Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
242 results about "Application posture" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The term application posture characterizes the nature of a software application's interaction with its user. The term was coined by Alan Cooper, who characterized four 'postures' for applications: sovereign, transient, daemonic and parasitic.
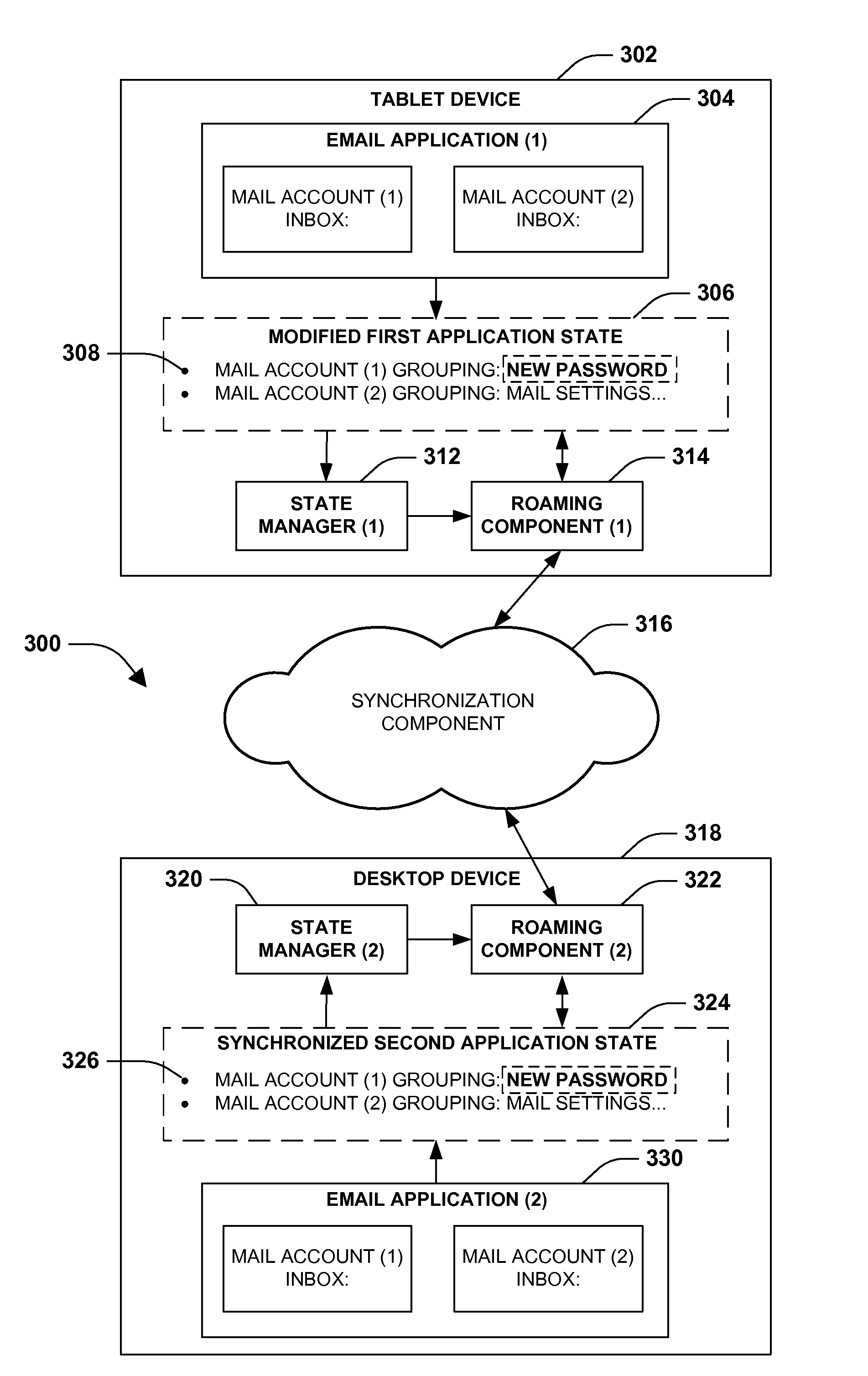
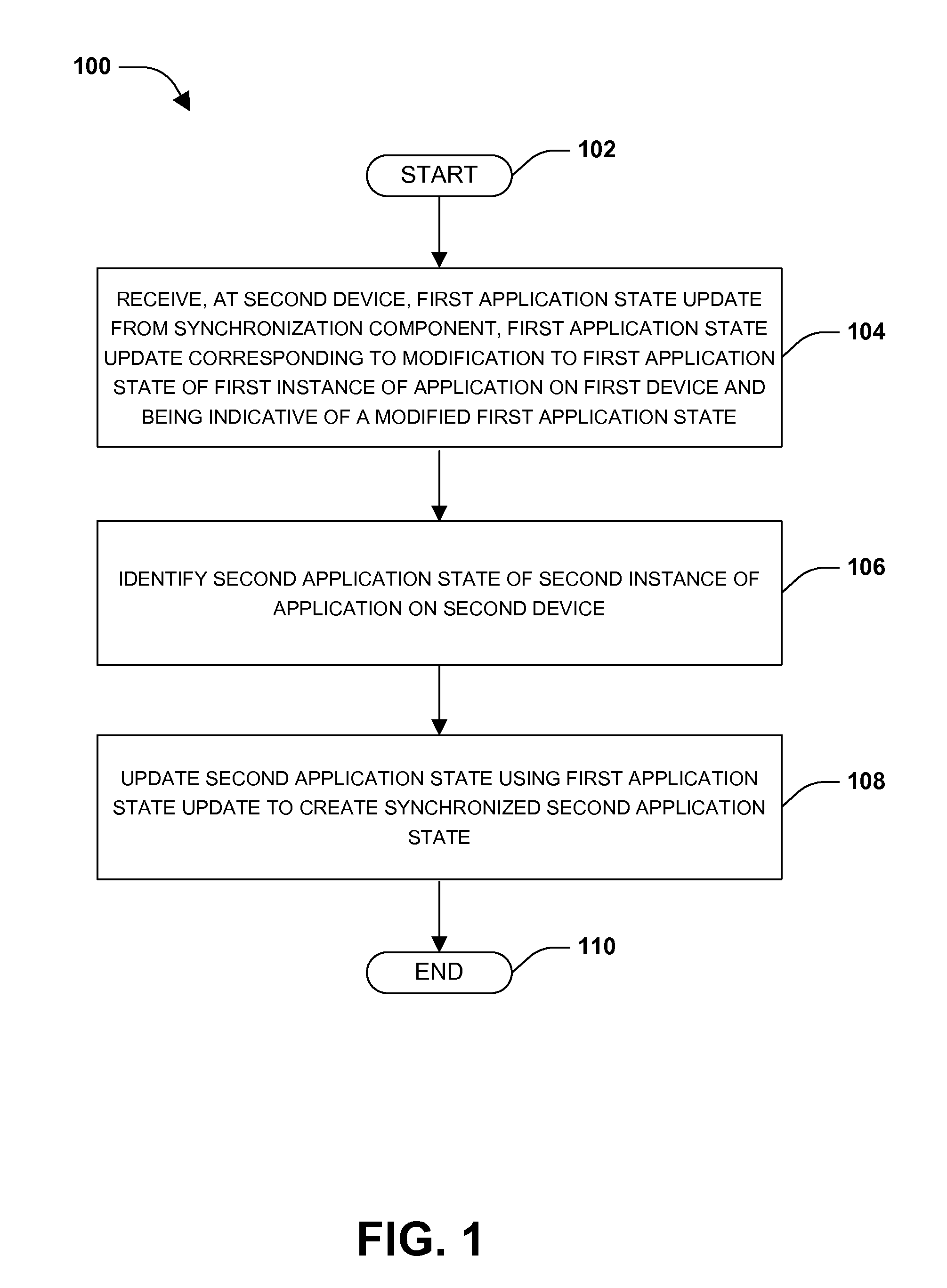
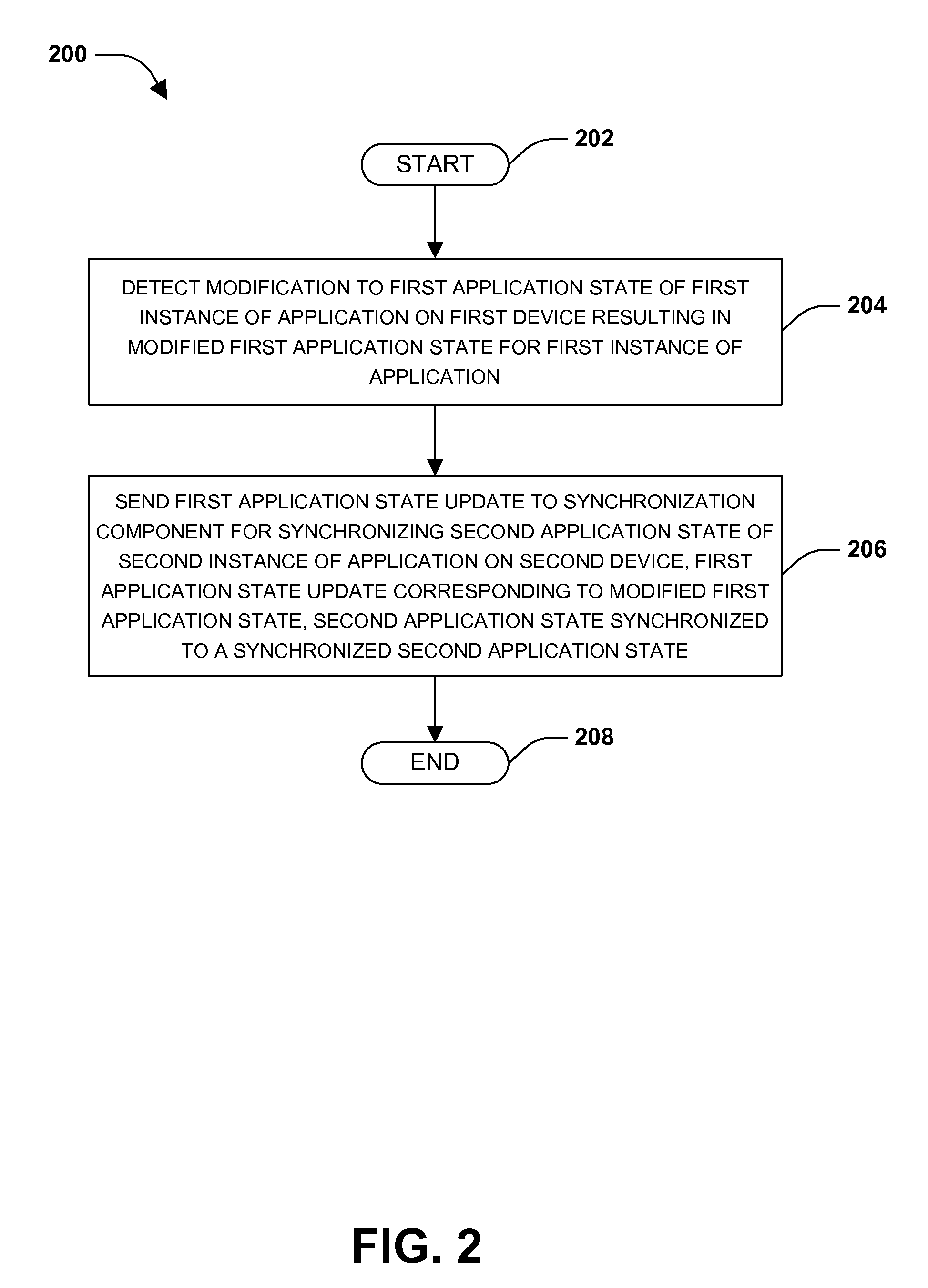
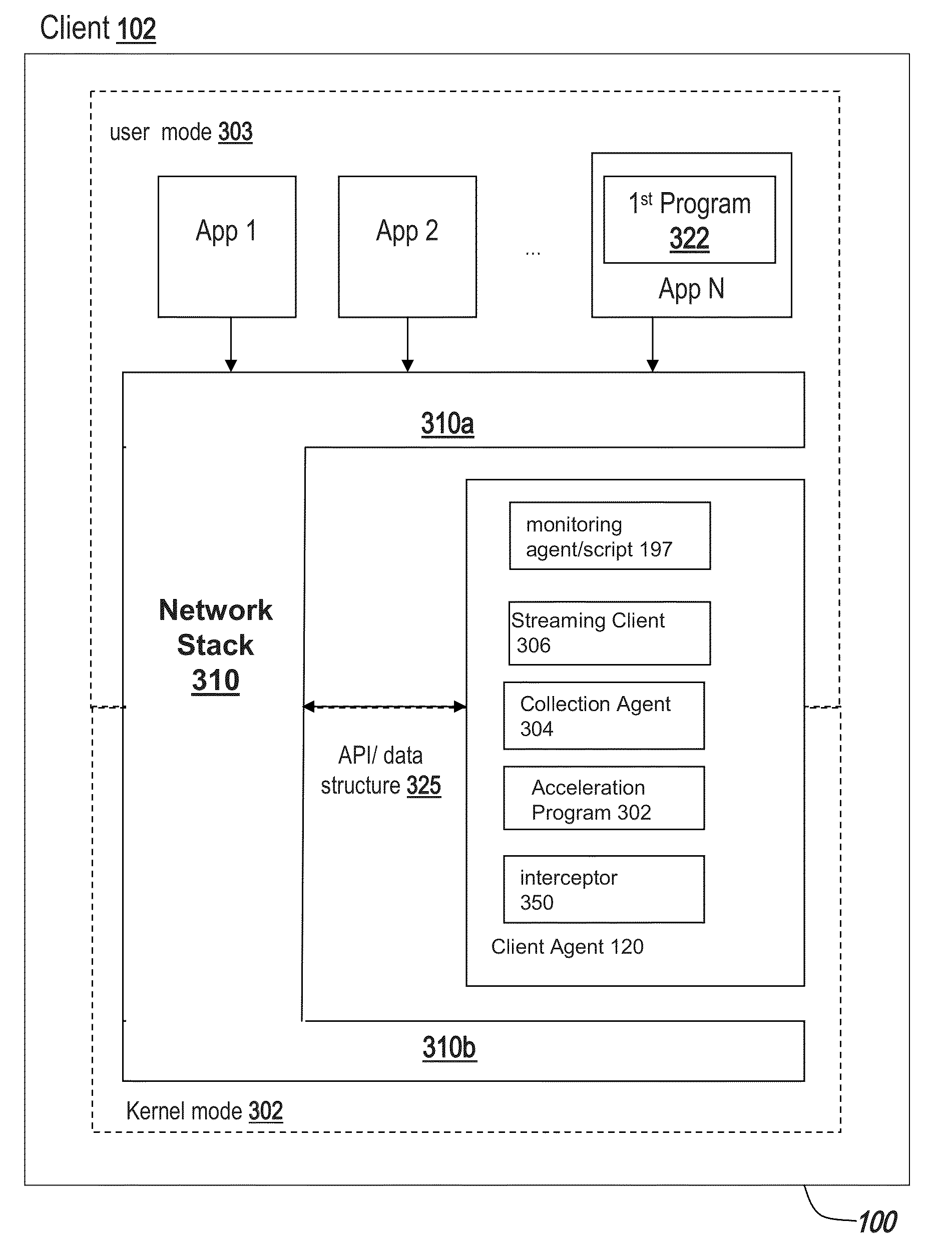
Application state synchronization
InactiveUS20130066832A1Good synchronizationDigital data processing detailsSpecial data processing applicationsApplication softwareWorld Wide Web
One or more techniques and / or systems are provided for synchronizing application state between one or more instances of an application on one or more devices. In particular, an application state, such as application settings, may be synchronized between a first instance of an application on a first device and a second instance of the application on a second device. For example, a user may configure a new email account within a first instance of an email application on a laptop device. The new email account may be synchronized with a second instance of the email application on a tablet device. During synchronization, various conflict resolution, version verifications, and / or consistency verifications may be performed. In this way, the user may be provided with a seamless and consistent experience between the laptop and tablet device.
Owner:MICROSOFT TECH LICENSING LLC
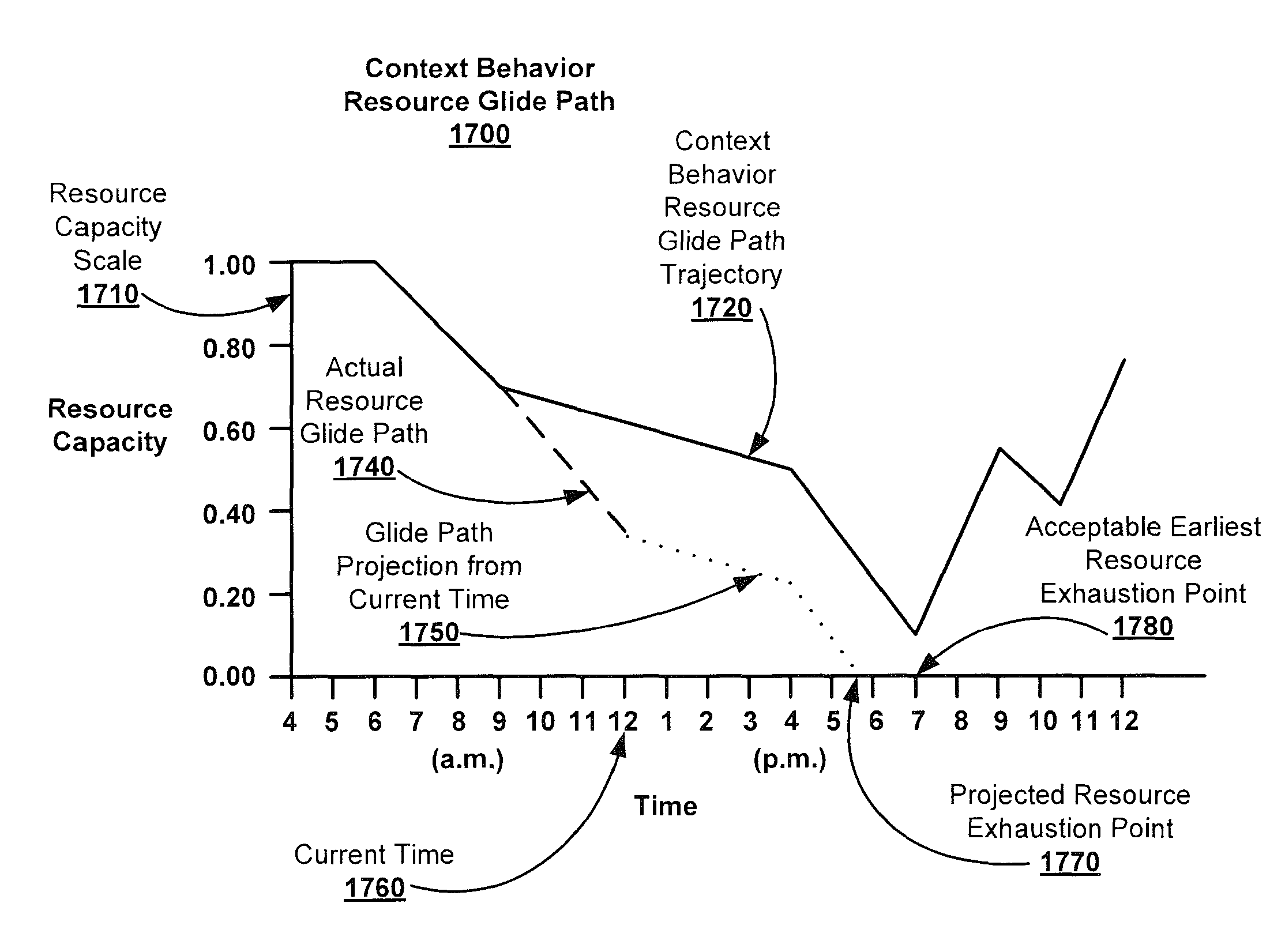
System and method for developing, updating, and using user device behavioral context models to modify user, device, and application state, settings and behavior for enhanced user security
ActiveUS8655307B1Reduce battery usageImprove battery usageEnergy efficient ICTPower managementUser deviceContext model
Security is enhanced for a user of a mobile device by monitoring and controlling resource usage. Usage information associated with a mobile device is collected. The collected information is used to build a usage model for a user of the mobile device that describes a set of contexts in which the mobile device is used. User activity on the device is monitored and the model is consulted to determine a first time after which it will be acceptable for a battery of the mobile device to fall below a threshold charge level. Based on the monitored activity, a prediction of a second time is made for when the battery will fall below the threshold charge level. If the second time is before or a predetermined amount of time before the first time, usage of the battery is reduced, else, usage of the battery is not reduced.
Owner:LOOKOUT MOBILE SECURITY
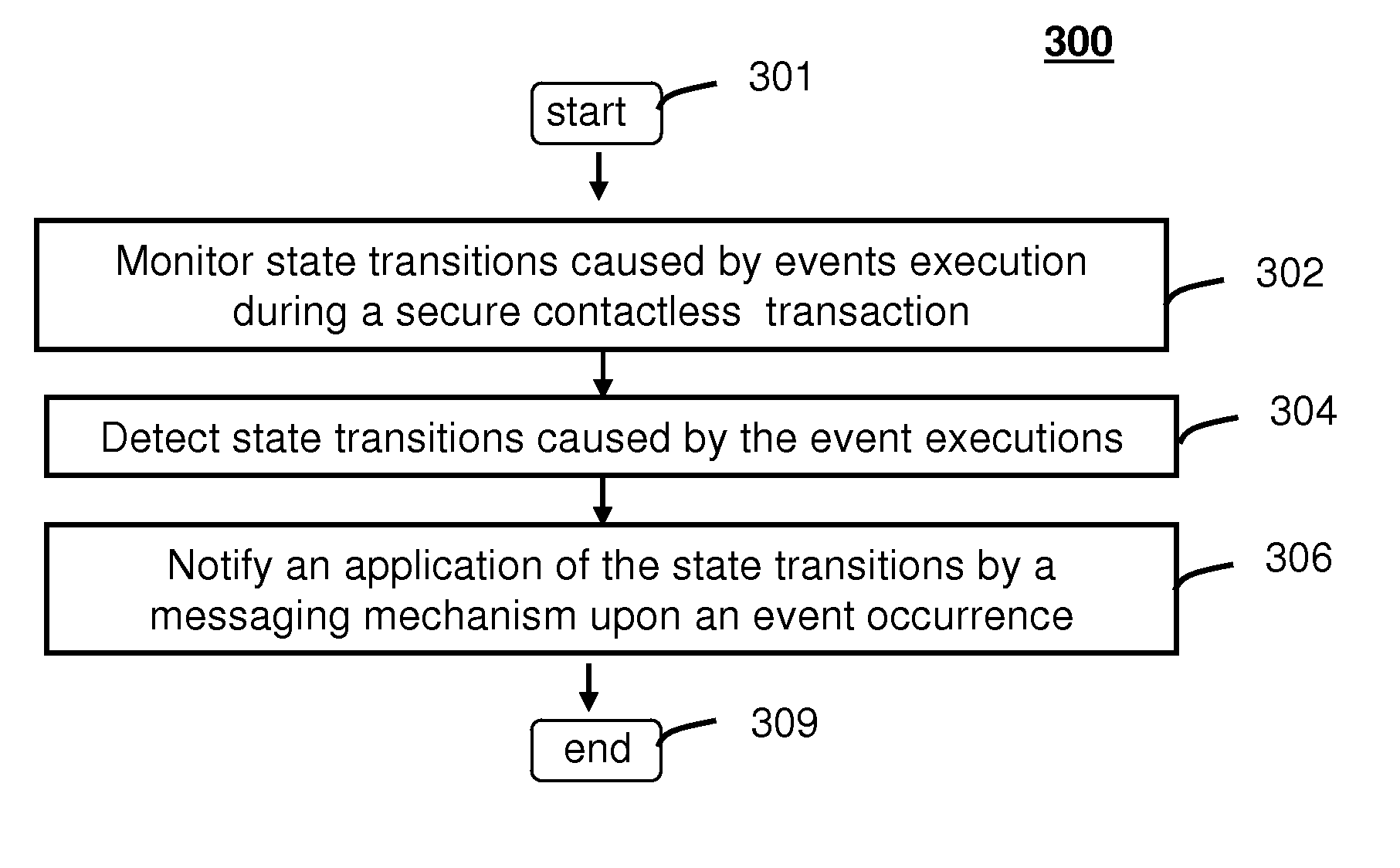
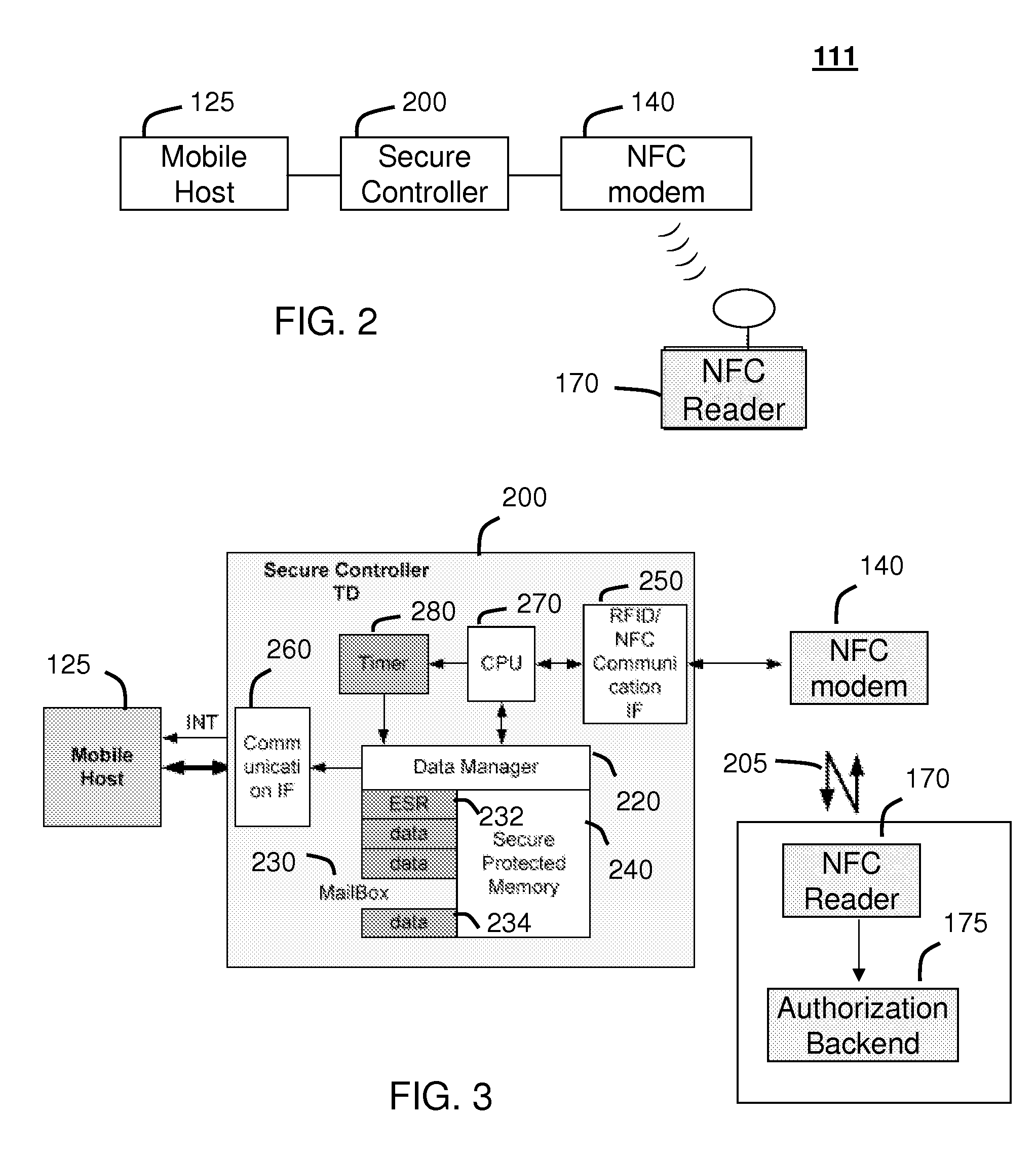
Method and system for monitoring secure application execution events during contactless rfid/nfc communication
ActiveUS20080162361A1Radio transmissionSecuring communicationCommunications securityTechnical communication
A system (211) and method (300) for reliable monitoring of secure application execution events is provided. The system can include a Near Field Communication (NFC) modem (140) for communicating transaction events of a secure contactless transaction (358) with a NFC reader (170), a secure controller (200) for monitoring state transitions caused by the transaction events, and a mobile host communicatively coupled to the secure controller for receiving hardware event notifications of the state transitions. The secure controller can generate message using a hardware interrupt to a mobile host based on secure applet state transition monitoring by setting up the events flag such as a Transaction Completion Flag (TCF) (372) into an Events Status Register (232) to identify a status of a secure contactless transactions
Owner:GOOGLE TECH HLDG LLC
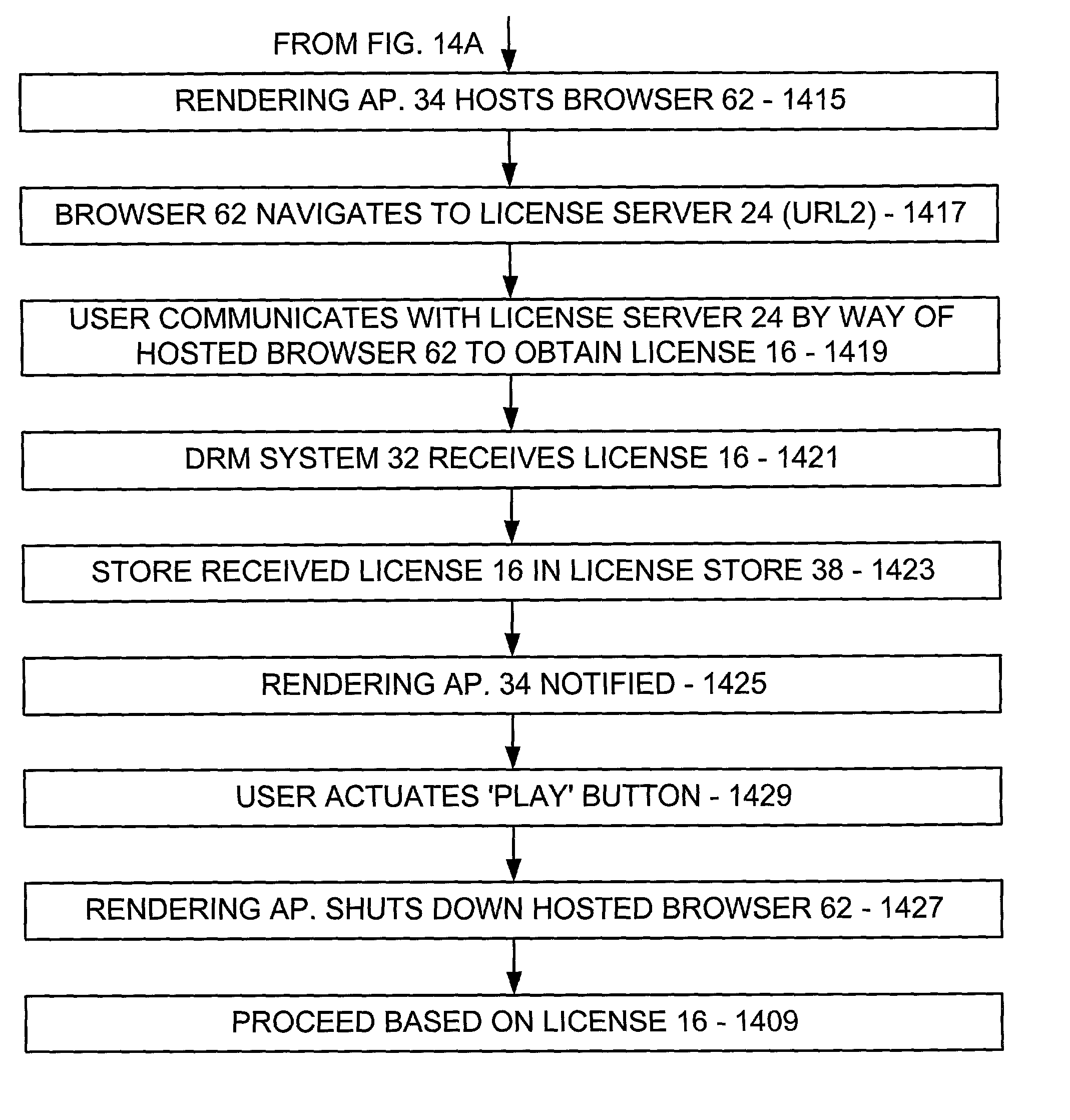
Supervised license acquisition in a digital rights management system on a computing device
InactiveUS7065507B2Satisfies needPayment protocolsBuying/selling/leasing transactionsDigital contentDigital rights management system
A rendering application on a computing device requests a digital rights management (DRM) system on the computing device to authorize digital content rendering based on a corresponding digital license. If unavailable, the DRM system attempts to silently acquire the license from a license server without the intervention of a user. In the course thereof, the rendering application receives status information from the DRM system relating to the attempted license acquisition thereby and displays the received status information in a rendering application status display portion. If silent acquisition fails, the rendering application hosts a browser, causes the browser to navigate to a license server, allows a user to communicate with the license server by way of the hosted browser to acquire the license, and shuts down the hosted browser upon reception of the license from the license server.
