Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
4763 results about "Host (network)" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A network host is a computer or other device connected to a computer network. A host may work as a server offering information resources, services, and applications to users or other hosts on the network. Hosts are assigned at least one network address.
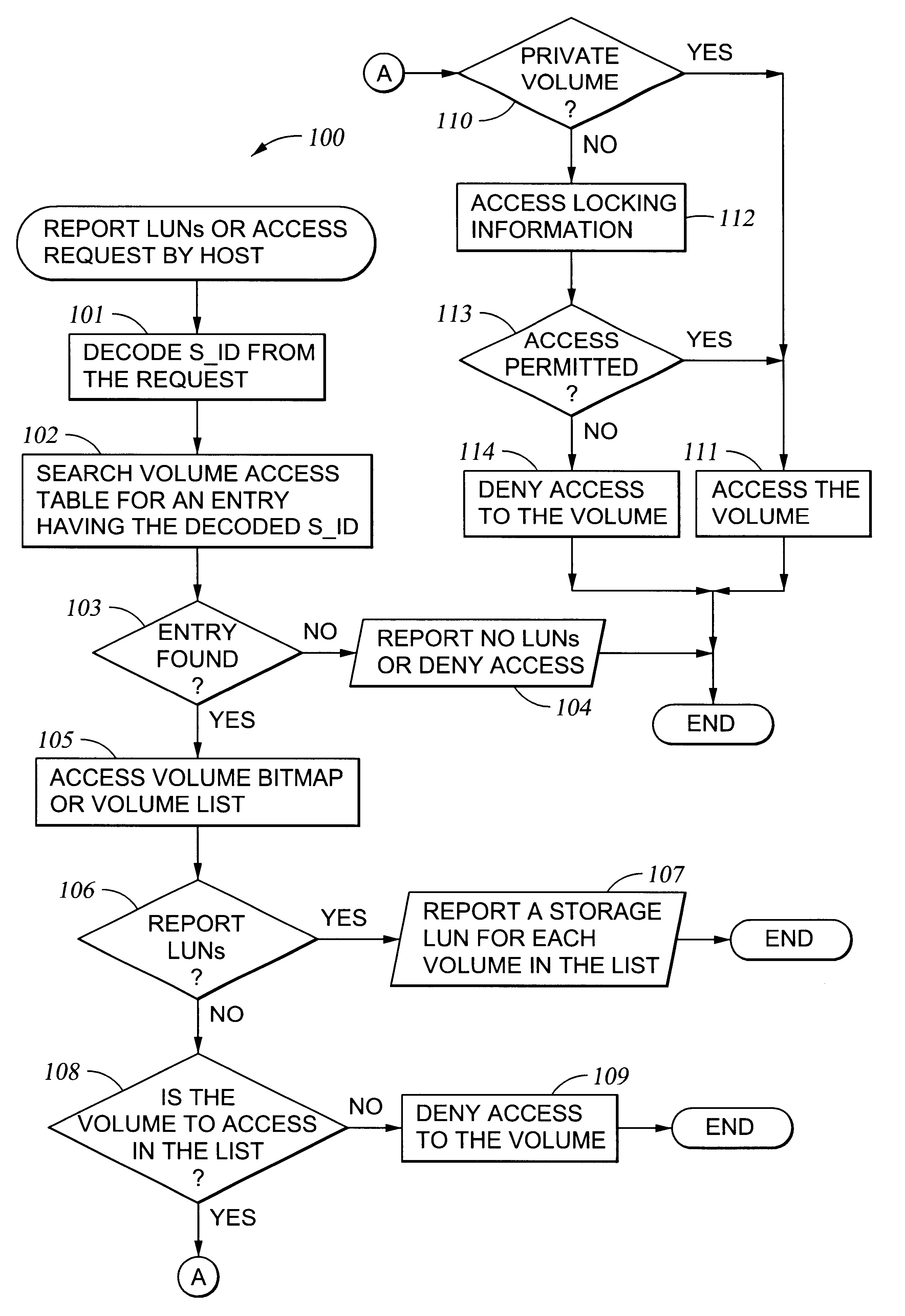
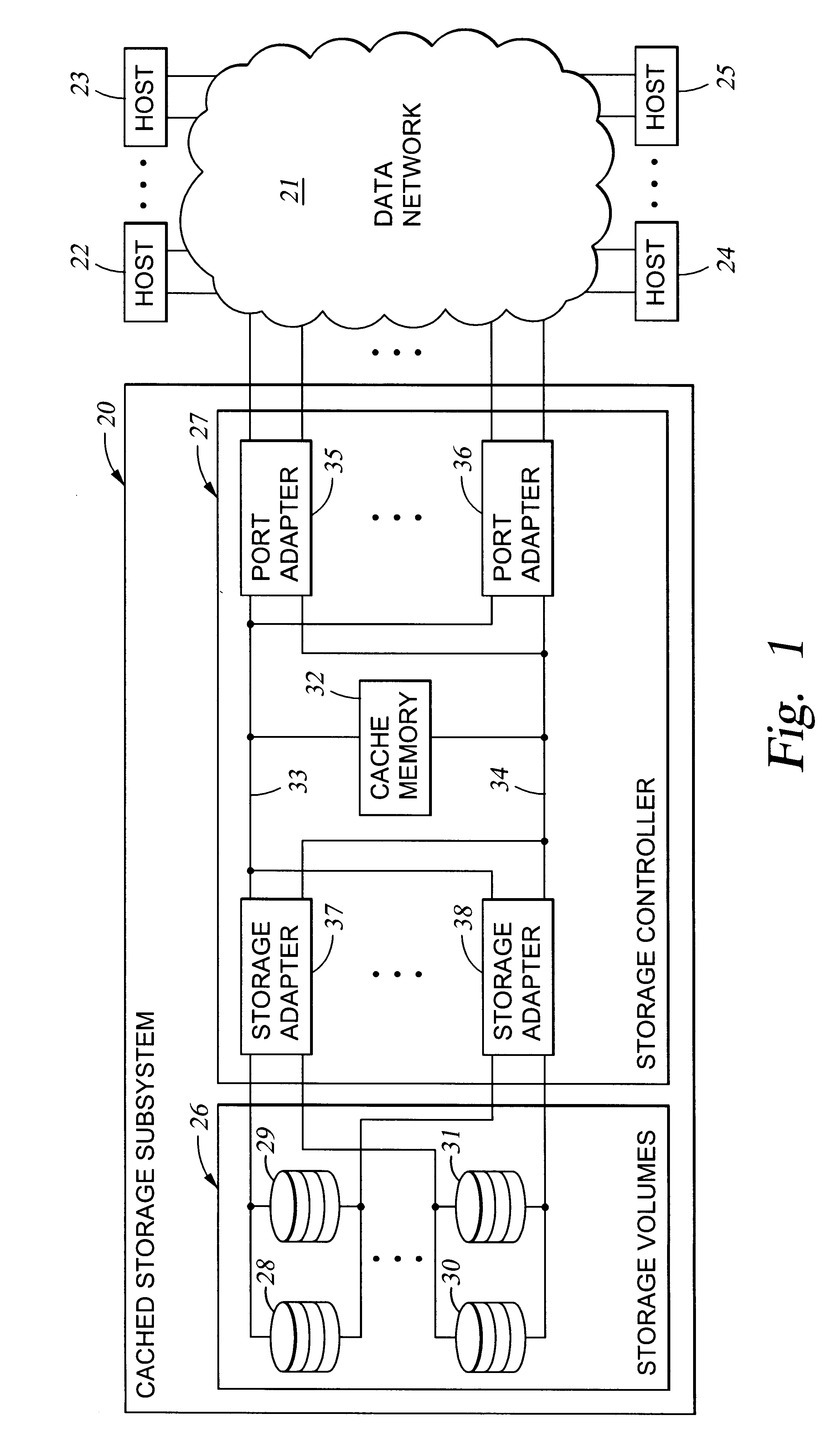
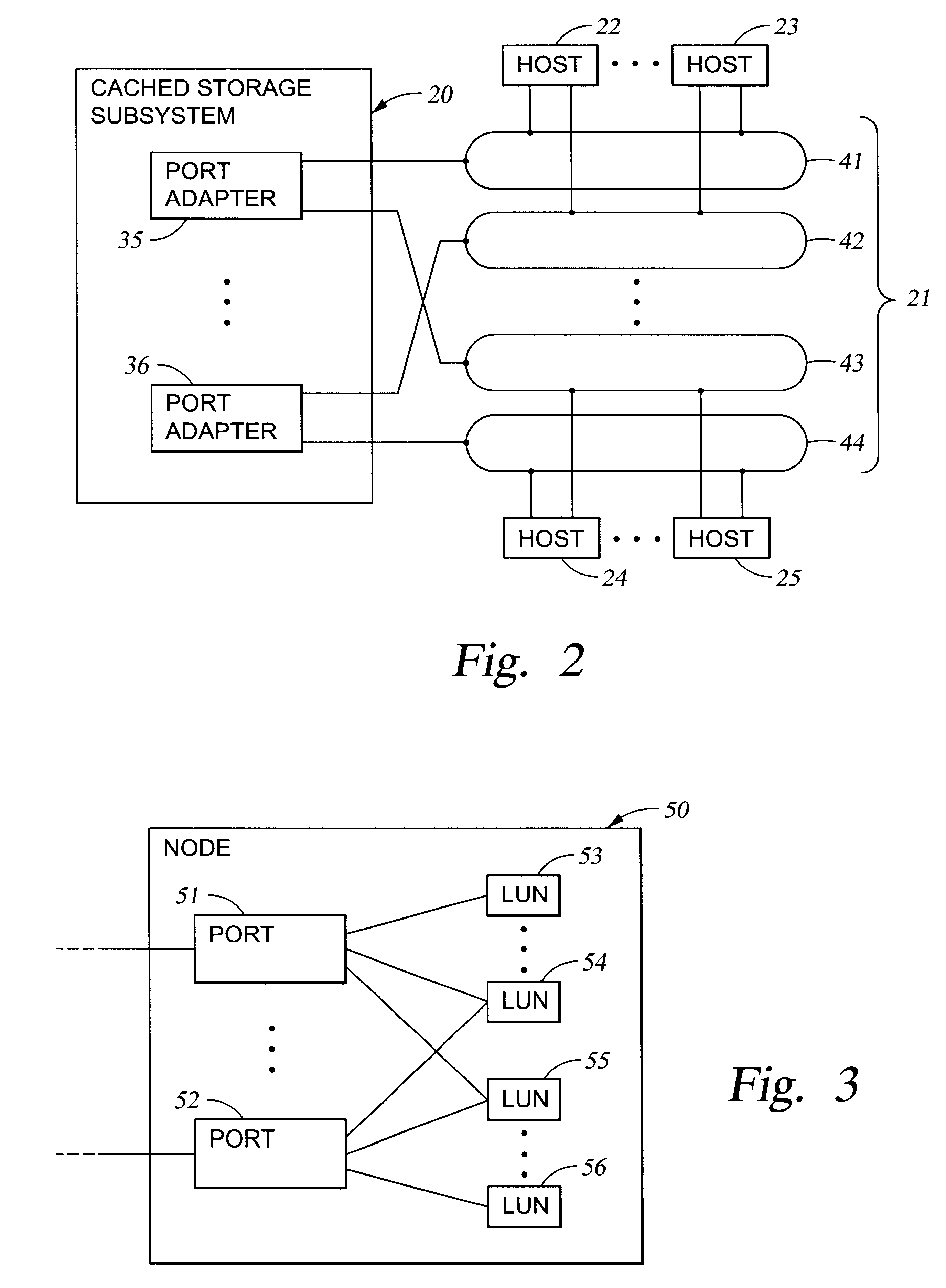
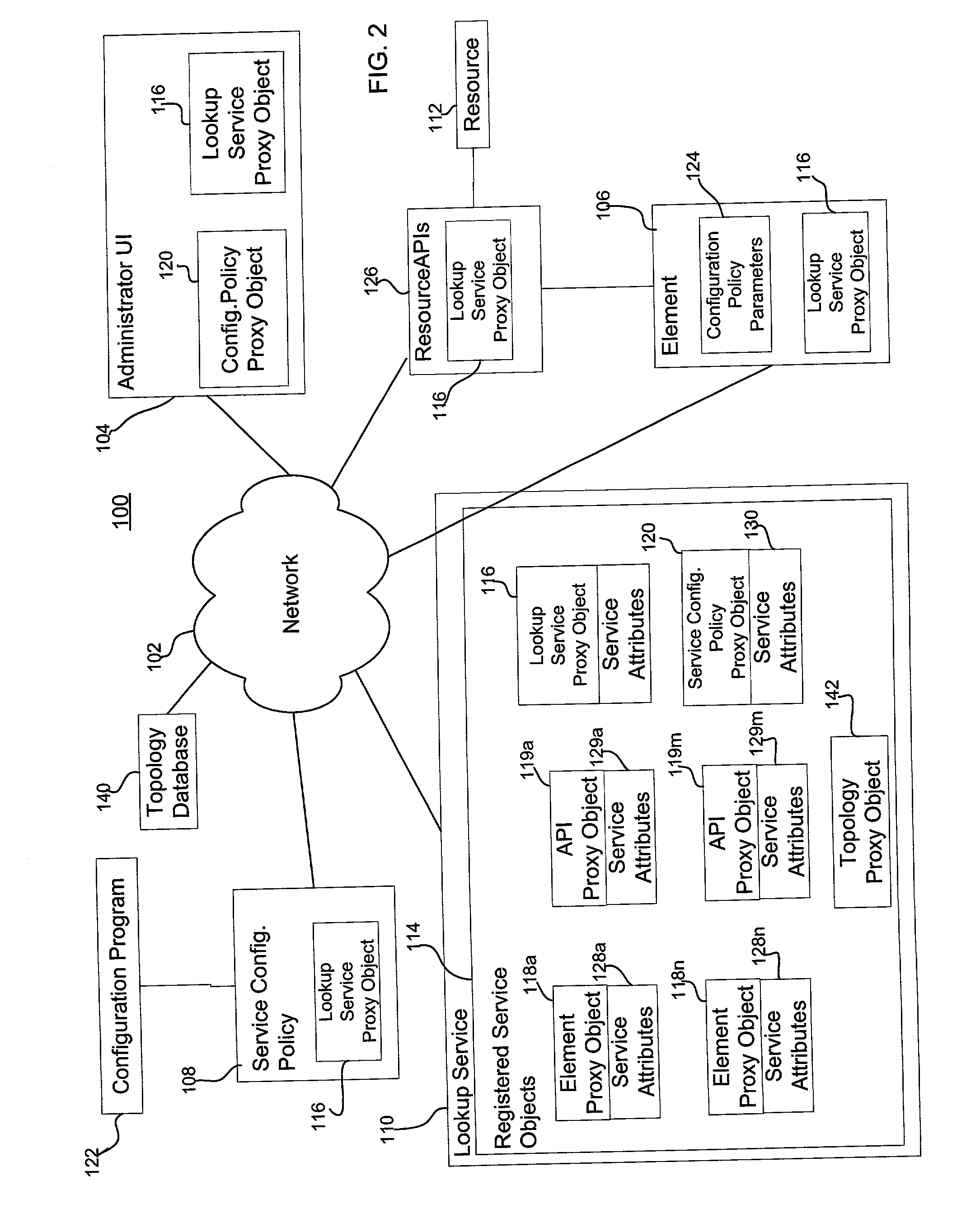
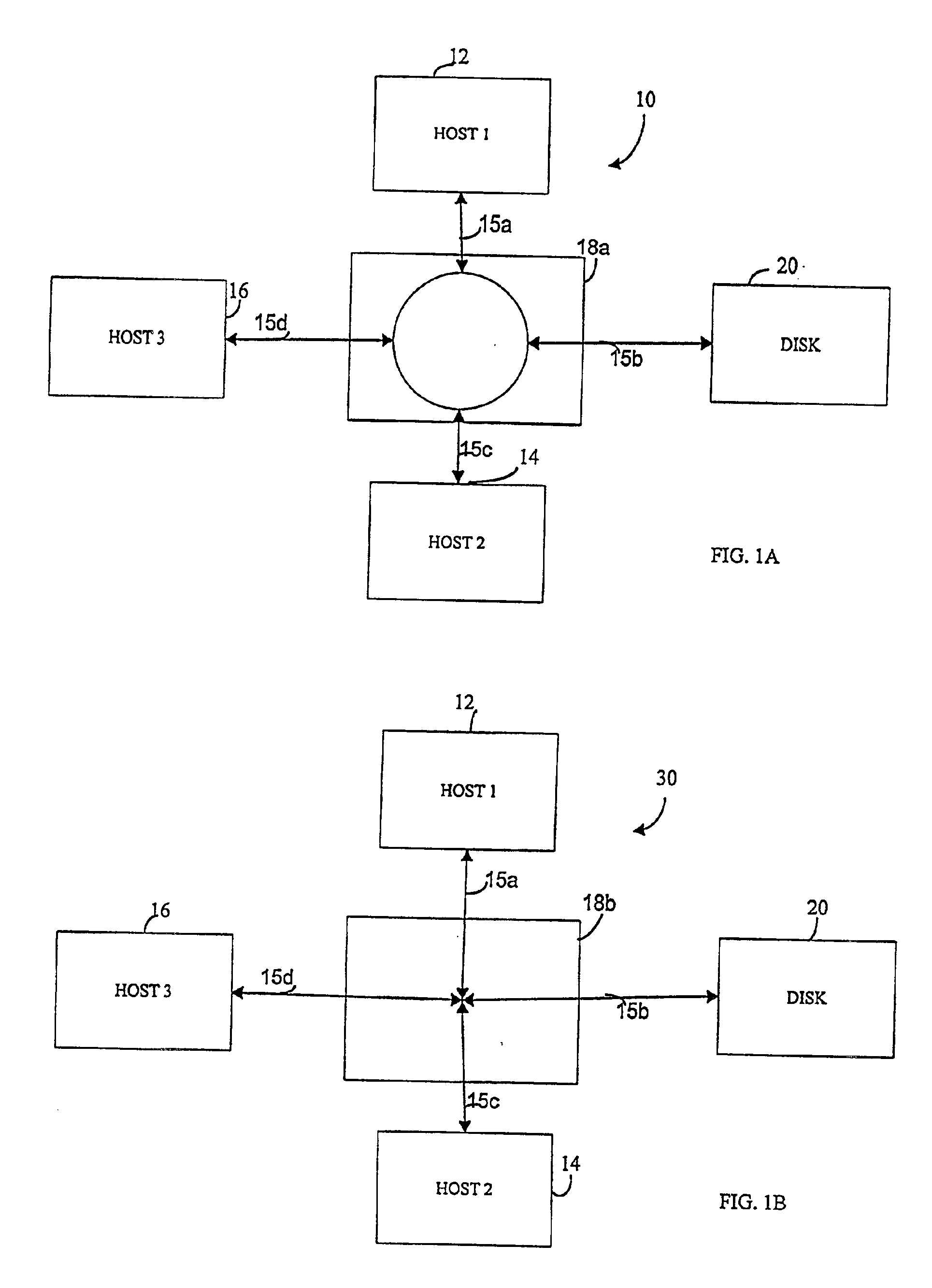
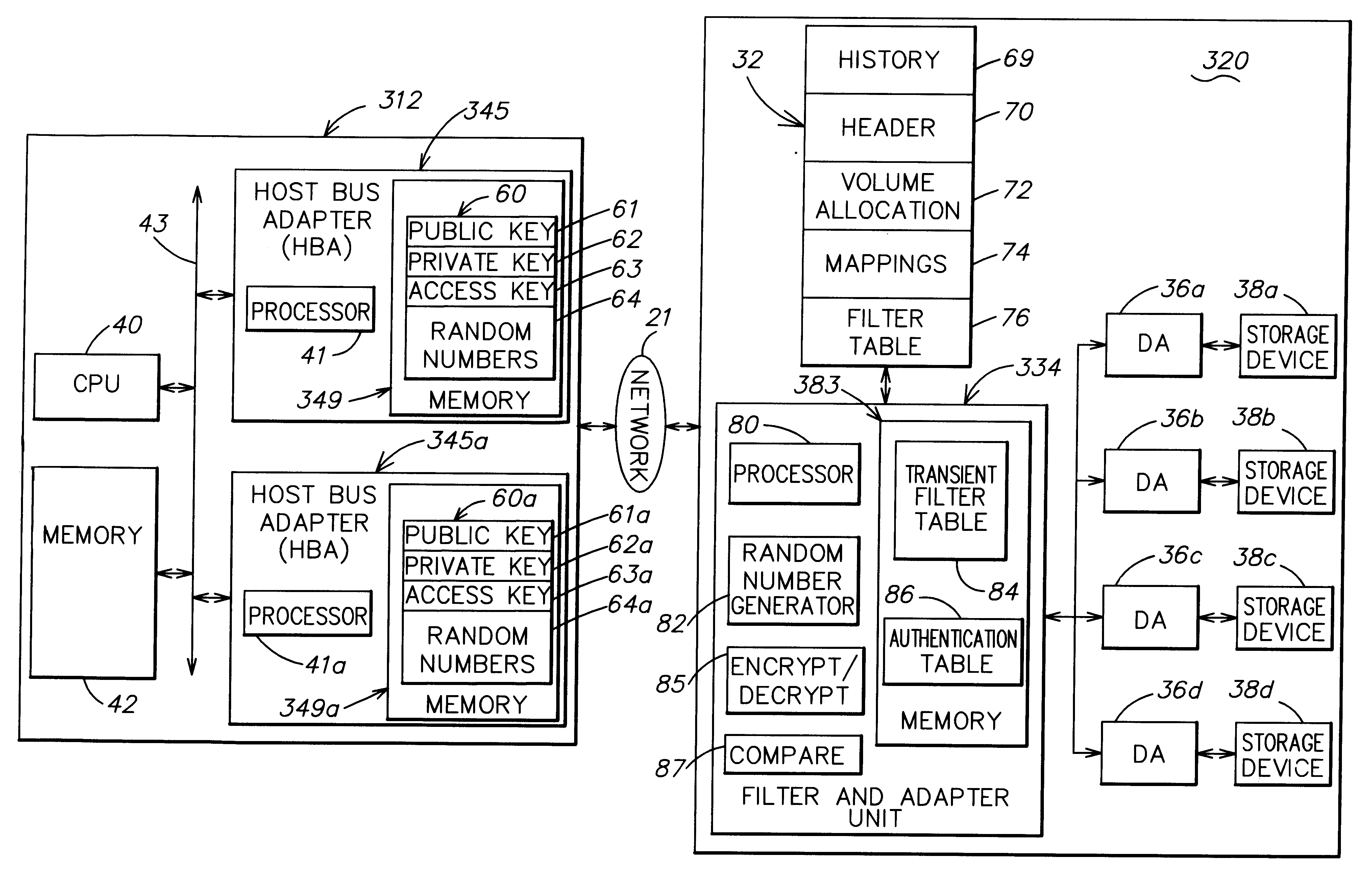
Storage mapping and partitioning among multiple host processors in the presence of login state changes and host controller replacement
InactiveUS6260120B1Input/output to record carriersData processing applicationsData portControl store
A storage controller for controling access to data storage has a memory and at least one data port for a data network including host processors. The memory is programmed to define a respective specification for each host processor of a respective subset of the data storage to which access by the host processor is restricted, and each specification is associated with a host identifier stored in the memory. When the storage controller receives a data access request from a host processor, it decodes a host identifier from the data access request, and searches the memory for a host identifier matching the host identifier decoded from the request. Upon finding a match, the respective specification of the respective subset for the host processor is accessed to determine whether or not storage specified by the storage access request is contained in the respective subset. If so, then storage access can continue, and otherwise, storage access is denied. Preferably the host identifier decoded from the request is a temporary address assigned by the network, and also stored in the memory in association with each respective specification is a relatively permanent identifier for the host processor.
