Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2090 results about "Master processor" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
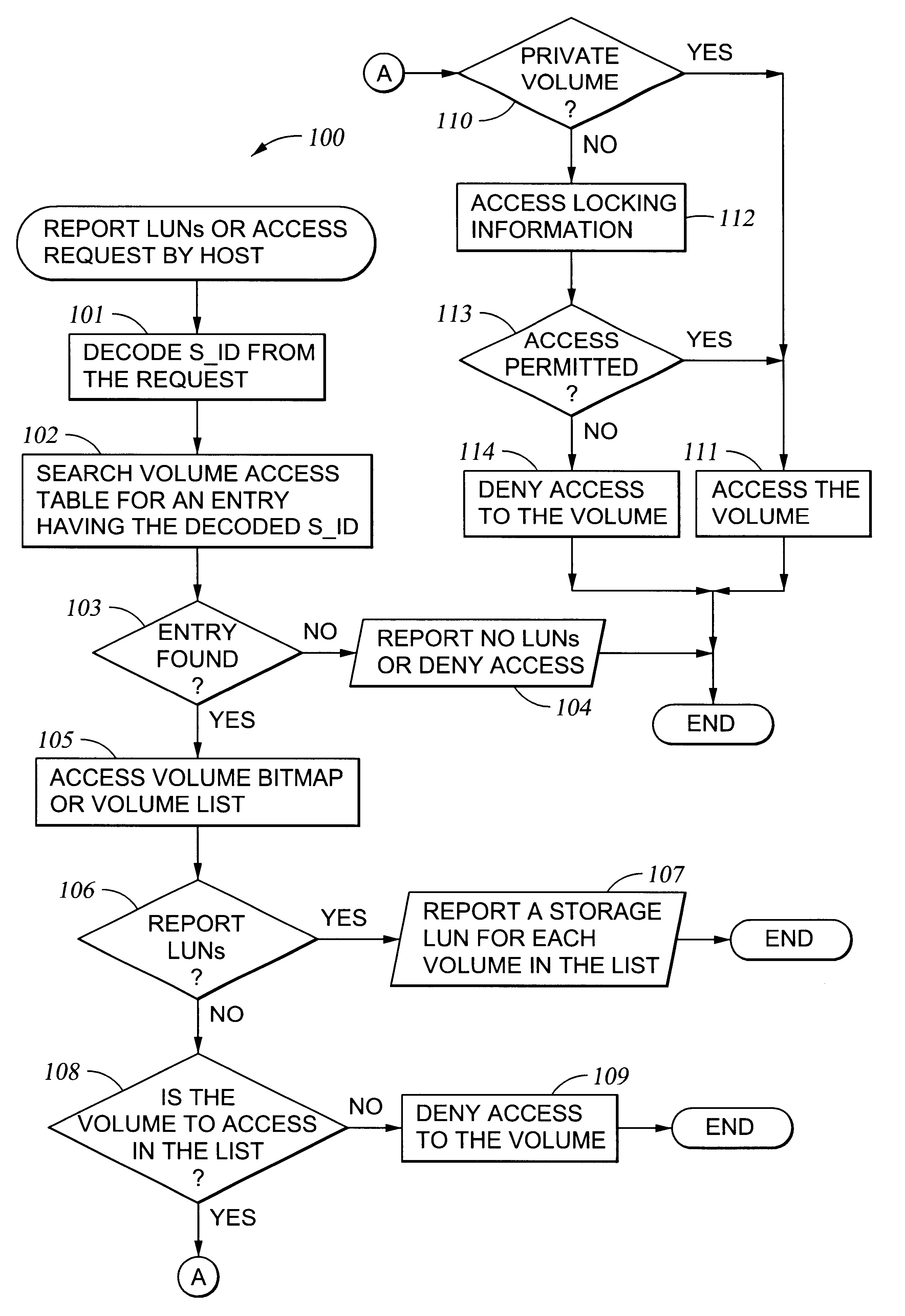
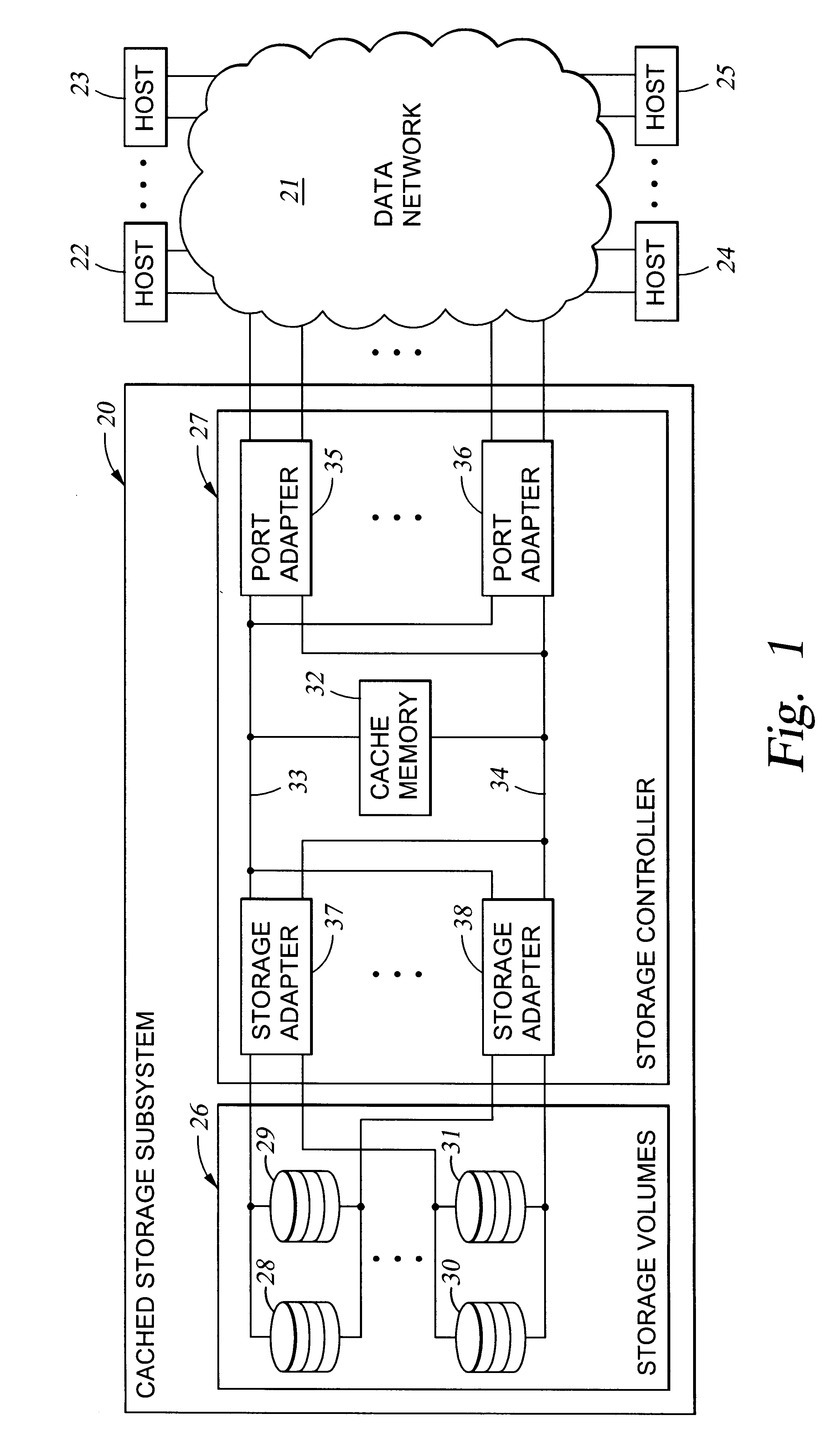
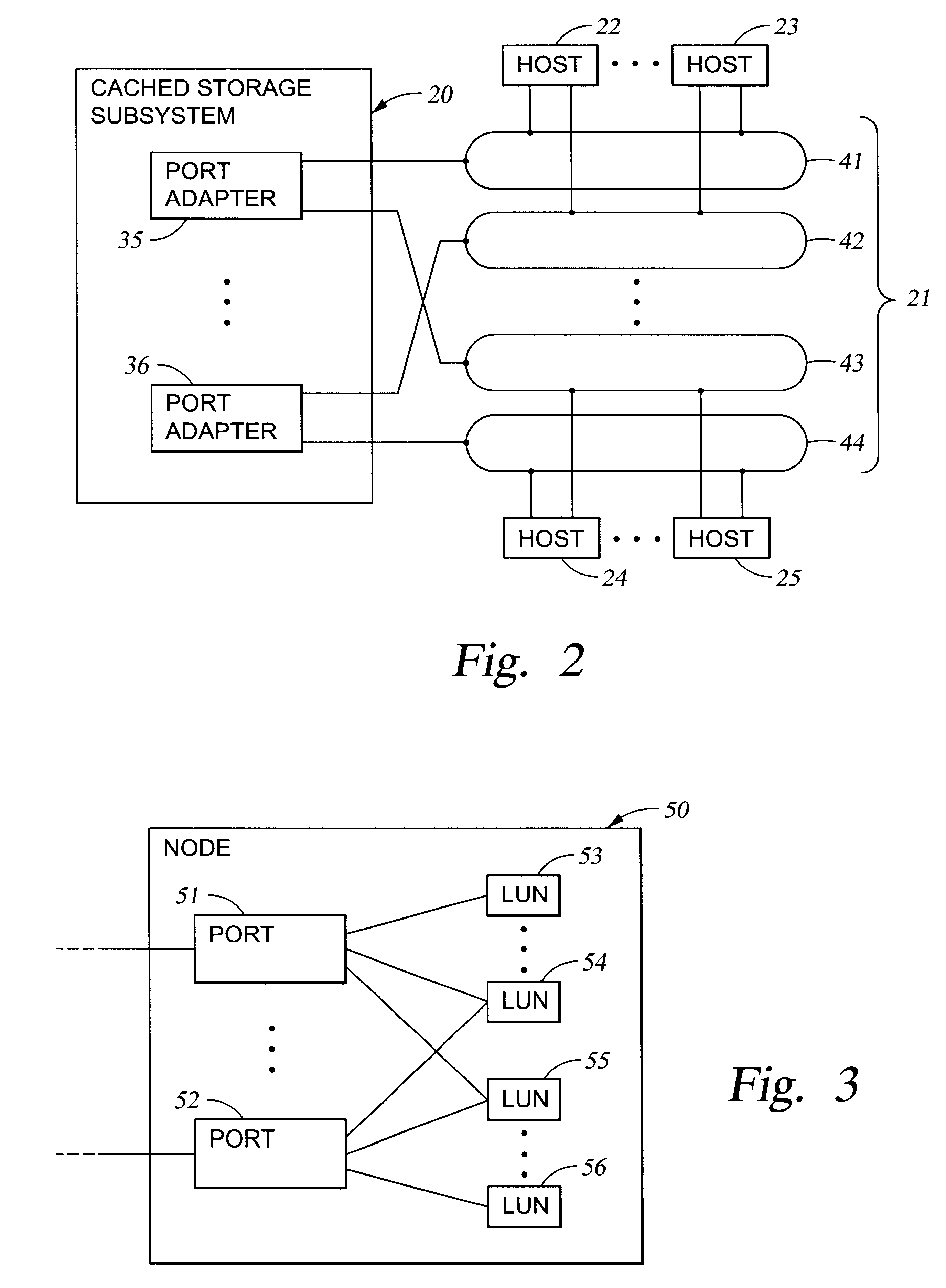
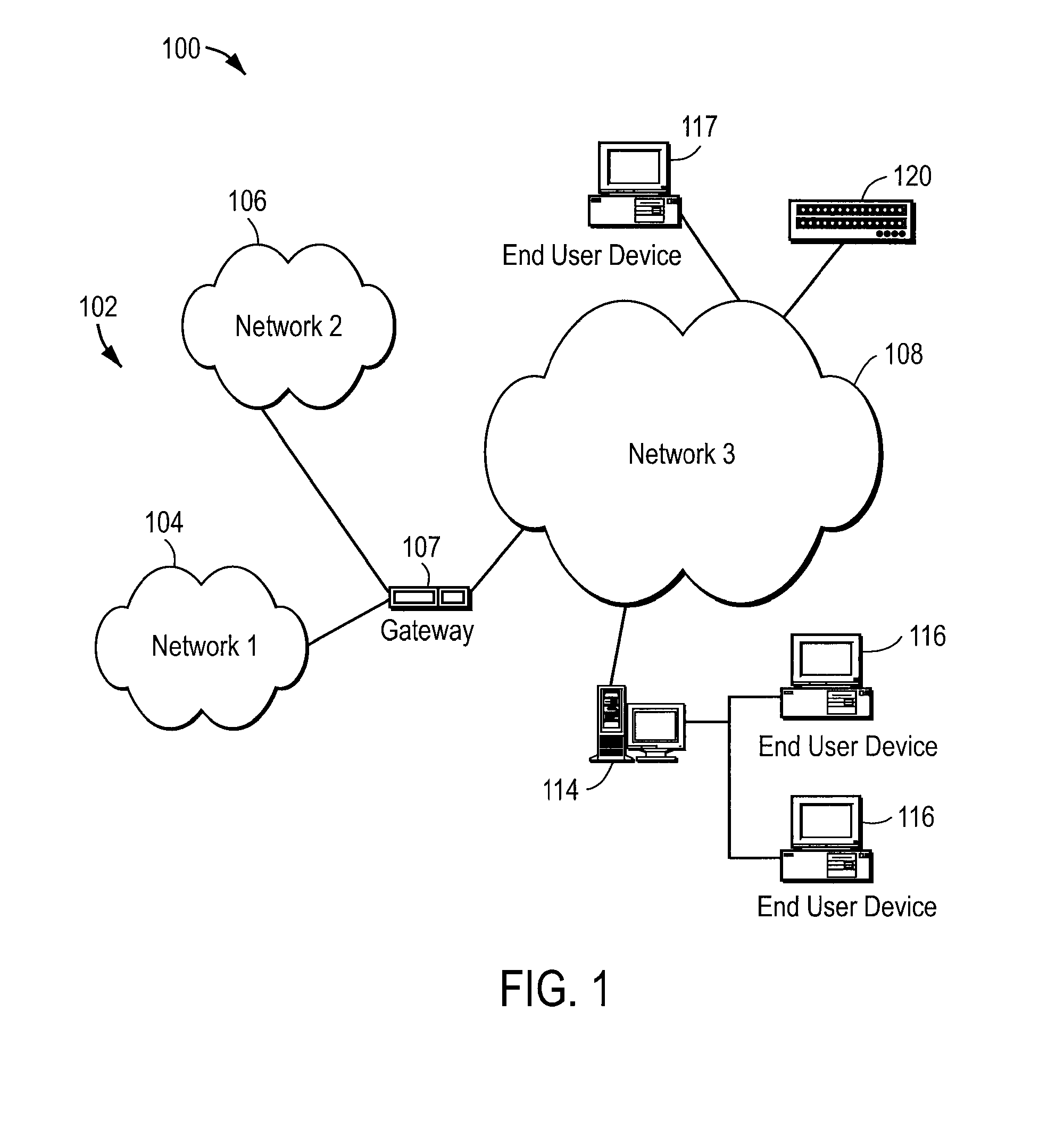
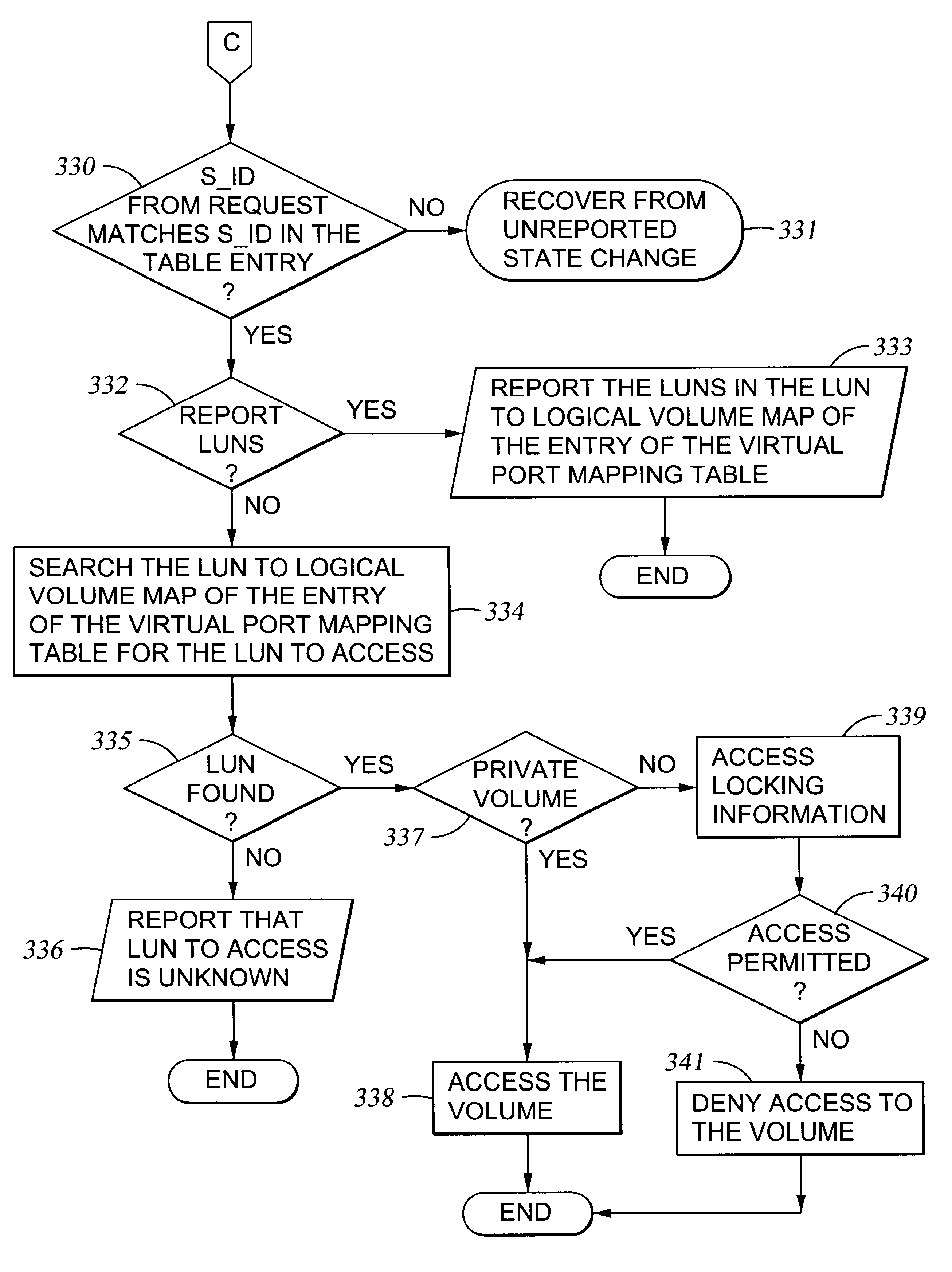
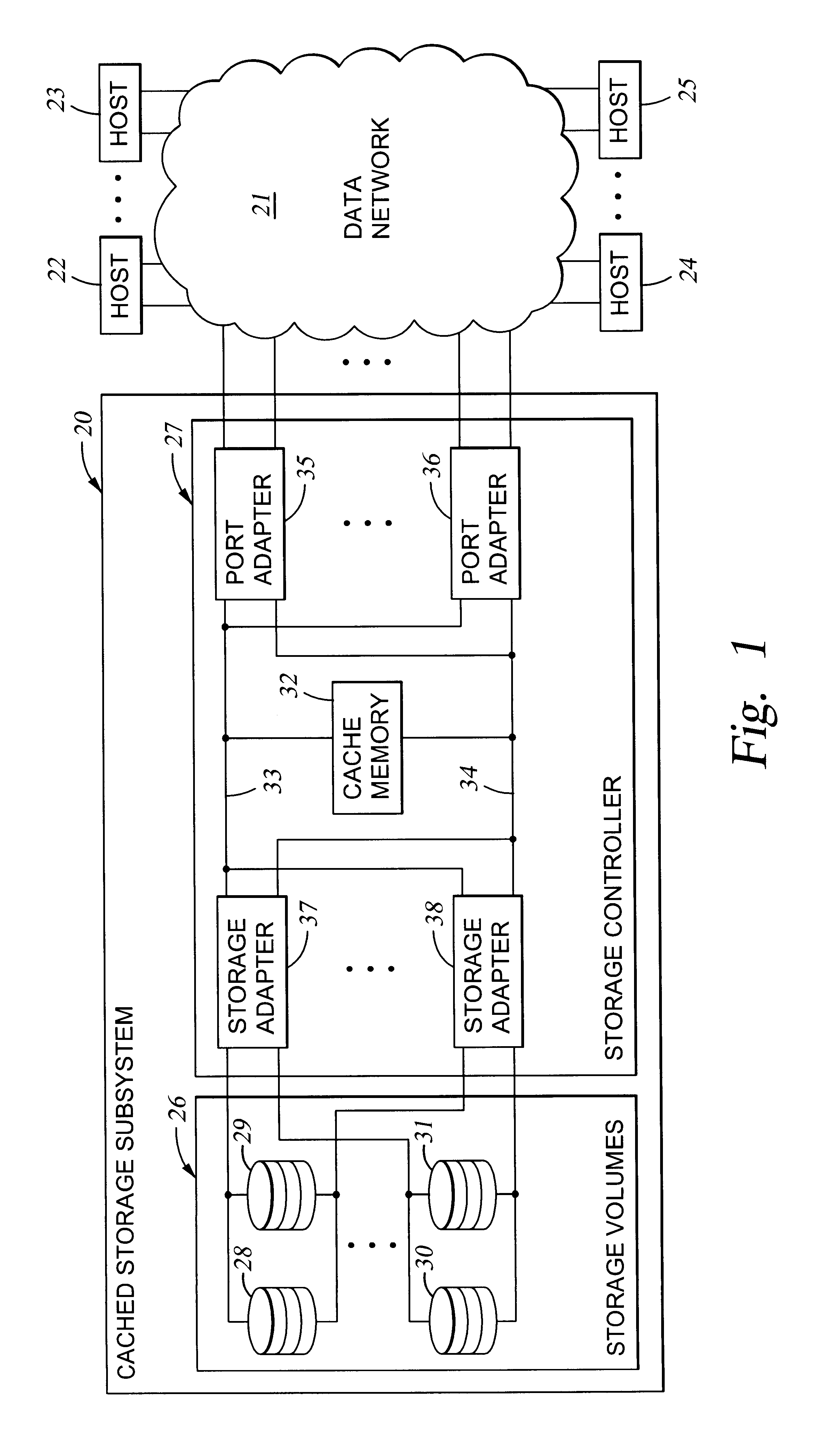
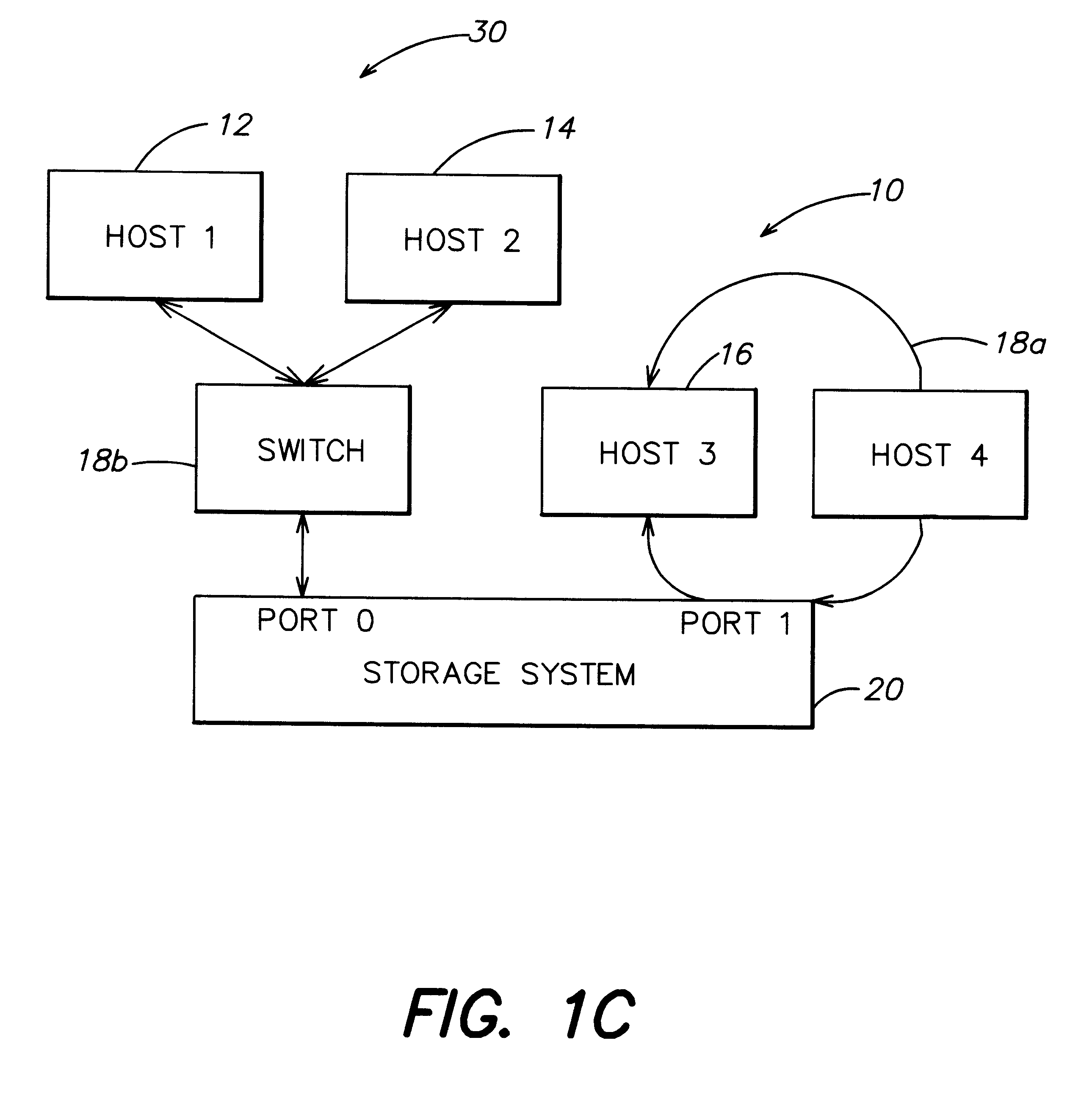
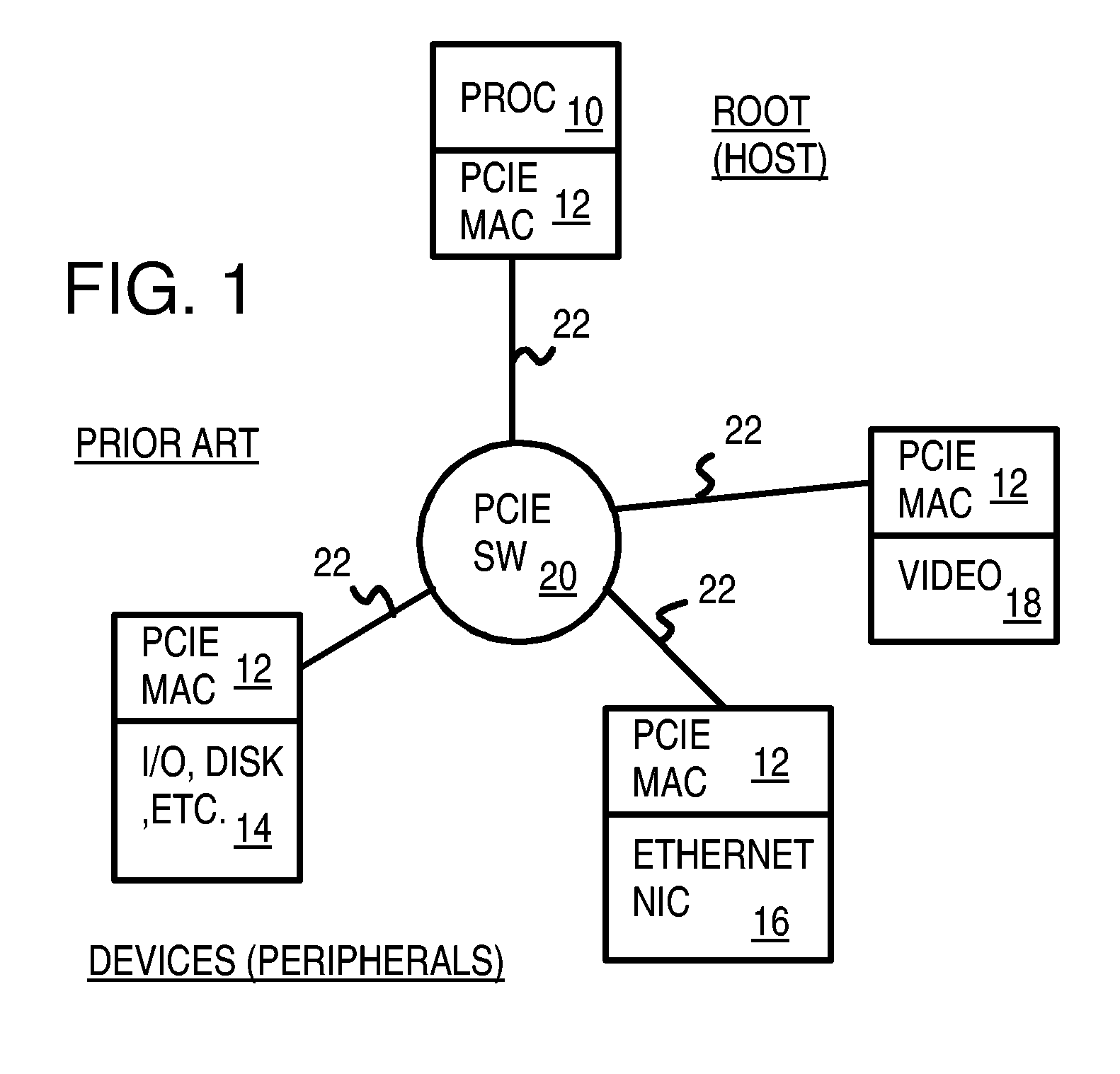
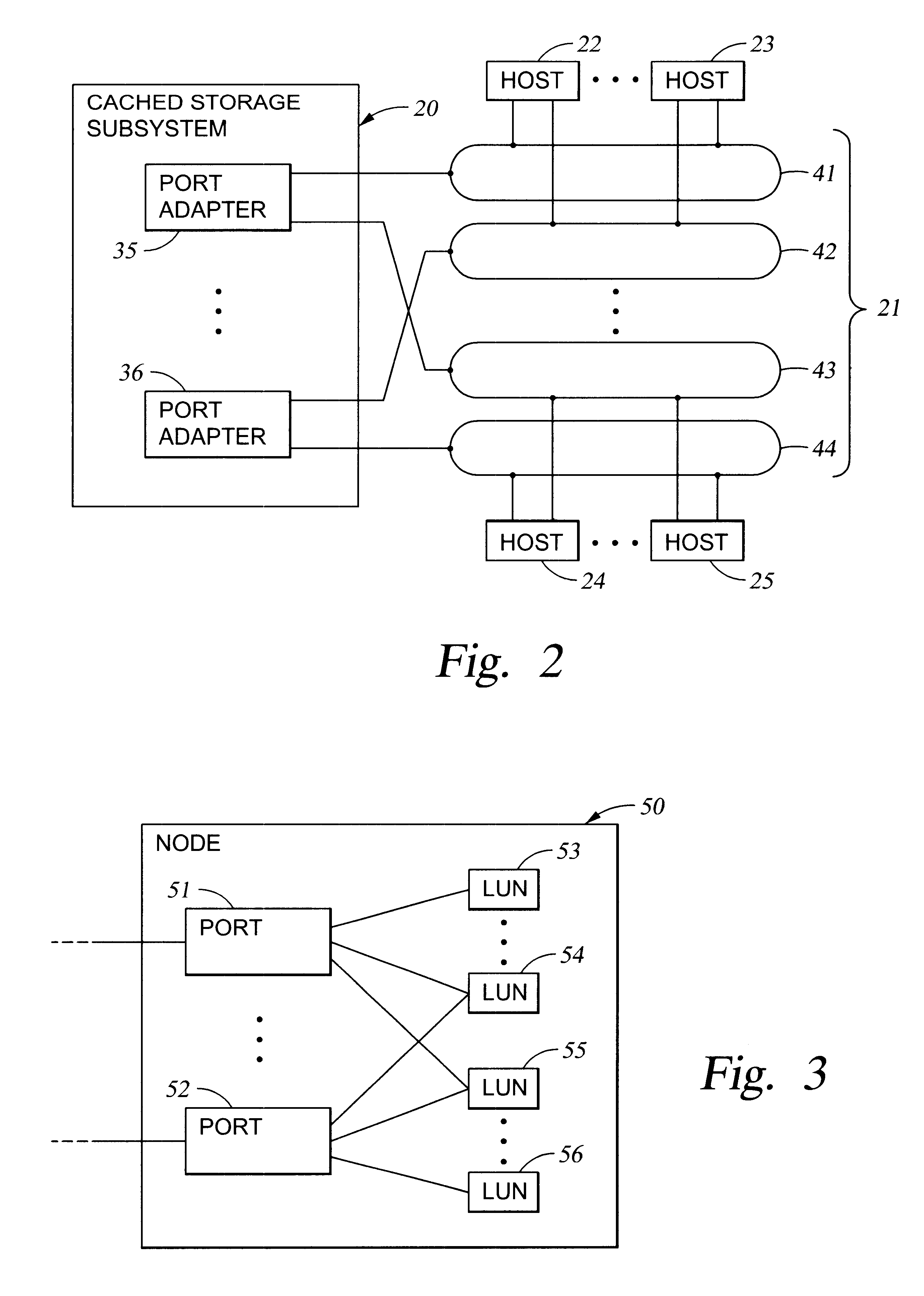
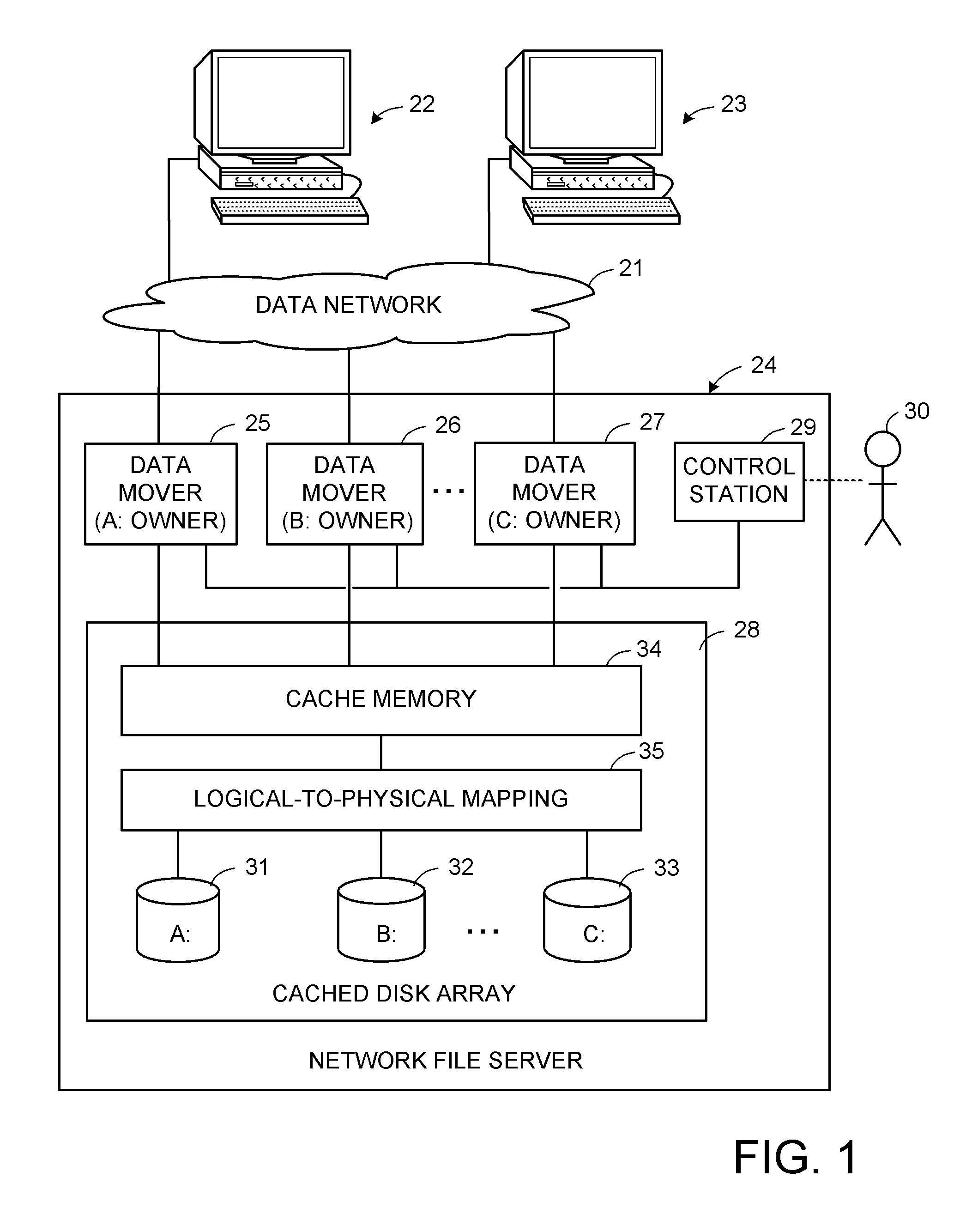
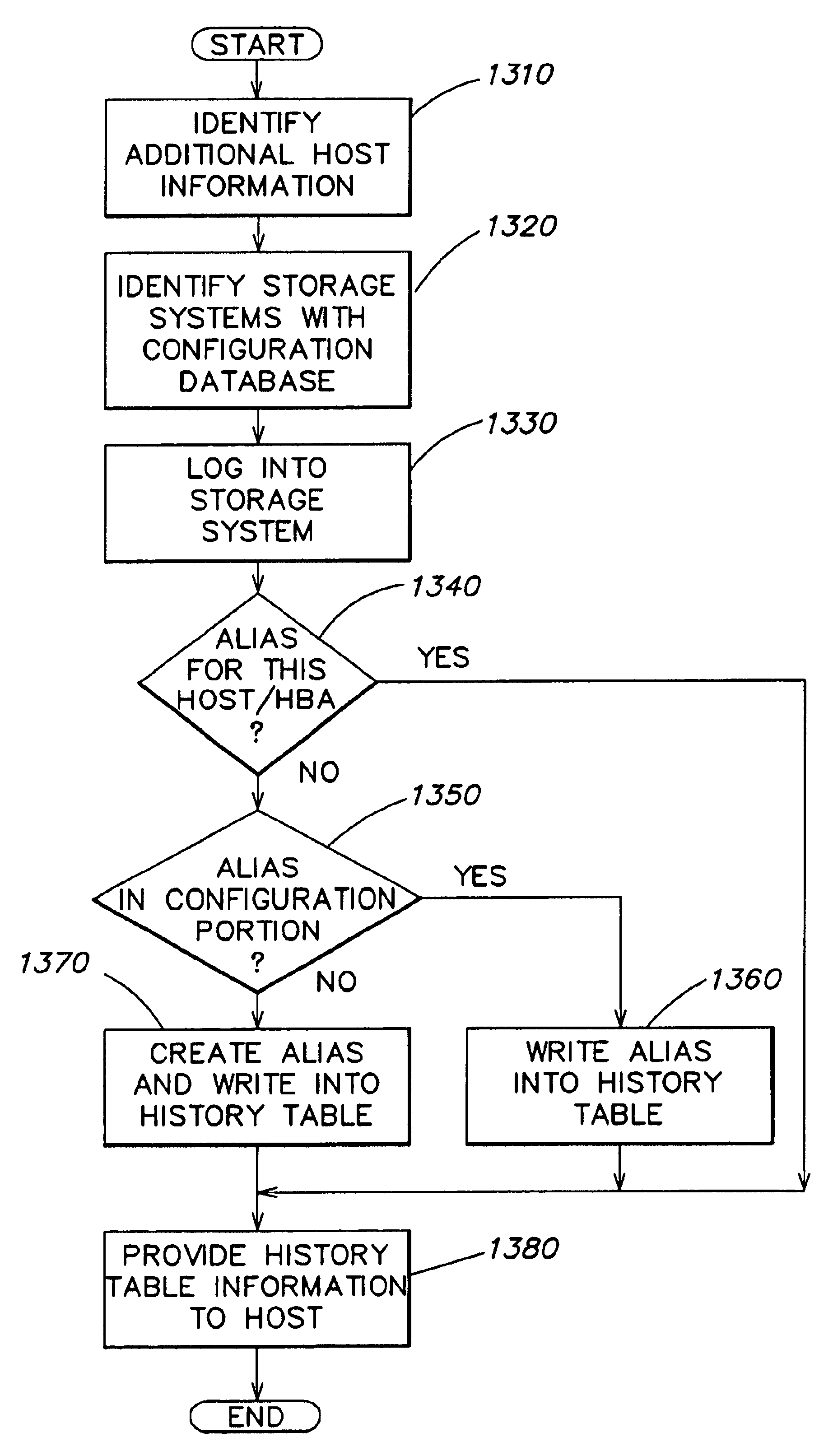
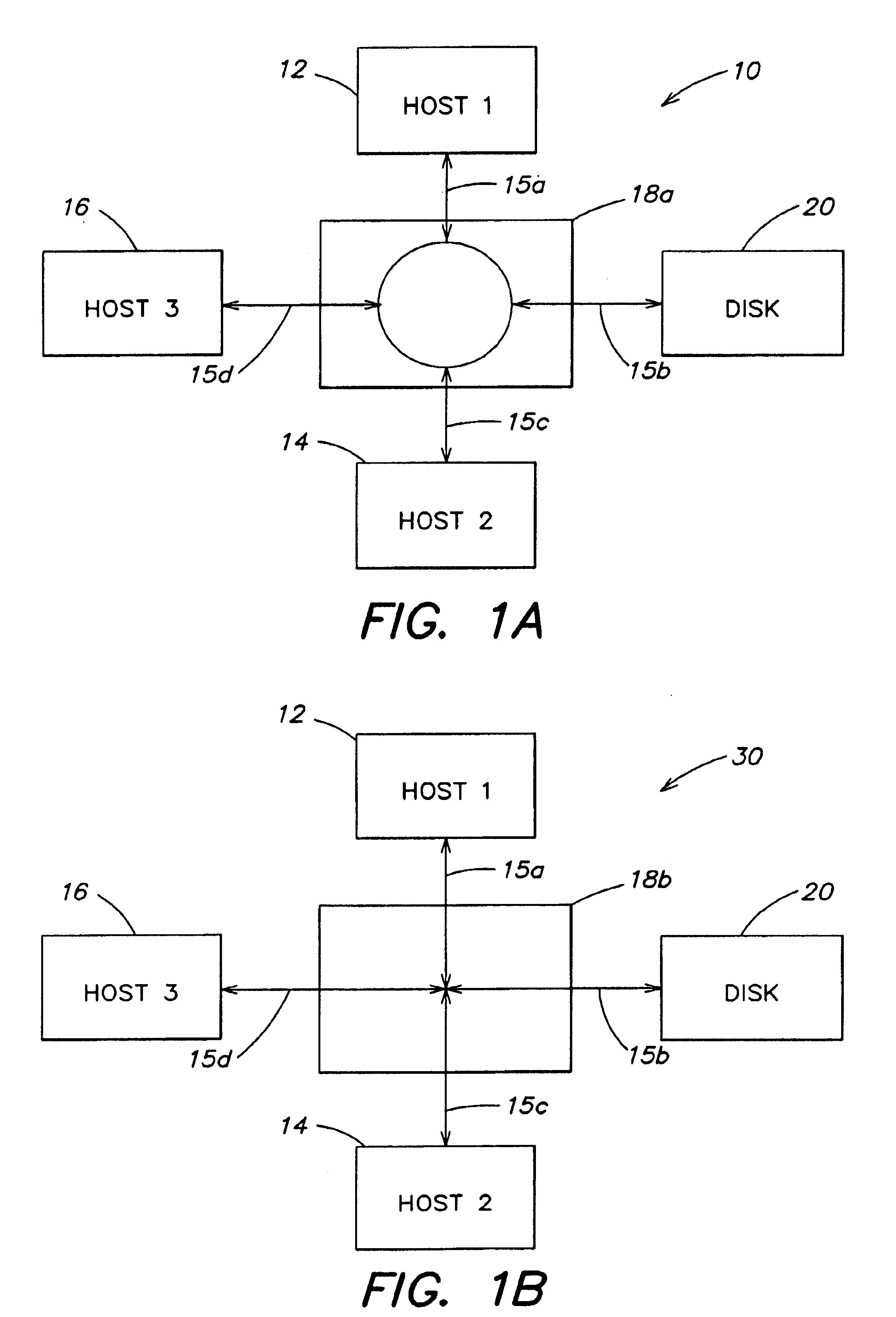
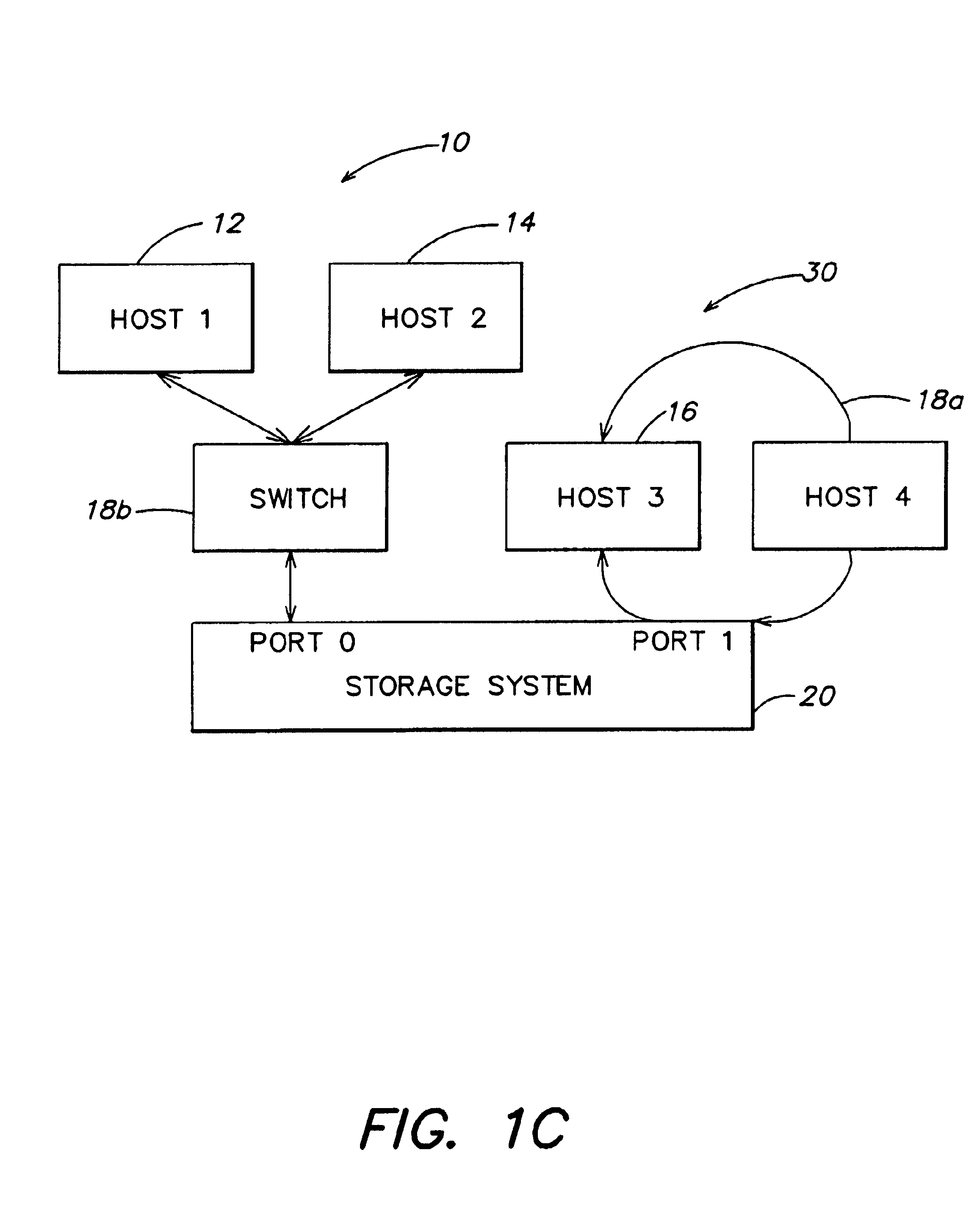
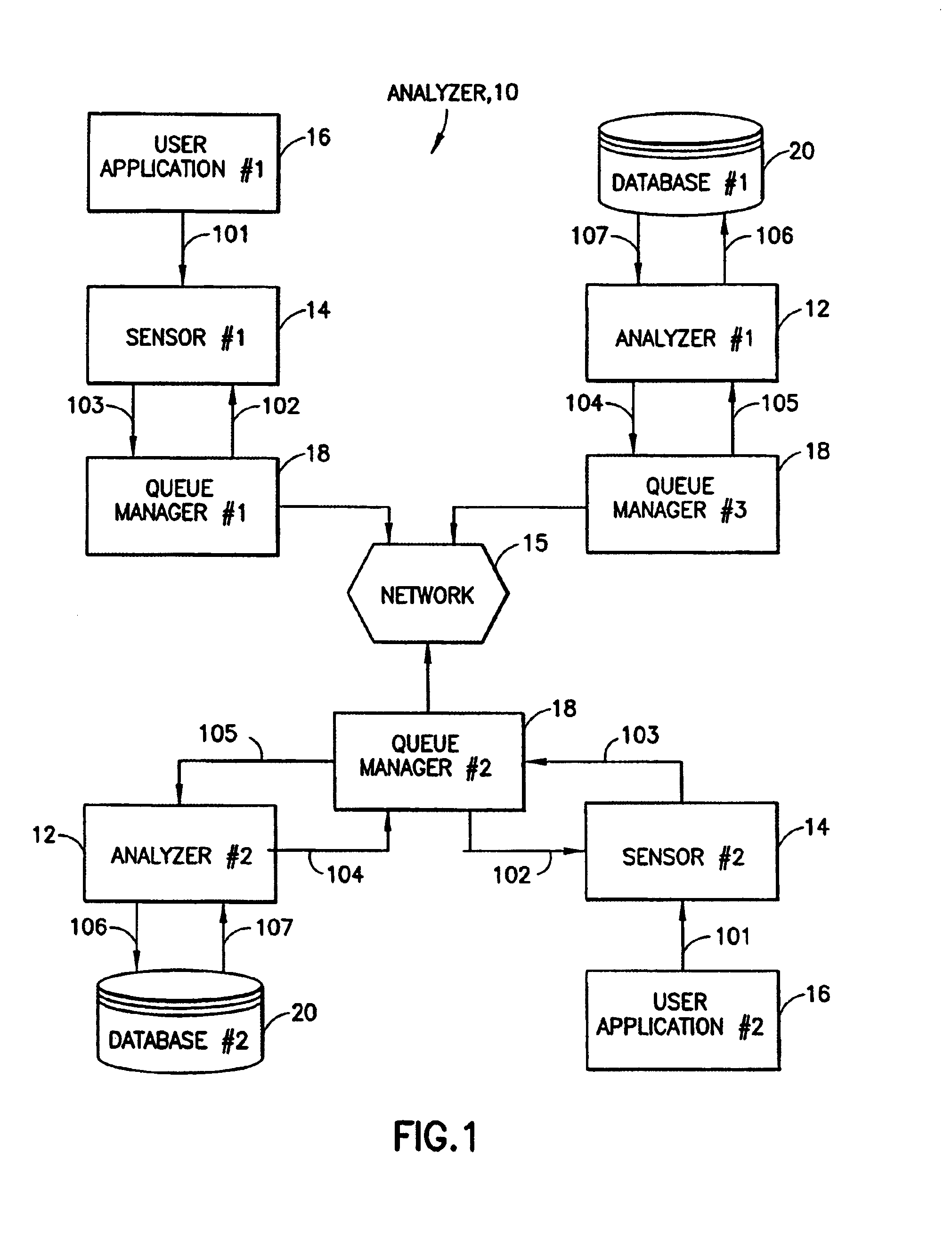
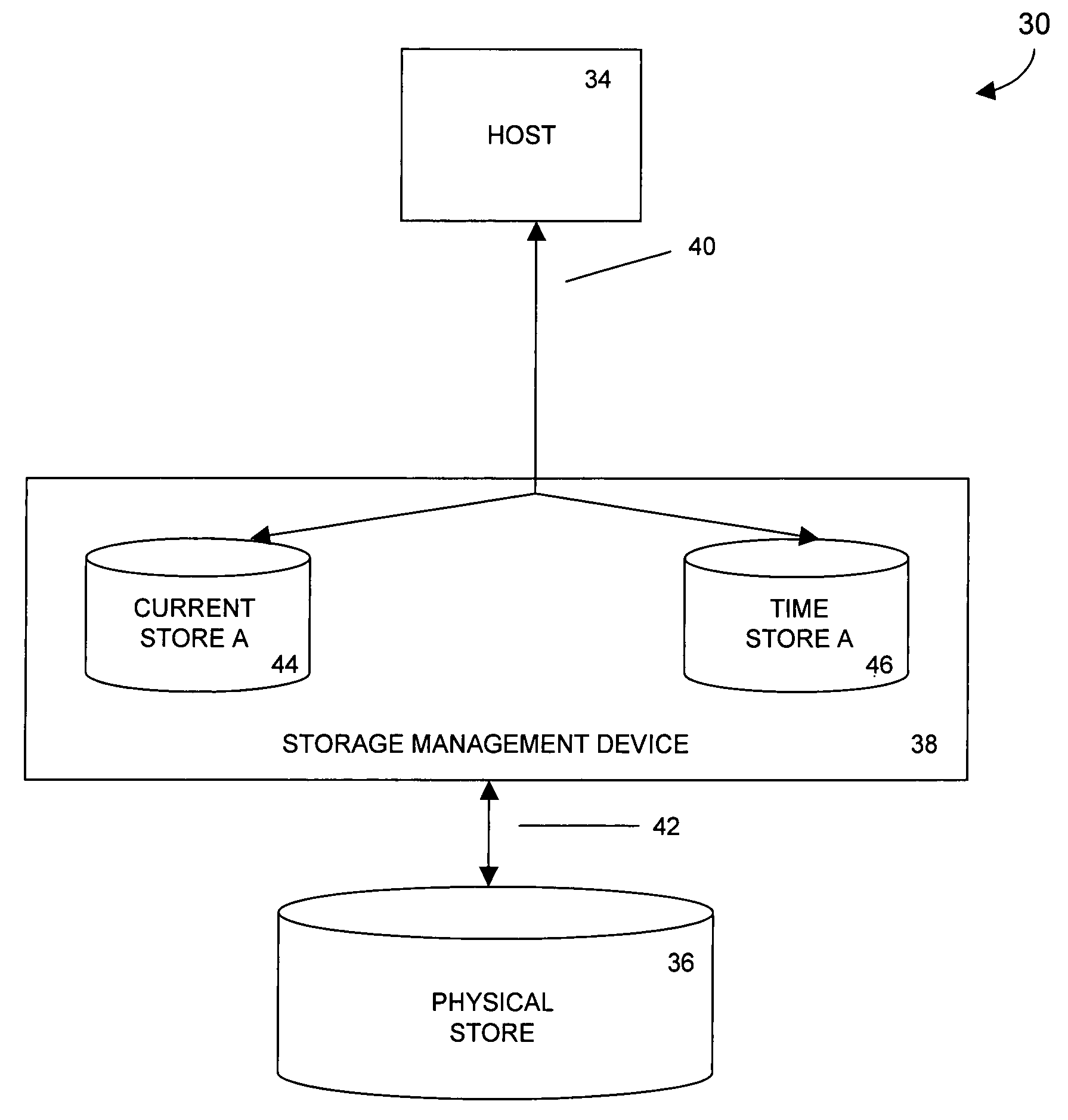
