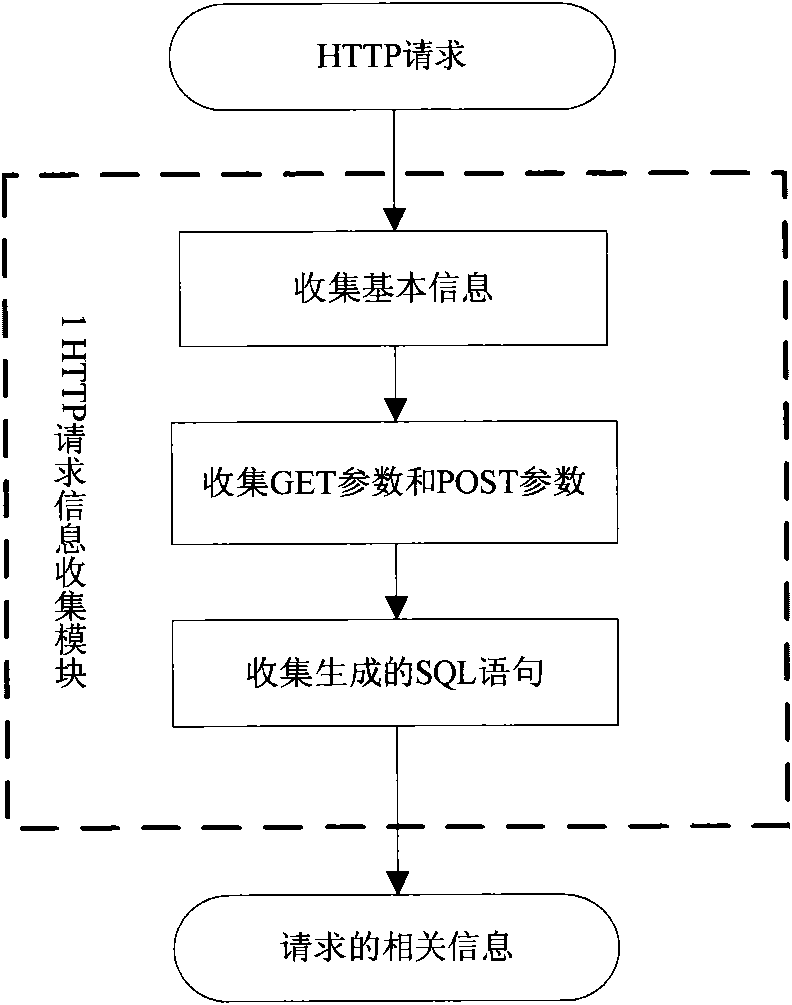
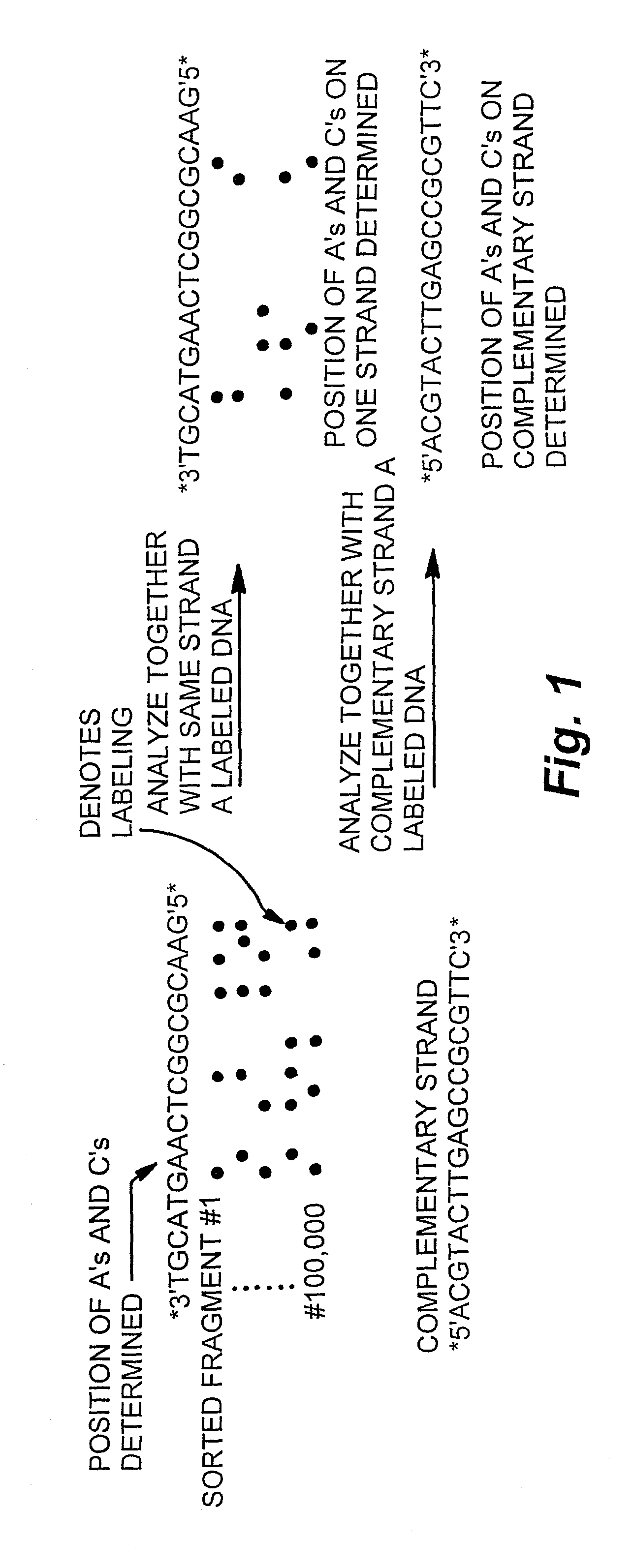
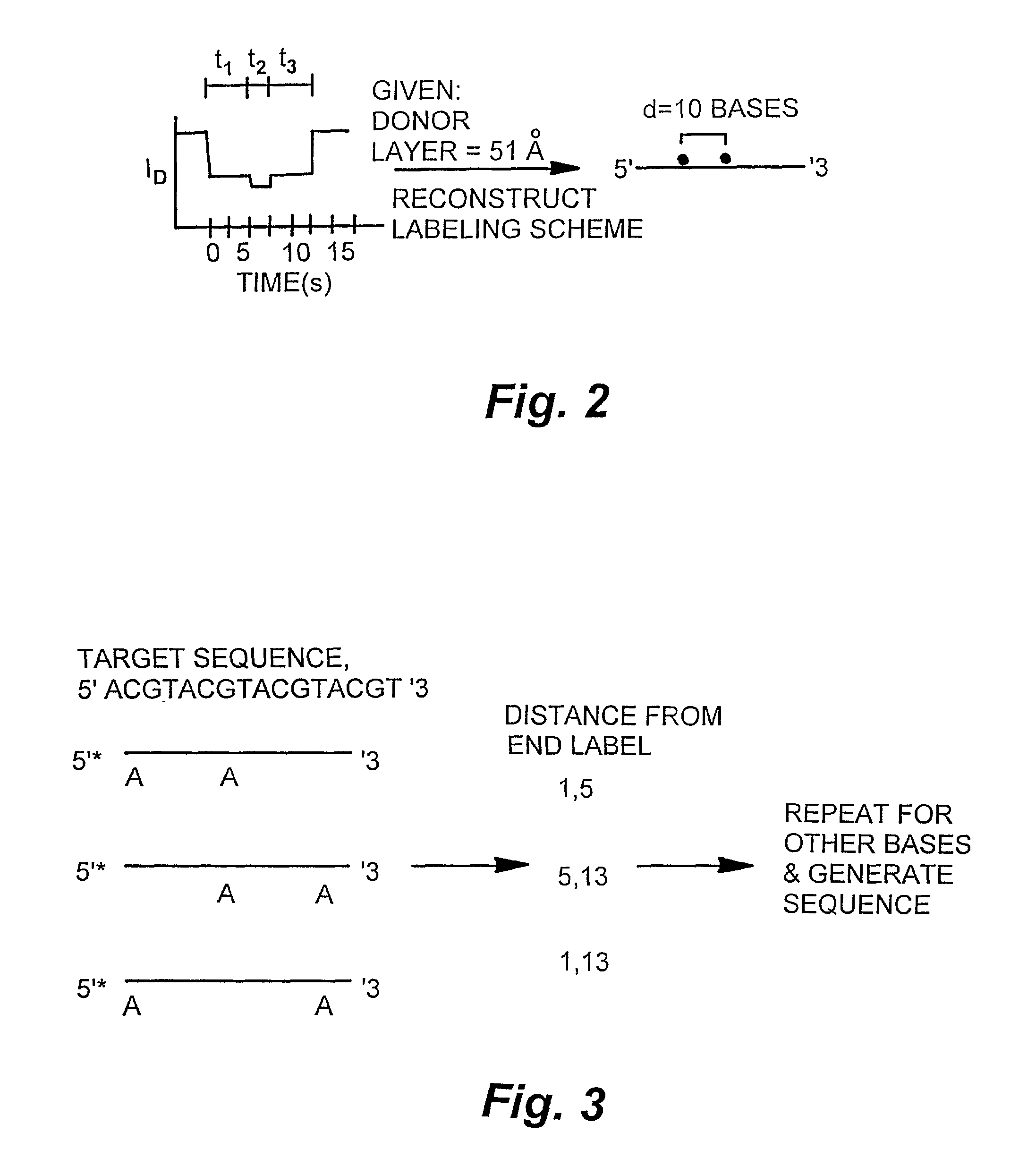
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
734results about How to "Quick discovery" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
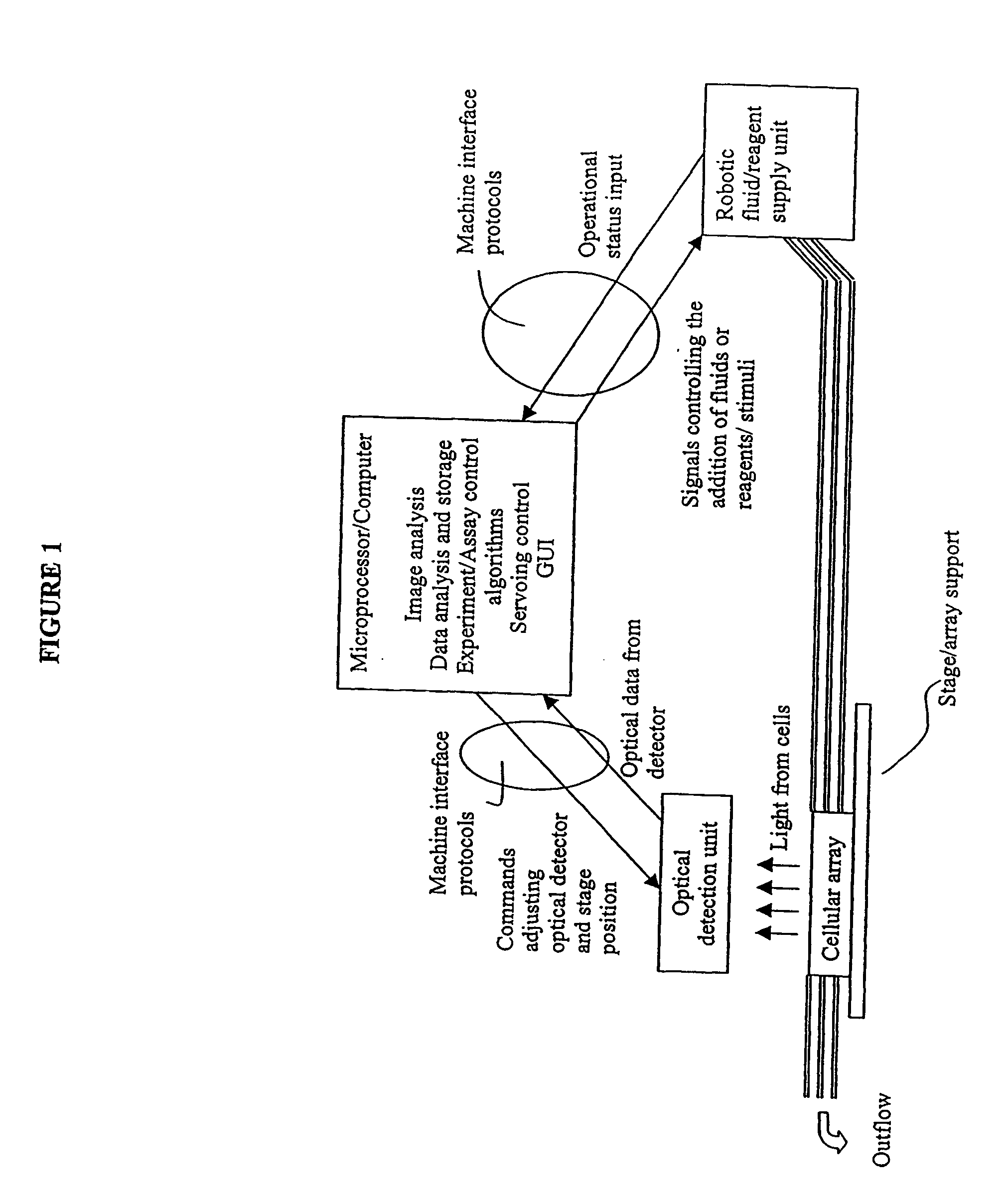
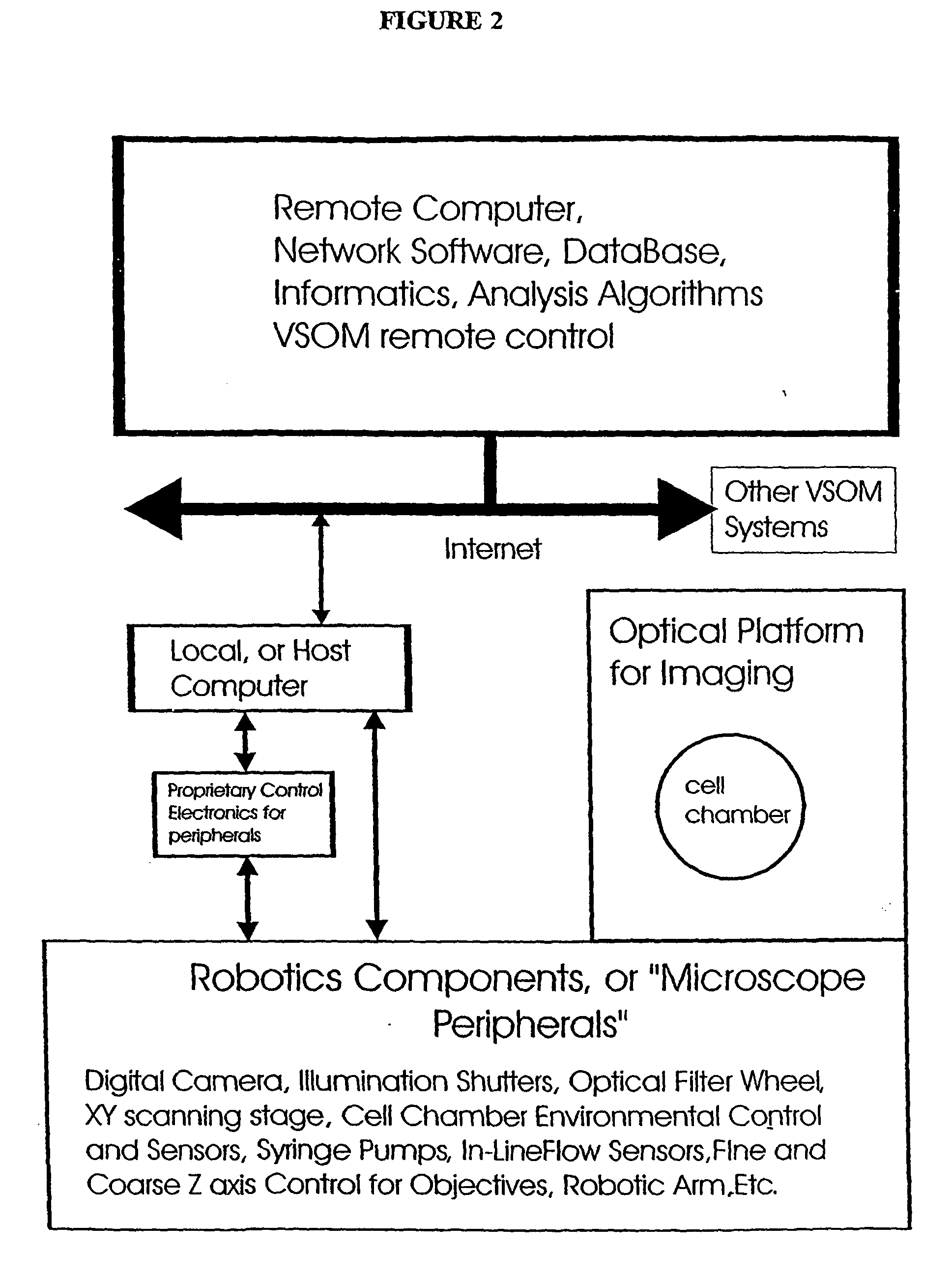
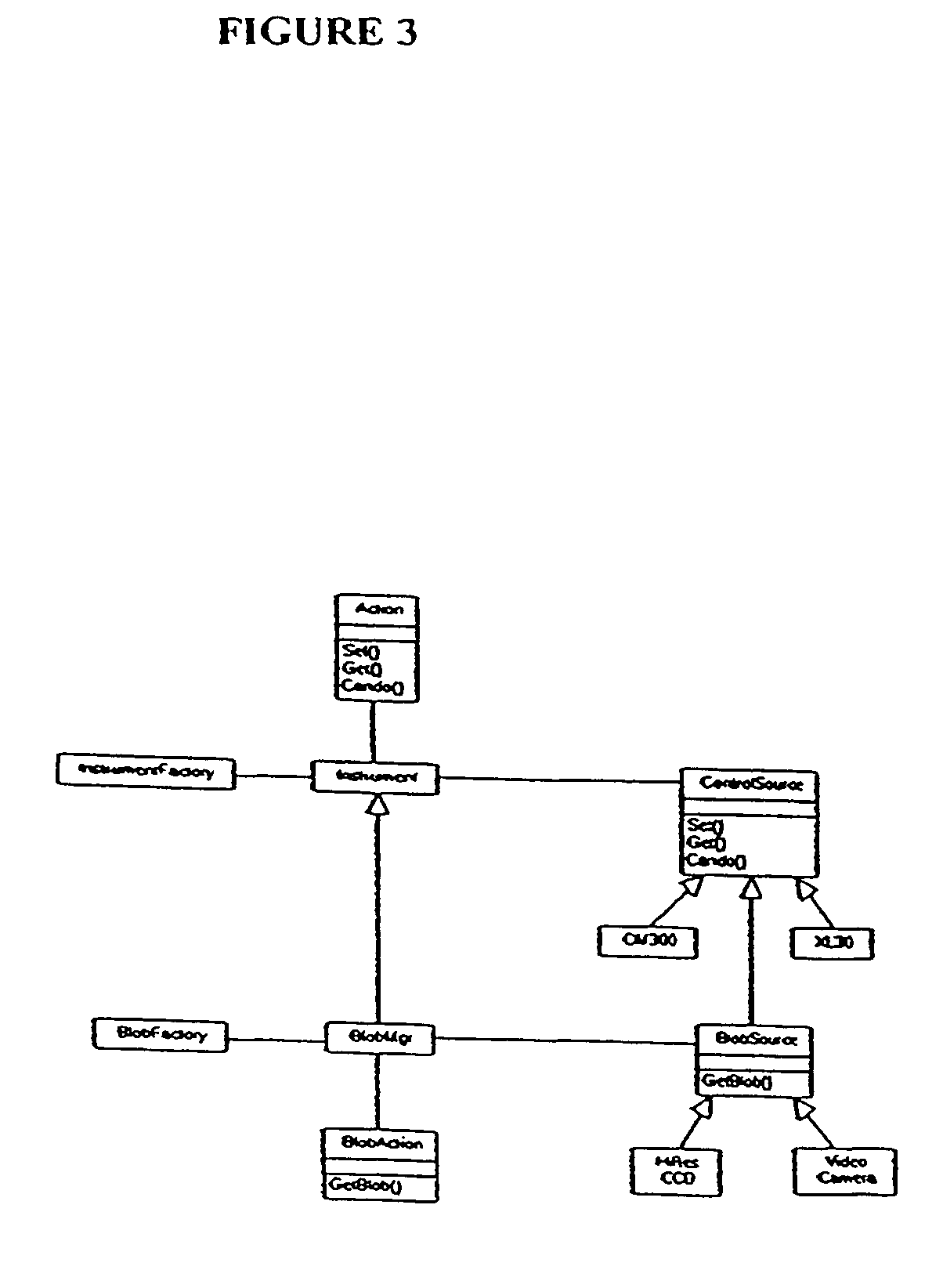
Visual-servoing optical microscopy
InactiveUS20040029213A1Close monitoringOptimize culture conditionsImage enhancementImage analysisCell typeCell stimulation
The present invention provides methods and devices for the knowledge-based discovery and optimization of differences between cell types. In particular, the present invention provides visual servoing optical microscopy, as well as analysis methods. The present invention provides means for the close monitoring of hundreds of individual, living cells over time: quantification of dynamic physiological responses in multiple channels; real-time digital image segmentation and analysis; intelligent, repetitive computer-applied cell stress and cell stimulation; and the ability to return to the same field of cells for long-term studies and observation. The present invention further provides means to optimize culture conditions for specific subpopulations of cells.
Owner:RGT UNIV OF CALIFORNIA
Processing a video for vascular pattern detection and cardiac function analysis
InactiveUS20130322729A1Quick discoveryEffective toolImage enhancementImage analysisPattern detectionLength wave
What is disclosed is a non-contact system and method for determining cardiac function parameters from a vascular pattern identified from RGB and IR video signals captured simultaneously of a region of exposed skin of a subject of interest. In one embodiment, a video of a region of exposed skin is captured using a video camera that captures color values for pixels over visible channels and an IR camera that measures pixel intensity values in wavelength ranges of interest. Pixel intensity values are processed to generate a vascular binary mask that indicates pixel locations corresponding to the vascular pathways. The IR images are registered with corresponding data from the camera's visible channels such that pixels that correspond to the vascular pattern can be isolated in each frame of the video of visible color data. Once processed, pixels associated with the isolated vascular patterns are analyzed to determine desired cardiac function parameters.