Owner:EMC IP HLDG CO LLC
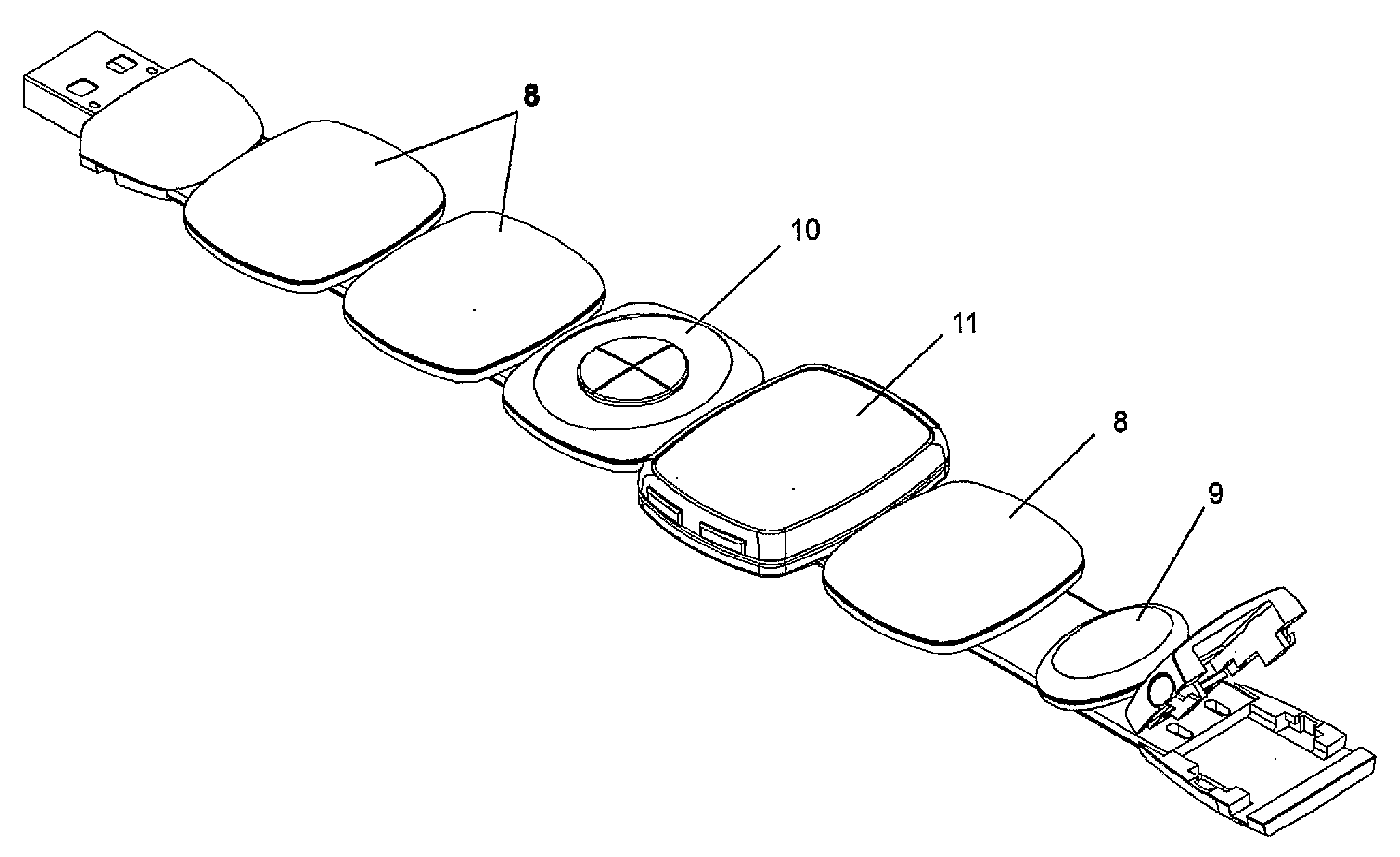
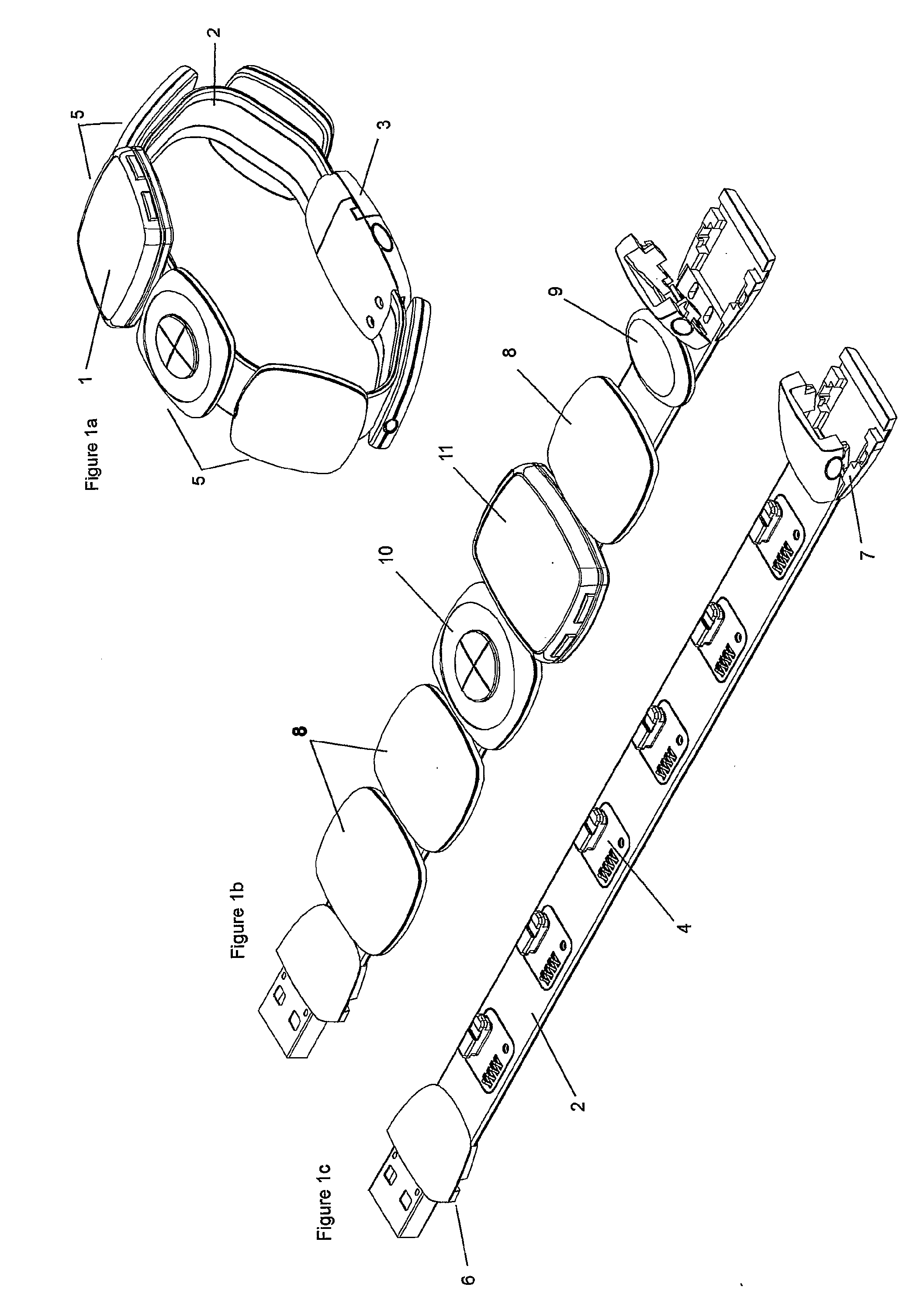
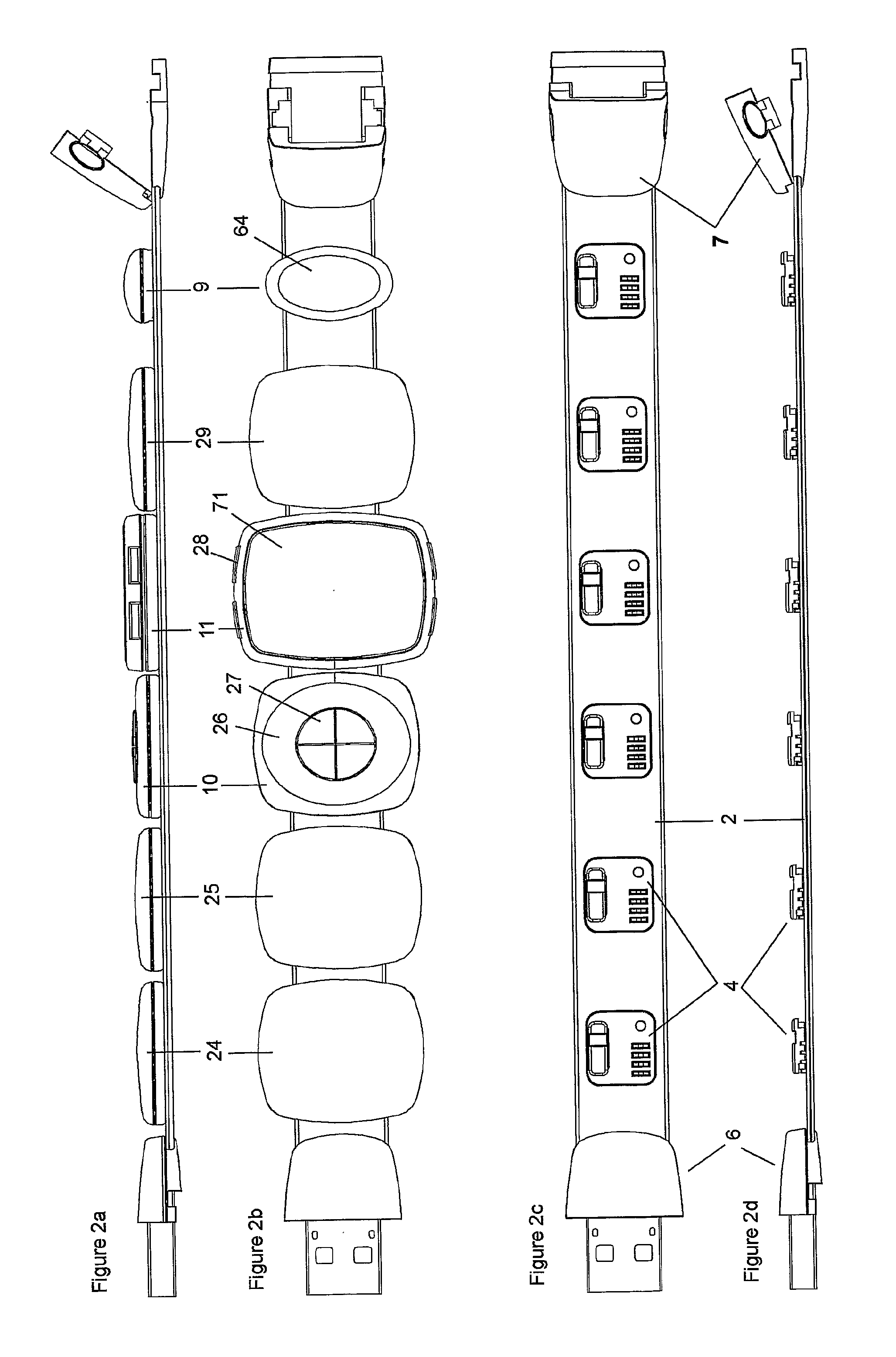
Wearable Modular Interface Strap
A wearable modular interface strap device for supporting multiple module units comprising a flexible strap with a plurality of electrically connected nodes acting as docking points to serial bus interface and mechanically connect removable modules, with the strap being 10 mechanically lockable in a loop by a clasp containing hub and host circuitry to enable network communication between modules and to a universal connector plug for recharging and data-exchange. Said strap containing a plurality of electrical wires between control circuitry and nodes and arranged to be wearable as a wristband, alternatively as a wrist device that when opened forms a curved handset with audio input and outputs at alternate ends, or arranged in a necklace configuration. Said device capable of supporting interchangeable modules such as displays, control devices, rechargeable batteries, a module with removable earpiece units, and a plurality of functional modules suitable for communication, data storage, location and environment sensing.
Owner:DANIEL SIMON R +1
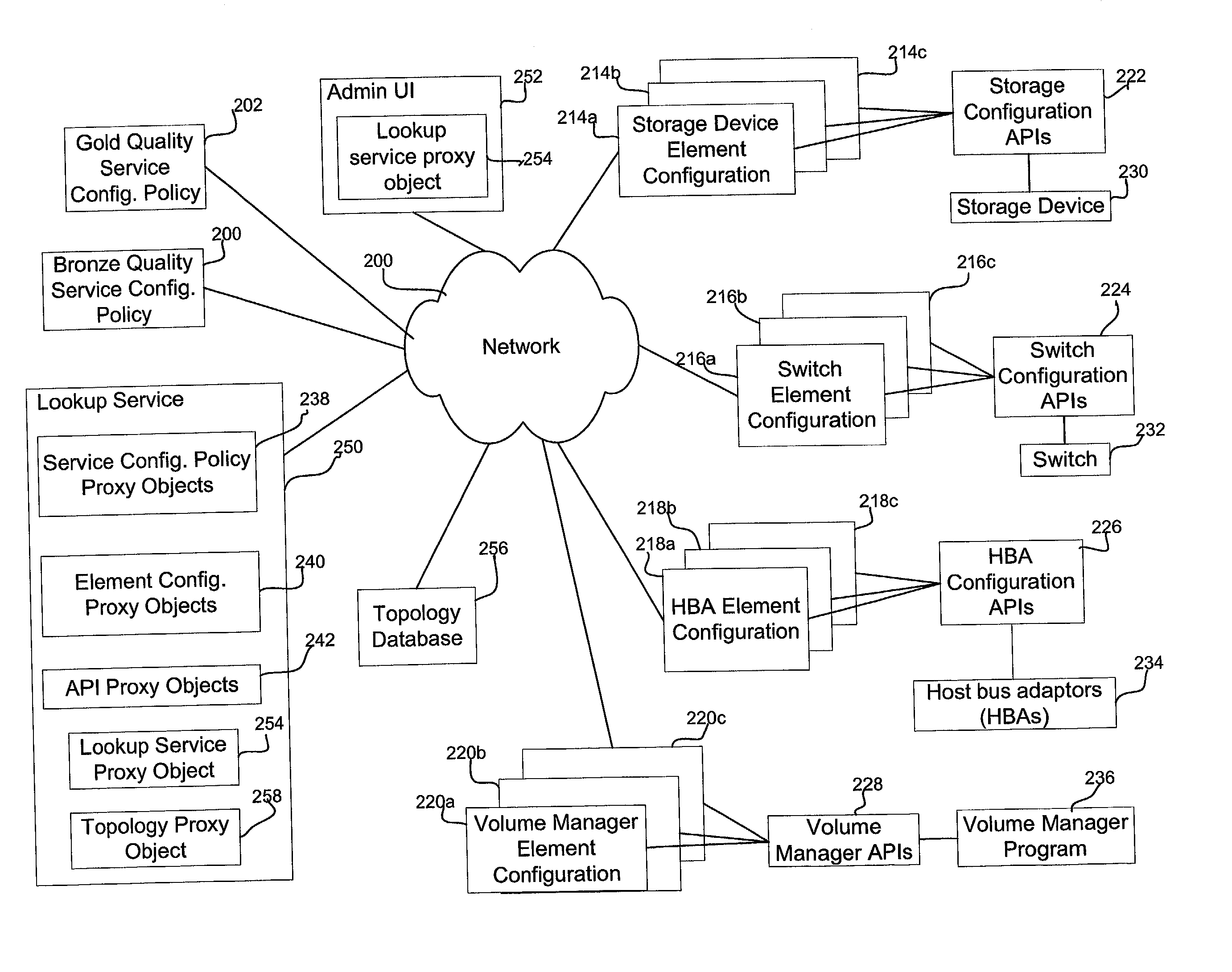
Method, system, and program for determining a modification of a system resource configuration
InactiveUS20030135609A1Resource allocationMultiple digital computer combinationsManagement systemReal-time computing
Provided are a method, system, and program for managing multiple resources in a system at a service level, including at least one host, network, and a storage space comprised of at least one storage system that each host is capable of accessing over the network. A plurality of service level parameters are measured and monitored indicating a state of the resources in the system. A determination is made of values for the service level parameters and whether the service level parameter values satisfy predetermined service level thresholds. Indication is made as to whether the service level parameter values satisfy the predetermined service thresholds. A determination is made of a modification to one or more resource deployments or configurations if the value for the service level parameter for the resource does not satisfy the predetermined service level thresholds.
Owner:SUN MICROSYSTEMS INC
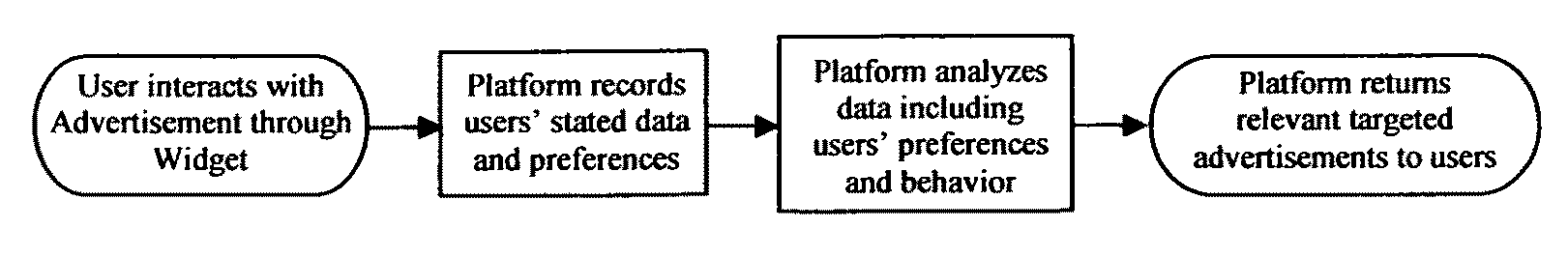
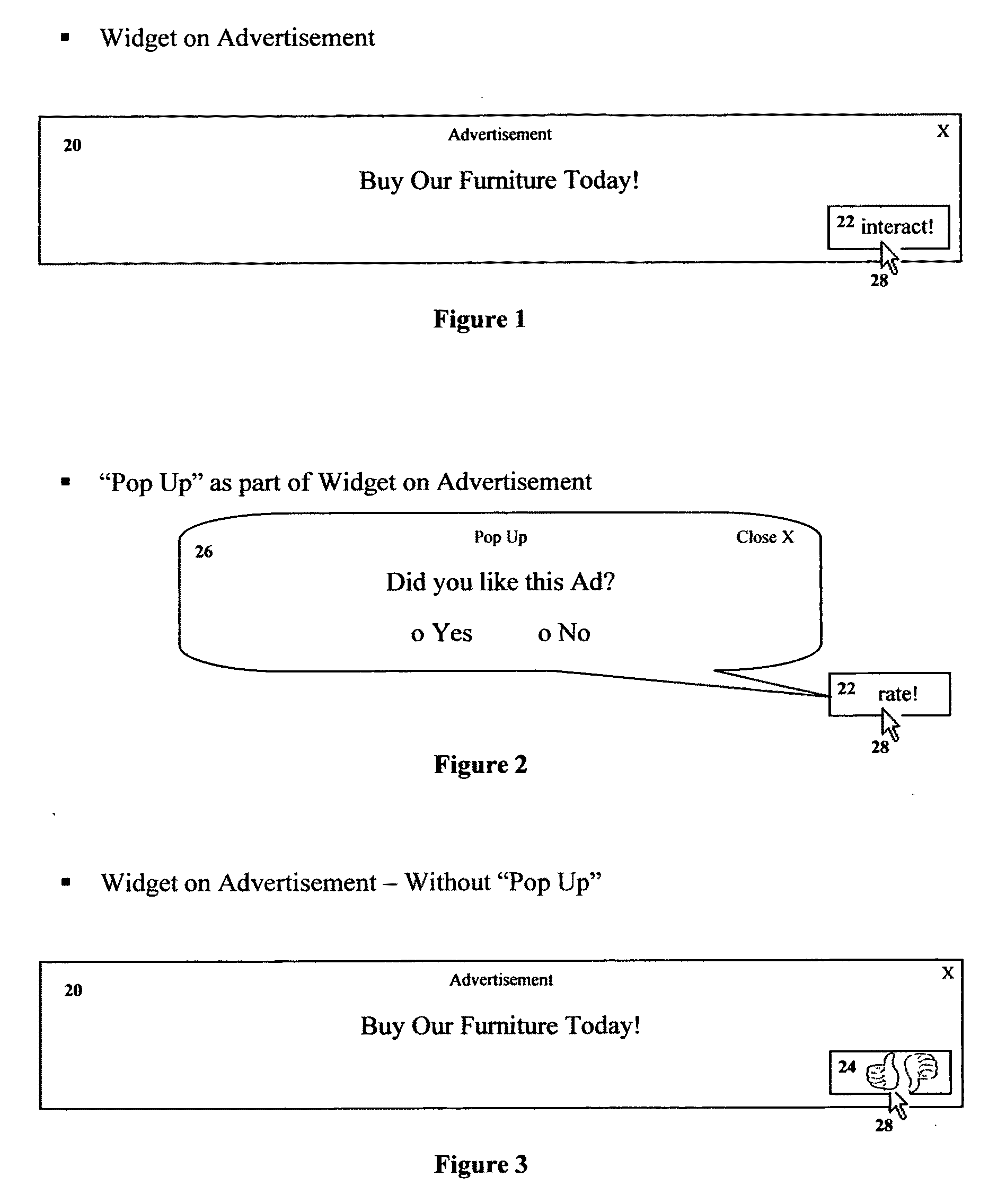
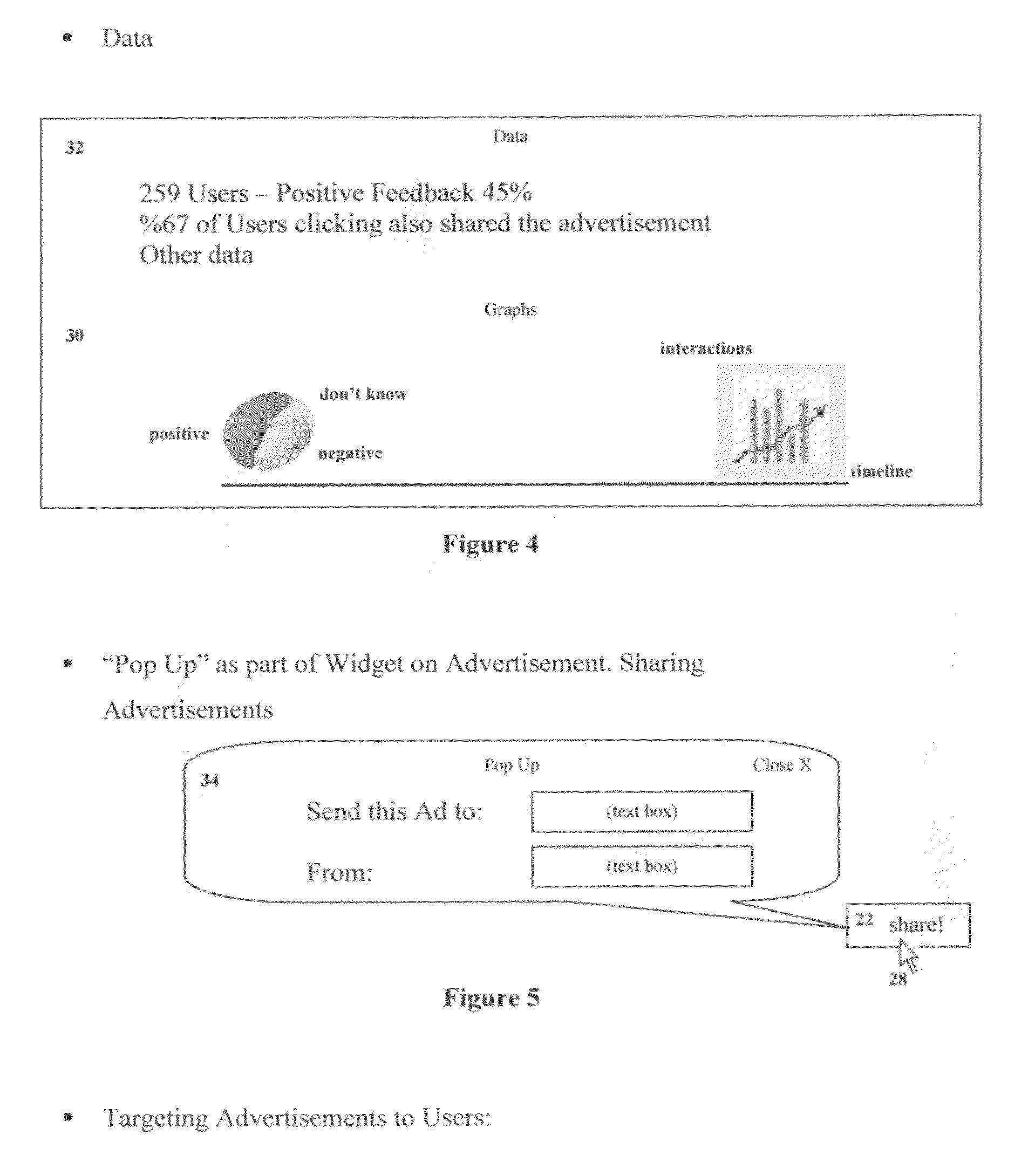
Method and system for user interaction with advertisements sharing, rating of and interacting with online advertisements
InactiveUS20090292608A1Large user baseIncreasing relevancy of advertisements to usersMultiple digital computer combinationsMarketingDistribution systemThe Internet
A platform includes an overall system for user interaction, associated with a particular advertisement. The process enables users to interact with a widget directly associated with an advertisement and express themselves in regards to the advertisement. Advertisement displayed in the Internet or similar distributed computer network-based information distribution system. Such user interactions include engagement methods such as rating advertisements, sharing them with other users, commenting on them, and more. The platform can also include a host site, storing and processing data received by users. As well as means for targeting advertisements and serving them to users according to data collected through the platform directly inserted by the users or collected by the platform in regards to their interaction with the platform.
