Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
448 results about "Write protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
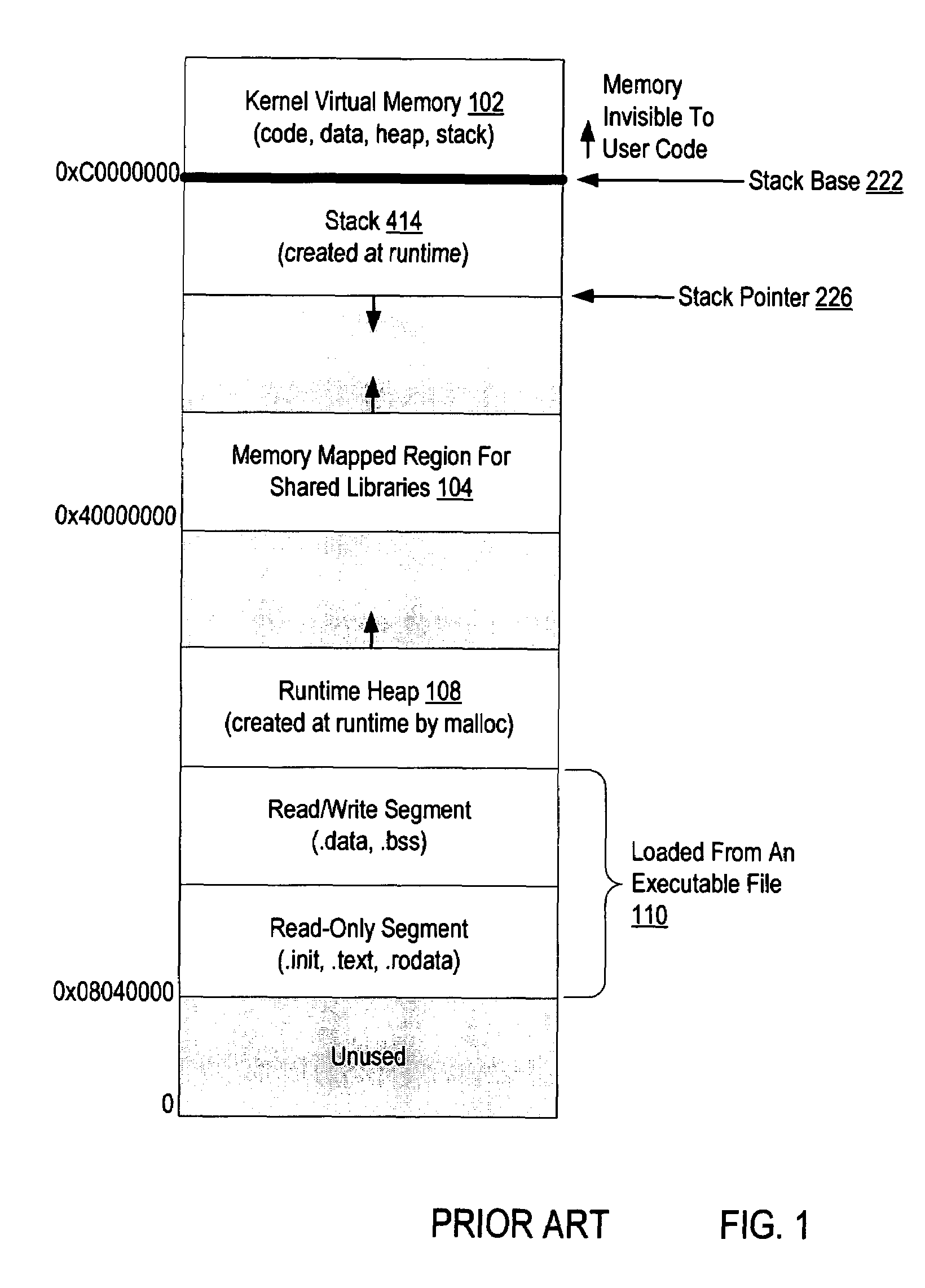
Write protection is any physical mechanism that prevents modification or erasure of valuable data on a device. Most commercial software, audio and video is sold pre-protected.
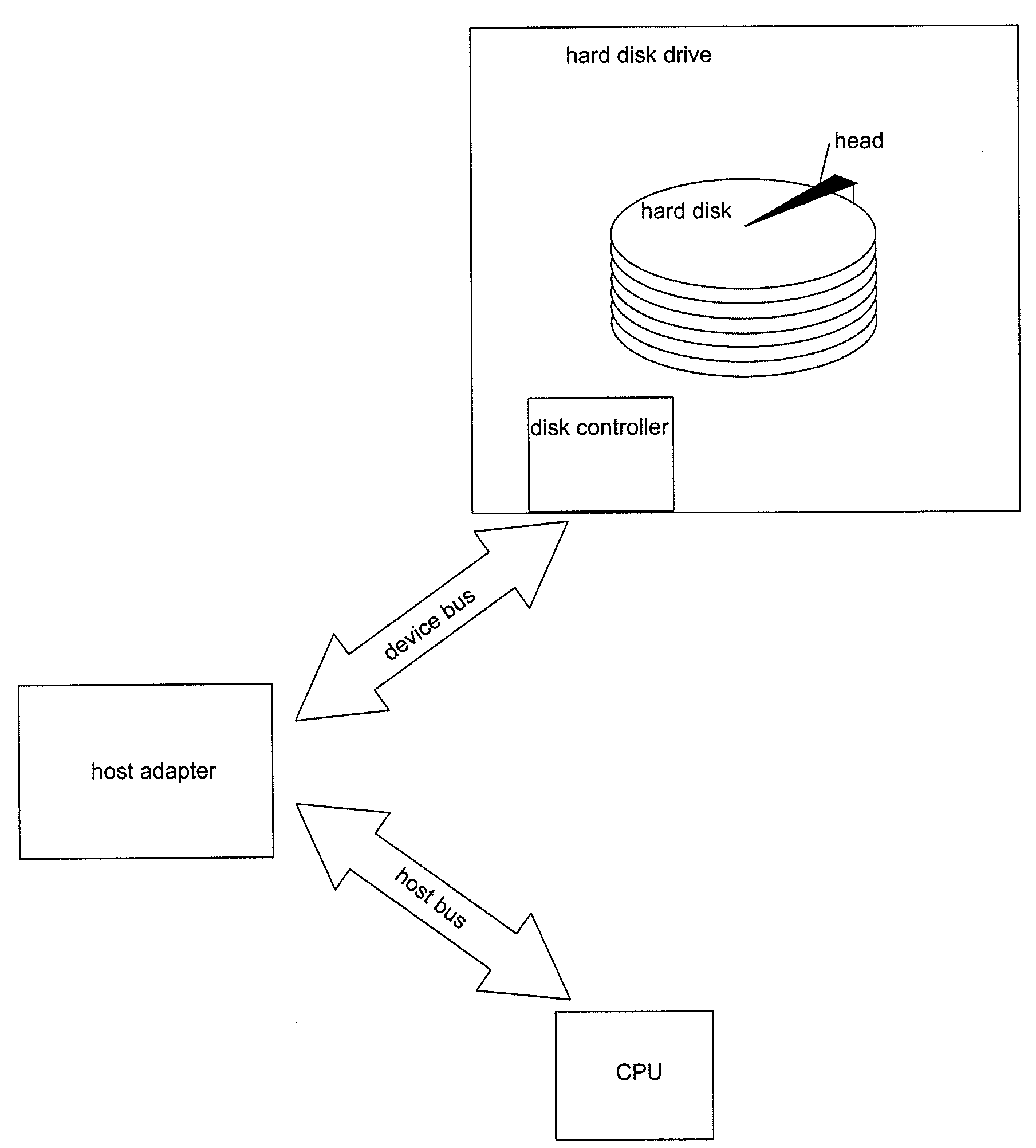
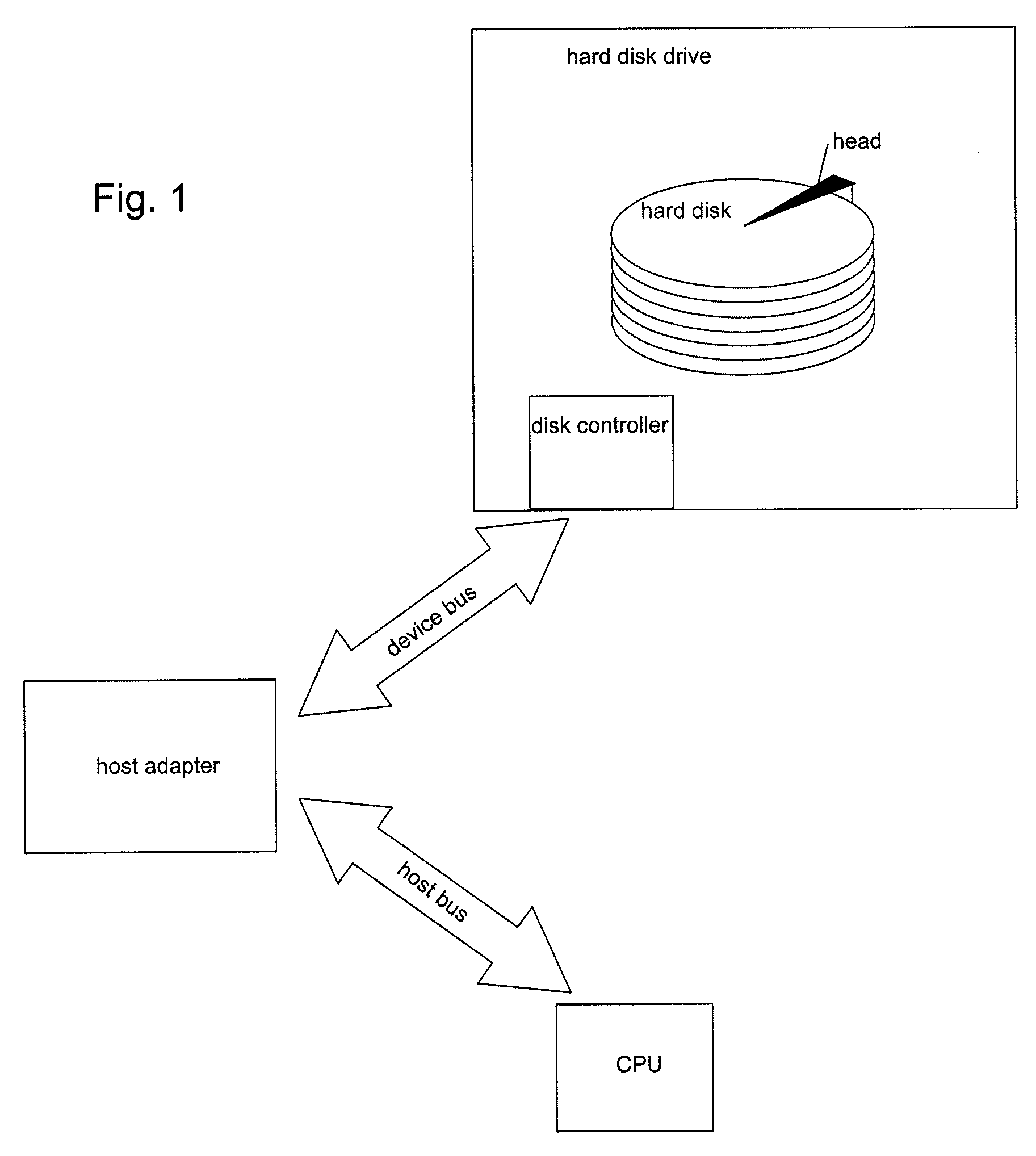
Write protection for computer long-term memory devices
InactiveUS6813682B2Input/output to record carriersDigital data processing detailsWrite protectionHard disc drive
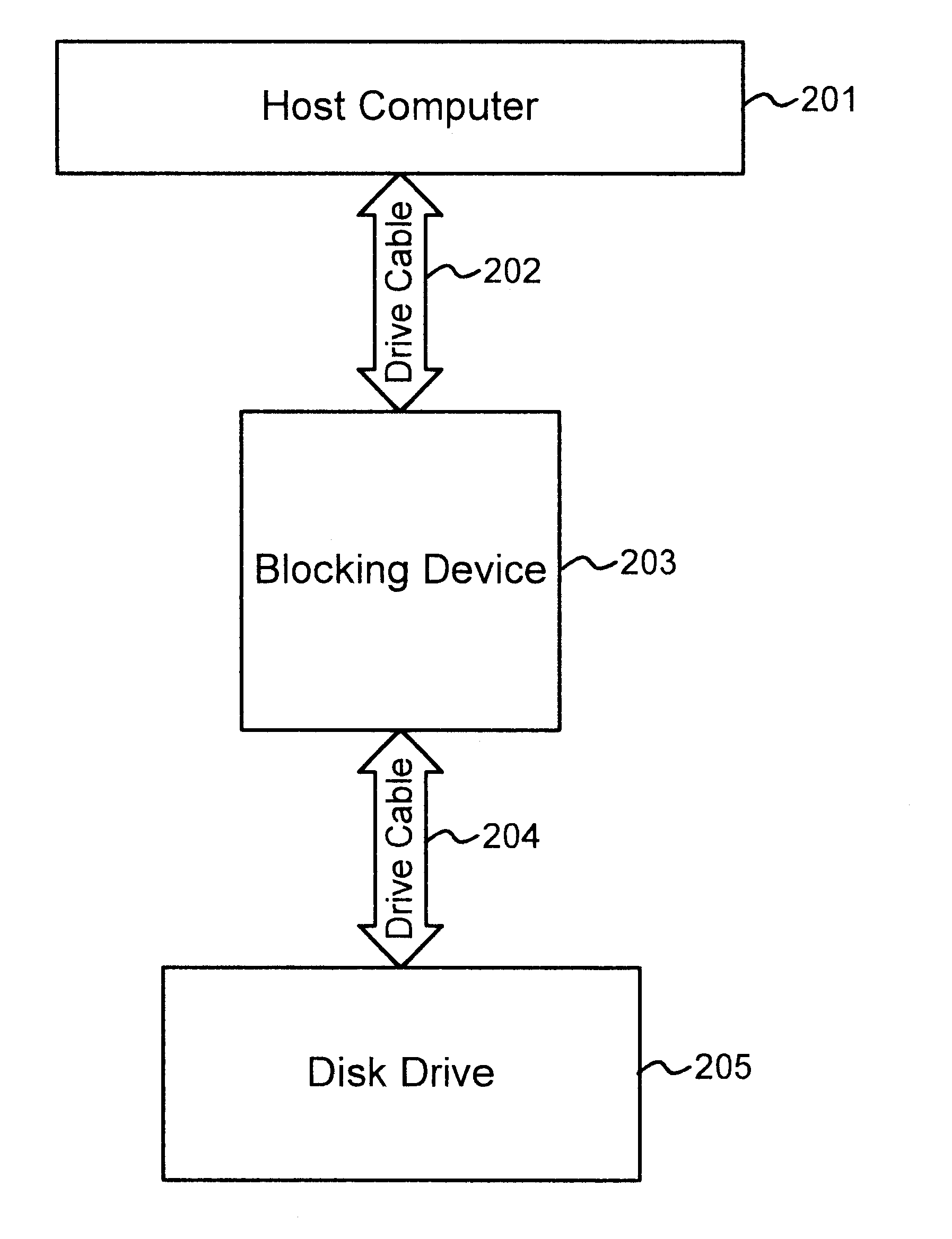
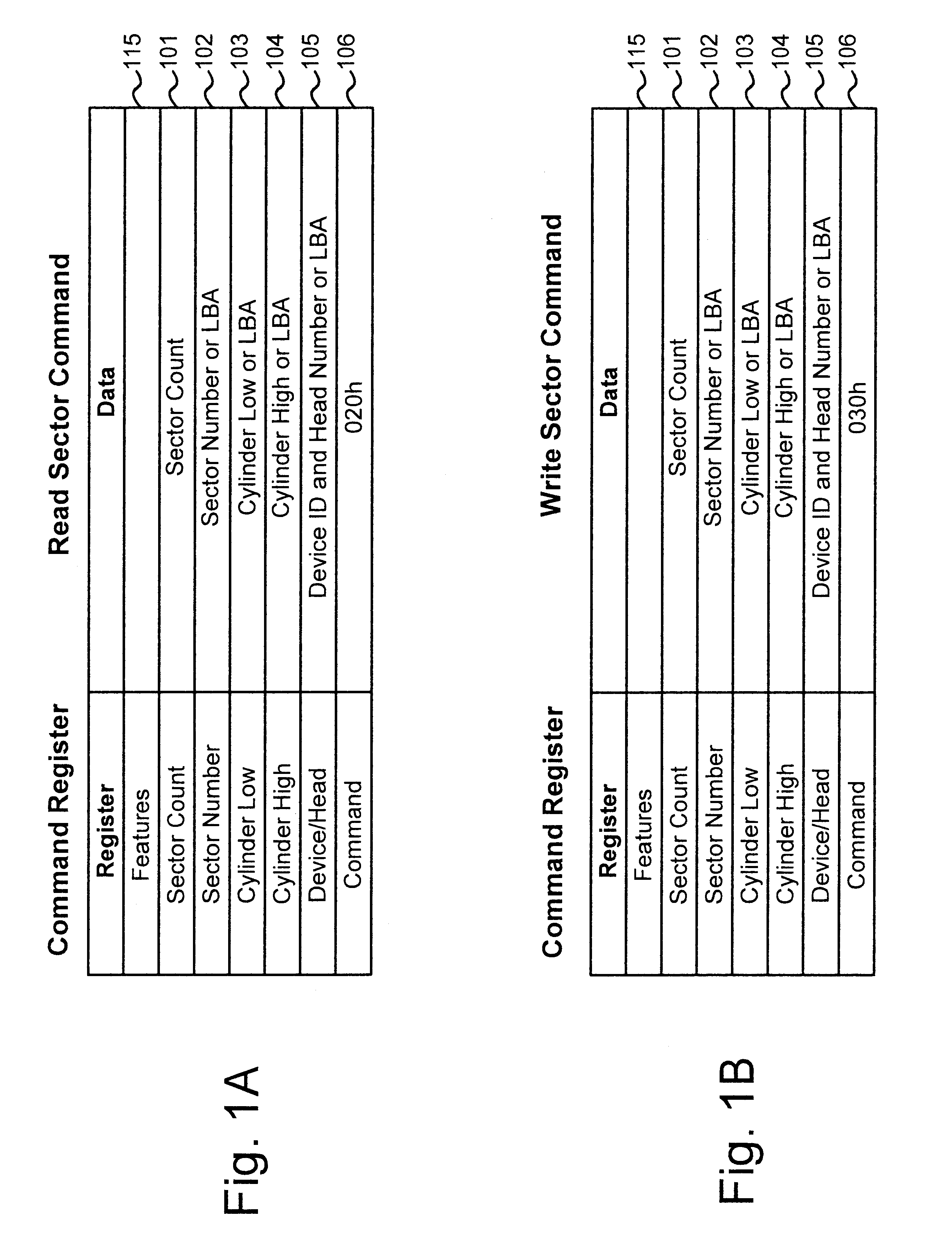
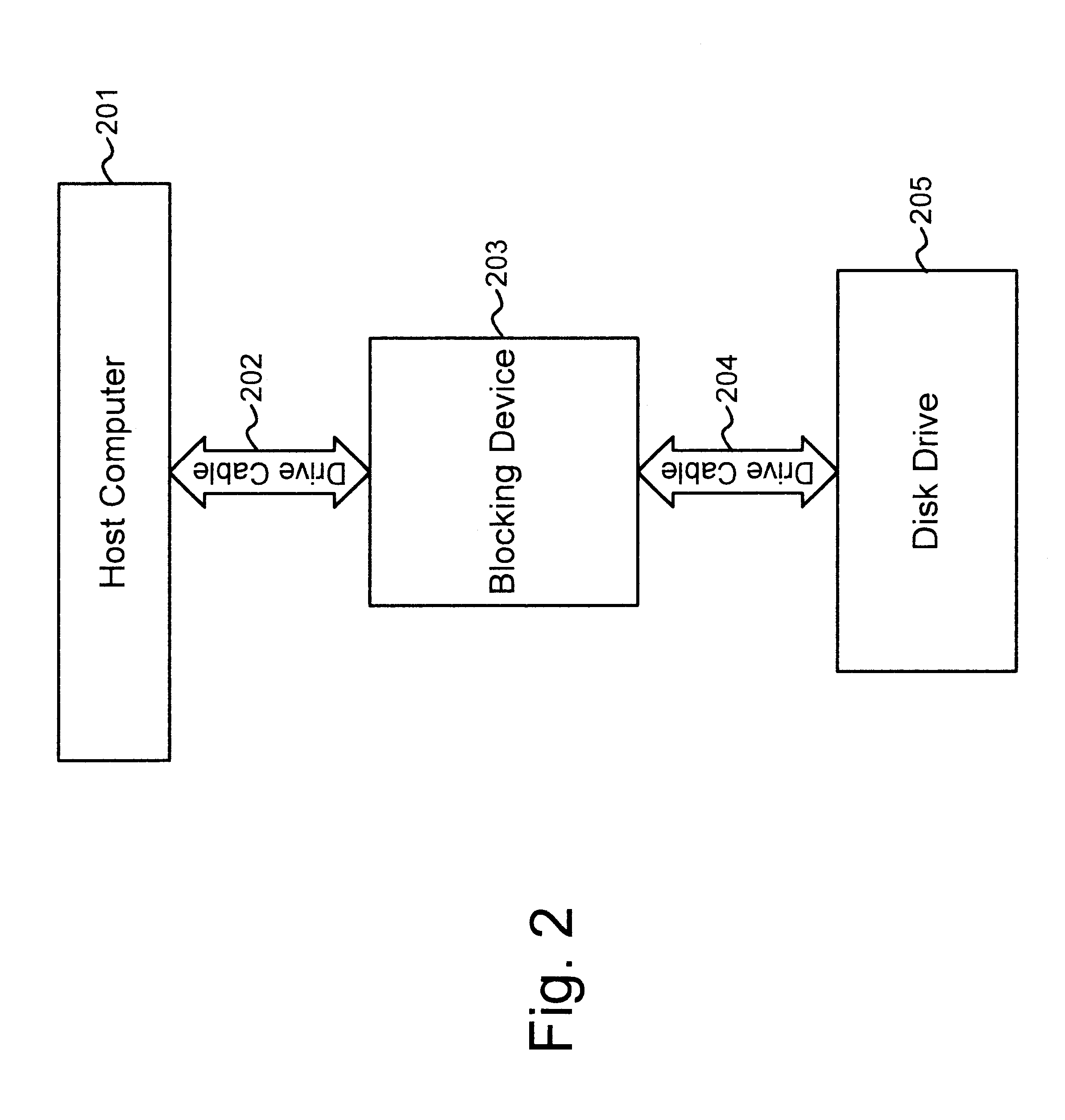
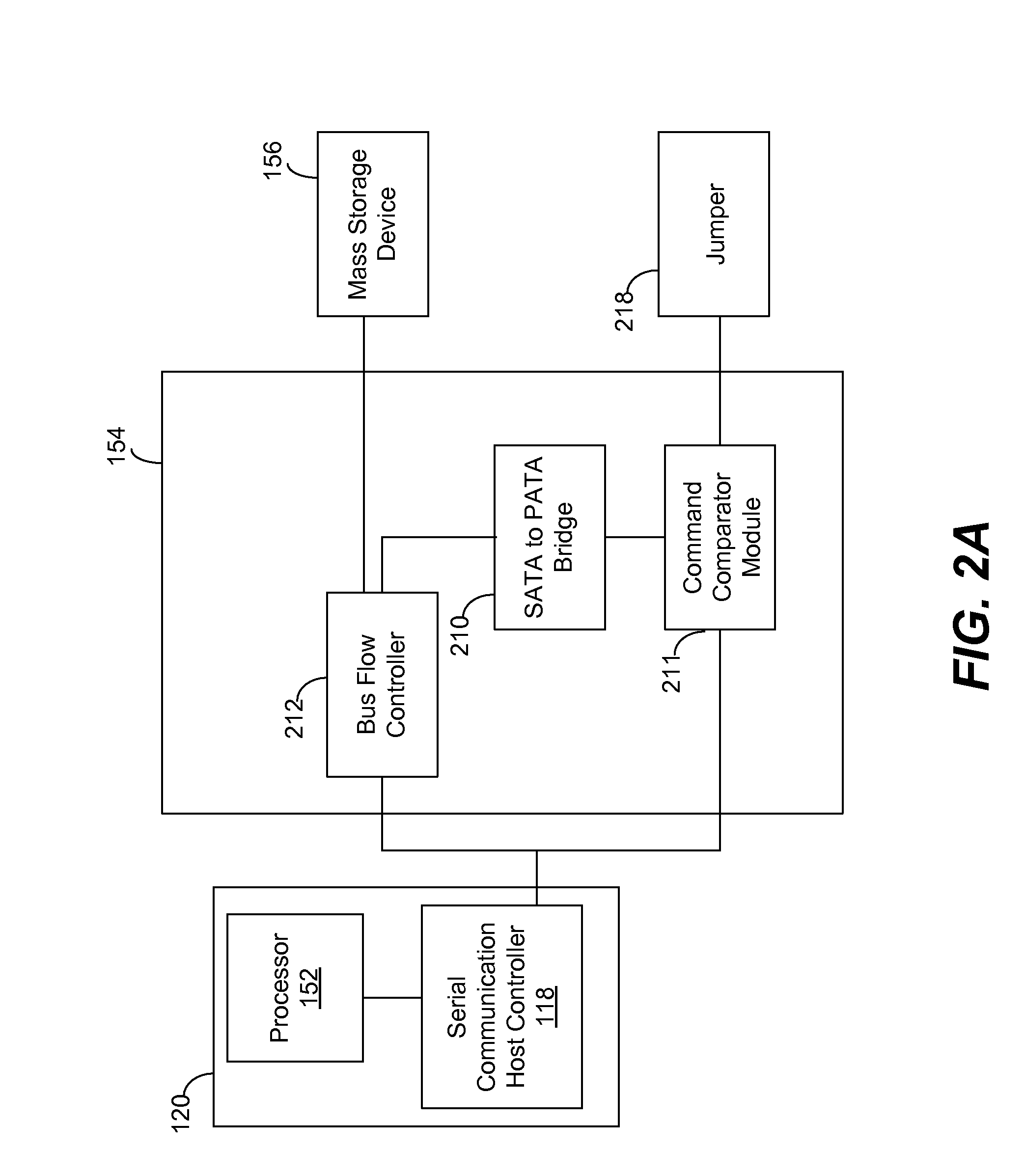
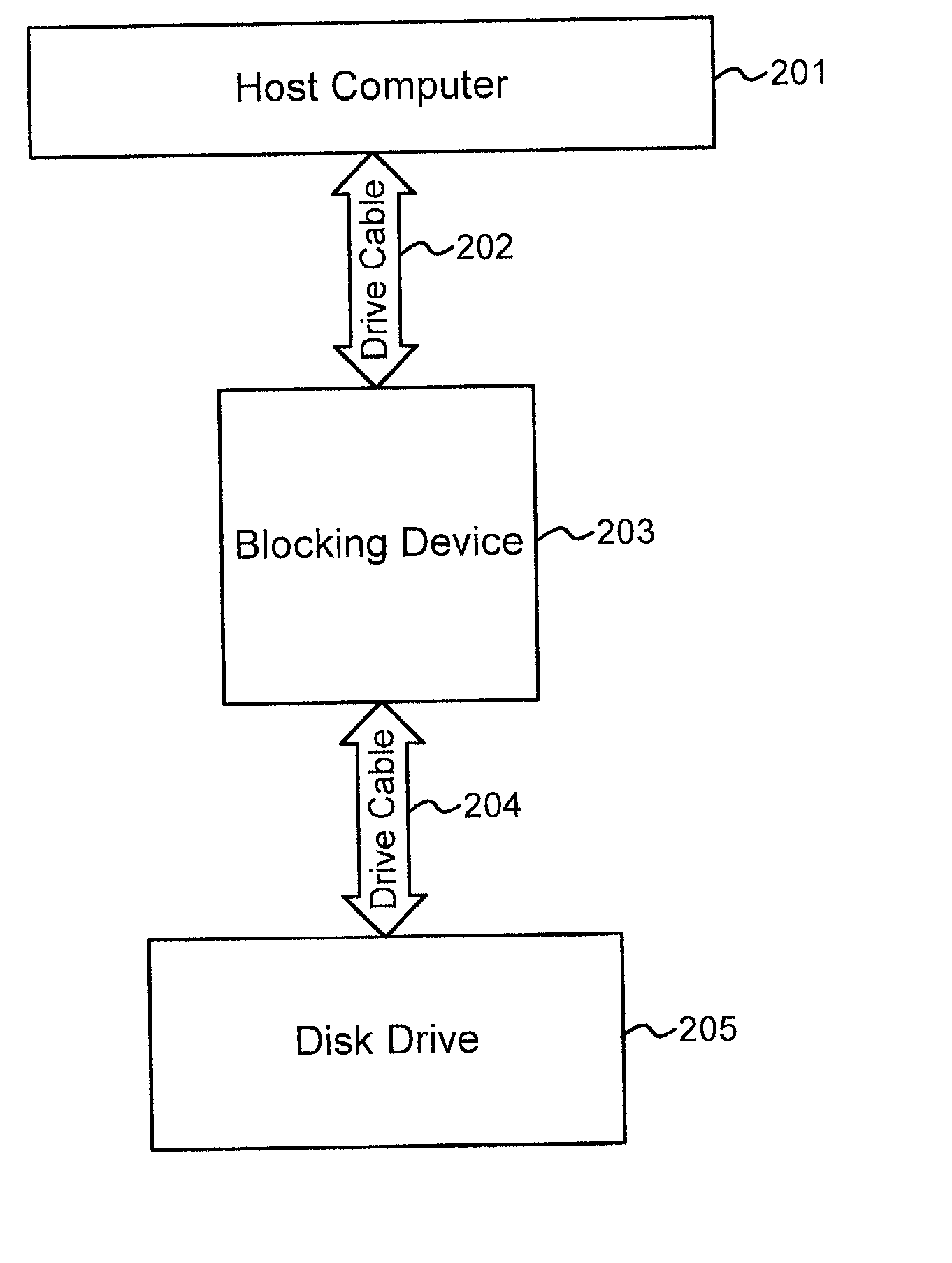
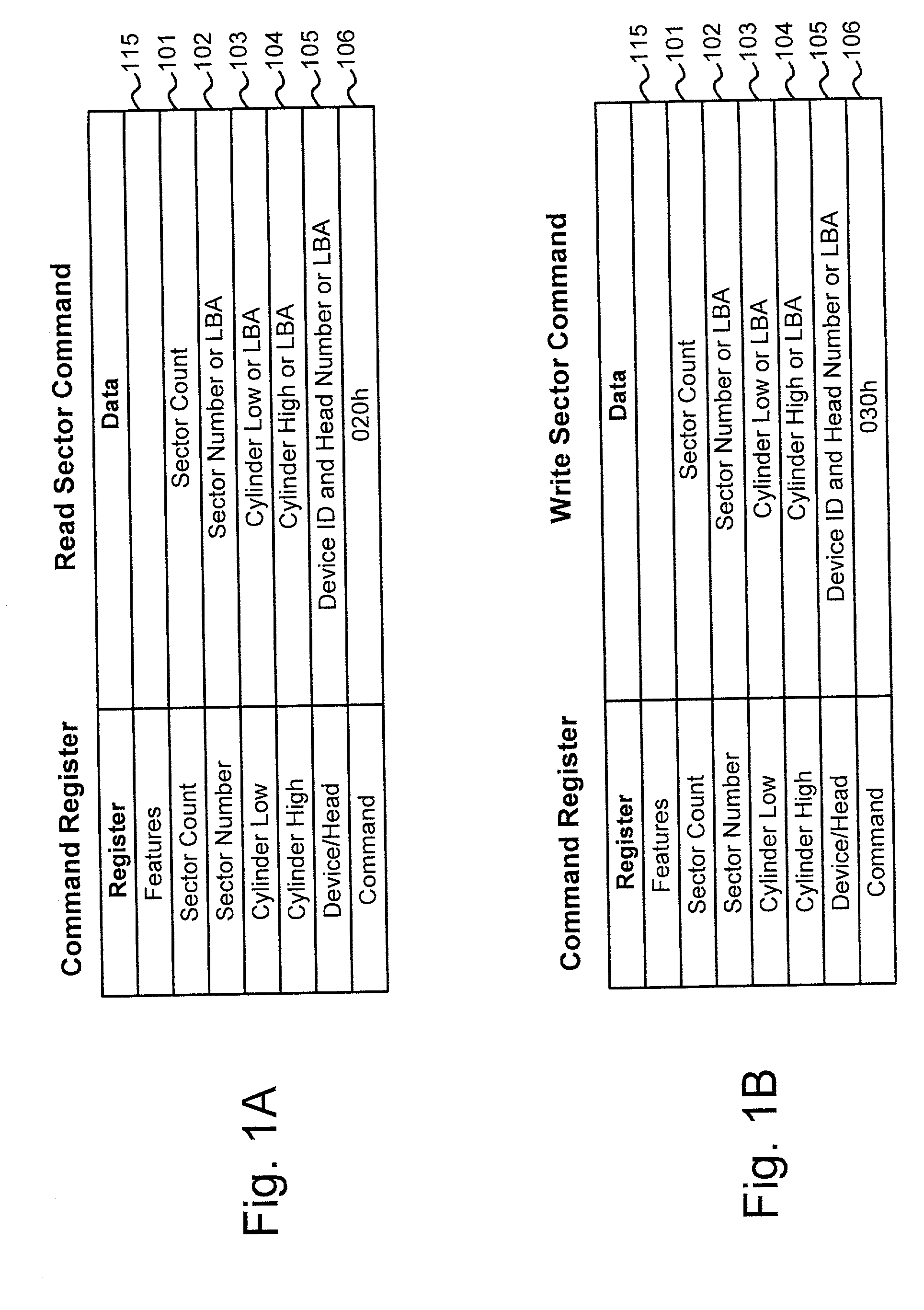
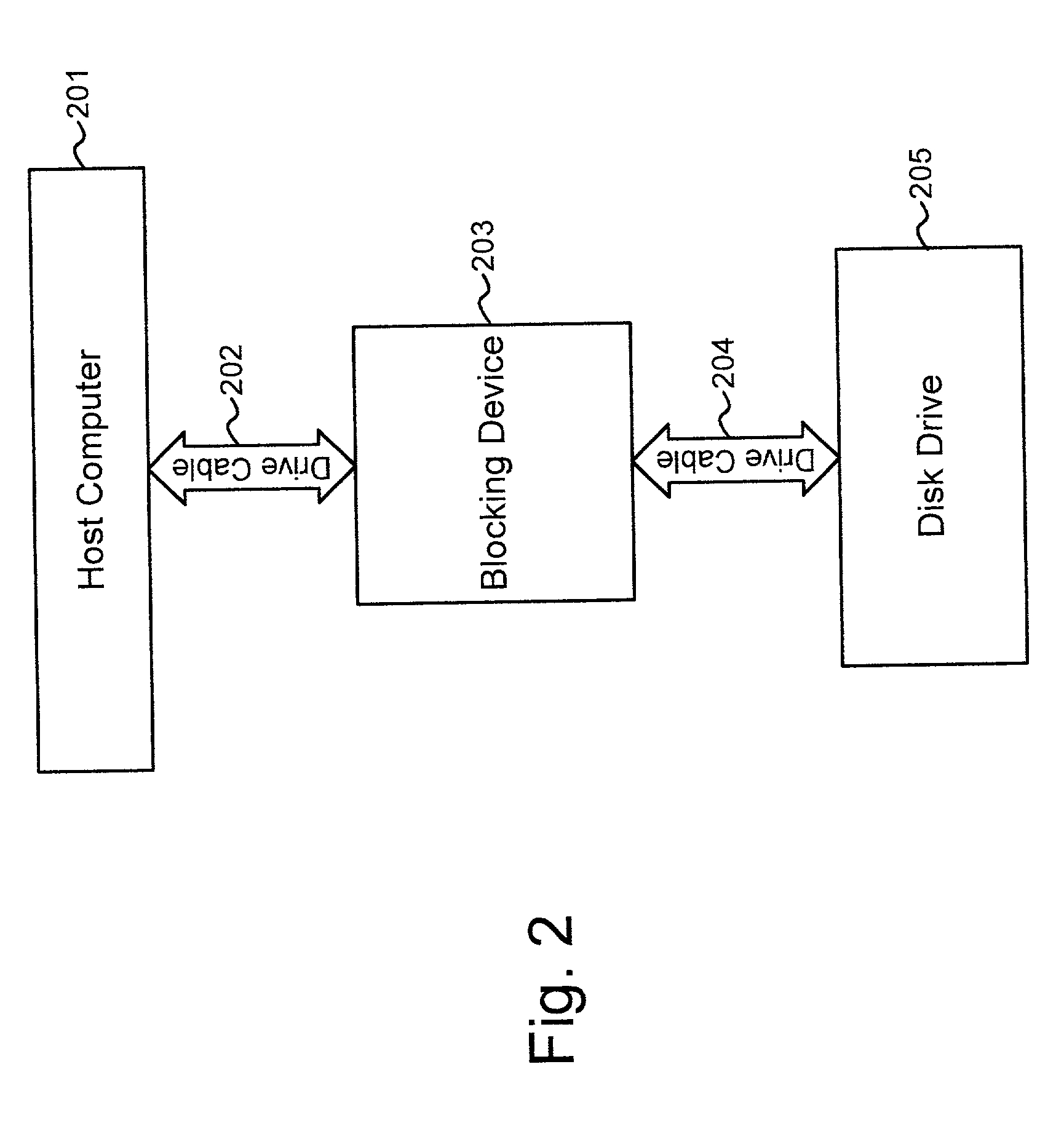
A blocking device provides read and write protection for computer long-term storage devices, such as hard drives. The blocking device is placed between a host computer and the storage device. The blocking device intercepts communications between the host and the storage device and examines any commands from the host to the storage device. Certain commands, such as commands that may modify the storage device, may be discarded.
