Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1152results about How to "Discovered in time" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
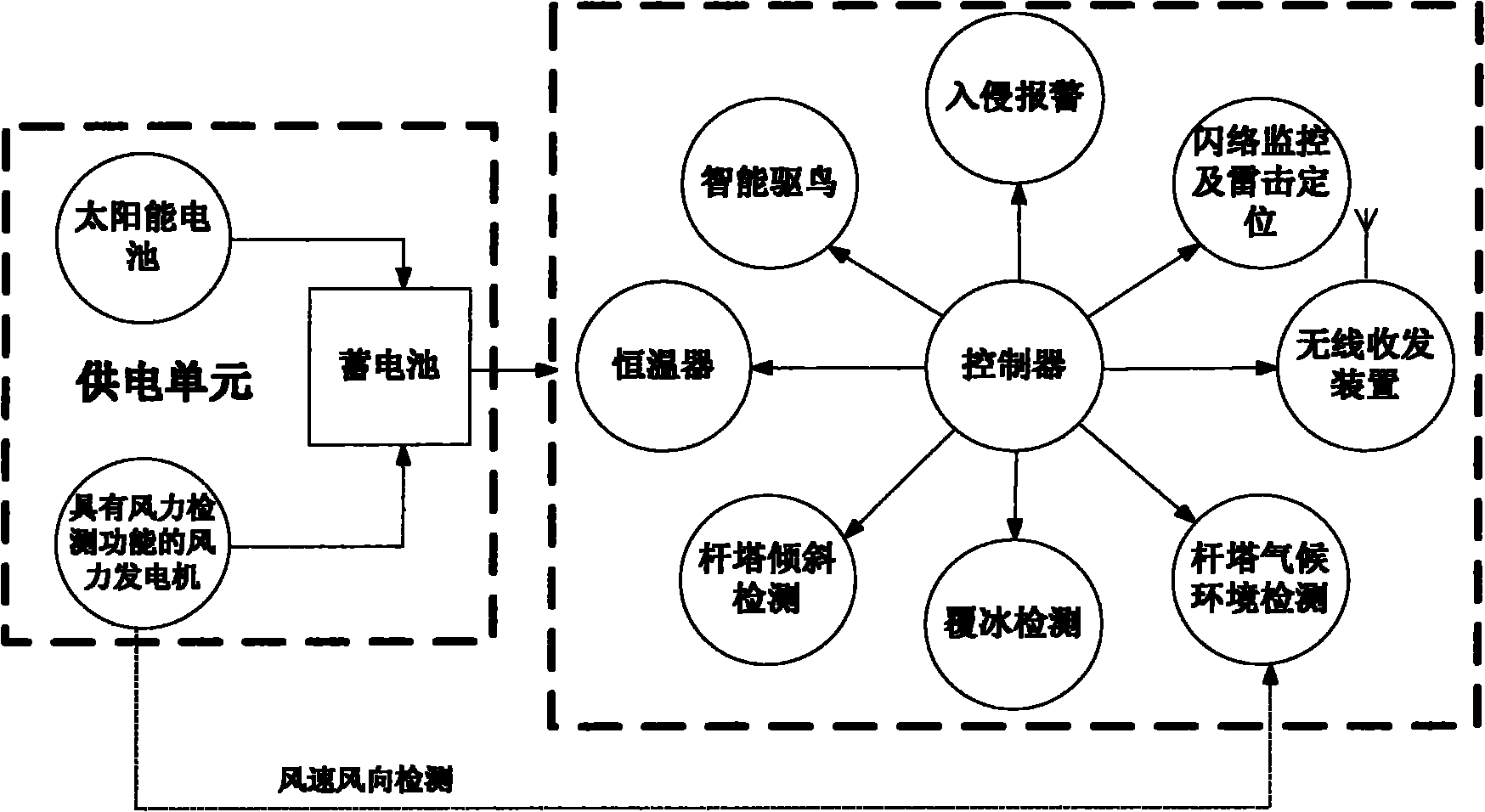
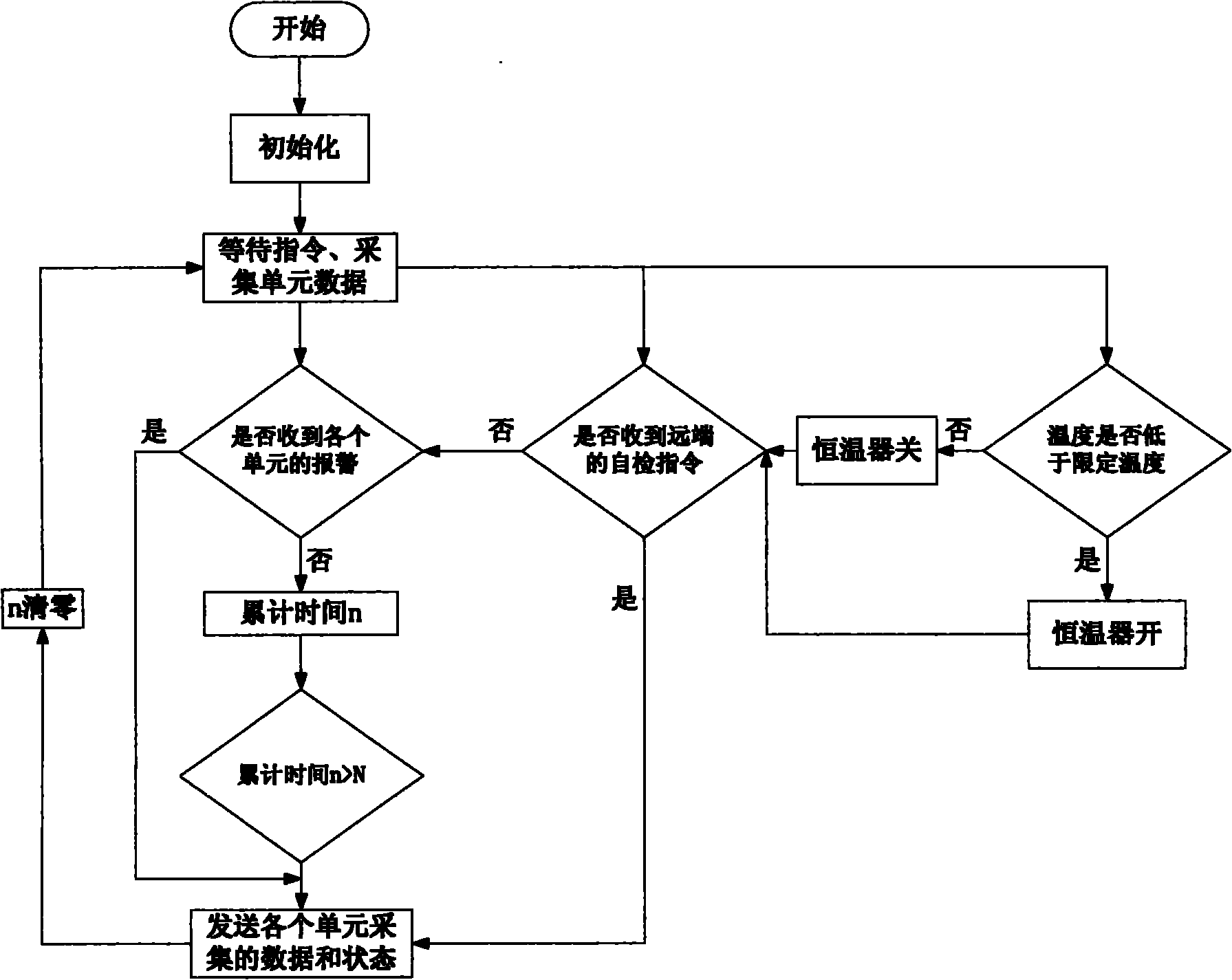
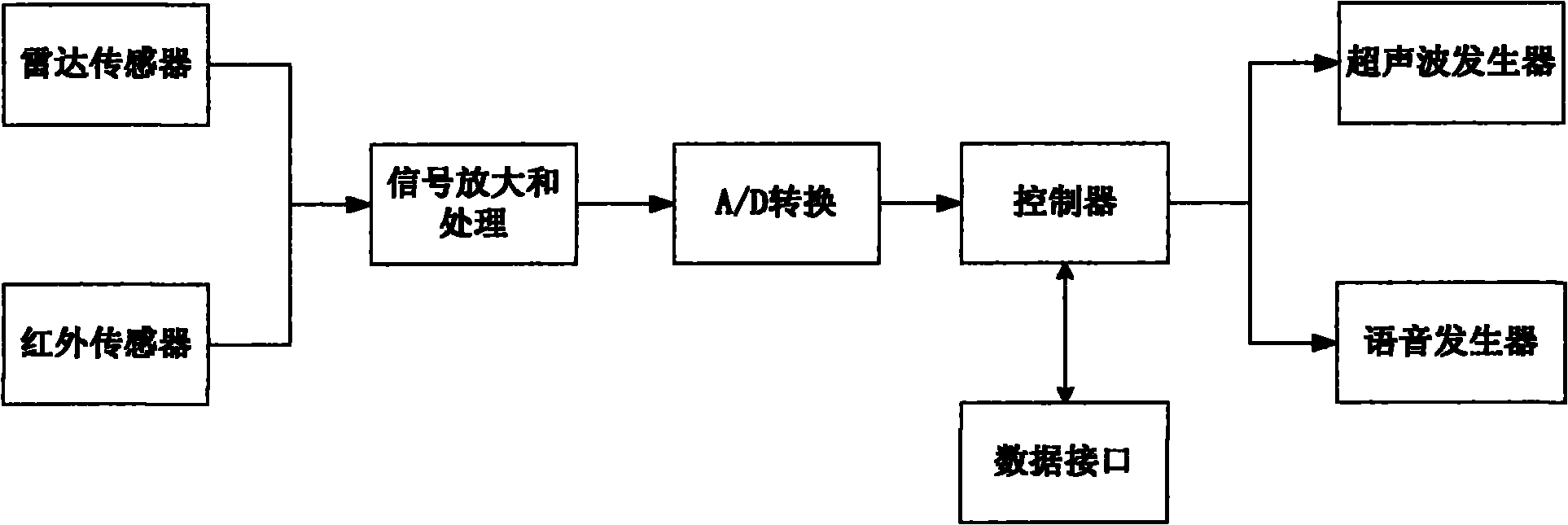
Comprehensive measuring and controlling device of high voltage pole tower
InactiveCN101989767AReduce pollutionReduce power consumptionCircuit arrangementsIndication of weather conditions using multiple variablesGeneral Packet Radio ServiceSmart grid
The invention relates to a comprehensive measuring and controlling device of a high voltage pole tower, mainly comprising a power supply unit, an intelligent bird driving unit, a flashover and lightning stroke location detection unit, a pole tower inclination detection unit, a pole tower meteorological environment detection unit, a pole tower intrusion alarm unit, an transmission line icing parameter detection unit, a central controller, a wireless transceiving device and a thermostat, wherein the power supply unit comprises two parts which are a solar battery and a wind turbine, the wind turbine also fulfills the functions of wind speed and wind direction detection and is an important component part of the pole tower meteorological environment detection unit, the power supply unit stores collected electric quantity into a storage battery through a collection circuit and supplies the power to the device, and the wireless transceiving device sends information collected in situ to a distant monitor center through a GPRS (General Packet Radio Service) or a wireless local network. The invention can fulfill the functions of intelligent bird driving, flashover and lightning stroke location, pole tower inclination detection, meteorological environment detection, intrusion alarm, icing parameter detection and the like and has strong environment adaptability because the wind power and the solar power generation accord with the environment self-powered requirement, thereby enhancing the maintenance free performance of a system. The device is an important component part of an intelligent power grid, accords with the requirement of intelligent power grid establishment of a national power grid and has higher practical value and wide application prospect.
Owner:中电国科技术有限公司 +1
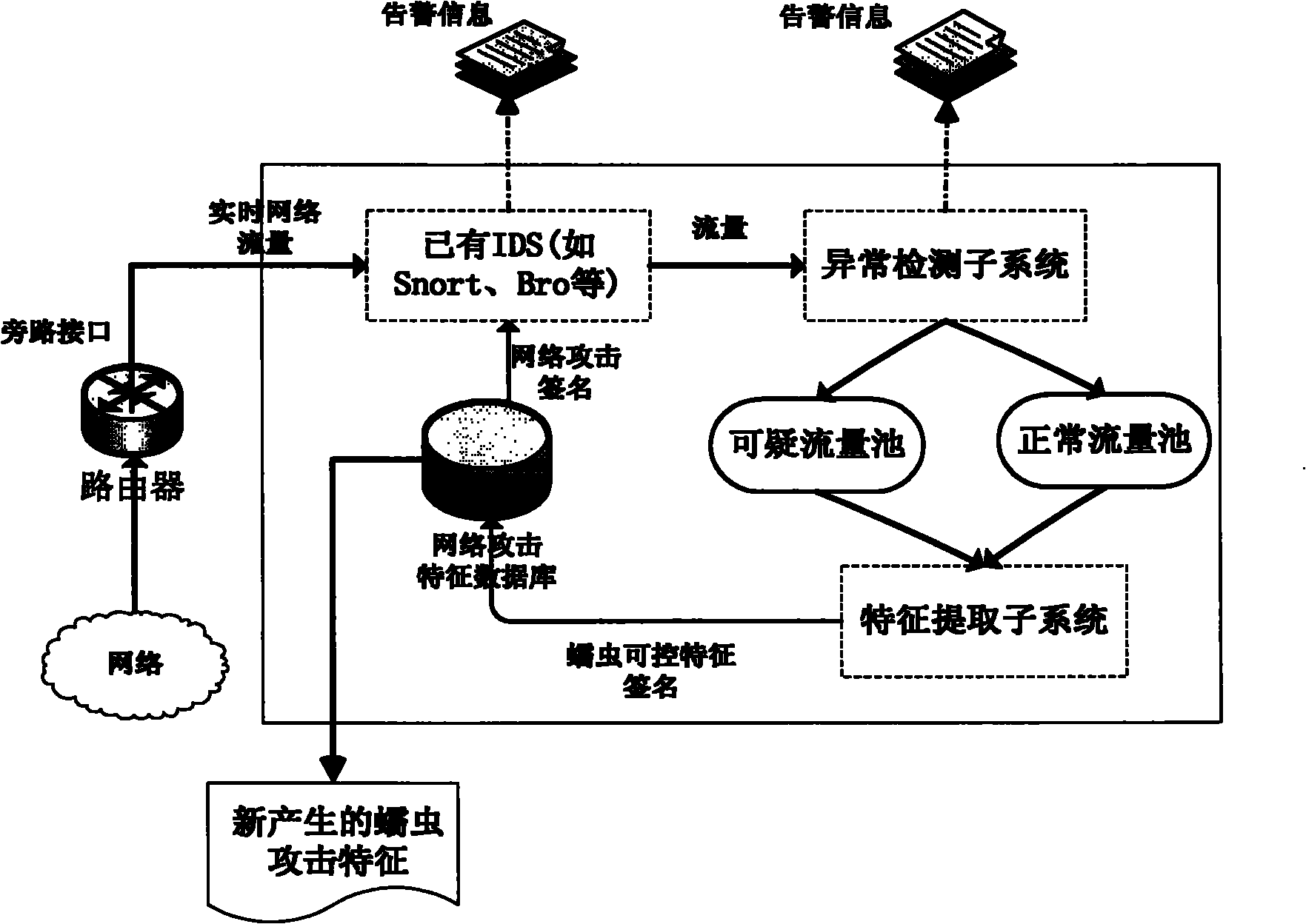
Network worm detection and characteristic automatic extraction method and system
InactiveCN101895521AStop the spreadAccurate discoveryData switching networksFeature extractionAnomaly detection
The invention discloses a network worm detection and characteristic automatic extraction method and a network worm detection and characteristic automatic extraction system and belongs to the technical field of network safety. The method comprises the following steps of: 1) performing abnormal detection on captured network data packets, and dividing the data packets into suspicious network flow and normal network flow according to detection results; 2) storing the suspicious network flow in a suspicious flow pool, and storing the normal network flow in a normal flow pool; 3) clustering the network flow in the suspicious flow pool and the normal flow pool, and extracting a characteristic signature; and 4) updating the extracted characteristic signature in a network attack database, and detecting the network worm. The system comprises an abnormal detection subsystem, a characteristic extraction subsystem, a network attack characteristic database, and a misuse detection system. The methodand the system can more accurately and timely discover the network worm, can automatically extract the worm characteristics and update the attack characteristic database of the existing misuse detection system. Therefore, the aim of suppressing worm propagation is really fulfilled.
Owner:GRADUATE SCHOOL OF THE CHINESE ACAD OF SCI GSCAS
Power distribution cabinet monitoring system and method
InactiveCN110264679AReduce data trafficDiscovered in timeTransmission systemsCircuit arrangementsPower equipmentEngineering
The invention discloses a power distribution cabinet monitoring system and a method. The system comprises a fault detection module, an intelligent fire protection module and a main control platform. The fault detection module is used for real-time data monitoring and fault analysis for a power distribution cabinet, the main control center is used for receiving the fault information of a power device, according to the fault position, an alarm module A is started to control the intelligent fire protection module to start an alarm unit B and a fire protection control unit, the execution mechanism at the field of the power distribution cabinet is controlled to control the automatic regulation of the temperature and the humidity at the internal portion of the power distribution cabinet, on-off of the loop power supply of the power distribution cabinet and the automatic switch-on of the fire protection device are controlled. The multi-level fault analysis and monitoring from the operation condition of the power equipment to the microenvironment of the cabinet and the like are achieved, and multiple detection modes are set through multi-level fault early warning and flexible threshold values, so that potential crisis can be timely found, and meanwhile, the power supply of the power device in the power distribution cabinet can be controlled to be switched on and off and the fire protection device can be controlled to be switched on and off according to the fault warning, so that the bidirectional development of monitoring quantity and control quantity is balanced.
Owner:国网山东省电力公司沂南县供电公司 +1
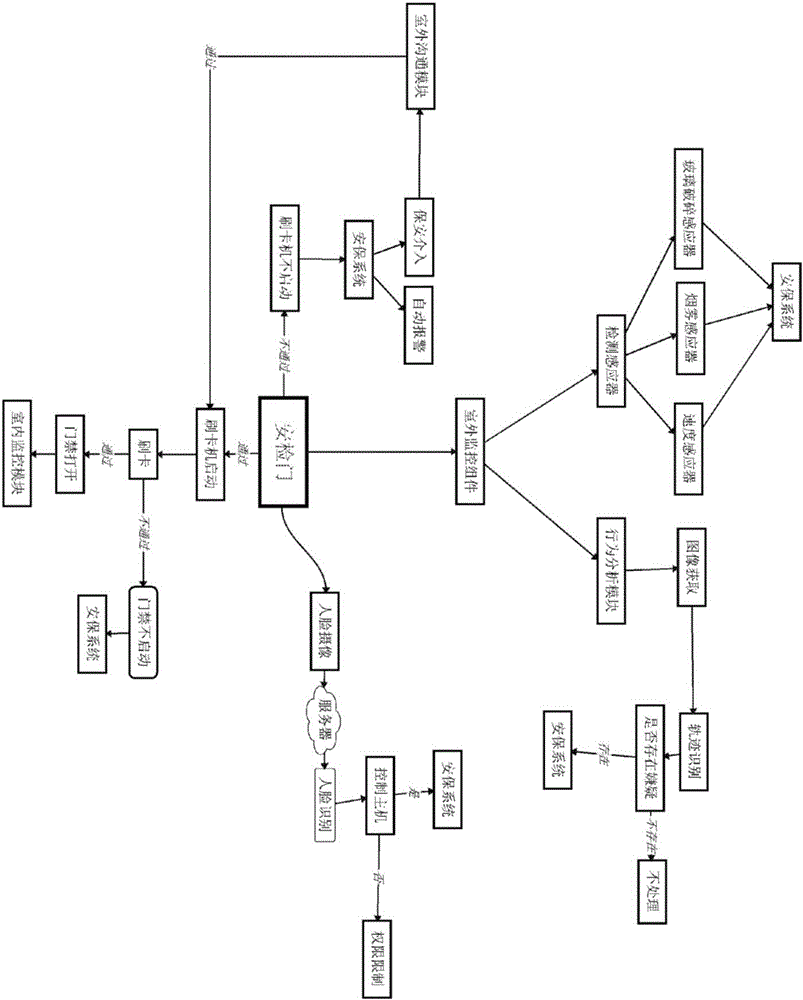
Intelligent monitoring system of self-service bank and monitoring method thereof
ActiveCN106373240ADiscovered in timeInsightComplete banking machinesATM surveillanceService controlMonitoring system
The invention discloses an intelligent monitoring system of a self-service bank. The intelligent monitoring system of the self-service bank comprises an outdoor monitoring module used for monitoring or analyzing environment out of an entrance guard of the self-service bank, an indoor monitoring module used for monitoring or analyzing environment in the entrance guard of the self-service bank and providing a user identification function, a security module used for timely warning or sending an alarm for suspicious or illegal actions, a server used for storing user information and providing related calculation service, a control host computer used for connecting with the outdoor monitoring module, the indoor monitoring module, the security module, the server and a pre-authorization module and sending control instructions to the outdoor monitoring module, the indoor monitoring module, the security module, the server and the pre-authorization module, and the pre-authorization module used for enabling a client to pre-authorize business to be handled in the bank or pre-authorize an appointed agent. The invention further discloses a monitoring method based on the intelligent monitoring system of the self-service bank. According to the intelligent monitoring system of the self-service bank and the monitoring method thereof, an overall monitoring system of the self-service bank is integrated, and overall monitoring, intelligent analysis, and timely discovery of the suspicious actions and suspicious personnel are achieved.