Owner:FLAKKES MEDIA 2009
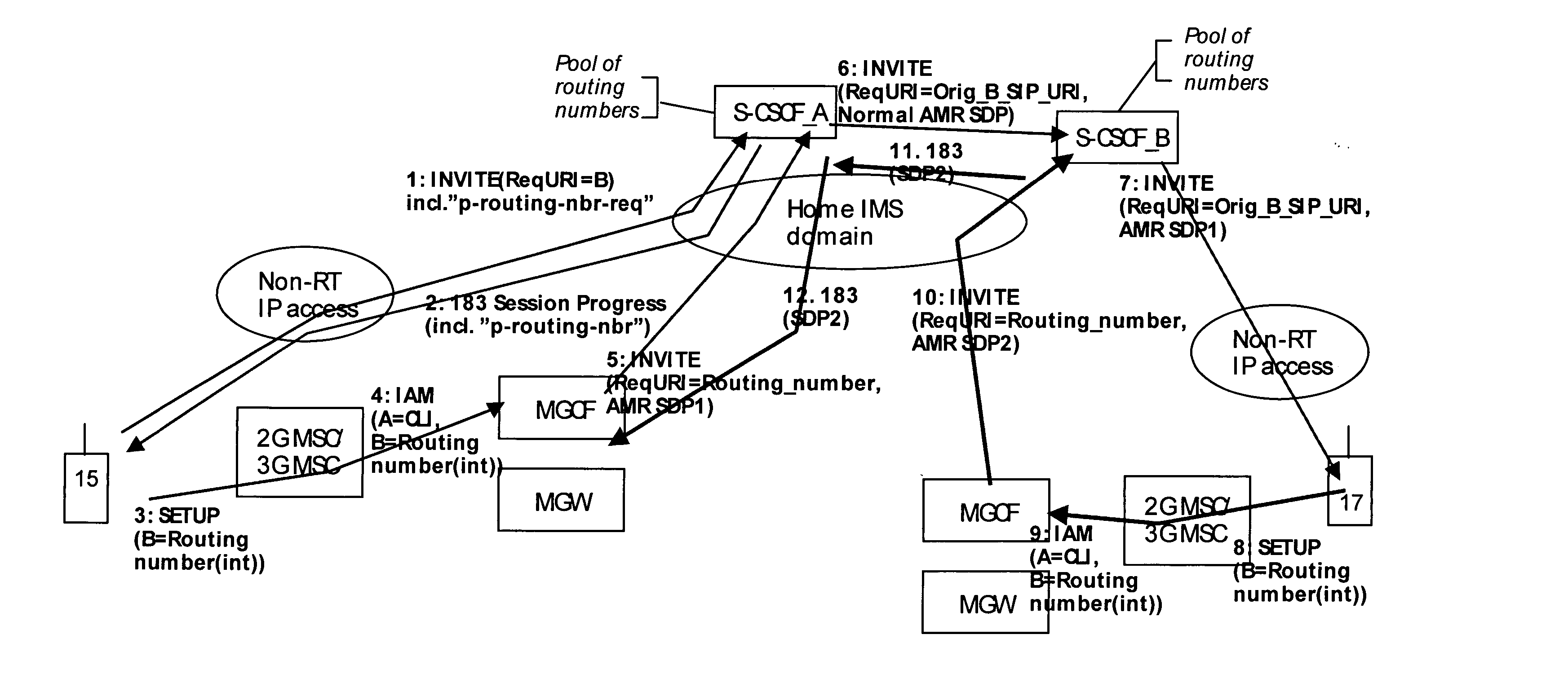
IP-based services for circuit-switched networks
ActiveUS20050058125A1Multiplex system selection arrangementsInterconnection arrangementsRadio access networkVoice over IP
A mechanism for providing a connection from an IP-based network to a circuit-switched network, such as a GSM network is disclosed. A temporary routing number for the circuit-switched network, such as an E.164 number, is delivered to a user terminal, and a circuit-switched call leg is established from the user terminal to the IP-based network using the routing number. Thereby, IMS-services are provided for end users which are located in the radio access network not having sufficient QoS required for voice over IP. In the example of a conference call service, a request for a conference call may forwarded via a data channel or data path to an application server which provides that conference call service. The application server then selects a conference routing number and returns the routing number to the conference host terminal via the data channel. Using the received conference routing number, the conference host terminal can then set up a circuit-switched connection as a call leg of the conference call.
Owner:NOKIA TECHNOLOGLES OY
System and method for incentive programs and award fulfillment
InactiveUS7054830B1Improve abilitiesIncrease powerCash registersMarketingOrder fulfillmentMultimedia
A method and system for providing incentive programs over a computer network is provided in which a host may provide sponsoring companies with the capability to buy prepackaged or self-built incentive programs, offer such incentive programs to consumers, provide sponsoring companies and retailers with the capability to associate prizes with incentive programs, provide sponsoring companies, retailers and consumers with convenient fulfillment of prizes, and store and manipulate databases regarding all of the foregoing.
Owner:KROY IP HLDG
Resilient trust network services
ActiveUS8843997B1Digital data processing detailsUser identity/authority verificationComposite applicationIntegration platform
A Resilient Trust Network (RTN) is a set of servers that provide: an application integration platform for developing and publishing services and user interface for services, building derived services, subscribing to services, and embedding services into host applications, and building composite applications composed from multiple diverse services. The RST can also provide a platform for defining security requirements and accessing shared trust services that implement those requirements for services regardless of where or how those services are used.
Owner:DATA443 RISK MITIGATION INC
Systems and methods for remote power management using 802.11 wireless protocols
InactiveUS20050055432A1Reduce power consumptionLow costTariff metering apparatusNetwork topologiesTerminal equipmentUsage data
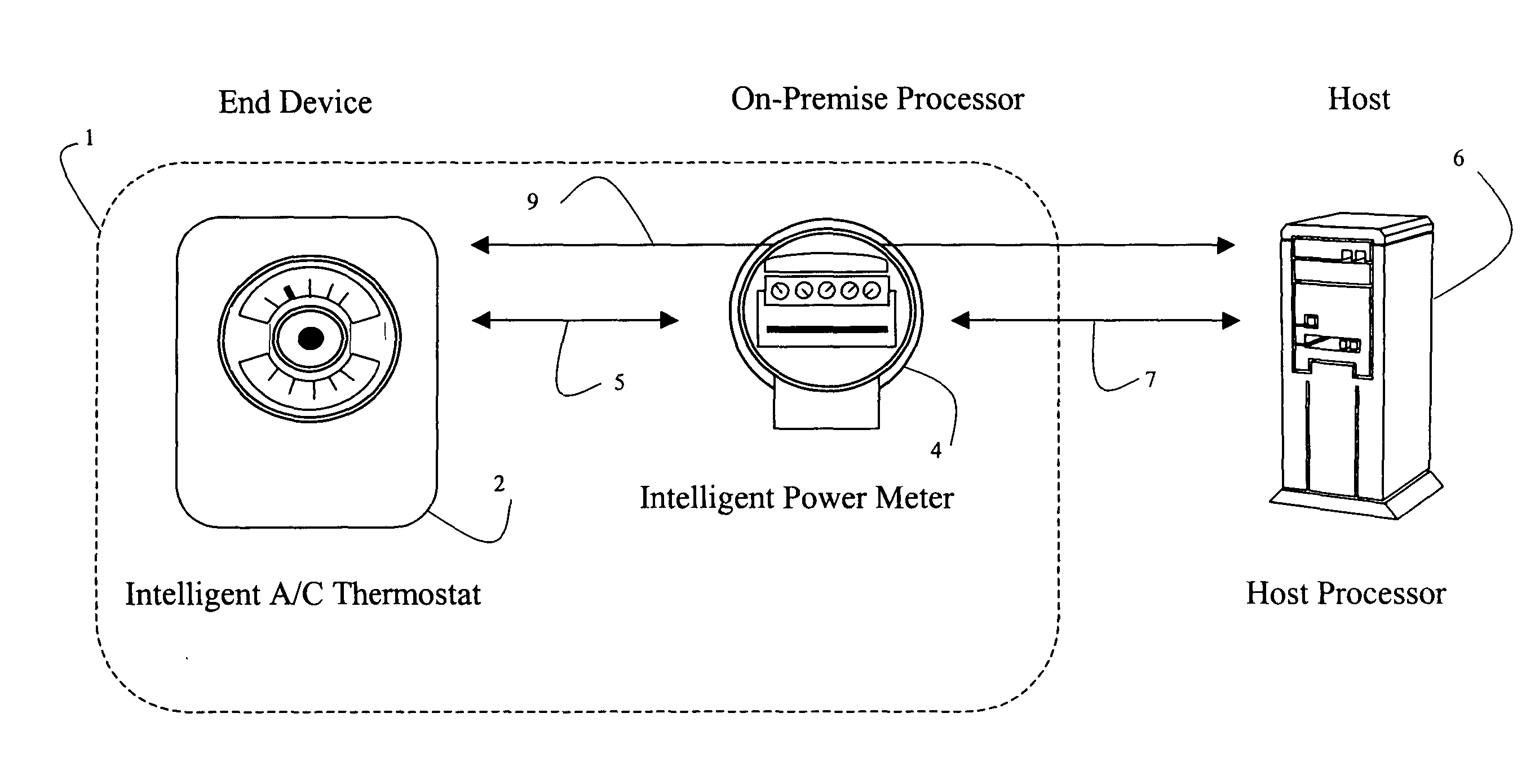
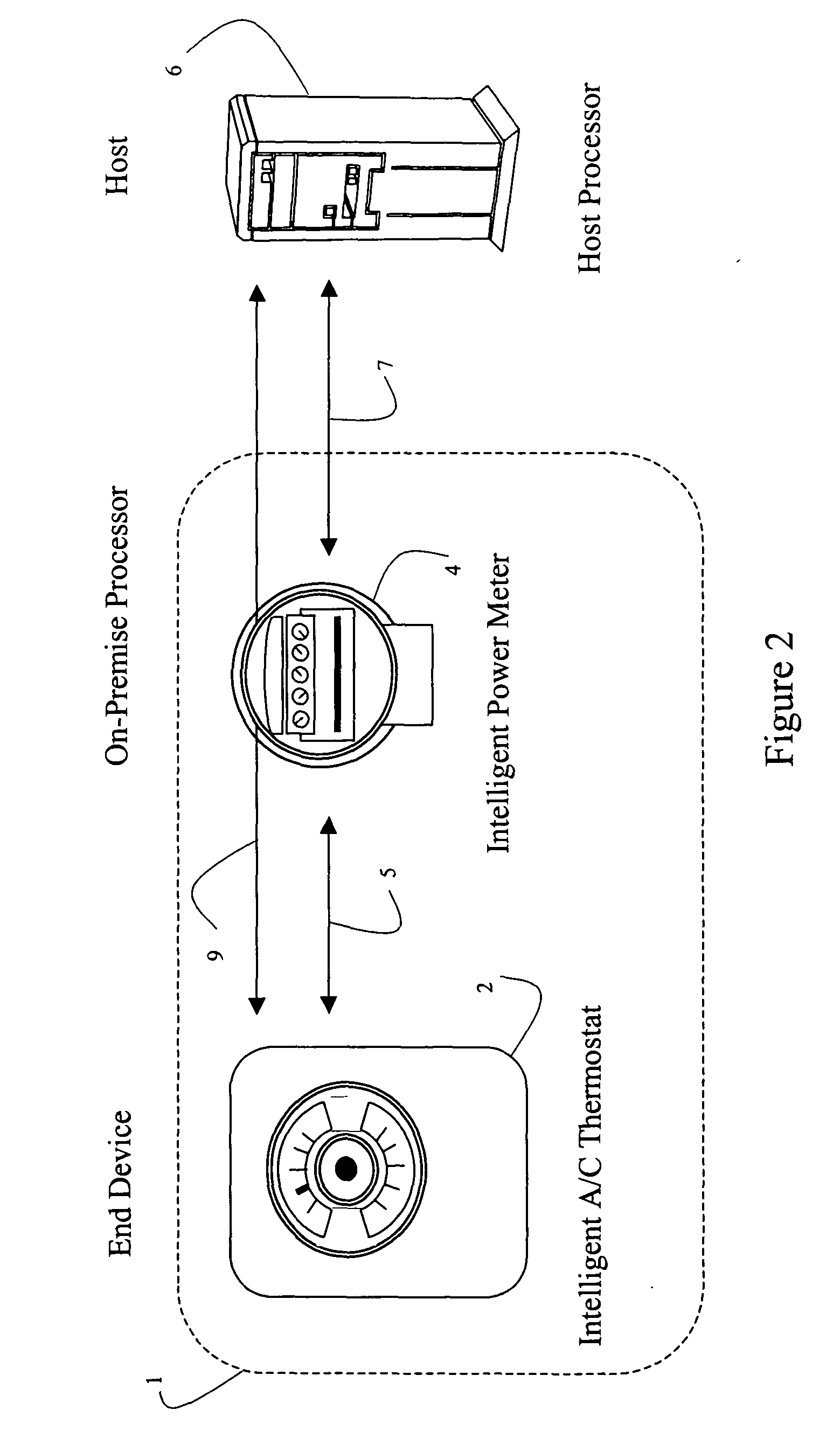
Systems and methods are disclosed for using 802.11 based wireless protocols in various energy management applications wherein a host controller uses various types of communication networks to distribute information to an on-premise processor that in turn uses 802.11 based wireless protocols to communicate with various types of end devices, such as utility meters. Various forms of communication are defined between the end device, the on-premise processor, and the energy management host for accomplishing power load control, including determining when to activate or deactivate a load, requesting permission to activate a load, reading usage data, activating or deactivating a meter, and determining rate schedules. A flexible scheme allows control to be shifted to be resident in various entities. The architecture is applicable not only for power load control, but other control type and metering devices.
Owner:SMARTSYNCH
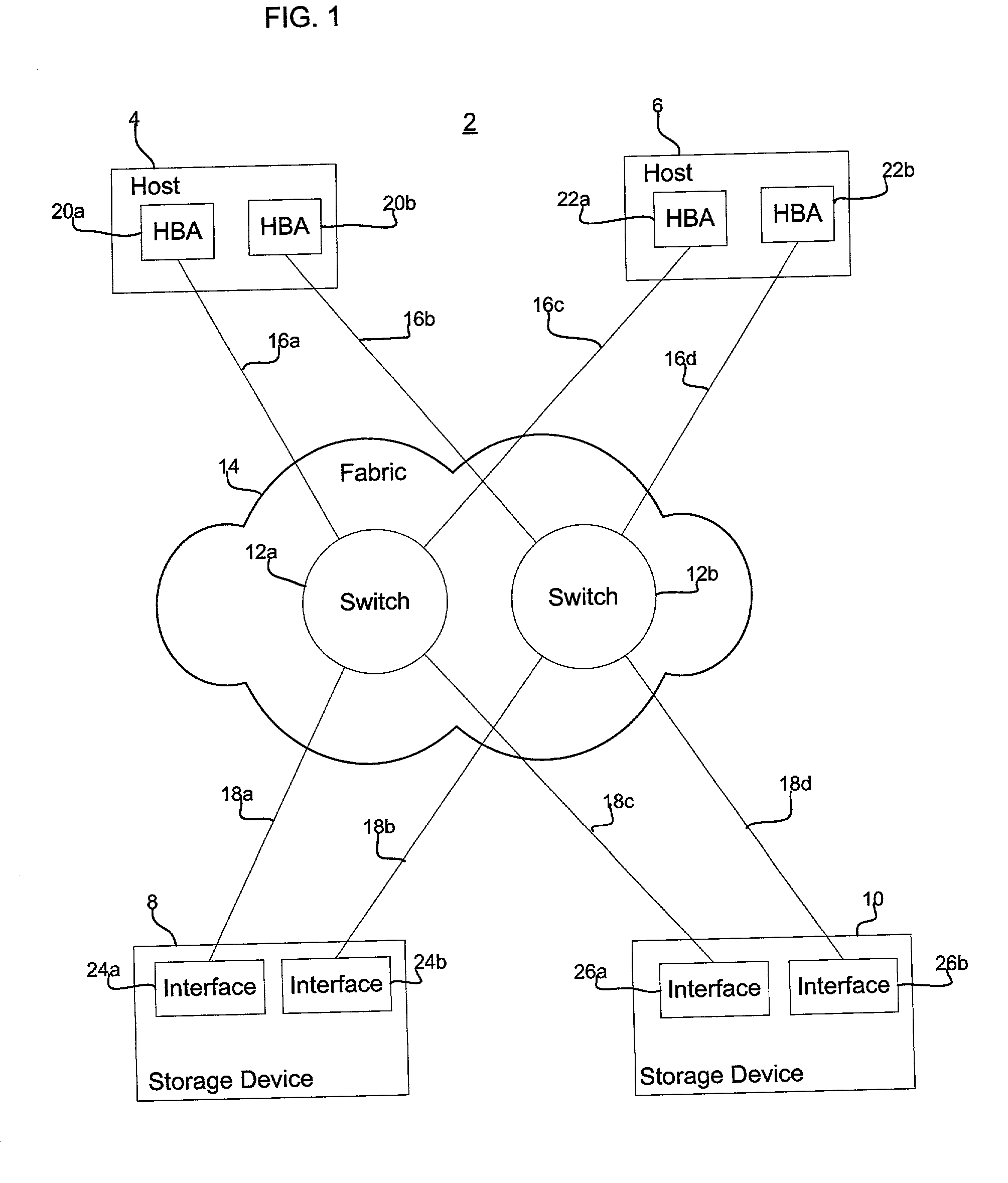
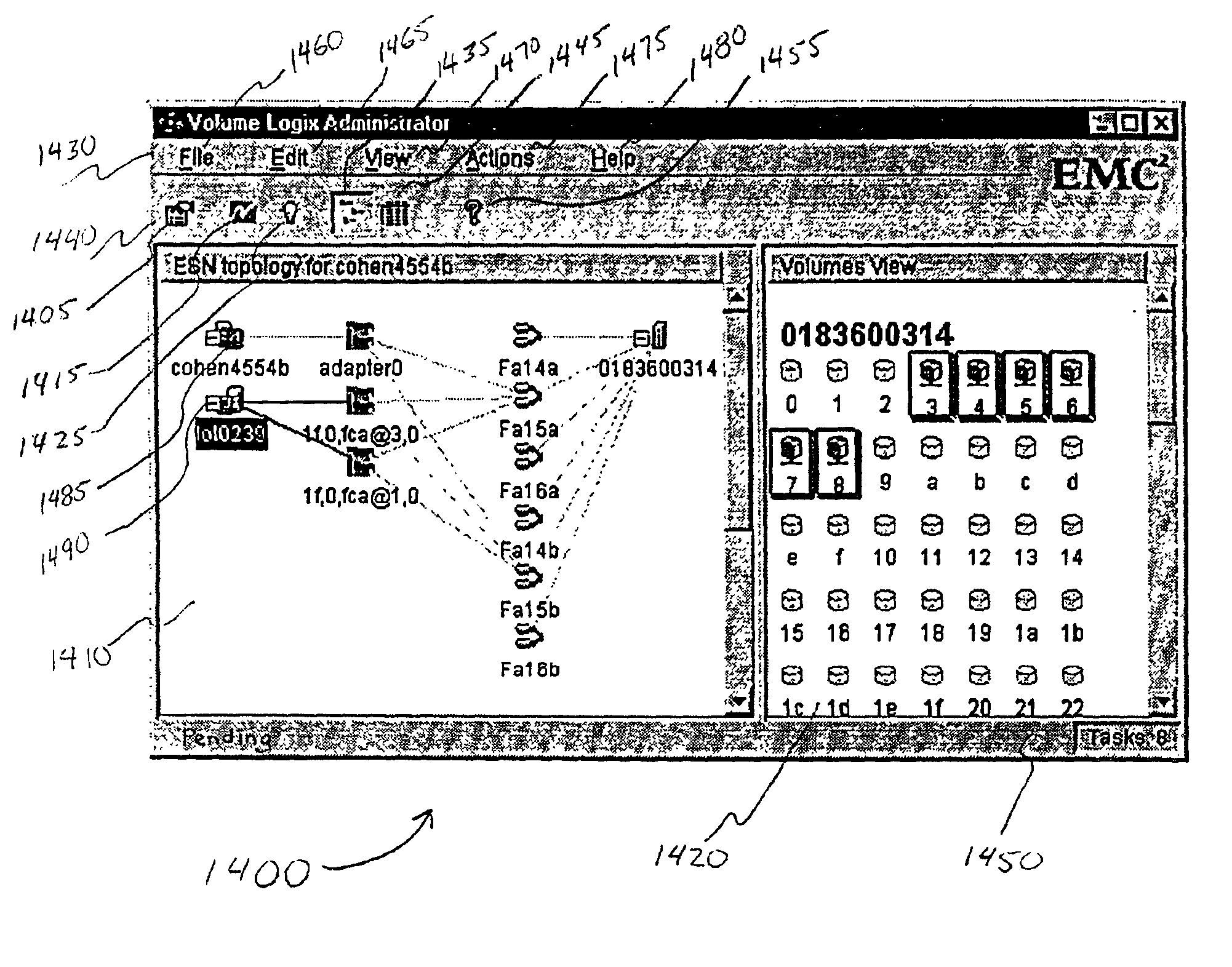
User interface for managing storage in a storage system coupled to a network
A method and apparatus for managing the availability and assignment of data in a storage system that is coupled to a network. A user interface is provided that executes on a host processor that is coupled to the storage system over the network. The user interface communicates with a configuration database in the storage system to identify host processors that are logged into the storage system over the network, to identify storage volumes on the storage system, to identify whether access to a particular storage volume on the storage system is permitted from a particular host processor, and to identify a network path by which host processors are logged into the storage system over the network. In one embodiment, a graphical user interface is provided that can be used to graphically represent host processors, host bus adapters, storage systems, and storage system adapters and storage volumes on the storage system. The graphical representation provided by the graphical user interface permits a user to graphically view a topology of the network at varying levels of detail, selectable by the user. The graphical user interface also permits a user to allow or deny access to storage systems or a particular storage volume on storage system from one or more of the host processors, host bus adapters, etc., by selecting and manipulating graphical representations thereof. In another embodiment, a command line user interface is provided with similar functionality.
