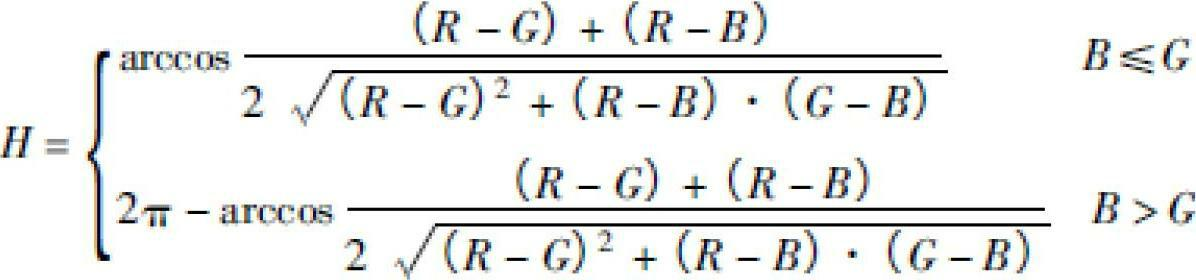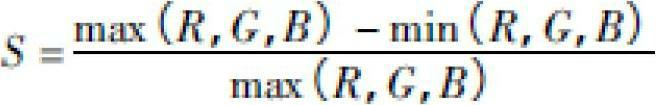Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
538results about How to "Save memory resources" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
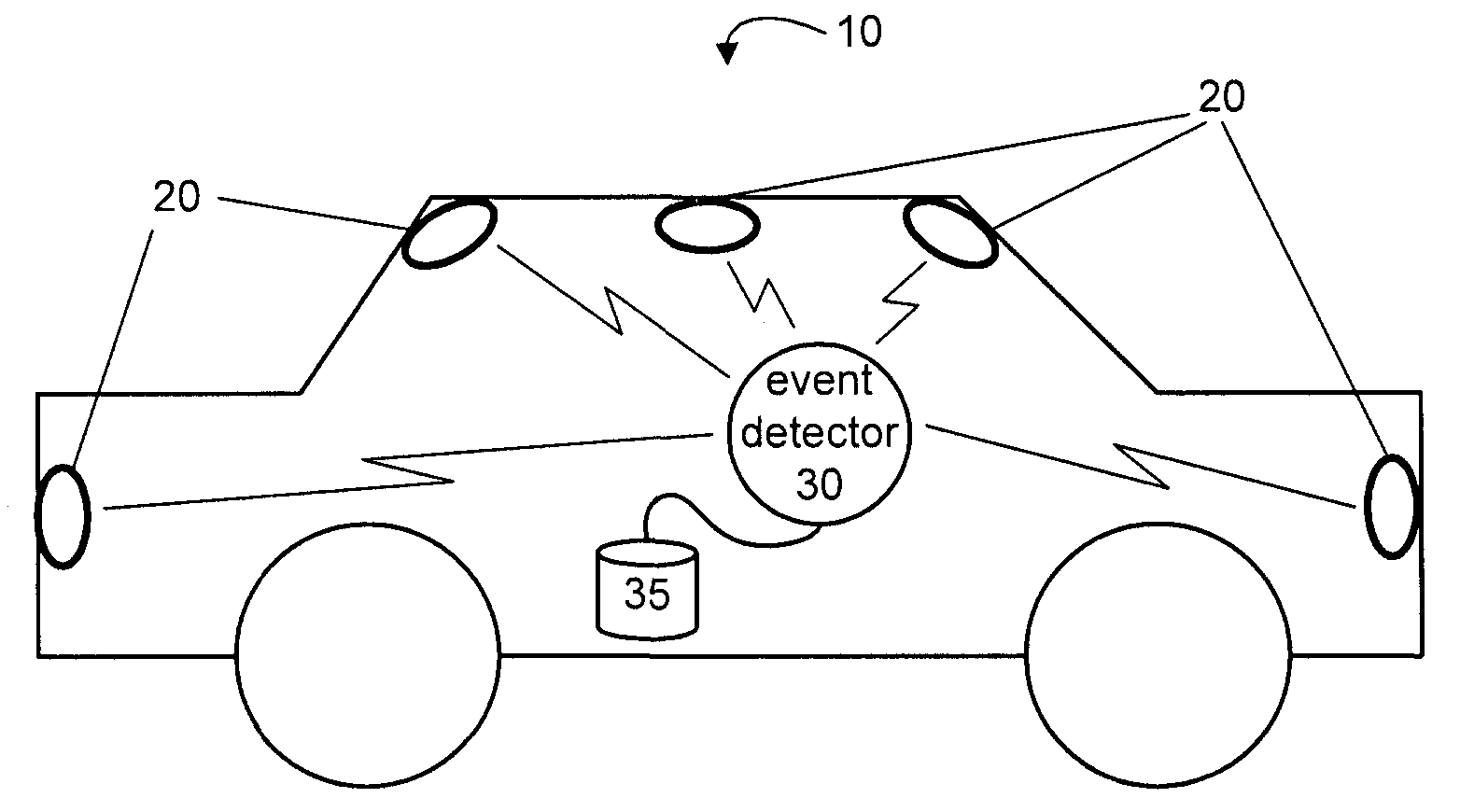
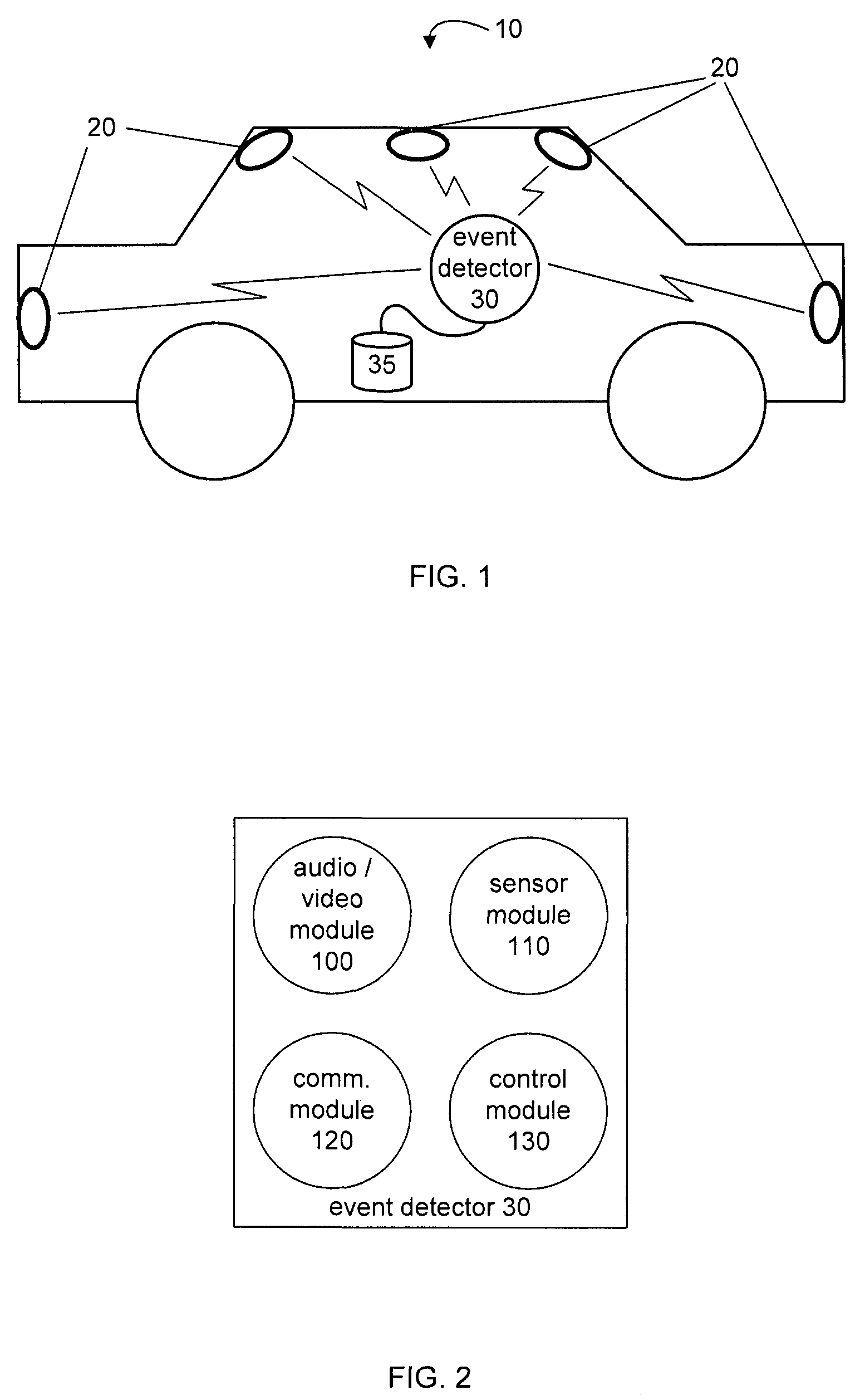
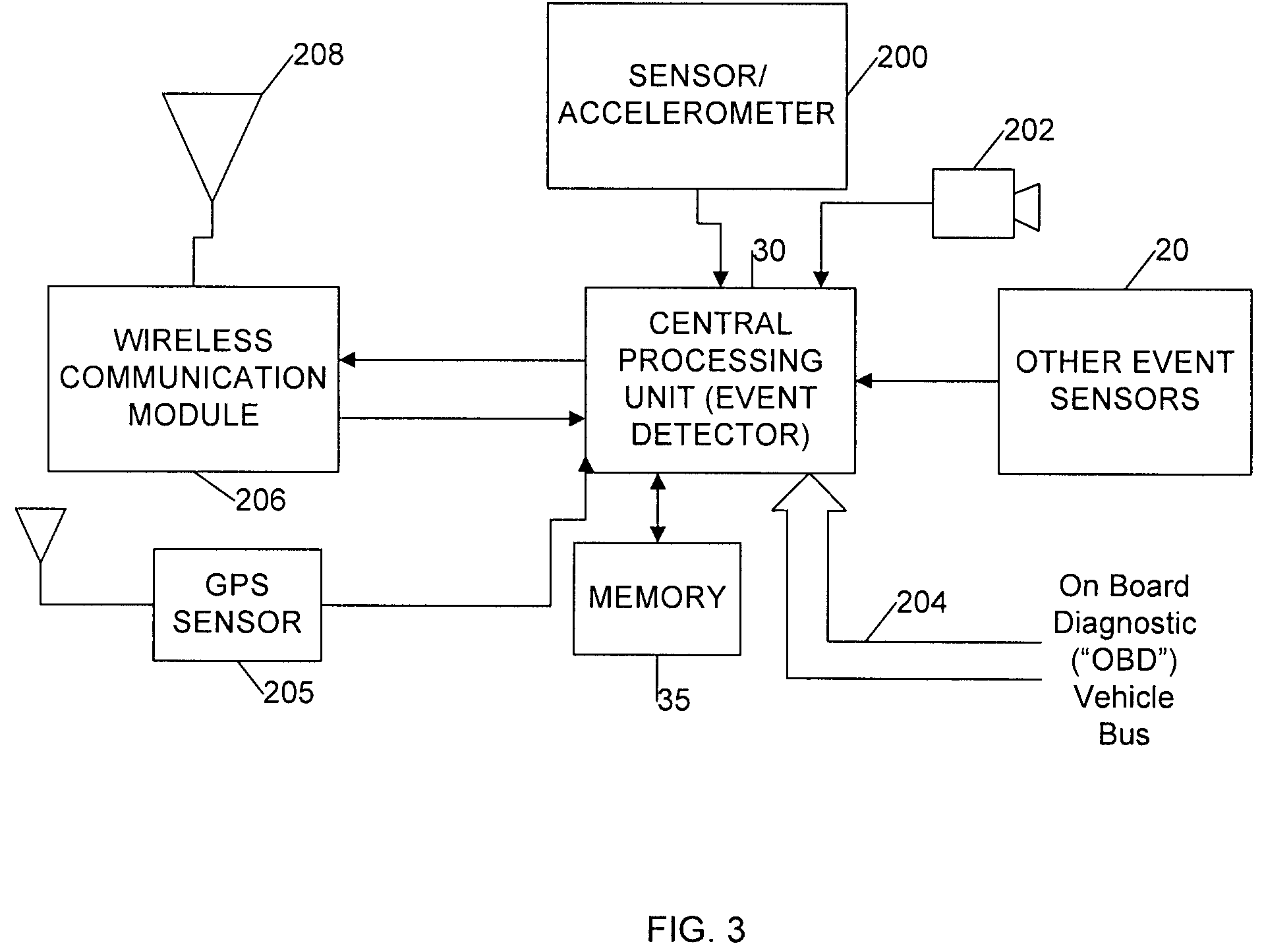
System and method for wireless delivery of event data
ActiveUS7536457B2Save memory resourcesVehicle testingRegistering/indicating working of vehiclesEvent dataData-driven
Driving events are captured at an event detector in a vehicle and stored in an associated data storage area. The output of a sensor in the vehicle is monitored, and the stored driving event data is sent to an evaluation server over a wireless communication network when a data transfer condition is detected. Driving event data is sent to the evaluation server when a predetermined output from the sensor is detected and the vehicle is in the transmission range of an access point. The predetermined sensor output may be from a motion sensor in the vehicle indicating that the vehicle is substantially stopped, or from a vehicle location sensor indicating that the vehicle is within transmission range of an access point.
Owner:DRIVECAM
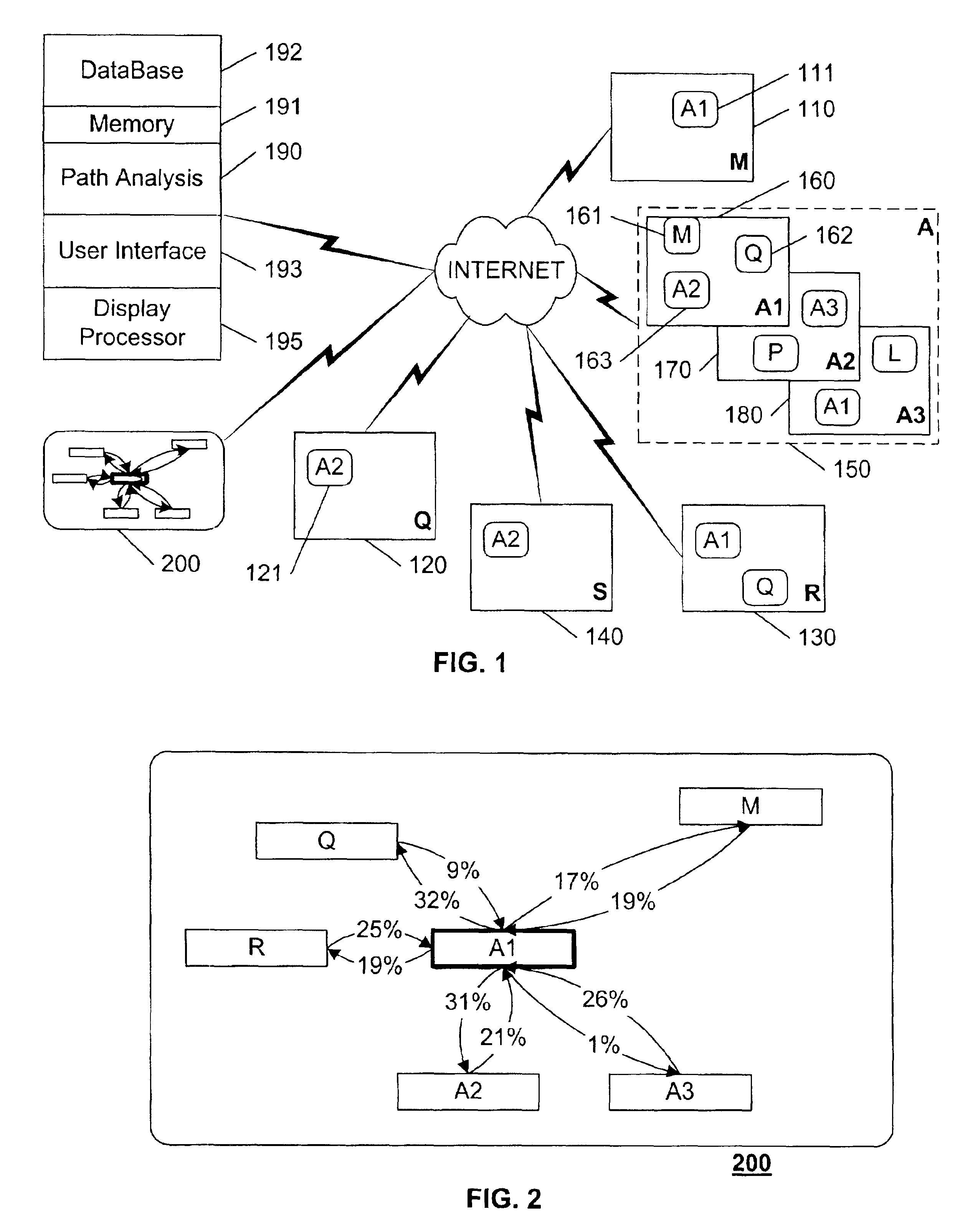
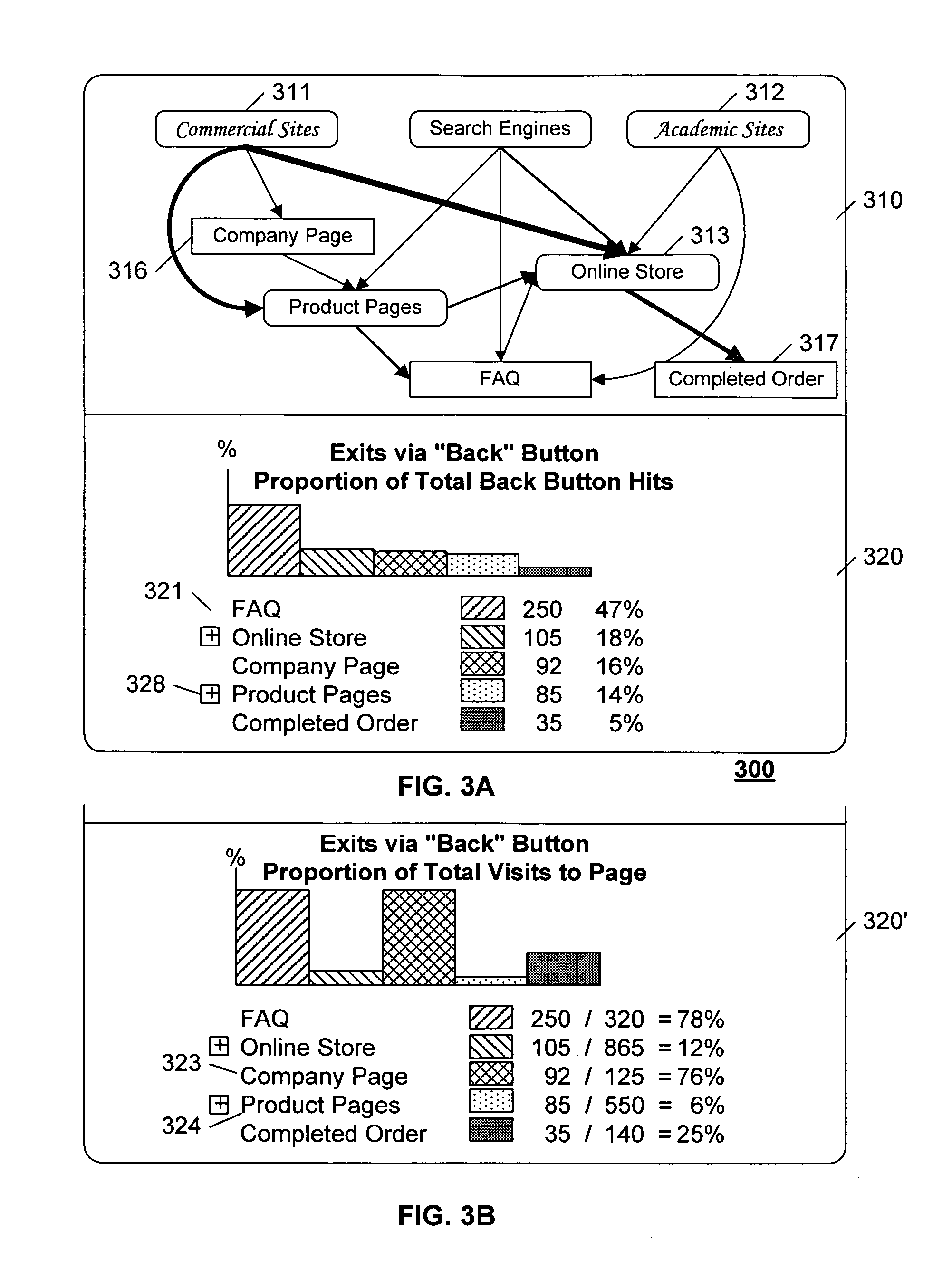
Web-site performance analysis system and method utilizing web-site traversal counters and histograms
InactiveUS6963874B2Ease of evaluationHigh trafficDigital data processing detailsMultiple digital computer combinationsWeb siteProcessor register
A data collection system collects statistics related to each visit to each web-page within a web-site. In addition to collecting path information related to traversals to and from each web-page, the system collects information regarding the particular session, such as the visitor's connection speed, the time required to download the web-page to the visitor's system, the duration of time that the visitor spent at the page, whether the user clicked the ‘back’ button to leave the site, and so on. The data reporting system presents statistics based on the collected data in an easy-to-use and easy-to-understand form that is customizable by the user. By collecting and reporting performance factors related to each web-page, or sets of web-pages within a web-site, marketers and webmasters can address any perceived deficiencies and / or can optimize the performance of select pages to achieve specific marketing objectives. To optimize performance and minimize storage requirements, the data collection system uses a two-stage storage architecture. Data is collected in one or more registers in a sequential fashion, and transferred to a database periodically.
Owner:DIGITAL RIVER INC
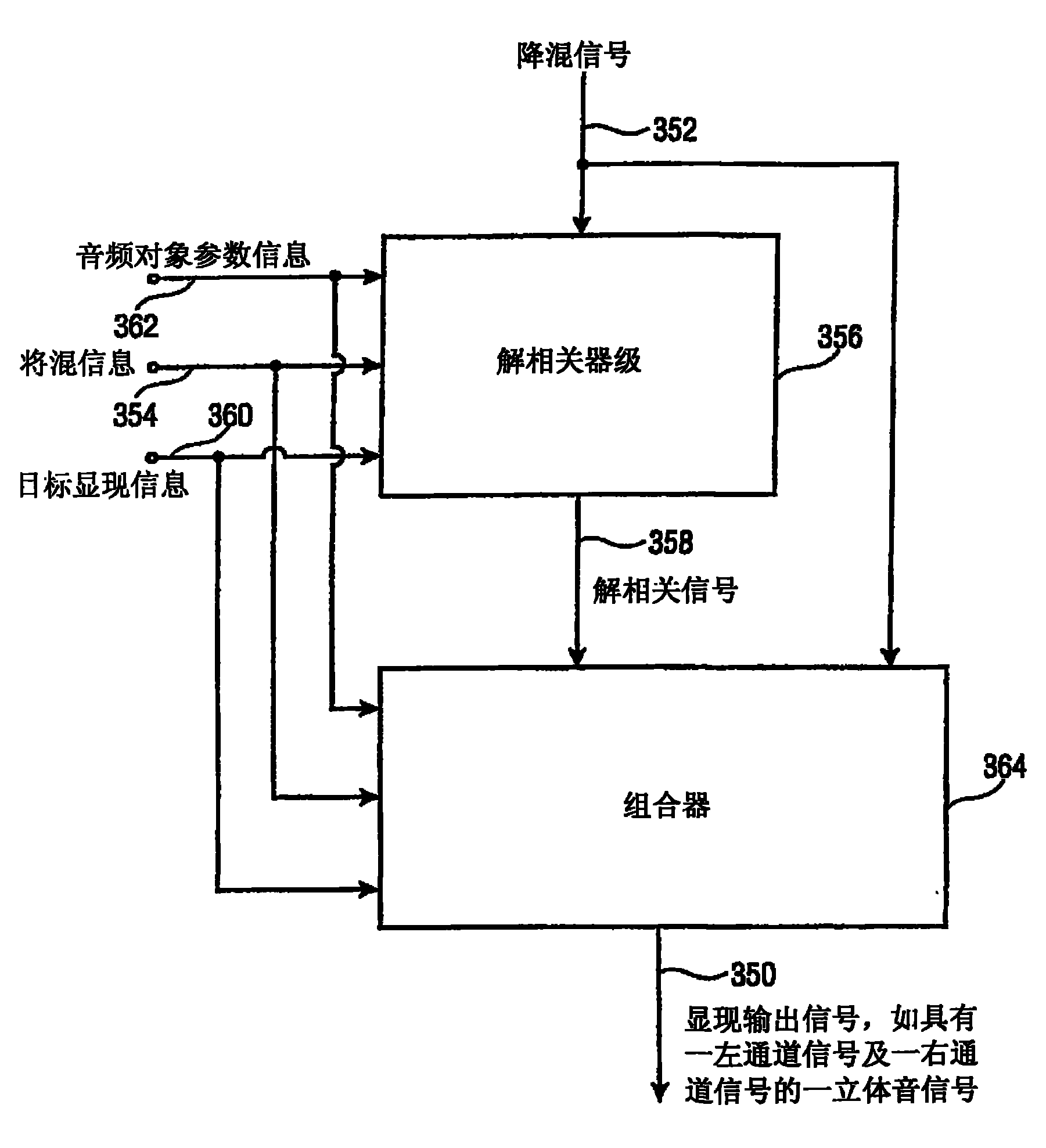
Apparatus and method for synthesizing an output signal
ActiveCN101809654AReduce complexitySave memory resourcesSpeech analysisTwo-channel systemsDecorrelationAudio frequency
An apparatus for synthesizing a rendered output signal having a first audio channel and a second audio channel includes a decorrelator stage (356) for generating a decorrelator signal based on a downmix signal, and a combiner (364) for performing a weighted combination of the downmix signal and a decorrelated signal based on parametric audio object information (362), downmix information (354) andtarget rendering information (360). The combiner solves the problem of optimally combining matrixing with decorrelation for a high quality stereo scene reproduction of a number of individual audio objects using a multichannel downmix.
