Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
9941 results about "Magnetic disks" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
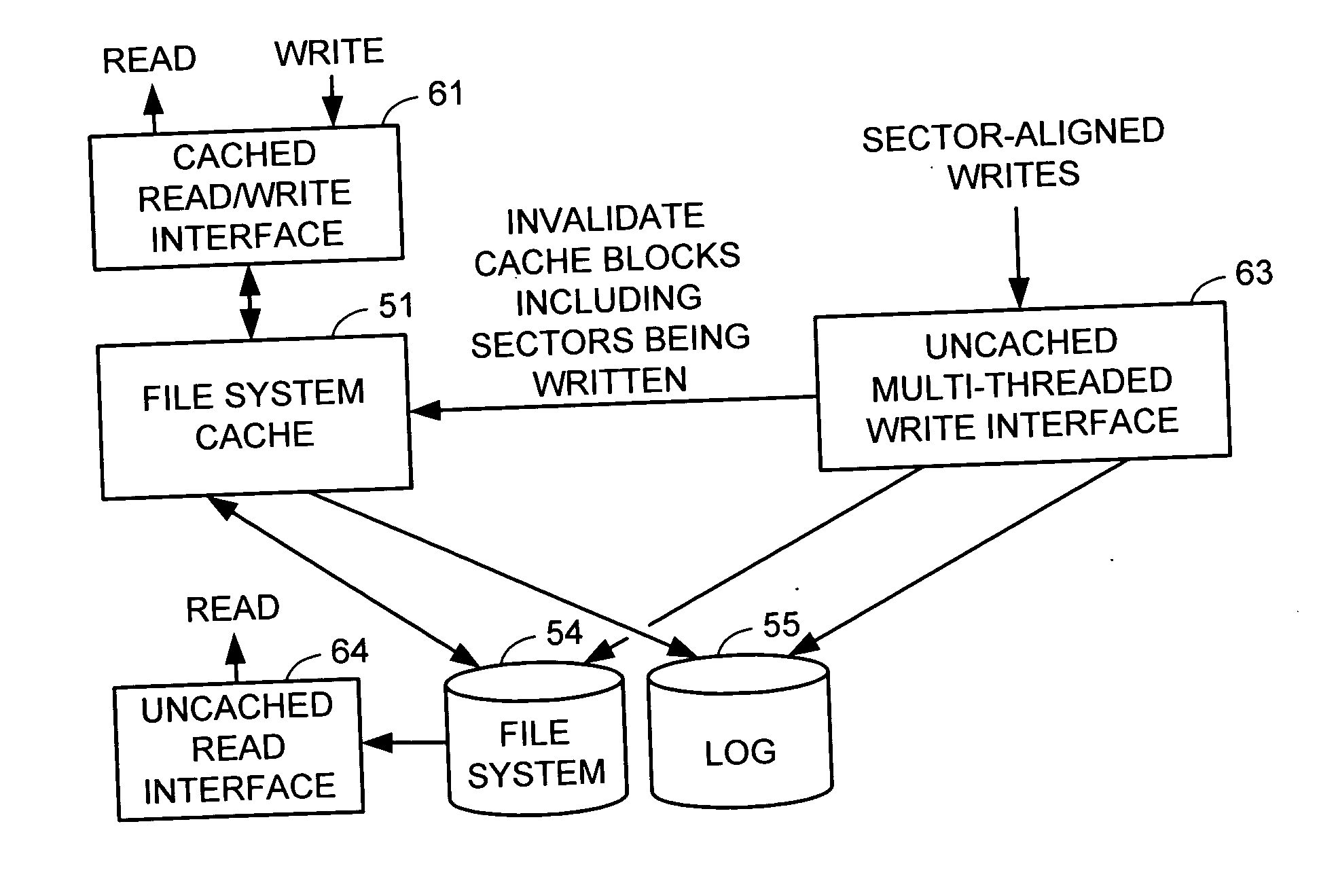
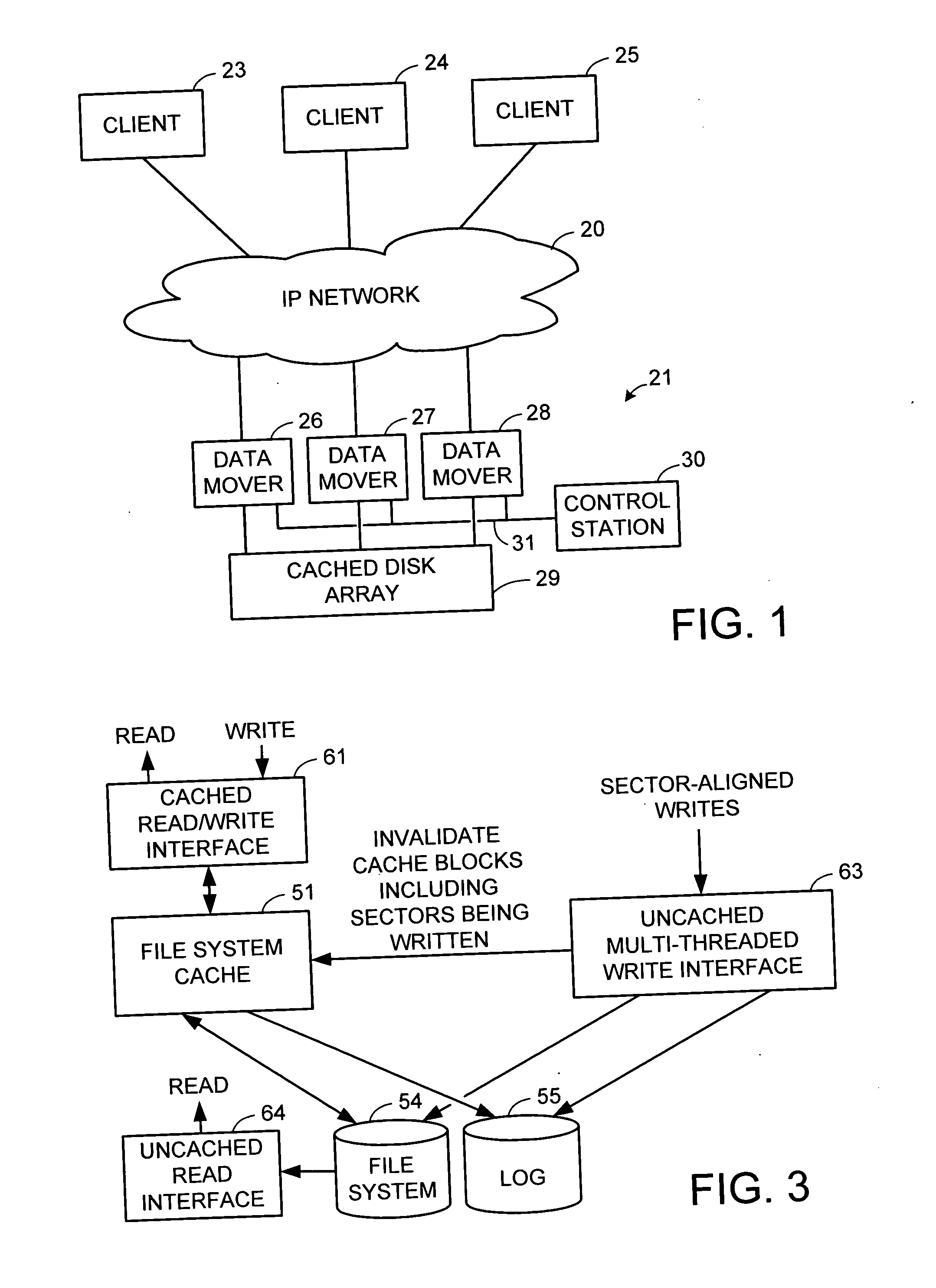
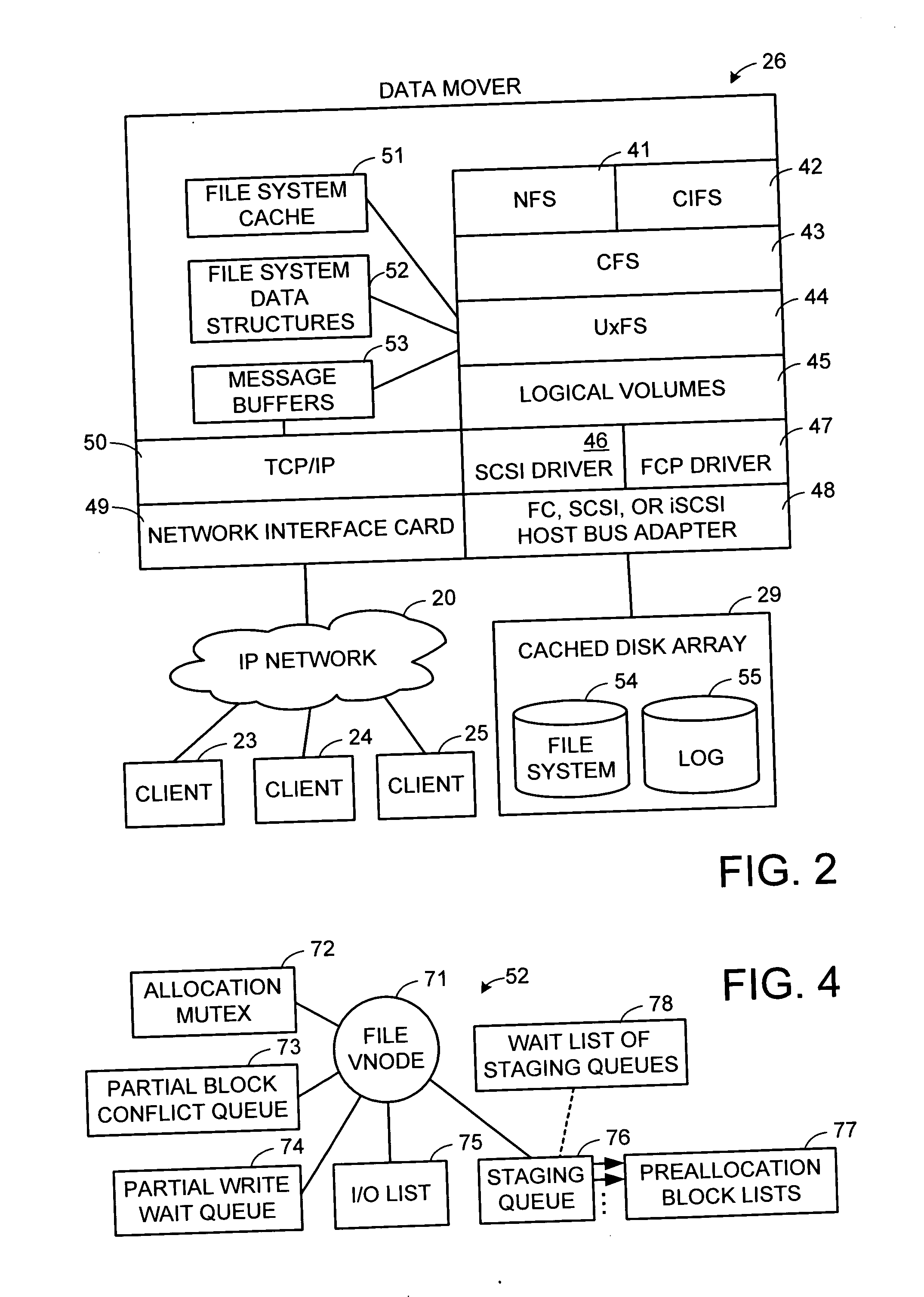
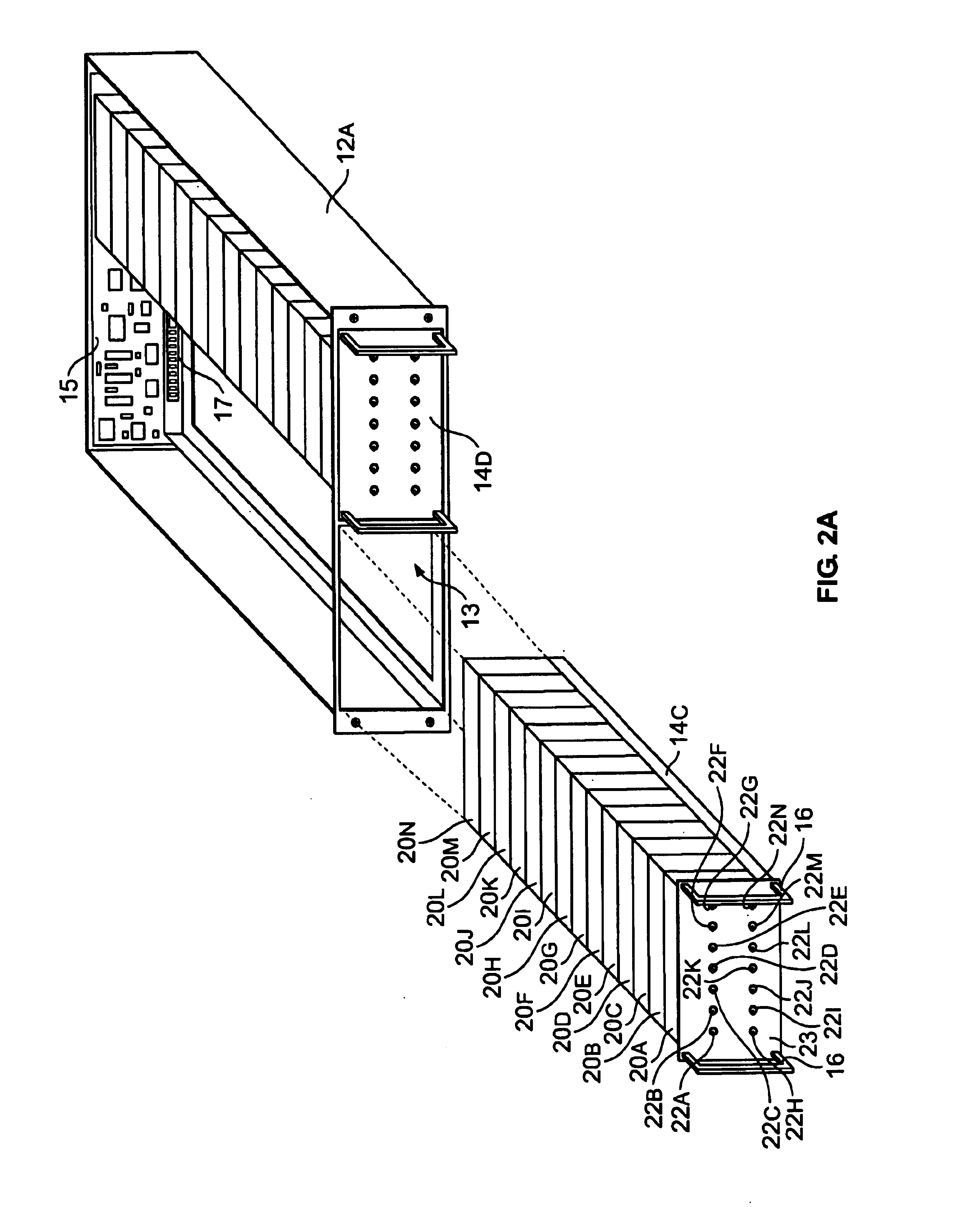
Multi-threaded write interface and methods for increasing the single file read and write throughput of a file server
ActiveUS20050066095A1Digital data information retrievalDigital data processing detailsData integrityFile allocation
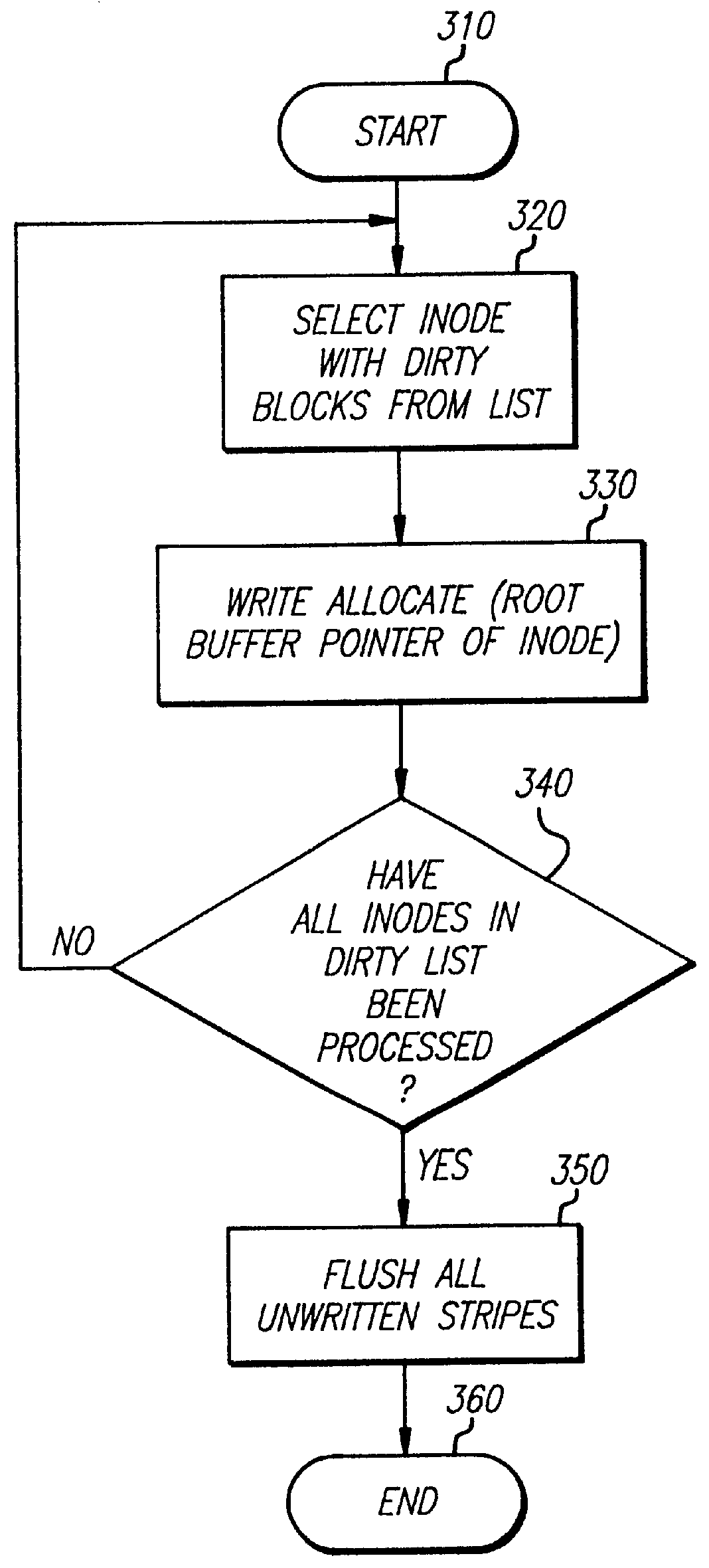
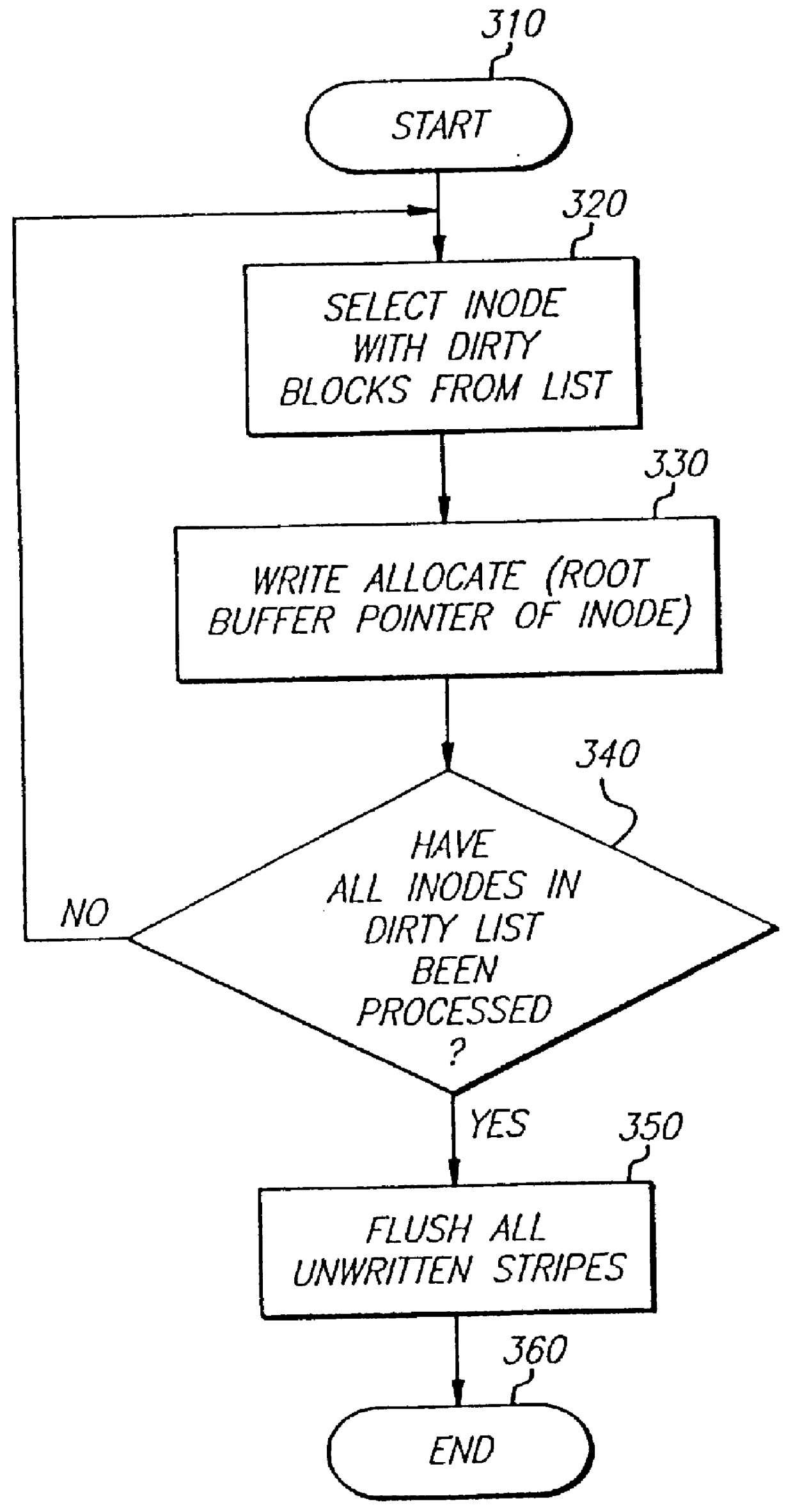
A write interface in a file server provides permission management for concurrent access to data blocks of a file, ensures correct use and update of indirect blocks in a tree of the file, preallocates file blocks when the file is extended, solves access conflicts for concurrent reads and writes to the same block, and permits the use of pipelined processors. For example, a write operation includes obtaining a per file allocation mutex (mutually exclusive lock), preallocating a metadata block, releasing the allocation mutex, issuing an asynchronous write request for writing to the file, waiting for the asynchronous write request to complete, obtaining the allocation mutex, committing the preallocated metadata block, and releasing the allocation mutex. Since no locks are held during the writing of data to the on-disk storage and this data write takes the majority of the time, the method enhances concurrency while maintaining data integrity.
Owner:EMC IP HLDG CO LLC
Method for allocating files in a file system integrated with a RAID disk sub-system
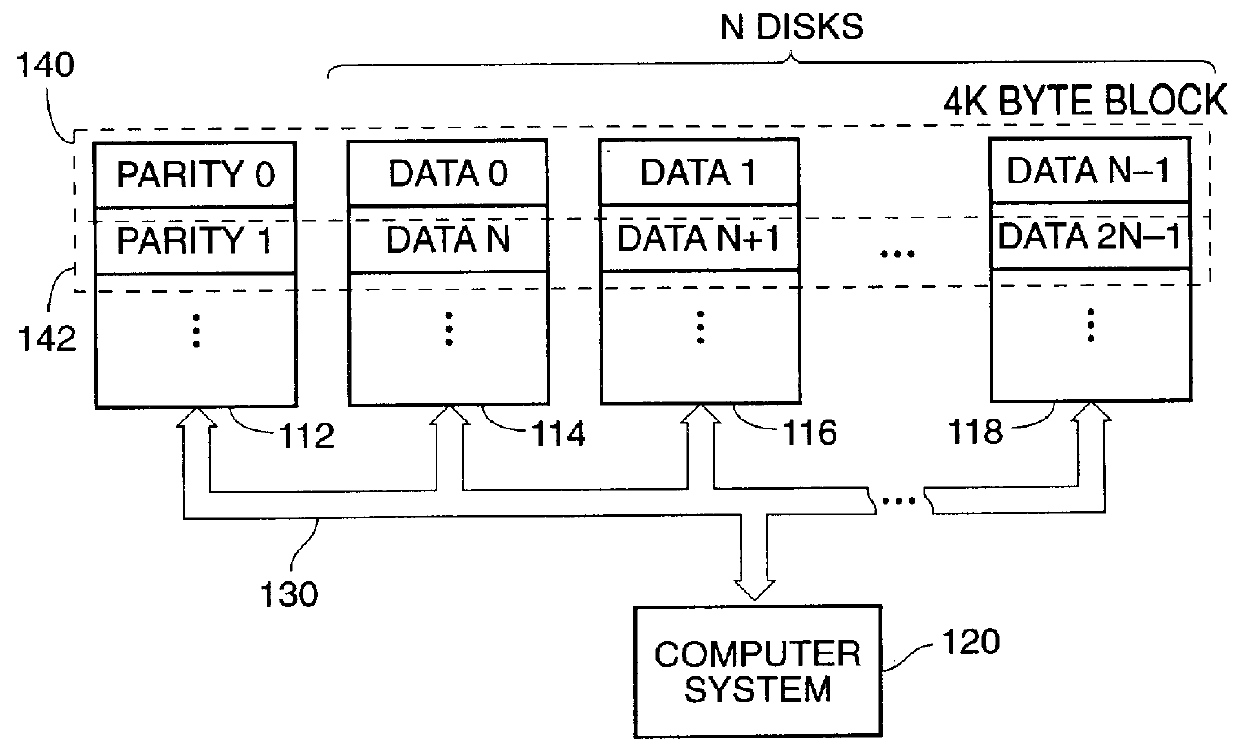
The present invention is a method for integrating a file system with a RAID array that exports precise information about the arrangement of data blocks in the RAID subsystem. The file system examines this information and uses it to optimize the location of blocks as they are written to the RAID system. Thus, the system uses explicit knowledge of the underlying RAID disk layout to schedule disk allocation. The present invention uses separate current-write location (CWL) pointers for each disk in the disk array where the pointers simply advance through the disks as writes occur. The algorithm used has two primary goals. The first goal is to keep the CWL pointers as close together as possible, thereby improving RAID efficiency by writing to multiple blocks in the stripe simultaneously. The second goal is to allocate adjacent blocks in a file on the same disk, thereby improving read back performance. The present invention satisfies the first goal by always writing on the disk with the lowest CWL pointer. For the second goal, a new disk is chosen only when the algorithm starts allocating space for a new file, or when it has allocated N blocks on the same disk for a single file. A sufficient number of blocks is defined as all the buffers in a chunk of N sequential buffers in a file. The result is that CWL pointers are never more than N blocks apart on different disks, and large files have N consecutive blocks on the same disk.
