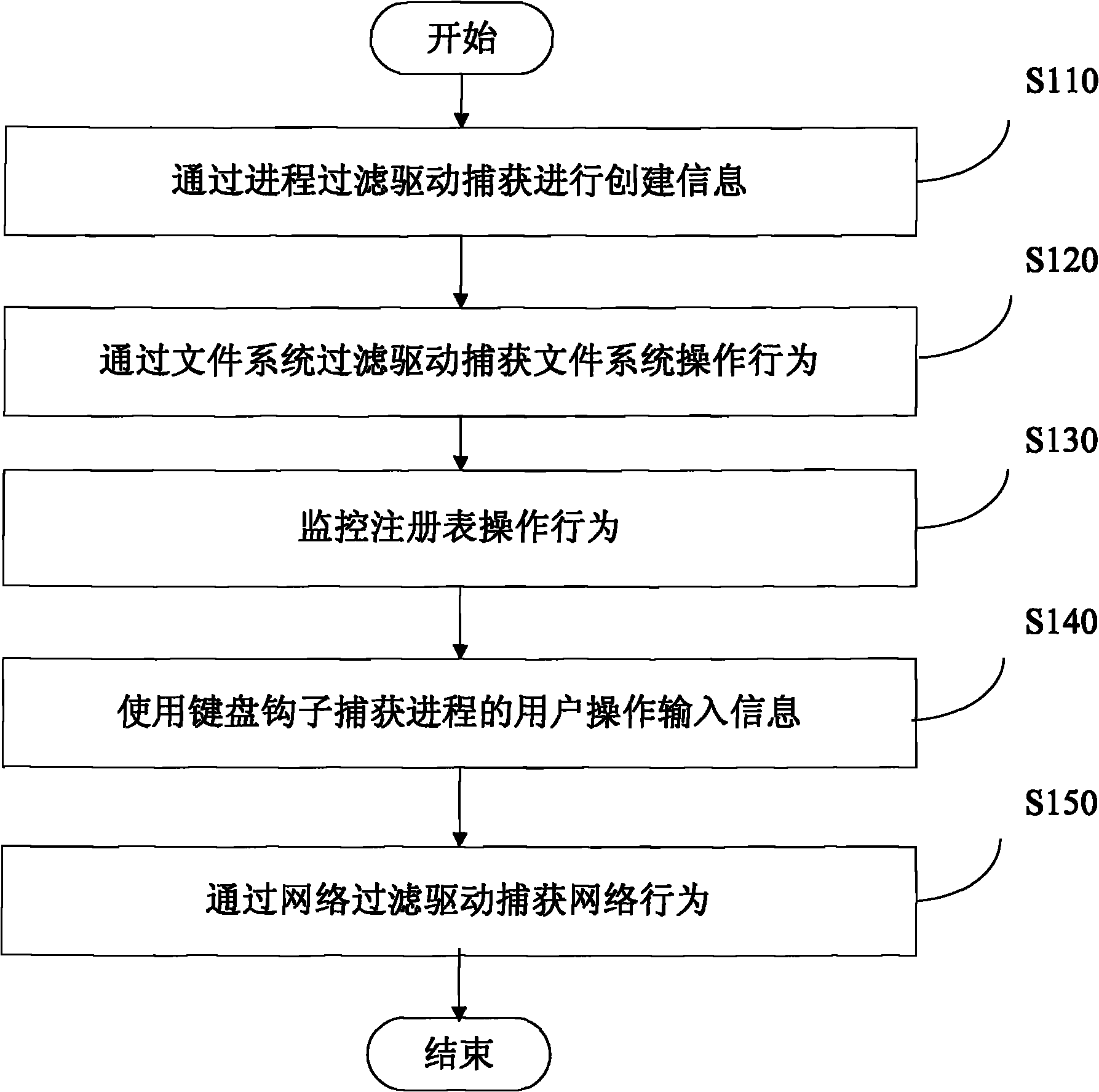
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
207 results about "Parent process" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
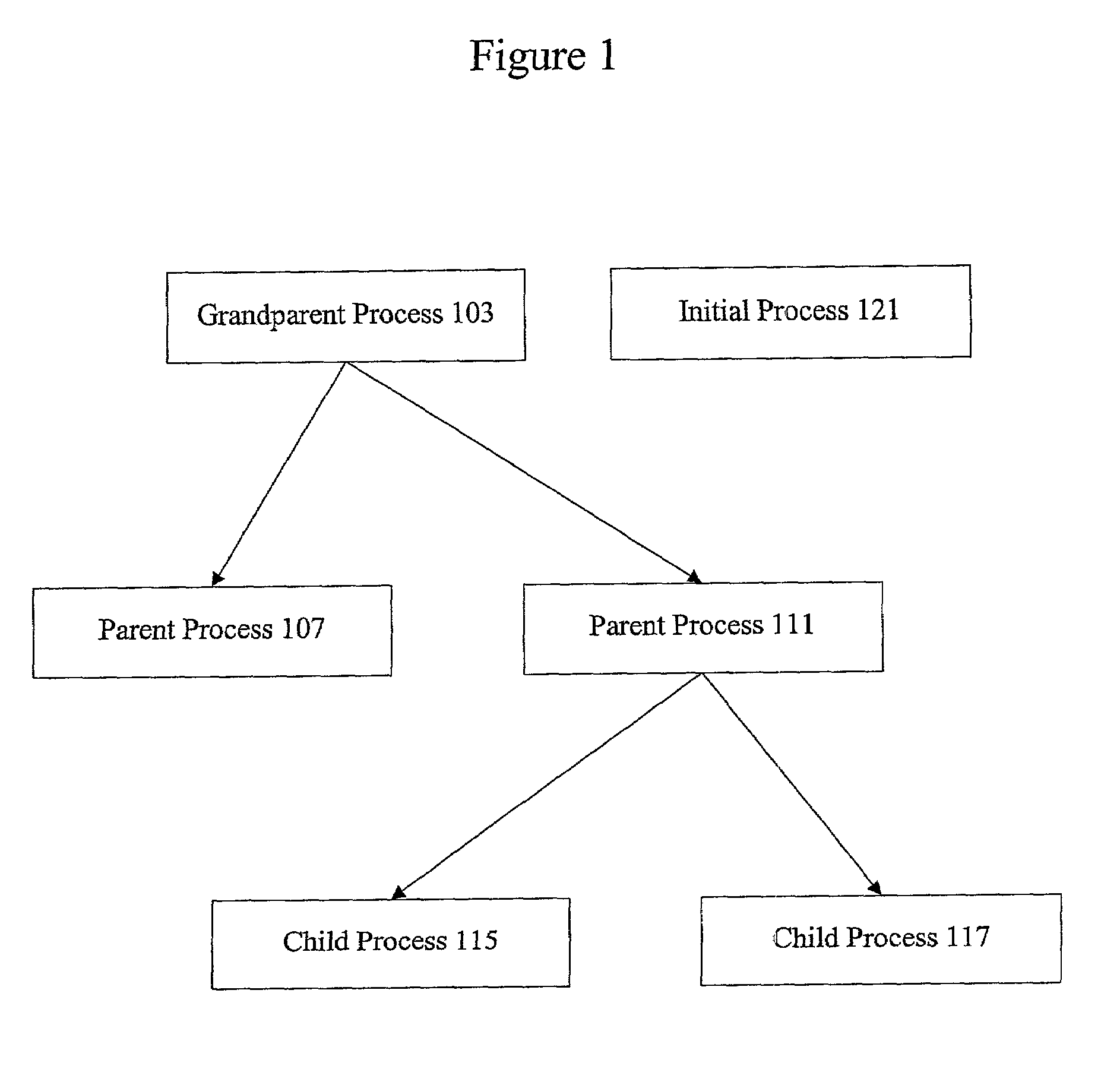
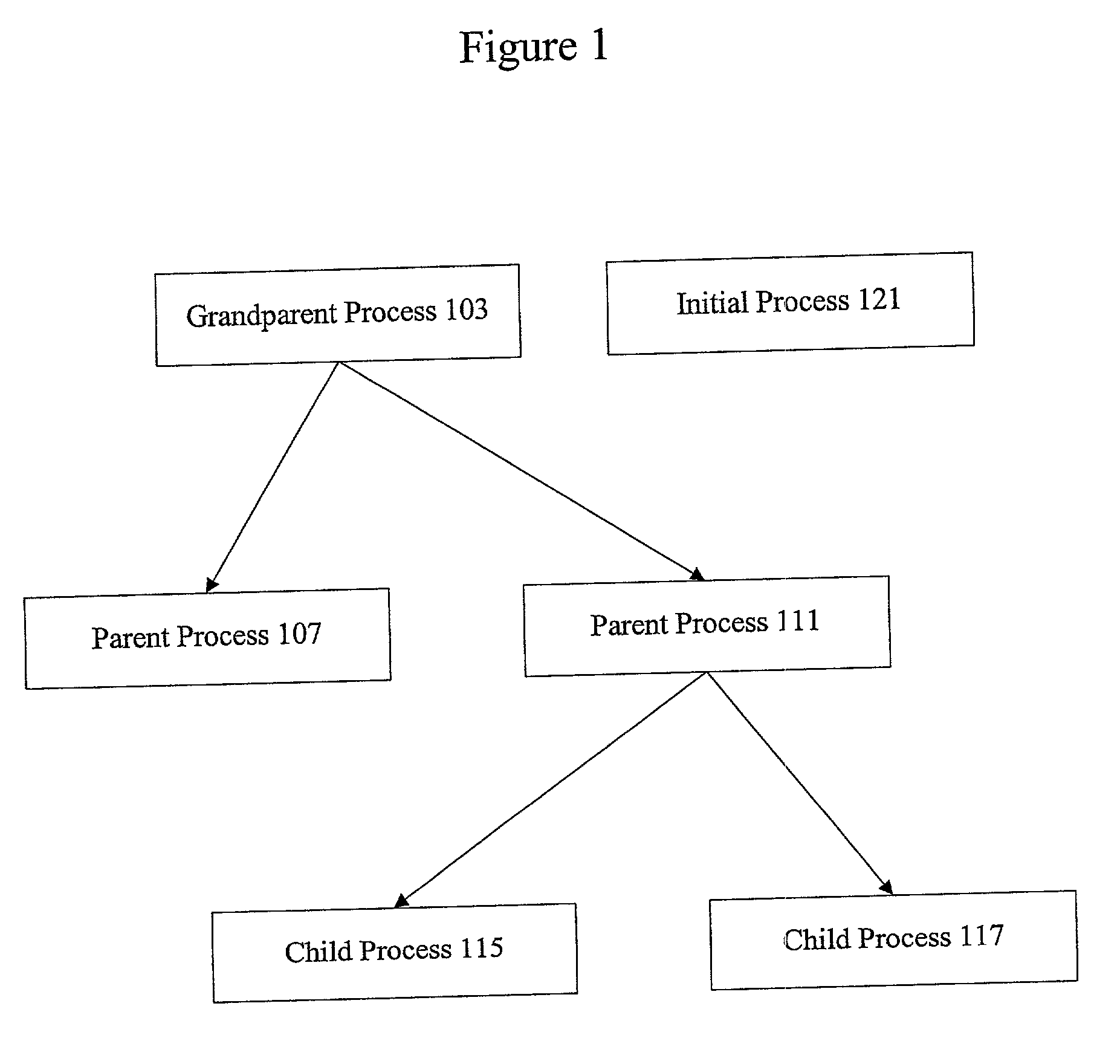
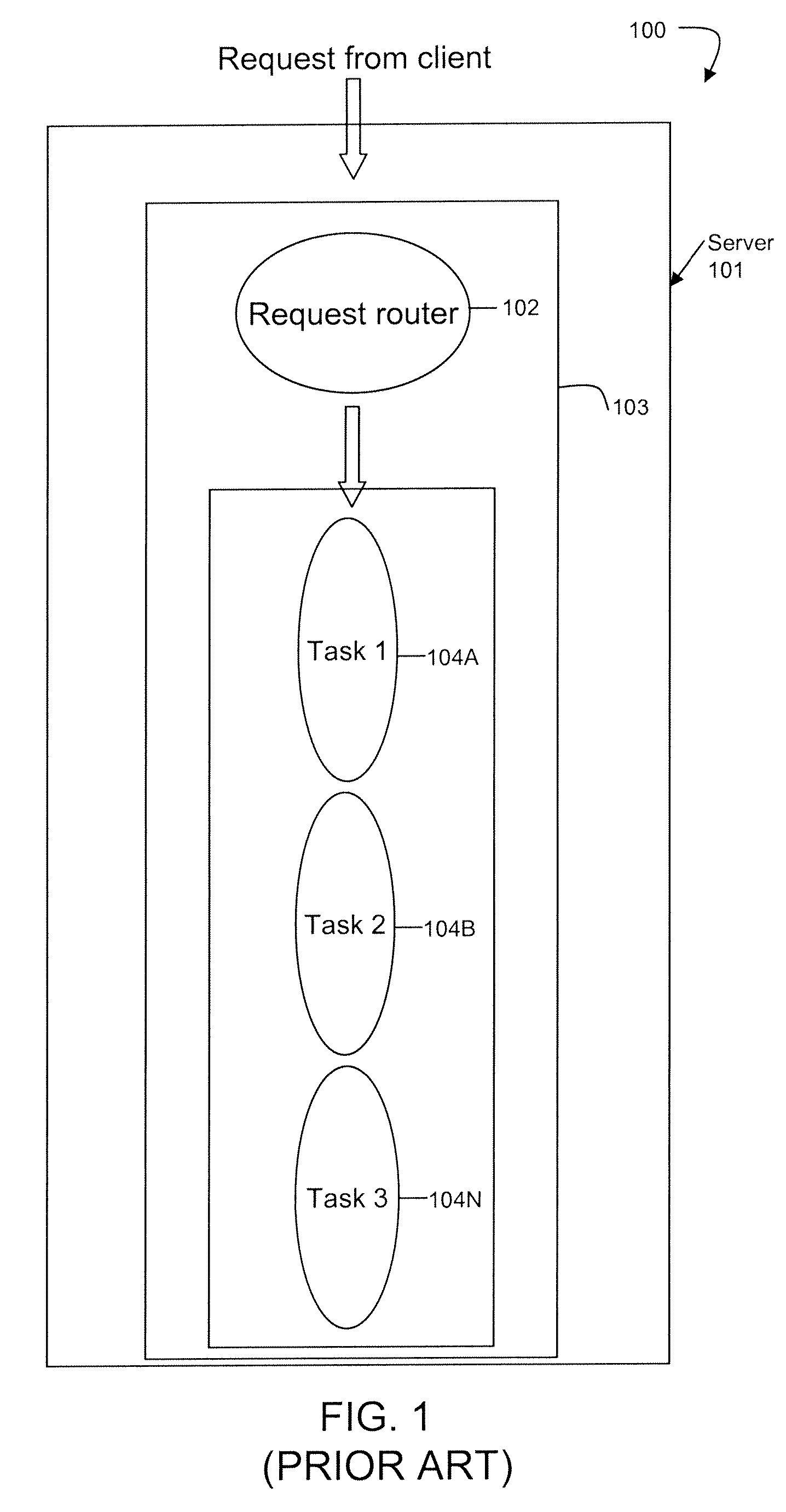
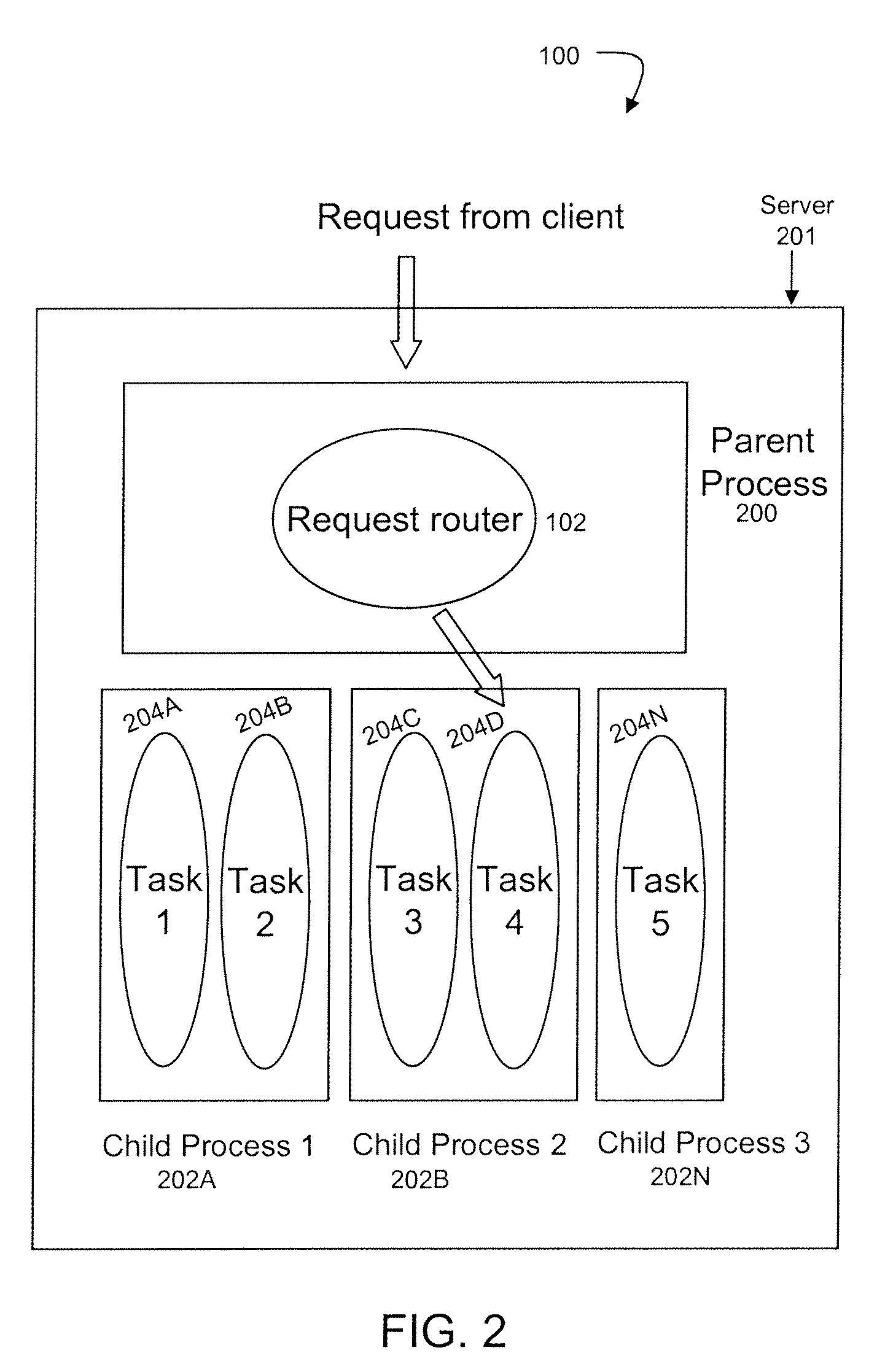
In computing, a parent process is a process that has created one or more child processes.
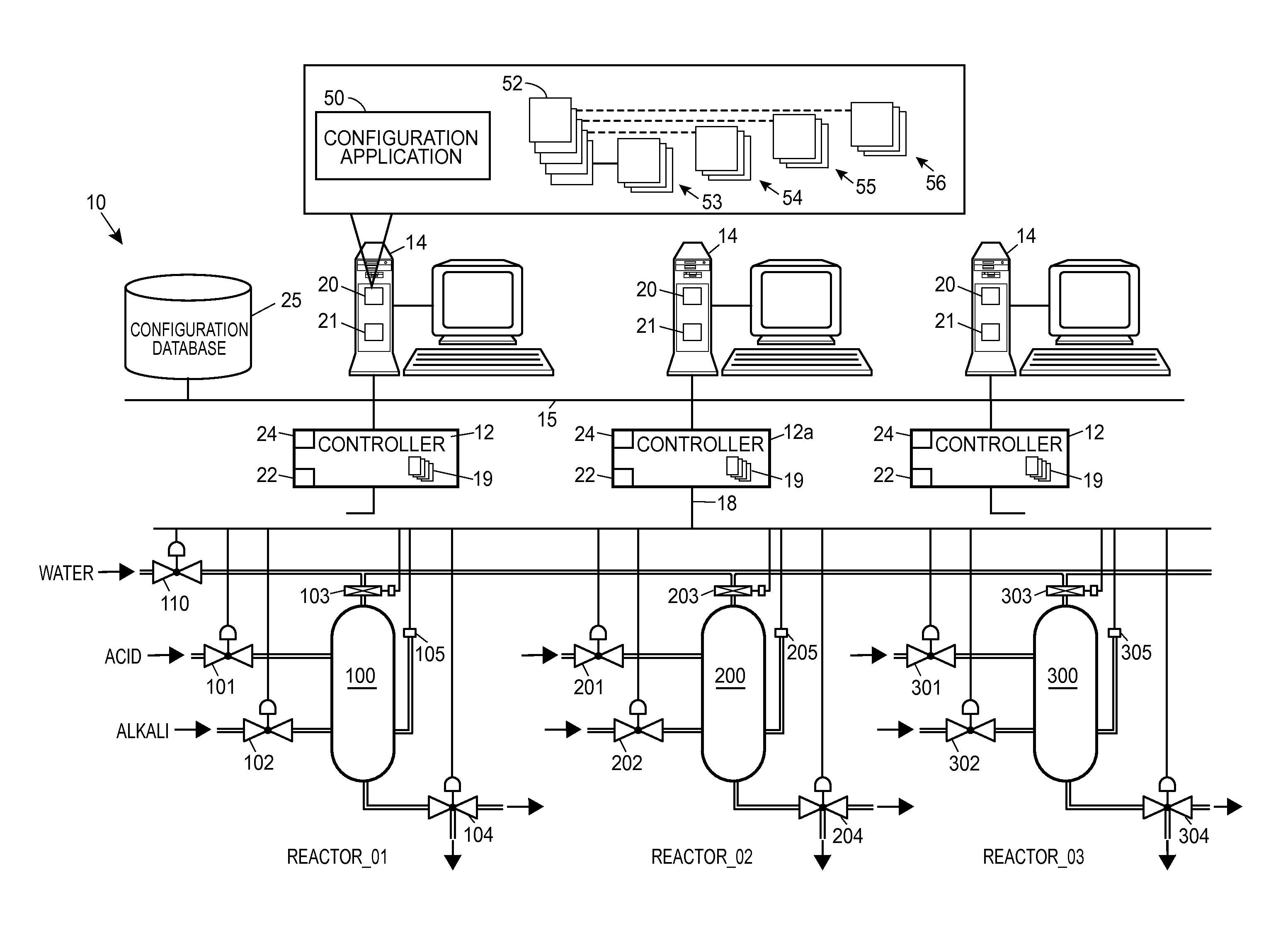
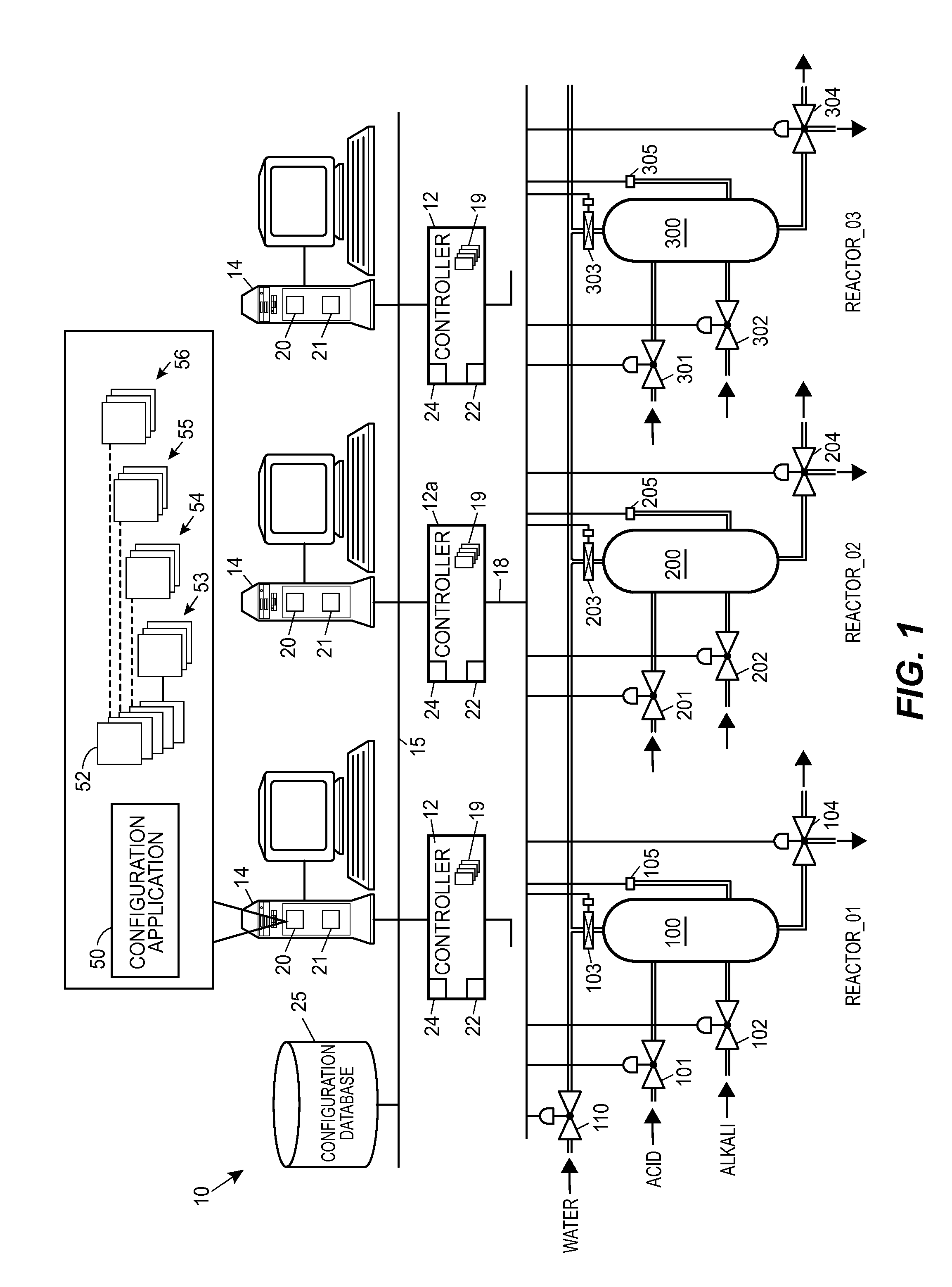
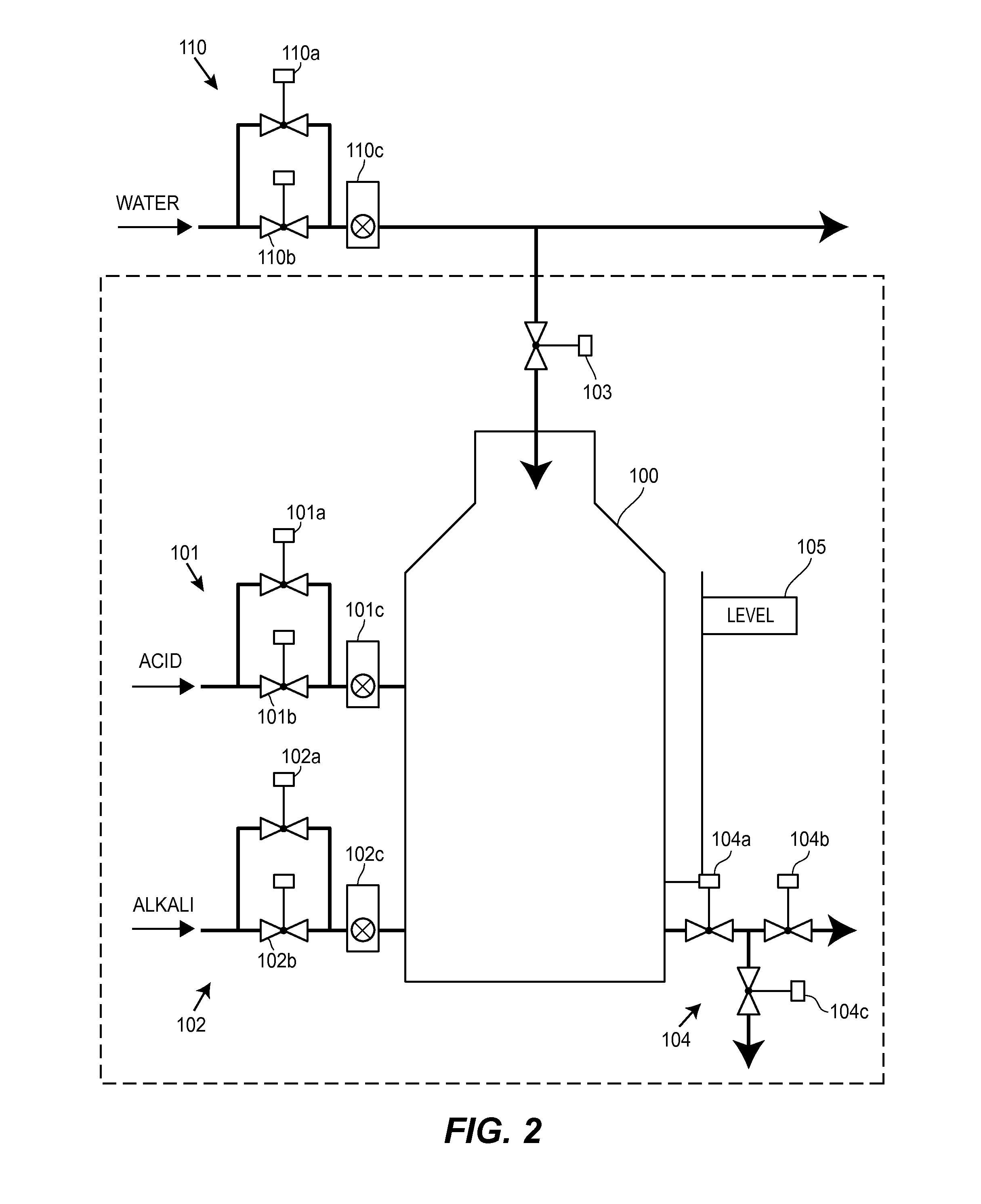
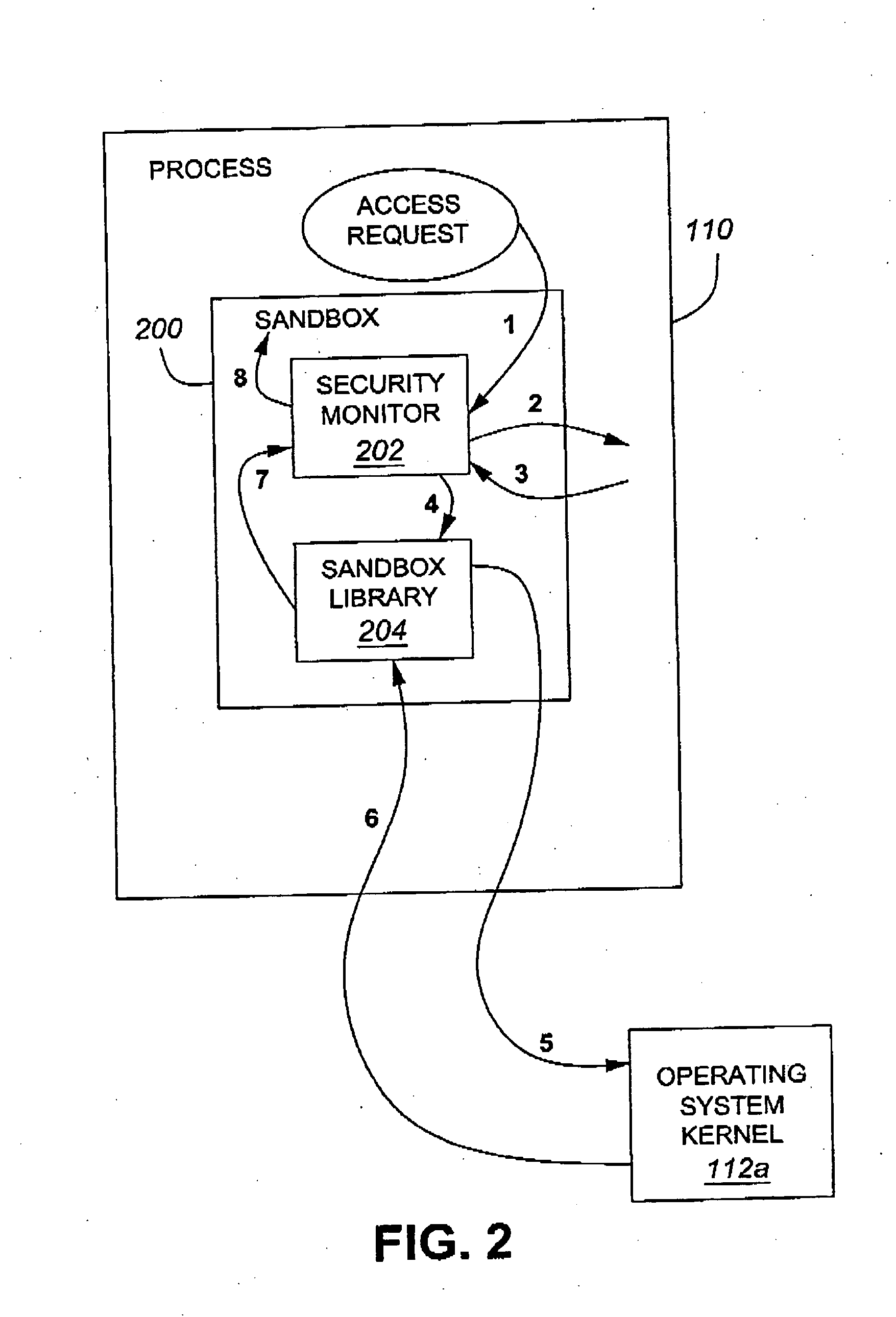
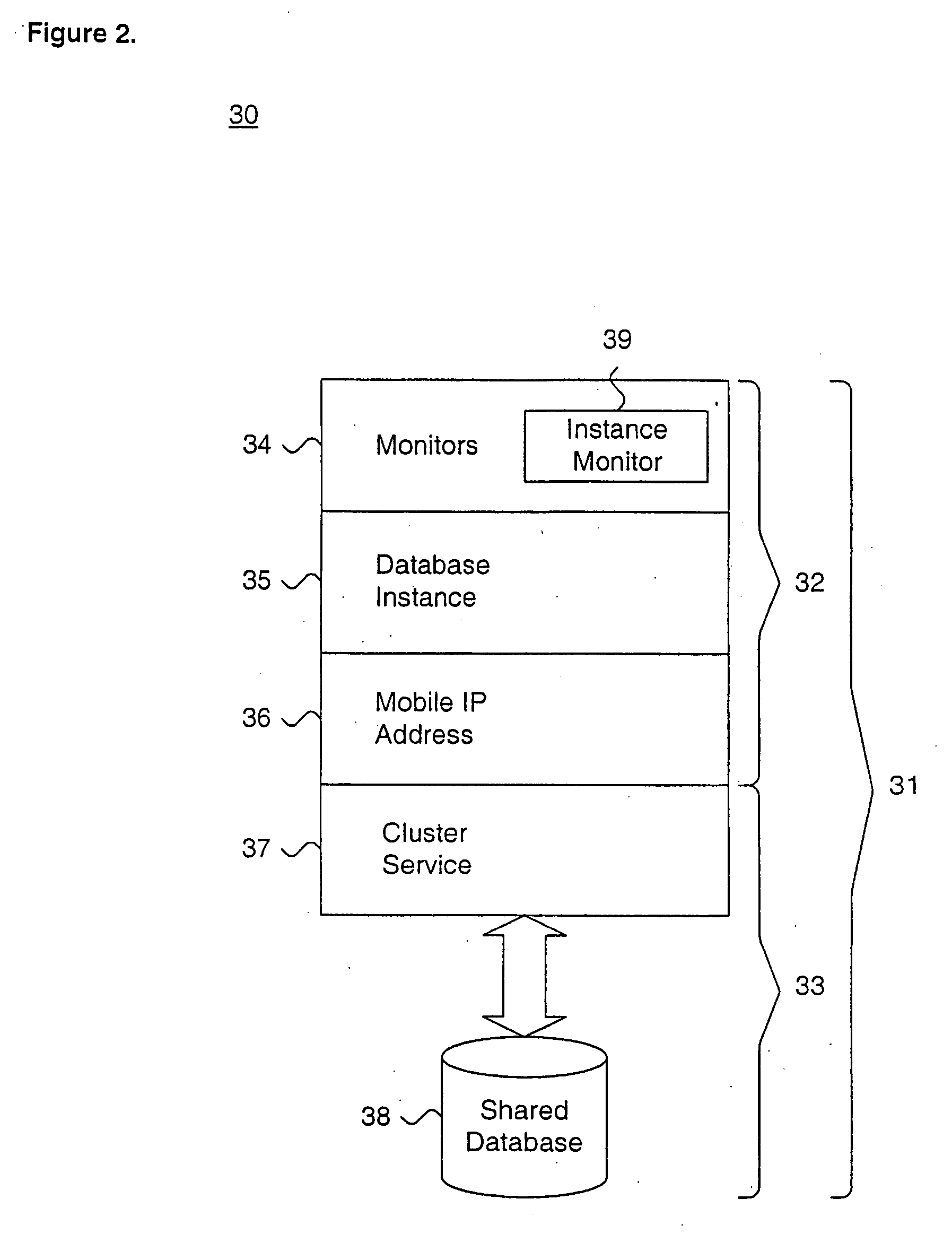
Method and apparatus for managing process control configuration
ActiveUS20140100668A1Sure easyEasy to createComputer controlElectric testing/monitoringControl systemEnvironment of Albania
Owner:FISHER-ROSEMOUNT SYST INC
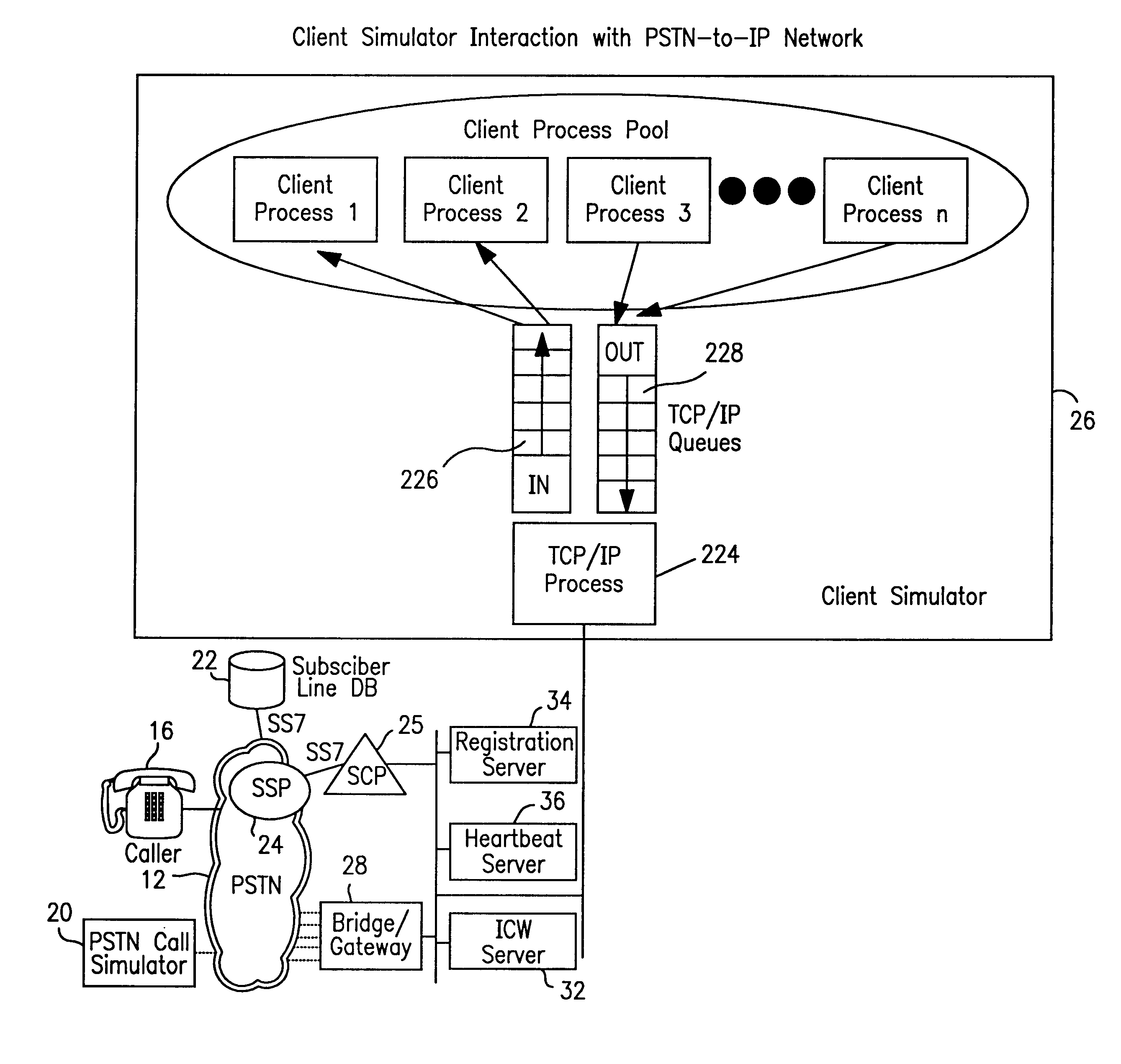
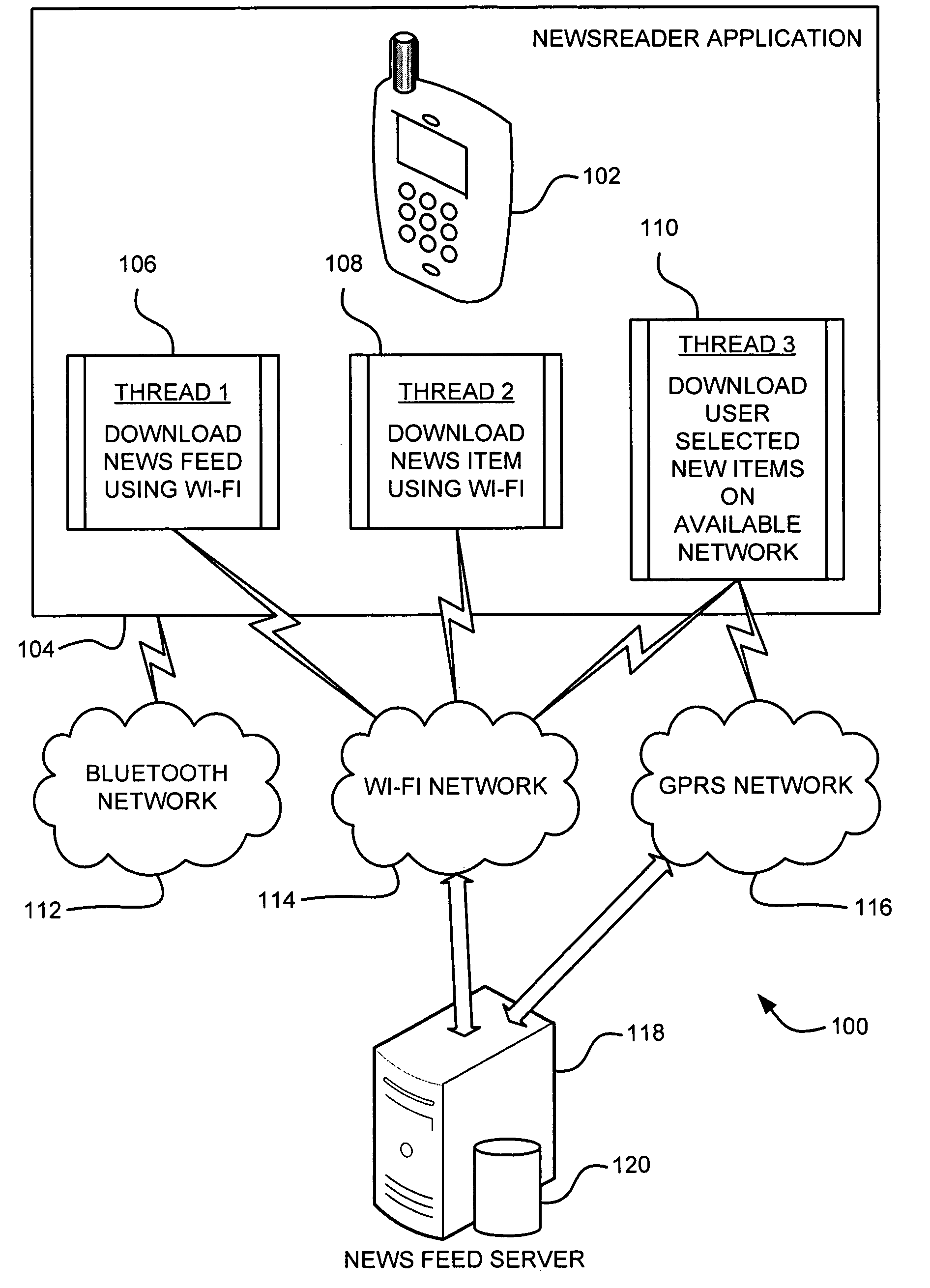
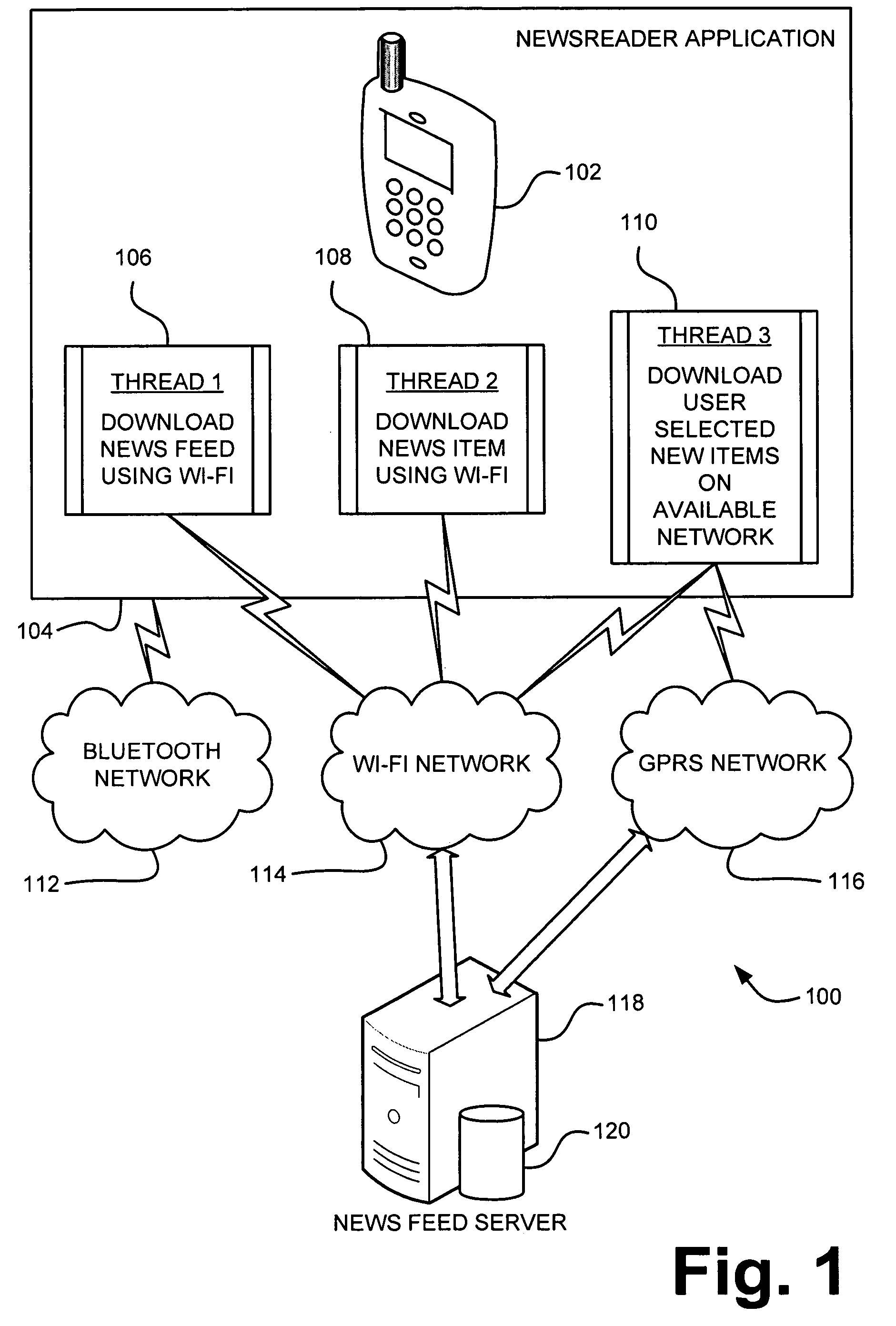
Client simulator and method of operation for testing PSTN-to-IP network telephone services for individual & group internet clients prior to availability of the services
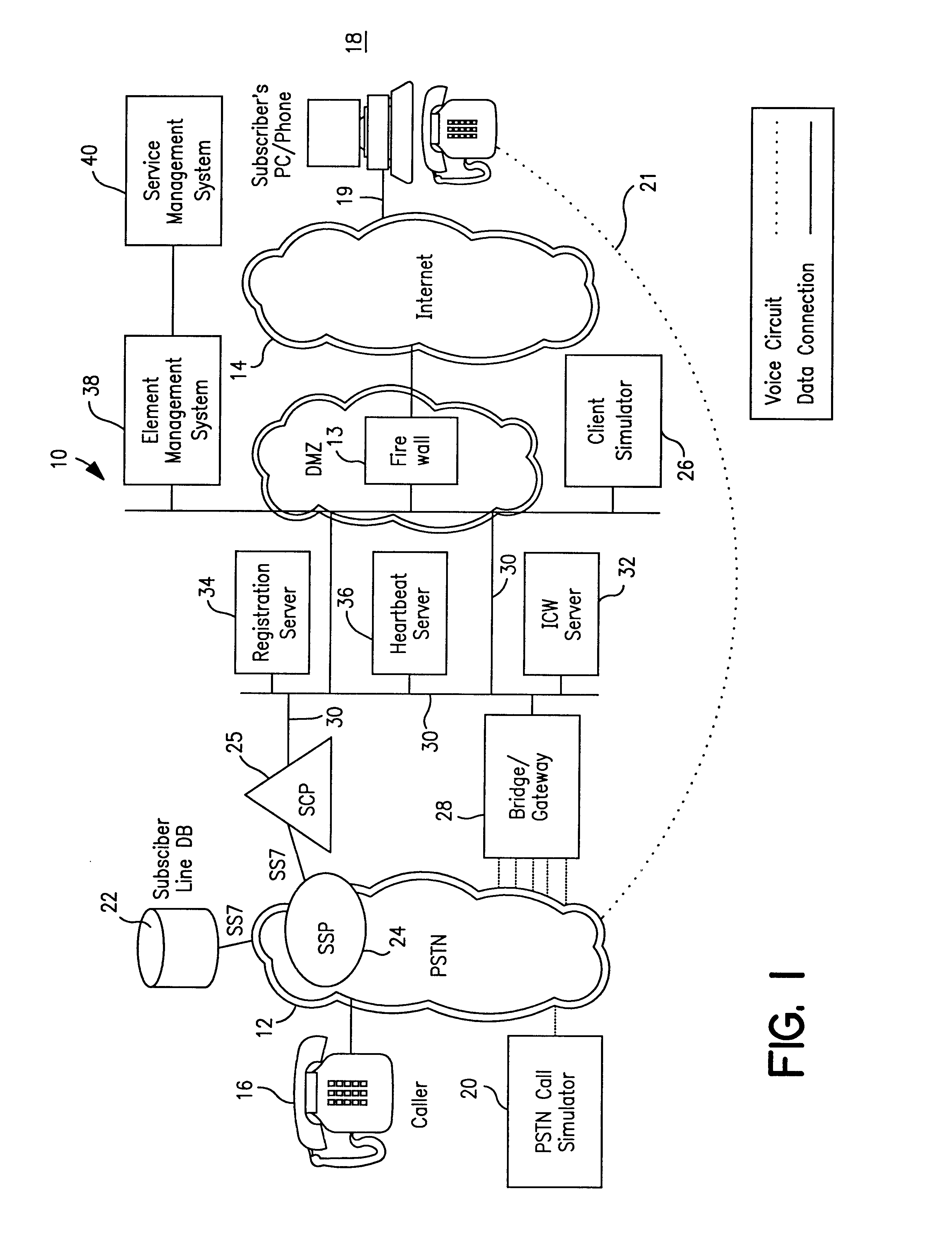
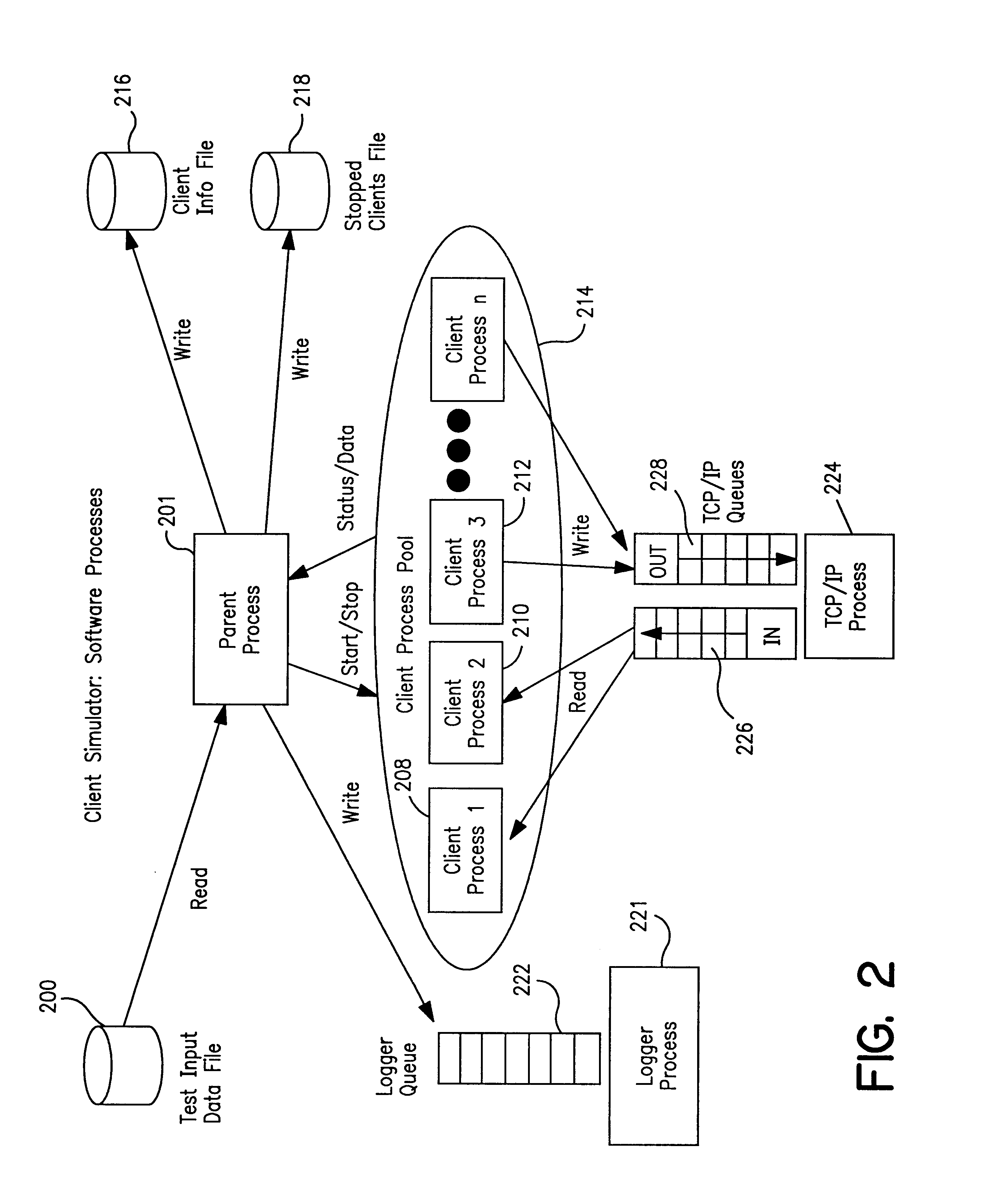
InactiveUS6421424B1Telephone data network interconnectionsSupervisory/monitoring/testing arrangementsTest inputNetwork link
A client simulator for simulating client behavior in groups or individuals to telephone services in a test system for testing telephone services between subscribers in a PSTN and clients in a distributed information network, for example, the Internet (IP Network), prior to availability of the telephone services to the subscribers and clients. A processor is coupled to a TCP / IP data network linked to the PSTN via a System Control Point (SCP) and the IP Network via an application server. A storage means is coupled to the processor through input / output registers and includes stored instruction for a parent process and a pool of client processes. e storage means further includes: a) a test input data file which contains client behavior profiles of either groups or individual client processes to call data messages; b) a logger queue file which allows the parent process to write event messages indicating start or stopped client processes with time stamp; c) a client information file which contains information and data for the total number of processes identified as being part of the test; d) a stopped client file used to track client processes that have stopped. The parent process is responsible for reading the test input data file and passing the client process behavior profile to the client processes. Each client process is responsible for returning state information to the PSTN; call handling actions and providing call handling statistics. The client process includes a client behavior control functions which processes and maintains the behavior parameters passed by the parent process. The behavior function, inter alia, accepts the call message, forward the call message according to the client behavior profile. The client process further includes a send / receive function to read and write to the registers coupled to the TCP / IP data network and support voice over IP protocols. A test originated by the PSTN is passed to the test input data file by the SCP and application file. The parent processes passes the call message to the client process. The client process provides a variety of call handling options including (a) accepting the call on the client's PC; sending a voice message to the caller. The call data messages responses are sent back to the SCP through the application server. The SCP directs the PSTN on how to handle the message call response.