Owner:MYKEY TECH
Serial advanced technology attachment write protection: mass storage data protection device
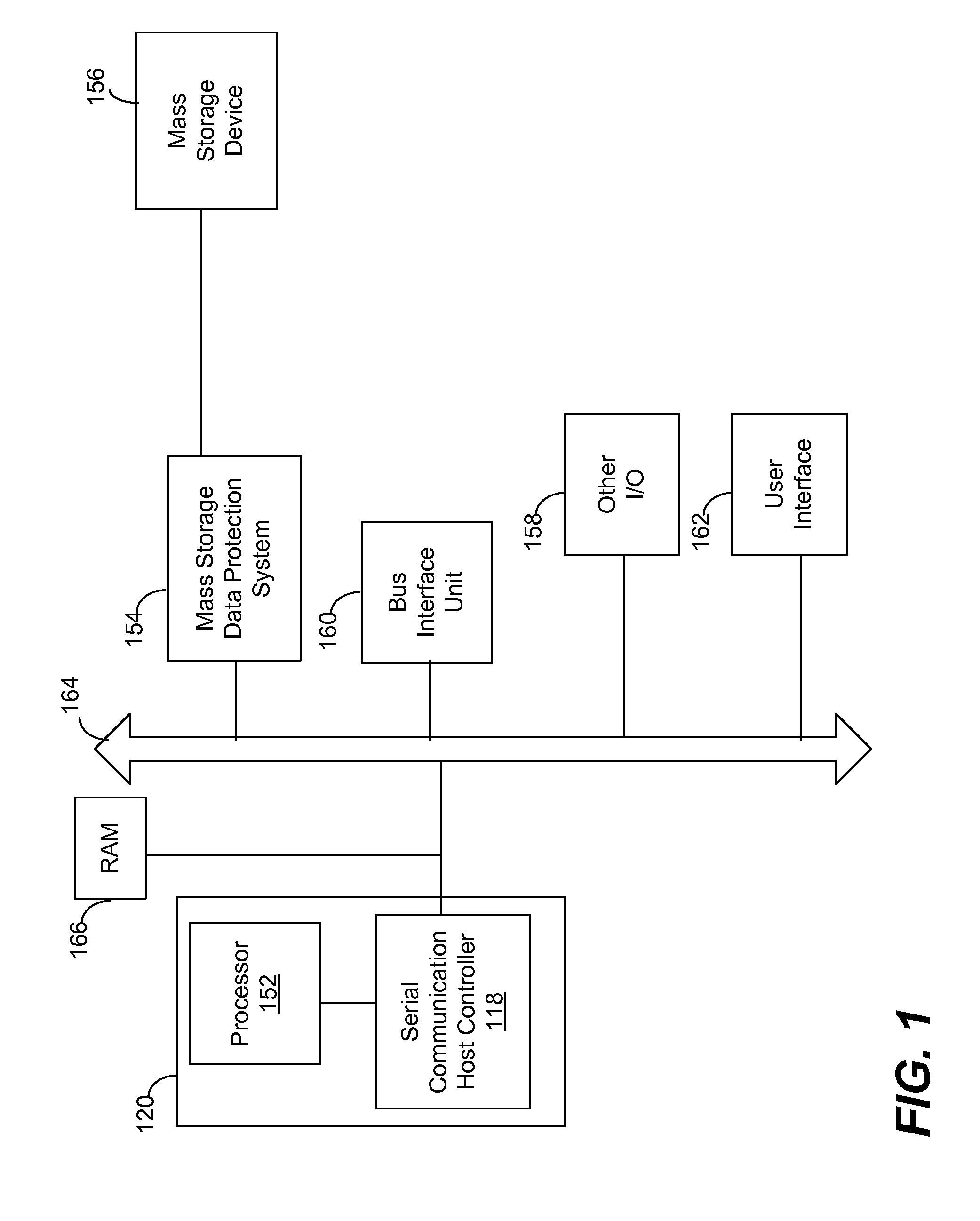
A mass storage device protection system may have a mass storage device, a processor configured to generate at least one serial write command signal to the mass storage device via a serial communication link, and a storage protector configured for communication with the processor and mass storage device, the storage protector configured to do the following: intercept the at least one serial write command signal, and determine whether the at least one serial write command signal comprises an authorized command signal or an unauthorized command signal.
Owner:IGT
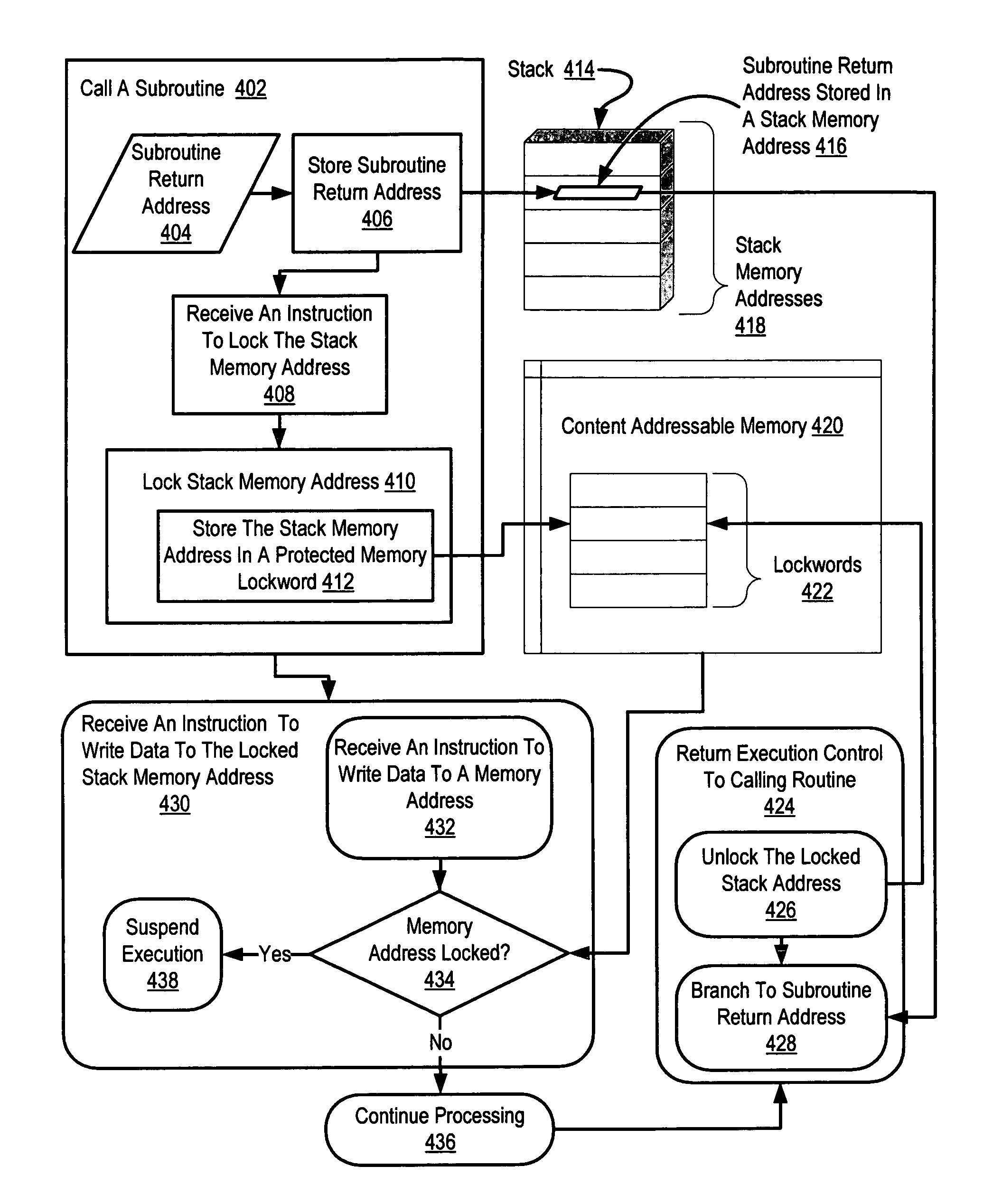
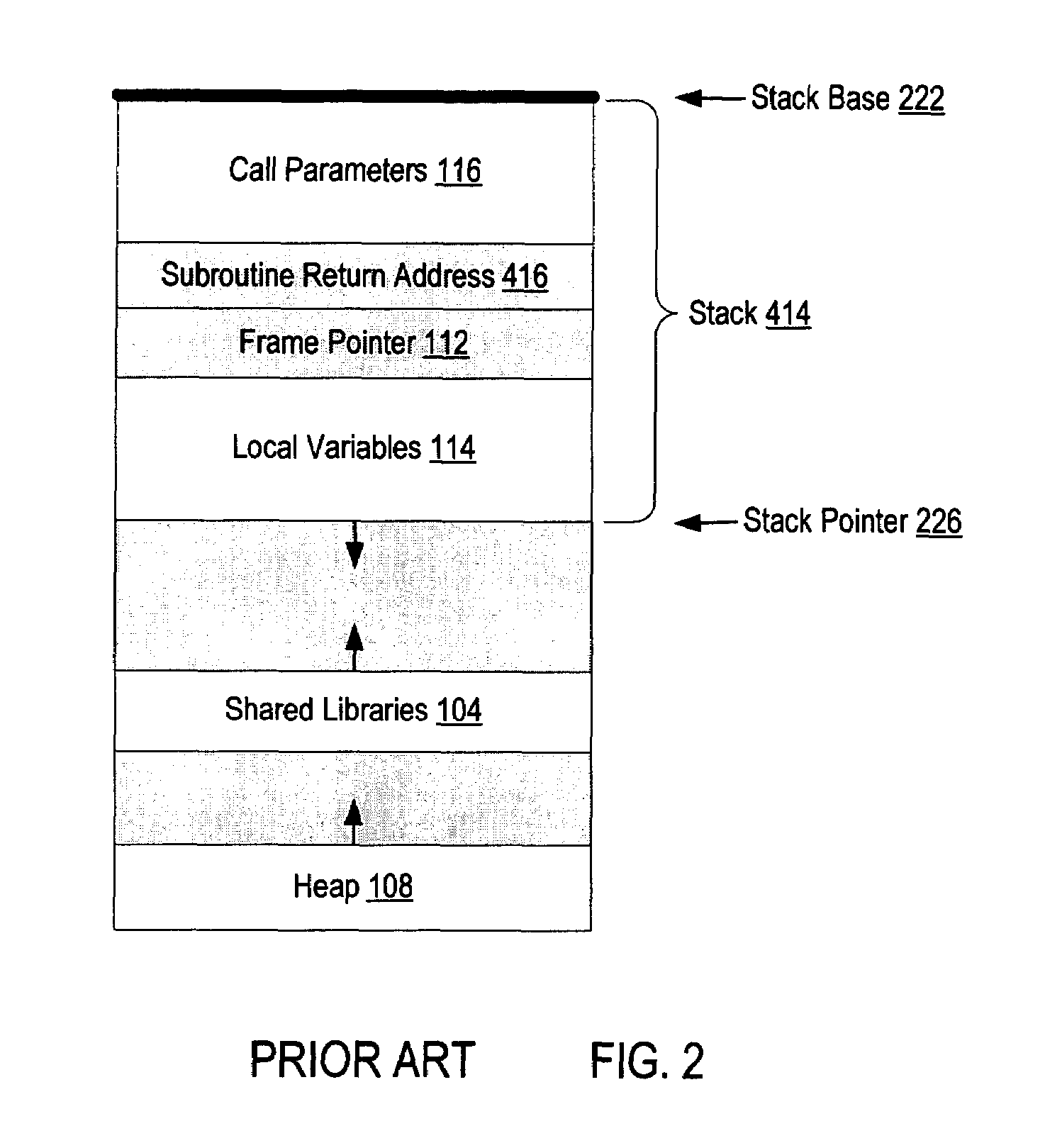
Write protection of subroutine return addresses
Exemplary methods, systems, and products are described that operate generally by moving subroutine return address protection to the processor itself, in effect proving atomic locks for subroutine return addresses stored in a stack, subject to application control. More particularly, exemplary methods, systems, and products are described that write protect subroutine return addresses by calling a subroutine, including storing in a stack memory address a subroutine return address and locking, by a computer processor, the stack memory address against write access. Calling a subroutine may include receiving in the computer processor an instruction to lock the stack memory address. Locking the stack memory address may be carried out by storing the stack memory address in a protected memory lockword. A protected memory lockword may be implemented as a portion of a protected content addressable memory.
Owner:IBM CORP
Write protection for computer long-term memory devices
InactiveUS20020040418A1Input/output to record carriersDigital data processing detailsWrite protectionHard disc drive
A blocking device provides read and write protection for computer long-term storage devices, such as hard drives. The blocking device is placed between a host computer and the storage device. The blocking device intercepts communications between the host and the storage device and examines any commands from the host to the storage device. Certain commands, such as commands that may modify the storage device, may be discarded.
Owner:MYKEY TECH
Safety guide device and method for embedded system
InactiveCN101751273AImplement complex functionsPrevent malicious substitutionProgram loading/initiatingWrite protectionOperational system
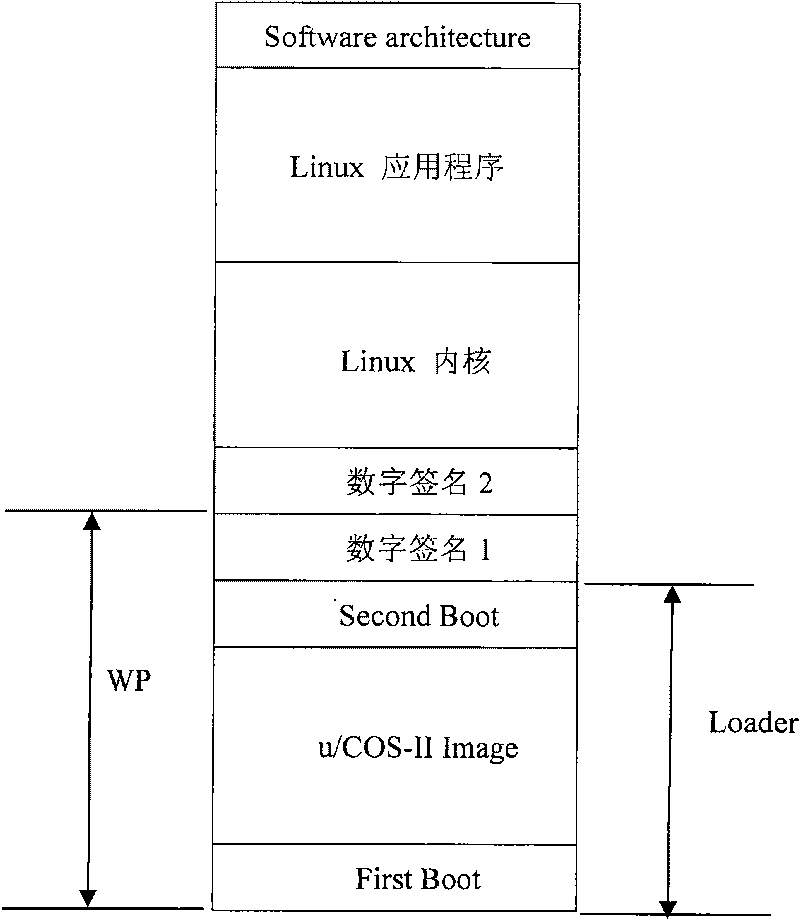
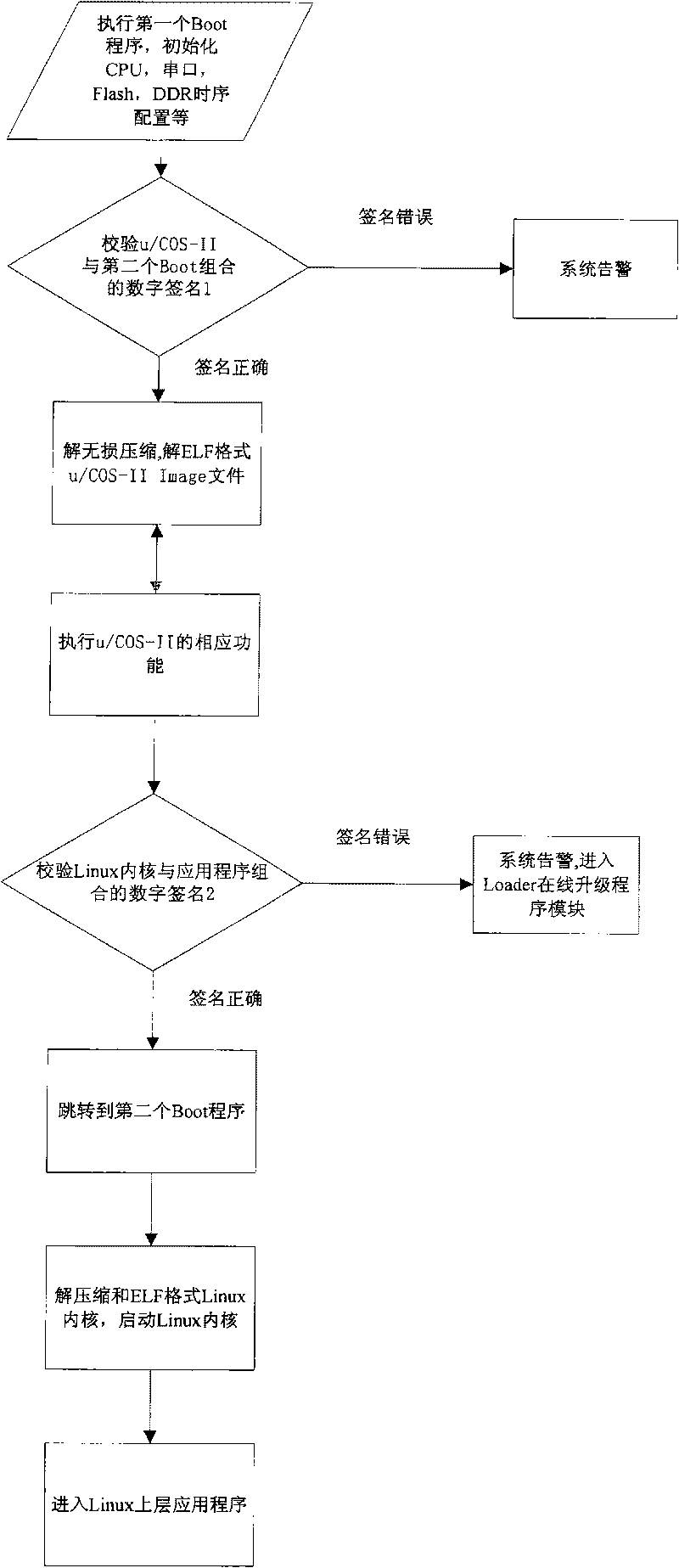
The invention provides a safety guide device for an embedded system, which comprises a loading module installed in a memory write protection region and is characterized in that the loading module comprises a first guide program module, a loading region operating system and a second guide program module; the first guide program module is used for initializing system hardware after starting up and then starting a loading region operating system; the loading region operating system is provided with a jump thread, and the jump thread is used for jumping the program to an initial address of the second guide program module after execution of other threads of the loading region operating system; and the second guide program module is used for initializing the system hardware again, and then a main operating system is started. In addition, the invention also provides a corresponding safety guide method. The invention can realize a plurality of complex functions at a safety guide phase. If an upper application program and a main operating system kernel are actively updated online, the invention fast displays a colorful start-up picture, realizes check step by step and the like.
Owner:INST OF ACOUSTICS CHINESE ACAD OF SCI +1
Tape library emulation with automatic configuration and data retention
ActiveUS20060200623A1Memory loss protectionError detection/correctionWrite protectionAuto-configuration
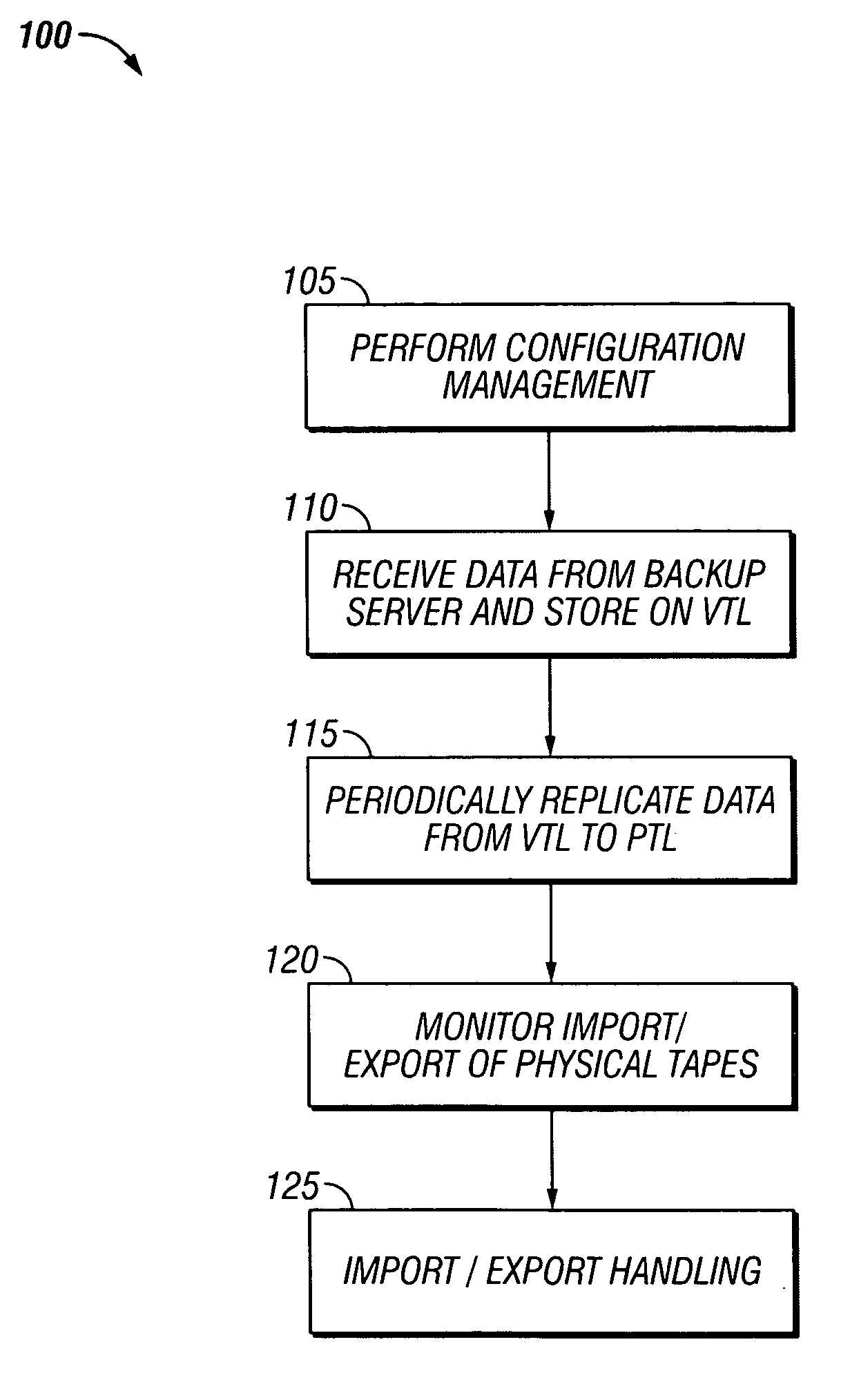
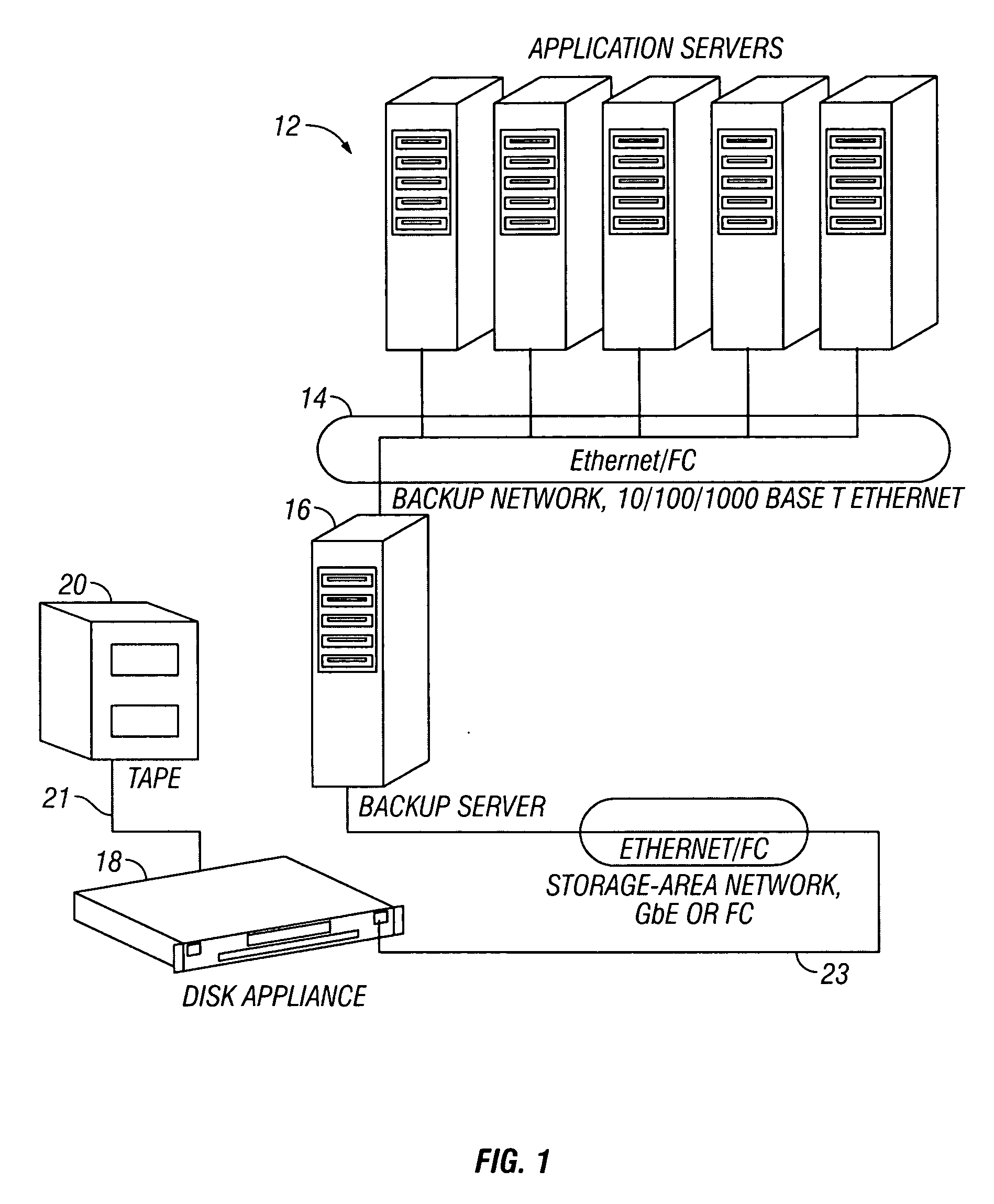
Disk based emulation of tape libraries is provided with features that allow easier management and administration of a backup system and also allow increased flexibility to both archive data on tape at a remote location and also have fast restore access to archived data files. Features include automatic emulation of physical libraries, and the retention and write protection of virtual tapes that correspond to exported physical tapes.
