Construction method based on hash table of memory, text searching method and corresponding device
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
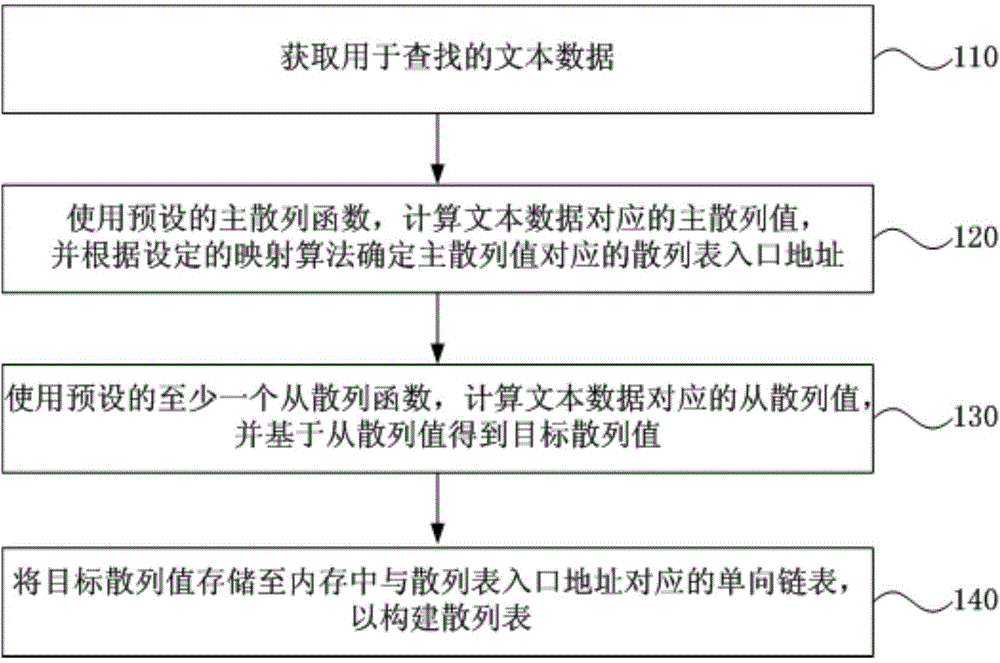
[0037] figure 1 It is a schematic flowchart of a method for constructing a memory-based hash table provided in Embodiment 1 of the present invention. This embodiment is applicable to the case of constructing a hash table for searching whether text data exists in memory. In the embodiment of the present invention, the text data may be data in any text format such as Weibo comments. The method can be executed by a device for constructing a memory-based hash table, and the device can be implemented by software and / or hardware. Aiming at the problem of memory shortage in the traditional chain address method when constructing a hash table of a large amount of text, this embodiment uses multiple hash functions to construct each single-linked list in the chain address method to achieve the purpose of further saving memory.
[0038] see figure 1 The method for constructing a memory-based hash table provided in this embodiment specifically includes the following operations:
[0039...
Embodiment 2
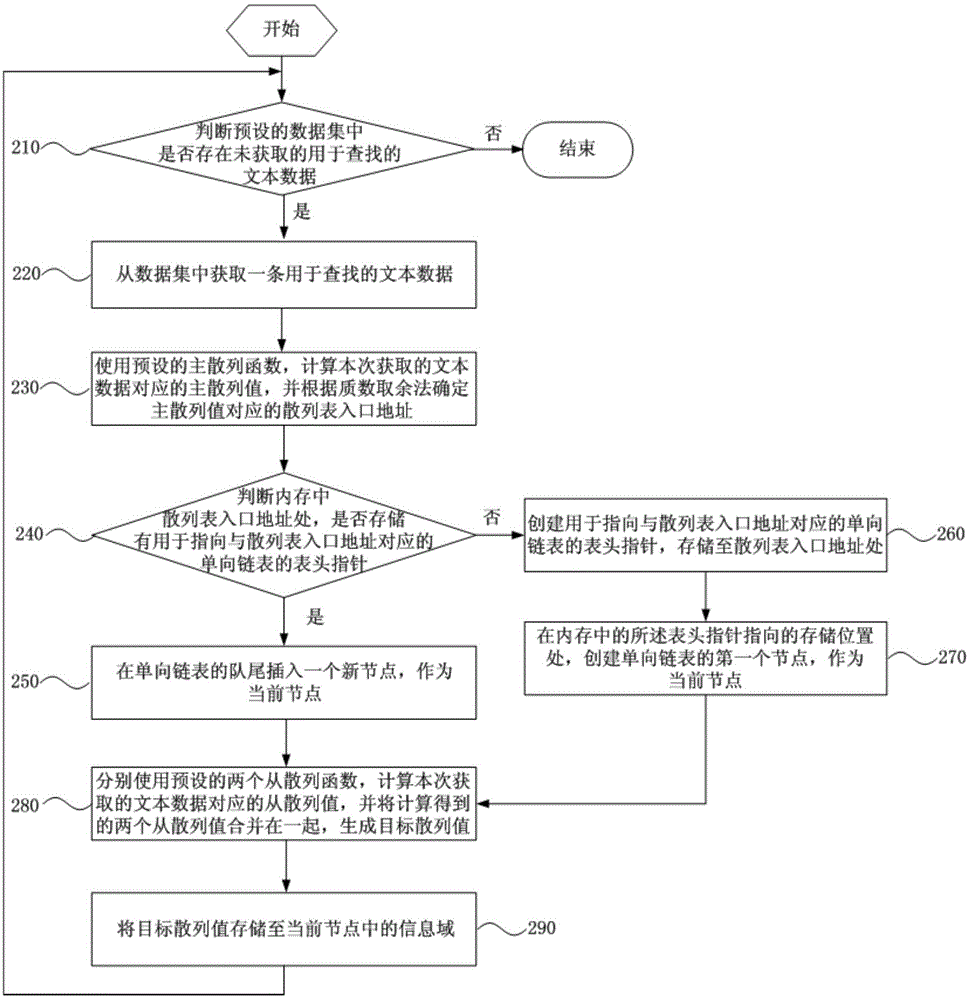
[0056] Figure 2A It is a schematic flowchart of a method for constructing a memory-based hash table provided in Embodiment 2 of the present invention. This embodiment provides a preferred embodiment on the basis of the first embodiment above. The construction method of the memory-based hash table provided by the present embodiment can be carried out under the windows2008server system of the intel core i7CPU with the main frequency of 2.2GHz, the hardware environment of 32GB of internal memory and the development environment based on Visual C++. see Figure 2A The method for constructing a memory-based hash table provided in this embodiment specifically includes the following operations:
[0057] Operation 210, judging whether there is unacquired text data for searching in the preset data set. If yes, perform operation 220, otherwise end the process.
