Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
731 results about "Content type" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
MRCM reference set attribute which indicates the type of SNOMED CT content over which the given concept model rule applies.
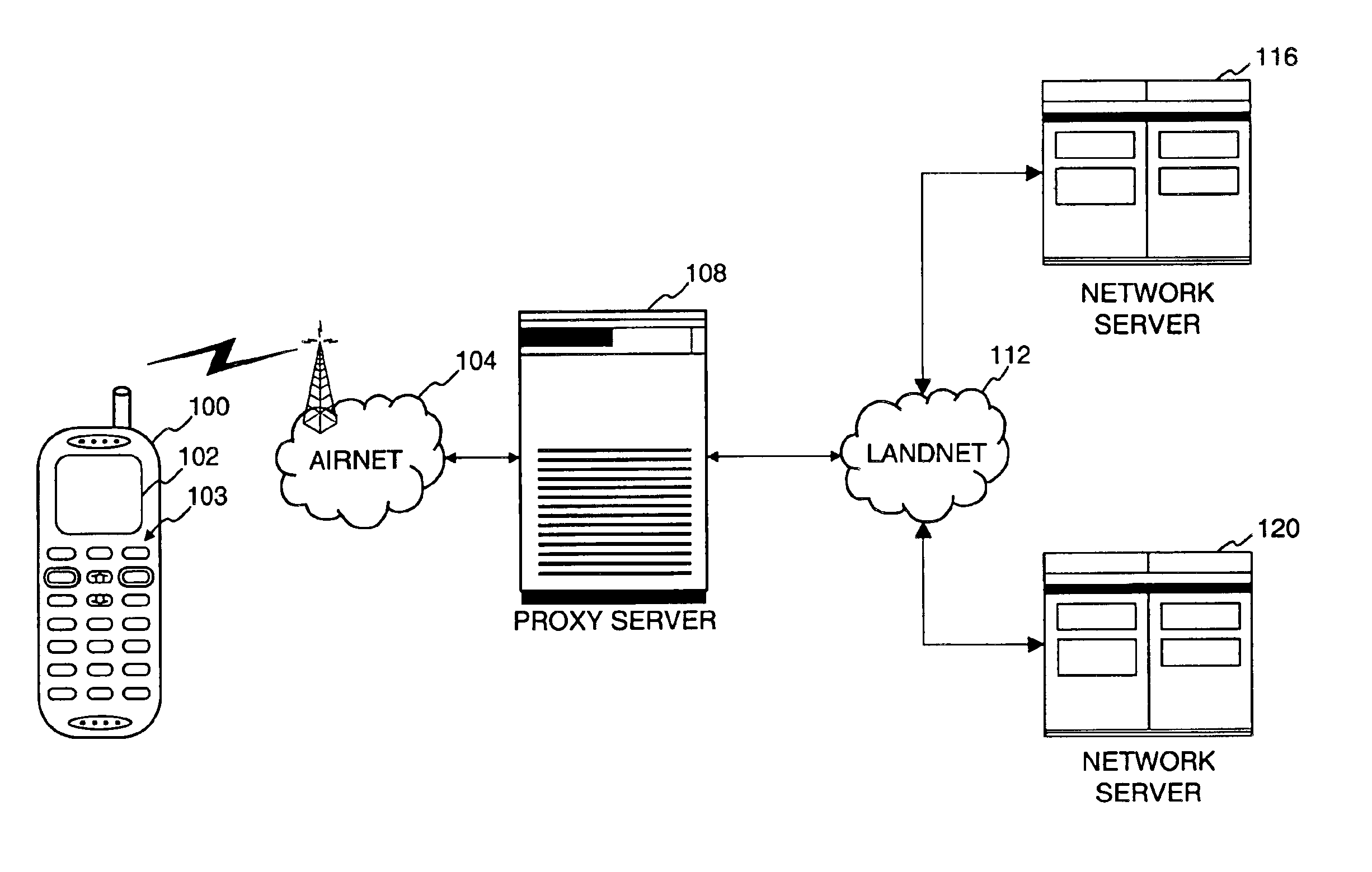
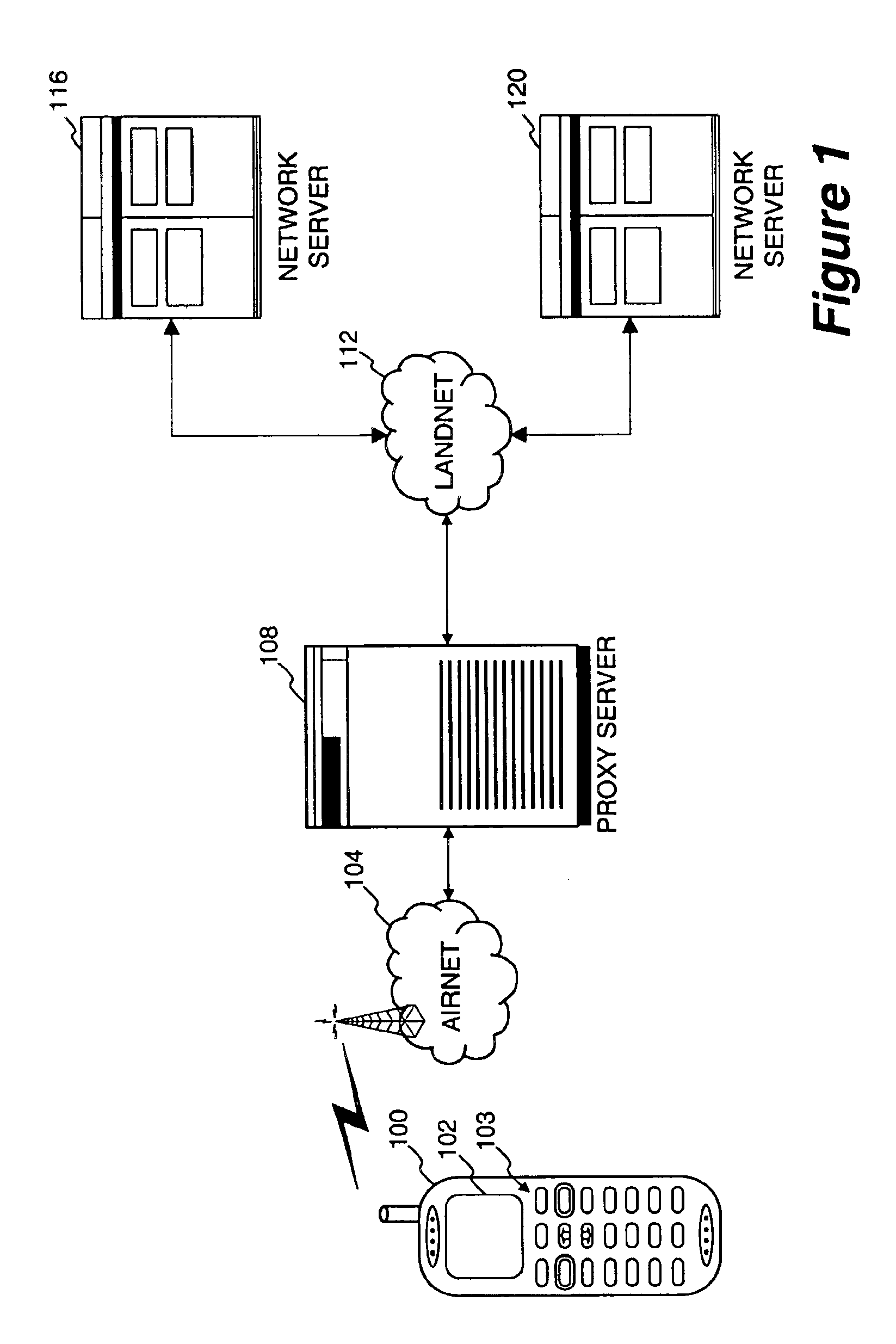
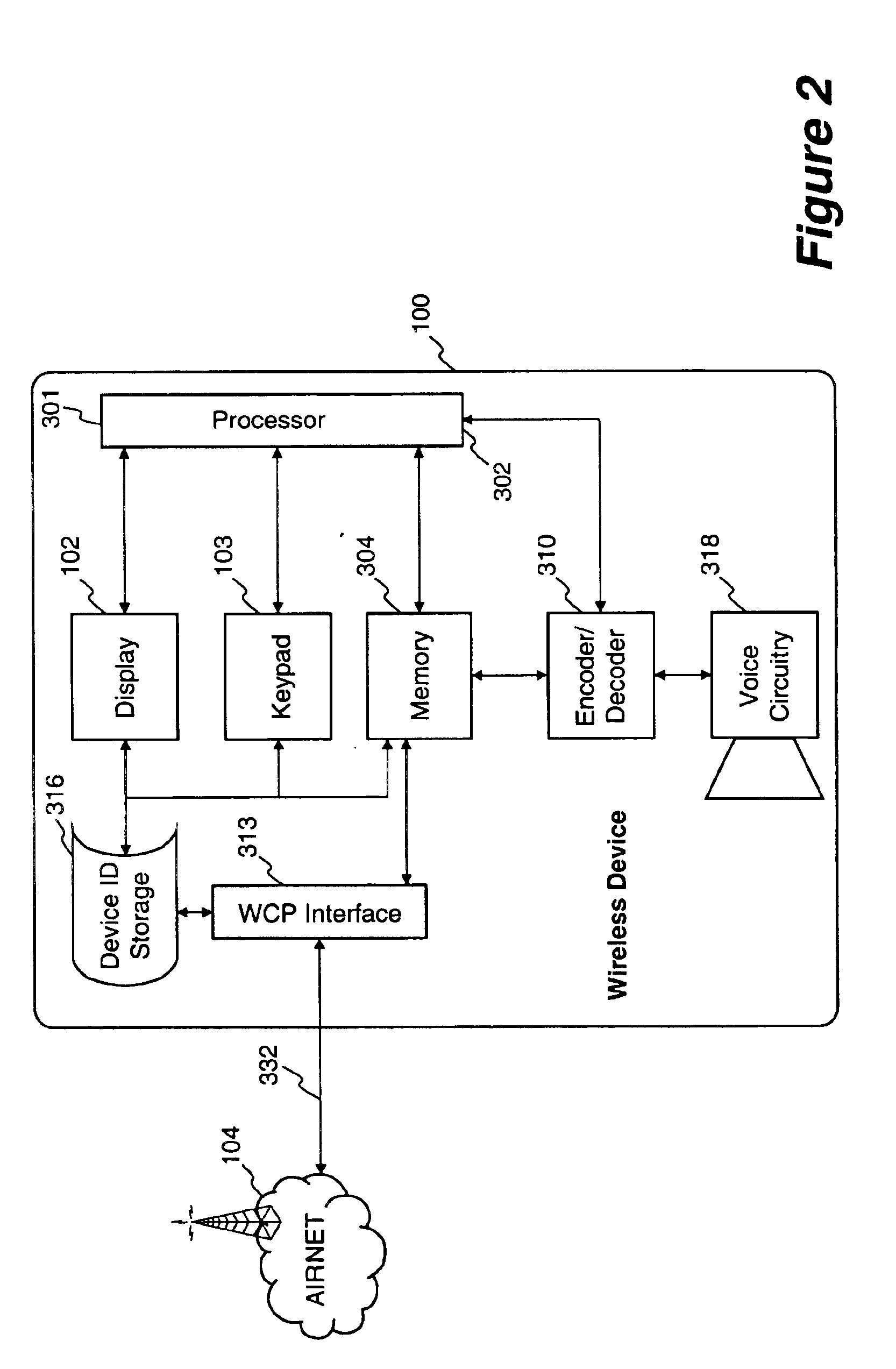
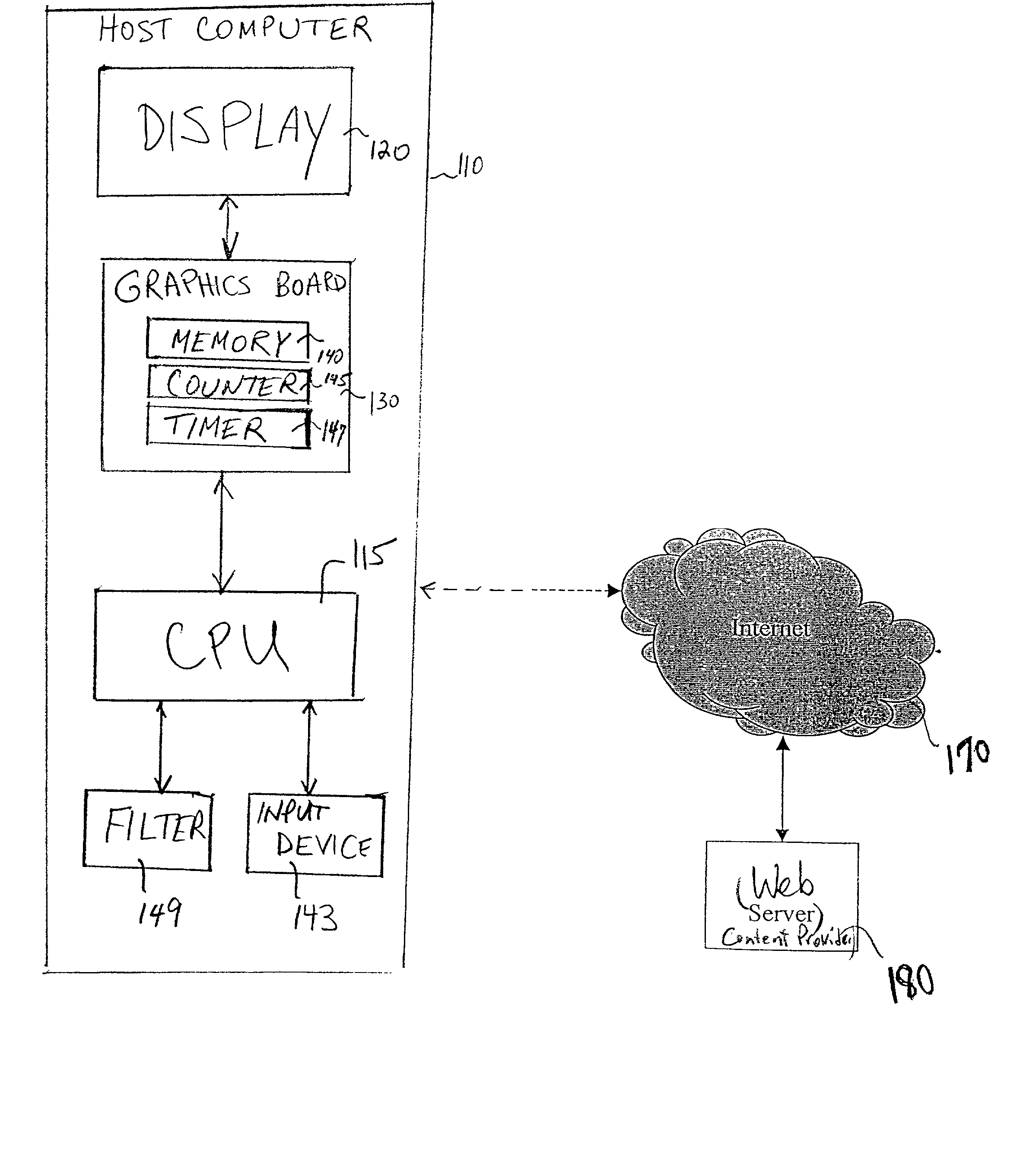
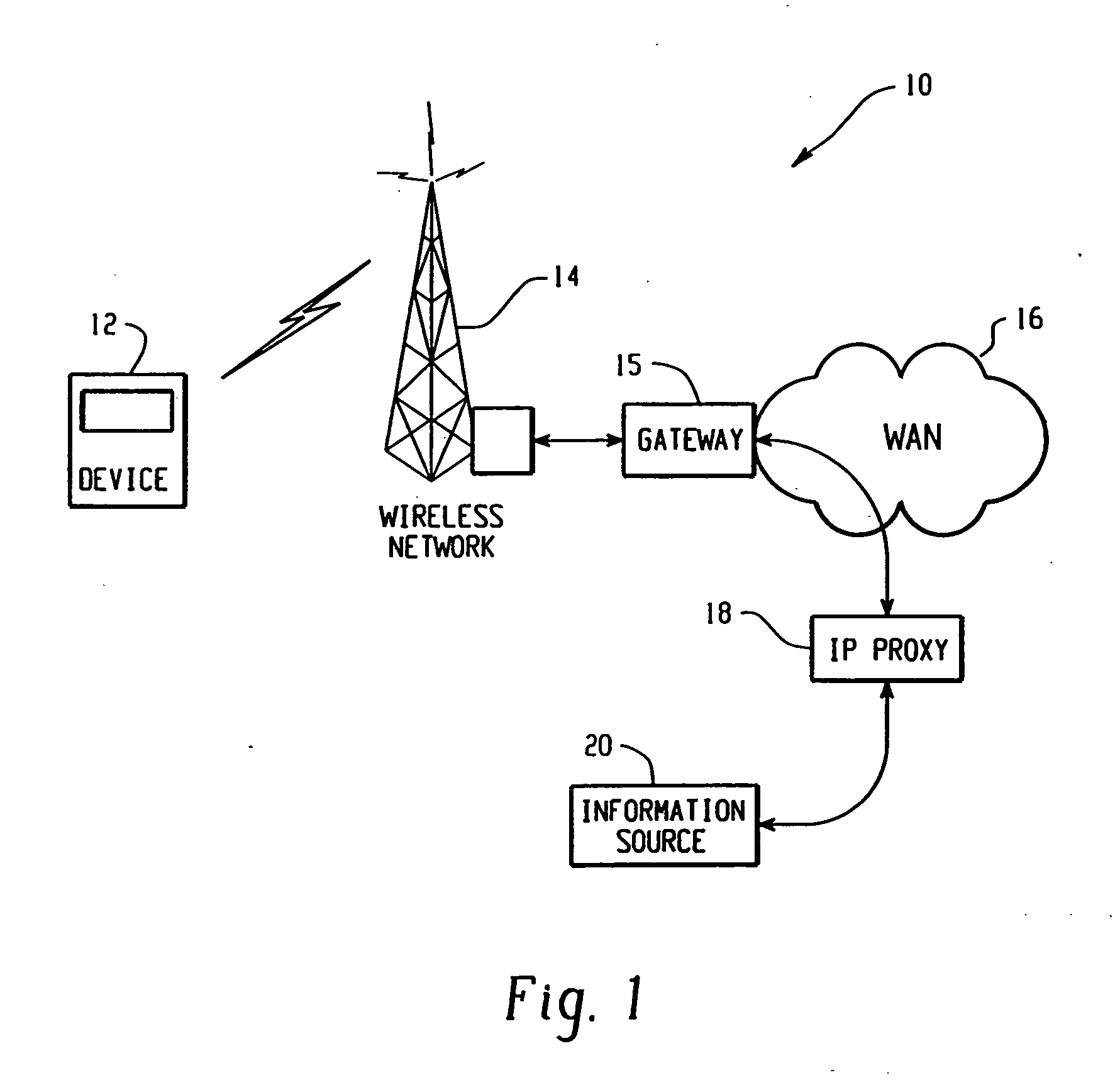
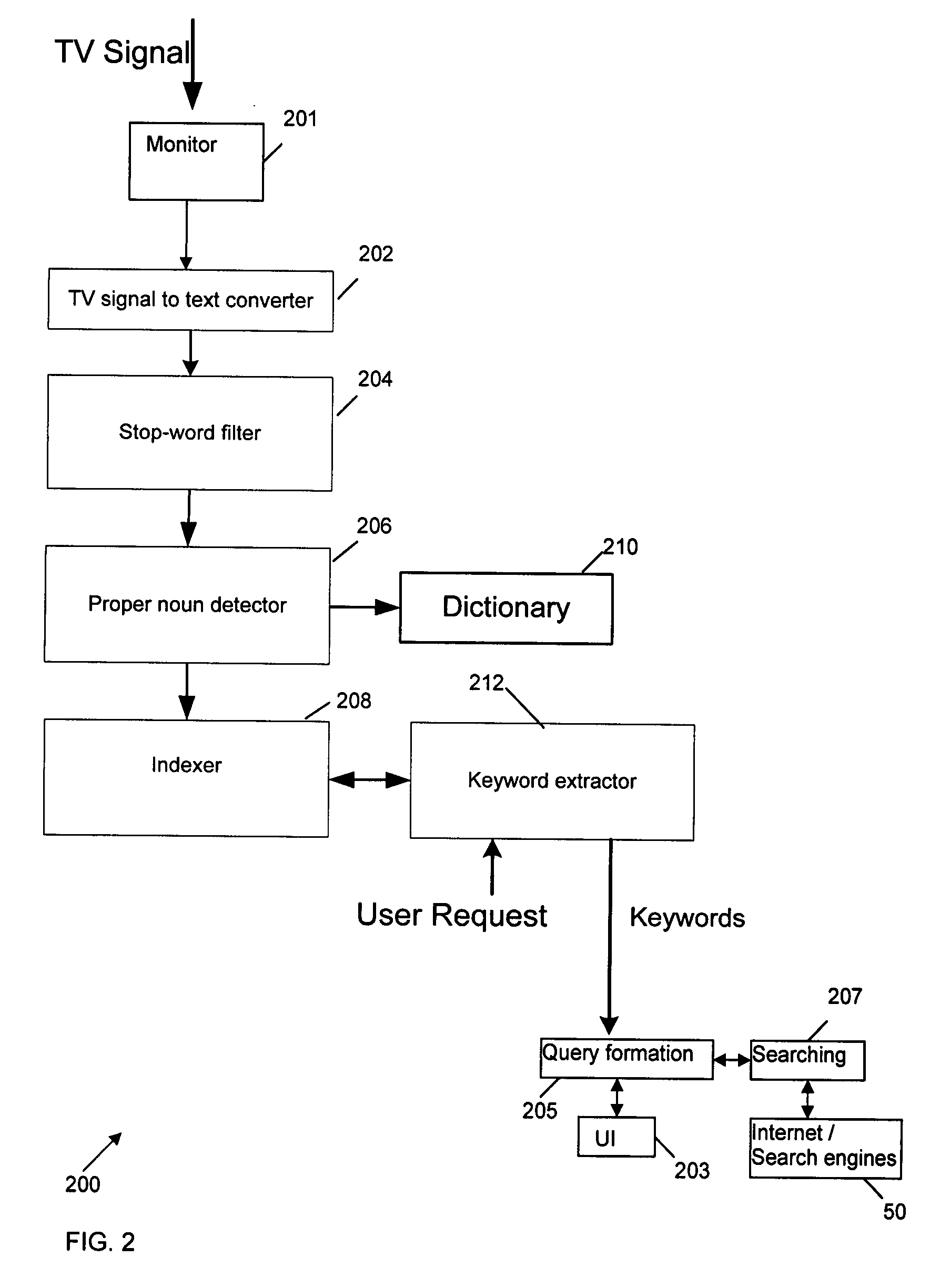
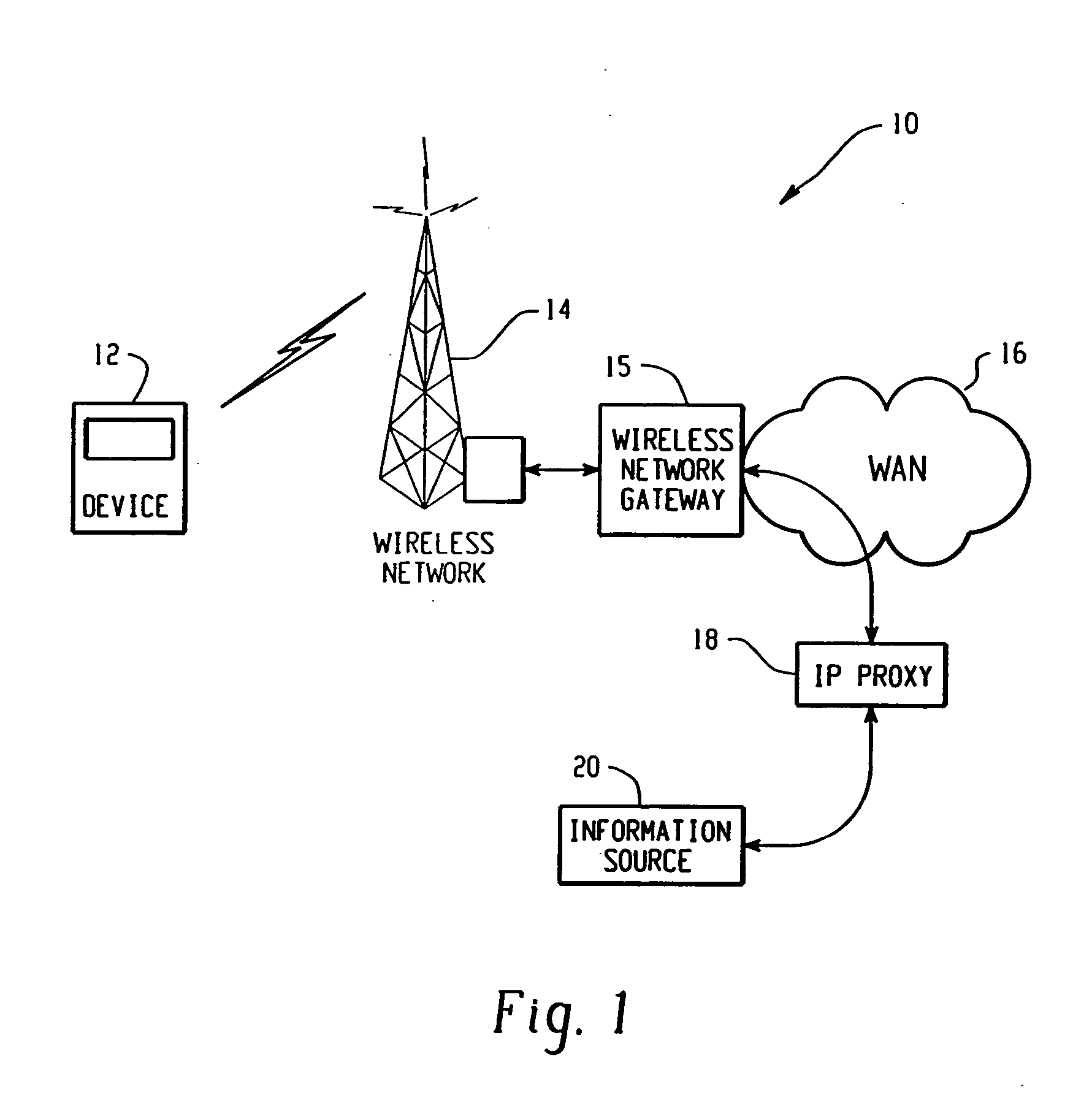
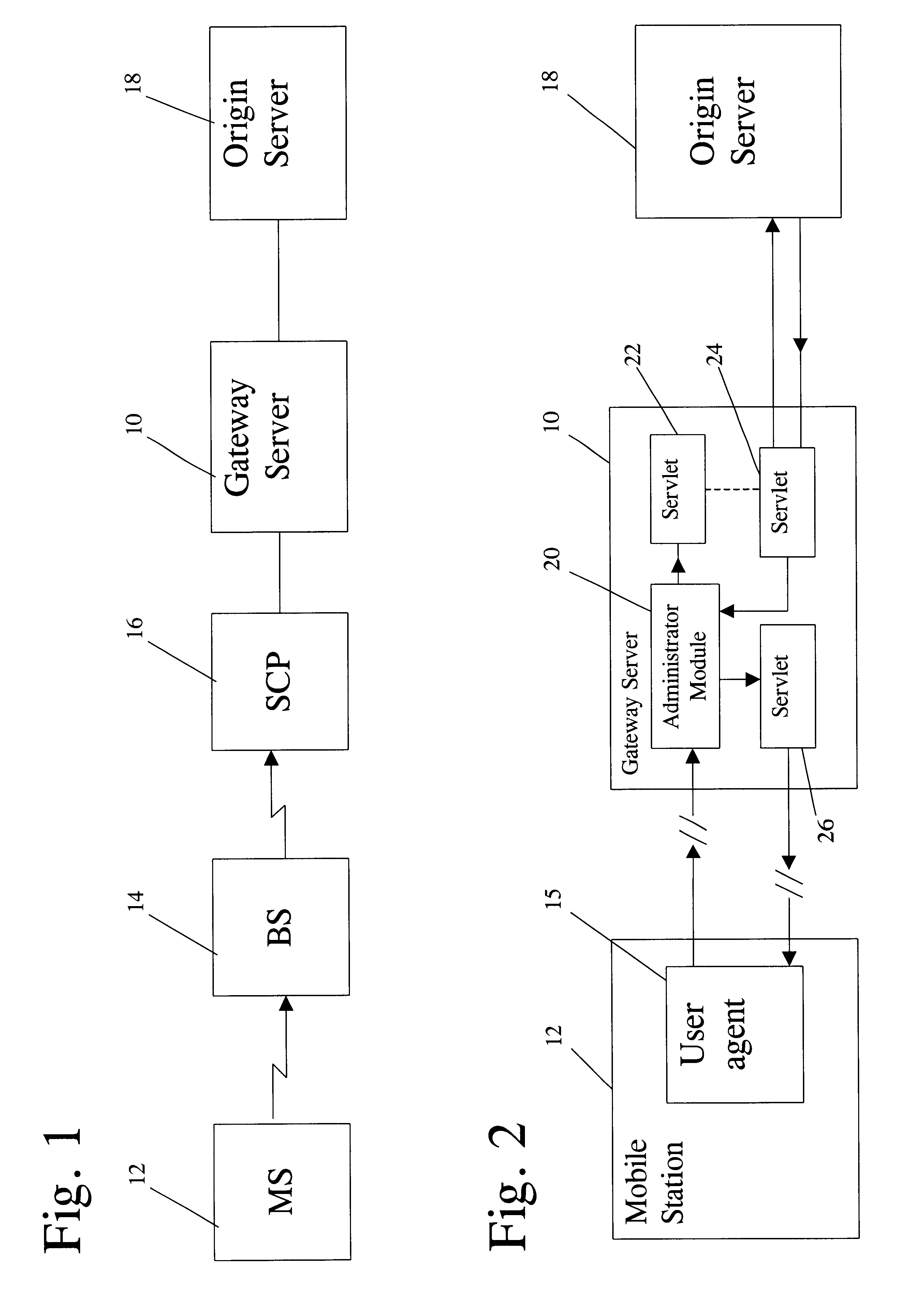
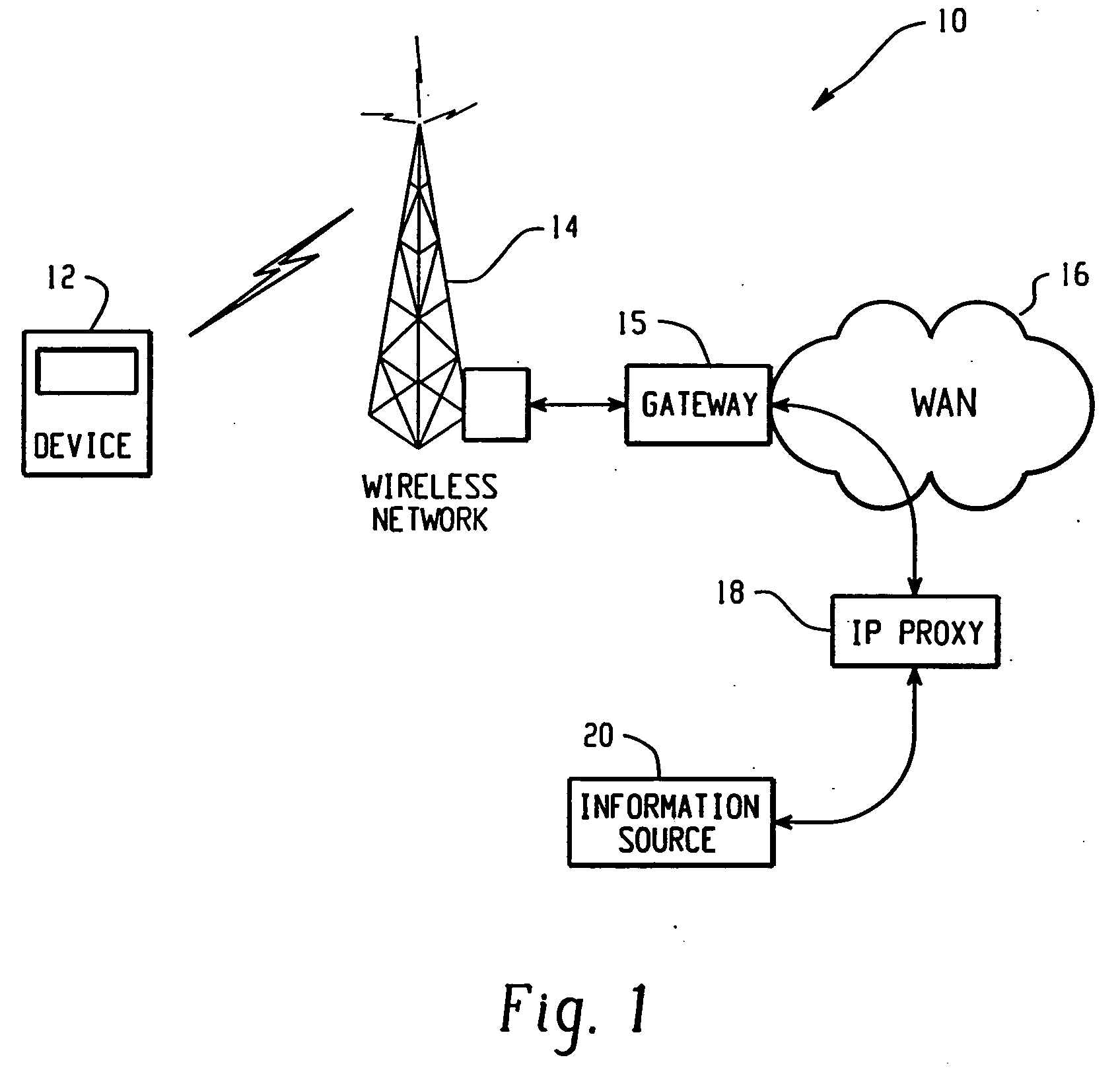
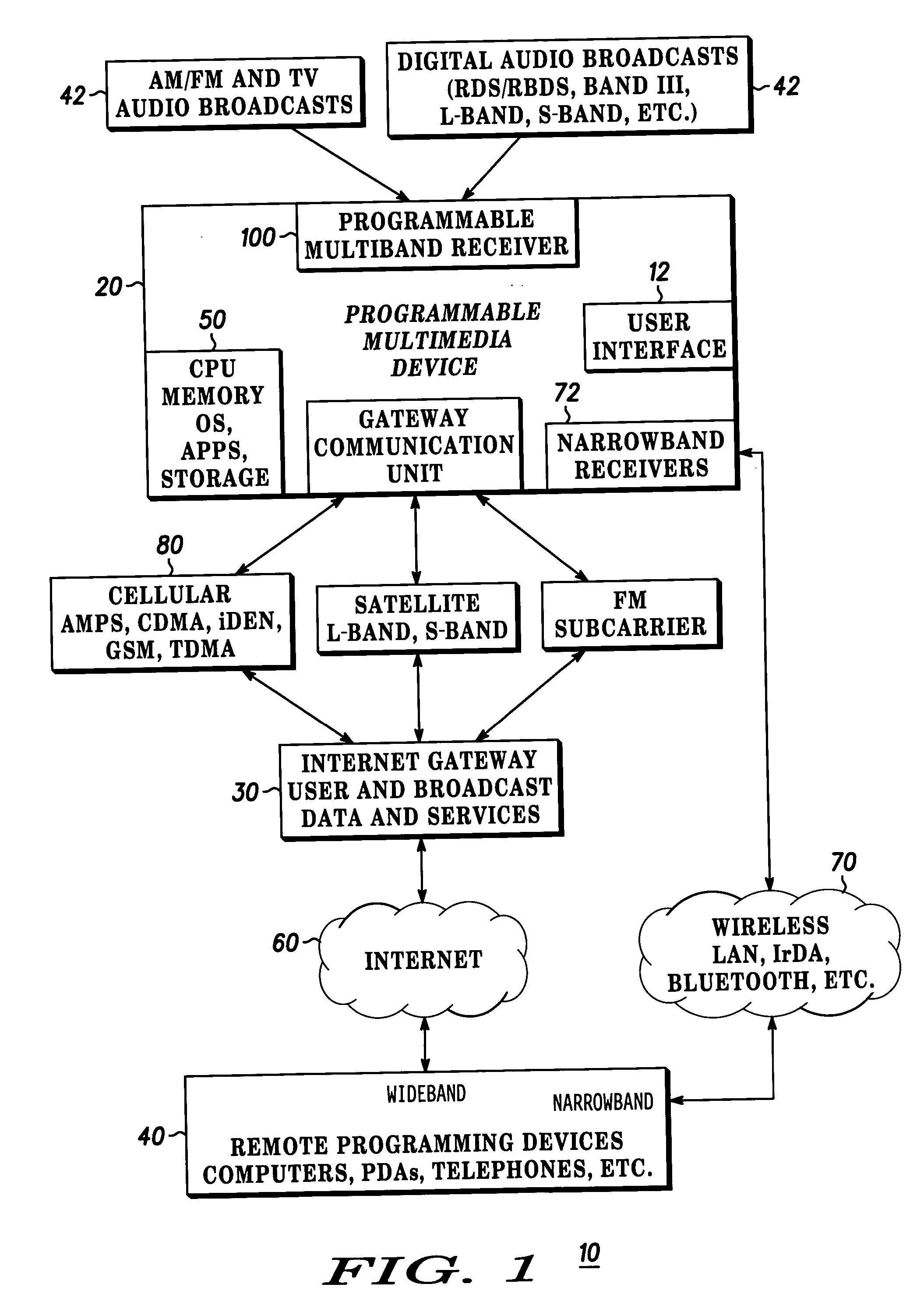
Method and apparatus for providing internet content to SMS-based wireless devices
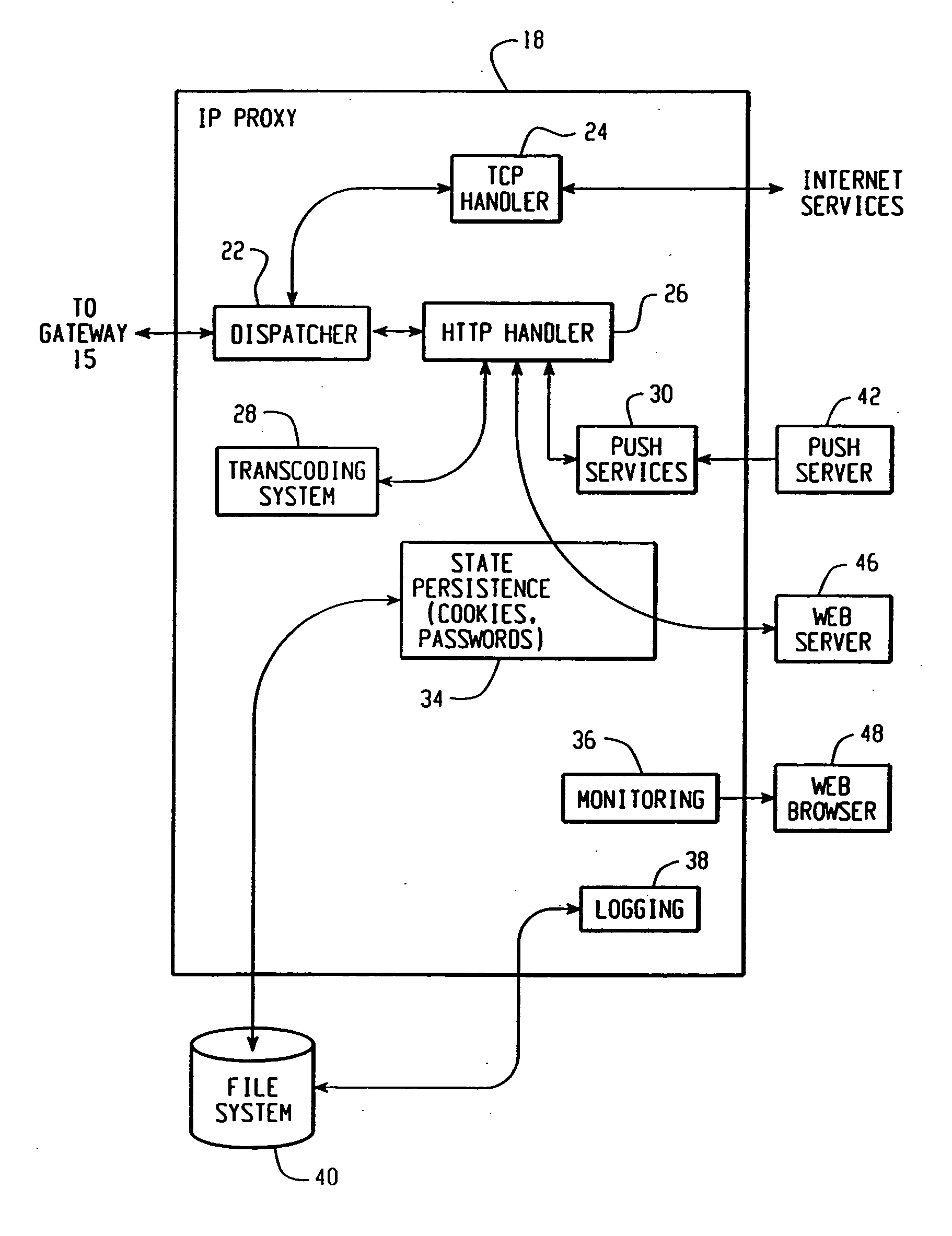
A method and apparatus for providing hypermedia content maintained remotely on a network to a wireless device without a browser are described. A Short Message Service (SMS) request for Internet-based content is received from the wireless device at a proxy server, via an SMS Center (SMSC). The SMS request is transmitted to the SMSC on a wireless network. The proxy server transcodes the SMS request from a character set of the SMSC to a character set of an application and extracts a keyword from the trancoded request. The proxy server maintains a mapping of keywords to URLs. The proxy server looks up the extracted keyword in the keyword-to-URL mapping to identify the URL of an application associated with the keyword. The proxy server constructs an HTTP POST operation containing the keyword and the URL, and submits the HTTP POST operation to the application over a wireline network such as the Internet. Upon receiving an HTTP response