Owner:OVERLAND STORAGE
Locking method and unlocking method
InactiveCN101026834AProtection of legitimate rights and interestsConvenient lock netUnauthorised/fraudulent call preventionUnauthorized memory use protectionWrite protectionHandset
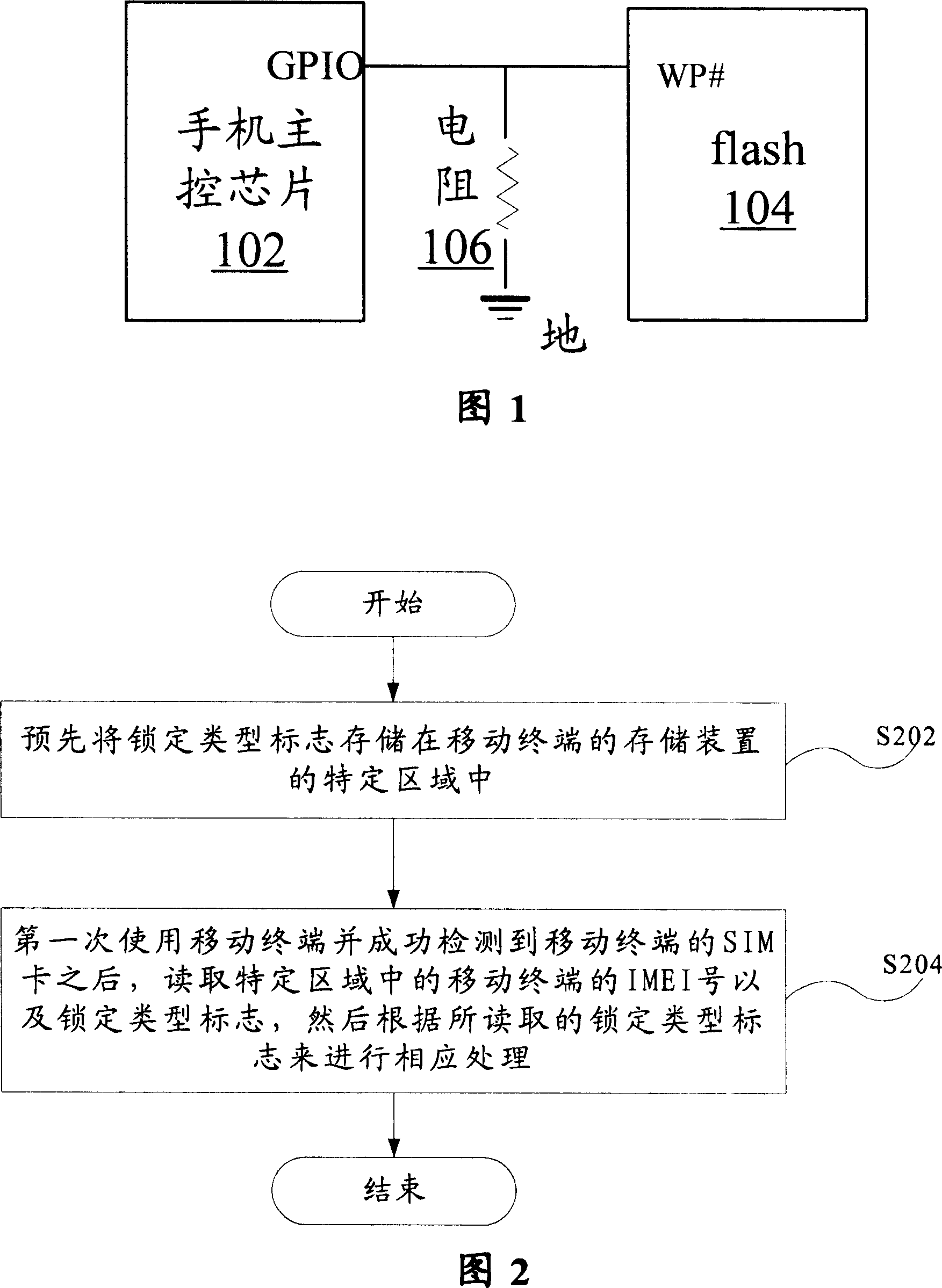
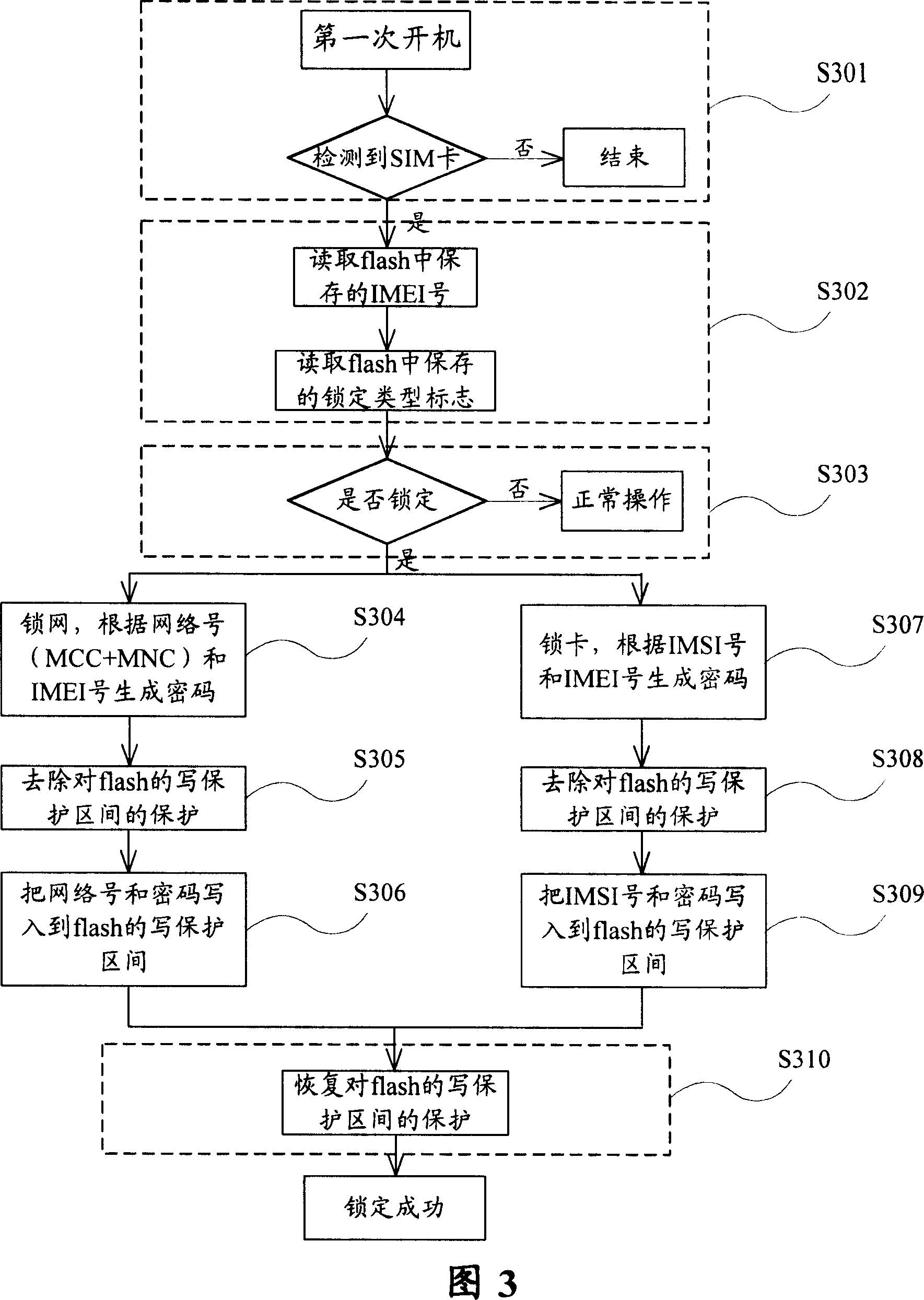
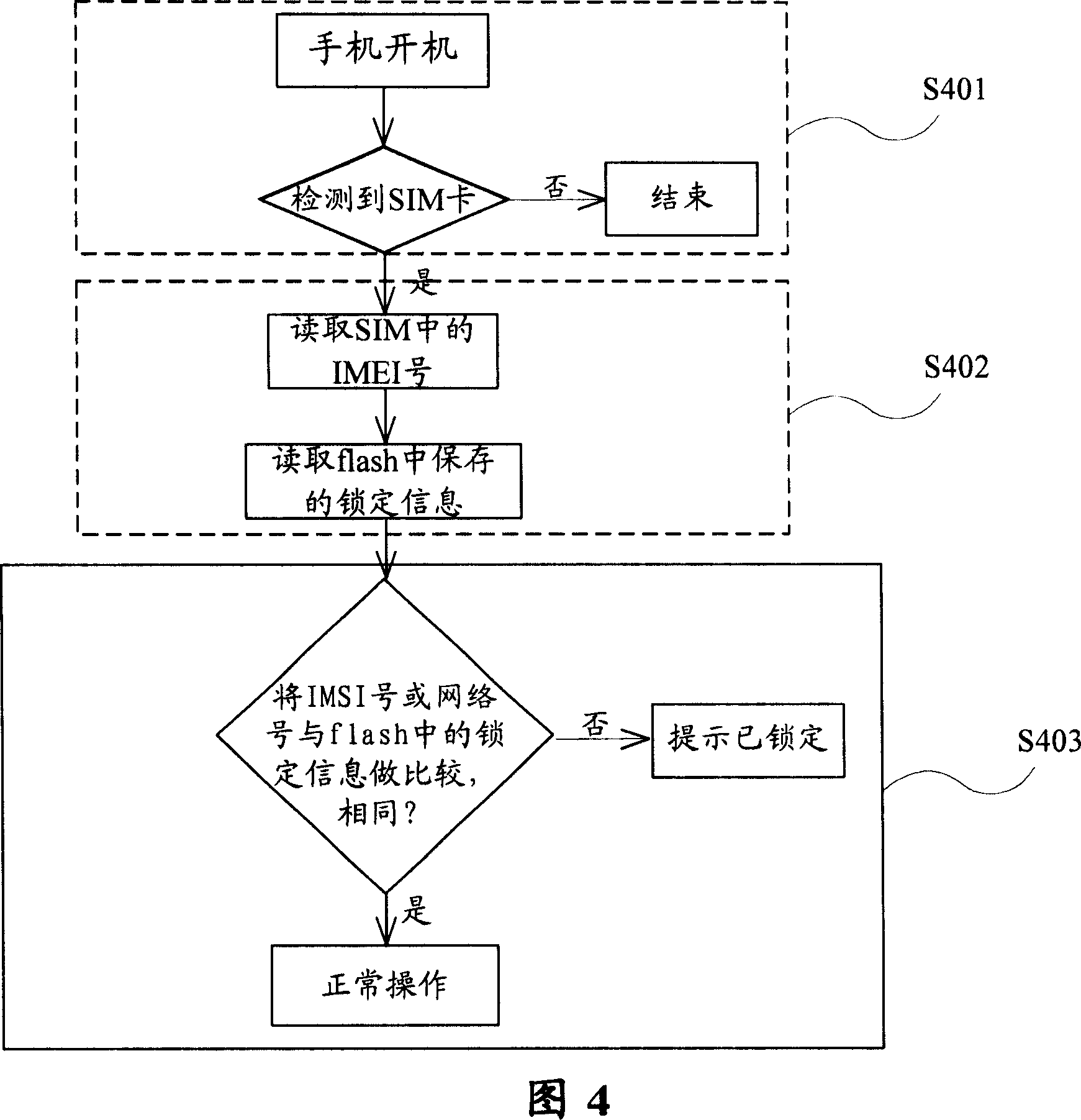
The locking method includes following steps: step S202, storing symbol of locking type in specific area of memory device of mobile terminal in advance; step S204, after first time to use mobile terminal, and detecting SIM card of mobile terminal successfully, reading IMEI number of mobile terminal in specific area, and symbol of locking type, and then based on read symbol of locking type to carry out corresponding process. Thus, it is convenient for operation manager to carry out operation of locking network, locking cards for centralized purchased handsets. Using specific network and specific SIM cards can operate the locked handsets, or other SIM cards will not make locked handsets work. The locked information is stored in write protection area of protected flash so as to protect the locked information from rewriting unlawfully. Based on requirement, locked handsets can be unlocked in order to solve maintenance issue after sale.
Owner:ZTE CORP
Multicore DSP device having shared program memory with conditional write protection
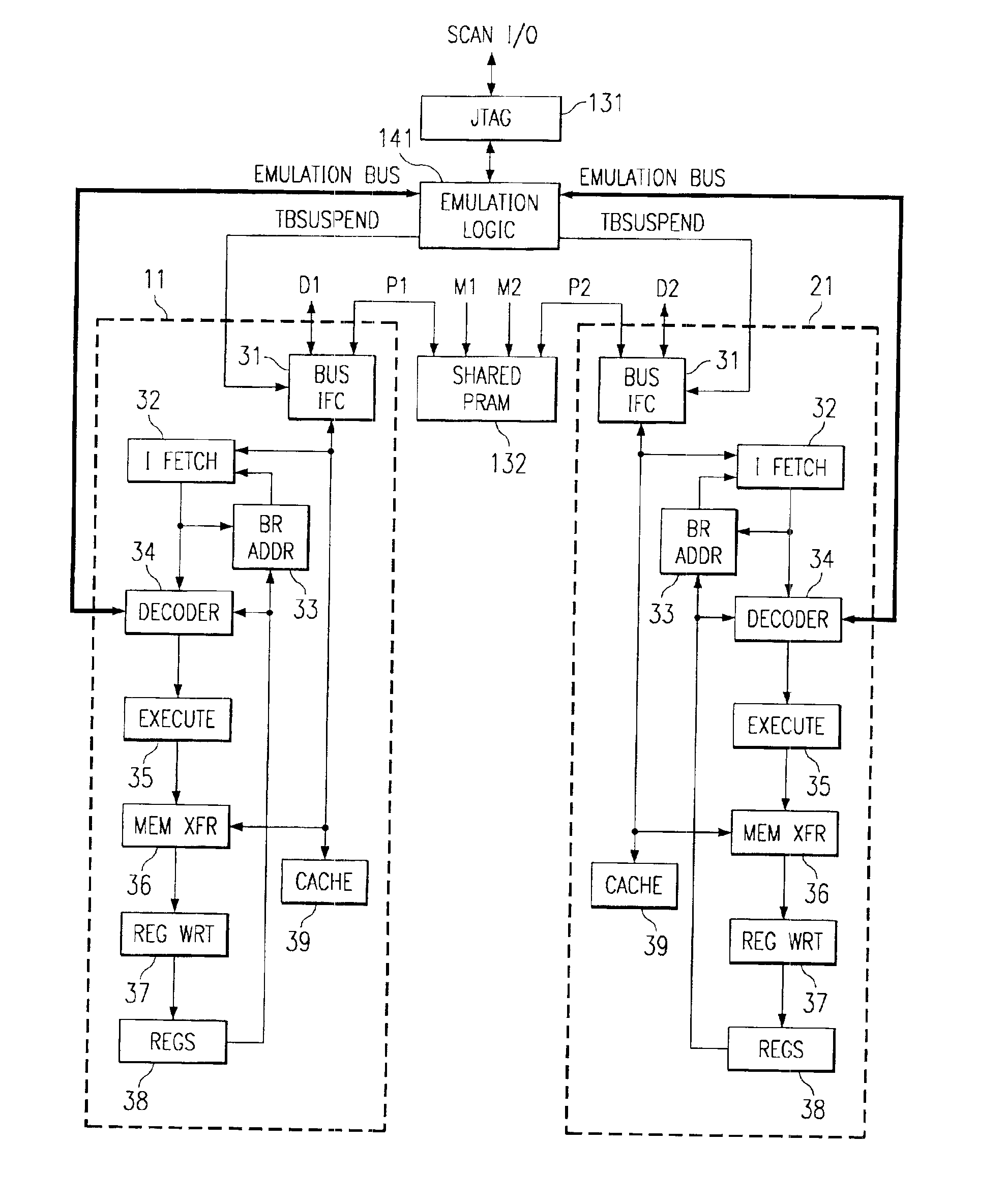
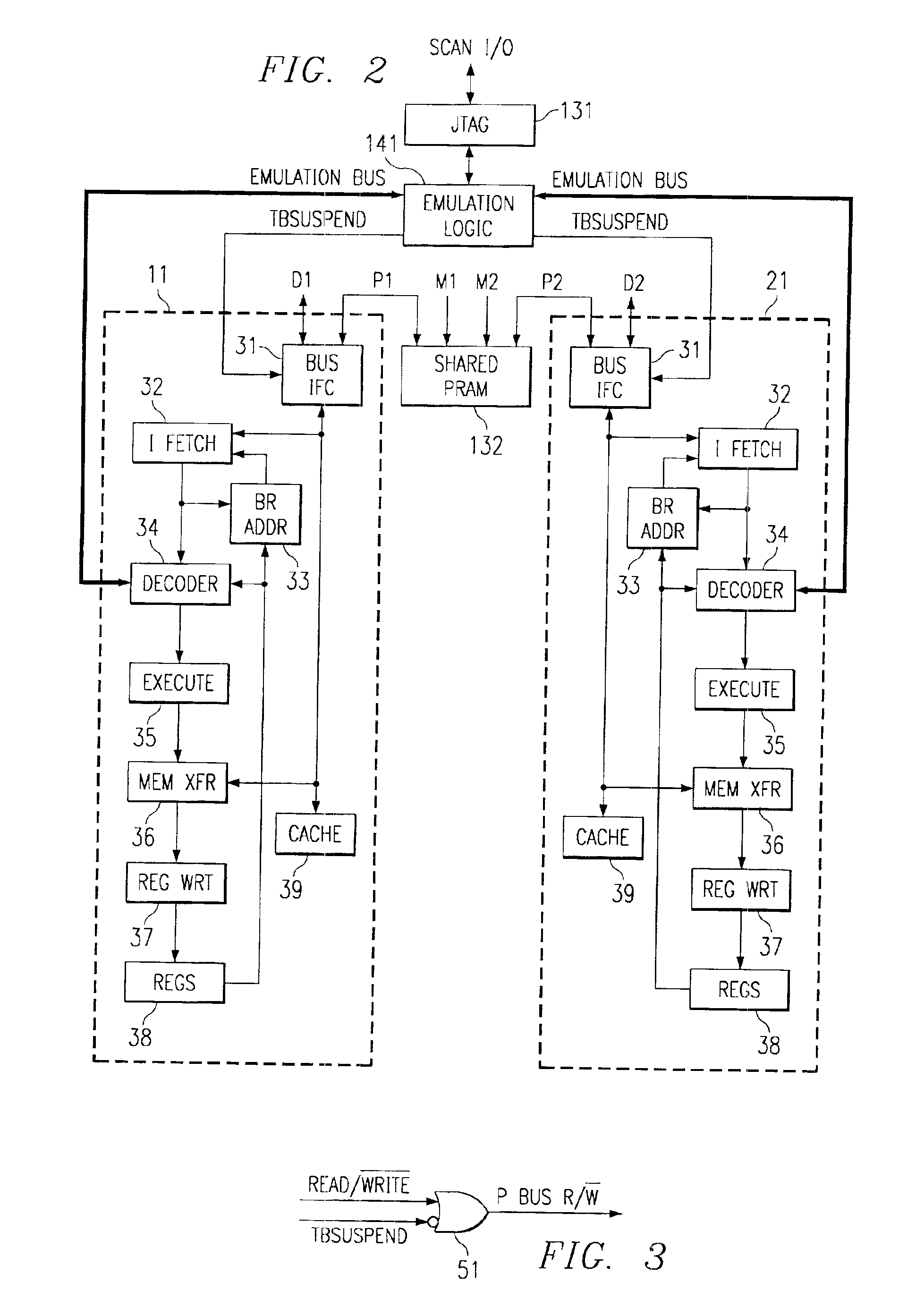
InactiveUS6895479B2Unauthorized memory use protectionGeneral purpose stored program computerWrite protectionDigital signal processing
A multi-core digital signal processor is disclosed having a shared program memory with conditional write protection. In one embodiment, the digital signal processor includes a shared program memory, an emulation logic module, and multiple processor cores each coupled to the shared program memory by corresponding instruction buses. The emulation logic module preferably determines the operating modes of each of the processors, e.g., whether they are operating in a normal mode or an emulation mode. In the emulation mode, the emulation logic can alter the states of various processor hardware and the contents of various registers and memory. The instruction buses each include a read / write signal that, while their corresponding processor cores are in normal mode, is maintained in a read state. On the other hand, when the processor cores are in the emulation mode, the processor cores are allowed to determine the state of the instruction bus read / write signals. Each instruction bus read / write signal is preferably generated by a logic gate that prevents the processor core from affecting the read / write signal value in normal mode, but allows the processor core to determine the read / write signal value in emulation mode. In this manner, the logic gate prevents write operations to the shared program memory when the emulation logic de-asserts a signal indicative of emulation mode, and allows write operations to the shared program memory when the emulation logic asserts the signal indicative of emulation mode. The logic gate is preferably included in a bus interface module in each processor core.
Owner:TEXAS INSTR INC
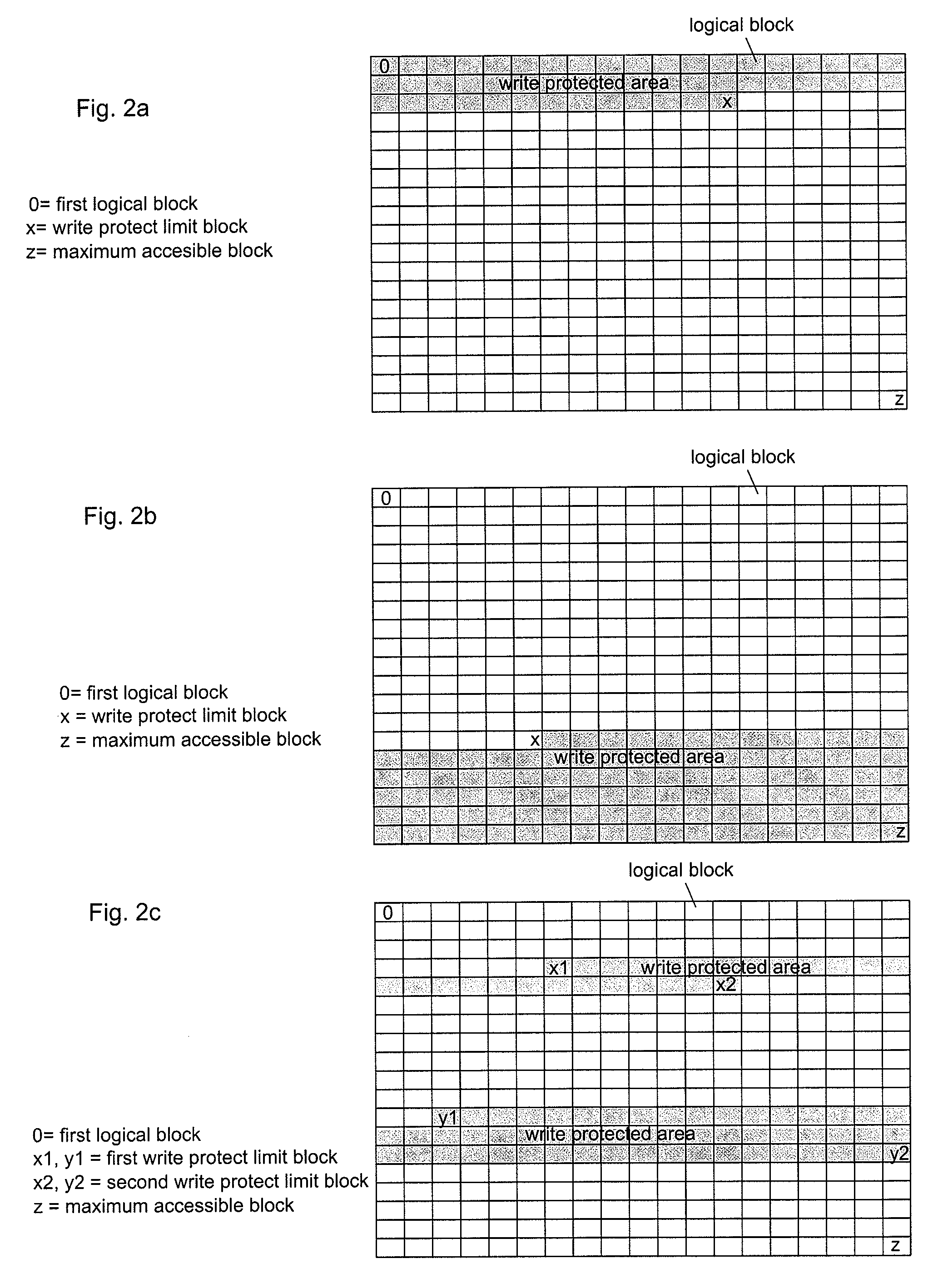
Write Protection For Memory Devices
InactiveUS20080250509A1Error detection/correctionVolume/mass flow measurementWrite protectionHard disc drive
Provided is a method for implementing write protection for a non-volatile rewritable memory device, such as a hard disk drive or flash memory module. A write protect command including a first write protect limit address is received, and the first write protect limit address is stored in a register, if it is within an accessible memory area of a memory device. Any subsequent write access to a write protected area is prevented, the write protected area being defined by the first write protect limit address. Associated devices, modules, and systems are also provided.
Owner:NOKIA CORP
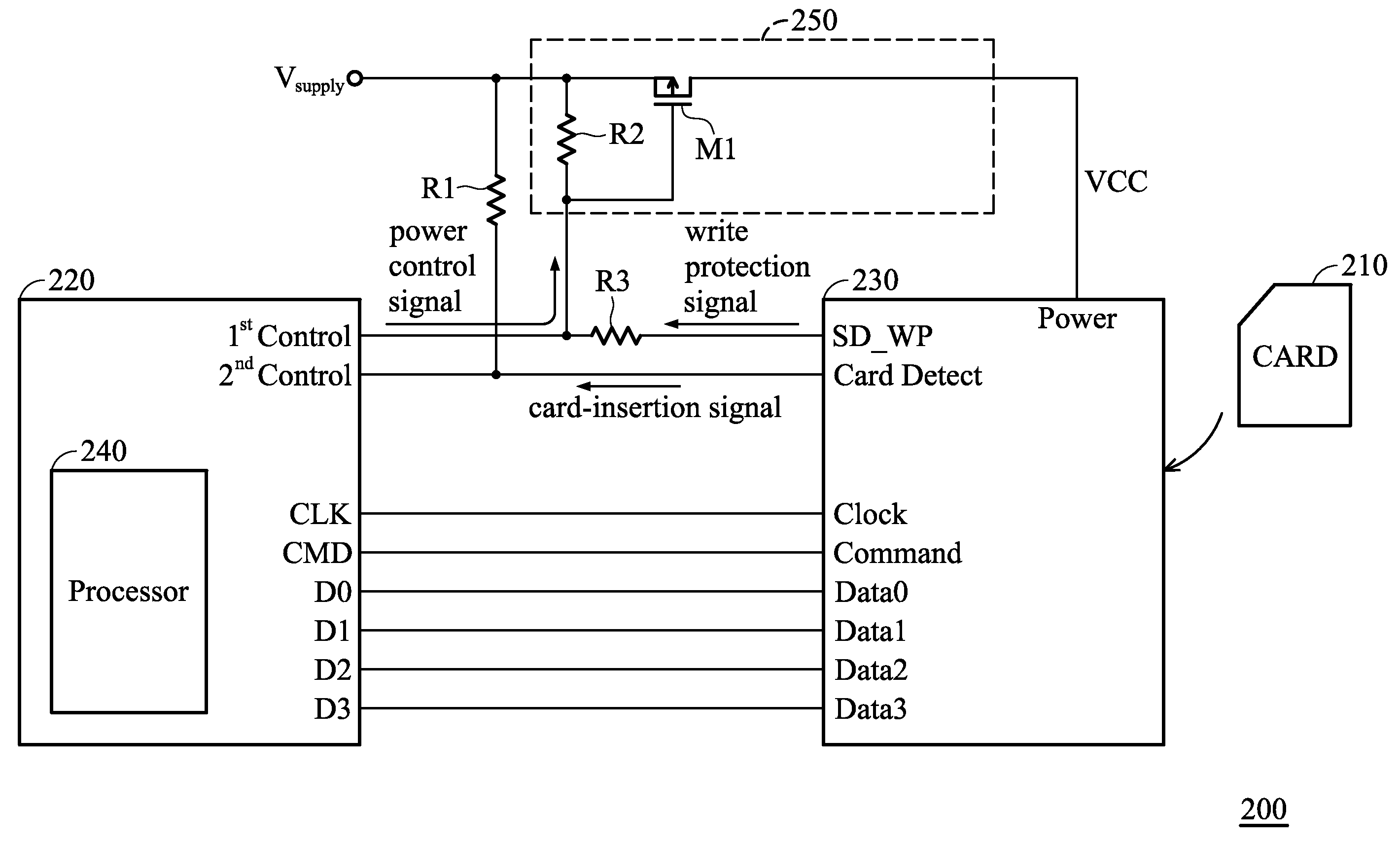
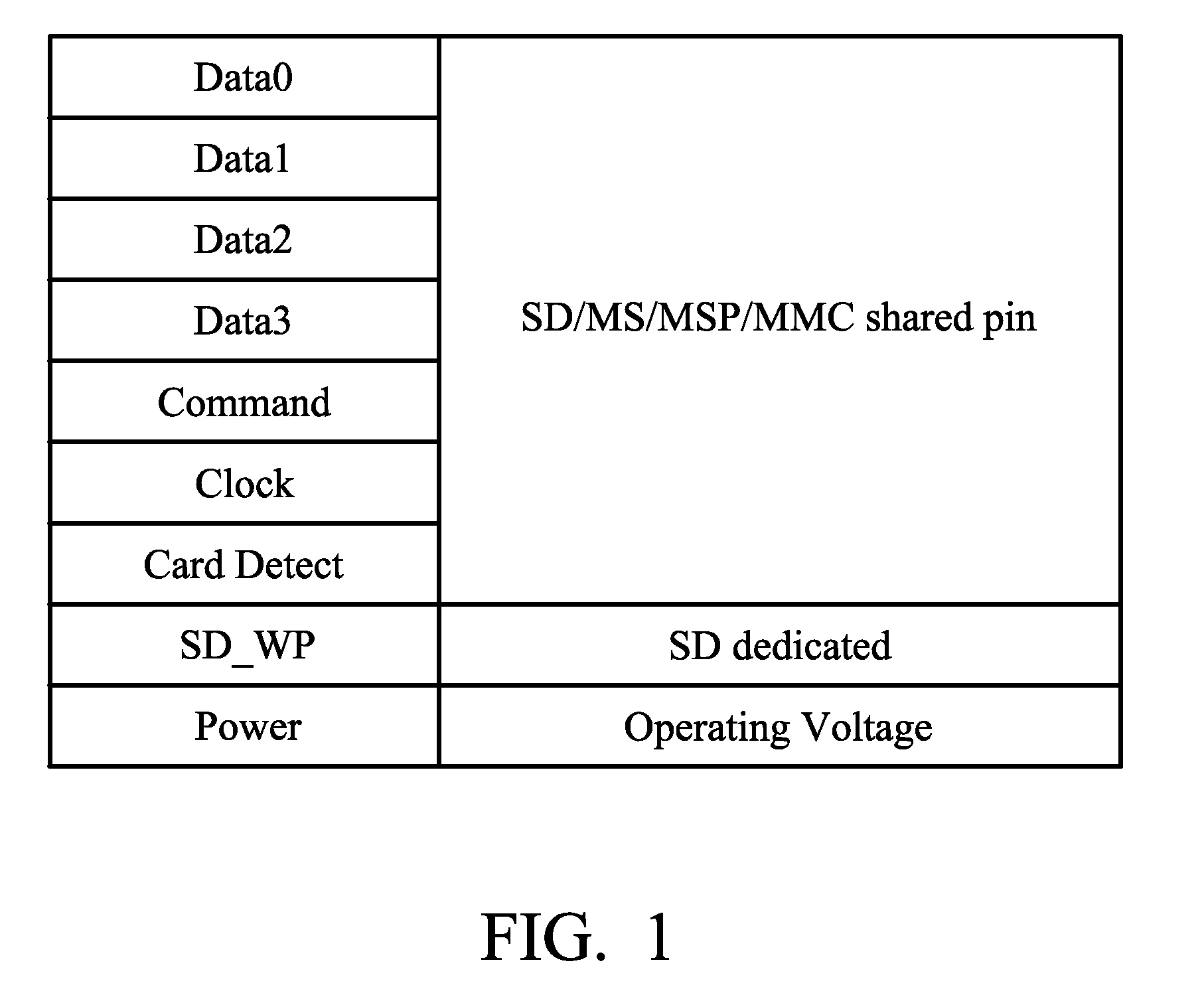
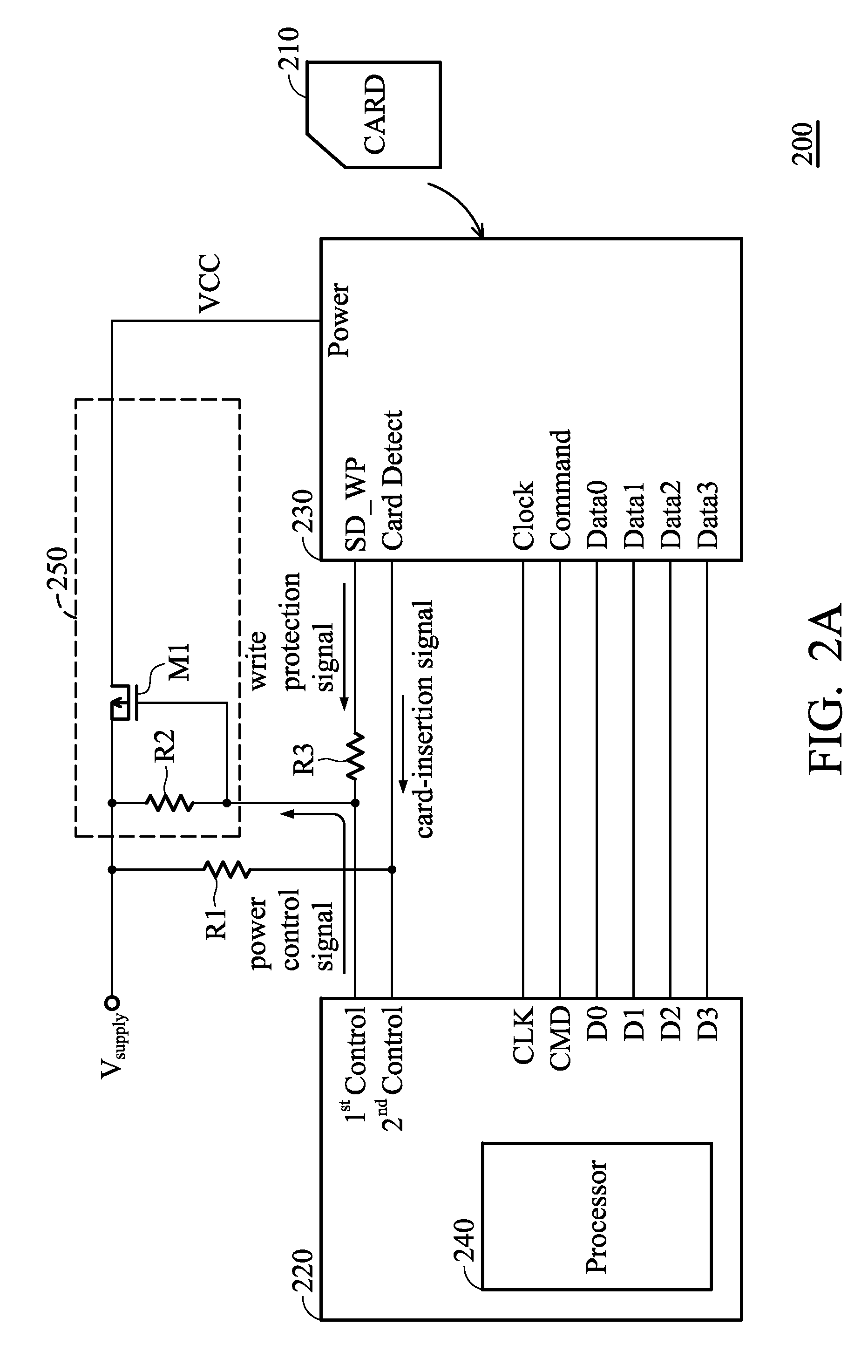
Systems for accessing memory card and methods for accessing memory card by a control unit
A system for accessing a memory card is provided. The system includes a control unit having a control pin and a processor. The processor senses a card-insertion signal from a socket via the control pin for indicating whether the memory card has been inserted into the socket. The processor provides a power control signal via the control pin to supply an operating voltage to the memory card when the sensed card-insertion signal indicates that the memory card has been inserted into the socket. The processor detects whether a write protection function of the memory card is present via the control pin.
