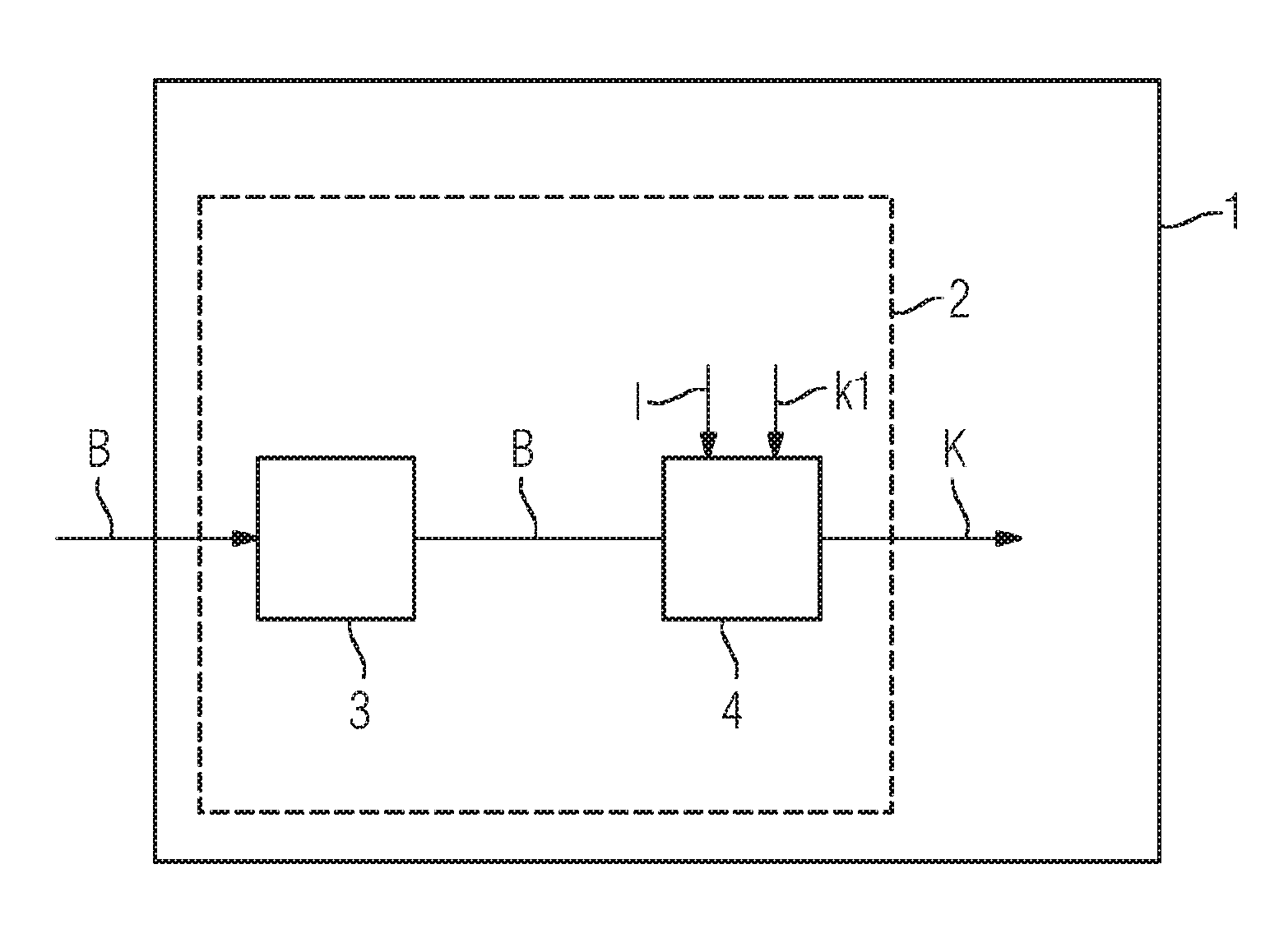
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
332results about How to "Guaranteed normal execution" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Decrypting data
ActiveUS9584311B2Prevent tamperingGuaranteed normal executionSecret communicationCommunication with homomorphic encryptionHomomorphic encryptionComputer program
A device for decrypting data includes a number of devices secured by at least one security device. The secured devices include a receiver for receiving calculation data encrypted using a homomorphic encryption function and a decryptor for decrypting the encrypted calculation data by carrying out the inverse of the homomorphic encryption function on the encrypted calculation data using a private key assigned to the homomorphic encryption function. A method and a computer program product for decrypting data are also provided.
Owner:SIEMENS AG
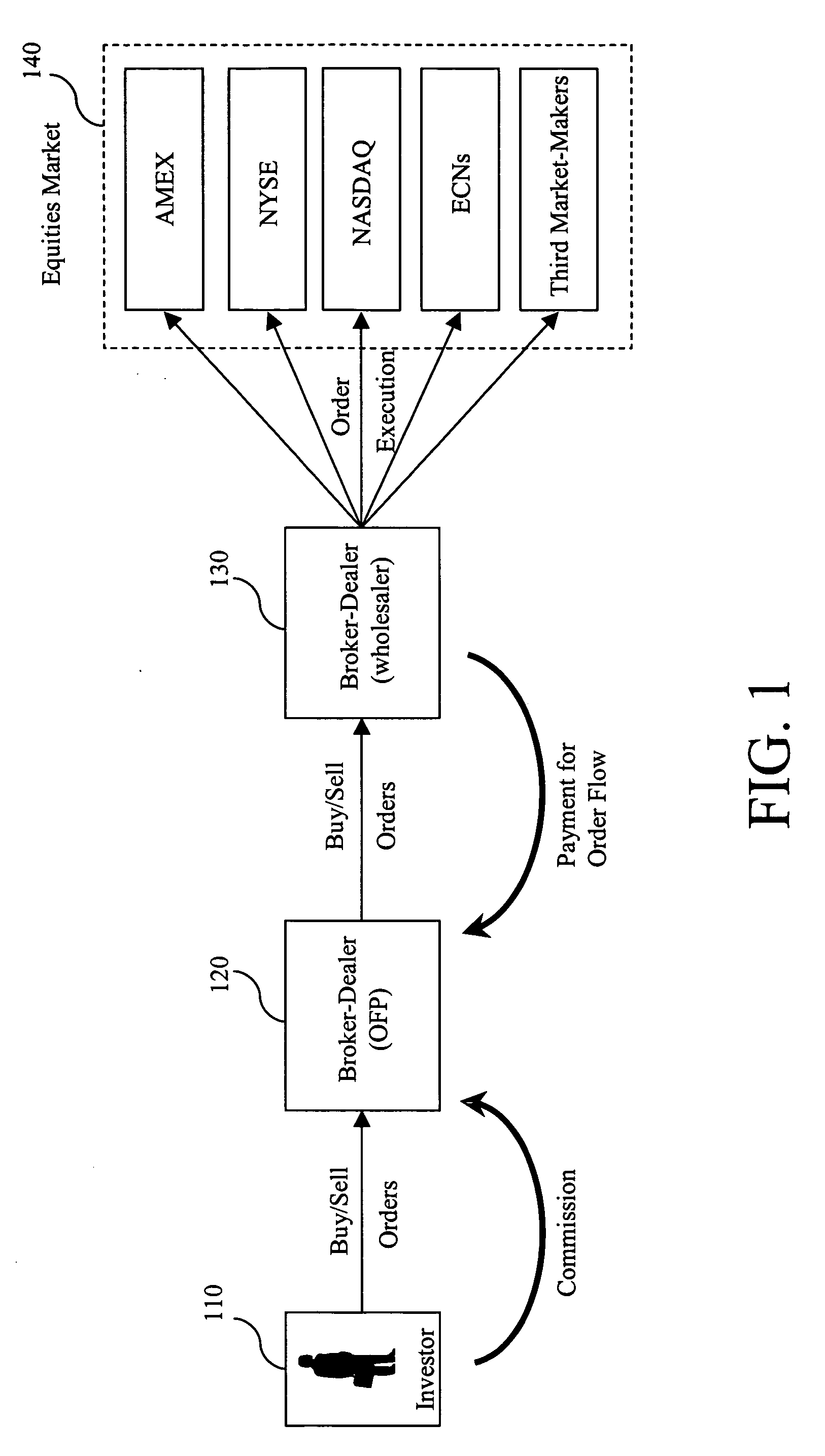
System and method for electronic trading of assets
A method for online trading of assets via transactionally linked virtual markets comprising the steps of defining attributes and behaviors of each of the virtual markets; placing individual buy or sell orders in each of the virtual markets; optionally defining trading strategies that will each span at least two virtual markets; calculating a price and amount for each order in the virtual markets defined by a trading strategy; generating an order in each of the virtual markets contained within a trading strategy; and matching and executing both the individual orders and orders generated by the defined trading strategies.
Owner:PLURATRADE
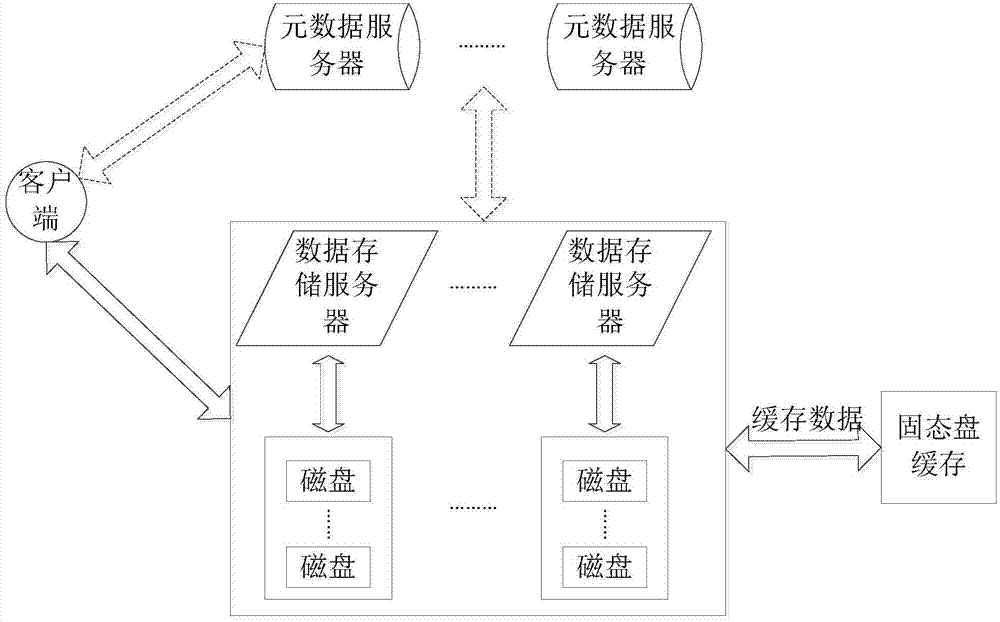
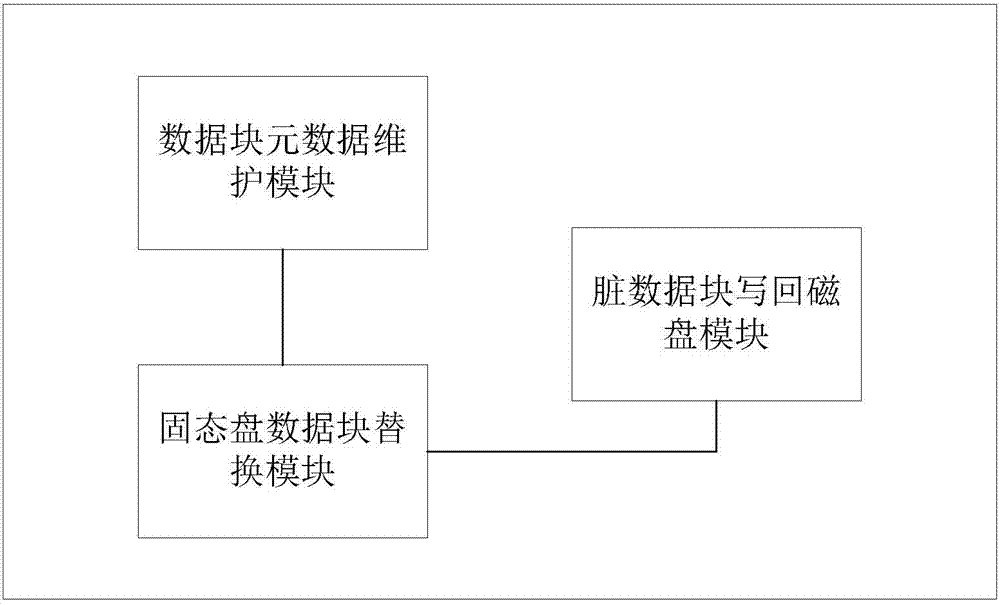
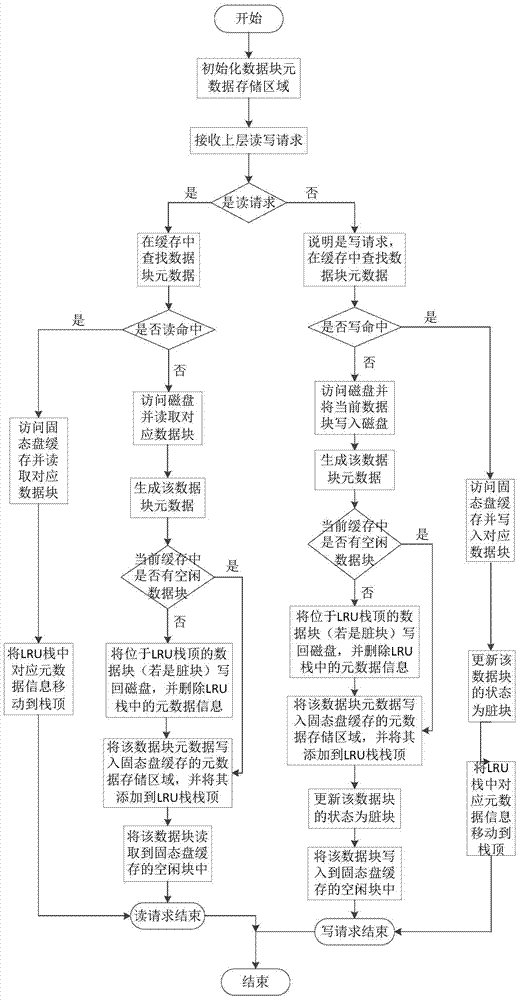
Magnetic disk cache system based on solid-state disk
ActiveCN103885728AImprove read and write performanceLower read latencyInput/output to record carriersMemory adressing/allocation/relocationMagnetic disksDirty data
The invention discloses a magnetic disk cache system based on a solid-state disk and belongs to the technical field of cache systems in computer data storage systems. The magnetic disk cache system based on the solid-state disk comprises a data block metadata maintenance module, a solid-state disk data replacement module and a dirty data block writing-back disk module. According to the magnetic disk cache system based on the solid-state disk, the reading and writing performance of disk data in a large-scale storage environment is improved through the solid-state disk, and the data block reading and writing hit rate and the cache space utilization rate are high; meanwhile, it is guaranteed that data blocks cached under the condition that a computer is restarted due to faults can not be lost easily, the cold-to-hot convergence time of solid-state disk equipment is shortened, and the problems that according to a computer data storage system in the prior art, the cache space is limited, cached data can be lost easily, and the cache space can not be fully utilized can be solved.
Owner:HUAZHONG UNIV OF SCI & TECH
Computer implemented and/or assisted methods and systems for providing guaranteed, specified and/or predetermined execution prices in a guaranteed, specified and/or predetermined timeframe on the purchase or sale of, for example, listed options
ActiveUS20060069636A1Lower Level RequirementsImprove execution qualityFinanceComputer scienceTime windows
Owner:CITADEL INVESTMENT GROUP
Database operation method, apparatus and system
InactiveCN101916298AImprove business processing performanceEnhance business service scalabilitySpecial data processing applicationsMessage queueData operations
The embodiment of the invention relates to a database operation method, which mainly comprises the steps that: an interfere-level database proxy is responsible for receiving data operation requests from a variety of application businesses, caches the obtained data operation requests in a message queue, and sends the data operation requests according to the sequence of the message queue to a selected target next-level database proxy so as to perform corresponding database processing. The embodiment of the invention also provides an apparatus and a system corresponding thereto. Thus, the data operation requests are cached and the target next-level database proxy is selected from one or a plurality of next-level database proxies to perform database processing, the processing of a plurality of data operation requests can be performed simultaneously, equalization for access load of distributed databases can be achieved, business processing ability of the databases is enhanced, business service expandability of the databases is strengthened, and normal performance of the processing of the data operation requests is ensured in order to enhance the safety of database operation.
Owner:深圳市领航创展实业有限责任公司
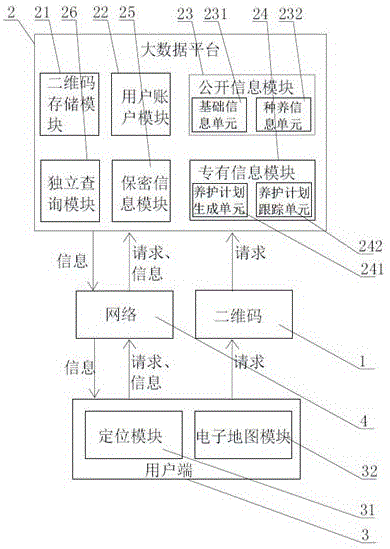
Plant management system and method for garden and landscape engineering based on two-dimensional codes
InactiveCN105844408AImprove confidentialitySolve the problem of limited display contentResourcesRecord carriers used with machinesAgricultural engineeringLandscape engineering
The invention discloses a plant management system and method for garden and landscape engineering based on two-dimensional codes. The system comprises: nameplates which are provided with two-dimensional codes and are fixed on trees for identifying the trees; a big data platform which is provided with configuration software and is used for receiving, processing, storing and outputting tree information corresponding to the two-dimensional codes; multiple user sides which are provided with configuration software and two-dimensional code scanning function, and are used for reading tree information in the big data platform through different permissions and / or scanning two-dimensional codes, inputting tree information into the big data platform and downloading applications from the big data platform; and a network which is used for interactive communication between the big data platform and user sides. According to the system and the method, the two-dimensional code technology is combined with the big data platform technology which helps users obtain comprehensive information of trees so that the problem that display content is limited by the limitation of nameplate area is solved; and planter information is kept secret to prevent information leakage.