Owner:XEROX CORP
Failure recognition method and system based on neural network self-learning
ActiveCN103914735ASpeed up fault identificationAccelerateBiological neural network modelsReal time acquisitionMonitoring data
The invention discloses a failure recognition method and system based on neural network self-learning. The method comprises the steps that (1), various set monitoring quantities of track traffic equipment are monitored and collected, and the collected monitoring data are converted into sample data applicable to training the neural network; (2), the sample data are classified according to the types of failures, and a sample data set corresponding to each type of failure is obtained; (3), one neural network is designed for each type of failure, then the sample data sets of the failures are used for training, and a recognition model of each type of failure is obtained; (4), the recognition models of all the types of failures are fused to be one neutral network, and failure recognition is carried out on the monitoring data collected in real time. The method can calmly cope with complex equipment failures and train operation accidents.
Owner:BEIJING TAILEDE INFORMATION TECH
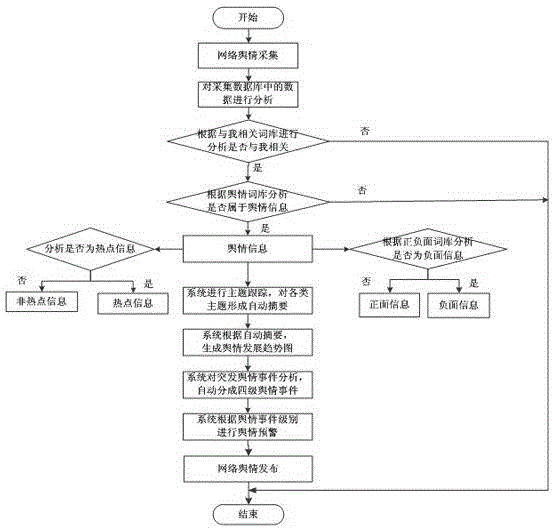
Funnel type data gathering, analyzing and pushing system and method for online public opinion
InactiveCN104408157AImplement topic tracking analysisRealize network public opinion monitoringData processing applicationsWeb data indexingProcess moduleThe Internet
The invention discloses a funnel type data gathering, analyzing and pushing system and method for online public opinion. The funnel type data gathering, analyzing and pushing system comprises an online public opinion gathering module, an online public opinion processing module and an online public opinion publishing module, and the modules comprise a directed precise gathering sub-module, a non-directive gathering sub-module, a hot spot and sensitive topic identifying sub-module, a topic tracking sub-module, an automatic abstracting sub-module, a comprehensive analysis sub-module, a public opinion pre-warning sub-module and a multi-dimensional public opinion information display sub-module. The funnel type data gathering, analyzing and pushing method for the online public opinion uses a special public opinion funnel algorithm and uses the lexicons of three types of keywords of related to me, public opinion and positive and negative aspects to analyze, judge and classify the gathered data and warn early to grasp the latent change rule. The funnel type data gathering, analyzing and pushing system and method for the online public opinion reduce the manual public opinion event polling burden, duly and precisely grasp the development trend of the public opinion event, form the latest, hottest and sensitive topics in the recent period on the Internet, and detect the public opinion message what the user is concerned about and give an early warning in the first time.
Owner:SICHUAN ESLITE ELECTRONICS COMMERCE CO LTD
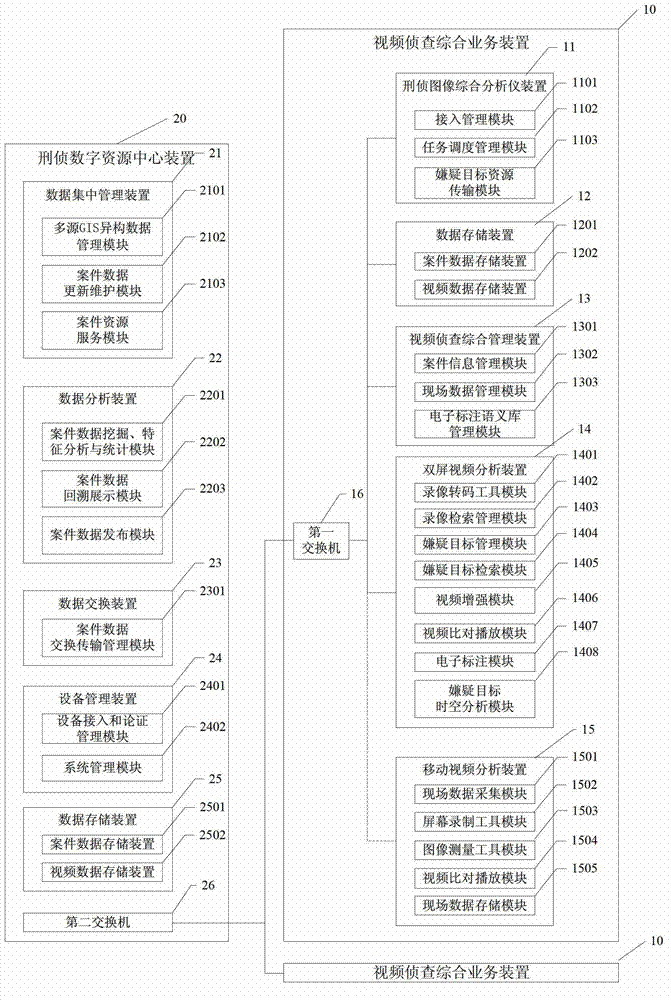
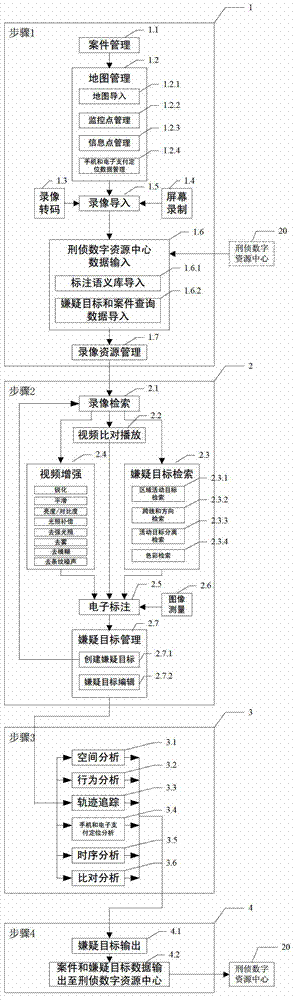
Suspected target analyzing system and method by video investigation
ActiveCN102819578AImprove playbackAvoid latency effectsImage analysisSpecial data processing applicationsPattern recognitionTarget analysis
The invention discloses a suspected target analyzing system and a method by a video investigation, belonging to the field of a criminal investigation video analysis. The system comprises a video investigation comprehensive business device and a criminal investigation digital resource center device which are connected to each other through an exchanger. By using the system, the case field information is structured, various monitoring video formats are transcoded to an uniform format; each frame image of a fuzzy video including a suspected target is enhanced to form a video enhanced segment; a suspected target video segment is obtained through the suspected target index with zero loss and low false drop rate; the unified semantic electronic mark is carried out on the suspected target video segment; the suspected target is found, screened and tracked by performing the space analysis, action analysis, trajectory tracking, positioning trace analysis of telephone and electronic payments, time sequence analysis, feature contrasting and analysis; furthermore, the system and the method can be widely applied to the video investigation and case solution.
Owner:WUHAN DAQIAN INFORMATION TECH
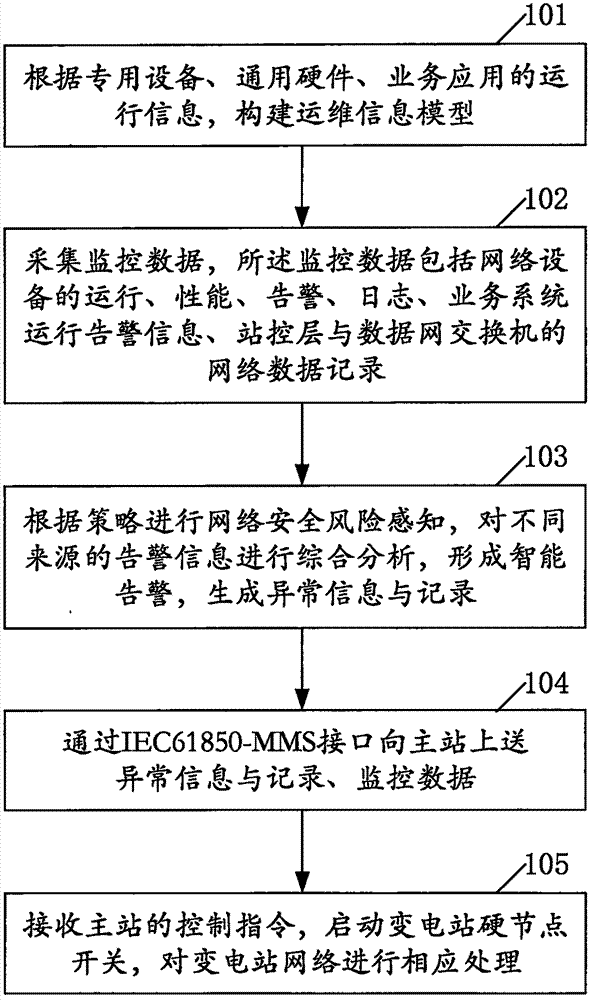
Network risk monitoring method and system for substation
The invention relates to the substation management control field, and discloses a network risk monitoring method and system for a substation. The network risk monitoring method for a substation includes the steps: according to the operating information of special equipment, general hardware and business application, constructing an operation information model; acquiring the monitoring data which includes operation, performance, alarm and logs of network equipment, business system operation alarm information, and network data record of a station control layer and a data network switch; according to a strategy, performing network safety risk induction, and performing comprehensive analysis on the alarm information from different sources to form intelligent alarm and generate abnormal information and record; uploading the abnormal information and record, and the monitoring data to a main station through an IEC61850-MMS interface; and receiving a control command of the main station, starting a substation hard node switch, and performing corresponding processing on the substation network. The operation information model based on the substation monitoring system can more quickly find the fault, can trace the generation source of the fault, can locate the area of effect of the fault, and can predict the propagating trend of the fault.
Owner:珠海市鸿瑞信息技术股份有限公司
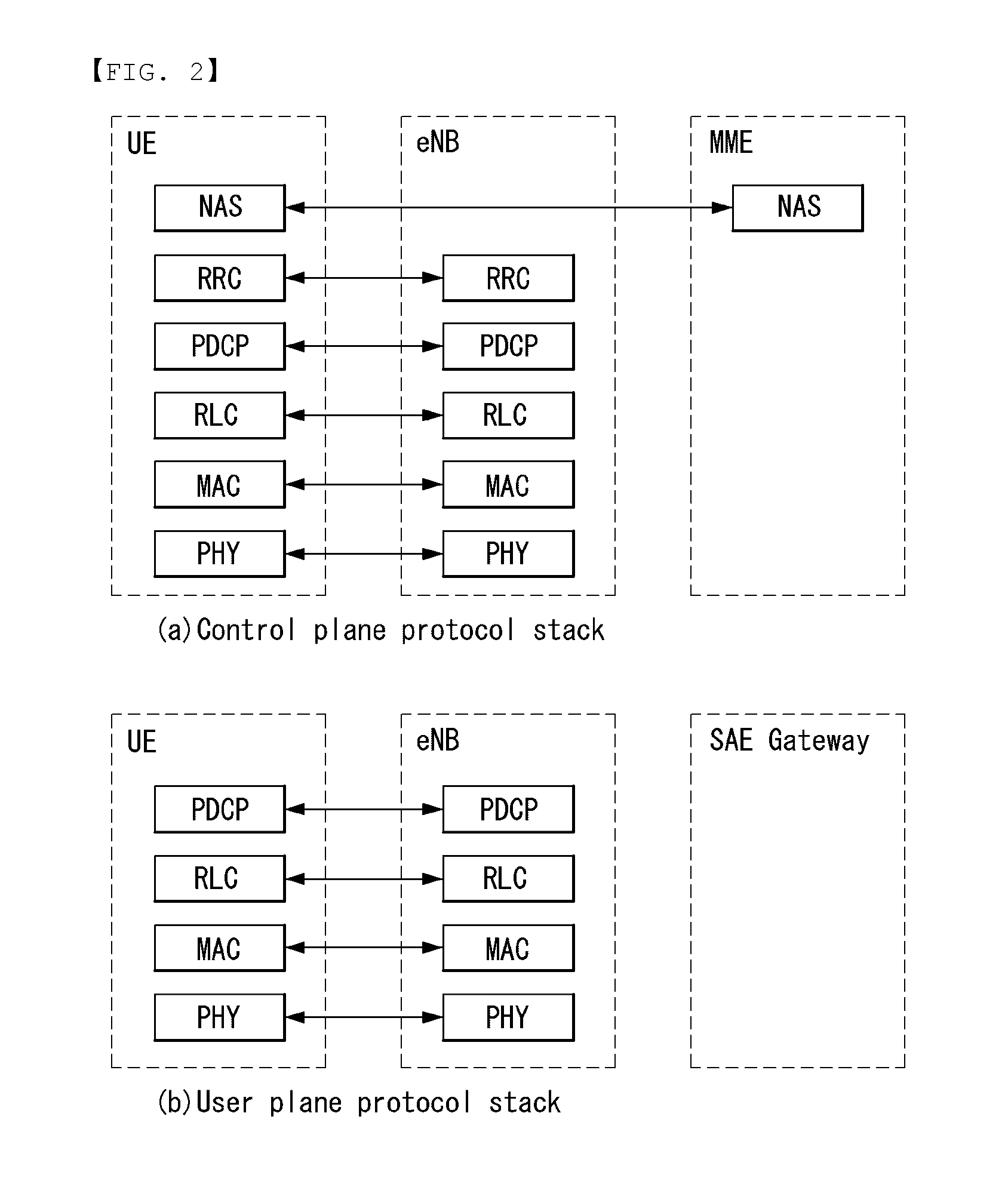
Method for transmitting and receiving discovery message in wireless communication system, and apparatus for same
InactiveUS20160373915A1Reduce overheadQuick discoveryConnection managementNetwork data managementCommunications systemComputer science
Disclosed herein are a method and apparatus for transmitting and receiving discovery messages in a wireless communication system. Specifically, a method for transmitting and receiving discovery messages in a wireless communication system supporting communication between user equipments (UEs) includes receiving, by a UE in a Radio Resource Control_IDLE (RRC_IDLE) state, information about an allocated resource for transmitting a discovery message from a network and transmitting, by the UE, the discovery message in the resource for transmitting the discovery message. The resource for transmitting the discovery message may be allocated based on a tracking area in which the device is located.
Owner:LG ELECTRONICS INC +1
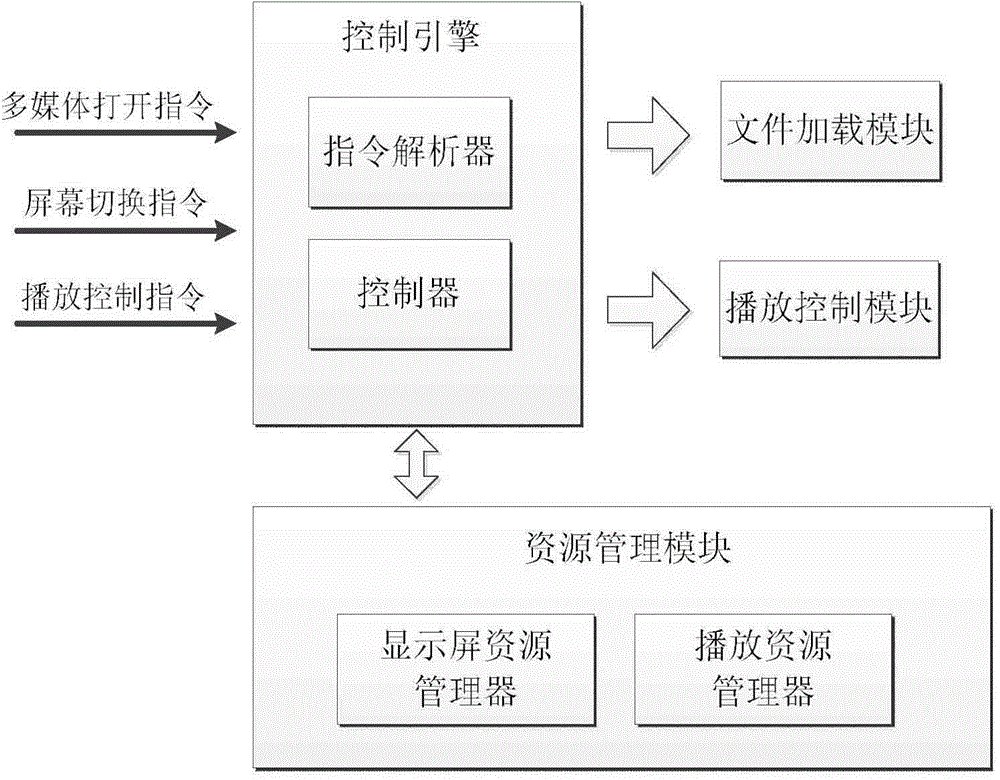
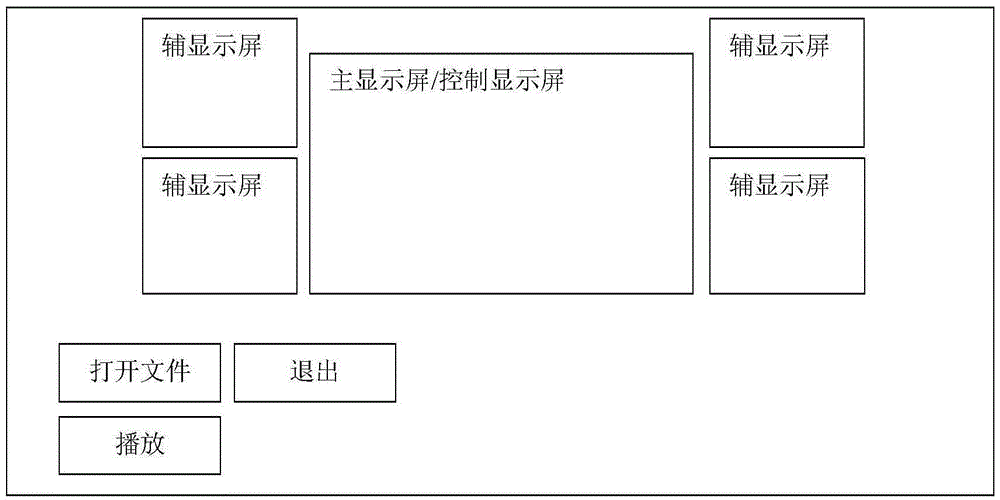
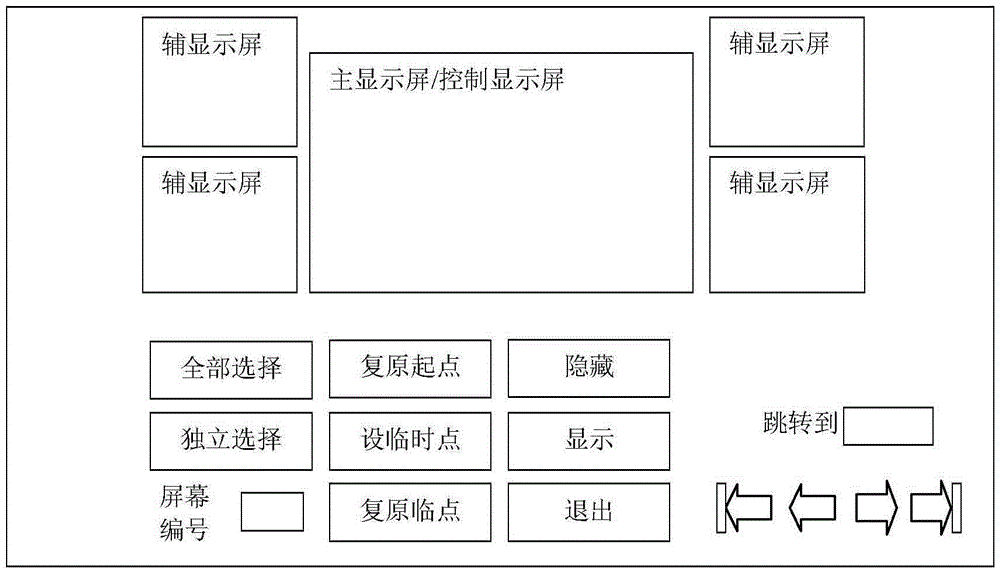
Multimedia display interaction control system under multi-screen environment
InactiveCN104540027AGood speechEffective speech effectSelective content distributionInteraction controlControl system
The invention provides a multimedia display interaction control system under multi-screen environment. According to the system, a set of multimedia files are played on different screens under one set of application environment, and unified linkage or respective play control can be carried out. The multimedia display interaction control system comprises a resource management module, a file loading module, a play control module and a control engine, wherein the resource management module maintains an opened multimedia file list and a display screen resource list. A multimedia file play object and a play window handle value are generated in a code every time a new multimedia file is opened and played. The multimedia play objects and the play window handle values are maintained in the multimedia file list, screen resource information of the system is maintained in the display screen resource list, certain-screen play or multi-screen switching display is carried out on the multimedia files through the control engine, and arbitrary combination and switching of respective control and linkage control over multiple display screens can be achieved through the play control module.