Owner:MEDIATEK INC
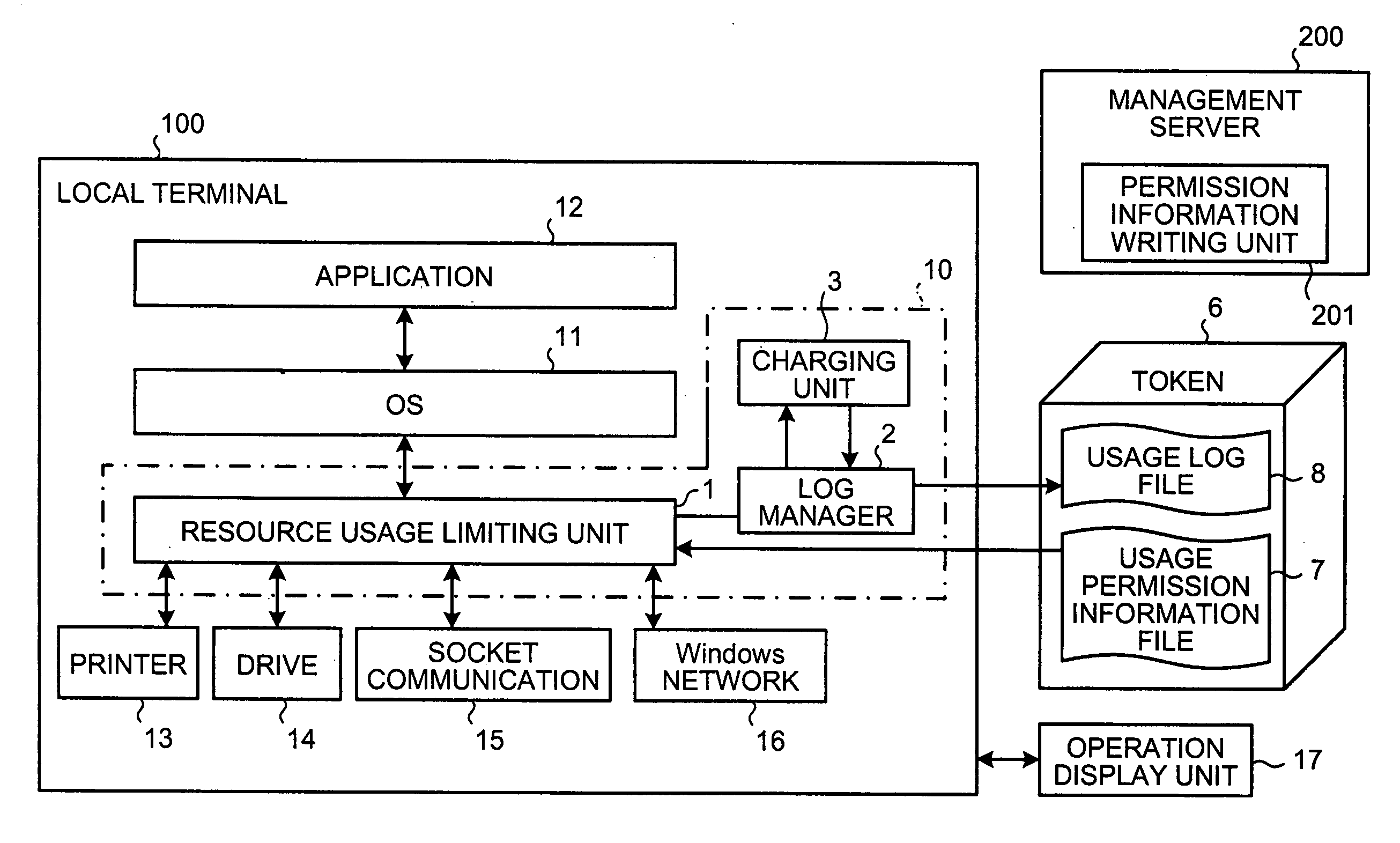
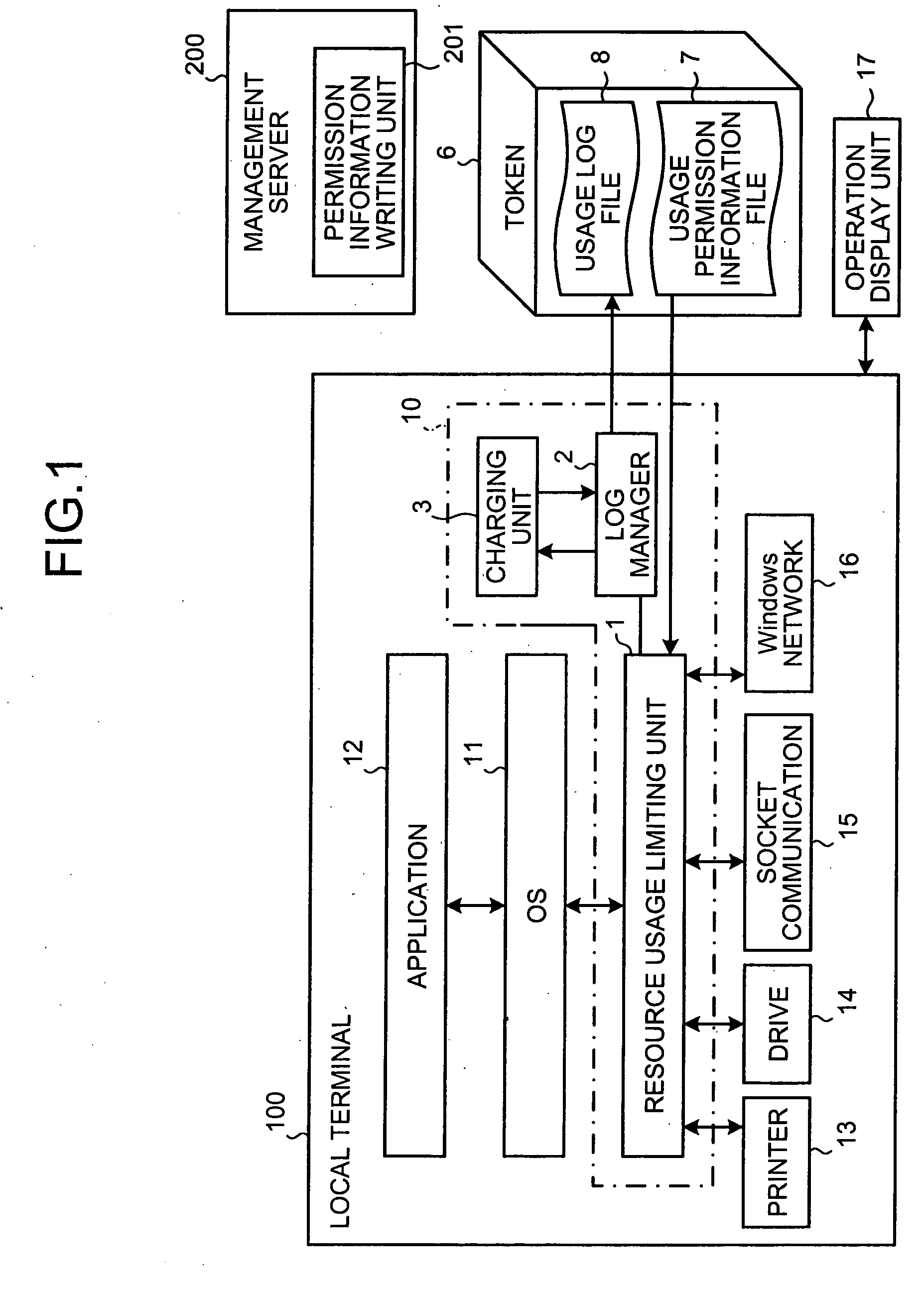
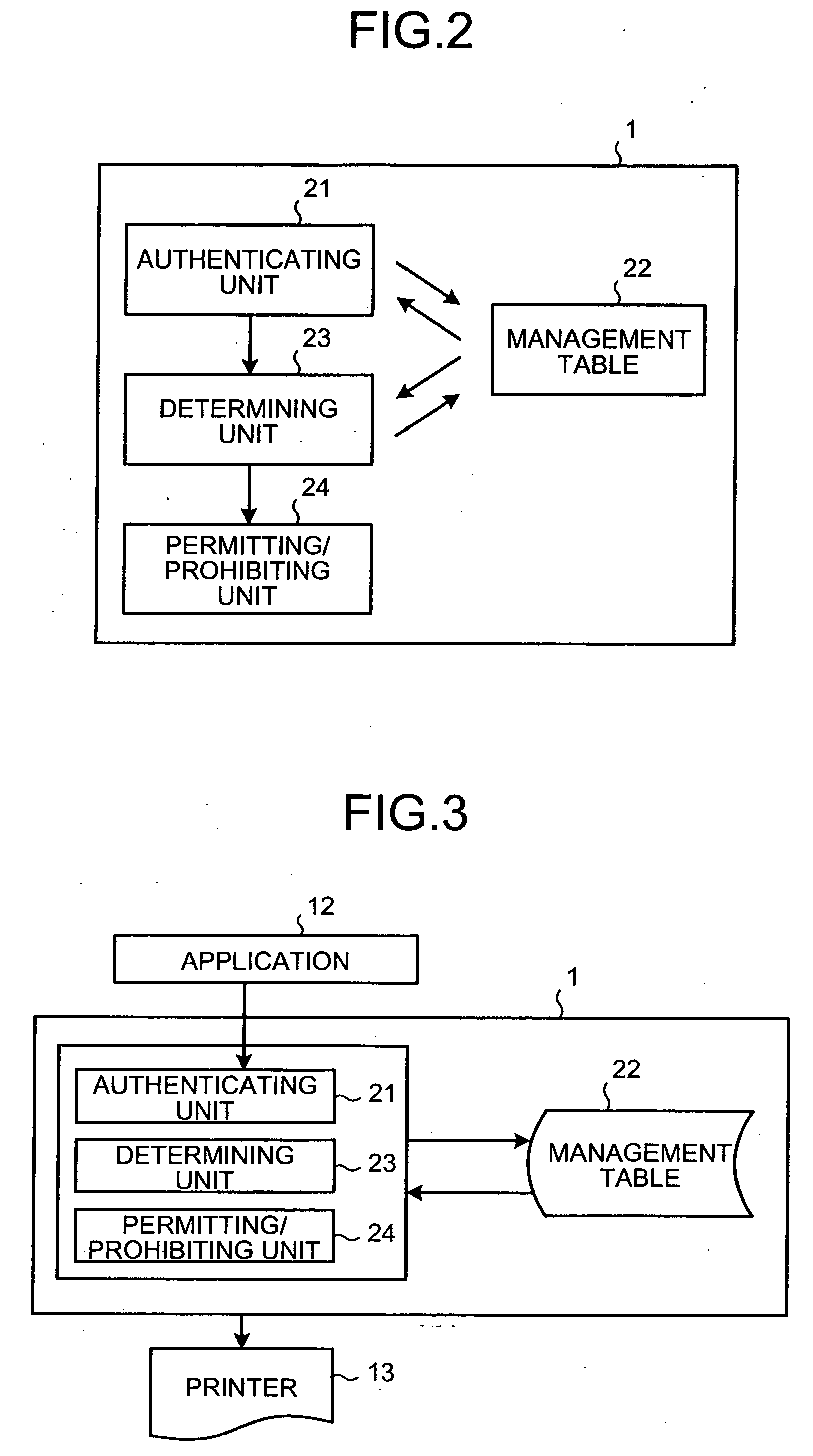
Method and system for acquiring resource usage log and computer product
InactiveUS20050216466A1Digital data processing detailsError detection/correctionWrite protectionProduct base
Based on user permission information read from a write-protected portable medium, it is determined whether an application is permitted to use a resource. If the application is permitted to use the resource, the write protection of the portable medium is released, usage log information is written into the medium.
Owner:FUJITSU LTD
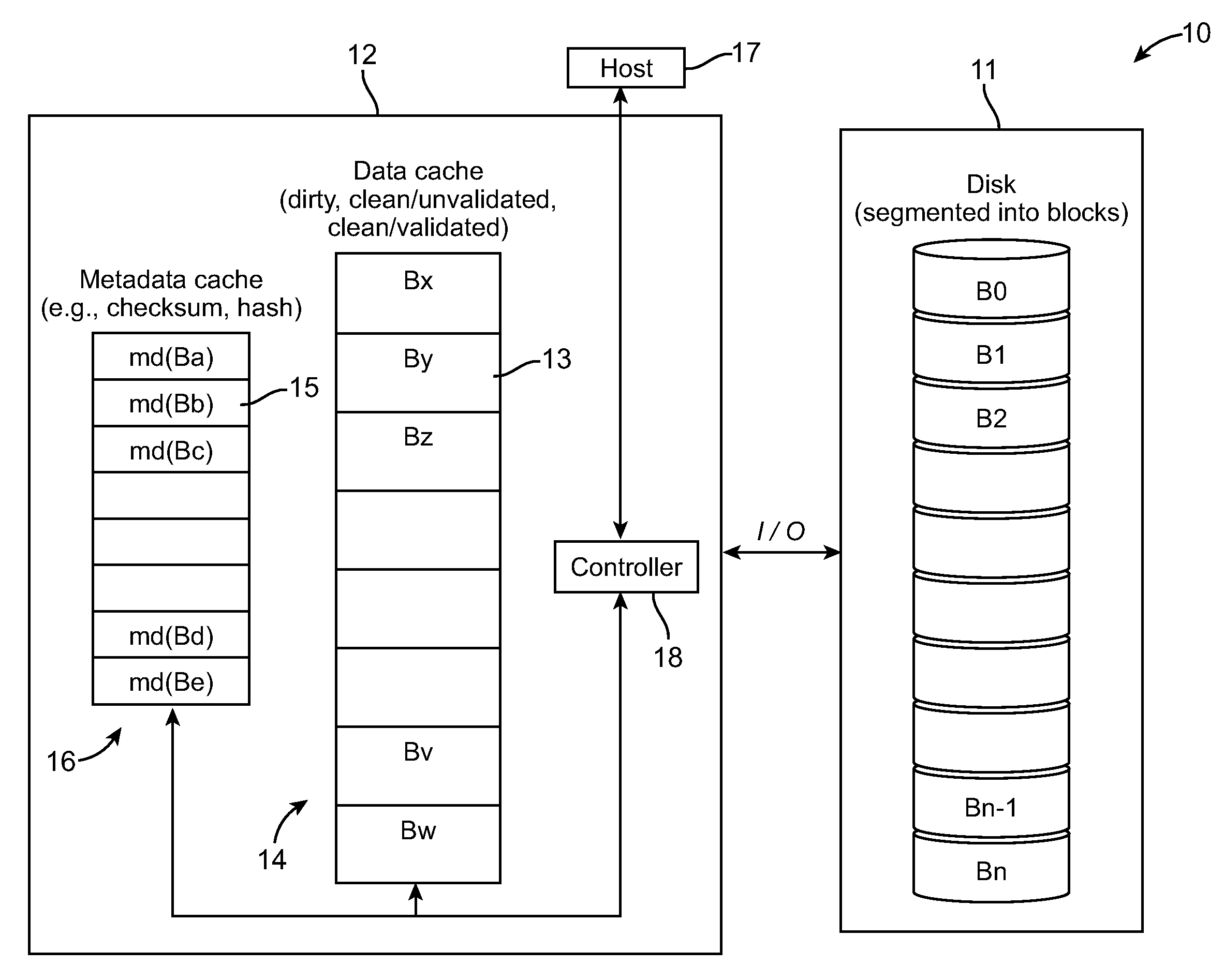
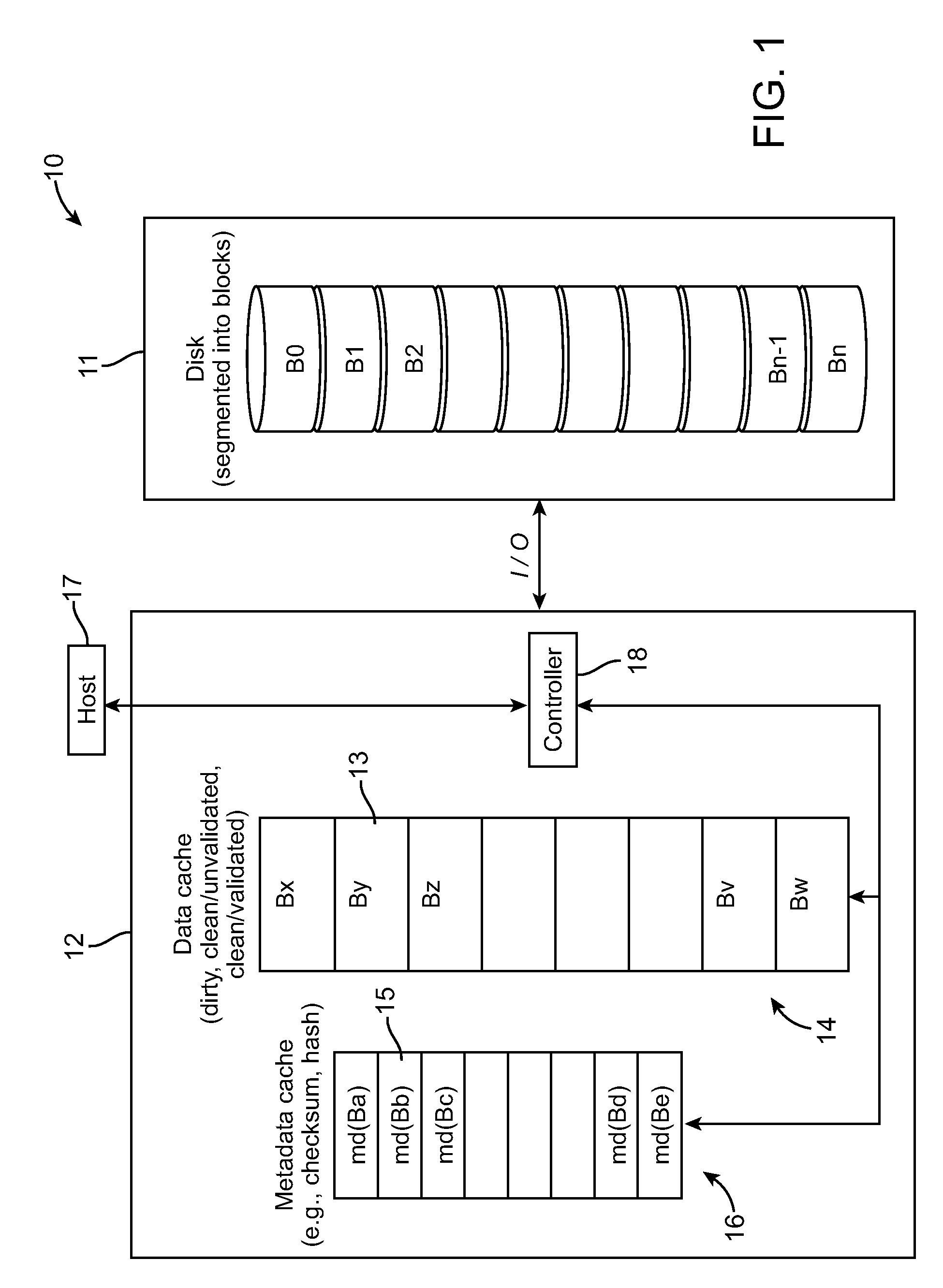
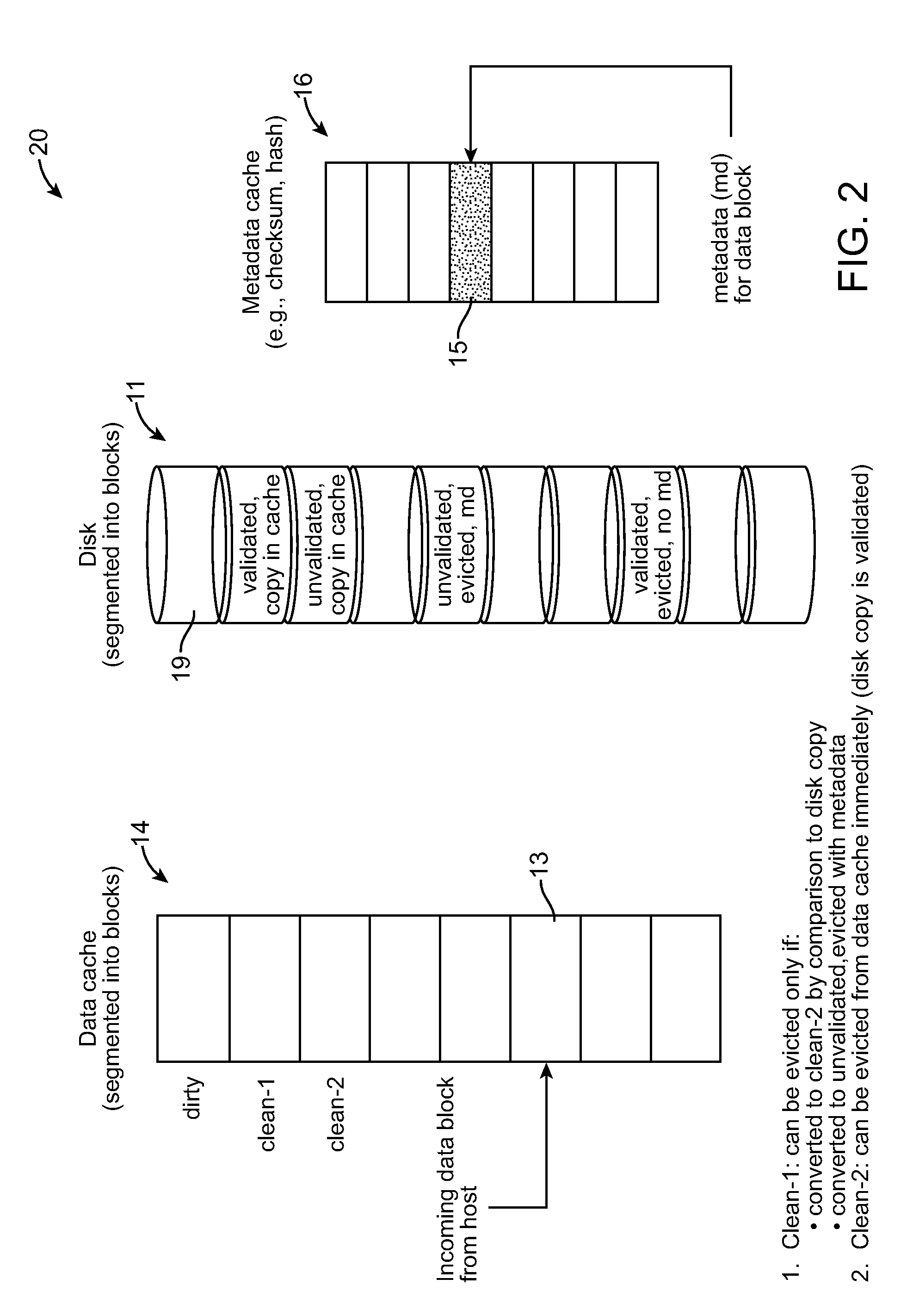
Method and system for cache-based dropped write protection in data storage systems
InactiveUS20090228744A1Error detection/correctionRecord information storageWrite protectionData needs
A method and system for cache-based dropped write protection in data storage systems are provided. An implementation involves detecting undetected write errors in a storage system, by writing data to a storage medium from a data cache; maintaining a copy of the data in the data cache until said data on the storage medium is validated or said data needs to be evicted from the data cache; and prior to eviction of said data from the data cache, maintaining metadata for said data in a metadata cache until the data written to the storage medium has been validated against the metadata.
Owner:GLOBALFOUNDRIES INC
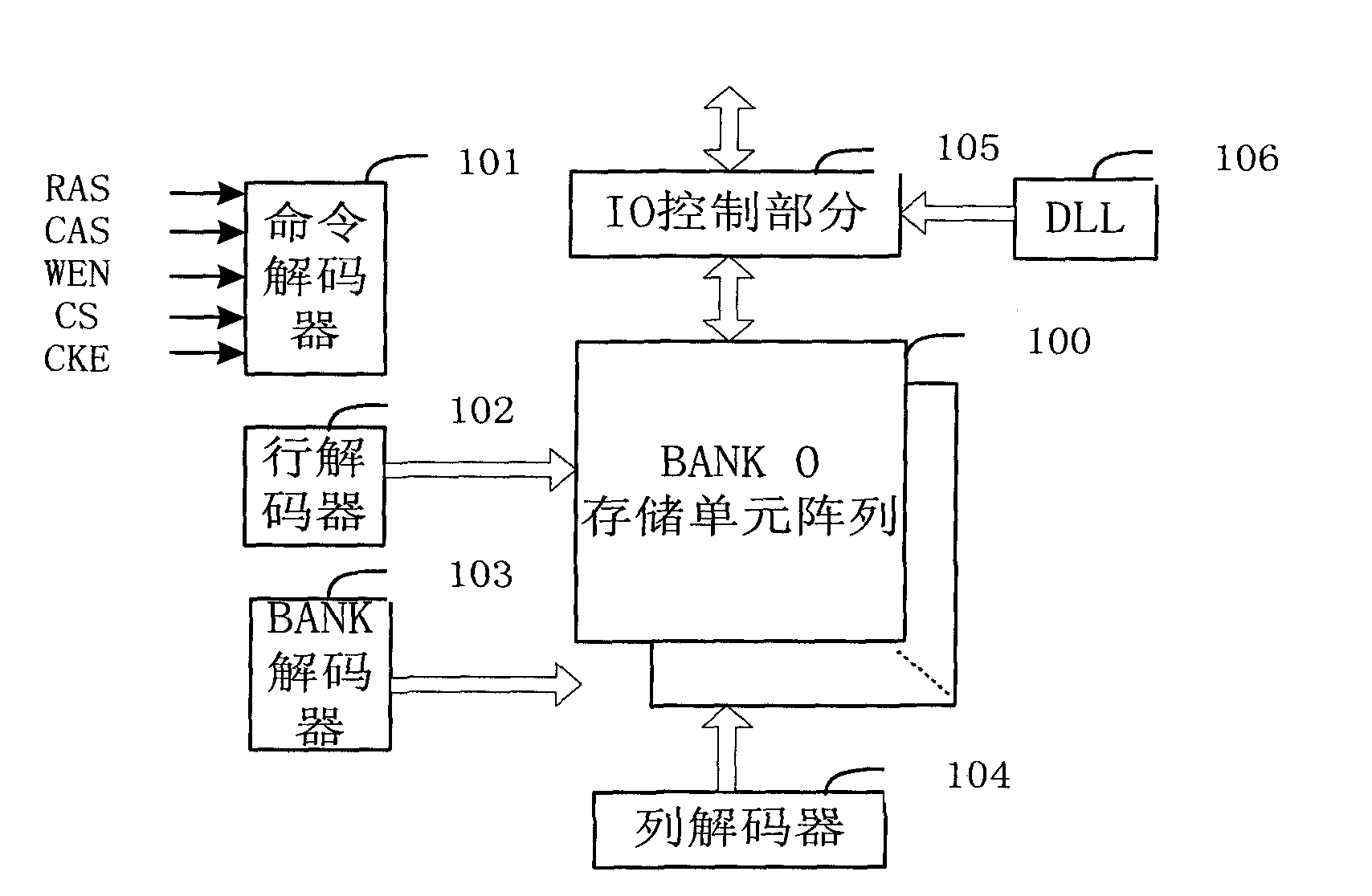
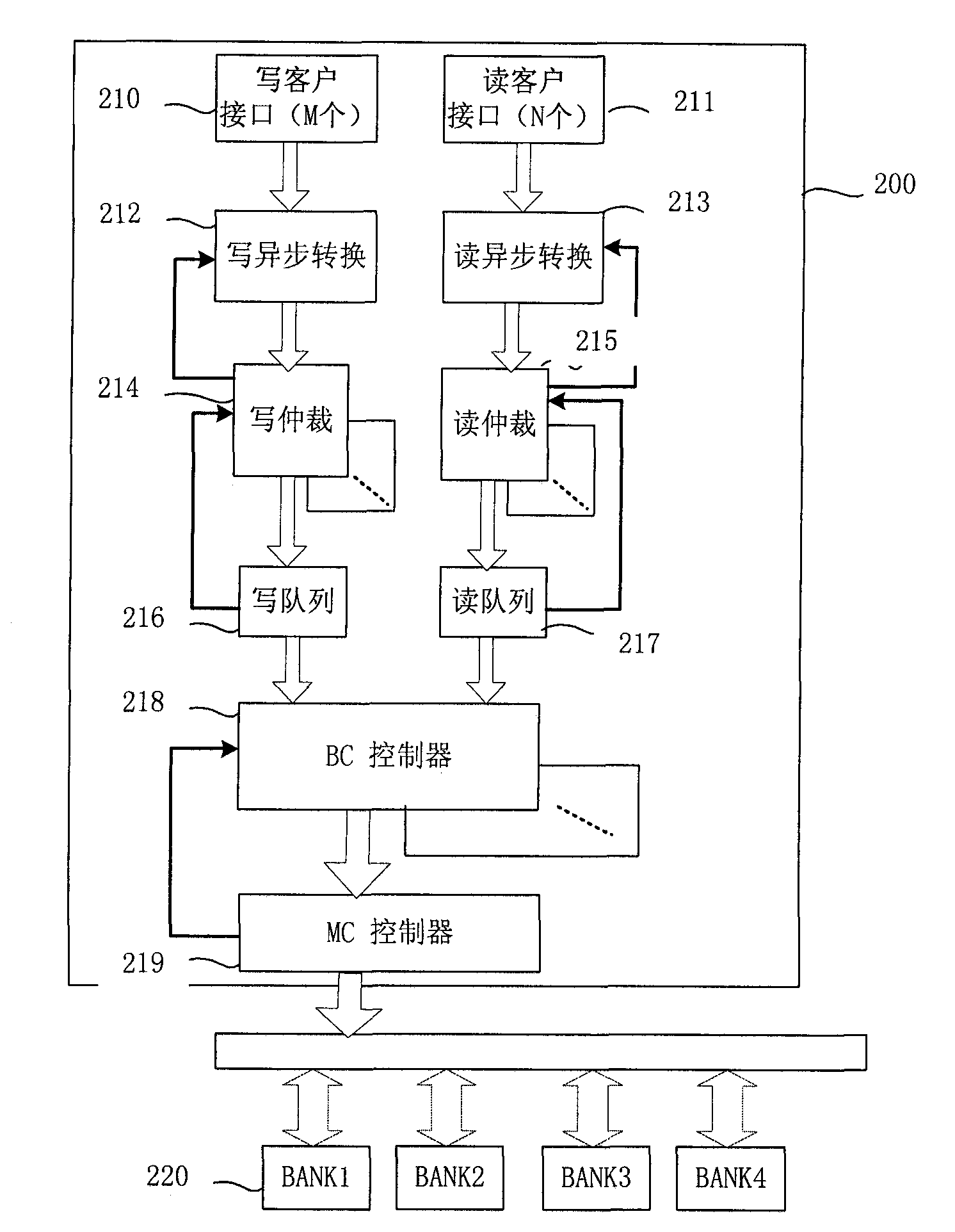
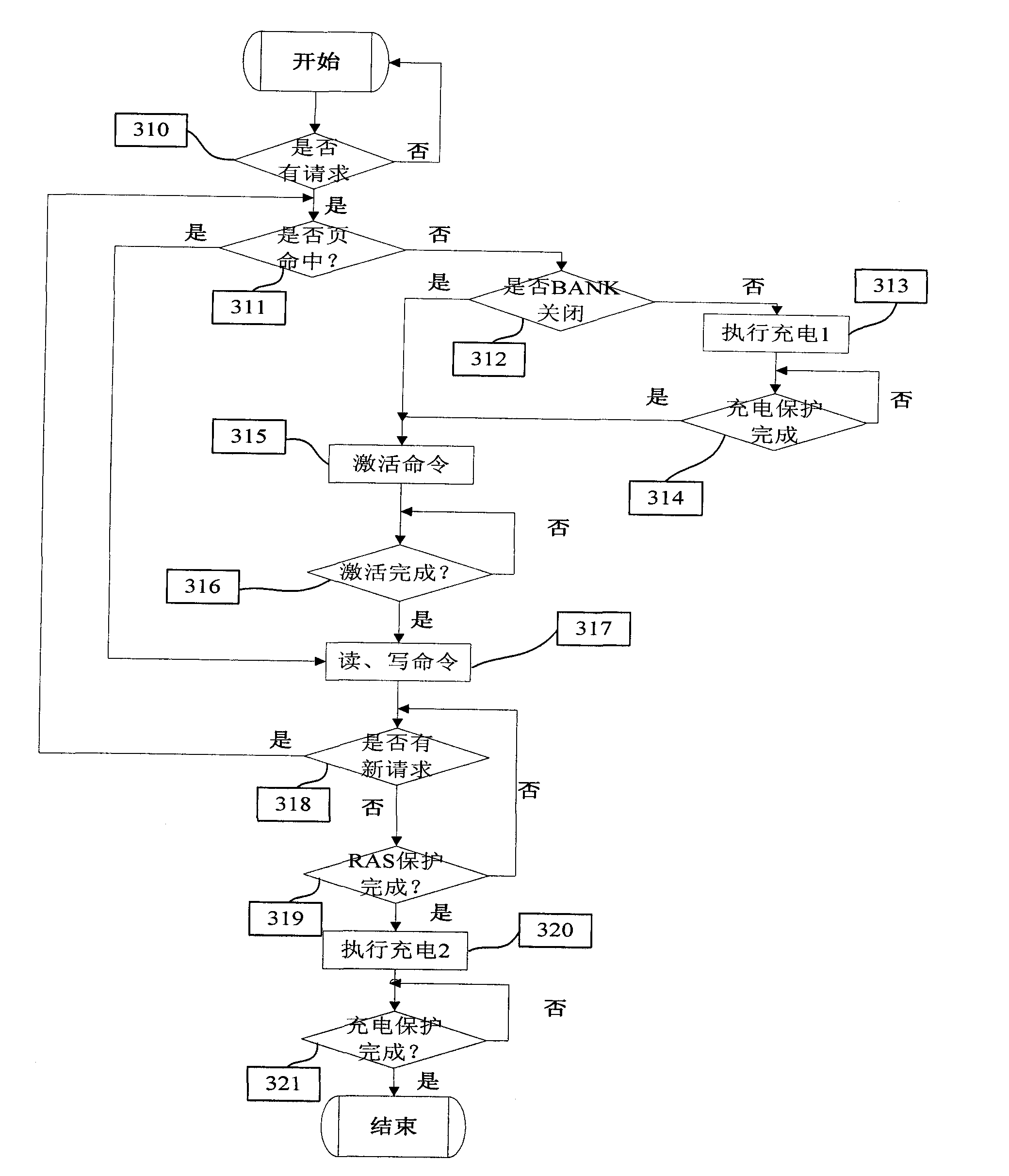
DRAM (Dynamic Random Access Memory) storage control method and device
The invention discloses DRAM storage control method and device. The method comprises the following steps of: A10. decoding read and write requests and rearranging into a plurality of BANK-based read and write request arrays according to BANK addresses; A20. respectively arbitrating the read and write requests; A30. respectively generating respective read and write request commands and activating commands and / or precharge commands; and A40. sending the read and write request commands to a command bus, and on the premise of satisfying the read and write protection time limit of a DRAM, inserting the activating commands and / or percharge commands of the read and write command requests in the other BANKs based read and write request arrays before the read and write command request in the BANK-based read and write request array. In the invention, the activating commands and the precharge commands can be completely hidden in the data transmission process, and seemingly, a DRAM data bus always transmits data, and therefore, the bus efficiency of the DRAM is greatly improved.