containing the requested content from the application in response to the POST operation, the proxy server extracts the content from the HTTP response. The proxy server then translates the content from the content-type used by the application to the content-type used by the SMSC and transcodes the content from the character set used by the application to the character set used by the SMSC. The proxy server then sends the translated and transcoded content in an SMS response to the SMSC, for subsequent delivery to wireless device as an SMS message.
Owner:UNWIRED PLANET
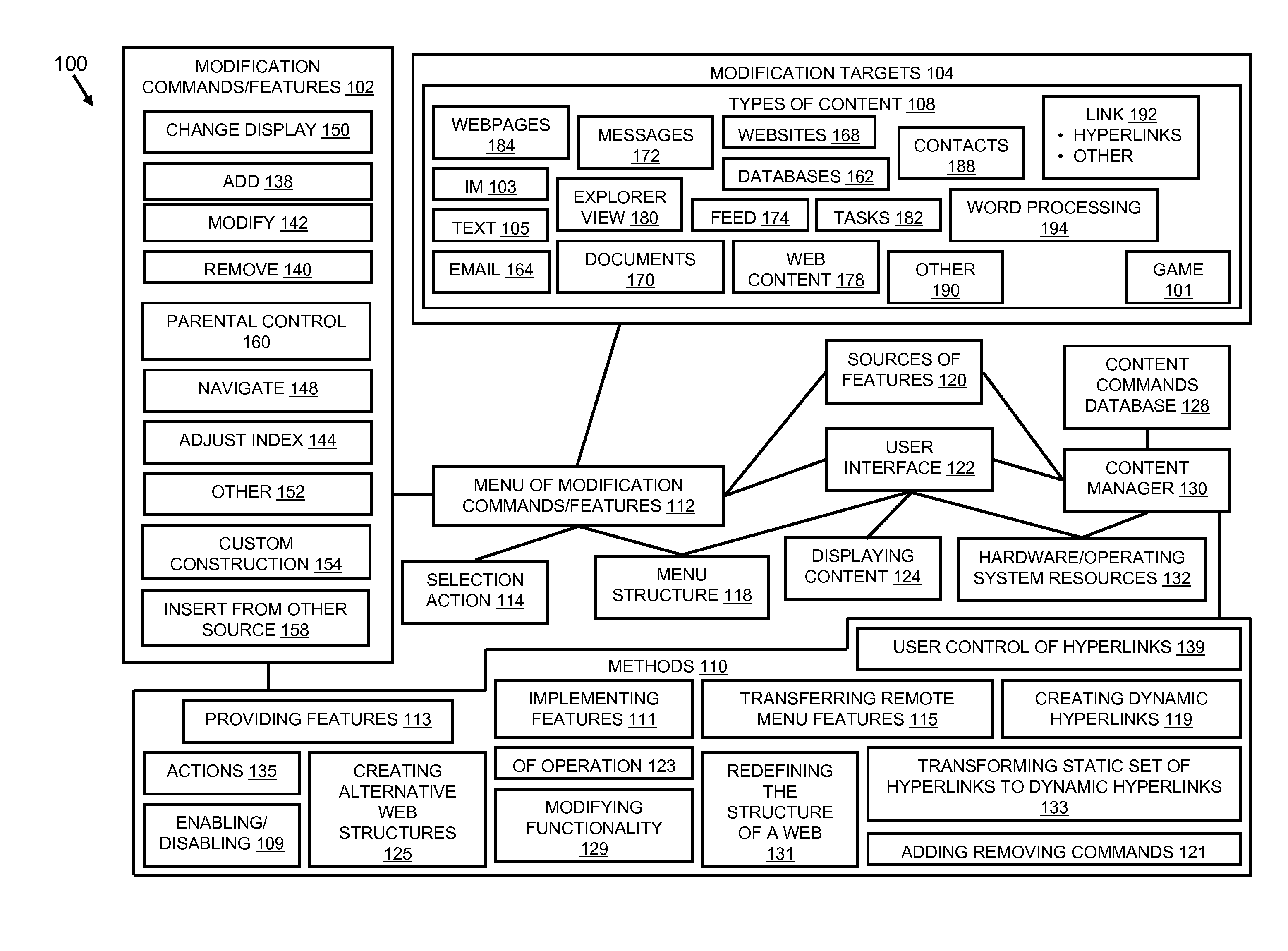
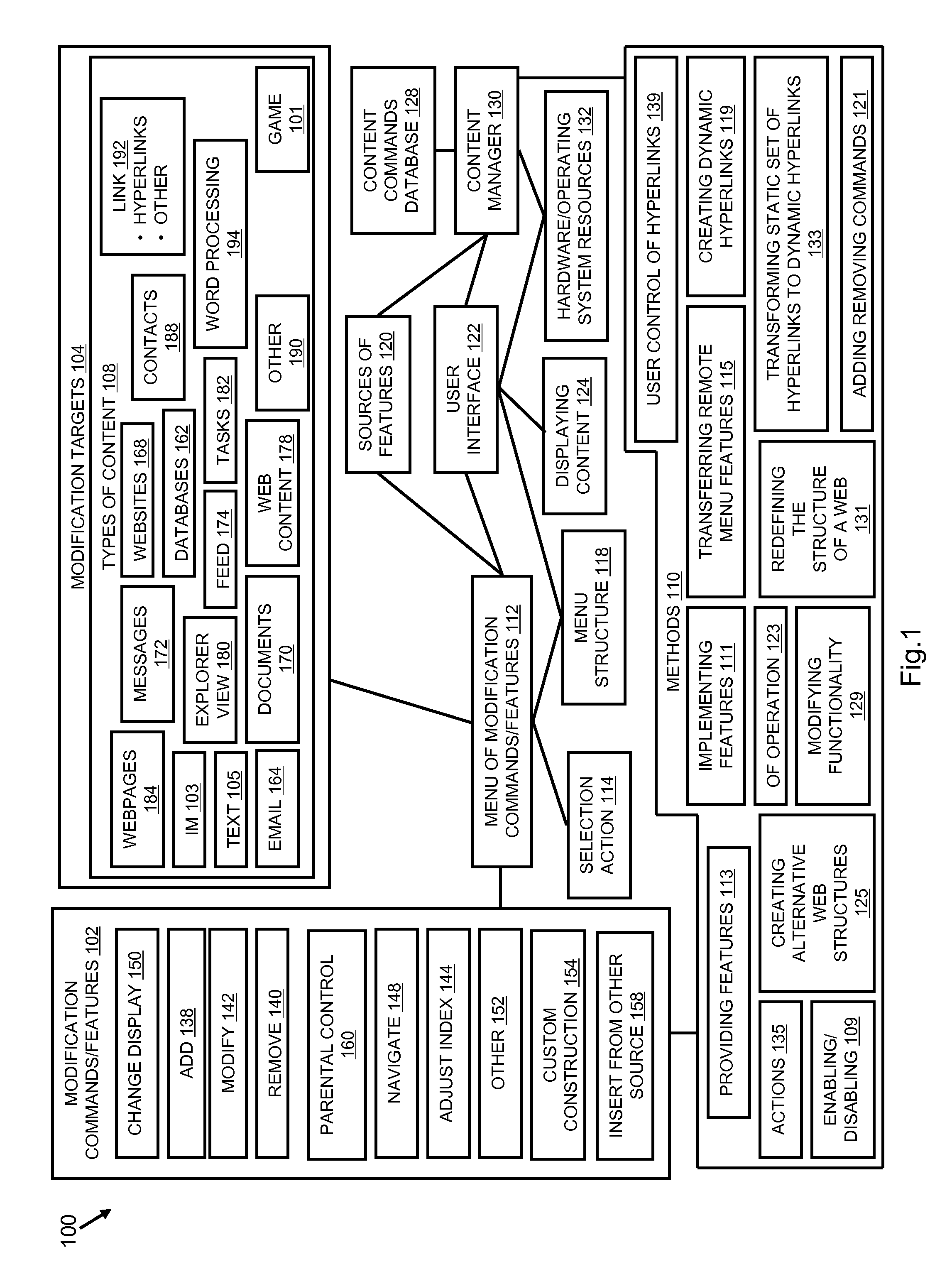
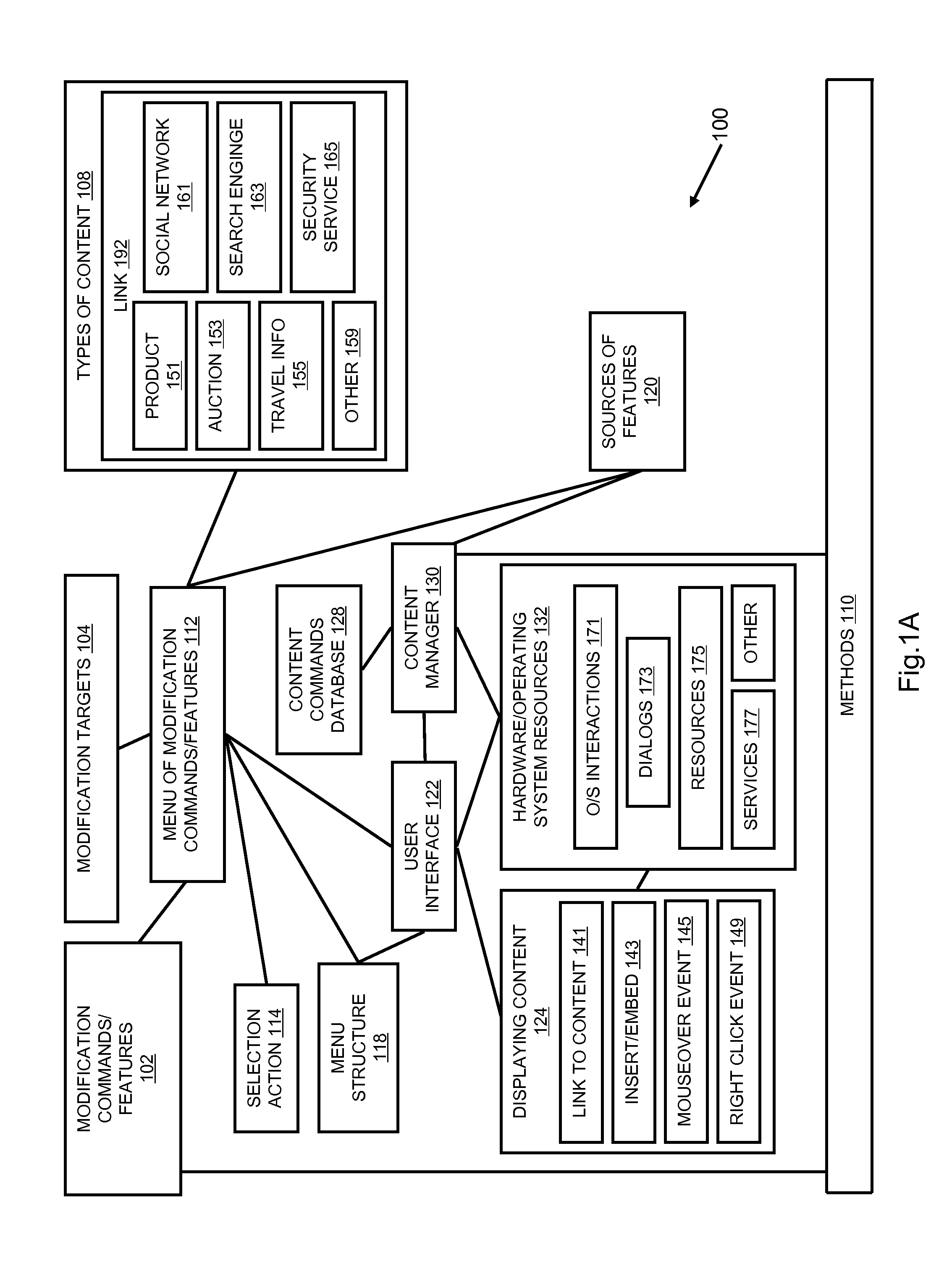
Personalized content control
InactiveUS20070208751A1Improve customizationOffice automationSpecial data processing applicationsPersonalizationThe Internet
A content modification platform facilitates personalized presentation and interaction associated with content such as web content, document content, transactional content, multimedia content, and the like. The platform provides sharing of personalization features to facilitate developing a community view of content, such as the internet Menu features are configured to modify source content through simple commands such as add, delete, replace targeted toward content and links to content. The content modification platform is beneficially and effectively used in a variety of on-line content types, environments, transactions, business activity, e-commerce, stock trading, education, human resources and many others. By facilitating a user defining what relationships between and among content is important to them, a customized view of the internet can be presented to the user.
