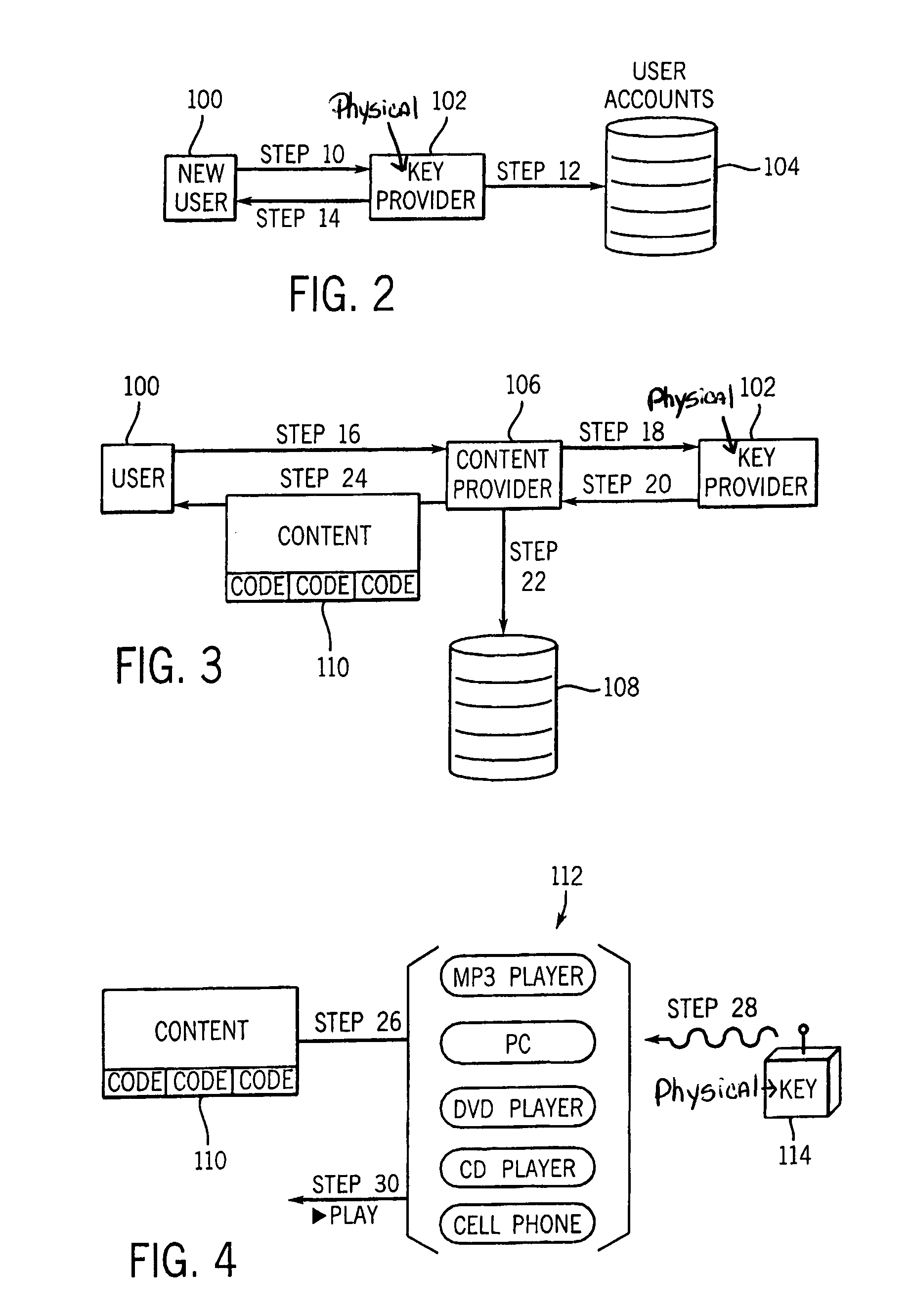
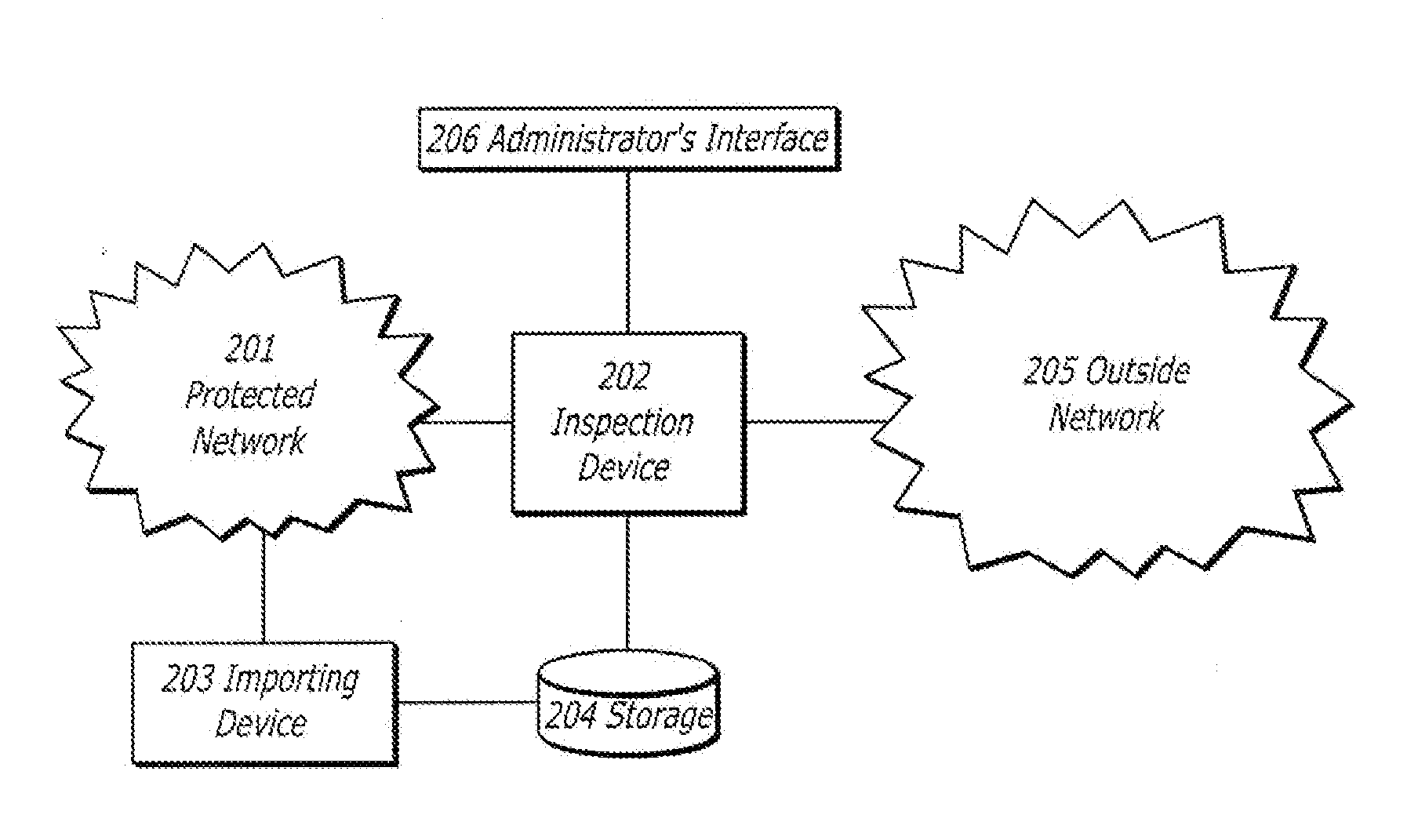
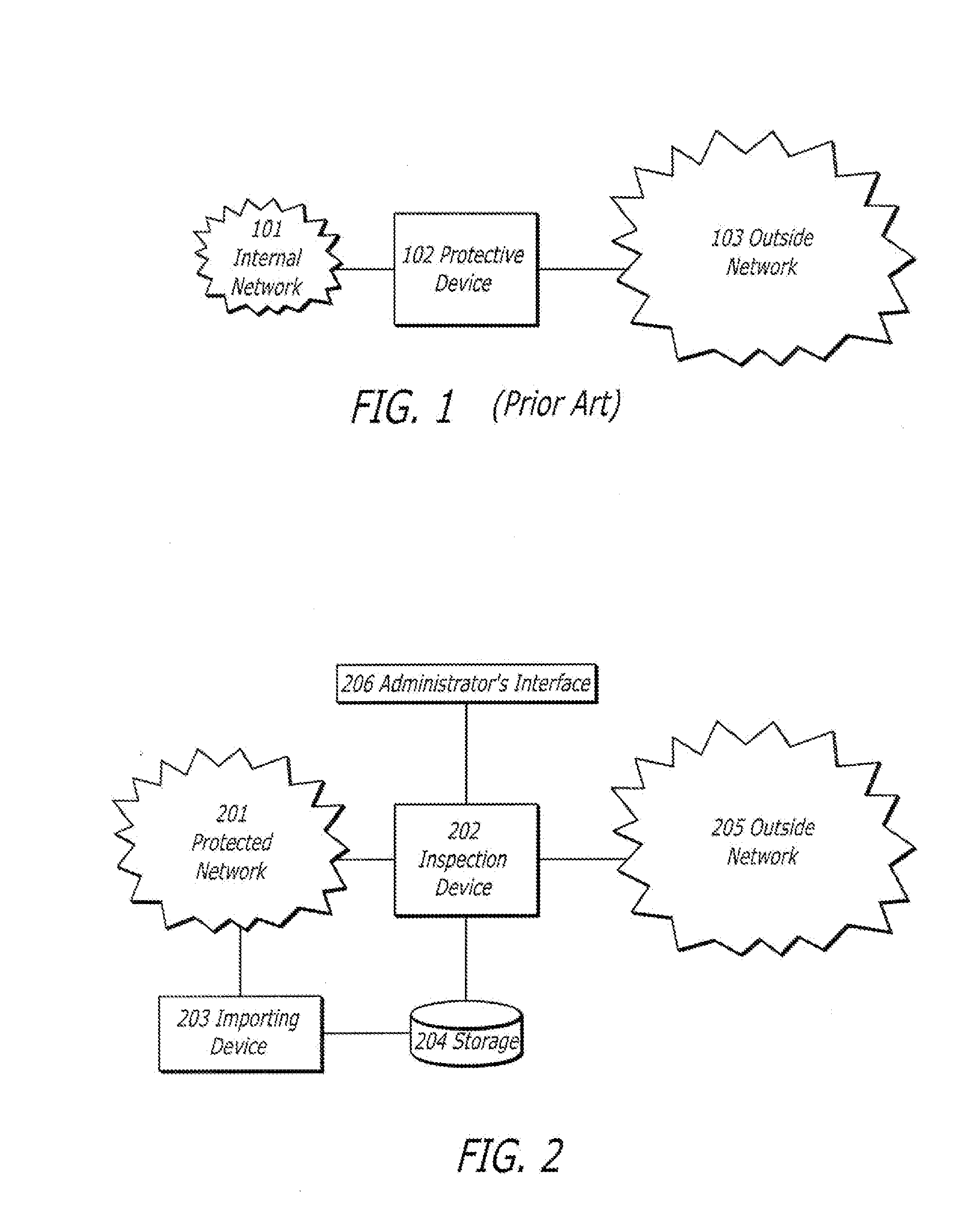
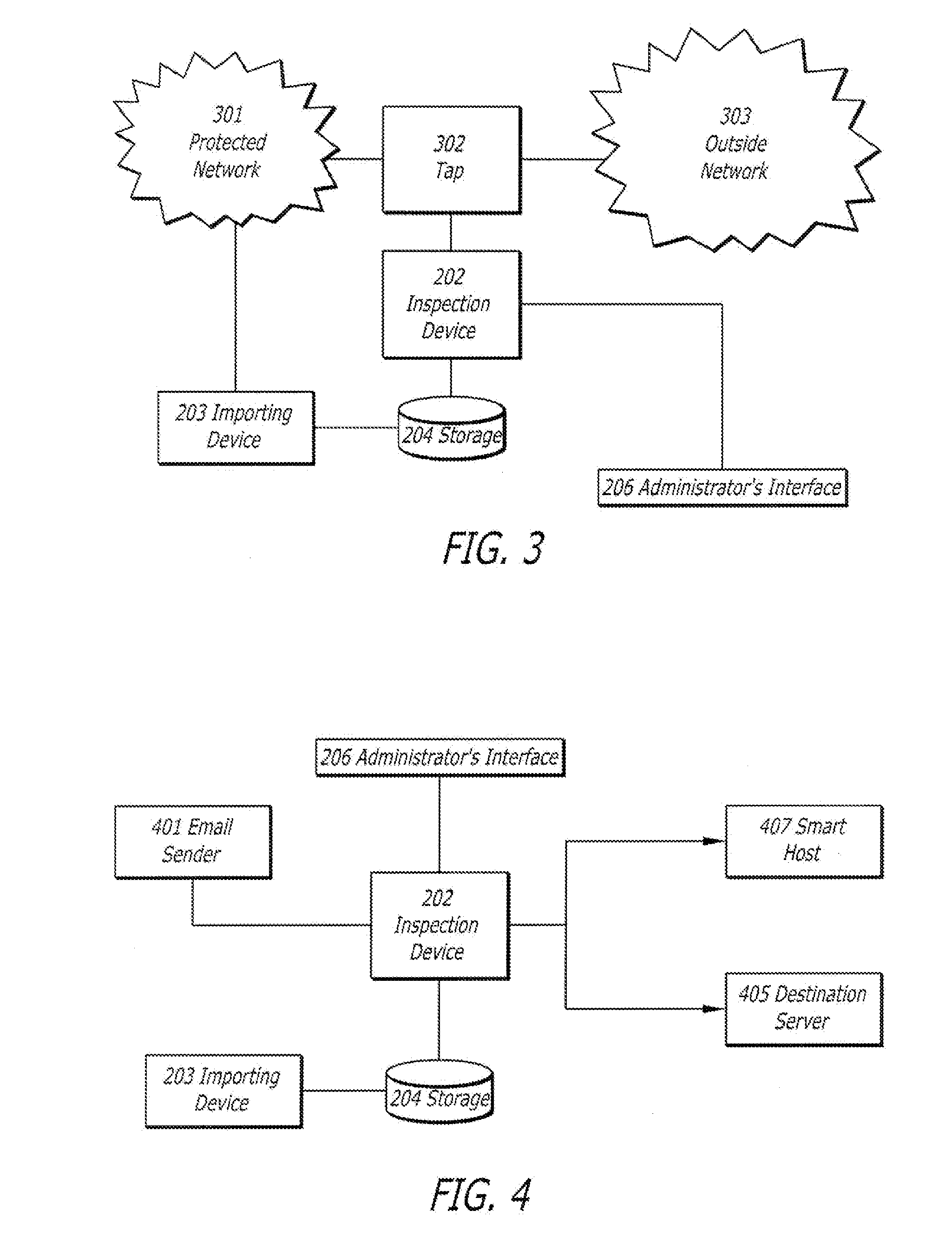
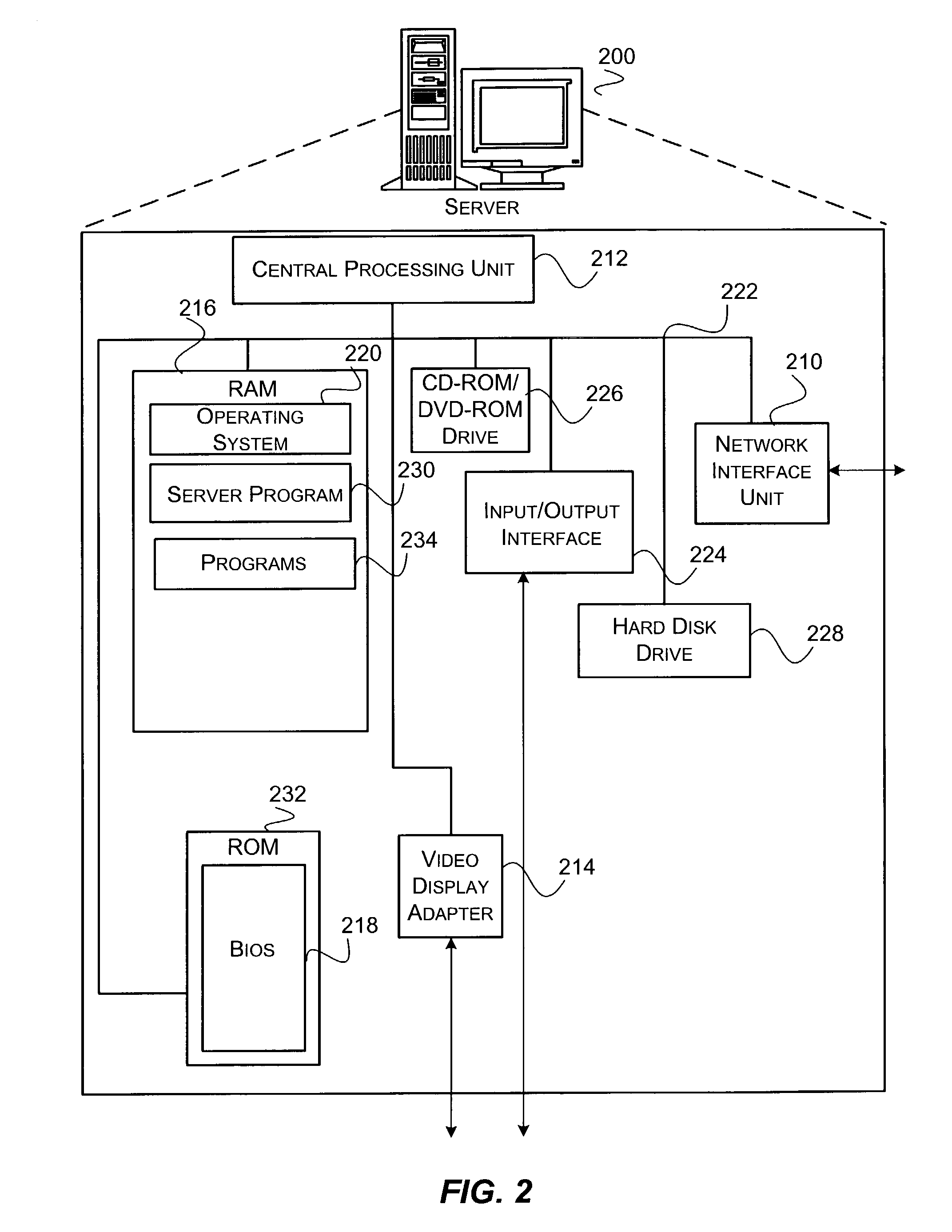
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
275 results about "Content security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Content security layer providing long-term renewable security
InactiveUS20020141582A1Unparalleled flexibilityIncrease sampling rateTelevision system detailsKey distribution for secure communicationAttackMediaFLO
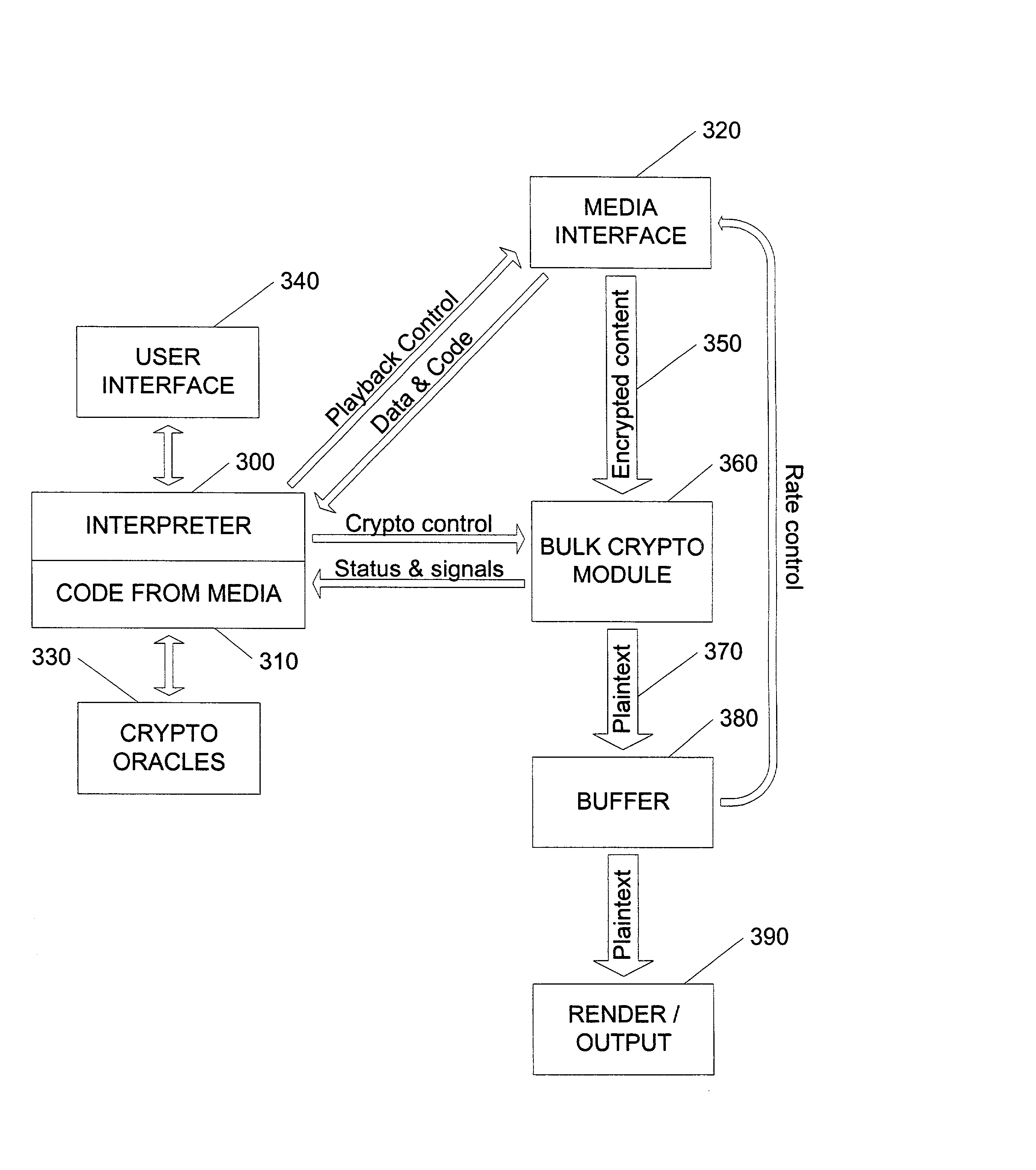
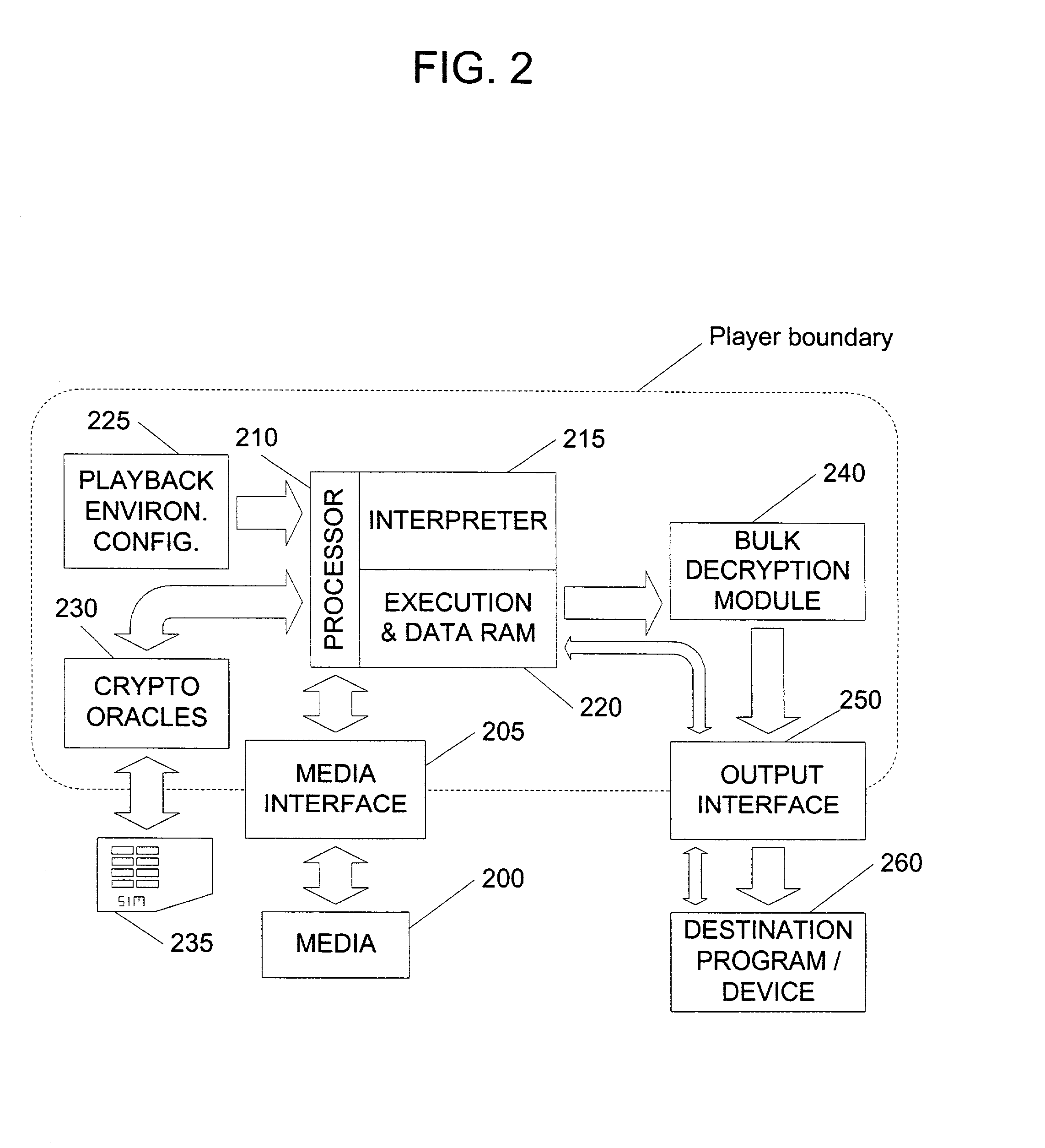
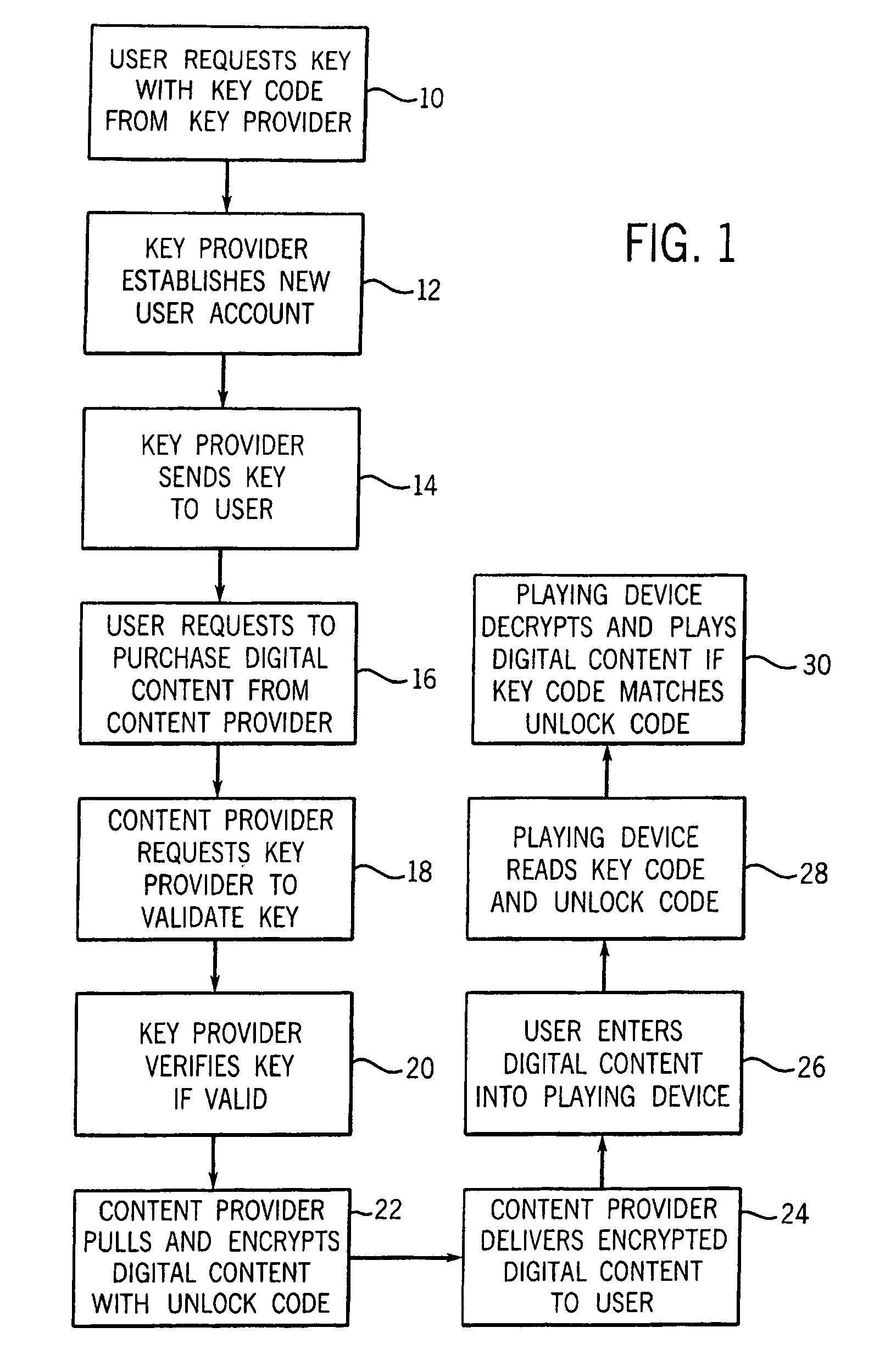
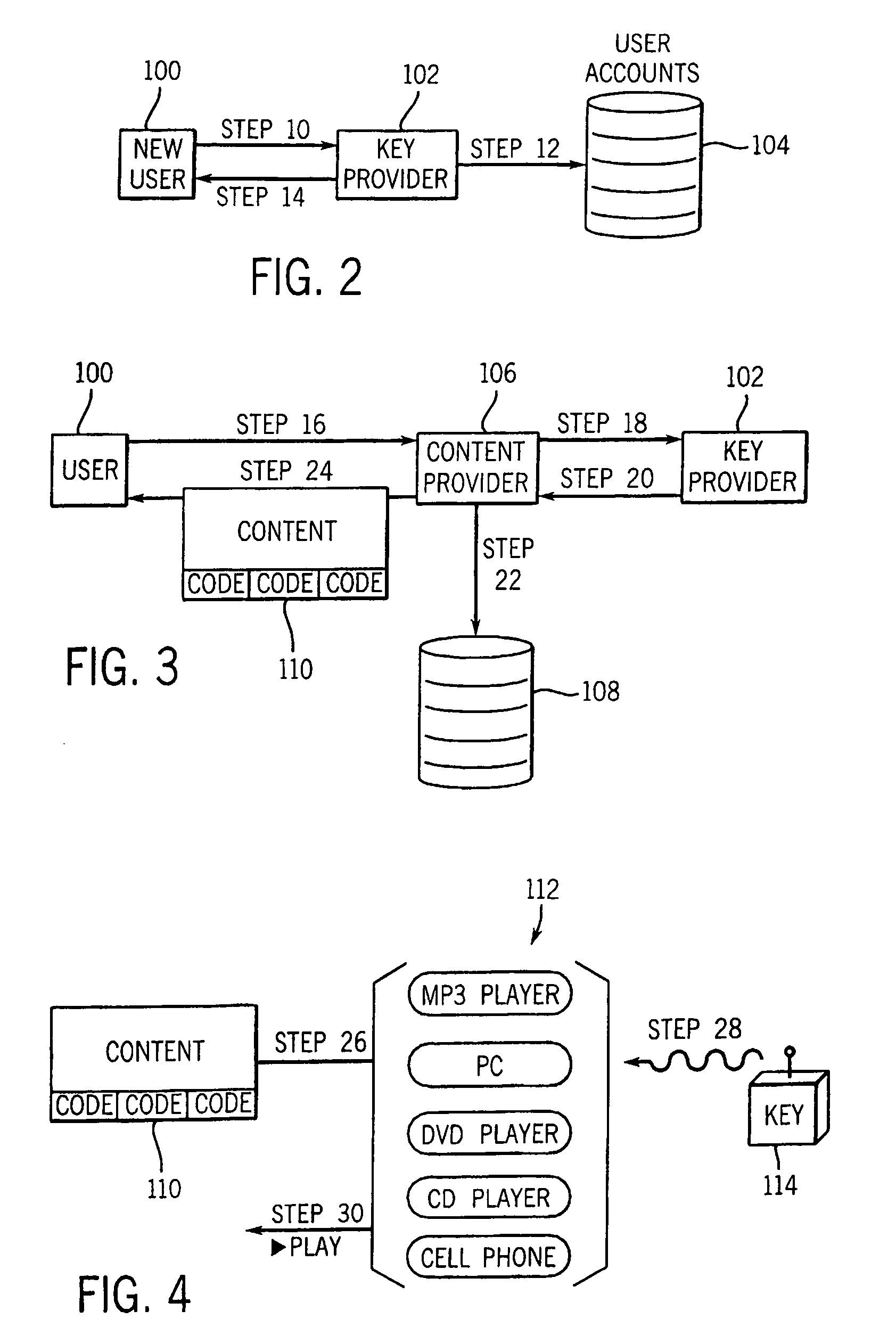
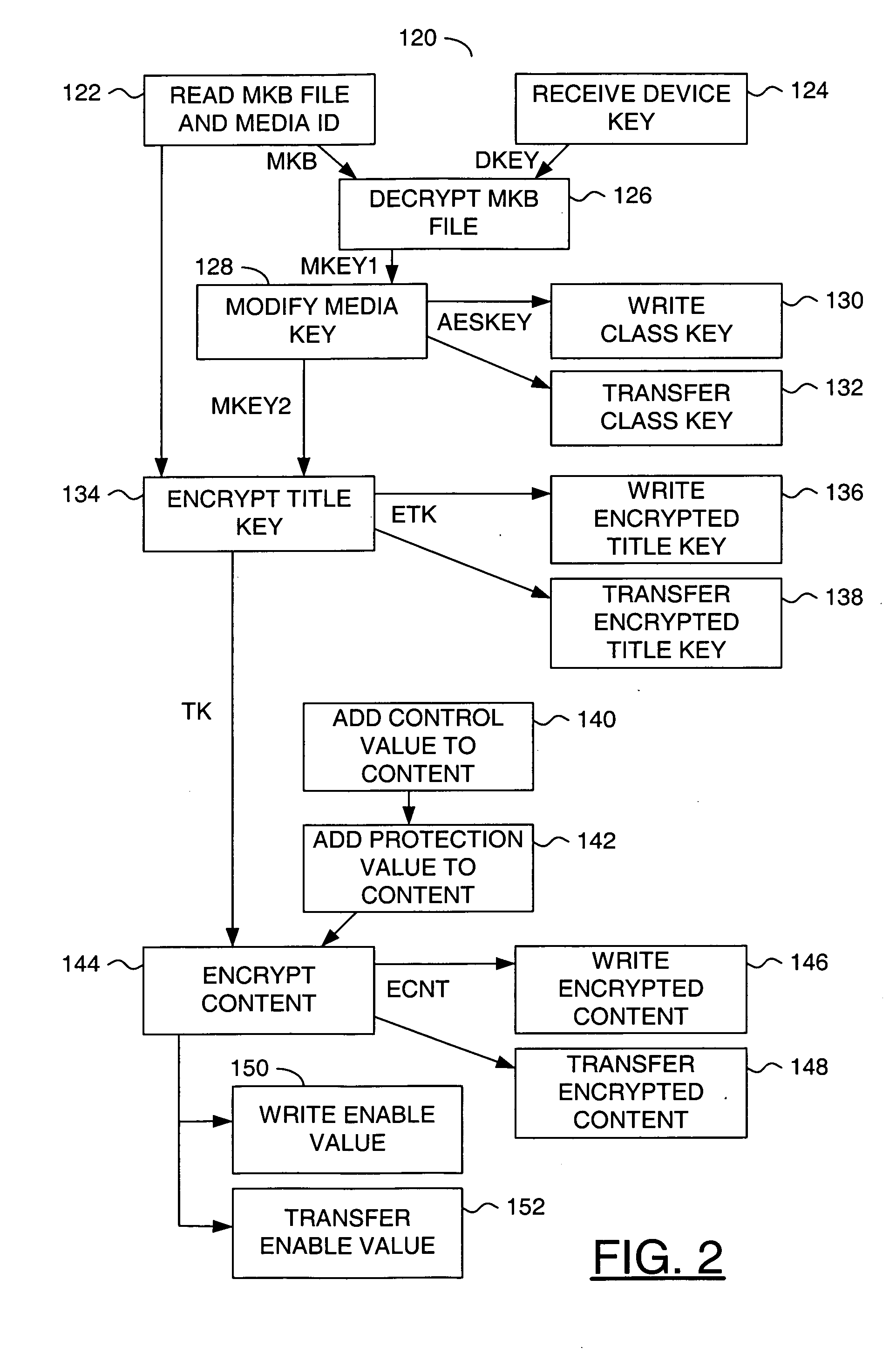
In an exemplary embodiment, digital content is mastered as a combination of encrypted data and data processing operations that enable use in approved playback environments. Player devices having a processing environment compatible with the content's data processing operations are able to decrypt and play the content. Players can also provide content with basic functions, such as loading data from media, performing network communications, determining playback environment configuration, controlling decryption / playback, and / or performing cryptographic operations using the player's keys. These functions allow the content to implement and enforce its own security policies. If pirates compromise individual players or content titles, new content can be mastered with new security features that block the old attacks. A selective decryption capability can also be provided, enabling on-the-fly watermark insertion so that attacks can be traced back to a particular player. Features to enable migration from legacy formats are also provided.
