Network sensitive information-oriented screenshot discovery and locking callback method
A sensitive information and network technology, applied in special data processing applications, instruments, electronic digital data processing, etc., can solve the problem of no sensitive public opinion analysis method, etc., to facilitate browsing and viewing, increase the difficulty and workload.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The specific embodiments of the present invention will be described in detail below with reference to the drawings.
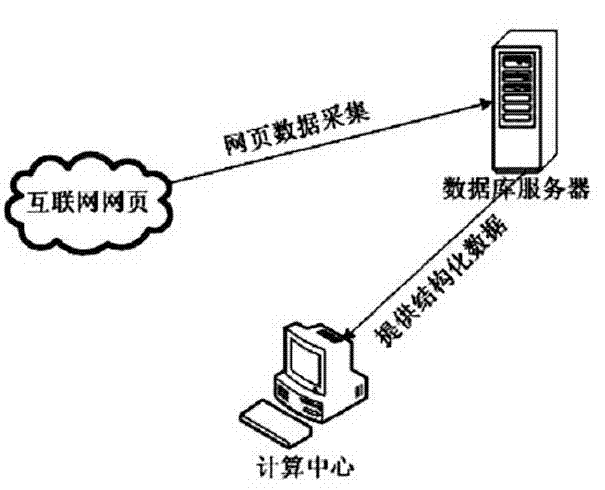
[0033] Such as figure 1 As shown, the system of the present invention for taking screenshots of sensitive network information and locking back visits includes a computing center and a database server, and the computing center communicates with the database server.
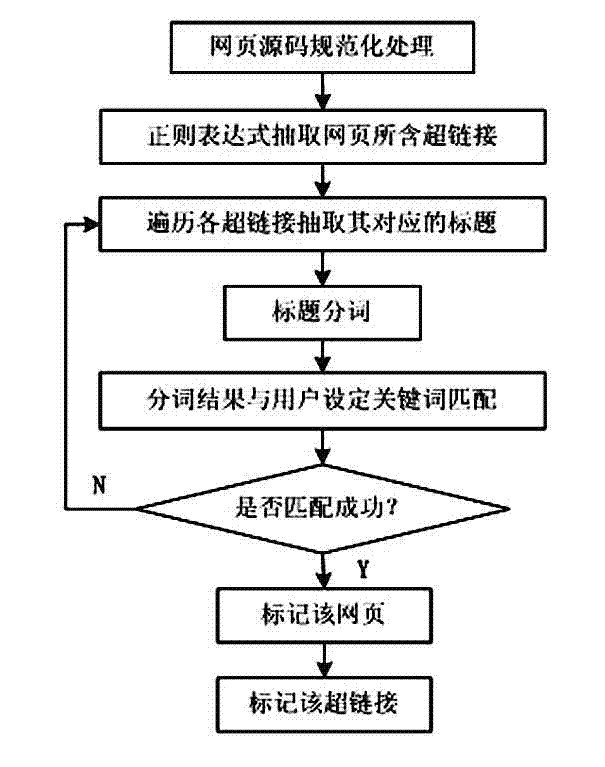
[0034] Such as Picture 10 As shown, the method steps of the present invention are as follows:
[0035] (1) Webpage data collection
[0036] The collection of webpage data is the data basis for the screenshot forensics of sensitive network information. The present invention uses a web crawler (spider) named LoalaSam for collection. LoalaSam is a web crawler developed by VC6.0 and running on the Windows platform. It can efficiently obtain massive resources from the Internet. These resources include web page text information, pictures, audio, video, and other types of file resources. The latest ve...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com