Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
625results about How to "Avoid threats" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
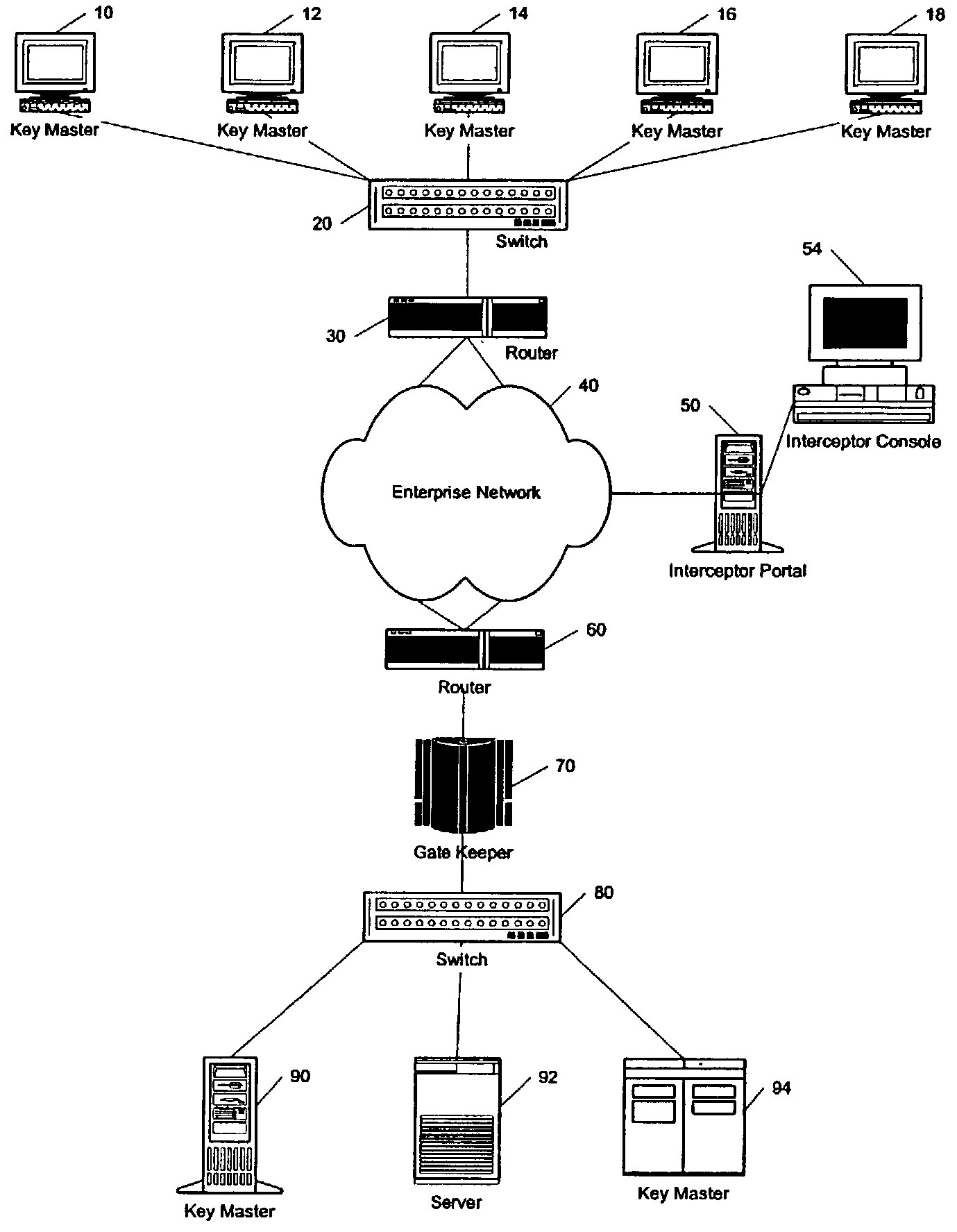
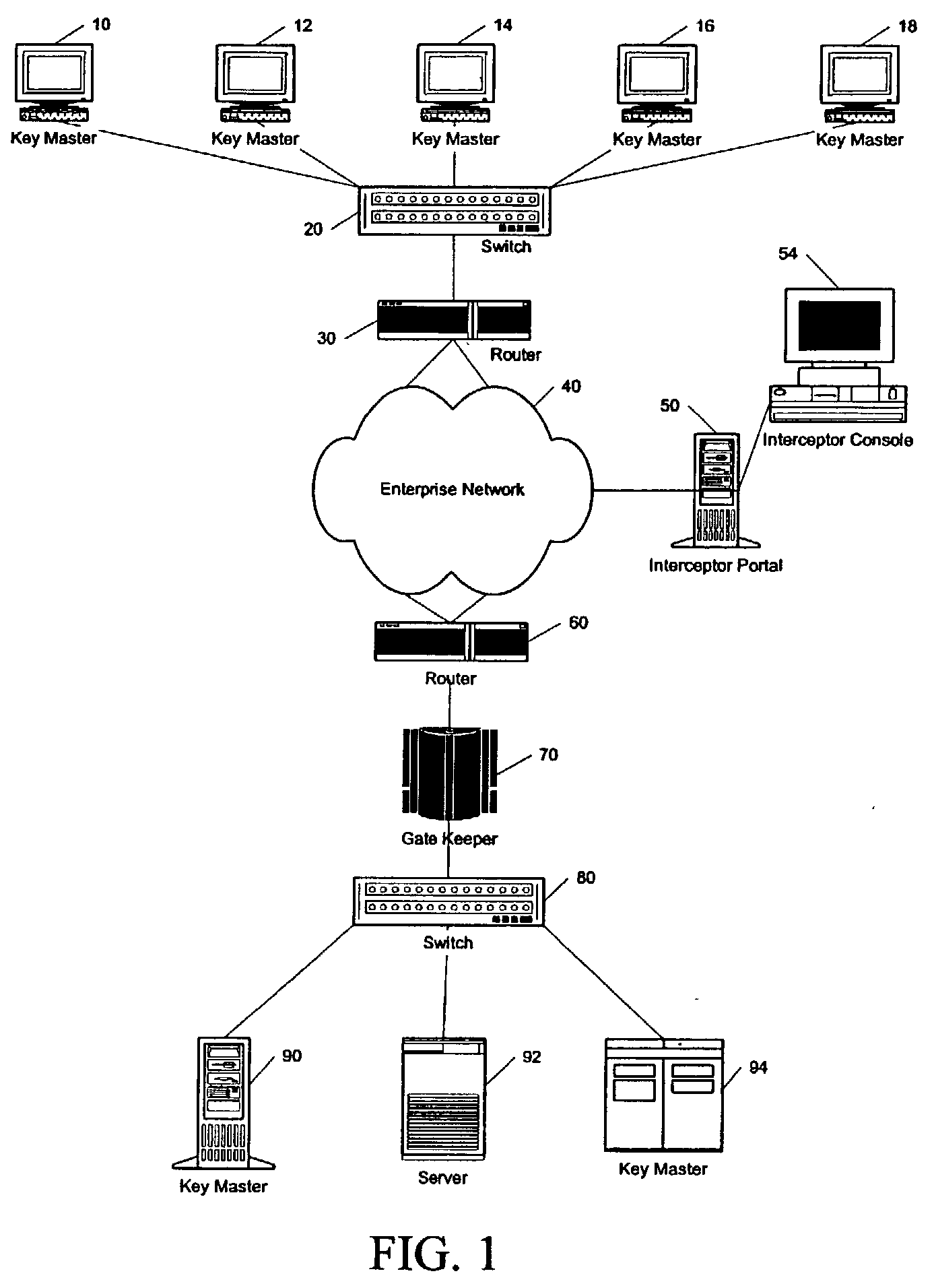
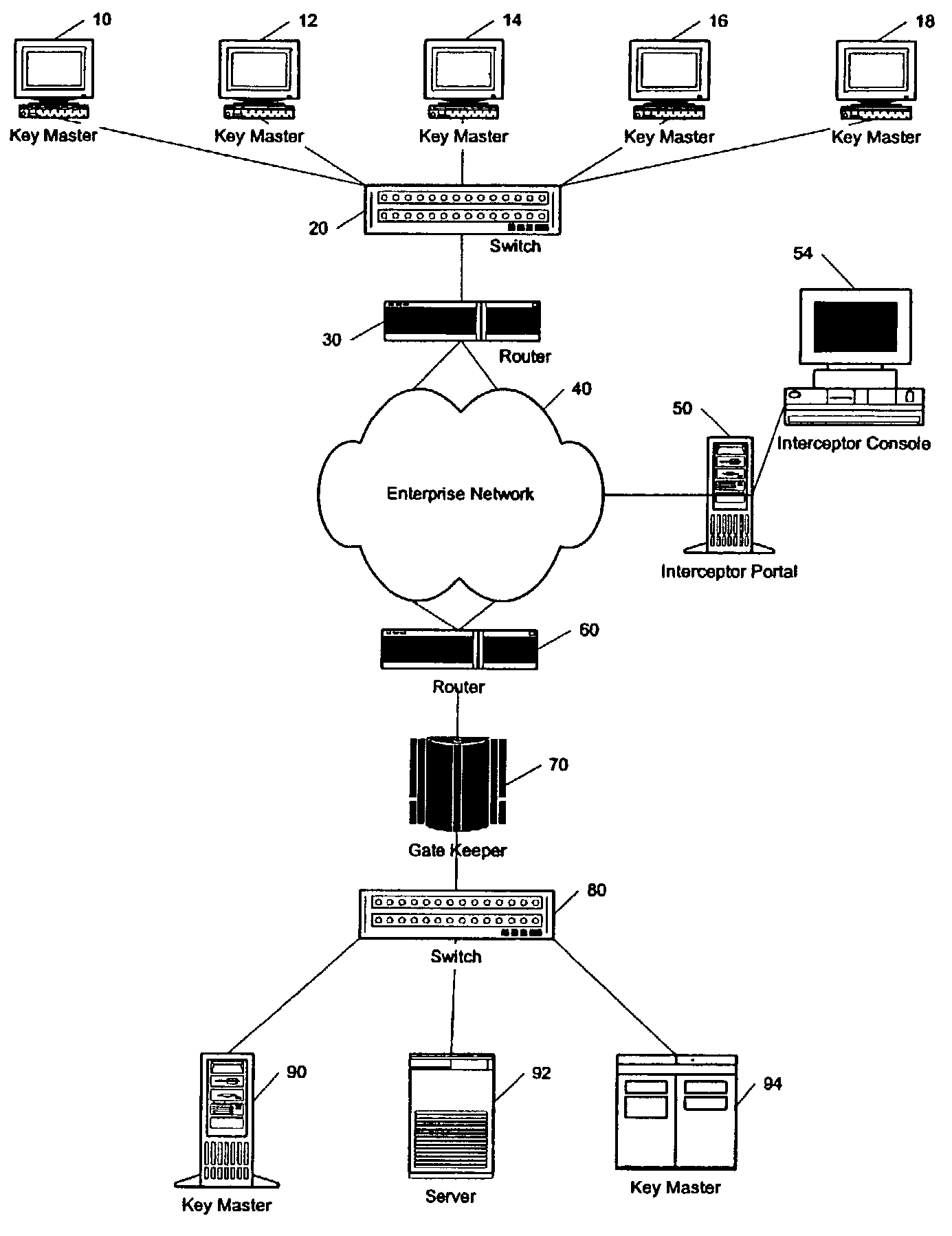
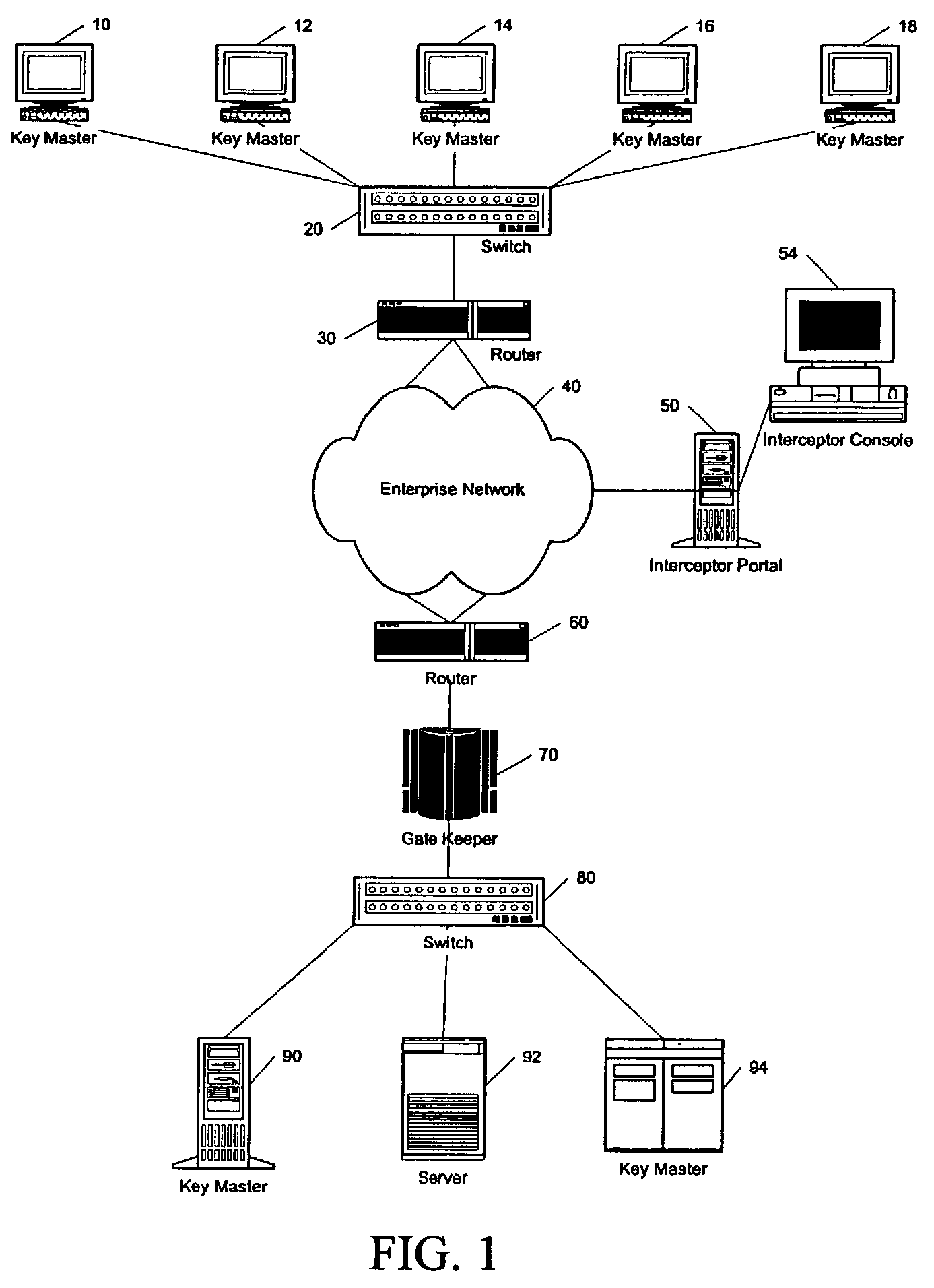
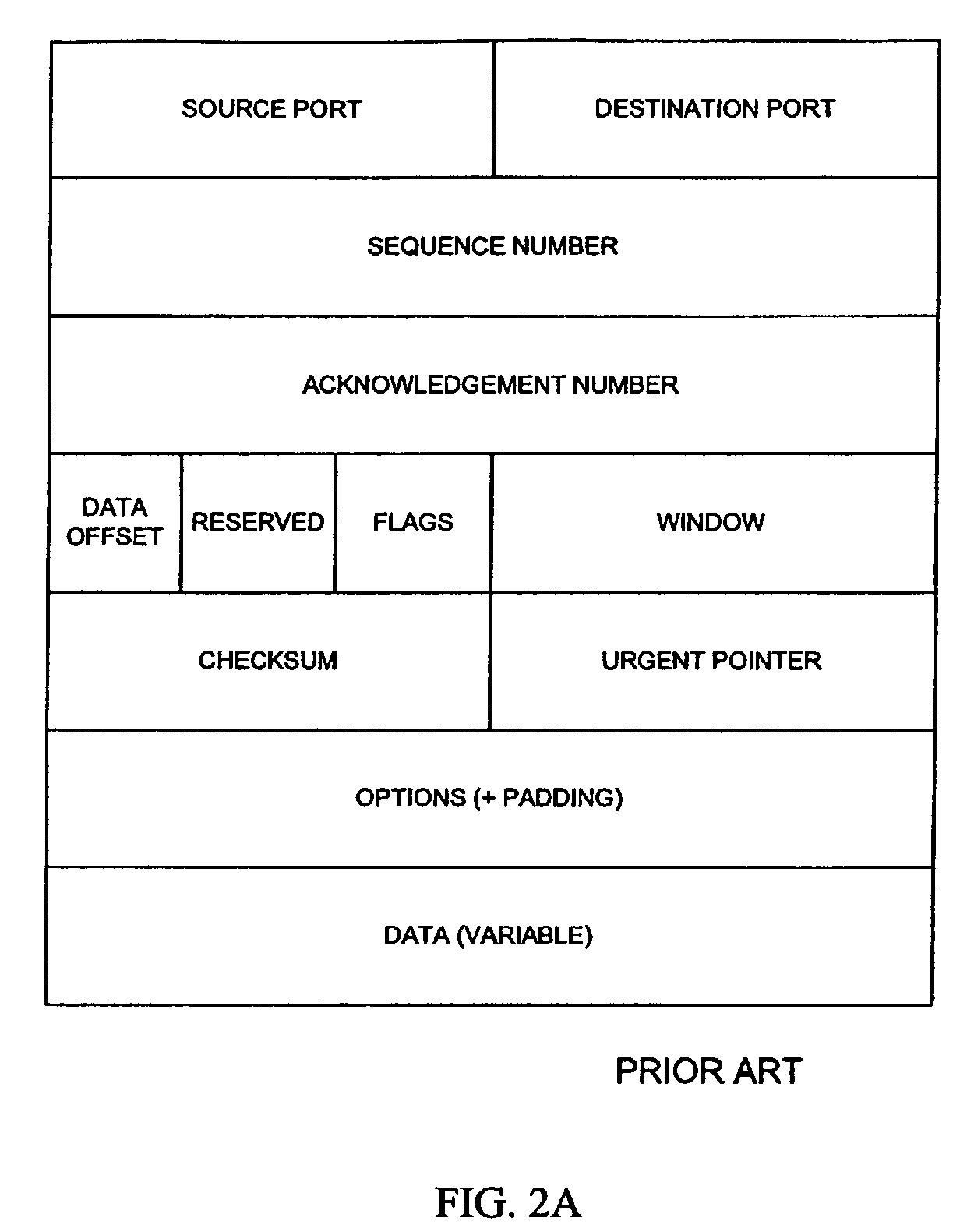
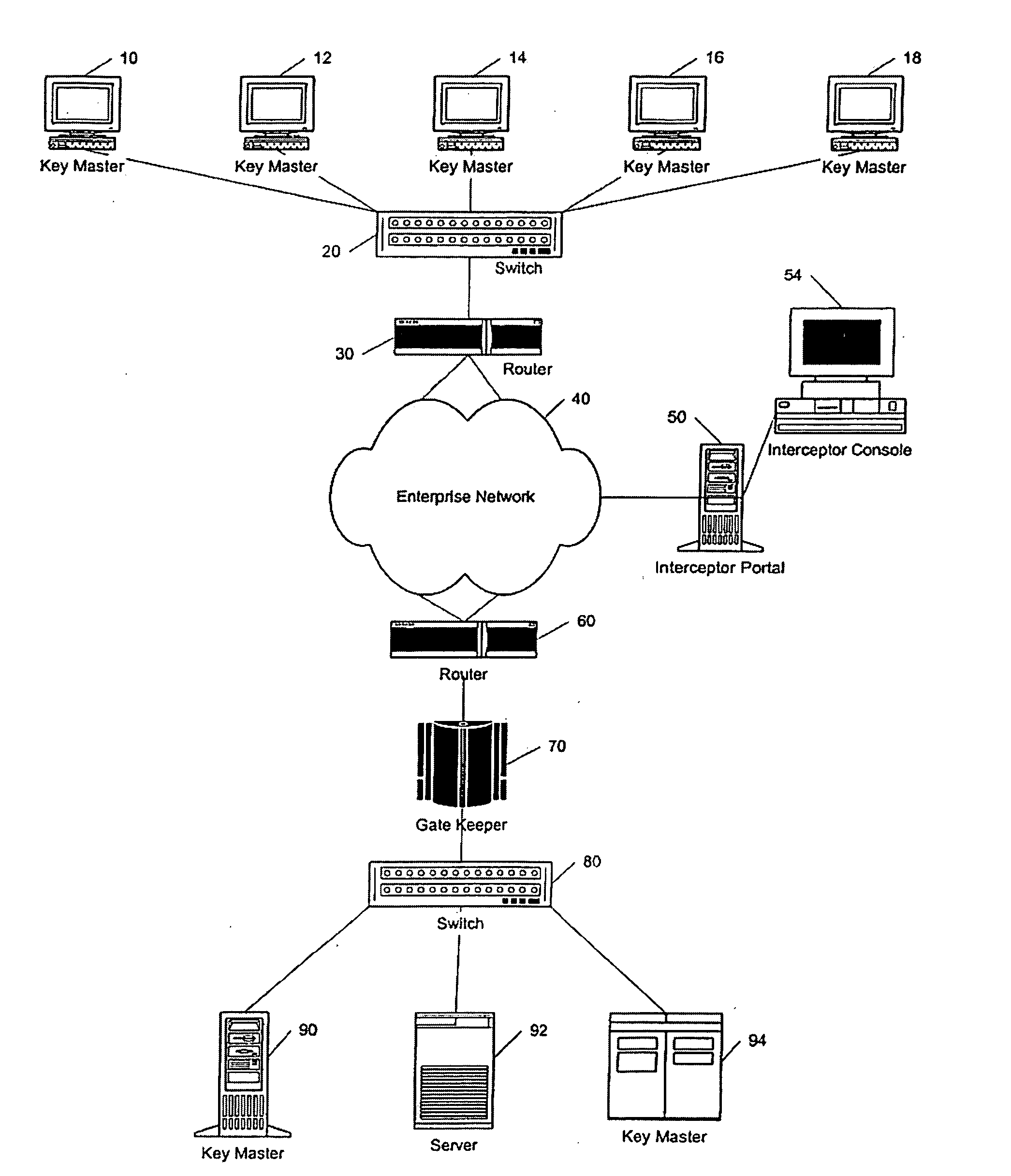
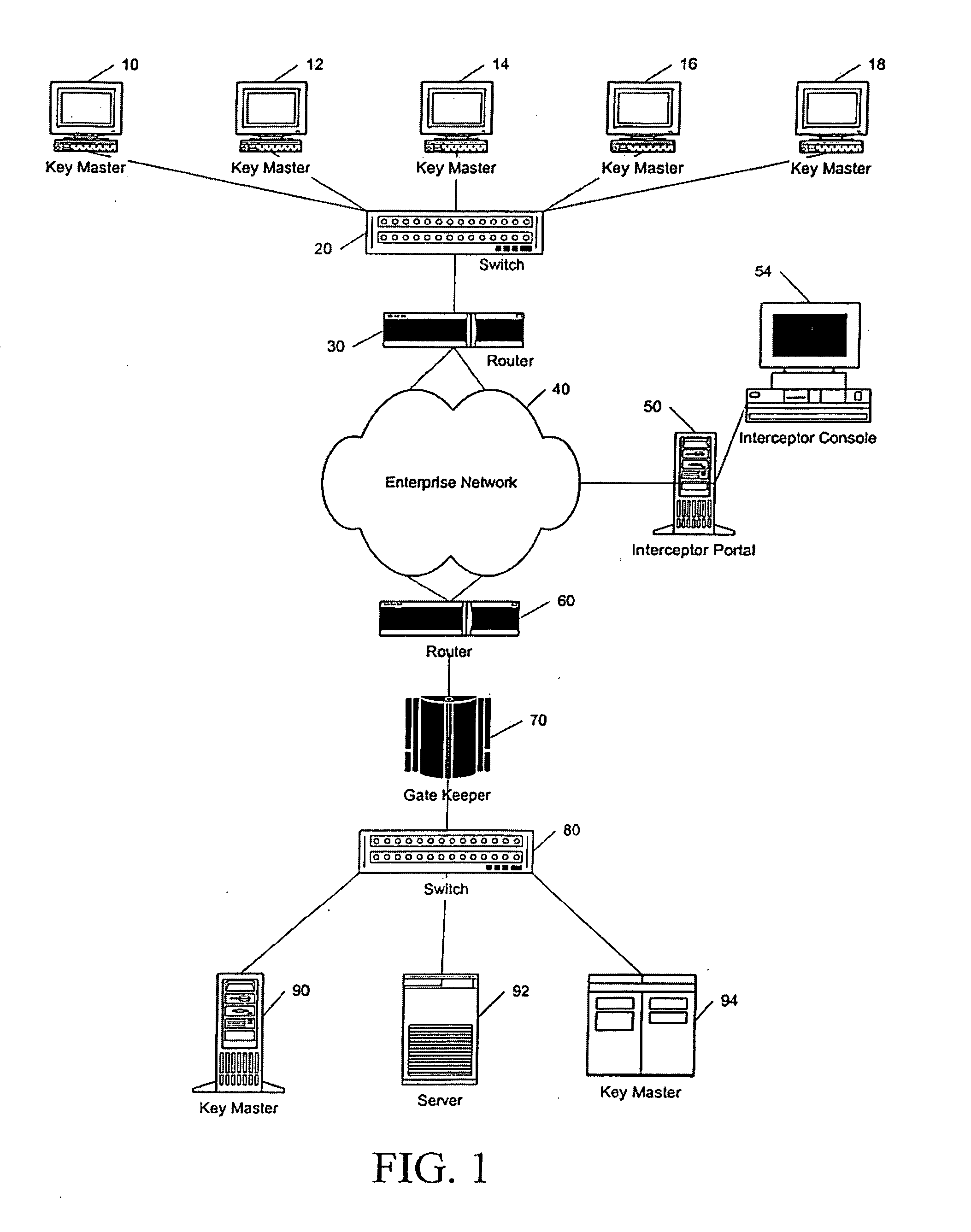
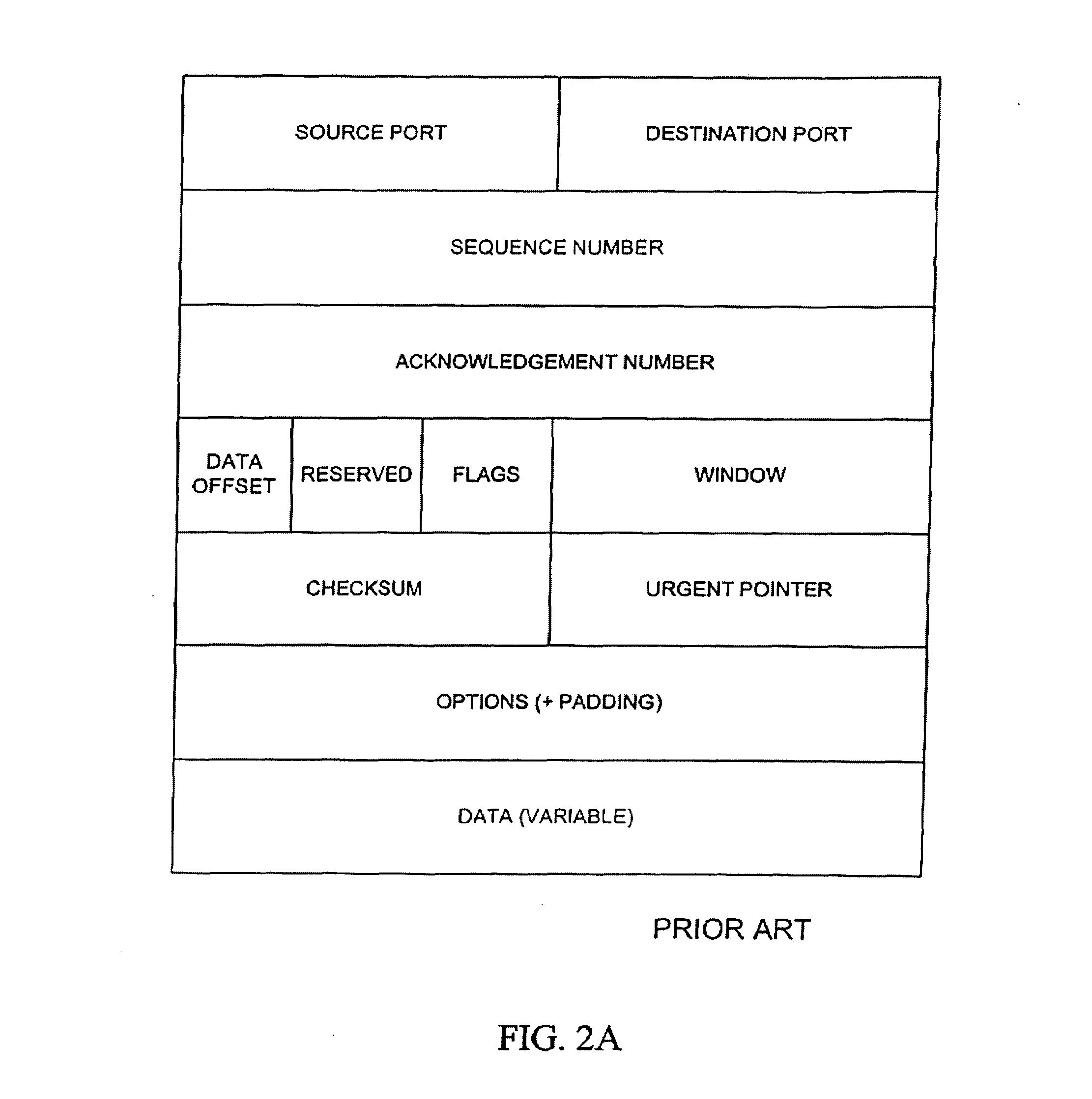
System and method for intrusion prevention in a communications network
InactiveUS20050160289A1Prevents unwanted connectionIncrease resourcesDigital data processing detailsAnalogue secracy/subscription systemsDatabase accessWeb resource
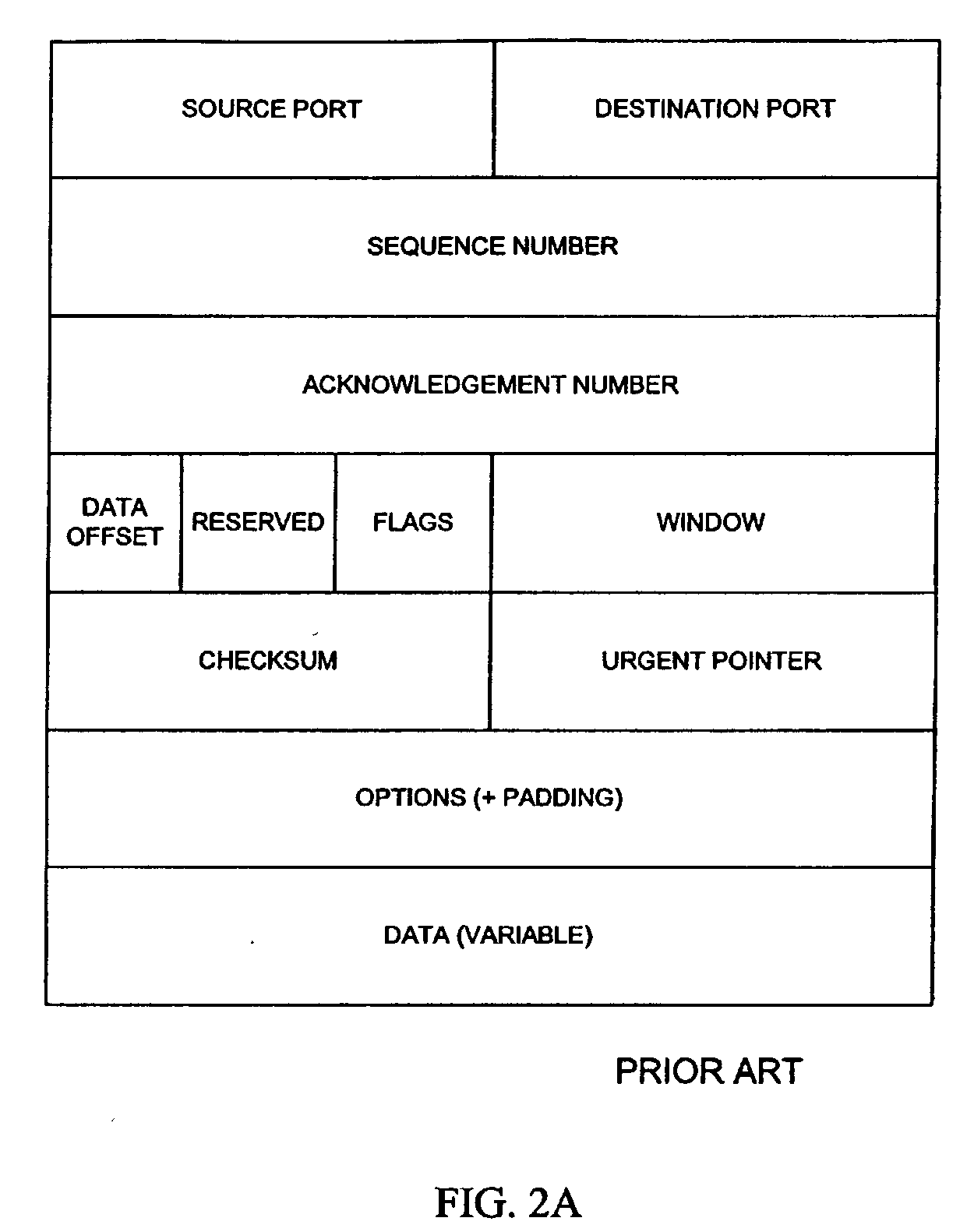
A method, system and program for preventing intrusion in a communications network. A source node initiates a request for network services, such as session establishment, database access, or application access. Known network resources and authorized user information is stored in a database at a network portal along with access policy rules that are device and user dependent. Identification of the source node is required before the source node can construct a transformed packet header that is included with a synchronization packet before transmission to a destination node. An appliance or firewall in the communications network receives and authenticates the synchronization packet before releasing the packet to its, intended destination. The authentication process includes verification of the access policy associated with the source node. Once received at the destination node, the transformed packet header is reformed by extracting a key index value. The extracted key index is subsequently used to transform the packet header in the response transmitted to the source node.