Owner:GROUPON INC
Statistical metering and filtering of content via pixel-based metadata
Data supplied to a display having a plurality of pixels comprises both content to be displayed and metadata that identifies the content of the respective pixel as being of a particular type by setting the metadata for each pixel to a value that is one of a predefined set of values. The identification of the content as being of a particular type enables the classification of the pixels on a per pixel basis into one or more categories. Pixels containing data for an advertisement can be identified and metered to determine the total display space they occupy and length of time they are displayed, which are both considered measures of the effectiveness of the advertisement. This metering can therefore be used to more equitably charge for advertising on web pages because an advertiser can be charged on the basis of what a user actually sees on the display. If only a percentage of the advertisement is visible, the advertiser pays an amount in proportion to the percentage of the advertisement that is visible. Pixels belonging to an advertisement can also be metered by a video game in a manner that gives an incentive to a game player to view advertisements. Additionally, metadata can be used to identify a pixel as containing objectionable content or some other information or type of content not desired by a user. The pixels containing objectionable or undesired content, which usually are pixels that display an object or portions thereof, can then be filtered out of the picture in a more precise way to either delete or leave a blurred image of the object or objectionable / undesirable portion thereof only, without hiding an entire screen of data.
Owner:NOKIA TECHNOLOGLES OY
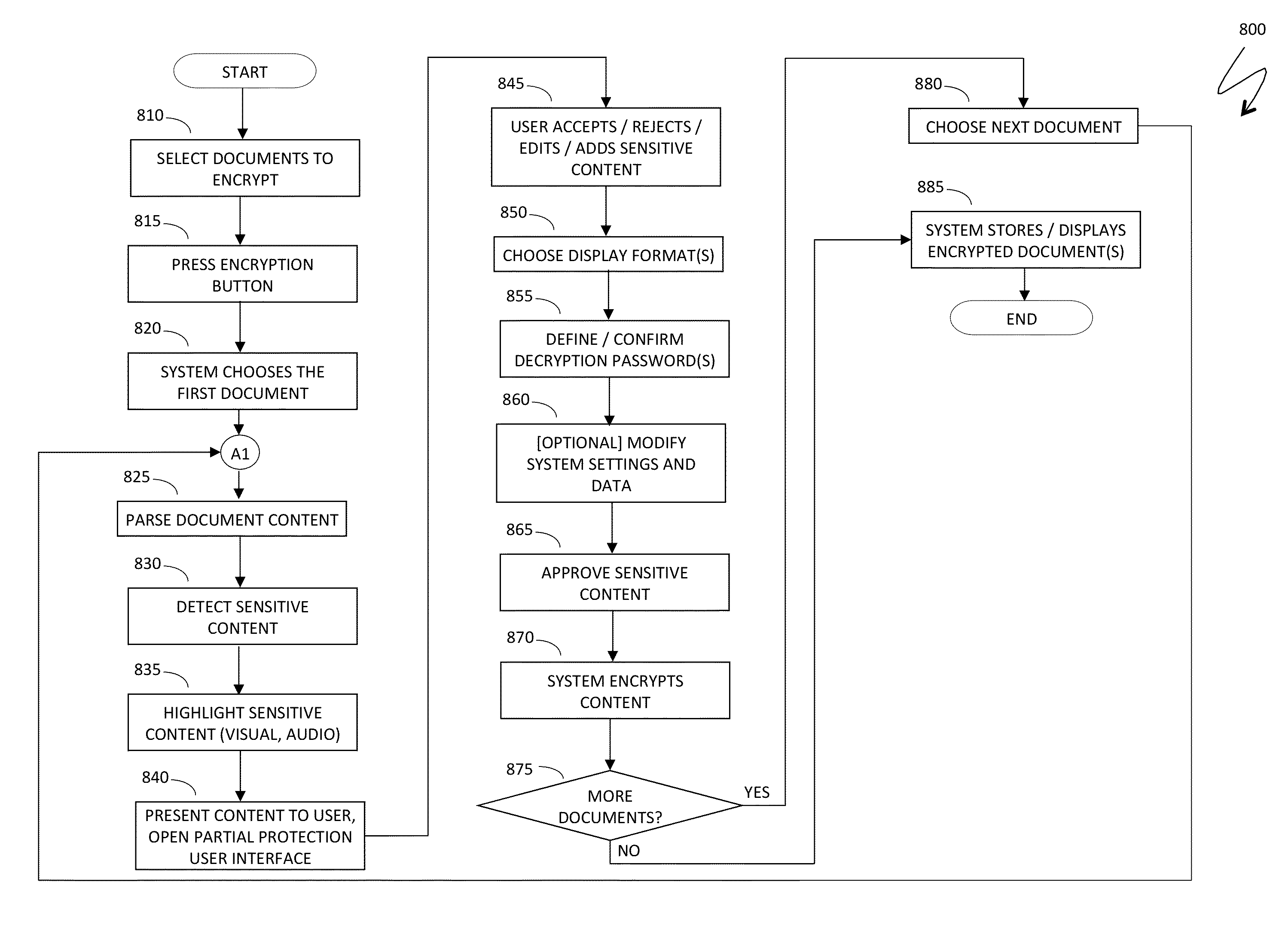
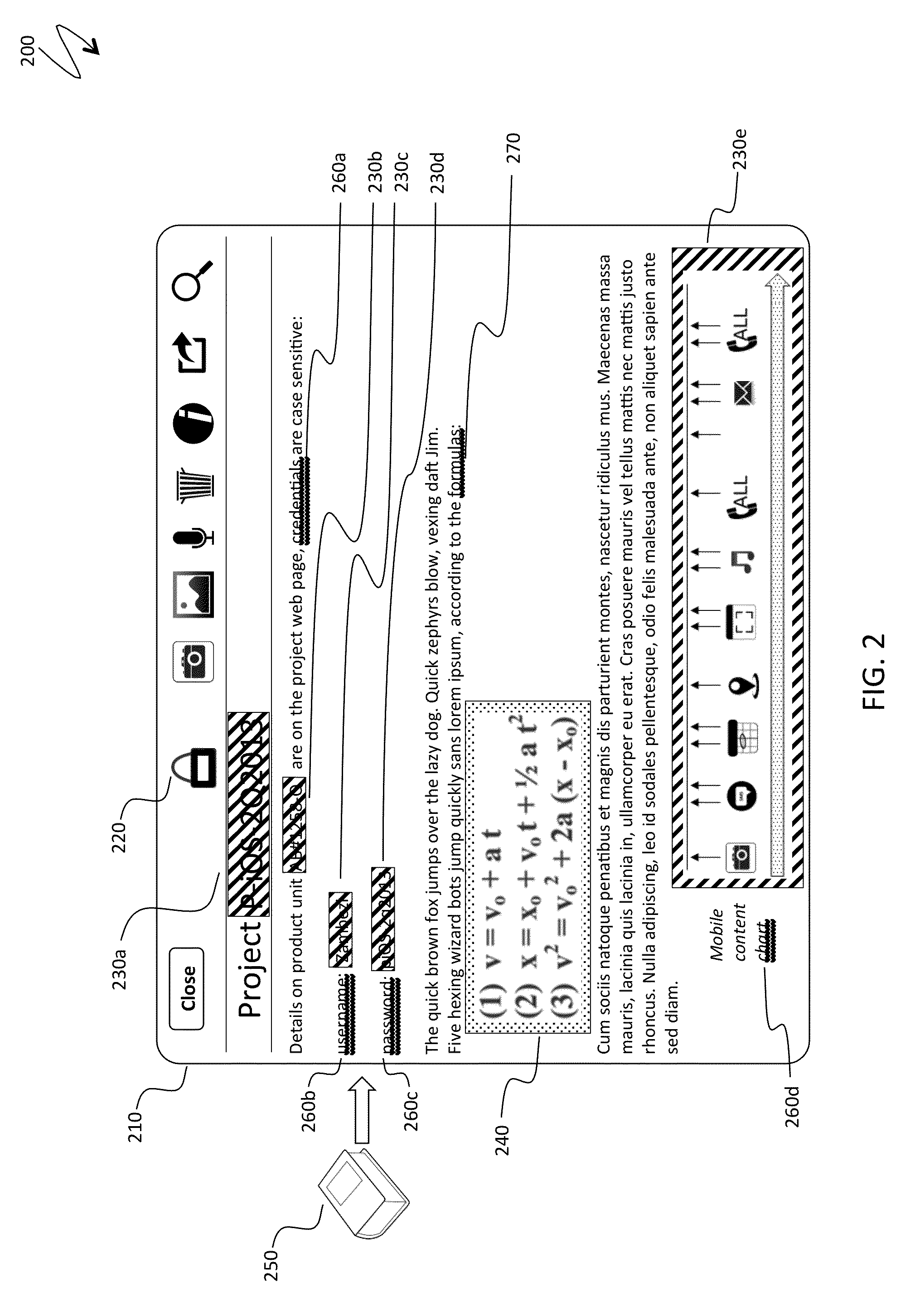
Automatic protection of partial document content
ActiveUS20140208418A1Reduce the amount requiredDigital data processing detailsUnauthorized memory use protectionPasswordDocumentation
Protecting a fragment of a document includes automatically detecting the fragment without user intervention based on the content of the fragment and / or the context of the fragment within a set of documents, selectively encrypting the fragment to prevent unauthorized access, and providing an alternative view of the fragment that prevents viewing and access of content corresponding to the fragment unless a decryption password is provided. Automatically detecting the fragment may include detecting numbers and alphanumeric sequences of sufficient length that do not represent commonly known abbreviations, detecting generic terms, detecting proper names, detecting terms signifying a type of content, detecting mutual location of terms and sensitive content, and / or detecting user defined terms. The generic terms may correspond to password, passcode, credentials, user name, account, ID, login, confidential, and / or sensitive. The proper names may be names of financial organizations and security organizations.
Owner:EVERNOTE
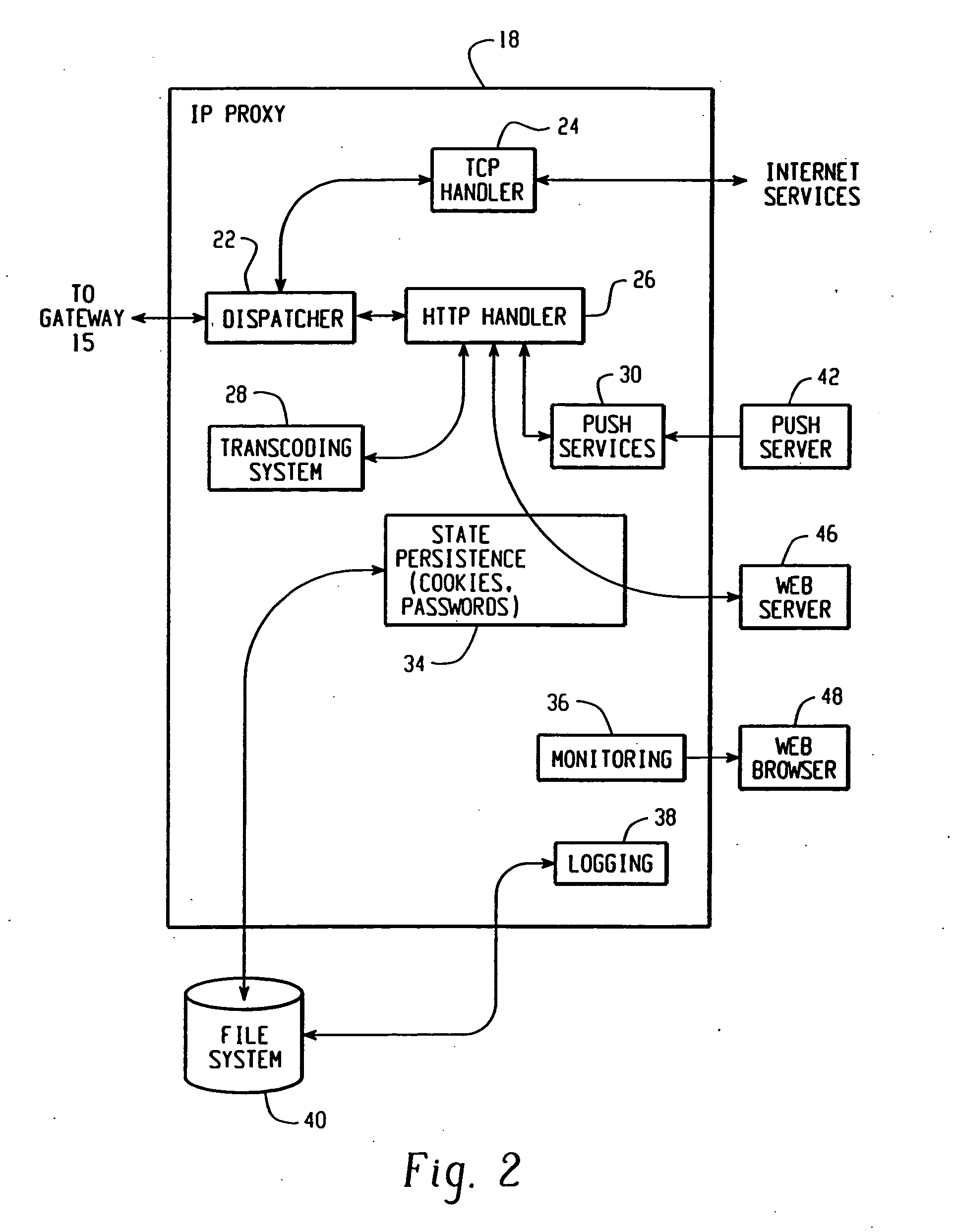
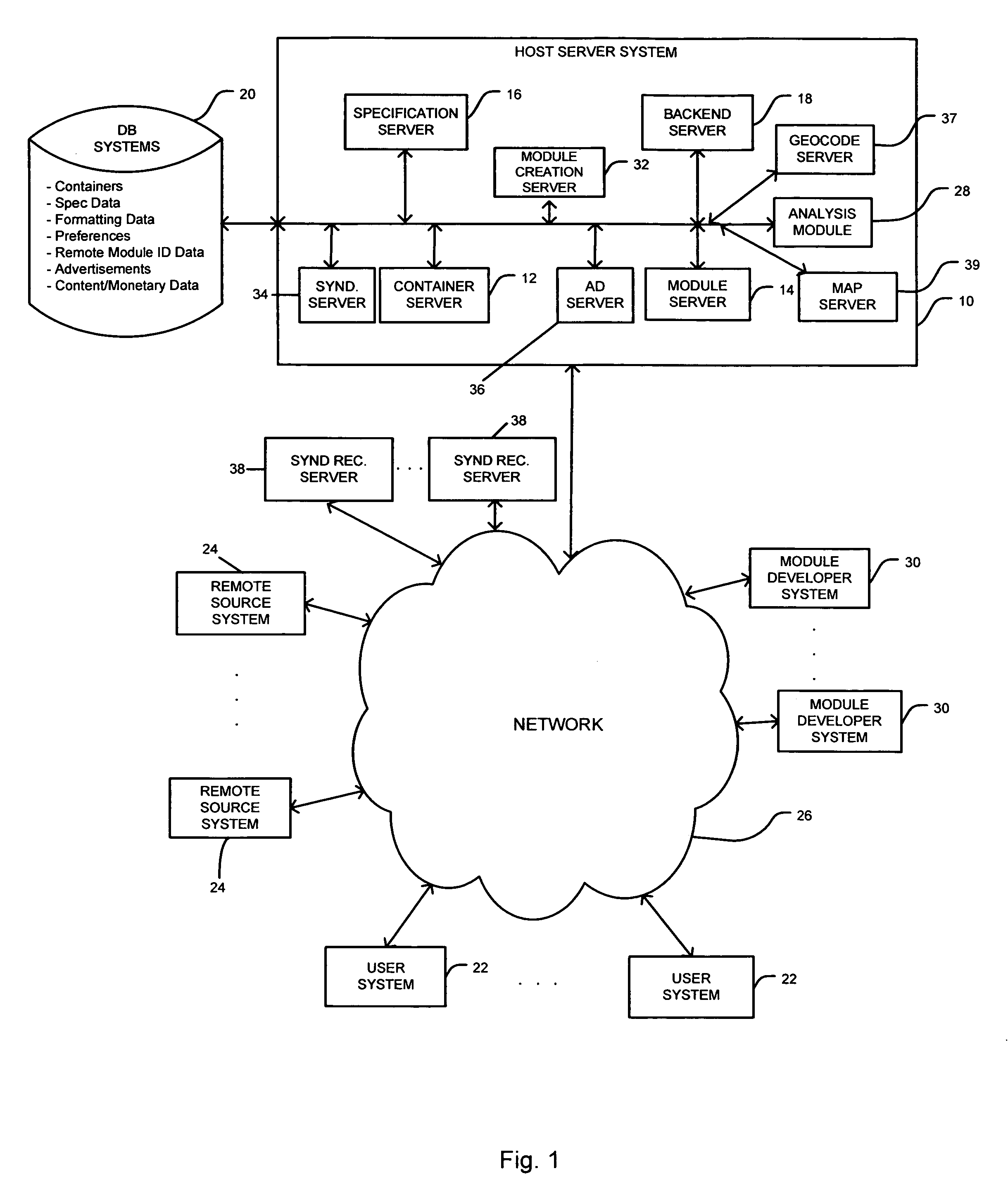
System and method for providing remote data access for a mobile communication device
ActiveUS20040170155A1Digital data information retrievalData processing applicationsData accessTranscoding
In one exemplary embodiment, a system for providing data access between an information source and a mobile communication device includes a transcoding system and a first network device. The transcoding system includes a plurality of transcoders, and each transcoder is operable to transcode information content from a respective first content type into a respective second content type. The first network device is in communication with the transcoding system and includes a connection handler system. The connection handler system is operable to receive connection data for a connection between the information source and the mobile communication device and to select a corresponding connection handler. The connection handler is operable to select one or more transcoders from the plurality of transcoders to transcode the information content.
Owner:MALIKIE INNOVATIONS LTD
Methods and apparatuses for advertisements on mobile devices for communication connections
Methods and apparatuses to present advertisements on mobile devices for communication connections of multiple content types. In one embodiment, a method includes: providing an advertisement to a mobile device, the advertisement to include a communication reference to be used by the mobile device to request a communication connection; and billing for the advertisement in response to an initiation of a communication, comprising more than one of text, voice, audio, image, and video, via the communication reference.
Owner:THRYV INC
System and method for controlling and organizing metadata associated with on-line content
Owner:JOHNSON DEACON
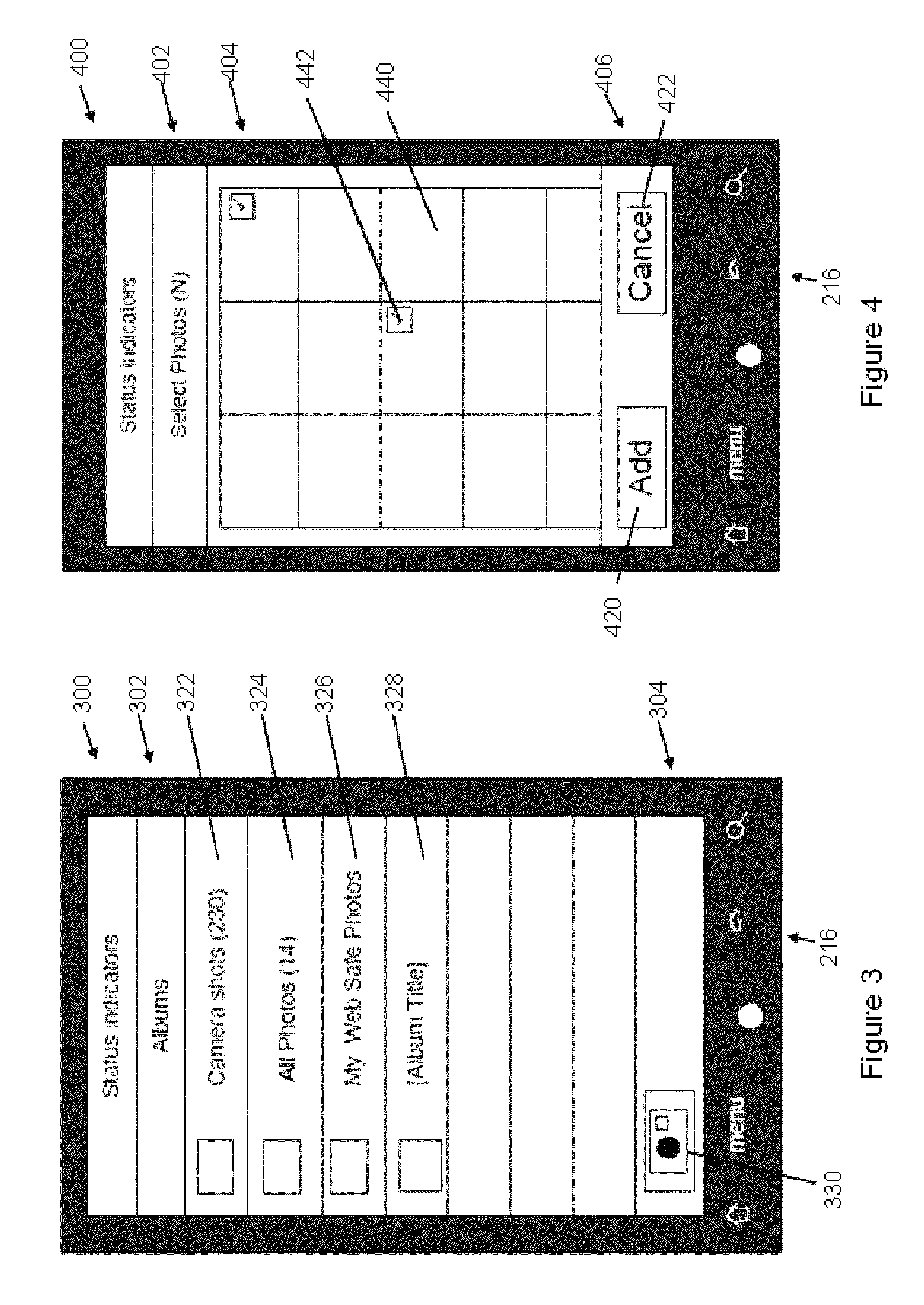
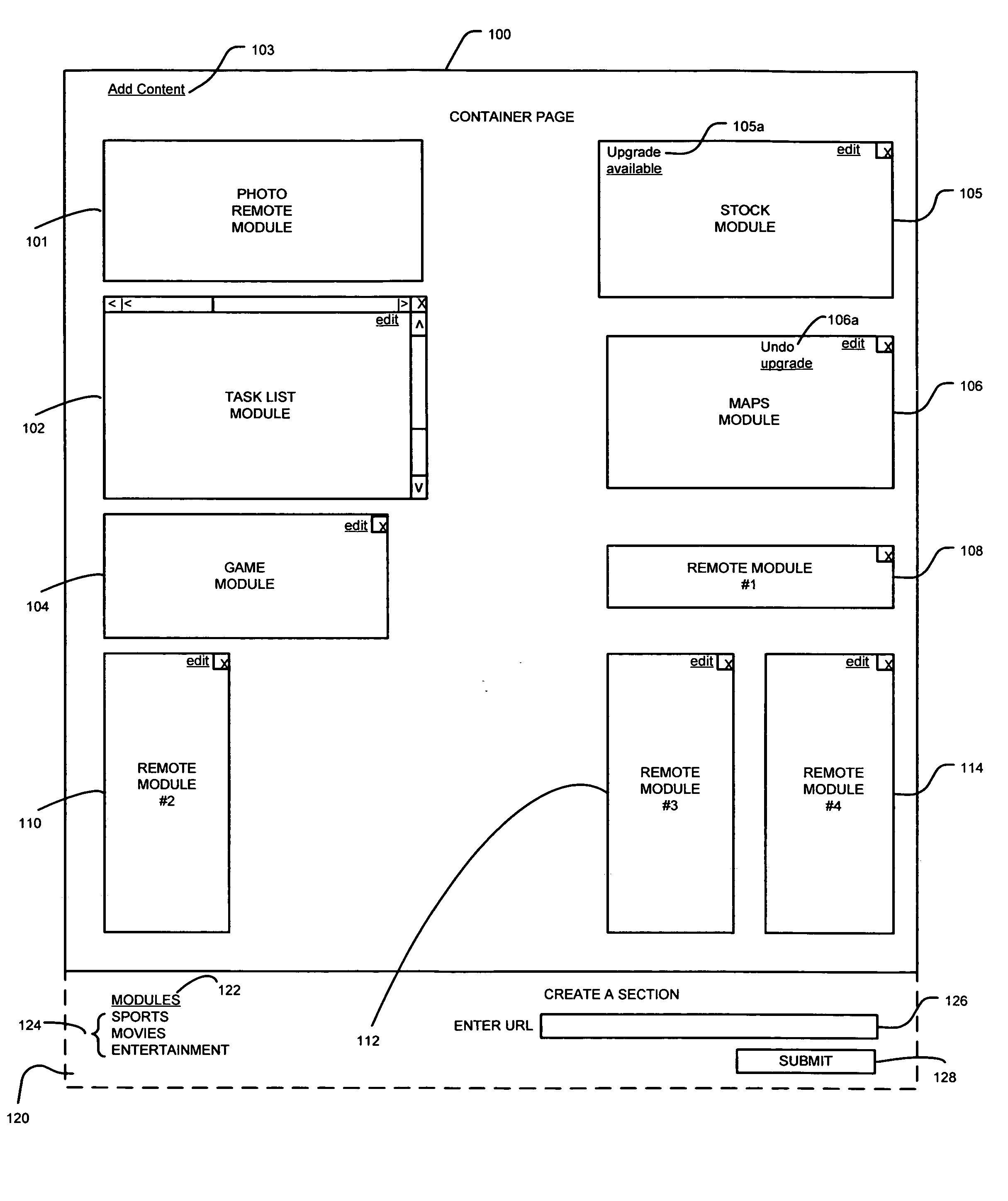
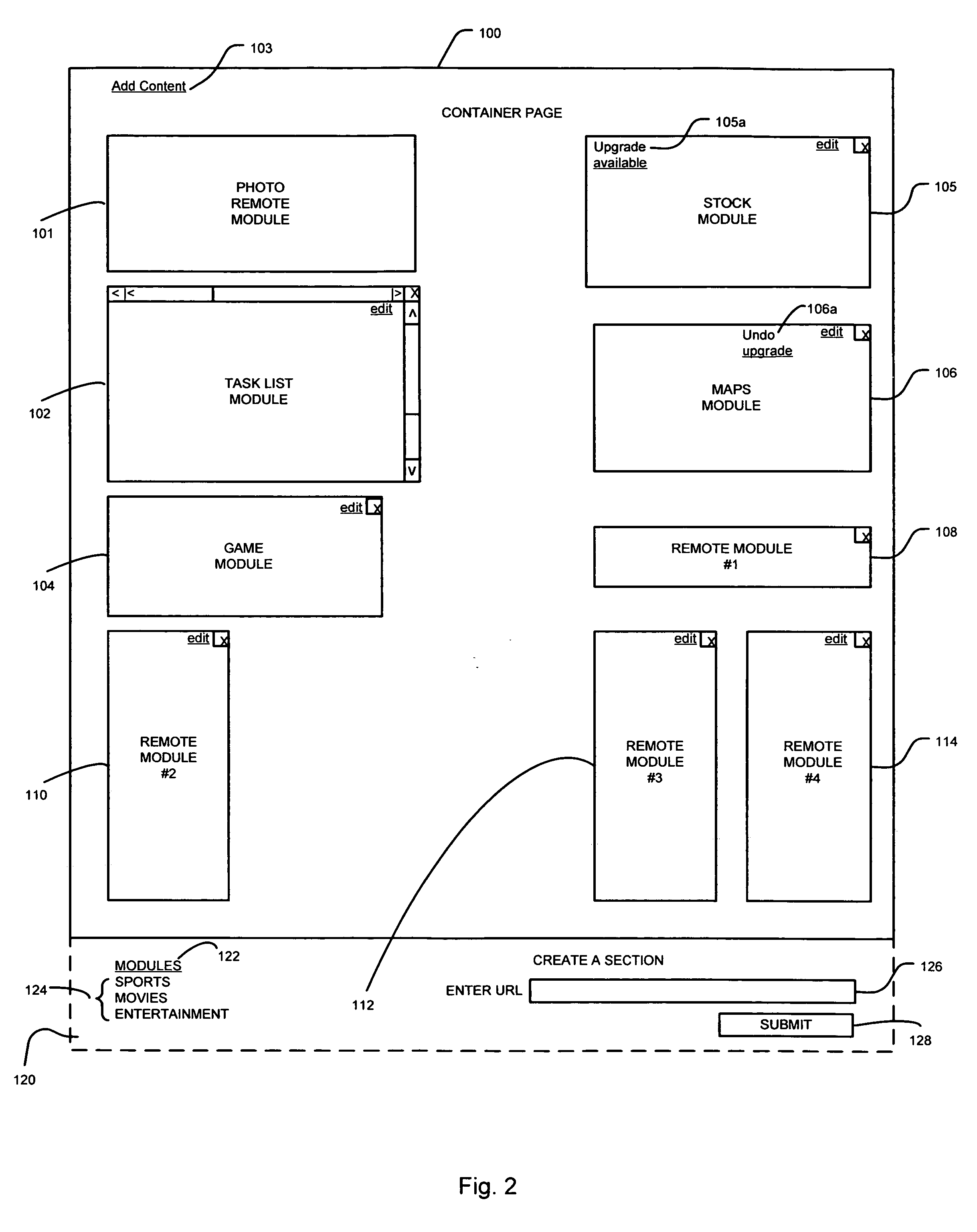
Module specification for a module to be incorporated into a container document
ActiveUS8185819B2Natural language data processingWebsite content managementElectronic documentPersonalization
A computer readable medium, an electronic document or a system that uses one of these that includes particular code that specifies a first module selectively designated for inclusion in a personalized container document and additional code that specifies a second module selectively designated for inclusion in the personalized container document. The container document designates a plurality of modules included in the container document. Each module in the plurality of modules is adapted for rendering module data for presenting in the container document. The first module is adapted to render module data based at least in part on the particular code, the particular code including a first content type element, a first content element, and one or more preference elements. The second module is adapted for rendering module data for presenting in the container document based at least in part on the additional code, the additional code including a second content type element, a second content element and one or more preference elements. The first content type element is different than the second content type element.
