Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
35 results about "Program tracing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Program tracing is the process where you run a program through each instruction and see the complete end to end flow of the program. This helps us to debug code when there are many flows through which a code can execute.
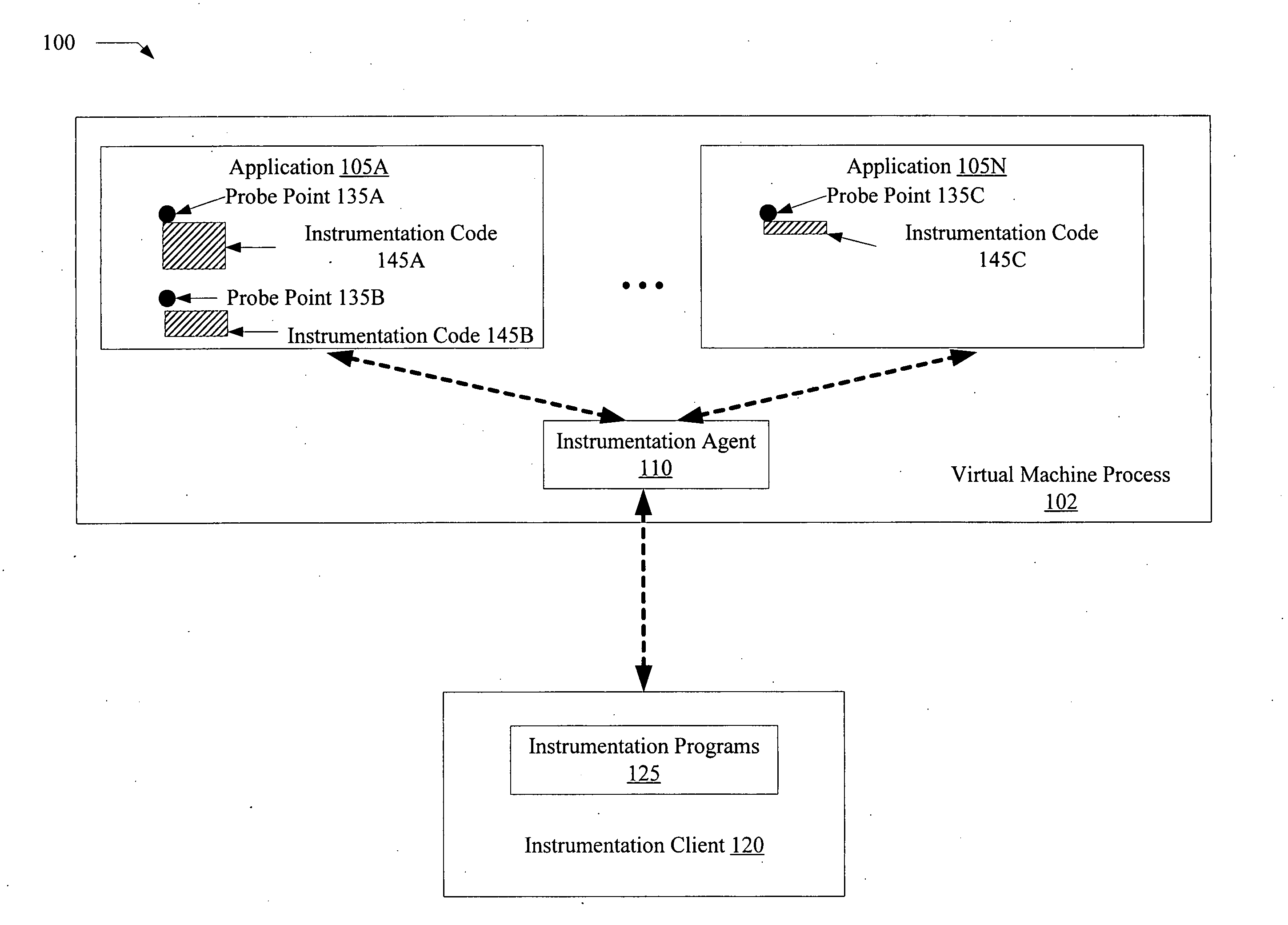
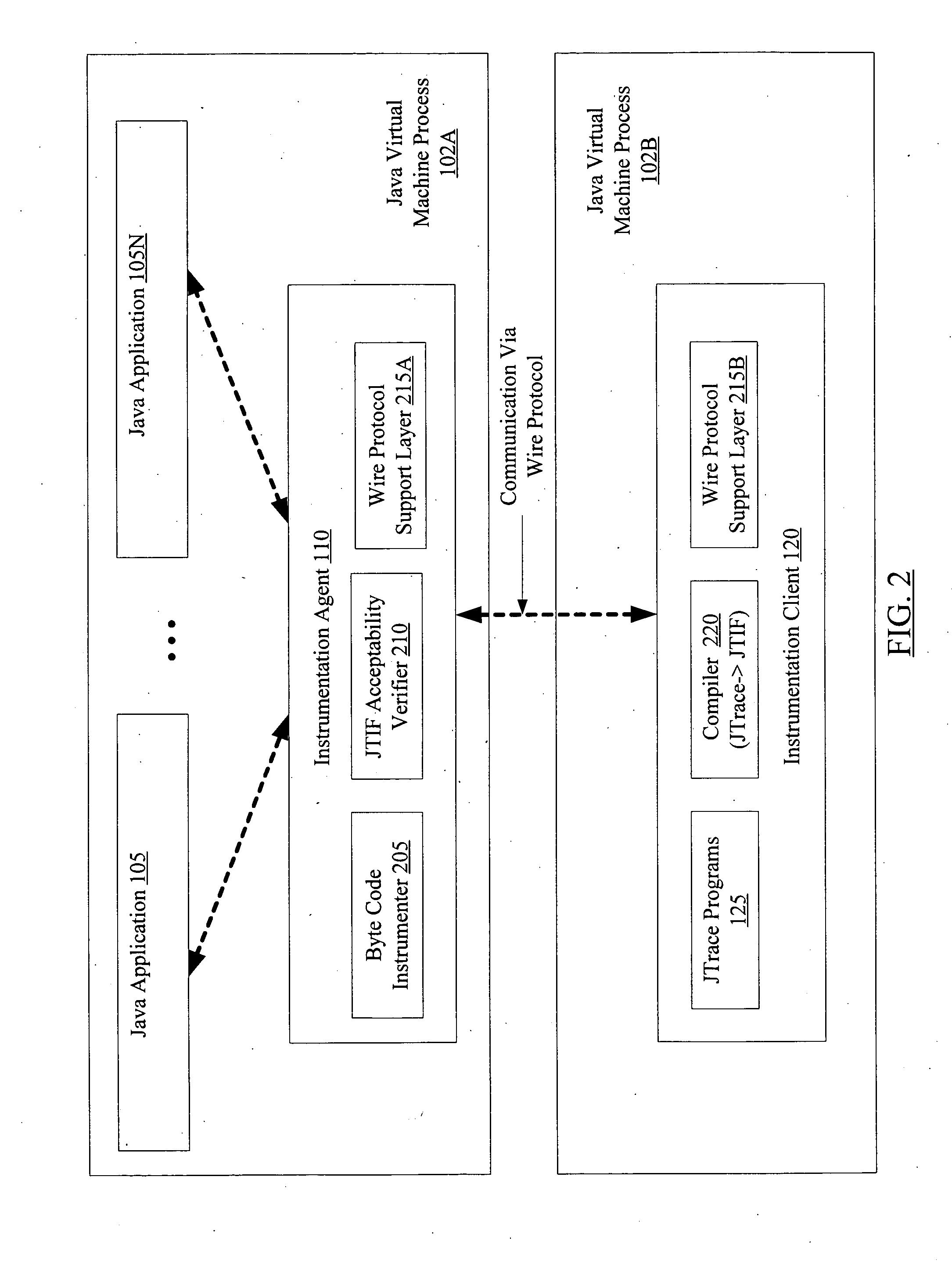
Dynamic application tracing in virtual machine environments
ActiveUS20070180439A1Promote generationError detection/correctionSpecific program execution arrangementsProgram tracingParallel computing
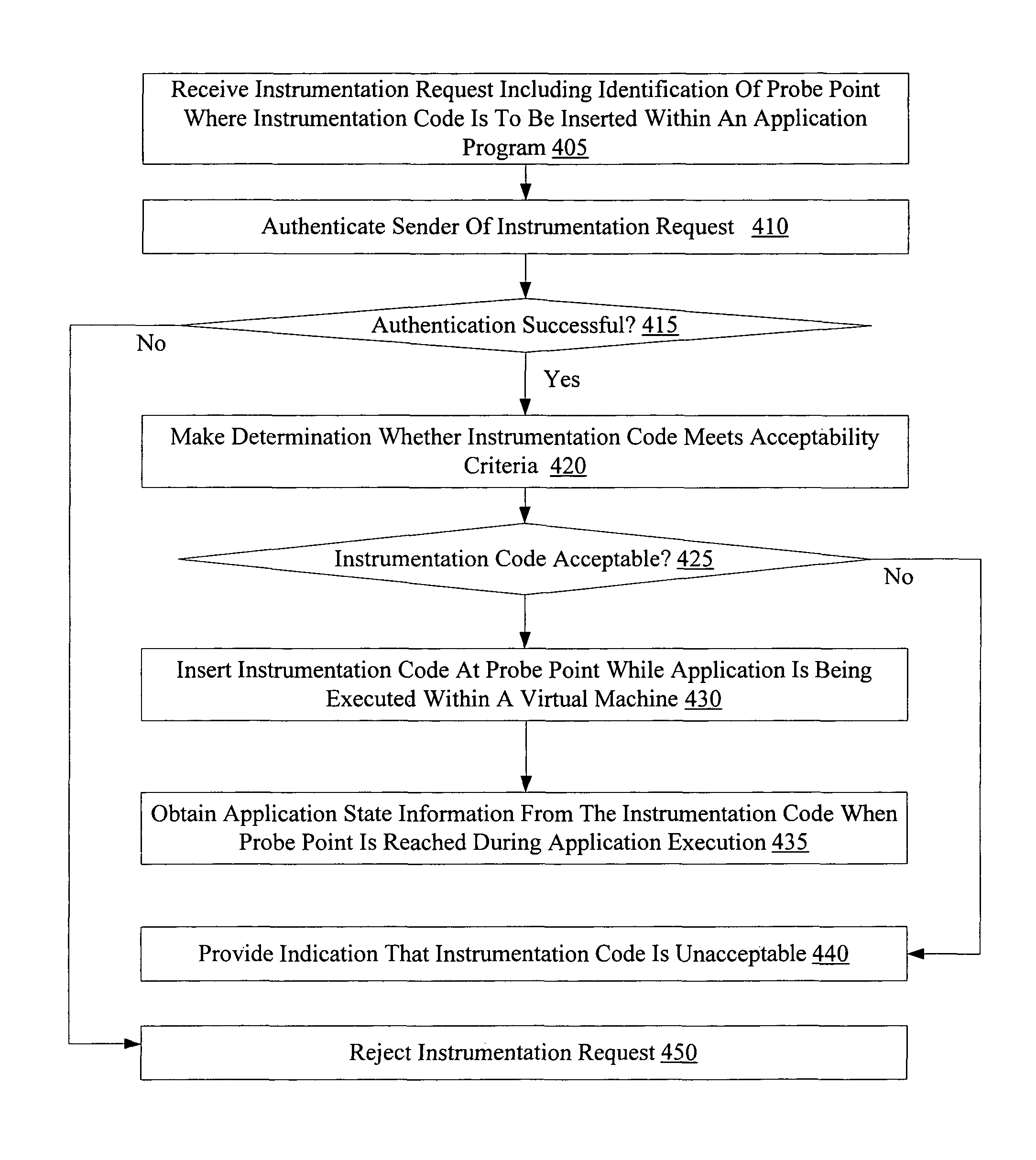
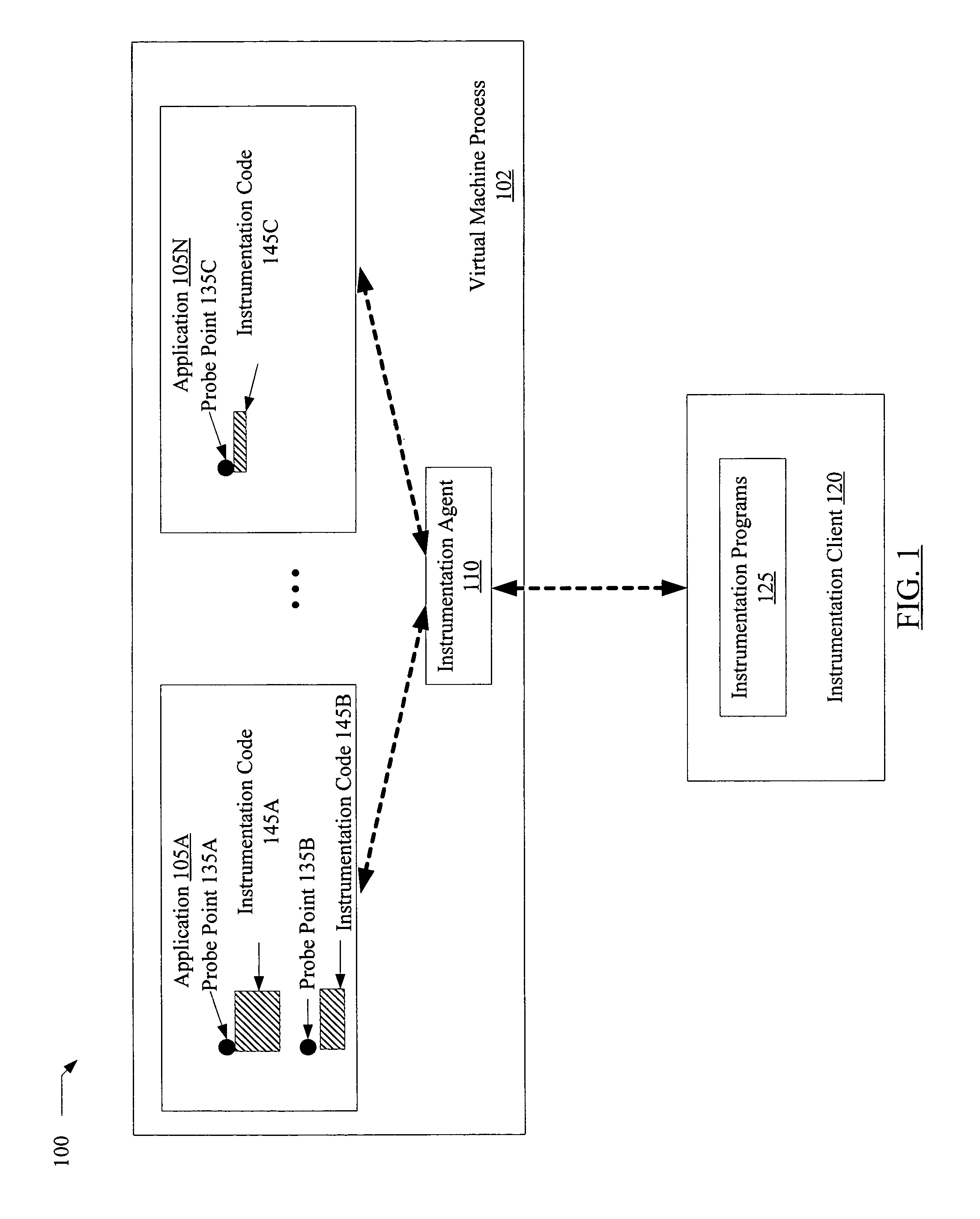
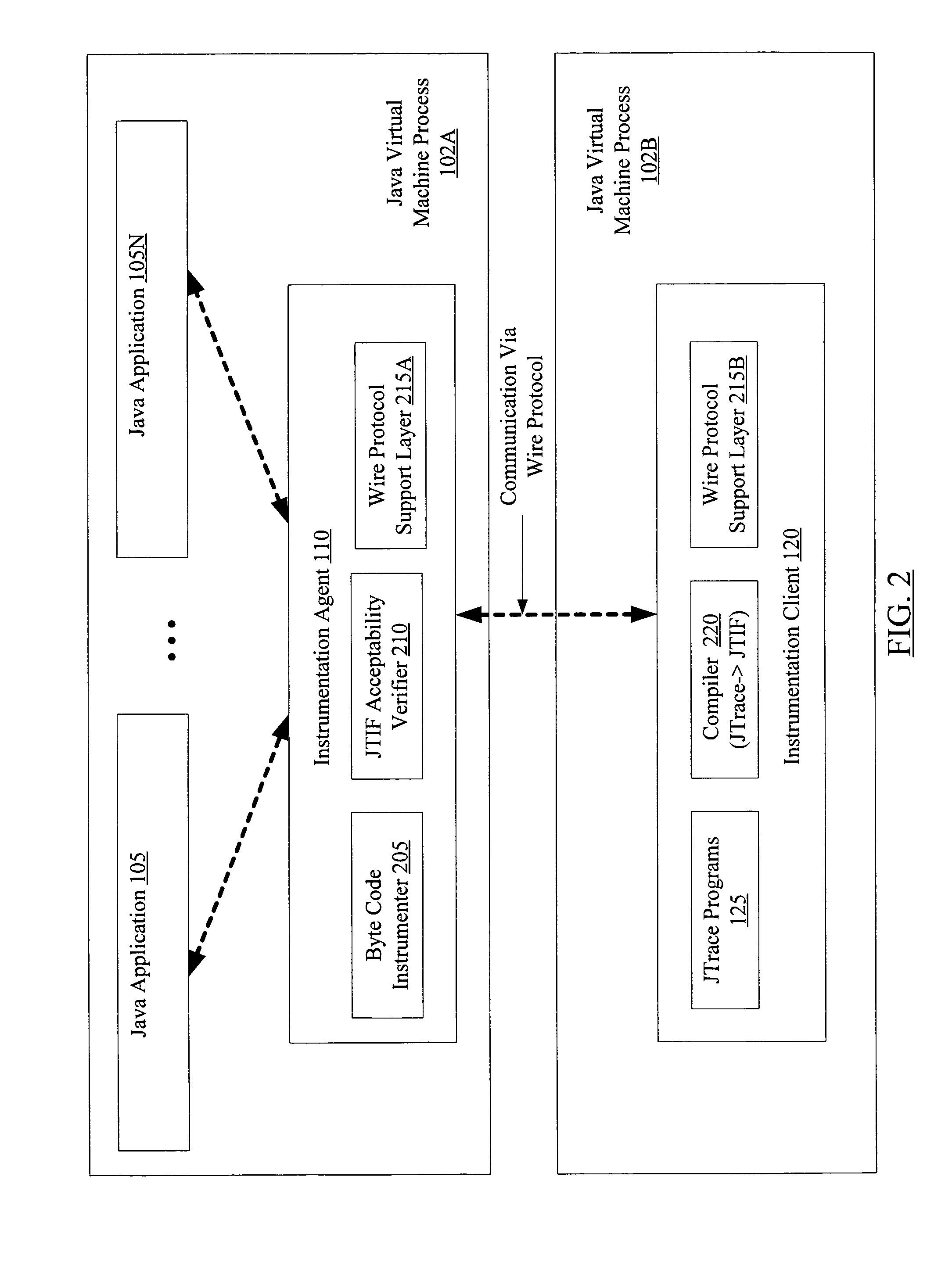
A method for dynamic application tracing in virtual machine environments comprises receiving an instrumentation request that includes an identification of a probe point at which instrumentation code is to be inserted within an application. The method may further comprise making a determination whether the instrumentation code meets one or more acceptance criteria. If the instrumentation code is found to be acceptable, the method may further comprise inserting the instrumentation code at the probe point within the application while the application is executing within a virtual machine, and obtaining information indicative of application state from an execution of the instrumentation code when the probe point is reached during application execution.
Owner:ORACLE INT CORP
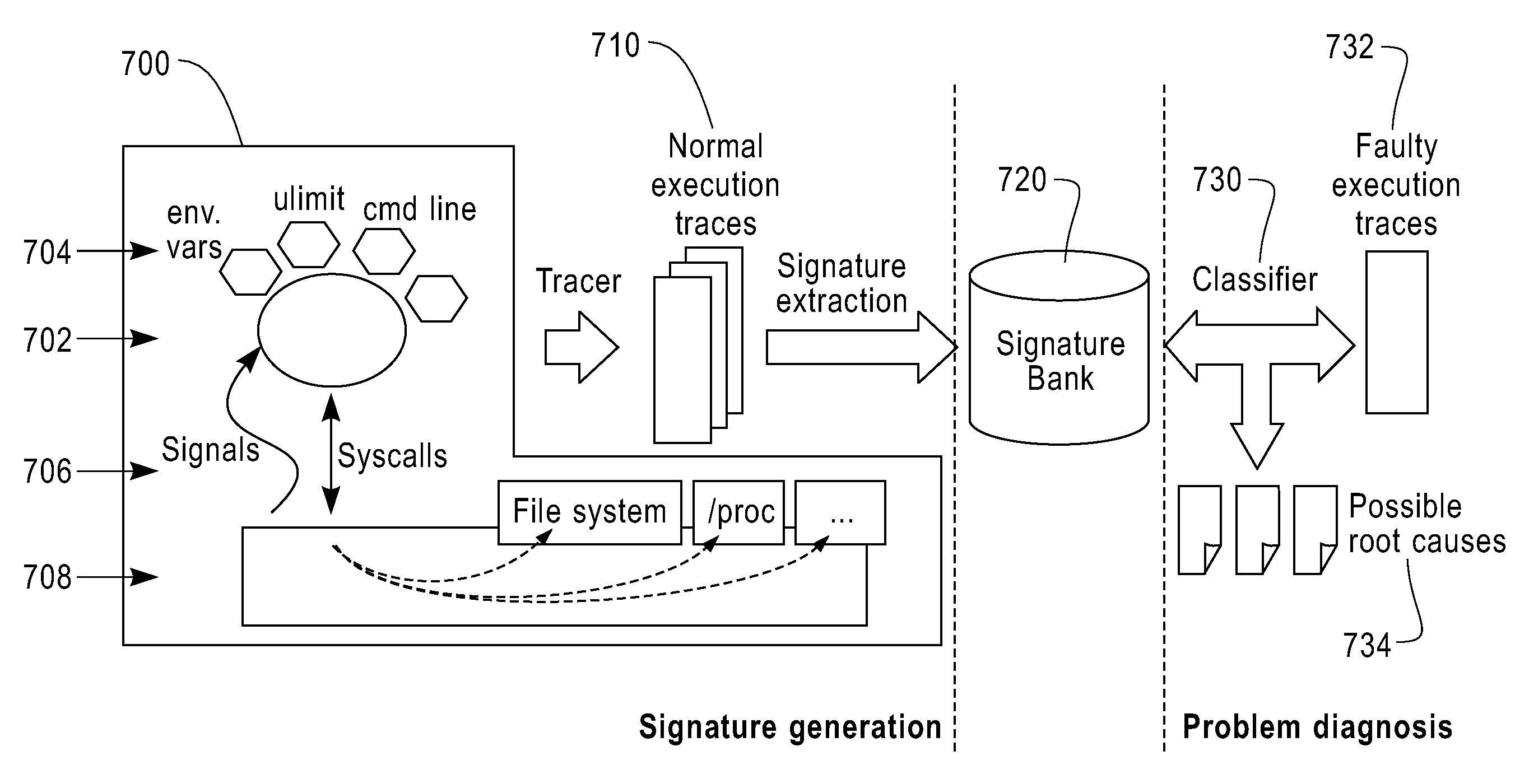
Automatic software fault diagnosis by exploiting application signatures
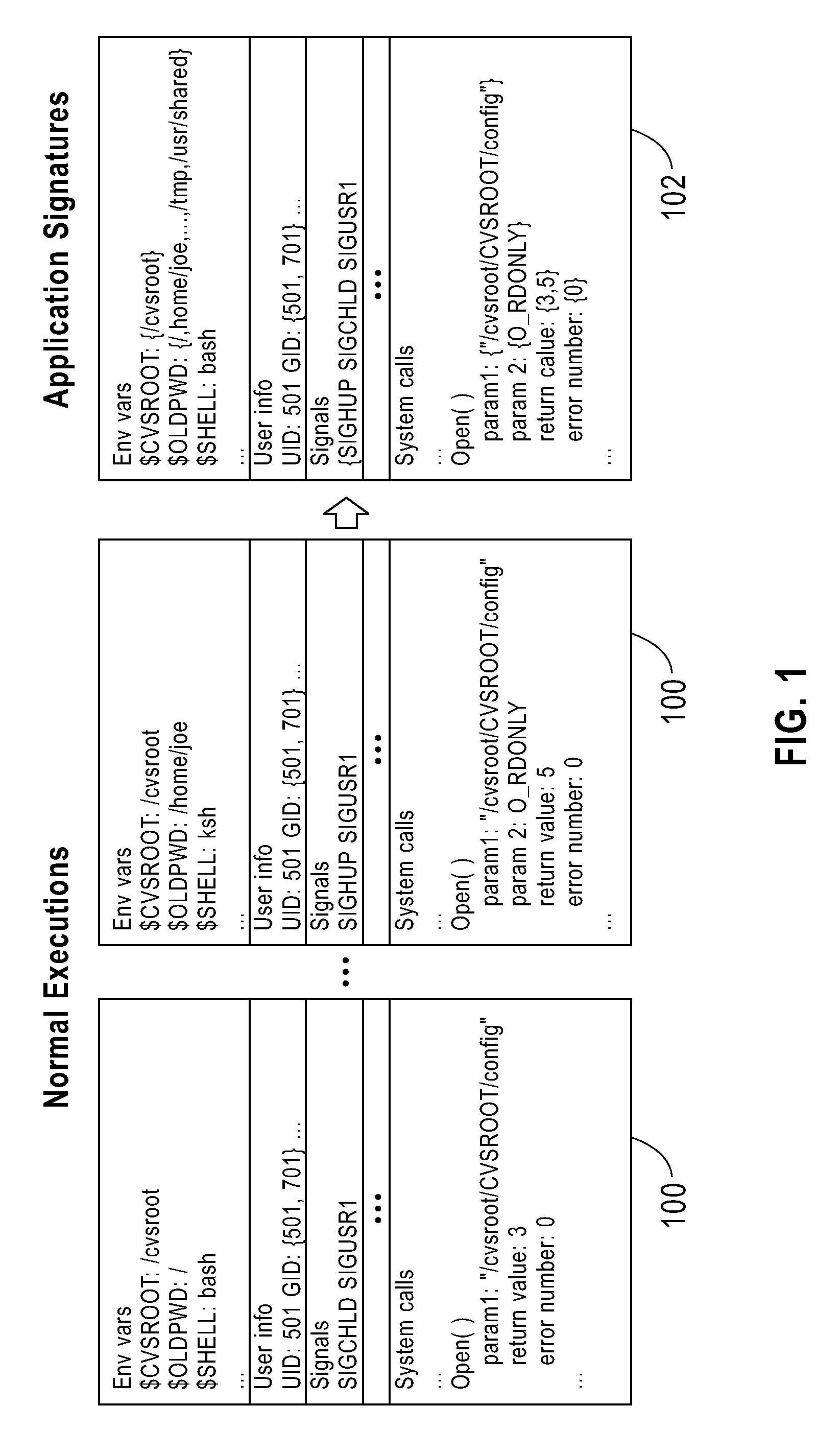
InactiveUS20100100774A1Lower requirementReduce the impactDatabase updatingFault responseProgram tracingSoftware fault
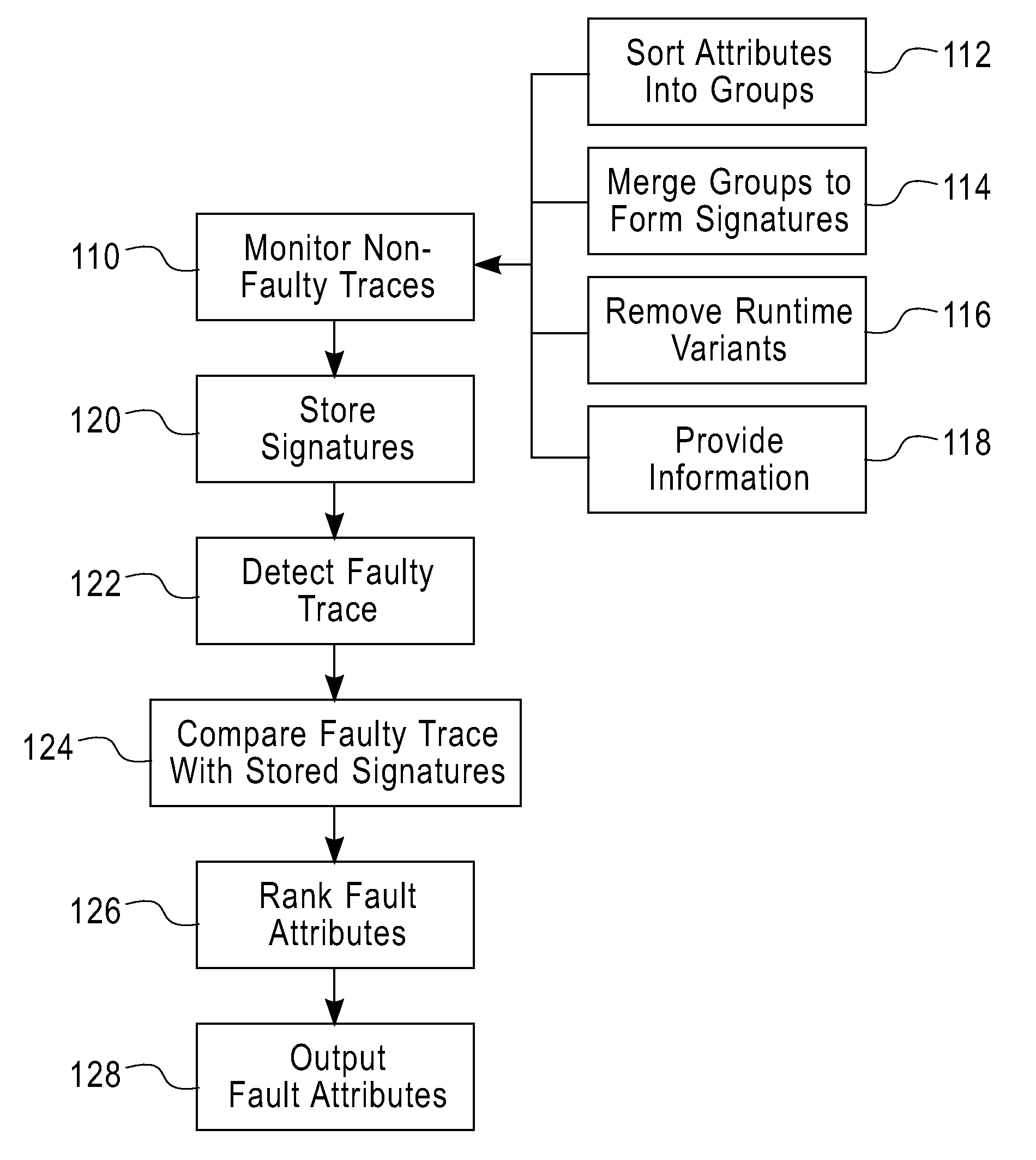
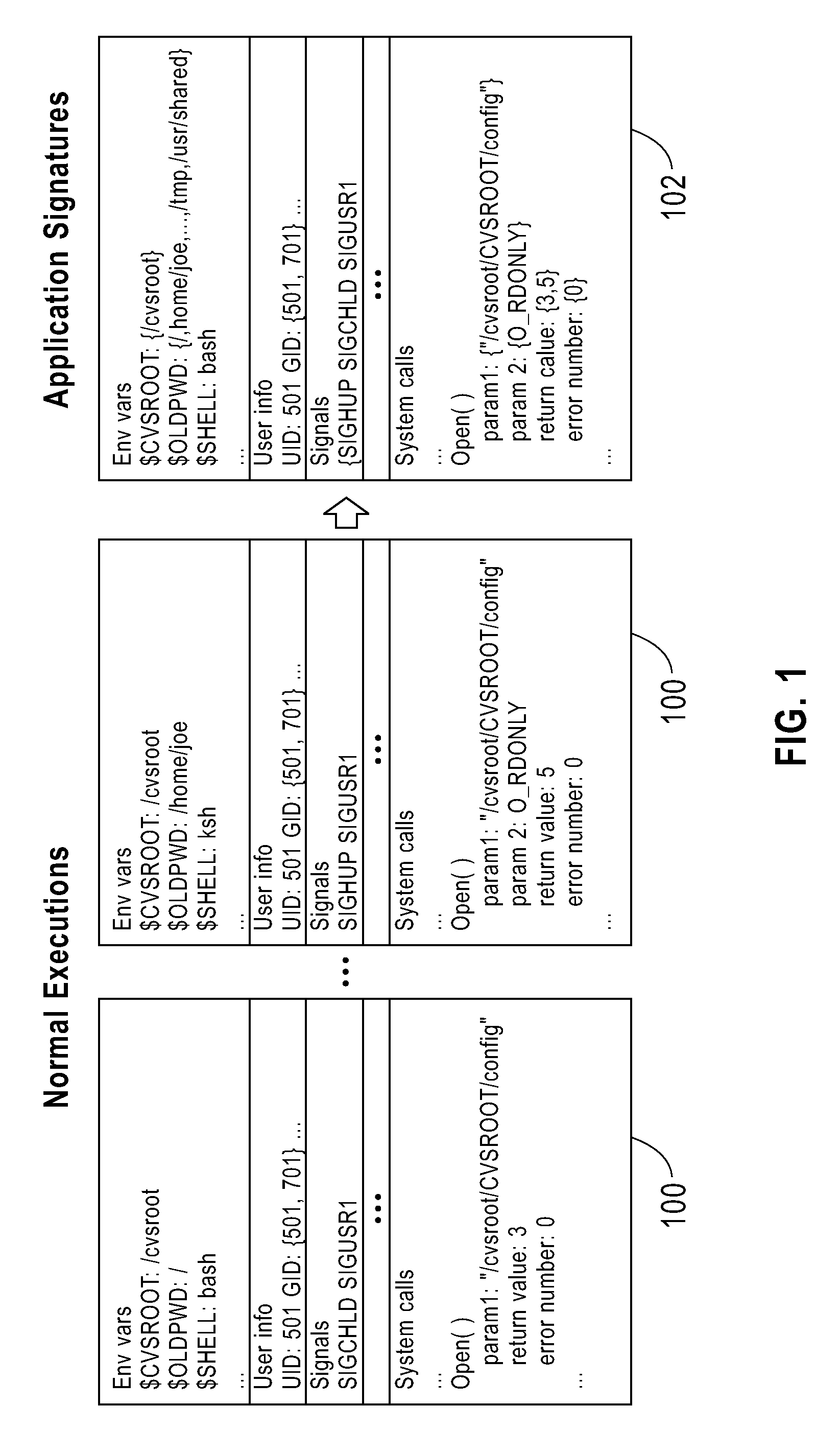
A method monitors non-faulty application traces of a computer application with the runtime environment during fault-free activities to create non-faulty runtime signatures for the computer application. Once obtained, the method stores the non-faulty runtime signatures. The method then detects a faulty application trace of the computer application and compares the faulty application trace with the non-faulty runtime signatures by comparing a call graph of the faulty application trace with call graphs of non-faulty application traces of the application signatures to identify differences between the two (e.g., fault attributes). Then the invention outputs the fault attributes to allow the user to identify a fault cause.