Owner:WEIRONG TECH CO LTD
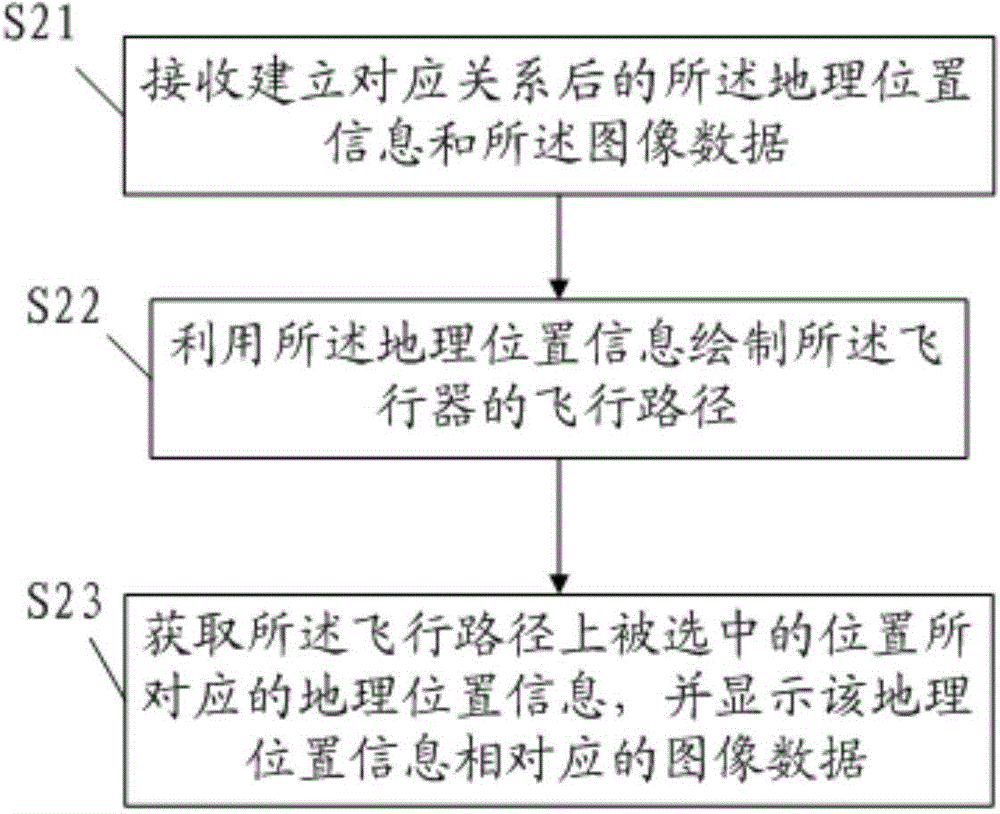
Aircraft tracing method and aircraft tracing system
InactiveCN104679873AMonitor flight statusEasy accessClosed circuit television systemsSpecial data processing applicationsFlight vehicleGeolocation
The invention provides an aircraft tracing method and an air aircraft tracing system. The method comprises the following steps: acquiring geographical location information of an aircraft and image data of an aircraft flyover area; establishing a corresponding relationship of the geographical location information and the image data which are acquired at the same moment; sending the data with the corresponding relationship; receiving the geographical location information and the image data with the established corresponding relationship at a receiving end; drawing a flight path of the aircraft by utilizing the geographical location information; obtaining the geographical location information corresponding to a position selected in the flight path and displaying the image data corresponding to the geographical location information. According to the aircraft tracing method disclosed by the invention, the geographical location information corresponding to each frame image is added in video information by establishing the corresponding relationship of the geographical location information and the image data, so that the geographical location corresponding to each frame video image can be conveniently obtained subsequently, and basis is provided for tracing a track of the aircraft and monitoring the flight condition of the aircraft.
Owner:SHENZHEN AUTEL INTELLIGENT AVIATION TECH CO LTD
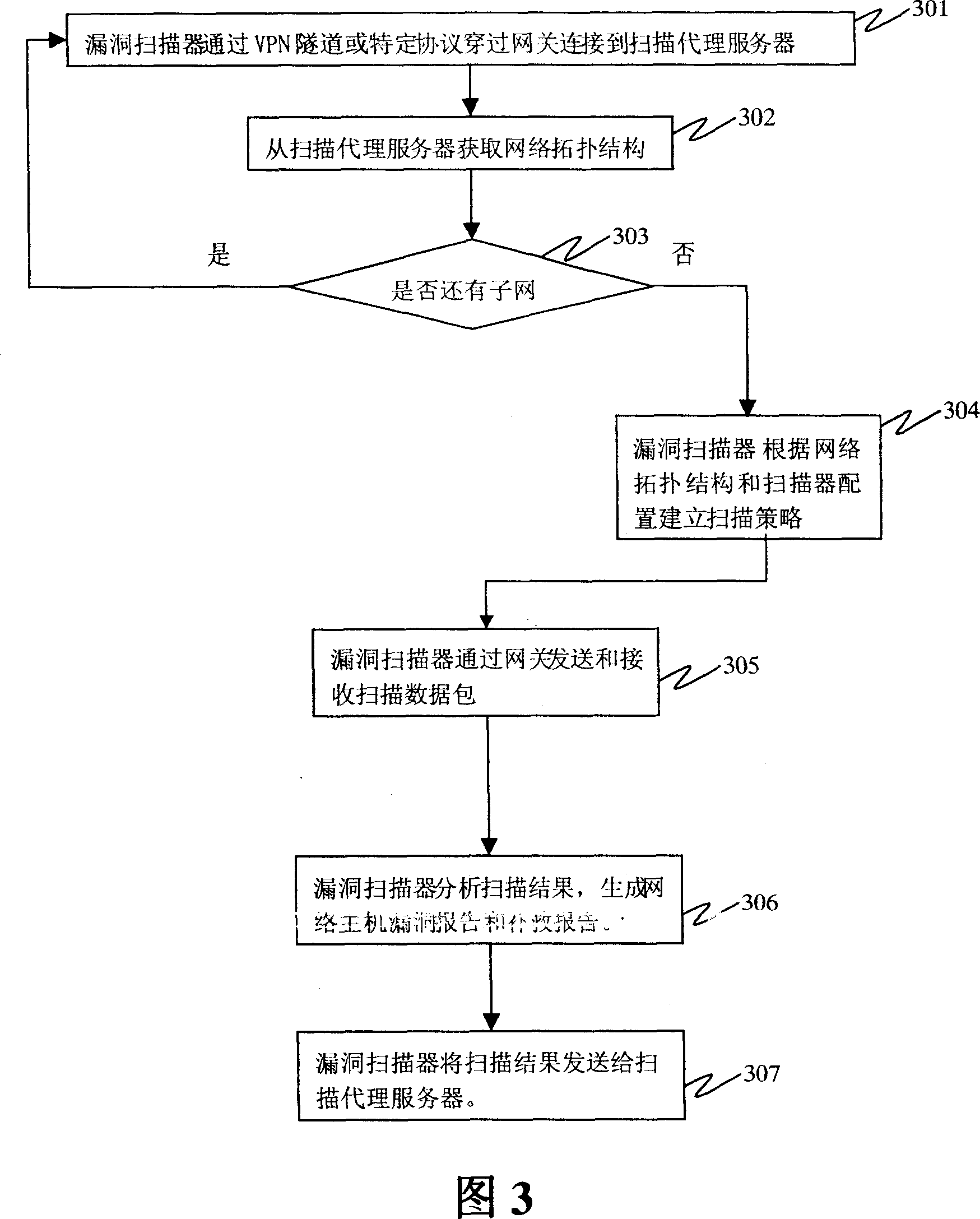
Computer network risk evaluation device and method therefor
ActiveCN101064736AImprove the protective effectLow costData switching by path configurationProxy serverRisk evaluation
The invention discloses a device and method for assessing the risk of computer network, the device in invention includes: gateway, which can obtain the network topology structure information; loophole scanner, which can obtain the network topology structure information from the scanning agent sever, and builds the scanning strategy according to the network topology structure information and the allocation. The method in the invention includes following steps: step1. The scanning agent sever obtains the network topology structure information from the gateway; step 2, loophole scanner obtains the network topology structure information from the scanning agent sever; step 3, the loophole scanner builds the scanning strategy according to the network topology structure information, and scans according to the scanning strategy; step 4, the loophole scanner analyzes the scanning result, and generates the loophole report and / or remedy report. Using the invention it can protect the risk in the internal web effectively.
Owner:FORTINET
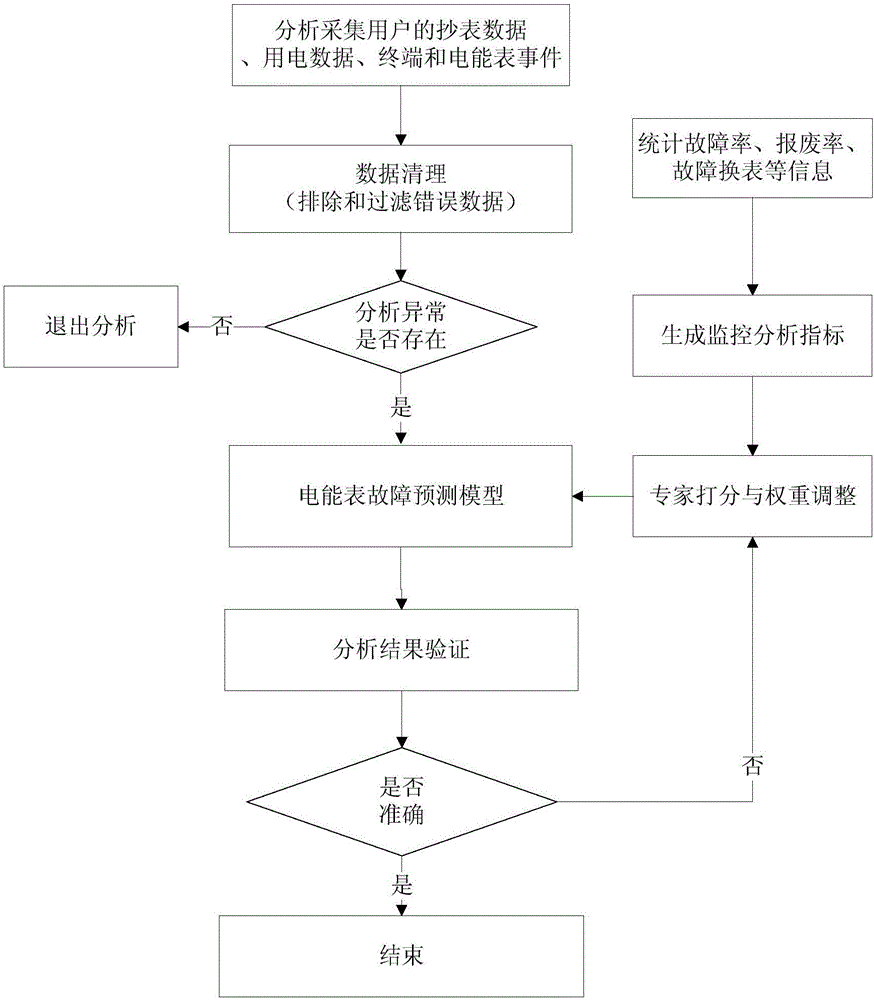
Electric energy meter fault prediction method based on decision tree algorithm
ActiveCN106154209ADiscovered in timeReduce the risk of complaintsElectrical measurementsElectricityLow voltage
The invention discloses an electric energy meter fault prediction method based on a decision tree algorithm. The electric energy meter fault prediction method comprises the following steps: acquiring relevant data of a user by using an acquirer and eliminating wrong data; analyzing whether electric energy meters which have abnormal environments and abnormal quality exist in specific power transformer users and low-voltage users within statistical time buckets; counting whether metering and electricity utilization abnormal events which meet requirements of fault judgment exist for the special power transformer users, and counting whether metering abnormal events which meet requirements of fault judgment exist for the low-voltage users; establishing an electric energy meter fault prediction model by using the decision tree algorithm according to manufacturers corresponding to the electric energy meter and information of failed batches and on the basis of electric energy meter metering fault information of a marketing system; judging whether the result is accurate or not; if the result is accurate, finishing the process; and if the result is inaccurate, continuing judging faults. By the electric energy meter fault prediction method based on the decision tree algorithm, failed electric energy meters can be found out accurately in time, so that workload of field investigation and metering fault treatment of an examination department is reduced.
Owner:NARI TECH CO LTD +3
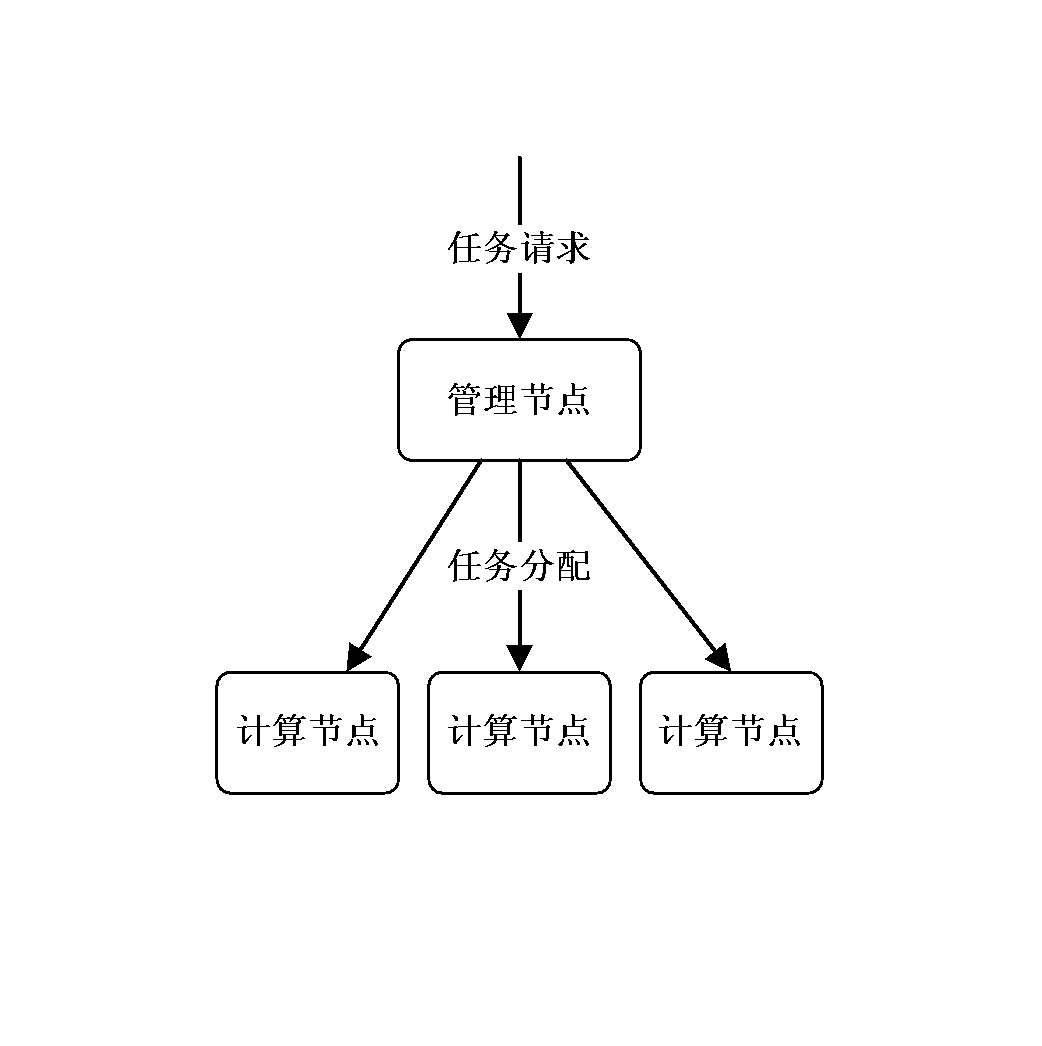
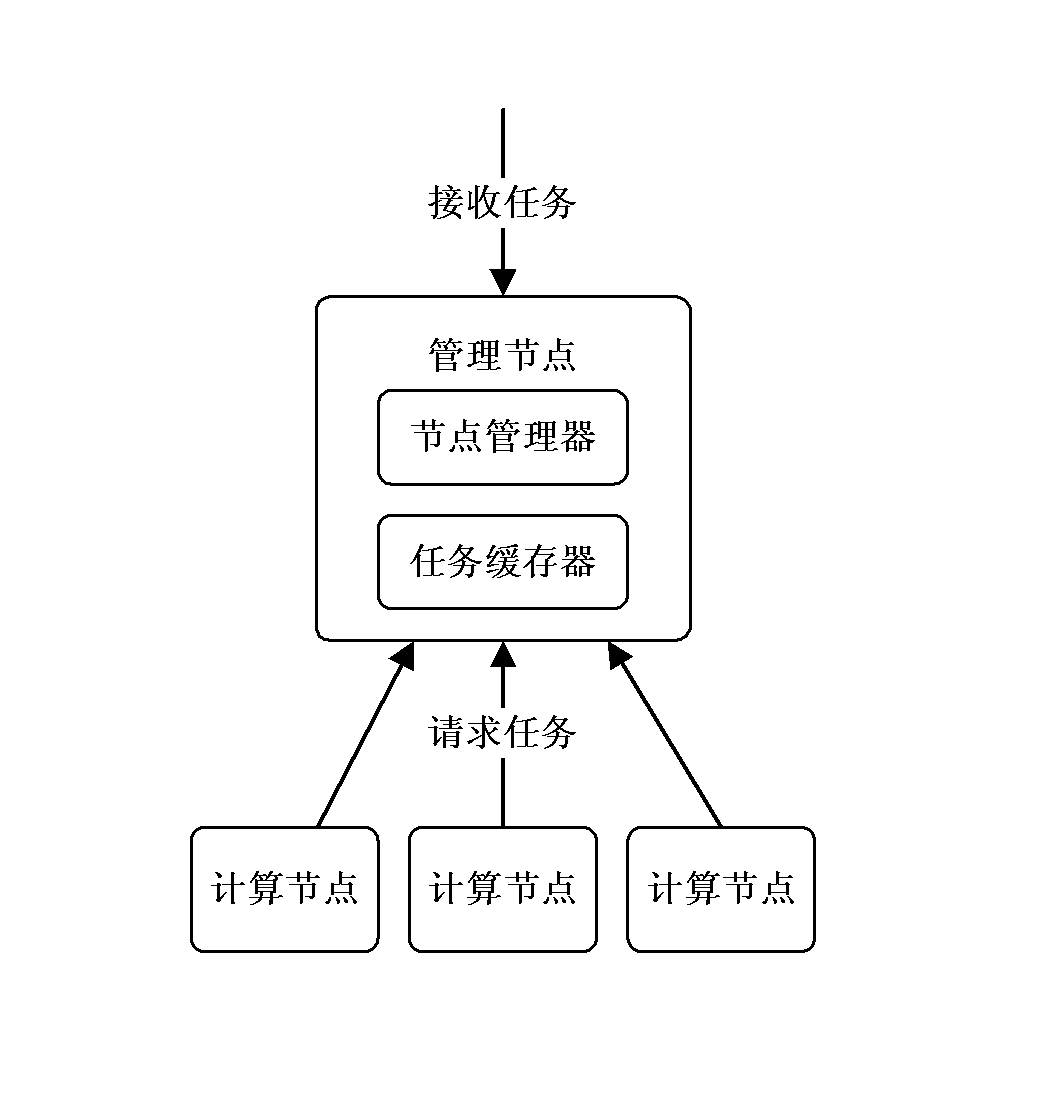
Distributed system node processing task method
InactiveCN103581225AFully automatedDiscovered in timeTransmissionComputational problemDistributed computing
The invention provides a distributed system node processing task managing method which includes the steps of receiving an external task request, storing a task in a task buffer of a management node, when some computational node is connected and asks for the task, sending the task to the computational node, and receiving task results when the task processing results are sent by the computational node. By means of the distributed system node processing task method, automation of the whole task processing process is achieved through simple configuration, the management cost is reduced, and in-time finding and in-time processing on the computational node with faults are facilitated.