Owner:LIQUIDWARE LABS
System and method for intrusion prevention in a communications network
InactiveUS7386889B2Avoid connectionIncrease resourcesDigital data processing detailsAnalogue secracy/subscription systemsIntrusion prevention systemNetwork service
A method, system and program for preventing intrusion in a communications network. A source node initiates a request for network services, such as session establishment, database access, or application access. Known network resources and authorized user information is stored in a database at a network portal along with access policy rules that are device and user dependent. Identification of the source node is required before the source node can construct a transformed packet header that is included with a synchronization packet before transmission to a destination node. An appliance or firewall in the communications network receives and authenticates the synchronization packet before releasing the packet to its, intended destination. The authentication process includes verification of the access policy associated with the source node. Once received at the destination node, the transformed packet header is reformed by extracting a key index value. The extracted key index is subsequently used to transform the packet header in the response transmitted to the source node.
Owner:LIQUIDWARE LABS
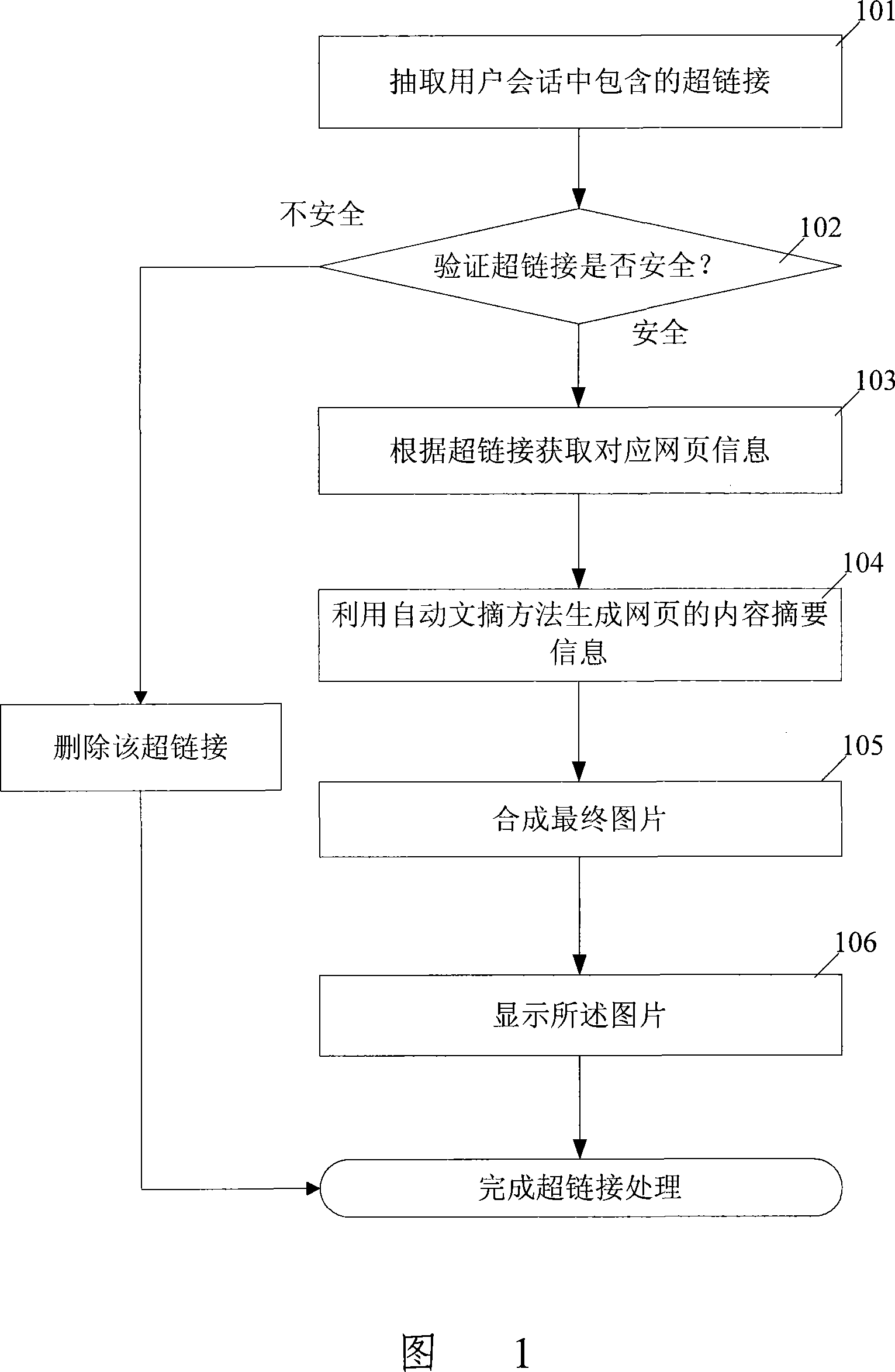
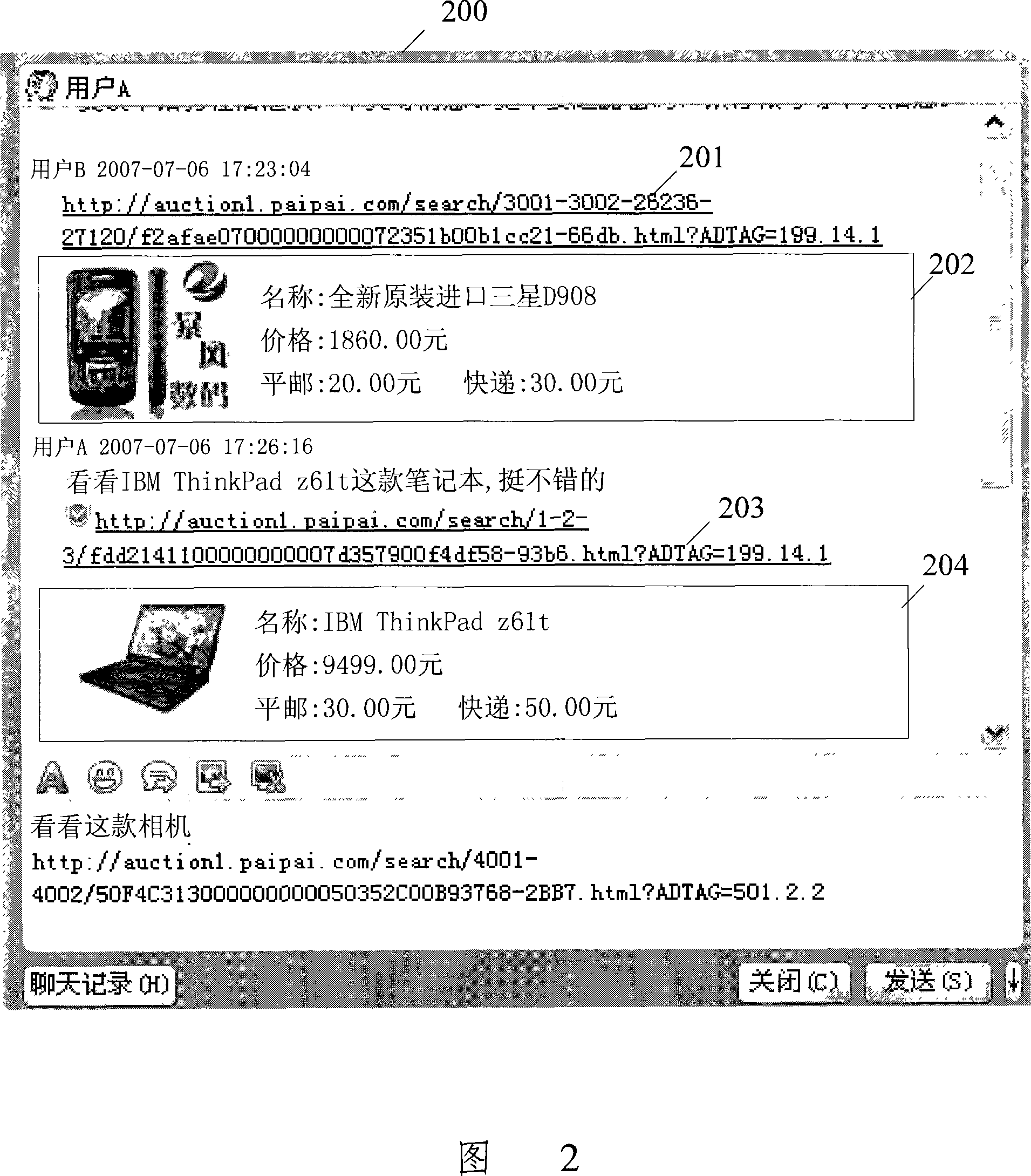
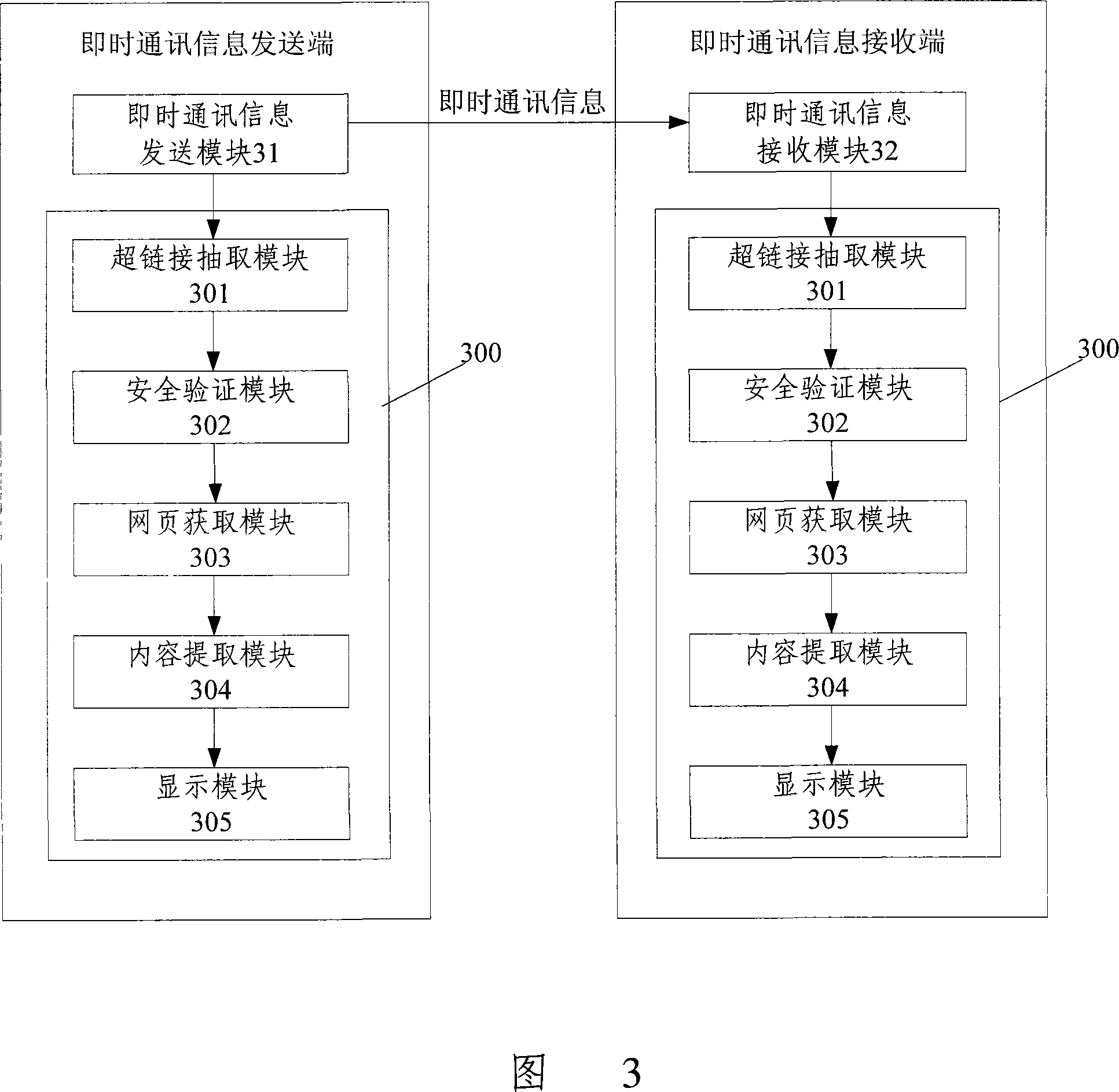
Processing method and device for instant communication information including hyperlink
ActiveCN101102255AConvenient instant messaging operationImprove interactivityDigital data information retrievalStore-and-forward switching systemsHyperlinkComputer terminal
Owner:TENCENT TECH (SHENZHEN) CO LTD
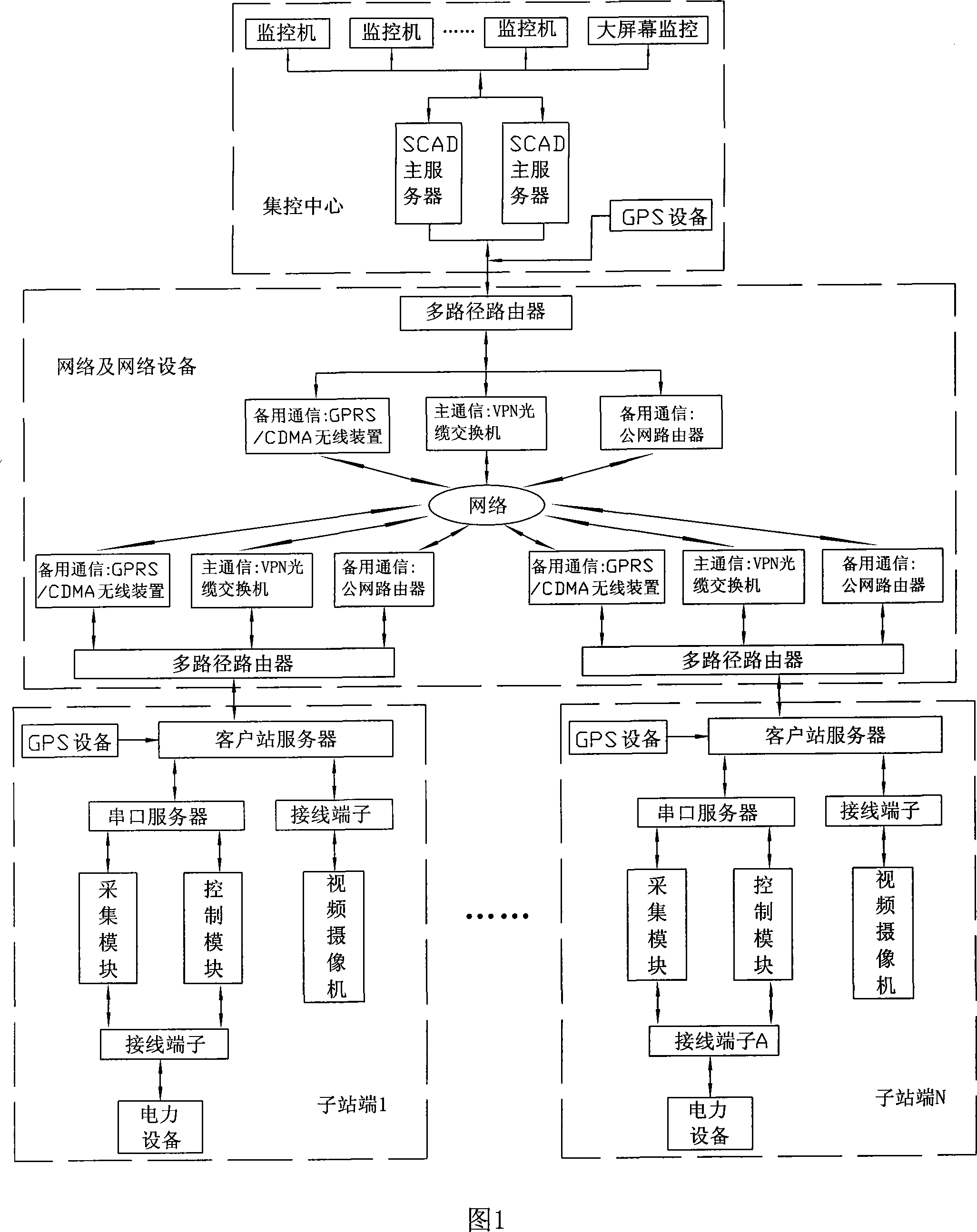
Client distribution automation remote real time monitoring system
InactiveCN101216709AReduce maintenance costsGuaranteed uptimeTotal factory controlProgramme total factory controlLow voltagePower grid
The invention relates to a client distribution network automatic remote real-time monitoring system, which conducts remote real-time monitoring on electrical equipments of at least one low-voltage and mid-voltage substation via a main network or a standby network. The system comprises a centralized control center and a plurality of subsite terminals which are communicated with the centralized control center via the network. The system has the advantages of that: a set of automatic management systems are constructed on the subsite terminals, and the centralized control center conducts uniform real-time monitoring on a client substation through the management mode of communicating the network with the centralized control center; thereby ensuring the safe operation of the client substation when unattended, creating an automatic monitoring system, supplying the automatic remote monitoring system of a gap that a prior domestic substation can only be used in a large-scaled substation in the main grid of the power network due to high cost and challenging communication requirements and a common low-voltage and mid-voltage substation is unable to realize automatic remote monitoring due to financial and technical reasons, and establishing the technical basis for major electrical users to achieve socialized professional operation and maintenance.