Owner:MICROSOFT TECH LICENSING LLC
Associating application states with a physical object
InactiveUS7397464B1Simple methodCathode-ray tube indicatorsInput/output processes for data processingApplication softwareInteractive displays
An application state of a computer program is stored and associated with a physical object and can be subsequently retrieved when the physical object is detected adjacent to an interactive display surface. An identifying characteristic presented by the physical object, such as a reflective pattern applied to the object, is detected when the physical object is positioned on the interactive display surface. The user or the system can initiate a save of the application state. For example, the state of an electronic game using the interactive display surface can be saved. Attributes representative of the state are stored and associated with the identifying characteristic of the physical object. When the physical object is again placed on the interactive display surface, the physical object is detected based on its identifying characteristic, and the attributes representative of the state can be selectively retrieved and used to recreate the state of the application.
Owner:MICROSOFT TECH LICENSING LLC
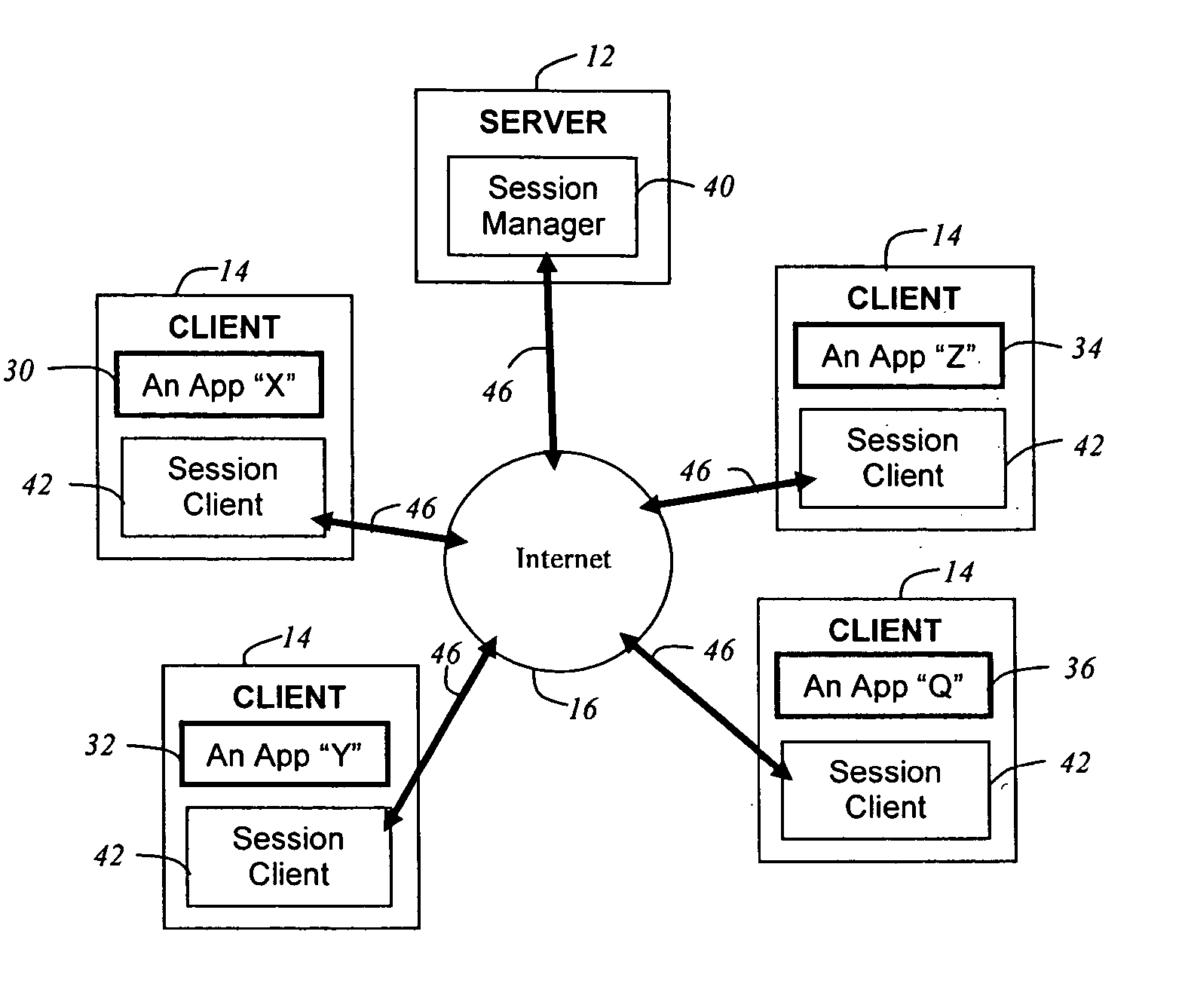
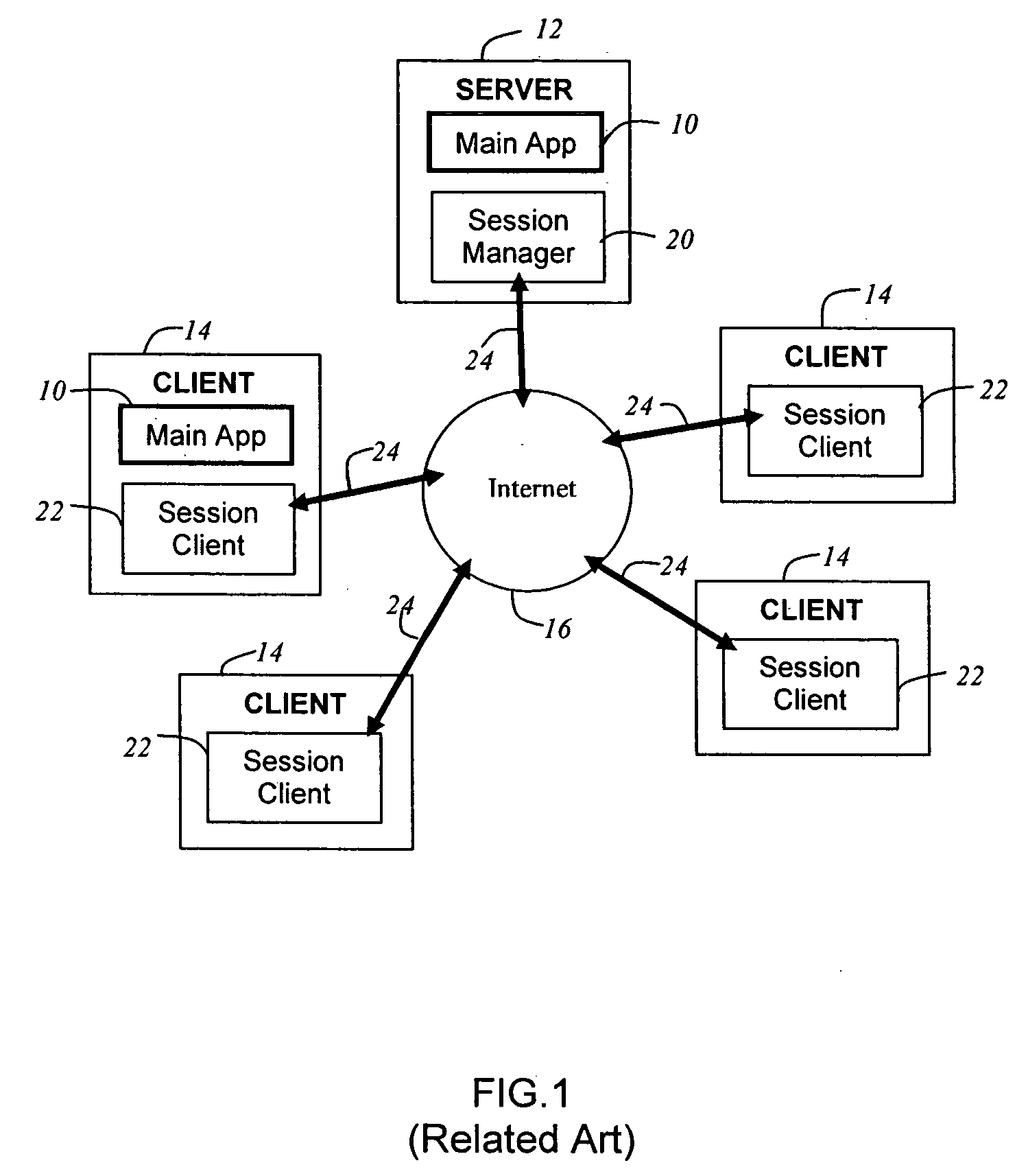
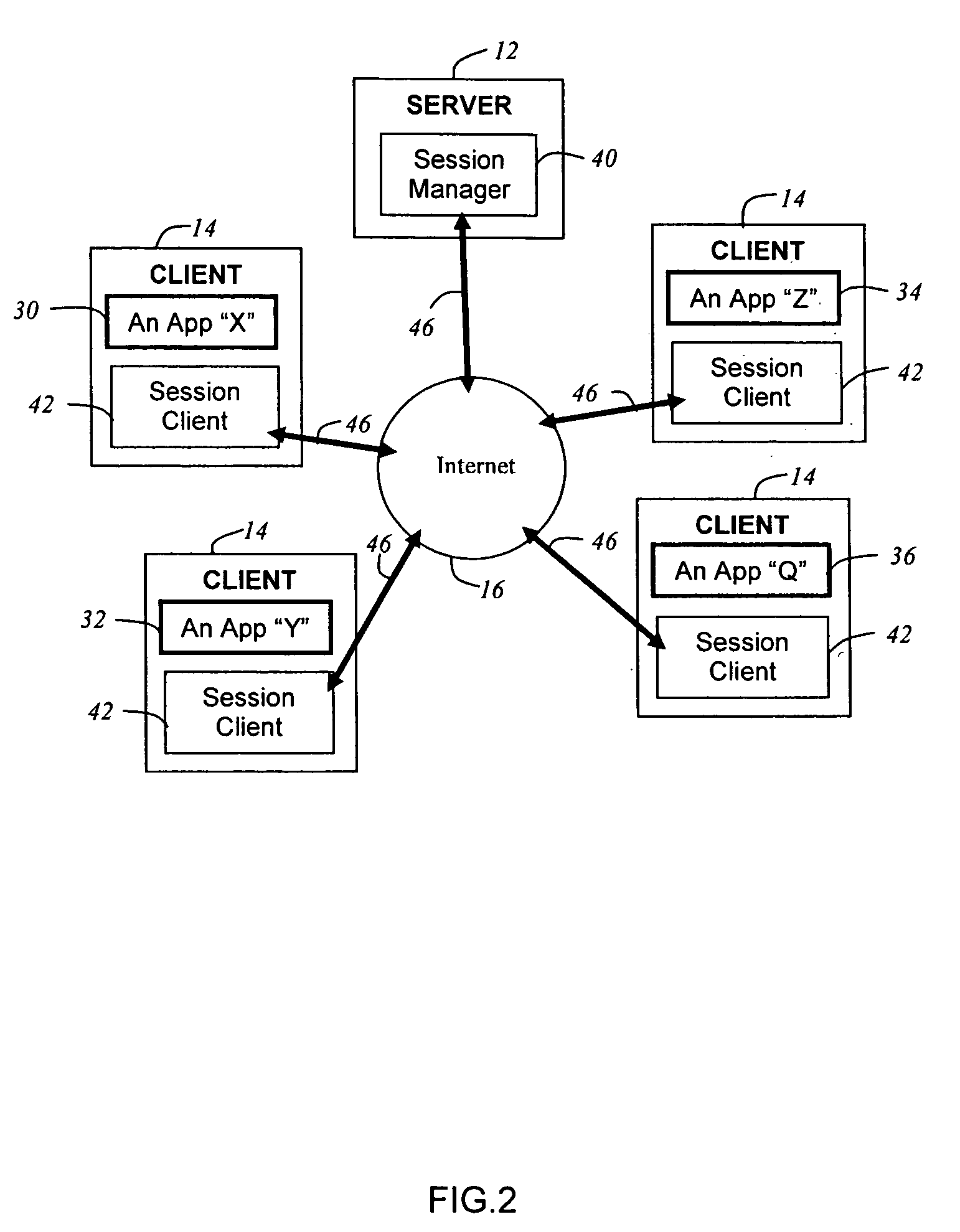
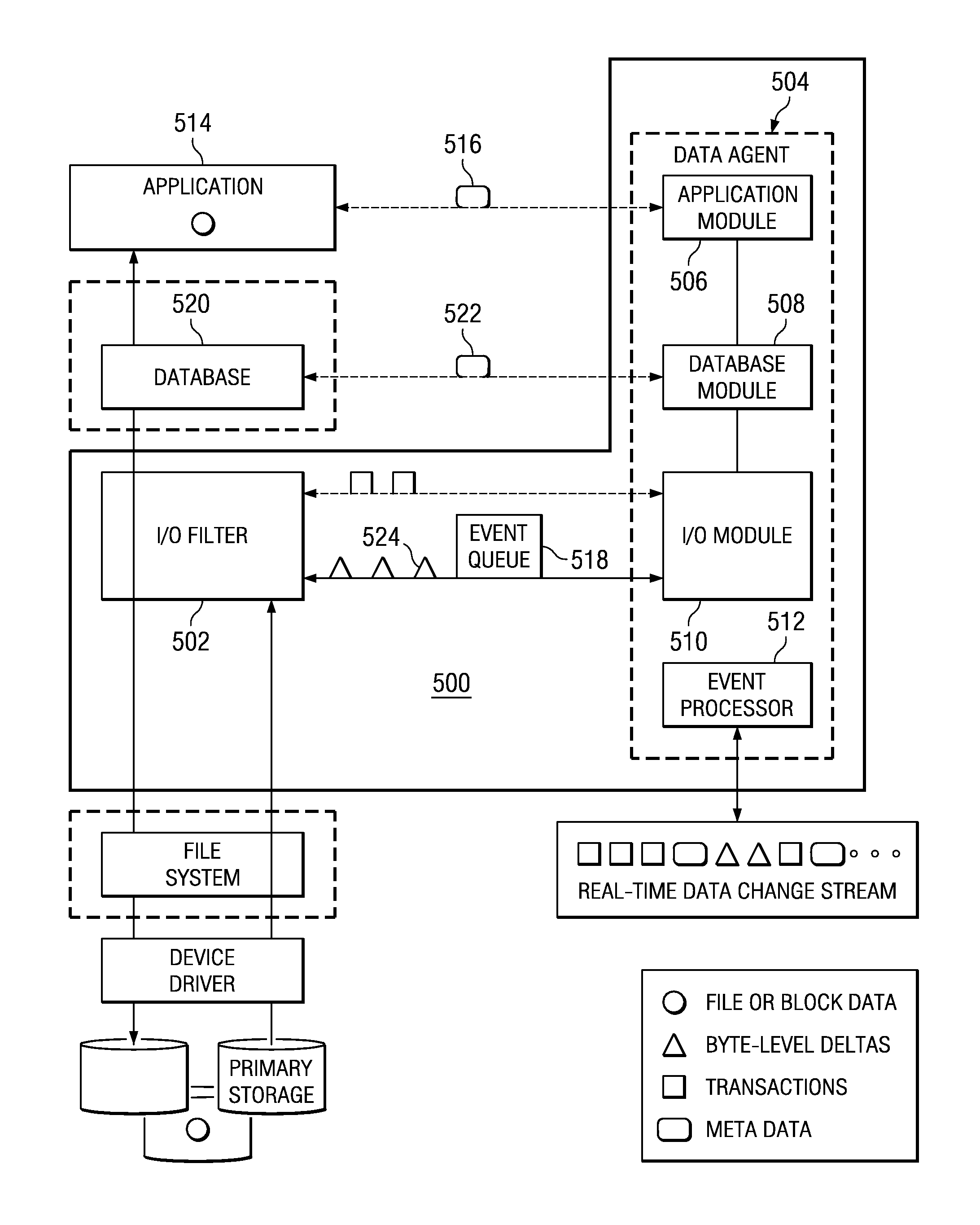
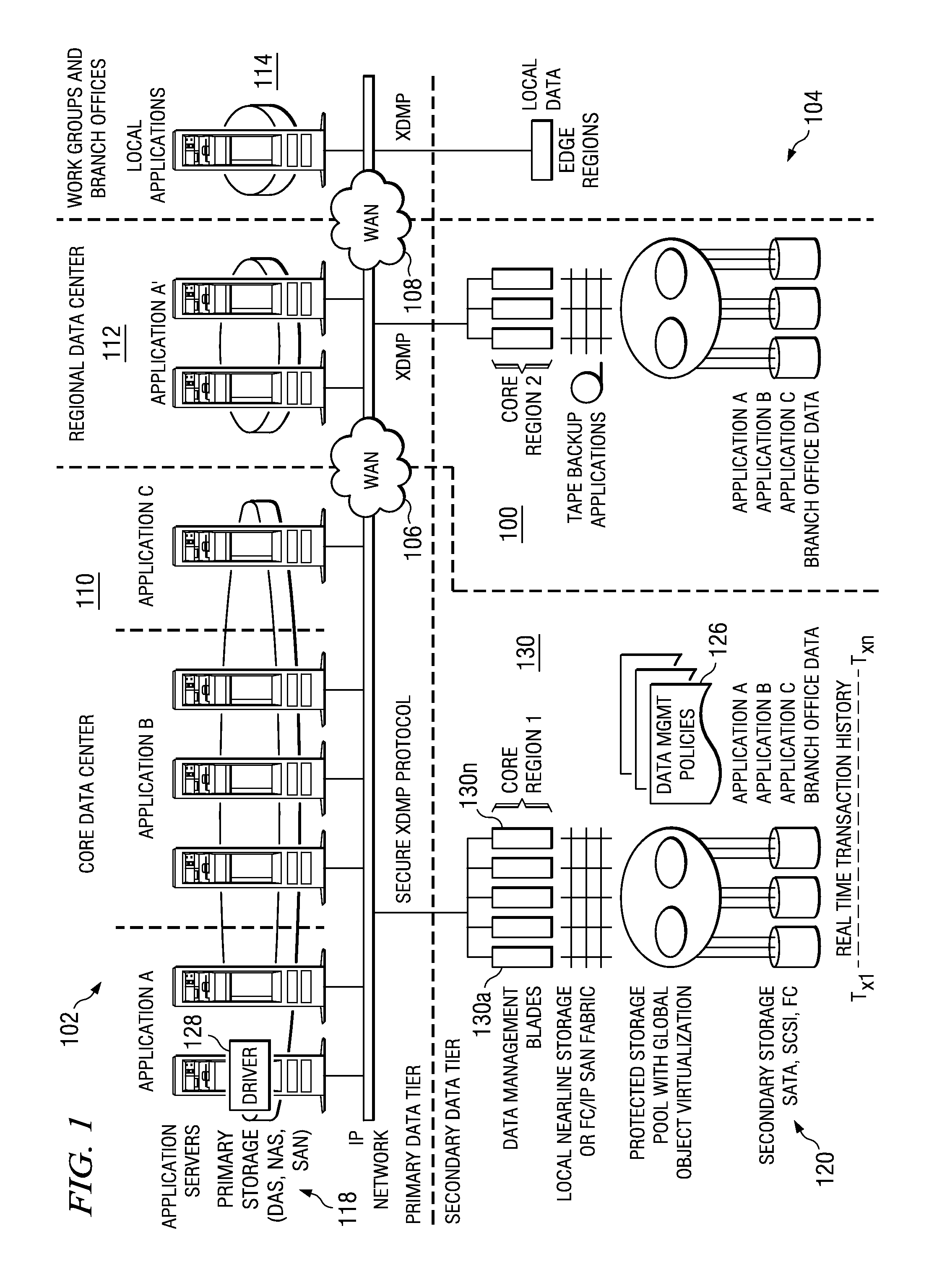
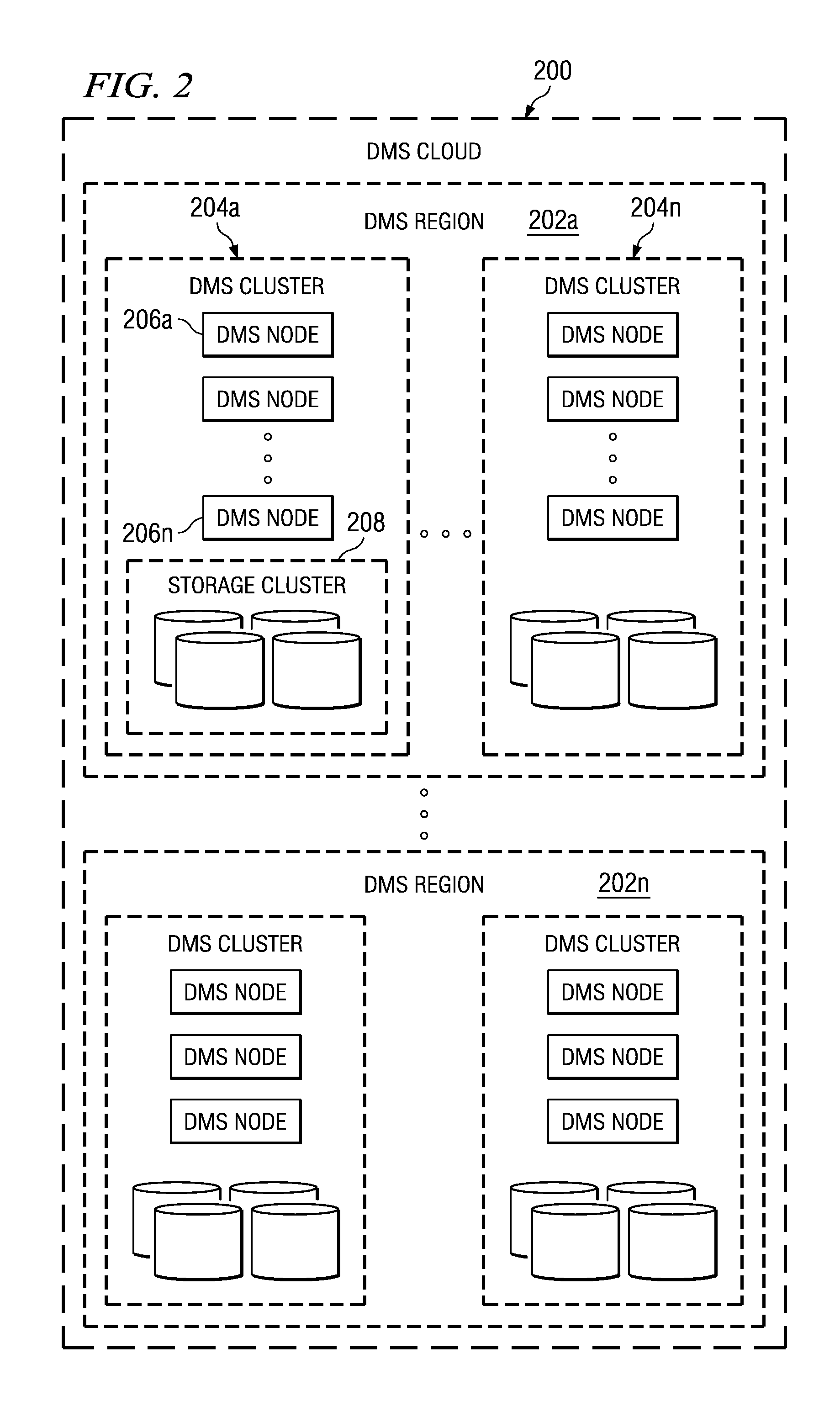
Method and system for real-time event journaling to provide enterprise data services
ActiveUS20050251540A1Good data serviceDigital data information retrievalError detection/correctionData connectionData stream
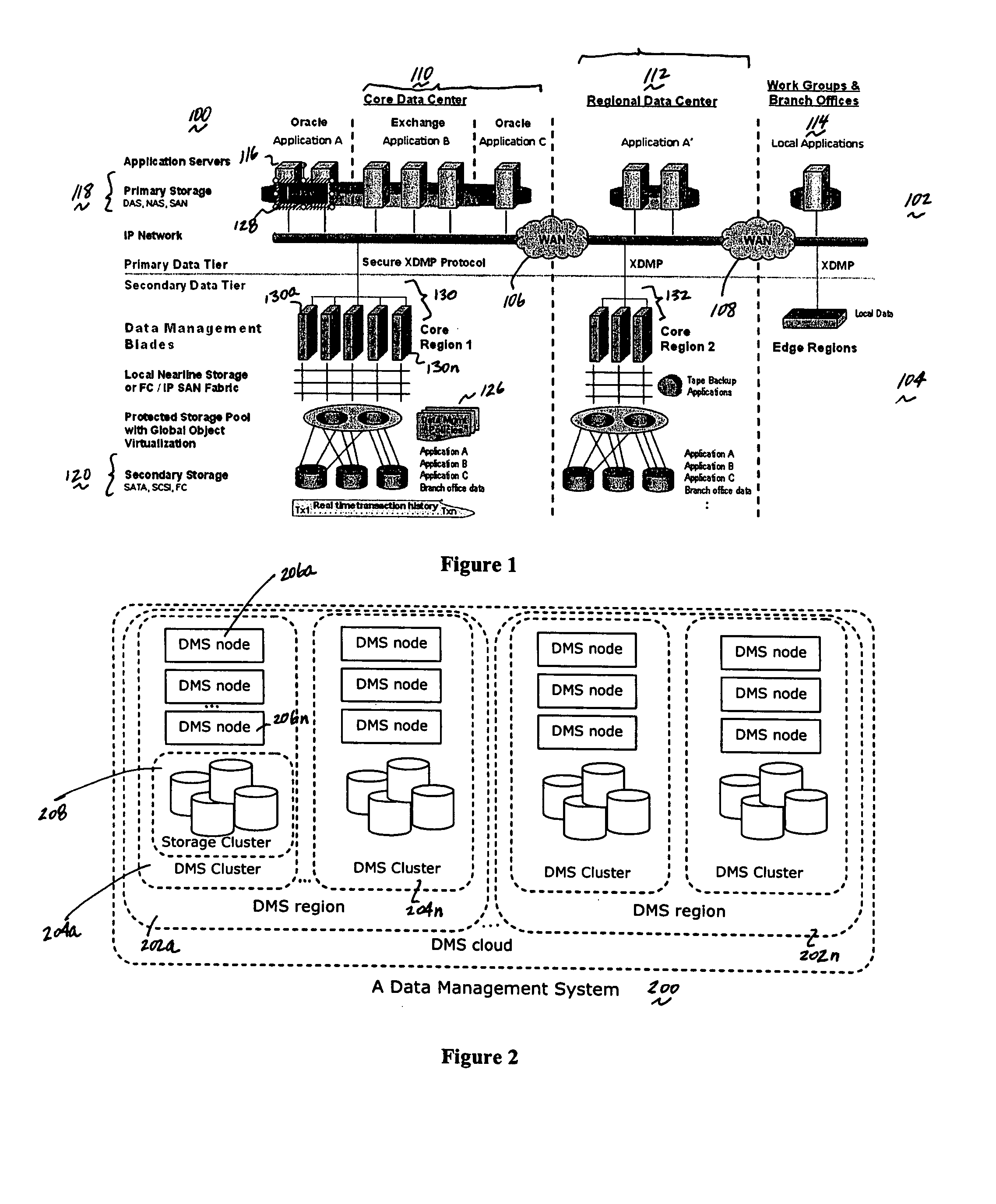
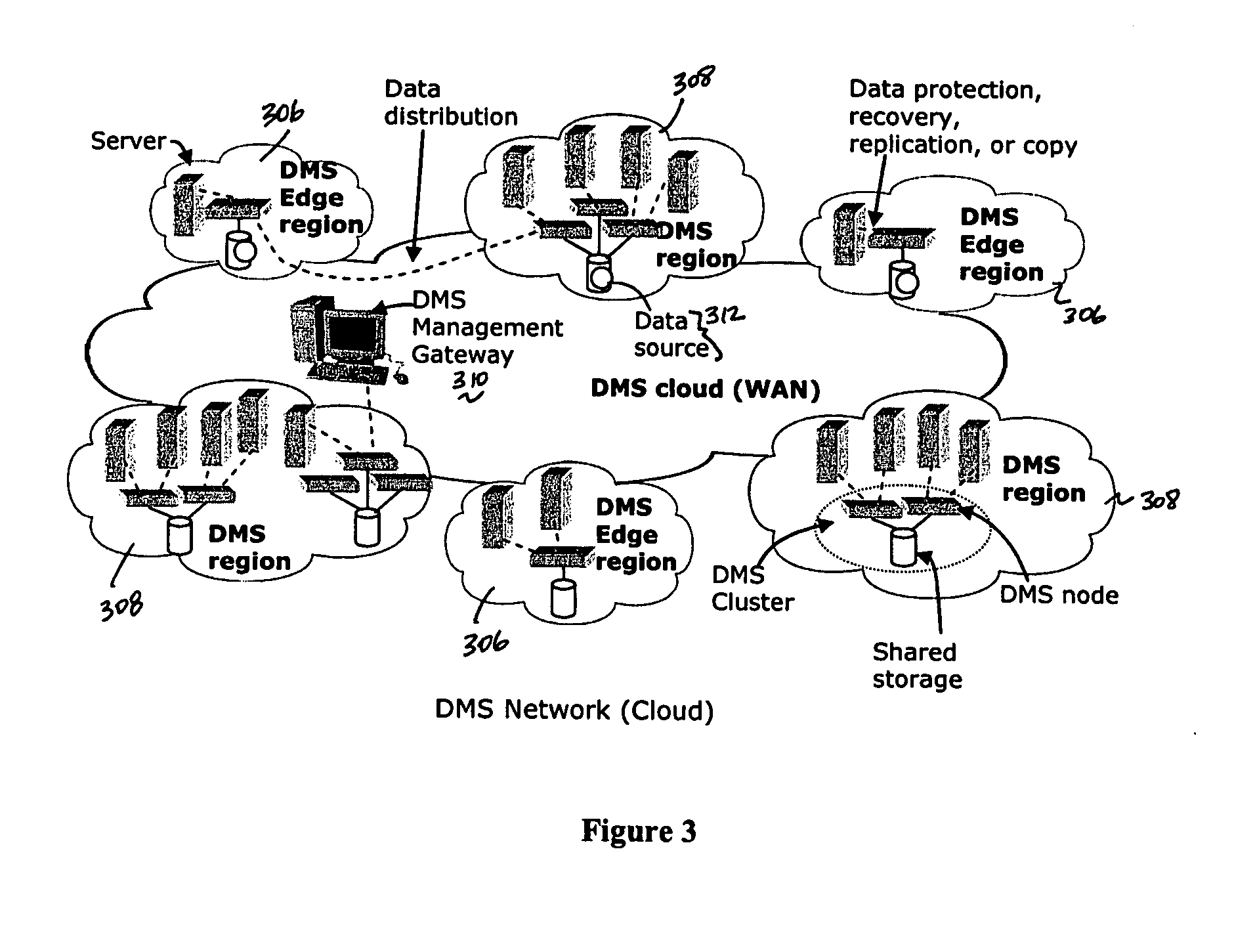
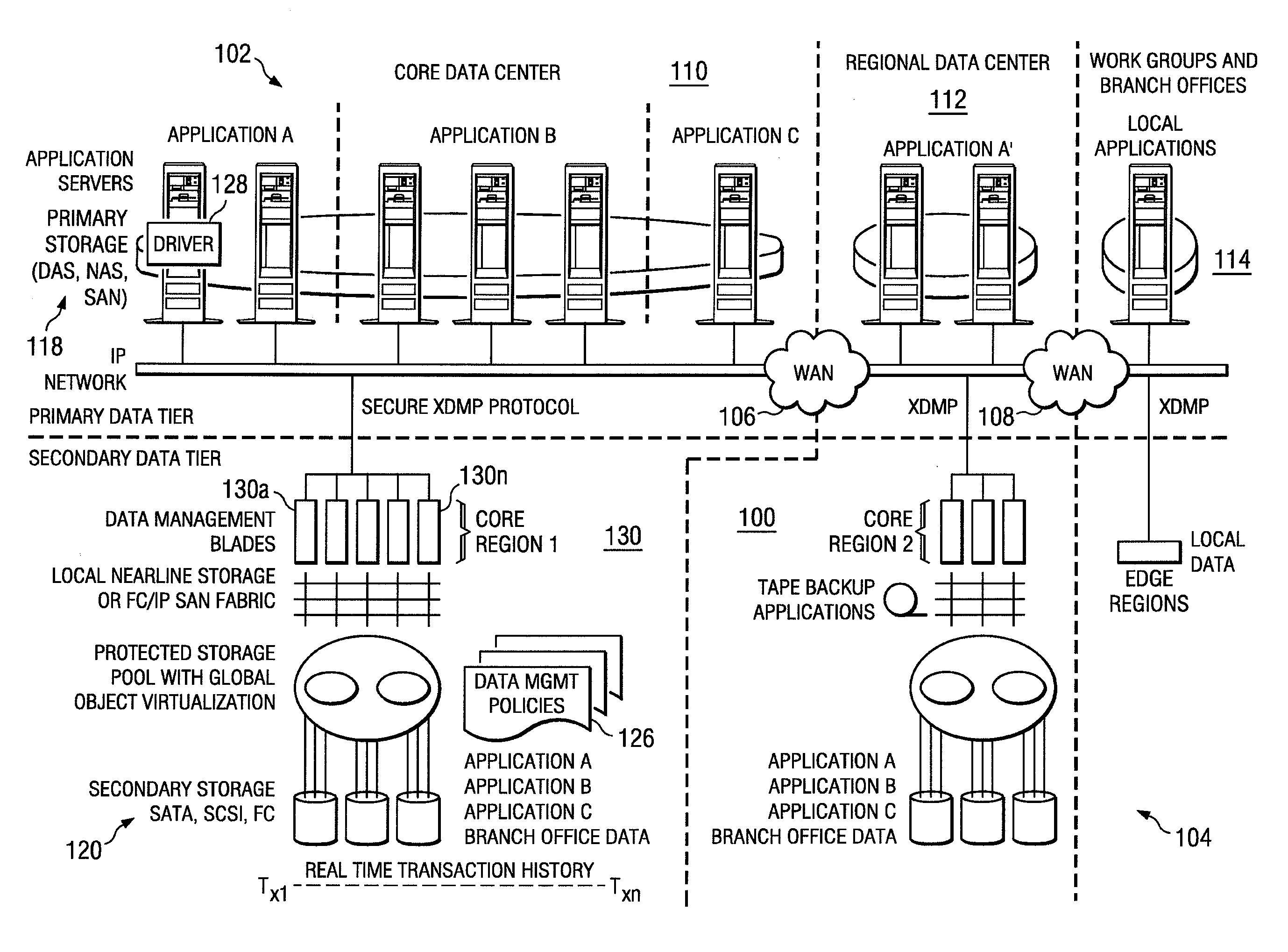
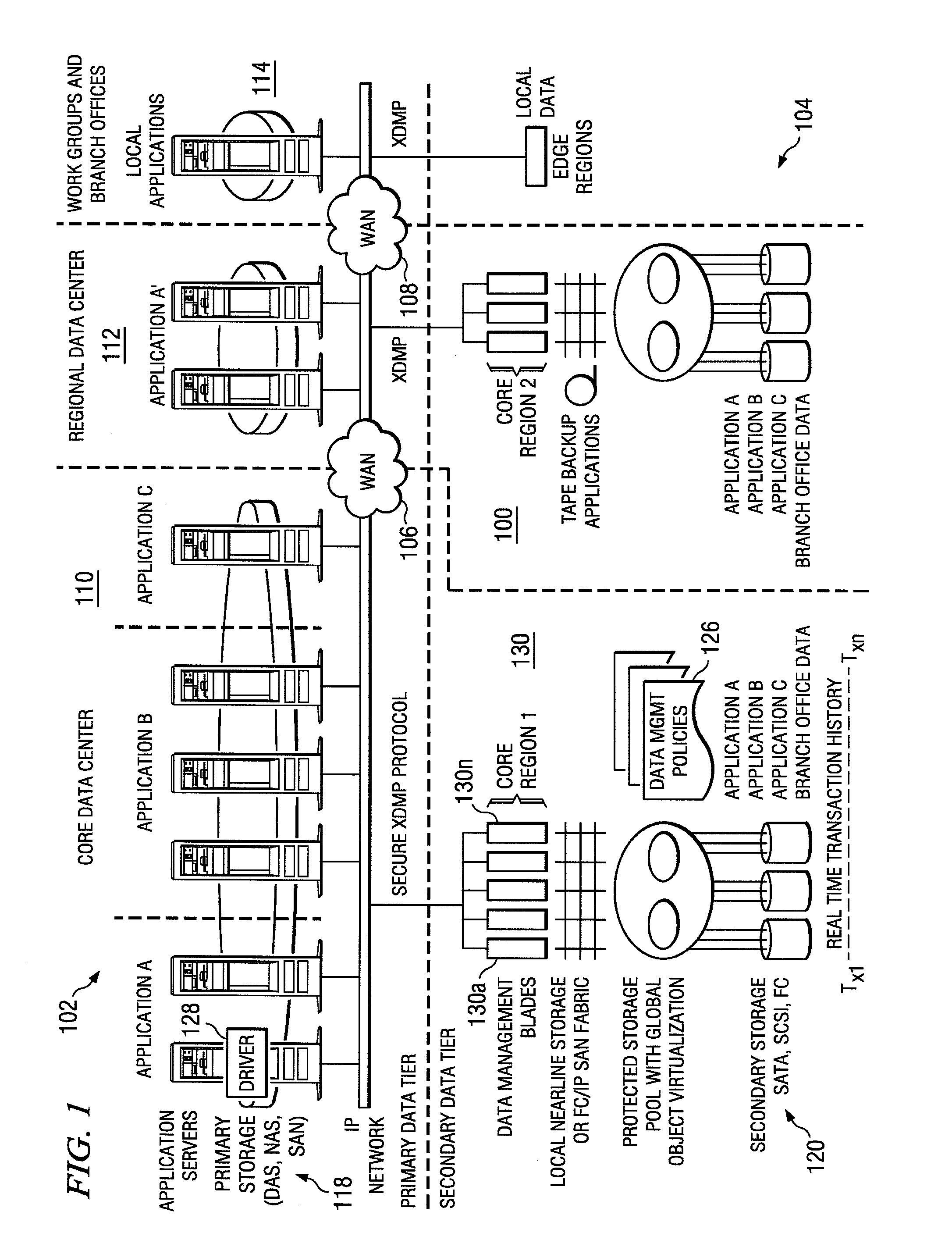
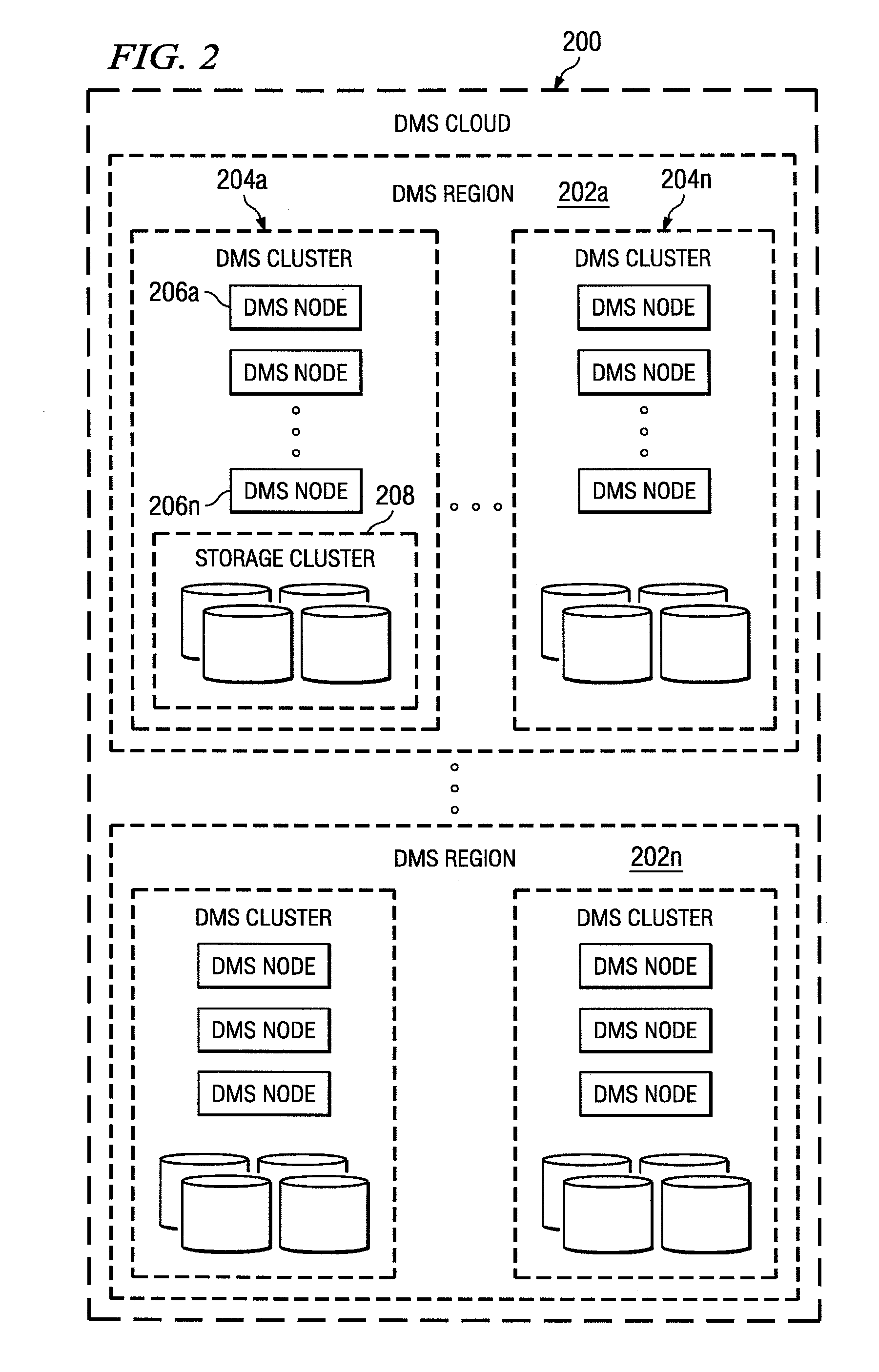
A data management system or “DMS” provides a wide range of data services to data sources associated with a set of application host servers. The data management system typically comprises one or more regions, with each region having one or more clusters. A given cluster has one or more nodes that share storage. To facilitate the data service, a host driver embedded in an application server connects an application and its data to a cluster. The host driver provides a method and apparatus for capturing real-time data modifications and application state notifications and, in response, generating data transactions in the form of an event journal that is provided to the data management system. The driver functions to translate traditional file / database / block I / O into a continuous, application-aware, output data stream. Using the streams generated in this manner, the DMS offers a wide range of data services that include, by way of example only: data protection (and recovery), and disaster recovery (data distribution and data replication).