Owner:GOOGLE LLC
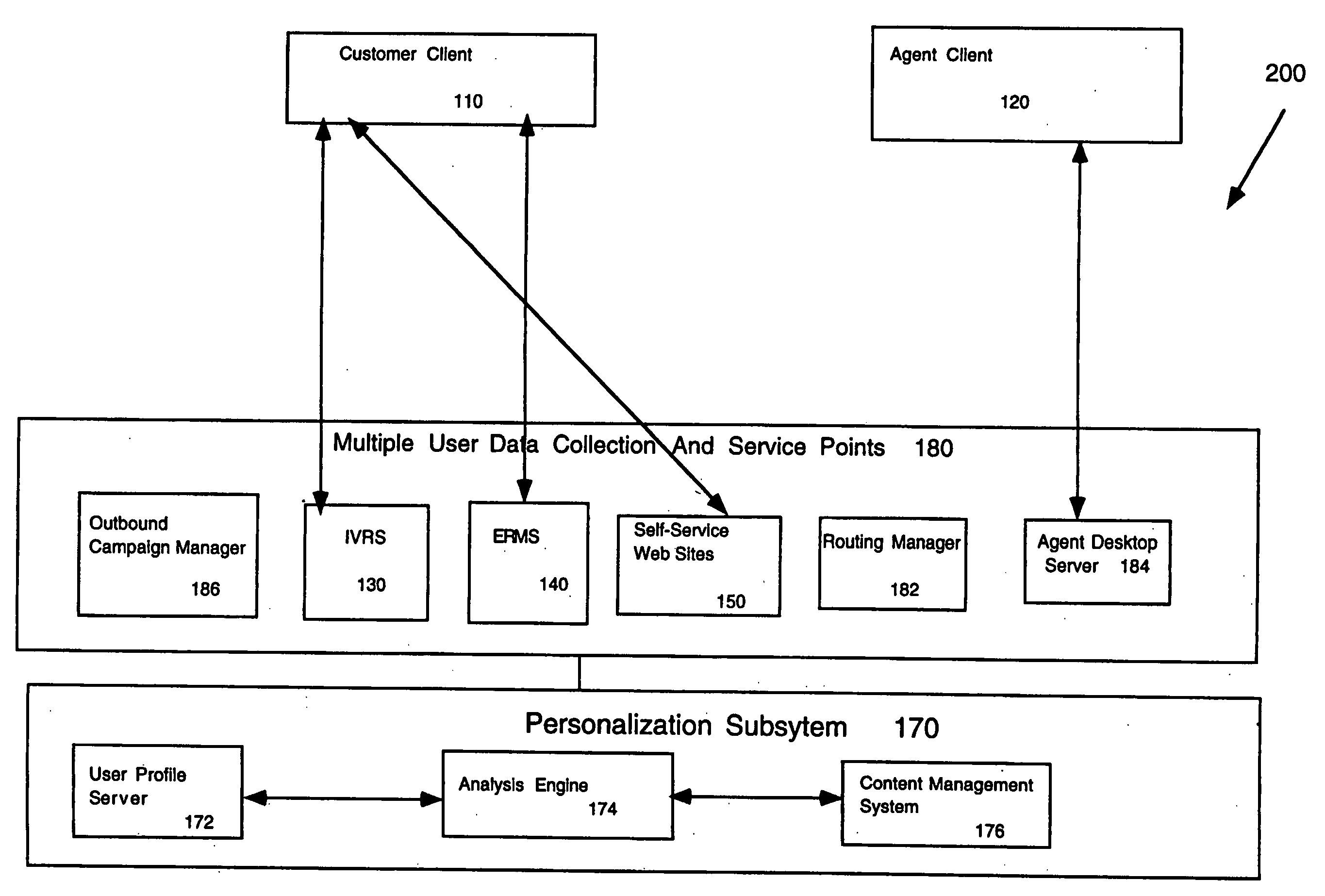
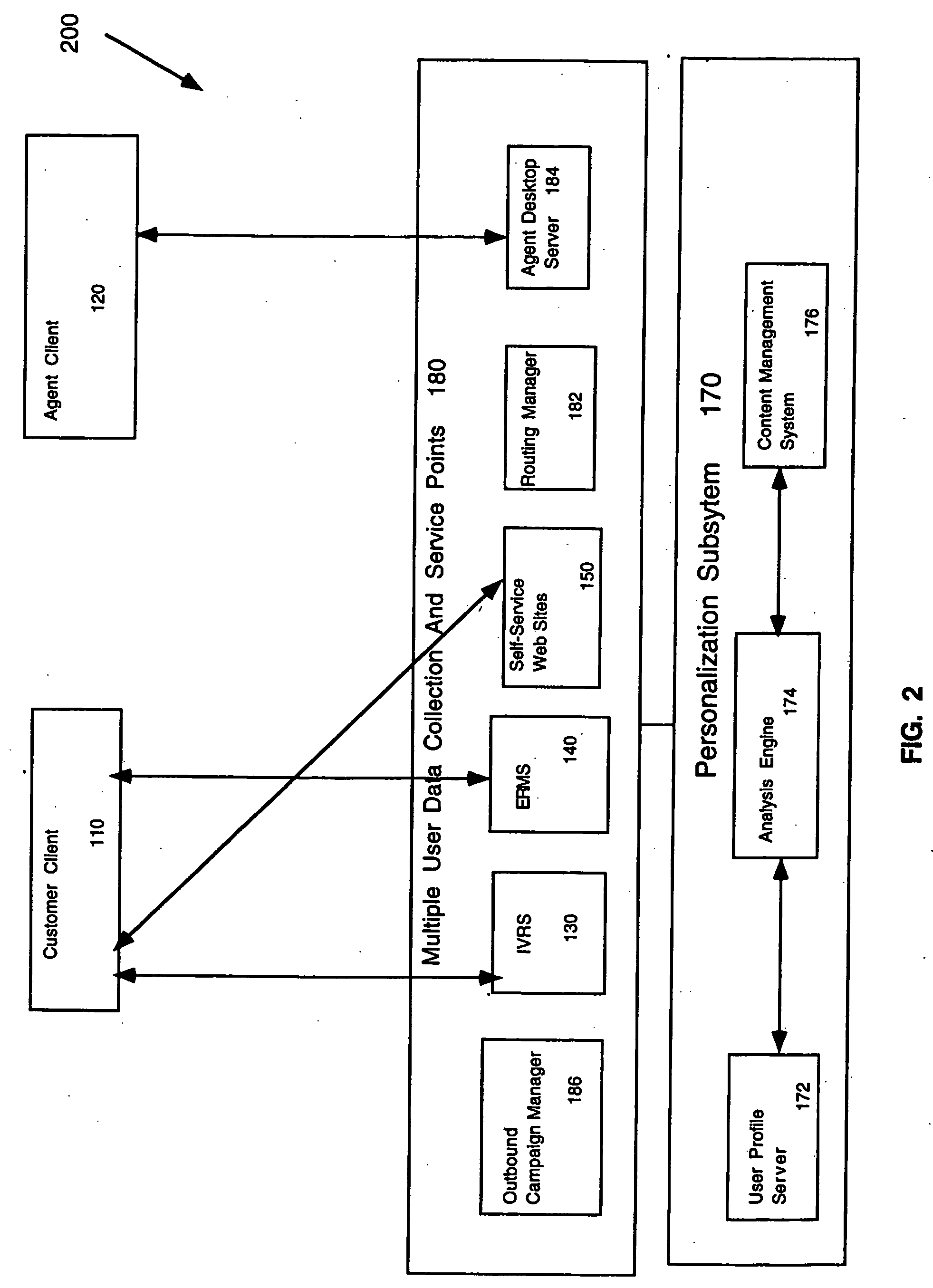
Method and system for providing personalized service over different contact channels
InactiveUS20050135596A1Data processing applicationsDigital data information retrievalUser profileFile server
A system comprising an analysis engine that interacts with a user profile server and a content management system. The user profile server is used to collect and manage data. The content management system manages a plurality of content types for a plurality of service points in real-time. A service point supports a content type.
Owner:ASPECT COMM
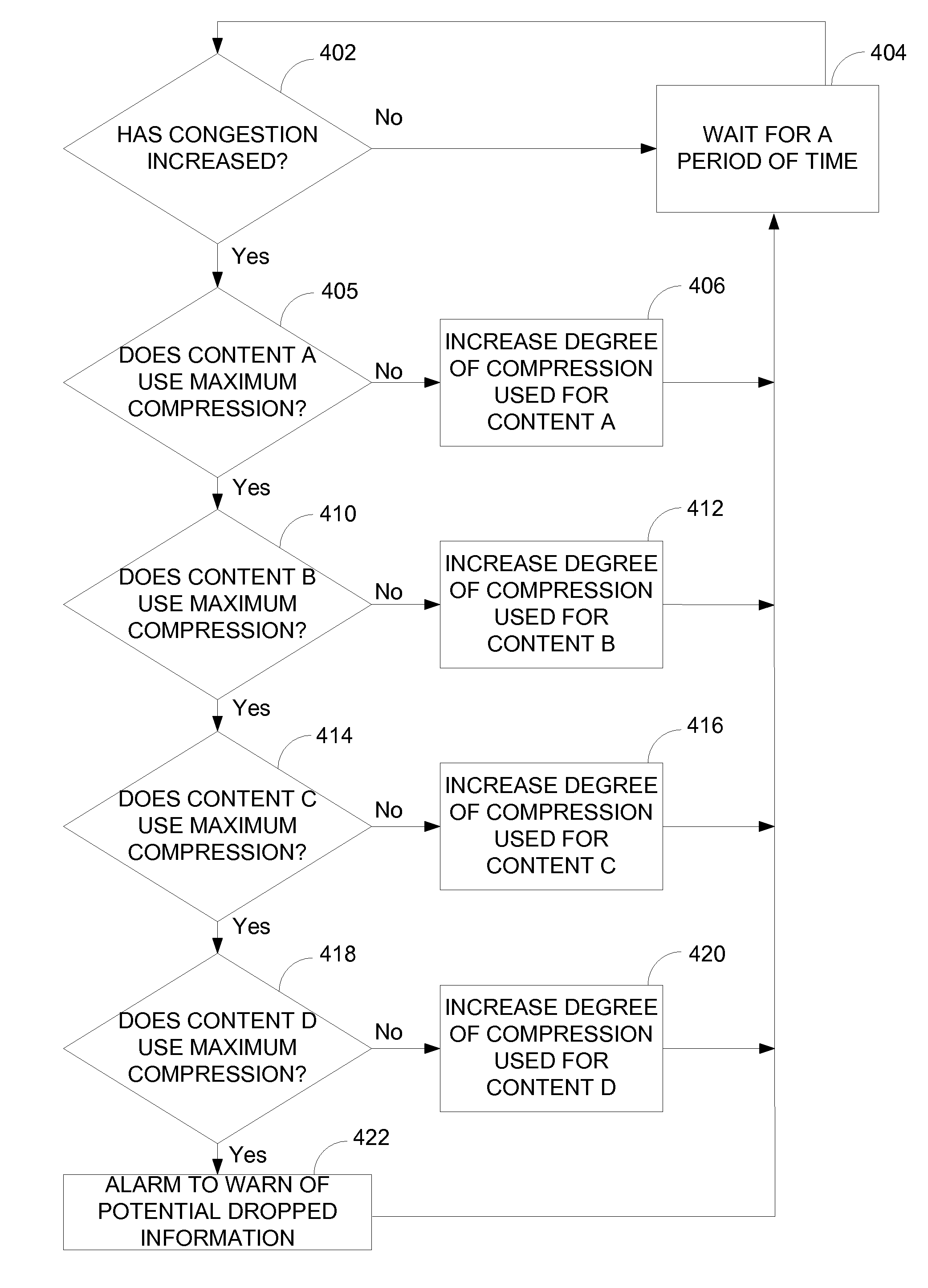
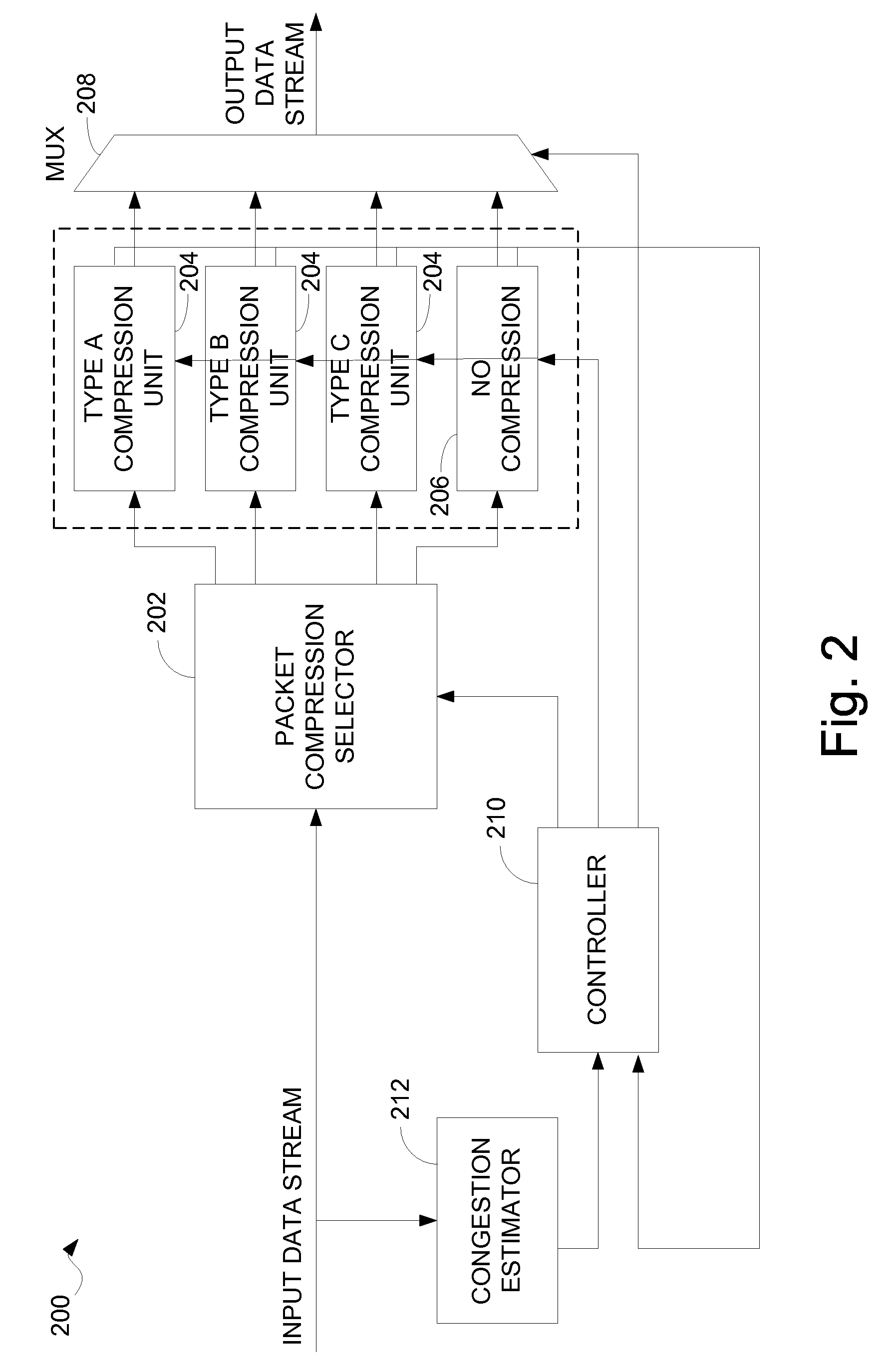
Communication system with content-based data compression
InactiveUS7069342B1Multiple digital computer combinationsTransmissionData compressionCommunications system
Methods and apparatus for dynamically adapting the degree of compression used in compressing data based upon the type of contents contained within a packet are disclosed. According to one aspect of the present invention, an apparatus that forwards data across a digital communications network includes a compression switch, a compression system, and an output interface. The compression switch receives the data, determines a content type associated with the data by examining the data, and assigns a compression level to the data in response to the determined content type. The compression system is arranged to compress the data based upon the compression level, while the output interface forwards the compressed data across the network. In one embodiment, the apparatus also includes a network congestion estimator that determines a level of network congestion.
Owner:CISCO TECH INC
Method and system for extracting relevant information from content metadata
InactiveUS20080204595A1Digital data information retrievalPicture reproducers using cathode ray tubesRelevant informationContent type
A method and system for extracting relevant information from content metadata is provided. User access to content is monitored. A set of extraction rules for information extraction is selected. Key information is extracted from metadata for the content based on the selected extraction rules. Additionally, a type for the content can be determined, and a set of extraction rules is selected based on the content type. The key information is used in queries for searching information of potential interest to the user, related to the content accessed.
Owner:SAMSUNG ELECTRONICS CO LTD
Method for paging a device in a wireless network
InactiveUS7197025B2Avoiding all setup messagingEffective controlPower managementFrequency-division multiplex detailsWireless mesh networkMessage flow
A method for access control in a wireless network having a base station and a plurality of remote hosts includes the optional abilities of making dynamic adjustments of the uplink / downlink transmission ratio, making dynamic adjustments of the total number of reservation minislots, and assigning access priorities by message content type within a single user message stream. The method of the invention further provides for remote wireless host paging and for delayed release of active channels by certain high priority users in order to provide low latency of real-time packets by avoiding the need for repeated channel setup signaling messages. In the preferred embodiment, there are N minislots available for contention in the next uplink frame organized into a plurality of access priority classes. The base station allows m access priority classes. Each remote host of access priority class i randomly picks one contention minislot and transmits an access request, the contention minislot picked being in a range from 1 to Ni where N(i+1)<Ni and N1=N. In an alternate embodiment of a method for access control according to the present invention, each remote host of access priority class i and with a stack level that equals 0, then transmits an access request with a probability Pi where P(i+1)<Pi and P1=1.
Owner:WSOU INVESTMENTS LLC
Method of Providing Content to a Wireless Computing Device
InactiveUS20080109528A1Prohibitively expensive to buildMaintenance becomes more and difficultVersion controlComputer security arrangementsMobile contentApplication software
A customised Network Application suitable for a specific type of Wireless Computing Device is automatically generated and sent to that Device. The Application is able to download a preview of content on demand by an end-user from a Server that stores the content and to play the preview of the content. It can also display an option or function that enables the end-user to download and buy that content from the Server. Attributes for that type of Wireless Computing Device are defined as Metadata; attributes for various different kinds of mobile content are also defined as Metadata; the Server then determines what content is compatible with the Wireless Computing Device by comparing the Metadata of the content and the Wireless Computing Device. The kind of content that can be provided includes ringtones, wallpapers / pictures, screensavers, realtones / truetones, full music downloads, video, SMS & MMS alerts, and mobile games.
Owner:OMNIFONE LTD
Replicated data deleting method based on file content types
InactiveCN101706825AAdd recognition stepsImprove performanceSpecial data processing applicationsRedundant operation error correctionDigital fingerprintContent type
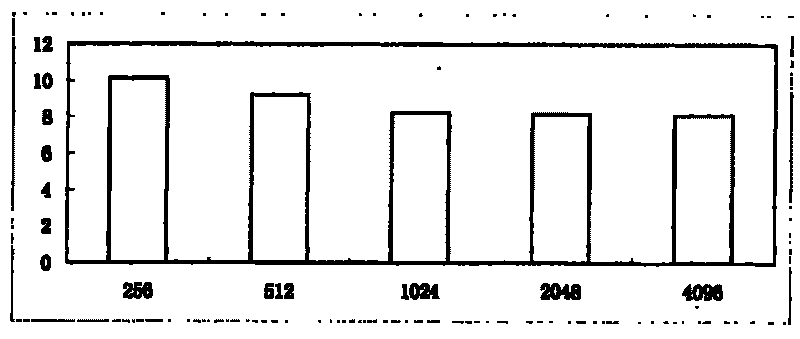
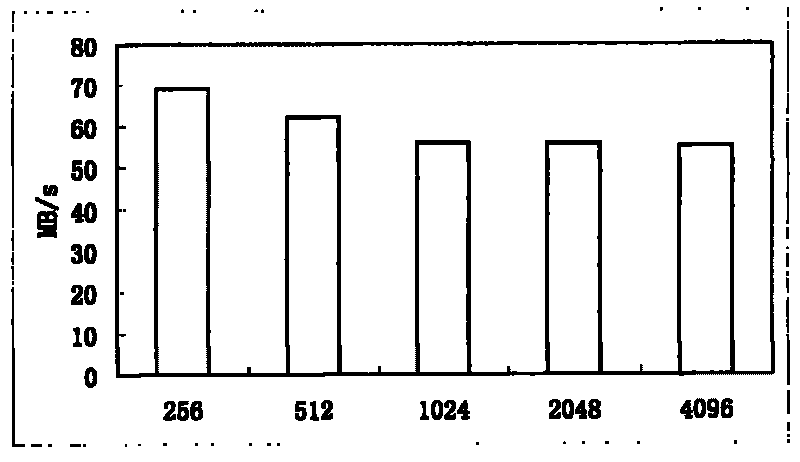
The invention discloses a replicated data deleting method based on file content types, which belongs to the replicated data deleting method of computer data backup, is applicable to disk-based backup systems, and solves the problems that the existing replicated data deleting method is single in block strategies and can not carry out optimization according to the file content types. The deleting method carries out a block boundary characteristic calculation step in advance, and then comprises the following steps sequentially: content type identification, file blocking, digital fingerprint calculation, replicated data block judgment and ending. The deleting method carries out classification on backup files based on content types, computes the optimal block boundary characteristic value aiming at every content type; and when the backup files are processed, the file content type identification step is added, and the block boundary characteristic is selected according to identification result, therefore, the overall effectiveness of the replicated data deleting method is improved when the complex backup files are processed.