Owner:毛建良
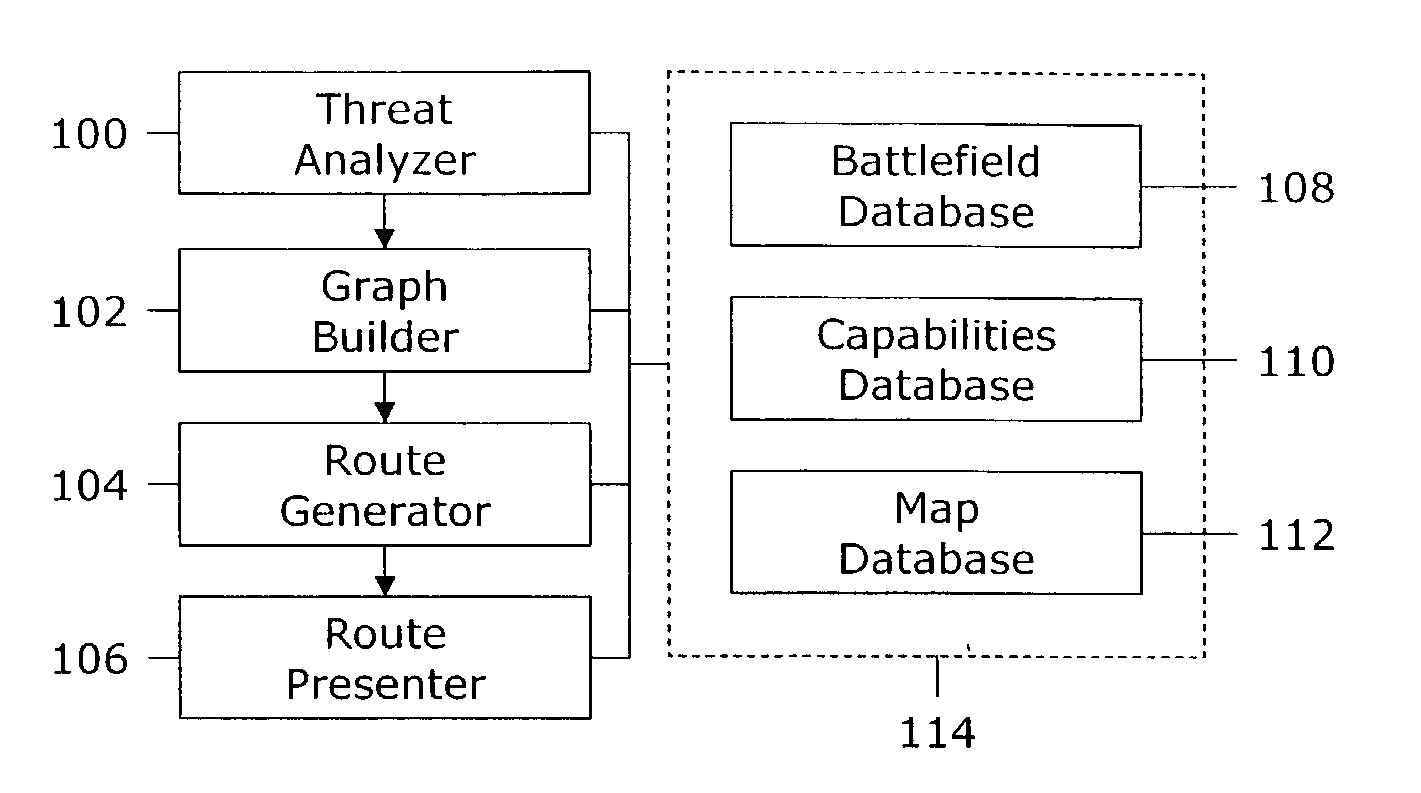
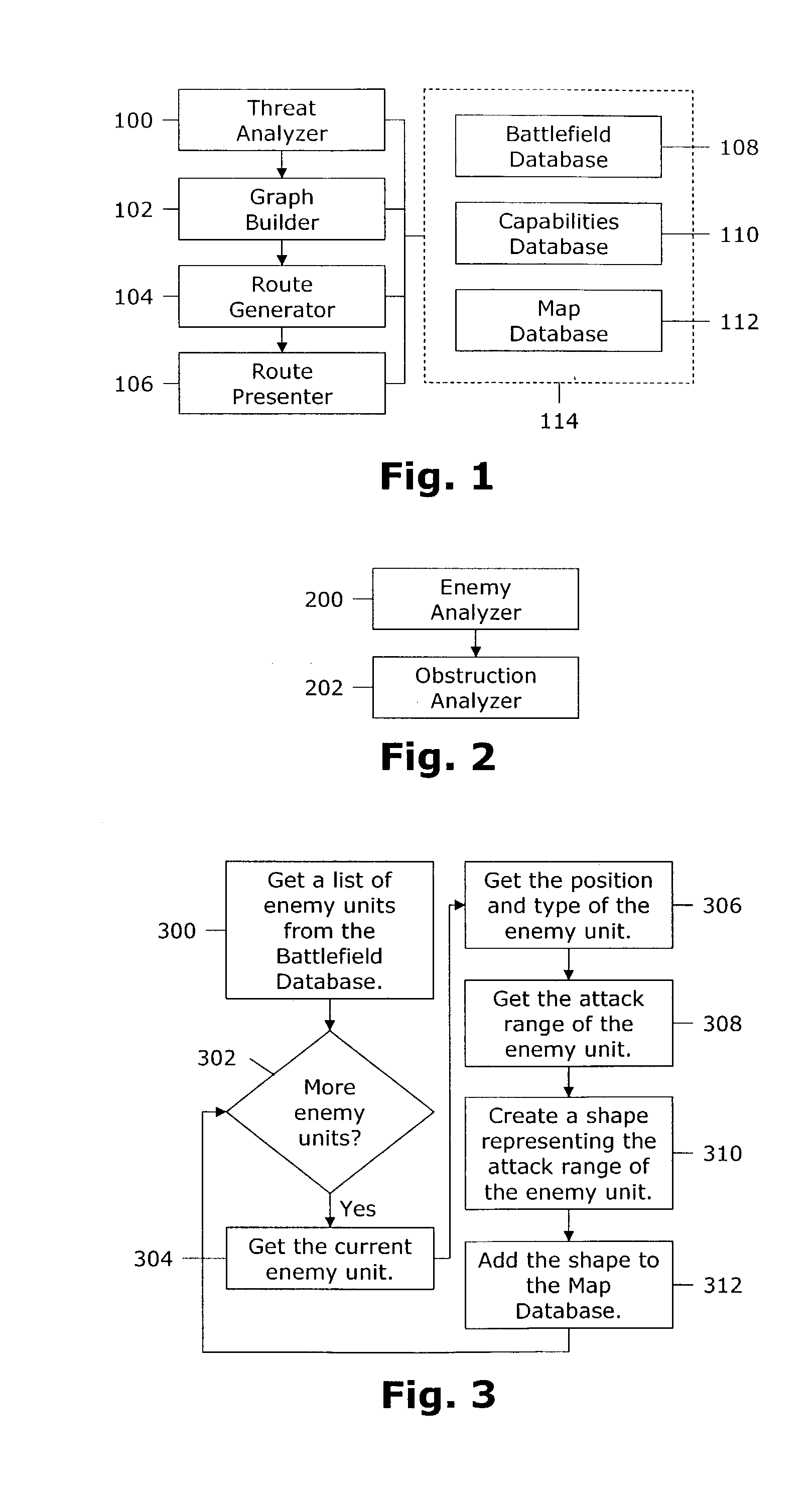
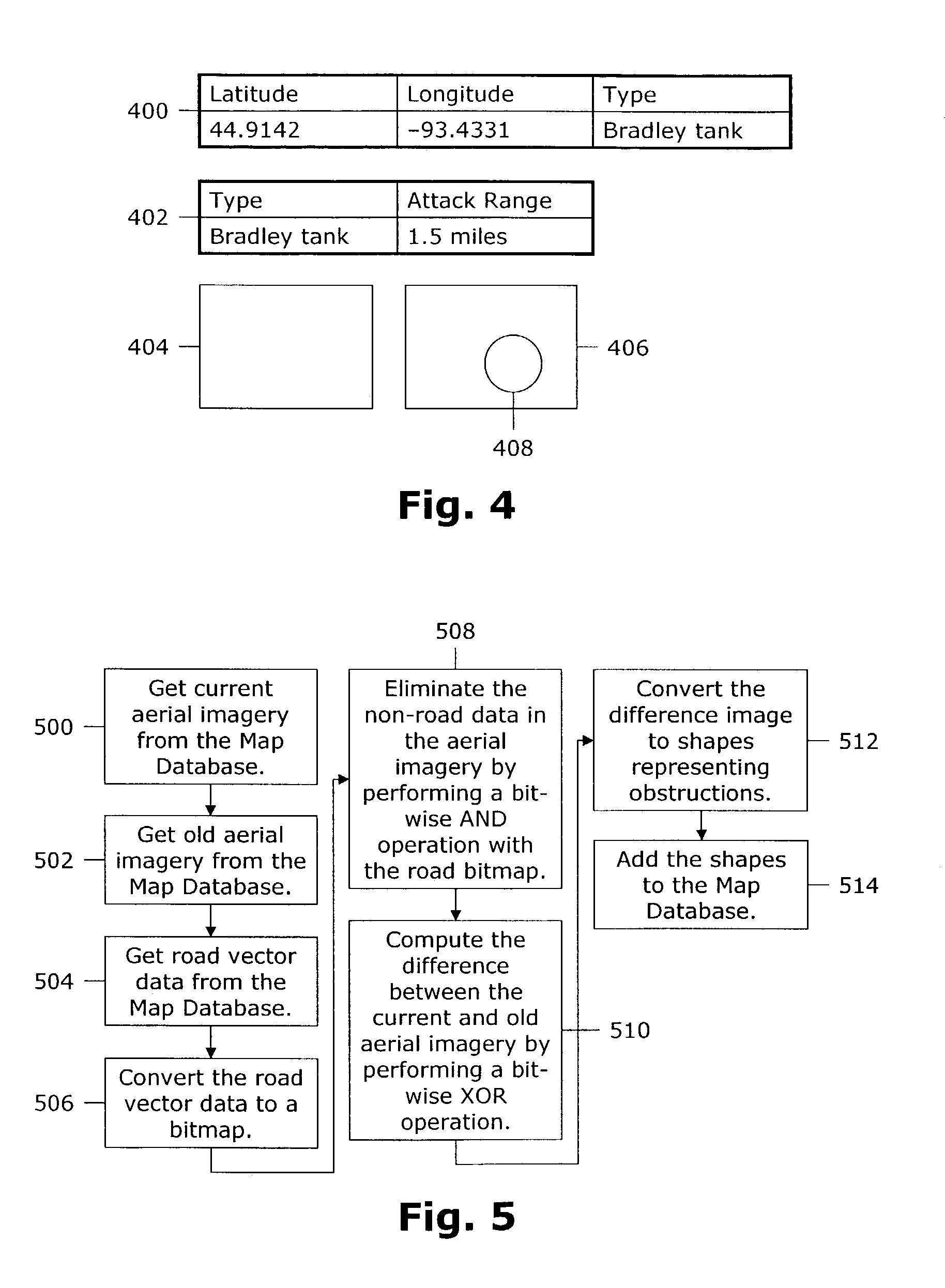
Routing soldiers around enemy attacks and battlefield obstructions
InactiveUS6963800B1Stay focusedSafely routedDefence devicesInstruments for road network navigationHead-up displayGraphics
A computer-implemented method for safely routing a soldier to a destination on the battlefield. The method includes a Threat Analyzer (100) for assessing threats to the soldier, a Graph Builder (102) for building a graph representing the battlefield, a Route Generator (104) for generating a route that avoids the threats, and a Route Presenter (106) for guiding the soldier along the route. The Threat Analyzer (100) includes an Enemy Analyzer (200) for determining the attack range of enemy units and an Obstruction Analyzer (202) for detecting obstructions in aerial imagery. The Graph Builder (102) includes a Cost Evaluator (712) that takes into account traversal speeds for soldiers across various types of terrain. The Route Presenter (106) overlays the route on live video in the soldier's heads-up display.
Owner:PRIMORDIAL
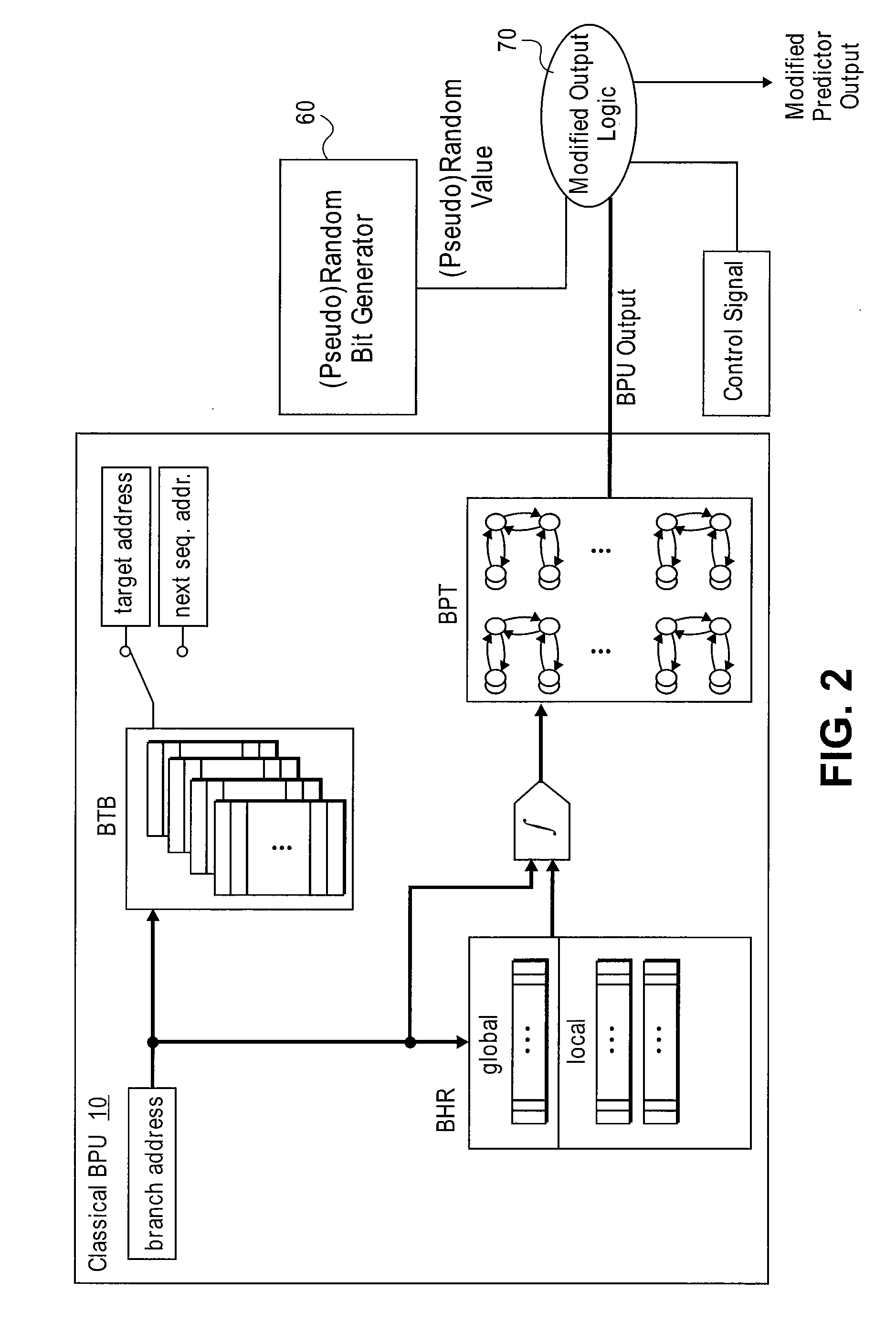
Systems and methods for providing security for computer systems
ActiveUS20080052499A1Reduce and eliminate vulnerabilityReduce vulnerabilityRandom number generatorsDigital computer detailsCountermeasureComputerized system
Hardware and / or software countermeasures are provided to reduce or eliminate vulnerabilities due to the observable and / or predictable states and state transitions of microprocessor components such as instruction cache, data cache, branch prediction unit(s), branch target buffer(s) and other components. For example, for branch prediction units, various hardware and / or software countermeasures are provided to reduce vulnerabilities in the branch prediction unit (BPU) and to protect against the security vulnerabilities due the observable and / or predictable states and state transitions during BPU operations.
