Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
850 results about "Bytecode" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
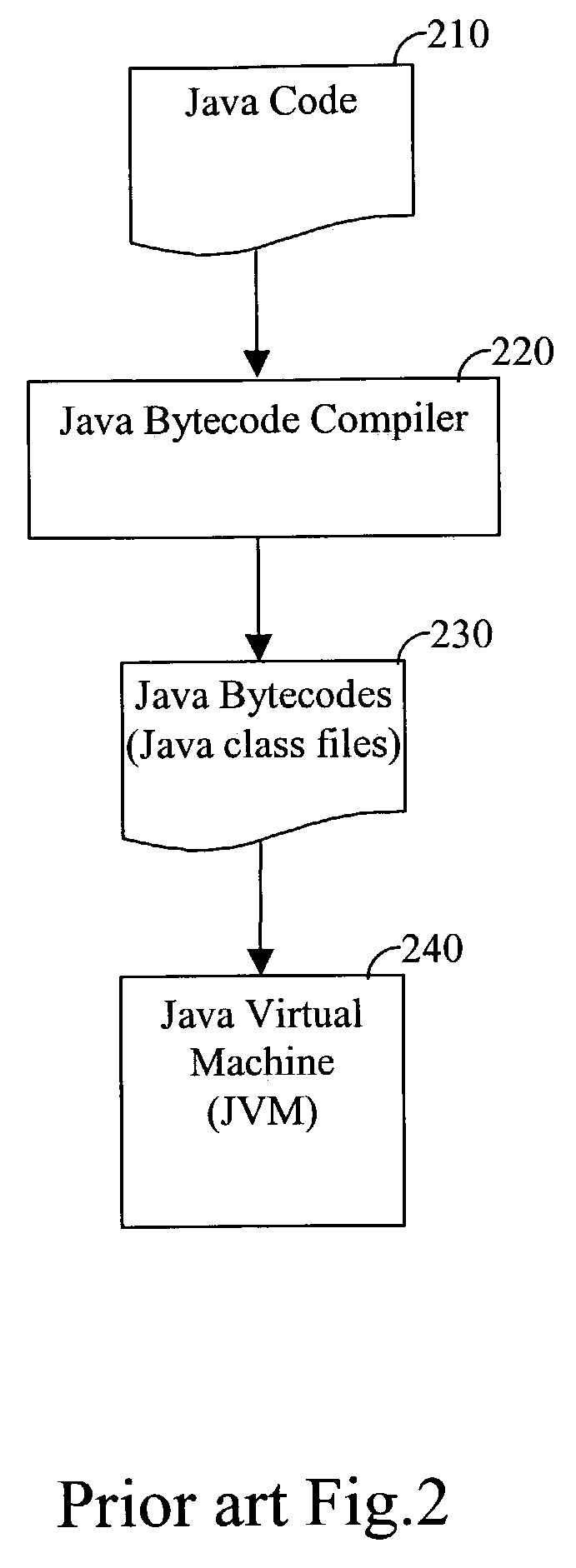
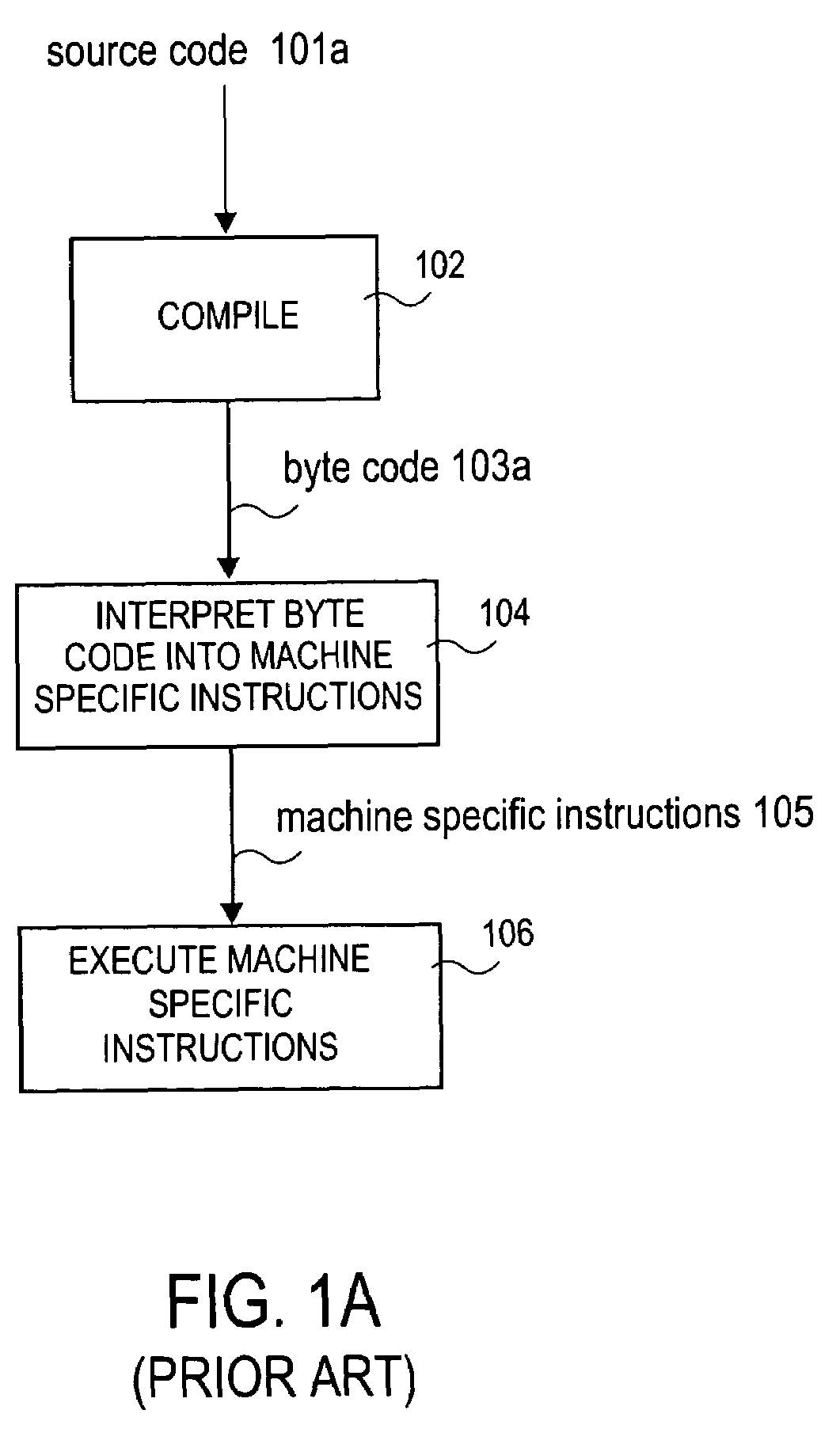
Bytecode, also termed portable code or p-code, is a form of instruction set designed for efficient execution by a software interpreter. Unlike human-readable source code, bytecodes are compact numeric codes, constants, and references (normally numeric addresses) that encode the result of compiler parsing and performing semantic analysis of things like type, scope, and nesting depths of program objects.
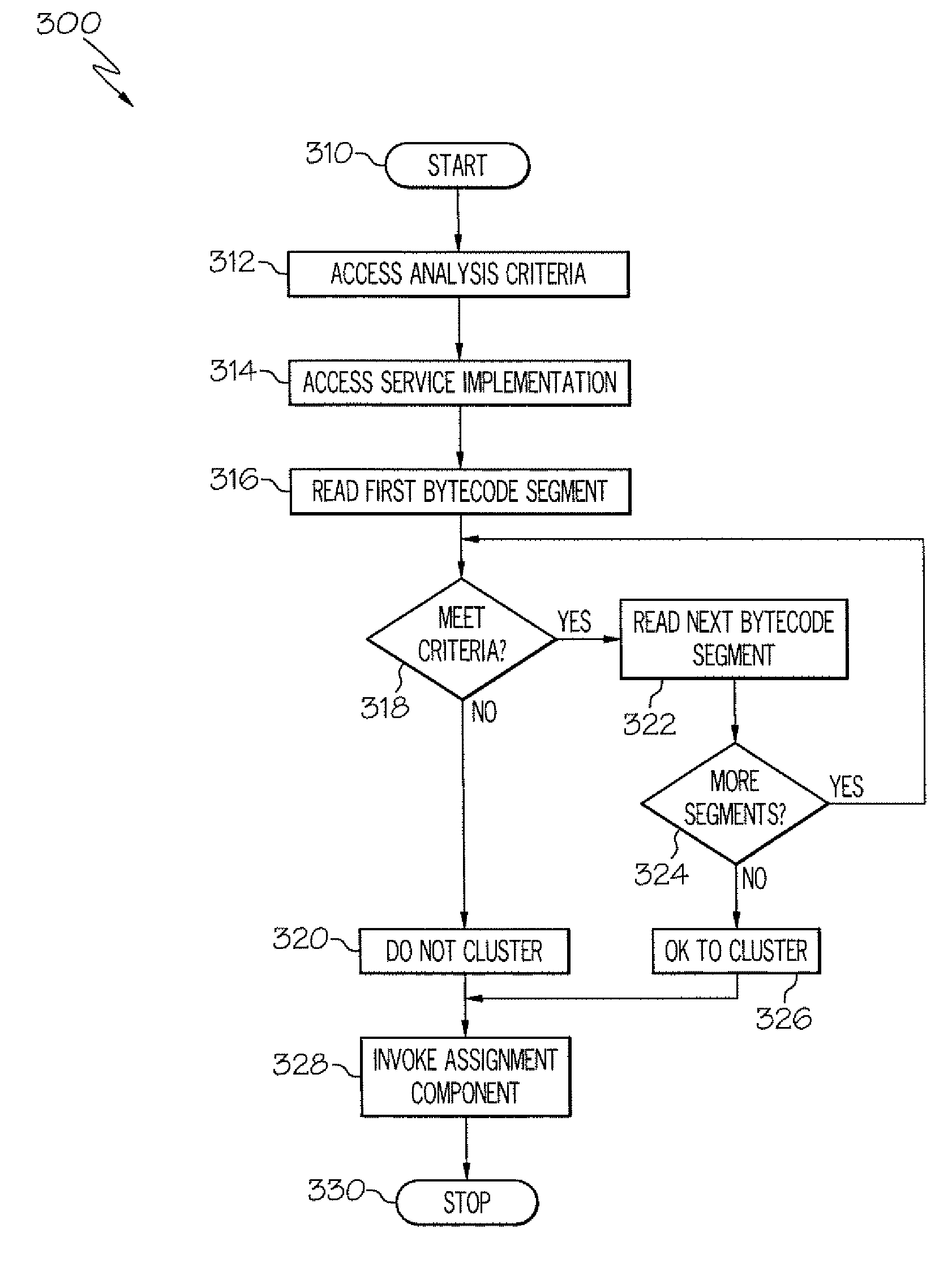
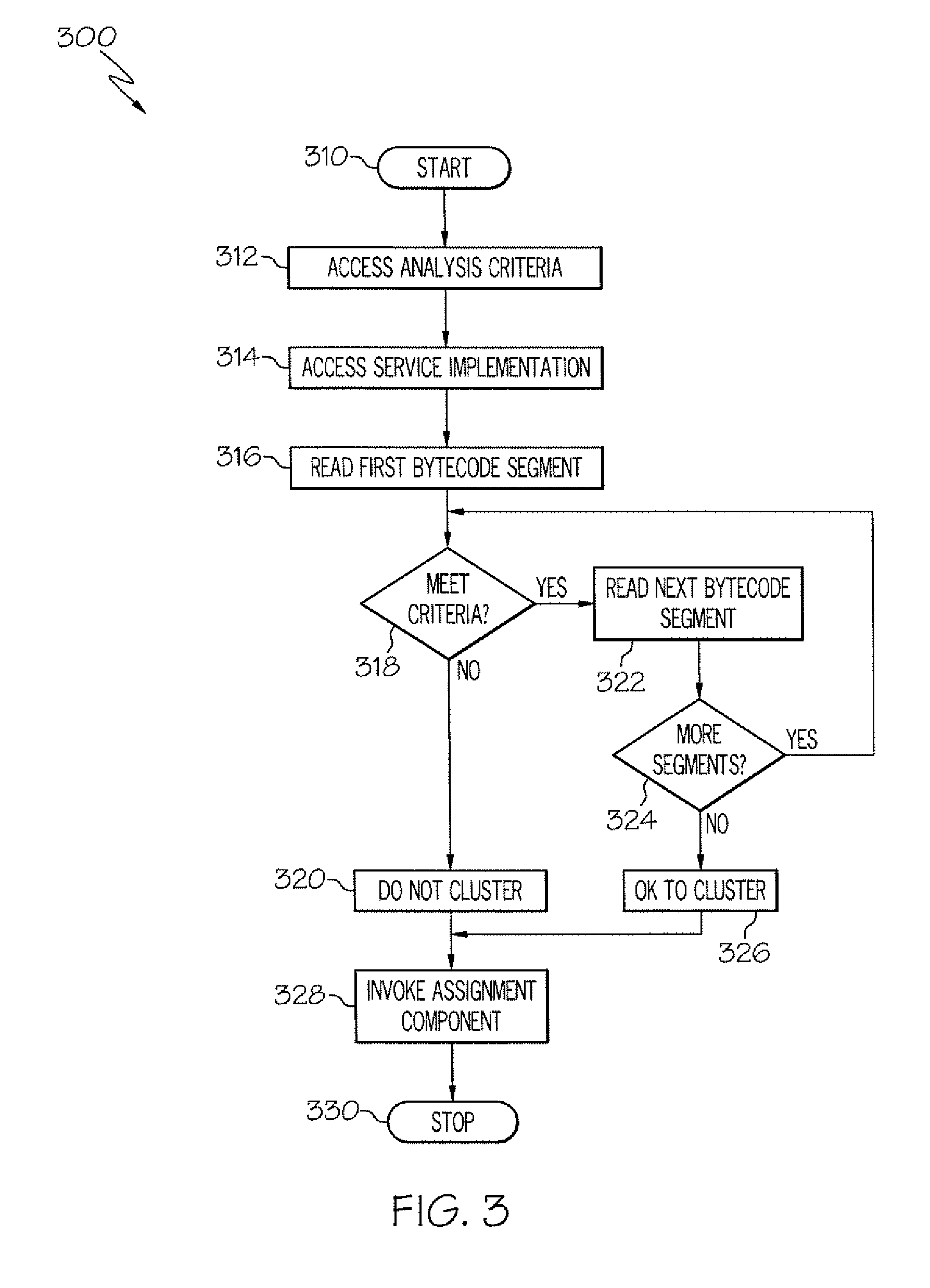
Method and apparatus for determining a service cluster topology based on static analysis
InactiveUS8171473B2Multiprogramming arrangementsSoftware simulation/interpretation/emulationStatic timing analysisCoding conventions
The service assignment tool analyzes a service to determine whether the service can execute on a cluster. If the service cannot execute on a cluster, the service is assigned to a single virtual machine. The service assignment tool identifies non-cluster friendly services by performing a static analysis on the bytecode of the service. The bytecode of the service is analyzed by comparing each segment of bytecode to a list of known good and bad coding conventions. If each segment of bytecode in a service meets the good coding convention criteria, then the service is cluster friendly. If one segment of bytecode does not meet the good coding convention criteria, then the entire service is considered to be not cluster friendly.
Owner:INT BUSINESS MASCH CORP
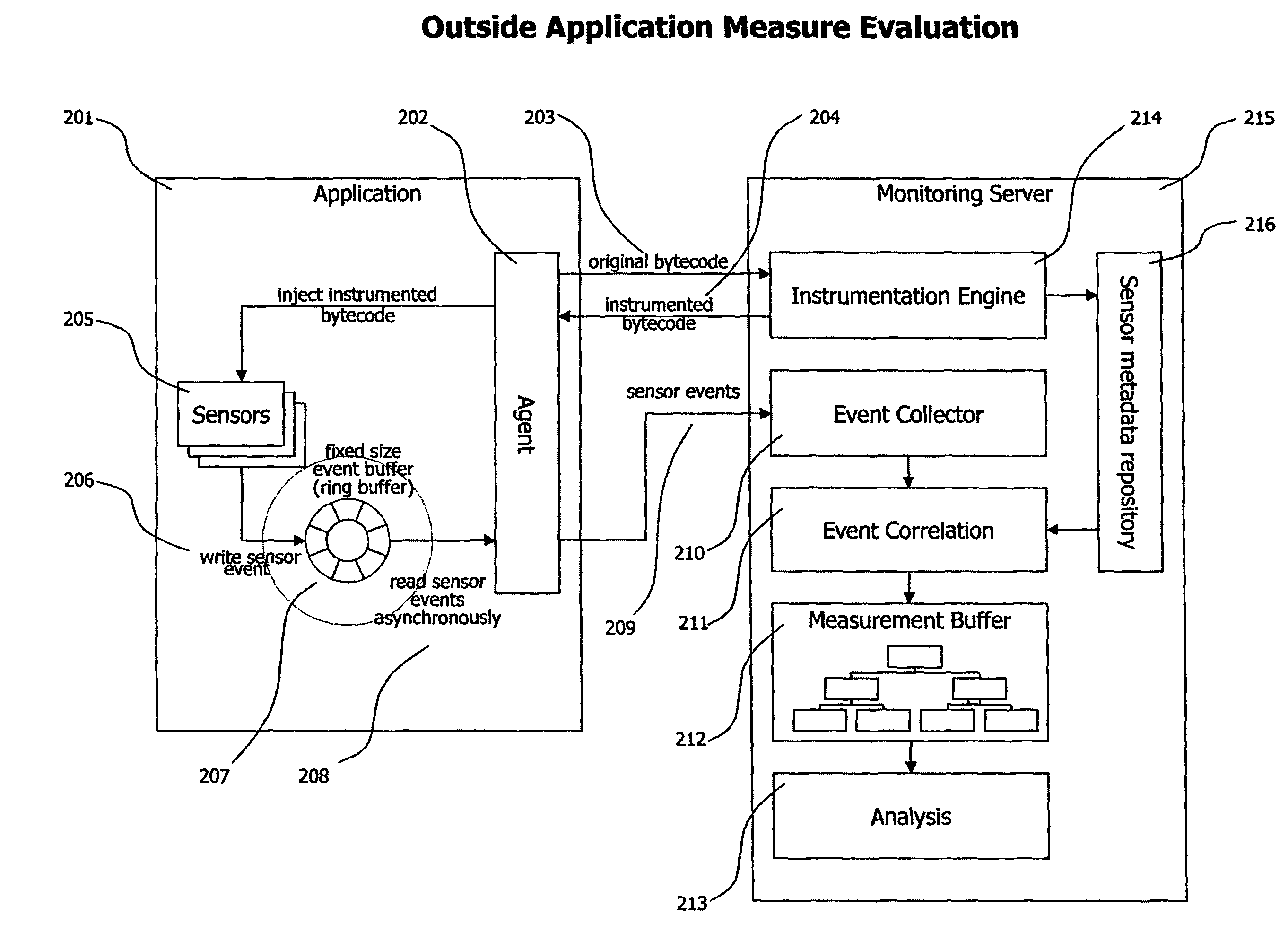
Method and system for processing application performance data outside of monitored applications to limit overhead caused by monitoring
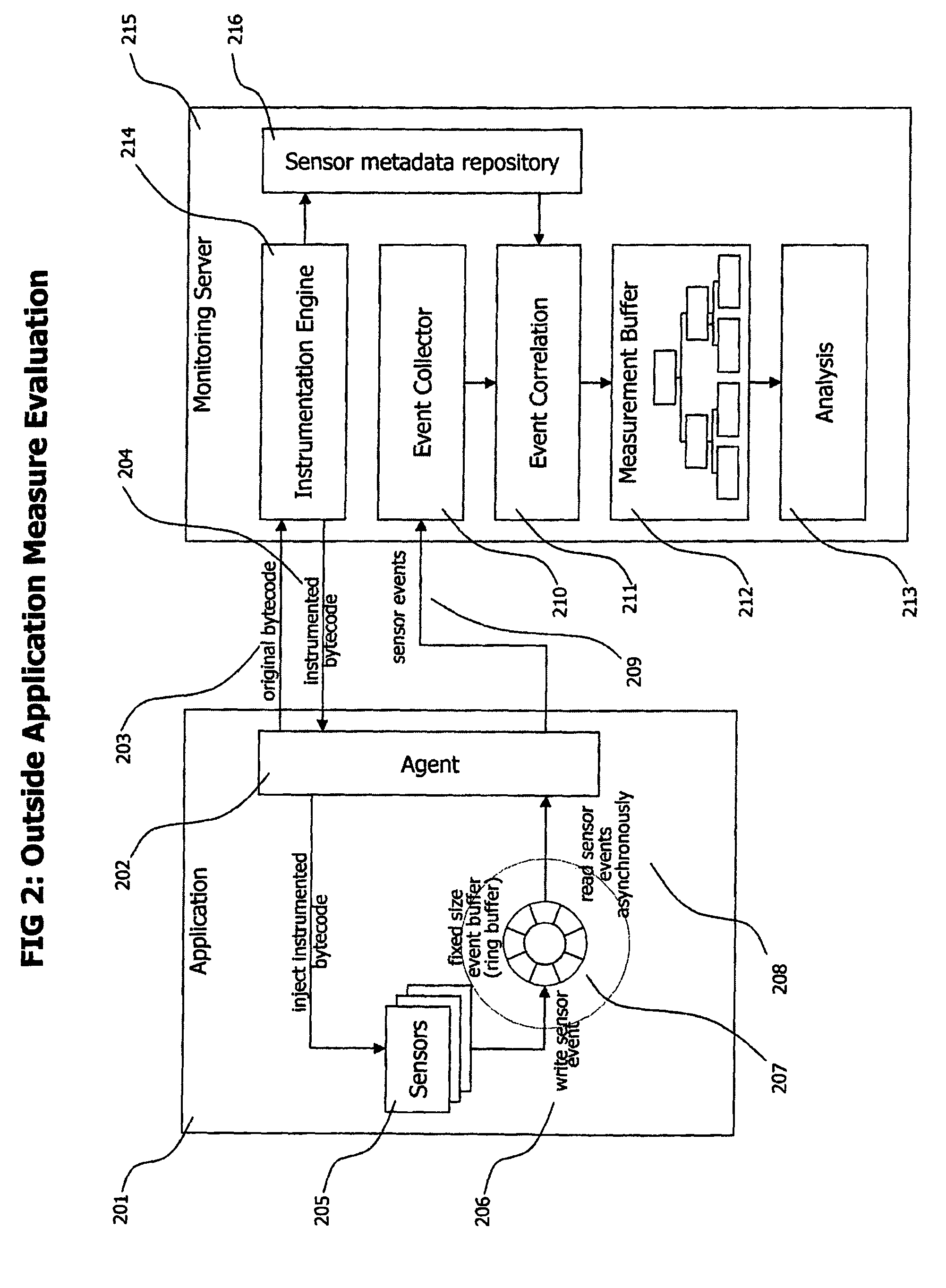
The present invention provides a system and method that aggregates and processes monitoring data acquired inside a monitored application outside of the said application to reduce overhead caused by monitoring tasks in the monitored application. Monitoring data acquired by monitoring sensors is stored in a ring buffer after acquisition, which decouples acquisition of data and its transfer, enabling asynchronous sending of performance data to a monitoring server for analysis. Memory consumption of said ring buffer is limited to a fixed size which keeps memory consumption caused by monitoring processes low and predictable. Correlation, analysis, all computation of monitoring data, and bytecode manipulation to place sensors is performed outside of the monitored application, by a monitoring server.