Owner:GLOBALFOUNDRIES INC
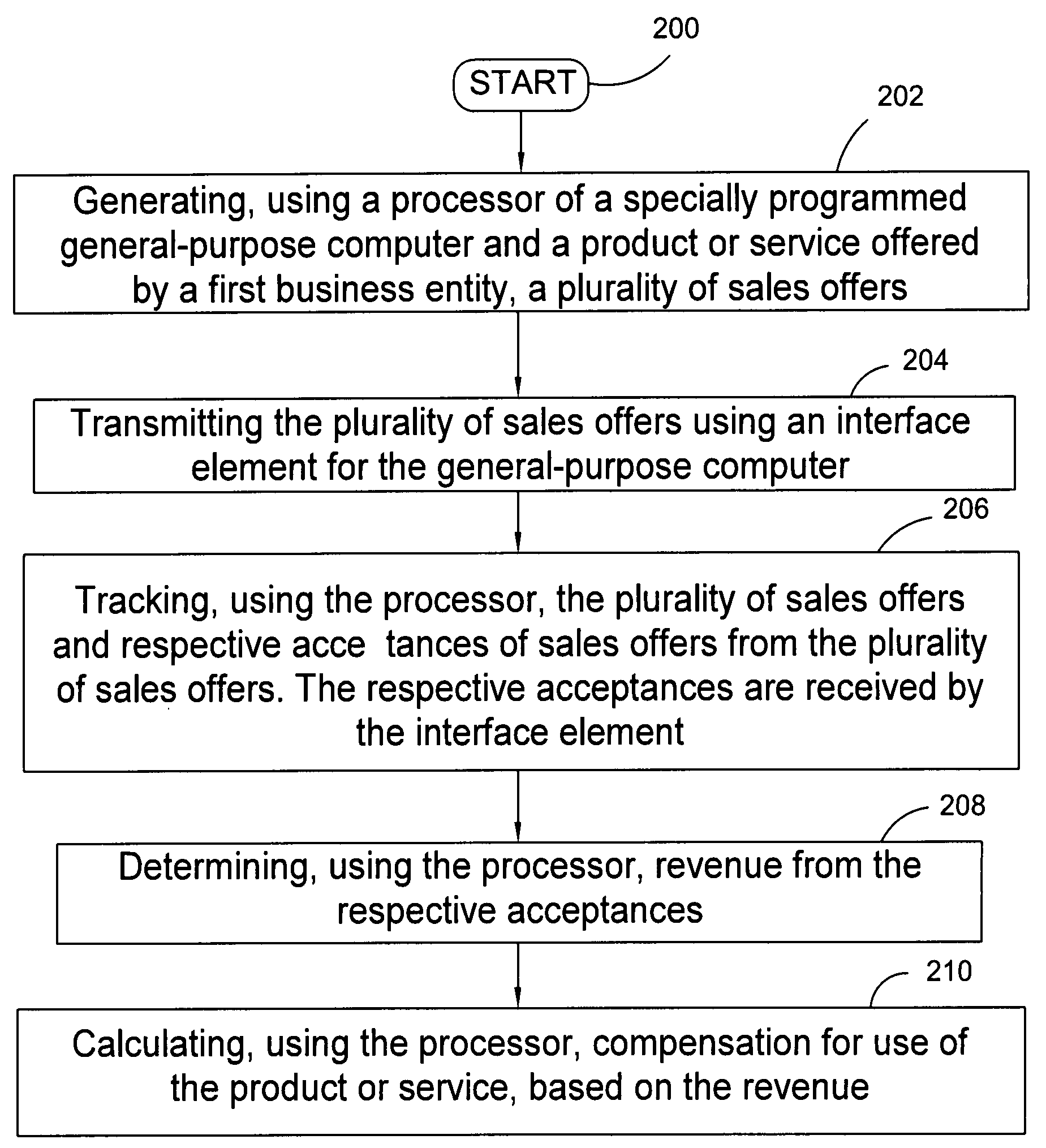
Upsell system embedded in a system and controlled by a third party
InactiveUS20090182677A1Readily appreciableComplete banking machinesFinanceThird partyGeneral purpose computer
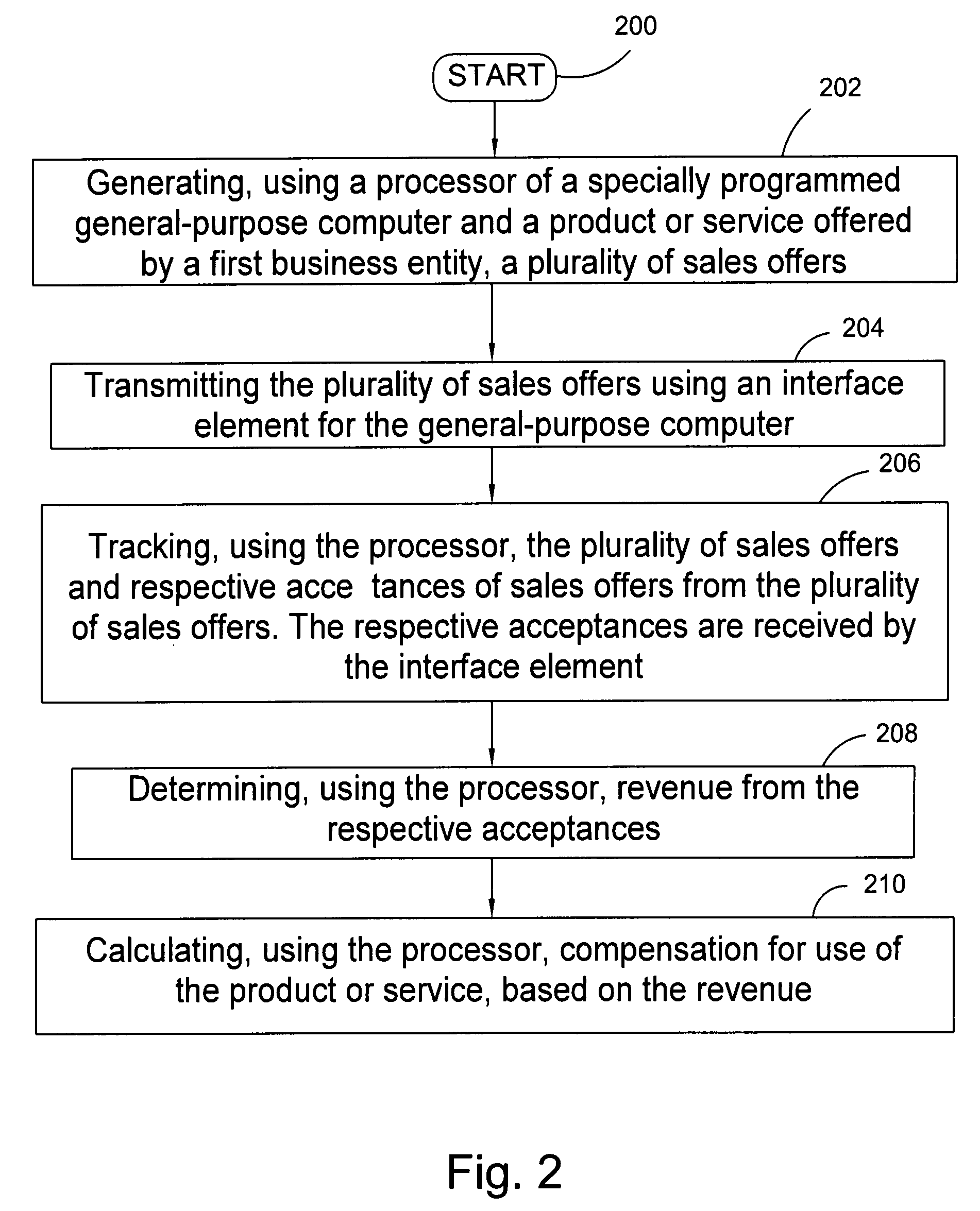
A method of determining compensation, including the steps of: generating, using a processor of a specially programmed general-purpose computer and a first software program stored in a memory element of the general-purpose computer and offered by a first business entity, at least one sales offer; transmitting the at least one sales offer using an interface element for the general-purpose computer; tracking, using the processor and a second software program stored in the memory element and supplied by a third business entity, the at least one sales offer and respective acceptances of sales offers from the at least one sales offer, the respective acceptances received by the interface element; determining, using the processor and the second software program, revenue from the respective acceptances; and calculating, using the processor and the second software program, compensation for use of the product or service, based on the revenue.
Owner:RETAILDNA
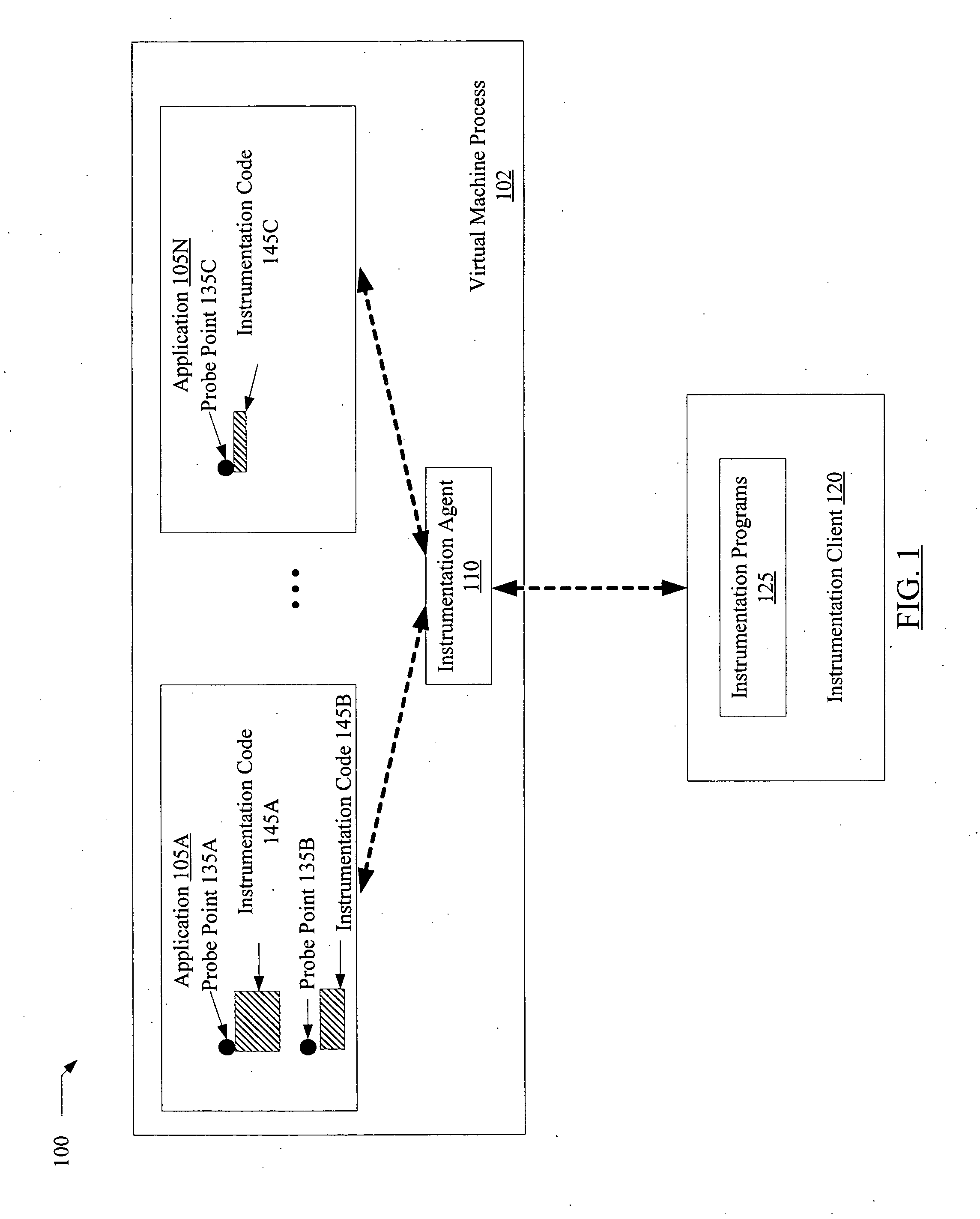
Dynamic application tracing in virtual machine environments
ActiveUS7818721B2Promote generationError detection/correctionSpecific program execution arrangementsProgram tracingParallel computing
A method for dynamic application tracing in virtual machine environments comprises receiving an instrumentation request that includes an identification of a probe point at which instrumentation code is to be inserted within an application. The method may further comprise making a determination whether the instrumentation code meets one or more acceptance criteria. If the instrumentation code is found to be acceptable, the method may further comprise inserting the instrumentation code at the probe point within the application while the application is executing within a virtual machine, and obtaining information indicative of application state from an execution of the instrumentation code when the probe point is reached during application execution.