Owner:KOC PH D CETIN KAYA
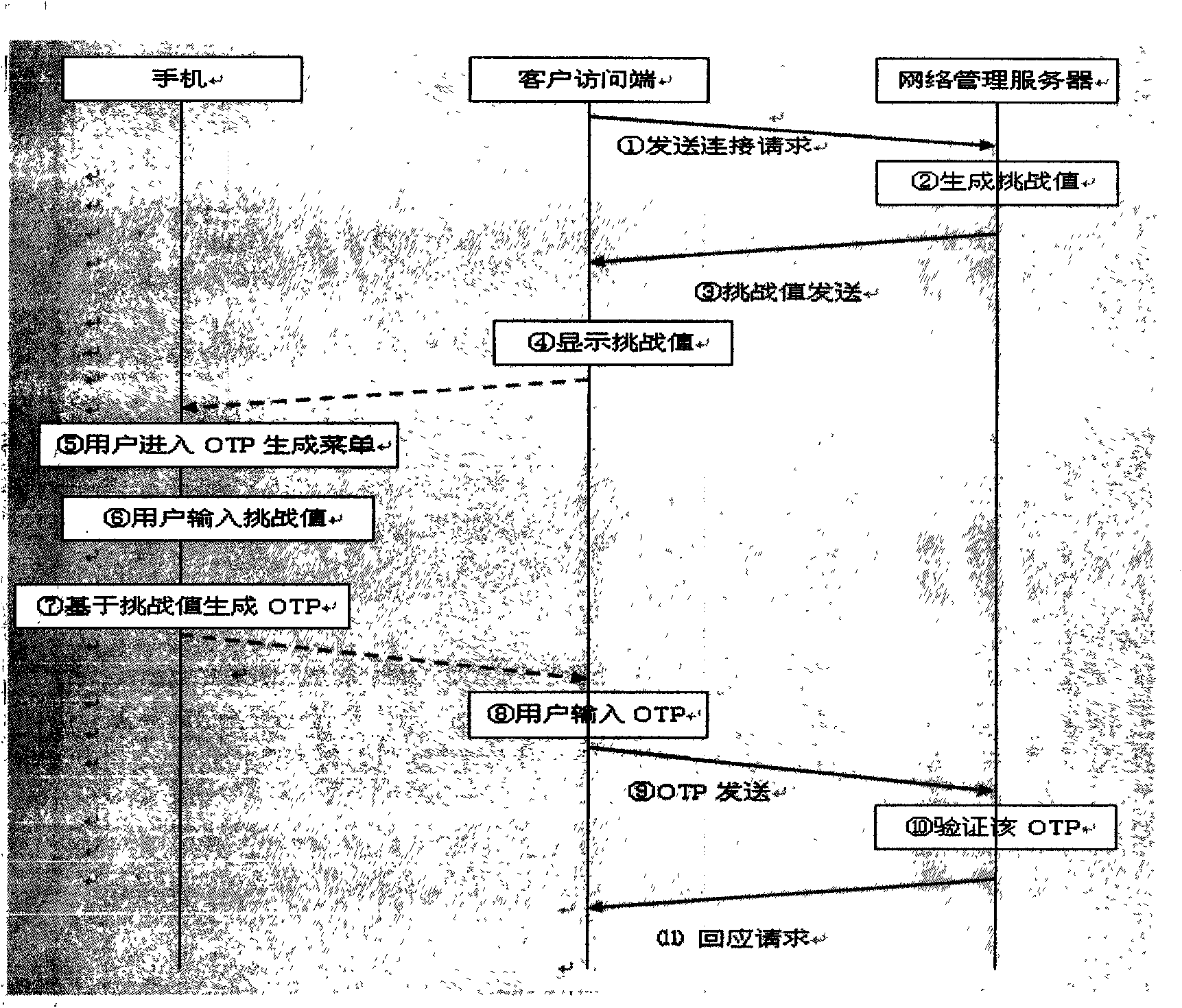
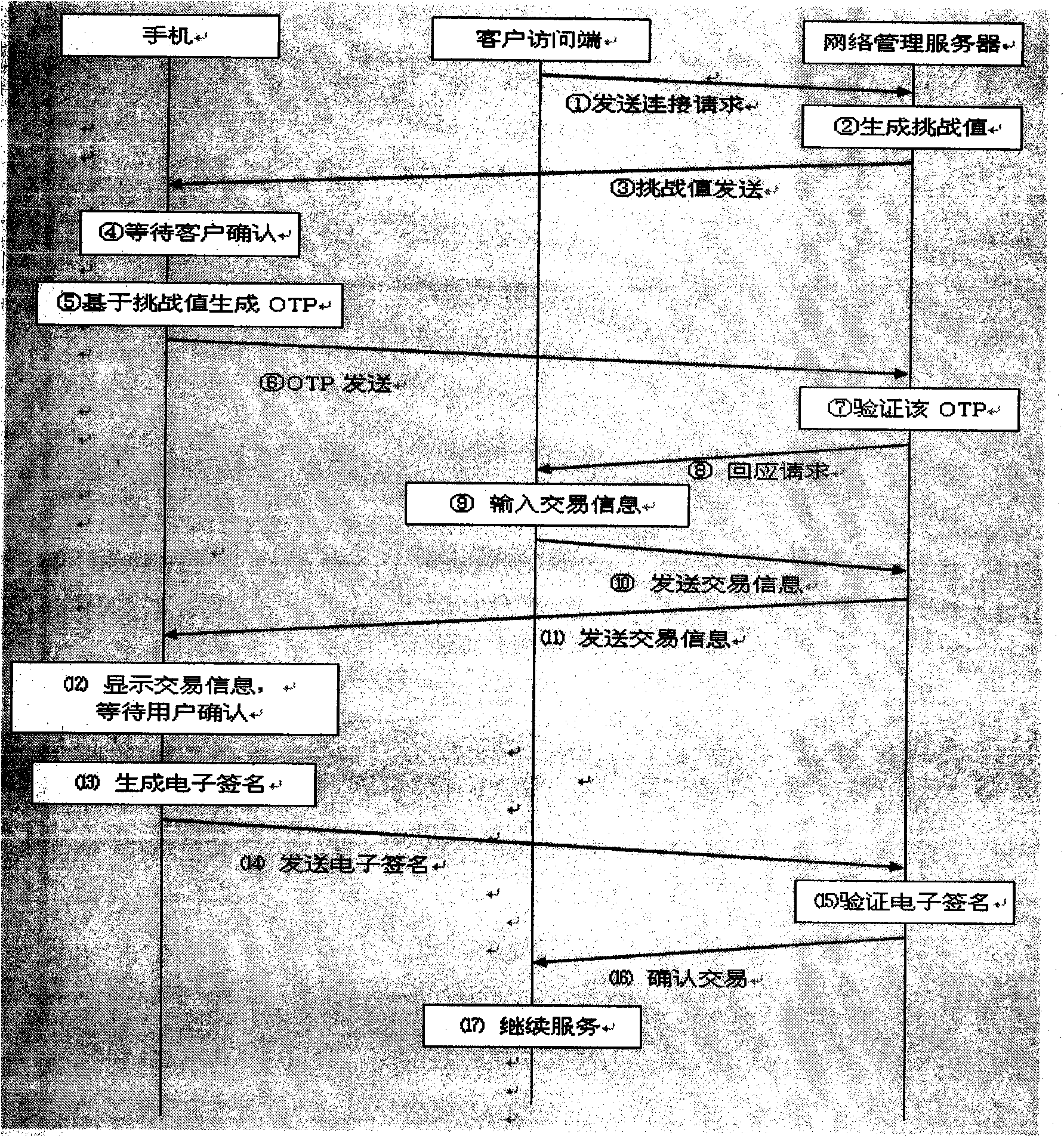
Safe dynamic password authentication method based on mobile phone
The invention discloses a method for generating dynamic password (OTP) by a mobile phone, and mainly solves the security problems of the current online banking system and electronic business system, thus not only preventing threats from Trojan programs and cheats from 'phishing sites', but also avoiding expressed problems of leakage and incapacity for tracing in the current mobile phone text message dynamic password.
Owner:SHENZHEN DTEC ELECTRONICS TECH
System And Method For Intrusion Prevention In A Communications Network
InactiveUS20080276297A1Avoid connectionIncrease resourcesMemory loss protectionError detection/correctionComputer networkUnique user
A method and system for monitoring UDP communications and for preventing unauthorized UDP communications within a computer network. A method for managing access to a resource comprises assigning a unique user identifier to each authorized user, upon initiation of a UDP communication initialed by a specific authorized user for access to a specific resource, appending the unique user identifier of the specific authorized user to each UDP packet of the UDP communication, intercepting the plurality of UDP packets within the computer network, extracting the unique user identifier from each UDP packet to identify the specific authorized user associated with the respective UDP packet, and allowing each respective UDP packet to reach the specific resource as a function of the unique user identifier extracted from the respective UDP packet.
Owner:LIQUIDWARE LABS
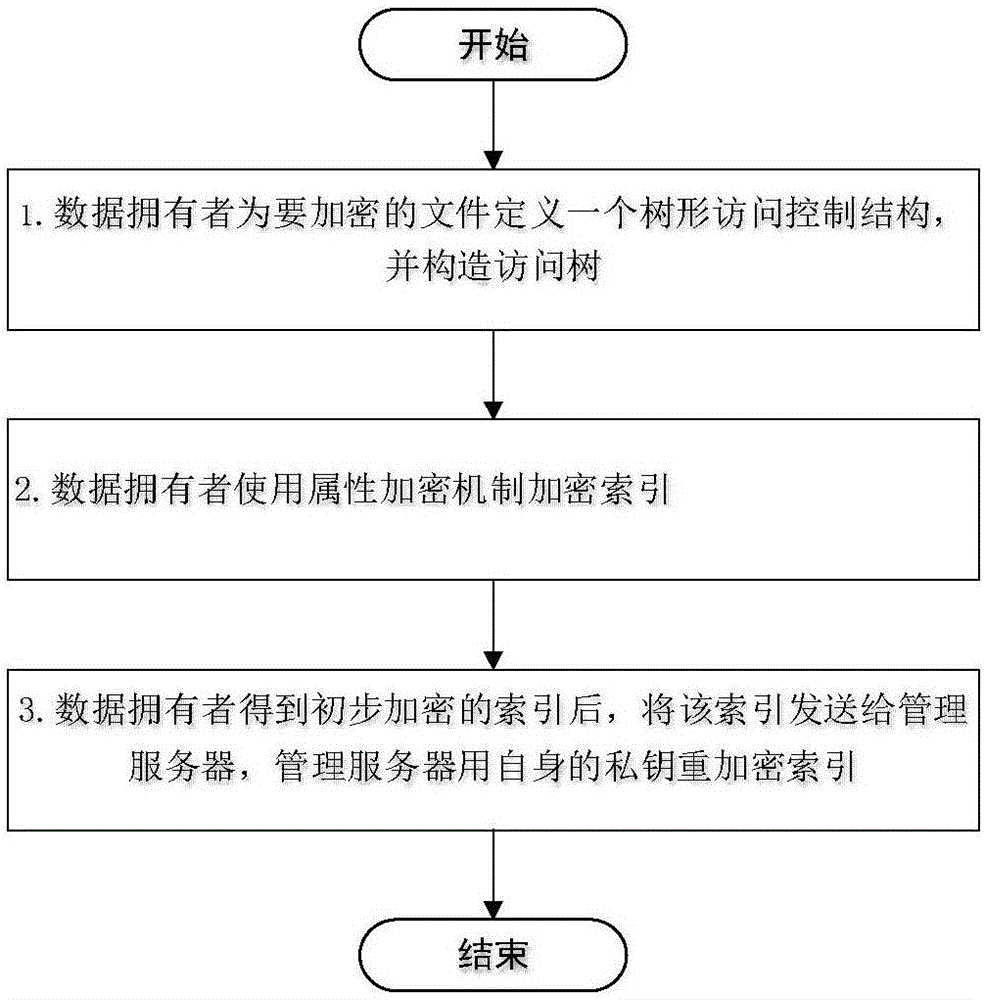
Property base keyword searching method supporting efficient revocation in cloud environment
ActiveCN106330865ASystem Architecture SupportAnti-attackPublic key for secure communicationOther databases queryingUser privacyTrusted third party
The invention discloses a property base keyword searching method supporting efficient revocation in the cloud environment. The method comprises the following steps: (1) initializing a system and managing a server to generate a public key and a master key; (2) registering a new user in a trusted third party and an authorized agency to obtain a register secret key and a property secret key; (3) allowing a data owner to generate encrypted files and indexes that are respectively sent to a cloud server and a management server, and allowing the management server to re-encrypt the index and send the new index to the cloud server; (4) in order to verify the identity of the user during the query phase, allowing the cloud server to generate a query mark; (5) allowing the user to generate an encrypted trapdoor to the management server, so that the management server re-encrypts and sends the received trapdoor to the cloud server; (6) when the cloud server receives the encrypted index and trapdoor, carrying out the keyword search; and (7) completing the user property revocation. The invention realizes searchable encryption based on the property encryption mechanism, so as to protect the user privacy and reduce the user expense.
Owner:ANHUI UNIVERSITY
Bovine left abomasal displacement operative reduction apparatus with reduction needle transmitting range setting function
InactiveCN103690269BEasy to control the lengthLimit launch distanceSurgical veterinarySurvival probabilitySurgery
The invention discloses a bovine left abomasal displacement operative reduction apparatus with a reduction needle transmitting range setting function. The bovine left abomasal displacement operative reduction apparatus comprises a reduction needle transmitting device and a reduction needle with a line binding hole. The outer edge of the reduction needle transmitting device is smooth, the reduction needle transmitting device comprises a transmitting tube, an ejection portion and a trigger, the ejection portion is positioned at the rear of the transmitting tube and is communicated with the transmitting tube, the reduction needle is straight, the rear end of the reduction needle is arranged in the ejection portion, the other portion of the reduction needle is positioned in the transmitting tube, and the line binding hole is positioned on a needle body in the transmitting tube; the reduction needle transmitting device is further provide with a suture line position lock, and the length of a suture line is locked by the suture line position lock, so that the transmitting range of the reduction needle can be controlled. The bovine left abomasal displacement operative reduction apparatus has the advantages that the traditional double-side incision operation can be simplified onto single-side incision operation, so that the survival probability of seriously ill cattle can be effectively increased; the reduction needle further can be effectively protected, the transmitting distance of the reduction needle can be controlled, accordingly, accidents can be reduced, and the success rate of operation can be increased.
Owner:广州市九新生物科技有限公司
A mobile crowdsourcing data acquisition and processing system and method based on a block chain
PendingCN109726887ARealize processingImprove efficiencyKey distribution for secure communicationEncryption apparatus with shift registers/memoriesChain networkChain system
The invention belongs to the technical field of transmission control regulations, such as data link level control regulations, and discloses a mobile crowdsourcing data acquisition and processing system and method based on a block chain. The miner discovers other miner nodes in the block chain network, downloads the block chain content and builds a block chain system together; The user issues thetask to the block chain through the miner, and the miner recruits the working node to complete the corresponding task. Collection and trust evaluation of feedback information: after the task is completed, a miner collects the feedback information of each node participating in the task and completes trust evaluation work of the nodes. Block generation and selection: a miner checks whether the information on the block satisfies a condition of generating a new block, generates the new block if the information on the block satisfies the condition of generating the new block, and broadcasts the block in the block chain network to achieve consistency. According to the invention, an incentive mechanism and system security of a miner are realized without depending on the presence of online currency; The bifurcation problem existing in the existing block chain technology is solved; Execution efficiency is high.