Owner:CHINA UNIONPAY
Intelligent self-service bank system
The invention discloses an intelligent self-service bank system, and the system comprises a recognition system which is used for recognizing a client or client information; a monitoring system which is used for monitoring and analyzing the internal and external environments of a self-service bank; a security system which is used for timely finding a suspected behavior, and reminding the security personnel of a suspected person or warning against the suspected person; an authority control system which is used for controlling and matching with the authorities needed by all services; a remote authorization module; and a server. Through the matching of a risk coefficient and an authority coefficient, the system determines the authority of business handling and risk early warning. The system employs a multistage recognition mode, and can effectively provide a recognition authority matched with a to-be-handled business for the client. The system is integrated with an overall monitoring system of the self-service bank, and can achieve the comprehensive monitoring, intelligent analysis and timely finding of suspected motion and persons. The system enables the suspected behaviors found by the monitoring system to be graded, limits the transaction authority of the self-service bank according to different levels, and can control risks from the source.
Owner:WEIRONG TECH CO LTD
Course monitoring method based on non-gauss component extraction and support vector description
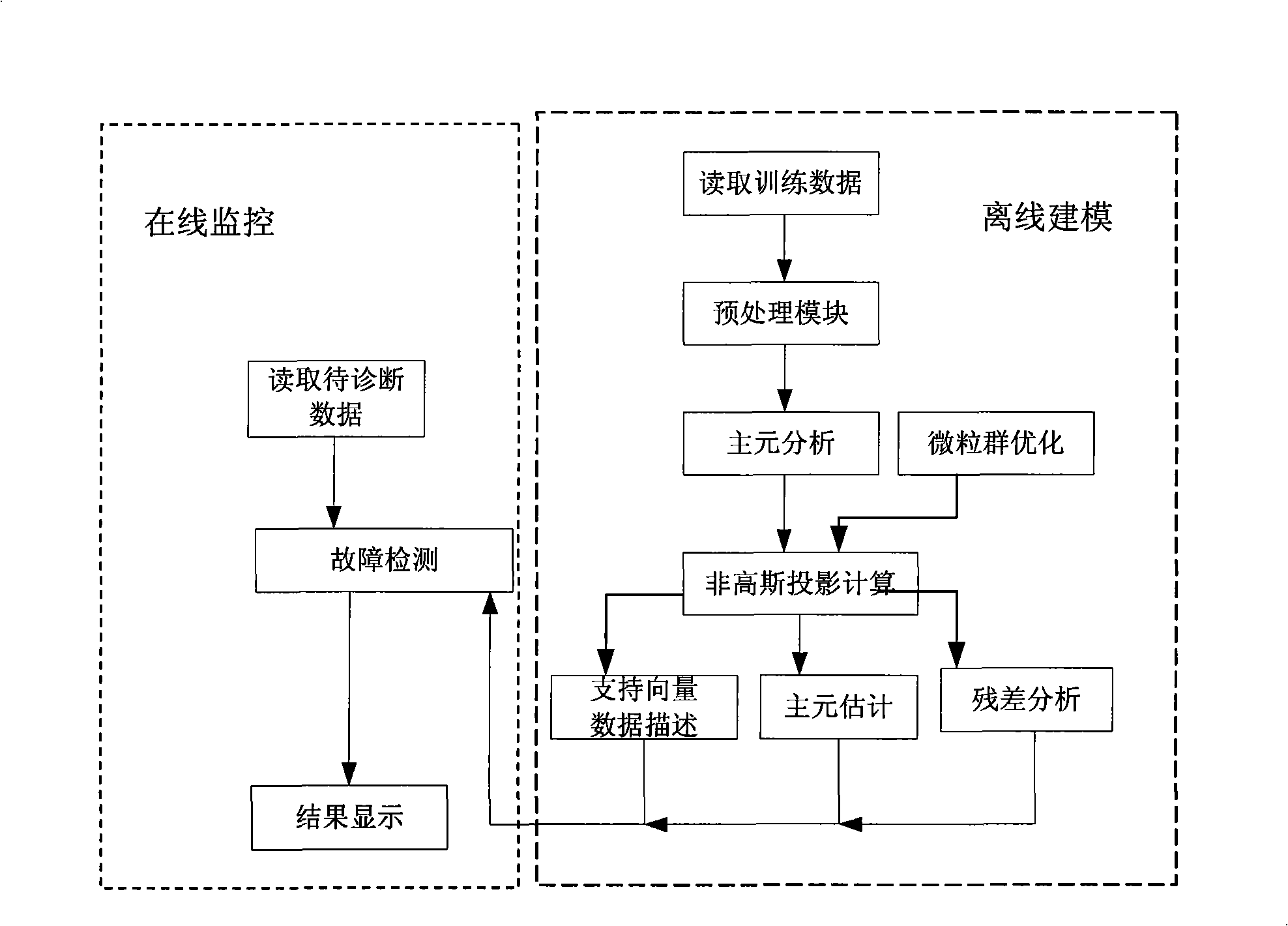
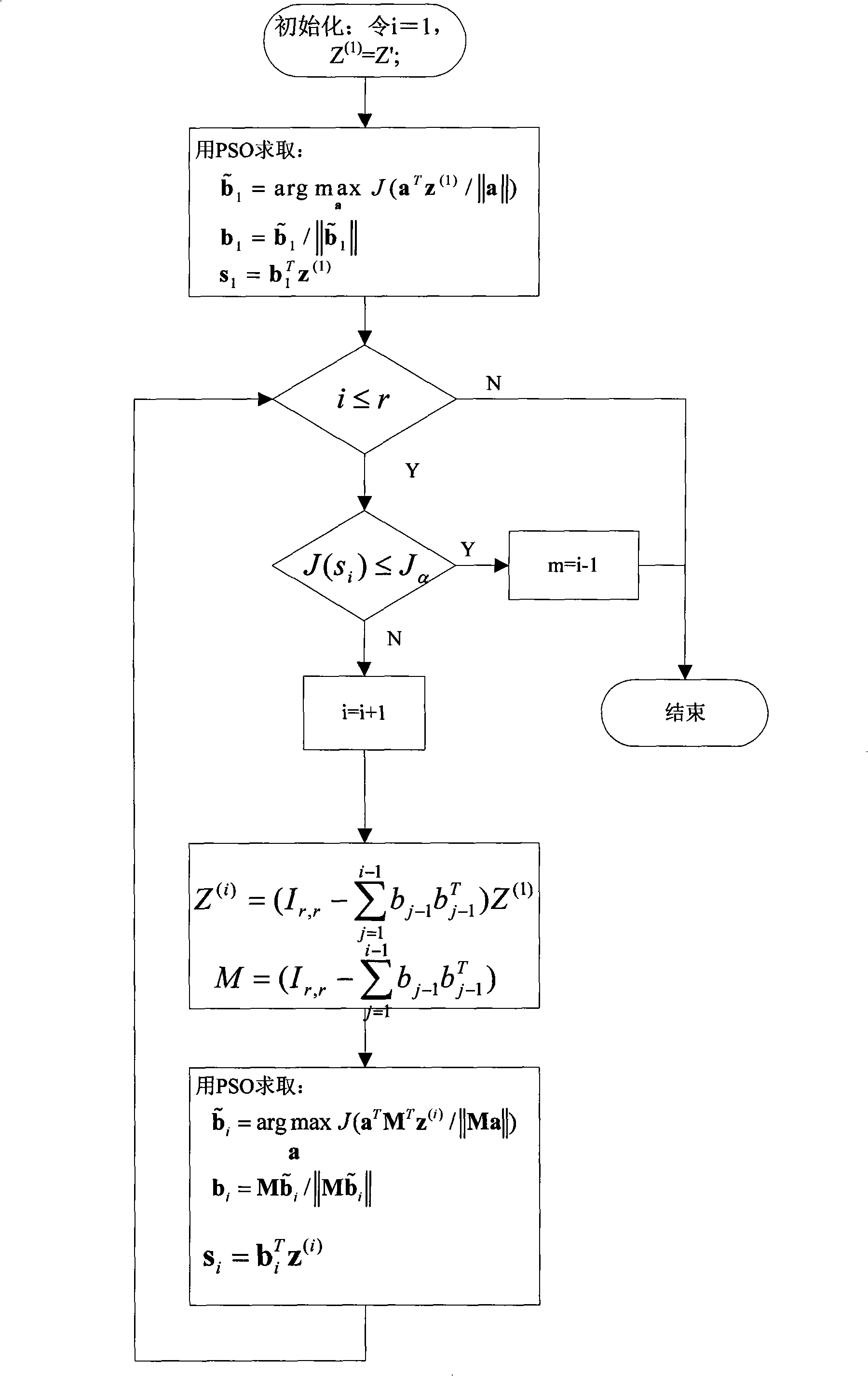
InactiveCN101403923AOvercome the shortcoming of easy to fall into local minimumAvoid the shortcoming of assuming a normal distributionElectric testing/monitoringData descriptionNon-Gaussianity
The invention discloses a process monitoring method which is based on non-Gaussian component extraction and support vector description. The method comprises the following steps: read-in of training data and data to be diagnosed, data preprocessing, establishment of a principal component analysis model, particle swarm optimization algorithm, non-Gaussian projection calculation, support vector data description, residual analysis, principal component estimation, fault detection and the model updating. By the method, the non-Gaussian components can be automatically extracted from operating data of an industrial process, thus avoiding the disadvantage that the conventional statistical process monitoring method assumes that data is subject to normal distribution, and the non-Gaussian projection algorithm based on the particle swarm optimization algorithm ensures the maximization of the non-Gaussian properties of the extracted independent components, and avoids the problem that the independent component analysis method is easy to be involved in the locally optimal solution. Compared with the conventional statistical process monitoring method, the method can find abnormity in time, effectively reduce the rate of false alarm, and obtain better monitoring effect.
Owner:ZHEJIANG UNIV
Network sensitive information-oriented screenshot discovery and locking callback method
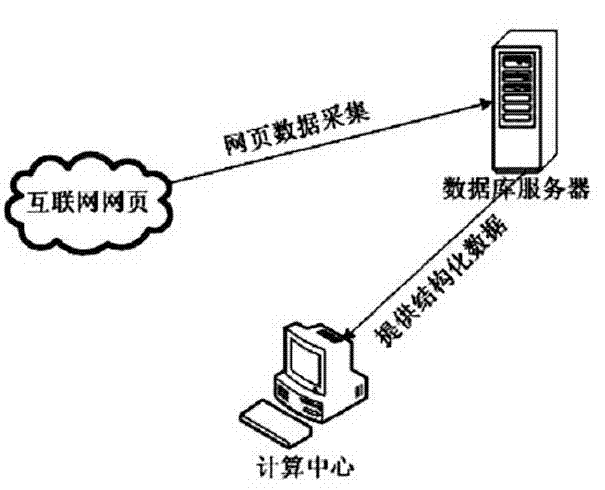
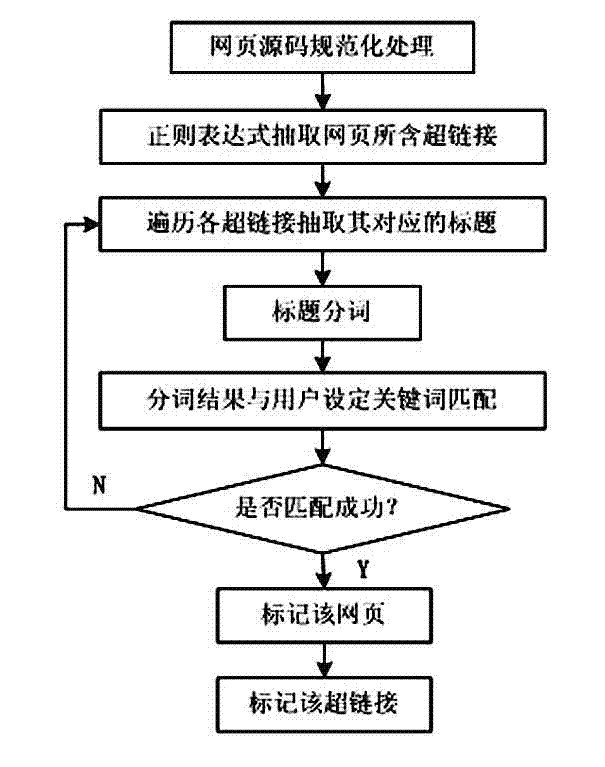
InactiveCN102902703ADiscovered in timeQuick discoverySpecial data processing applicationsComputer securityNetwork on
The invention discloses a network sensitive information-oriented screenshot discovery and locking callback method which comprises the steps of: acquiring webpage data of a website to be monitored; normally treating the webpage data, extracting a webpage title and a link on the basis of a regular expression, matching sensitive information on the basis of the webpage title and the link; carrying out outer page and inner page screenshot on the sensitive information; carrying out locking callback on the sensitive information for preventing resurgence; and storing and inquiring a sensitive information screenshot result. For the sensitive information on a network, by adopting the network sensitive information-oriented screenshot discovery and locking callback method, the sensitive information can be found within shortest time and is subjected to screenshot storage, the webpage is prevented from being updated or deleted in future, file discovery and immediate disposition of relative disposing mechanisms are facilitated, and a website for frequently issuing the sensitive information is disposed. In addition, the method provided by the invention can effectively meet the monitoring and disposing demand of the sensitive information of a network, and is suitable for implementation of a network public opinion analysis system.
Owner:NAT UNIV OF DEFENSE TECH
Method and device for identifying legality of website service
The invention discloses a method and a device for identifying the legality of a website service, which are used for improving access security when a user accesses the internet. The method comprises the steps of: when a client requires to use the website service, based on random numbers transmitted by the client, a server generates the corresponding temporary communication key by adopting a negotiated and appointed method, encrypts identification information by adopting the temporary communication key and transmits the encrypted identification information to the client; and the client decryptsthe received encrypted identification information by adopting a temporary communication key generated based on the same method and identifies the legality of the website service provided by the server based on the decrypted result and by adopting the preset mode. Therefore, the client can judge the legality of the website service according to the correctness of the identification information and effectively prevents information from being altered and intercepted midway, so that the security of using the website service by the user is effectively improved and the quality of the website serviceis improved. The invention also discloses the device for identifying the legality of the website service.
Owner:CHONGQING SHAHAI INFORMATION TECH
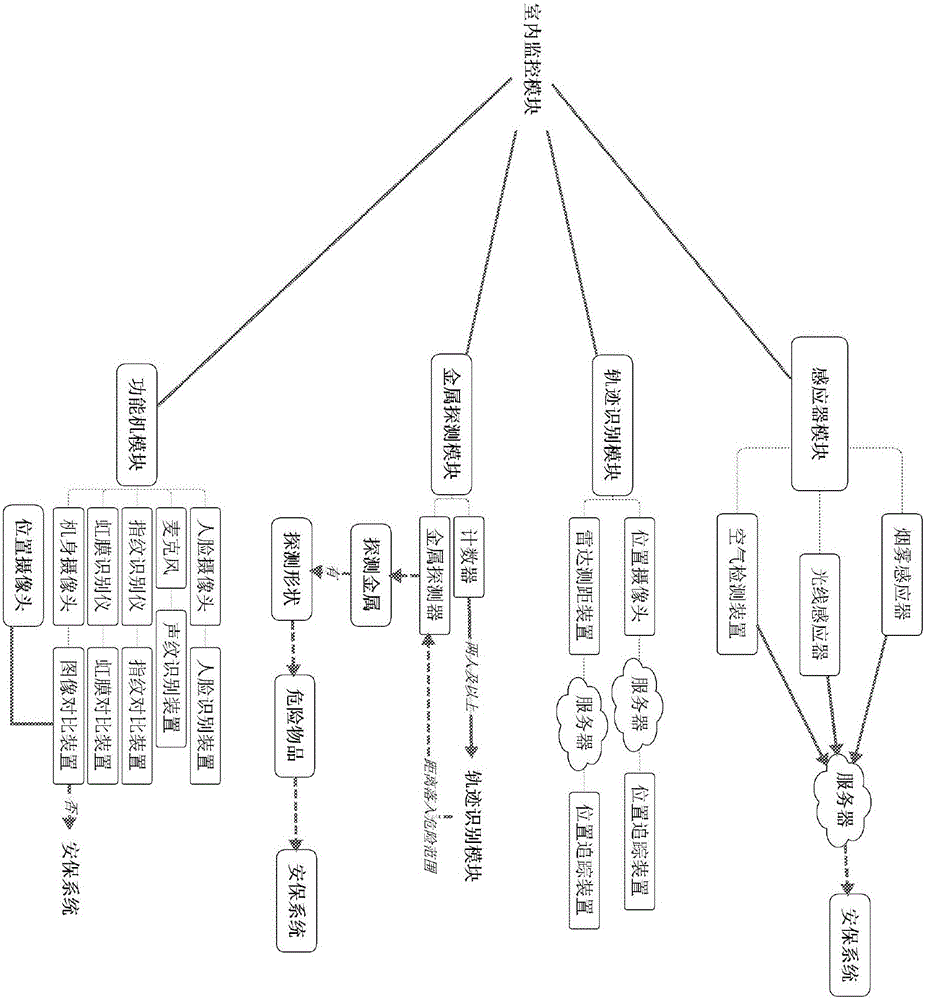
Smart community monitoring system
InactiveCN106358021AAvoid enteringImprove securityData processing applicationsCharacter and pattern recognitionVideo monitoringMonitoring system
The invention discloses a smart community monitoring system, including an access control system for opening a door when the first human body feature information of a person trying to open a corresponding door is verified to be successful, an elevator control unit for unlocking the button for a target floor in an elevator for a first preset time when the second human body feature information of a passenger is verified to be successful, a video monitoring unit for acquiring real-time video images in a community, a security detection unit for detecting whether someone fall down according to the video images and alarming when a person falls down over a second preset time, a person recognition unit for detecting a facial image in the video images and comparing the facial image with a prestored target person image and alarming when detecting a facial image consistent with the target person image, a rubbish detection unit for alarming when detecting the rubbish quantity at a rubbish spot exceeds standards, and a smart home unit for performing indoor safety protection and environmental conditioning. According to the invention, real-time smart monitoring and safeguard of the community are achieved.
