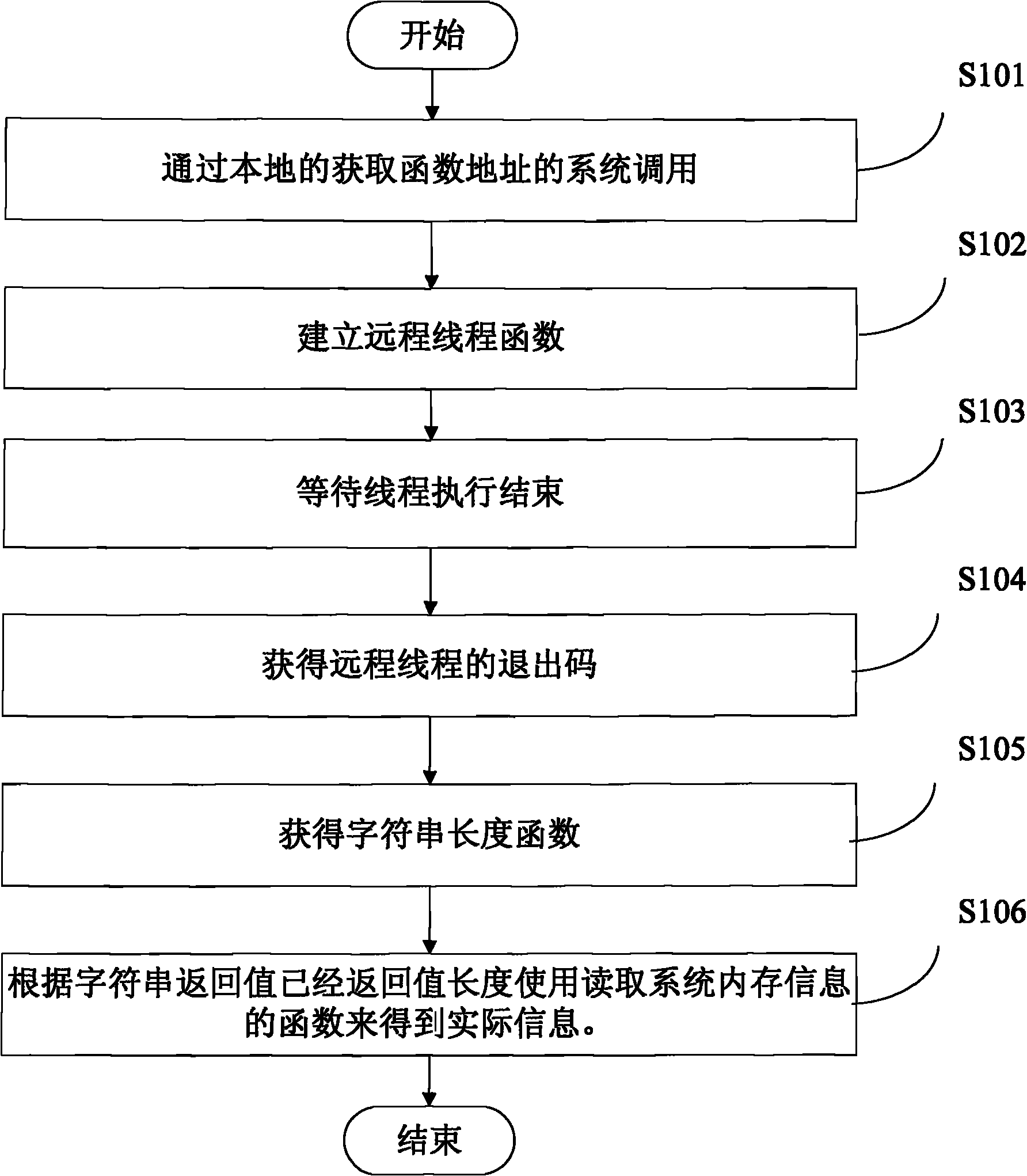
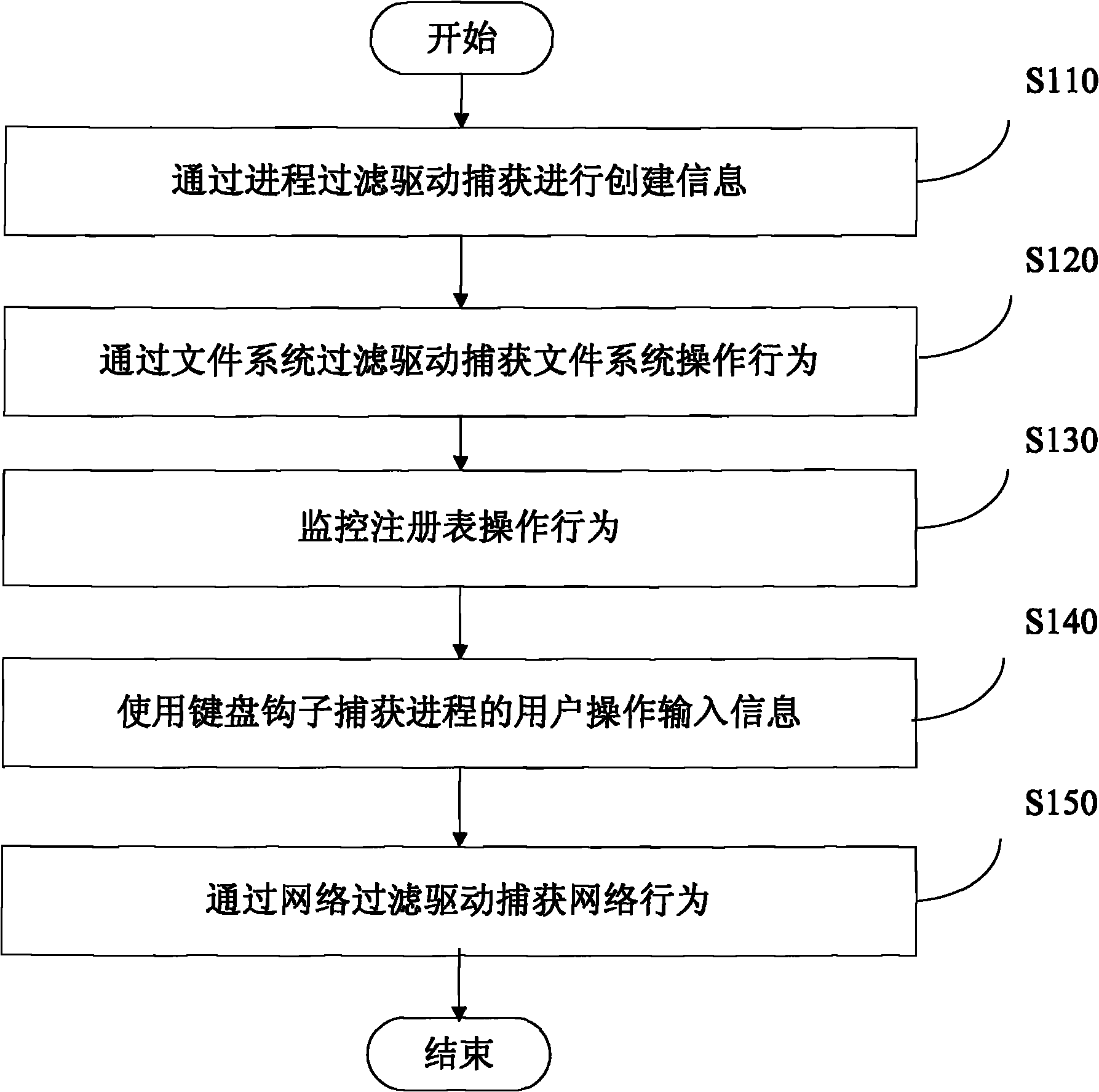
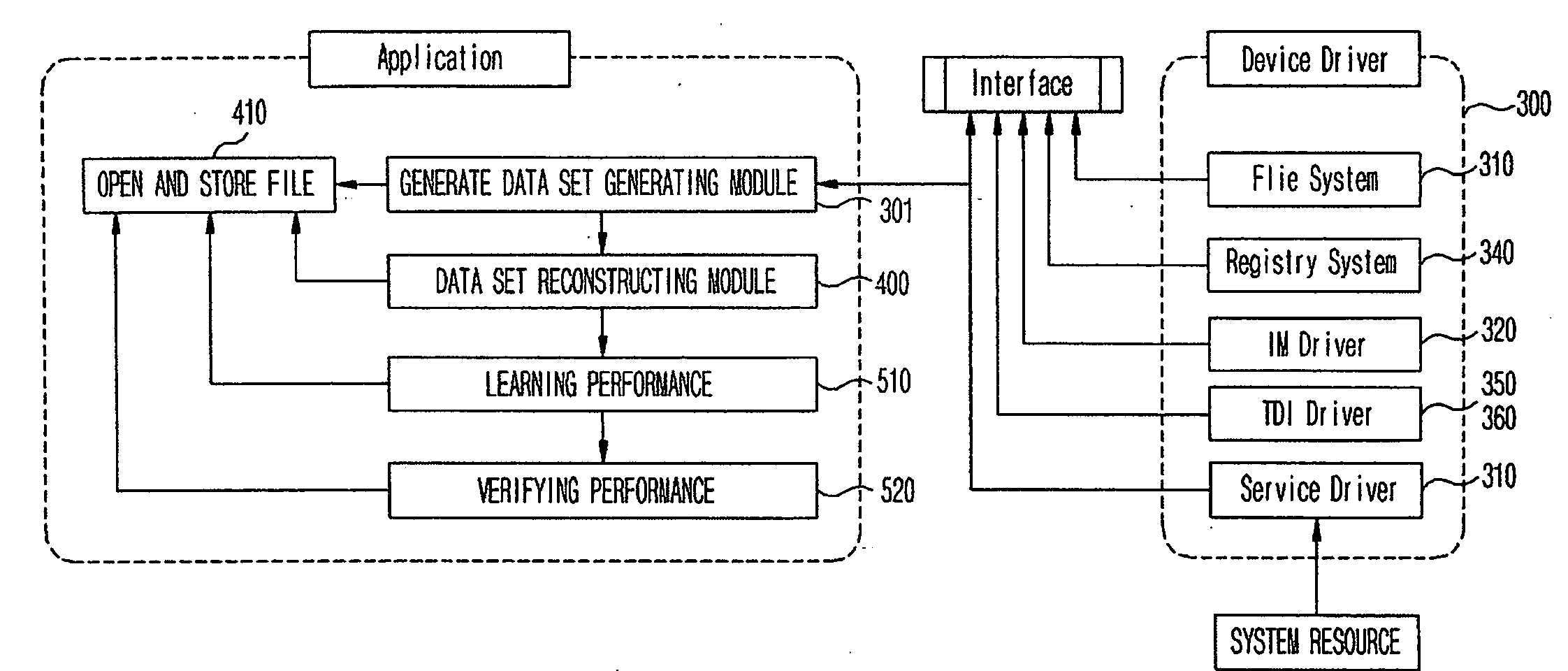
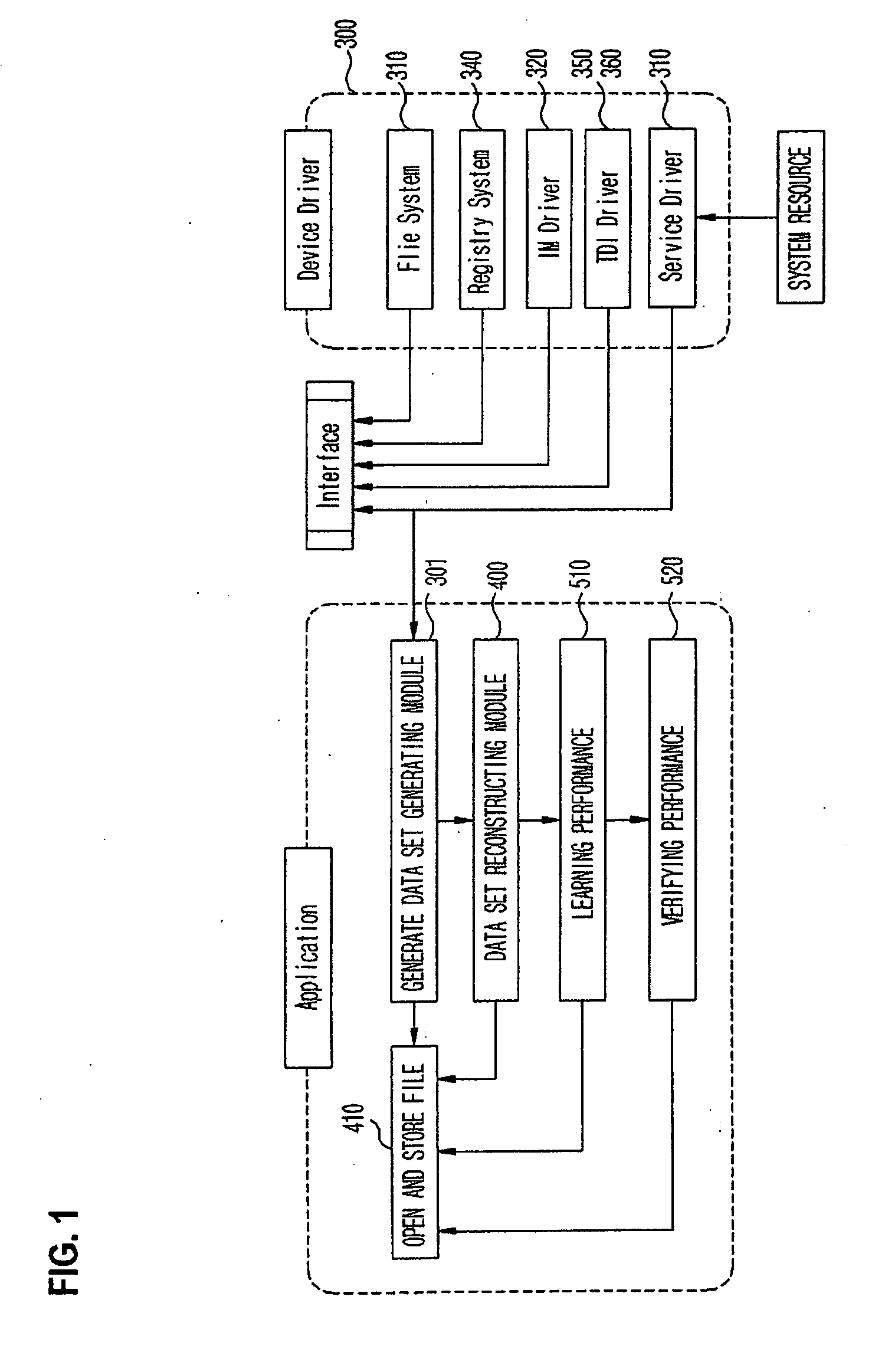
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
102 results about "Process behavior" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
PROCESS OF BEHAVIOUR. We assume that behaviour is caused and this assumption is true. Behaviour takes place in the form of a process. It is based on the analysis of behaviour process over the period of time.
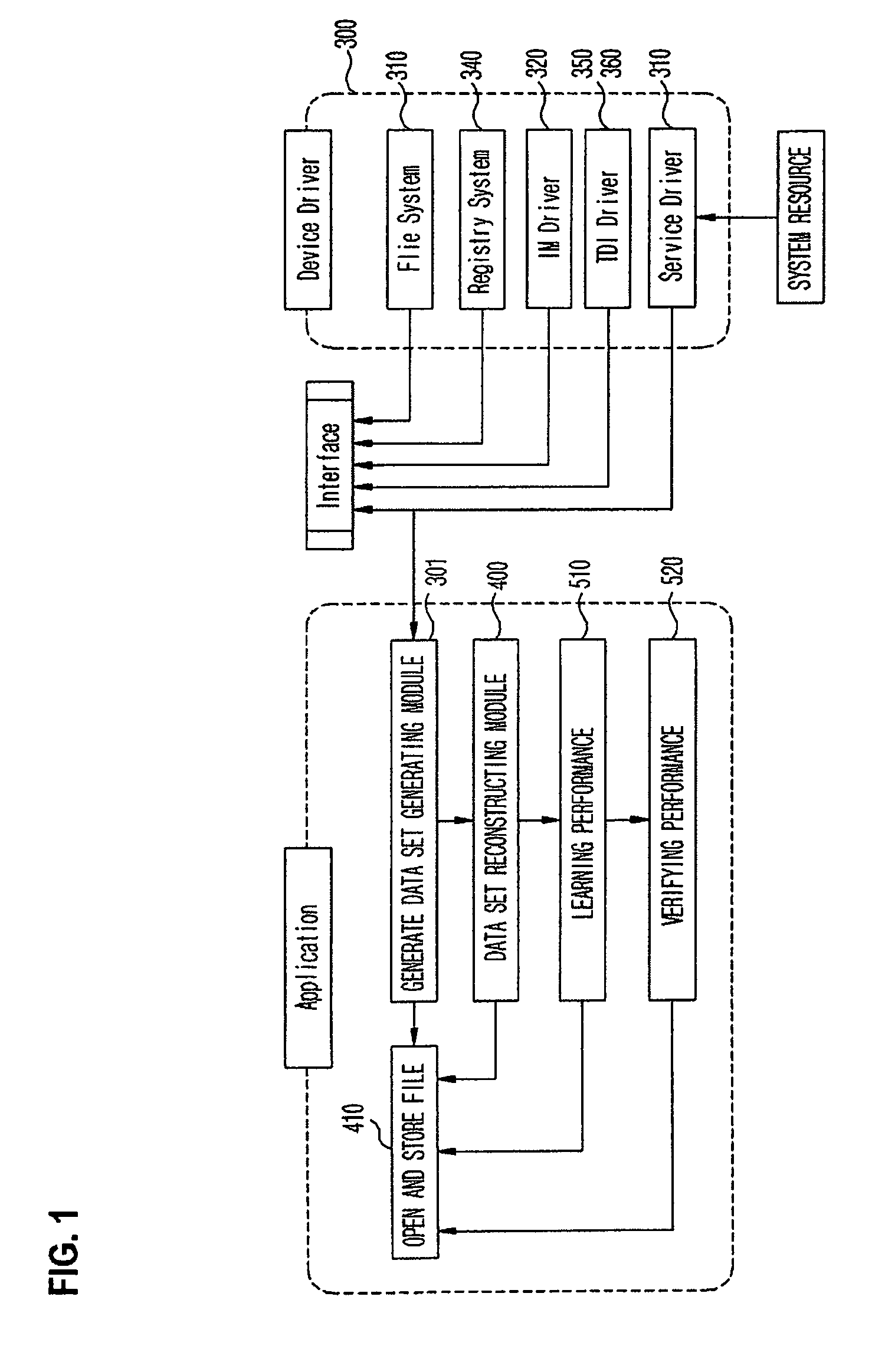
Antivirus protection system and method for computers
InactiveUS20080066179A1Reduce in quantitySimple methodMemory loss protectionUnauthorized memory use protectionProcess behaviorProgram behavior
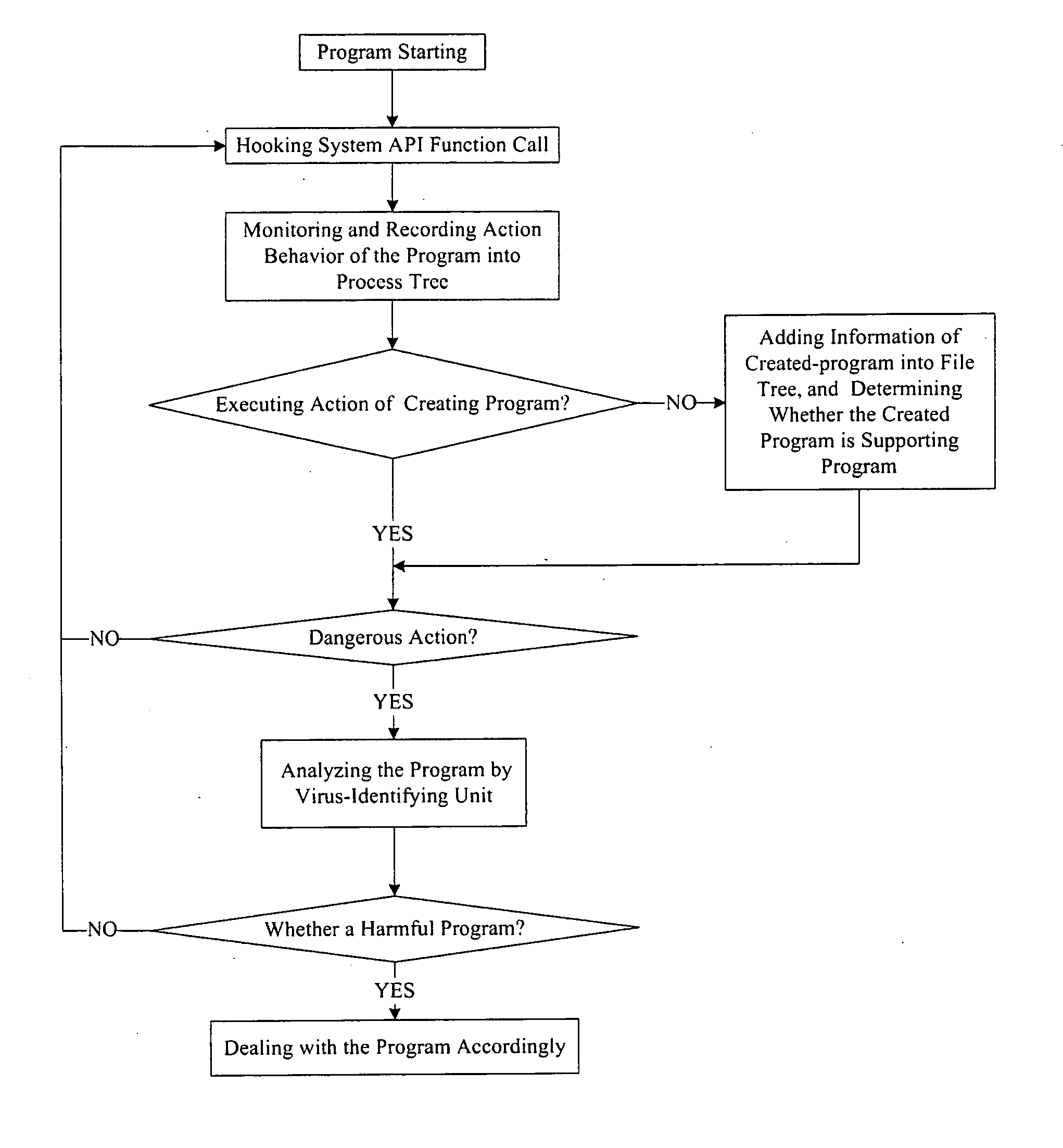
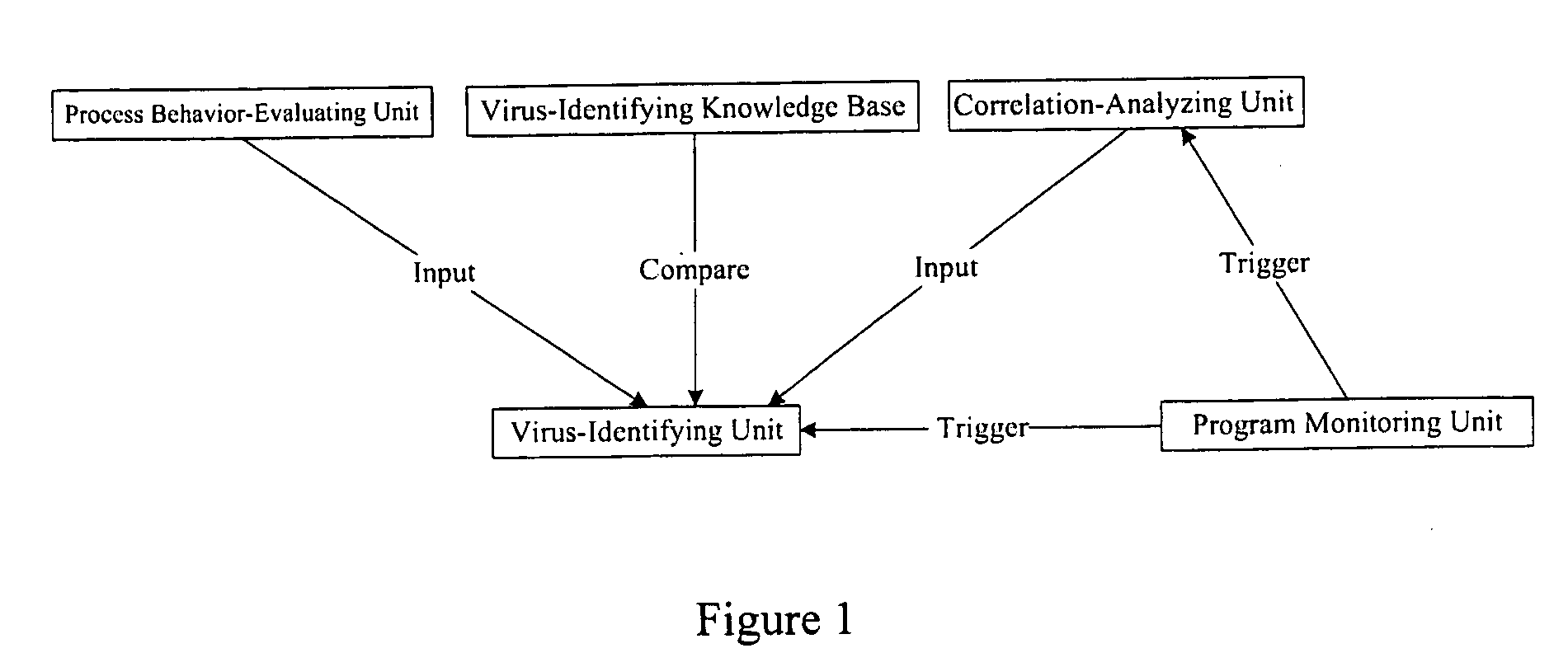
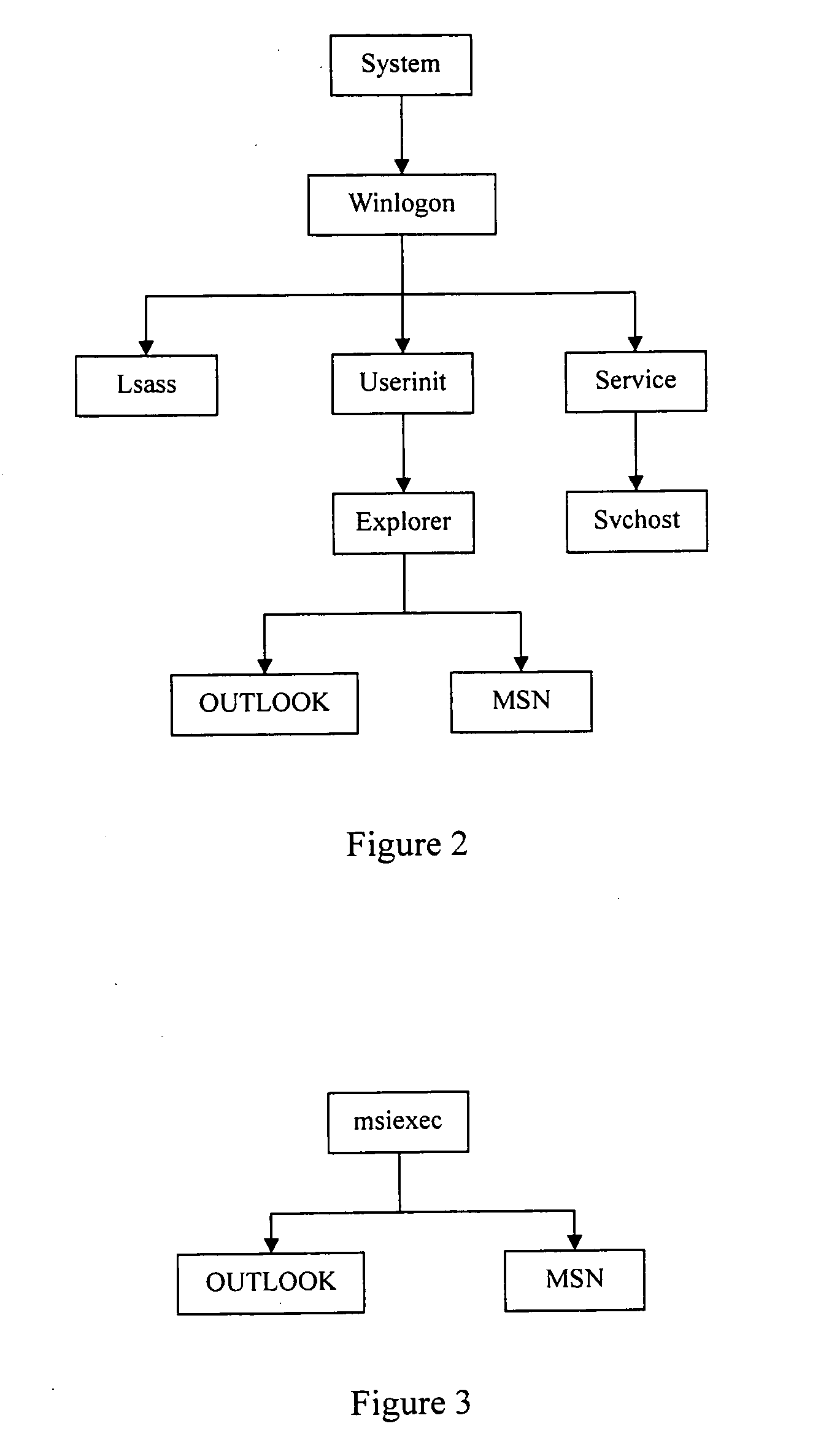
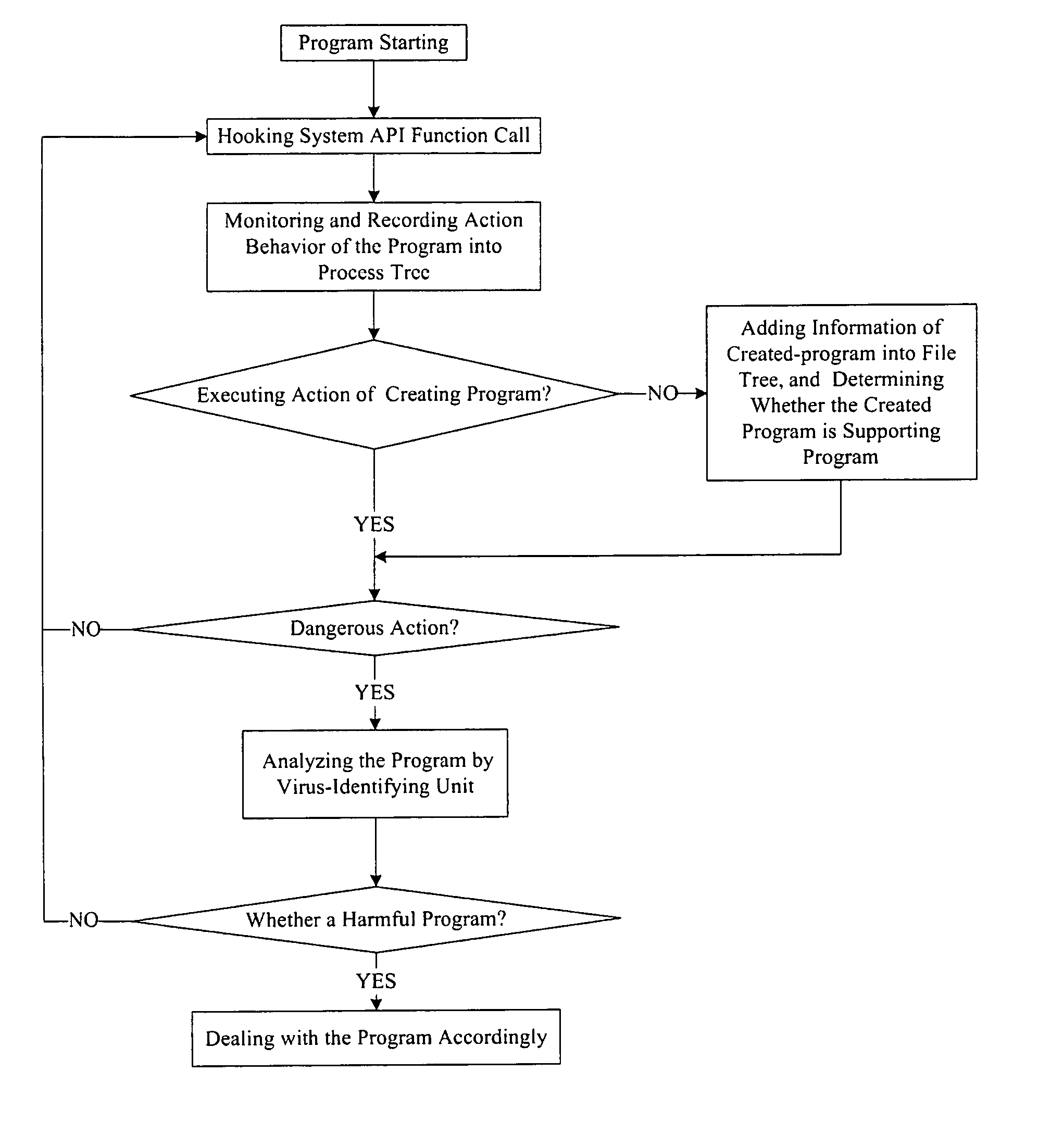
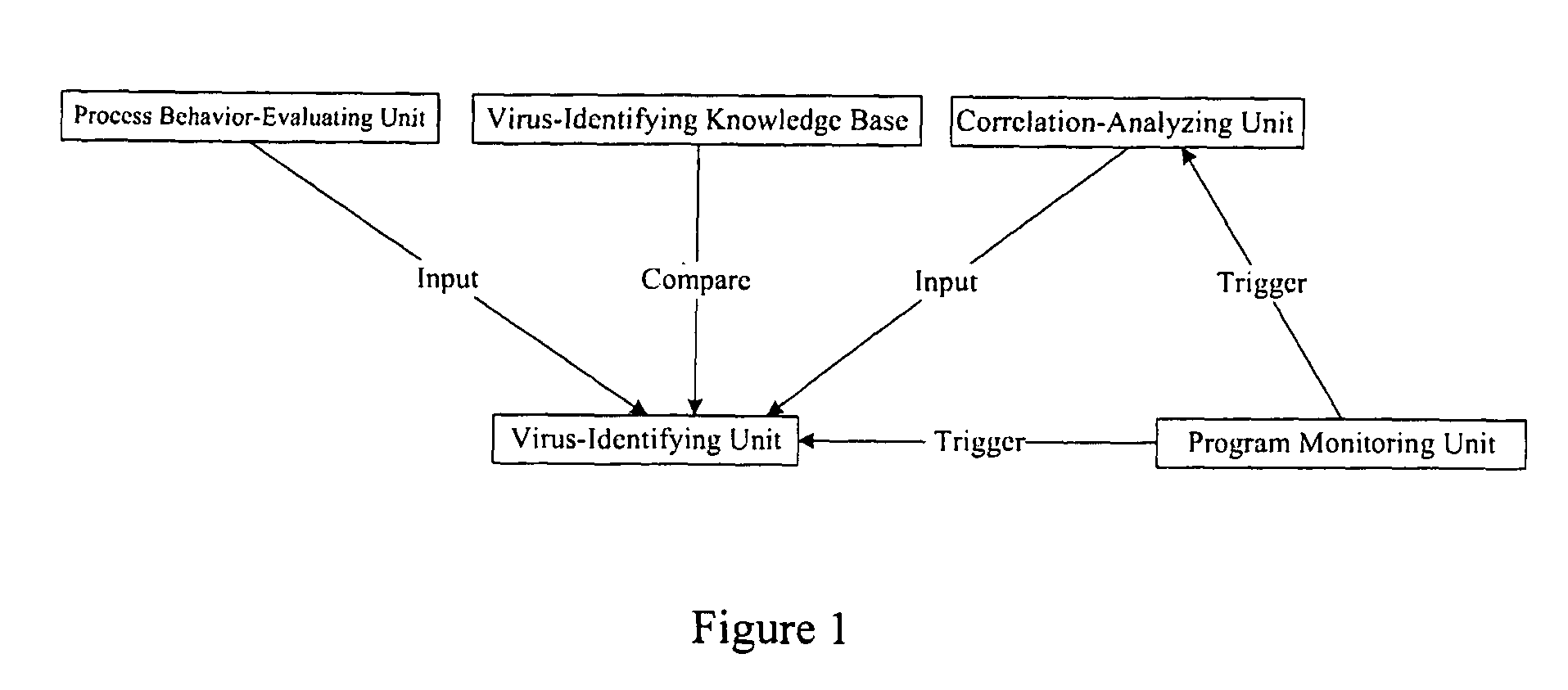
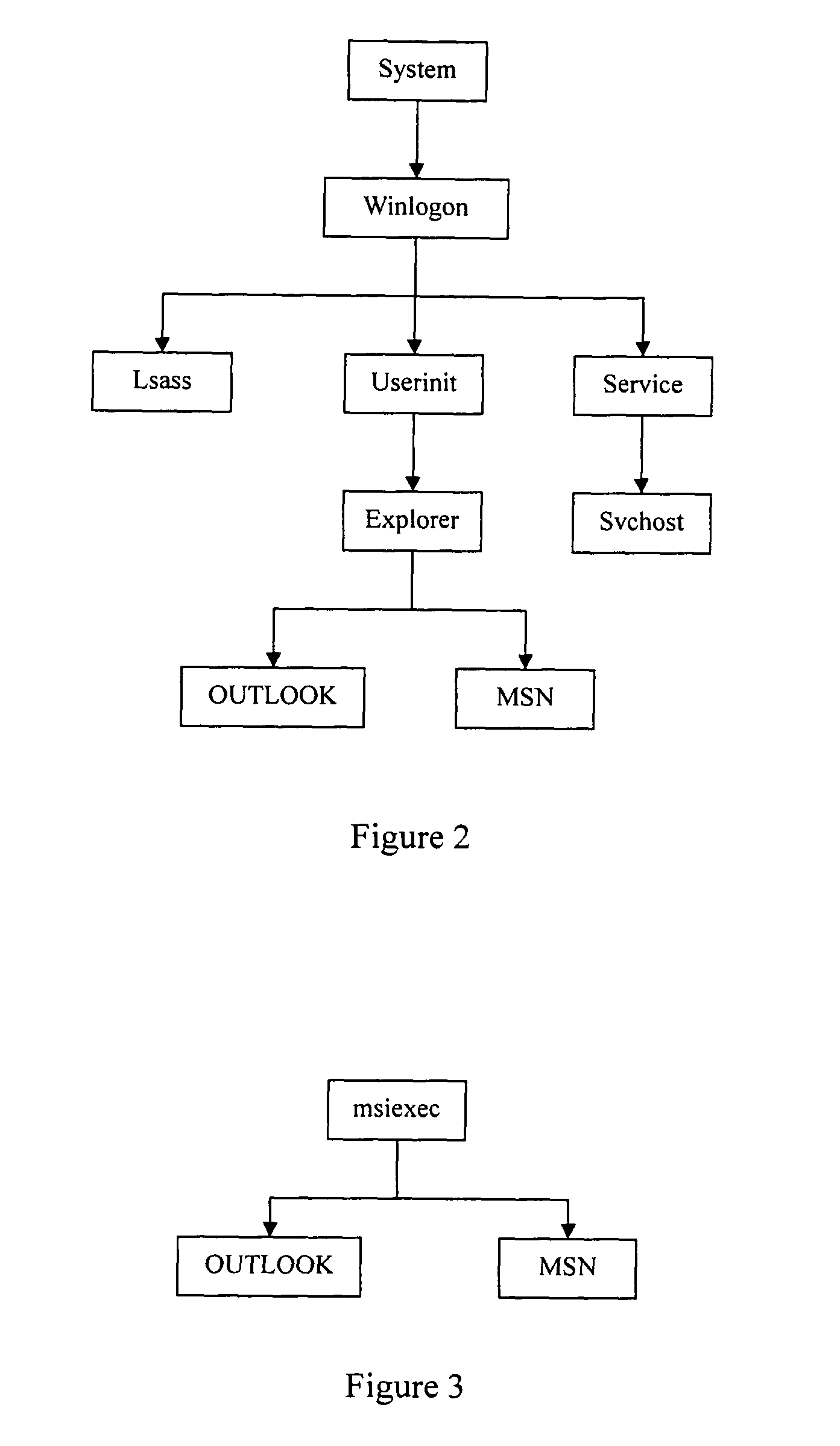
The example embodiments herein relate to an antivirus protection system and method for computers based on program behavior analysis. The antivirus protection system may comprise: a Process Behavior-Evaluating Unit for identifying the programs existing in the user's computers and classifying them into normal programs and suspect programs; a Program-Monitoring Unit for monitoring and recording the actions and / or behaviors of programs; a Correlation-Analyzing Unit for creating correlative trees and analyzing the correlations of actions and / or behaviors of programs, the correlative trees comprising a process tree and a file tree; a Virus-Identifying Knowledge Base, comprising a Program-Behavior Knowledge Base and a Database of Attack-Identifying Rules; a Virus-Identifying Unit for comparing captured actions and / or behaviors to the information in the Virus-Identifying Knowledge Base to determine whether the program is a virus program. With the techniques of certain example embodiments, it may be possible to increase efficiency and reduce the need to upgrade virus codes after viruses become active, while also effectively blocking unknown viruses, Trojans, etc.