Owner:QUEST SOFTWARE INC
Method and system for real-time event journaling to provide enterprise data services
InactiveUS20100031274A1Digital data information retrievalError detection/correctionData connectionData stream
A data management system or “DMS” provides a wide range of data services to data sources associated with a set of application host servers. The data management system typically comprises one or more regions, with each region having one or more clusters. A given cluster has one or more nodes that share storage. To facilitate the data service, a host driver embedded in an application server connects an application and its data to a cluster. The host driver provides a method and apparatus for capturing real-time data modifications and application state notifications and, in response, generating data transactions in the form of an event journal that is provided to the data management system. The driver functions to translate traditional file / database / block I / O into a continuous, application-aware, output data stream. Using the streams generated in this manner, the DMS offers a wide range of data services that include, by way of example only: data protection (and recovery), and disaster recovery (data distribution and data replication).
Owner:QUEST SOFTWARE INC
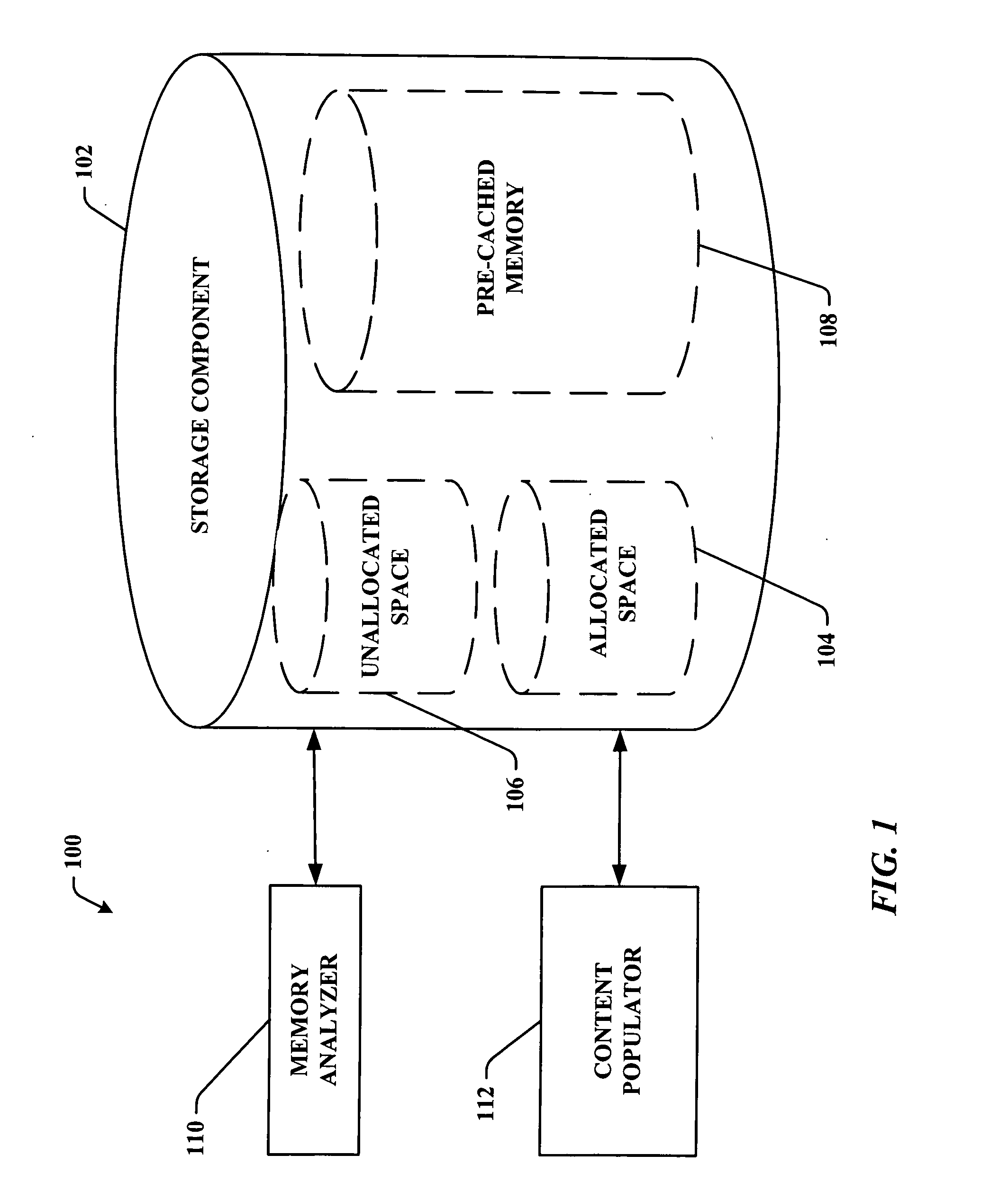
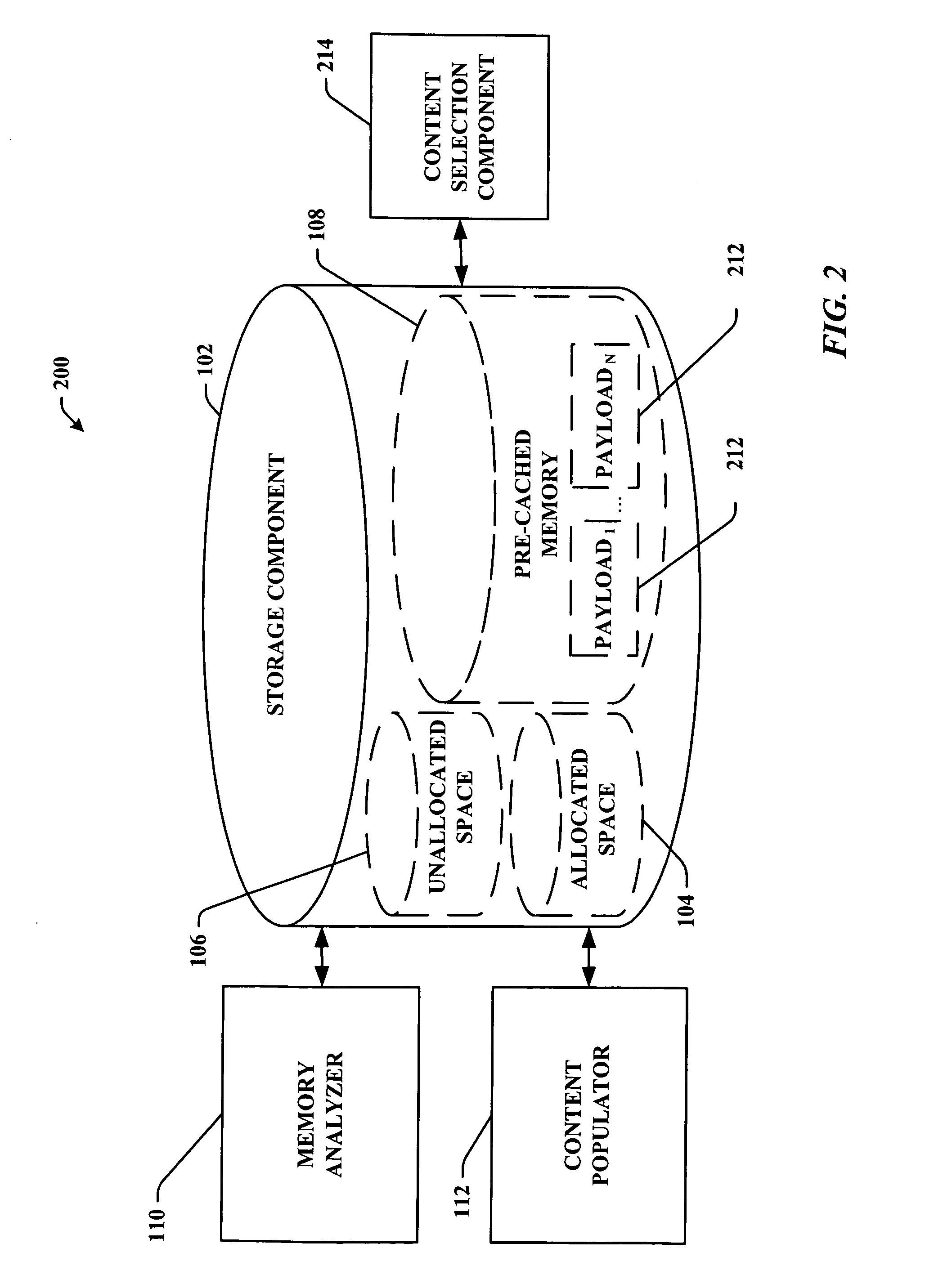
Pre-storage of data to pre-cached system memory
ActiveUS20070136533A1Improve utilizationImprove computing powerAdvertisementsTransmissionOperational systemData access
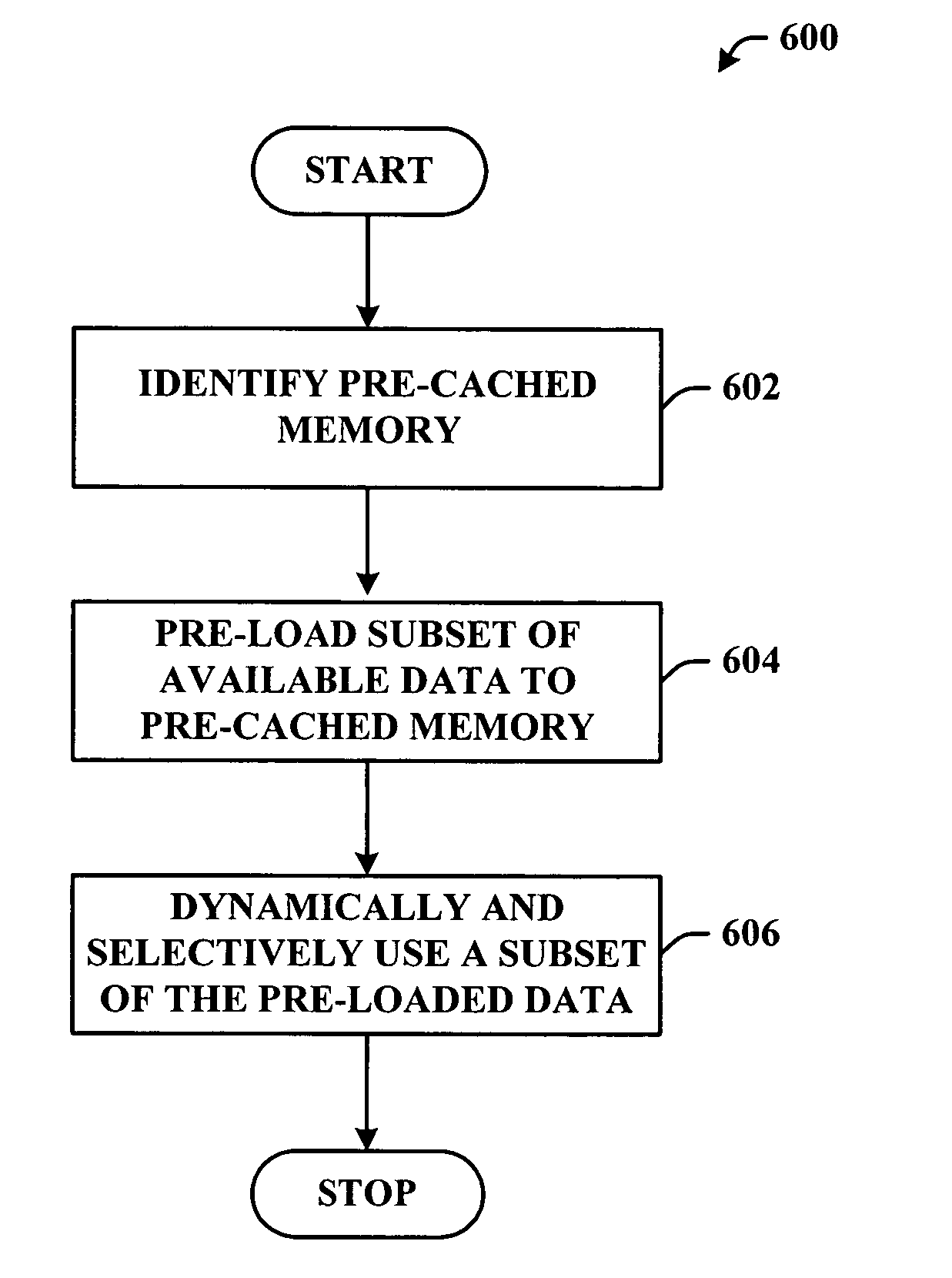
System(s) and method(s) that facilitate utilizing pre-cached disk space. Pre-cached memory space within a storage device is identified, and a subset of the pre-cached memory space is pre-populated with data so that the data can be selectively and dynamically accessed. During use of a computer (e.g., in a web-browsing session) a subset of the pre-stored data can be dynamically and selectively exposed to the user as a function of user and / or computer application state. Pre-storage of the data on pre-cached memory of the computer mitigates delayed data access (e.g., due to insufficient transmission bandwidth) thereby enhancing user computing experience. The user can utilize the device without having to distinguish between pre-cached and free memory. In other words, the operating system can present the cached memory to the user so that it appears as free memory without the user having to direct the system to do so.