Owner:CHENGDU HONGRUAN SCI & TECH IND CO LTD
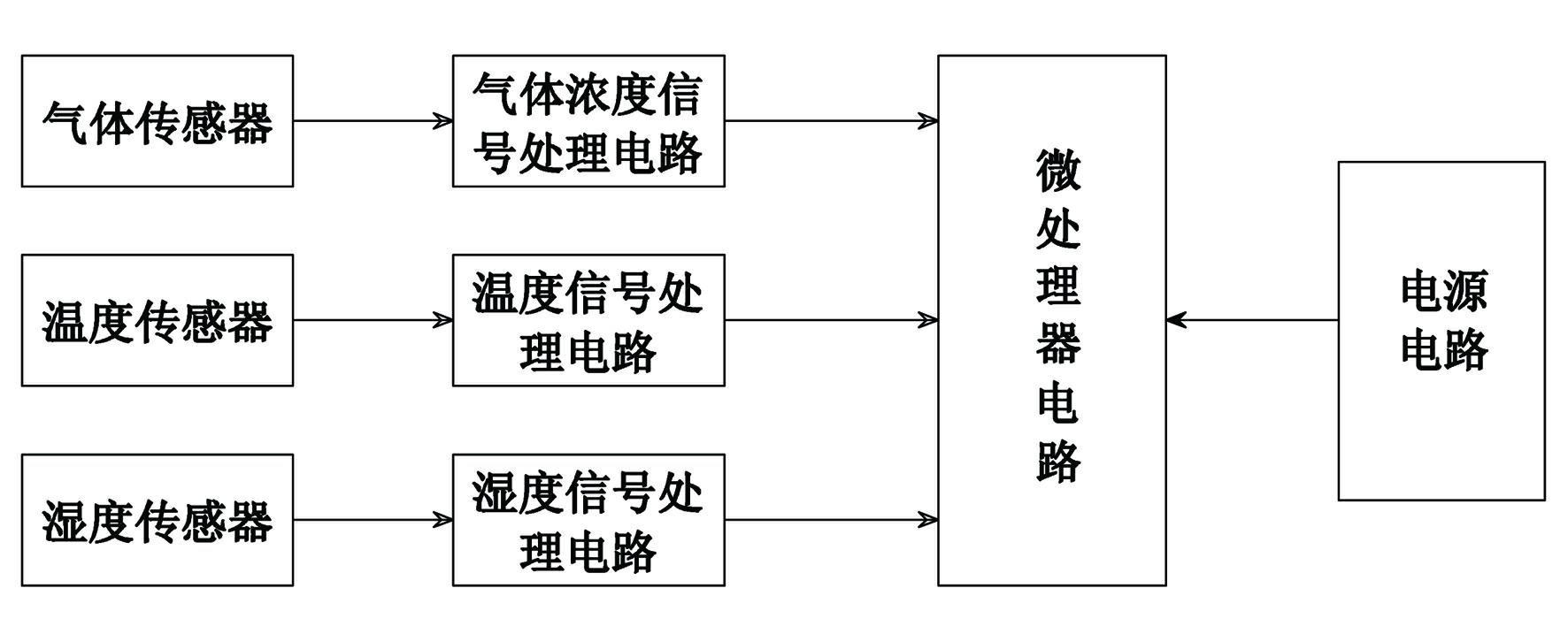
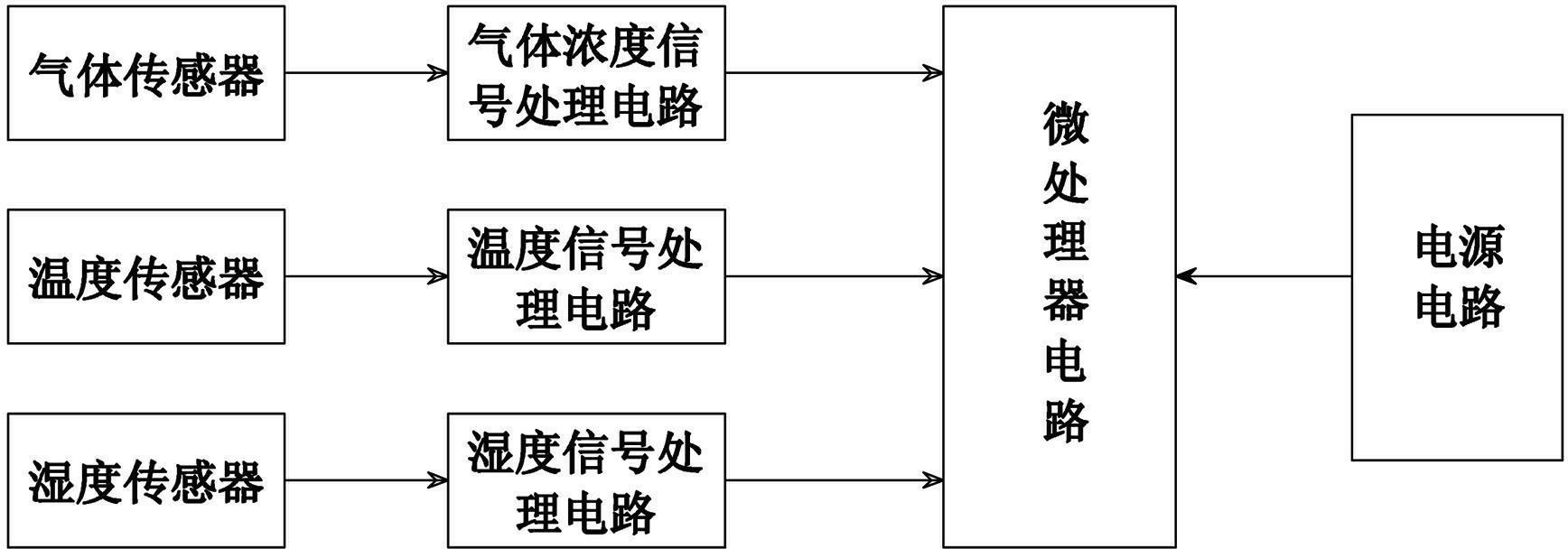
Compensation type gas sensor and humiture compensation method thereof
InactiveCN102680518ADiscovered in timeAccurate discoveryMaterial heat developmentHigh humiditySignal processing circuits
The invention provides a compensation type gas sensor and a humiture compensation method thereof. The compensation type gas sensor comprises a microprocessor circuit, a gas sensor, a temperature sensor, a humidity sensor, a gas concentration signal processing circuit, a temperature signal processing circuit, a humidity signal processing circuit and a power supply circuit. The humiture compensation method comprises the following steps of: creating a compensation factor searching database; obtaining a gas concentration measured value C0, a temperature measured value T and a humidity measured value H through actual measurement; searching a compensation factor @ corresponding to the gas concentration measured value C0, the temperature measured value T and the humidity measured value H from the compensation factor searching database according to the gas concentration measured value C0, the temperature measured value T and the humidity measured value H; and obtaining a gas concentration true value C1 of the gas sensor by multiplying the gas concentration measured value C0 with the compensation factor @ according to the searched compensation factor @. The compensation type gas sensor provided by the invention has the advantages of being high in detection accuracy, reliable in performance, and suitable for the high-temperature high-humidity environment detection; and the humiture compensation method provided by the invention has the advantages of being simple and practical, and beneficial for increasing the detection accuracy of the gas sensor.
Owner:HENAN HANWEI ELECTRONICS
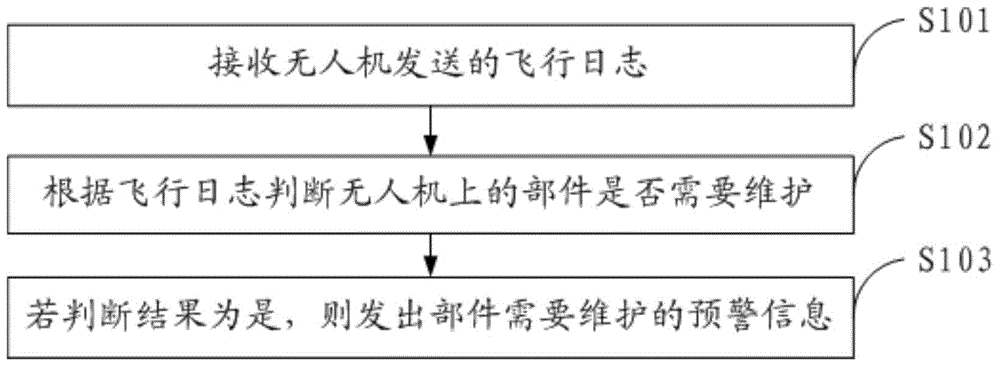
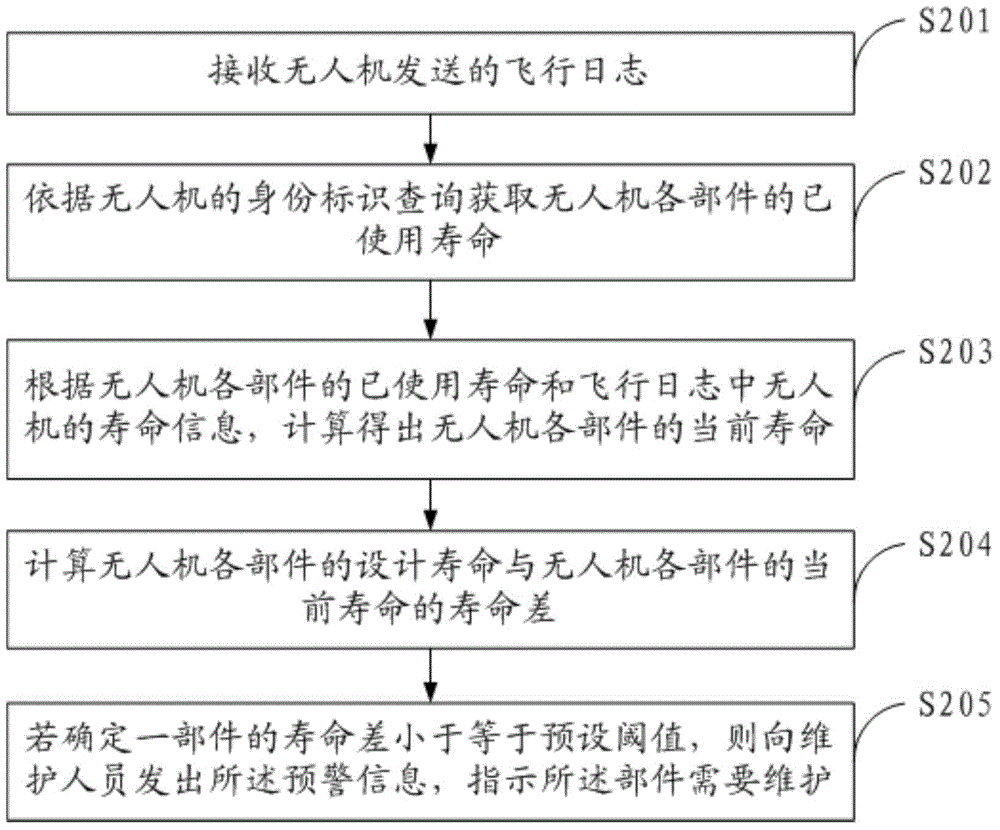
Maintenance method and apparatus for unmanned aerial vehicle
ActiveCN105069507AImprove maintenance efficiencyDiscovered in timeInstrumentsUncrewed vehicleEngineering
Owner:GUANGZHOU XAIRCRAFT TECH CO LTD
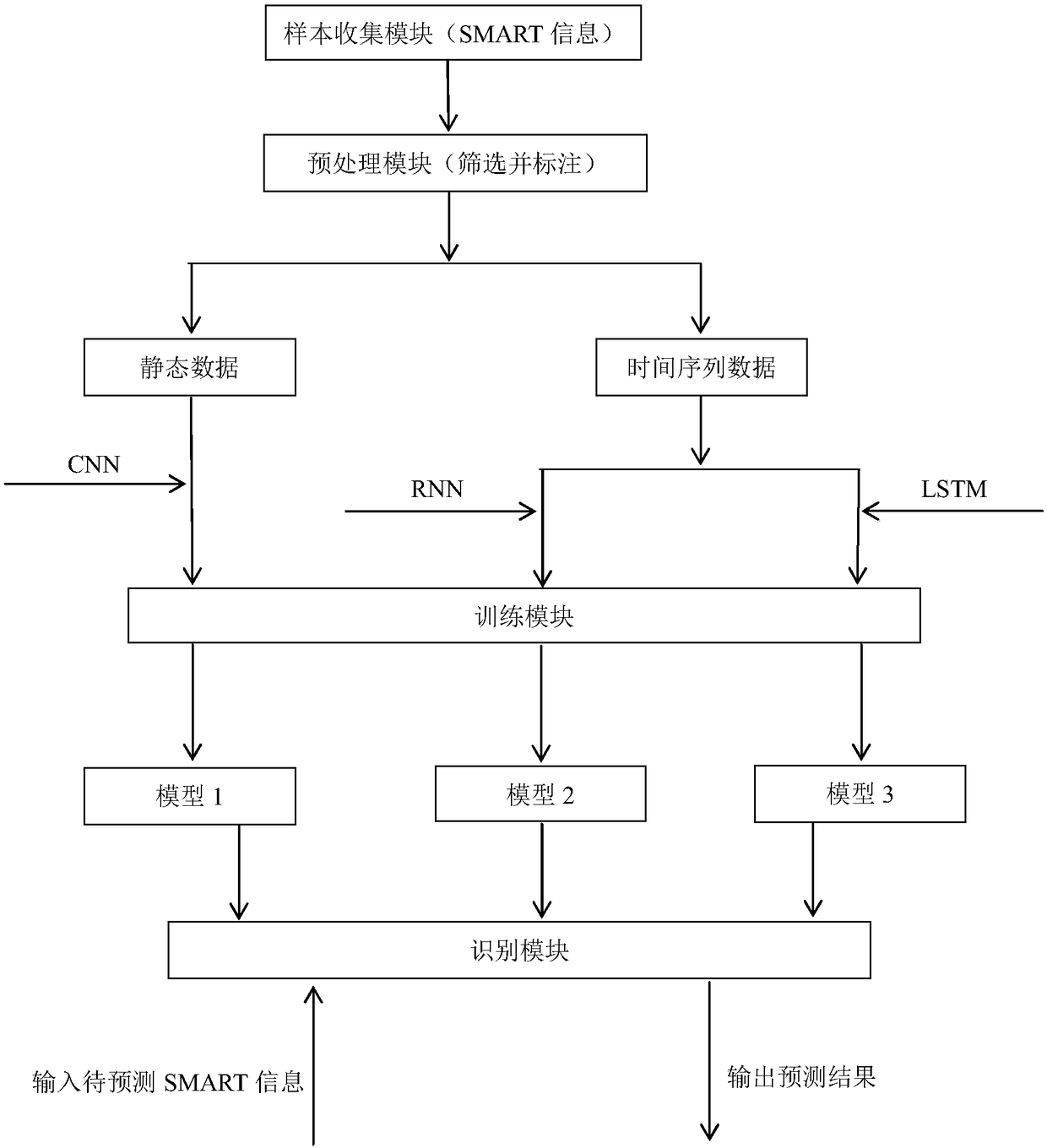
SMART information and deep learning-based hard disk damage prediction method and device
ActiveCN108647136AImprove accuracyImprove usabilityHardware monitoringNeural architecturesAlgorithmData center
The invention discloses a SMART information and deep learning-based hard disk damage prediction method and device. The method comprises the following steps of: collecting SMART information of different hard disk in different time periods as original sample data, and selecting two types of training sample data such as static data and time sequence data from the original sample data; screening the training sample data, extracting an effective parameter set related with hard disk faults and carrying out labeling to obtain labeled training data; respectively constructing at least one neural network model to carry out deep learning on the labeled static data and the labeled time sequence data so as to obtain corresponding neural network models for optimizing model parameters; and obtaining SMART information data of a hard disk in a storage system according to a set timing strategy, and extracting the effective parameter set to input into the neural network model so as to predict whether thehard disk is going to be damaged. The method and device are capable discovering correctly hard disk conditions in time before mechanical hard disks are going to be damaged, so as to carry out timelychange before hard disk failure, thereby greatly improving the high availability and data safety of data centers.
Owner:南京道熵信息技术有限公司
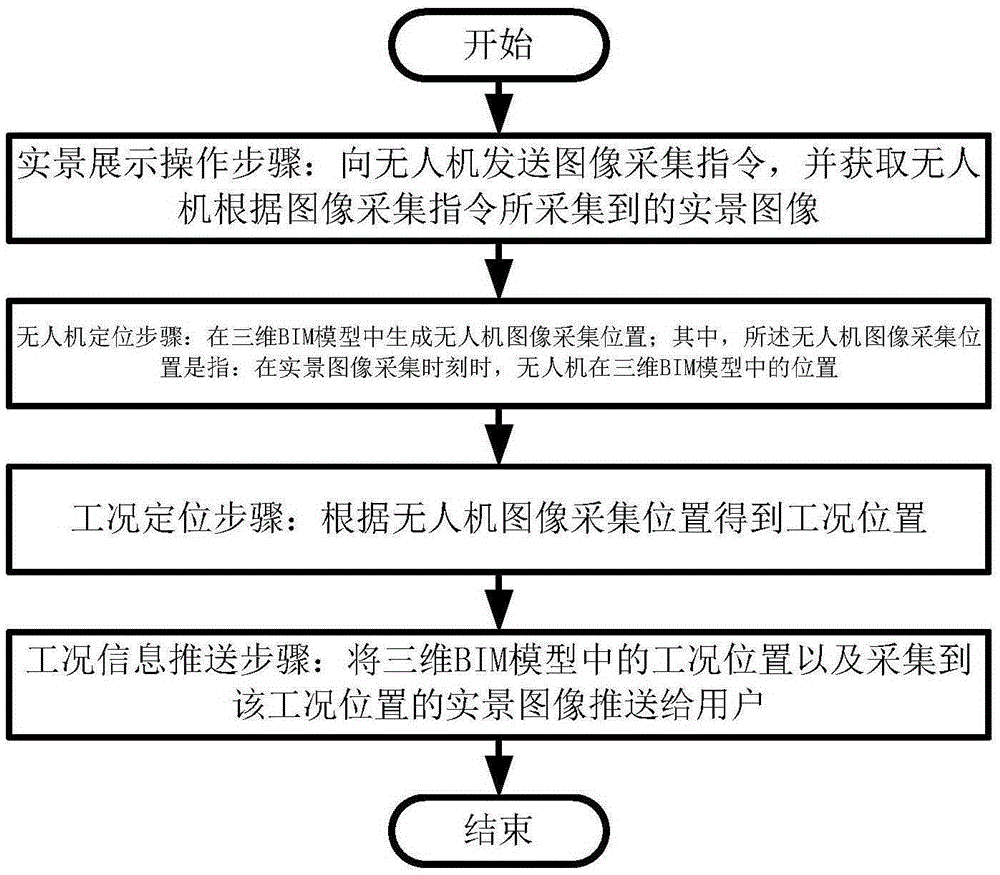
BIM-based unmanned aerial vehicle monitoring method and system
InactiveCN105334862AImprove work efficiencyAccurate monitoringClosed circuit television systemsPosition/course control in three dimensionsUncrewed vehicleVehicle positioning
The invention provides a BIM-based unmanned aerial vehicle monitoring method and system. The method comprises a real scene operation step, an unmanned aerial vehicle positioning step and a work condition positioning step. According to the real scene operation step, an unmanned aerial vehicle is operated, an image collection instruction is transmitted to the unmanned aerial vehicle, and real scene images collected by the unmanned aerial vehicle according to the image collection instruction are obtained. According to the unmanned aerial vehicle positioning step, an unmanned aerial vehicle image collection position is generated in a three-dimensional BIM model, wherein the unmanned aerial vehicle image collection position is the position of the unmanned aerial vehicle in the three-dimensional BIM model at a real scene image collection moment. According to the work condition positioning step, a work condition position can be obtained according to the unmanned aerial vehicle image collection position. According to the BIM-based unmanned aerial vehicle monitoring method and system of the invention, the unmanned aerial vehicle and the BIM model are combined together, so that information obtained through aerial monitoring can be recorded, displayed and pushed through the BIM model, and therefore, the working efficiency of monitoring personnel can be enhanced, and manpower can be greatly saved, and the shortening of a construction period can be benefitted.