Owner:BEIJING ZHENGWEN TECH +1
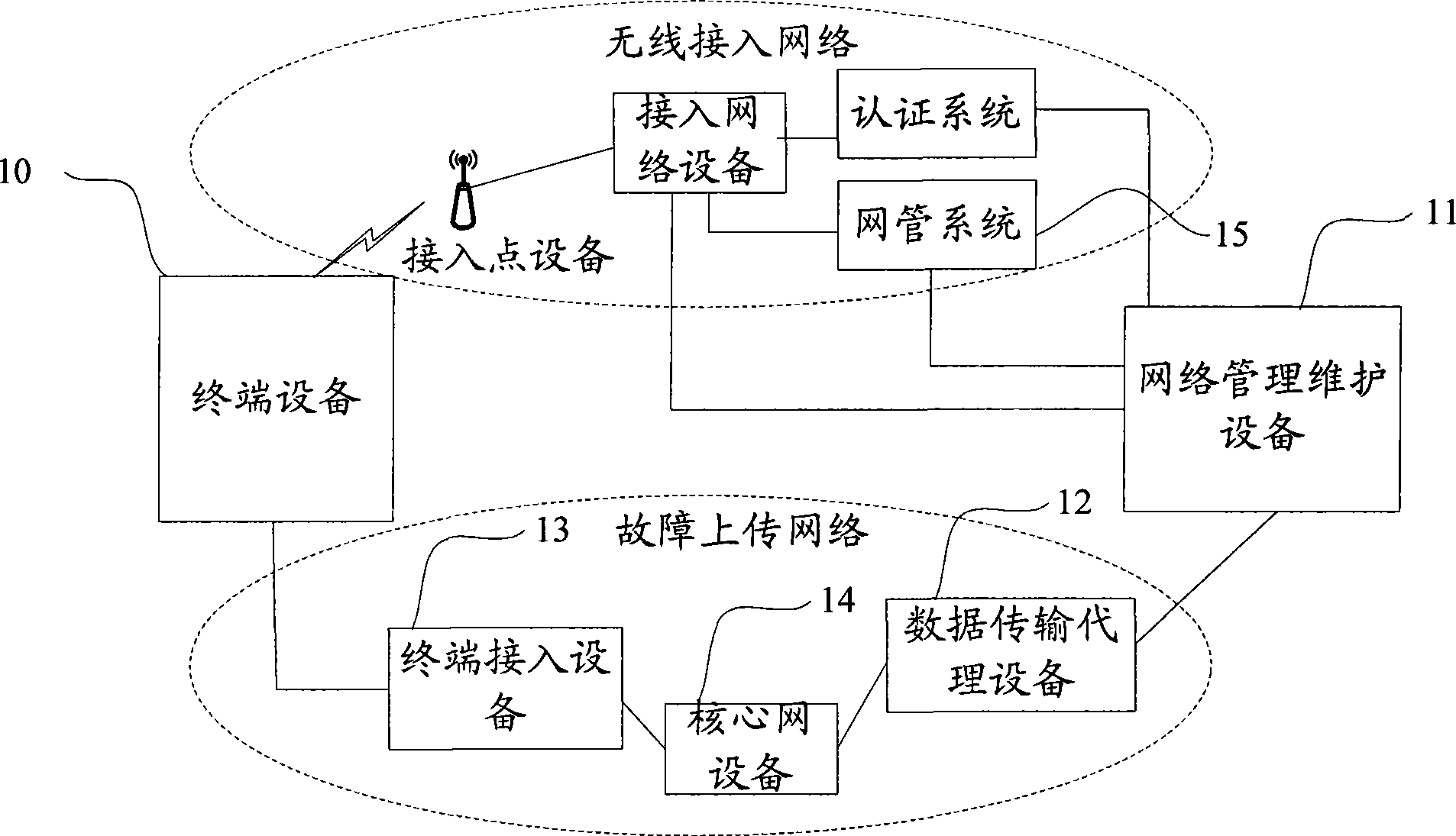
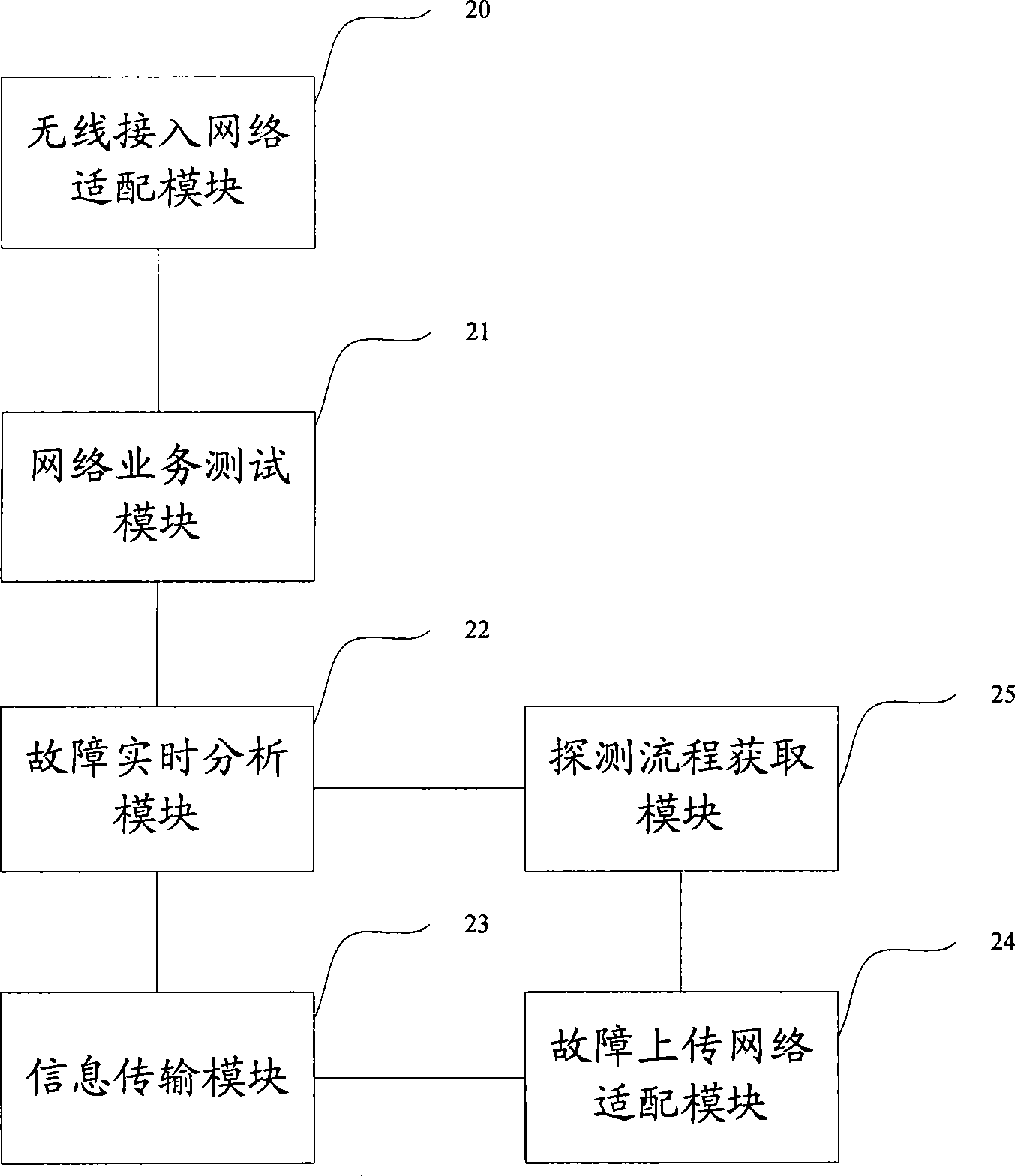
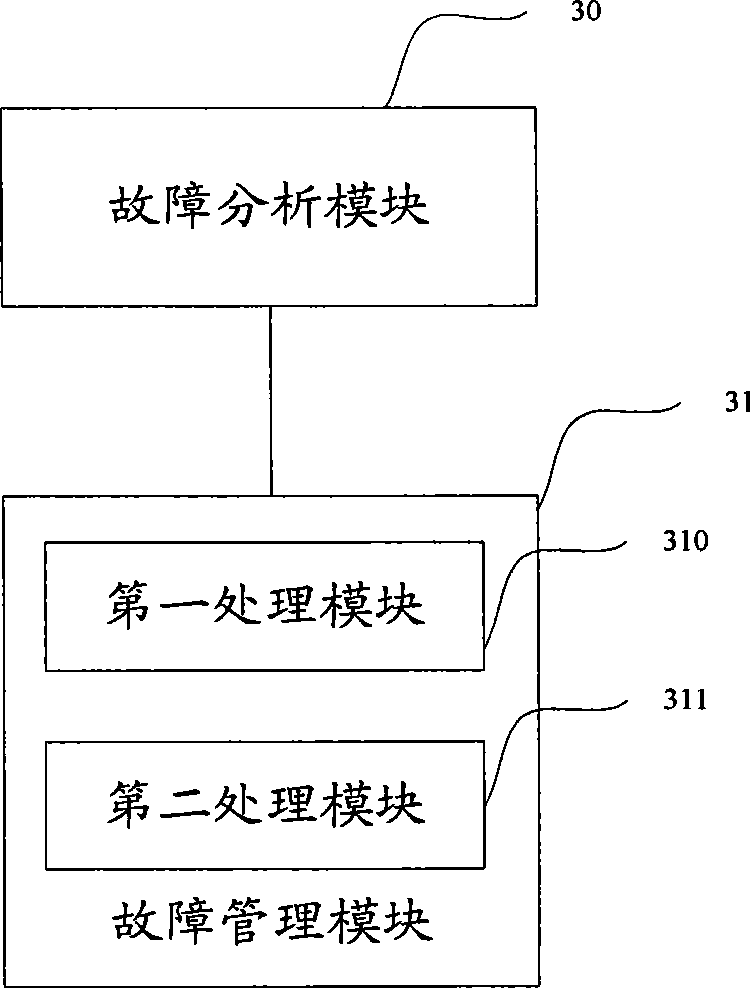
Method, system and device for processing wireless access network faults
The embodiment of the invention discloses a system for processing wireless access network faults, which comprises a terminal unit and a network management maintenance facility, wherein, the terminal unit is used for confirming the faults occurring in a wireless access network and sending fault information to the network management maintenance facility; and the network management maintenance facility is used for determining the fault type according to the fault information sent from the terminal unit, determining the fault processing manner corresponding to the fault type according to the preset corresponding relation between the fault type and the fault processing manner, and processing the faults according to the determined fault processing manner. The embodiment of the invention further discloses a method and a device for processing the wireless access network faults. By adopting the system, the method and the device, the real-time performance for processing the wireless access network faults can be increased effectively.
Owner:CHINA MOBILE GRP BEIJING
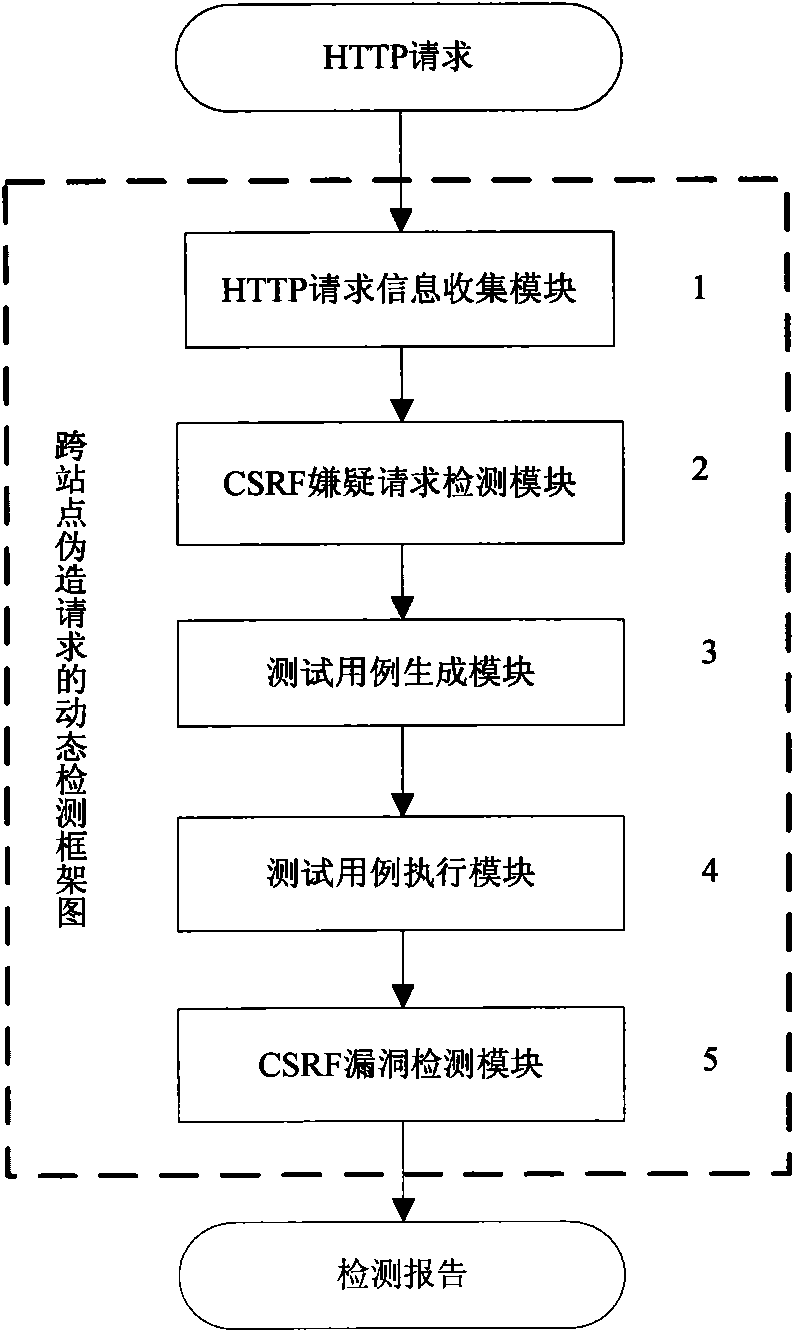
Dynamic detection method for cross-site forged request
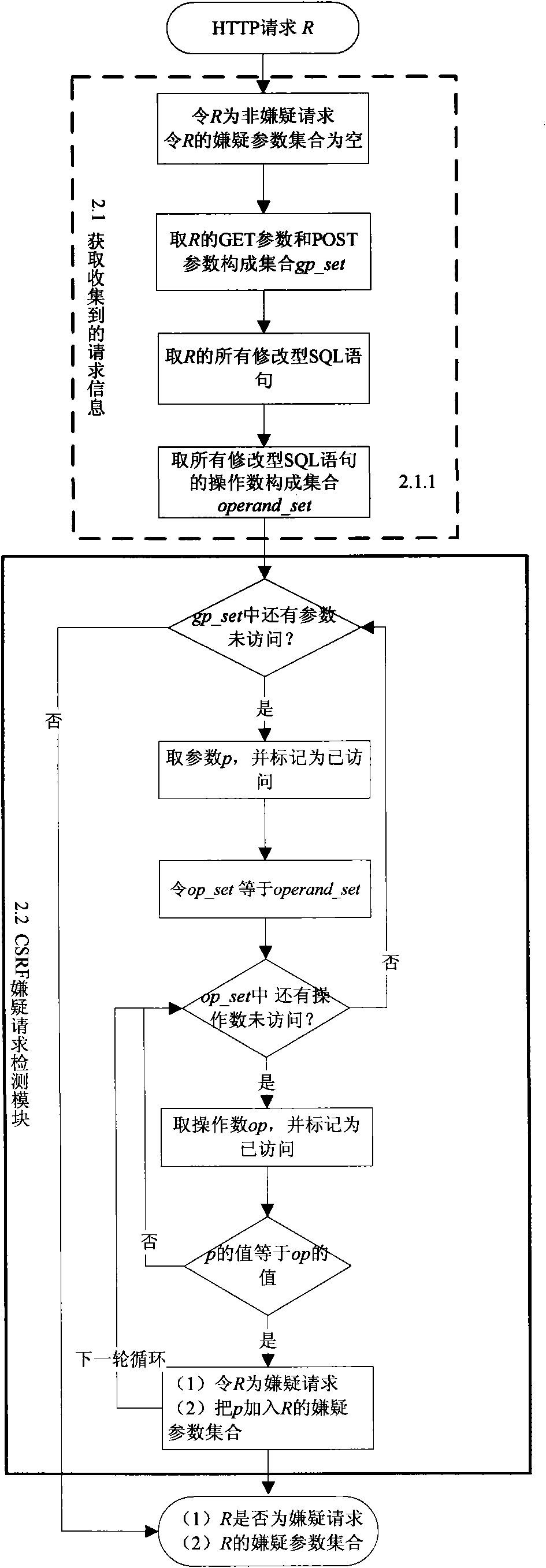
InactiveCN101883024AQuick and accurate discoveryImprove test efficiencyData switching networksWeb applicationDynamic testing
The invention discloses a dynamic detection method for a cross-site forged request, which comprises the following steps: collecting HTTP request information; analyzing whether a request is a CSRF suspect request or not according to the collected information; generating a test case aiming at the suspect request and finding out all suspect parameters contained by the suspect request; using the suspect parameters to generate a plurality of forged requests and generating a test case for each forged request; when an environment in which the suspect request is generated recurs, executing the forged request corresponding to each test case; detecting CSRF vulnerabilities; and according to the suspect request, the execution information of the suspect request, the forged requests and the execution information of the forged requests, analyzing whether the forged requests find the CSRF vulnerabilities in Web application or not, forming a report and helping a Web application developer to repair the vulnerabilities. Since the dynamic detection method is used for detecting the CSRF vulnerabilities, the CSRF vulnerabilities in the Web application can be rapidly and accurately found out at low cost.
Owner:NANJING UNIV
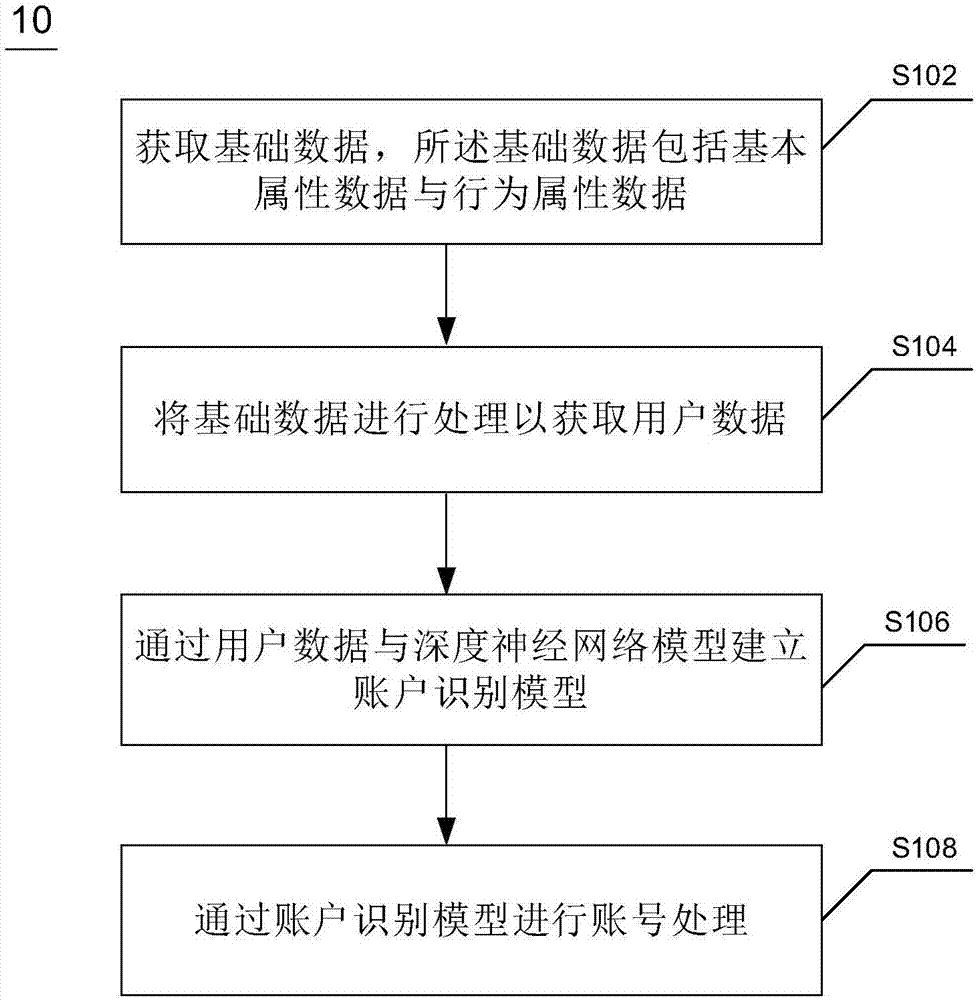
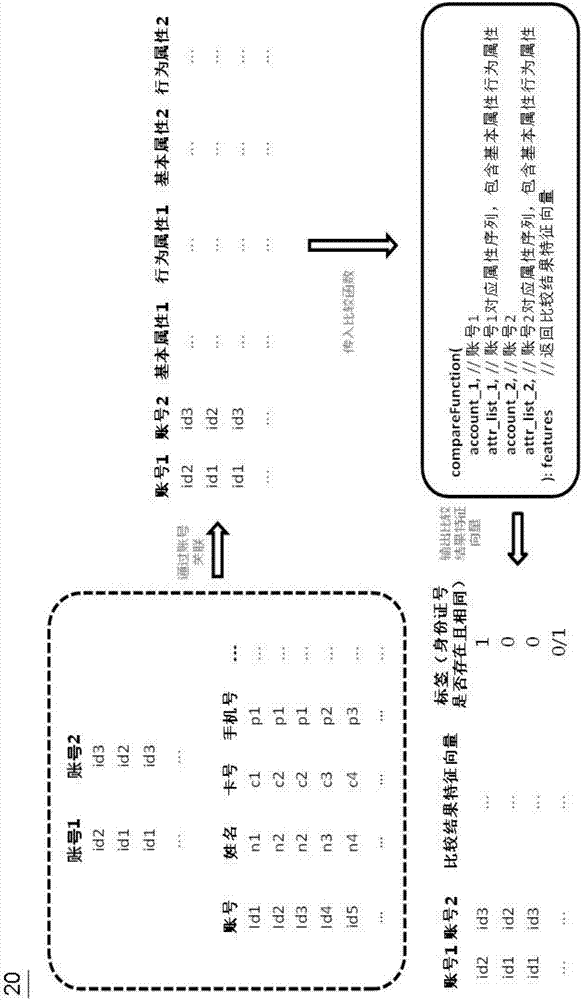
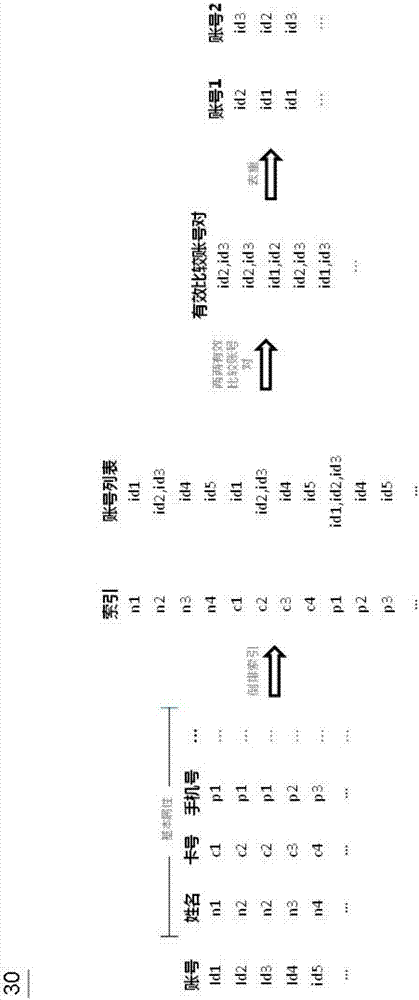
Account processing method and device and electronic equipment
ActiveCN107066616AQuick comparisonQuick identificationCharacter and pattern recognitionMulti-dimensional databasesNetwork modelDeep neural networks
Owner:JINGDONG TECH HLDG CO LTD
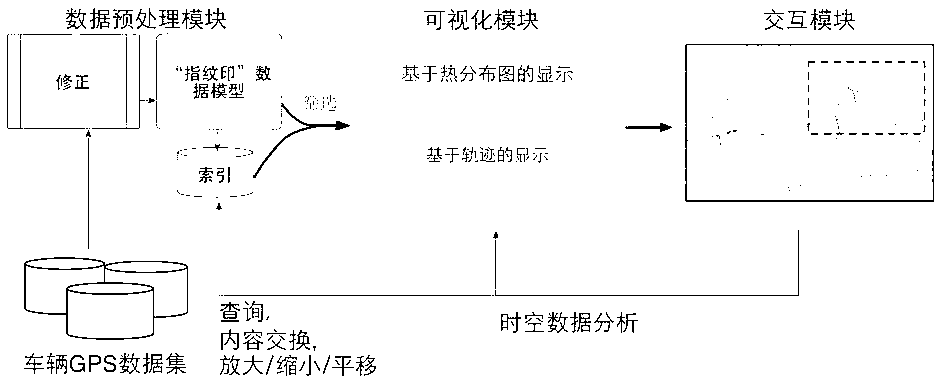
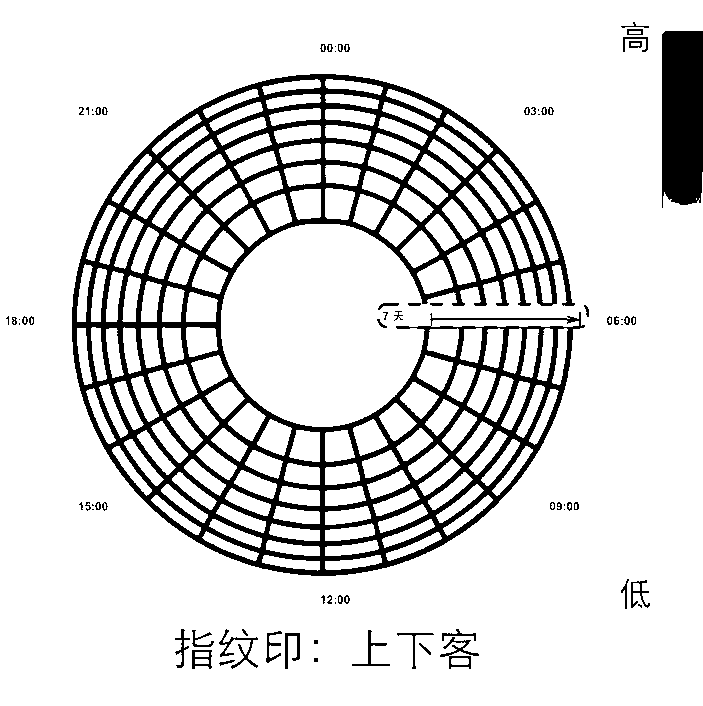
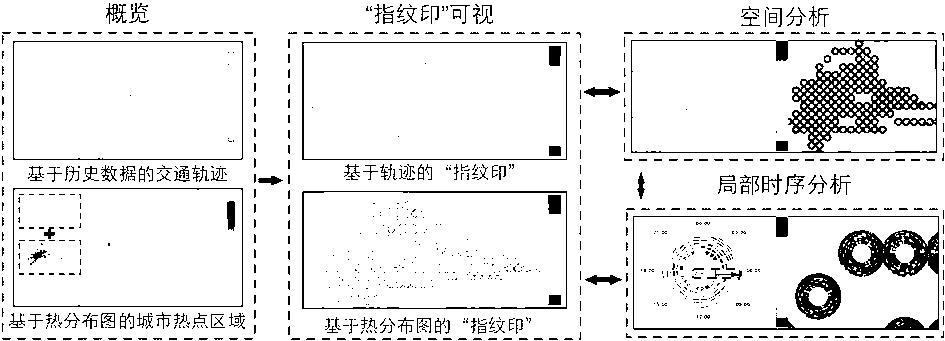
Visual mining method for vehicle GPS (global positioning system) data analysis and abnormality monitoring
ActiveCN103020222AQuick understandingQuick discoverySpecial data processing applicationsTime responseAbstract concept
The invention relates to a visual mining method based on a visualization technology for vehicle GPS (global positioning system) data analysis and abnormality monitoring. Original vehicle GPS data are converted by a data conversion module into a unique visual ''fingerprint stamp'' data model, a data index for real-time response to user interaction is provided to help a user to analyze data; and a visual vehicle data model is combined with a display based on a heat distribution map and a trajectory through a visualization module, detection of urban hot spot areas and traffic trajectory abnormality monitoring based on historical data are performed, and certain abstract concepts in the data, such as frequent rules and periodic rules, are displayed in an easy-to-understand way for an analyzer. The analysis threshold can be lowered, the scope of application can be expanded, and the analysis efficiency can be improved. Rich interaction operations can be realized through a user interaction module, monitoring and analysis can be performed by the user, and analysis and support can be provided for decisions of the user.