Owner:DYNATRACE
System and method for minimizing inter-application interference among static synchronized methods
InactiveUS6557168B1Multiple digital computer combinationsGenerating/distributing signalsStatic fieldApplication software
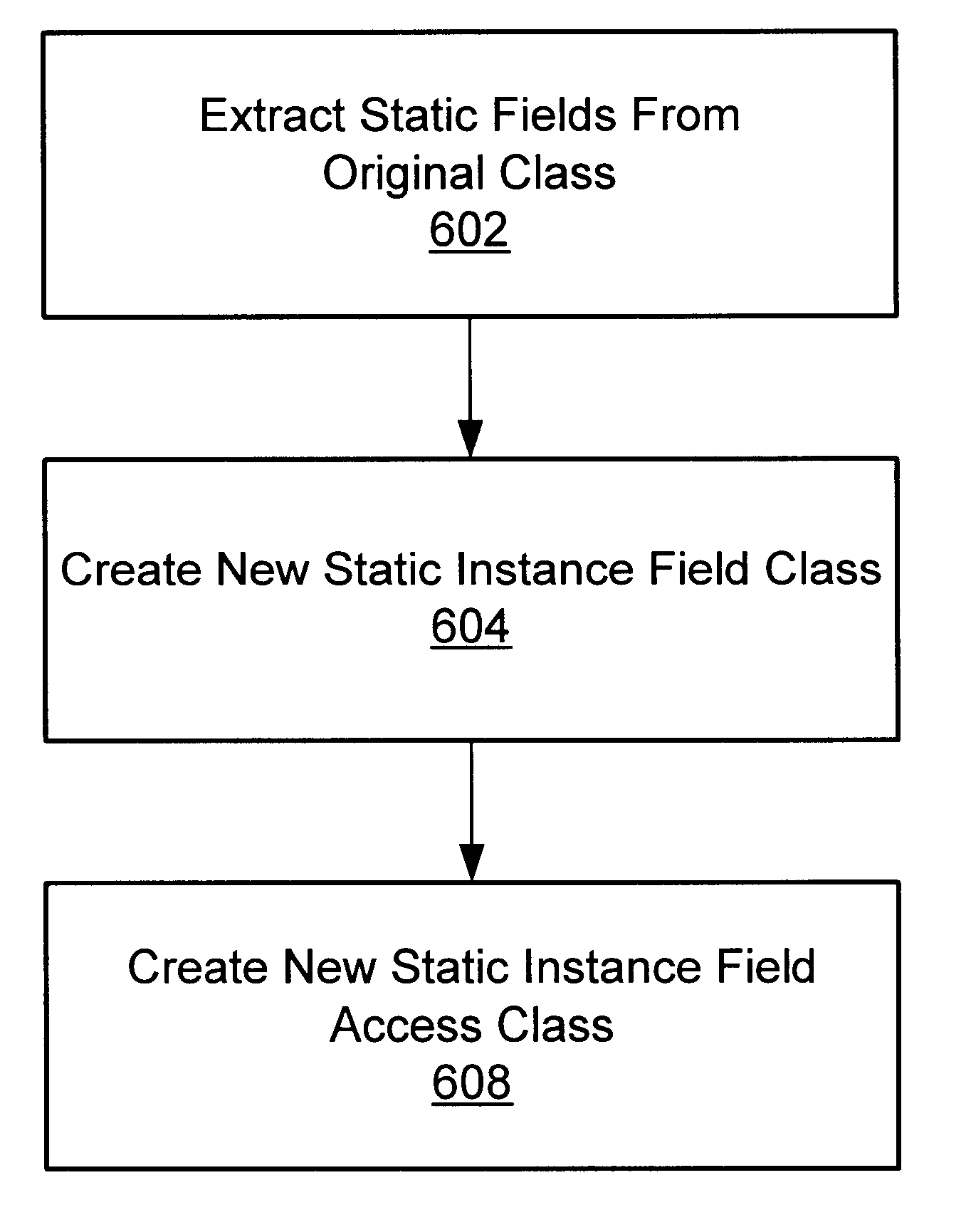
A system and method for isolating the execution of a plurality of applications. A plurality of monitors are provided for a plurality of applications to access a static synchronized method. The applications are enabled to call the static synchronized method concurrently by accessing the static synchronized method through the plurality of monitors. A plurality of threads within one of the applications are excluded from calling the static synchronized method concurrently. The source code or bytecode for the synchronized method may be transformed by removing a method-level monitor and adding the plurality of monitors inside the method. In one embodiment, each static synchronized method is replaced with a corresponding static non-synchronized method. The applications may be further isolated by placing the static fields of shared classes into a static field class, which has one instance per utilizing application. The static non-synchronized method includes the body of the corresponding static synchronized method, wherein the body is synchronized on the instance of the static field class that corresponds to the utilizing application.
Owner:ORACLE INT CORP
Fast just-in-time (JIT) scheduler
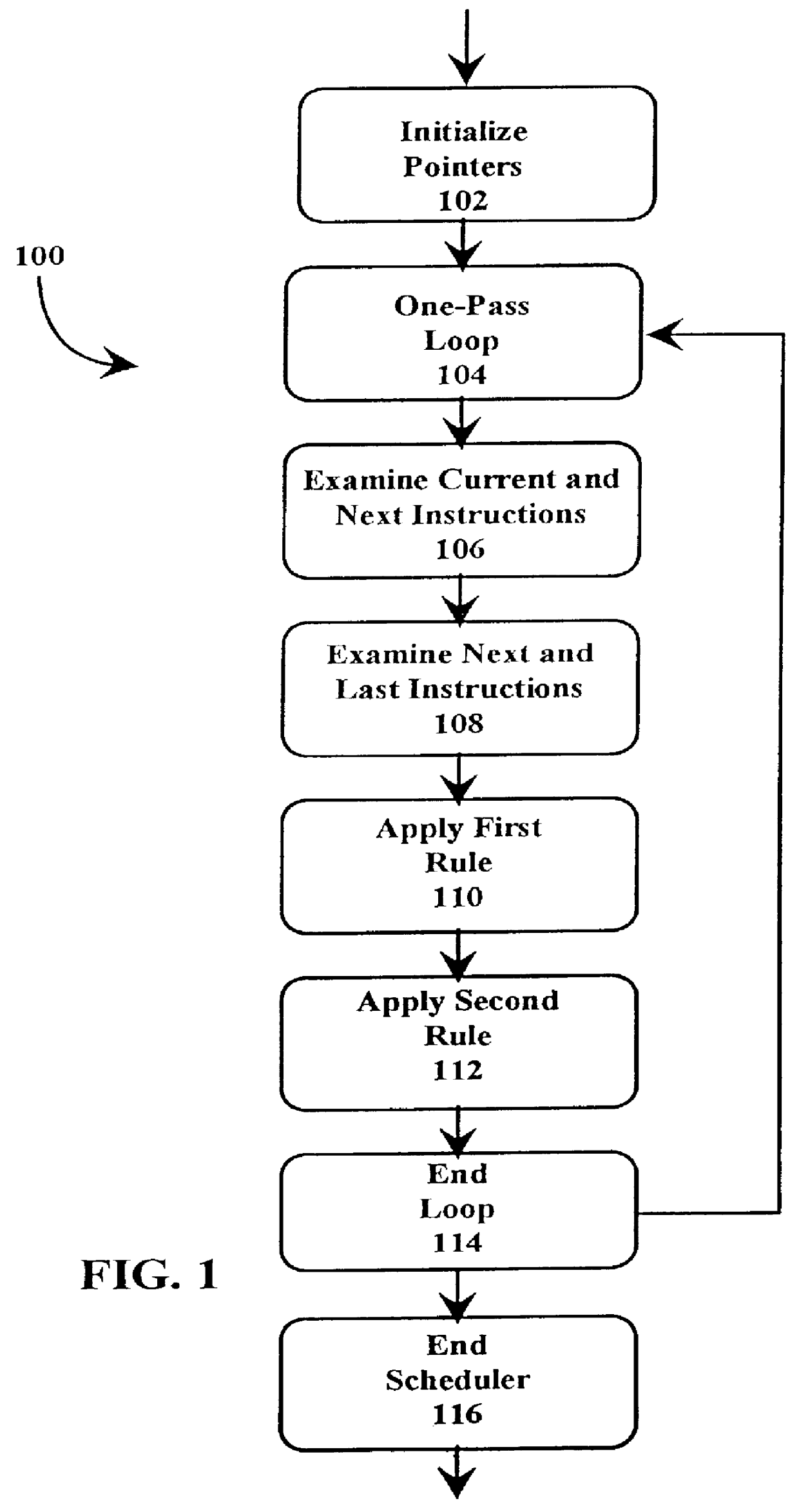
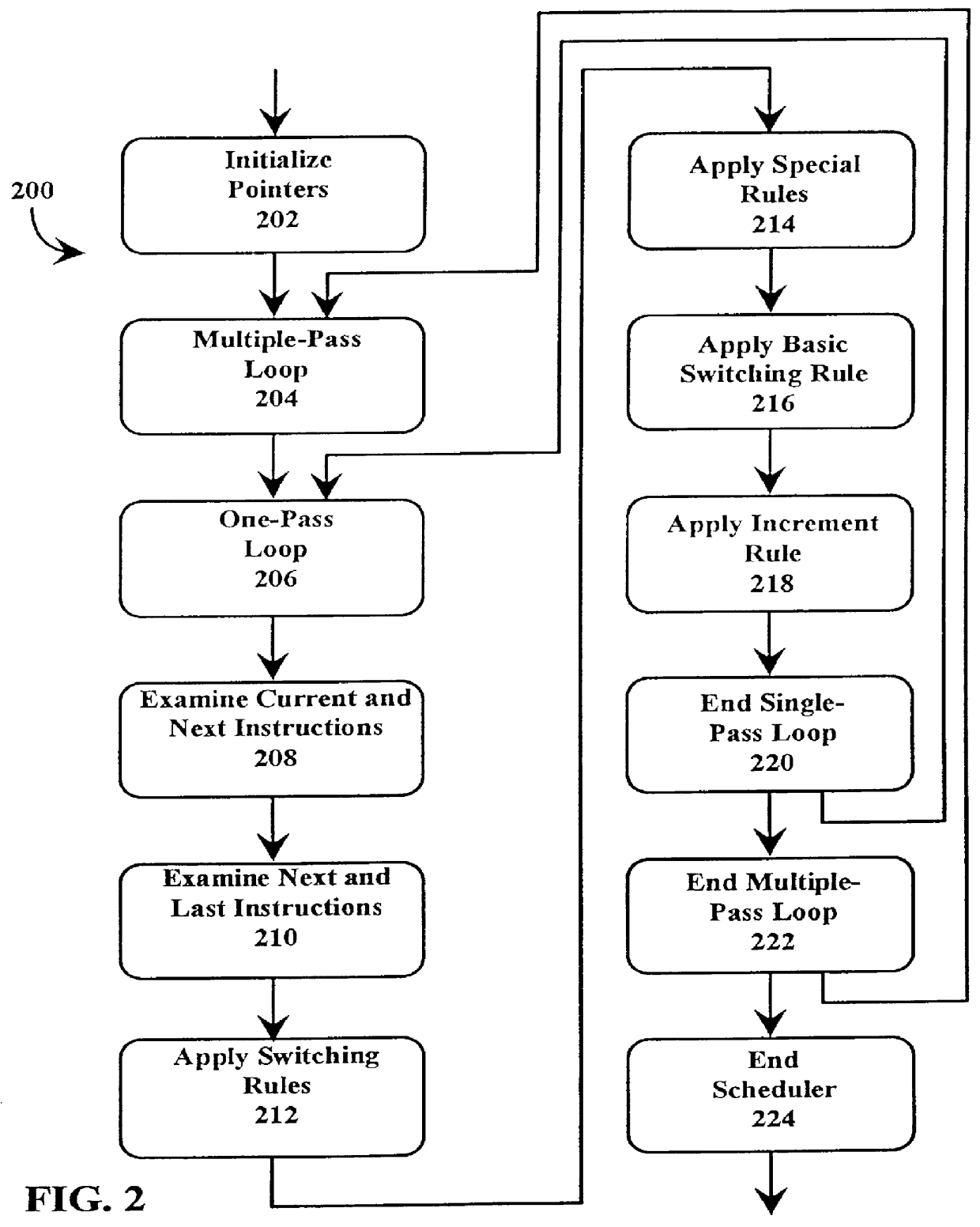
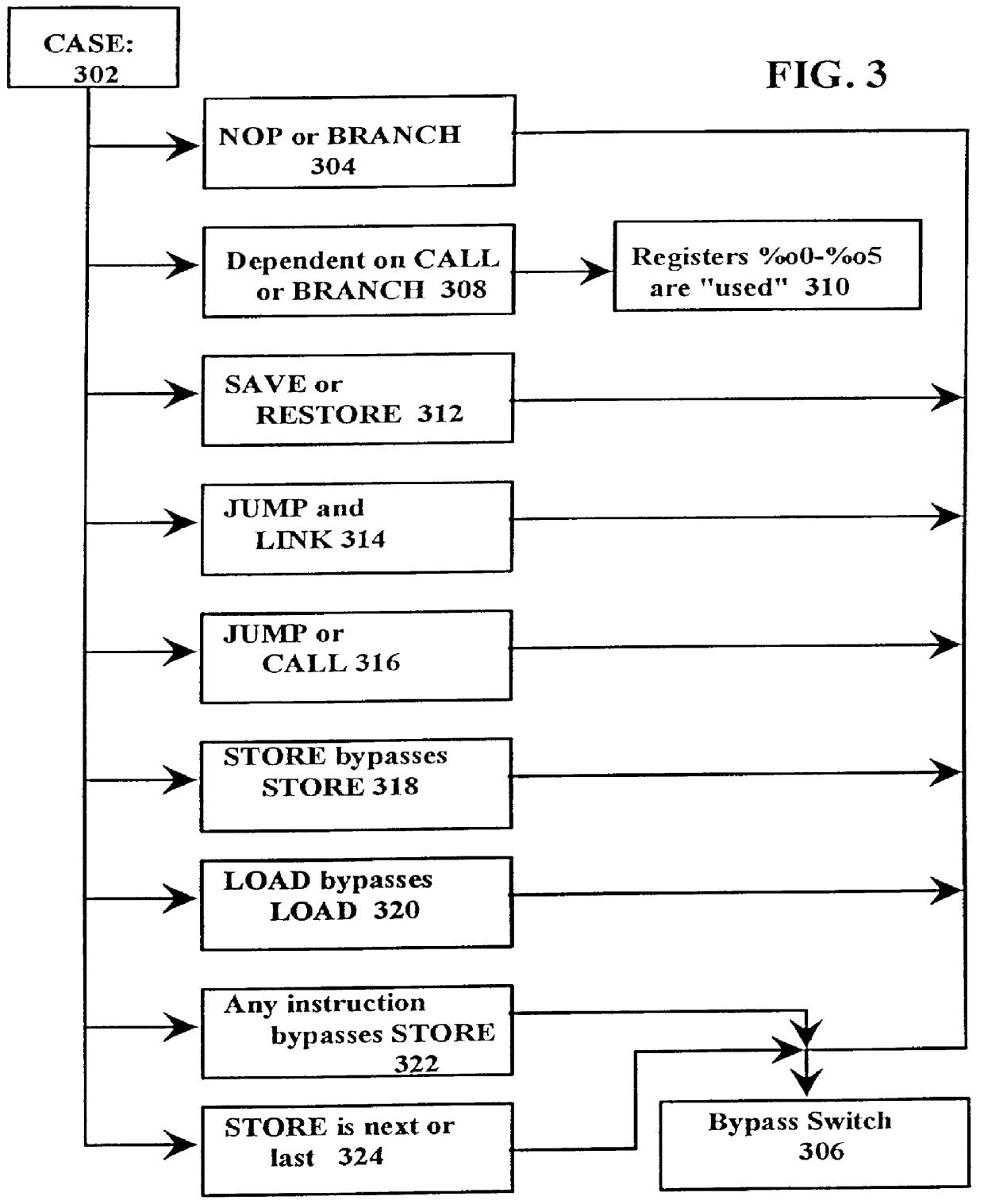
A just-in-time (JIT) compiler typically generates code from bytecodes that have a sequence of assembly instructions forming a "template". It has been discovered that a just-in-time (JIT) compiler generates a small number, approximately 2.3, assembly instructions per bytecode. It has also been discovered that, within a template, the assembly instructions are almost always dependent on the next assembly instruction. The absence of a dependence between instructions of different templates is exploited to increase the size of issue groups using scheduling. A fast method for scheduling program instructions is useful in just-in-time (JIT) compilers. Scheduling of instructions is generally useful for just-in-time (JIT) compilers that are targeted to in-order superscalar processors because the code generated by the JIT compilers is often sequential in nature. The disclosed fast scheduling method has a complexity, and therefore an execution time, that is proportional to the number of instructions in an instruction block (N complexity), a substantial improvement in comparison to the N2 complexity of conventional compiler schedulers. The described fast scheduler advantageously reorders instructions with a single pass, or few passes, through a basic instruction block while a conventional compiler scheduler such as the DAG scheduler must iterate over an instruction basic block many times. A fast scheduler operates using an analysis of a sliding window of three instructions, applying two rules within the three instruction window to determine when to reorder instructions. The analysis includes acquiring the opcodes and operands of each instruction in the three instruction window, and determining register usage and definition of the operands of each instruction with respect to the other instructions within the window. The rules are applied to determine ordering of the instructions within the window.