[0058] Operation 220, acquire a piece of text data for searching from the data set. Execute operation 230 .
[0059] Ope...
Embodiment 3
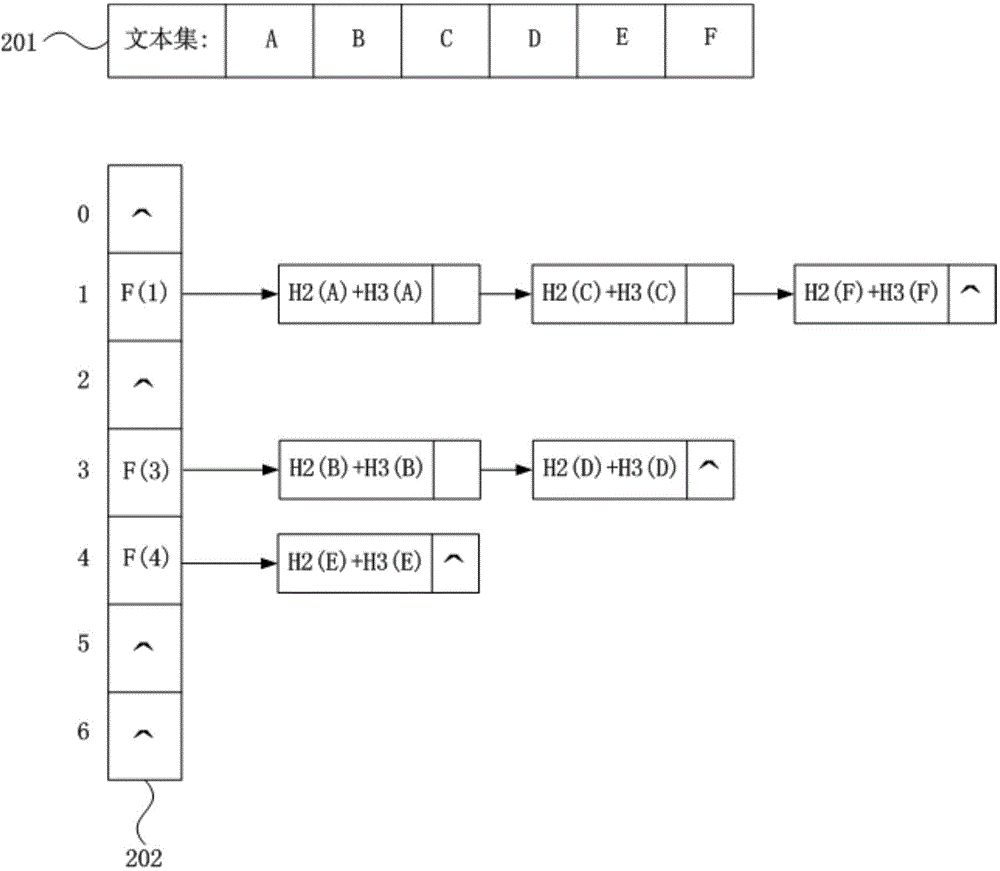
[0081] image 3 It is a schematic flowchart of a text search method provided in Embodiment 3 of the present invention. After the construction method of the memory-based hash table is executed, this embodiment further provides a method for searching text data, which can be executed by a text searching device, and the device is implemented by software and / or hardware. see image 3 , the text search method provided in this embodiment specifically includes the following operations:
[0082] Operation 310, acquire the text data to be searched this time.
[0083] Operation 320: Use the preset primary hash function to calculate the primary hash value corresponding to the text data to be searched this time, and determine the entry address of the hash table corresponding to the primary hash value according to the set mapping algorithm.
[0084] Operation 330: Using at least one preset secondary hash function, calculate a secondary hash value corresponding to the text data to be sear...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com