Owner:HUAZHONG UNIV OF SCI & TECH
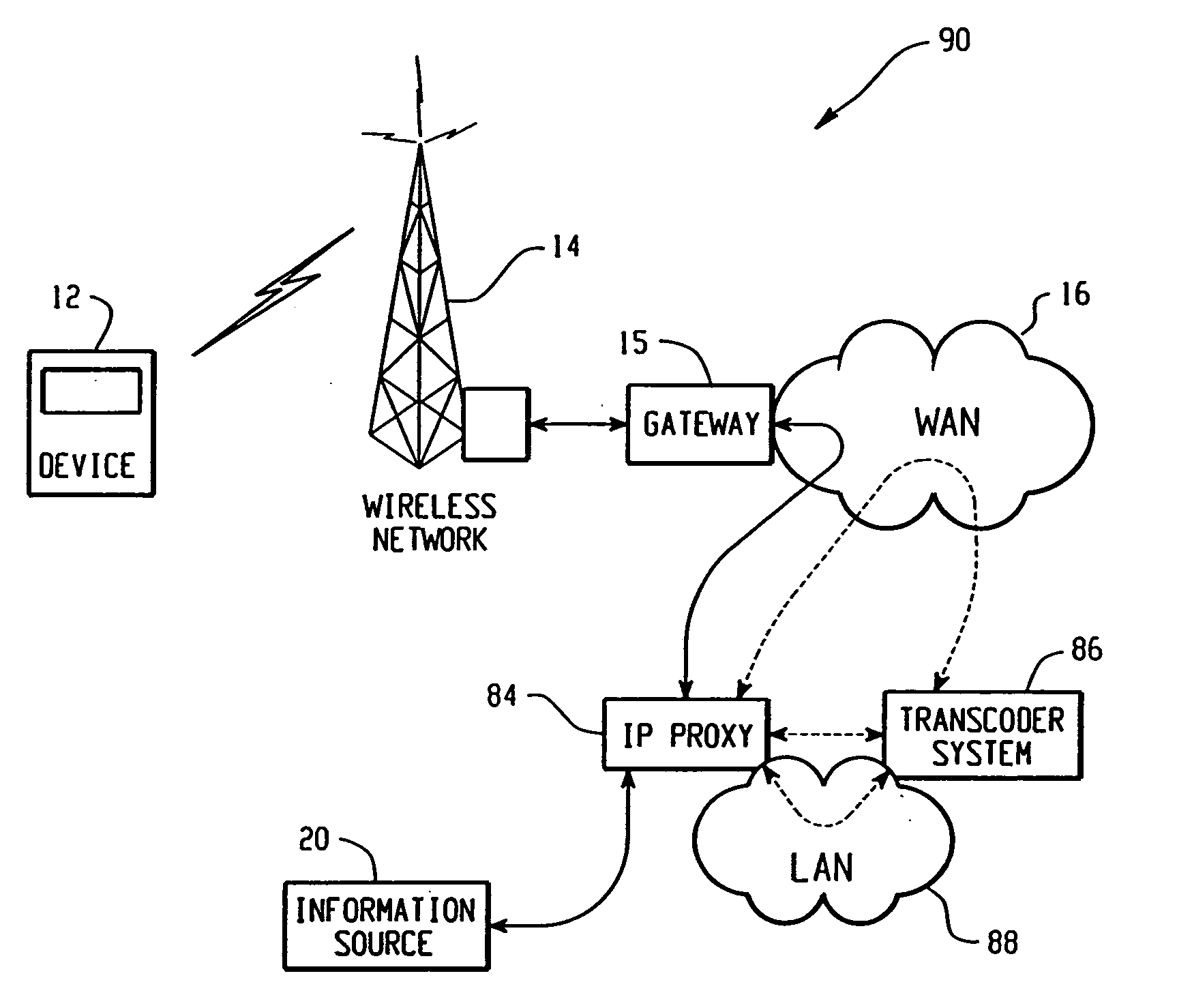
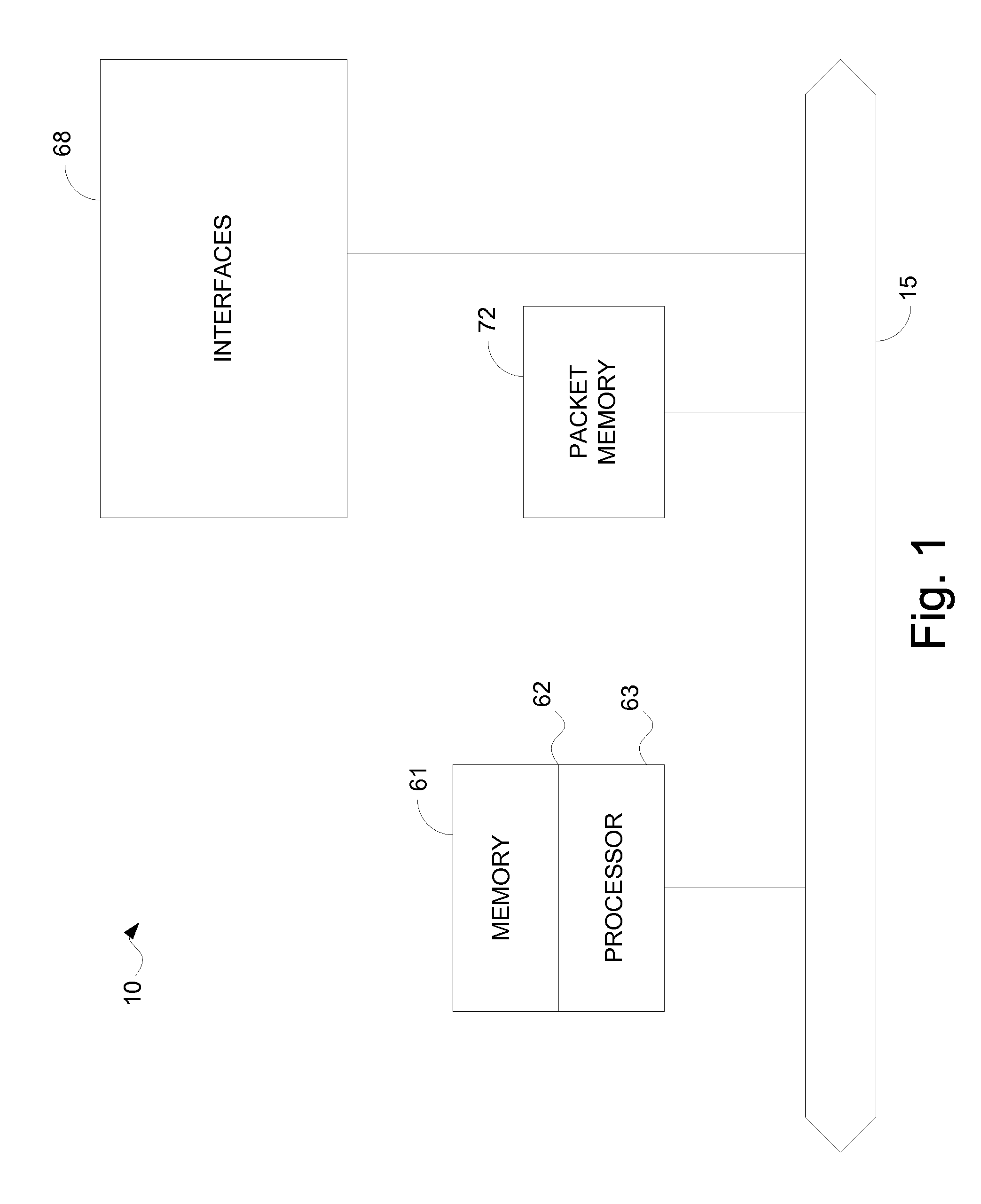
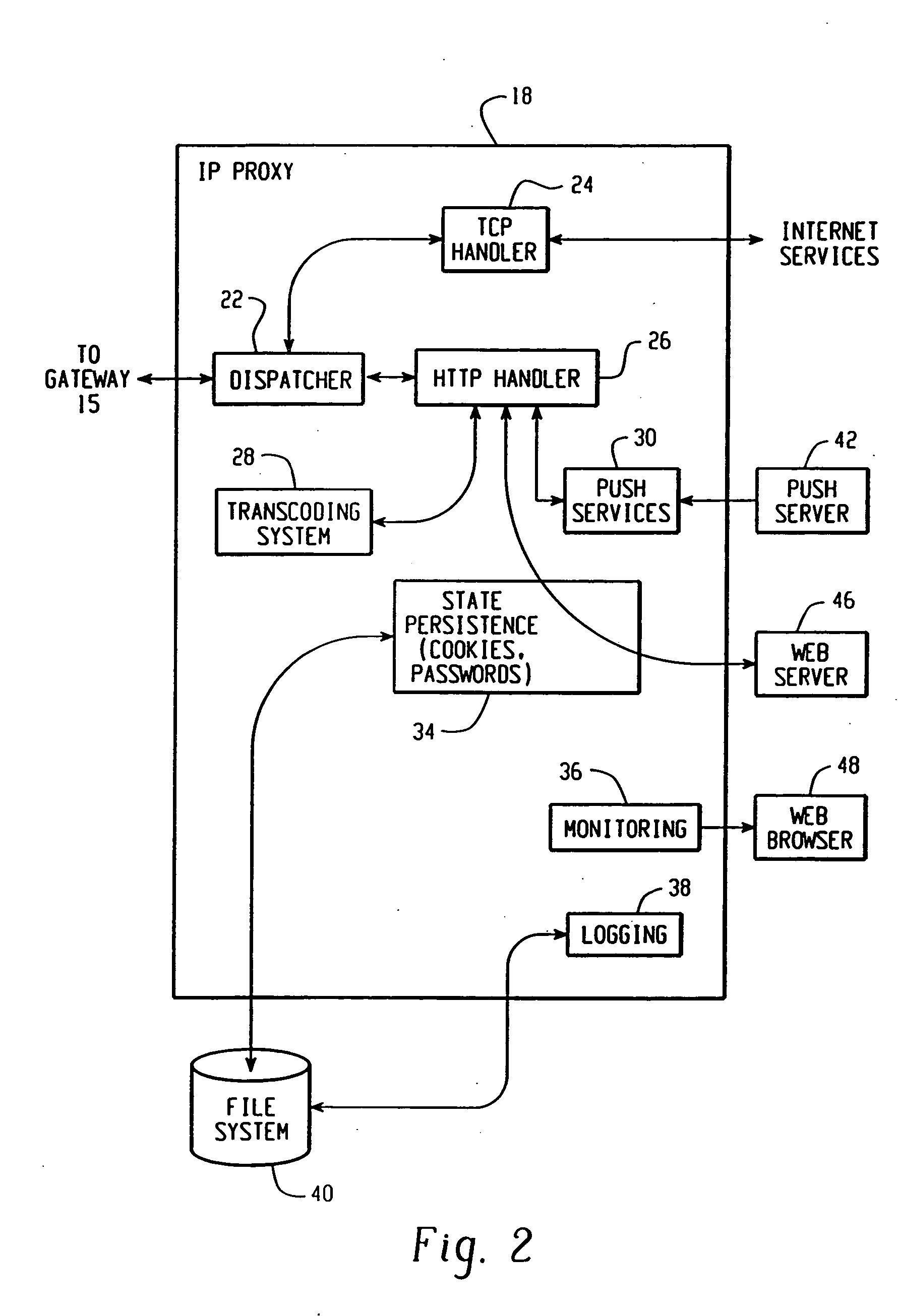
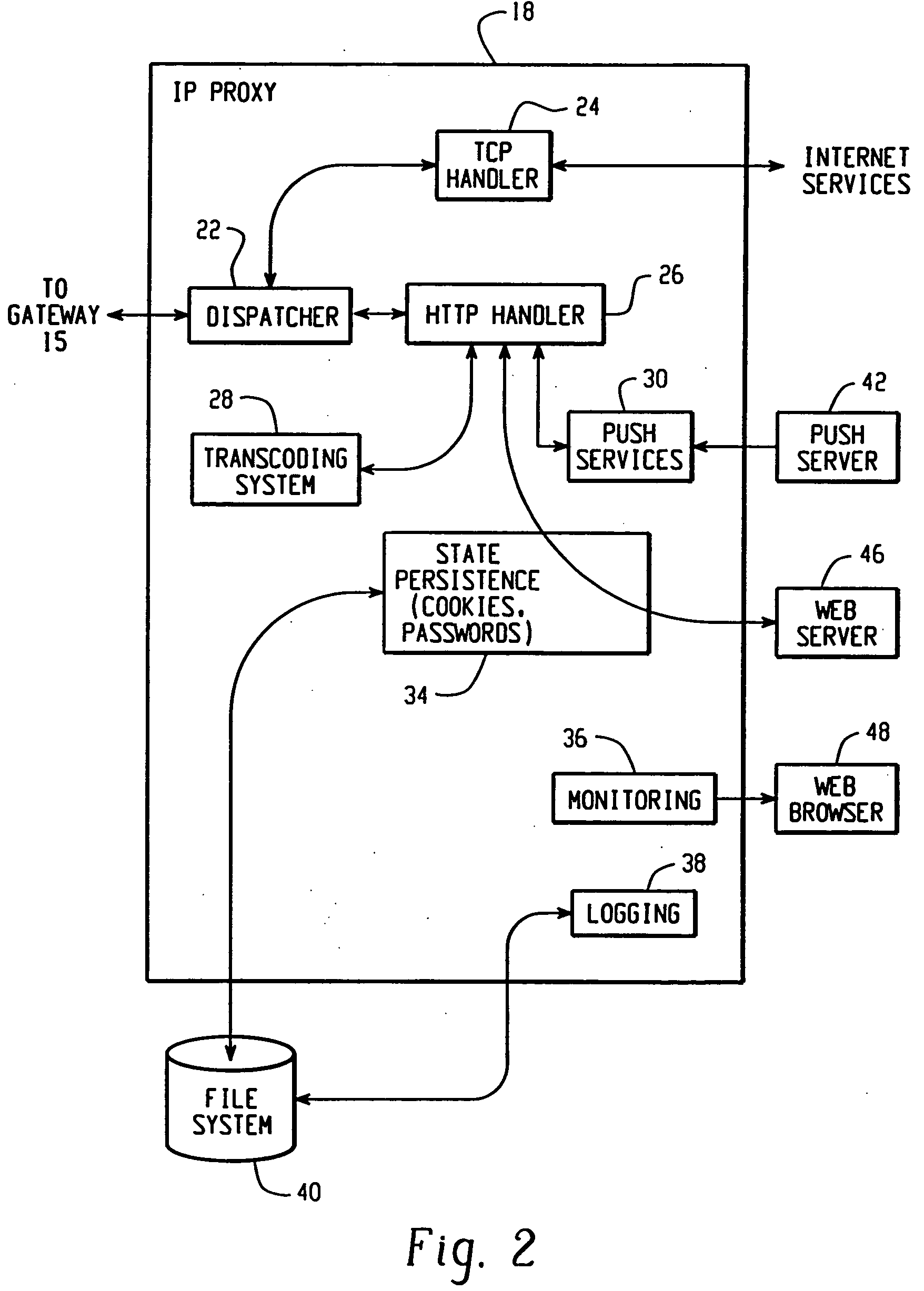
System and method for pushing data from an information source to a mobile communication device including transcoding of the data
A system for pushing information content from an information source to a mobile communication device over a network includes a transcoding system and a first network device. The transcoding system includes a plurality of transcoders, each transcoder operable to transcode the information content from a respective input content type into a respective output content type. The first network device is in communication with the transcoding system, and includes a push module. The push module is operable to receive a connection request from the information source. The connection request includes an identifier associated with the mobile communication device. The push module is further operable to select a corresponding connection handler that is operable to select one or more transcoders from the plurality of transcoders to transcode the information content.
Owner:MALIKIE INNOVATIONS LTD
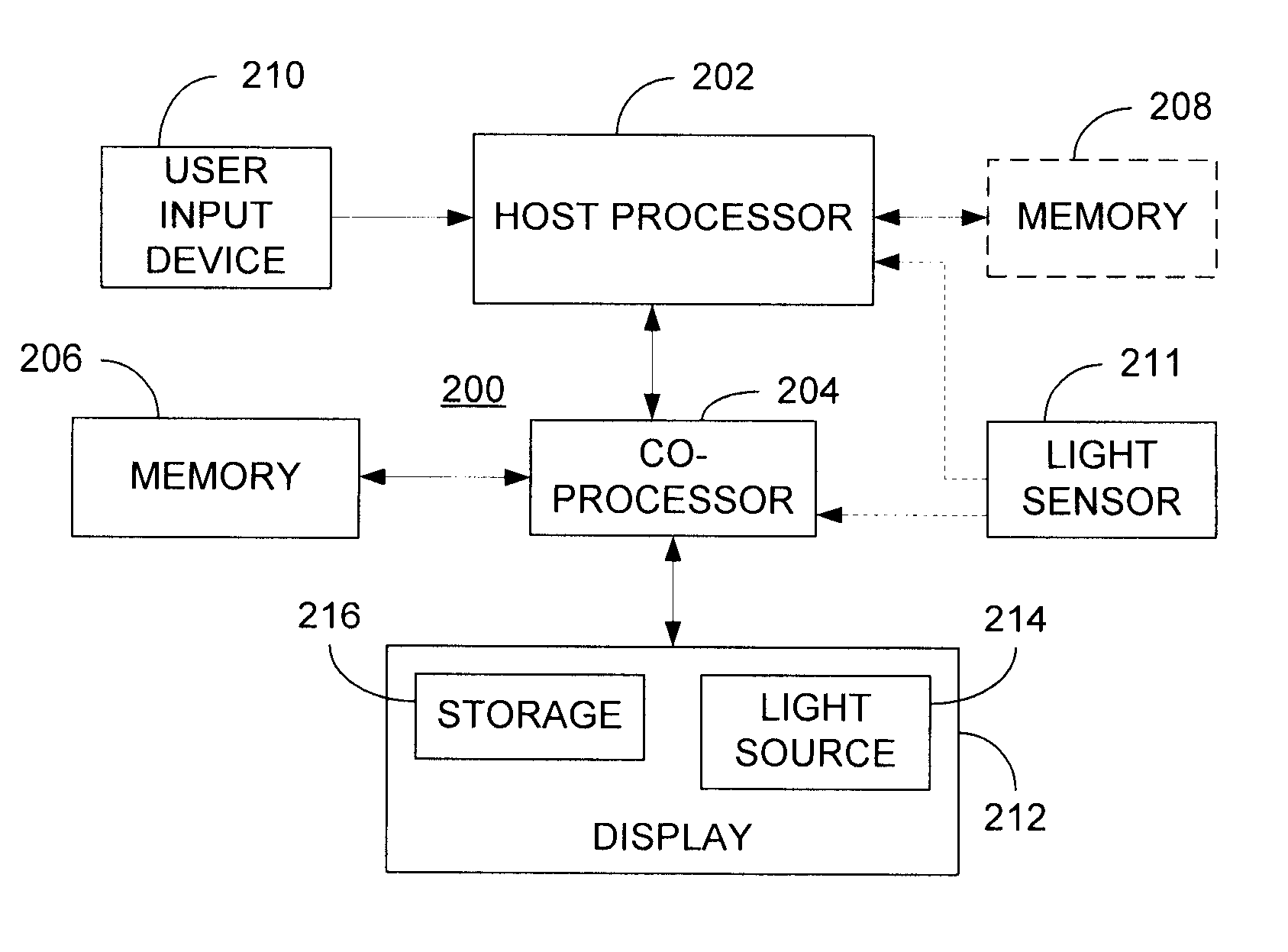
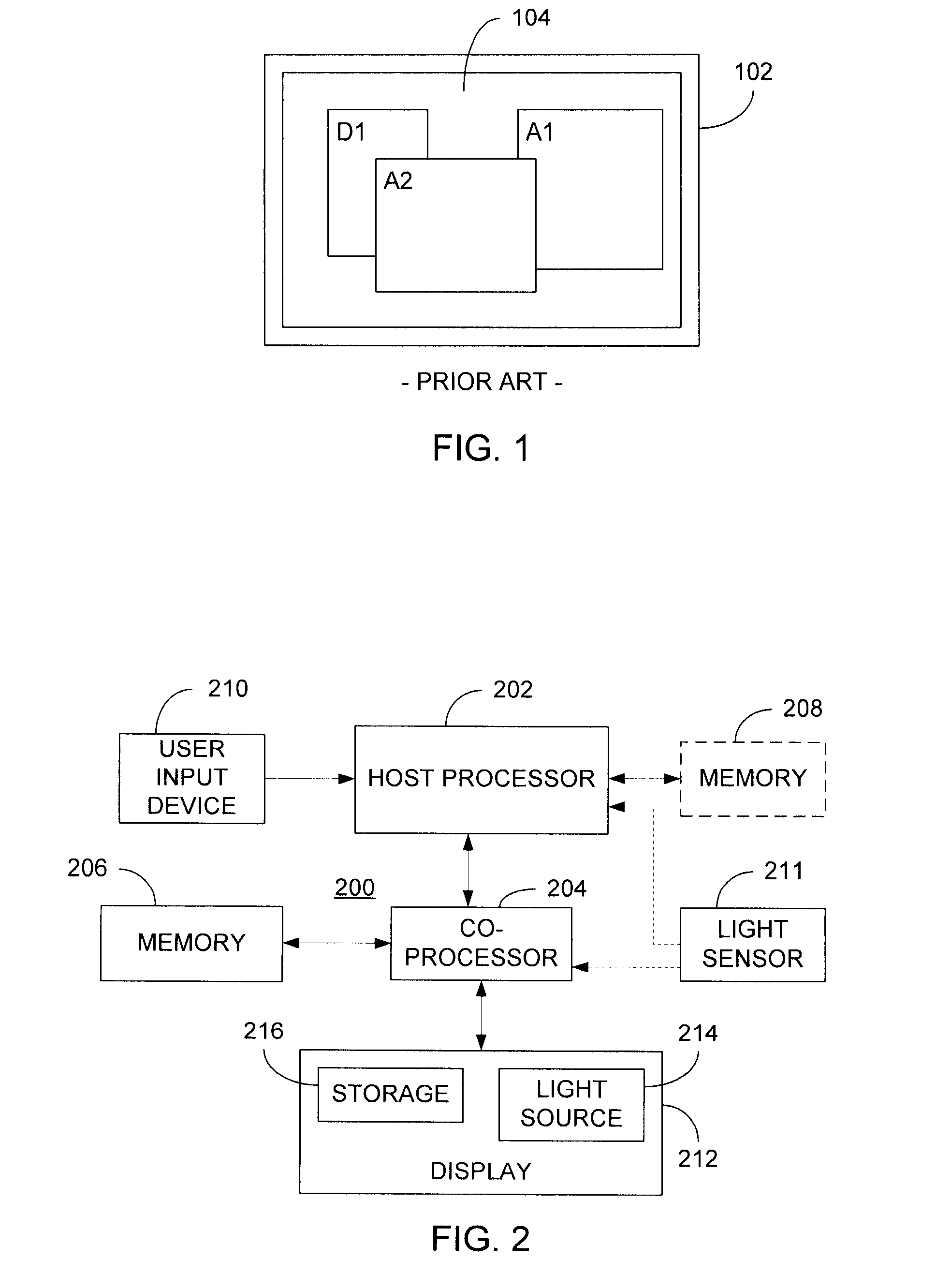
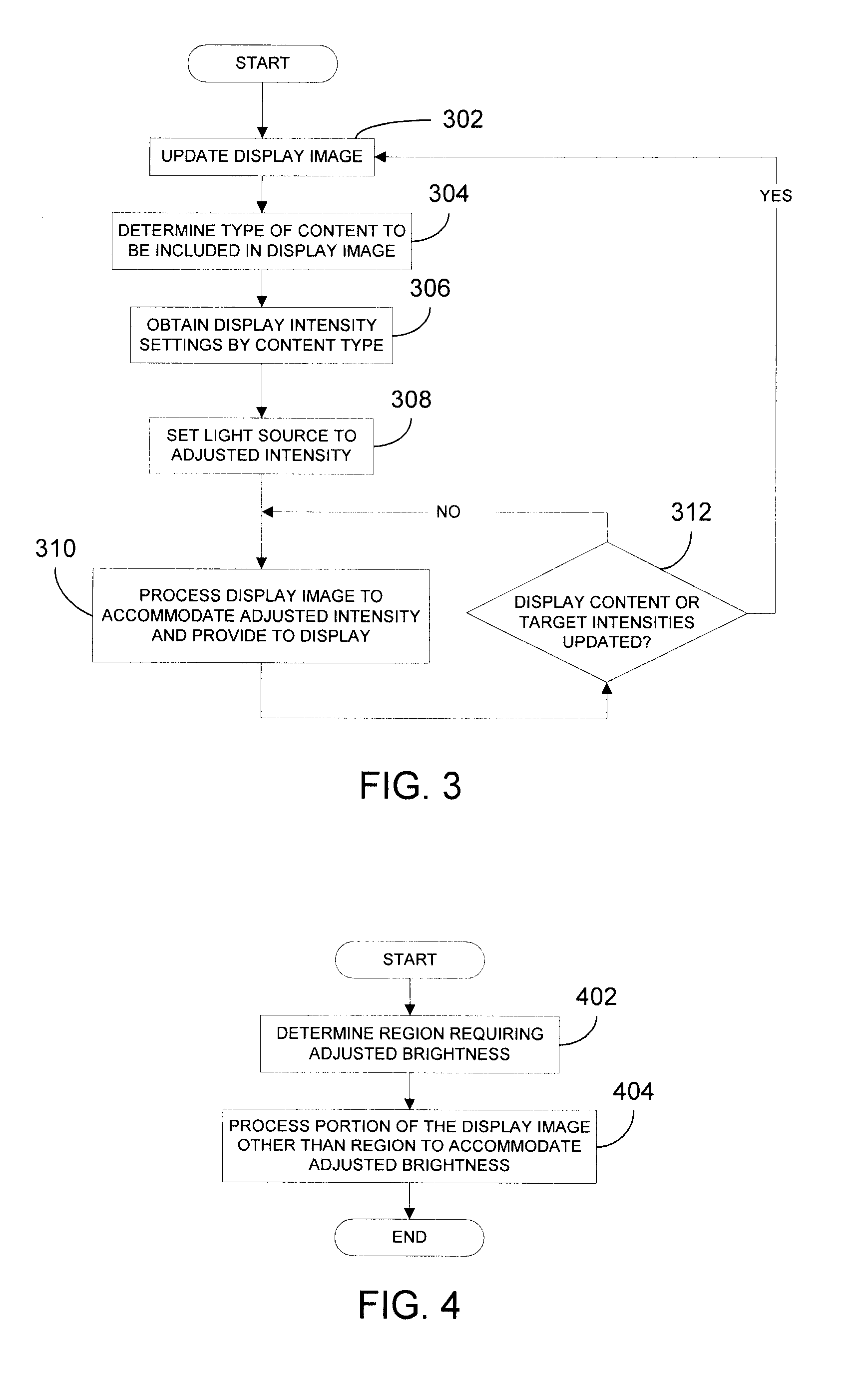
Adjusting brightness of a display image in a display having an adjustable intensity light source
To adjust brightness of at least a portion of a display image, a type of content to be included within the display image is determined and, based on the identified content type, the light source of the display is set to an adjusted intensity. Thereafter, that portion of the display image unrelated to the content requiring adjusted brightness is processed to account for the adjusted intensity of the light source. Because the processing in accordance with the present invention is performed entirely on one or more processors that provide the display images to the display, the present invention overcomes the added complexity and cost associated with prior art techniques, while simultaneously providing the flexibility to quickly adjust display brightness based on types of content being included in the displayed image.