Owner:ORACLE INT CORP
Computer multi-tasking via virtual threading using an interpreter
InactiveUS7234139B1Eliminate dependenciesDifferent operationalProgram initiation/switchingInterprogram communicationLocal variablePseudocode
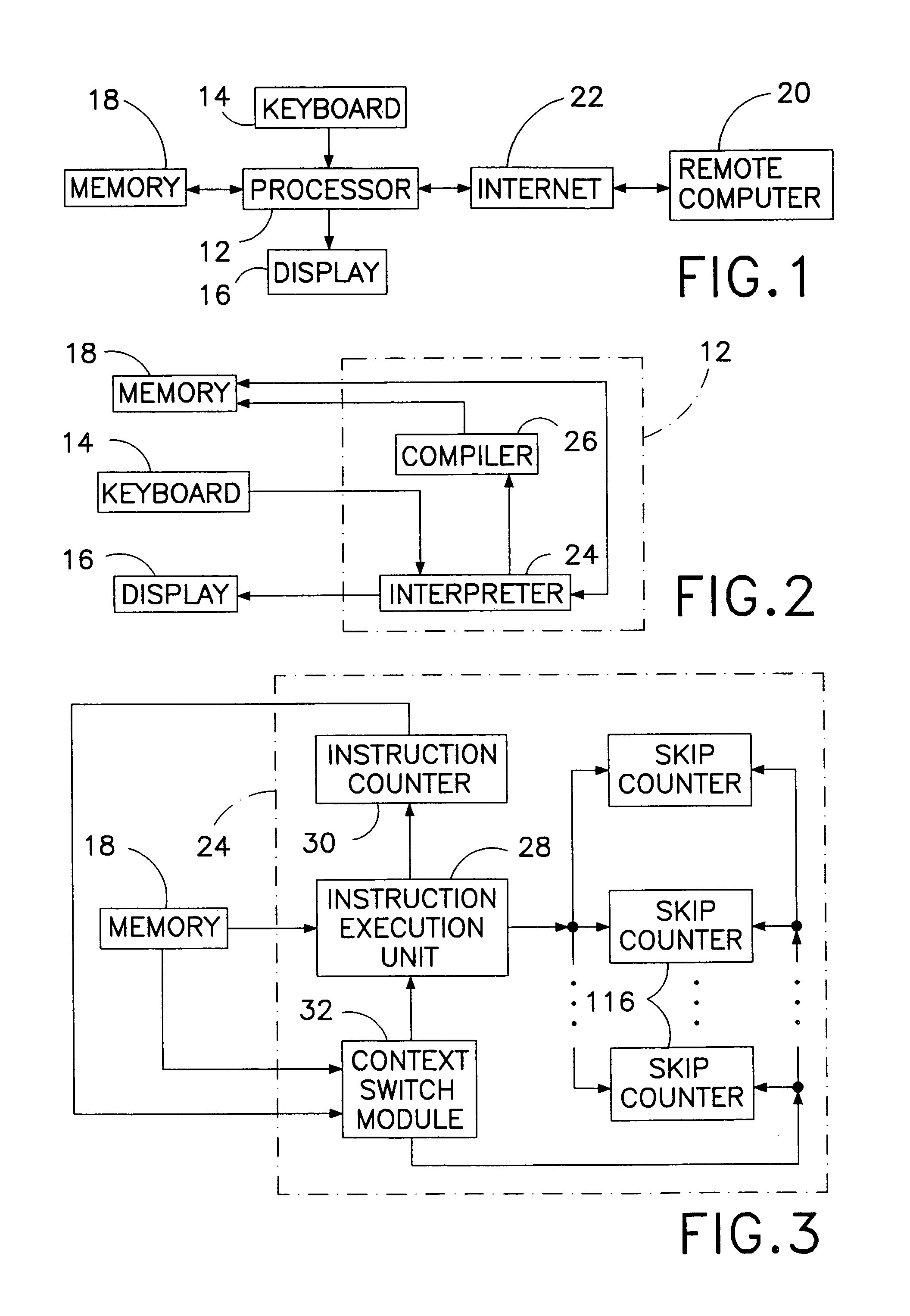
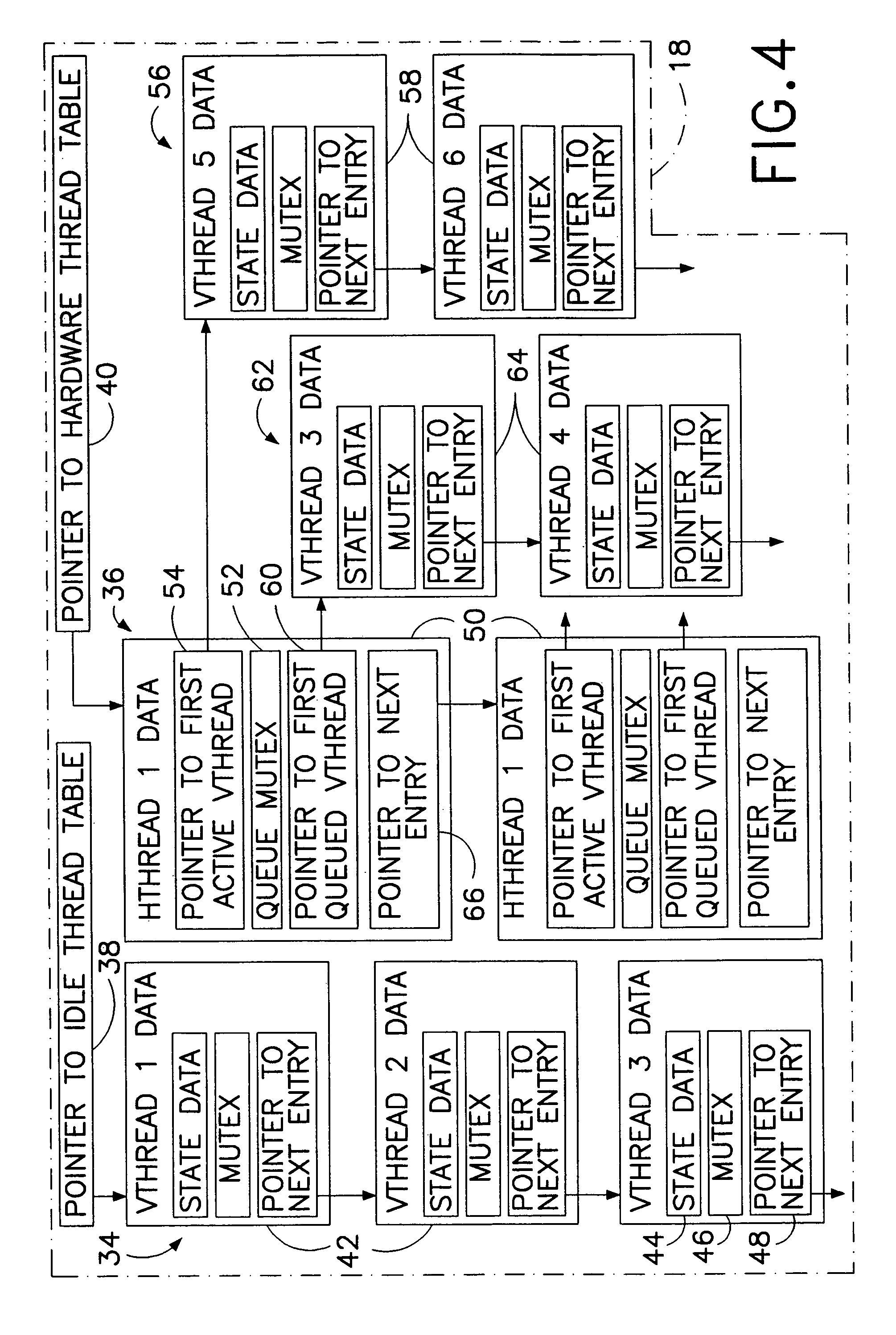
In the operation of a computer, a plurality of bytecode or pseudocode instructions, at least some of the pseudocode instructions comprising a plurality of machine code instructions, are stored in a computer memory. For each of a plurality of tasks or jobs to be performed by the computer, a respective virtual thread of execution context data is automatically created. The virtual threads each include (a) a memory location of a next one of the pseudocode instructions to be executed in carrying out the respective task or job and (b) the values of any local variables required for carrying out the respective task or job. At least some of the tasks or jobs each entails execution of a respective one of the pseudocode instructions comprising a plurality of machine language instructions. Each of the tasks or jobs are processed in a respective series of time slices or processing slots under the control of the respective virtual thread, and, in every context switch between different virtual threads, such context switch is undertaken only after completed execution of a currently executing one of the pseudocode instructions.
Owner:CERINET USA
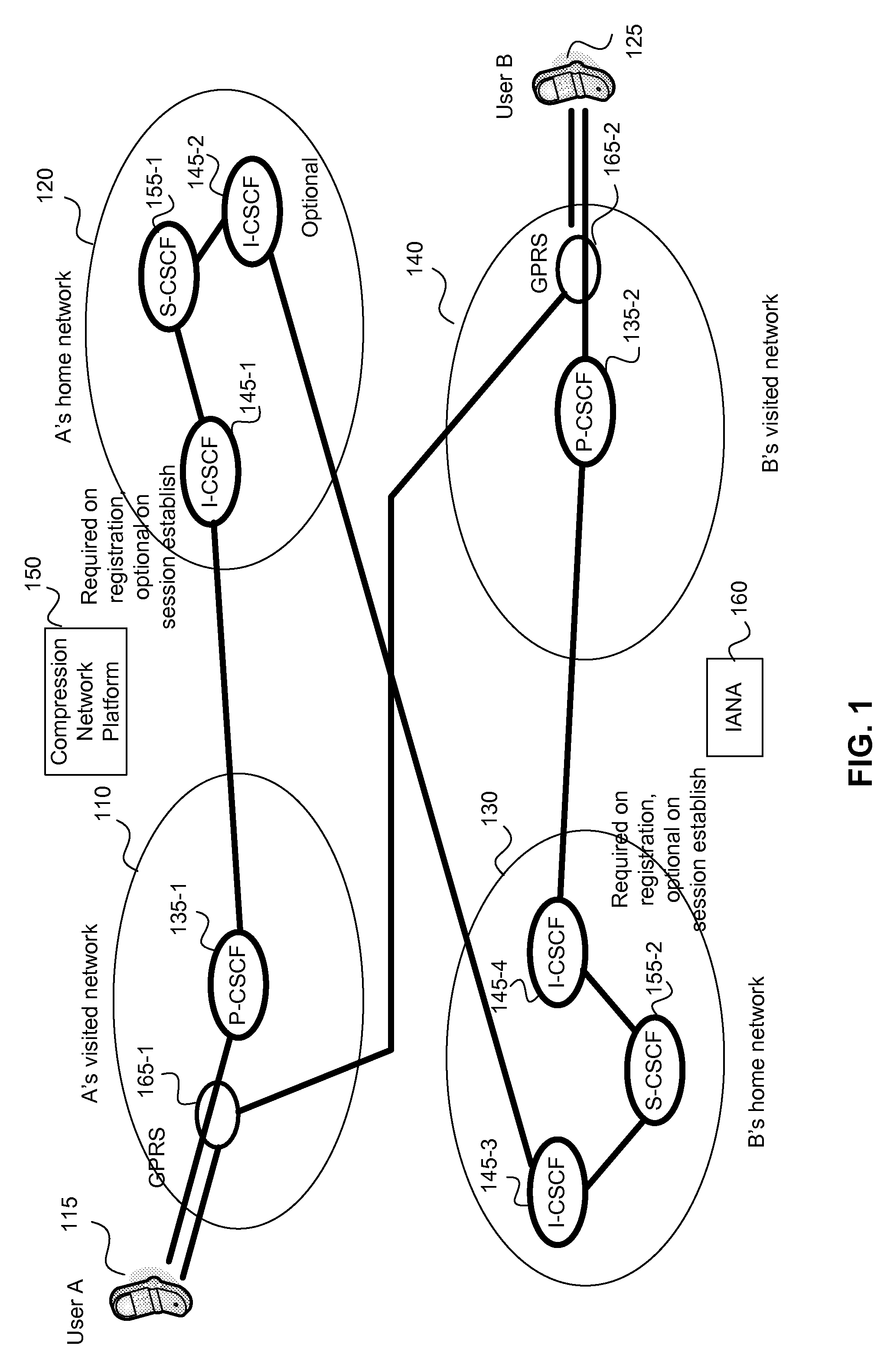
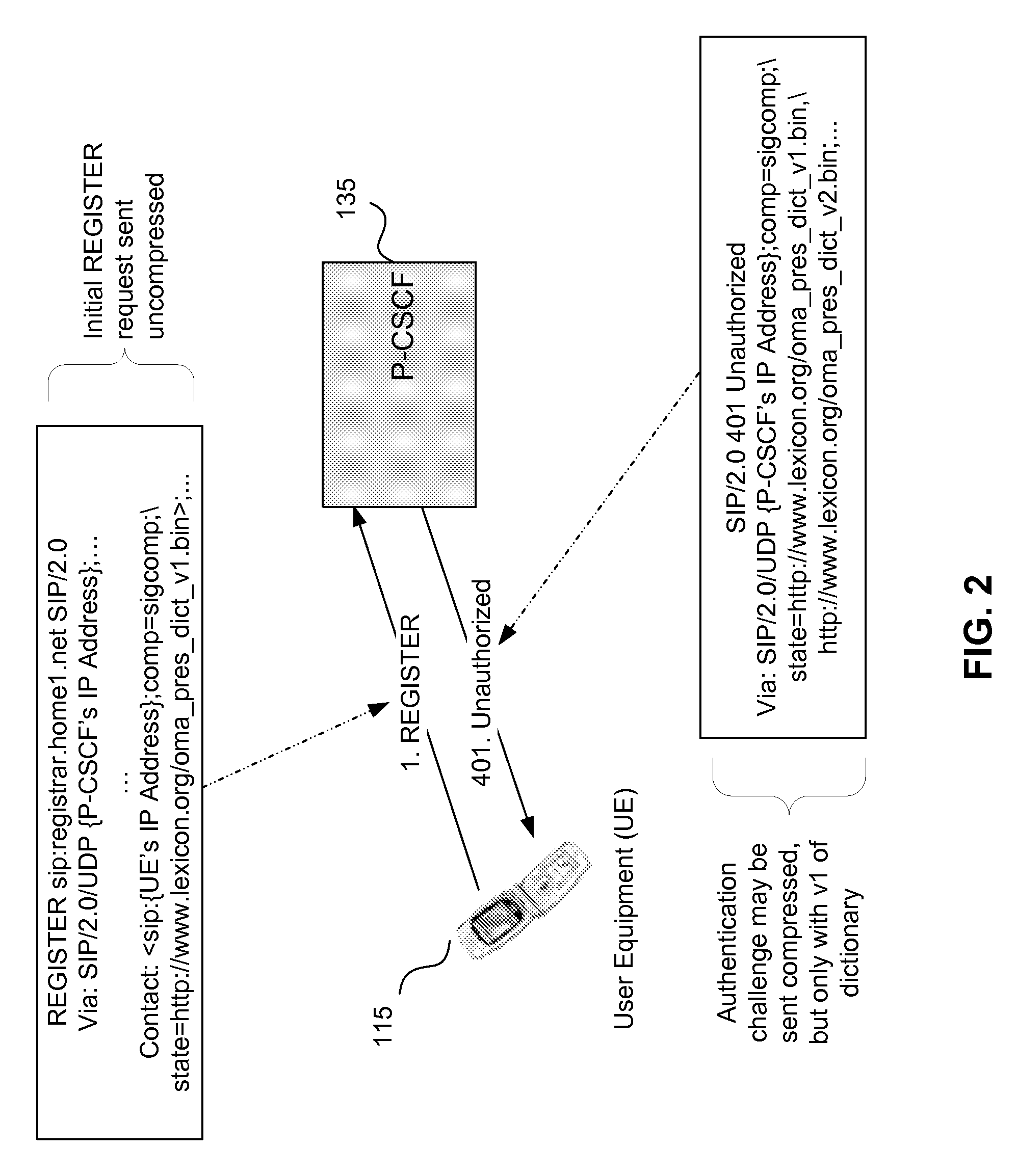
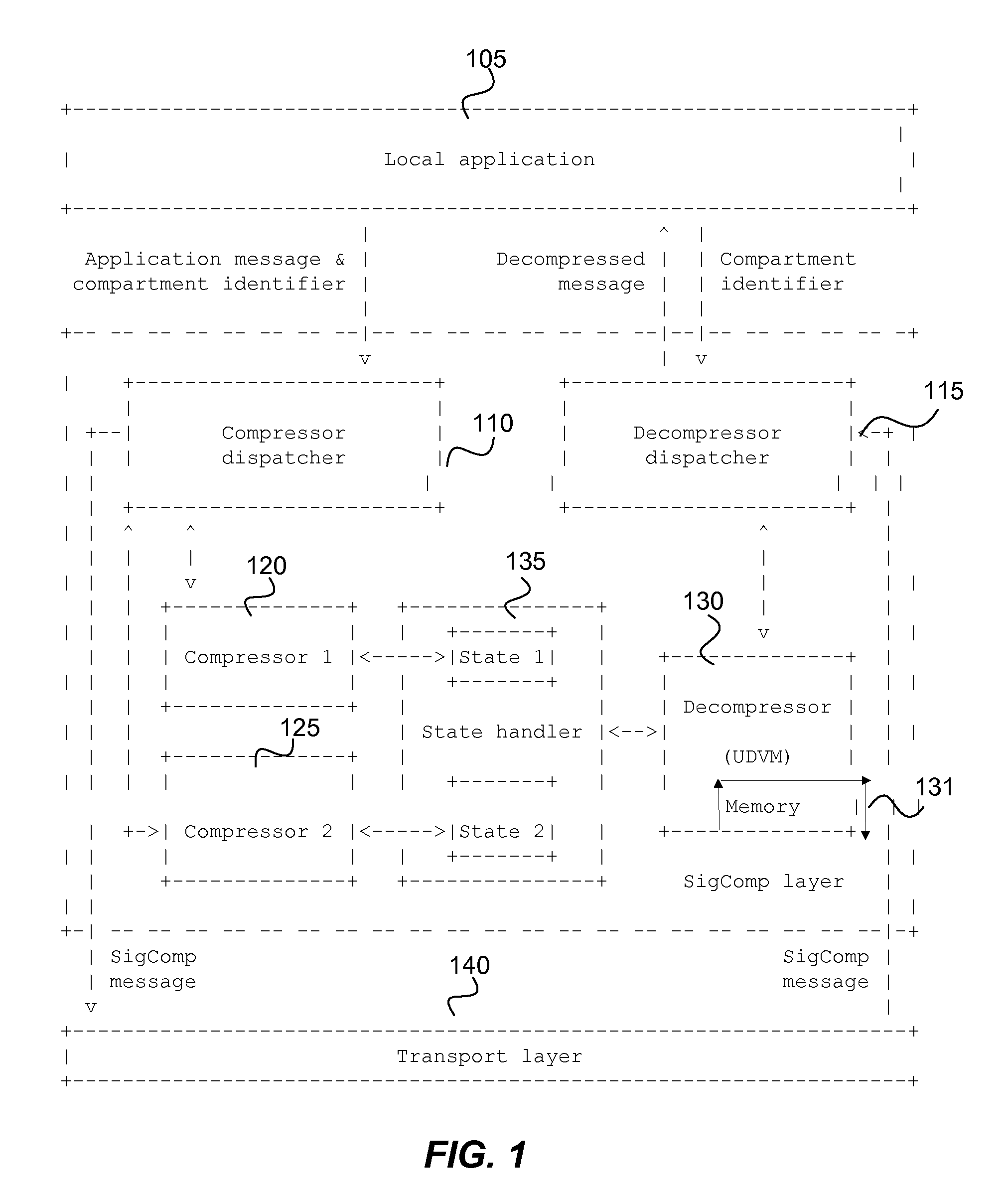
Optimizing static dictionary usage for signal compression and for hypertext transfer protocol compression in a wireless network
InactiveUS20080115125A1TransmissionSoftware simulation/interpretation/emulationSession controlData signal
Methods and apparatus including a virtual machine and a compression network platform are provided especially for improving the application of compression algorithms and unique identifiers for algorithms, bytecode and HTTP common phrases of HTTP messages utilized to advantage in wireless networks. In particular, a given virtual machine need only identify to a receiving virtual machine the unique identifier for one of an algorithm, a static dictionary or a hash for decompressing a received data signal. Universal decompressor virtual machines may receive uploaded compression algorithms, bytecode identifiers or static dictionary identifiers and the like from proxy call session control functions of a wireless network, the compressing machine or a compression network platform resource which in one embodiment may comprise an IANA database. The methods and apparatus may find particular application in improving the efficiency of presence / group list management.