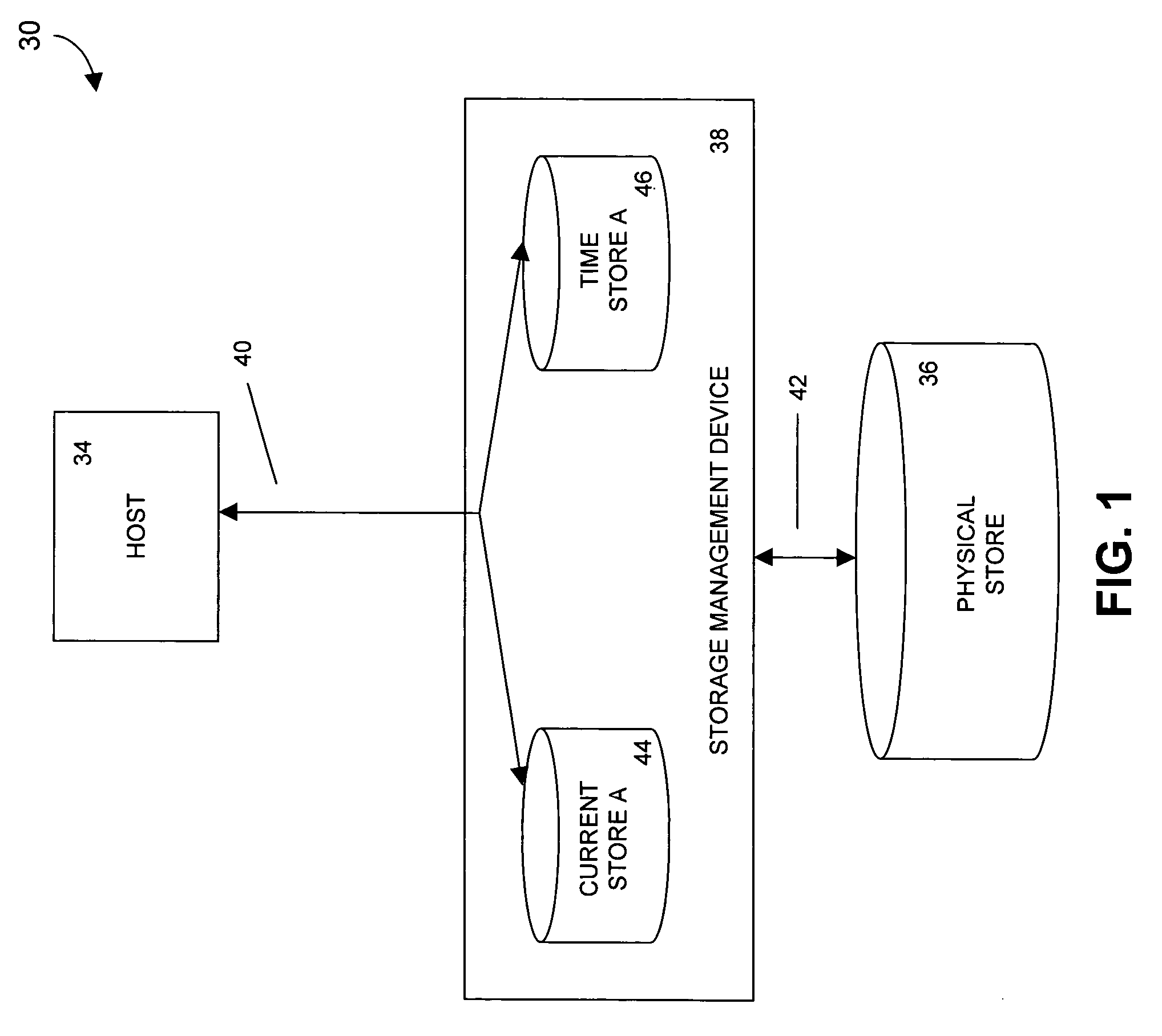
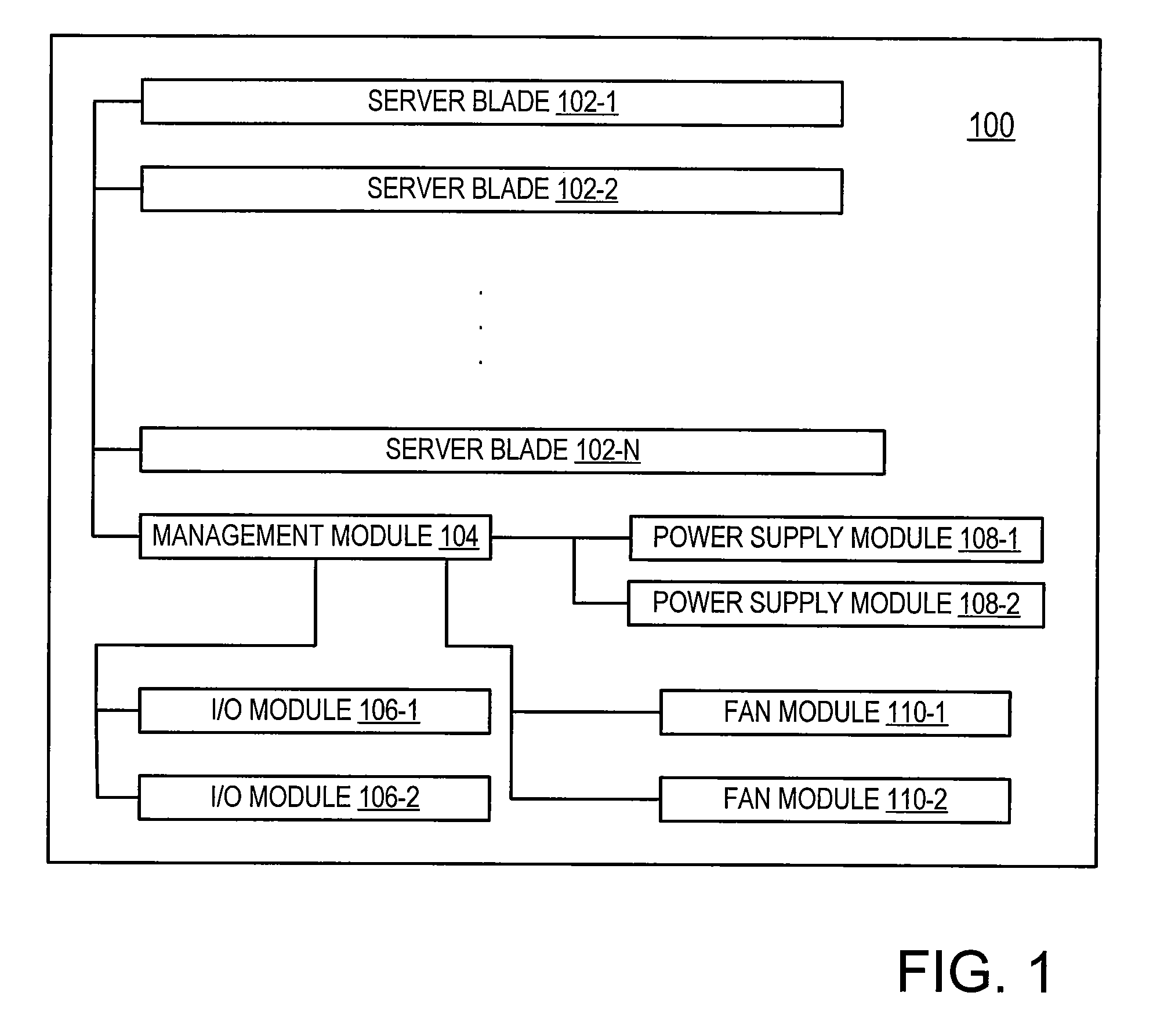
Storage mapping and partitioning among multiple host processors in the presence of login state changes and host controller replacement
InactiveUS6260120B1Input/output to record carriersData processing applicationsData portControl store
A storage controller for controling access to data storage has a memory and at least one data port for a data network including host processors. The memory is programmed to define a respective specification for each host processor of a respective subset of the data storage to which access by the host processor is restricted, and each specification is associated with a host identifier stored in the memory. When the storage controller receives a data access request from a host processor, it decodes a host identifier from the data access request, and searches the memory for a host identifier matching the host identifier decoded from the request. Upon finding a match, the respective specification of the respective subset for the host processor is accessed to determine whether or not storage specified by the storage access request is contained in the respective subset. If so, then storage access can continue, and otherwise, storage access is denied. Preferably the host identifier decoded from the request is a temporary address assigned by the network, and also stored in the memory in association with each respective specification is a relatively permanent identifier for the host processor.