Owner:ATI TECH INC
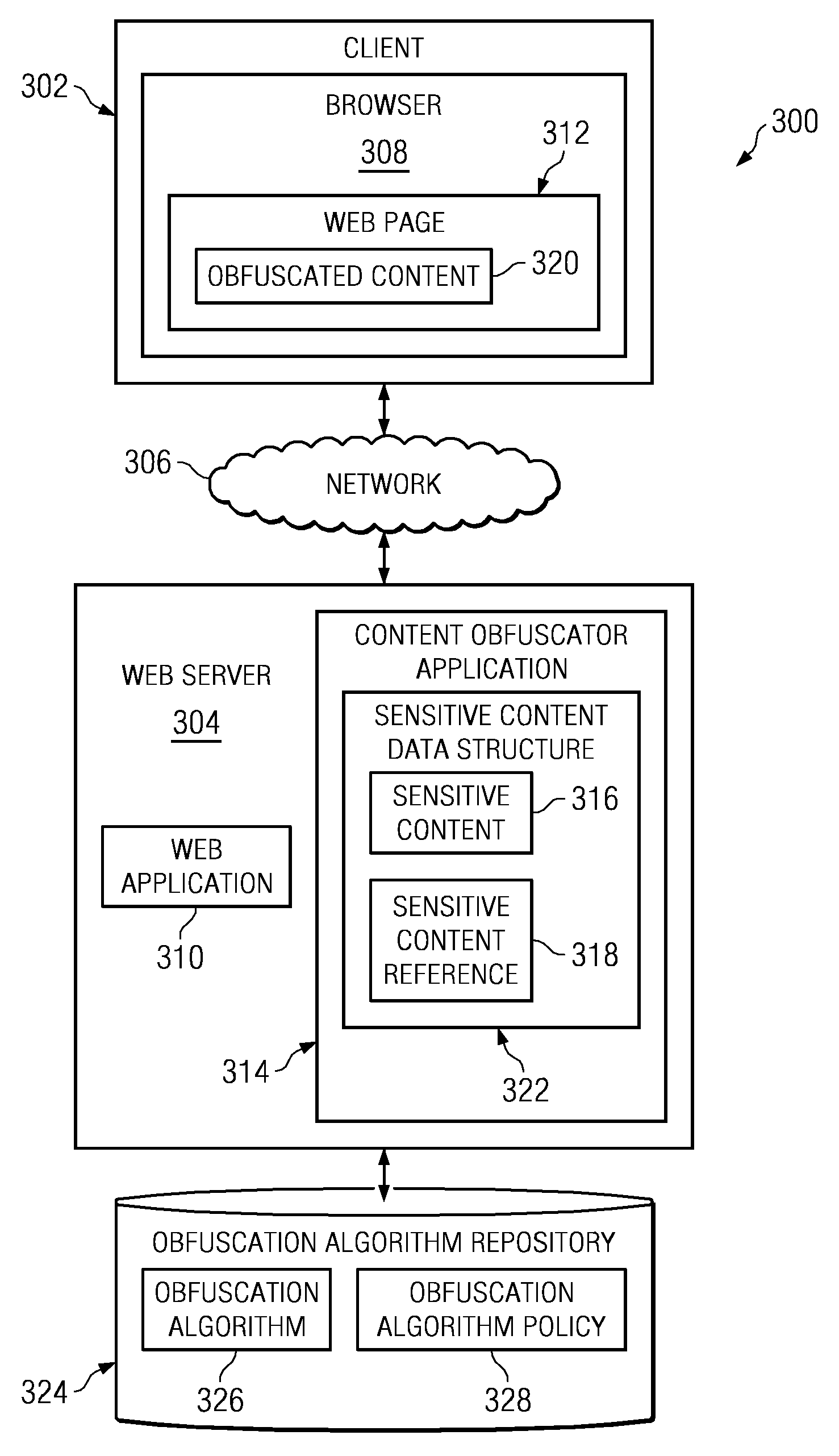
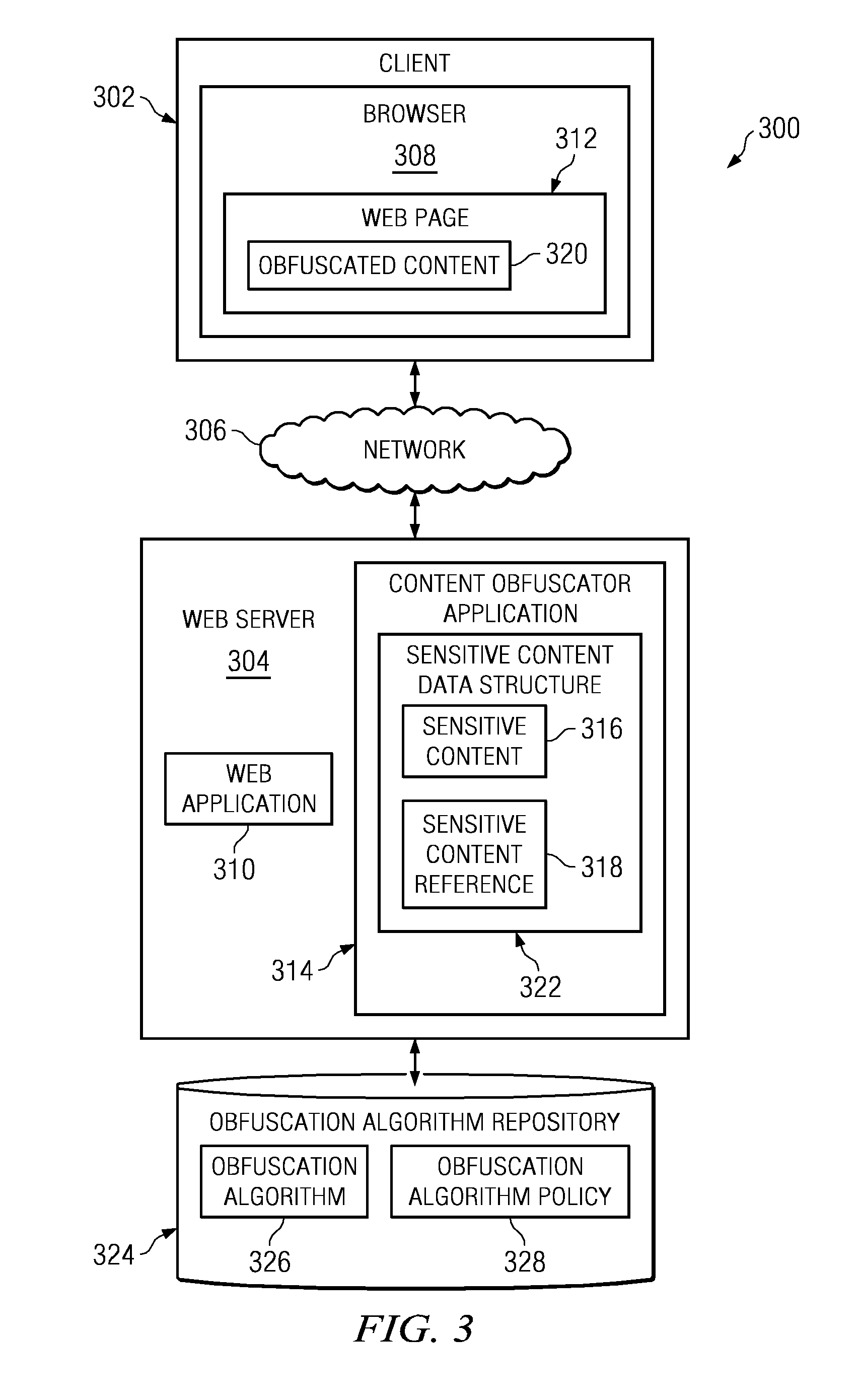
Method and apparatus to protect sensitive content for human-only consumption
InactiveUS20090144829A1Memory loss protectionDigital data processing detailsObfuscationWorld Wide Web
A computer implemented method, apparatus, and computer usable program product for protecting sensitive content. In response to receiving a selection of content, the process determines whether the content is of a sensitive content type based on a policy. The process then designates the content as the sensitive content in response to the content being of a sensitive content type. Thereafter, the process generates a sensitive content reference for publication and stores the sensitive content in a data structure, wherein the data structure associates the sensitive content with the sensitive content reference. Subsequently, in response to receiving a request from a requester for the sensitive content reference, the process obfuscates the sensitive content using a selected obfuscation algorithm to form obfuscated content, and returns the obfuscated content to the requester.
Owner:IBM CORP
System and method to associate content types in a portable communication device
InactiveUS20060041632A1Easy to demonstrateOptimize allocationMetadata multimedia retrievalMultiple digital computer combinationsContent typePortable communications device
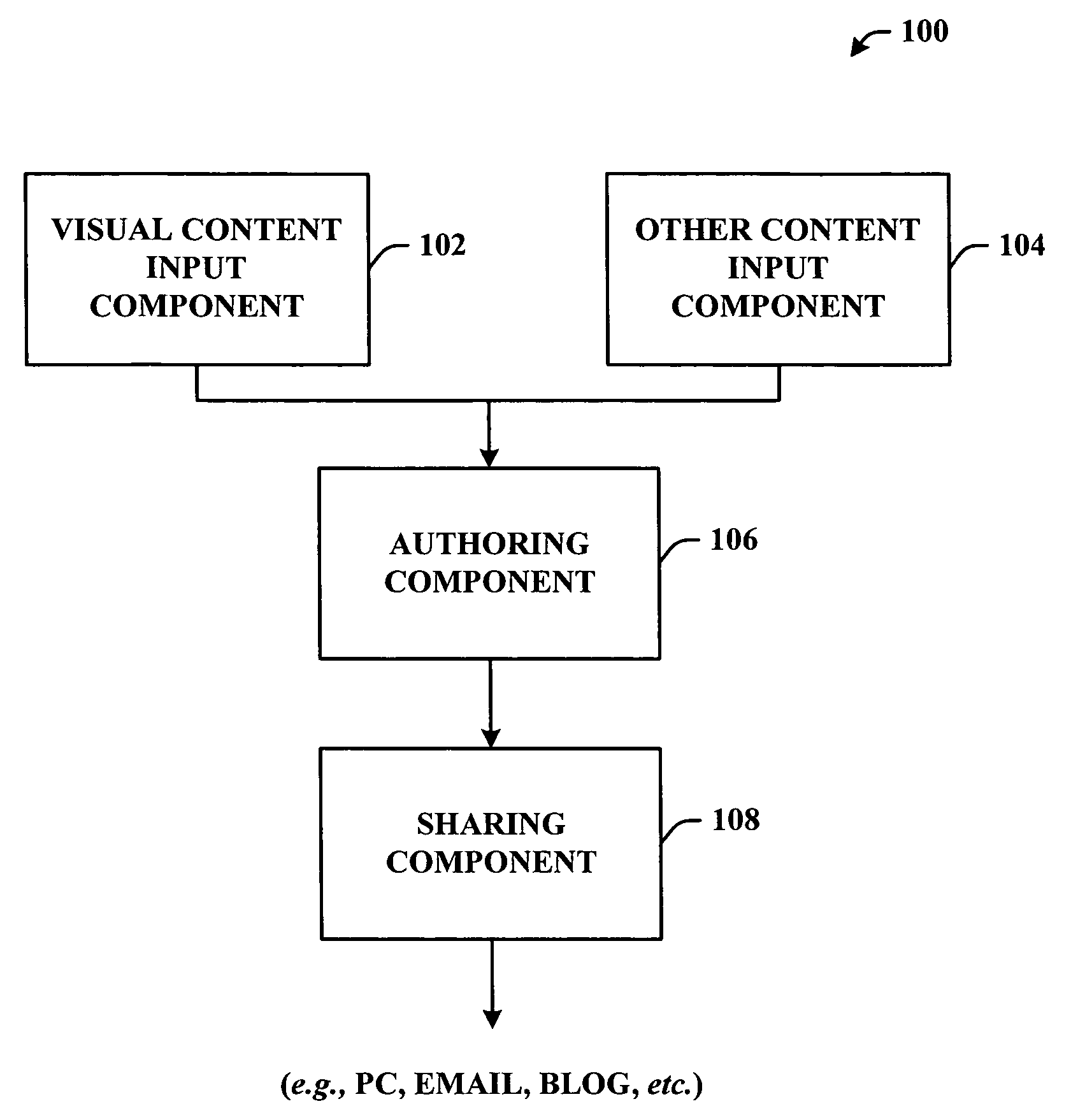
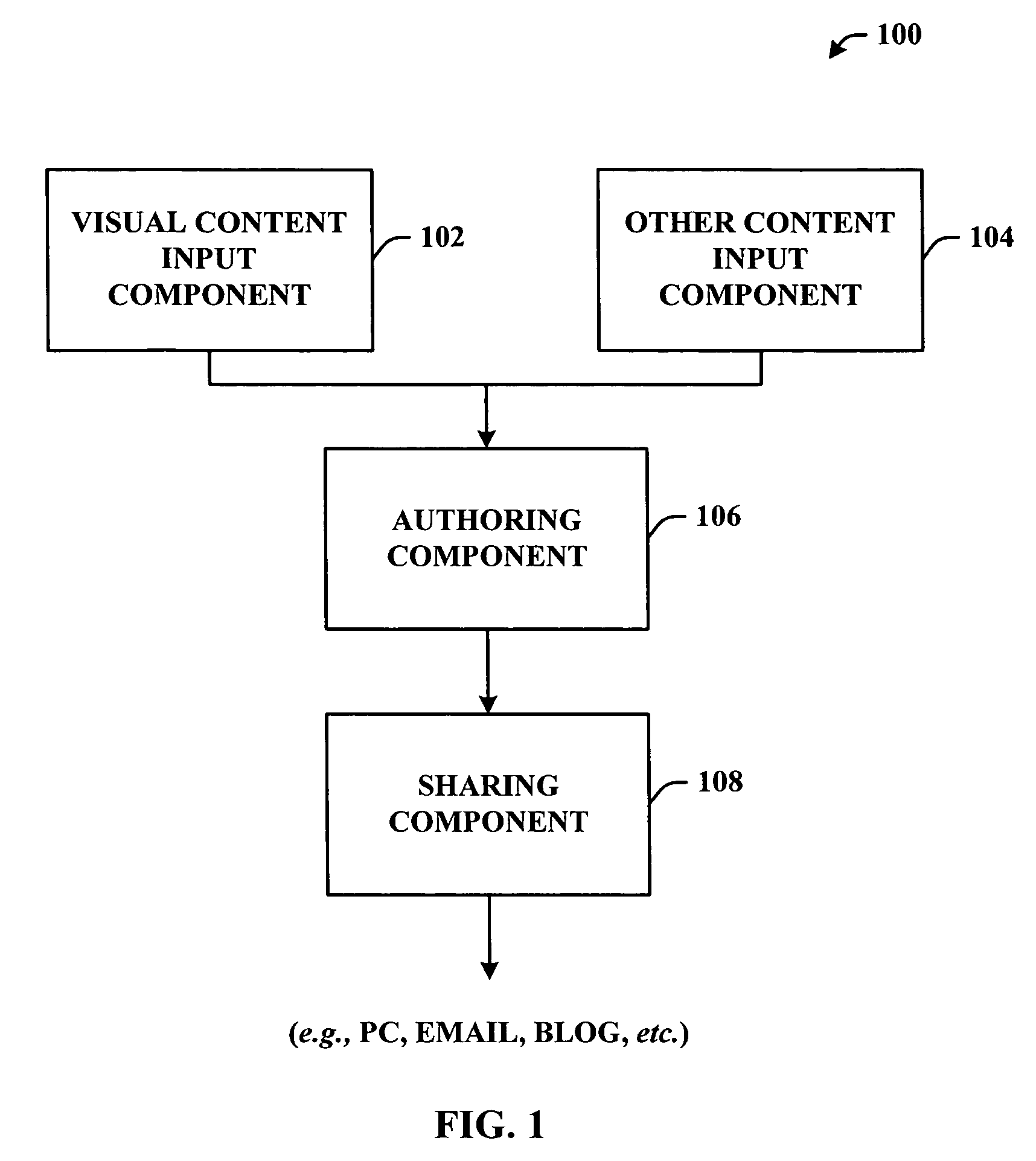
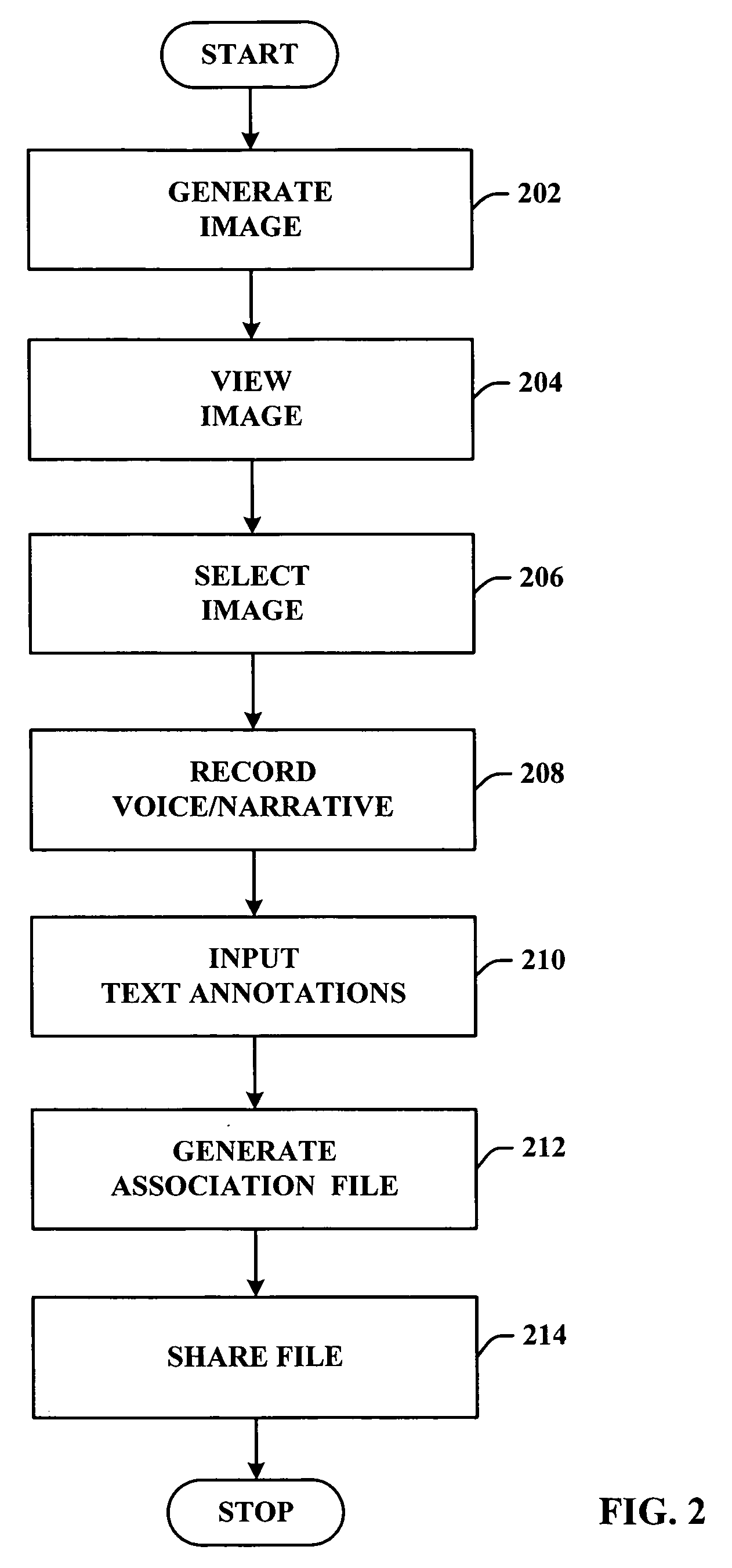
A system and or / methodology that facilitates organizing content on a portable communications device to generate a compilation (e.g., presentation) containing the organized content. The system and / or methodology includes an authoring component that associates content of a first type with a subset of other content and a sharing component that communicates and distributes the associated content. The subject invention can include a visual content input component that receives visual content and another content input component that can generate and organize other content in accordance with a user preference. The other content can include any content type known in the art including, but not limited to, visual, audible, text or the like.
Owner:MICROSOFT TECH LICENSING LLC
Dynamic content filter in a gateway
InactiveUS6678518B2Data processing applicationsDigital data information retrievalMobile stationWorld Wide Web
Owner:CALLAHAN CELLULAR L L C
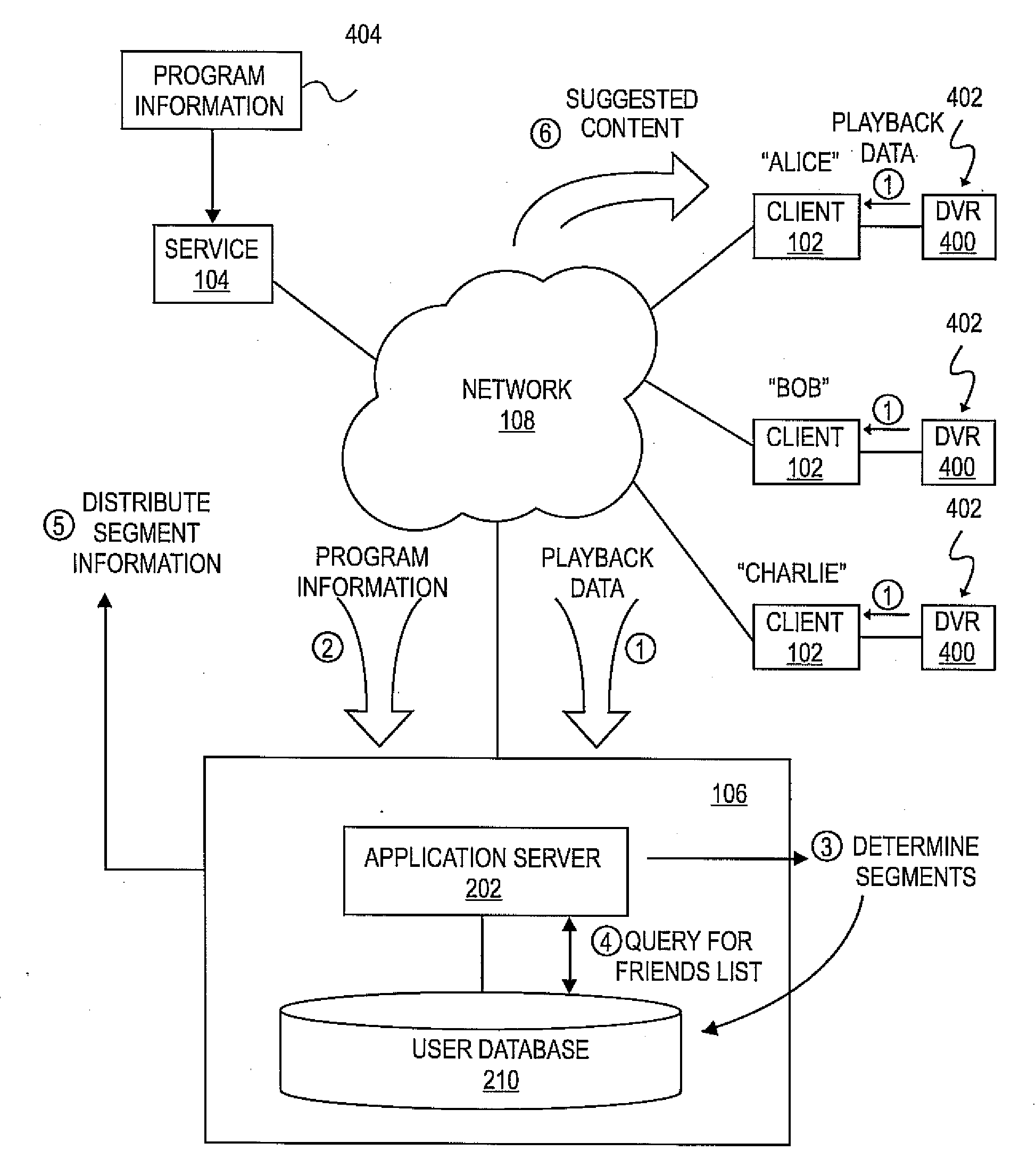
Method and system for preloading suggested content onto digital video recorder based on social recommendations
ActiveUS20080134039A1Metadata audio data retrievalTelevision system detailsDigital videoSocial network
Owner:RED HAT
Real-time or near real-time streaming
ActiveUS20110246621A1Multiple digital computer combinationsTelevision systemsTransfer systemClient-side
Owner:APPLE INC
System and method for providing remote data access and transcoding for a mobile communication device
A system for providing information content over a network to a mobile communication device includes a transcoding system and a first network device. The transcoding system includes a plurality of transcoders. Each transcoder is operable to transcode the information content from a respective input content type into a respective output content type. The first network device is in communication with the transcoding system and includes a connection handler system. The first network device is operable to receive a first connection request that includes transcoder request data and to select a corresponding connection handler. The connection handler is operable to select one or more transcoders from the plurality of transcoders based on the transcoder request data.