Owner:ROVI SOLUTIONS CORP
Content protection management system
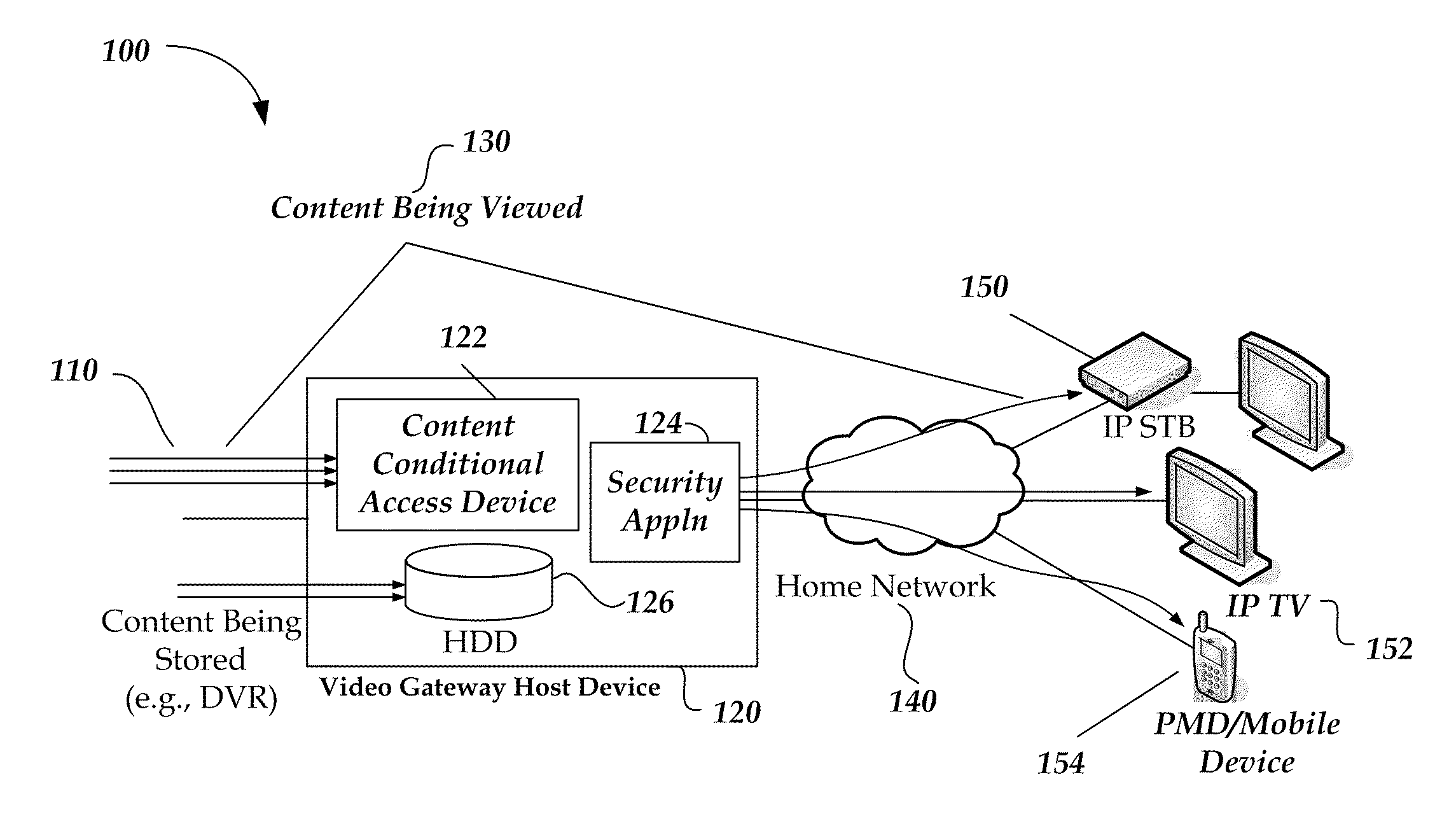
ActiveUS20100287609A1Simple and consistent and reliableMultiple digital computer combinationsProgram controlSecurity domainContent security
A content protection management system that enables interoperability with other Content Protection and DRM technologies. A managed security domain provides a simple, consistent and reliable experience to whole-home network subscribers. The architectural concept for the whole-home network includes an underlying control plane with an overlaying content security control plane running a particular DRM technology.
Owner:COX COMMUNICATIONS
Securing digital content system and method
InactiveUS20070033397A1Key distribution for secure communicationDigital data processing detailsDigital contentContent security
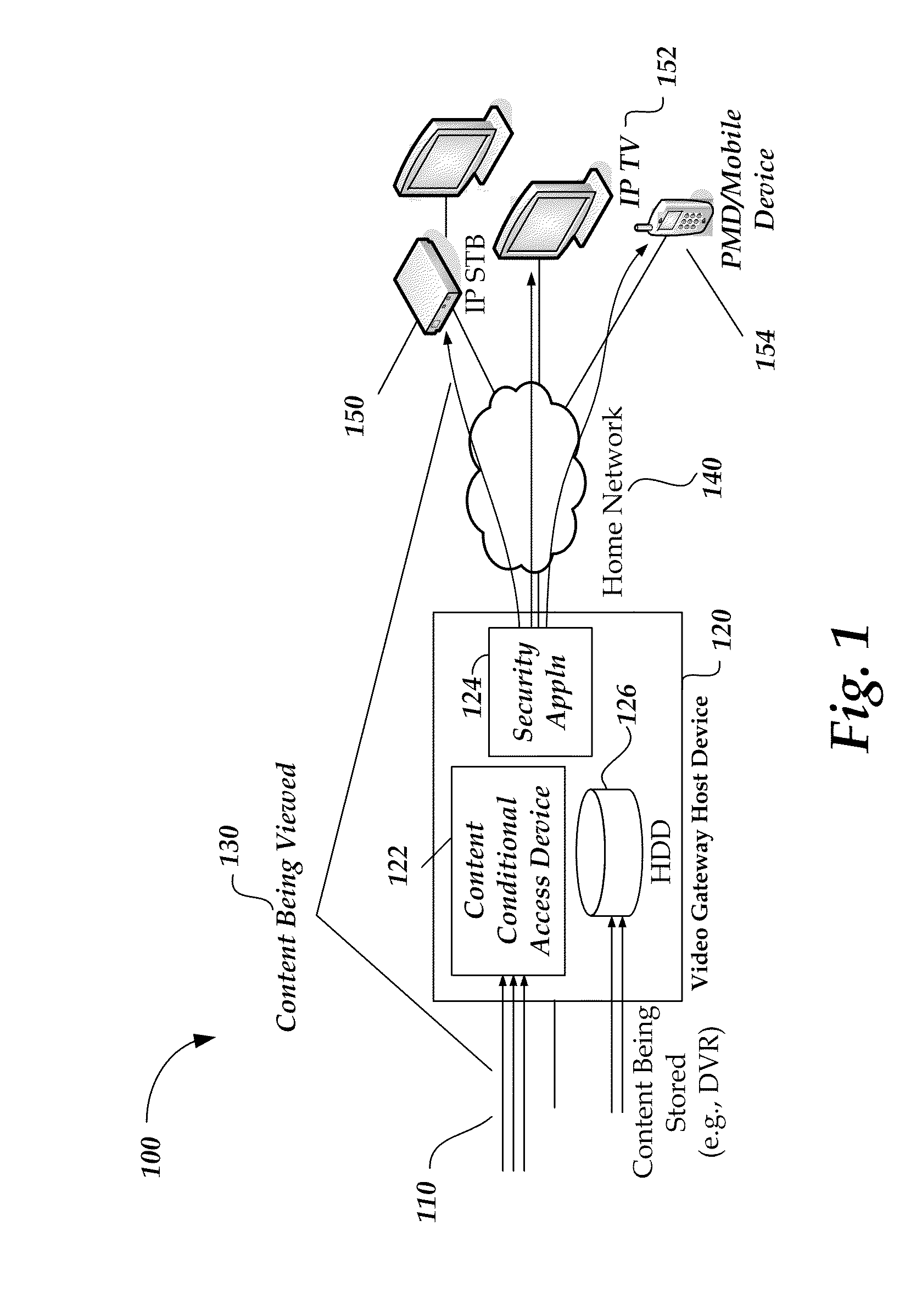
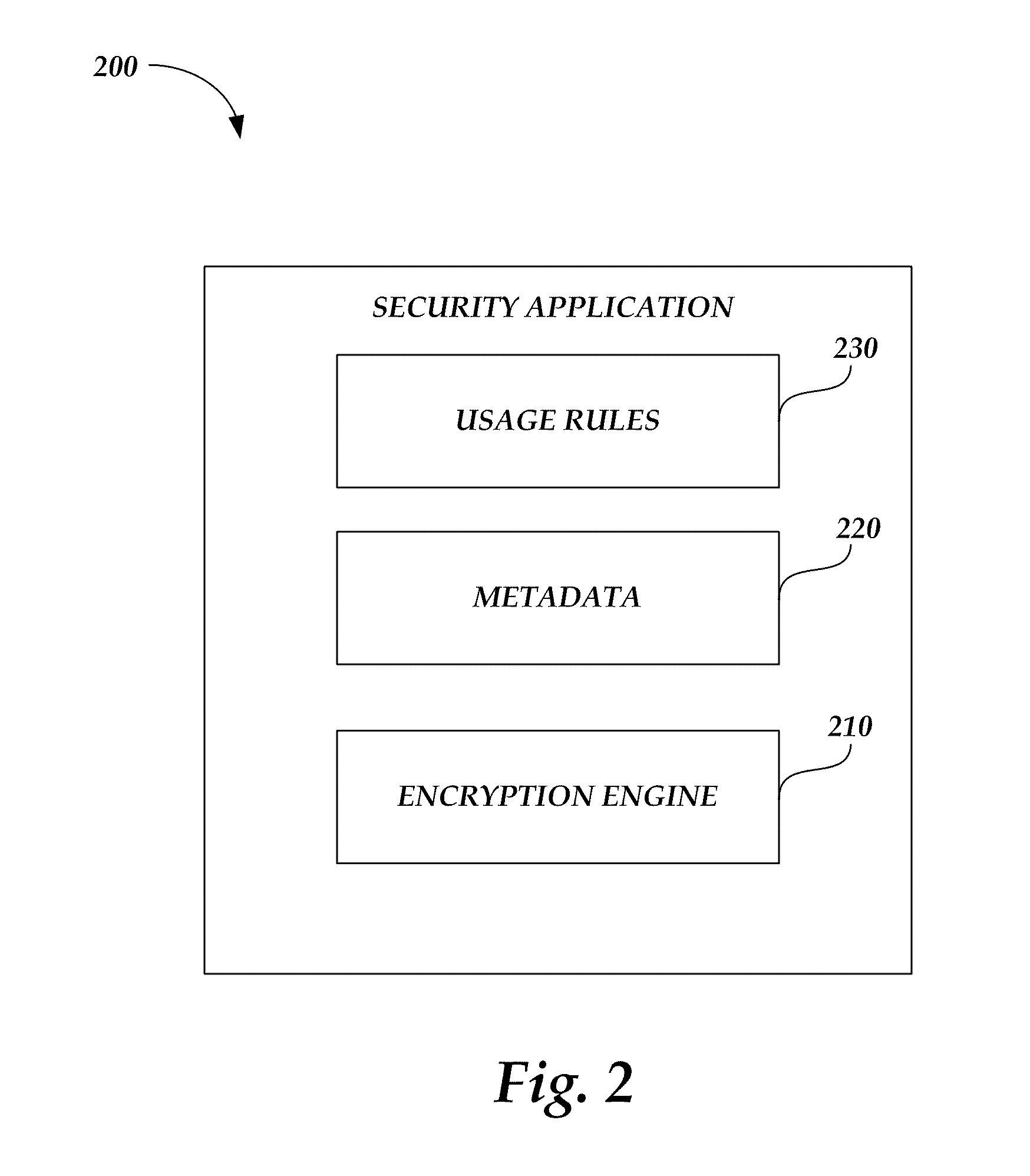
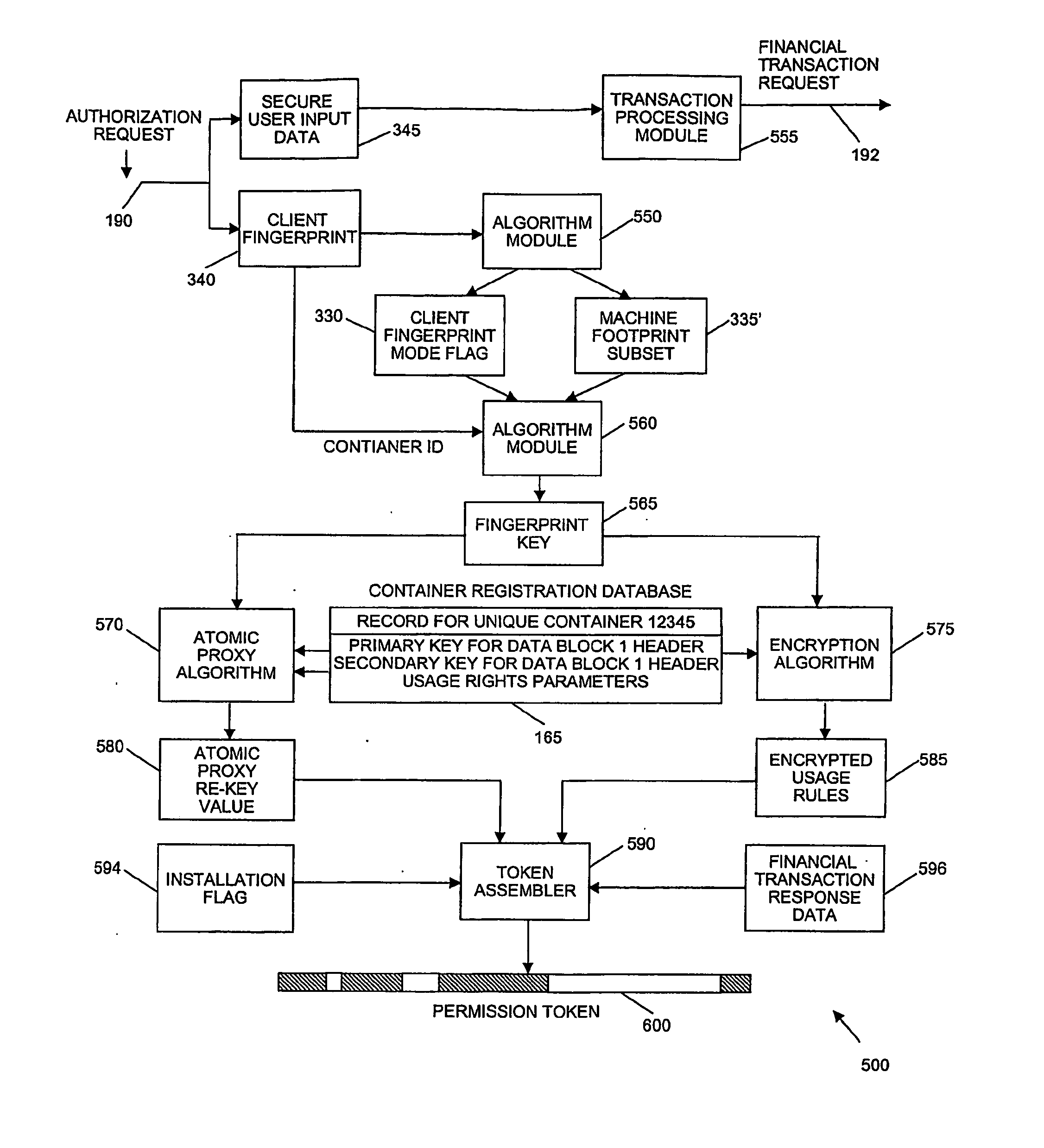
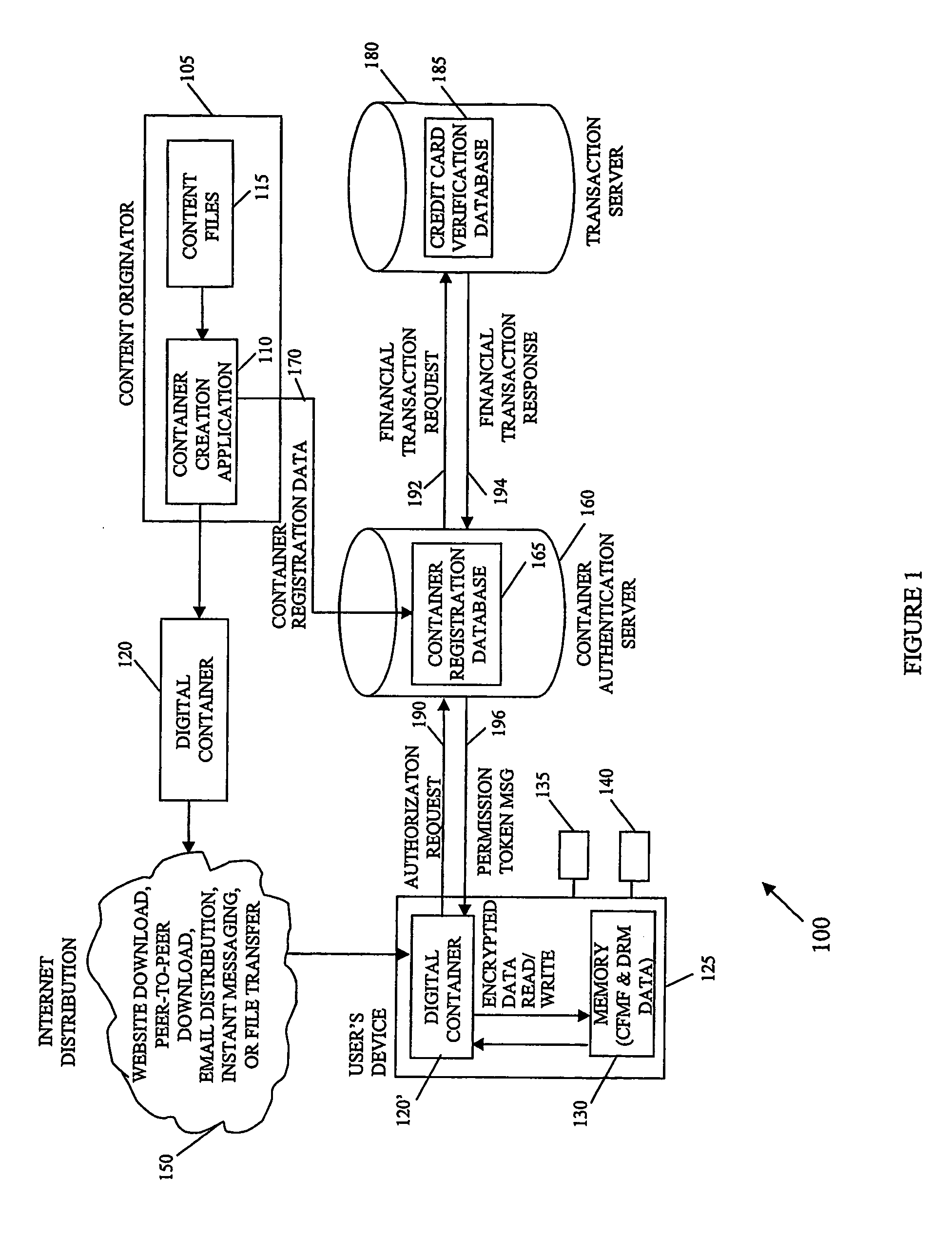
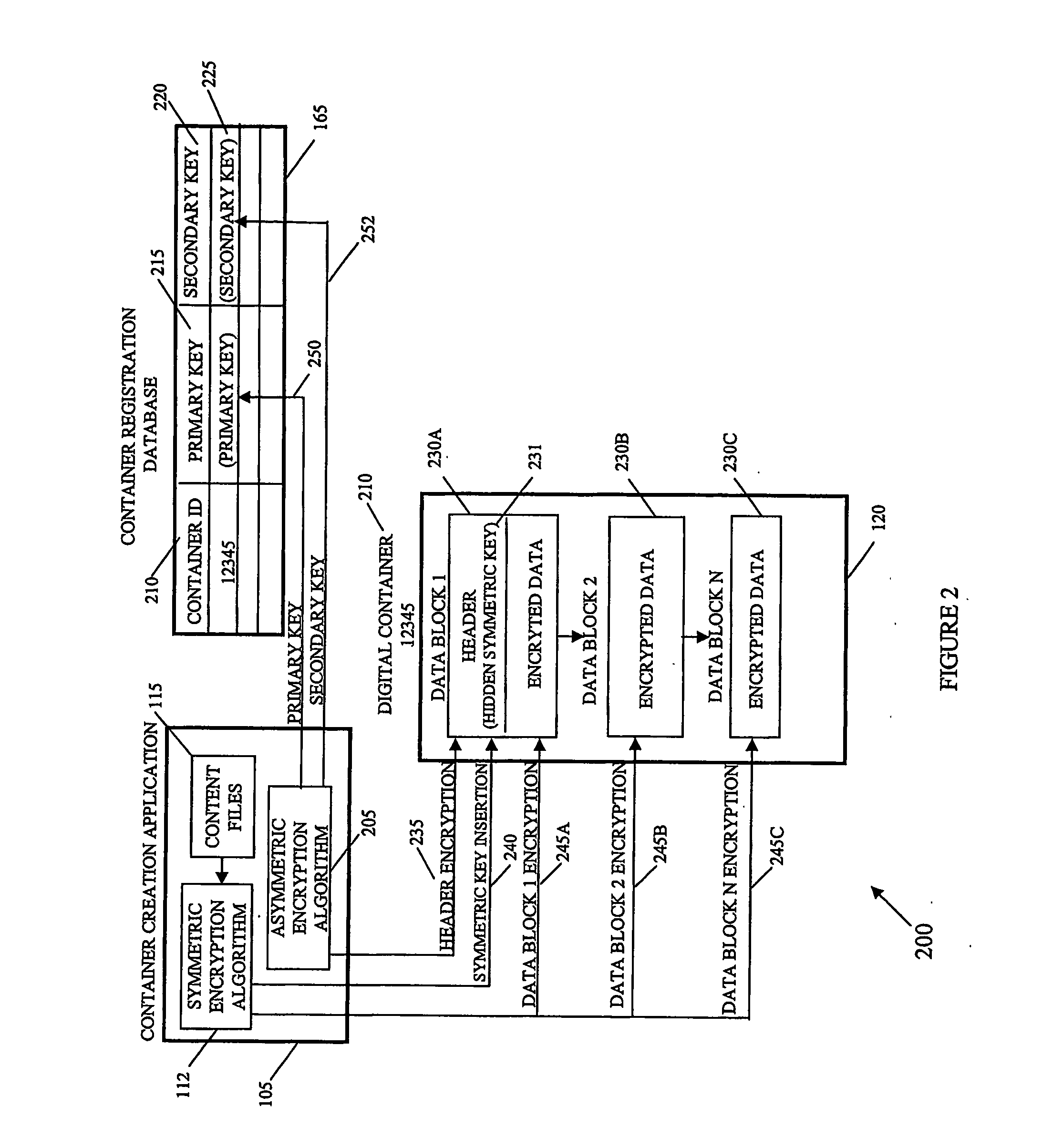
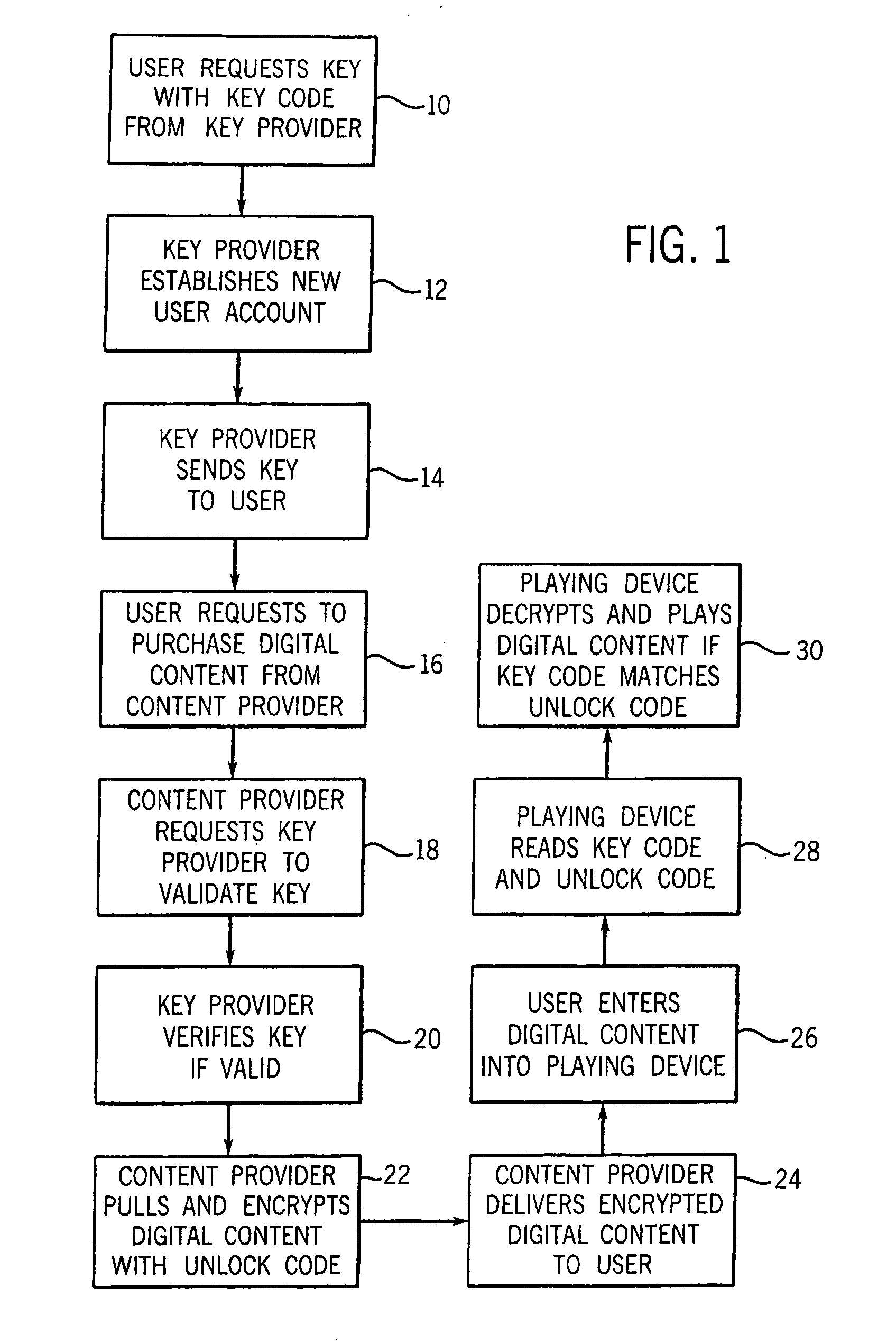
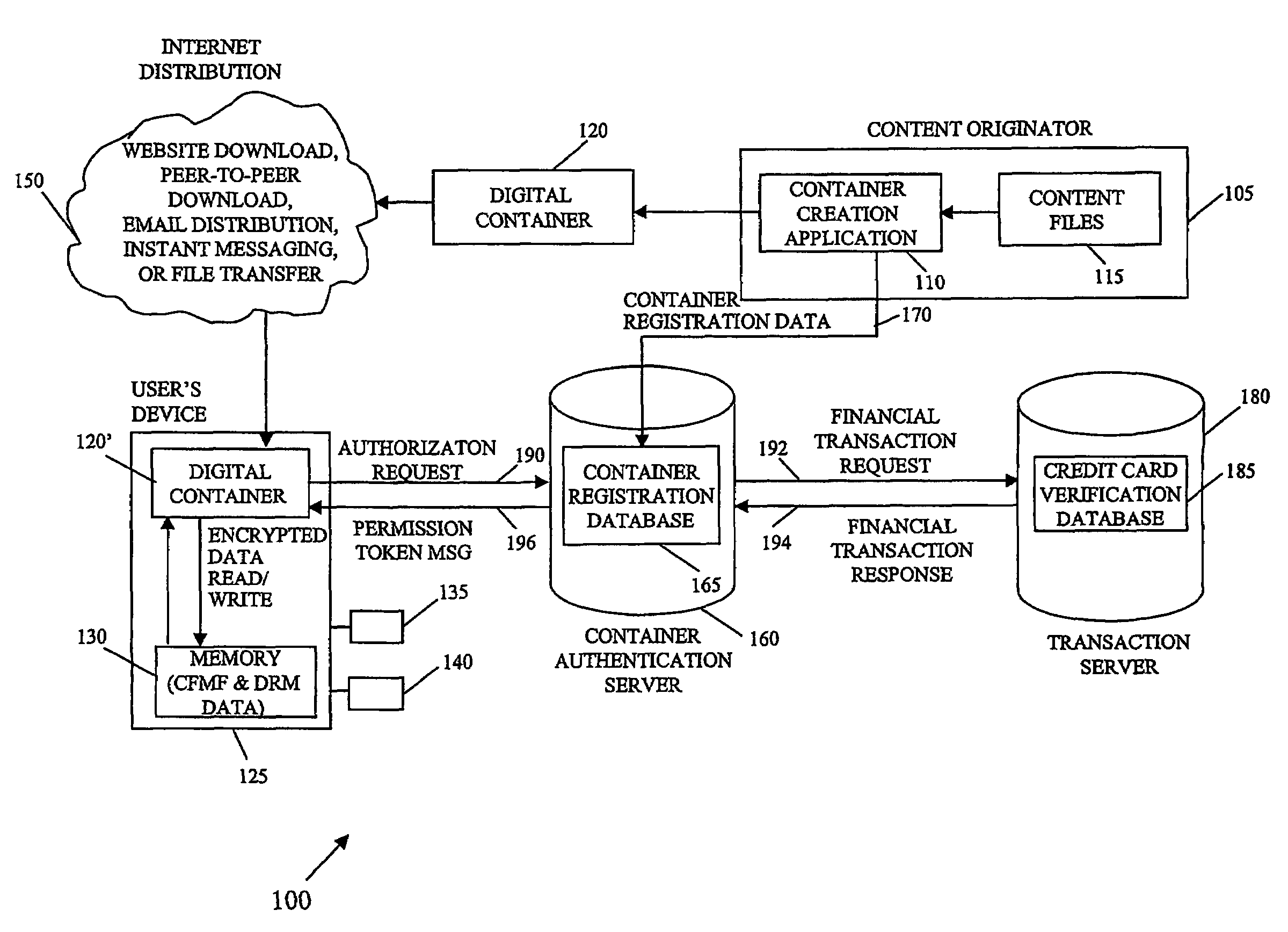
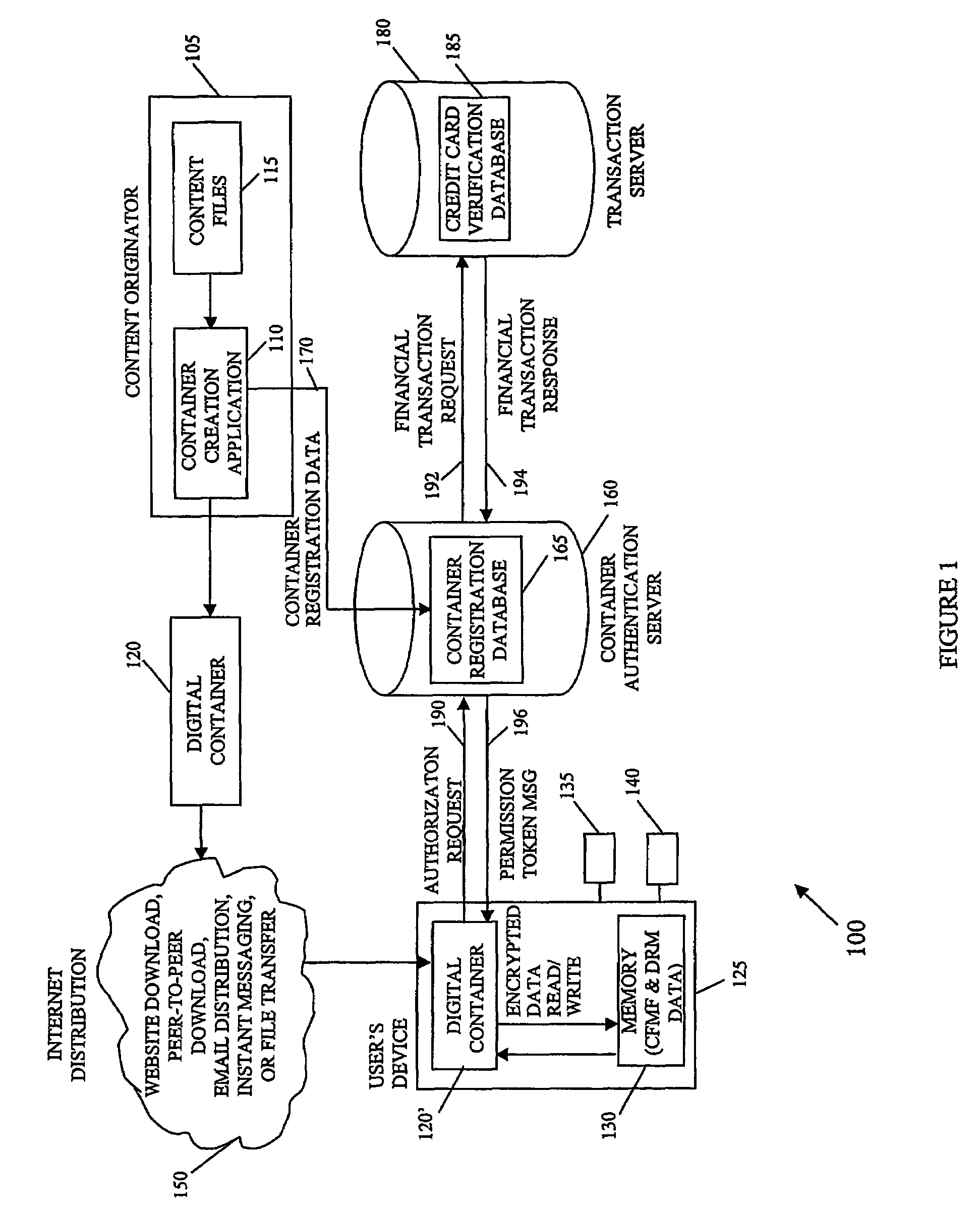
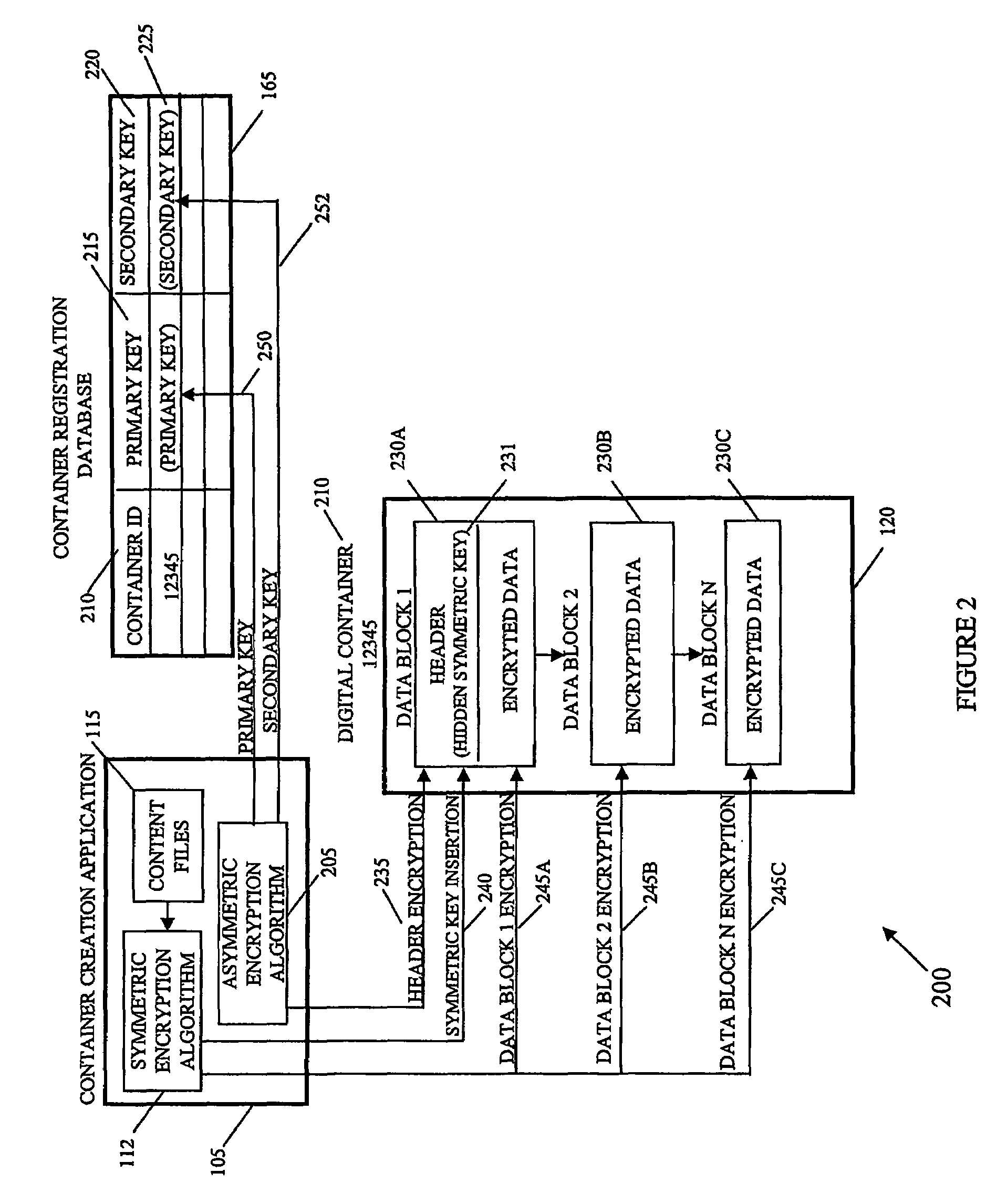
A system and method of encrypting digital content in a digital container and securely locking the encrypted content to a particular user and / or computer or other computing device is provided. The system uses a token-based authentication and authorization procedure and involves the use of an authentication / authorization server. This system provides a high level of encryption security equivalent to that provided by public key / asymmetric cryptography without the complexity and expense of the associated PKI infrastructure. The system enjoys the simplicity and ease of use of single key / symmetric cryptography without the risk inherent in passing unsecured hidden keys. The secured digital container when locked to a user or user's device may not open or permit access to the contents if the digital container is transferred to another user's device. The digital container provides a secure technique of distributing electronic content such as videos, text, data, photos, financial data, sales solicitations, or the like.
Owner:DIGITAL REG OF TEXAS
Content security in a social network
ActiveUS20130091582A1Digital data processing detailsServices signallingInternet privacyPrivate network
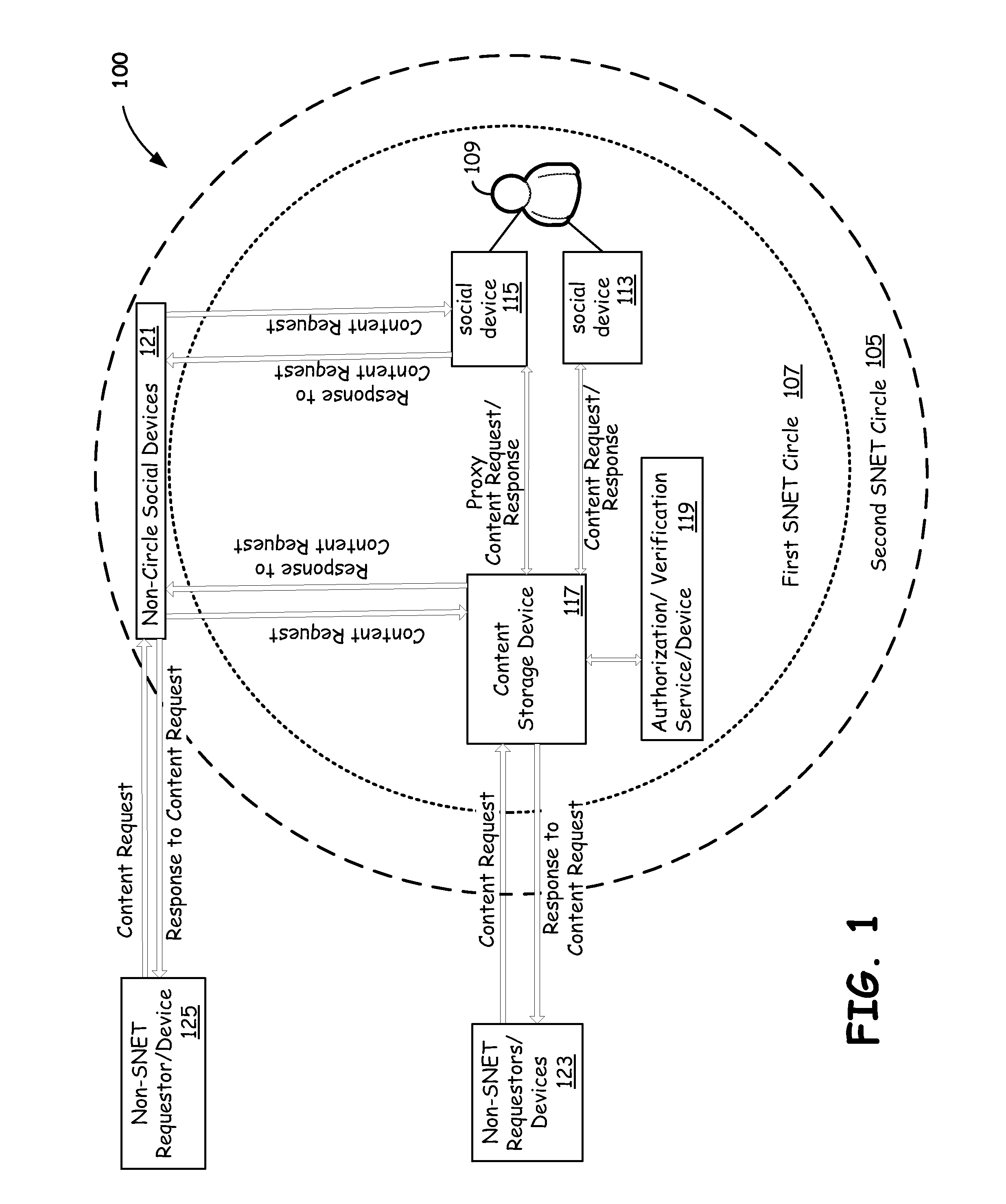
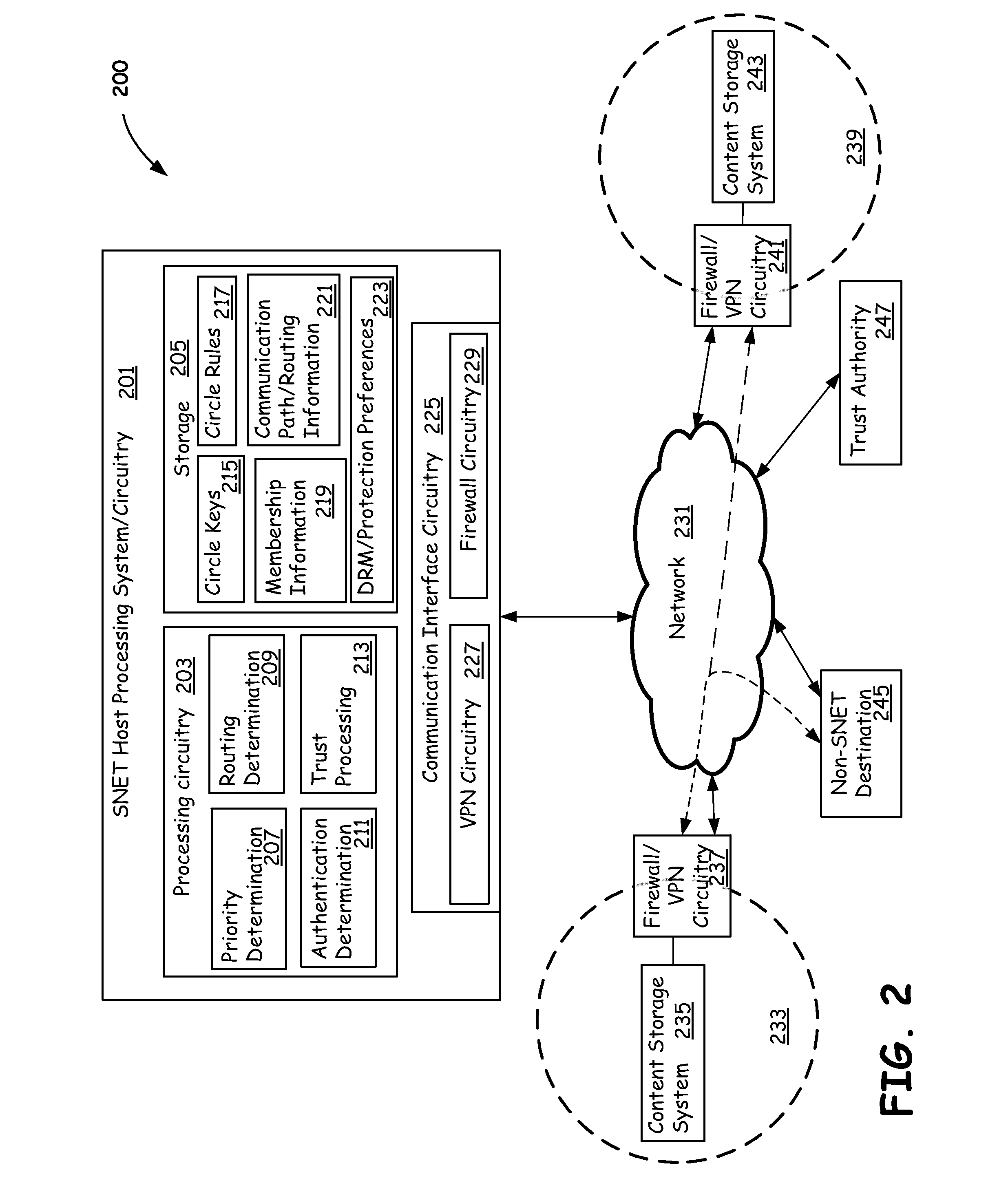