Owner:GUANGZHOU HKUST FOK YING TUNG RES INST
Methods and products for analyzing polymers
InactiveUS8168380B2Improve abilitiesUsed to determineSugar derivativesMaterial analysis by observing effect on chemical indicatorPolymerStructural property
Owner:LIFE TECH CORP
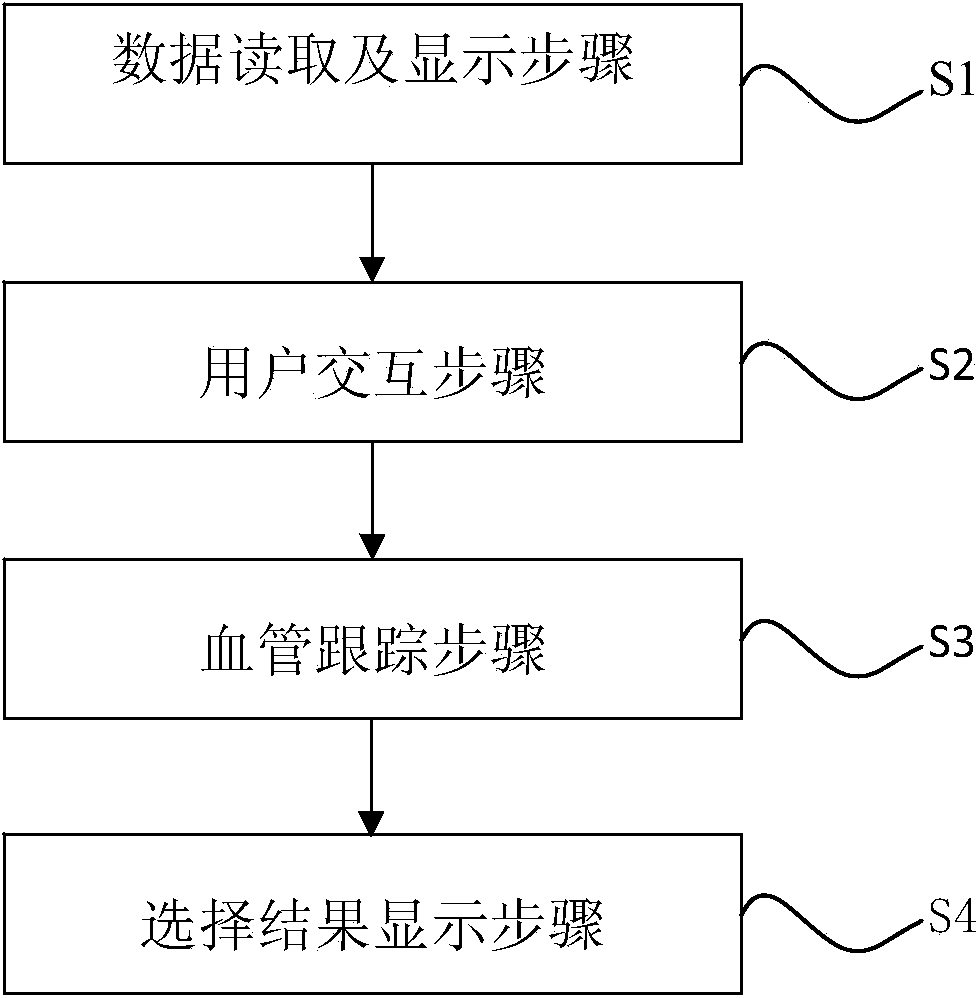
Method for rapidly selecting and displaying interested blood vessel in magnetic resonance blood vessel image
InactiveCN103886312AImprove the efficiency of clinical diagnosisSolve the problem of manual segmentationImage analysisCharacter and pattern recognitionRegion of interestResonance
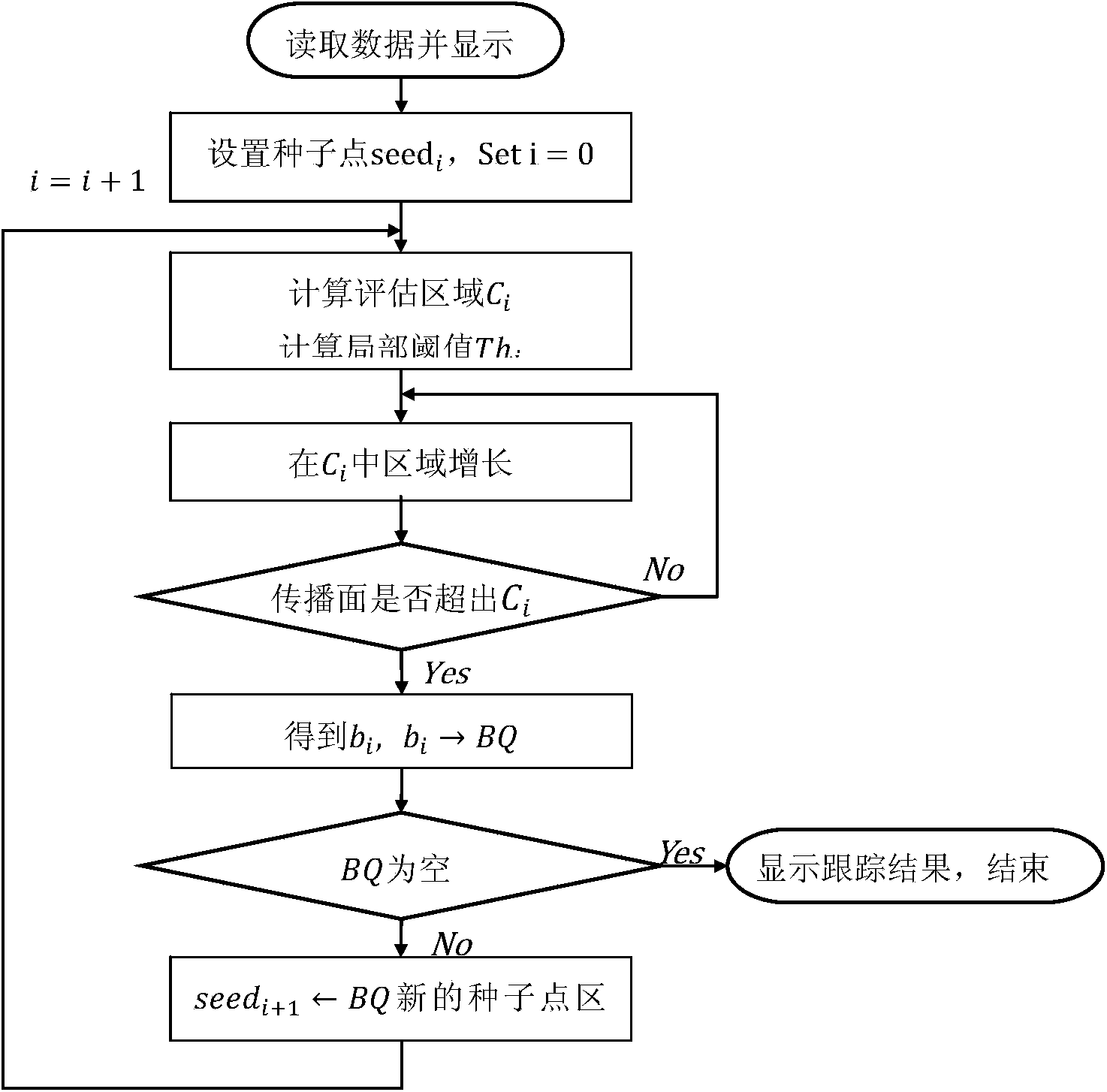
The invention discloses a method for rapidly selecting and displaying an interested blood vessel in a magnetic resonance blood vessel image. The method comprises the following steps that data are read and displayed, and data of an original image are loaded and the original image is displayed on a terminal; users interact with each other, a starting point is selected in interested areas of the blood vessel selected from the original image, and the growth direction of the blood vessel is determined; the blood vessel is tracked, orientation area growth is carried out from the starting point in the growth direction of the blood vessel to obtain part of the intersected blood vessel areas until all the intersected blood vessel areas are obtained; the selection result is displayed, all the areas of the interested blood vessel are displayed in a three-dimensional rebuilding process. Through the method for rapidly selecting and displaying the interested blood vessel in the magnetic resonance blood vessel image, the interested blood vessel in the magnetic resonance blood vessel image can be rapidly, stably and practically selected.
Owner:EAST CHINA NORMAL UNIVERSITY
Network sensitive information-oriented screenshot discovery and locking callback method
InactiveCN102902703ADiscovered in timeQuick discoverySpecial data processing applicationsComputer securityNetwork on
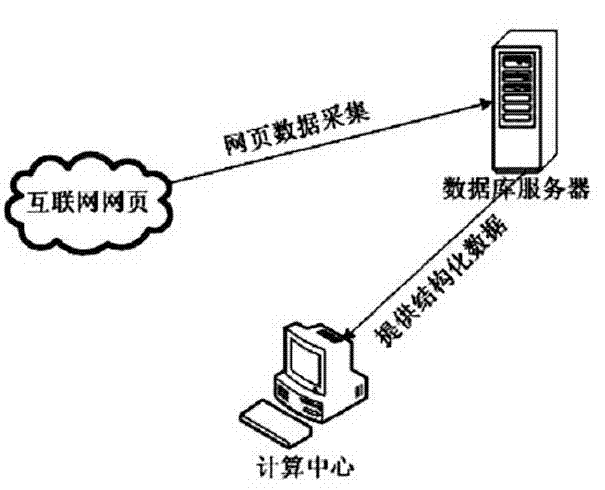
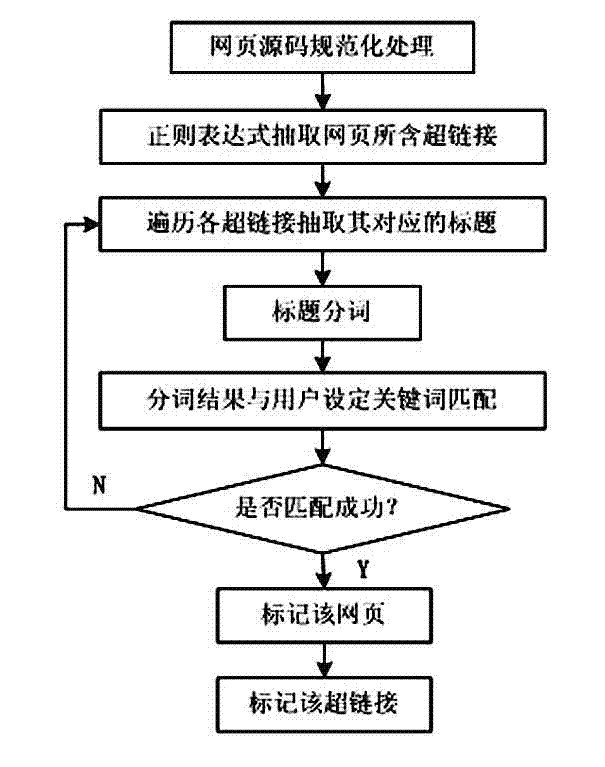
The invention discloses a network sensitive information-oriented screenshot discovery and locking callback method which comprises the steps of: acquiring webpage data of a website to be monitored; normally treating the webpage data, extracting a webpage title and a link on the basis of a regular expression, matching sensitive information on the basis of the webpage title and the link; carrying out outer page and inner page screenshot on the sensitive information; carrying out locking callback on the sensitive information for preventing resurgence; and storing and inquiring a sensitive information screenshot result. For the sensitive information on a network, by adopting the network sensitive information-oriented screenshot discovery and locking callback method, the sensitive information can be found within shortest time and is subjected to screenshot storage, the webpage is prevented from being updated or deleted in future, file discovery and immediate disposition of relative disposing mechanisms are facilitated, and a website for frequently issuing the sensitive information is disposed. In addition, the method provided by the invention can effectively meet the monitoring and disposing demand of the sensitive information of a network, and is suitable for implementation of a network public opinion analysis system.