Owner:NETWORK APPLIANCE INC
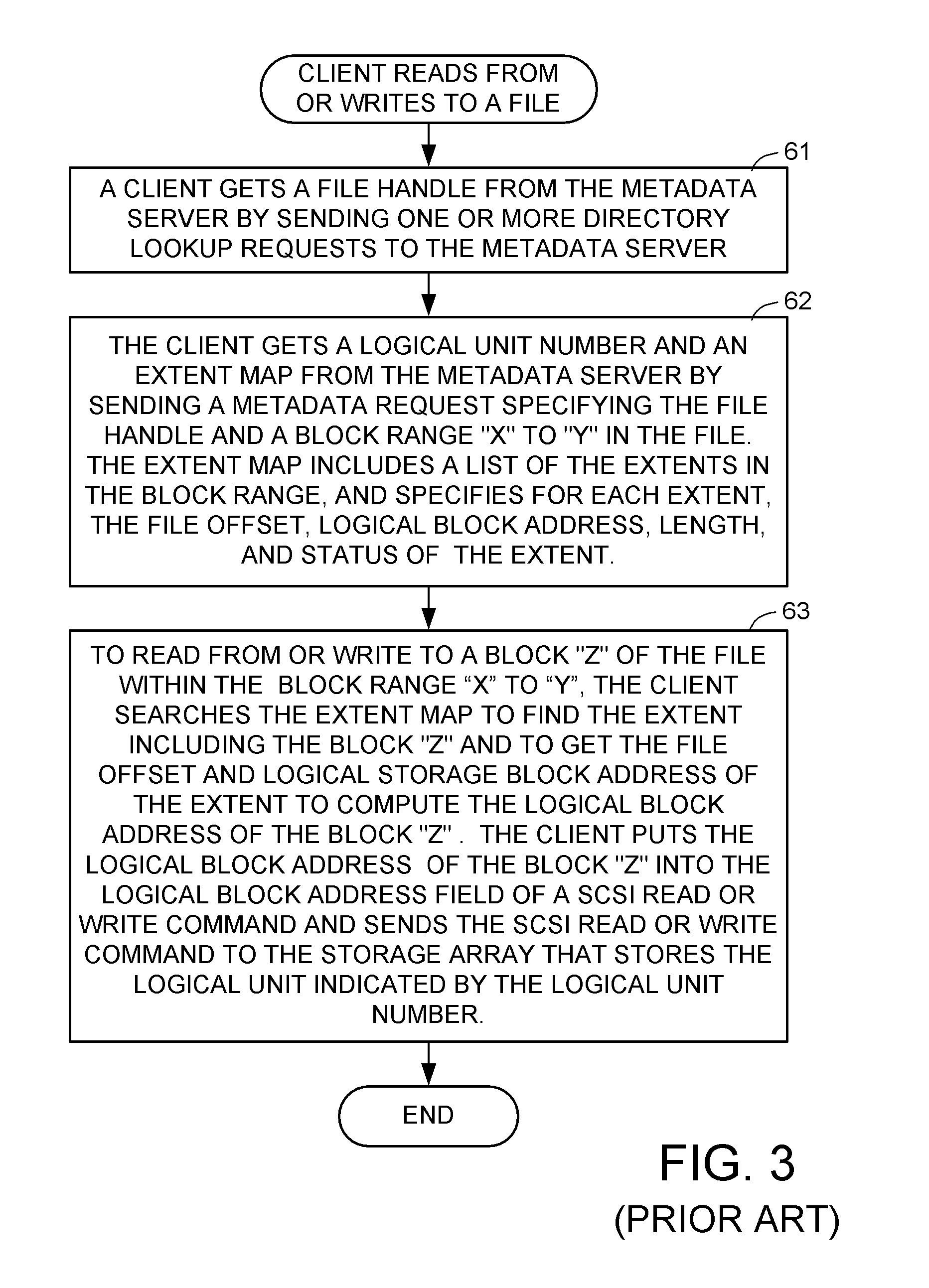
Access control to block storage devices for a shared disk based file system
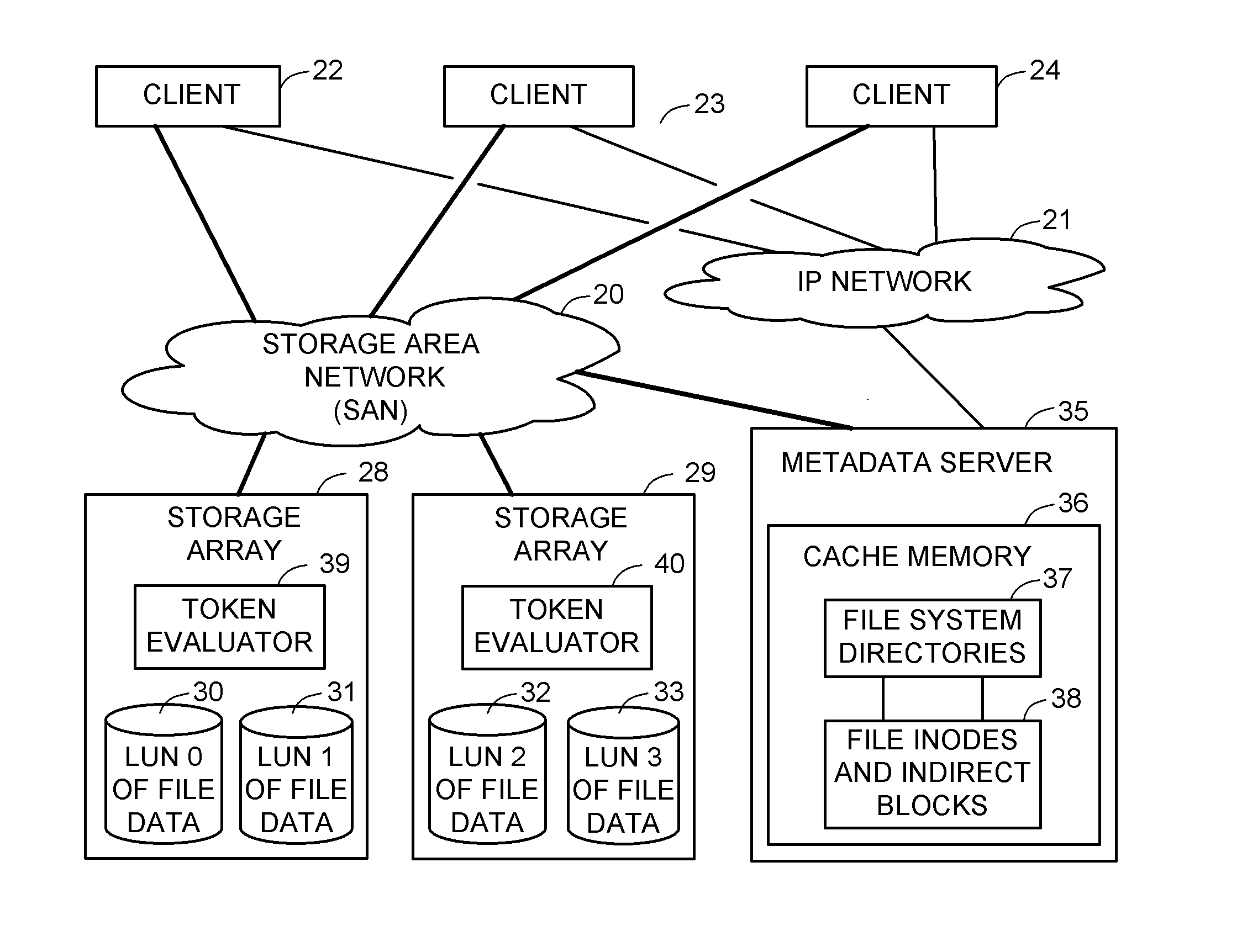
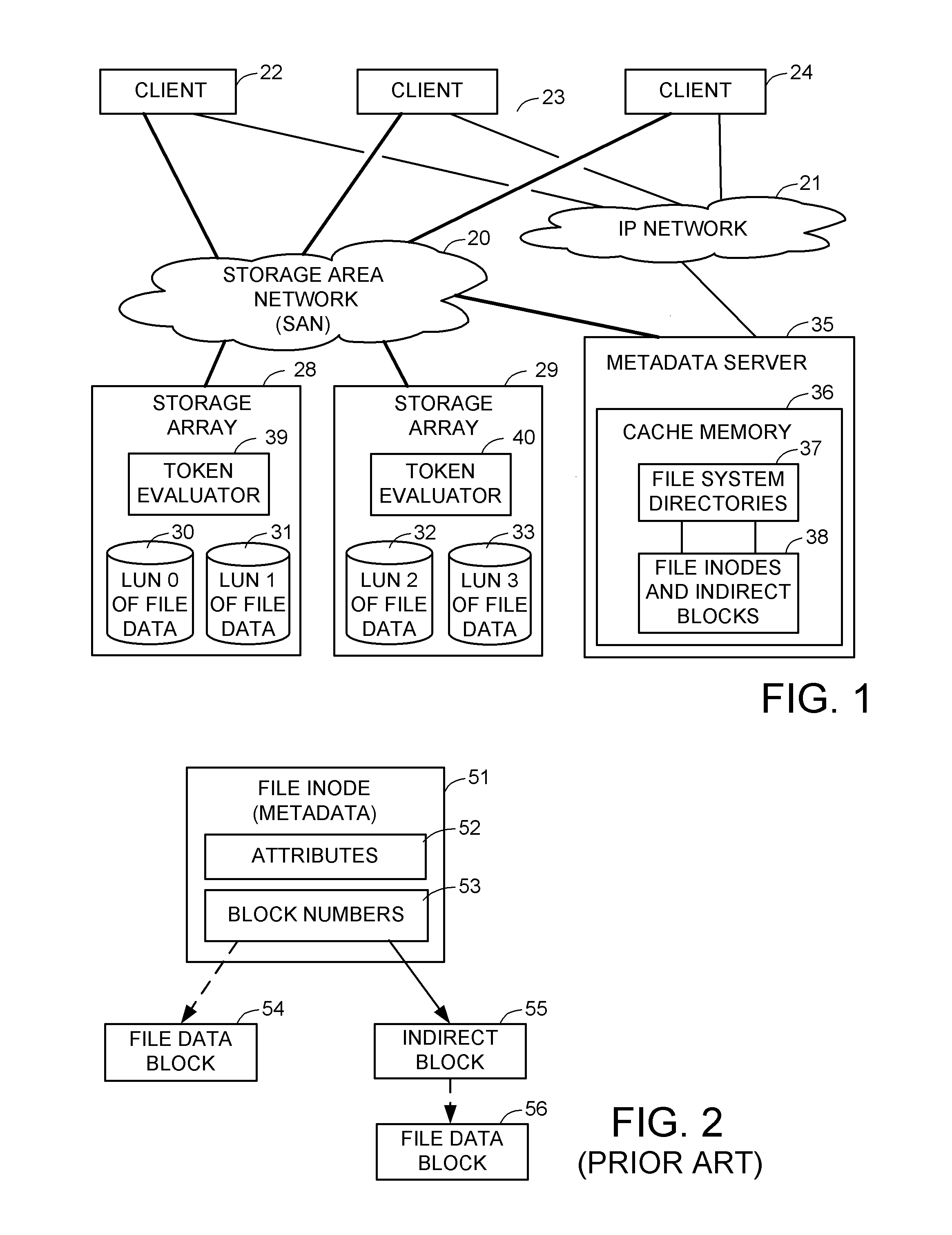
ActiveUS8086585B1Improve securityChangeDigital data information retrievalDigital data processing detailsSCSILogical block addressing
For enhanced access control, a client includes a token in each read or write command sent to a block storage device. The block storage device evaluates the token to determine whether or not read or write access is permitted at a specified logical block address. For example, the token is included in the logical block address field of a SCSI read or write command. The client may compute the token as a function of the logical block address of a data block to be accessed, or a metadata server may include the token in each block address of each extent reported to the client in response to a metadata request. For enhanced security, the token also is a function of a client identifier, a logical unit number, and access rights of the client to a particular extent of file system data blocks.
Owner:EMC IP HLDG CO LLC
Method, software and apparatus for saving, using and recovering data
InactiveUS6016553ADigital data information retrievalInput/output to record carriersOperational systemOriginal data
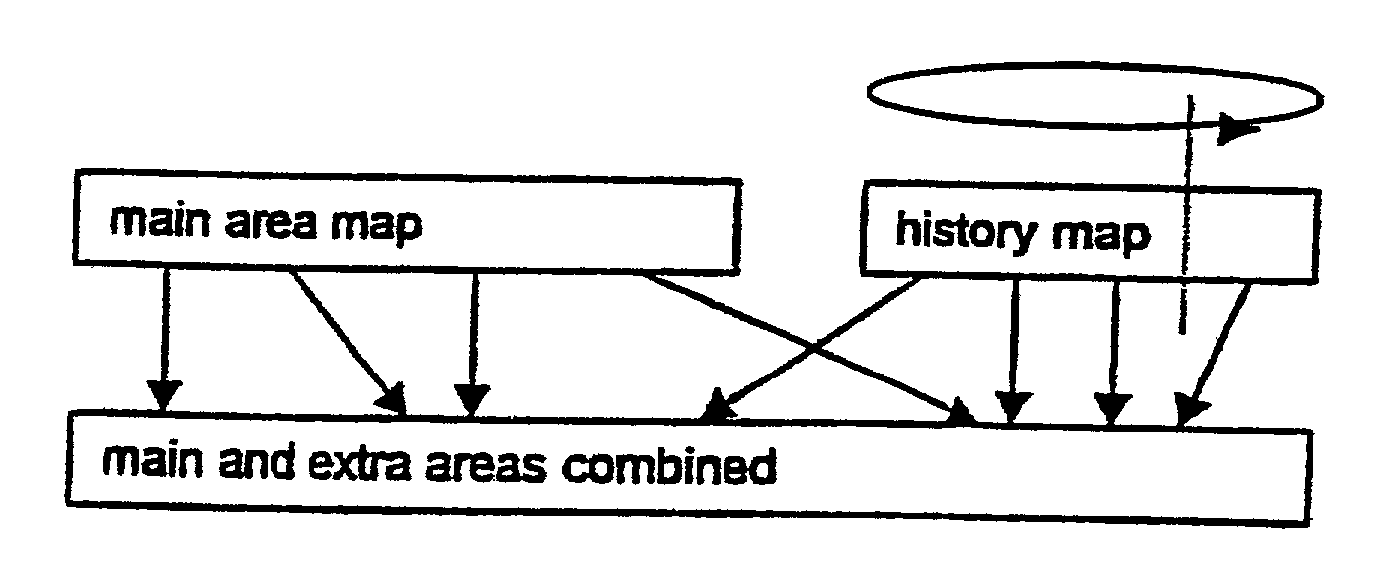
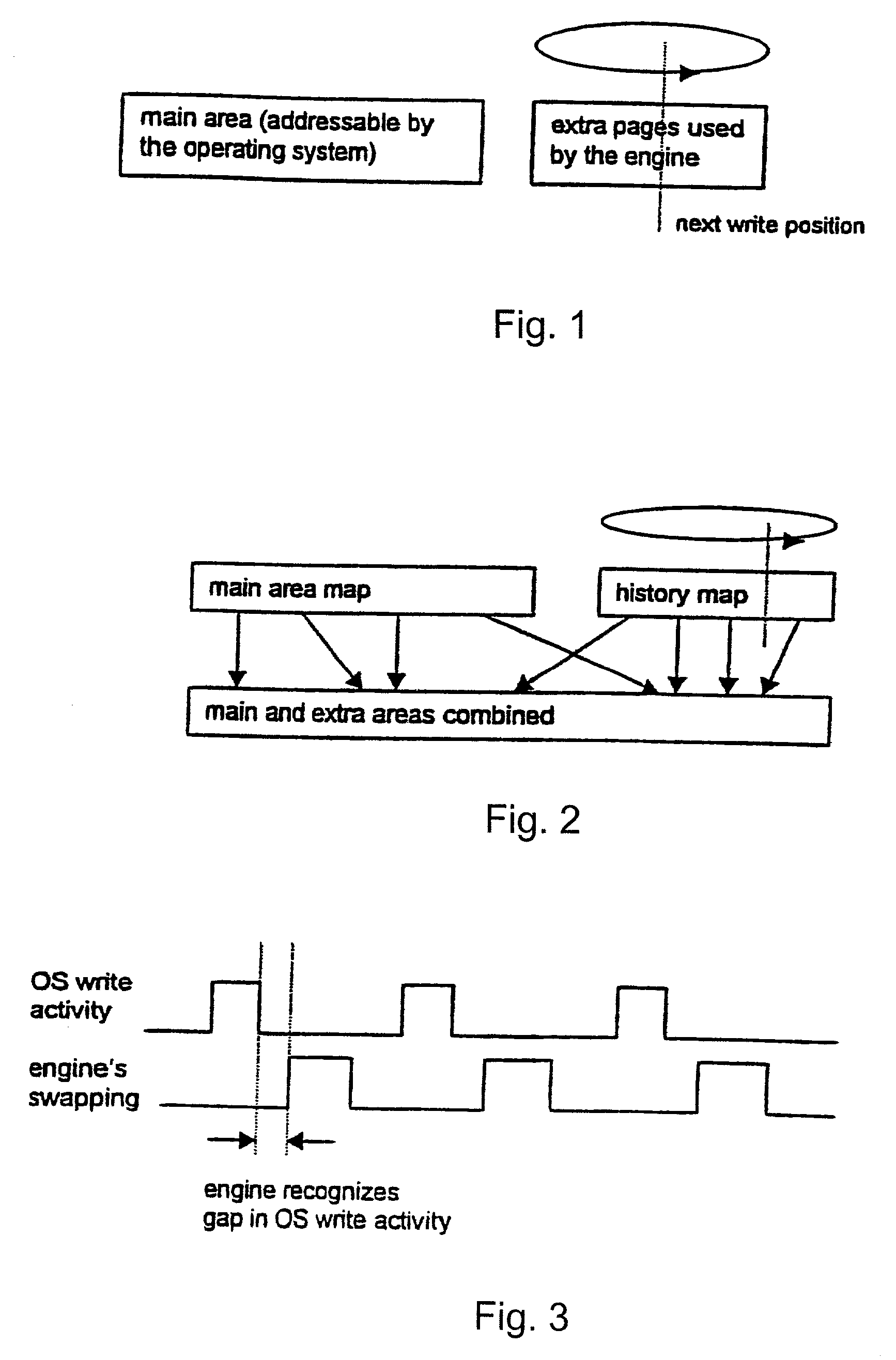
A method and apparatus for reverting a disk drive to an earlier point in time is disclosed. Changes made to the drive are saved in a circular history buffer which includes the old data, the time it was replaced by new data, and the original location of the data. The circular history buffer may also be implemented by saving new data elements into new locations and leaving the old data elements in their original locations. References to the new data elements are mapped to the new location. The disk drive is reverted to an earlier point in time by replacing the new data elements with the original data elements retrieved from the history buffer, or in the case of the other embodiment, reads to the disk are mapped to the old data elements stilled stored in their original locations. The method and apparatus may be implemented as part of an operating system, or as a separate program, or in the controller for the disk drive. The method and apparatus are applicable to other forms of data storage as well. Also disclosed are method and apparatus for providing firewall protection to data in a data storage medium of a computer system.
Owner:POWER MANAGEMENT ENTERPRISES
Multi-Level Striping and Truncation Channel-Equalization for Flash-Memory System
InactiveUS20090240873A1Memory architecture accessing/allocationError preventionLogical block addressingData access
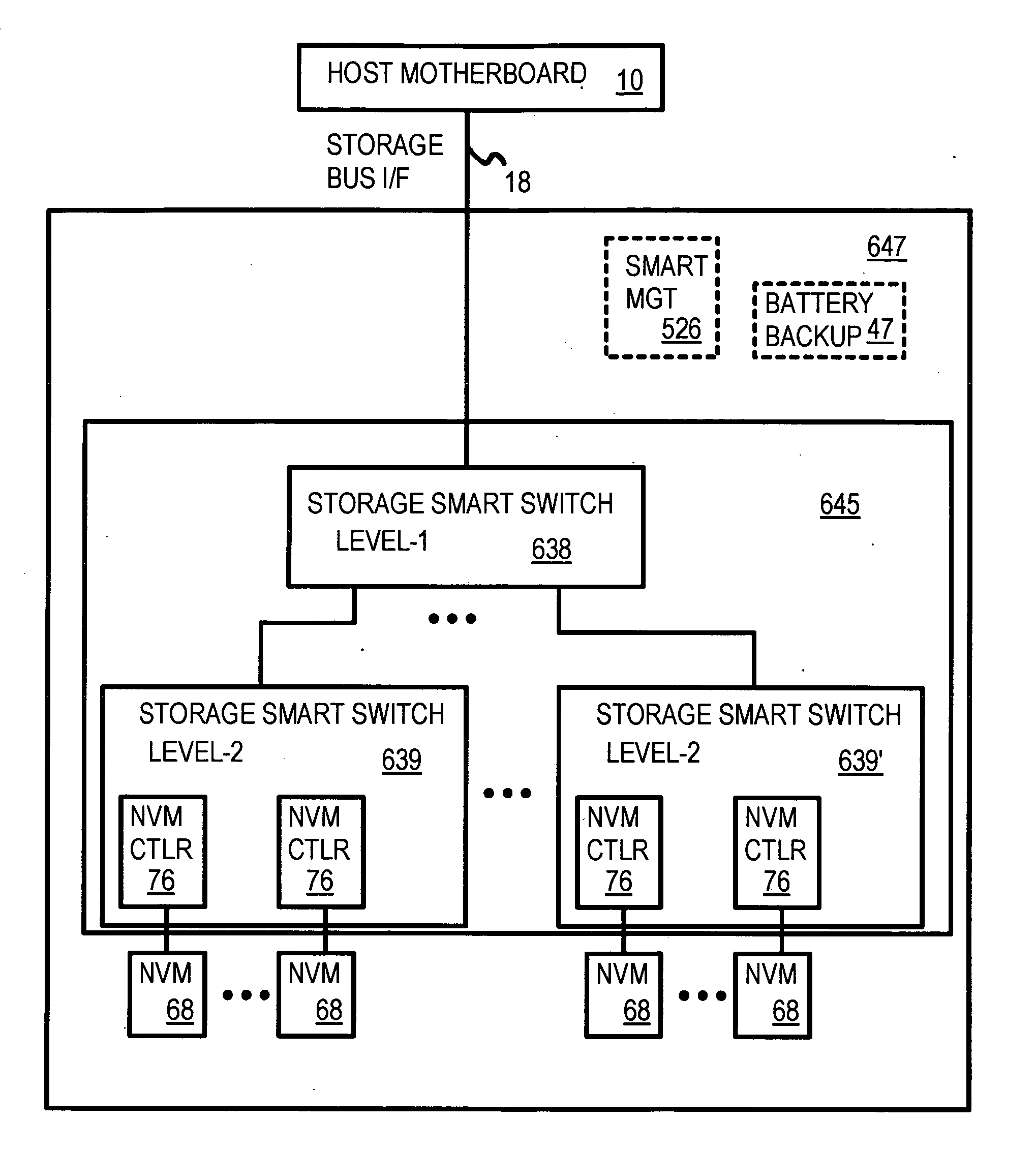
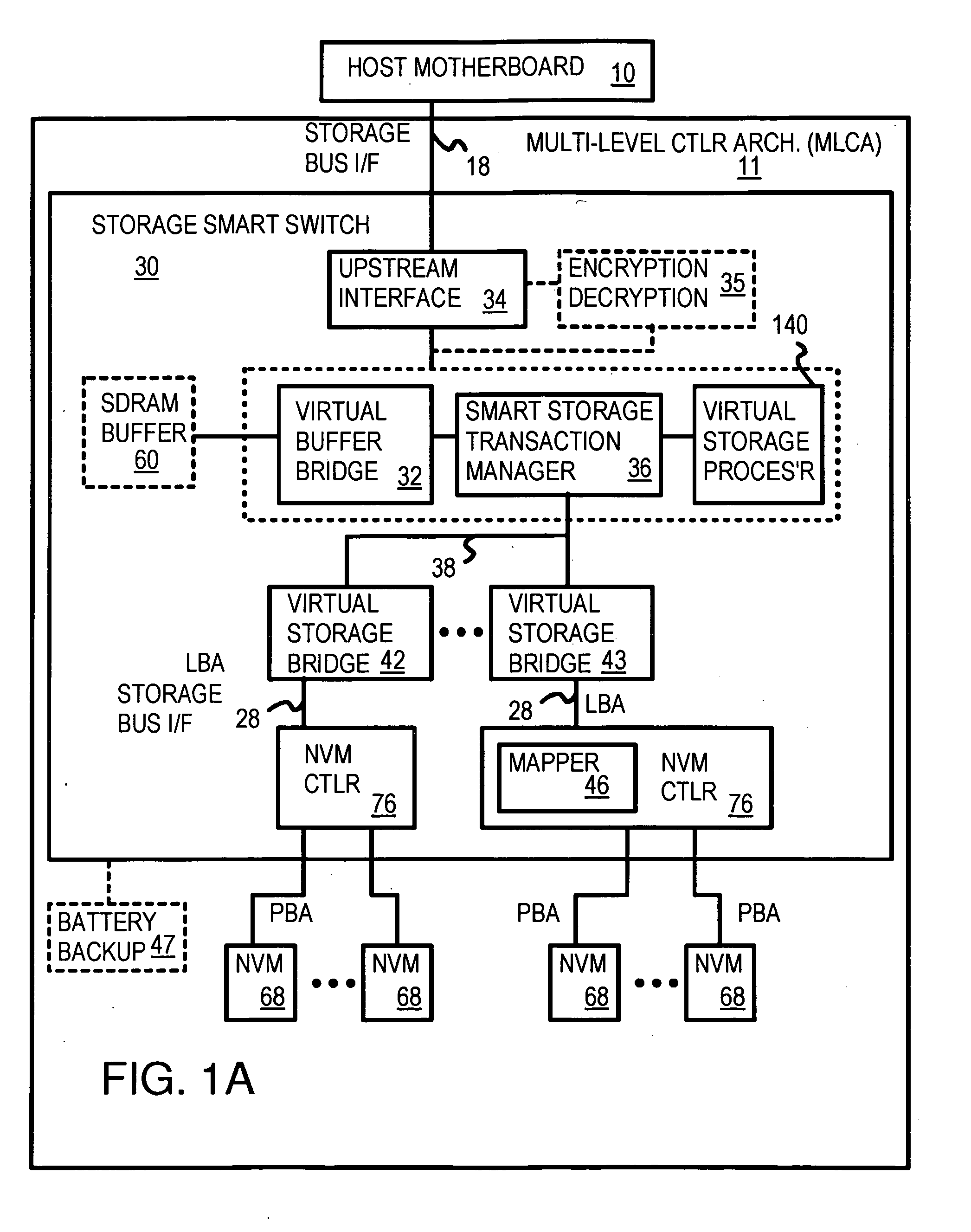
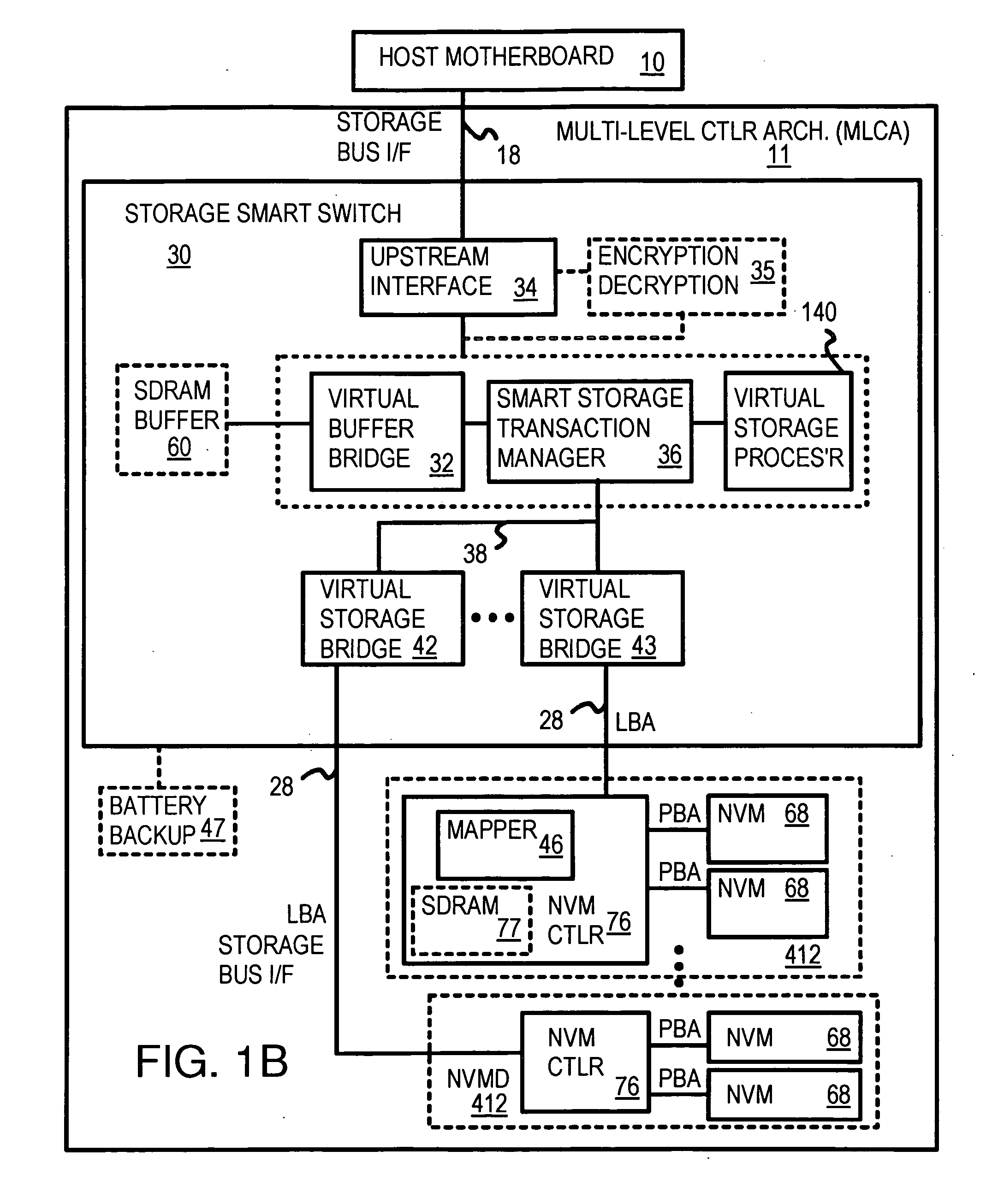
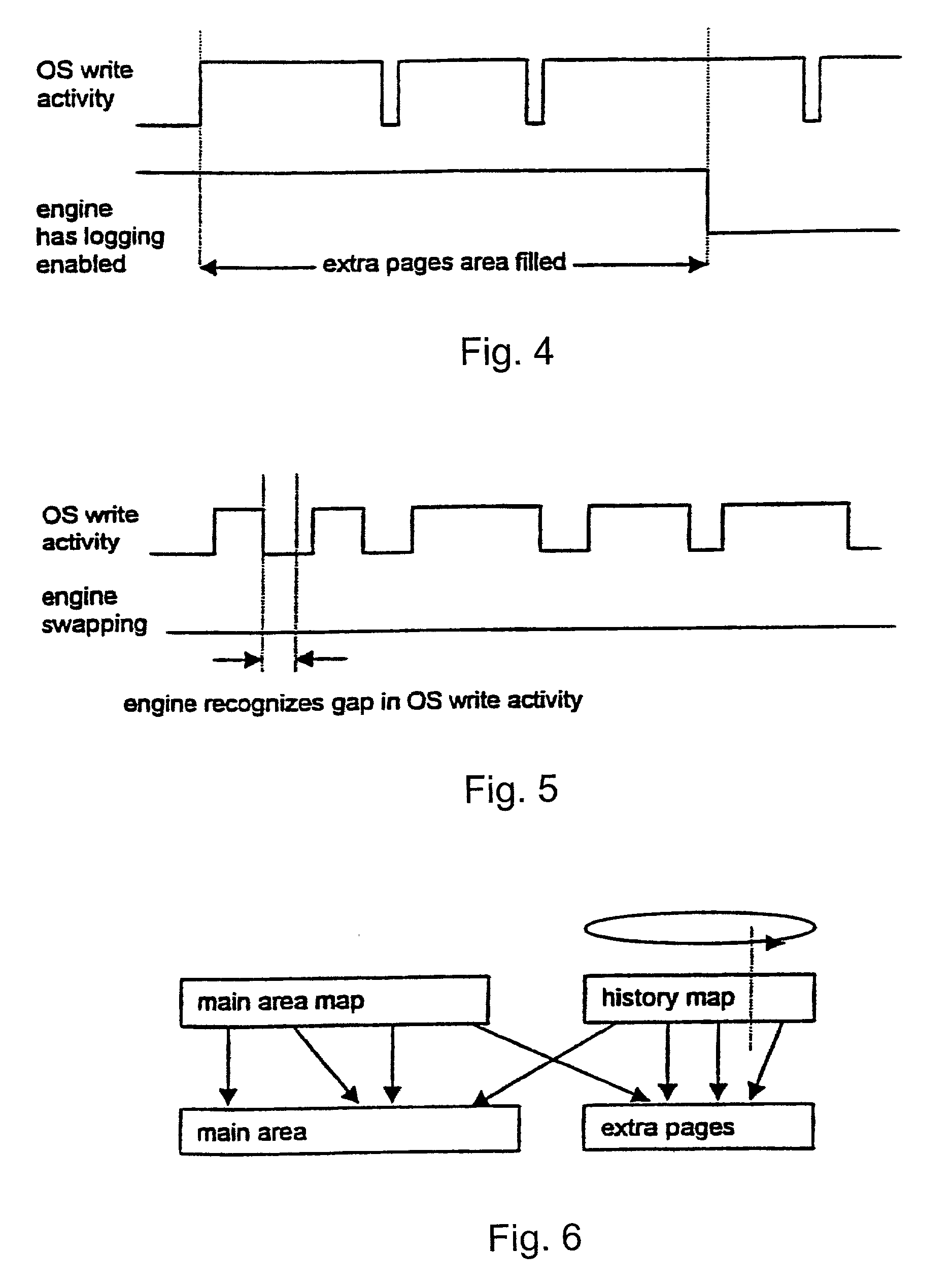
Truncation reduces the available striped data capacity of all flash channels to the capacity of the smallest flash channel. A solid-state disk (SSD) has a smart storage switch salvages flash storage removed from the striped data capacity by truncation. Extra storage beyond the striped data capacity is accessed as scattered data that is not striped. The size of the striped data capacity is reduced over time as more bad blocks appear. A first-level striping map stores striped and scattered capacities of all flash channels and maps scattered and striped data. Each flash channel has a Non-Volatile Memory Device (NVMD) with a lower-level controller that converts logical block addresses (LBA) to physical block addresses (PBA) that access flash memory in the NVMD. Wear-leveling and bad block remapping are preformed by each NVMD. Source and shadow flash blocks are recycled by the NVMD. Two levels of smart storage switches enable three-level controllers.
Owner:SUPER TALENT TECH CORP
System and method for restoring a computer system after a failure
InactiveUS20020049883A1Memory adressing/allocation/relocationInternal/peripheral component protectionOperational systemOriginal data
A method and apparatus for reverting a disk drive to an earlier point in time is disclosed. Changes made to the drive are saved in a circular history buffer which includes the old data, the time it was replaced by new data, and the original location of the data. The circular history buffer may also be implemented by saving new data elements into new locations and leaving the old data elements in their original locations. References to the new data elements are mapped to the new location. The disk drive is reverted to an earlier point in time by replacing the new data elements with the original data elements retrieved from the history buffer, or in the case of the other embodiment, reads to the disk are mapped to the old data elements stilled stored in their original locations. The method and apparatus may be implemented as part of an operating system, or as a separate program, or in the controller for the disk drive. The method and apparatus are applicable to other forms of data storage as well. Also disclosed are method and apparatus for providing firewall protection to data in a data storage medium of a computer system.