Owner:SHANGHAI TONGZHU INFORMATION TECH
Fuzzy dynamic allocation method for cloud storage resource
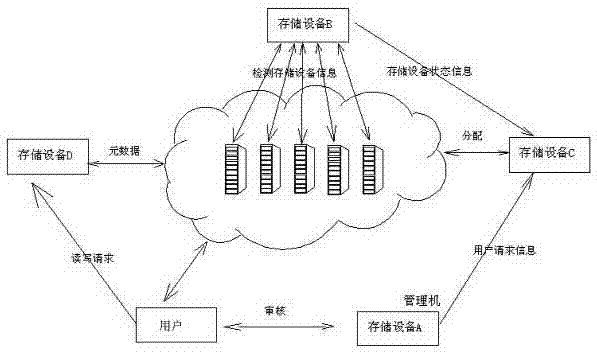
InactiveCN102404399AReal-time monitoring statusDiscovered in timeTransmissionCloud storage systemDistributed computing
The invention provides a fuzzy dynamic allocation method for cloud storage resources, which increases the efficiency of the cloud storage system by detecting the state information of storage equipment in real time and complementing fuzzy dynamic balanced allocation of the cloud storage resources according to the cloud storage state information and the user storage request resource parameters. Corresponding physical storage equipment is selected for storing the user data according to the storage and copy quantity by learning and computing the targeting fuzzy possibility of the storage resources, and the physical storage equipment is registered. The storage allocation mechanism can effectively and dynamically balance the load of the storage equipment and optimize the accessing efficiency of the resources.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Multiple-input multiple-output (MIMO)-orthogonal frequency division multiplexing (OFDM) cognitive radio communication method
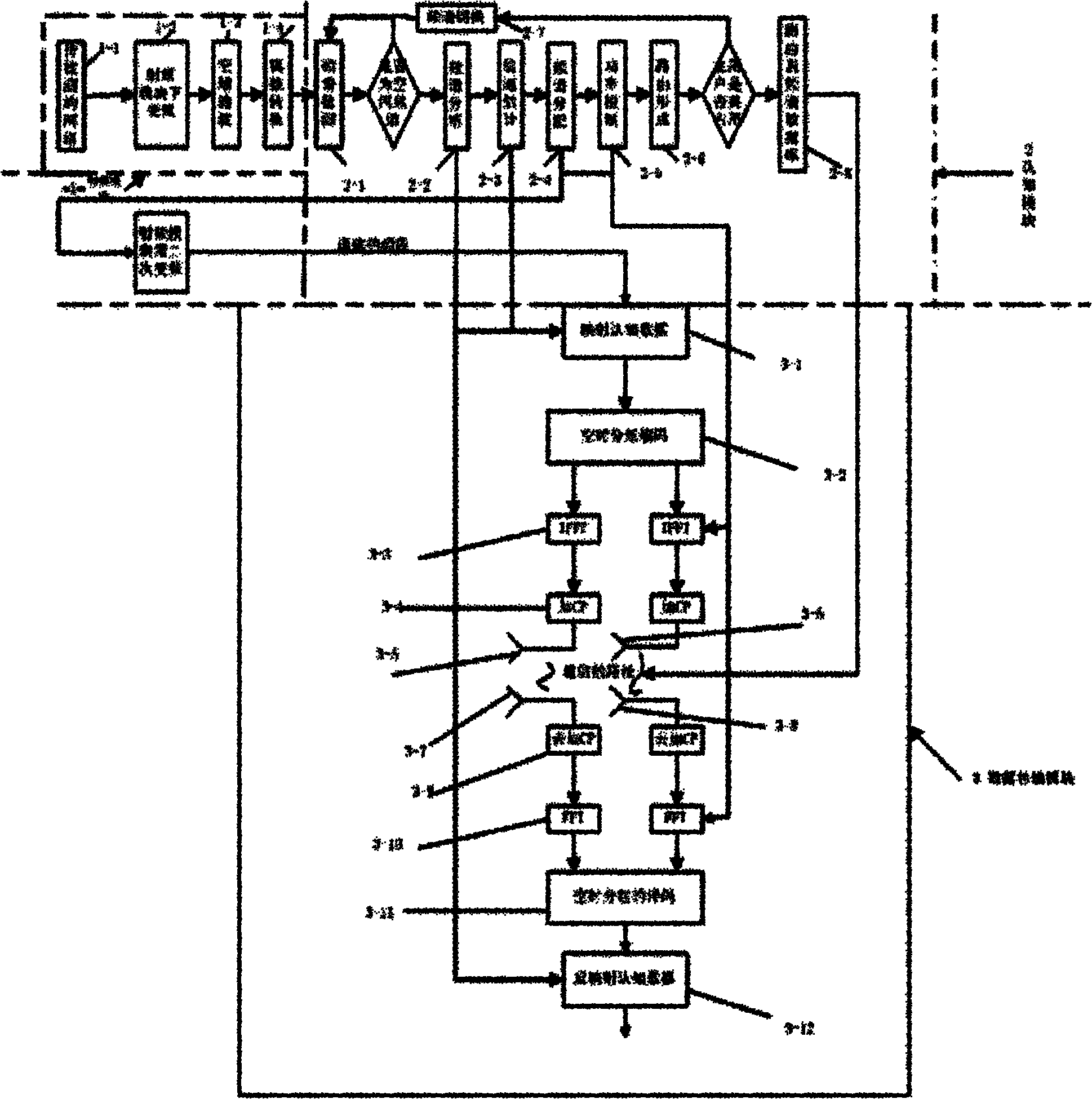
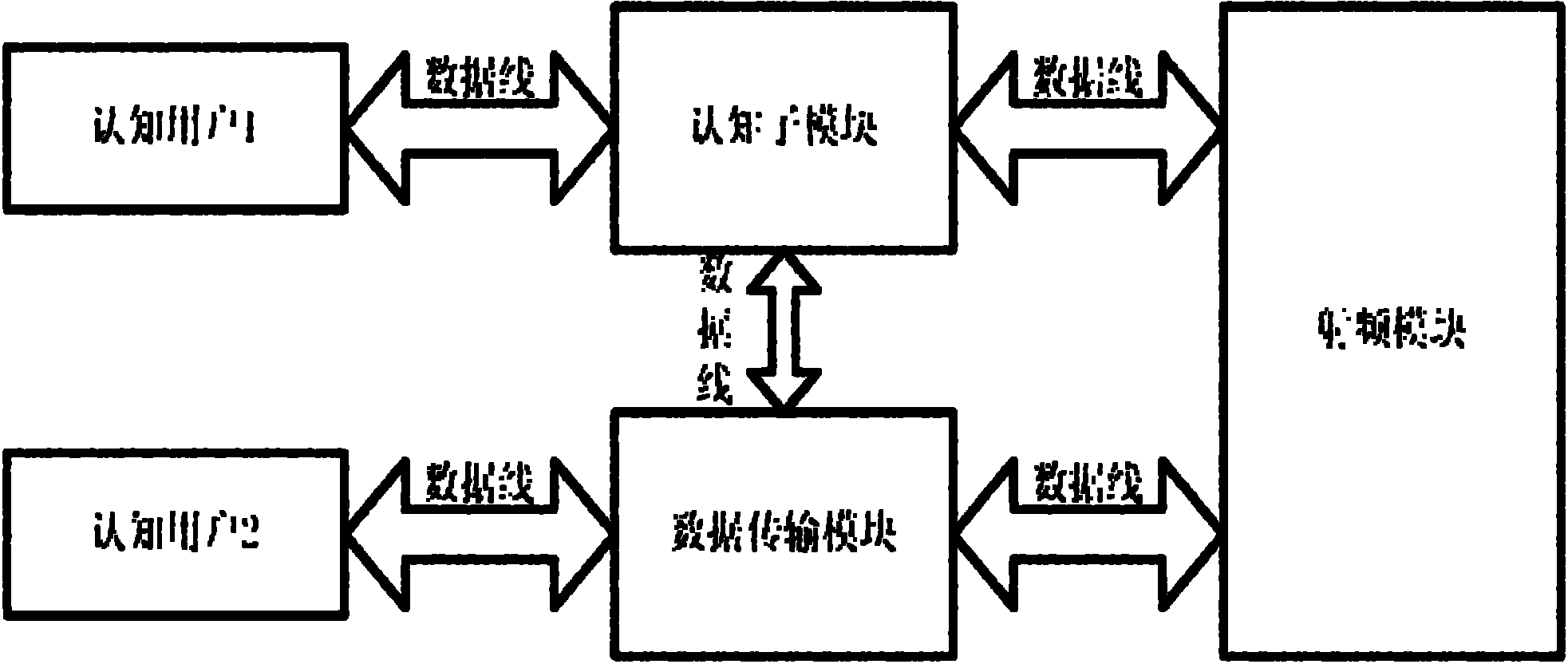
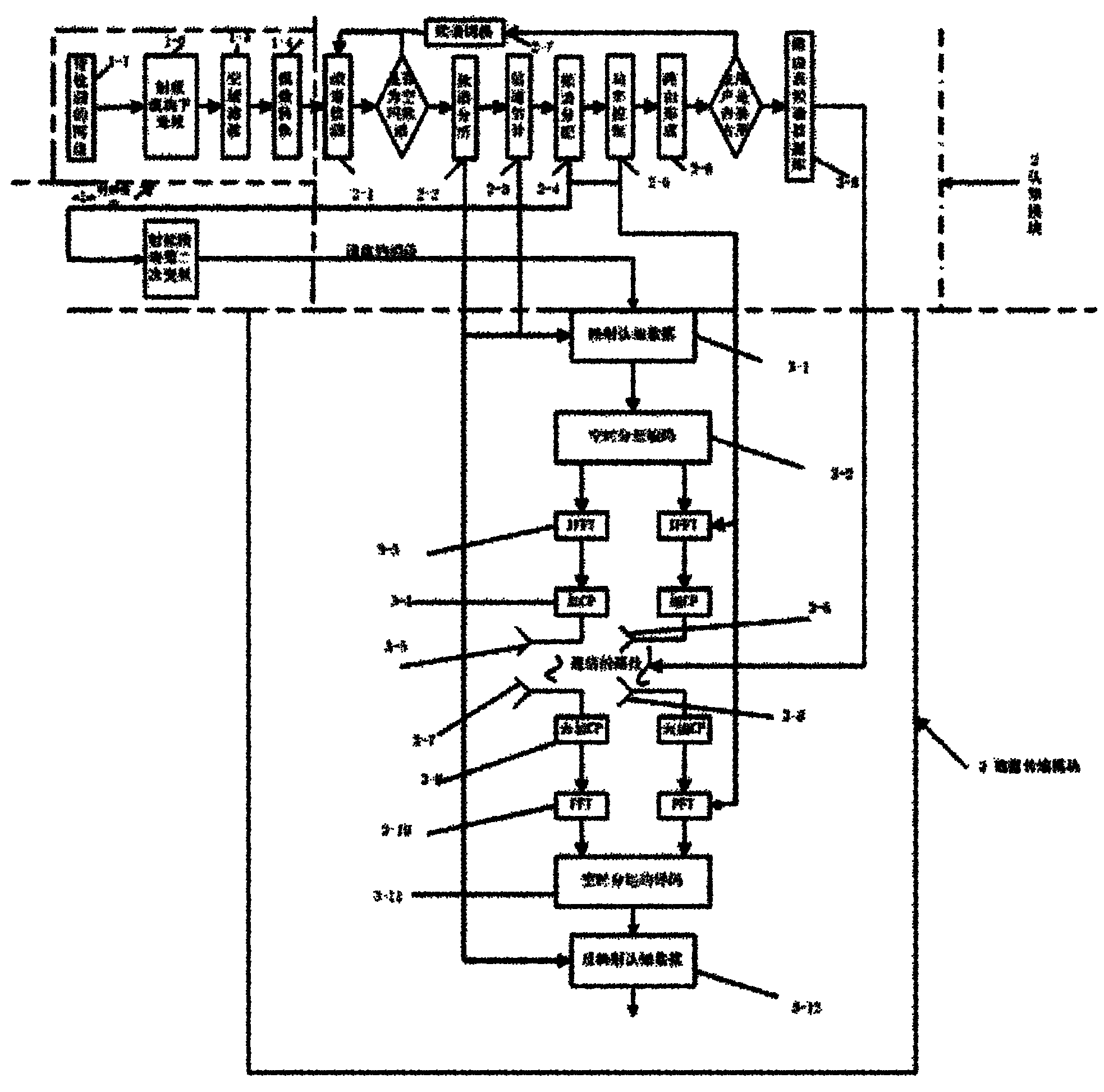
InactiveCN102075950AImprove transmission qualityDiscovered in timeTransmission monitoringNetwork planningCognitive userFrequency spectrum
The invention provides a multiple-input multiple-output (MIMO)-orthogonal frequency division multiplexing (OFDM) cognitive radio communication method. A radio-frequency module outputs intermediate-frequency data which is used for spectrum detection to determine whether a spectrum is an idle spectrum or not, if so, optimum spectrum analysis and channel estimation are conducted to determine the characteristic of the spectrum, then optimum spectrum allocation is conducted to determine routing lines for information transmission, and when a master user requires to use the current frequency band, other routing lines are selected and used for data transmission; a cognitive module transmits a control signal to the radio-frequency module, wherein the control signal is used for setting the parameters of the secondary frequency variation of the radio-frequency module and setting the communication frequency band of a data transmission module; and each cognitive user has two transmitting and receiving antennas which are used for transmitting and receiving data, and signaling information is transmitted between the cognitive module and the data transmission module and is used for selecting transmission lines and proper transmission power. The method has the advantages that the spectrum utilization ratio is improved, the channel switching times are reduced, the data transmission quality is improved and the goal of stably transmitting cognitive data to the cognitive users is achieved.
Owner:HARBIN ENG UNIV
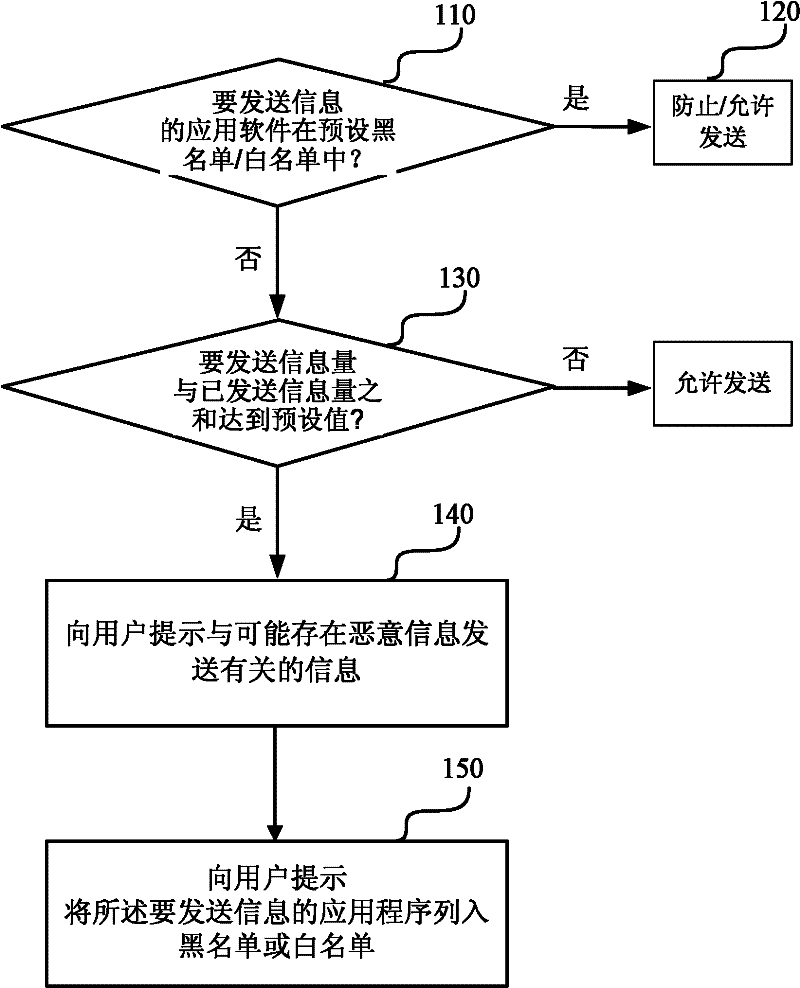
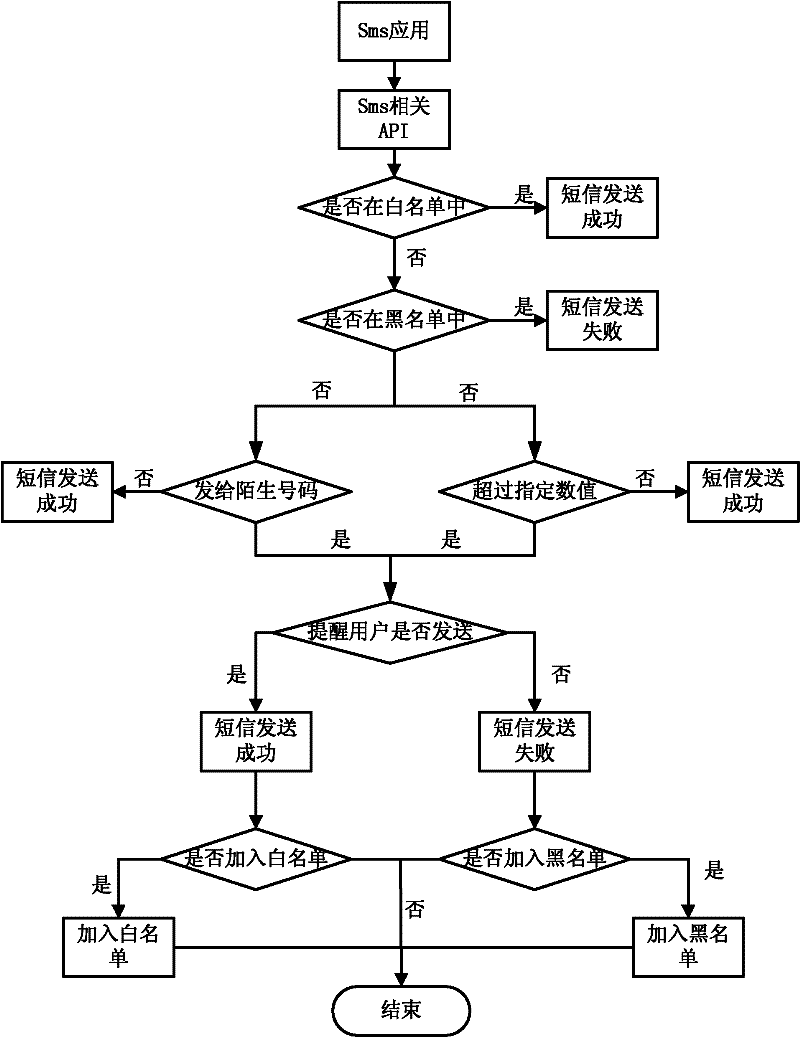
Malicious information transmission preventing method and system of mobile intelligent terminal
InactiveCN102395128AEfficiently prevent malicious information from being sentImprove real-time performancePlatform integrity maintainanceSecurity arrangementWhitelistApplication software
The invention discloses a malicious information transmission preventing method and system of a mobile intelligent terminal. The method comprises the following steps of: judging, namely judging whether an information transmission object is in a preset blacklist or whitelist or not when the application program of the mobile intelligent terminal is about to transmit information; and processing, stopping the transmission of the information if the information transmission object is in the preset blacklist and allowing the transmission of the information if the information transmission object is in the preset whitelist, wherein the blacklist is a list of application software untrusted by the mobile intelligent terminal, and the whitelist is a list of application software trusted by the mobile intelligent terminal. By applying the method and system disclosed by the invention, the transmission of the malicious information can be efficiently prevented.