Owner:MICROSOFT TECH LICENSING LLC
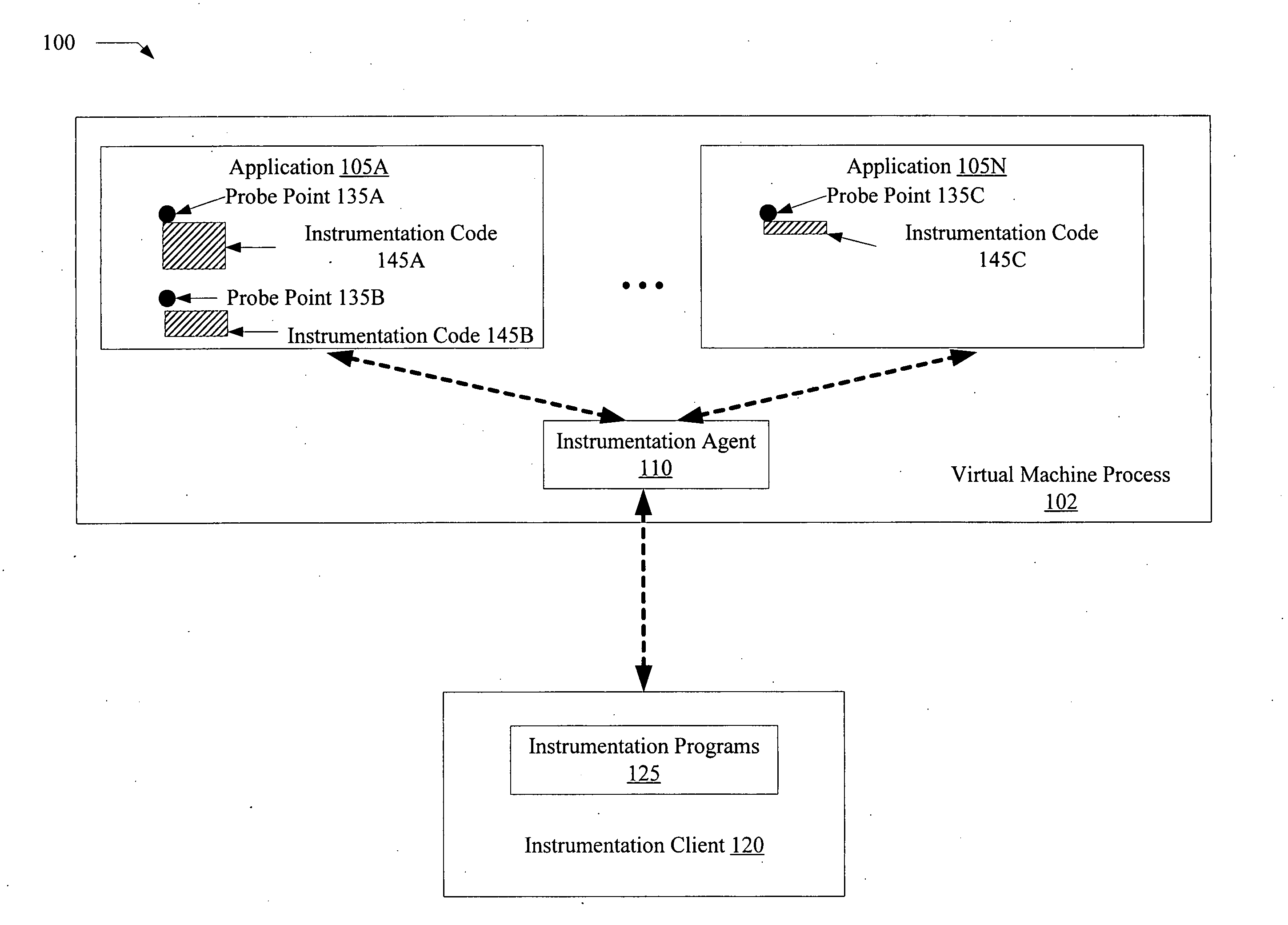
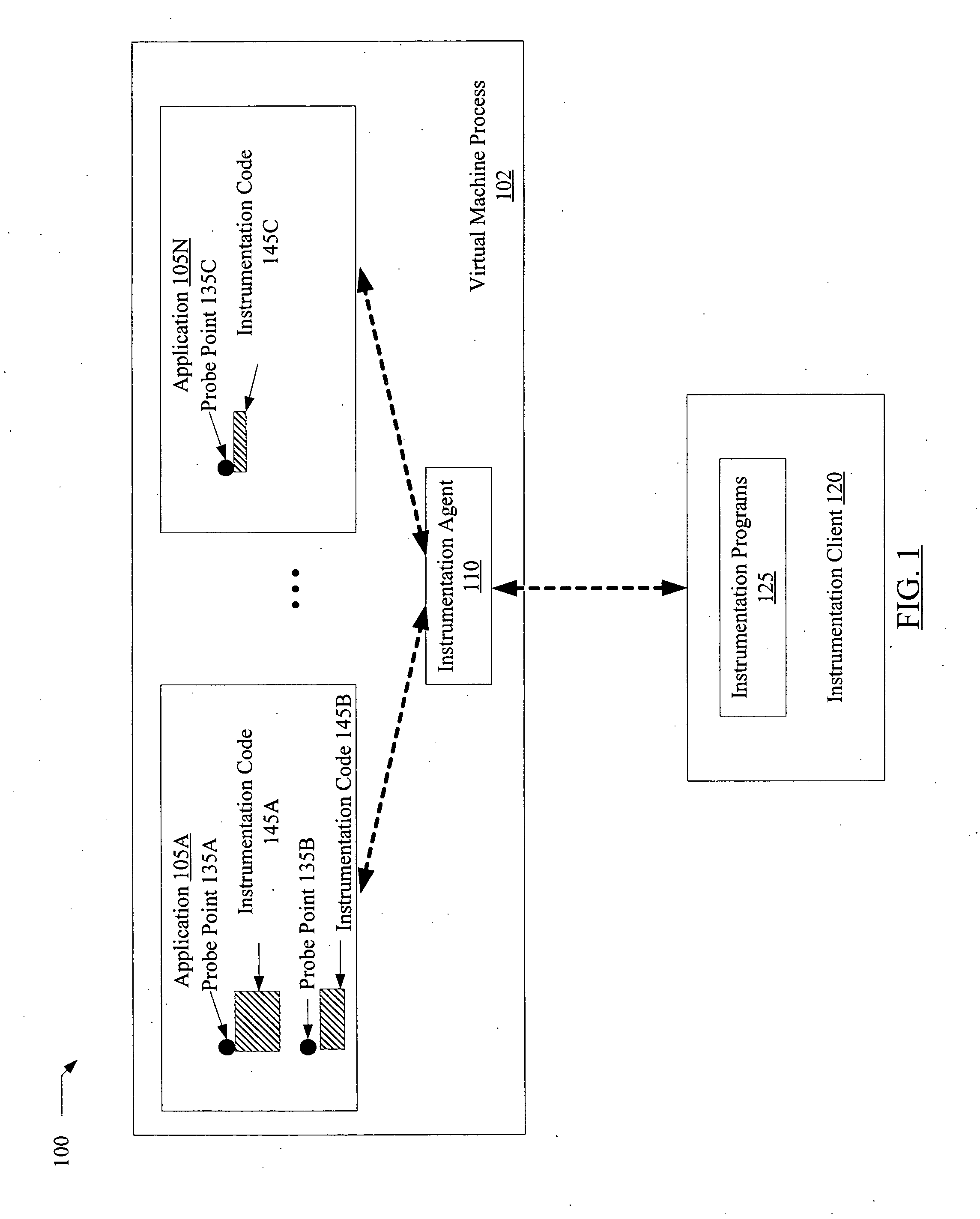
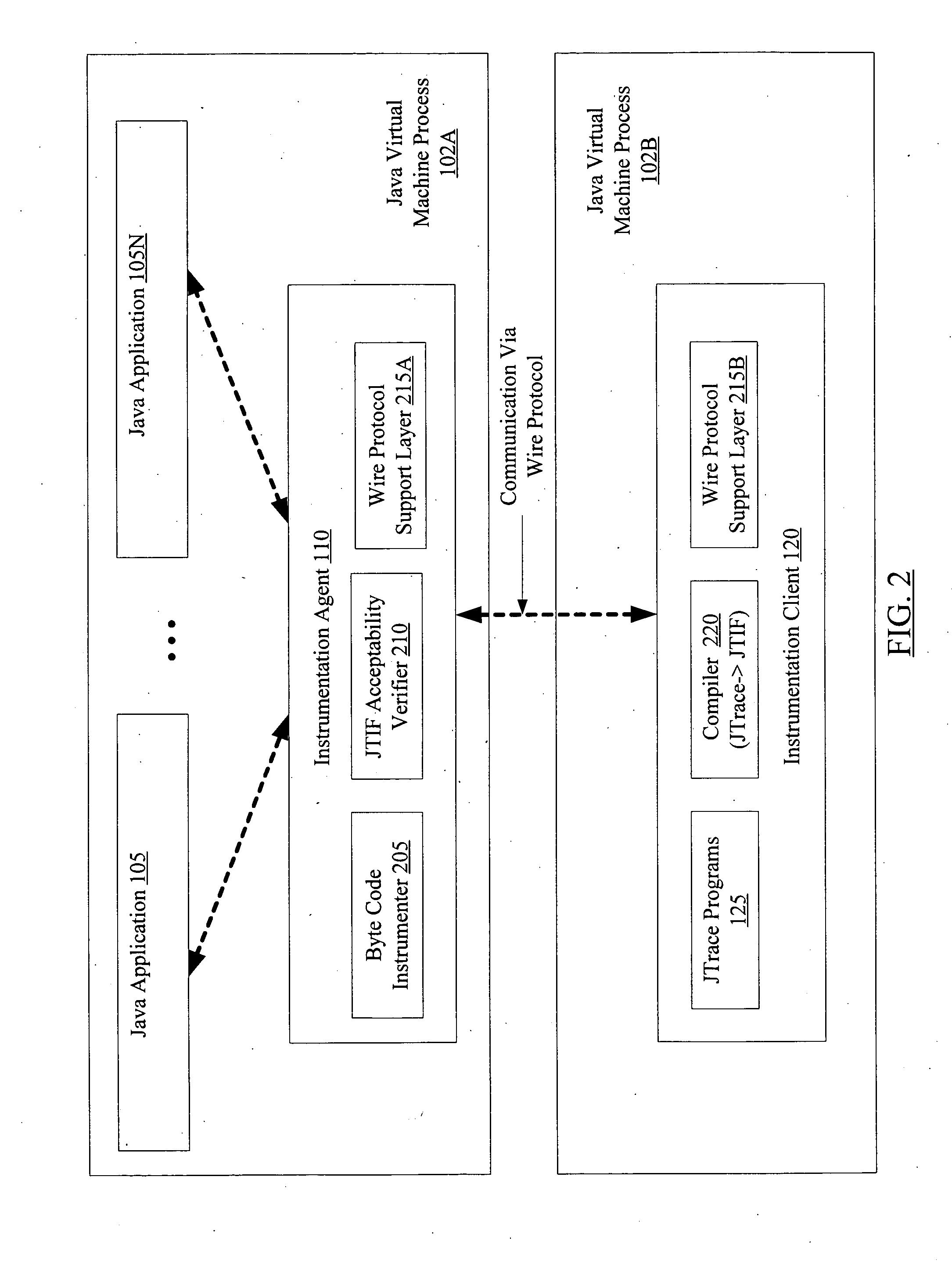
Dynamic application tracing in virtual machine environments
ActiveUS20070180439A1Promote generationError detection/correctionSpecific program execution arrangementsProgram tracingParallel computing
A method for dynamic application tracing in virtual machine environments comprises receiving an instrumentation request that includes an identification of a probe point at which instrumentation code is to be inserted within an application. The method may further comprise making a determination whether the instrumentation code meets one or more acceptance criteria. If the instrumentation code is found to be acceptable, the method may further comprise inserting the instrumentation code at the probe point within the application while the application is executing within a virtual machine, and obtaining information indicative of application state from an execution of the instrumentation code when the probe point is reached during application execution.
Owner:ORACLE INT CORP
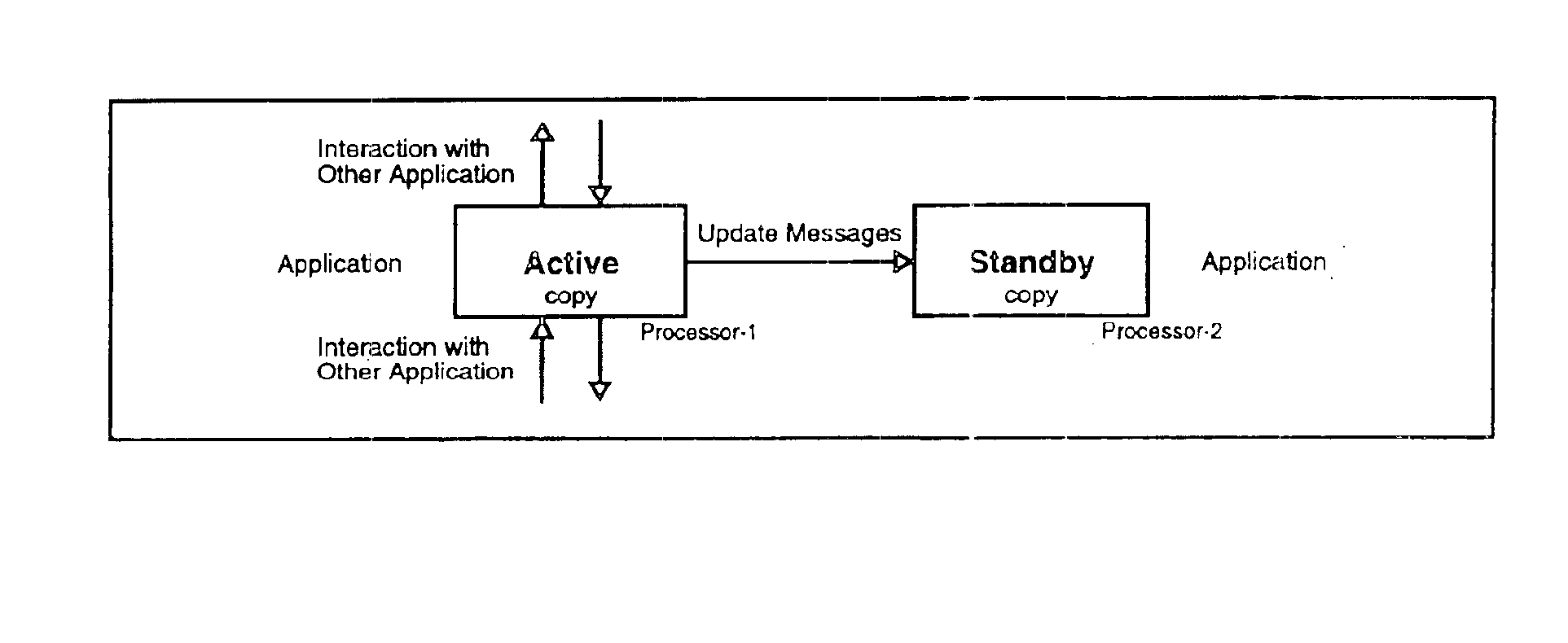
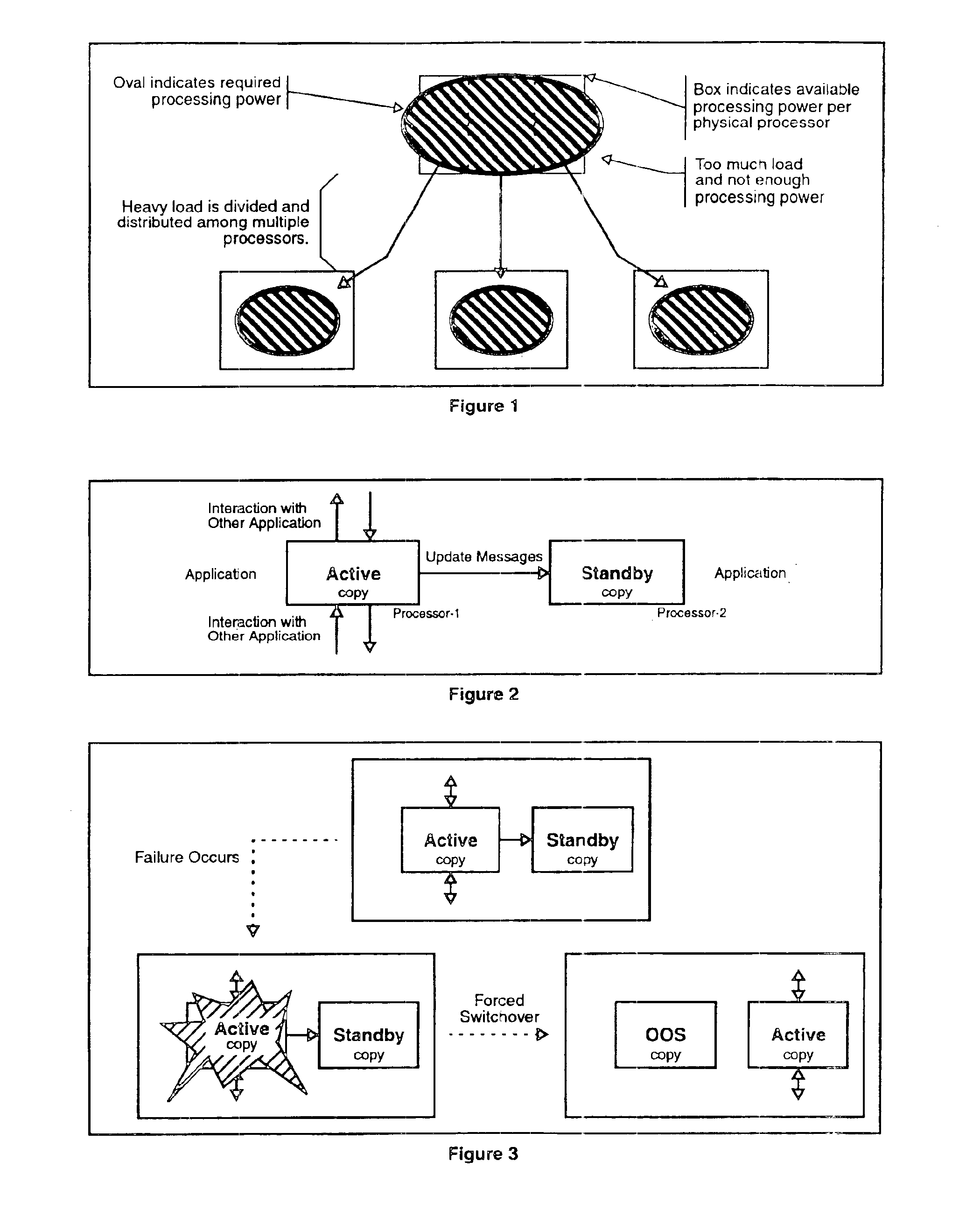
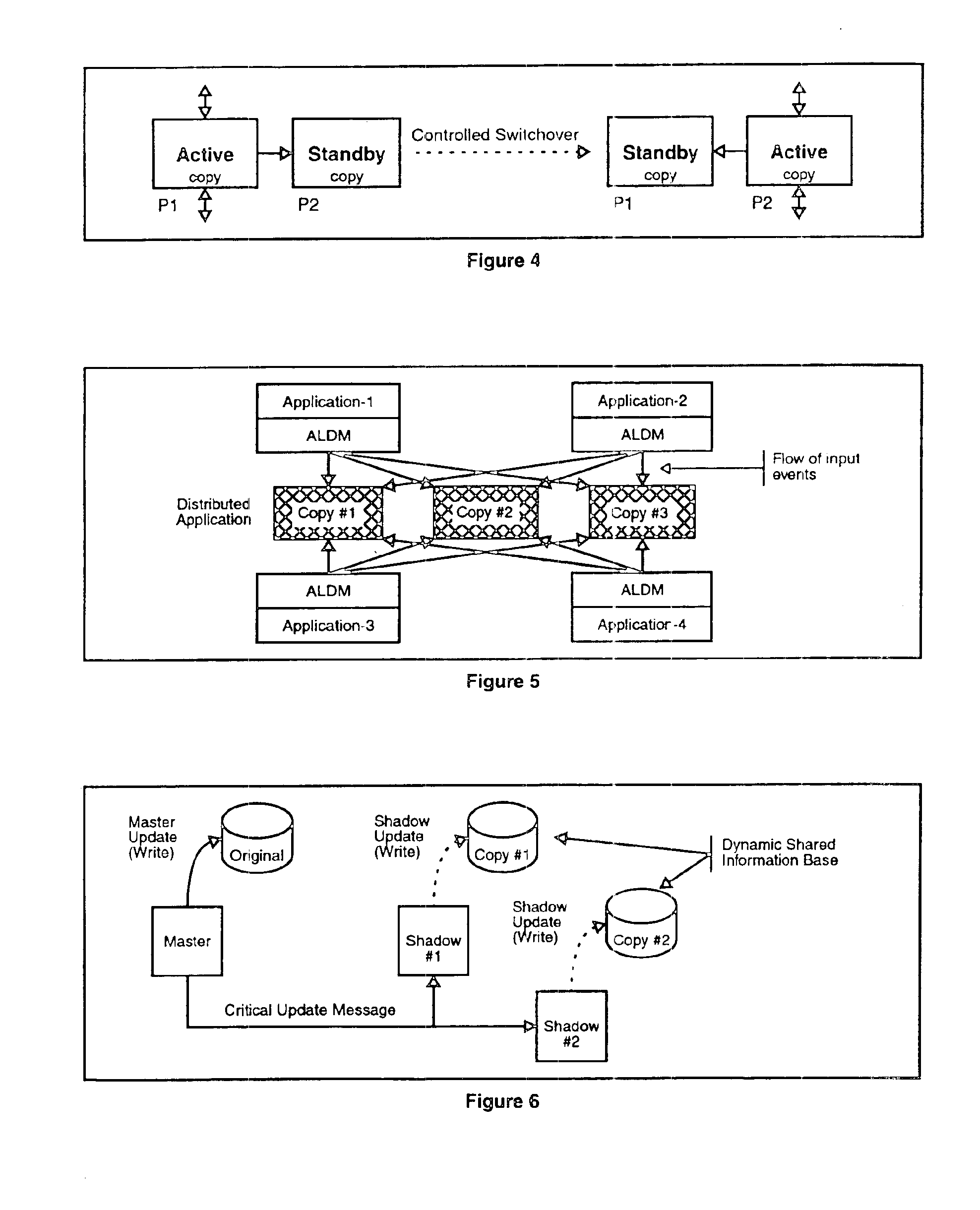
Apparatus and method for building distributed fault-tolerant/high-availability computed applications
InactiveUS6865591B1Multiple failureOptimal hardware utilizationMultiprogramming arrangementsTransmissionOperational systemSystem maintenance
Software architecture for developing distributed fault-tolerant systems independent of the underlying hardware architecture and operating system. Systems built using architecture components are scalable and allow a set of computer applications to operate in fault-tolerant / high-availability mode, distributed processing mode, or many possible combinations of distributed and fault-tolerant modes in the same system without any modification to the architecture components. The software architecture defines system components that are modular and address problems in present systems. The architecture uses a System Controller, which controls system activation, initial load distribution, fault recovery, load redistribution, and system topology, and implements system maintenance procedures. An Application Distributed Fault-Tolerant / High-Availability Support Module (ADSM) enables an applications( ) to operate in various distributed fault-tolerant modes. The System Controller uses ADSM's well-defined API to control the state of the application in these modes. The Router architecture component provides transparent communication between applications during fault recovery and topology changes. An Application Load Distribution Module (ALDM) component distributes incoming external events towards the distributed application. The architecture allows for a Load Manager, which monitors load on various copies of the application and maximizes the hardware usage by providing dynamic load balancing. The architecture also allows for a Fault Manager, which performs fault detection, fault location, and fault isolation, and uses the System Controller's API to initiate fault recovery. These architecture components can be used to achieve a variety of distributed processing high-availability system configurations, which results in a reduction of cost and development time.
Owner:TRILLIUM DIGITAL SYST
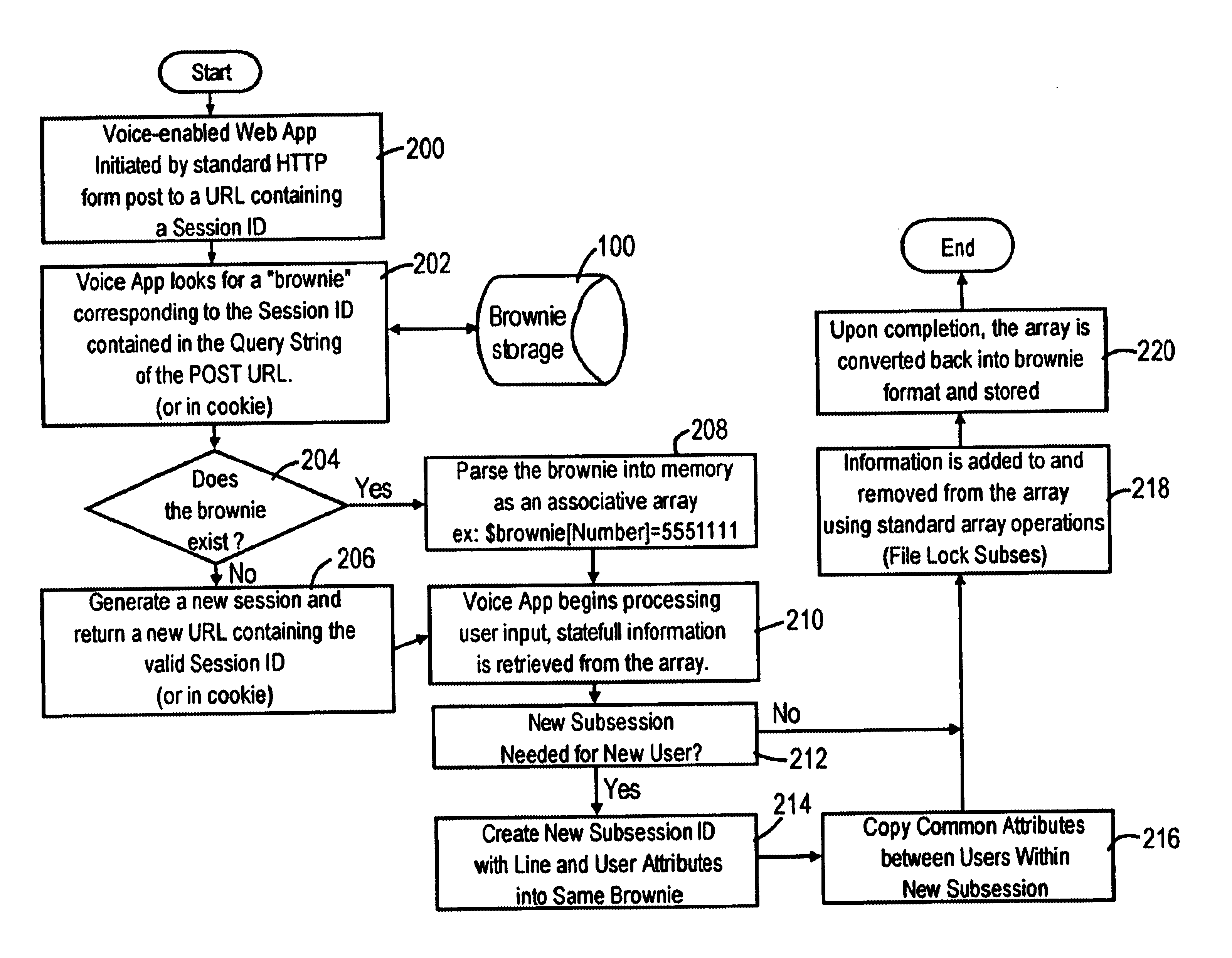
Apparatus and method for providing server state and attribute management for multiple-threaded voice enabled web applications
InactiveUS6883015B1Multiple digital computer combinationsSpeech recognitionSingle sessionWeb application
An application server generates and maintains a server-side data record, also referred to as a “brownie”, that includes application state information and user attribute information for multiple users within a single session controlled by a web-based browser. The brownie includes a session identifier that uniquely identifies the session, and a subsession identifier that uniquely identifies each corresponding user of the application session. As each new user is added to the session, for example by initiating a call to the new user, the application server stores the subsession identifier and corresponding application state information for the new user in the same brownie. In response to receiving a second web page request from the browser that includes the session identifier, the application server initiates a new web application instance, and recovers the brownie from the memory based on the session identifier included in the second page request.
