Malicious behavior blocking method and device
A behavioral and malicious technology, applied in the computer field, can solve the problems of ineffective blocking of malicious behavior, low efficiency and accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
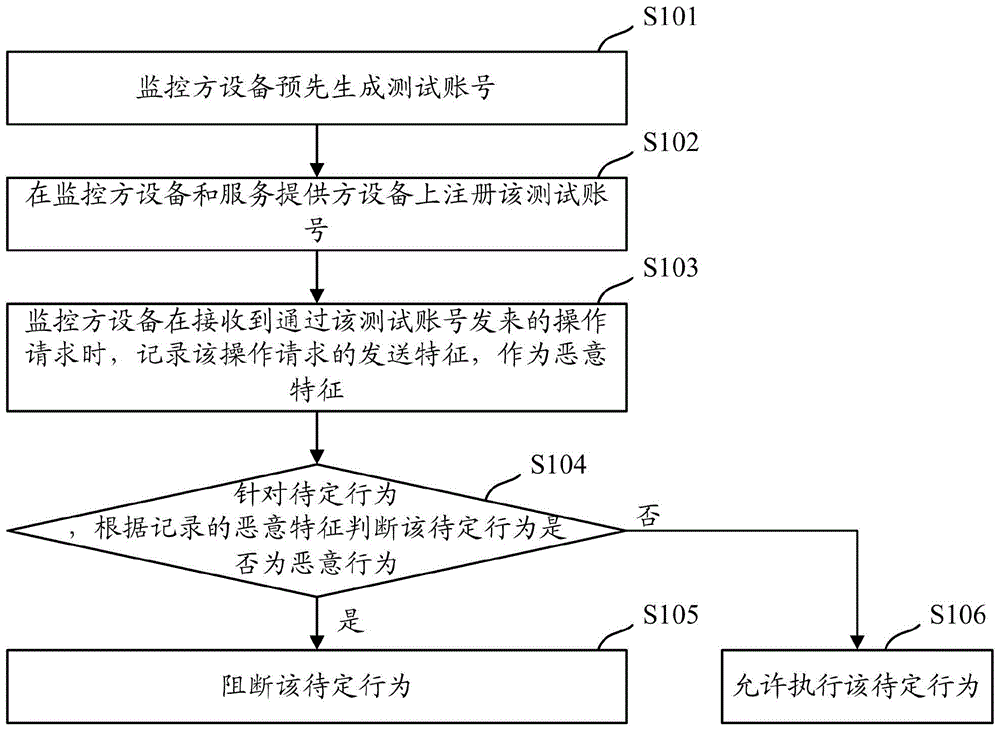
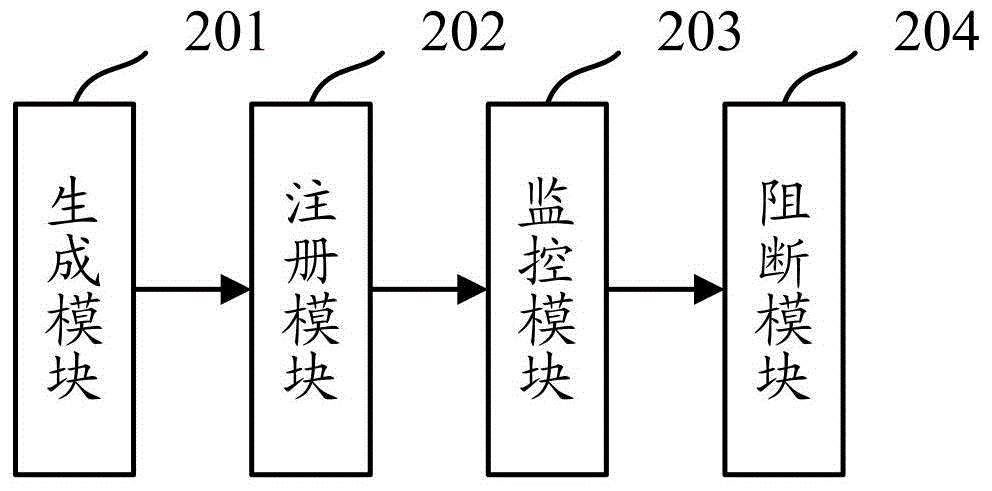
[0024] Because the existing technology needs to analyze a large amount of historical data to extract the characteristics of malicious behaviors, this method is too passive and needs to filter out malicious behaviors and extract features from a large number of normal behaviors, so it is not only inefficient, but also accurate. Also very low. However, in the embodiment of the present application, malicious behaviors are monitored by registering an unused test account on the service provider device (for example, a website server, an application server, etc.), and once it is found that someone has sent an operation request through the test account, the It is determined that the operation must be a malicious behavior, so as to directly record the sending characteristics of the operation request as malicious characteristics, which can effectively improve the efficiency of obtaining the characteristics of malicious behaviors, and the accuracy is also high, and the follow-up can be bas...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com