Owner:EMC IP HLDG CO LLC
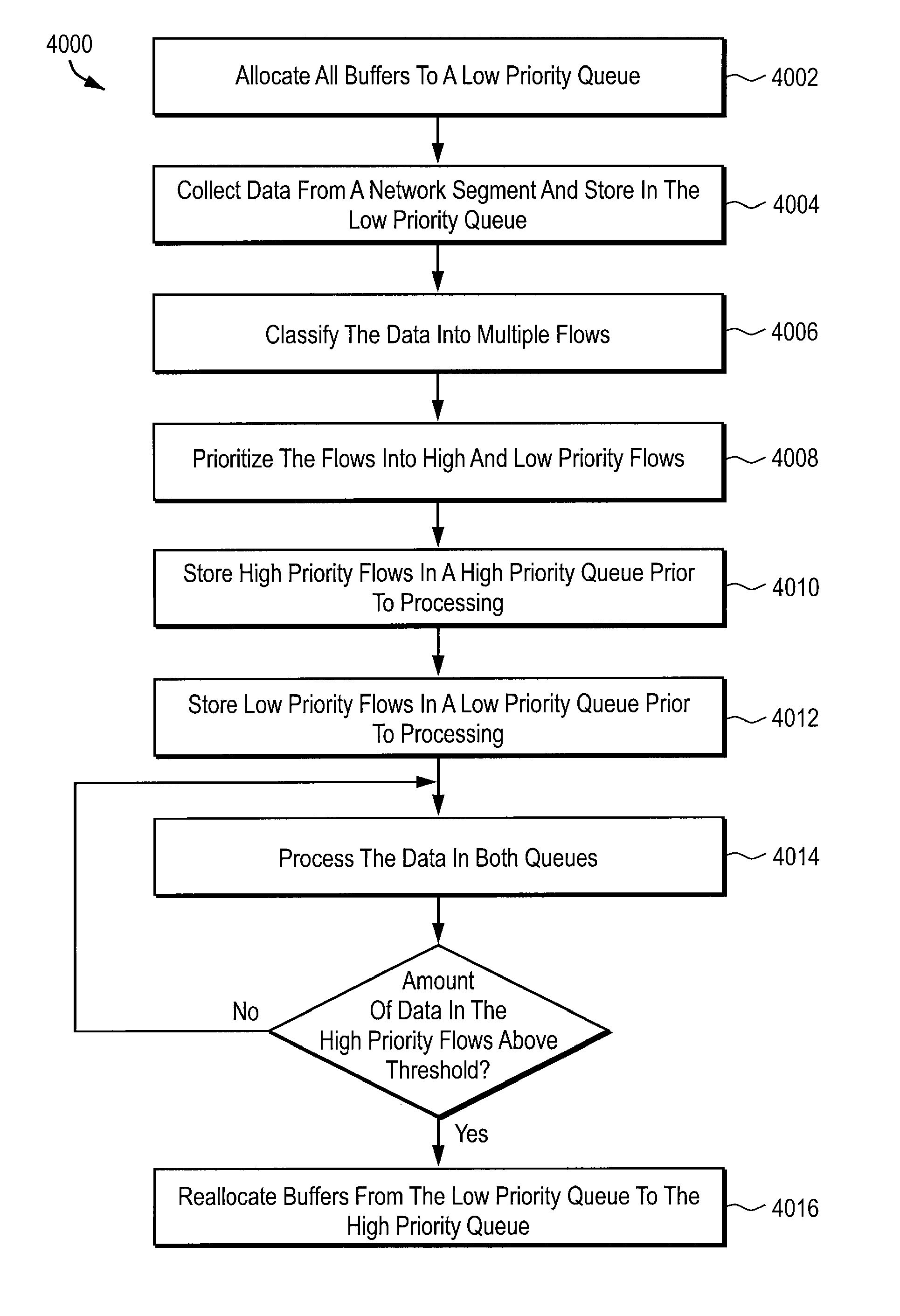
Media module apparatus and method for use in a network monitoring environment
InactiveUS7299277B1Avoid data lossReduce probabilityError preventionTransmission systemsApplication softwareMaster processor
A probe apparatus, method and computer program product for application monitoring are provided. A data collection module collects data from a network segment. A flow processor coupled to the data collection module classifies the collected data into a plurality of flows. A capture system coupled to the flow processor filters and buffers the collected data. A main processor processes the filtered data.
Owner:NETWORK GENERAL TECH
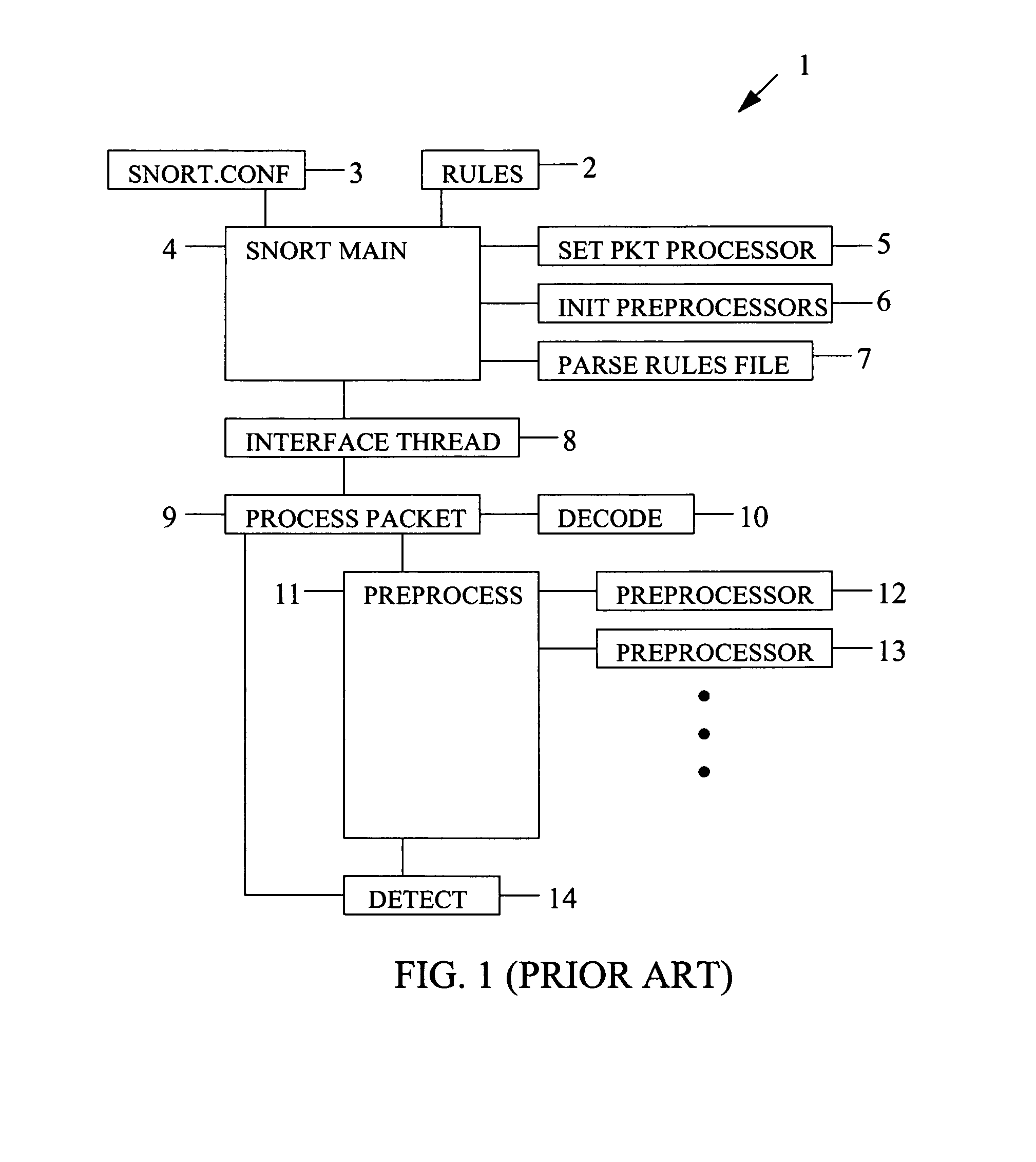
Device for and method of wireless intrusion detection
A device for and method of detecting intrusion into a wireless network that includes a configuration file, a rules files, a main processor, a set packet processor, an initialize preprocessor, a parse rules file, an interface thread unit, a process packet unit, a decoder, a preprocess unit connected to the process packet unit; at least one preprocessor consisting of a rogue access point and transmit channel preprocessor, a NETSTUMBLER preprocessor, a MAC spoofing preprocessor, a DEAUTH flood preprocessor, an AUTH flood preprocessor, a rogue client preprocessor, a bridged network preprocessor, a rogue client valid access point preprocessor, valid client rogue access point preprocessor, an ad-hoc network preprocessor, a wrong channel preprocessor, a cloaking policy violation preprocessor, an encryption policy violation preprocessor, and a null SSID association policy violation preprocessor; and a detector.
Owner:NATIONAL SECURITY AGENCY
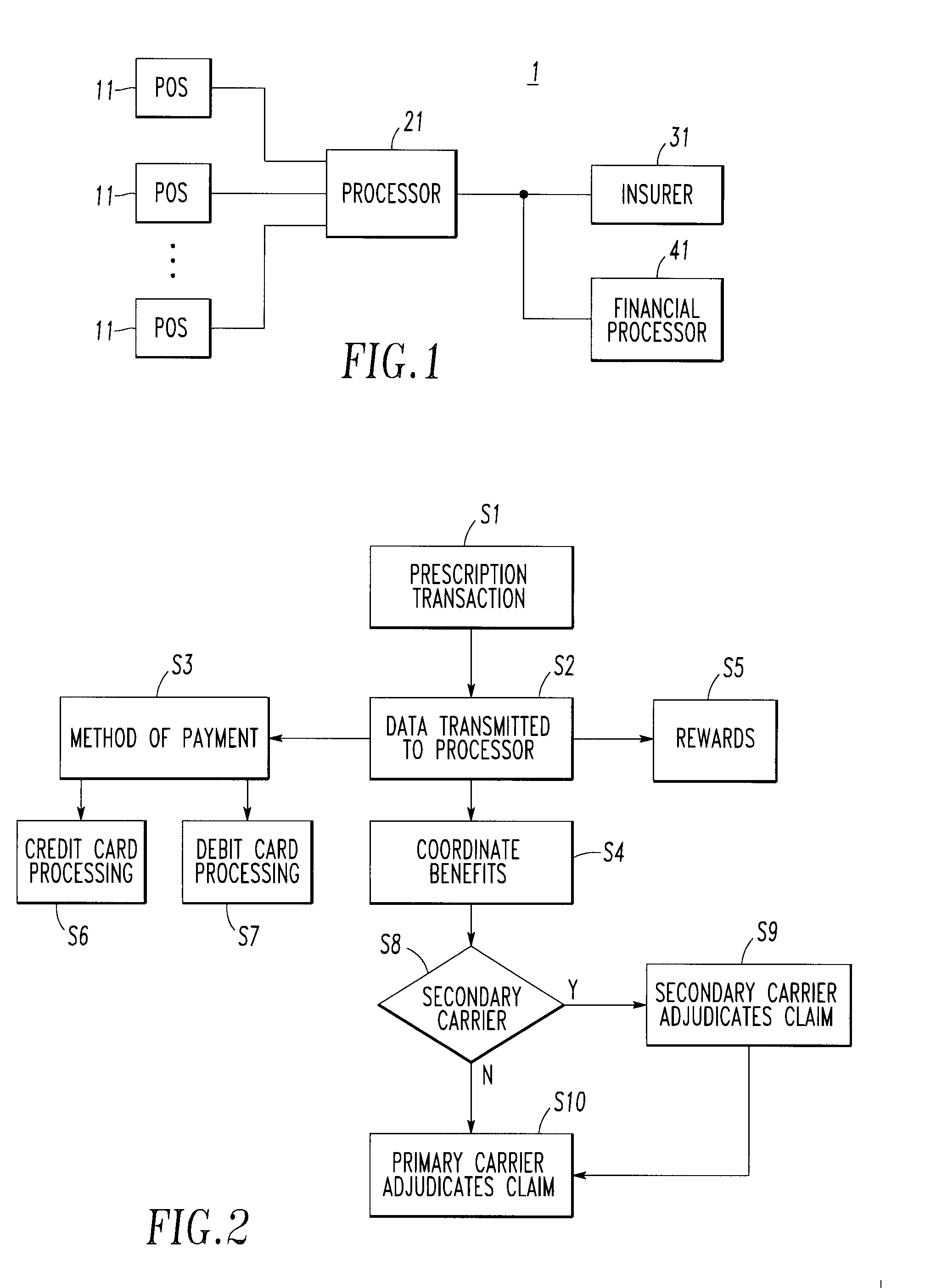
Integrated pharmaceutical accounts management system and method
InactiveUS20020002495A1Facilitate real-time adjudicationEasy to processHand manipulated computer devicesDrug and medicationsData warehouseDrug interaction
<heading lvl="0">Abstract of Disclosure< / heading> An integrated suite of services for consumers, service providers and manufacturers in the pharmaceutical industry is disclosed. The present invention utilizes one or more of the NCPDP standard formats and adopts the switch for an integrated system of, for example, instant adjudication of prescriptions, consumer data warehousing and / or incentive rewards for the consumer. A participating consumer with one card, can instantly purchase pharmaceuticals and charge the transaction to a credit card and earn and apply savings dollars redeemable for pharmaceutical purchases. For a participating service provider, instant adjudication and instant validation of consumer eligibility can be performed. Moreover, a service provider may receive messages related to the patient's medications. Significantly, data is recorded for consumers even when consumers make the pharmaceutical purchase with cash. The system includes a unique card issued to participating consumers. The card is adapted to encode conventional credit or debit card information specific to the participating consumer so that the consumer can consummate a transaction for the purchase of pharmaceuticals without possession of an additional credit card. The system further includes a host processor coupled to the point of sale at the service provider through a leased line or public switch network or the like. When a customer performs a pharmaceutical transaction at the point of sale of the service provider, the host processor coordinates any benefits and data with other prescription benefit management systems through messages transmitted and received from any primary or secondary carrier systems. The host processor further is adapted to facilitate real-time adjudication of claims and checks for any dangerous drug-to-drug interactions. The host processor additionally facilitates any financial processing including the accumulation and redemption of any bonus dollars earned by the consumer. Furthermore, since the card used by the consumer can be encoded with credit or debit card information, the host processor determines the desired payment method and performs the actual financial transaction. Even if the transaction at the point of sale is a cash purchase, the consumer may desire to use his unique card for the accrual of bonus dollars. Therefore, data concerning the transaction (i.e., pharmacy number, prescription number, etc.) can be recorded even for transactions conducted with cash.