Owner:CINGULAR WIRELESS II LLC
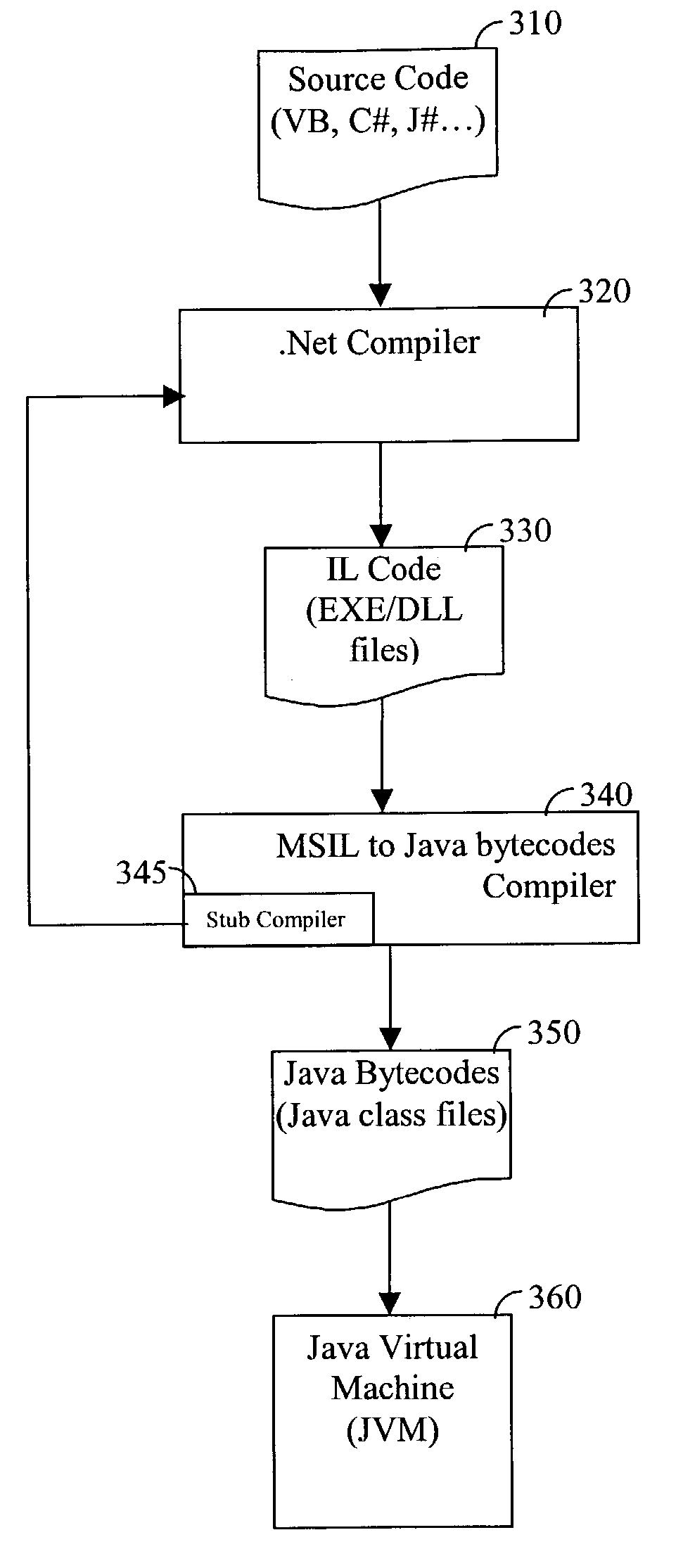
Compiler and software product for compiling intermediate language bytecodes into Java bytecodes
InactiveUS7380242B2Simple to executeSoftware engineeringSpecific program execution arrangements.NET FrameworkApplication software
Compiler and software product for compiling intermediate language (IL) bytecodes, such as Microsoft IL (MSIL) instructions into Java bytecodes, are provided. The provided compiler decodes the IL instructions, generates the stack content, and produces Java bytecodes based on the stack content. Furthermore, the compiler is specially designed to allow a programmer to develop software applications using the .Net framework that could be easily executed using a Java runtime environment.
Owner:HARMON IE R&D
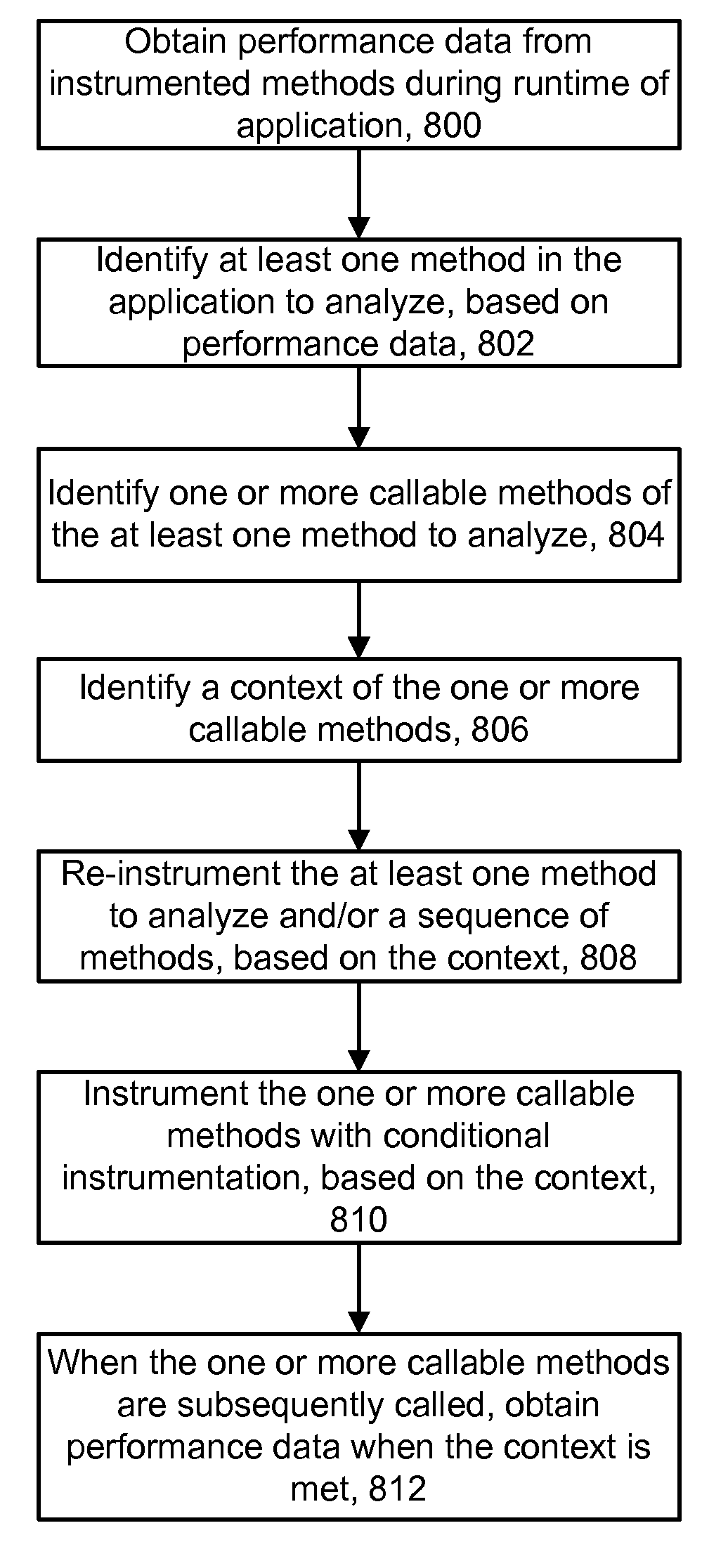
Conditional dynamic instrumentation of software in a specified transaction context
ActiveUS20110283263A1Error detection/correctionSoftware maintainance/managementDynamic instrumentationTransaction data
Techniques for analyzing software in which un-instrumented components can be discovered and conditionally instrumented during a runtime of the software. Initially, software such as an application can be configured with a baseline set of instrumented components such as methods. As the application runs, performance data gathered from the instrumentation may indicate that the performance of some methods is below expectations. To analyze this, any methods which are callable from a method at issue are discovered, such as by inspecting the byte code of loaded classes in a JAVA Virtual Machine (JVM). To limit and focus the diagnosis, the instrumentation which is added to the discovered components can be conditional, so that the instrumentation is executed only in a specified context. The context can involve, e.g., a specified sequence of components in which a discovered component is called, and / or transaction data in which a discovered component is called.
Owner:CA TECH INC
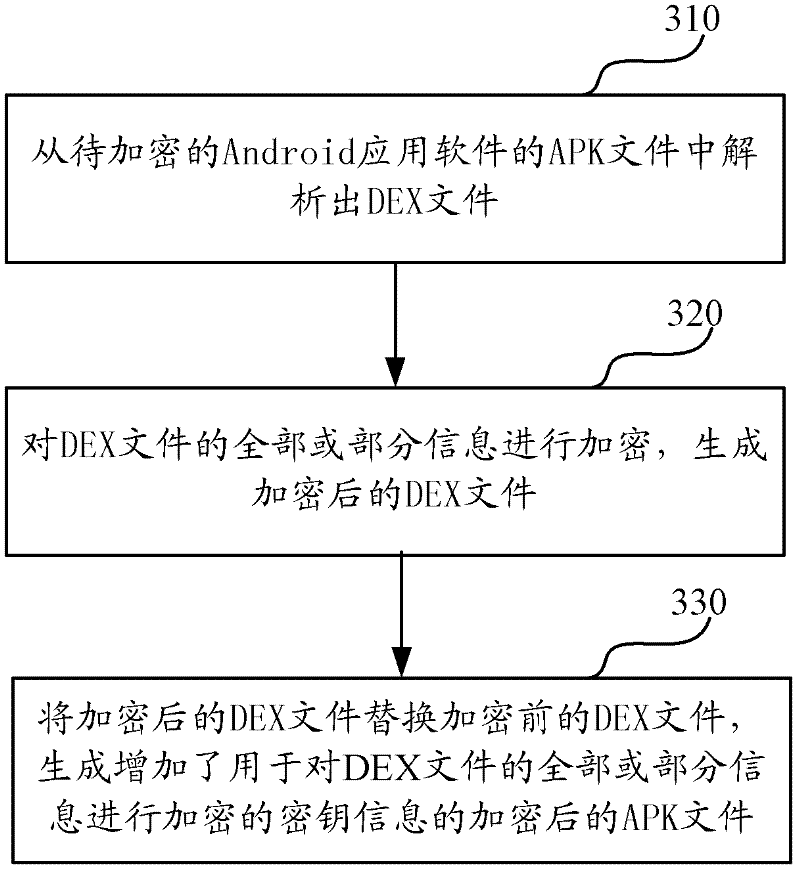
Software protection method and system applicable to Android system
InactiveCN102236757AImprove protectionImprove execution efficiencyProgram/content distribution protectionByteSoftware protection
The invention discloses a software protection method and system applicable to an Android system. The method comprises the following steps of: analyzing: analyzing a DEX file from an APK (Android Package) file of Android application software to be encrypted; encrypting: encrypting all or a part of information of the DEX file to generate an encrypted DEX file; and generating, substituting the DEX file before encryption with the encrypted DEX file to generate the APK file formed by encrypting all or a part of the information of the DEX file and a digest file formed by performing MD5 (Message Digest 5) encryption on a key. Since the method only aims at the encryption protection of key information (such as a DEX file header, byte codes in the DEX file and the like) of the DEX file in the APK file, the execution efficiency of encryption and decryption is greatly increased.
Owner:BEIJING UNIV OF POSTS & TELECOMM
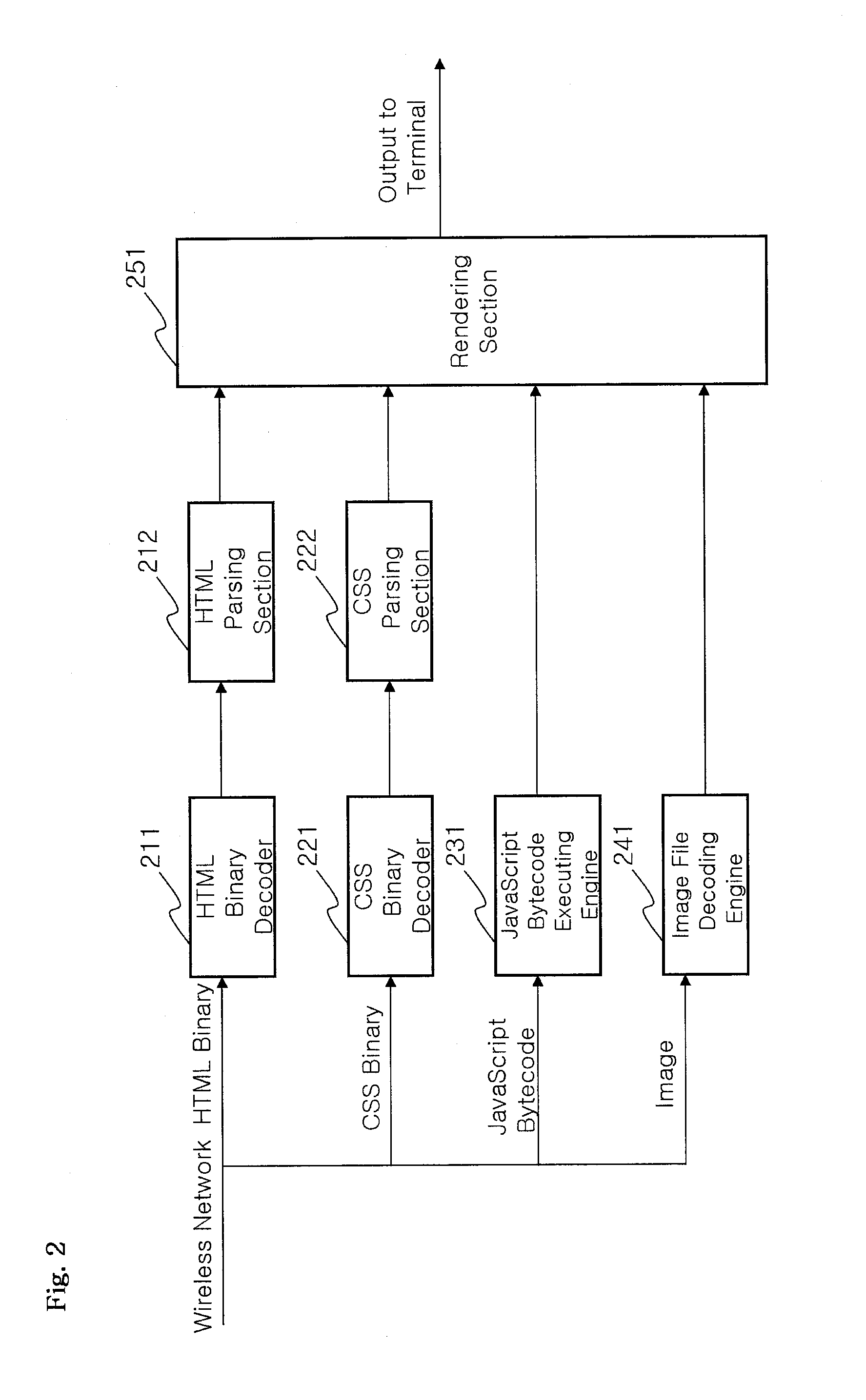
Web browser system of mobile communication terminal, using proxy server
InactiveUS20100050089A1Improve processing speedDecreasing an amount of wireless transmission dataMultiple digital computer combinationsTransmissionFile transmissionWeb browser
A web browser system includes a mobile communication terminal configured to implement decoding and parsing for HTML and CSS binary files, execute a JavaScript bytecode, decode an image file, and implement rendering for respective results, for web browsing of a web browser built therein; a proxy server configured to, in correspondence to a web address transmitted thereto, transmit a page access command to a web server of the corresponding web address via a wired network, implement grammar indentifying binary encoding for HTML and CSS transmitted from the web server to decrease capacity, convert quality for an image file to decrease capacity, compile JavaScript into a bytecode to decrease capacity, and transmit those files to the mobile communication terminal via a wireless network; and a web server configured to transmit files constituting a web page including the HTML, CSS, JavaScript and image files, to the proxy server.
