft system and the anti-theft method, the automobiles with fake license plates can be accurately found and anti-theft effect of the automobiles can be realized.
Owner:陈淼
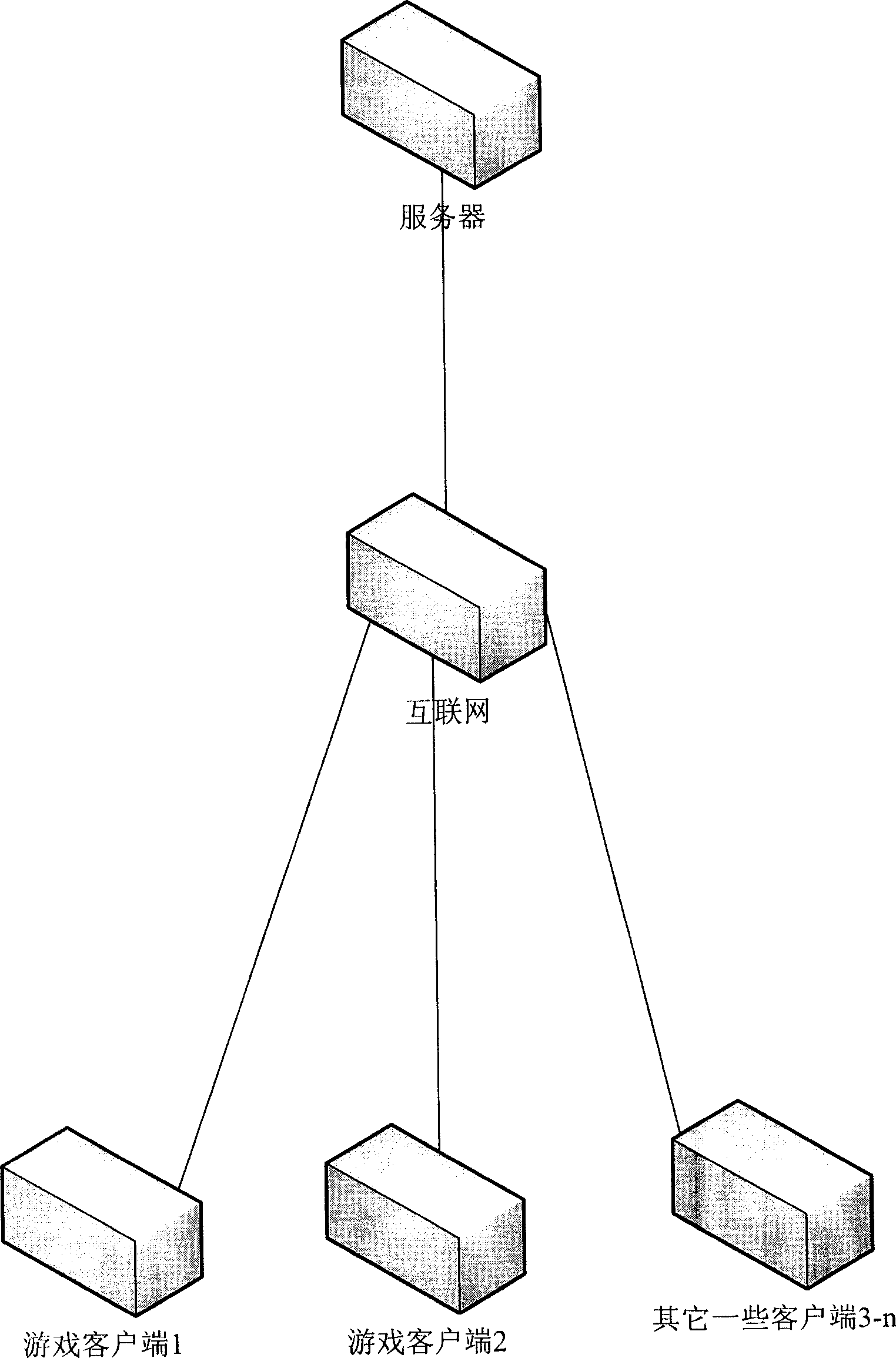
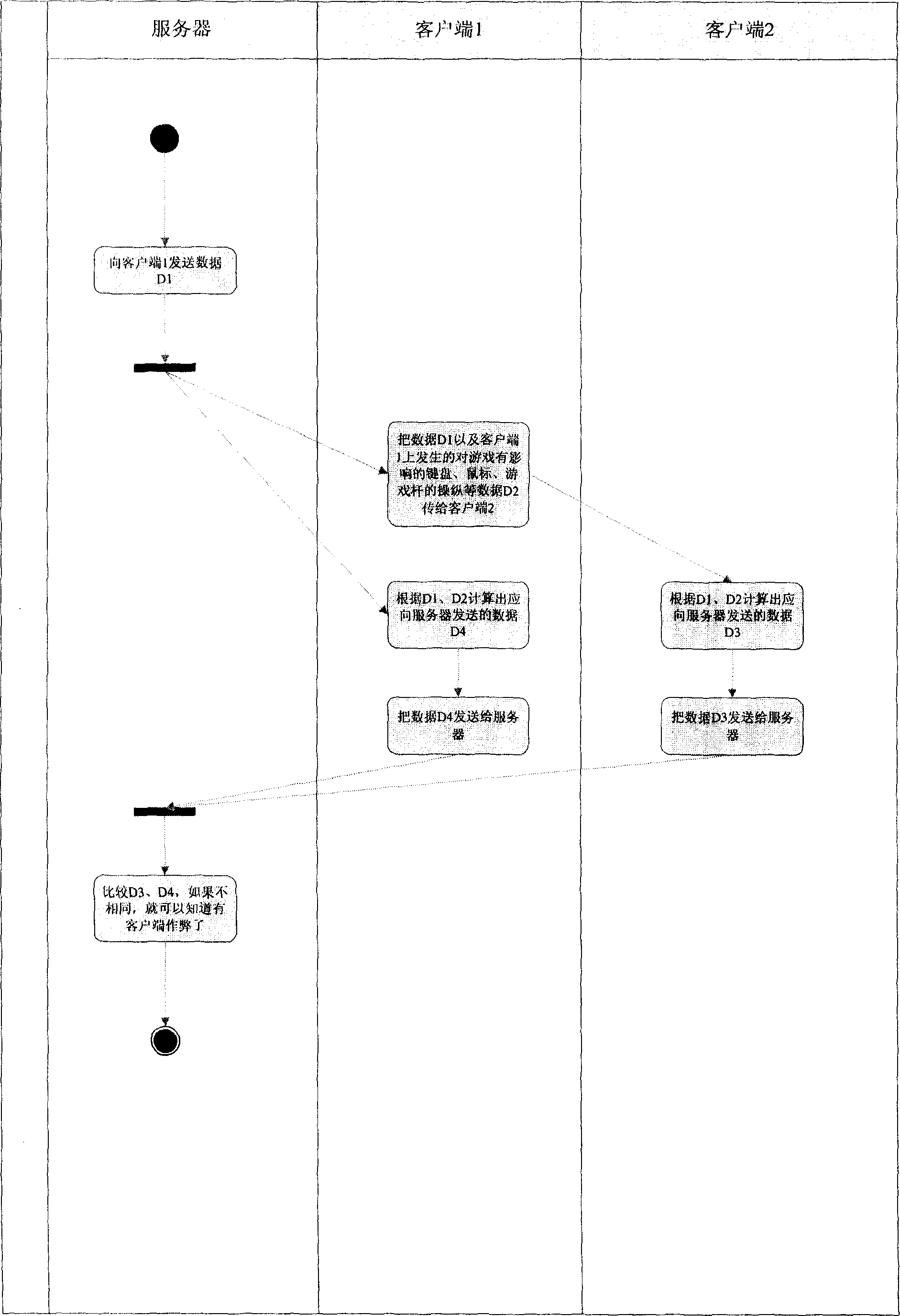
Method for detecting network game cheat
InactiveCN1893347AAccurate cheatingPrevent cheatingVideo gamesData switching networksClient-sideGame client
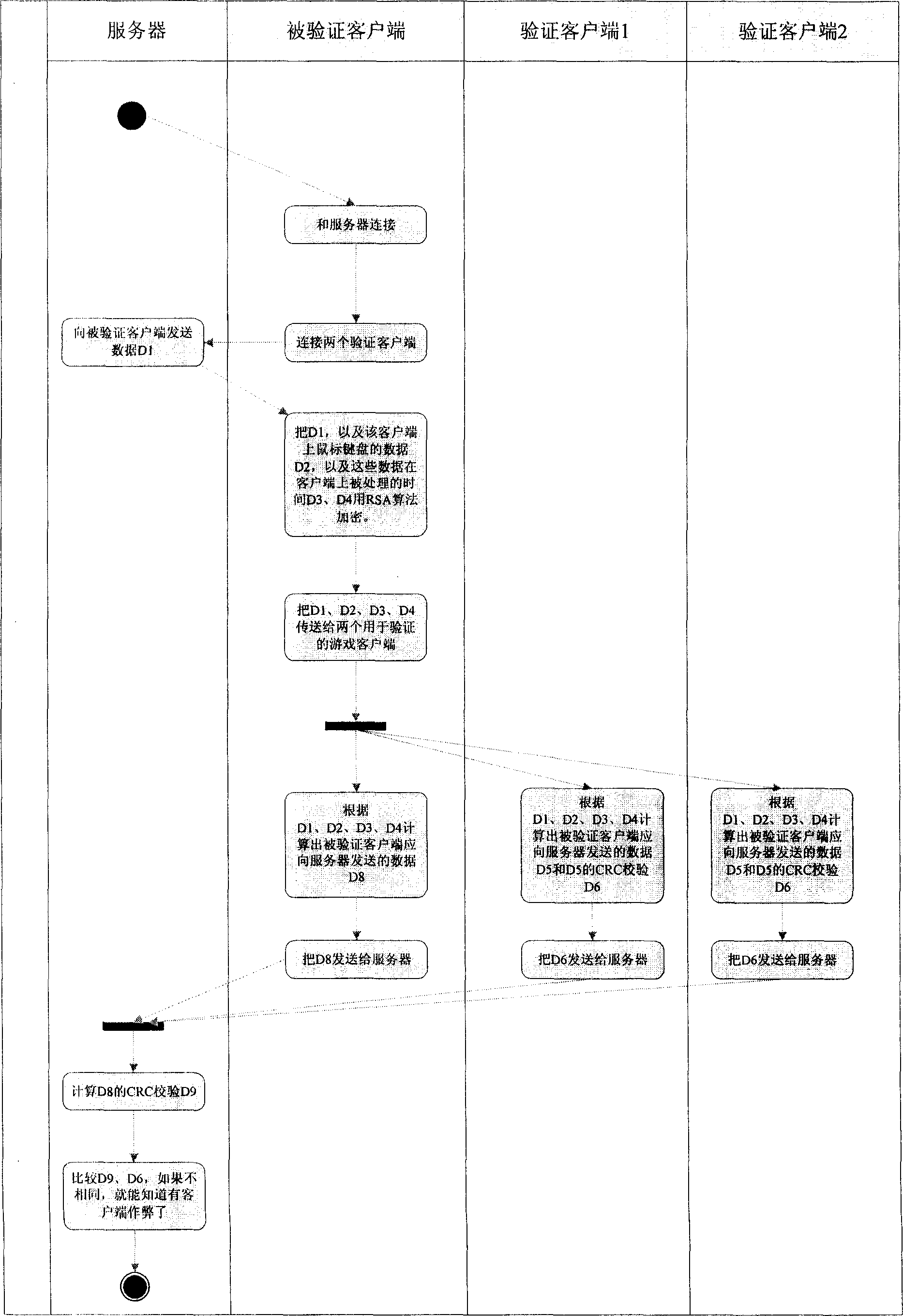
The method includes steps: client end to be validated and validating client end receive data 1 sent from server; the client end to be validated sends operation data 2 with influence on game happened on the client end to the validating client end, and then calculating out data 3, which should be sent to server from the client end to be validated; the validating client processes data 1 and data 2 so as to obtain data 3'; comparing data 3 with data 3', if they are not identical, then conclusion can be made that there is cheat action has done by at least one client end. Through validation each other between client ends on network game, the invention detects cheat action correctly. Moreover, external hanging mode to make cheat action also can be detected out. The invention ensures that game is carried out fairly as well as reduces loss of earnings of operational manager.