Owner:ORACLE INT CORP
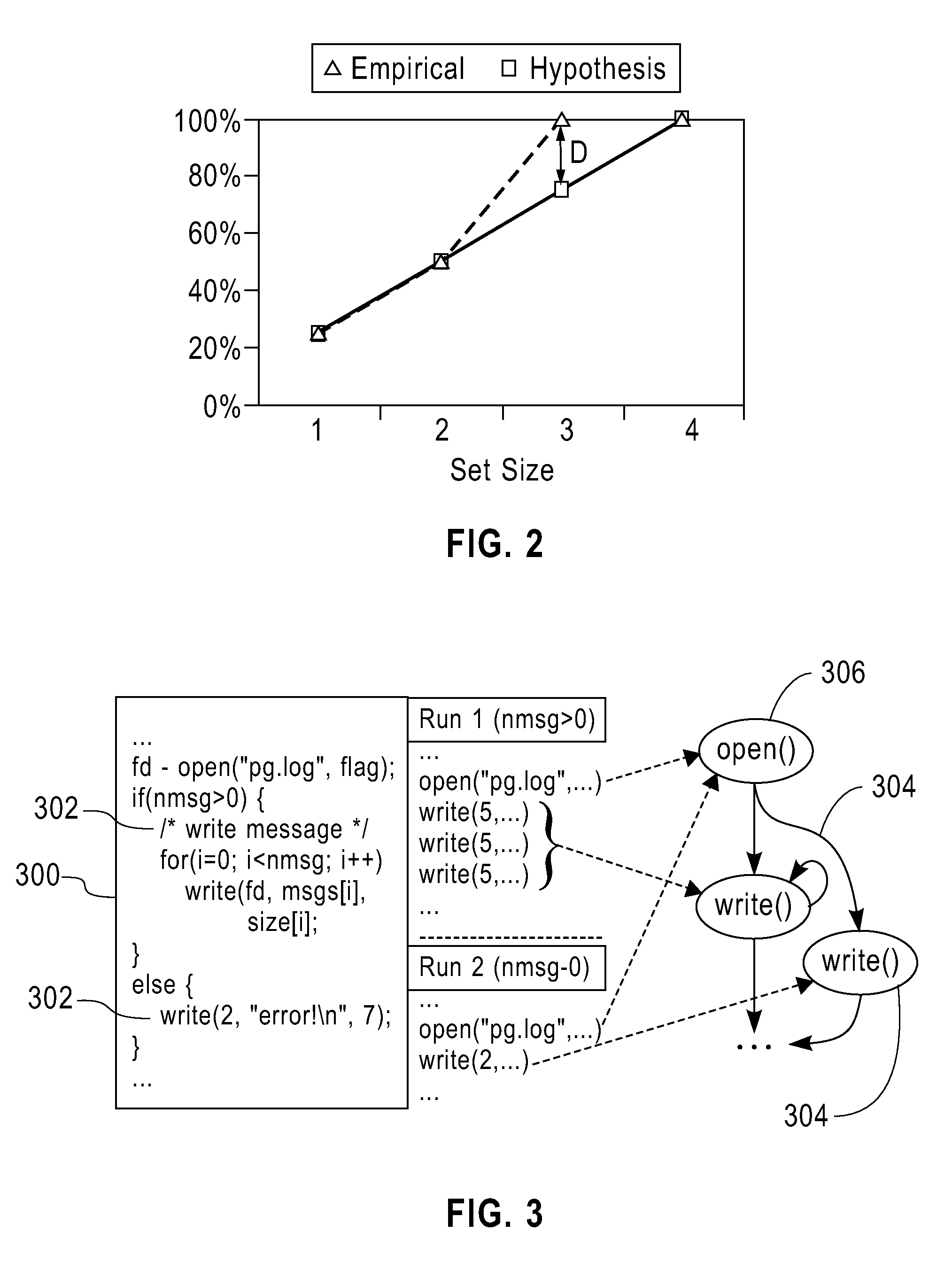
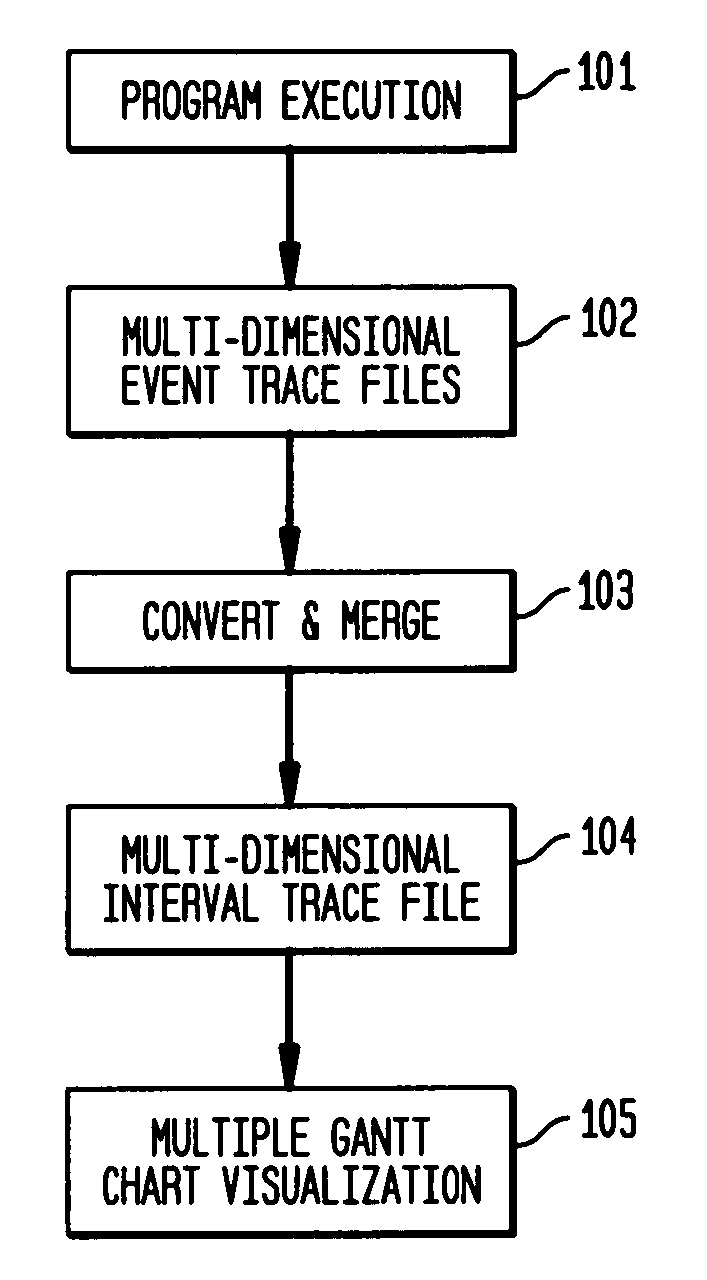
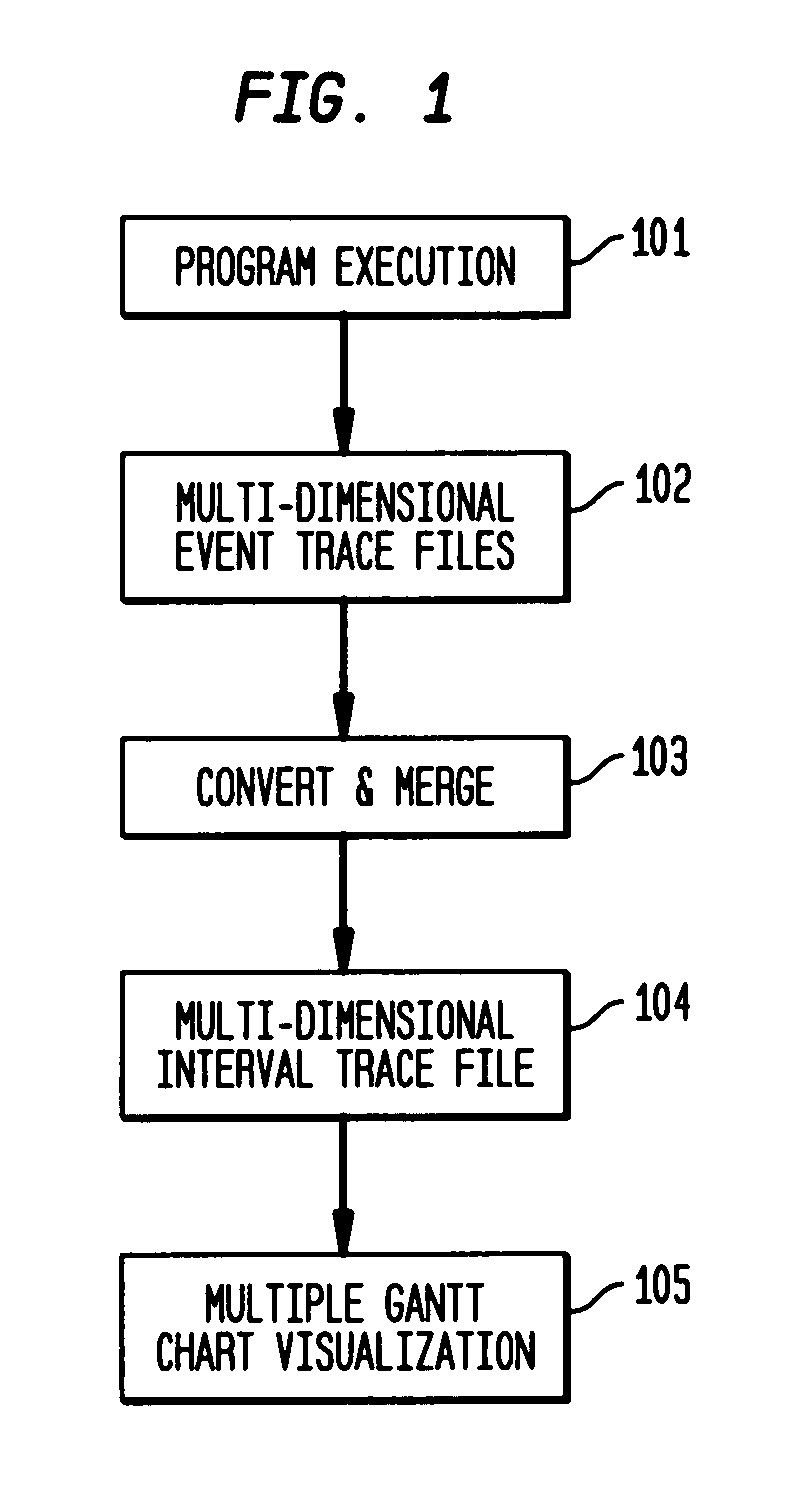
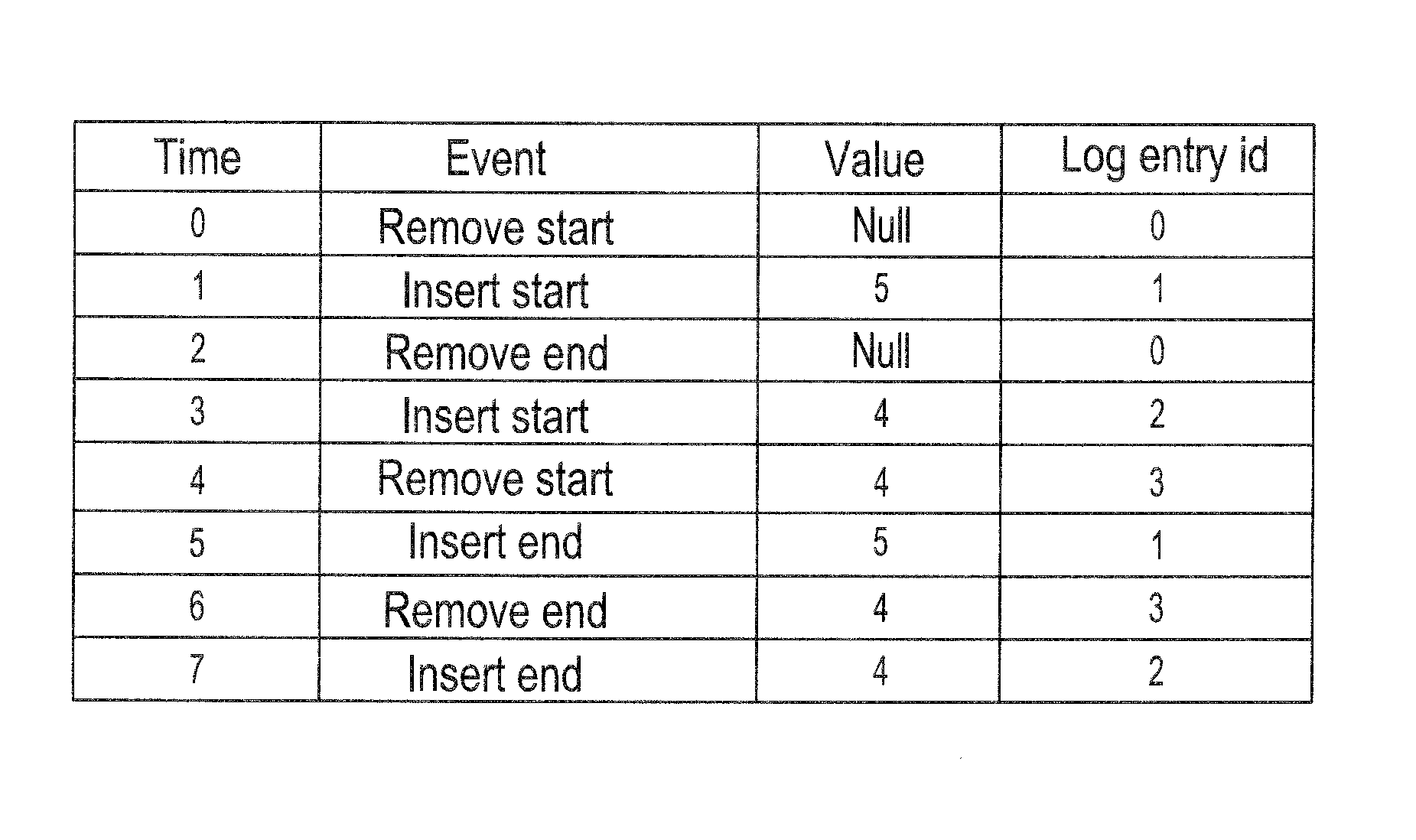
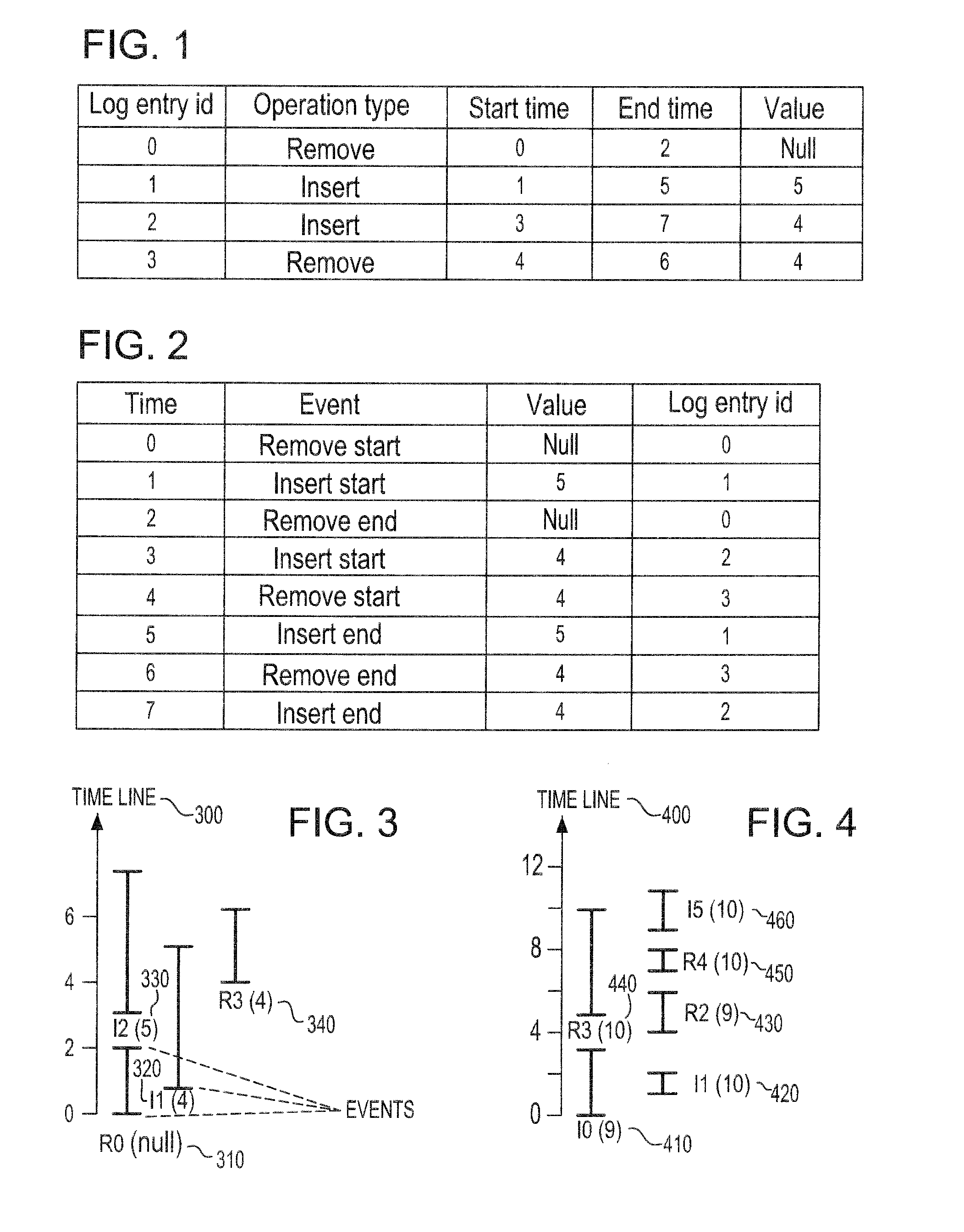
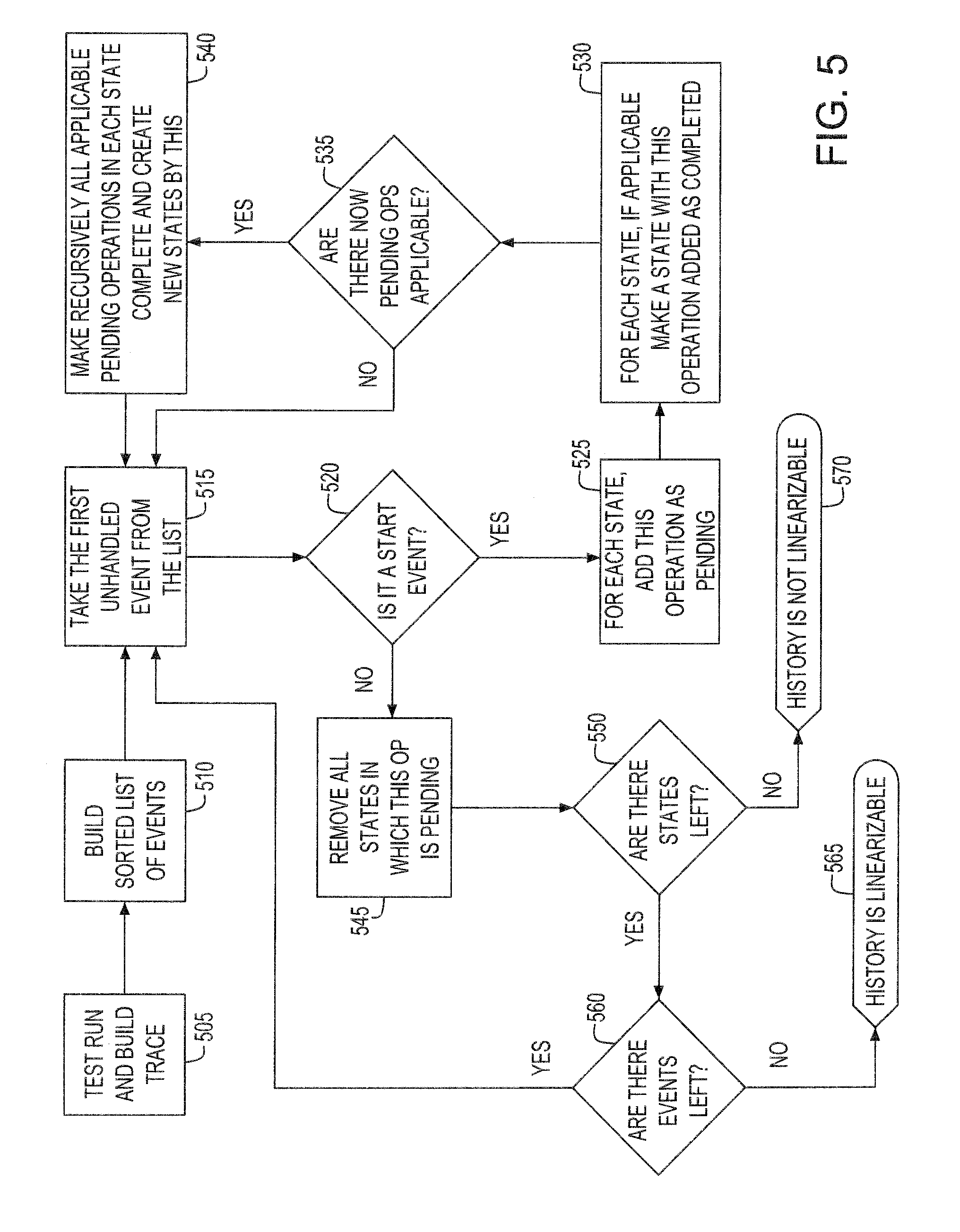
System and method on generating multi-dimensional trace files and visualizing them using multiple Gantt charts
InactiveUS7131113B2Elimination of trace file explosionEasy to understandError preventionError detection/correctionGantt chartMultiple dimension
A system and method for visualizing data in two-dimensional time-space diagrams including generating multi-dimensional program trace files, converting and merging them into interval trace files, and generating multiple time-space diagrams (multiple Gantt charts) to visualize the resulting multi-dimensional interval trace files. The needed events and trace information required to form multi-dimensional event traces are described in event trace files typically gathered from running programs, such as parallel programs for technical computing and Web server processes. The method includes converting event traces into interval traces. In one selectable design, the two-dimensional time-space diagrams includes three discriminator types (thread, processor, and activity) and six discriminator-legend combinations, capable of producing seven possible views. The six discriminator-legend combinations are thread-activity, thread-processor, processor-thread, processor-activity, activity-thread, and activity-processor. Each discriminator-legend combination corresponds to one time-space diagram, except that the thread-activity combination has two possible views: Thread-Activity View and Connected Thread-Activity View.
Owner:IBM CORP
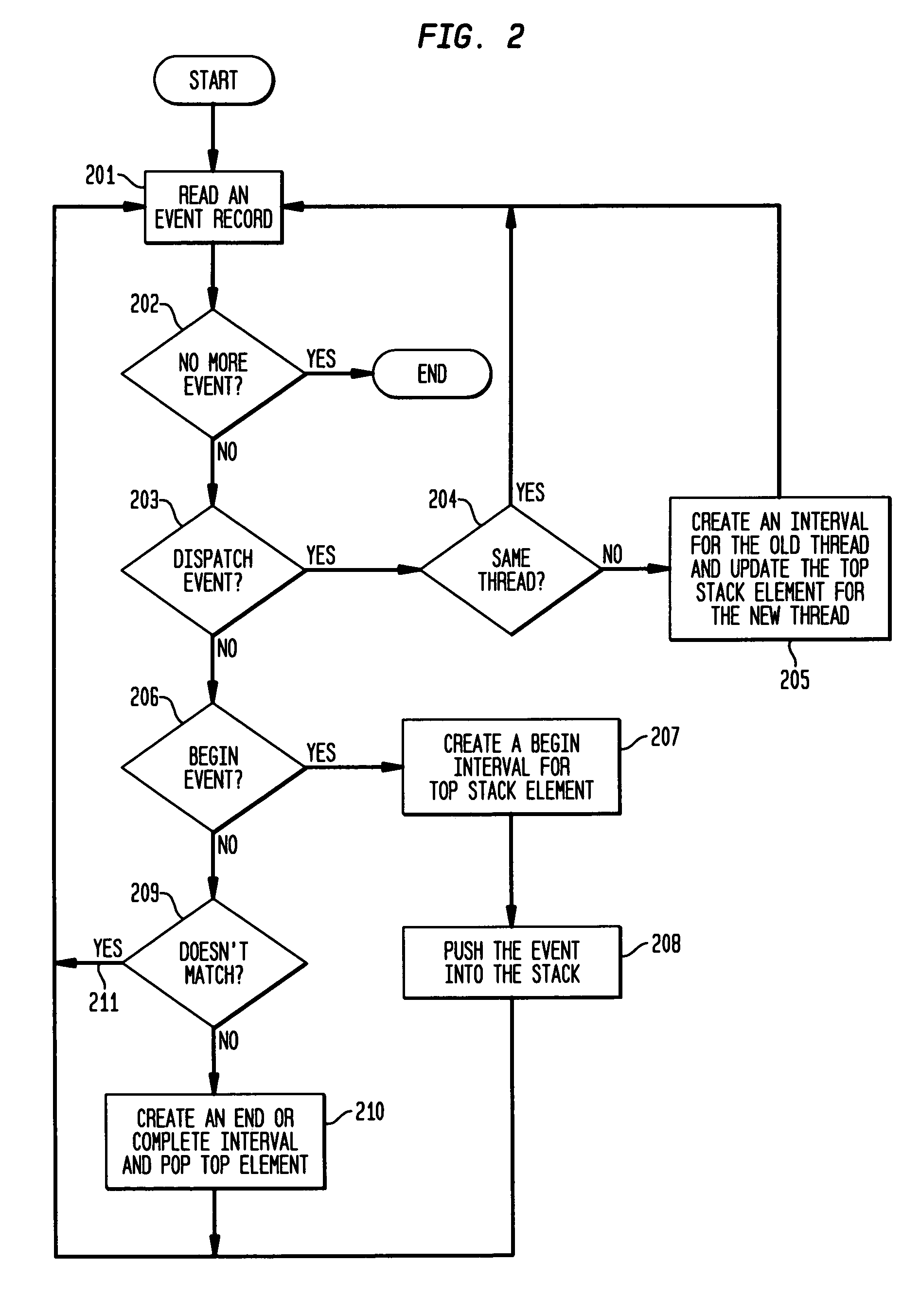
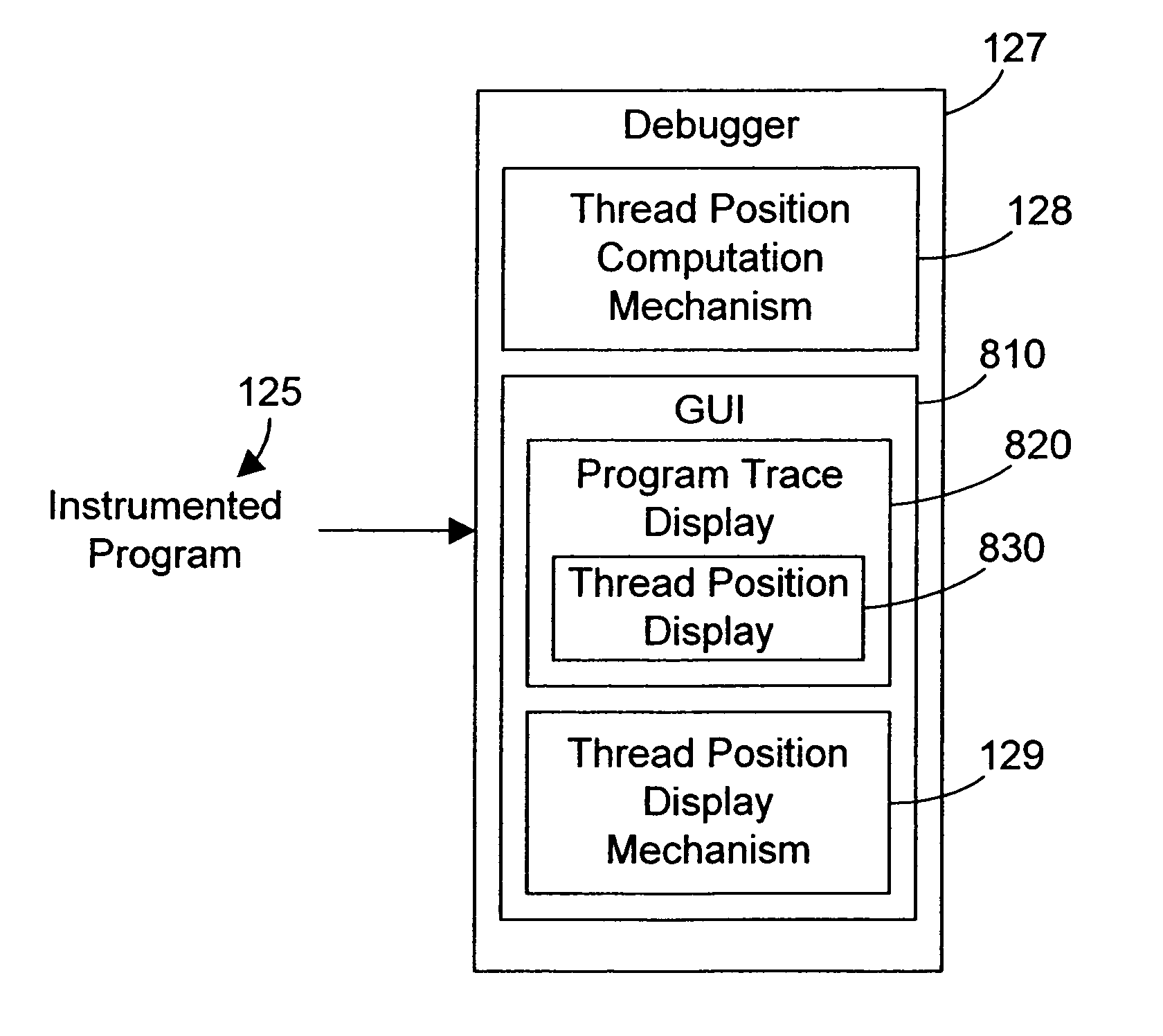
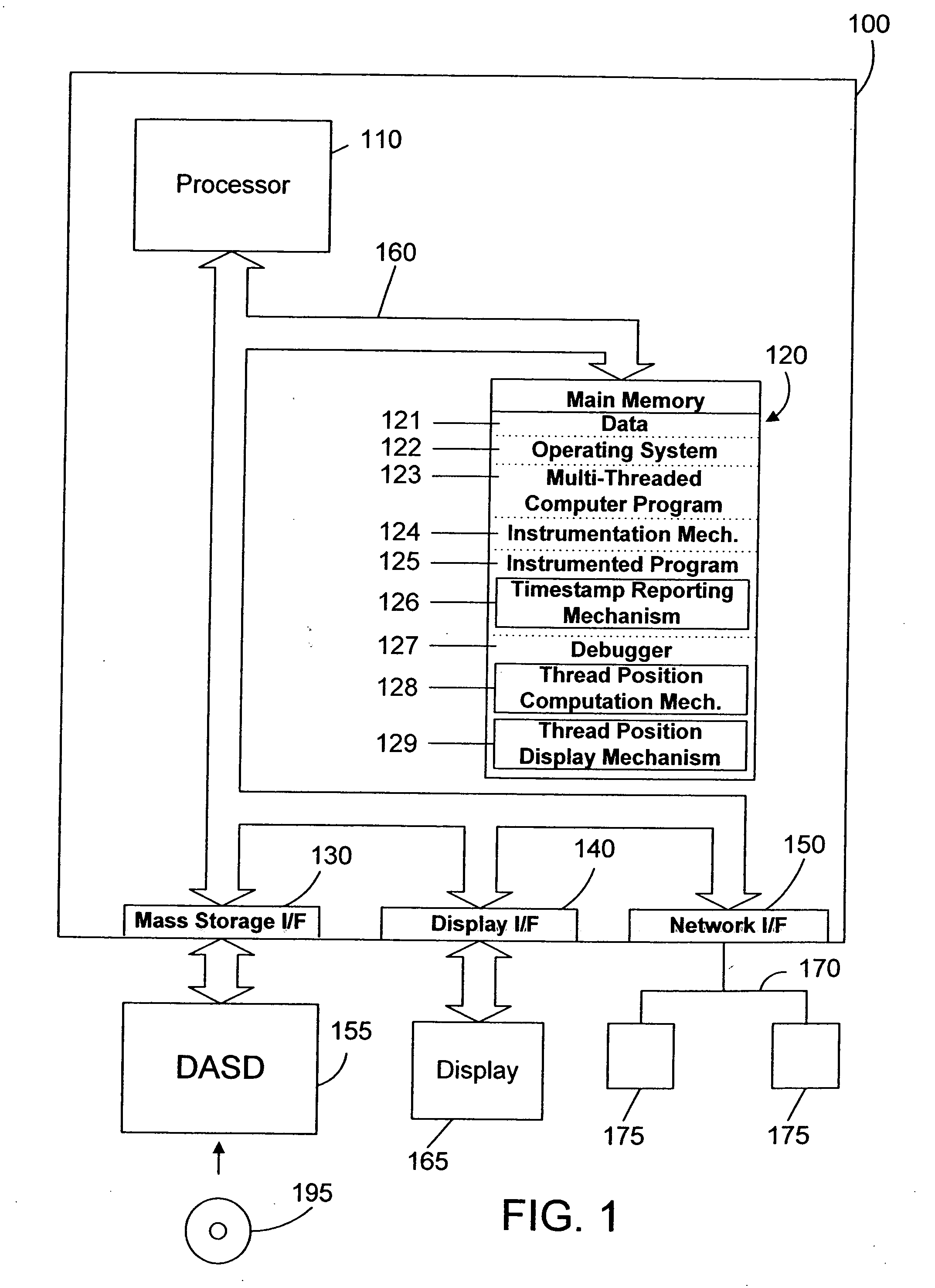
Debugger apparatus and method for indicating time-correlated position of threads in a multi-threaded computer program
InactiveUS20070168968A1Error detection/correctionSpecific program execution arrangementsTimestampProgram trace
A debugger inserts instrumentation hooks in a multi-threaded computer program that allow collecting a program trace and that provide timestamps that correspond to the program trace. When a breakpoint in a first thread is encountered, a timestamp corresponding to the breakpoint is retrieved. Execution of the other threads may continue until the debugger is able to halt their execution. Once the execution of all threads has been halted, the program trace for each thread is traced backwards to a point where the timestamp is less than the breakpoint timestamp. Instructions are then executed, one by one, until the execution time of the instructions plus the timestamp is approximately the same as the breakpoint timestamp. The instruction in the program trace display is then highlighted to indicate the instruction that was likely being executed when the breakpoint in the first thread is encountered.