Owner:FUJIAN EASTERN MICROPOINT INFO TECH
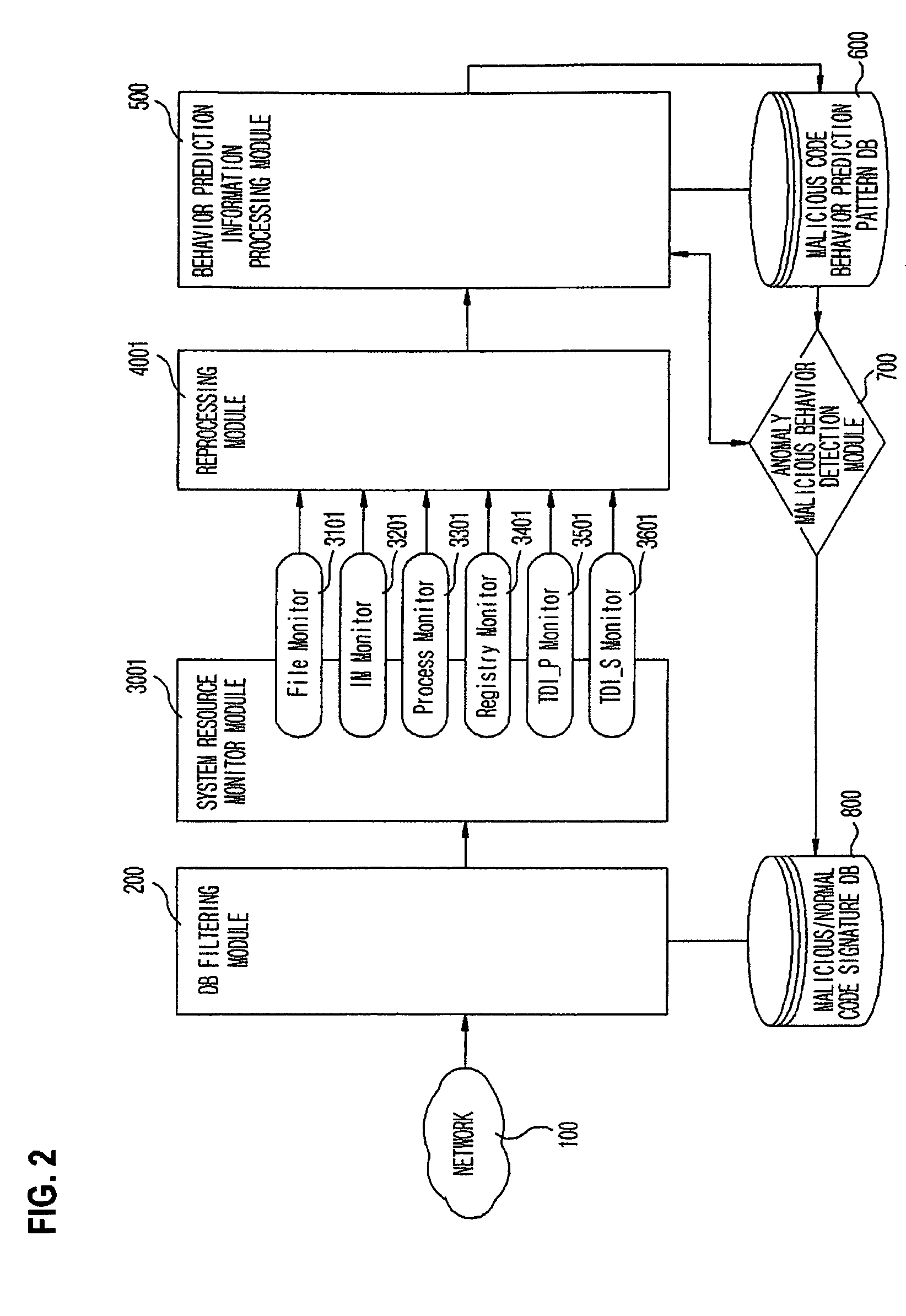
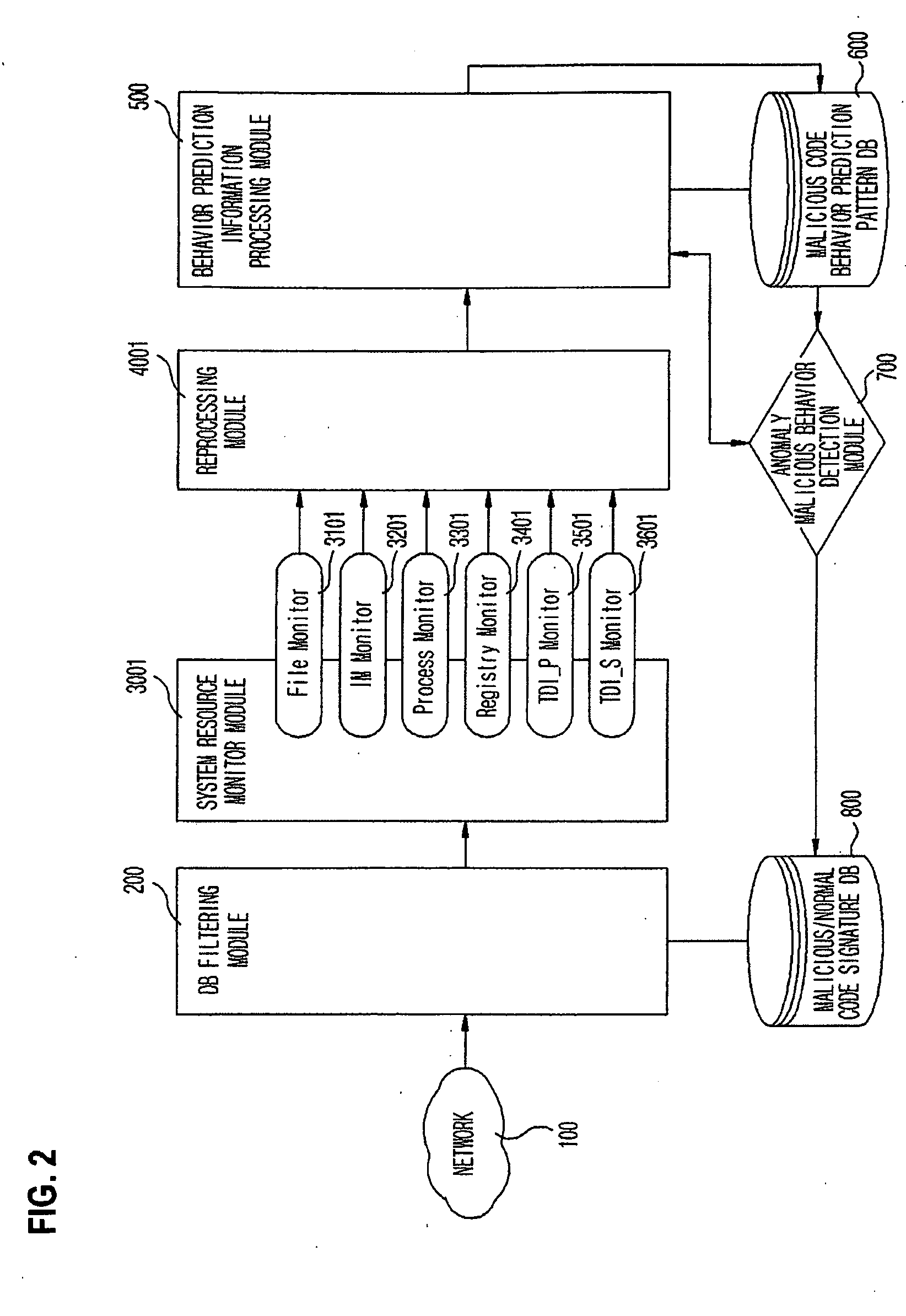
System and method of detecting anomaly malicious code by using process behavior prediction technique
InactiveUS8181248B2Memory loss protectionUser identity/authority verificationProcess behaviorSchema analysis
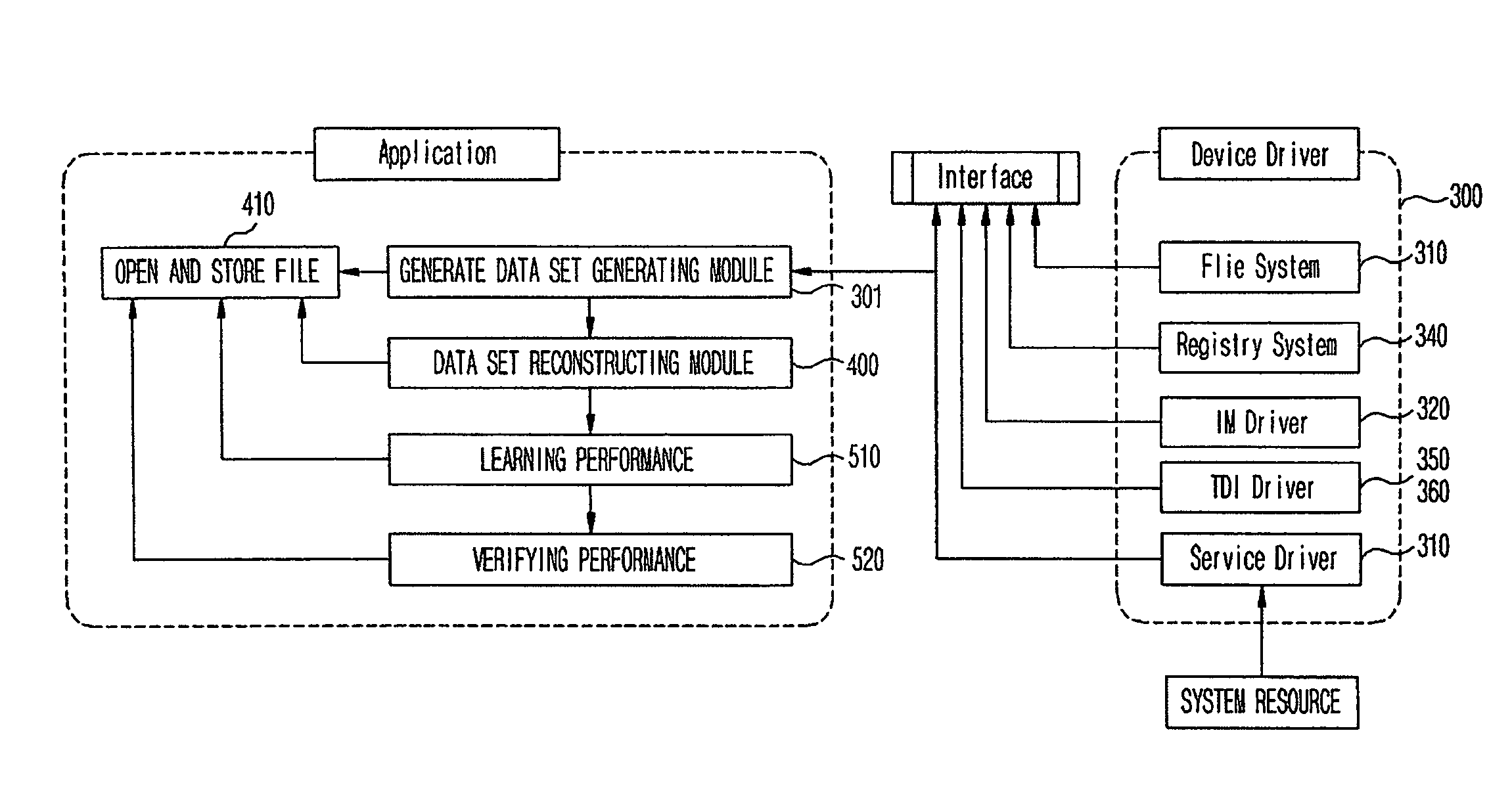
Provided are a pattern analyzing / detecting method and a system using the same that are capable of detecting and effectively preventing an unknown malicious code attack. To detect such an attack, the method monitors the system to combine all behaviors exhibited within the system due to corresponding malicious codes, reprocess and learn the behaviors, analyze existing malicious behavior feature values (prediction patterns), and compare them with a behavior pattern exhibited by an execution code.
Owner:F1 SECURITY INC
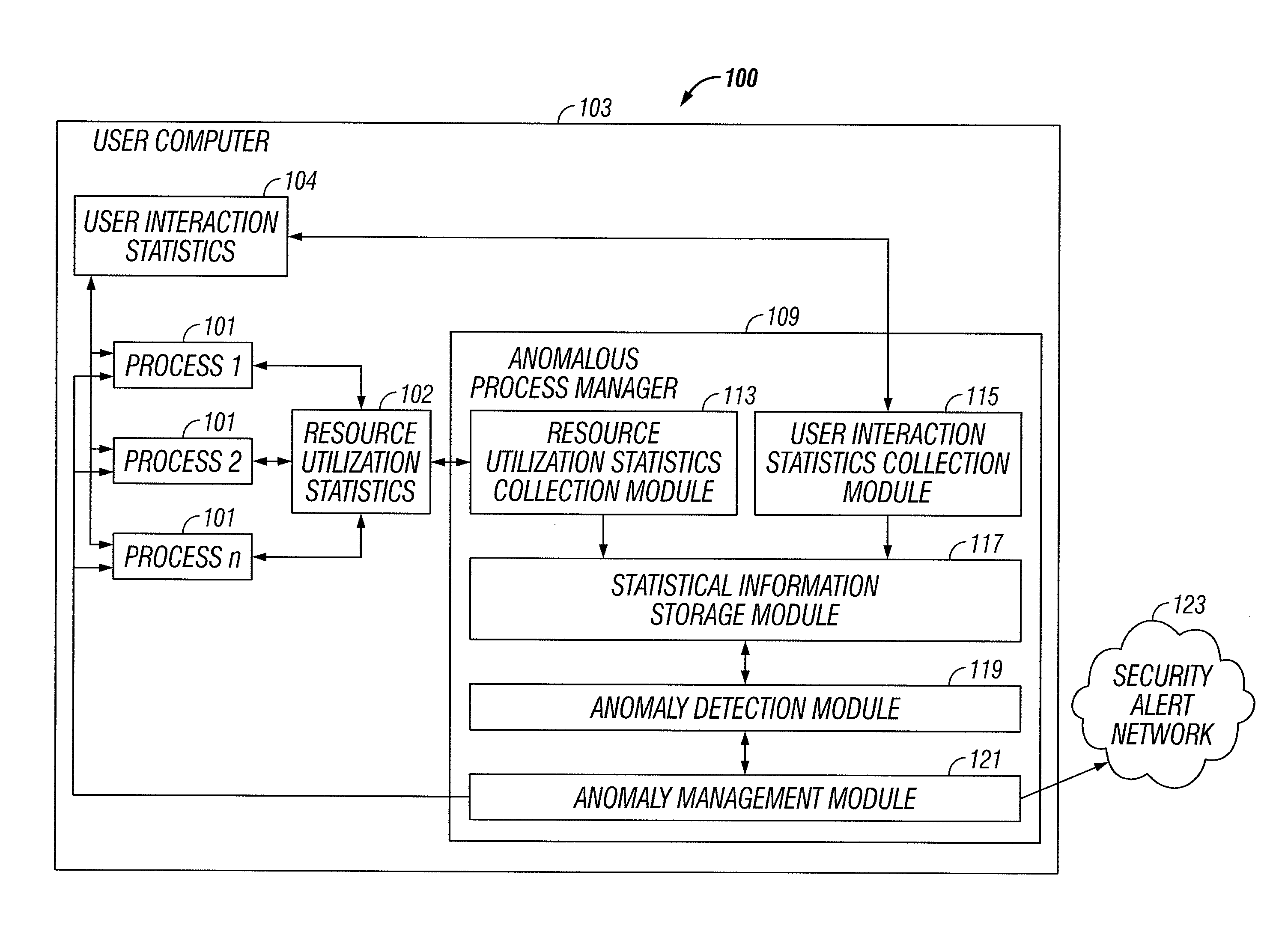
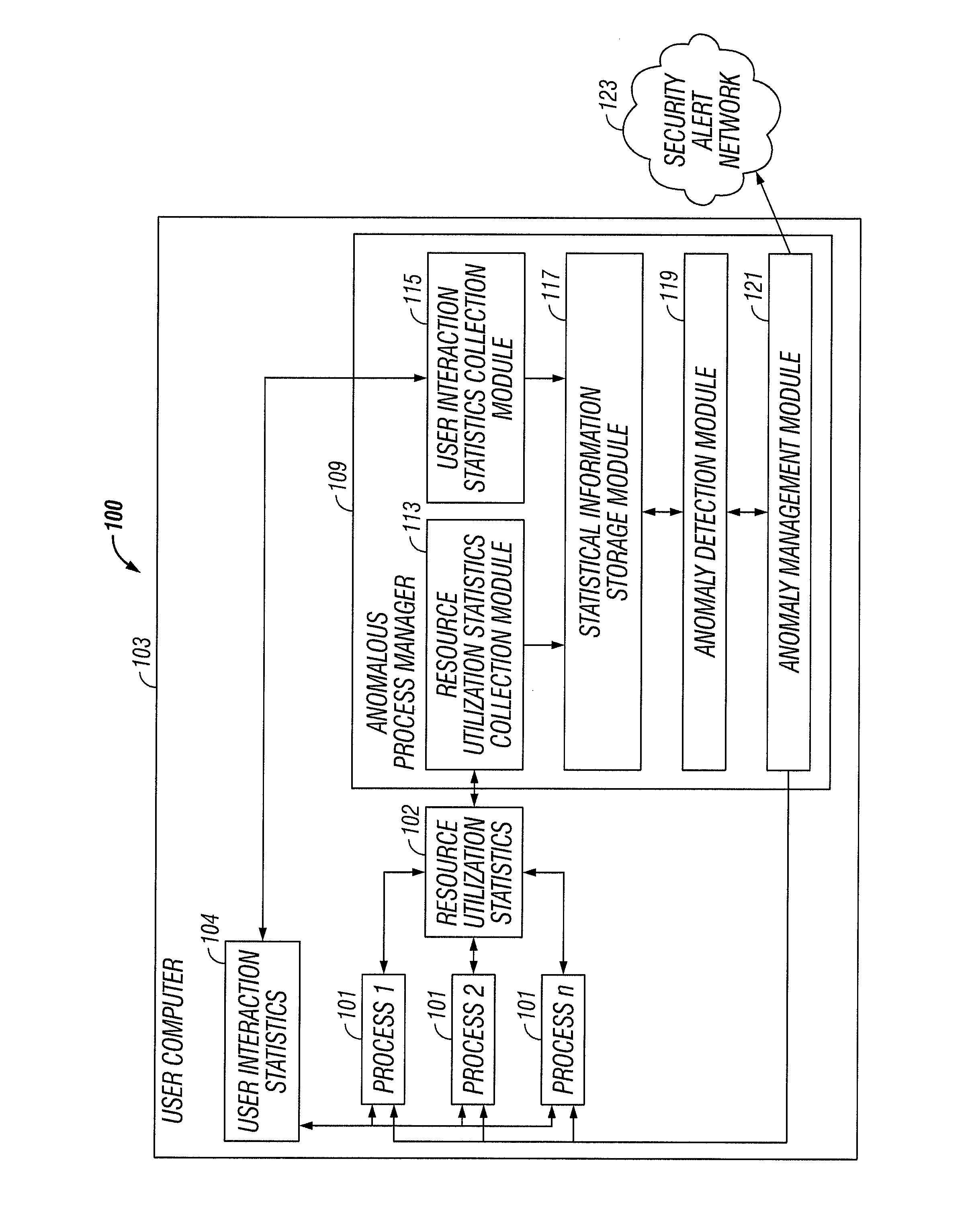
Process profiling for behavioral anomaly detection
ActiveUS8171545B1Memory loss protectionError detection/correctionRelevant informationProcess behavior
An anomalous process behavior manager uses statistical information concerning running processes to detect and manage process behavioral anomalies. The anomalous process behavior manager collects per process statistical data over time, such as resource allocation statistics and user interaction statistics. Current collected statistical data is analyzed against corresponding historical statistical data to determine whether processes are behaving in expected ways relative to past performance. Appropriate corrective steps are taken when it is determined that a process is behaving anomalously. For example, the process's blocking exclusions can be revoked, the process can be uninstalled, the process and / or the computer can be scanned for malicious code, the user can be alerted and / or relevant information can be shared with other parties.