Owner:SUZHOU GREEN PLANT FULL STACK INFORMATION TECH CO LTD
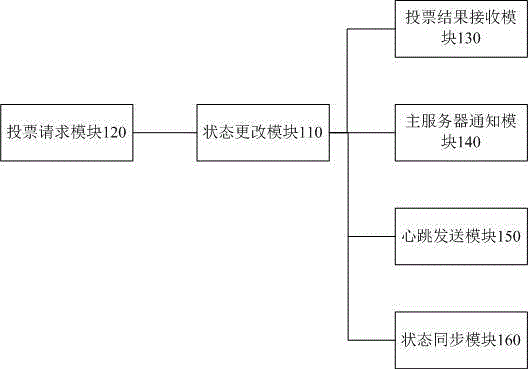
Cluster election method and system
InactiveCN106789197AGuaranteed normal executionImprove availabilityData switching networksHigh availabilityData operations
The invention relates to the field of large data computing, and more specifically relates to a cluster election method and system for large data operations. The method comprises the following steps: when a slave server cannot obtain the heartbeat of a master server, changing the state of the slave server into a candidate server, and sending a voting request of sending the slave server as the master server to the rest servers; when the candidate server receives the votes of the server exceeding a preset threshold number, electing the candidate server as the master server, and changing the state of the candidate server into the master server; when the candidate server waits for the voting result, electing the other servers as the master server, and changing the state of the candidate server into the slave server; and when no candidate server is elected as the master server, sending the voting request again by the candidate server until a candidate server becomes the master server. According to the cluster election method and system, all kinds of application clusters are formed by a distributed voting protocol, so that the system without high availability has high availability.
Owner:GOSUNCN TECH GRP
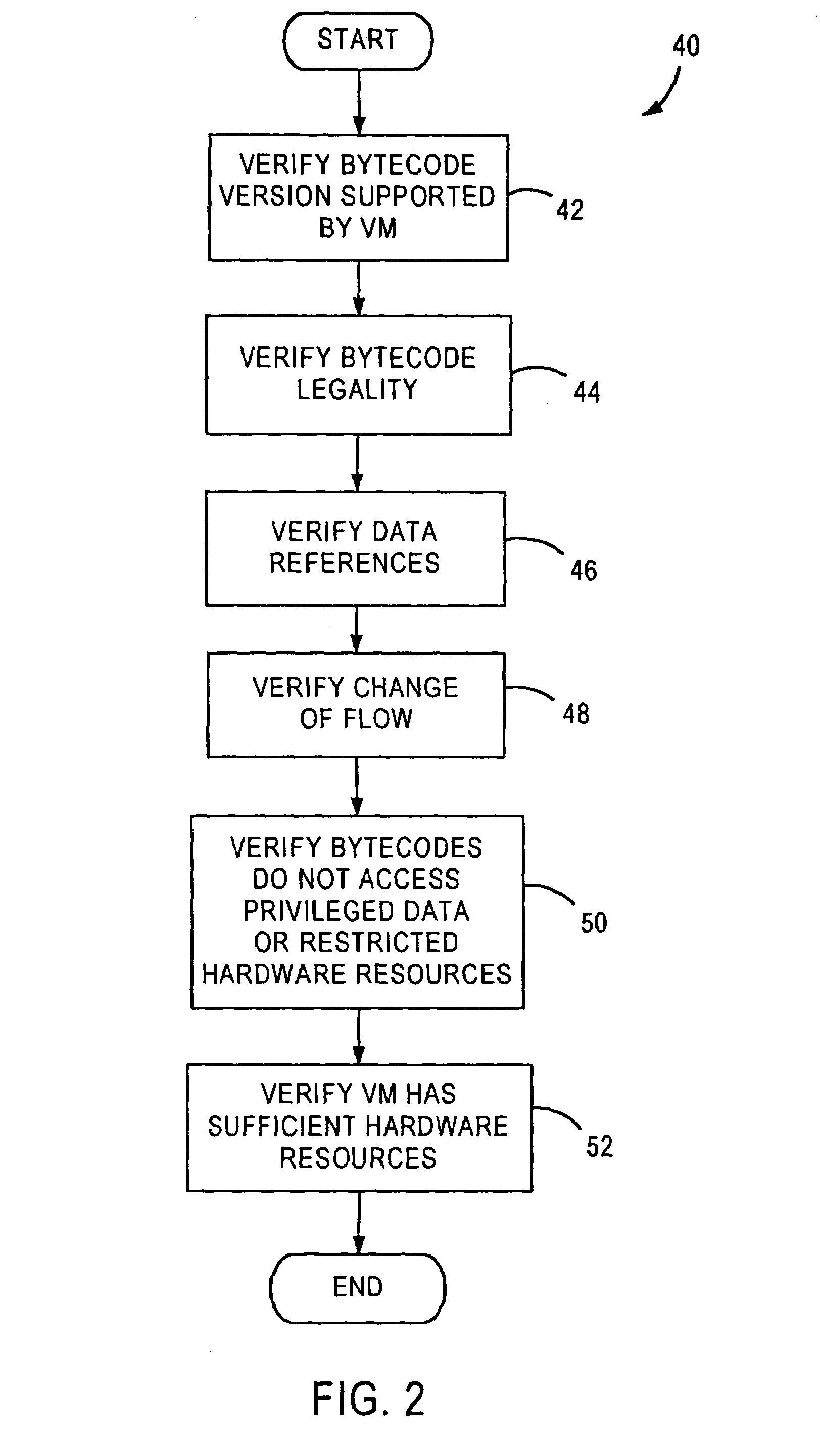
Method, system and devices for transmitting data in streaming media service
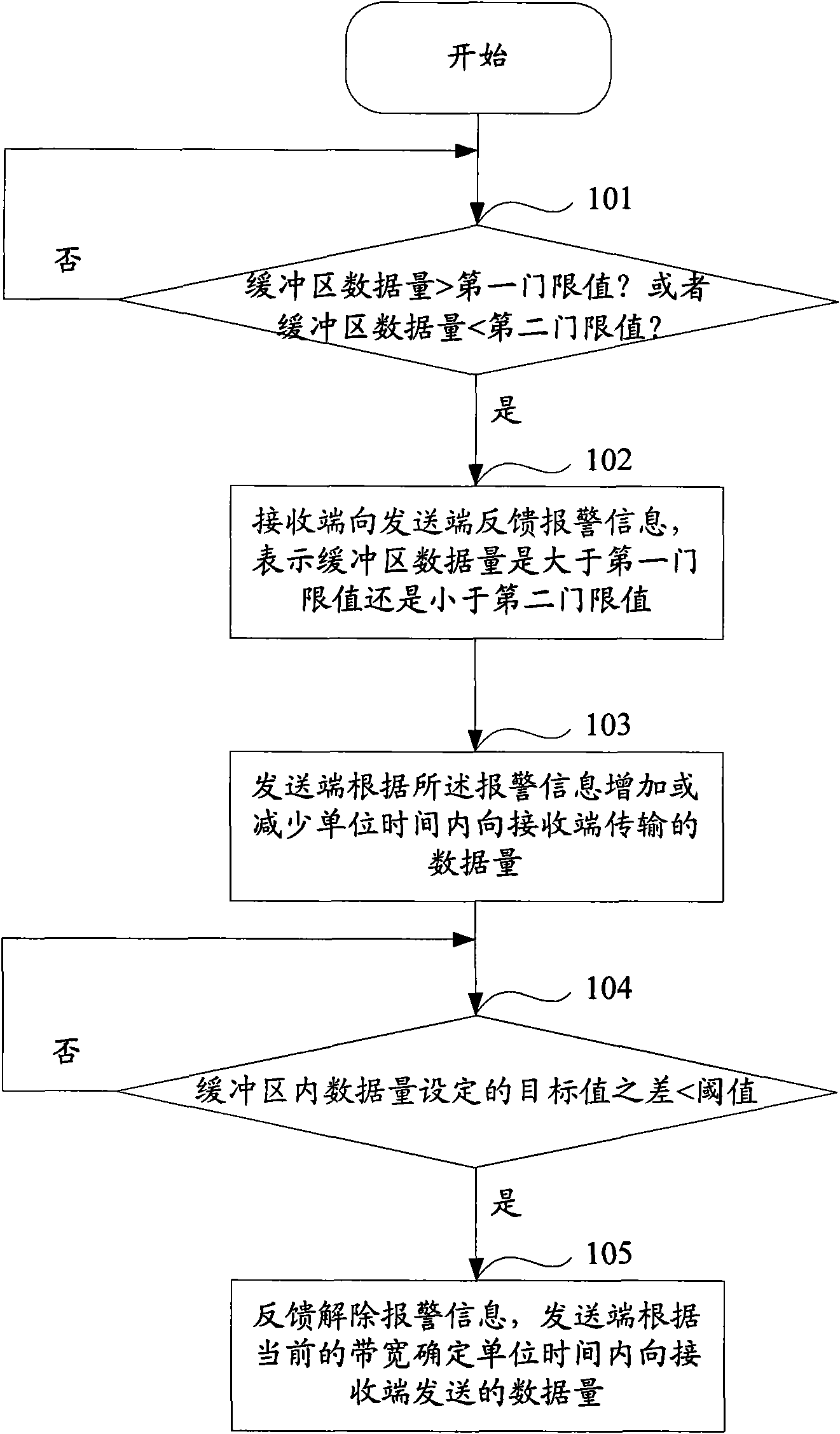
InactiveCN101577672AGuaranteed normal executionQuick responseData switching networksData transmission
The invention discloses a method for transmitting data in streaming media service, which comprises the following steps: detecting data quantity in a buffer area of a current receiving end, and determining that the data quantity is greater than a first threshold or smaller than a second threshold, wherein the first threshold is greater than the second threshold; sending alarm information to a sending end, wherein the alarm information shows that the data quantity in the buffer area is greater than the first threshold or smaller than the second threshold; and adjusting the data quantity transmitted to the receiving end in unit time by the sending end according to the alarm information, and transmitting data according to the adjusted data quantity. The method makes the receiving end and the sending end timely respond to the change of data transmission quantity caused by the change of the quality of network channels so as to ensure the normal execution of the streaming media service. The invention also discloses a system for transmitting data in streaming media service, a data sending device and a data receiving device.
Owner:CHINA MOBILE COMM GRP CO LTD
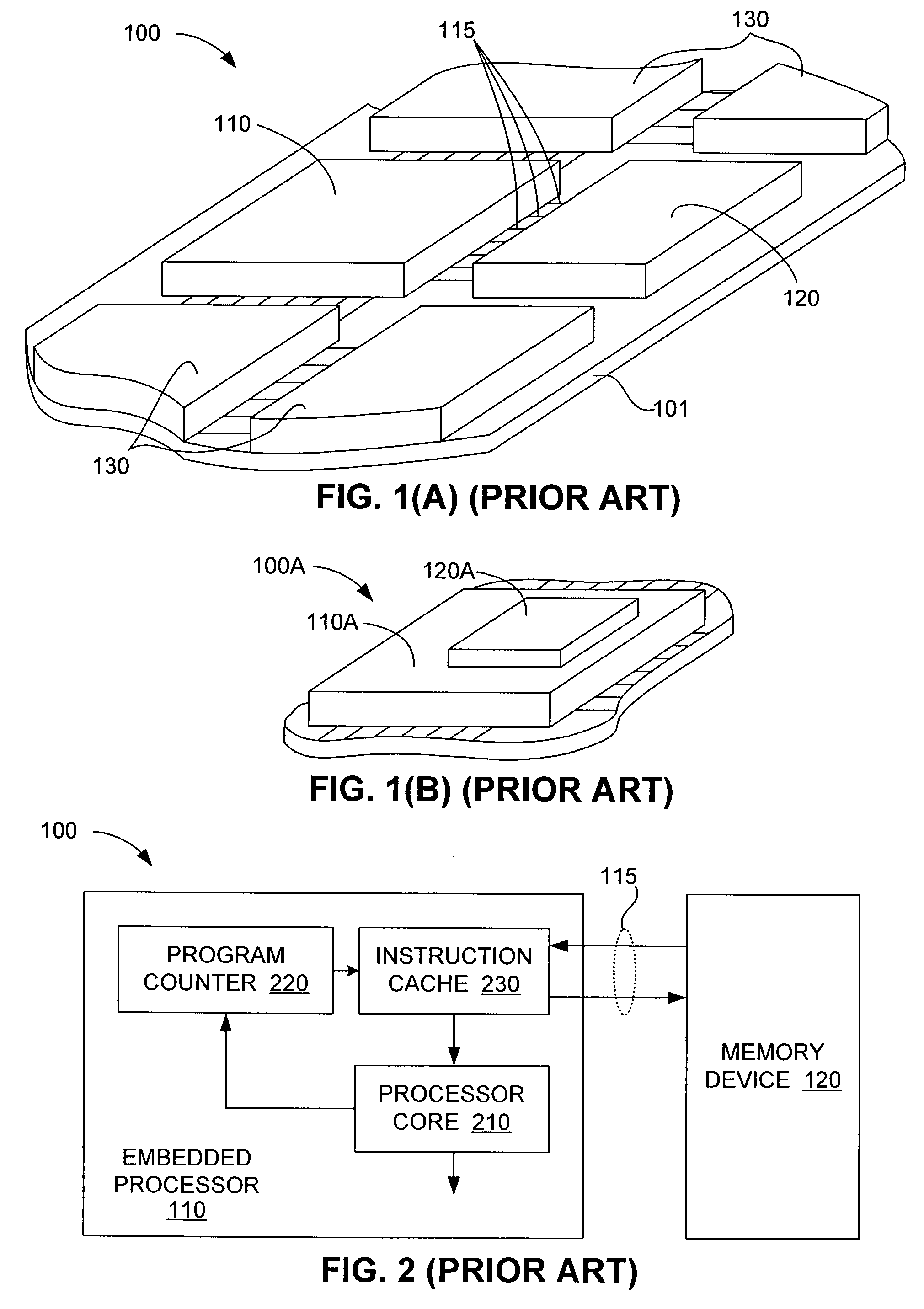
Multi-threaded embedded processor using deterministic instruction memory to guarantee execution of pre-selected threads during blocking events
ActiveUS7062606B2Increase processor efficiencyIncreasing costMemory architecture accessing/allocationEnergy efficient ICTInstruction memoryExternal storage
A multi-threaded embedded processor that includes an on-chip deterministic (e.g., scratch or locked cache) memory that persistently stores all instructions associated with one or more pre-selected high-use threads. The processor executes general (non-selected) threads by reading instructions from an inexpensive external memory, e.g., by way of an on-chip standard cache memory, or using other potentially slow, non-deterministic operation such as direct execution from that external memory that can cause the processor to stall while waiting for instructions to arrive. When a cache miss or other blocking event occurs during execution of a general thread, the processor switches to the pre-selected thread, whose execution with zero or minimal delay is guaranteed by the deterministic memory, thereby utilizing otherwise wasted processor cycles until the blocking event is complete.
Owner:INFINEON TECH AG
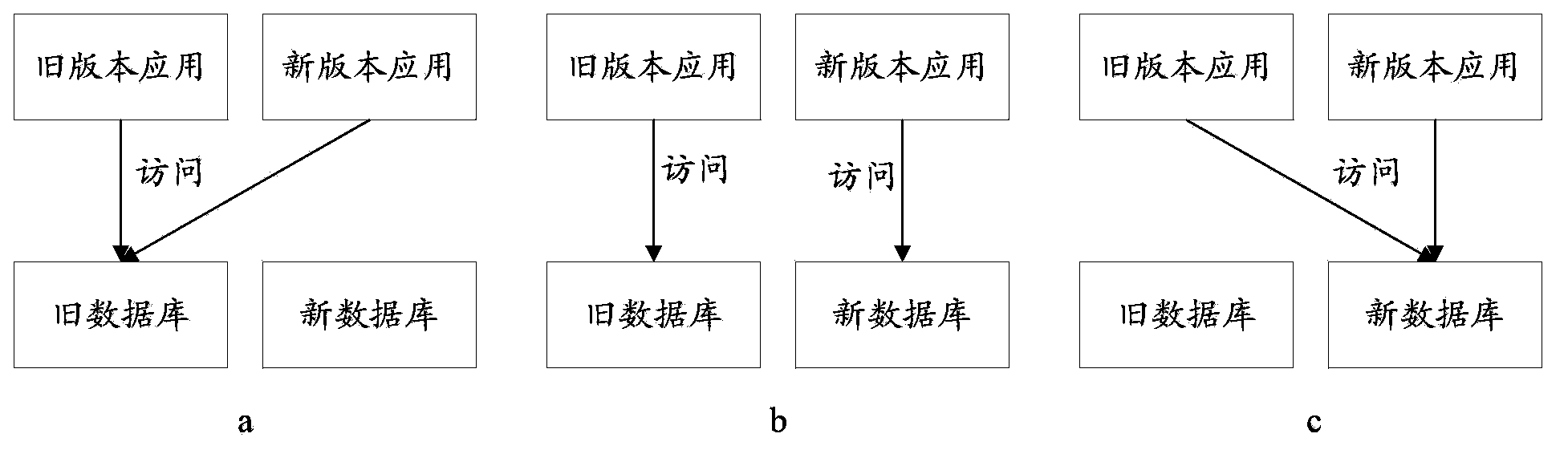
Data on-line migration method and device for updating applications in network platform
The invention provides a data on-line migration method and device for updating applications in a network platform in order to solve the problem that services fail to be executed in the prior art. The method includes the steps that at the first stage of updating, a new version application and an old version application are run simultaneously, and the new version application and the old version application have access to an old database in the running process; the first stage of updating is finished, data in the old database are all synchronized to a new database, the second stage of updating is carried out, the new version application and the old version application are run simultaneously, the new version application has access to the new database in the running process, and the old version application has access to the old database; the second stage of updating is finished, the third step stage of updating is carried out, the new version application and the old version application are run simultaneously, and the new version application and the old version application have access to the new database in the running process; when the third stage of updating is finished, the new version application is run, and the new version application has access to the new database in the running process.