Owner:DOLBY INT AB +1
Convenient information search method, system and an input method system
ActiveCN101231636AImprove search efficiencyReduce stepsSpecial data processing applicationsInternet searchingInternet search engines
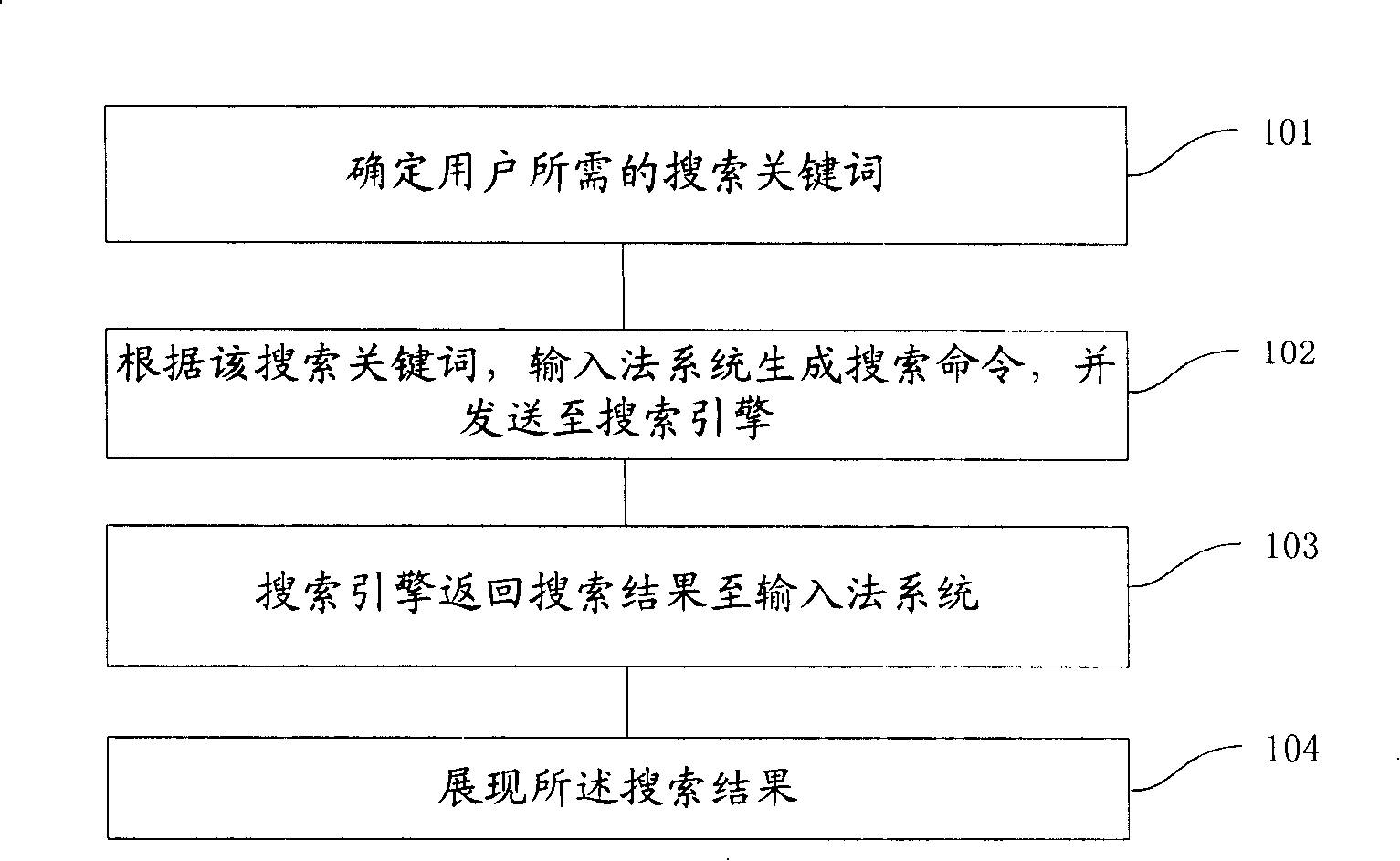
The invention provides a method and a system for searching information, as well as an input method system, wherein, the method for searching the information comprises the following steps that: a searching keyword required by a user is determined; according to the searching keyword, the input method system generates a searching command, which is sent out to a searching engine; the searching enginereturns the searching result to the input method system; the searching result is displayed. The invention can greatly improve the searching efficiency, reduce the operation steps of the user, and avoid the invalid data exchange and the invalid data processing. For some simple searching results, the invention can also directly call the display of an affiliated window or candidate word window, thereby a browse is avoided to be called, thus saving the resources of the system and calculating the sources. The invention is applicable to various internet searching engines as well as various local searching engines, and is also applicable to various searching tools or searching websites.
Owner:BEIJING SOGOU TECHNOLOGY DEVELOPMENT CO LTD
Methods, systems, and computer program products for compressing a computer program based on a compression criterion and executing the compressed program
InactiveUS6865664B2Improve adaptabilitySave memory resourcesDigital computer detailsSpecific program execution arrangementsHigh frequencyComputer program
Embodiments of systems, methods, and computer program products are provided for compressing a computer program based on a compression criterion and executing the compressed program. For example, a computer program may be compressed by scanning an initial computer program to identify one or more uncompressed instructions that have a high frequency of use. A storage mechanism, such as a data structure, may then be populated with the identified uncompressed instructions. A compressed computer program may be generated by respectively replacing one or more of the identified uncompressed instructions with a compressed instruction that identifies a location of the corresponding uncompressed instruction in the storage mechanism. Additional compression of the computer program may be achieved by scanning the compressed computer program to identify one or more uncompressed instructions that have a high frequency of use when at least a portion of their instruction operand is ignored. A second storage mechanism, such as a data structure, may then be populated with the identified uncompressed instructions. Finally, a further compressed computer program may be generated by respectively replacing one or more of the identified uncompressed instructions with a second type of compressed instruction that identifies a location of the corresponding uncompressed instruction in the second storage mechanism.
Owner:MACOM TECH SOLUTIONS HLDG INC
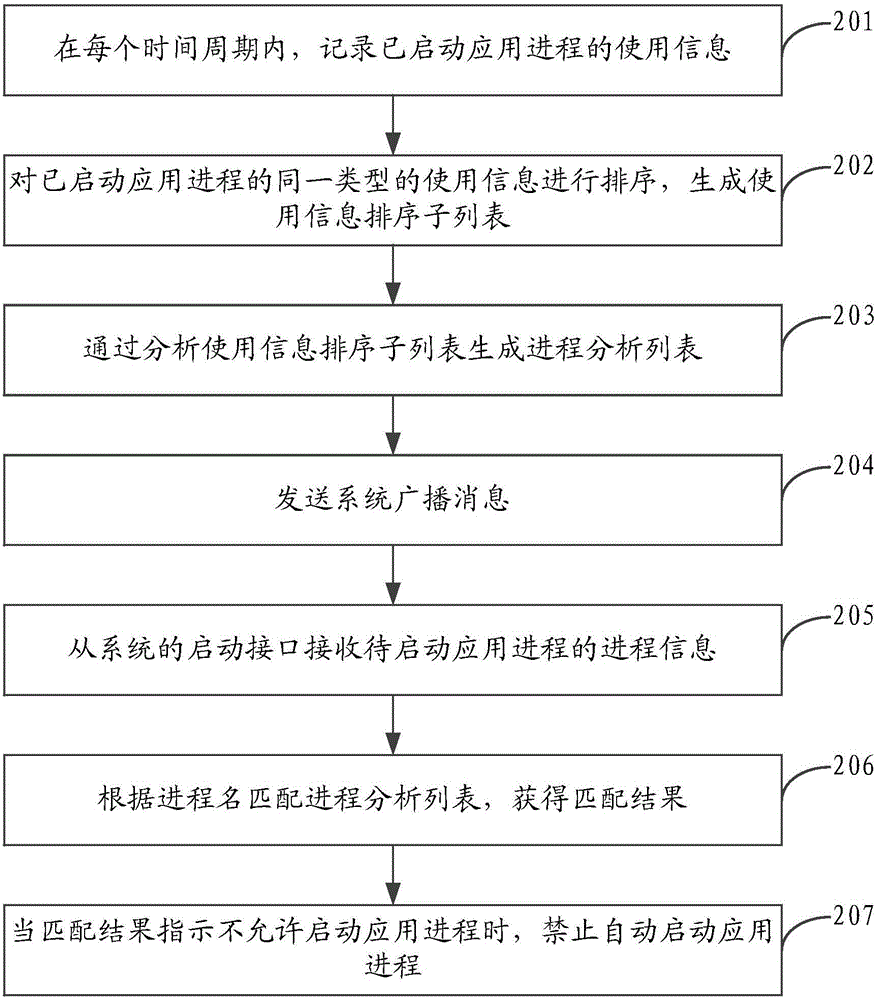
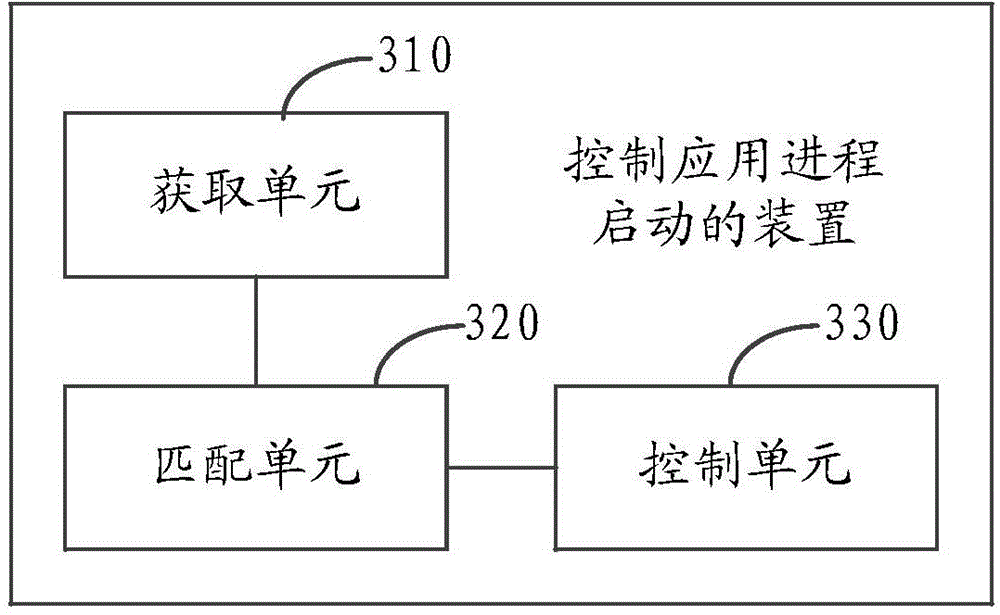
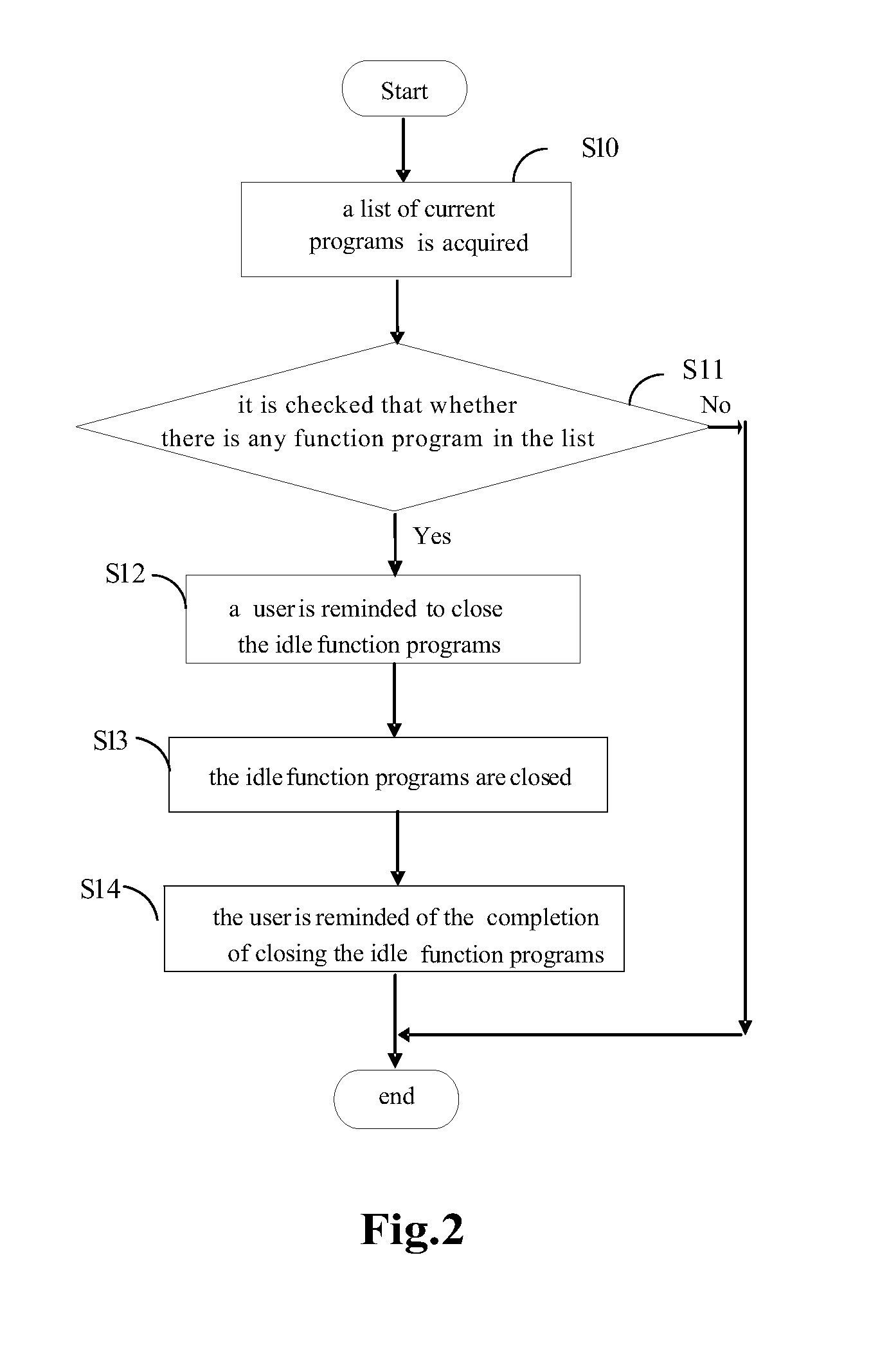
Application process starting control method and device
ActiveCN104461725ASave memory resourcesImprove user experienceProgram initiation/switchingResource allocationOperational systemSoftware engineering
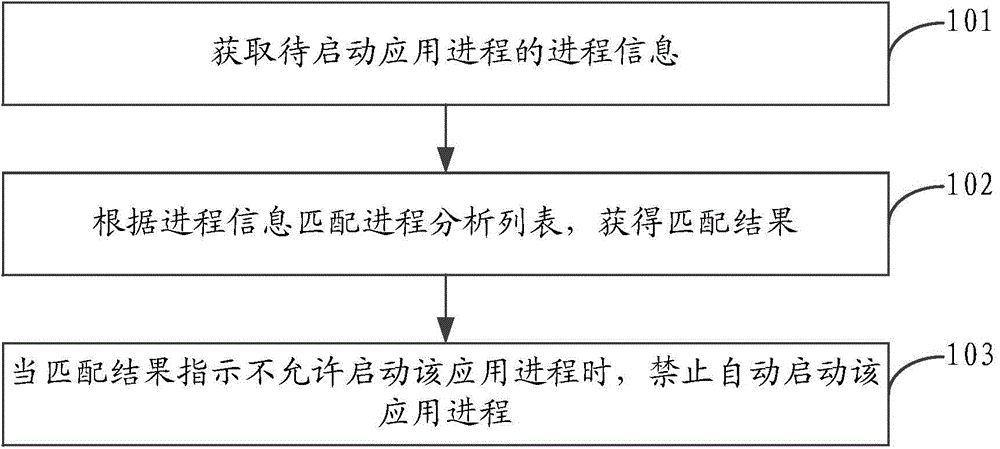
The invention discloses an application process starting control method and device. The application process starting control method comprises the steps of obtaining process information of an application process to be started, matching a process analysis list according to process information to obtain a matching result, and forbidding automatic starting of the application process when the matching result indicates that starting of the application process is not allowed. Due to the fact that automatic starting of application processes which are not needed in a terminal is avoided by matching the process analysis list, internal storage resources of the terminal can be saved, the operation speed of a terminal operating system is ensured, and accordingly the terminal usage experience of a user is improved.
Owner:XIAOMI INC
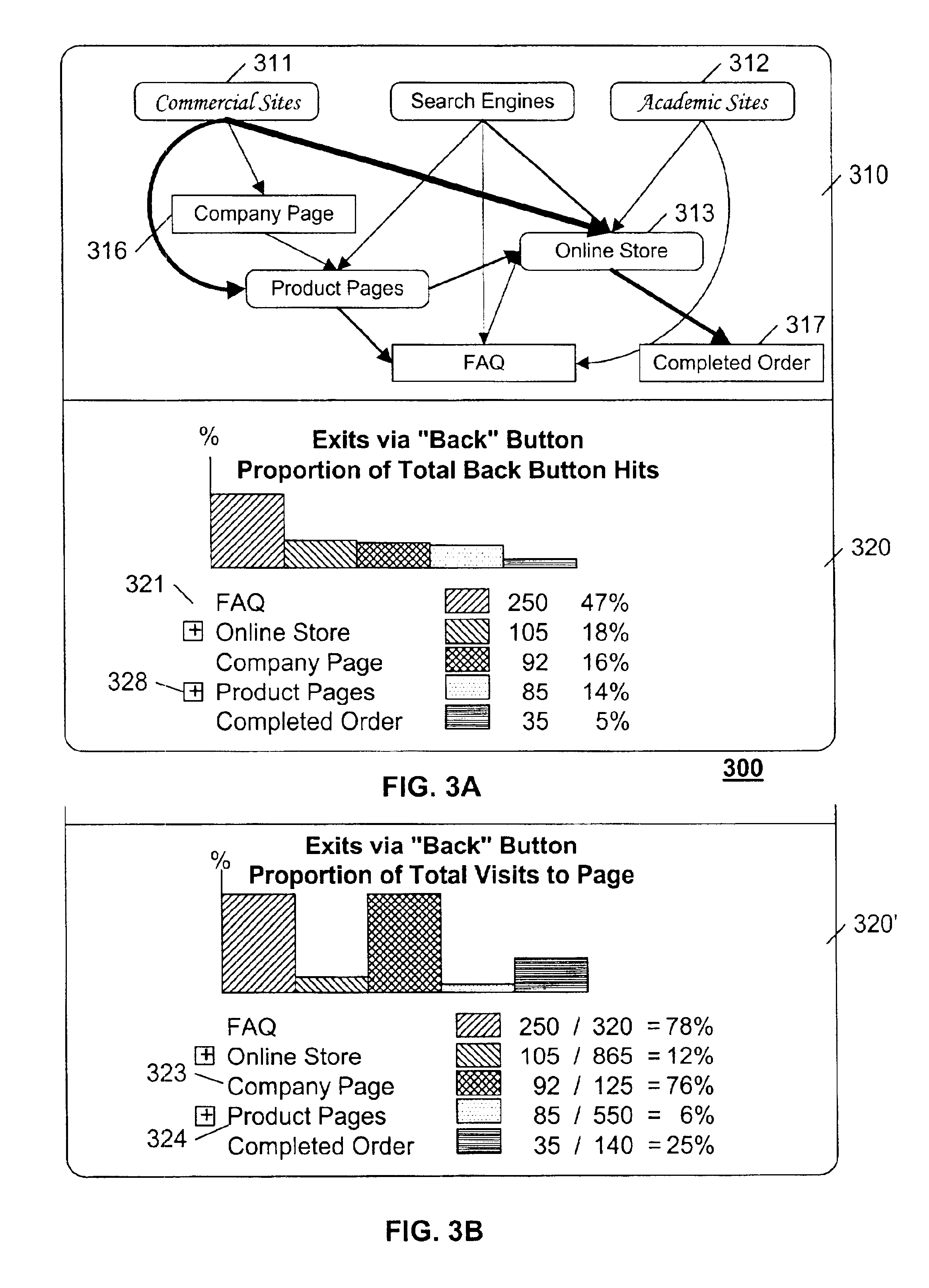
Web-site performance analysis system and method of providing a web-site performance analysis service
InactiveUS20060036400A1Ease of evaluationHigh trafficNuclear monitoringHardware monitoringWeb siteWeb page
A method of providing a web-site performance analysis service is disclosed that gathers data relative to visits to web-pages that are associated with a web-site. Traversals are identified that correspond to each visit to the web-pages. Each identified traversal has an identification of either an incoming link from which each visit originated or an outgoing link to which each visit terminated. A time duration is measured that corresponds to each visit. A chart of a statistical distribution of pages-per-visit of the identified traversals is formed. The identified traversals and time duration corresponding to each visit is stored in a memory. The stored data from the memory is transferred to a database. Performance measures are produced that correspond to each visit to the web-pages based on the stored data in the database. A web-site performance analysis system that implements this method also is disclosed.
Owner:DIGITAL RIVER INC
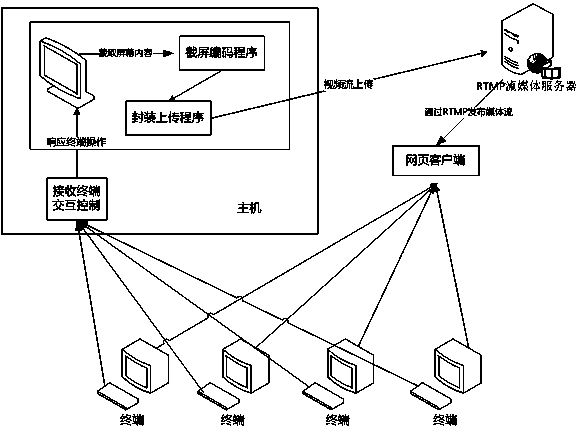
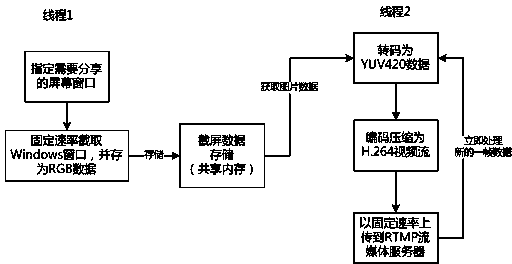
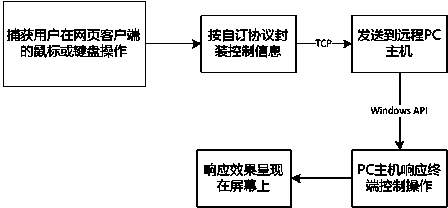
PC screen content sharing/interaction control method
ActiveCN103414751AImprove experienceGuaranteed real-timeTelevision systemsTransmissionResponse effectInteraction control
The invention relates to a PC screen content sharing / interaction control method, specifically, relates to improvement of an existing method of PC screen content sharing. The PC screen content sharing / interaction control method comprises the following steps that: S1, a remote PC host assigns a window of which the content is required to be shared; S2, screen RGB data are obtained in a shared memory data buffer; S3, a software encoder is utilized to perform encoding and compression on data a YUV420 format so as to obtain H.264 video streams; S4, the screen content video streams which have been subjected to encoding and compression are uploaded to a stream media server through an RTMP protocol; S5, a user logs into a Webpage client address which releases media streams of the remote PC host through a browser; S6, control information is transmitted to the remote PC host through a TCP protocol; S7, the remote PC host parses received control information of a user end and displays the received control information on a PC screen; and S8, screen response effect is presented on a Webpage client which the client logs into. With the PC screen content sharing / interaction control method adopted, a user can directly browse the content of the screen through a Webpage browser, and remote interaction control protocols can be customized, and a lightweight system used for PC screen content sharing / interaction can be realized.