Owner:IBM CORP
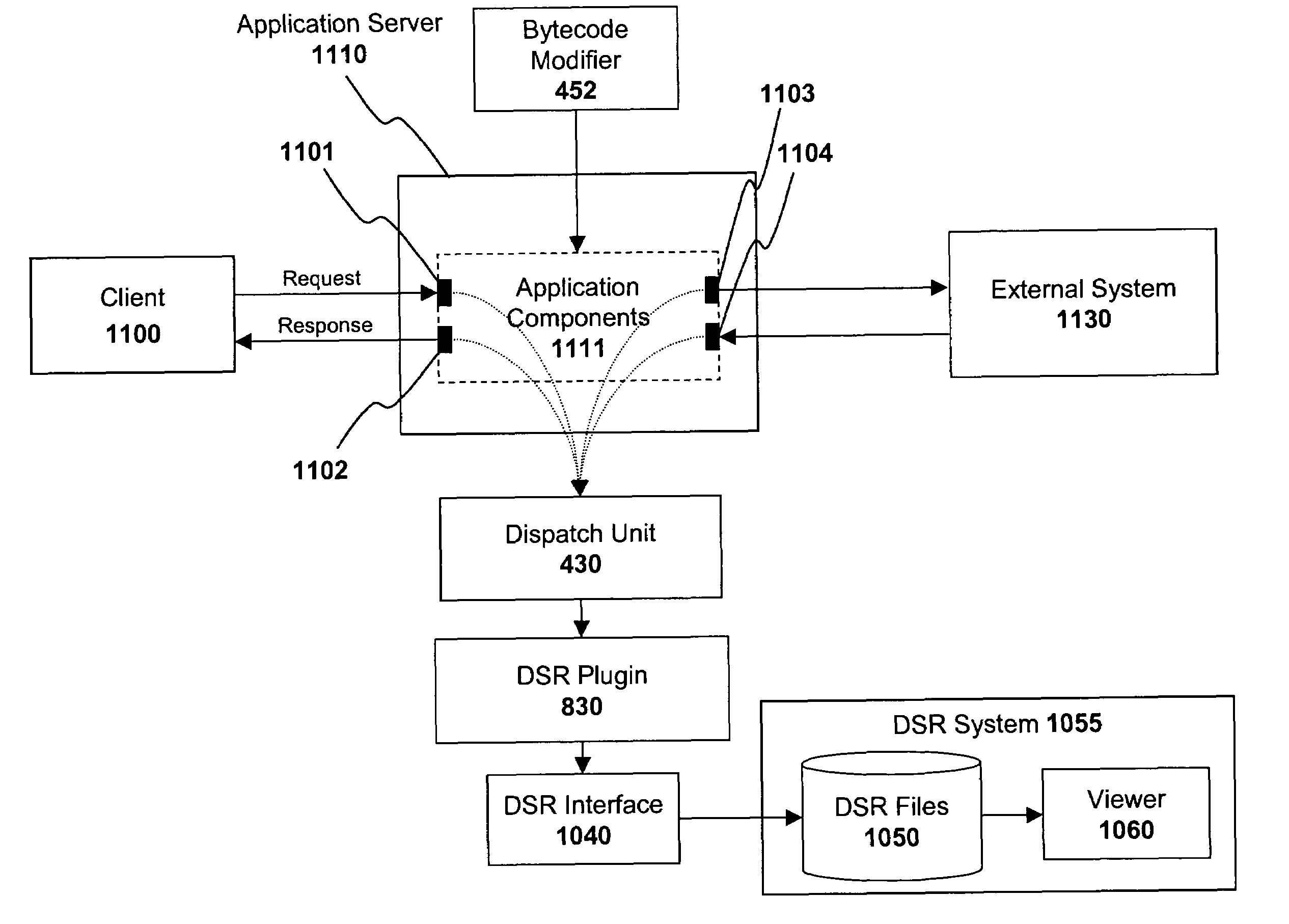
System and method combining application tracing and distributed statistical records
ActiveUS7506315B1Flexible and scalable architectureError detection/correctionSpecific program execution arrangementsProgram tracingApplication server
A system and method for coupling a distributed statistical records (“DSR”) collection system with a tracing system utilizing bytecode modification techniques. In one embodiment, a distributed statistical records (“DSR”) module initially identifies one or more application components within the application server to be traced. A bytecode modification module responsively modifies the bytecode of the one or more application components. The modifications are directed to a particular set of methods of the application components (e.g., methods which are relevant to DSR data). A dispatch unit registers the method invocations and method-related information associated with the particular set of methods and provides the method-related information to the DSR module. Finally, a DSR interface module translates the method-related information to a format employed within a DSR system and forwards the translated information to the DSR system.
Owner:SAP AG
Automatic software fault diagnosis by exploiting application signatures
InactiveUS7877642B2Reduce in quantityExcessive weightDatabase updatingError detection/correctionProgram tracingSoftware fault
A method monitors non-faulty application traces of a computer application with the runtime environment during fault-free activities to create non-faulty runtime signatures for the computer application. Once obtained, the method stores the non-faulty runtime signatures. The method then detects a faulty application trace of the computer application and compares the faulty application trace with the non-faulty runtime signatures by comparing a call graph of the faulty application trace with call graphs of non-faulty application traces of the application signatures to identify differences between the two (e.g., fault attributes). Then the invention outputs the fault attributes to allow the user to identify a fault cause.
Owner:GLOBALFOUNDRIES INC
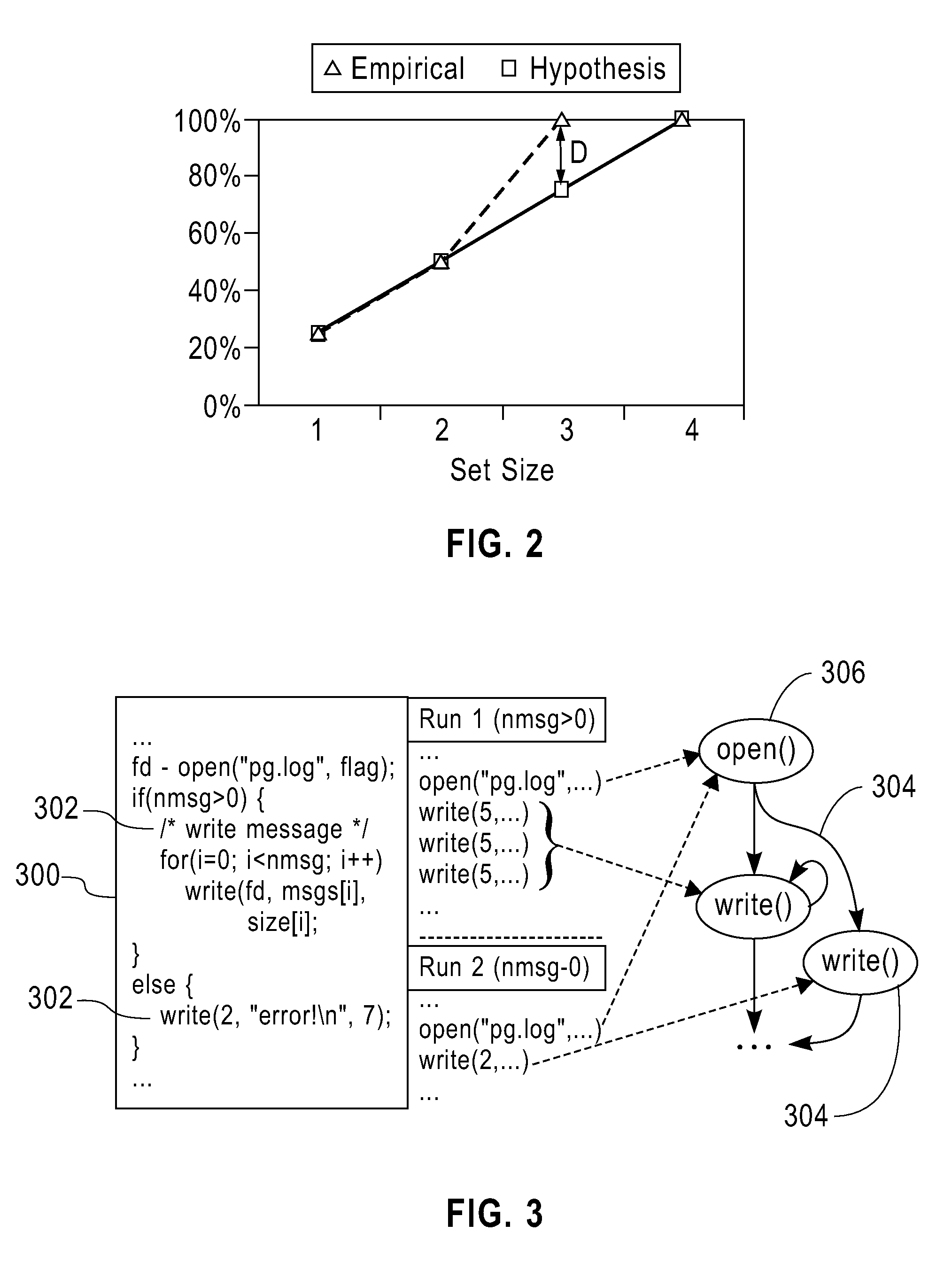
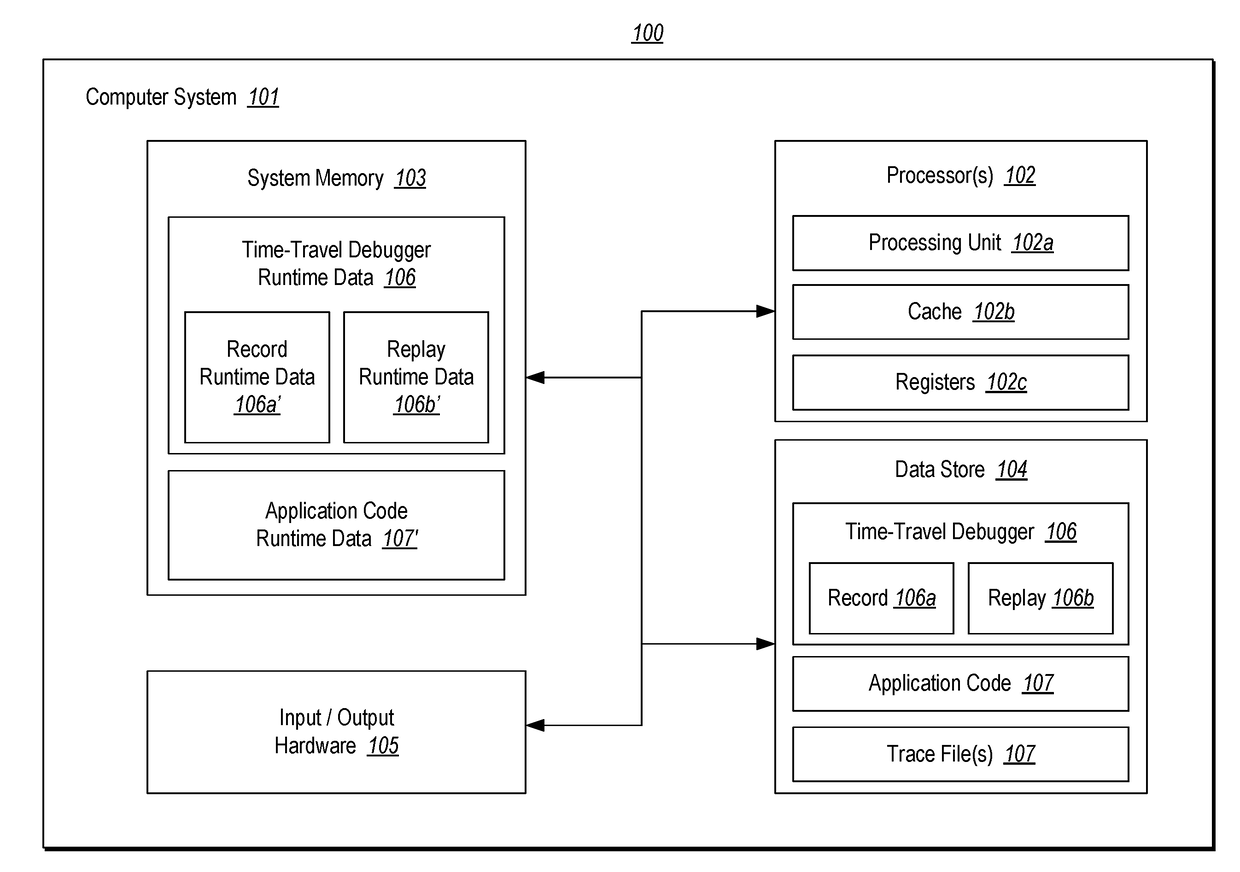
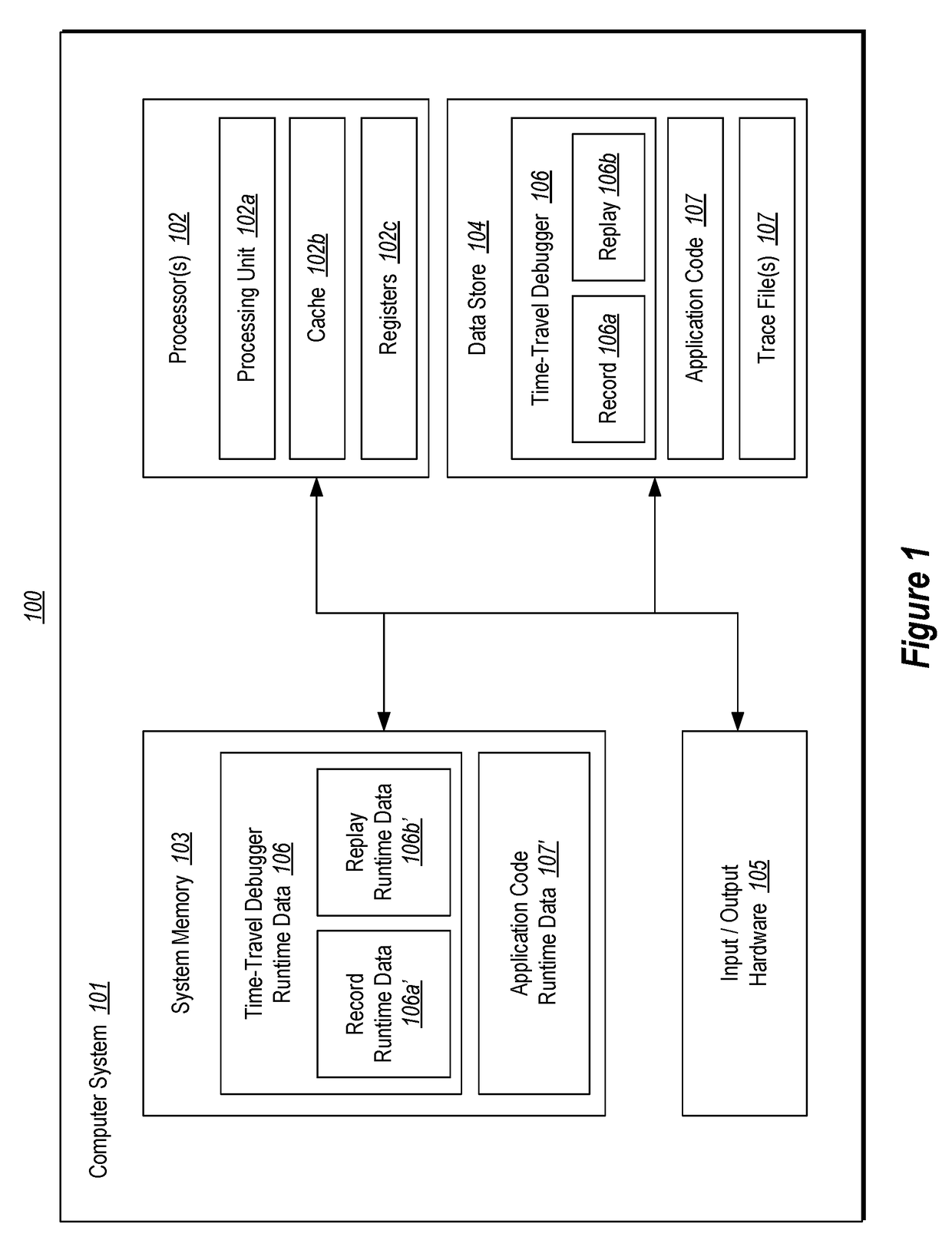
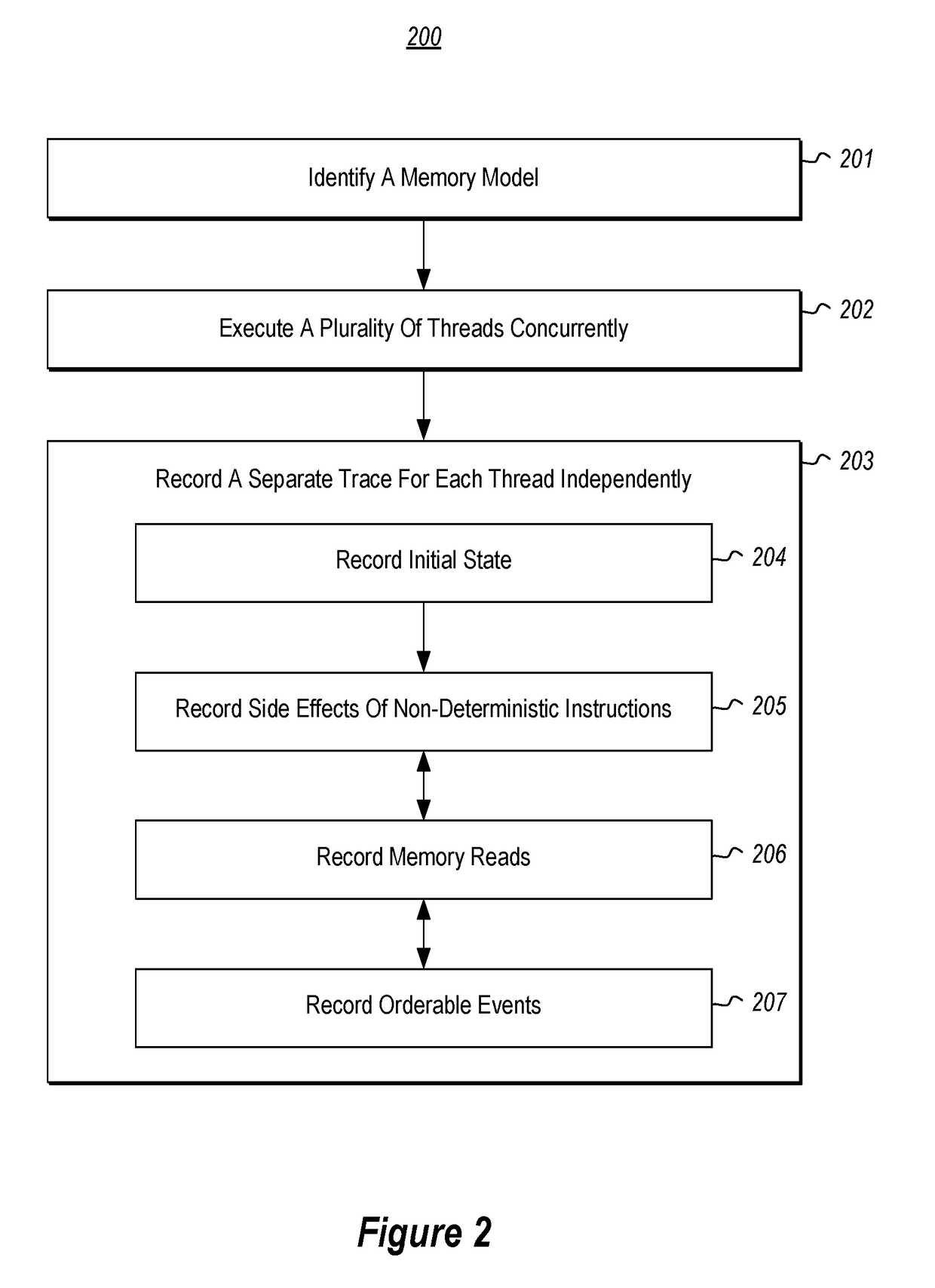
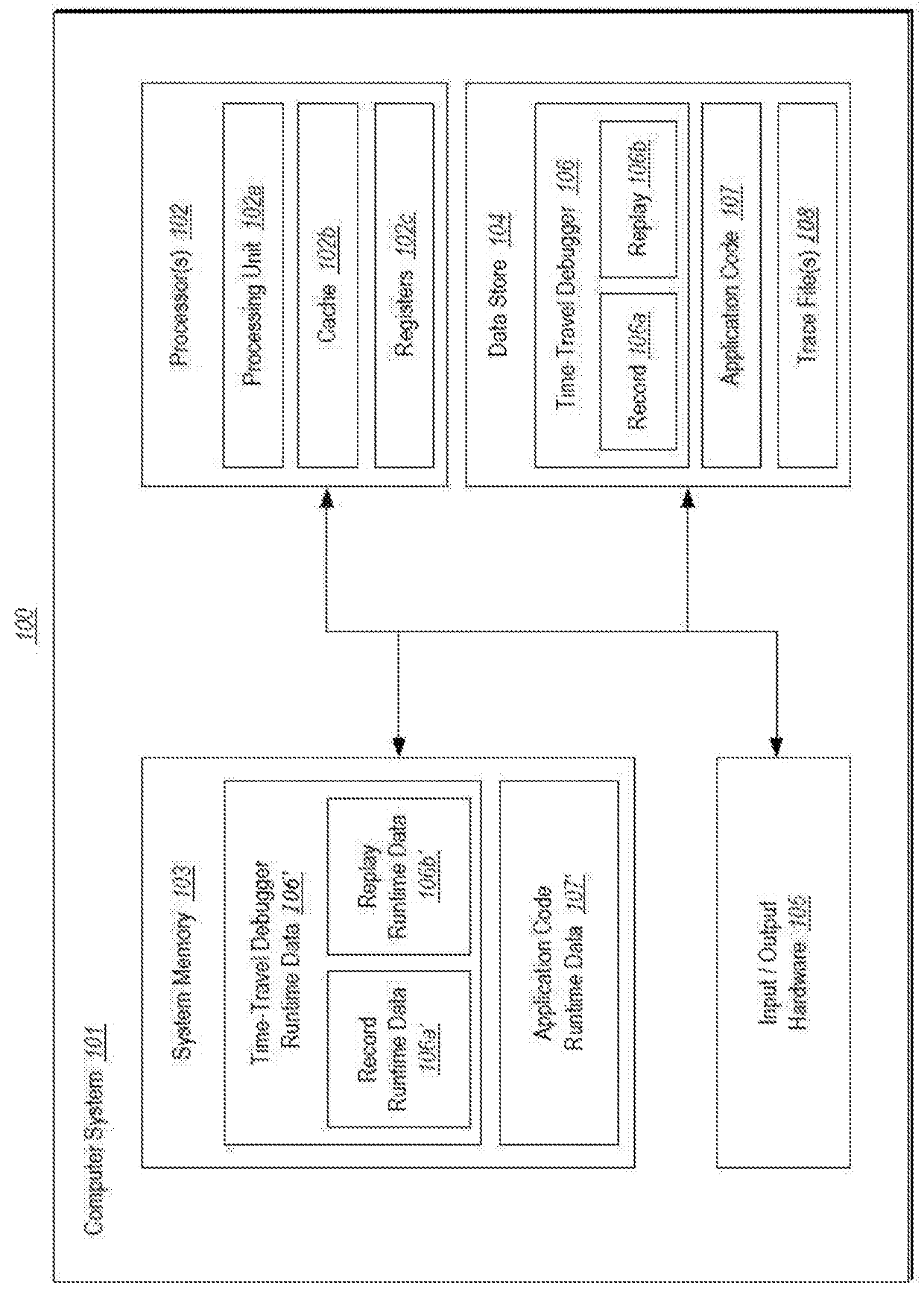
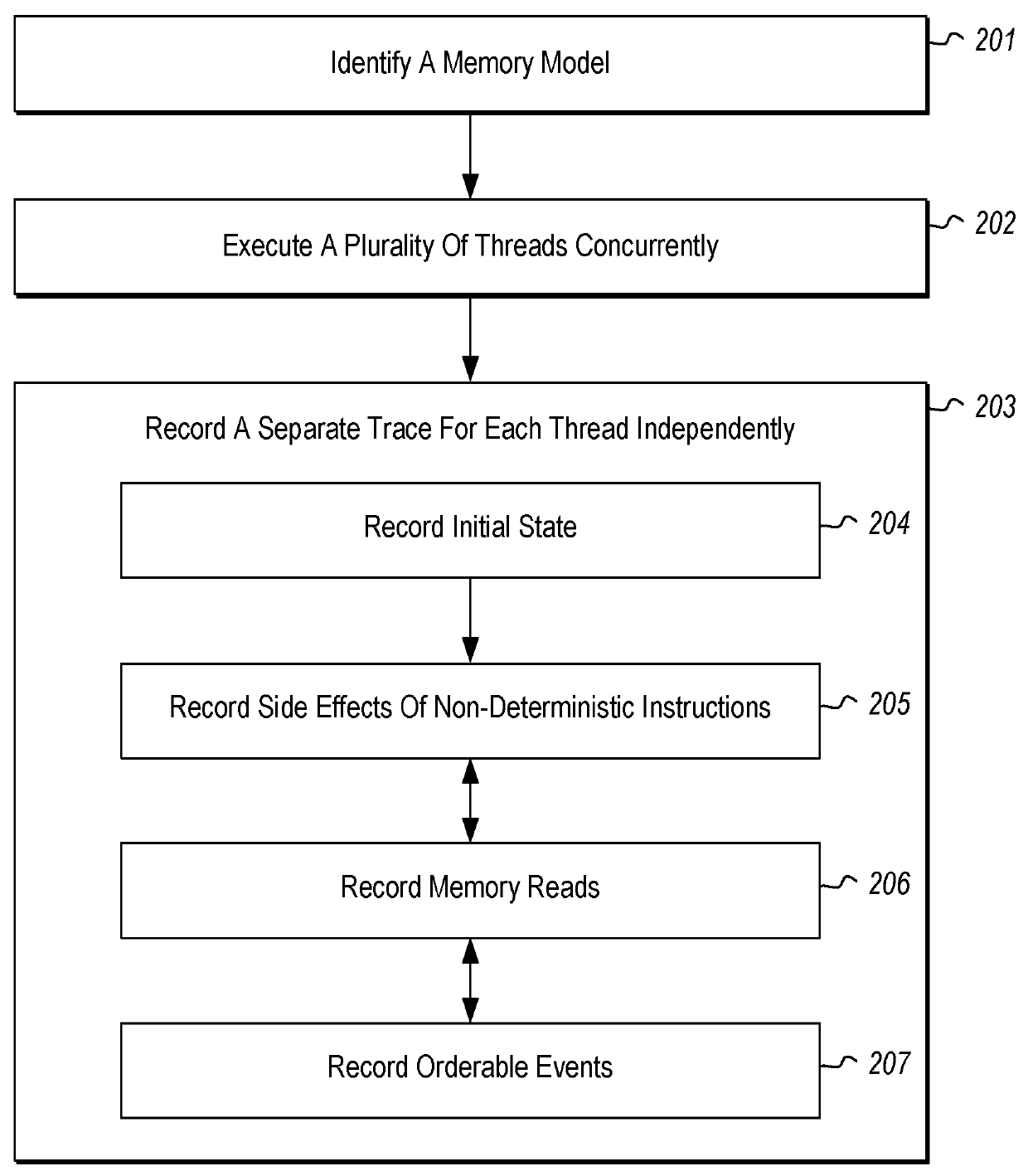
Program tracing for time travel debugging and analysis
ActiveUS20180060213A1Improve performanceSmall sizeSoftware testing/debuggingProgram tracingProcessing element
Recording a replay-able trace of execution of a multi-threaded process includes identifying a trace memory model that defines one or more orderable events that are to be ordered across a plurality of threads of the multi-threaded process. The plurality of threads are executed concurrently across one or more processing units of one or more processors. During execution of the plurality of threads, a separate replay-able trace is recorded for each thread independently. Recording includes, for each thread, recording initial state for the thread, recording at least one memory read performed by at least one processor instruction executed by the thread that takes memory as input, and recording a least one orderable event performed by the thread with a monotonically increasing number that orders the event among other orderable events across the plurality of threads.