Owner:NORTONLIFELOCK INC
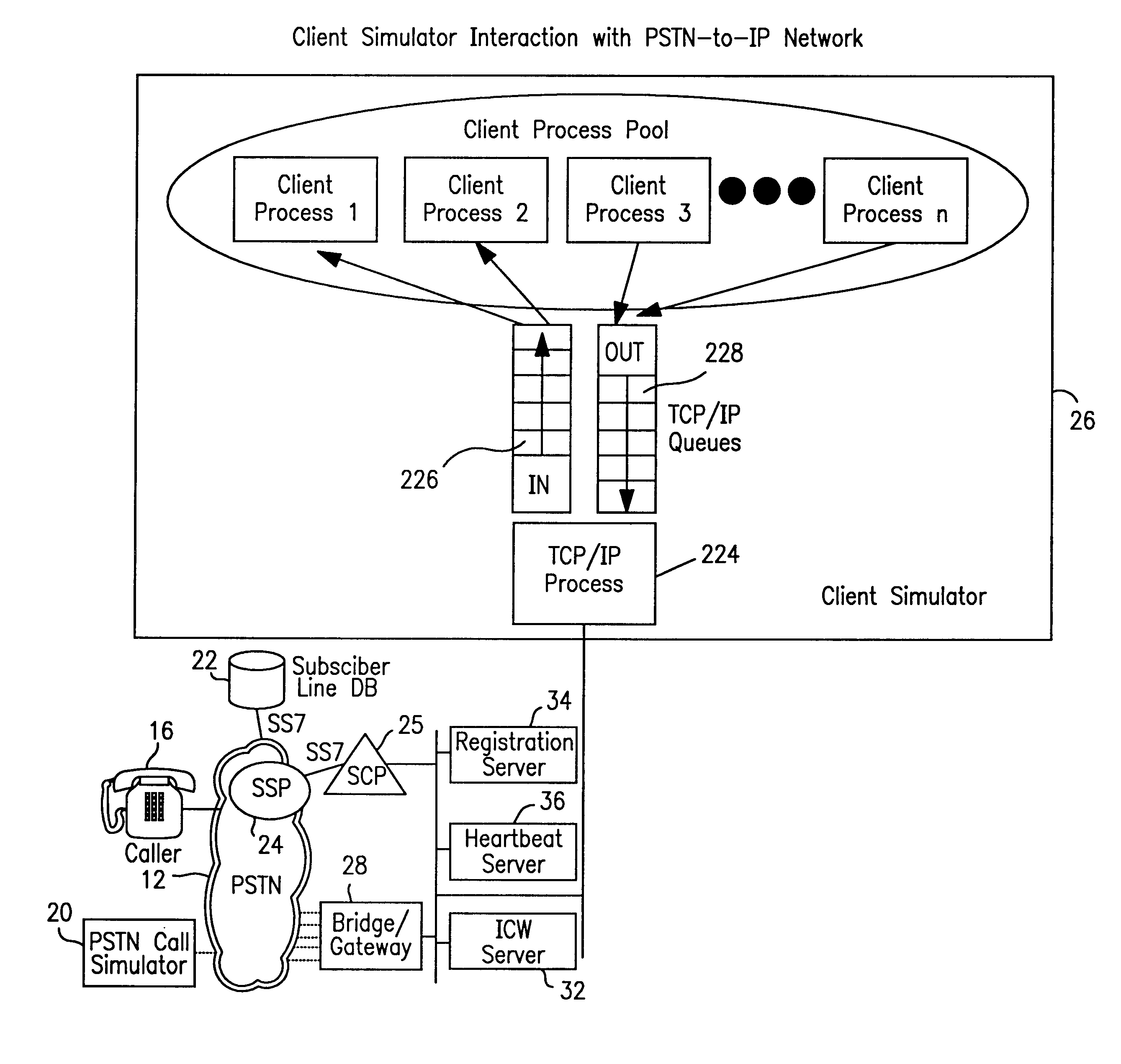
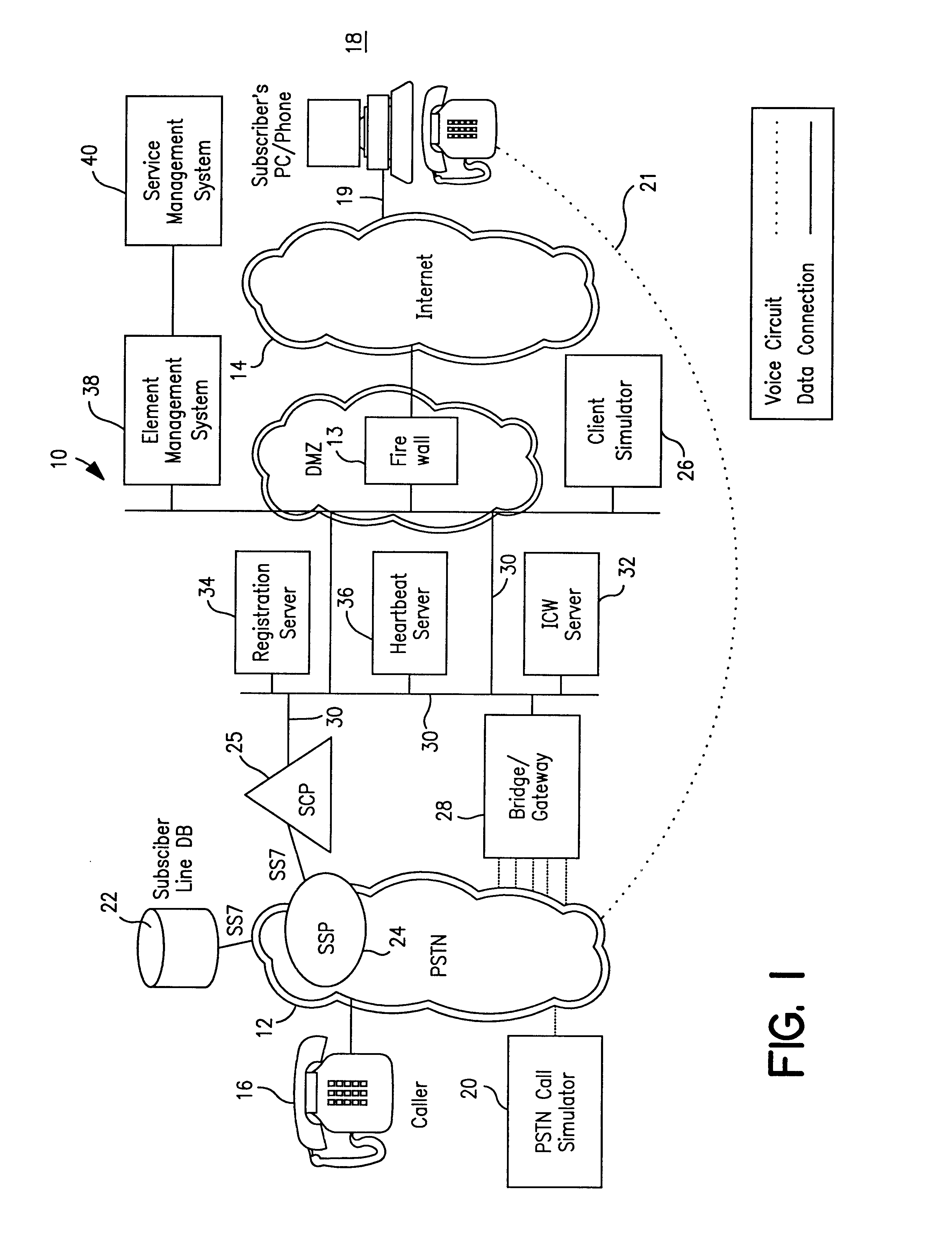
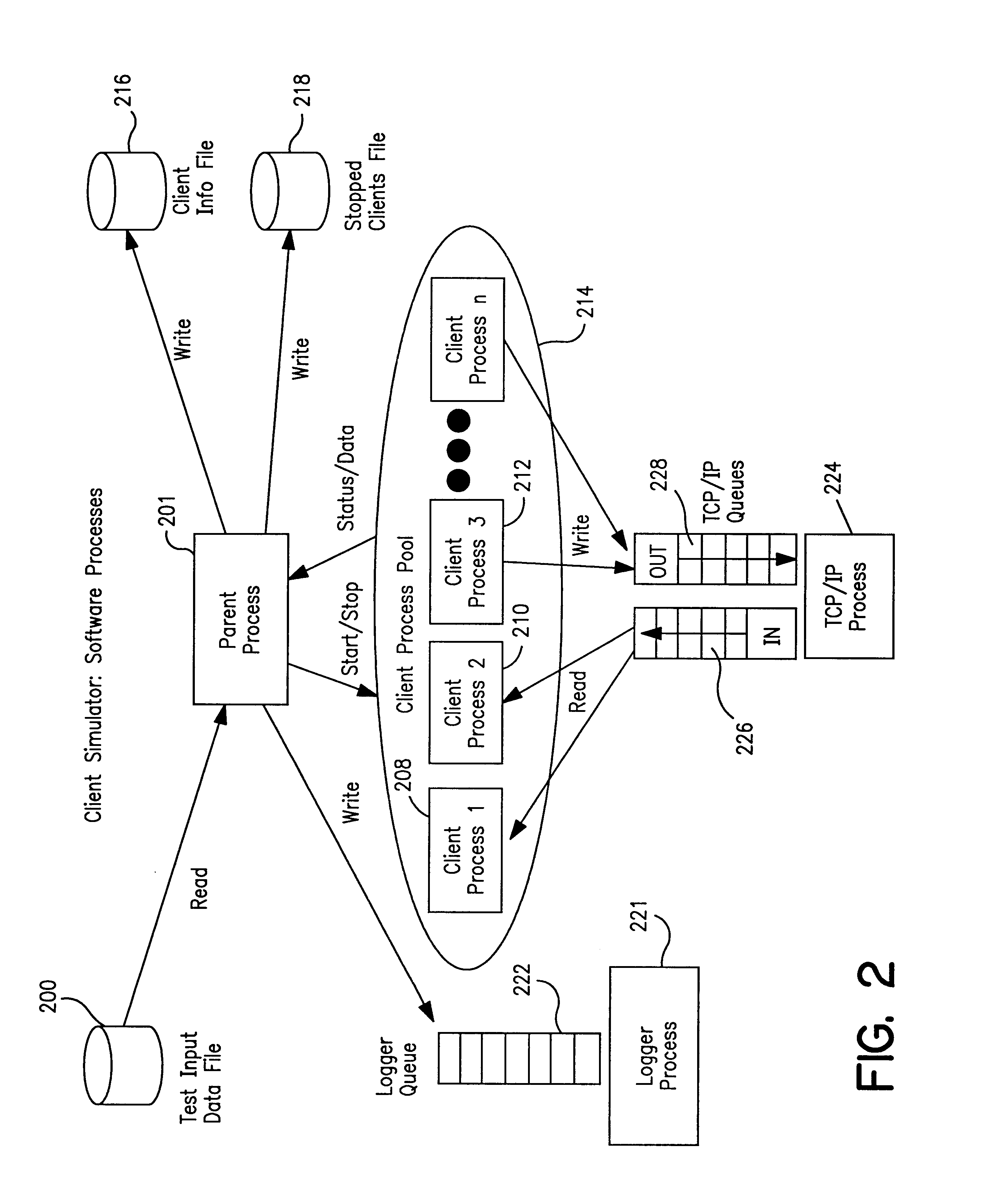
Client simulator and method of operation for testing PSTN-to-IP network telephone services for individual & group internet clients prior to availability of the services
InactiveUS6421424B1Telephone data network interconnectionsSupervisory/monitoring/testing arrangementsTest inputNetwork link
A client simulator for simulating client behavior in groups or individuals to telephone services in a test system for testing telephone services between subscribers in a PSTN and clients in a distributed information network, for example, the Internet (IP Network), prior to availability of the telephone services to the subscribers and clients. A processor is coupled to a TCP / IP data network linked to the PSTN via a System Control Point (SCP) and the IP Network via an application server. A storage means is coupled to the processor through input / output registers and includes stored instruction for a parent process and a pool of client processes. e storage means further includes: a) a test input data file which contains client behavior profiles of either groups or individual client processes to call data messages; b) a logger queue file which allows the parent process to write event messages indicating start or stopped client processes with time stamp; c) a client information file which contains information and data for the total number of processes identified as being part of the test; d) a stopped client file used to track client processes that have stopped. The parent process is responsible for reading the test input data file and passing the client process behavior profile to the client processes. Each client process is responsible for returning state information to the PSTN; call handling actions and providing call handling statistics. The client process includes a client behavior control functions which processes and maintains the behavior parameters passed by the parent process. The behavior function, inter alia, accepts the call message, forward the call message according to the client behavior profile. The client process further includes a send / receive function to read and write to the registers coupled to the TCP / IP data network and support voice over IP protocols. A test originated by the PSTN is passed to the test input data file by the SCP and application file. The parent processes passes the call message to the client process. The client process provides a variety of call handling options including (a) accepting the call on the client's PC; sending a voice message to the caller. The call data messages responses are sent back to the SCP through the application server. The SCP directs the PSTN on how to handle the message call response.
Owner:LINKEDIN
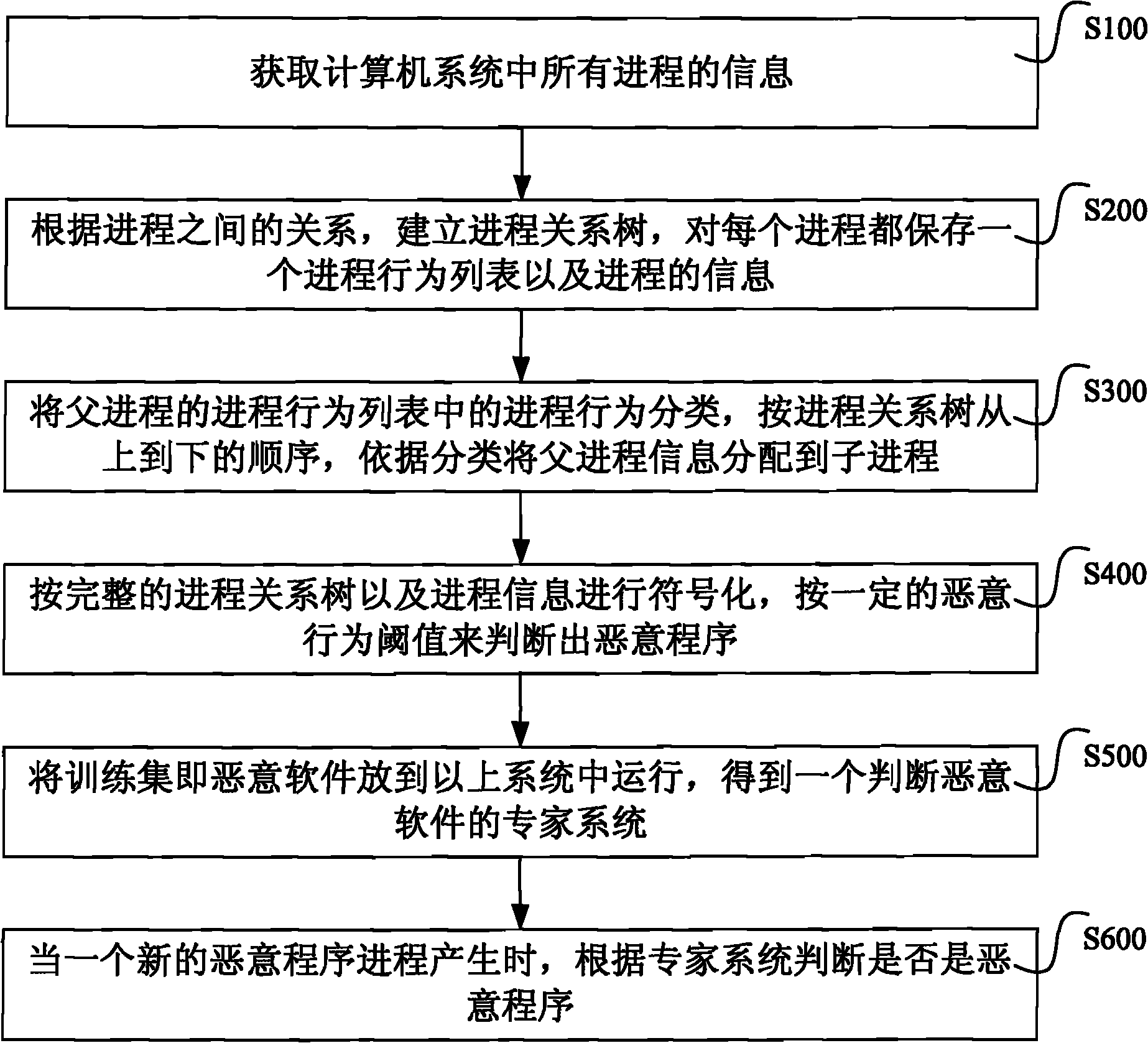
Method and system for identifying malicious program
ActiveCN101944167AThe accuracy of the killing effect is lowHigh false positive rateMultiprogramming arrangementsPlatform integrity maintainanceProcess behaviorComputerized system
The invention relates to a method and a system for identifying a malicious program. The method comprises the following steps: 1. acquiring information and acts of all processes in a computer system, establishing a process relational tree according to the set membership among the processes, and storing a process information and a process behavior list corresponding to each process; 2. classifying the process behaviors in the process behavior list of the parent process, and allocating the information of the parent process to sub-process according to the classification and the order of the process relation tree from top to bottom; 3. symbolizing according to the process relation tree and the process information, judging a malicious program based on a preset malicious behavior threshold, and running the malicious program in the computer system to obtain an expert system for judging the malicious program; and 4. when the process of a new program is created, using the expert system to judge whether the new program is a malicious program. Compared with the prior art, the invention lowers the implementation complexity and can improve the efficiency.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
System and method of detecting anomaly malicious code by using process behavior prediction technique
InactiveUS20080127346A1Memory loss protectionUser identity/authority verificationProcess behaviorBehaviour pattern
Provided are a pattern analyzing / detecting method and a system using the same that are capable of detecting and effectively preventing an unknown malicious code attack. To detect such an attack, the method monitors the system to combine all behaviors exhibited within the system due to corresponding malicious codes, reprocess and learn the behaviors, analyze existing malicious behavior feature values (prediction patterns), and compare them with a behavior pattern exhibited by an execution code.
Owner:F1 SECURITY INC
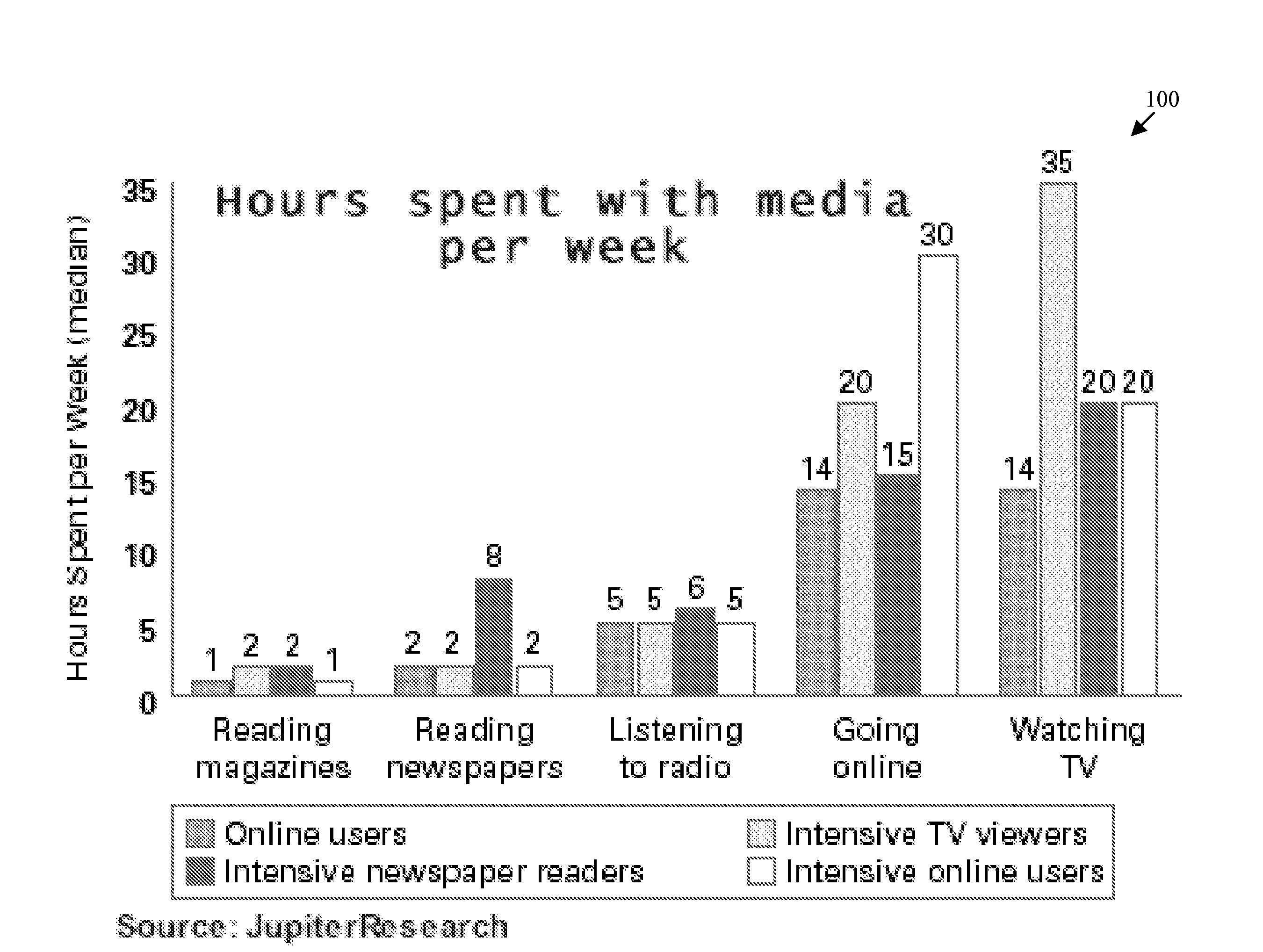
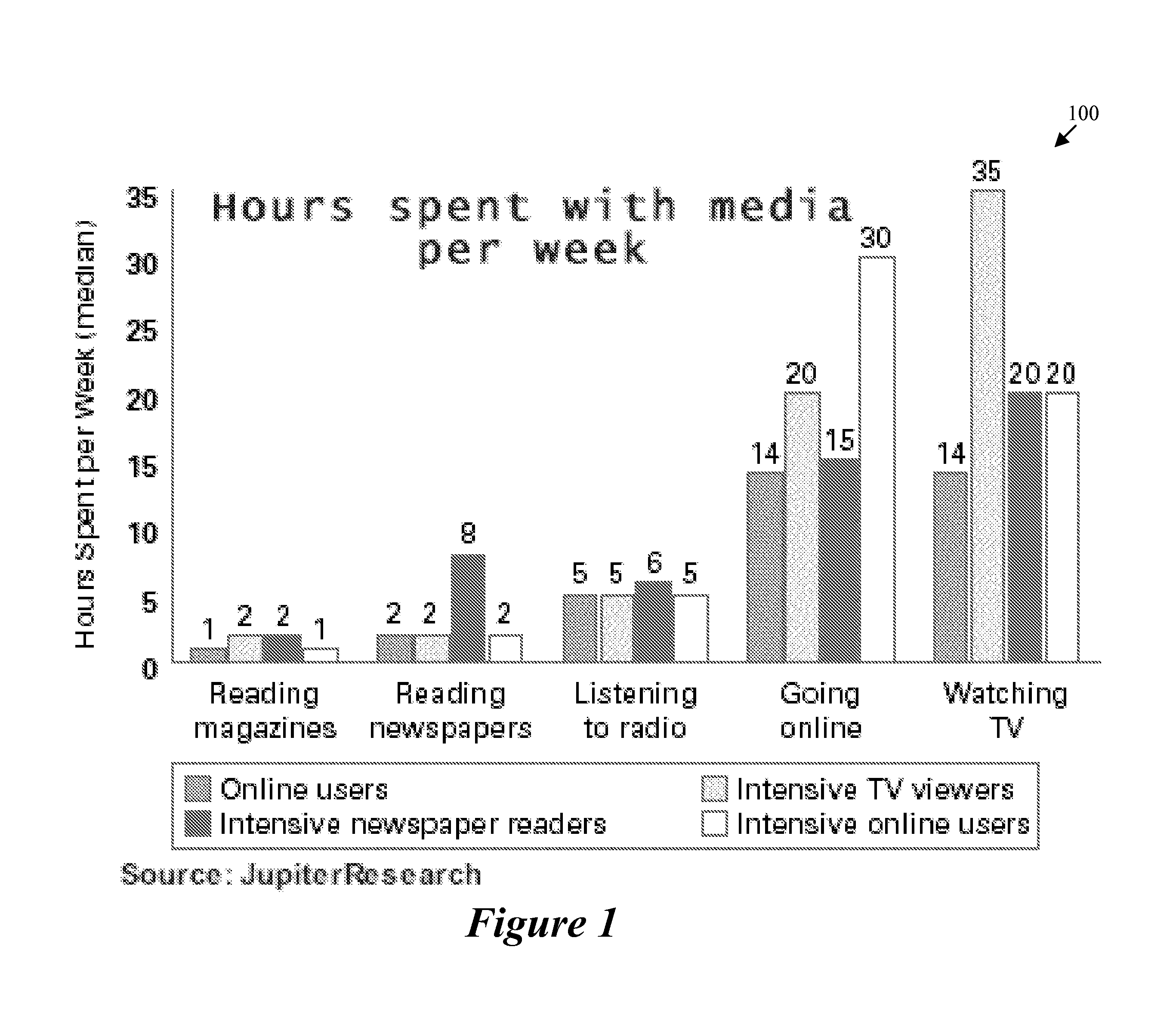
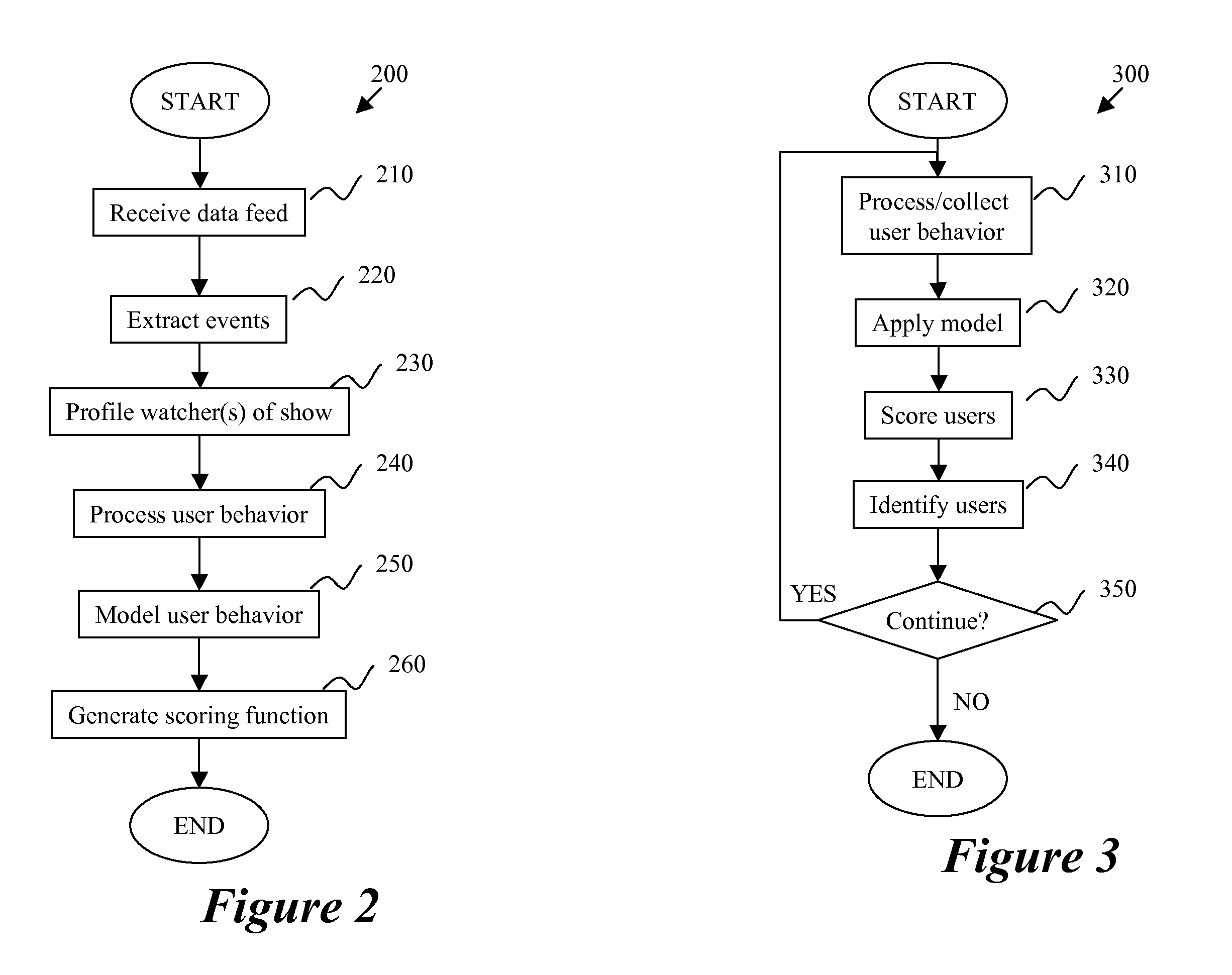
Television Audience Targeting Online
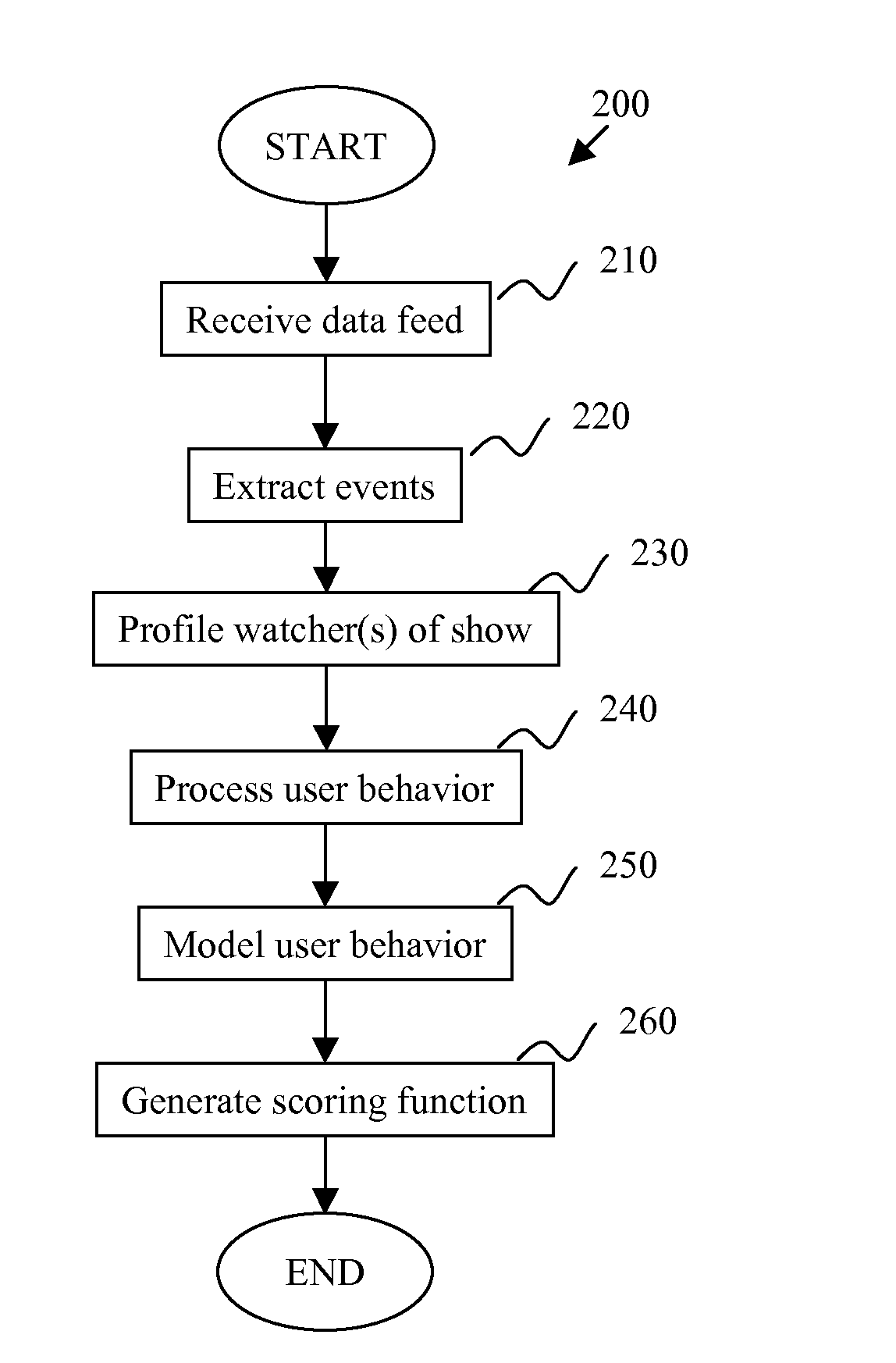
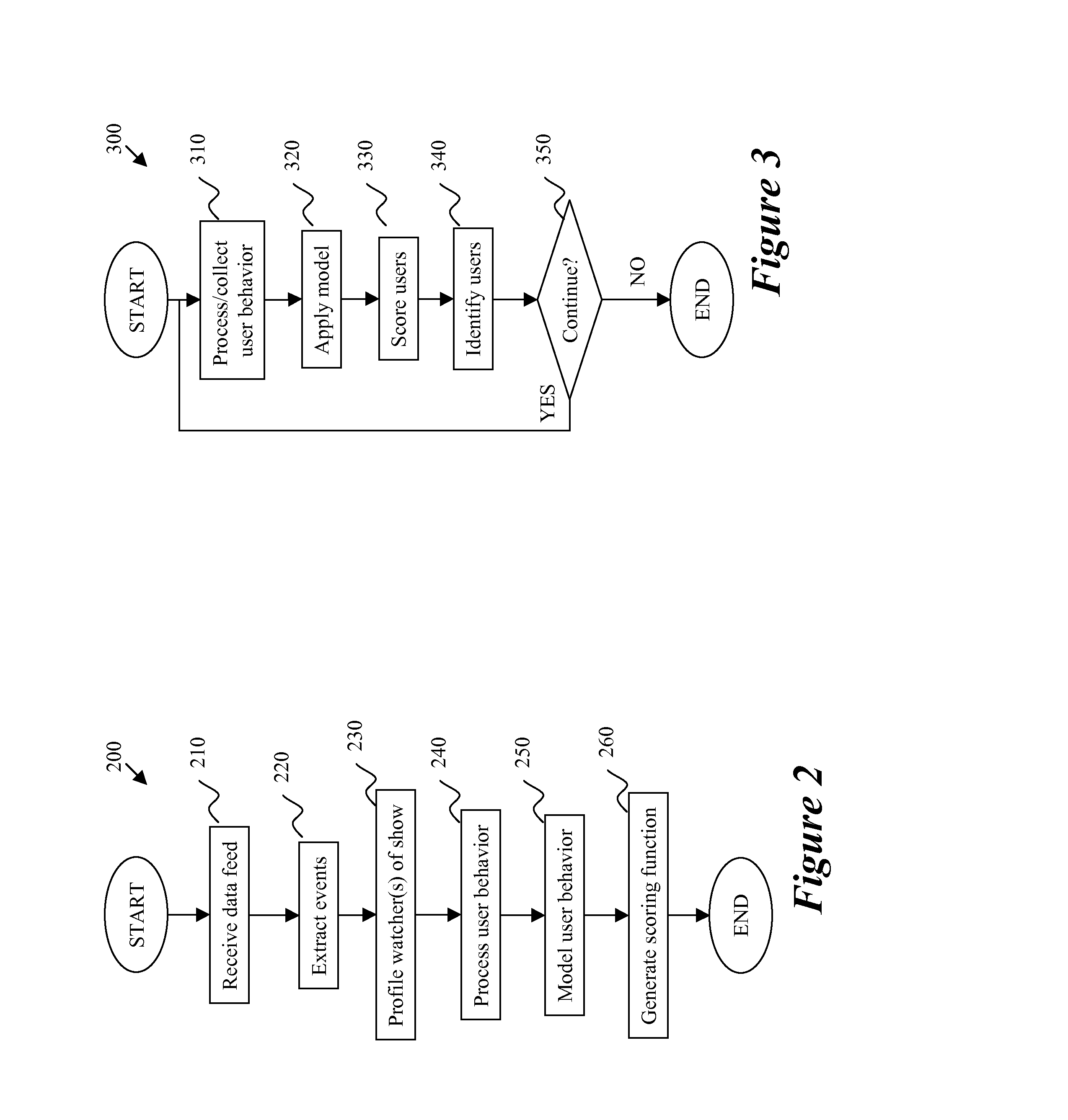
InactiveUS20080300894A1Easy maintenanceTelevision systemsSelective content distributionData feedProcess behavior
A method of targeting users receives a data feed that has information relating to a first media and extracts events from the received data feed. The method generates a profile relating to a first item in the first media, and processes behavior of a first group of users of a second media. The method models the behavior of the first group of users, and generates a scoring function by using the modeling. A system for targeting a user includes a data feed, an event extractor, one or more profiles, a behavior processor, and a model. The data feed has information relating to a first media. The event extractor is for receiving the data feed and extracting particular information based on a second media. The profile(s) are based on the extracted information. The behavior processor is for receiving the profile and comparing the profile to a first group of users of the second media. The model space is for receiving an output of the behavior processor and modeling user behavior by using the profile.