Members of a social network (SNET) circle can share content with other members of SNET circle, members of the same SNET that are not members of the same circle, or send content to people or devices outside of SNET. Different levels of content security can be applied to the shared content, depending on who requests the content, the destination of the content, user preferences, content type, SNET, SNET circle, or other security parameters. Content can be tagged to limit the number of times it can be accessed, the length of time access is allowed, and to otherwise control redistribution. Content can also be protected by limiting host network access to the content, implementing SNET circle firewalls and virtual private networks, or transcoding content before allowing transmission to non-SNET circle or SNET members. Docking of devices into an SNET security circle can be restricted to properly secured devices.
Owner:AVAGO TECH INT SALES PTE LTD
Digital content security system
InactiveUS6973576B2Provide protectionDigital data processing detailsUser identity/authority verificationHard disc driveOperational system
A Personal Digital Key Digital Content Security System (PDK-DCSS) is used to protect computers from unauthorized use and protect the digital content stored on computers from being wrongfully accessed, copied, and / or distributed. The basic components of the PDK-DCSS are (1) a standard hard drive device, with the addition of a PDK Receiver / Decoder Circuit (PDK-RDC) optionally integrated into the hard drive's controller, and (2) a PDK-Key associated with the PDK-RDC. The PDK-Key and RDC technology is utilized to provide two categories of protection: (1) hard drive access control for providing Drive-Level and Sector-Level protection and (2) operating system-level independent file protection for providing File-Level and Network-Level protection.
Owner:PROXENSE
Method and a system for advanced content security in computer networks
InactiveUS20090064326A1Memory loss protectionUnauthorized memory use protectionNetworking protocolContent security
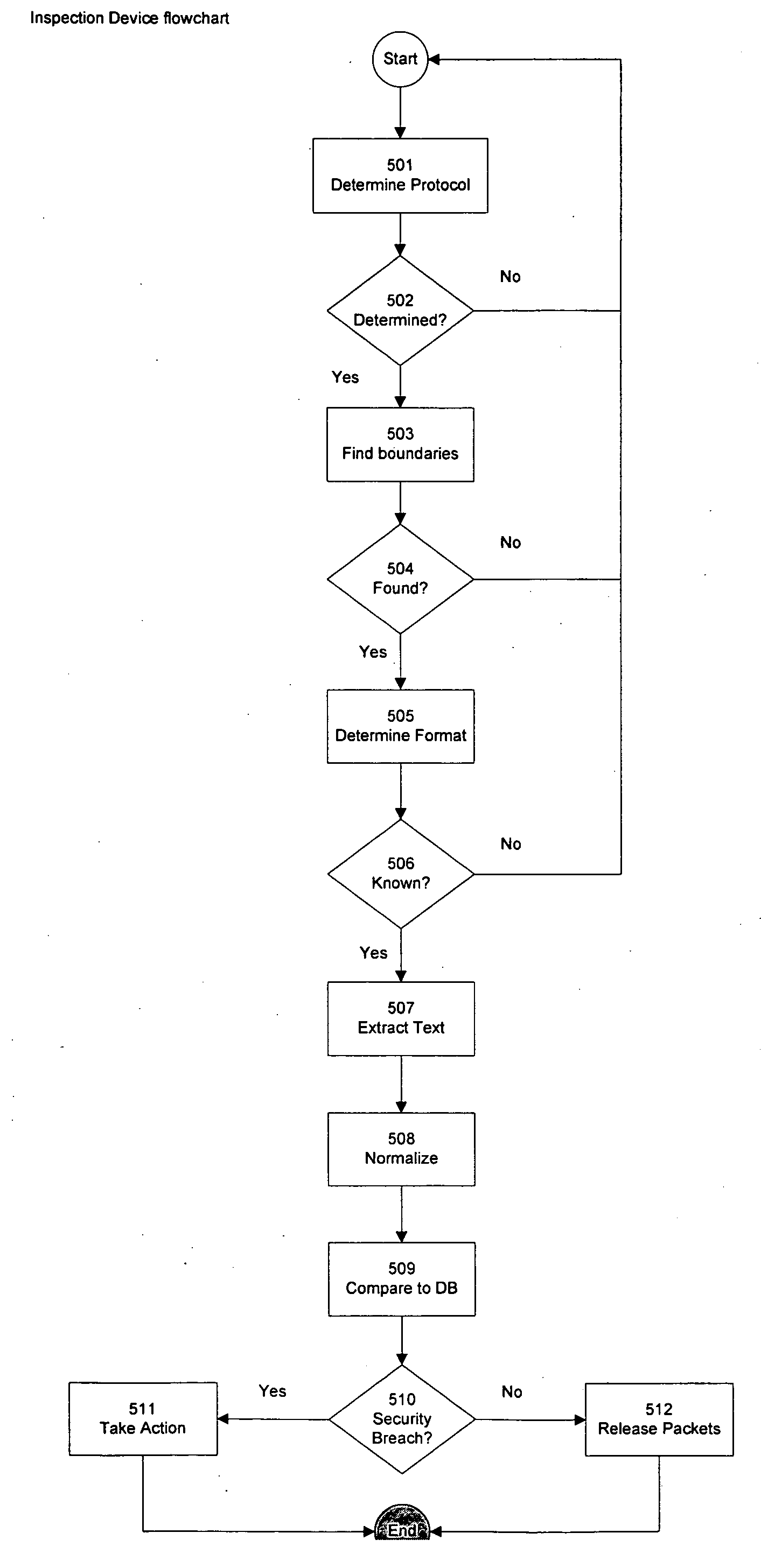
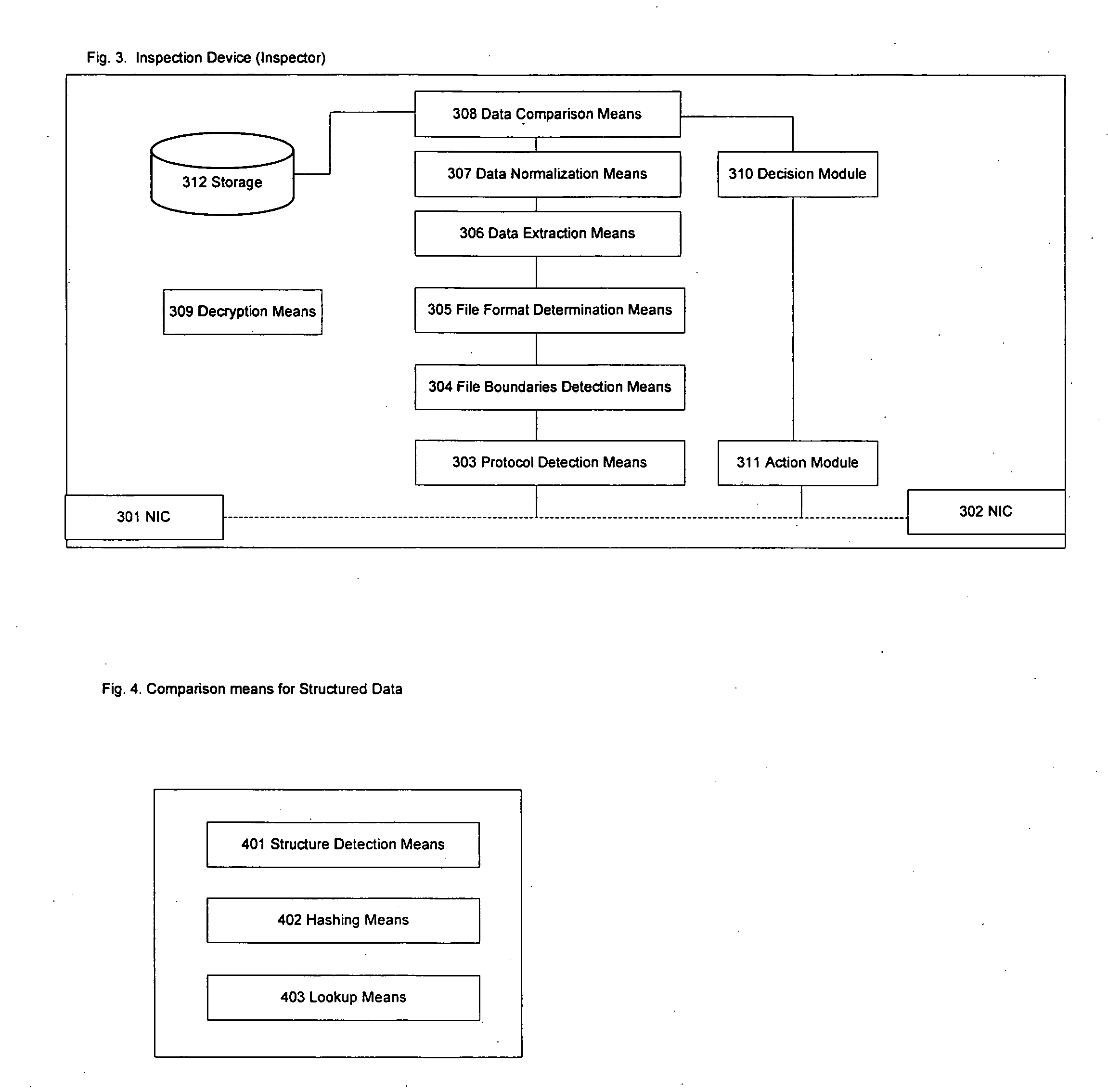
The present invention relates to a method and a system for protecting data in a computer network. A device is placed on a network edge in such a way, that all outgoing data has to pass through it. Separately, a set of data that is not allowed to leave the network is defined and stored in a secure form (typically, one way hash). The device determines the network protocol, file type, transforms and normalizes the passing data, and seeks the presence of the data from the defined set. If a threshold amount of the protected data is present, the device takes one of the following actions: block, alert, log, redact, store, redirect, encrypt, notify sender.