Owner:王荣
Compensation type gas sensor and humiture compensation method thereof
InactiveCN102680518ADiscovered in timeAccurate discoveryMaterial heat developmentHigh humiditySignal processing circuits
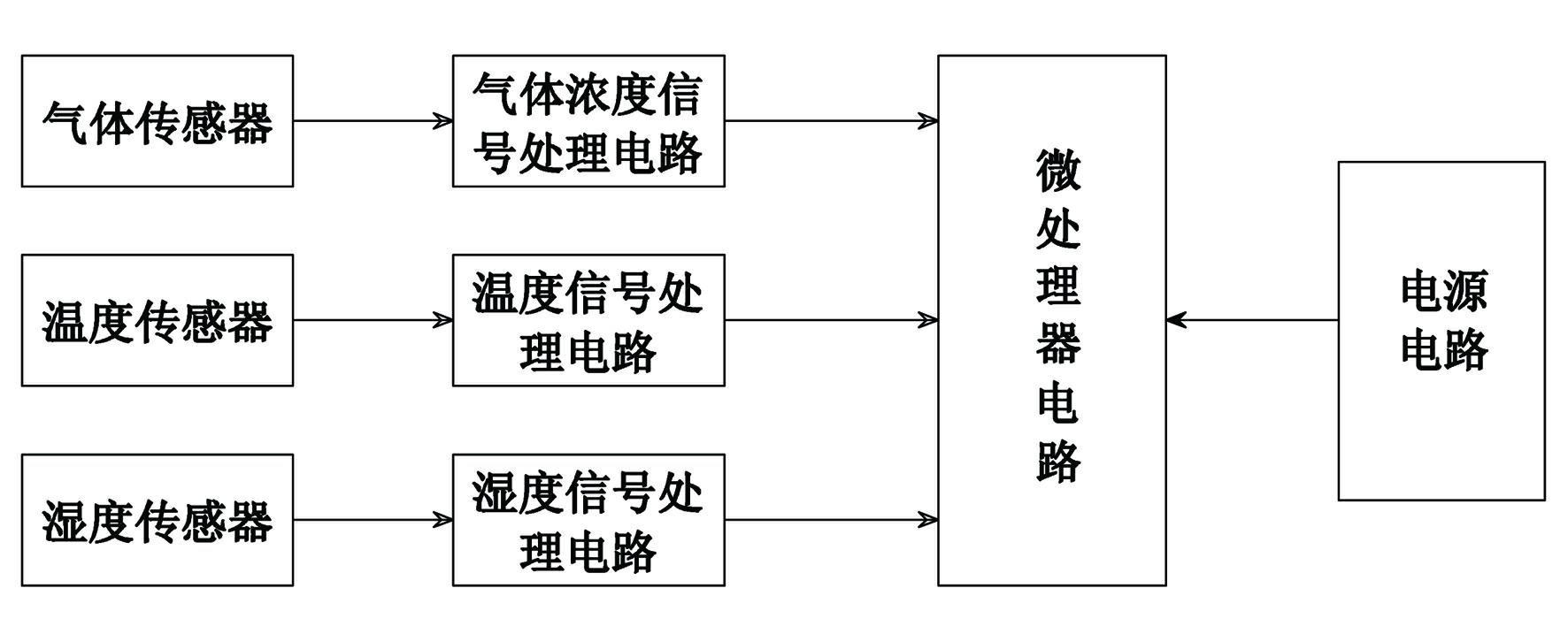
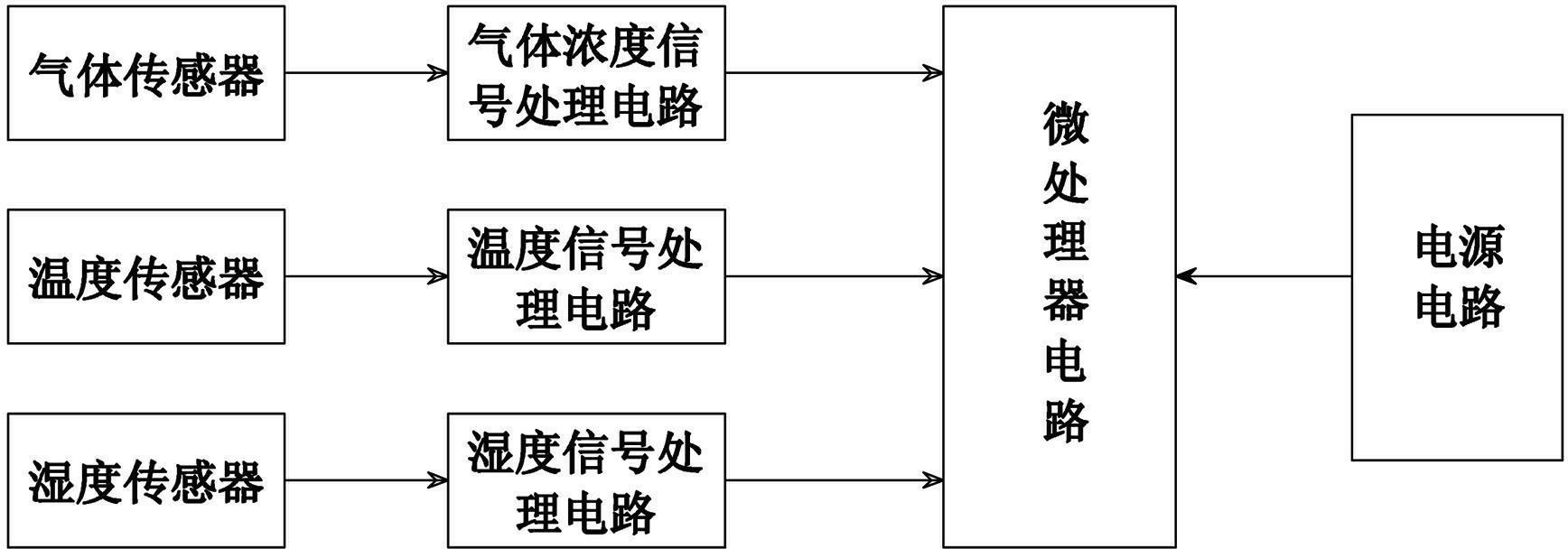
The invention provides a compensation type gas sensor and a humiture compensation method thereof. The compensation type gas sensor comprises a microprocessor circuit, a gas sensor, a temperature sensor, a humidity sensor, a gas concentration signal processing circuit, a temperature signal processing circuit, a humidity signal processing circuit and a power supply circuit. The humiture compensation method comprises the following steps of: creating a compensation factor searching database; obtaining a gas concentration measured value C0, a temperature measured value T and a humidity measured value H through actual measurement; searching a compensation factor @ corresponding to the gas concentration measured value C0, the temperature measured value T and the humidity measured value H from the compensation factor searching database according to the gas concentration measured value C0, the temperature measured value T and the humidity measured value H; and obtaining a gas concentration true value C1 of the gas sensor by multiplying the gas concentration measured value C0 with the compensation factor @ according to the searched compensation factor @. The compensation type gas sensor provided by the invention has the advantages of being high in detection accuracy, reliable in performance, and suitable for the high-temperature high-humidity environment detection; and the humiture compensation method provided by the invention has the advantages of being simple and practical, and beneficial for increasing the detection accuracy of the gas sensor.