Owner:EMC IP HLDG CO LLC
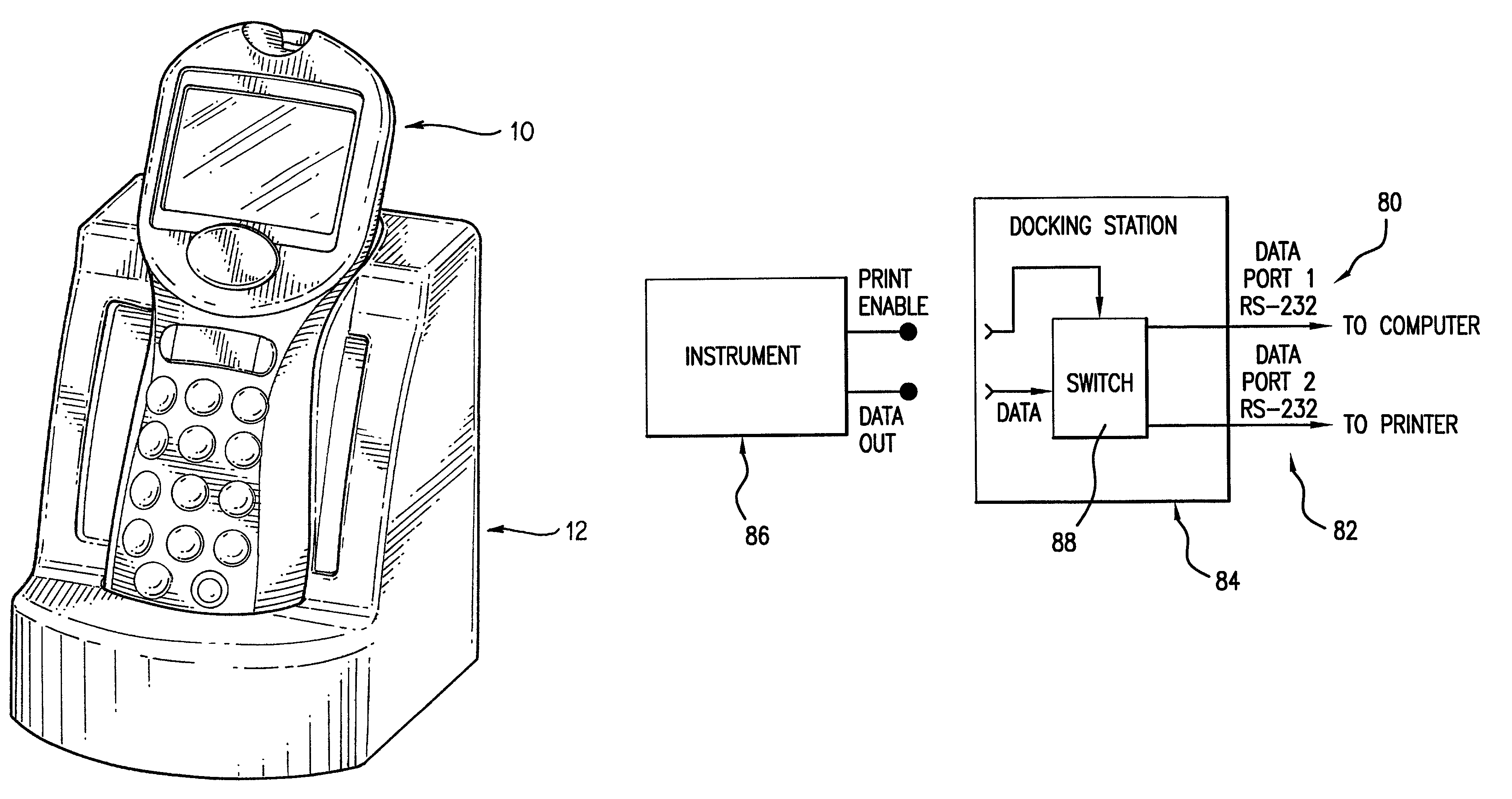
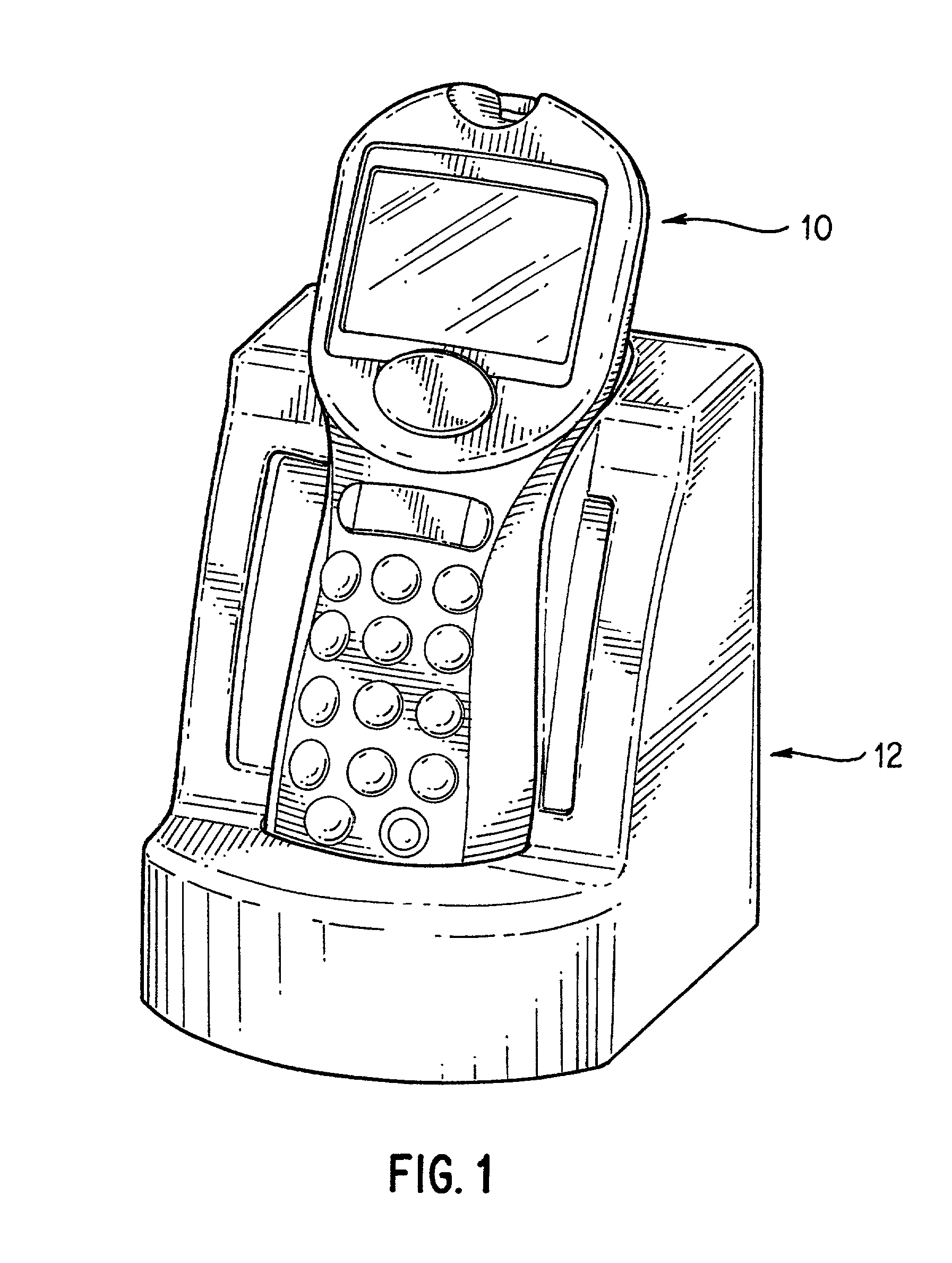
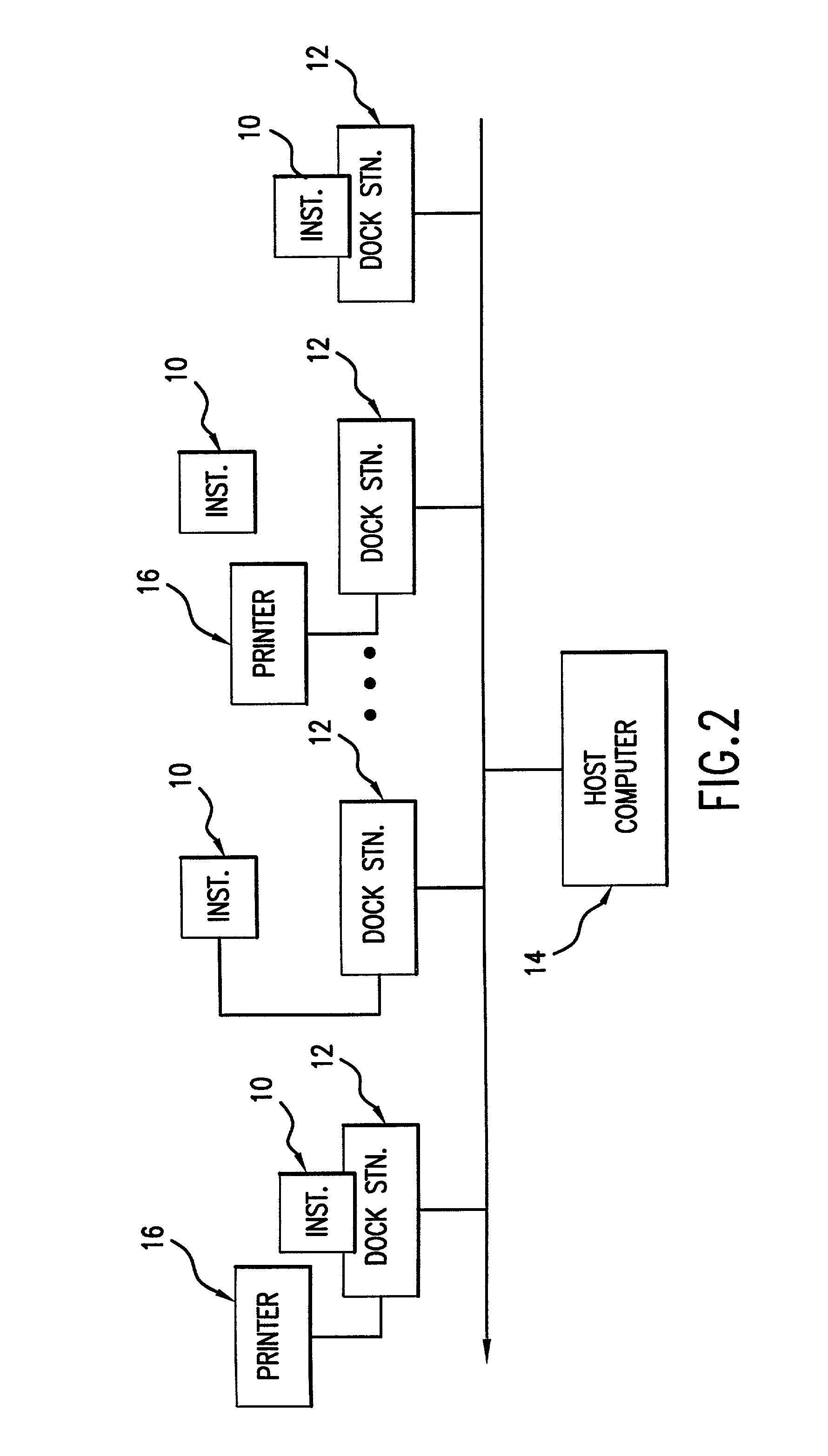
Analyte test instrument system including data management system
InactiveUS7077328B2Computer-assisted medical data acquisitionCharacter and pattern recognitionSwitched communication networkInstrumentation
A method of managing data for a plurality of analyte test instruments connected to a data communication network. The method comprises the steps of: detecting via a host computer the connection of each instrument to the data communication network; uploading data received from each instrument to the host computer; processing the uploaded data on the host computer for operator review; and downloading configuration data from the host computer to each test instrument, the downloaded data comprising instrument-specific setup and control data. The invention further involves a hand-held analyte test instrument and a docking station for the test instrument.
Owner:ABBOTT DIABETES CARE INC
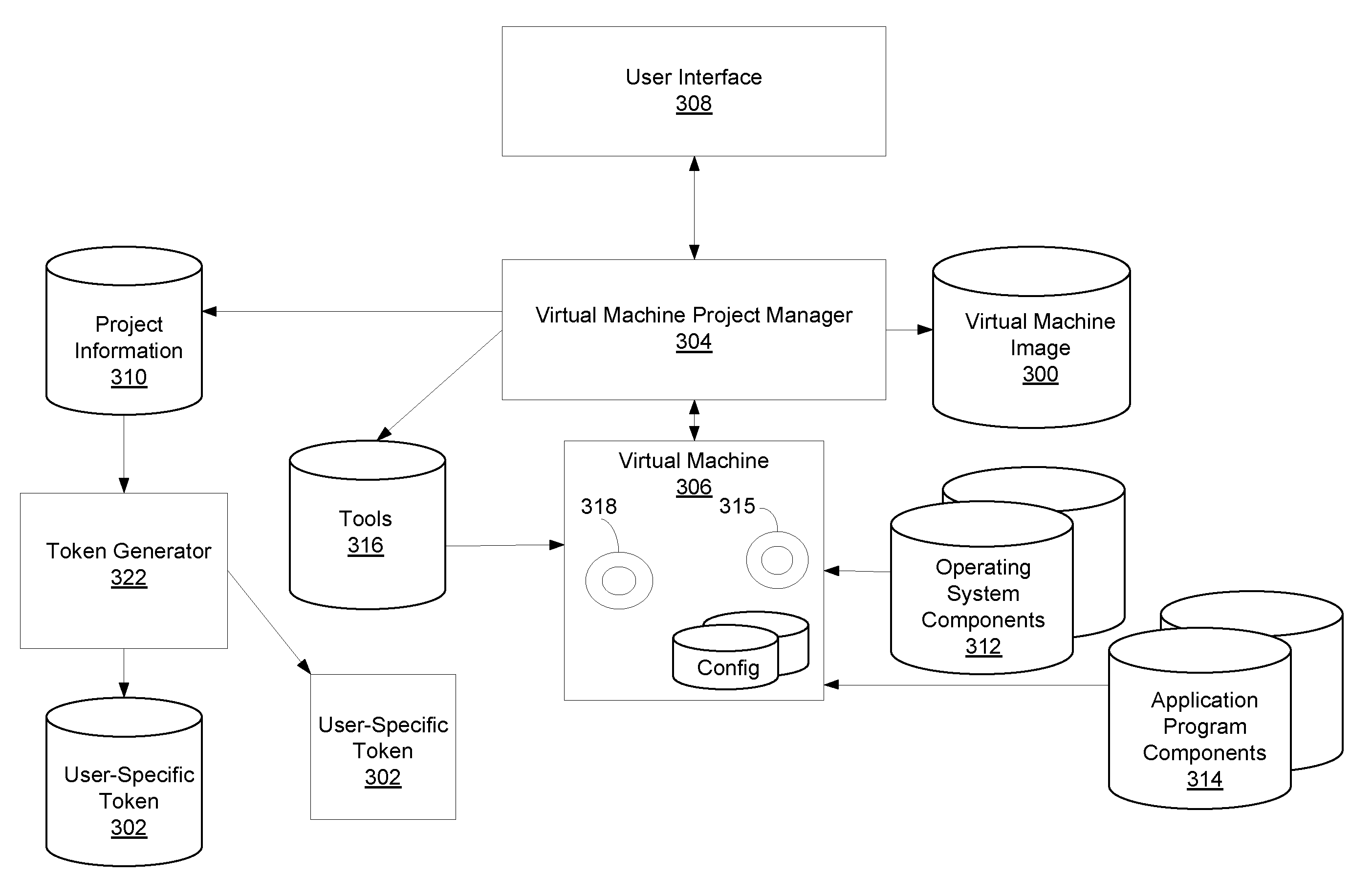
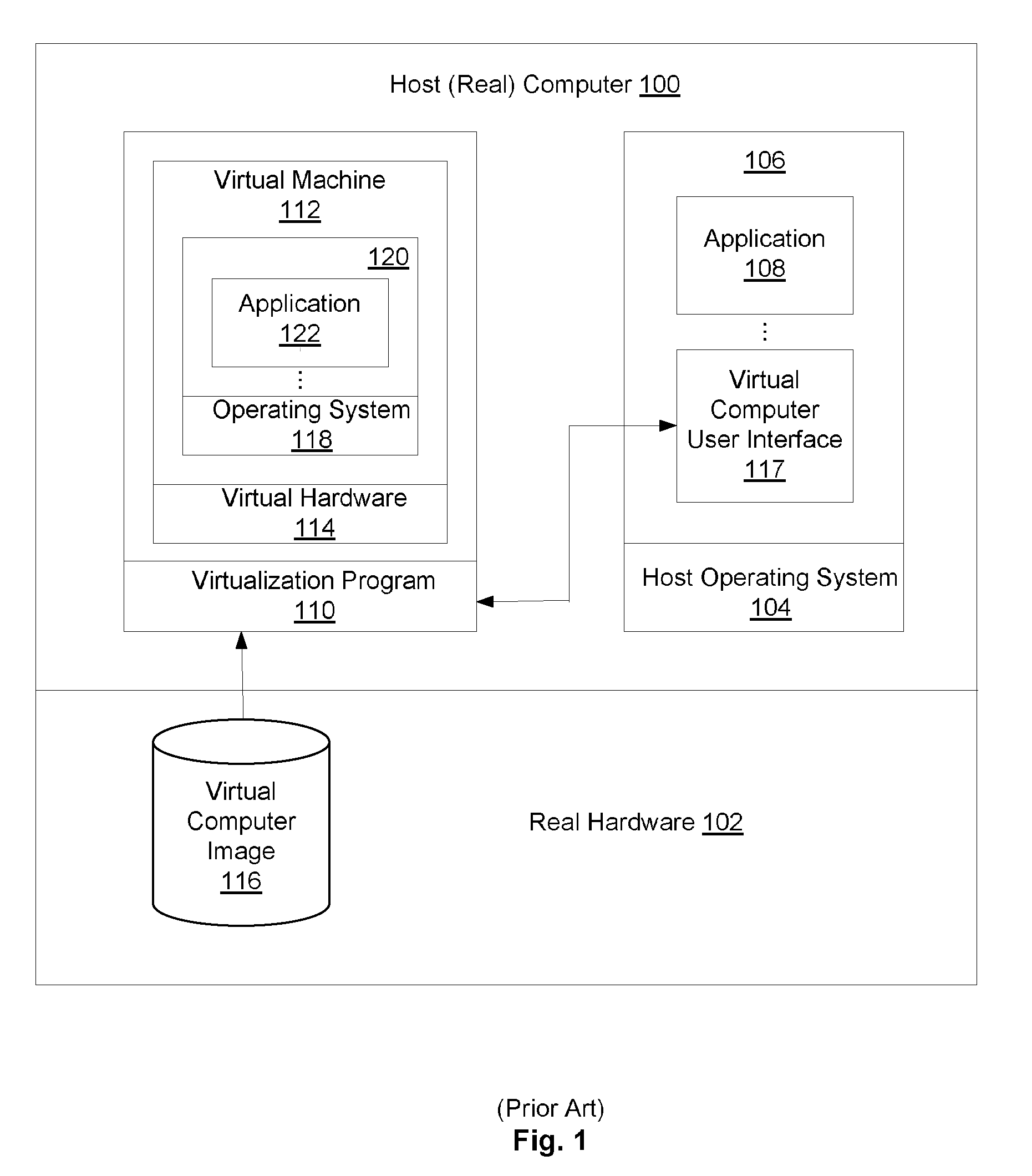
Remote Network Access Via Virtual Machine
ActiveUS20070300220A1User identity/authority verificationMultiple digital computer combinationsPrivate networkSoftware engineering
A virtual machine project manager creates a generic, i.e., not user-specific, virtual machine image file. Copies of this image file may be distributed to one or more users, each of whom may then use an automated procedure to generate a user-specific virtual machine image file and, thus, a user-specific virtual machine on his / her remote host computer. The generic virtual machine image file may be distributed on computer-readable media, such as a DVD disks, or the file may be stored on a server and downloaded (such as via the Internet) by the users. Each user also receives or downloads a token, which contains a small amount of user-specific information that is used by the automated procedure to provision the generic virtual machine image file for the particular user. A virtual machine accesses a security token connected to a host computer to automatically authenticate or re-authenticate a user, such as when a virtual private network connection is restarted. Substantially identical session identifiers are used by a host computer and a virtual machine, or by two or more virtual machines and, when communicating with an integrated access server. A file server stores virtual machine images that are accessed by a plurality of host computers.
Owner:MICROSOFT TECH LICENSING LLC
Method and device for audience monitoring on multicast capable networks
InactiveUS20060294259A1Eliminates need of cooperationCost effectiveSpecial service provision for substationBroadcast-related systemsData packUser equipment
The presented idea is a cheap solution for audience monitoring in multicast capable networks e.g. Ethernet, IP or UMTS. There is no need for user equipment in order to monitor the viewers' watching behavior. The measurement is done in the operator's network; therefore, there is no need to contact the end user. The idea can be applied in systems comprising multicast capable network contention server, network devices and user equipment. The content is carried in data packets to the end user. The network devices are remote manageable. The user can choose between several contents. The aim is to measure the user statistics regarding the chosen content. According to the invention it is enough to place a measurement host with our proposed software block in the network, which collects data from the network devices in the edge of the network periodically in order to make a content access survey.
Owner:TELEFON AB LM ERICSSON (PUBL)
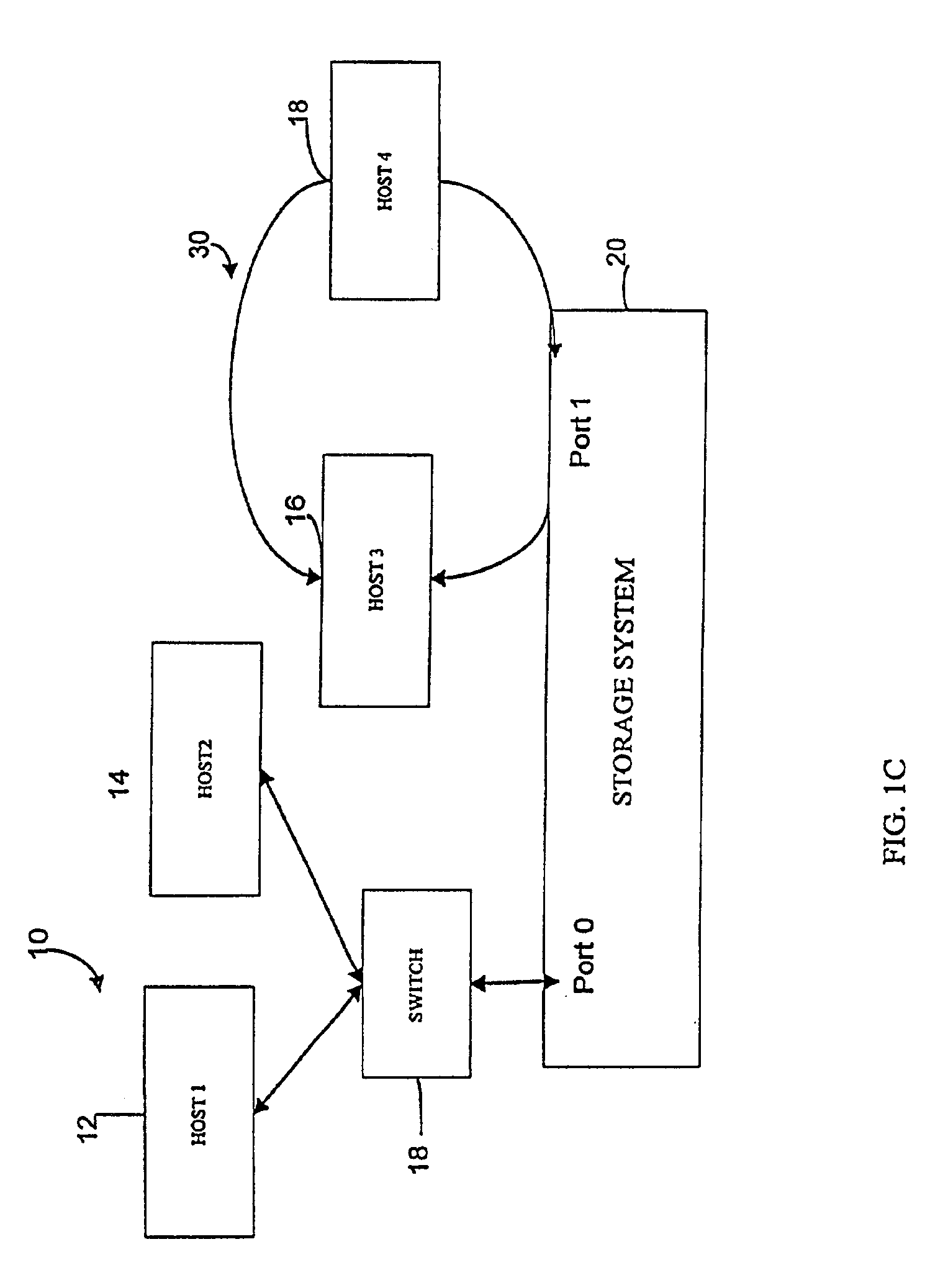
Method and apparatus for authenticating connections to a storage system coupled to a network
InactiveUS6263445B1Key distribution for secure communicationInput/output to record carriersData accessData management
A data management technique for managing accesses to data at a shared storage system includes a filter at the storage system. The filter is coupled to a configuration table, which identifies which of a number of coupled host processors have accesses to each of the resources at the device. During operation, requests received from the host devices are filtered by the filter, and only those requests to resources that the individual host devices have privilege to access are serviced. Advantageously, data security is further enhanced by authenticating each of the requests received by the storage system to verify that the host processor that is represented as forwarding the request is the indicated host processor. In addition, transfers of data between the storage system and the host processor may be validated to ensure that data was not corrupted during the data transfer.