Owner:GTB TECH
Method, Apparatus and System for Secure Distribution of Content
InactiveUS20090290711A1Analogue secracy/subscription systemsDigital data protectionSmart cardContent security
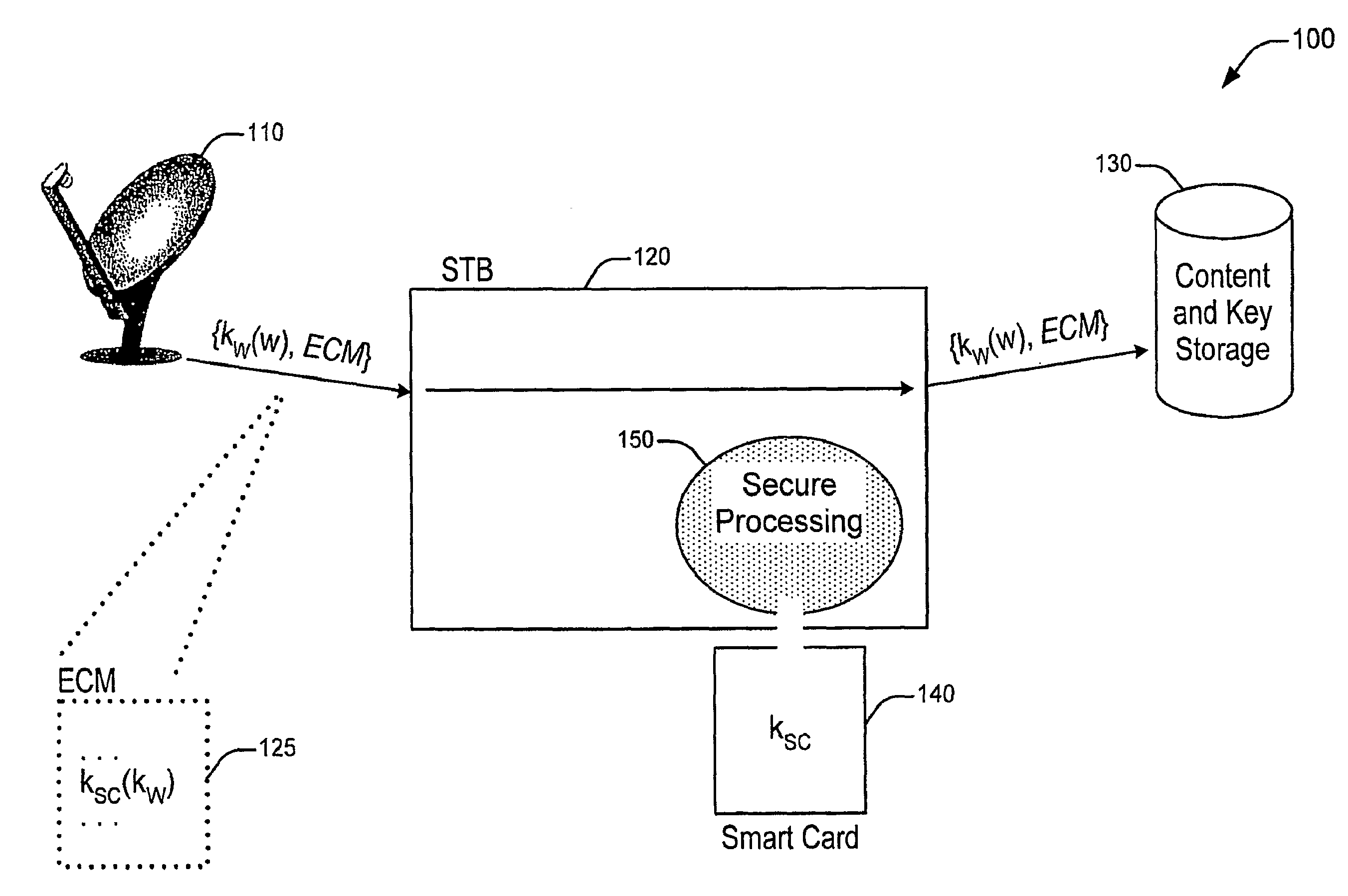
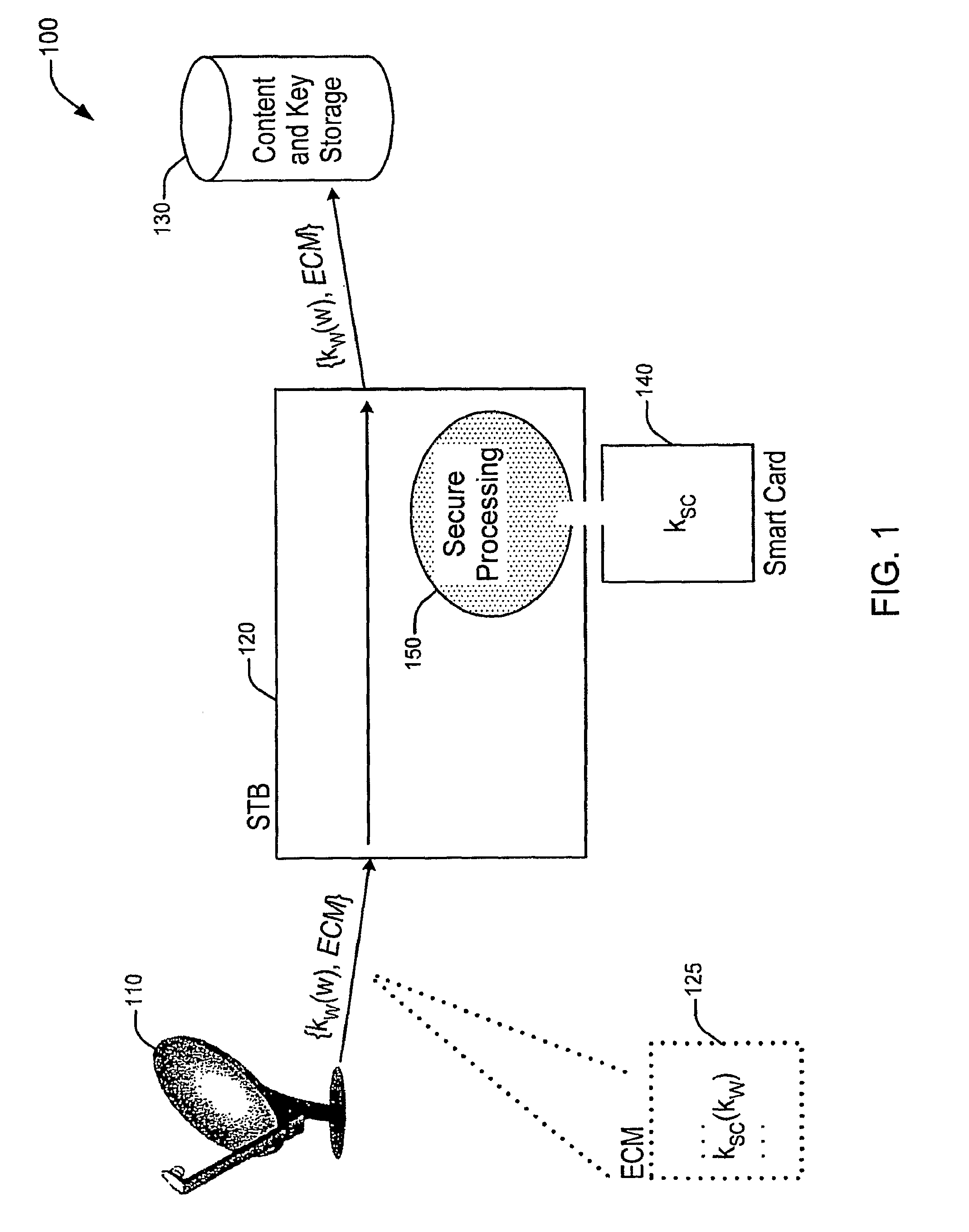
Embodiments of the present invention provide a method, apparatus and system for the secure distribution of content such as audiovisual content in a way that prevents users from misusing the content and provides a mechanism for tracking pirated material back to the original location of misappropriation. A security device, in accordance with one embodiment of the present invention, incorporates encryption methods to insure the broadcast encryption key remains secure. A marking device, in accordance with one embodiment of the present invention, incorporates, for example, digital watermarking methods that attach to the content information to identify a location of origin of the misappropriation, such as a Set-top Box (STB) and / or smart card.
Owner:THOMSON LICENSING SA
Digital content security system
InactiveUS20060064605A1Digital data processing detailsUser identity/authority verificationHard disc driveOperational system
Owner:PROXENSE
Method and a system for outbound content security in computer networks
InactiveUS20070198420A1Computer security arrangementsSecuring communicationNetworking protocolContent security
The present invention relates to a method and a system for protecting data in a computer network. A device is placed on a network edge in such a way, that all outgoing data has to pass through it. Separately, a set of data that is not allowed to leave the network is defined and stored in a secure form (typically, one way hash). The device determines the network protocol, file types, transforms and normalizes the passing data, and seeks the presence of the data from the defined set. If a threshold amount of the protected data is present, the device interrupts the connection or takes another appropriate action.
Owner:GTB TECH
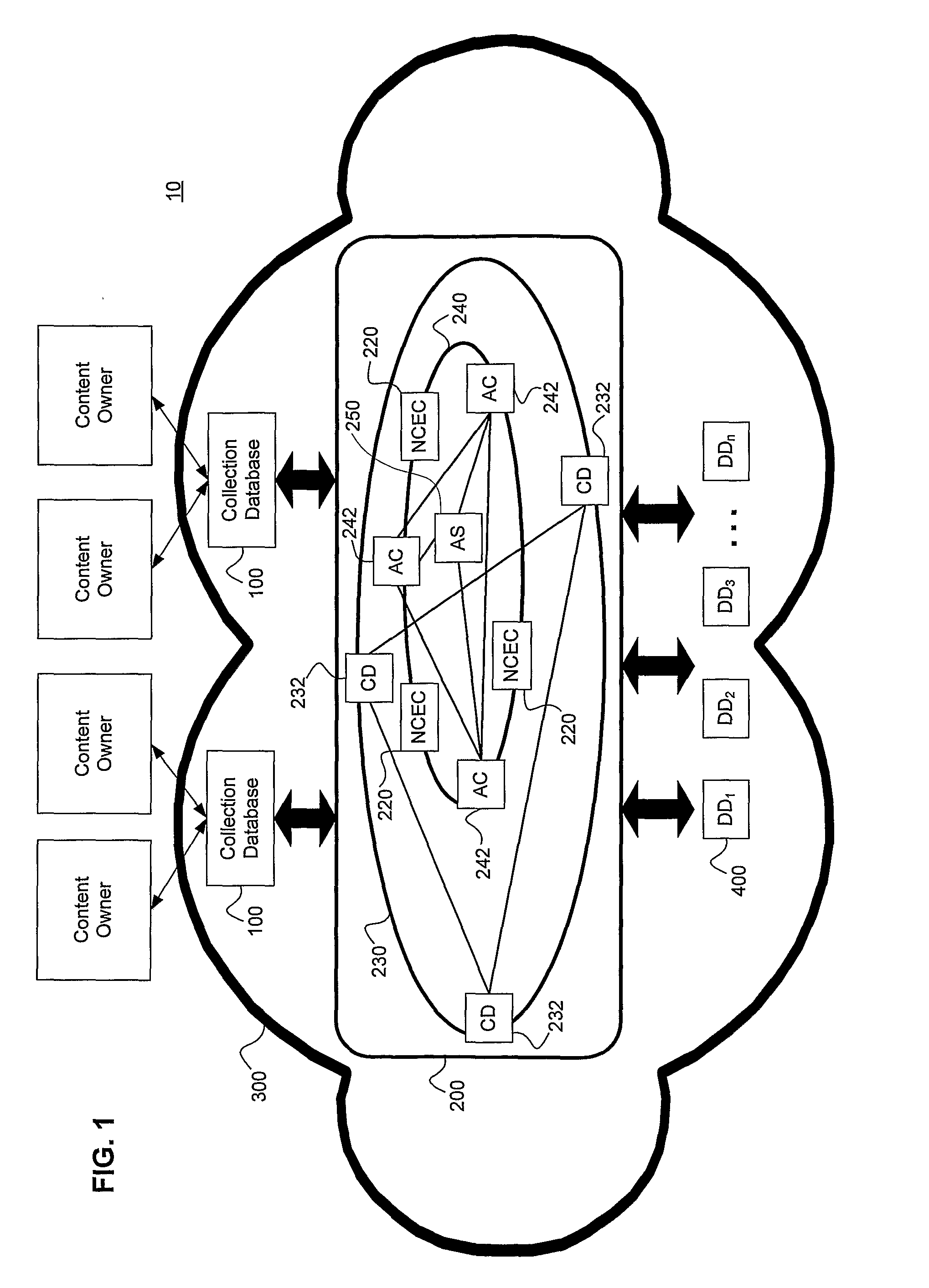
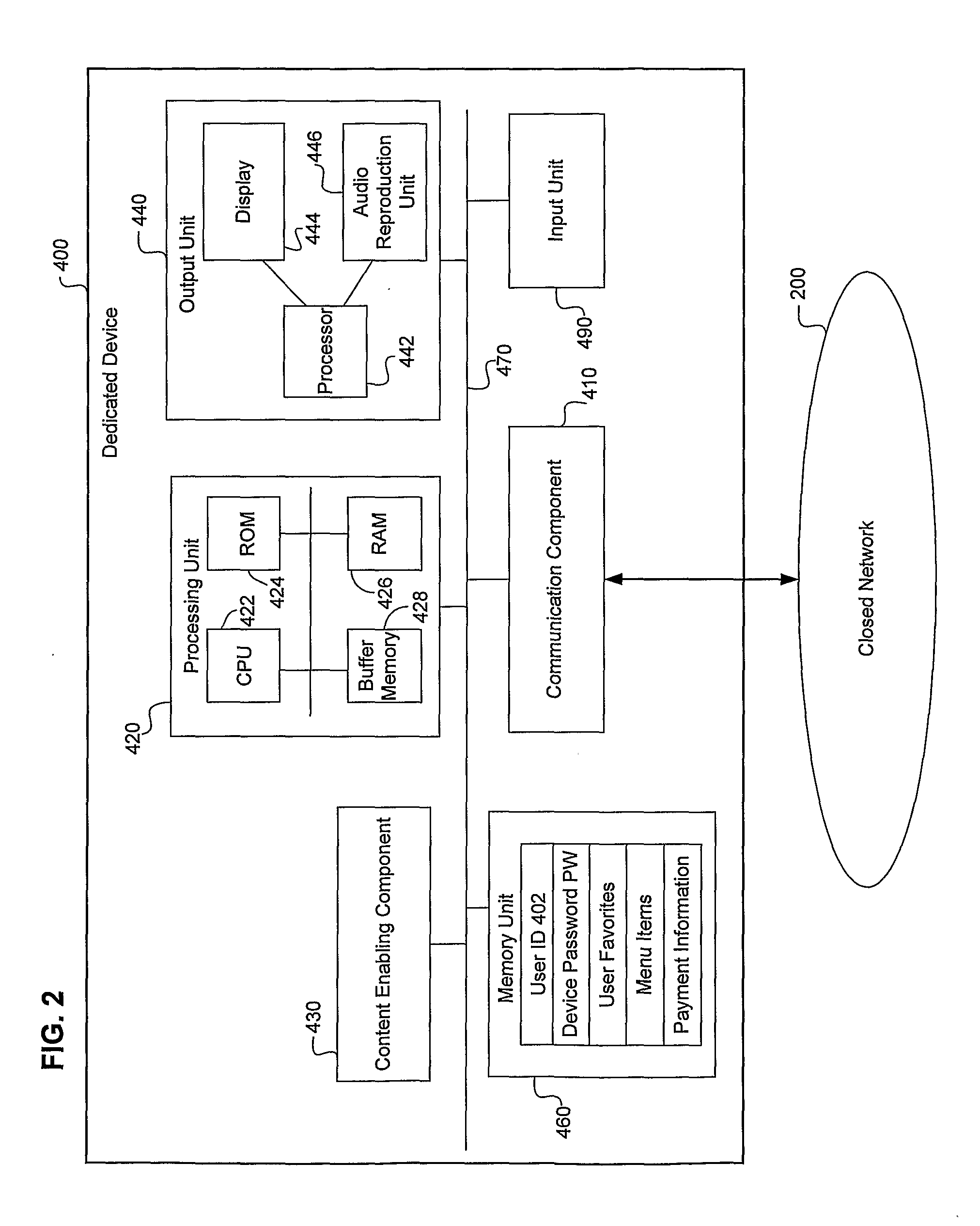
System and Method For Securely Communicating On-Demand Content From Closed Network to Dedicated Devices, and For Compiling Content Usage Data in Closed Network Securely Communicating Content to Dedicated Devices
ActiveUS20100241753A1Communication securityUser identity/authority verificationMultiple digital computer combinationsStreaming dataNetwork on
A system for securely communicating content as streaming data is provided. The system includes a closed network created on a public network, and a dedicated device for receiving twice-encrypted streamed content from the closed network. Upon authentication of the dedicated device, a content enabling component in the closed network twice-encrypts previously once-encrypted streamed content by using randomly selected encryption algorithms, and streams the twice-encrypted streamed content to the dedicated device during a closed network communication session and through a closed connection established between the closed network and the dedicated device. The dedicated device includes a content enabling component having a unique content enabling component identifier and a unique decryption key. The dedicated device decrypts the twice-encrypted streamed content by using its unique information and decryption key as well as randomly selected information received from the closed network during the closed network communication session and through the closed connection.
Owner:ZEBIC GREGOR
Digital content security system
InactiveUS7305560B2Digital data processing detailsUnauthorized memory use protectionHard disc driveOperational system
A Personal Digital Key Digital Content Security System (PDK-DCSS) is used to protect computers from unauthorized use and protect the digital content stored on computers from being wrongfully accessed, copied, and / or distributed. The basic components of the PDK-DCSS are (1) a standard hard drive device, with the addition of a PDK Receiver / Decoder Circuit (PDK-RDC) optionally integrated into the hard drive's controller, and (2) a PDK-Key associated with the PDK-RDC. The PDK-Key and RDC technology is utilized to provide two categories of protection: (1) hard drive access control for providing Drive-Level and Sector-Level protection and (2) operating system-level independent file protection for providing File-Level and Network-Level protection.
Owner:PROXENSE
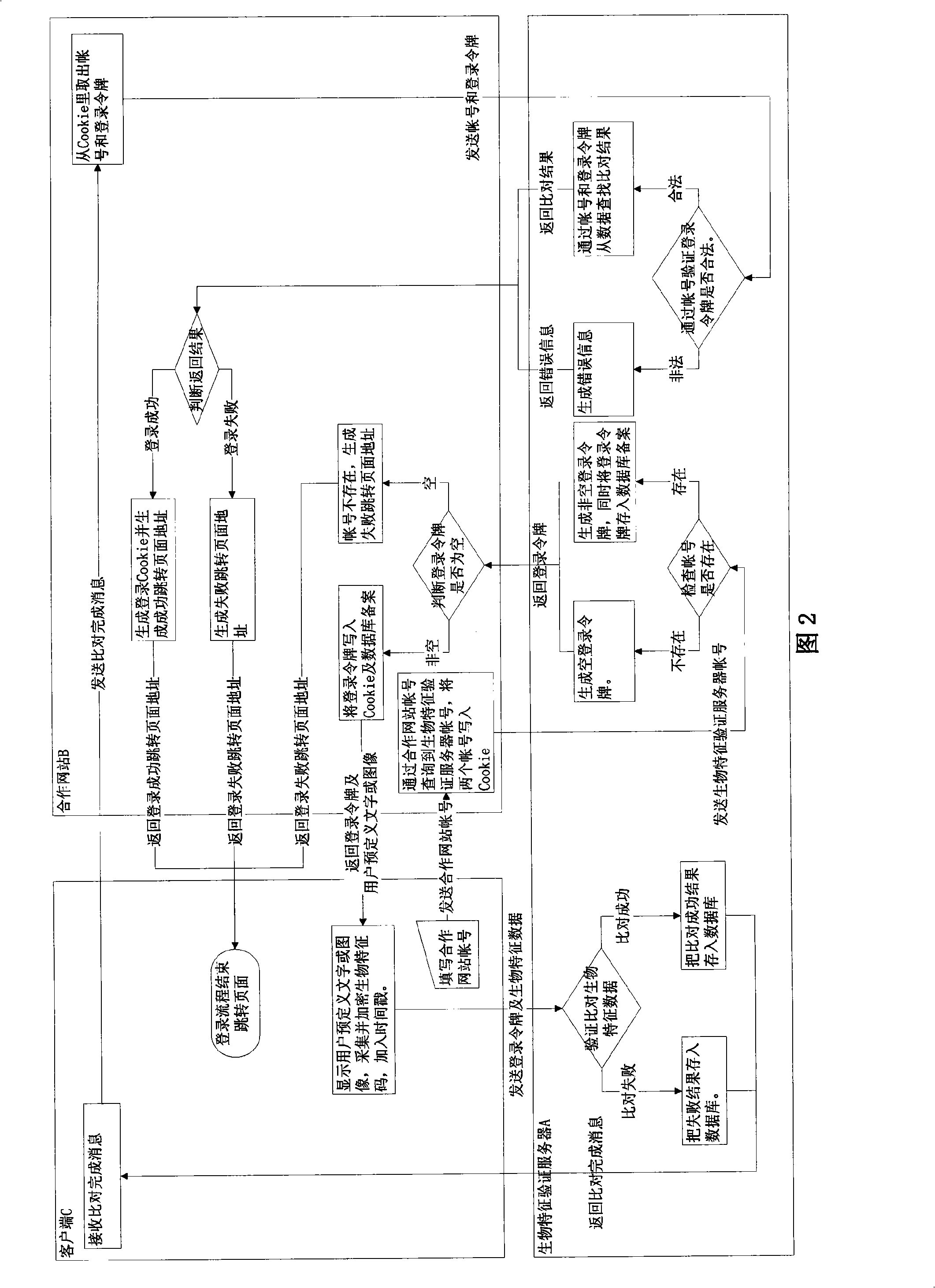
Network identity verification method based on internet third party biological characteristic validation
InactiveCN101316169AGuaranteed reliabilityEnsure safetyUser identity/authority verificationCharacter and pattern recognitionMultiple encryptionApplication software
The invention provides a network identity authentication method based on the biological characteristic authentication of a third party on the Internet. The biological characteristics (fingerprint, human face, iris, lip membrane and so on) are used as the identity identification of the user, the user can obtain an authentication request from the third party by submitting the biological characteristic codes through a client terminal widget provided by the third party, the identity authentication is carried out through the request password process and the matching algorithm, the Internet identity authentication can be carried out through a fully cooperative website or an application program provided by a cooperative network in a self-help mode, the third party provides request interfaces containing the registration, verification, reset of the biological characteristics, binding information,etc., the third party needs not to know the name of the user in the cooperative website or the application program provided by the cooperative network, thus avoiding to obtain the other information of the user in the cooperative website or the application program provided by the cooperative network, the reliability at the service terminal and the communication safety among the three parties can be guaranteed through the complete active service request of the cooperative website or the application program provided by the cooperative network, the Cookie, SSL, multi-encryption, digital signature of the widget, user-defined words or pictures,etc.