Owner:HENAN HANWEI ELECTRONICS
Testing method and system, testing server, testing terminal and storage medium
InactiveCN108052451AMonitor Performance DataMonitoring log informationSoftware testing/debuggingRegression testingTest script
The invention discloses a testing method and system, a testing server, a testing terminal and a storage medium. The method comprises the following steps that according to a to-be-executed testing script, a testing task is created; the testing task is sent to the corresponding testing terminal, wherein the testing task is used for triggering the testing terminal to run a to-be-tested program according to the testing script and release the running data generated in the to-be-tested program running process into a corresponding subject; the running data received by the subscribed subject is obtained through a subscriber object; the received running data is sent to a front-end user side, wherein the running data is used for triggering the front-end user side to display the running data on a display interface of the subject corresponding to the running data. Based on the testing method, visual automatic regression testing can be achieved, and the testing efficiency is improved.
Owner:NETEASE (HANGZHOU) NETWORK CO LTD
Method of classifying web text information sentiments
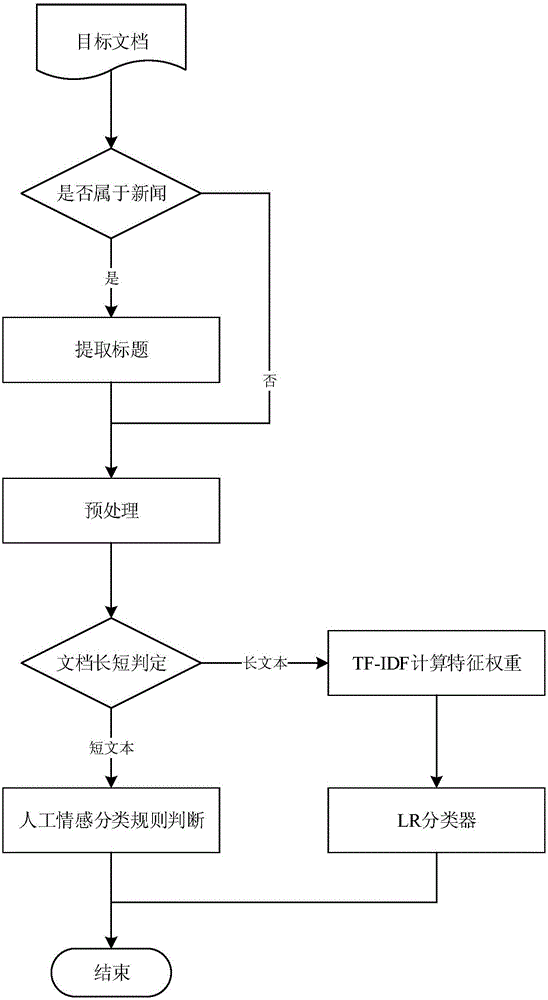
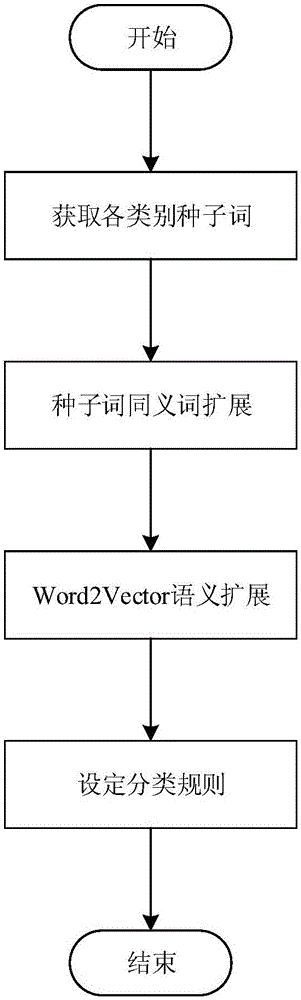
InactiveCN106202372AAccurate discoverySpecial data processing applicationsText database clustering/classificationClassification ruleDocument preparation
The invention discloses a method of classifying web text information sentiments, comprising the following steps of 1, judging whether a document is news, if yes, just extracting a title for sentiment classification, and if not, carrying out sentiment classifying on the whole document; 2, preprocessing the document to be classified; 3, classifying the document according to text length: calculating a feature weight for a document longer than 140 characters by using TF-IDF (term frequency-inverse document frequency), and carrying out classification by using a trained logistic regression classifier; and carrying classification on a document longer than 140 characters by using manual sentiment classification rules. Compared with the prior art, the method has the advantages that a technical route combining a classifier and field expert formulated classification features is constructed by using machine learning algorithm according to different features of long and short texts, and it is possible to timely find related reactionary information, sensitive information and negative information in online public opinions.
Owner:CHINA ELECTRONICS TECH CYBER SECURITY CO LTD
Intelligent analysis system for all-media detection and monitoring big data behaviors
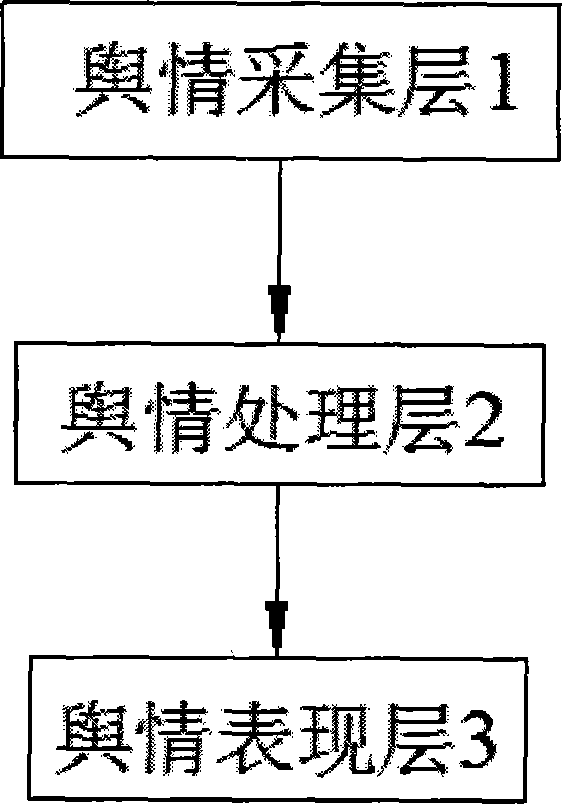
InactiveCN104504081AAccurate discoveryImprove complianceSpecial data processing applicationsThe InternetContent analytics
The invention discloses an intelligent analysis system for all-media detection and monitoring big data behaviors and relates to an all-media monitoring system. The intelligent analysis system comprises a public opinion collection layer, a public opinion processing layer and a public opinion presentation layer, wherein the public opinion collection layer is connected with the public opinion processing layer; the public opinion processing layer is presented by the public opinion presentation layer; in the public opinion collection layer, a distributed and oriented collection engine collects news, forums, blogs, micro blogs, print media, questions and answers and other public opinion information from the Internet, and stores the information into a distributed database and a file system. The intelligent analysis system realizes data content analysis, semantic analysis and descriptive analysis on media monitoring big data, builds a data analysis model based on media, a media big data structure and a content analysis multilevel description method, realizes functions of a super-large scale media data content conceptual analysis model and is an intelligent data behavior analysis system for understanding all-media data content.