Owner:NPAX
Media processing method and device
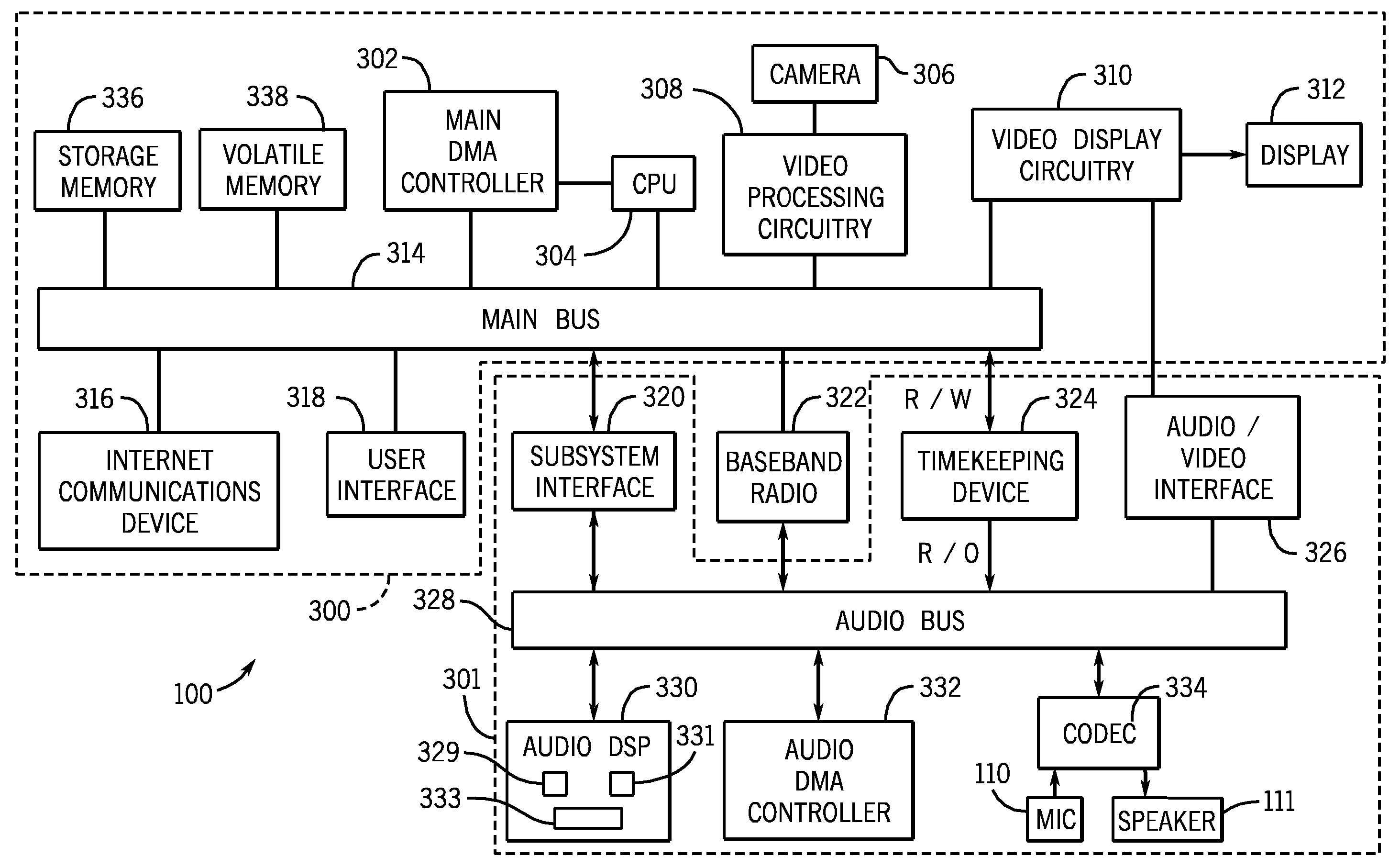
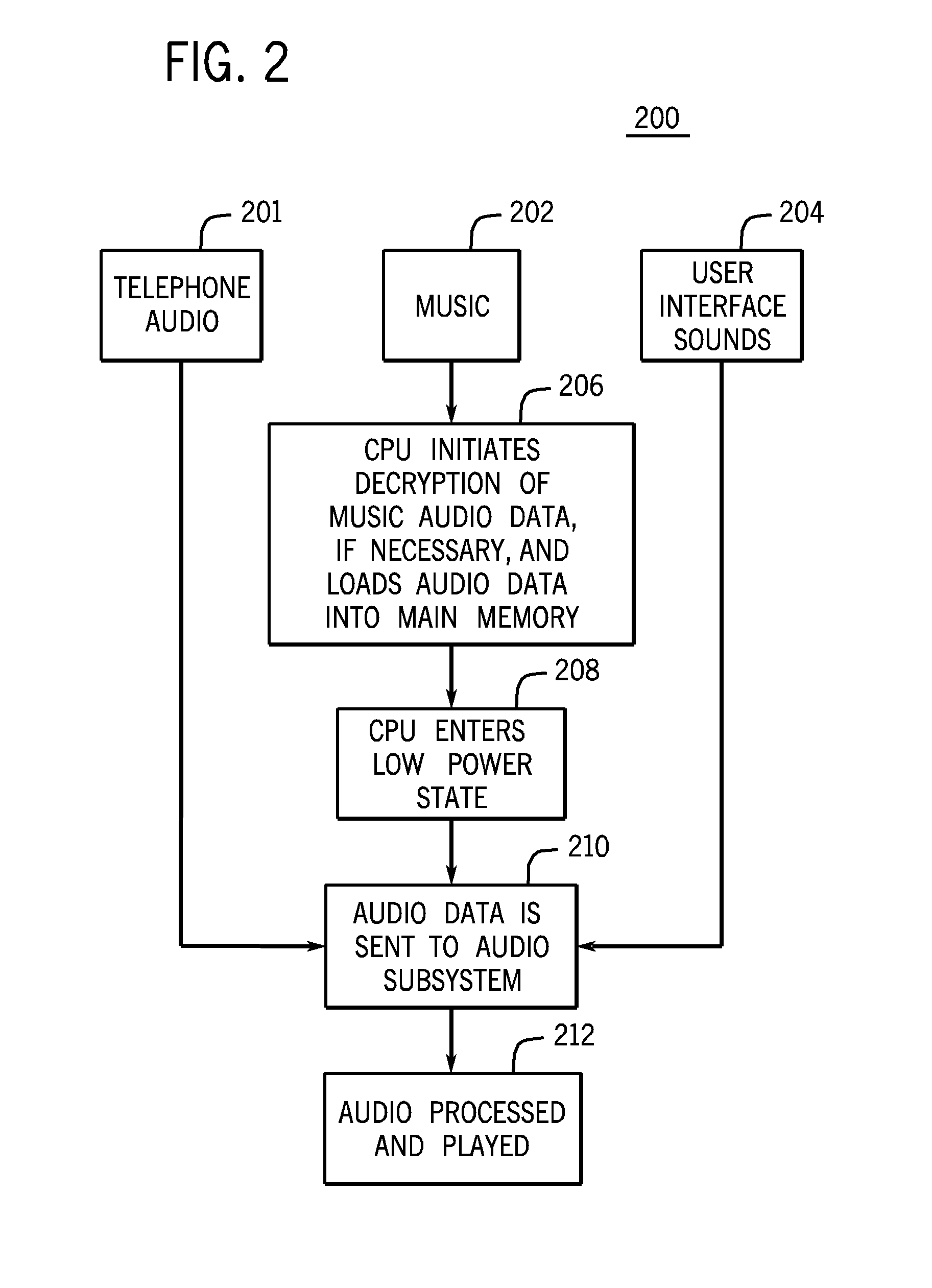
A media processing system and device with improved power usage characteristics, improved audio functionality and improved media security is provided. Embodiments of the media processing system include an audio processing subsystem that operates independently of the host processor for long periods of time, allowing the host processor to enter a low power state. Other aspects of the media processing system provide for enhanced audio effects such as mixing stored audio samples into real-time telephone audio. Still other aspects of the media processing system provide for improved media security due to the isolation of decrypted audio data from the host processor.
Owner:APPLE INC
Storage mapping and partitioning among multiple host processors
InactiveUS6799255B1Input/output to record carriersData processing applicationsData portControl store
A storage controller for controling access to data storage has a memory and at least one data port for a data network including host processors. The memory is programmed to define a respective specification for each host processor of a respective subset of the data storage to which access by the host processor is restricted, and each specification is associated with a host identifier stored in the memory. When the storage controller receives a data access request from a host processor, it decodes a host identifier from the data access request, and searches the memory for a host identifier matching the host identifier decoded from the request. Upon finding a match, the respective specification of the respective subset for the host processor is accessed to determine whether or not storage specified by the storage access request is contained in the respective subset. If so, then storage access can continue, and otherwise, storage access is denied. Preferably the host identifier decoded from the request is a temporary address assigned by the network, and also stored in the memory in association with each respective specification is a relatively permanent identifier for the host processor.
Owner:EMC IP HLDG CO LLC
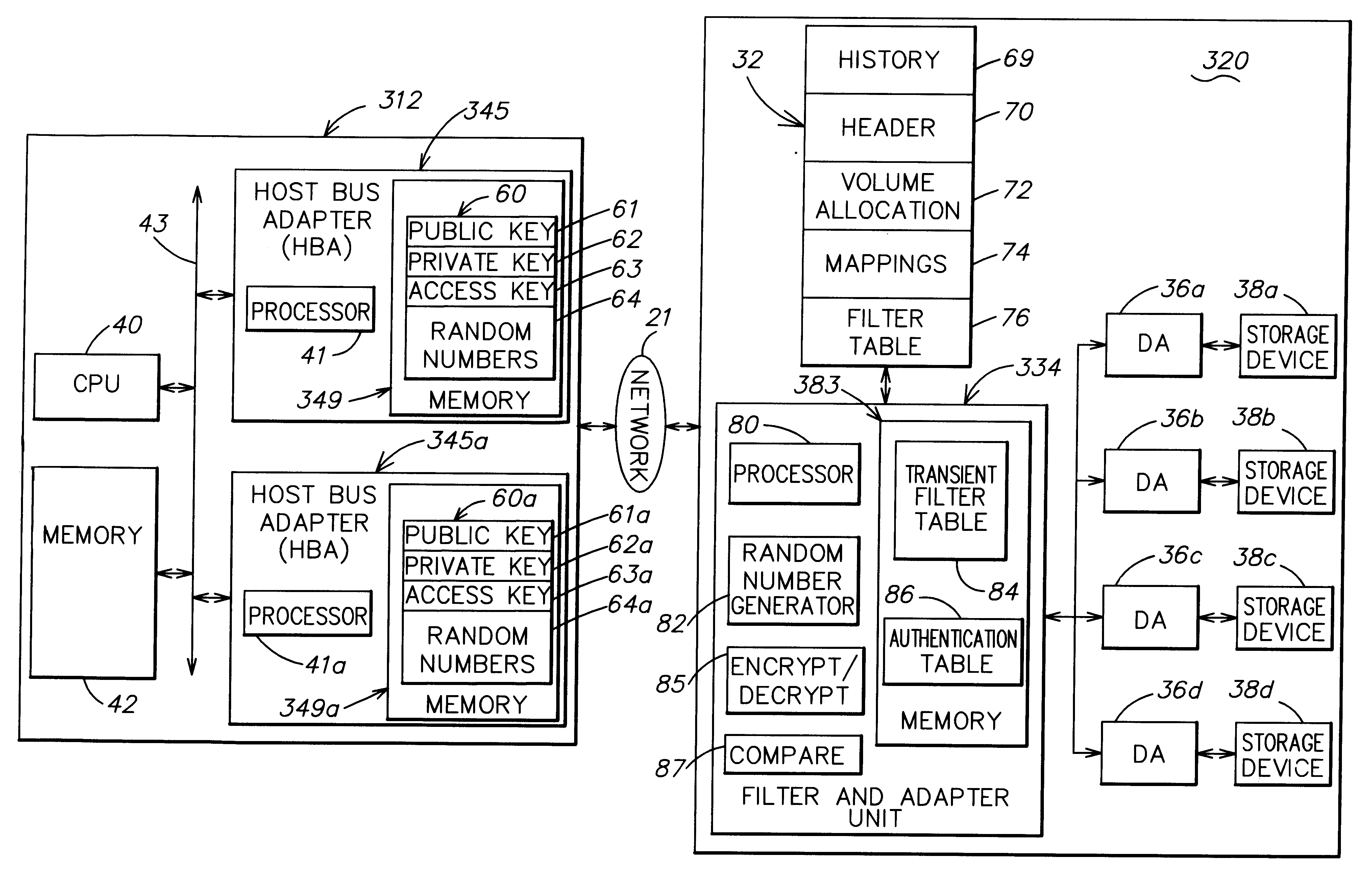
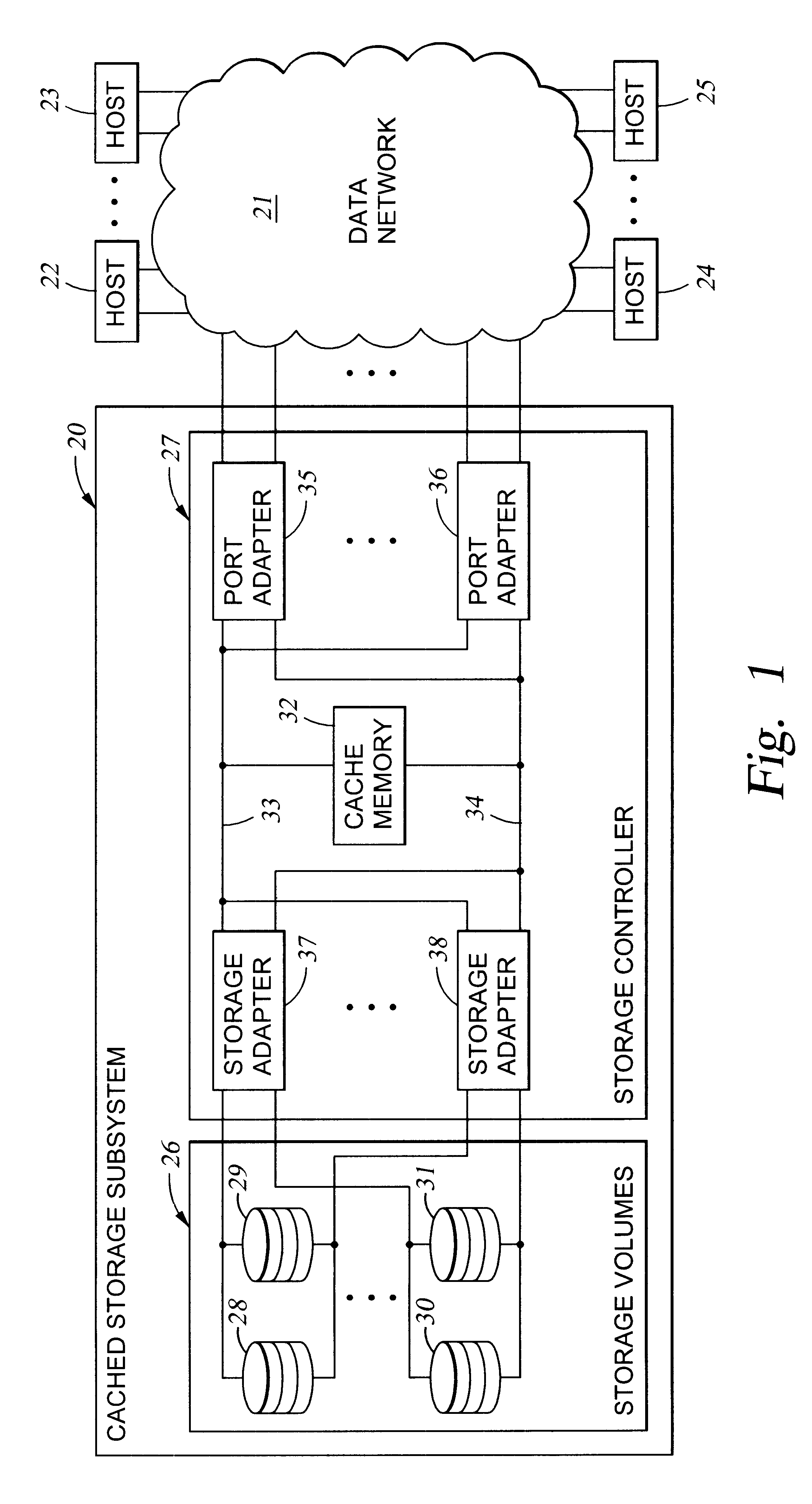
Method and apparatus for authenticating connections to a storage system coupled to a network
InactiveUS6263445B1Key distribution for secure communicationInput/output to record carriersData accessData management
A data management technique for managing accesses to data at a shared storage system includes a filter at the storage system. The filter is coupled to a configuration table, which identifies which of a number of coupled host processors have accesses to each of the resources at the device. During operation, requests received from the host devices are filtered by the filter, and only those requests to resources that the individual host devices have privilege to access are serviced. Advantageously, data security is further enhanced by authenticating each of the requests received by the storage system to verify that the host processor that is represented as forwarding the request is the indicated host processor. In addition, transfers of data between the storage system and the host processor may be validated to ensure that data was not corrupted during the data transfer.
Owner:EMC IP HLDG CO LLC
Scanning device for coded data
InactiveUS7128270B2Input/output for user-computer interactionDigital data processing detailsPhotovoltaic detectorsPhotodetector
A scanning device for scanning coded data indicative of a plurality of locations disposed on a surface is provided. The device generates interaction data based on the sensed coded data. The scanning device comprises a laser source for exposing a coded data portion, a photodetector, an analog to digital converter, a framestore, an image processor and a host processor.