Owner:张曌 +2
Retail point of sale (RPOS) apparatus for internet merchandising
InactiveUS7003500B1Easy to optimizeCash registersApparatus for meter-controlled dispensingCredit cardThe Internet
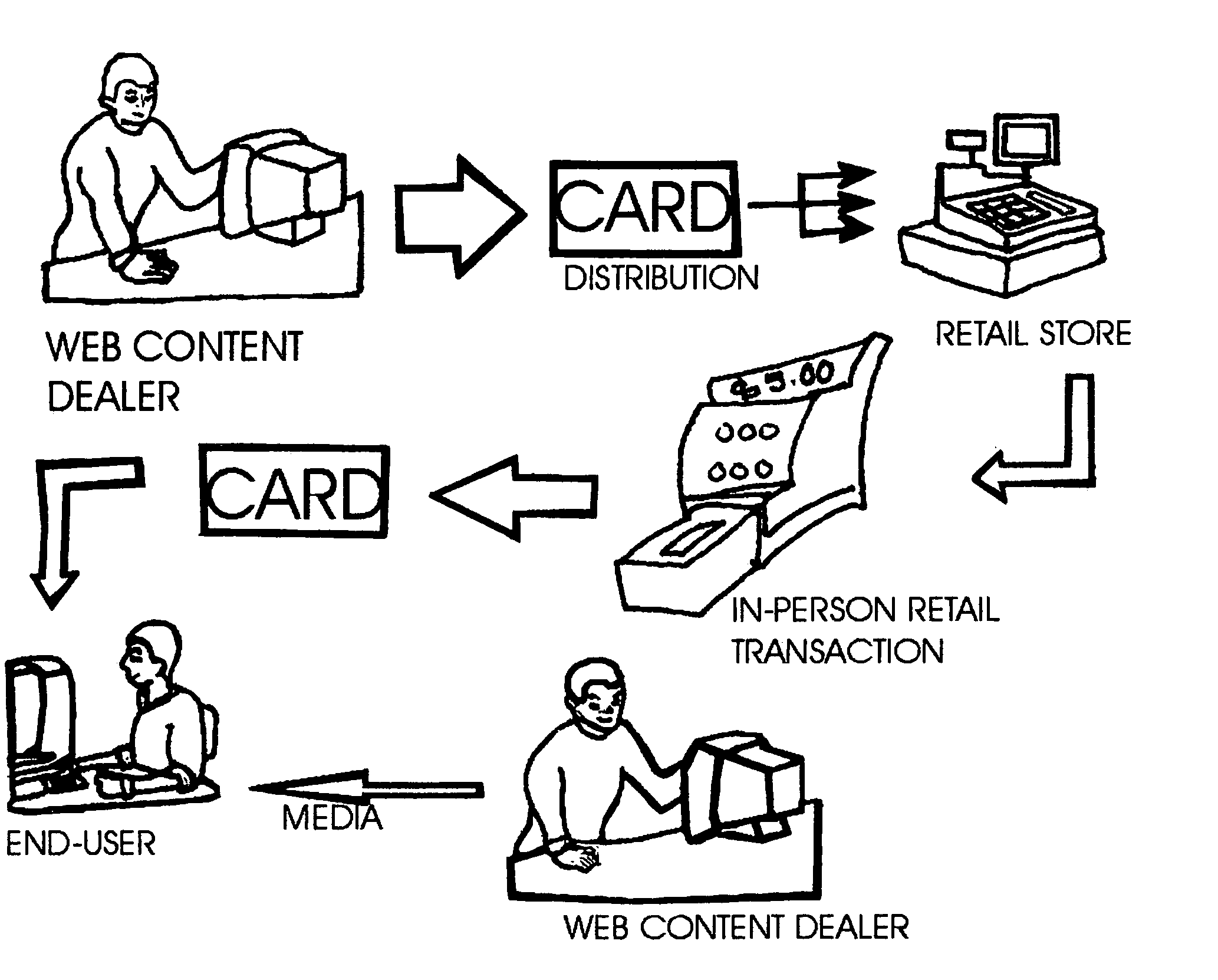
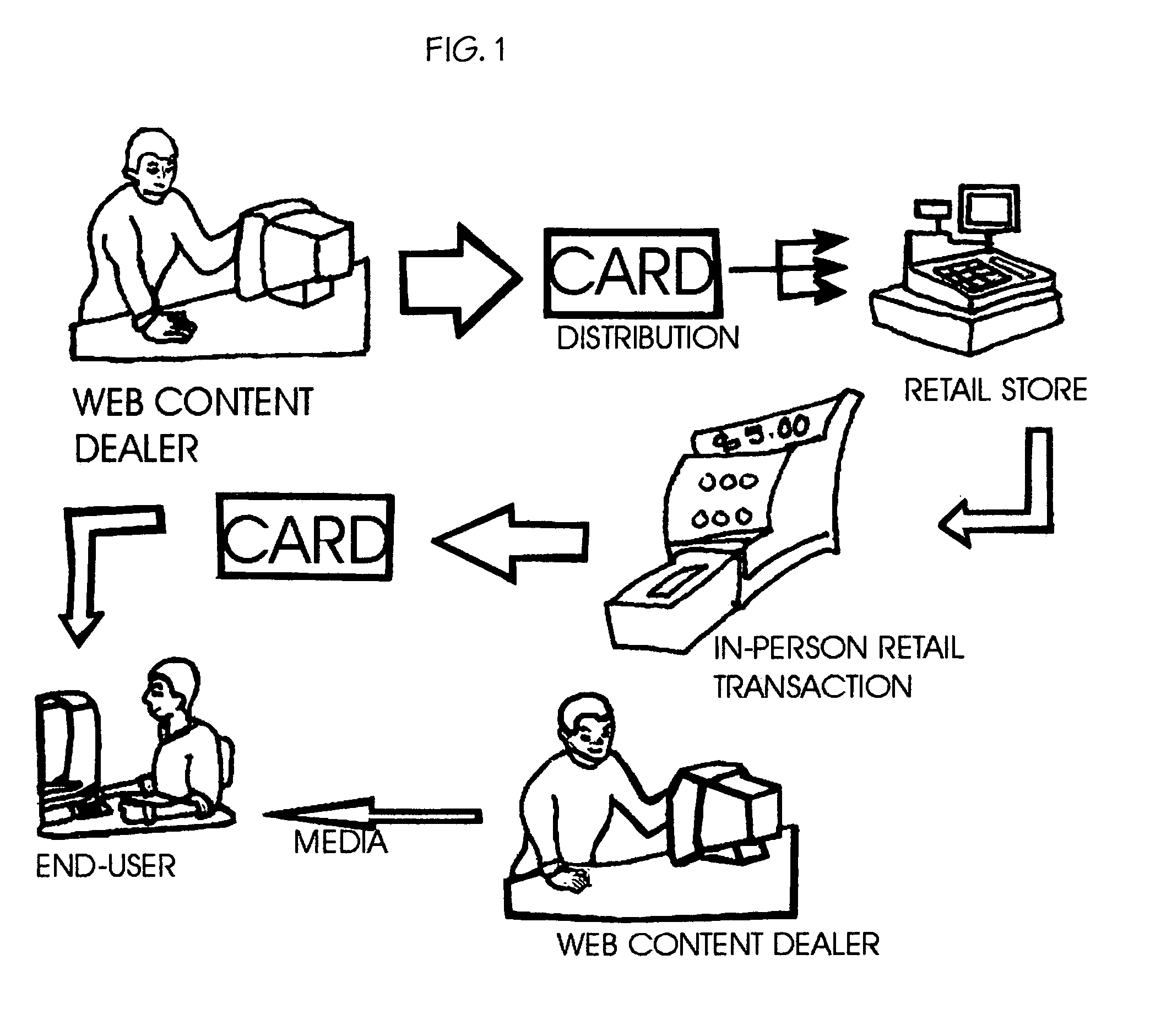
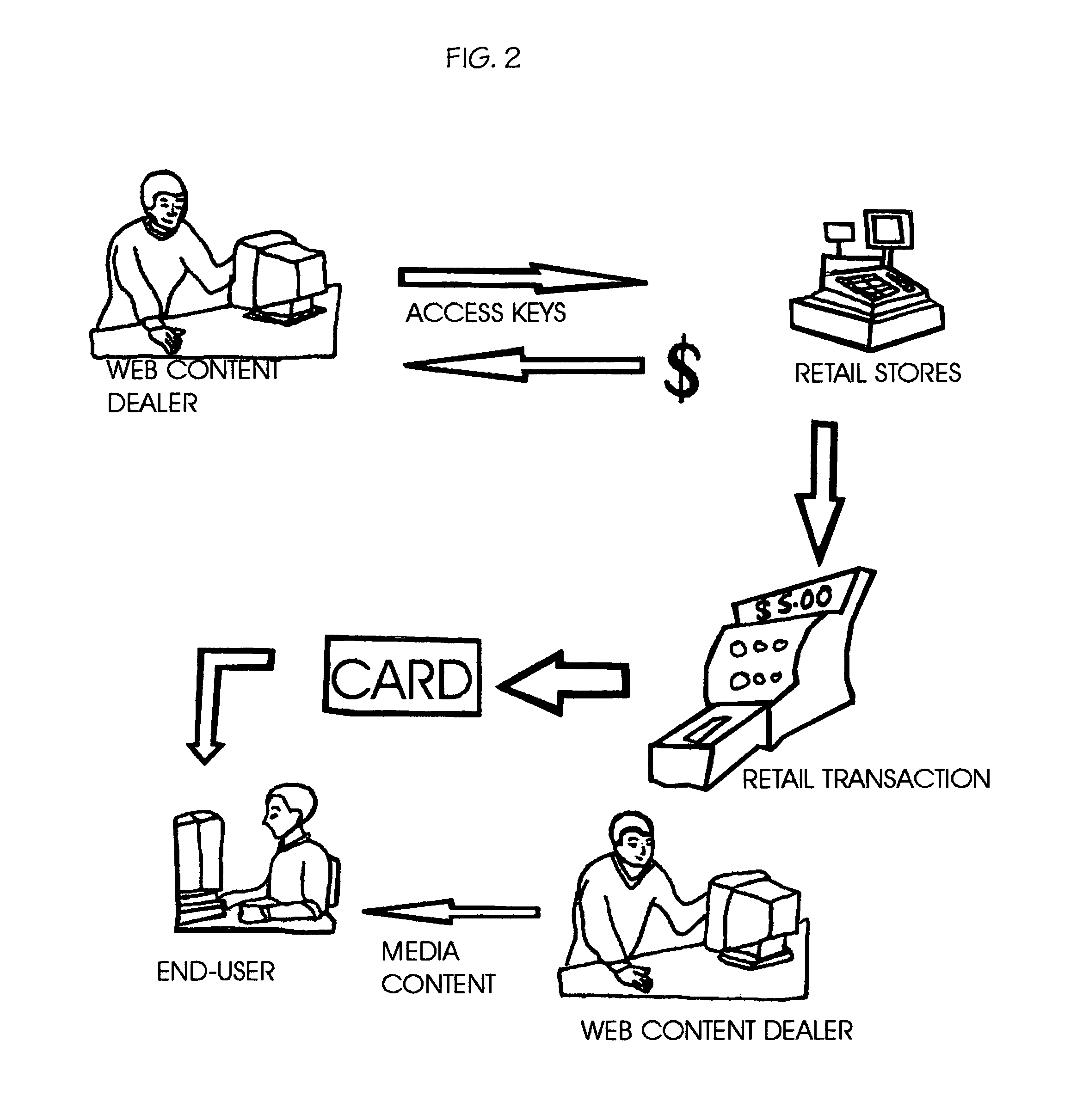
The present invention is an apparatus for the money transactions required in the selling of merchandise or media content on the Internet and uses at least one in-person contact with the buyer. A predefined transaction originating at a real place of business authorizes access to web content or merchandise from a place off the web. Purchasers (end-users) must physically go to a retail location to choose the Internet media or merchandise shopping cart they wish to acquire where age can be verified if necessary and payment can be made with or without a credit card. Content security using a non-audible or invisible code signal sequence(s) can provide traceability as well as absolute anonymity for the purchaser. This apparatus can be used to conduct transactions off the web so that business can be done on the web.
Owner:DRIESSEN MARGUERITE A
Digital content security system
InactiveUS7404088B2Digital data processing detailsUser identity/authority verificationHard disc driveOperational system
A Personal Digital Key Digital Content Security System (PDK-DCSS) is used to protect computers from unauthorized use and protect the digital content stored on computers from being wrongfully accessed, copied, and / or distributed. The basic components of the PDK-DCSS are (1) a standard hard drive device, with the addition of a PDK Receiver / Decoder Circuit (PDK-RDC) optionally integrated into the hard drive's controller, and (2) a PDK-Key associated with the PDK-RDC. The PDK-Key and RDC technology is utilized to provide two categories of protection: (1) hard drive access control for providing Drive-Level and Sector-Level protection and (2) operating system-level independent file protection for providing File-Level and Network-Level protection.
Owner:PROXENSE
Content security system for screening applications
ActiveUS20050278257A1Frustrate unauthorized digital copyingEasy to controlKey distribution for secure communicationRecord information storageInternet privacyMediaFLO
Owner:AVAGO TECH INT SALES PTE LTD
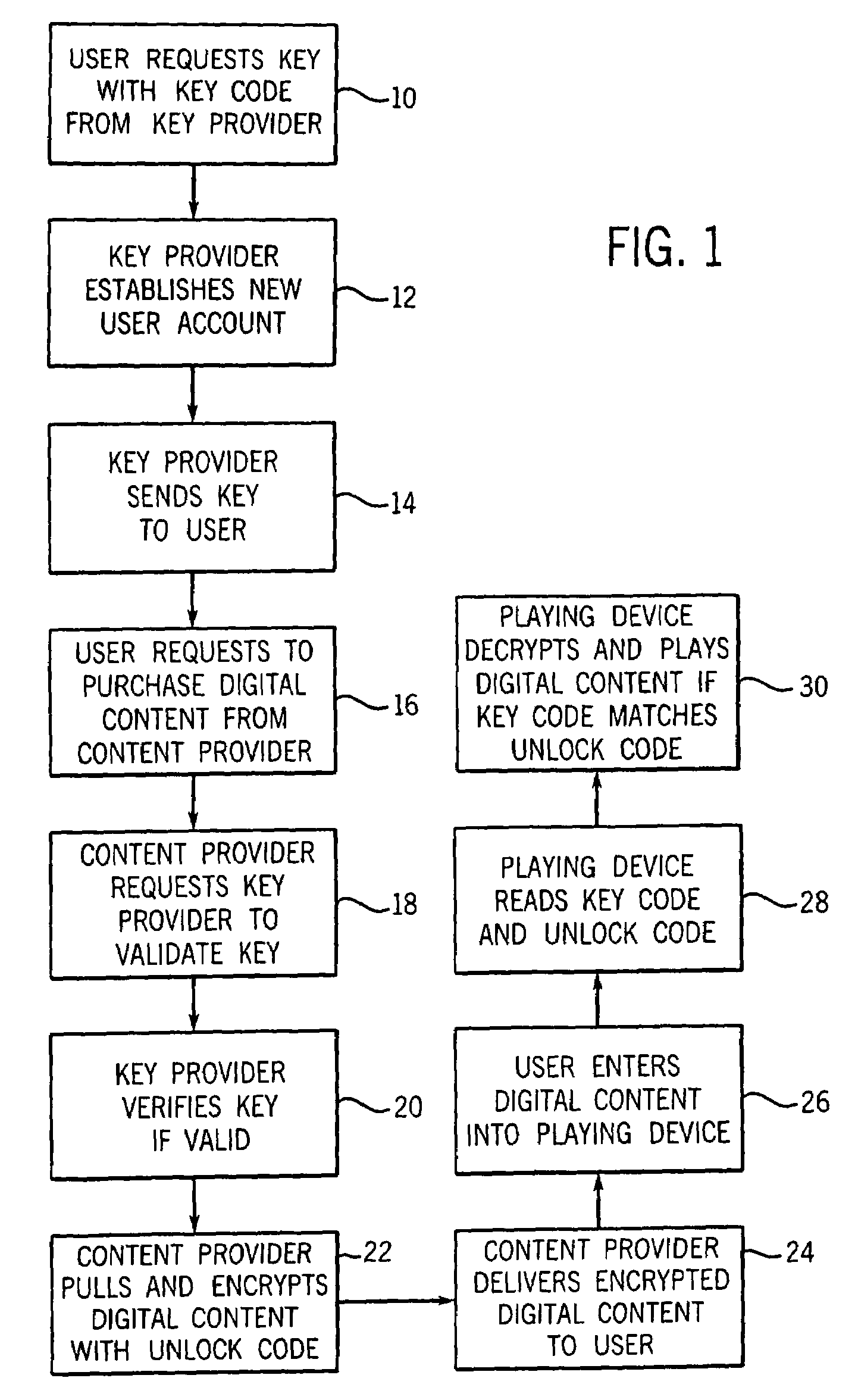
Securing digital content system and method
InactiveUS7421741B2Secure deliveryKey distribution for secure communicationPublic key for secure communicationDigital contentContent security
A system and method of encrypting digital content in a digital container and securely locking the encrypted content to a particular user and / or computer or other computing device is provided. The system uses a token-based authentication and authorization procedure and involves the use of an authentication / authorization server. This system provides a high level of encryption security equivalent to that provided by public key / asymmetric cryptography without the complexity and expense of the associated PKI infrastructure. The system enjoys the simplicity and ease of use of single key / symmetric cryptography without the risk inherent in passing unsecured hidden keys. The secured digital container when locked to a user or user's device may not open or permit access to the contents if the digital container is transferred to another user's device. The digital container provides a secure technique of distributing electronic content such as videos, text, data, photos, financial data, sales solicitations, or the like.
Owner:DIGITAL REG OF TEXAS
Method, System and Program Product for Secure Storage of Content
ActiveUS20140140508A1Key distribution for secure communicationSecret communicationPassword hashingMaster key
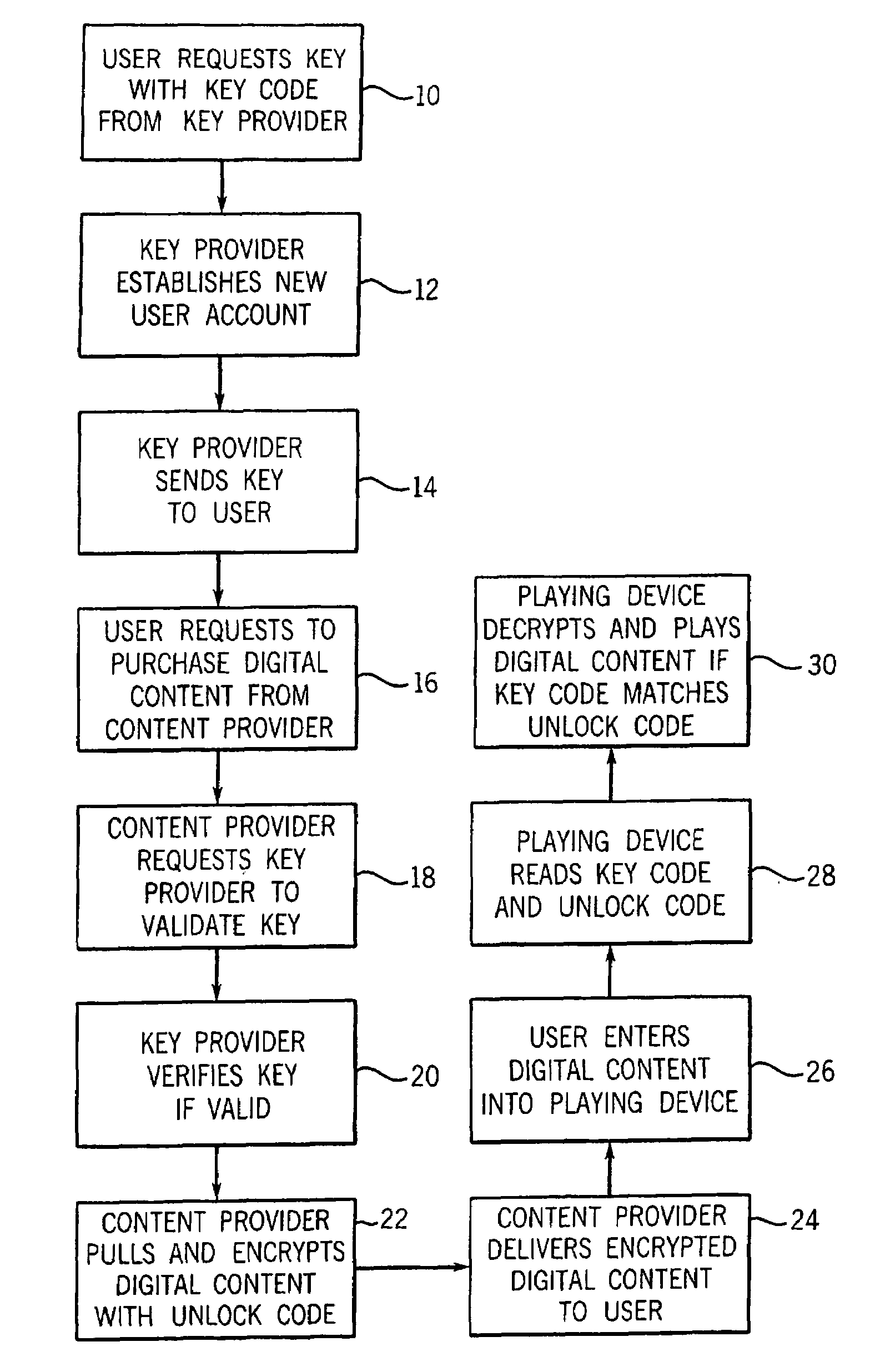
A method, system and program product comprise obtaining a user's username and password. A random key is generated for use as a master key. The master key is encrypted using the password to create an encrypted master key. A hash function is performed on the password to create a password hash. A random key is generated for use as a content key for encrypting the user's selected content. The content key is encrypted using the master key to create an encrypted content key. The selected content is encrypted using the content key to create encrypted content. The username, password hash, encrypted master key, first encrypted content key, and encrypted content is communicated to a server for storage in the user's account in which the possibility of decrypting at least the encrypted content by operations on the server is mitigated.
Owner:KAMATH DEEPAK +1
System and method for providing telephonic content security service in a wireless network environment
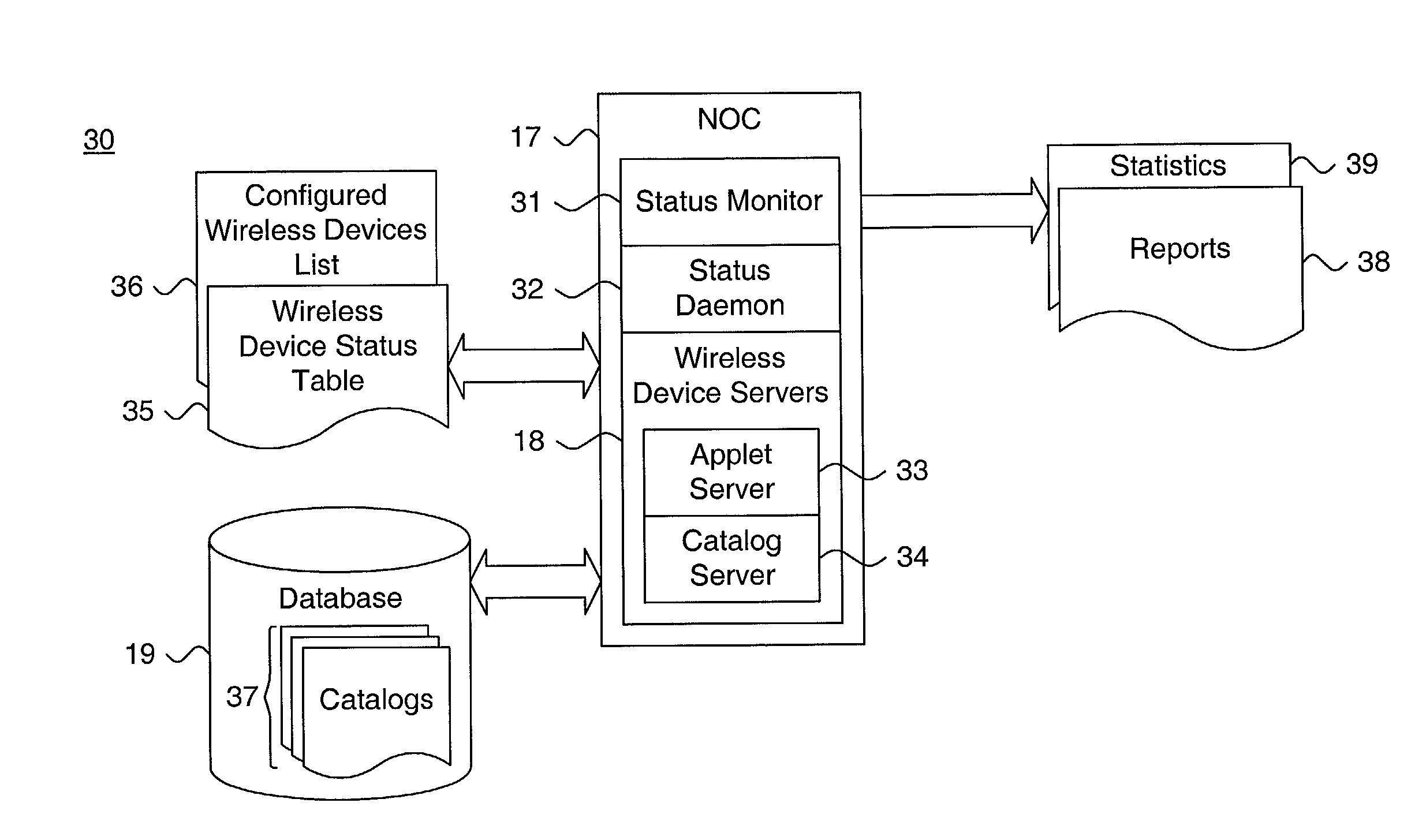
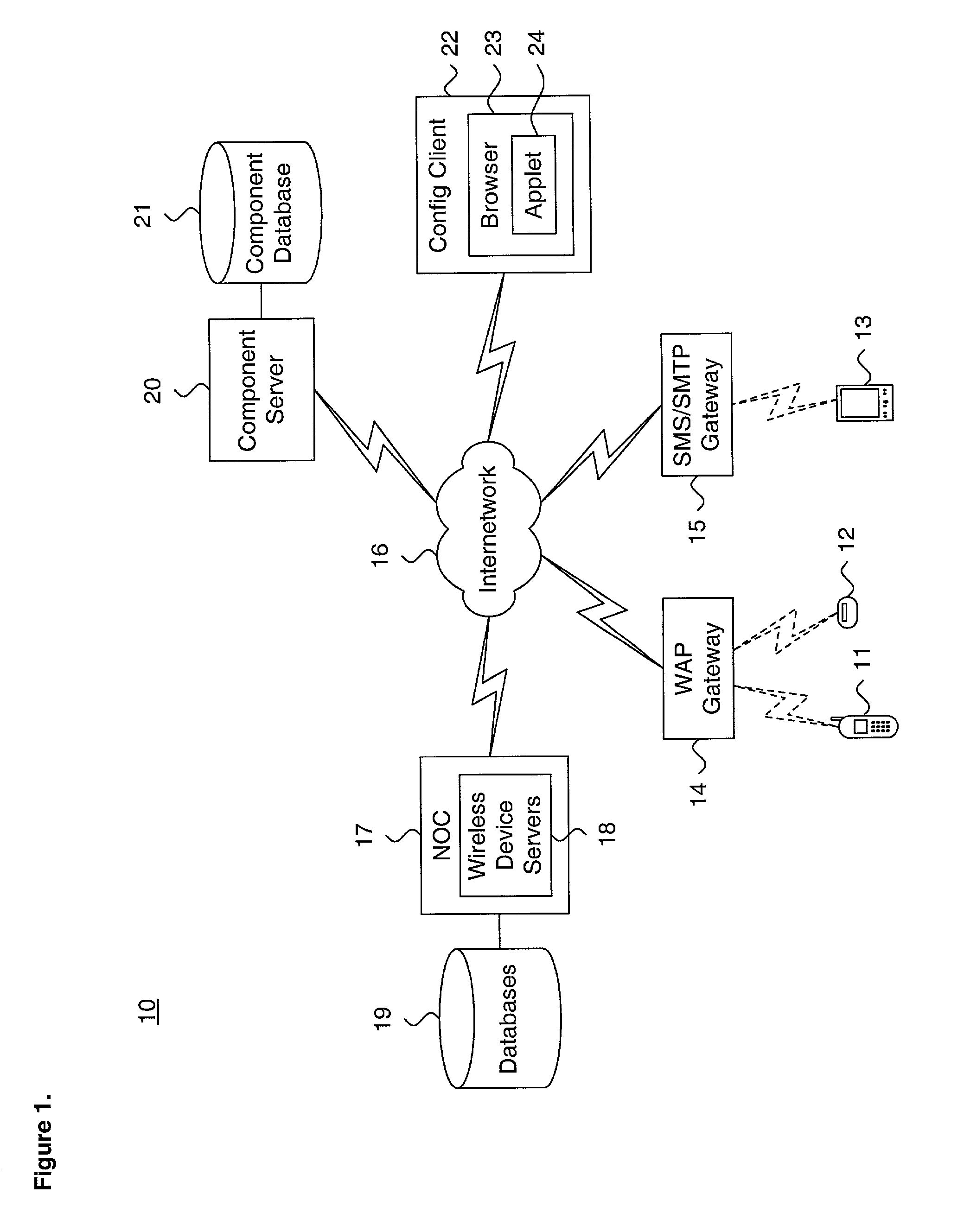
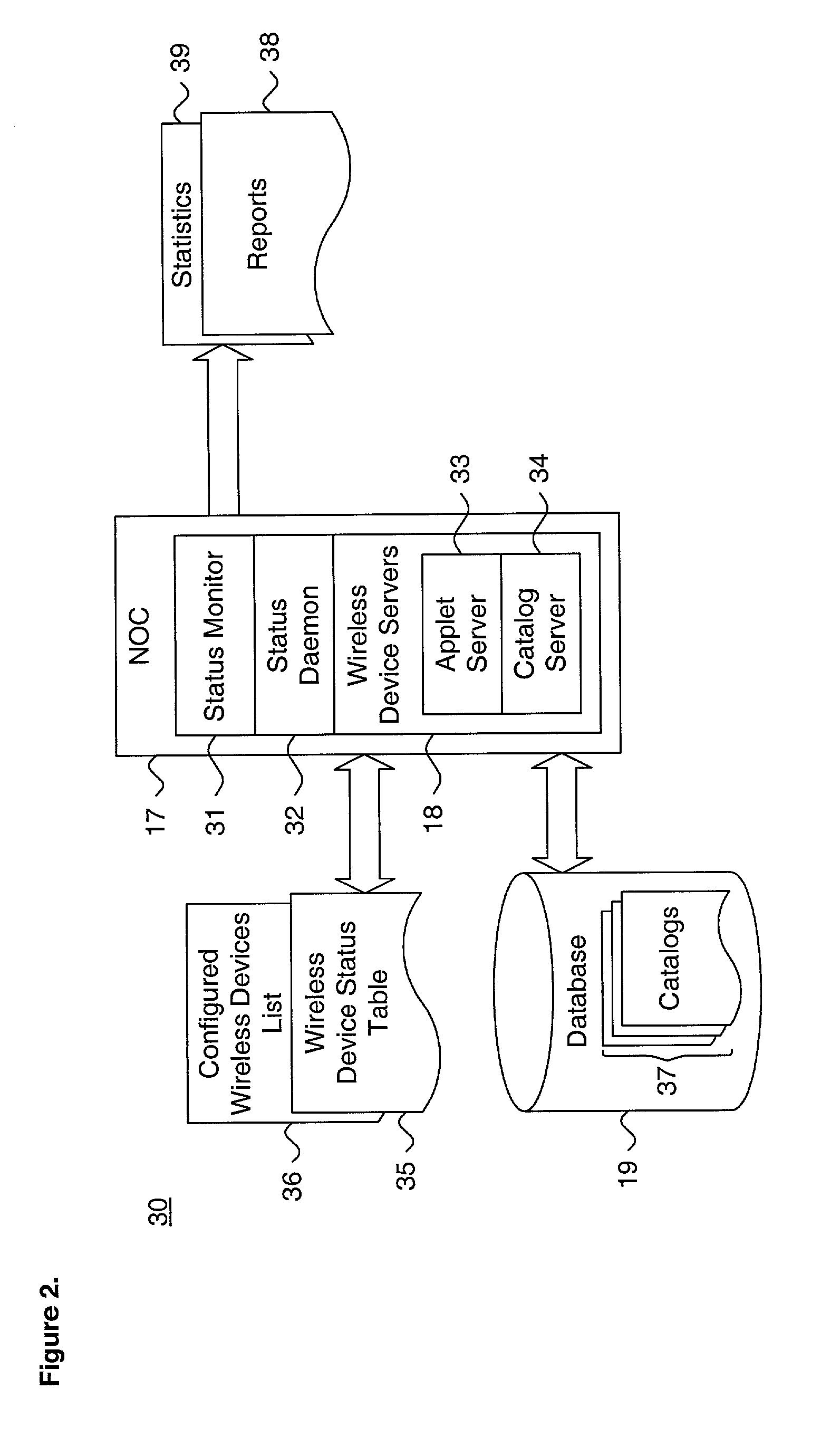
ActiveUS7146155B2Configures applicationEasy to configureUnauthorised/fraudulent call preventionEavesdropping prevention circuitsNetwork connectionNetwork operations center
A system and method for providing telephonic content security service in a wireless network environment is described. A plurality of wireless devices interfacing over a network providing wireless telephonic services through a layered service architecture. Content security services are provisioned to the wireless devices via the layered service architecture. Each content security service is delivered through applications executing in a user layer on each wireless device. The provisioning of the content security services to each wireless device are supervised from a network operations center at which are maintained a master catalog of the applications and configured wireless devices list. Configuration of each wireless device is managed from a configuration client by consulting the master catalog and the configured wireless devices list and downloading the applications to each wireless device. The content security services are delivered as functionality provided through execution of the applications on each wireless device.