Owner:COMPANY 100 LNC
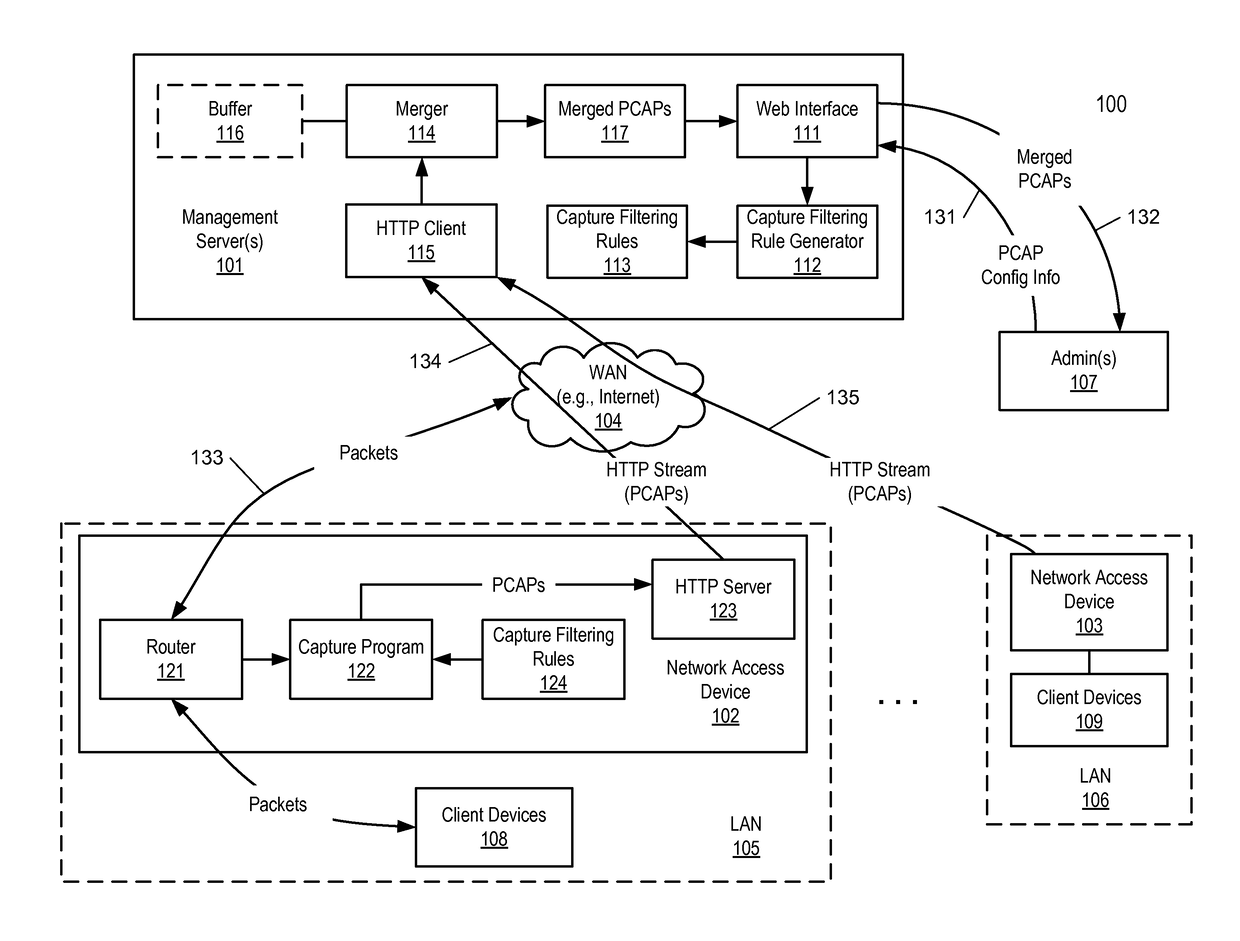
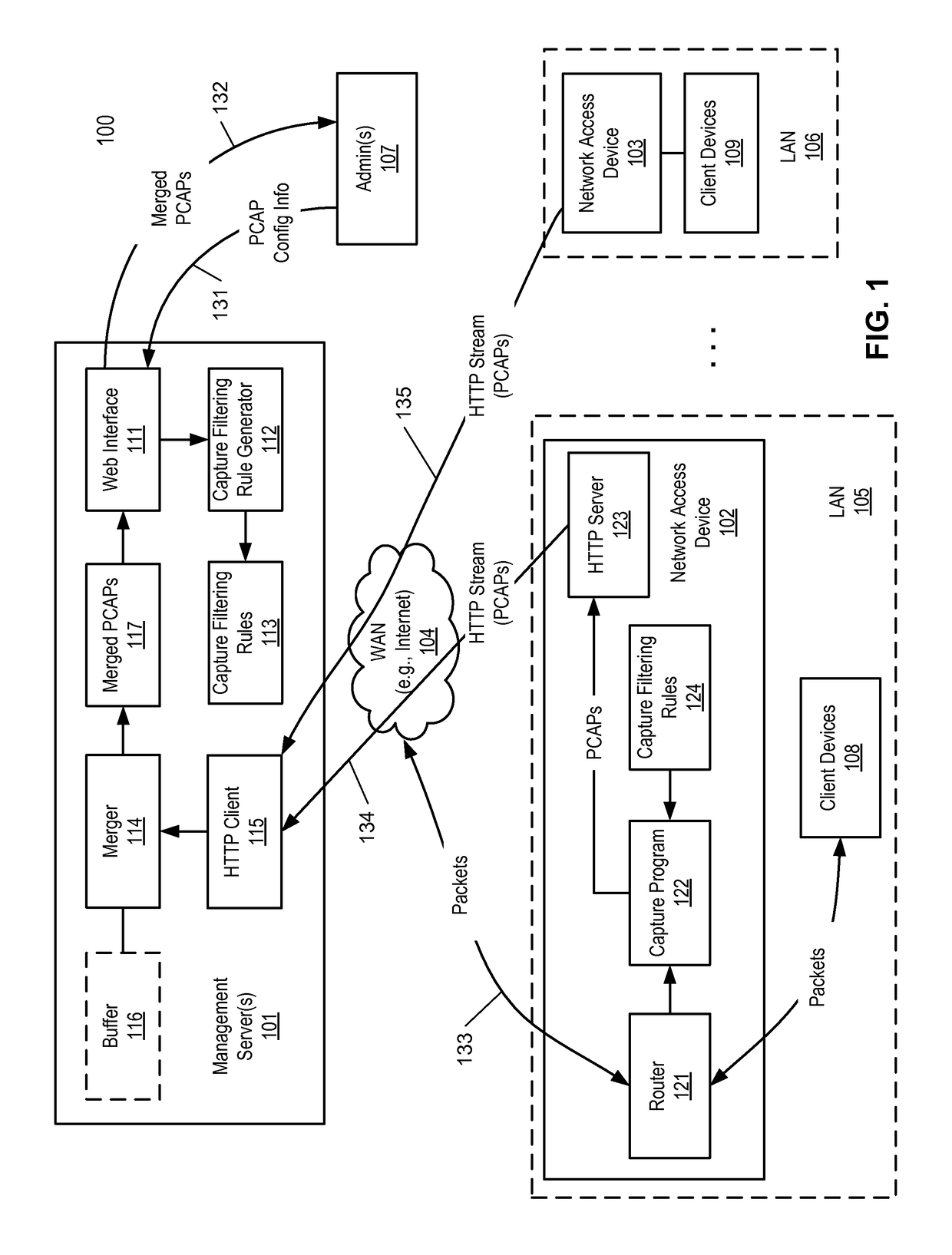
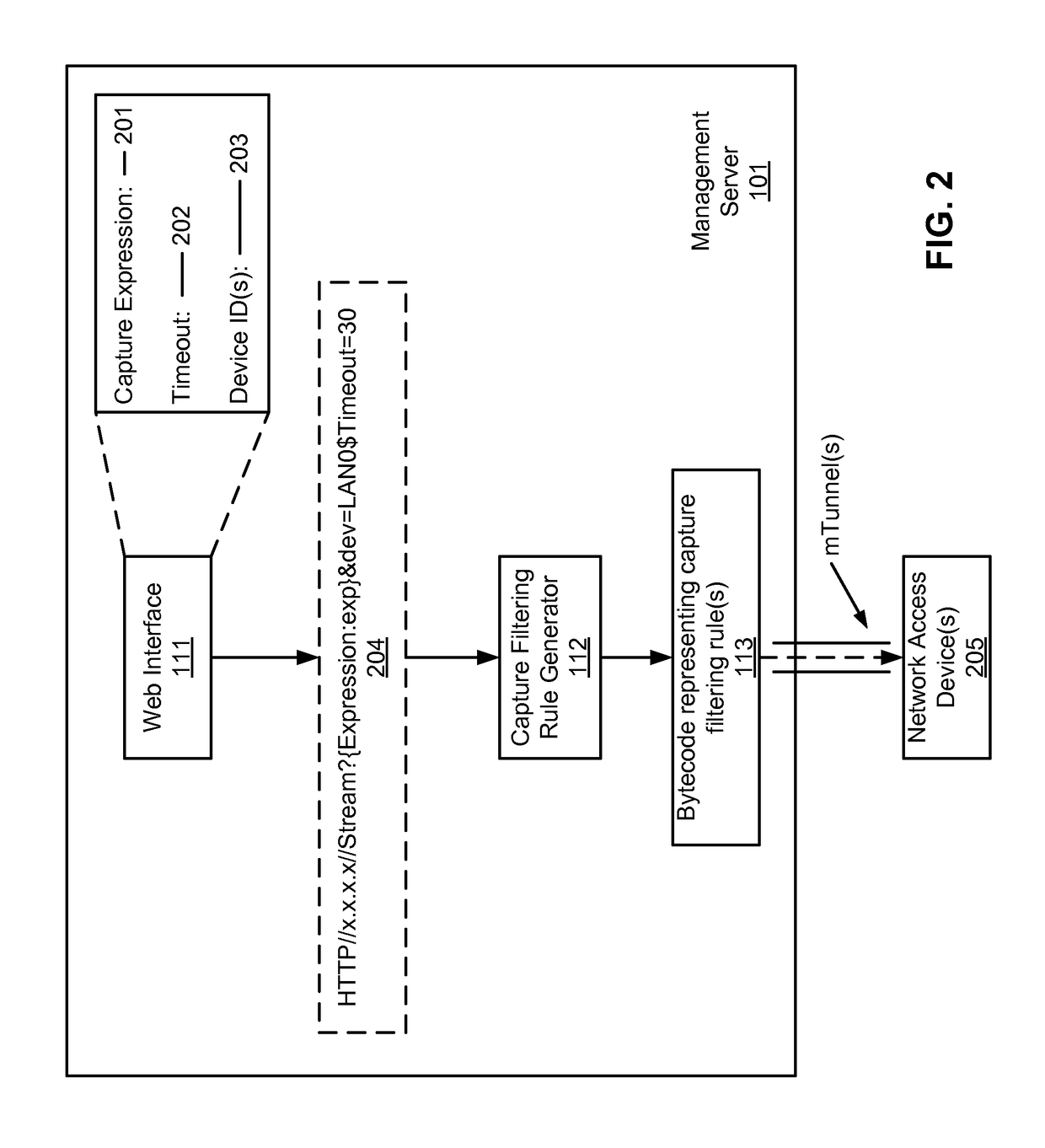
Method for streaming packet captures from network access devices to a cloud server over HTTP
ActiveUS9692802B2Multiple digital computer combinationsData switching networksNetwork access serverNetwork packet
A system for streaming packet captures over the Internet includes multiple network access devices, each operating as one of a gateway device, a wireless access point, and a network switch, and a management server communicatively coupled to the network access devices over the Internet for managing the network access devices. The management server maintains a persistent hypertext transport protocol (HTTP) connection with each of the network access devices over the Internet. The management server is to generate a bytecode based on a filtering expression for packet captures (PCAPs) representing one or more PCAPs filtering rules, transmit the bytecode to the network access devices without requiring the network access devices to compile the PCAPs filtering rules, receive PCAPs from the network access devices captured by the network access devices based on the PCAPs filtering rules, and merge the PCAPs received from the network access devices into merged PCAPs.
Owner:CISCO TECH INC
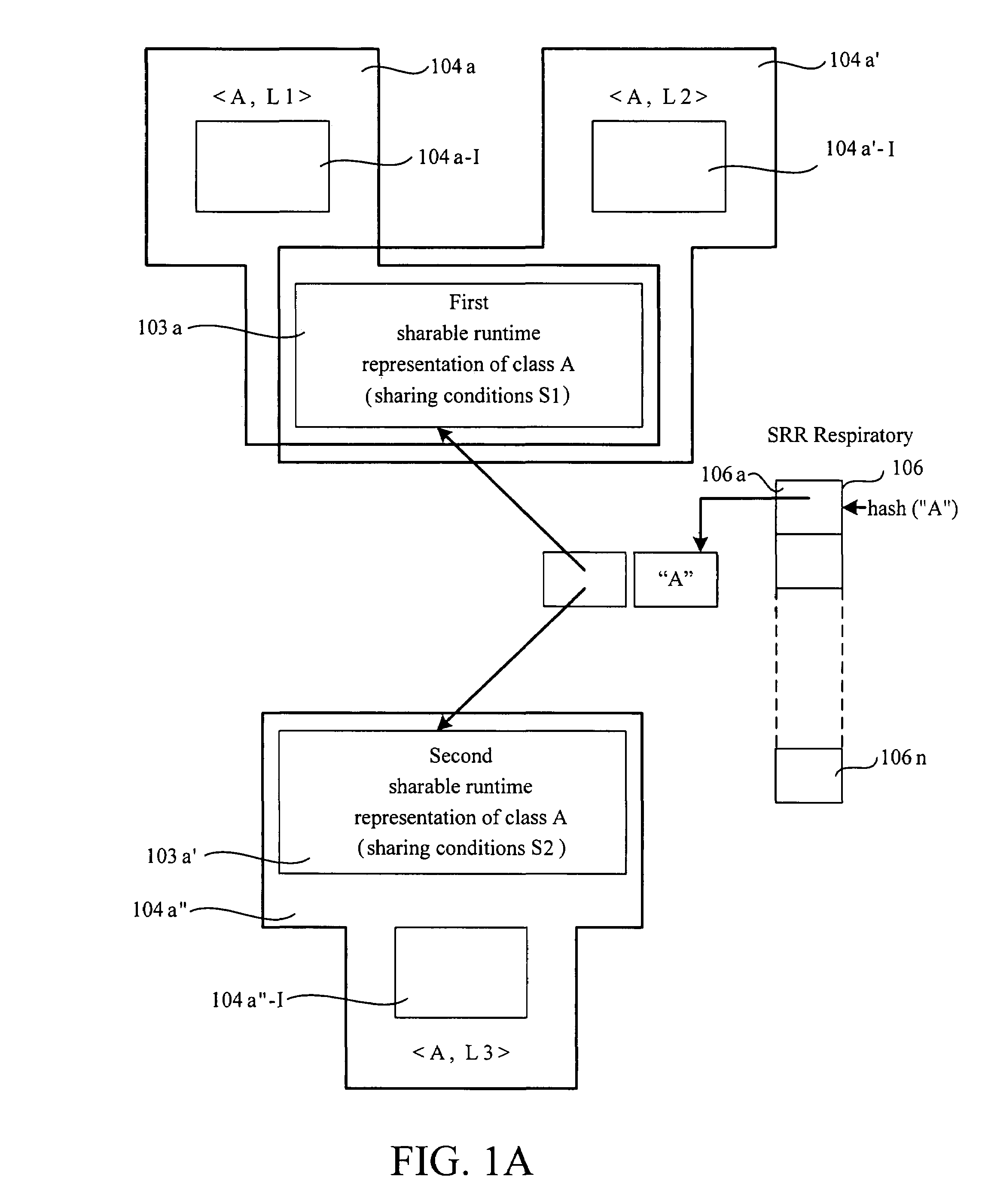
Methods for sharing conditionally across class loaders dynamically compiled code
A method for conditionally sharing dynamically compiled code between different class loaders is provided. In this method, bytecodes of a first class type are compiled into a compiled code if the bytecodes have not been compiled. The locations of sequence of instructions in the compiled code that are loader dependent are then recorded. Thereafter, the loader dependencies in the compiled code are compared to determine whether the compiled code can be used by a method of a second class type. If the loader dependencies of the second class type are different from the loader dependencies of the first class type, the compiled code for the method of the first class type is cloned. Subsequently, portions of the cloned code that are loader dependent are modified to enable the method of the second class type to use the cloned code.
Owner:SUN MICROSYSTEMS INC
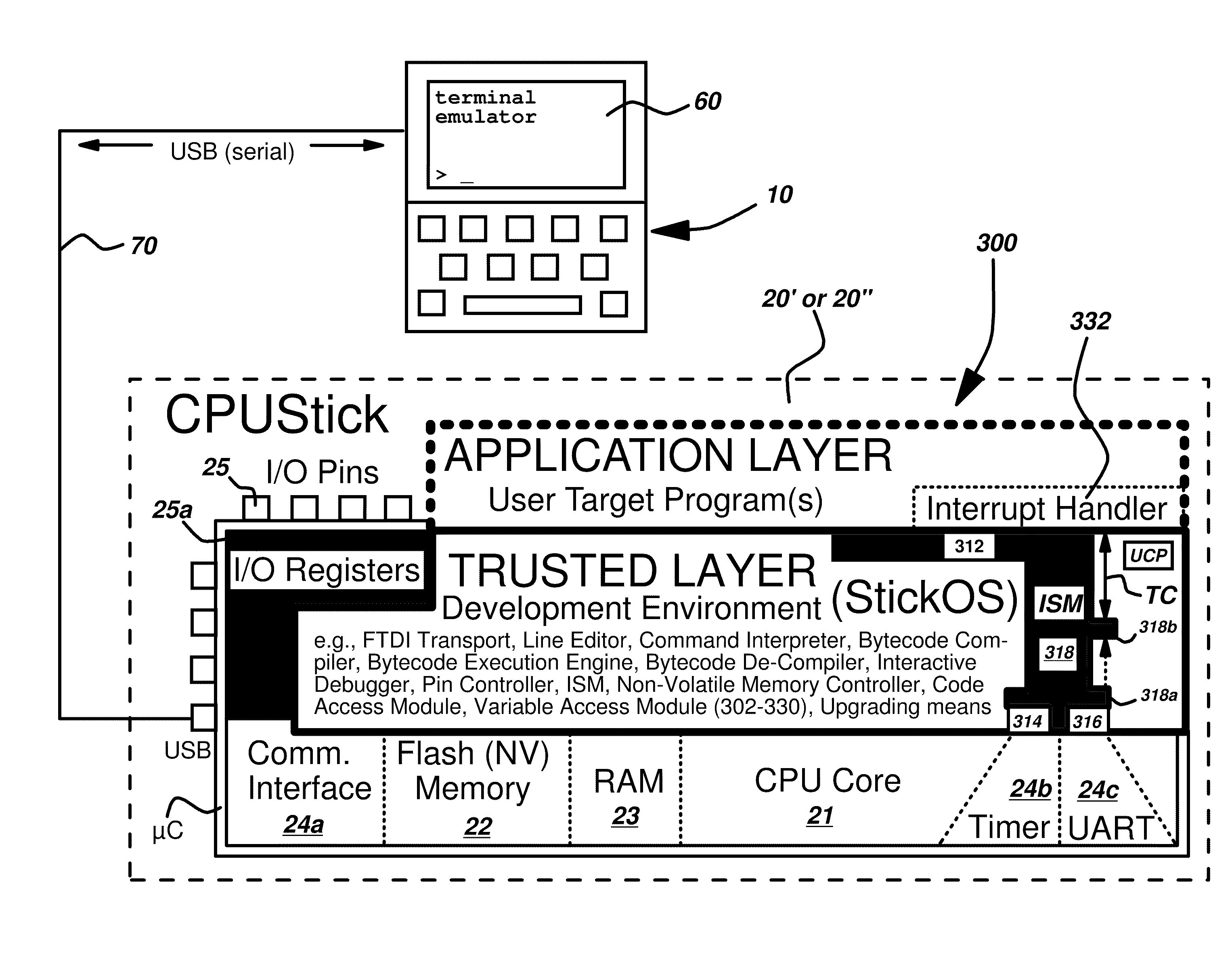
Microcontroller-resident software development environment supporting application-level asynchronous event handling, interactive debugging and pin variables for embedded systems
An operating system including a software development environment is programmed into the on-chip flash memory of a system-on-a-chip type microcontroller. The software development environment is configured to reside entirely in the microcontroller's on-chip flash memory and includes an editor, a line-by-line bytecode compiler, a flasher, and an interactive debugger. A user operating a terminal emulator on a host computer connects to the microcontroller chip by means of a serial (USB) connection based on an FTDI protocol, or other serial link, in order to develop a BASIC program for the embedded system. The operating system is configured to permit external I / O pins on the microcontroller chip to be mapped to special “pin variables” for manipulation or examination by the user program, and to manage internal peripherals (timers, UARTs) of the microcontroller chip so as to permit application-level interrupt handling.