Owner:NAT UNIV OF DEFENSE TECH
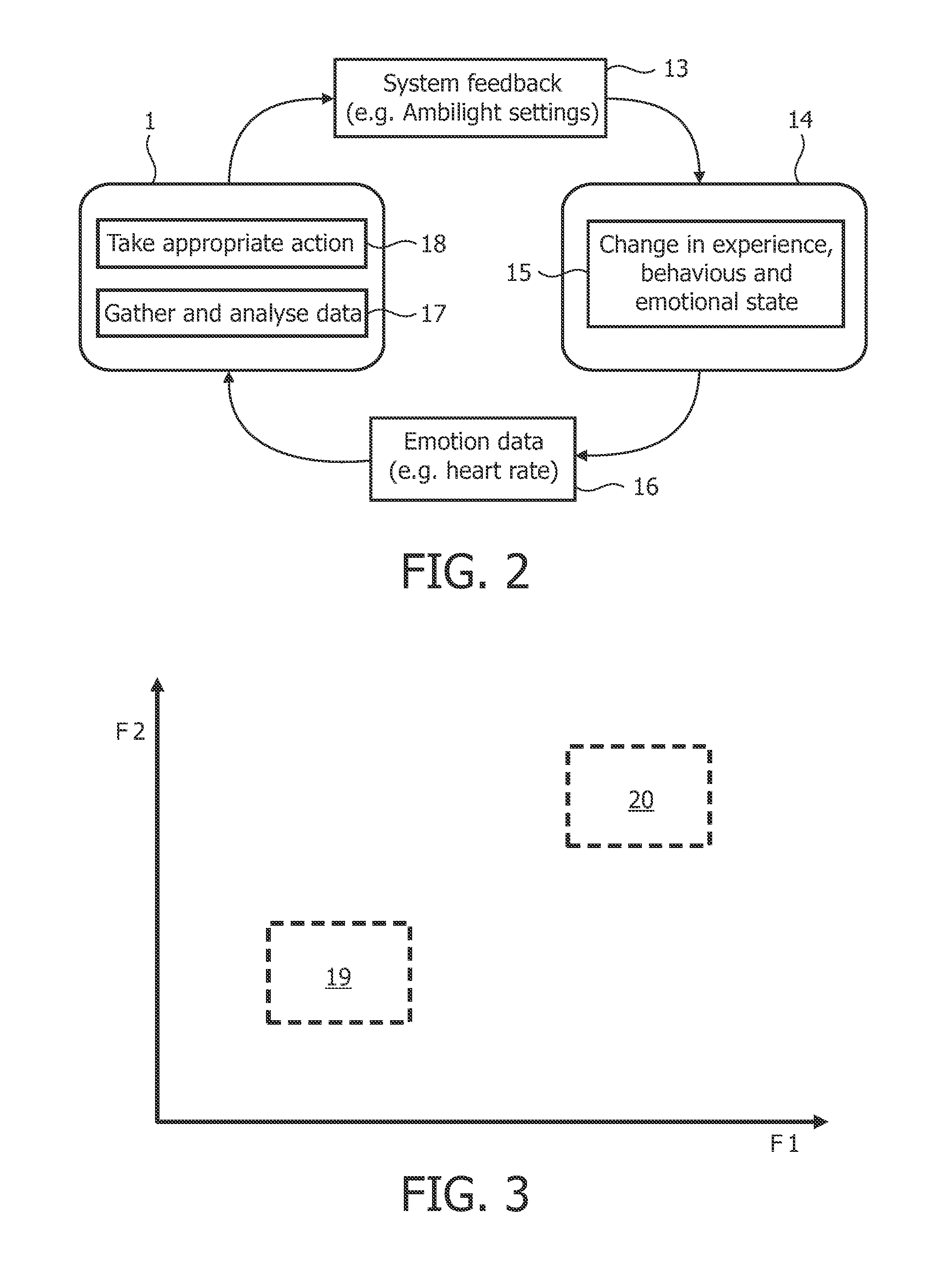
Controlling an influence on a user in a rendering environment
ActiveUS20110207100A1Optimize the player's enjoymentSimple processTeaching apparatusInput/output processes for data processingSelf reportUser expectations
A method of controlling an influence on a user (14) in a rendering environment comprises: obtaining signal data (16) representing one or more physiological conditions of a user (14) in response to an influence caused by system feedback (13) of the rendering environment; obtaining data corresponding to a user's desired emotional state (19,20;32-36), which data is based on the user's self-reports and data representative of accompanying signal data (16) representing one or more physiological conditions of the user (14) over a last period before the accompanying self-report; —determining whether the desired emotional state (19,20;32-36) is reached; and if the state (19,20;32-36) is not reached, adapting the system feedback (16) provided by the rendering environment correspondingly.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
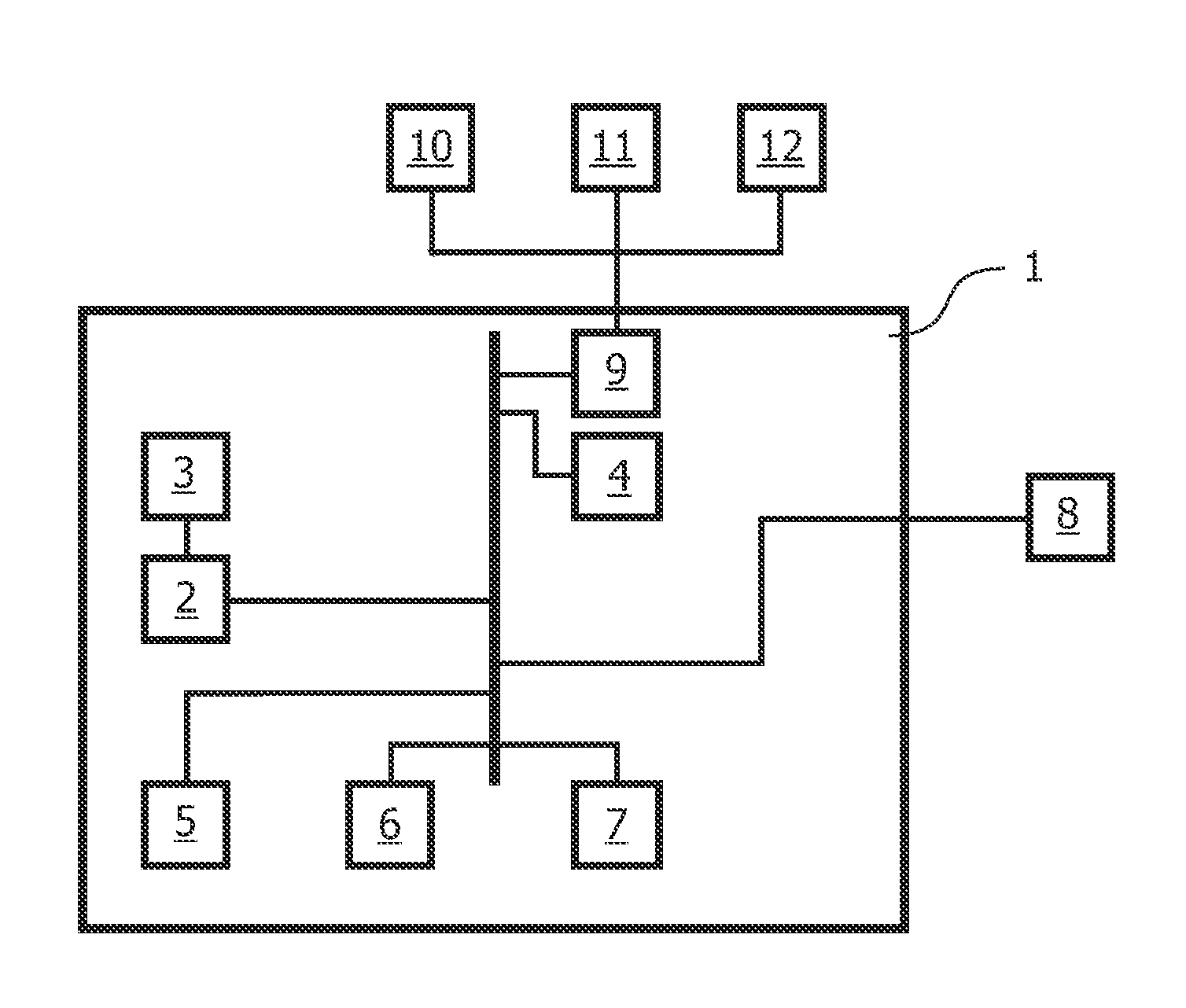
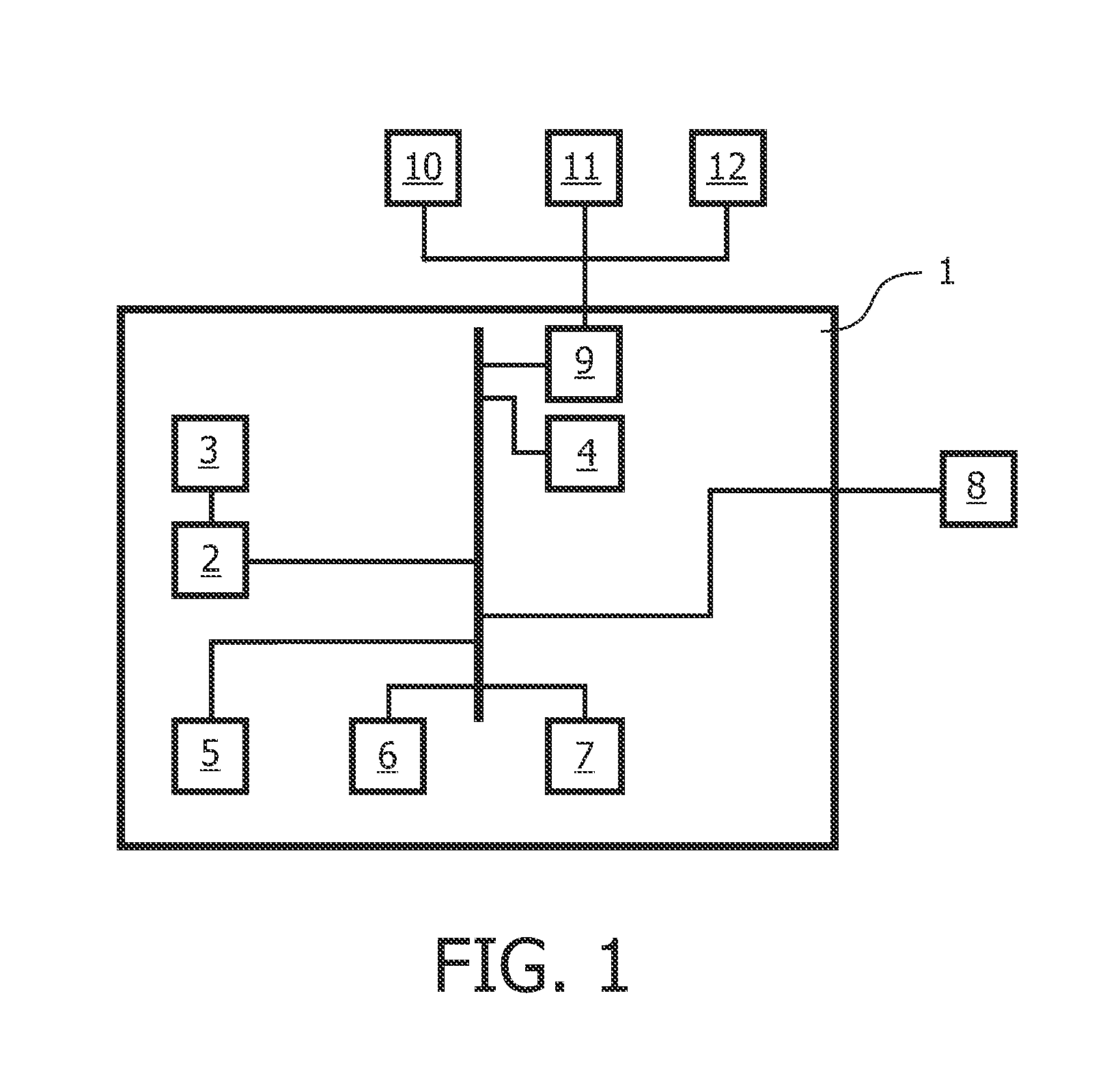
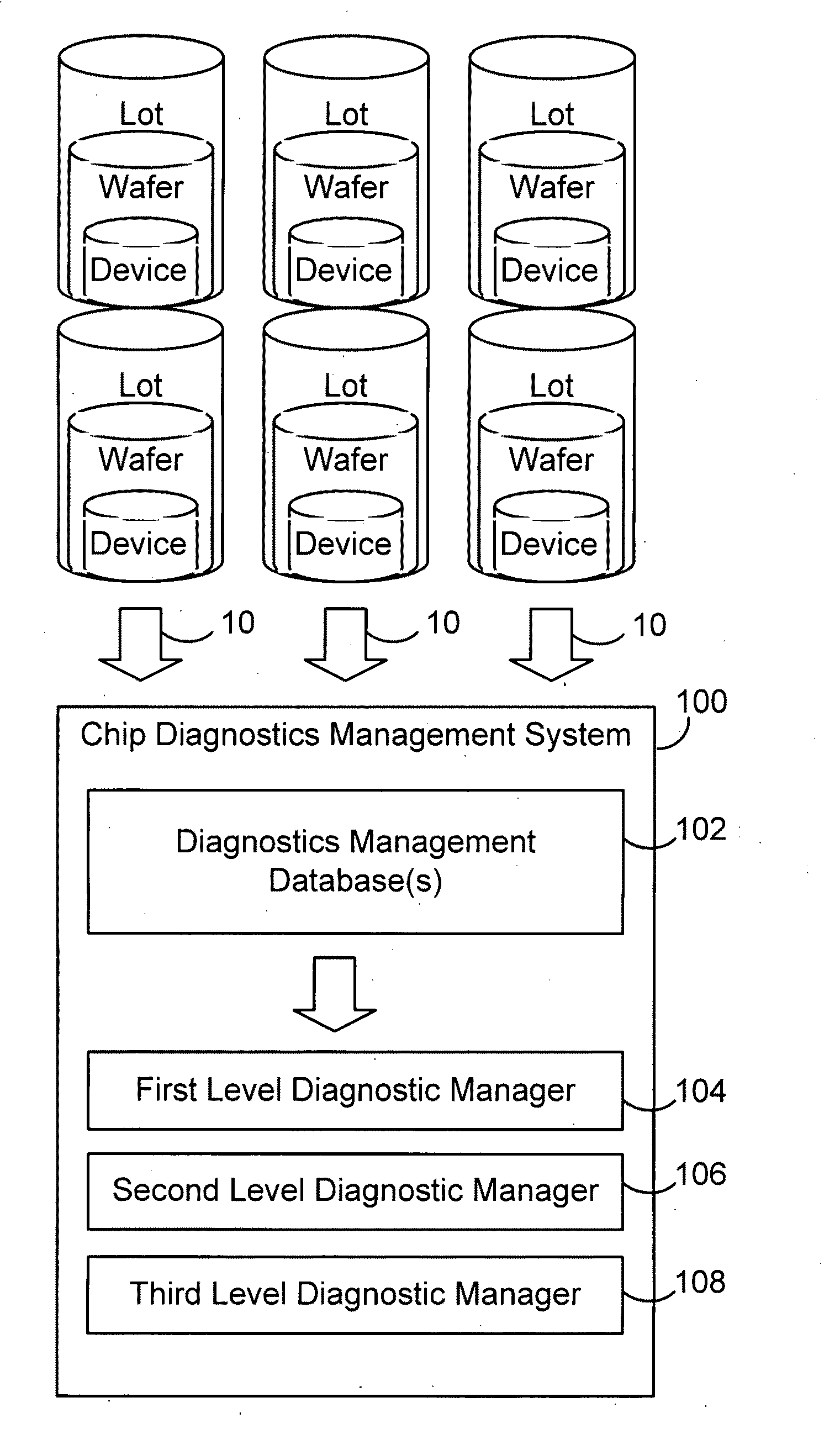
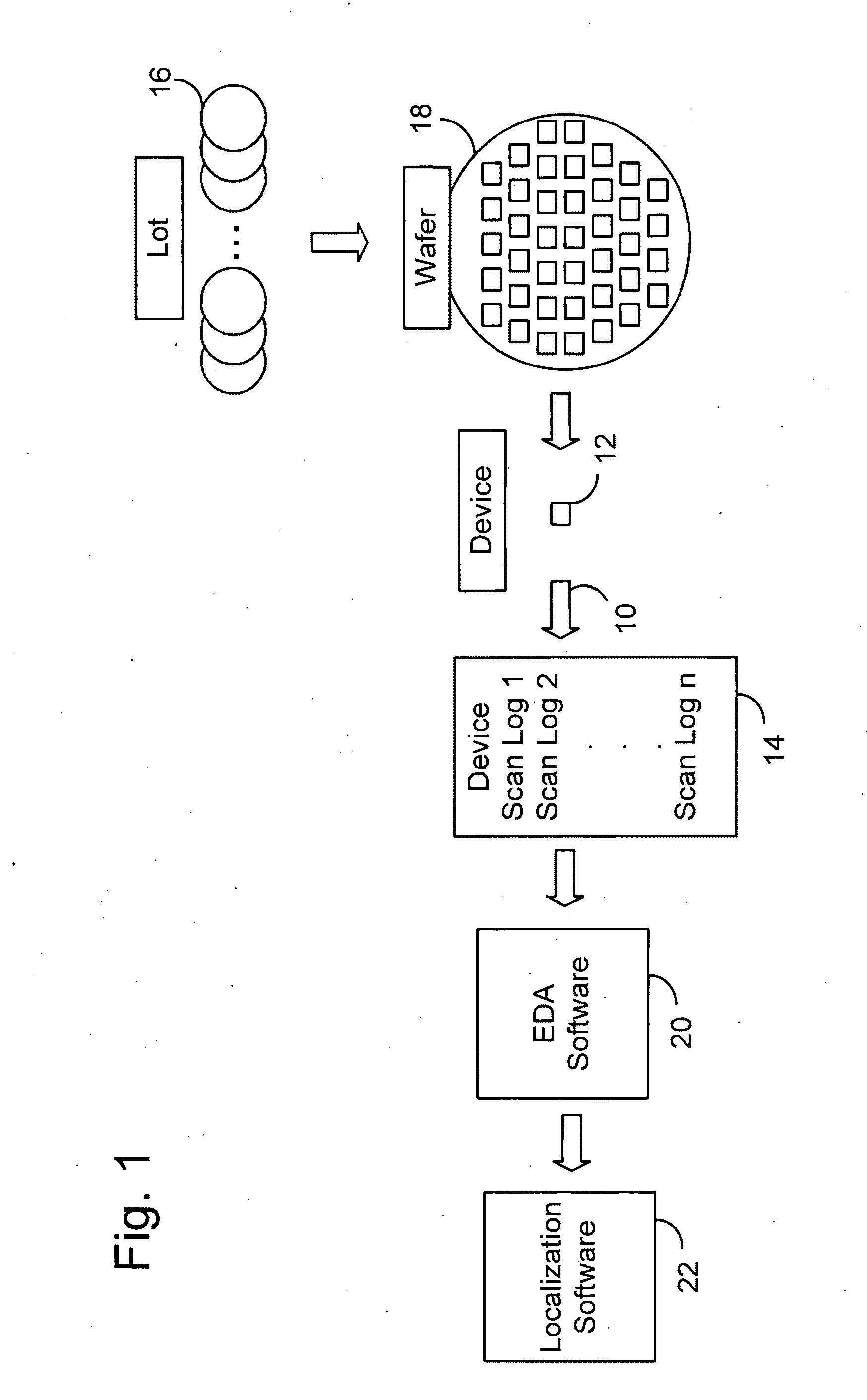
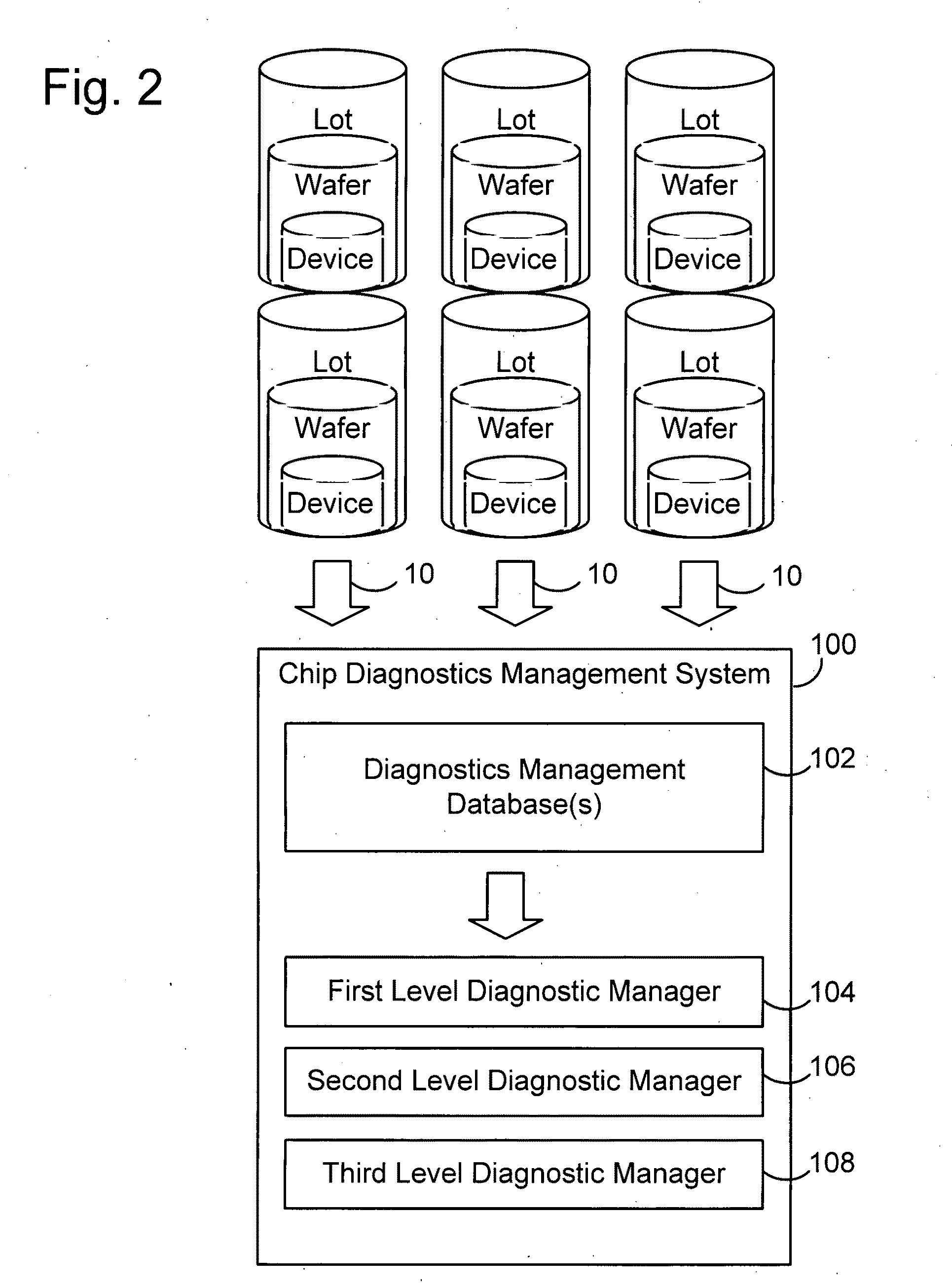
Secure test-for-yield chip diagnostics management system and method
ActiveUS20100332172A1Quick discoveryElectrical testingSpecial data processing applicationsSecurity designDiagnosis management
A chip diagnostics management system includes secure design information that define production features of integrated circuit devices and are accessible according to selected levels of access privilege. A database of device defect information includes information of defects of devices produced according to the production features of the design information and associated wafers, production lots, and dies in or with which the devices were produced. A diagnostic manager correlates device defect information from plural wafers with the design information to identify a device location with a probability of being associated with the device defect information. A diagnostic manager viewer indicates the device location together with an amount of design information correlated the level of access privilege assigned to a selected user.
Owner:TESEDA CORP
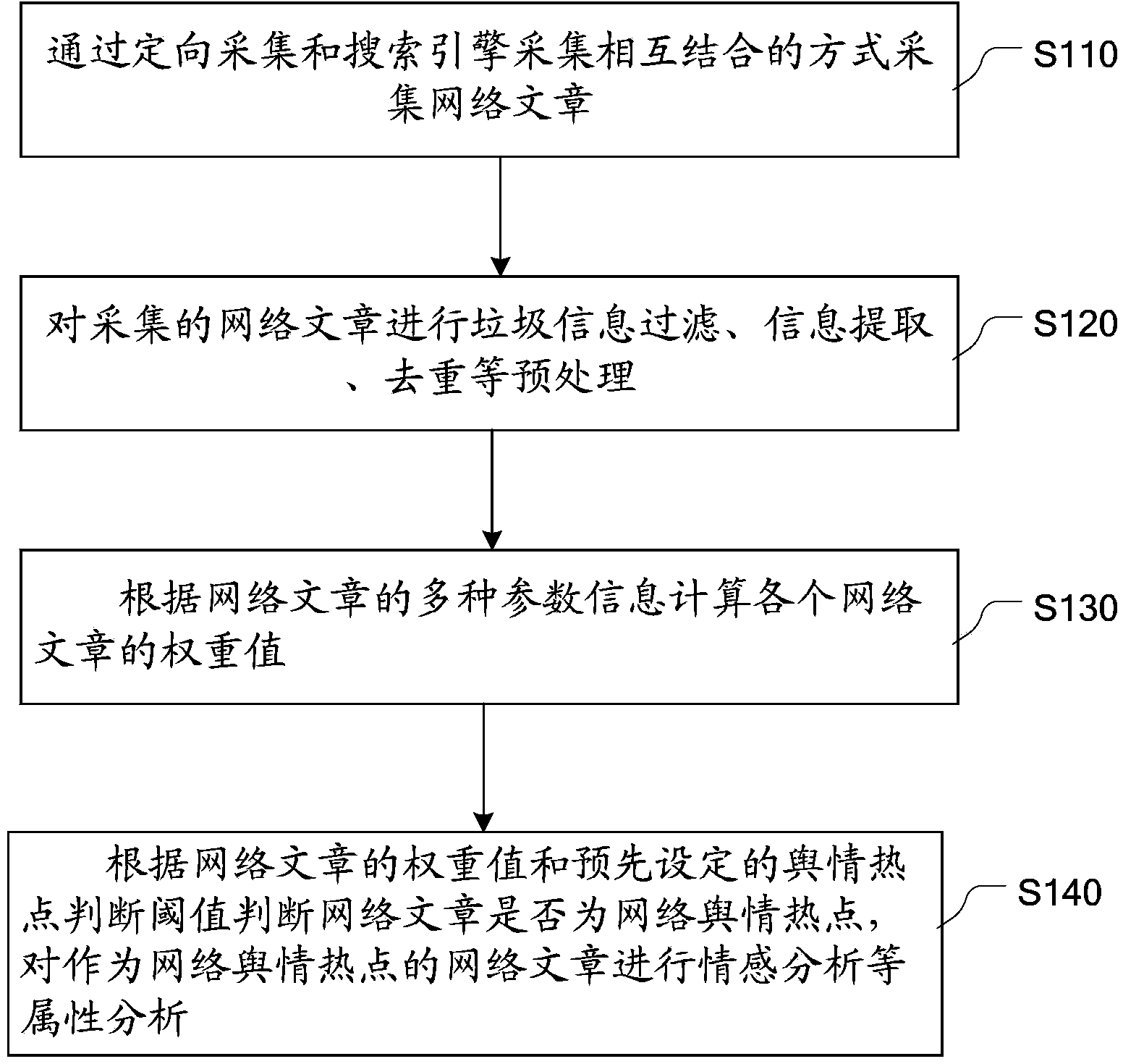
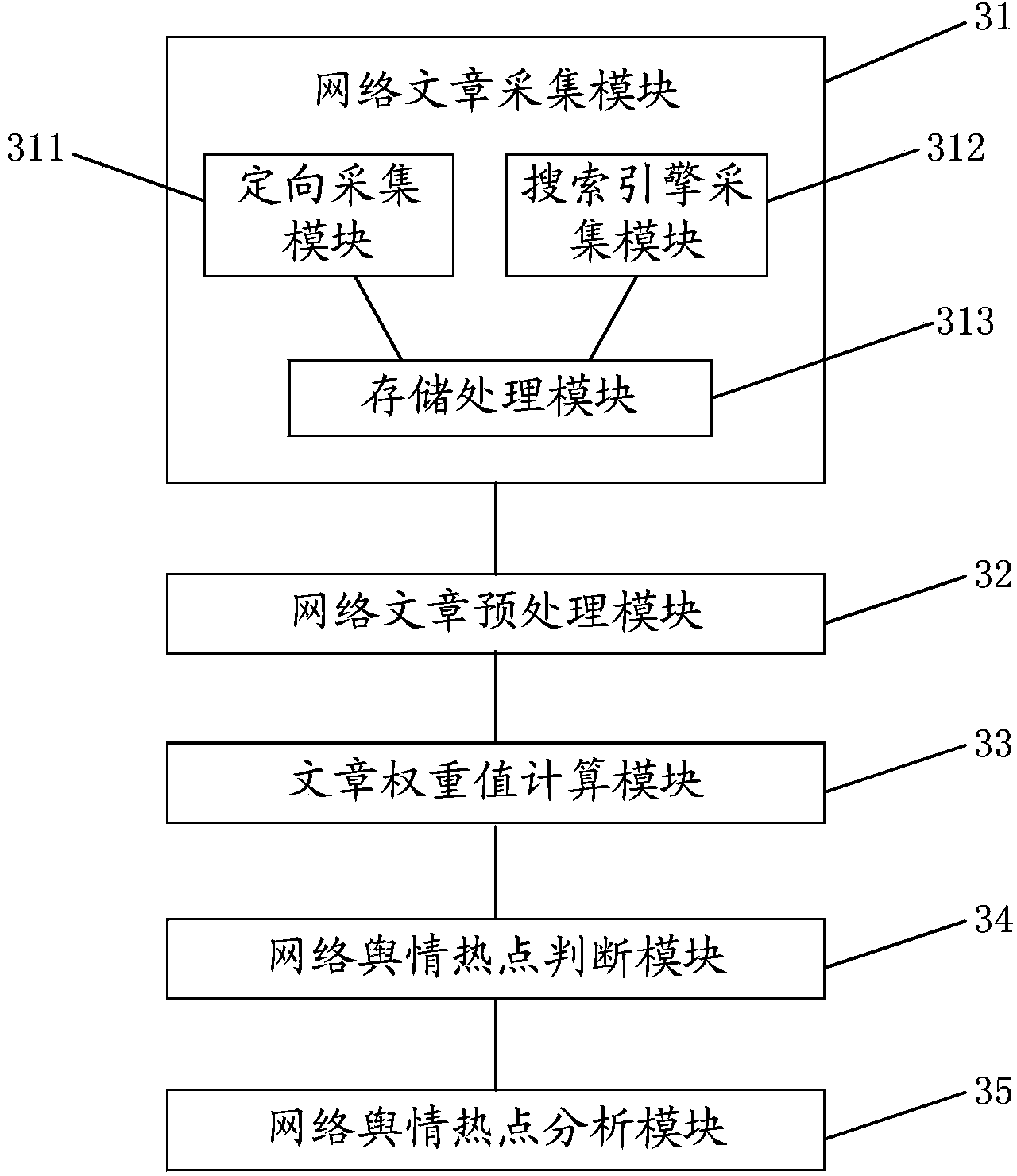
Method and device for finding network public opinion hotspots based on network article attributes
ActiveCN104077377AQuick discoveryDiscovered in timeSpecial data processing applicationsData scienceWeight value
The embodiment of the invention provides a method and a device for finding network public opinion hotspots based on network article attributes. The method mainly comprises collecting network articles in the way which integrates oriented collection with search engine collection, calculating the weighted value of each network article according to several kinds of parameter information of the network article, judging whether the network articles are the network public opinion hotspots according to the weighted values of the network articles and a preset public opinion hotspot judgment threshold value, and analyzing the attributes of the judged network public opinion hotspots. According to the method and device for finding the network public opinion hotspots based on the network article attributes, the network public opinion hotspots can be found rapidly and timely. The accuracy of finding the network public opinion hotspots is improved by firstly performing pretreatment, such as filtering junk information and de-weighting, on the network articles, and then judging values of the network articles according to several kinds of parameter attributes of the network articles.
