Process monitoring method and device and intelligent terminal
A process monitoring and sub-process technology, applied in the field of communication, can solve problems such as inability to monitor native sub-processes, and achieve the effect of improving security, avoiding threats and ensuring system security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0085] figure 1 It is a method for process monitoring in the embodiment of the present application, which can be implemented based on an intelligent terminal; as figure 1 As indicated, it may specifically include:
[0086] S101: When a parent process creates a child process, intercept the creation of the child process, and use an injector to replace the child process, thereby creating an injector.
[0087] Among them, when the parent process creates a child process, the creation of the child process is intercepted, and the injector is used to replace the child process, thereby creating an injector, including:
[0088] When the parent process creates a child process, the parent process first creates a mirror image of the child process through the fork function, and then calls the path parameter corresponding to the child process through the Execve function, thus completing the creation of the child process. However, in order to obtain an injector in this application, it is nece...
Embodiment 2
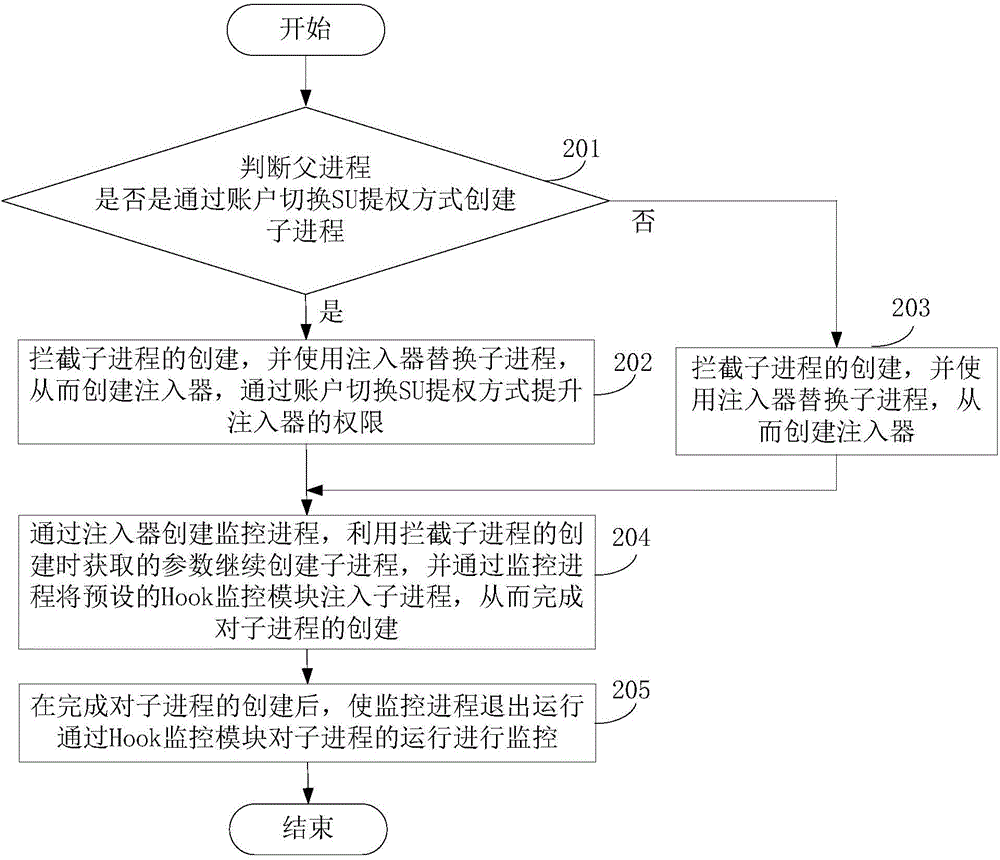
[0099] figure 2 It is the process monitoring method of the second embodiment of the present application, which can be implemented based on an intelligent terminal; as figure 2 As indicated, it may specifically include:
[0100] S201: When the parent process creates a child process, determine whether the parent process creates the child process through account switching SU privilege escalation, if yes, execute S202; otherwise, execute S203.
[0101] Among them, judging whether the parent process creates a child process by means of account switching SU privilege escalation includes:
[0102] Determine whether the child process contains a function that shares the S attribute;
[0103] If it contains a function with the S attribute, it is determined that the child process is created through SU privilege escalation;
[0104] If the function of the S attribute is not included, it is determined that the child process is not created through SU privilege escalation.
[0105] S202...
Embodiment 3
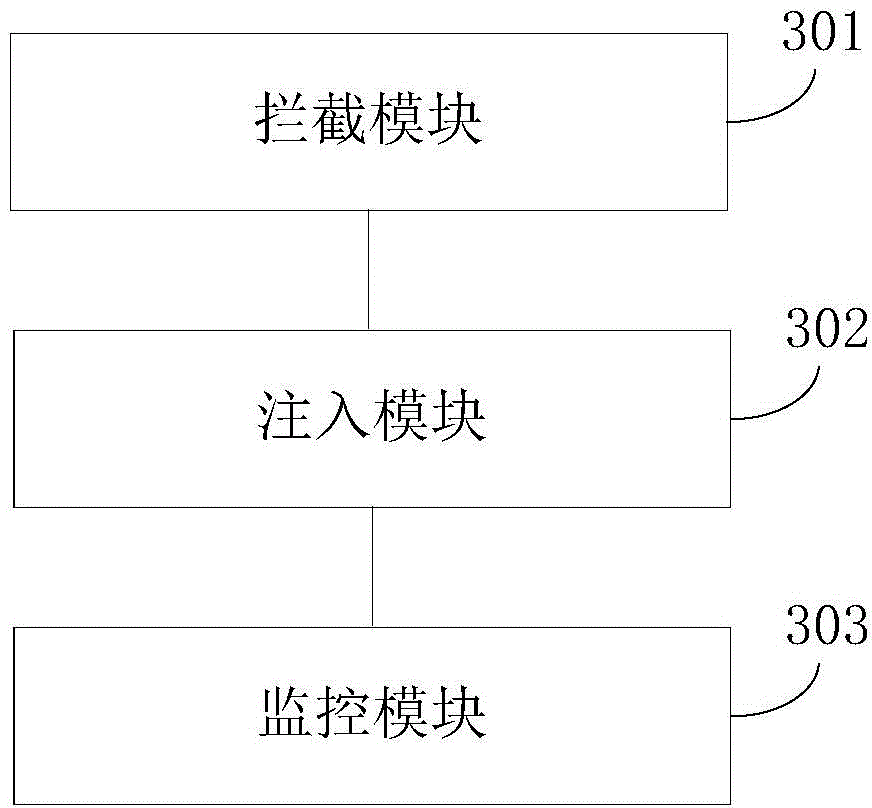
[0118] image 3 It is the device for process monitoring in the third embodiment of the present application, which can be implemented based on an intelligent terminal; for example image 3 As indicated, it may specifically include:
[0119] The interception module 301 is used to intercept the creation of the child process when the parent process creates the child process, and use the injector to replace the child process, thereby creating the injector;
[0120] The injection module 302 is used to create a monitoring process through the injector, continue to create the sub-process by using the parameters obtained when intercepting the creation of the sub-process, and inject the preset Hook monitoring module into the sub-process through the monitoring process, thereby completing the creation of the sub-process ;
[0121] The monitoring module 303 is configured to cause the monitoring process to quit running after the creation of the sub-process is completed, and monitor the opera...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com