Owner:FENGHUO COMM SCI & TECH CO LTD +1
Method and system for operating multiple virtual machines
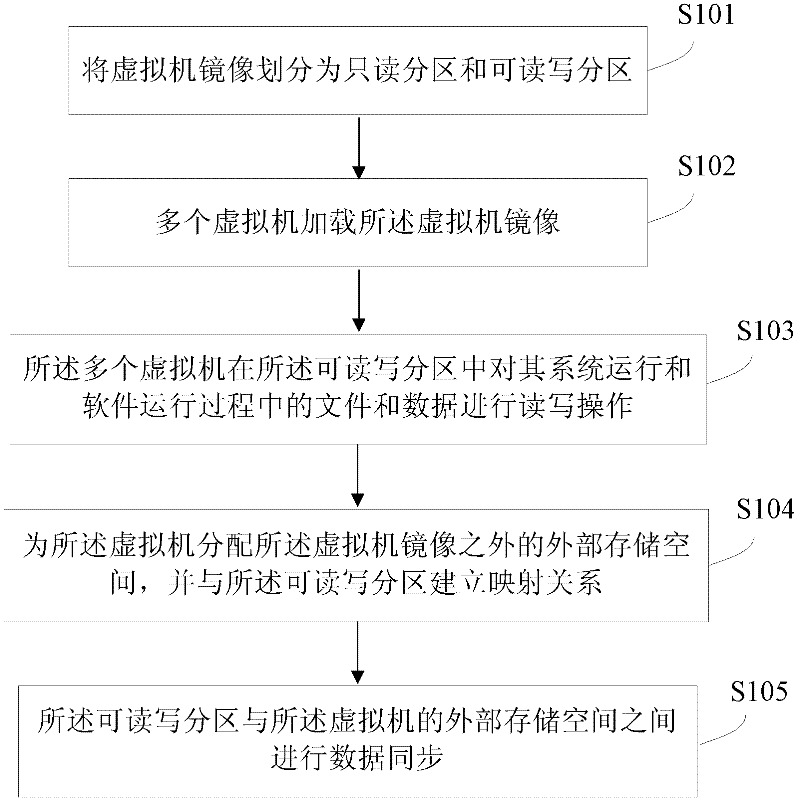
InactiveCN102521016APromote migrationEasy maintenanceSoftware simulation/interpretation/emulationWrite protectionBitwise operation
The invention discloses a method and a system for operating multiple virtual machines. The method comprises: a virtual machine mirror image is divided into a read-only partition and a read-write partition, wherein the read-only partition stores data which needs write-protection in a virtual machine mirror image; multiple virtual machines upload the virtual machine mirror image, wherein the multiple virtual machines perform reading / writing operation to files and data during system operation and software operation in the read-write partition. The system comprises a partition dividing module, a multiple virtual machine uploading module and a data reading / writing module. With the method and the system provided by the invention, the problem of file reading / writing conflict when multiple virtual machines operate on one same mirror image is avoided. In addition, updating and upgrade of virtual servers can be only performed to one mirror image to be synchronized to all nodes, such that not only the maintenance cost of virtual servers is saved, but also the maintenance time is shortened, furthermore, error possibility during updating and upgrade can be reduced or completely avoided.
Owner:ZTE CORP
Write protection of subroutine return addresses
Owner:INT BUSINESS MASCH CORP
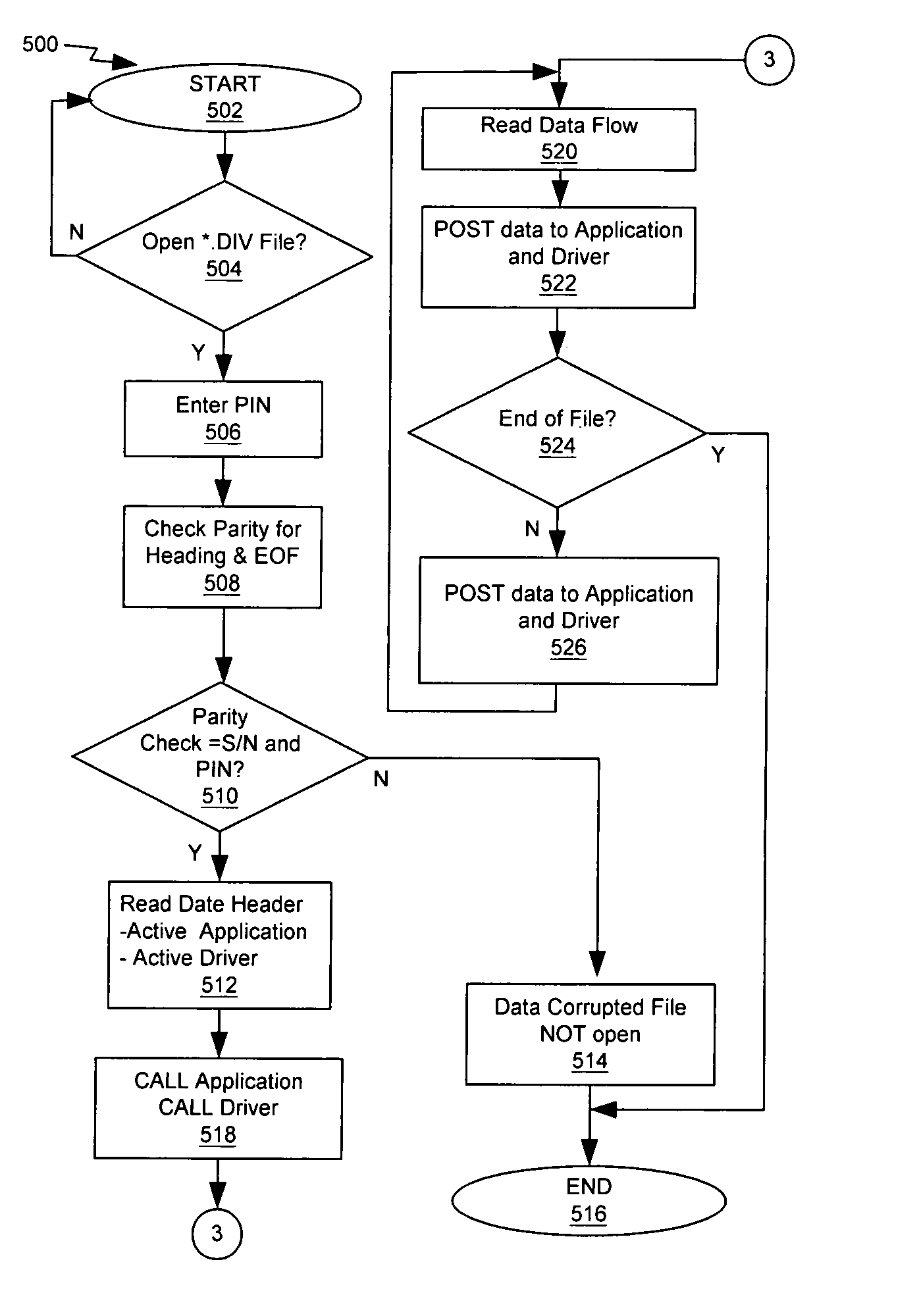
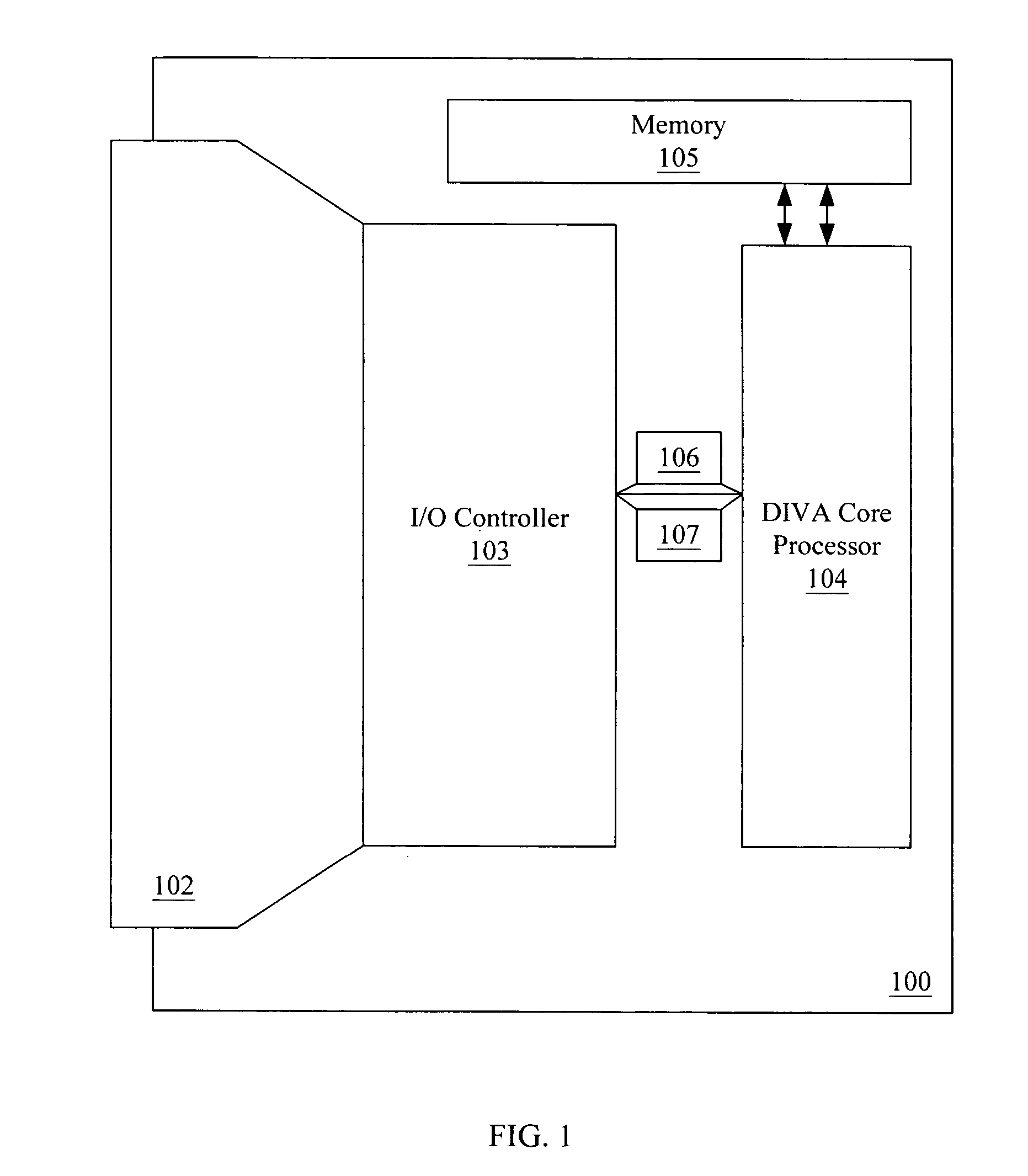
Digital image validations system (DIVA)
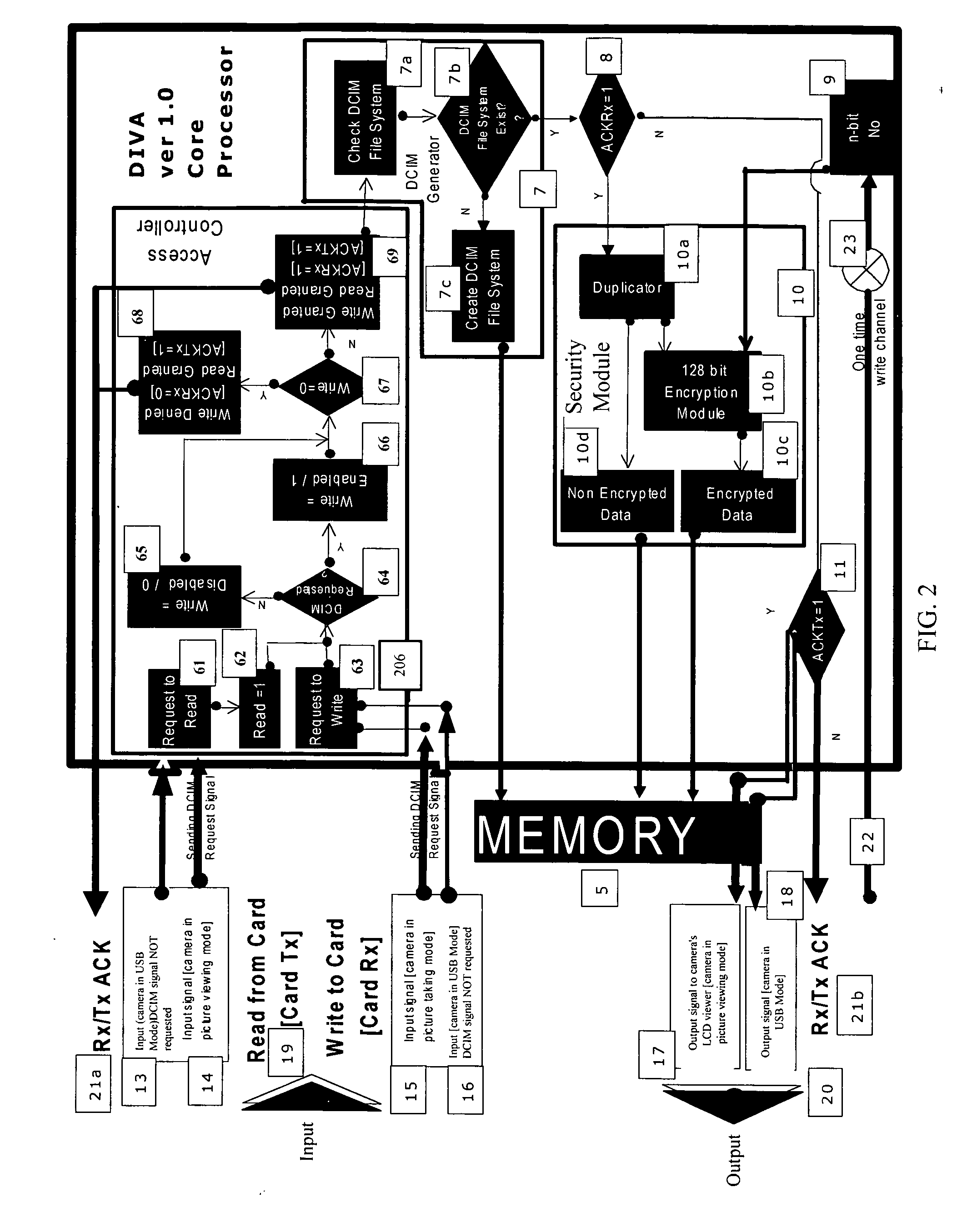
InactiveUS20050108540A1Avoid interceptionUser identity/authority verificationComputer security arrangementsWrite protectionDigital imaging
The DIVA stands for Digital Imaging Validation: is an external electronic device equipped with controlled microprocessor, which includes write protection, data encryption, and duplication capabilities. This electronic device is equipped with flash memory chips to hold / store digital image data produced by any digital imaging devices. This electronic device is packaged in small form factor housing (including compact flash form, dongle form, PCMCIA form etc) with abilities to act as storage memory device of the digital imaging device and can be directly inserted or attached to the interface port of the corresponding imaging device. The DIVA is also known as Programmable Microprocessor-Integrated Encryption External Storage Media. Furthermore, DIVA is also comprises of a system utilizing secured web-based application to deploy its full capability.
Owner:KUSNOTO BUDI +1
Data recording device
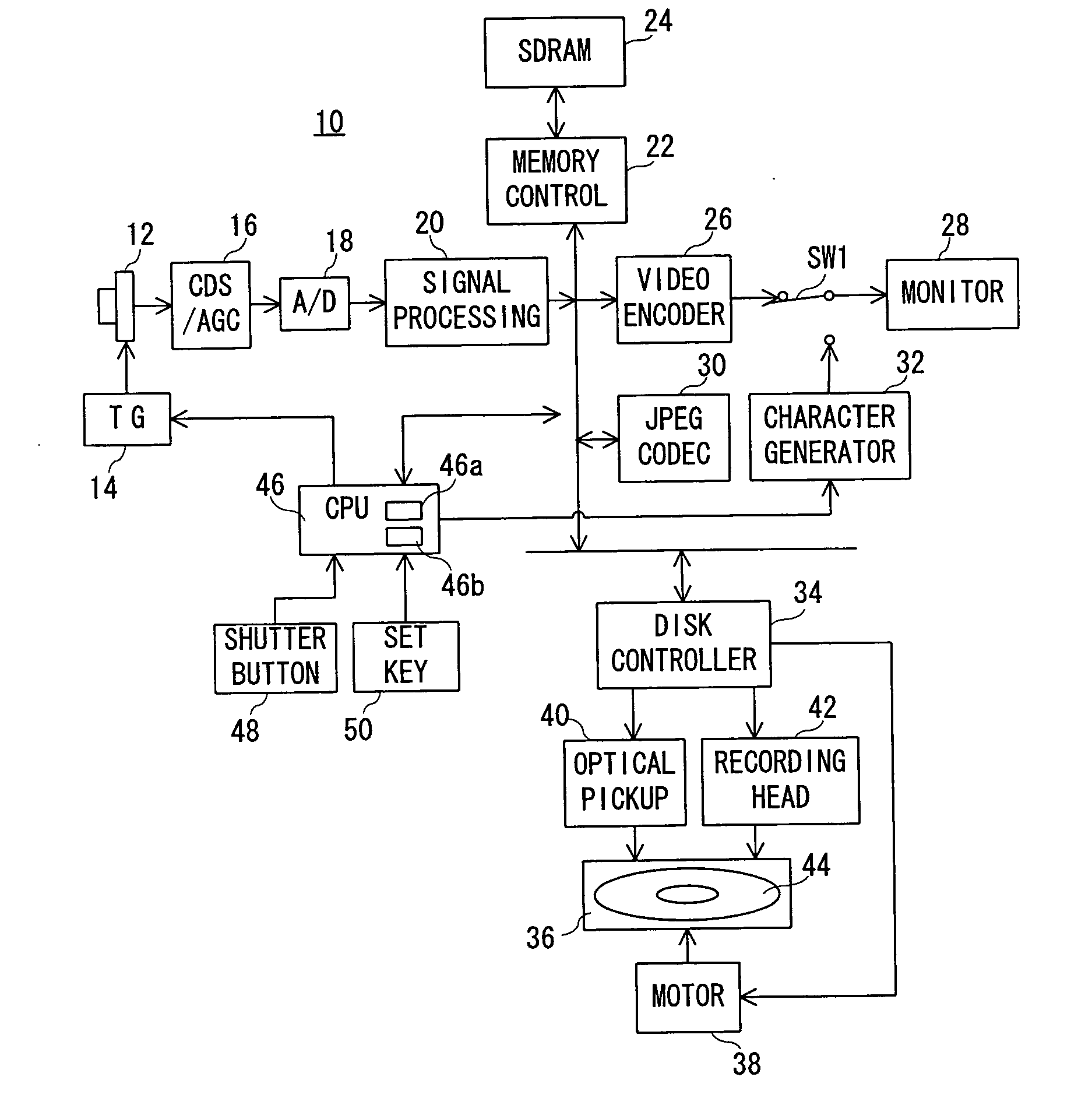
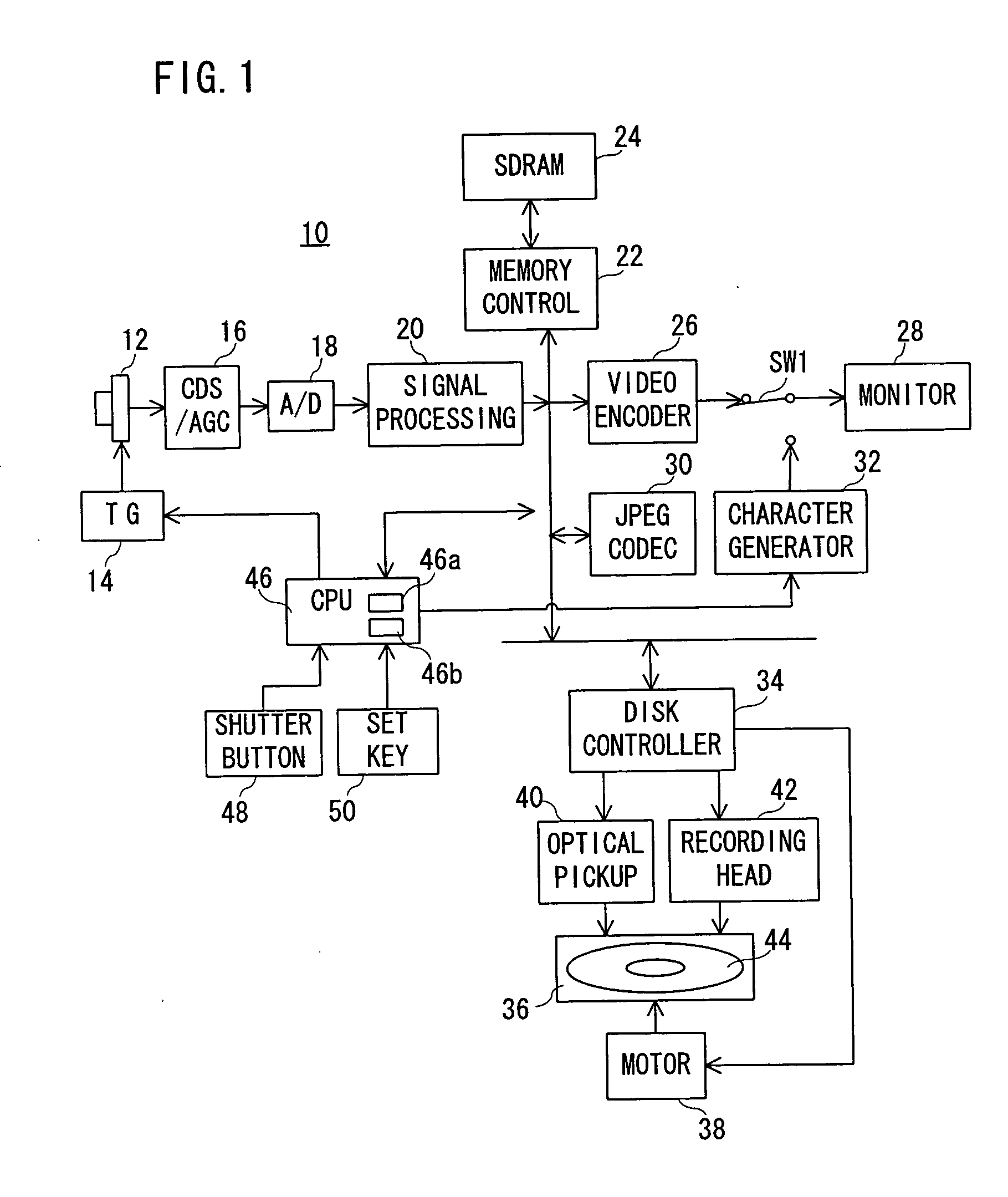
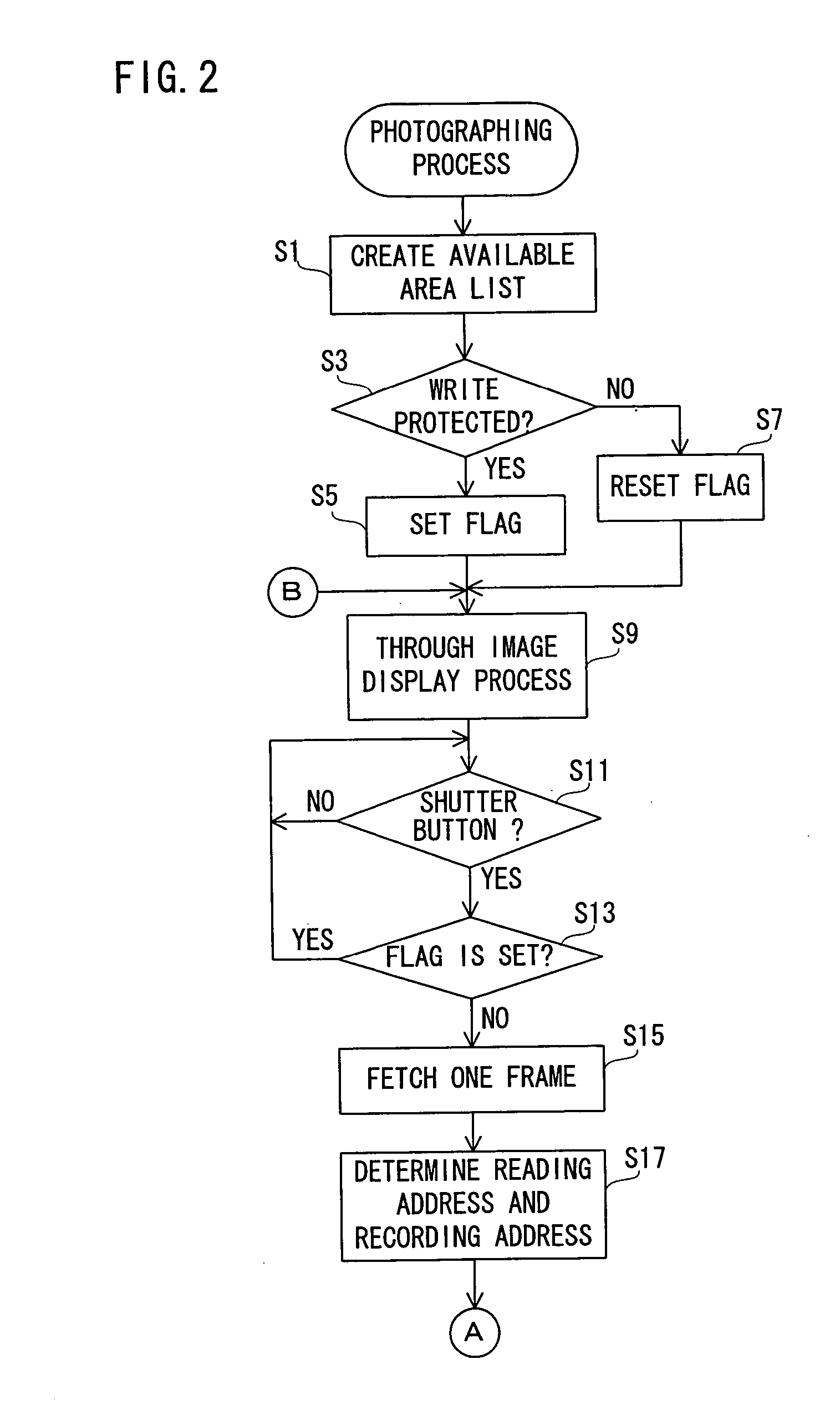
InactiveUS20040034617A1Easy to operateTelevision system detailsDigital data processing detailsWrite protectionData recording
A digital camera (10) includes a CPU (46). When a power source is turned on, the CPU (46) determines an available area of a recording destination on the basis of an FAT recorded on a magneto-optical disk (44). Compressed image data created on the basis of an operation of a shutter button (48) is recorded on the determined available area. When succeeding in recording, the FAT is renewed. When failing in recording due to a defect of the magneto-optical disk (44), a message is displayed on a monitor (28). When a set key (50) is operated after displaying the message, a write protection is set on the magneto-optical disk (44).
Owner:XACTI CORP
Memory devices with data protection
ActiveUS20090089526A1Avoid state changesAvoid writingRead-only memoriesDigital storageWrite protectionMemory protection
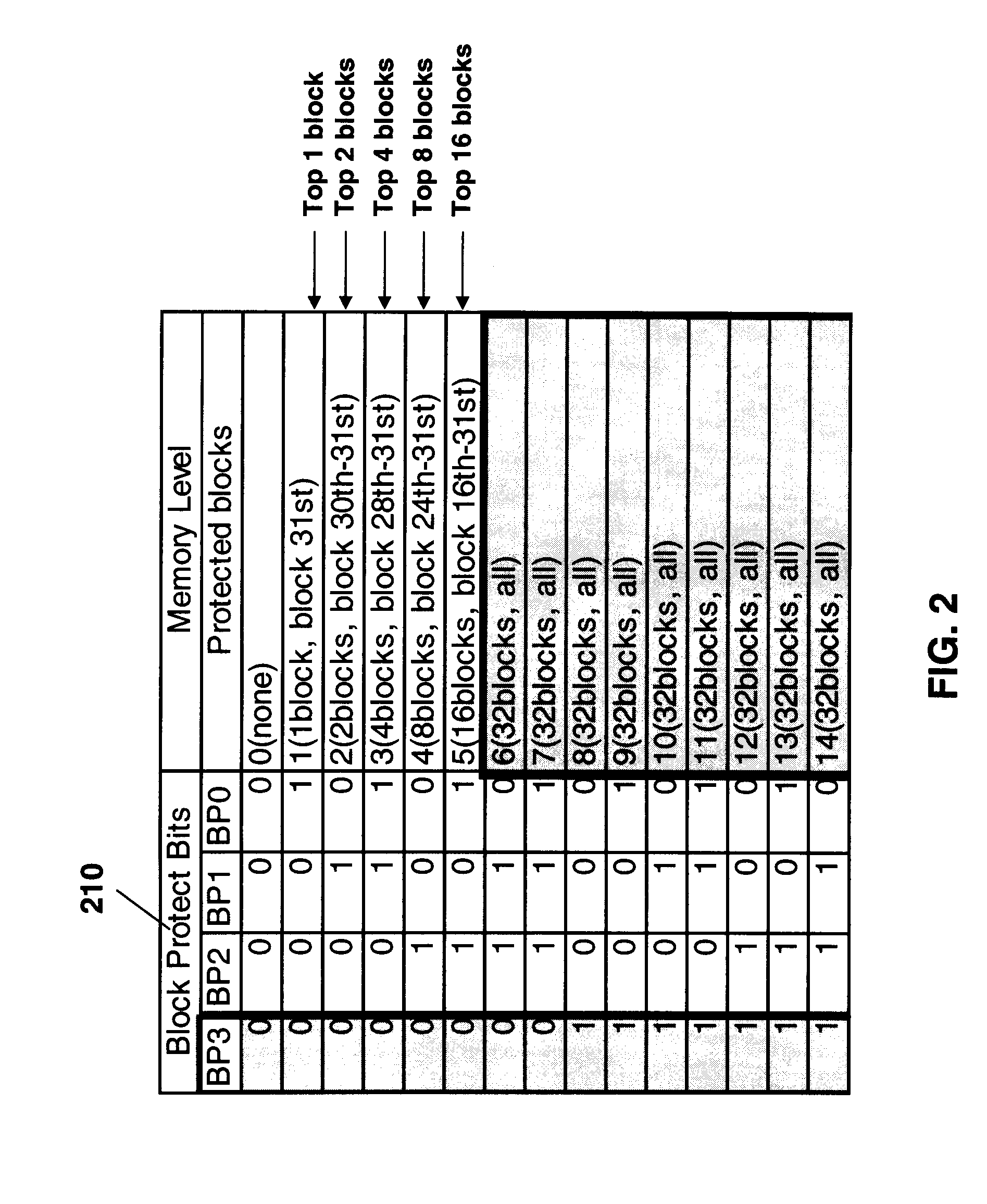
A memory device comprises a memory array, a status register coupled with the memory array, and a security register coupled with the memory array and the status register. The memory array contains a number of memory blocks configured to have independent access control. The status register includes at least one protection bit indicative of a write-protection status of at least one corresponding block of the memory blocks that corresponds to the protection bit. The security register includes at least one register-protection bit. The register-protection bit is programmable to a memory-protection state for preventing a state change of at least the protection bit of the status register. The register-protection bit is configured to remain in the memory-protection state until the resetting of the memory device.