Owner:NORTONLIFELOCK INC
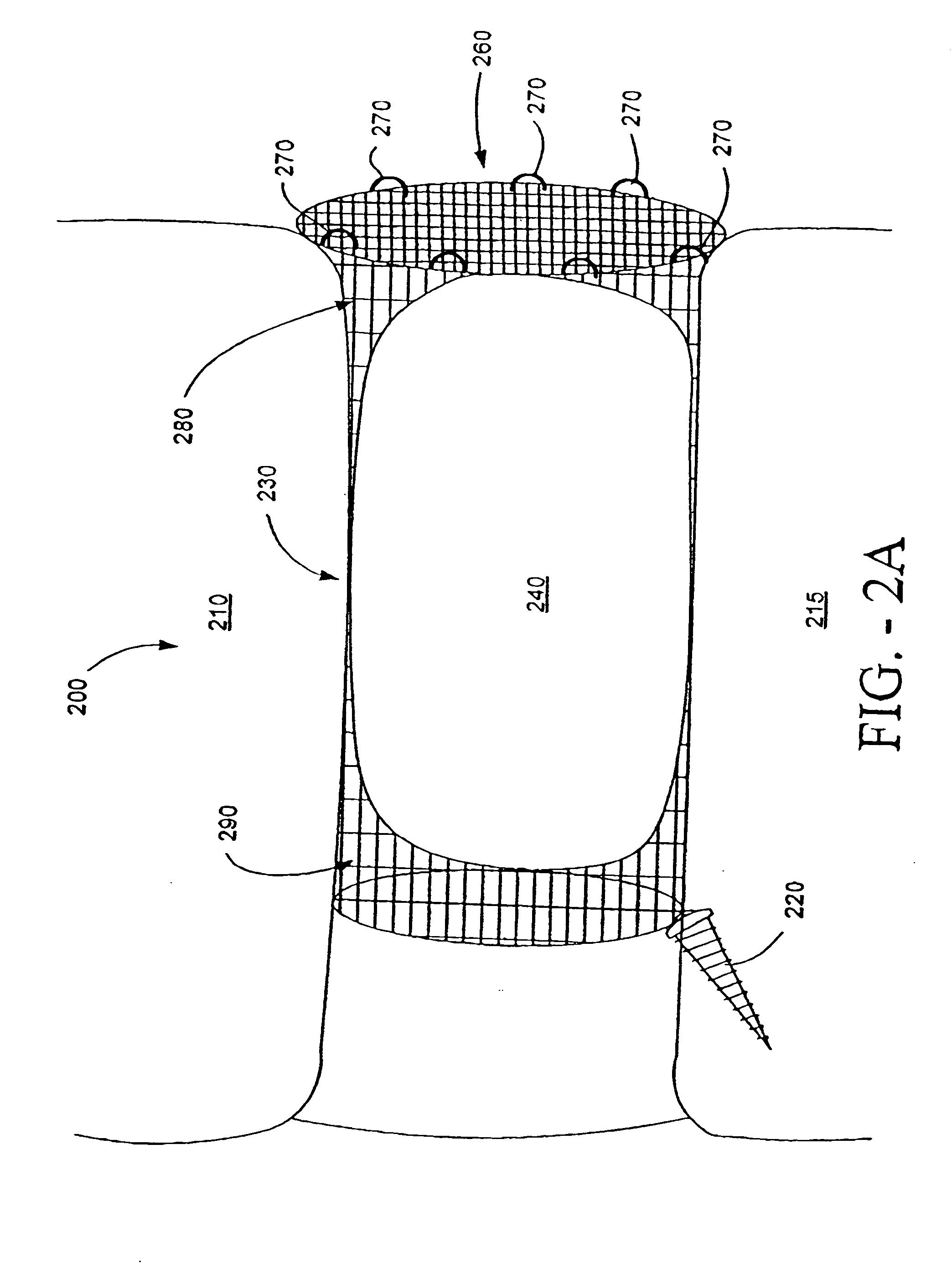
Disk repair structures for positioning disk repair material
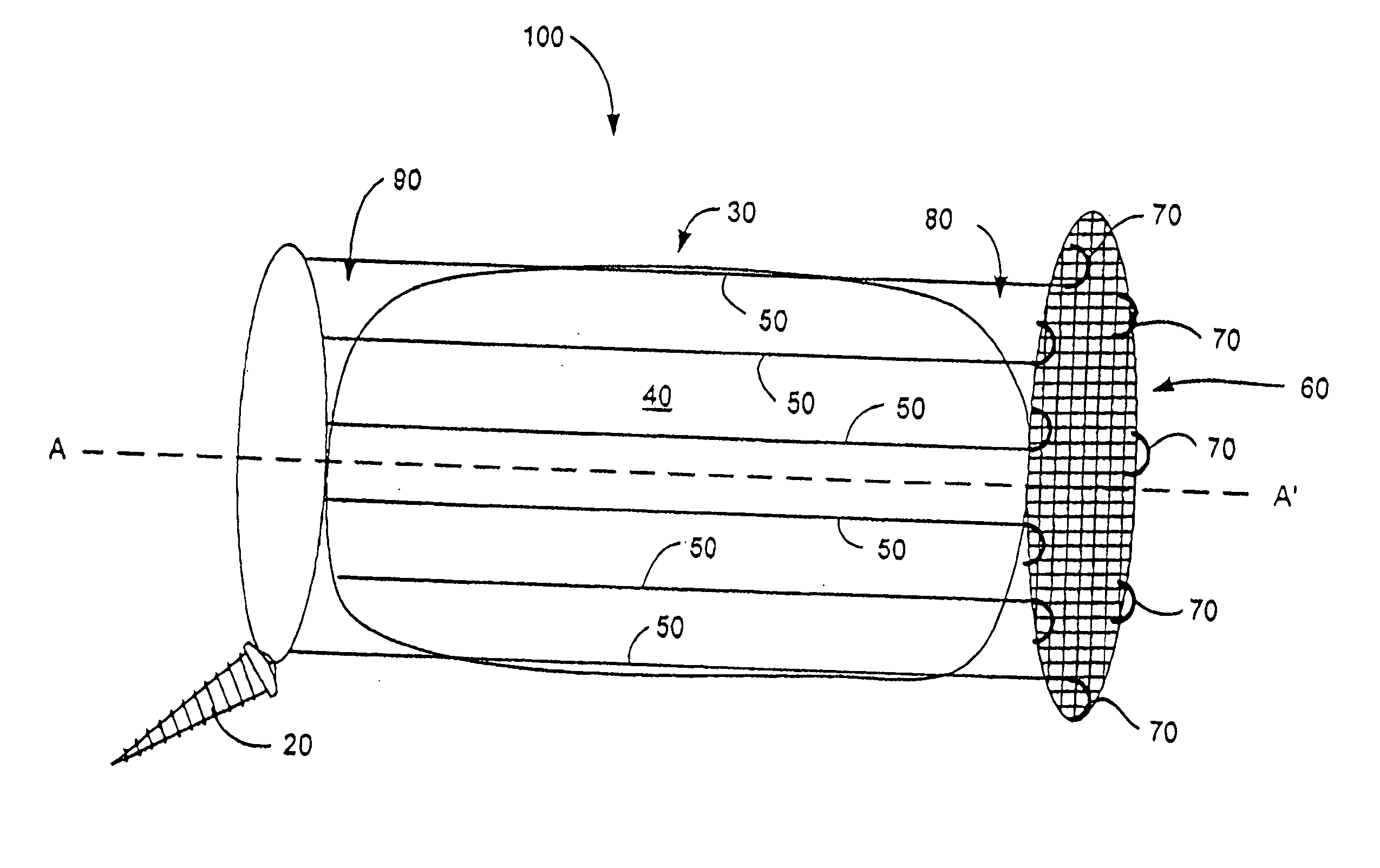
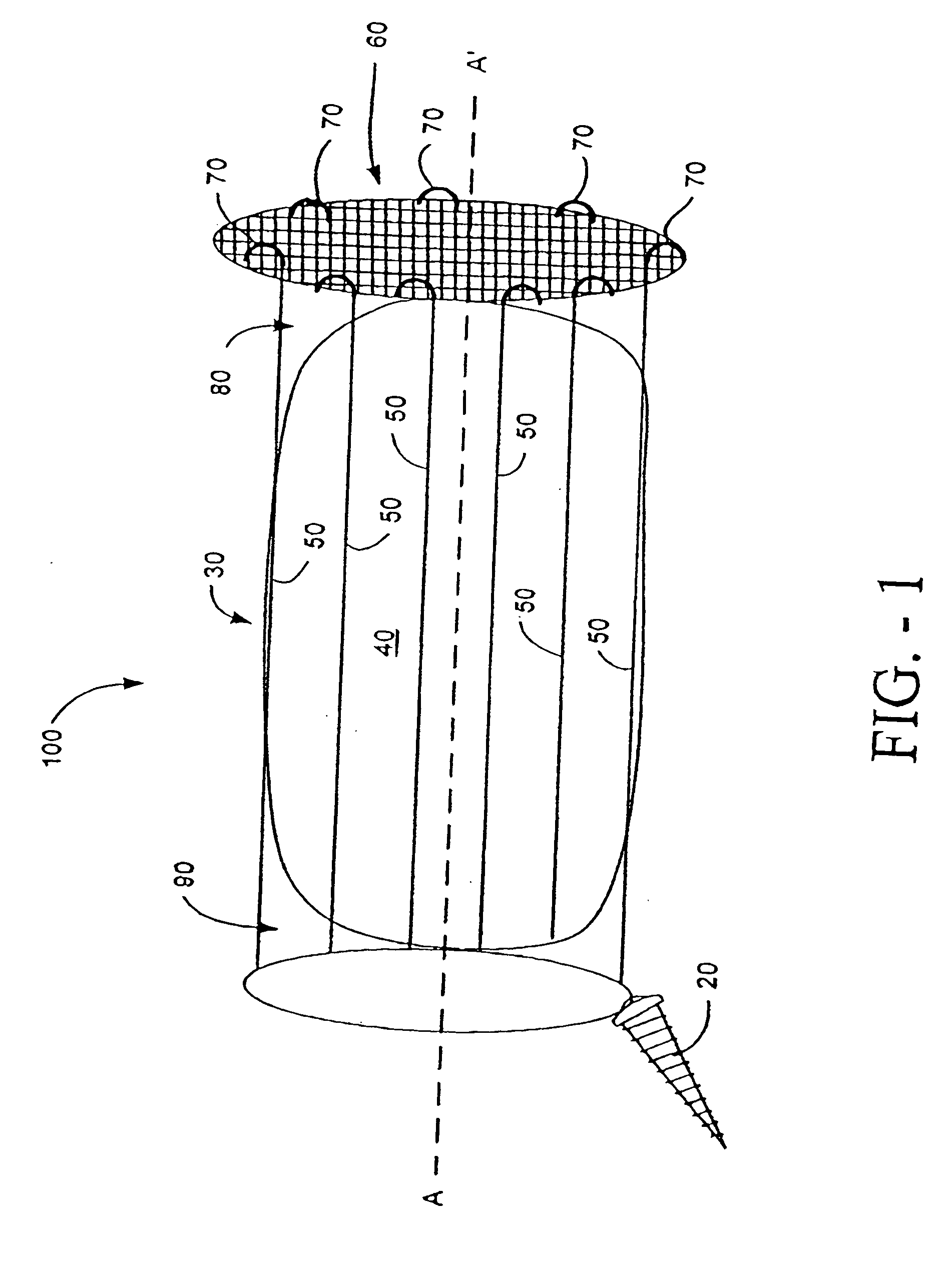
The present invention is directed to a device that can be placed between two adjacent vertebrae, and that is used to repair an injury or defect in the anulus of the intervertebral disk. The implant is characterized by having a flexible structure anchored to the vertebral bone, the flexible structure connected with a patch held in place over the injury or defect. The flexible structure has a hollow interior space which can sustain inside it a hydrogel cushion. The hydrogel cushion acts as a shock absorber for the spine, maintains height of the intervertebral disk space, and prevents further disk herniation due to the narrowing of the intervertebral disk space.
Owner:KYPHON
Storage virtualization by layering virtual disk objects on a file system
InactiveUS7107385B2Input/output to record carriersData processing applicationsOperational systemFile system
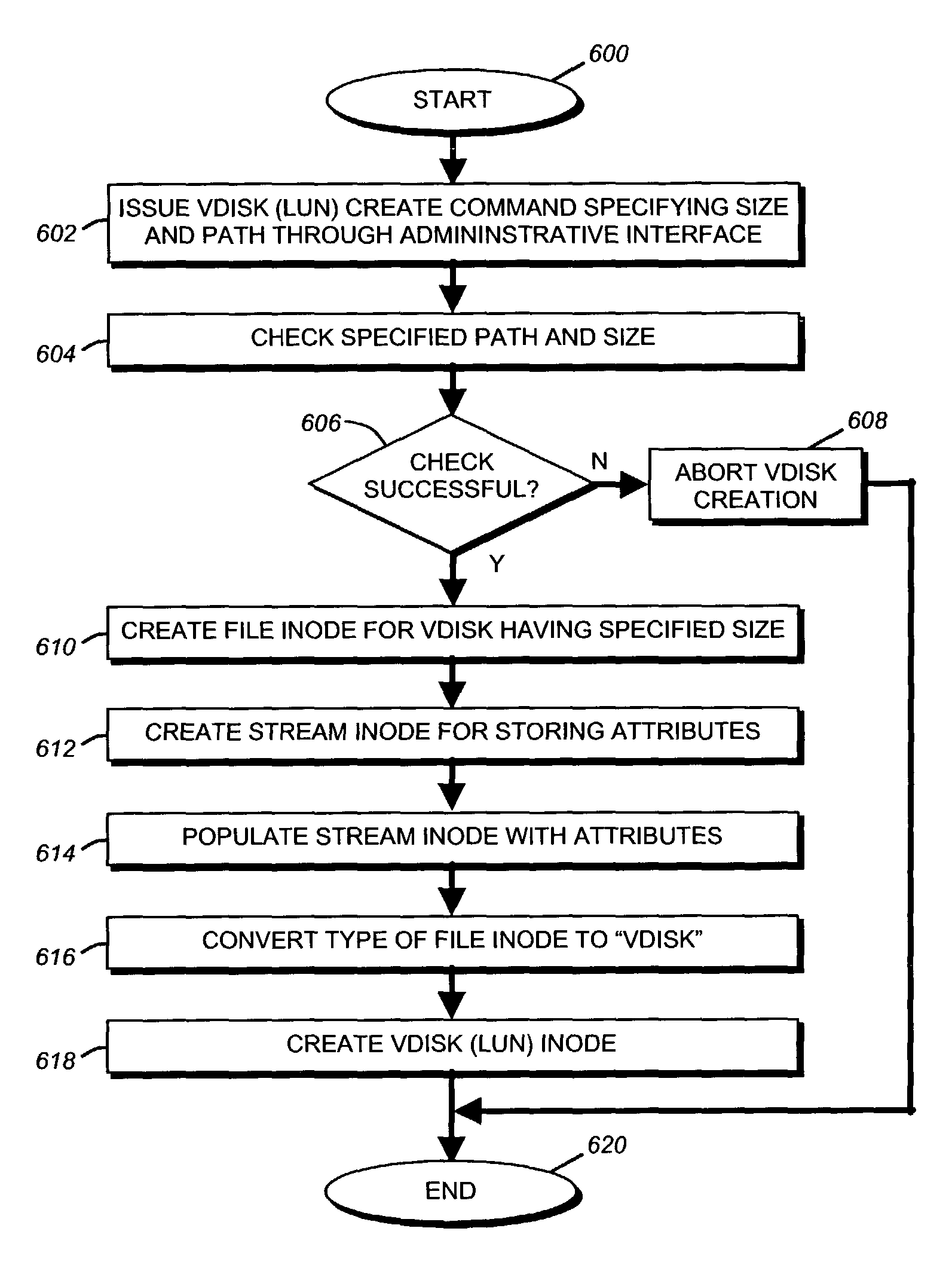
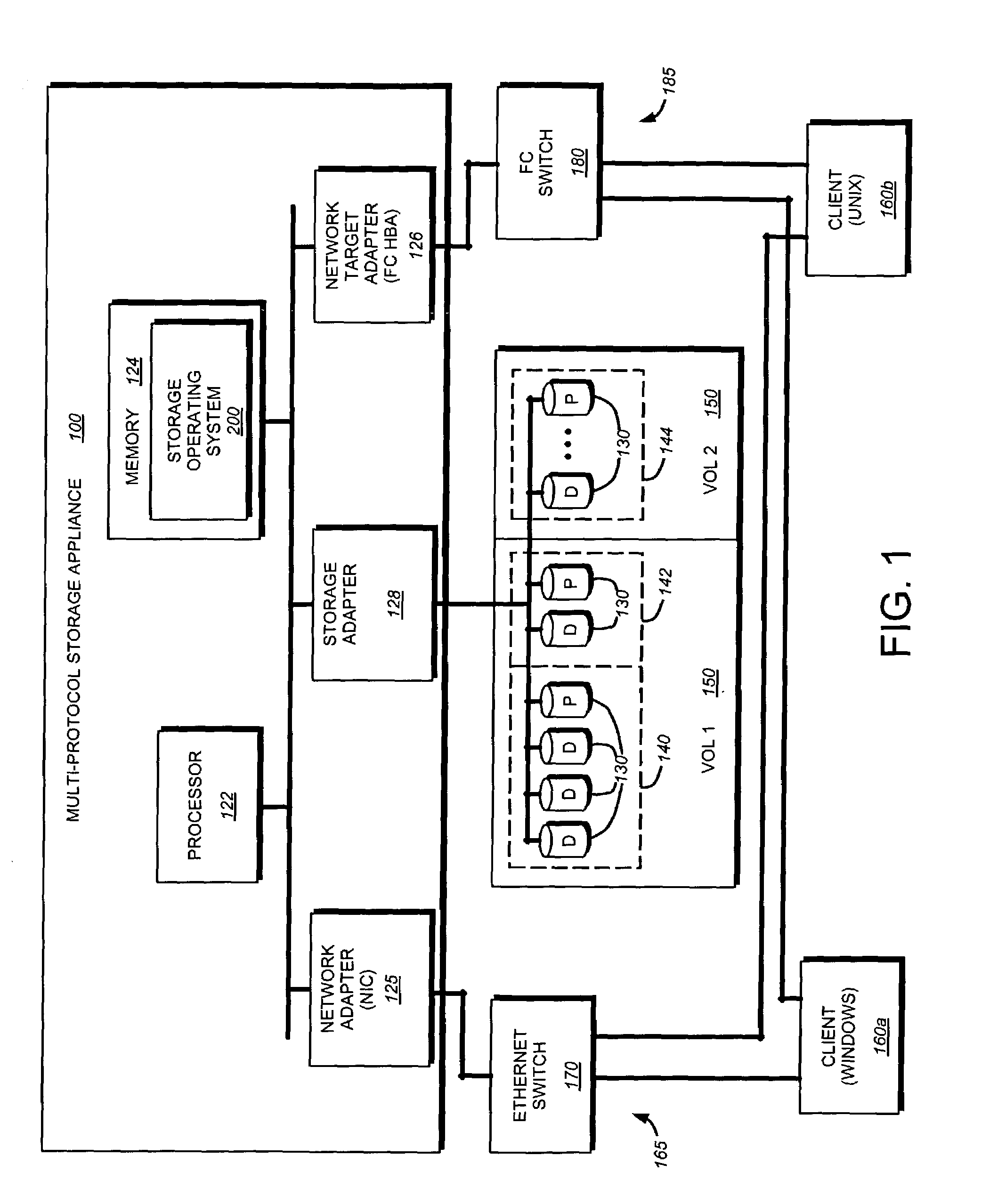
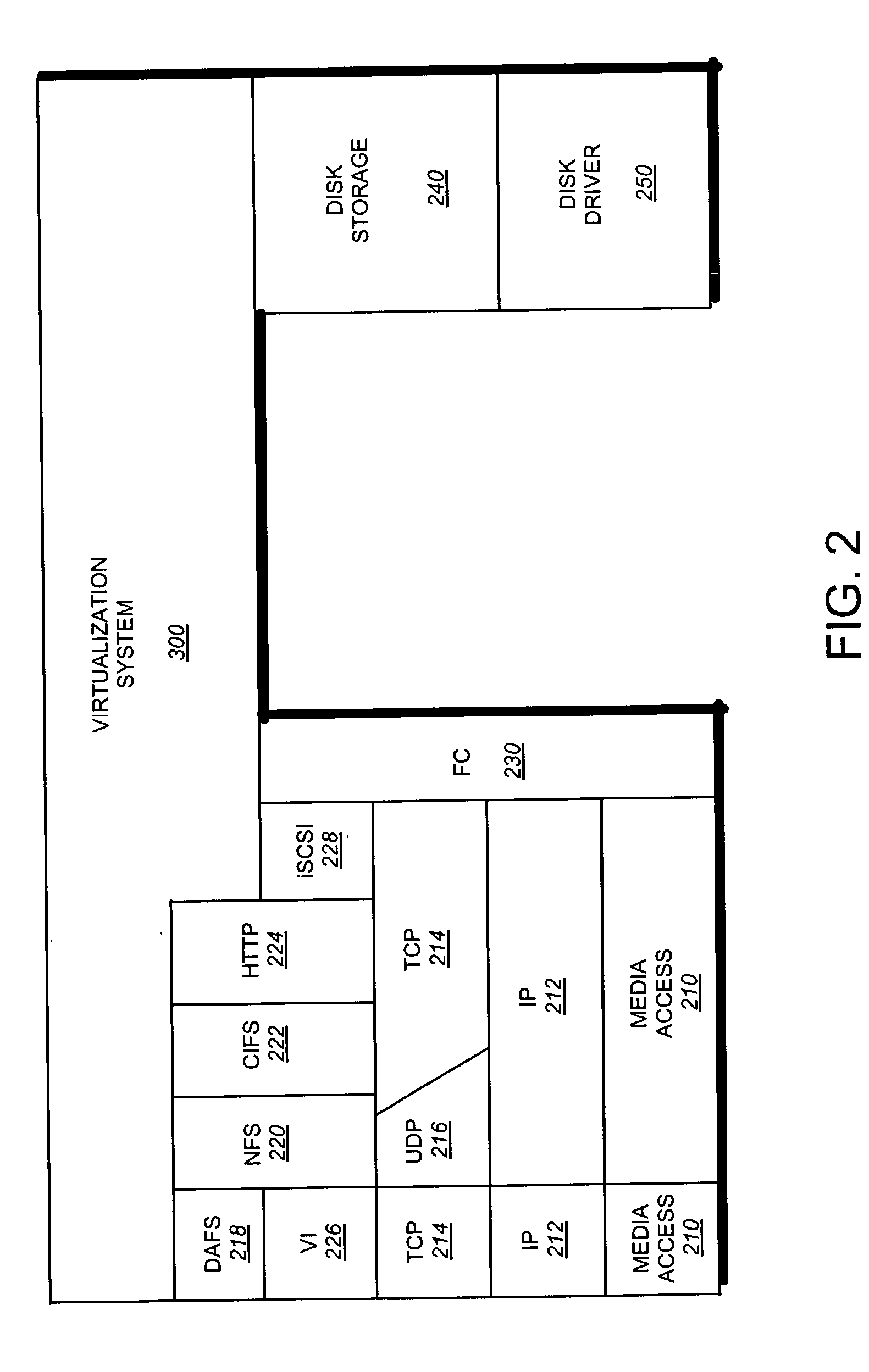
A storage virtualization selection technique “automates” a virtualization selection process to create virtual disk (vdisk) storage objects over a volume of a file system implemented by a storage operating system of a multi-protocol storage appliance. The file system provides a virtualization system that aggregates physical storage of a set of disks or portions (e.g., extents) of disks into a pool of blocks that can be dynamically allocated to form a vdisk. The file system also provides reliability guarantees for the vdisks in accordance with its underlying architecture. That is, the file system organizes its storage within volumes created among the managed disks. The vdisk is thereafter created as a storage object within a volume and, thus, inherits the underlying reliability configuration associated with that volume. The portions are aggregated and allocated as a vdisk with reliability guarantees in response to a request to create the vdisk from a user of the storage appliance and without further user involvement.
Owner:NETWORK APPLIANCE INC
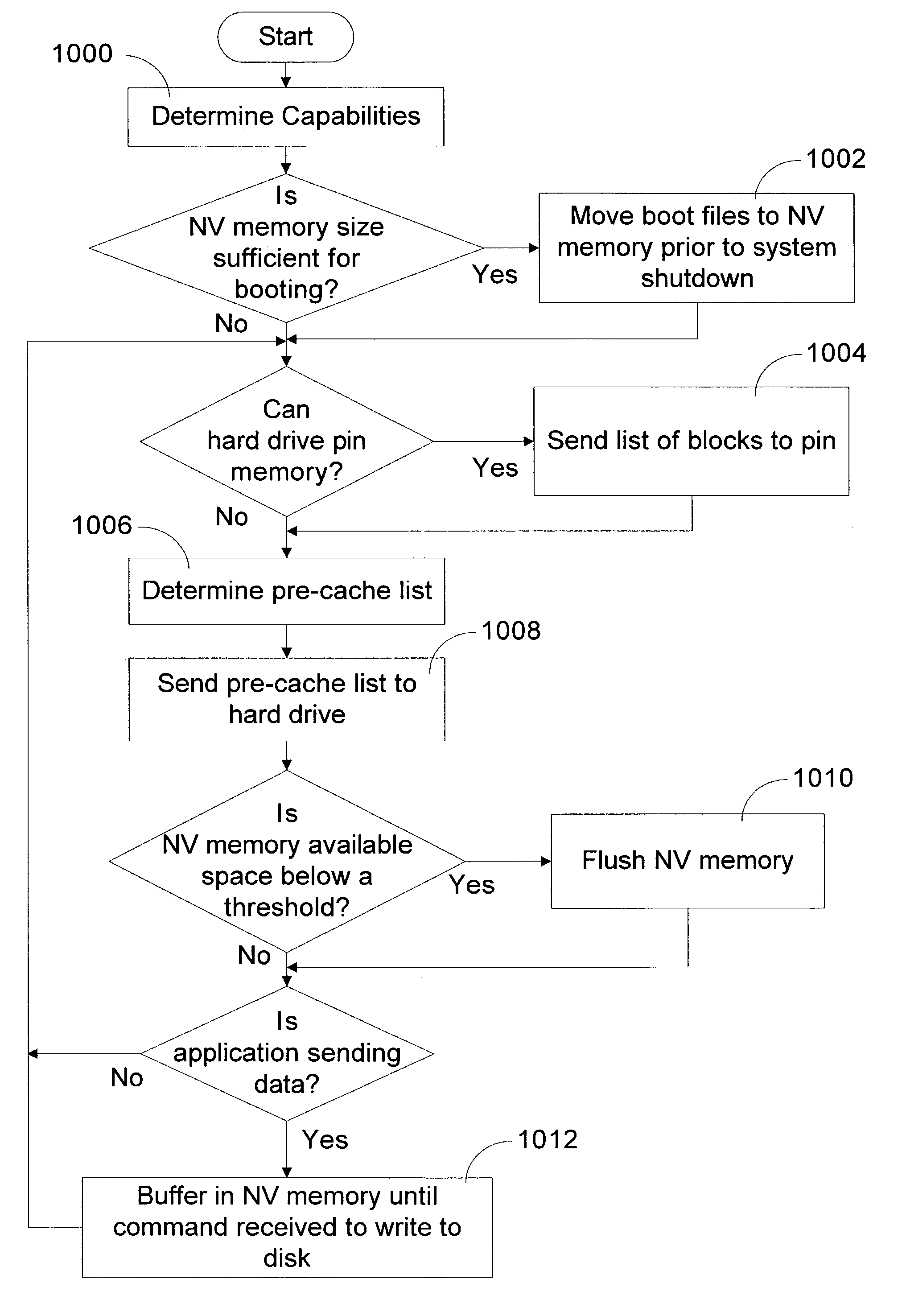
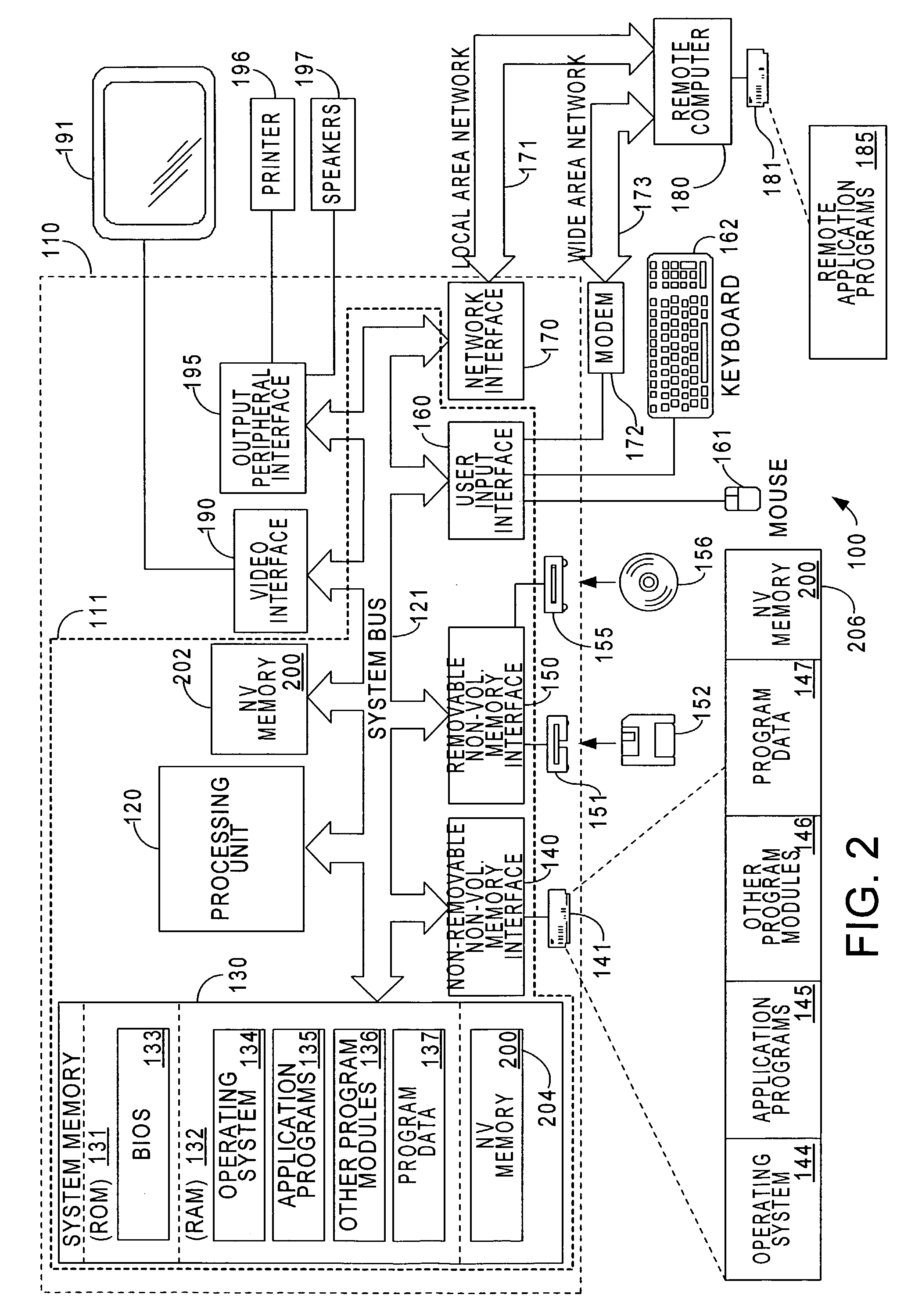
In-line non volatile memory disk read cache and write buffer
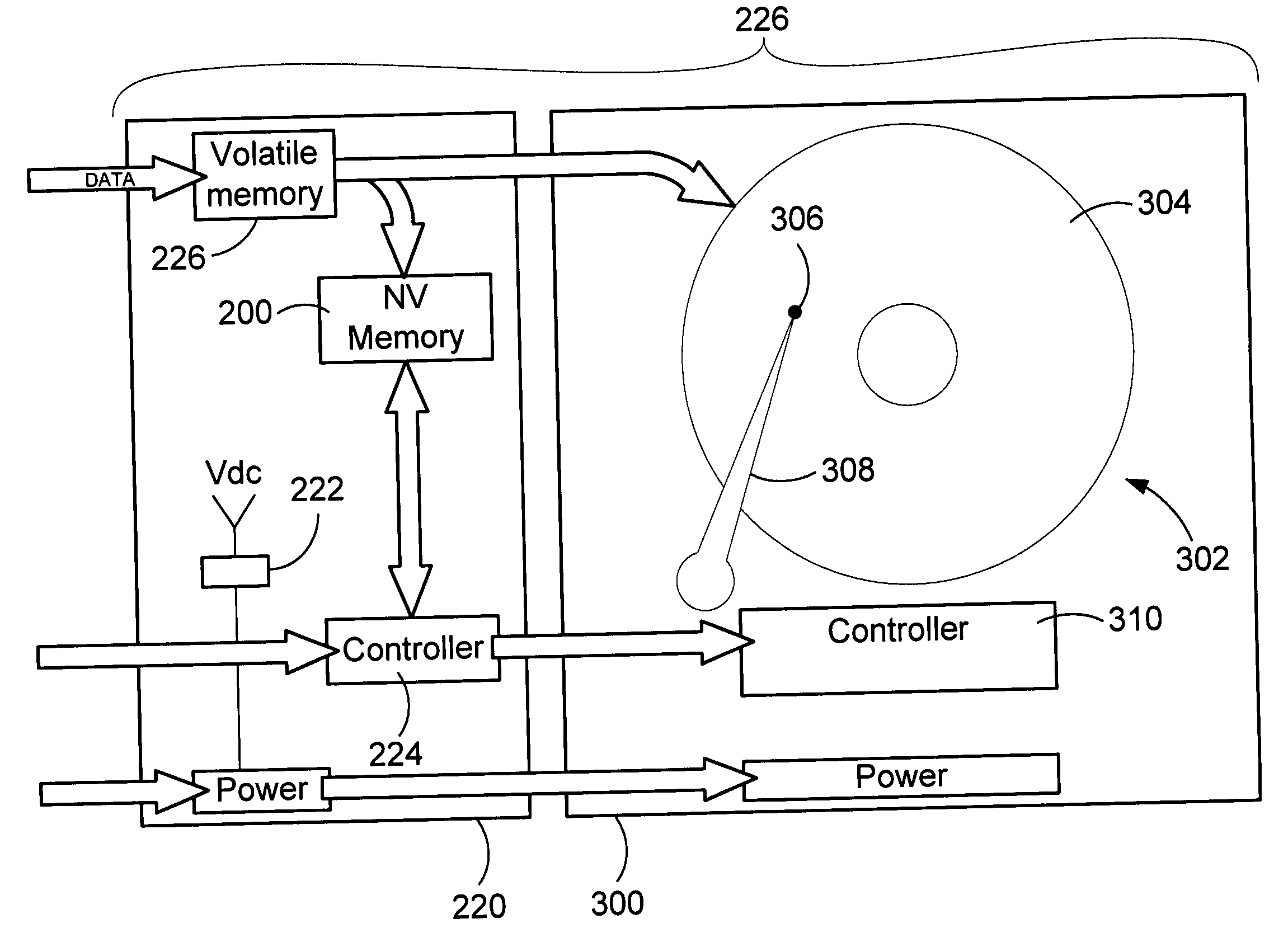
ActiveUS20060248387A1Read/write performance of hardReduce the number of timesData buffering arrangementsError detection/correctionHard disc driveWrite buffer
A method and apparatus to improve the read / write performance of a hard drive is presented. A device having solid state, non-volatile (NV) memory is added in-line to the conventional hard drive and acts as a read / write cache. Data specified by the operating system is stored in the NV memory. The operating system provides a list of data to be put in NV memory. The data includes data to be pinned in NV memory and data that is dynamic. Pinned data persists in NV memory until the operating system commands it to be flushed. Dynamic data can be flushed by the hard drive controller. Data sent by an application for storage is temporarily stored in NV memory in data blocks until the operating system commits it to the disk.