Owner:TESTARDI RICHARD PAUL
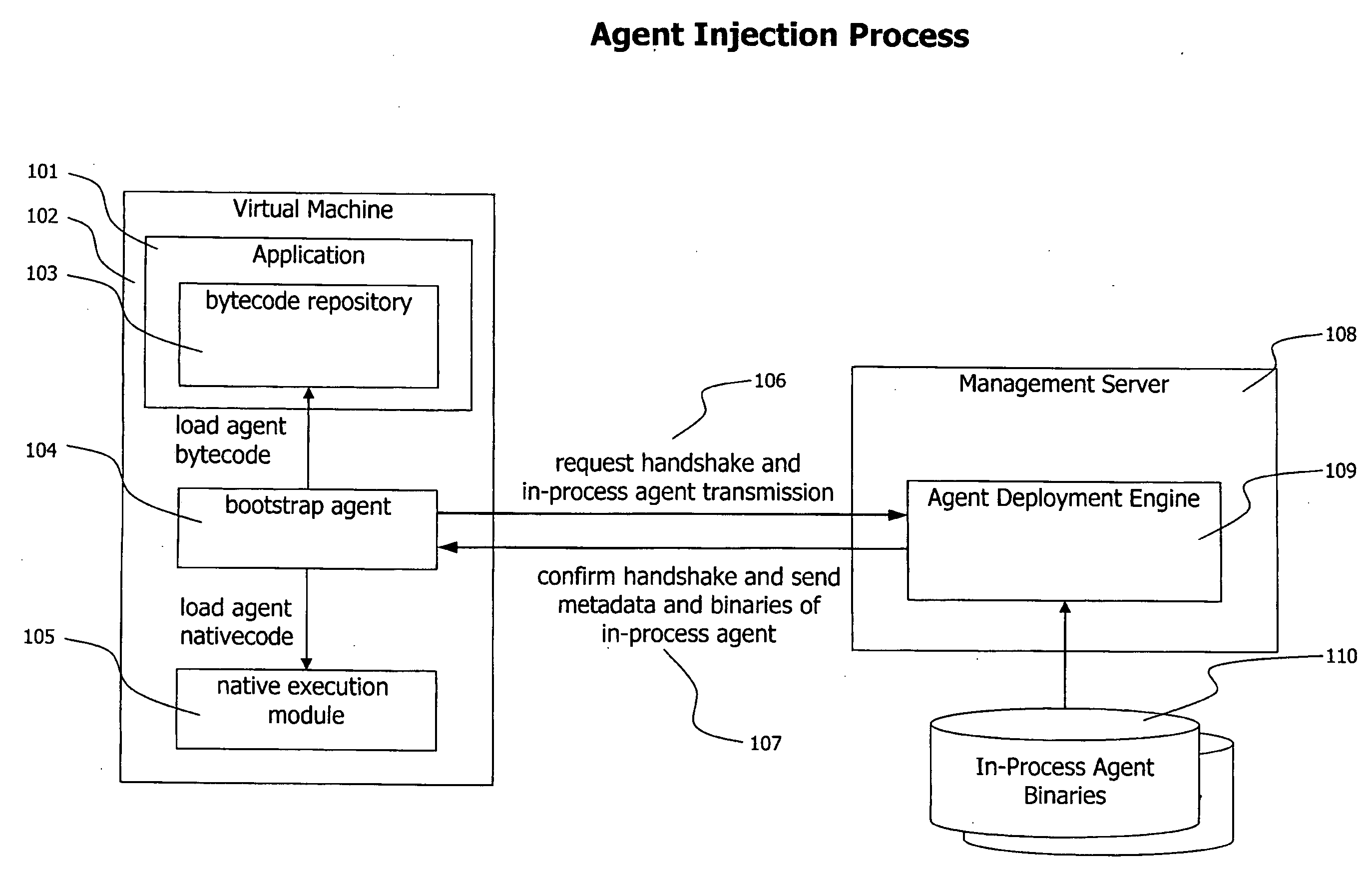
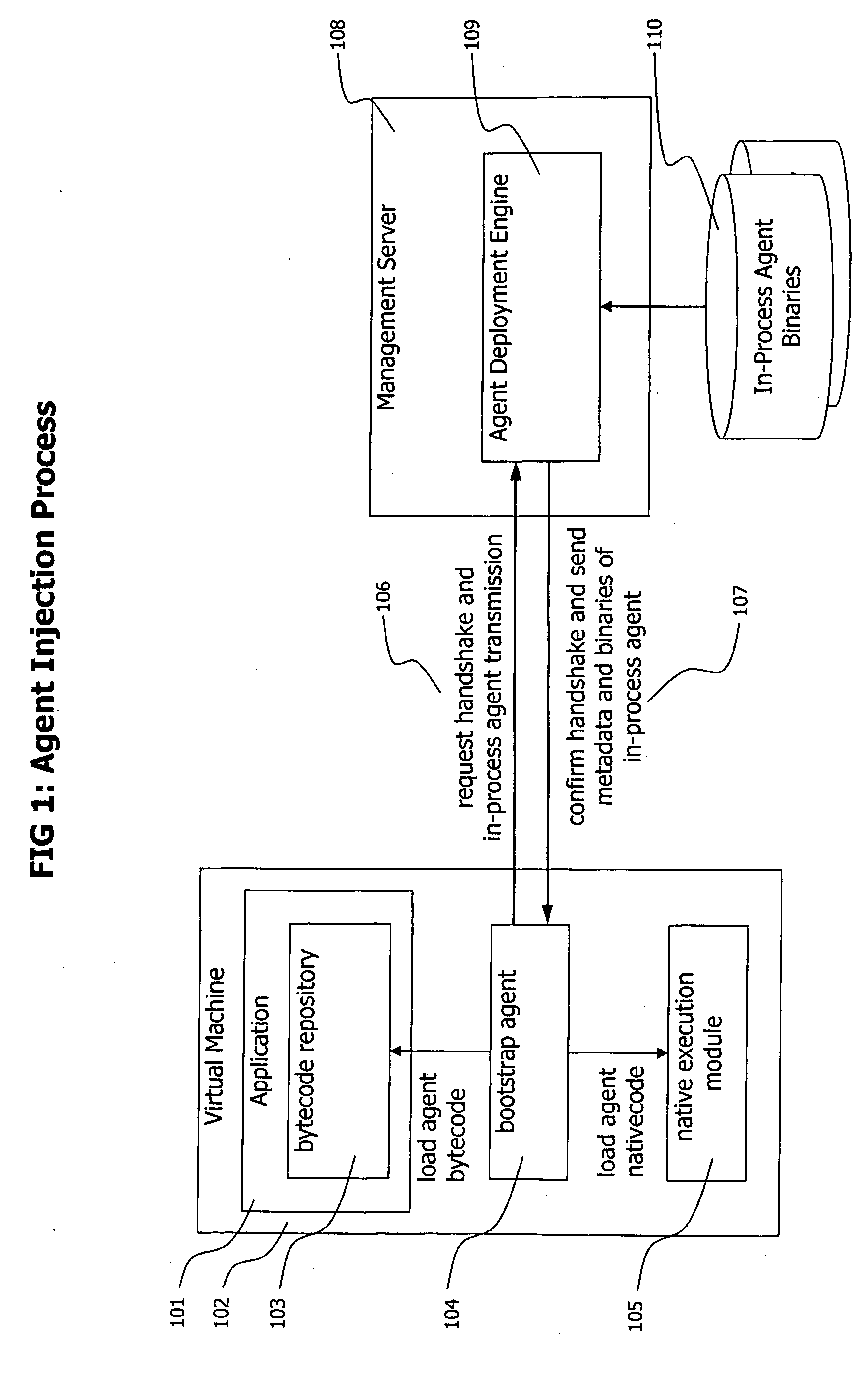
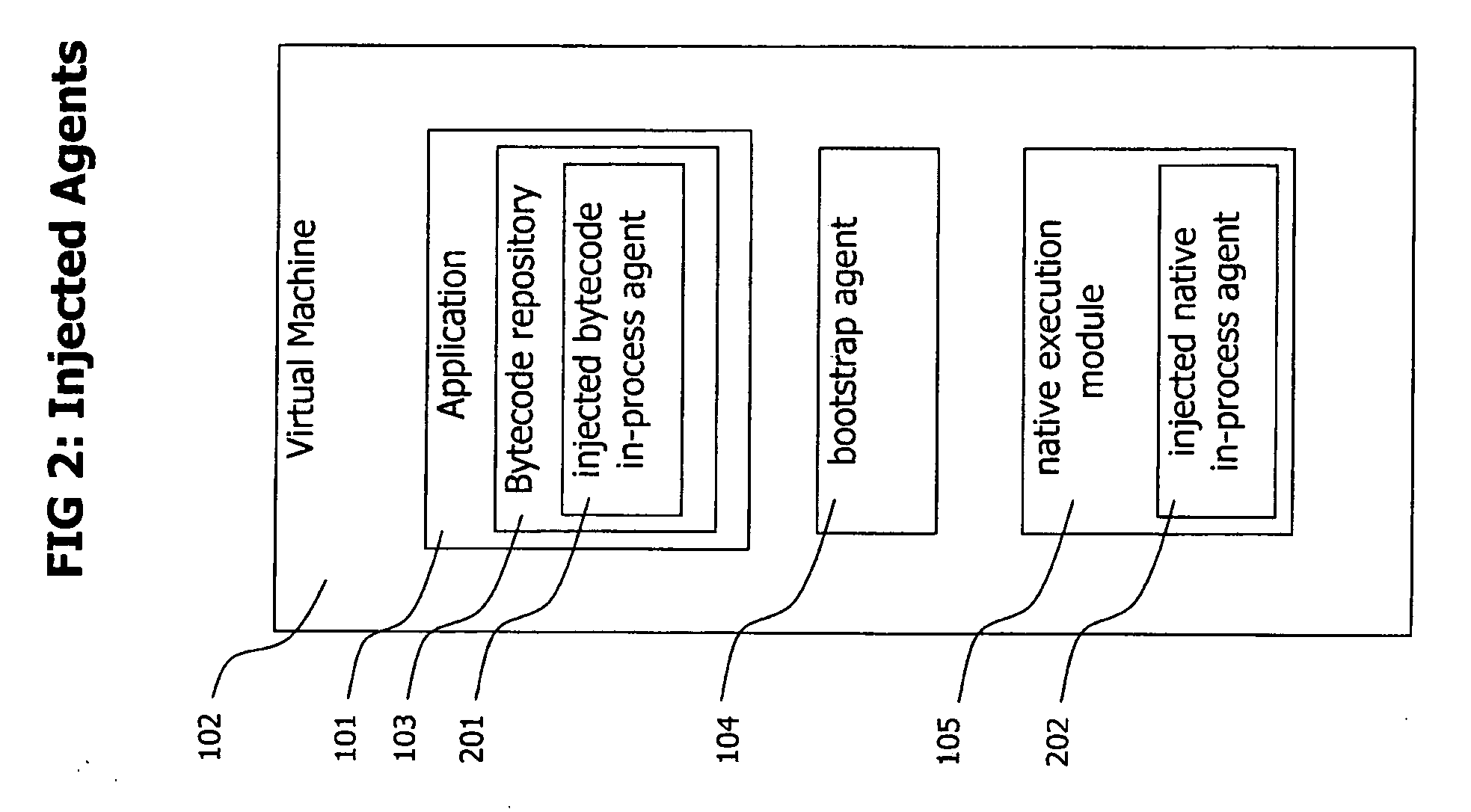
Method and System for Dynamic Remote injection of In-process Agents into Virtual Machine based Applications
A method and system for dynamic and adaptive deployment of in-process agents to virtual machine based applications which may run on remote hosts is provided. A bootstrap agent is injected into the application, using standardized interfaces provided by virtual machine based systems like Sun Microsystems' Java or Microsoft's .NET. Said bootstrap agent establishes a network connection to a management server which provides binaries representing in-process agents in bytecode or native code format. The bootstrap agent sends data identifying its runtime environment to the management server, which determines the matching in-process agent binaries for the runtime environment of the connected agent and sends the selected binaries to the bootstrap agent. The bootstrap agent receives the binaries and installs them to its hosting virtual machine, according to their format (bytecode or native code).
Owner:DYNATRACE
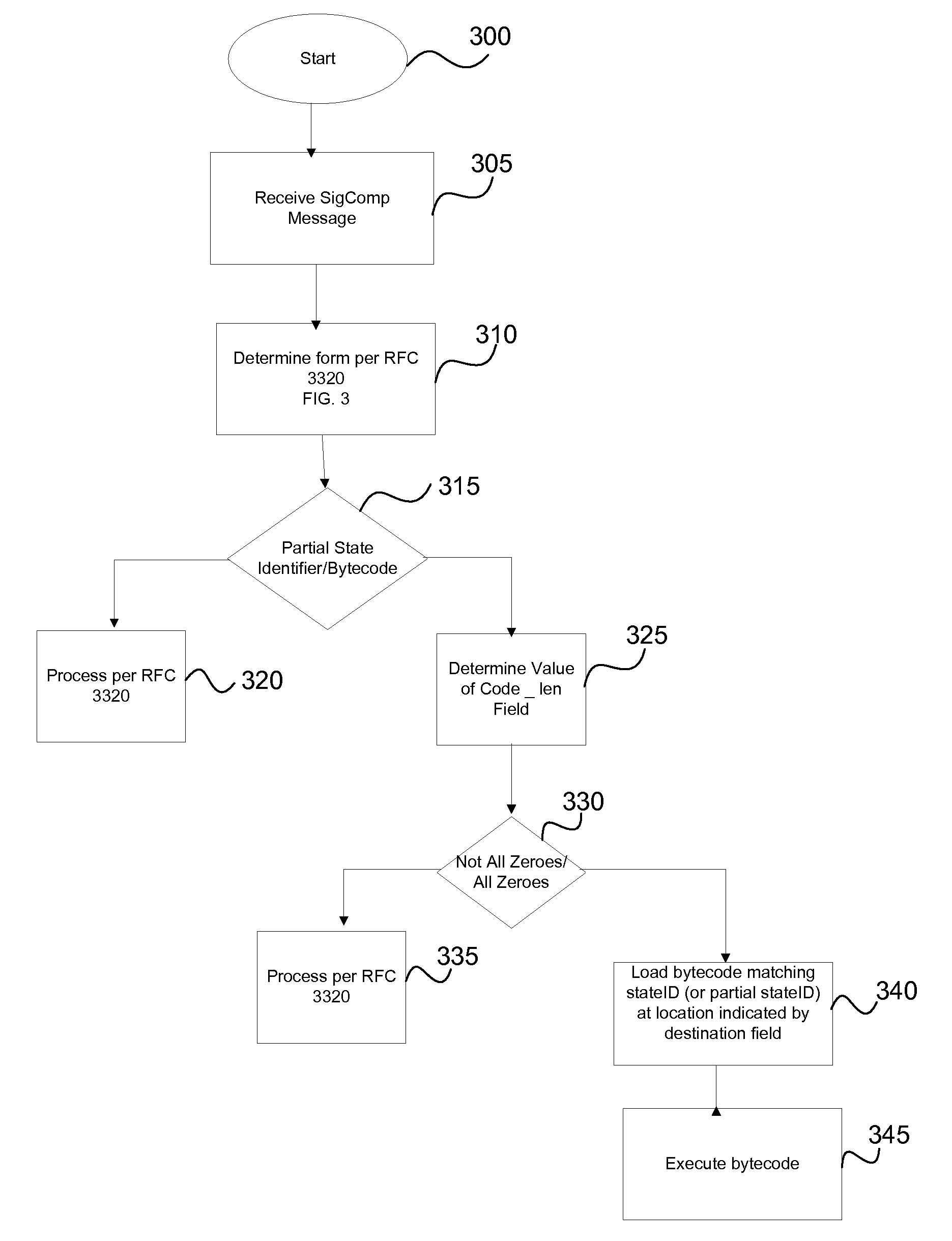
Optimizing static dictionary usage for signal, hypertext transfer protocol and bytecode compression in a wireless network
InactiveUS20080112411A1Network traffic/resource managementTime-division multiplexSession controlData signal
Methods and apparatus including a virtual machine and a compression network platform are provided especially for improving the application of compression algorithms and unique identifiers for bytecode and bytecode packages including associated static dictionaries utilized to advantage in wireless networks. In particular, a given virtual machine need only identify to a receiving virtual machine the unique package identifier for one or more of an algorithm, a static dictionary or a hash for decompressing a received data signal. The receiving virtual machine may advertise what it has locally available to it so that no uploading is necessary. The actuation of bytecode by identifier may be requested at a given destination within the parameters set by RFC 3320. Universal decompressor virtual machines may receive uploaded compression algorithms, bytecode identifiers, package identifiers or static dictionary identifiers and the like from proxy call session control functions of a wireless network, the compressing machine or a compression network platform resource which in one embodiment may comprise an IANA database. The methods and apparatus may find particular application in improving the efficiency of presence / group list management.
Owner:CINGULAR WIRELESS II LLC
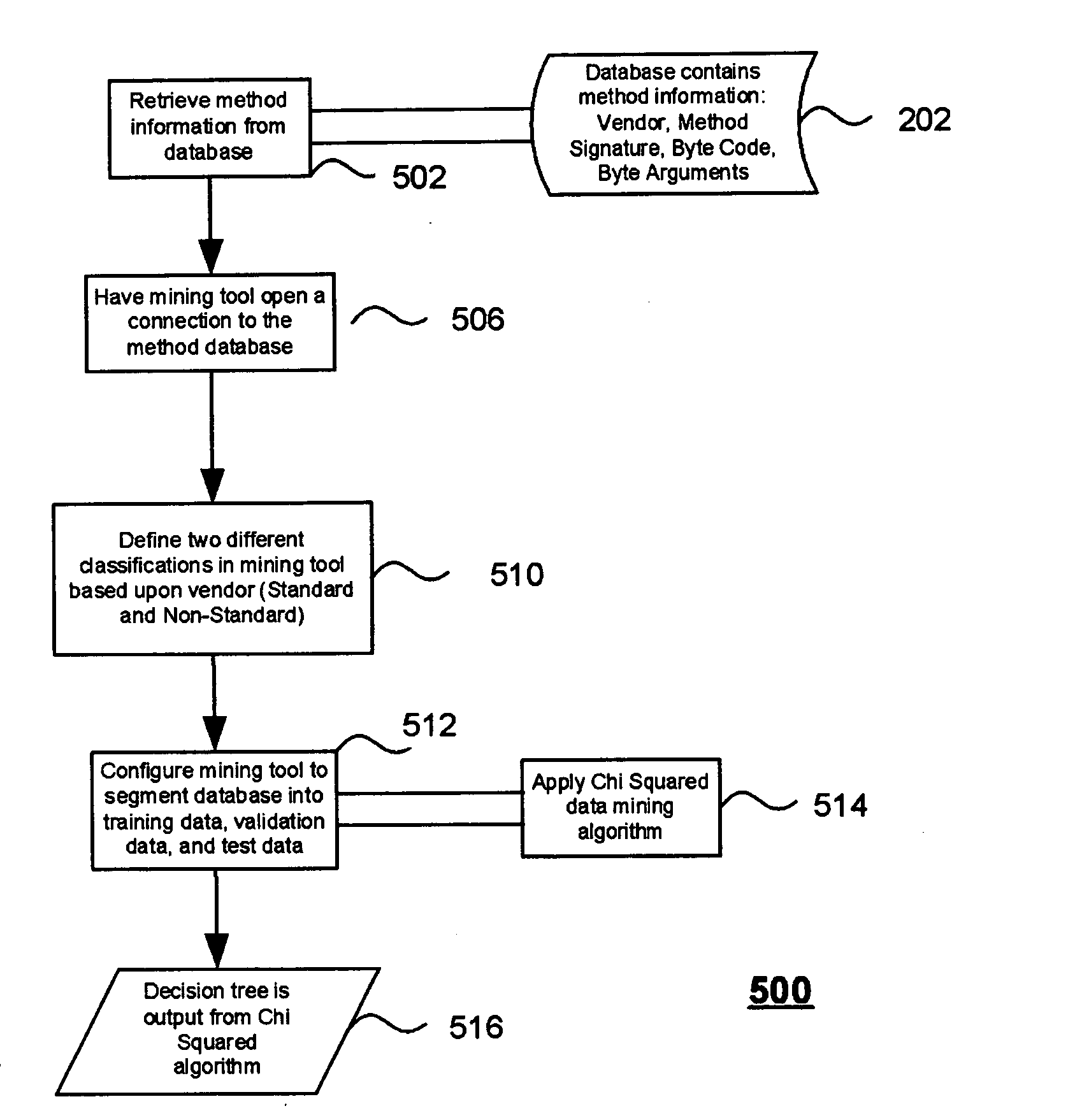
Method, system and program product for optimizing java application performance through data mining
InactiveUS20060005177A1Program documentationSpecific program execution arrangementsGood practiceJava classes
Metadata describing common Java classes is extracted and utilized to optimize a Java program's performance based on the code requirements of the application. Data mining techniques extract metadata and other information about different sets of JVM byte code written by multiple vendors to determine the design choices and optimizations made by each vendor in implementing their JVM. Then, byte code in a Java application being programmed is analyzed in comparison to each vendor's JVM metadata and information. Based upon the application's requirements (for example footprint, performance, etc.), recommendations are generated that yield a newly compiled rt.jar that combines the best practices of each vendor together or recommends a particular vendor's standard JVM that is best suited for the application.