Owner:GUANGDONG UNIV OF TECH
Local-sensitive hash high-dimensional indexing method based on distribution entropy
ActiveCN102609441AImprove retrieval performanceSave memory resourcesSpecial data processing applicationsData setAlgorithm
The invention provides a local-sensitive hash high-dimensional indexing method based on distribution entropy. The method comprises: firstly, generating a local-sensitive hash function candidate set; secondly, calculating the distribution entropy of each hash function in the local-sensitive hash function candidate set according to a training data set, and selecting L hash functions with the highest distribution entropy as the local-sensitive hash function set; thirdly, storing a data set to be indexed to a hash table according to the local-sensitive hash function set; and querying the above hash table by adopting a query algorithm based on triangle inequality filtering and Euclidean distance sorting to obtain a result set similar to the query data. The method can well suit the data distribution by selecting the hash functions with the highest distribution entropy, thereby optimizing the hash table index structure, reducing memory consumption for indexing, and ensuring more accurate and efficient query.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
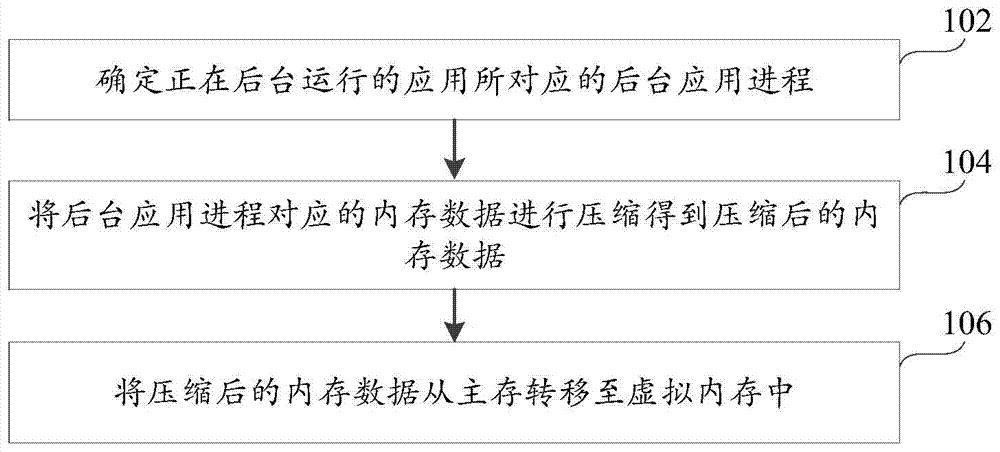
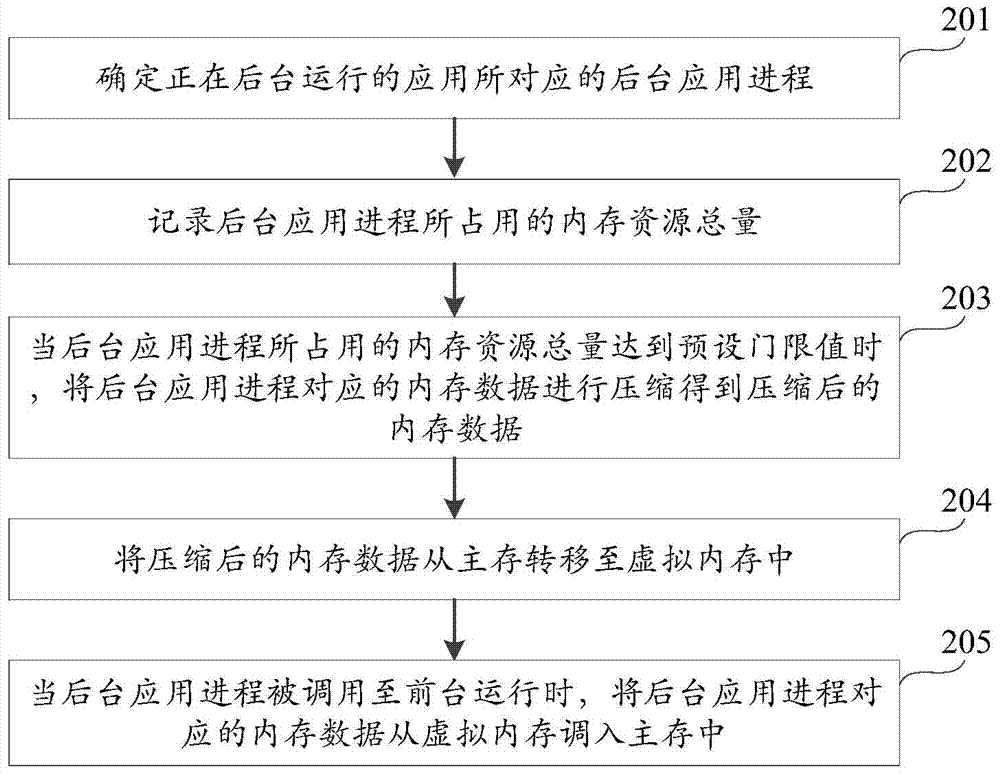
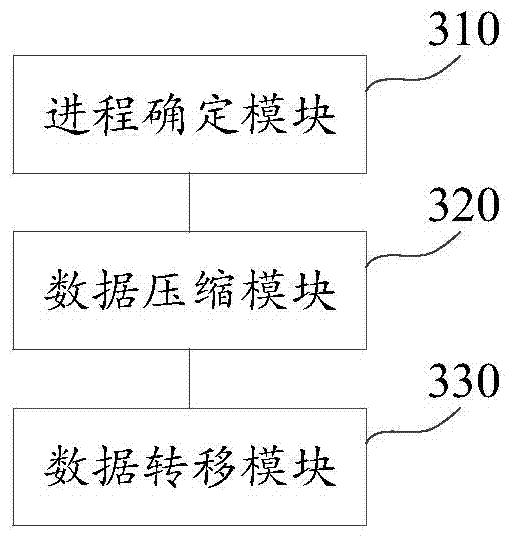
Memory management method and device
InactiveCN104503740AEasy to useSave memory resourcesSpecific program execution arrangementsResource savingMemory management unit
The utility model discloses a memory management method and device and belongs to the technical field of computers. The method comprises the following steps: determining a background application process corresponding to an application running in the background; compressing memory data corresponding to the background application process, and thus obtaining the compressed memory data; transferring the compressed memory data from a main memory into a virtual memory. The memory data corresponding to the background application process is compressed, and the compressed memory data is transferred from the main memory into the virtual memory, so that the memory management method solves the problem that when the memory resource is released by a correlation technique, useful progresses are killed; as a result, the normal use of equipment is influenced. On the basis that the normal running of the useful processes is ensured, the background application process not used by a system and a user is compressed for storage, so that the purpose of memory resource saving is achieved, while the normal use of the equipment is ensured.
Owner:XIAOMI INC
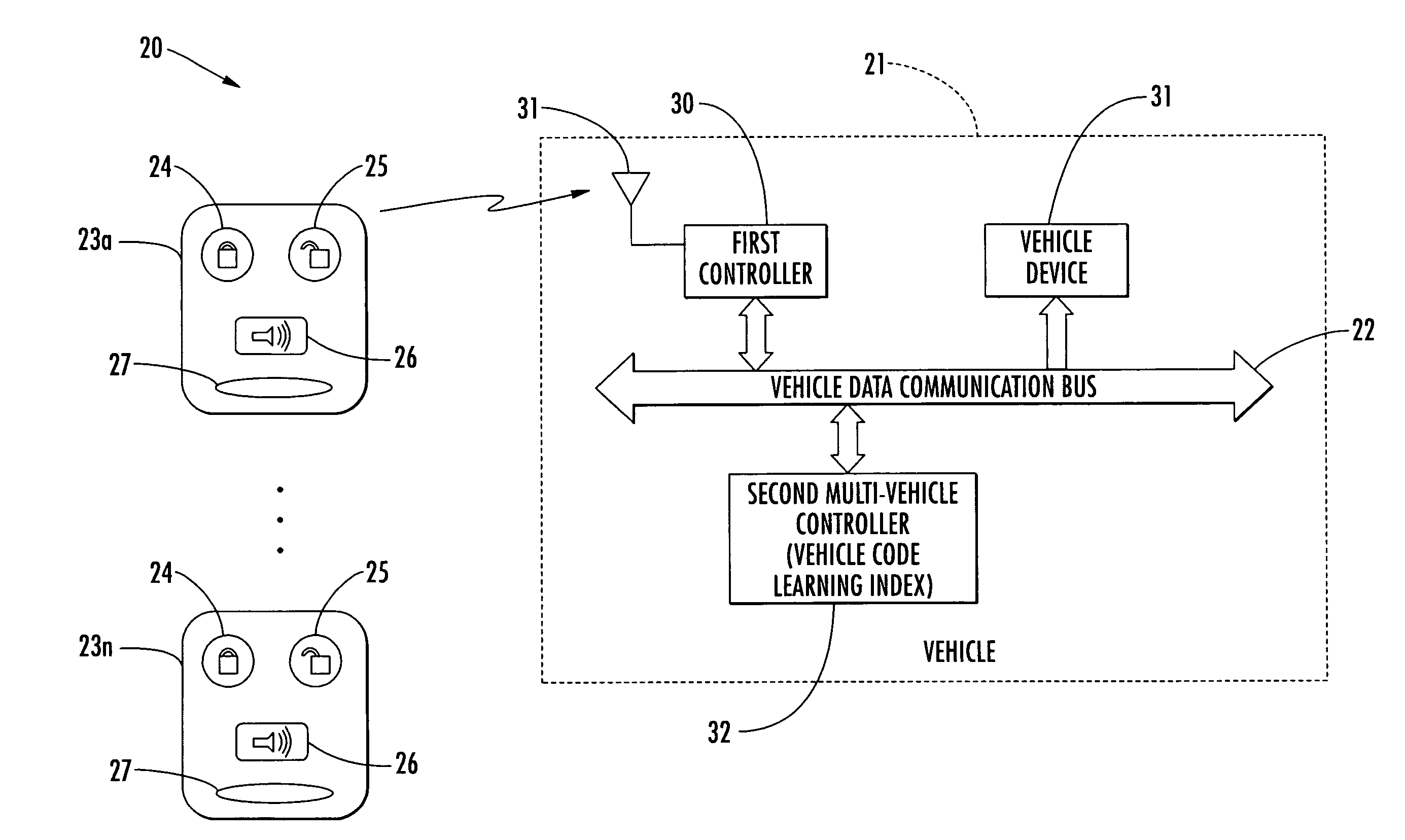
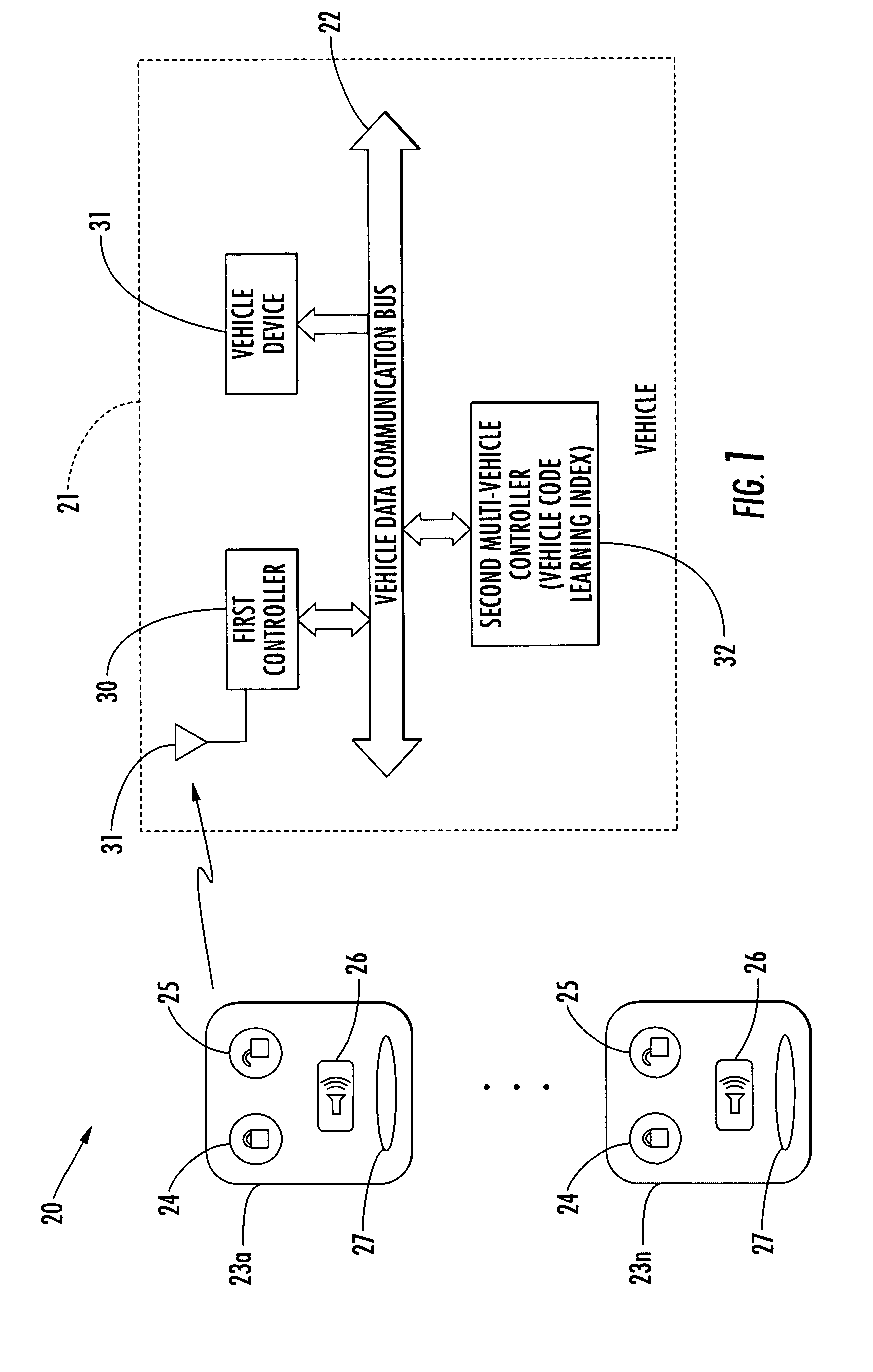
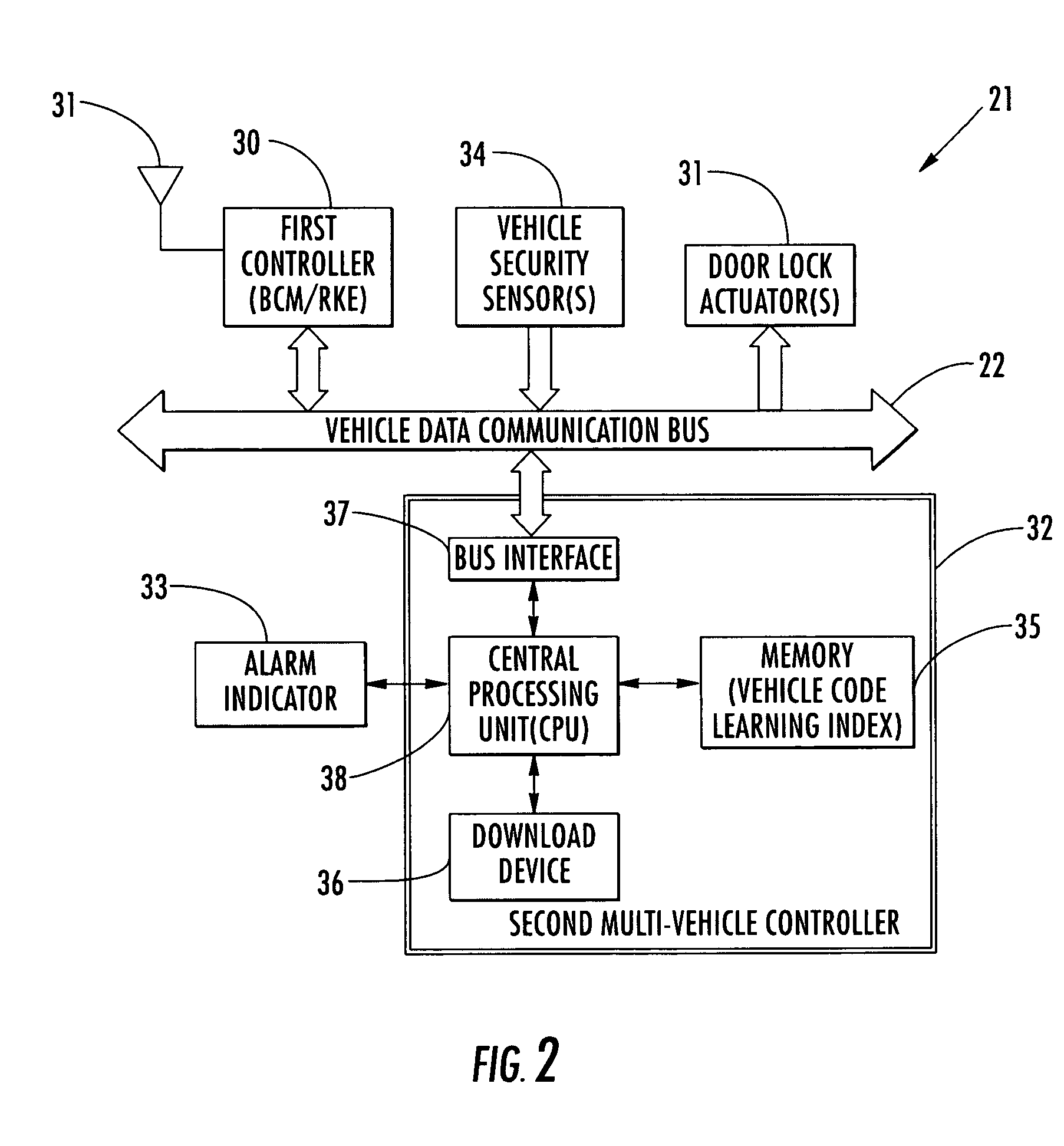
Vehicle control system including multi-vehicle controller using vehicle code learning index and related methods
ActiveUS7010402B2Easy to installQuickly and easily configuredElectric devicesElectrical apparatusControl systemSeries data
A vehicle control system is for a vehicle including a vehicle data communication bus extending throughout the vehicle and may include a plurality of user control devices, and a first controller at the vehicle for generating a data bus code on the bus from among a series of data bus codes based upon a respective user control device. Each data bus code of the series may have a common function portion and an identity portion that is different for each respective user control device. Moreover, a second multi-vehicle controller at the vehicle may compare a data bus code on the bus with a vehicle code learning index to determine the vehicle from a plurality of different vehicles. The index may include possible data bus codes each including a respective common function portion for each different vehicle with a don't care condition specified for each identity portion.