Owner:ADVANCED NEW TECH CO LTD
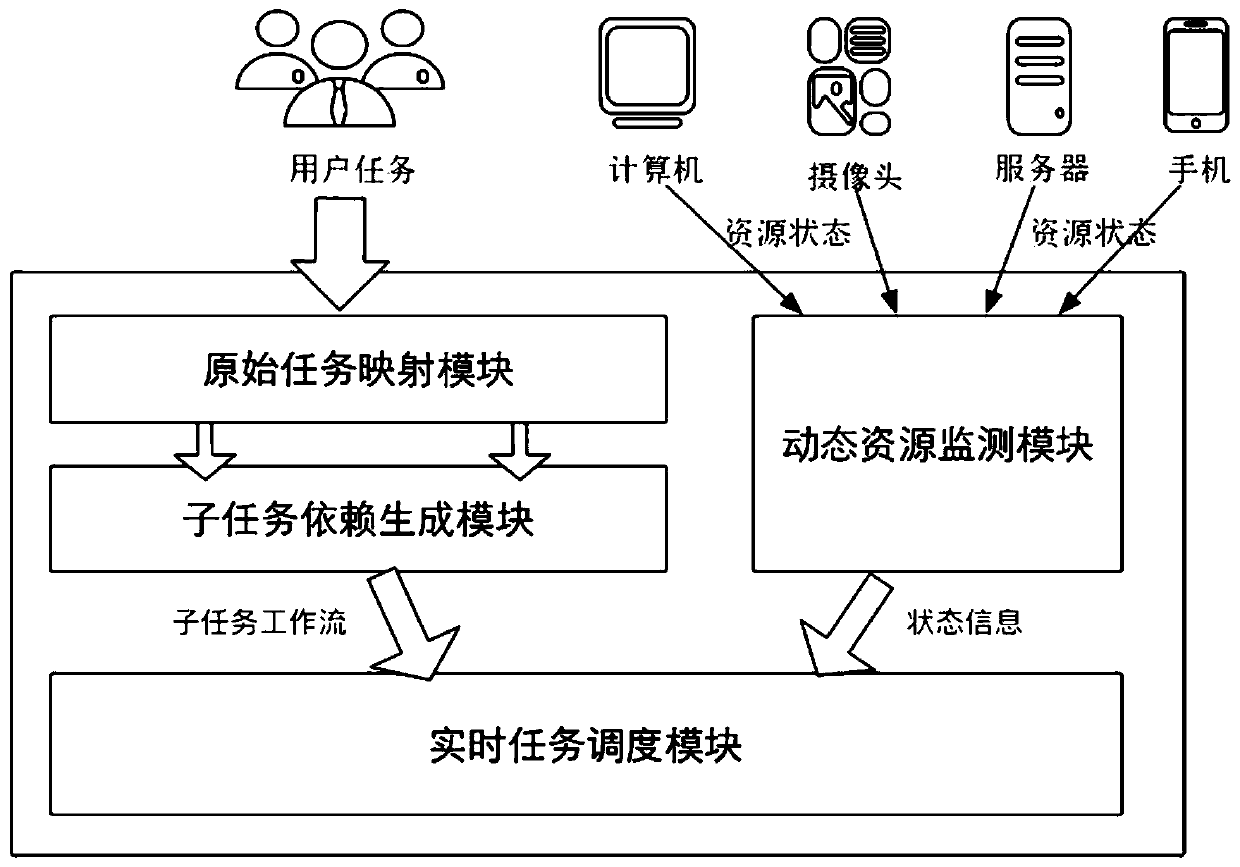
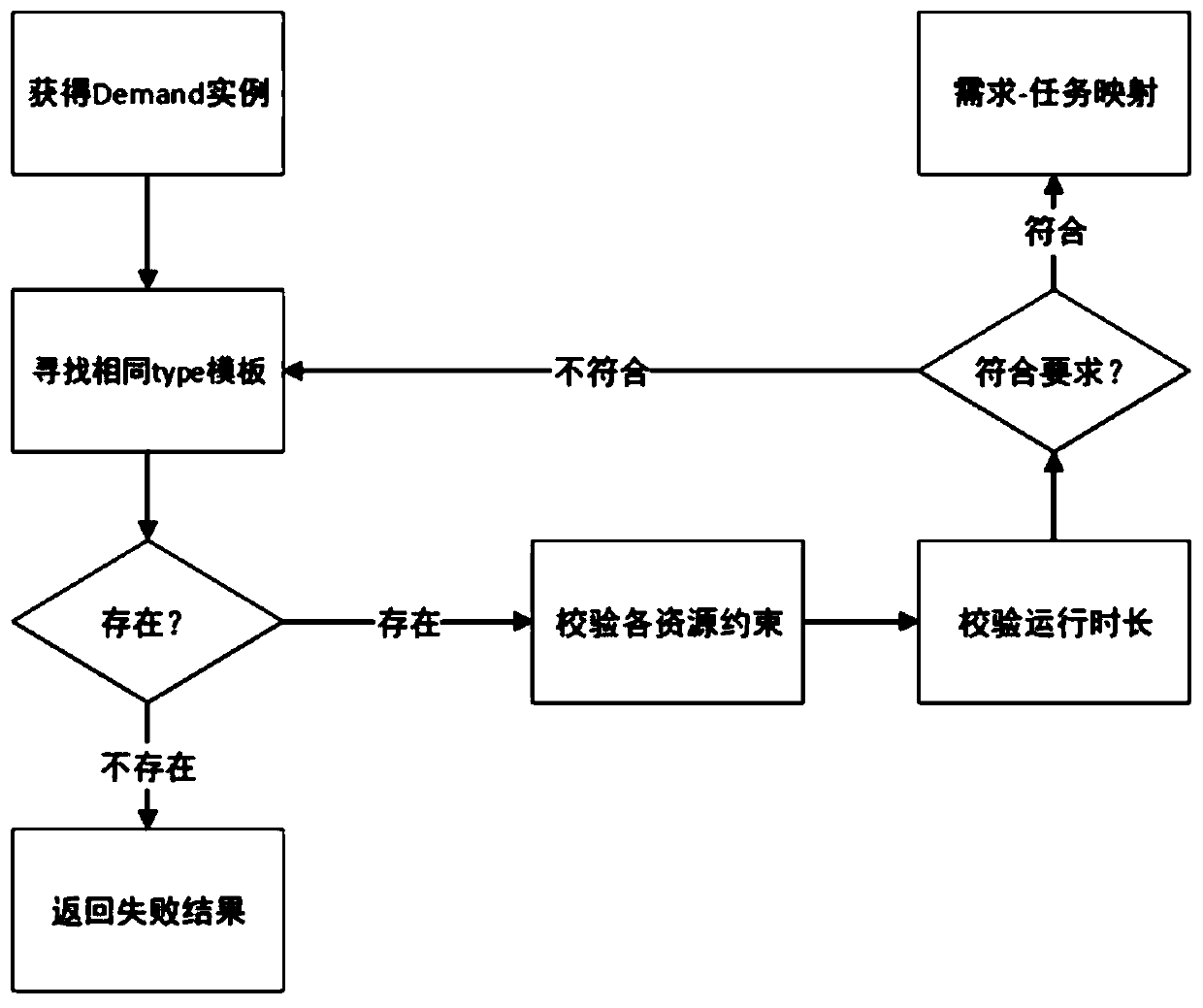
Real-time task matching scheduling system and method based on resource monitoring in edge computing
ActiveCN111427681AGuaranteed normal executionTake advantage ofResource allocationTask analysisUser needs
The invention provides a real-time task matching scheduling system and method based on resource monitoring in edge computing. The method comprises the steps of detecting user demands and then converting the user demands into a task unit set; carrying out sub-task analysis on each task in the task unit set, and integrating and deduplicating the repeated sub-tasks to form a sub-task workflow; monitoring the real-time resource and task state of each edge server; and performing real-time mode matching on the sub-tasks and the edge server, and performing task scheduling according to the sub-task sorting sequence and the task priority. According to the method, the average running time of each task can be minimized as much as possible on the basis of ensuring normal execution of the task and meeting corresponding limiting conditions in an environment of multiple edge servers, and meanwhile, each resource can be more fully utilized, so that dynamic high-throughput low-delay task response is provided for task matching scheduling.
Owner:SHANGHAI JIAO TONG UNIV
Application task processing method, device and system
ActiveCN107491346AGuaranteed normal executionReasonable useProgram initiation/switchingTerminal systemReal-time computing
The invention provides an application task processing method, device and system. The method comprises the following steps of: storing background tasks of an application in a task queue; monitoring whether the application is located in an idle state or not; and when the fact that the application is located in the idle state is monitored, triggering a preset task thread to execute the tasks stored in the task queue according to a serial execution manner. According to the method, device and system provided by the invention, an application-idle task processing mechanism is proposed for the application lag problem caused by multiple tasks, so that the application starting performance and processing performance can be effectively improved. Aiming at the characteristic that terminal system resources are limited, a manner of serially executing background tasks by using single threads is proposed, so that the normal execution of the background tasks is ensured, the terminal system resources can be reasonably utilized, and the influences on foreground tasks of applications are decreased as much as possible when the background tasks are executed.
Owner:ALIBABA GRP HLDG LTD
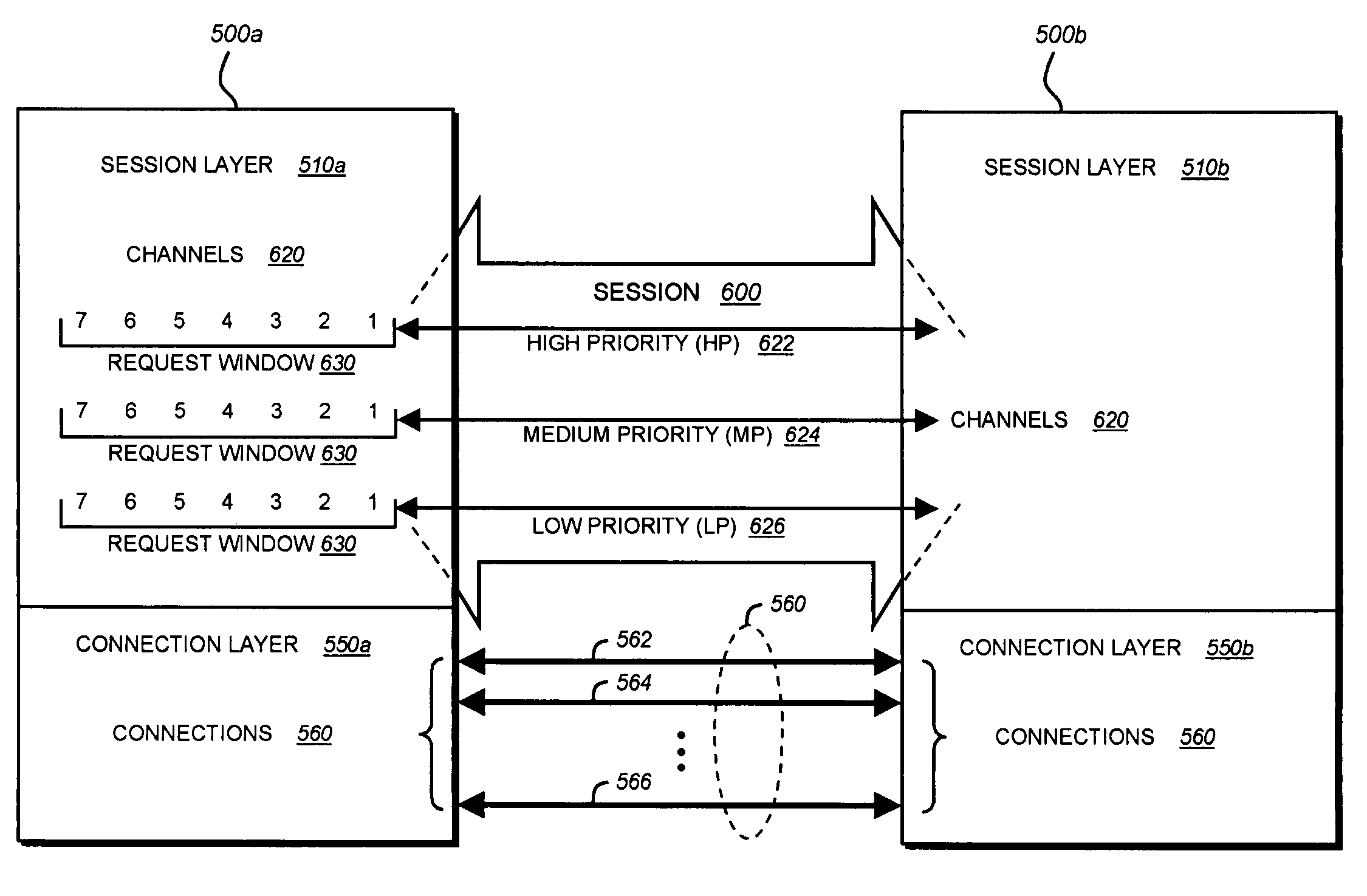
System and method for multiplexing channels over multiple connections in a storage system cluster
ActiveUS7443872B1Guaranteed normal executionTime-division multiplexData switching by path configurationNetworking protocolData access
A system and method multiplexes channels over multiple connections between one or more nodes. Each node includes a cluster fabric interface module adapted to implement a novel network protocol that enables intra-cluster communication among the nodes. The network protocol is a multi-layered protocol that integrates a session infrastructure and an application operation set into a session layer. The network protocol is illustratively a request / response protocol wherein a node (requester) receiving a data access request from a client redirects that request to another node (responder) that services the request and, upon completion, returns a response.
Owner:NETWORK APPLIANCE INC
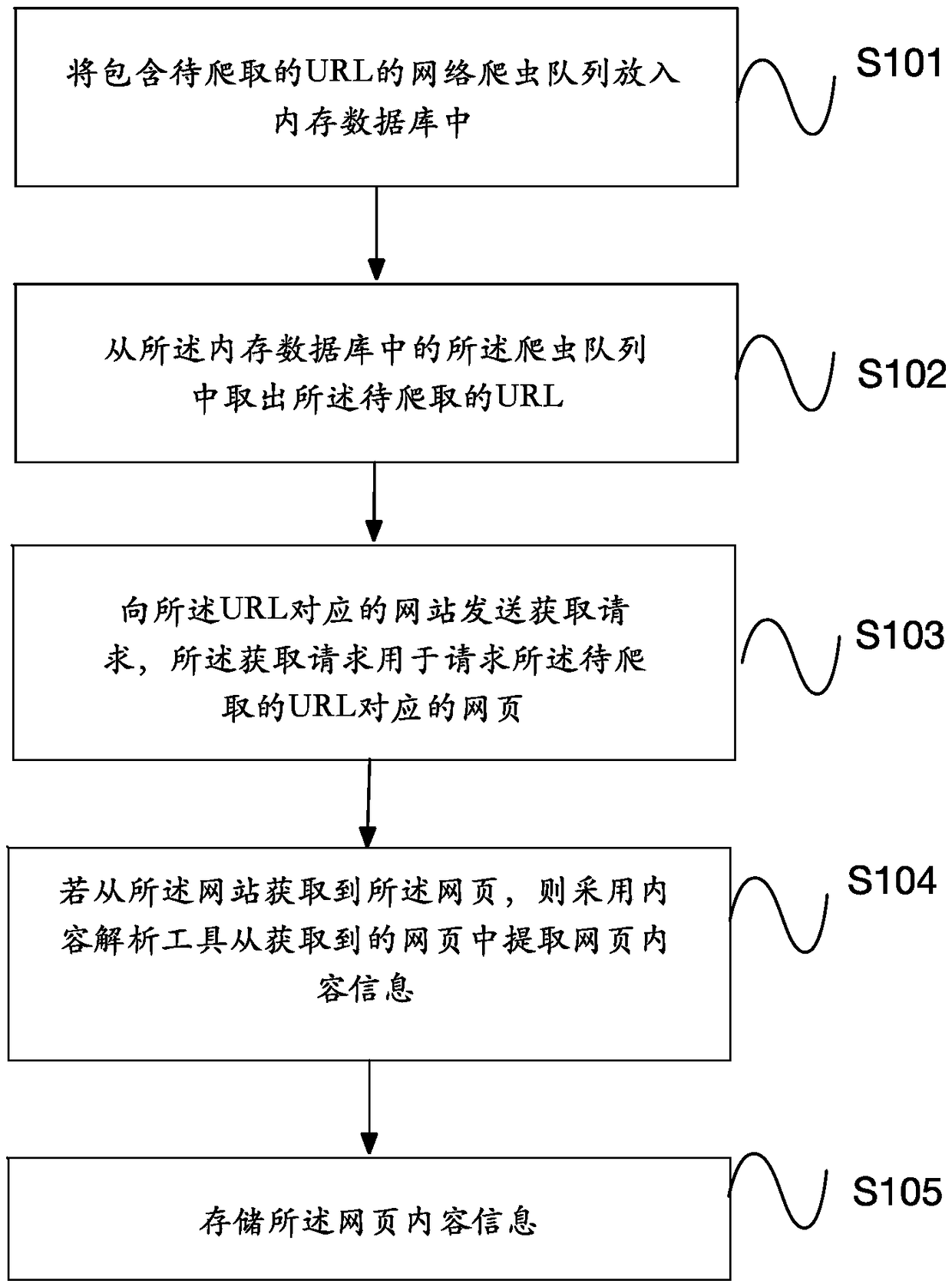
Method and device for obtaining web page information, and computer-readable medium
PendingCN109033195AFast readGuaranteed normal executionSpecial data processing applicationsIn-memory databaseAnalysis tools
It is an object of the present application to provide a method and device for obtaining web page information, and a computer-readable medium By putting the network crawler queue containing the UniformResource Locator (URL) to be crawled into the in-memory database before web page collection, the invention avoids the problem that the URL stored in the memory will disappear when the network crawlersystem needs to be restarted, and can ensure that after the network crawler system is restarted, the URL to be crawled can be quickly read from the network crawler queue of the memory database, and the normal execution of the network crawler system can be ensured. By adopting the content analysis tool to extract the web page content information from the obtained web page, the web page content iscleaned, and finally the web page content information is stored, and the web page content information is put into the warehouse, thereby improving the obtaining efficiency and reliability of the web page content information.