Owner:MICROSOFT TECH LICENSING LLC
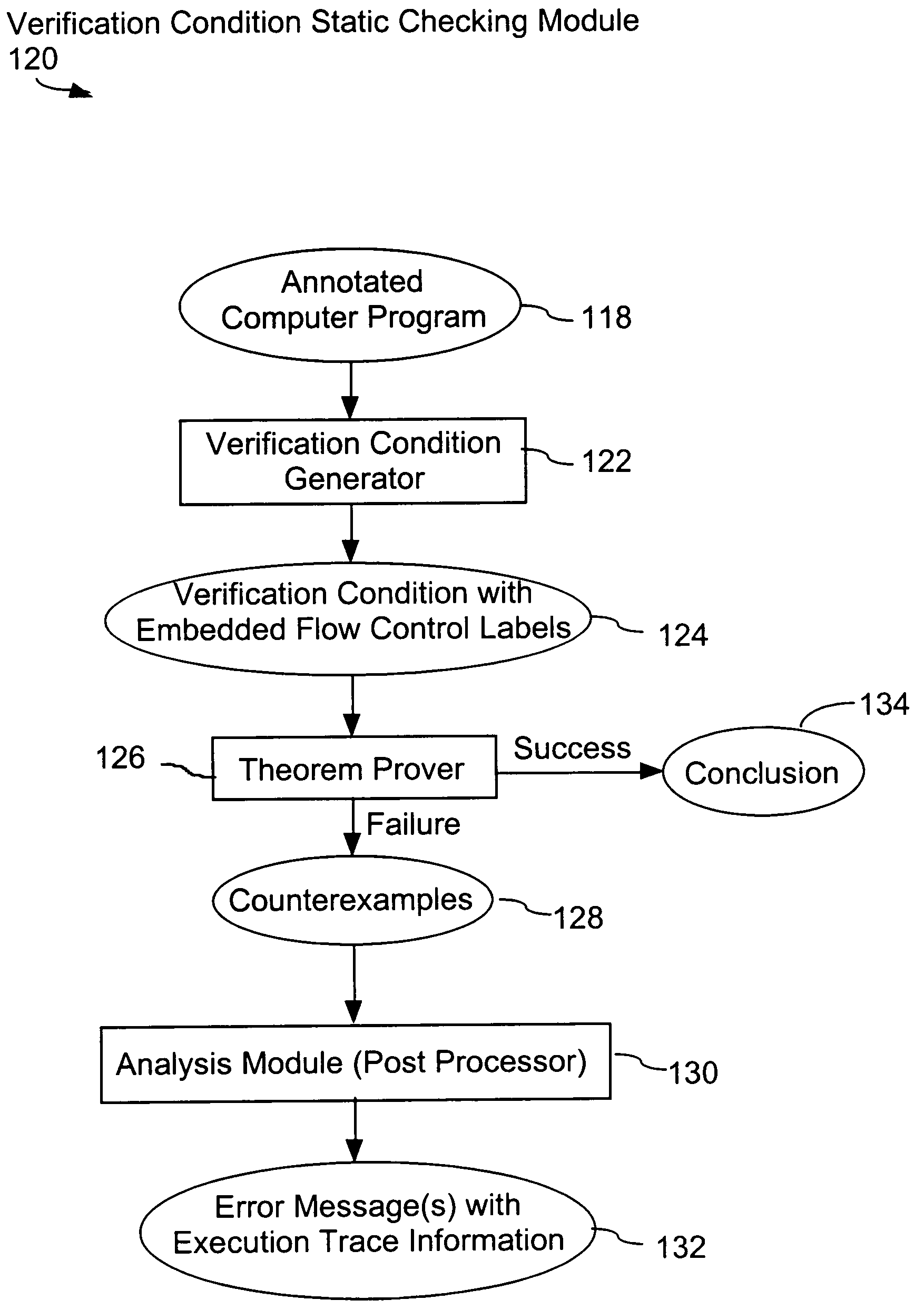
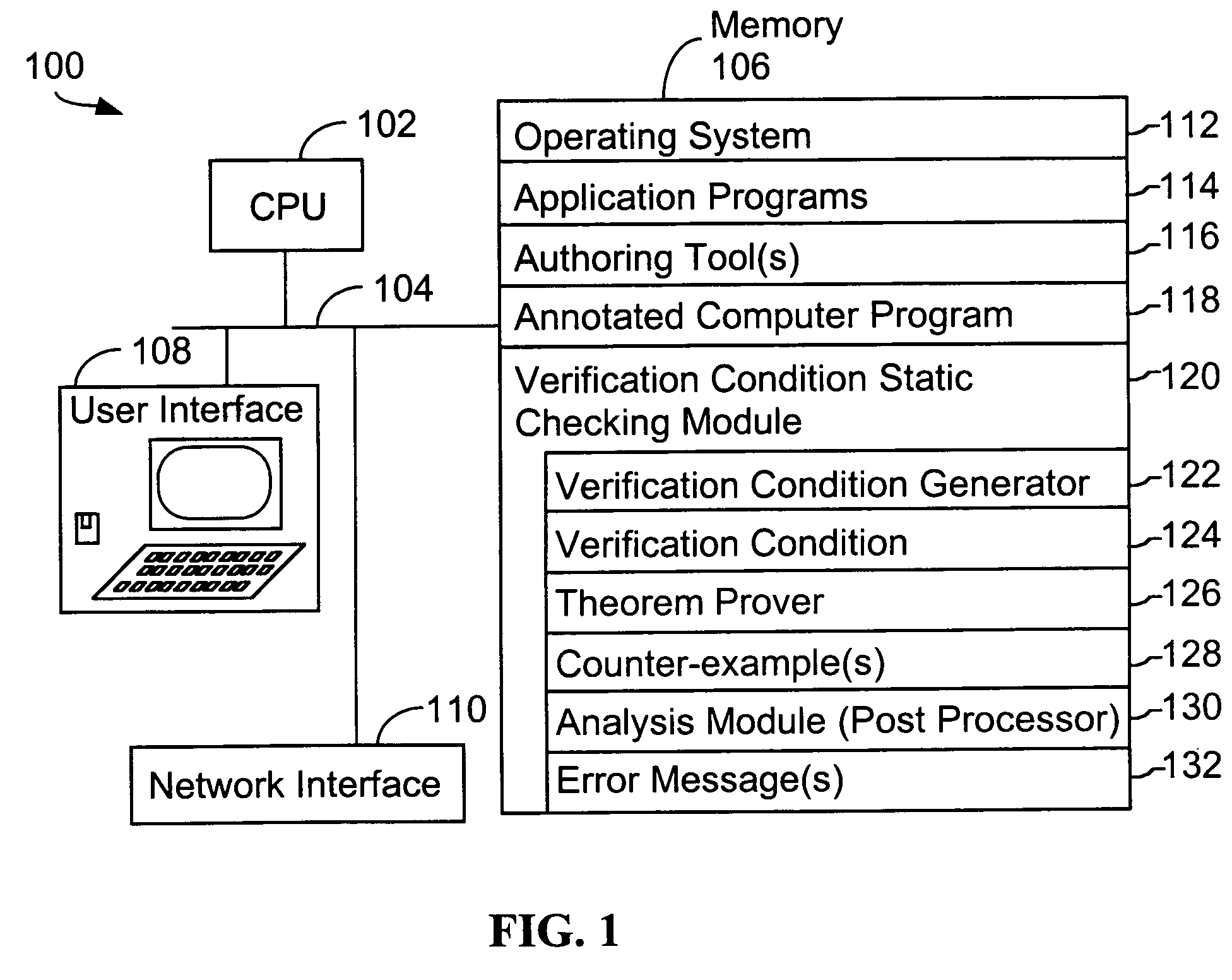
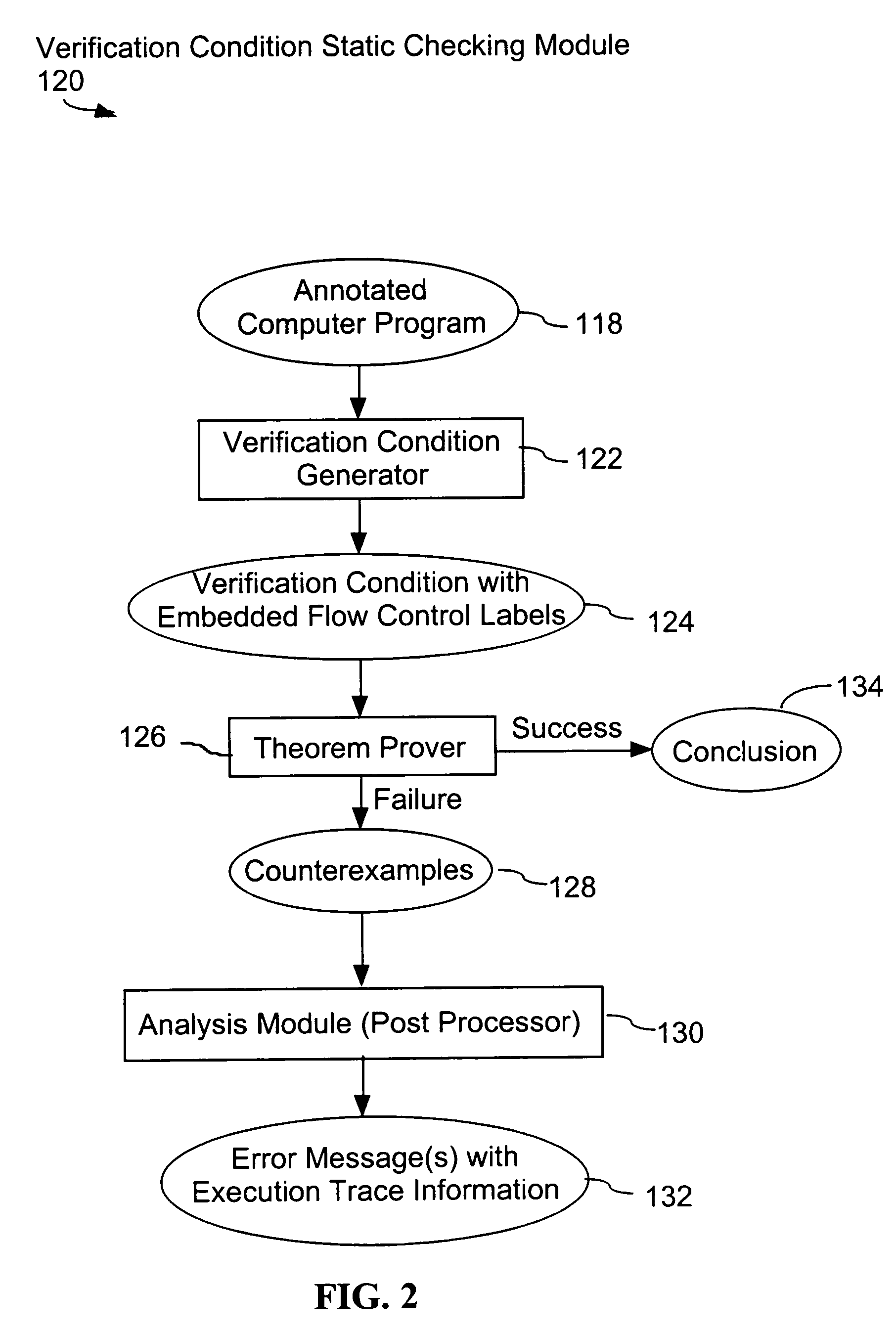
System and method for verifying computer program correctness and providing recoverable execution trace information
In a system for statically analyzing a specified computer, a verification condition generator converts the program into a logical equation, called a verification condition, and inserts program flow control labels into the sub-equations of the verification condition. The flow control labels identify conditional branch points in the specified computer program. A theorem prover is applied to the logical equation to determine truth of the logical equation, and when the truth of the logical equation cannot be proved, the theorem prover generates at least one counter-example identifying one of the conditions, one or more variable values inconsistent with that condition, and any of the flow control labels for conditional branch points of the program associated with the identified variable values. A post processing module converts each counter-example into an error message that includes a program trace when the counter-example identifies one or more of the flow control labels.
Owner:HEWLETT PACKARD DEV CO LP
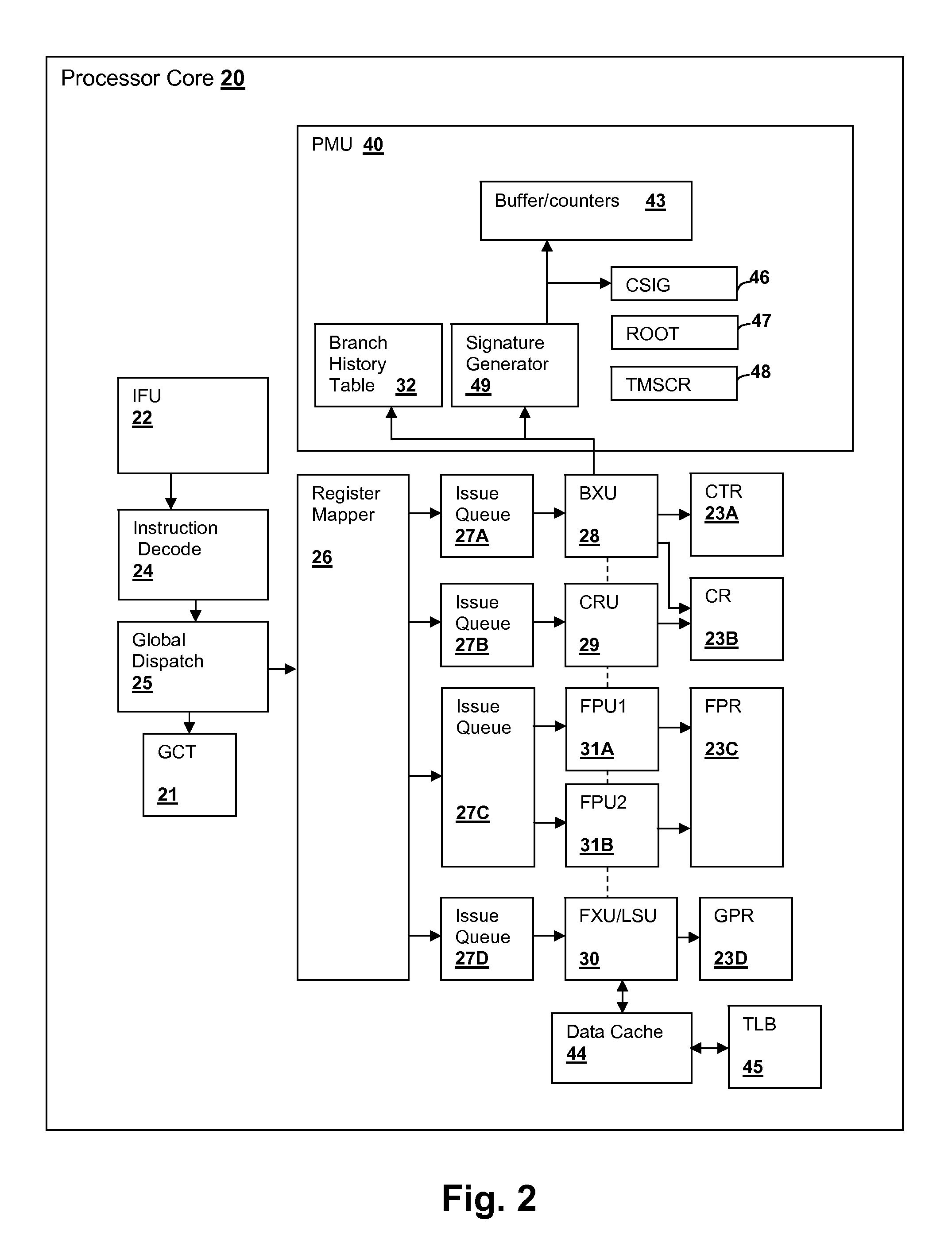
Hardware-assisted program trace collection with selectable call-signature capture
Hardware-assisted program tracing is facilitated by a processor that includes a root instruction address register, a program trace signature computation unit and a call signature register. When a program instruction having an address matching the root instruction address register is executed, a program trace signature is captured in the call signature register and capture of branch history is commenced. By accumulating different values of the call signature register, for example in response to an interrupt generated when the root instruction is executed, software that performs program tracing can obtain signatures of all of the multiple execution paths that lead to the root instruction, which is also specified by software in order to set different root instructions for program tracing. In an alternative implementation, a storage for multiple call signatures is provided in the processor and read at once by the software.
Owner:IBM CORP
Program tracing for time travel debugging and analysis
Recording a replay-able trace of execution of a multi-threaded process includes identifying a trace memory model that defines one or more orderable events that are to be ordered across a plurality of threads of the multi-threaded process. The plurality of threads are executed concurrently across one or more processing units of one or more processors. During execution of the plurality of threads, a separate replay-able trace is recorded for each thread independently. Recording includes, for each thread, recording initial state for the thread, recording at least one memory read performed by at least one processor instruction executed by the thread that takes memory as input, and recording a least one orderable event performed by the thread with a monotonically increasing number that orders the event among other orderable events across the plurality of threads.
Owner:MICROSOFT TECH LICENSING LLC
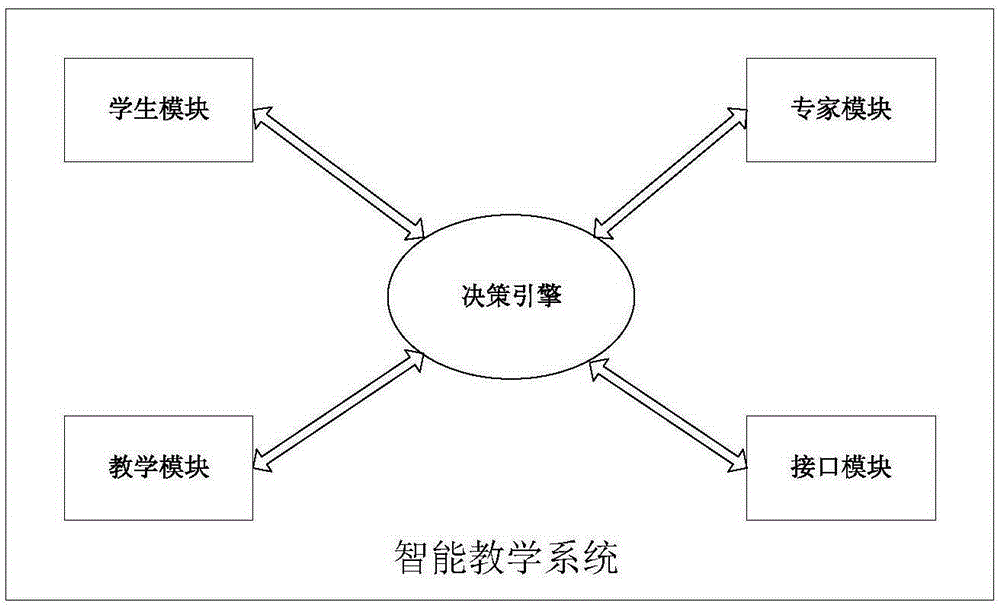
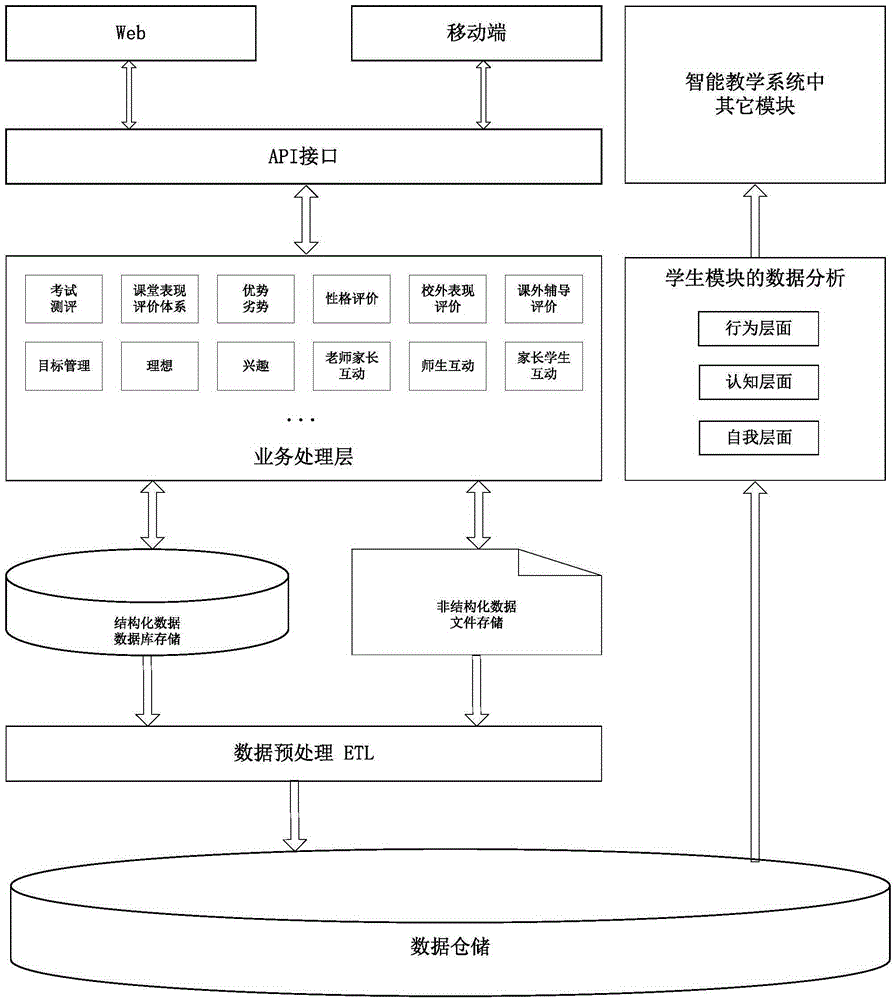
Intelligent teaching method and system based on mobile terminal
InactiveCN105243146APrecise arrangementElectrical appliancesSpecial data processing applicationsProgram tracingTeam working
The invention discloses an intelligent teaching method and system based on a mobile terminal. The method comprises the following steps: a parent user program, a teacher user program and a student user program on the mobile terminal are independently loaded or stored, and each student user, each parent user and each teacher user independently track and record the learning situation of the student through the user programs on the mobile terminal, wherein the learning situation of the user not only comprises objective data including examinations, appraisal and the like but also comprises certain subjective assessment, such as characteristics of personality, teamwork characteristics and the like. Recorded mass data is subjected to data mining and analysis processing through a background program to obtain the knowledge level summary of the student and learning path guidance.
Owner:NANJING PLASO NETWORK TECH CO LTD
Designing method for computer CPU anti-interference
InactiveCN1677363AMonitor interference in real timeEasy resetSoftware testing/debuggingProgram tracingProcessor register
The invention relates to a designing method for anti-interference property of computer CPU, comprising adding program tracking address register (PTAR), program tracking flag register (PTFR) and program interference flag register (PIFR) and additionally adding three select two counter (CPC), three select two instruction register (ICR) and adding nonscreened interruption (NSI). And a computer designed by this method can both effectively monitor program counter (PC) interference and instruction interference and records the interference interruption point and restoration interruption of the program, therefore provided with the characters of stronger anti-interference property, more accurate and reliable interference judgment, more effective failure treatment as well as real-time property, repairability and scientificalness.