Owner:MICROSOFT TECH LICENSING LLC
Systems, Methods, and Computer Program Products for Instant Recovery of Image Level Backups
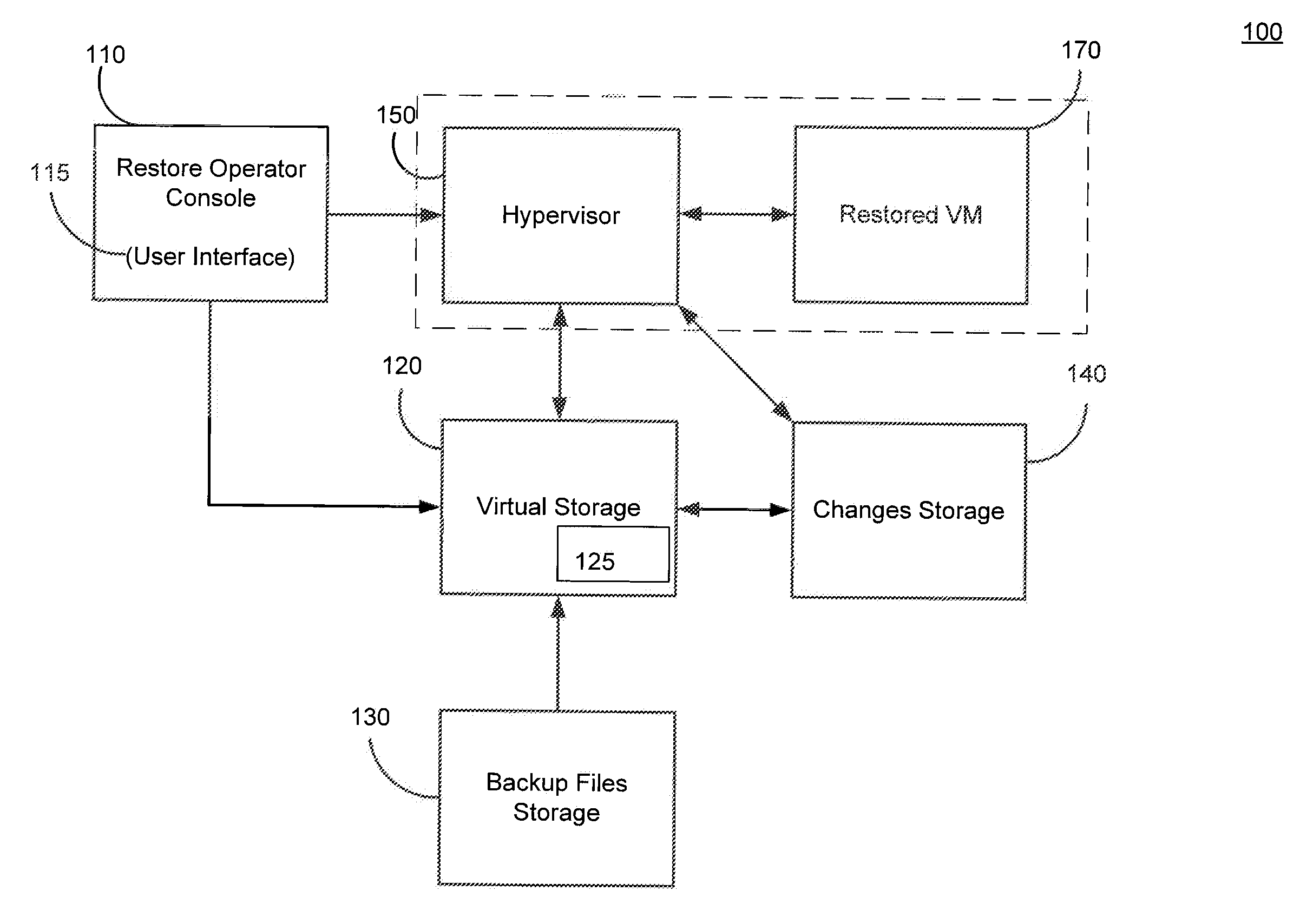
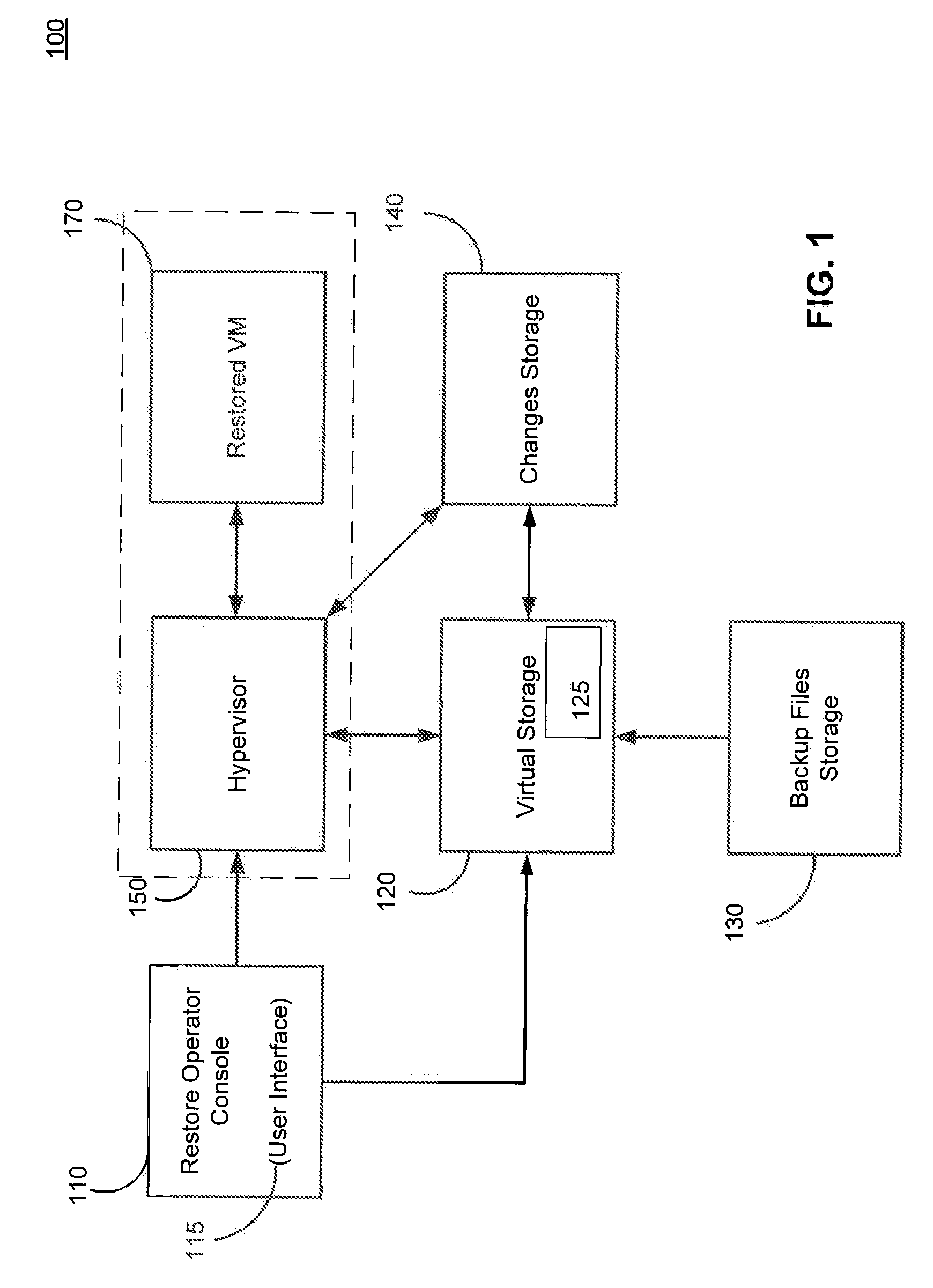
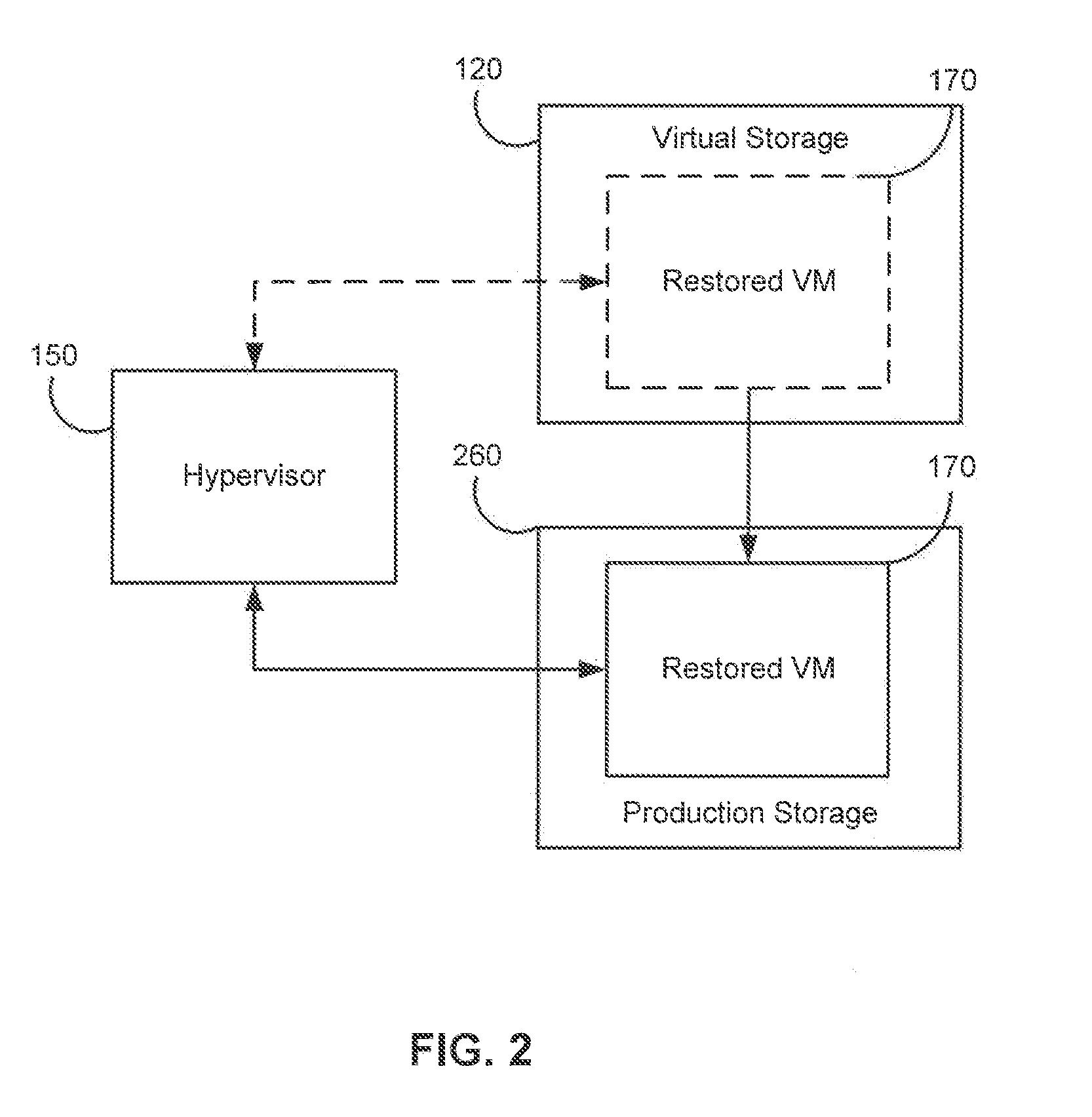
ActiveUS20120017114A1Fault responseSoftware simulation/interpretation/emulationOperational systemDowntime
Systems, methods, and computer program products are provided for instant recovery of a virtual machine (VM) from a compressed image level backup without fully extracting the image level backup file's contents to production storage. The method receives restore parameters and initializes a virtual storage. The method attaches the virtual storage to a hypervisor configured to launch a recovered VM. The method stores virtual disk data changes inflicted by a running operating system (OS), applications, and users in a changes storage. The method provides the ability to migrate the actual VM disk state (taking into account changed disk data blocks accumulated in changes storage) so as to prevent data loss resulting from the VM running during the recovery and accessing virtual storage, to production storage without downtime. In embodiments, the method displays receives restore parameters in an interactive interface and delivers the recovery results via an automated message, such as an email message.
Owner:VEEAM SOFTWARE GROUP GMBH
Method for allocating files in a file system integrated with a raid disk sub-system
A method is disclosed for integrating a file system with a RAID array that exports precise information about the arrangement of data blocks in the RAID subsystem. The file system examines this information and uses it to optimize the location of blocks as they are written to the RAID system. Thus, the system uses explicit knowledge of the underlying RAID disk layout to schedule disk allocation. The method uses separate current-write location (CWL) pointers for each disk in the disk array where the pointers simply advance through the disks as writes occur. The algorithm used has two primary goals. The first goal is to keep the CWL pointers as close together as possible, thereby improving RAID efficiency by writing to multiple blocks in the stripe simultaneously. The second goal is to allocate adjacent blocks in a file on the same disk, thereby improving read back performance. The method satisfies the first goal by always writing on the disk with the lowest CWL pointer. For the second goal, a new disks chosen only when the algorithm starts allocating space for a new file, or when it has allocated N blocks on the same disk for a single file. A sufficient number of blocks is defined as all the buffers in a chunk of N sequential buffers in a file. The result is that CWL pointers are never more than N blocks apart on different disks, and large files have N consecutive blocks on the same disk.
Owner:NETWORK APPLIANCE INC
Secure data storage in raid memory devices
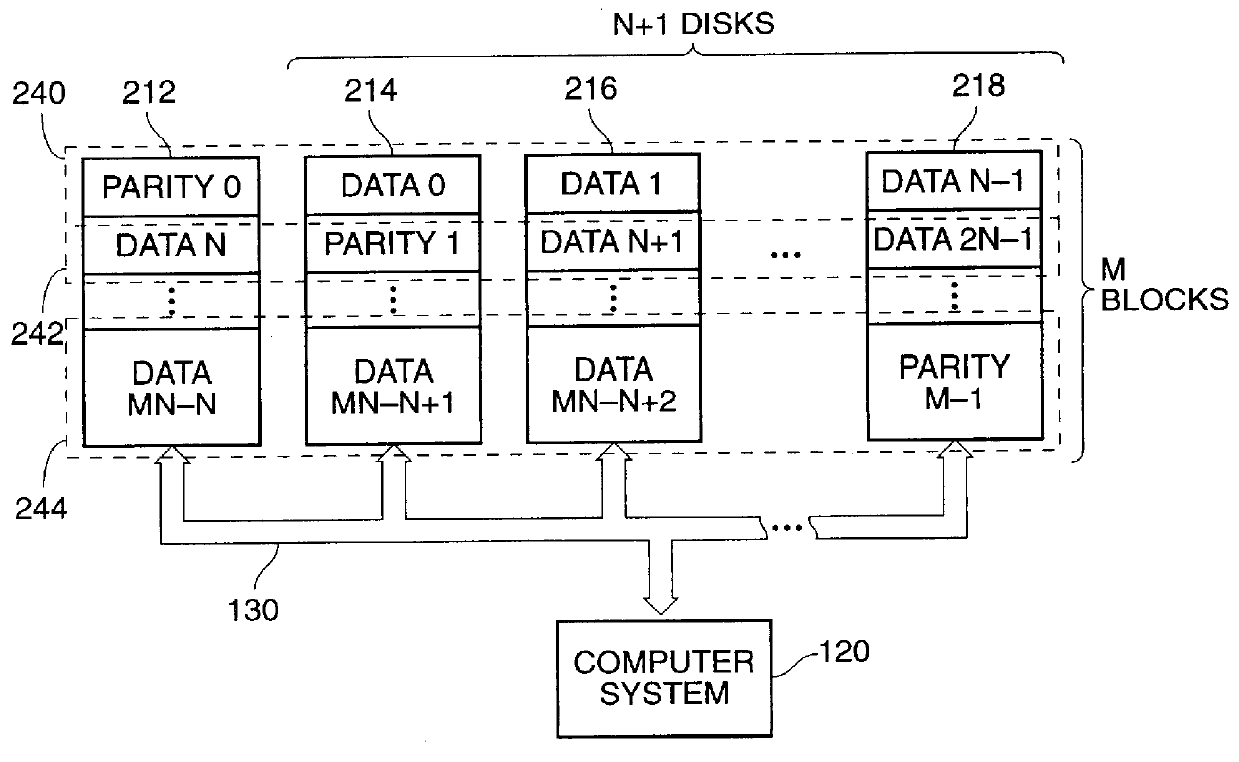
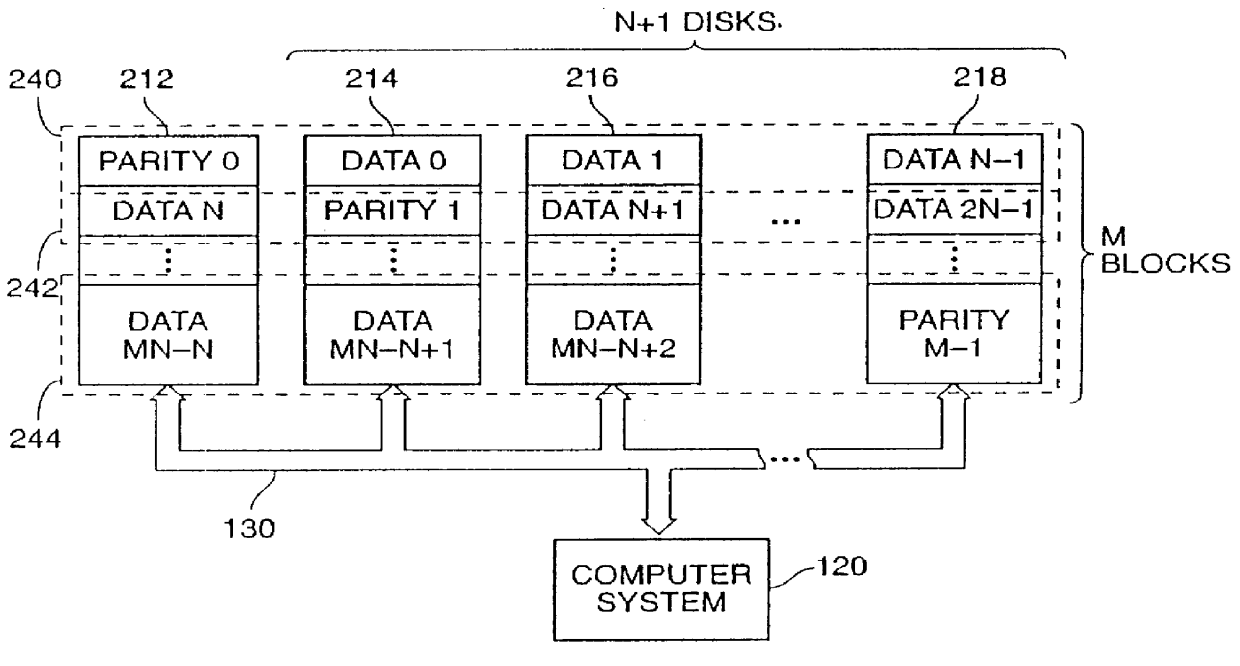
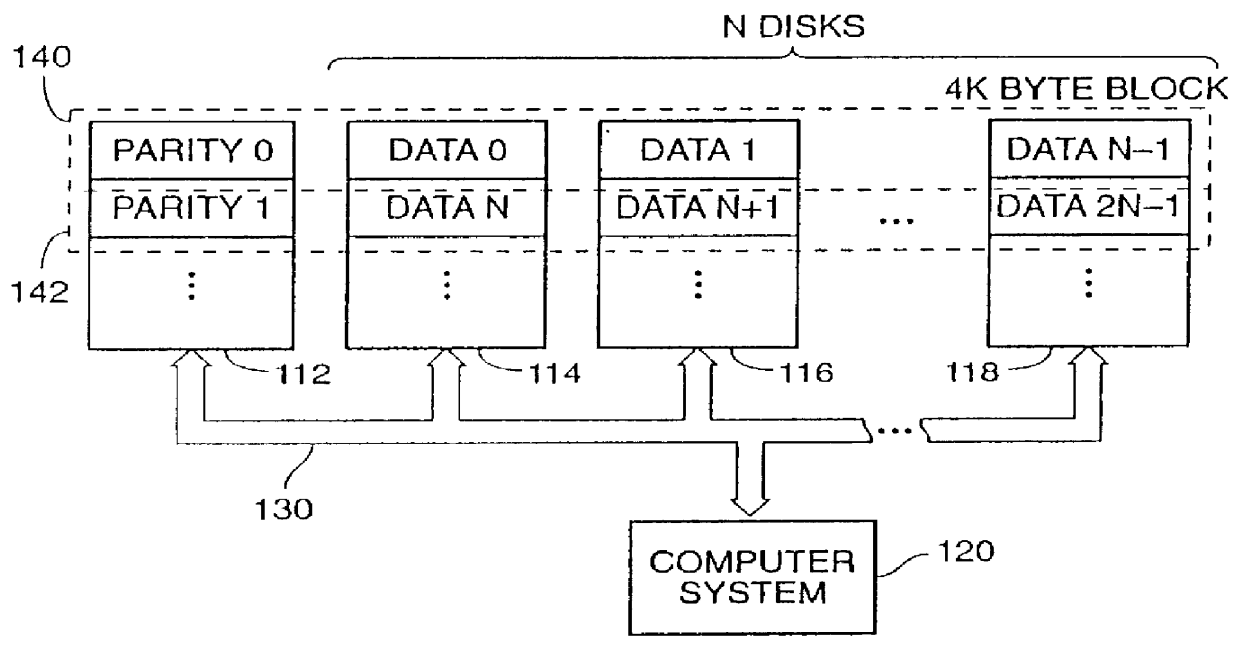
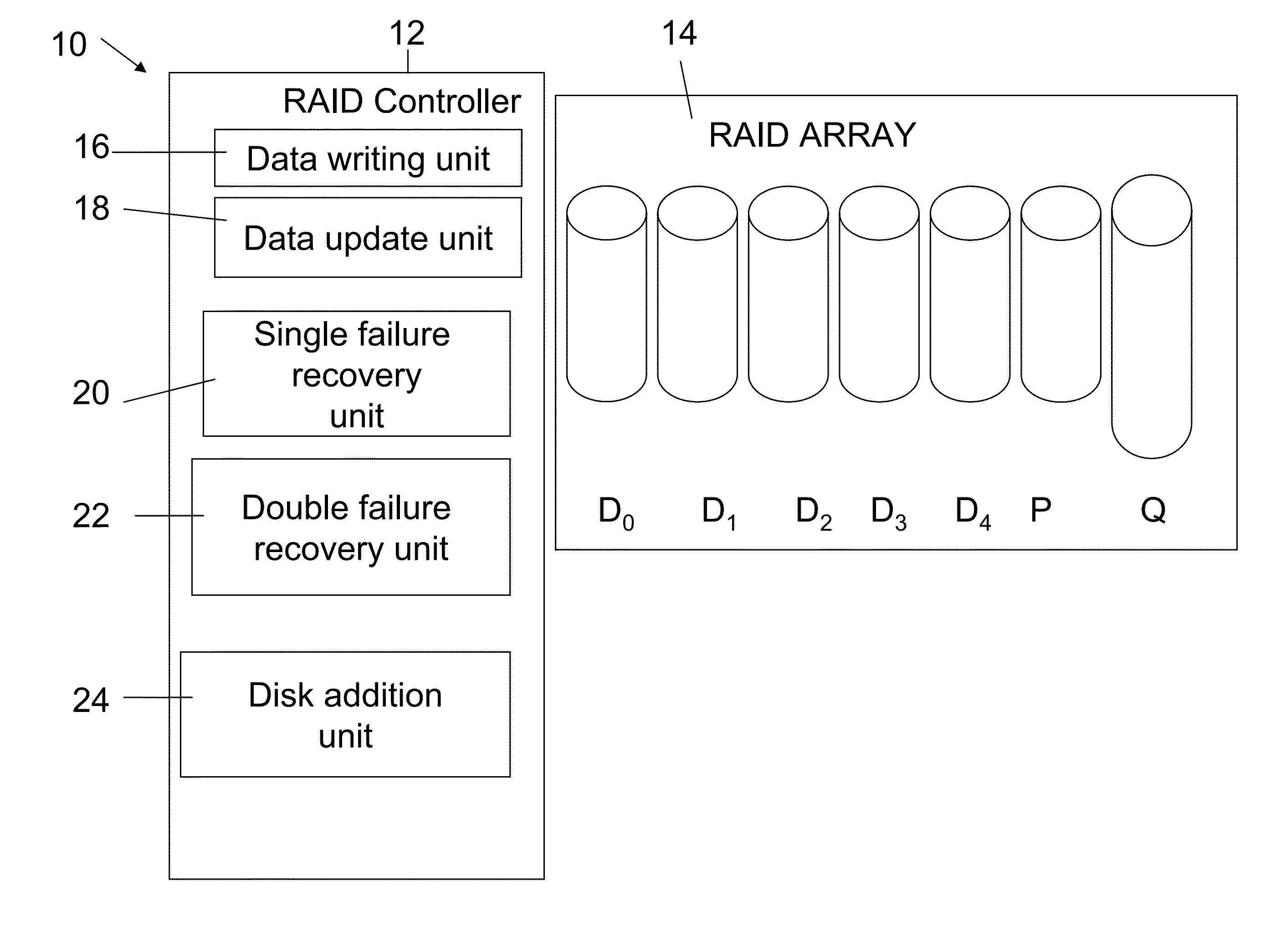
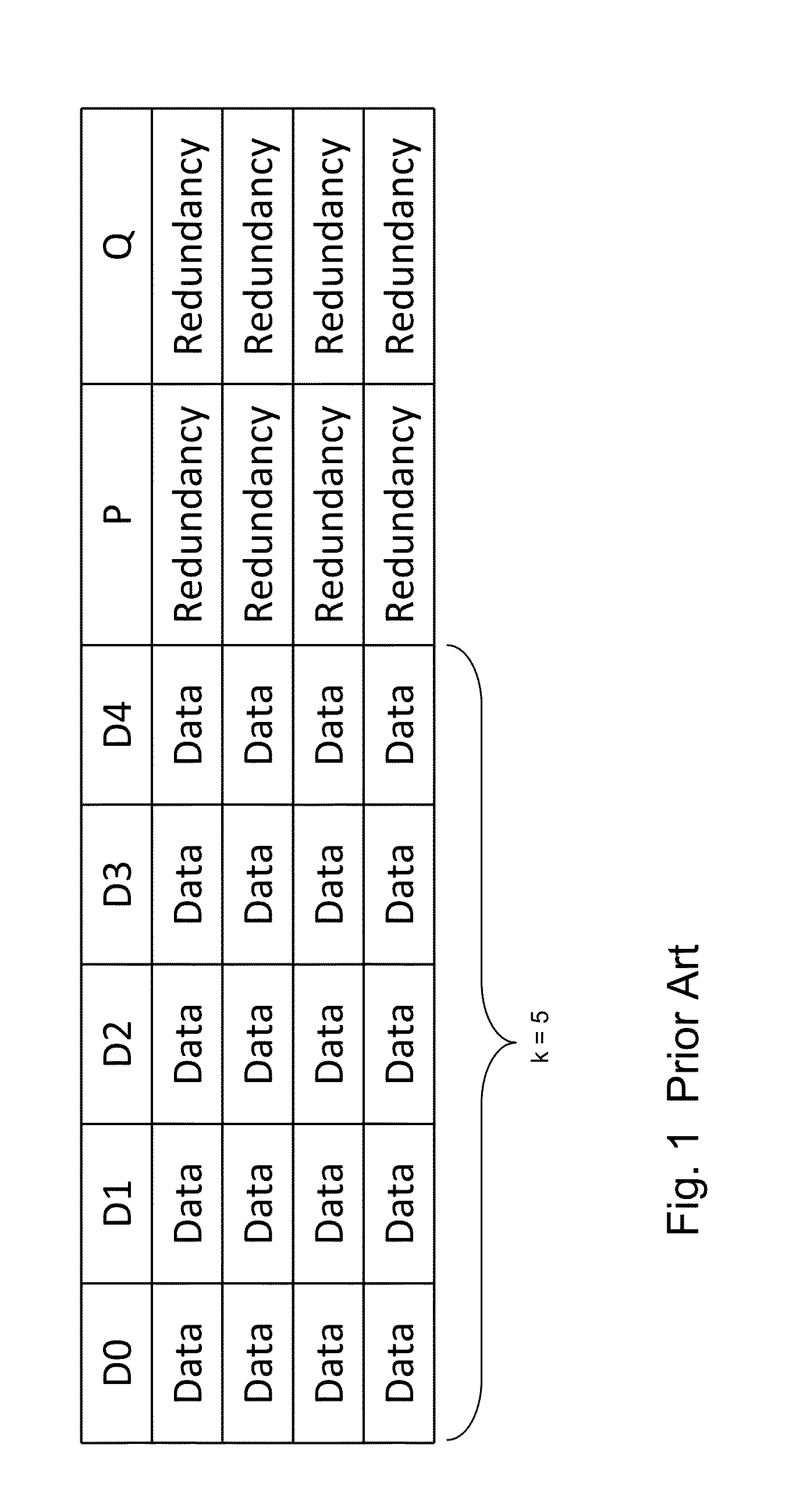
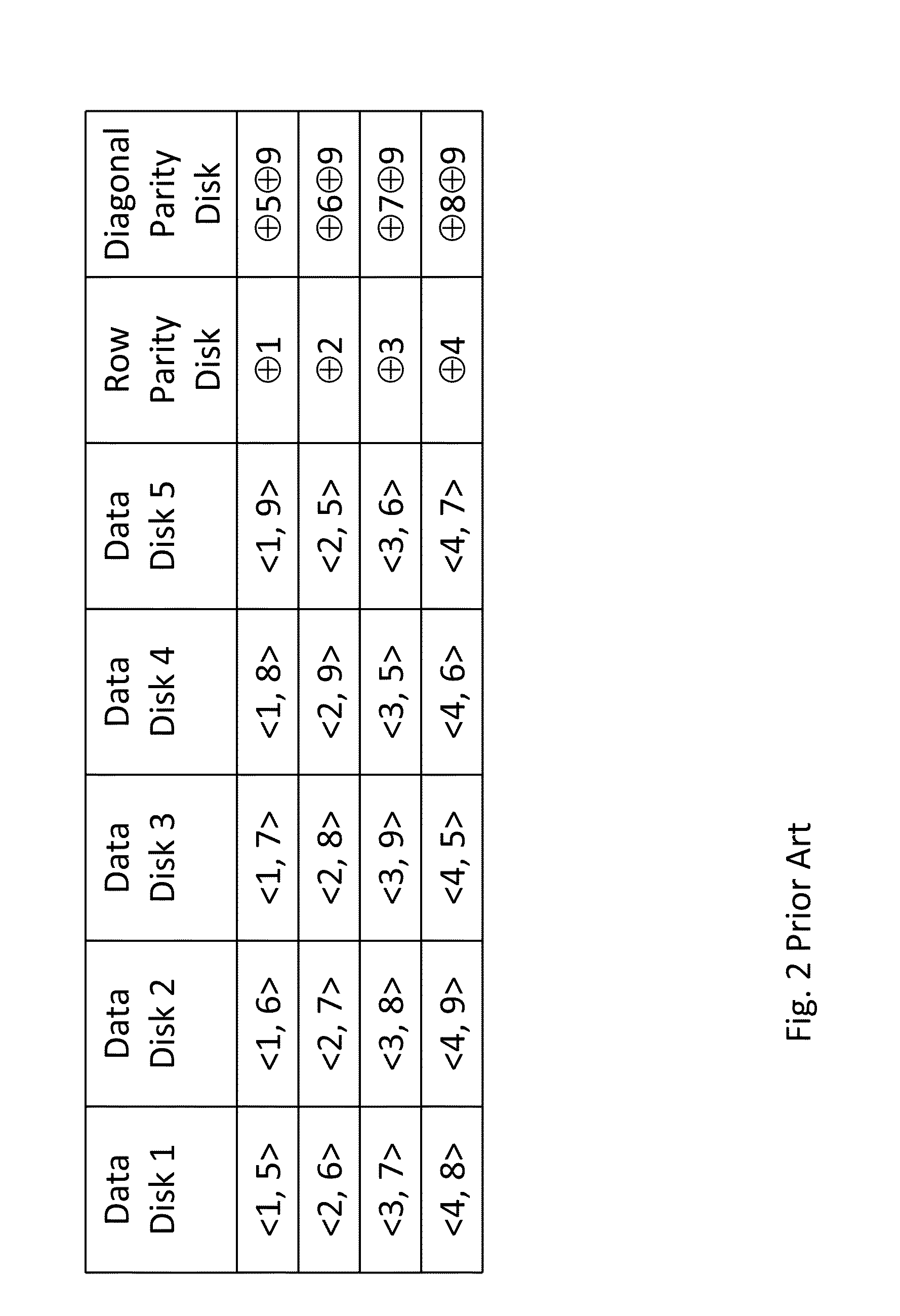
ActiveUS20130124776A1Reduce overheadUtility and advantageMemory loss protectionError detection/correctionRAIDComputer architecture
A redundant array of independent disk (RAID) memory storage system comprising data storage blocks arranged in a first plurality of data rows and a second plurality of data columns, wherein parity data is stored in additionally defined parity blocks, and wherein numbers of data blocks in respective columns are different, to accommodate the additional diagonal parity data block that the geometry of the system requires. The system is suitable for an SSD array in which sequential disk readout is not required.