Owner:LINKEDIN
Method and system for identifying malicious program
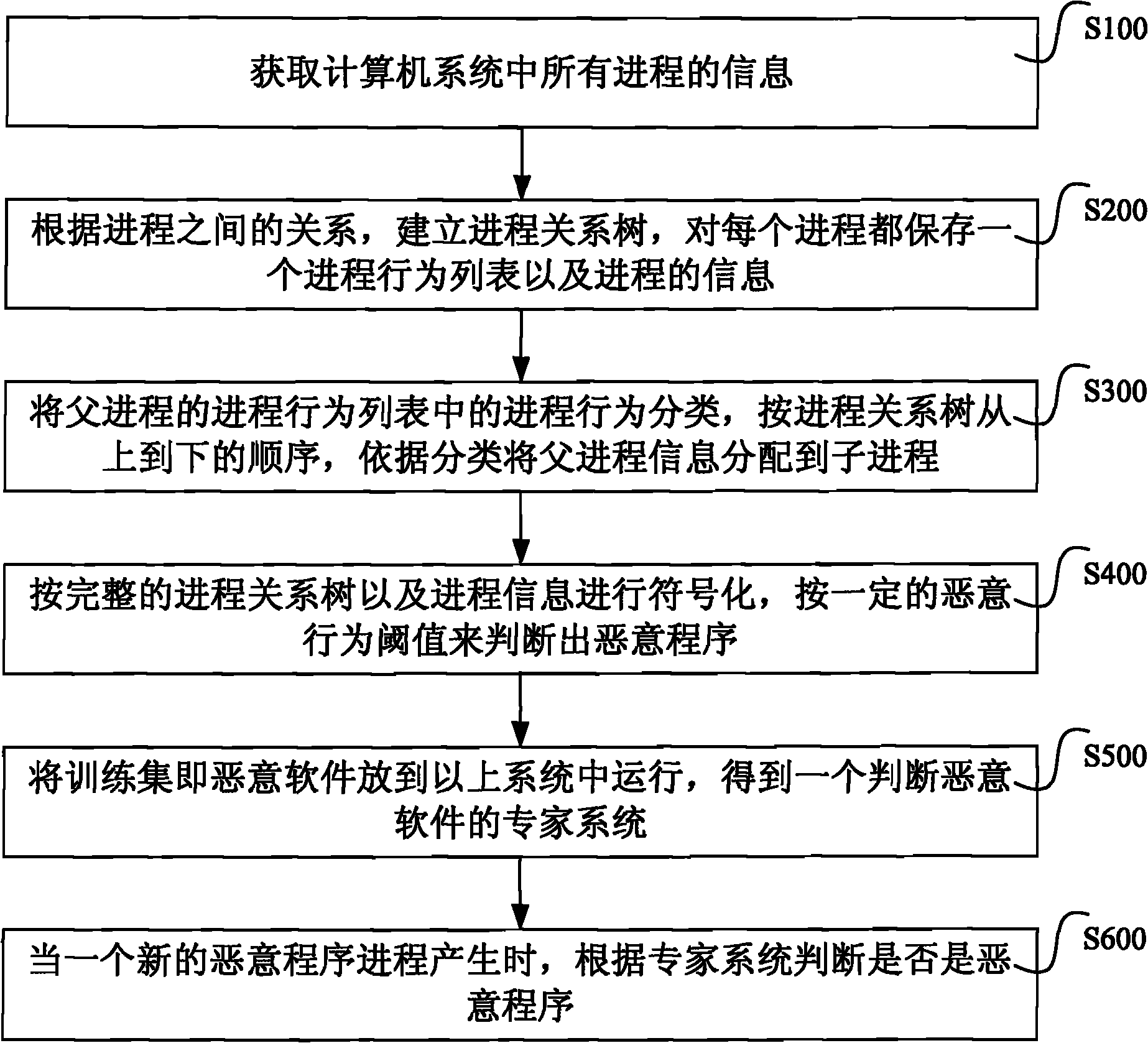
ActiveCN101944167AThe accuracy of the killing effect is lowHigh false positive rateMultiprogramming arrangementsPlatform integrity maintainanceProcess behaviorComputerized system
The invention relates to a method and a system for identifying a malicious program. The method comprises the following steps: 1. acquiring information and acts of all processes in a computer system, establishing a process relational tree according to the set membership among the processes, and storing a process information and a process behavior list corresponding to each process; 2. classifying the process behaviors in the process behavior list of the parent process, and allocating the information of the parent process to sub-process according to the classification and the order of the process relation tree from top to bottom; 3. symbolizing according to the process relation tree and the process information, judging a malicious program based on a preset malicious behavior threshold, and running the malicious program in the computer system to obtain an expert system for judging the malicious program; and 4. when the process of a new program is created, using the expert system to judge whether the new program is a malicious program. Compared with the prior art, the invention lowers the implementation complexity and can improve the efficiency.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
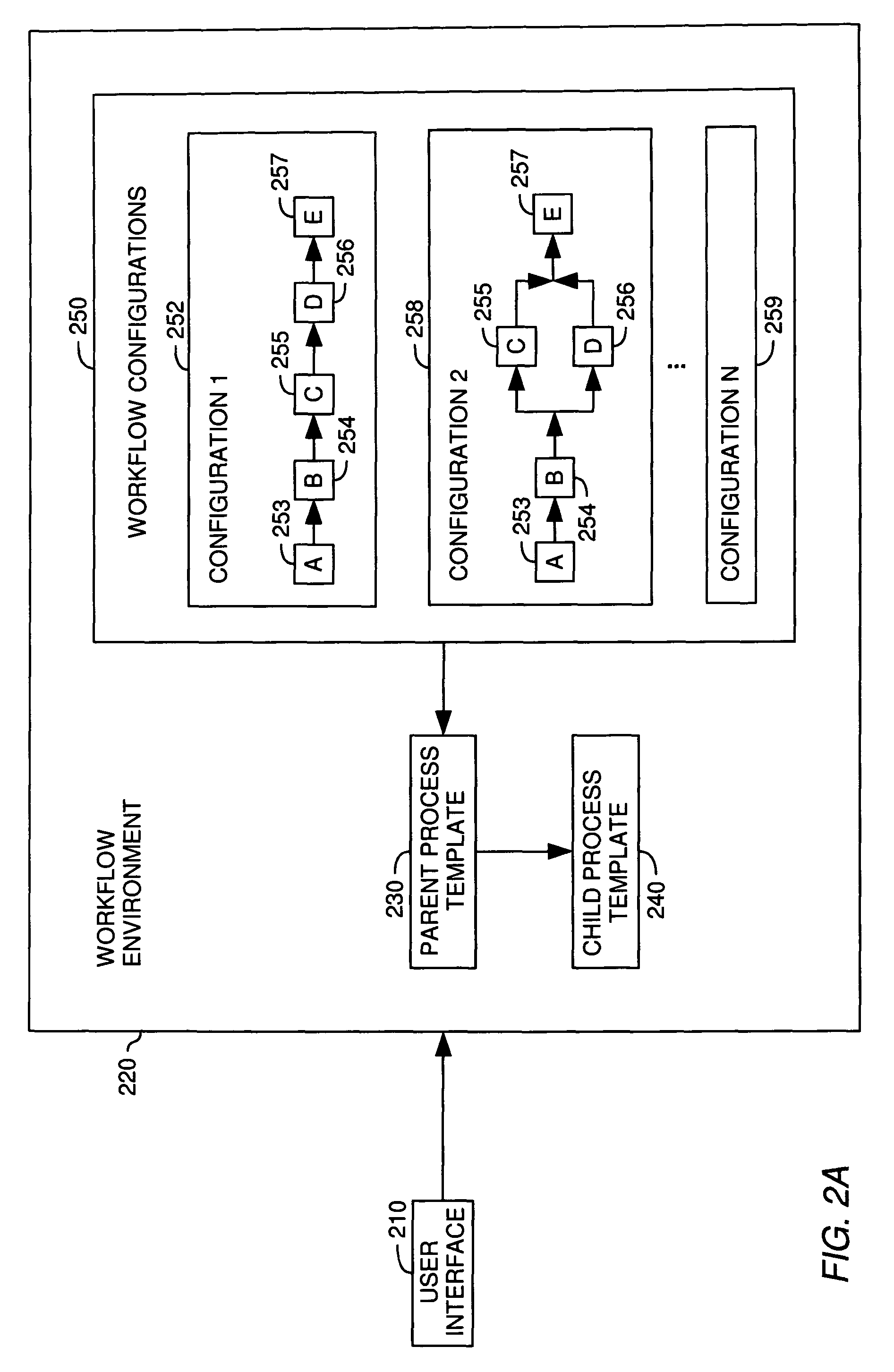
Data driven dynamic workflow
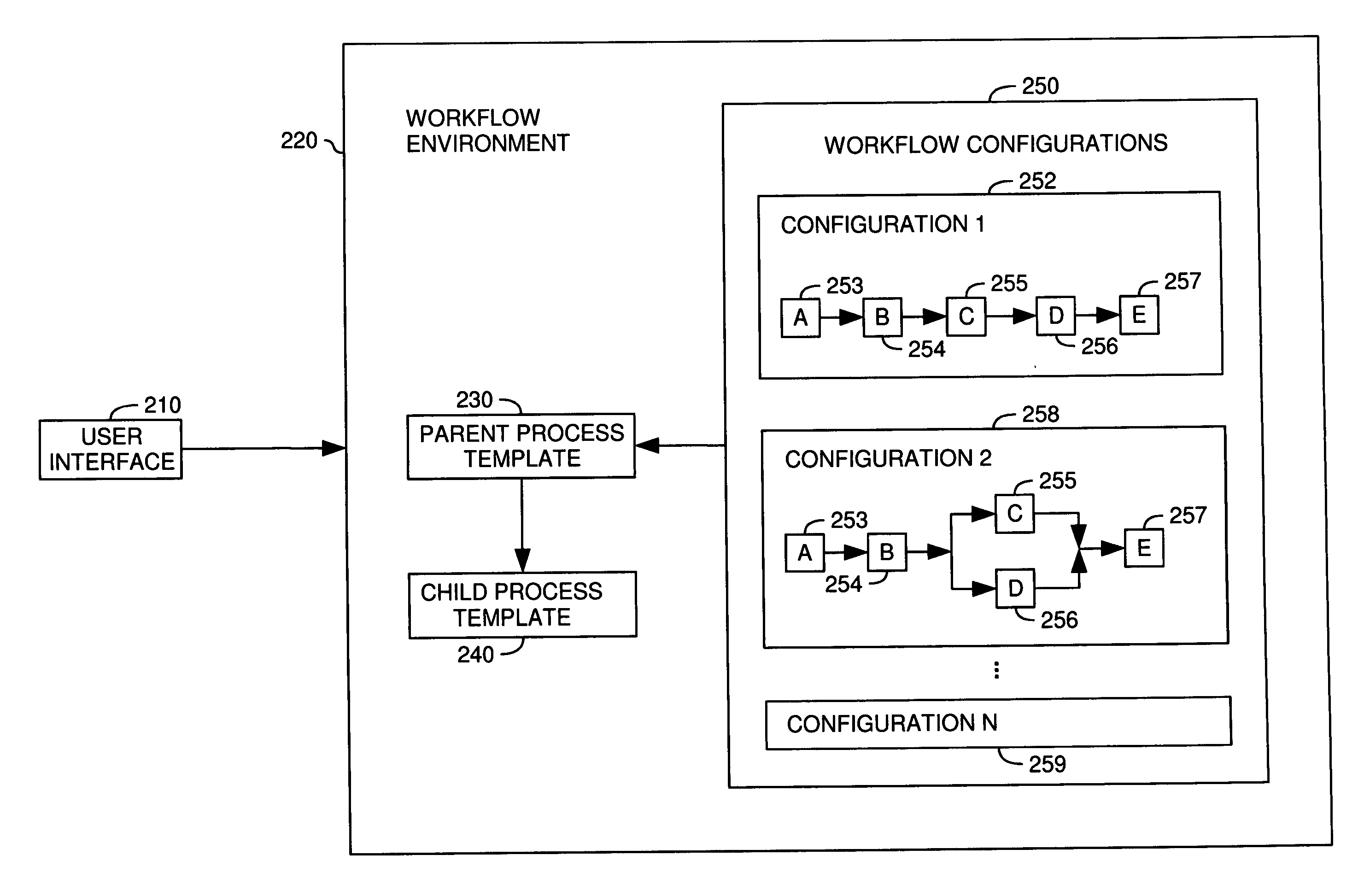
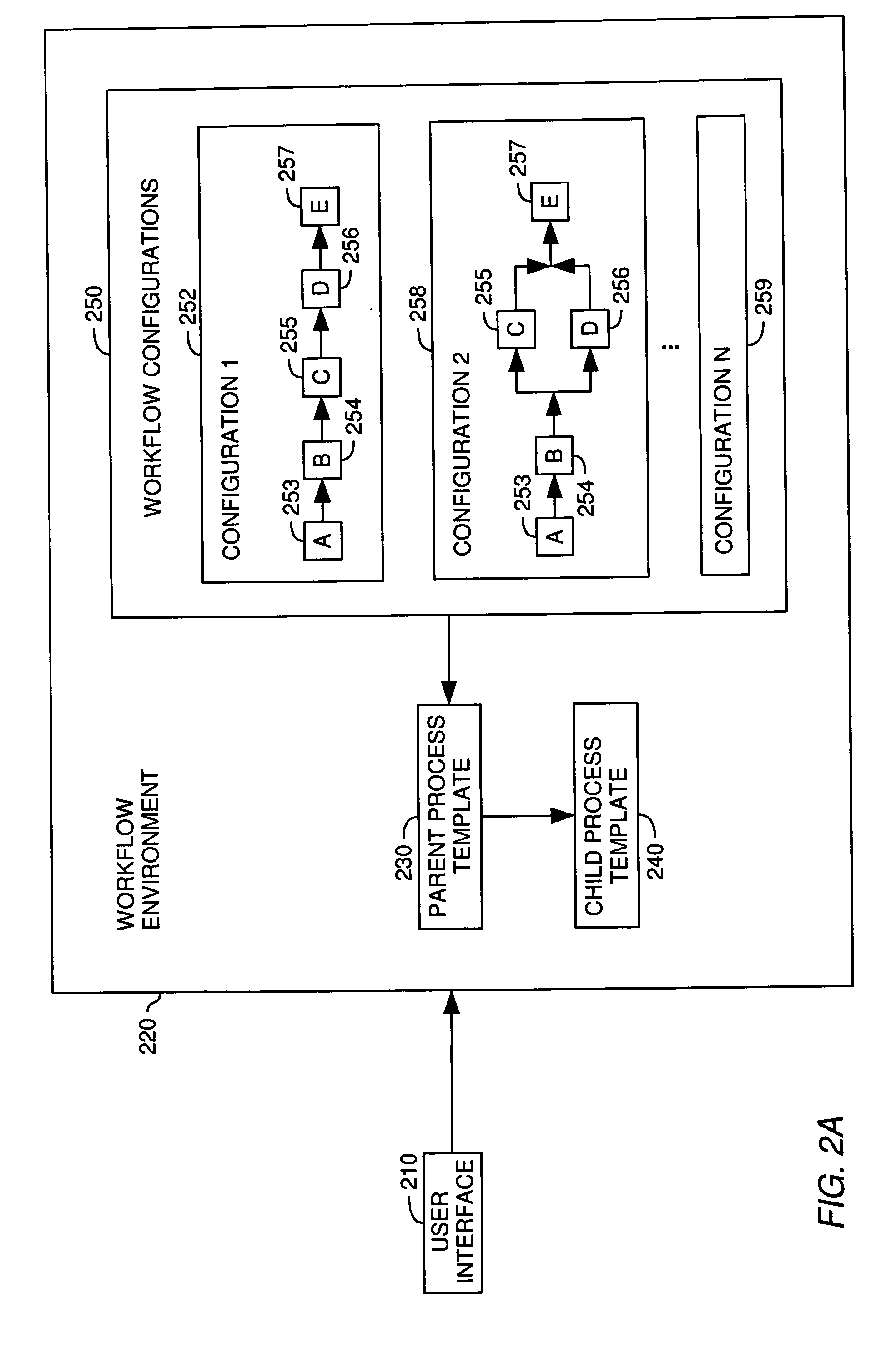
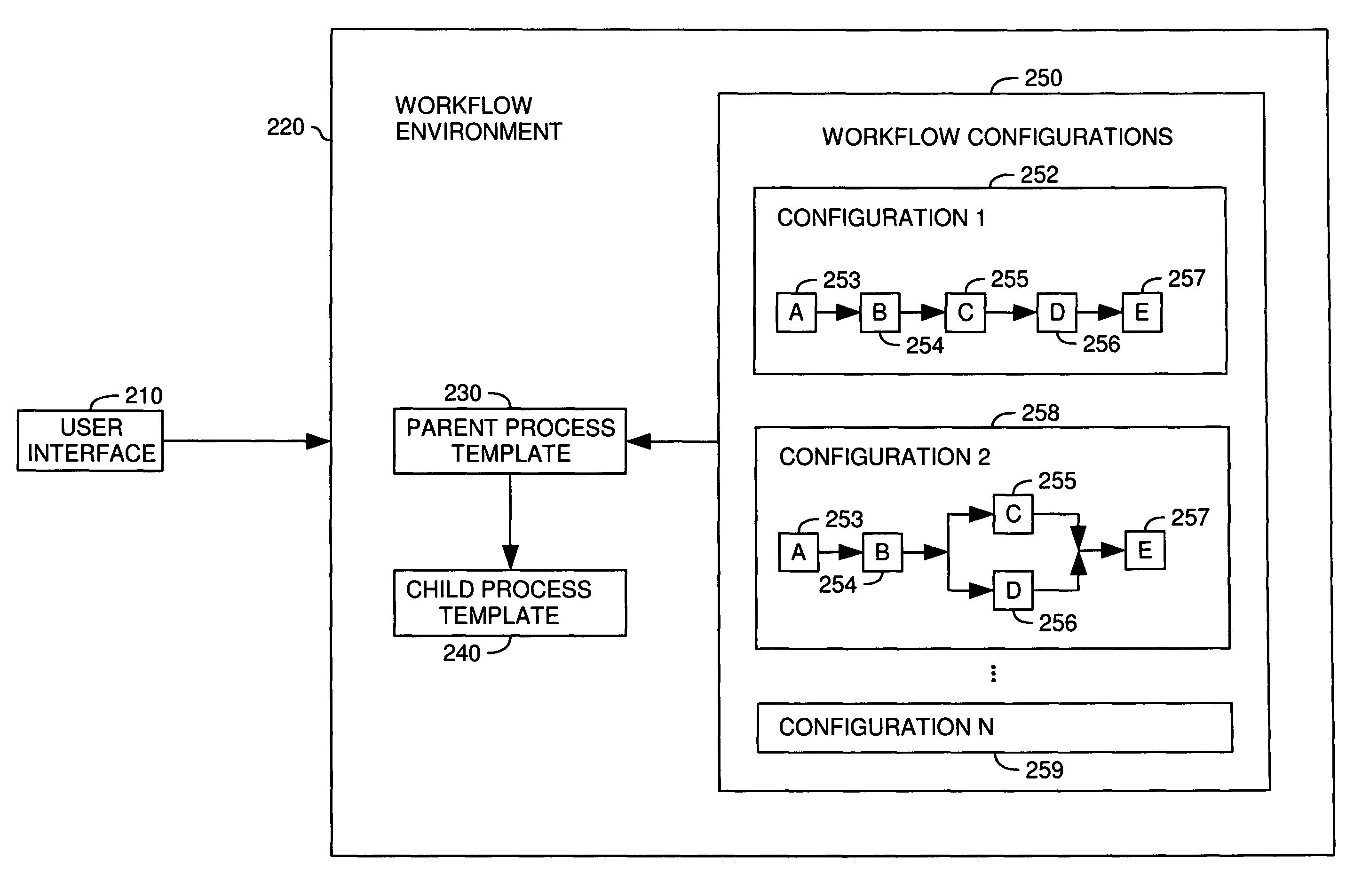
A method, system and article of manufacture for workflow processing and, more particularly, for managing creation and execution of data driven dynamic workflows. One embodiment provides a computer-implemented method for managing execution of workflow instances. The method comprises providing a parent process template and providing a child process template. The child process template is configured to implement an arbitrary number of workflow operations for a given workflow instance, and the parent process template is configured to instantiate child processes on the basis of the child process template to implement a desired workflow. The method further comprises receiving a workflow configuration and instantiating an instance of the workflow on the basis of the workflow configuration. The instantiating comprises instantiating a parent process on the basis of the parent process template and instantiating, by the parent process template, one or more child processes on the basis of the child process template.
Owner:IBM CORP
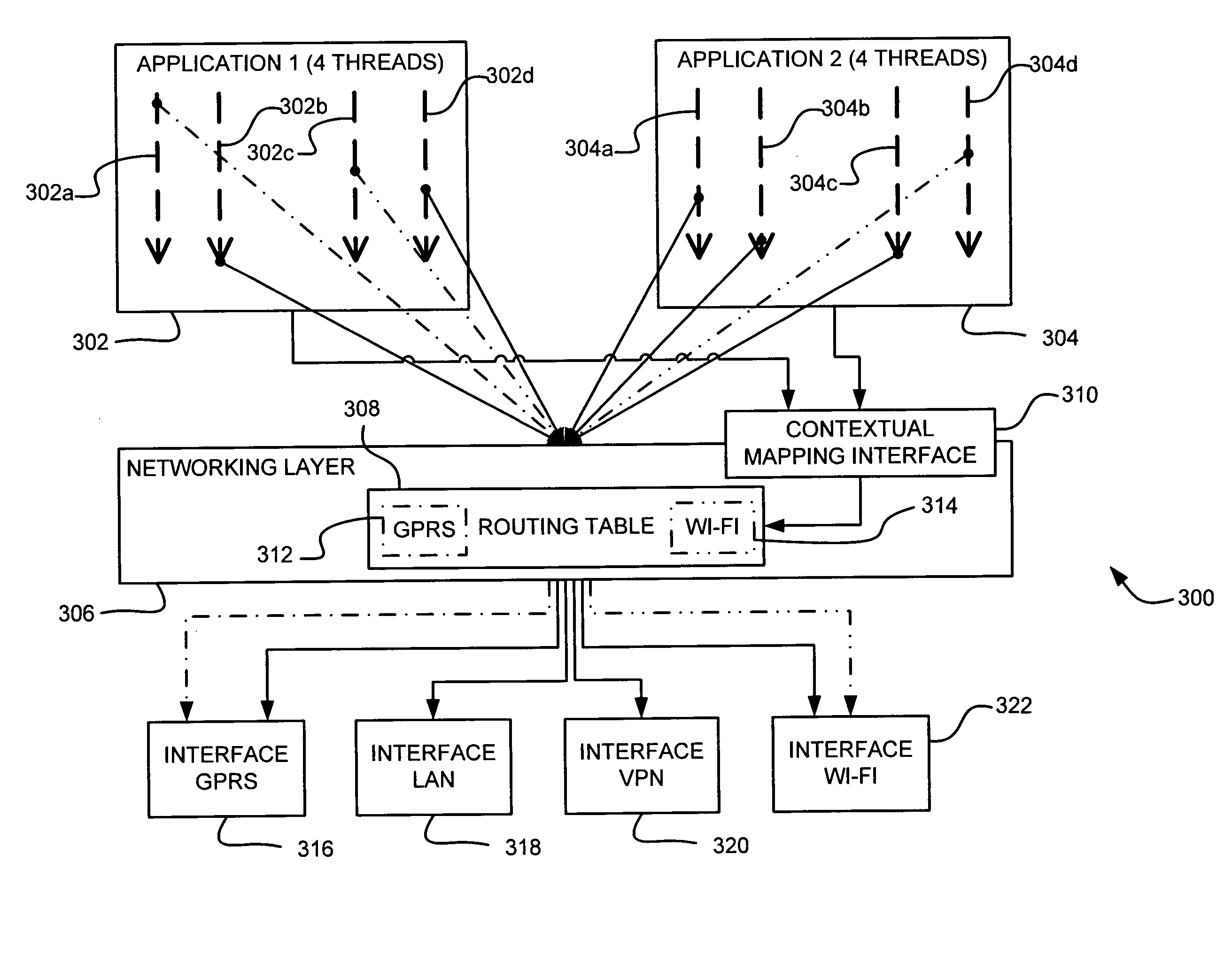
Network interface routing using computational context
InactiveUS20070211690A1Network traffic/resource managementData switching by path configurationOperational systemNetwork connection
Knowledge of the computational context of a computer operating environment, for example, awareness of process threads, is used to route IP traffic in the presence of multiple active network connections. An additional protocol may be added to the network layer of an operating system in order to map certain computational contexts to particular network interfaces. Any process with identification parameters associated with a mapped computational context requesting data transfer via a communication network is bound to the network interface previously associated with the computational context rather than an alternate network interface that otherwise might be the default. Further, process threads created by a parent process thread may be caused to inherit the computational context of the parent thread in order to assign traffic to the same network interface. This routing framework may have particular application with respect to multihomed host devices, for example, mobile computing devices.