Owner:XIAN UNIV OF SCI & TECH
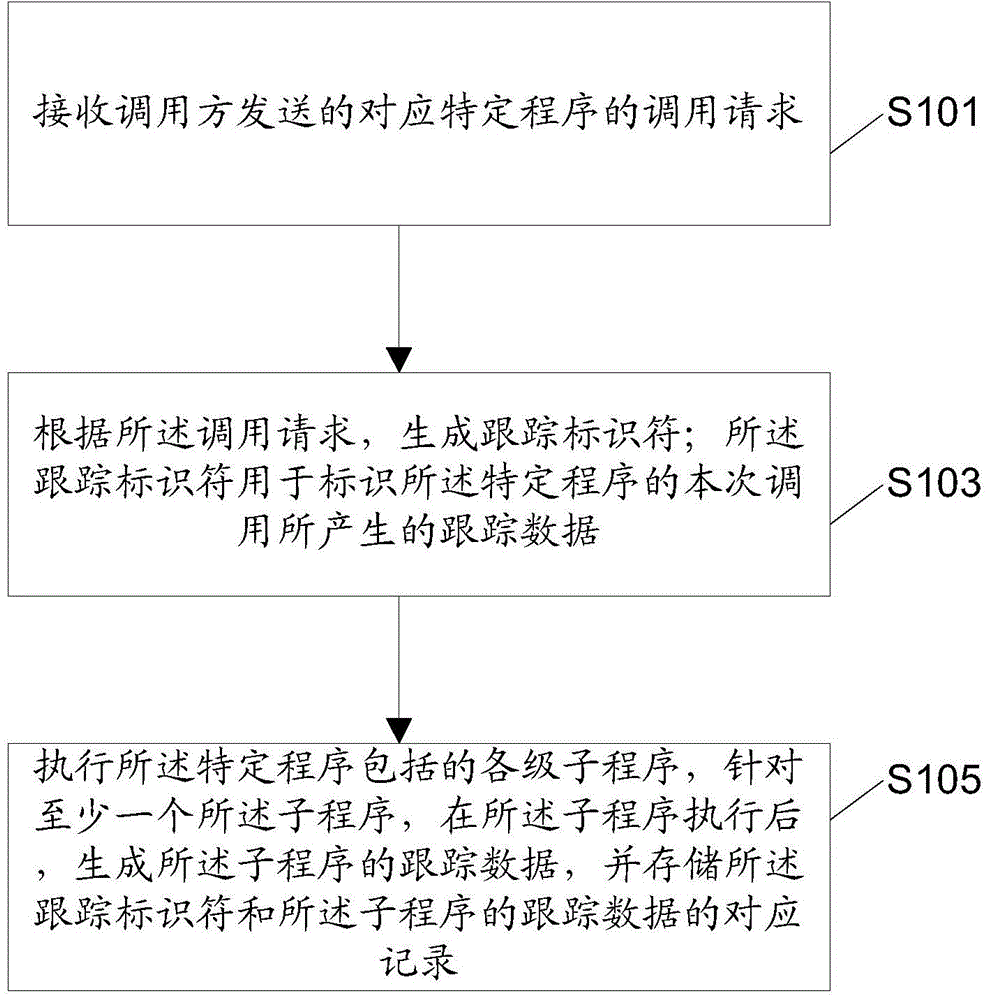
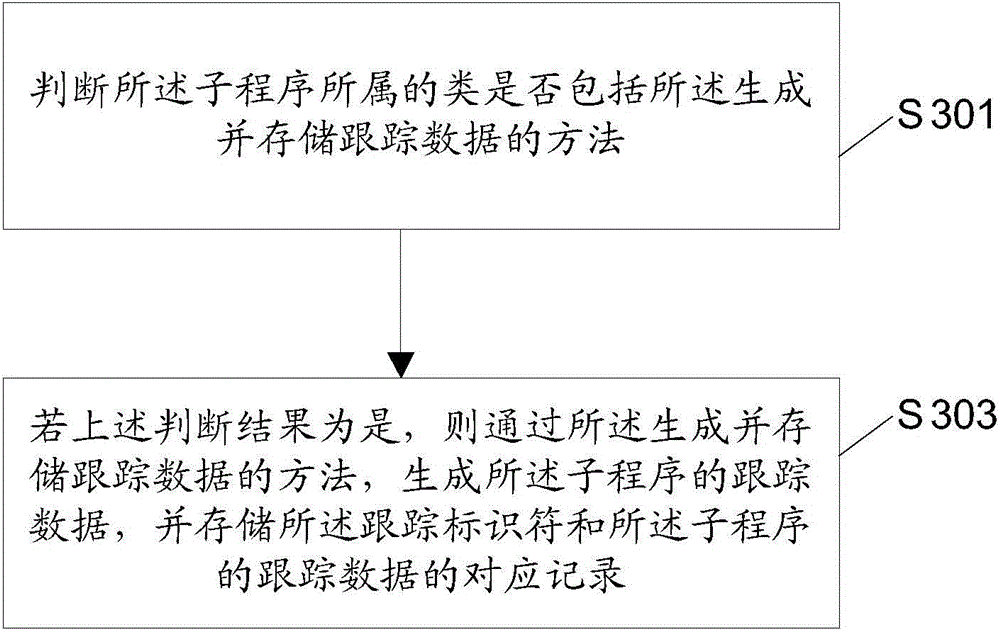
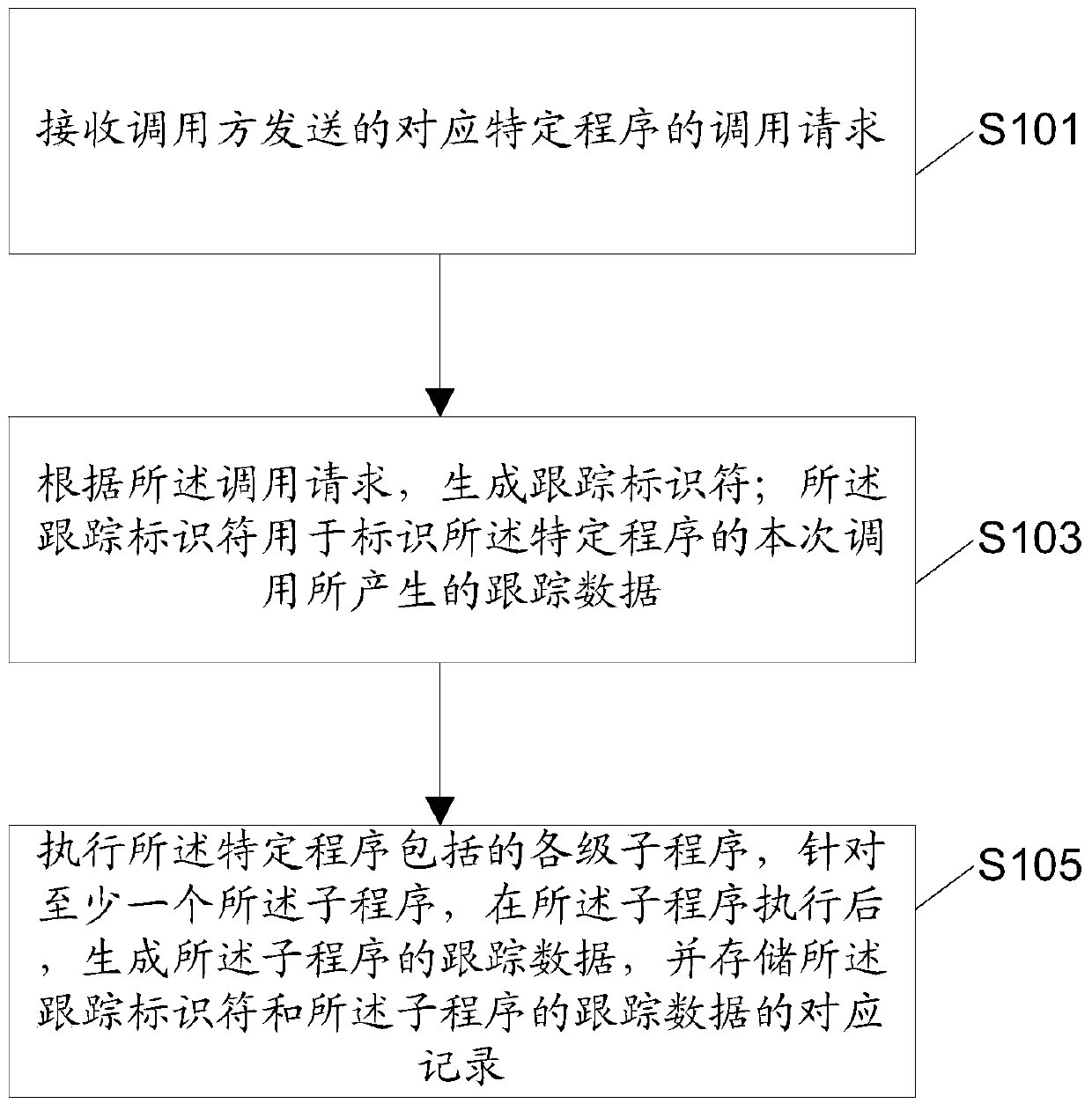
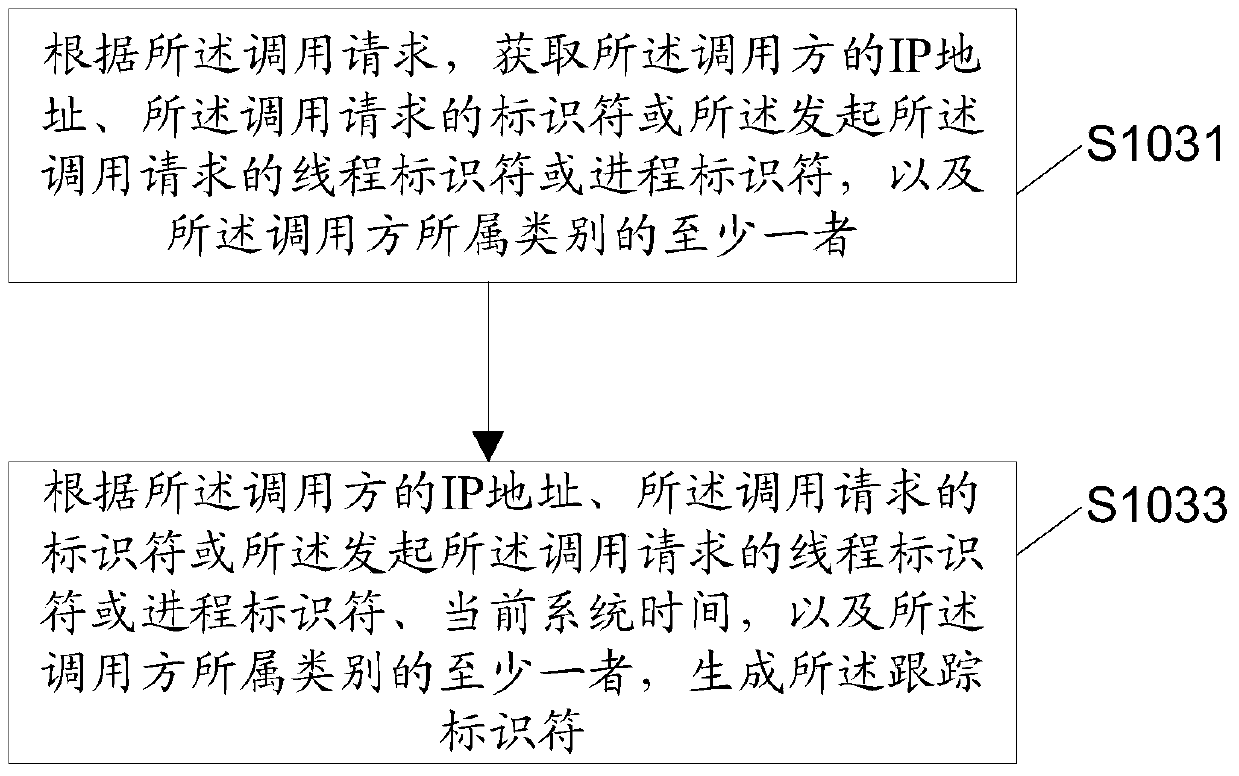
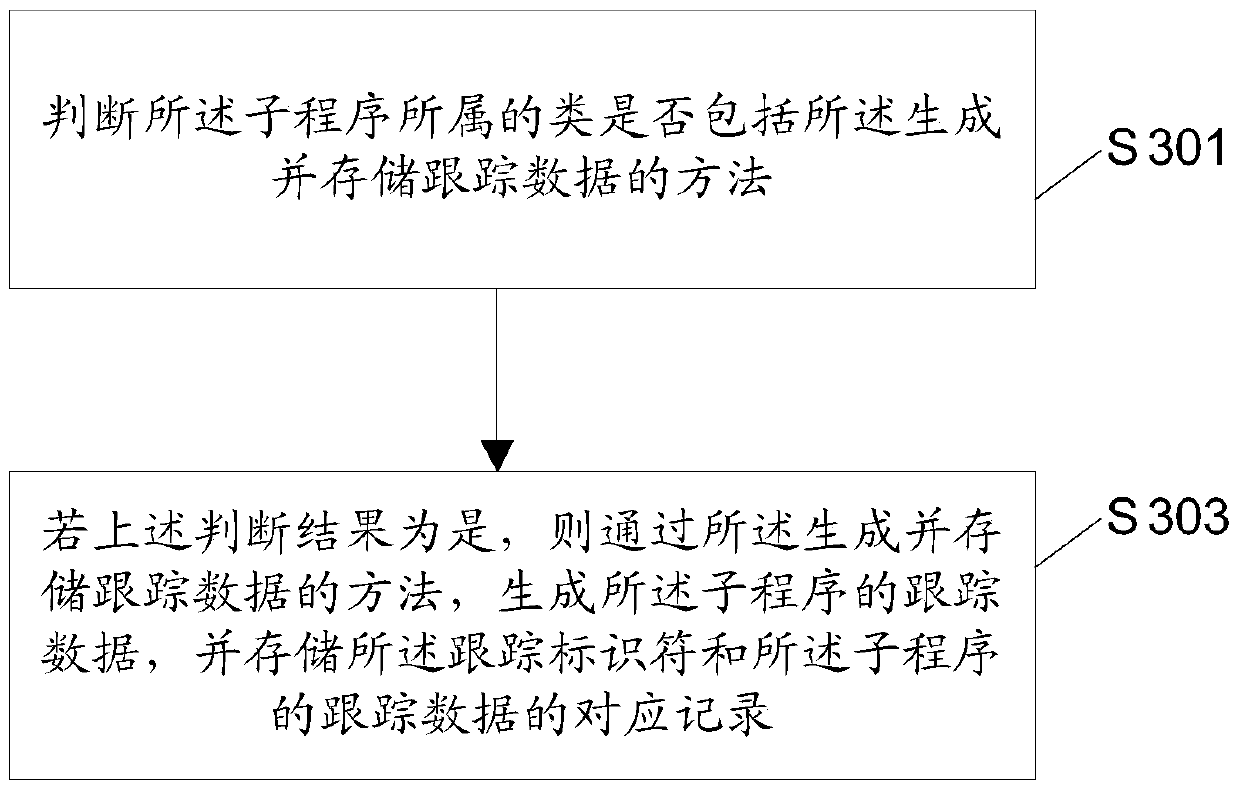
Method and device used in program tracking and electronic device
ActiveCN106326099AAvoid remodelingDoes not affect reliabilitySoftware testing/debuggingTraffic capacityProgram tracing
The invention discloses a method and a device used in program tracking and an electronic device, as well as a traffic control method and device and the electronic device. The method used in the program tracking comprises the steps of receiving a calling request which is sent by a calling party and is corresponding to a special program; according to the calling request, and generating a tracking identifier; and executing each level of subprogram included in the special program, generating tracking data of the subprogram for at least one subprogram after the subprogram is executed, and storing corresponding records of the tracking identifier and the tracking data of the subprogram. By adopting the method provided by the invention, a non-OSGi (Open Service Gateway initiative) application program, when tracking and recording a function operating condition of the OSGi subprogram, can separate a tracking processing logic and a service processing logic of the subprogram, and the transformation at a source code level on each subprogram is prevented; and thus, the effect of not affecting the robustness and the reliability of non-OSGi application program service processing is achieved.
Owner:ALIBABA GRP HLDG LTD
System and method for demonstrating the correctness of an execution trace in concurrent processing environments
InactiveUS8413122B2Avoid backtrackingError detection/correctionSpecific program execution arrangementsGeneral purposeProgram trace
Since multi-core processors have become the standard architecture for general purpose machines, programmers are required to write software optimized for parallelism. Verification of correctness is an important issue for parallel code because of its complexity. There are still tools missing that provide verification for complex code, such as testing the execution of code provides. Consequently, described herein are systems and methods to evaluate the correctness of program traces. Furthermore, the systems and methods described herein do not demand excessive computational requirements and the size of the program trace being evaluated increases.
Owner:GLOBALFOUNDRIES INC
Device and method for tracing cracks of rock sample
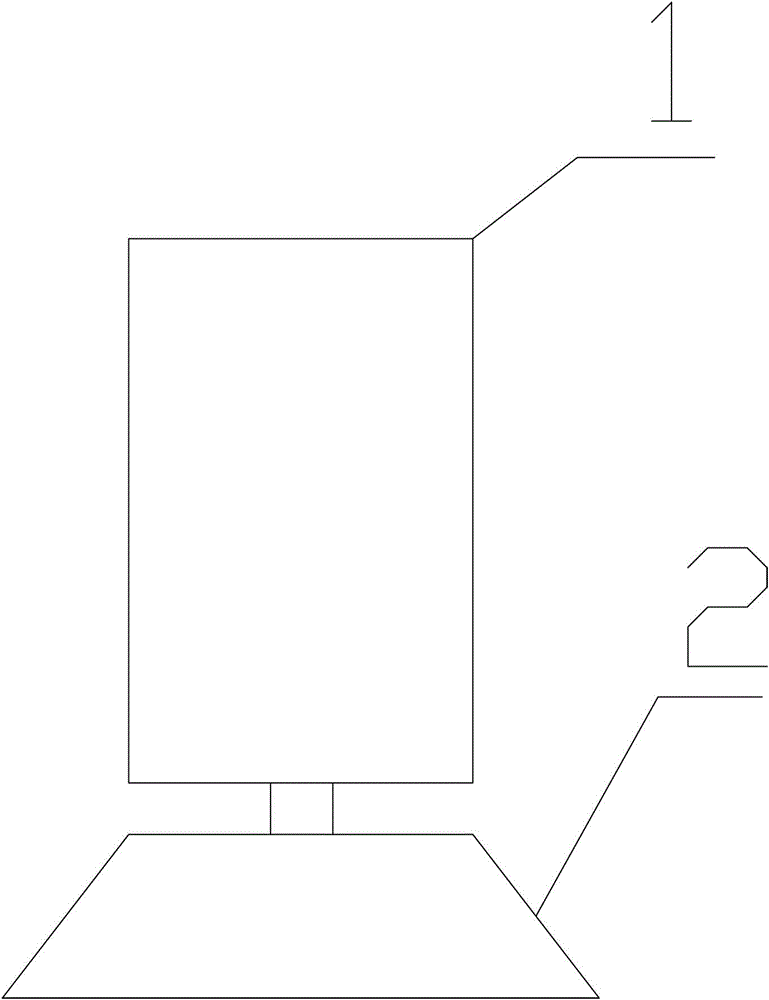
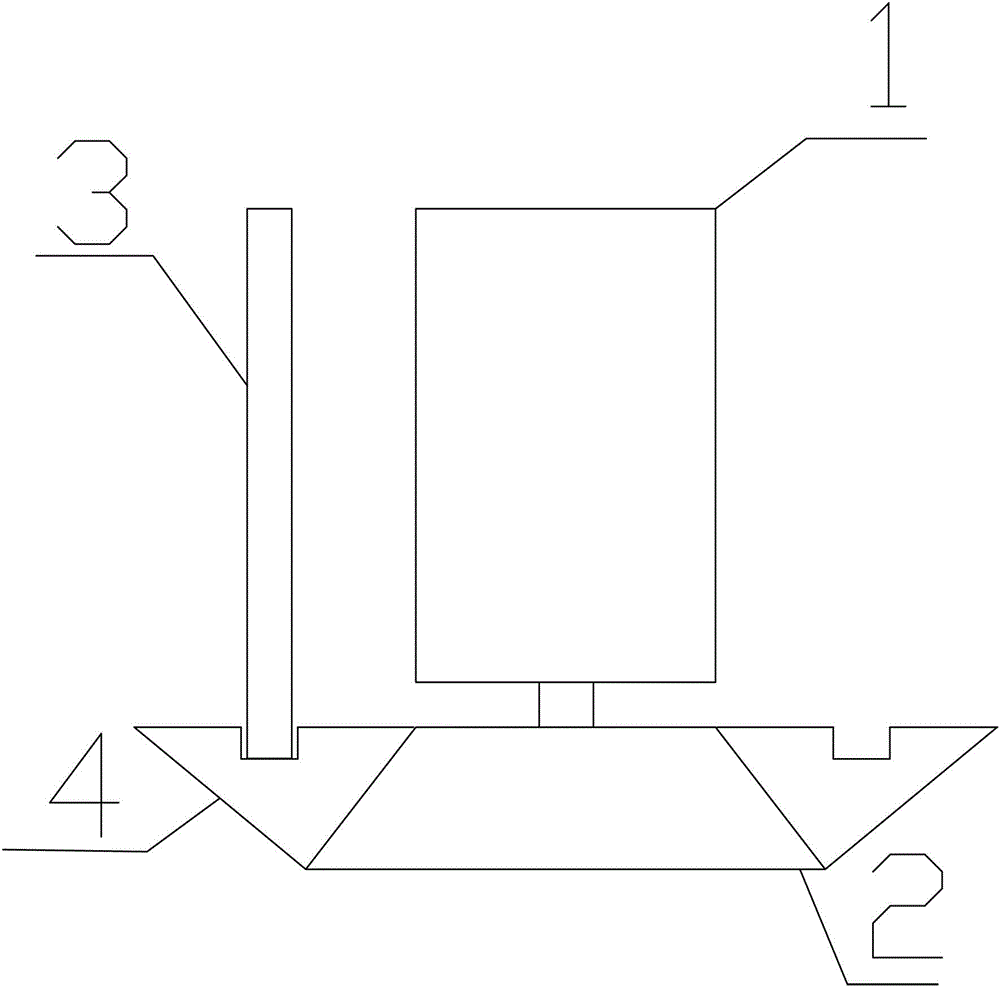
ActiveCN103837406AImprove accuracyEasy to refactorStrength propertiesProgram tracingImaging processing
The invention provides a device and a method for tracing cracks of a rock sample. The device comprises a tracer and a support platform, wherein the tracer comprises a transparent container with the Y-coordinate and the X-coordinate, the support platform is connected with the transparent container by bearings, and the transparent container can rotate relative to the support platform. The method comprises the following steps of installing the rock sample, tracing points, and imaging; or installing the rock sample, scanning and carrying out image processing. The device for tracing the cracks of the rock sample has the advantages of simpleness in manufacturing, high precision, convenience in operation and maintenance, and realization in programmed tracing; the method for tracing the cracks of the rock sample has the advantages of high working efficiency and convenience.
Owner:CHINA THREE GORGES UNIV
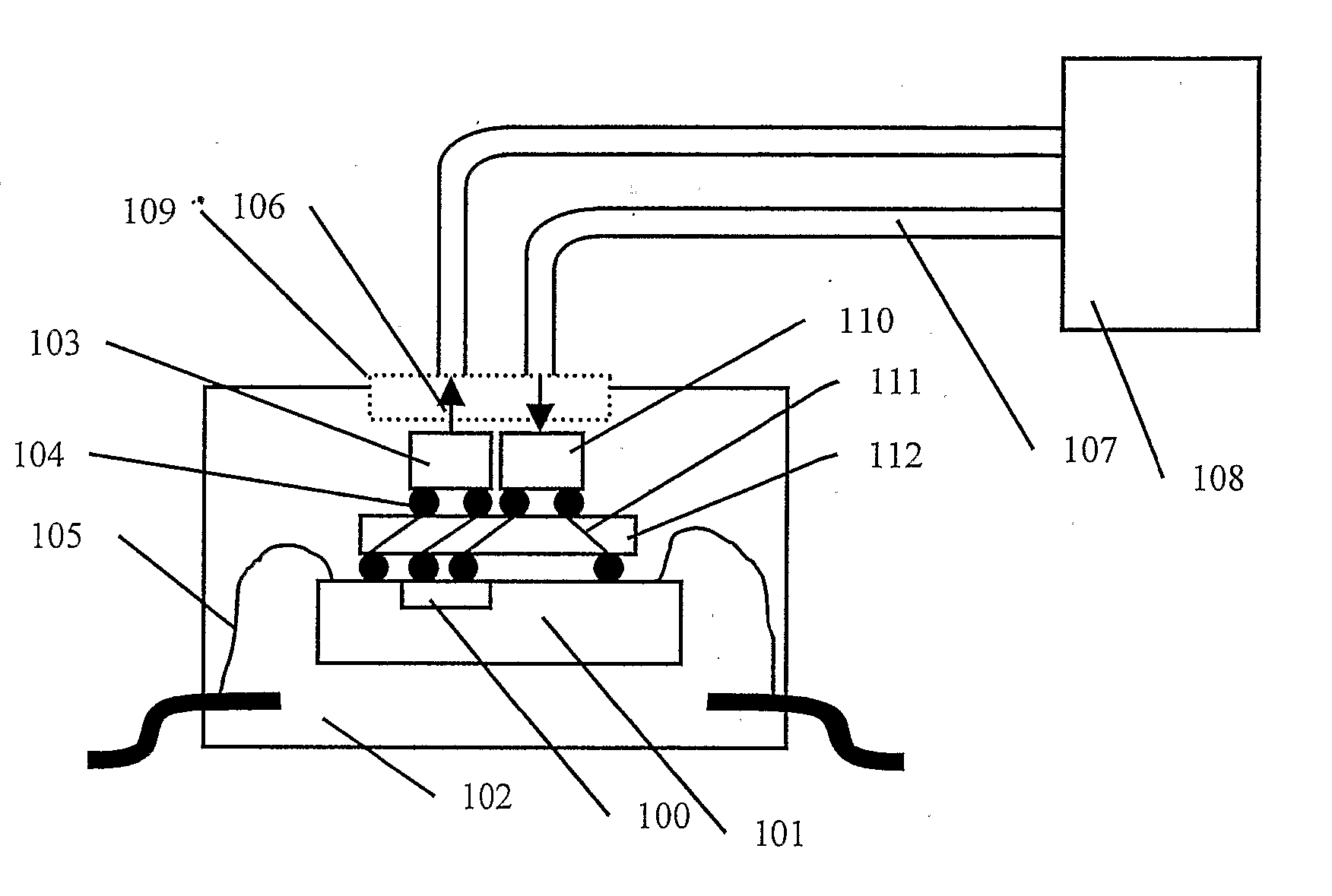
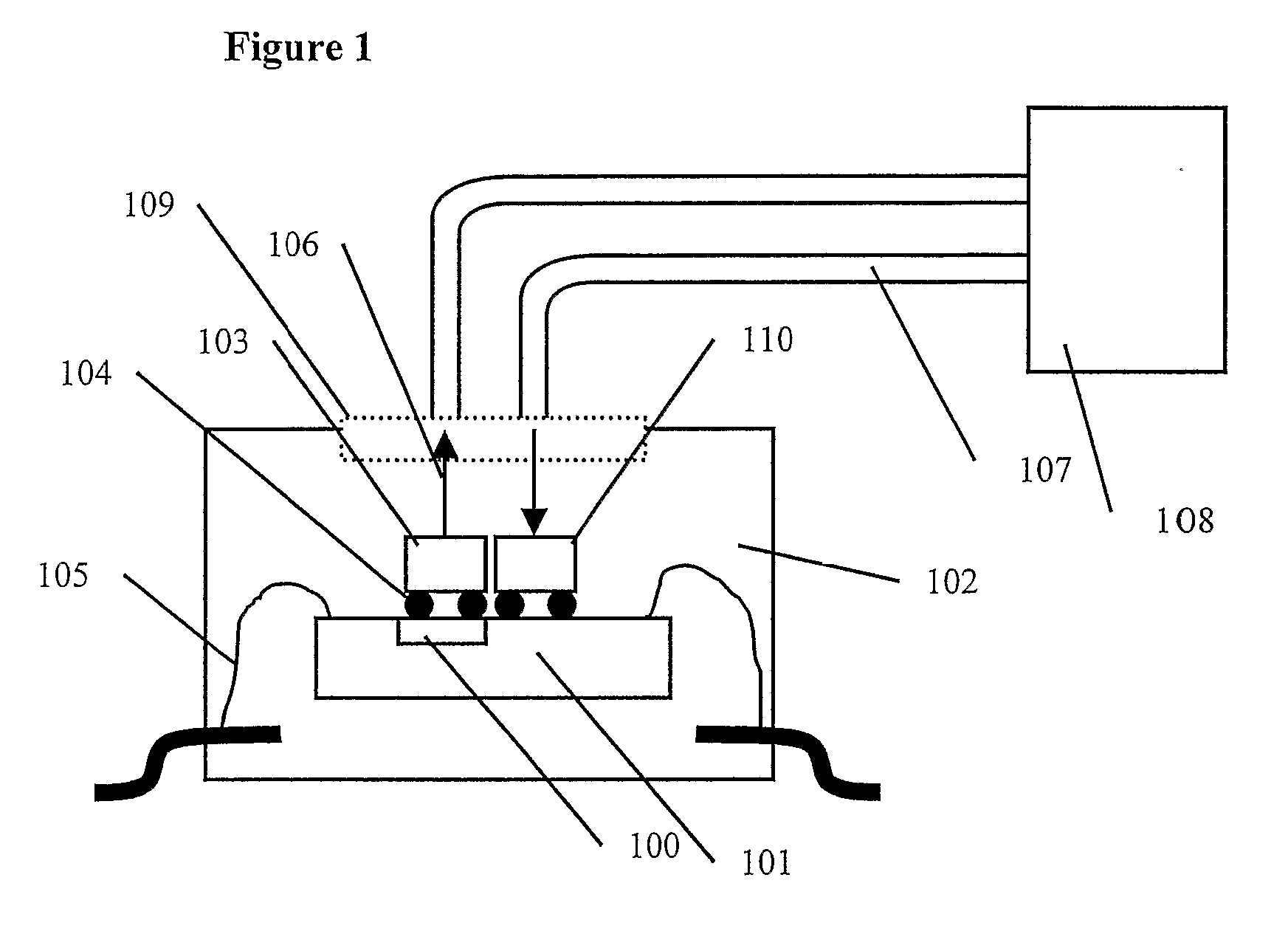
Integrated Circuit with Debug Support Interface
InactiveUS20070283191A1Reduce functionMinimal costDigital circuit testingSolid-state devicesProgram tracingHigh bandwidth
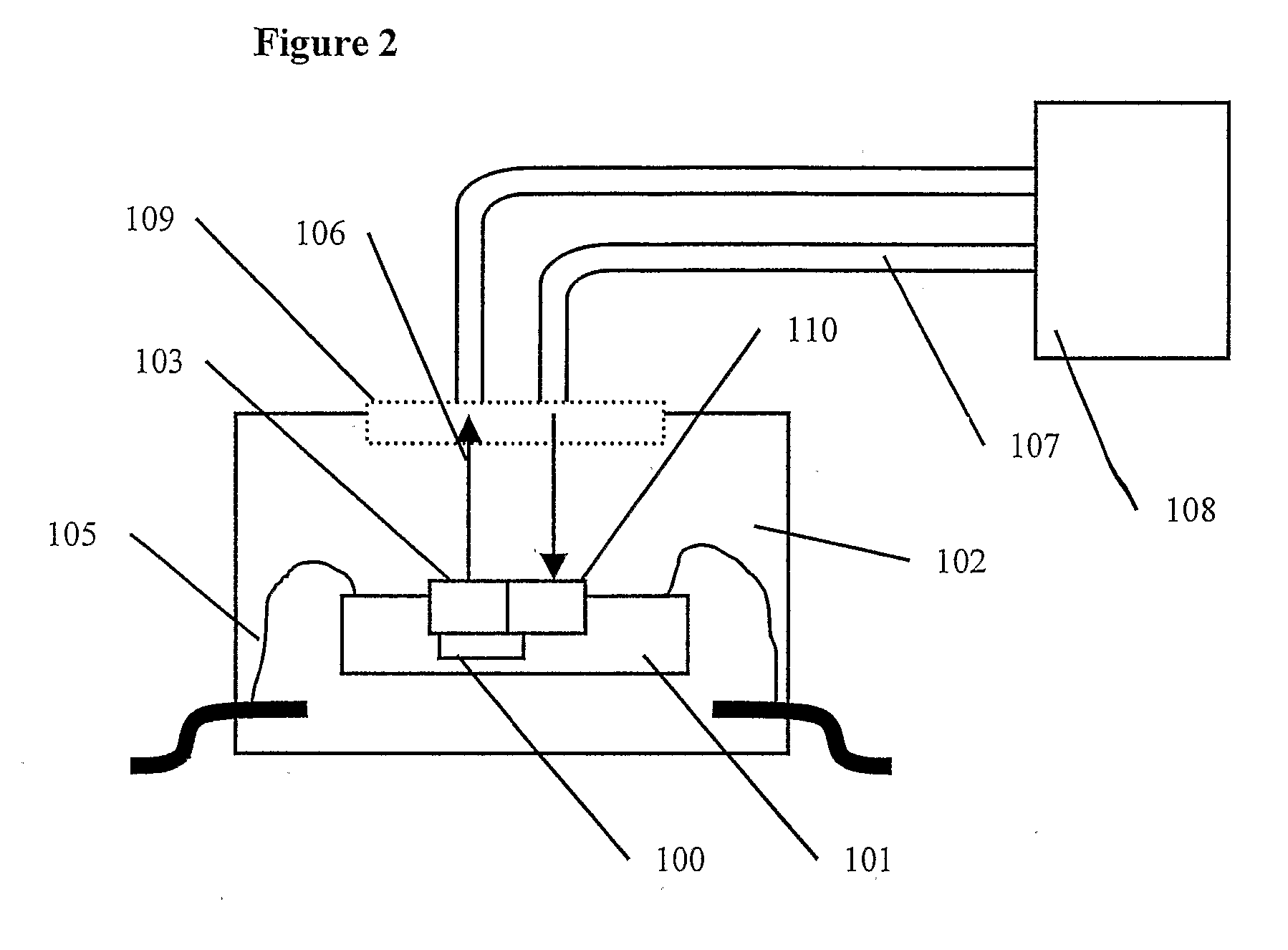
A high speed debug support interface has circuits to interface on-chip debug support circuits to a high bandwidth communications port means located on the surface of a system integrated circuit (101) and to on-chip debug support circuits (100). The communication port means can be realised by bonding or integrating special sender and or receiver cells preferably optical sender cells (103) and or optical receiver cells (110) onto the surface of the system integrated circuit (101). The high speed debug support interface communicates with on-chip or in-assembly debug support circuits and an external development tool (108) to permit hardware and software related debugging and development activities, including program tracing, data tracing and memory substitution. The high speed debug support interface has circuits to interface on-chip debug support circuits to system resources such as memory located within the device assembly (102) and connected by the system interconnect.