Owner:EMC IP HLDG CO LLC
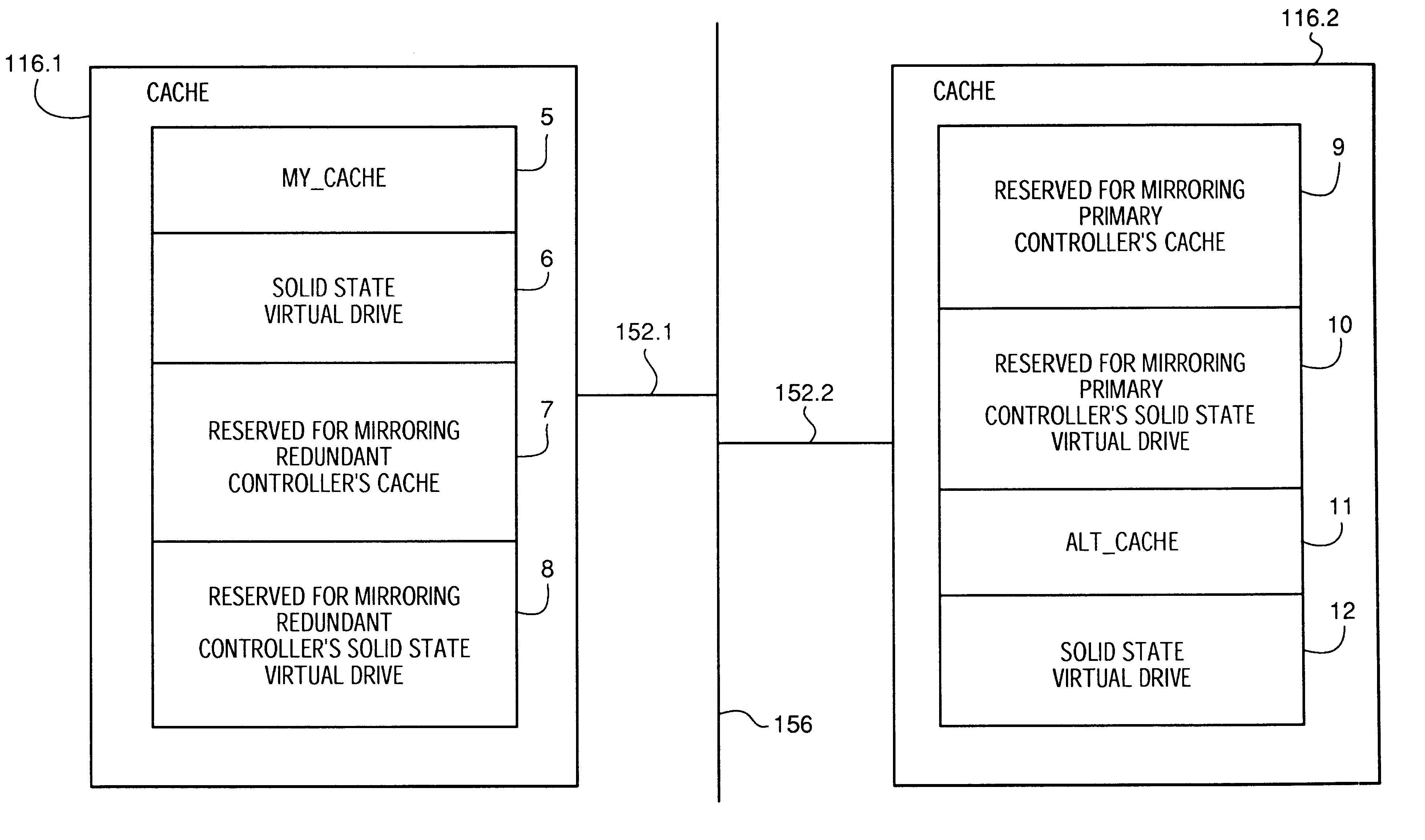
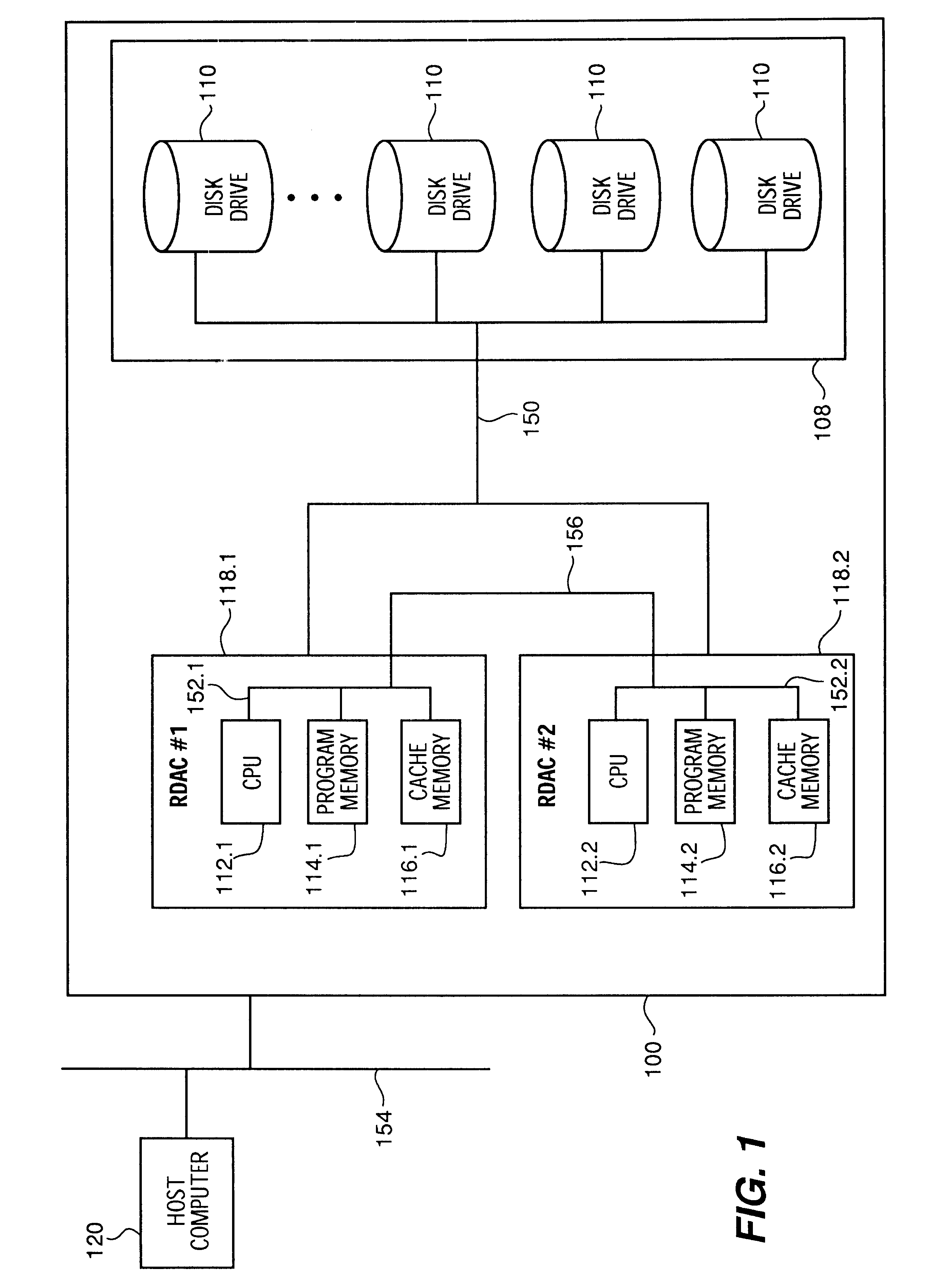
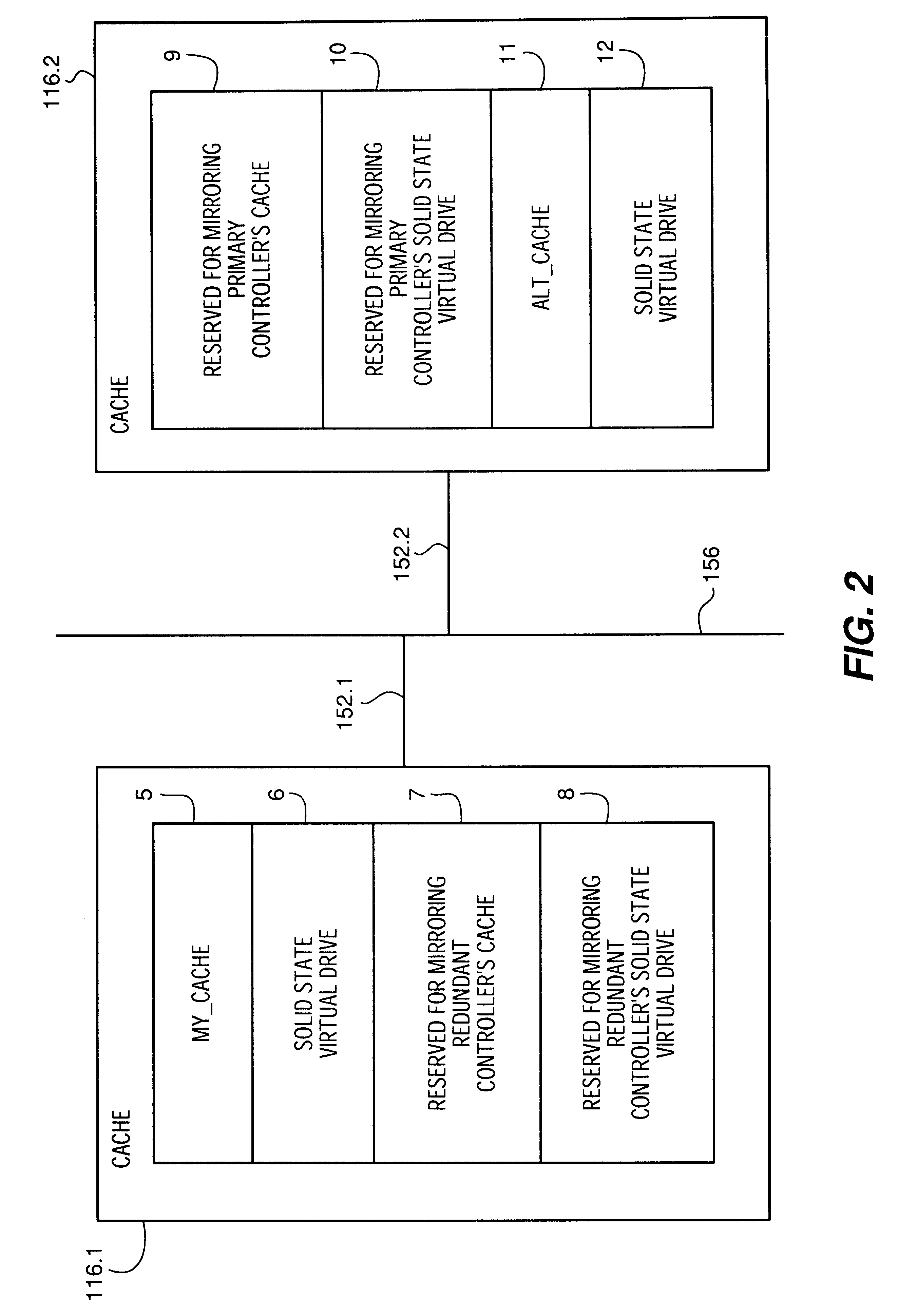
Apparatus and method to provide virtual solid state disk in cache memory in a storage controller
InactiveUS6567889B1Reduce in quantityImprove I/O performanceMemory architecture accessing/allocationInput/output to record carriersRAIDControl store
A portion of a storage controller's cache memory is used as a virtual solid state disk storage device to improve overall storage subsystem performance. In a first embodiment, the virtual solid state disk storage device is a single virtual disk drive for storing controller based information. In the first embodiment, the virtual solid state disk is reserved for use by the controller. In a second embodiment, a hybrid virtual LUN is configured as one or more virtual solid state disks in conjunction with one or more physical disks and managed using RAID levels 1-6. Since the hybrid virtual LUN is in the cache memory of the controller, data access times are reduced and throughput is increased by reduction of the RAID write penalty. The hybrid virtual LUN provides write performance that is typical of RAID 0. In a third embodiment, a high-speed virtual LUN is configured as a plurality of virtual solid state disks and managed as an entire virtual RAID LUN. Standard battery backup and redundant controller features of RAID controller technology ensure virtual solid state disk storage device non-volatility and redundancy in the event of controller failures.
Owner:NETWORK APPLIANCE INC
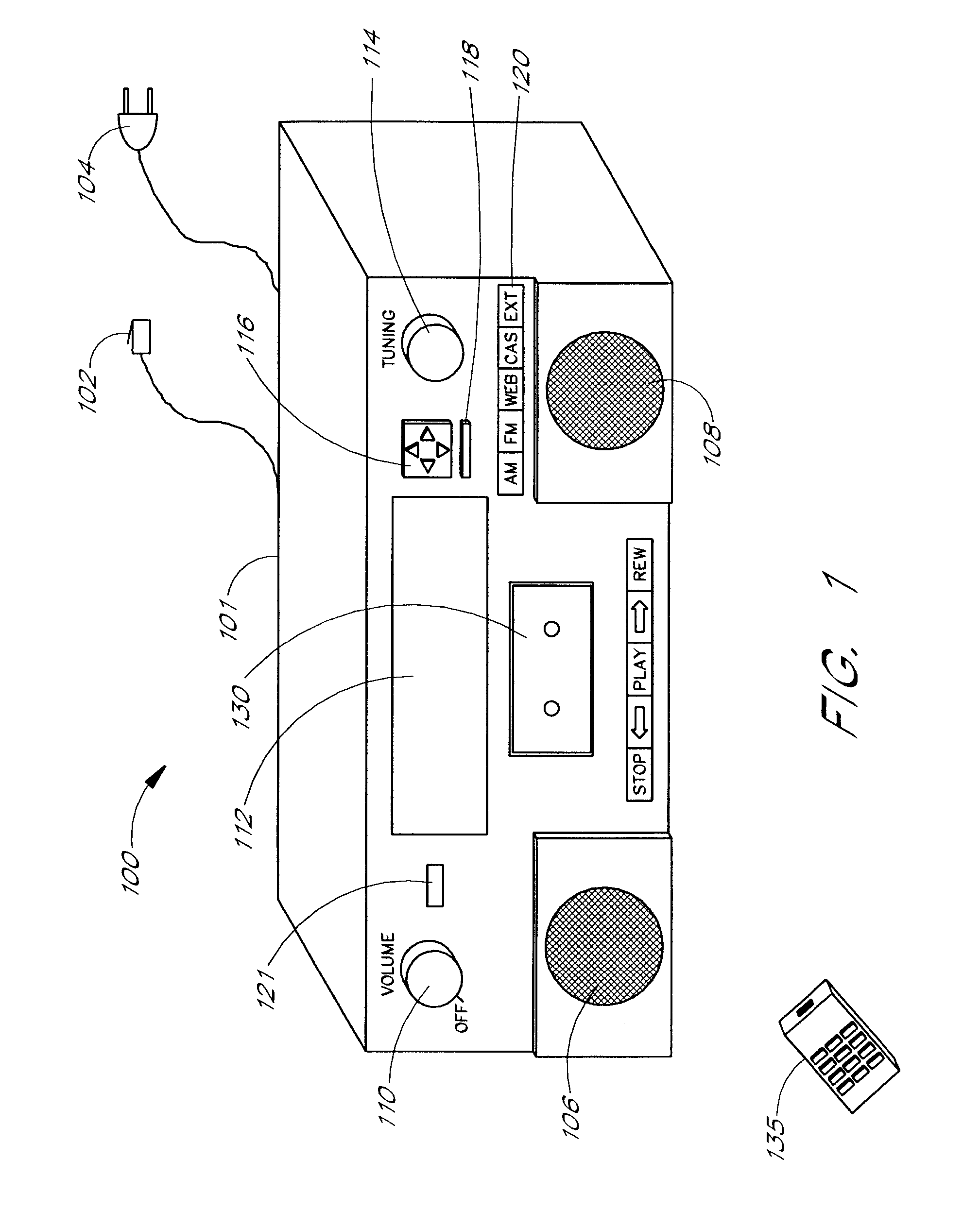
Network-enabled audio device
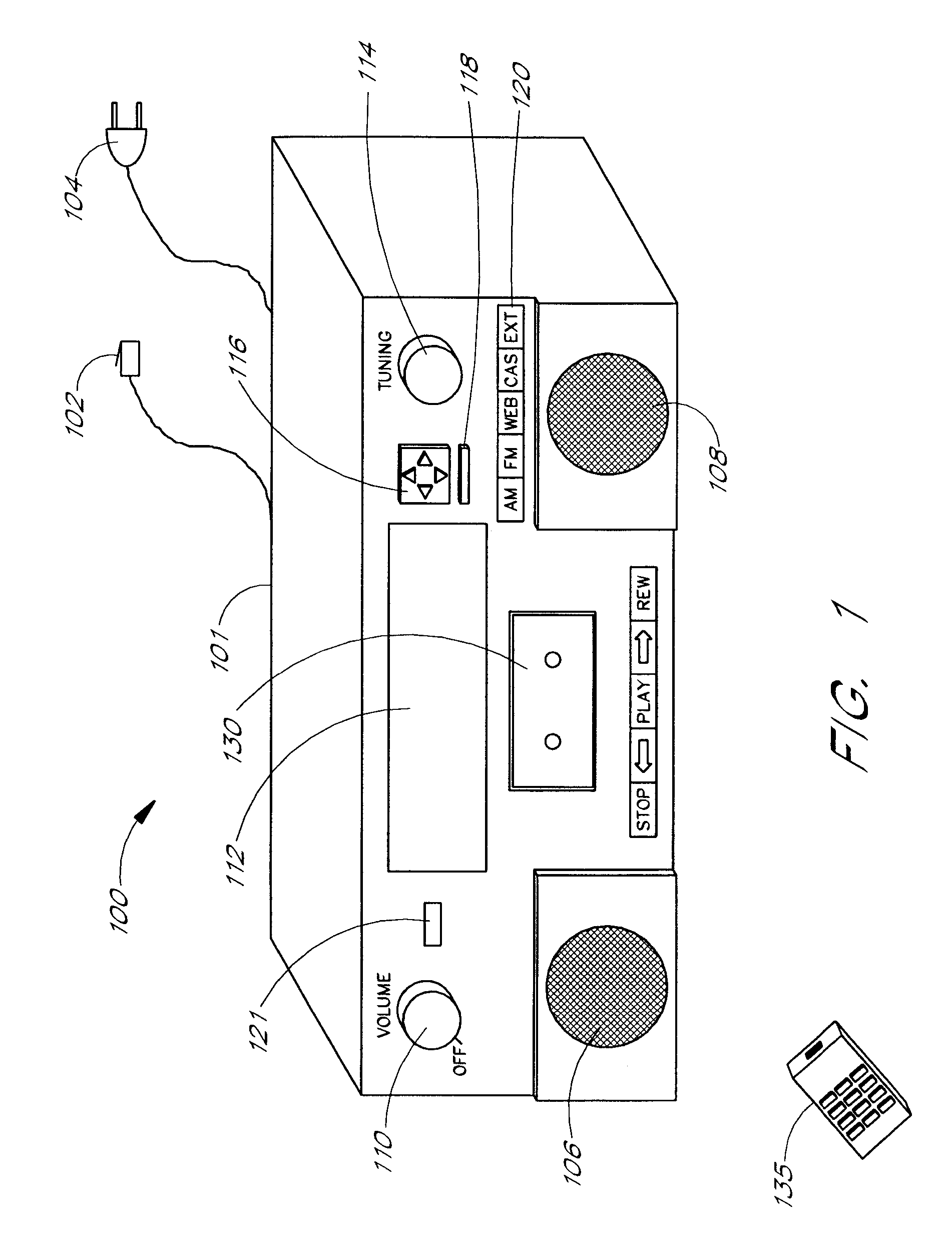
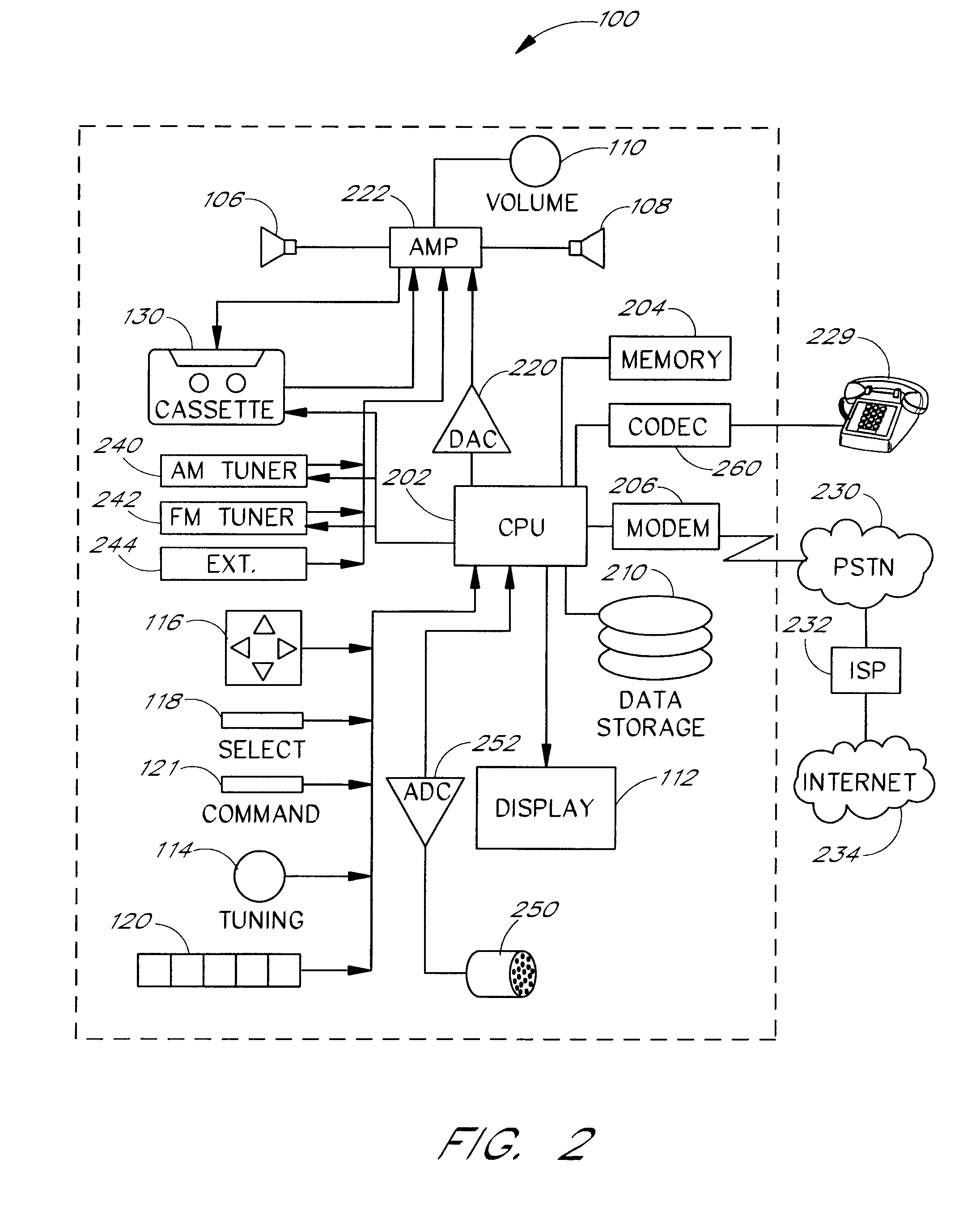
InactiveUS20070089132A1Optimize allocationReception of a broadcast from the World Wide Web is no more complicatedTelevision system detailsGain controlThe InternetDisplay device
A network-enabled audio device that provides a display device that allows the user to select playlists of music much like a jukebox is disclosed. The user can compose playlists from disk files, CD's, Internet streaming audio broadcasts, online music sites, and other audio sources. The user can also select a desired Web broadcast from a list of available Web broadcasts. In addition, the user can play standard audio CD's and MP3 encoded CD's and have access to local AM / FM stations. Further, the software, the user controls, and the display in the network-enabled audio device are operably configured and connected such that the user can listen to playlists that include CD's and other audio sources just as the user would choose a playlist in a jukebox. The user accesses a server site via a PC and the Internet. From the server site, the user obtains a list of the devices in his or her Internet Personal Audio Network (IPAN) and what songs are on those devices. The IPAN includes an IPAN server, an IPAN client, and IPAN software stored on the network-enabled audio device. Thus, the network-enabled audio device provides people who are or are not comfortable with computers a way of taking music from various sources and putting it into one place for listening pleasure. In one embodiment, the Personal Computer (PC) is used to compose the playlists, but the user is able to listen to playlists and other audio sources without using the PC.
Owner:GOLDEN IP LLC
Removable disk storage array emulating tape library having backup and archive capability
InactiveUS6957291B2Enhance system functionsLow costInput/output to record carriersError detection/correctionData connectionHard disc drive
A hard disk drive based data archive system emulating a tape archive system includes a hot pluggable multi-drive magazine having a housing for holding a plurality of hard disk drives, each drive connected to receive power and data from the magazine in a controlled fashion, and at least one magazine receiving system for physically receiving the magazine and for thereupon providing power, data and control connections to the magazine, such that when the magazine is received within the magazine receiving system, the hard disk drives selectively receive power and data connections via the magazine and receiving system from a host computer. The magazine may be hot-disconnected from an active computing system environment and removed to an archive rack wherein each disk drive is periodically checked to ensure functionality and to provide some limited-bandwidth data retrieval functions via a network connection to the archive rack. A file mark structure enables a disk drive in the magazine to emulate functionality of a tape cartridge.
Owner:QUANTUM CORP
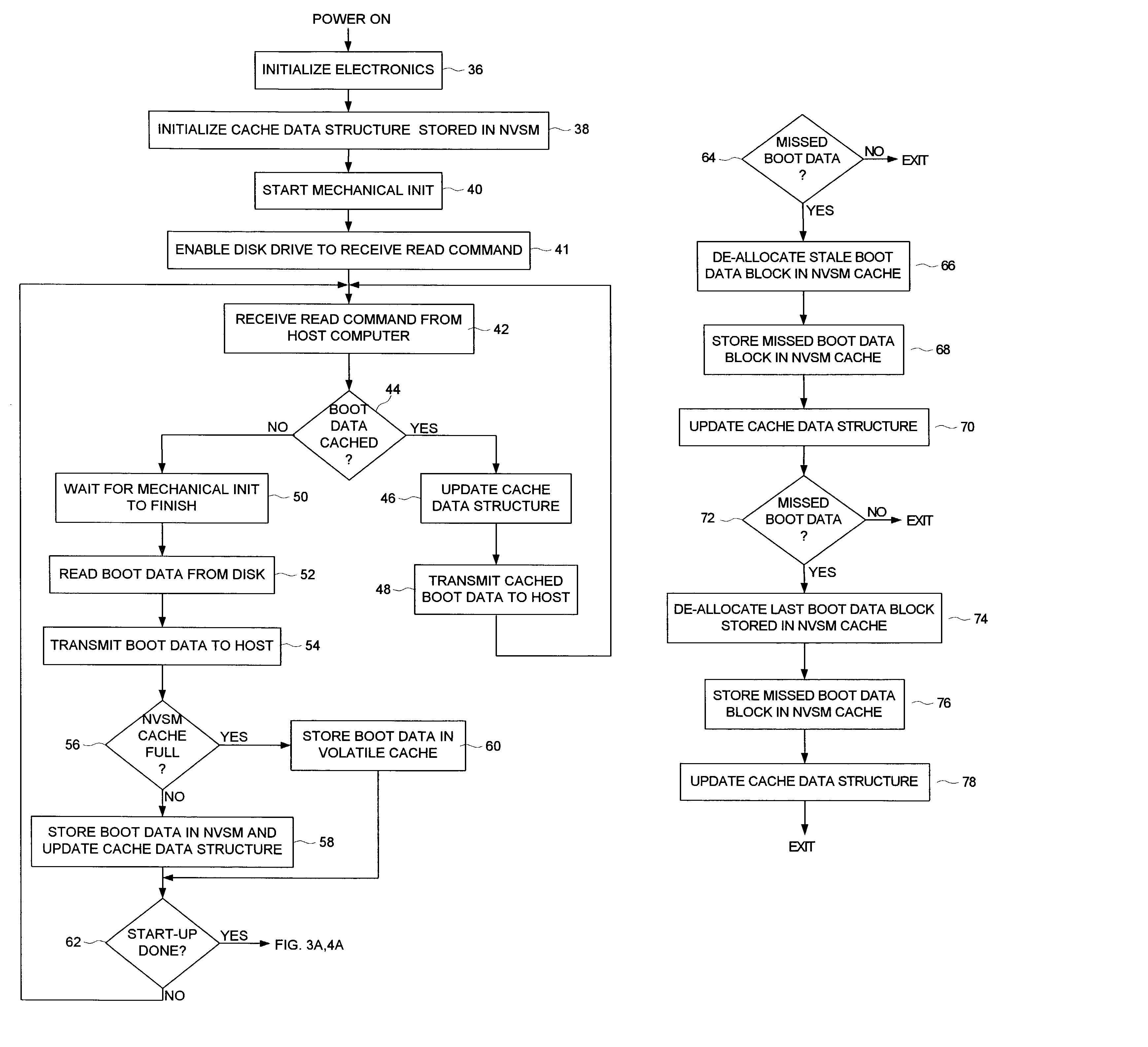
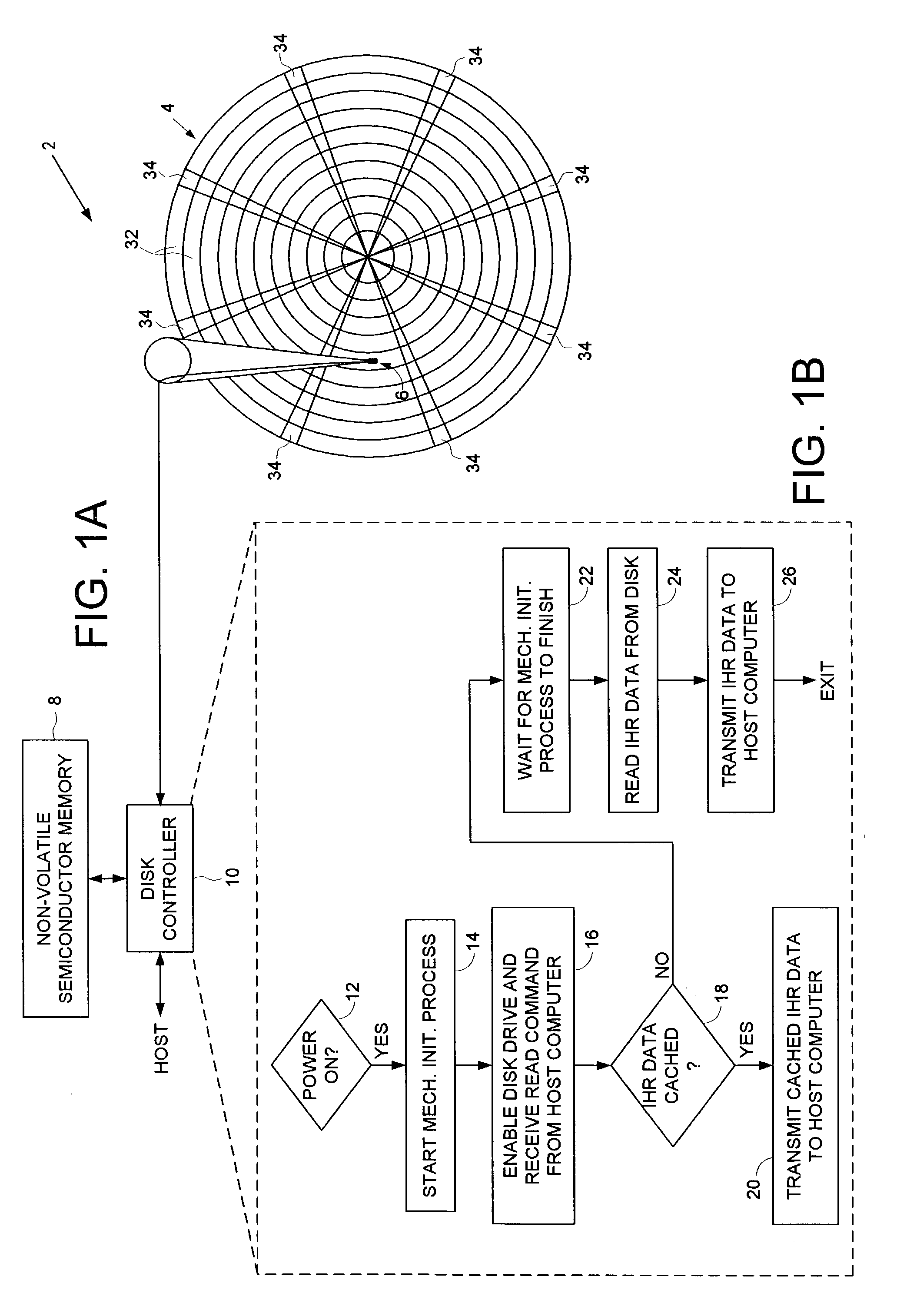
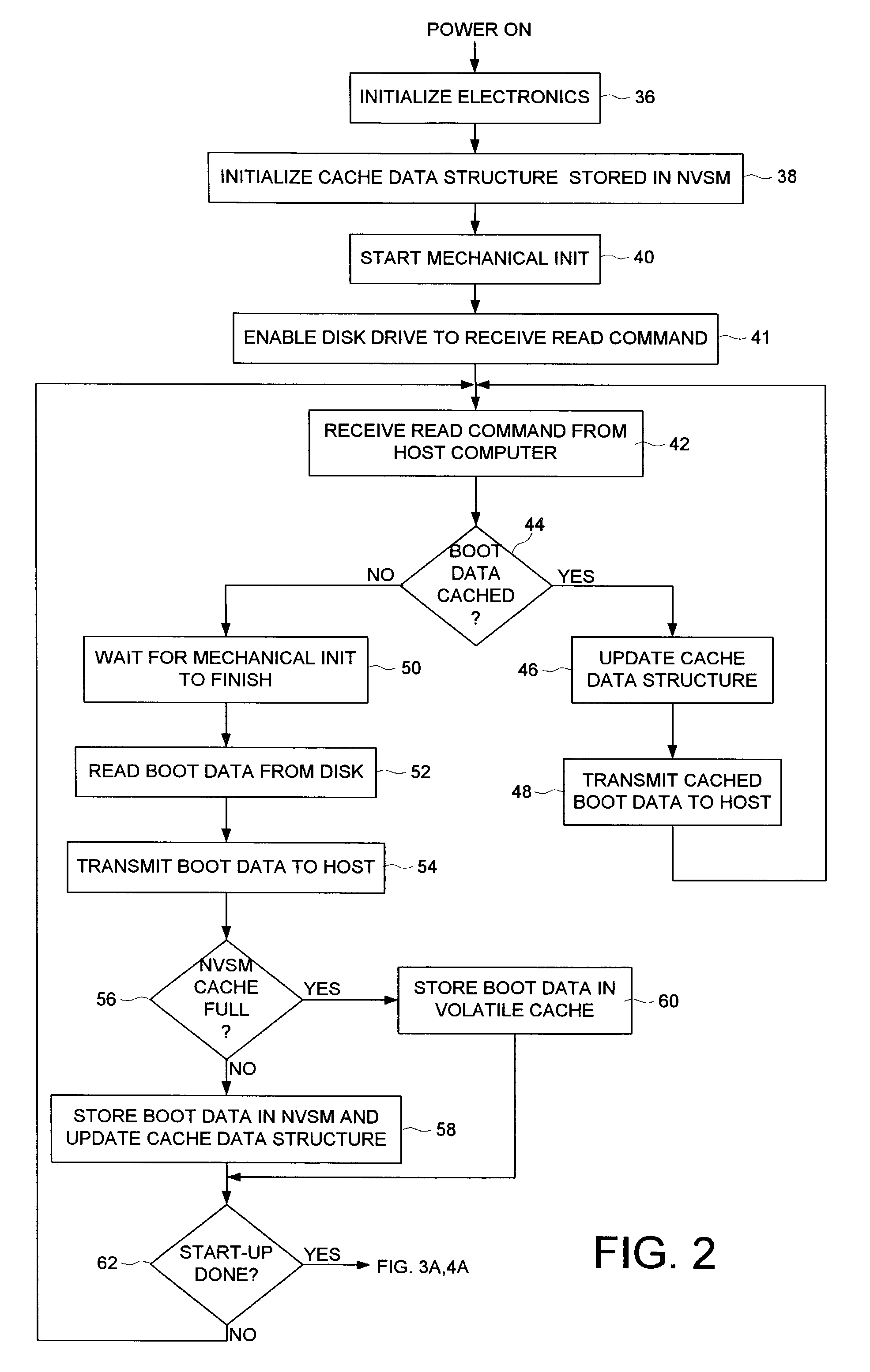
Disk drive caching initial host requested data in non-volatile semiconductor memory to reduce start-up time of a host computer
A disk drive is disclosed comprising a disk for storing initial host requested (IHR) data requested by a host computer during a start-up process of the host computer, a head actuated radially over the disk, and a non-volatile semiconductor memory (NVSM) for caching at least part of the IHR data. The disk drive transmits the cached IHR data from the NVSM to the host computer during the start-up process thereby avoiding the delay associated with initializing the mechanics of the disk drive as well as conserving battery power for mobile applications.