Owner:BEIJING EASTERN PRESSCLIPPING INT CONSULTANTS
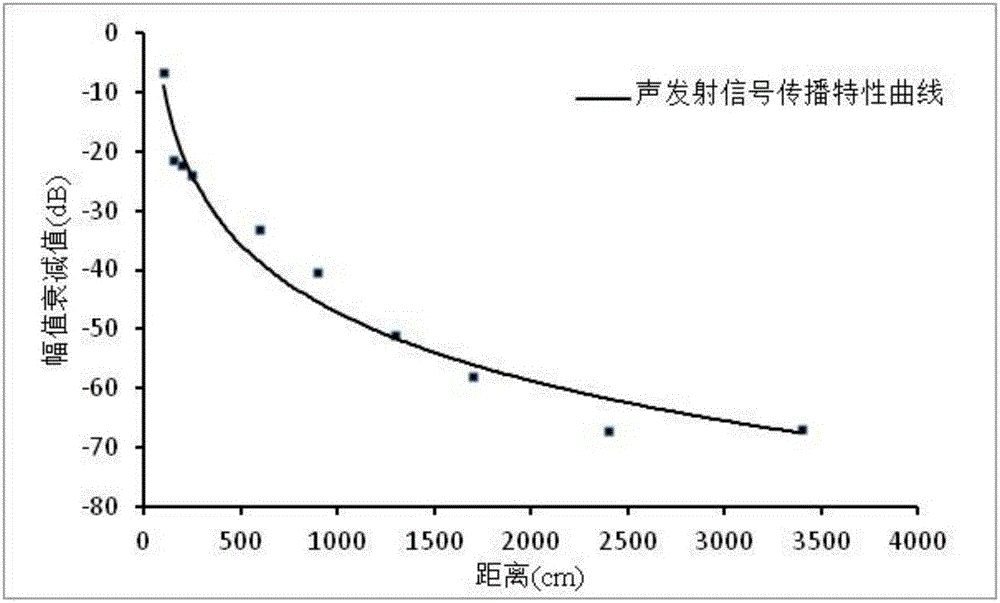
Multilayer buried pipeline leakage source locating device and method based on acoustic emission inspection
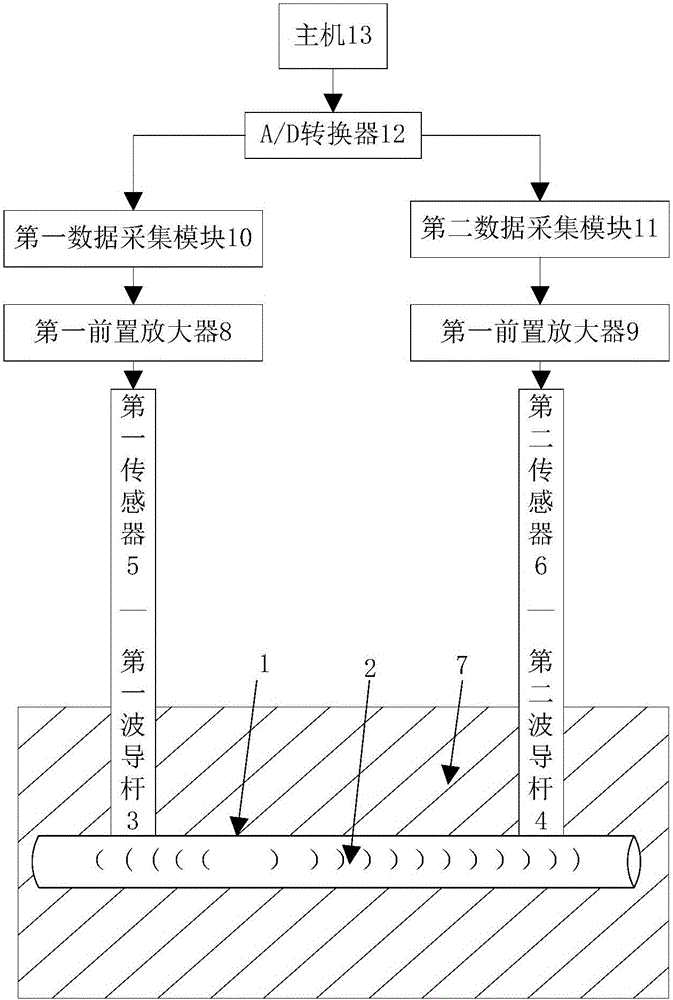
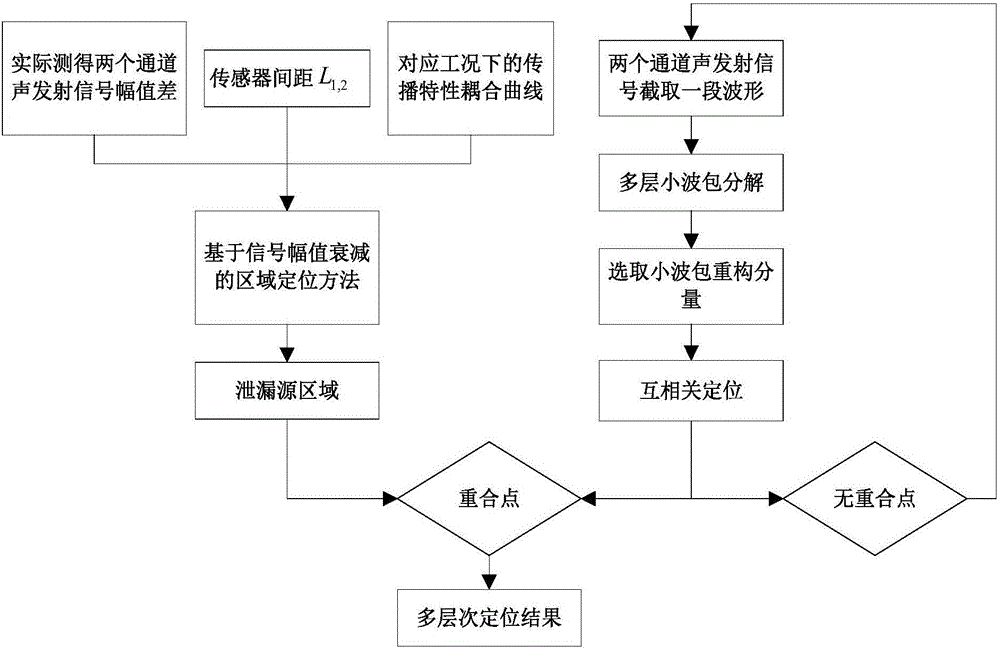
ActiveCN105042341AOvercome the speed of soundOvercome timePipeline systemsAudio power amplifierAcoustic emission
The invention belongs to the field of pipeline detection, and particularly relates to a multilayer buried pipeline leakage source locating device and method based on acoustic emission inspection. The locating device is characterized in that a first waveguide rod and a second waveguide rod are fixed to the two sides of a leakage source respectively; the lower end of a first piezoelectric acceleration sensor and the lower end of a second piezoelectric acceleration sensor are bonded to the surfaces of the first waveguide rod and the second waveguide rod respectively; the upper end of the first piezoelectric acceleration sensor and the upper end of the second piezoelectric acceleration sensor are connected with a first preamplifier and a second preamplifier respectively through wires; then signals are transmitted to a first data acquisition module and a second data acquisition module; the signals are transmitted to an A / D converter through the two data acquisition modules to be converted to digital signals; the A / D converter transmits the digital signals to a host, and the host determines the position of the leakage source of a pipeline finally. According to the multilayer leakage source locating method, local locating and accurate locating are combined, local locating based on signal amplitude damping is adopted, accurate locating of the pipeline leakage source under a complex working condition is achieved finally based on acoustic emission inspection, and the method is suitable for locating of leakage of the pipeline under a buried condition.
Owner:CHINA UNIV OF PETROLEUM (EAST CHINA)
Static detection method for privacy information disclosure in mobile applications
ActiveCN103577324AAccurate discoveryImprove detection efficiencySoftware testing/debuggingControl flowOperational system
The invention discloses a static detection method for privacy information disclosure in mobile applications. The method comprises the steps as follows: firstly, the completeness of codes is checked, if the codes are incomplete, preparatory work is performed on source codes, state machine description files corresponding to the privacy disclosure are loaded, related state machine information is obtained, the source codes are compiled to obtain detailed information of classes, functions and the like, pre-analysis is performed on the source codes, basic data structures such as abstract syntax trees and the like are generated, and call relations among the functions are obtained; and then detection and analysis is performed in units of the functions, state machine instances are created for all state machines with associated methods in the state machines, state machine instance iteration is performed on control flow diagrams corresponding to the functions, when the state machine instances are in error states, errors are reported, after detection is finished, the detected errors are checked manually, and detection results are confirmed. With the adoption of the method, the privacy disclosure codes existing in application programs of different operating system platforms can be effectively detected, so that the privacy information disclosure of users can be effectively prevented.