Owner:OMEGA PATENTS
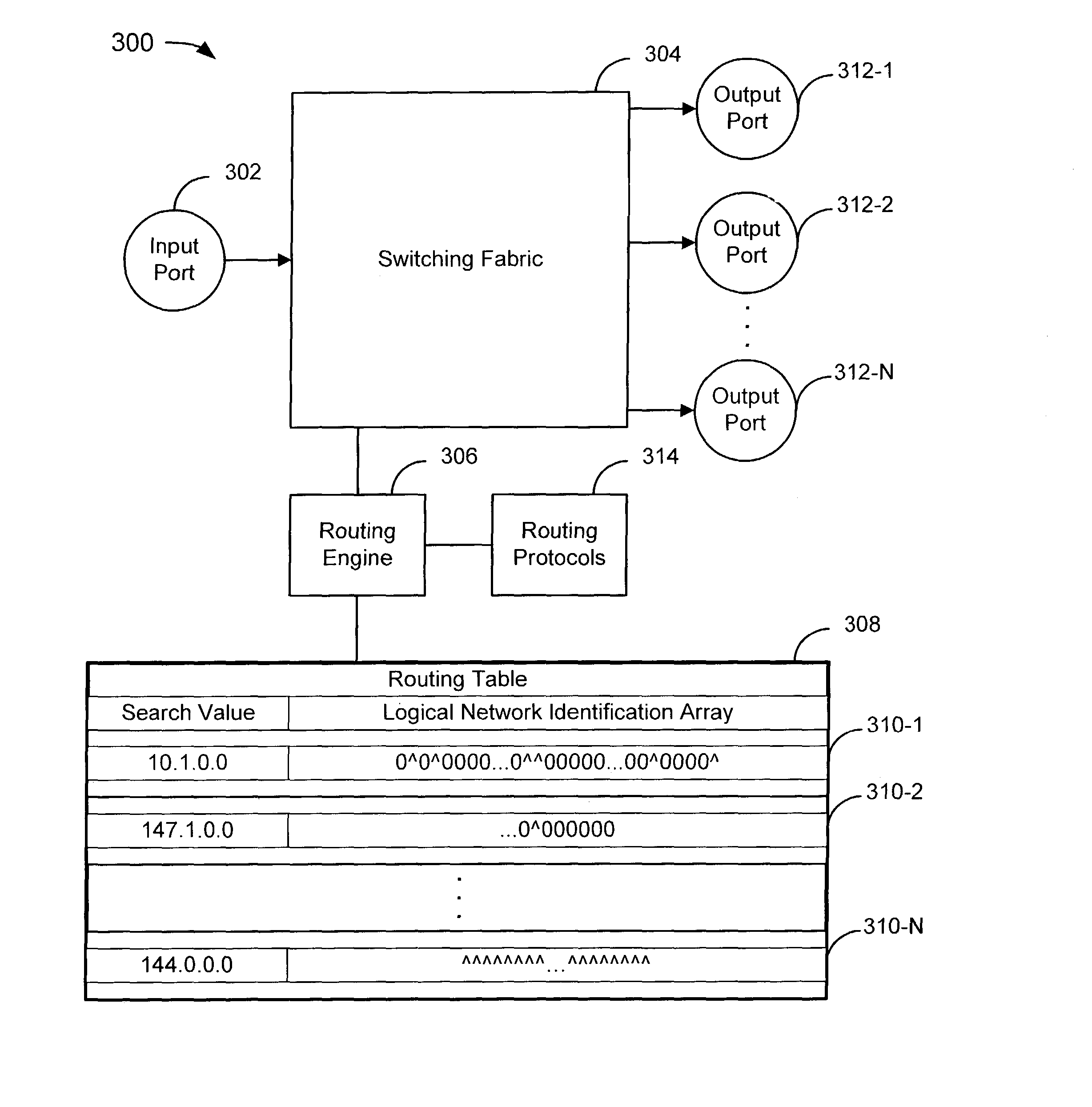
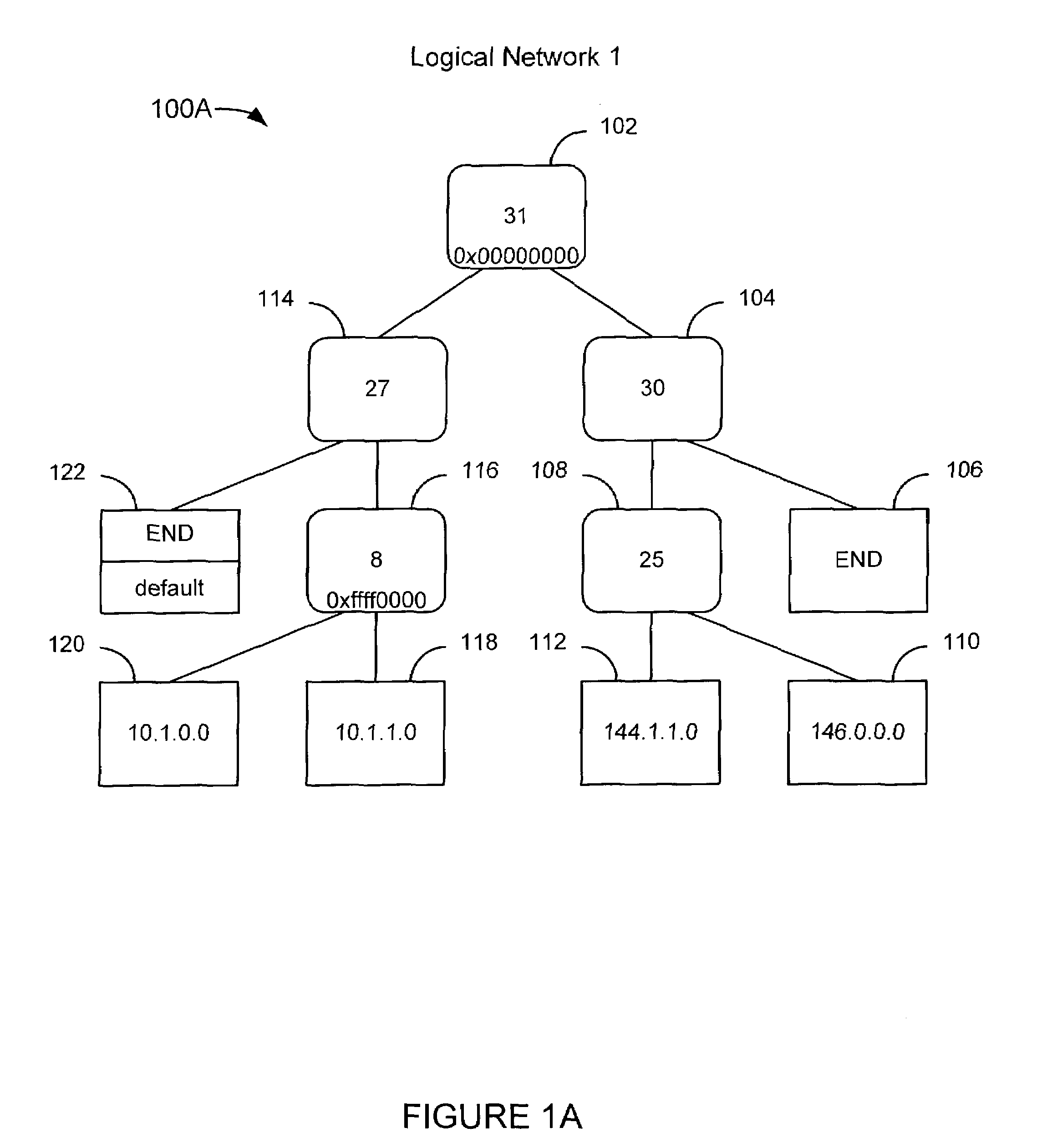
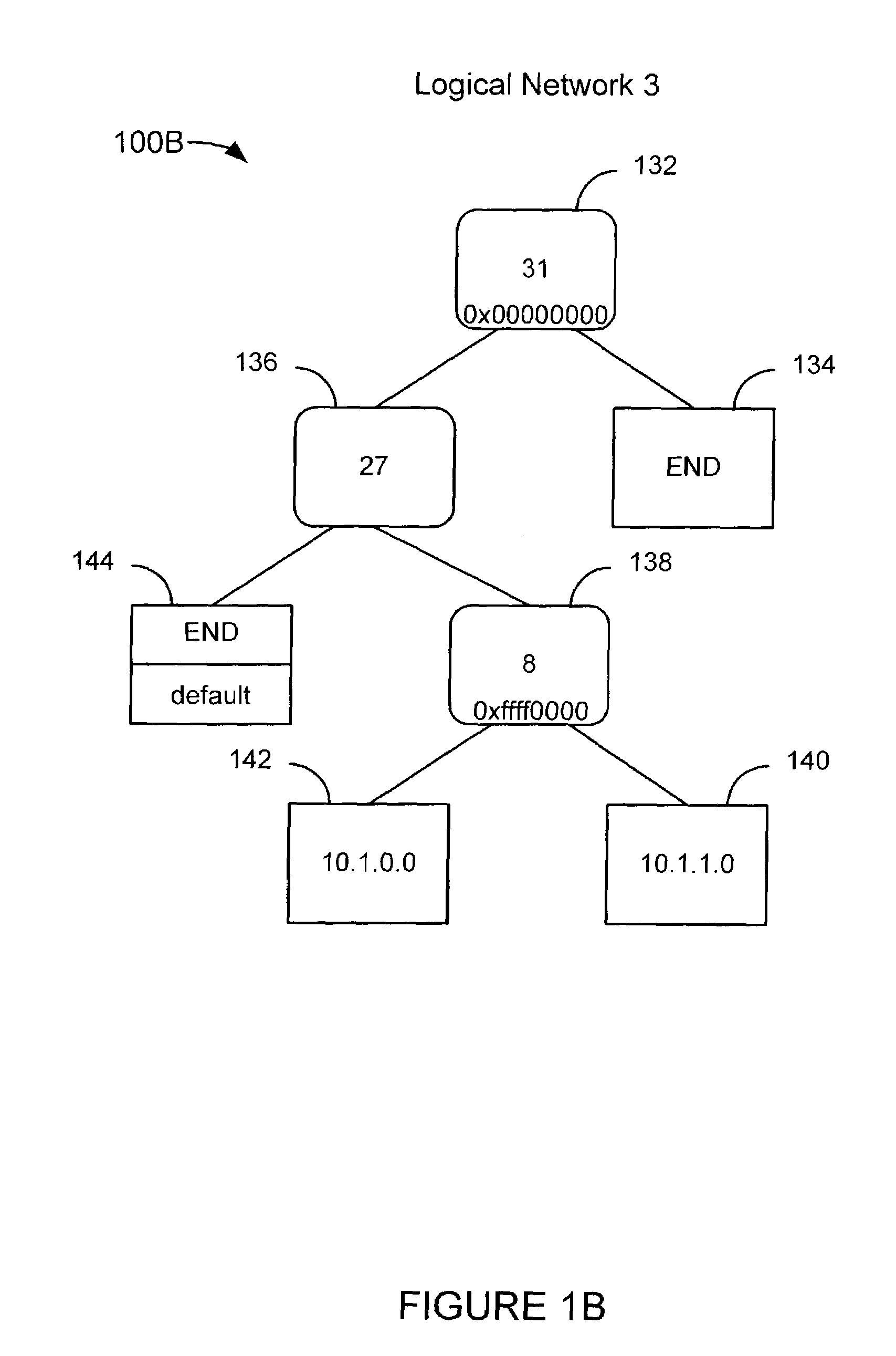
Forwarding traffic in a network using a single forwarding table that includes forwarding information related to a plurality of logical networks
ActiveUS7325071B2Memory resource is valuableOptimizationData switching by path configurationMultiple digital computer combinationsTraffic capacityRouting table
A method and system for forwarding traffic from a plurality of logical networks using a single forwarding table. Traffic is received in the form of packets with a key and a logical traffic identifier. The routing table is traversed to a forwarding table entry having a longest prefixed search value that matches the key and having a logical network identification array in which the logical traffic identifier may be represented. If the logical traffic identifier is represented in the logical network identification array, then the packet is forwarded in accordance with forwarding information associated with the forwarding table entry.
Owner:WSOU INVESTMENTS LLC +1
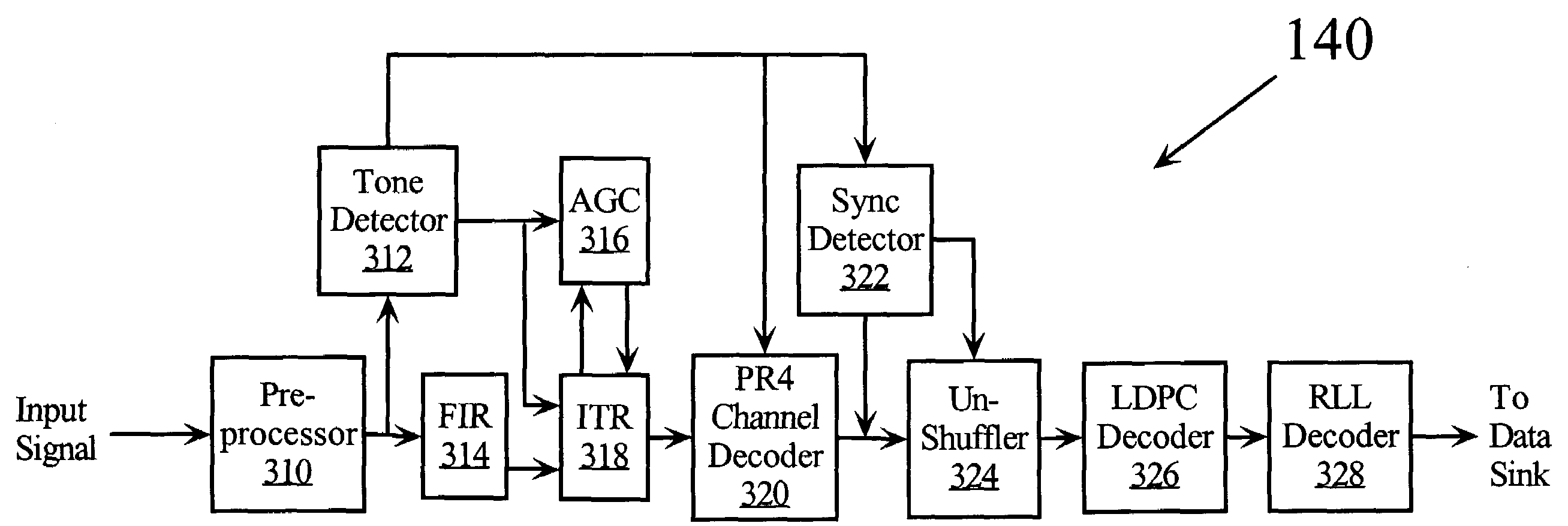
Channel processor using reduced complexity LDPC decoder
InactiveUS7222289B2Simple processSave memory resourcesError correction/detection using multiple parity bitsCode conversionParity-check matrixTheoretical computer science
A low-density parity check device can process data using a special low-density parity check matrix having a size of n-rows by m-columns. By styling the matrix such that the matrix is composed of p equal-size sqaure sub-matrices, only the first row of the first sub-matrix need be generated and stored. By then further constraining each of the sub-matrices to form various sub-portions, with each sub-portion constructed such that any two columns within the sub-portion will have no common location containing a non-zero entry, processing advantages are gained.
Owner:QUANTUM CORP
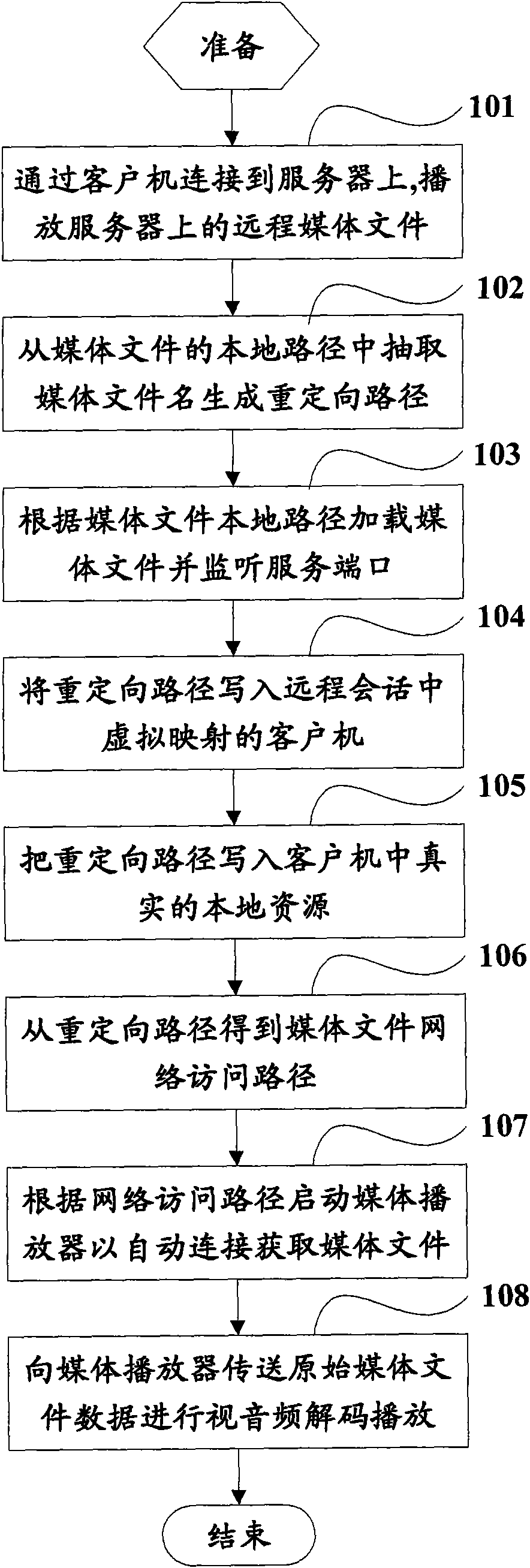
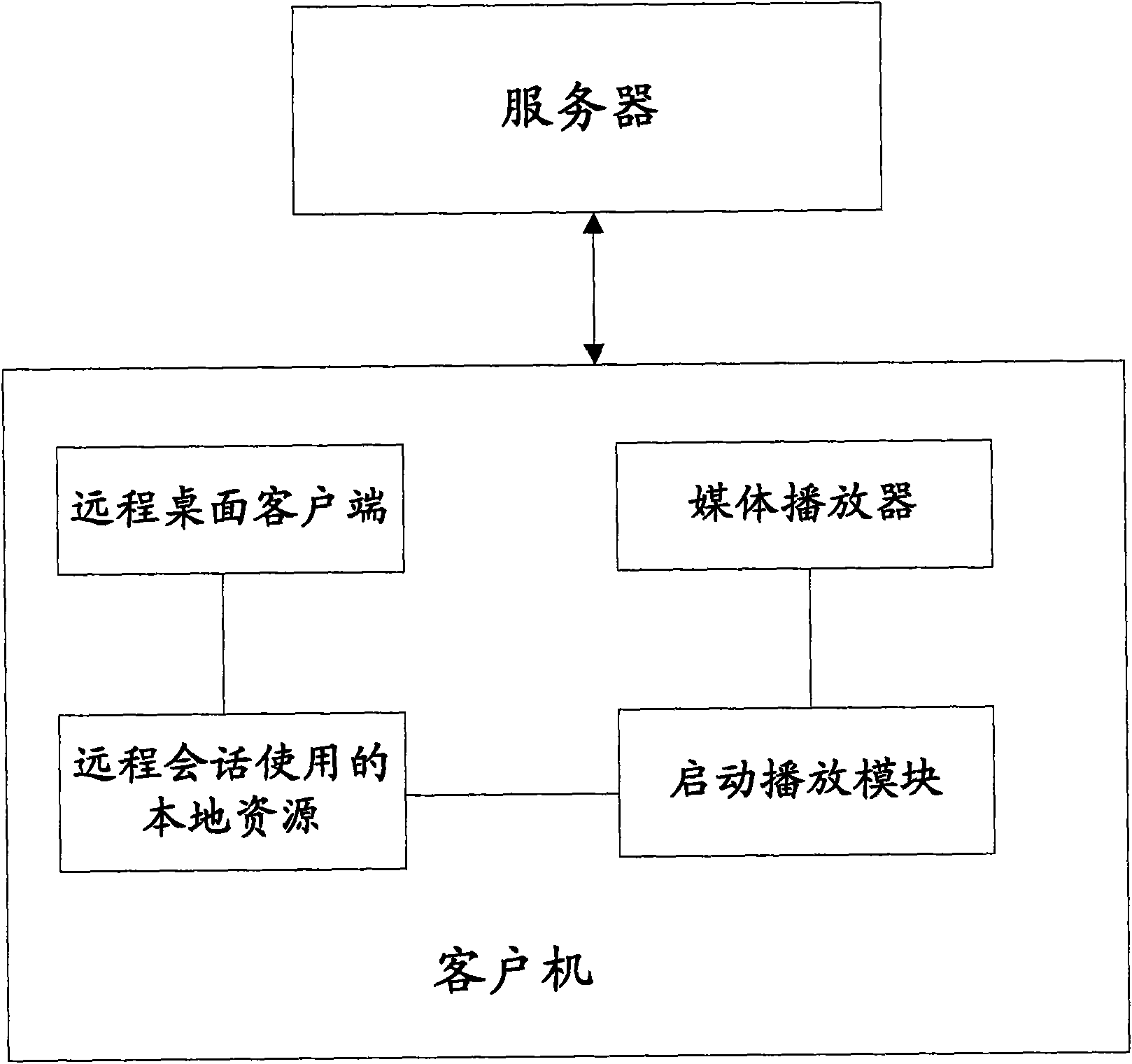
Method for realizing redirection of playing remote media and system
ActiveCN101582926ASave memory resourcesGuaranteed performanceSpecial service provision for substationAudio frequencyLarge networks
The invention discloses a method for realizing the redirection of playing remote media, a system, a client machine and a server. The method comprises the following steps of: playing a remote media file by connecting the client machine to the server; acquiring a local path of the media file and extracting a media file name therefrom so as to generate a redirection path; according the local path, loading the media file, monitoring a service port and waiting for the client machine to connect the acquired media file; writing the redirection path into the client machine of virtual mapping in a remote session; writing the redirection path into a local resource in the client machine; acquiring the data of the local resource used by the remote session and obtaining network access path of the media file; according to the network access path of the media file, starting a media player installed locally to automatically connect so as to acquire the media file; and transmitting the original media file data to the media player, and carrying out decoding and playing of video-audio frequency to the received media file data. The invention solves the problem that the server has heavy operation load and large network bandwidth occupation, and the audio frequency playing is limited by the hardware configuration of the server.
Owner:CHINA TELECOM CORP LTD
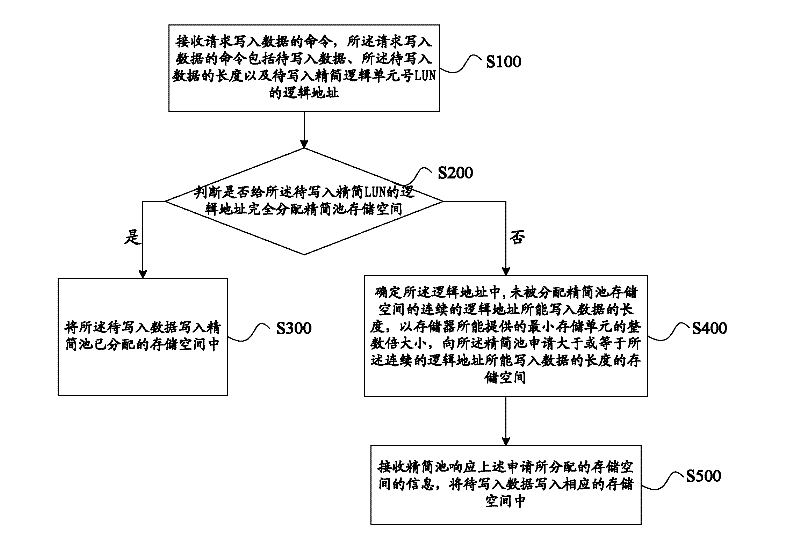
Method and system for writing data
ActiveCN102650931AAvoid wastingSave memory resourcesInput/output to record carriersOperating systemLogical address
The embodiment of the invention provides a method and system for writing data. The method comprises the following steps of: receiving a command for requesting to write data; judging whether a compacted cell storage space is completely allocated for a logic address to be written in a compacted LUN (Logic Unit Number) or not, if so, writing the data to be written into a storage space allocated by the compacted cell and otherwise, determining the length of the data which can be written by a continuous logic address for which the compacted cell storage space is not allocated in the logic address and applying the storage space which is greater than or equal to the length of the data which can be written into the continuous logic address for the compacted cell according to the magnitude of integral multiple of a minimum storage unit provided by a memory; and receiving information responding to the storage space allocated by the application by the compacted cell and writing the data to be written into the corresponding storage space. According to the method and system disclosed by the invention, effective utilization of system resources is realized.
Owner:HUAWEI TECH CO LTD
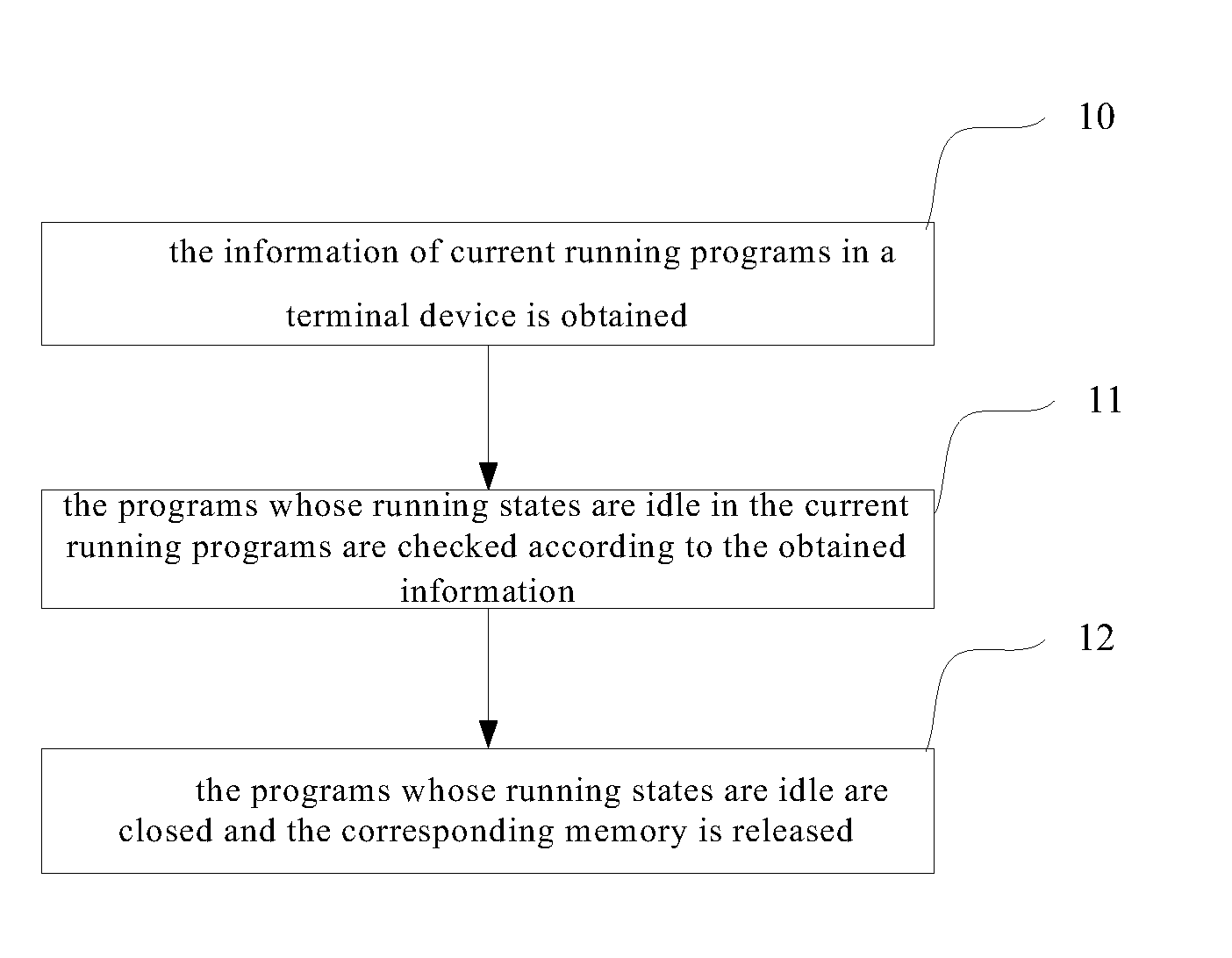
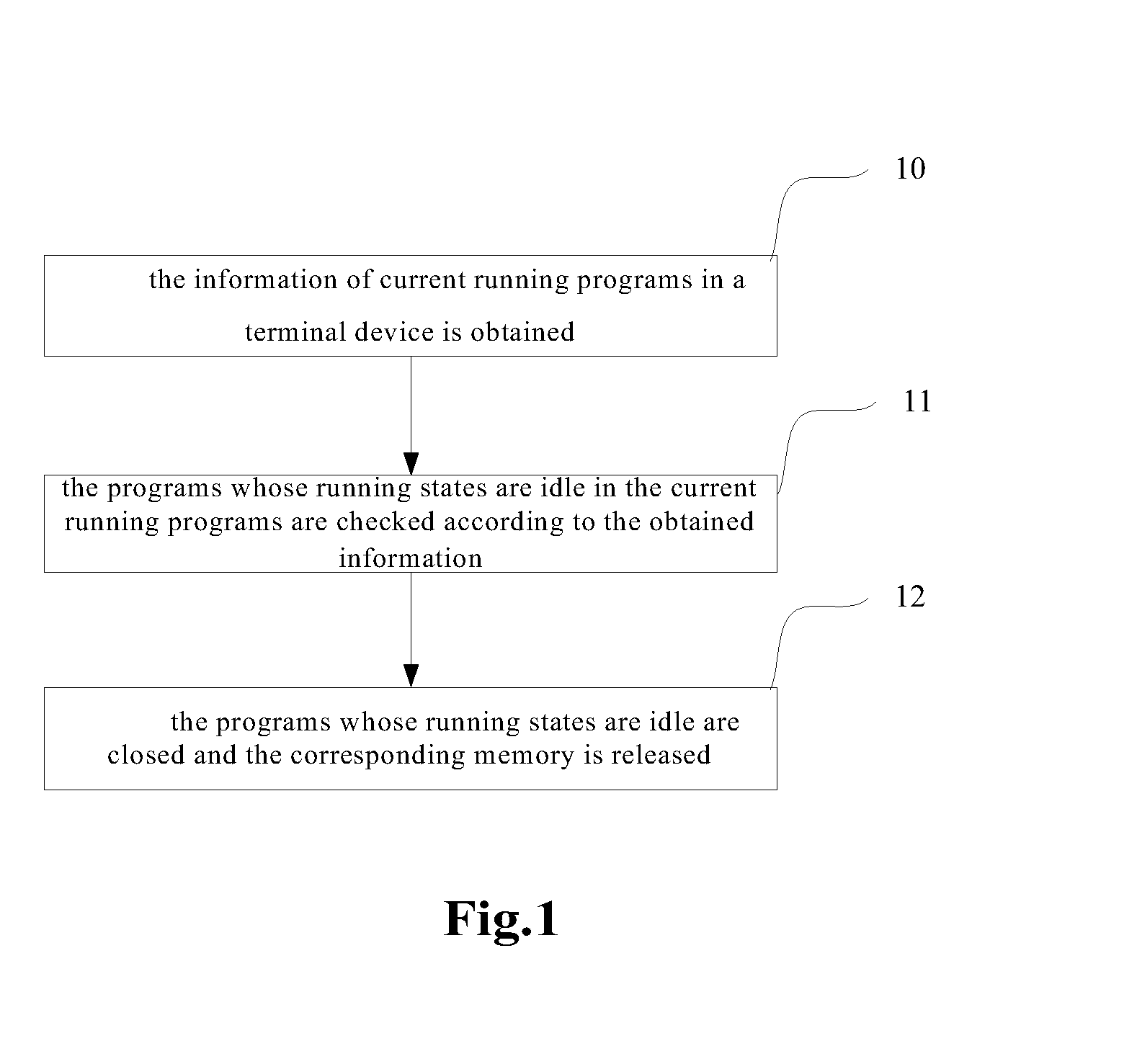
Control method and control device for releasing memory
ActiveUS20130074082A1Improve user experienceSave memory resourcesError detection/correctionMultiprogramming arrangementsProgram managementReal-time computing
A control method and a control device for releasing memory are provided by the embodiments of the present invention. The present invention relates to the technical field of terminal device program management, which is used for solving the problem of wasting memory resource of terminal devices. The present invention comprises: obtaining information of current running programs in a terminal device; checking programs whose running states are idle in the current running programs according to the obtained information; closing programs whose running states are idle and releasing corresponding memory. According to the present invention, idle programs can be quickly found and then closed, and thereby the memory is saved and user experience is improved.