Owner:HONG MAI JUXIN SOFTWARE TECH BEIJING
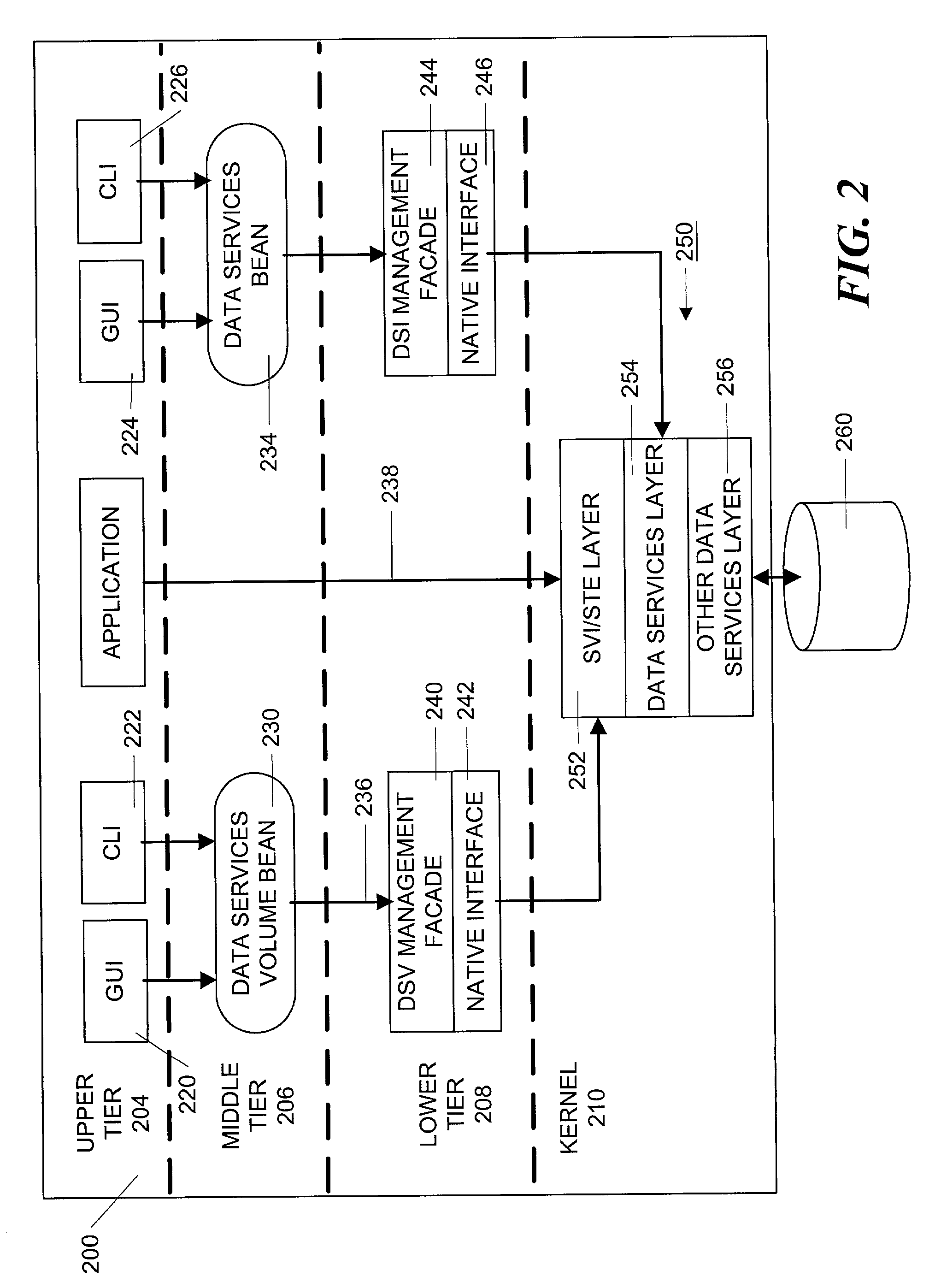
Method and apparatus for managing data services in a distributed computer system
InactiveUS7000235B2Quick discoveryInput/output to record carriersData switching networksSystems managementJava
Data services are managed by a three-tiered system. The lowest tier comprises management facade software running on each machine that converts a platform-dependent interface written with the low-level kernel routines that actually implements the data services to platform-independent method calls. The middle tier is a set of federated Java beans that communicate with the management facades and with the upper tier of the system. The upper tier of the inventive system comprises presentation programs that can be directly manipulated by management personnel to view and control the system.
Owner:ORACLE INT CORP
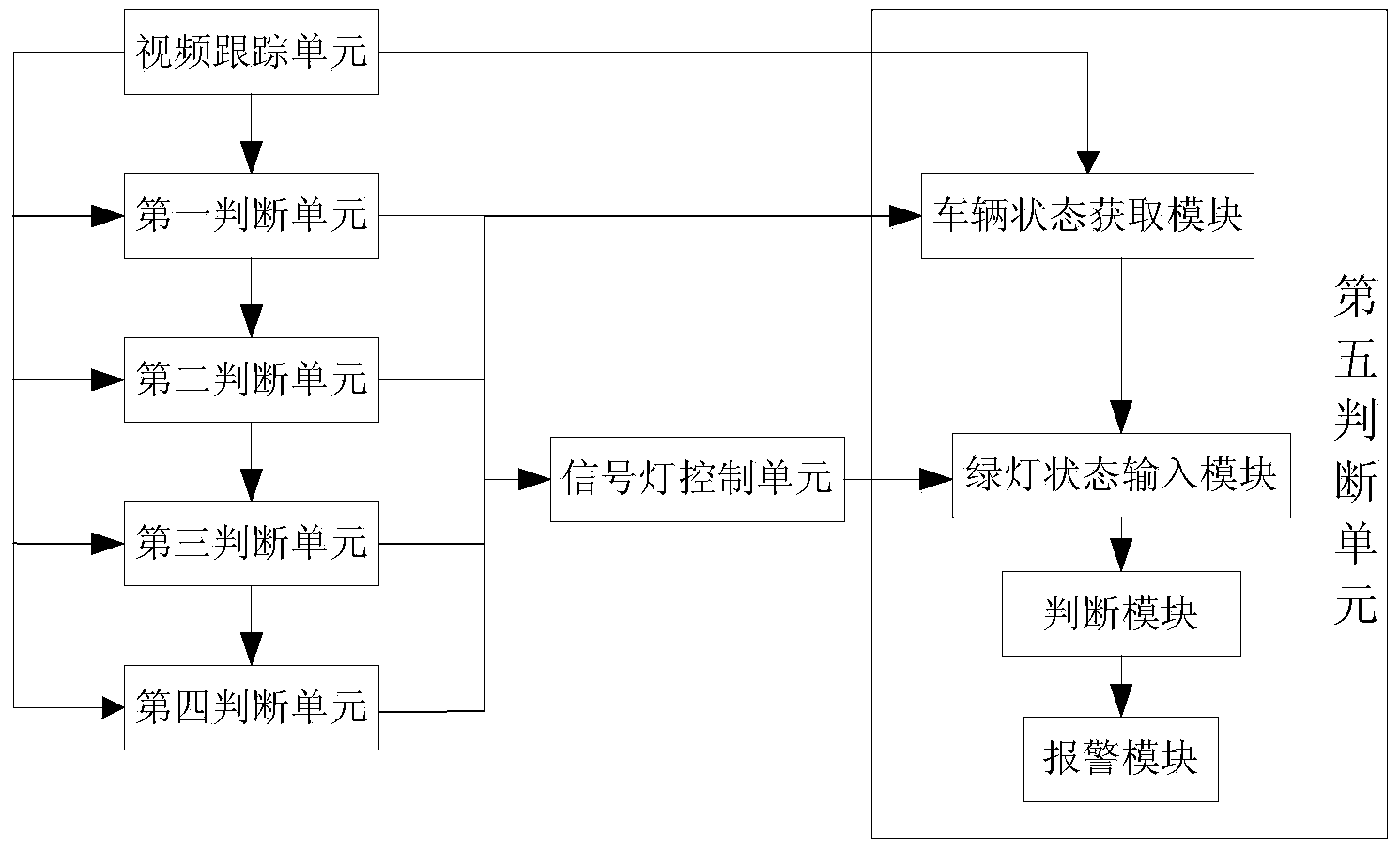
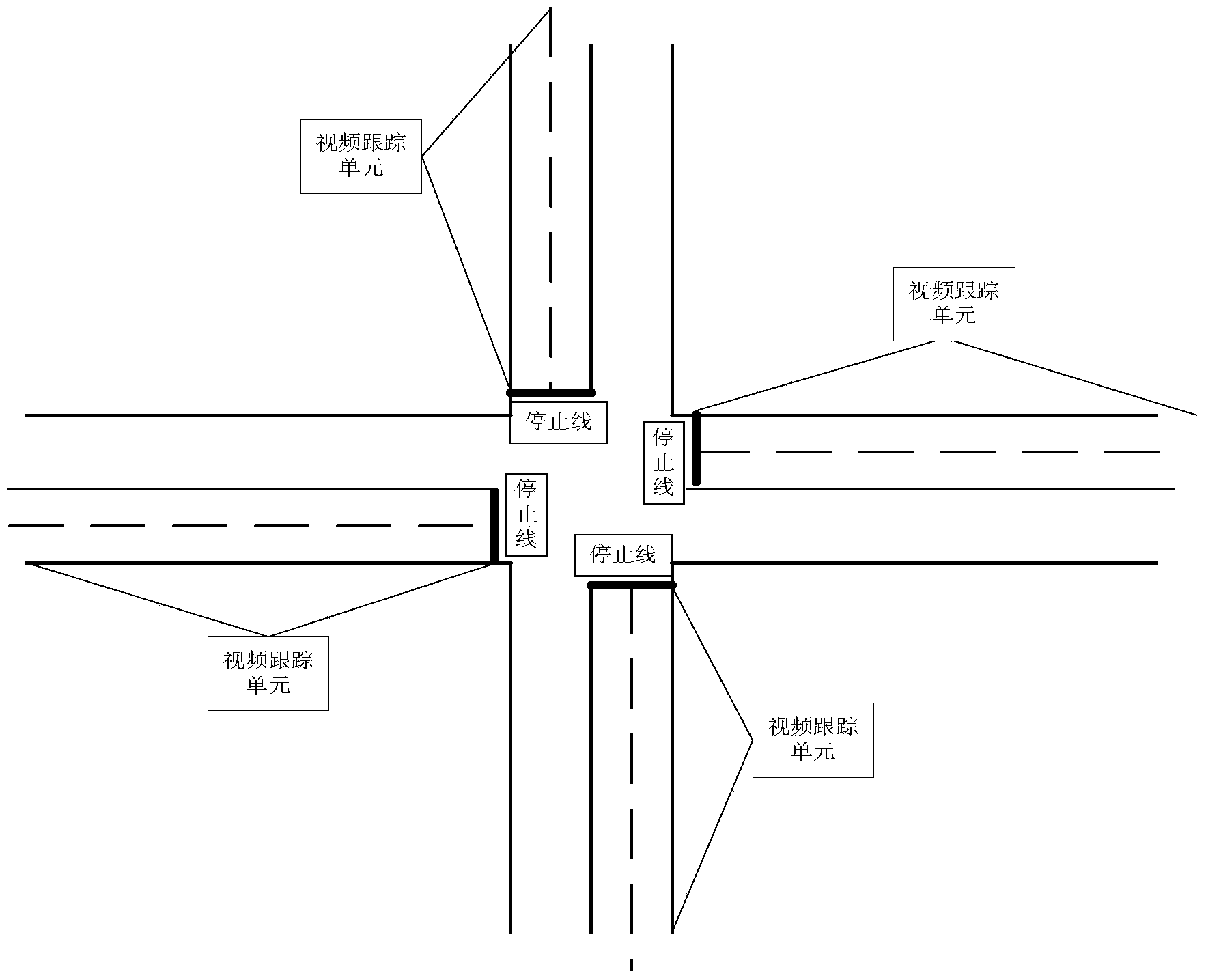
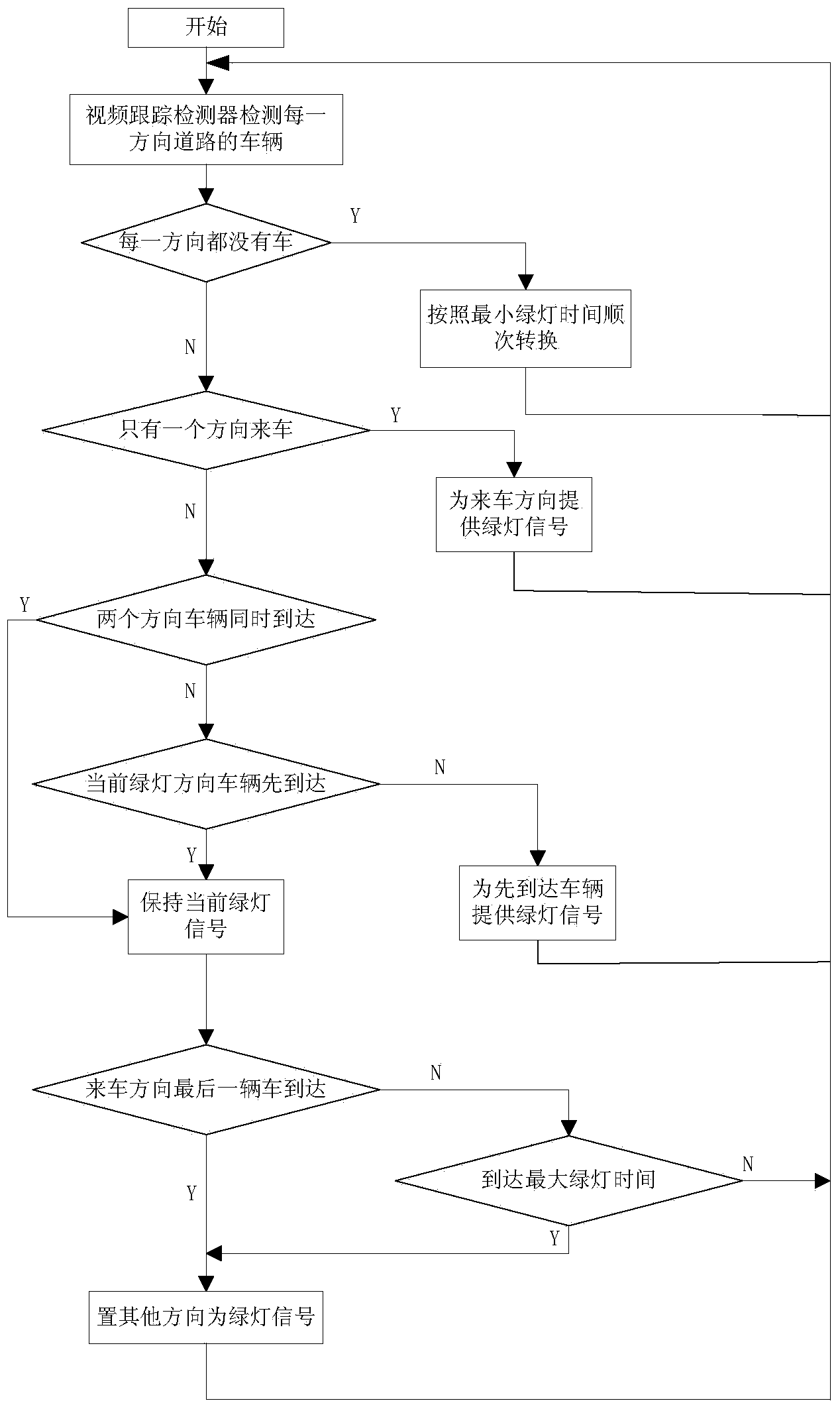
Intersection control machine capable of shortening green light lost time and control method
ActiveCN103956060AImprove efficiencyMake sure it's offControlling traffic signalsCurrent velocityEngineering
The invention provides an intersection control machine capable of shortening green light lost time and a control method. Detectors with the video tracking function are used for continuously tracking all vehicles passing an intersection, the time for each vehicle to reach an intersection stop line at a current speed can be accurately detected, when vehicles come from two directions at the same time, the vehicles which reach the stop line first can be accurately measured under the current road traffic conditions, on the premise that the current speeds of the vehicles in the two directions are kept, a green light signal can be preferentially provided for the vehicles which reach the stop line first, and the efficiency of the green light is improved. According to the technical scheme of the intersection control machine, the problem caused by the mode that only one or more detectors can be embedded in the cross section, nearby the intersection stop line or with a certain distance from the intersection stop line, of the intersection is solved.