Owner:CISCO TECH INC
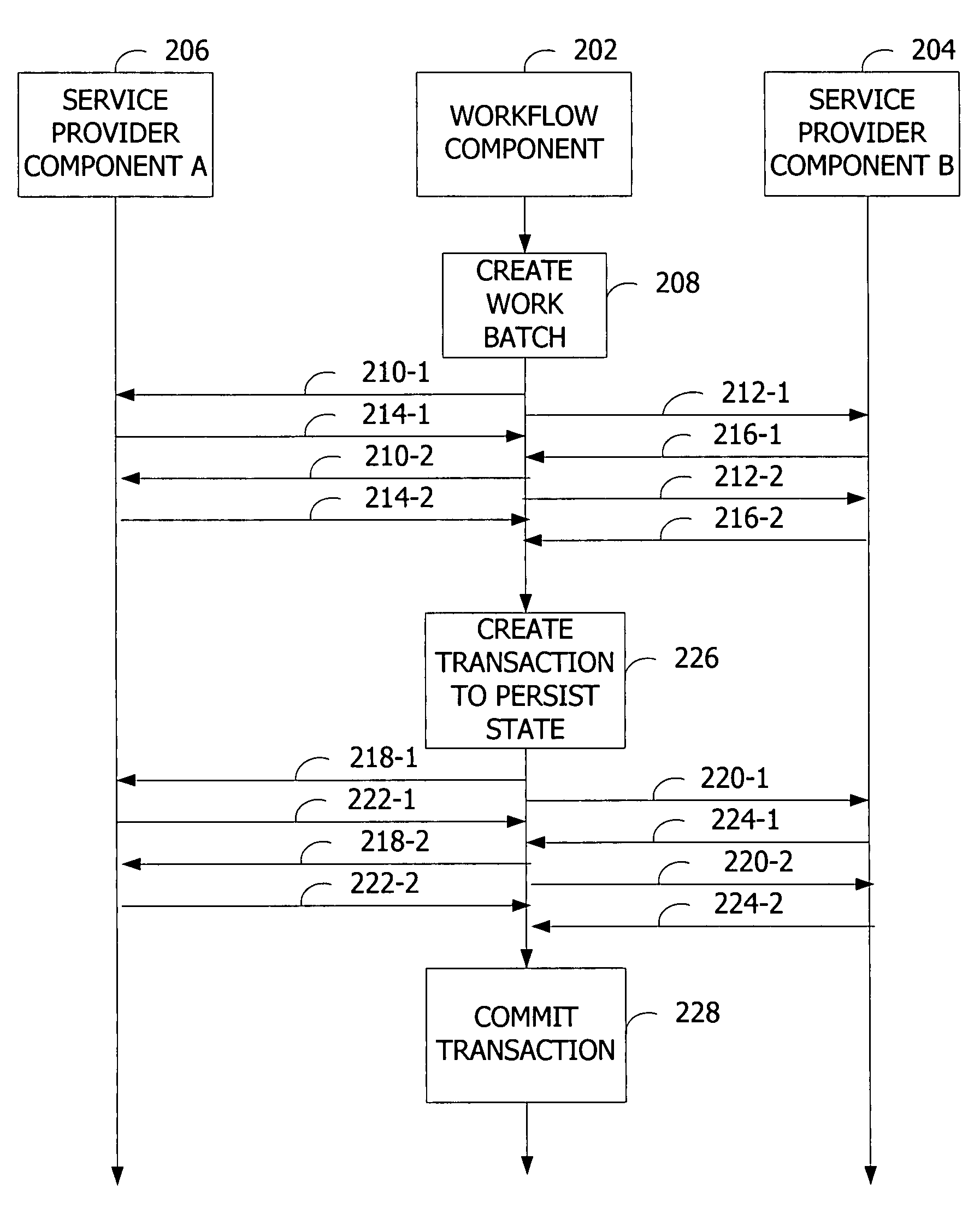
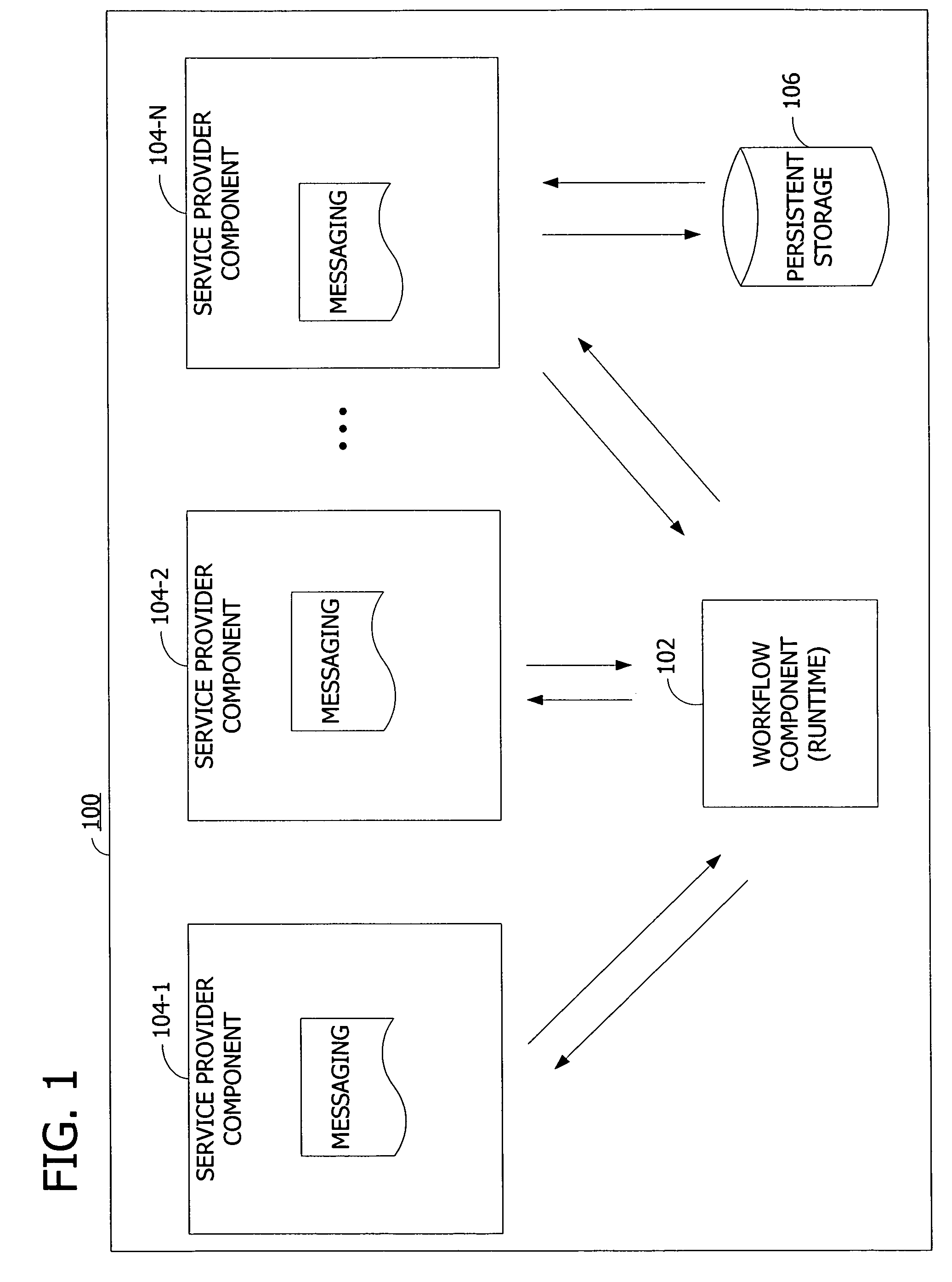
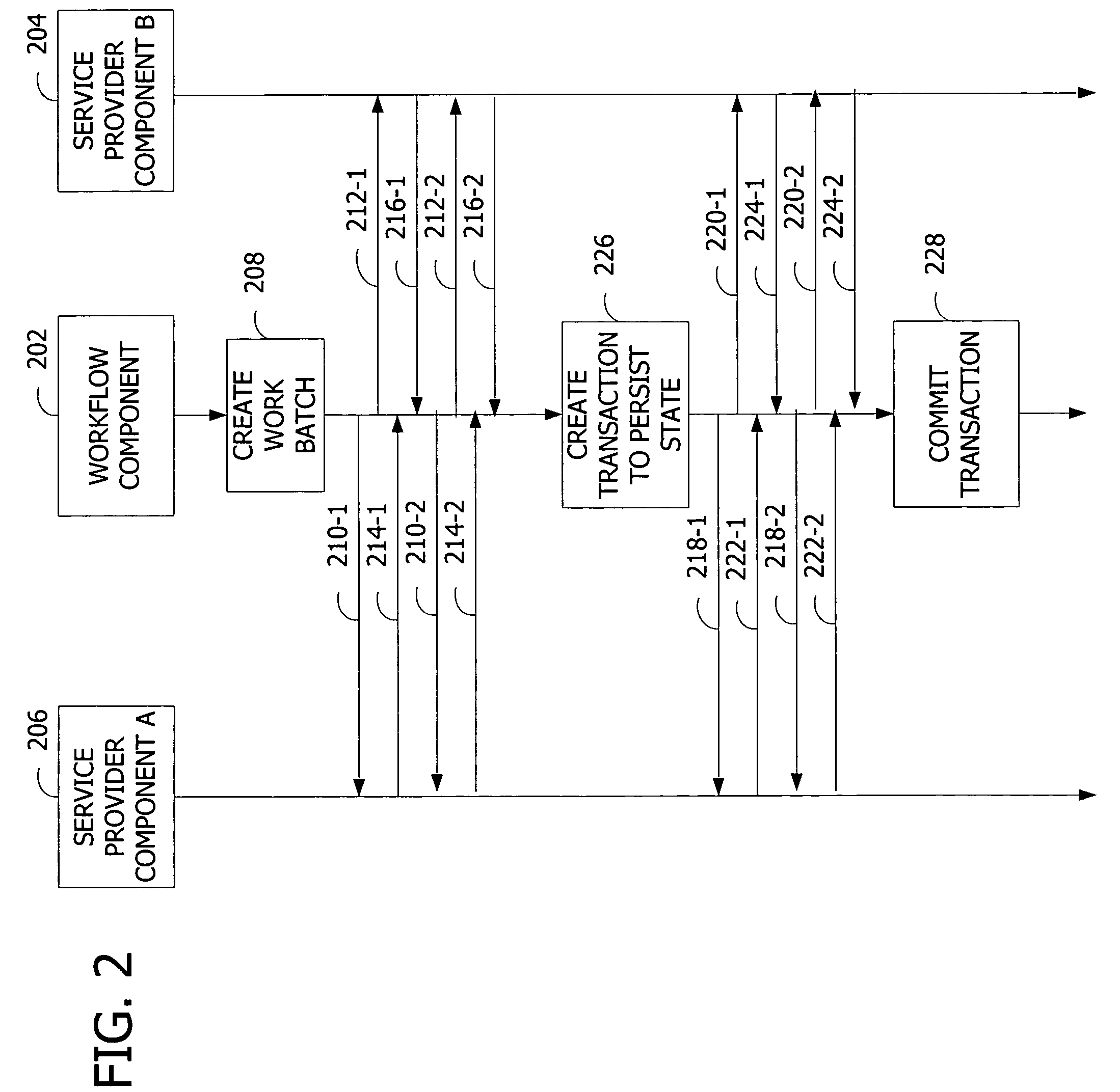
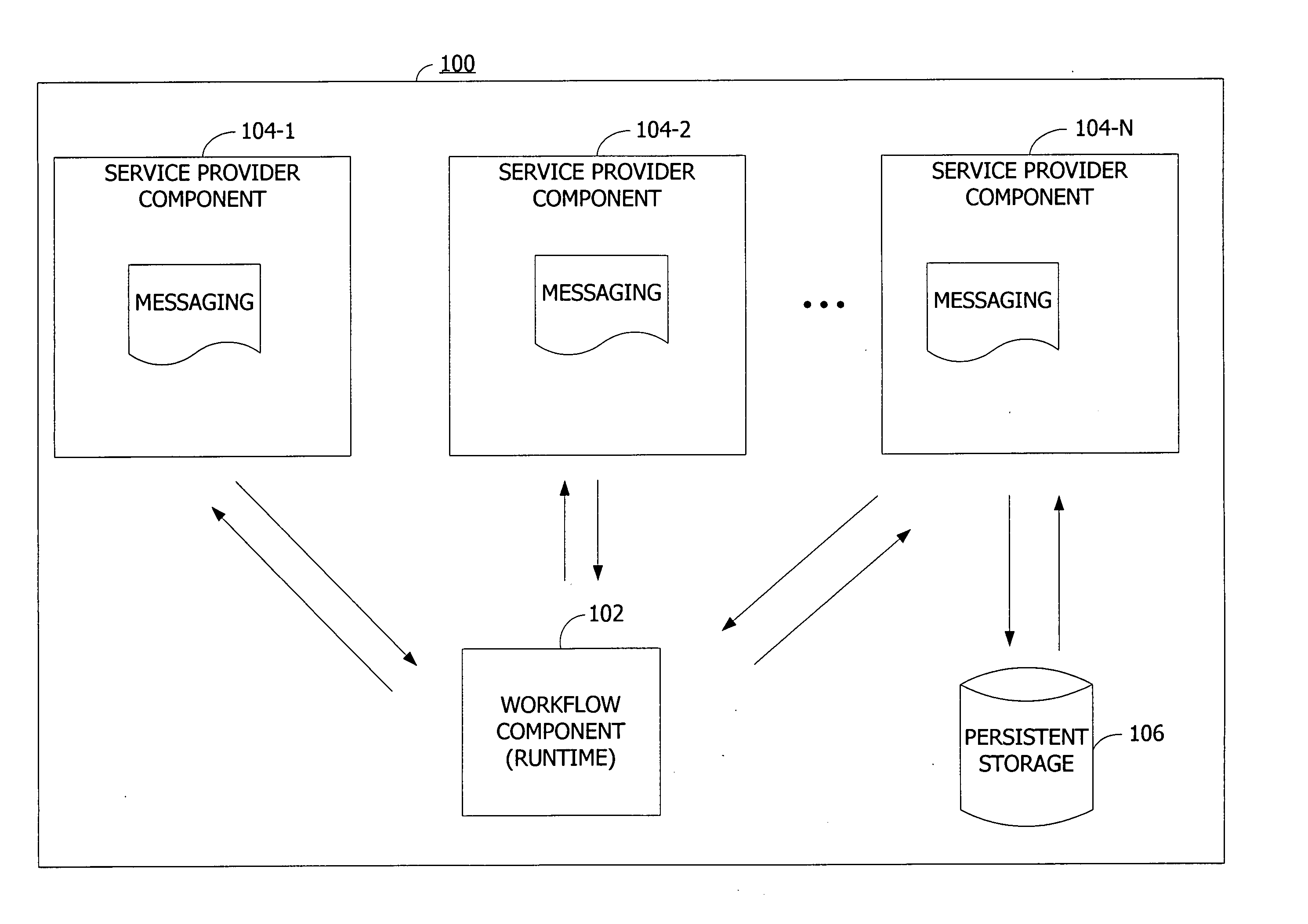
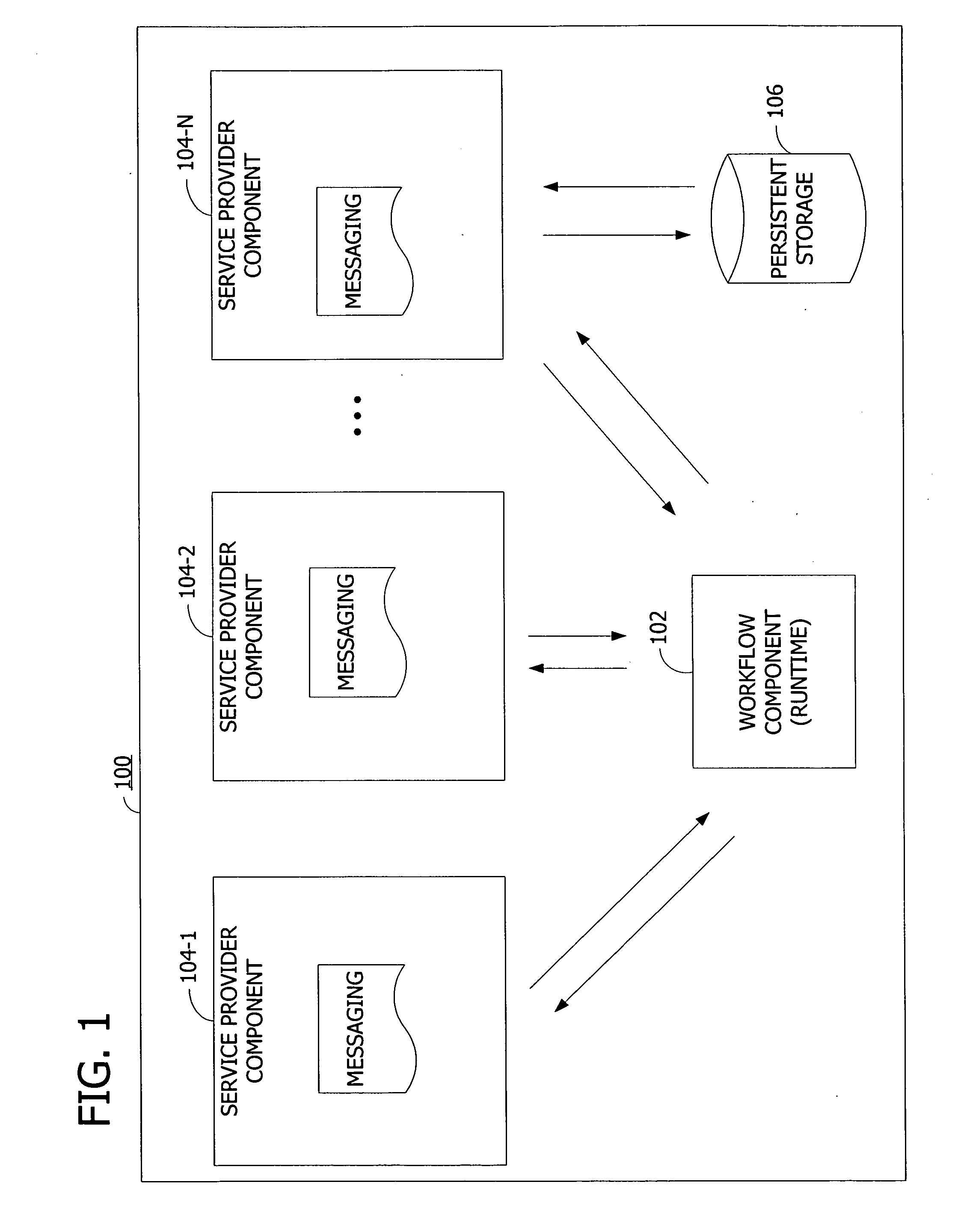
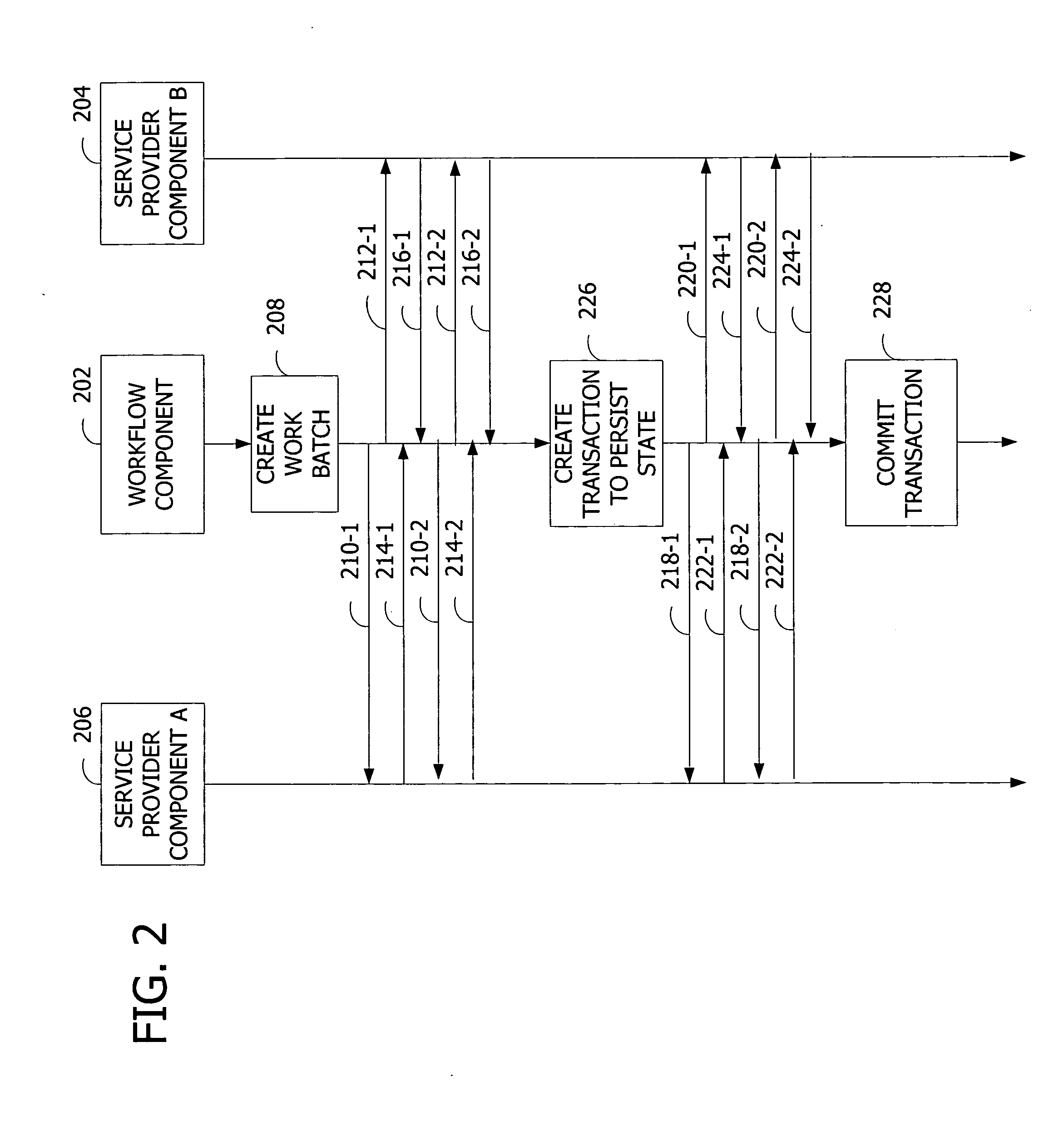
Synchronization of runtime and application state via batching of workflow transactions
ActiveUS7665093B2Easy to shareProgram control using stored programsDigital data processing detailsApplication softwareComputer science
Workflow management for maintaining consistency of persisted state across communicating components via batching of uncommitted work. A workflow component defines a workflow containing work items to be performed by service provider components. The workflow component assigns the work items to the service provider components, and the service provider components acknowledge the assigned work items. The workflow component appends the assigned work items to a work batch. The workflow component creates a transaction containing the batched work items. The workflow component commits to the workflow by requesting the service provider components to perform the work items. The workflow component checks the state of the execution of the work items and stores the state in a persistent storage.
Owner:MICROSOFT TECH LICENSING LLC
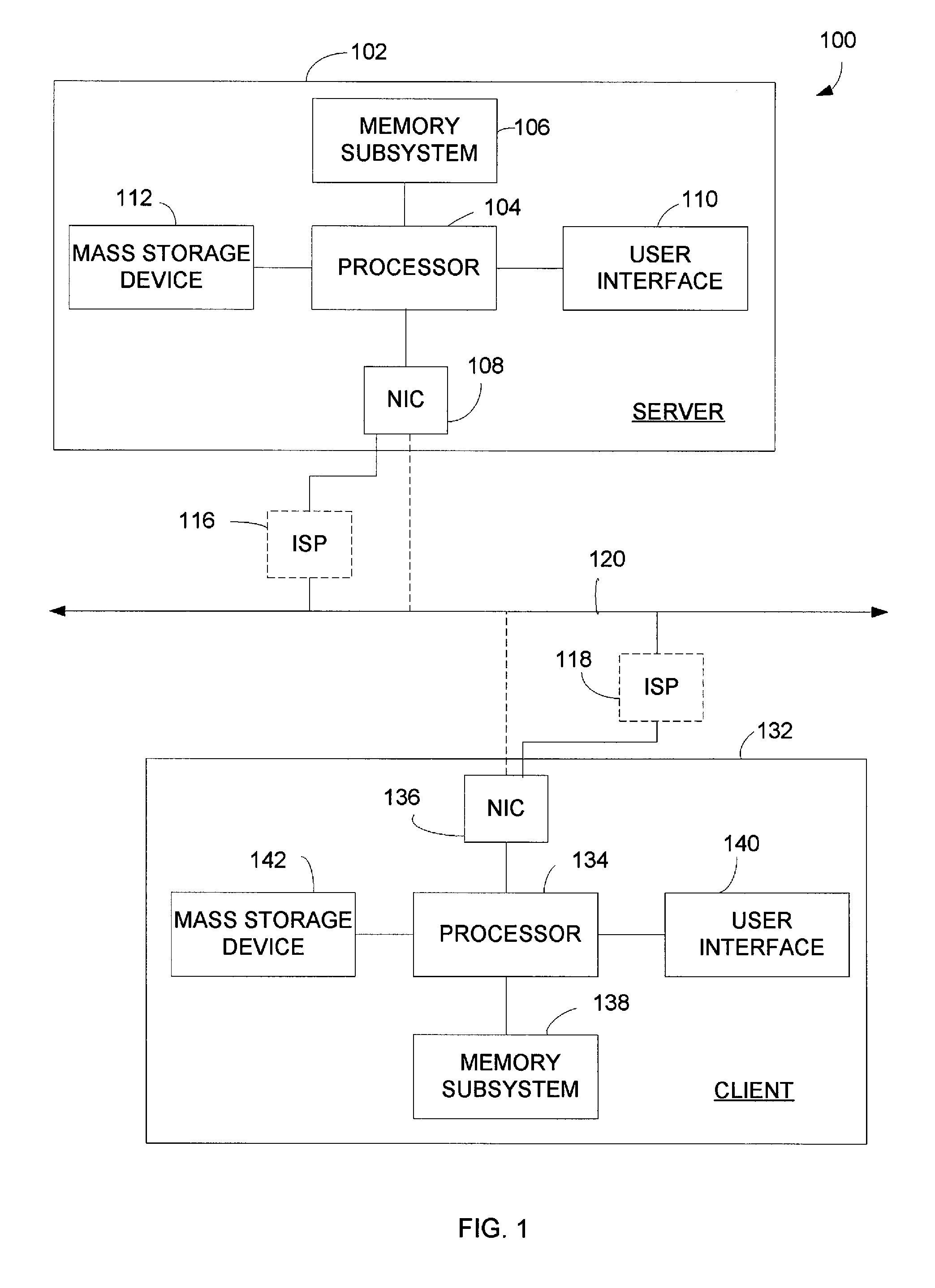
Synchronous and asynchronous collaboration between heterogeneous applications
ActiveUS20050160396A1Specific program execution arrangementsMemory systemsClient-sideDistributed computing
A network-based collaboration system and method can be used to create, modify or otherwise manipulate a design using heterogeneous applications on clients connected to a network. The system and method enables design collaboration between the heterogeneous applications each having a different design abstraction and a different local data model by exchanging application states normalized at a design abstraction level recognized by each of the heterogeneous applications.
Owner:PARAMETRIC TECH CORP
Method and system for real-time event journaling to provide enterprise data services
ActiveUS7565661B2Digital data information retrievalError detection/correctionData connectionData stream
A data management system or “DMS” provides a wide range of data services to data sources associated with a set of application host servers. The data management system typically comprises one or more regions, with each region having one or more clusters. A given cluster has one or more nodes that share storage. To facilitate the data service, a host driver embedded in an application server connects an application and its data to a cluster. The host driver provides a method and apparatus for capturing real-time data modifications and application state notifications and, in response, generating data transactions in the form of an event journal that is provided to the data management system. The driver functions to translate traditional file / database / block I / O into a continuous, application-aware, output data stream. Using the streams generated in this manner, the DMS offers a wide range of data services that include, by way of example only: data protection (and recovery), and disaster recovery (data distribution and data replication).
Owner:QUEST SOFTWARE INC
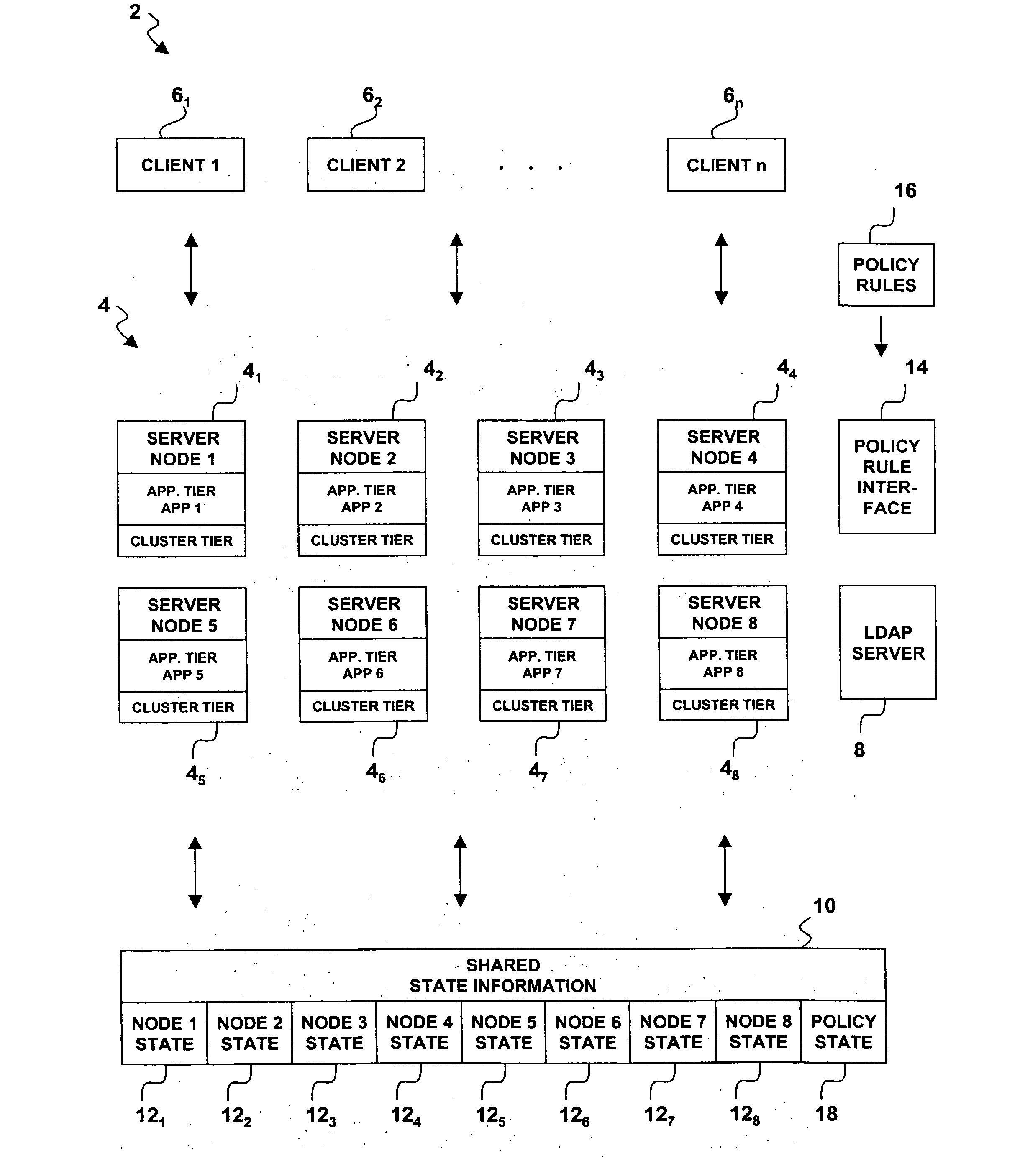
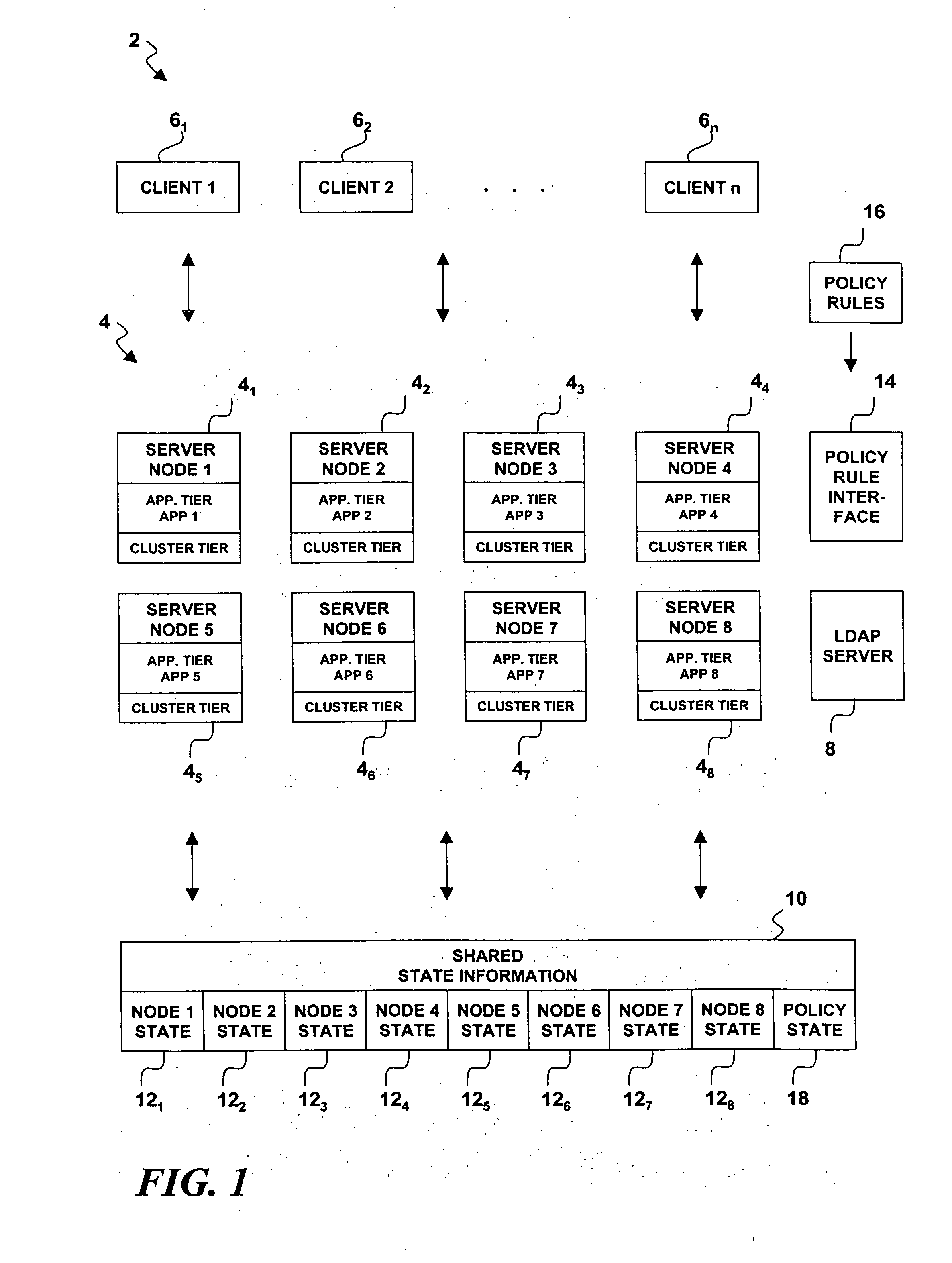
Policy-based, cluster-application-defined quorum with generic support interface for cluster managers in a shared storage environment
A system, method and computer program product for use in a server cluster having plural server nodes implementing a server tier in a client-server computing architecture in order to determine which of two or more partitioned server subgroups has a quorum. A determination is made of relative priorities of the subgroups and a quorum is awarded to the subgroup having a highest relative priority. The relative priorities are determined by policy rules that evaluate comparative server node application state information. The server node application state information may include one or more of client connectivity, application priority, resource connectivity, processing capability, memory availability, and input / output resource availability, etc. The policy rules evaluate the application state information for each subgroup and can assign different weights to different types of application state information. An interface may be provided for receiving policy rules specified by a cluster application.
