Secure routing protocol based on trust detection in vehicle-mounted ad hoc network
A technology of vehicular ad hoc network and routing protocol, which is applied in the field of vehicular ad hoc network, and can solve the problem of deliberate discarding of malicious nodes with short survival time of vehicular network links
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] The specific embodiments of the present invention will be further described below in conjunction with the accompanying drawings, but the implementation and protection scope of the present invention are not limited thereto.
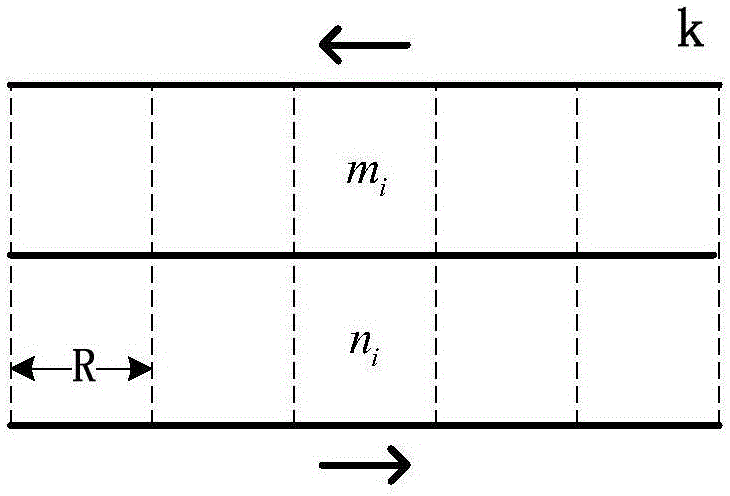
[0049] Such as figure 1 Shown is the model established by the traffic density sensing method in the multi-channel selective monitoring mechanism of the present invention. First, the road is divided into k units, and the interval of each unit is a single communication distance R, and the value of the number of cells k is given by The ratio of the length of each road to a single communication distance is determined. According to the division of cells, the distribution of the number of vehicles in two opposite directions in different cells of the road is defined as two one-dimensional arrays, which are expressed as M[k ]=[m 1 ,m 2 ,...,m i ,...,m k ], 1≤i≤k and N[k]=[n 1 ,n 2 ,...,n i ,...,n k ], 1≤i≤k, where m i and n i respectively represen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com