Owner:IBM CORP
Method and system for translating exception handling semantics of a bytecode class file
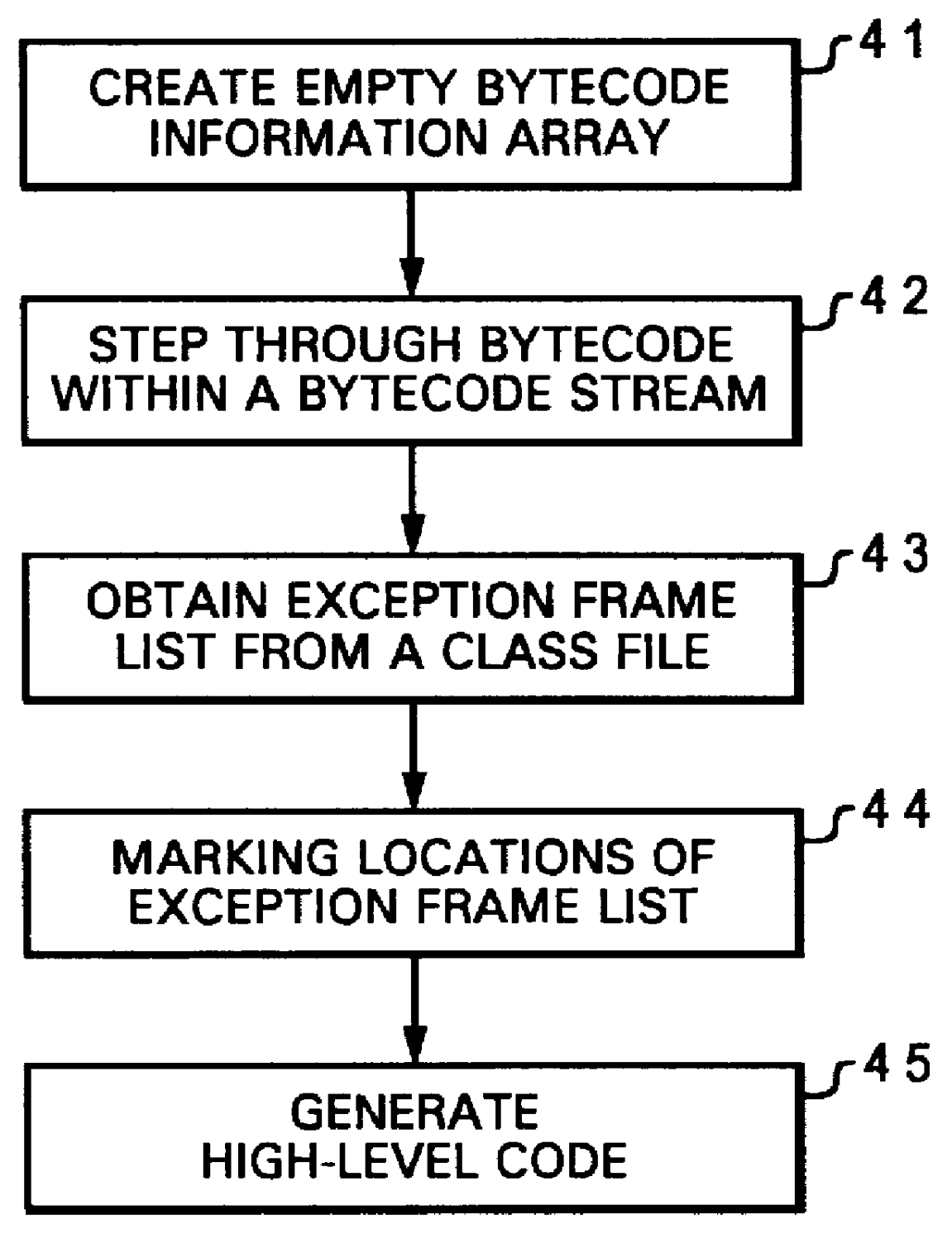
InactiveUS6131187ABinary to binarySpecific program execution arrangementsRelevant informationArray data structure
A method for translating exception handling semantics of a bytecode class file within a computer system is disclosed. An empty bytecode information array is first established. Pertinent information is then obtained by examining bytecodes within a bytecode stream, and such information are inserted into the bytecode information array. An exception framelist, which includes an exception handling routine, is subsequently obtained from a class file for the bytecode stream. The entries within the bytecode information array corresponding to a starting location and an ending location of the exception framelist are marked. Finally, a high-level code sequence is generated utilizing the bytecode information array.
Owner:IBM CORP
Process and system for dynamically compiling a partially interpreted method
InactiveUS6851109B1Improve method performanceSpecific program execution arrangementsMemory systemsDynamic compilationByte
A process and system for dynamically compiling a partially interpreted method is provided. A set of bytecodes for a method is interpreted within a virtual machine. During the interpretation of the method, it is determined, according to the satisfaction of predetermined criteria, that the method contains an execution hot spot and should be just-in-time compiled (JITed) in order to increase the processing speed of the method. The interpretation of the method is halted with a halted execution state and at a halted execution location. Another method is constructed using information from the partially interpreted method and its execution state. The newly constructed method is just-in-time compiled and invoked in such a manner that the newly constructed method recreates the execution state of the partially interpreted method. Once the newly constructed method recreates the execution state of the partially interpreted method, the execution flow follows the bytecode sequence of the partially interpreted method.
Owner:IBM CORP
Method for generating a Java bytecode data flow graph
InactiveUS6233733B1Software engineeringSpecific program execution arrangementsParallel computingJava bytecode
According to a first aspect of the present invention, a method for linking bytecodes of an uninterrupted block of bytecodes in the formation of a data flow graph comprises the steps of scanning the uninterrupted block of bytecodes in a forward manner to identify the start of each of the bytecodes, scanning in a backward manner bytecodewise each of the bytecodes in the uninterrupted block of bytecodes, and generating a link in the data flow graph that links each of the bytecodes to all other of the bytecodes used by the each of the bytecodes.According to a second aspect of the present invention, a method for linking bytecodes between uninterrupted blocks of bytecodes in the formation of a data flow graph, the uninterrupted blocks of bytecodes having links according to an order of execution of the uninterrupted blocks and wherein a stack state has been generated for each of the uninterrupted blocks of bytecodes, comprises the steps of stepping through a first path of a plurality of paths of the order of execution that terminates in a join to generate a link in the data flow graph between each bytecode producing a value in one of the uninterrupted blocks and each bytecode consuming the value in another of the uninterrupted blocks in the first path, and duplicating each link in the first path with a link for each bytecode in all of the plurality of paths other than the first path for each bytecode producing a value having a similar stack location to each bytecode producing a value in one of the uninterrupted blocks in the first path.
Owner:ORACLE INT CORP
Distributing workloads in a computing platform
InactiveUS20110289519A1Transformation of program codeResource allocationProgram instructionParallel computing
Techniques are disclosed relating to distributing workloads between processors. In one embodiment, a computer system includes a first processor and a second processor. The first processor executes program instructions to receive a first set of bytecode specifying a first set of tasks and to determine whether to offload the first set of tasks to the second processor. In response to determining to offload the first set of tasks to the second processor, the program instructions are further executable to cause generation of a set of instructions to perform the first set of tasks, where the set of instructions are in a format different from that of the first set of bytecode, and where the format is supported by the second processor. The program instructions are further executable to cause the second processor to execute the set of instructions by causing the set of instructions to be provided to the second processor.
Owner:ADVANCED MICRO DEVICES INC
System and method combining application tracing and distributed statistical records
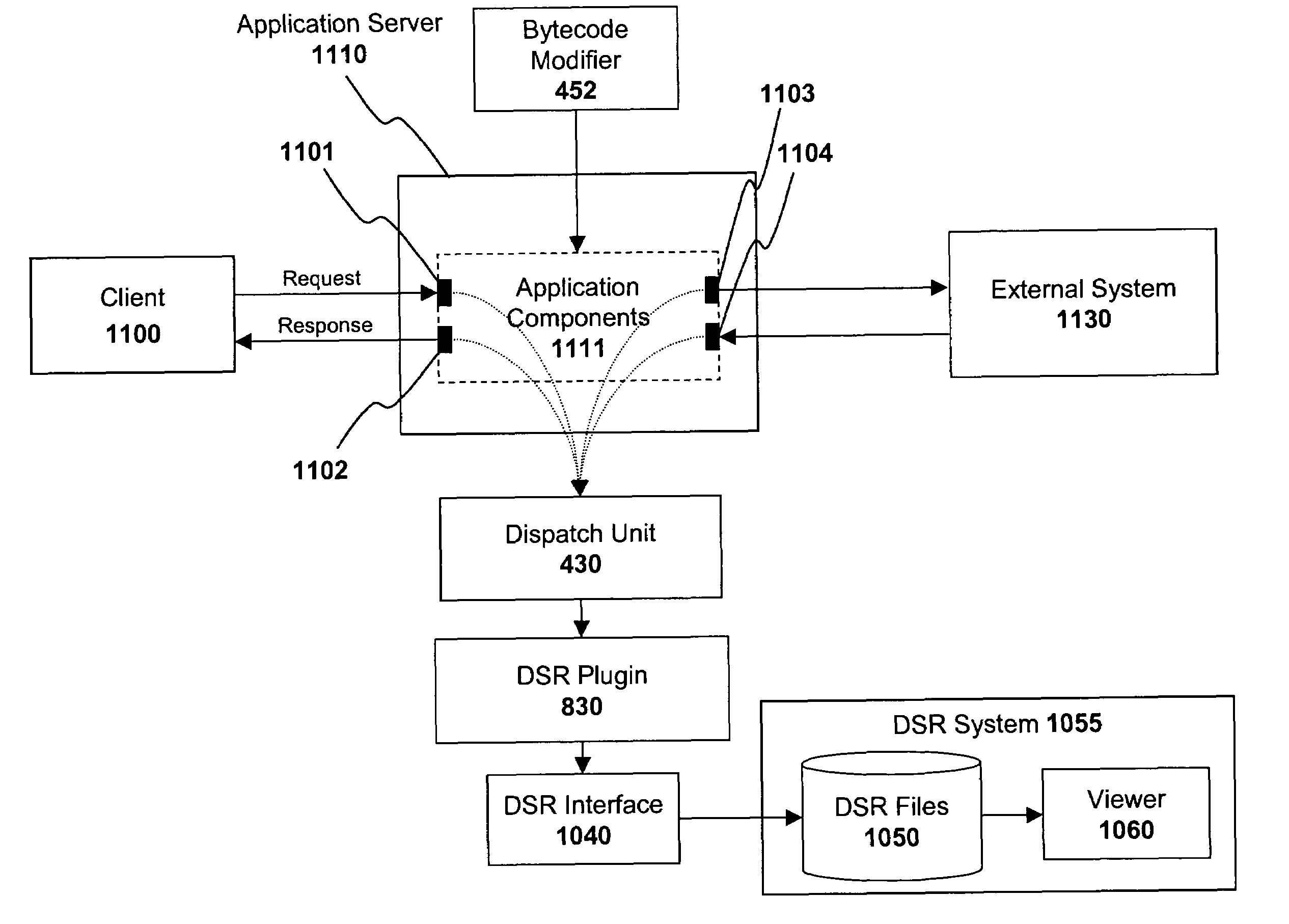
ActiveUS7506315B1Flexible and scalable architectureError detection/correctionSpecific program execution arrangementsProgram tracingApplication server
A system and method for coupling a distributed statistical records (“DSR”) collection system with a tracing system utilizing bytecode modification techniques. In one embodiment, a distributed statistical records (“DSR”) module initially identifies one or more application components within the application server to be traced. A bytecode modification module responsively modifies the bytecode of the one or more application components. The modifications are directed to a particular set of methods of the application components (e.g., methods which are relevant to DSR data). A dispatch unit registers the method invocations and method-related information associated with the particular set of methods and provides the method-related information to the DSR module. Finally, a DSR interface module translates the method-related information to a format employed within a DSR system and forwards the translated information to the DSR system.
Owner:SAP AG
Automatic customization of classes
InactiveUS20050071810A1Improve programming efficiencySoftware reuseSpecific program execution arrangementsObject ClassProgram Efficiency
A method and computer readable medium for automatic replacement of object classes in a library with custom classes to improve program efficiency. The method begins with static analysis preformed on a program containing a plurality of objects in order to determine type-correctness constraints and to detect unused functionality in one or more of the objects to be replaced. The plurality of objects is instrumented to detect usage patterns of functionality in one or more objects. Customized classes are generated based upon the static analysis and usage patterns detected. Bytecode is rewritten which is used for generating classes. The present invention provides transparency in the replacement of the objects.
Owner:IBM CORP
Automatic adapter/stub generator
InactiveUS6381737B1Readily apparentSpecific program execution arrangementsMemory systemsByteComputer science
Systems and methods for automatically providing an adapter or a stub in a runtime environment are provided. An adapter generator is provided with input parameters that are in turn processed and input to a compiler. The compiler, in turn, is coupled to an adapter library used to store the generated adapters. The adapter library, in turn, provides adapters, on demand to a runtime system when executing a bytecode, or a series of bytecodes.
Owner:ORACLE INT CORP
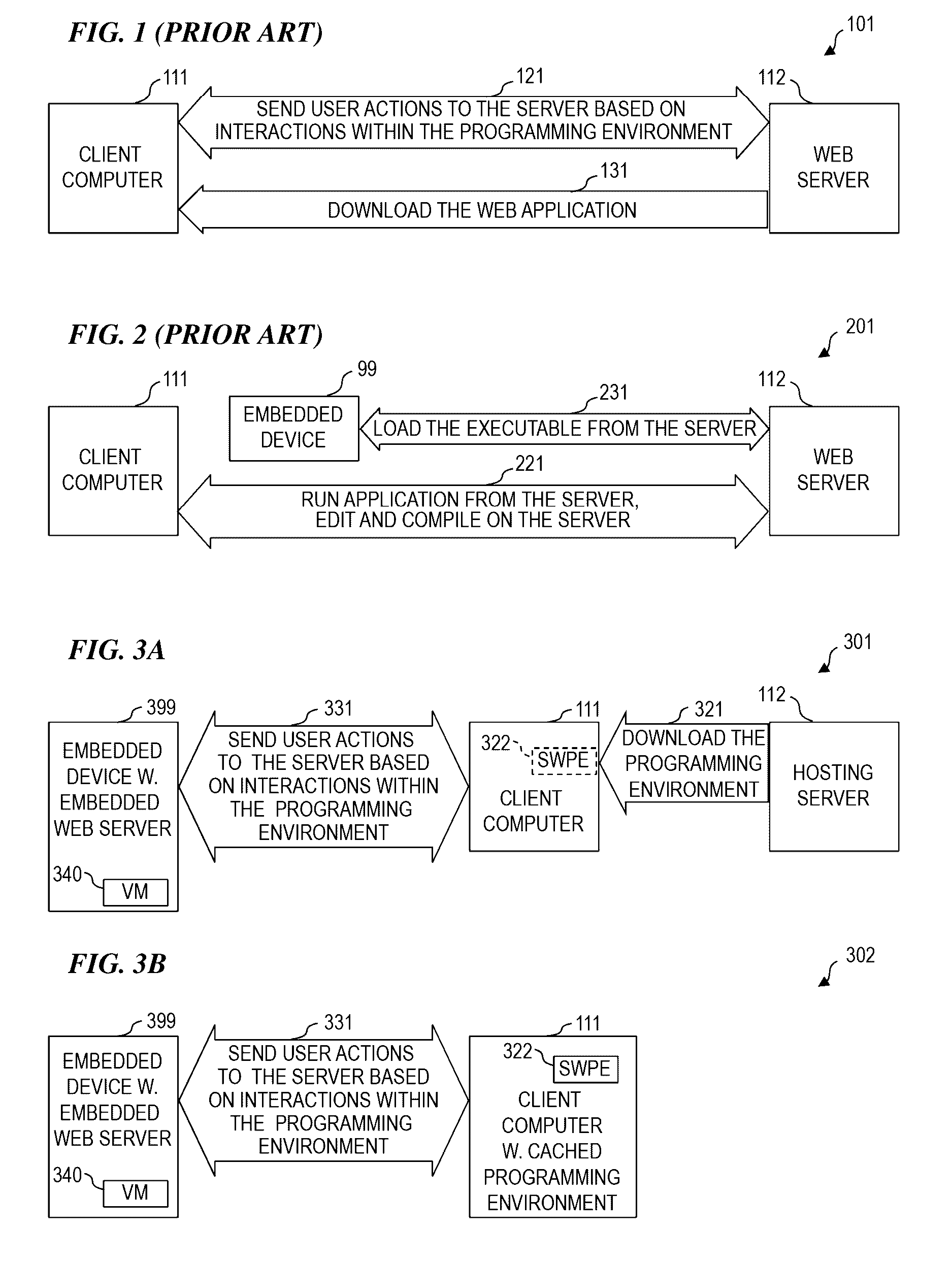
Web-Based Programming Environment for Embedded Devices
A programming environment and a simple programming language that runs on Ethernet block-input / output (block-IO) devices and hosting servers. In some embodiments, the ARGEE™ system includes a web-based programming environment that compiles a GUI program into a bytecode program of a virtual machine; and the virtual machine that runs in the device firmware and executes the bytecode program representing the GUI program created by a user. There are many programming languages that provide a web-based programming environment. Some such languages apply to embedded devices. However, the ARGEE™ system, considered as a whole, is unique in that the programming environment is not hosted on the same embedded device it controls. The system reduces the FLASH-memory requirements of the device by hosting the environment on an external server. The system also facilitates a faster update cycle of the environment software, making it easier to distribute changes to customers when environment changes.