Owner:LINKEDIN
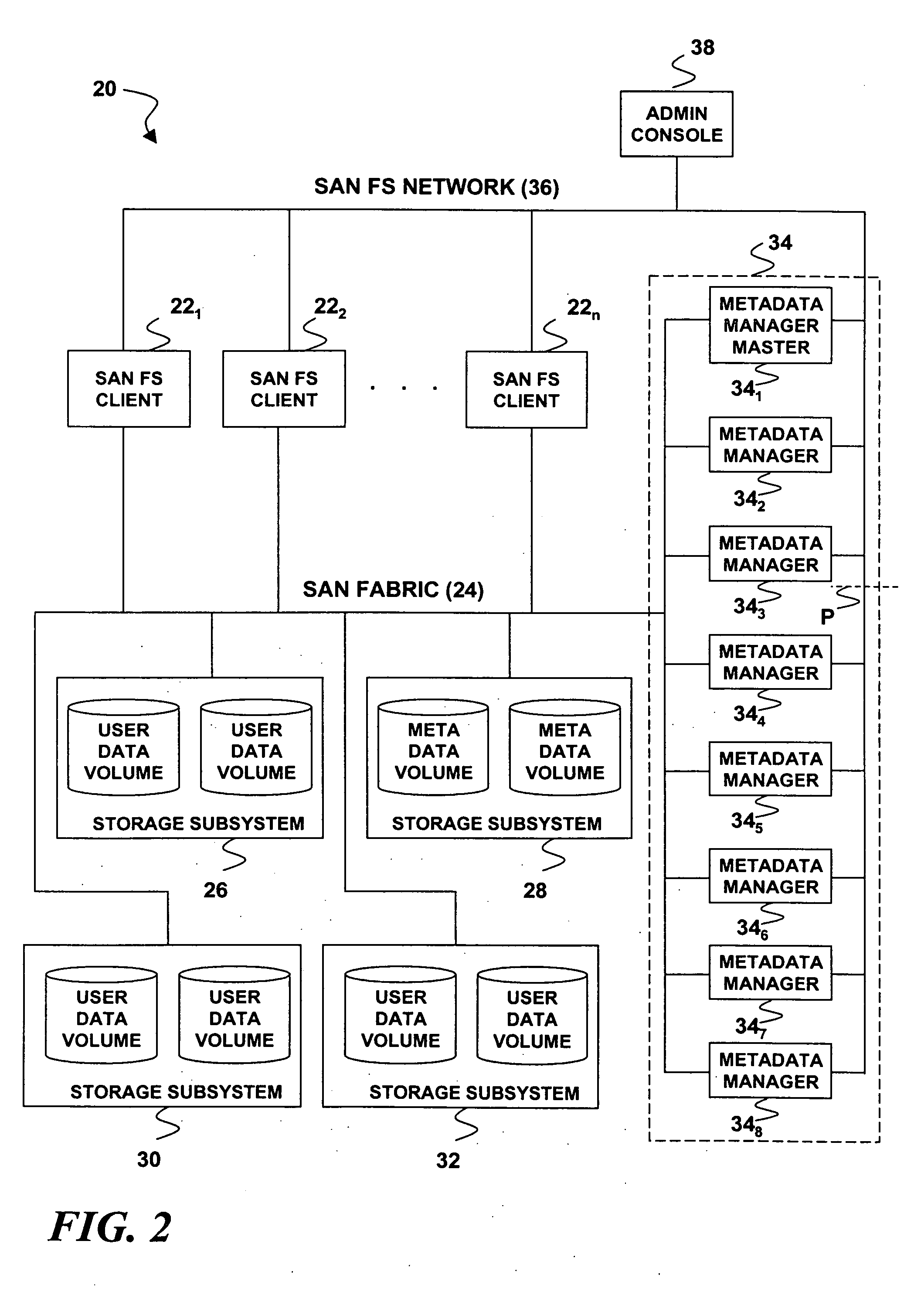
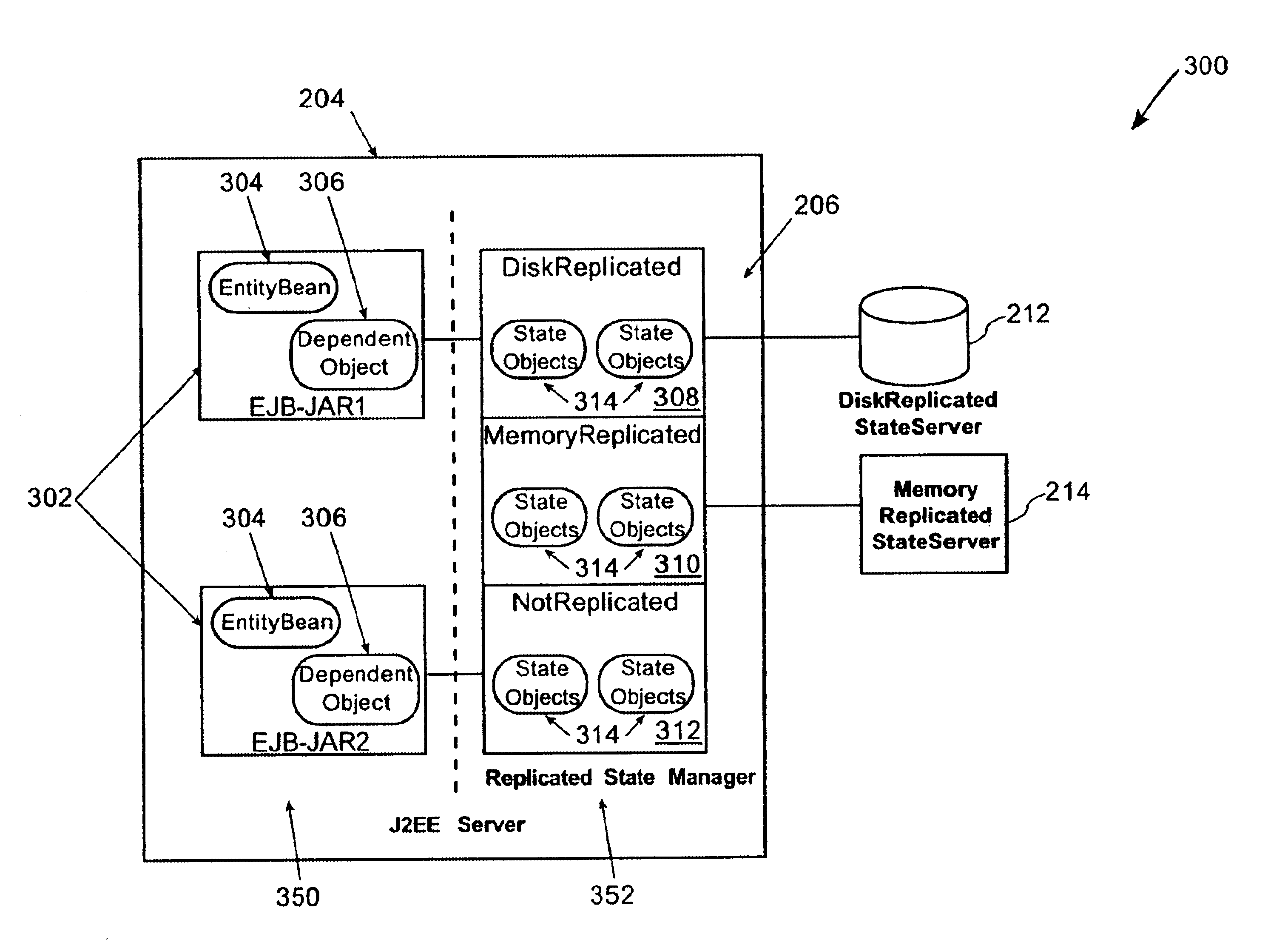
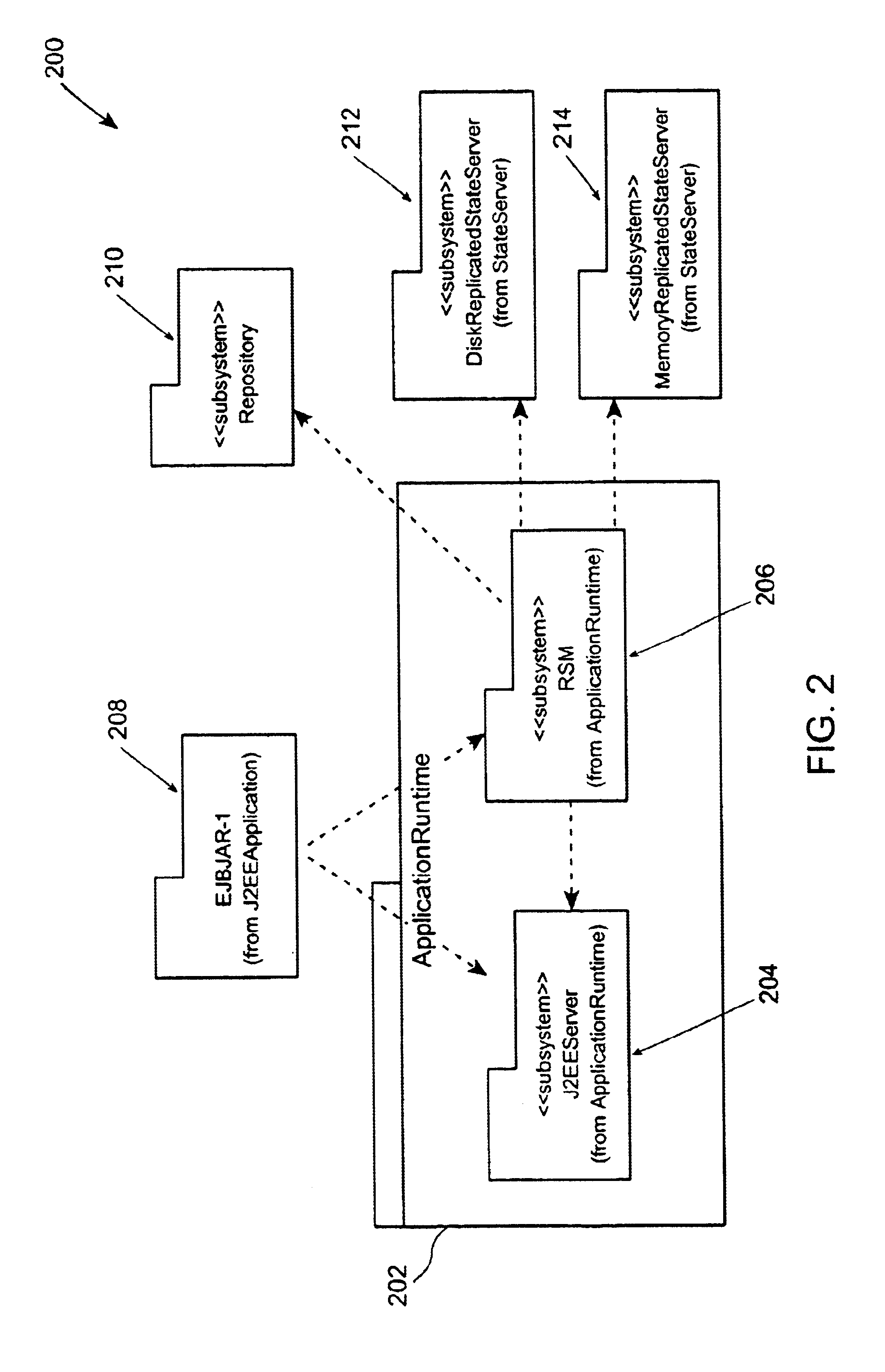
Method and apparatus for managing replicated and migration capable session state for a Java platform
InactiveUS6877111B2Facilitate application state managementError preventionResource allocationProgram instructionEnterprise Java Bean
An invention is disclosed managing the replicated and migration capable state for an enterprise Java bean (EJB) application. The invention includes executing a Java application on a server that includes an entity bean. In addition, a replicated state manager is executed that includes program instructions for managing an in-memory state of the Java application, and program instructions for replicating the in-memory state of the Java application to a replicated state server. The replicated state server can be a memory replicated state server, or a disk replicated state server. To facilitate application state management, embodiments of the present invention store states of the entity beans objects using state objects, which are updated in response to changes in the state of the application. Hence, the embodiments of the present invention define a logical separation between the application and the state objects.
Owner:ORACLE INT CORP
Systems and methods for application-state distributed replication table hunting
ActiveUS20140304231A1Digital data processing detailsDatabase distribution/replicationHash tableDistributed computing
The present application is directed towards systems and methods of hunting for a hash table entry in a hash table distributed over a multi-node system. More specifically, when entries are created in an ASDR table, the owner node of the entry may replicate the entry onto a non-owner node. The replica can act as a backup of the ASDR table entry in the event the node leaves the multi-mode system. When the node returns to the multi-node system, the node may no longer have the most up to date ASDR table entries, and may hunt to find the existence of the value associated with the entry. Responsive to receiving a request for an entry that may be outdated on the node, the node sends a request down a replication chain for an updated copy of the ASDR table entry from one of the replicas. Responsive to receiving the replica copy of the entry, the node responds to the client's request for the entry.
Owner:CITRIX SYST INC
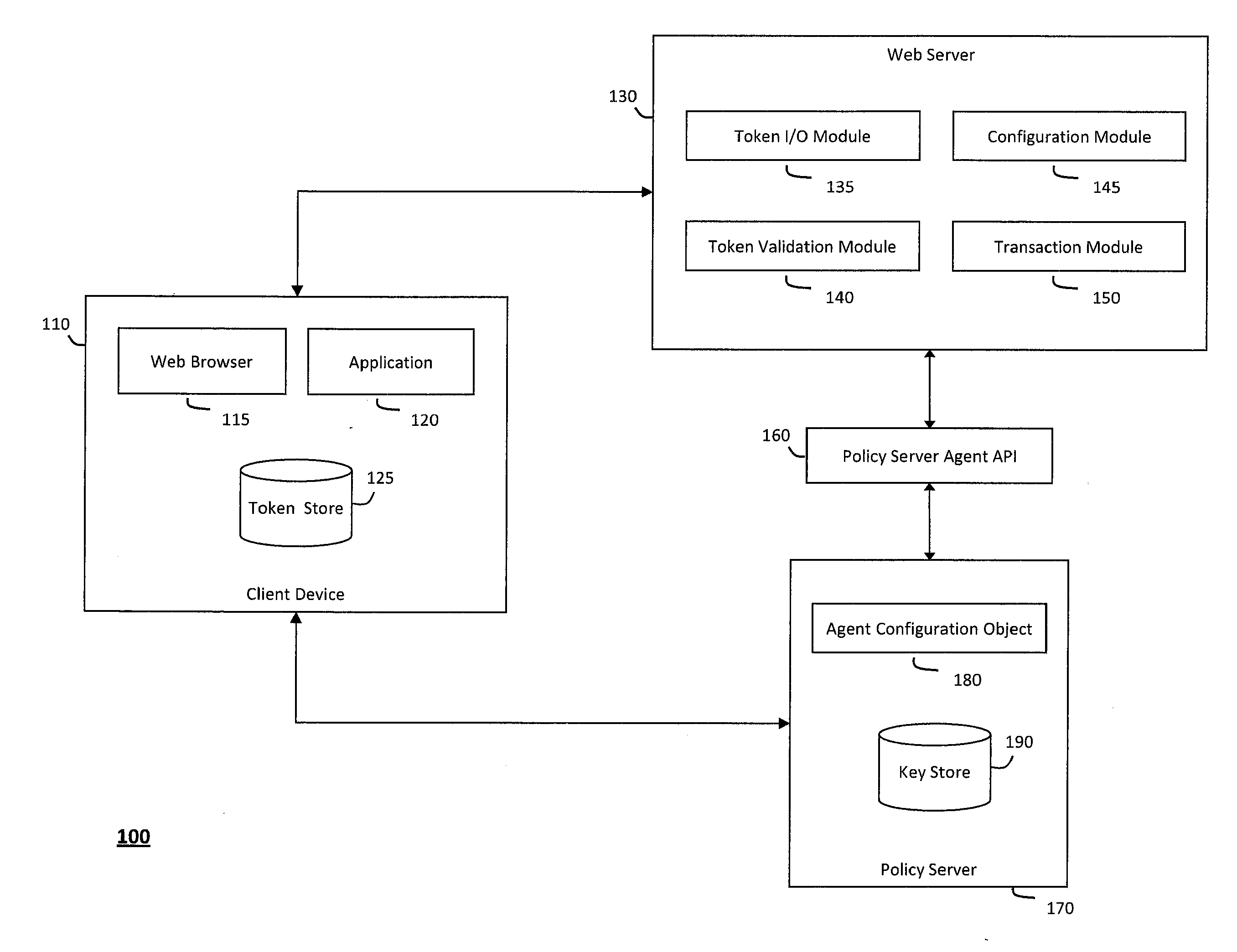
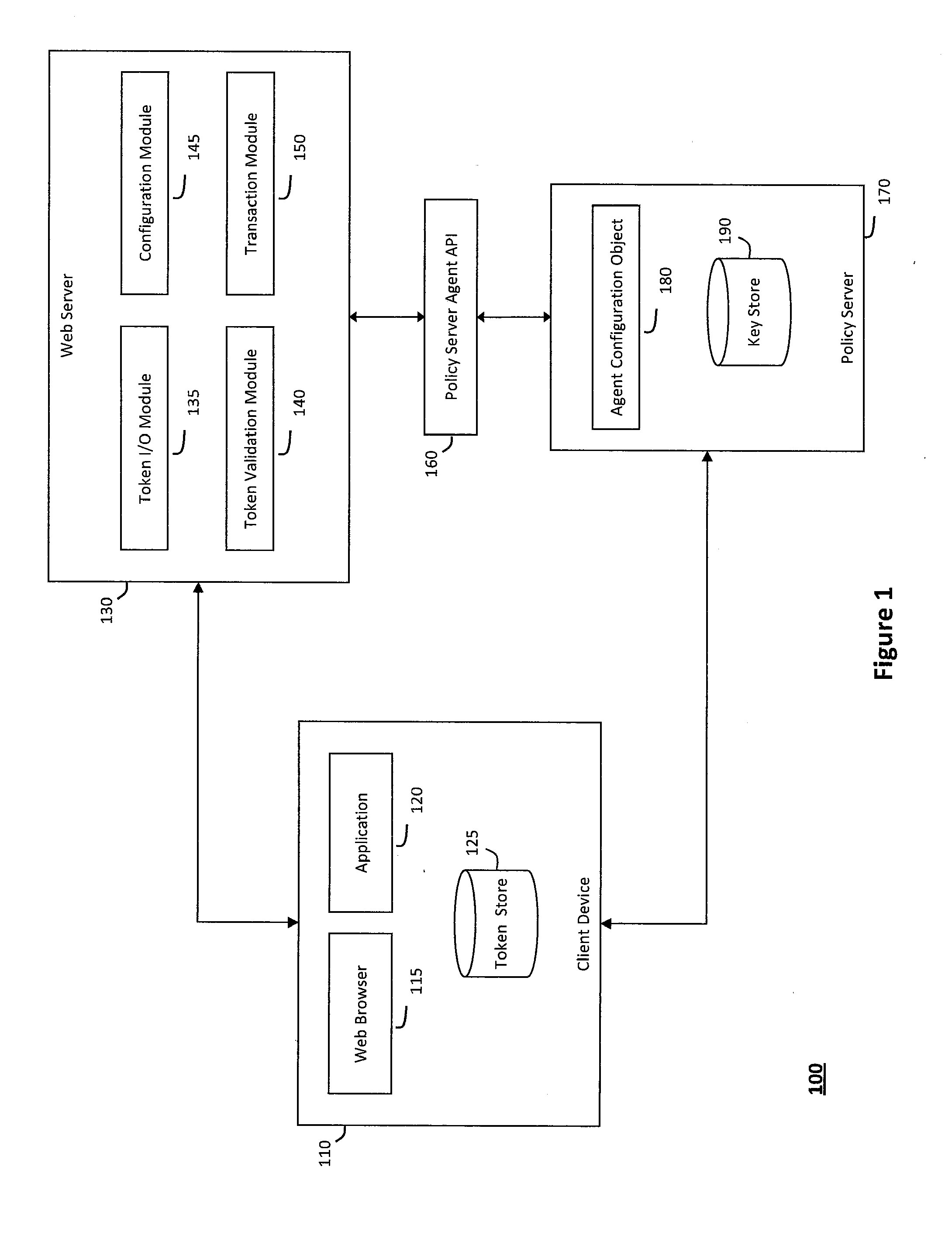
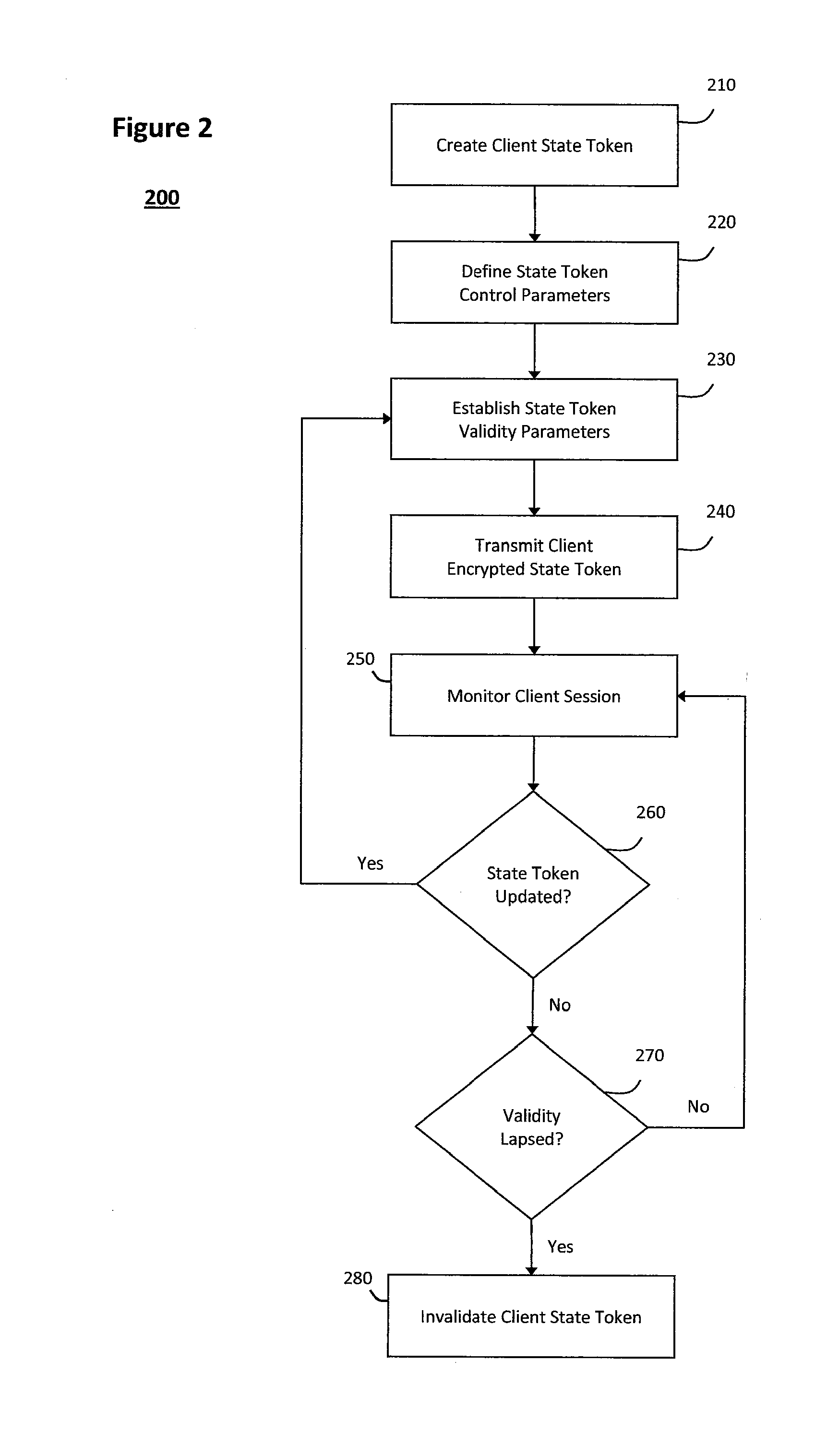
System and method for controlling state tokens
ActiveUS20120110318A1Digital data processing detailsUser identity/authority verificationSemanticsApplication software
The system and method for controlling state tokens described herein may secure sensitive application state tokens, link one application state token to other state tokens that represent certain identities or communication sessions, and maintain application state tokens to integrate various different systems or applications. In particular, the system and method described herein may provide a mechanism to override scheme that applications use to manage state information and thereby enforce policies that provide fine-grained control over any semantics the applications otherwise use to manage state information. Furthermore, a first application state token may be linked to another state token representing a session or identity to validate whether the session or identity represented therein created the first application state token, and state tokens that represent active communication sessions may be copied from browser processes to various external clients to integrate or otherwise share state information across the various external clients.
Owner:CA TECH INC
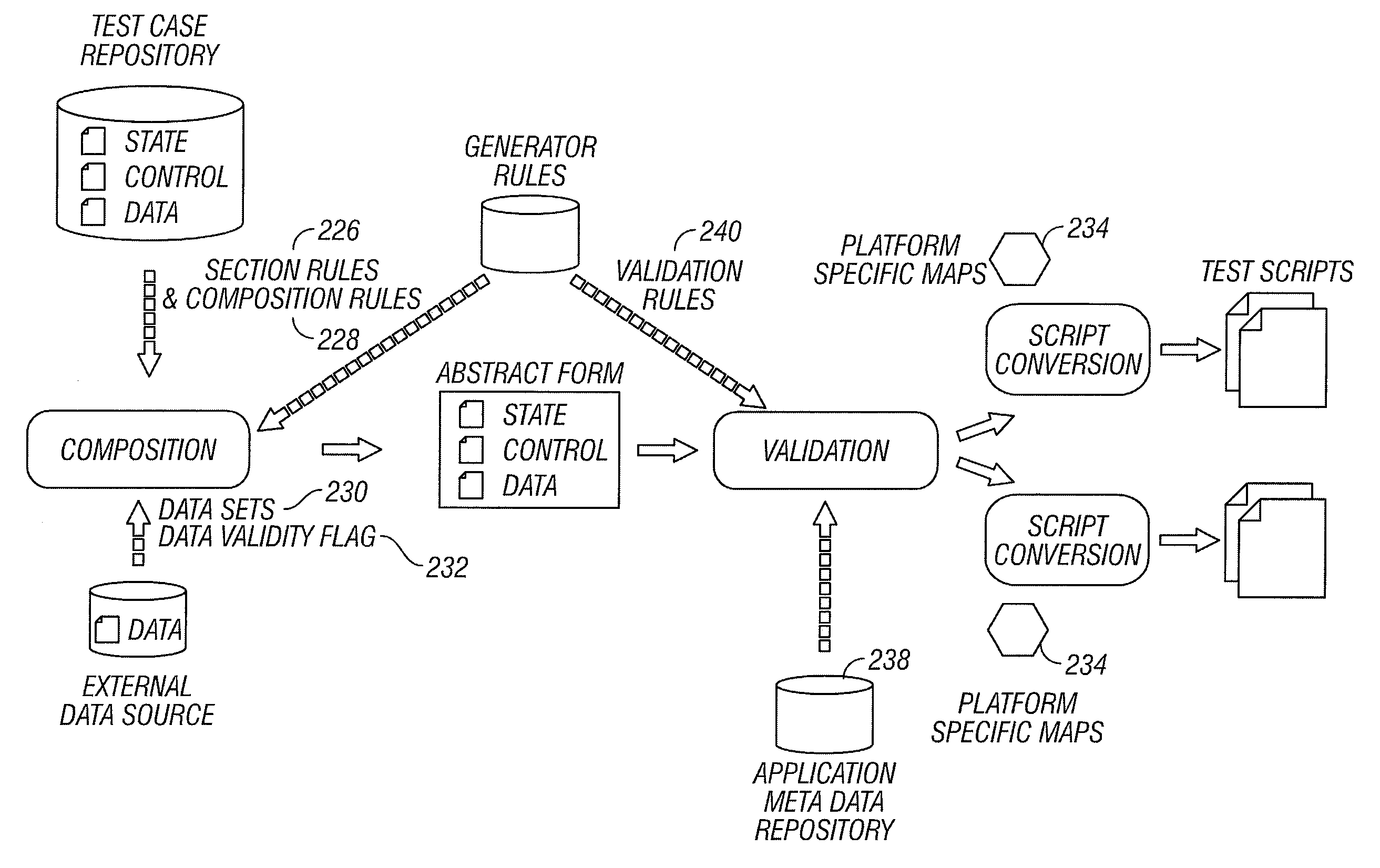
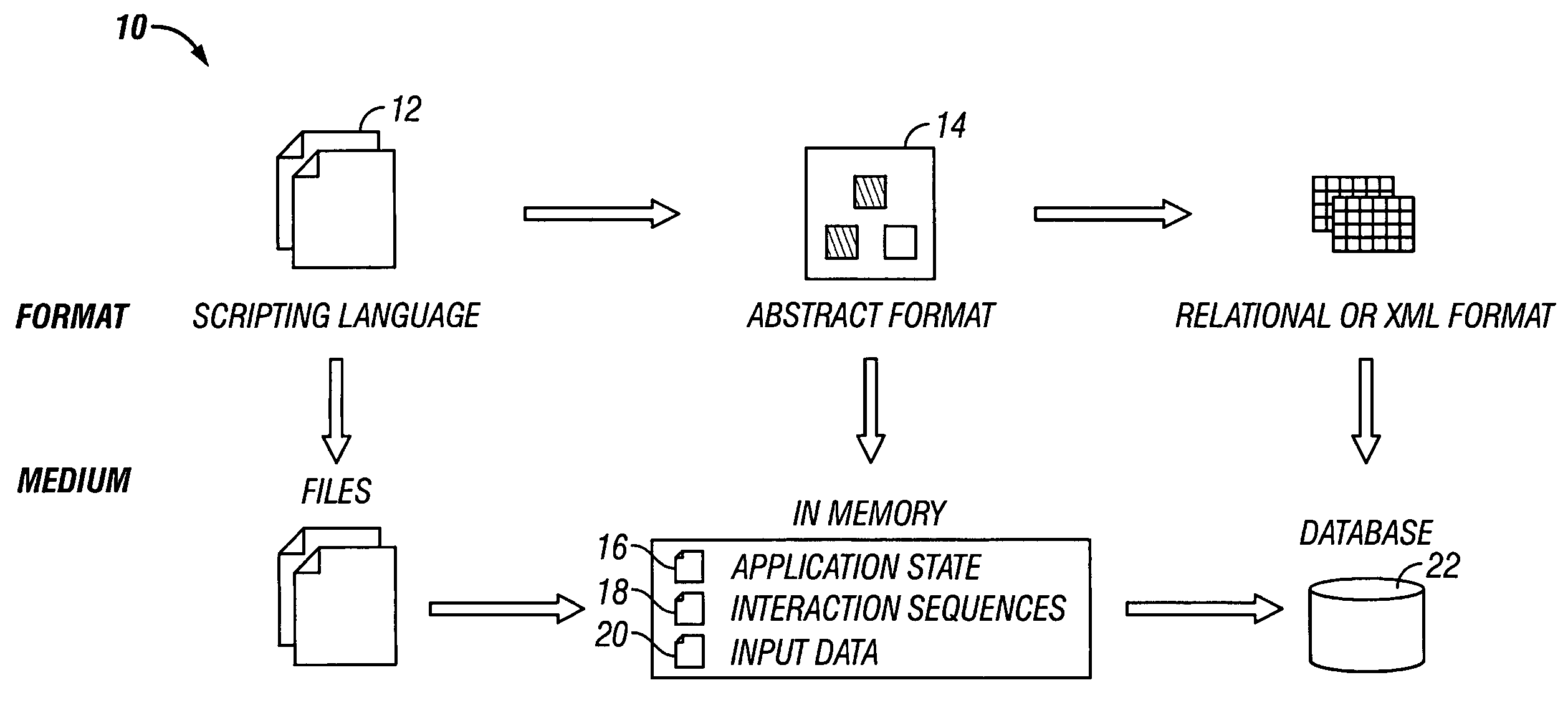
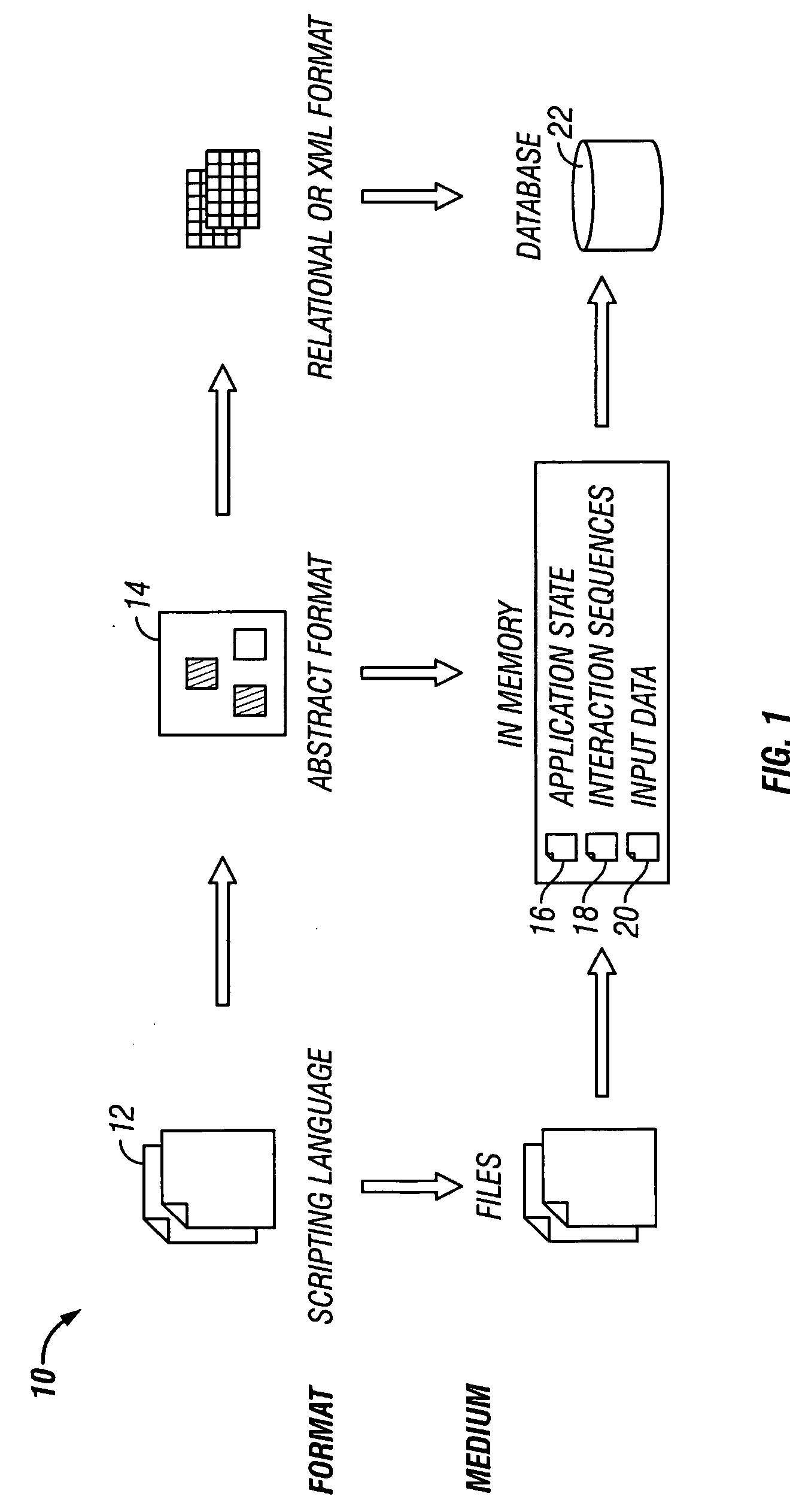
Method and system for rule-based generation of automation test scripts from abstract test case representation
A general rule-based technique is provided for generating a test case from an abstract internal test case representation. The abstract internal test case representation is based on a test case representation model that includes application states (state information), external interaction sequences (control flow information) and input data. The abstract representation in essence provides a platform independent representation of test cases. An application object model provides the representational capabilities required for capturing structural and behavioral properties of the application under test. Rules can be specified to define which application states (state information), external interaction sequences (control information) and input data sets should be used in the generation of the test case. A technique based on platform mapping is provided to convert a test case into an automation test script for any specific test script execution environment for any specific application platform.