Owner:SHANGHAI SHENGPAY E PAYMENT SERVICE CO LTD
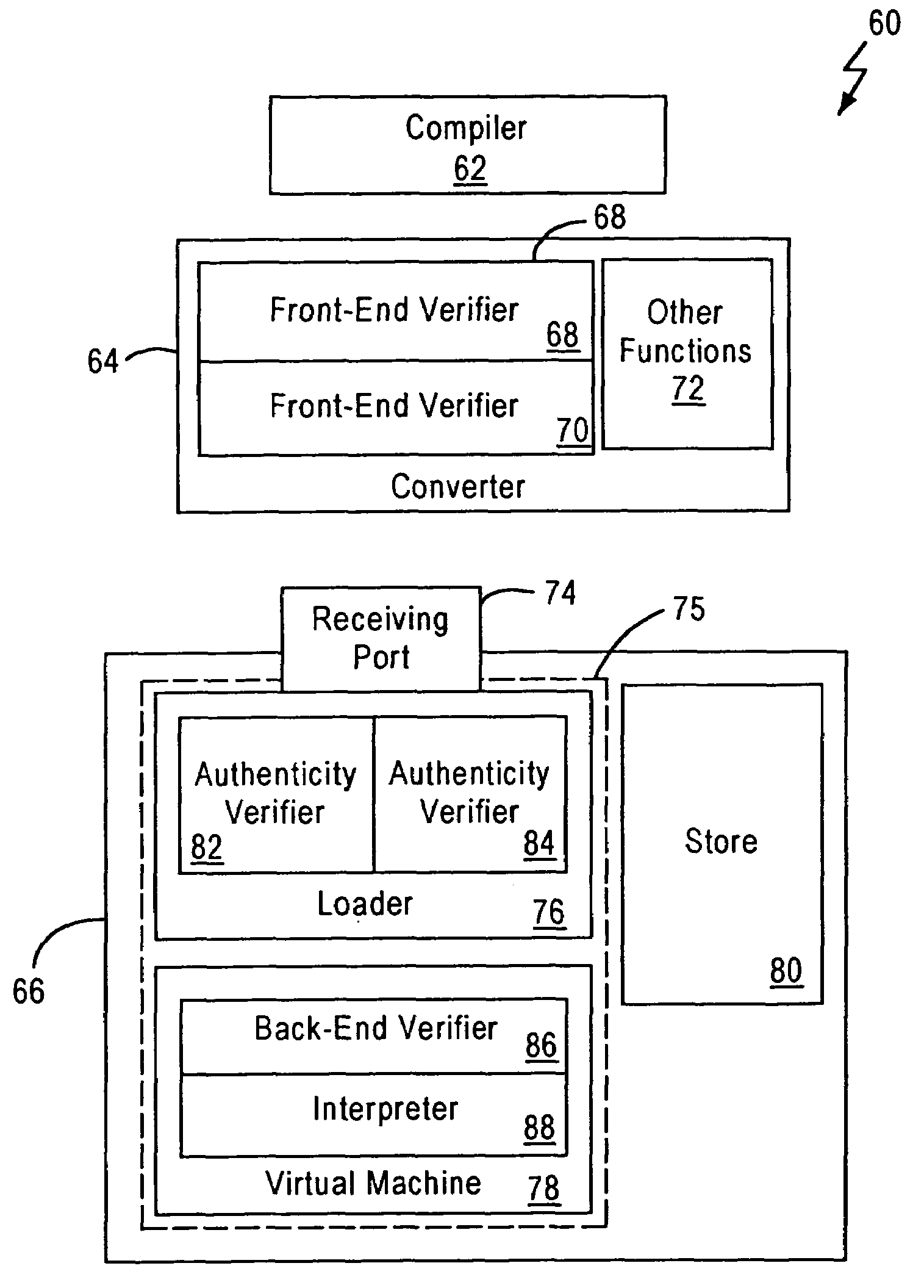
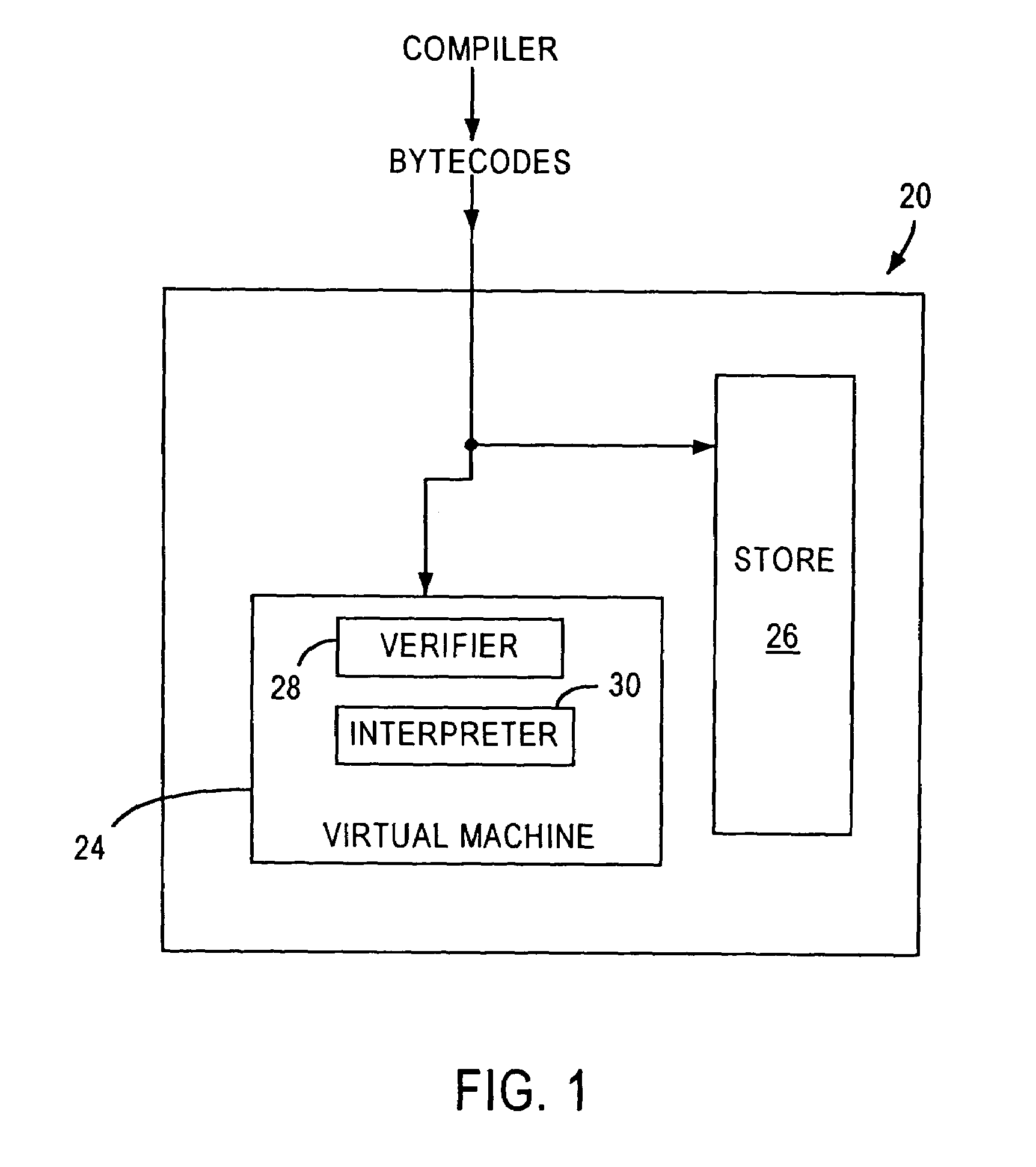
Virtual machine with securely distributed bytecode verification
InactiveUS7334136B2Reduce memory sizeImprove processing speedDigital data processing detailsUnauthorized memory use protectionApplication softwareComputing systems
A system for executing a software application comprising a plurality of hardware independent bytecodes is provided comprising a computing system that generates bytecodes, a virtual machine, remote to the computing system, that receives a plurality of bytecodes from said computing system, and executes said plurality of bytecodes, a system for testing said bytecodes against a set of predetermined criteria in which the testing is securely distributed between said virtual machine and said computing system so that the bytecode verification completed by the computing system is authenticated by the virtual machine prior to the execution of the bytecodes by said virtual machine. A method for distributed bytecode verification is also provided.
Owner:ORACLE INT CORP
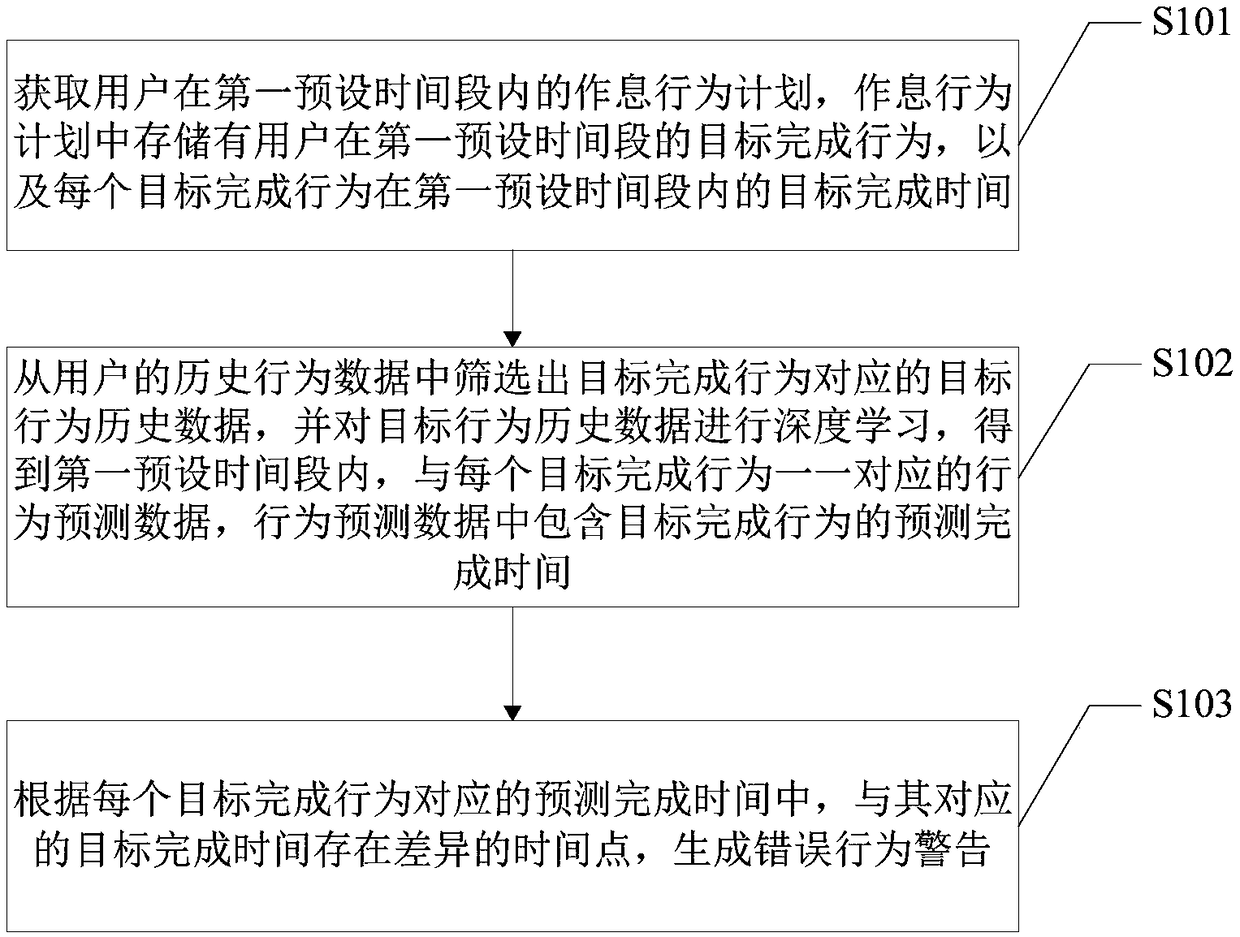
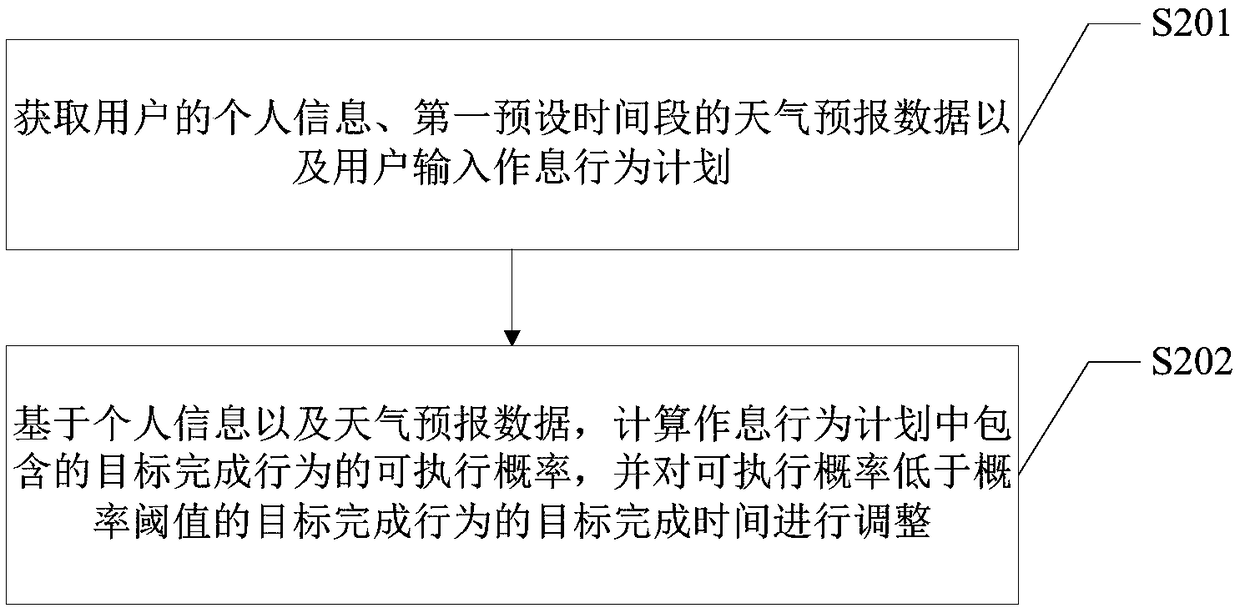
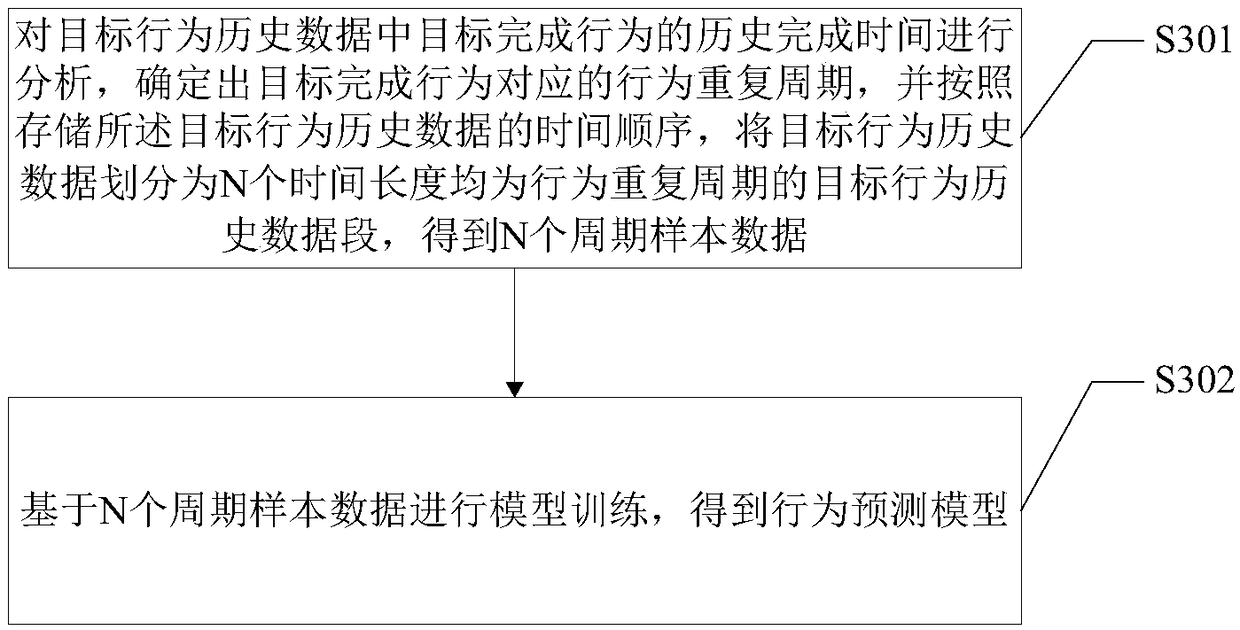
User behavior prompt generation method and terminal device
ActiveCN108876284AGuaranteed normal executionHigh degree of intelligenceForecastingOffice automationCompletion timeSimulation
The invention provides a user behavior prompt generation method and a terminal device and is applicable to the technical field of data processing. The method comprises the following steps: obtaining aschedule of work and rest behaviors of a user during a first preset time period; screening out target historical behavior data corresponding to a target completion behavior from the historical behavior data of the user, and performing deep learning on the target historical behavior data to obtain behavior prediction data corresponding to each target completion behavior in the first preset time period, wherein the behavior prediction data comprises a prediction completion time of the target completion behavior; and generating an error behavior warning according to the time point at which the target completion time corresponding to each target completion behavior differs from the prediction completion time corresponding to the target completion behavior. According to the embodiment of the invention, the purpose of intelligently providing behavior suggestions for the work and rest of the user according to the actual situation of the user is realized, and the intelligence degree of an application program is greatly improved.