Owner:BEIJING E HUALU INFORMATION TECH +1
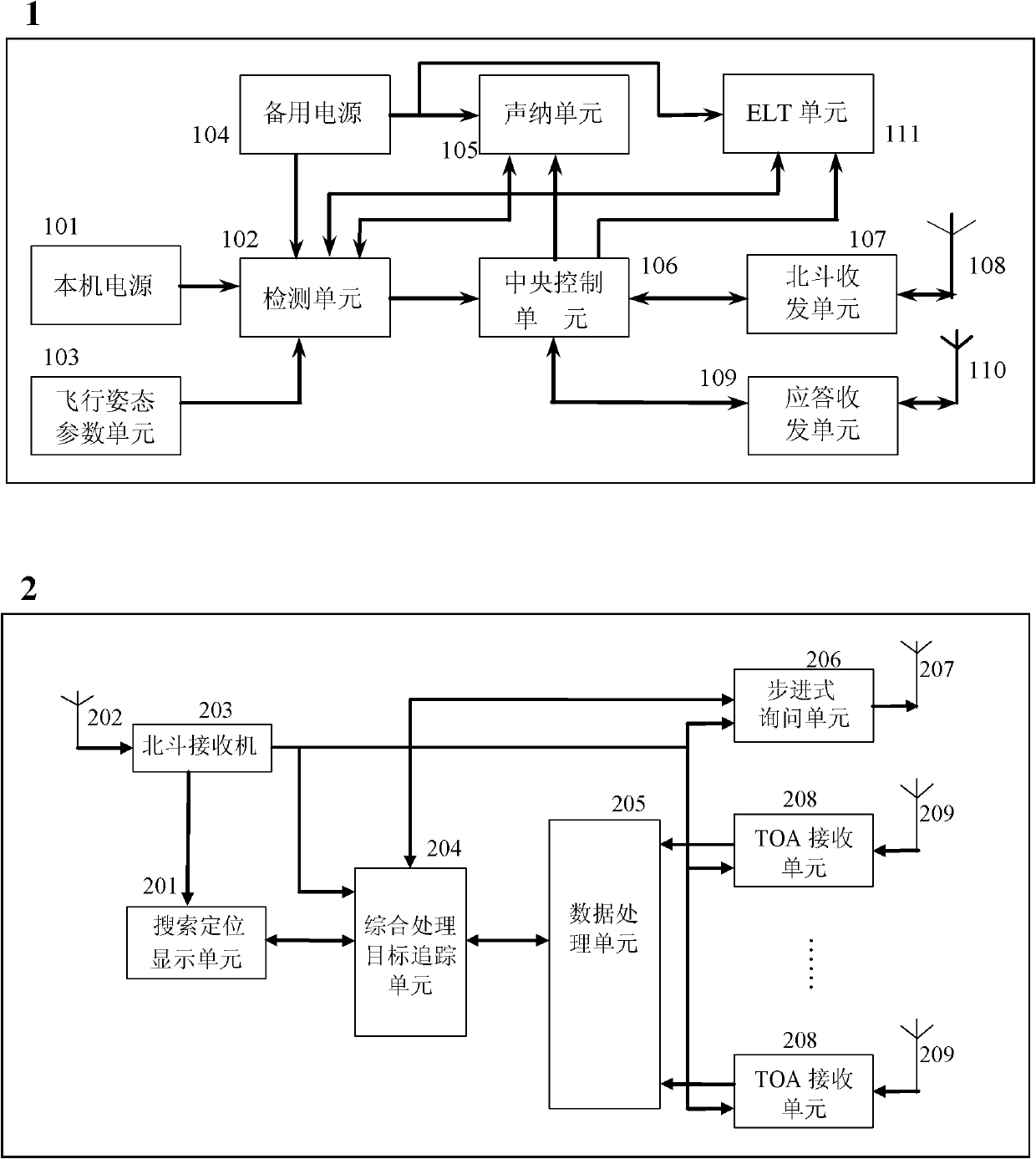
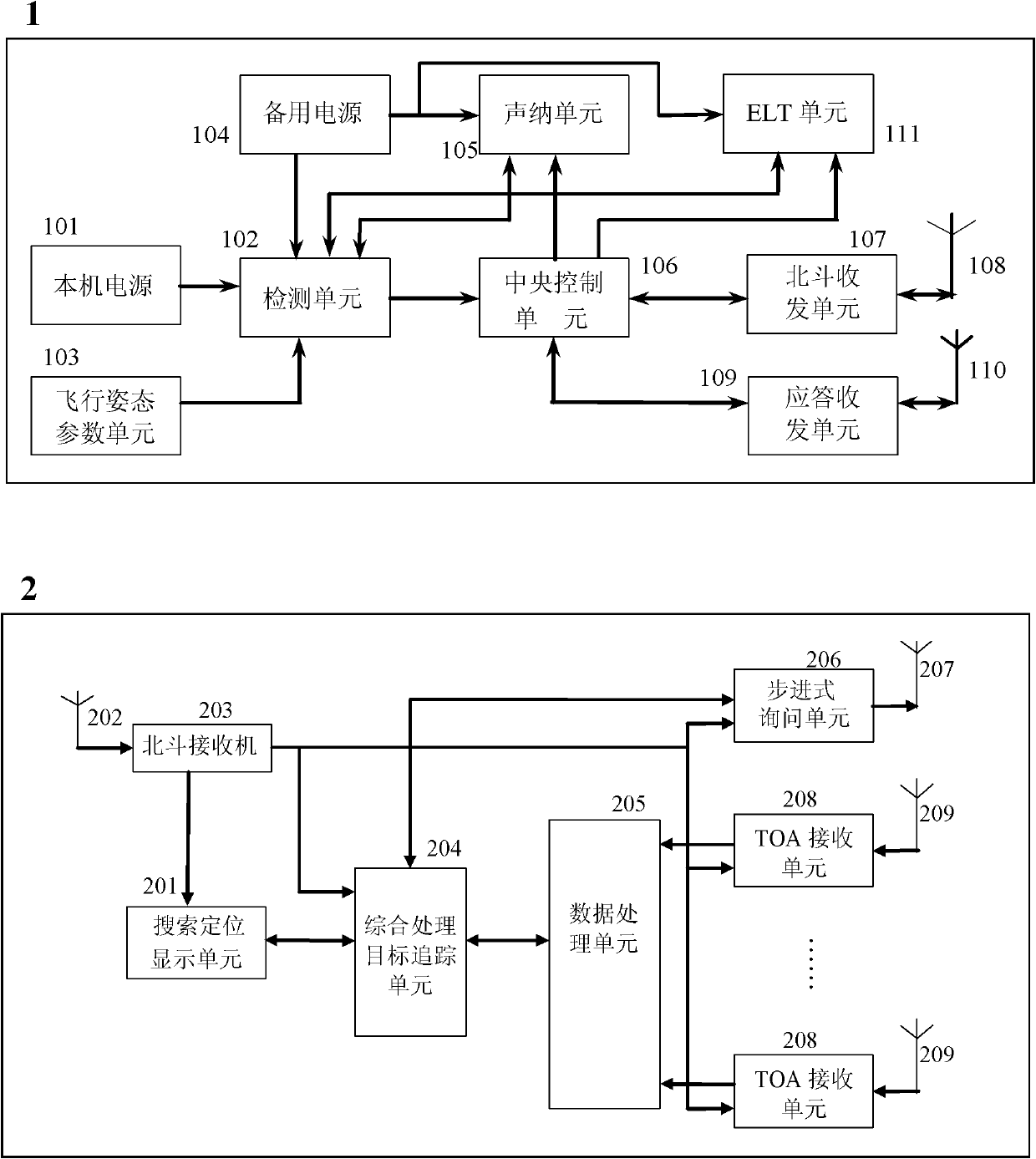
Stepping inquiry-response locating system for flight data recorder
InactiveCN102608636AQuick discoverySave human effortSatellite radio beaconingBroadcast packetJet aeroplane
The invention discloses a stepping inquiry-response locating system for a flight data recorder. The stepping inquiry-response locating system comprises a flight data recorder (FDR) airborne triones locating device and a ground mobile searching and locating device, wherein the FDR airborne triones locating device is installed in the flight data recorder; and the ground mobile searching and locating device is installed in a mobile ground station for search and rescue. The stepping inquiry-response locating system for the flight data recorder adopts a triones navigating and locating system, an inquiry-response mode and a multi-point locating system, and transmits a radio data packet which contains an identification code and position coordinates and has a designated response signal frequency,a searching and locating method comprises a mutual corroborating mode of the position coordinates of a cooperative and related locating algorithm, so research and rescue personnel can quickly find the flight data recorder of a wrecked airplane according to the received triones coordinate information and designated frequency, accordingly, the purpose of quickly finding an object is realized, a great deal of manpower, resources, financial resources and time can be saved, and the rescue efficiency is improved.
Owner:CIVIL AVIATION UNIV OF CHINA
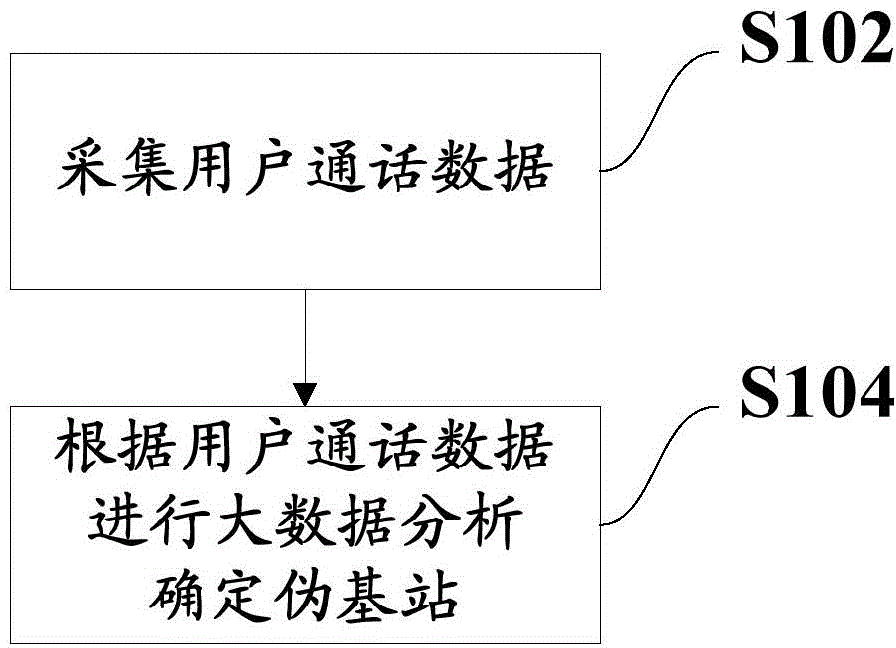
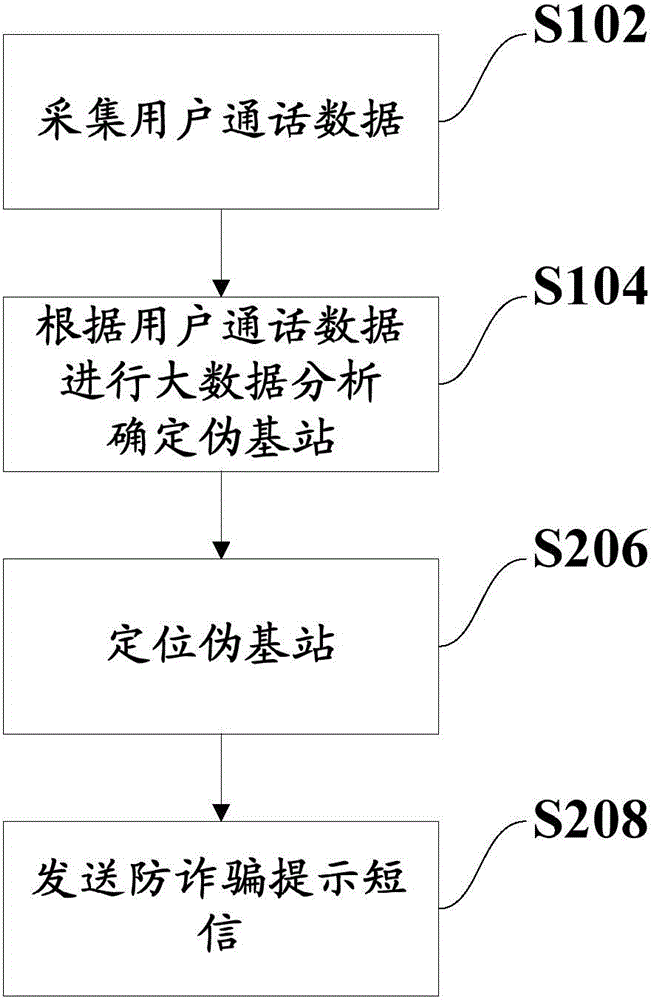
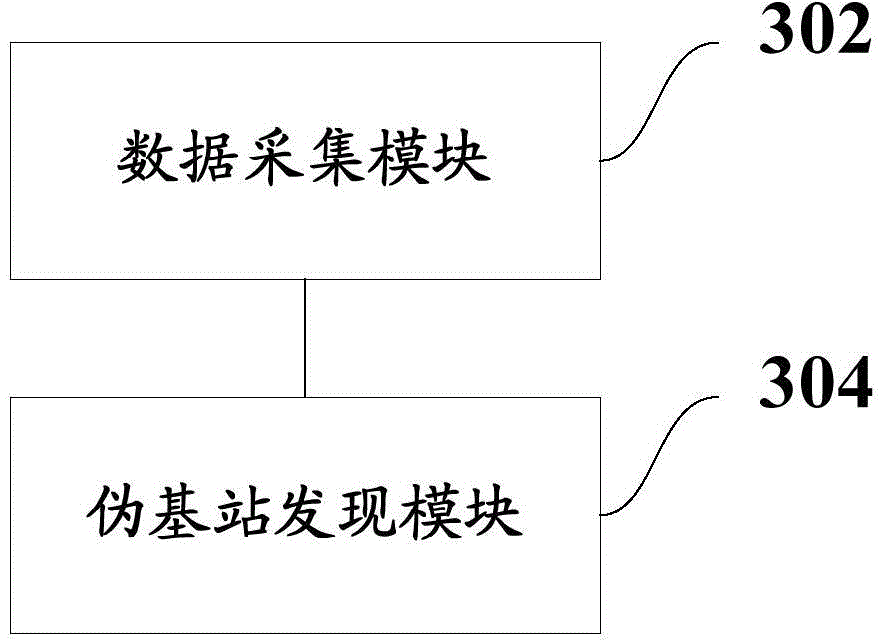
Pseudo base station discovery method and system
The invention discloses a pseudo base station discovery method and system, and relates to the field of wireless communication. According to an embodiment, big data analysis is performed on user call data through acquisition of the user call data which comprises one kind of information of a call establishment characteristic information, service quality-related information, call process behavior information, call release-related information and off-networking information, and a pseudo base station is discovered rapidly according to abnormal characteristic information, reflected in the user call data, of a terminal when the pseudo base station works. And a fixed pseudo base station can be discovered, and a moving pseudo base station can also be discovered.
Owner:CHINA TELECOM CORP LTD
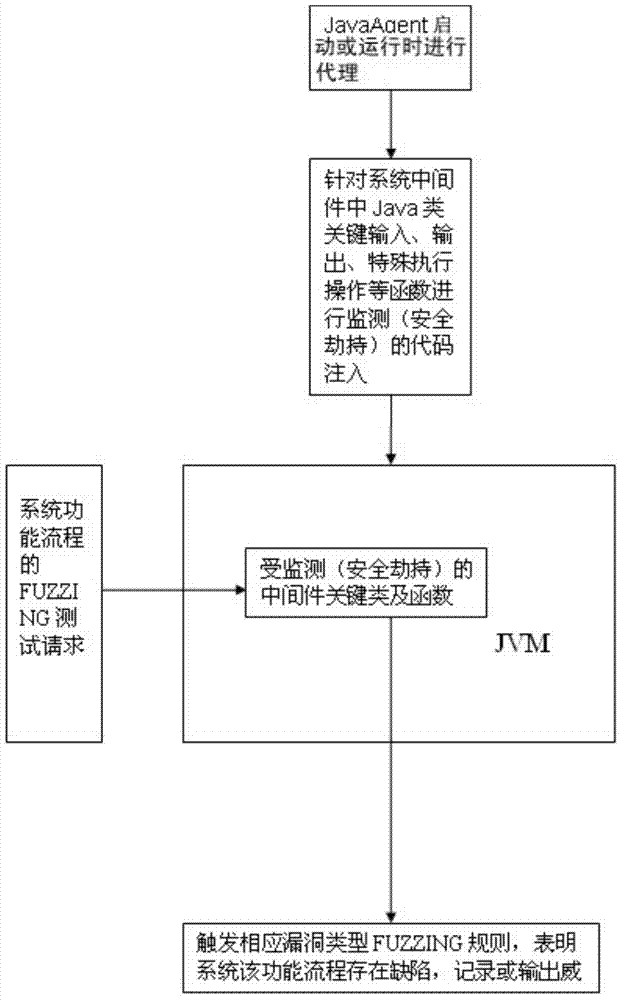
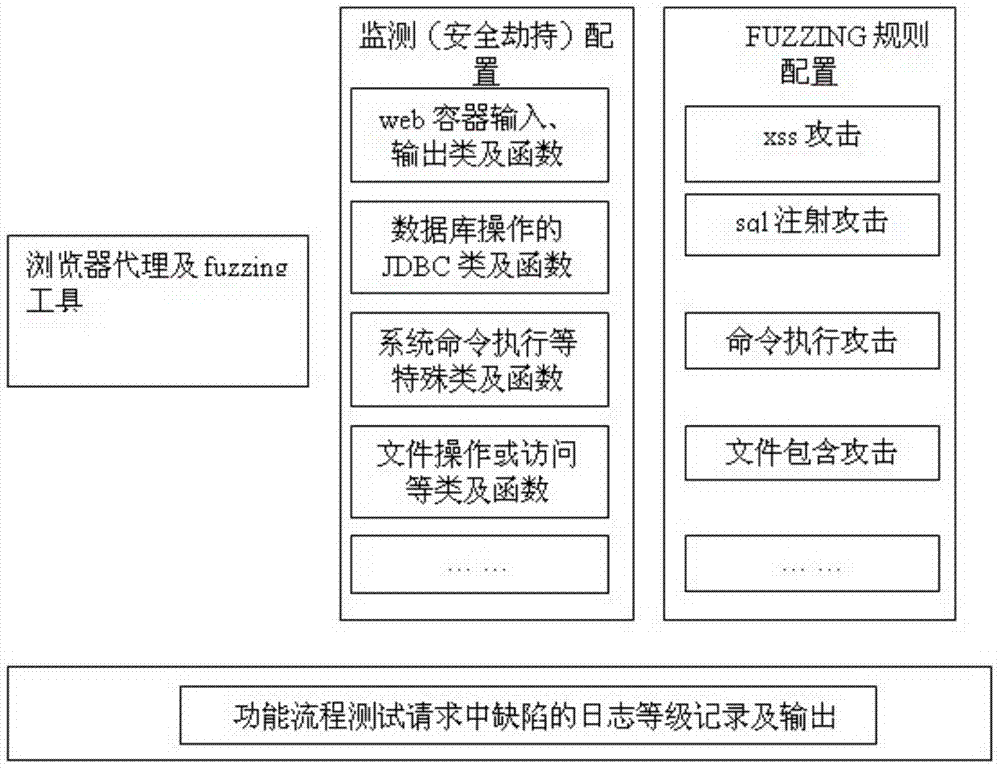
WEB dynamic security flaw detection method based on JAVA
The invention relates to a security test of WEB application, and aims to provide a WEB dynamic security flaw detection method based on JAVA. The WEB dynamic security flaw detection method based on JAVA is used for detecting the security flaws of a WEB application system, and comprises the following steps: modifying JAVA middleware; performing fuzzing test and dynamic flaw tracking. Due to the adoption of the WEB dynamic security flaw detection method, more WEB security flaw problems can be found rapidly, the security flaw range of black box test can be better covered, more deep WEB security problems can be found, the problem of high cost in white box test can be solved, the specific position of a flaw code can be determined more accurately, and lower missing report rate and error report rate in a detection process are ensured.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
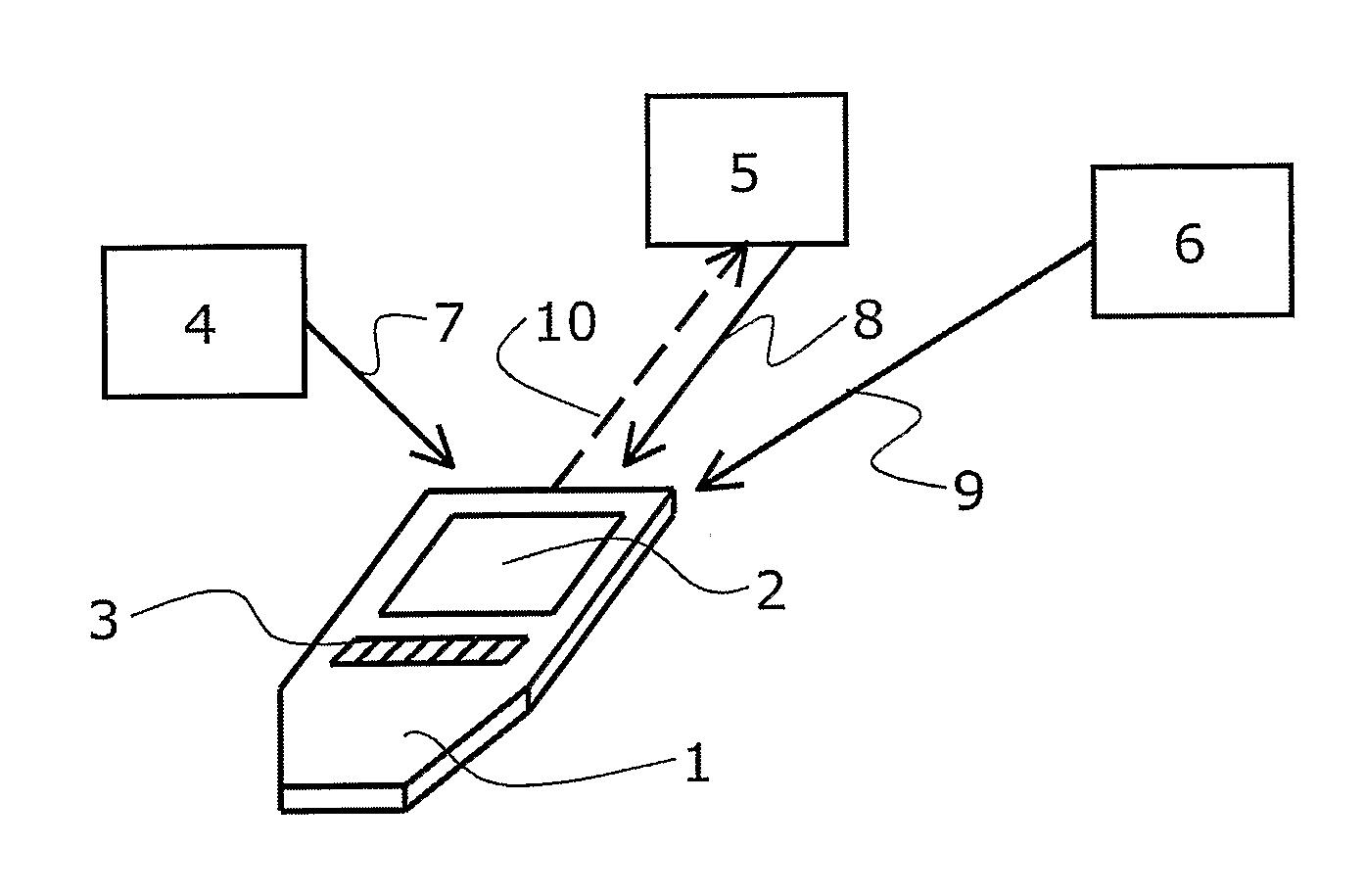
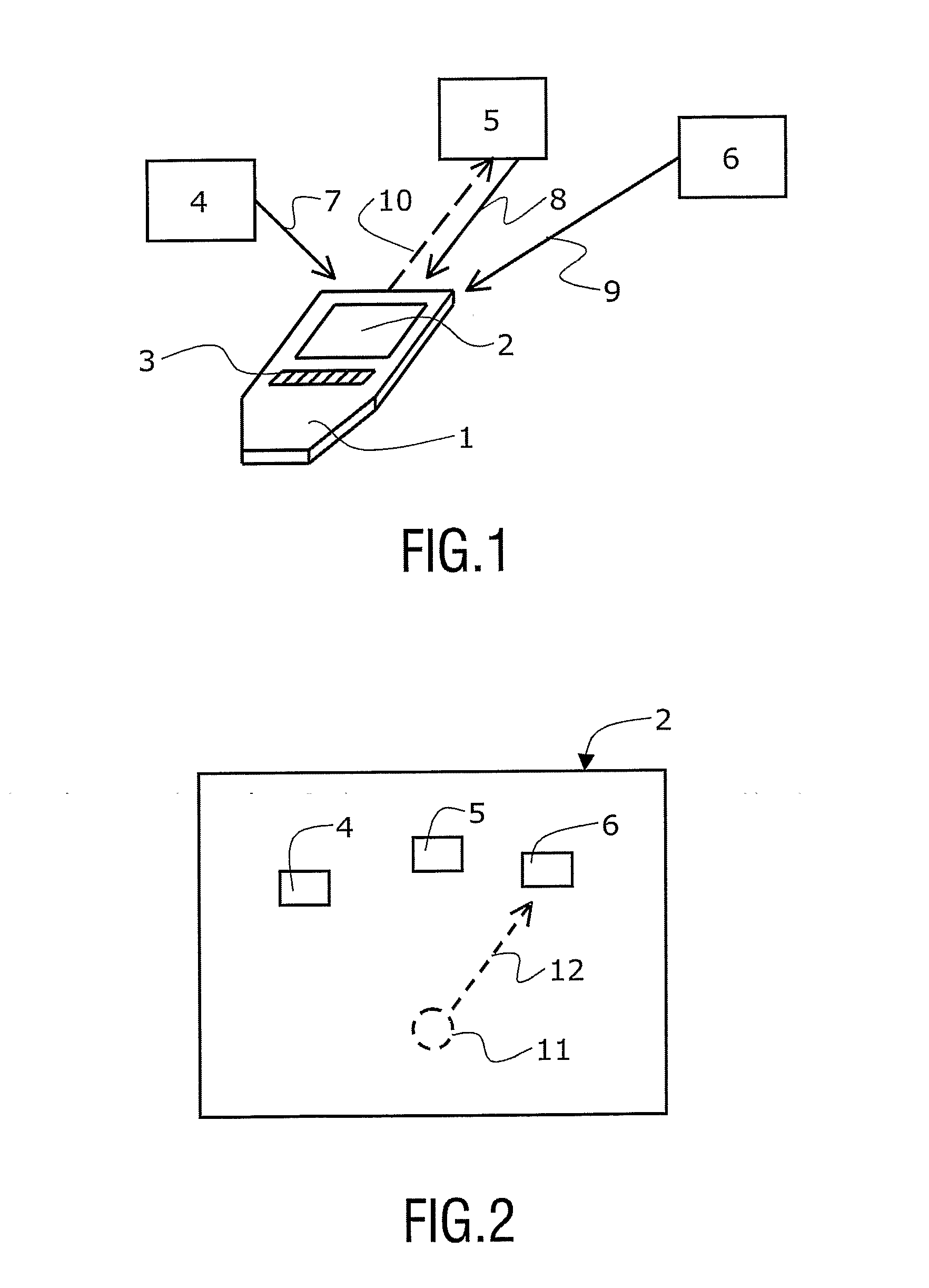
Spatial Interaction System
InactiveUS20070252721A1Quickly pinpointBreed fastTransmission systemsComputer controlRemote controlHuman–computer interaction
The present invention relates to a remote control device and a computer program product for control of a plurality of consumer-electronic devices. The remote control device comprises a user interface and means for determining an orientation of the remote control device relative to at least one of the consumer-electronic devices. The remote control device further comprises means for adapting the user interface based on said orientation of the remote control device.