Owner:BEIJING UNIV OF POSTS & TELECOMM
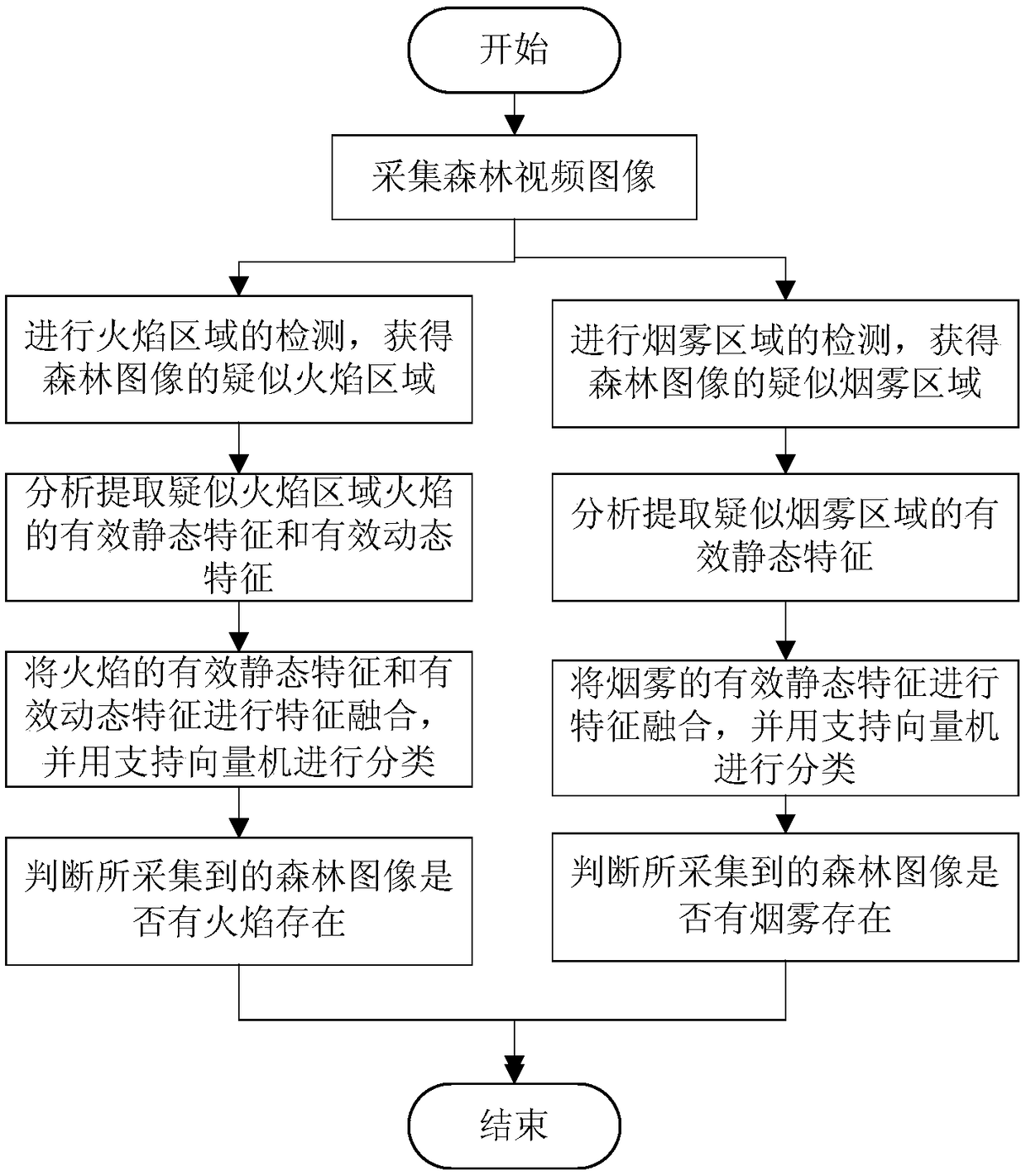
An early forest fire detection method based on a video image
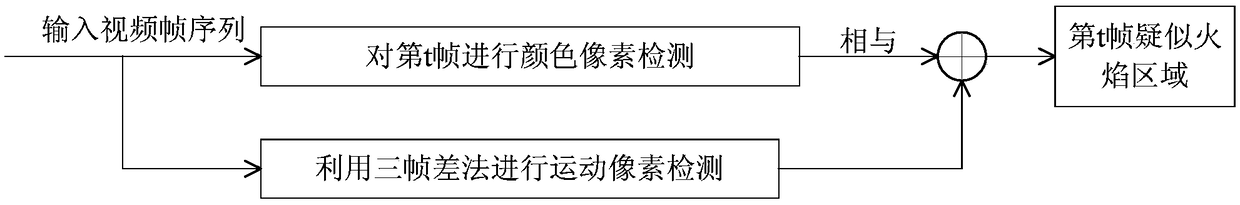
ActiveCN109165577AAccurate discoveryEliminate the effects ofCharacter and pattern recognitionSupport vector machineFlame detection
The invention provides an early forest fire detection method based on a video image, which relates to the technical field of video remote monitoring fire. The method includes flame detection and smokedetection. First, the suspected flame region of the forest video image is obtained by flame detection. The effective static and dynamic characteristics of the flame are extracted from the suspected flame area, and the characteristics are fused. Then the forest images are classified by support vector machine to judge whether there is flame or not. Smoke detection first obtains the suspected smog area of the forest video image. The effective static features of smoke are extracted from the suspected smoke area, and the features are fused. Then the support vector machine is used to classify the smoke image to determine whether there is smoke in the collected forest image. The early forest fire detection method based on a video image simultaneously takes into account the identification of smoke and flame, and can detect the fire in the video in real time, eliminate the influence of disturbances in the forest environment, and accurately discover the early fire situation.
Owner:NORTHEASTERN UNIV
Defect quantified comprehensive safety judgment method for on-service pressure container
ActiveCN103868985AEliminate subjective arbitrarinessAccurate discoveryMaterial magnetic variablesEvaluation resultMagnetic memory
The invention discloses a defect quantified comprehensive safety judgment method for an on-service pressure container. The method comprises the steps of detecting a defect of the on-service pressure container by a magnetic memory detection method, and quantifying the defect by a calculation formula; performing planar defect breakage evaluation and planar defect fatigue evaluation on the on-service pressure container according to a magnetic memory detection result; constructing a comprehensive judgment matrix by a fuzzy comprehensive judgment system, calculating a total damage rate according to the damage rate, caused by each ineffectiveness factor, on the pressure container and a weight of the influences on the safety of the pressure container, determining a relation of the influences, and making comprehensive safety judgment. The defect quantified comprehensive safety judgment method for the on-service pressure container is high in reliability and high in operability, and an evaluation result can objectively and really reflect actual situations of engineering.
Owner:SOUTHWEST PETROLEUM UNIV
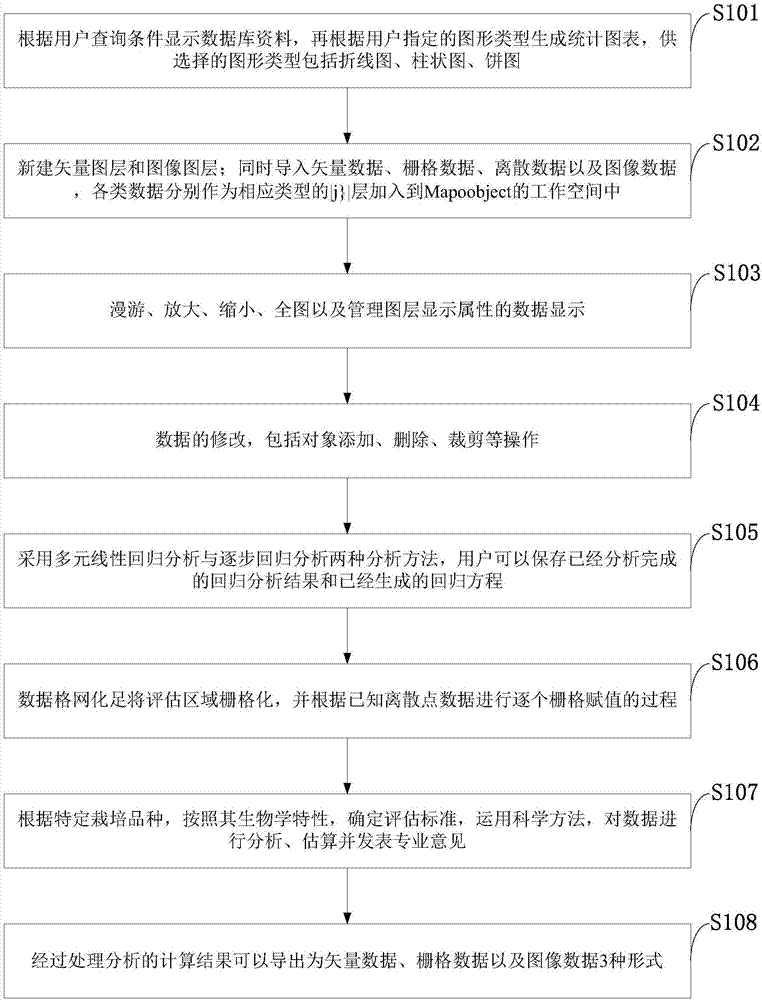
Land crop planting suitability evaluation method
InactiveCN107274297AEfficient managementGuaranteed accuracyData processing applicationsComplex mathematical operationsMultiple linear regression analysisTechnical standard
The invention belongs to the technical field of land crop planting and discloses a land crop planting suitability evaluation method. The method comprises steps: data in a database are displayed according to a user query condition and a statistical chart is then generated according to a chart type specified by a user, wherein selectable chart types comprise a broken line chart, a column chart and a pie chart; a vector layer and an image layer are built newly; roaming, zoom in, zoom out, full chart and management on layer display attribute data are realized; data are modified; a multiple linear regression analysis method and a stepwise regression analysis method are adopted; data gridding and gridding of an evaluation area are carried out; according to a specified cultivated variety, based on biological characteristics, the evaluation standard is determined, a scientific method is applied, the data are analyzed and estimated, and a professional suggestion is given; and a calculation result through processing and analysis is outputted. The method of the invention has a high-efficiency massive data management ability, and an important role is played in guiding adjustment and layout of an agricultural production structure.
Owner:贵州中北斗科技有限公司 +1
Method for detecting anti-seepage effect of anti-seepage film
InactiveCN101706354AEasy to measureEasy to masterFluid-tightness measurement using electric meansEngineeringHigh pressure
The invention discloses a method for detecting the anti-seepage effect of an anti-seepage film, belonging to the anti-seepage detection field of anti-seepage films. The method comprises the following steps: adopting a high-pressure pulse power supply to apply electric potentials onto the upper side and the lower side of the anti-seepage film by current electrodes the positions of which are fixed; arranging a fixed electrode and a movable electrode in an upper detection region of the anti-seepage film, wherein the position of the fixed electrode is fixed; and distributing detection points at 1-5m *1-5m intervals by the movable electrode. In measurement, a high-pressure pulse is applied onto the current electrodes to measure an electric potential difference between the movable electrode and the fixed electrode until all measuring points are measured; and the distribution of the electric potential differences is distorted in loophole positions so as to judge the existence and the positions of leakage. The invention is a nondestructive measurement method and has high detection precision and simple and convenient operation.