Owner:PING AN TECH (SHENZHEN) CO LTD
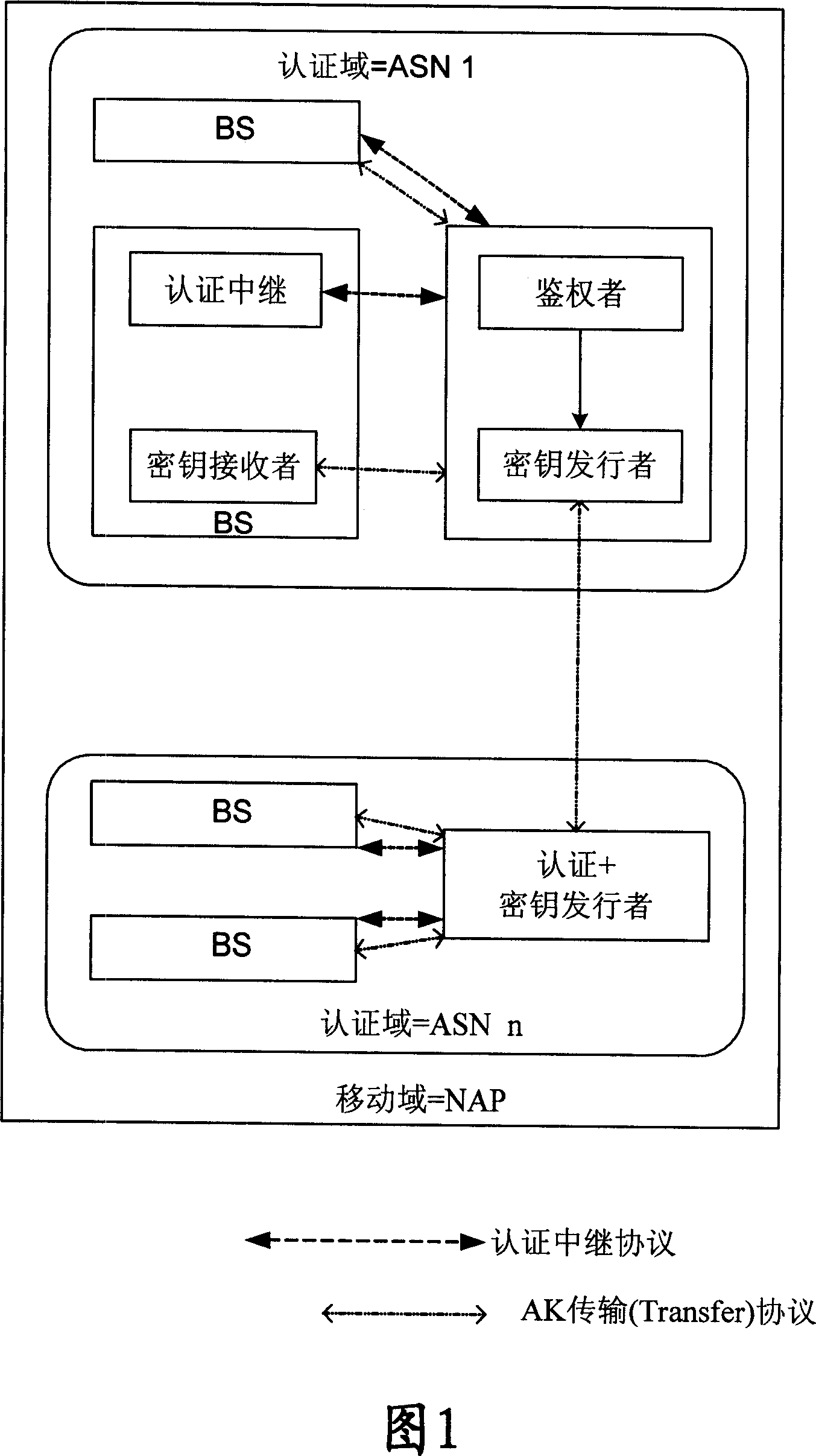
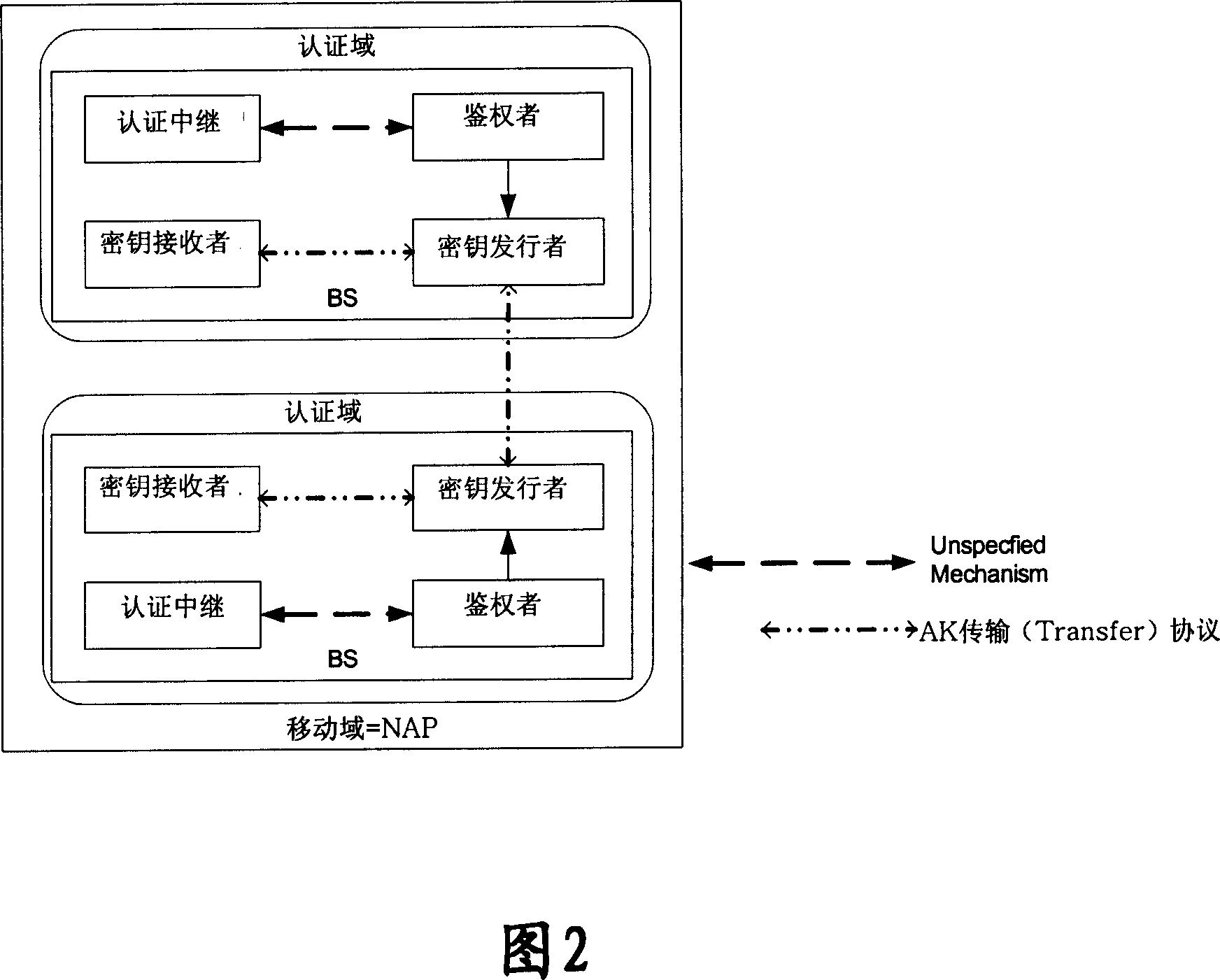
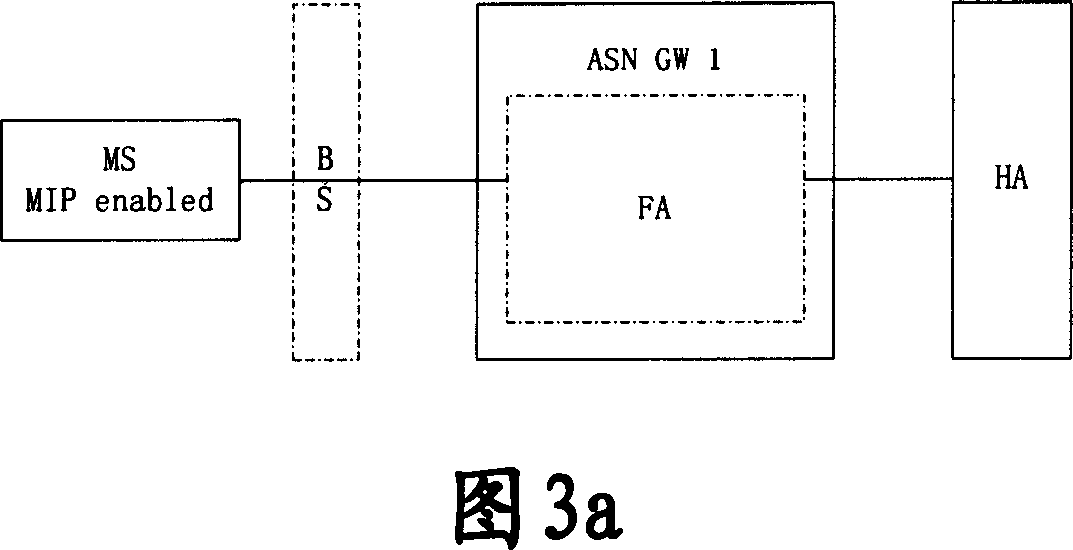
Generation and distribution method and system of mobile IP secret key after second authentication
ActiveCN101079705AGuaranteed normal executionUser identity/authority verificationRadio/inductive link selection arrangementsDistribution methodMobile IP
The invention discloses a generating and distributing method of mobile IP key after reidentifying and recognizing, which comprises the following steps: the terminal and identification authorizing charging AAA server generates the main conversation expanding key EMSK in the reidentifying authorizing course; the terminal generates new relative key of mobile joint according to the EMSK, which replaces old mobile joint key; the home agency obtains new mobile IP key from AAA server, which replaces the old mobile IP key; the AAA server hands out key information to anchor identifier which obtains new mobile IP key from external agency according to the key information to transmit to the external agency; the outer agency replaces the old mobile IP key. The invention ensures the execution of MIP register after the reidentifying and authorizing course.
Owner:HUAWEI TECH CO LTD
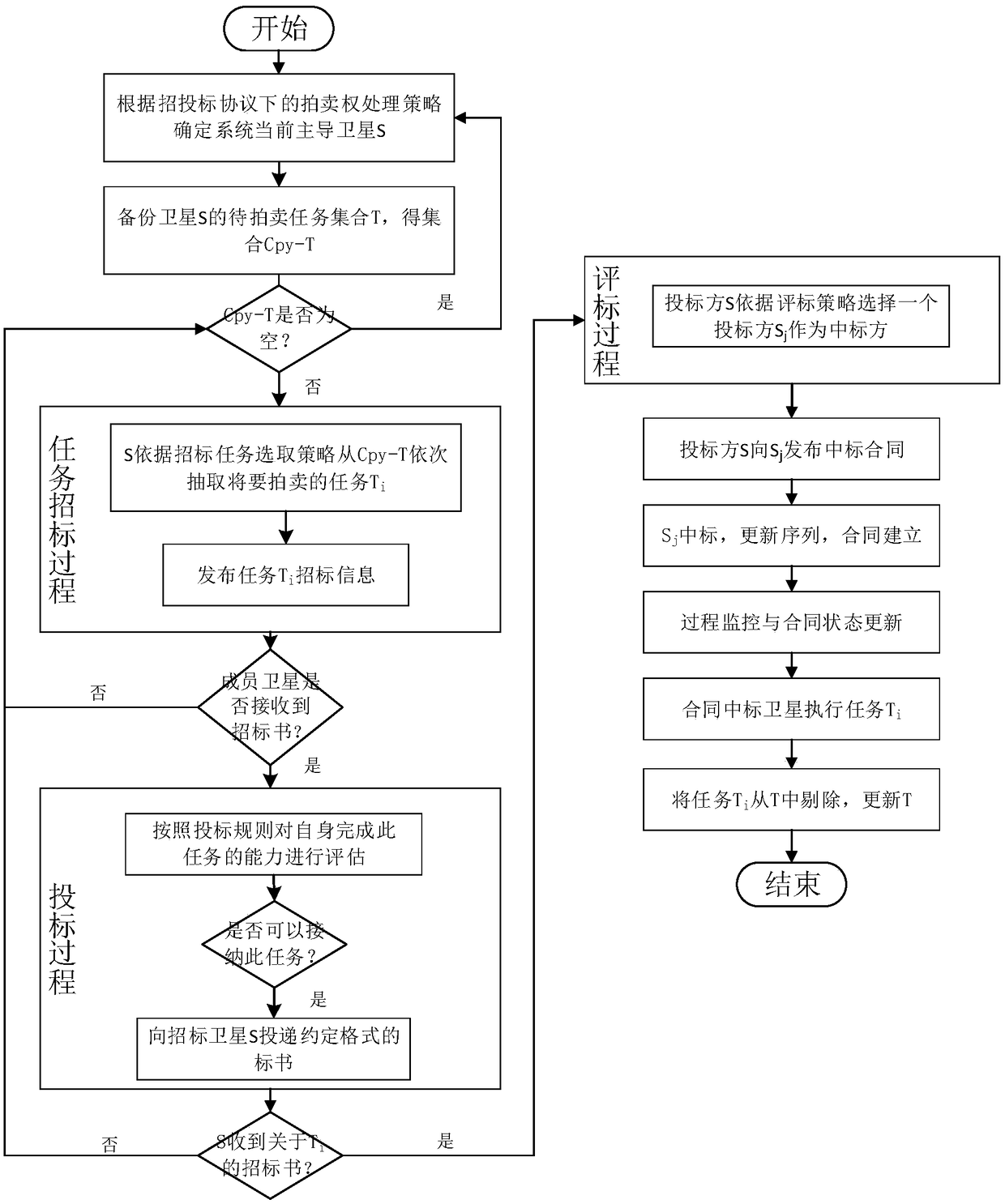
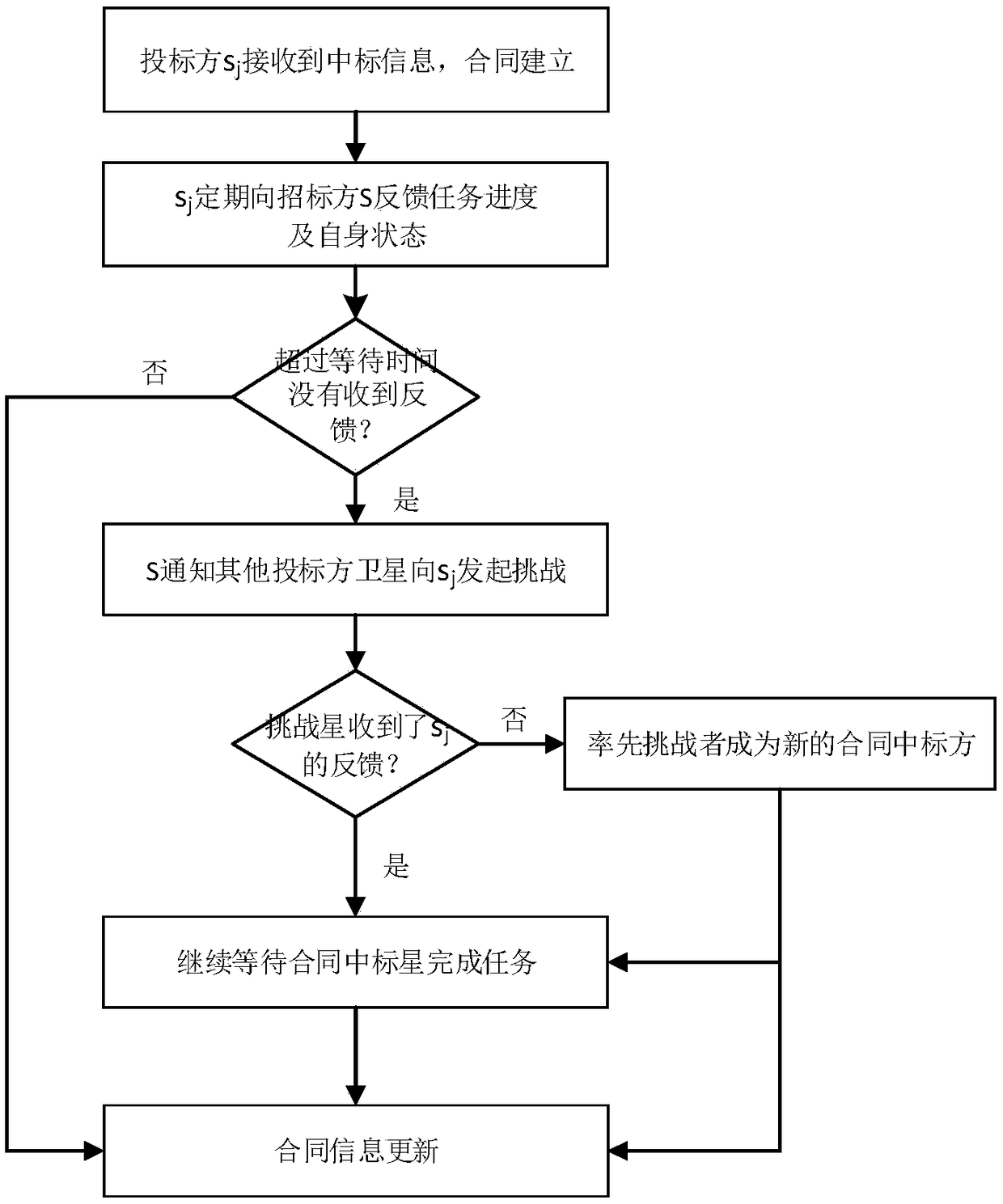
Online dynamic task planning terminal and planning method for medium and low orbit micro satellites
InactiveCN108832989AImprove online planning capabilitiesImprove real-time responseRadio transmissionTransceiverParallel processing
The invention provides an online dynamic task planning terminal and planning method for medium and low orbit micro satellites. The terminal of the invention adopts an online task planning module of aparallel processing structure, and when the satellite maintains communication with a ground measurement and control station, the communication and coordination among multiple satellites, and dynamic task planning are achieved in combination with a Beidou short message transceiver. The method of the invention adopts the form of an auction contract network, and comprises: processing auction rights,selecting a dominant satellite, and selecting the current auction task. The dominant satellite performs bidding on member satellites for the task. A bidder performs task bidding according to an own state. A tenderee completes bidding evaluation according to a bidding evaluation strategy and selects a contract satellite. Contract establishment, and process monitoring and contract information updateare completed, and the contract is terminated after the task is completed. By adoption of the online dynamic task planning terminal and planning method provided by the invention, the online dynamic task distribution and rational planning of a plurality of medium and low orbit micro satellites can be achieved, the efficiency is relatively high, the planning result is feasible, and it has practicalsignificance for improving the on-orbit autonomy and joint planning capability of the micro satellites.