Owner:MCAFEE LLC
Apparatus for generating secure key using device and user authentication information
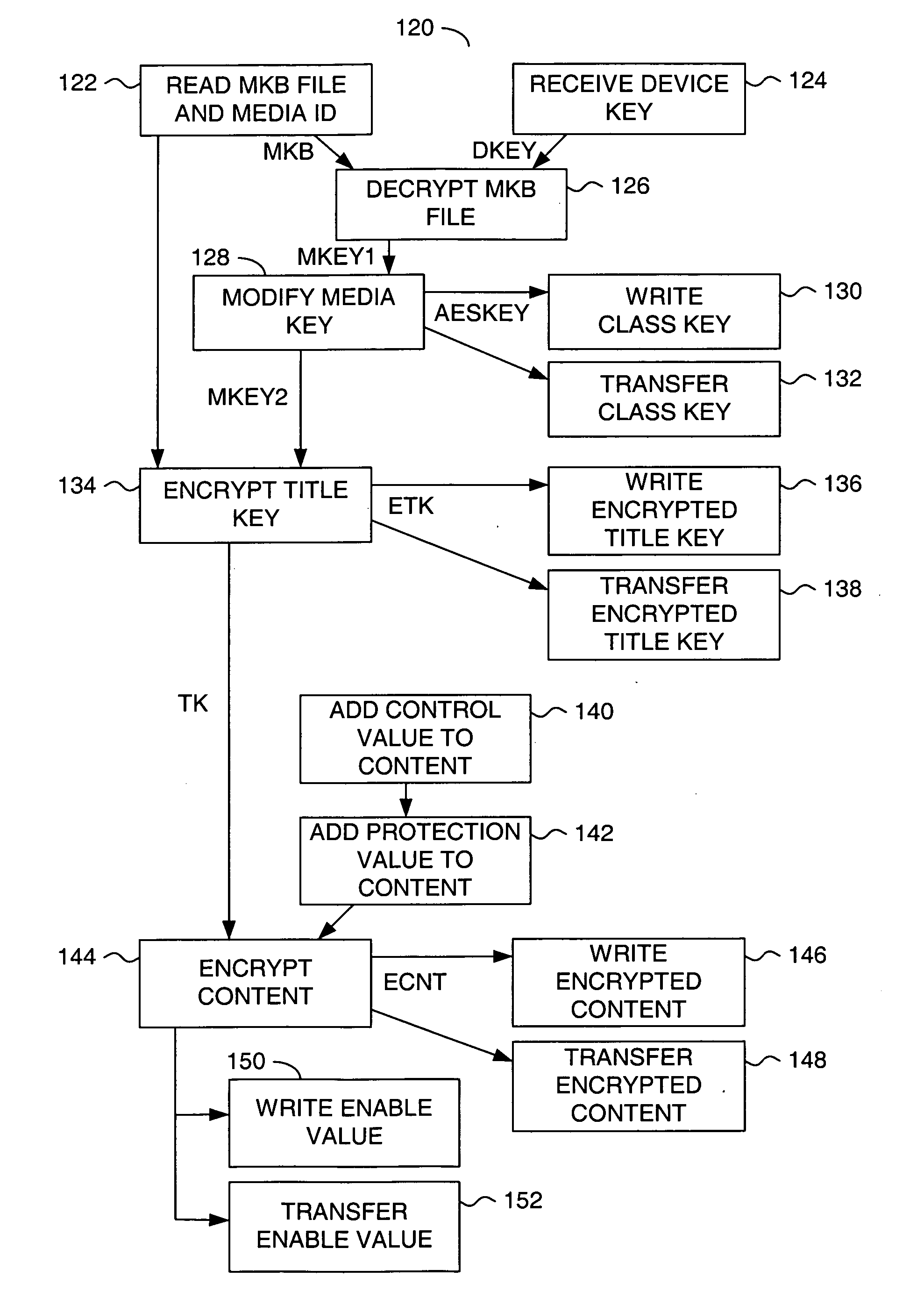
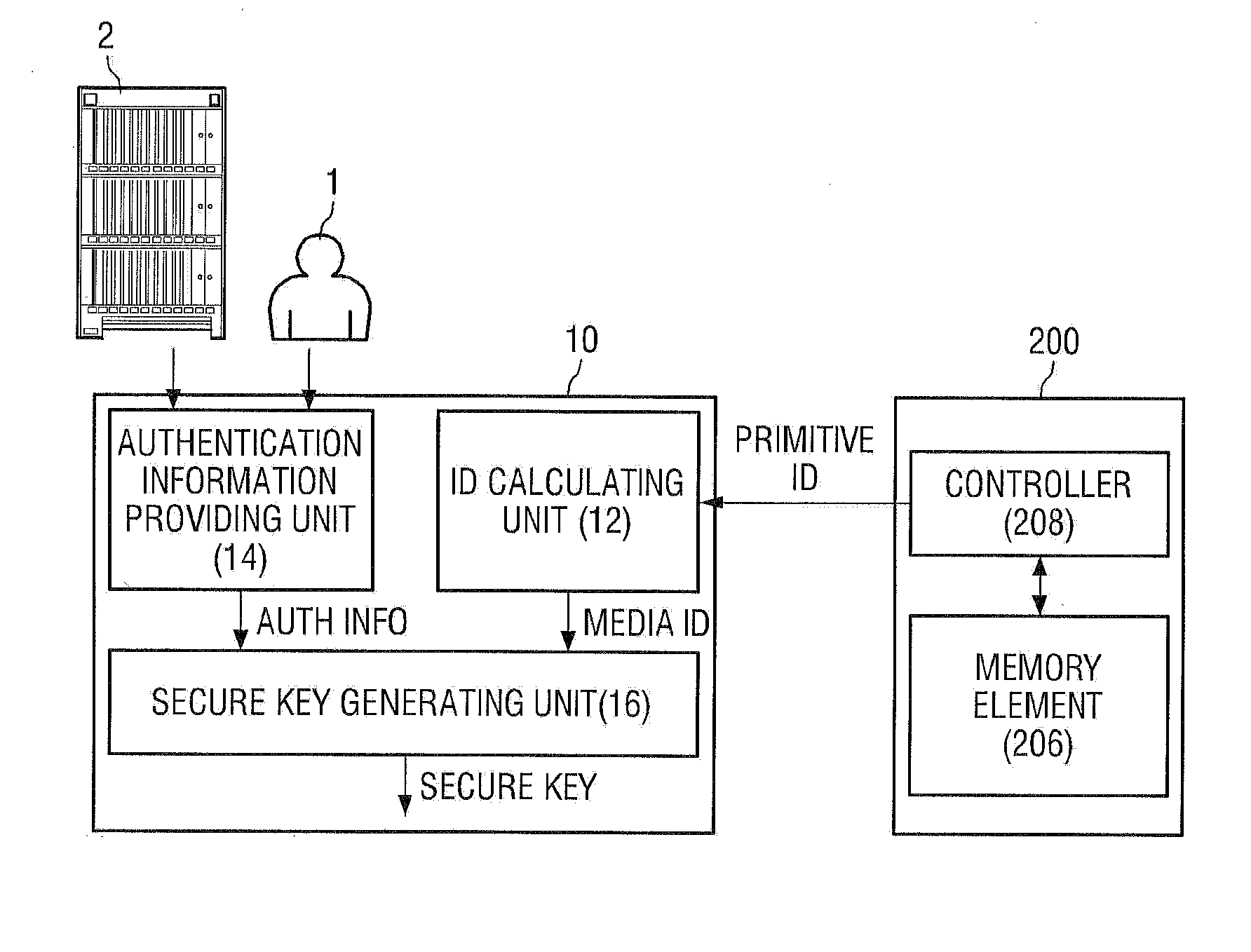
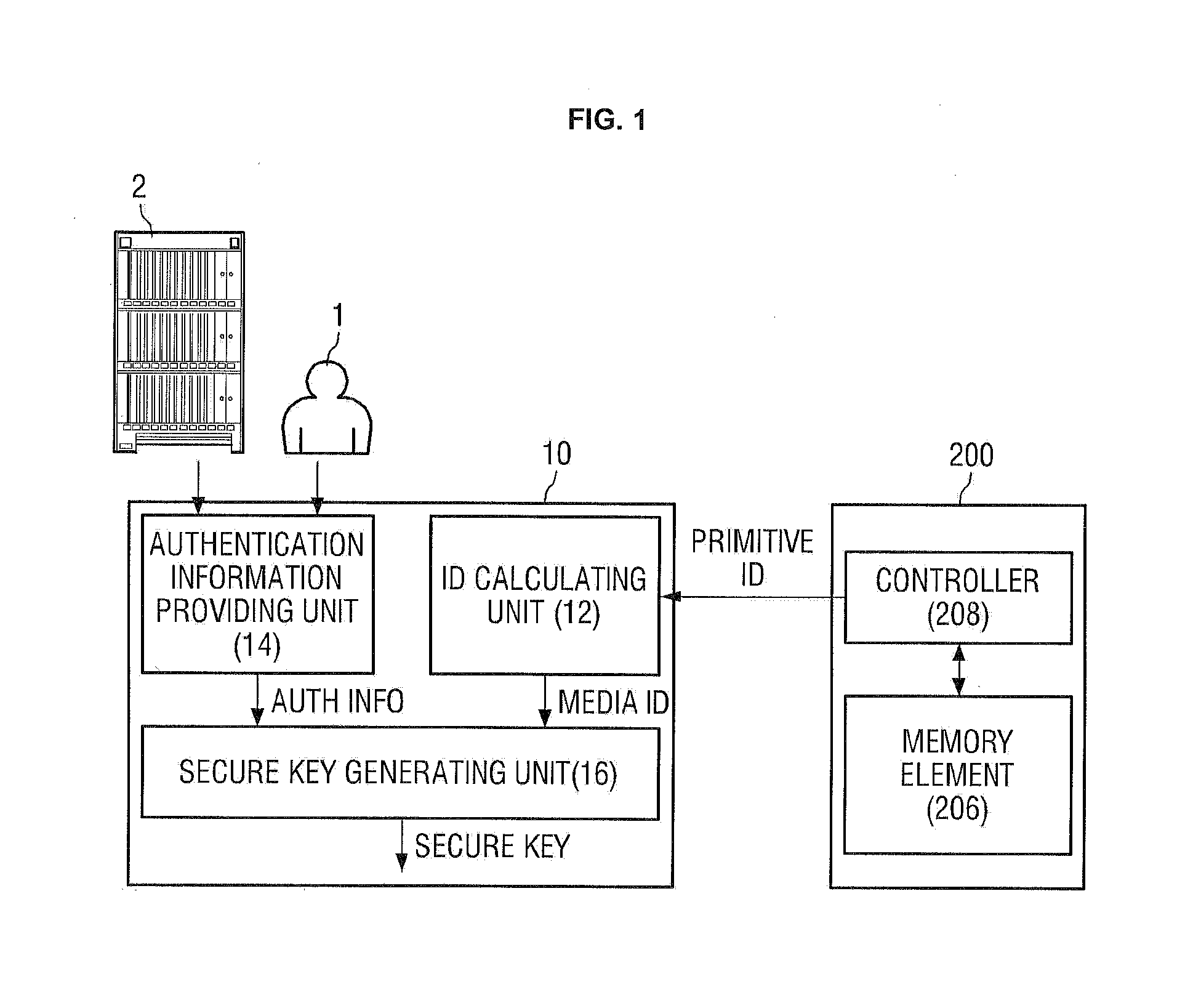
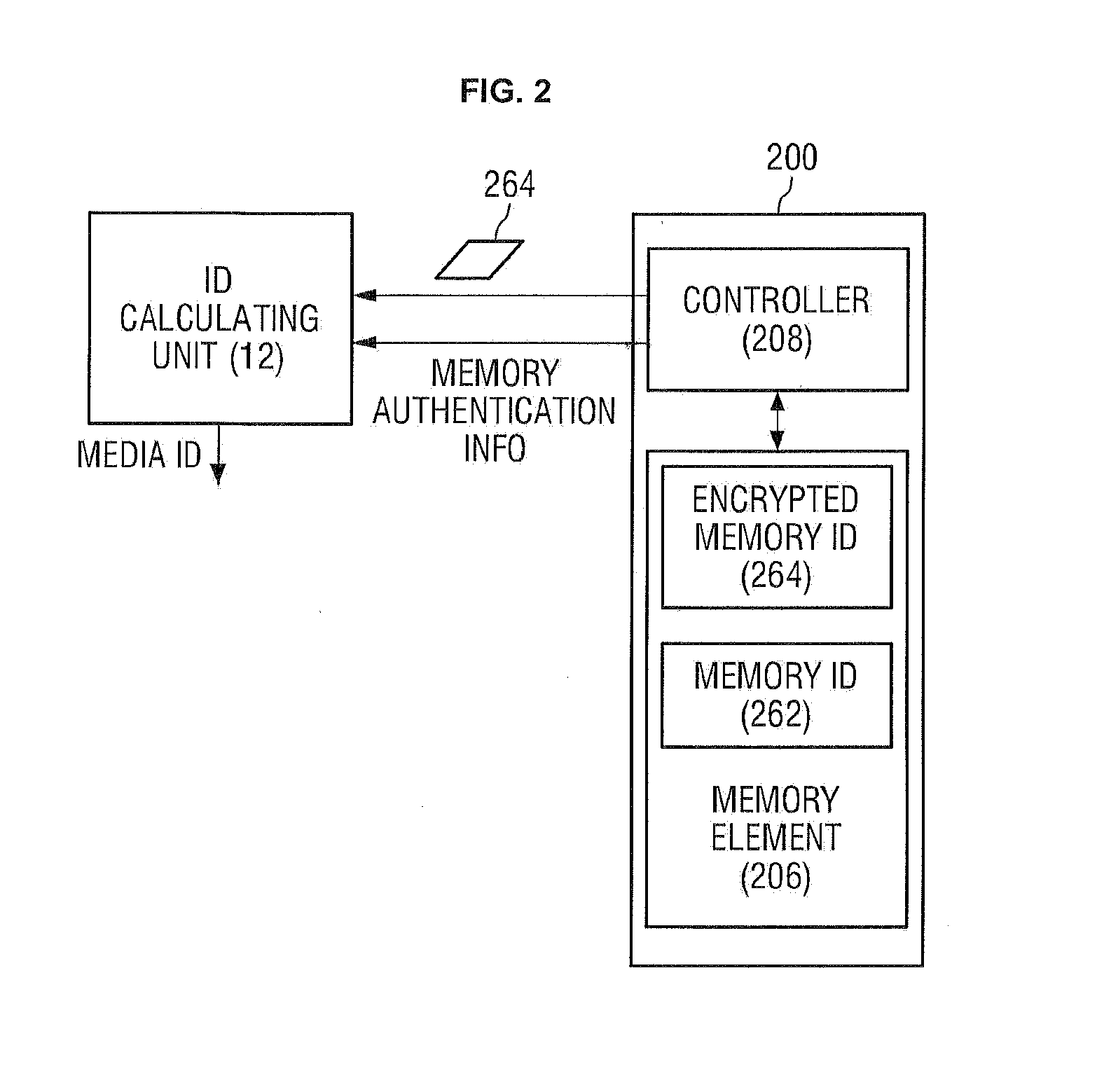
ActiveUS20130318358A1Privacy protectionGuaranteed safe generationKey distribution for secure communicationDigital data authenticationUnique identifierUser authentication
A secure key generating apparatus comprising an ID calculating unit receiving a primitive ID from a first storage device and calculating a first media ID, (a unique identifier of the first storage device), from the first primitive ID; a user authentication information providing unit providing user authentication information for authenticating the current; and a secure key generating unit for generating a first Secure Key using both the first media ID and the first user's authentication information. The Secure Key is used to encrypt / decrypt content stored in the first storage device. The secure key generating unit generates a first different Secure Key using a second media ID of a second storage device, and generates a second different Secure Key using second user's user authentication information. Only the first Secure Key can be used to decrypt encrypted content stored in the first storage device that was encrypted using the first Secure Key.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and system for enabling content security in a distributed system
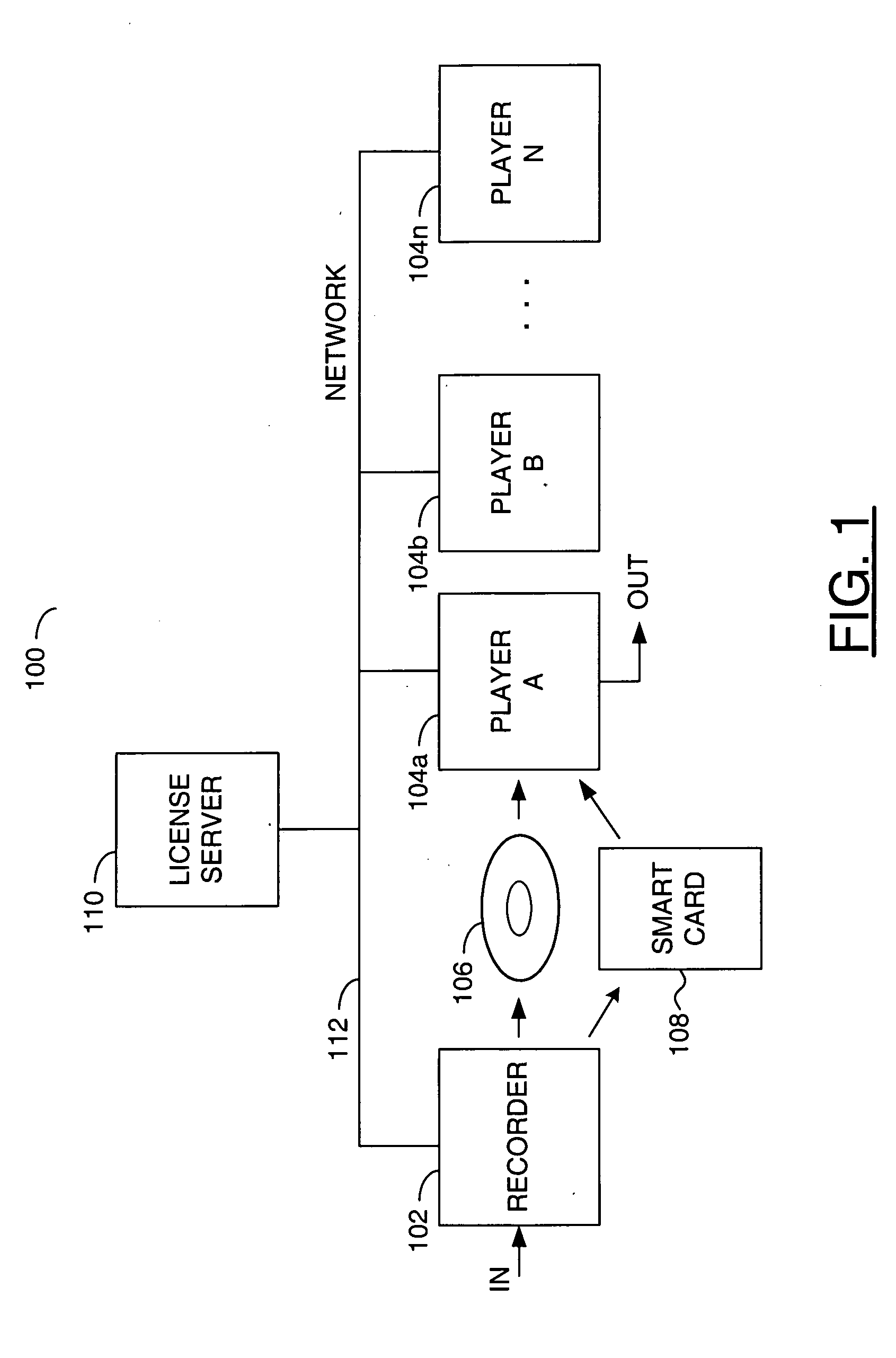
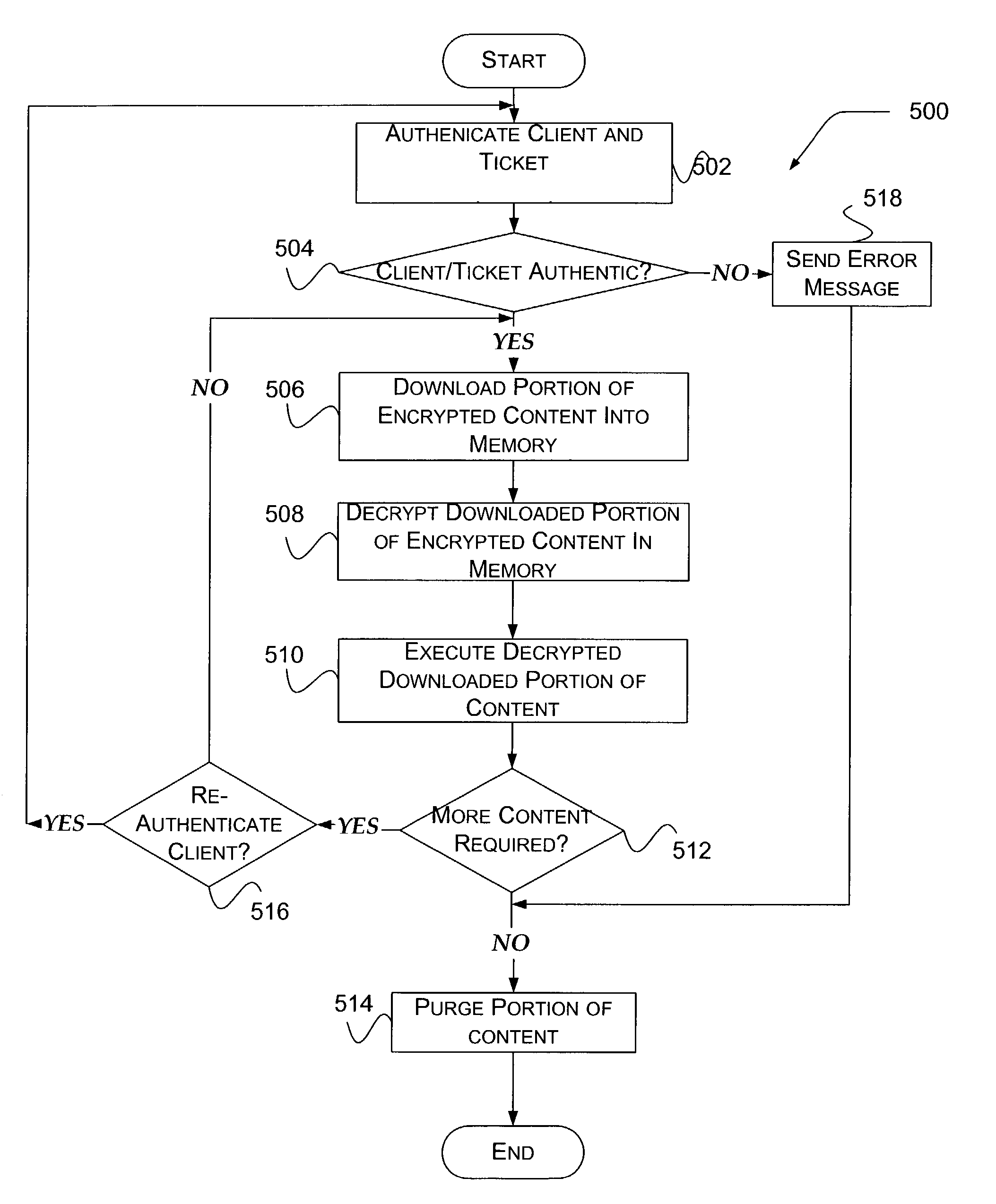
ActiveUS7243226B2Reduce theftUser identity/authority verificationDigital computer detailsDigital signatureClient-side
A method and system are directed towards enabling content security in a distributed environment. The system includes a data store for content associated with an application that may be tagged as exclusively memory resident at a client. The content may also be encrypted and digitally signed. When an authenticated client requests the content, it is provided at a constrained rate that enables a portion of the content to start execution on the client before the application associated with the content is completely downloaded. Additional portions of the content are provided to the client when the additional portions are required for execution by the application.