Owner:SILICON VALLEY BANK
Database computer system using logical logging to extend recovery
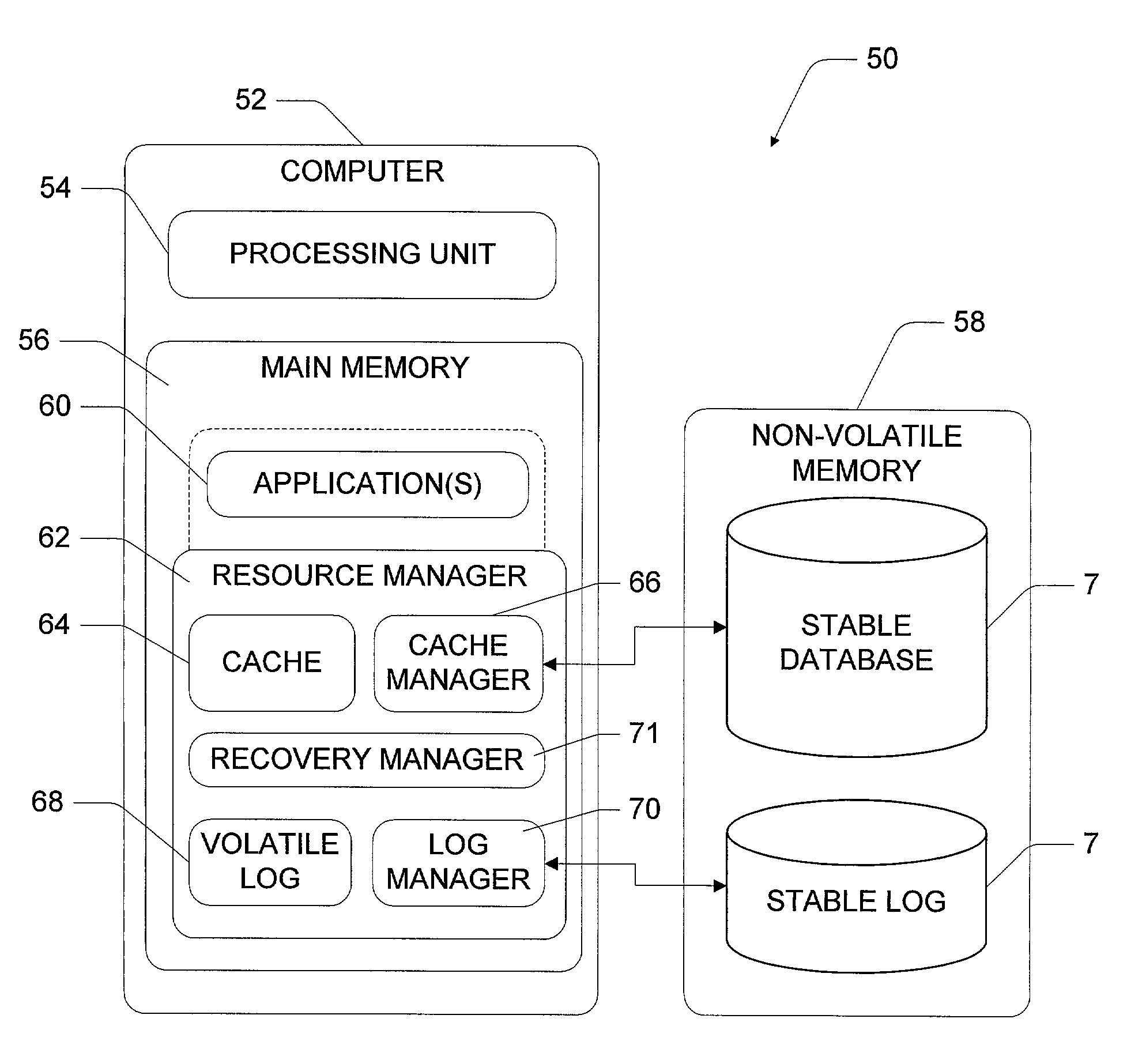
InactiveUS6978279B1Reduce data volumeData processing applicationsError detection/correctionCheck pointDatabase machine
This invention concerns a database computer system and method for making applications recoverable from system crashes. The application state (i.e., address space) is treated as a single object which can be atomically flushed in a manner akin to flushing individual pages in database recovery techniques. To enable this monolithic treatment of the application, executions performed by the application are mapped to logical loggable operations that can be posted to the stable log. Any modifications to the application state are accumulated and the application state is periodically flushed to stable storage using an atomic procedure. The application recovery integrates with database recovery, and effectively eliminates or at least substantially reduces the need for check pointing applications. In addition, optimization techniques are described to make the read, write, and recovery phases more efficient. Atomic flush sets, whether generated from cyclic flush dependencies or otherwise, can be broken apart. This enables an ordered flushing sequence of first flushing a first object and then flushing a second object, rather than having to flush both the first and second objects simultaneously and atomically.
Owner:MICROSOFT TECH LICENSING LLC +1
Method for providing guaranteed distributed failure notification
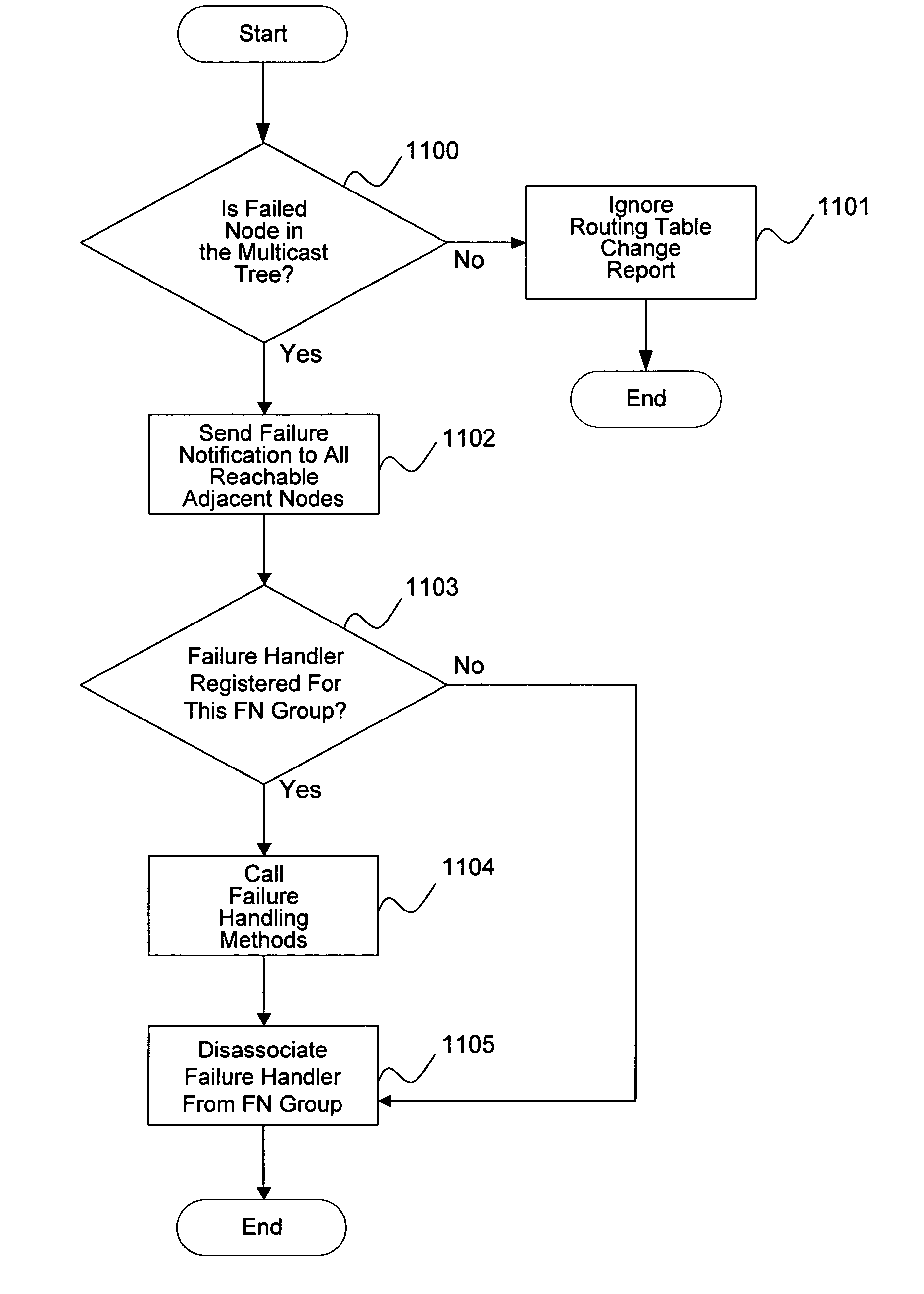
InactiveUS20050083834A1Reliability failureAccurate associationSpecial service provision for substationError preventionSystem failureComputer science
A guaranteed distributed failure notification method is described, wherein a failure notification (FN) facility allows applications using the facility to create FN groups to which the application associates an application state. The application registers failure handlers with the FN facility on nodes in the FN group; each failure handler is associated with a specific FN group. When, on a given node, the FN facility learns of a failure in the FN group, the facility executes the associated failure handler on that node. System failures detected by the application are signaled to other FN group members using the facility. The facility detects system failures that occur in an overlay network on which the facility is implemented, and signals a failure notification to the other FN group members.
Owner:MICROSOFT TECH LICENSING LLC
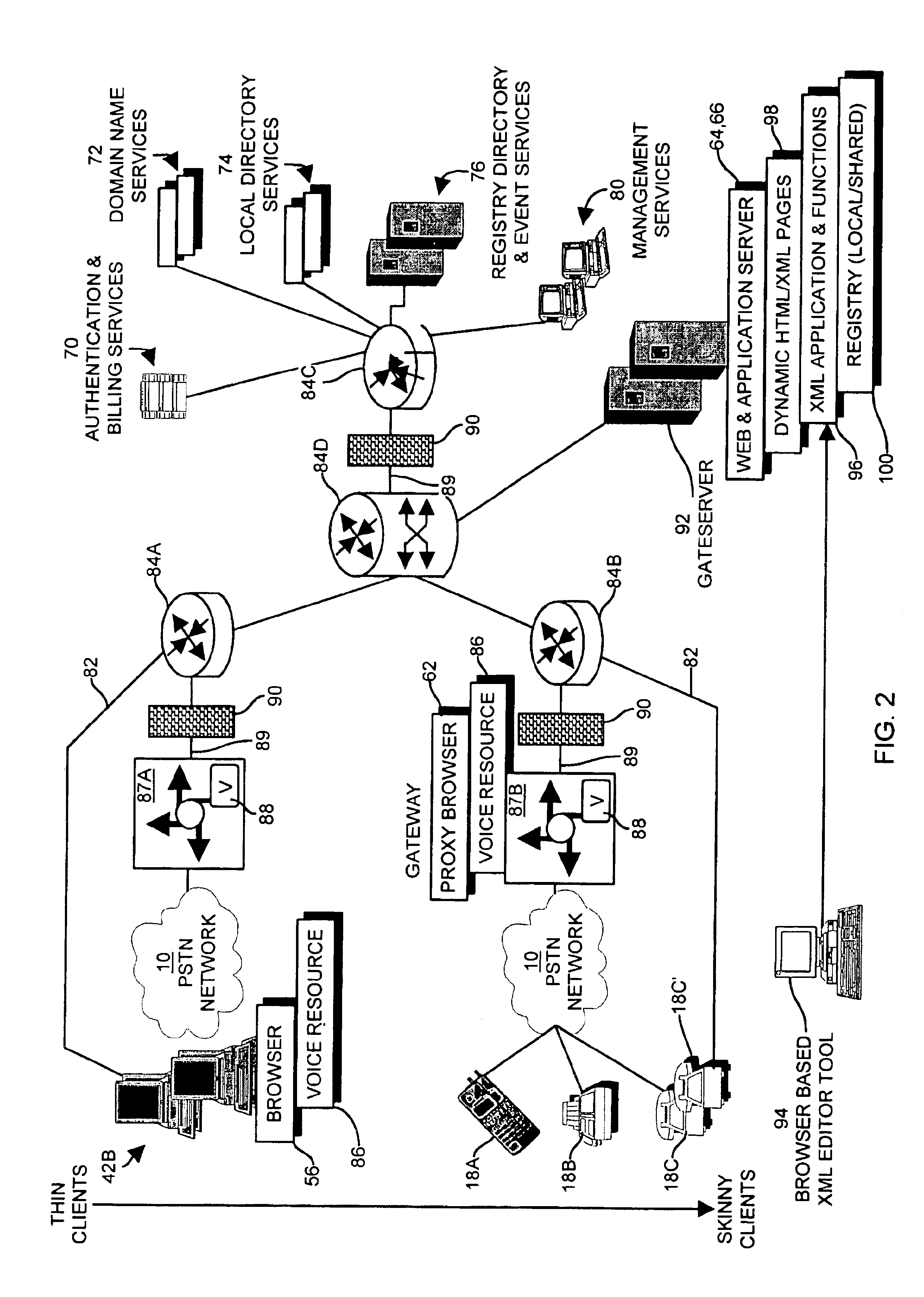
Apparatus and methods for providing an event driven notification over a network to a telephony device
InactiveUS6907455B1Multiple digital computer combinationsTransmissionWeb applicationApplication software
The invention is directed to techniques for notifying a client device of the occurrence of an event using a web application activated based on an application-state data record. A persistent process monitors incoming data for the occurrence of an event and provides the application-state data record that can be used to activate a session of an event notification application. The persistent process provides an event indicator to a proxy browser which then activates the event notification application. The event notification application provides an event notification to the proxy browser, which in turn provides an audio notification of the event to the client device, which may be a telephony device or other two-way audio communication device. The user of the client device can then respond to the event notification or otherwise interact with the event notification application via the proxy browser.
Owner:CISCO TECH INC
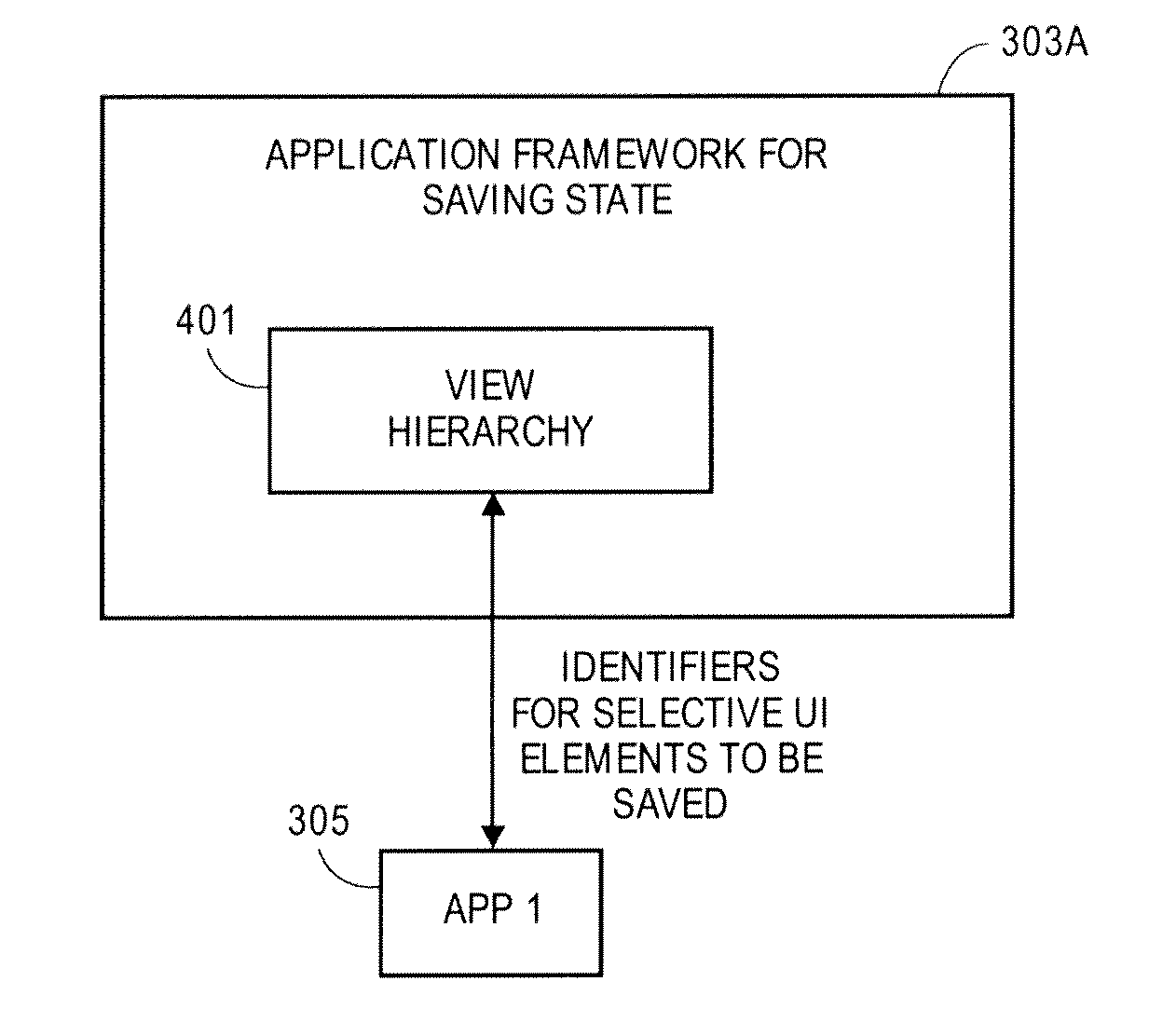
Extensible application state preservation architecture
ActiveUS20130332846A1Input/output for user-computer interactionError detection/correctionUser interfaceComputer engineering
The preservation of the user interface state of first application on a first device allows, in one embodiment, a user to resume use of at least a portion of the user interface state on a second application on second devices. The first and second applications can be the same or different (with some common user interface UI features or elements and other UI features that are different). Other embodiments are also described.
Owner:APPLE INC
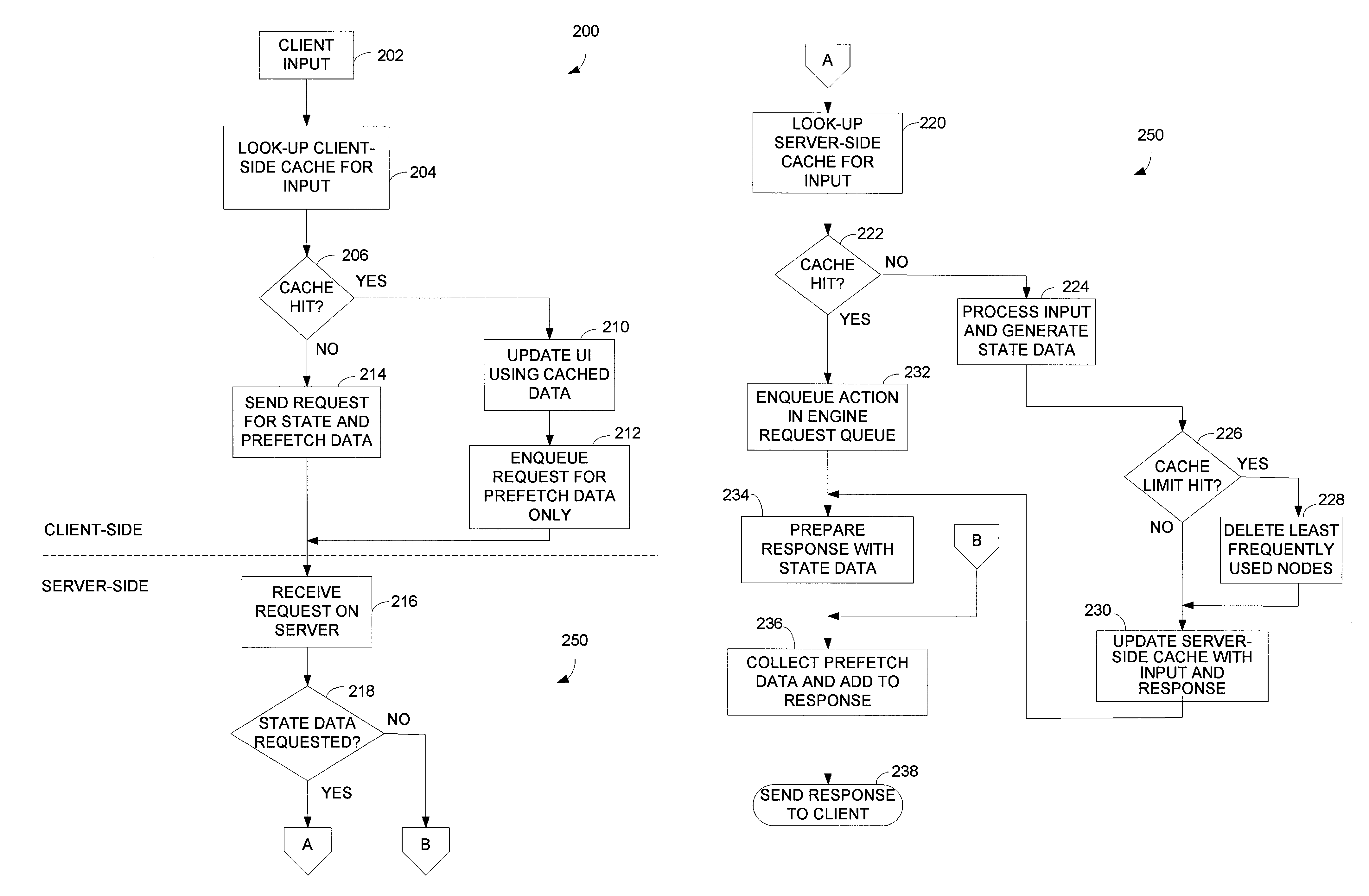
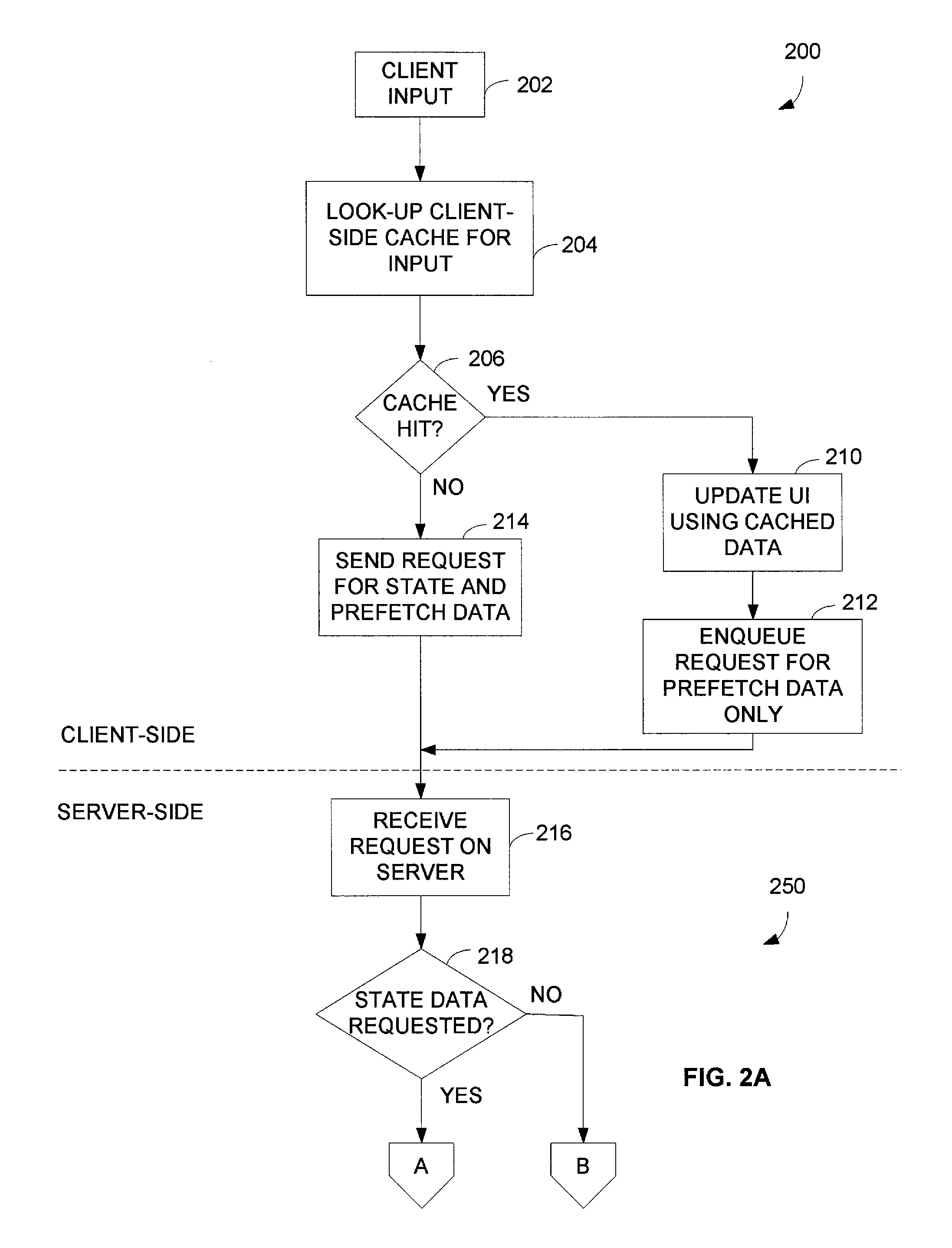
Application state server-side cache for a state-based client-server application
ActiveUS8019811B1Reduce delaysAvoid delayMultiple digital computer combinationsProgram controlResponse delayClient-side
Response delay associated with a state-based client-server application can be reduced with utilization of an application state server-side cache. A server caches data for a set of one or more possible states of a client-server application that may follow a current state of the application. The server rapidly responds to a client request with data that corresponds to an appropriate new state of the application in accordance with the application state server-side cache. The server determines that the application will transition to the appropriate new state from the current state of the application with the application state server-side cache based, at least in part, on an operation indicated by the client request.