Owner:HARBIN ENG UNIV
Hardware energy-saving processing method and device
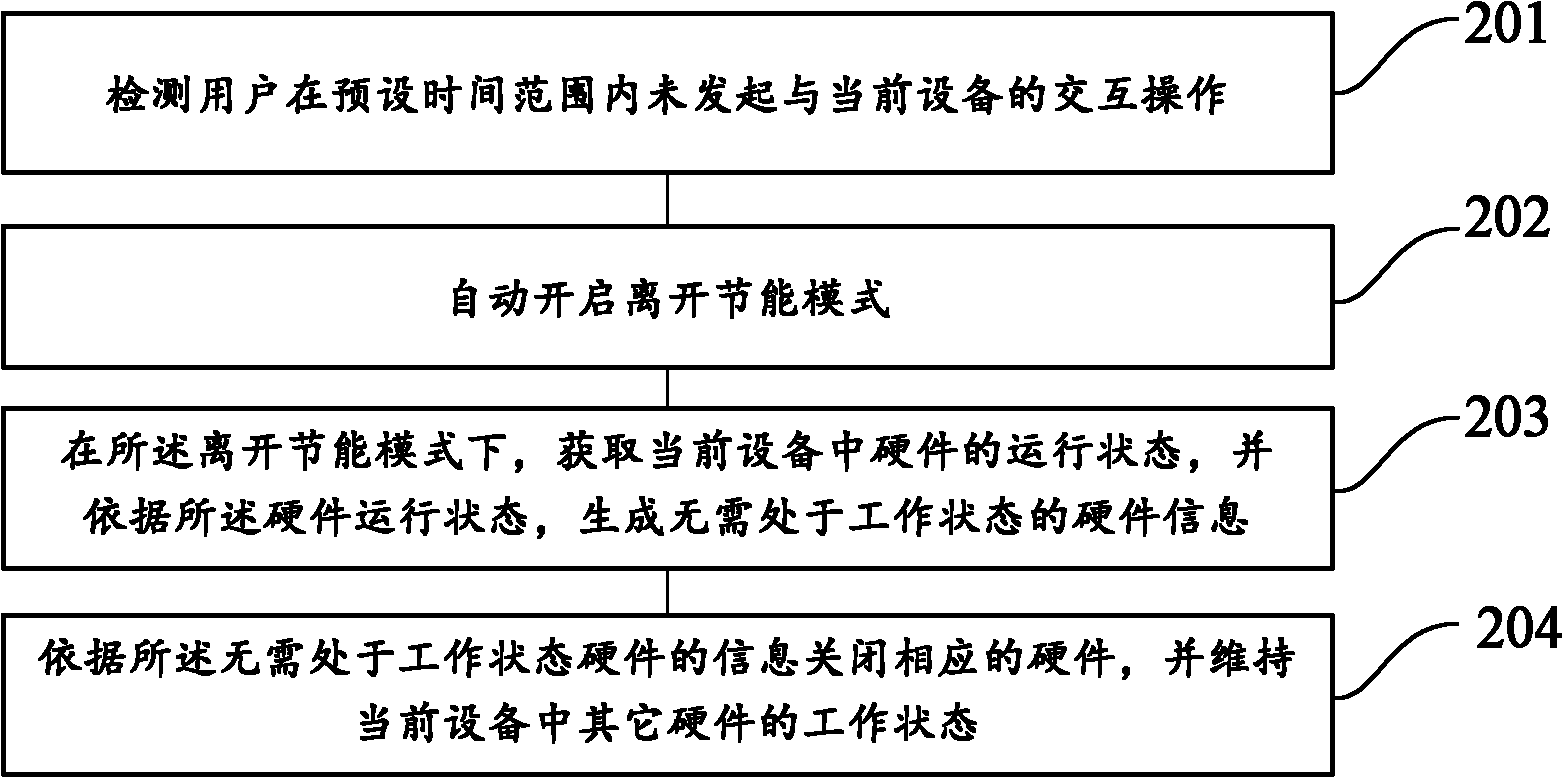
InactiveCN102156534AExtended service lifeGuaranteed normal executionPower supply for data processingWork statusEmbedded system
The invention provides a hardware energy-saving processing method. The method comprises the following steps: starting an off energy-saving mode; in the off energy-saving mode, closing hardware which is unnecessary in a working state in the current equipment, and maintaining the working state of other hardware in the current equipment. By the method and the device, electric energy can be saved as much as possible on the basis of ensuring user task execution.
Owner:QIZHI SOFTWARE (BEIJING) CO LTD
Method and system for controlling transaction amount to enter into account
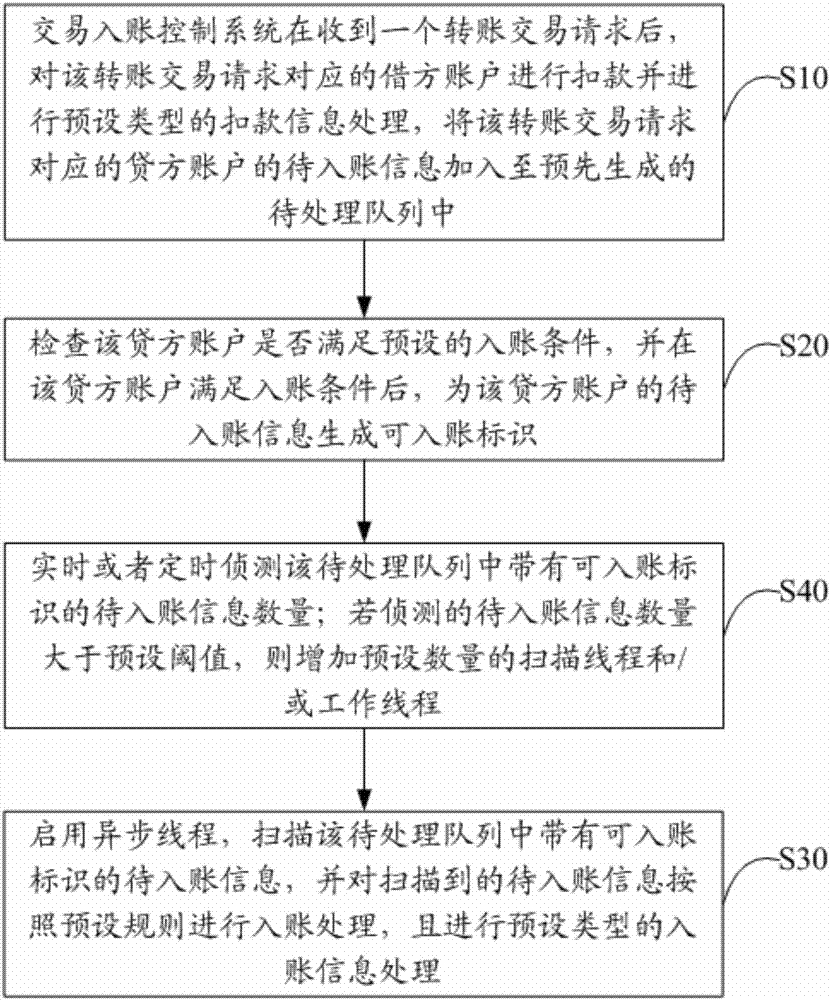
ActiveCN107015869AReduce the pressure of entryGuaranteed normal executionFinanceProgram synchronisationInformation processingControl system
The invention discloses a method and system for controlling a transaction amount to enter into an account. The method includes the steps that after the system for controlling the transaction amount to enter into the account receives a transfer transaction request, deduction and deduction information processing of a preset type are conducted on a debit account corresponding to the transfer transaction request, and pre-entering information of a creditor account corresponding to the transfer transaction request is added into a pending queue which is generated in advance; whether or not the creditor account meets preset entering conditions is inspected, and after the creditor account meets the entering conditions, an enterable identifier for the pre-entering information of the creditor account is generated; asynchronous threads are started, the pre-entering information with the enterable identifier in the pending queue is scanned, entering processing is conducted on the scanned pre-entering information according to preset rules, and entering information processing of the preset type is conducted. By the adoption of the method and system for controlling the transaction amount to enter into the account, the execution speed and handling capacity of transaction are improved, and normal execution of business is ensured.
Owner:PING AN BANK CO LTD
Method for generating and distributing movable IP Key
InactiveCN101075870AGuaranteed normal executionUser identity/authority verificationBroadcastingMobile IP
The method comprises: during authentication process, the authentication, authorization and accounting (AAA) server sends the key information to the anchor authenticator; according to said key information, the authenticator gets the key between the mobile node and the external agent and the key between the external agent and the home agent; when receiving a broadcast message from the external agent, according to the address of the external agent, the terminal figures out the key between the mobile node and the external agent, and triggers the mobile IP registration request; the home agent processes the registration request, and after success of registration, returns the request confirmation; according to ht e received registration confirmation, said terminal gets the address of the home agent, and figures out the key between the mobile node and the home agent.
Owner:HUAWEI TECH CO LTD
Flight navigation method and device and unmanned aerial vehicle
InactiveCN109307510AGuaranteed normal executionHigh precisionNavigational calculation instrumentsForecastingRegional planningComputer science
The embodiment of the invention provides a flight navigation method and device and unmanned aerial vehicle. The flight navigation method is applied to the unmanned aerial vehicle and comprises the steps that first map data and a flight route planned in an operation area in the first map data are obtained; when the unmanned aerial vehicle flies according to the flight route, second map data and theflight position are obtained; the operation area of the first map data is matched with the second map data, so that the flight offset of the flight position deviating from the flight route is calculated; and flight correction is conducted according to the flight offset, and thus the flight position is corrected to the flight route. Deviation brought by positioning in the mode of GPS and the likeis corrected through the relationship between the two map data, the positioning accuracy is improved, the robustness of a system in the unmanned aerial vehicle is improved, thus the probability of deviating from the flight route during flying is decreased, and normal executing of the flight task is ensured.
Owner:GUANGZHOU XAIRCRAFT TECH CO LTD
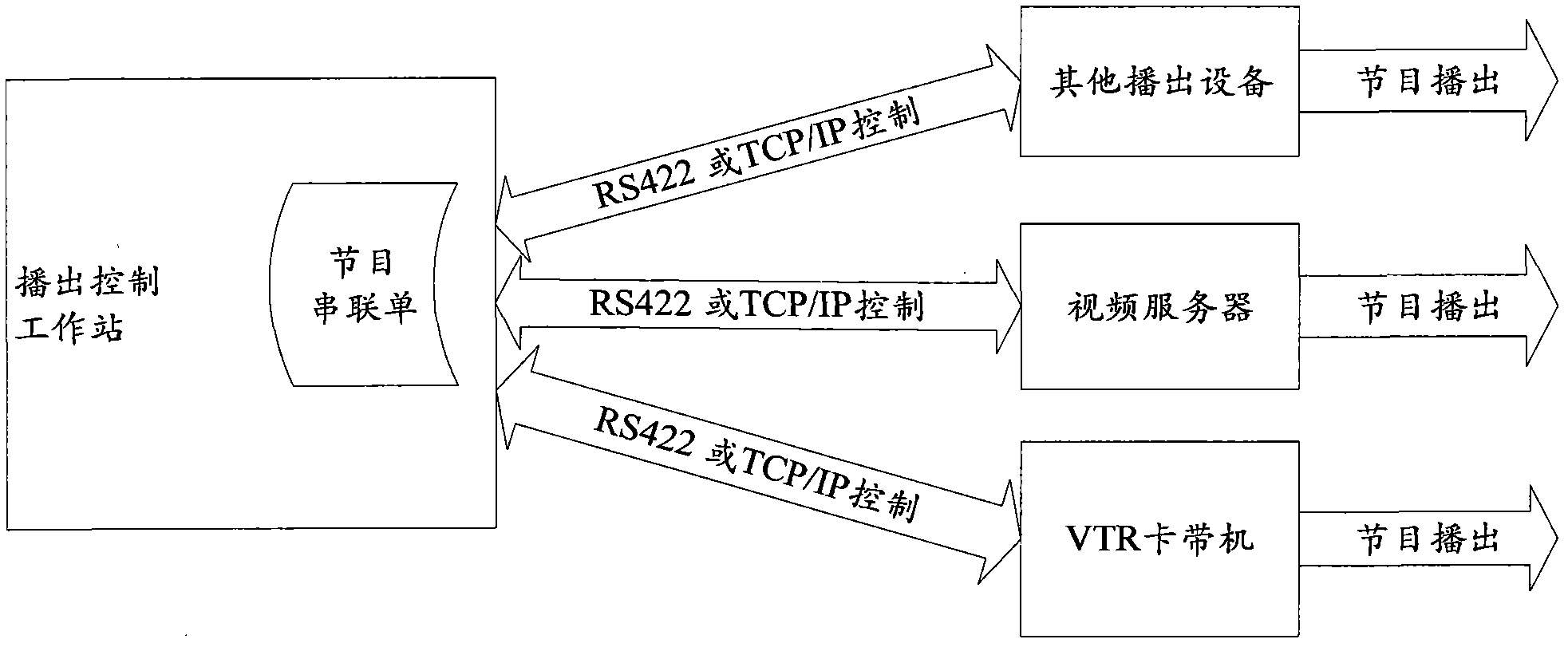
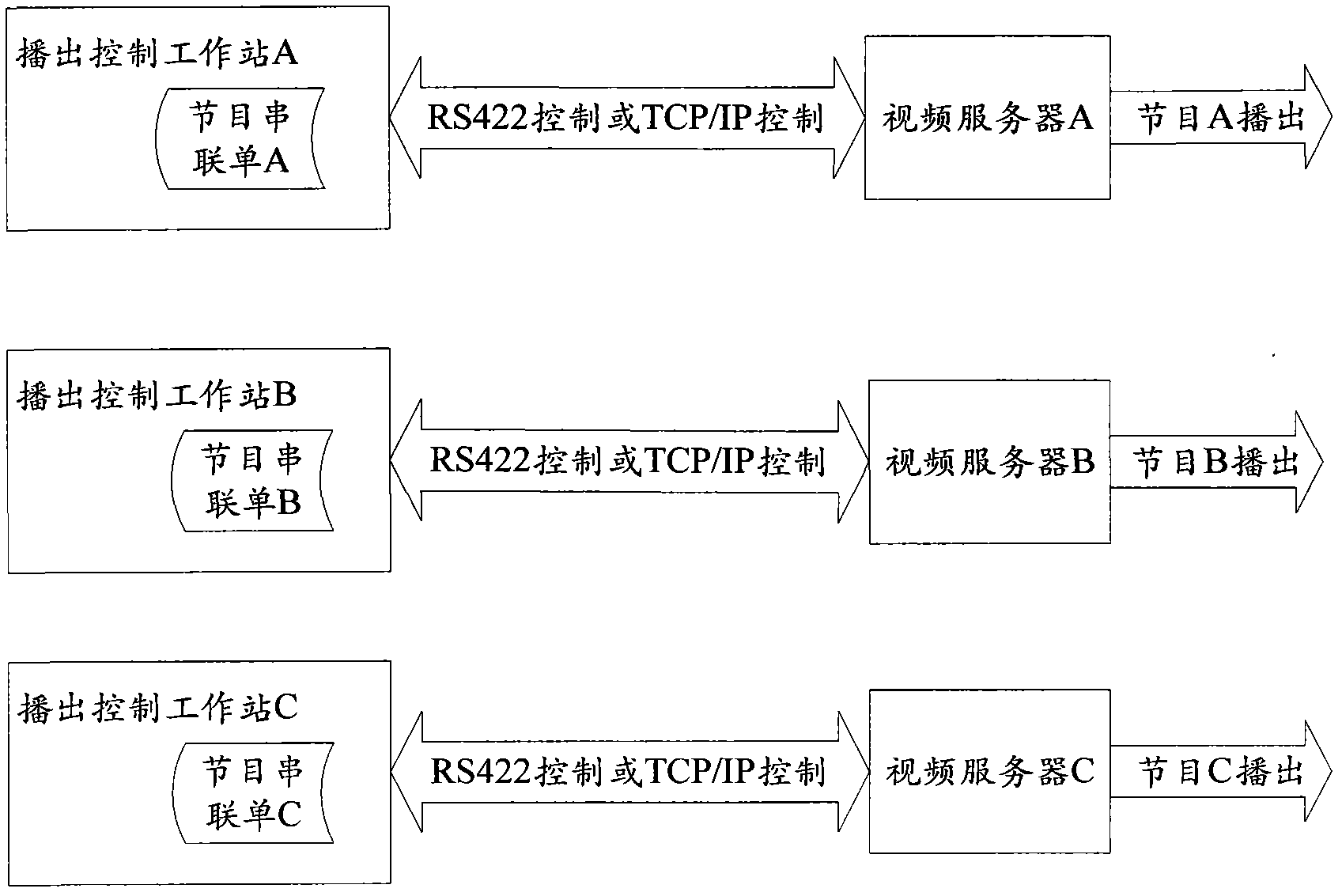
Broadcast control method, device and system for broadcast television
InactiveCN102497498AImprove resource utilizationImprove securityTelevision system detailsColor television detailsControl systemResource utilization
The invention provides a broadcast control system for broadcast television. The system comprises at least one broadcast control workstation, a control server and at least one piece of controlled equipment, wherein the broadcast control workstation sends a command to the controlled equipment through the control server, and receives the state information of the controlled equipment and the state information of a program series list from the control server; the control server is used for controlling corresponding controlled equipment according to the command of the broadcast control workstation, obtaining the state information of the controlled equipment from the controlled equipment, and broadcasting the state of the controlled equipment and the state information of the program series list to the broadcast control workstation; and the controlled equipment is used for broadcasting according to the control of the control server, and sending the self state information to the control server. The invention also provides a control server and a broadcast control method for broadcast television. According to the invention, the resource utilization rate of the broadcast equipment can be improved, and the security of the broadcast control system is enhanced.