Owner:MALIKIE INNOVATIONS LTD
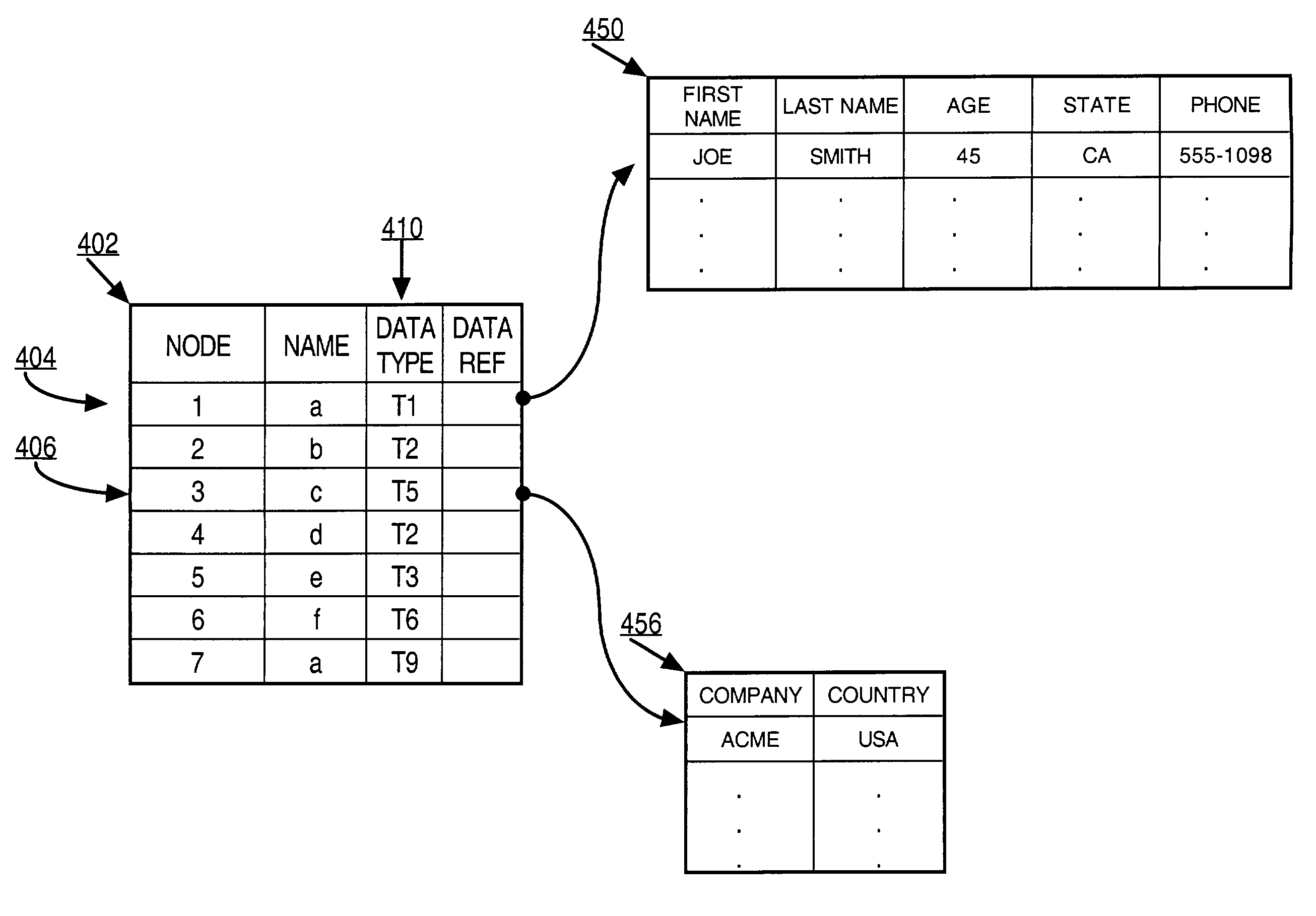
Mechanisms for storing content and properties of hierarchically organized resources
Various techniques are provided for facilitating the management of hierarchical data within a relational database system. One such technique involves separating the storage structures used to store data that captures the information about the hierarchy (the “hierarchy structures”), from the storage structures used to store the content of the resources that belong to the hierarchy (the “content structures”). Techniques are also provided for allowing users to customize the metadata attributes associated with resources that belong to the information hierarchy. One technique involves registering XML schemas that specify the metadata attributes desired by a user. Another technique involves storing attributes that do not correspond to any declared field in a “catch-all” column within the resource table. Techniques are provided for determining how to store resources as they are added to the database. According to one technique, the database server searches the data of the resource to find content-type information. If content-type information is found, then the database server consults a content-type to content-structure mapping to determine where to store the content of the resource.
Owner:ORACLE INT CORP
Graphically rich, modular, promotional tile interface for interactive television
Owner:COMCAST CABLE COMM MANAGEMENT LLC
Content cryptographic firewall system
ActiveUS20100058072A1Digital data processing detailsUser identity/authority verificationData operationsStorage type
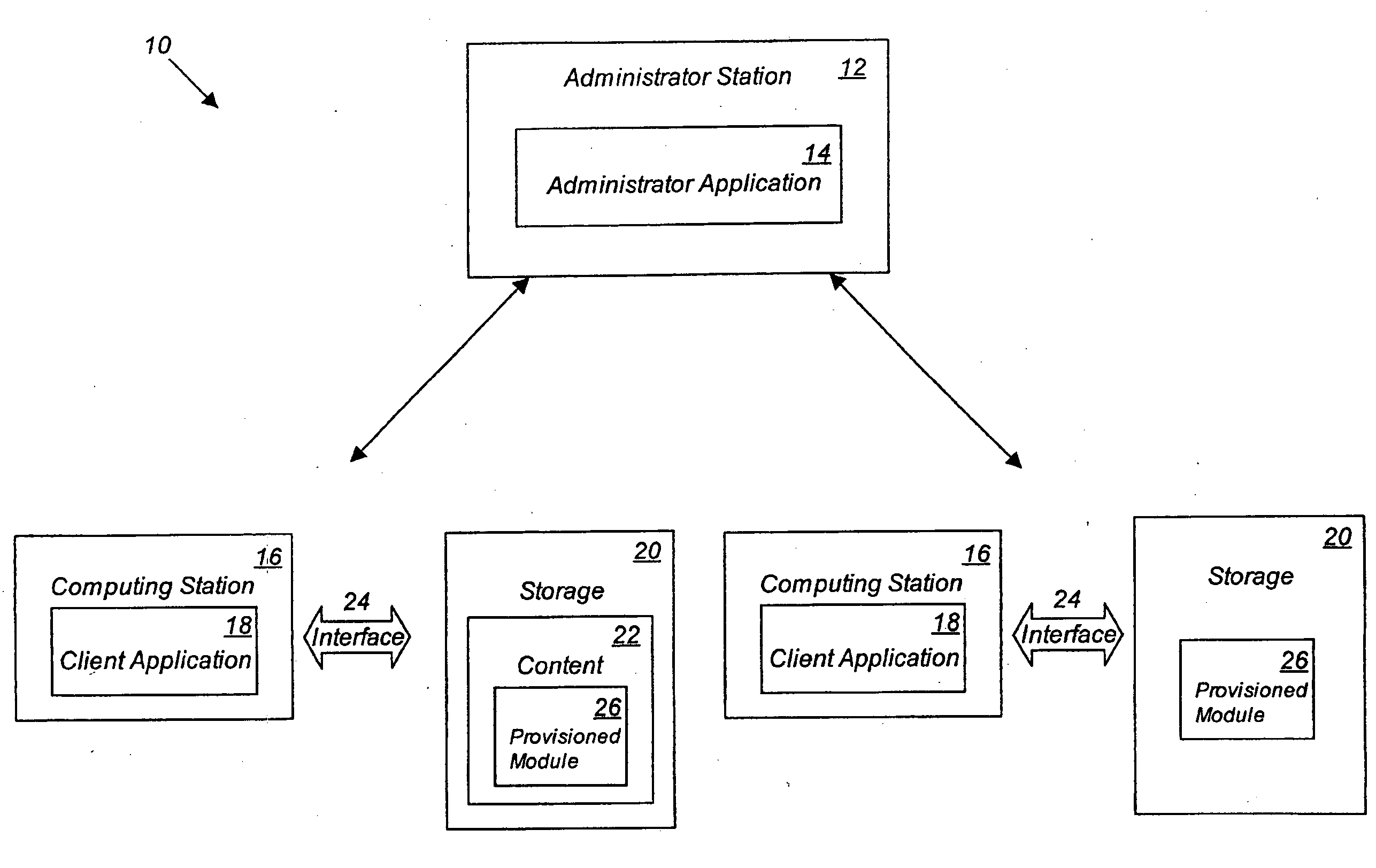
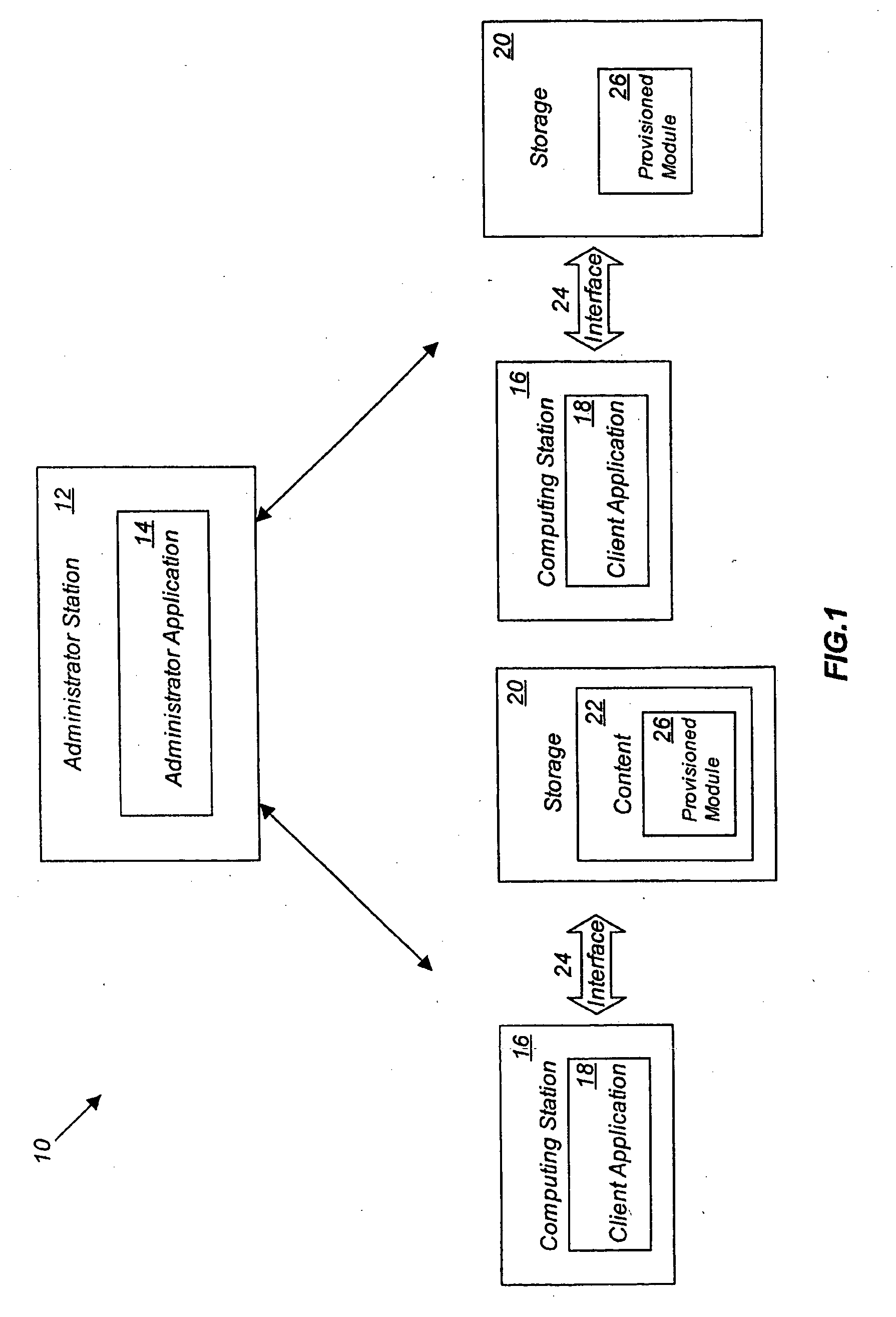
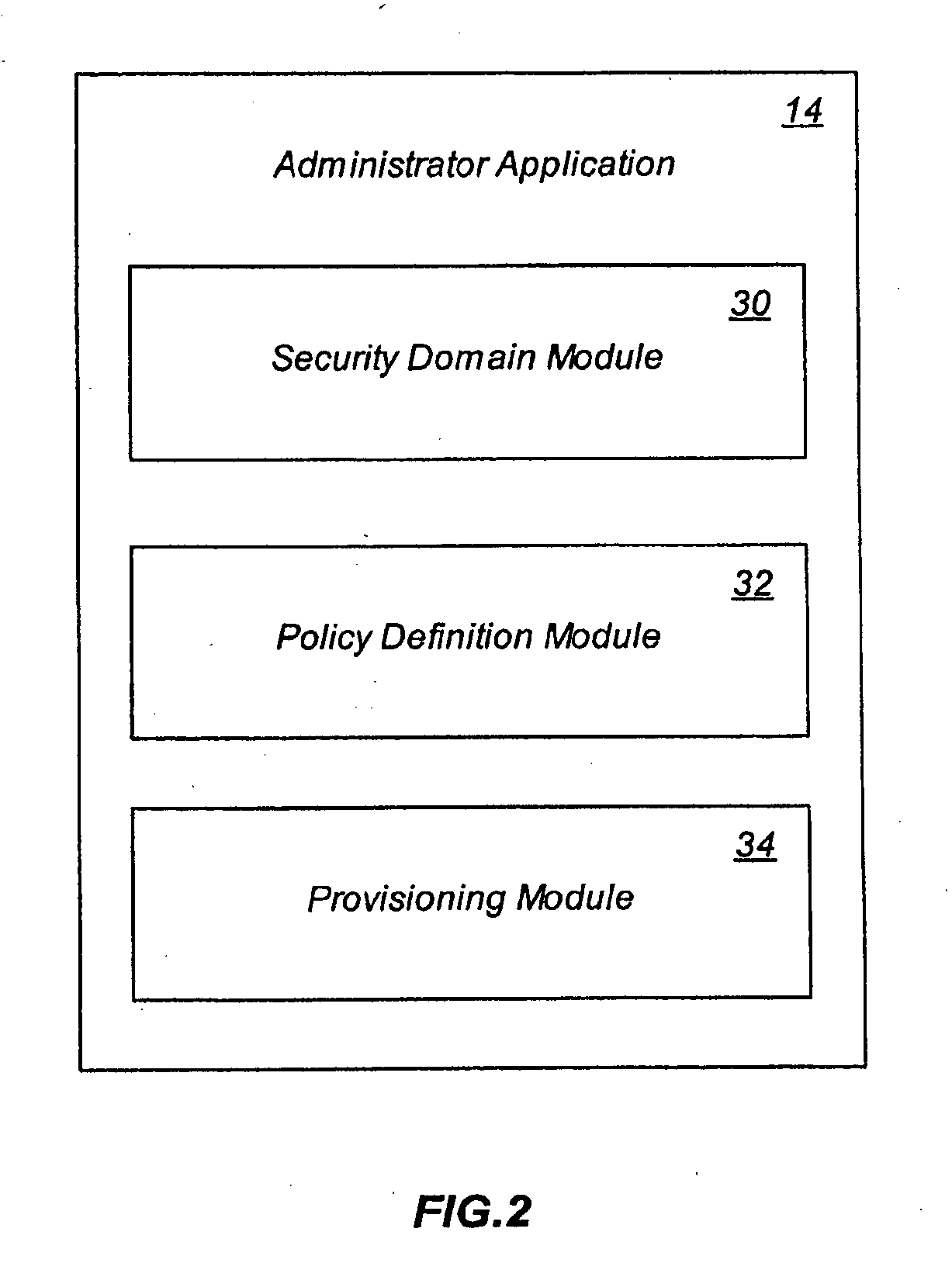
A system and method that regulates the various operations between computing stations and storage or content. Any operation that involves or may lead to the exchange or accessing of content (data) between storage or hosting content container and computing station may be regulated by means of a policy which comprise a set of rules. Rules may be defined according to specific criteria, including the type of storage, the type of content, the attributes of the content, and other attributes associated with the storage device and / or the content. The policy will be dynamically installed / updated upon a computing station for specific User(s) and will regulate the data operations that may take place between the computing stations and storage or content based on evaluation of the policy. Based on the evaluation of the policy, the requested operation is permitted, restricted in some areas, or denied.
Owner:CRYPTOMILL
Method and apparatus for playing content
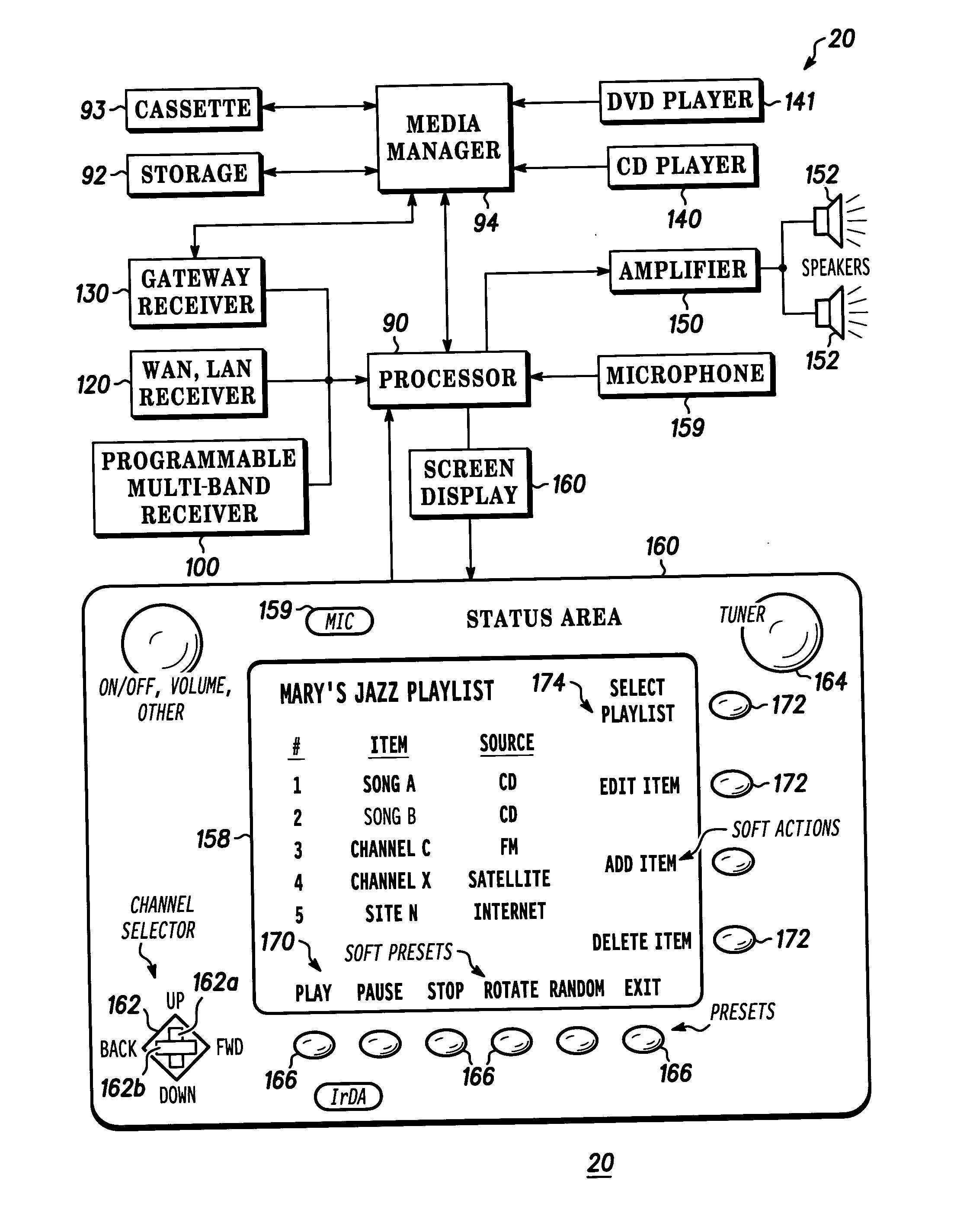
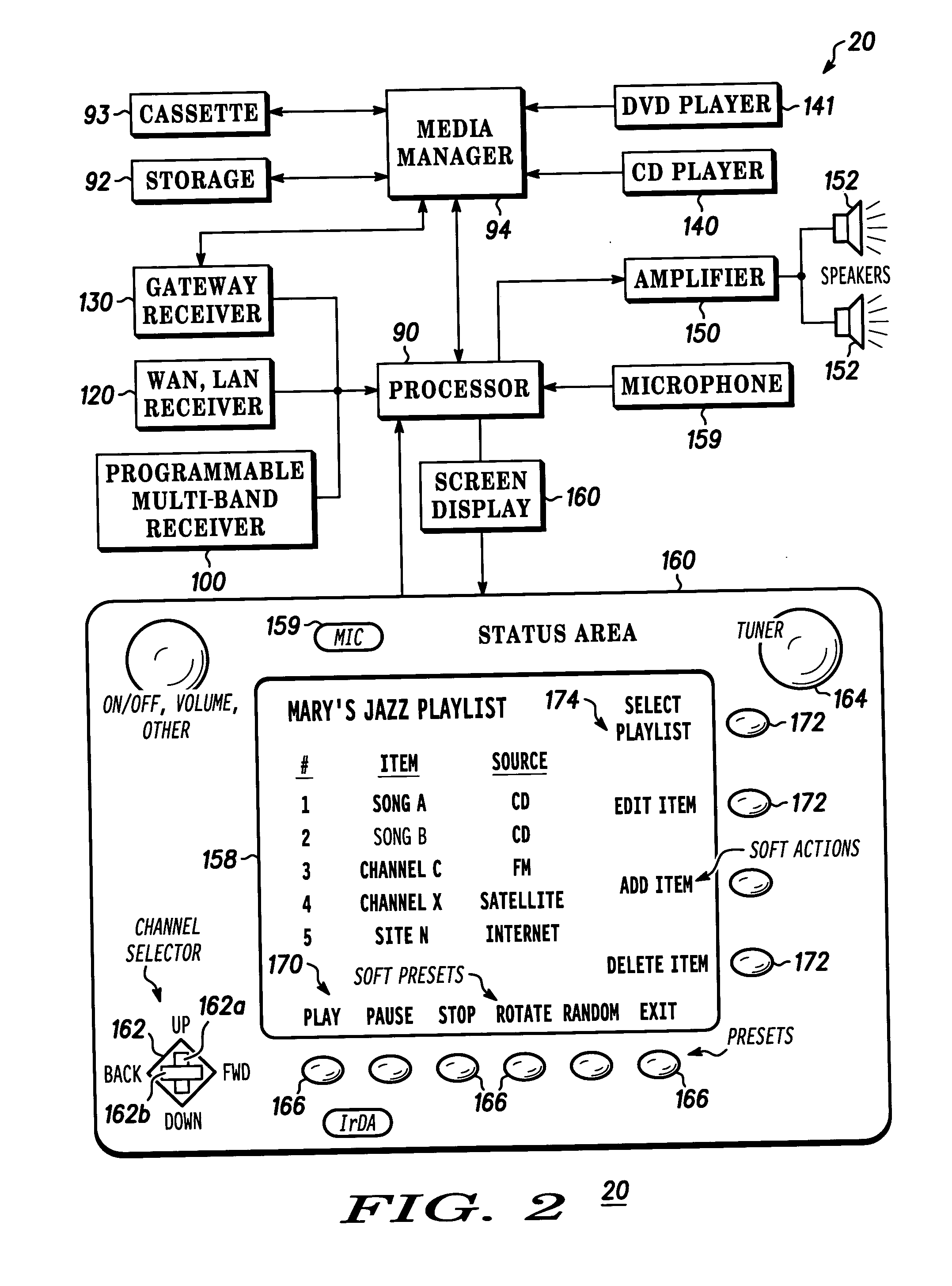
InactiveUS20060059535A1Television system detailsMetadata audio data retrievalStart timeCommunication device
A receiver such as in an automobile and / or wireless communication device is configured for a method of playing of live and recorded multimedia content. A desired genre of content is first defined. Both recorded and live content of that desired genre is identified and assembled into a playlist. Live content that is near a beginning of its being played can be rotated to a top of the playlist. In this way, live content, which a user may not have heard is given a priority of recorded content of the user. Since a start time of live content typically will not coincide with an end time of recorded content being played, the receiver can fade-in and fade-out to a the live content or buffer it for delayed play.