Owner:XIDIAN UNIV
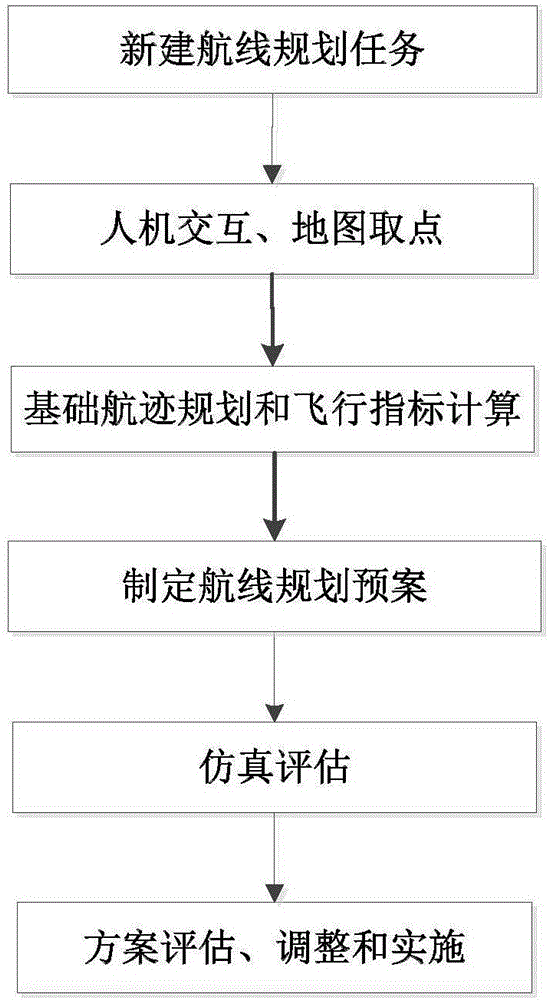
Route planning method for low-altitude medium- and long-distance ferry flights
ActiveCN106781707AImprove operational efficiencyQuick planningFlight plan managementShortest distanceCivil aviation
The invention discloses a route planning method for low-altitude medium- and long-distance ferry flights. The route planning method can plan a flight route with minimum flight cost for an aircraft, and multi-aircraft and multi-route collaborative task planning can be achieved herein. The route planning method is characterized in that a route is divided into a route-entering path P1, a flight path P2 and a route-exiting path P3; the route-entering path P1 and the route-exiting path P3 employ the shortest distances avoiding static threats; the flight on a flight path is a flight performed below a planned civil aviation route, and the shortest flight path is found by utilizing DijKstra algorithm; multiple aircrafts fly in a simulated manner on a digital map according the planned basic route; safety detection and warning are performed according to the current flight states of the aircrafts and the preset environment information on the digital map, and warning information is output; route optimization is finally performed according to the warning information.
Owner:华北计算技术研究所 +1
Real-time path planning method for unmanned aerial vehicle based on deep reinforcement learning
ActiveCN110488872AImprove autonomous flight capabilitiesStrong adaptability and real-timeInternal combustion piston enginesPosition/course control in three dimensionsTelecommunications linkNetwork model
The invention discloses a real-time path planning method for an unmanned aerial vehicle based on deep reinforcement learning. The method comprises the steps of S1, obtaining the current environment state of the unmanned aerial vehicle from a simulation environment, calculating the threat degree of a target object defense unit to the unmanned aerial vehicle according to a situation evaluation model, and constructing a situation map of a task area of the unmanned aerial vehicle; constructing a main network and a target network of the convolutional neural network and the competitive neural network to perform action selection; S2, obtaining the current environment state of the unmanned aerial vehicle according to the communication link, calculating a threat value of the target object defense unit to the unmanned aerial vehicle according to the situation evaluation model, constructing a situation map of the task areas of the unmanned aerial vehicle, constructing a competitive dual-Q network, loading the trained network model, evaluating the Q value of each action in the current state, selecting the action corresponding to the maximum Q value, determining the flight direction of the unmanned aerial vehicle, and completing the flight task. According to the invention, the autonomous decision-making ability of the unmanned aerial vehicle can be effectively improved, and the method has high robustness and application value.
Owner:NAT UNIV OF DEFENSE TECH
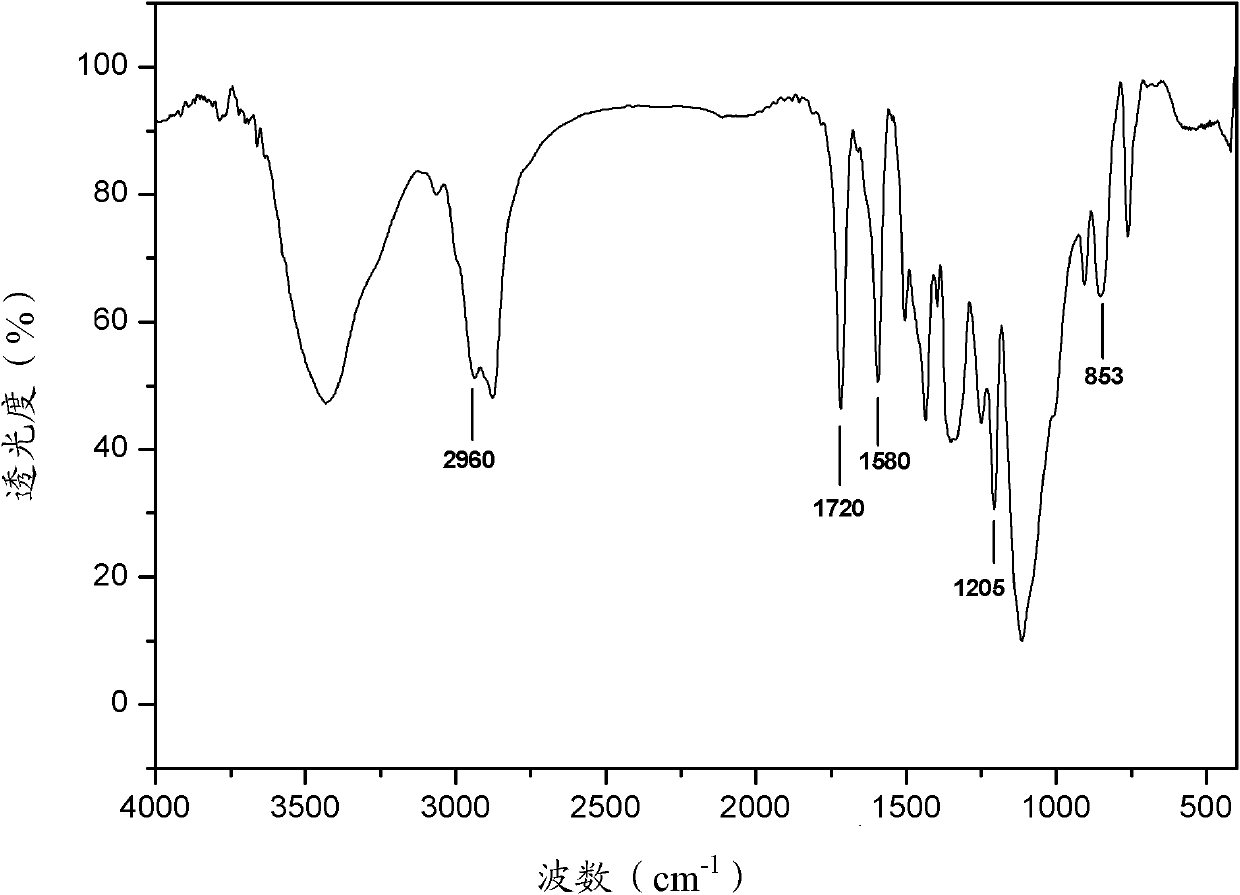
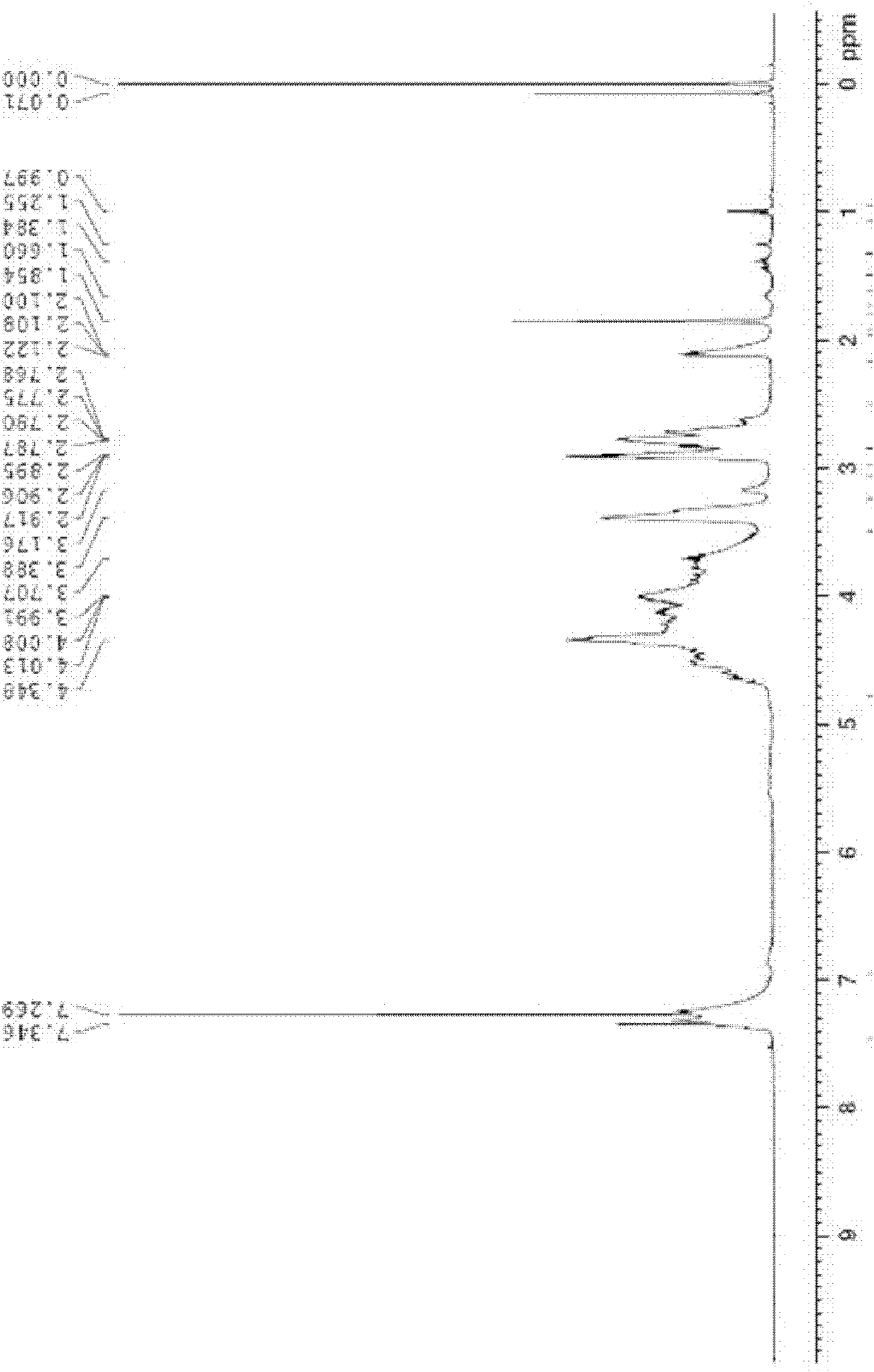
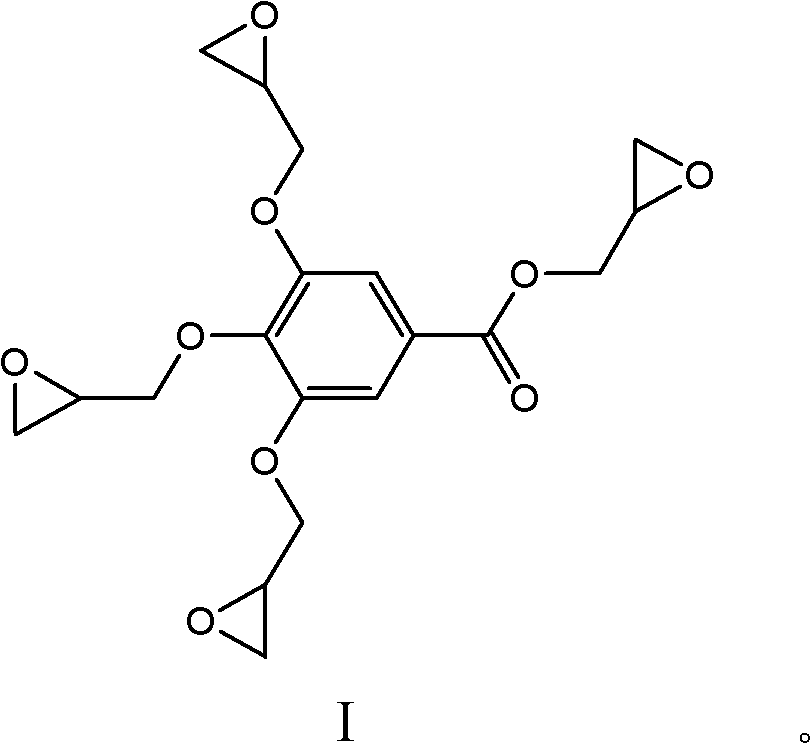
A kind of epoxy resin based on gallic acid and its preparation method and application
ActiveCN102276788AHigh epoxy valueIncrease crosslink densityEpoxy resin adhesivesEpoxy resin coatingsPolymer scienceGallic acid ester
The invention discloses an epoxy resin based on gallic acids with a structure shown as the formula I, which has high epoxy values and also has higher crosslinking density after being cured, thus having good mechanical property and thermal property. The invention also discloses a preparation method of the epoxy resin based on the gallic acids, comprising the following steps: mixing the gallic acids, epoxy halogenopropane and a catalyst and reacting for 2-5 hours at the temperature of 100-120 DEG C; cooling to 20-40 DEG C; adding alkaline compounds and water and continuing to react for 2-5 hours; and washing, removing a solvent and drying to obtain the epoxy resin based on the gallic acids. The preparation method is simple in process, good in controllability and easy to implement industrially. The invention also provides an application of the epoxy resin based on the gallic acids. The epoxy resin based on the gallic acids is particularly applied to preparing composite materials, epoxy adhesives and coatings.
Owner:NINGBO INST OF MATERIALS TECH & ENG CHINESE ACADEMY OF SCI
Device with microbubble-induced superhydrophobic surfaces for drag reduction and biofouling prevention and device for biofouling prevention
InactiveUS20120247383A1Increase the areaLarge specific surface areaVessel cleaningWatercraft hull designHydrogenMicrobubbles
A device with microbubble-induced superhydrophobic surfaces for drag reduction and biofouling prevention includes an anodic microporous plate, a cathodic microporous plate, and a DC power supply. The anodic microporous plate and the cathodic microporous plate are mounted to a hull surface of a ship. The DC power supply includes a positive pole electrically connected to the anodic microporous plate and a negative pole electrically connected to the cathodic microporous plate. Seawater is electrolyzed to generate hydrogen microbubbles adjacent to a surface of the cathodic microporous plate and to generate oxygen microbubbles adjacent to a surface of the anodic microporous plate, forming superhydrophobic surfaces on the surfaces of the anodic microporous plate and the cathodic microporous plate. Electric current flows through the anodic microporous plate and the cathodic microporous plate to prevent biofouling.
Owner:WU KEE RONG +4
Unmanned ship route optimization method based on environment forecast information
ActiveCN108564202AImprove work efficiencyEfficient designWaterways transportForecastingGlobal Positioning SystemComputer science
The invention relates to an unmanned ship route optimization method based on environment forecast information. According to the method, environment information factors possibly influencing marine navigation of an unmanned ship are collected through meteorological forecast, the current position of the unmanned ship is confirmed through a global positioning system, and an accurate unmanned ship navigation state is obtained; modeling is performed on the environment of a sea area by considering the influences of static barriers in an unmanned ship navigation area and the meteorological factor of ocean currents on the unmanned ship in combination with obtained environment data; and design is performed based on an unmanned ship route planning algorithm of a particle swarm optimization algorithm,an unmanned ship route designed through the planning algorithm avoids the static barriers as much as possible, and the ocean current area beneficial for unmanned ship navigation is utilized. Throughthe method, the unmanned ship can design the route according to the environment forecast information, the route can be timely adjusted at any time according to weather environment changes, the situation that a bad environment on the sea area threatens the safety of the unmanned ship is avoided, and the economy and safety of unmanned ship navigation are improved.