Owner:刘少峰
Method, system and device for implementing overload control in packet network
InactiveCN101296177AImprove usabilityGuaranteed normal executionData switching networksOverload controlUsability
The invention discloses a method for realizing overload control in a packet based network, which comprises the steps that: when a server is over loaded, a client end judges whether a current service request received meets preset service request routing conditions or not; if the current service request received meets the preset service request routing conditions, the client end routes the current service request to the server. The invention also discloses a system and a device for realizing overload control in the packet based network. The application of the invention does not means carrying out respective process according to the characteristics of the request instead of not transmitting any request to an overload server simply, thereby promoting the usability of the packet based network. Besides, the invention also ensures that session of urgency priority can be carried out.
Owner:HUAWEI TECH CO LTD
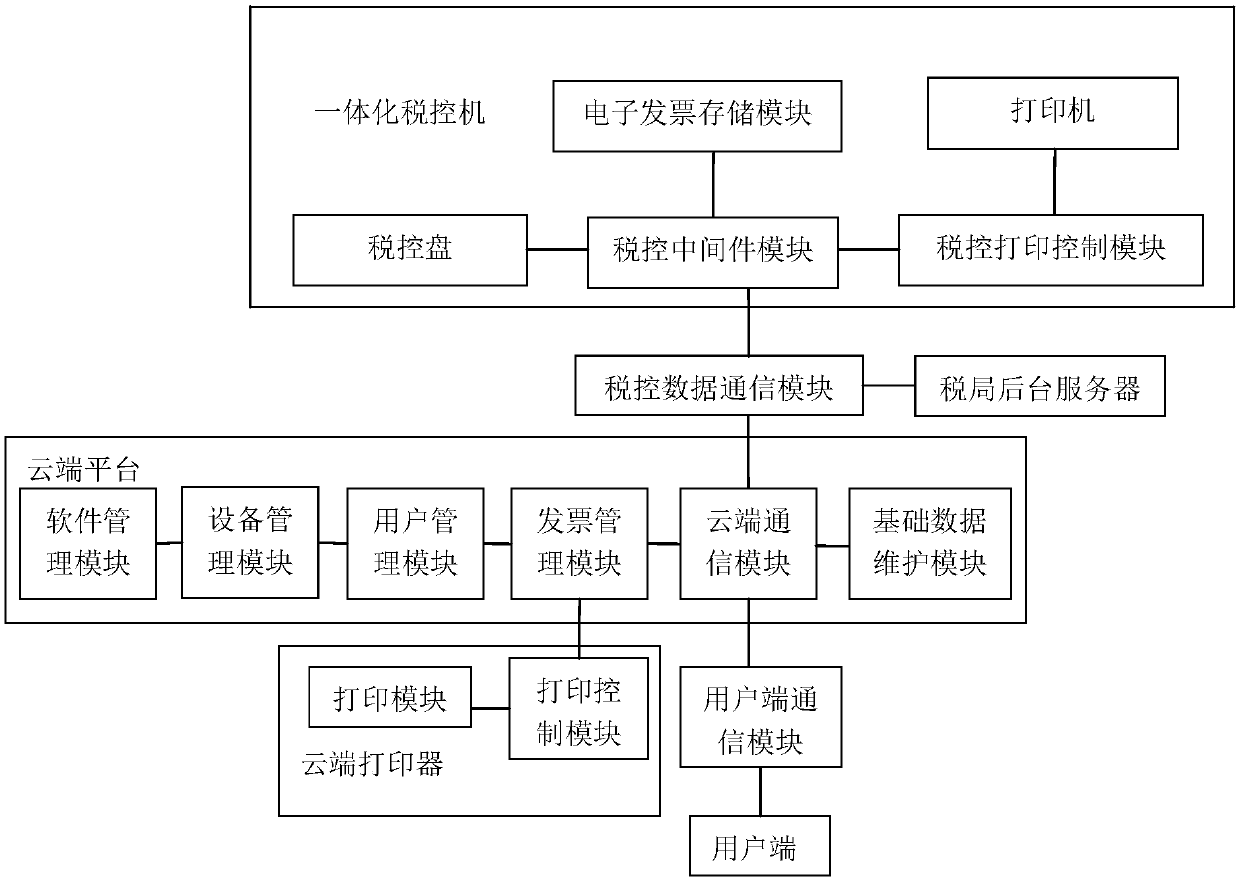
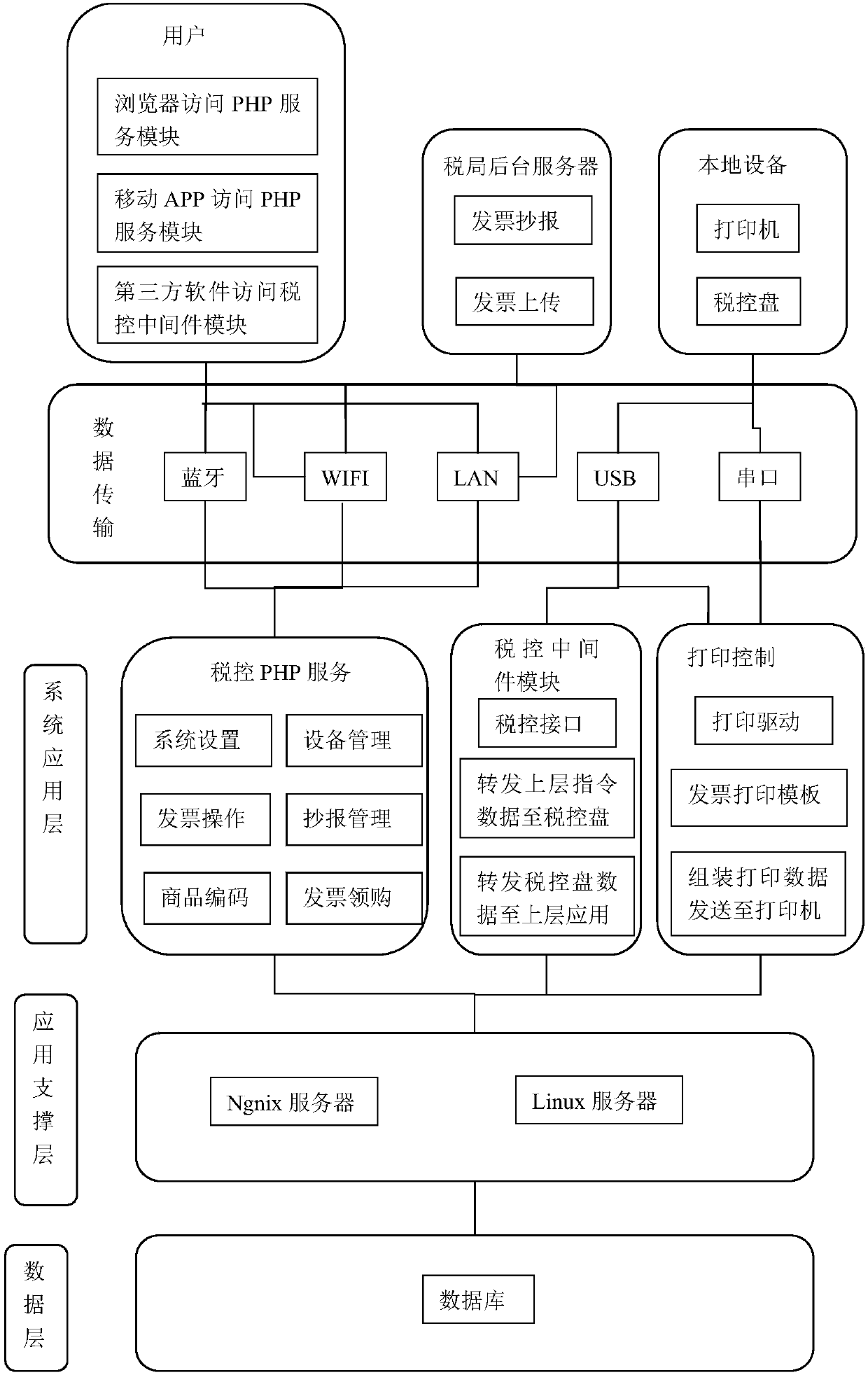
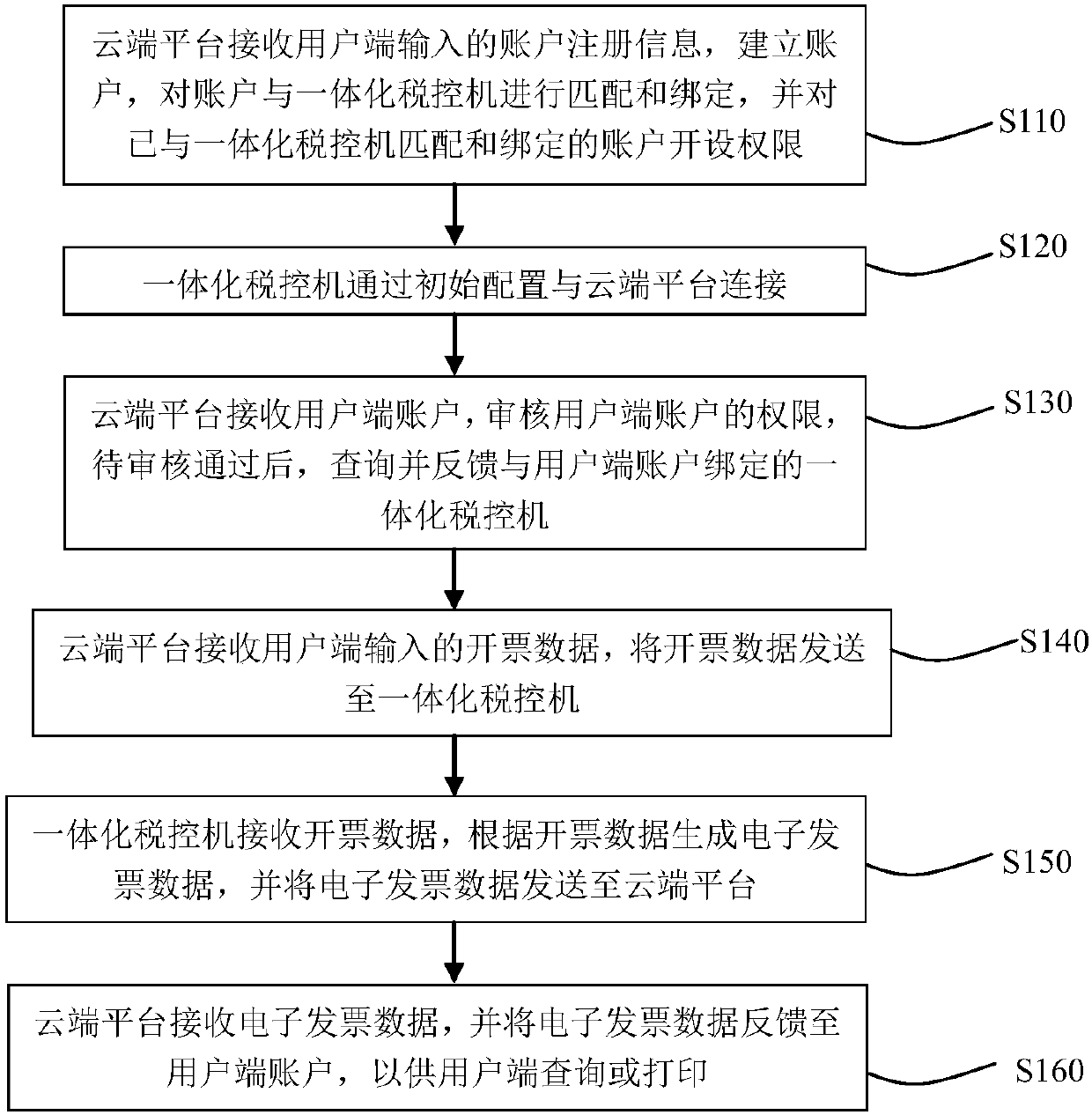
Cloud-side invoicing system and invoicing method based on integrated tax control machine
InactiveCN107784532AImprove applicabilityGuaranteed normal executionBilling/invoicingTransmissionInvoiceElectronic data
The invention relates to a cloud-side invoicing system and invoicing method based on an integrated tax control machine. The cloud-side invoicing system includes a user side, a user-side data communication module, a cloud-side platform and the integrated tax control machine. The user side is used for sending invoicing data to the user-side data communication module. The user-side data communicationmodule is used for receiving the invoicing data and forwarding the invoicing data to the cloud-side platform. The cloud-side platform is used for receiving account registration information input by the user side, creating an account, matching and binding the account with the integrated tax control machine, receiving a user-side account, auditing the permission of the user-side account, querying and linking the integrated tax control machine which is bound with the user-side account after the user-side account passes the audit successfully, receiving the voicing data and sending the voicing data to the tax control data communication module. The tax control data communication module is used for receiving the voicing data and forwarding the data to the integrated tax control machine. The integrated tax control machine is used for receiving the voicing data sent by the tax control data communication module and generating electronic data invoices according to the invoicing data.