Owner:WESTERN DIGITAL TECH INC
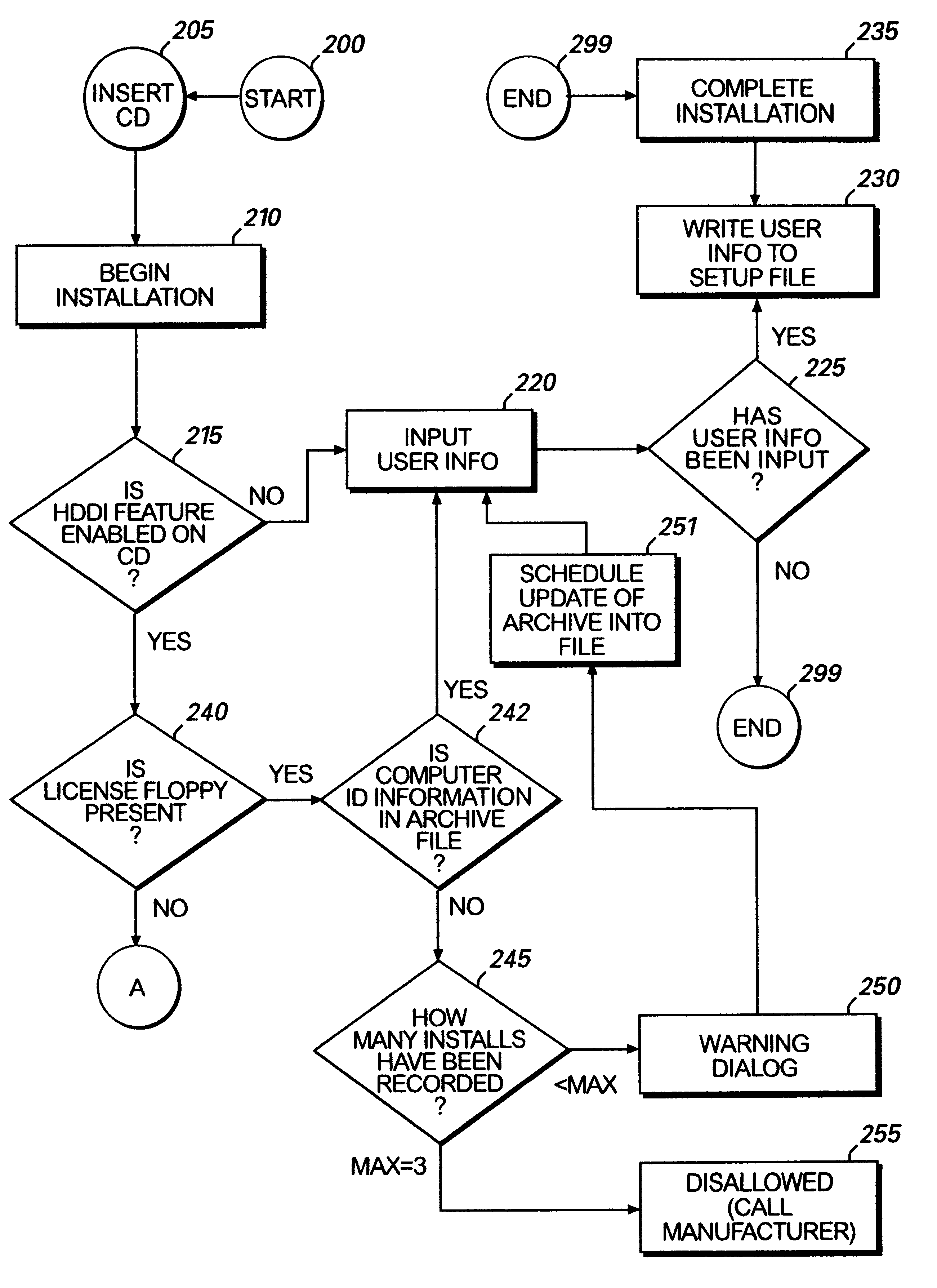
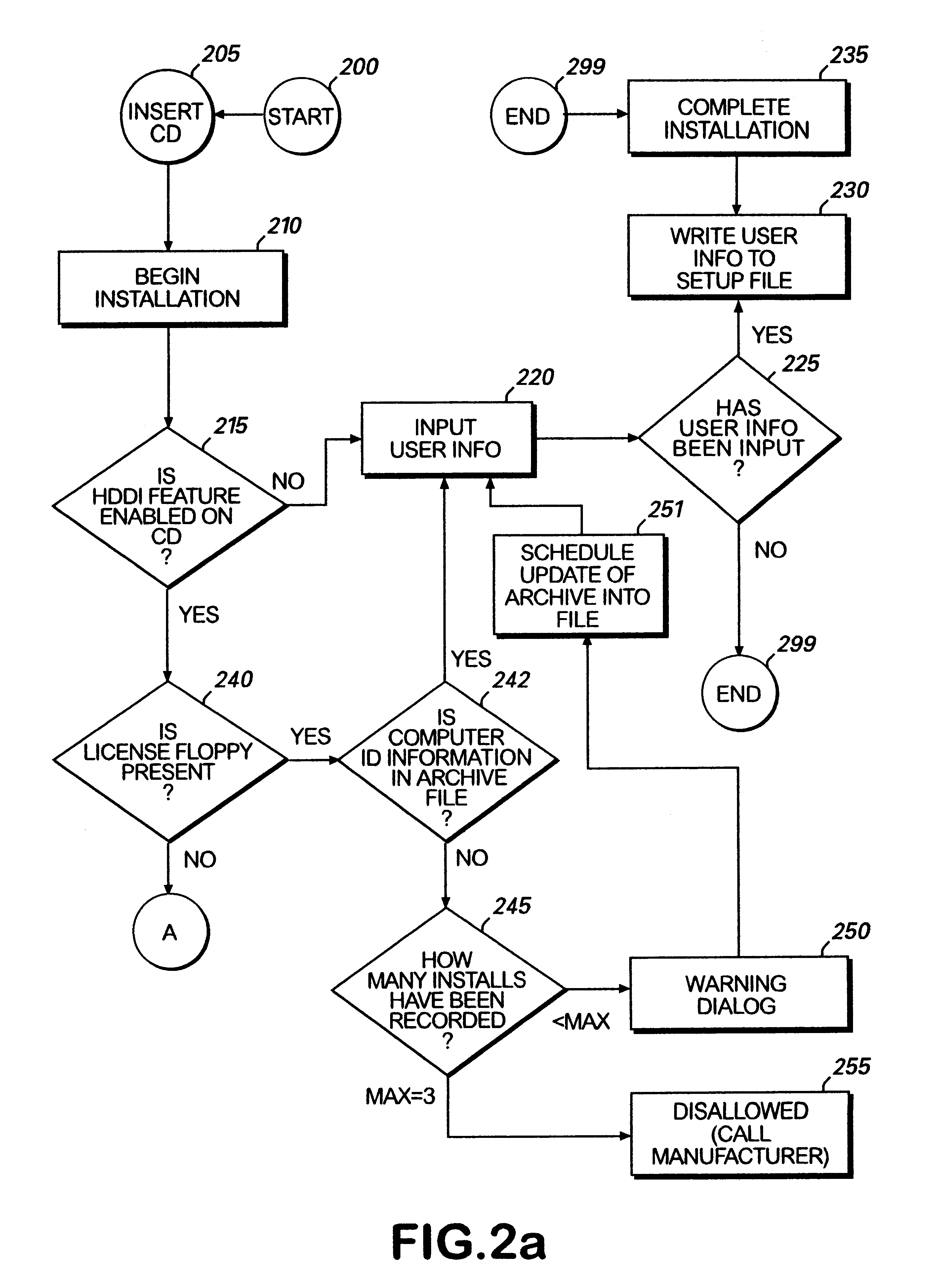
Method for preventing software piracy during installation from a read only storage medium
InactiveUS6226747B1Easy to installDigital data processing detailsRecord information storageSoftware licenseComputer software
The method and system for limiting the number of installations of a computer software program located on a read only disk from the read only disk to a computer. The read only disk is linked to a removable read / write memory by data on the removable read / write memory corresponding to data on the read only disk. Prior to installation of the computer software program from the read only disk to the computer, software residing on the removable read / write memory determines whether the installation is authorized. Such determination is made by comparing identification information corresponding to computers on to which the computer software program has previously been installed to installation limitations dictated by a software license agreement.
Owner:MICROSOFT TECH LICENSING LLC
Network-enabled audio device
InactiveUS20070089135A1Reception of a broadcast from the World Wide Web is no more complicatedOptimize allocationTelevision system detailsGain controlThe InternetDisplay device
A network-enabled audio device that provides a display device that allows the user to select playlists of music much like a jukebox is disclosed. The user can compose playlists from disk files, CD's, Internet streaming audio broadcasts, online music sites, and other audio sources. The user can also select a desired Web broadcast from a list of available Web broadcasts. In addition, the user can play standard audio CD's and MP3 encoded CD's and have access to local AM / FM stations. Further, the software, the user controls, and the display in the network-enabled audio device are operably configured and connected such that the user can listen to playlists that include CD's and other audio sources just as the user would choose a playlist in a jukebox. The user accesses a server site via a PC and the Internet. From the server site, the user obtains a list of the devices in his or her Internet Personal Audio Network (IPAN) and what songs are on those devices. The IPAN includes an IPAN server, an IPAN client, and IPAN software stored on the network-enabled audio device. Thus, the network-enabled audio device provides people who are or are not comfortable with computers a way of taking music from various sources and putting it into one place for listening pleasure. In one embodiment, the Personal Computer (PC) is used to compose the playlists, but the user is able to listen to playlists and other audio sources without using the PC.
Owner:GOLDEN IP LLC
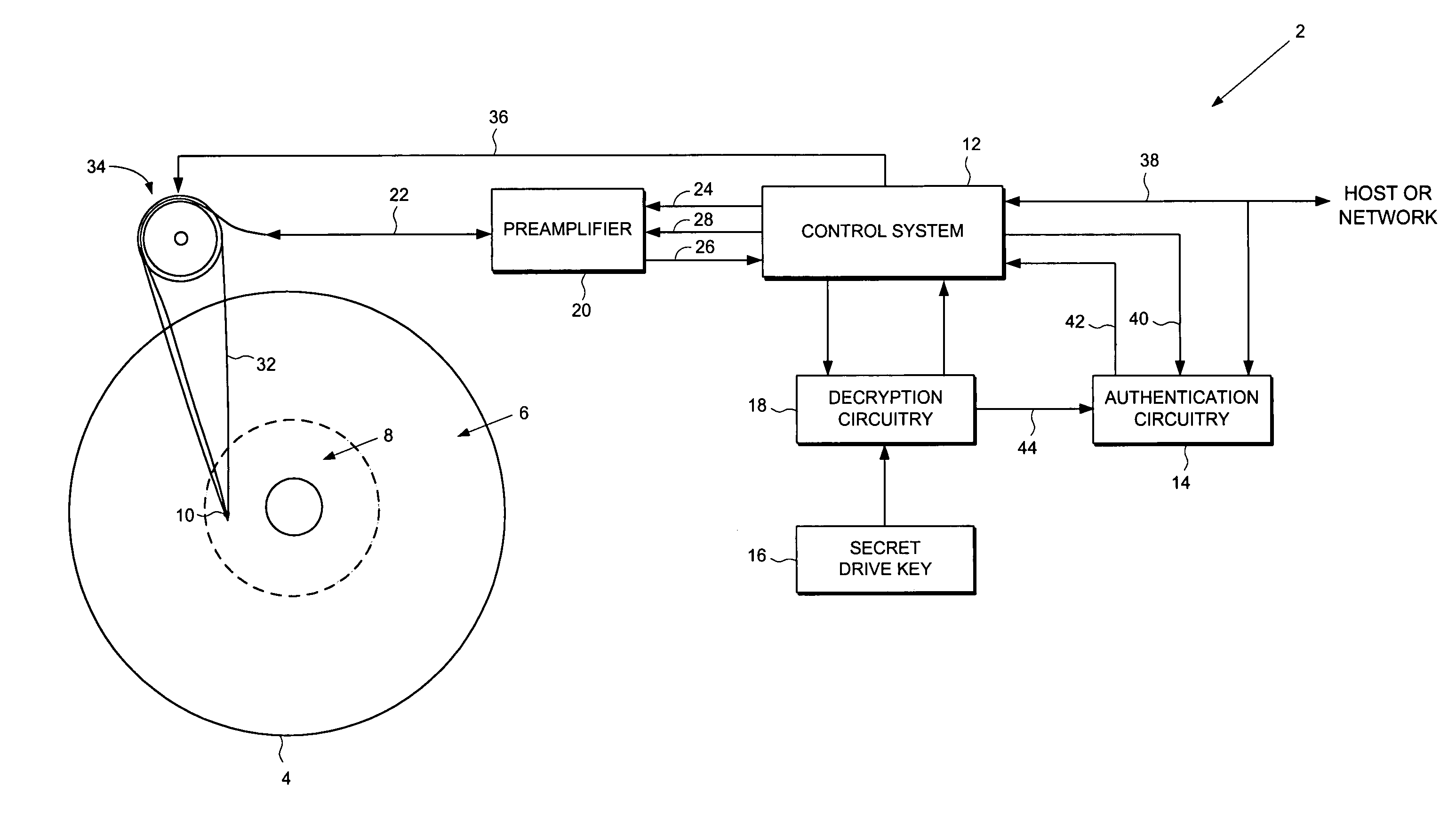
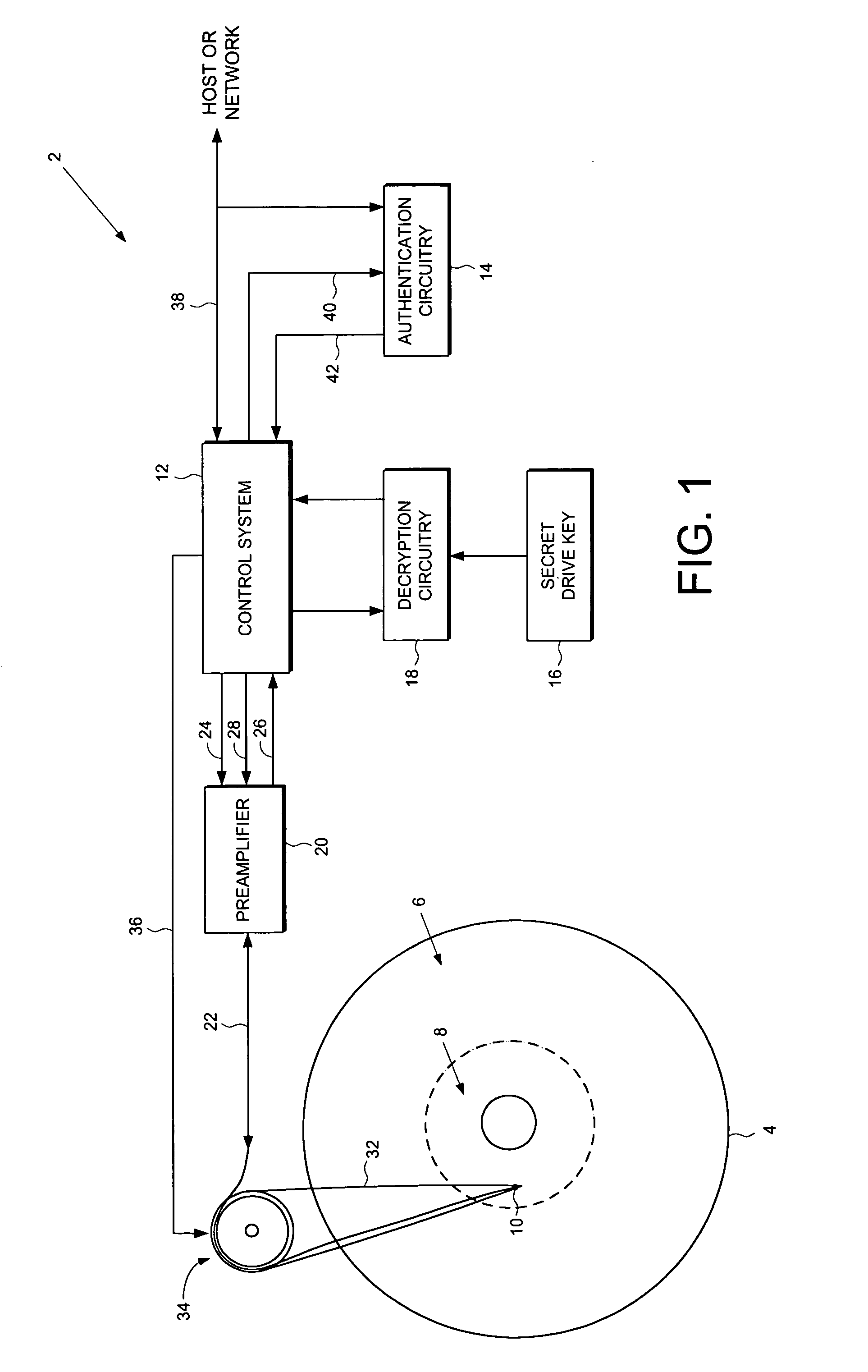
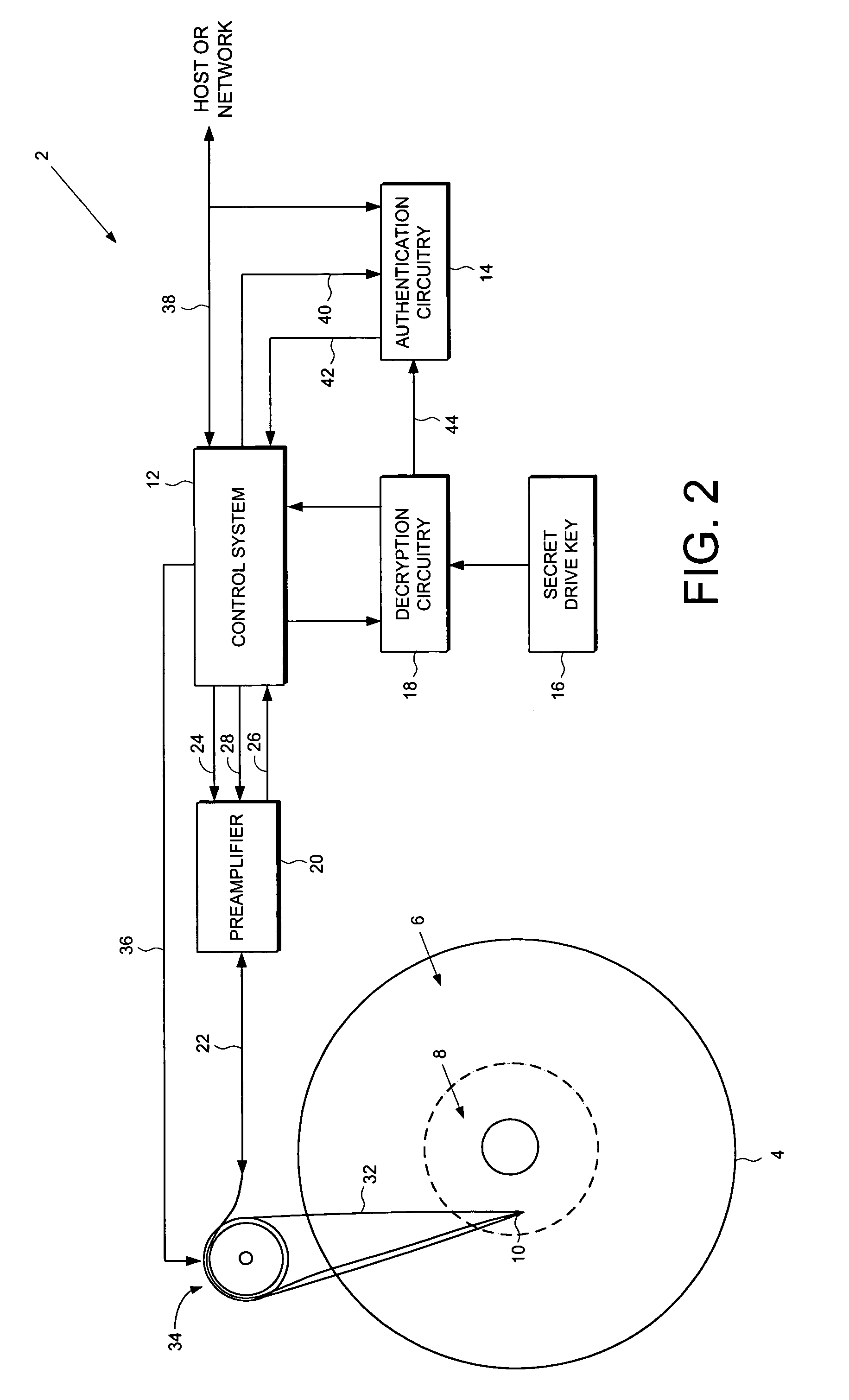
Disk drive employing a disk with a pristine area for storing encrypted data accessible only by trusted devices or clients to facilitate secure network communications
A disk drive is disclosed comprising a disk for storing data, the disk comprising a public area for storing plaintext data and a pristine area for storing encrypted data. The disk drive comprises a head for reading the encrypted data from the pristine area of the disk, and a control system for controlling access to the pristine area of the disk. Authentication circuitry within the disk drive is provided for authenticating a request received from an external entity to access the pristine area of the disk and for enabling the control system if the request is authenticated. The disk drive further comprises a secret drive key, and decryption circuitry responsive to the secret drive key, for decrypting the encrypted data stored in the pristine area of the disk.
Owner:WESTERN DIGITAL VENTURES
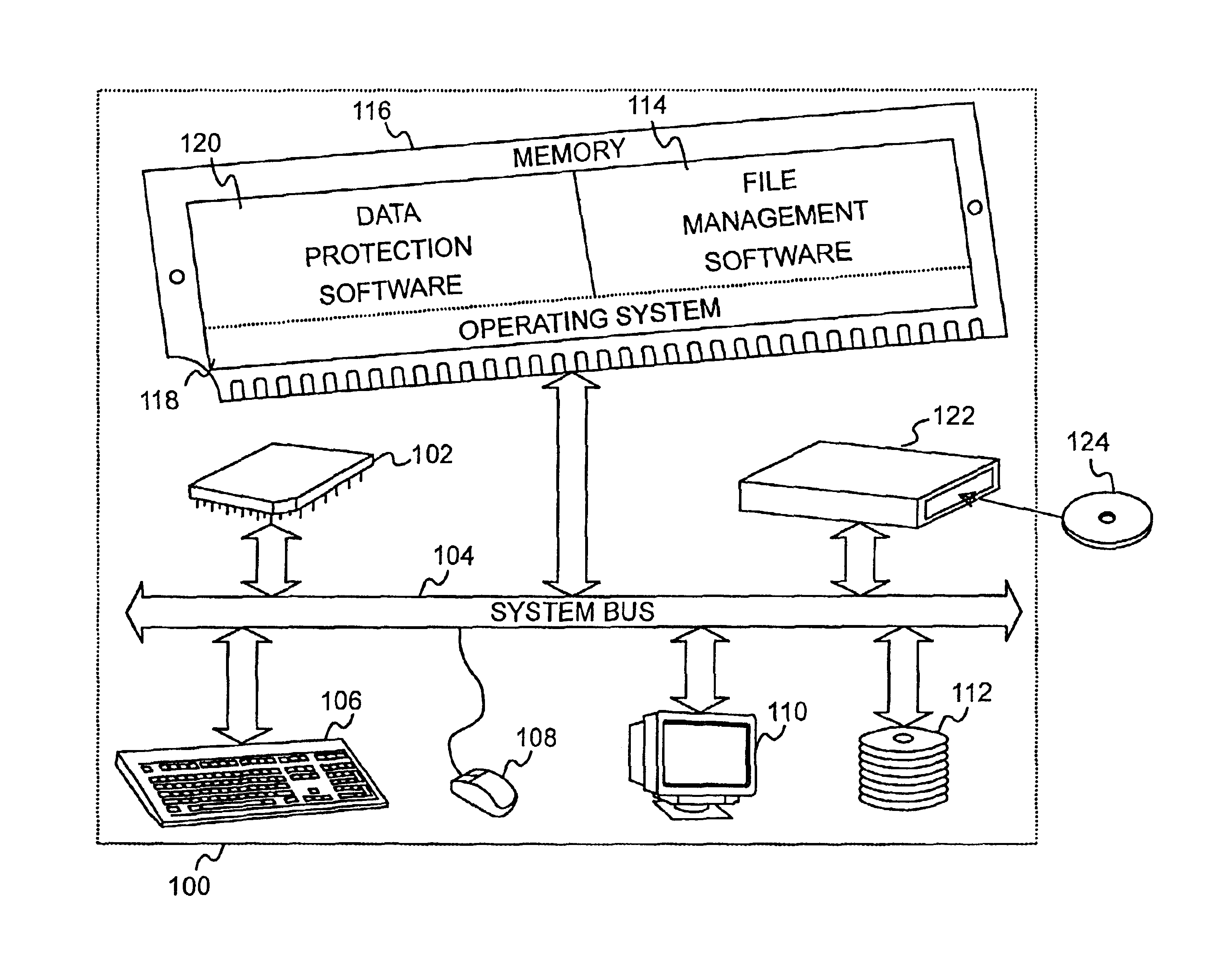
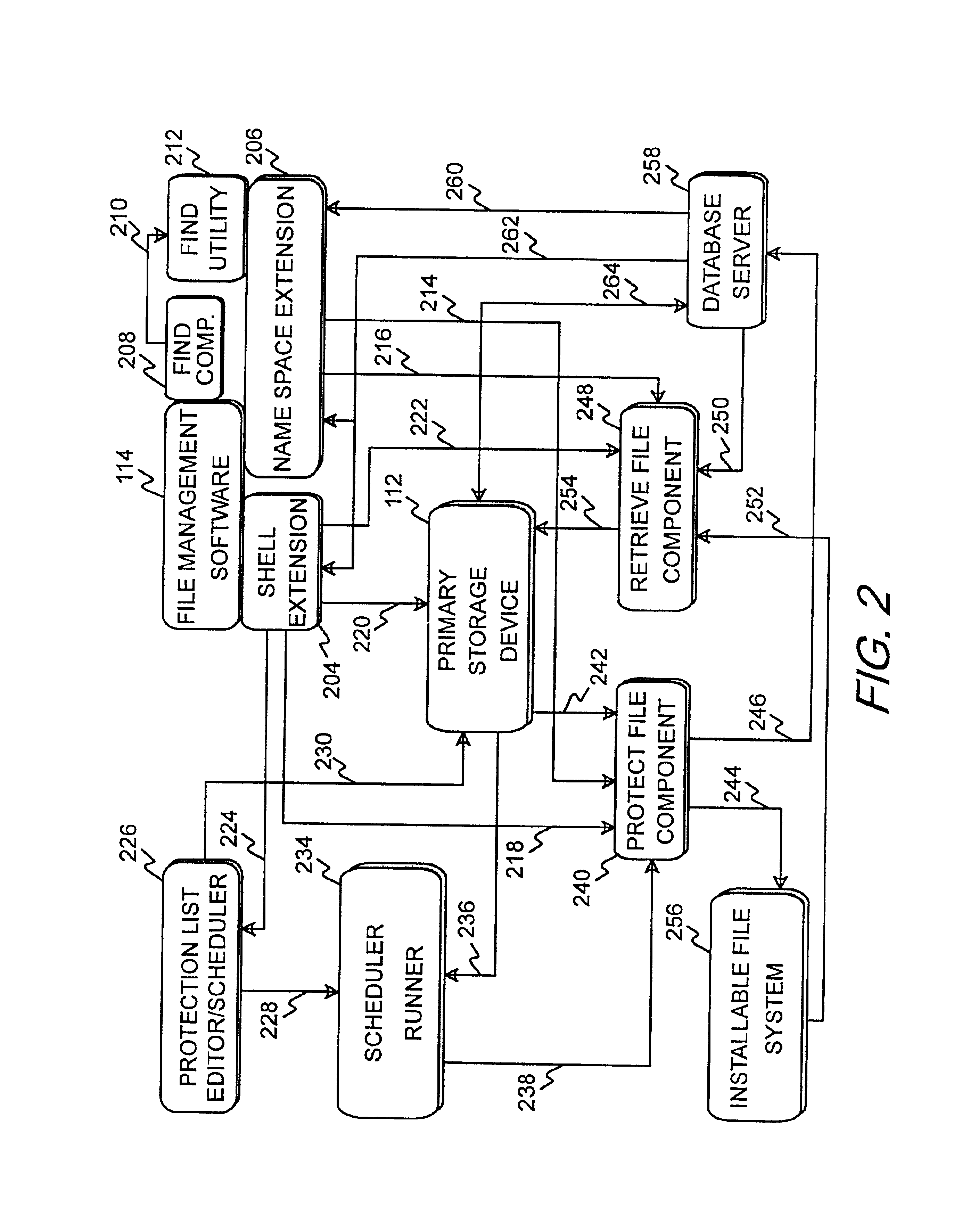
Integration of a database into file management software for protecting, tracking, and retrieving data
InactiveUS6839721B2Simple and efficientAccurate identificationData processing applicationsSpecial data processing applicationsProgram planningProtection system
A data protection system that integrates a database with Windows Explorer in the Microsoft Windows 9X and NT Environments that mimics the Windows Explorer user interface, enabling the user to apply already known use paradigms. The data protection system appears as an extension to Windows Explorer and visibly appears as a folder item called the data vault. The data vault is a virtual disk that represents the underlying database. The database creates records and stores information about files backed up to removable secondary storage medium. Files may be backed up manually or automatically. A schedule can be set up for automatic protection of selected files and file types. The database can be searched to find files for restoration purposes without having to load secondary storage medium. Once a file or files are selected, the data protection system indicates which labeled removable secondary storage medium must be loaded for retrieval.