Owner:MICROSOFT TECH LICENSING LLC
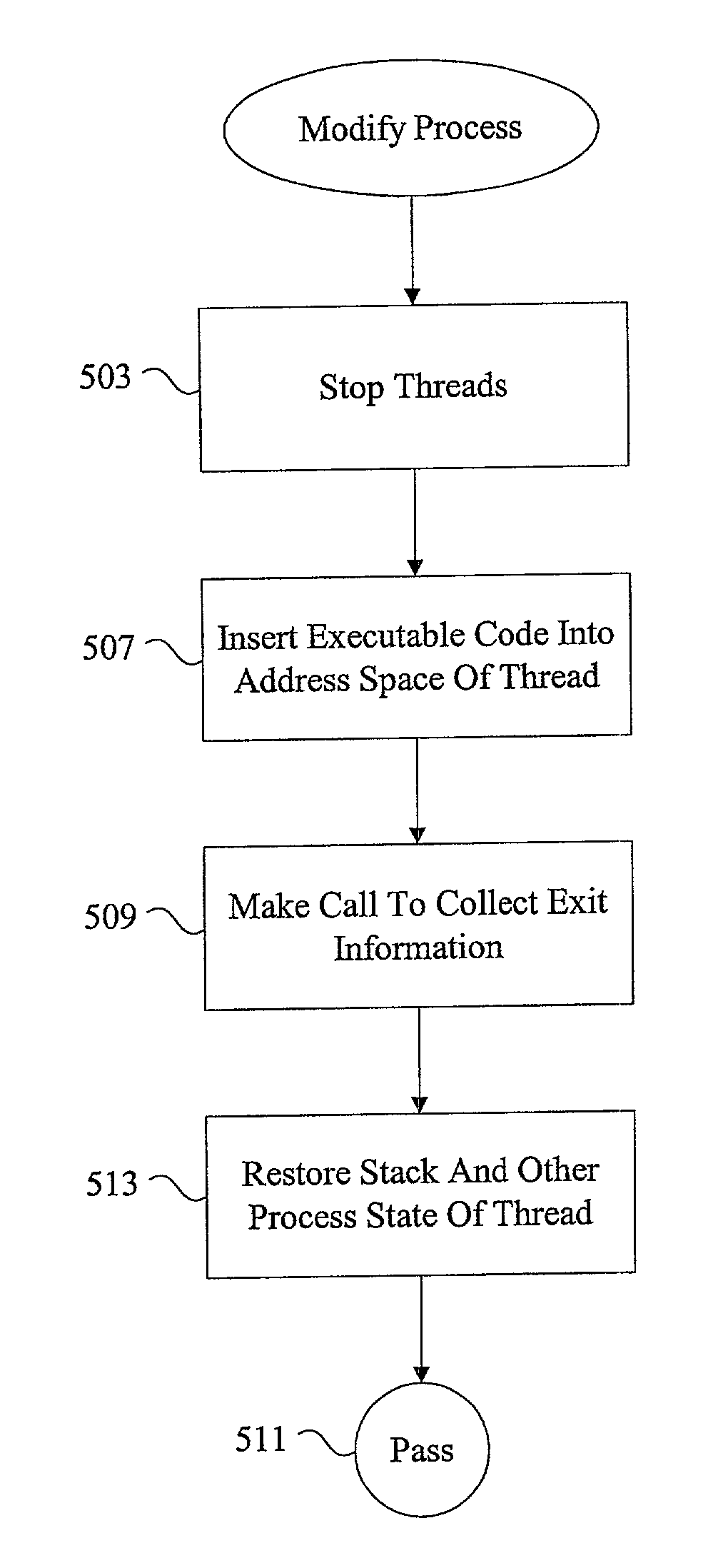
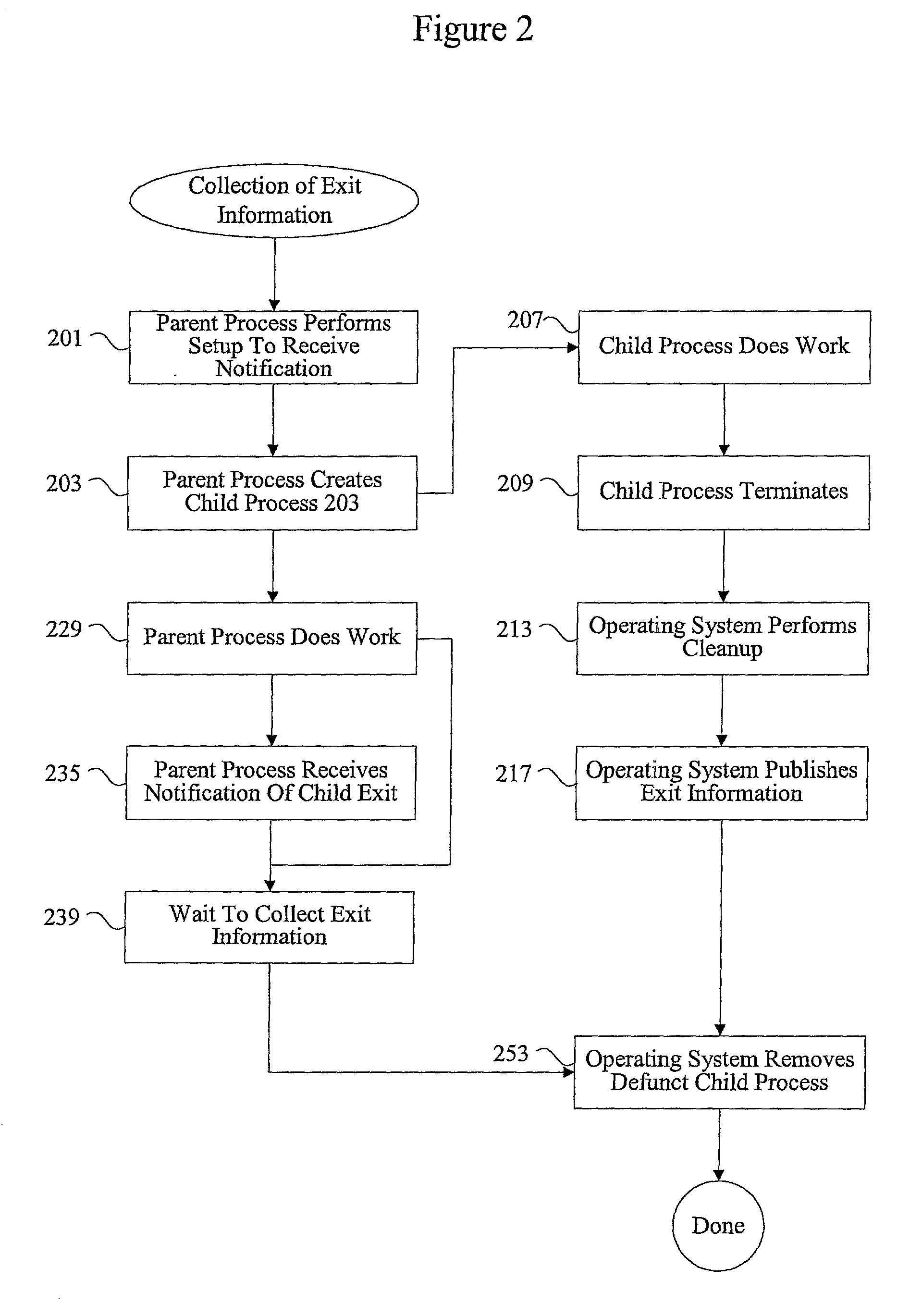
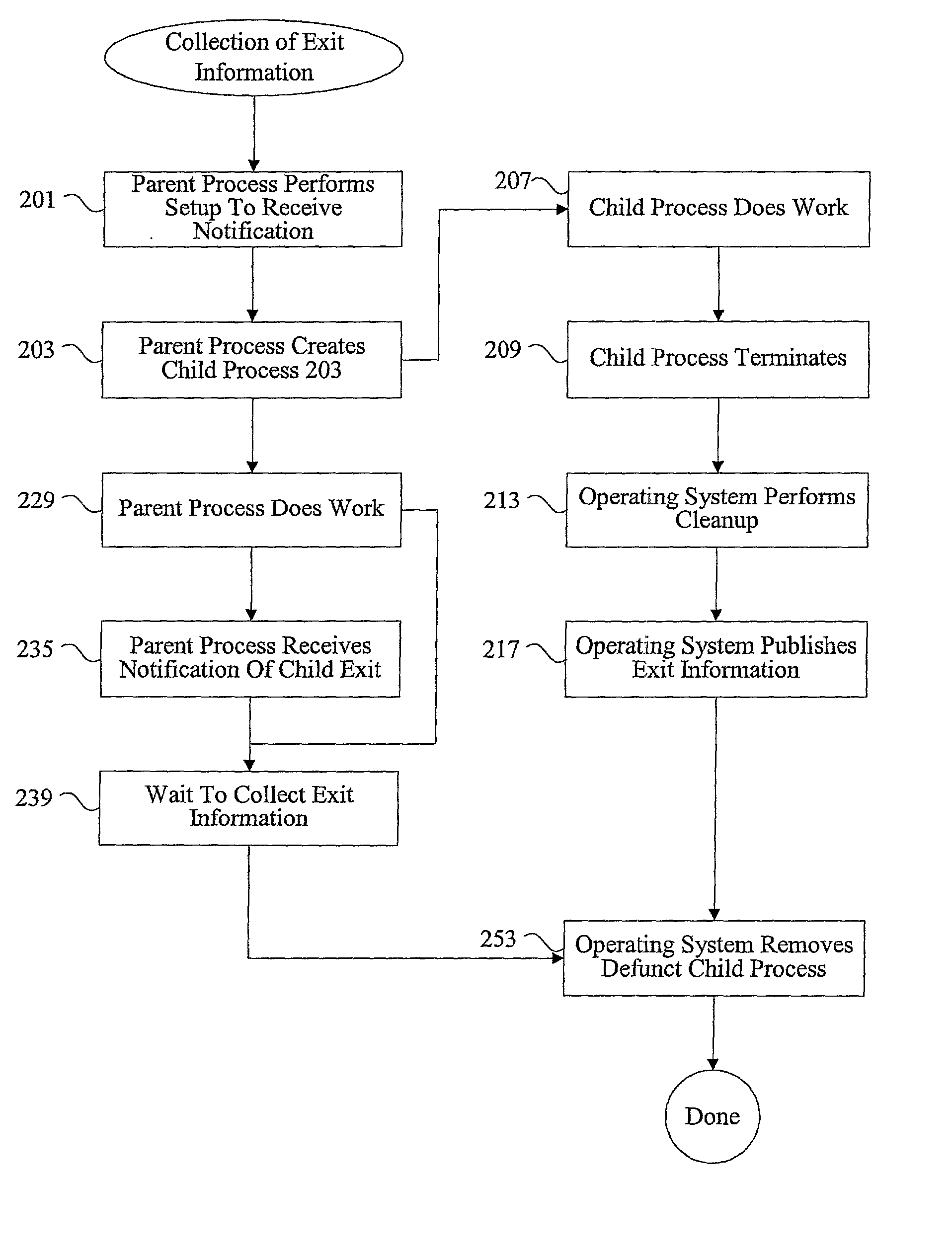
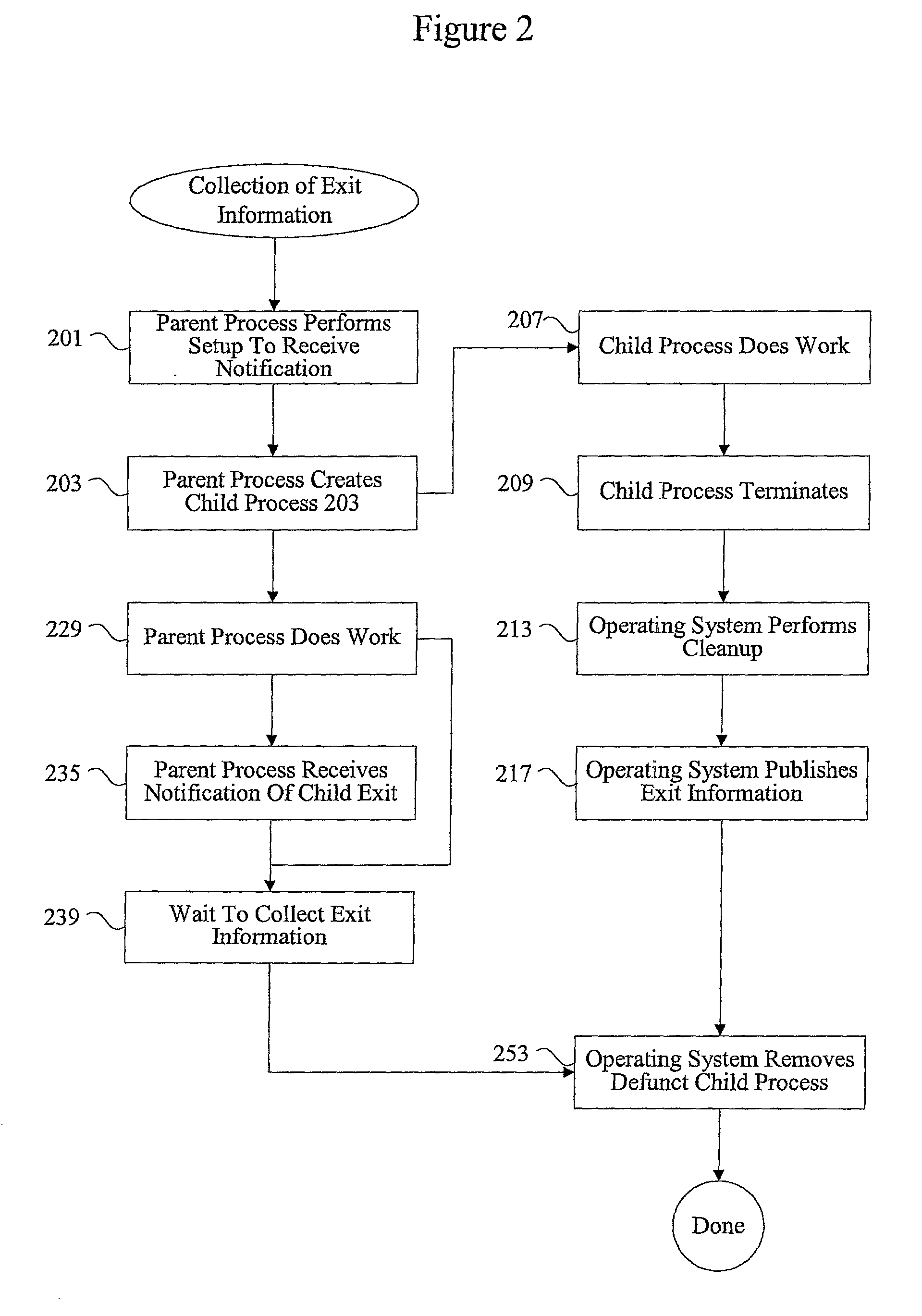
Methods and apparatus for managing defunct processes
InactiveUS7124403B2Program initiation/switchingSpecific program execution arrangementsSoftware engineeringParent process
The present invention relates to managing defunct processes. A parent process that does not collect exit information associated with a child process may leave a defunct child process. A defunct child process is identified. The parent process of the defunct child process is modified. The parent process can be modified by changing an existing thread or instantiating a new thread to collect exit information associated with the child process. Collecting exit information causes the removal of the defunct child process.
Owner:ORACLE INT CORP
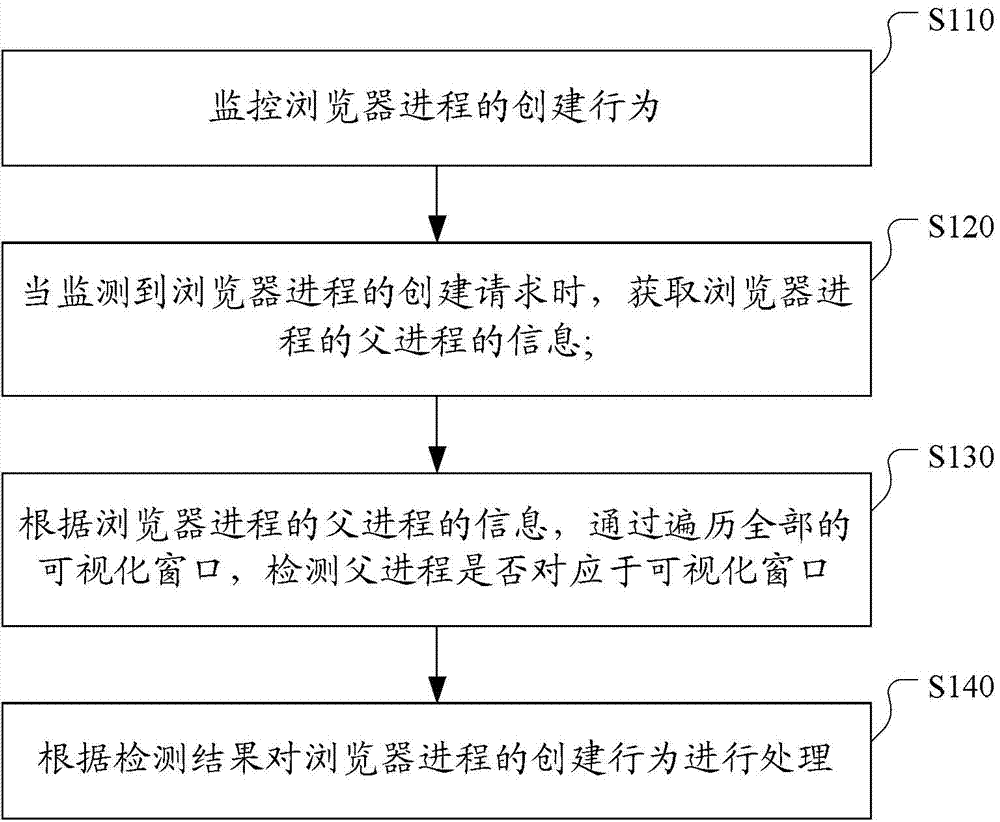
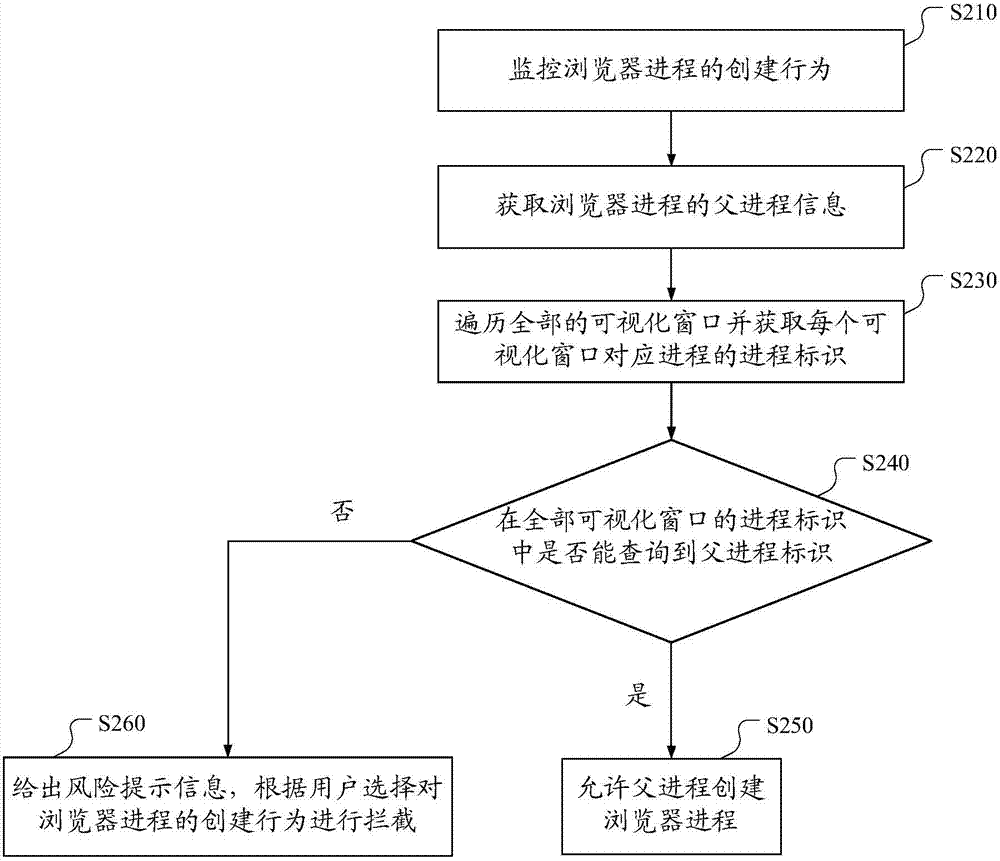
Method, device and system for intercepting advertisement programs based on cloud security
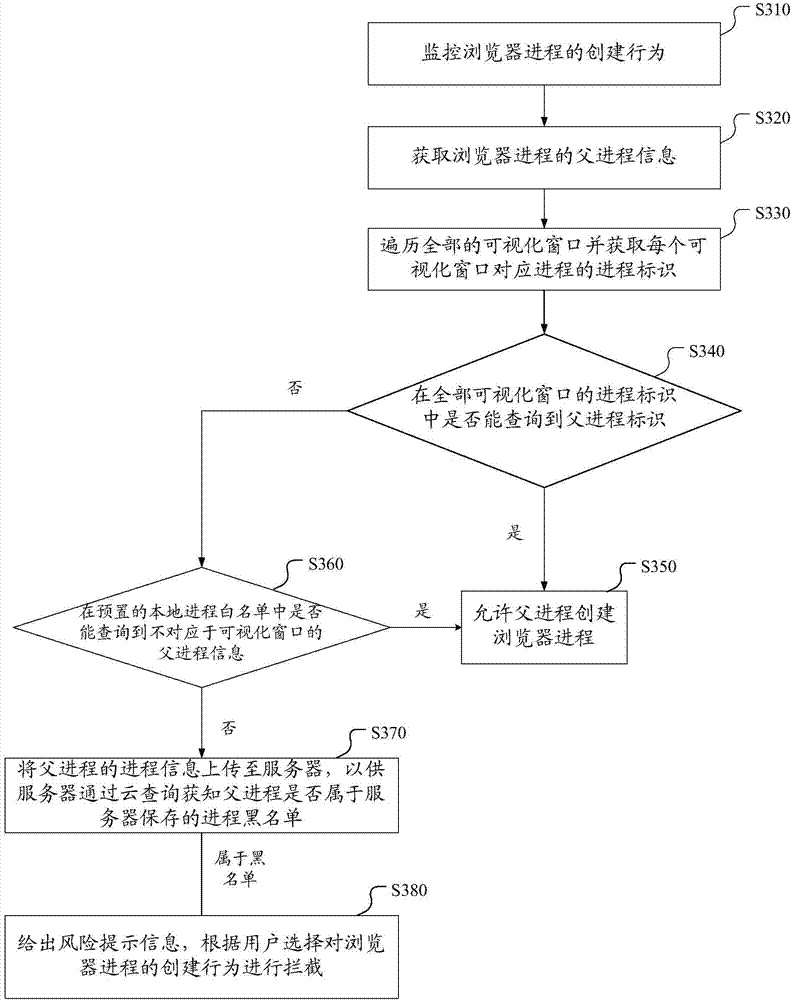
ActiveCN103617395AAvoid interferencePrevent cheatingPlatform integrity maintainanceTransmissionWeb pageBackground process
The invention discloses a method, device and system for intercepting advertisement programs based on cloud security. The method comprises the steps that the creation behavior of a browser process is monitored; when the creation request of the browser process is monitored, the information of a parent process of the browser process is obtained; according to the information of the parent process of the browser process, all visual windows are traversed, and whether the parent process corresponds to the visual windows or not is detected; the creation behavior of the browser process is processed according to a detection result. According to the scheme, advertisements, phishing websites and other browser web pages, popped up without the agreement of users, of background processes of hidden windows can be effectively intercepted, the users are prevented from being interfered by the advertisements and other ineffective information and being deceived by false information of various malicious websites, and the safety of user network operations is improved.
Owner:BEIJING QIHOO TECH CO LTD
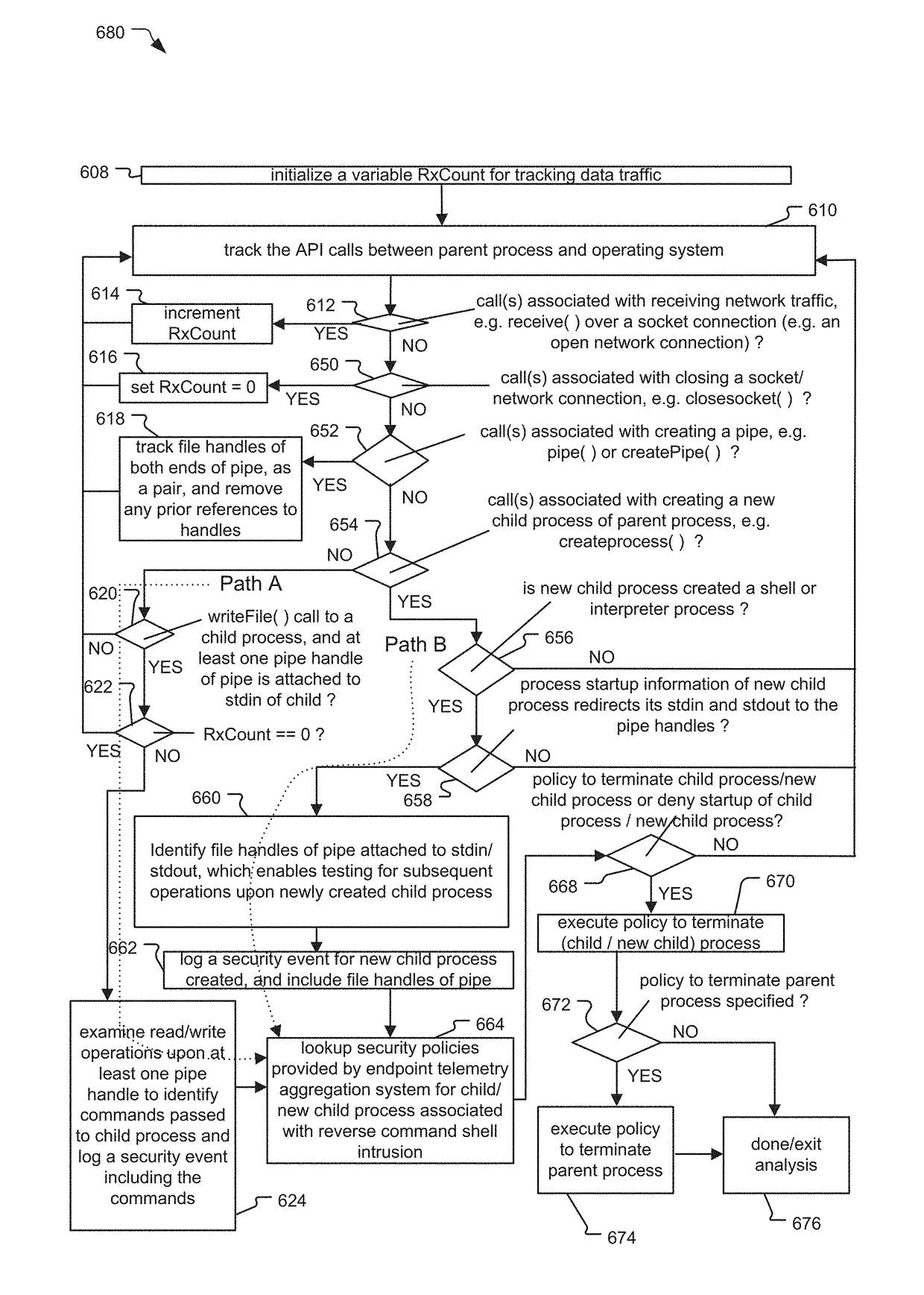
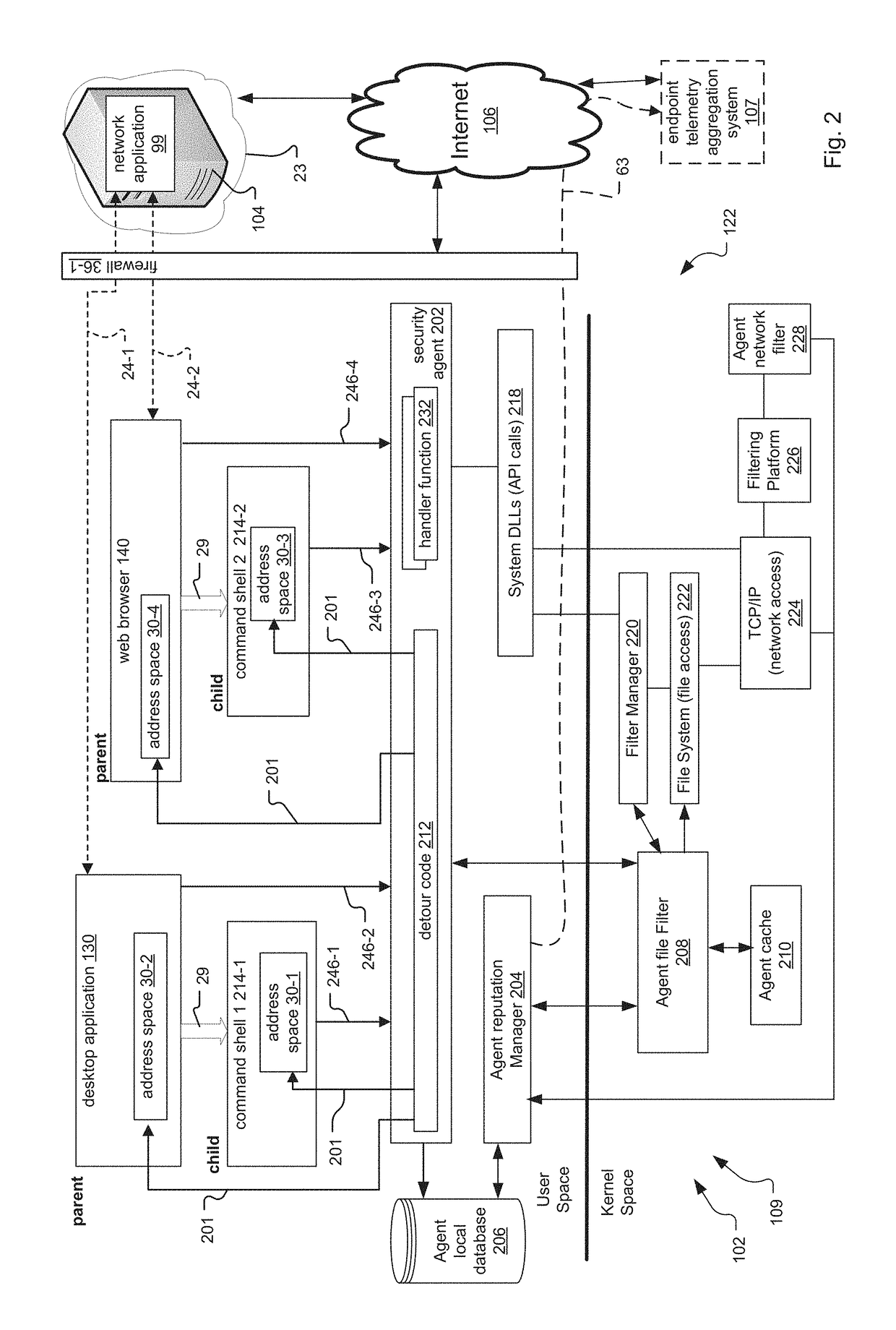
System and Method for Reverse Command Shell Detection
A system and method for detecting reverse command shell intrusions at a process-level on a user device is disclosed. In one embodiment, the system detects each process starting on an operating system of the user device, such as a mobile phone or laptop computer, and monitors Application Programming Interface (API) calls between each process and the operating system. The system then determines whether each process is associated with a reverse command shell intrusion based on information associated with each process and / or the API calls, and executes security policies against the processes associated with the reverse command shell intrusion to remediate the processes. In another embodiment, the system determines whether processes starting on a user device are associated with a reverse command shell intrusion by monitoring and analyzing information associated with the parent process of each process and / or API calls between each parent process and the operating system.