Owner:EMC IP HLDG CO LLC
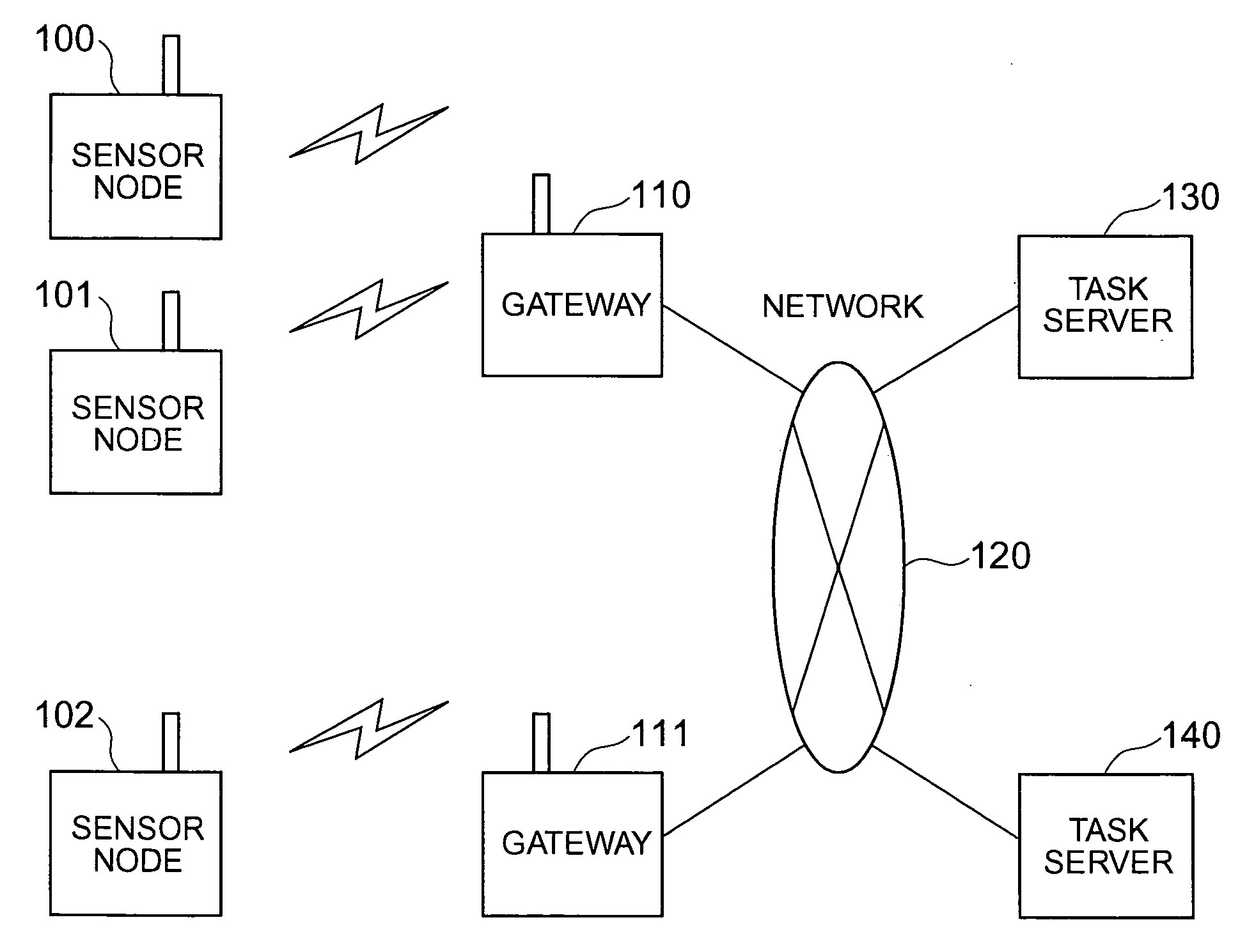
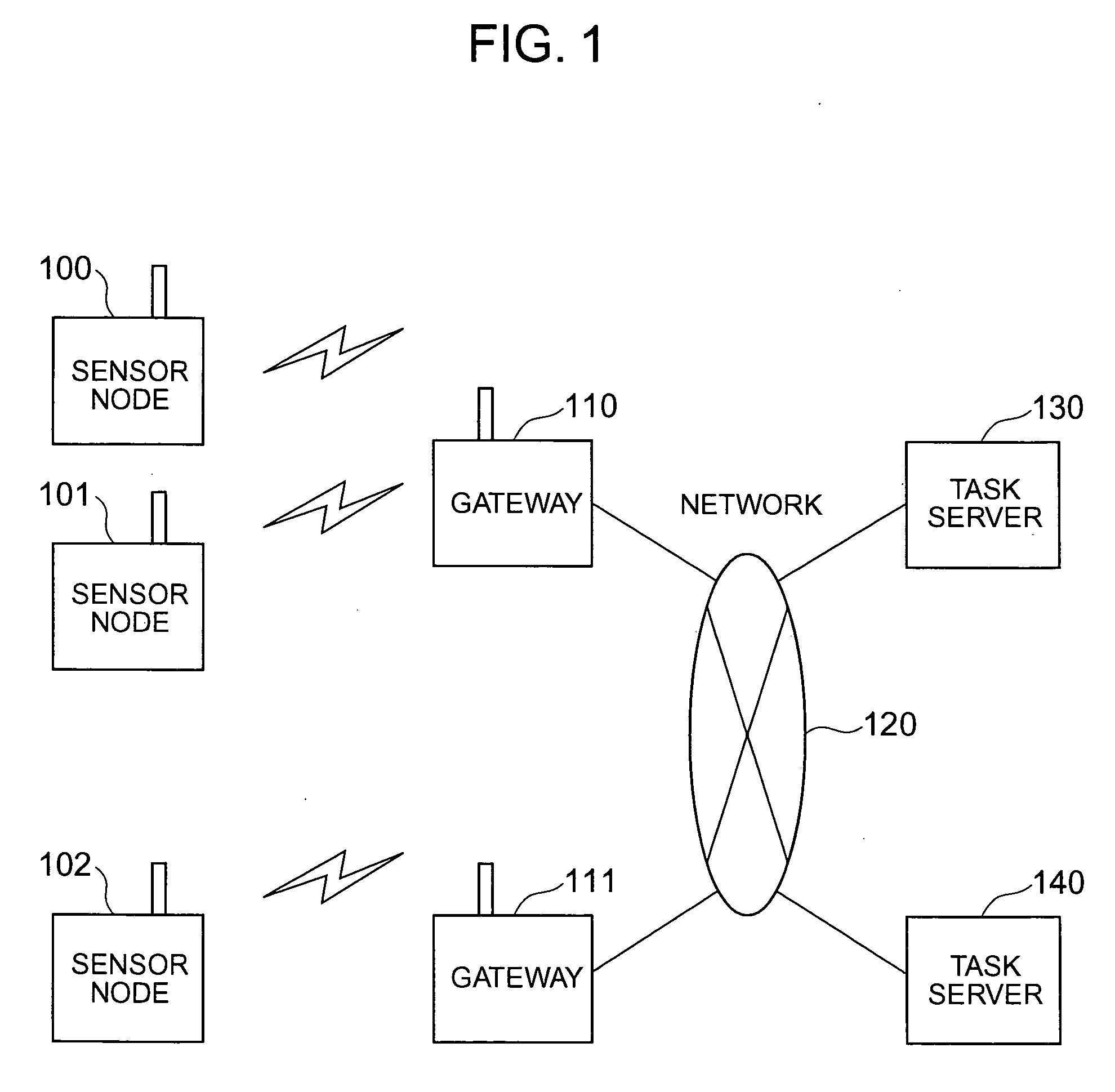
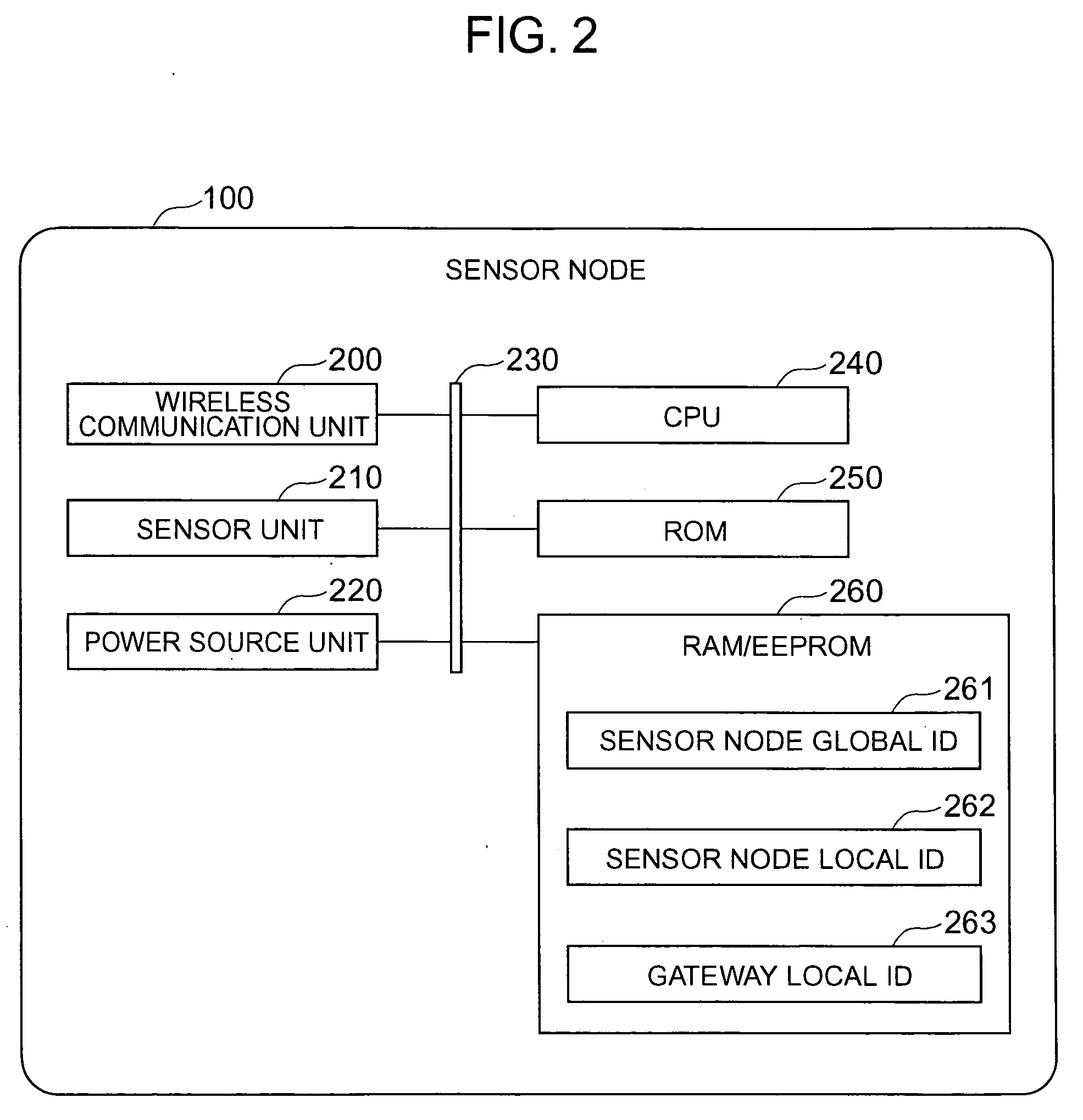
Sensor network management system
InactiveUS20060190458A1Easily lookIncrease freedomDigital data processing detailsActive radio relay systemsTrunkingNetwork management
An attribute value of a matter accompanied by a sensor is transmissibly accessible in a sensor node system constituted by wireless terminal computers having the sensor, the wireless communication base stations and server computers. The wireless terminal computer reports at the time of wireless communication an identification number of a wireless communication base station with which it communicates previously. A relay processing service is dynamically constituted so that when a wireless communication base station different from itself is reported, the wireless base station as the communication counter-part can transmissbly look up the wireless terminal computer from a host computer.
Owner:HITACHI LTD
End-to-end virtualization
InactiveUS20120099602A1Facilitates end-to-end virtualizationData switching by path configurationData virtualizationNetwork virtualization
One embodiment of the present invention provides a system that facilitates end-to-end virtualization. During operation, a network interface residing on an end host sets up a tunnel. The network interface then encapsulates a packet destined to a virtual machine based on a tunneling protocol. By establishing a tunnel that allows a source host to address a remote virtual machine, embodiments of the present invention facilitate end-to-end virtualization.
Owner:AVAGO TECH INT SALES PTE LTD
Communications network incorporating agent oriented computing environment
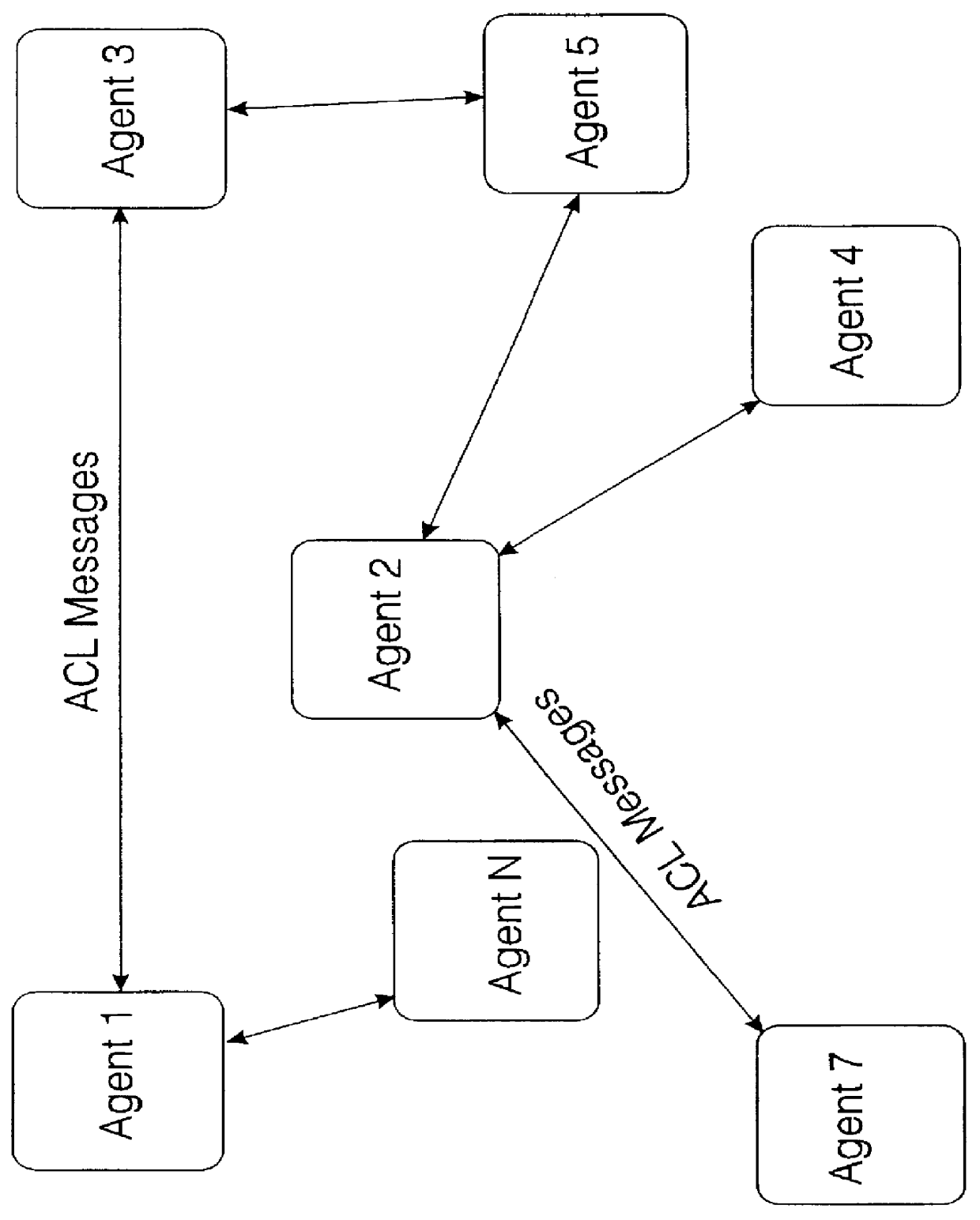
InactiveUS6049819AEfficiently identify each otherQuick functionResource allocationMultiple digital computer combinationsProxy serviceCommunication language
An agent oriented computing environment is disclosed comprising an "agent shell" means which can be used by developers for constructing agent computing entities according to their own functionality requirements; an agent enabling layer, providing basic communication, brokering, and negotiation facilities between agent computing entities; and an underlying transport mechanism based on a prior art CORBA platform. Agents communicate with each other using an agent communication language enabling them to interact to domain specific problems. Agents can pass information to each other in ACL messages describing their own vocabularies concerning logic (ontologies). Various services for locating and connecting agents are provided in the agent oriented environment, such as a broker service for locating and finding agents. A collection of agents may communicate with each other where the agents remain static, maintaining their physical locations on their corresponding host physical resource devices, or alternatively agents may be transported across a plurality of physical resources, through the CORBA platform. The environment supports encapsulation of legacy objects, databases, standard and proprietary protocols and interfaces.
Owner:RPX CLEARINGHOUSE
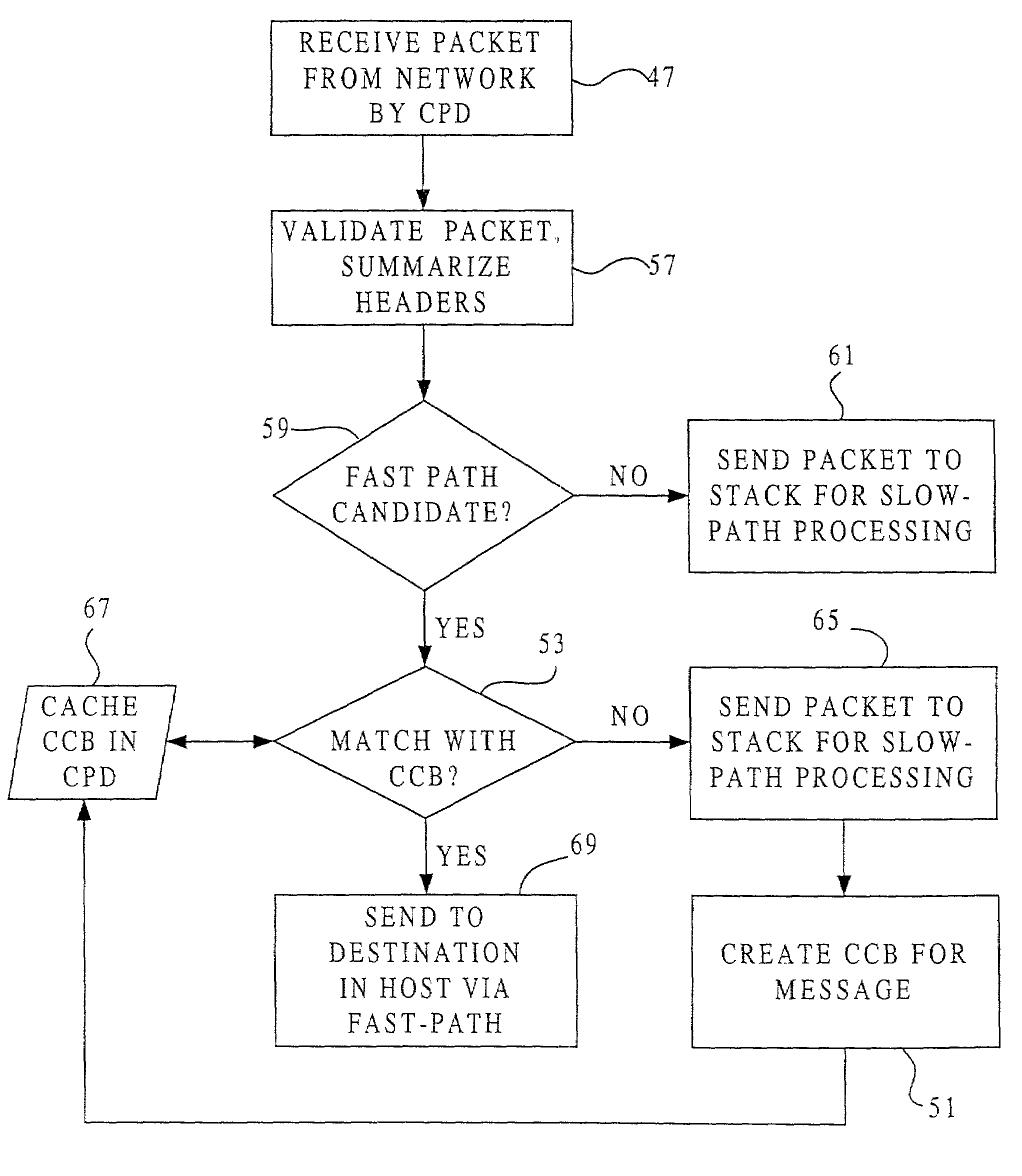
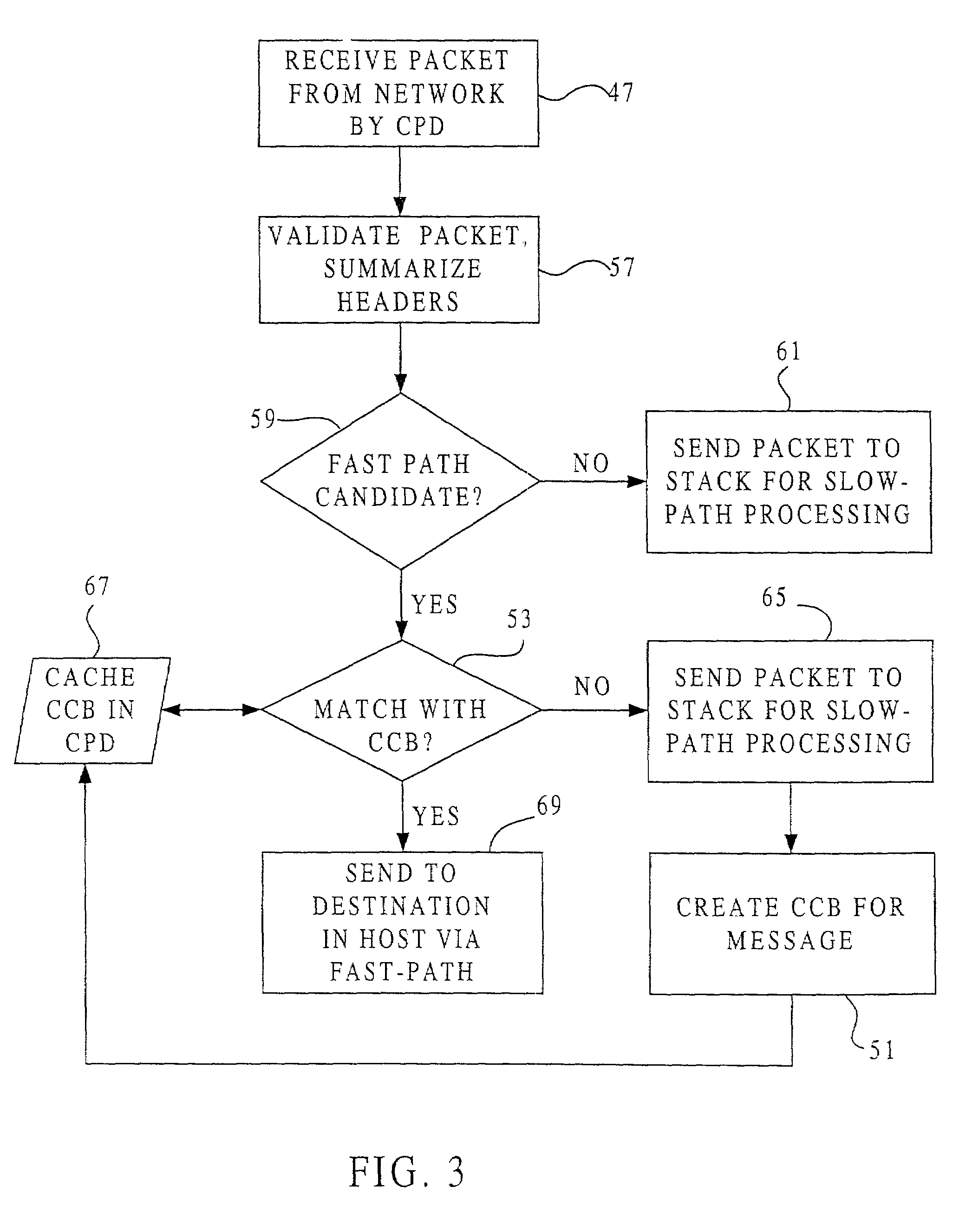
Fast-path processing for receiving data on TCP connection offload devices
ActiveUS7089326B2Negligibly effectMove quicklyMultiple digital computer combinationsData switching networksFast pathProtocol processing
A network interface device provides a fast-path that avoids most host TCP and IP protocol processing for most messages. The host retains a fallback slow-path processing capability. In one embodiment, generation of a response to a TCP / IP packet received onto the network interface device is accelerated by determining the TCP and IP source and destination information from the incoming packet, retrieving an appropriate template header, using a finite state machine to fill in the TCP and IP fields in the template header without sequential TCP and IP protocol processing, combining the filled-in template header with a data payload to form a packet, and then outputting the packet from the network interface device by pushing a pointer to the packet onto a transmit queue. A transmit sequencer retrieves the pointer from the transmit queue and causes the corresponding packet to be output from the network interface device.
Owner:ALACRITECH
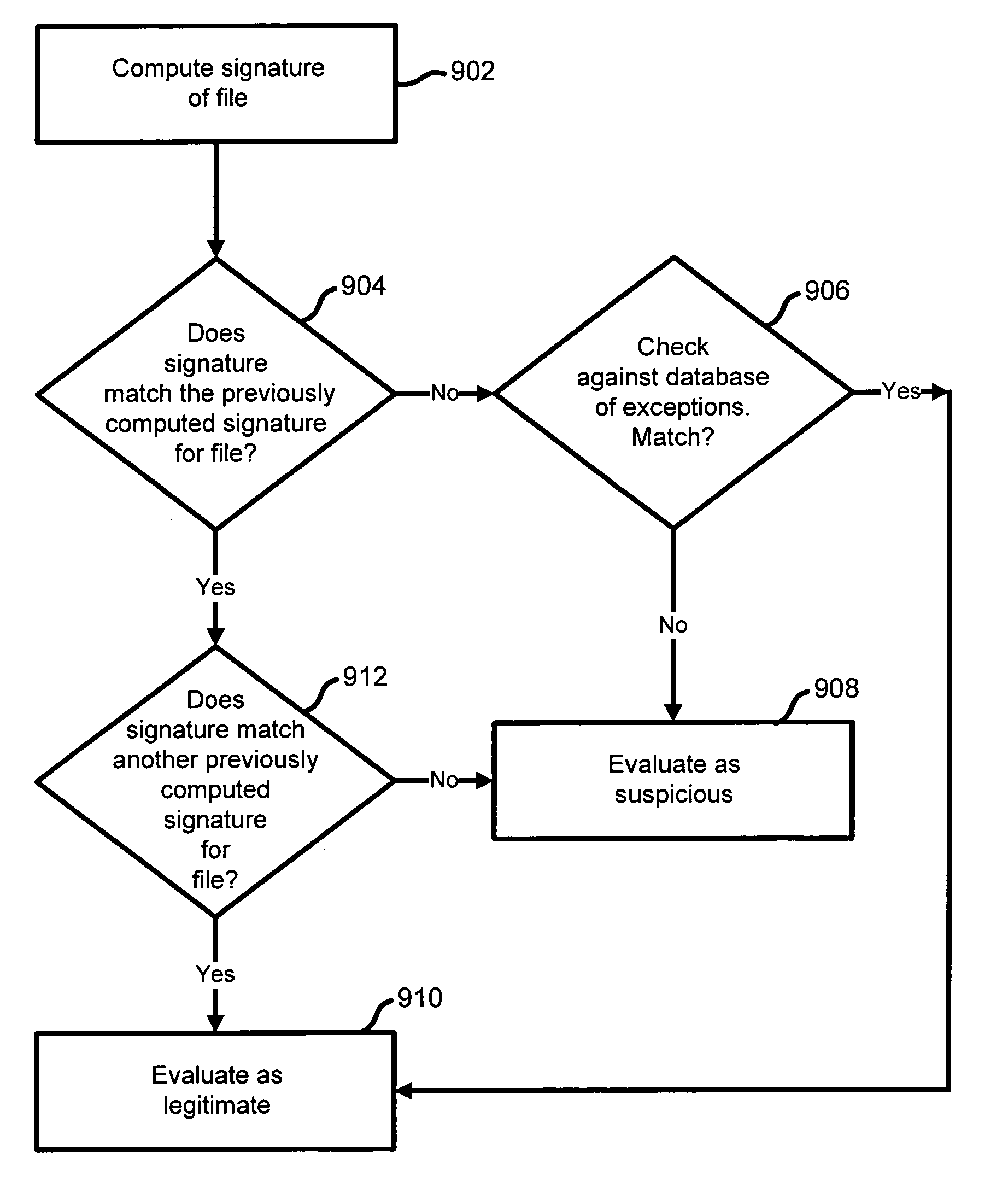
System and method for using signatures to detect computer intrusions
InactiveUS7032114B1Problem can be overcomeEnabling detectionMemory loss protectionUser identity/authority verificationIntrusion detection systemContinuation
A system and method are disclosed for detecting intrusions in a host system on a network. The intrusion detection system comprises an analysis engine configured to use continuations and apply forward- and backward-chaining using rules. Also provided are sensors, which communicate with the analysis engine using a meta-protocol in which the data packet comprises a 4-tuple. A configuration discovery mechanism locates host system files and communicates the locations to the analysis engine. A file processing mechanism matches contents of a deleted file to a directory or filename, and a directory processing mechanism extracts deallocated directory entries from a directory, creating a partial ordering of the entries. A signature checking mechanism computes the signature of a file and compares it to previously computed signatures. A buffer overflow attack detector compares access times of commands and their associated files. The intrusion detection system further includes a mechanism for checking timestamps to identify and analyze forward and backward time steps in a log file.