Owner:PACE MICRO TECH
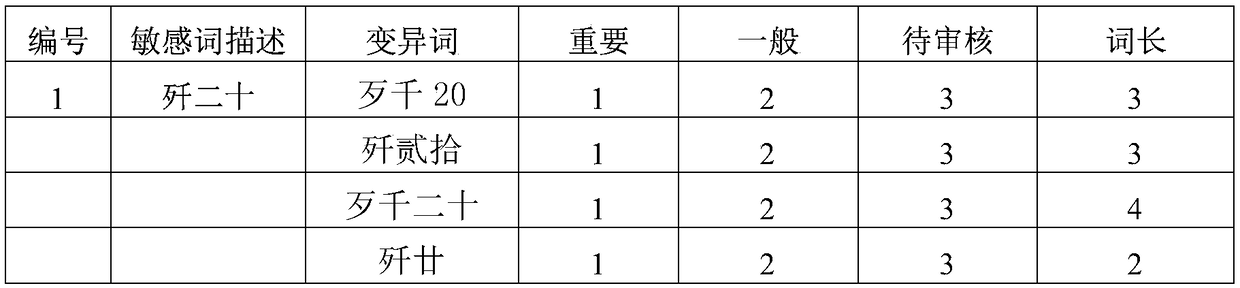
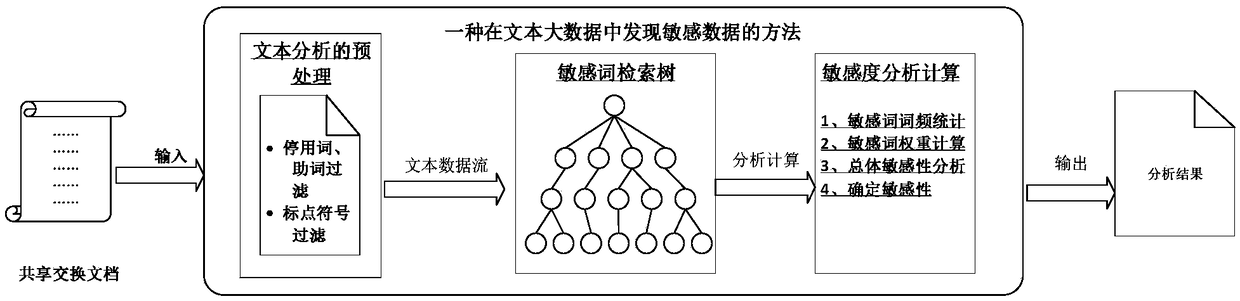
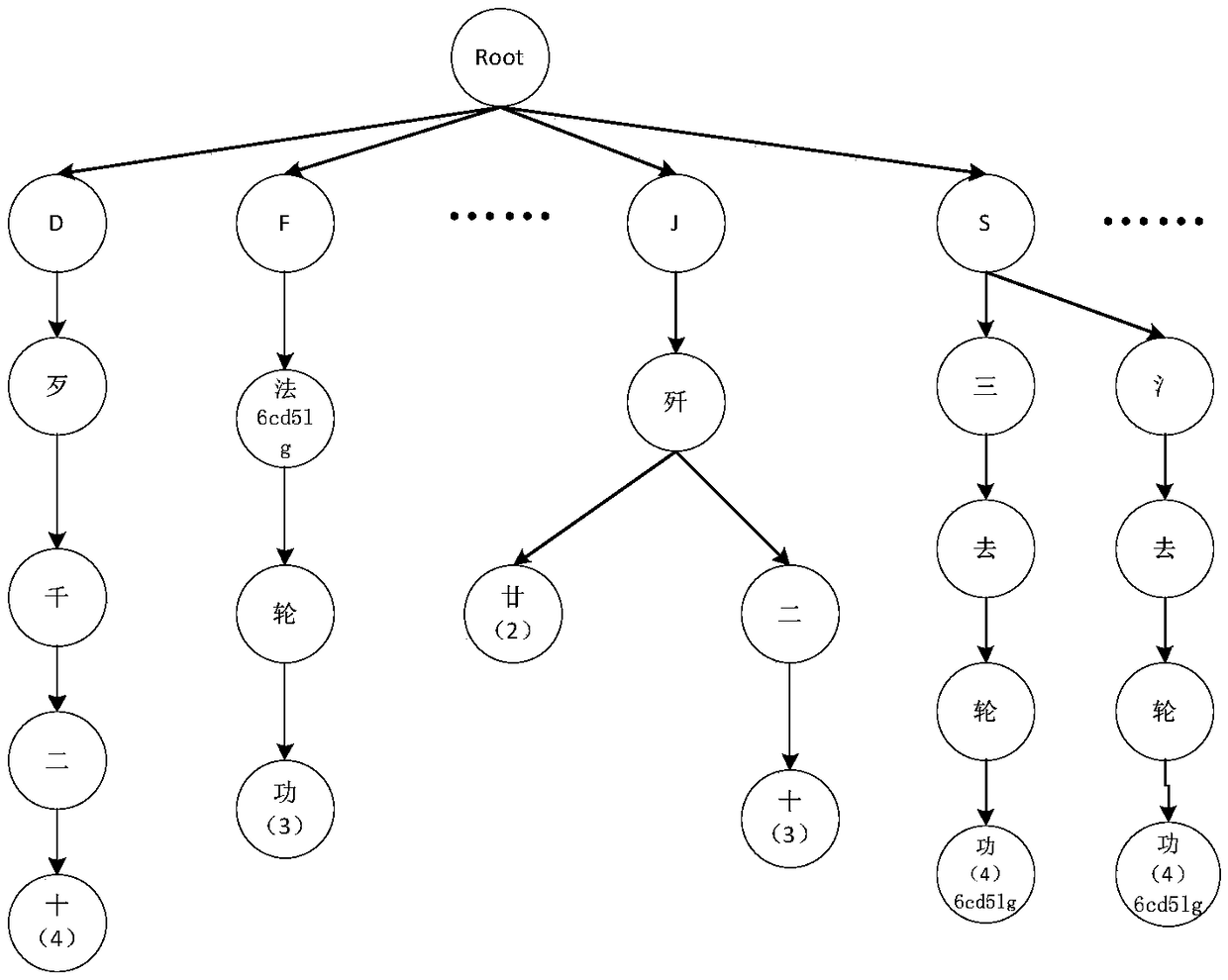
Method for discovering sensitive data in text big data
InactiveCN108280130AImprove efficiencyPrecise searchSpecial data processing applicationsInformation retrievalData science
The invention discloses a method for discovering sensitive data in text big data. The method comprises the following steps that a sensitive word information base is established; a sensitive word retrieval tree is established for all sensitive words in the sensitive word information base; sensitive word retrieval discover is carried out on a pretreated text with a character streaming through the retrieval tree, and the occurrence frequency of each sensitive word is counted; the sensitivity of a to-be-retrieved text is calculated by using the occurrence frequency of the sensitive words, documentclass, and weight rank of the sensitive words; the sensitivity of the to-be-retrieved text is compared with a preset threshold, and a retrieval text of which a sensitivity value exceeds the thresholdis determined to be a sensitive text. According to the method for discovering the sensitive data in the text big data, a method to quickly discover sensitive information of normalized and non-normalized description for massive heterogeneous texts is provided, the mode of the quick and accurate search combined with the fuzzy retrieval of the sensitive information achieves the quick discover of thepotential sensitive information.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
Method for locating meter reading fault source of low-voltage area
ActiveCN103760874APrecise positioningAccurate repairTotal factory controlProgramme total factory controlEmbedded systemReliability engineering
The invention discloses a method for locating a meter reading fault source of a low-voltage area. The method is characterized by comprising the following steps of obtaining a meter reading topology structure of the low-voltage area, defining a fault source recognition model, and utilizing the classification recognition method and the input data of the fault source recognition model to locate the fault source according to the topology structure and the meter reading results of meters. The method can locate the meter reading fault point accurately and effectively, and operation staff can remove faults timely and conveniently.
Owner:STATE GRID CORP OF CHINA +1
Depth study-based network risk early warning method
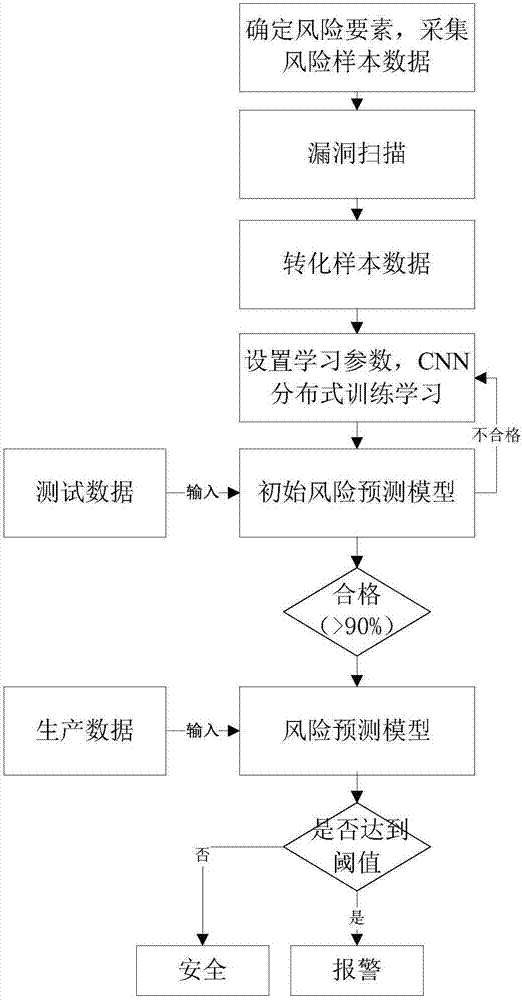
ActiveCN107104978AQuick discoveryQuick responseTransmissionSpecial data processing applicationsData miningRisk evaluation
The invention discloses a depth study-based network risk early warning method. The method comprises the following steps of: A1. collecting cyberspace asset risk sample data of a full network segment, and storing the cyberspace asset risk sample data in a database; A2. extracting data from the database, and performing convolutional neural network distributed training study, so as to form an initial risk prediction model; and A3. inputting production data into the risk prediction model, evaluating a risk value of the production data, if the risk value reaches an early warning threshold, alarming. Through adoption of the method and device, security risk evaluation and early warning are performed on multiple target networks or targets without obvious vulnerability, and the security state of one network can be evaluated overall; the response speed is improved, and the risk points can be found rapidly; and the maintenance cost is lowered, and the manpower is saved.
Owner:赖洪昌
Active-avoidance-based routing in a wireless ad hoc network
InactiveUS8509060B1Quick discoveryError preventionFrequency-division multiplex detailsNatural barrierWireless ad hoc network
Conventional multi-hop routing of ad hoc wireless networks involves considerations such as costs, connection quality, distances, and numbers of hops. A conventional wireless routing algorithm may fail when a destructive event takes place and is rapidly expanding in area, as the route discoveries may perpetually lag behind the rate of expansion of the destructive area. As typically embodied, the present invention's wireless routing algorithm detects a destructive event early, assumes rapid expansion of the destruction area, establishes “subnets” of nodes, and predetermines one or more routes that circumvent the rapidly expanding destruction area by exiting from and returning to the subnet in which the destructive event originates. Typical inventive practice avails itself of the architectural character of the physical setting for the wireless network, for instance by establishing subnets corresponding to compartments formed by wall-like structures (e.g., shipboard bulkheads), which represent natural barriers to expansion of a destruction area.
Owner:THE UNITED STATES OF AMERICA AS REPRESENTED BY THE SECRETARY OF THE NAVY
Virtual machine fault detection method and system based on data mining
InactiveCN106201828AQuick analysisQuick discoveryDetecting faulty computer hardwareHardware monitoringCluster algorithmTopological graph
The invention discloses a virtual machine fault detection method and system based on data mining. The system comprises a data collection module, a data analysis module and a display and alarm module. The method comprises the steps that real-time and historical data is collected through VMware vSphere SDK and a vCenter database; a coarse fine granularity combined collection way is used for obtaining data for providing necessary conditions for data mining; multiple algorithms are combined for analyzing mass data to build a fault diagnosis model, the state of a virtual machine is analyzed through a cluster algorithm, and a fault tree is further built for judging the fault type of the virtual machine; nodes with abnormal data mining results are reported to a user, and system conditions are displayed through a topological graph. Through tests, the system can well judge virtual machine health conditions and diagnose the fault type, the performance can sufficiently meet requirements of the user, and the system can be well compatible with other programs. Meanwhile, the system provides a unified solution for virtual machine fault detection.
Owner:云南电网有限责任公司信息中心
Forest fire detection method based on deep convolutional model with convolution kernels of multiple sizes
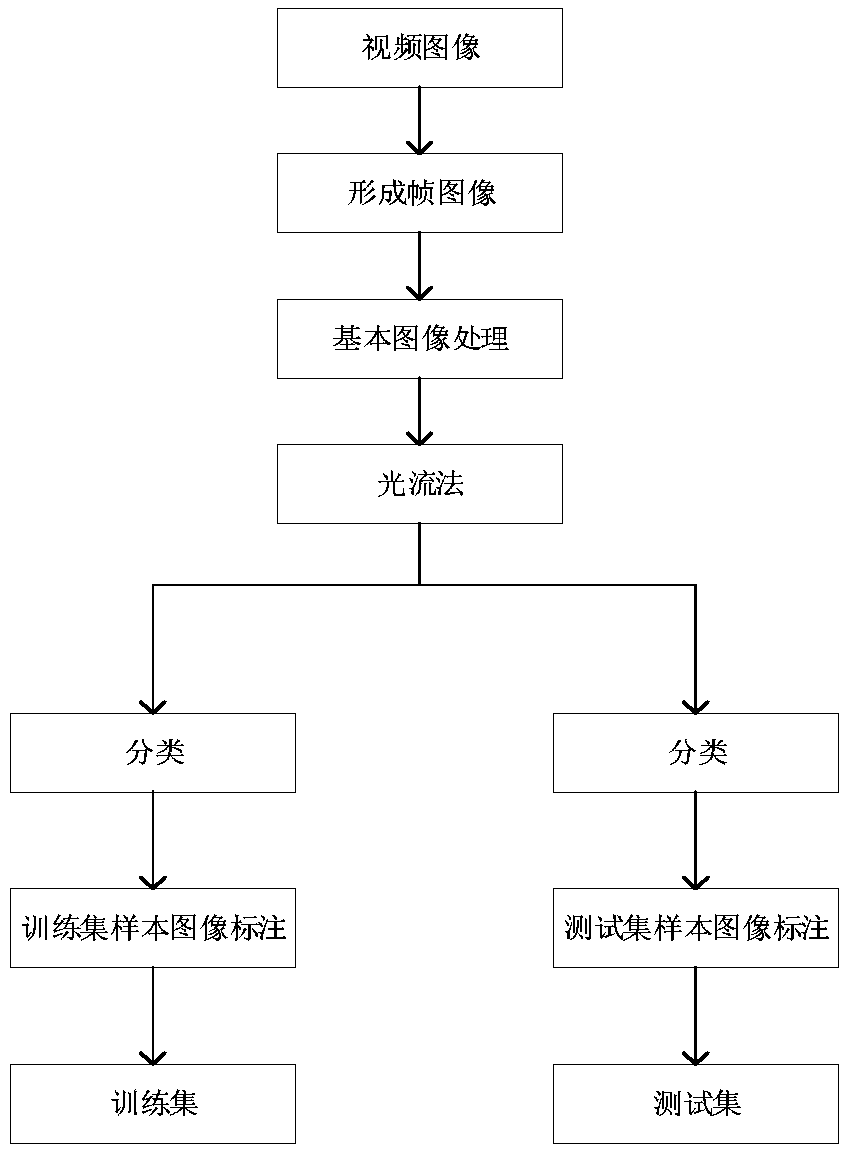
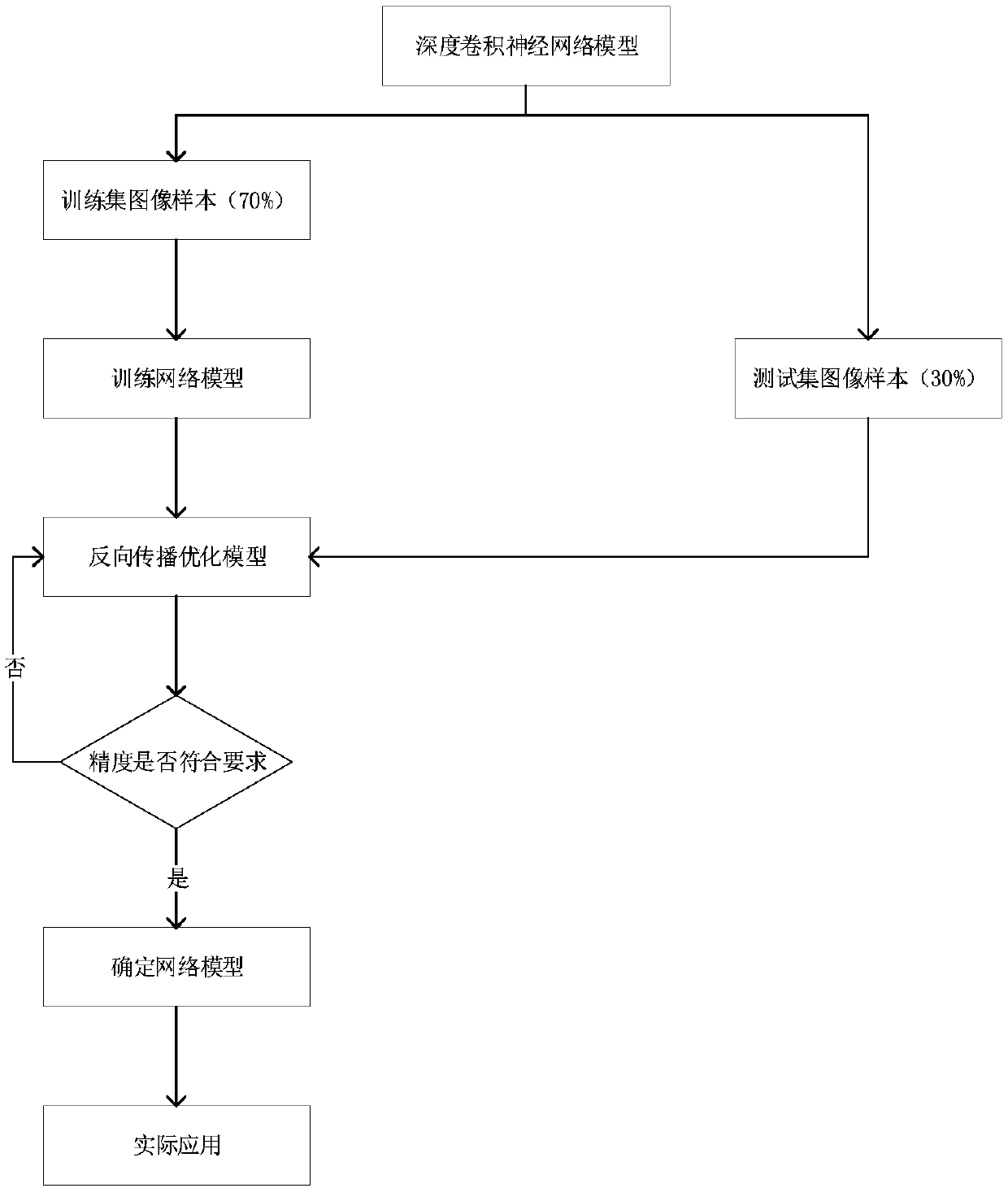
InactiveCN108921039AEfficient collectionImprove accuracyForest fire alarmsCharacter and pattern recognitionOptical flowConvolution theorem
The invention discloses a forest fire detection method based on a deep convolutional model with convolution kernels of multiple sizes, and relates to the technical field of deep learning video recognition. The method comprises the steps of collecting video image information; wirelessly transmitting data; forming an optical flow field; building a convolutional neural network model in deep learning;predicting a result; and the like. By training the deep convolutional neural network model with the convolution kernels of different sizes, an existing algorithm is improved; and in combination withexisting hardware conditions, the forest fire judgment speed is increased, the prediction precision of the whole model is improved, and the problems that an existing forest fire is not timely discovered and the economic loss is relatively serious can be effectively solved; and therefore, the method has a certain practical value.
Owner:南京启德电子科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com