Owner:CARBON BLACK
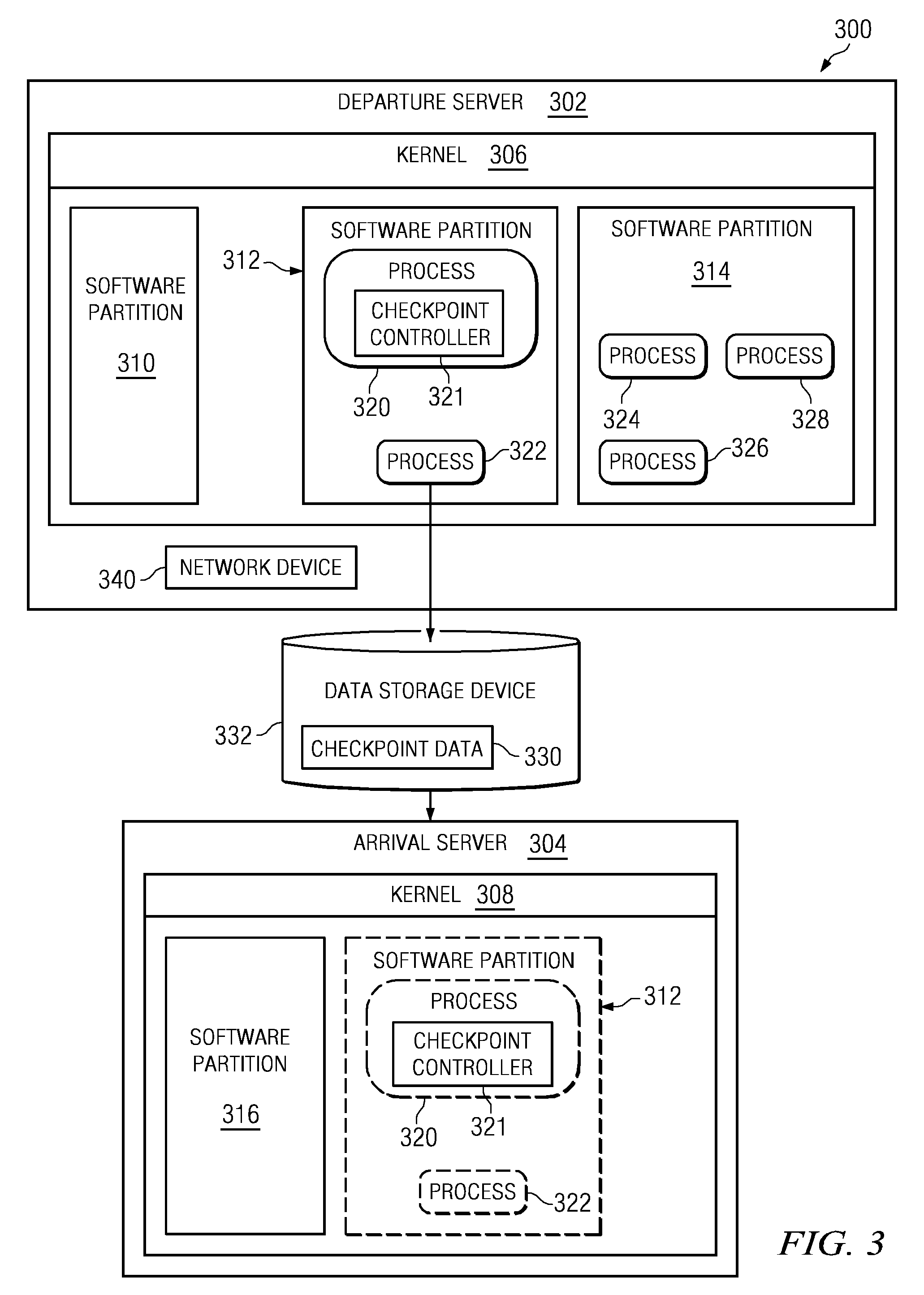
Checkpoint and restartable applications and system services
ActiveUS20090094582A1Specific program execution arrangementsMemory systemsApplication softwareComputer science
A computer implemented method, apparatus, and computer program product for checkpoint and restart of a process. In one embodiment, a process shell representing a restartable process is created on an arrival server in response to identifying a process on a departure server that is a restartable process. The process shell is frozen. A name of the restartable process, an identifier of the restartable process, and an identifier of a parent process of the restartable process is assigned to the process shell. The process shell is then unfrozen and exits. A parent process restarts the restartable process when the process shell exits.
Owner:IBM CORP
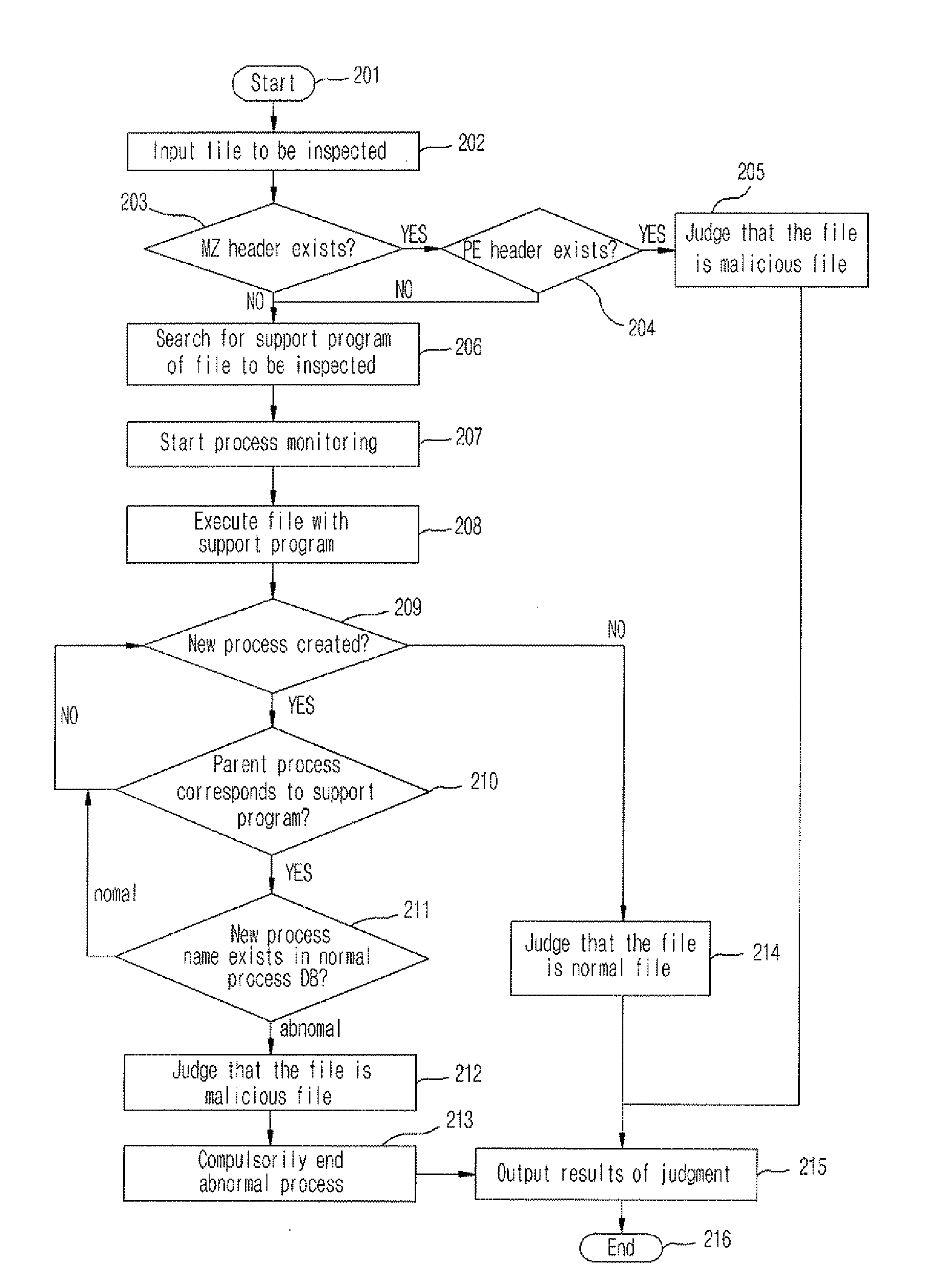
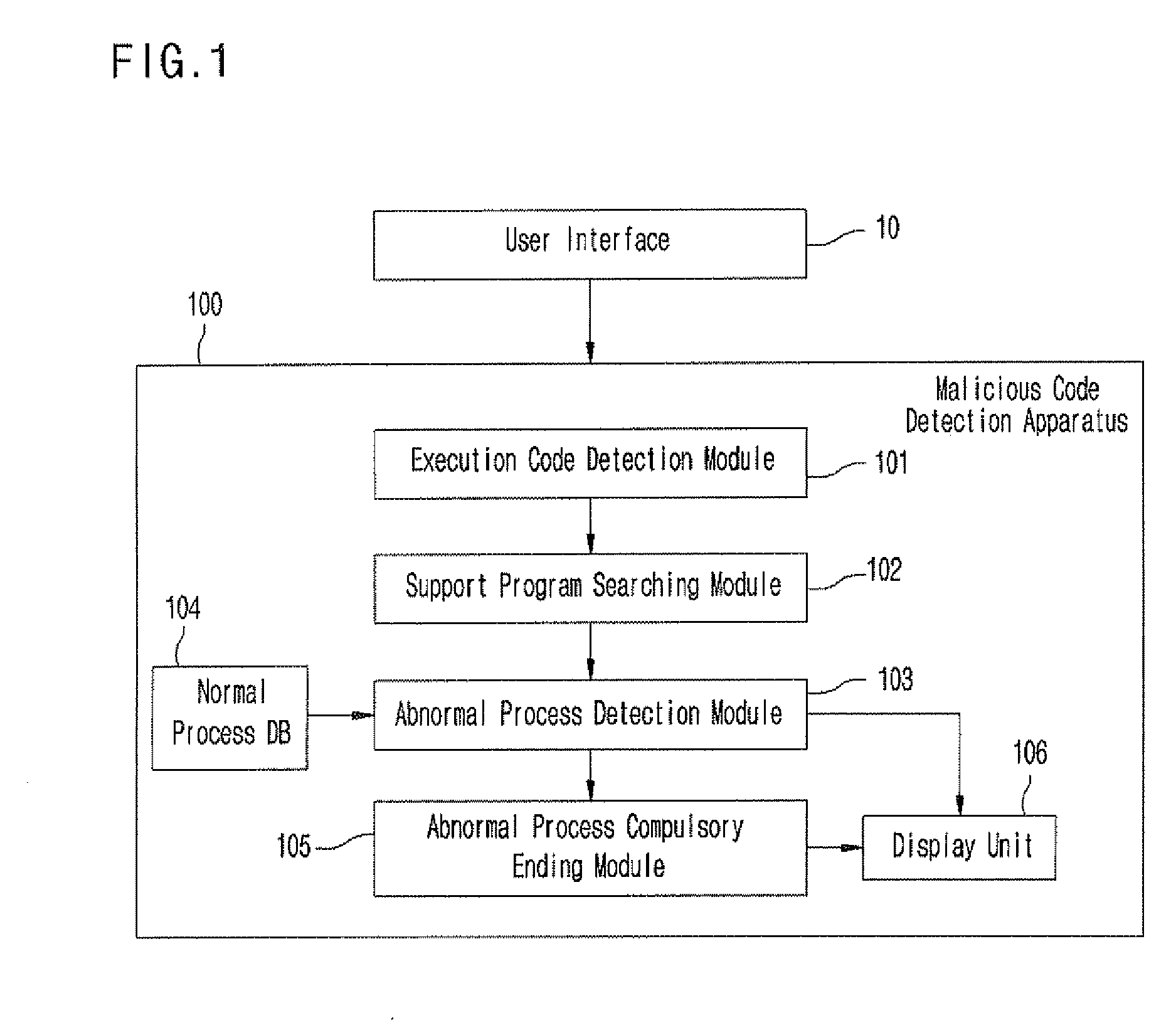
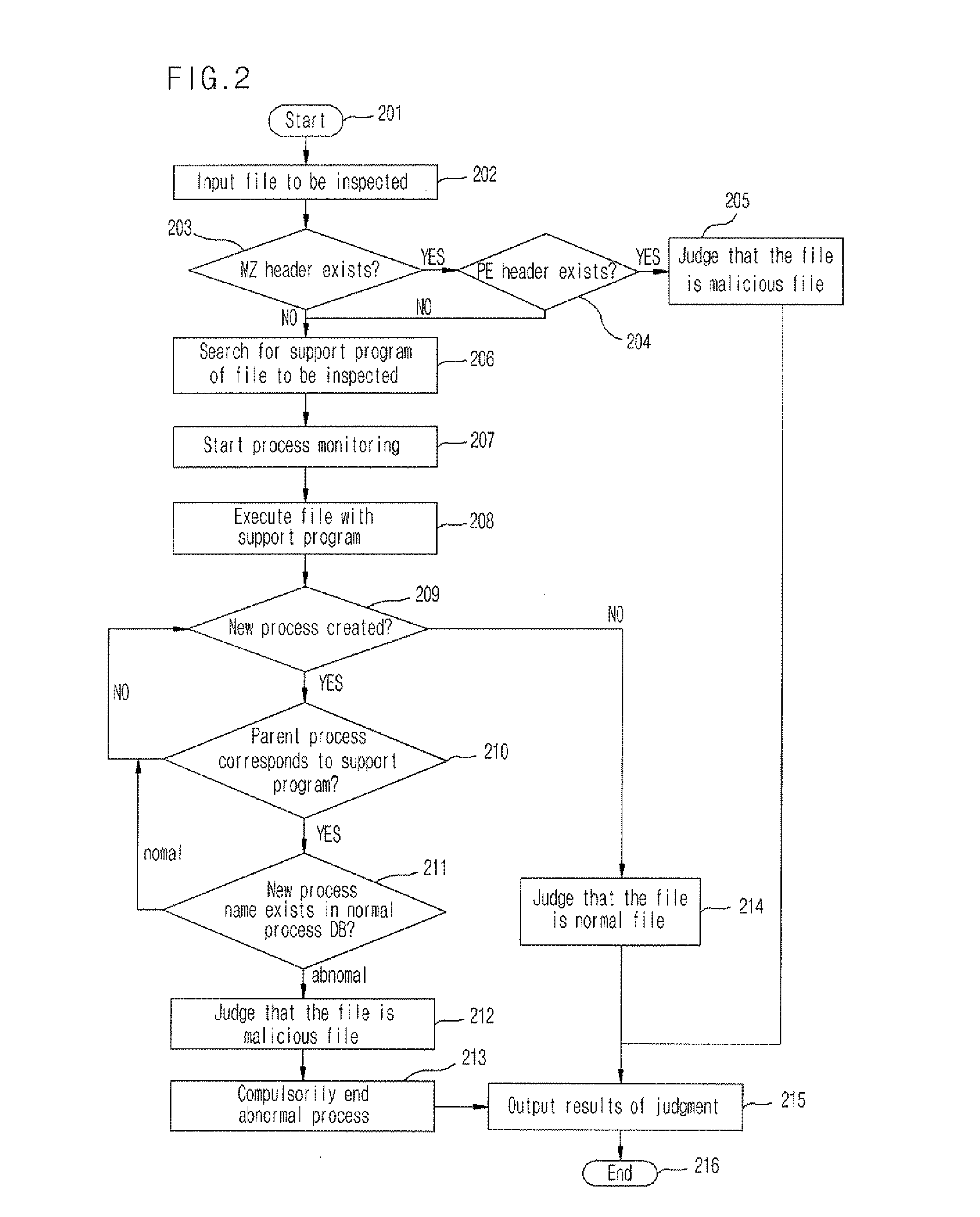
Apparatus and method of detecting file having embedded malicious code
InactiveUS20080115219A1Memory loss protectionError detection/correctionException handlingParent process
An apparatus and method of detecting a file having an embedded malicious code by confirming normality / abnormality of a process that operates in a file process is disclosed. The apparatus includes an execution code detection module for detecting whether an executable file format is included in a file to be inspected through a static analysis, a support program searching module for searching for a support program according to an extension of the file to be inspected and reporting a corresponding process name and an execution path, an abnormal process detection nodule for monitoring the searched support process and judging whether a parent process of a newly created process is normal using a tree structure of the process, and an abnormal process compulsory ending module for compulsorily ending the newly created process if it is judged that the file to be inspected is the file having the embedded malicious code. Accordingly, execution of all abnormal processes can be checked.
Owner:ELECTRONICS & TELECOMM RES INST
Customizing Policies for Process Privilege Inheritance
InactiveUS20090328129A1Digital data processing detailsUnauthorized memory use protectionSoftware engineeringParent process
An approach is provided that uses policies to determine which parental privileges are inherited by the parent's child processes. A parent software process initializes a child software process, such as by executing the child process. The parent process is associated with a first set of privileges. The inheritance policies are retrieved that correspond to the parent process. A second set of privileges is identified based on the retrieved inheritance policies, and this second set of privileges is applied to the child software process.
Owner:IBM CORP
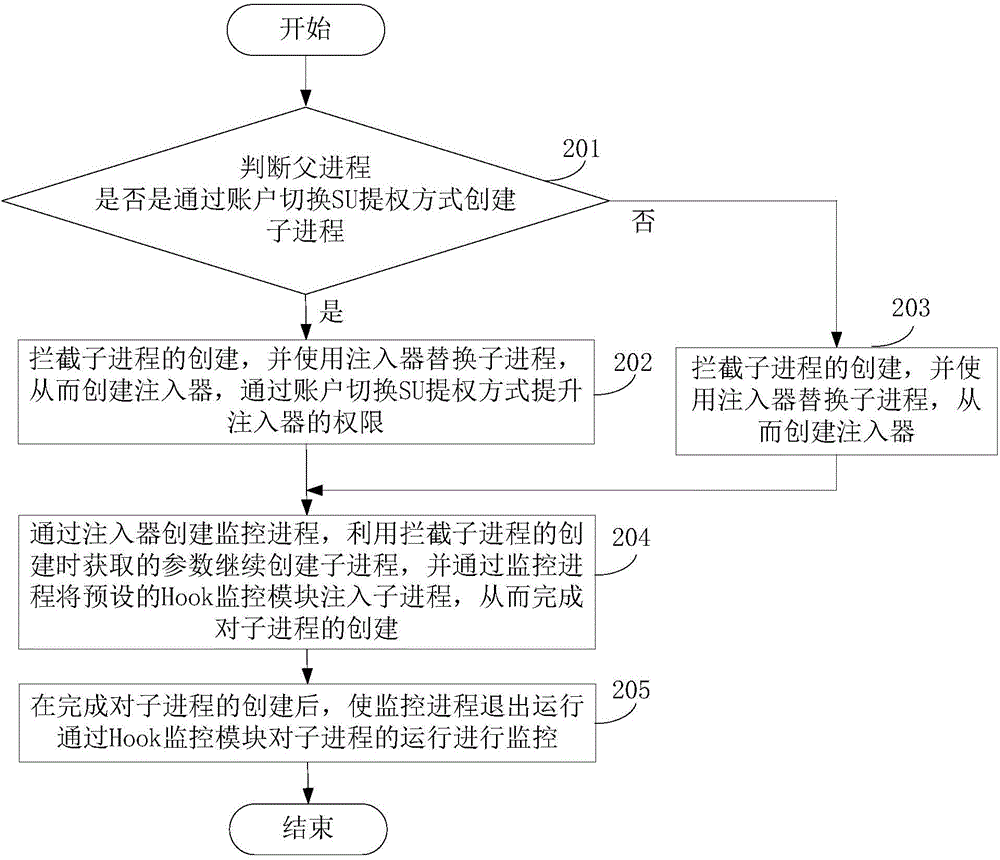
Process monitoring method and device and intelligent terminal
ActiveCN104156662AMalicious Behavior BlockingAvoid threatsPlatform integrity maintainanceEngineeringParent process
The invention discloses a process monitoring method and device and an intelligent terminal and belongs to the technical field of communication. The method comprises the steps that when a parent process establishes a child process, the establishment of the child process is intercepted, an injector is used for replacing the child process, and thus the injector is established; a monitoring process is established through the injector, the child process is established continually by using parameters obtained when the establishment of the child process is intercepted, a preset Hook monitoring module is injected into the child process through the monitoring process, and thus the establishment of the child process is completed; after the establishment of the child process is completed, the monitoring process stops operating, and the operation of the child process is monitored through the Hook monitoring module. The device comprises an intersecting module, an injecting module and a monitoring module. The intelligent terminal comprises a distributing platform and a Hook platform. The process monitoring method and device and the intelligent terminal can monitor any child process.
Owner:BEIJING QIHOO TECH CO LTD
Methods and apparatus for managing defunct processes
InactiveUS20030037290A1Program initiation/switchingEmergency protective arrangements for automatic disconnectionSoftware engineeringParent process
The present invention relates to managing defunct processes. A parent process that does not collect exit information associated with a child process may leave a defunct child process. A defunct child process is identified. The parent process of the defunct child process is modified. The parent process can be modified by changing an existing thread or instantiating a new thread to collect exit information associated with the child process. Collecting exit information causes the removal of the defunct child process.
Owner:ORACLE INT CORP
System and method for executing a process on a microprocessor-enabled device
InactiveUS20060174078A1Specific access rightsUnauthorized memory use protectionOperational systemMicroprocessor
The invention provides a system and a method for controlling a request for a resource from a process operating on a microprocessor-enabled machine is provided. The method comprises regulating access of the process to the resource associated with the machine via a parent process when the process initiates the request to an operating system associated with the machine, the parent process operating outside of the operating system. In the method, the parent process may spawn the process. In the method the request may initially be received by an access process in the operating system. Then, the access process may initiate a second request to the parent process to check whether the process has clearance to access the resource. Then, the parent process may provide a signal to the access process indicating whether the process has such clearance.