Owner:BEIJING UNIV OF POSTS & TELECOMM
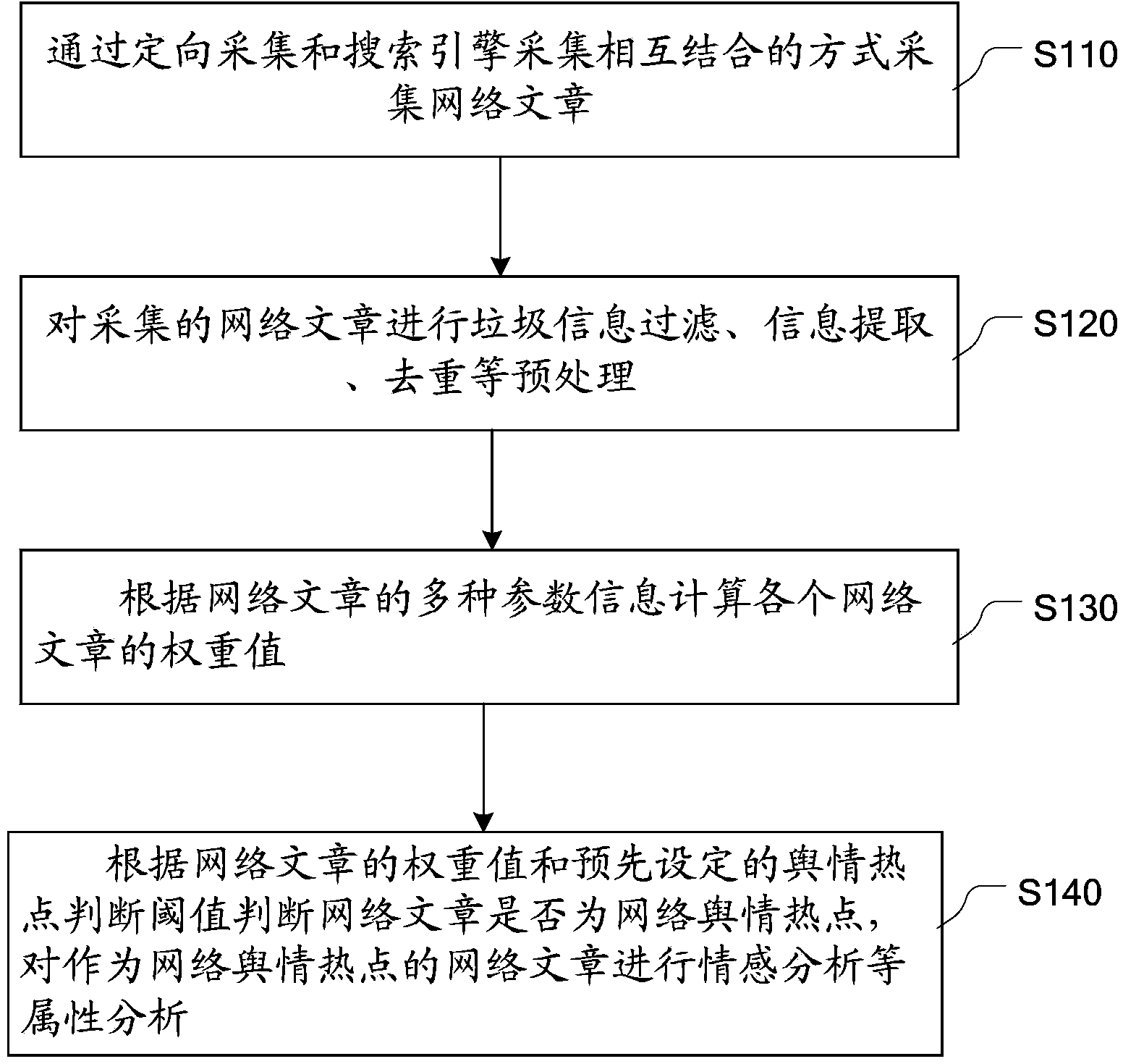
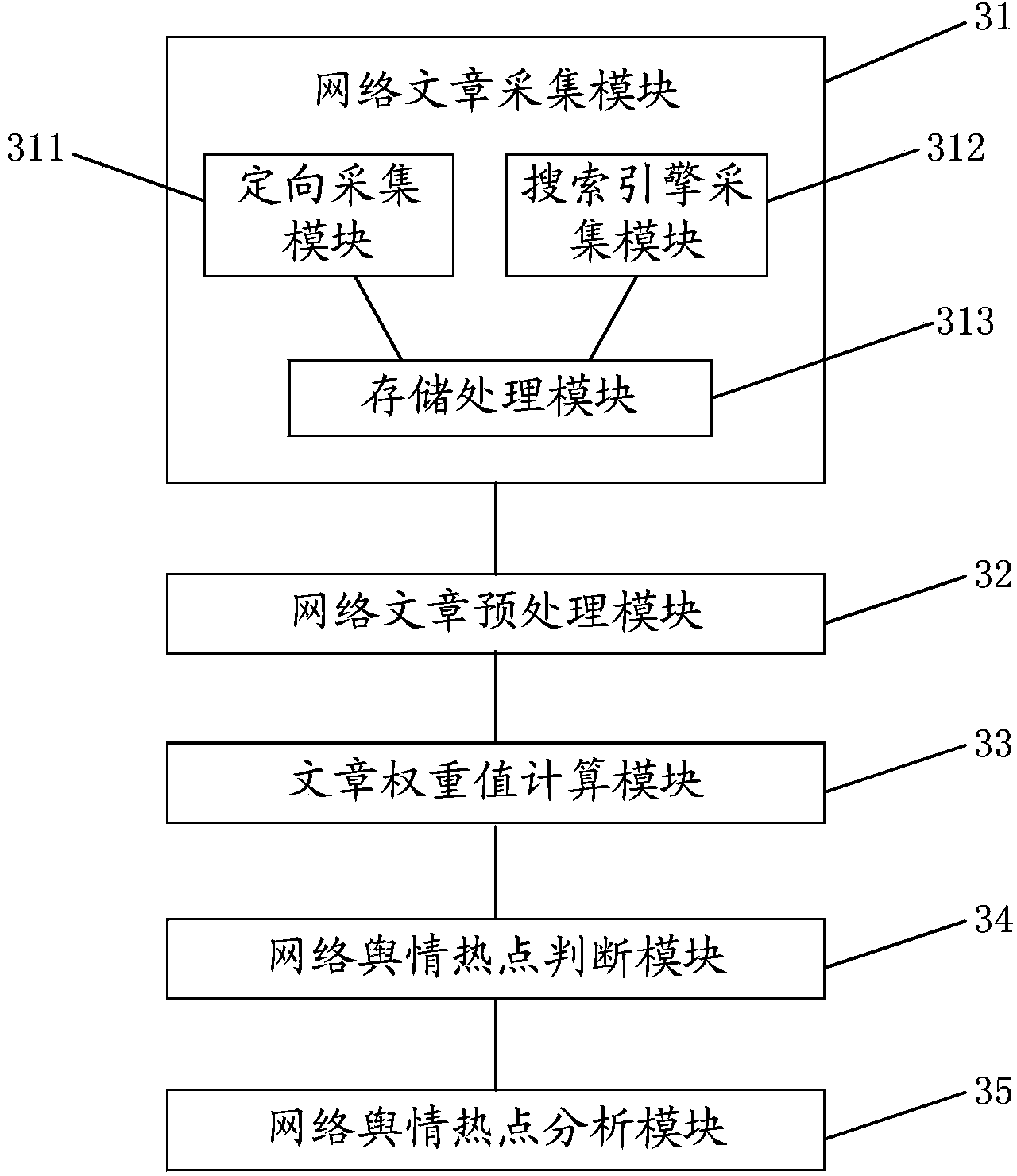
Method and device for finding network public opinion hotspots based on network article attributes
ActiveCN104077377AQuick discoveryDiscovered in timeSpecial data processing applicationsData scienceWeight value
The embodiment of the invention provides a method and a device for finding network public opinion hotspots based on network article attributes. The method mainly comprises collecting network articles in the way which integrates oriented collection with search engine collection, calculating the weighted value of each network article according to several kinds of parameter information of the network article, judging whether the network articles are the network public opinion hotspots according to the weighted values of the network articles and a preset public opinion hotspot judgment threshold value, and analyzing the attributes of the judged network public opinion hotspots. According to the method and device for finding the network public opinion hotspots based on the network article attributes, the network public opinion hotspots can be found rapidly and timely. The accuracy of finding the network public opinion hotspots is improved by firstly performing pretreatment, such as filtering junk information and de-weighting, on the network articles, and then judging values of the network articles according to several kinds of parameter attributes of the network articles.
Owner:HONG MAI JUXIN SOFTWARE TECH BEIJING
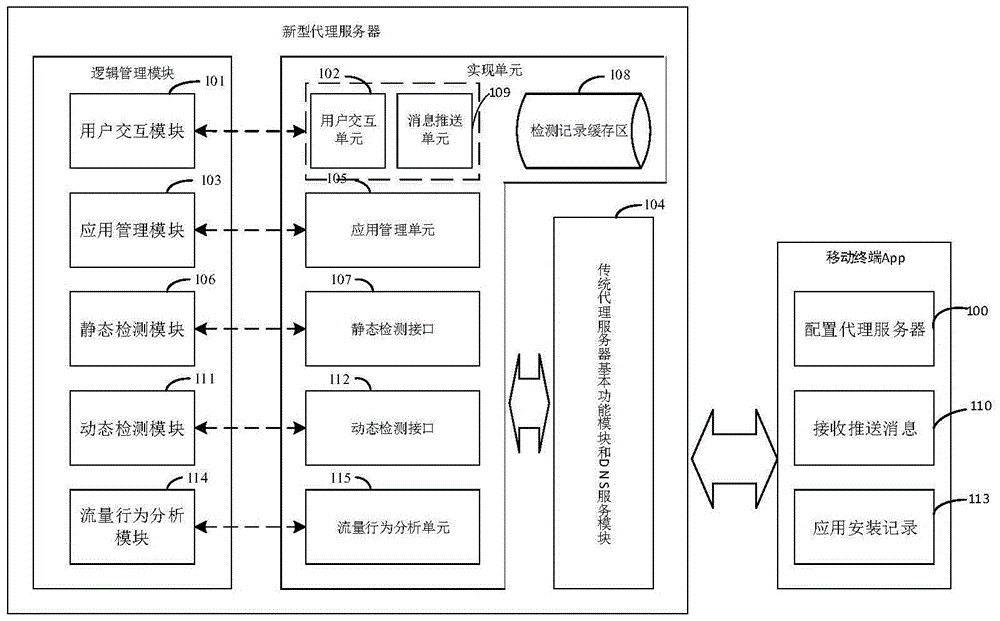
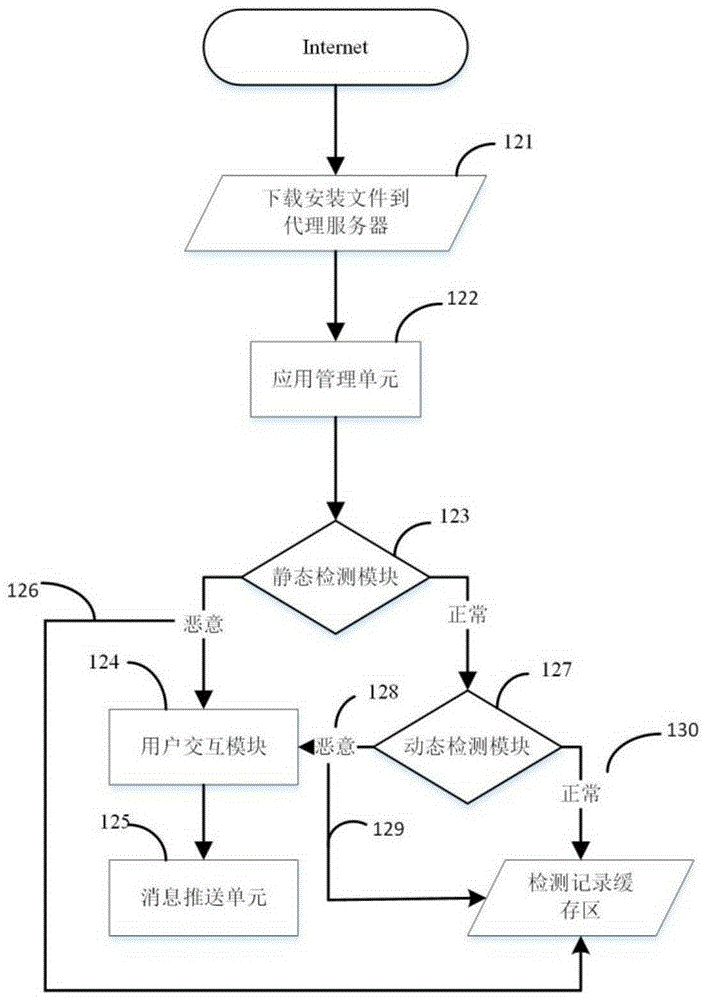
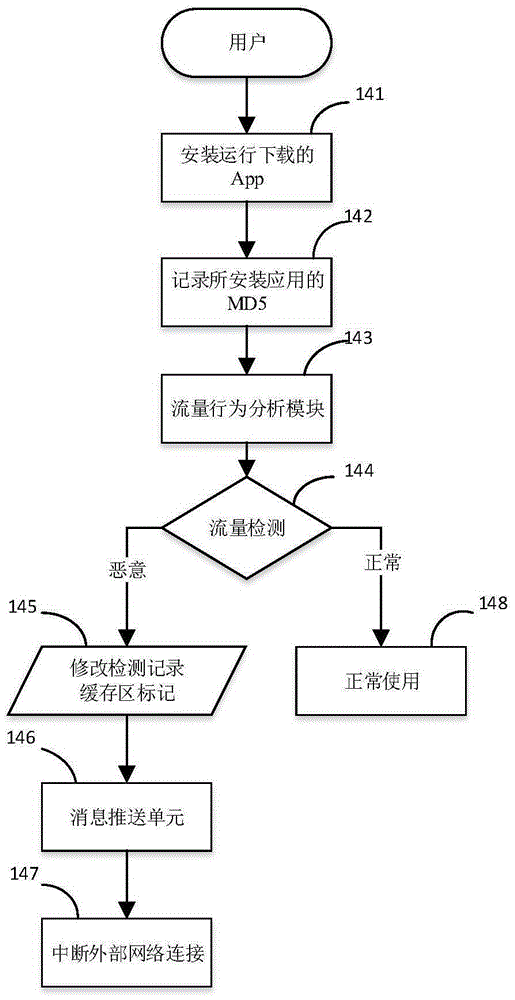
Proxy server having mobile terminal malicious software behavior detection capability and method
The invention discloses a proxy server having a mobile terminal malicious software behavior detection capability and a method. The proxy server comprises a static detection module, a dynamic detection module and a flow behavior analysis module, wherein the static detection module is used for performing static detection on downloaded mobile applications by calling a static detection interface; the dynamic detection module is used for performing secondary detection on the mobile applications which are detected to be normal by the static detection module by calling an API interface provided by a third-party dynamic detection service; and the flow behavior analysis module is used for processing flow of applications installed by a user and detecting whether flow behaviors are generated by malicious software or not through a flow detection service model. A novel proxy server having a triple detection capability is designed. Through primary and secondary detection, the security of the mobile applications installed by the user is basically ensured. Through tertiary flow detection, effective identification of malicious behaviors generated by the malicious software is ensured.