Owner:OATH INC
Method and apparatus for monitoring a computer to detect operating system process manipulation
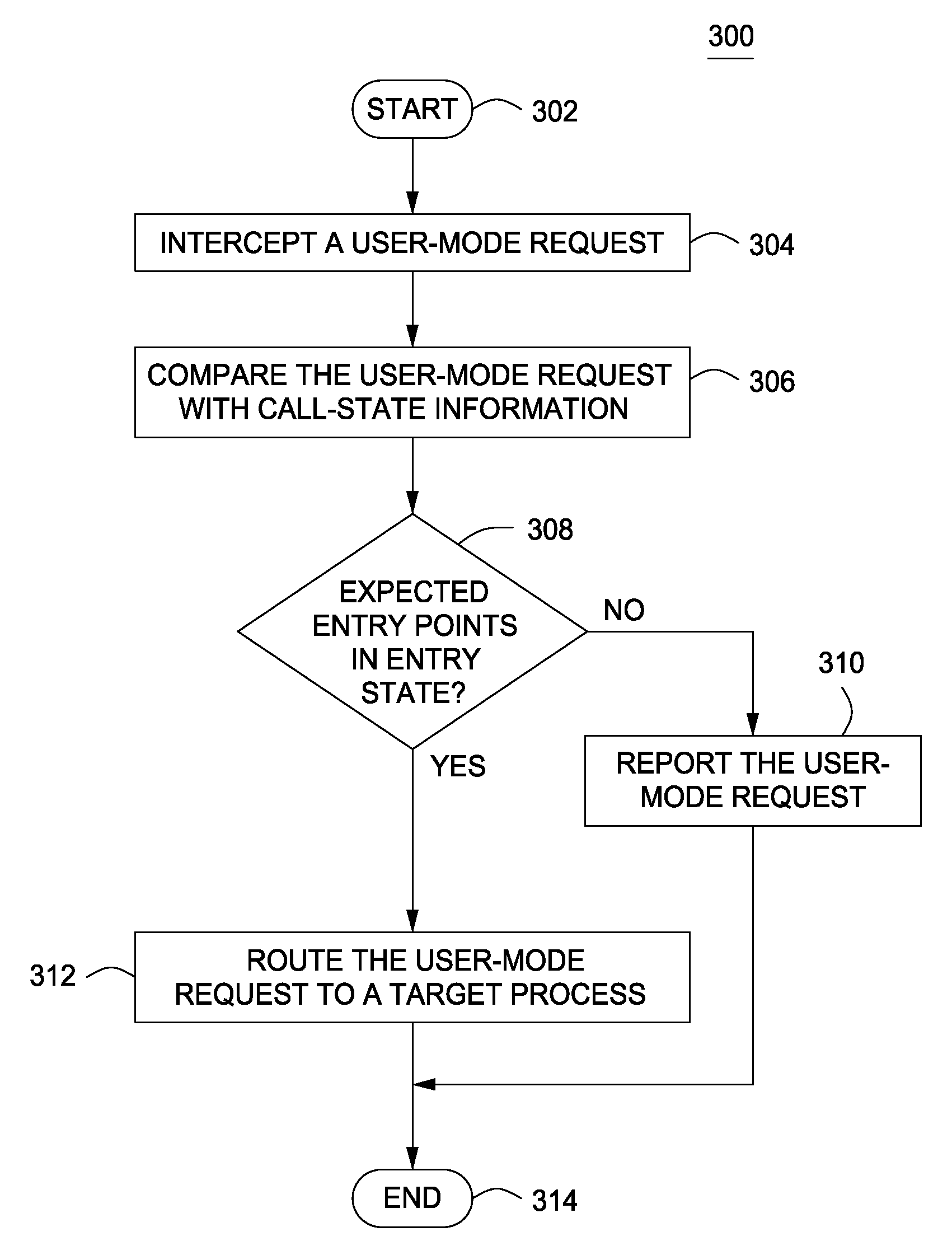
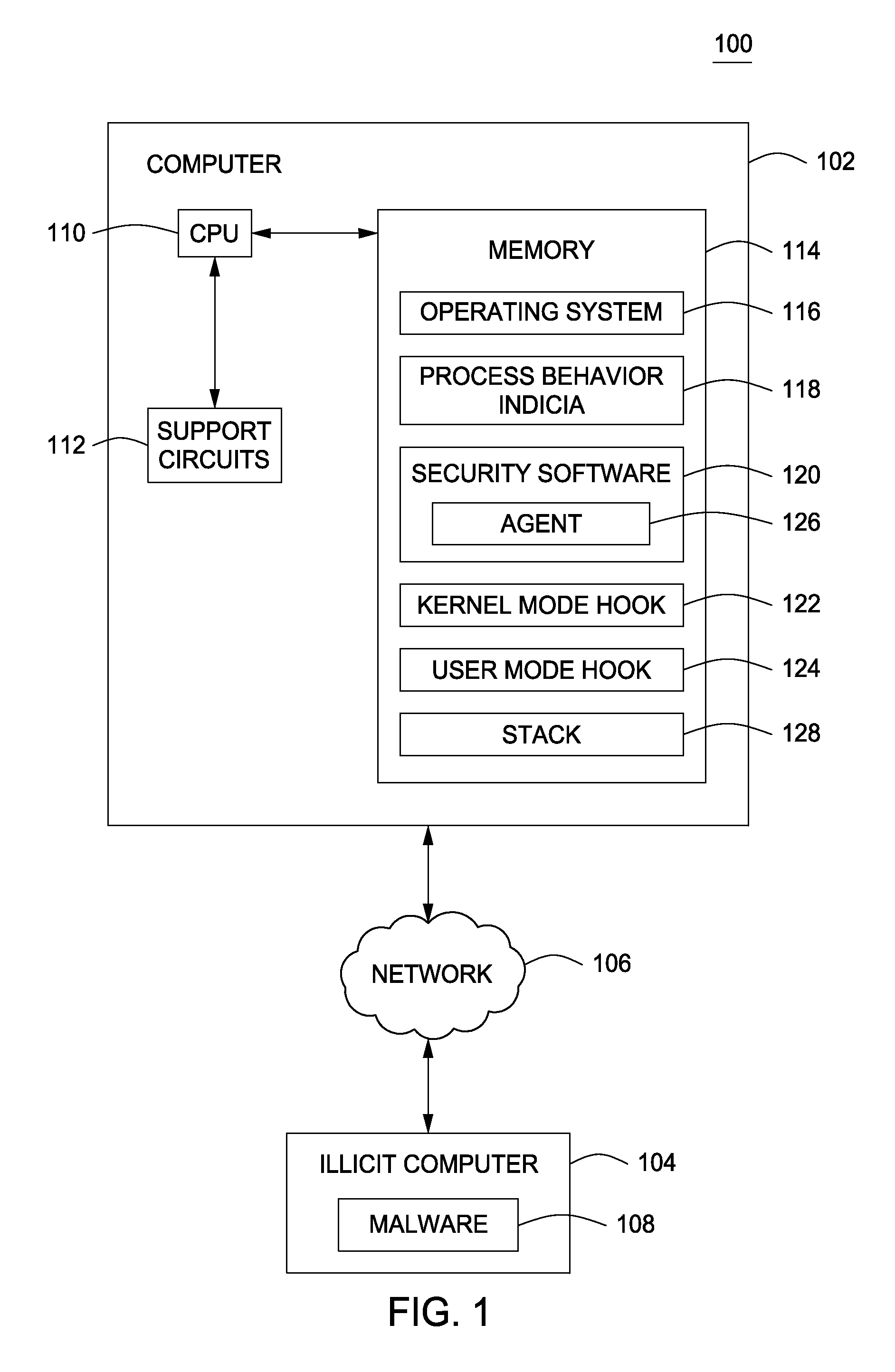
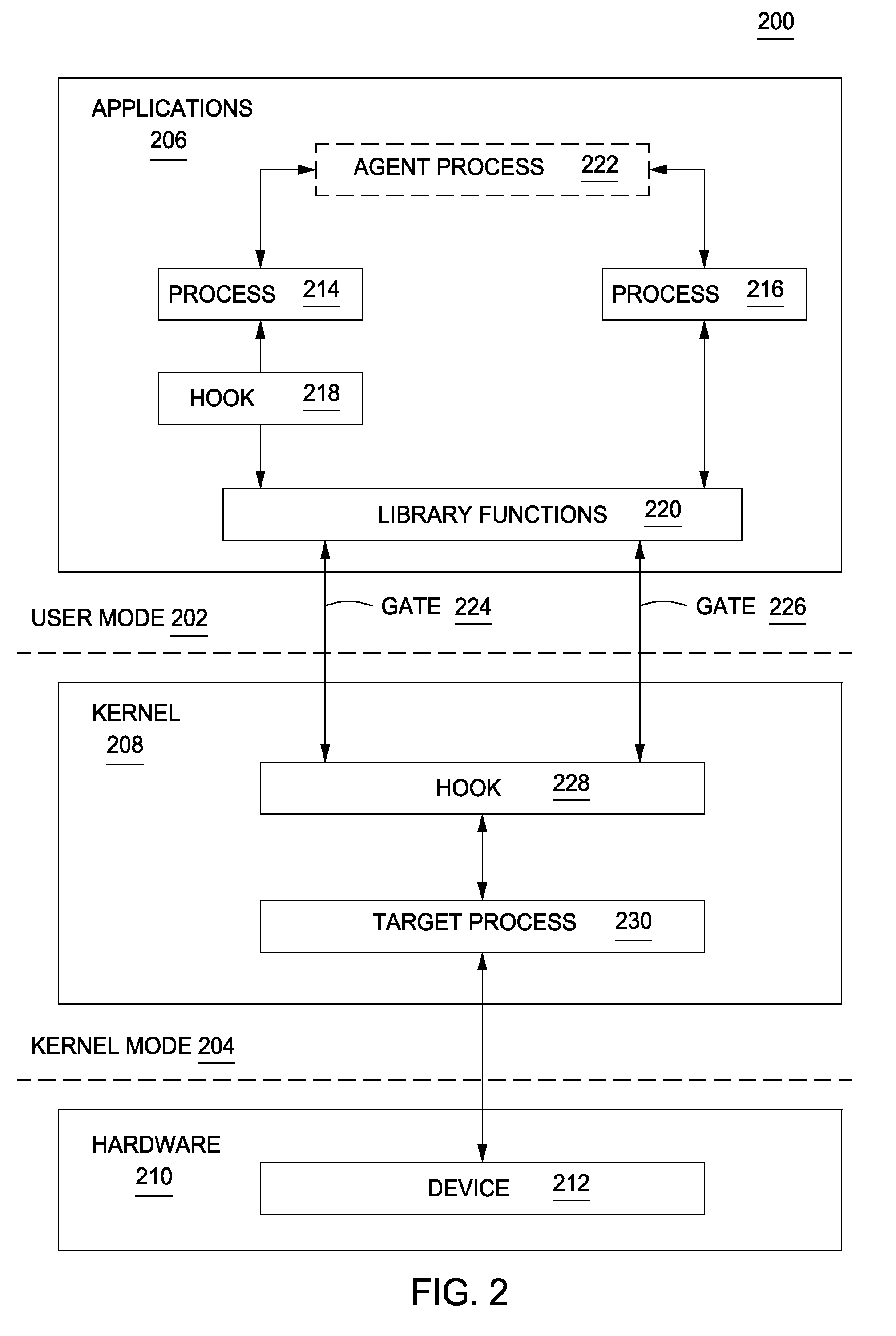
A method and apparatus for monitoring a computer to detect operating system process manipulation by malicious software programs is disclosed. In one embodiment, a method for detecting operating system process manipulation through unexpected process behavior includes accessing process behavior indicia regarding memory addresses used by at least one user mode process to request computer resources and comparing the process behavior indicia with a user mode request to identify operating system process manipulation.
Owner:CA TECH INC
Method and system for detecting anomalous process behavior
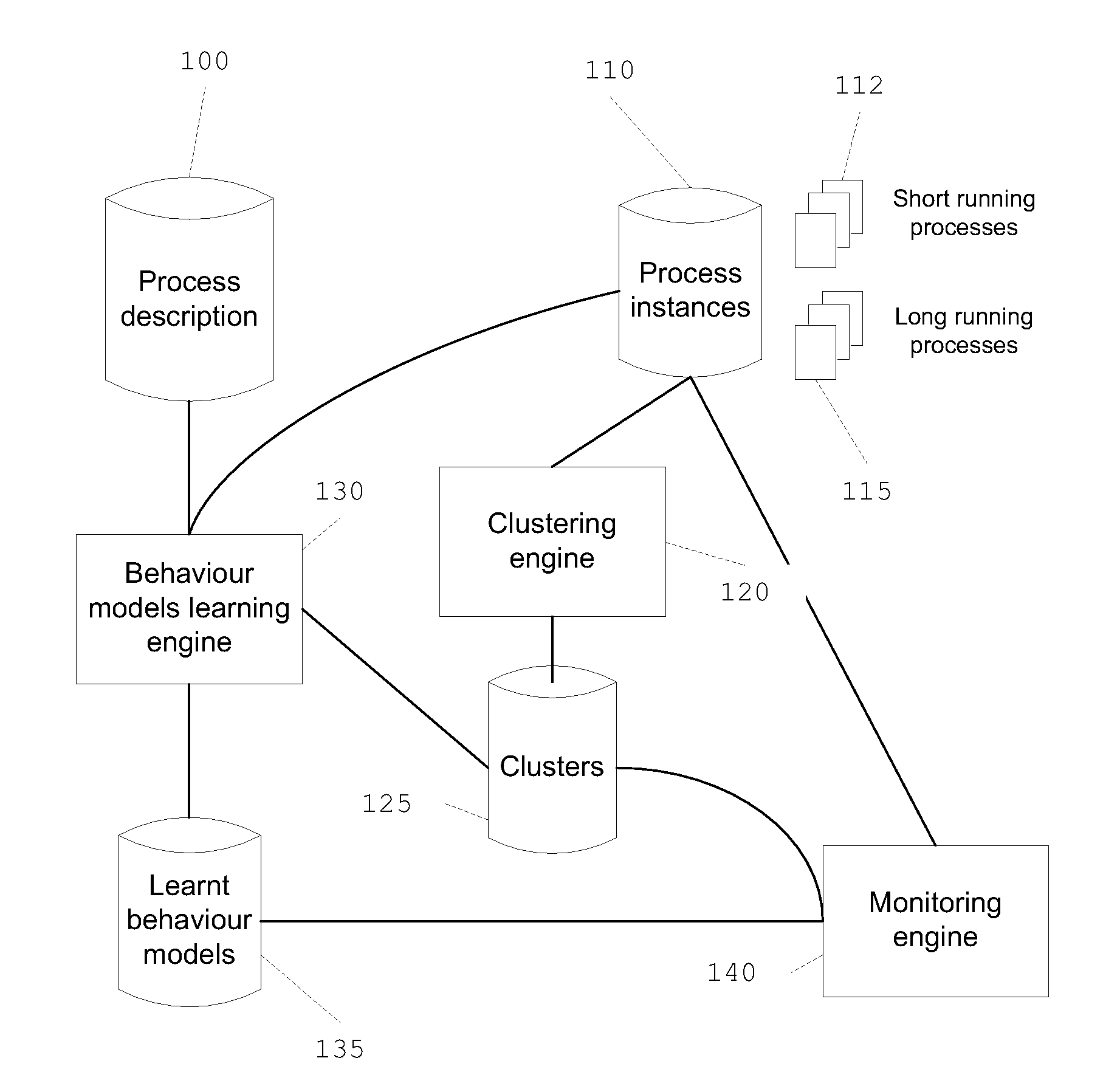
InactiveUS20090018983A1Easily install methodEasy to getMathematical modelsError detection/correctionProcess behaviorData mining
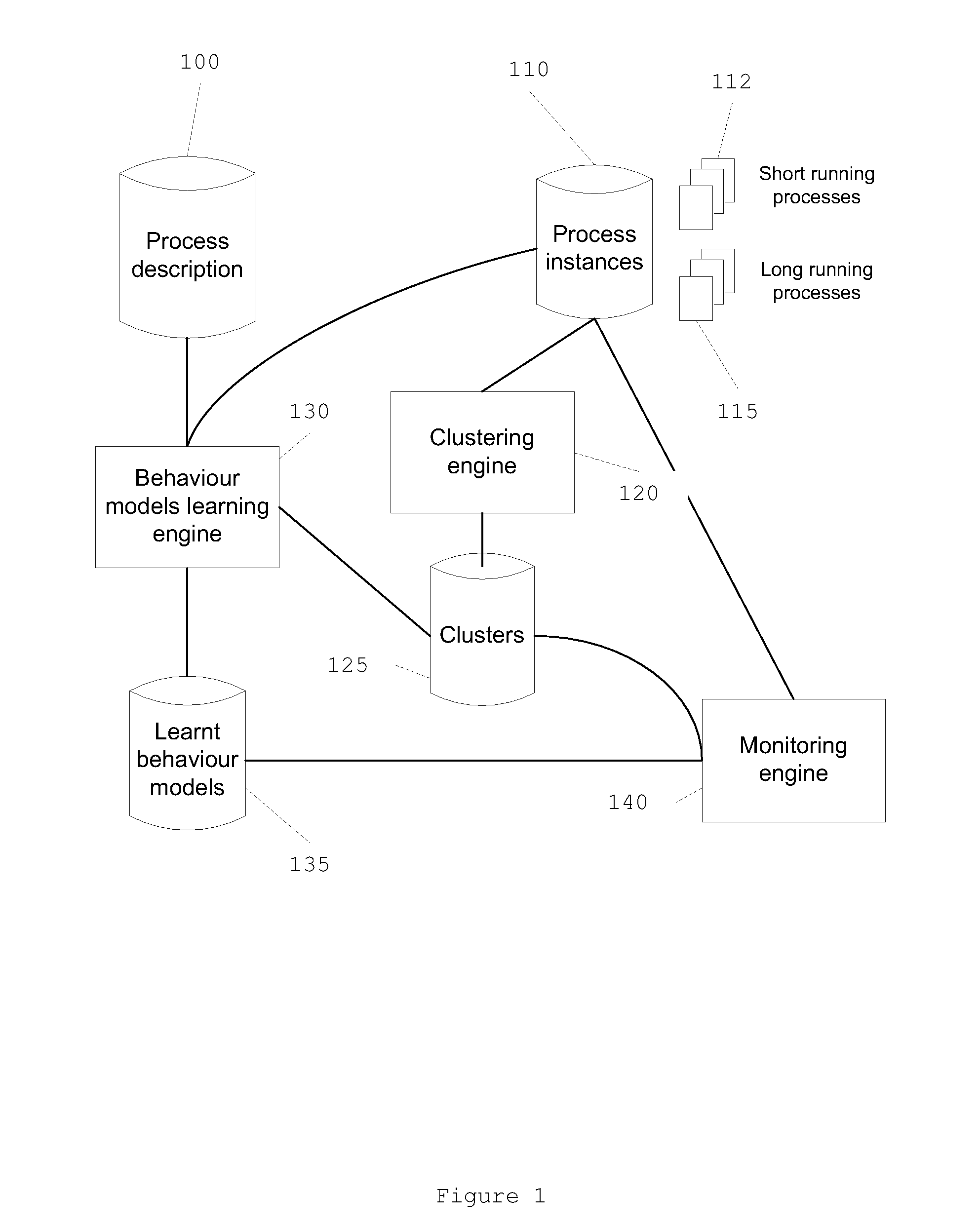
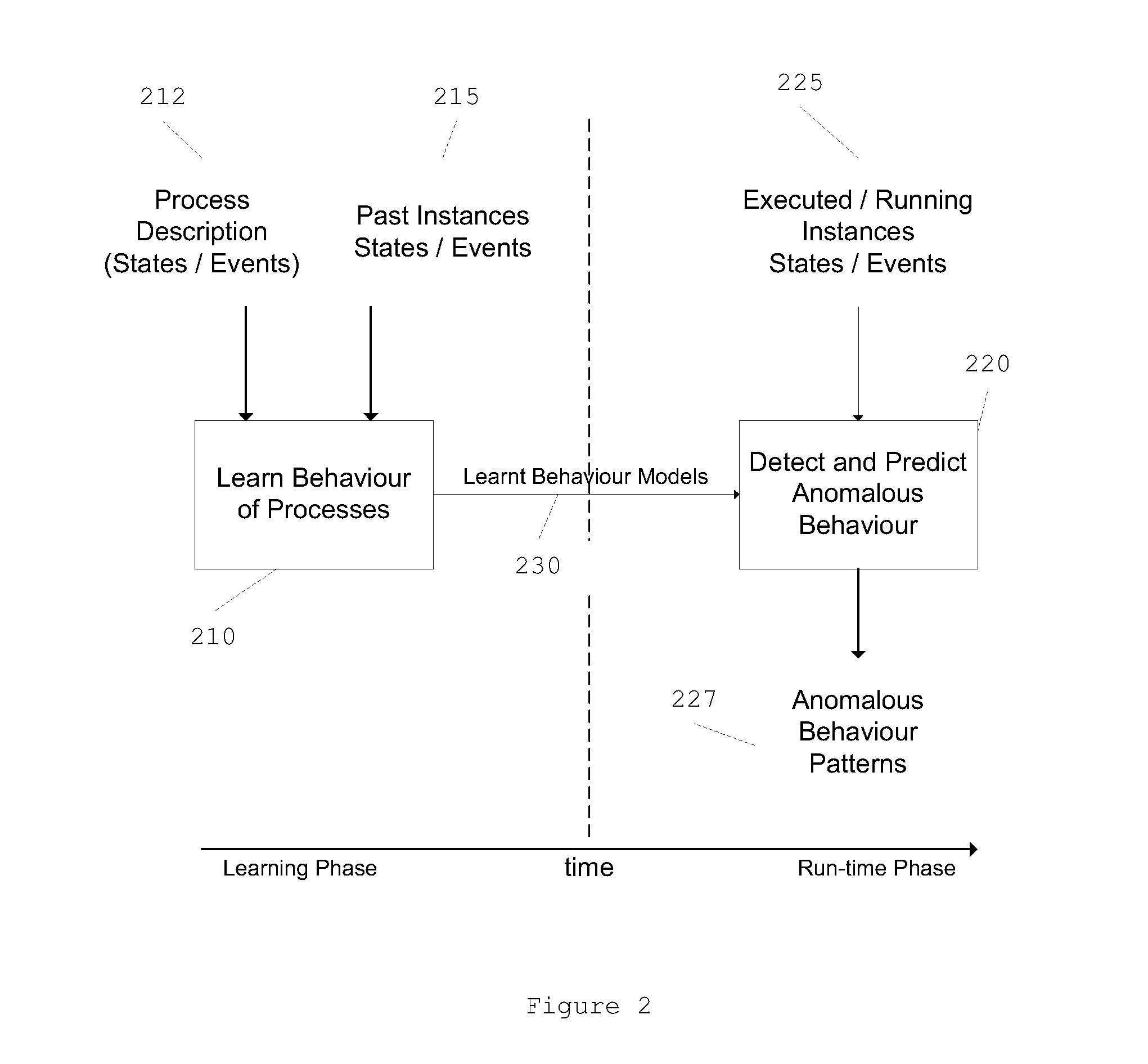
A method for learning a process behavior model based on a process past instances and on one or more process attributes, and a method for detecting an anomalous process using the corresponding process behavior model.