Owner:MOTOROLA INC
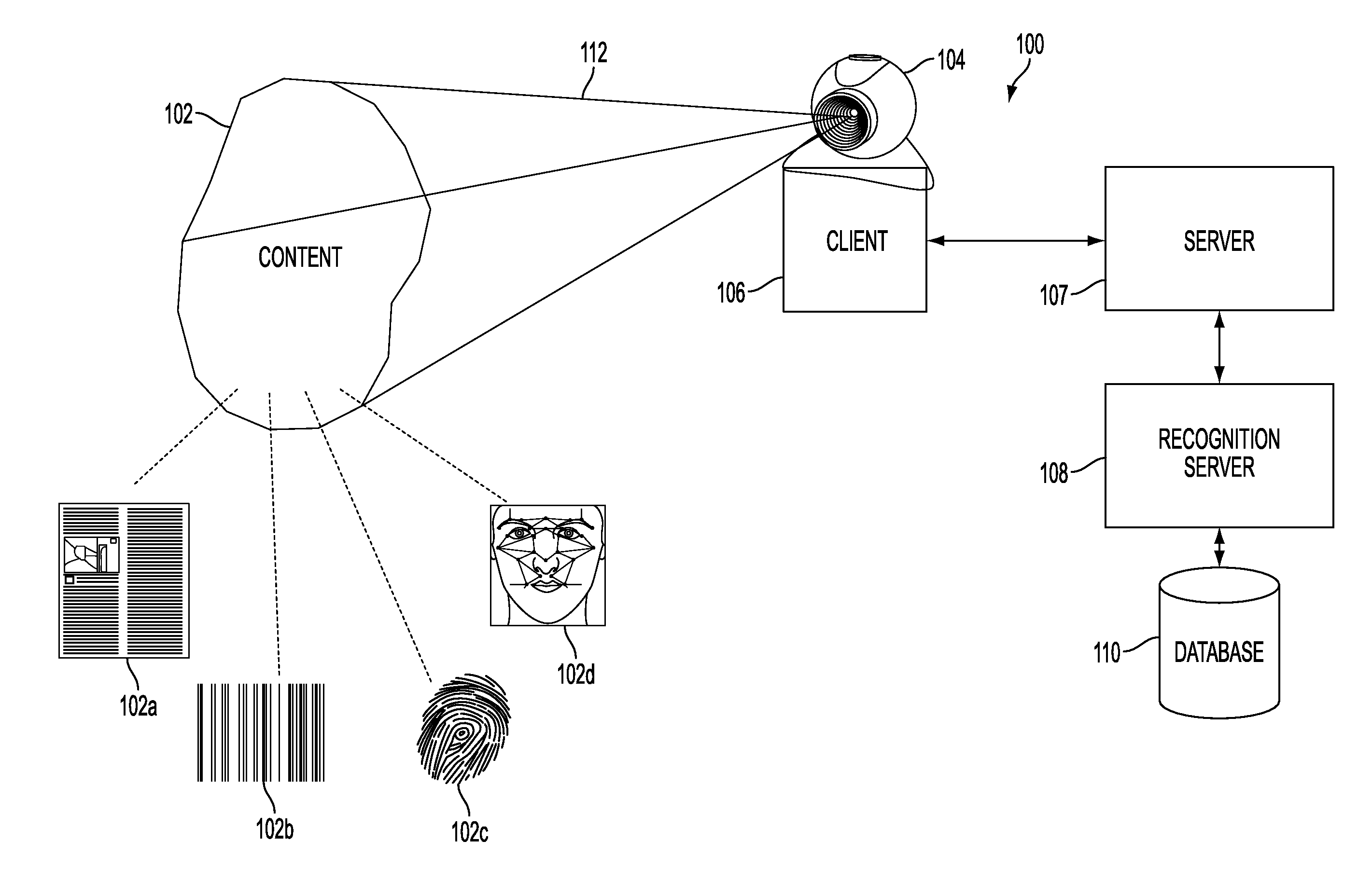
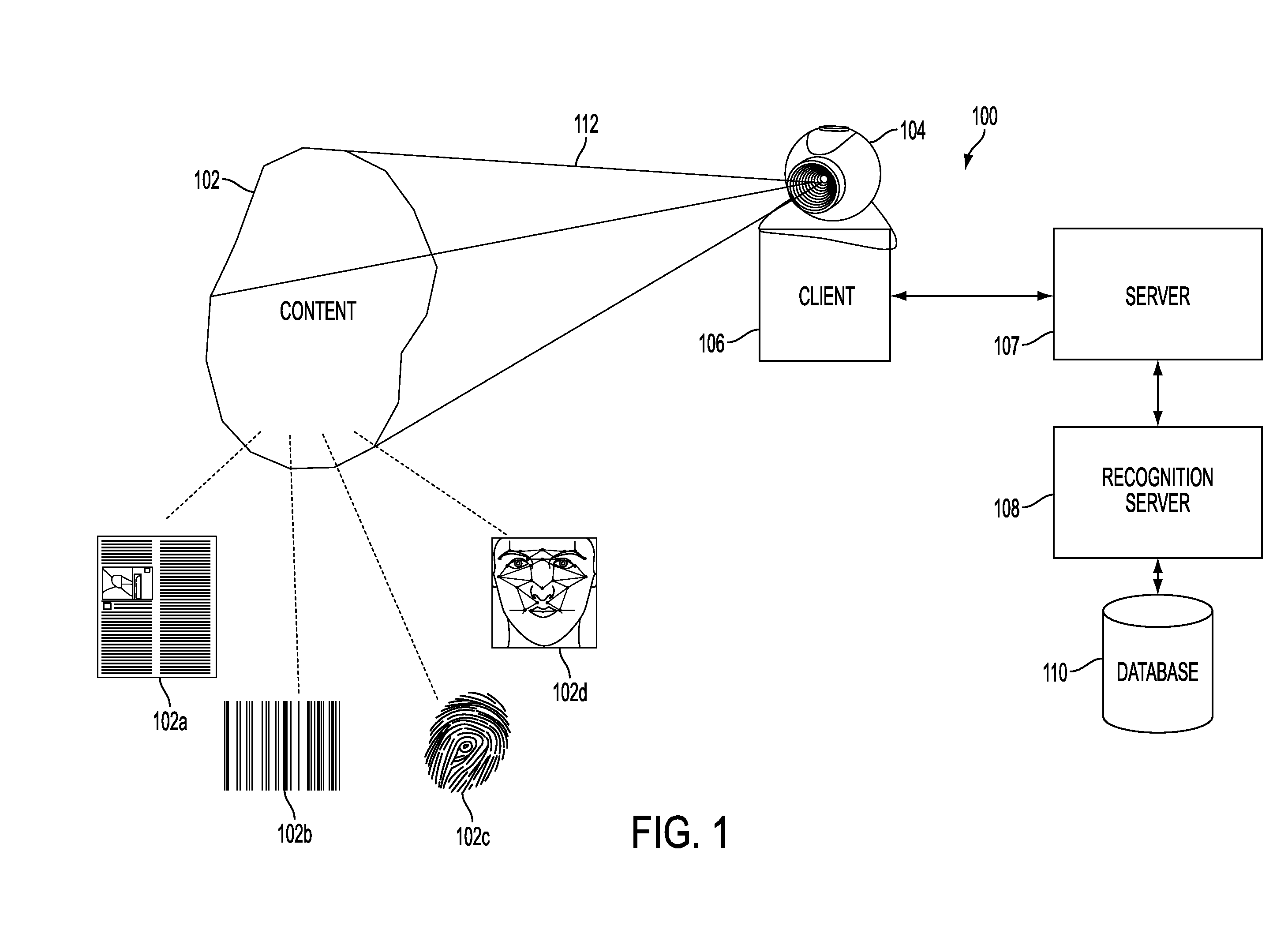
Web-Based Content Detection in Images, Extraction and Recognition
ActiveUS20090285444A1Overcome deficienciesEasy qualityDigital data information retrievalCharacter and pattern recognitionPattern recognitionWeb browser
A web-based image detection system includes: an image capture device, a web browser, a plug-in, and a recognition server. A captured image is processed by the plug-in to assess whether a pre-determined content type is contained with in the image. Once an initial analysis at the browser plug-in detects a pre-determined content type in an image, the image is transmitted to a recognition server for content recognition of the image by content type. The system thus enables users to link documents or other image types to electronic data using only a capture device and a web browser.
Owner:PIECE FUTURE PTE LTD
Technique for enabling remote data access and manipulation from a pervasive device
InactiveUS6925481B2Easy accessEfficient and cost-effectiveMultiple digital computer combinationsElectric digital data processingData accessWorld Wide Web
Methods, systems, and computer program instructions for enabling users of pervasive devices to remotely access and manipulate information in ways that might otherwise be impossible or impractical because of inherent limitations of the device. The disclosed techniques enable a wide variety of data manipulation operations to be performed on behalf of the pervasive device, for a wide variety of content types. In preferred embodiments, no modifications or add-ons are required to the pervasive device.
Owner:CLOUDING
Tag data structure for maintaining relational data over captured objects
ActiveUS20050132079A1Increase searchImprove abilitiesDigital data processing detailsDigital data protectionLabeled dataContent type
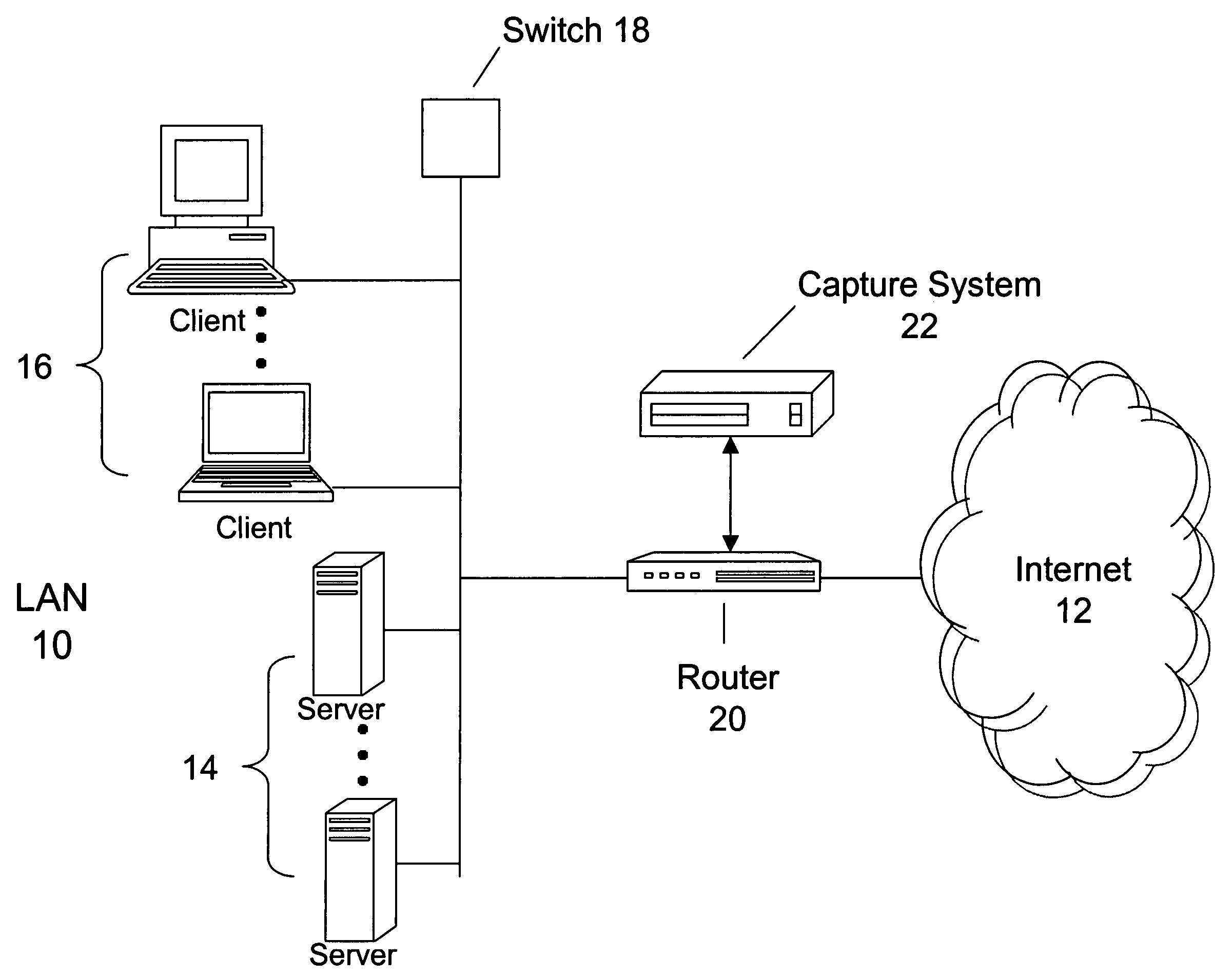
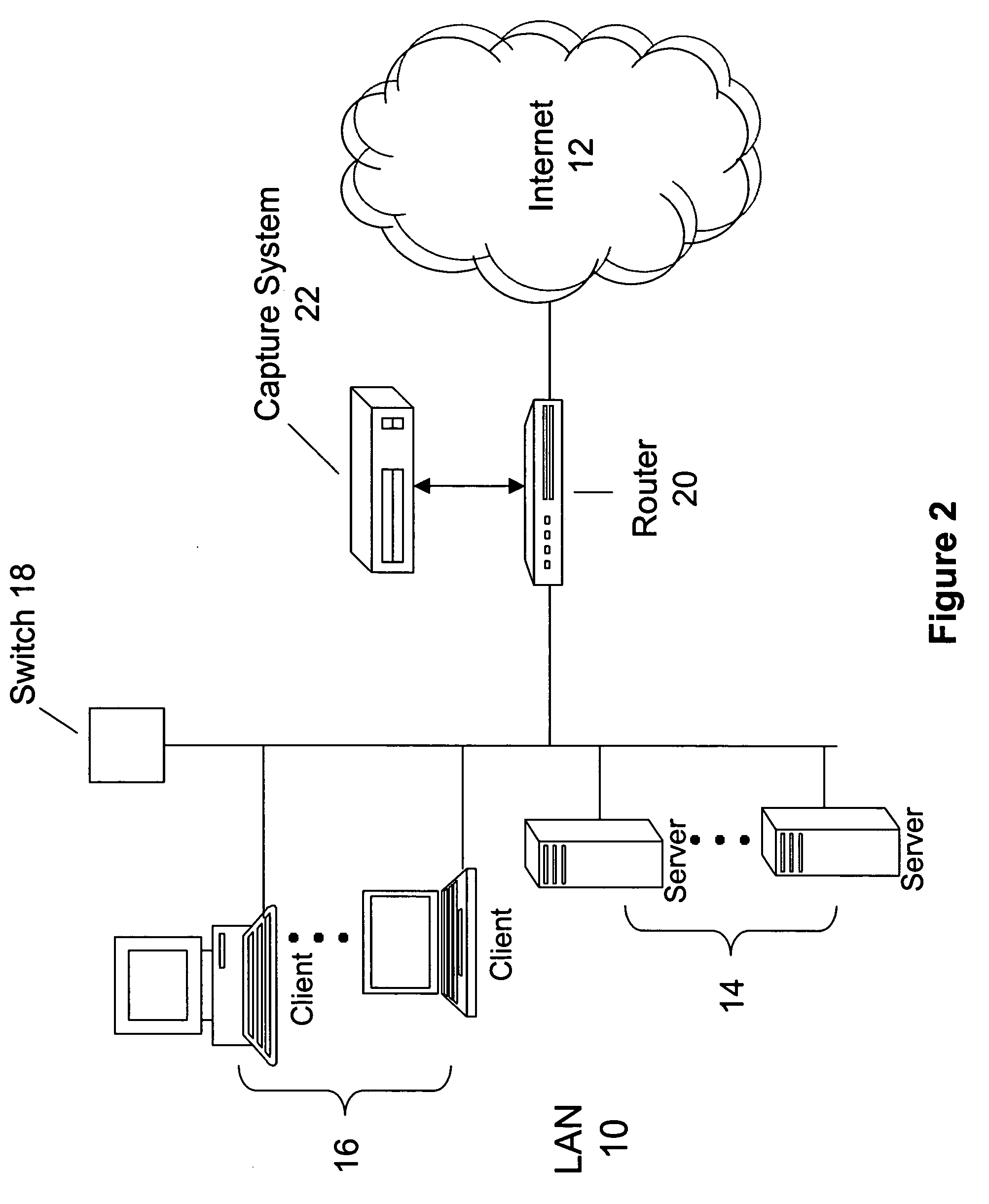
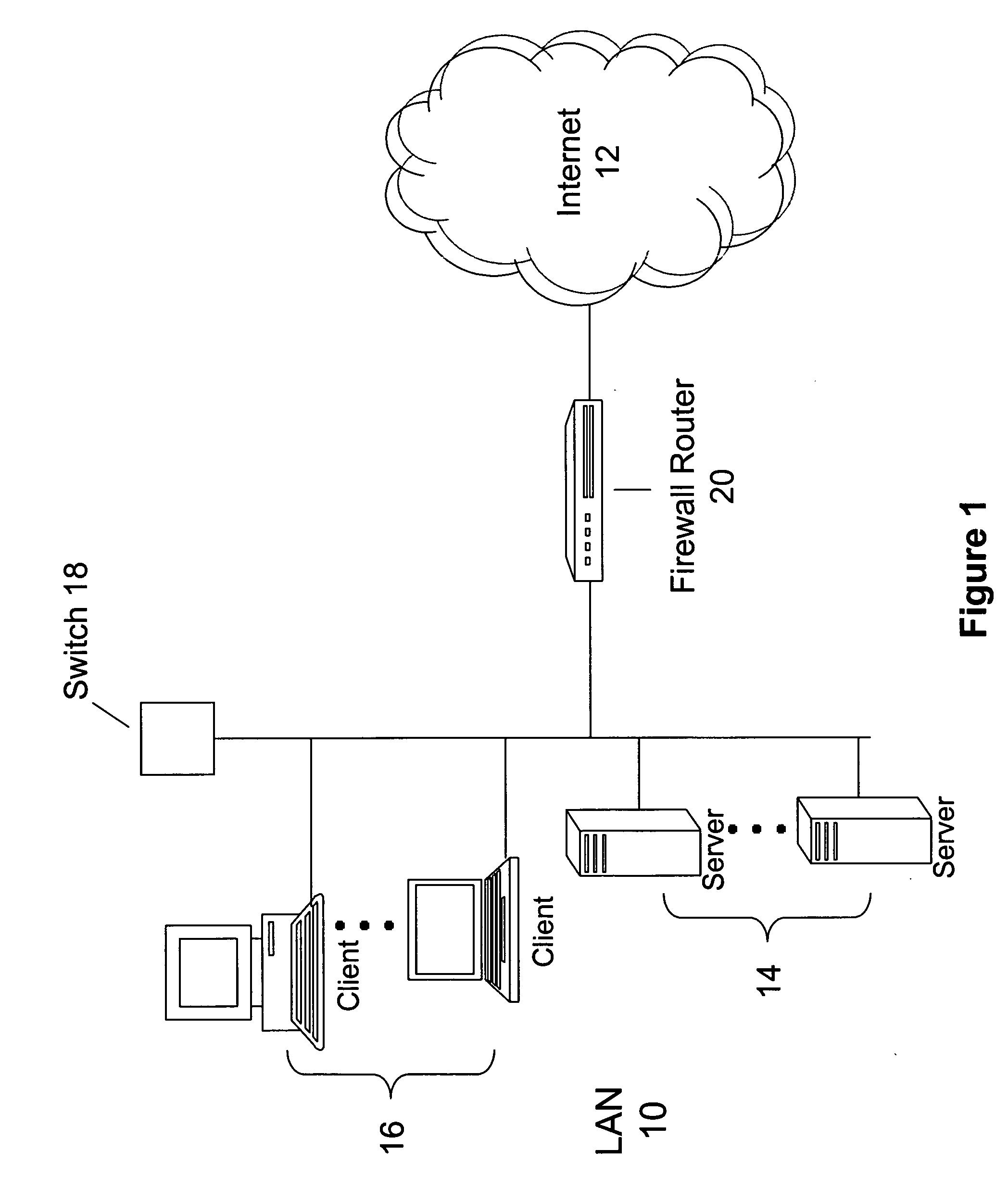
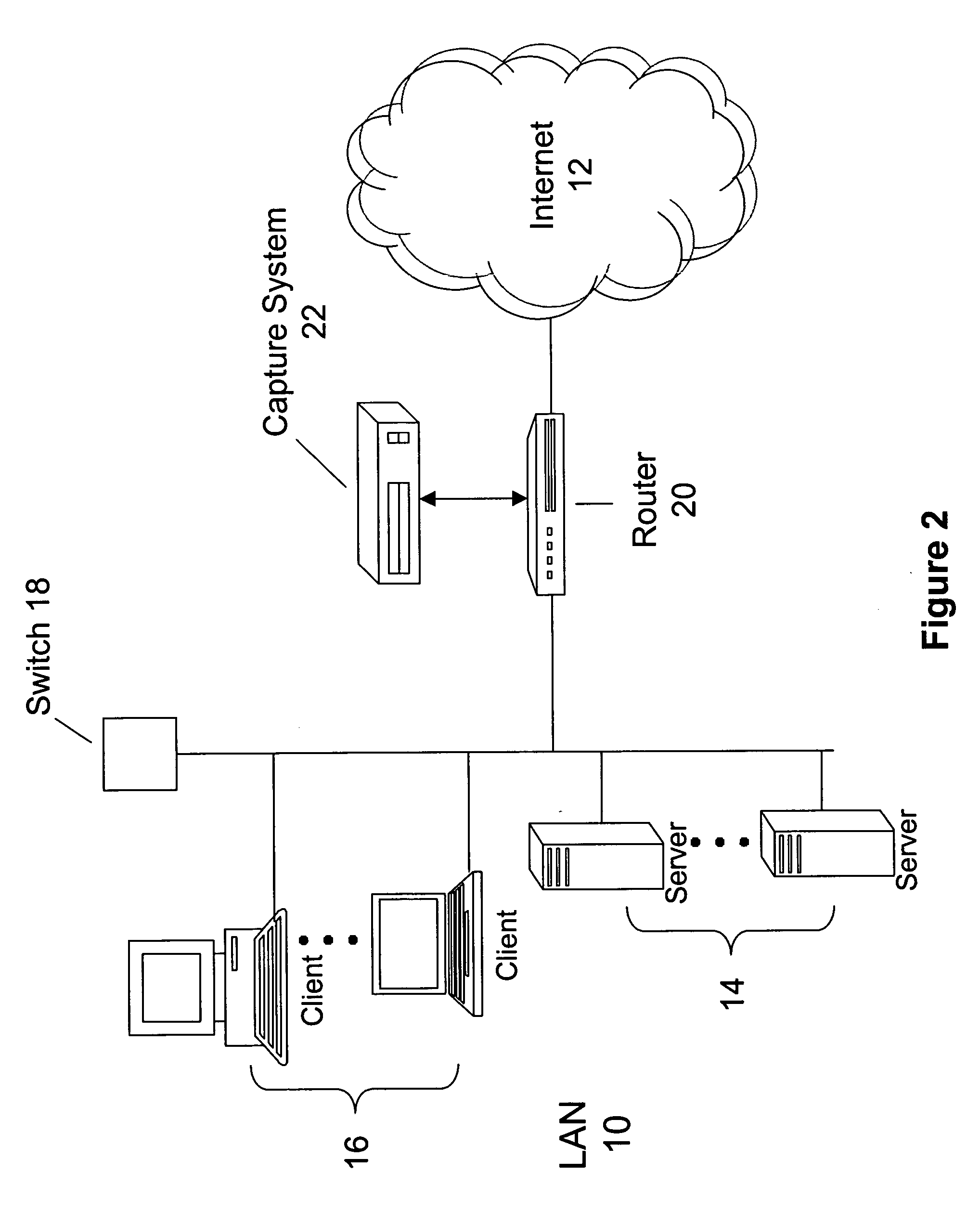
Objects captured over a network by a capture system can be indexed to provide enhanced search and content analysis capabilities. In one embodiment the objects can be indexed using a data structure having a source address field to indicate an origination address of the object, a destination address field to indicate a destination address of the object, a source port field to indicate an origination port of the object, a destination port field to indicate a destination port of the object, a content field to indicate a content type from a plurality of content types identifying a type of content contained in the object, and a time field to indicate when the object was captured. The data structure may also store a cryptographic signature of the object to ensure the object is not altered after capture.
Owner:MCAFEE LLC
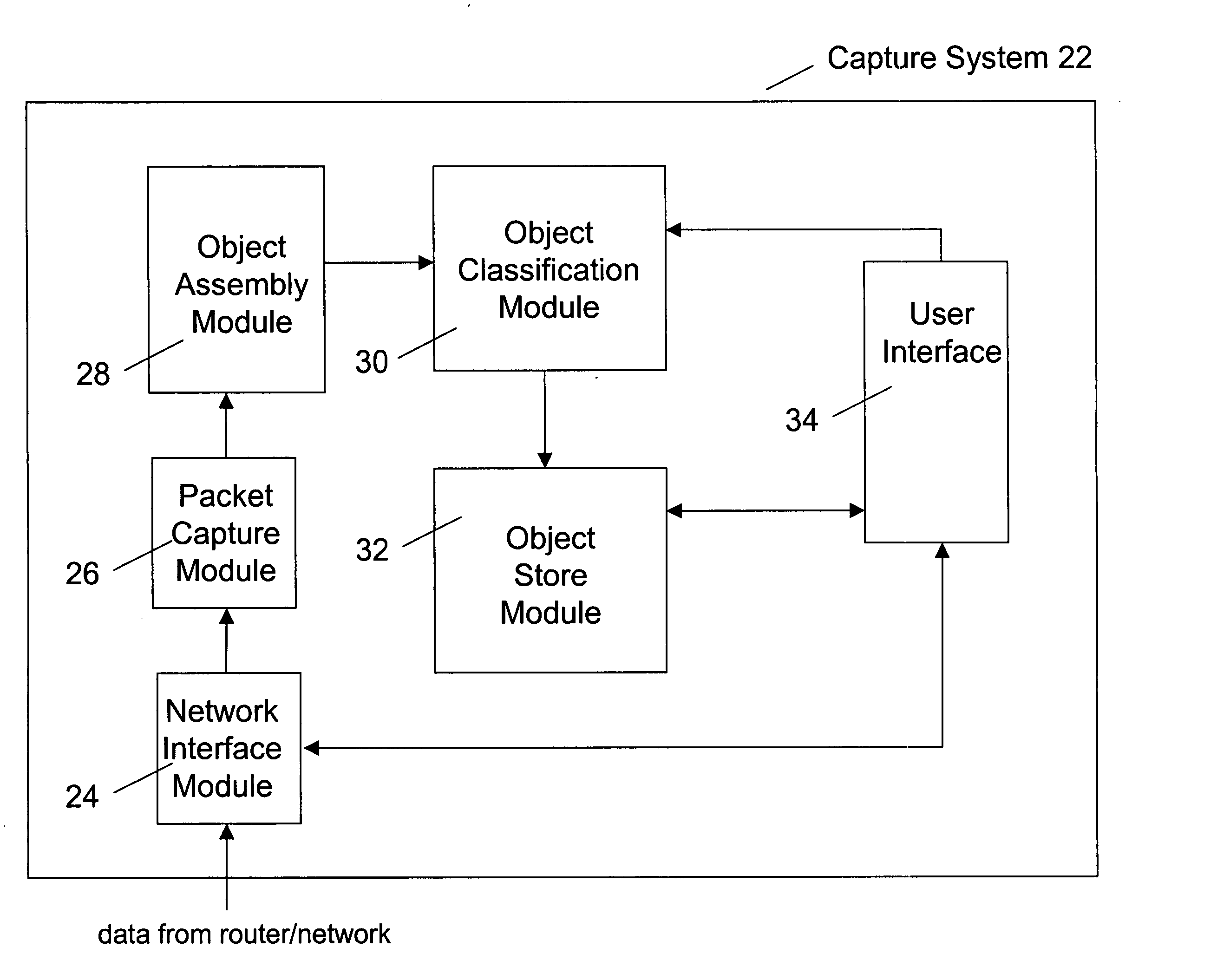
Object classification in a capture system
Owner:MCAFEE LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com