Owner:SYMANTEC CORP
Instant messaging account system
InactiveUS7200634B2Multiple digital computer combinationsData switching networksThe InternetUnique identifier
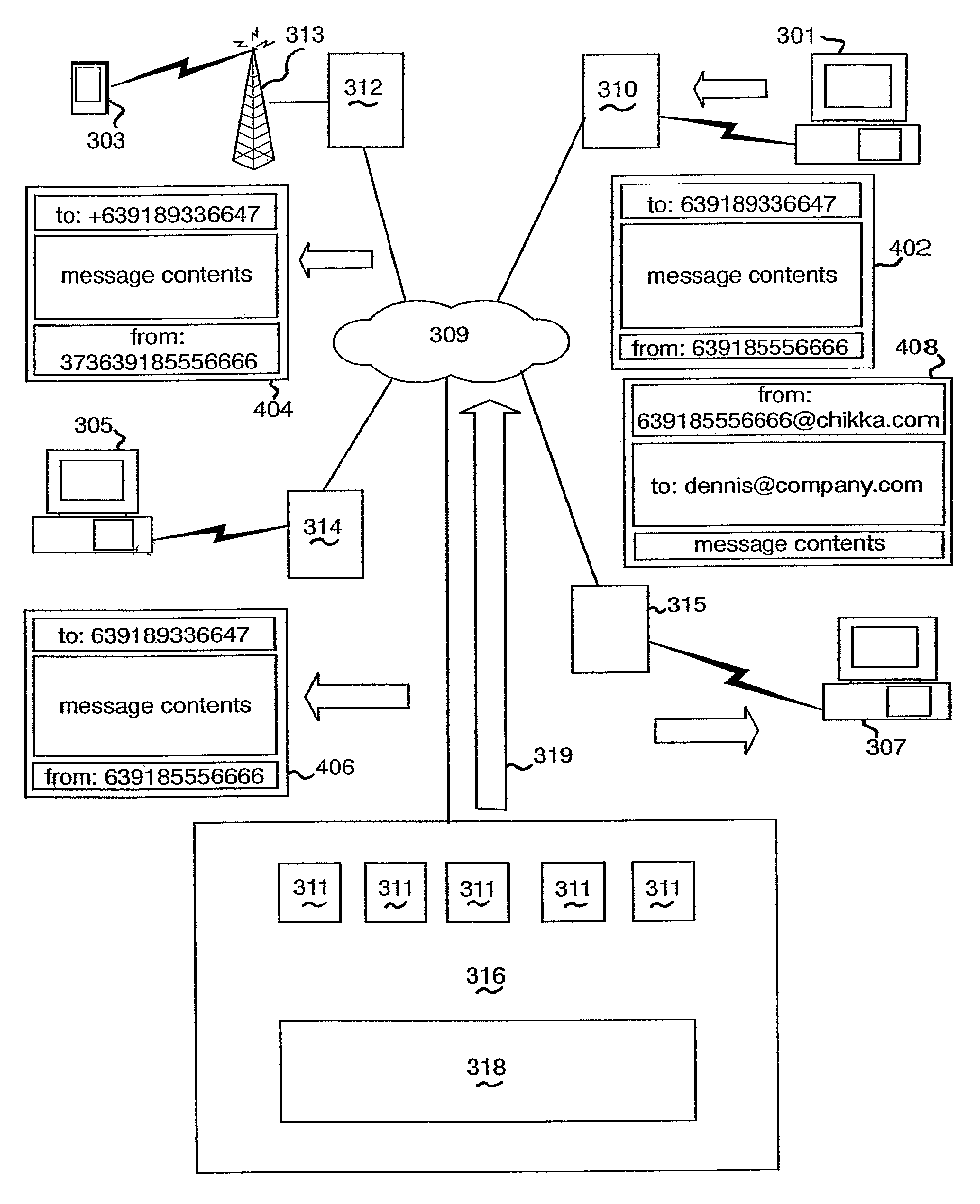
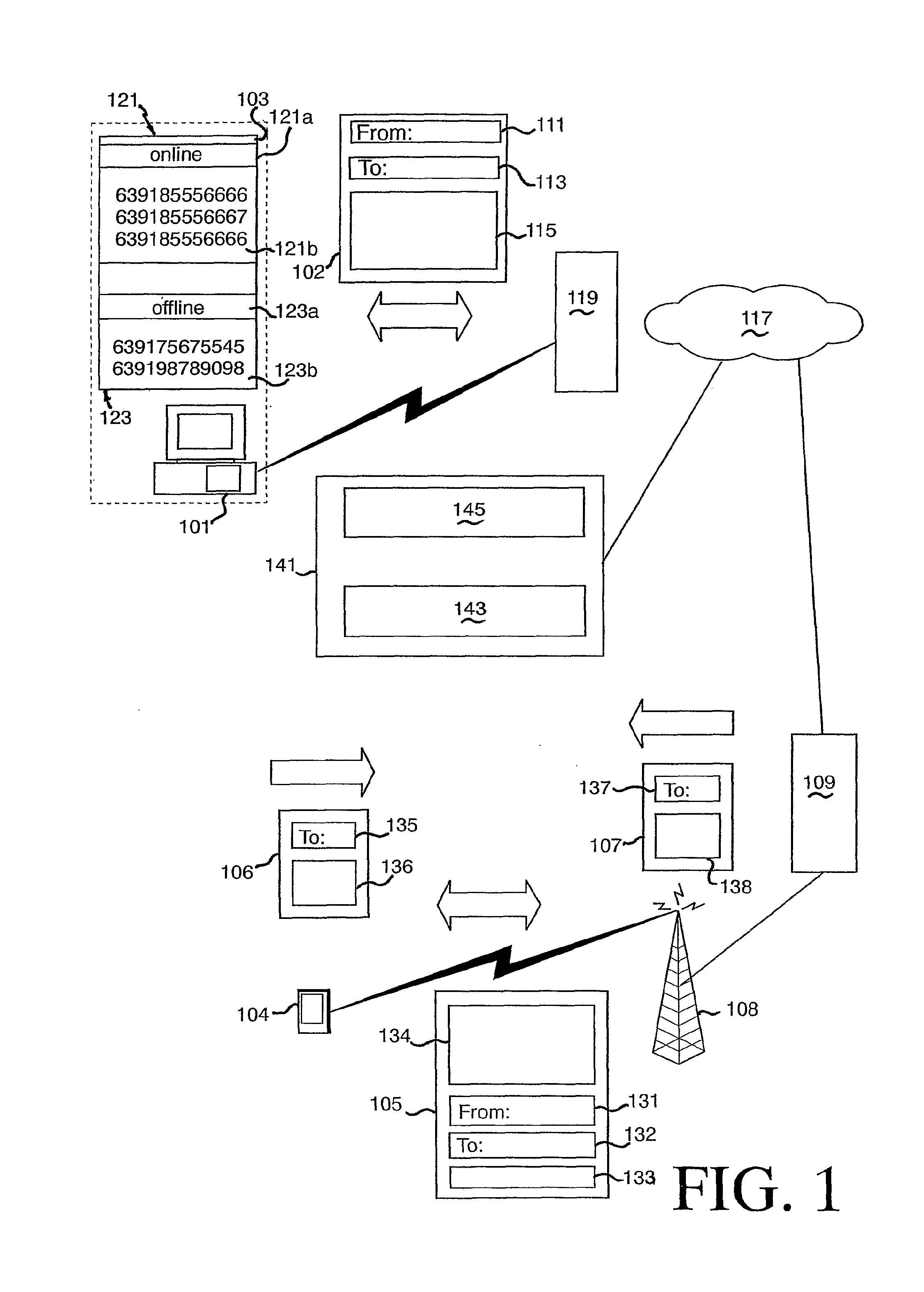
An instant messaging system and a method of instant messaging between a plurality of clients having IM applications of the same or different types. The IM system includes a plurality of clients having IM client applications of the following types: a PC-based instant messaging client application program (101, 301); a GSM device (104, 303) forming part of a GSM network; an internet browser-based client application 201, 305; and an email-based client application (208, 307). An IM system host (141, 211, 316) including an IM server (143, 217, 311) is selectively connected to each of the clients via the direct electronic links or the internet (117, 213, 309) and provides a prescribed range of functionality to the clients. This functionality includes sending an IM, receiving an IM and identifying which members of a group of clients that a client is a member, or prospective member, of are online. Each client type has a unique identifier to enable access thereto via the internet (117, 213, 309) and each client has a single account on the IM host / server for all of its client types that can access the IM server (143, 217, 311). The account is identified by a unique identification number (“UIN”) common to all of the client types of that client and each unique identifier of each client type of a client is matched to the UIN of the particular client.
Owner:CHIKKA COM
Usage statistics collection for a cable data delivery system
InactiveUS6308328B1Broadband local area networksBroadcast transmission systemsData connectionNetwork management
Apparatus for recording and collecting usage and other statistical data from components of a cable data network comprises a network manager for maintaining and collecting the statistics. Internet protocol addresses are associated with components of the network. The component maintains a software agent that manages a statistics database. Responsive to a manager request generated at a service provider defined time interval, the component software agent provides the usage statistics to the network manager in real-time during an Internet session with a host. When the host to Internet or other data connection is torn down due to failure, disconnect or inactivity time-out, remaining usage statistics data is collected and the session duration updated with the time of tear down. Usage statistics collected include the amount of data transferred to / from a host, the amount of data that is discarded due to insufficient resource capacity and amount of data that cannot be corrected despite forward error correction used in a downstream high capacity channel to the host. Data traps may be defined and downloaded to components of the network for implementation. As a result, billing of users of the cable data network can be usage sensitive and determined based on actual data transferred (including credit given for errored data) and / or time sensitive based on session duration.
Owner:CISCO TECH INC
Methods, systems, and products for intrusion detection
InactiveUS7971053B2Reduce rogue accessReduce intrusionMemory loss protectionError detection/correctionComputer networkComputerized system
Methods, systems, and products are disclosed for detecting an intrusion to a communications network. One embodiment describes a system for detecting intrusions. The system has a peripheral card coupled to a host computer system. The peripheral card has a communications portion and a processor managing the communications portion. The communications portion has only a capability for receiving data packets via a communications network. The communications portion lacks capability of transmitting the data packets via the communications network. The communications portion of the peripheral card reduces intrusion of the communications network.
Owner:BELLSOUTH INTPROP COR
Cardiac rhythm management device and sensor-suite for the optimal control of ultrafiltration and renal replacement therapies
ActiveUS20070175827A1ElectrotherapyMechanical/radiation/invasive therapiesUltrafiltrationOptimal control
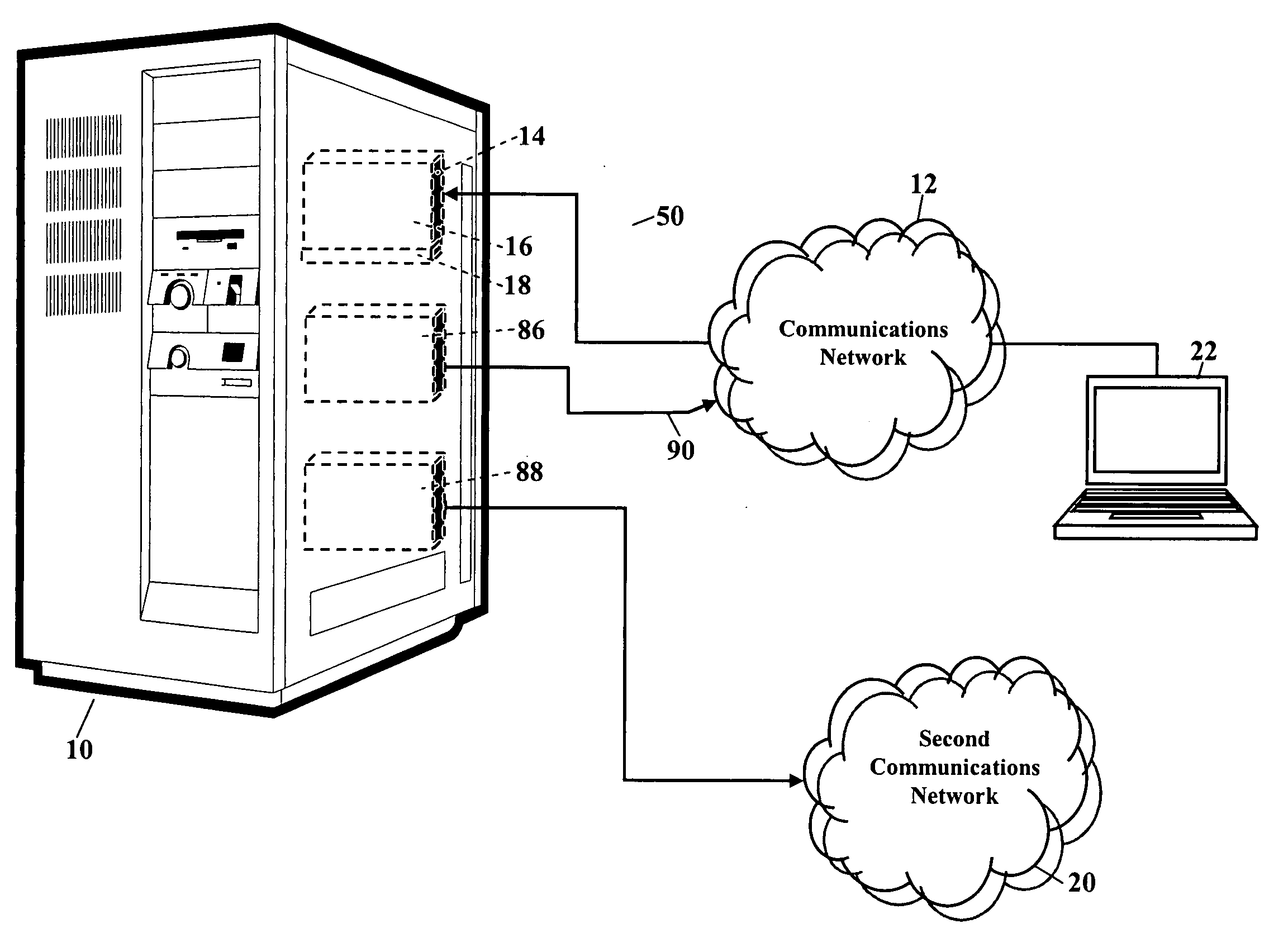
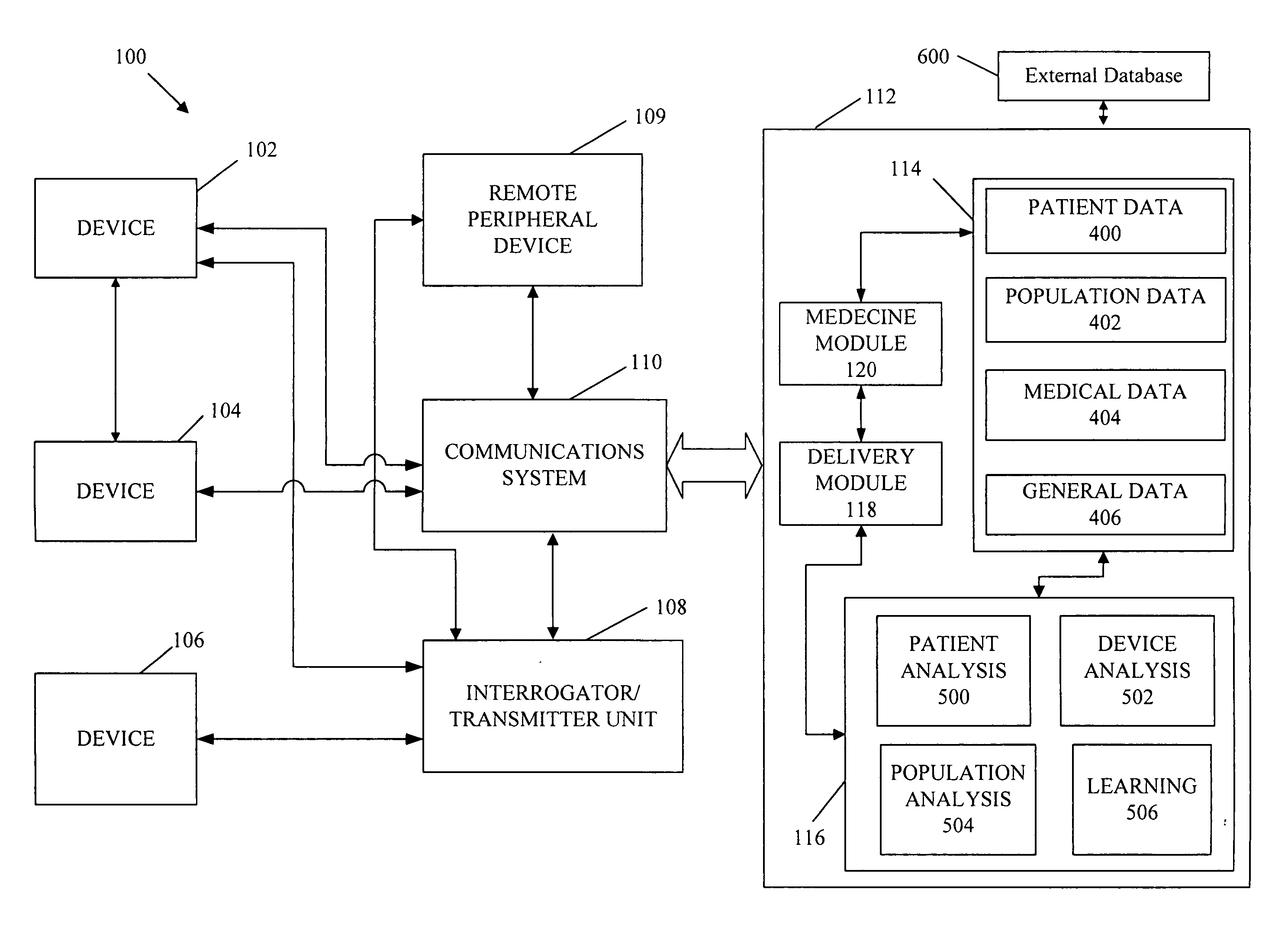
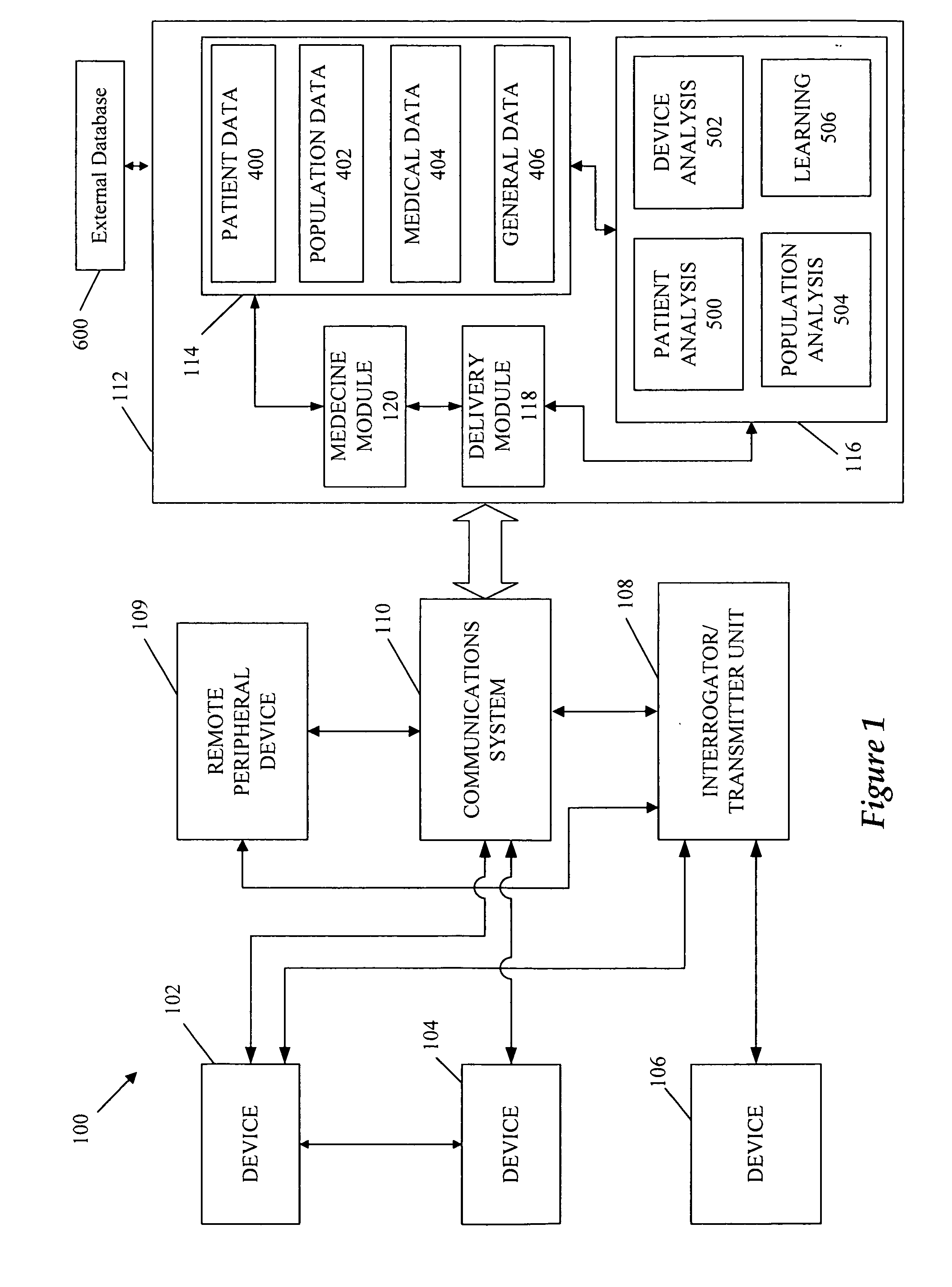
A cardiorenal patient monitoring system comprising, either implanted or non-implanted device(s), remote peripheral device(s), computer network(s), host, and communication means between the device(s), computer network(s), and host. The preferred embodiment shows an advanced patient monitoring system for using an implanted cardiac device and a dialysis machine in renal therapy. In addition, the method of advanced patient monitoring is in conjunction with the advanced patient monitoring system is disclosed.