Owner:AIRBNB
Methods for behavioral detection and prevention of cyberattacks, and related apparatus and techniques
ActiveUS20190121978A1Reduce the amount of calculationReduce false alarm ratePlatform integrity maintainanceTransmissionRansomwareProcess behavior
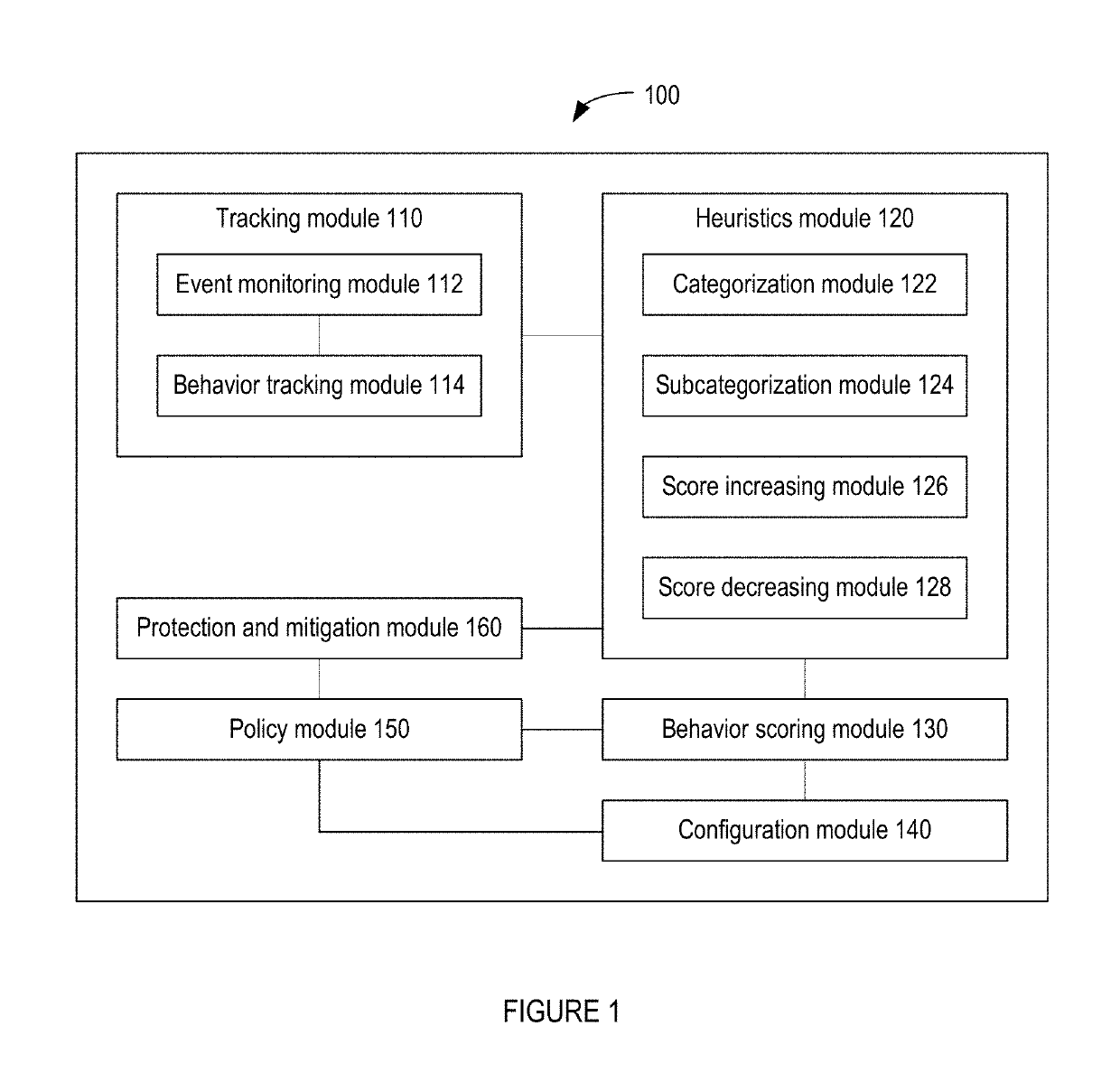
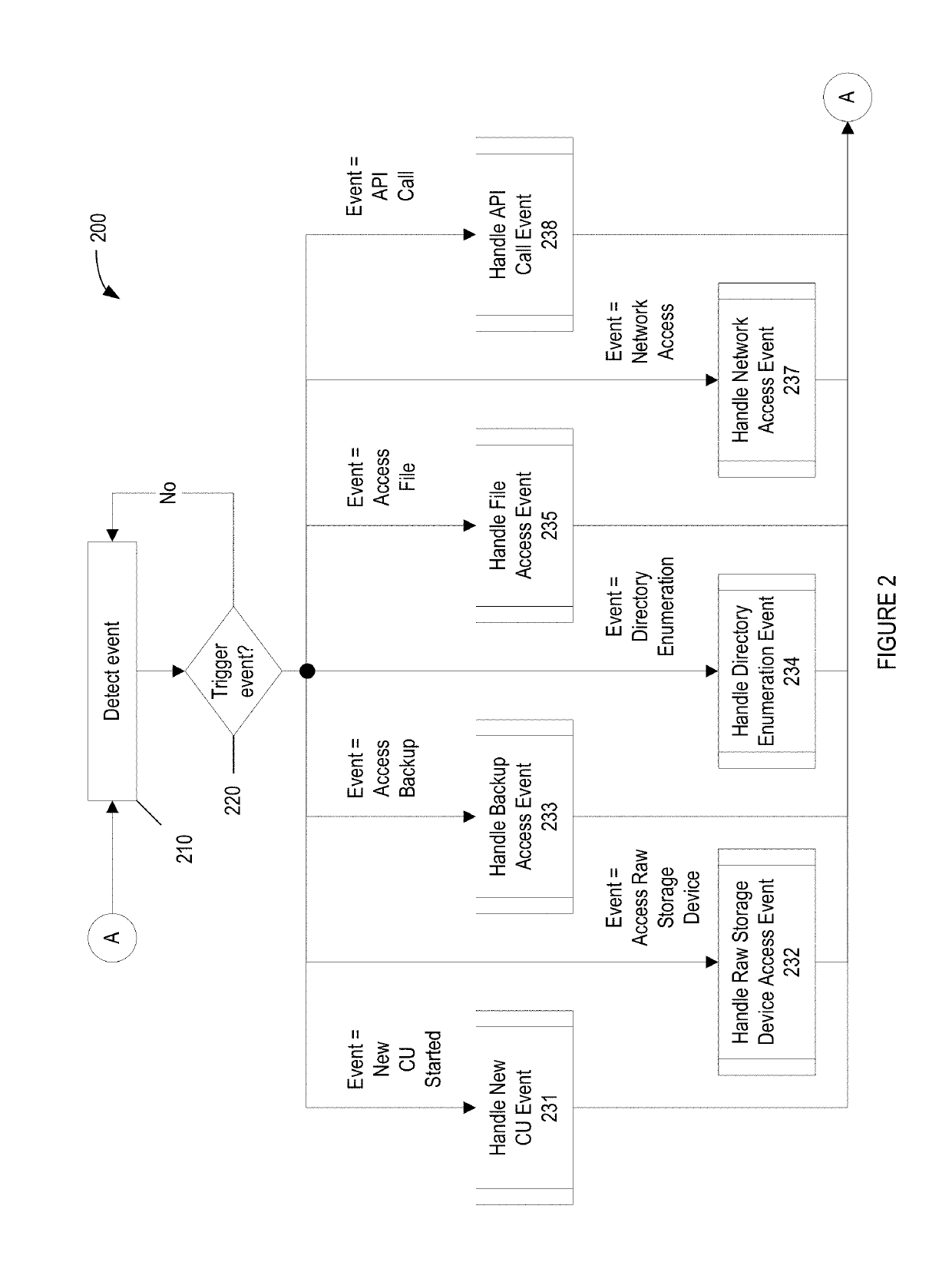
A security engine may use event-stream processing and behavioral techniques to detect ransomware. The engine may detect process behavior associated with encrypting a file, encrypting a storage device, or disabling a backup file, and may assign a ransomware category to the process based thereon. The engine may initiate protection actions to protect system resources from the process, which may continue to execute. The engine may monitor the process for specific behavior corresponding to its ransomware category. Based on the extent to which such specific behavior is detected, the engine may determine that the process is not ransomware, assign a ransomware subcategory to the process, or adjust the process's threat score. Monitoring of the process may continue, and the threat score may be updated based on the process's behavior. If the threat score exceeds a threshold corresponding to the ransomware category (or subcategory), a corresponding policy action may be initiated.
Owner:CARBON BLACK
Apparatus and method for detecting abnormal behavior
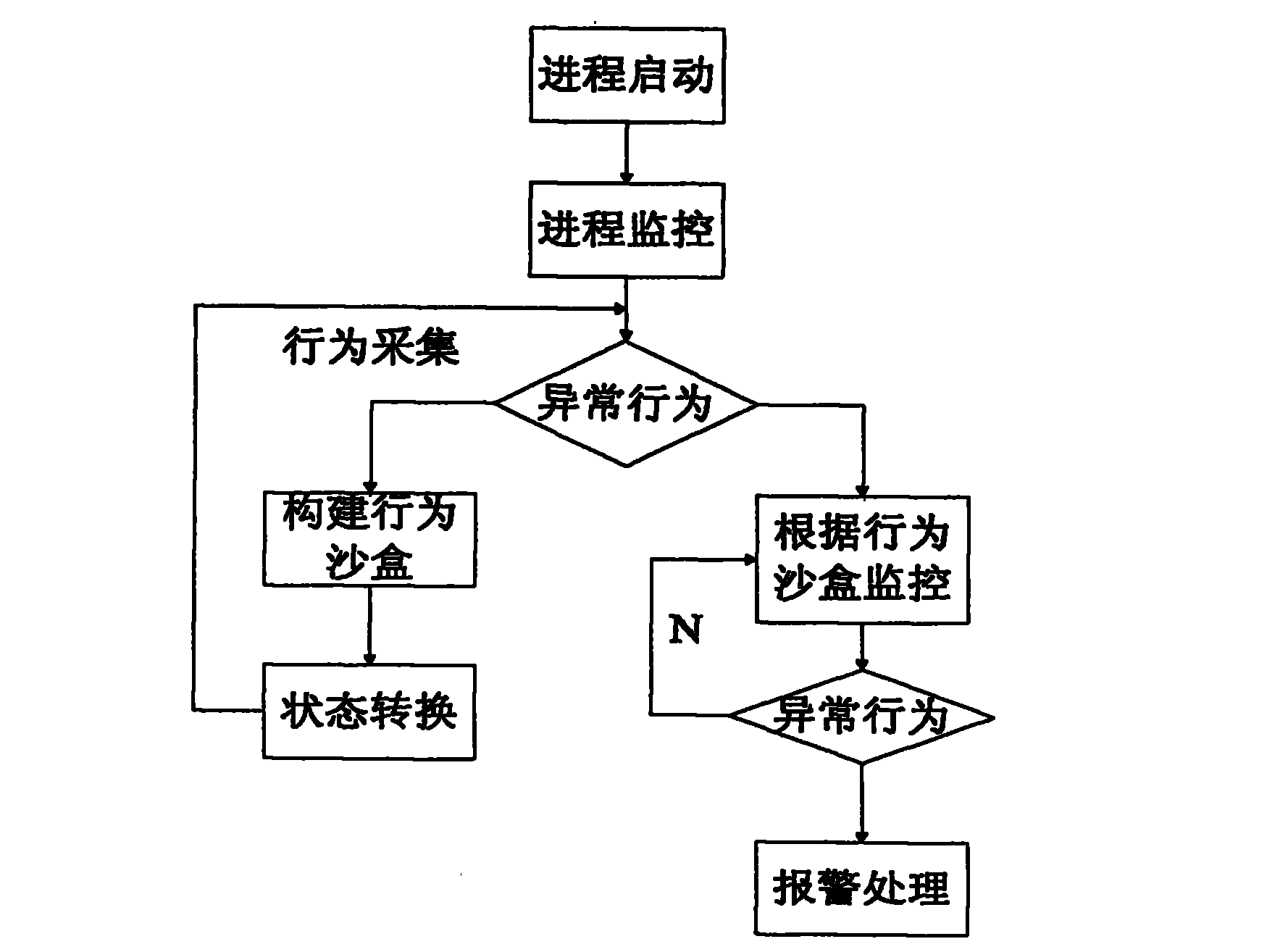
InactiveUS20150199512A1Easy to detectMemory loss protectionError detection/correctionBehavioral analyticsProcess behavior
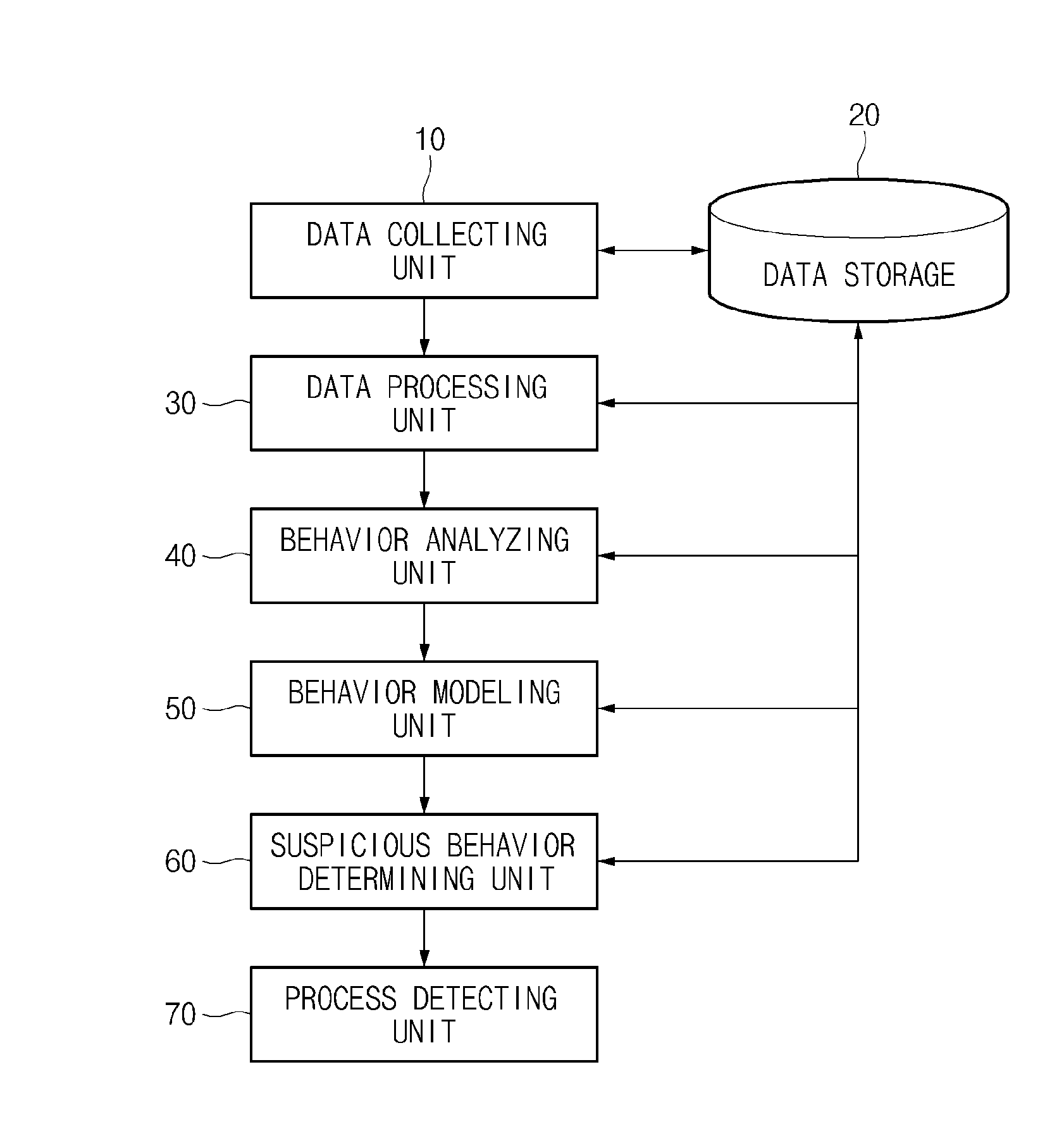
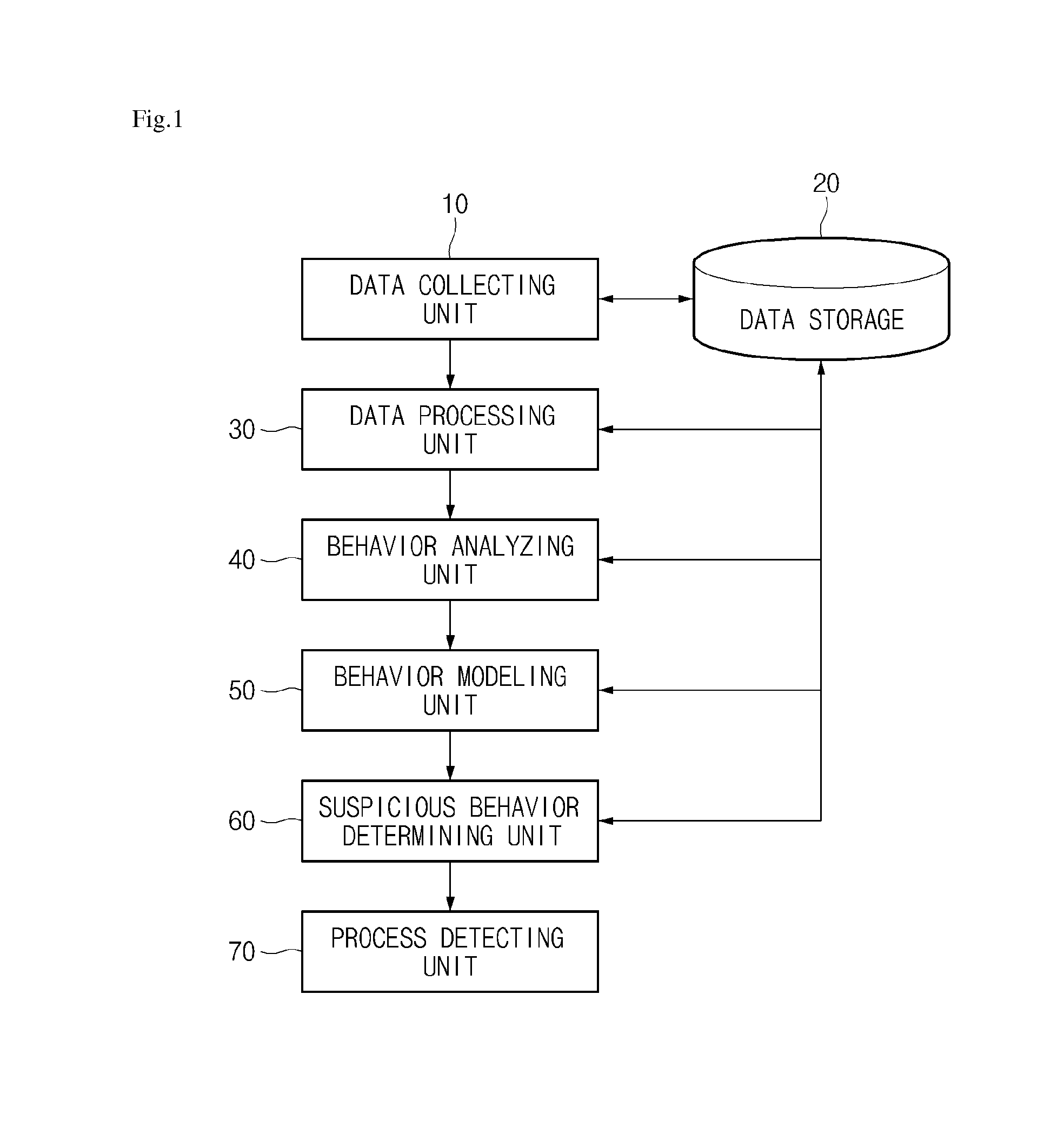
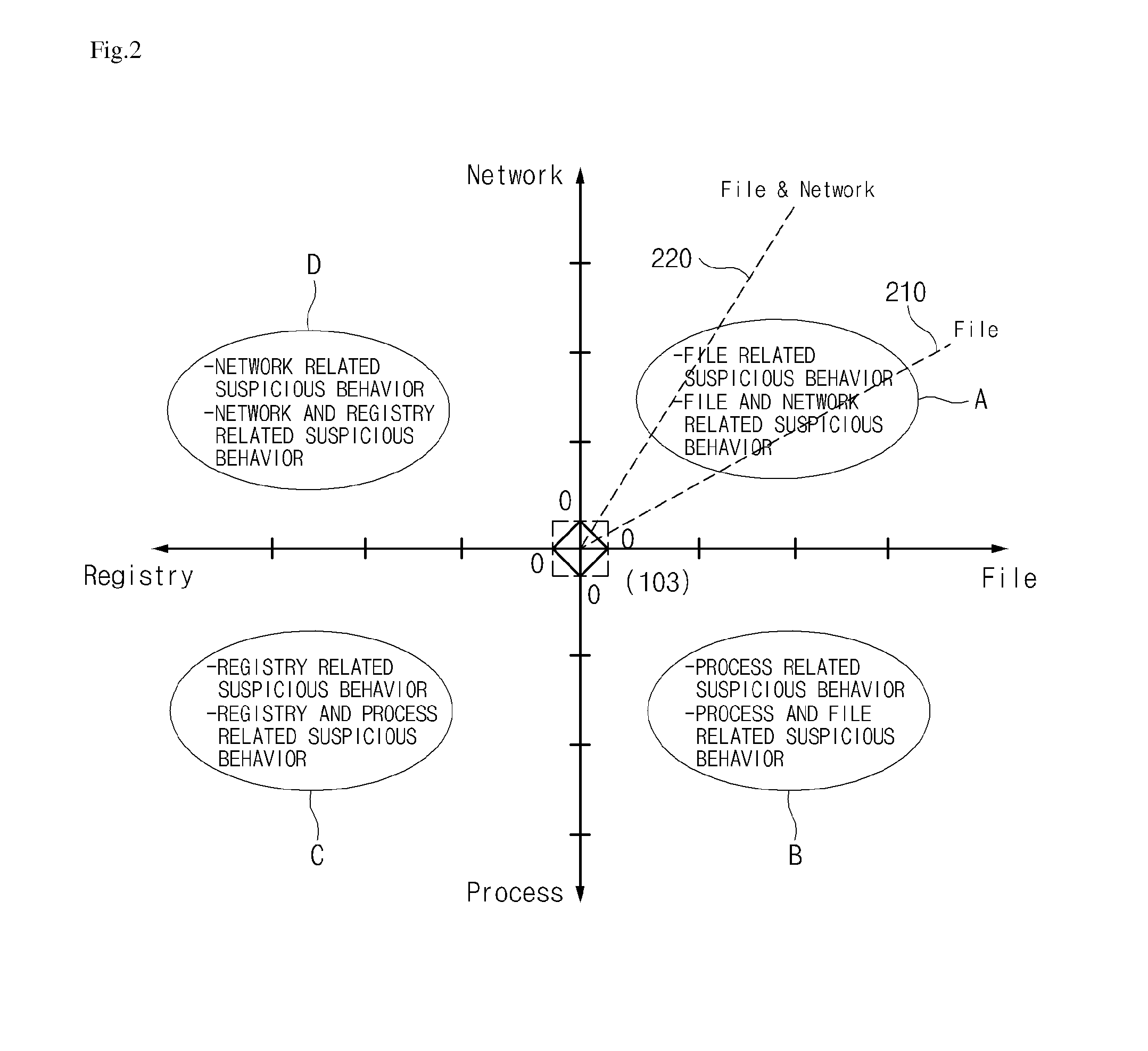
Provided are abnormal behavior detecting apparatus and method and the abnormal behavior detecting apparatus, includes: a behavior analyzing unit which analyzes a behavior which occurs for resources of a system based on data collected from a process while the process is executed on the system; a behavior modeling unit which models a behavior analysis result for the resources of the system on a coordinate which is generated based on the behavior for the resources of the system to create a process behavior model corresponding to the resources of the system; a suspicious behavior determining unit which determines a suspicious behavior of the process in accordance with the type of the process behavior model which is implemented on the coordinate; and a process detecting unit which detects a process in which the suspicious behavior occurs as an abnormal behavior process.
Owner:ELECTRONICS & TELECOMM RES INST
Antivirus protection system and method for computers
InactiveUS7870612B2Reduce in quantitySimple methodMemory loss protectionUnauthorized memory use protectionProcess behaviorCorrelation analysis
Owner:FUJIAN EASTERN MICROPOINT INFO TECH
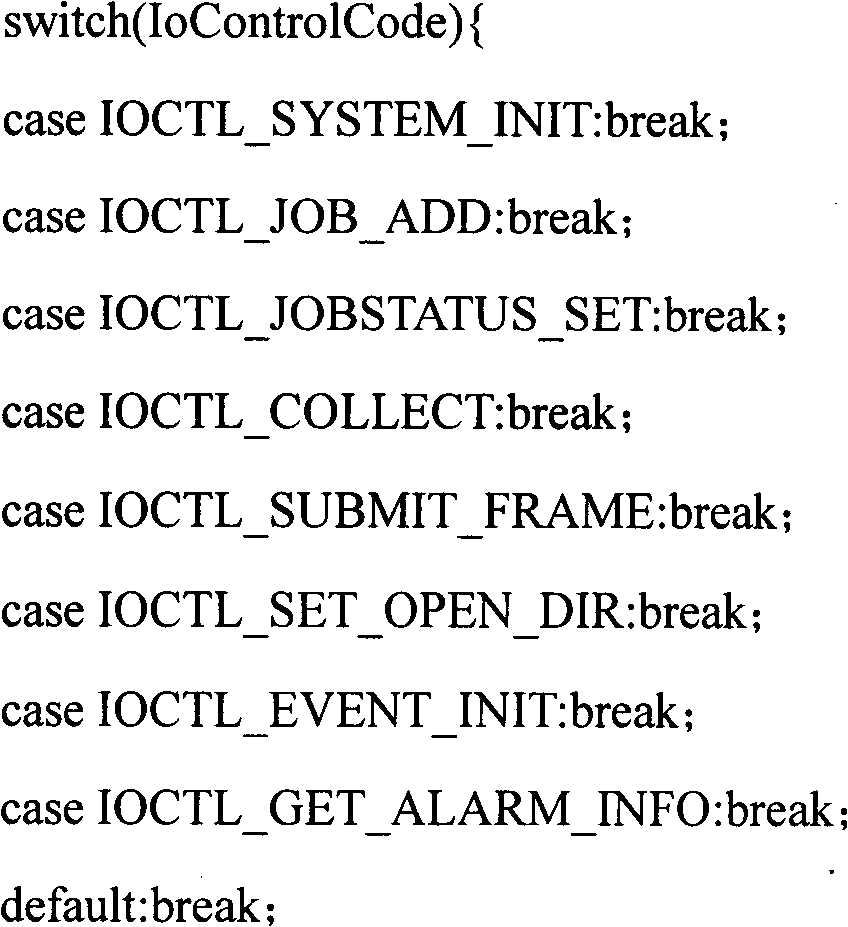
Kernel hook based process behavior monitoring method
ActiveCN105068916AImprove securityHardware monitoringPlatform integrity maintainanceProcess behaviorReal-time computing
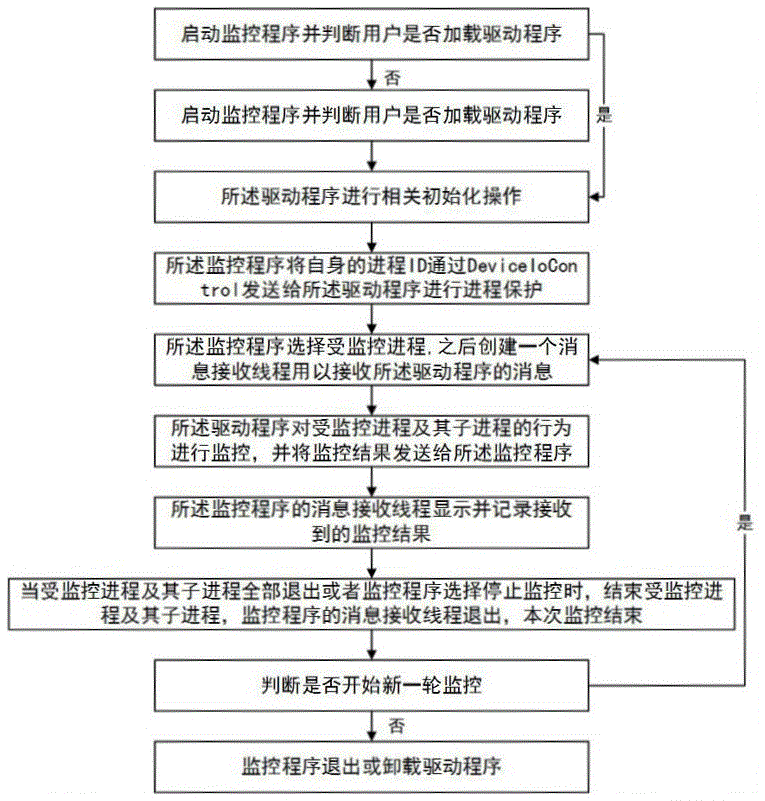
The invention relates to a kernel hook based process behavior monitoring method. Firstly a monitoring program is started and whether a user loads a driving program is judged, if the user does not load the driving program, the user is prompted to load the driving program, then initialization operation is performed, and the monitoring program sends a process ID of the monitoring program to the driving program through DeviceIoControl and performs process protection; the monitoring program selects a monitored process and creates a message receiving thread for receiving a message of the driving program; the driving program monitors behaviors of the monitored process and sub-processes, and sends a monitoring result to the monitoring program; the message receiving thread of the monitoring program displays and records the received monitoring result; and when the monitored process and the sub-processes are all exited or the monitoring program selects stopping of monitoring, the monitored process and the sub-processes are ended, the message receiving thread of the monitoring program is exited, the current monitoring is ended, and the steps are repeated for performing a new round of monitoring. According to the method, the occurrence of malicious process behaviors can be effectively prevented.