Owner:百望金赋科技有限公司
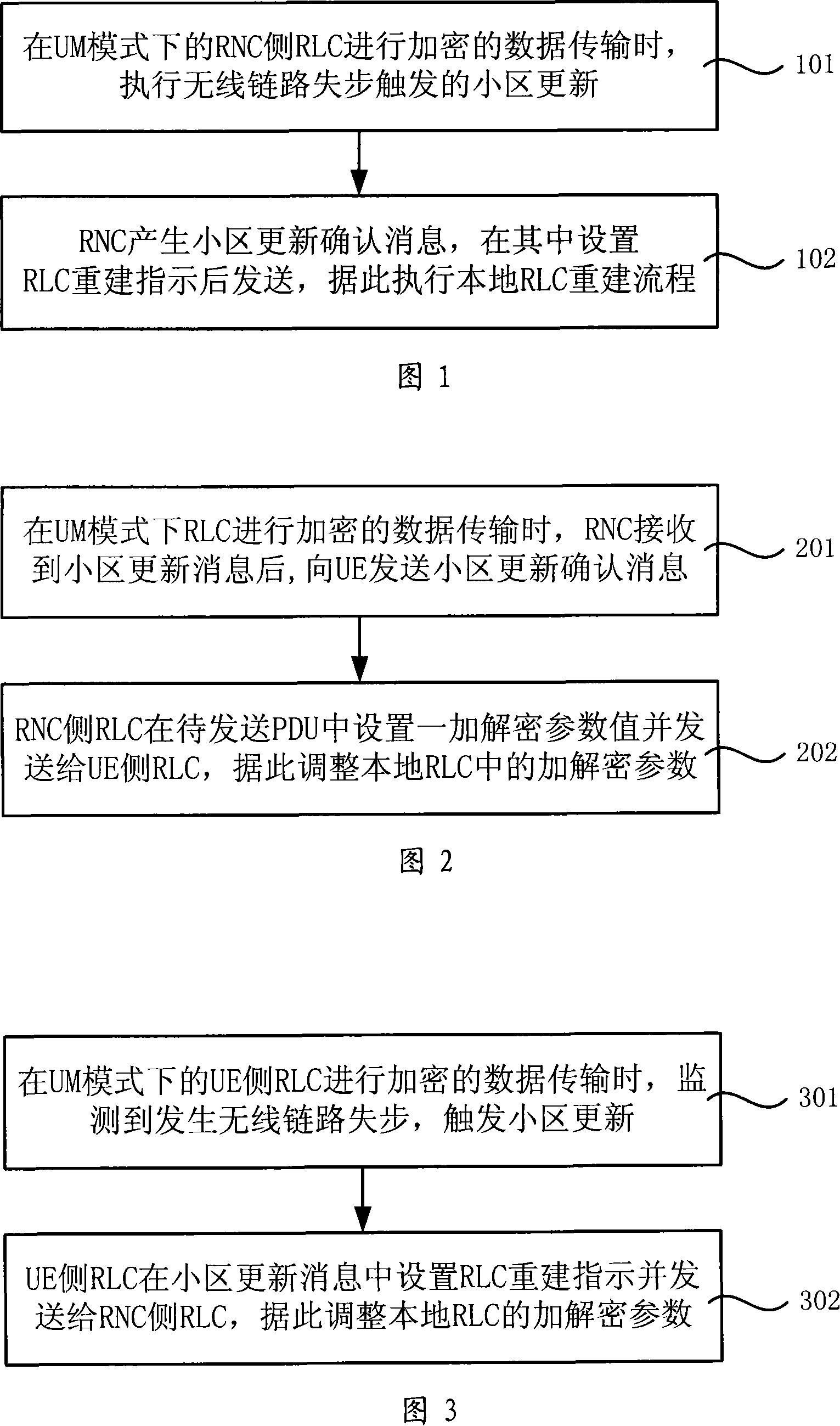
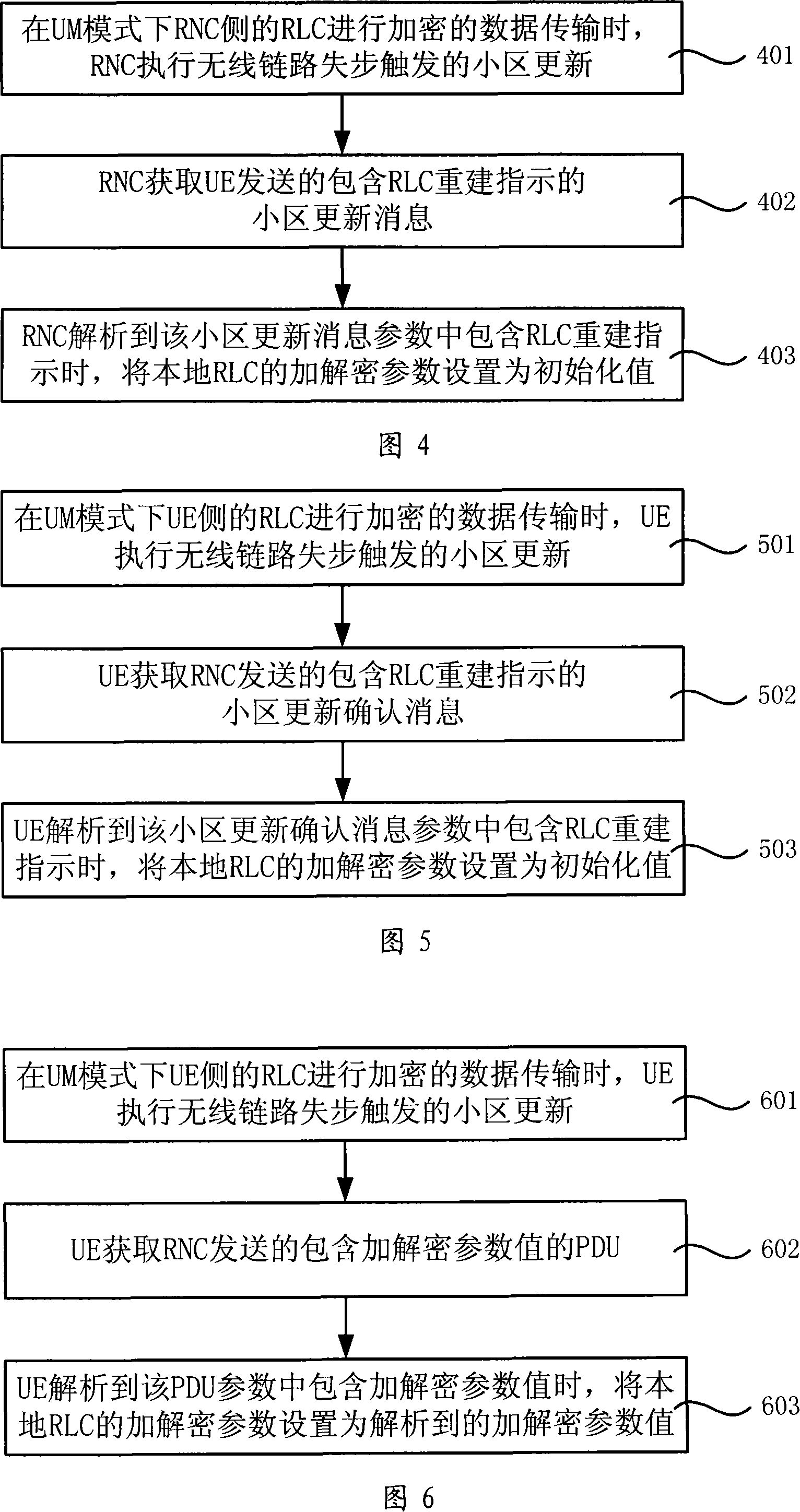
Parameter synchronization method and device
InactiveCN101150866AGuaranteed normal executionKey distribution for secure communicationSynchronisation arrangementComputer hardwareData transmission
The invention provides a parameter synchronization method and a device, the method includes: when the RCL transmits the encrypted data under a UM mode, executes the cell updataing triggerd by the wireless links; generating encryption and decryption parameter changing information and sending or acquiring the encryption and decryption parameter changing information, adjusting the local RLC encryption and decryption parameter based on the encryption and decryption parameter changing information. The device includes a module for executing the parameter synchronization method. After the cell update is triggered by the wireless links, the invention ensures the normal encryption and decryption operation when doing encrypted data transmission.
Owner:HUAWEI TECH CO LTD
Method for realizing group broadcast channel quick switching
ActiveCN1716902AEasy to operateTroubleshooting Multicast Streaming IssuesSpecial service provision for substationData switching by path configurationBroadcast channelsTelecommunications
This invention relates to a quick switch realization method for multicast channels including: when a user terminal leaves the current placed multicast channel, it is judged if said position information in said multicast channel has other accessed user terminals based on the position information accessed by said user terminal and the multicast duplicate list of the related channel is maintained according to the judgment result, which realizes that there is always only one multicast flow bandwidth on a user terminal circuit and solves the problem of existing multicast flows on the circuit during the switch.
Owner:HUAWEI TECH CO LTD
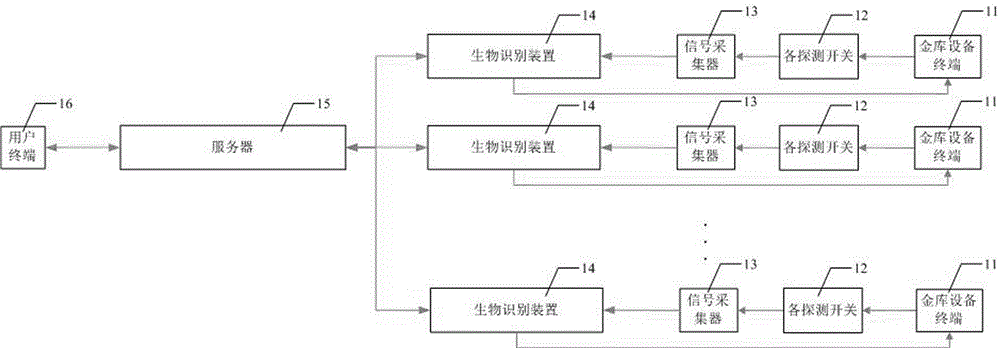
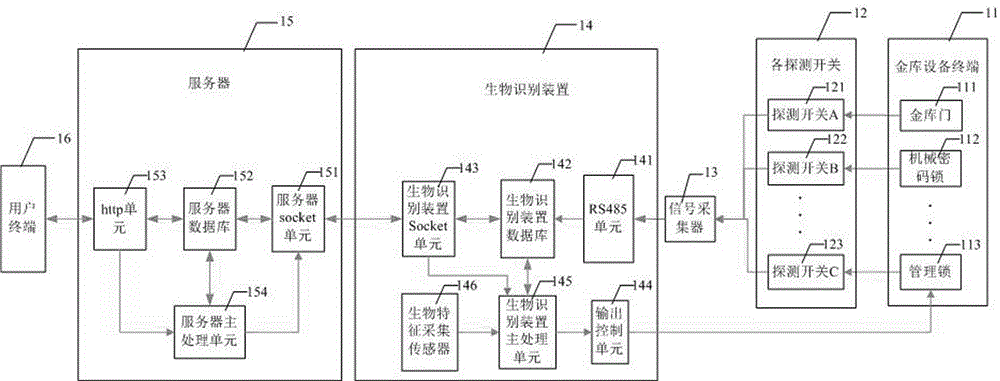
Management and control system and management and control method of bank vault door
ActiveCN104574584AImprove regulatory efficiencyGuaranteed normal executionFinanceIndividual entry/exit registersAuthorizationReal-time computing
The invention discloses a management and control system and a management and control method of a bank vault door. The system comprises vault device terminals, detection switches, signal acquiring devices, biological recognition devices, a server and a user terminal. On the one hand, the biological recognition devices are used for acquiring the information of the vault device terminals by the signal acquiring devices, and the server is used for integrating the different biological recognition devices so as to have communication with the remote user terminal, end-users can view the data; on the other hand, vault opening scheduling authorization is set by the end-users and is downloaded into the biological recognition devices by the server, and the door opening can be controlled by a management door. The system and the method have the remarkable effects that the informatization management of a bank vault and the authorization control of vault door opening are realized, so that the supervision efficiency is improved while the safety guarantee is obtained.
Owner:沈阳赛普顿科技有限公司
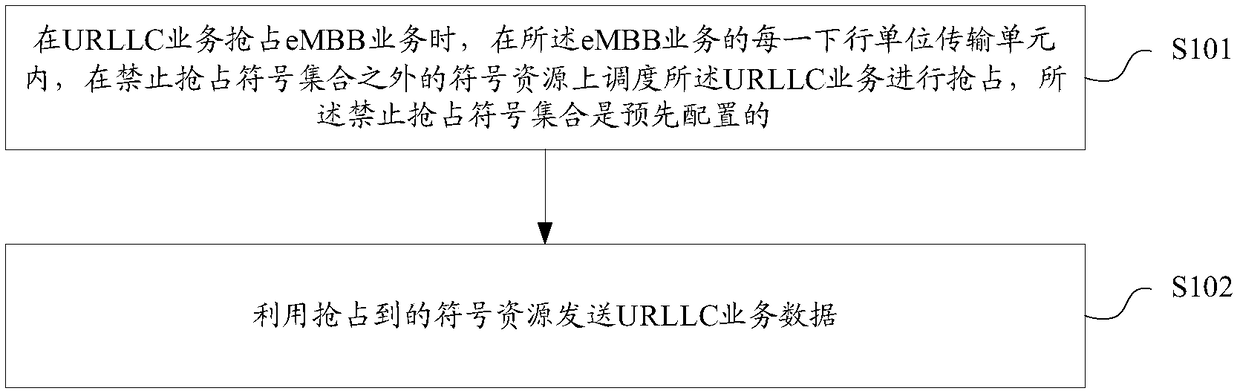
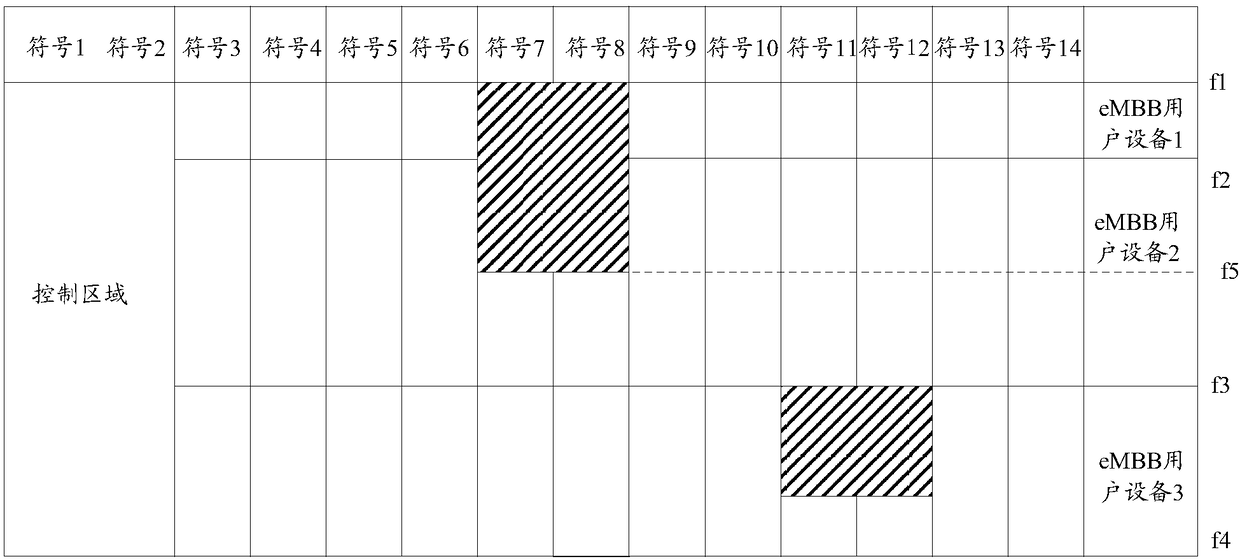
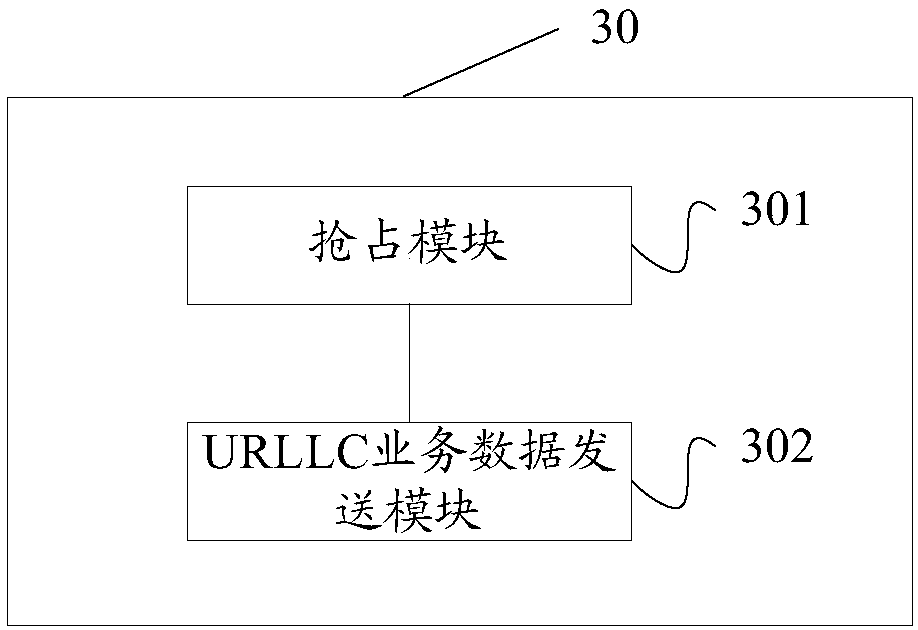
Service preemption method and device and base station
ActiveCN108633023AGuaranteed performanceGuaranteed normal executionWireless communicationLatency (engineering)Base station
The invention relates to a service preemption method and device and a base station. The service preemption method comprises the steps of when a URLLC (Ultra-reliable low-latency communication) servicepreempts an eMBB (Enhance mobile broad-band) service, scheduling the URLLC service to preempt on symbol resources beyond a preemption prohibition symbol set within each downlink unit transmission unit of the eMBB service, wherein the preemption prohibition symbol set is preconfigured; and transmitting URLLC service data by using the preempted symbol resources. The technical scheme of the invention can reduce influences imposed on the performance of the eMBB service by URLLC service preemption.
Owner:SPREADTRUM COMM (SHANGHAI) CO LTD
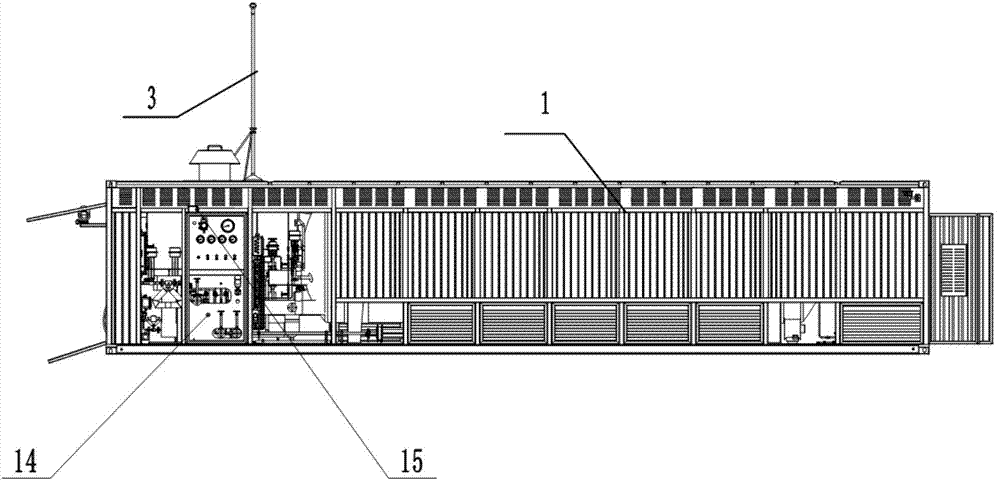
Container-type LNG (Liquefied Natural Gas) filling device and station control method
ActiveCN104500966AAvoid safety hazardsSolve the problem of long-distance transportation fixed-point refuelingPipeline systemsContainer discharging methodsVideo monitoringOperation mode
The invention discloses a container-type LNG (Liquefied Natural Gas) filling device and a station control method, belongs to the technical field of LNG. The container-type LNG aerated device comprises a container, wherein a storage tank area is arranged in the container and used for accommodating a storage tank; two ends of the container are respectively provided with an operating area and a control room, the operating area is internally provided with gas filing equipment, unloading equipment and an LNG pipeline system, and the gas filling equipment and the unloading equipment are connected with the storage tank by virtue of the LNG pipeline system; the control chamber is internally provided with a monitoring instrument; a instrument and a pipeline valve on the LNG pipeline system are connected with the monitoring instrument and controlled by the monitoring instrument. The LNG storage tank and the gas filling equipment are integrated in the container, the potential safety hazard that the gas filling equipment is exposed is solved; the purpose of filling LNG while unloading can be realized, the pressure rating of a steel bottle can be automatically identified, and different steel bottle pressures are automatically and safely filled by virtue of a control system; the temperature and pressure of the storage tank can be detected, when the alarm happens, the container-type LNG filling device performs unloading automatically, and the alarm information is sent to a preset mobile phone in a short message service manner; a video monitoring system has no dead angle, drivers can automatically add LNG, and an unattended operation mode is realized.
Owner:HOPE CLEAN ENERGY (GRP) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com