Owner:UNIV OF JINAN
Method for finding radio local area network in mobile network
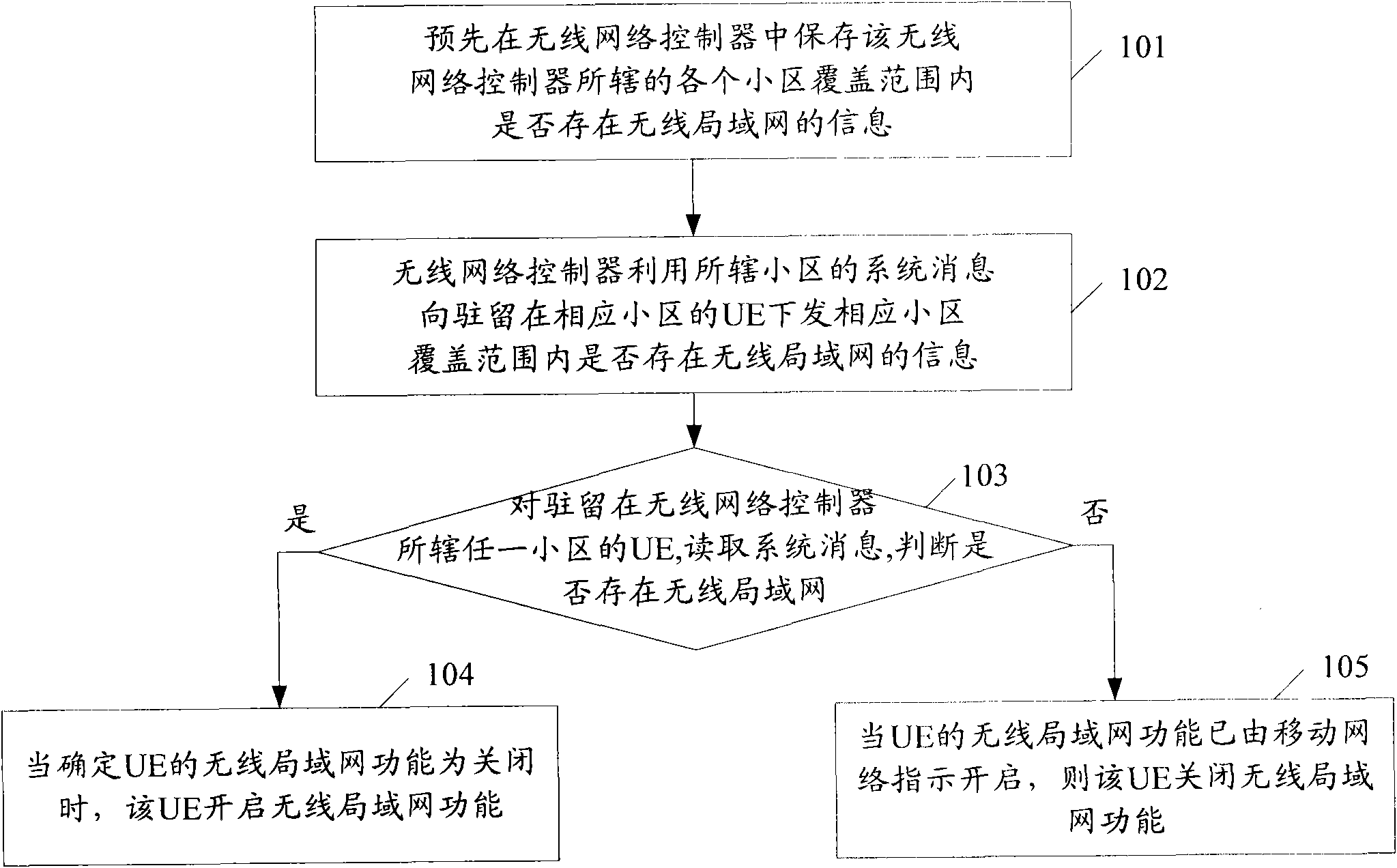
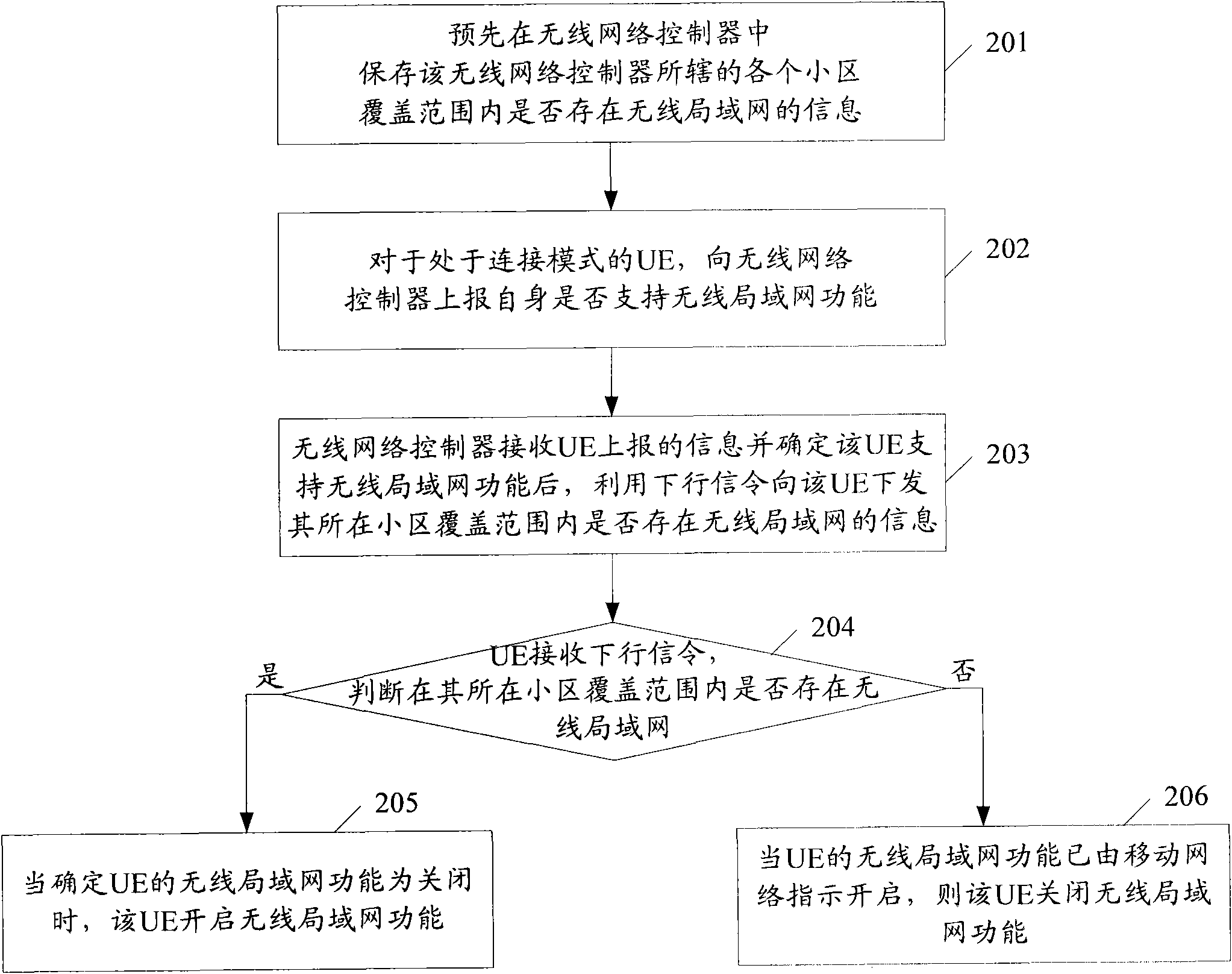
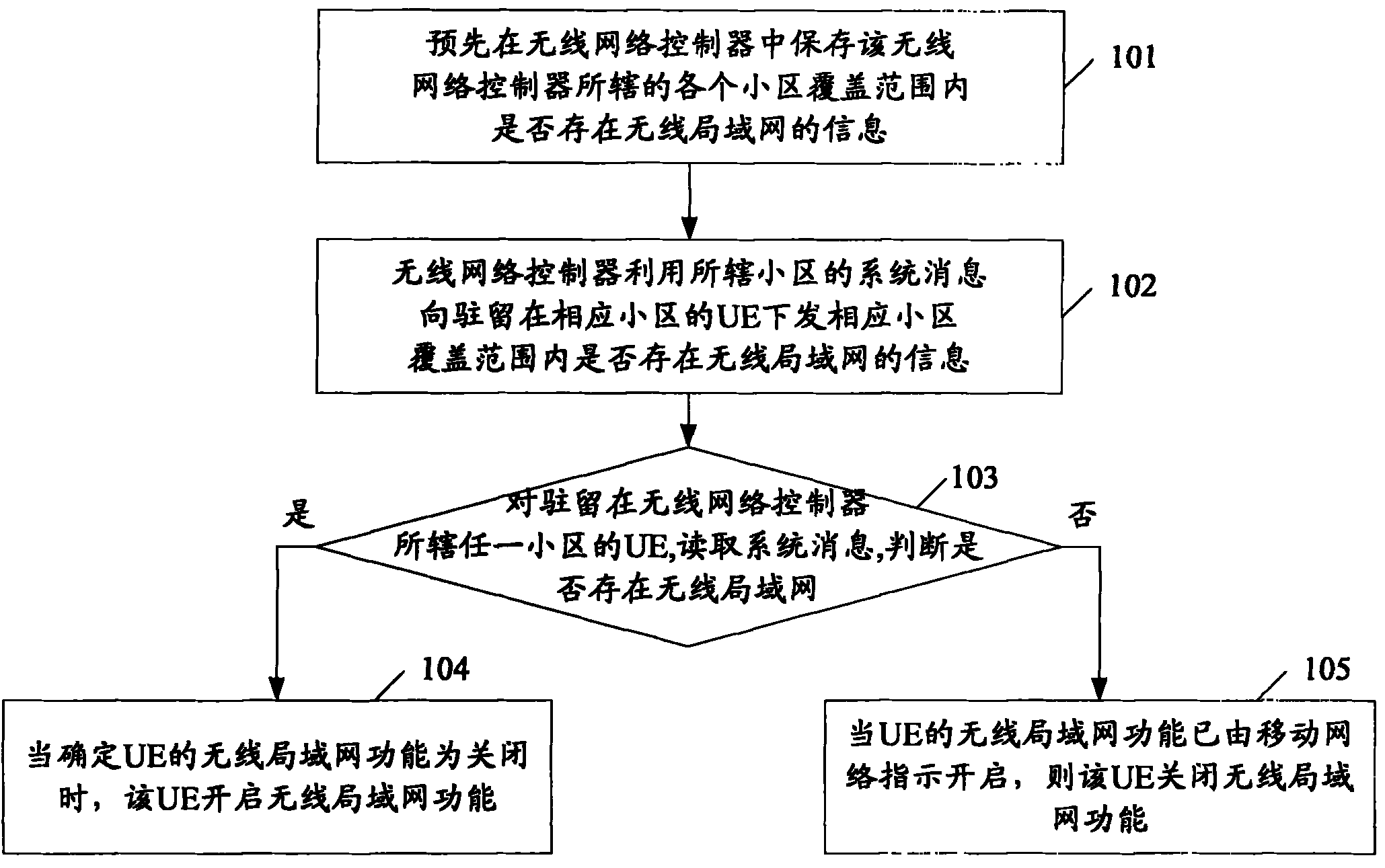
InactiveCN102256334ADiscovered in timeEnergy efficient ICTAssess restrictionTelecommunicationsRadio Network Controller
The invention provides a method for finding a radio local area network in a mobile network, which comprises the following steps of: pre-storing information whether the radio local area network exists in the coverage area of each cell controlled by a radio network controller in the radio network controller, wherein the radio network controller carries the information whether the radio local area network exists in the coverage area of each cell in a system message of the corresponding cell; issuing the information whether the radio local area network exists in the coverage area of the cell wherein UE (User Equipment) locates to the UE through the system message or downlink signaling; activating the radio local area network function after the UE determines that the radio local area network exists in the coverage area of the cell where the UE locates, if the radio local area network function is otherwise activated at present through an instruction of the mobile network, deactivating the radio local area network function. Therefore, the purposes of saving end power and timely finding the radio local area network for switching are realized.
Owner:TD TECH COMM TECH LTD
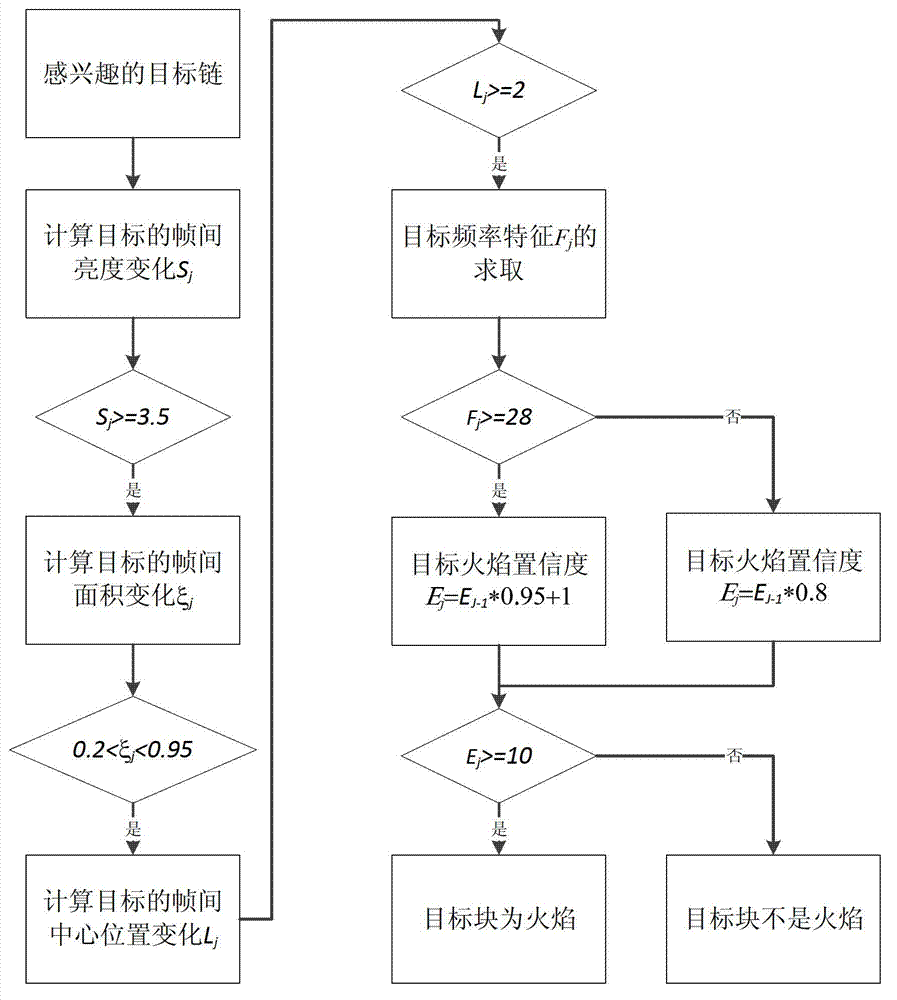
Flame detection method based on video frame image
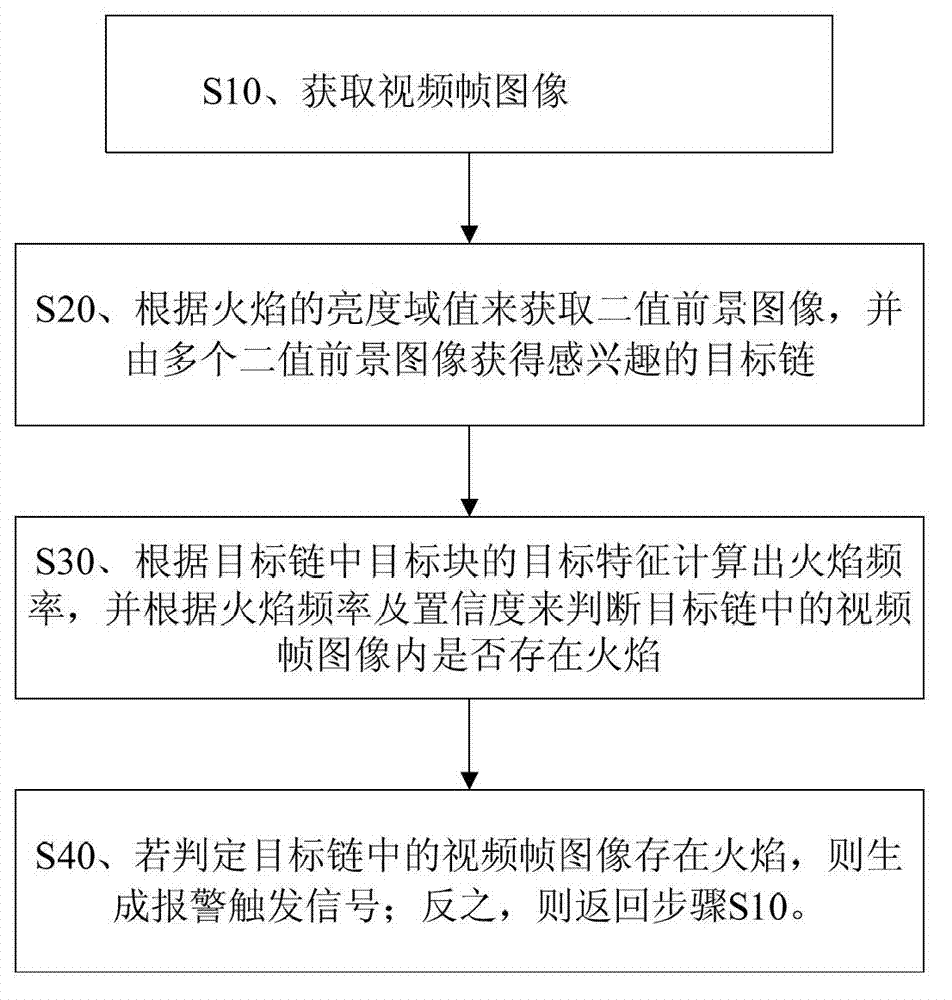
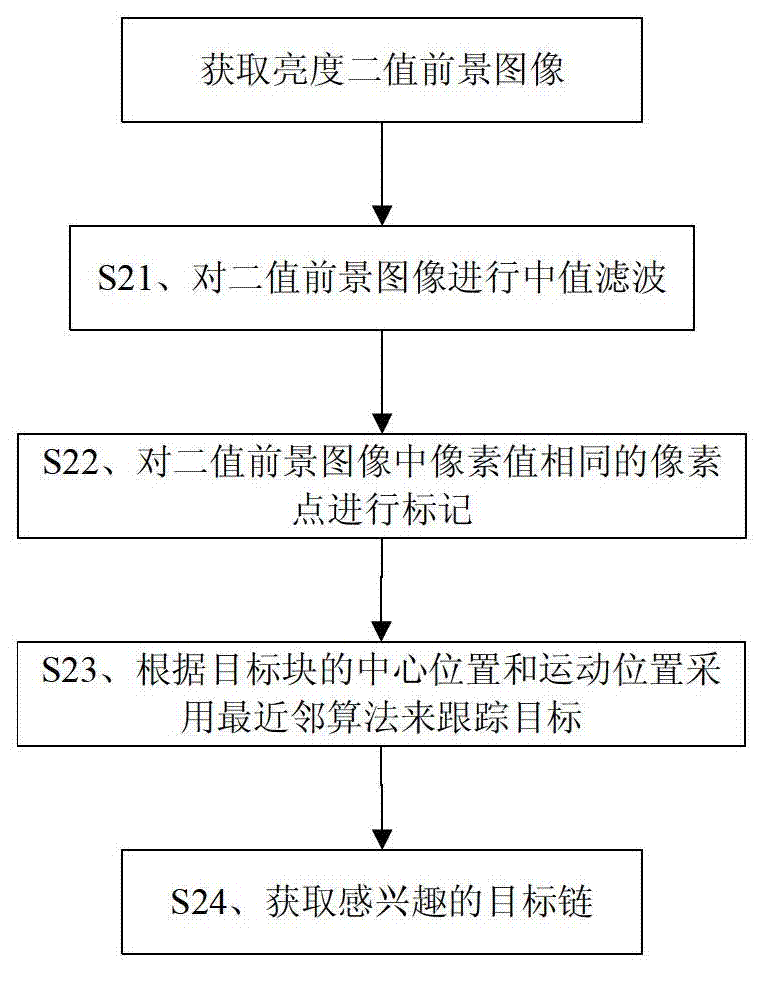
InactiveCN102819735ATimely detectionDiscovered in timeImage analysisCharacter and pattern recognitionFlame detectionFalse alarm
The invention provides a flame detection method based on a video frame image, which is characterized by comprising the following steps of: S10) obtaining a video frame image; S20) according to a flame luminance threshold, obtaining binary foreground images, and obtaining an interested target chain by a plurality of binary foreground images; S30) according to the target characteristic of a target block in a target chain, calculating flame frequency, and judging whether flame exists in the video frame image in the target chain according to the flame frequency and the confidence coefficient, wherein the target characteristic comprises the average luminance variation, the area variation and the center position shake of the target block; S40) if the flame exists in the video frame image in the target chain, generating an alarm triggering signal; and otherwise, returning to step S10). According to the flame detection method based on the video frame image, which is disclosed by the invention, the flame can be accurately detected, so that the flame false alarm rate is greatly lowered so as to lighten the pressure of working personnel, and the working efficiency of the working personnel is improved.
Owner:深圳辉锐天眼科技有限公司
Log auditing method and platform
The invention relates to a computer technology, and discloses a log auditing method and platform, which are used for log real-time auditing in cloud environment. The method comprises the following steps that an auditing platform respectively collects a corresponding system log from each kind of platform at a cloud end; the obtained system log is cached into a distributive asynchronous queue; when the condition that the preset triggering condition is met is determined, the system log conforming to the triggering condition is read from the distributive asynchronous queue; the auditing is performed on the system log on the basis of a rule model, wherein the rule model is generated after the machine learning training performed on the basis of the historical auditing data. Therefore compared with the single rule in the prior art, the rule model formed through data modeling on the basis of the historical auditing data has the advantages that the complicated auditing conditions can be better described; the system log generated due to complicated early warning events can be conveniently picked out, so that management personnel can conveniently and timely discover the condition and perform management.
Owner:ALIBABA GRP HLDG LTD
Detection method, device and terminal for cheating traffic
ActiveCN106355431ARealize OKDetermine the implementation to be testedMarketingData miningTraffic volume
A cheating detection method, device and terminal including: determining the data to be detected, and select the observation index to be observed as well as a variety of dimensions, each dimension has to be observed at least one value; According to the plurality of dimensions to be observed, the values of each dimension to be observed are combined to form a plurality of observation dimension combinations; According to the data to be tested, the index value of the observed index is calculated for each observation dimension combination; The candidate anomaly combination in the observation dimension combination is determined according to the index value; Based on the historical data, the candidate anomaly combination is analyzed to determine the abnormal combination in the candidate anomaly combination.The abnormal combination is used to determine the flow of cheating. The technical scheme of the invention can detect the flow of cheating.