Owner:ZTE CORP
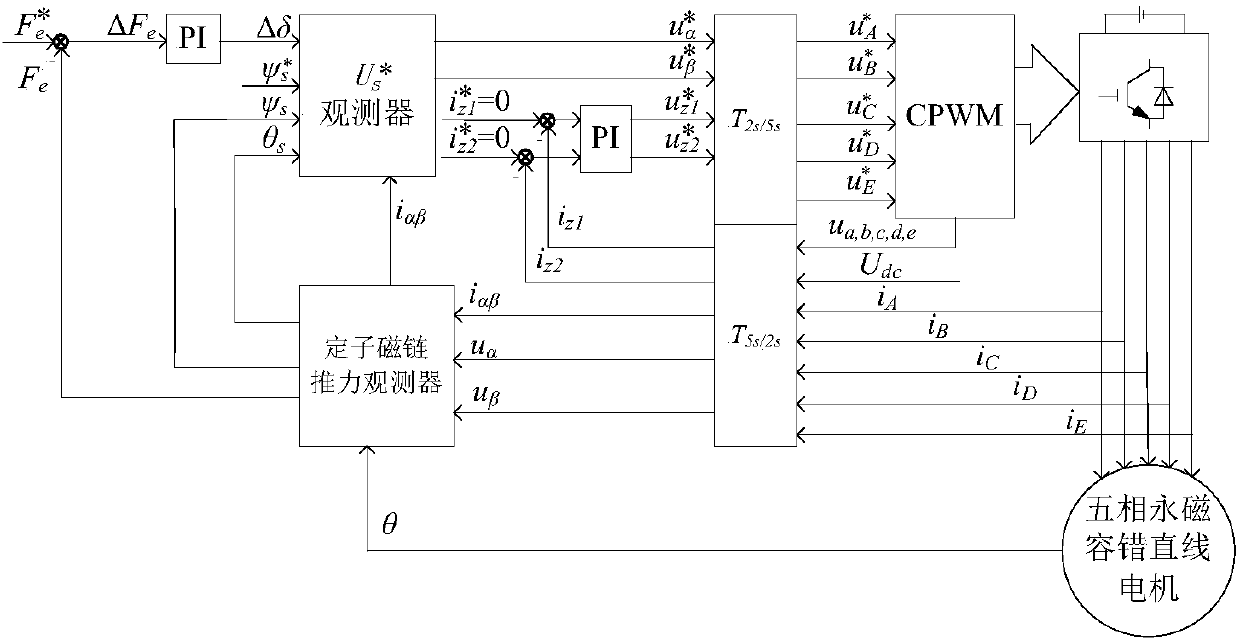
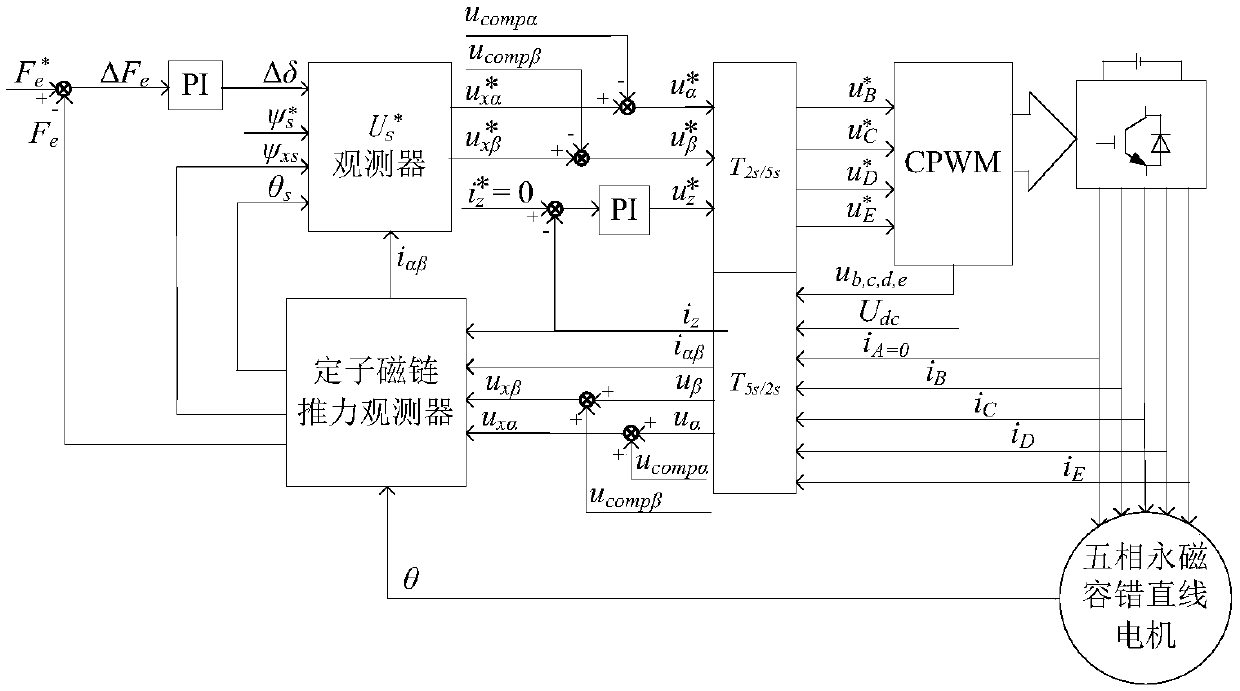
One-phase open-circuit fault-tolerant direct thrust control method for five-phase permanent magnet linear motor
InactiveCN108306571AIncreased complexitySave memory resourcesElectric motor controlVector control systemsPhase currentsModulation function
The invention discloses a one-phase open-circuit fault-tolerant direct thrust control method for a five-phase permanent magnet linear motor. Firstly, a Clark transform matrix and an inverse matrix thereof are derived based on fault-tolerant phase current. On the above basis, a stator flux linkage on alpha-beta is derived, a stator virtual flux linkage is defined according to the requirements of acircular stator flux linkage trajectory, and thus the voltage compensation on alpha-beta is derived. The stator actual voltage on the alpha-beta is derived by a modulation function of a voltage sourceinverter, and voltage is combined with voltage compensation and stator current, and a stator virtual flux linkage and thrust are observed by a stator flux observer and a thrust observer. Then statorvirtual target votlage is calculated according to given thrust, a given stator flux linkage amplitude and the observed stator virtual flux linkage and thrust. Finally, the stator actual voltage is calculated by the voltage and the voltage compensation, and the motor is controlled by the voltage by the voltage source inverter. According to the method, a thrust fluctuation caused by a motor failureis suppressed, and more importantly, the dynamic performance and steady state performance are consistent with that in a normal condition.
Owner:JIANGSU UNIV
Implementation method for operator reuse in parallel database
ActiveCN102323946AReduce readSave memory resourcesSpecial data processing applicationsQuery planDirected graph
The invention discloses an implementation method for operator reuse in a parallel database, comprising the following steps of: step 1, generating a serial query plan for query through a normal query planning method, wherein the query plan is a binary tree structure; step 2, executing the query plane by scanning from top to bottom, searching materialized reusable operators, changing the query plane structure, and changing thread level materialized operators into global reusable materialized operators; step 3, parallelizing the query plan changed in the step 2, and generating a plan forest for parallel execution of a plurality of threads; step 4, executing global reusable operator combination on the plan forest generated in the step 3, and generating a directed graph plan for the materialized reusable operators capable of being executed by the plurality of threads in parallel; step 5, executing own plan part in the directed graph by each thread in parallel, wherein the thread which executes the global reusable operator firstly is called a main thread, the main thread locks the global reusable operator and truly executes the operator and the plan of the operator, and other threads wait; step 6, unlocking the global reusable operator by the main thread after execution, wherein other threads start to read data from the global reusable operator and continue to execute own plan tree;and step 7, releasing the materialized data of the operator by the main thread after all the plans read the data of the global reusable operator.
Owner:天津神舟通用数据技术有限公司
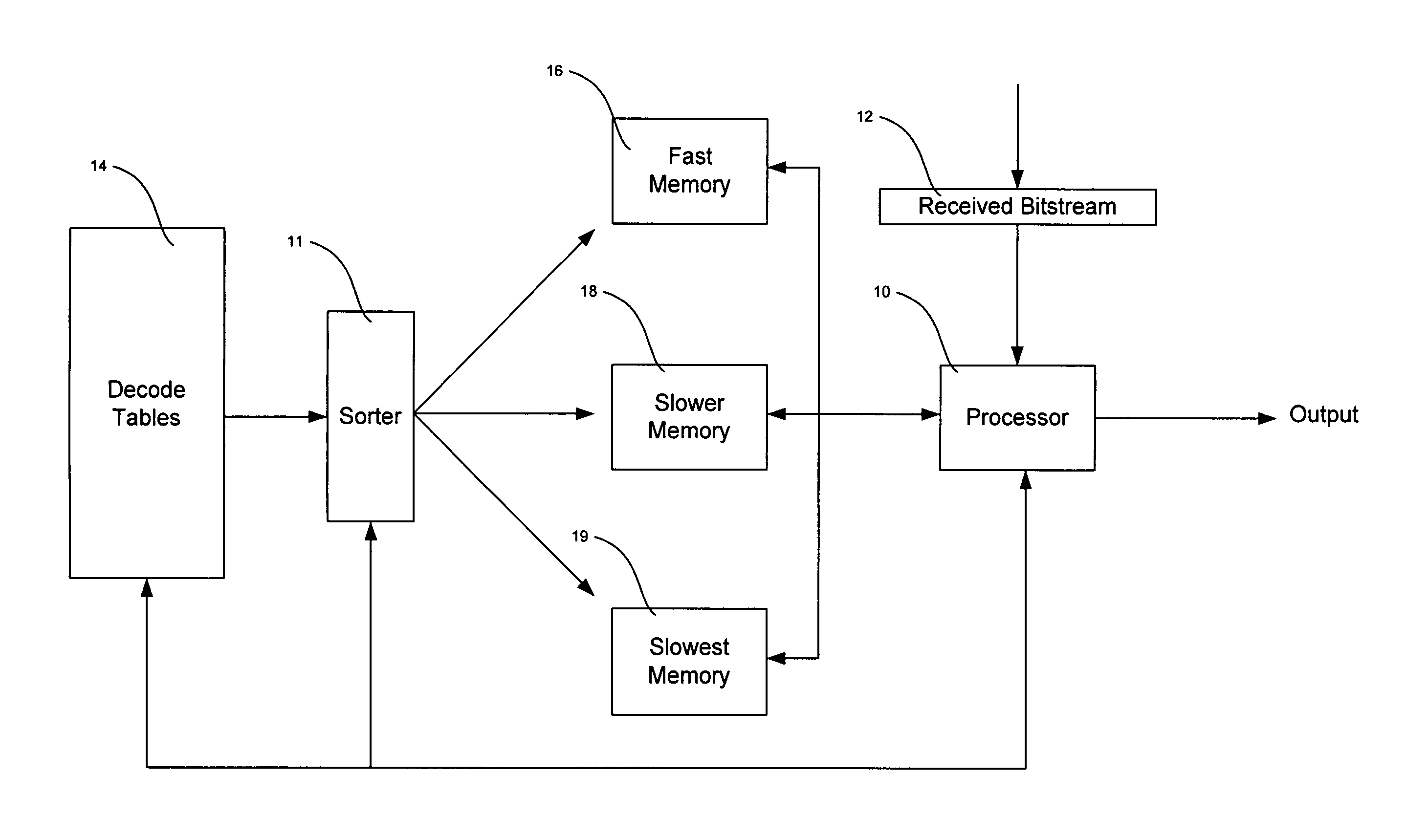
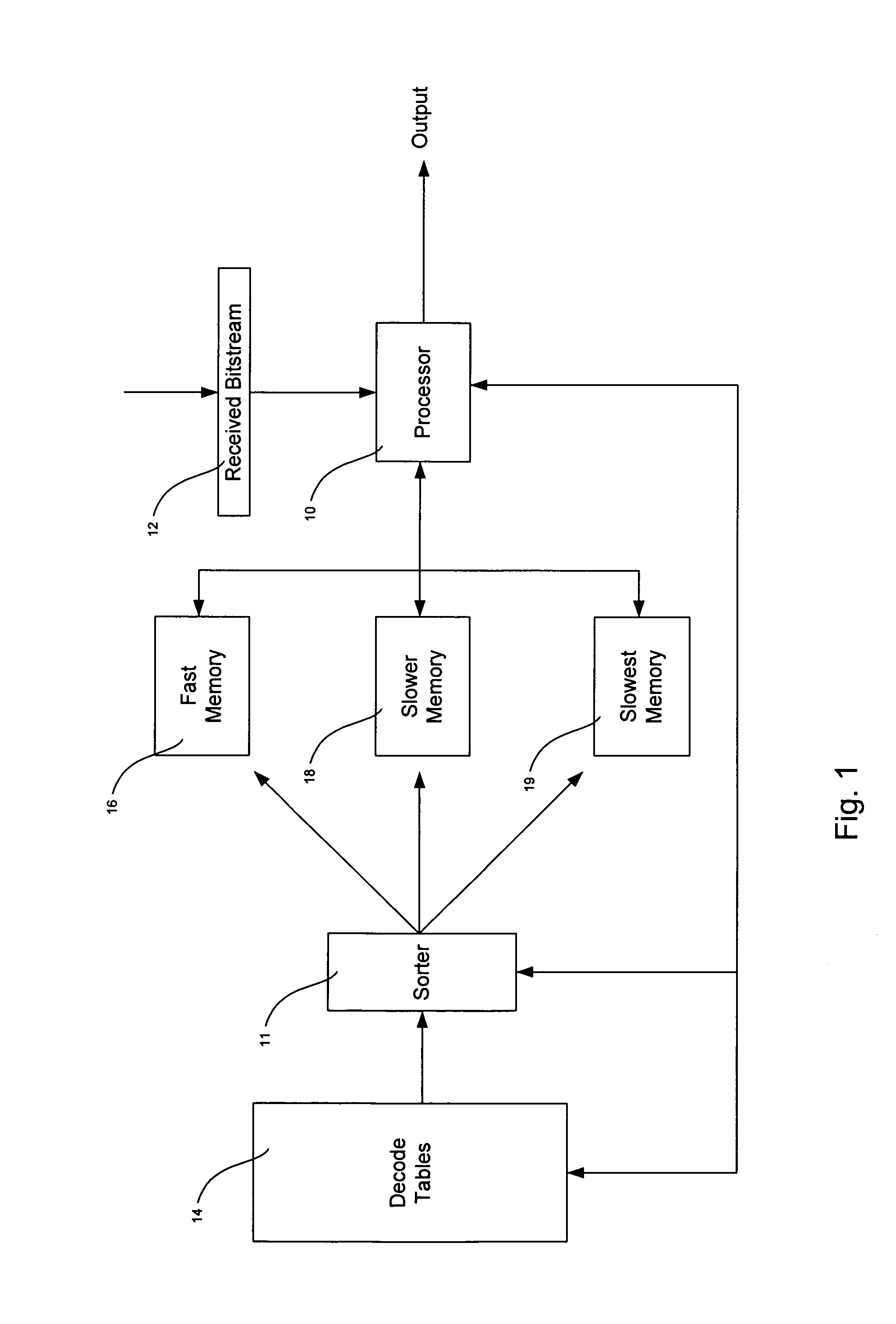
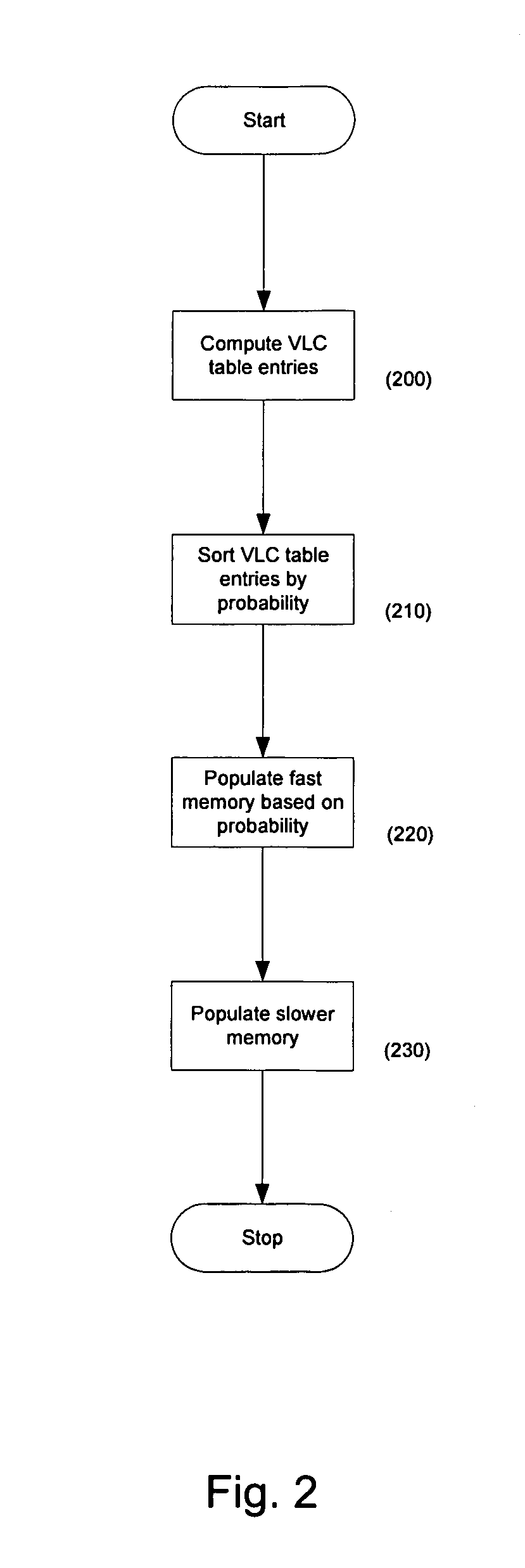
Optimization of decoder memory usage for VLC tables
ActiveUS7324026B2Optimizing storage of VLC tablesSave memory resourcesCode conversionDigital video signal modificationVariable lengthData mining
Systems and methods for optimizing system performance in variable length decoding systems are described. Embodiments are described in which decode tables are analyzed and elements of the tables sorted by probability of occurrence. Storage of elements can be determined by probability of occurrence and embodiments of the present invention can optimize system efficiency by storing most likely entries into fast-memory and least likely entries in slowest memory. In certain embodiments, a single large table is provided that cannot fit into decoder fast-memory. In some embodiments, individual elements can be optimized for storage in fast-memory by selecting more frequently occurring entries or groups of entries into decoder memory.