Owner:HEWLETT PACKARD DEV CO LP
Artificial spinal disk
InactiveUS20050107881A1Rotational shiftingInternal osteosythesisBone implantLateral bendingIntervertebral disk
An artificial spinal disk comprises a central capsule that is configured to slide laterally within the disk space with one or more of flexion, extension, and lateral bending of the spine so as to shift an instantaneous center of rotation of the artificial disk. In one embodiment, the invention comprises an artificial spinal disk comprising a first plate having an inwardly directed surface, a second plate having an inwardly directed surface facing generally toward the inwardly directed surface of the first plate, and a central capsule with outwardly directed opposed faces that slidably mate with the inwardly directed surfaces of the first and second plates.
Owner:SMART DISC
Method and device for protecting digital data by double re-encryption
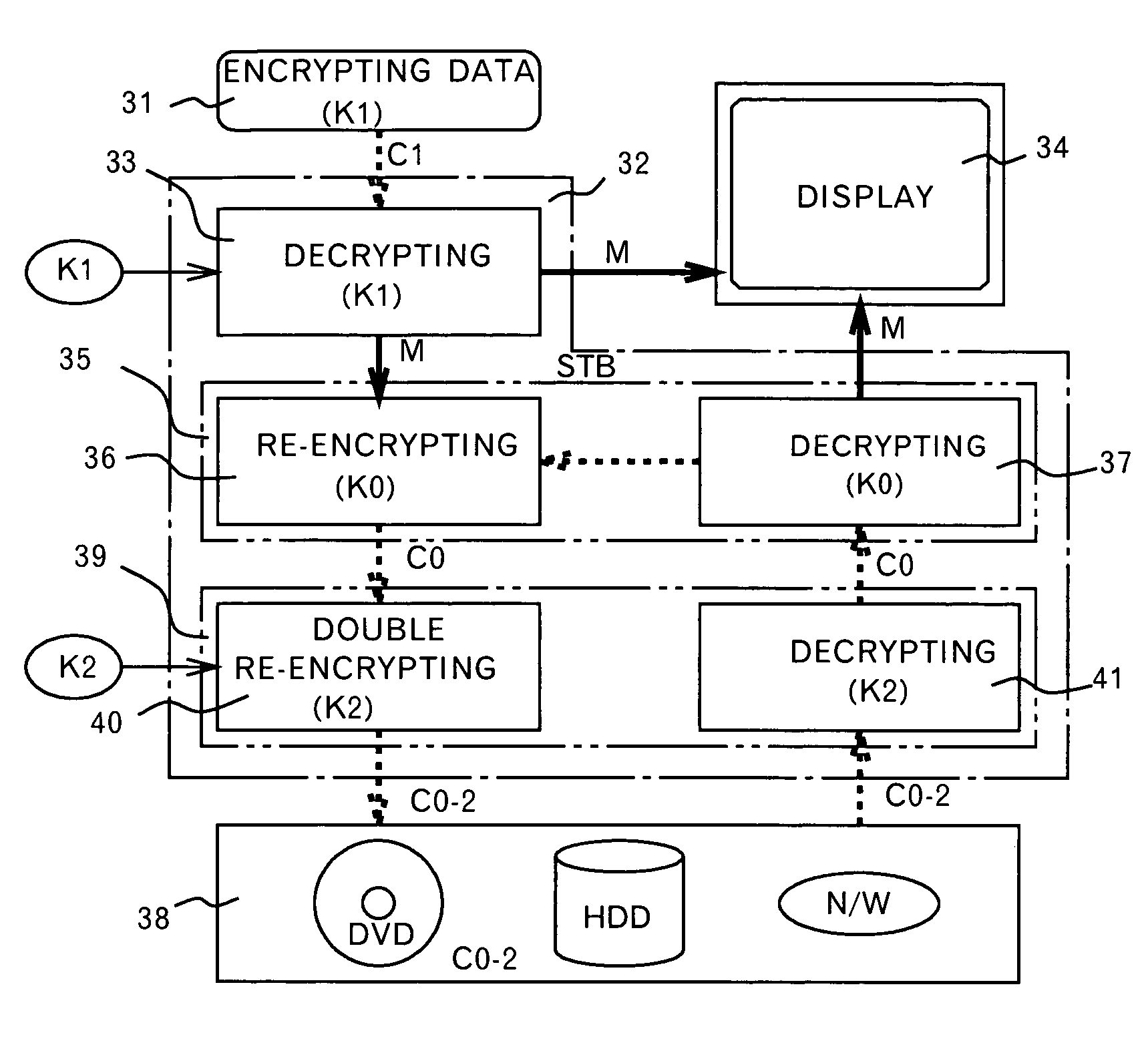
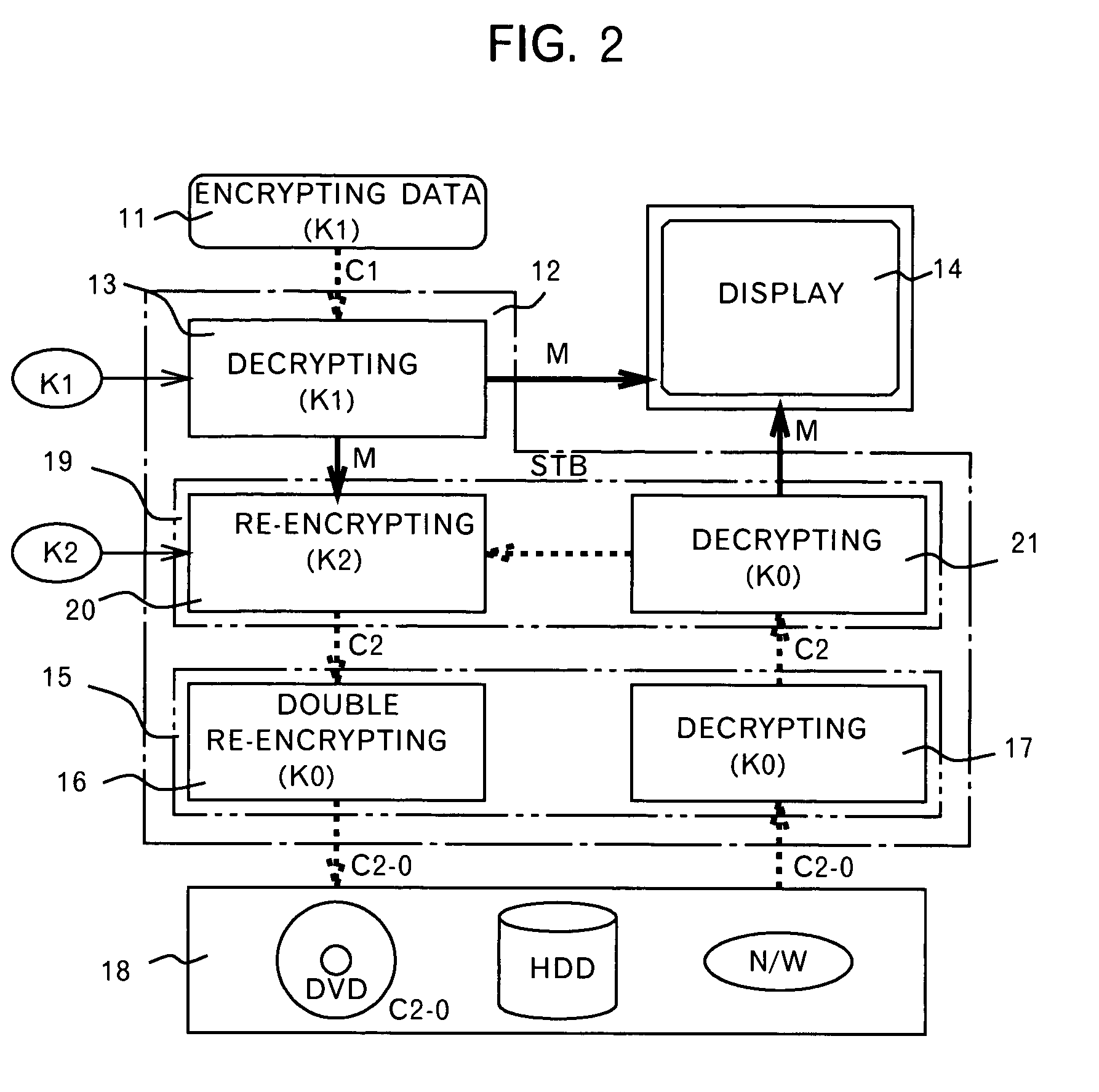
InactiveUS7093295B1Television system detailsKey distribution for secure communicationDigital videoDigital data
A method and an apparatus ensuring protection of digital data are provided. In addition to re-encrypting the data using an unchangeable key, the data is double re-encrypted using a changeable key. The changeable key is used first and the unchangeable key is then used, or in another case, the unchangeable key is used first, and the changeable key is then used. In the aspect of embodiments, there is a case adopting a software, a case adopting a hardware, or a case adopting the software and the hardware in combination. The hardware using the unchangeable key developed for digital video is available. In adopting the software, encryption / decryption is performed in a region below the kernel which cannot be handled by the user to ensure the security for the program and for the key used. More concretely, encryption / decryption is performed with RTOS using a HAL and a device driver, i.e., a filter driver, a disk driver and a network driver, in an I / O manager. Either one of two filter drivers, with a file system driver between them, may be used. Further, both filter drivers may be used.
Owner:KIOBA PROCESSING LLC
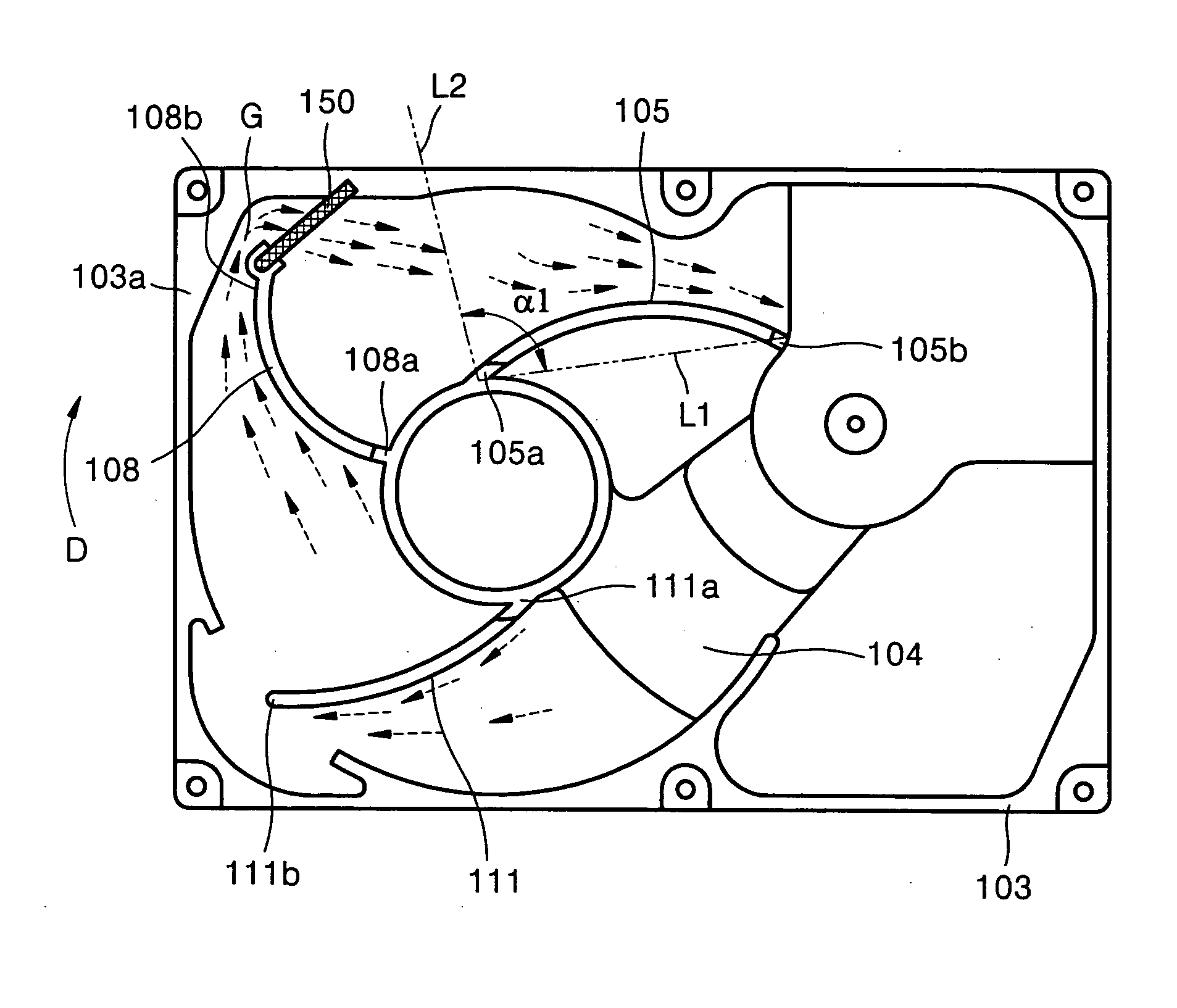
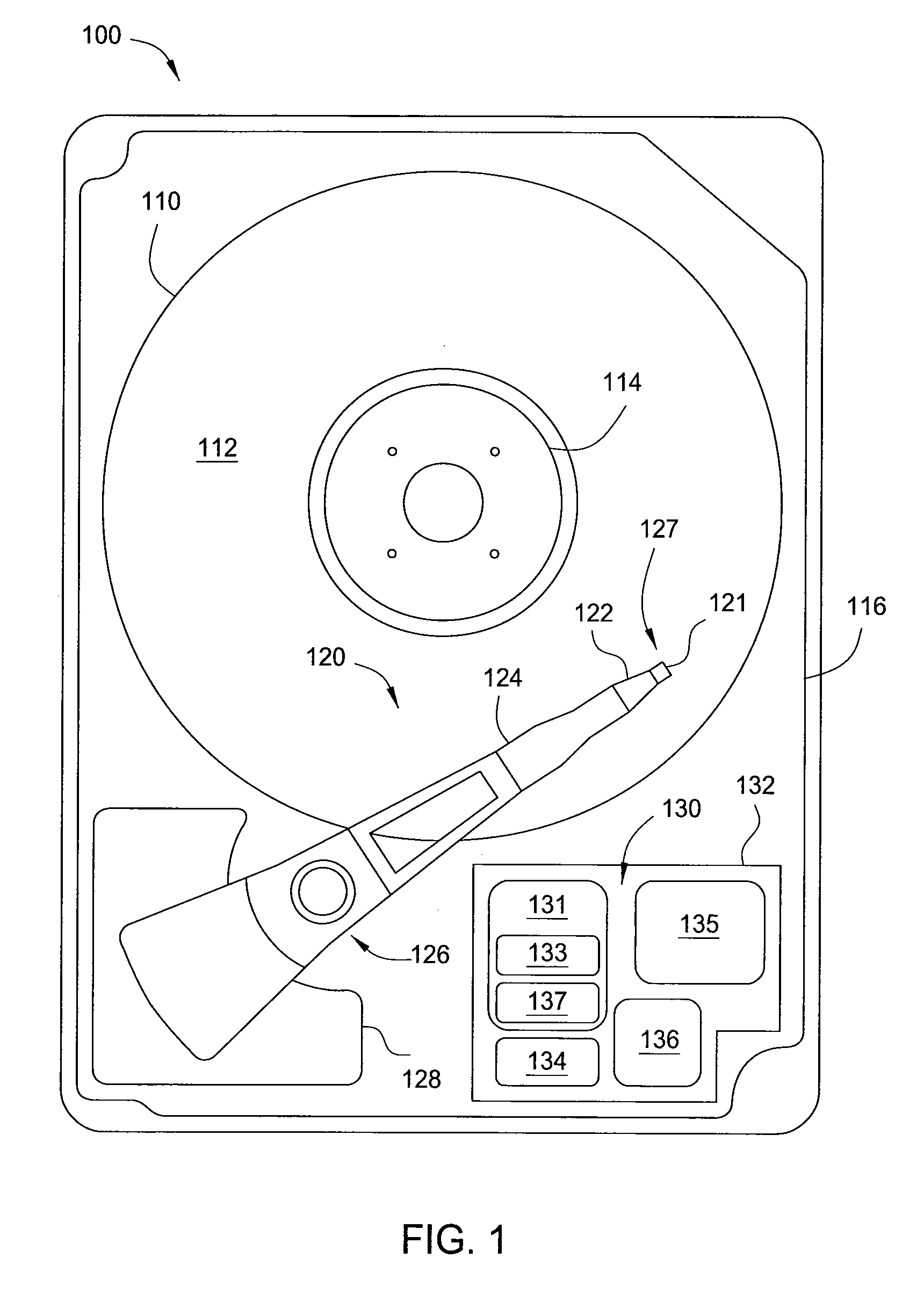
Hard disk drive
A hard disk drive having a housing with a base and a cover connected to each other, a spindle motor connected to the base, a disk mounted on the spindle motor and rotating with respect to the base, and an actuator rotatably connected to the base and supporting a slider with a magnetic head mounted on a front end thereof. The magnetic head writes and / or reads data to and / or from the disk. The hard disk drive also has a blade protruding from a surface of the base and / or a portion of the cover facing the disk. The blade guides an air flow caused by rotation of the disk toward an outer edge of the disk.
Owner:SAMSUNG ELECTRONICS CO LTD
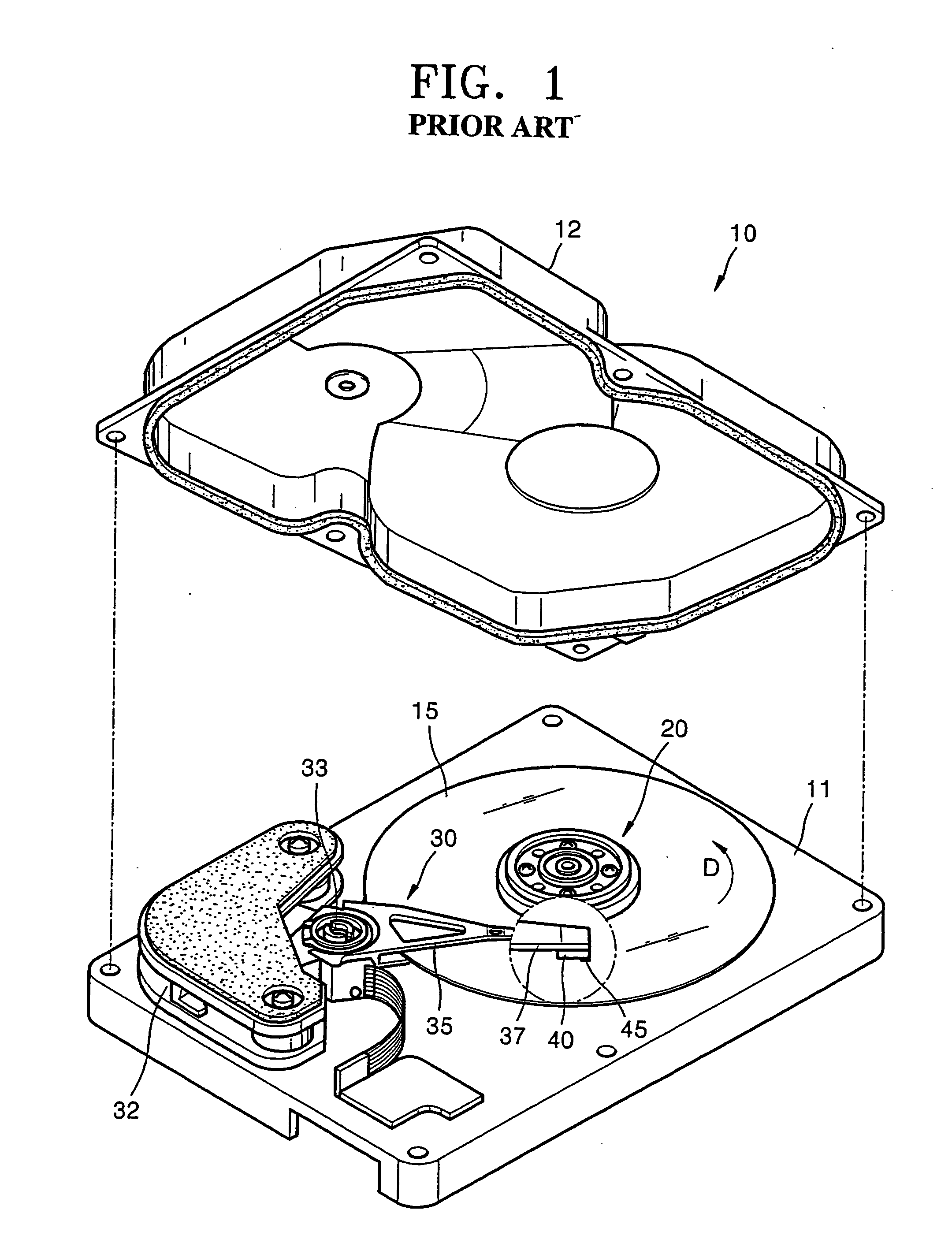
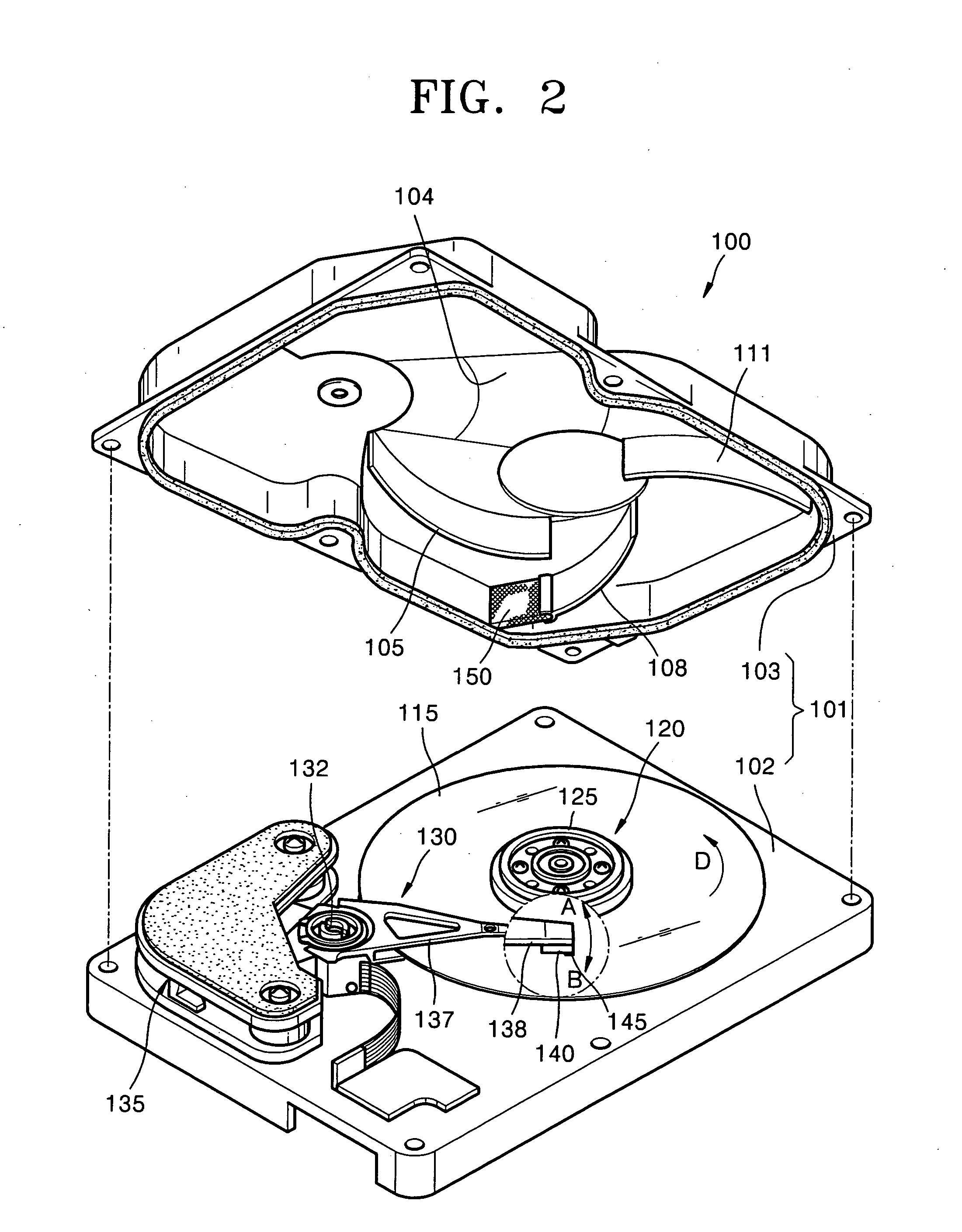
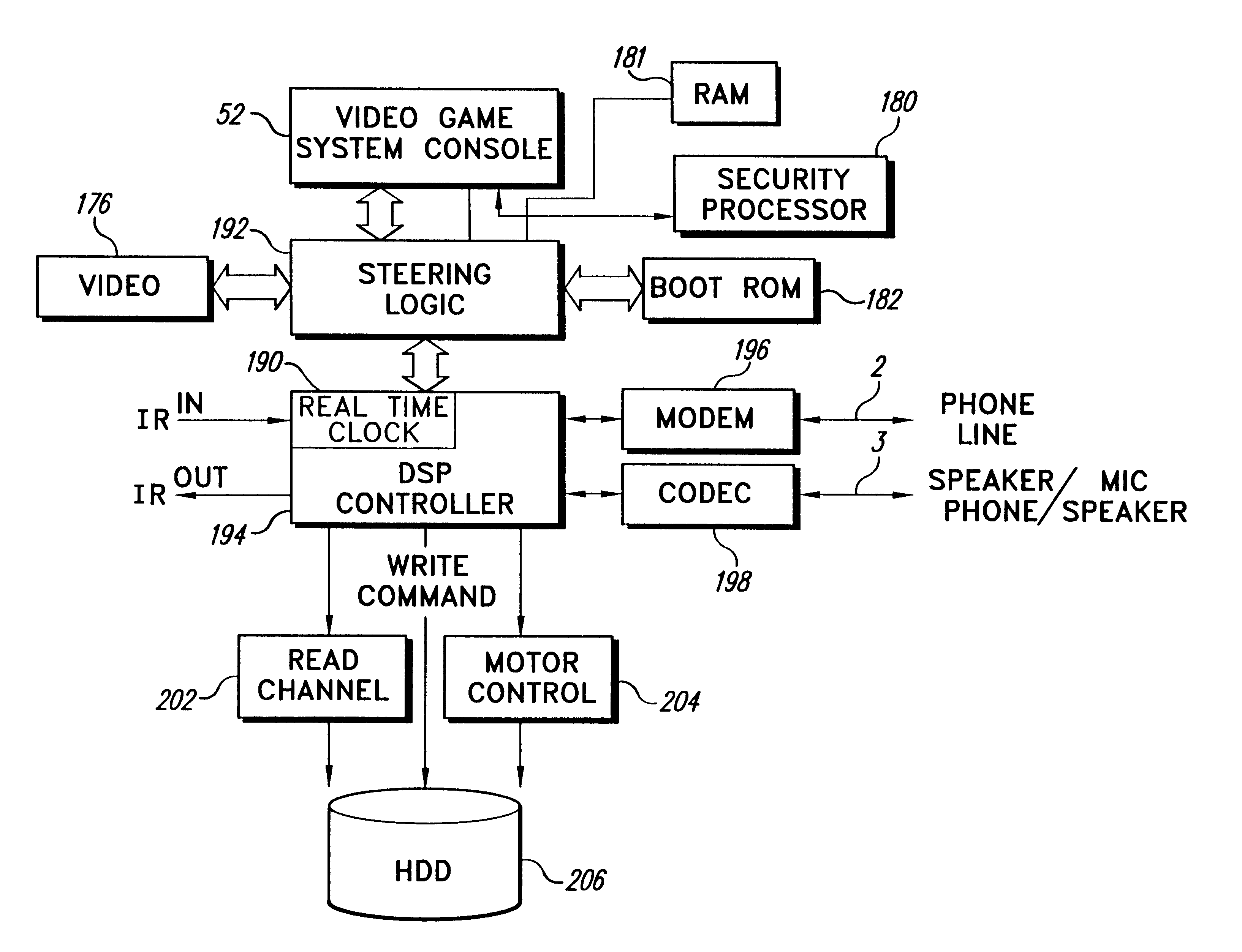
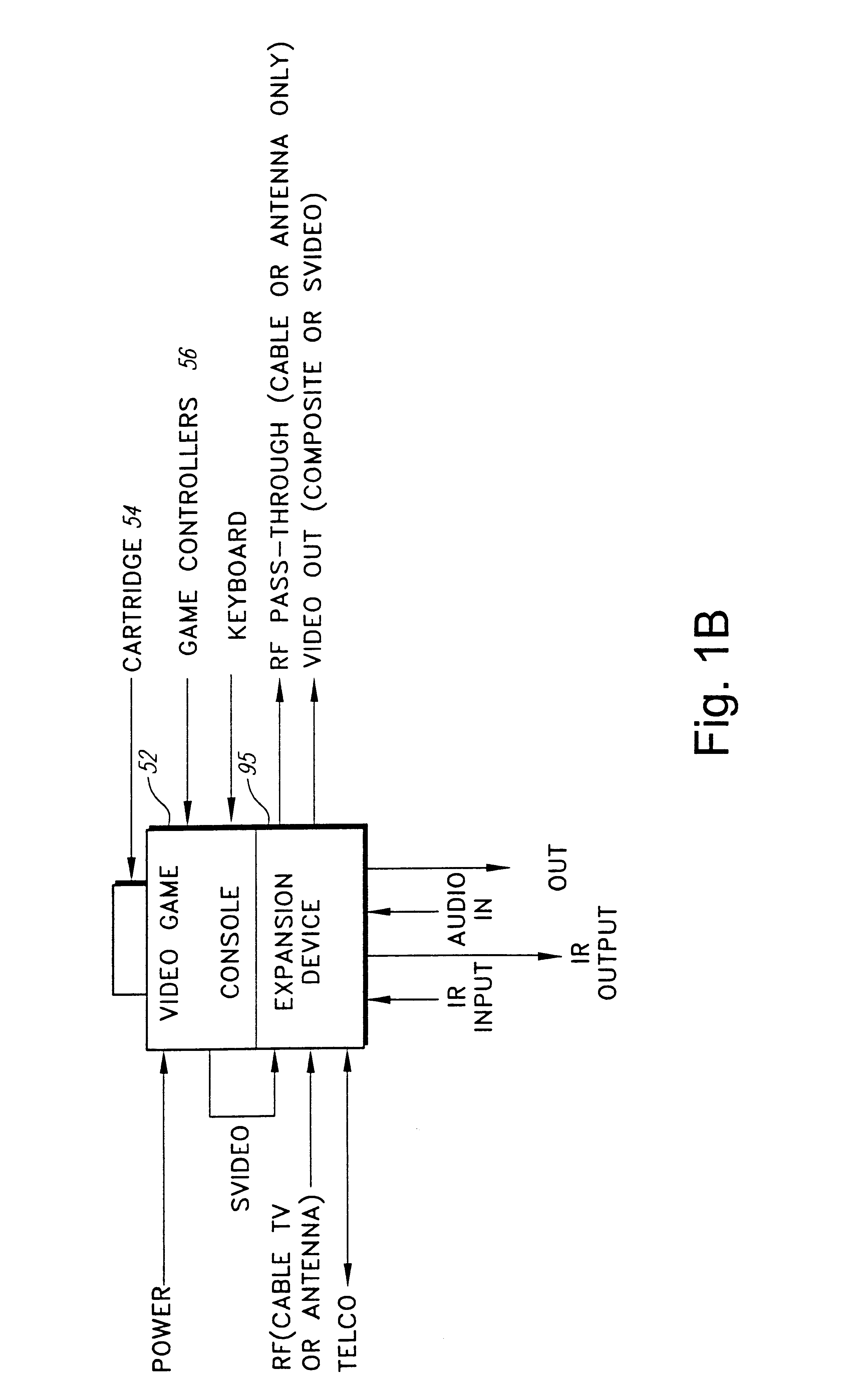
Security system for video game system with hard disk drive and internet access capability
An existing video game system is modified to include additional communication and storage capability via a modem and hard disk drive. In accordance with one embodiment of the present invention, the primary system security features are incorporated into a video game system expansion device having a hard disk drive. The security system does not rely on the relatively insecure video game system. The present exemplary embodiment focuses security control in a disk drive / mass media controlling engine which is physically disposed within the expansion device housing as close as possible to the hard disk drive and the downloaded video games and other data it is designed to protect. Security features are incorporated into, for example, a disk drive controlling processing engine to provide security features which extend far beyond simplistic password systems which have heretofore been utilized in conjunction with disk drive controllers. In accordance with an exemplary embodiment of the present invention, the disk controller also incorporates an encrypting engine which encrypts in accordance with a highly secure encrypting algorithm. A further level of security is provided in the illustrative embodiments by partitioning the hard drive into various partitions whose security / accessibility is tightly controlled. Each application program, e.g., a video game, has a predetermined number of private partitions, including a read only encrypted partition.