Owner:JINGZAN ADVERTISING SHANGHAI CO LTD
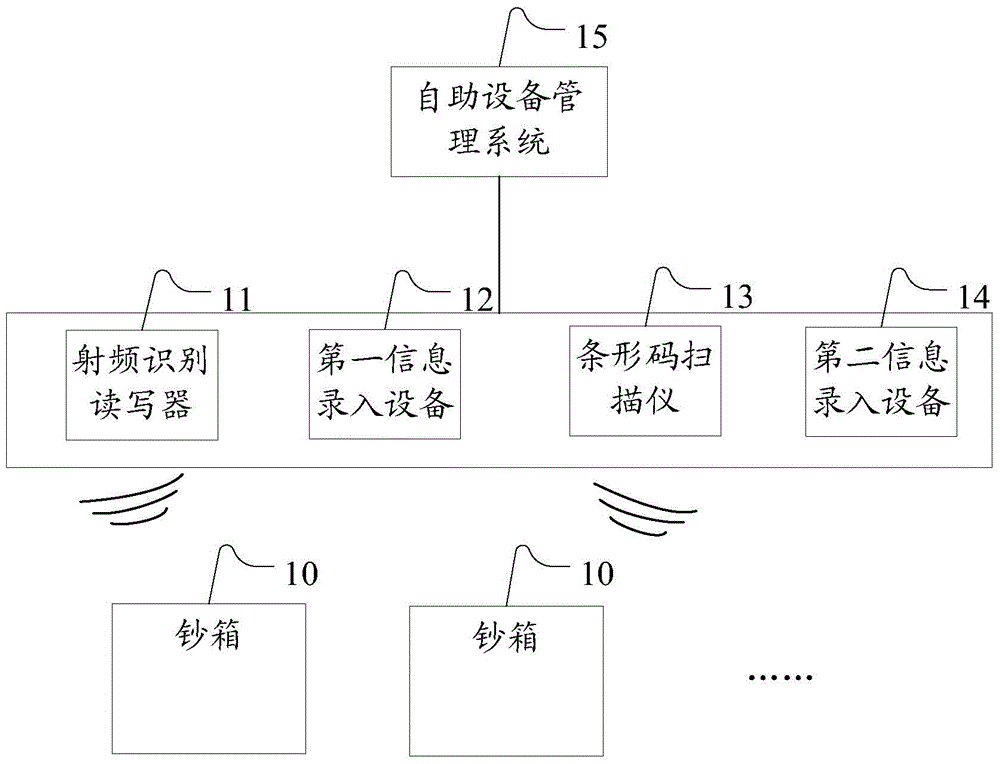
Information processing system and information processing method for managing self-service equipment
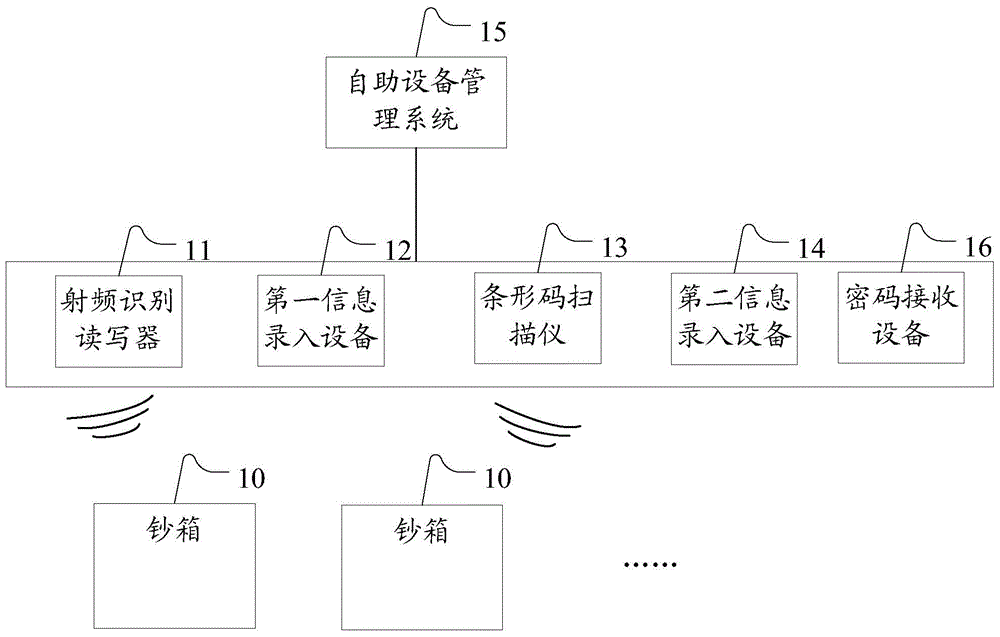
ActiveCN104103133AImprove efficiencyImprove accuracyComplete banking machinesCo-operative working arrangementsControl levelRisk prevention
The invention provides an information processing system and an information processing method for managing self-service equipment. The system comprises a plurality of cash boxes, a radiofrequency recognition reader, first information entry equipment, a scanning instrument for the bar codes (comprising one-dimensional bar codes and two-dimensional bar codes), a second information entry equipment and a self-service equipment management system, wherein bar codes (comprising the one-dimensional bar codes and the two-dimensional bar codes) and radio frequency identification labels are fixed on the cash boxes; numbers of the cash boxes are stored in the bar codes; the radiofrequency recognition reader is used for acquiring information of the cash boxes discharged from a storehouse in batches when the cash boxes are discharged from the storehouse; the first information entry equipment is used for entering the number of the self-service equipment and the numbers of the cash boxes which are fed in the self-service equipment when the self-service equipment is neatened and cashes are fed in the self-service equipment; the scanning instrument for the bar codes (comprising the one-dimensional bar codes and the two-dimensional bar codes) is used for acquiring the information of the cash boxes stored in the storehouse one by one during clearing at the integral point; the second information entry equipment is used for entering the rest cashes of the cash boxes stored in the storehouse during clearing at the integral point; and the self-service equipment management system is used for account checking. By the information processing system and the information processing method for managing the self-service equipment, information can be quickly and accurately acquired, the automation degree on management of the self-service equipment is improved, and the whole efficiency and the risk prevention and control level on the management of the self-service equipment are improved.
Owner:CHINA CONSTRUCTION BANK
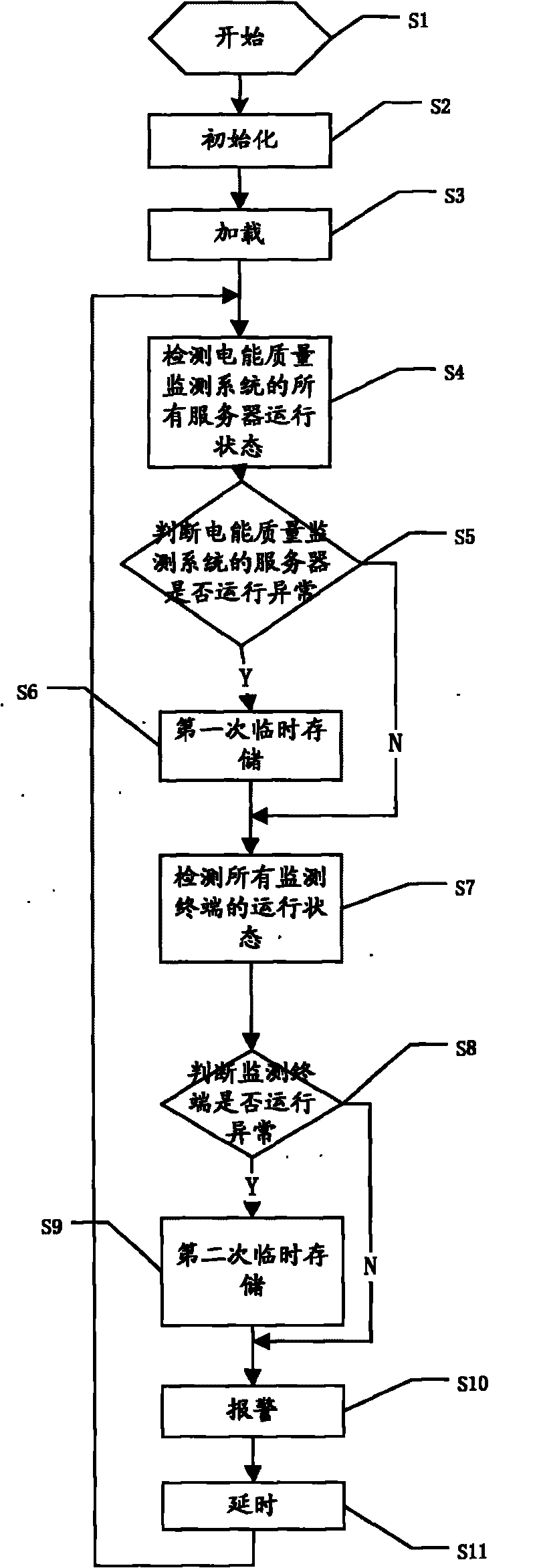
Real-time monitoring method for power quality monitoring system and terminal running state
ActiveCN101726681AReal-time monitoring of running statusMonitor running statusCircuit arrangementsElectrical testingPower qualityLoad step
The invention discloses a real-time monitoring method for a power quality monitoring system and a terminal running state; a network topological graph or a GIS geographic information map is adopted to carry out real-time monitoring to the power quality monitoring system and the monitoring terminal, and the fault message is displayed; the real-time monitoring method comprises the following steps: starting, initialization, loading, running state detection of all servers of the power quality monitoring system, judging whether the running of the servers of the power quality monitoring system is normal, first temporary storage, running state detection of all the monitoring terminals, judging whether the running of the monitoring terminal is normal, second temporary storage, alarming and time delaying; the real-time monitoring method for the power quality monitoring system and the terminal running state can monitor the power quality monitoring system and the terminal monitoring, ensure to find problems timely and solve the problems timely, and ensure the integrity of the monitoring data.
Owner:SHANGHAI MUNICIPAL ELECTRIC POWER CO +2
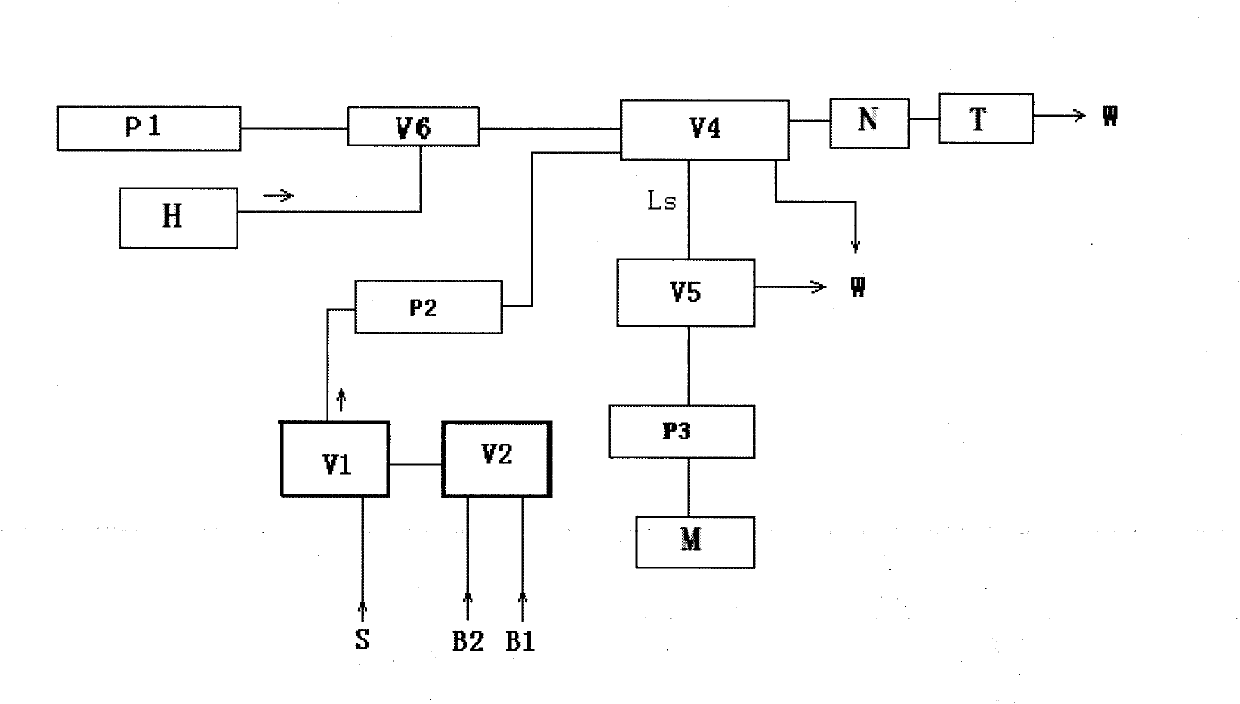
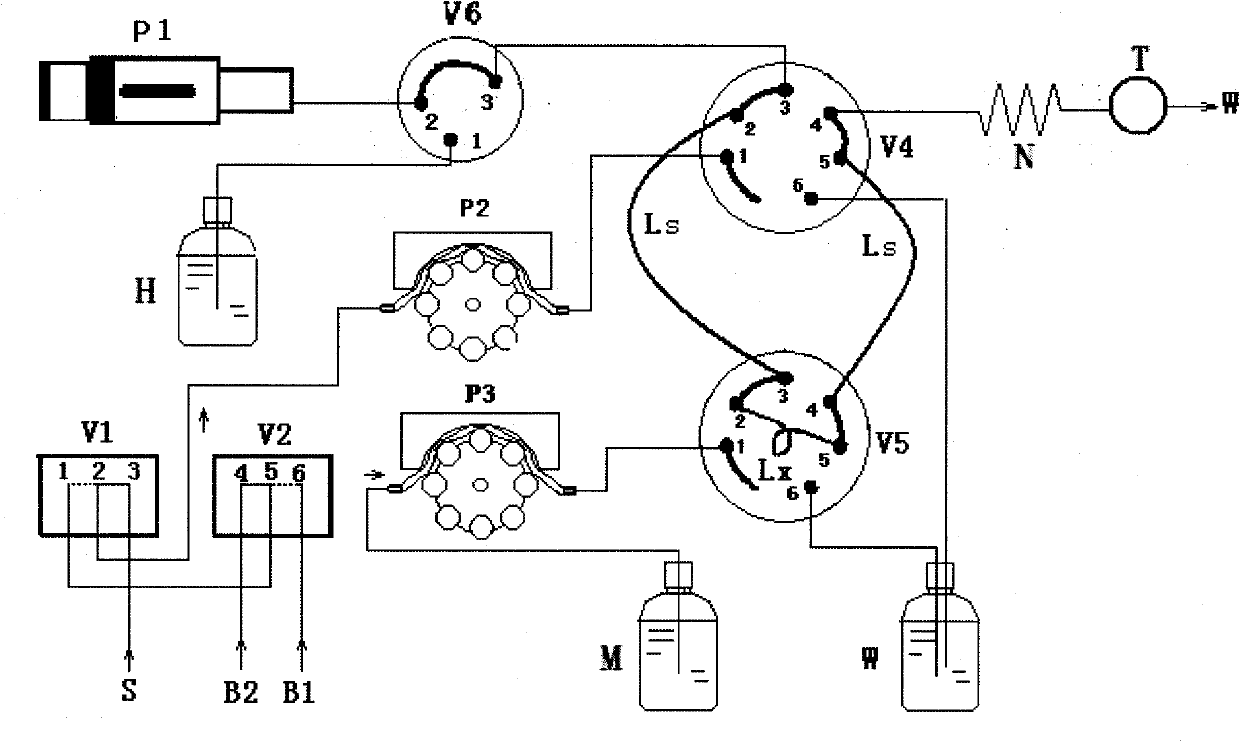
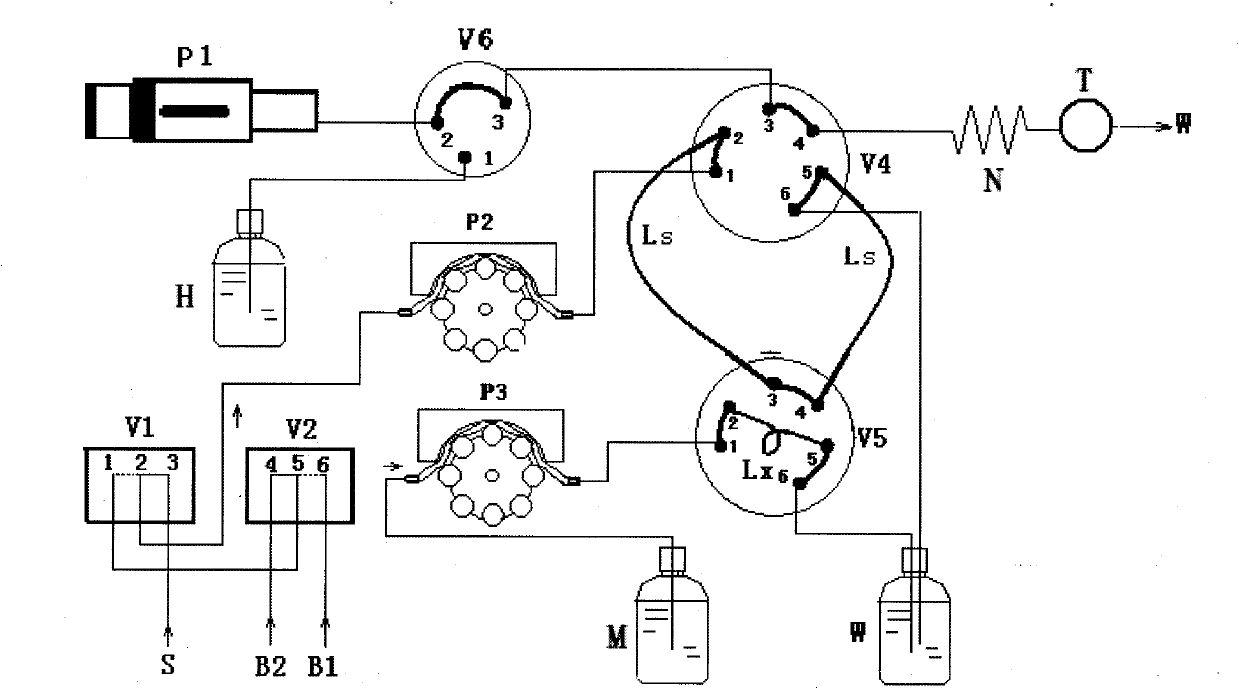
Device for fluidly injecting and rapidly analyzing residual chlorine of water quality and analysis method thereof
InactiveCN101793902AQuantitatively accurateAccurate measurementMaterial analysis by observing effect on chemical indicatorColor/spectral properties measurementsPeristaltic pumpReal time analysis
The invention discloses a device for fluidly injecting and rapidly analyzing residual chlorine of water quality and an analysis method thereof. The device comprises a photoelectric flow cell, a reacting tube, an indicator liquid storage vase, a current-carrying liquid storage vase, a first peristaltic pump, a current-carrying liquid injection pump, a second peristaltic pump, a current-carrying liquid three-way valve, a first sampling six-way valve, a second sampling six-way valve, a capillary tube, a sampling capillary tube, a first guide sample source, a second guide sample source, a first electromagnetic valve and a second electromagnetic valve, wherein the first electromagnetic valve and the second electromagnetic valve are switched with a water sample source. In the invention, the sampling capillary tube with a fixed length is adopted, the water sample ration is accurate, the dispersed state of the sample in the current-carrying liquid has high repeatability in a certain retained time, the measurement result is accurate, and the flow path is simple, thereby being easy for realizing automation, real-time and on-line monitoring and low failure rate. The invention can be used for on-line monitoring of the residual chlorine in drinking water and industrial recirculating cooling water, conveniently and rapidly obtaining real-time analysis data, and especially finding, reporting and handling water pollution accidents with serious idiopathic.
Owner:HOHAI UNIV
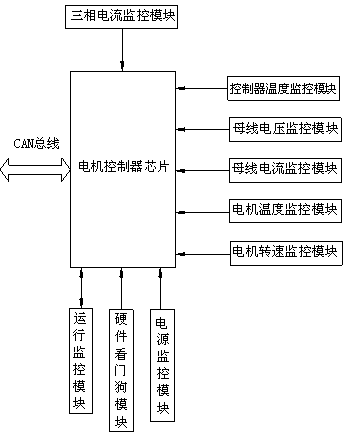
Vehicle electrical motor control system with safety monitoring function and monitoring method of vehicle electrical motor control system
ActiveCN103738198AImprove securityDiscovered in timeSpeed controllerElectric devicesControl systemTemperature monitoring
The invention provides a vehicle electrical motor control system with a safety monitoring function and a monitoring method of the vehicle electrical motor control system. The vehicle electrical motor control system aims to meet the ever-growing requirement for vehicle safety. The vehicle electrical motor control system with the safety monitoring function comprises an electrical motor controller chip controlling operation of an electrical motor, the electrical motor controller chip is connected with a CAN bus, a power source monitoring module, a bus voltage monitoring module, a bus current monitoring module, a three-phase current monitoring module, a controller temperature monitoring module, an electrical motor temperature monitoring module, an electrical motor rotating-speed monitoring module and an operation monitoring module, and the operation monitoring module is communicated with an electrical motor controller. According to the vehicle electrical motor control system, many hardware monitoring modules and software monitoring functions are added and constitute a two-level monitoring network together, it is guaranteed that all fault information can be found timely and processed timely, and therefore the whole control system has higher safety and meets the requirement related to safety in the vehicle industry.
Owner:CHERY AUTOMOBILE CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com