Owner:HARBIN ENG UNIV
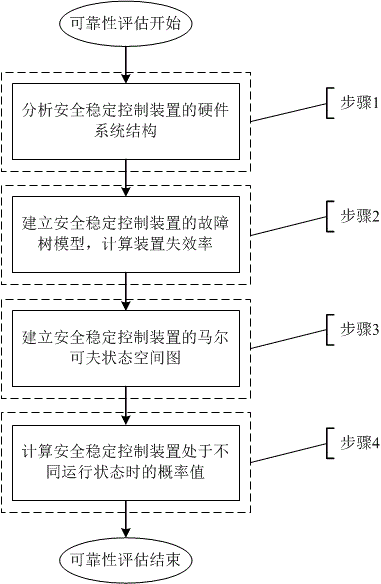
Safety and stability control device reliability analysis method in consideration of multistate operation
InactiveCN104898636AAvoid threatsAvoid lostElectric testing/monitoringFailure rateElectric power system
The invention discloses a safety and stability control device reliability analysis method in consideration of multistate operation, which belongs to the technical field of power system control. A hardware system structure of the safety and stability control device is firstly analyzed; a fault tree model for the safety and stability control device is then built based on a fault tree method, and the failure rate of the safety and stability control device is acquired; and finally, on the basis of Markov state space, a reliability evaluation model for the safety and stability control device is built, and the probability values of the safety and stability control device in four different operation states are calculated. The hardware system structure of the safety and stability control device and the importance degree of each stable control module for composing the device in the device are considered, the fault tree method and the Markov state space method are combined to carry out reliability evaluation on the safety and stability control device, the reliability degree of the device is thus judged, influences on reliability of the device by external faults are considered during the evaluation process, and the evaluation result is more objective and more accurate.
Owner:STATE GRID CORP OF CHINA +3
Wine cap
InactiveUS6029836ASlow venting of gas pressureAvoid explosionCapsPower operated devicesWine bottleEngineering
A cap device, particularly for a wine bottle, is disclosed as including a cap having a recessed top opening for receiving a screw for threadable insertion into the cork of the wine bottle. The recess at the top of the cap is of basically square shape with two recess extensions for receiving a butter knife, or the like, for turning the cork and screw as a unit and thereby unscrewing the cap, which is threadably attached to the outside of the neck of the wine bottle. The threading direction of the threads of the cap and neck of the wine bottle are opposite to the threading direction between the cork and the screw. Additionally, the cap is structured to extend a distance above the extent of the cork in the neck of the wine bottle, the cork is bullet-shaped and channels are defined transverse to the threads extending outwardly of the neck of the wine bottle, in order to allow the escape of compressed carbon dioxide in a sparkling wine or champagne bottle as the cap is unscrewed and the cork lifted. The top of the screw defines a spherical projection in order to assist guiding the cork in, with respect to the recess of the cap, when reinserting the cork after use.
Owner:LIGERAS ACHILLES P
Coating device and coating method
InactiveCN103586169AStrong repeatabilityImprove coating efficiencyLiquid surface applicatorsCoatingsMeasurement deviceBiomedical engineering
The invention discloses a coating device and a coating method. The coating device comprises a needle head, a clamp, an imaging device, a height measurement device and a control device, wherein paint is sprayed on the needle head, the clamp is positioned under the needle head, and the clamp and the needle head can relatively move in a transverse direction and a longitudinal direction; the imaging device, the height measurement device and the control device are positioned above the clamp; the needle head can vertically move relative to the clamp; the needle head is connected with a flow control device, and the imaging device, the height measurement device and the flow control device are connected with the control device. During coating, the injection quantity of the paint of the needle head and the opening and closing of a valve are controlled through the flow control device. In the injection process, the control device controls the relative positions of the clamp and the needle head in the transverse direction and the longitudinal direction so as to ensure that the needle head carries out point injection according to a point injection track determined in advance, and controls the needle head to vertically move relative to the clamp so as to ensure that the distance between the needle head and the surface of a product to be coated is constant.
Owner:SWELL MARUI GUANGZHOU AUTOMOBILE PARTS
Solar street lamp for traffic management support
PendingCN106918016AExpand the range of exposureQuick stopPhotovoltaic supportsMechanical apparatusEnergy absorptionSolar street light
The invention discloses a solar street lamp for traffic management support. The solar street lamp comprises a lamp holder, a lamp pole and a solar panel support plate, wherein a revolving shaft is arranged on the top of the lamp pole, and is rotatably connected with the solar panel support plate through the revolving shaft; an illumination sensor is arranged at the lower end of the solar panel support plate; an angle adjusting mechanism is arranged on the upper surface of a support platform in a sliding way; the angle adjusting mechanism comprises a motor seat, an adjusting motor, a gear disk, a rack, a guide wheel, a guide seat, a support rod and a carrier rod; a vehicle stopping mechanism is arranged on the side wall of the lamp holder; the vehicle stopping mechanism consists of a slope, a belt, a runner, an energy absorption pad, an anti-collision plate and a mounting groove. In the solar street lamp, sunlight is sensed by the illumination sensor, and the controller is used for controlling the adjusting motor to rotate in order to adjust the illumination angle of a solar panel; the vehicle stopping mechanism can separate front wheels of a vehicle from the ground, so that forward moving power is lost, the vehicle is stopped rapidly, and a vehicle in accident is prevented from threatening the safety of other pedestrians and vehicles.
Owner:李姗姗
Secure routing protocol based on trust detection in vehicle-mounted ad hoc network
InactiveCN105163308AShorten the timeGuaranteed stabilitySecurity arrangementRouting decisionTelecommunications link
The invention discloses a secure routing protocol based on trust detection in a vehicle-mounted ad hoc network. The secure routing protocol comprises the steps of firstly, according to multi-channel selection monitoring mechanism, allowing vehicle nodes with a consistent movement trend to work on the same service channel and achieve data monitoring and transmission tasks on the same service channel; the vehicle nodes acquiring routing packet forwarding behaviors of adjacent nodes through channel monitoring to establish direct trust of the adjacent nodes; and meanwhile, detecting the received hello message packets periodically transmitted by the adjacent nodes, obtaining recommend trust through a node trust list attached to the packets, then calculating and maintaining the trust list of the adjacent nodes, and assisting the nodes in making routing decisions. The routing protocol can maintain a relatively stable communication link in a vehicle-mounted environment with a rapid change in the topology, has high delivery rate and low transmission delay, and can also effectively avoid malicious behaviors of discarding routing packets by nodes through trust detection.
Owner:SOUTH CHINA UNIV OF TECH
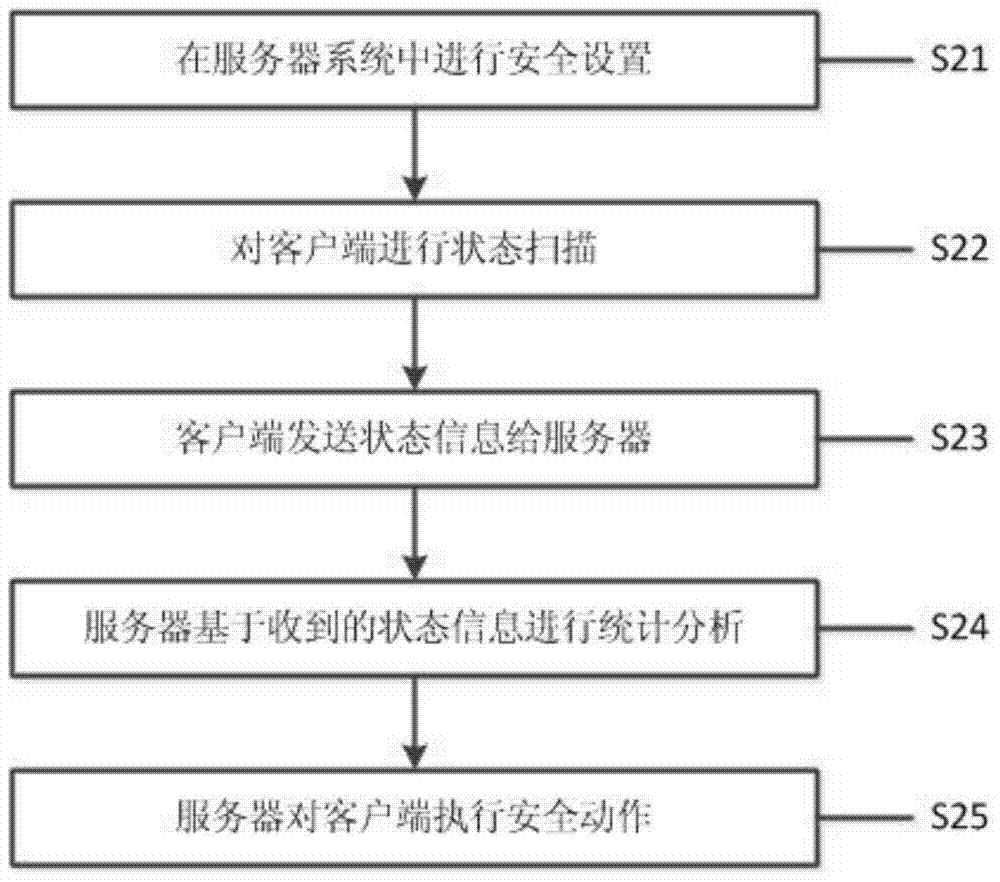
Health degree monitoring method of cloud network equipment
InactiveCN103929323AAvoid threatsReduce security risksPlatform integrity maintainanceData switching networksSecure stateSafe handling
Provided is a health degree monitoring method of cloud network equipment. The method includes the steps that state scanning is conducted on a client; state information obtained through scanning is sent to a server; the server conducts health degree analysis and processing according to the state information. According to the method, an active mode is used for monitoring the safety of the cloud equipment in a cloud network uniformly, and the situation that client equipment in the cloud network is threatened can be effectively avoided; dynamic centralized monitoring is conducted on scanning software installed on the cloud equipment, the safe state of the cloud equipment is analyzed, therefore, corresponding safety processing actions can be sent out in real time so as to conduct processing uniformly, and the overall safety risk of the cloud equipment in the cloud network is reduced to the minimum level.
Owner:OPZOON TECH
Attribute-based online/offline keyword search method in mobile cloud environment and cloud computing application system thereof
InactiveCN107547530AImplement searchReduce computational costKey distribution for secure communicationEncryption apparatus with shift registers/memoriesCiphertextMobile cloud
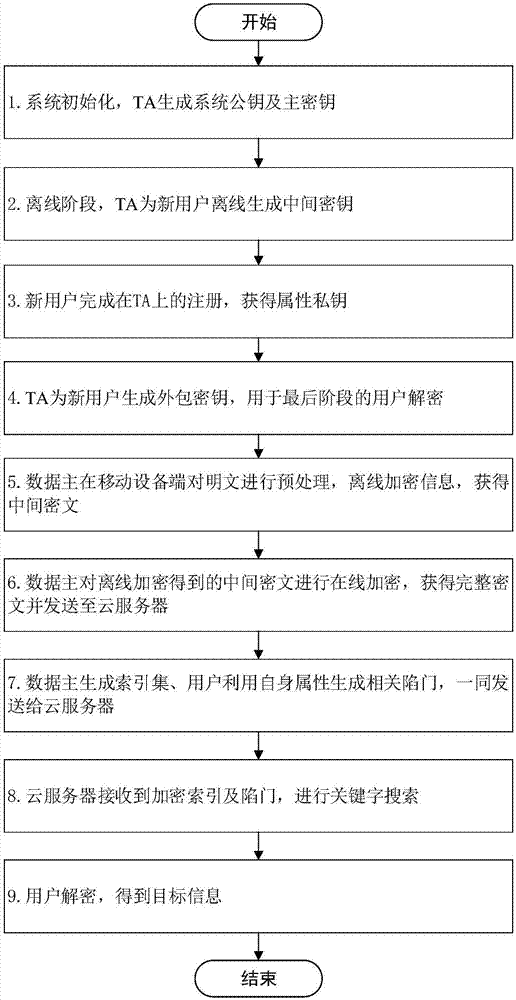
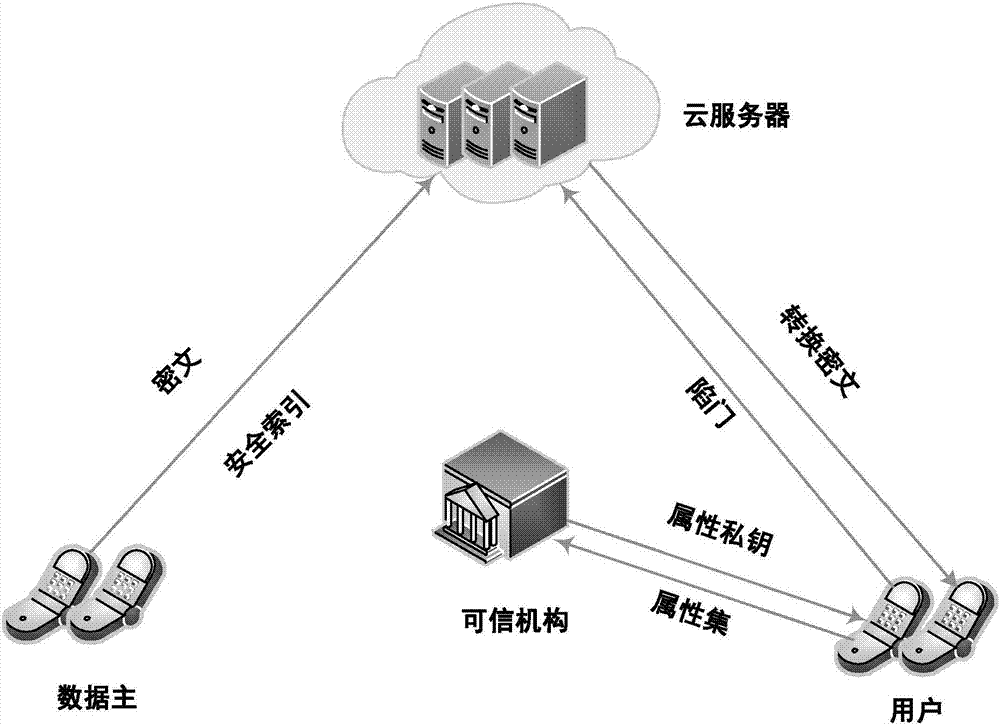
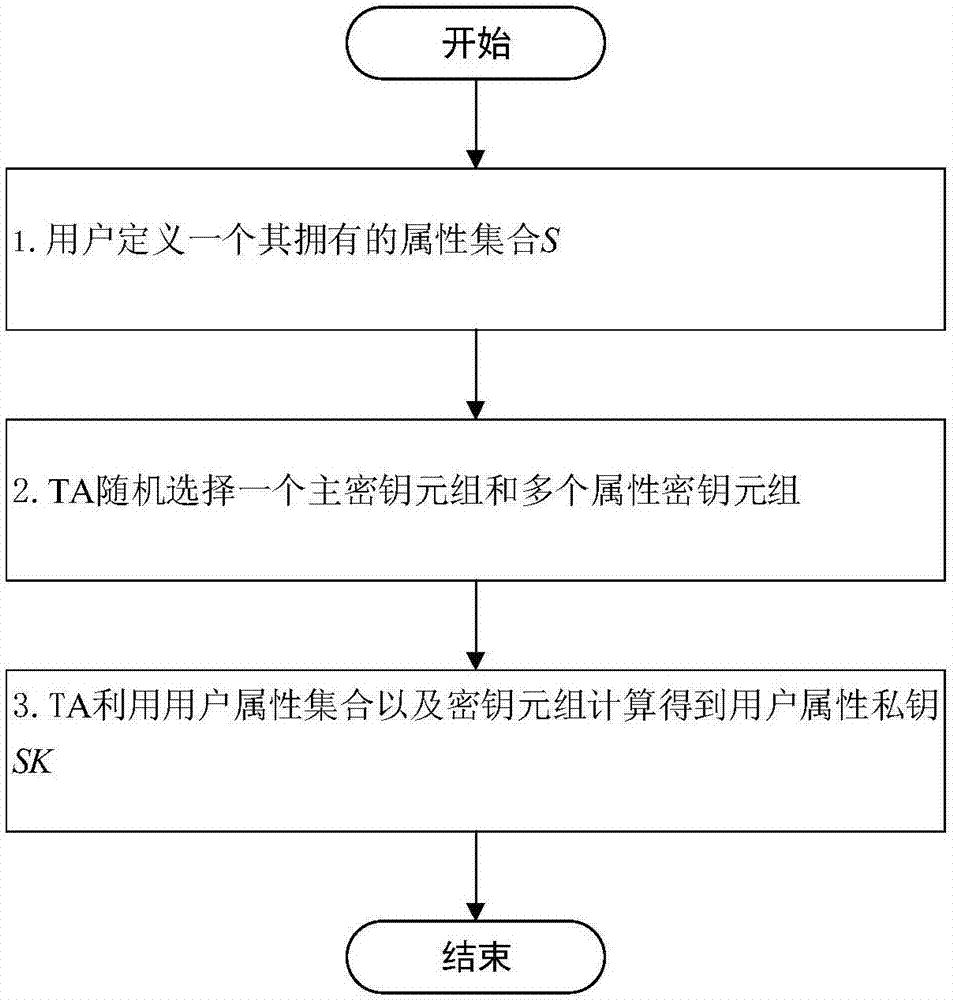
The invention discloses an attribute-based online / offline keyword search method and its cloud computing application system in a mobile cloud environment, comprising the following steps: system initialization, TA generates a public key and a master key; TA generates an intermediate key offline for a new user After the new user completes the registration, TA generates its attribute private key; TA generates an outsourced key for the new user; the data master encrypts the information offline on the mobile device side to obtain the intermediate ciphertext;) the data master encrypts the intermediate ciphertext online to obtain the complete ciphertext The data master generates an index set, and the user uses its own attributes to generate relevant trapdoors, and sends them to the cloud server together; the cloud server receives the encrypted index and trapdoor, and searches for keywords; the user decrypts to obtain the target information. The present invention realizes searchable encryption based on an attribute encryption mechanism and online / offline technology, protects user privacy, and greatly reduces user expenses.