Owner:ALCATEL LUCENT SAS
Crossed dynamic software testing method and device
InactiveCN102508780AAvoid falling intoReduce overheadSoftware testing/debuggingCoding blockCode coverage
The invention discloses a crossed dynamic software testing method and a crossed dynamic software testing device. The crossed dynamic software testing method comprises the following steps: 1, executing a random detection on a tested application by a dynamic random testing method and detecting application bugs; if an abnormal application is detected, recording abnormal information and exiting the test; otherwise, after completion of the current test, computing a code coverage and detecting whether the code coverage is saturated; if the code coverage is saturated, invoking a symbol switching function and switching into dynamic symbolic execution to hold on a parent process; otherwise, continuing to execute the next test till the code coverage is detected to be saturated; and 2, searching a new uncovered code block by a dynamic symbolic execution method; if a new code block is detected, restoring the state to a random executing state in the step 1; and if all basic blocks are covered, exiting the test. By the crossed dynamic software testing method, relatively large applications can be tested in an all-around way, so that a relatively high code coverage can be obtained and the explosion problem of a dynamic symbolic execution route can be relieved.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA +1
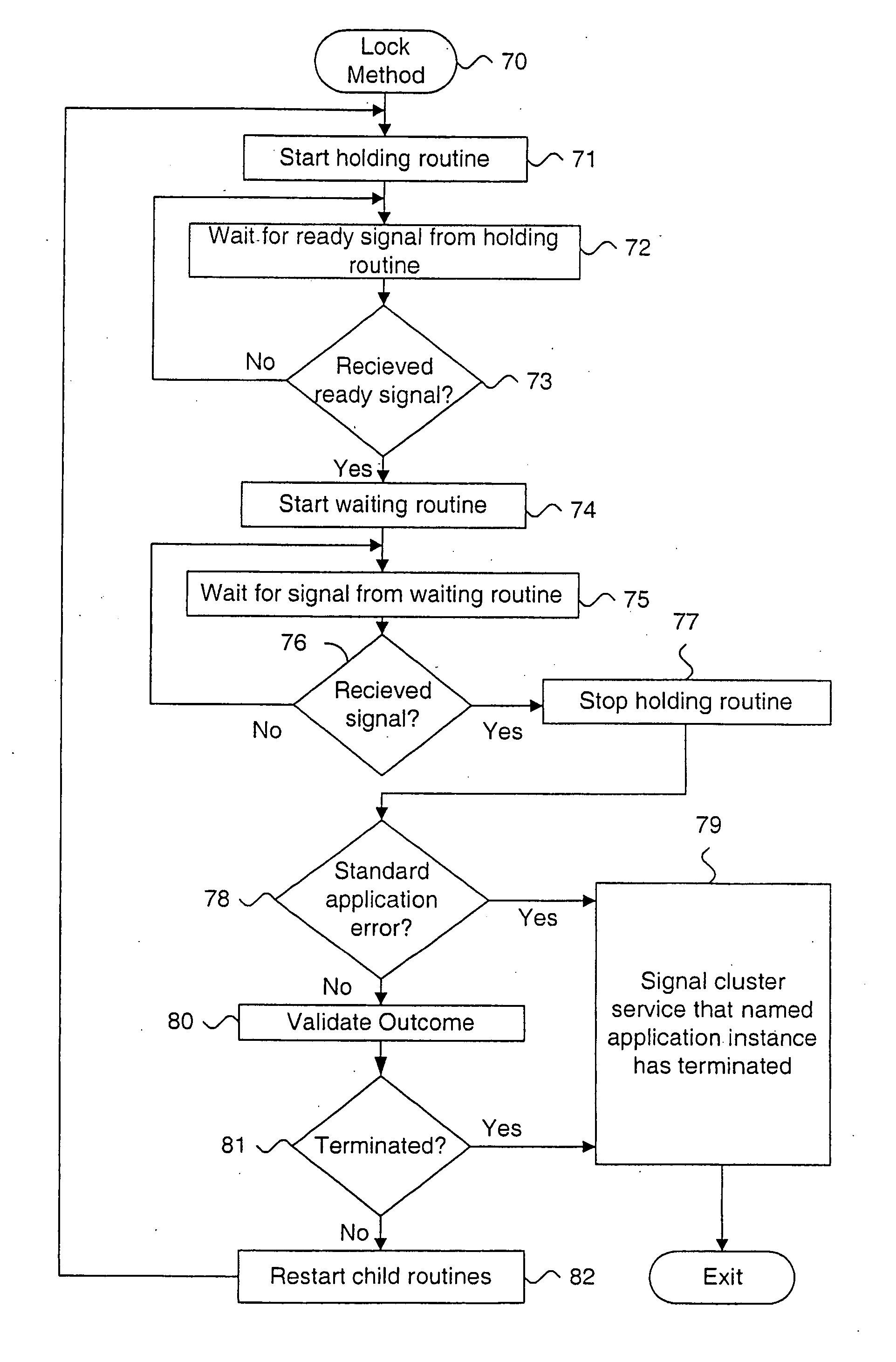
System and method for detecting termination of an application instance using locks
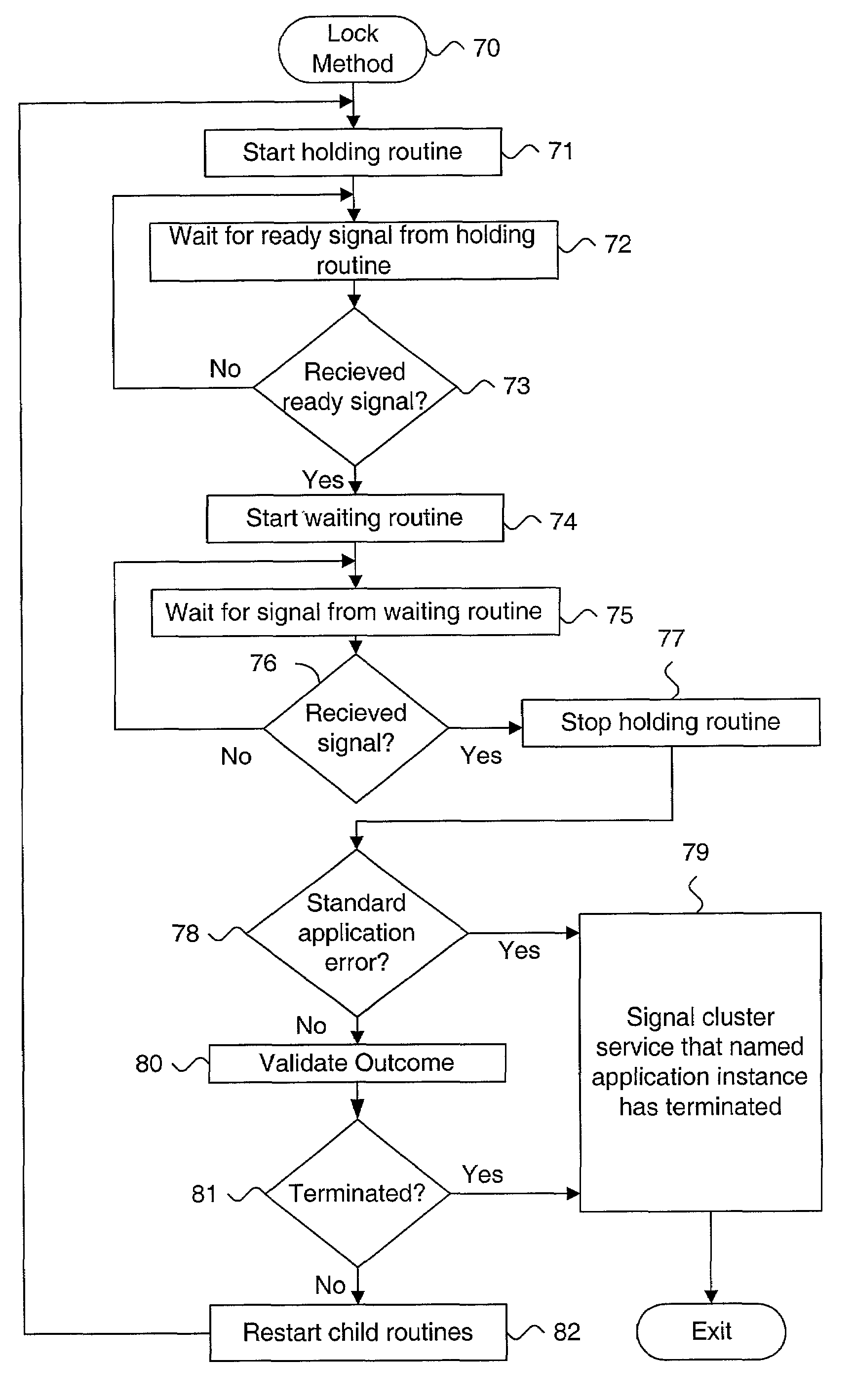
InactiveUS7058629B1Digital data information retrievalData processing applicationsApplication procedureData bank
A system and method for detecting termination of an application, such as a database instance, that uses locks is described. A holding child process is started from a parent process. The holding child process connects to a monitored application instance, acquires an exclusive lock on the monitored application instance and returns a ready signal upon successfully acquiring the exclusive lock. A waiting child process is started from the parent process subsequent to the holding child process. The holding child process connects to the monitored application instance, blocks on the exclusive lock on the monitored application instance and returns a result signal upon at least one of acquiring the exclusive lock and clearing the block on the exclusive lock. The return signal is processed at the parent process. Using locks provides immediate detection that the application has terminated. Methods for blocking against the application are also described.
Owner:ORACLE INT CORP
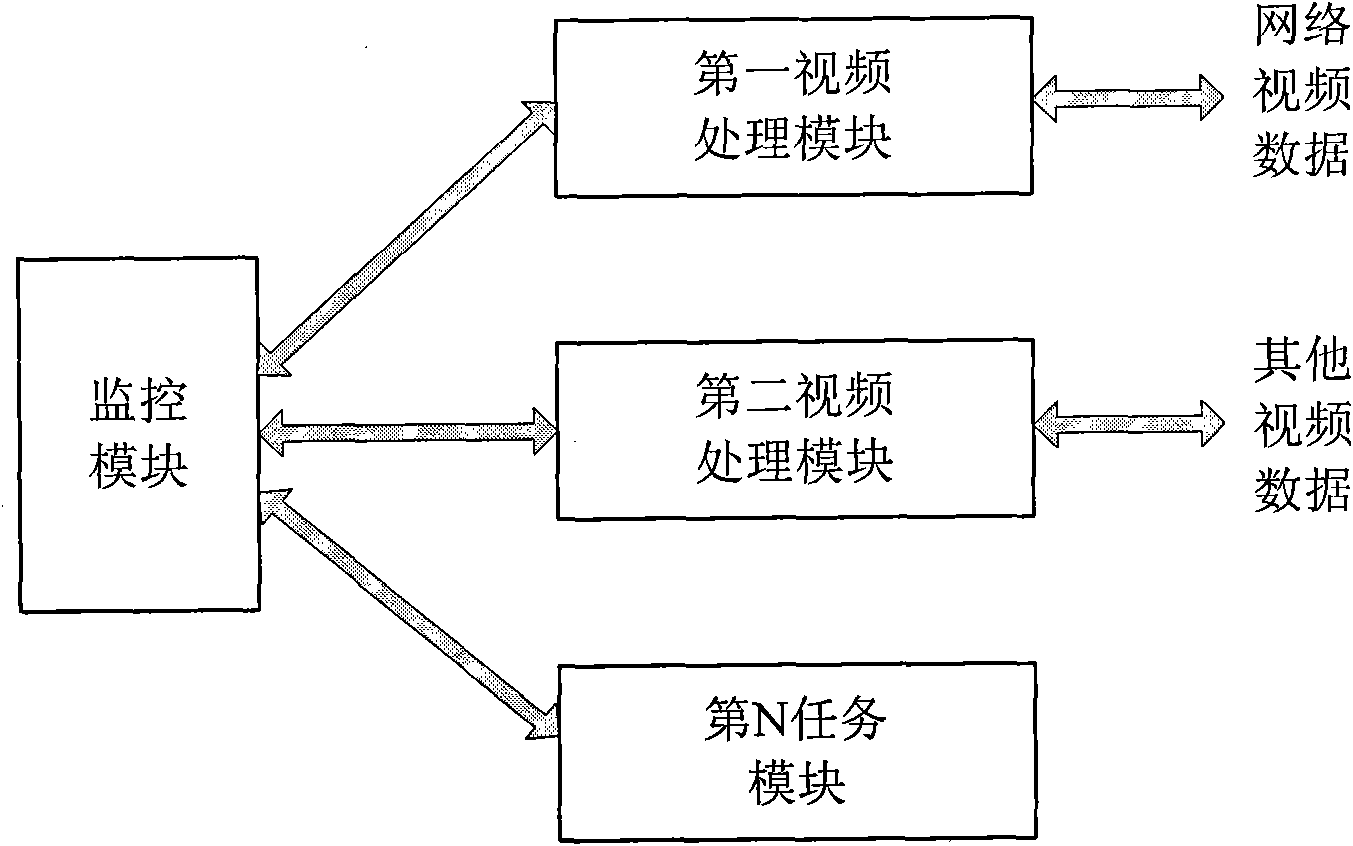
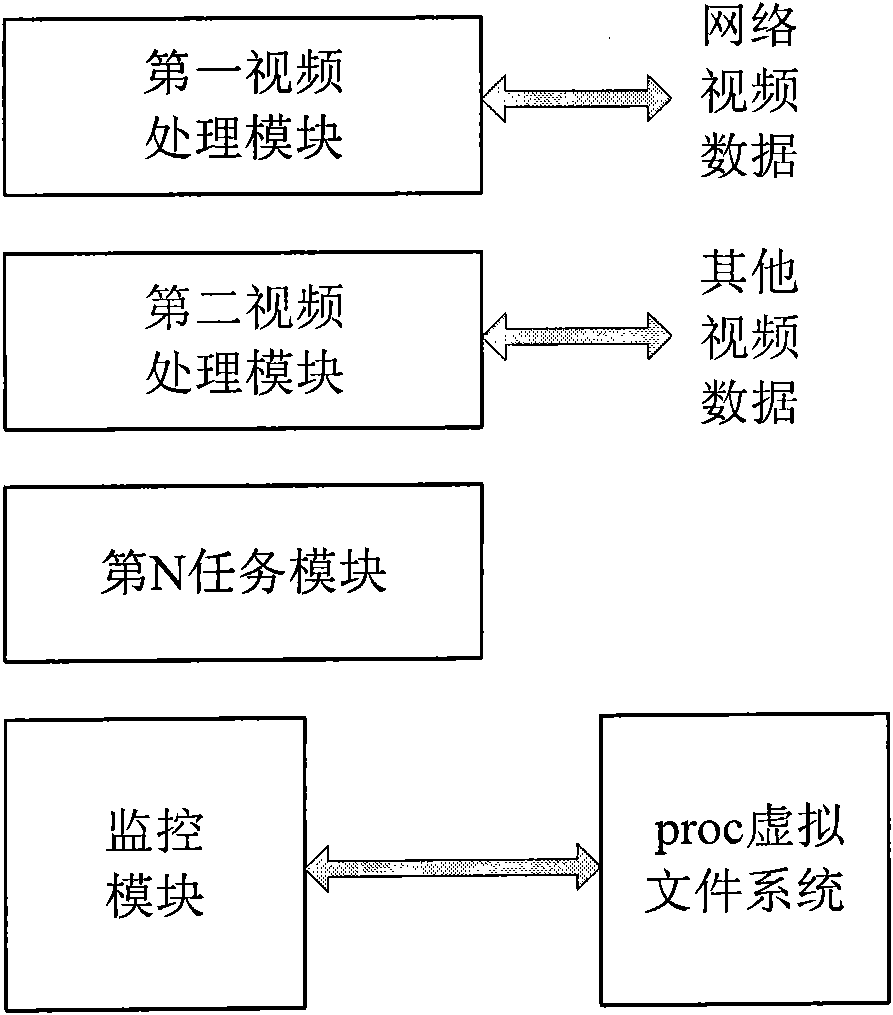
Method and system for multi-task monitoring process of videos
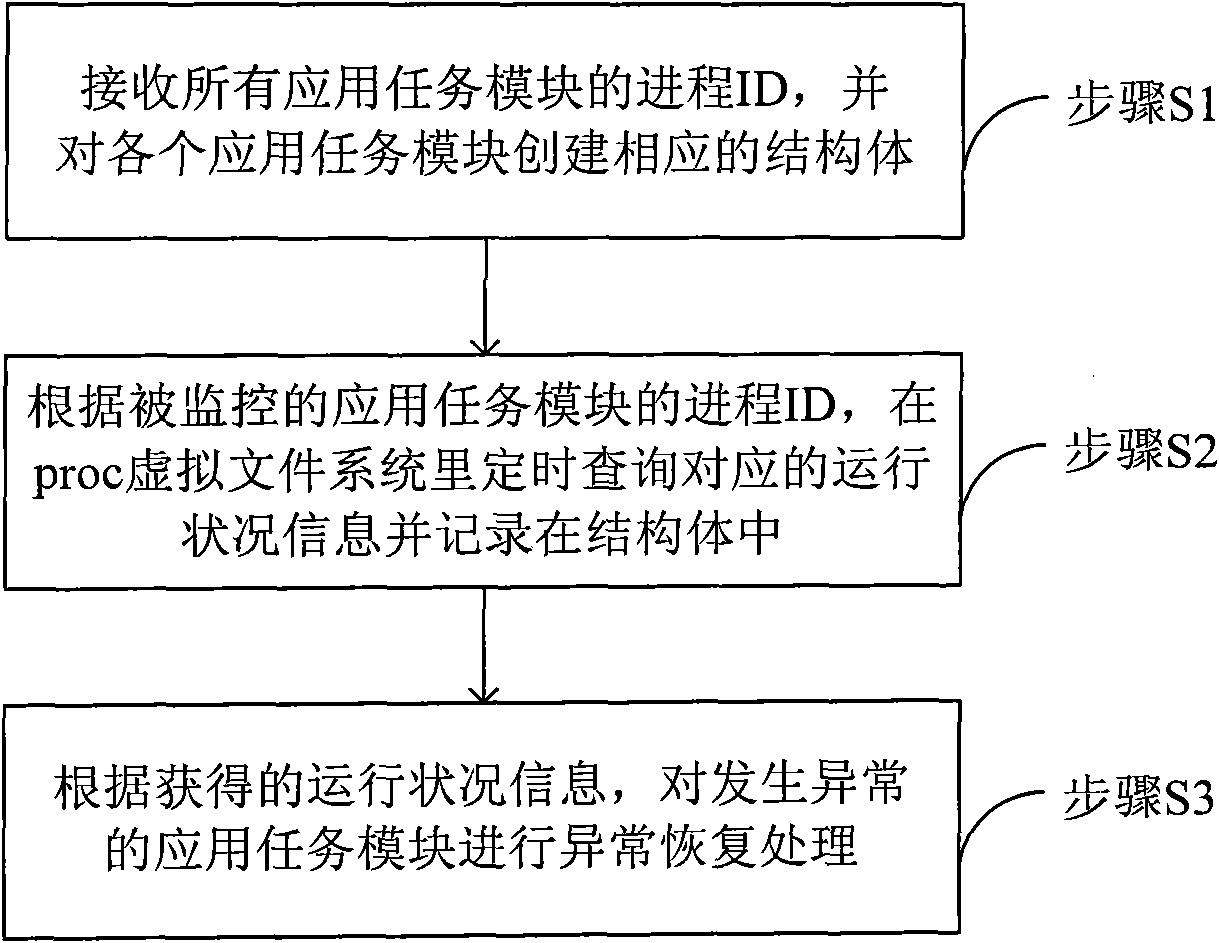
InactiveCN101674465ADoes not affect processing efficiencyLower latencyProgram initiation/switchingClosed circuit television systemsVirtual file systemFile system
The invention relates to the field of multi-task monitoring and provides a method for the multi-task monitoring process of videos. The method comprises the following steps: receiving the process IDs of all the application task modules and creating a corresponding structural body for each application task module, wherein, the structural body is used for recording the information on the process running state of the application task module; inquiring the corresponding information on the running state regularly in a proc virtual file system according to the process IDs of the monitored applicationtask modules, and recording the information on the running state thereof in the structural body; and detecting exceptions, and handling the exceptions of the application task module. Meanwhile, the invention further provides a system for the multi-task monitoring process of videos. The system comprises a parent process, a monitoring module, a plurality of application task modules and the proc virtual file system. The invention can monitor the application task modules and handle the exceptions without influencing the data processing efficiency of the video; moreover, the invention can reduce the picture delay.
Owner:NANTONG BEICHEN MACHINERY EQUIP MFGCO
System and method for detecting termination of an application instance using locks
InactiveUS20060190453A1Data processing applicationsDigital data information retrievalApplication procedureData bank
A system and method for detecting termination of an application, such as a database instance, that uses locks is described. A holding child process is started from a parent process. The holding child process connects to a monitored application instance, acquires an exclusive lock on the monitored application instance and returns a ready signal upon successfully acquiring the exclusive lock. A waiting child process is started from the parent process subsequent to the holding child process. The holding child process connects to the monitored application instance, blocks on the exclusive lock on the monitored application instance and returns a result signal upon at least one of acquiring the exclusive lock and clearing the block on the exclusive lock. The return signal is processed at the parent process. Using locks provides immediate detection that the application has terminated. Methods for blocking against the application are also described.
Owner:ORACLE INT CORP
Network interface routing using computational context
InactiveUS7821985B2Network traffic/resource managementData switching by path configurationOperational systemNetwork connection
Knowledge of the computational context of a computer operating environment, for example, awareness of process threads, is used to route IP traffic in the presence of multiple active network connections. An additional protocol may be added to the network layer of an operating system in order to map certain computational contexts to particular network interfaces. Any process with identification parameters associated with a mapped computational context requesting data transfer via a communication network is bound to the network interface previously associated with the computational context rather than an alternate network interface that otherwise might be the default. Further, process threads created by a parent process thread may be caused to inherit the computational context of the parent thread in order to assign traffic to the same network interface. This routing framework may have particular application with respect to multihomed host devices, for example, mobile computing devices.
Owner:MICROSOFT TECH LICENSING LLC
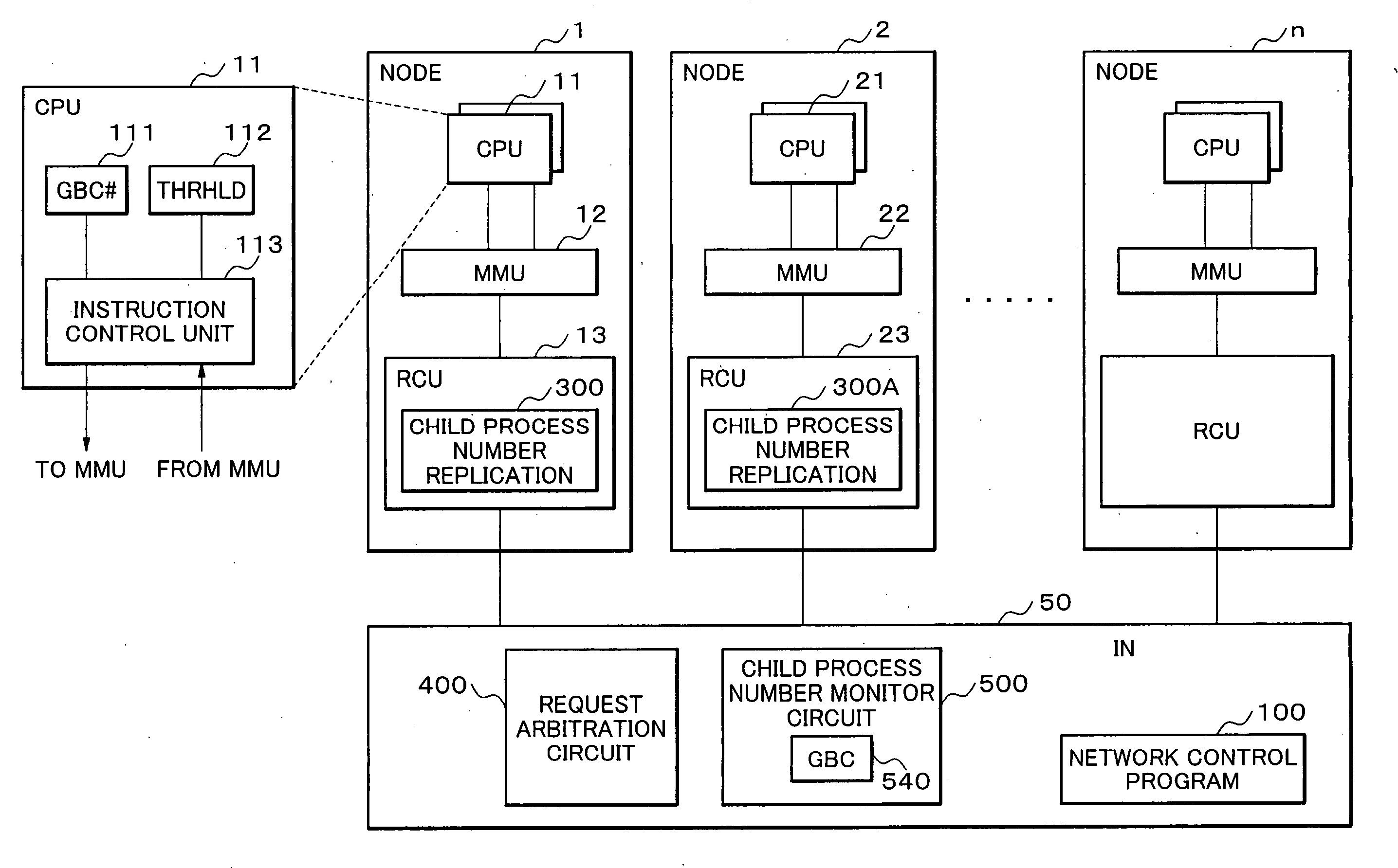
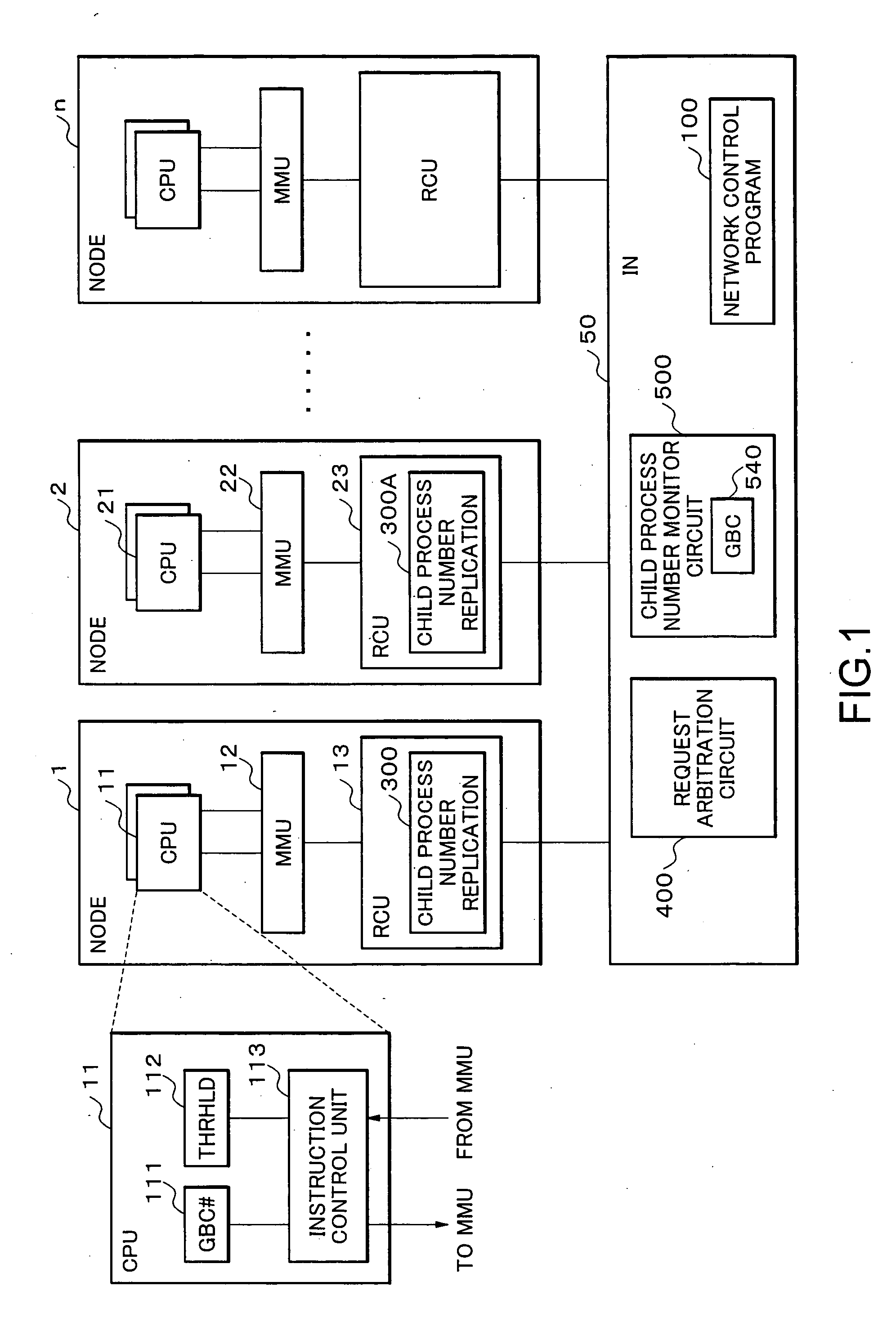
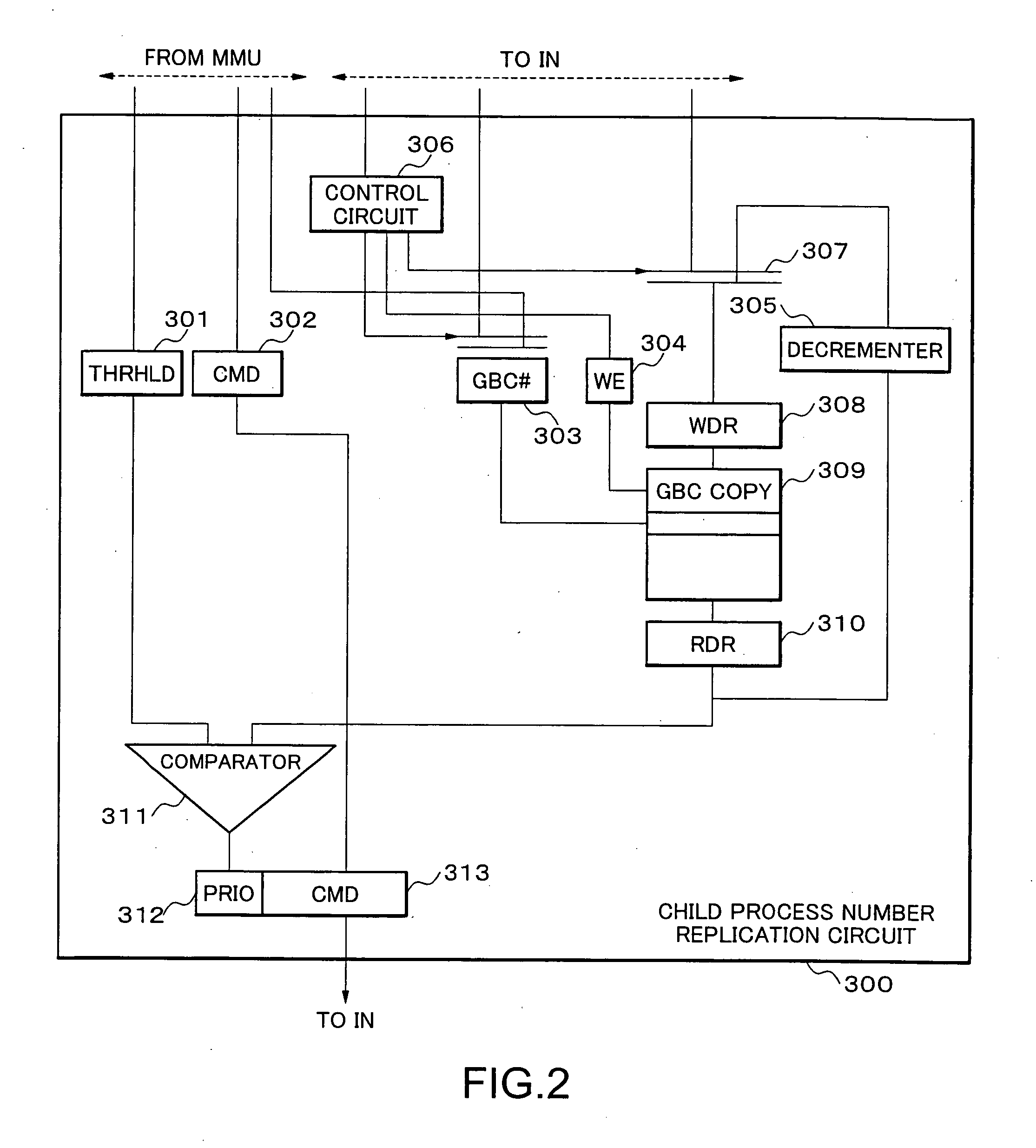
Parallel processing system, interconnection network, node and network control method, and program therefor
InactiveUS20060059489A1Shortened TATImprove system efficiencyProgram synchronisationMemory systemsNetwork controlInterconnection
The parallel processing system includes a plurality of nodes which are interconnected over an interconnection network; wherein the parallel processing system divides a computer job into parallel jobs by a parent process performed by a computer arranged in the nodes, and the parallel jobs are processed by the plurality of child processes using the plurality of computers arranged in the plurality of nodes; and a transfer process through the interconnection network from a slow child process in the child processes is performed on a basis of priority over other transfer processes.