Owner:NVIDIA CORP
Method for extracting compressed video key frames
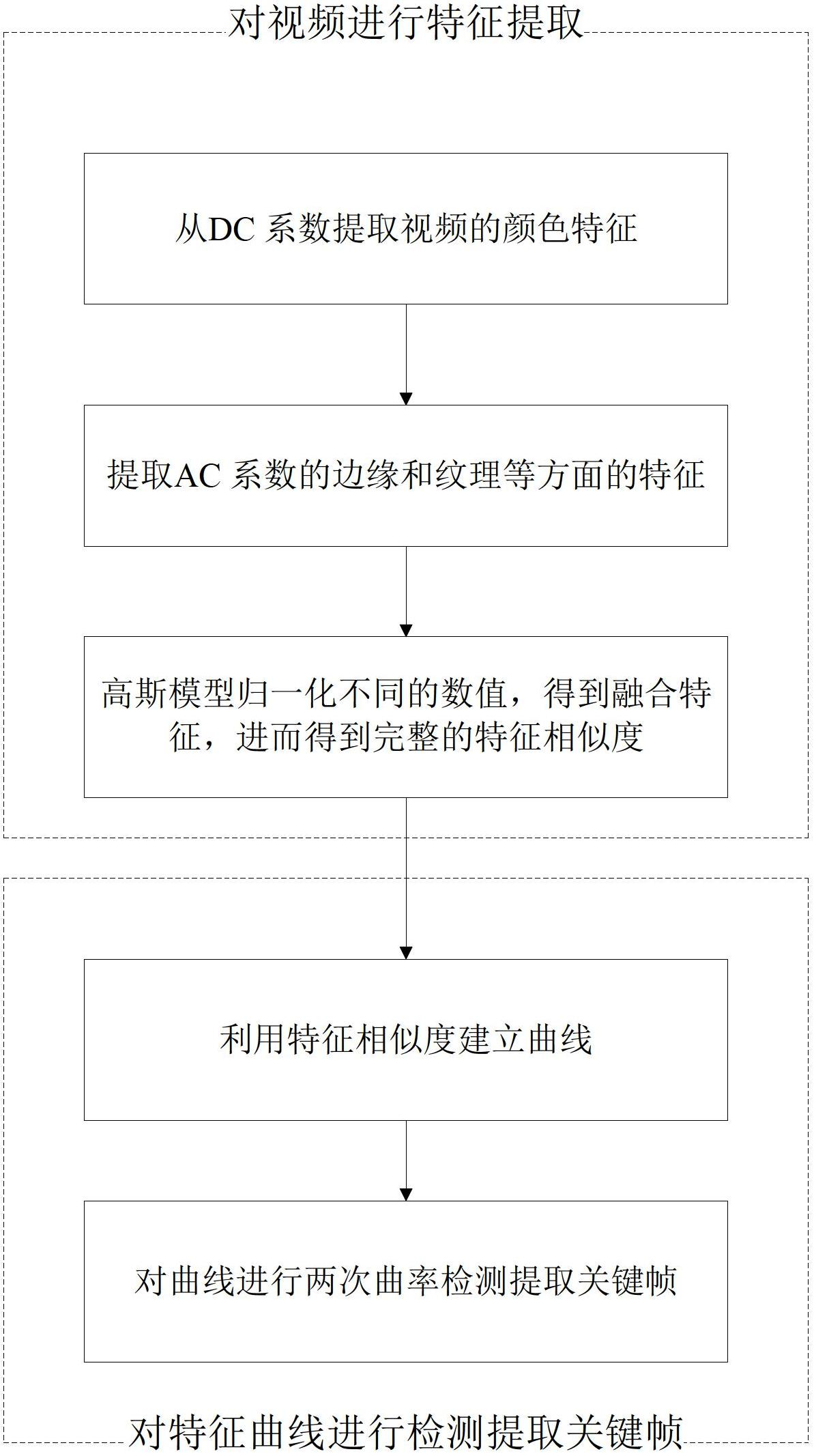
InactiveCN102695056ARealize automatic extractionMake up for incomplete descriptionTelevision systemsDigital video signal modificationPattern recognitionAc coefficient
The invention discloses a method for extracting compressed video key frames. The method includes: firstly, extracting color characteristics of a video from a DC coefficient, then extracting characteristics of edges, textures and the like of an AC coefficient and normalizing different values by means of a Gaussian model to obtain fusion characteristics, so that complete characteristic similarities are obtained to improve representativeness and increase the accuracy rate of the key frames; and then establishing a curve by the aid of the complete characteristic similarities, and performing curvature detection for the curve for twice so as to extract the key frames. By the method, the key frames capable of reflecting main contents of the video can be accurately extracted, and the defect of incomplete video content descriptions by using DC coefficient characteristic information only is made up. Moreover, automatic extraction of the key frames is realized by means of two-time curve detection, and artificial determination of the amount of the key frames is avoided.
Owner:SUN YAT SEN UNIV
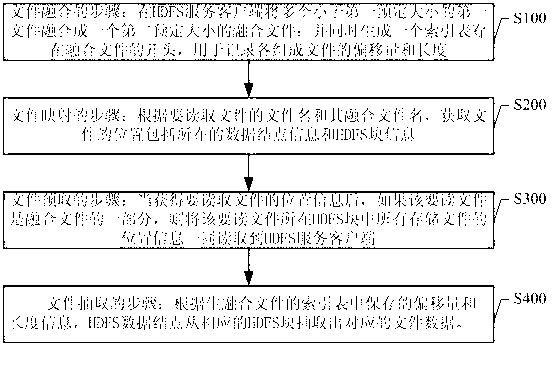
Video file index method and system
InactiveCN103279474ASave memory resourcesImprove reading efficiencySpecial data processing applicationsClient-sideIndex method
The invention discloses a video file index method and system. The method includes the steps of file merging and file extraction. According to the step of file extraction, data nodes of an HDFS extract corresponding file data from corresponding HDFS blocks according to offset and length information saved in an index table of a generated merged file. More specifically, the method includes the steps of merging small files into the large file, establishing an index for the merged file, storing the merged file onto the HDFS, acquiring a corresponding storage position at namenodes with the method of file mapping in the process of reading the merged file from the HDFS, and improving read efficiency by direct communication between an HDFS service client-side and the data nodes and by file prefetching at the HDFS service client-side. The video file index method and system can manage the small files in the HDFS efficiently, save internal storage resources of the namenodes of the HDFS, improve the efficiency in reading the small files, and save storage resources of the data nodes of the HDFS.
Owner:SHENZHEN KONKA TELECOMM TECH
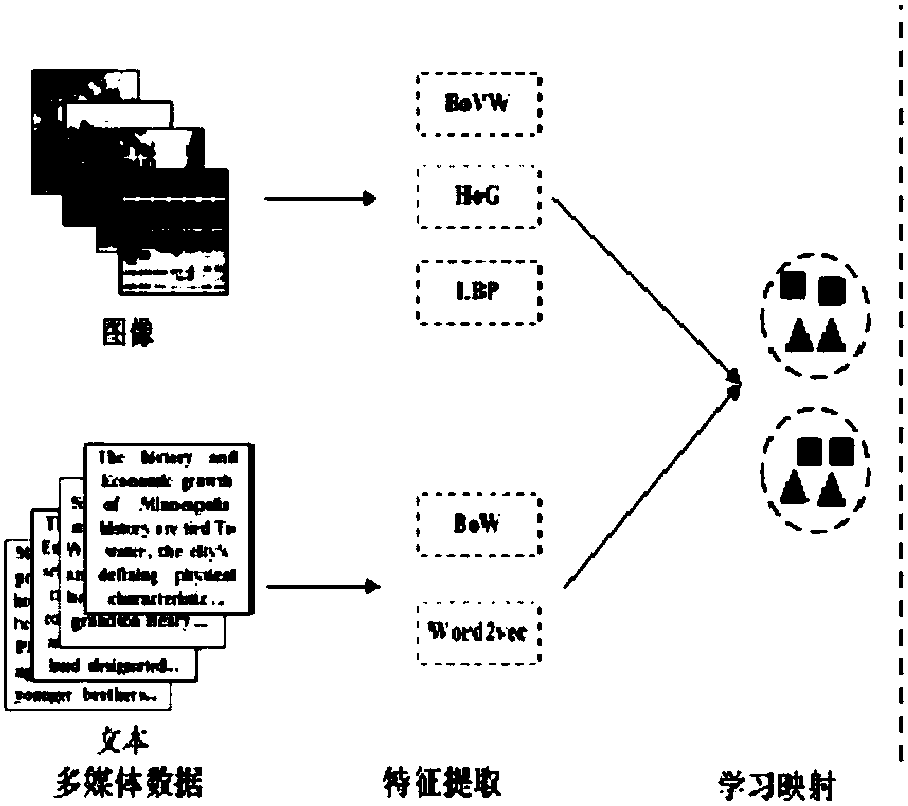
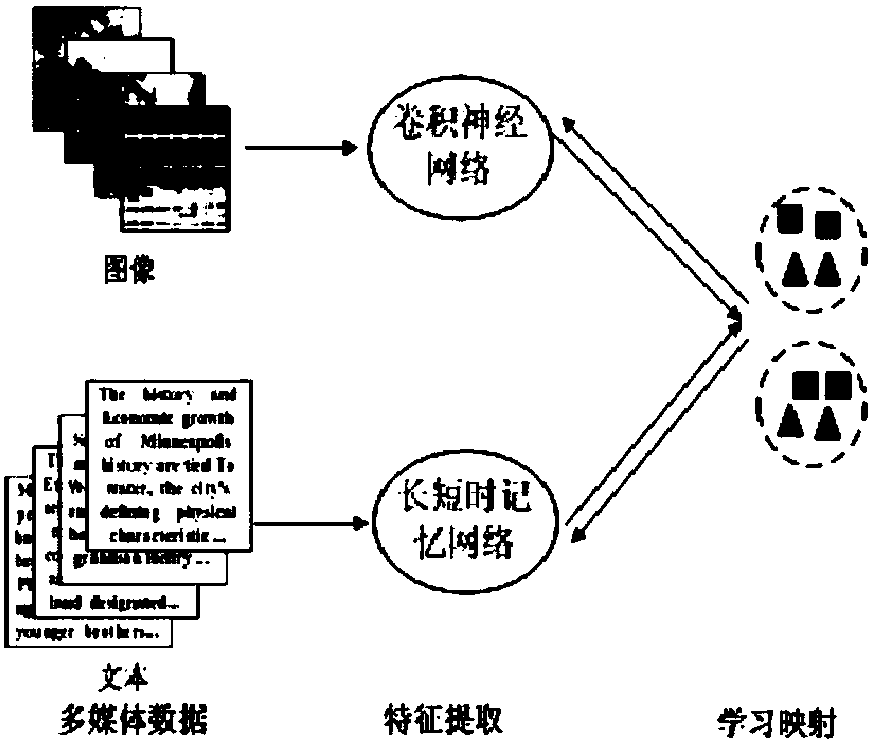
Cross-media training and retrieval method based on depth discrimination sorting learning
ActiveCN107657008AEasy to handleEffectively Mining Semantic AssociationsMetadata multimedia retrievalCharacter and pattern recognitionFeature vectorAcquired characteristic
The invention relates to a cross-media training and retrieval method based on depth discrimination sorting learning. The method comprises the following steps that: utilizing a deep network to extractfeatures from an image sample and a statement sample in a training set, and obtaining a feature vector pair, wherein the feature vector pair comprises an image feature vector used for showing the image sample, and a statement feature vector used for showing the statement sample; mapping the obtained feature vector pair to a common space, and calculating a similarity between the image feature vector and the statement feature vector; and utilizing a bidirectional discrimination sorting target function to sort the feature vector, and obtaining a training model.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
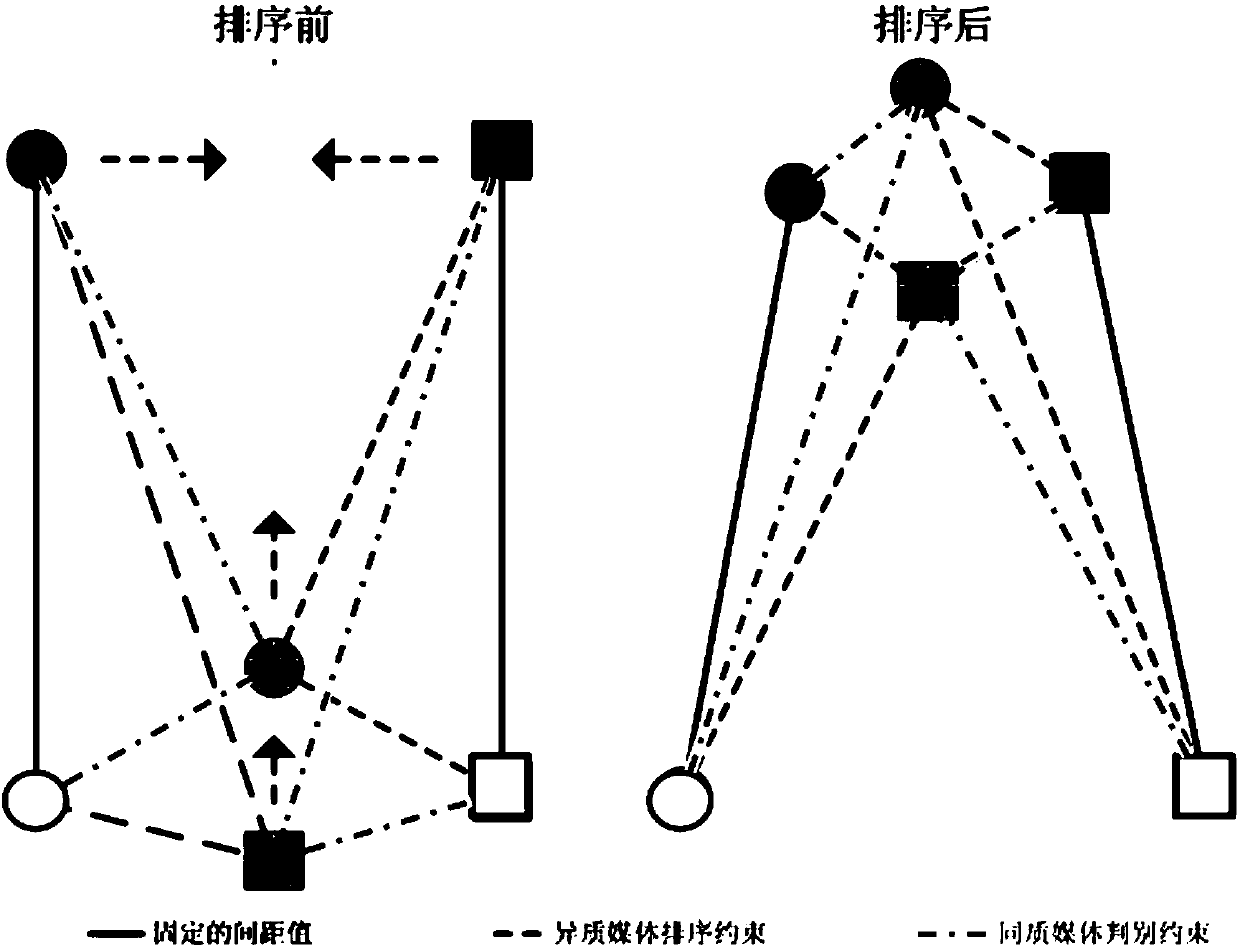
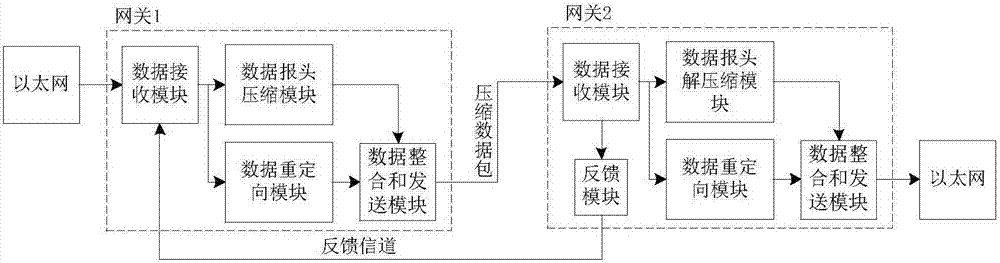
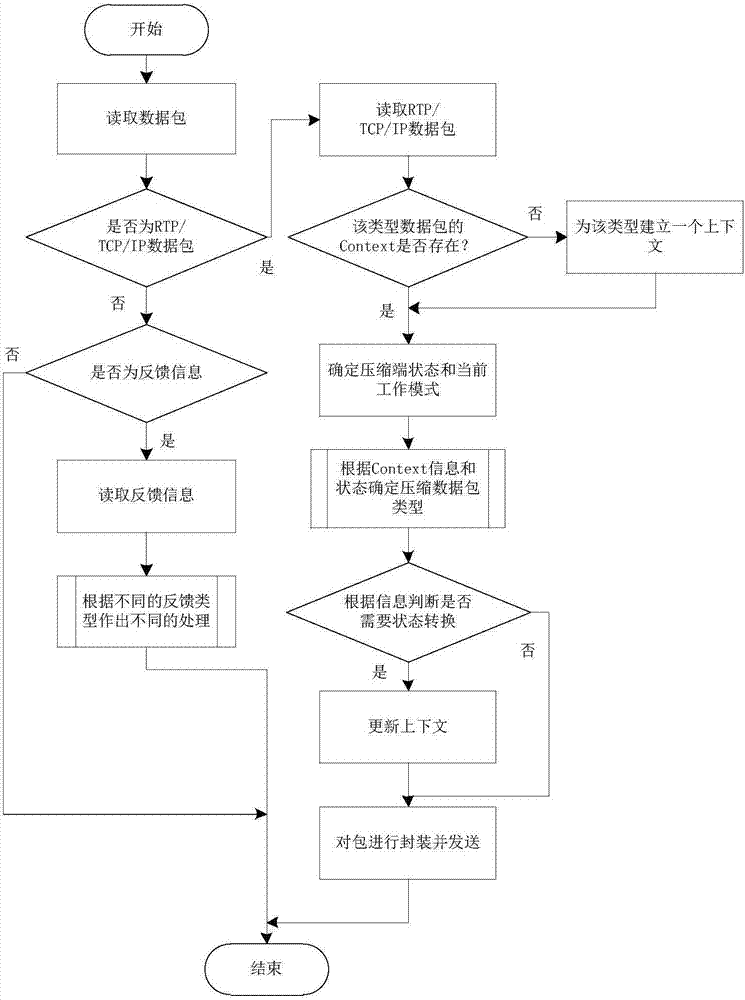
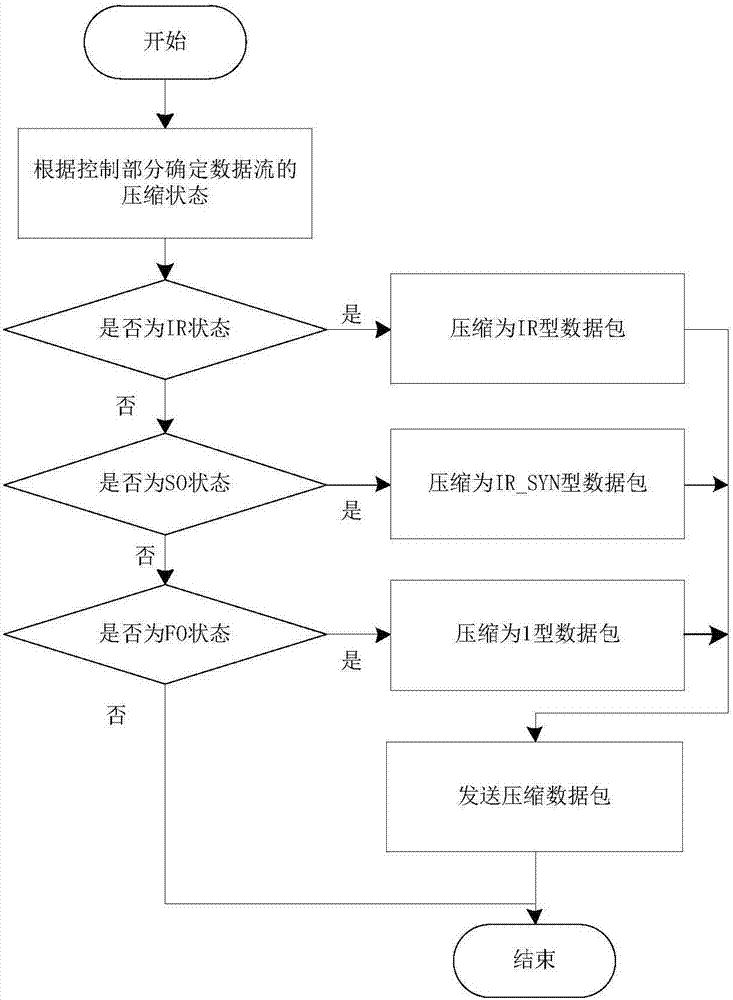
Inter-network data header compression realization method
InactiveCN107347046AClear layersReduce relevanceTransmissionAddress Resolution ProtocolTelecommunications link
The present invention relates to an inter-network data header compression realization method. According to the method, two embedded ARM (Acorn RISC Machine) processors are adopted as a hardware basis, and the kinds of hardware are designed into gateways in different network domains by means of gateway data forwarding; a multi-processing mechanism is adopted to perform classification processing on the different data packet types of the different gateways; and a network address and physical address mapping method is adopted to achieve host communication between different local area networks. The inter-network data header compression method can be applied to an OSI (Open System Interconnection) seven-layer model-based network protocol. Different from a traditional a third-layer switching technology, the inter-network data header compression method of the present invention uses the network address and physical address mapping method in the ARP (Address Resolution Protocol) technology to process the data packets of a data link layer, so that the gateways can directly forward the data after receiving data without making the data processed by the upper layer of a network protocol, and therefore, the forwarding efficiency of the data can be increased by 15%; the quantity of data transmission in a communication link can be reduce by 12%; and good anti-jamming performance can be realized when video voice data packets are transmitted.
Owner:BEIJING UNIV OF CHEM TECH
Display of images with transparent pixels
InactiveUS7012616B1Save memory resourcesImage memory managementCathode-ray tube indicatorsAnimationDisplay device
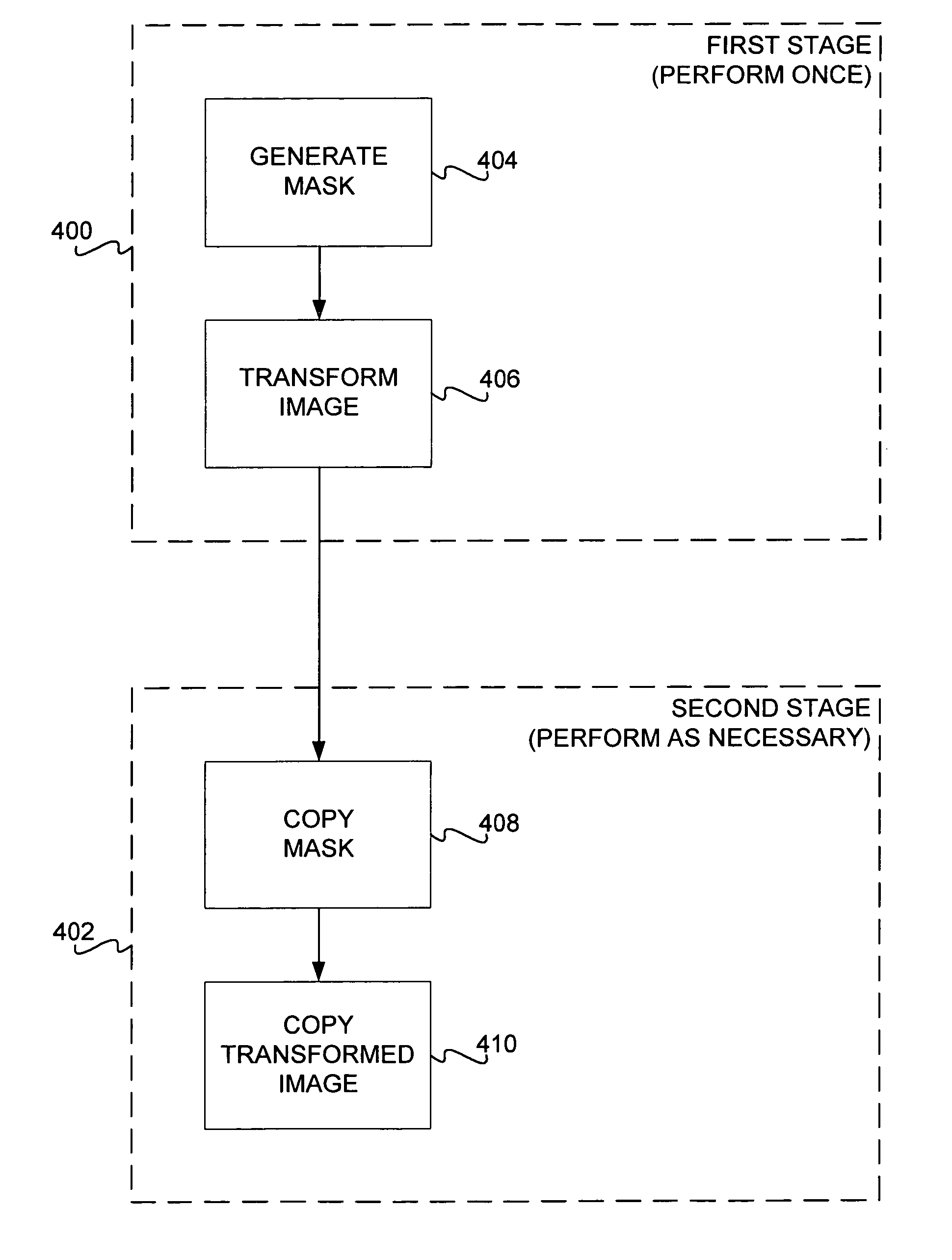
Displaying images having pixels thereof that are meant to be transparent is disclosed. In one embodiment, a method includes a first stage and a second stage. The first stage is performed once, to transform the image and generate a mask thereof. The second stage is performed each time the image is to be displayed, to copy the transformed image and the mask onto the display. In one embodiment, the transparent image is shrunk and / or stretched when displayed. The cases of animated images and dithering for alpha blending are also disclosed and covered by the invention.