Owner:ANHUI UNIVERSITY
Multiple upper protective-seam gas burst-preventing exploitation method used in the exploitation of coal seams
InactiveCN1542257AGood pressure relief effectAdd depthUnderground miningSurface miningEnvironmental engineeringProtection layer
The grouped coal bed exploiting method features that grouped coal bed exploiting process from top to bottom includes the first exploitation of the upper non-protuberant coal bed as protecting layer; the subsequent exploitation of lower protected coal bed; and final exploitation of the protected coal bed with ever serious protuberant danger, so as to form multiple protection of the protuberant coal bed while releasing gas pressure of the protected coal bed for forced pumping. The said method can prevent effectively coal and gas burst disaster radically to double the extracting progress, lower gas pumping cost and realize the safe and efficient intensive extraction of high gas content and low penetration coal bed.
Owner:HUAINAN MINING IND GRP +1
Process of nickel citrate for catalyzing thiosulfate to leach gold
ActiveCN104789792AReduce consumptionReduce the amount of decompositionProcess efficiency improvementSulfateAmmonia
The invention discloses a novel process of nickel citrate for catalyzing thiosulfate to leach gold. The novel process is characterized in that the nickel citrate catalysis is used for substituting the traditional copper ammonia catalysis, namely the nickel sulfate and the citric acid (or sodium citrate) are added in the thiosulfate gold leaching pulp to substitute the adding of the copper sulfate and the ammonia. By adopting the process, the oxygenolysis effect of the Cu(NH3)4<2+> and S2O3<2-> is eliminated so that the consumption of the thiosulfate is obviously reduced; and besides, the use of the ammonia is cancelled so as to avoid the risk of the NH3 on the environment. The gold leaching rate is equal to that of the copper ammonia catalysis.
Owner:CENT SOUTH UNIV
A block chain anonymous transport protocol based on ring signature
ActiveCN109104284AImprove securityImprove communication transmission efficiencyUser identity/authority verificationTransmission protocolRing signature
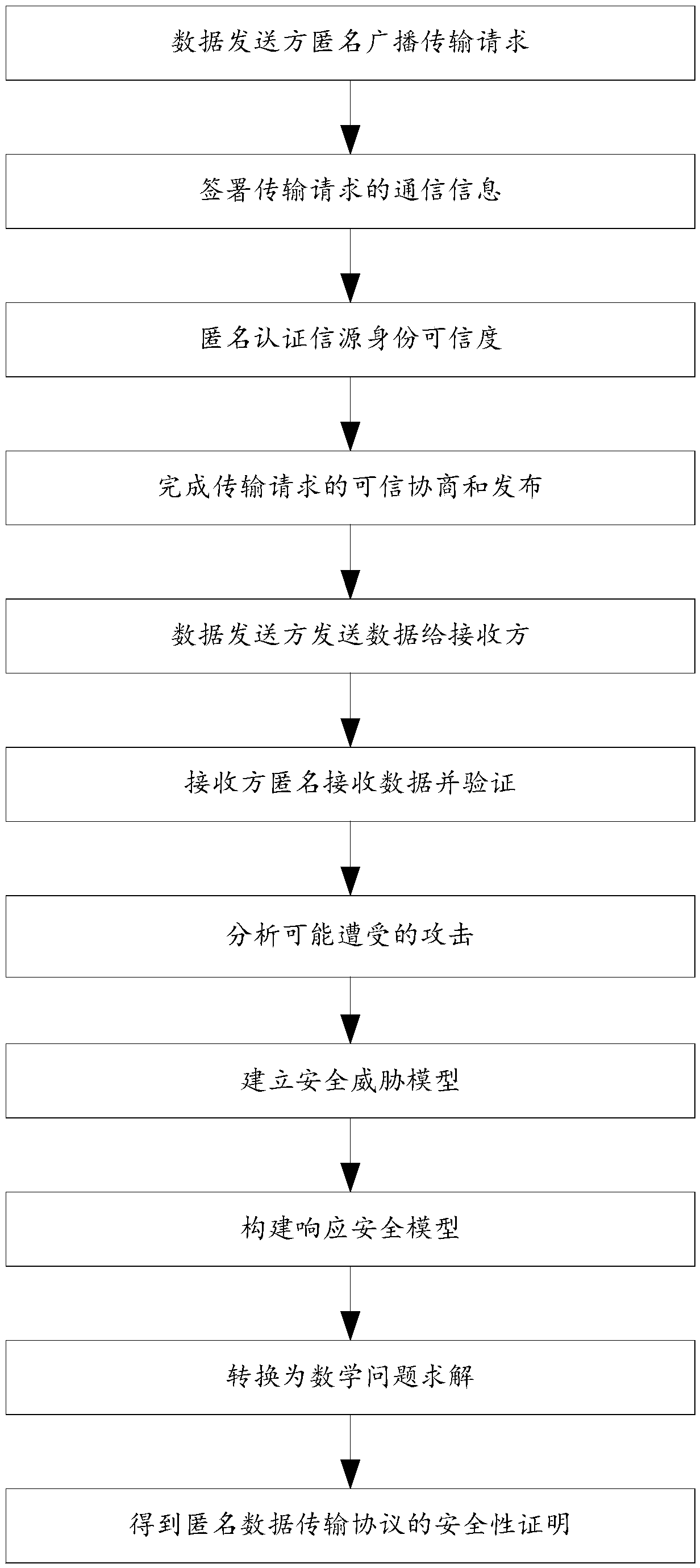
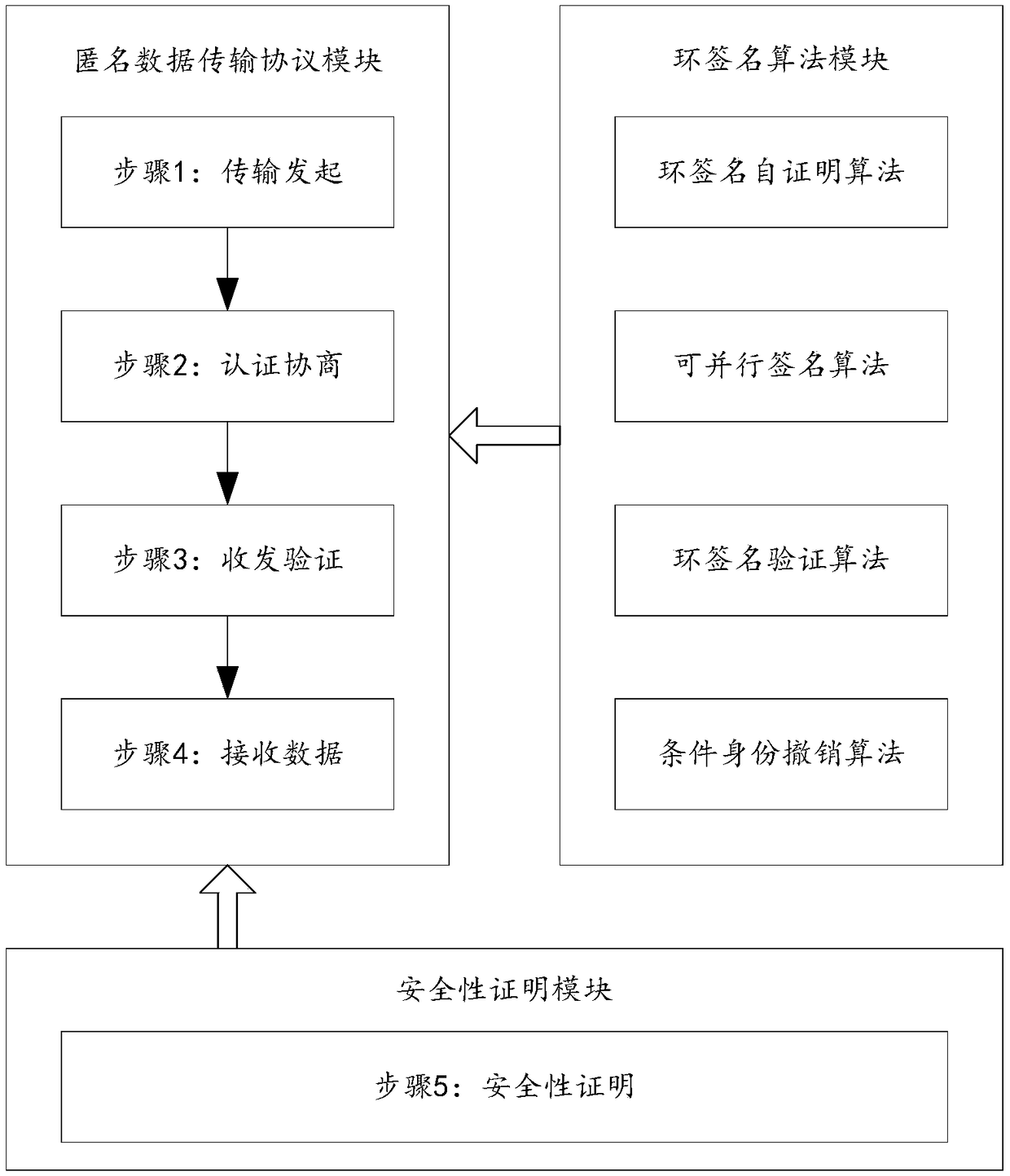
The invention discloses a block chain anonymous transmission protocol based on ring signature, belonging to the technical field of network security. The method comprises steps of 1,anomynously broadcasting a transmission request by a data sender; 2, signing the communication information of the transmission request, anonymously authenticating the trustworthiness of the information source identity of the data sender, obtaining the trustworthiness mechanism and parameters of the transmission request, and issuing the transmission request; 3, the data sender broadcasts and transmits data accordingto the negotiation mechanism and parameters of the step 2; 4, anonymously receiving, verifying and restoring the content of the data by the receiver; Step 5: proving the security of the anonymous datatransfer protocol. The invention solves the problems of poor transmission efficiency and low transmission security of the data transmission protocol on the existing block chain, as well as low sourcereliability and data security of the sending and receiving sides on the block chain, and the invention also solves the problems of low transmission efficiency and low transmission security of the data transmission protocol on the existing block chain.
Owner:SICHUAN UNIV
Method and device for detecting hijacking of DNS (Domain Name Server)
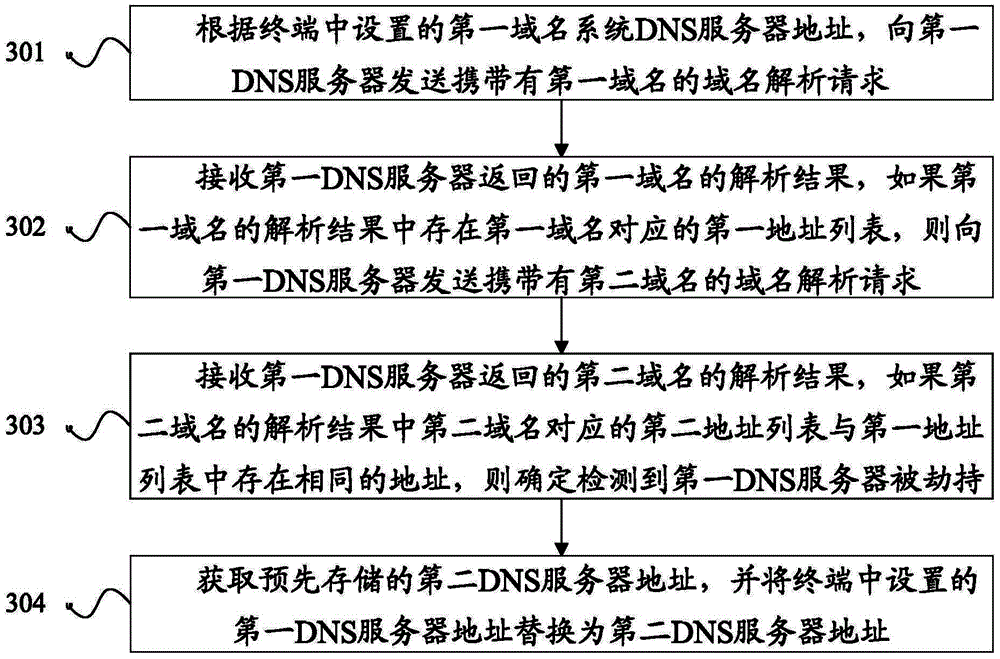
The invention discloses a method and a device for detecting hijacking of a DNS (Domain Name Server), and belongs to the technical field of Internet. The method comprises the following steps: sending a domain name solving request which carries a first domain name to a first DNS, wherein the first domain name is a domain name which does not exist in a network; receiving the solving result of the first domain name returned by the first DNS, and sending a domain name solving request which carries a second domain name to the first DNS if a first address list corresponding to the first domain name exists in the solving result of the first domain name, wherein the second domain name is a domain name which exists in a network needing to be accessed in a target application; receiving a solving result of the second domain name returned by the first DNS, and determining that hijacking of the first DNS is detected if the same addresses exist in a second address list corresponding to the second domain name in the solving result of the second domain name and the first address list. By adopting the method and the device, the function of actively detecting the DNS server is realized, threat caused by access to the Internet by a terminal after hijacking of the DNS is avoided, and the security of the terminal is enhanced.
Owner:XIAOMI INC
Safety mobile office method based on WMI software whitelist mechanism
ActiveCN104573494AObserve the actual effectEasy to managePlatform integrity maintainanceGlobal softwareMonitoring program
The invention relates to a safety mobile office method based on a WMI software whitelist mechanism and belongs to the technical field of terminal equipment safety office. The method is characterized in that the various attributes, serving as software attribute parameters, of software and setting number form an application software whitelist, system PE files during initial system installation of a computer form a system software whitelist, and the application software whitelist and the system software whitelist jointly form a global software whitelist; the global software whitelist is divided into the software whitelist of each department according to the requirements of the corresponding department, and the software whitelist is issued to the safety mobile office terminals of department staff; a user transmits a software request to a server end through an authentication code formed by a department identification code and a staff PIN code; a monitoring program is built on the basis of WMI on the corresponding safety mobile office terminal, the monitoring program performs starting detection on software installation and operation, comparison with the whitelist is performed, and installation and operation are allowed after the comparison is passed. Compared with existing application program mounting control methods, the method is good in stability, safety and compatibility, and mounting efficiency and operation efficiency are increased.
Owner:BEIJING UNIV OF TECH
Static behavior analysis method of mobile smart terminal software
InactiveCN104751053AAvoid threatsStable and efficient analysisPlatform integrity maintainanceSoftware development processFeature vector
The invention discloses a static behavior analysis method of mobile smart terminal software. The static behavior analysis method includes steps of decompressing and decompiling to obtain software source codes by comparing signatures and machine learning concept, extracting kind function calling information and signature information, comparing the signature information at cloud and generating characteristic vectors of numeric types by an SDK (software development kit) dictionary, reducing Weka attribute to obtain behavior characteristics finally, and finally analyzing static behavior of the software by the machine learning algorithm. Accuracy and detecting rate are guaranteed while malicious software behaviors can be more precisely detected. Meanwhile, potential safety hazards during operating of the software are avoided and software behaviors of the mobile smart terminal can be more stably and efficiently analyzed.
Owner:CHANGSHU RES INSTITUE OF NANJING UNIV OF SCI & TECH
Landslide disaster risk regionalization map generation method
ActiveCN111858803AForecast refinementComprehensive descriptionForecastingGeographical information databasesSoil scienceData set
The invention relates to a landslide disaster risk regionalization map generation method, belongs to the technical field of landslide risk prediction and early warning, and solves the problem of low accuracy of an existing landslide risk prediction method. The method comprises the following steps: identifying landslide disaster points and non-disaster stable areas in a research area, and obtaininga training set layer and a verification set layer; obtaining and combining geological-environmental factors related to a plurality of landslide disasters in the research area, and constructing a multilayer geological-environmental factor data set; training a landslide risk prediction model by taking the constructed data set as an input variable and the training set layer as a dependent variable,and verifying the trained landslide risk prediction model by utilizing the constructed data set and the verification set layer to obtain a successfully verified landslide risk prediction model; and inputting the constructed data set into the verified landslide risk prediction model, carrying out processing to obtain a grid value of each grid in the research area, and drawing a landslide disaster risk regionalization map of the research area based on a corresponding relationship between the grid values and risk levels.
Owner:EAST CHINA UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com