Owner:MACRONIX INT CO LTD
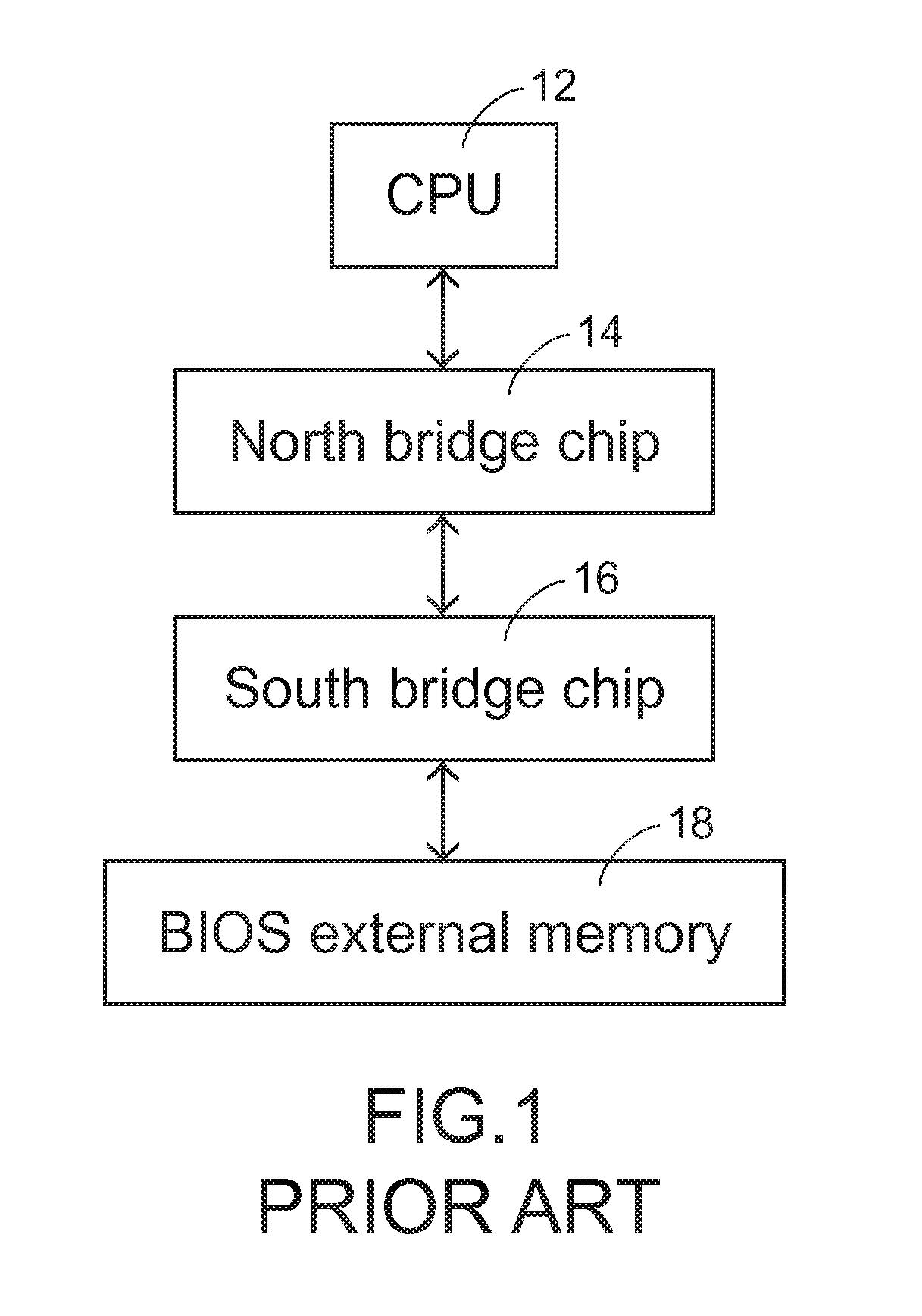
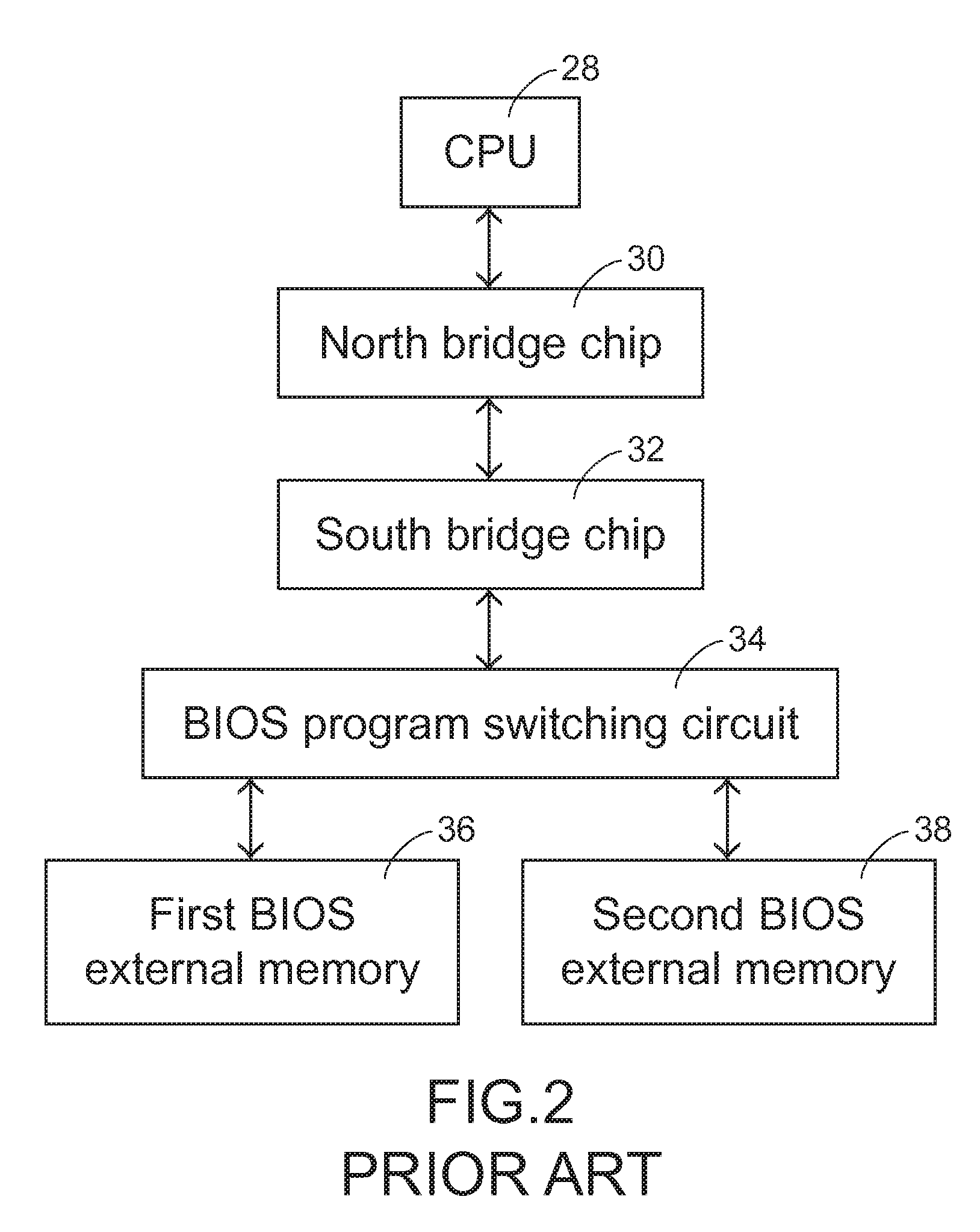
Computer system having dual BIOS program protecting function and control method thereof
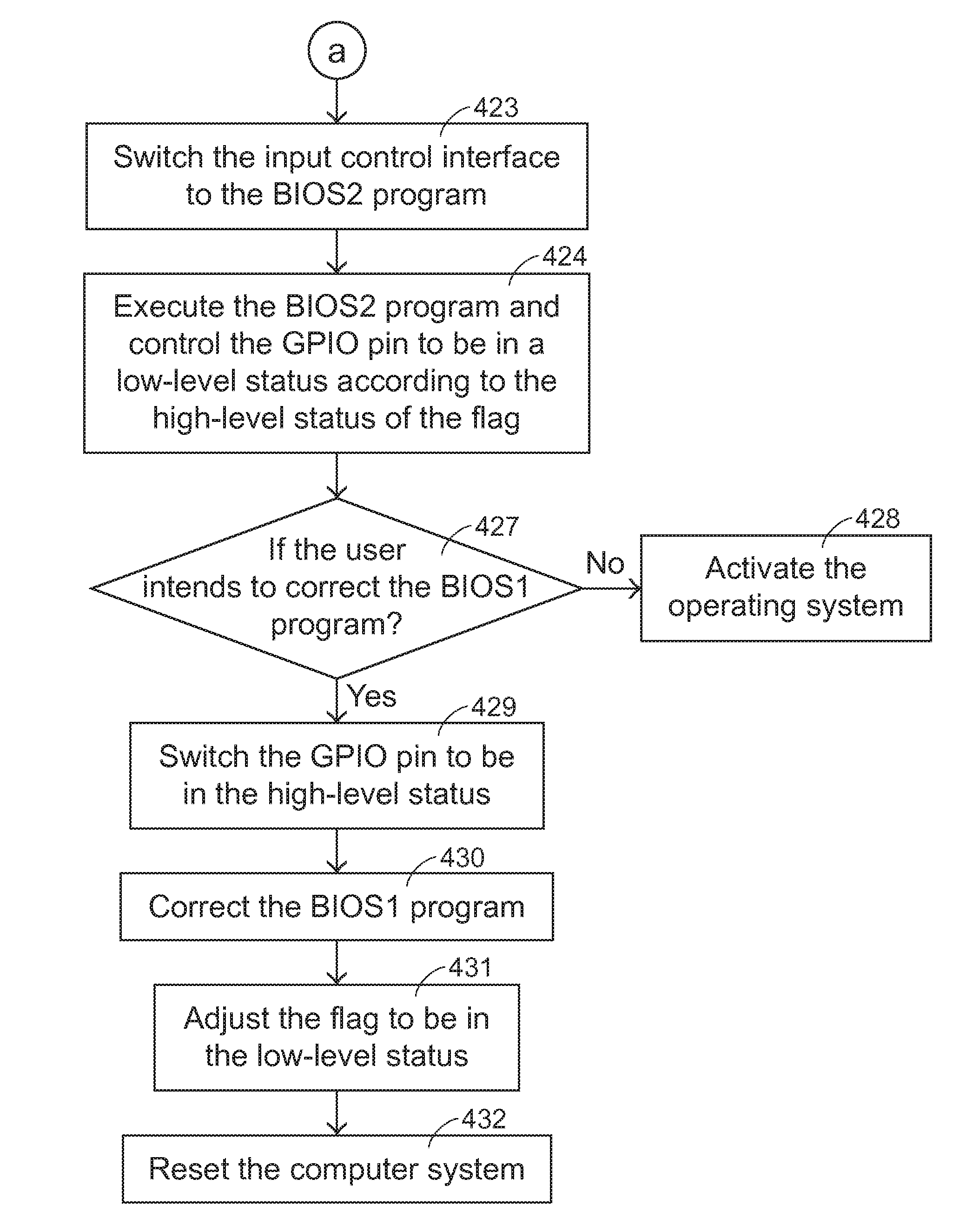
ActiveUS20100100720A1Error detection/correctionDigital computer detailsWrite protectionControl signal
A dual BIOS program protecting method is provided for protecting a first BIOS program and a second BIOS program of a computer system. Firstly, a flag is switched from a first status to a second status during the refreshing of the first BIOS program. If the first BIOS program is successfully refreshed, the flag is switched from the second status to the first status. If the flag is in the second status when the computer system is booted, a first control signal is generated and the second BIOS program enters a write protection mode according to the first control signal.
Owner:ASUSTEK COMPUTER INC
Apparatus and method for securely isolating hard disk
InactiveUS20050172144A1Improve scalabilityEasy compatibilityMemory loss protectionError detection/correctionWrite protectionOperational system
The invention presents an apparatus and method of realizing secured and compatible partition or absolute separation of multiple sections on a single hard disk for multiple OS as well as other software programs. One-way lockup device and set address lock device together constitute a complete and secured apparatus to separate OS and other software programs on a single hard disk. Furthermore, with hard disk reserved section, write-protection section in the front of hard disk, write-protection section at the back of hard disk, and hard disk Address Offset technology, it can realize secured and compatible absolute separation of multiple OS or software programs on a single hard disk with data exchange or one-way data exchange at the same time.
Owner:SHAO TONG
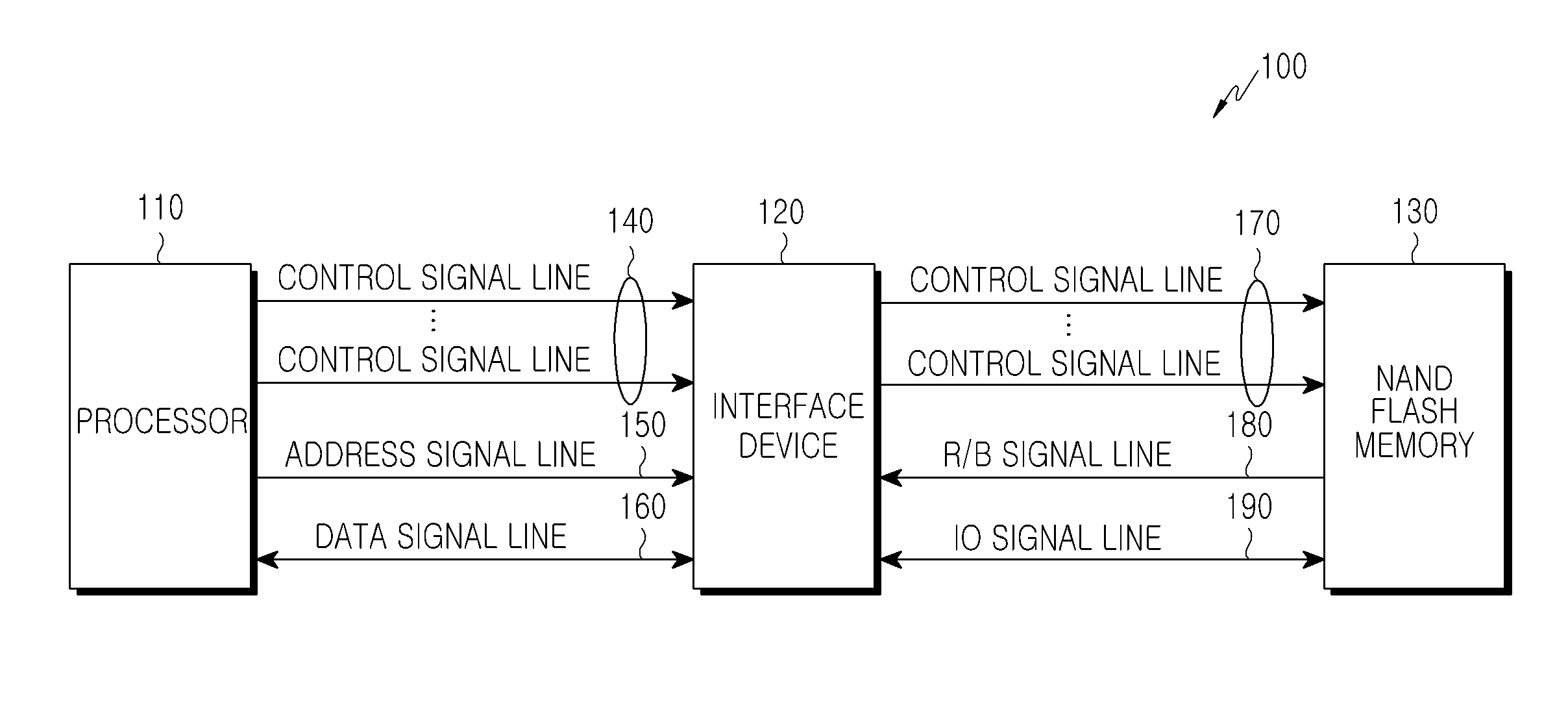
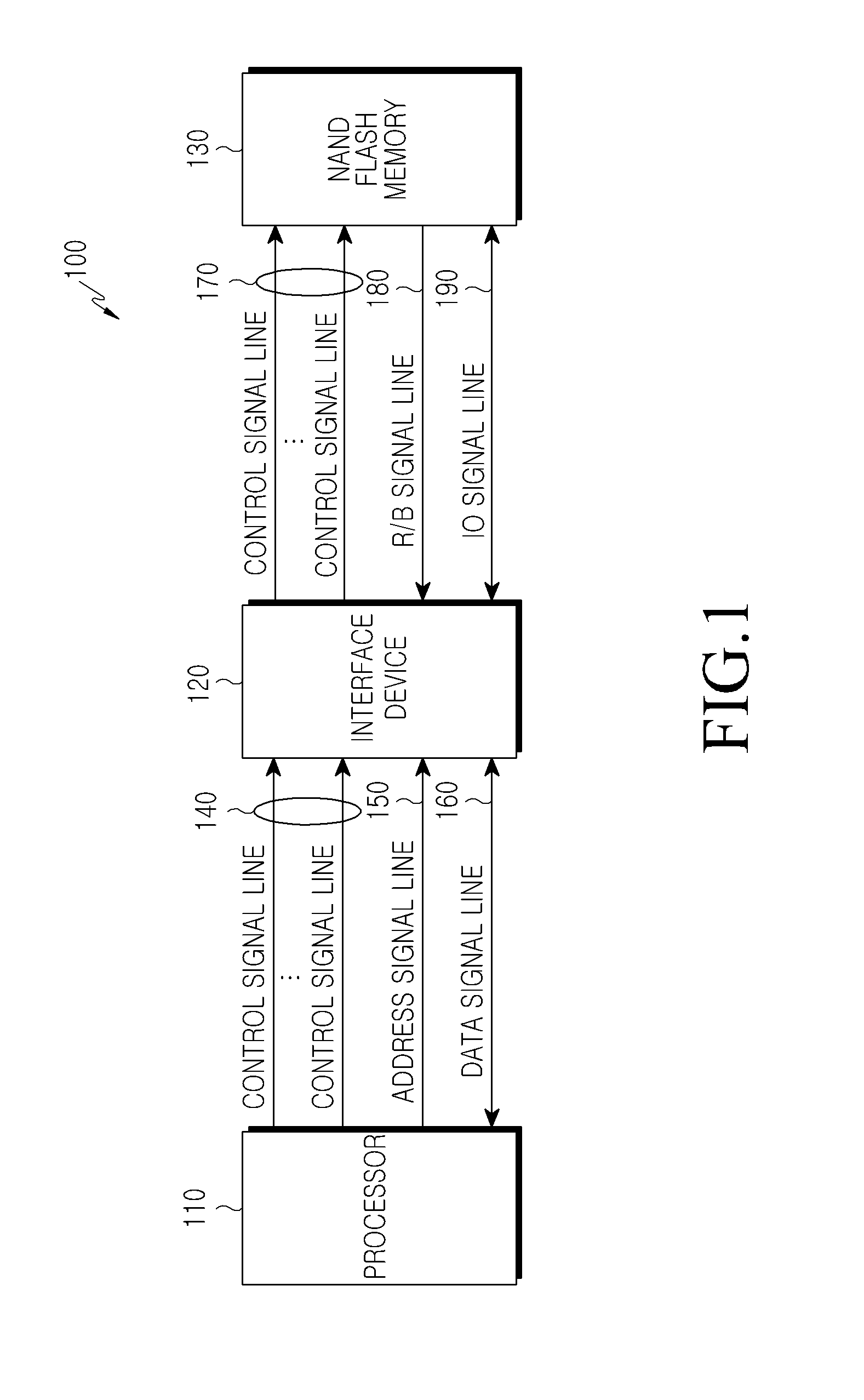
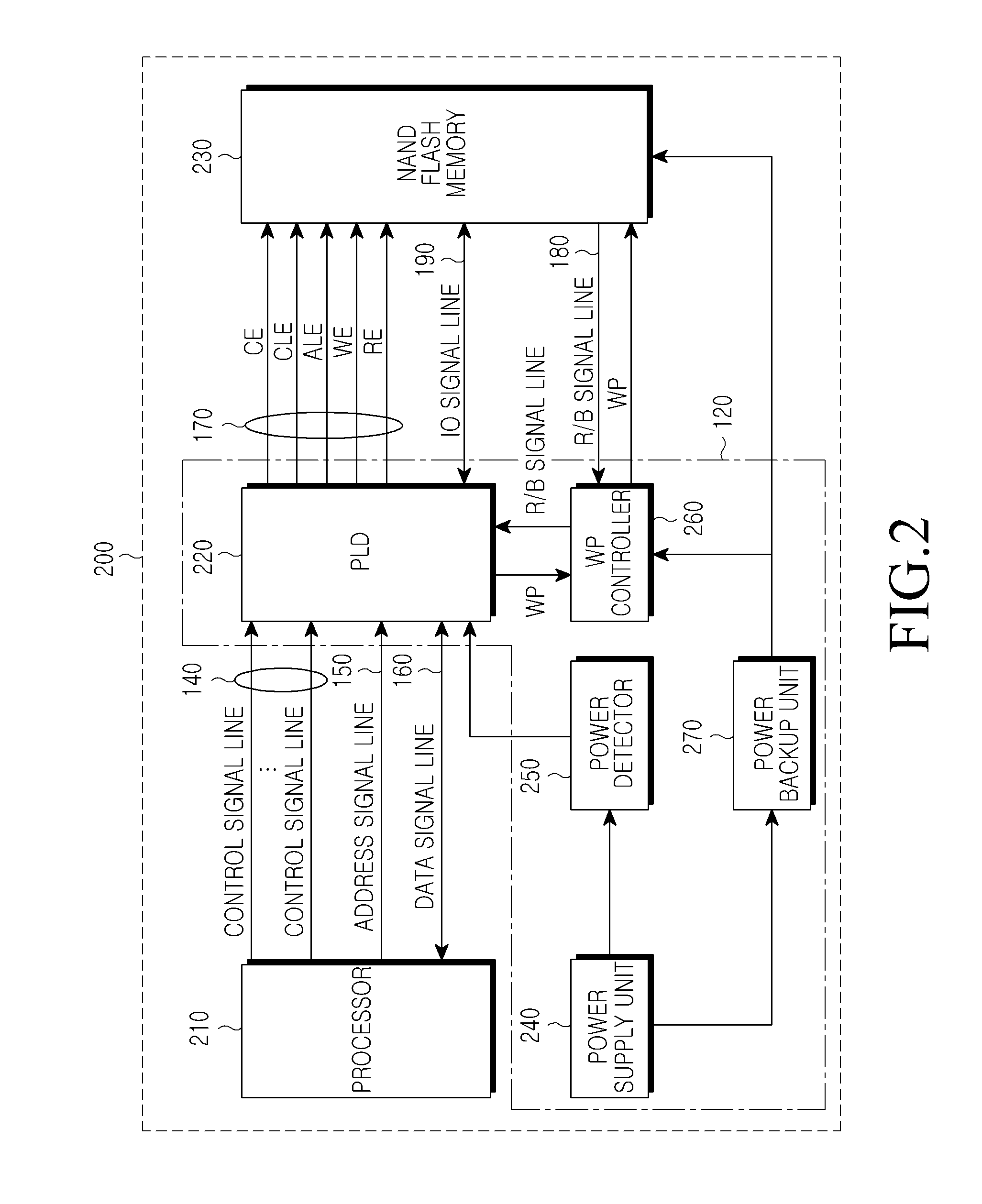
Apparatus and method for protecting data in flash memory
An apparatus for securely protecting data in a flash memory upon power off is disclosed. In the apparatus, a power detector monitors a voltage output from a power supply unit, and outputs a power fail signal when the voltage drops by a predetermined reference voltage or more. A Programmable Logic Device (PLD) outputs a Write Protect (WP) signal for performing write protection on the flash memory upon receiving the power fail signal from the power detector. A WP controller outputs the WP signal output from the PLD to the flash memory, according to a Ready / Busy (R / B) state of the flash memory.
Owner:SAMSUNG ELECTRONICS CO LTD
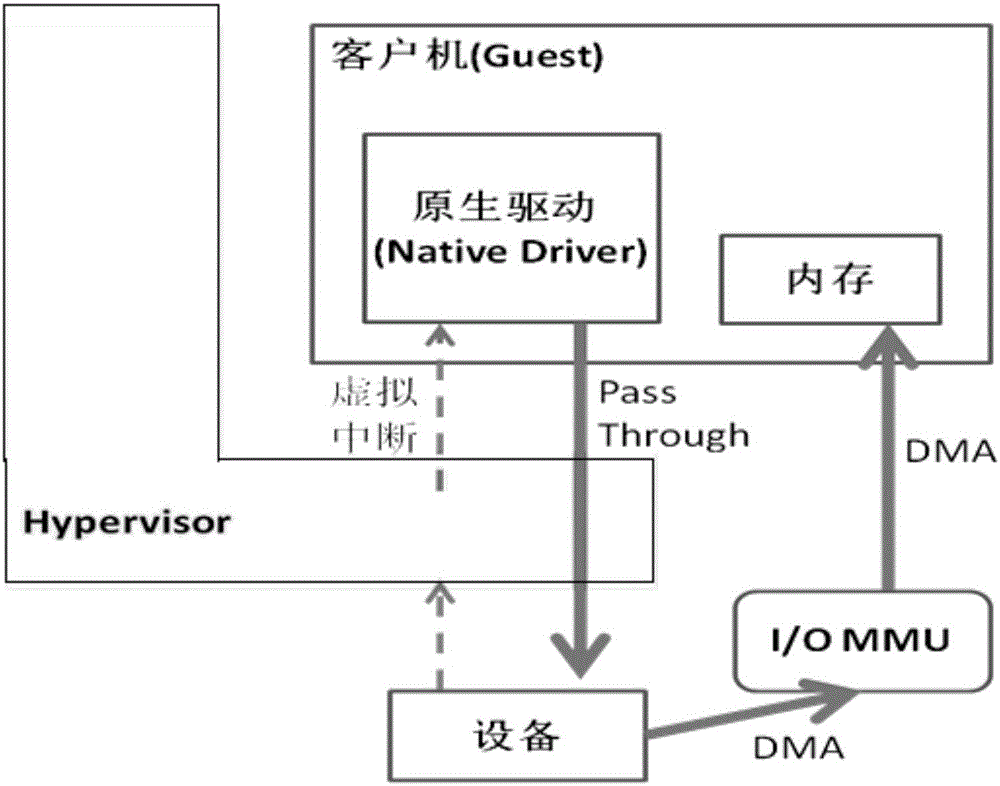
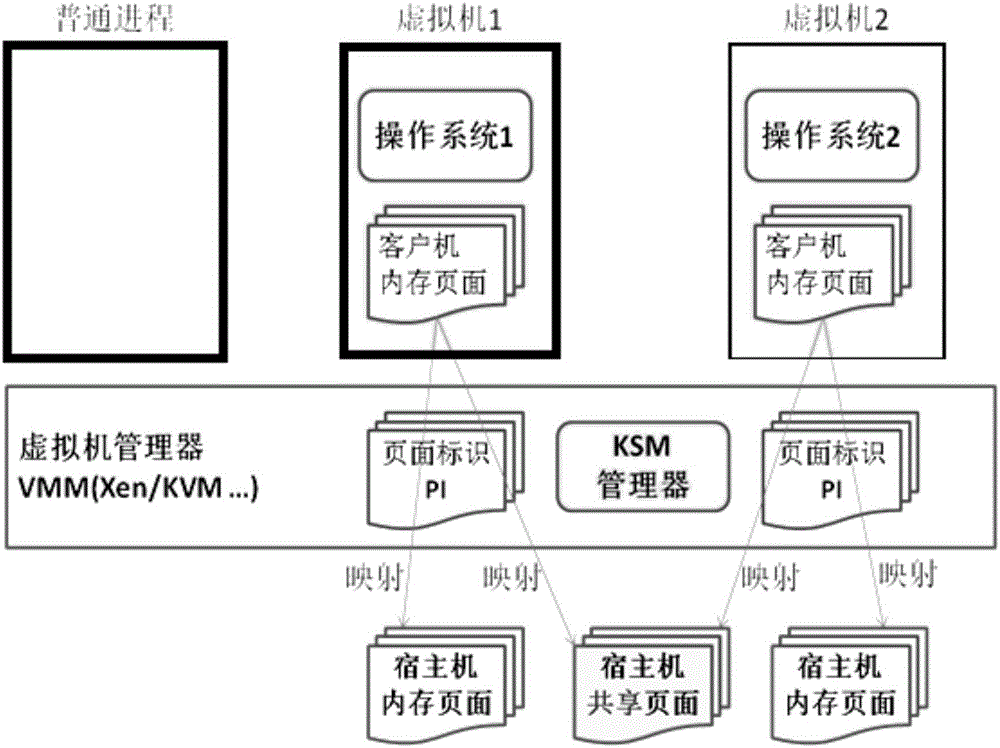
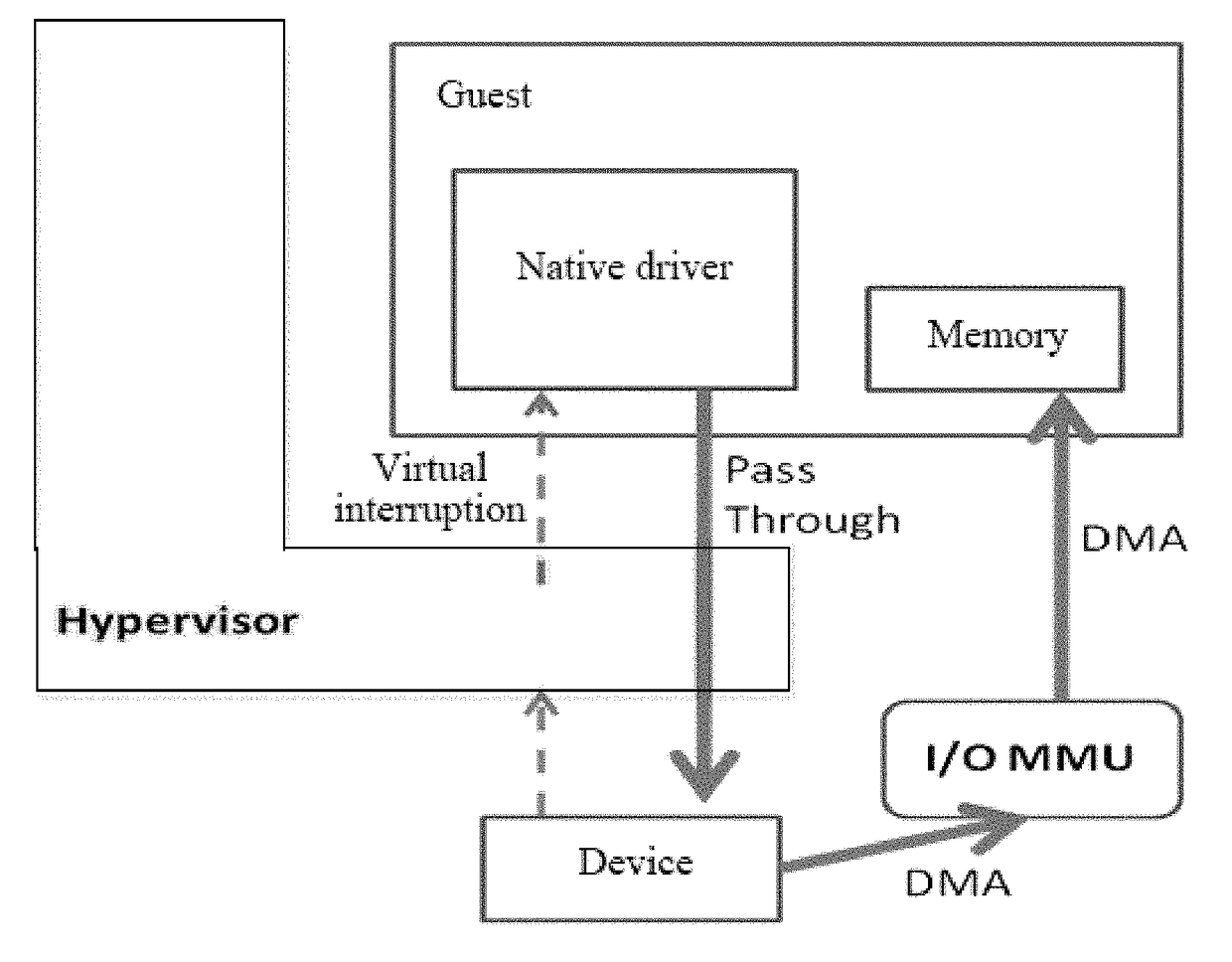
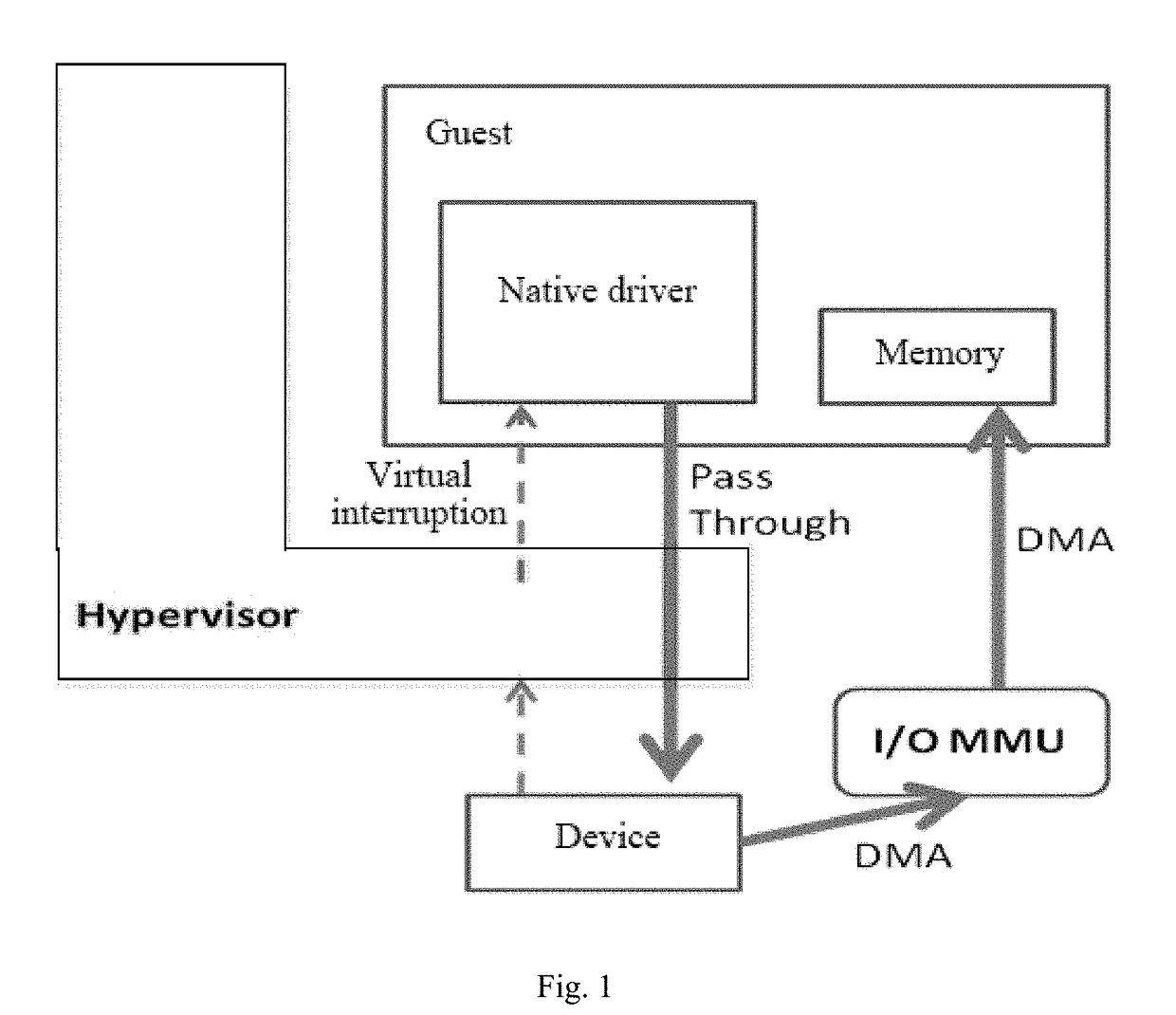
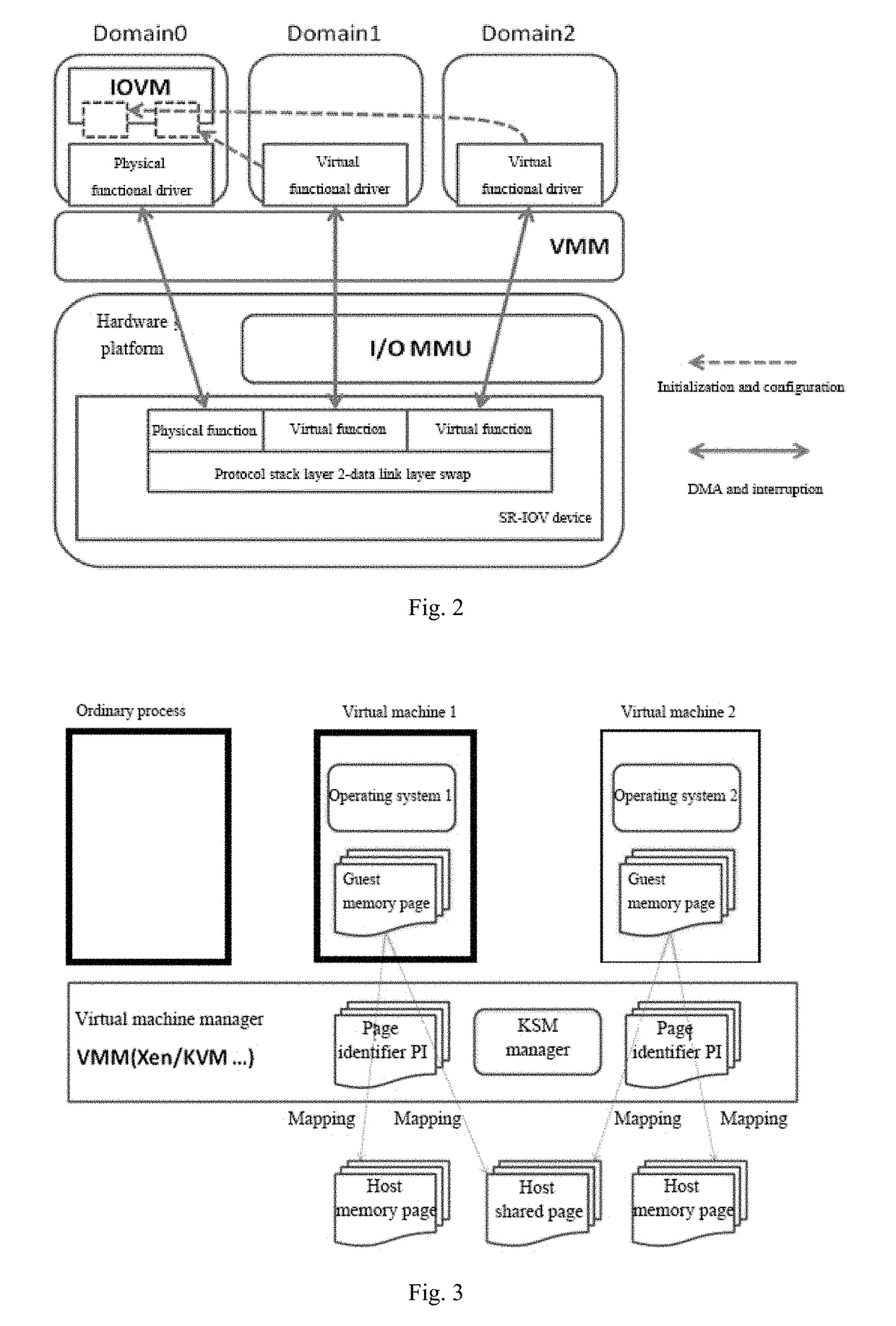
Virtual machine memory sharing method based on combination of KSM and Pass-through
ActiveCN106155933ATroubleshooting Shared Merge IssuesEasy to operateMemory architecture accessing/allocationSoftware simulation/interpretation/emulationWrite protectionDirect memory access
The invention discloses a virtual machine memory sharing method based on the combination of KSM and Pass-through. The virtual machine memory sharing method specifically comprises the following steps: judging whether an operating system of each client uses an IOMMU (Input / Output Memory Management Unit) or not by a virtual machine manager; if not, not participating in sharing mapping of a KSM technology; if so, judging a memory page of each client and determining whether the memory page is a mapping page or not; if so, mapping the mapping page of each client into a host; if not, under the condition of keeping Pass-through properties, utilizing the KSM technology for all non-mapping pages and combining the memory pages with the same content in a plurality of sets of virtual machines; and meanwhile, carrying out writing protection processing. The memory pages of the clients are distinguished into special use for DMA (Direct Memory Access) and non-DMA uses, so that the KSM technology is only selectively applied to the non-DMA pages; and under the condition of keeping the Pass-through properties, the aim of saving memory resources is realized.