Owner:UNIVERSITY OF KENT
Application program tracing method and device
ActiveCN105653433AImprove controllabilityImprove acceleration performanceHardware monitoringProgram tracingSoftware engineering
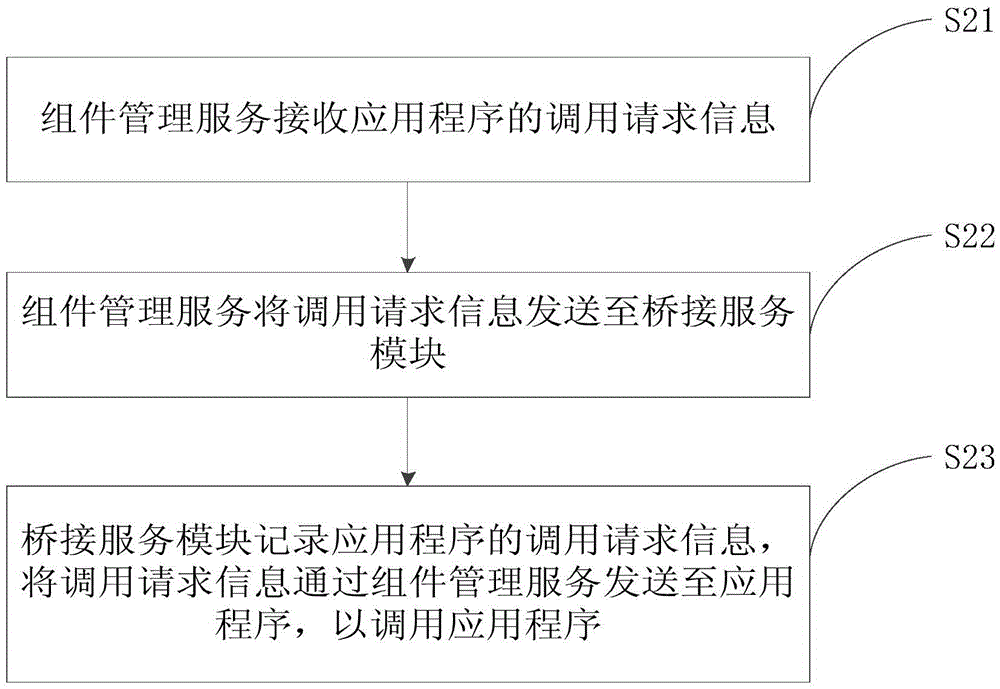
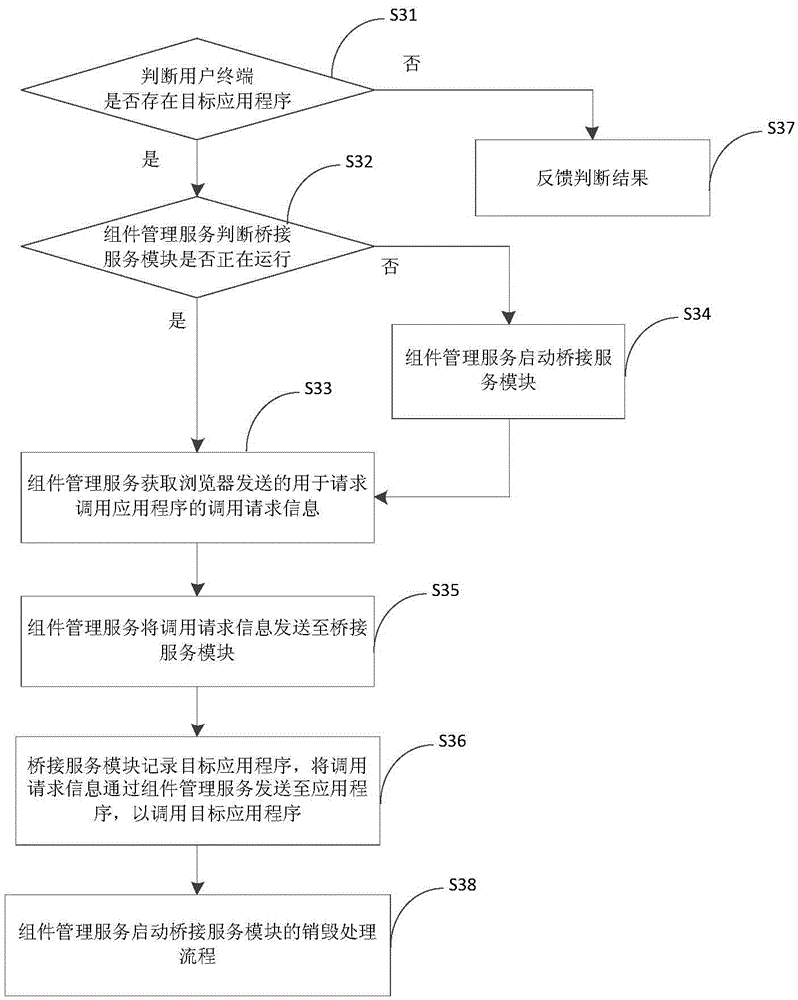
Embodiments of the invention provide an application program tracing method and device, and relates to the field of browsers. The method comprises the following steps: obtaining, by a component management server, calling request information which is sent by a browser and is used for calling application programs, wherein the calling request information comprises related information of a target application program; sending the calling request information to a bridging service module by the component management server; and recording the target application program by the bridging service module, and sending the calling request information to the target application program through the component management server so as to call the target application program. The invention aims at providing a tracing method and device for calling application programs, so as to improve the problem that the existing tracing method for calling application programs is low in controllability and extendibility due to being limited by the application programs.
Owner:ALIBABA (CHINA) CO LTD
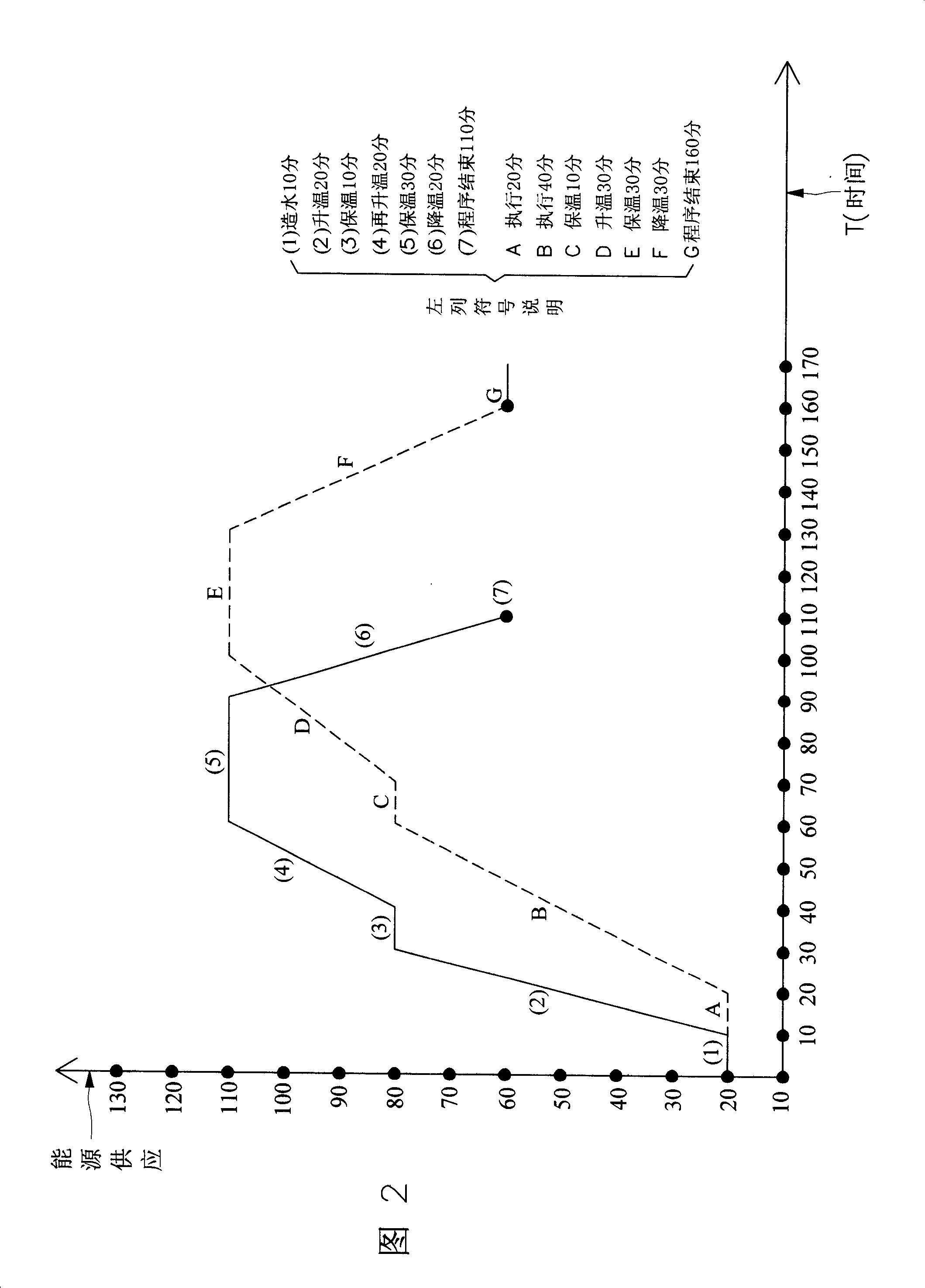
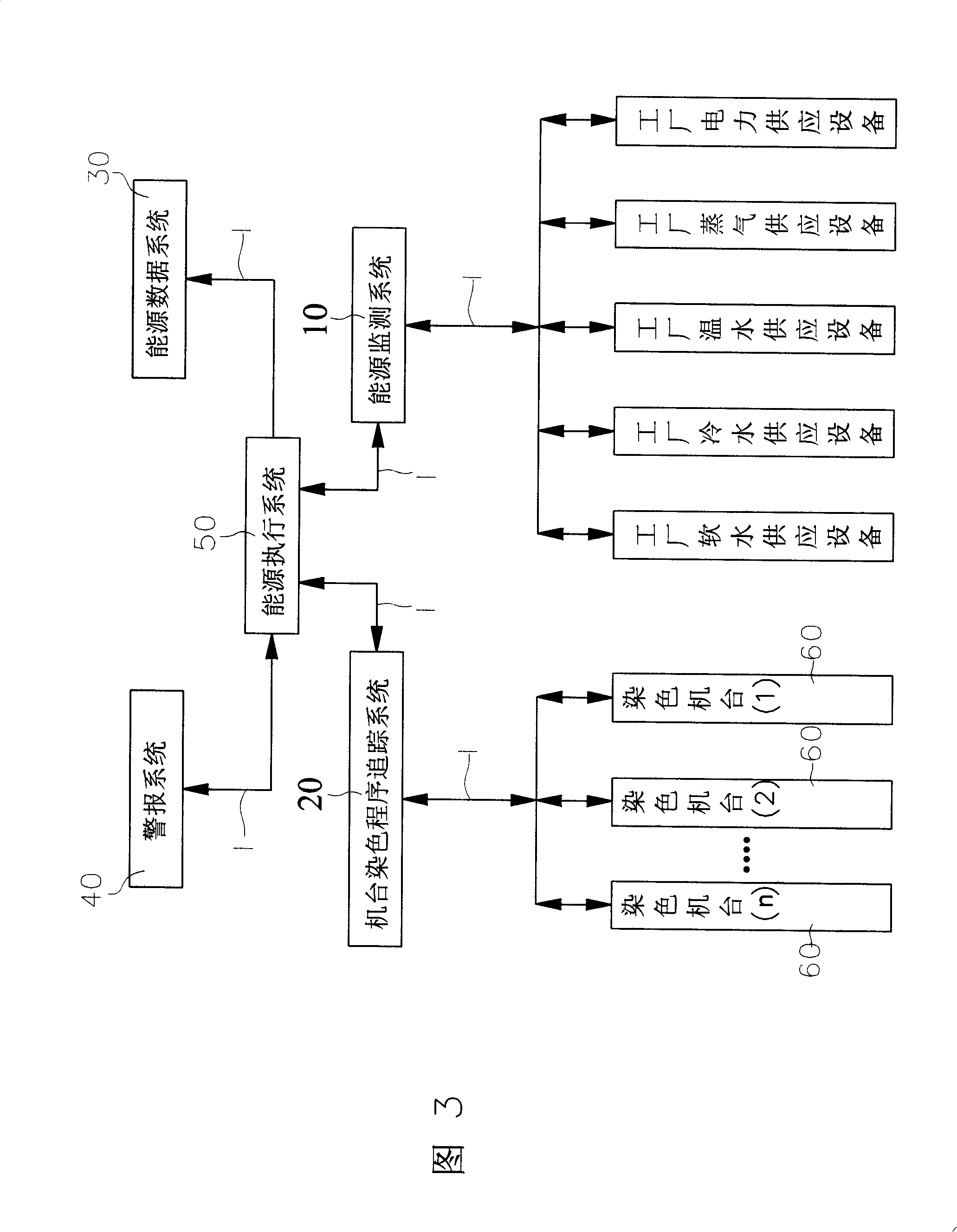
Method for reducing integer energy consumption of colour dyeing machine in dyeing and finishing manufactory
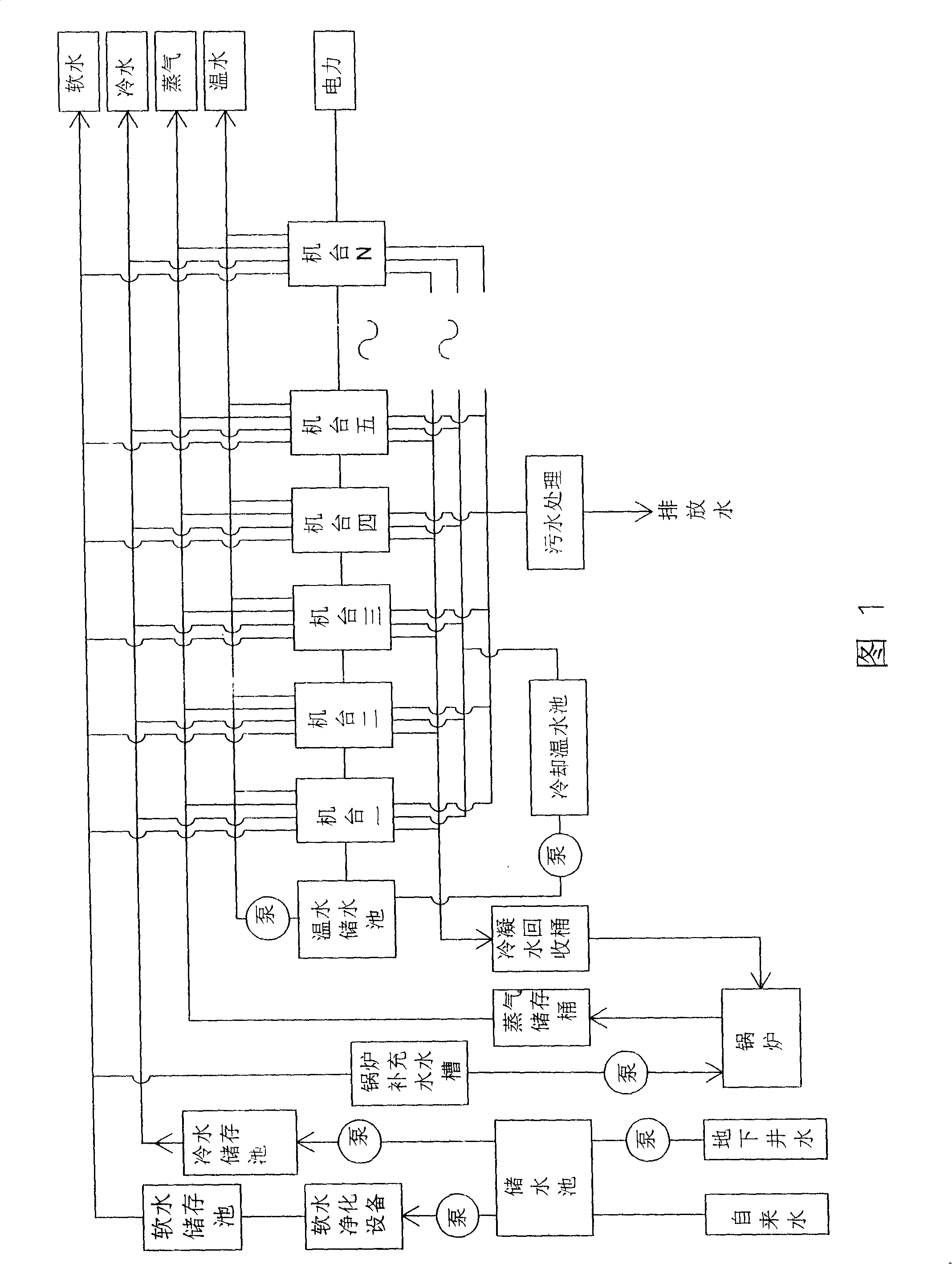
InactiveCN101231512AEasy to recordEasy to analyzeProgramme controlComputer controlProgram tracingReal time analysis
A method for reducing the total energy consumption of dyeing machines in a dyeing / finishing plant is provided. The method involves an energy monitoring system, a dyeing program tracing system, an energy data system, an alarm system and an energy execution system. The energy monitoring system comprises a plurality of detectors. The dyeing program tracing system is connected with the dyeing machines in the dyeing / finishing plant. The energy data system is preset with energy supply capacity response curve data, energy need data and response curve data of the dyeing / finishing plant. The alarm system can provide alarm signals when detecting abnormality in energy consumption of all the dyeing machines. The energy execution system comprises a central control computing and is connected with the energy monitoring system, the dyeing program tracing system, the energy data system and the alarm system via a local network in the dyeing / finishing plant. The energy execution system has the production modes for reception and transfer of data of each system, real-time analysis of energy consumption data of the plant and execution of optimal energy utilization, thereby minimizing the energy consumption.
Owner:巫协森
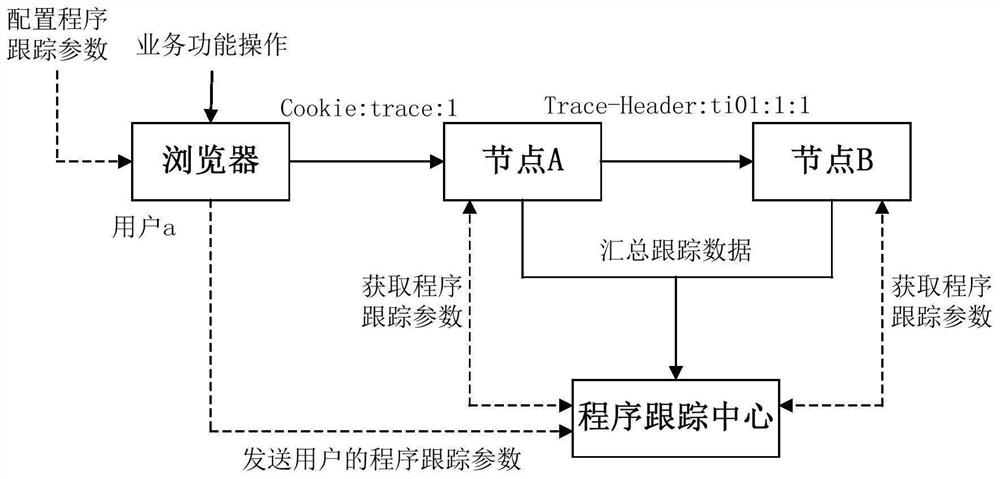
Program tracking method and device supporting micro-service architecture and medium
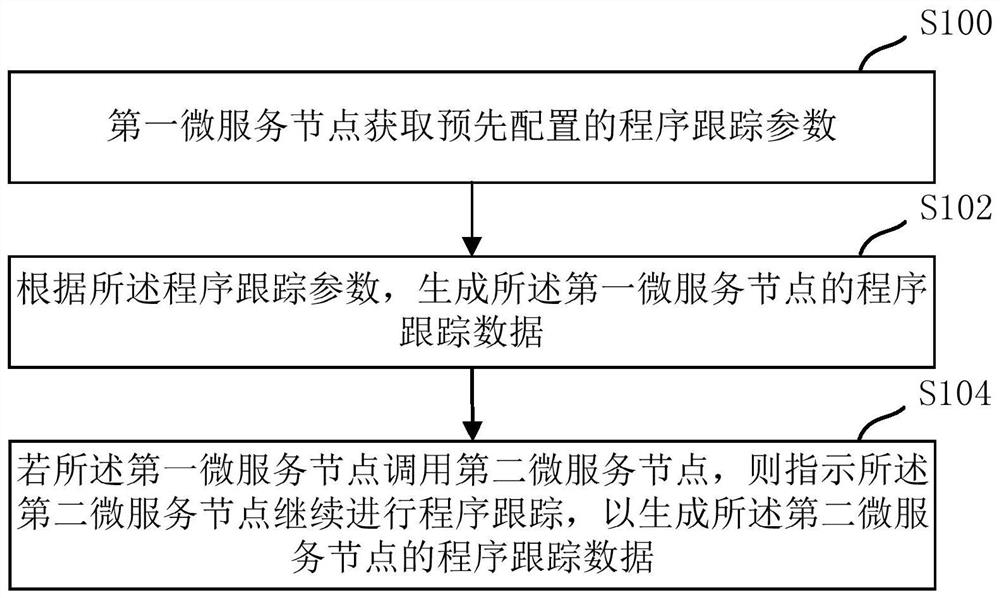
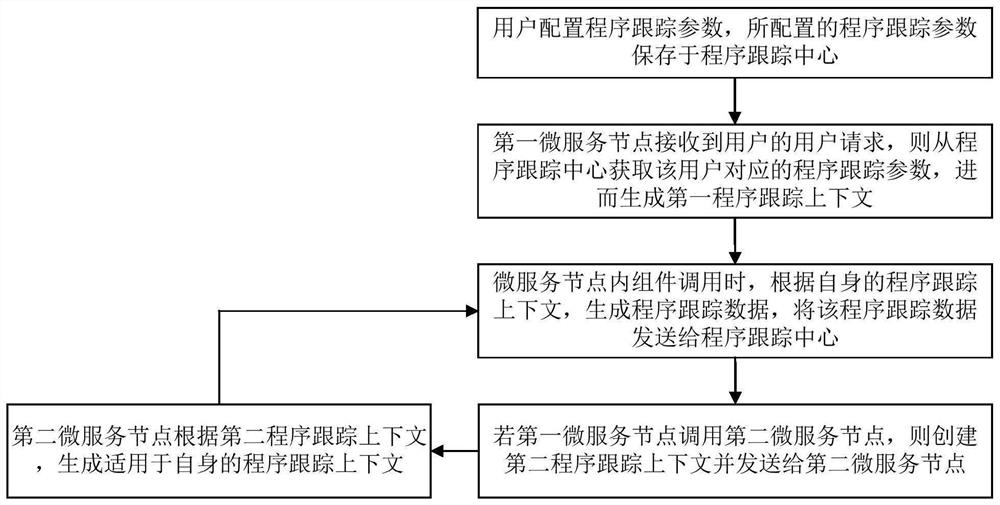
PendingCN111913789AEasy to locate business function problemsProgram initiation/switchingSoftware testing/debuggingProgram tracingComputer network
The invention discloses a program tracking method and device supporting a micro-service architecture and a medium. The method comprises the steps that a first micro-service node acquires a pre-configured program tracking parameter; program tracking data of the first micro-service node is generated according to the program tracking parameter; and if the first micro-service node calls the second micro-service node, the second micro-service node is indicated to continue program tracking so as to generate program tracking data of the second micro-service node. According to the application, programtracking can be carried out on the currently working micro-service nodes, and if calling between the micro-service nodes occurs, the currently working micro-service nodes can indicate the called micro-service nodes to continue to carry out program tracking, therefore, program tracking data with continuity and integrity meeting requirements on the whole calling link can be recorded, and the service function problem can be conveniently positioned.
Owner:INSPUR COMMON SOFTWARE
Method, apparatus, and computer program product for improved tracking of state data
ActiveUS20180336194A1Easy to trackReducing and minimizing numberDatabase updatingSpecial data processing applicationsProgram tracingSoftware engineering
A method, apparatus, and computer program product is provided for tracking state data of objects during a session, and saving the data to a database. The tracking may be performed by a reusable set of computer program code accessible by a plurality of user interface applications. Temporary data may be stored as insert objects, update objects, and delete objects and maintained during a session of a user interface application. The temporary data may be updated as additional data is manipulated by the user interface application, but does not need to be tracked by the user interface application. The user interface application indicates if data is to be deleted, or is current (e.g., new or modified). Upon completion of the session, calls are made to update the database based on the temporary data.
Owner:HEALTHSTREAM INC
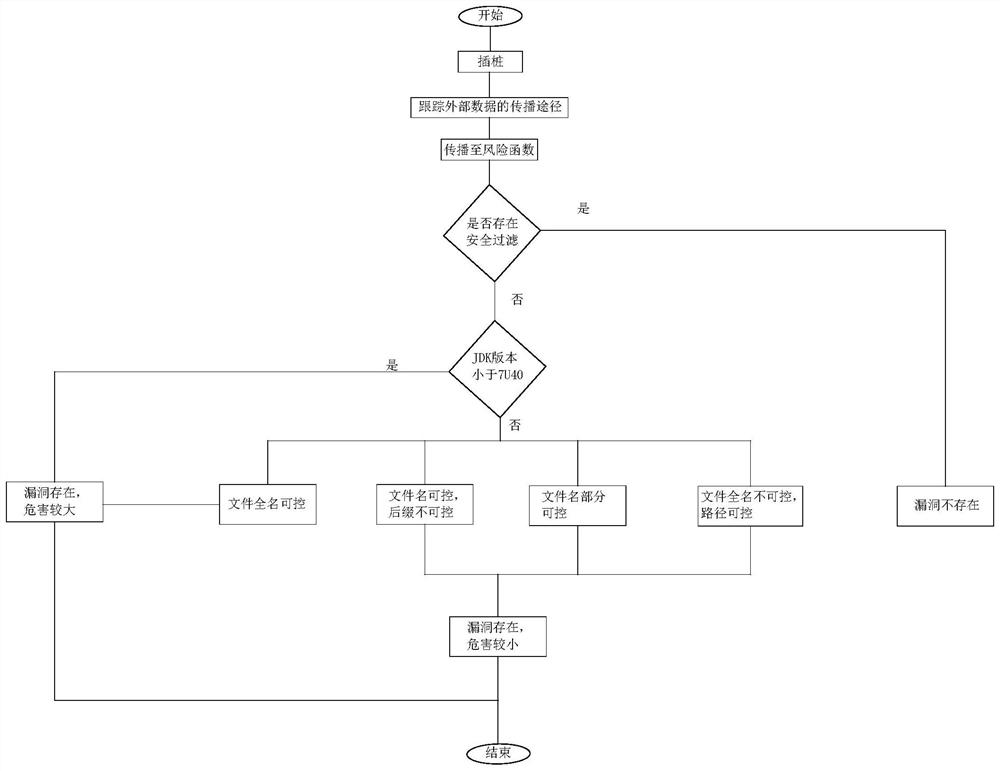
Path traversal vulnerability detection method
The invention discloses a path traversal vulnerability detection method. The method comprises the following steps of 1, performing program instrumentation on a Java EE program through a byte code enhancement method; 2, by the instrumentation program, tracking the propagation path of data, obtained from the outside by the Java EE program, in the program; 3, when the instrumentation program finds that external data is directly propagated to the path traversal risk method without passing through a security filtering method, performing vulnerability detection logic judgment; and when the instrumentation program finds that the external data is propagated through the security filtering method, determining that the vulnerability does not exist. According to the method, the data flow direction during running of the application program can be tracked in real time during running of the Java EE program, the real forming process of the vulnerability and the specific code position of the vulnerability can be detected, and online, real-time, comprehensive and accurate vulnerability detection is achieved. Meanwhile, whether the vulnerability exists or not can be determined by analyzing the propagation paths of the stains in different scenes, and the possible utilization harm of the vulnerability can be given separately.