Owner:NEC CORP
System and method for ensuring mobile device data and content security
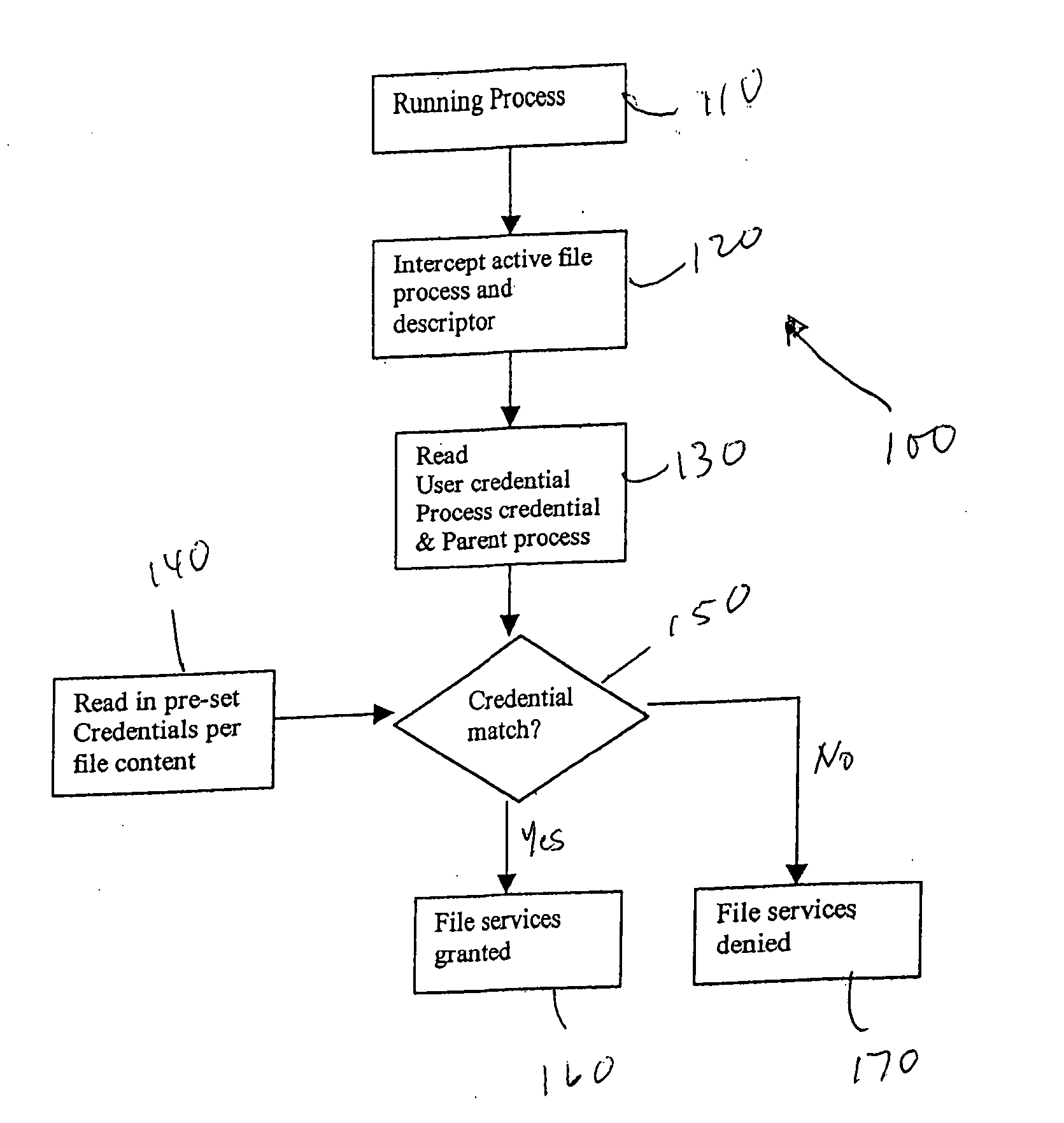
InactiveUS20050015605A1Computer security arrangementsSecret communicationMobile deviceContent security
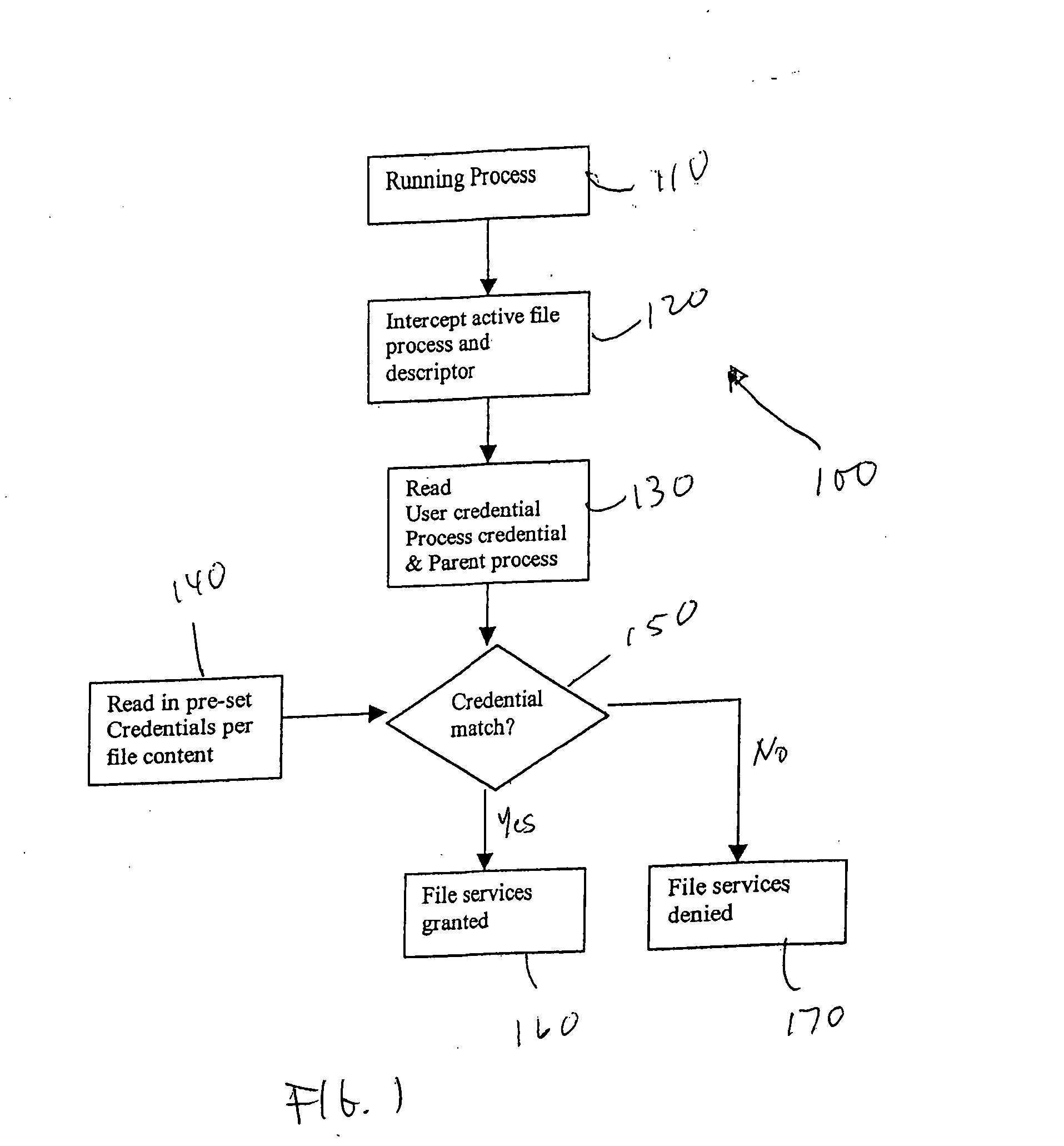
A method for ensuring mobile device data and content security includes the steps of intercepting an active file process, reading a user credential, a process credential and a parent process, reading a pre-set credential, comparing the user credential and the process credential with the pre-set credential, allowing the active file process to proceed if the user credential and the process credential match the pre-set credential, and denying the active file process to proceed if the user credential and the process credential do not match the pre-set credential.
Owner:LIN JEOU KAI
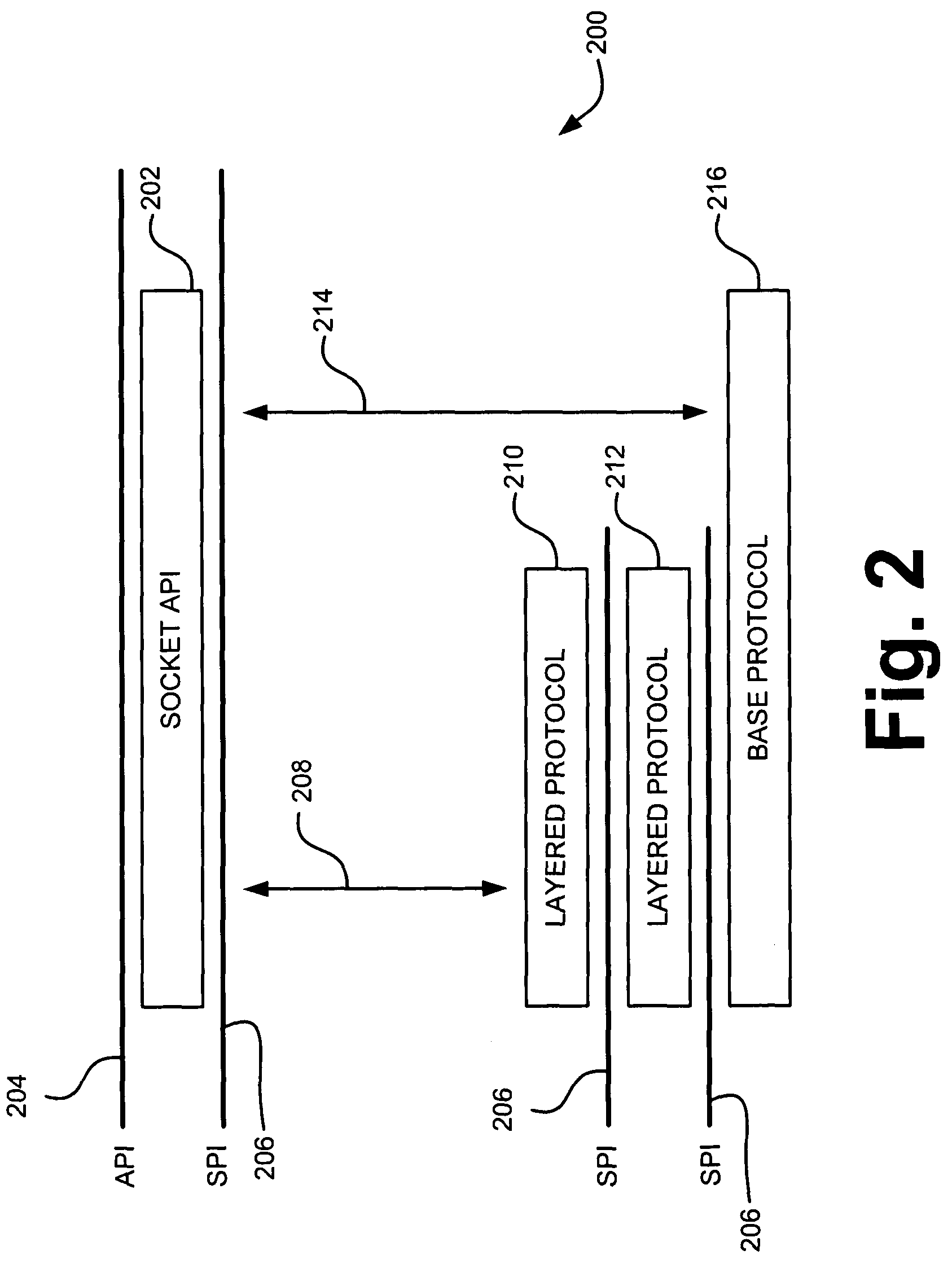
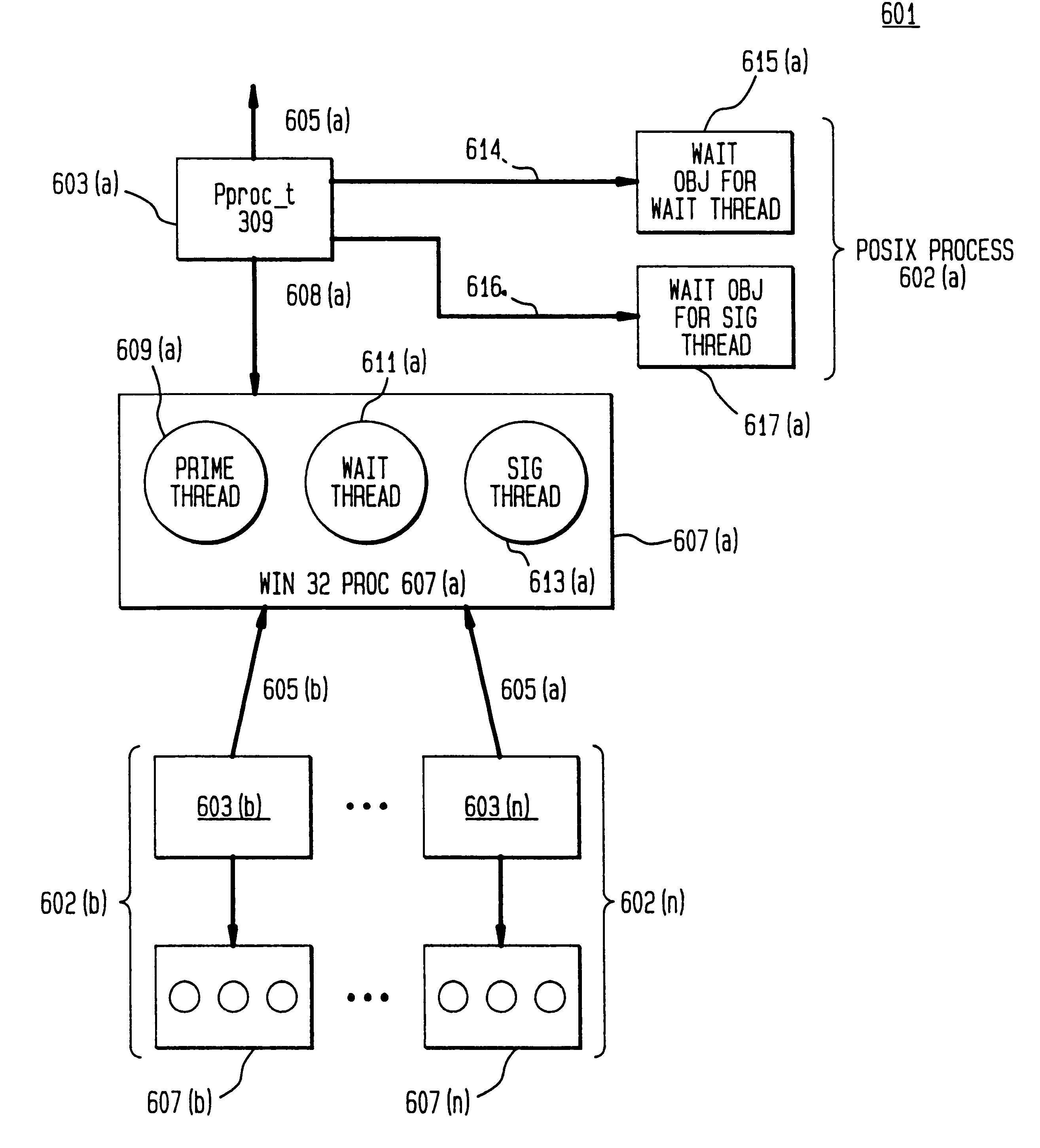
Porting POSIX-conforming operating systems to Win32 API-conforming operating systems
InactiveUS6292820B1Multiprogramming arrangementsProgram code adaptionOperational systemSignal processing
Techniques for porting operating systems of a first class whose representatives include operating systems implementing the POSIX standard to operating systems of a second class whose representatives include operating systems implementing the Win32 API. Processes belonging to operating systems of the first class are characterized by a single thread, parent-child relationships, and signal handlers that execute on the top of the stack; processes belonging to operating systems belonging to the second class have multiple threads, do not have parent-child relationships, and do not necessarily execute their signal handlers at the top of the stack. Techniques are disclosed for implementing signal handling as required for operating systems of the first class and providing a signal to a parent process of the first class when one of its child processes terminates. Processes of the second class adapted for implementing processes of the first class are disclosed, as well as implementations of the POSIX fork and exec functions using those processes.
Owner:RAKUTEN INC
Method for jointly demodulating MSK and DSSS and demodulator thereof
InactiveCN101515915AReduce consumptionReduce power consumptionMulti-frequency code systemsTransmitter/receiver shaping networksCommunications systemFrequency compensation
The invention belongs to the technology filed of wireless communication, relating to a method for jointly demodulating MSK (minimum shift keying) and DSSS (direct sequence spread spectrum) and a demodulator thereof. The demodulator comprises an error information obtaining module, a match filter module, a synchronous information trapping module, a demodulating module and a tracking module; and the method for jointly demodulating MSK and DSSS comprises the following steps of: (1) obtaining error information, (2) matching and filtering the error information, (3) trapping synchronous information, (4) demodulating, (5) tracking, or the like, and sending demodulation results to parent process so as to complete communication process. The invention has the advantage of better frequency compensation ability, thereby, solving the problems that a method for dispreading and demodulating direct sequence spread spectrum signals needs to be frequency offset estimated, complex extraction of PN code synchronization and bit synchronization, etc. Compared with the existing dispreading and demodulating method, the invention is simple as needing no carrier recovery module nor bit timing module, and is applicable to the wireless communication system.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
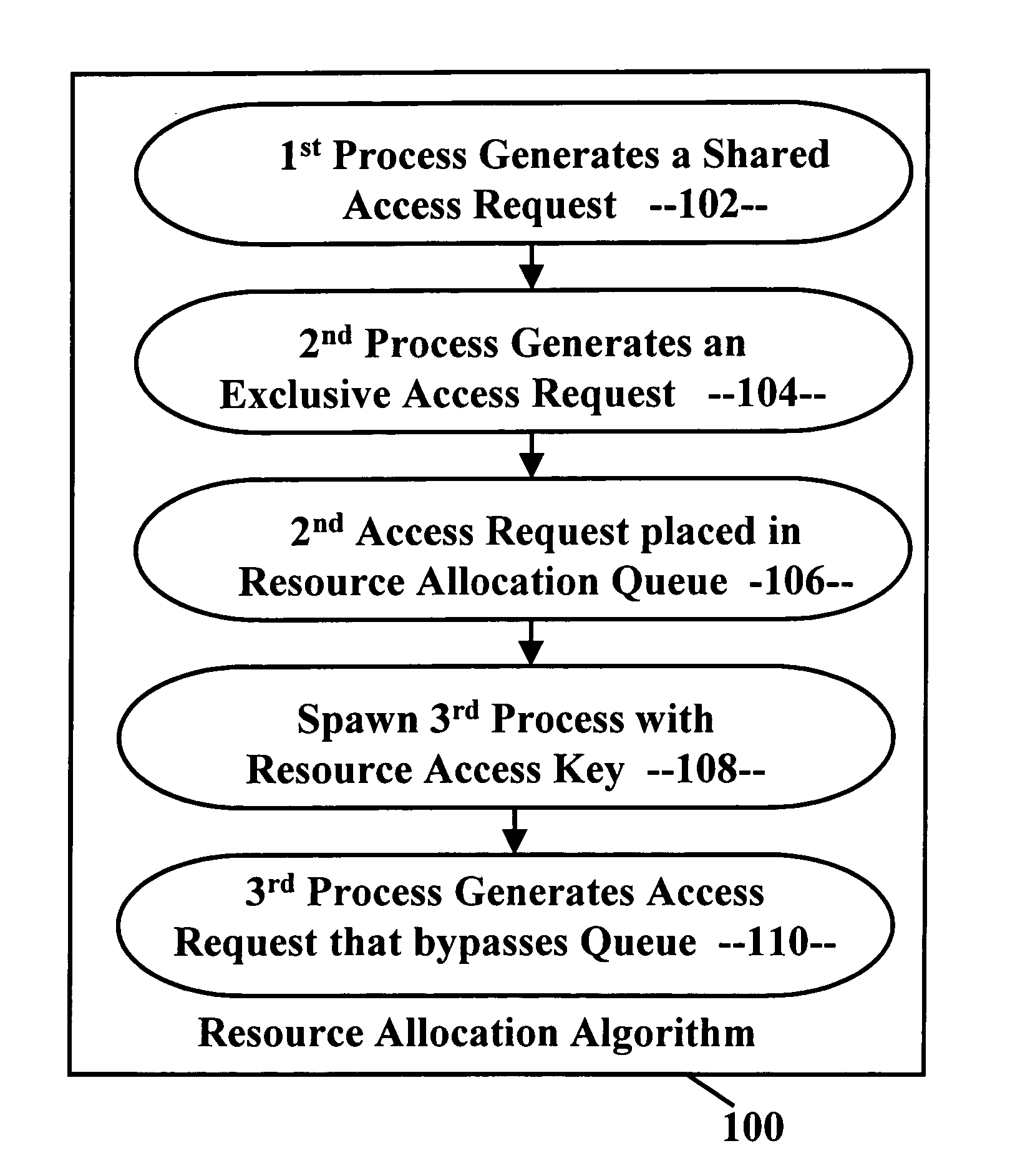
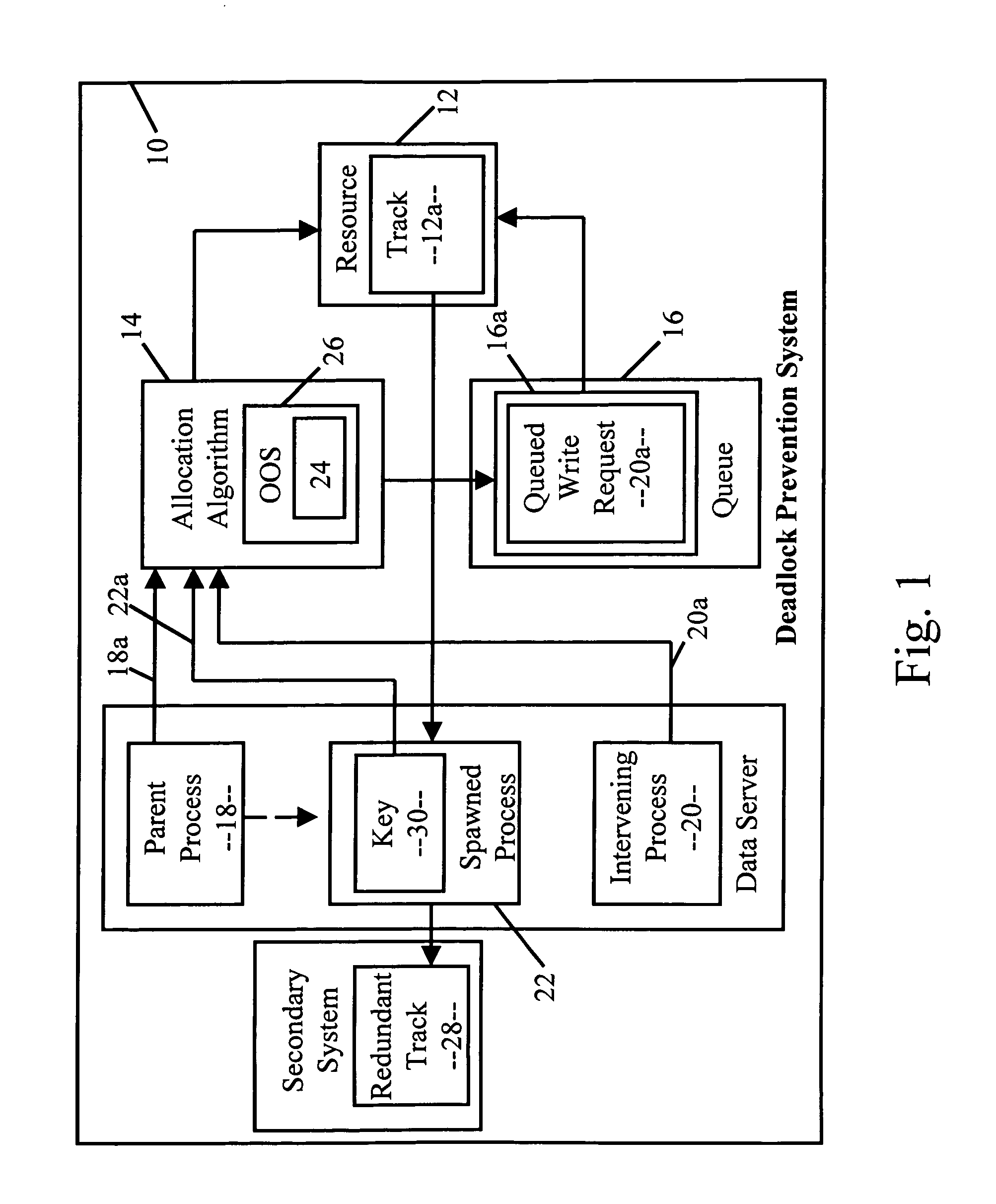
Deadlock-prevention system
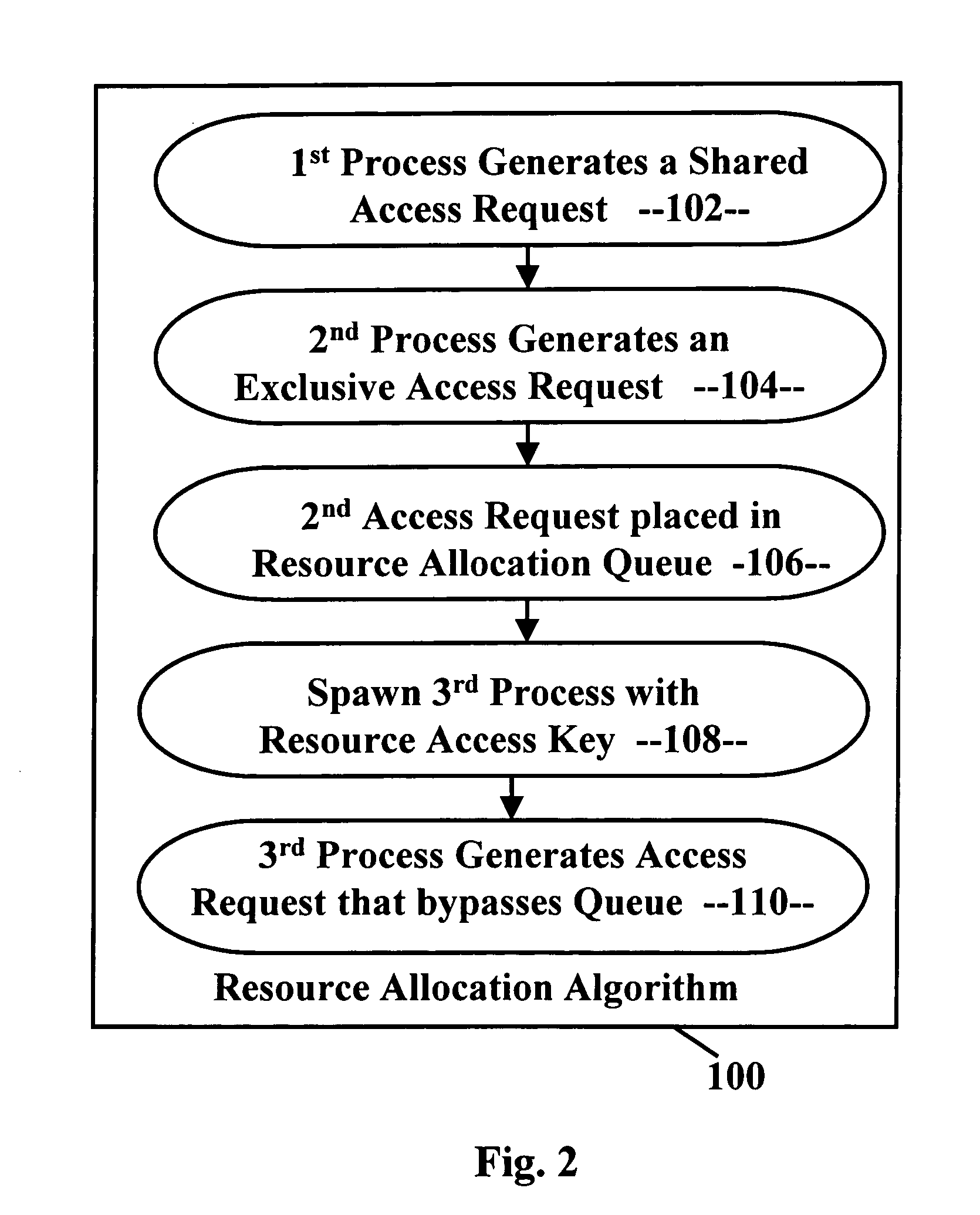
A deadlock-prevention system includes a resource-access key passed from a parent process to a spawned process that includes the parent processes' level of access to a system resource. Optionally, the resource-access key includes a shared-access request based on the expectation by the parent process that the child process will need shared-access to a system resource. The resource-access key is presented by the child process to a resource-allocation algorithm. The resource-allocation algorithm identifies the resource-access key, allows the child process to bypass a resource-allocation queue, and grants shared access to the resource to the child process, preventing deadlock.