Owner:TURCK HLDG
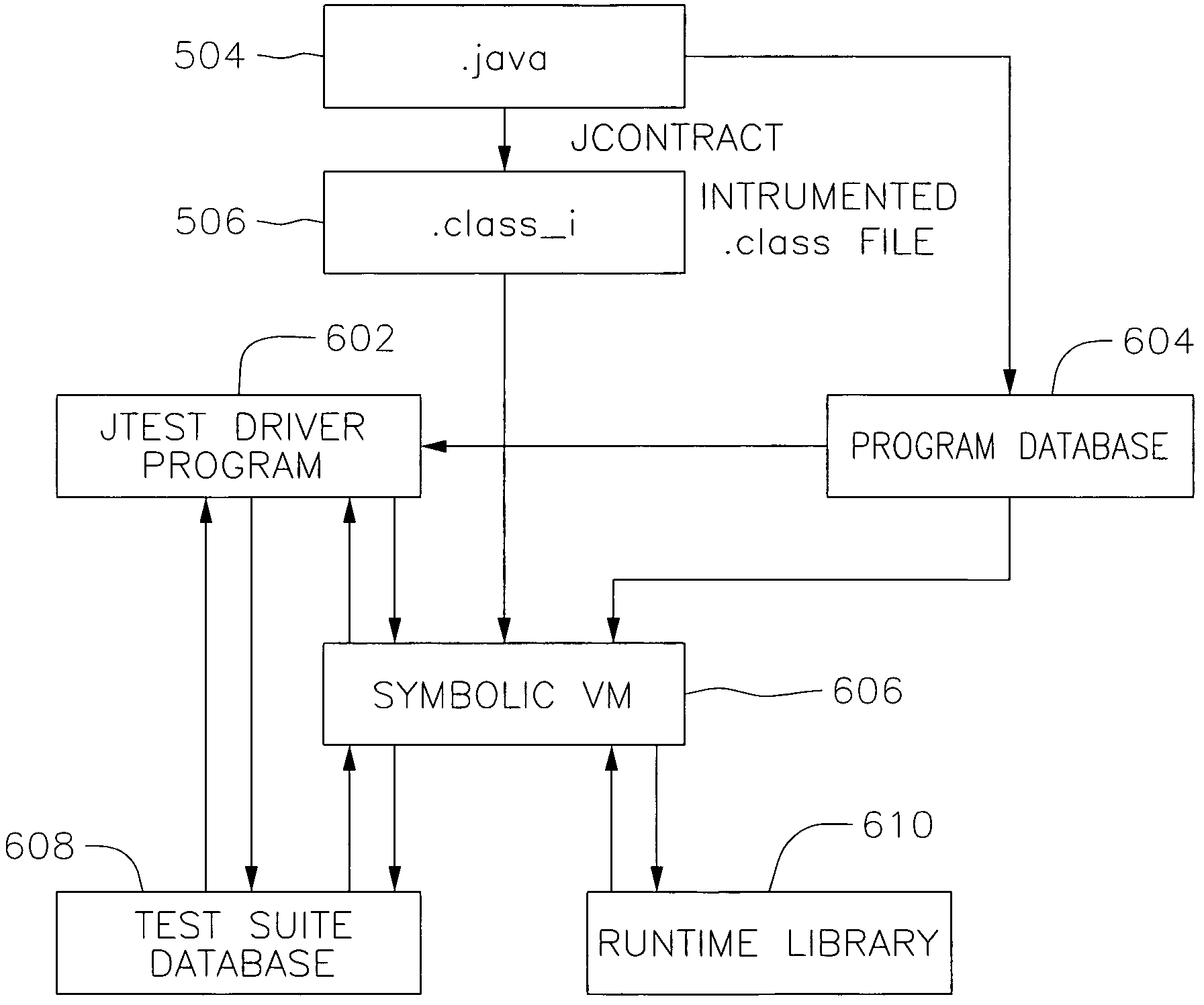
Method and system for dynamically invoking and/or checking conditions of a computer test program
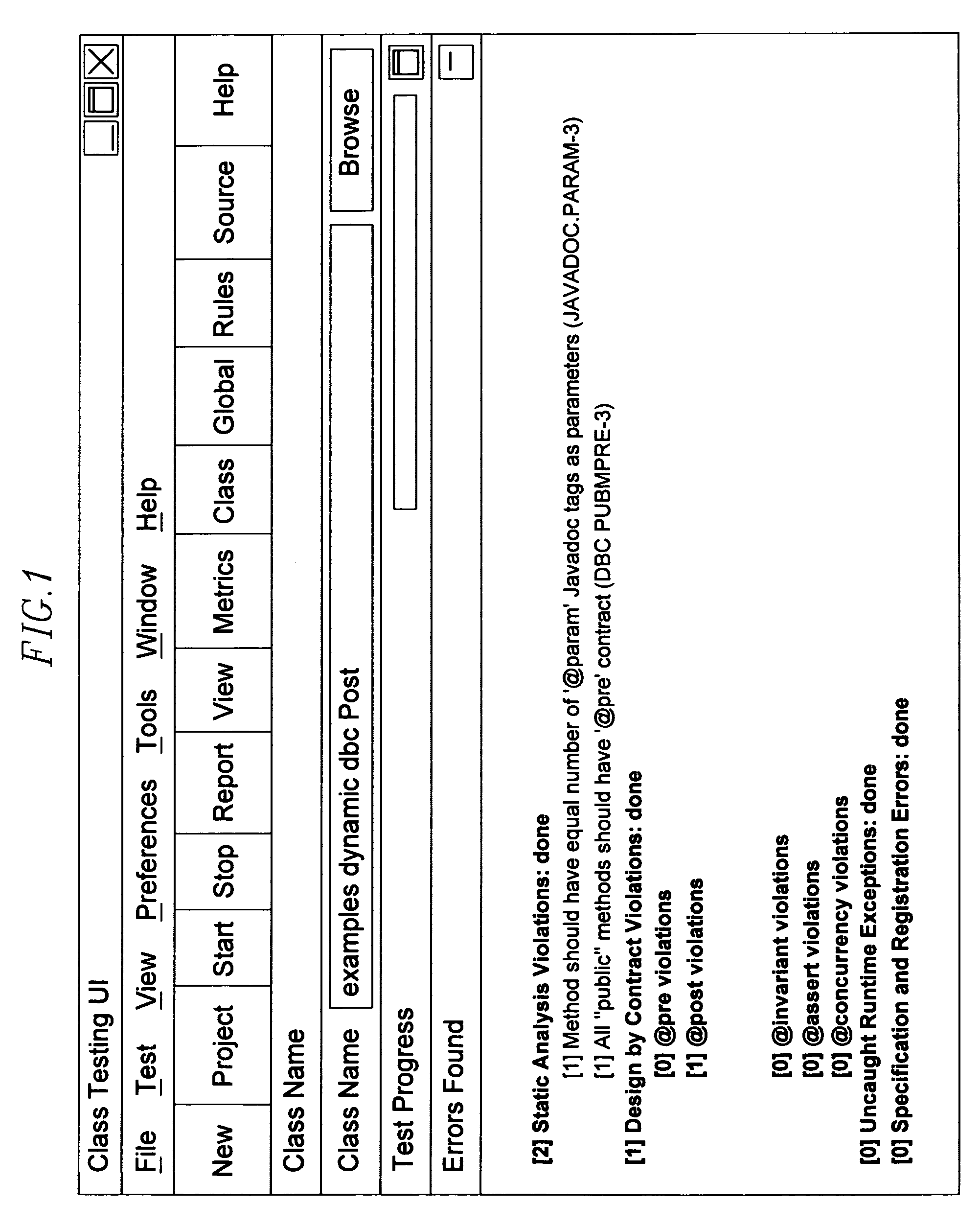
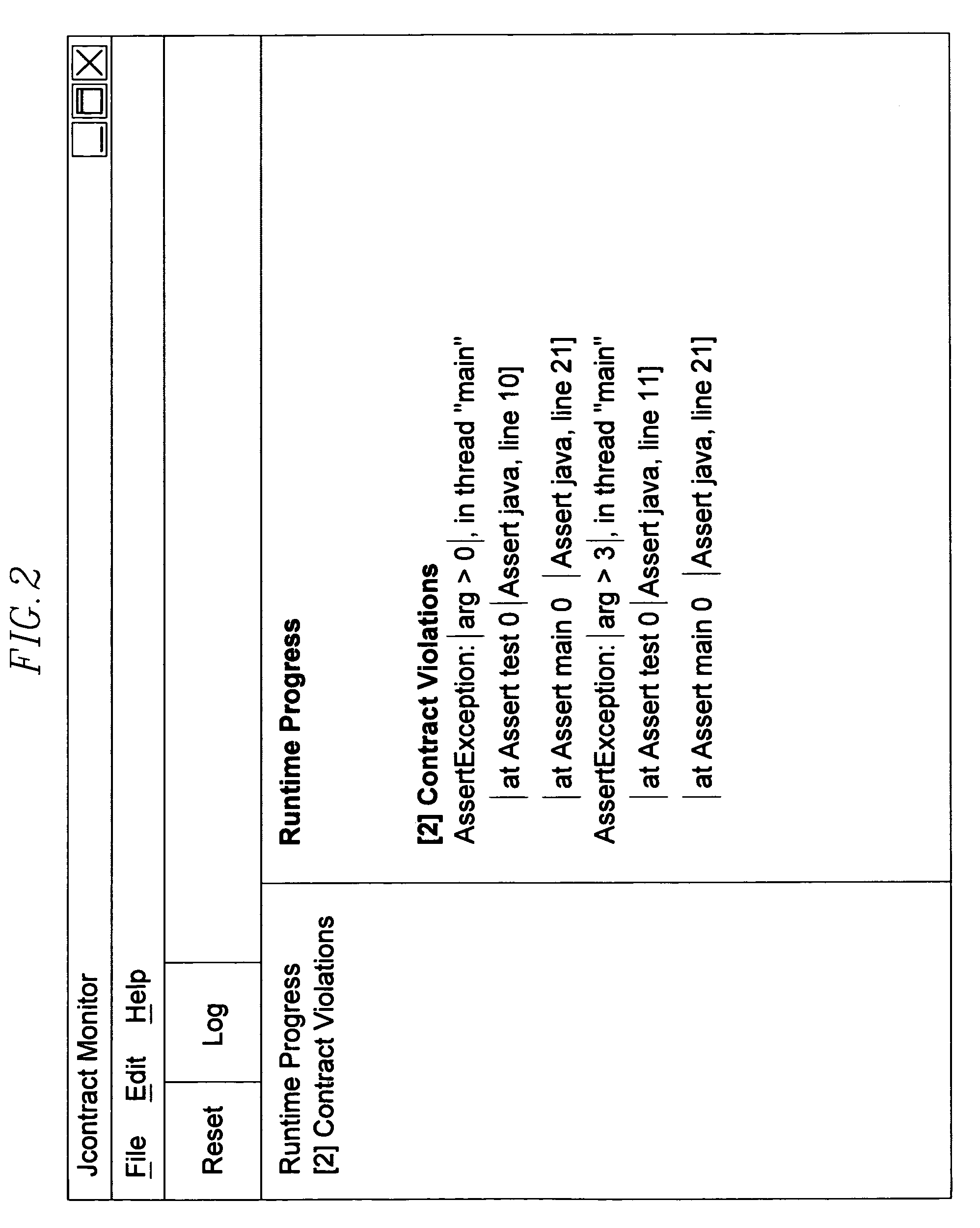
ActiveUS7266808B2Save resourcesShorten the timeError preventionError detection/correctionProgramming languageDBc
A method and system for dynamically invoking and / or checking conditions of a computer test program. Test cases that verify class / component functionality are automatically created from the DbC contracts. When the classes / components that contain DbC contracts are added to the system, the invention automatically verifies whether the system uses them correctly. The information in the contract continents is used to generate more comprehensive and better quality test cases.In one embodiment, a code's specification information is analyzed and a class with extra bytecodes that describe how the class is supposed to work and be used is generated. Next, the instrumented class is integrated into the system, and the system is run. The system is monitored as it runs and contract violations are automatically detected.
Owner:PARASOFT
Reverse index mixed compression and decompression method based on Hbase database
InactiveCN102708187AImprove query efficiencySave storage spaceSpecial data processing applicationsTable (database)Datasheet
The invention discloses a reverse index mixed compression method based on an Hbase database. The reverse index mixed compression method comprises the steps of processing the Hbase database to obtain an Hbase database reversed index data table including keys and values; compressing the key part by a key dictionary compression method; compressing the value part by a variable bytecode compression method; and writing the compressed content into files. The invention also discloses a decompression method of the compressed file key part after being compressed by the compression method. The decompression method comprises the steps of judging the length of each compressed data item, processing to obtain decompressed data according to two conditions of the length being less than or equal to 13, and the length being more than or equal to 25, otherwise, failing to decompress. According to the method adopts the classification mixed compression and the classification decompression method, the compression ratio is improved on the condition that the high decompression ratio is ensured possibly; the unified considerations of file reading and data decompression can be achieved; and the query efficiency of the reverse index can be improved completely and the storage space can be saved.
Owner:CHENGDU UNIV OF INFORMATION TECH
Java hardware accelerator using microcode engine
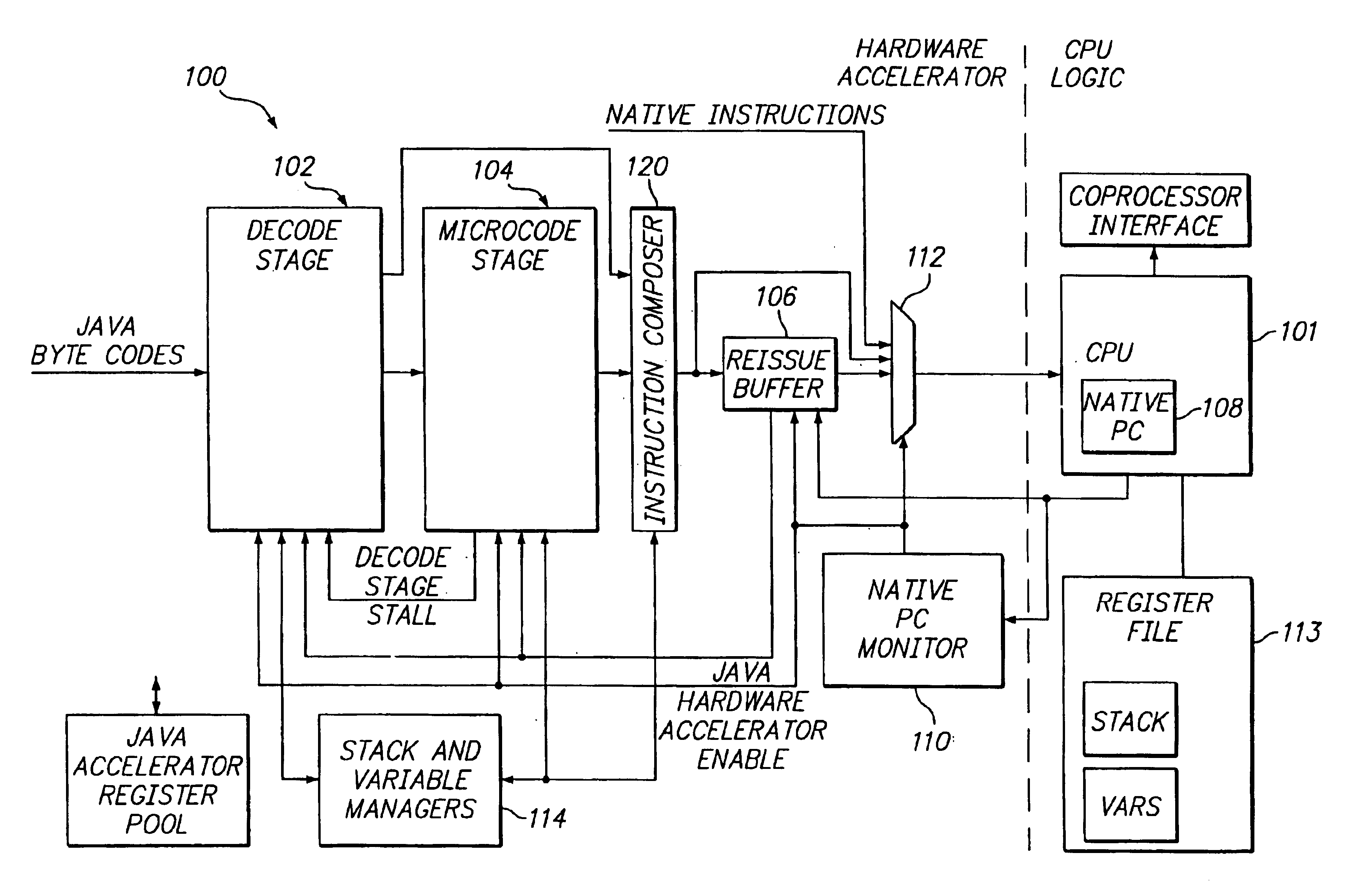
InactiveUS7225436B1Easy to handleGeneral purpose stored program computerSpecific program execution arrangementsOperating systemHardware acceleration
A hardware Java™ accelerator is comprised of a decode stage and a microcode stage. Separating into the decode and microcode stage allows the decode stage to implement instruction level parallelism while the microcode stage allows the conversion of a single Java™ bytecode into multiple native instructions. A reissue buffer is provided which stores the converted instructions and reissues them when the system returns from an interrupt. In this manner, the hardware accelerator need not be flushed upon an interrupt A native PC monitor is also used. While the native PC is within a specific range, the hardware accelerator is enabled to convert the Java™ bytecodes into native instructions. When the native PC is outside the range, the hardware accelerator is disabled and the CPU operates on native instructions obtained from the memory.
Owner:NAZOMI COMM
Smart contract execution method and device, equipment and medium
ActiveCN110096338AImplementationImprove execution efficiencySoftware simulation/interpretation/emulationCode compilationSource code fileSoftware engineering
The embodiment of the invention discloses a smart contract execution method and device, equipment and a medium. The method comprises the steps of obtaining a transaction request initiated based on a smart contract; in the process of executing the smart contract to process the transaction request, calling a contract dynamic link library file, wherein an intelligent contract bytecode file is decompiled into a target advanced language to obtain a contract source code file, and the contract source code file is compiled to obtain the contract dynamic link library file. Through the technical schemeprovided by the embodiment of the invention, the execution efficiency of the smart contract can be improved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Process and implementation for dynamically determining probe enablement using out of process correlating token
The present invention addresses the problem of linking cross-process and cross-thread subtransactions into a single user transaction. The mechanism of the present invention employs bytecode inserted probes to dynamically detect out of process correlating tokens in an inbound request. The bytecode inserted probes retrieve the correlating token in the inbound request. Based on the correlating token retrieved, the bytecode inserted probes are then used to dynamically determine if the inbound user request should be recorded and linked to a transaction that began in another thread or process.
Owner:INT BUSINESS MASCH CORP
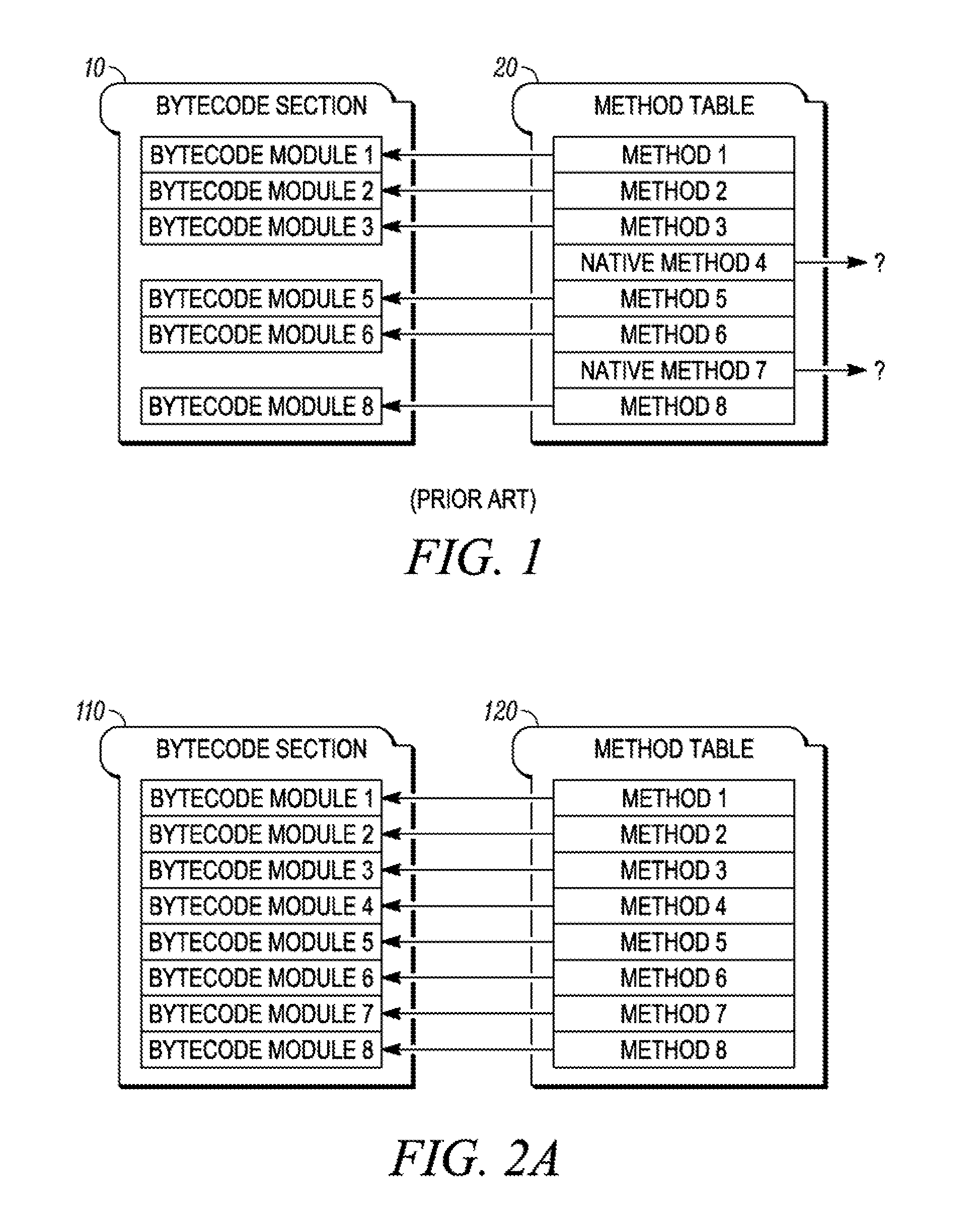
System for overriding intrepreted byte-code with native code
In a method of executing a program on an interpreted bytecode language, a plurality of interpreted bytecode modules (each having an associated name) is loaded. A pointer is directed from each method entry to a different interpreted bytecode module. A native code module library is loaded and includes a native code module (also having an associated name) that implements a function corresponding to an interpreted bytecode module. When the name of an interpreted bytecode module corresponds to the name of a native code module, the pointer directed to the interpreted bytecode module is redirected to the corresponding native code module. Each interpreted bytecode module and native code module pointed to by the each method entry in the method table is executed according to an application-controlled order of execution.
Owner:GOOGLE TECH HLDG LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com