Owner:FUZHOU BOKE WANGAN INFORMATION TECH CO LTD
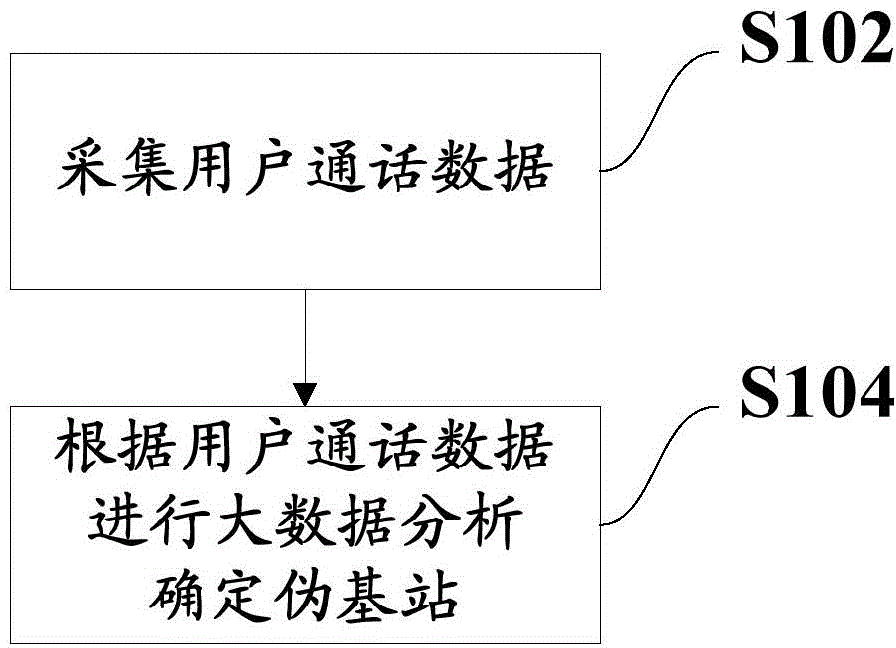
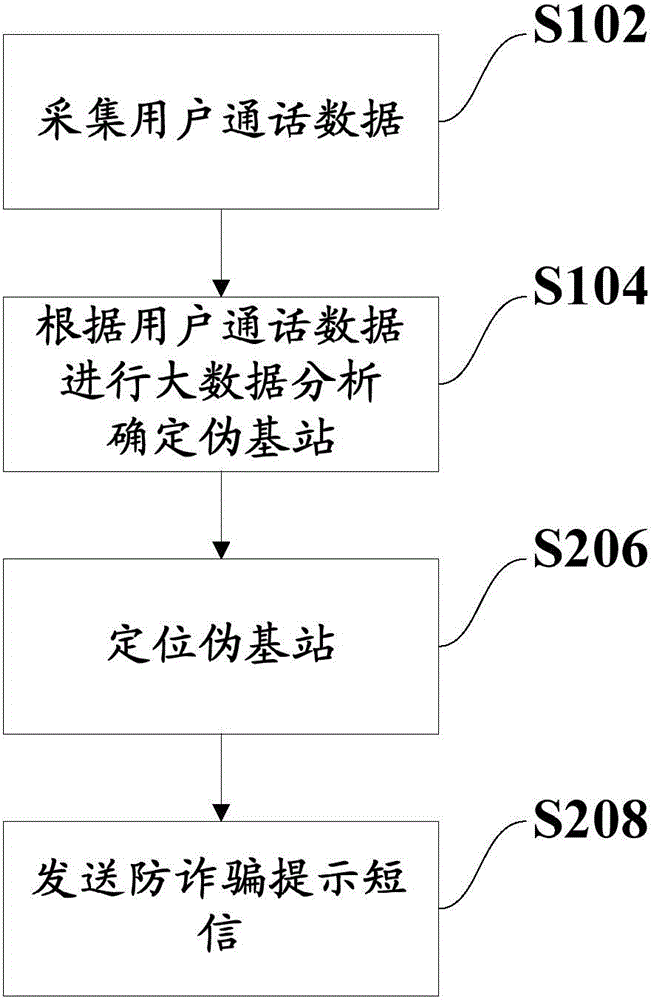
Pseudo base station discovery method and system
The invention discloses a pseudo base station discovery method and system, and relates to the field of wireless communication. According to an embodiment, big data analysis is performed on user call data through acquisition of the user call data which comprises one kind of information of a call establishment characteristic information, service quality-related information, call process behavior information, call release-related information and off-networking information, and a pseudo base station is discovered rapidly according to abnormal characteristic information, reflected in the user call data, of a terminal when the pseudo base station works. And a fixed pseudo base station can be discovered, and a moving pseudo base station can also be discovered.
Owner:CHINA TELECOM CORP LTD
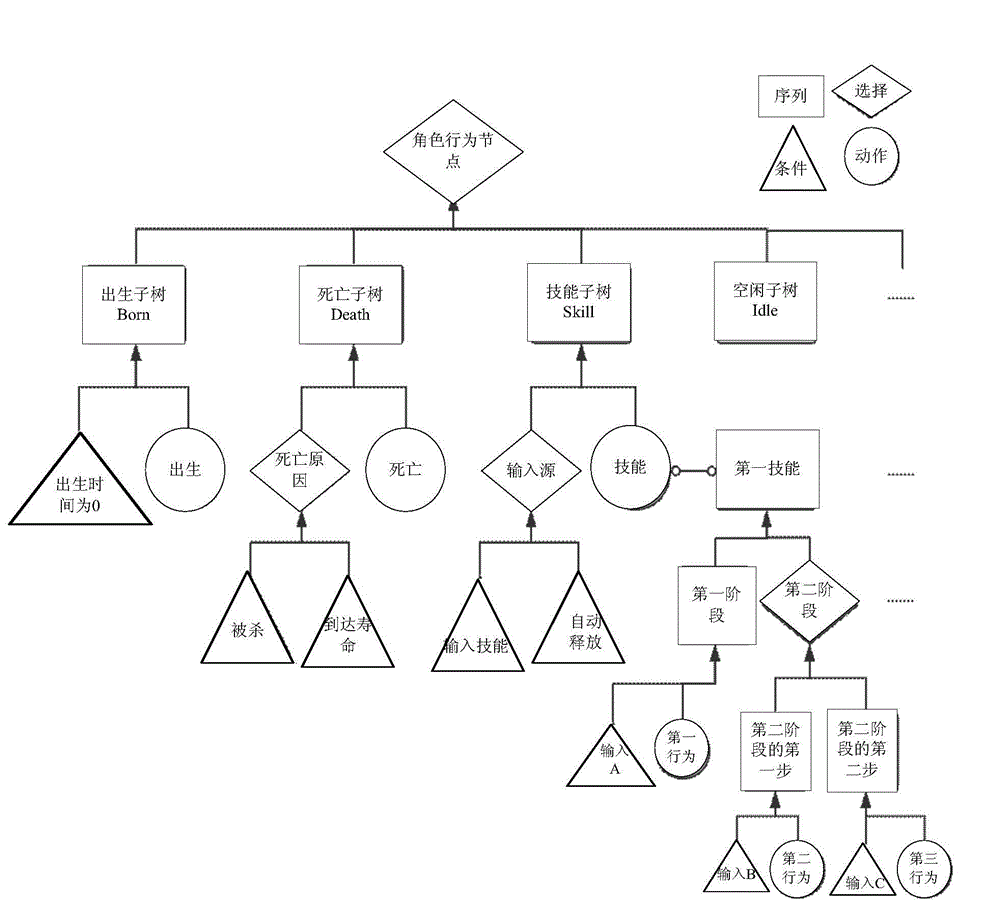
Behavior processing method and device
ActiveCN105117575ASimple designStrong scalabilitySpecial data processing applicationsProcess behaviorTheoretical computer science
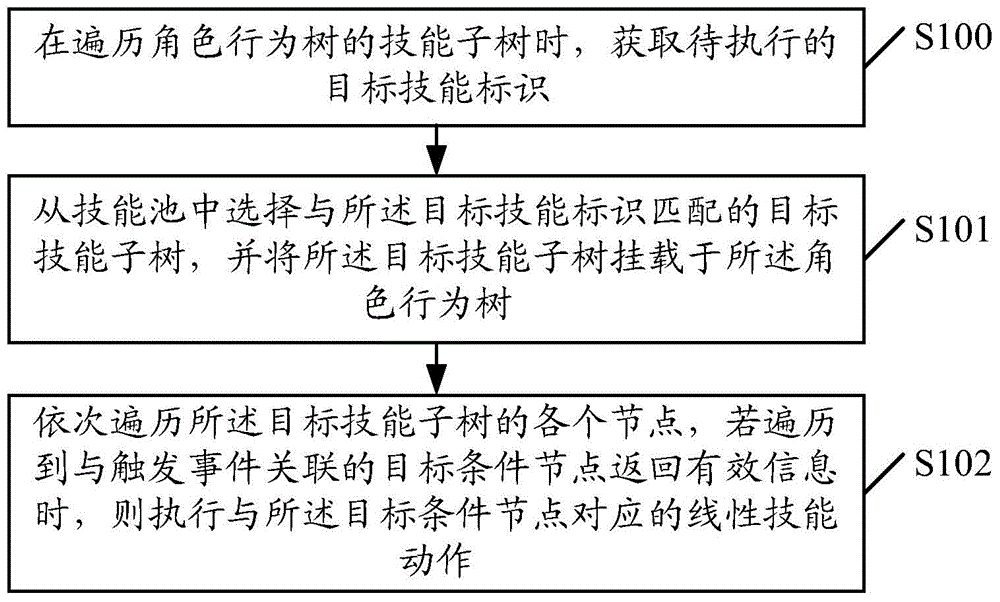
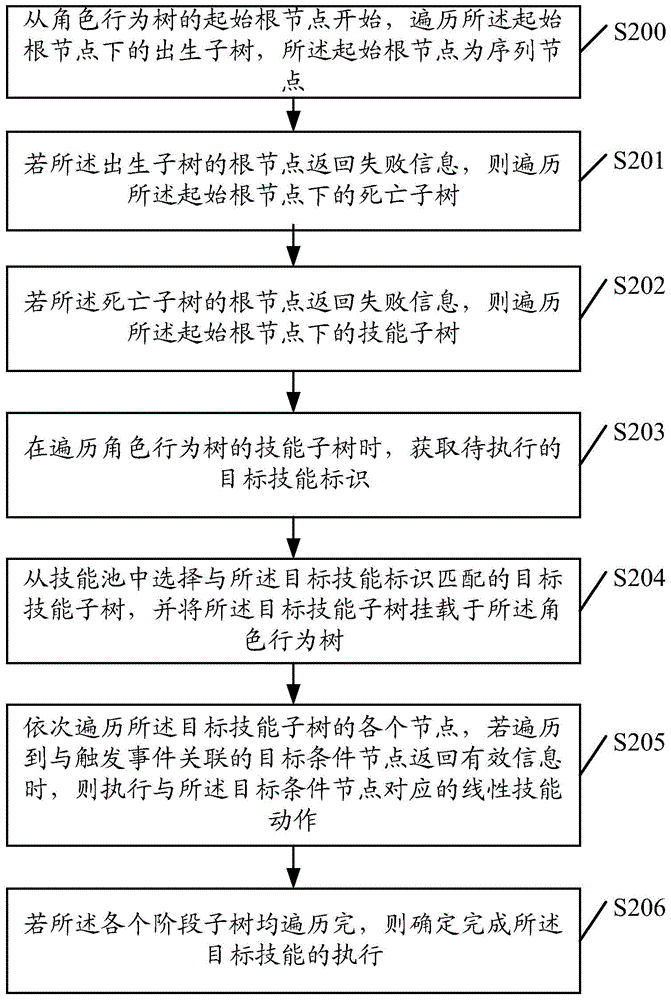
Embodiments of invention provide a behavior processing method and device. The method comprises acquiring a mark of a target ability to be executed after traversing an ability subtree of a role behavior tree; selecting a target ability subtree matching the mark of the target ability from an ability pool, and loading the target ability subtree on the role behavior tree; and sequentially traversing all nodes of the target ability subtree, and executing linear ability motion corresponding to a target condition node if that a target condition node associated with a trigger event returns effective information is traversed. According to the behavior processing method and device, a subtree of a target ability to be executed can be loaded on a role behavior to be traversed, features of recursion and logic of a behavior tree can be fully utilized, the design mode is simple, and the expansibility is excellent.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
Method, device and system for detecting malicious process behavior
ActiveCN103955645AImprove securityImprove reliabilityPlatform integrity maintainanceTransmissionSingle sampleProcess behavior
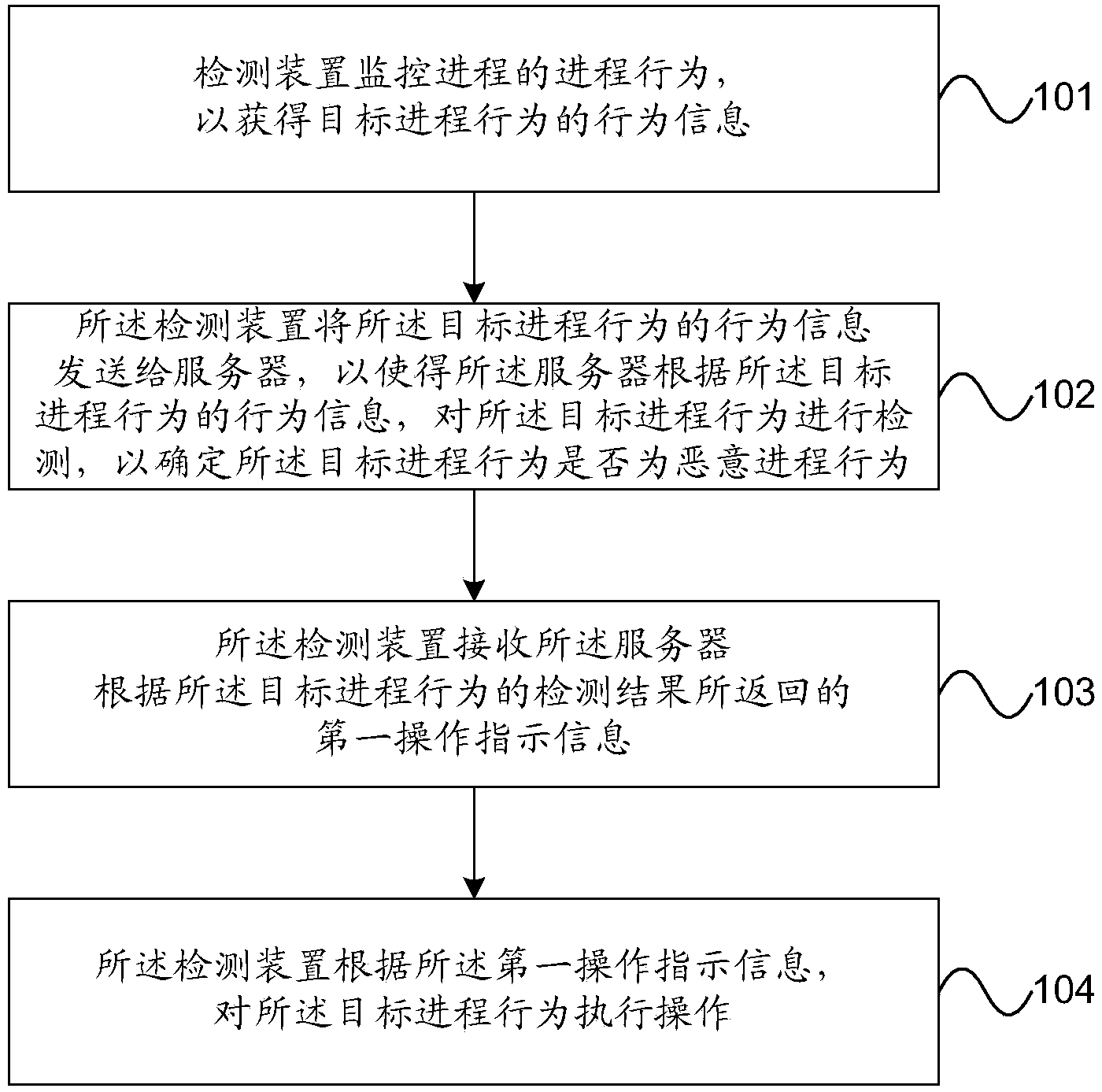
The embodiment of the invention provides a method, a device and a system for detecting a malicious process behavior. The detection device is used for monitoring a process behavior of a process so as to acquire behavior information of a target process behavior, and sending the behavior information of the target process behavior to a server; the server detects the target process behavior according to the behavior information of the target process behavior to determine whether the target process behavior is a malicious process behavior, so that the detection device can receive first operation indicating information returned by the server according to a detection result of the target process behavior, and operate the target process behavior according to the first operation indicating information. The target process behavior is subjected to comprehensive detection by the server according to the behavior information of the target process behavior instead of appointed feature analysis on a single sample by the detection device, so that the malicious process behavior can be detected in time, and the safety of the system is improved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Document leak protecting and tracking system
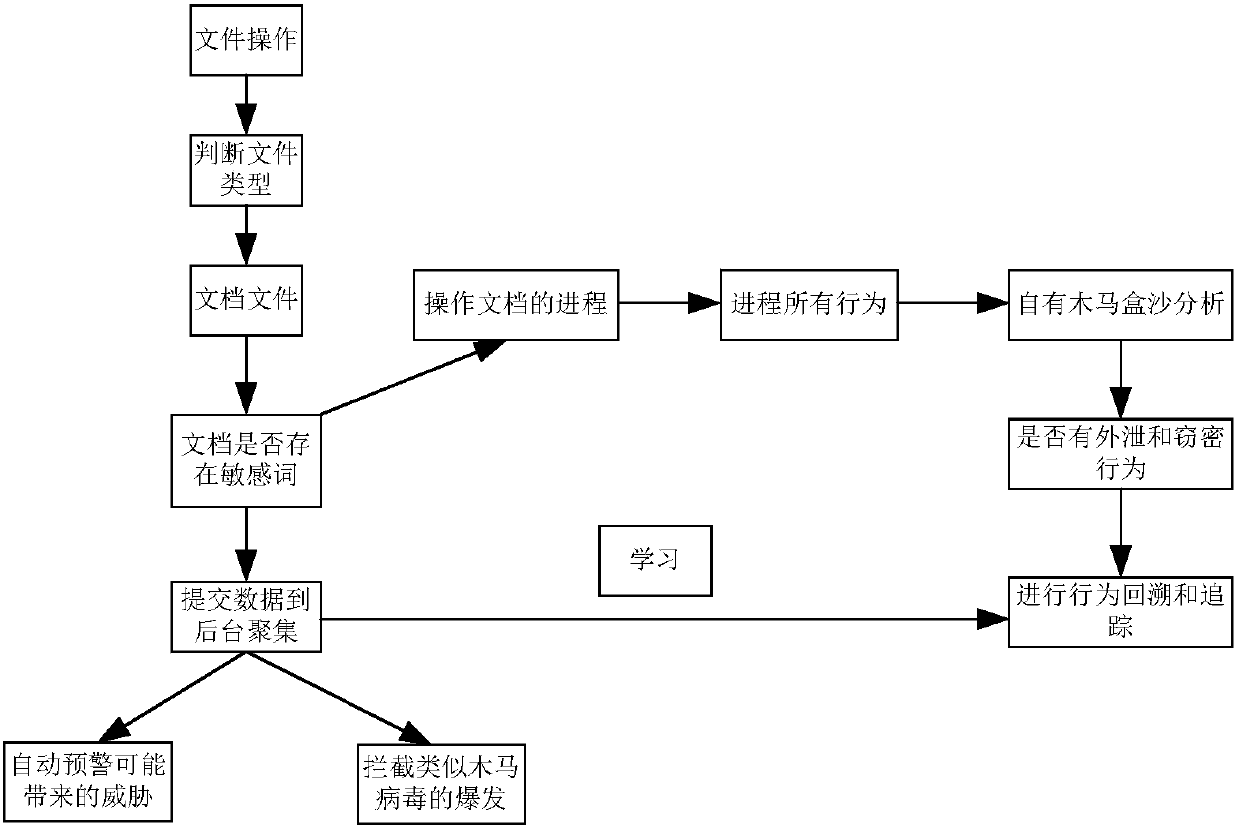
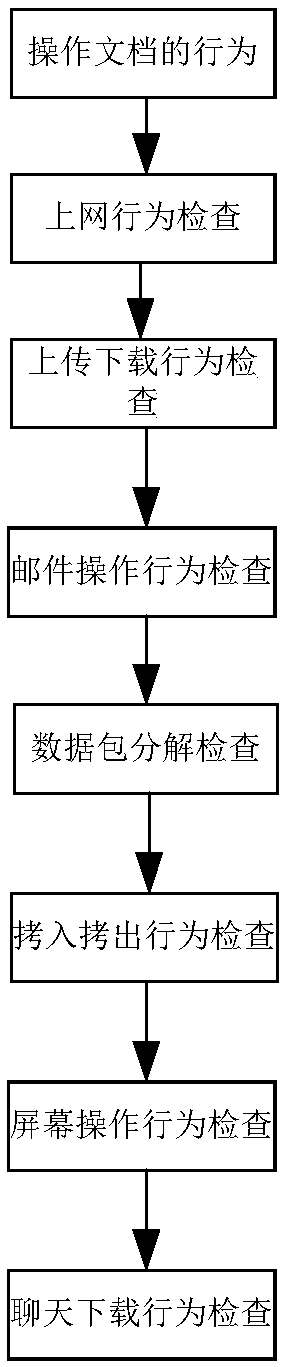
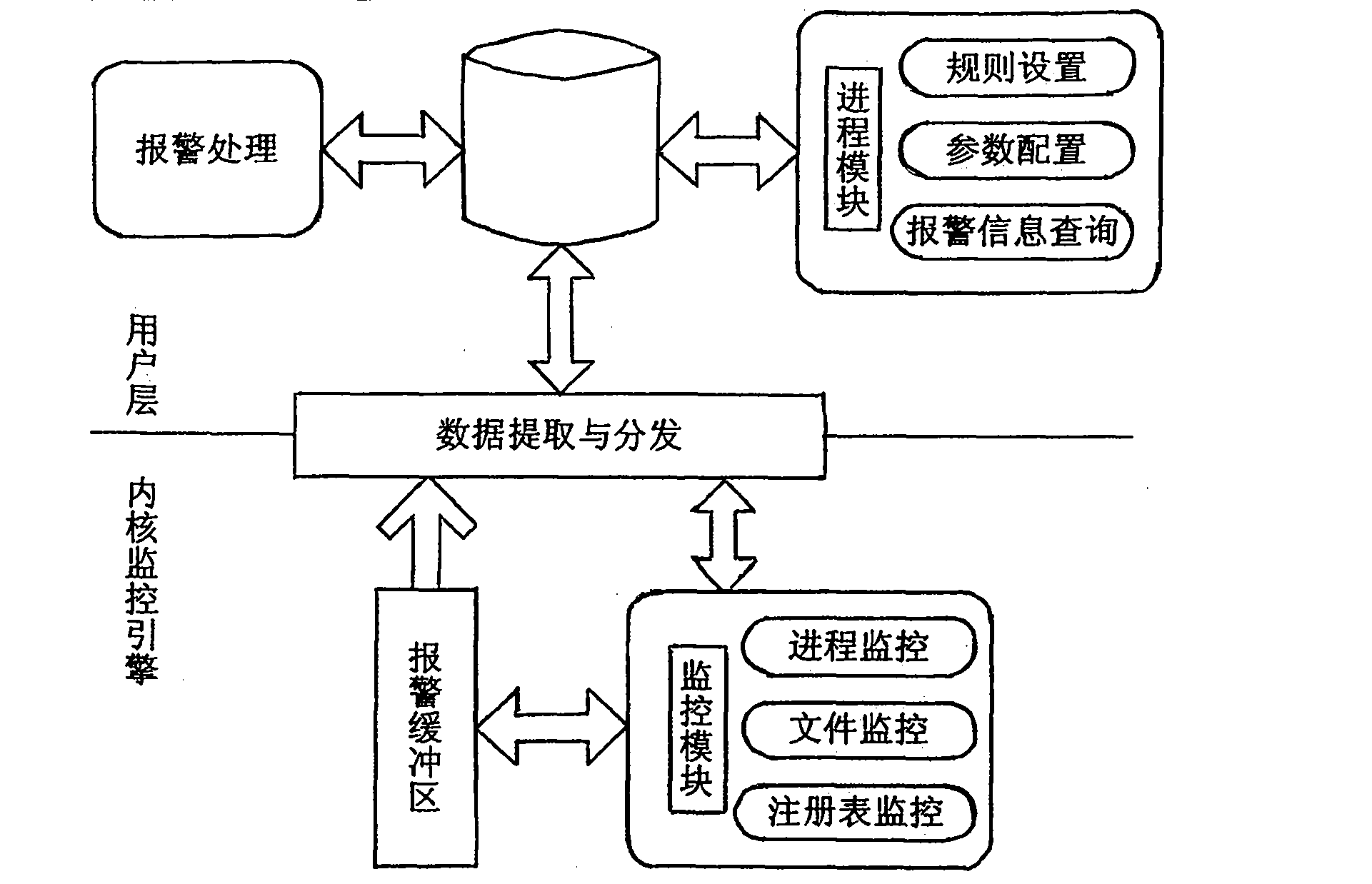
ActiveCN108121914AReal-time inspection and identification of stolenExamine and identify compromised behavior in real timeDigital data protectionPlatform integrity maintainanceBehavioral analyticsOperational system
The invention discloses a document leak protecting and tracking system which comprises a management module, a sensitive word matching module, a monitoring module, a behavior analysis module, a Trojansandbox module and an early warning analysis module, wherein the management module is used for setting sensitive word configuration information of the protecting and tracking system and user-defined rules as well as issuing planning tasks of document scanning and matching sensitive words for each host operating system; the sensitive word matching module is used for matching documents accessed by all processes for each host operating system as well as recognizing whether configuration key words exist in the documents or not; the monitoring module is used for monitoring local directories and files in real time and controlling access process behaviors of the local directories and files; the behavior analysis module is used for analyzing various behaviors of file access processes; the Trojan sandbox module is used for simulating and backtracking process behavior events with leak behaviors so as to recognize Trojan leak and Trojan outbreak; and the early warning analysis module is used forintercepting and early-warning all host clients when Trojan stealing behaviors are found. The system disclosed by the invention can be used for backtracking leaked and stolen sensitive files in computers as well as recognizing leaking and stealing modes.