Owner:HOHAI UNIV
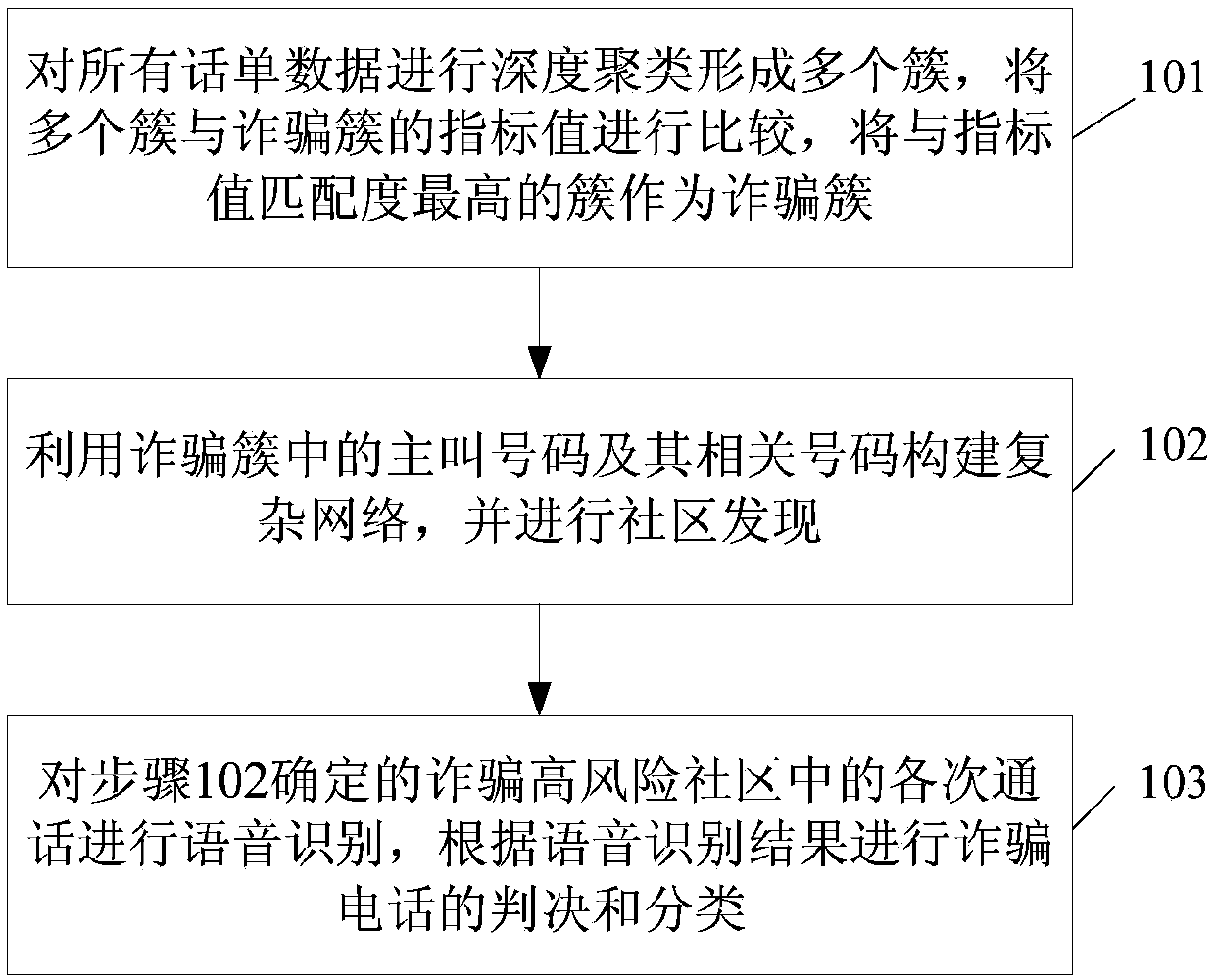
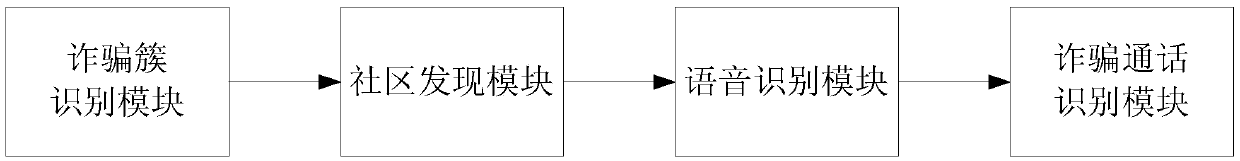
Deep clustering fraud detection method and device
ActiveCN109600752AAccurately determineAccurate discoverySupervisory/monitoring/testing arrangementsCharacter and pattern recognitionData miningComputer science
The invention discloses a deep clustering fraud call detection method, which comprises the following steps: carrying out deep clustering on all call bill data to form a plurality of clusters, comparing the plurality of clusters with index values of a fraud cluster, and taking the cluster with the highest matching degree with the index values as a fraud cluster; obtaining each called number calledby the calling number in the fraud cluster, determining all the calling numbers called by the called numbers according to the call bill data, and performing complex network modeling by utilizing the called numbers and all the calling numbers; performing community discovery in a complex network of modeling, and determining a fraud high-risk community according to the proportion of the calling number in the fraud cluster contained in each community; and carrying out voice recognition on each call in the fraud high-risk community, and judging and classifying fraud calls according to a voice recognition result. By applying the method and the device, the fraud call can be found more accurately on the basis of ensuring the real-time performance.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT +1
WSN (Wireless Sensor Network) abnormity detection method and system based on artificial immunization and k-means clustering
InactiveCN105791051AImprove search efficiencyPrecise positioningPower managementNetwork topologiesAnomaly detectionArtificial immune algorithm
The invention discloses a WSN abnormity detection method and system based on artificial immunization and k-means clustering. The method comprises that S1) original monitoring data collected by WSN nodes is obtained to form a time sequence, the time sequence is normalized, compression and dimension reduction are carried out on the normalized sequence, and the mean value and variance of each sequential segments in the compressed sequence are calculated; S2) the Euclidean distance between node data and each cluster head is calculated, and an artificial immunization algorithm is used to search an optimal initial cluster head set for K-means classification; S3) whenever new data is distributed into a corresponding cluster, iterative update is carried out on the cluster head value of the cluster till the amount of all data in the cluster does not change; and S4) the WSN determines abnormity according to the amount of data in the cluster in a K-means clustering result. According to the invention, abnormity information in monitoring data can be discovered accurately, the instantaneity and reliability of abnormity event detection of the WSN are improved, and energy and communication bandwidth of the WSN are greatly reduced.
Owner:CHINA UNIV OF GEOSCIENCES (WUHAN)
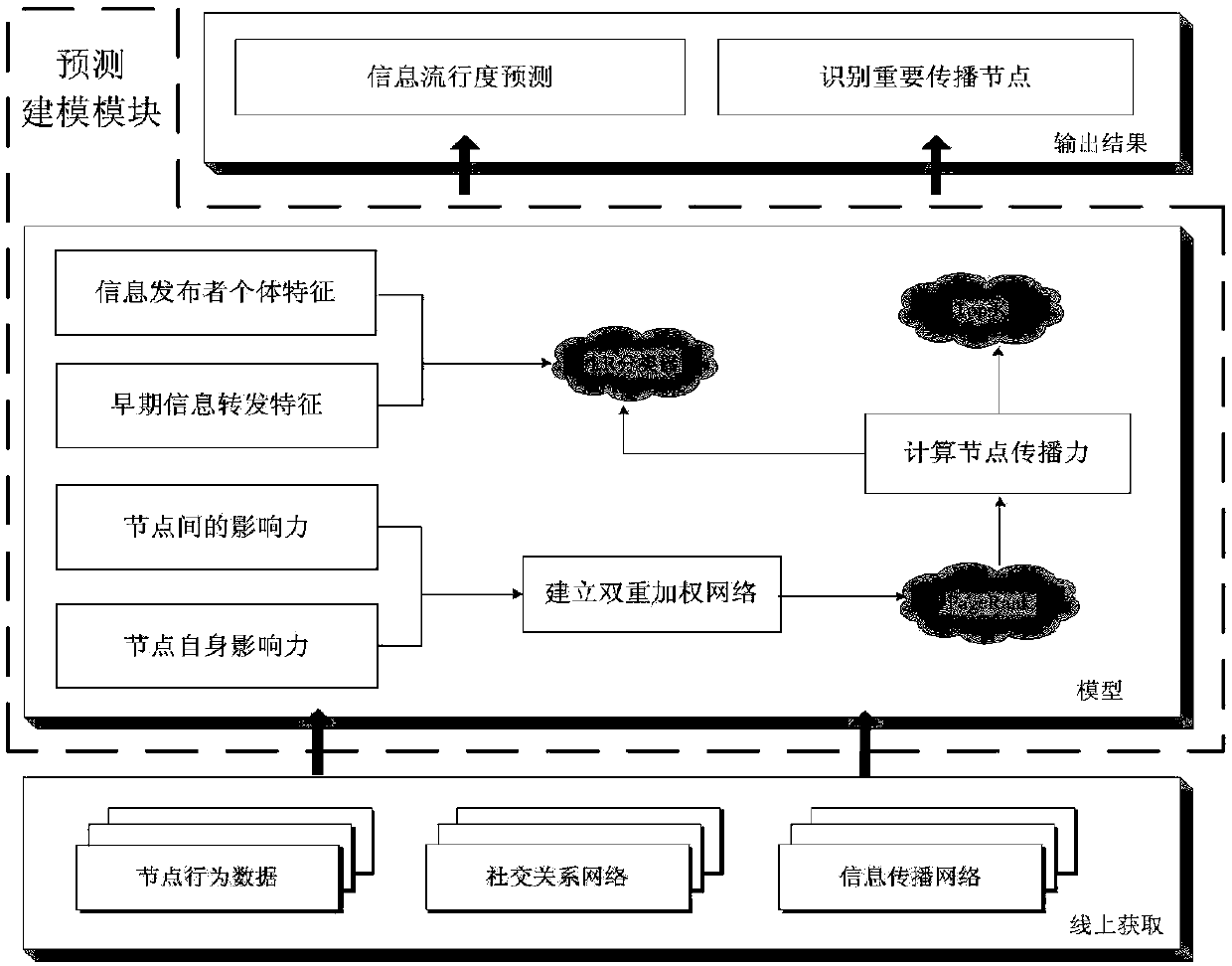
Method and system for predicting information popularity of social network
ActiveCN108304867AAccurate measurementAccurate discoveryData processing applicationsCharacter and pattern recognitionNODALInformation analysis
The invention belonging to the field of social network information analysis makes a request of protecting a method and system for predicting information popularity of a social network. The method comprises steps of data acquisition, attribute extraction, model construction and prediction analysis. An information dissemination network is refined by combining user relationships and node behavior data in a social network; attributes affecting the measure of propagation power are extracted by starting with an individual behavior dimension and a node interaction dimension and related definitions are provided; a dual-weighted social network is constructed again and a node propagating power in the network is measured based on an improved PageRank algorithm; and individual characteristics of an information publisher and forwarding characteristics of the information published within one hour are extracted by using the information as a center and training is carried out by using an LR classifierto obtain an information popularity prediction model. Therefore, the information popularity can be predicted effectively; and a network group event is found out timely and important propagation nodesin the information dissemination network are identified.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Current change rate-based coal mine power grid short-circuiting fault quick judging device and method
ActiveCN105572544ASignificant changeRapid changeFault location by conductor typesPower gridEngineering
The invention relates to a current change rate-based coal mine power grid short-circuiting fault quick judging device and method. The method includes the following four stages of judgment calculation: stage 1, current first-order derivative calculation; stage 2, current first-order derivative zero point crossing judgment; stage 3, current first-order derivative judgment; and stage 4, current second-order derivative calculation and judgment. The method specifically includes the following steps that: the current change rate of a coal mine power grid line is calculated uninterruptedly; whether a first-order derivative crosses a zero point is judged, if the first-order derivative crosses the zero point, the method enters the stage 4, current second-order calculation is started; if the first-order derivative does not cross the zero point, the method enters the stage 3, the first-order derivative is compared with a previous current change rate calculation result, if the current first-order derivative exceeds a set change range, it is judged that a short-circuiting fault occurs, otherwise, the method enters the stage 1, first-order derivative calculation is further executed; and a current second-order derivative is calculated, and is compared with a previous current change second-order derivative, if the current second-order derivative exceeds a set range, it is judged that a short-circuiting fault occurs, and corresponding operation is carried out, otherwise, the method returns to the stage 1. The current change rate-based coal mine power grid short-circuit fault quick judging device and method provided by the invention can quickly and accurately find faults at the moment when short-circuiting occurs.