Owner:VALVE
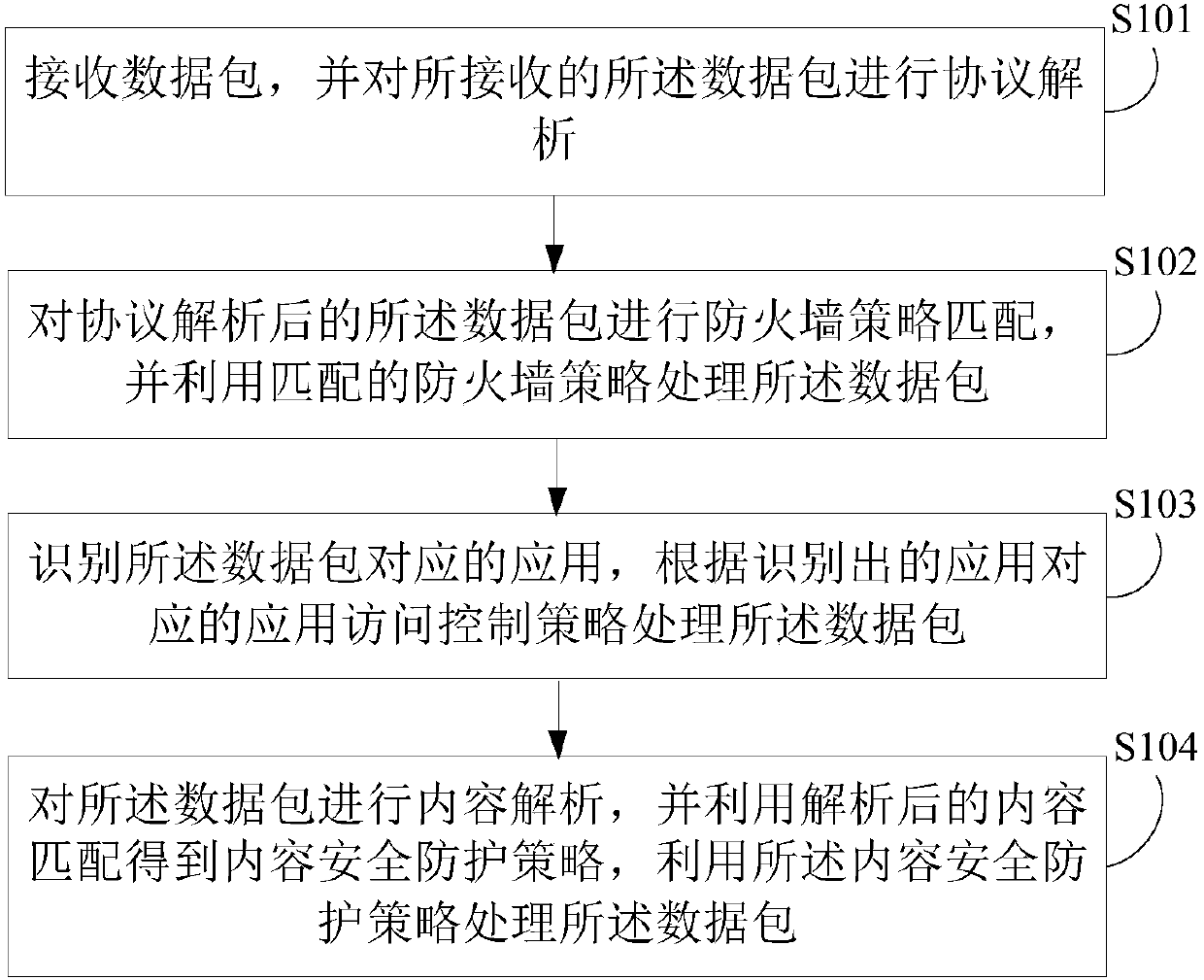
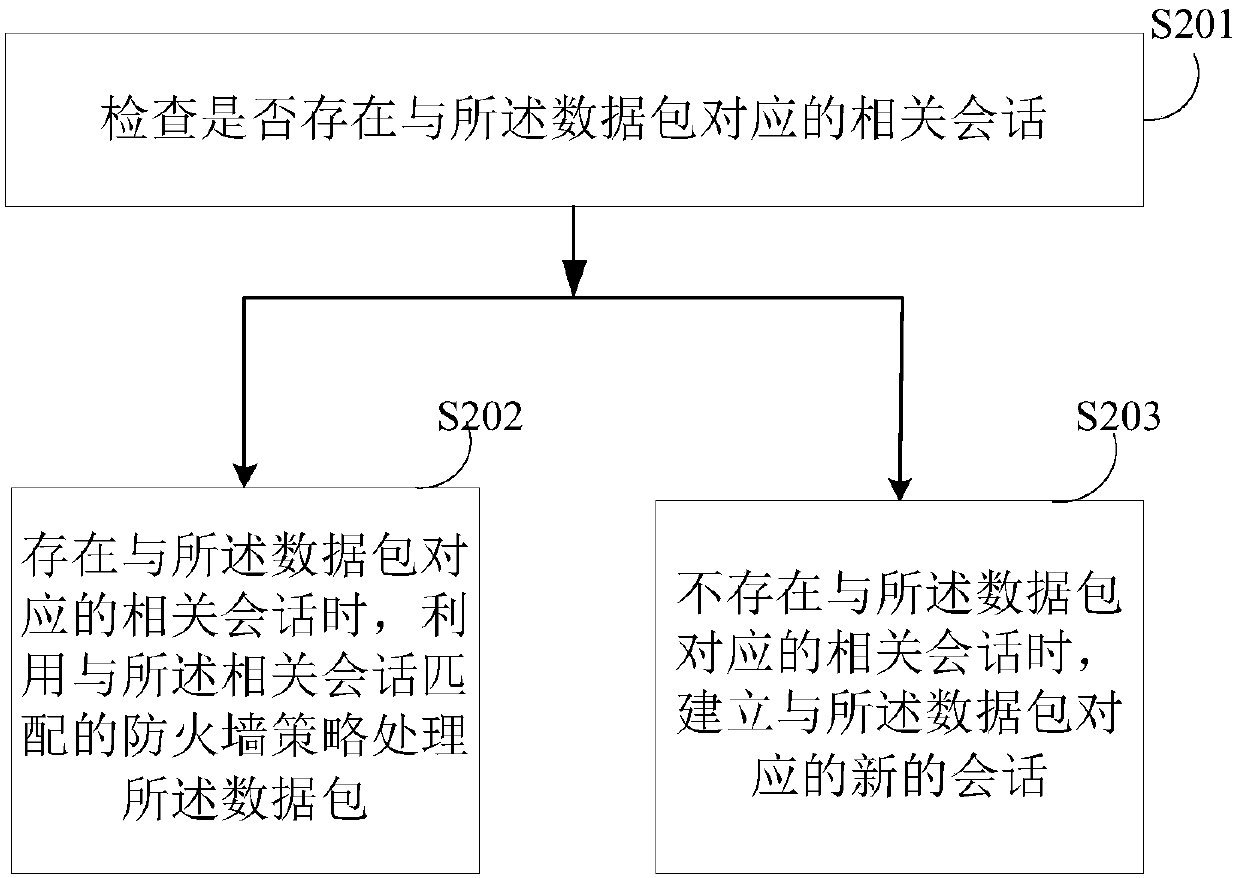
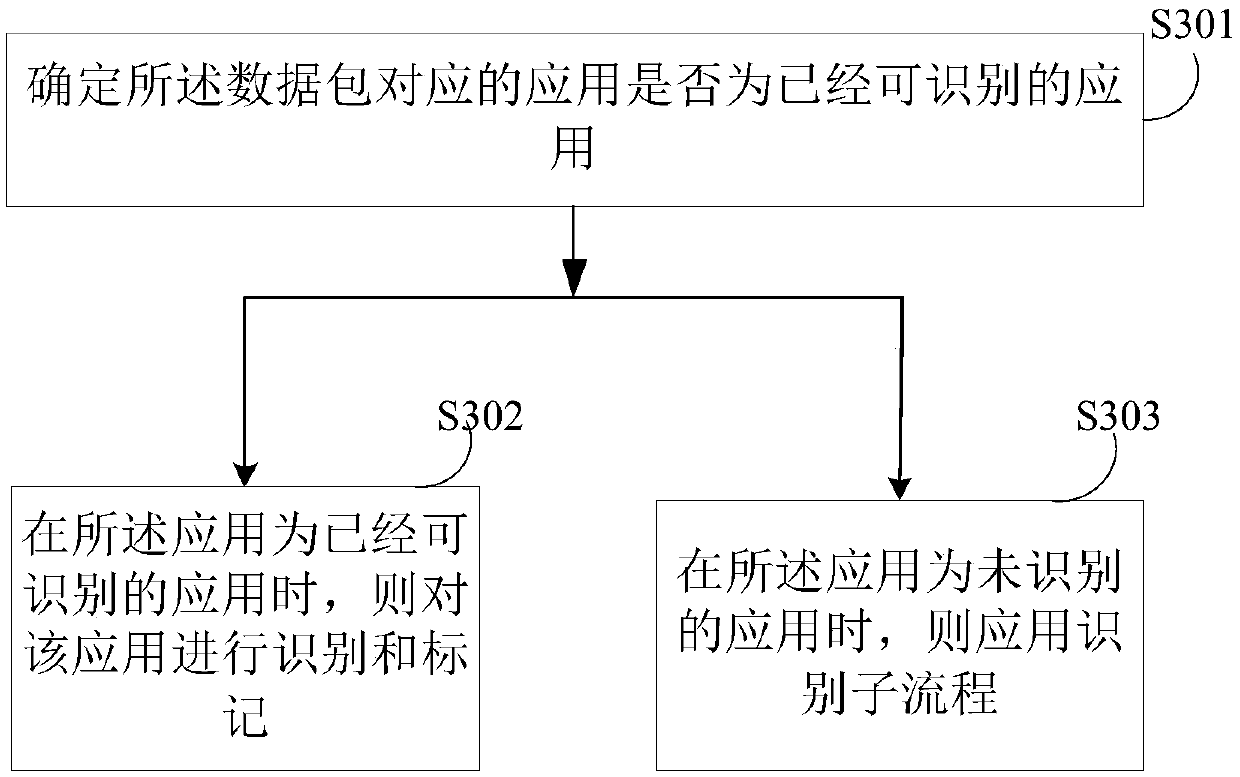
Network intrusion prevention method, device and system and computer readable storage medium
An embodiment of the invention discloses a network intrusion prevention method, device and system and a computer readable storage medium. The method includes: receiving a data packet, and subjecting the received data packet to protocol analysis; performing fire wall policy matching on the data packet subjected to protocol analysis, and processing the data packet by a matched fire wall policy; recognizing an application corresponding to the data packet, and processing the data packet according to an application access control policy corresponding to the recognized application; subjecting the data packet to content analysis, adopting a content obtained by analysis to obtain a content safety protection policy by matching, and processing the data packet by the content safety protection policy.After protocol analysis of the data packet, protocol and port detection is performed according to the fire wall policy, then application layer information is deeply read on the basis of application feature code recognition, and an application type is determined by comparison of analyzed application information with a background feature library.
Owner:深圳市利谱信息技术有限公司
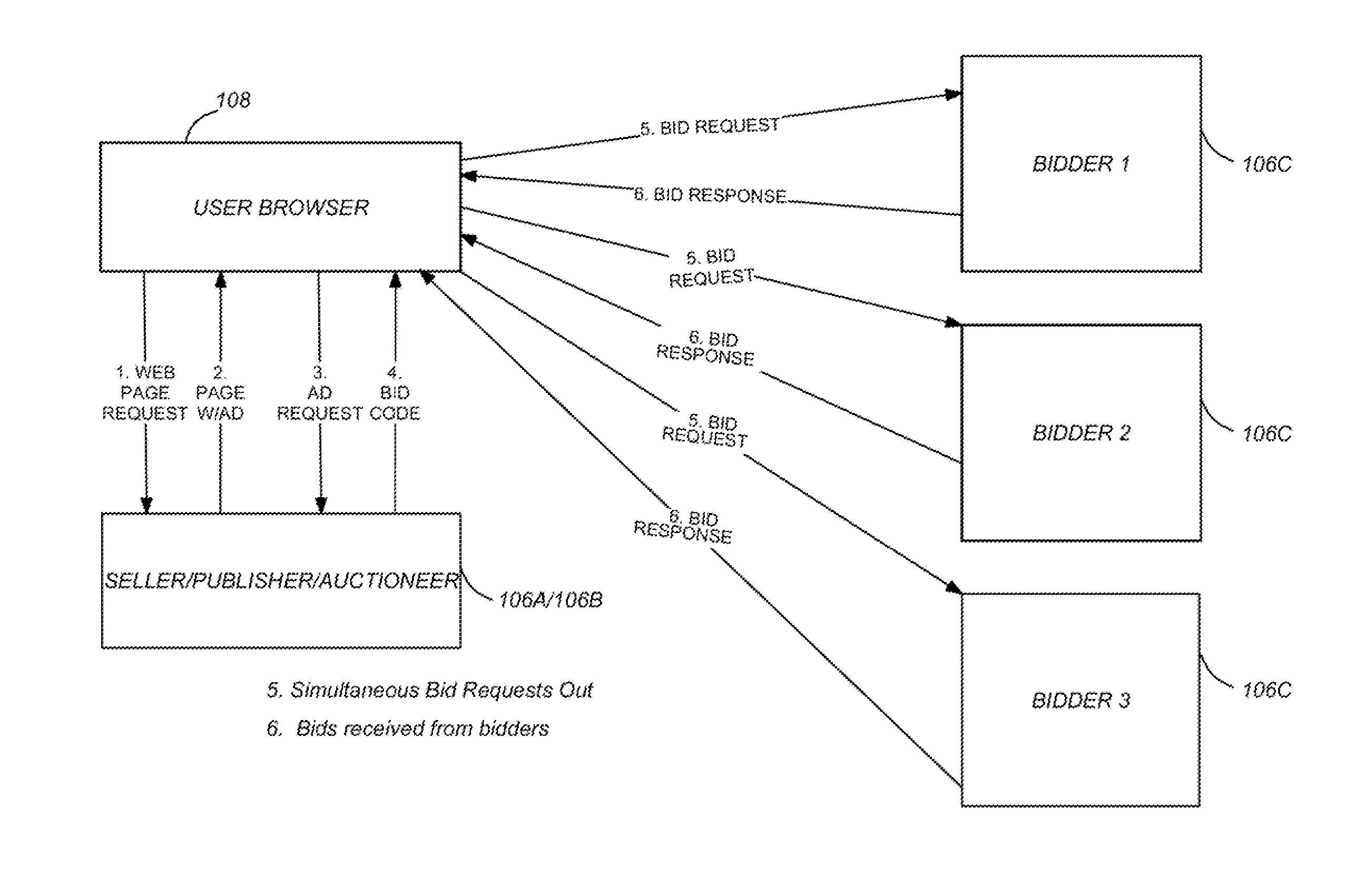
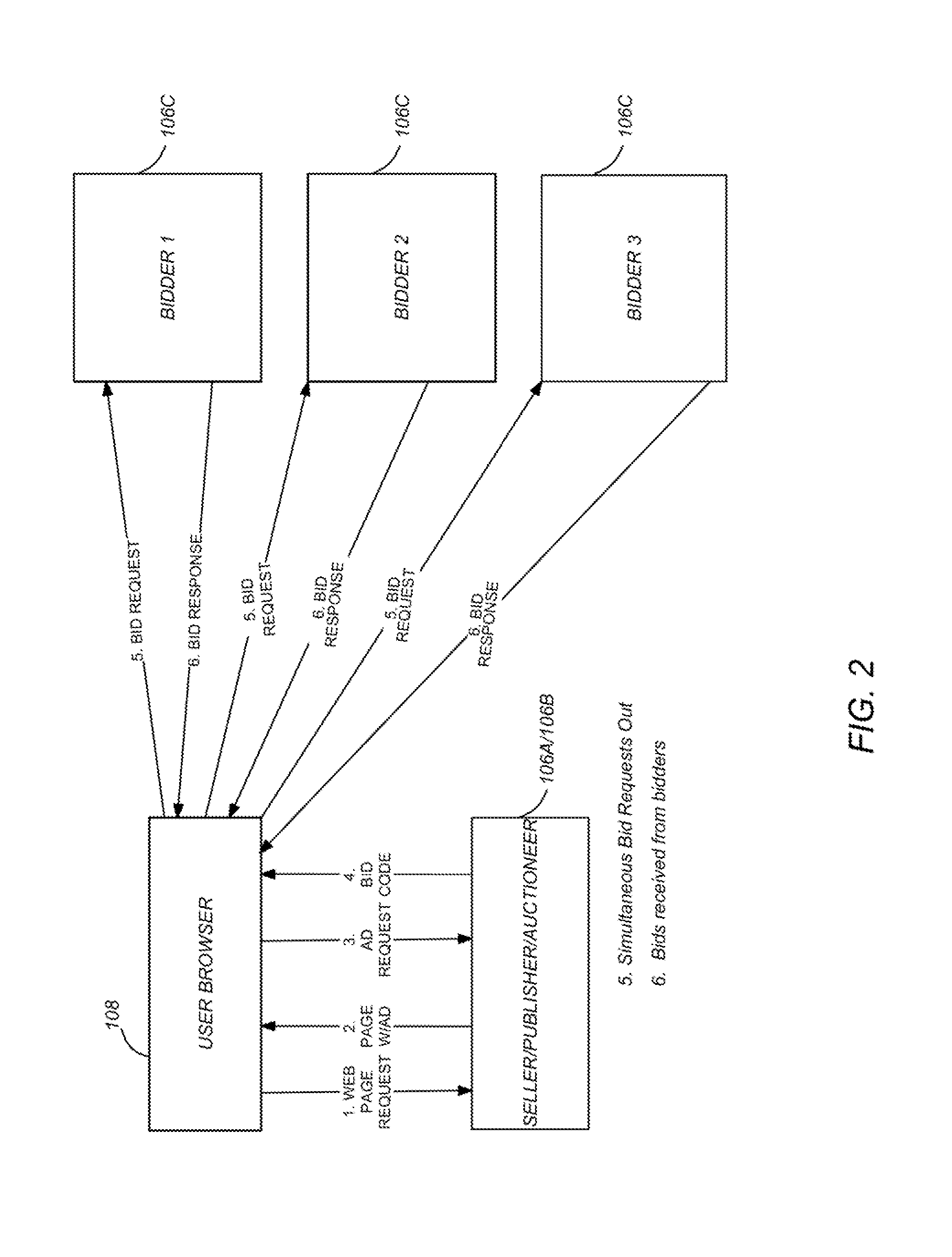
Content security for real-time bidding
ActiveUS20110173126A1AdvertisementsPublic key for secure communicationComputer networkContent security
Owner:FOX AUDIENCE NETWORK INC
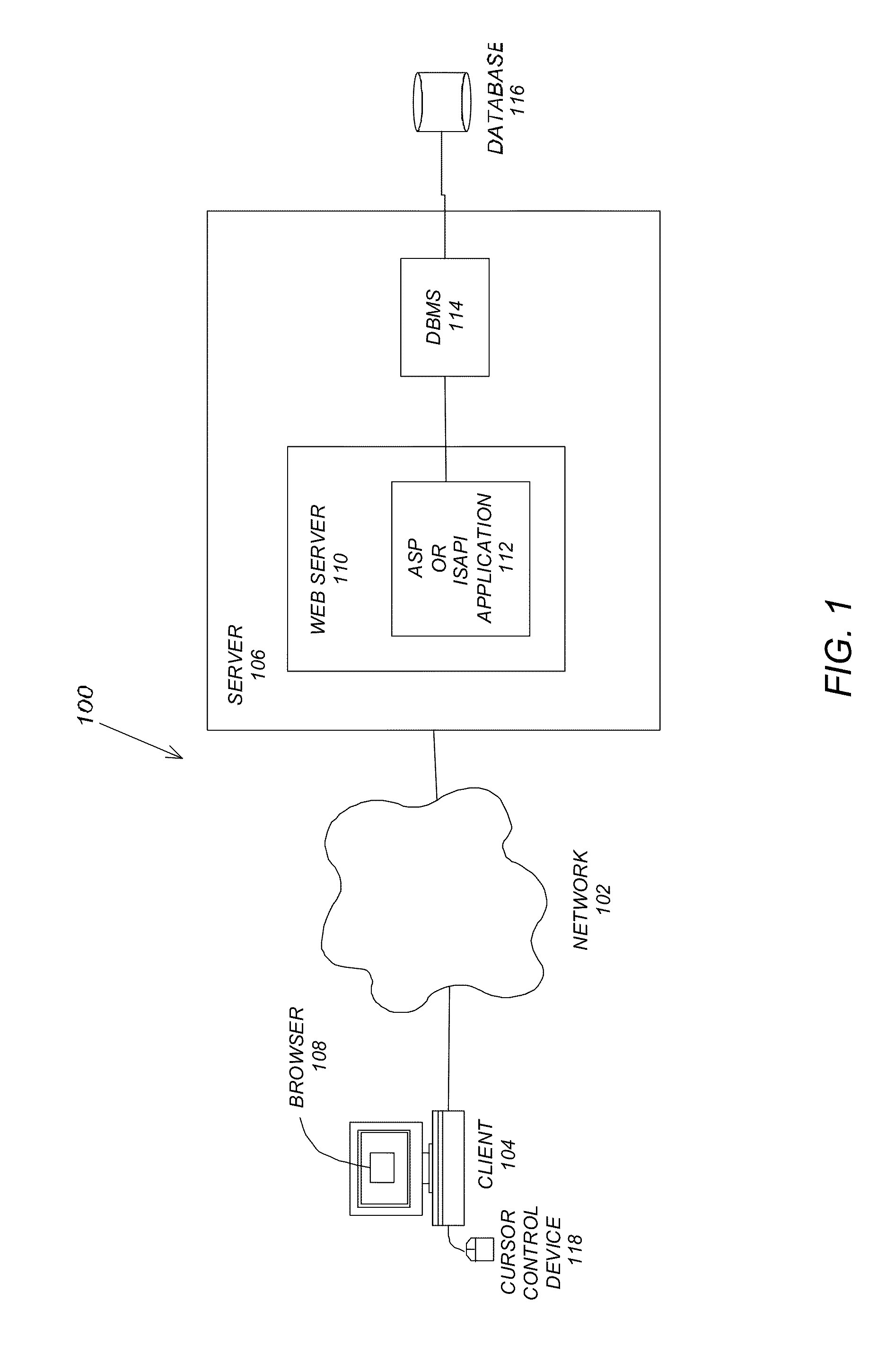
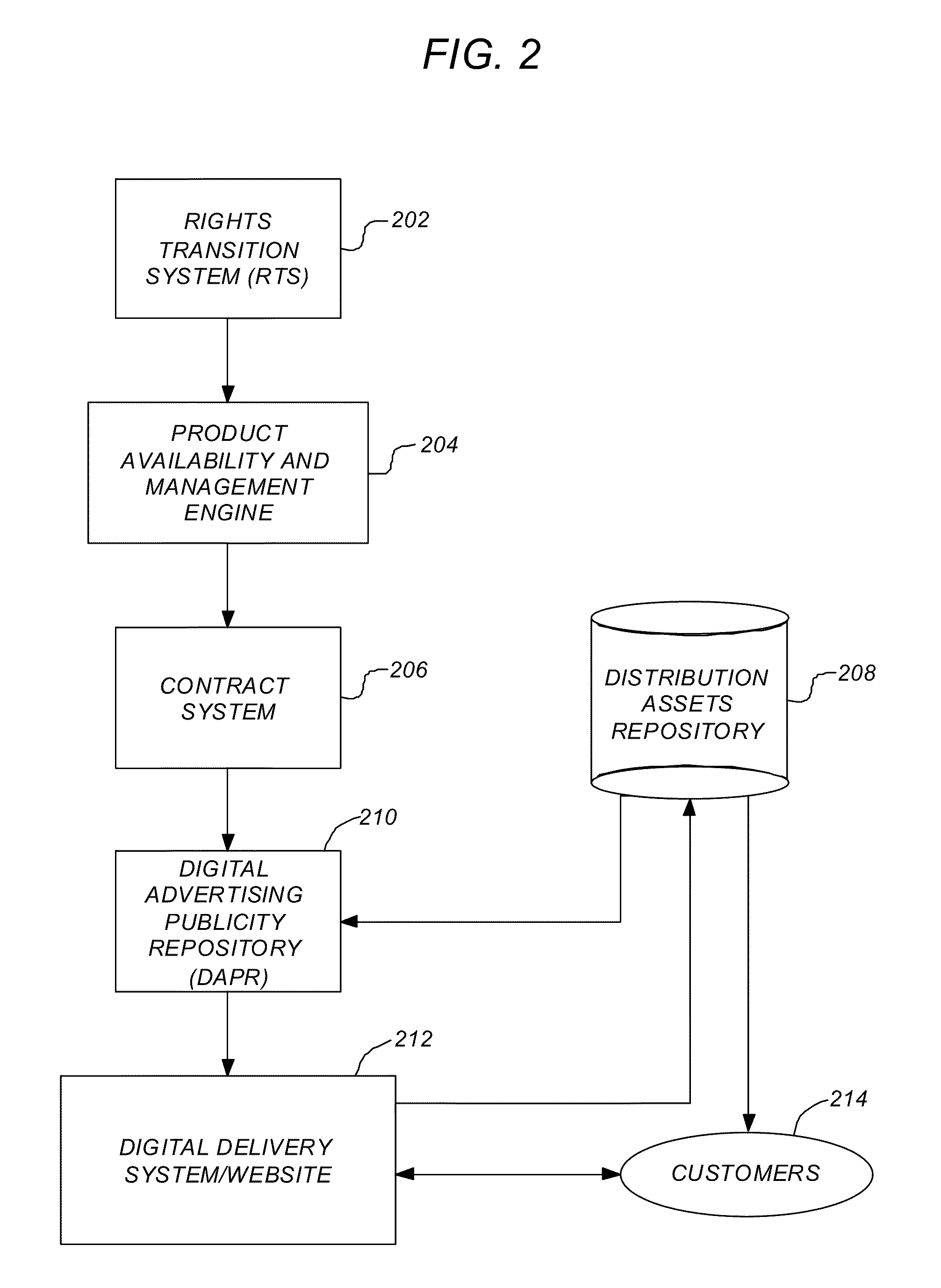
Media asset/content security control and management system
InactiveUS20110265150A1Eliminate needLow costDigital data processing detailsAnalogue secracy/subscription systemsDigital advertisingThe Internet
A system, method, apparatus, and computer readable storage medium provide the ability to deliver media content in a secure manner in a computer system. A storage repository stores media content and marketing assets for the media content. A server computer is coupled to the storage repository and enabled to provide access to the media content and marketing assets via a website accessible on the Internet worldwide to a user. A digital advertising publicity repository (DAPR) enables an administrator to define first access rights for the user to access the website and second access rights for the user to access the DAPR.
Owner:FOX ENTERTAINMENT GROUP
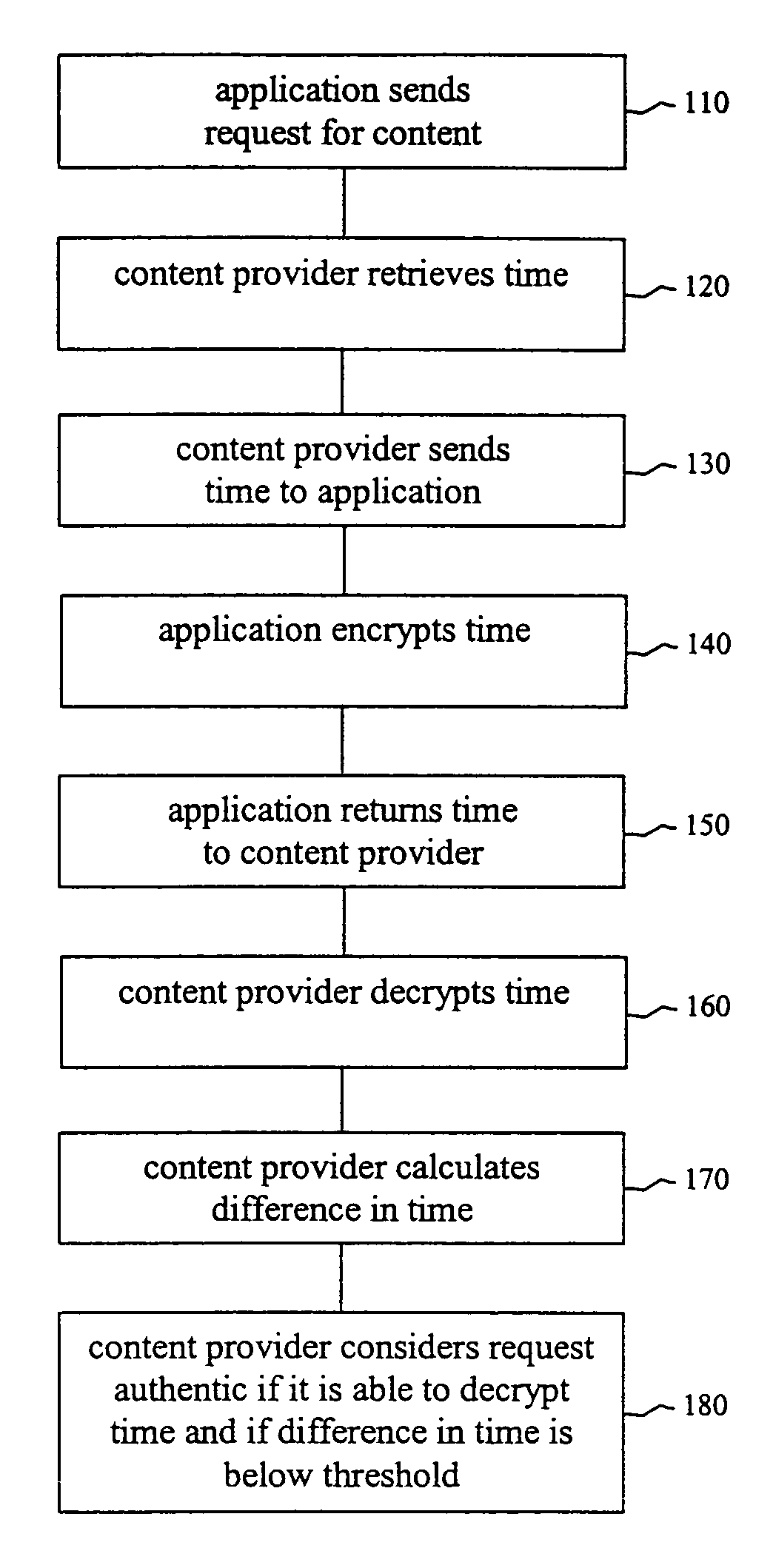
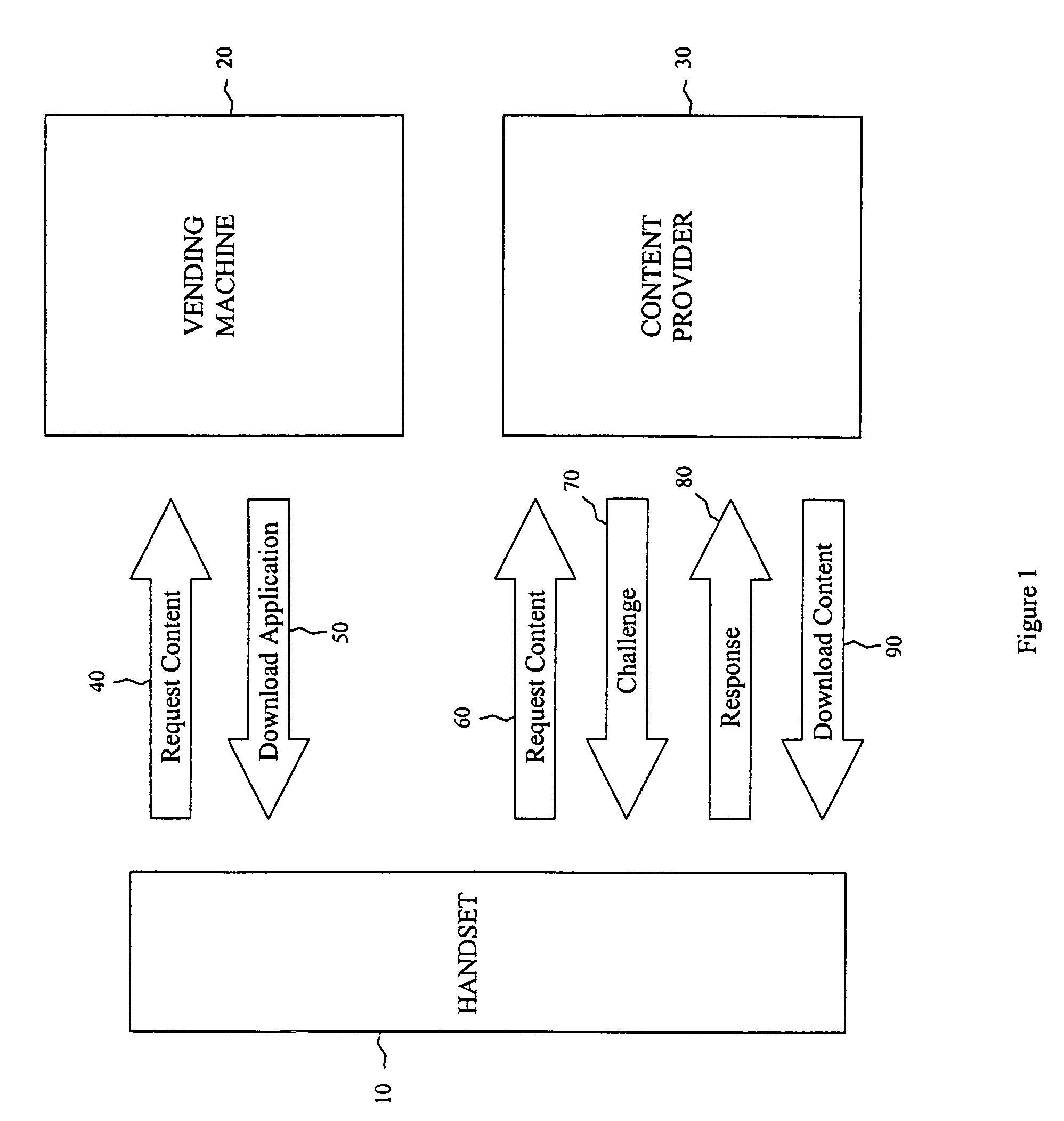
System and method for securing system content by automated device authentication
ActiveUS7480803B1Digital data processing detailsUser identity/authority verificationApplication softwareContent security
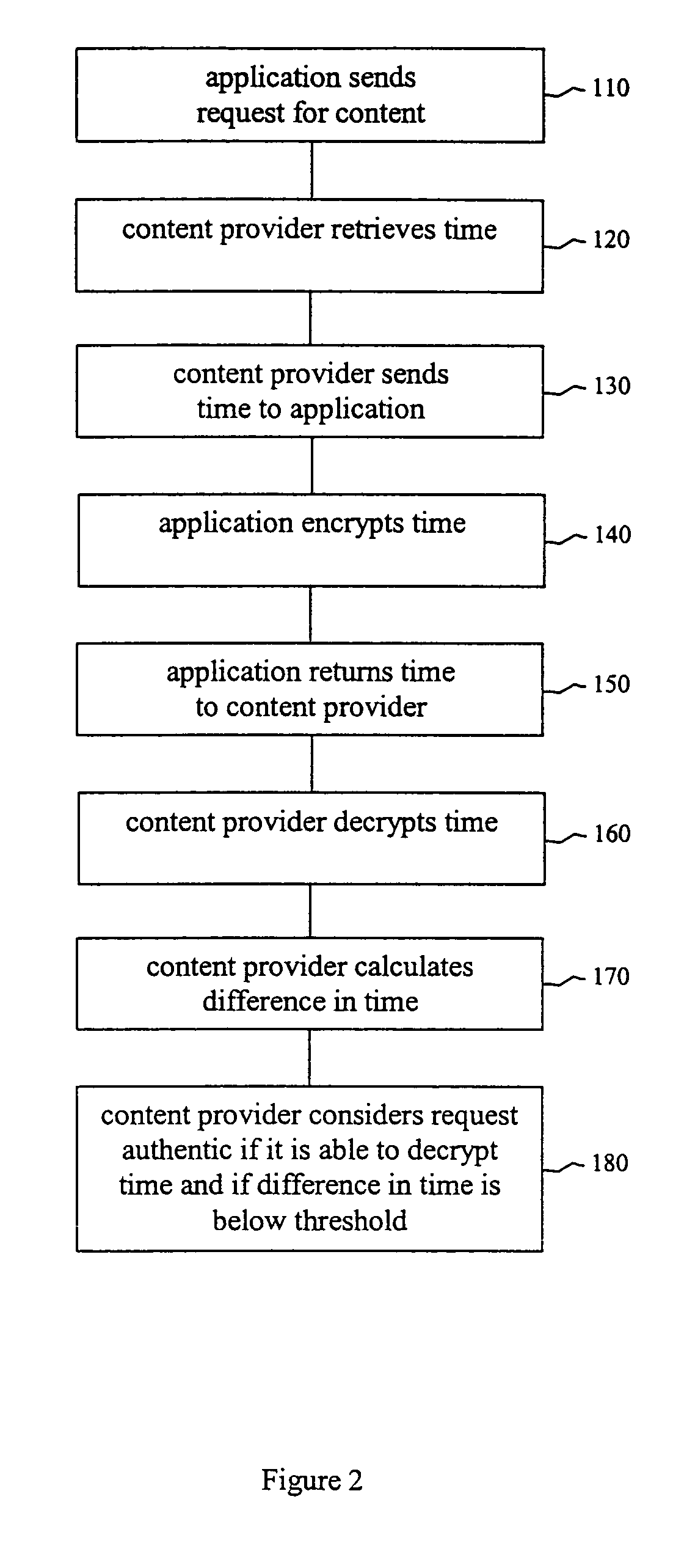
A system is provided for securely downloading content to a mobile telecommunications device. The system includes a mobile application to enable the mobile telecommunications device to send a request for content identified on a telecommunication provider system. The system includes a content application maintained by the content provider to retrieve content and promote delivery of the content to the mobile telecommunications device. The system also includes a challenge component and a response component, the response component communicates with the mobile application and encodes a challenge data. The challenge component communicates with the content application. The challenge component sends the challenge data to the mobile application and decodes the challenge data received from the mobile application to validate the response for delivery of the content to the mobile application.