Owner:MICROSOFT TECH LICENSING LLC
Implementation method and system for bus passing by station where no passengers get on and off without stopping
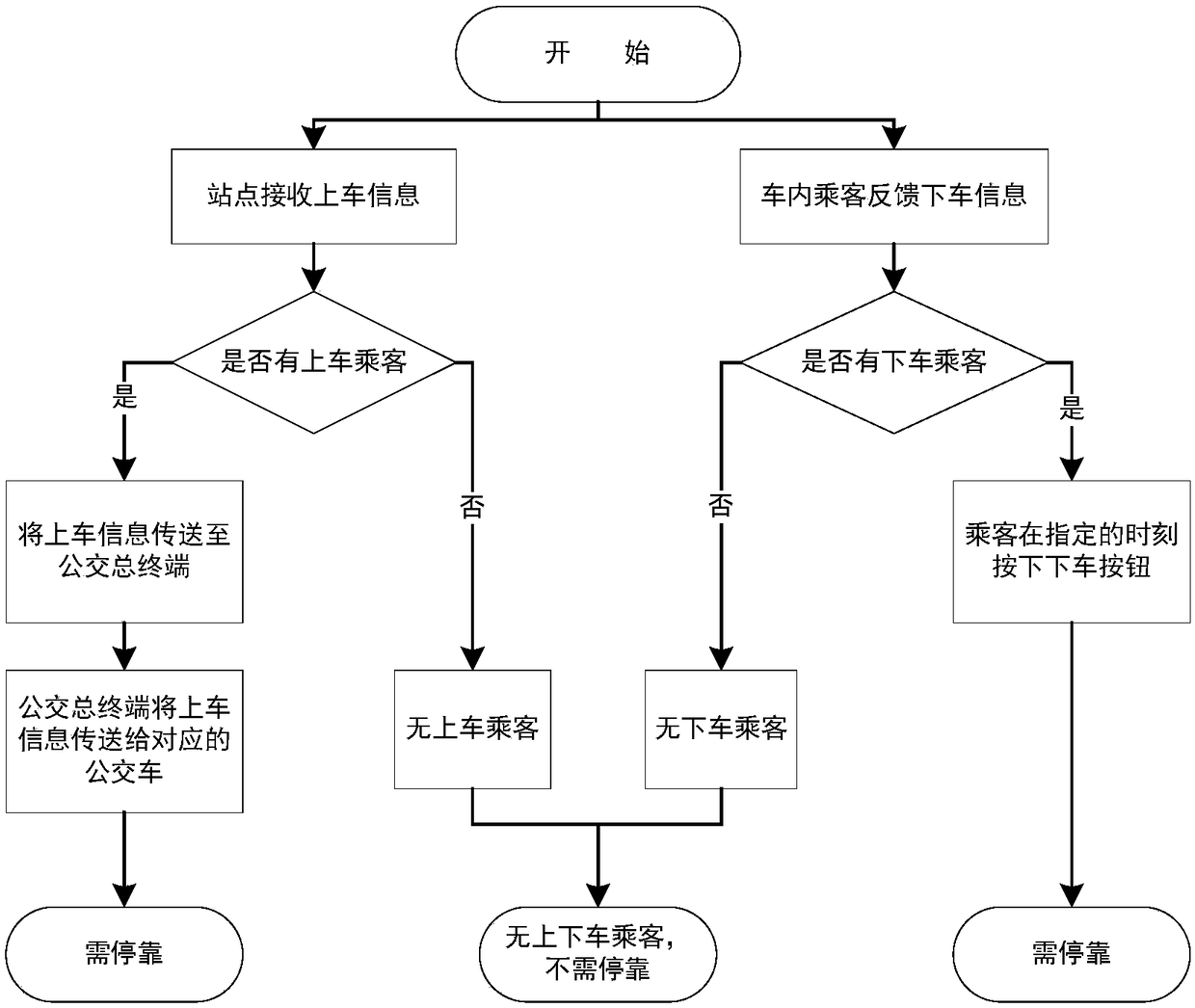
InactiveCN108335517ASave travel timeImprove ride satisfactionRoad vehicles traffic controlEmbedded systemTotal station
The invention discloses an implementation method and system for a bus passing by a station where no passengers get on and off without stopping. The system comprises a platform input panel, a get-on passenger information indicating lamp, a get-off feedback button, a get-off passenger information indicating lamp, a voice player and an information transmitter are arranged in a bus, and a bus total terminal is arranged on a bus total station; after a passenger inputs a needed bus path through the platform input panel, the station and the bus path are sent to the bus total terminal, and the bus sends the path position of the bus to the bus total terminal in real time; the bus total terminal selects a bus which is closest to the passenger path position to send passenger get-on information according to the received information; after the information transmitter of the bus receives the passenger get-on information, or when the passenger of the bus presses the get-off feedback button, a driverinformation receiving device in the bus can light up the corresponding get-on information indicating lamp and get-off information indicating lamp and plays get-on information and get-off information to a driver through voice, and the driver stops at a front platform. The implementation method and system have the advantages that the bus station-passing efficiency can be improved, energy is saved, the trip time is saved, and the riding satisfaction of the passenger is improved.
Owner:SOUTHEAST UNIV
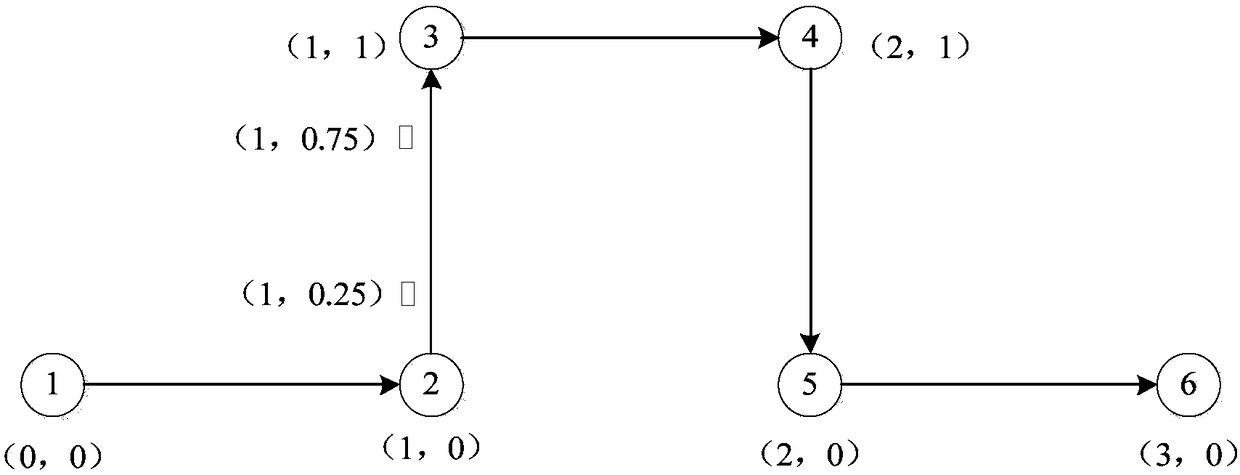
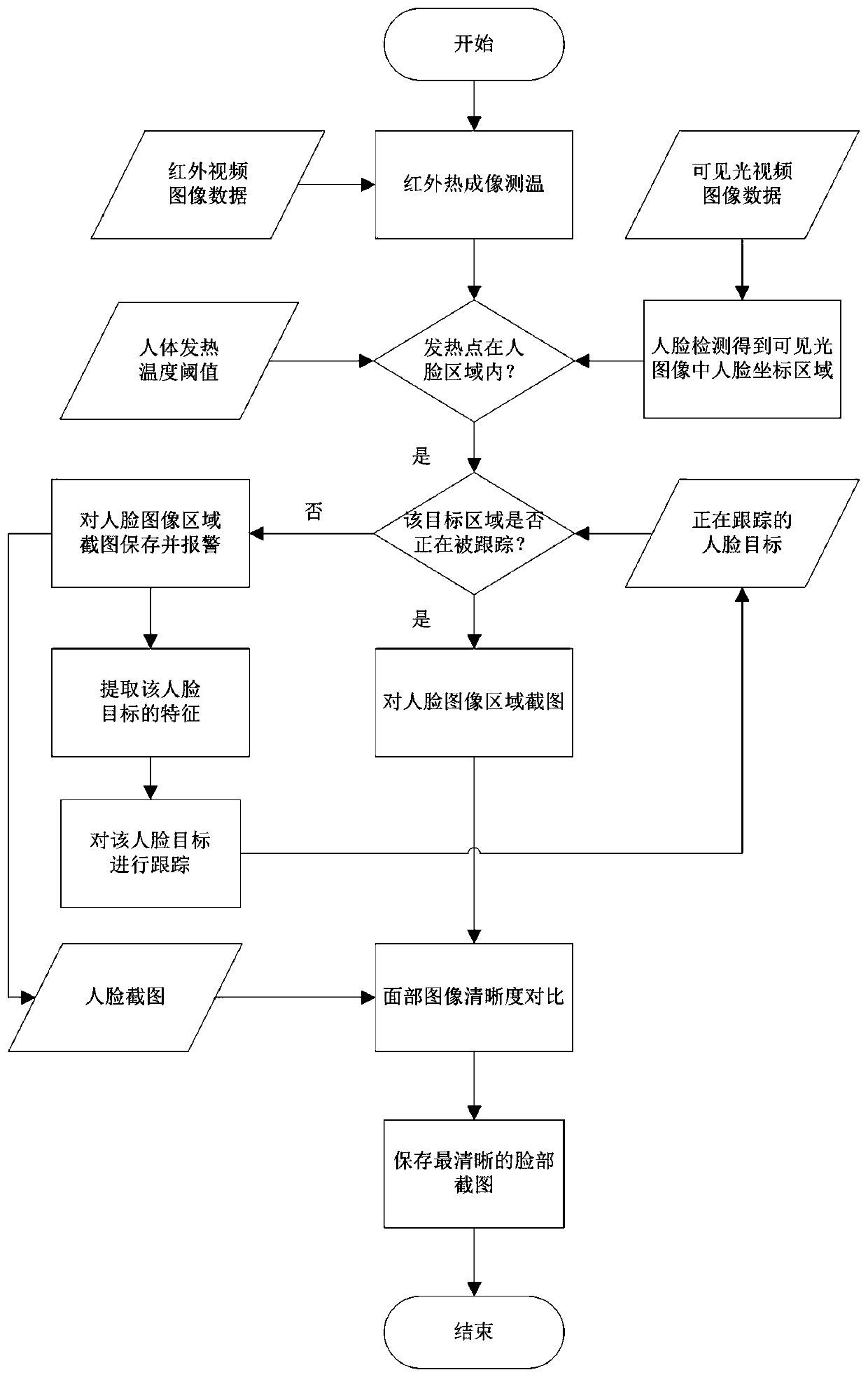
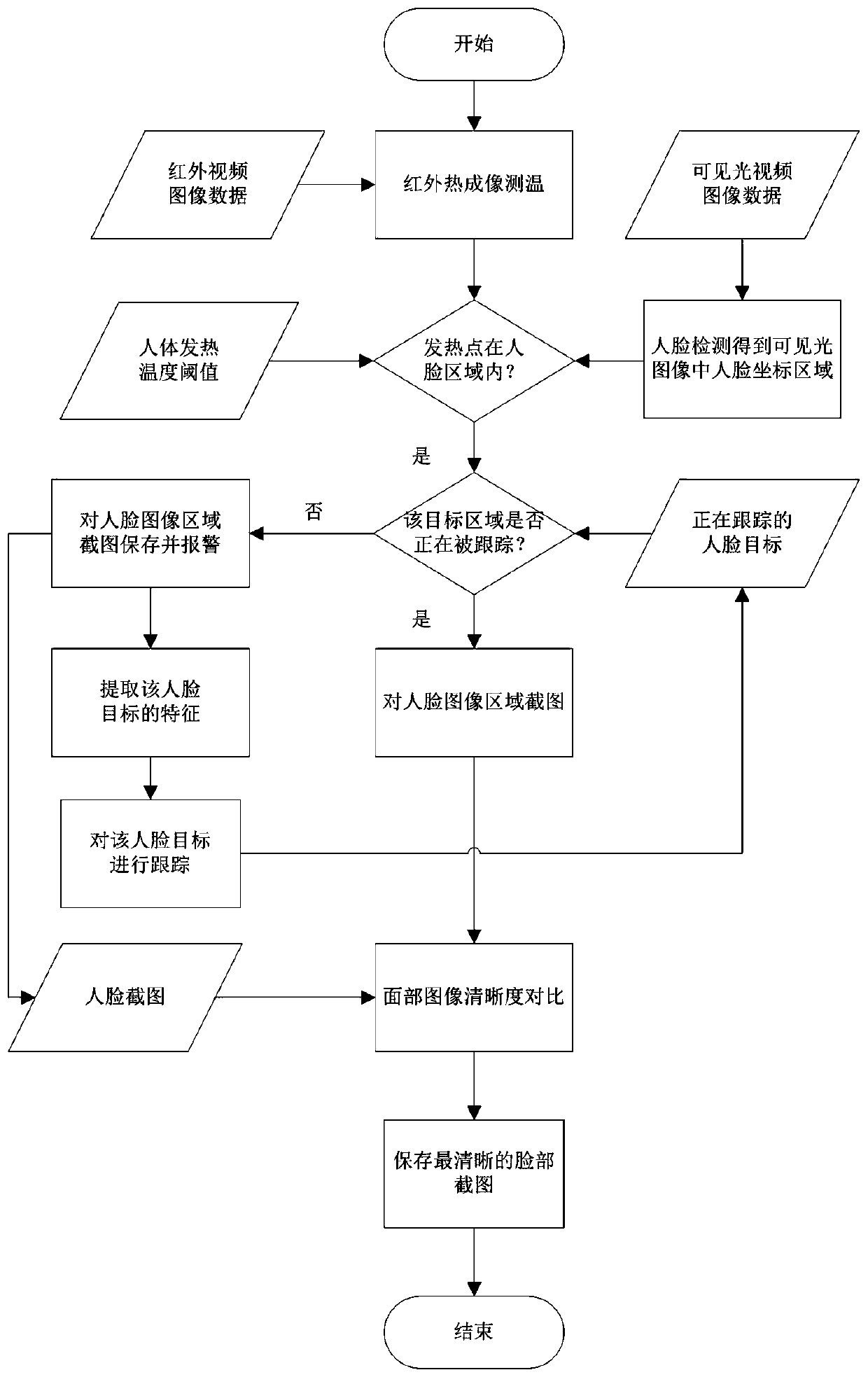
Method, device and equipment for avoiding repeated alarms in human body inspection and quarantine system
ActiveCN110044486AAvoid repeated alarmsRepeated alarms will notImage enhancementImage analysisHuman bodyQuarantine
The invention discloses a method, device and equipment for avoiding repeated alarms in a human body inspection and quarantine system. The method for avoiding repeated alarms in the human body inspection and quarantine system comprises the following steps that infrared video image data and visible light video image data of a human body are acquired, and heating personnel in the infrared video imagedata are measured by using an infrared thermal imaging temperature measurement method; when the heating personnel are monitored, a face image area of the heating personnel in a visible light video image is detected by using the matching relationship between an infrared image and the visible light image, and whether the face image area is tracked or not is judged; if the face image area is not tracked, screenshots of the face image area are saved, an alarm is given, and the face image area is tracked at the same time; and if the face image area is tracked, no alarm is given. The human body inspection and quarantine system is prevented from repeatedly alarming the same alarm personnel.
Owner:WUHAN GUIDE SENSMART TECH CO LTD
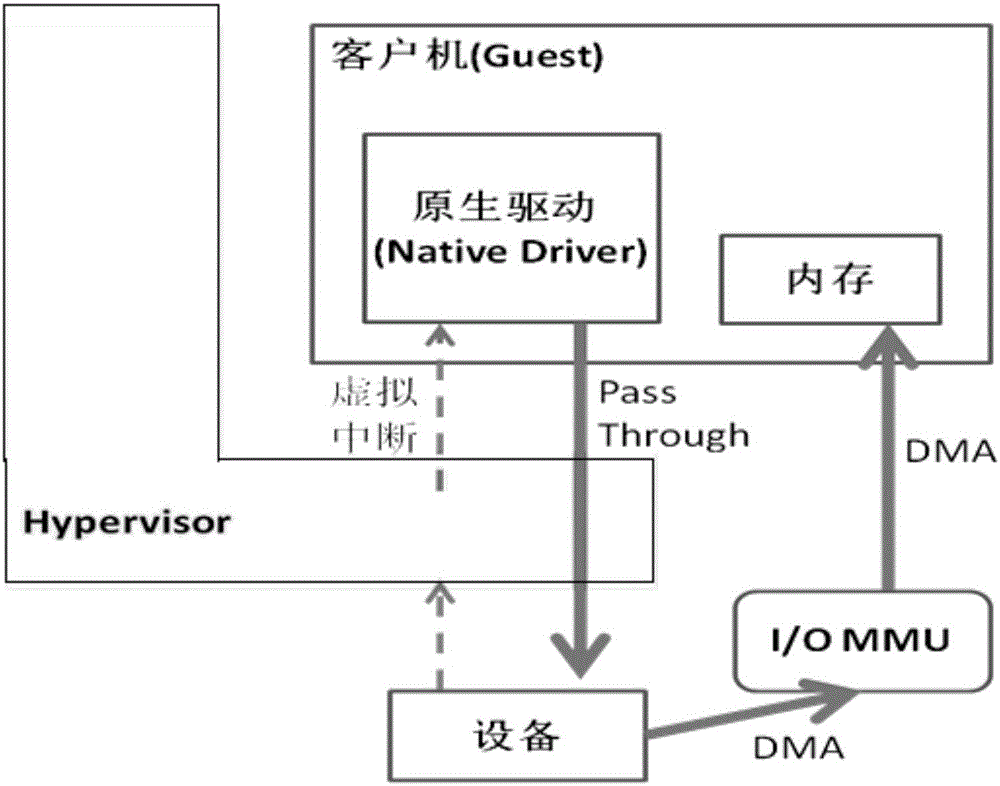
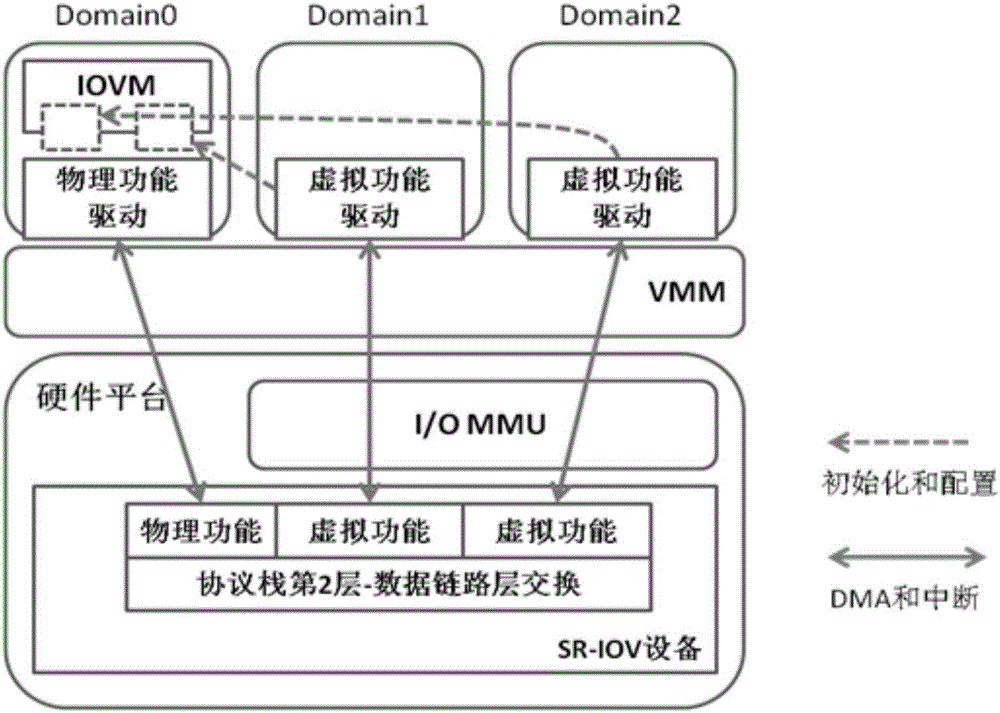
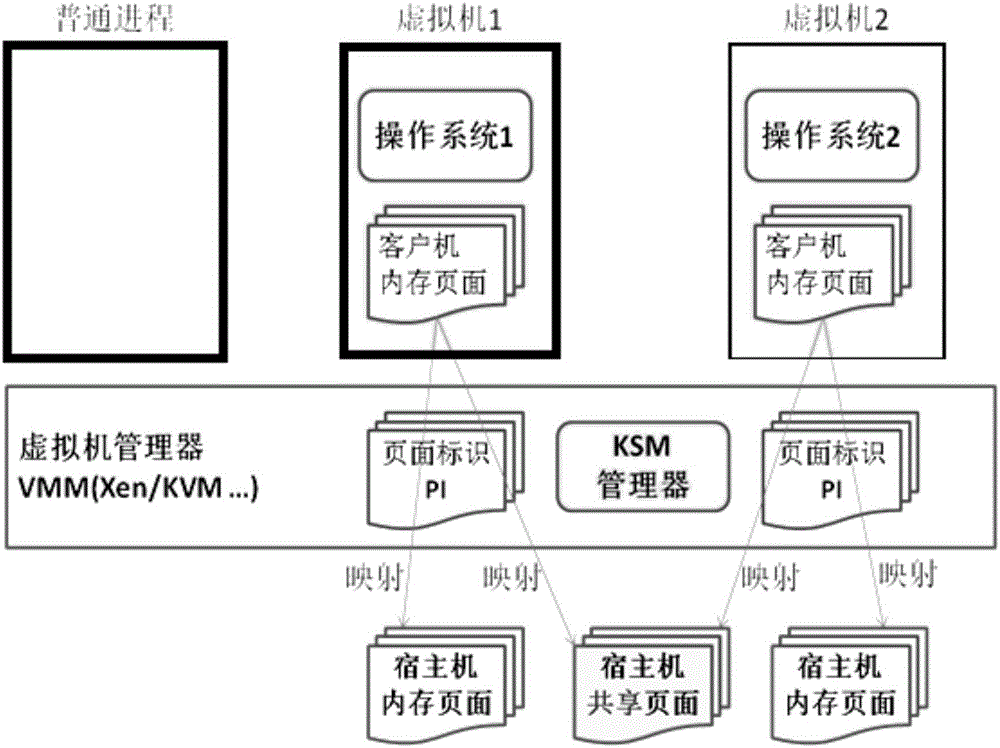
Virtual machine memory sharing method based on combination of KSM and Pass-through
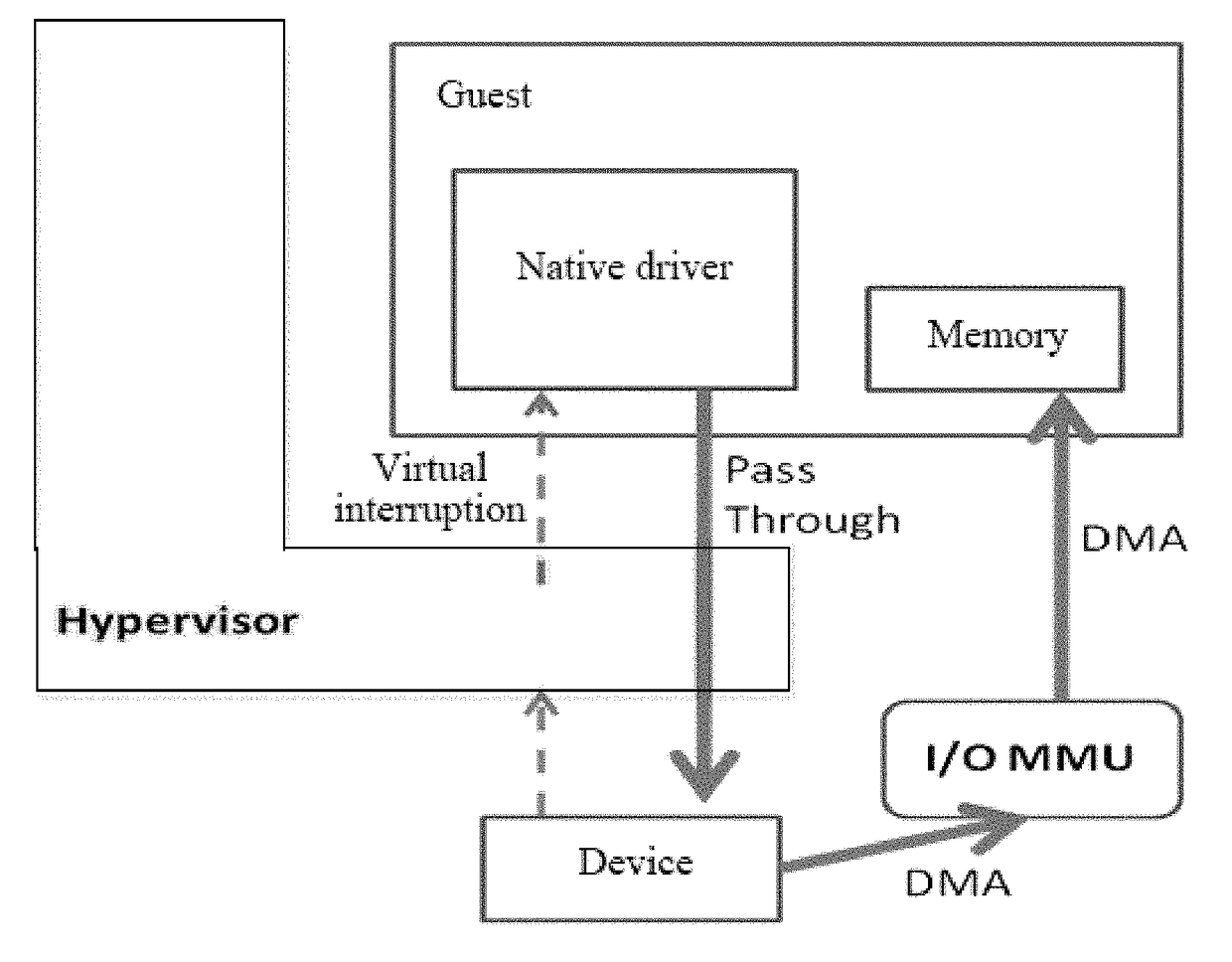
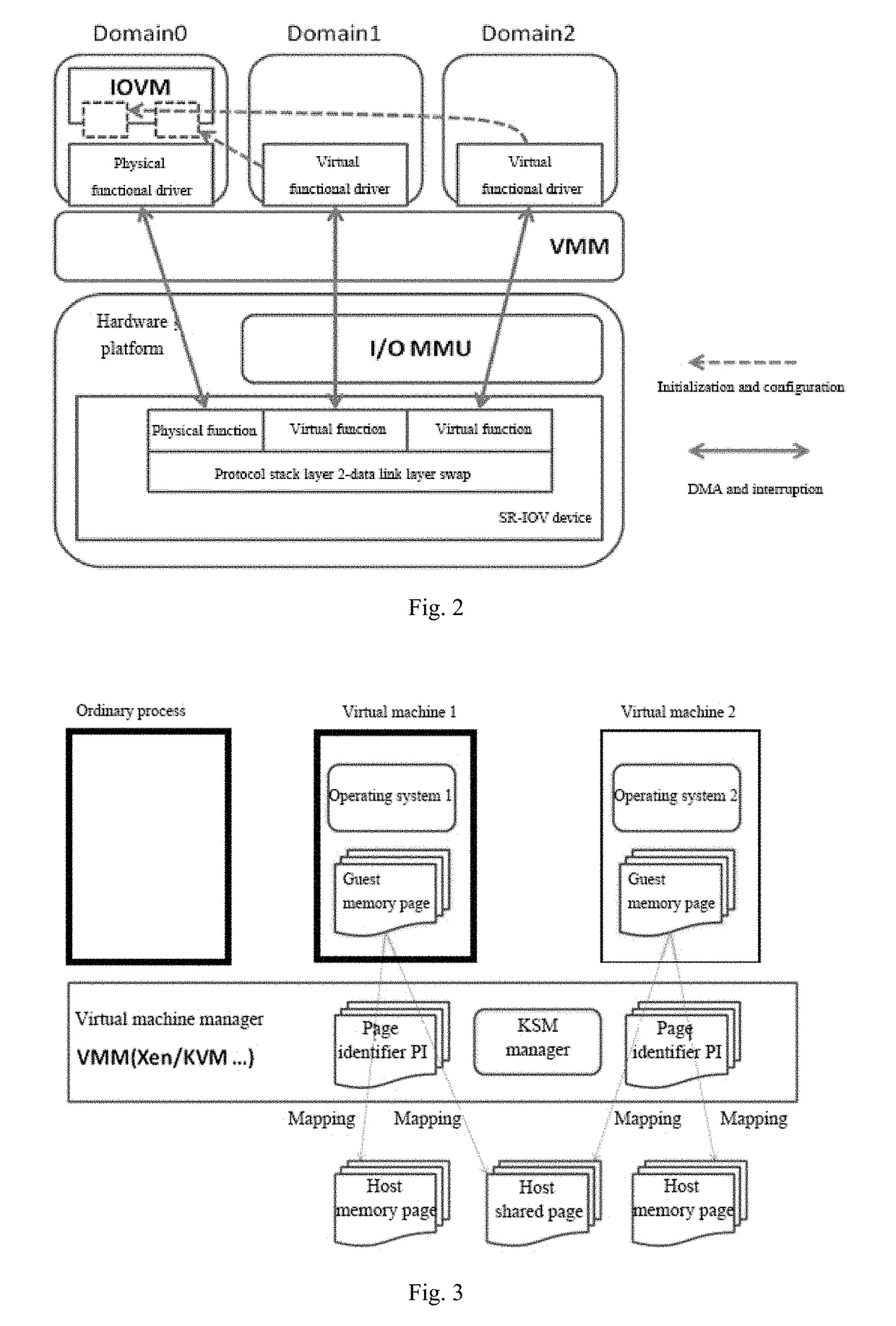
ActiveCN106155933ATroubleshooting Shared Merge IssuesEasy to operateMemory architecture accessing/allocationSoftware simulation/interpretation/emulationWrite protectionDirect memory access
The invention discloses a virtual machine memory sharing method based on the combination of KSM and Pass-through. The virtual machine memory sharing method specifically comprises the following steps: judging whether an operating system of each client uses an IOMMU (Input / Output Memory Management Unit) or not by a virtual machine manager; if not, not participating in sharing mapping of a KSM technology; if so, judging a memory page of each client and determining whether the memory page is a mapping page or not; if so, mapping the mapping page of each client into a host; if not, under the condition of keeping Pass-through properties, utilizing the KSM technology for all non-mapping pages and combining the memory pages with the same content in a plurality of sets of virtual machines; and meanwhile, carrying out writing protection processing. The memory pages of the clients are distinguished into special use for DMA (Direct Memory Access) and non-DMA uses, so that the KSM technology is only selectively applied to the non-DMA pages; and under the condition of keeping the Pass-through properties, the aim of saving memory resources is realized.