Owner:HENAN POLYTECHNIC UNIV
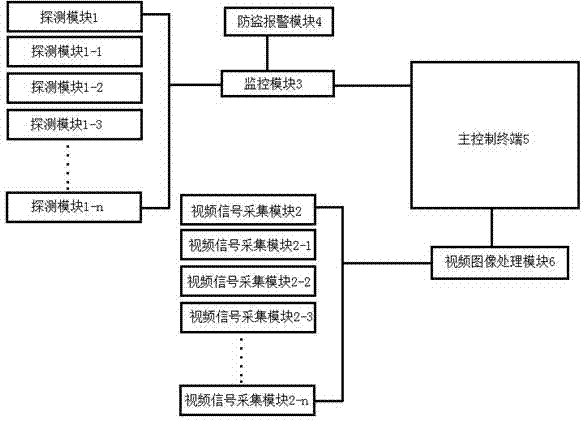
Security alarm system for residential area
InactiveCN103530967ACall the police in timeComprehensive and accurate monitoringClosed circuit television systemsBurglar alarmComputer hardwareAlarm message
The invention provides a security alarm system for a residential area. The security alarm system comprises a plurality of detection modules, a plurality of video signal acquisition modules, a monitoring module, an anti-theft alarm module, a master control terminal and a video picture processing module, wherein the plurality of detection modules and the plurality of video signal acquisition modules are arranged on walls or fences around the residential area; the monitoring module is mounted in a guard room or a duty room; the master control terminal is mounted in a monitoring center; the plurality of detection modules are gathered to the input end of the monitoring module through a network transmission bus; the output end of the monitoring module is connected with the anti-theft alarm module; the plurality of video signal acquisition modules are gathered to the input end of the video picture processing module through the network transmission bus; the video picture processing module transmits processed alarm information to the master control terminal; and the monitoring module is further connected with the master control terminal. By means of the security alarm system for the residential area, combination of the detection modules and the video signal acquisition modules is achieved, working amount of guards is reduced greatly, and living safety of residents is guaranteed.
Owner:KUNSHAN ZHIZHONG XINCHENG INFORMATION TECH CO LTD
Partial discharge monitoring system and method
ActiveCN106990340AImprove detection accuracyImprove field efficiencyTesting dielectric strengthElectricityMonitoring system
The invention discloses a partial discharge monitoring system and a method which aim to provide a monitoring system and a method featuring high detection precision, onsite high efficiency, and comprehensive detection of partial discharge. The technical schemes of the invention are as follows: prior to the testing, connecting an apparent discharge calibrator and a partial discharge detector to a cable; through the apparent discharge calibrator, outputting a fixed electricity quantity at two ends of the cable; adjusting the calibration coefficient; determining the measuring range of the partial discharge detector; obtaining the indirectly measured discharge quantity after the calibration of the apparent