Owner:CARDIAC PACEMAKERS INC
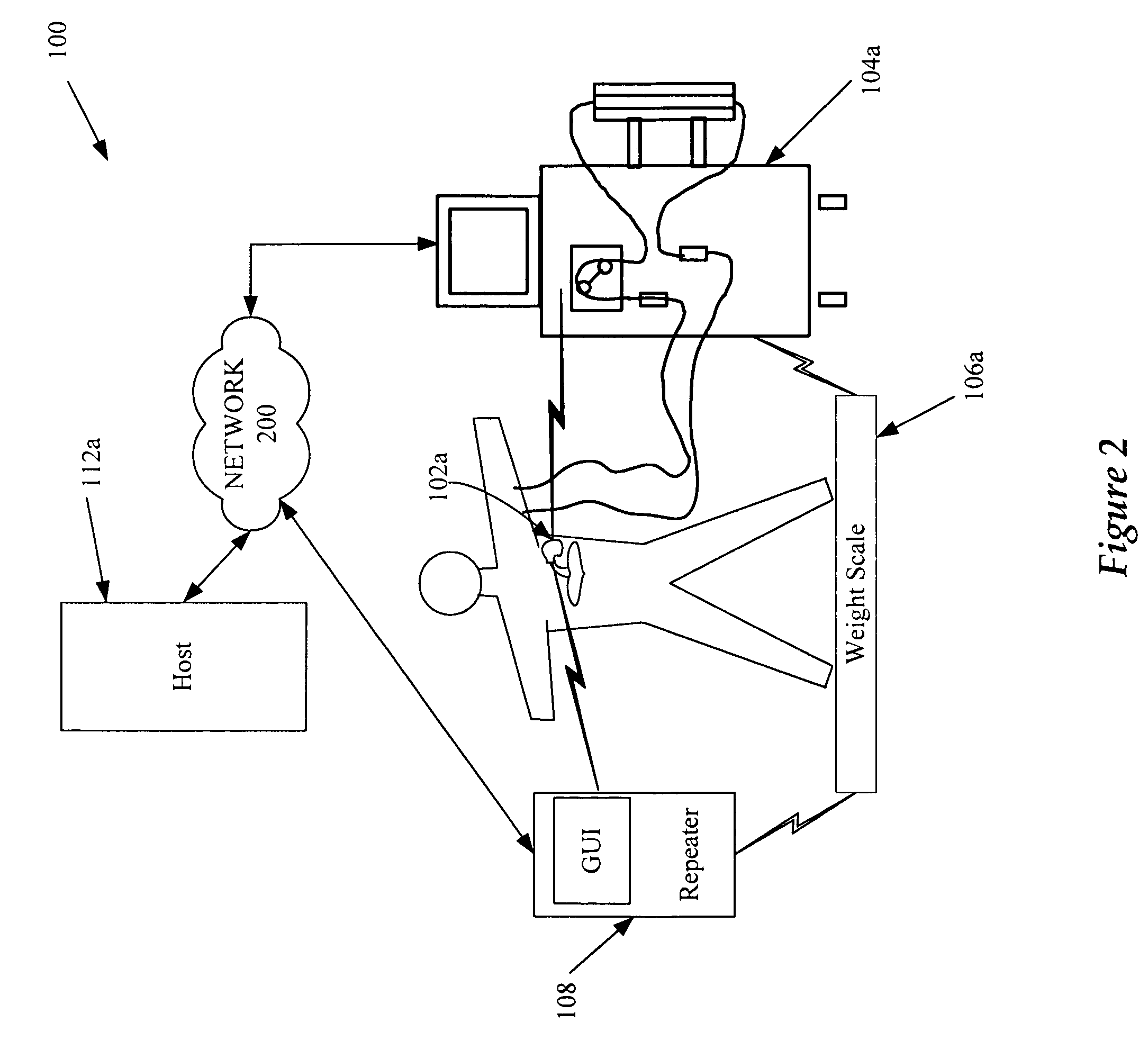
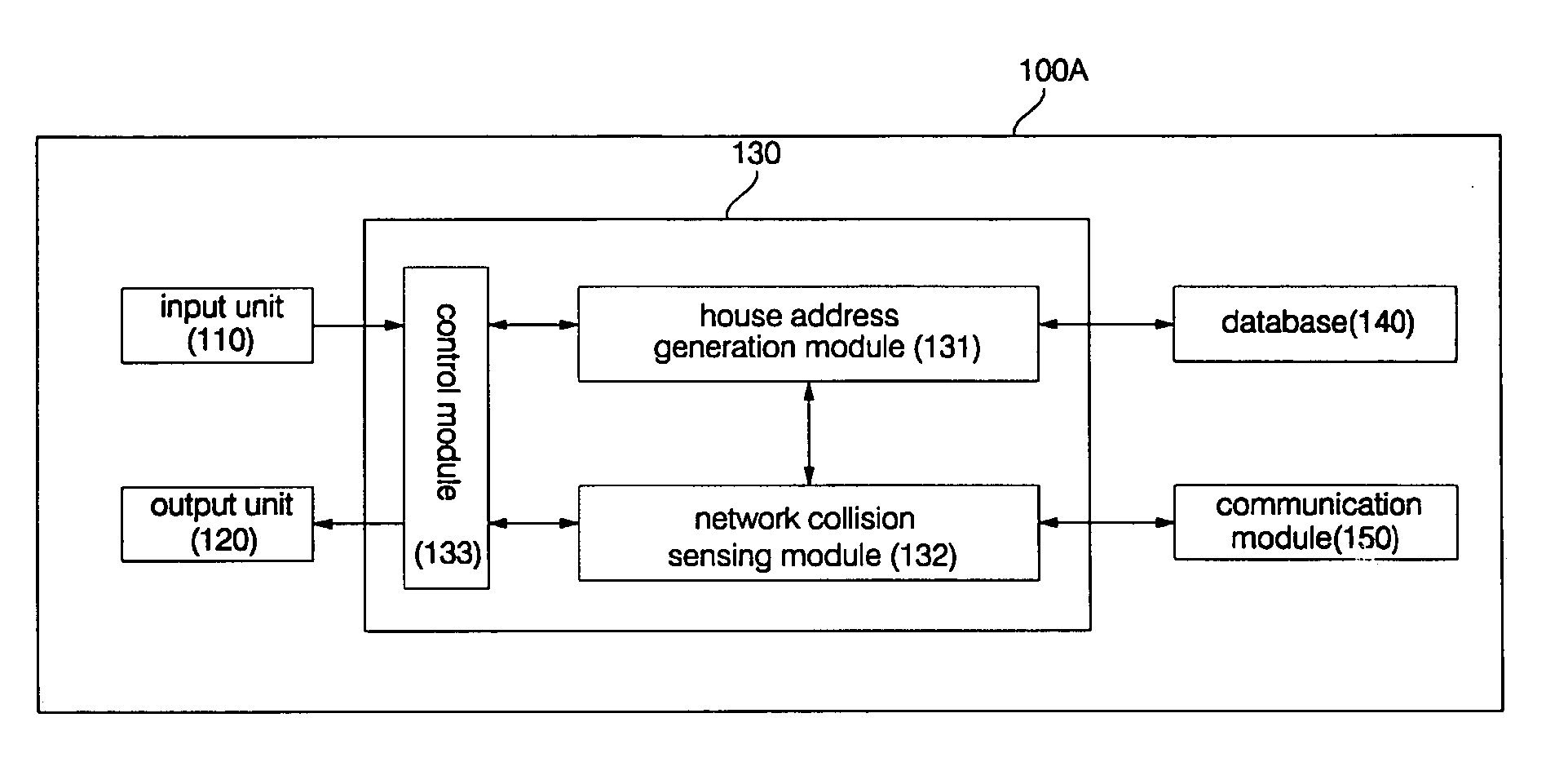
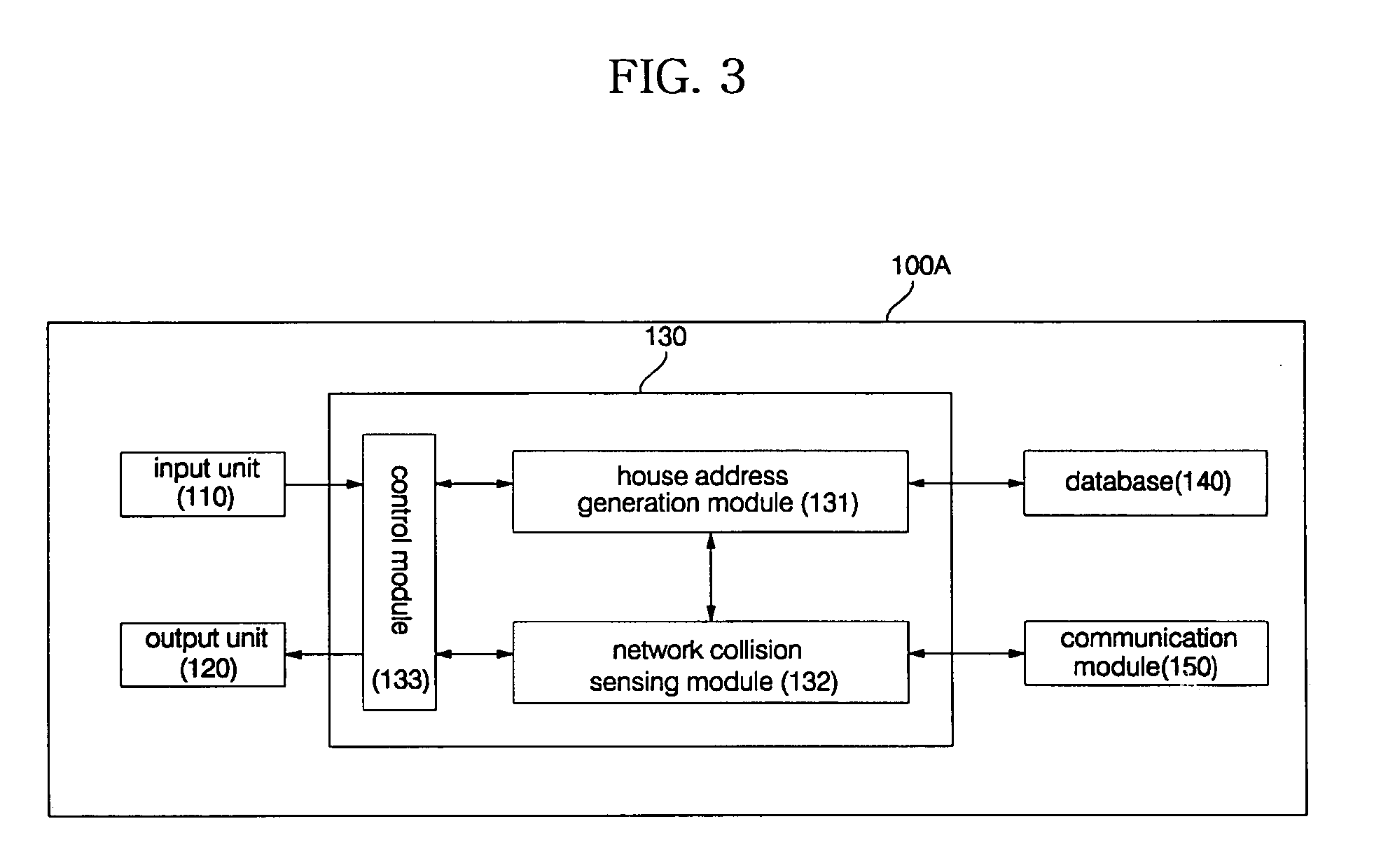
Home appliance network system and method for operating the same
InactiveUS20050002408A1Blocking in networkImprove ease of useInterconnection arrangementsPower distribution line transmissionEngineeringHome appliance
A home appliance network system and a method for operating the same, wherein a network master can not only automatically generate a unique house address of a corresponding home, but also sense a network collision of the corresponding home with a neighboring home to maintain house address uniqueness. The network master manages / controls one or more home appliances connected to a network of the corresponding home and determines whether the generated house address collides with that of the neighboring home. If the generated house address is determined to collide with that of the neighboring home, the network master automatically changes the house address to a new one to maintain house address uniqueness. As a result, the network master can prevent a network interference / collision with the neighboring home, thereby increasing security and stability of the home appliance network system at low cost.
Owner:LG ELECTRONICS INC
Method and apparatus for managing hardware address resolution
InactiveUS20070248085A1Data switching by path configurationAddress Resolution ProtocolAddress resolution
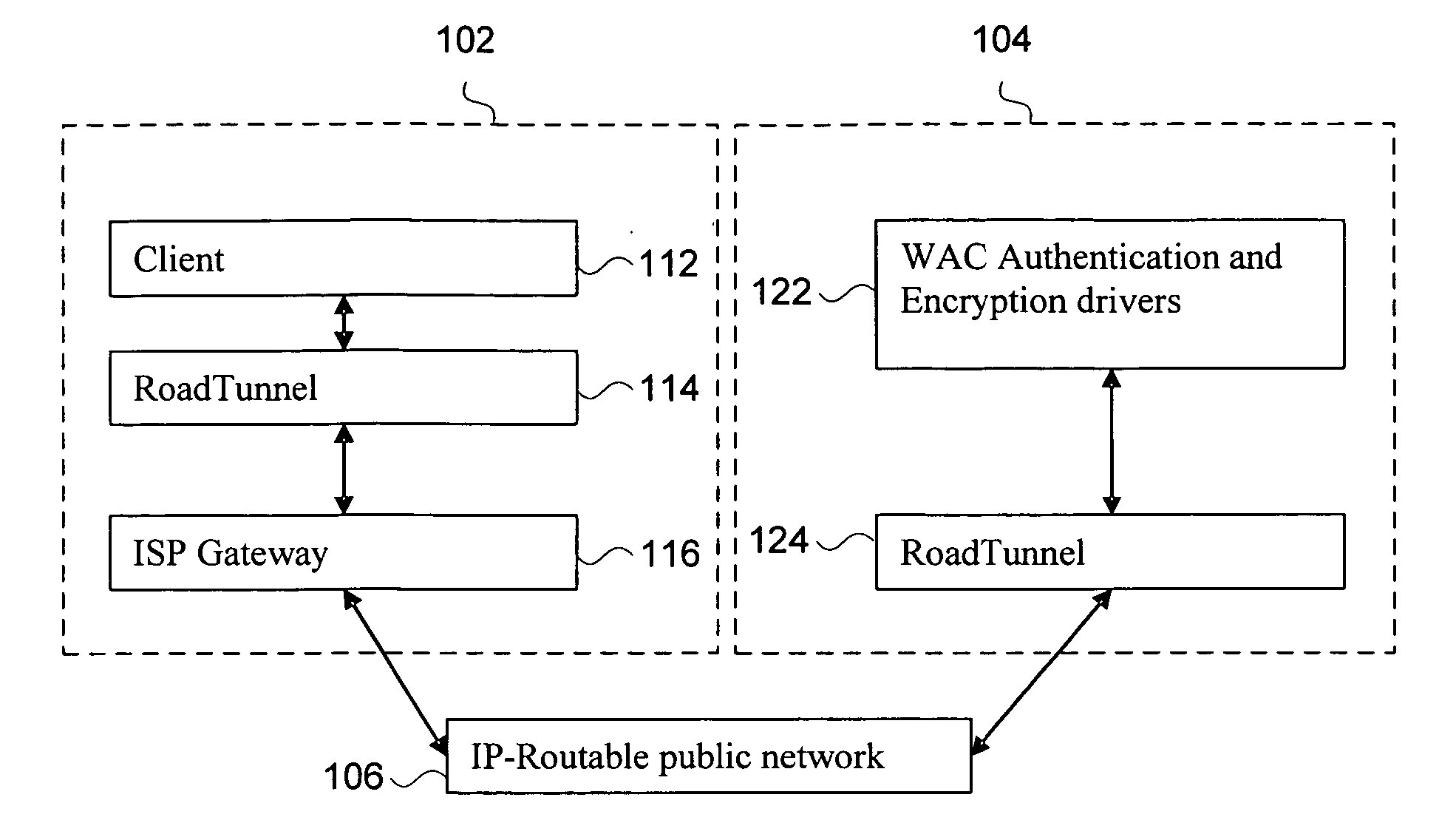
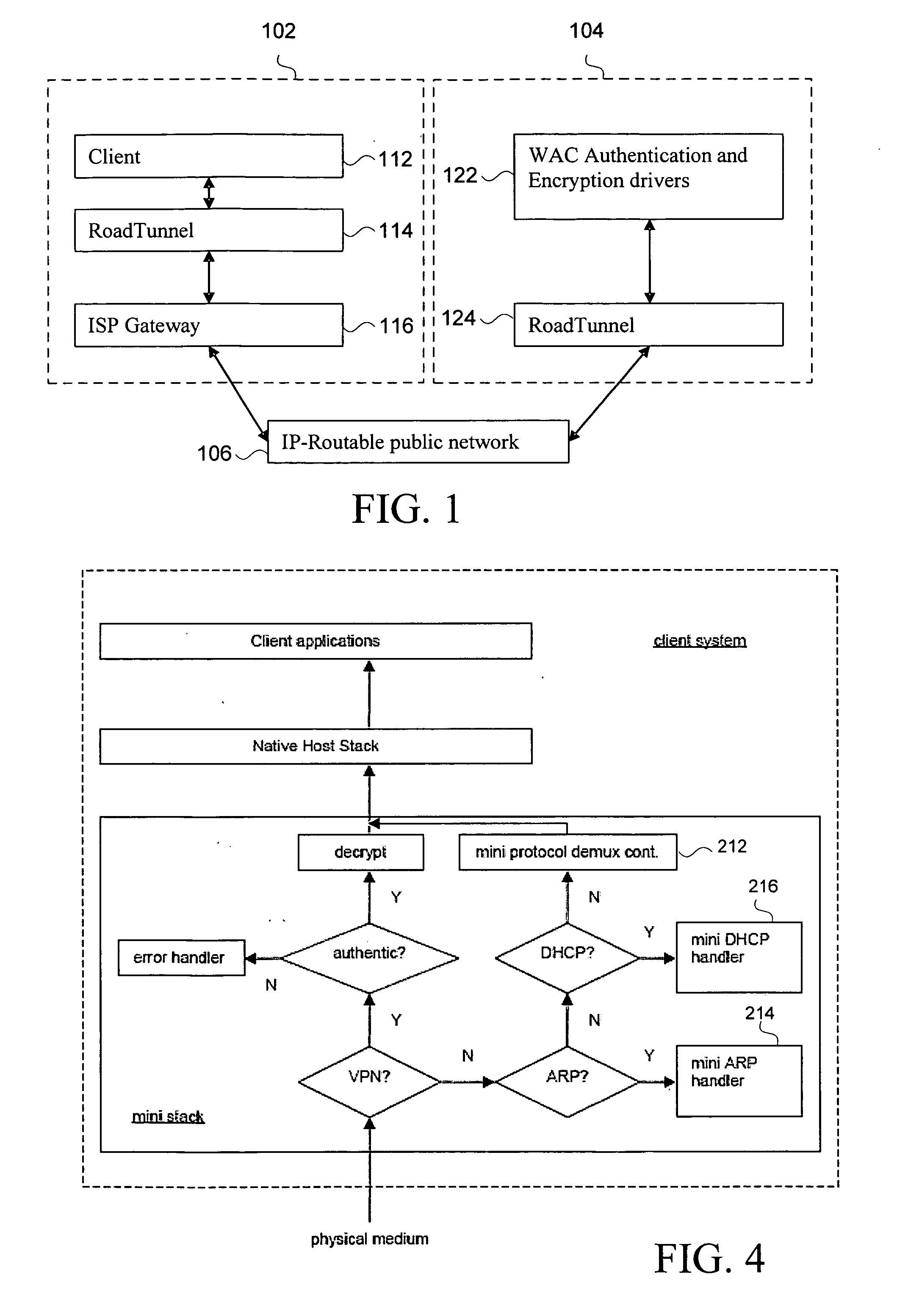
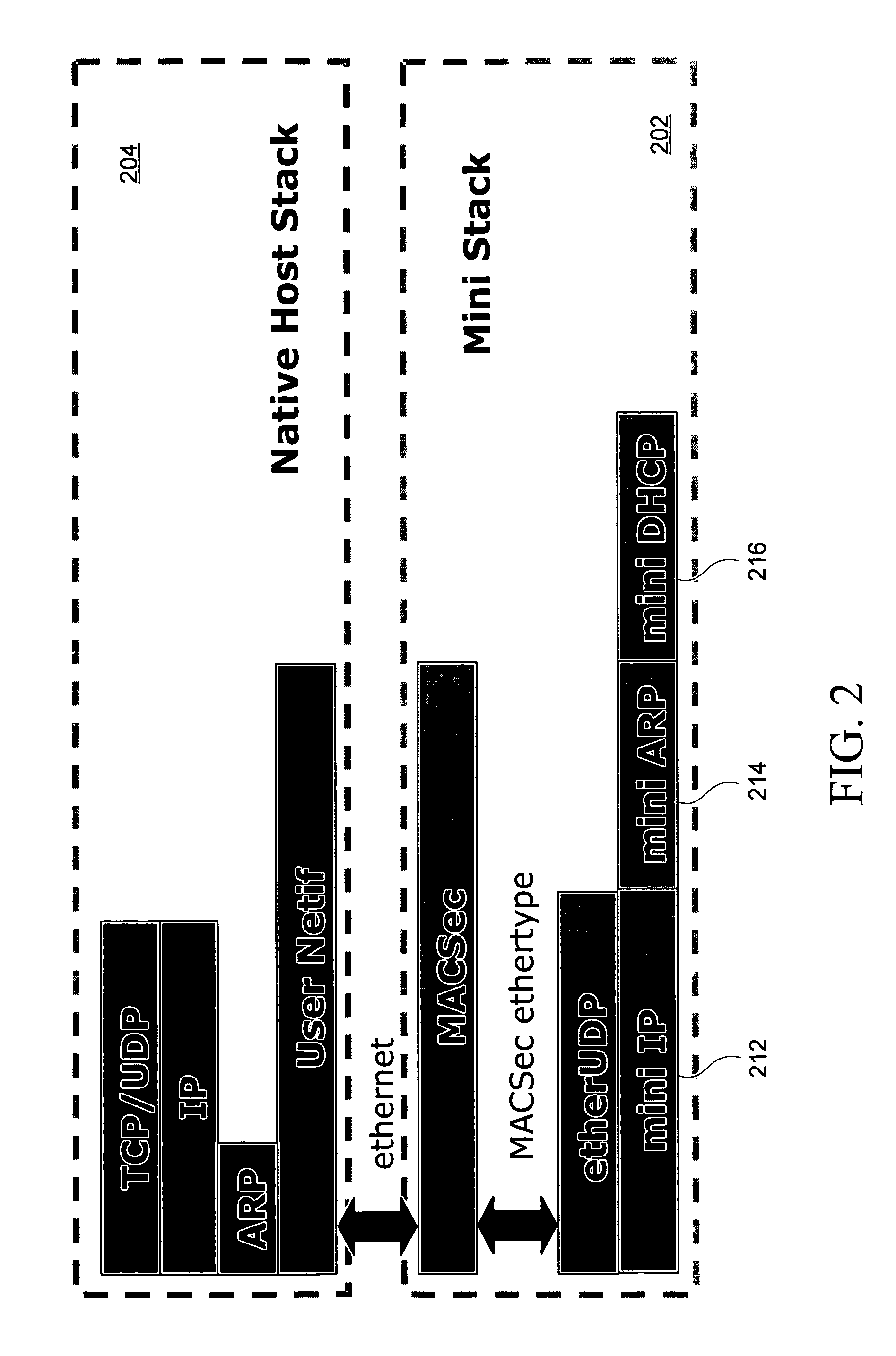
Disclosed herein is a network device, such as a host computer, that simultaneously has two IP identities: a local IP identity on a local network (e.g., a non-virtual private network) to which the host computer is connected; and a remote IP identity on a second network (e.g., virtual private network) that is remote to the host. Only the remote IP identity is visible to the host operating system's network stack. Each IP identity has its own ARP cache and Address Resolution Protocol (ARP). The local ARP cache is managed with respect to a connection of the host to a local subnet (e.g., an Internet Service Provider (ISP) subnet) and the remote ARP cache is managed with respect to a remote subnet reachable through a gateway on the local subnet.
Owner:E COLT SYST INC
Method, system, and program for managing memory for data transmission through a network
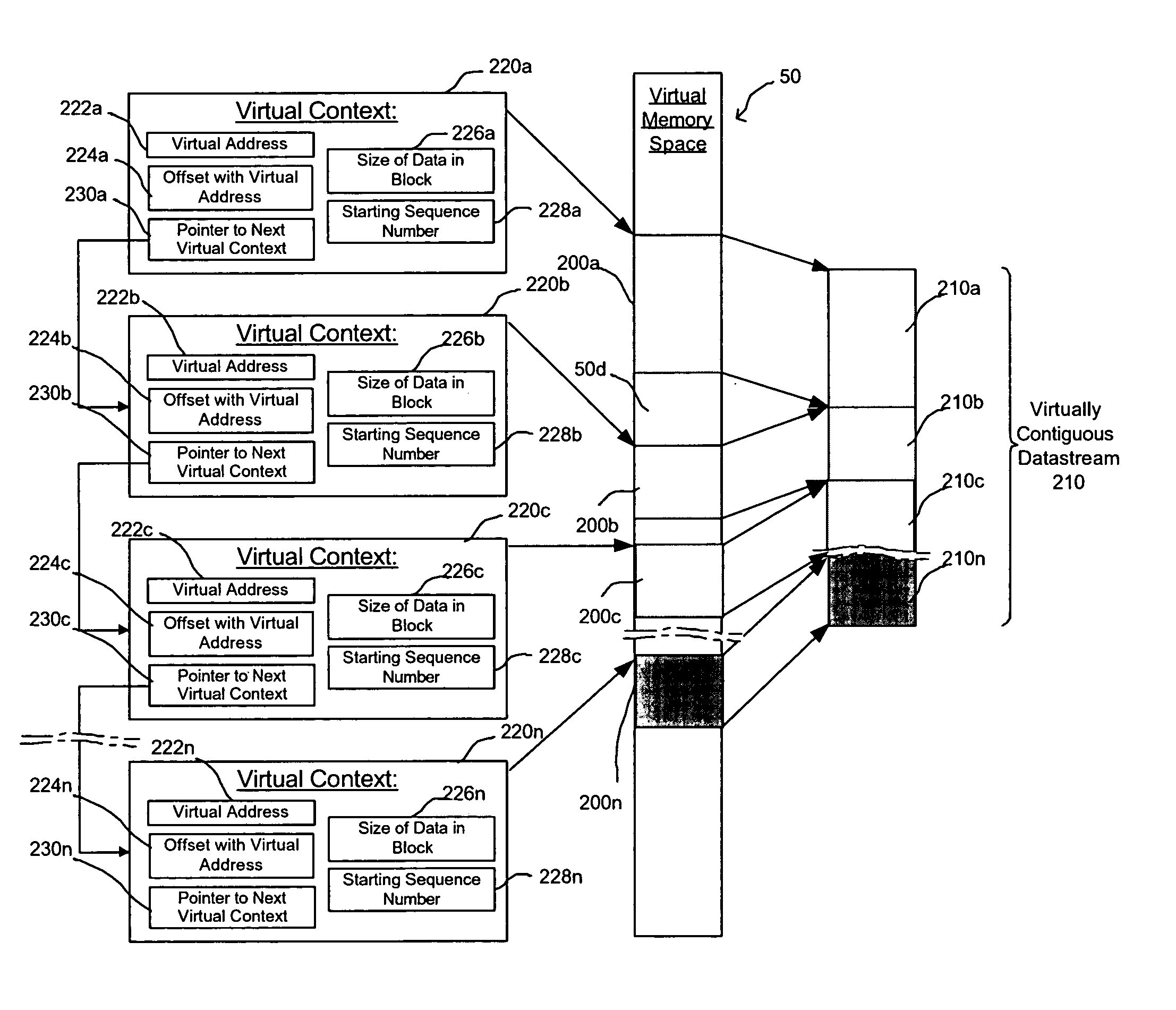
InactiveUS20050080928A1Memory adressing/allocation/relocationMultiple digital computer combinationsVirtual memoryData transmission
Provided are a method, system, and program for managing memory for data transmission through a network. Virtual memory addresses of the data to be sent are provided to a sending agent. The sending agent provides to a host the virtual addresses of requested data. In response, the requested data addressed by the virtual addresses or the physical memory locations of the requested data are provided to the sending agent for sending to a destination.
Owner:INTEL CORP
Multiple levels of logical routers
Some embodiments provide a managed network for implementing a logical network for a tenant. The managed network includes a first set of host machines and a second set of host machines. The first set of host machines is for hosting virtual machines (VMs) for the logical network. Each of the first set of host machines operates a managed forwarding element that implements a first logical router for the tenant logical network and a second logical router to which the first logical router connects. The implementation of the second logical router is for processing packets entering and exiting the tenant logical network. The second set of host machines is for hosting L3 gateways for the second logical router. The L3 gateways connect the tenant logical network to at least one external network.
Owner:NICIRA
Network access control system and method for devices connecting to network using remote access control methods
ActiveUS20090307753A1Digital data processing detailsMultiple digital computer combinationsControl systemUser authentication
A system and method for network access control (NAC) of remotely connected devices is disclosed. In embodiments, agents support role mapping and policy-based scanning. Embodiments automatically perform authentication, assessment, authorization, provisioning, and remediation. Capabilities include user authentication, role-based authorization, endpoint compliance, alarms and alerts, audit logs, location-based rules, and policy enforcement. Processes collect information about the user as well as the host being used from sources including, but not limited to, LDAP, the remote access device, and the agent. Once this data has been obtained, embodiments construct a comprehensive model of the host. This model is subsequently used to govern the actual host's network access when it connects to the network. Passive monitoring includes vulnerability scanning to control access rights throughout the duration of the connection.