Owner:杭州孝道科技有限公司
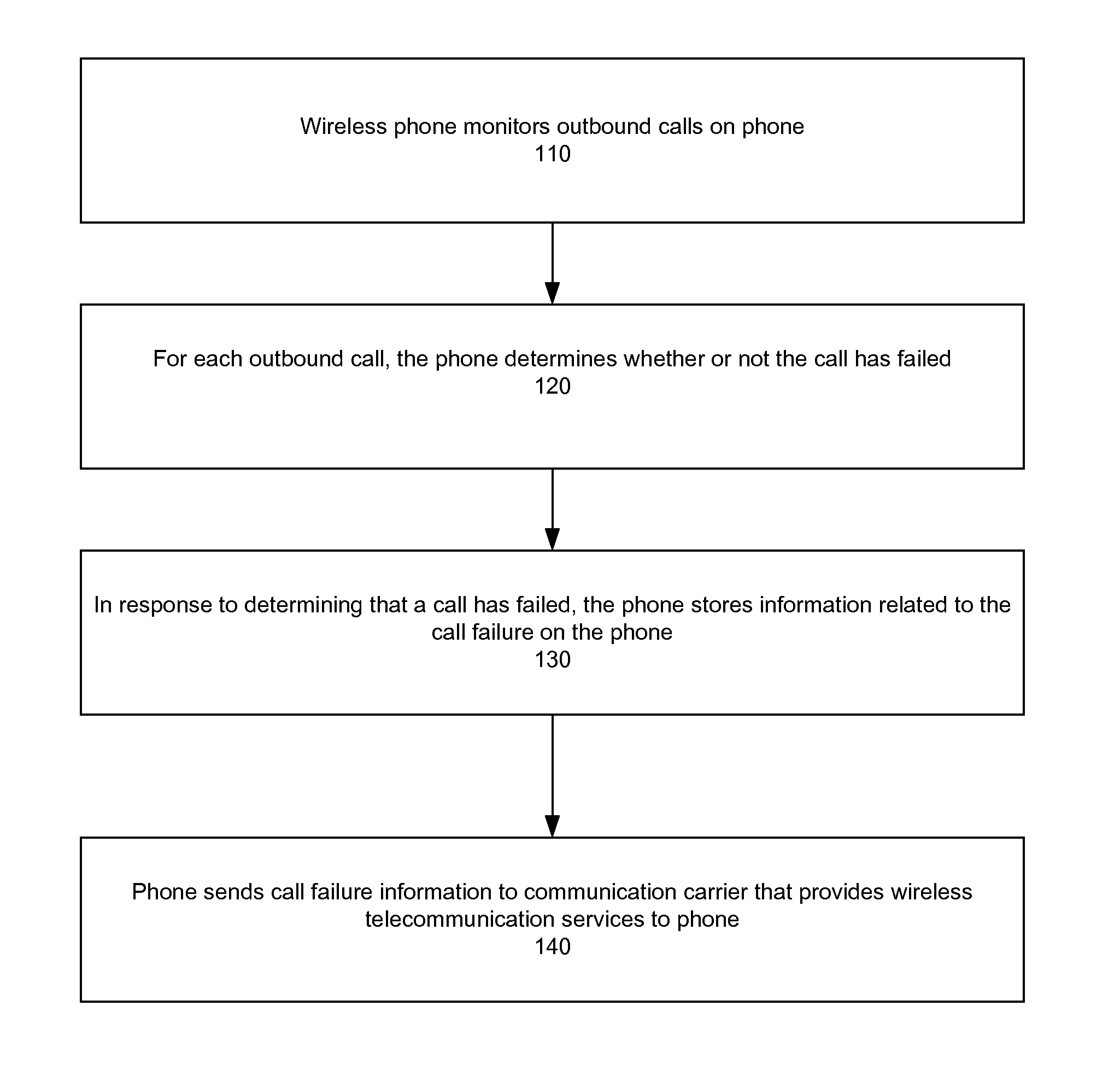
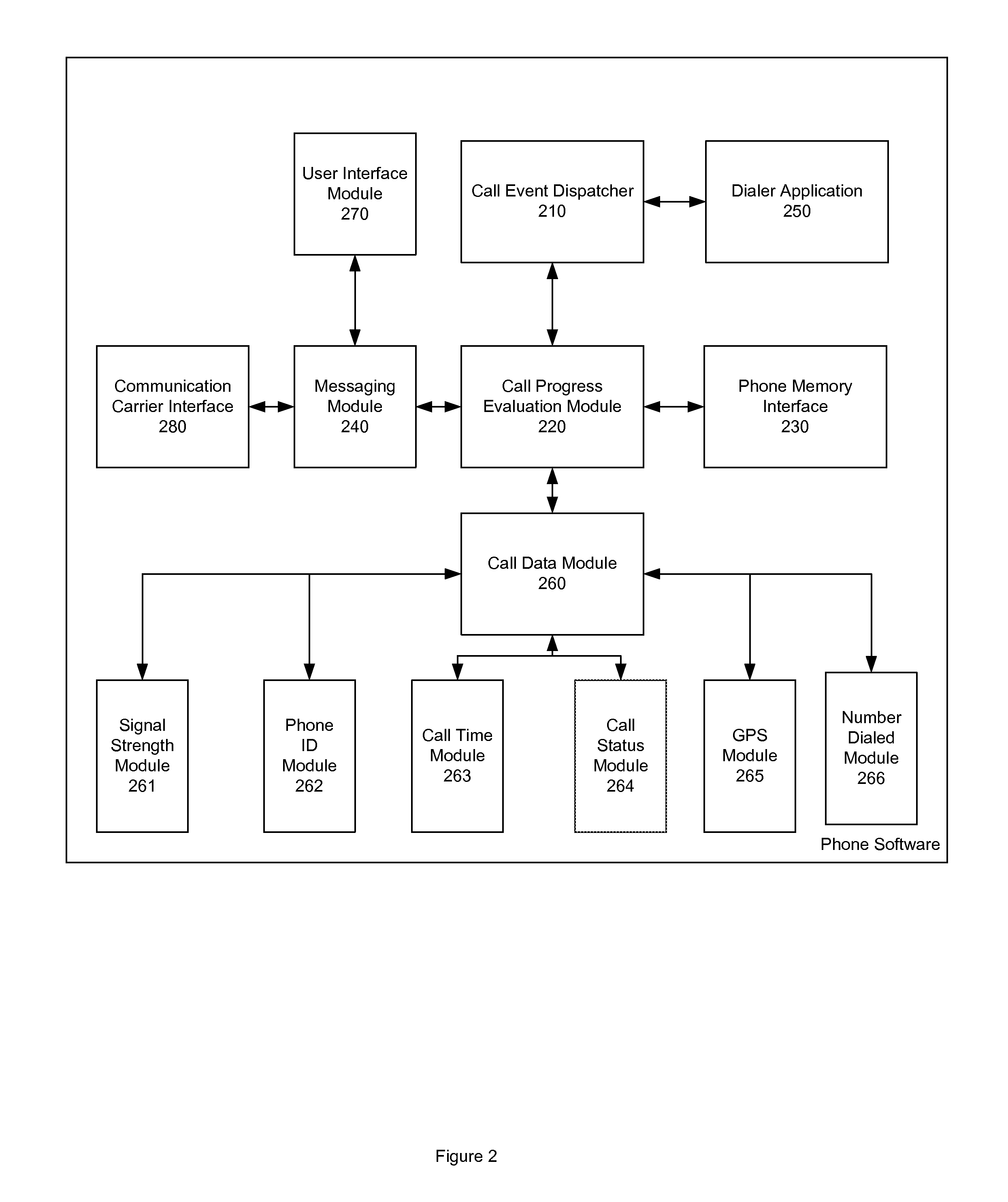
System, method, and software program product for tracking call failures on a wireless phone
Owner:MICROSOFT TECH LICENSING LLC
A rock sample crack drawing device and drawing method
ActiveCN103837406BImprove accuracyEasy to refactorStrength propertiesProgram tracingImaging processing
The invention provides a device and a method for tracing cracks of a rock sample. The device comprises a tracer and a support platform, wherein the tracer comprises a transparent container with the Y-coordinate and the X-coordinate, the support platform is connected with the transparent container by bearings, and the transparent container can rotate relative to the support platform. The method comprises the following steps of installing the rock sample, tracing points, and imaging; or installing the rock sample, scanning and carrying out image processing. The device for tracing the cracks of the rock sample has the advantages of simpleness in manufacturing, high precision, convenience in operation and maintenance, and realization in programmed tracing; the method for tracing the cracks of the rock sample has the advantages of high working efficiency and convenience.
Owner:CHINA THREE GORGES UNIV
Designing method for computer CPU anti-interference
InactiveCN1329839CMonitor interference in real timeEasy resetSoftware testing/debuggingProgram tracingProcessor register
The invention relates to a designing method for anti-interference property of computer CPU, comprising adding program tracking address register (PTAR), program tracking flag register (PTFR) and program interference flag register (PIFR) and additionally adding three select two counter (CPC), three select two instruction register (ICR) and adding nonscreened interruption (NSI). And a computer designed by this method can both effectively monitor program counter (PC) interference and instruction interference and records the interference interruption point and restoration interruption of the program, therefore provided with the characters of stronger anti-interference property, more accurate and reliable interference judgment, more effective failure treatment as well as real-time property, repairability and scientificalness.
Owner:XIAN UNIV OF SCI & TECH
A method, device and electronic equipment for program tracking
ActiveCN106326099BAvoid remodelingDoes not affect reliabilitySoftware testing/debuggingProgram tracingApplication software
The invention discloses a method and a device used in program tracking and an electronic device, as well as a traffic control method and device and the electronic device. The method used in the program tracking comprises the steps of receiving a calling request which is sent by a calling party and is corresponding to a special program; according to the calling request, and generating a tracking identifier; and executing each level of subprogram included in the special program, generating tracking data of the subprogram for at least one subprogram after the subprogram is executed, and storing corresponding records of the tracking identifier and the tracking data of the subprogram. By adopting the method provided by the invention, a non-OSGi (Open Service Gateway initiative) application program, when tracking and recording a function operating condition of the OSGi subprogram, can separate a tracking processing logic and a service processing logic of the subprogram, and the transformation at a source code level on each subprogram is prevented; and thus, the effect of not affecting the robustness and the reliability of non-OSGi application program service processing is achieved.
Owner:ALIBABA GRP HLDG LTD
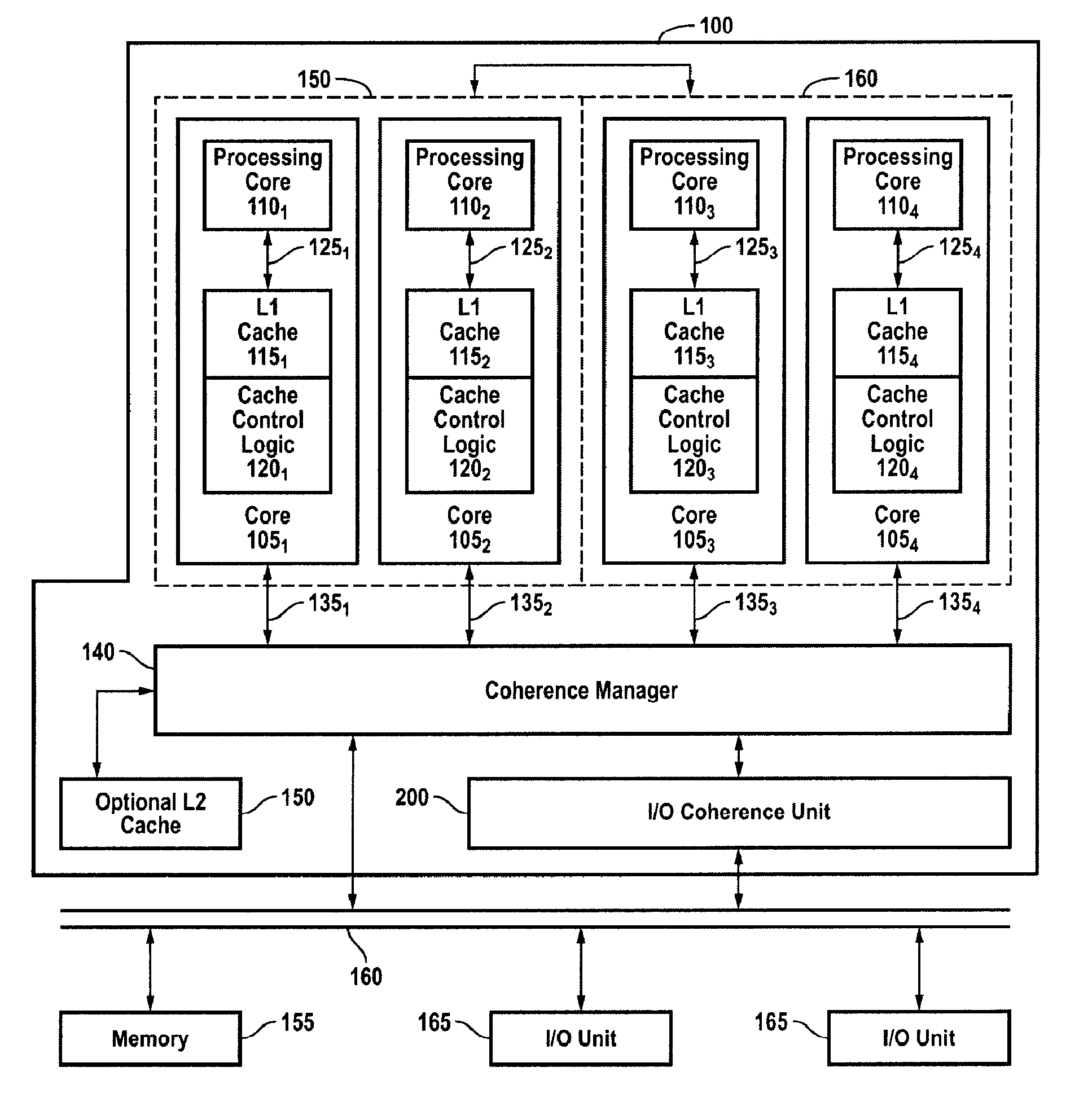
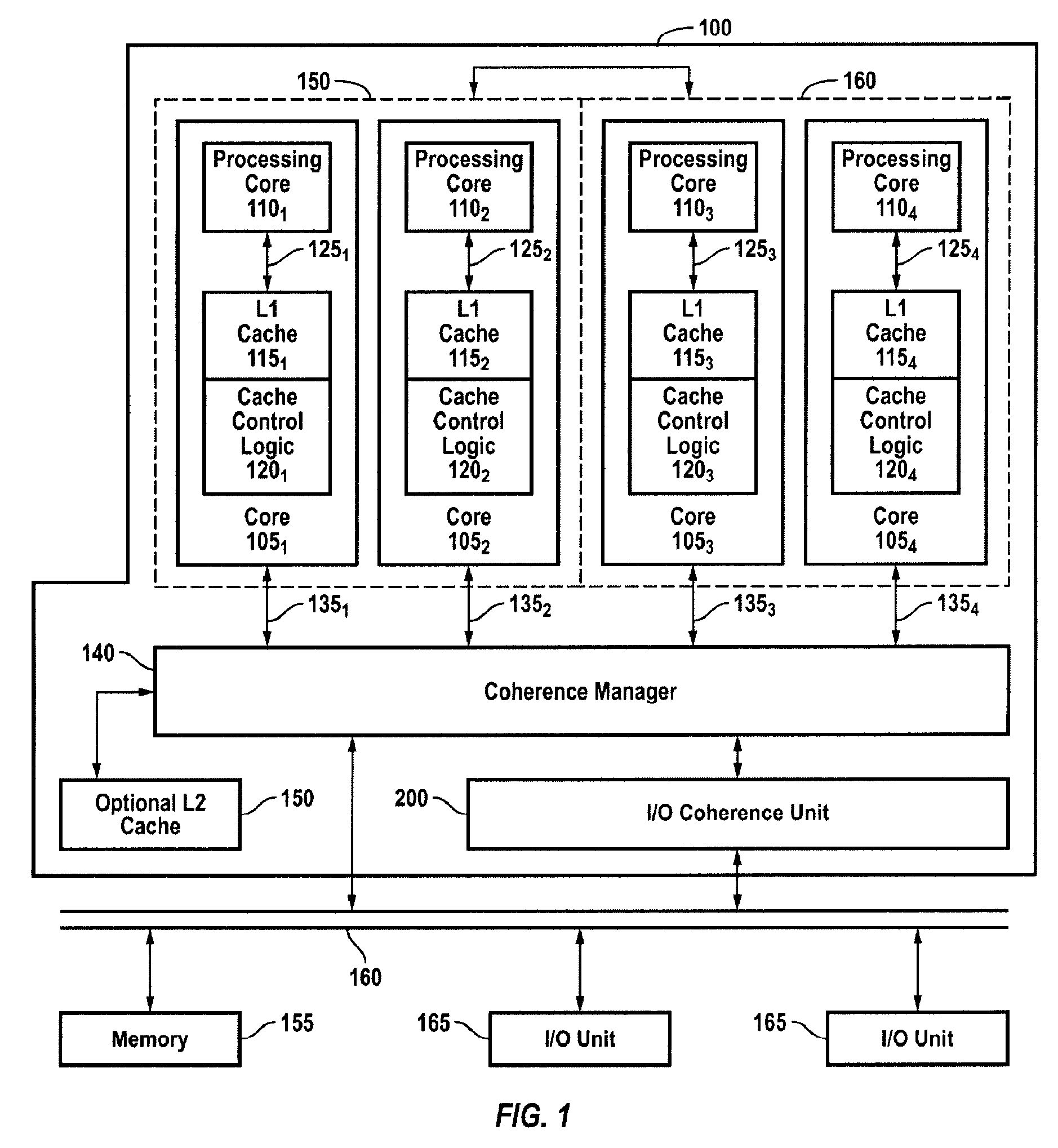
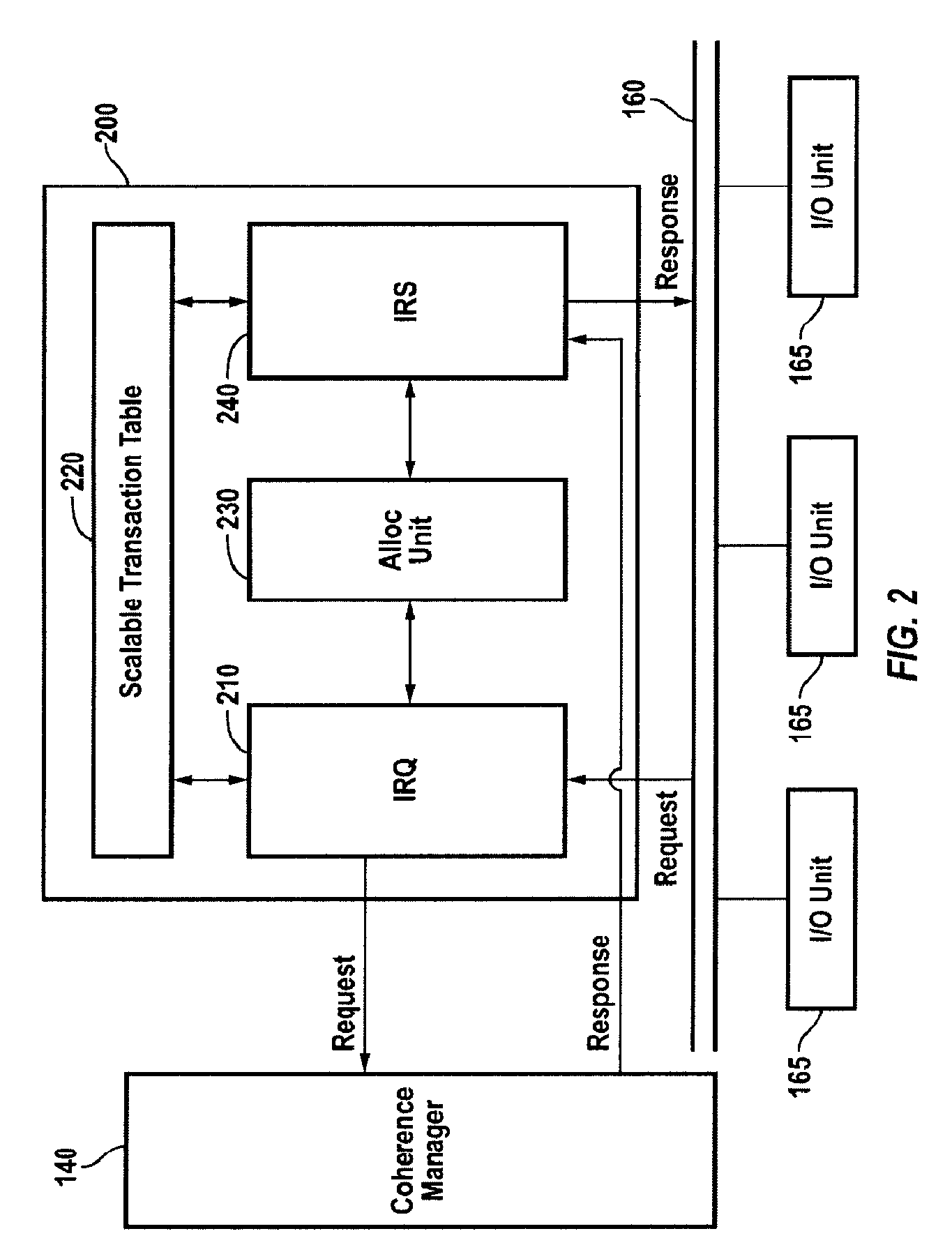
Efficient, scalable and high performance mechanism for handling IO requests
A system, apparatus and method for managing input / output requests in a multi-processor system is disclosed. An IO coherence unit includes an IO request handler, a variable size transaction table, and an IO response handler. The size of the transaction table varies according to the number of pending IO requests. The IO request handler stores information about pending IO requests in the transaction table to establish an order among related requests and to permit out-of-order handling of unrelated requests. The IO response handler tracks responses to the IO requests and updates the information in the transaction table. The IO coherence unit returns responses to requesting devices in compliance with device ordering requirements.
Owner:ARM FINANCE OVERSEAS LTD
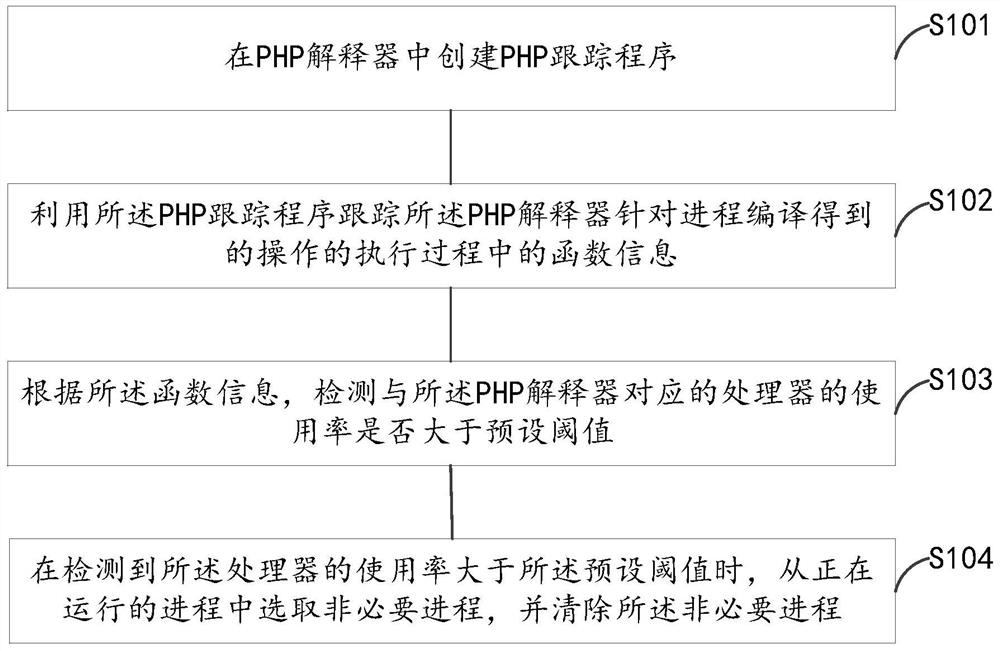
Process cleaning method and device
ActiveCN106897051BConvenient and quick positioningConvenient and quick positioning of PHP script problemsHardware monitoringBootstrappingProgram tracingSoftware engineering
The embodiment of the present invention provides a method and device for process cleaning, creating a PHP tracking program in the PHP interpreter; using the PHP tracking program to track the function information in the execution process of the operation compiled by the PHP interpreter for the process ; According to the function information, detect whether the usage rate of the processor corresponding to the PHP interpreter is greater than a preset threshold; when it is detected that the processor usage rate is greater than the preset threshold, from the running process Select non-essential processes in and clear the non-essential processes. The embodiment of the present invention can acquire and output function information in the execution process of an operation in real time, so that developers of PHP scripts can quickly locate PHP script problems.
Owner:BEIJING QIHOO TECH CO LTD
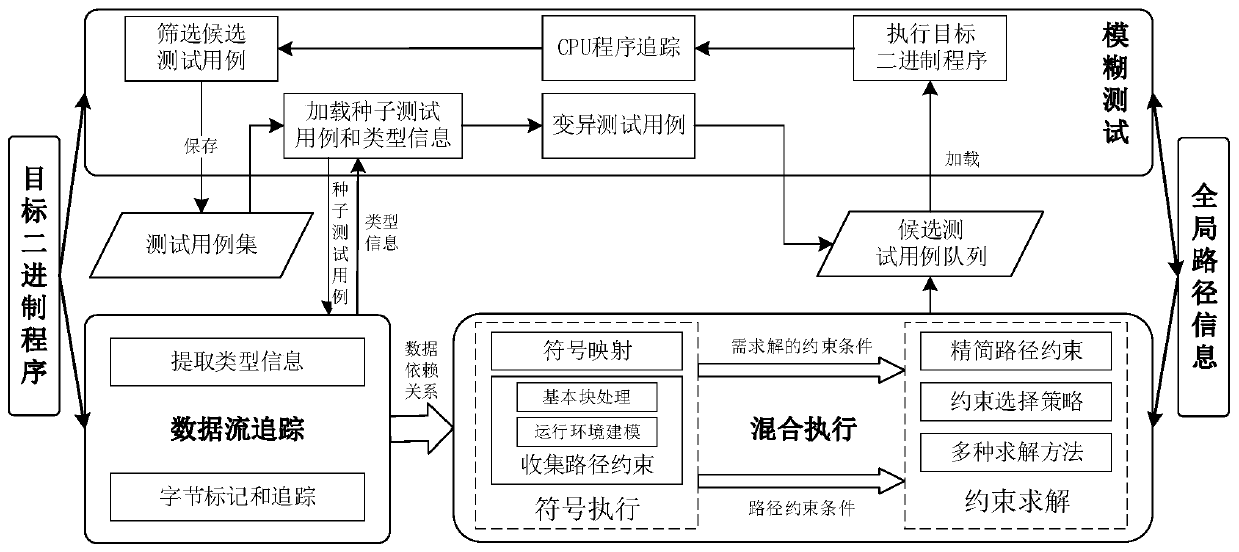
A Fuzzing System Based on Program Tracing and Mixed Execution
ActiveCN109739755BImprove efficiencyImprove effectivenessSoftware testing/debuggingProgram tracingPathPing
The invention provides a fuzzy test system based on program tracking and hybrid execution, and the system mainly comprises three modules: a fuzzy test module, a data flow tracking module, and a hybridexecution module. Wherein the input of the fuzzy test module is a target binary program, the type information of variables corresponding to byte sequences in a seed test case and the seed test case extracted by the data flow tracking module is output as a test case for triggering a new path; wherein the input of the data flow tracking module is a seed test case loaded by the target binary programand the fuzzy test module, and the output of the data flow tracking module is a dependency relationship between type information of variables corresponding to byte sequences in the seed test case anddata in the target binary program; wherein the input of the hybrid execution module is a dependency relationship of data in a target binary program provided by the data flow tracking module in real time, and the output of the hybrid execution module is a candidate test case which is newly generated by the module and can trigger a new path. Compared with the prior art, the system can improve the effectiveness of test case generation.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com