discharge calibrator; and correcting the detection data of the partial discharge detector; and in the testing, acquiring the partial discharge data and positioning the partial discharge events. With the system and the method, the detection precision can be increased; and through the reception of the ultrasonic wave signals generated from electric equipment by the instrument and the analysis to the tone quality and the intensity, it is possible to rapidly measure the partial discharge and to accurately position.
Owner:杭州纵波科技有限公司
Topic influence individual digging method based on relational network
ActiveCN103179198AAccurate discoveryTransmissionSpecial data processing applicationsMaximum entropy probability distributionComputer science
Owner:NAT UNIV OF DEFENSE TECH
Method for measuring user influence power in microblog network
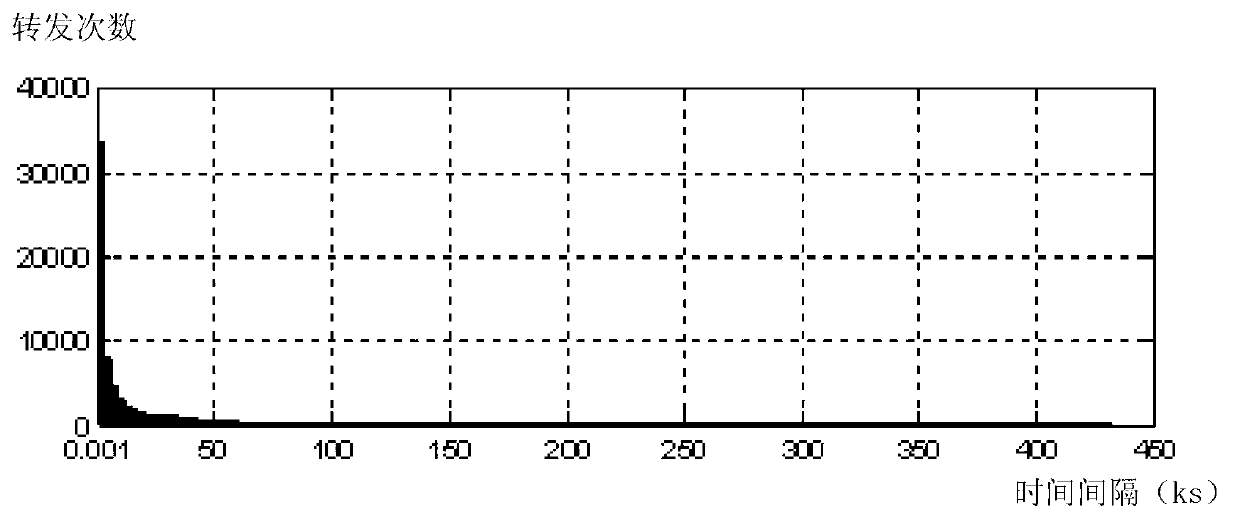
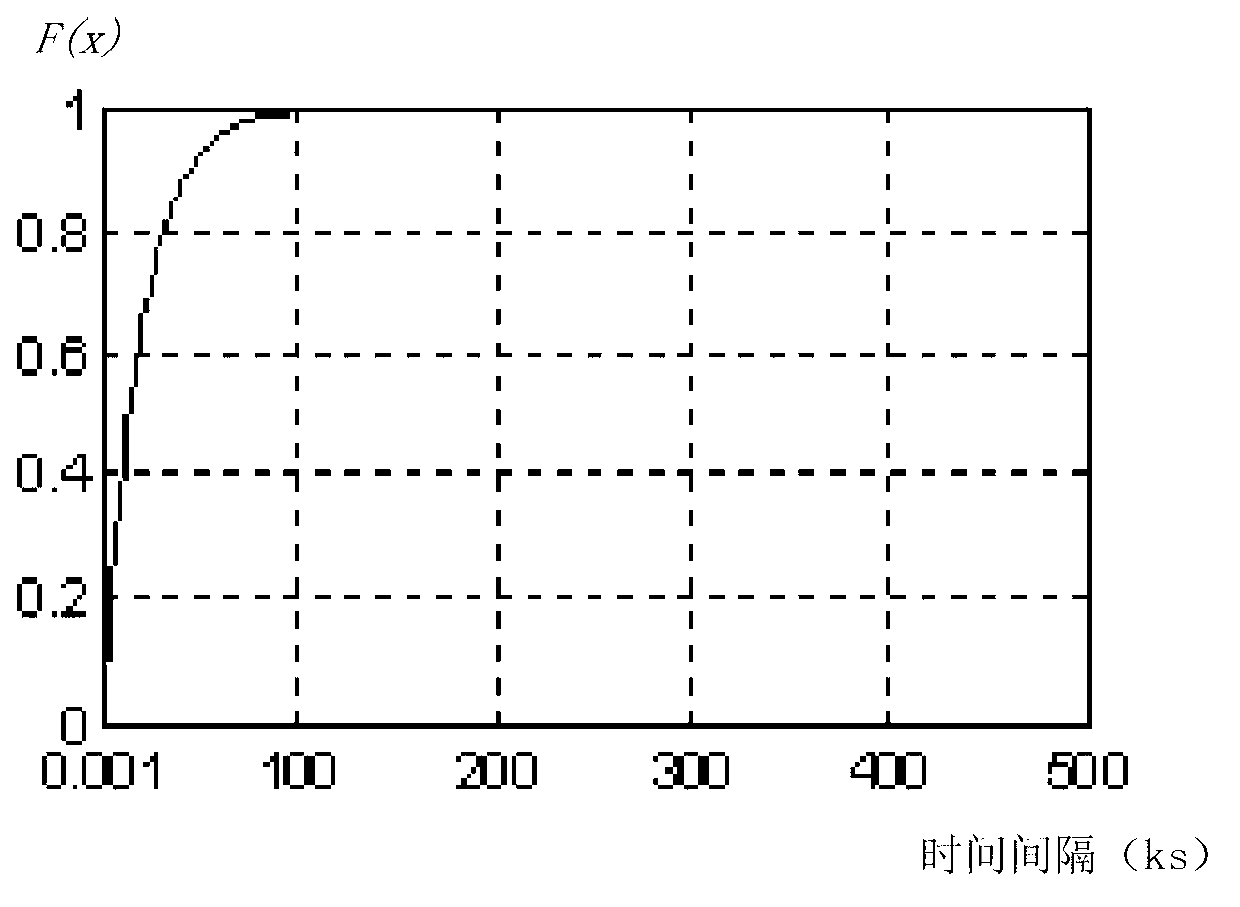
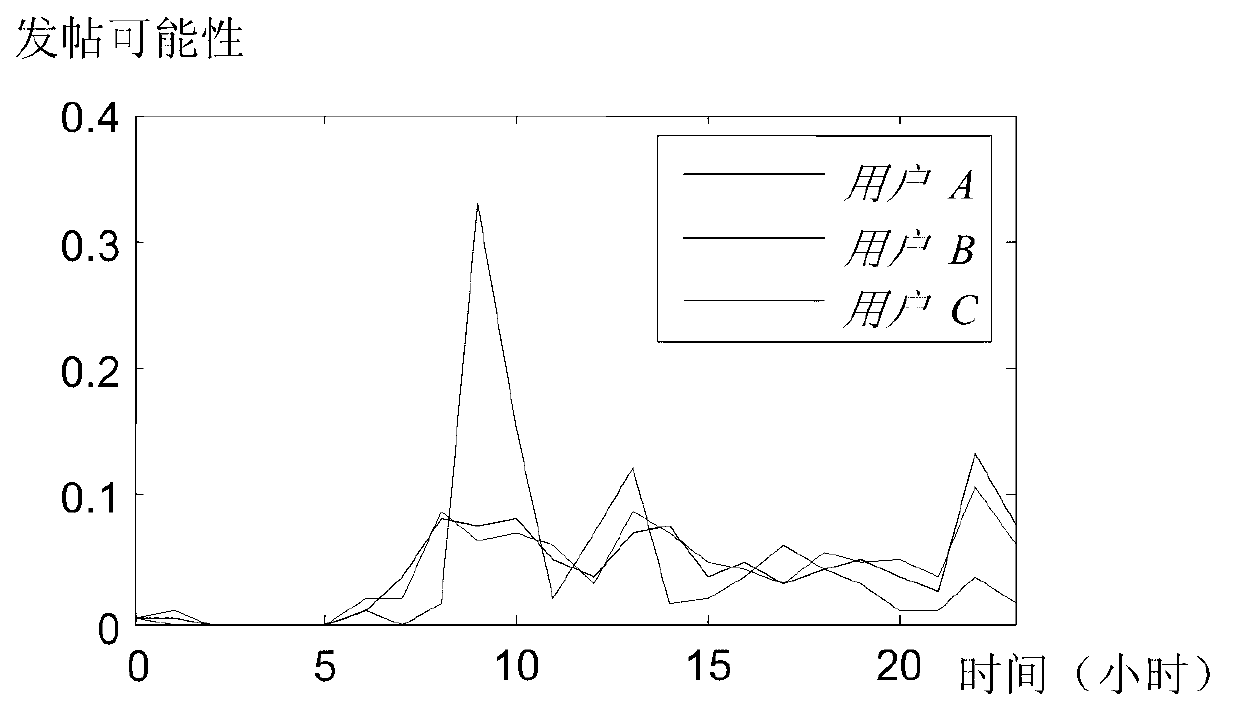
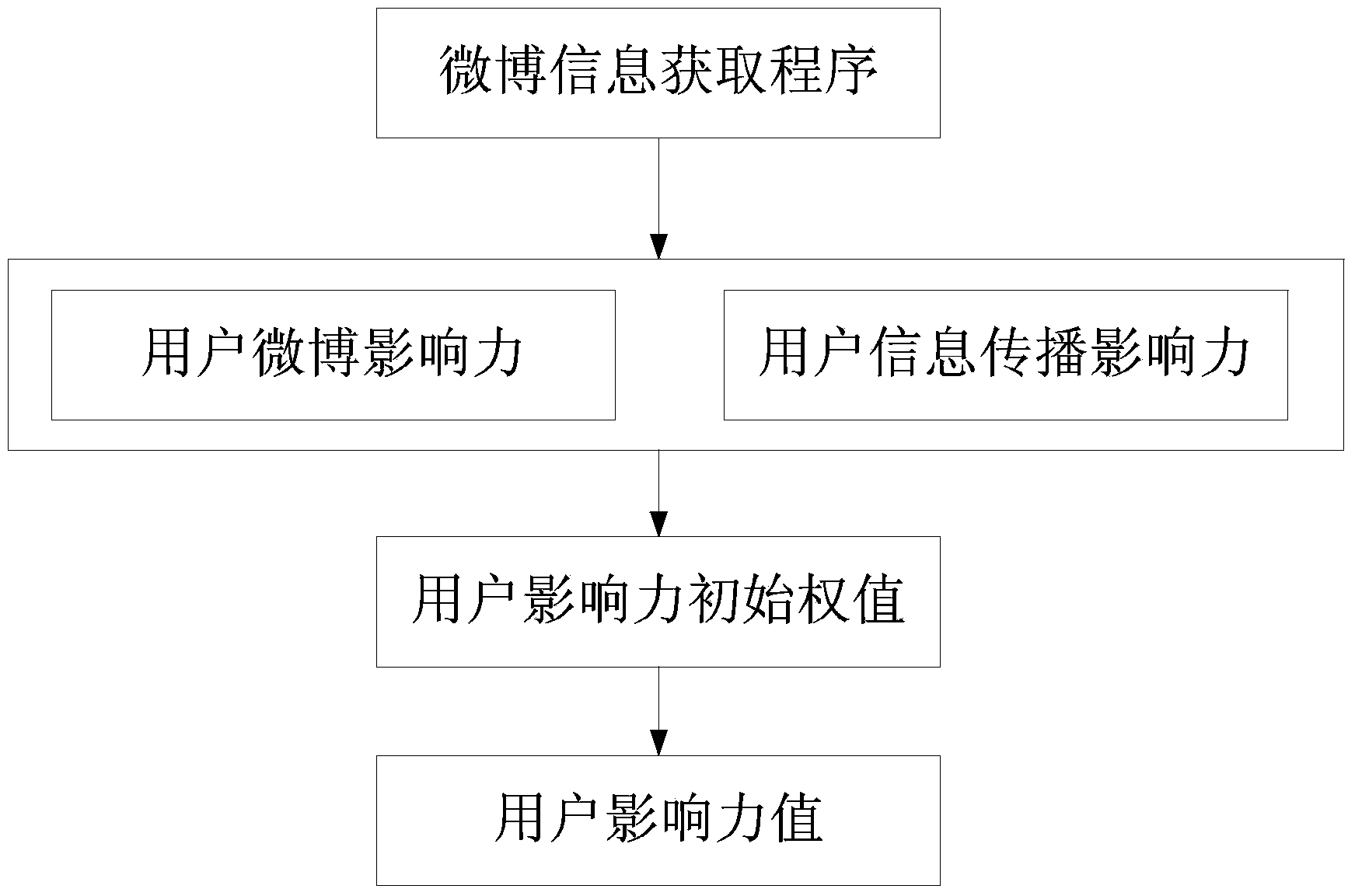
ActiveCN104298767AAccurate discoveryThe recognition effect is accurateWebsite content managementSpecial data processing applicationsInformation dispersalMicroblogging
The invention discloses a method for measuring user influence power in a microblog network. The method includes the following steps that (1) a program used for acquiring microblog user information and released microblog content is written, real microblog user information is acquired through an API port provided by a microblog platform, and the information about the read, forwarded and commented number of a microblog released by a user is extracted from the real microblog user information; (2) the microblog influence power It(u) value of the user is obtained; (3) the information dissemination influence power Id(u) value of the user is obtained; (4) the influence power initial weight value W(u) of the user is obtained according to the microblog influence power It(u) value of the user and the information dissemination influence power Id(u) value of the user; (5) iterative computation is conducted on the influence power value I(u) of the user according to the influence power initial weight value W(u) of the user, and thus the influence power of the user in the microblog network can be measured according to the influence power value I(u) of the user. By means of the method for measuring the user influence power in the microblog network, influence power individuals in the microblog network can be discovered and recognized more accurately.
Owner:XI AN JIAOTONG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com