Owner:FORTINET
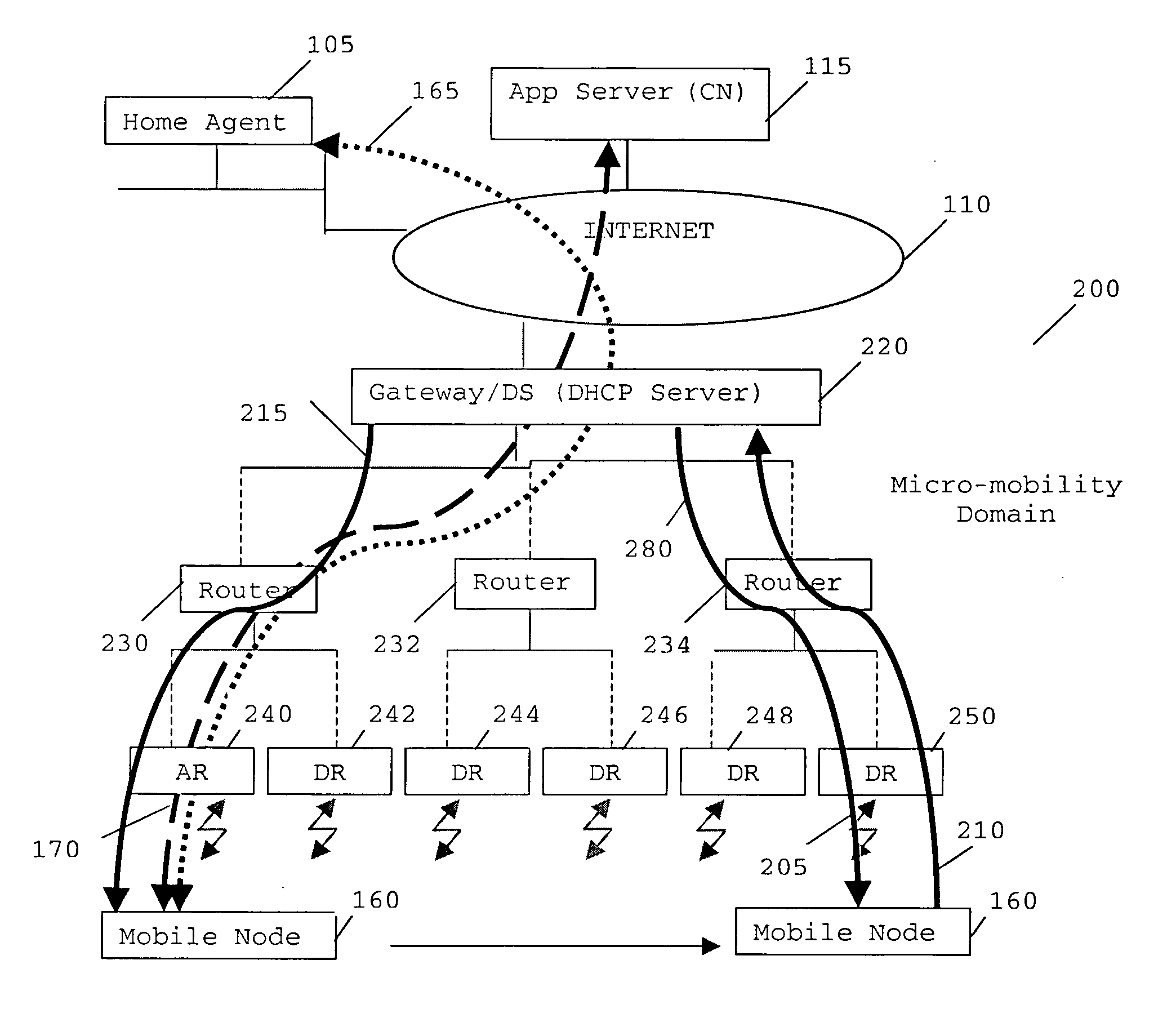
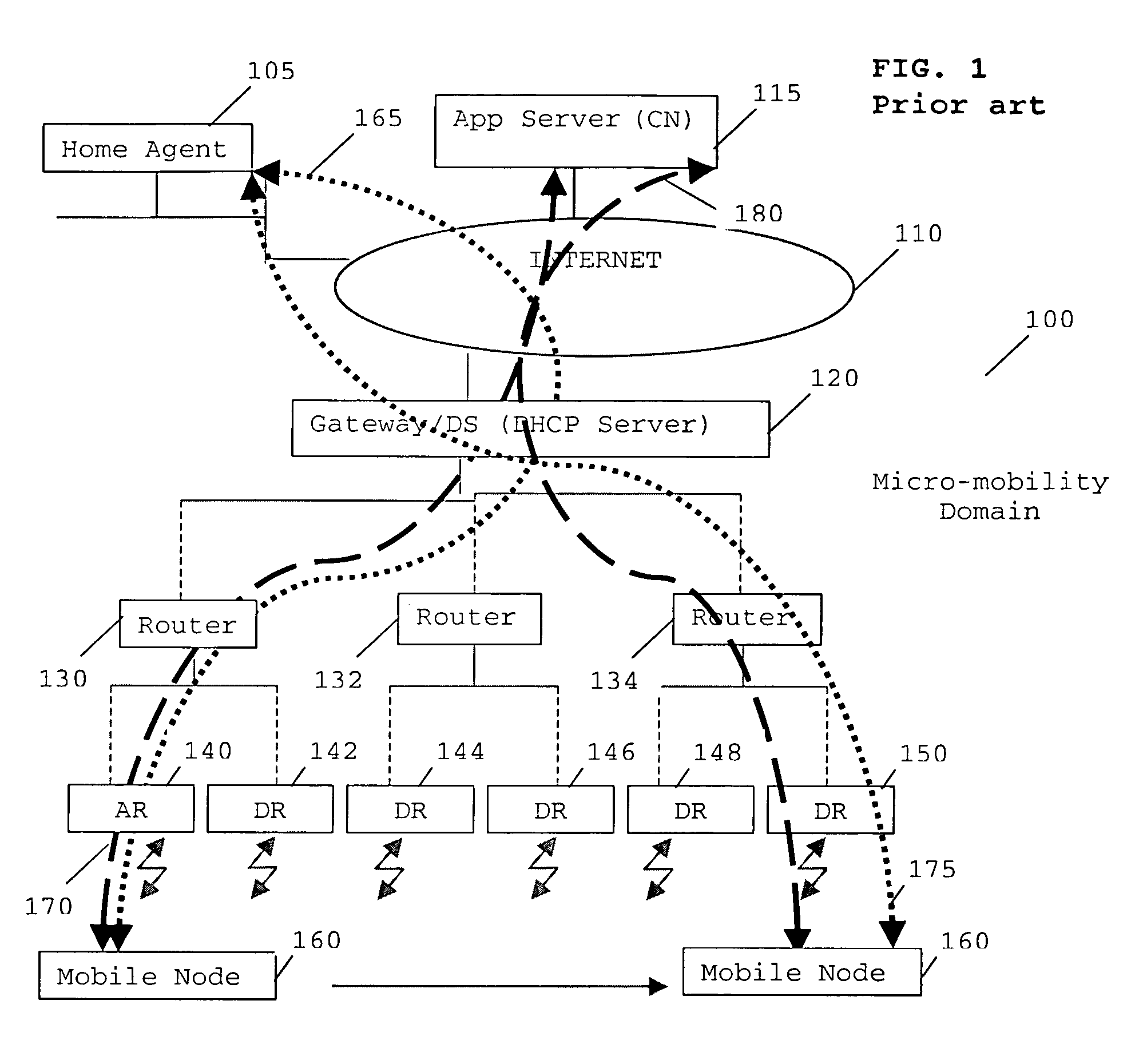
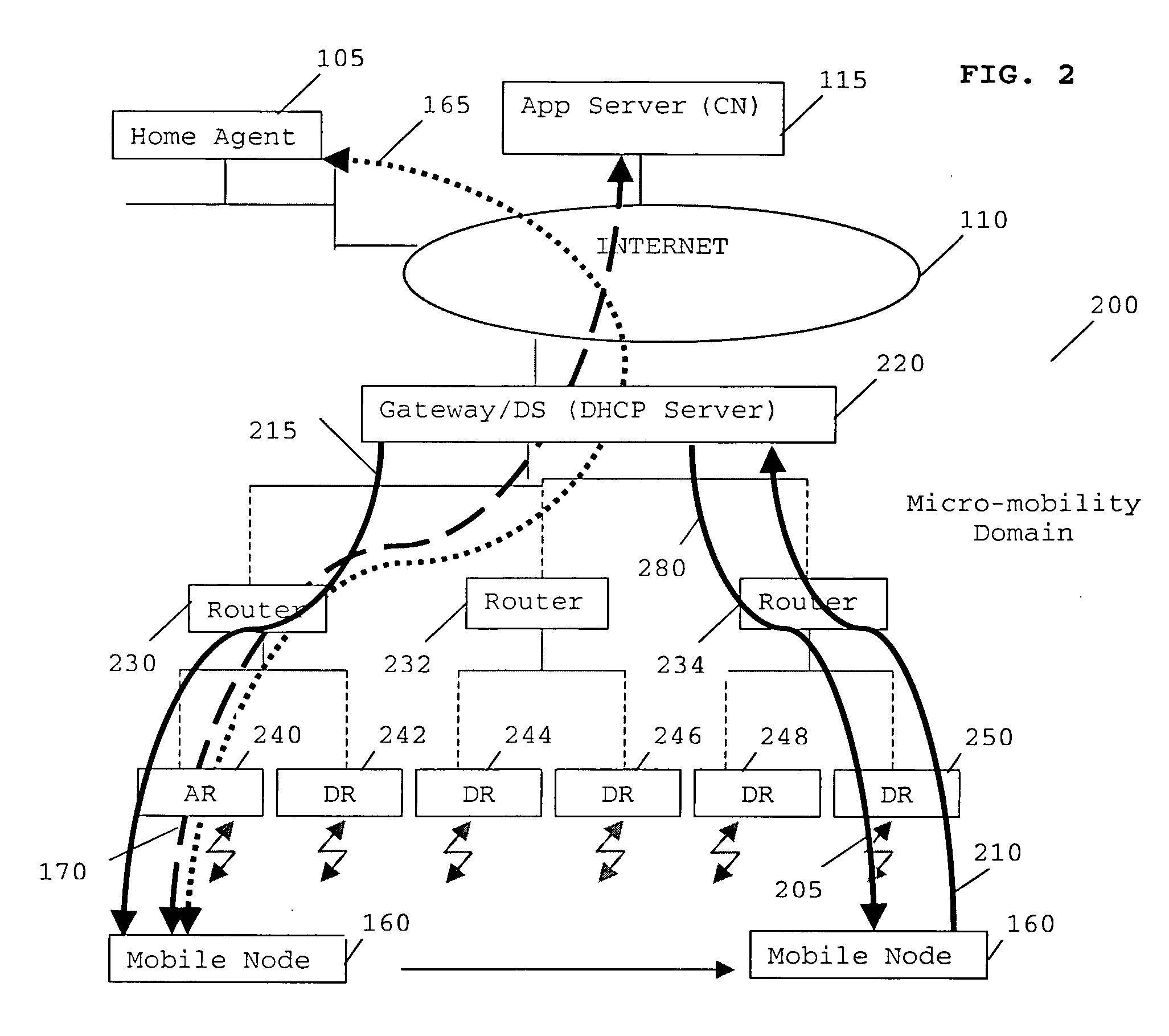
Routing in a data communication network
“A method of supporting mobility in an Internet Protocol (IP)-based data network. The method comprises the steps of generating a first stateful IP autoconfiguration message at a mobile node, whereby the message includes an address capable of use for routing maintenance. The mobile node transmits the generated message to a first access node, which incorporates its address and forwards the message to a dynamic host configuration protocol (DHCP) Server. The DHCP Server and access node analyse the message to determine a route to deliver data to and / or from the mobile node. One or more route update message are triggered from said access node and said DHCP server to a number of network elements between said access node and said DHCP server in the IP based data network to support mobility in an IP domain with minimum bandwidth use and minimum tunnelling required.”
Owner:GOOGLE TECH HLDG LLC
Method for extending a network map
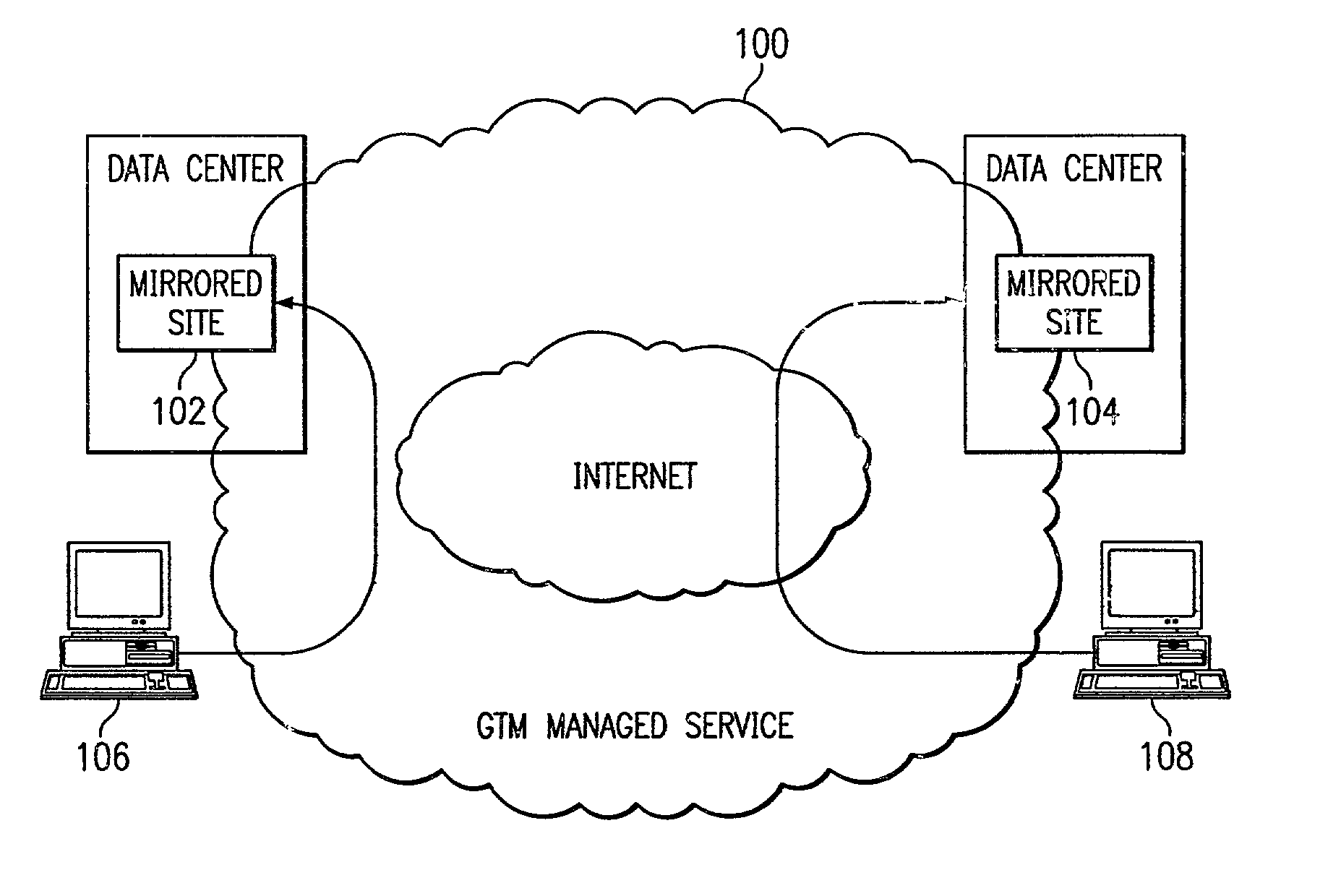
ActiveUS7028083B2Reduce dimensionalityOvercome problemsMultiple digital computer combinationsData switching networksSystem usageIp address
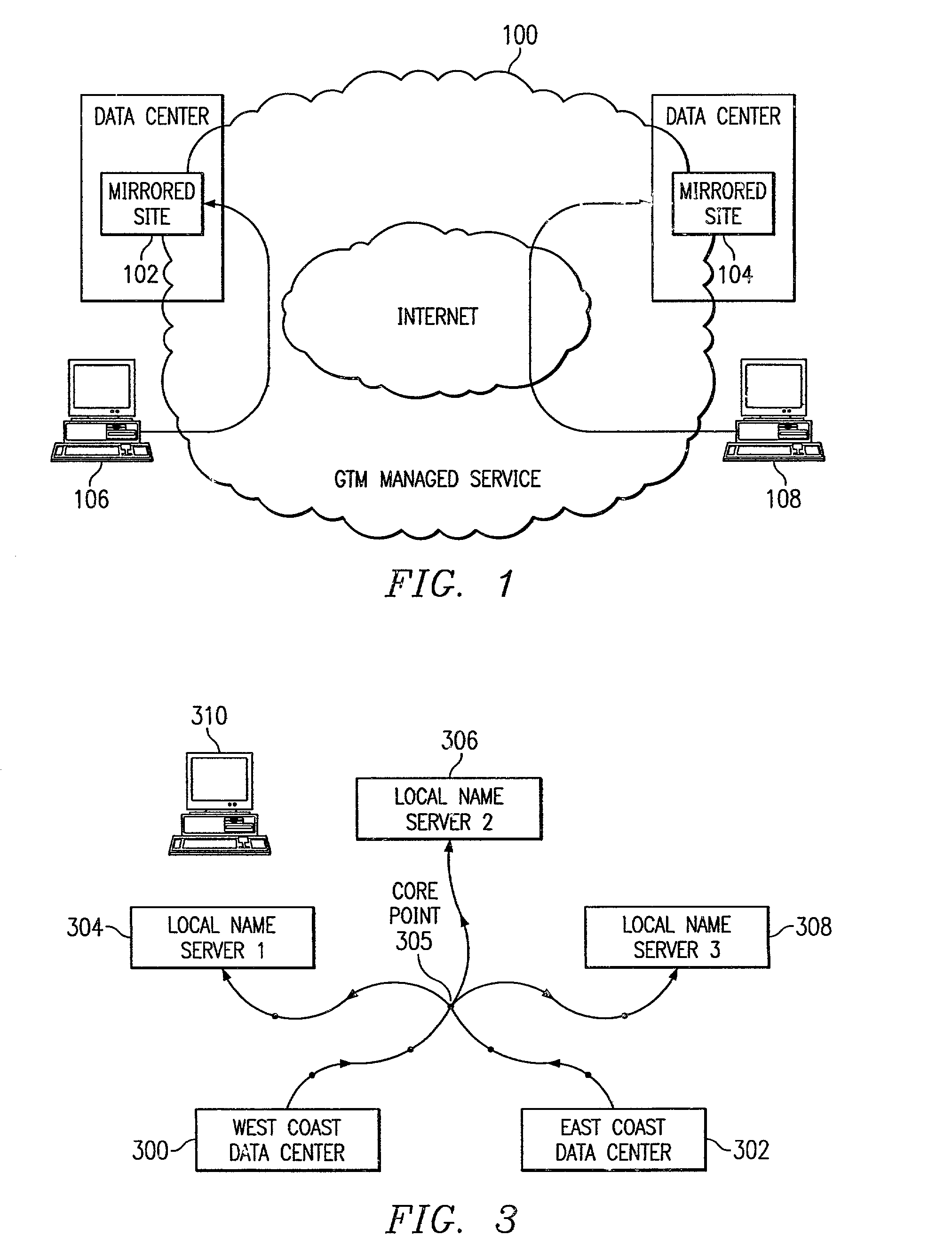
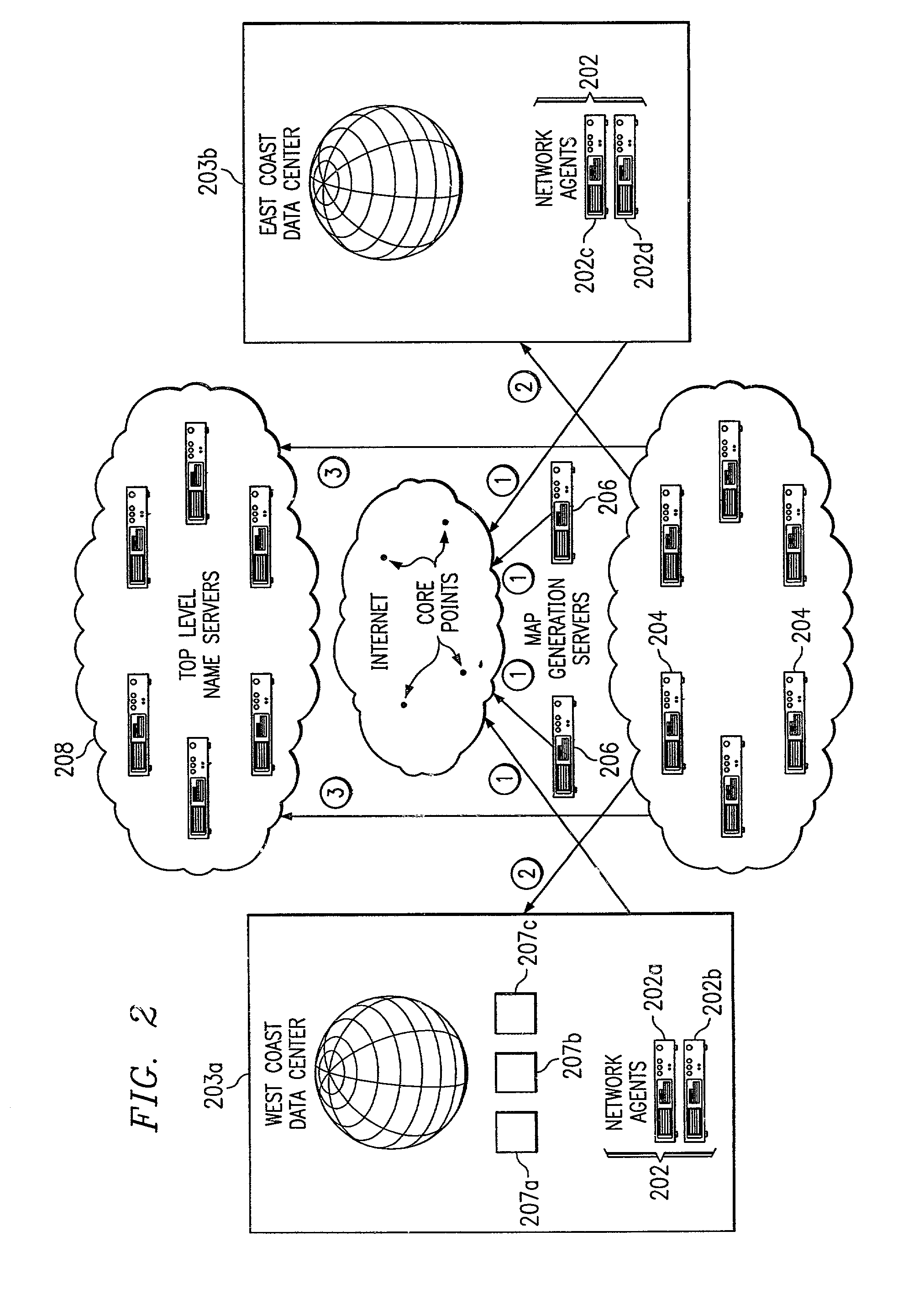
An intelligent traffic redirection system performs global load balancing. The system uses a network map that is generated in part by extending a “sparse” IP address data map. In particular, a method of extending an IP address block map begins by defining a set of one or more upper bound block(s). These upper bound blocks are then used to partition a space of IP addresses into subsets or “territories”, wherein each territory represents a largest set of IP addresses to which a piece of mapping data may be extended. The “piece” of mapping data typically consists of a host (usually a “name server” identified by the core point discovery process) IP address and some data about that host, namely, a “nearest” data center or a flag indicating that either “no data” exists for that host or that the system is “indifferent” as to which of a set of mirrored data centers the host should be mapped. A unification algorithm partitions the territory of each upper bound block into the largest possible sub-blocks in which a given unanimity criterion is satisfied and extends the mapping data in each such sub-block to all of the territory of that sub-block.
Owner:AKAMAI TECH INC
System for real-time network-based vulnerability assessment of a host/device via real-time tracking, vulnerability assessment of services and a method thereof
ActiveUS20050005169A1Not consuming high bandwidth and other resourceError preventionFrequency-division multiplex detailsComputer hardwareState variation
A system for real-time vulnerability assessment of a host / device, said system comprising an agent running on the host / device. The agent includes a a first data structure for storing the status of interfaces and ports on the interfaces of the host / device. An n executable agent module is coupled to the first data structure to track the status of interfaces and ports on the interfaces of the host / device and to store the information, as entries in said first data structure. The executable agent module compares the entries to determine a change in the status of interfaces and / or of ports on the interfaces of the host / device. A remote destination server is provided that includes a second data structure for storing the status of interfaces and the ports on the interfaces of the host / device. An executable server module is coupled to the second data structure to receive the information communicated by the agent executable module of the agent on the host / device. The executable server module stores the received information as entries in the second data structure wherein the entries indicate the state of each of the ports on each of the active interfaces of the host / device as received. The executable server module compares the entries in said data structures to determine the change in the status of interfaces and ports on the interfaces of the host / device. The executable server module runs vulnerability assessment tests on the host / device in the event of a change in the status of interface / ports.
Owner:RPX CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com