Owner:MASSCLOUDS INNOVATION RES INST (BEIJING) OF INFORMATION TECH
Method and system for implementing write protection of block memory stack
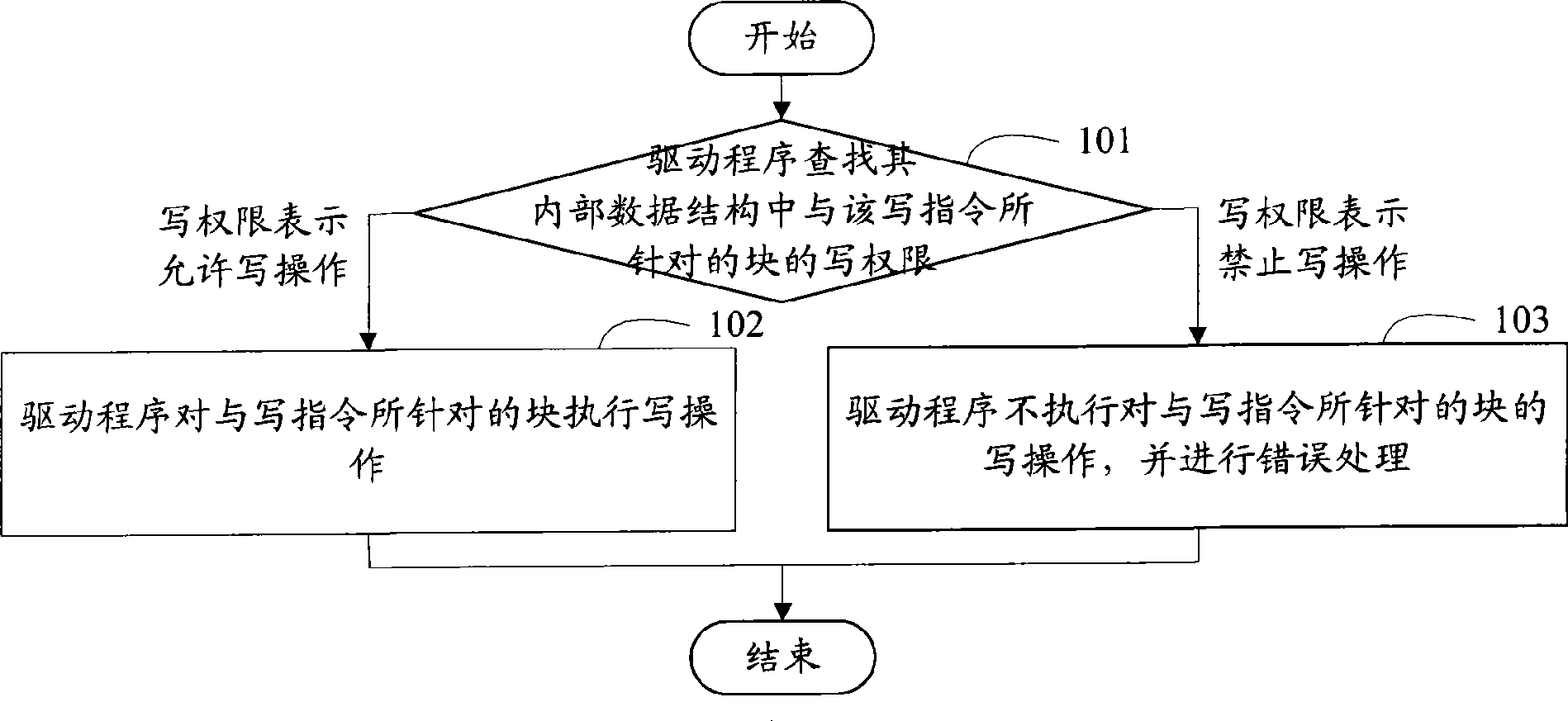
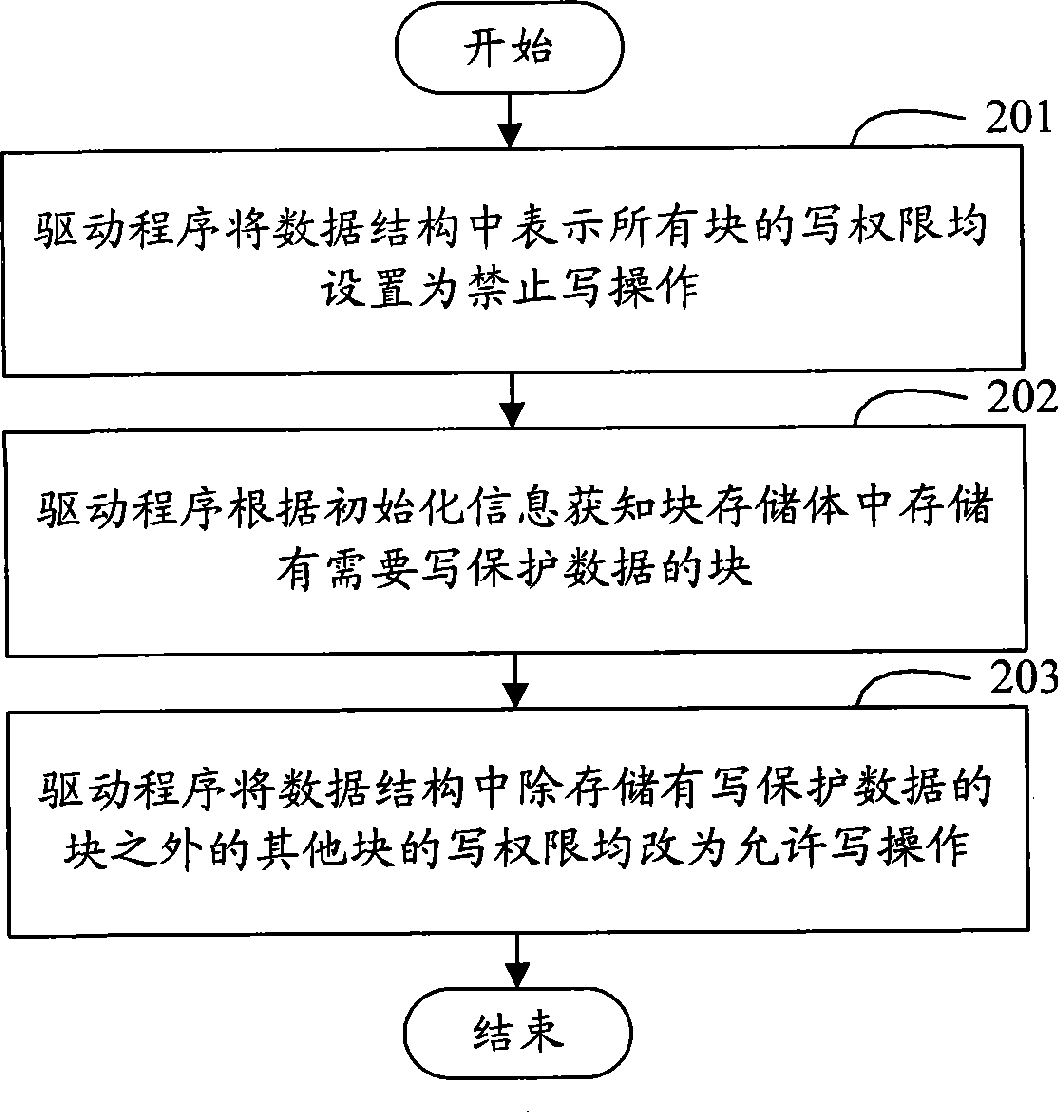
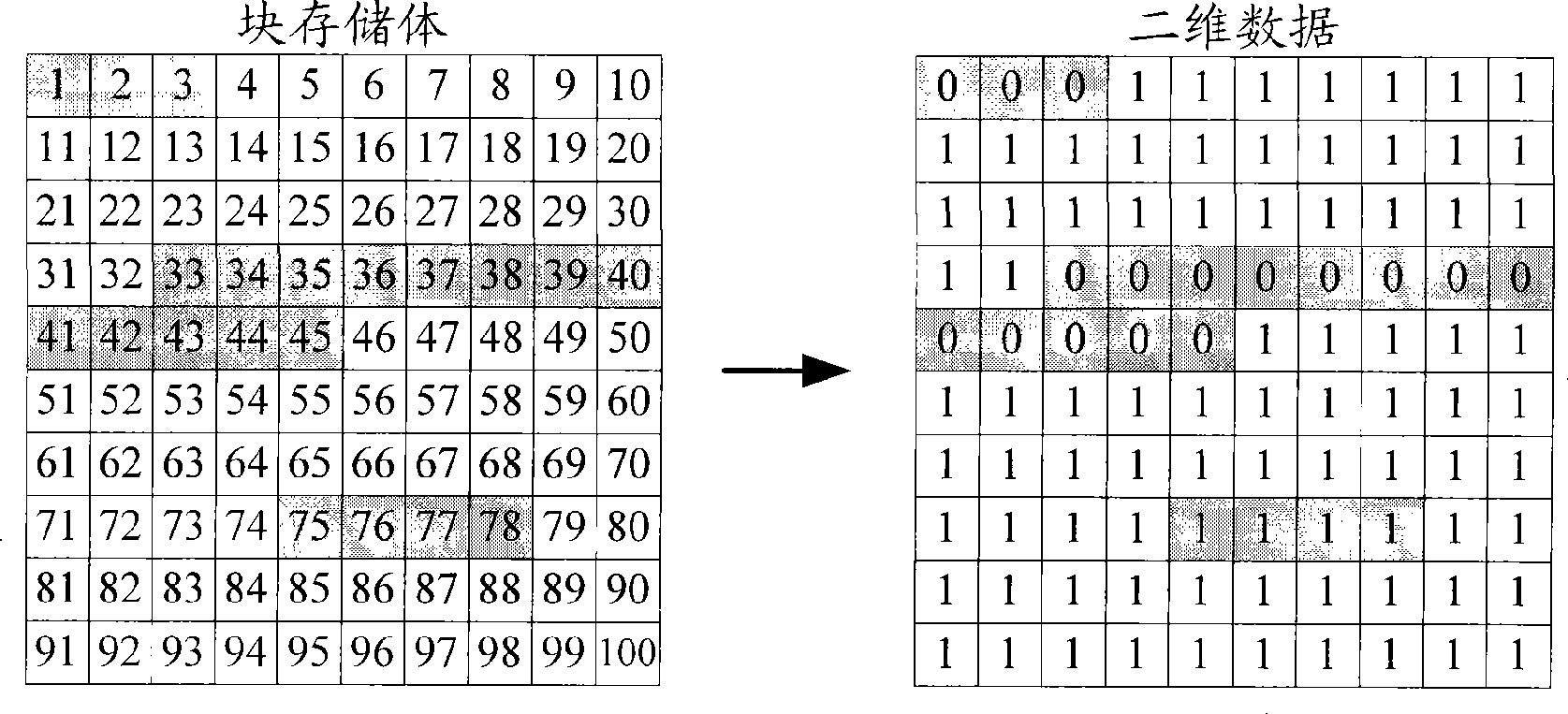
InactiveCN101464841AImplement write protectionImprove reliabilityUnauthorized memory use protectionSpecial data processing applicationsWrite protectionFile system
The invention discloses a method and a system for realizing write protection to a block memory bank. The invention utilizes the setting of the driving procedure of a block memory bank to indicate the data structure of the write permission of each block in the block memory bank and a driving procedure to judge whether write operation can be conducted to each block in the block memory bank or not. Therefore, whether a write command is given out by a file system or other application procedures, the driving procedure is used to execute write operation to each block in the block memory bank, so that due to the fact that the data structure is set for the driving procedure and the driving procedure judges whether conducting write operation according to the structure, under the circumstances that the file system or other application procedures give out write commands, the protection to the block memory bank can be realized, thereby increasing the reliability of the write protection to the block memory bank. In addition, in the invention, the realization of write protection to the block memory bank does not need the function expansion of the file system, and the cost of the write protection to the block memory bank is reduced.
Owner:NEW H3C TECH CO LTD
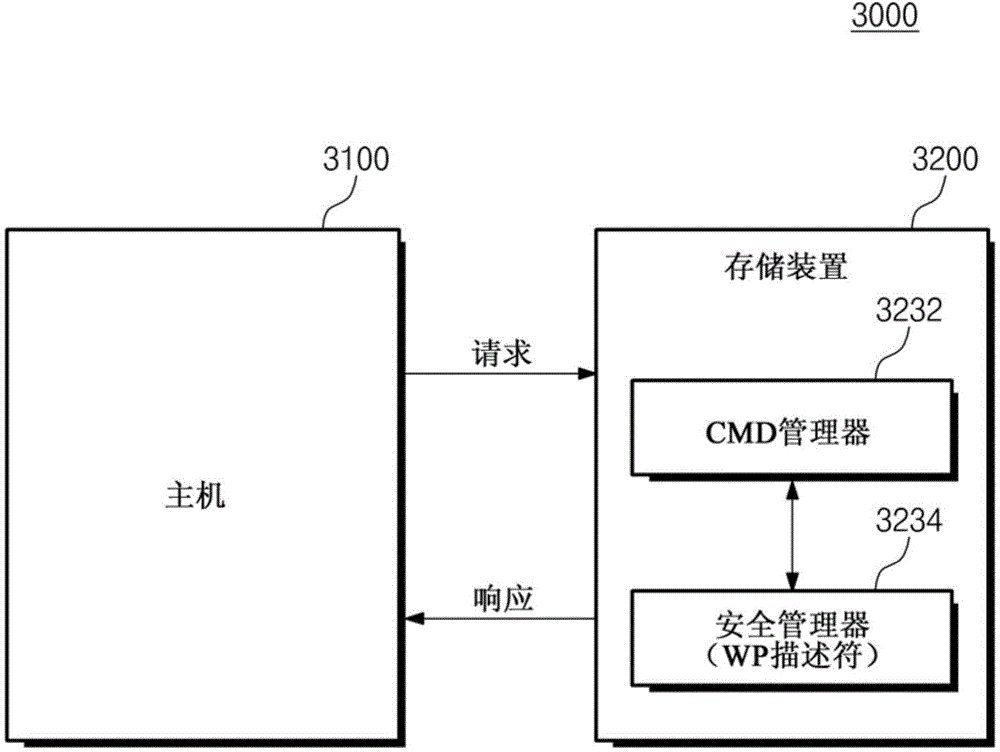
Storage system and method for performing and authenticating write-protection thereof
ActiveCN104951405AMemory adressing/allocation/relocationInternal/peripheral component protectionWrite protectionLogical block addressing
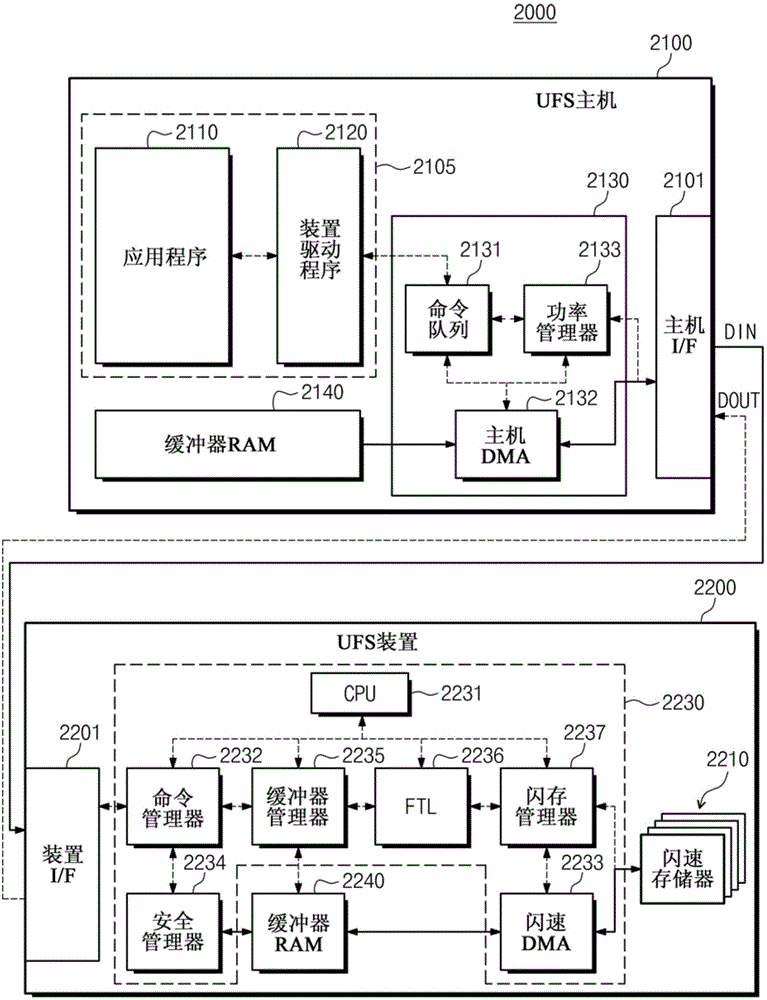
The invention relates to a storage system and a method for performing and authenticating write-protection thereof. The method includes receiving, at a storage device, a request. The request includes a request message authentication code and write protect information. The write protect information includes at least one of start address information and length information. The start address information indicates a logical block address at which a memory area in a non-volatile memory of the storage device starts, and the length information indicates a length of the memory area. The method also includes generating, at the storage device, a message authentication code based on at least one of the start address information and the length information, and a key stored at the storage device; authenticating, at the storage device, the request based on the generated message authentication code and the request message authentication code; and processing, at the storage device, the request based on a result of the authenticating.
Owner:SAMSUNG ELECTRONICS CO LTD
Method for recoverying basic inputting and outputting system chip
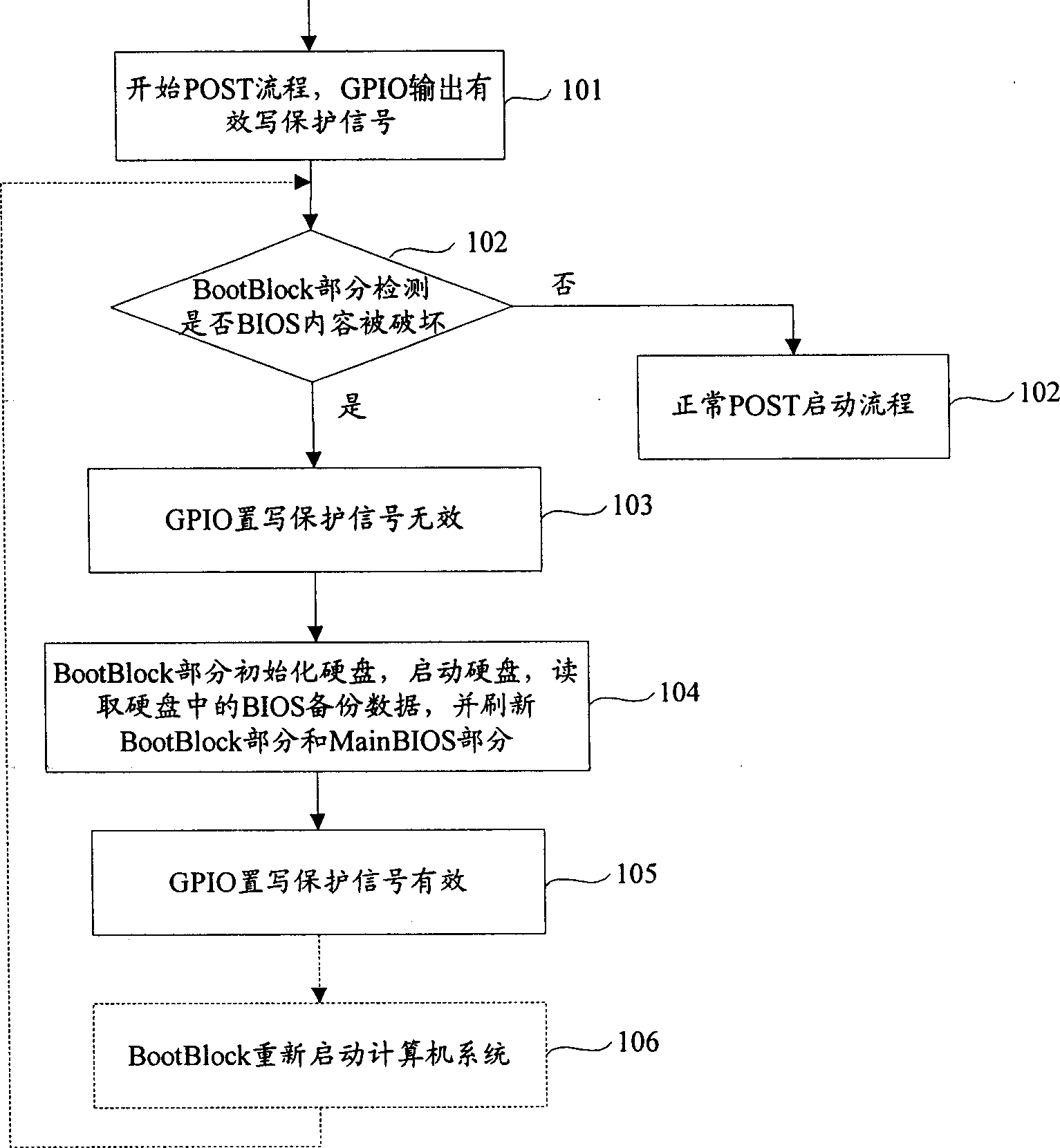
ActiveCN1707442AControl write protection signalRealize automatic self-testRedundant operation error correctionWrite protectionRestoration method
The present invention discloses BIOS chip restoring method, and the BIOS chip receives write protection signal from the mainboard and set as valid normally. The present invention features that the method also includes: A. informing the mainboard to set the write protection signal as invalid in case of detecting the damaged BIOS content in starting the computer system with the BIOS chip; B. starting the hard disc with the BIOS chip to read out the back-up BIOS data stored in the hard disc in advance and to update the BIOS content according to the read out back-up BIOS data; and C. informing the mainboard that the write protection signal is valid with the BIOS chip. Applying the said method can realize the automatic restoring of BIOS chip data and protect BIOS chip effectively.
Owner:LENOVO (BEIJING) CO LTD
Method and system for protecting software data in display panel
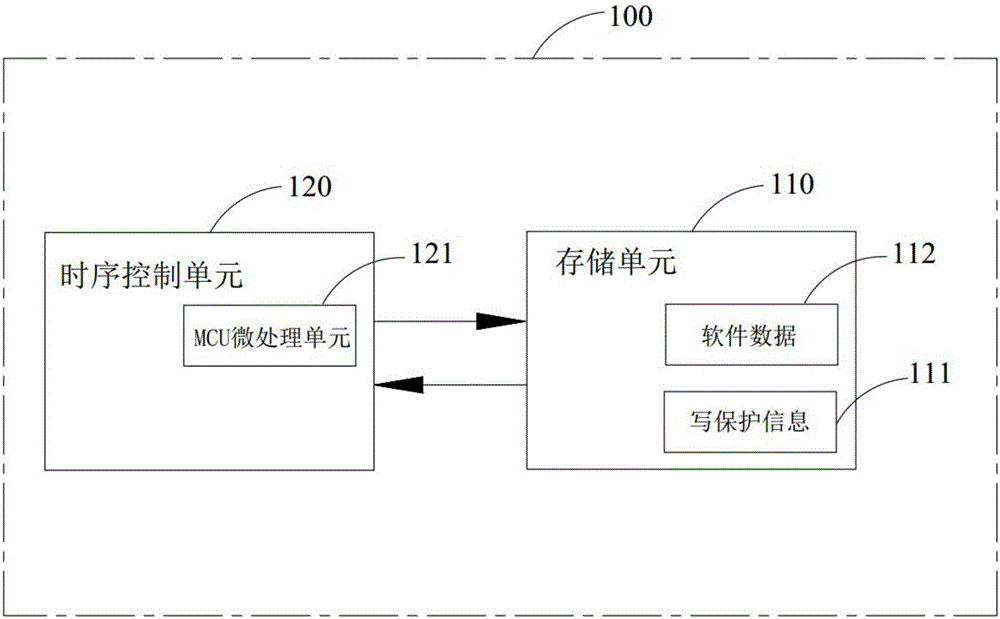
InactiveCN107526979AStatic indicating devicesInternal/peripheral component protectionWrite protectionSoftware
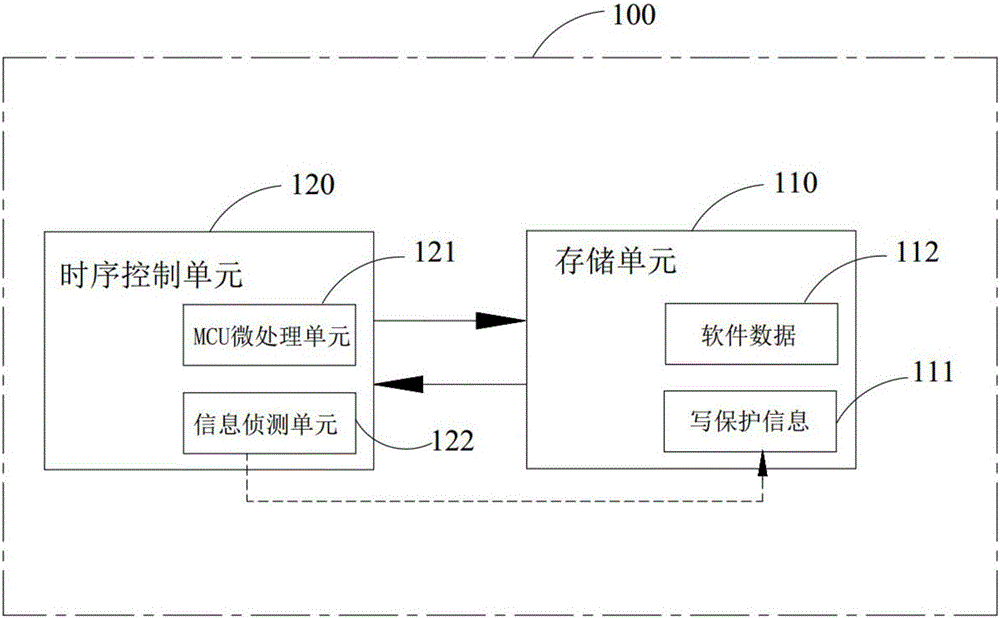
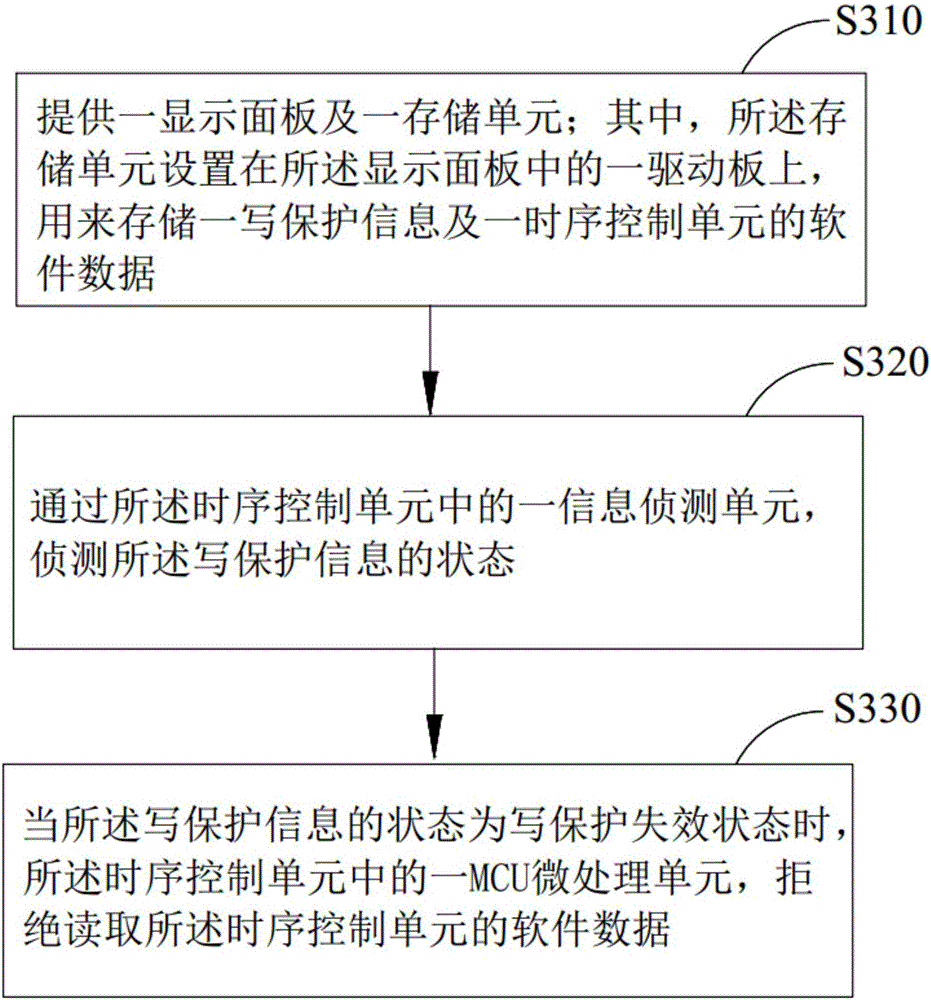
The invention discloses a method and a system for protecting software data in a display panel. The method comprises the following steps that: providing a display panel and a storage unit, wherein the storage unit is arranged on a driving board on the display panel for storing one piece of write protection information and the software data of a time sequence control unit; through one information detection unit in the time sequence control unit, the state of write protection information is detected; and when the state of the write protection information is a write protection failure state, one MCU (Microprogrammed Control Unit) micro-processing unit in the time sequence control unit refuses to read the software data of the time sequence control unit. Therefore, the software data on the storage unit can be prevented from being rewritten so as to avoid a situation that a picture displayed on the display panel is abnormal.