Owner:MASSCLOUDS INNOVATION RES INST (BEIJING) OF INFORMATION TECH
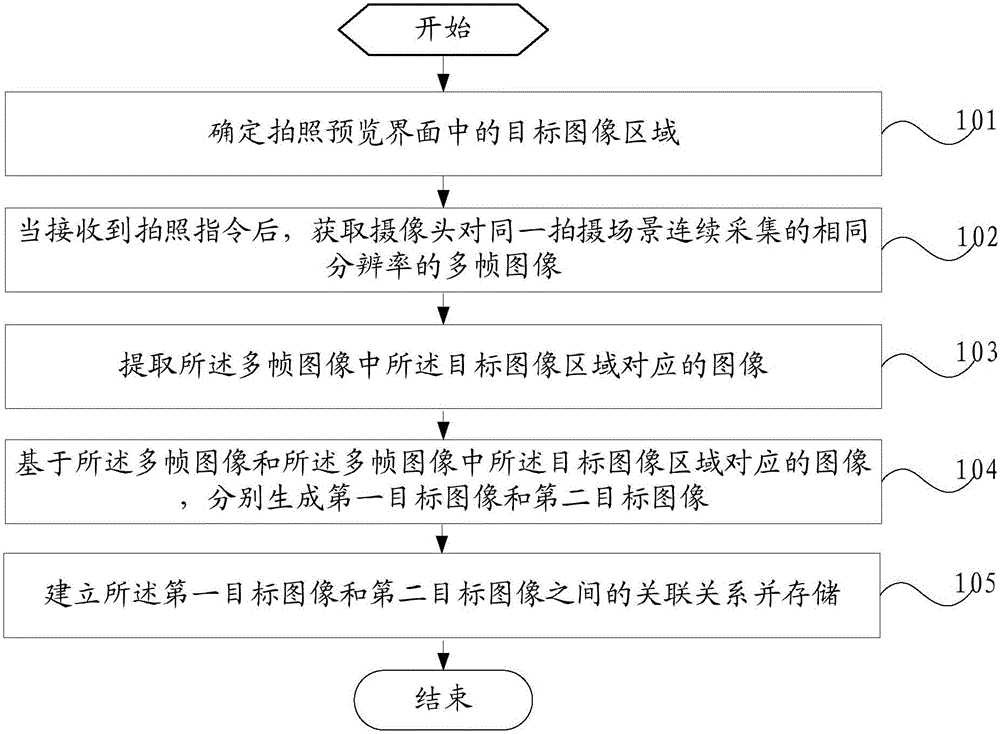
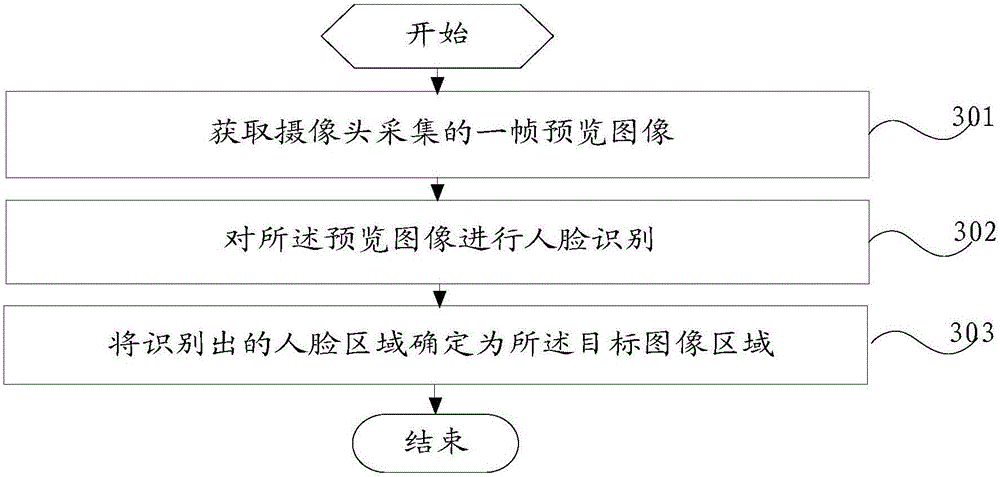
Image processing method and mobile terminal
ActiveCN106101545AReduce data volumeReduce occupancyTelevision system detailsColor television detailsImaging processingImage resolution
The invention provides an image processing method and a mobile terminal. The method comprises that a target image area in a shooting preview interface is determined; after that a shooting instruction is received, at least two frames of images, of the same resolution, collected by a camera continuously of the same shooting scene are obtained; images corresponding to the target image area are extracted from the at least two frames of images; based on the at least two frames of images and the images corresponding to the target image area in the two frame of images, a first target image and a second target image are generated; and association between the first target image and the second target image is established and stored. The resolution of the second target image is higher than that of the first target image. According to the method and mobile terminal provided by the invention, the target image area in the at least two frames of images are processed, and memory resource is saved effectively.
Owner:VIVO MOBILE COMM CO LTD
Construction method based on hash table of memory, text searching method and corresponding device
ActiveCN104572983AReduce occupancySolve the problem of hash collisionMemory adressing/allocation/relocationMemory systems with specific data encodingPoint of entryMapping algorithm
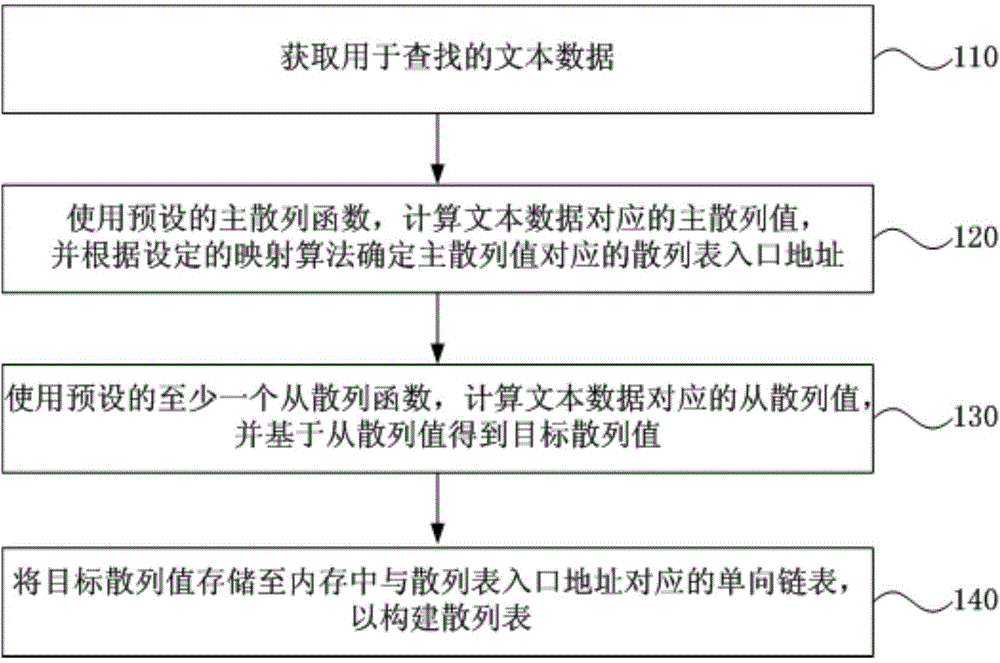
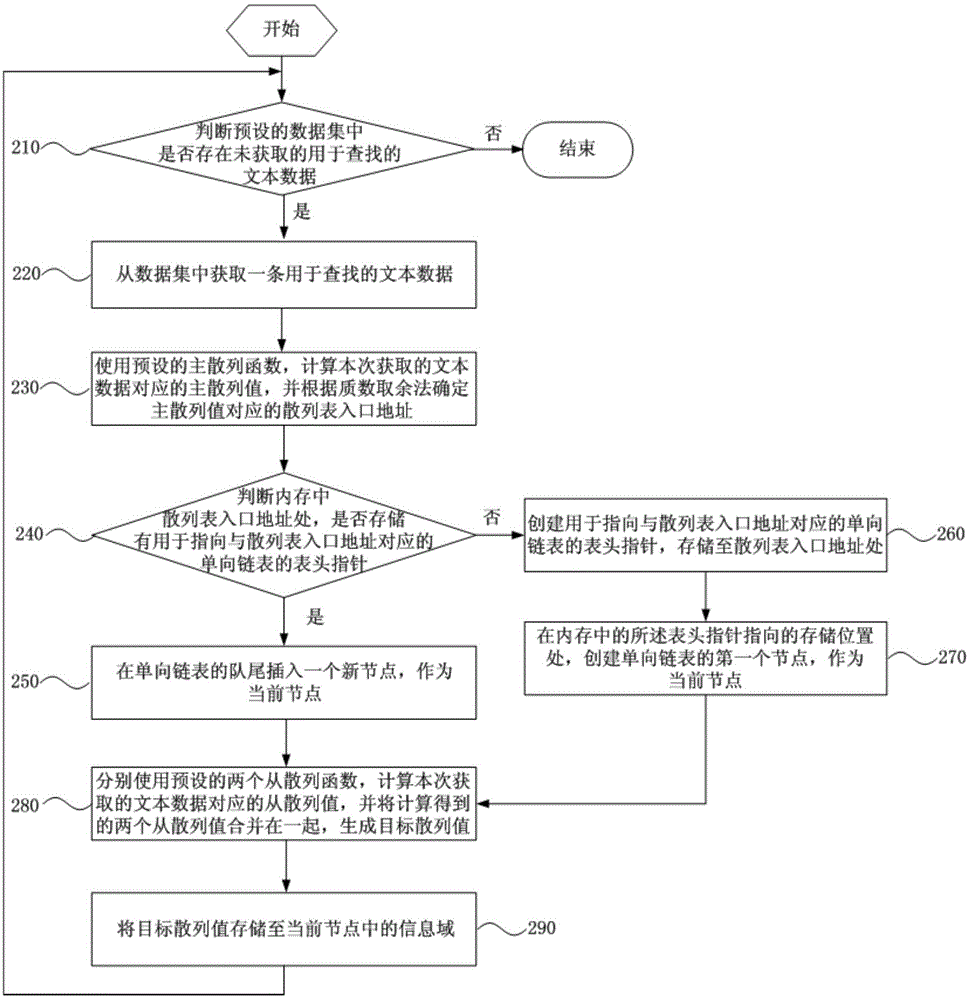
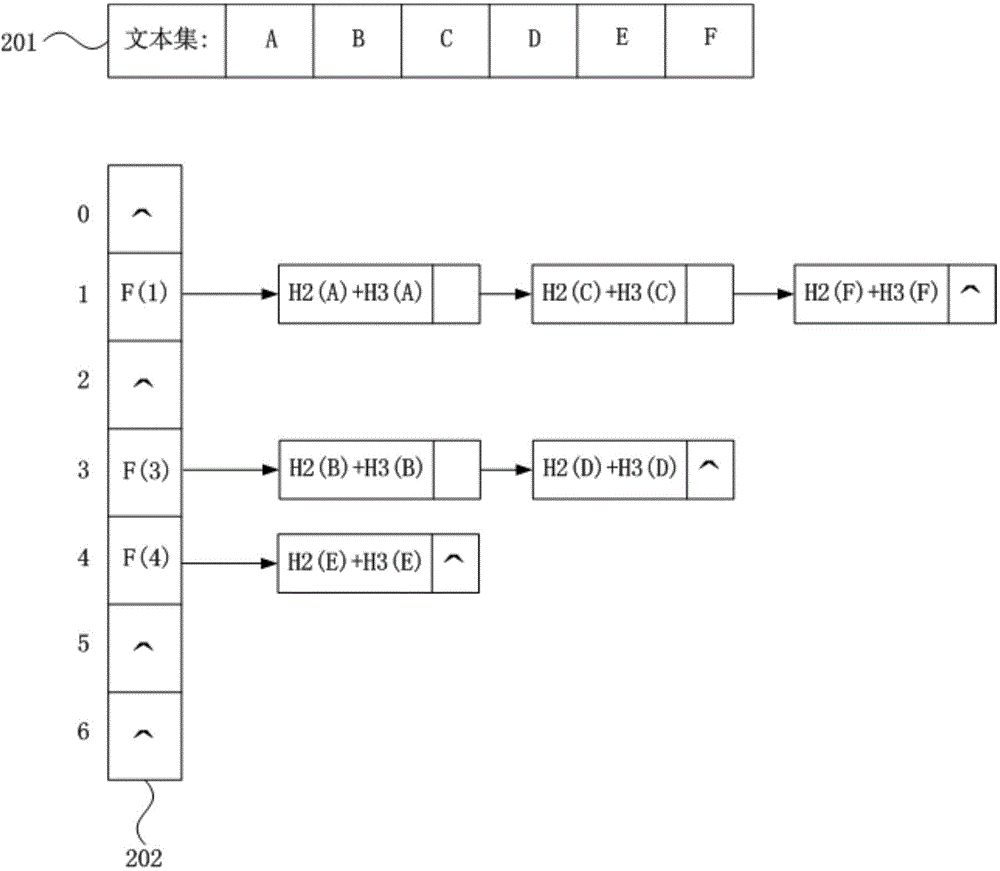
The embodiment of the invention discloses a construction method based on a hash table of a memory, a text searching method and a corresponding device, wherein the construction method based on the hash table of the memory comprises the following steps: obtaining text data for searching; using a preset main hash function, calculating a main hash value corresponding to the text data, determining a hash table inlet address corresponding to the has table inlet address in the memory according to a preset mapping algorithm; using at least one preset secondary hash function to calculate a corresponding secondary hash value of the text data, obtaining a target hash value from a secondary hash value; storing the target hash value into a corresponding one-way linked list corresponding to the hash table inlet address in the memory to construct a hash table. According to the technical scheme provided by the embodiment of the invention, the memory utilization rate can be increased better, and the memory is relatively saved.
Owner:RUN TECH CO LTD BEIJING
Memory sharing method of virtual machines based on combination of ksm and pass-through
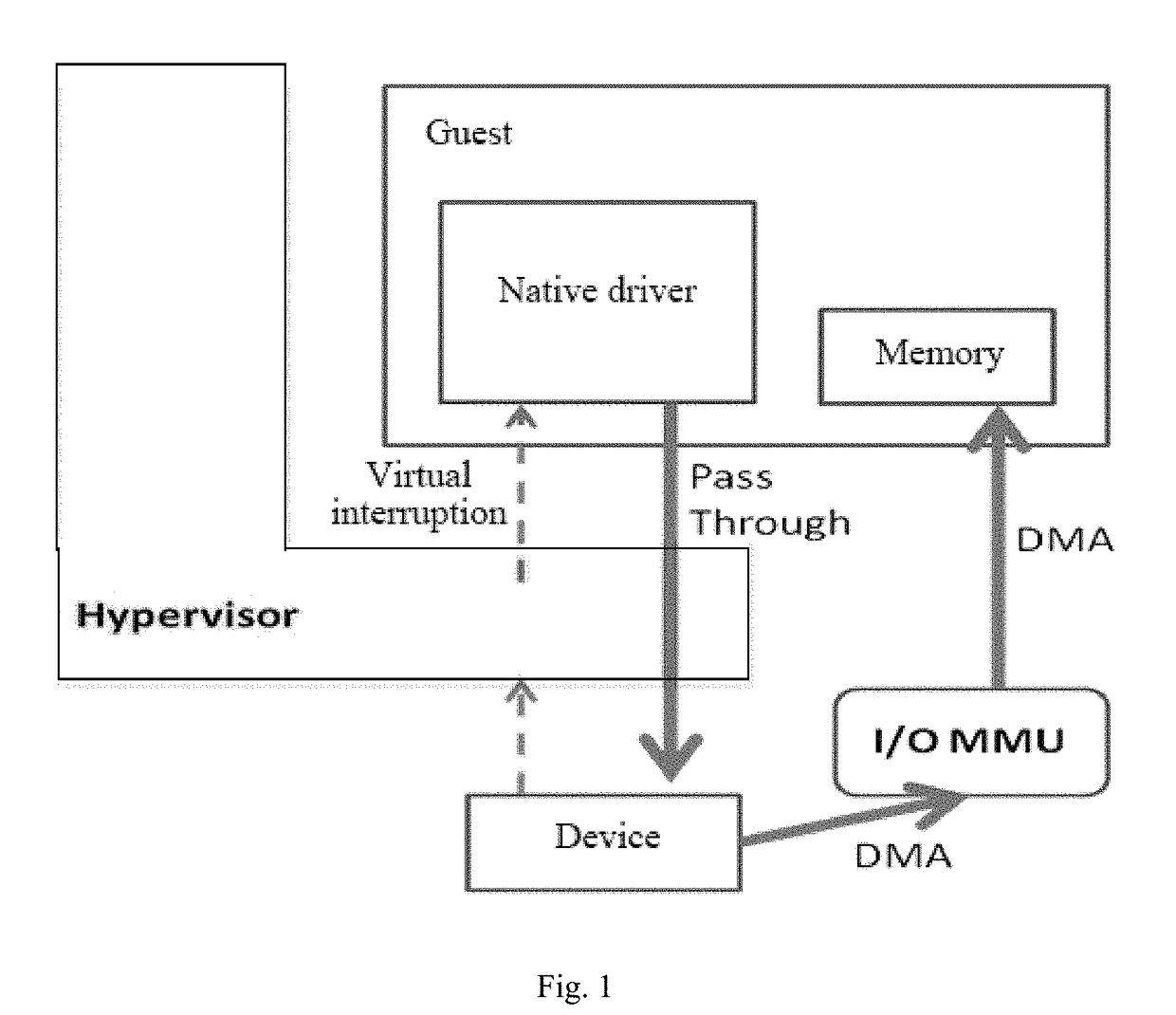
InactiveUS20180011797A1Improve balanceEfficient solutionMemory architecture accessing/allocationSoftware simulation/interpretation/emulationWrite protectionSoftware engineering
A memory sharing method of virtual machines through the combination of KSM and pass-through, including: a virtual machine manager judging whether operating systems of guests use IOMMU, if not, not participating in shared mapping of a KSM technology; if yes, judging memory pages of each guest to confirm whether the pages are mapping pages, if yes, remain the mapping pages into a host; and if not, on the premise of keeping the properties of Pass-through, using the KSM technology for all non-mapping pages to merge the memory pages with same contents among various virtual machines and perform write protection processing simultaneously. The guest memory pages are divided into those special for DMA and those for non-DMA purpose, then the KSM technology is only selectively applied to the non-DMA pages, and on the premise of keeping the properties of Pass-through, the object of saving memory resources is achieved simultaneously.
Owner:MASSCLOUDS INNOVATION RES INST (BEIJING) OF INFORMATION TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com