Owner:四川神虎科技有限公司
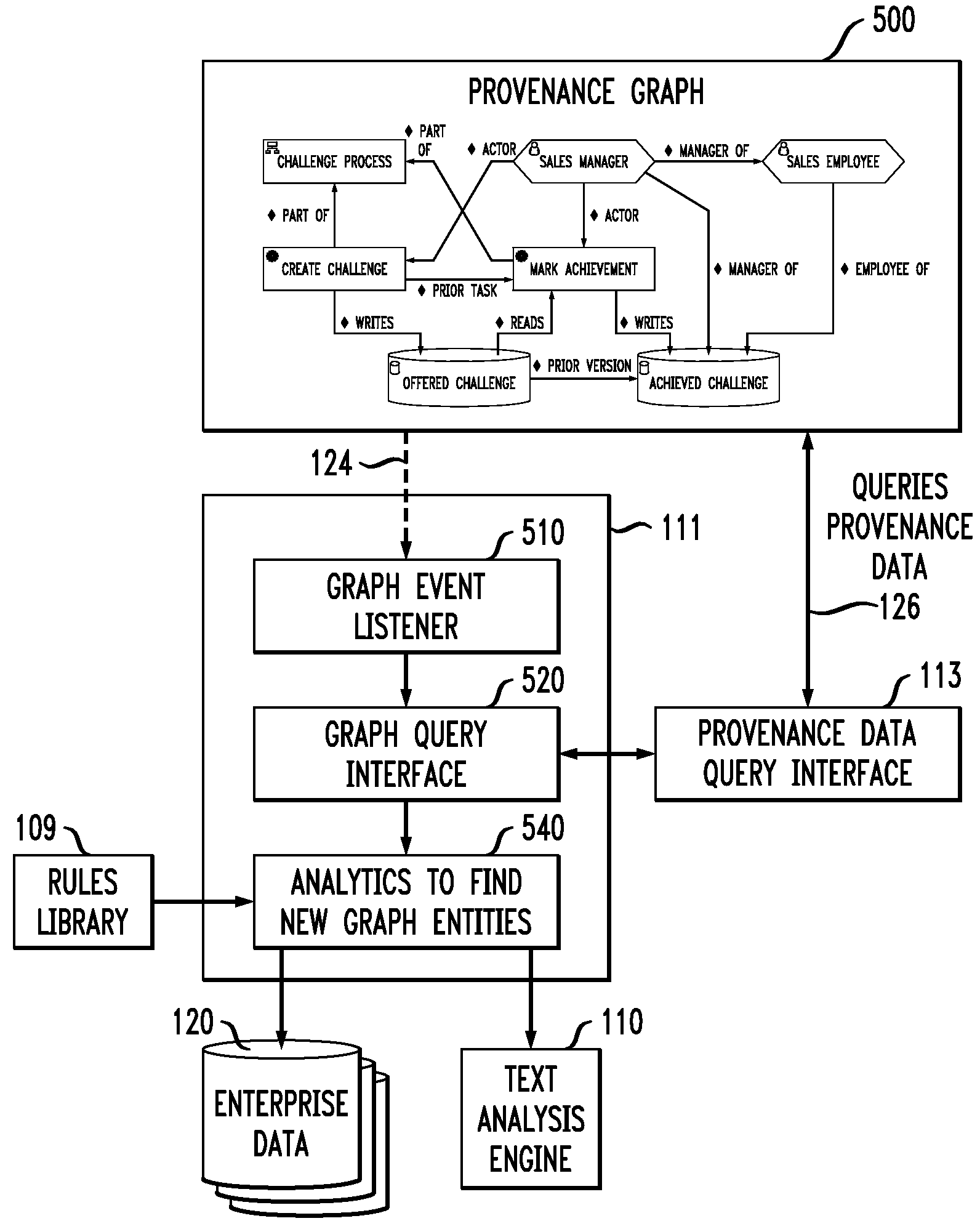
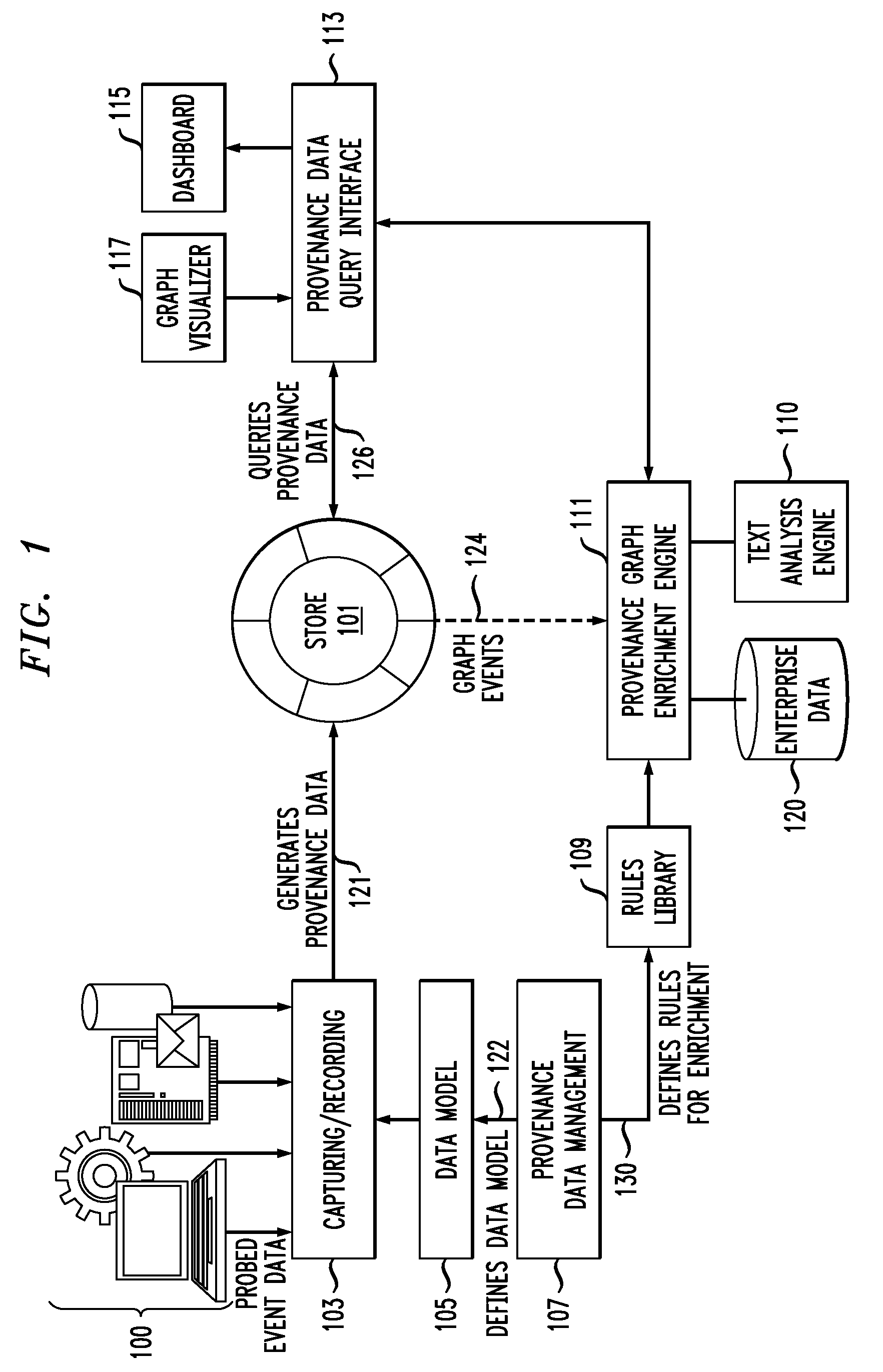
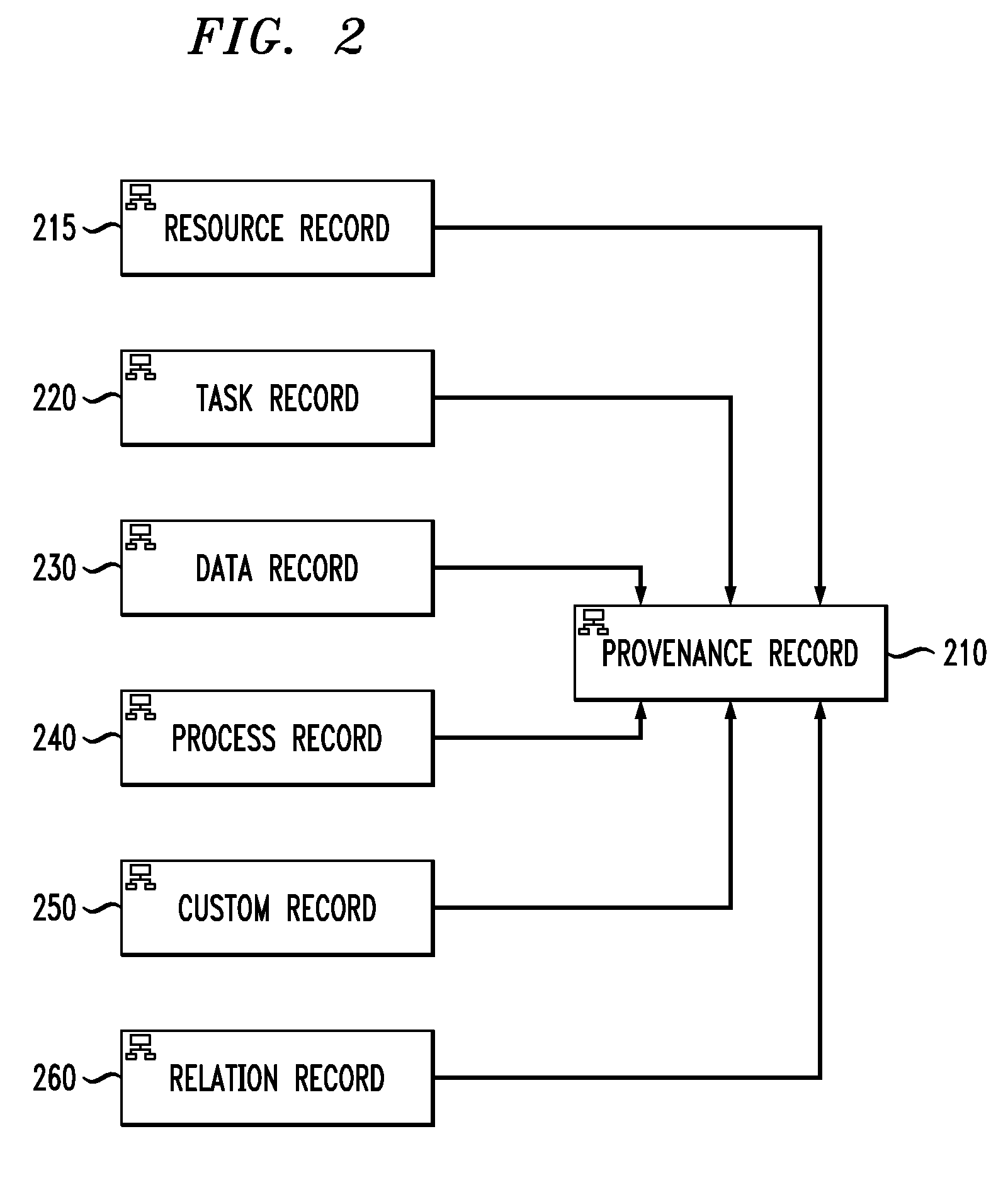
Influencing Behavior of Enterprise Operations During Process Enactment Using Provenance Data
InactiveUS20100114630A1Saves enterprises significantly against integrity lapses and penaltiesDrawing from basic elementsResourcesEnterprise processProcess behavior
Techniques are disclosed for influencing behavior of enterprise operations during process enactment using provenance data. For example, a computer-implemented method of influencing a behavior of an enterprise process comprises the following steps. Provenance data is generated, wherein the provenance data is based on collected data associated with at least a partial actual execution of the enterprise process and is indicative of a lineage of one or more data items. A provenance graph is generated that provides a visual representation of the generated provenance data, wherein nodes of the graph represent records associated with the collected data and edges of the graph represent relations between the records. At least a portion of the generated provenance data from the graph is analyzed to generate an execution pattern corresponding to the at least partial actual execution of the enterprise process. The execution pattern is compared to one or more previously stored patterns. A determination is made as to whether or not to alter the enterprise process based on a result of the comparison.
Owner:SERVICENOW INC
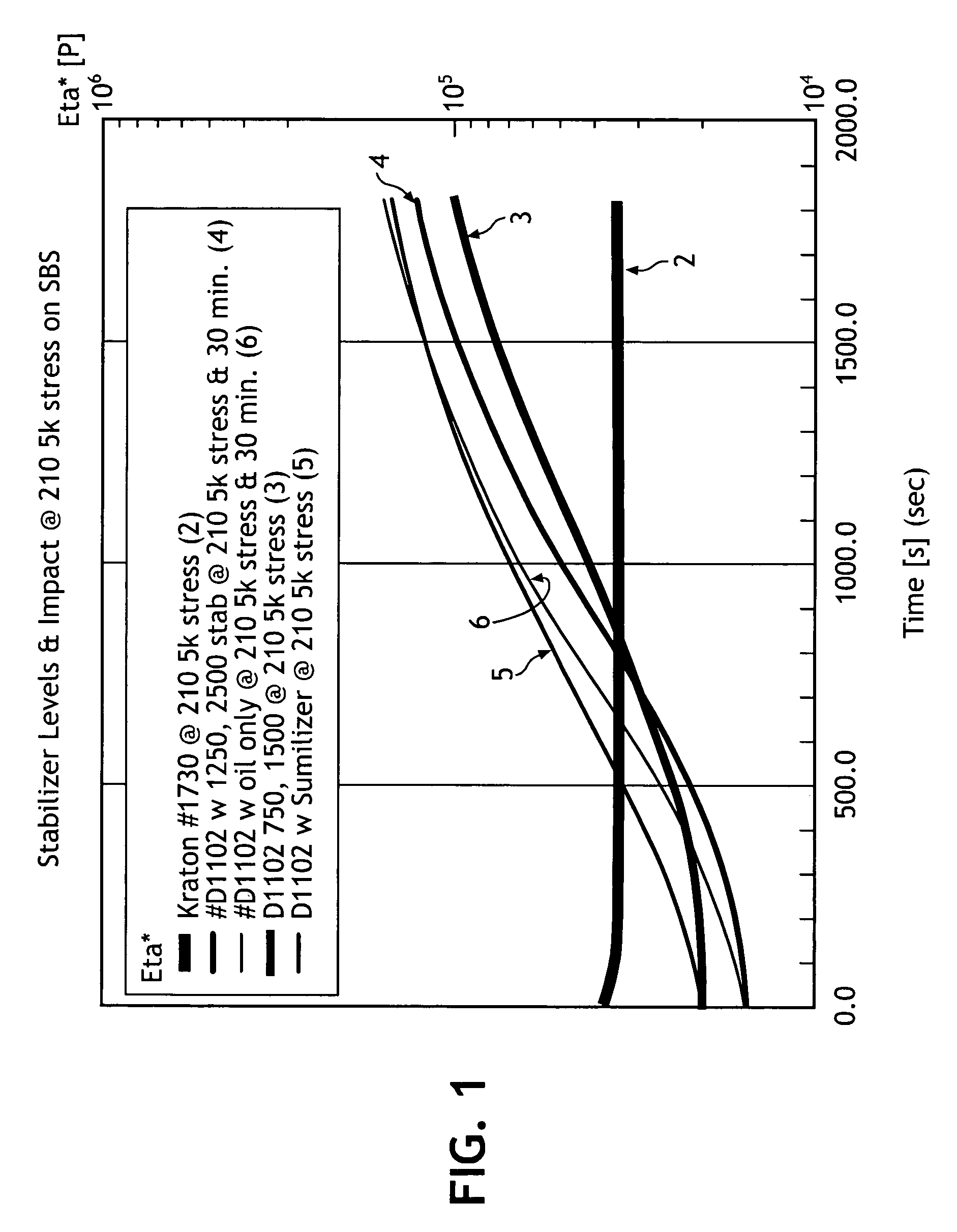
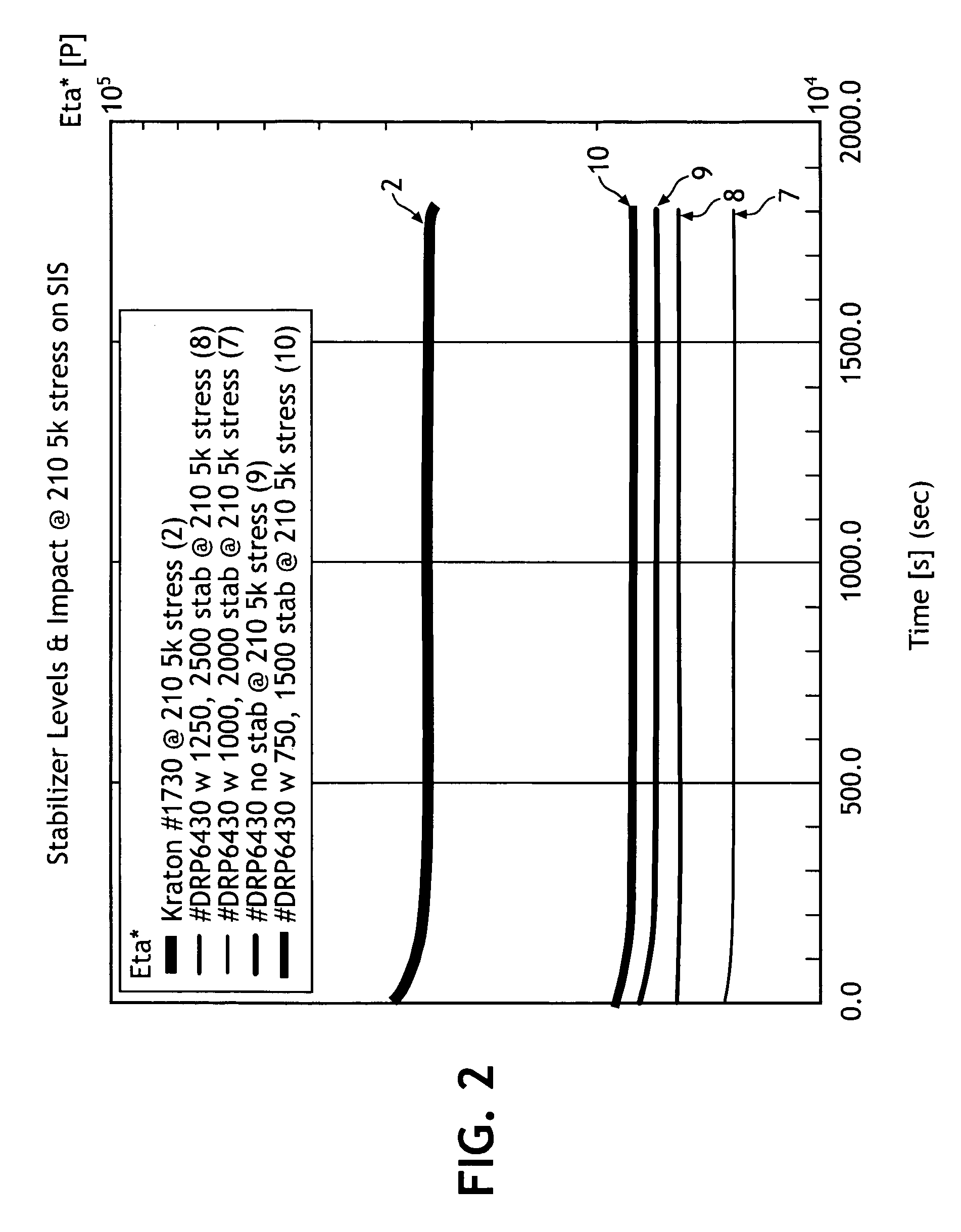
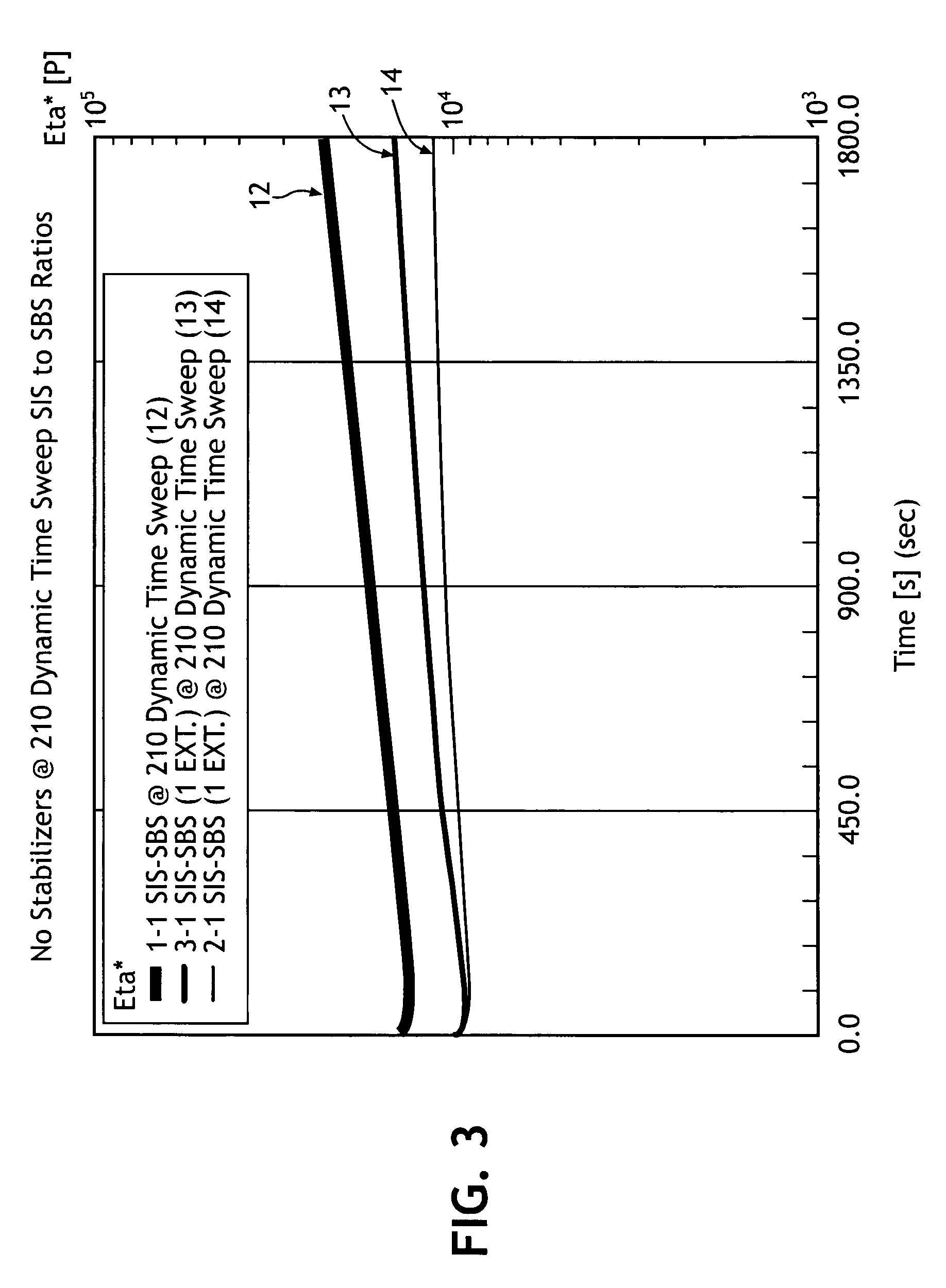
Thermal stabilization and processing behavior of block copolymer compositions by blending, applications thereof, and methods of making same
Owner:KIMBERLY-CLARK WORLDWIDE INC
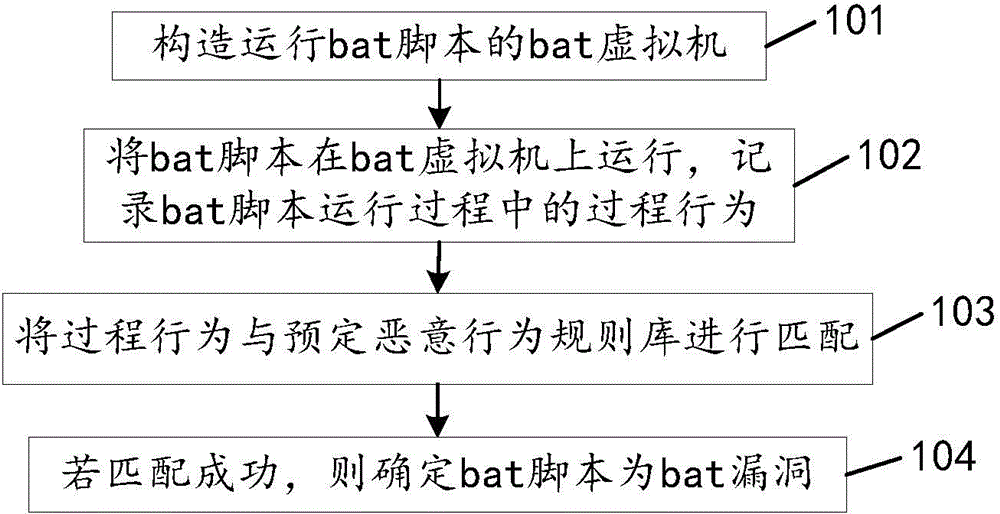
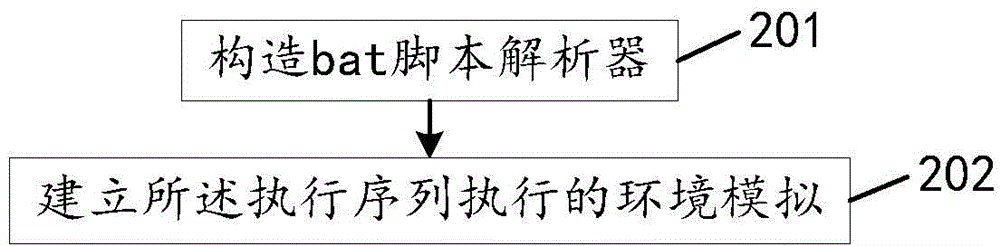
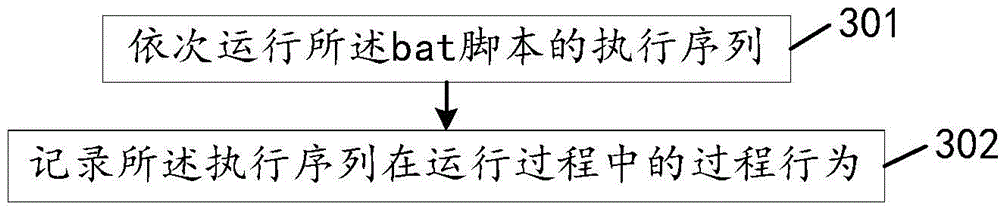
Detecting method and device of bat loopholes
The invention discloses a detecting method and device of bat loopholes and relates to the field of information safety. The bat loopholes in a bat script can be detected quickly and accurately so that the safety of a computer system can be protected. According to the main technical scheme, a bat virtual machine for bat script operation is established; the bat script operates on the bat virtual machine, and the process behavior of the bat script during operation is recorded; the process behavior and a preset malicious behavior base are matched, and the preset malicious behavior base comprises the judging rules of a know malicious behavior script; and if matching is successful, the fact that the bat script is the bat loopholes is determined. The detecting method and device are mainly used in the processing of bat loophole detecting.
Owner:BEIJING QIHOO TECH CO LTD +1
Television audience targeting online
InactiveUS20130104159A1Analogue secracy/subscription systemsBroadcast information monitoringProcess behaviorTv viewer
Owner:EXCALIBUR IP LLC
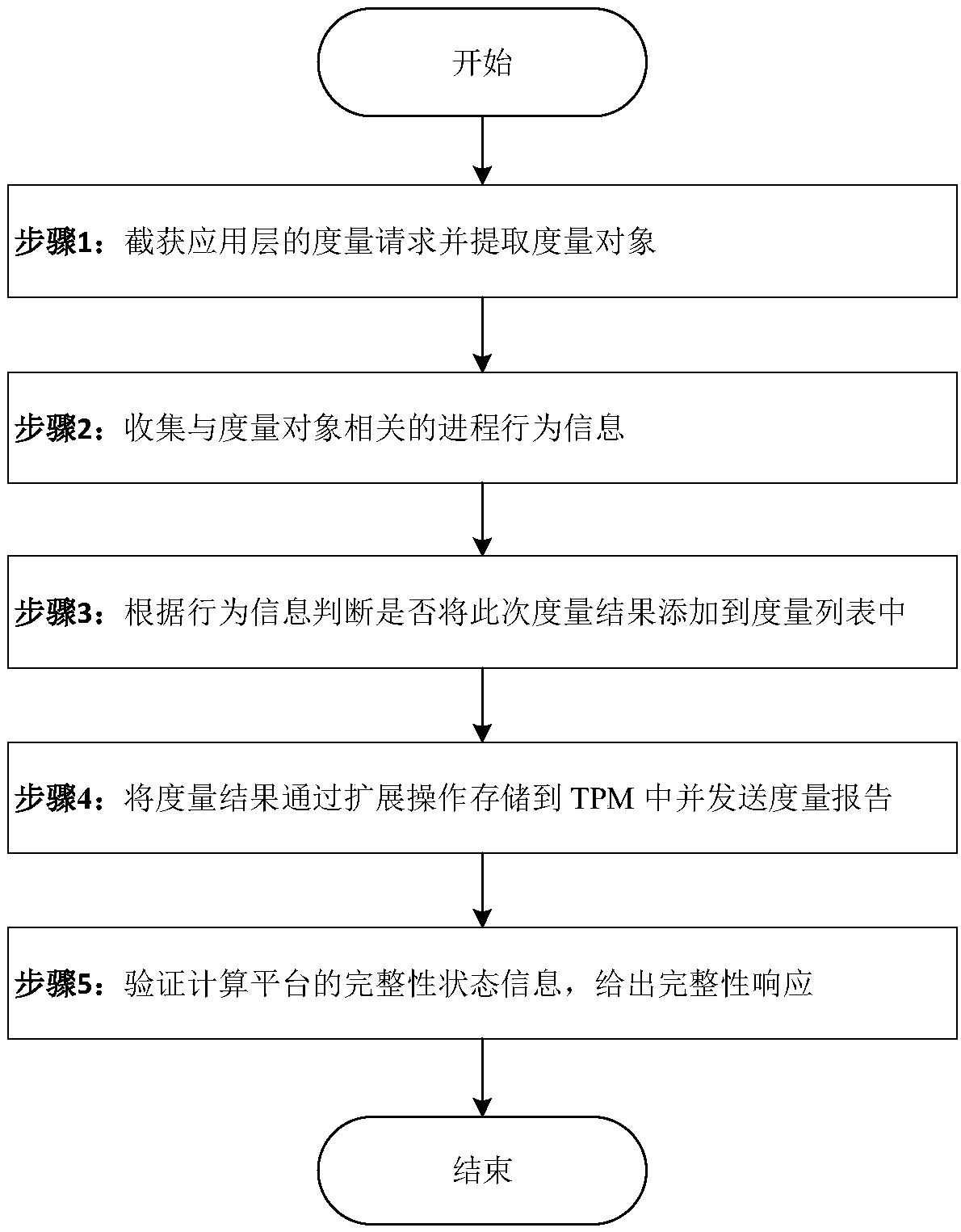
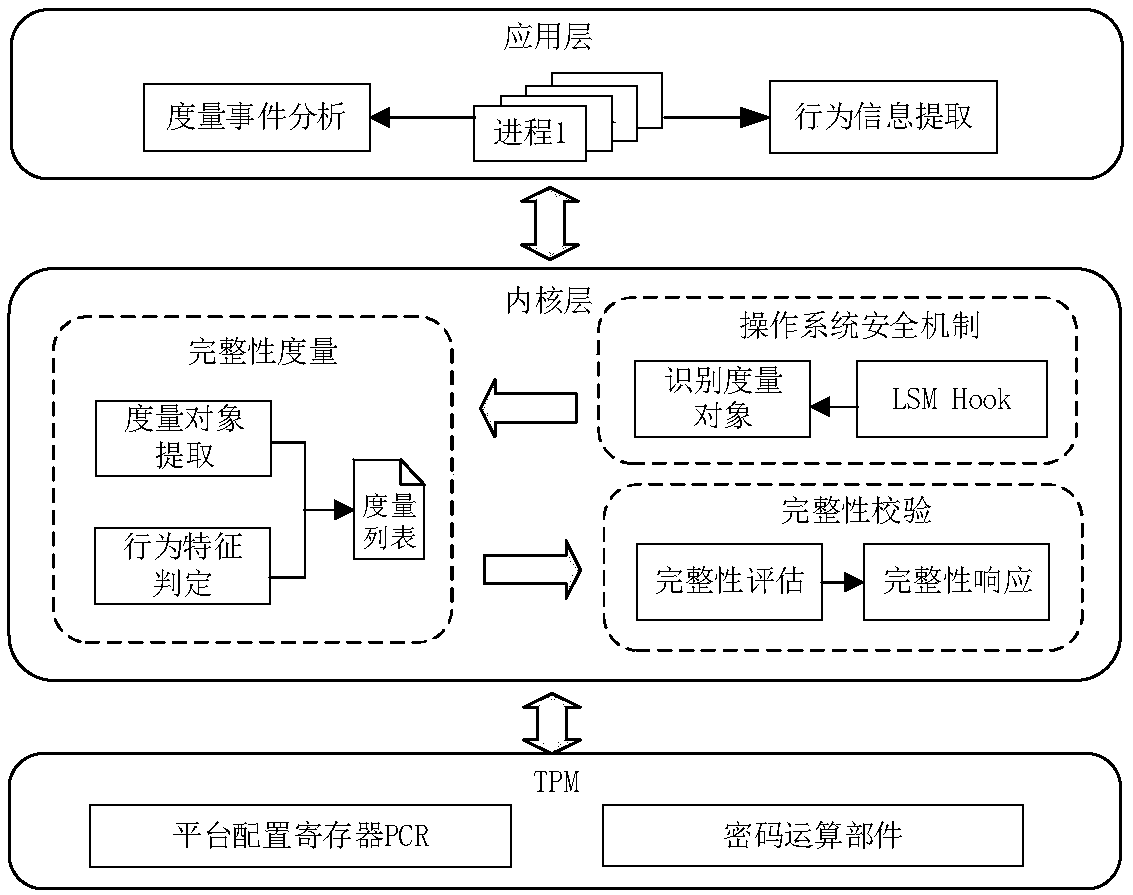
Process behavior-based platform integrity state information measurement method
ActiveCN108399338AImprove integrity measurement efficiencyEasy to measurePlatform integrity maintainanceComputer hardwareGranularity
The invention discloses a process behavior-based platform integrity state information measurement method. The method comprises the following steps of 1, capturing a measurement request of an application layer, and extracting a measurement object from an application; 2, analyzing a running state and an executive parameter of the application, and collecting process behavior information related to the measurement object; 3, according to a behavior characteristic, judging whether a current measurement result is added to a measurement list or not, and collecting the process behavior information related to the measurement object in the measurement list; 4, storing the measurement result in a specific PCR of a trusted platform module through expansion operation, generating a measurement report and sending the measurement report to a log audit mechanism of the application layer; and 5, according to the measurement list, a measurement log and the measurement result stored in the PCR, verifyingand calculating integrity state information of the platform. According to the higher-granularity integrity state information measurement method provided by the invention, the reflected to-be-verifiedand calculated security attribute information of the platform is more accurate, so that the measurement efficiency can be improved.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
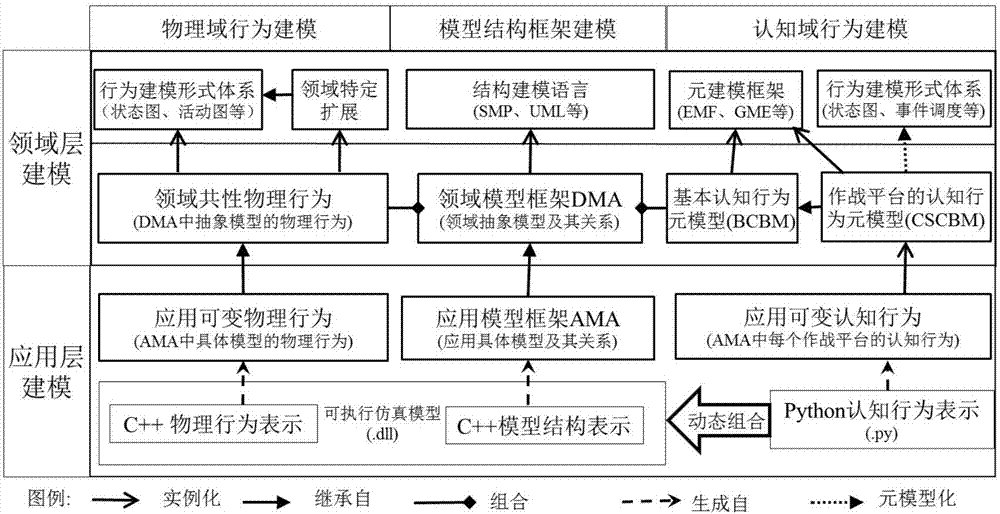
Novel combat effectiveness simulation modeling method
ActiveCN107967134ASupports semantic compositionEfficiently buildSoftware designVisual/graphical programmingMetamodelingProcess behavior
The invention discloses a novel combat effectiveness simulation modeling method, and the problems that a simulation model in combat effectiveness simulation is difficult to combine, reuse, expand andevolve, and a decision behavior model lacks flexibility and problem pertinence are solved. On the one hand, the method emphasizes clear distinction between two levels of knowledge including domain commonness non-variable knowledge and application variable knowledge of the combat effectiveness simulation, and describing the two levels of the knowledge separately; the domain commonness non-variableknowledge is applicable to the entire combat effectiveness field, accordingly a field abstract model is established; the application variable knowledge depends on specific combat effectiveness assessment questions, and an application-specific model which can be instantiated and deployed is established on the basis of the field abstract model. On the other hand, the method emphasizes the distinction between physical process behaviors of weapons and cognitive decision-making behaviors of combat commanders, the cognitive decision-making behaviors compared with the physical process behaviors havegreat difference in different applications according to missions and different choices of the commanders, and dynamic flexibility of the cognitive decision-making behaviors and pertinent expression ofquestions are realized by means of a script technology and a meta-modeling technology.