Owner:SILVERBROOK RES PTY LTD
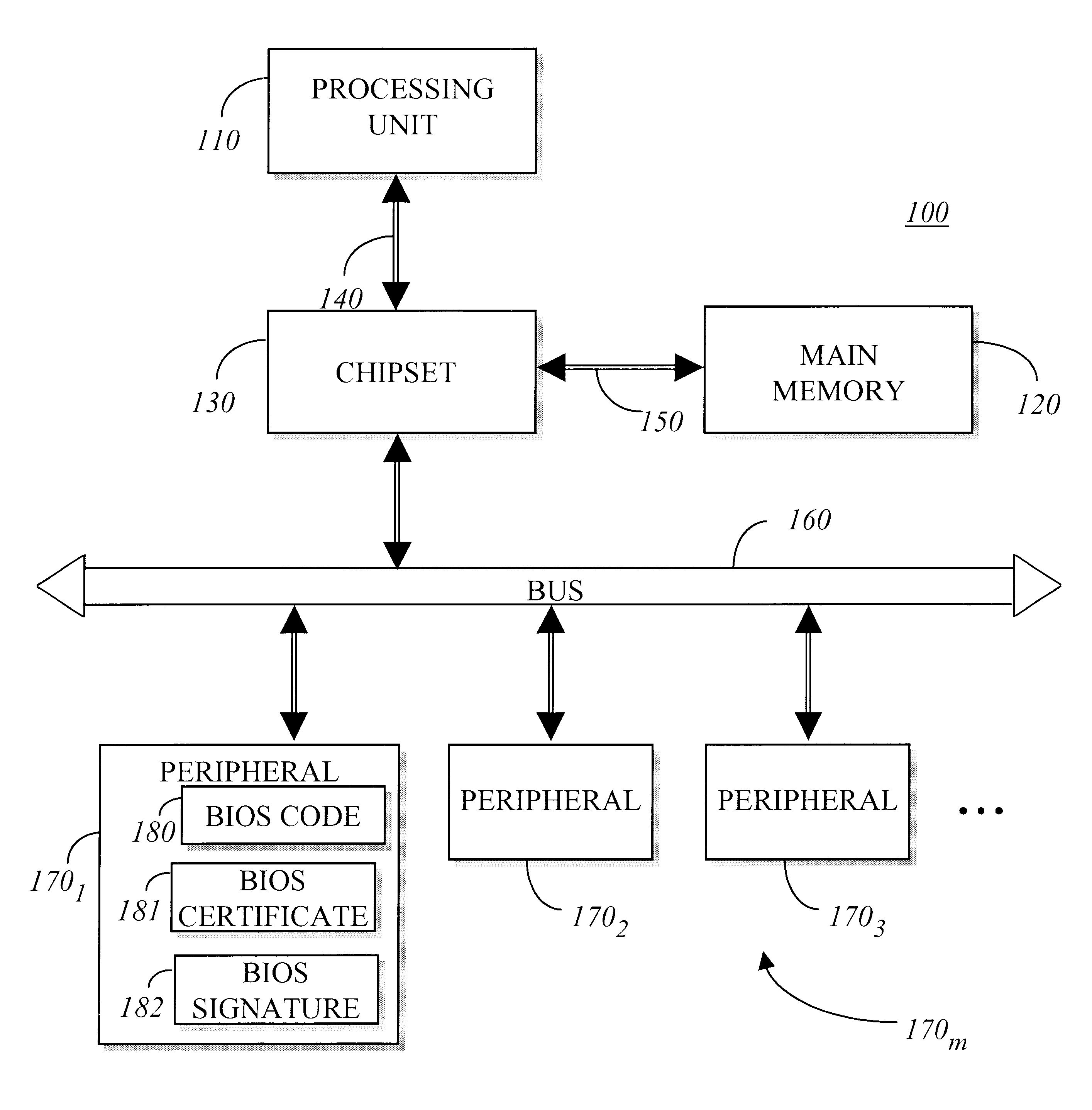
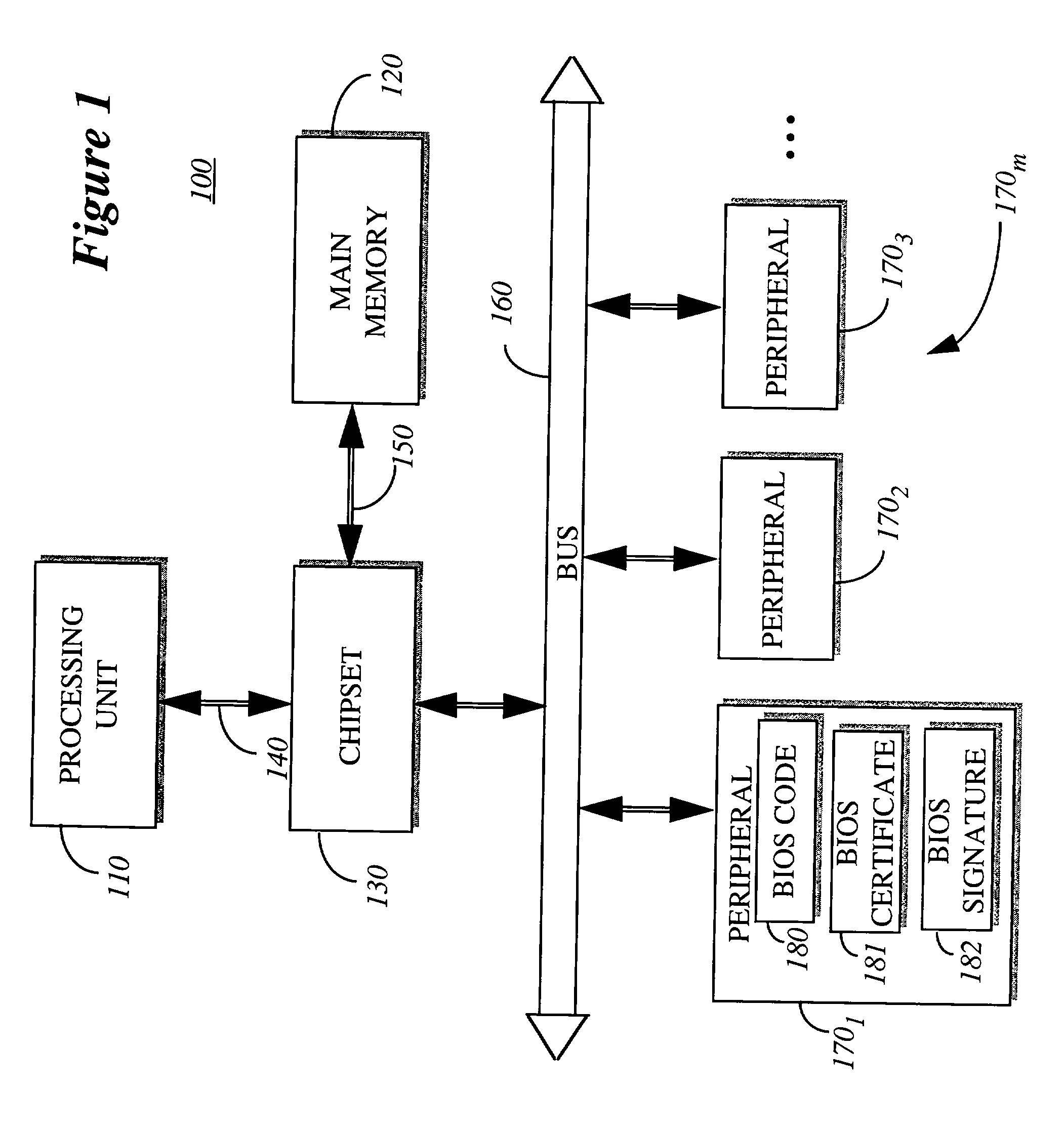
Method for BIOS authentication prior to BIOS execution
InactiveUS6401208B2User identity/authority verificationUnauthorized memory use protectionPower-on resetBIOS
Owner:INTEL CORP
Accelerated compositing of fixed position elements on an electronic device
A device, system and method are provided for processing structured documents for display. Content of a first viewable portion of the structured document having a fixed position in relation to a viewport is rendered as first rendered image data. Content of a second viewable portion that does not have a fixed position is rendered as second rendered image data. The first and second rendered image data are composited, and a resultant composited image is output for display. In response to a scroll or zoom command applied to the document, and in particular to the second viewable portion, the second rendered image data is updated and composited with the first rendered image data. Compositing can be carried out by a graphics processor separate from a main processor in the electronic device. When no fixed position elements are present in the structured document, the main processor renders the entire content without compositing.
Owner:BLACKBERRY LTD
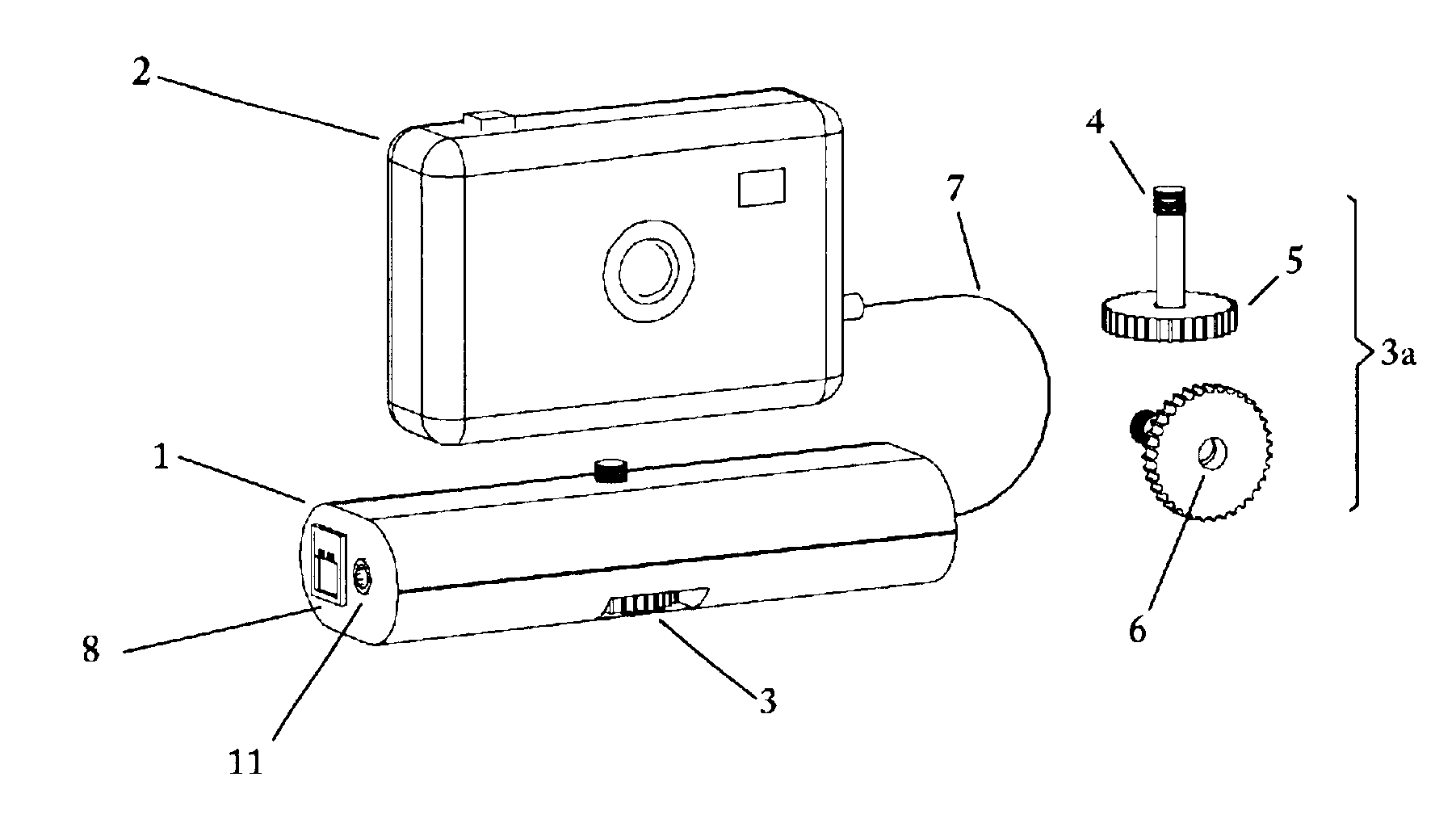
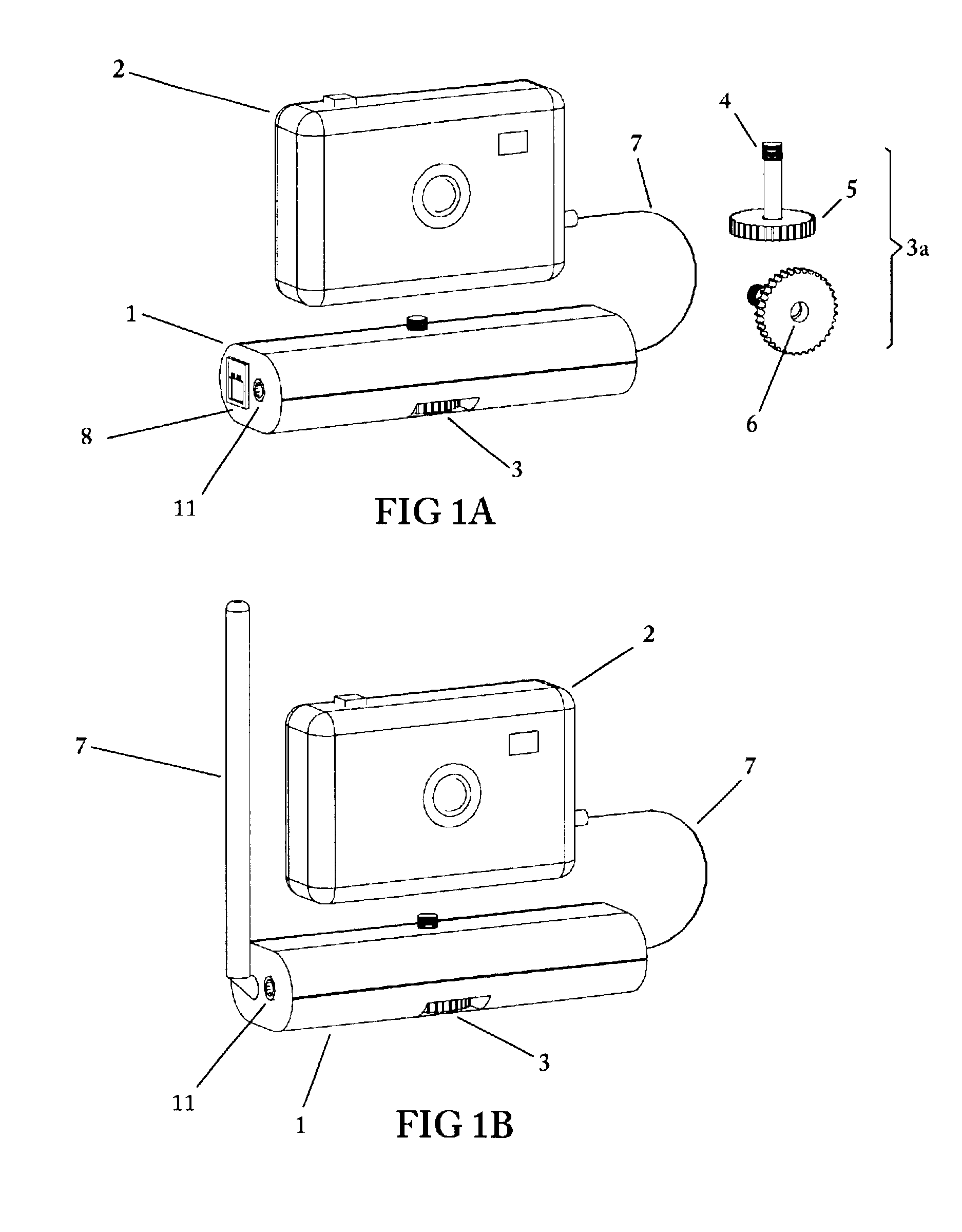
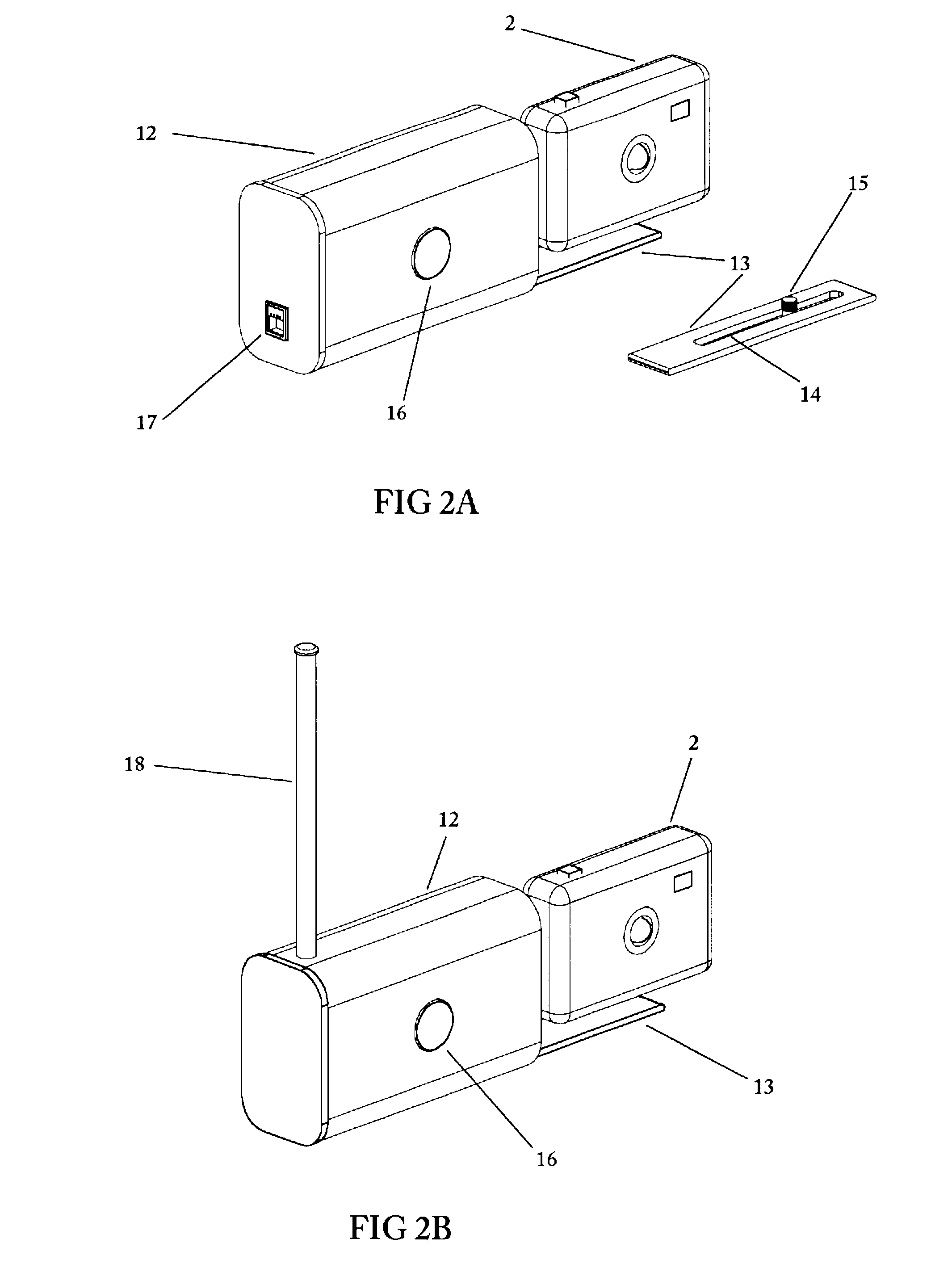
Remote camera relay controller method and apparatus
InactiveUS6400903B1Reduce transmit powerReduction in Eb/NoTelevision system detailsProjector film strip handlingModem deviceTelecommunications link
A remote camera relay method and apparatus for remotely operating a self-contained, unattended digital camera over a communications link. Format conversion means are included for transparently relaying control signals and remote image data between a local host processor and the remotely located digital camera, independently of specific camera command and image protocols. It thereby functions as a universal remote image transmission adapter, operable as an attachment for use with self-contained digital cameras. A portable enclosure is provided for accommodating the remote relay communications and control electronics and for attaching a hand-held digital camera thereto. Further means are included for remotely actuating the pan and tilt orientation of the camera in accordance with field-of-view selection commands. Data rate conversion and error correction coding are included for providing reliable, low power image forwarding. The communications channel could be a dial-up telephone system, a network connection, modem, an infra-red link or a wireless RF link, for example. Additional control means are provided for remotely selecting the camera field of view for image capture, and includes the ability to access only those subsets of image scenes for which viewing permissions are authorized. A further mode of operation includes protocol training whereby host photographing commands are captured by the remote relay invention during on-line operation, then replayed at programmed times resulting in automatic scheduled remote image capture. Power management is provided for maximizing operating time when used in low power, portable, battery operation.