Owner:VERSATA DEV GROUP
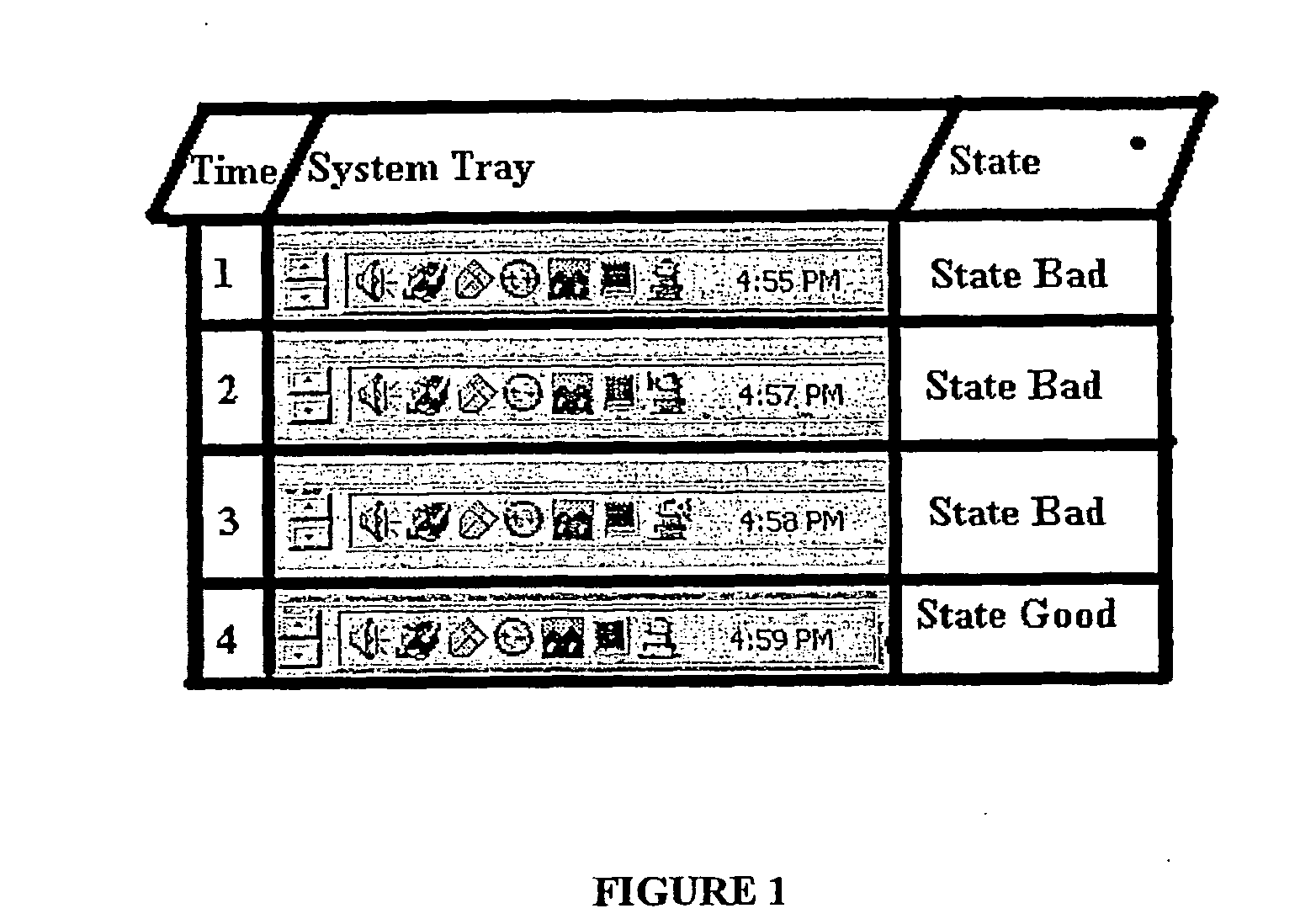
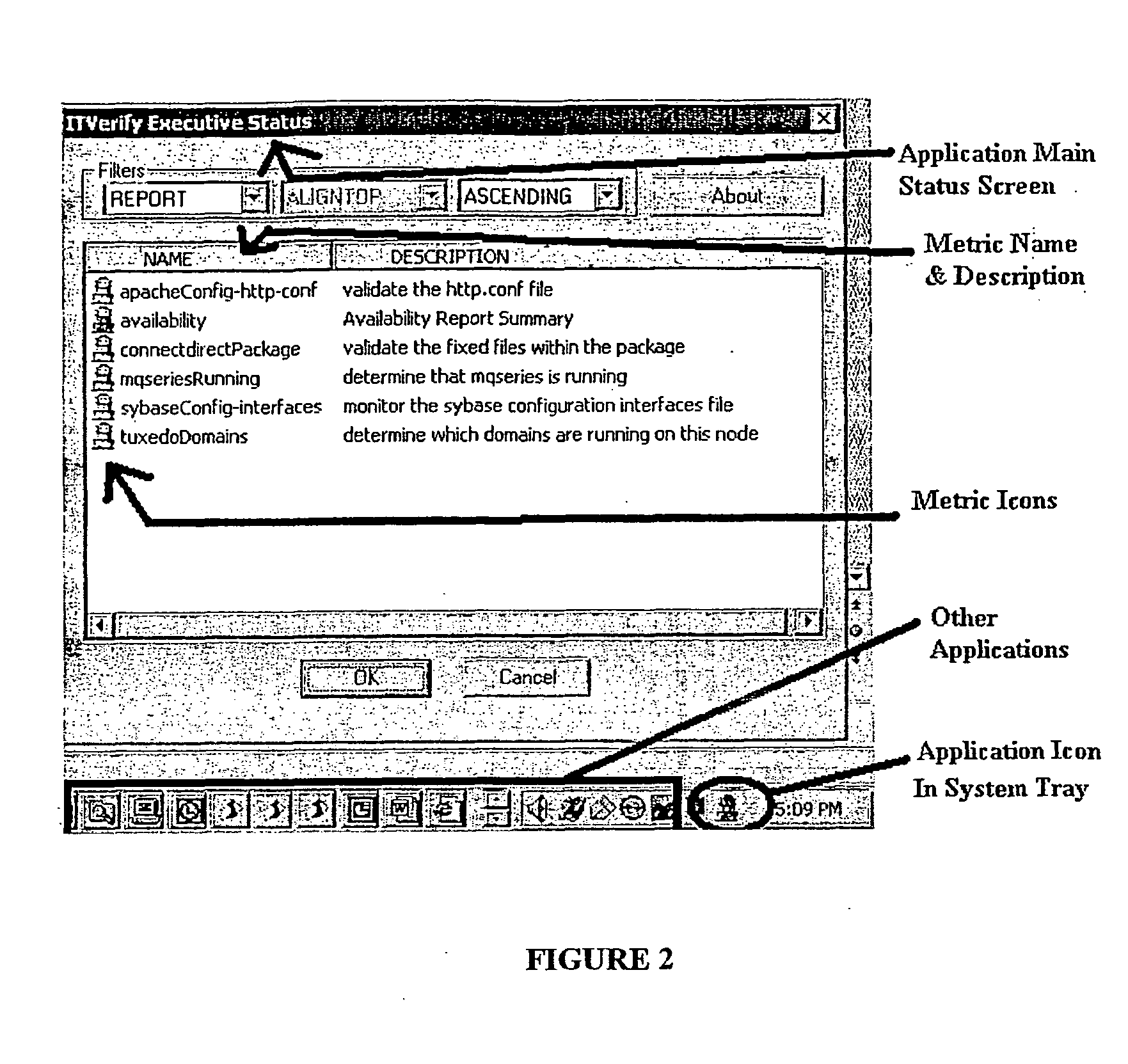
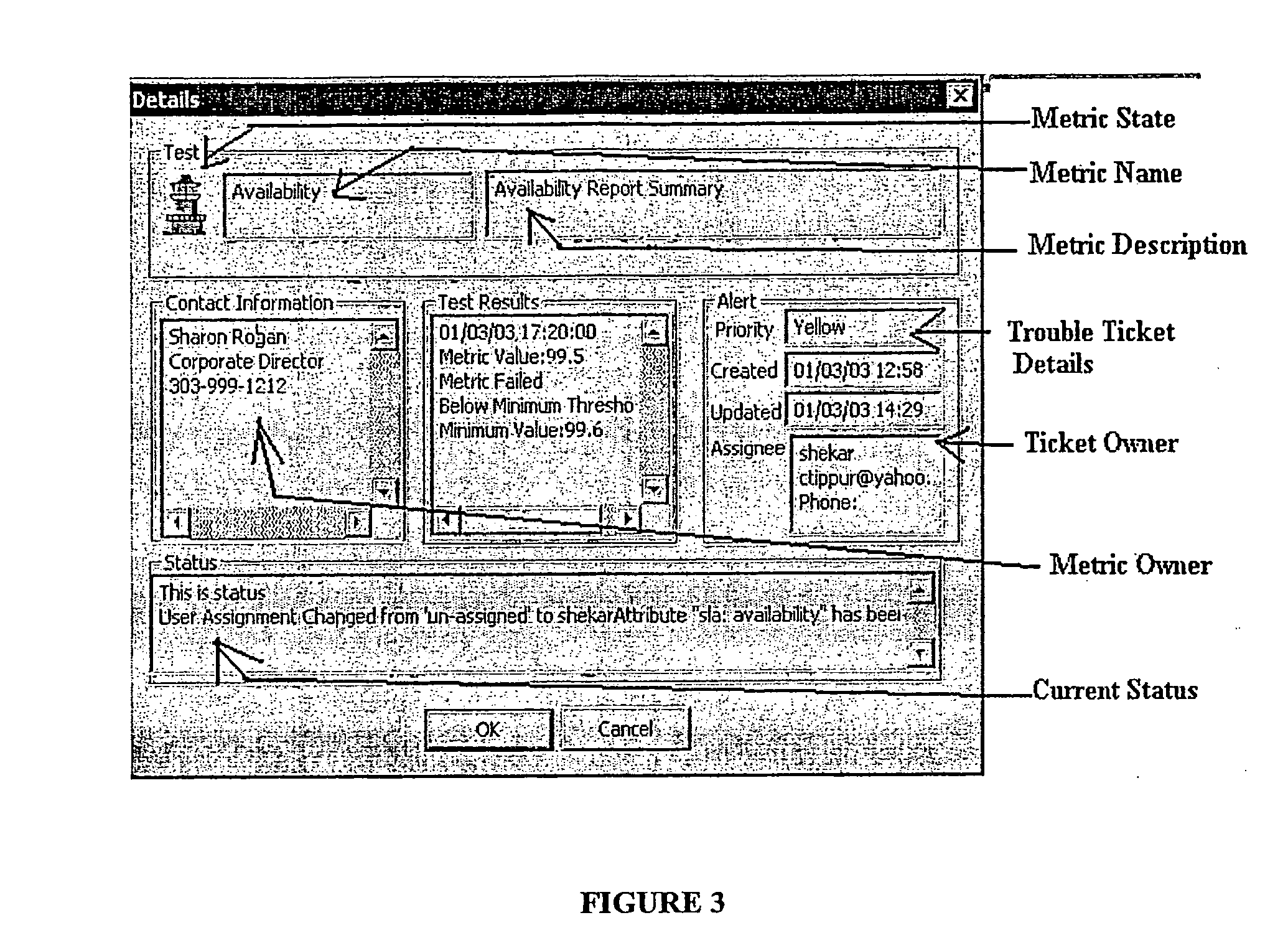
Apparatus method and article of manufacture for visualizing status in a compute environment
InactiveUS20060200773A1Digital computer detailsInput/output processes for data processingGraphicsDatabase query
There is provided herein an exemplary technique utilizing at least one application status icon for visualizing the status of important metrics of, e.g., one or more applications running within a compute infrastructure. In an exemplary embodiment, the application status icon is located on a device display, preferably as part of a graphical user interface icon tray, such as Microsoft® Windows® system tray. To generate the appropriate color of the application status icon, several predefined test or database queries are executed lo determine the status of a desired application. Thereafter, the determined status is compared to a plurality of threshold conditions, which determine the state of a given status metric and contribute to the overall color of the application status icon, preferably located on the display device. Thus, a user or manager need not run an application to check its status. Instead, the manager need only view the color of the application status icon on the display device to determine the overall health of a plurality of underlying metrics, which contribute to the creation of the application status icon's color.
Owner:VERIFICHI
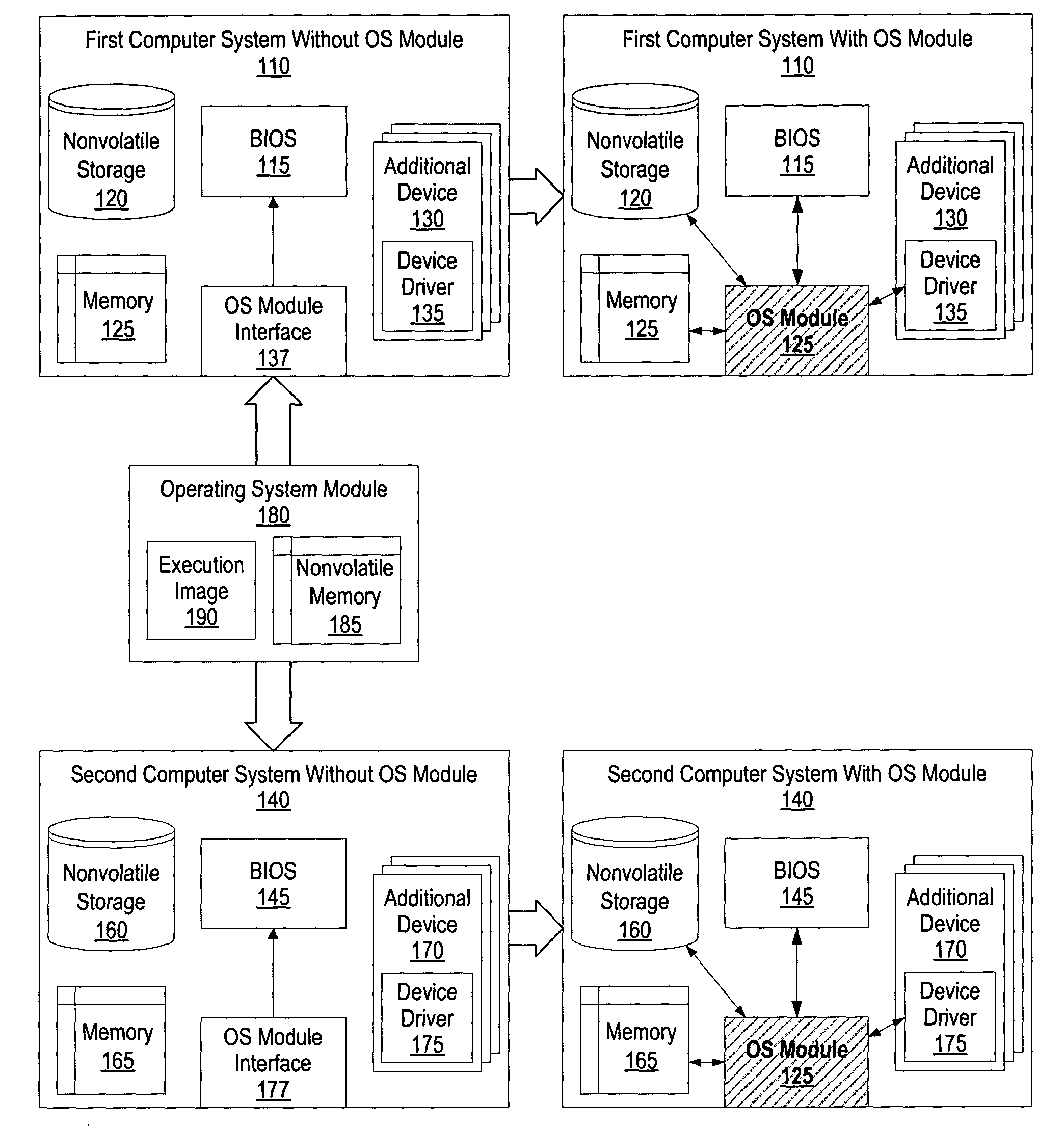
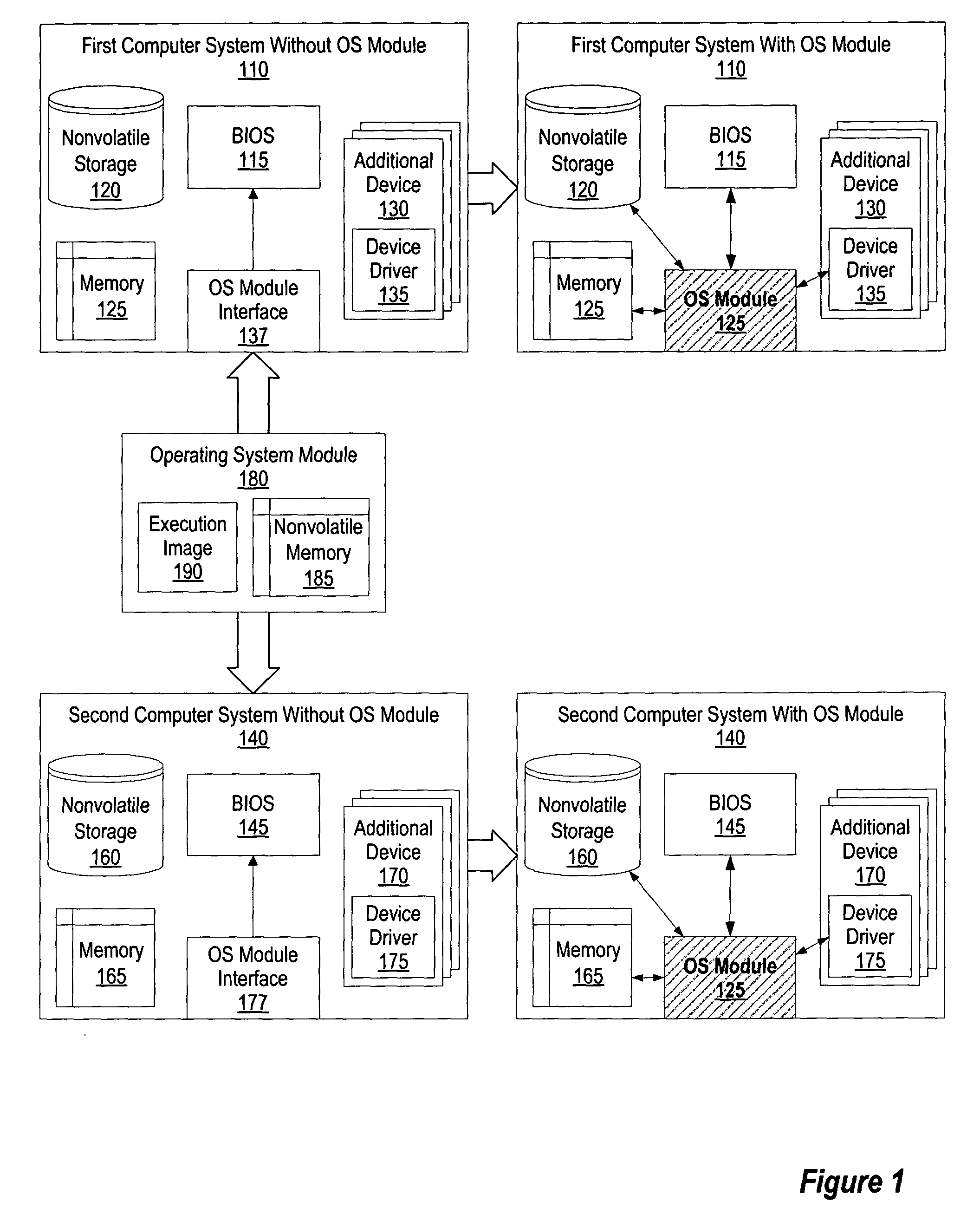
System and method for hibernating application state data on removable module
ActiveUS20050038933A1Digital computer detailsMultiprogramming arrangementsApplication IdentifierSoftware
A method and system for hibernating the state of executing applications on a removable module and resume the applications at later time using the saved applications state. After inserting the removable module into a computer system, the applications state information stored on the removable module is loaded. The application state information may include an application identifier, a file identifier of a file being accessed by the application, and user preferences related to the application. One or more software applications are loaded from a nonvolatile storage device accessible by the computer system to a memory accessible by the computer system, and the loaded applications are executed. The state of each of the executed software applications is set based upon the corresponding application state information.
Owner:LENOVO PC INT
Synchronization of runtime and application state via batching of workflow transactions
ActiveUS20060136279A1Easy to shareProgram control using stored programsDigital data processing detailsBatch processingWorkflow
Workflow management for maintaining consistency of persisted state across communicating components via batching of uncommitted work. A workflow component defines a workflow containing work items to be performed by service provider components. The workflow component assigns the work items to the service provider components, and the service provider components acknowledge the assigned work items. The workflow component appends the assigned work items to a work batch. The workflow component creates a transaction containing the batched work items. The workflow component commits to the workflow by requesting the service provider components to perform the work items. The workflow component checks the state of the execution of the work items and stores the state in a persistent storage.
Owner:MICROSOFT TECH LICENSING LLC
Flexible architecture for notifying applications of state changes
ActiveUS20050091219A1Digital data processing detailsInterprogram communicationProgram planningApplication programming interface
Described is a method and system a unified mechanism for storing device, application, and service state, as well as a rich notification brokerage architecture. Clients register with a notification broker to receive notifications for changes to state properties. When a registered state property changes, a notification broker determines which clients to notify of the state change and provides the client with a notification regarding the change. Clients may be notified whenever a state changes, when a state change meets a predetermined condition, or based on a schedule. An application may also be launched in response to a state change. An application programming interface (API) is provided that provides a unified way of accessing state change information across different components within the device.
Owner:MICROSOFT TECH LICENSING LLC
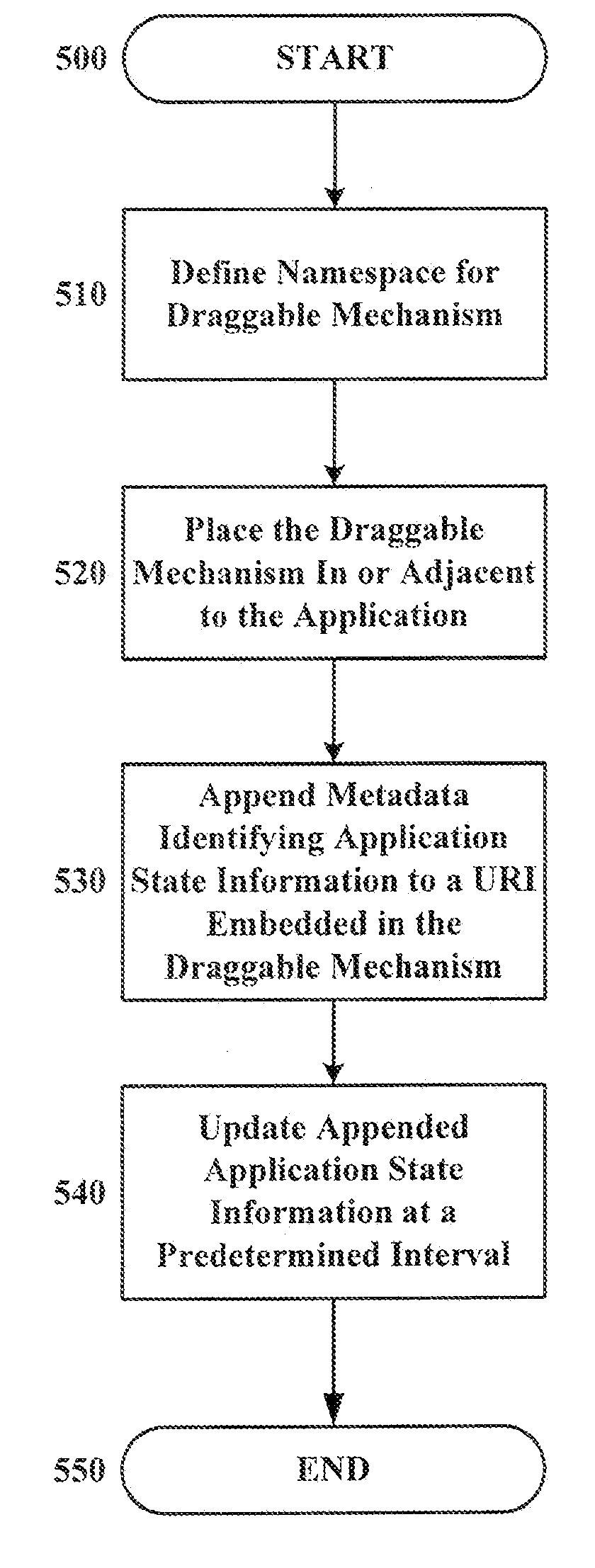
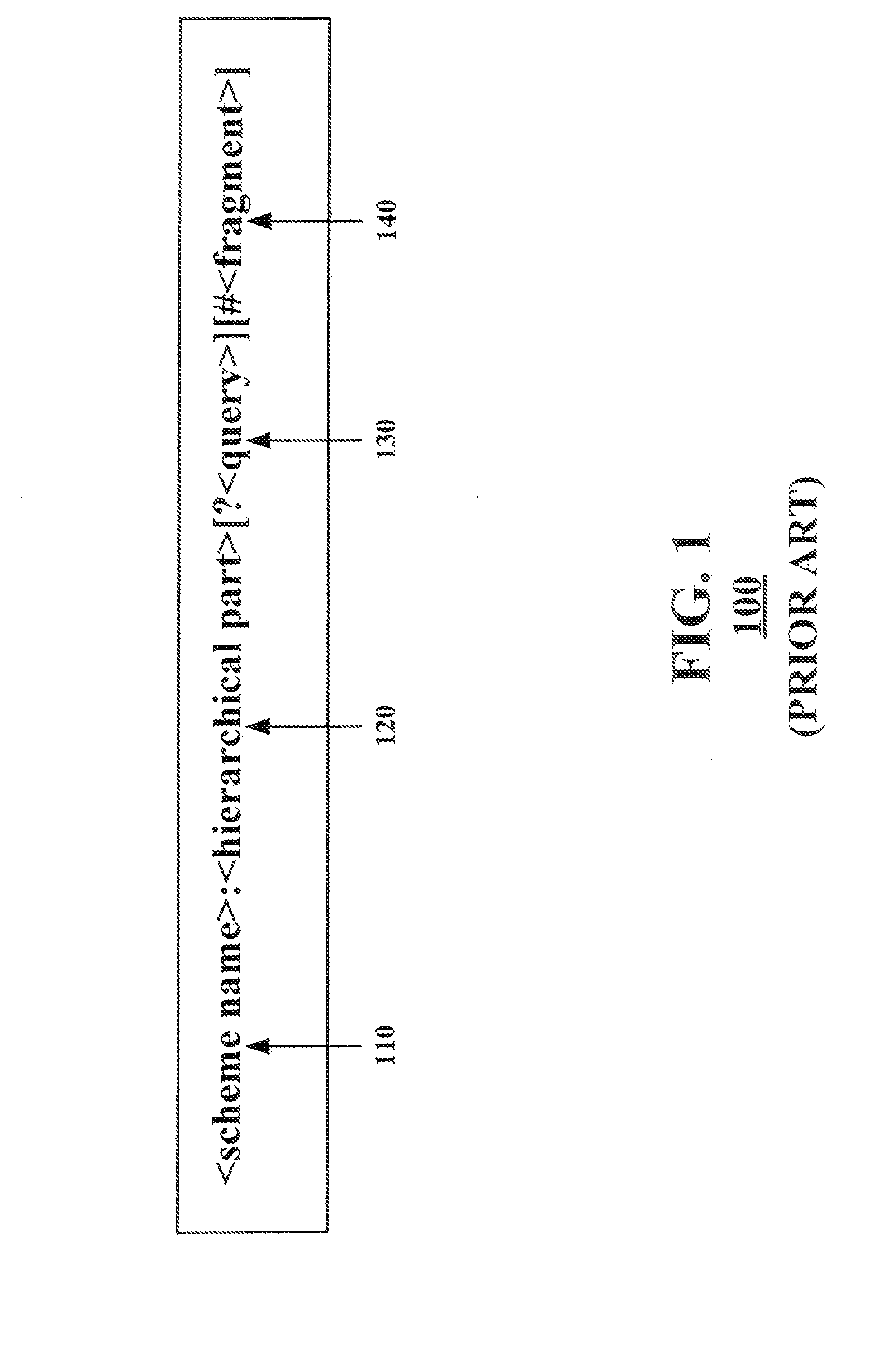
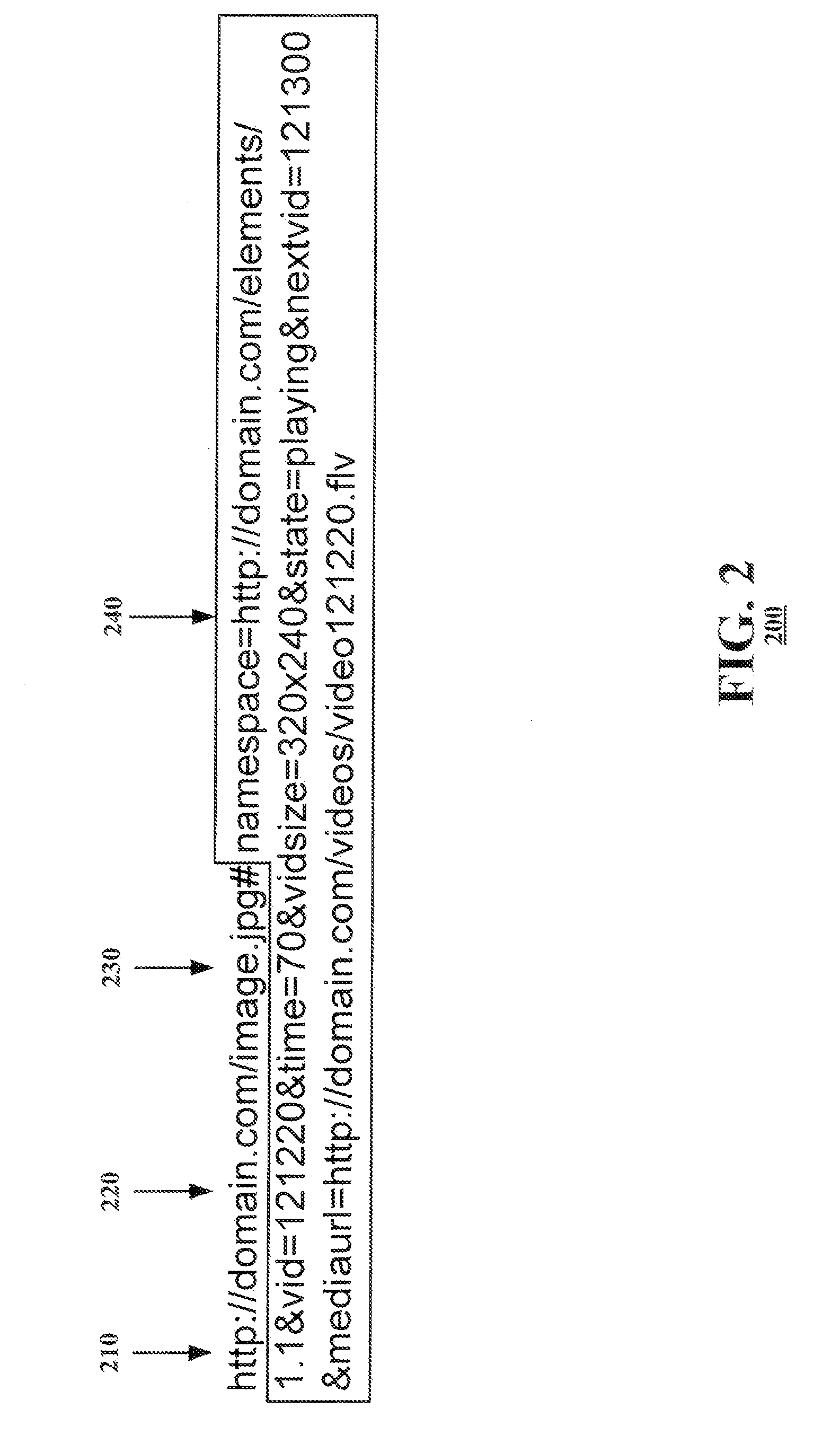
Draggable mechanism for identifying and communicating the state of an application
InactiveUS20090015599A1Cathode-ray tube indicatorsExecution for user interfacesUniform resource locatorApplication software
In a method and system for identifying and communicating a state of an application, a namespace is defined for a draggable mechanism. The draggable mechanism is located within an application window housing an application. Metadata identifying application state information is appended to a URL embedded within the draggable mechanism to reflect a first application state of the application. The metadata identifying the application state information is updated at a predetermined interval to reflect new application states.
Owner:OATH INC
Method and system for rule-based generation of automation test scripts from abstract test case representation
ActiveUS20050188271A1Detecting faulty computer hardwareSoftware testing/debuggingSpecific testTest script
A general rule-based technique is provided for generating a test case from an abstract internal test case representation. The abstract internal test case representation is based on a test case representation model that includes application states (state information), external interaction sequences (control flow information) and input data. The abstract representation in essence provides a platform independent representation of test cases. An application object model provides the representational capabilities required for capturing structural and behavioral properties of the application under test. Rules can be specified to define which application states (state information), external interaction sequences (control information) and input data sets should be used in the generation of the test case. Multiple data sets can be created and applied to support data-driven test case generation. A technique based on platform mapping is provided to convert a test case into an automation test script for any specific test script execution environment for any specific application platform.
Owner:SILICON VALLEY BANK
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com