Owner:T MOBILE INNOVATIONS LLC
Method and apparatus of drm systems for protecting enterprise confidentiality
InactiveUS20170329942A1Image watermarkingProgram/content distribution protectionConfidentialityBusiness enterprise
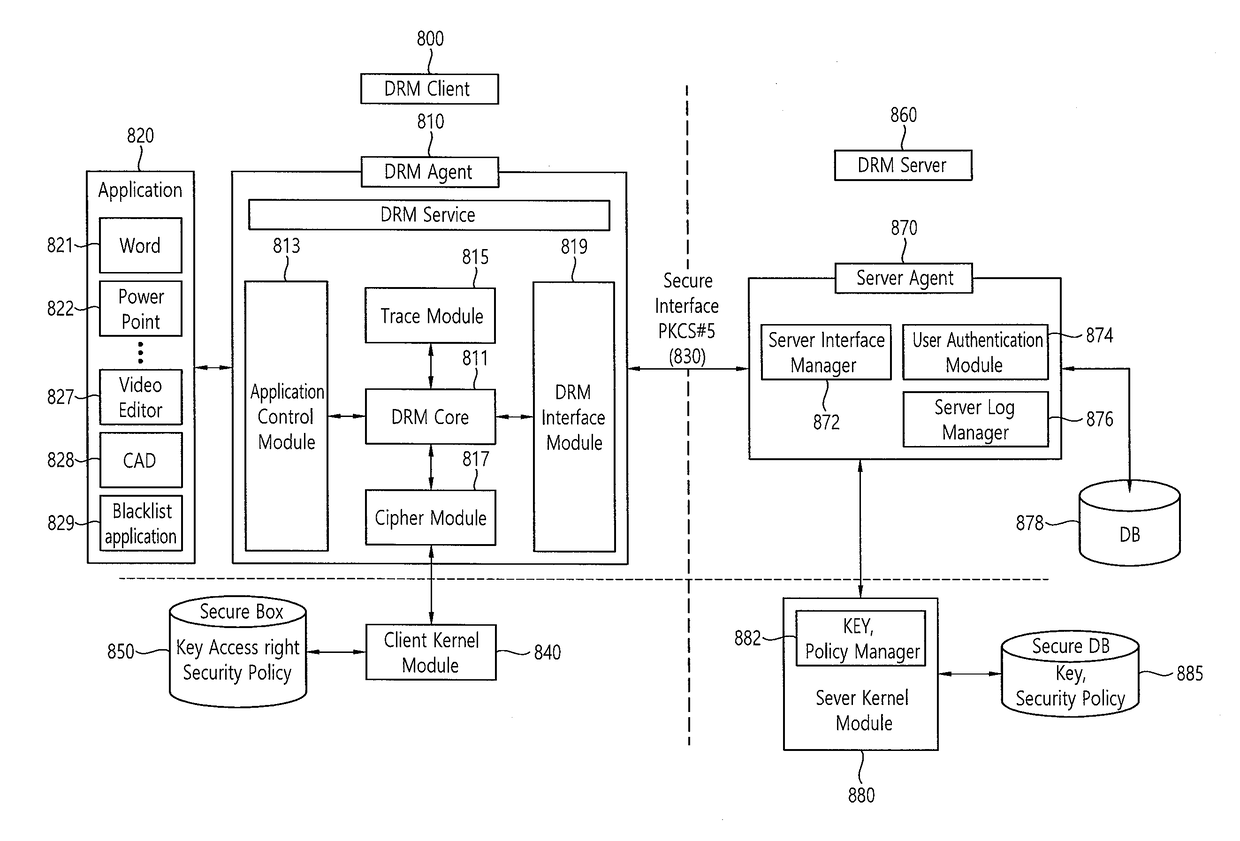
One aspect of the present invention discloses a device for content security. The device includes: an application execution unit configured to generate and control content in response to a content control command requested by a user; and a DRM agent configured to communicate with the application execution unit, to detect the content control command generated by the application execution unit, and to perform control on the content, and the DRM agent comprises a tracing module configured to insert security information into the content in order to prevent and trace content leakage.
Owner:MARKANY
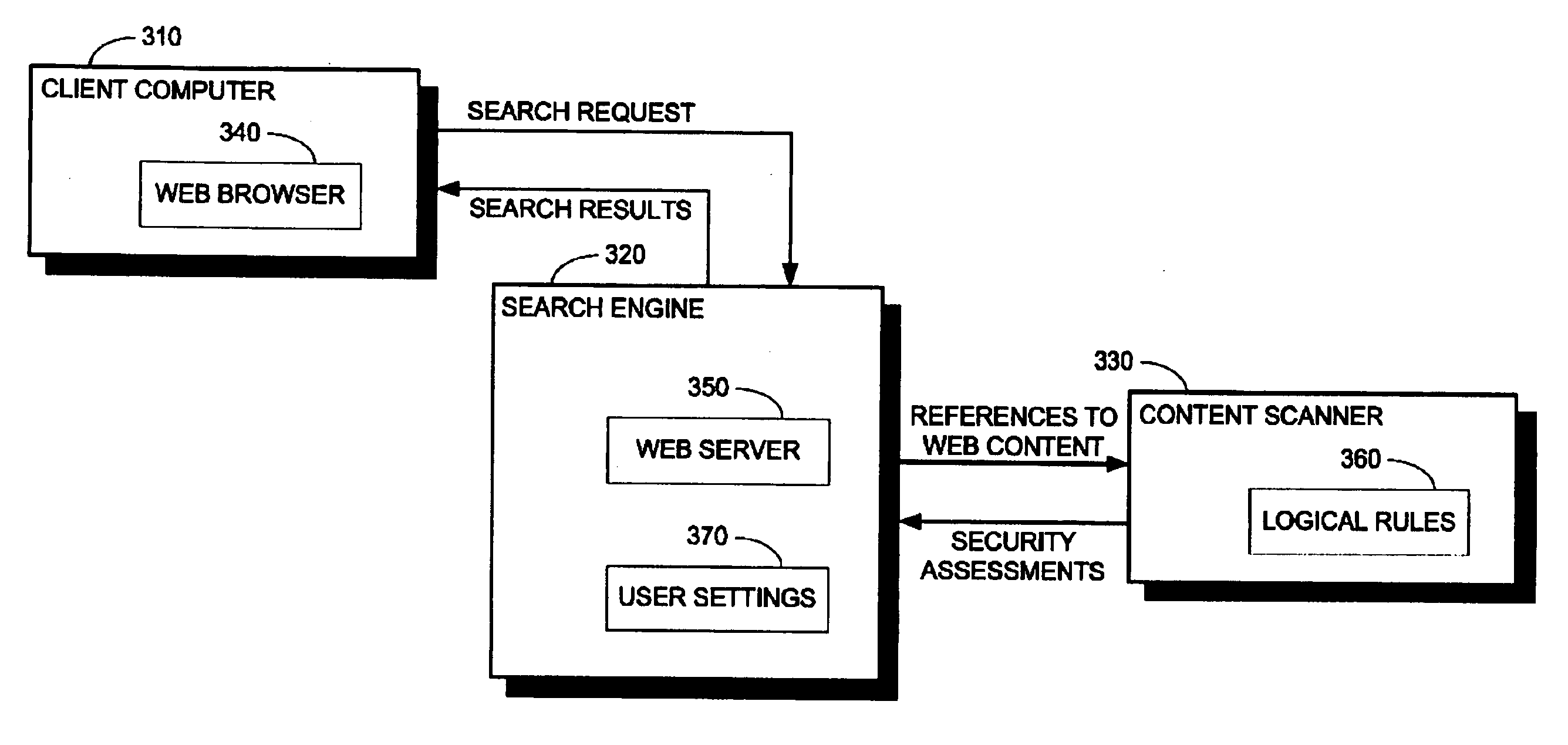
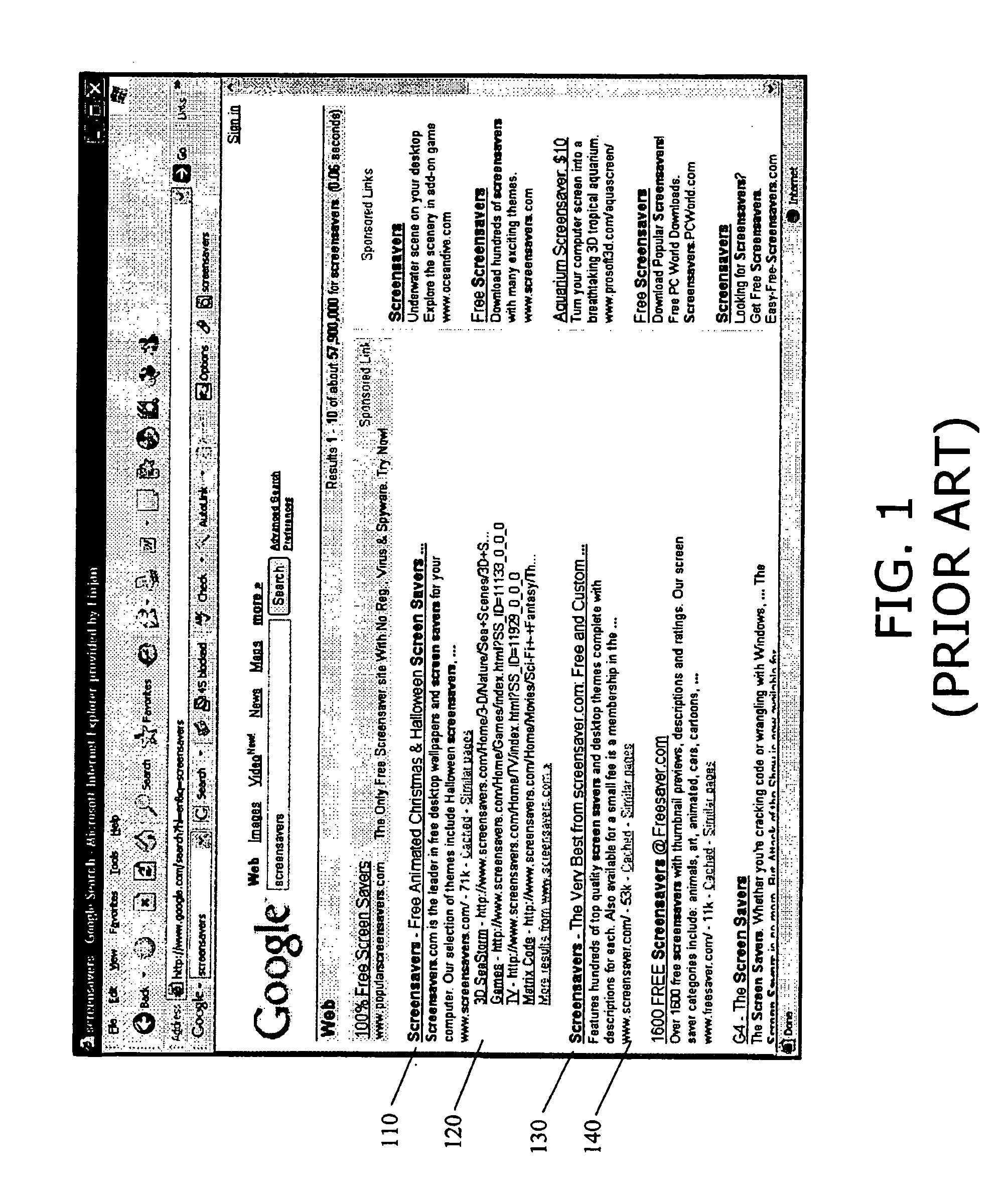
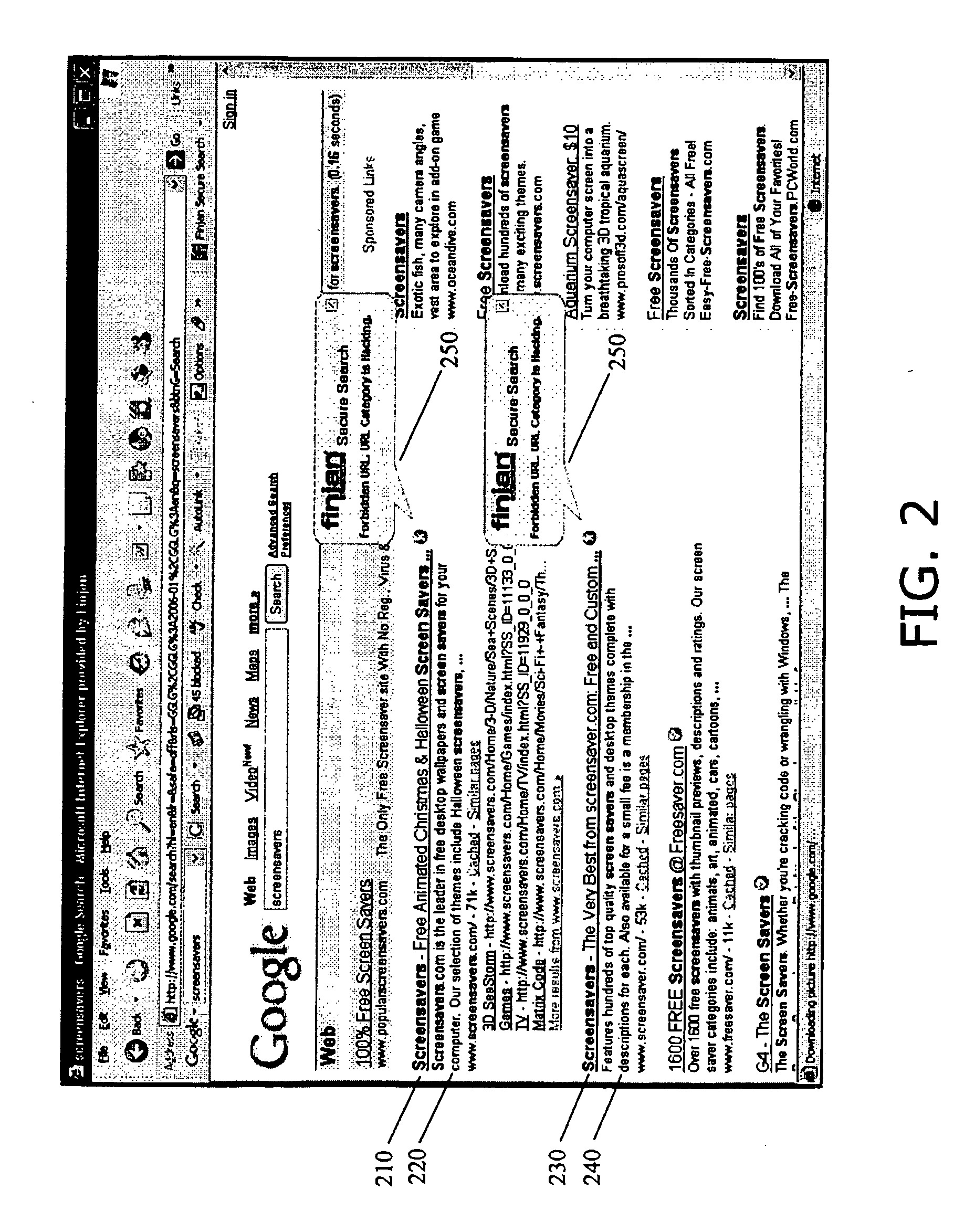
System and method for appending security information to search engine results
A system for appending security information to search engine results, including a search engine for locating, in a computer network, web pages that include at least one designated search term, for issuing a security analysis request to a content security scanner to assess at least one designated web page for potential security risks, and for preparing a search results summary that includes links to the located web pages and security assessments for the located web pages, a client computer communicatively coupled with the search engine for issuing a search request with at least one user designated search term, to the search engine, and for receiving the search results summary from the search engine, and a content security scanner communicatively coupled with the search engine for assessing security of content in at least one designated web page. A method and computer-readable storage media are also described and claimed.
Owner:FINJAN LLC
Video steganalysis method based on partial cost non-optimal statistics
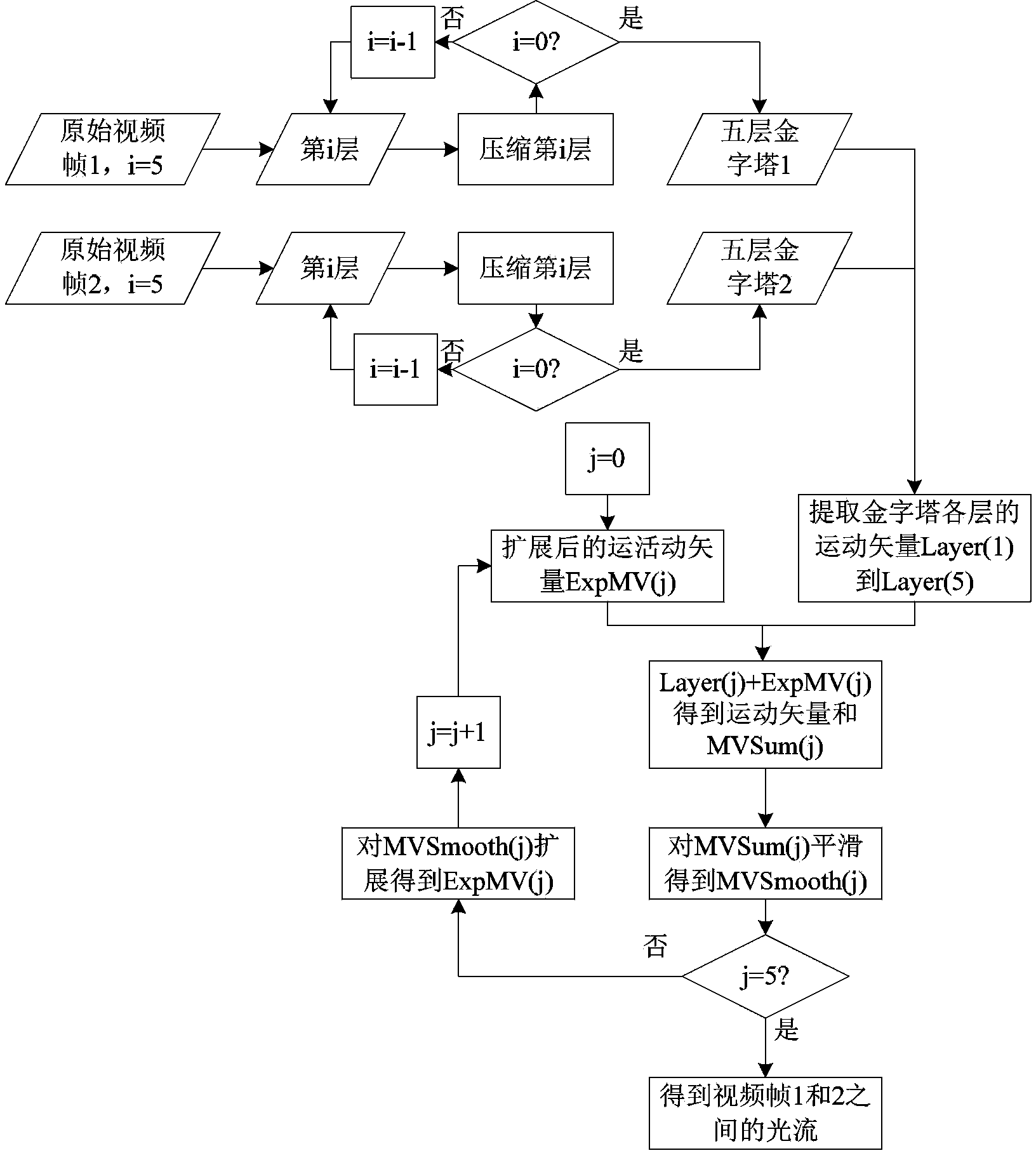
InactiveCN103108188AGood and wide versatilityHigh-precision detectionTelevision systemsDigital video signal modificationLocal optimumPattern recognition
The invention provides a video steganalysis method based on partial cost non-optimal statistics. A fundamental principle of producing a motion vector is deeply excavated in the steganalysis method. The video steganalysis method based on the partial cost non-optimal statistics starts from the local optimum characteristics which should be kept and produced by the motion vector, and thereby the steganalysis method is enabled not to be limited to a particular video coding standard and a coding tool, is applicable to video encoding formats adopting interframe prediction technology such as moving picture expert group (MPEG)-2, MPEG-4 and H.264 and has good and wide generality and a high detection accurate rate. The video steganalysis method based on the partial cost non-optimal statistics can be applied to national security, army, government and enterprise sectors, achieves effective detection and monitoring of video content security, prevents illegal personnel from transferring intelligence information with a large data amount through video data and has important research significance and application values for ensuring the national intelligence safety, preventing enterprise confidential information from being revealed and the like.
Owner:WUHAN UNIV
Website monitoring pre-warning method
InactiveCN104182478AImprove experienceEfficient searchComputer security arrangementsWebsite content managementThumbnailWebsite monitoring
The invention relates to a website monitoring pre-warning method, mainly adopts Java and Flex which are vanward in the industry to intelligently analyze and excavate various content information of a website. The method comprises the following steps: analyzing invisible web links, content variation, performance monitoring and DNS analyzing time of the website to be monitored, and website download time; reporting the information to a user to monitor a network environment in a real-time manner; when the website changes, generating a thumbnail of the website to local, and displaying the thumbnail in a 3-dimensional image wall of a system; sending the website variation to the user in forms such as mails and short messages to ensure network safety; evaluating the content security of the whole website through a network crawler; utilizing the Flex and combining a browser. The website monitoring pre-warning method provided by the invention has the advantages that the operation efficiency is high; the cost is reduced greatly; the user has a larger selection space while selecting similar website pre-warning products.
Owner:BEIJING HUAQING TAIHE TECH
Video inter-frame forgery detection method based on light stream consistency
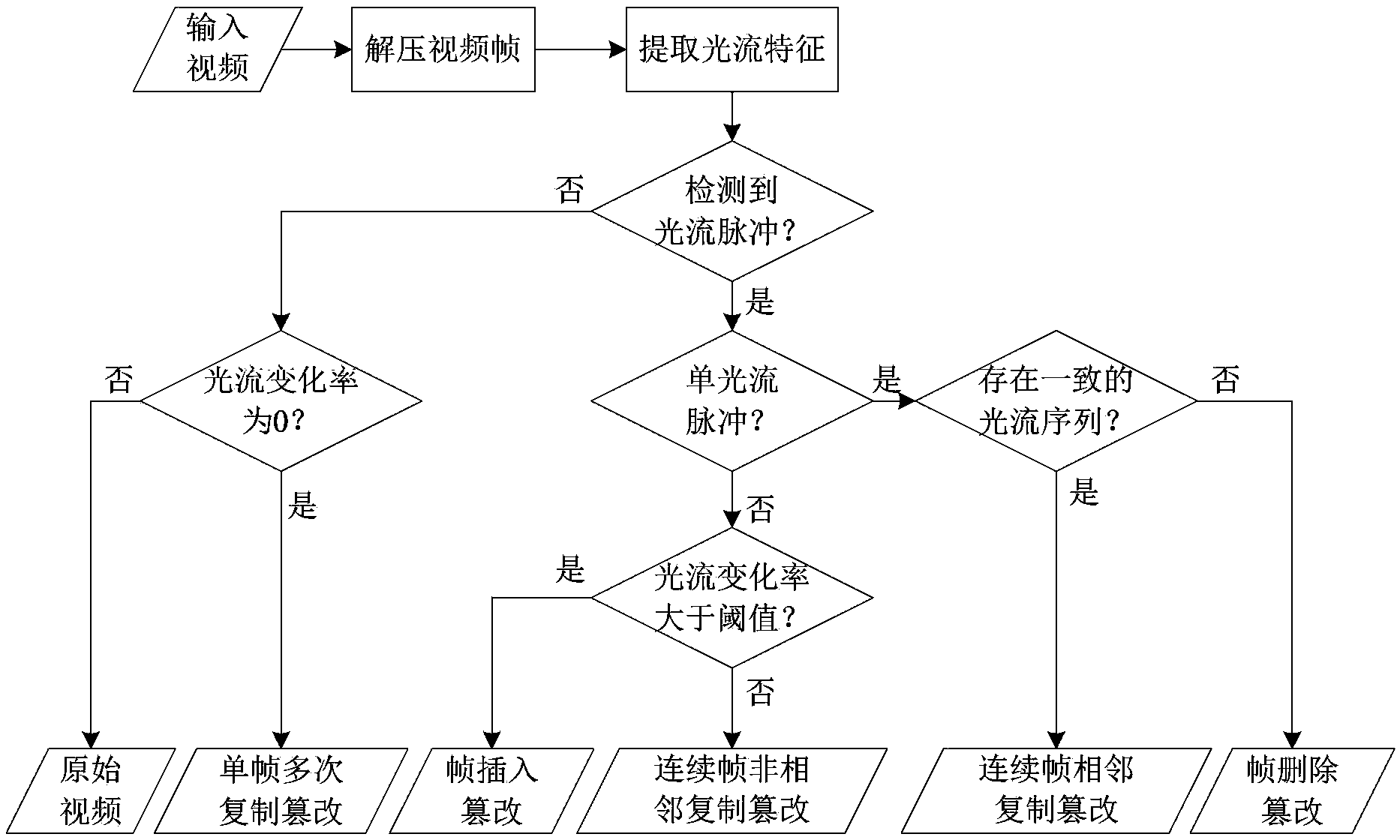
InactiveCN103384331ACumulative impactImprove time and efficiencyTelevision systemsSelective content distributionPassive detectionContent security
The invention provides a passive video inter-frame forgery detection method based on the light stream consistency in the field of video content safety. The detection method mainly comprises the steps of extracting light stream features of two adjacent frames in a surveillance video shot by a static camera, adding light stream absolute values in horizontal and vertical directions to generate two light stream sequences of the whole video in horizontal and vertical directions, analyzing the light stream sequences, and performing video inter-frame forgery detection for features of different inter-frame forgery modes. According to the detection method, through the light stream features which are high-robustness video features, five types of video inter-frame forgeries, including video frame insertion, frame deletion, repeated duplication of single frames, non-adjacent duplication of continuous frames and adjacent duplication of continuous frames can be detected effectively, and a forceful detection weapon is provided for the integrity and the authenticity of court testimony videos.
Owner:SHANGHAI JIAO TONG UNIV
Protecting Contents in a Content Management System by Automatically Determining the Content Security Level
An approach is provided to automatically classify and handle data. The approach is implemented by an information handling system. In the approach, data is received, from a sender, at a content management system. When the data is received, the system automatically utilizes an artificial intelligence (AI) engine (e.g., IBM Watson, etc.) to perform an unstructured information analysis using a pre-existing knowledge base. The result of using the AI engine is an identification of a confidentiality level of the data. The approach further performs an action based on the identified confidentiality level of the data.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com