Owner:CONOVAL PAUL
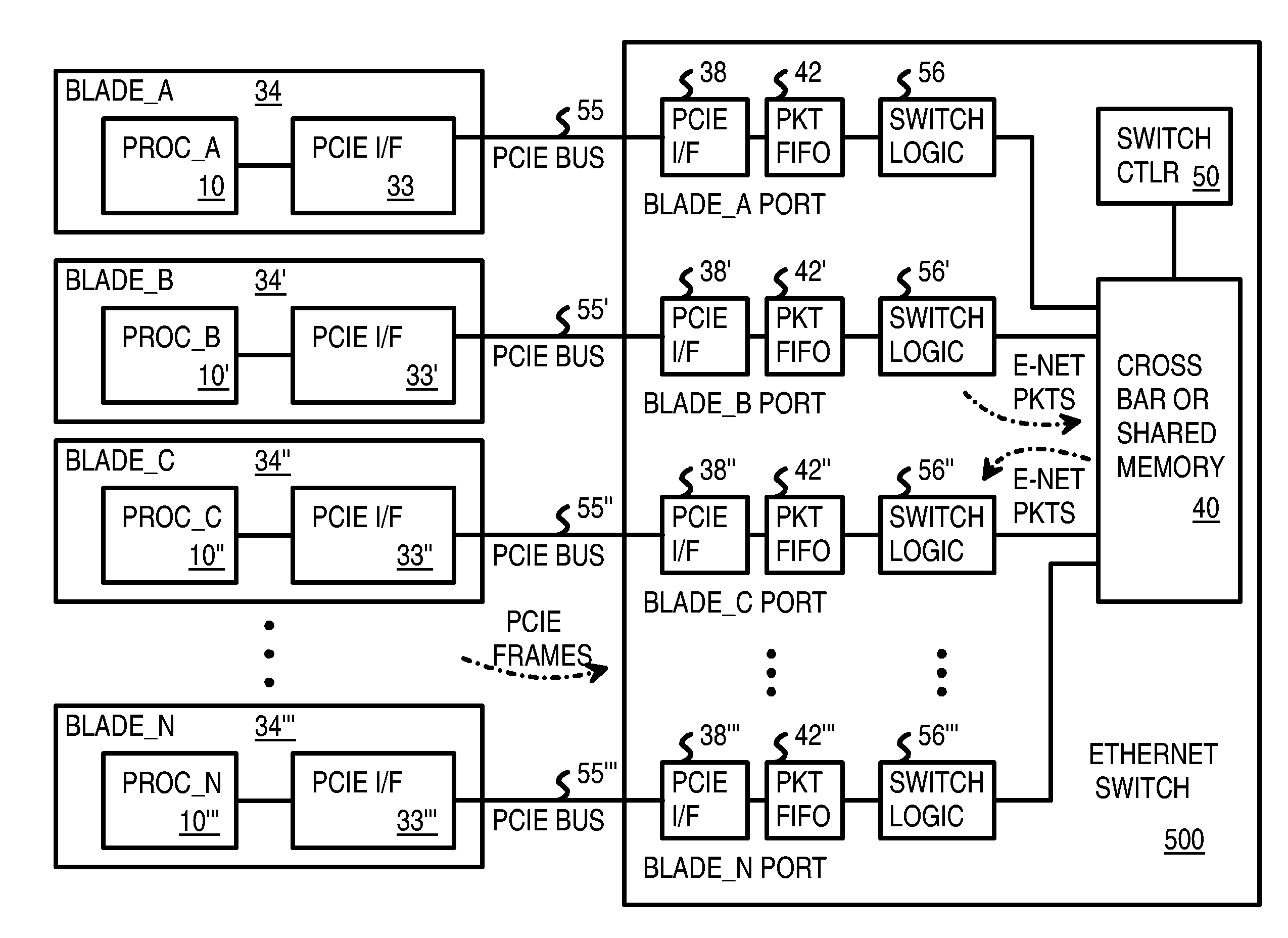
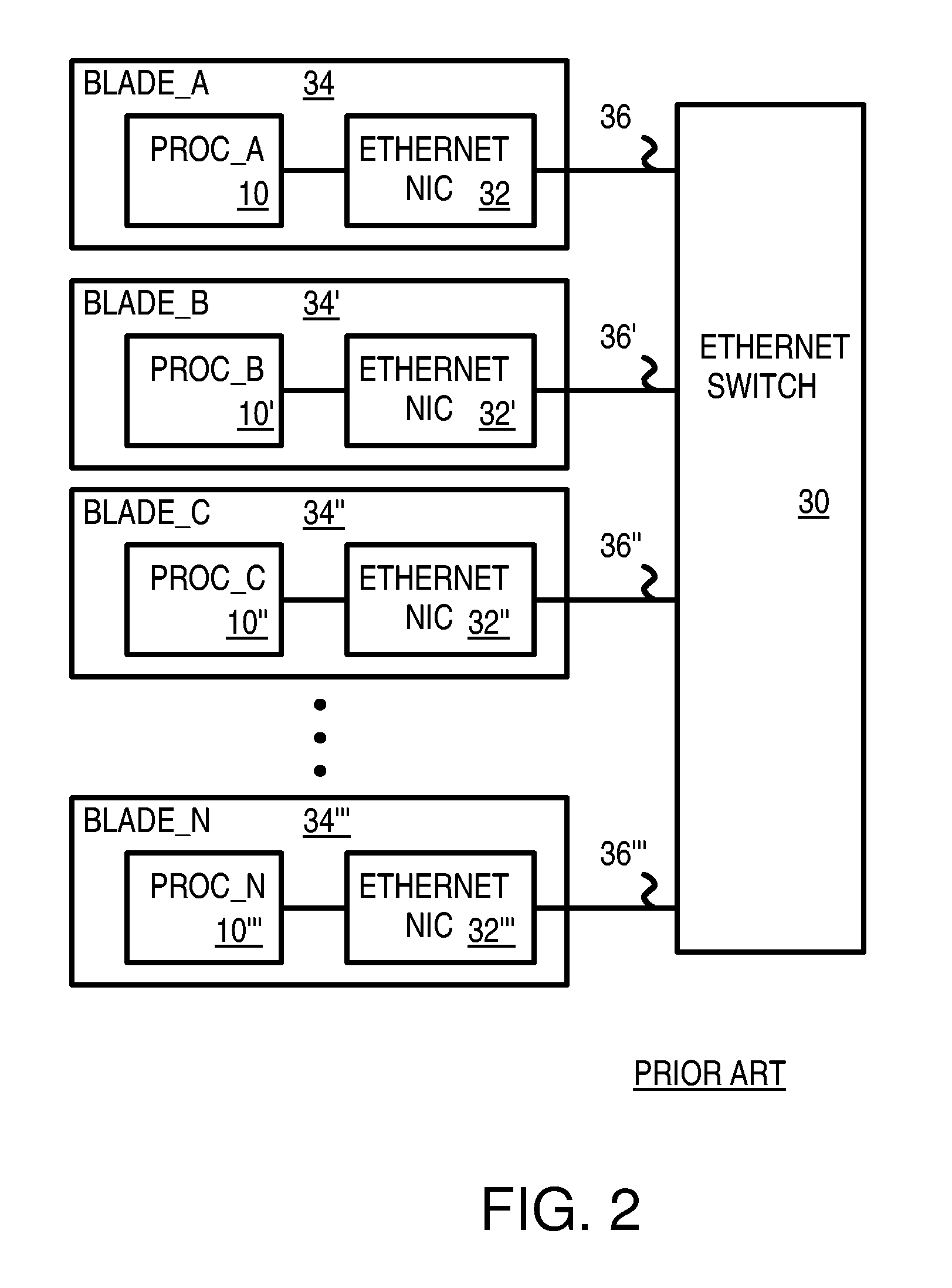
Pseudo-ethernet switch without ethernet media-access-controllers (MAC's) that copies ethernet context registers between PCI-express ports
A Pseudo-Ethernet switch has a routing table that uses Ethernet media-access controller (MAC) addresses to route Ethernet packets through a switch fabric between an input port and an output port. However, the input port and output port have Peripheral Component Interconnect Express (PCIE) interfaces that read and write PCI-Express packets to and from host-processor memories. When used in a blade system, host processor boards have PCIE physical links that connect to the PCIE ports on the Pseudo-Ethernet switch. The Pseudo-Ethernet switch does not have Ethernet MAC and Ethernet physical layers, saving considerable hardware. The switch fabric can be a cross-bar switch or can be a shared memory that stores Ethernet packet data embedded in the PCIE packets. Write and read pointers for a buffer storing an Ethernet packet in the shared memory can be passed from input to output port to perform packet switching.
Owner:DIODES INC
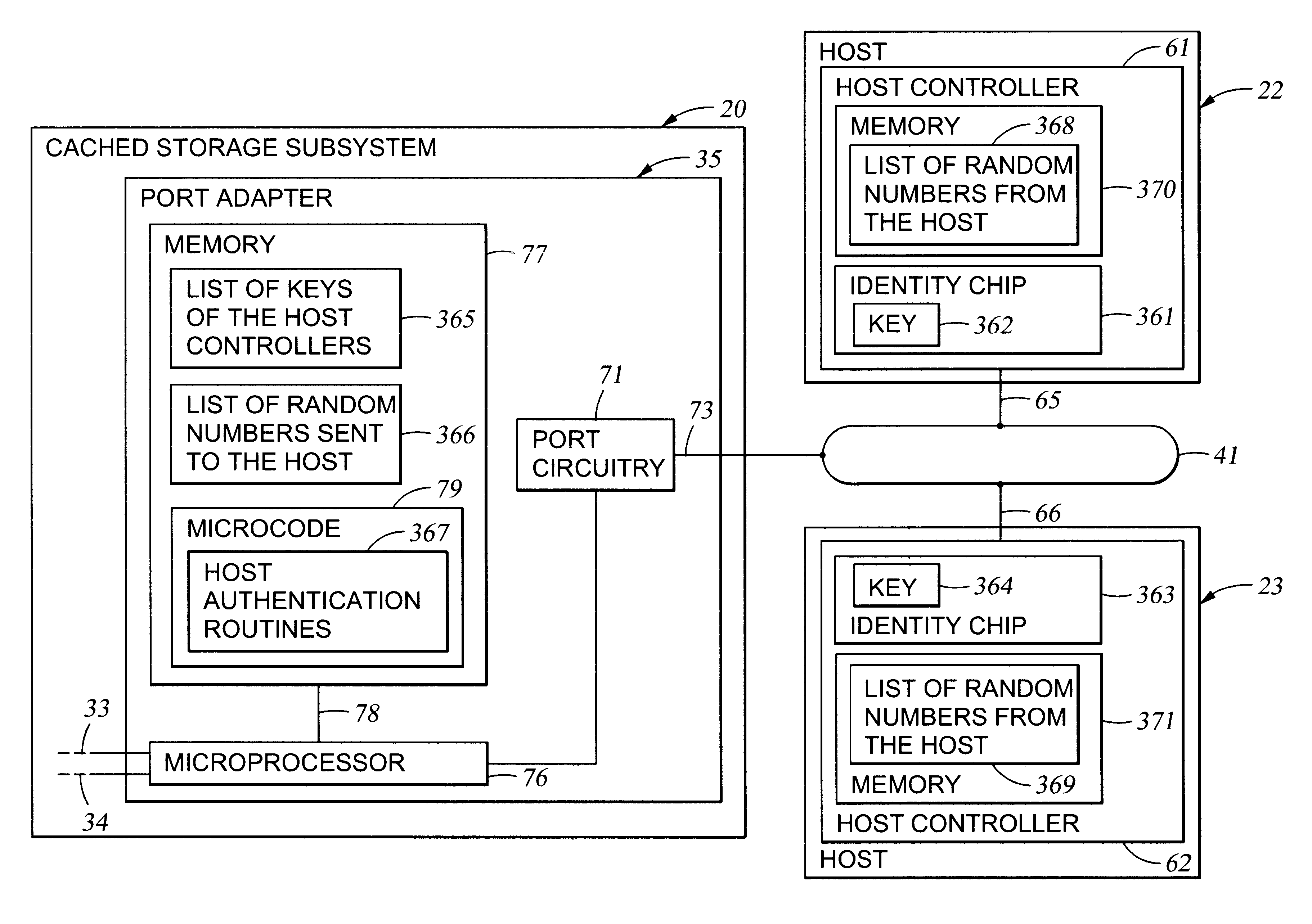
Authentication of a host processor requesting service in a data processing network
InactiveUS6493825B1Key distribution for secure communicationPublic key for secure communicationData processing systemVisual inspection
An object is authenticated by transmitting a random number to the object. The object has an integrated circuit chip including a memory and encryption circuitry. The memory stores information defining an encryption scheme preassigned to the object. The encryption circuitry reads the memory, and encrypts the random number according to the encryption scheme defined by the information read from the memory to produce encrypted data. The memory cannot be read from any output of the integrated chip, and the chip is constructed so that it is virtually impossible to recover the information contained in the memory by visual inspection, probing, or disassembly of the chip. The object is authenticated by checking whether the encrypted data is a correct result of encrypting the data using the encryption scheme pressigned to the object. The method can be used in a data processing system to authenticate each message transmitted by a host processor to a data processing device. For example, when a host logs into the data processing device, the data processing device transmits a series of random numbers to the host. The host encrypts the random numbers to produce a series of encrypted data, and the data processing device concurrently encrypts the random numbers to produce a series of encrypted values. The host inserts respective encrypted data into each message, and the data processing device authenticates each message by comparing the encrypted data in the message to a corresponding encrypted value.