Owner:JARVIS THOMAS C +1
Method and device for realizing high-performance cluster system for scheduling mirror images
ActiveCN106371889AProgram initiation/switchingSoftware simulation/interpretation/emulationCluster systemsMirror image
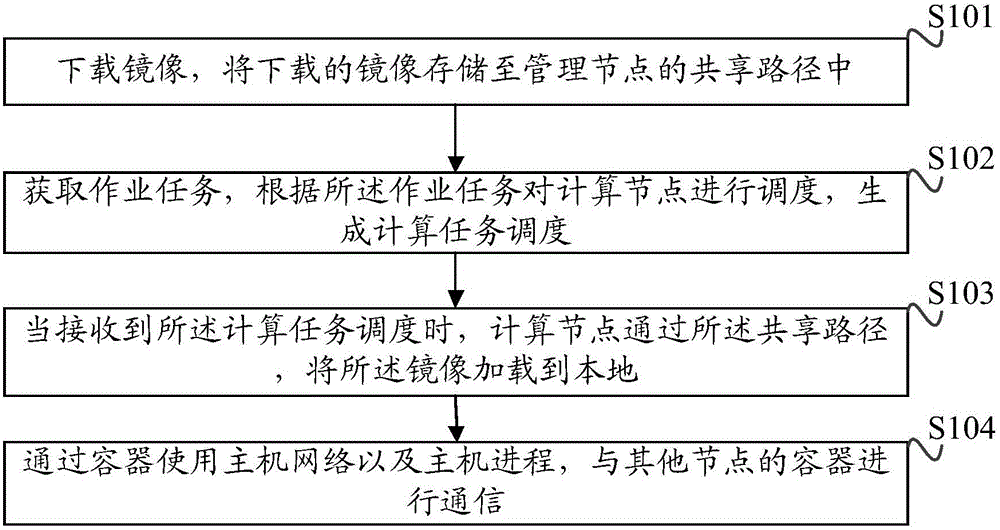
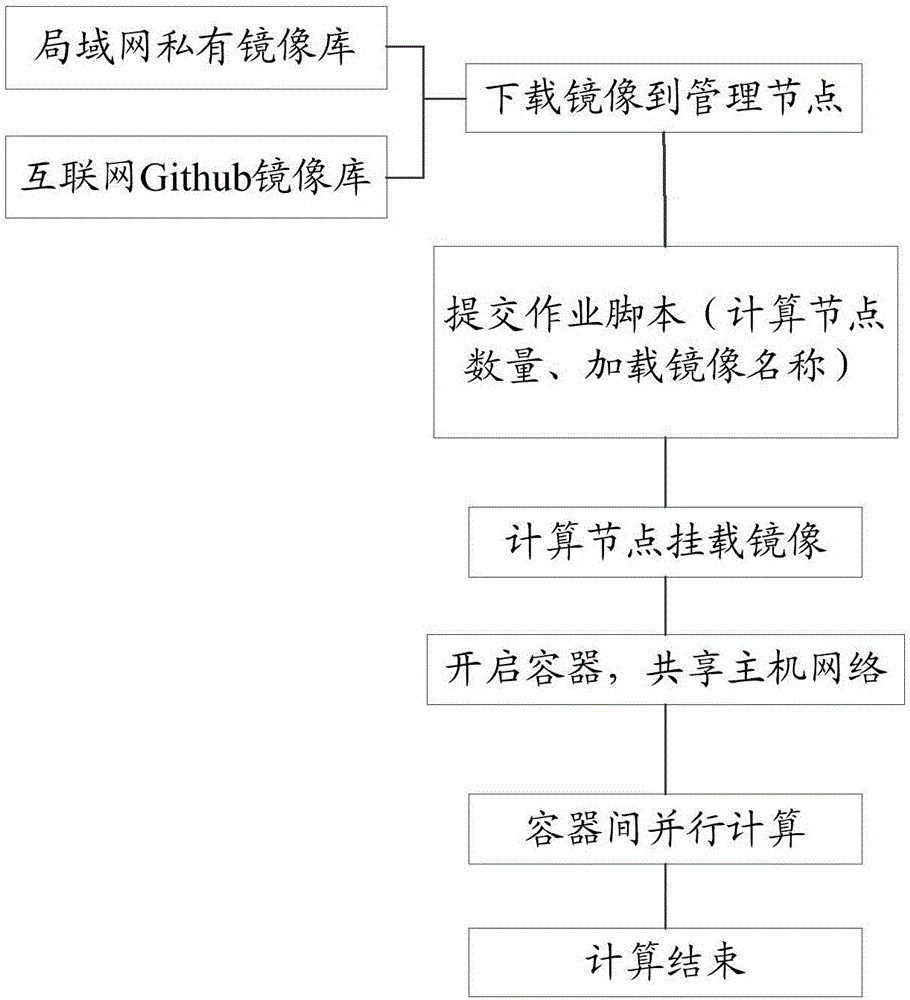
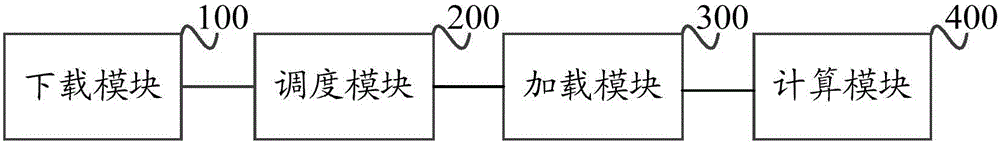
The invention discloses a method and device for realizing a high-performance cluster system for scheduling mirror images. The method comprises the following steps of: downloading a mirror image and storing the downloaded mirror image into a shared path of a management node; obtaining an operation task, and scheduling a computation node according to the operation task so as to generate computation task scheduling; when the computation task scheduling is received, loading the mirror image to the local by the computation node through the shared path; and enabling a host network and a host process to communicate with containers of other nodes through a container. According to the method and device for realizing the high-performance cluster system for scheduling mirror images, the management node provides a mirror image gateway function, the monitored idle computation node loads the mirror image to start the container, and a sub-process is started according to an MPI parent process so as to complete MPI parallel computation processing.
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
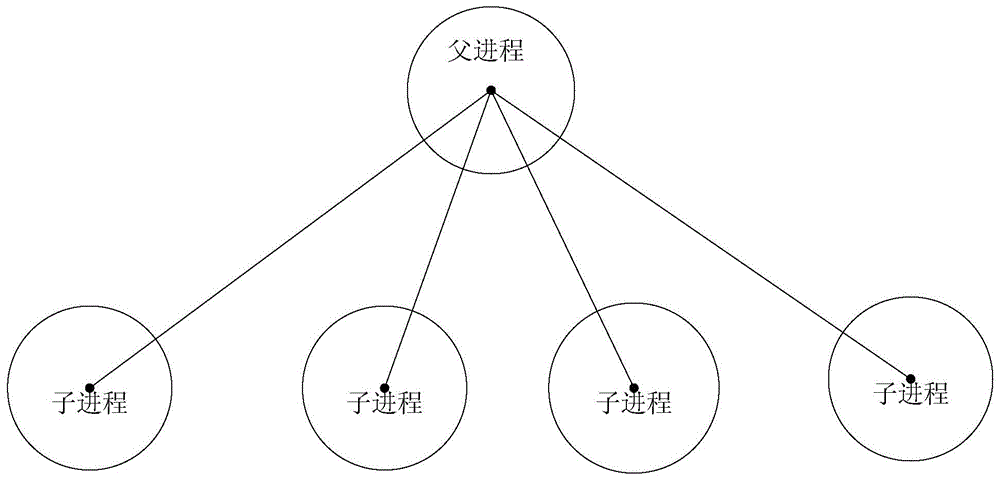
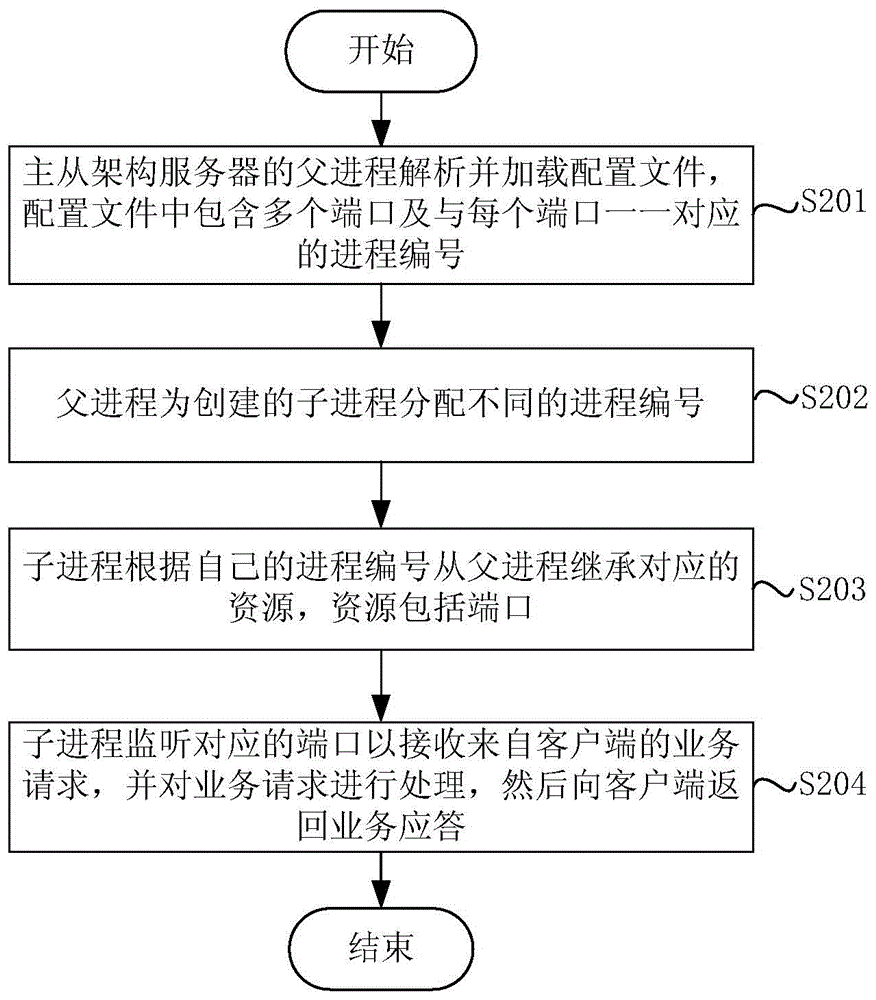
Master-slave architecture server, service processing method thereof and service processing system thereof
ActiveCN105337755AAvoid panic herdImprove processing efficiencyData switching networksSerial codeParent process
The invention discloses a master-slave architecture server, a service processing method thereof and a service processing system thereof. The service processing method of the master-slave architecture server comprises the steps of analyzing and uploading a configuration file by a parent process of the master-slave architecture server, wherein the configuration file includes multiple ports and a process serial number which is in one-to-one correspondence with each port; distributing different process serial numbers for established sub-processes by the parent process; inheriting corresponding resources from the parent process based on the process serial number by each sub-process, wherein the resources include ports; and, by the sub-processes, monitoring corresponding ports to receive a service request from a client, processing the service request and then returning a service response to the client. According to the embodiment of the invention, as different sub-processes respectively monitor reading-writing events of different ports, the service request of one port can be completely processed by one sub-process, the sub-processes are completely independent and no longer compete with each other for the service request, and a thundering-herd phenomenon is accordingly avoided.
Owner:TAOBAO CHINA SOFTWARE
Method and apparatus for a fast process monitor suitable for a high availability system
InactiveUS6964047B2Program initiation/switchingError detection/correctionHigh availabilityInter-process communication
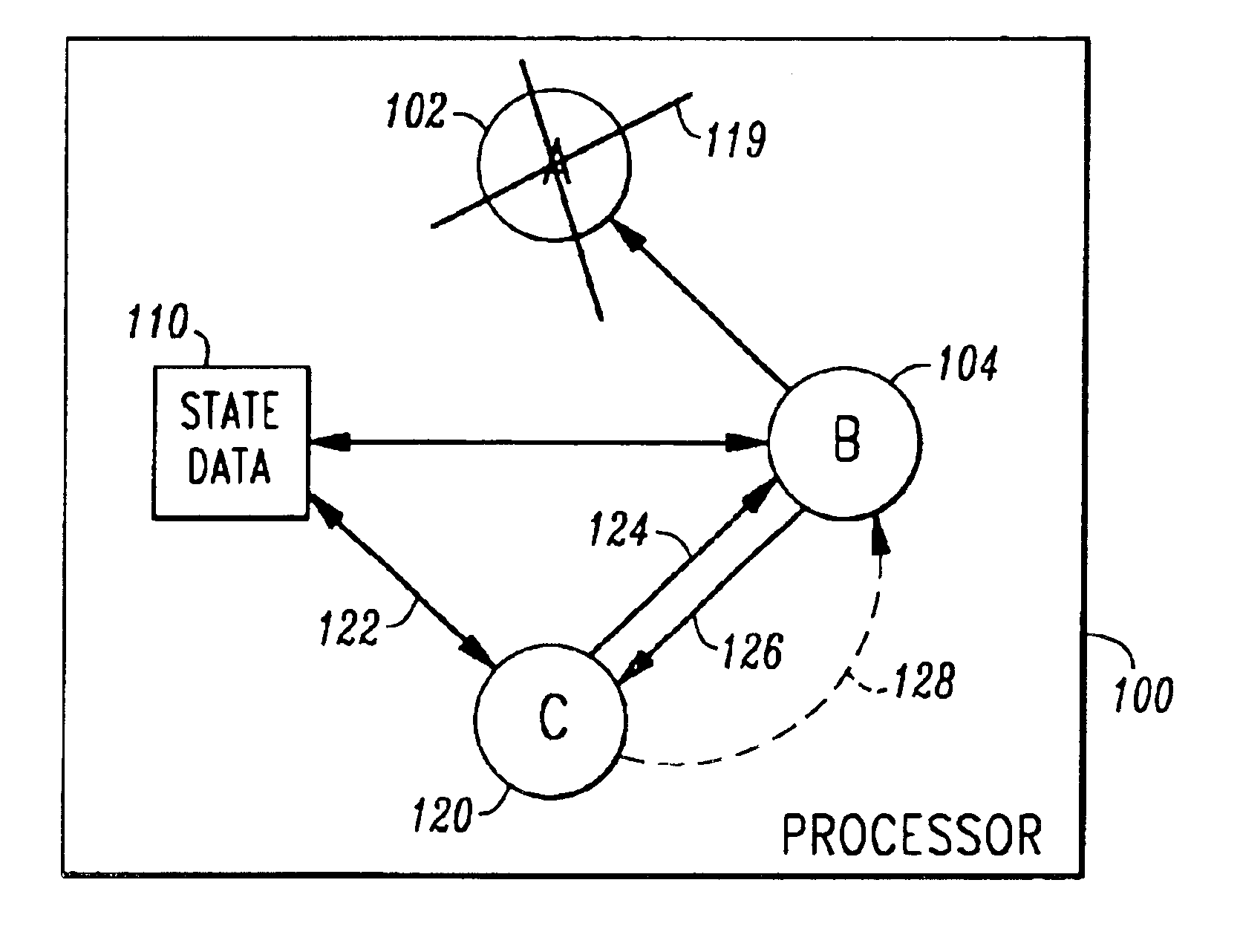
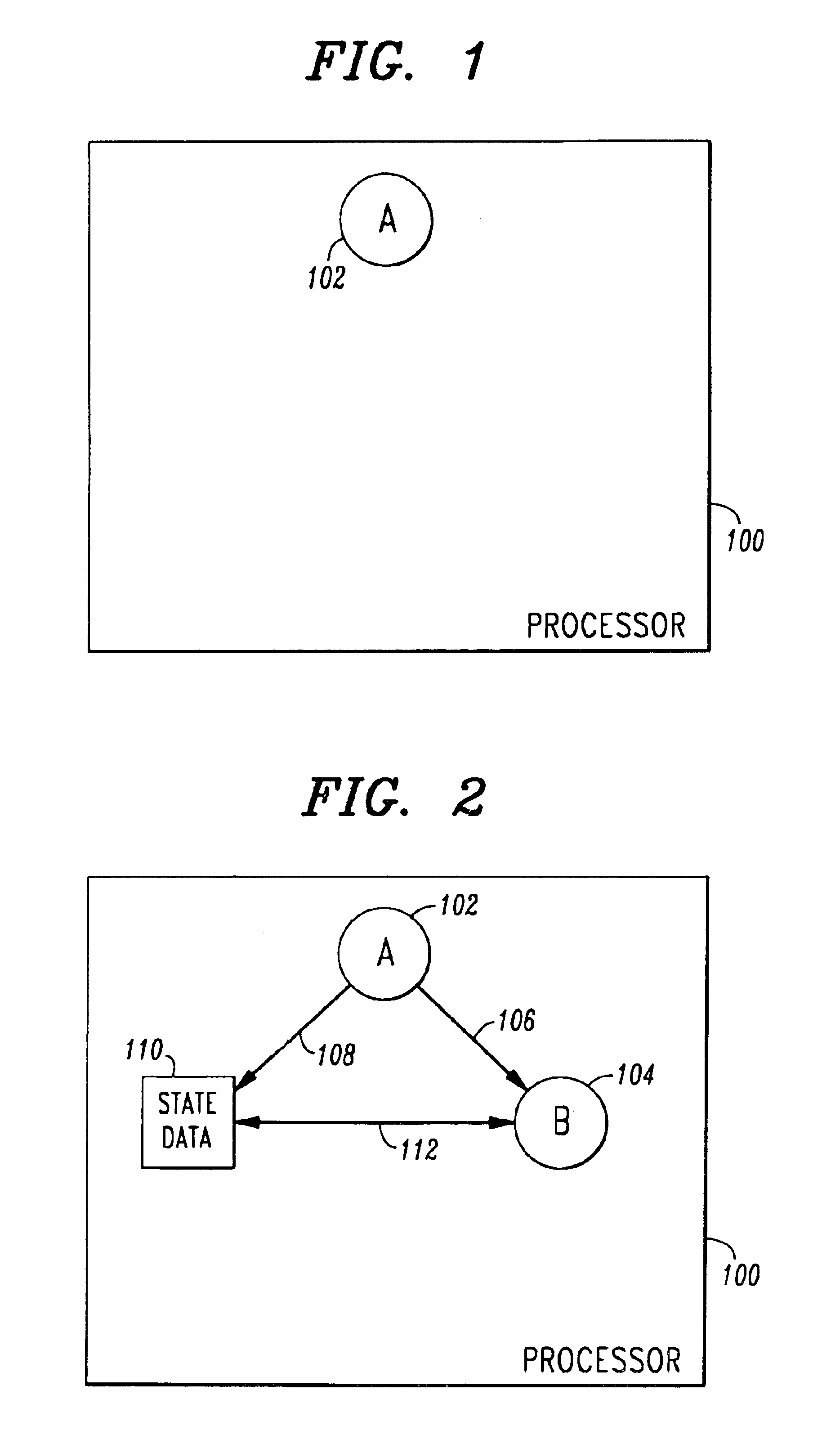
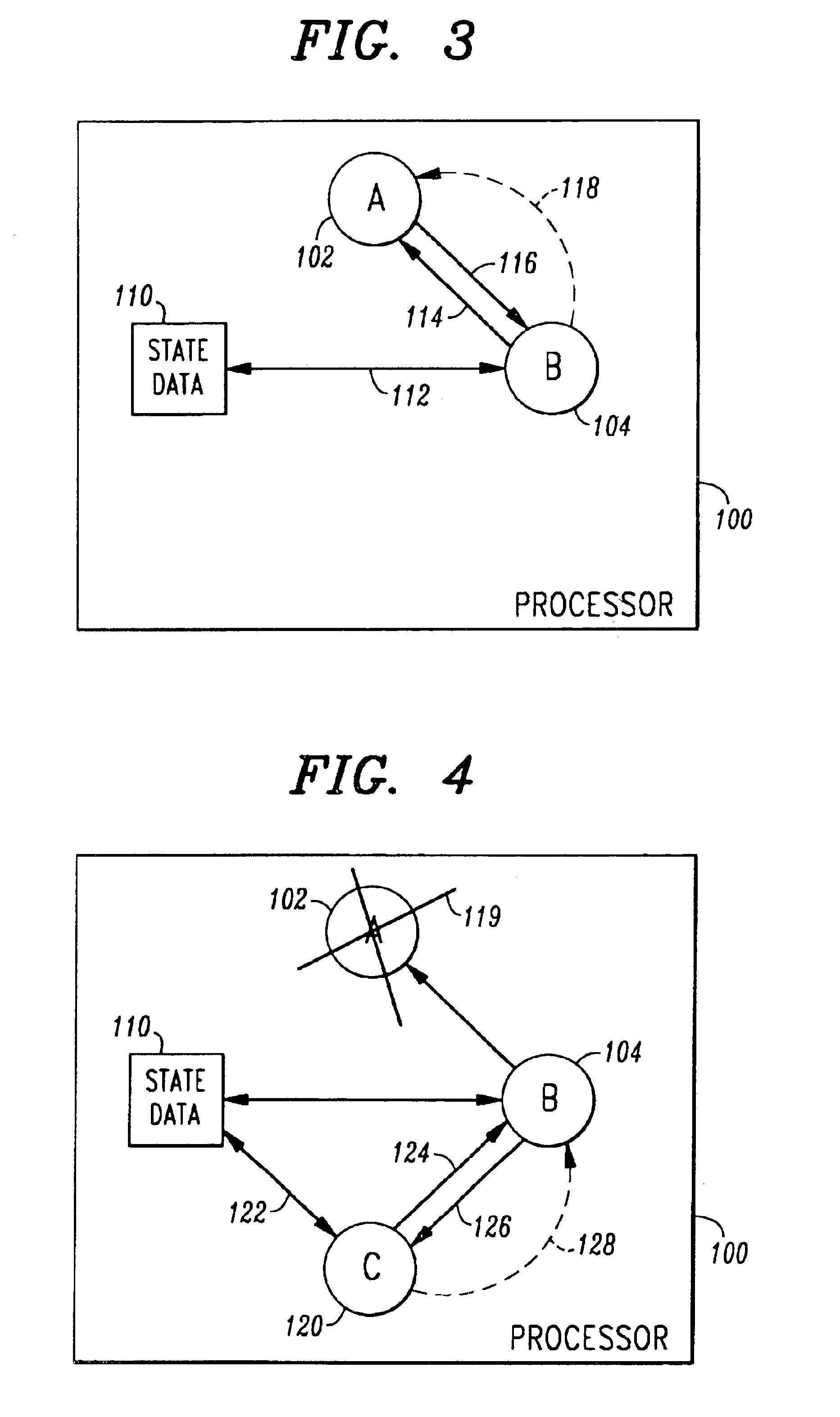
An application initiates a parent process (102) to begin executing the application. The parent process (102) creates a child process (104) to execute the application. The parent monitors the death of the child process using inter-process communications (118). The child process monitors the parent process using polling (114, 116). If the parent process detects the death of the child, the parent process creates another child to continue the processing of the dead child. If the child process detects the death of the parent process (119), the child creates another child process (120) to execute the application it previously executed. The original child, now a parent, monitors the child process via inter-process communication (128). The new child monitors the parent using polling (124, 126)
Owner:LUCENT TECH INC +1
Method for Anti-debugging
InactiveCN105793860AGuaranteed uptimeFree from attackSoftware engineeringHardware monitoringSoftware engineeringEmbedded system
The present invention relates to an anti-debugging method employed by an anti-debugging device. The anti-debugging method includes: a child process generation step; a parent process monitoring step in which a parent process is monitored by a child process; and a child process monitoring step in which the parent process monitors the child process.
Owner:INKA ENTWORKS INC
Apparatus and method for persistent report serving
A computer-readable medium is configured to receive a report processing request at a hierarchical report processor. The hierarchical report processor includes a parent process and at least one child process executing on a single processing unit, and is configured to process the report processing request as a task on the single processing unit.
Owner:BUSINESS OBJECTS SOFTWARE
Data driven dynamic workflow
A method, system and article of manufacture for workflow processing and, more particularly, for managing creation and execution of data driven dynamic workflows. One embodiment provides a computer-implemented method for managing execution of workflow instances. The method comprises providing a parent process template and providing a child process template. The child process template is configured to implement an arbitrary number of workflow operations for a given workflow instance, and the parent process template is configured to instantiate child processes on the basis of the child process template to implement a desired workflow. The method further comprises receiving a workflow configuration and instantiating an instance of the workflow on the basis of the workflow configuration. The instantiating comprises instantiating a parent process on the basis of the parent process template and instantiating, by the parent process template, one or more child processes on the basis of the child process template.
Owner:INT BUSINESS MASCH CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com