Owner:NAT UNIV OF DEFENSE TECH
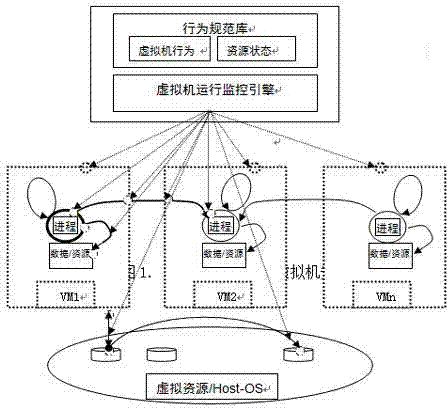
Virtual machine safety monitoring method based on behavior recognition
InactiveCN103793646AEffective Operation Safety Safety MonitoringRealize security protectionPlatform integrity maintainanceVirtualizationProcess behavior
The invention provides a virtual machine safety monitoring method based on behavior recognition. A series of virtual machines, key monitoring points in the relevant program running process behavior and virtual machine resource state critical identification points are set, and then corresponding characteristic parameter specifications are set. On the basis, virtual machines and relevant resources are monitored, and when it is found that the behaviors of the virtual machines and virtual machine applications or the relevant resource states of the virtual machines are abnormal, an abnormality alarm is given. Through a bottom layer operation system or monitoring system of the running environment of the virtual machines, corresponding protective measures can be taken according to the abnormality warning information, and thus the running safety of the virtual machines and a virtualized system can be effectively guaranteed.
Owner:INSPUR TIANYUAN COMM INFORMATION SYST CO LTD
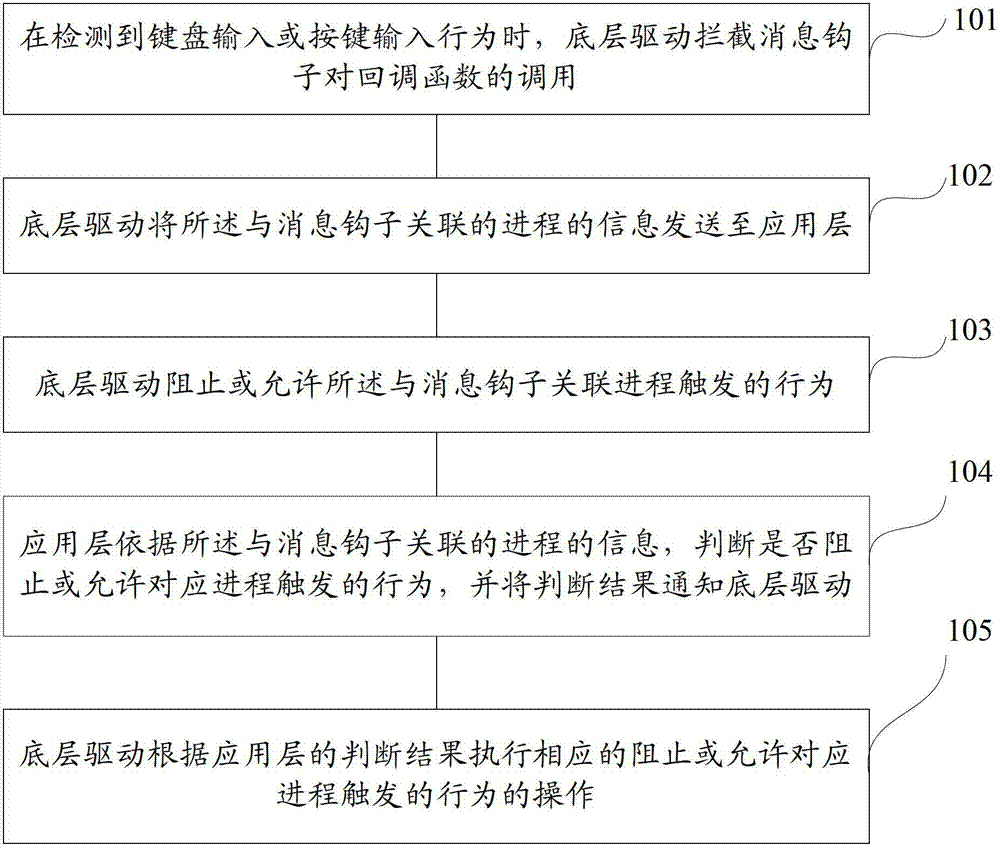
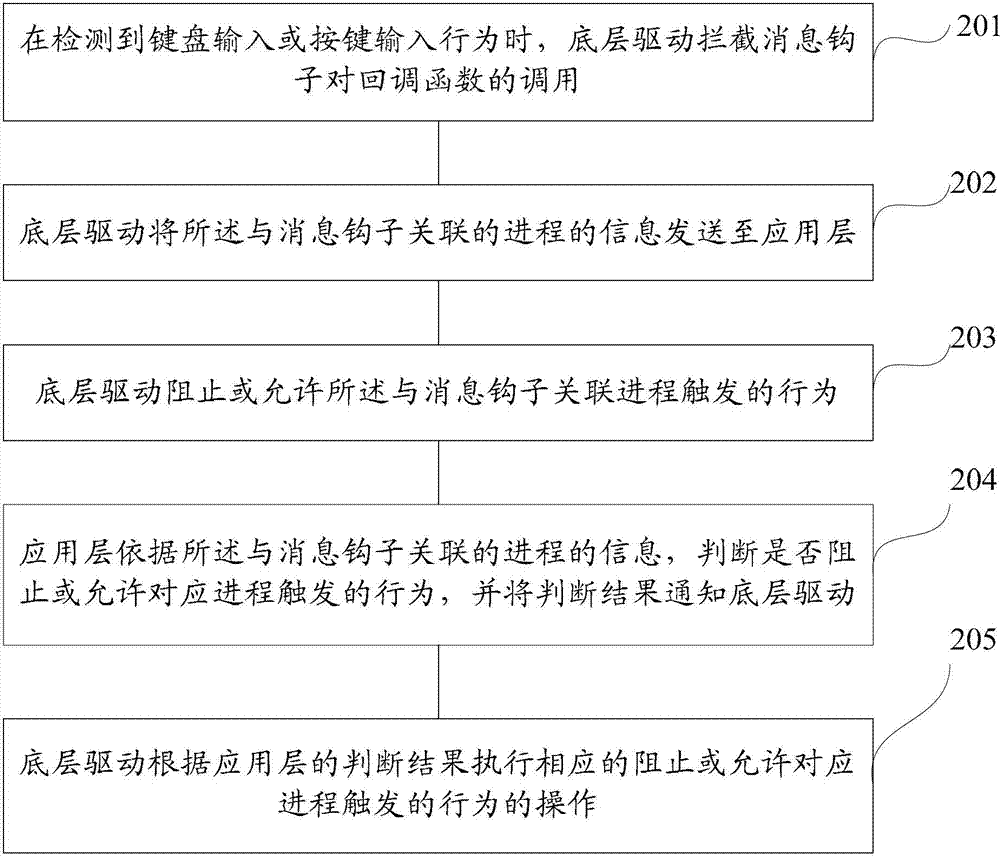
Process behavior control method and device
ActiveCN102890641AEnsure safetyGuaranteed stabilityMultiprogramming arrangementsPlatform integrity maintainanceProcess behaviorProtocol Application
The invention discloses a process behavior control method and a process behavior control device. The method comprises the following steps that: when detecting a keyboard input or key input behavior, an underlying driver intercepts the calling of a callback function by a message hook, wherein the message hook is associated with a process for triggering the current keyboard input or key input behavior; the underlying driver sends information of the process associated with the message hook to an application layer; the underlying driver stops or allows the behavior triggered by the process associated with the message hook; the application layer judges whether the behavior triggered by the corresponding process is stopped or allowed or not according to the information of the process associated with the message hook, and informs the underlying driver of a judgment result; and the underlying driver performs the corresponding operation of stopping or allowing the behavior triggered by the corresponding process according to the judgment result of the application layer. By the method and the device, the calling of the callback function by the message hook can be intercepted, and the stability of a system is ensured.
Owner:BEIJING QIHOO TECH CO LTD +1
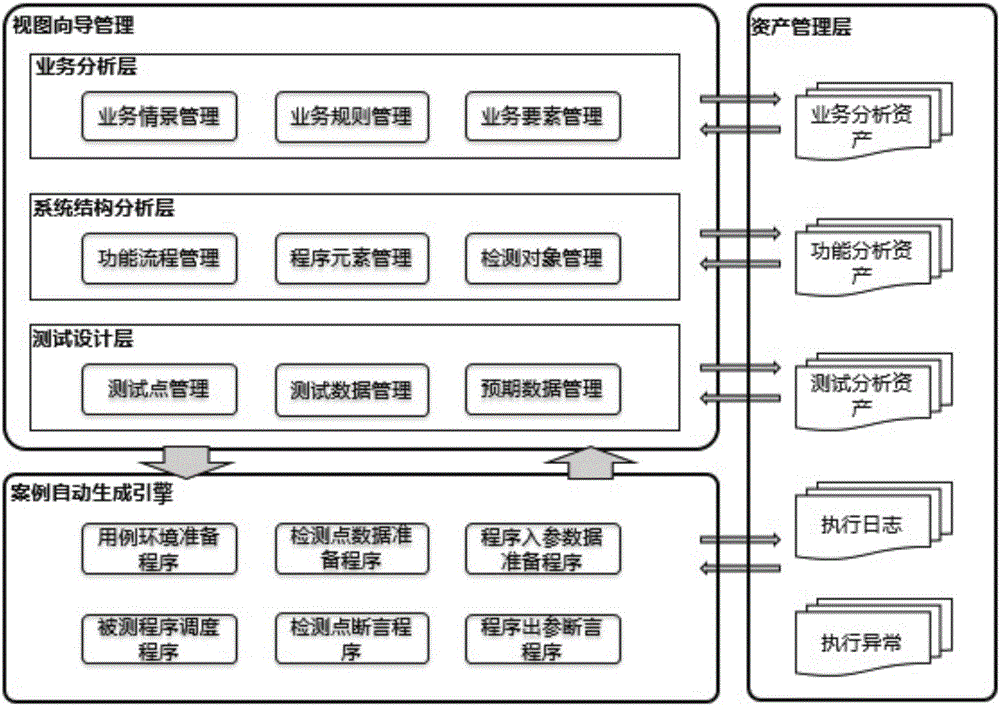
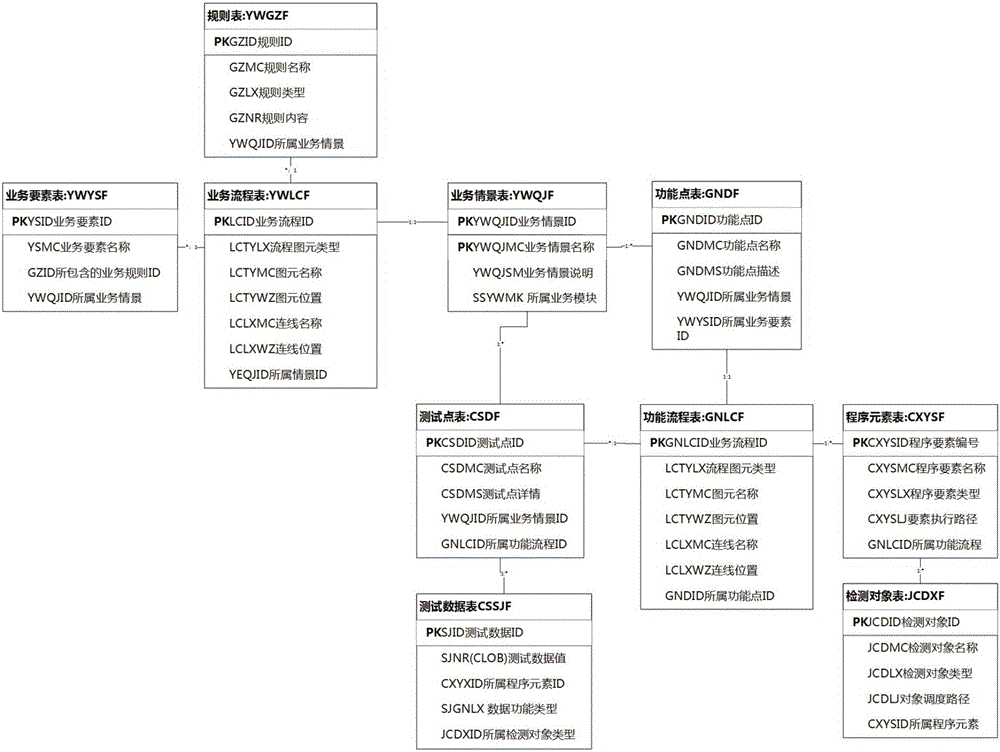
Service analysis based automatic test case generation system and method
ActiveCN106201899AIncrease productivityEffective Business Test Analysis ProcessSoftware testing/debuggingProcess behaviorSystem under test
The invention relates to a service analysis based automatic test case generation system and method. The service analysis based automatic test case generation system comprises a service analysis layer for determining the will of service achievement and clarifying a judgement criterion of the system, a system structure analysis layer for analyzing program elements, operating timing sequence and a detection object of a tested system and clarifying a program verification model for system testing, a testing design layer for performing test point analysis management and test data analysis management, an automatic test case generation engine for converting tested and analyzed data into test cases. By the adoption of the system and method, the problem that business personnel do not know techniques and accordingly 'demand distortion' of software design is caused, and the phenomenon that software function design does not meet the demand of service intent and accordingly frequent reworking is caused is avoided. The process behaviors of service, design and testing analysis are recorded through unified management practices and sediment to form properties of the software design process, and the service analysis based automatic test case generation system has a wide application range.
Owner:PRIMETON INFORMATION TECH
Detection method of web shell and web server
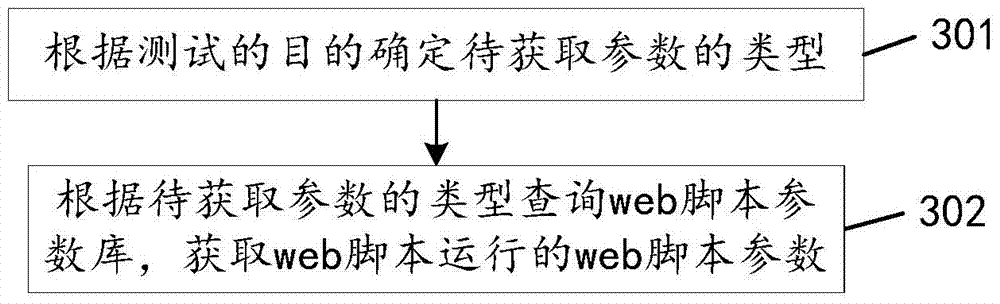
The invention discloses a detection method of web shell and a web server, relates to the field of information security, and mainly aims to detect the web shell in the web server rapidly and accurately in order to protect the security of the web server. According to the major technical scheme of the invention, the method comprises the following steps: constructing a web script virtual machine running a web server script; acquiring web script parameters of web scrip running according to different testing aims; running the web script parameters and the detected web server script on the web script virtual machine, and recording a process behavior in the running process of the web server script; matching the process behavior with a predetermined malicious script rule base; if the matching is successful, determining that the web server script is the web shell. The detection method is mainly applied to the detection process of the web shell.
Owner:三六零数字安全科技集团有限公司
Method for controlling software behavior based on least privilege principle
InactiveCN102208004AAvoid crossing the lineAvoid destructionPlatform integrity maintainanceFiltrationProcess behavior
Owner:江苏云木养老科技有限公司
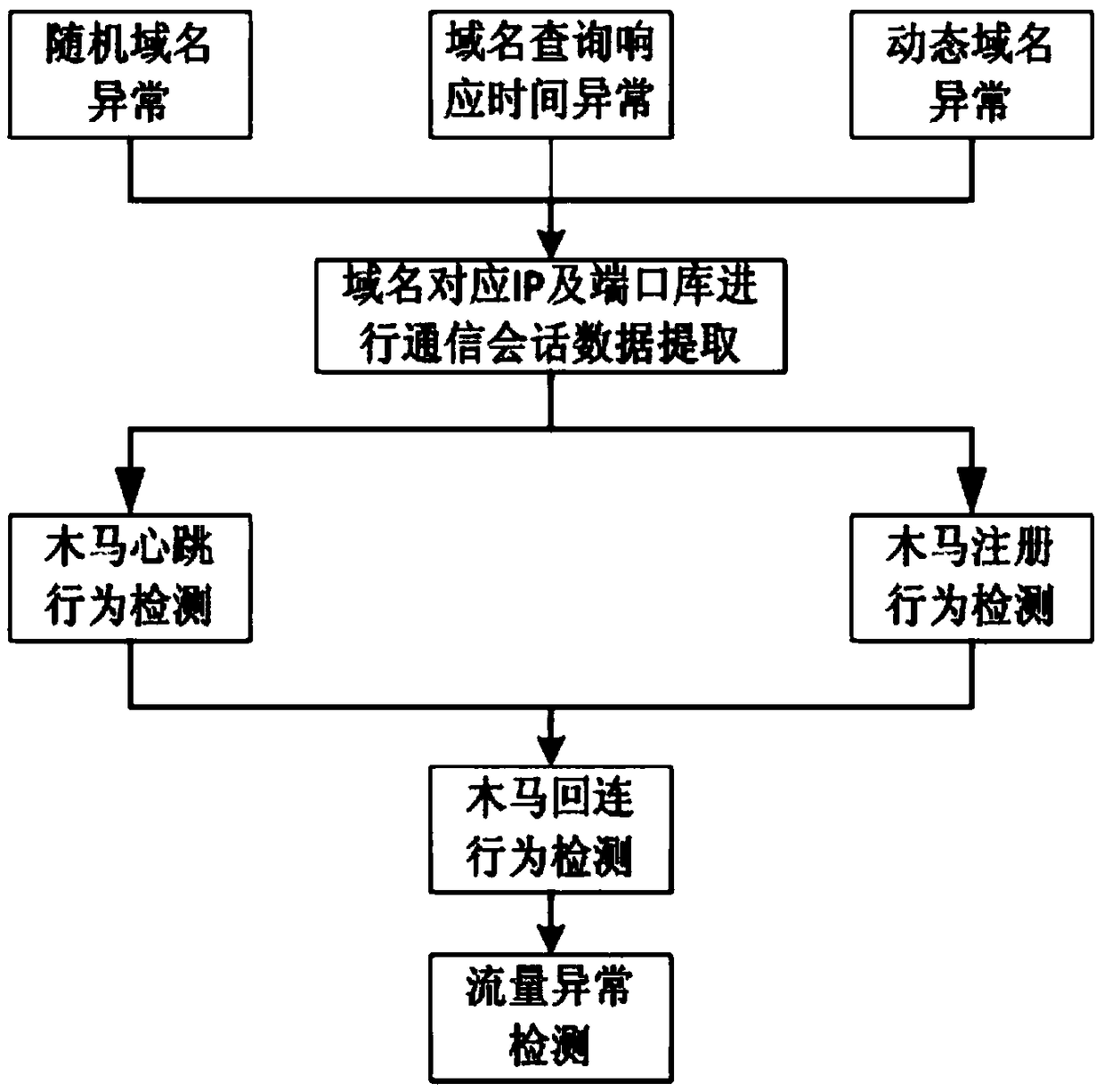
Attack chain behavior analysis based Trojan horse detection method and system
The invention relates to network safety and aims at providing an attack chain behavior analysis based Trojan horse detection method and system. The attack chain behavior analysis based Trojan horse detection system comprises a DNS domain name anomaly detection module, a Trojan horse incubation behavior anomaly detection module and a Trojan horse communication behavior anomaly detection module andcan perform anomaly detection on three behavior processes, including, a Trojan horse connection process, a Trojan horse incubation process and a Trojan horse communication process, in a Trojan horse permeation attacking process; when the anomaly detection condition of the Trojan horse connection process, the Trojan horse incubation process and the Trojan horse communication process is met, a factthat a Trojan horse is detected is confirmed and the Trojan horse detection is realized. By performing sequential associated analysis on the three Trojan horse behavior processes, including, the Trojan horse connection process, the Trojan horse incubation process and the Trojan horse communication process, the comprehensive and efficient Trojan horse detection method and system are provided respectively based on the behavior features of the three Trojan horse processes, the accuracy of Trojan horse detection is enabled to be higher, and the missing report rate is enabled to be lower.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
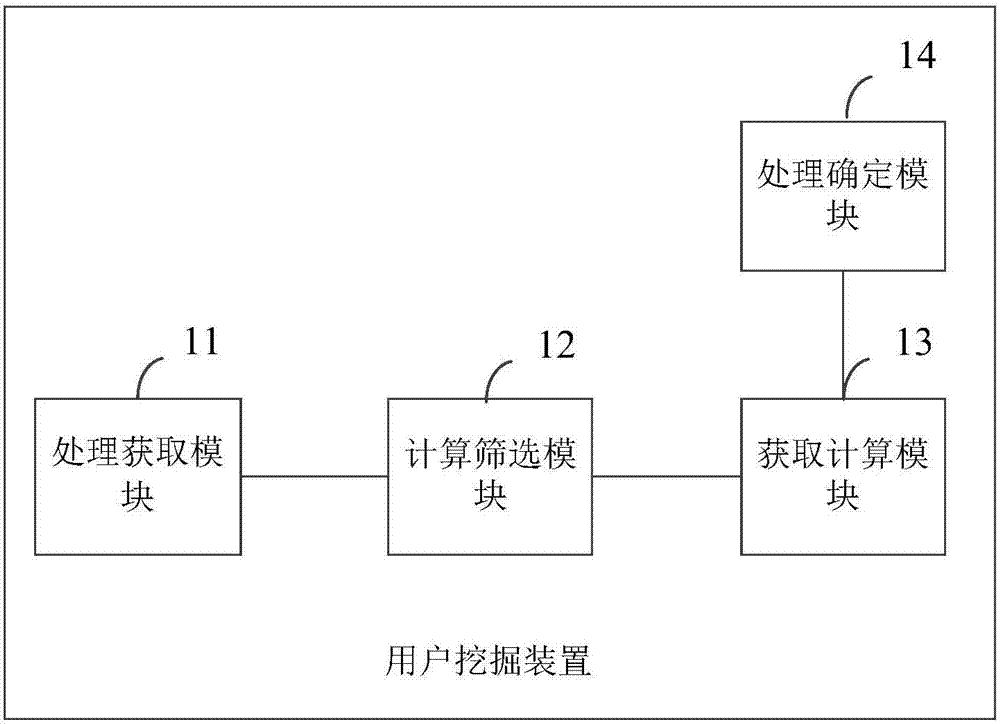
User mining method, apparatus and device
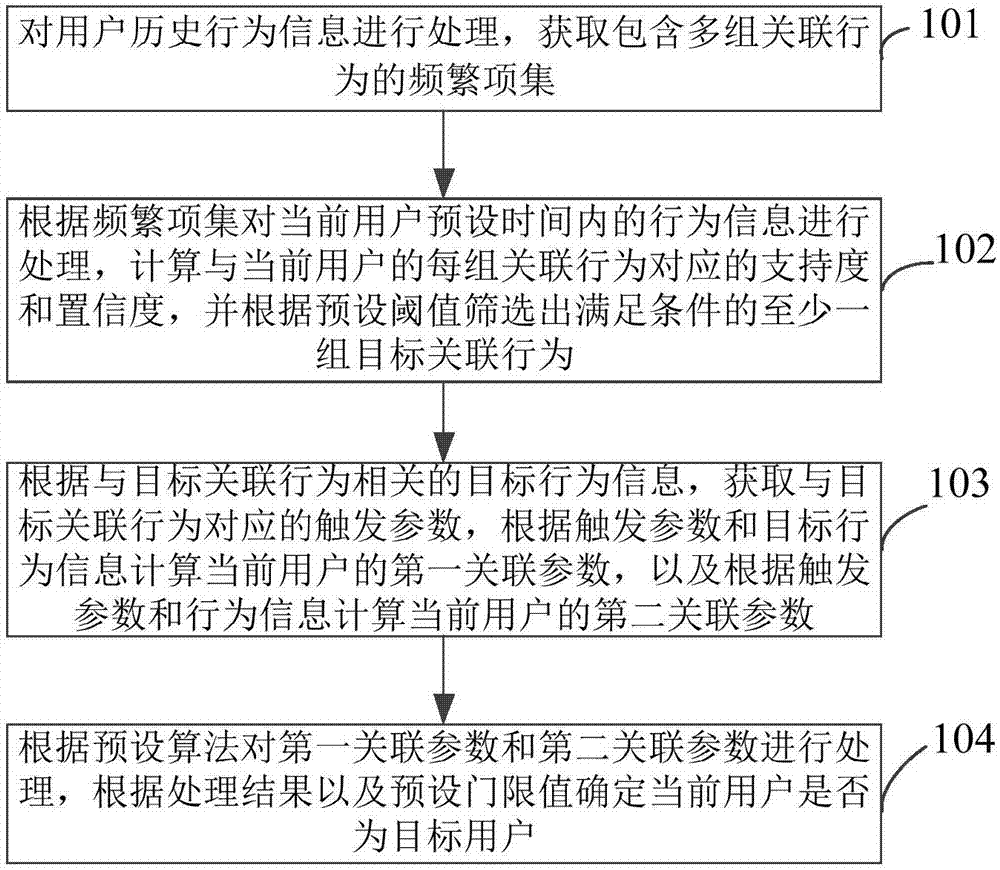
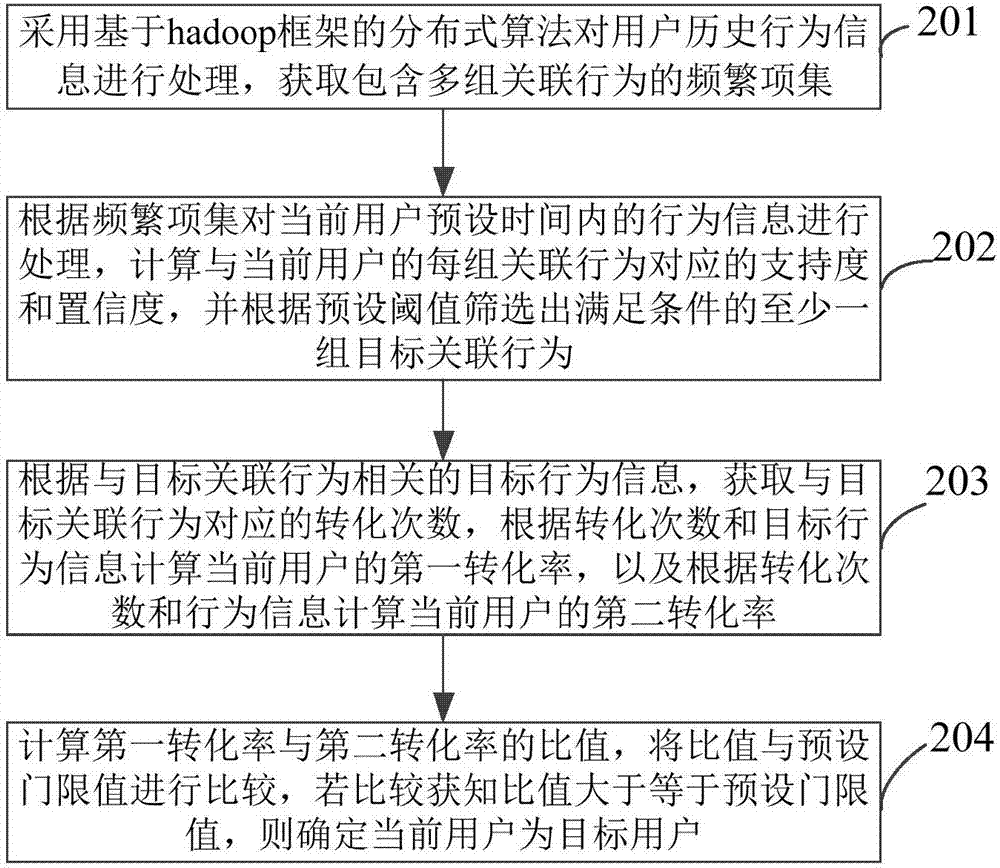
InactiveCN107392645AImprove the search experienceExcavate accuratelyMarket data gatheringProcess behaviorData mining
The invention provides a user mining method, apparatus and device. The method comprises the steps of processing historical behavior information of a user to obtain a frequent item set containing multiple groups of associated behaviors; processing behavior information in a preset time of the current user according to the frequent item set, calculating a support degree and a confidence degree corresponding to each group of the associated behaviors of the current user, and screening out at least one group of target associated behaviors meeting a condition according to a preset threshold; calculating first associated parameters and second associated parameters of the current user according to target behavior information related to the target associated behaviors and triggering parameters corresponding to the target behavior information; and processing the first associated parameters and the second associated parameters according to a preset algorithm to obtain a processing result, and determining whether the current user is a target user or not according to the processing result and a preset threshold. The target user can be accurately mined, and future possible behaviors of the user can be accurately predicted, so that commodities liked by the user are recommended, the search experience of the user is improved, and the conversion rate of a merchant is increased.
Owner:绿湾网络科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com