Owner:NINTENDO OF AMERICA
Method and apparatus to reduce power consumption and improve read/write performance of hard disk drives using non-volatile memory
InactiveUS7082495B2Read/write performance of hardReduce the number of timesEnergy efficient ICTInput/output to record carriersHard disc driveOperational system
A method and apparatus to improve the read / write performance of a hard drive is presented. The hard drive includes solid state, non-volatile (NV) memory as a read / write cache. Data specified by the operating system is stored in the NV memory. The operating system provides a list of data to be put in NV memory. The data includes data to be pinned in NV memory and data that is dynamic. Pinned data persists in NV memory until the operating system commands it to be flushed. Dynamic data can be flushed by the hard drive controller. Data sent by an application for storage is temporary stored in NV memory in data blocks until the operating system commits it to the disk.
Owner:MICROSOFT TECH LICENSING LLC
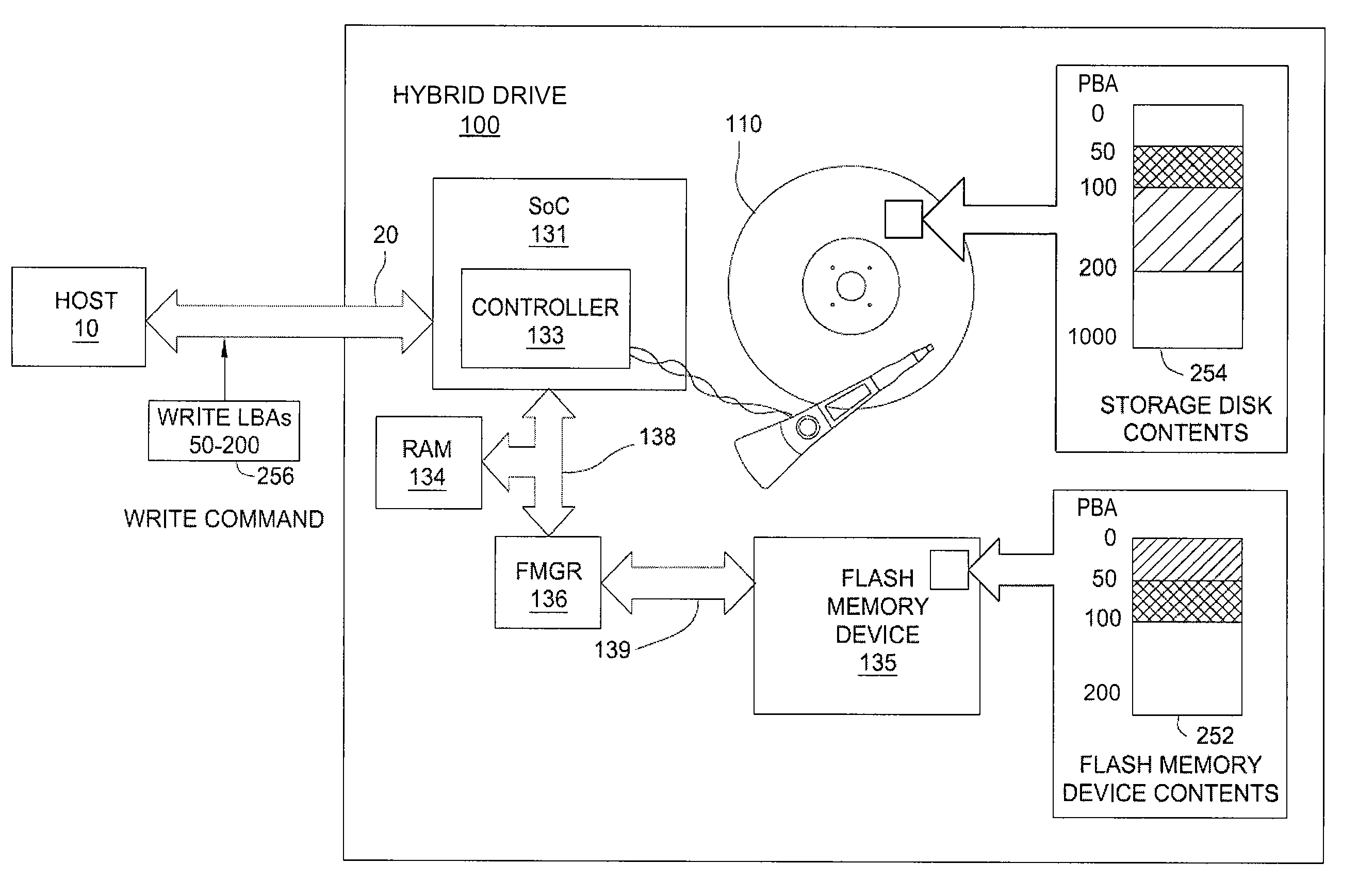
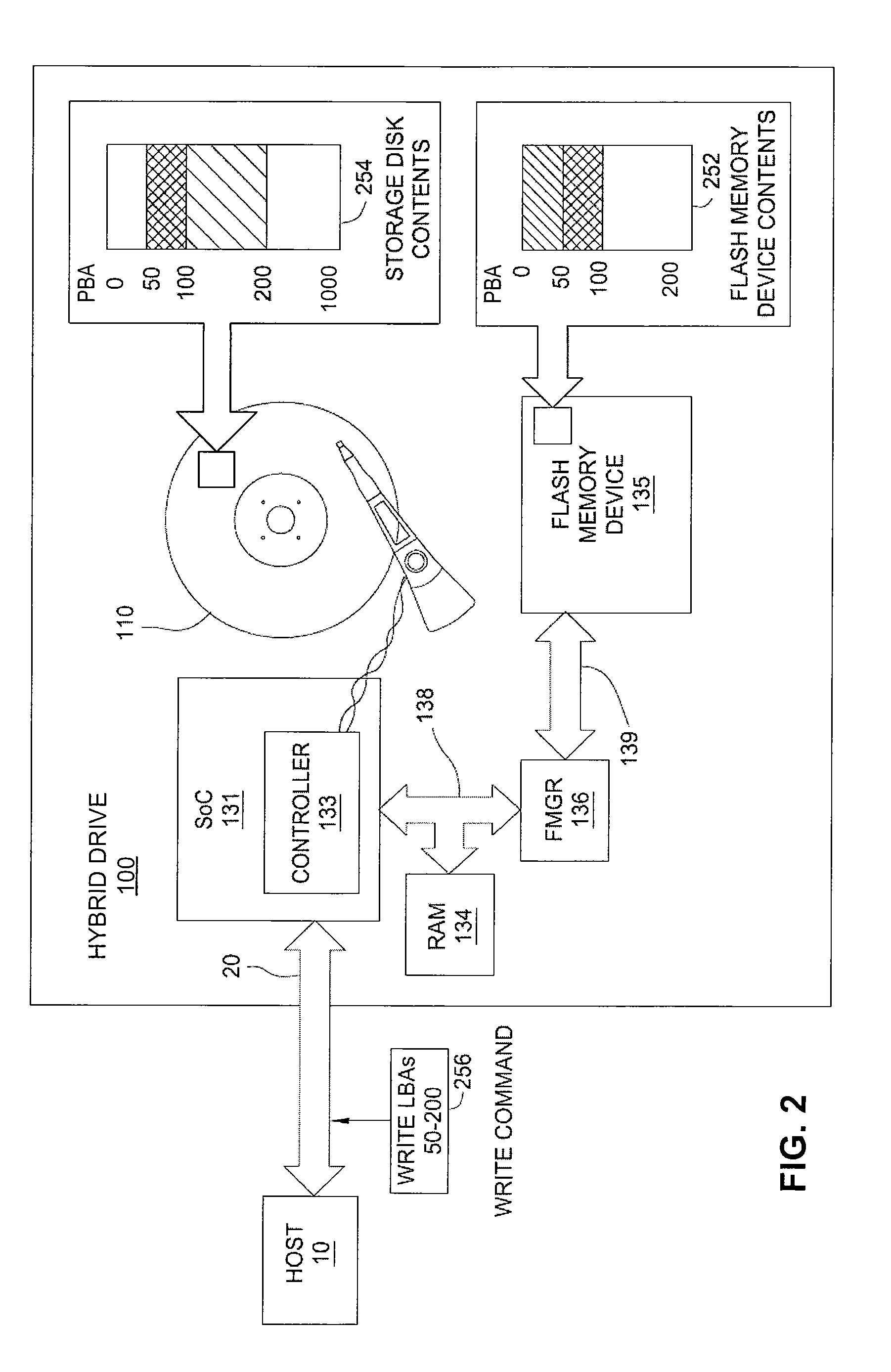
Hybrid drive that implements a deferred trim list
InactiveUS20140237164A1Prevent leakageMemory architecture accessing/allocationMemory adressing/allocation/relocationComputer scienceLogical address
A hybrid drive controller maintains a deferred trim list that holds a subset of logical addresses of writes performed on magnetic disks. For example, if a write command is issued to an LBA space that overlaps a portion stored in flash memory and the write is to be performed on the magnetic disks, the trimming of the overlapping portion in the flash memory will be deferred. Instead of trimming, the logical addresses associated with the overlapping portion will be added to the deferred trim list and trimming of the logical addresses in the deferred trim list will be carried out at a later time, asynchronous to the write that caused them to be added to the list.
Owner:KK TOSHIBA
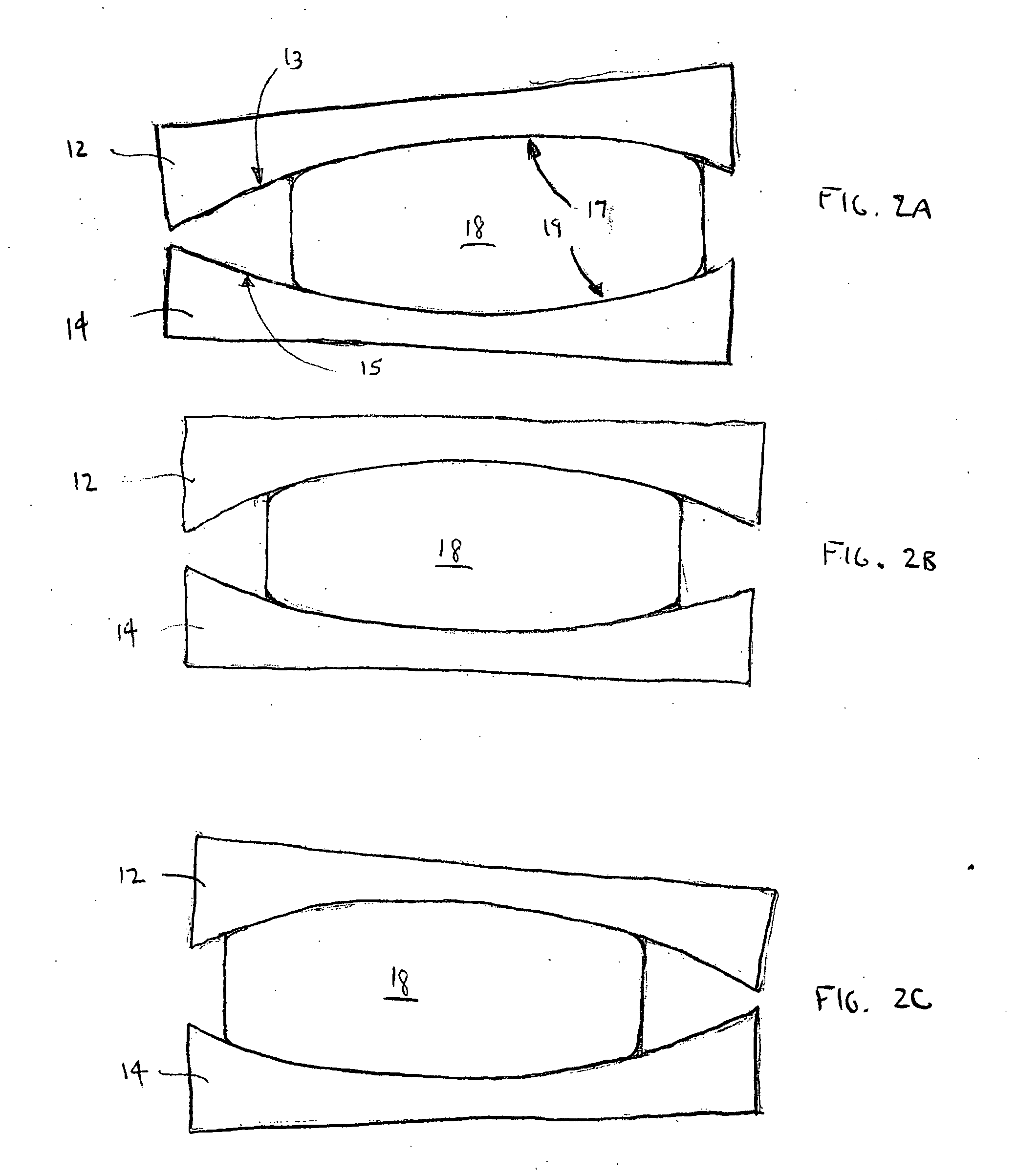
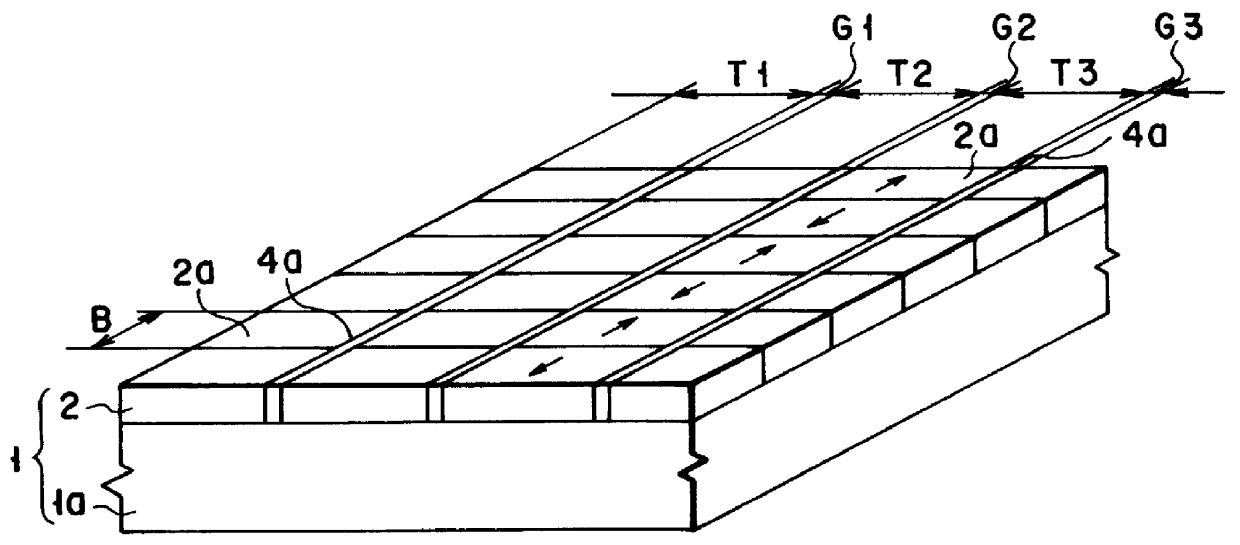
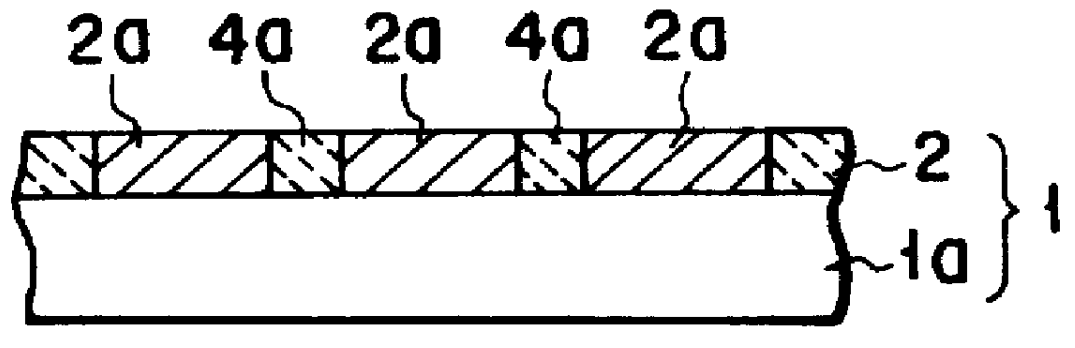
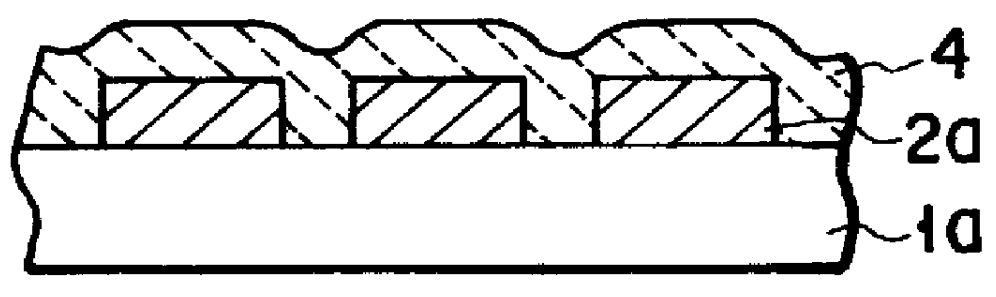
Magnetic disk with a guard band arrangement
A magnetic disk including a substrate, a recording track section which is made of a magnetic member for recording and reproducing information magnetically and is provided on the substrate, and a guard band member which is provided between the recording track sections adjacent to each other so that they are substantially continued in a track direction and is harder than the magnetic member and is made of a non-magnetic material. Moreover, the magnetic member is not provided or magnetic members with a different thickness from the magnetic member forming the recording track section is provided on a lower area of the guard band member.
Owner:KK TOSHIBA
Disc Space Sizing Devices And Methods Of Using The Same
A spacing device is provided for adjusting the spacing between adjacent vertebral bodies. The spacing device has a distal end with at least one distraction member adapted for insertion into an intervertebral disc space and movable between a low profile first configuration and a higher profile second configuration. Also provided is an actuator for moving the distraction member between the first configuration (for delivery of the distal end of the spacing device to a target disc space) and the second configuration (for manipulation of the space between adjacent vertebral bodies).
Owner:SPINAL ELEMENTS INC
User interface for a file system shell
InactiveUS7769794B2Adapt quicklyDigital data information retrievalSpecial data processing applicationsView basedFile system
A file system shell is provided. One aspect of the shell provides virtual folders which expose regular files and folders to users in different views based on their metadata instead of the actual physical underlying file system structure on the disk. Users are able to work with the virtual folders through direct manipulation (e.g., clicking and dragging, copying, pasting, etc.). Filters are provided for narrowing down sets of items. Quick links are provided which can be clicked on to generate useful views of the sets of items. Libraries are provided which consist of large groups of usable types of items that can be associated together, along with functions and tools related to the items. A virtual address bar is provided which comprises a plurality of segments, each segment corresponding to a filter for selecting content. A shell browser is provided with which users can readily identify an item based on the metadata associated with that item. An object previewer in a shell browser is provided which is configured to display a plurality of items representing multiple item types.
Owner:MICROSOFT TECH LICENSING LLC
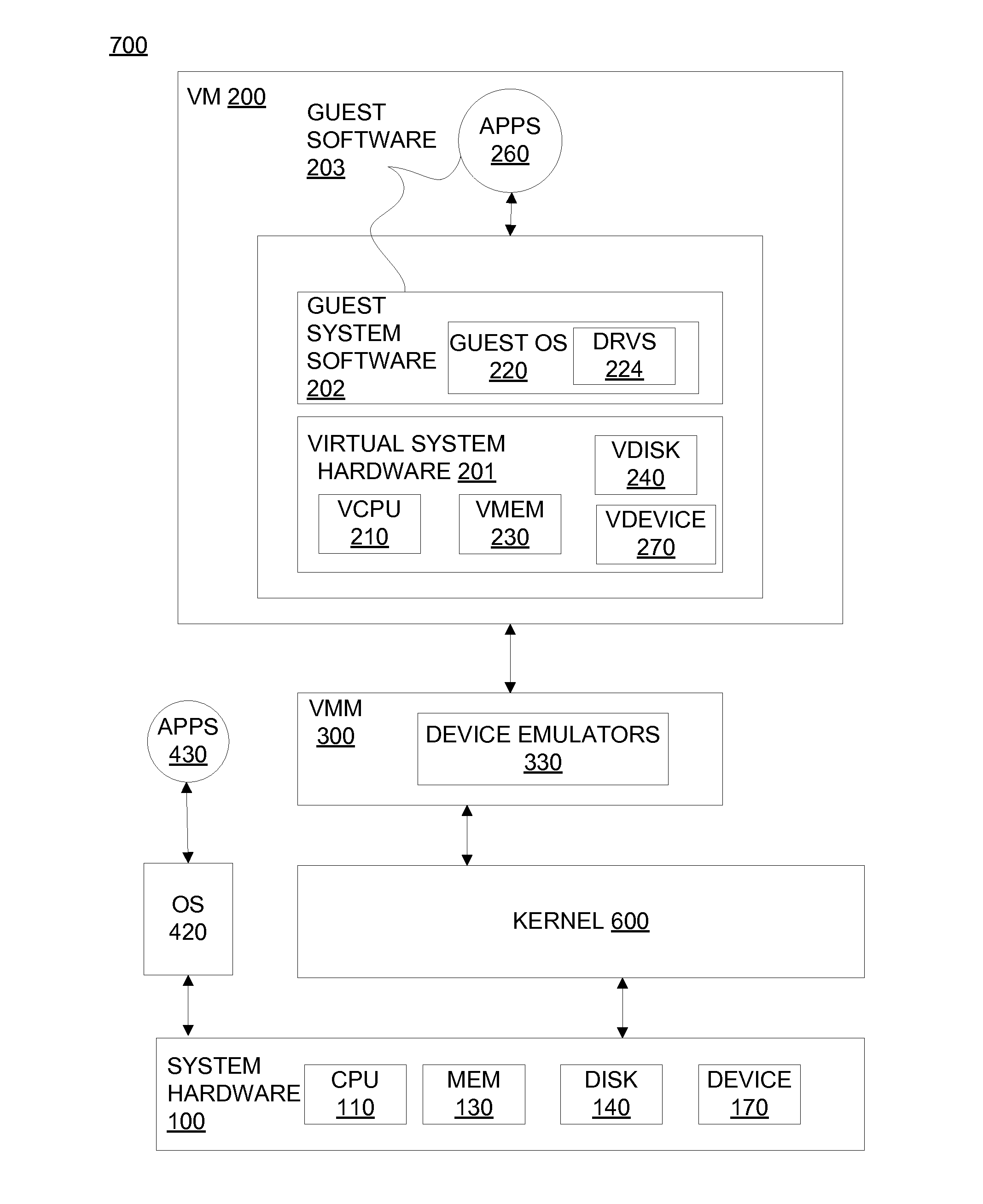
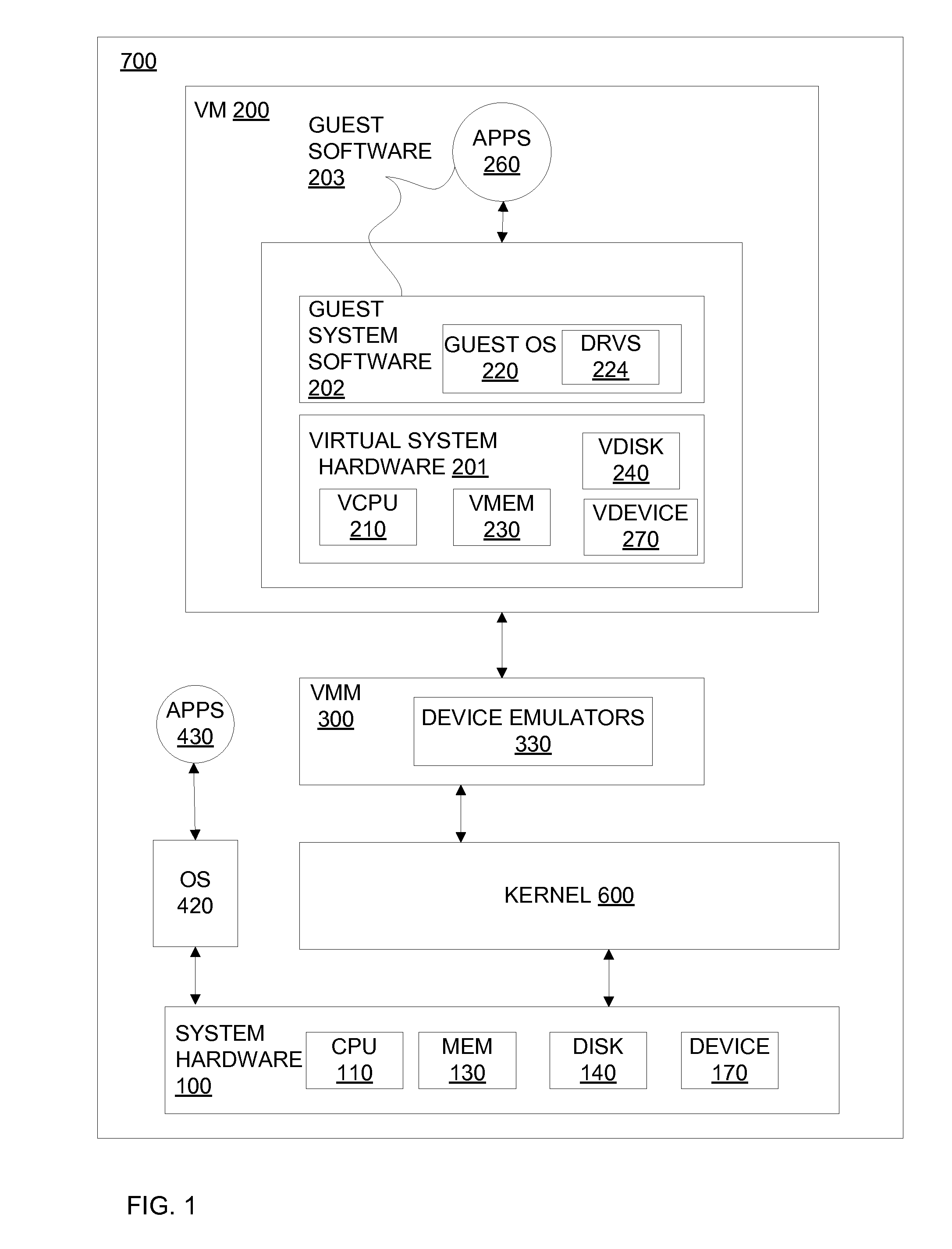
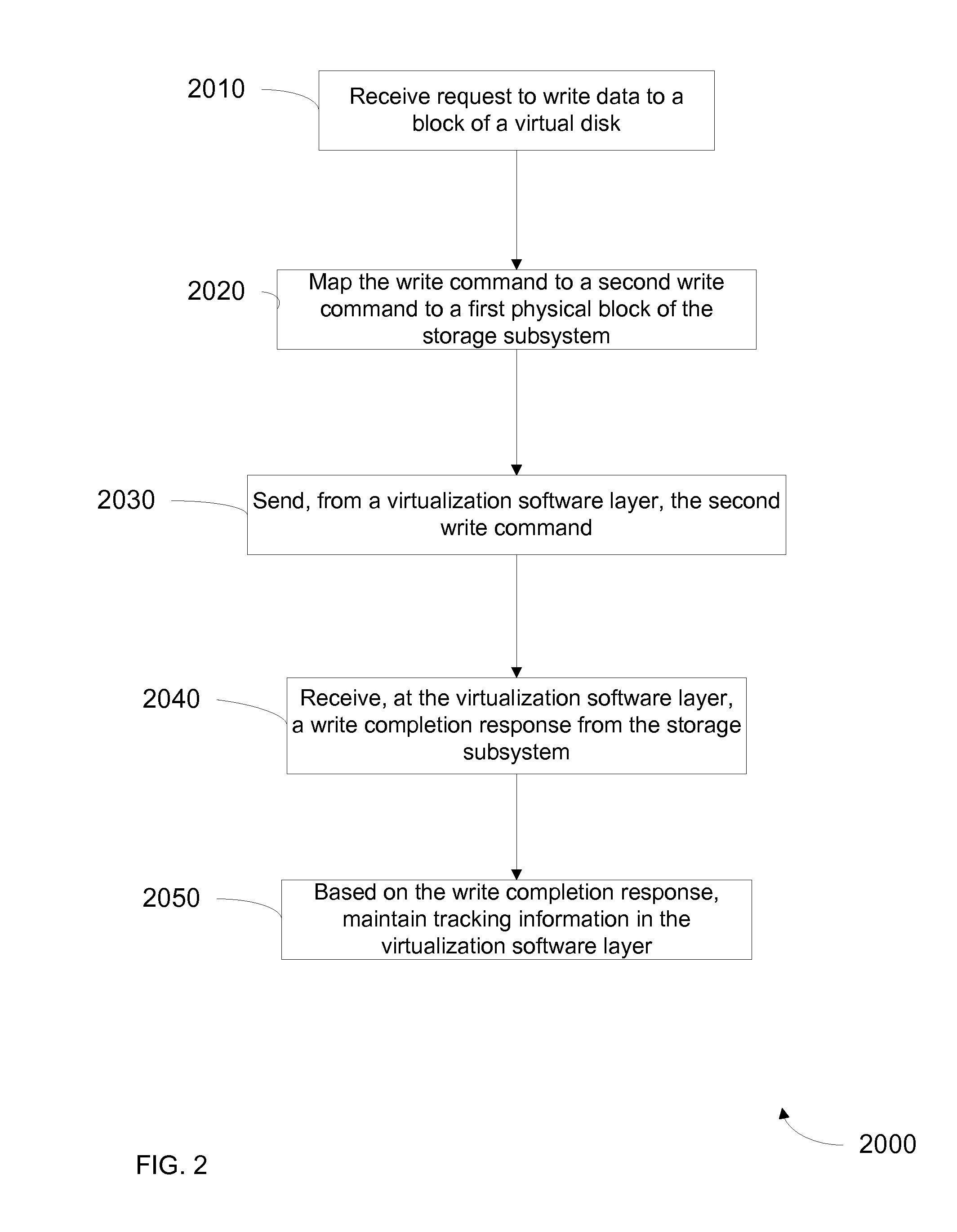
Method for tracking changes in virtual disks
ActiveUS20100228913A1Reduce the impactMore efficientMemory loss protectionError detection/correctionVirtualizationGranularity
Systems and methods for tracking changes and performing backups to a storage device are provided. For virtual disks of a virtual machine, changes are tracked from outside the virtual machine in the kernel of a virtualization layer. The changes can be tracked in a lightweight fashion with a bitmap, with a finer granularity stored and tracked at intermittent intervals in persistent storage. Multiple backup applications can be allowed to accurately and efficiently backup a storage device. Each backup application can determine which block of the storage device has been updated since the last backup of a respective application. This change log is efficiently stored as a counter value for each block, where the counter is incremented when a backup is performed. The change log can be maintained with little impact on I / O by using a coarse bitmap to update the finer grained change log.
Owner:VMWARE INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com