Owner:HKC CORP LTD +1
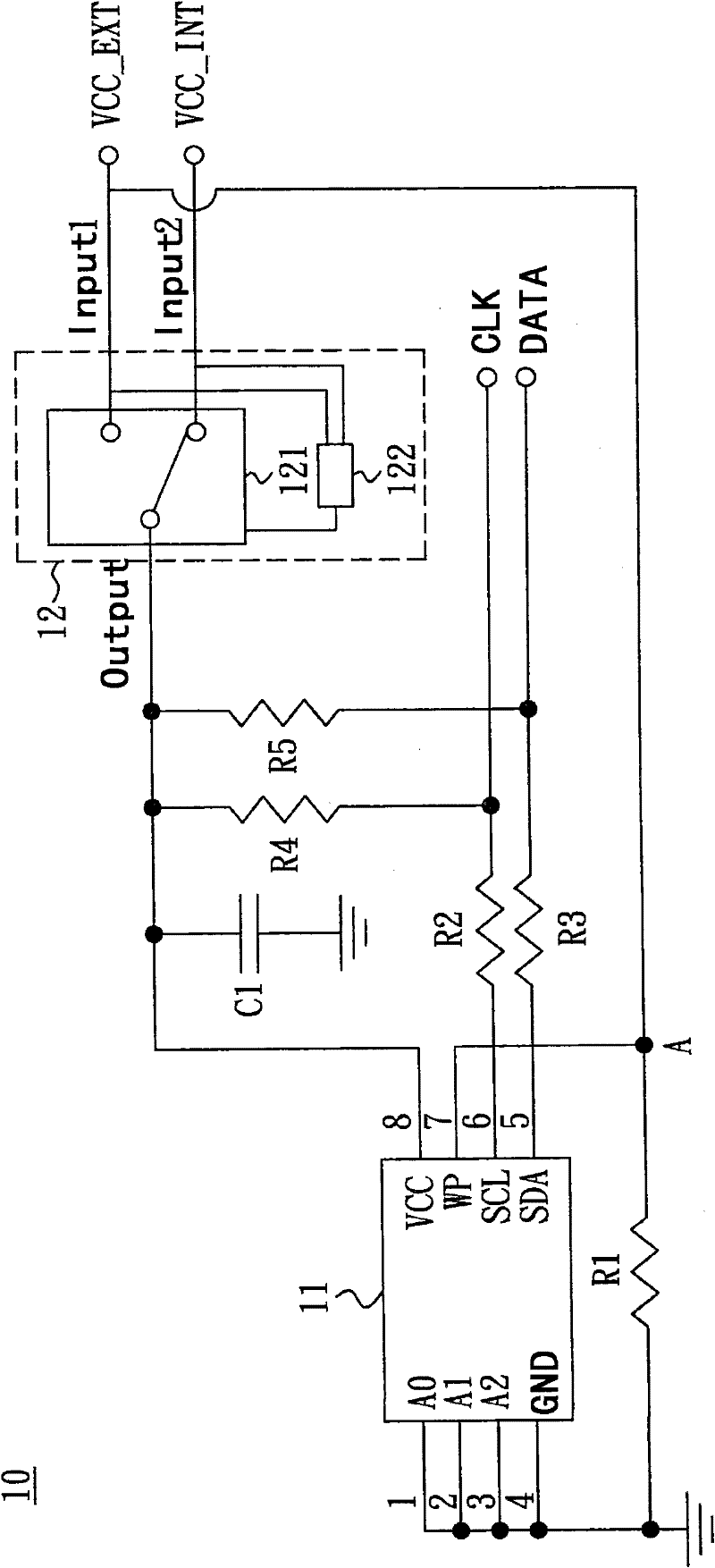
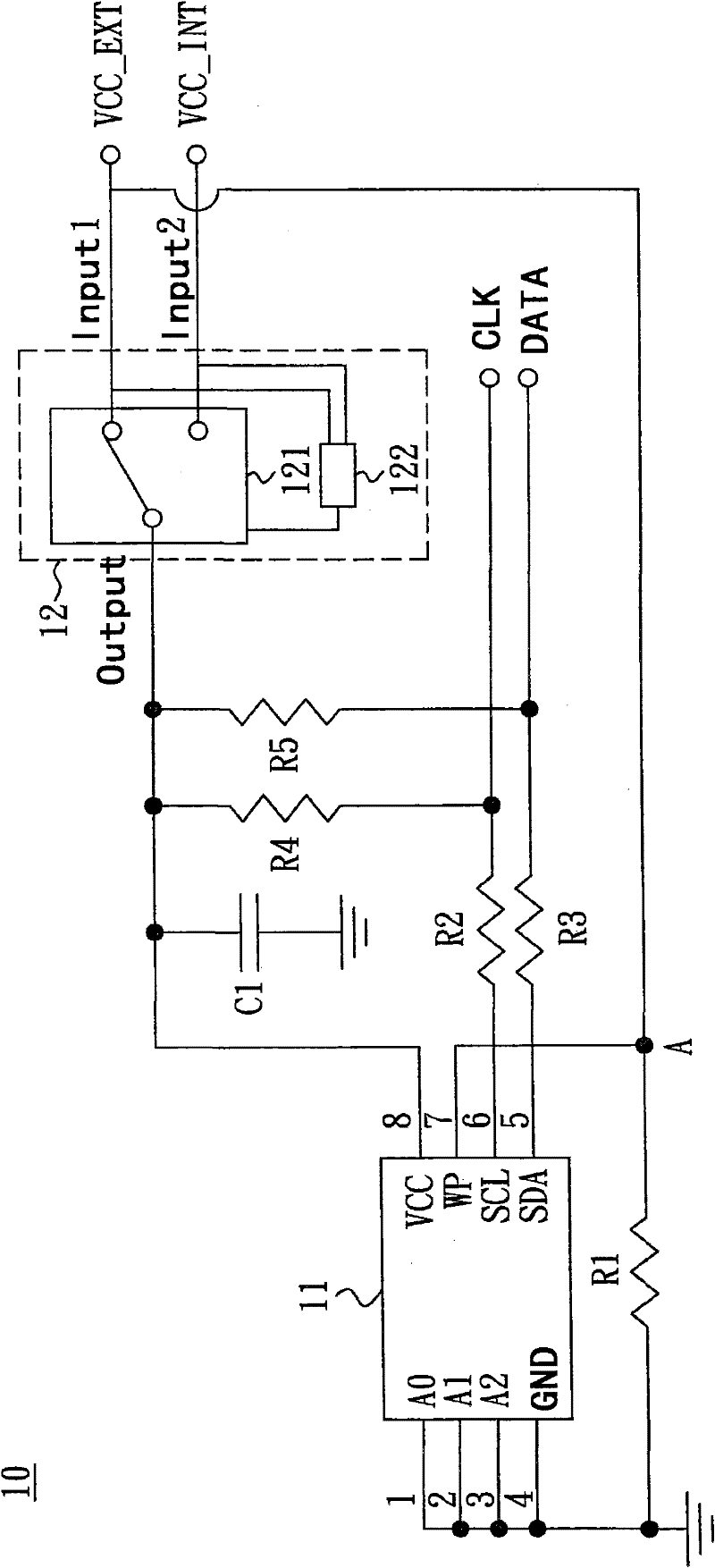
Read-write protection circuit
Embodiments of the invention provide a read-write protection circuit which mainly comprises a memory and a control circuit. The control circuit is provided for determining electric source received by the memory. The memory is provided with a pin for determining an access state of the memory. When the pin receives a high level voltage, the access state of the memory is set as a read-only state; when the pin receives a low level voltage, the access state of the memory is set as a readable-writable state. With the design of the control circuit provided by the present invention, a user of a manufacturing terminal can read and write data in the memory conveniently, and a user of a whole machine terminal only can read the data in the memory.
Owner:HANNSTAR DISPLAY CORPORATION
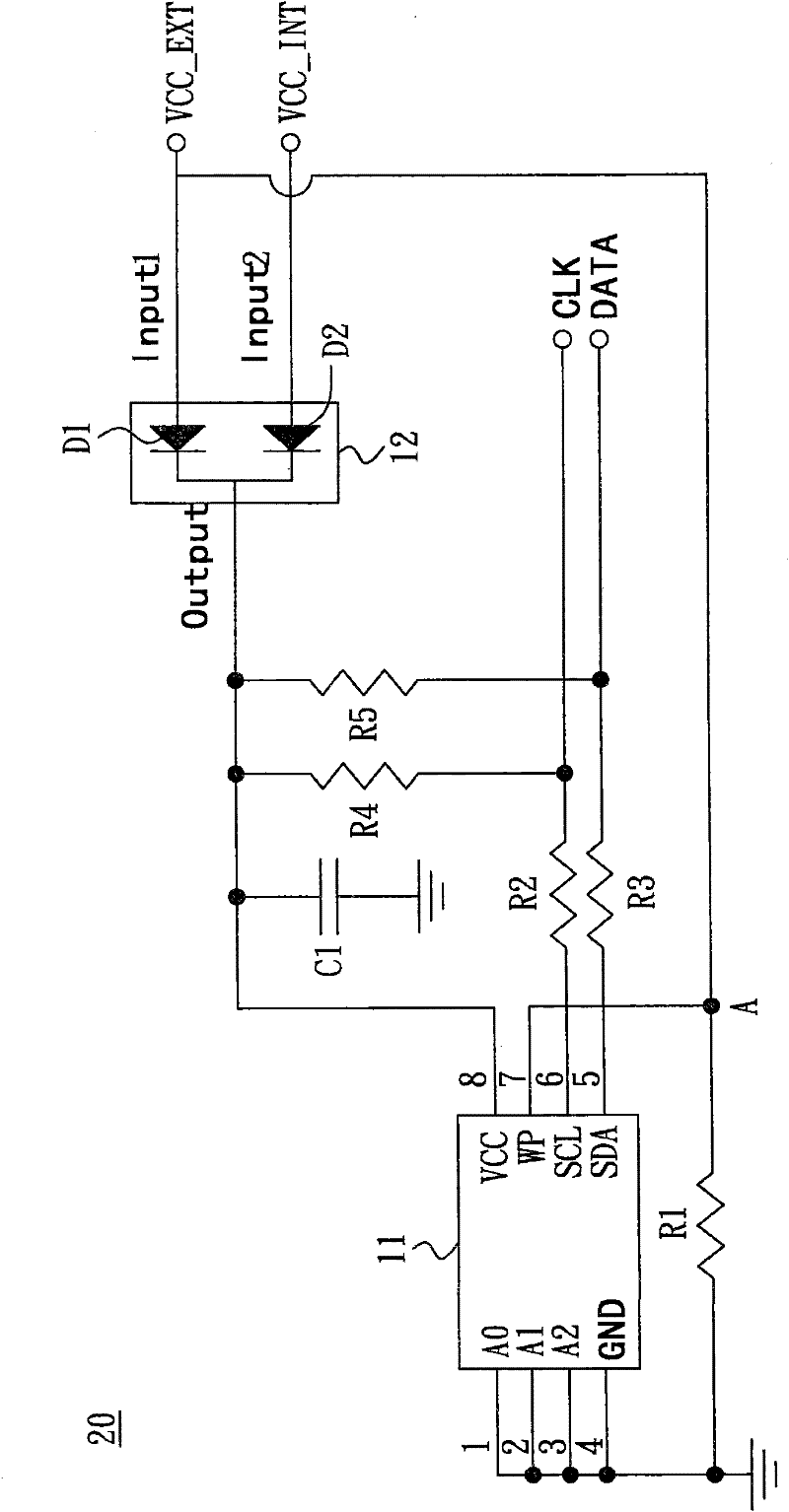
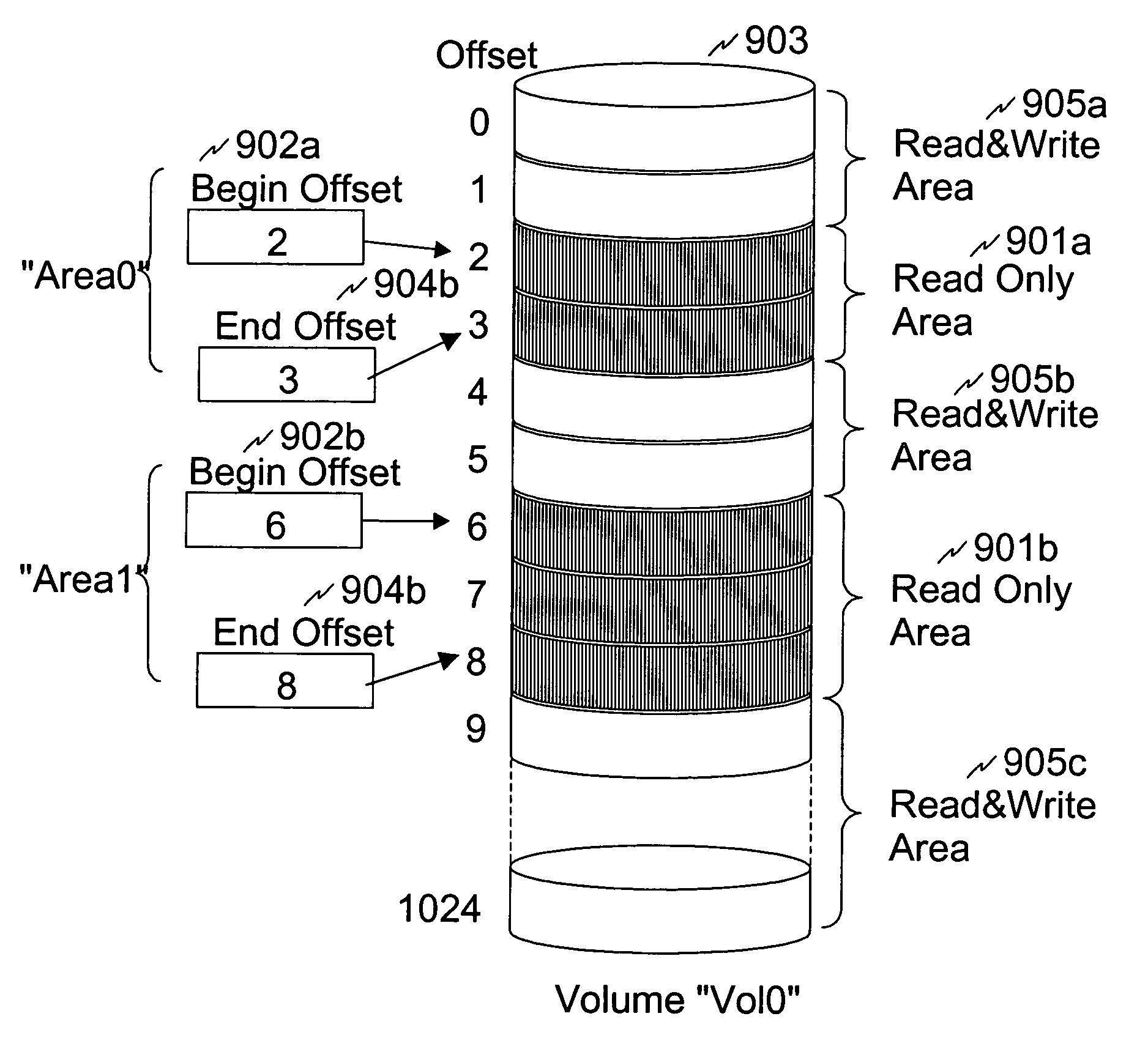
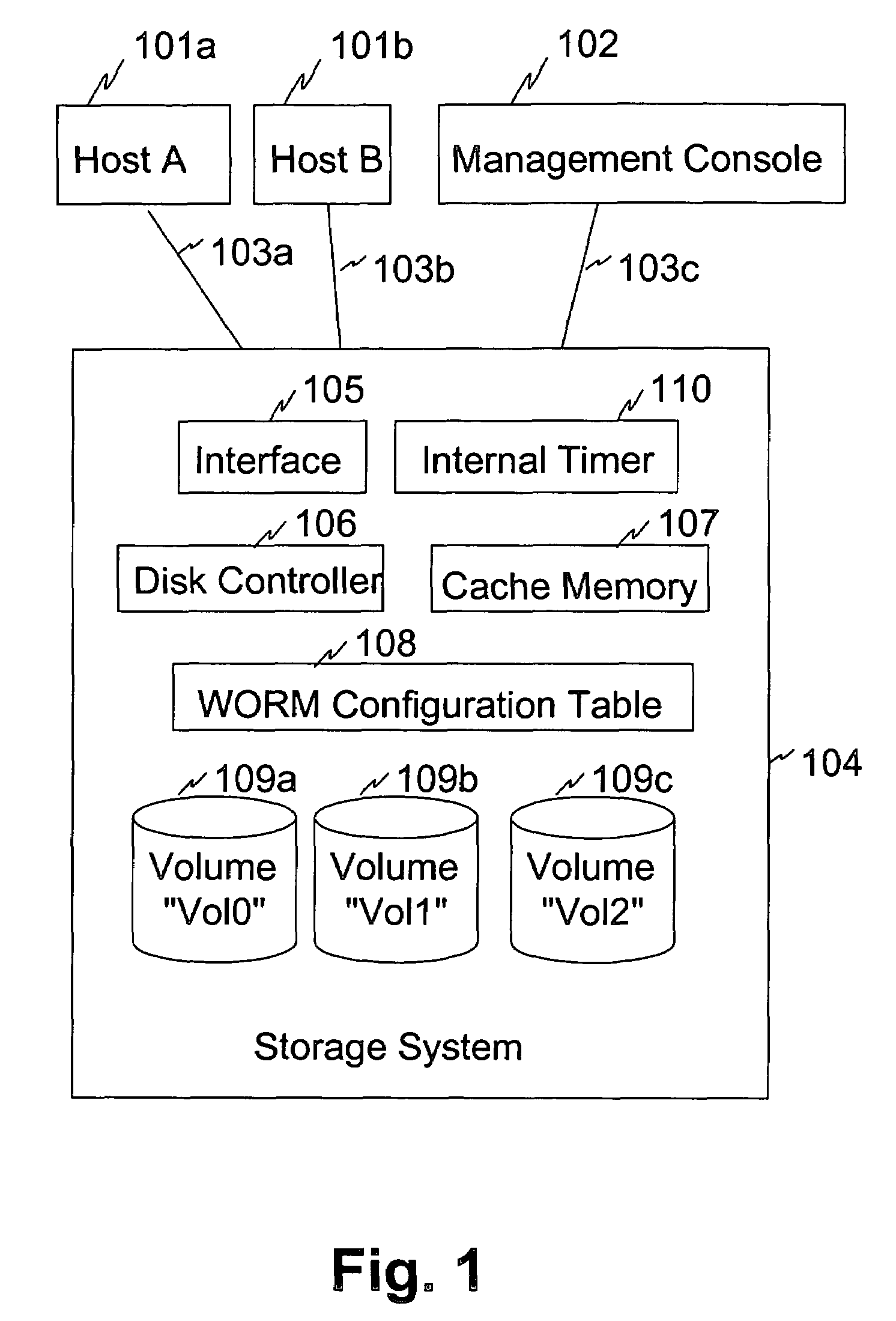
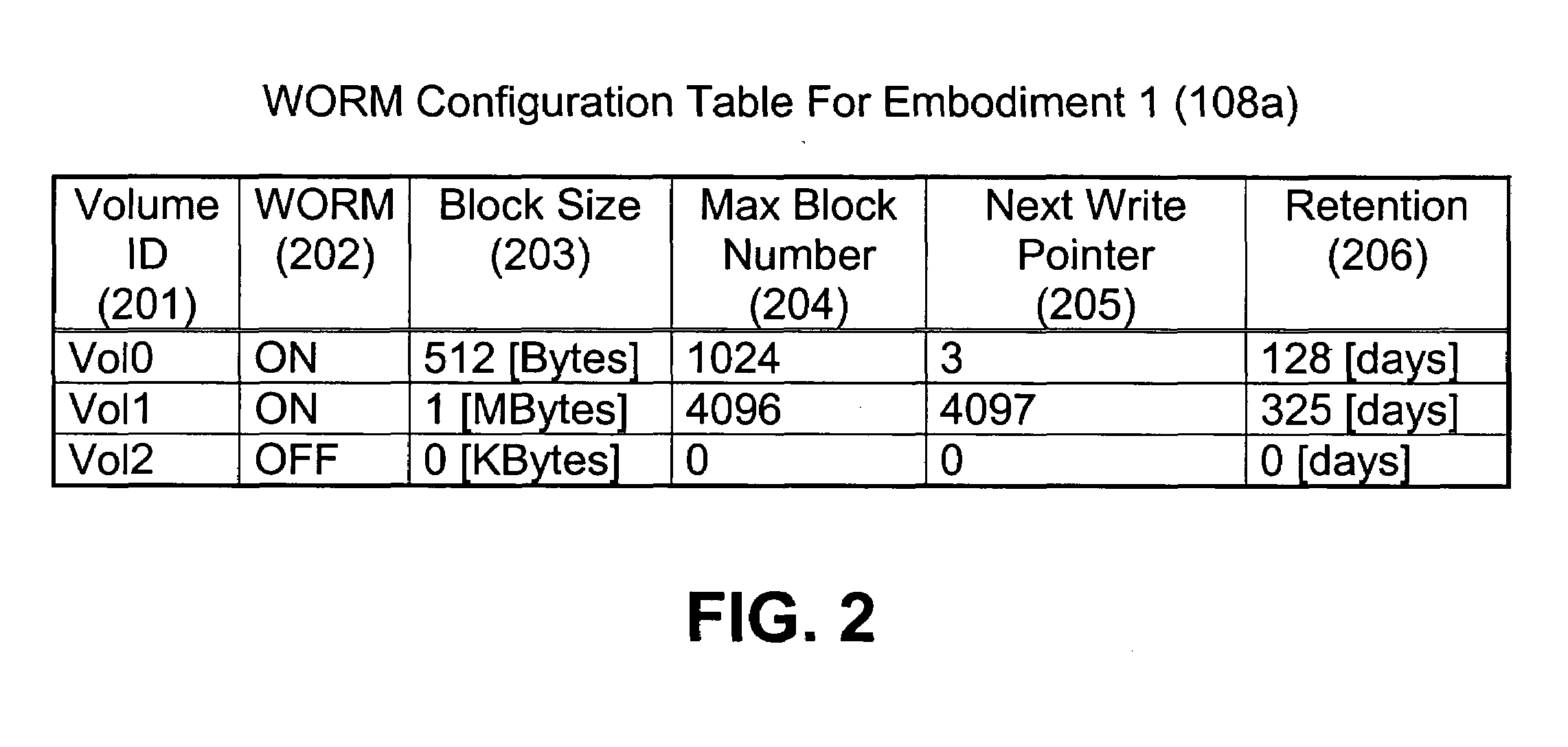
More granular and more efficient write protection for disk volumes
InactiveUS7162602B2Input/output to record carriersUnauthorized memory use protectionWrite protectionDisk controller
A storage system, method and system for protecting data stored on a volume of the storage system. The storage system includes a storage media upon which the volume is represented, a disk controller which controls the storage system, and a write once read many (WORM) configuration table having a plurality of entries which indicate by use of a next write pointer which of a plurality of areas of the volume is write protected. Alternatively, the entries of the WORM configuration table could indicate write protected areas of the volume each being defined by use of a beginning offset and an ending offset.
Owner:HITACHI LTD
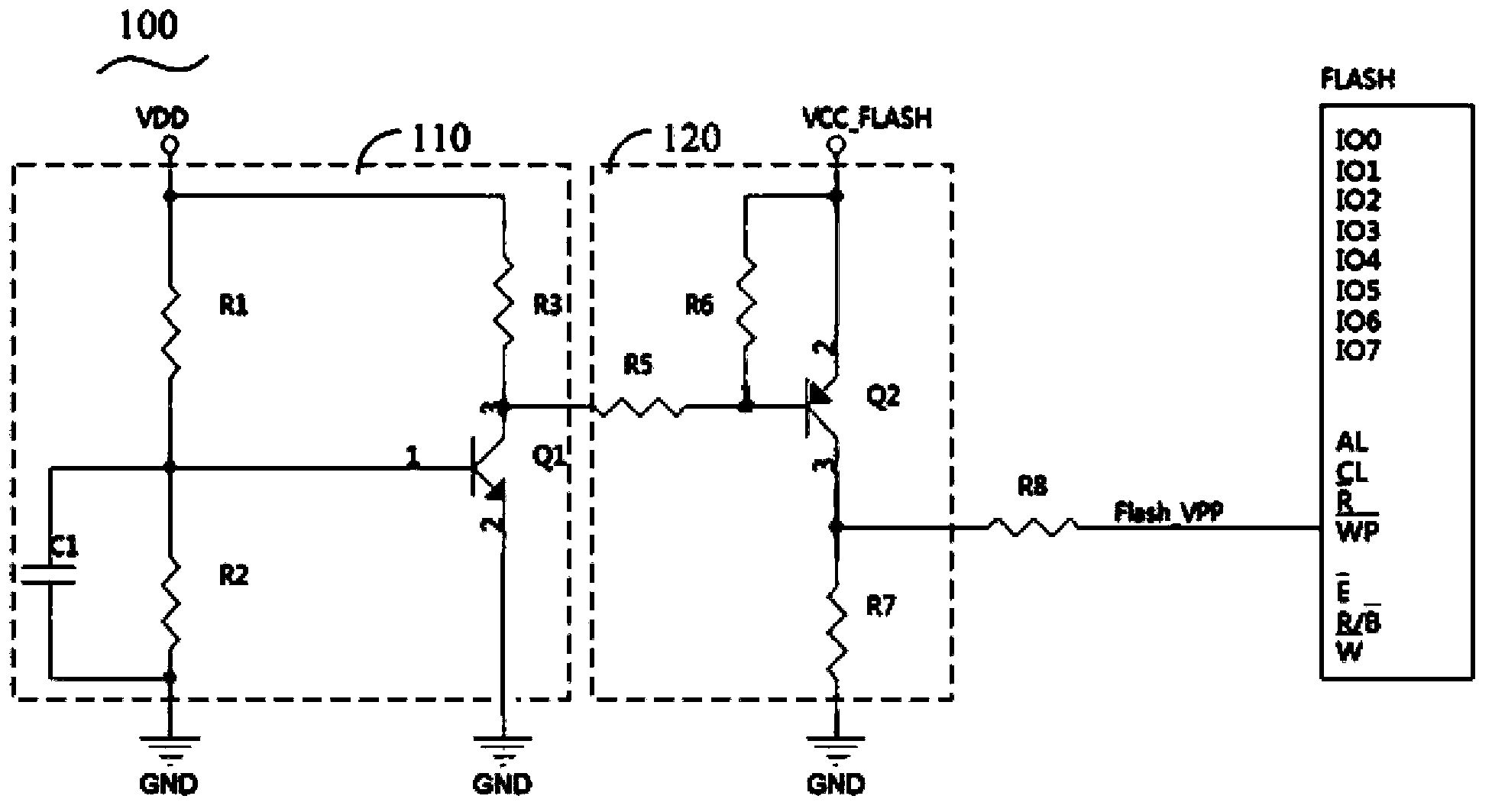
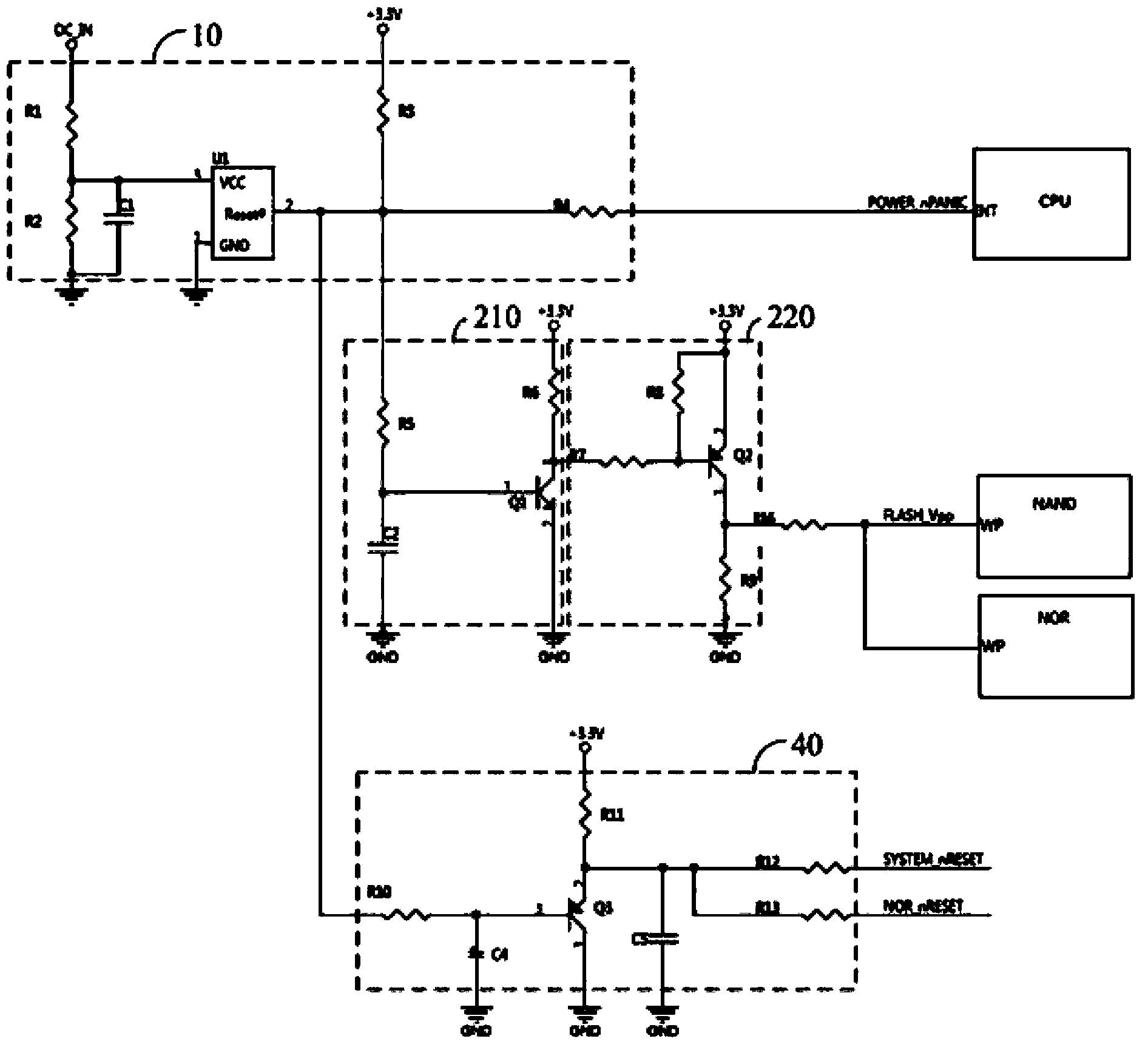
Power-fail protective circuit and power-fail protective sequential circuit for flash memory
The invention relates to a power-fail protective sequential circuit for a flash memory. The power-fail protective sequential circuit comprises an independent power supply converting module, a power supply monitoring module, a write-protection module and a reset module, wherein the independent power supply converting module is used for converting an exterior power supply into an internal power supply which is output through the output end of the independent power supply converting module, and thus the internal power supply power-fail at last is realized during the process of the exterior power supply power-fail; the power supply monitoring module is used for obtaining the exterior power supply, and outputting an alarm signal when the voltage of the exterior power supply is less than a power-fail threshold. The invention further relates to a power-fail protective circuit for the flash memory. The power-fail protective circuit is used for pulling the write-protection pin of the flash memory to a low level when the voltage of the exterior power supply decreases to be less than the power-fail threshold, the flash memory is put at a write-protection state until power-fail is finished. So that, during the power-fail process, data stored in the flash memory can not be erased, the safety of the stored data is improved.
Owner:SHENZHEN GONGJIN ELECTRONICS CO LTD
Memory sharing method of virtual machines based on combination of ksm and pass-through
InactiveUS20180011797A1Improve balanceEfficient solutionMemory architecture accessing/allocationSoftware simulation/interpretation/emulationWrite protectionSoftware engineering
A memory sharing method of virtual machines through the combination of KSM and pass-through, including: a virtual machine manager judging whether operating systems of guests use IOMMU, if not, not participating in shared mapping of a KSM technology; if yes, judging memory pages of each guest to confirm whether the pages are mapping pages, if yes, remain the mapping pages into a host; and if not, on the premise of keeping the properties of Pass-through, using the KSM technology for all non-mapping pages to merge the memory pages with same contents among various virtual machines and perform write protection processing simultaneously. The guest memory pages are divided into those special for DMA and those for non-DMA purpose, then the KSM technology is only selectively applied to the non-DMA pages, and on the premise of keeping the properties of Pass-through, the object of saving memory resources is achieved simultaneously.
Owner:MASSCLOUDS INNOVATION RES INST (BEIJING) OF INFORMATION TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com