Owner:EMC IP HLDG CO LLC
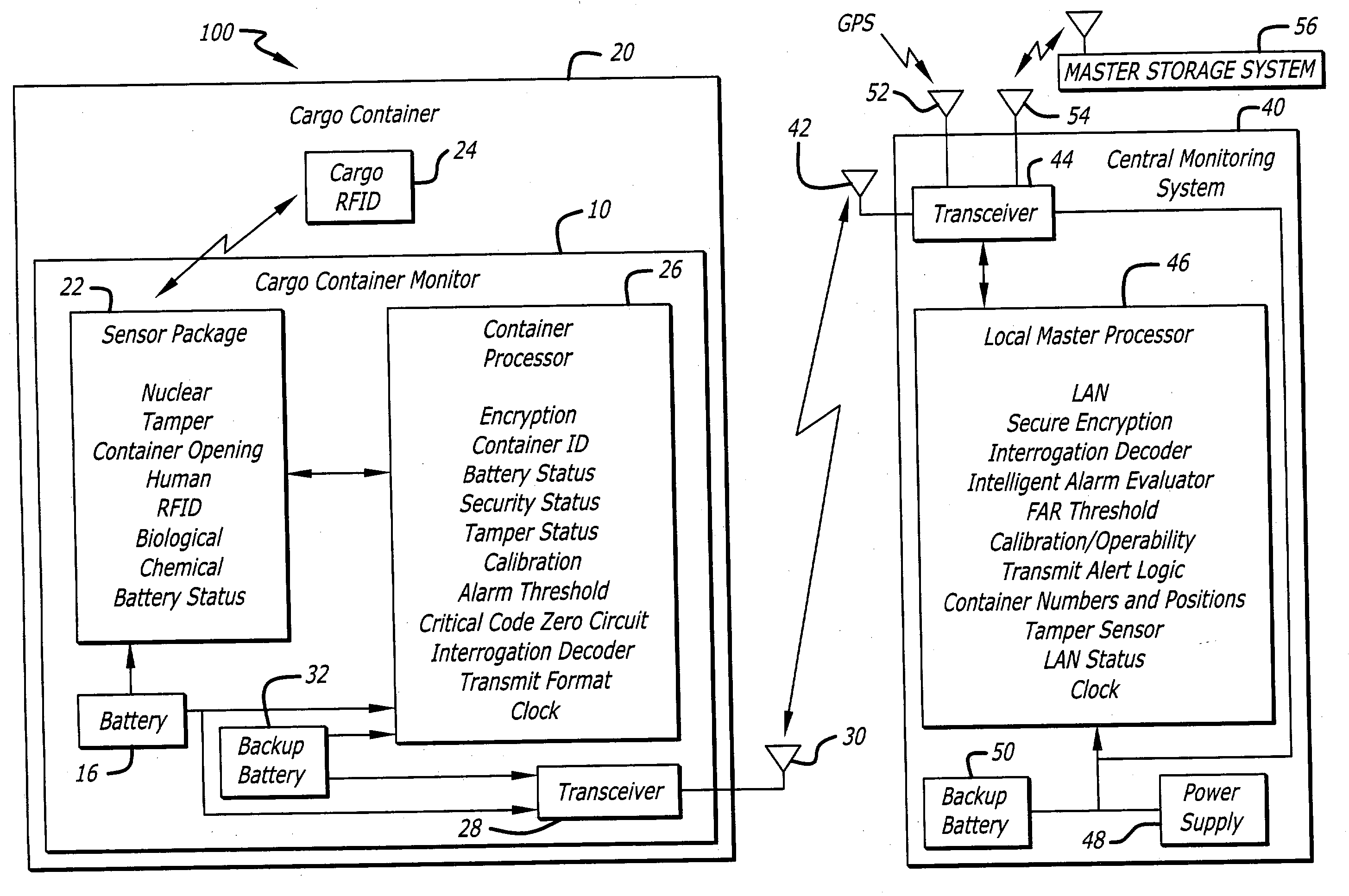
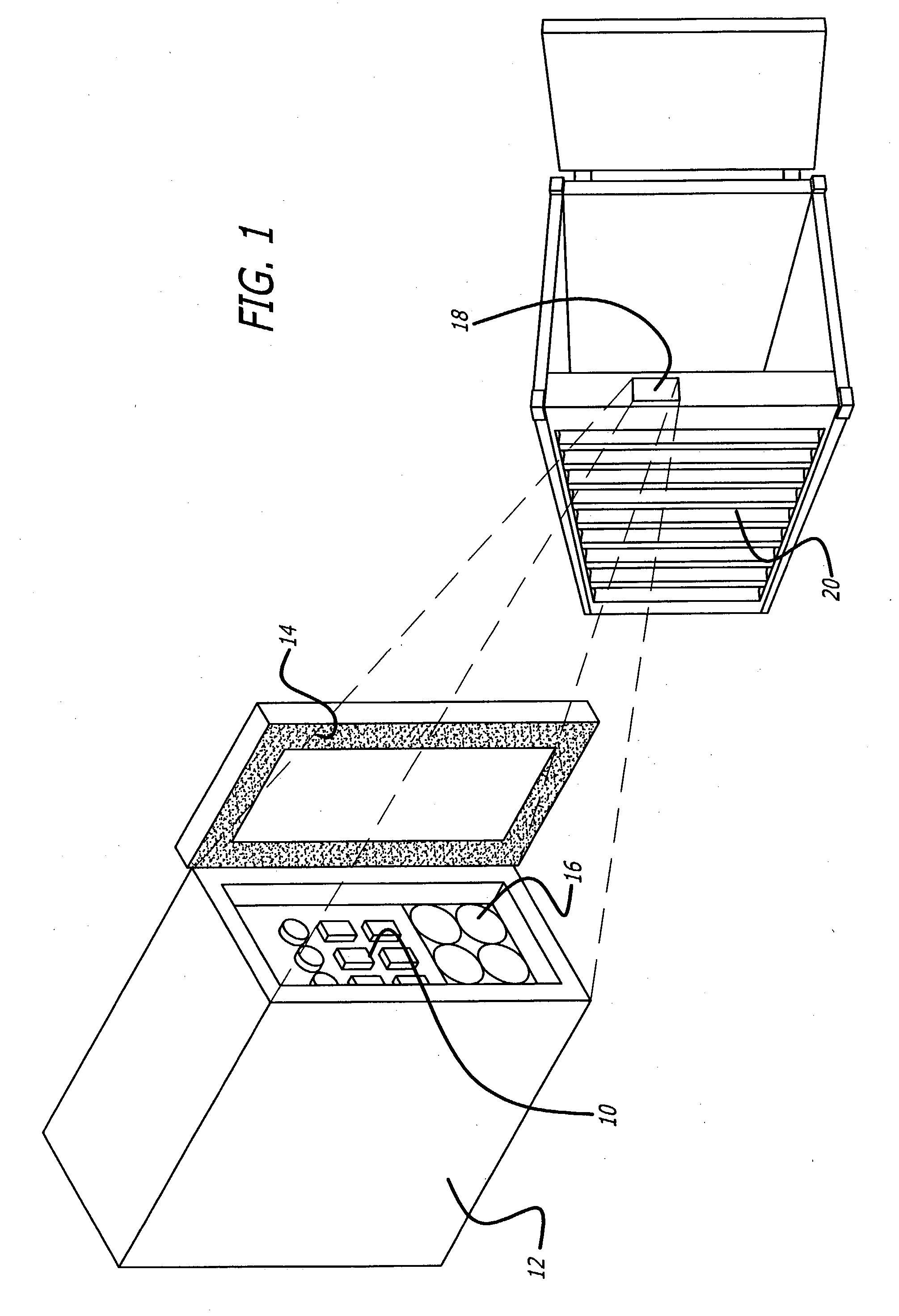
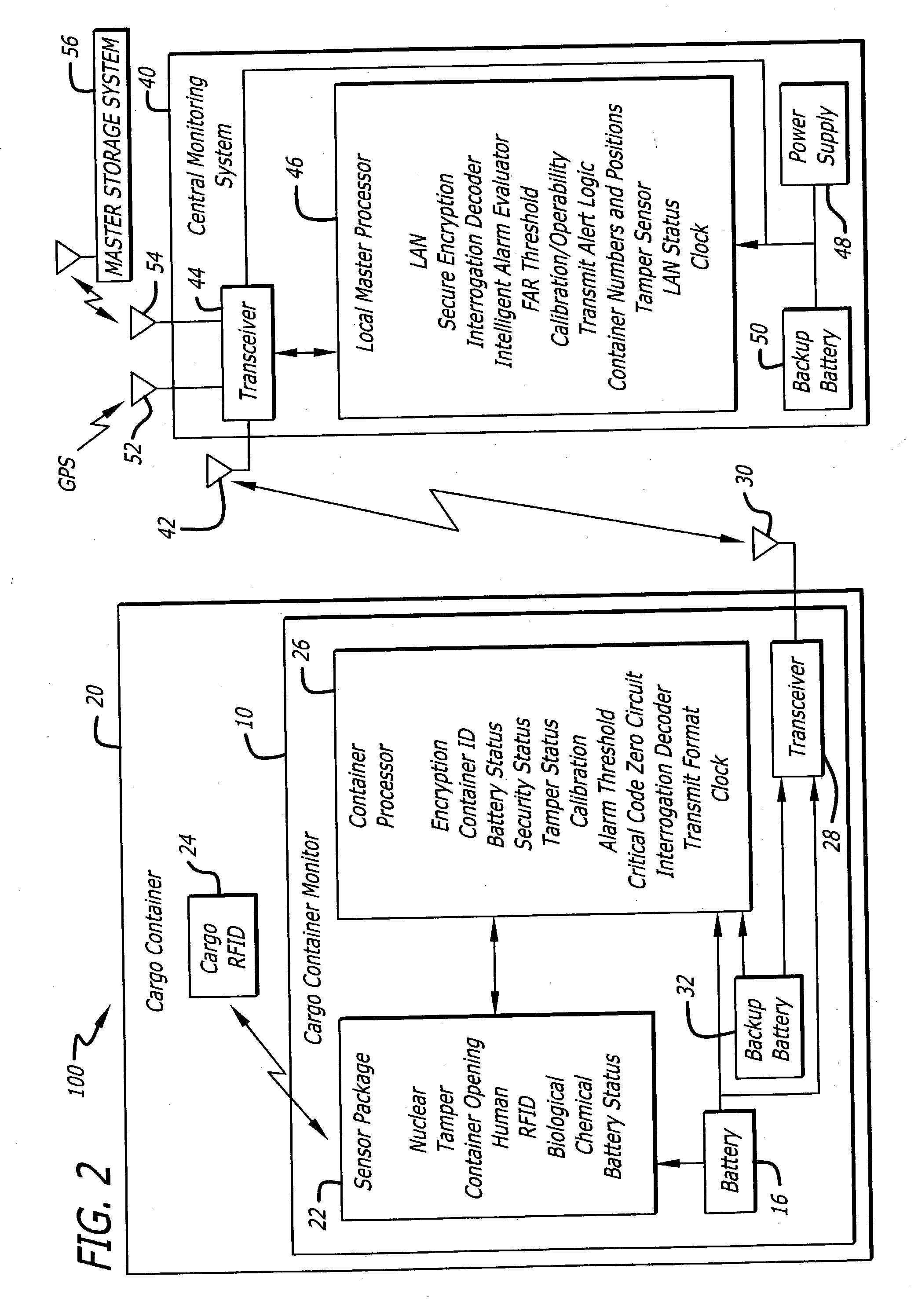
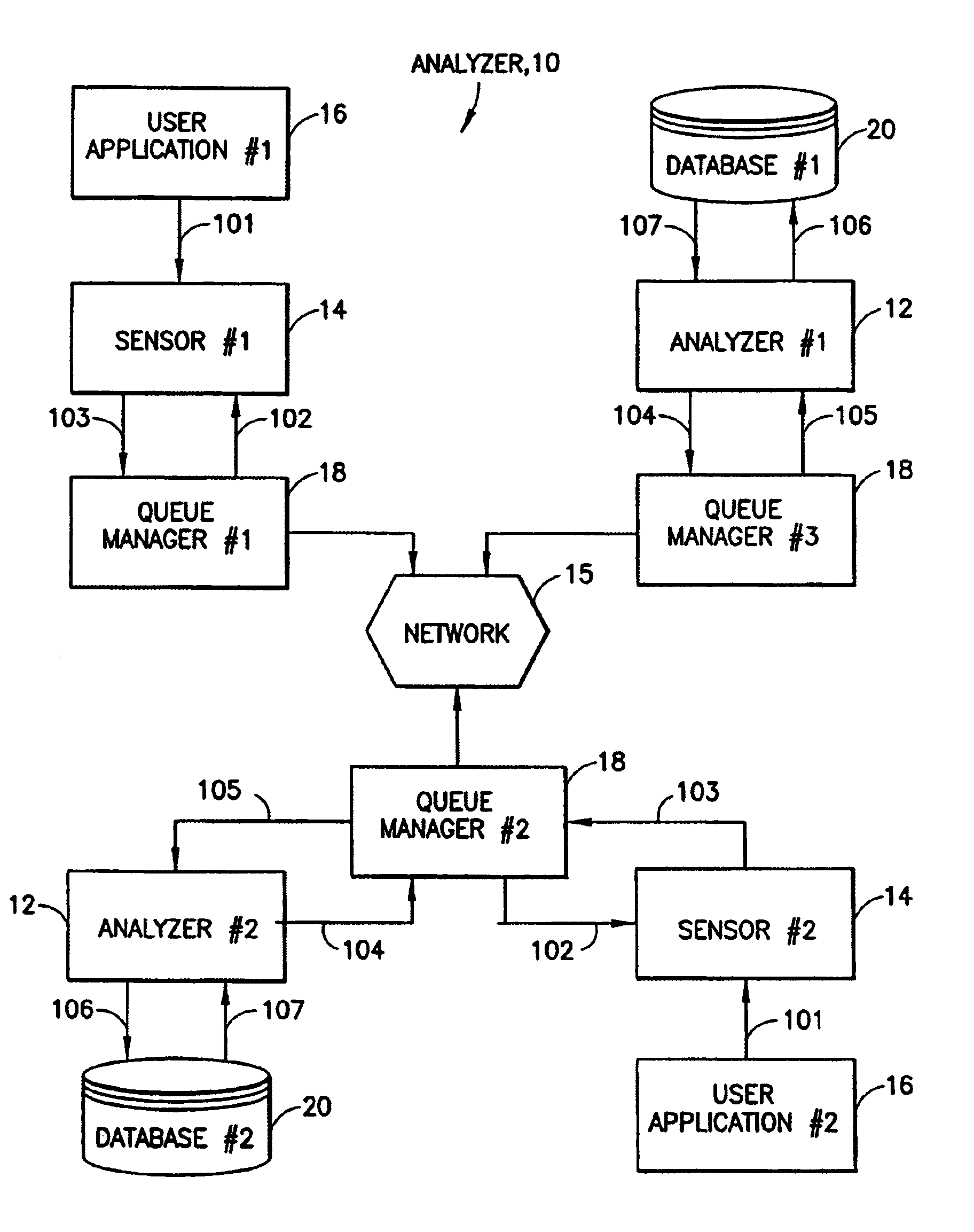
Sensor suite and communication system for cargo monitoring and identification
InactiveUS20040233055A1Frequency-division multiplex detailsTime-division multiplexTransceiverCommunications system
A system and method for monitoring a cargo container. The novel system (100) includes a sensor module (10) mounted in each target area (20) and a central monitoring system (40). Each sensor module (10) includes one or more sensors (22) and a transceiver (28) for transmitting data from the sensors to the central monitoring system (40). The central monitoring system (40) includes a transceiver (44) for receiving the data from all sensor modules (10) and a local master processor (46) for processing and analyzing the data. In the preferred embodiment, each transceiver (28) is capable of receiving and retransmitting signals of other sensor modules to relay signals of a particular sensor module (10) in a daisy chain fashion to and from the central monitoring system (40).
Owner:RAYTHEON CO
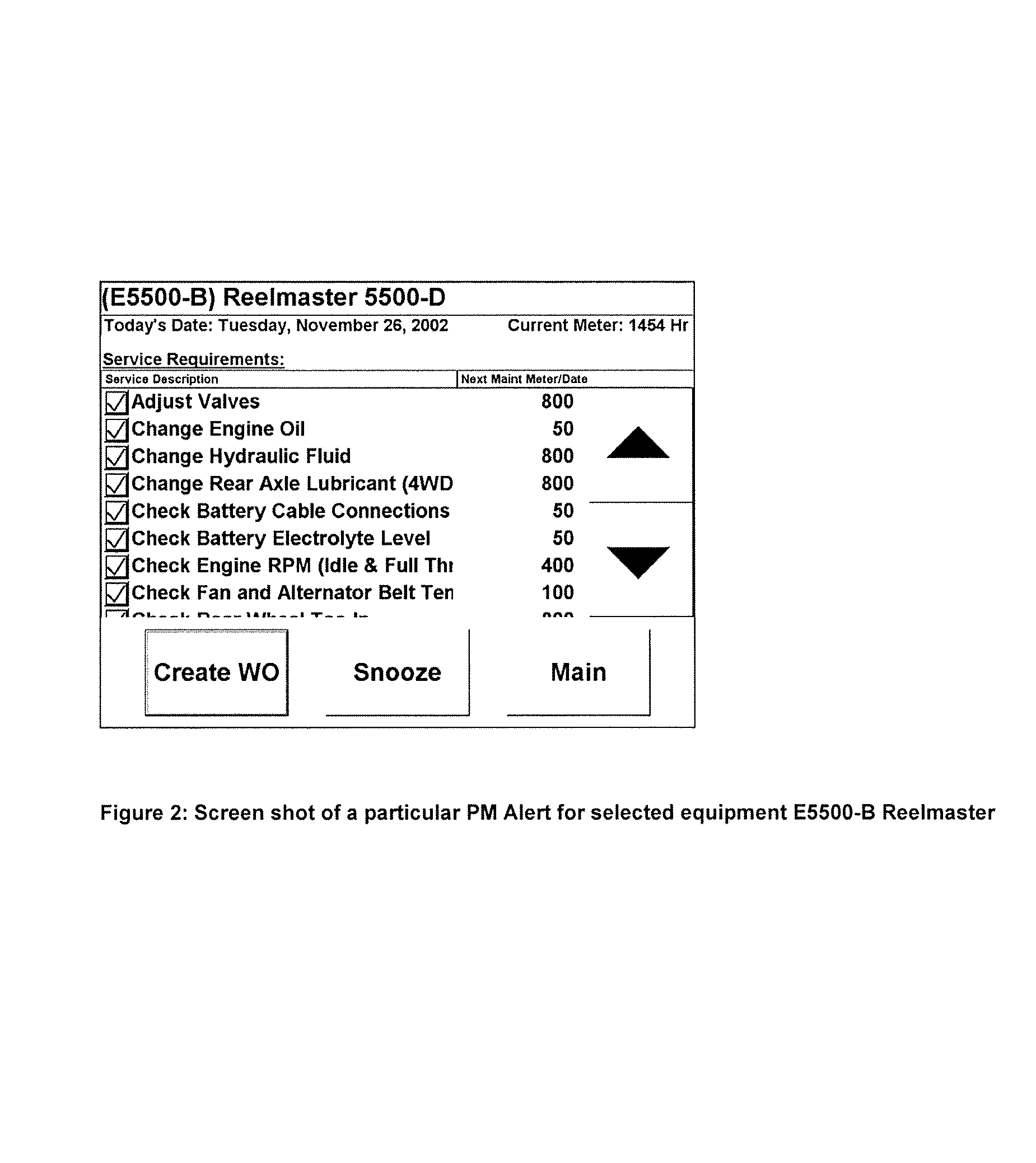
Integrated system for routine maintenance of mechanized equipment
ActiveUS7356393B1Easy accessEffective maintenanceVehicle testingRegistering/indicating working of vehiclesComputerized systemMaster processor
An apparatus and method for managing the preventative maintenance requirements and unscheduled repairs on a fleet of vehicles. The apparatus includes a computer system having a host processor and a database accessible by the host processor, and at least one maintenance response station communicating with the host processor. The database contains vehicle specific maintenance schedules indicating recommended maintenance intervals for scheduled maintenance, where each scheduled maintenance has associated maintenance tasks. The method involves periodically receiving signals at the host processor containing maintenance trigger data associated with a specific vehicle in the fleet of vehicles, comparing the received maintenance trigger data to maintenance schedule data contained in the database, and for each comparison, determining whether maintenance is indicated, and if so, identifying the vehicle at a vehicle response station.
Owner:TURFCENTRIC
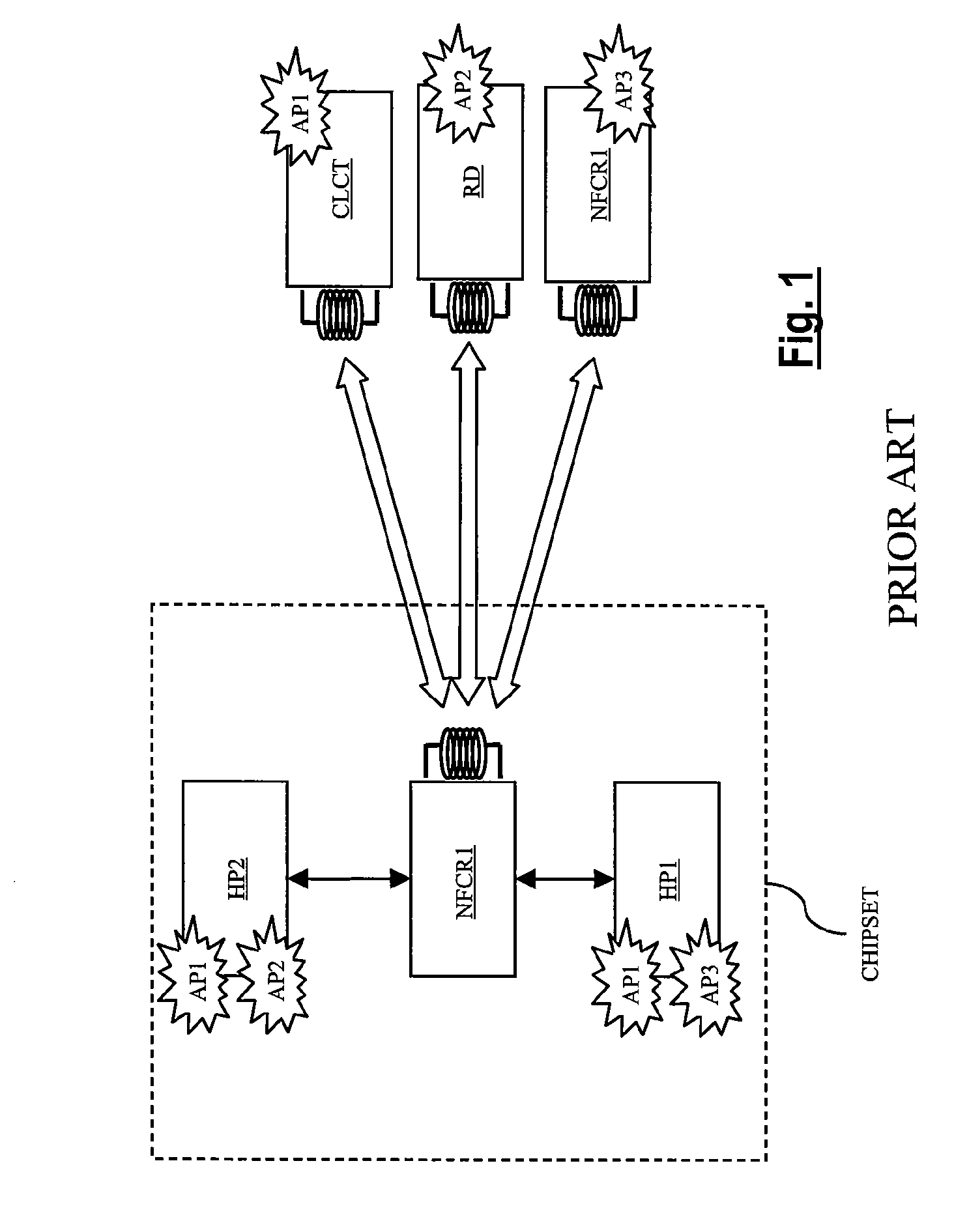
Method for routing incoming and outgoing data in an NFC chipset
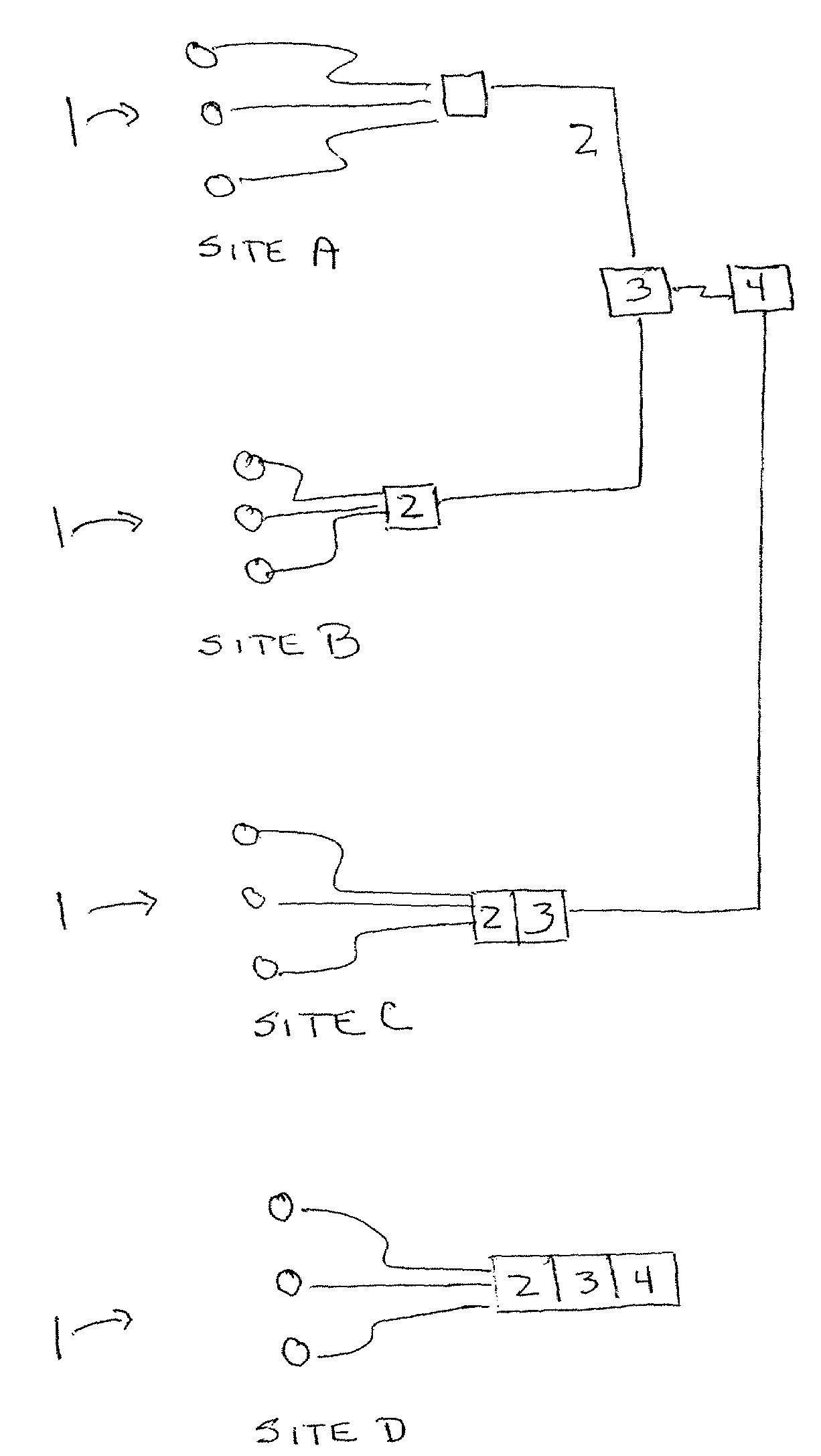
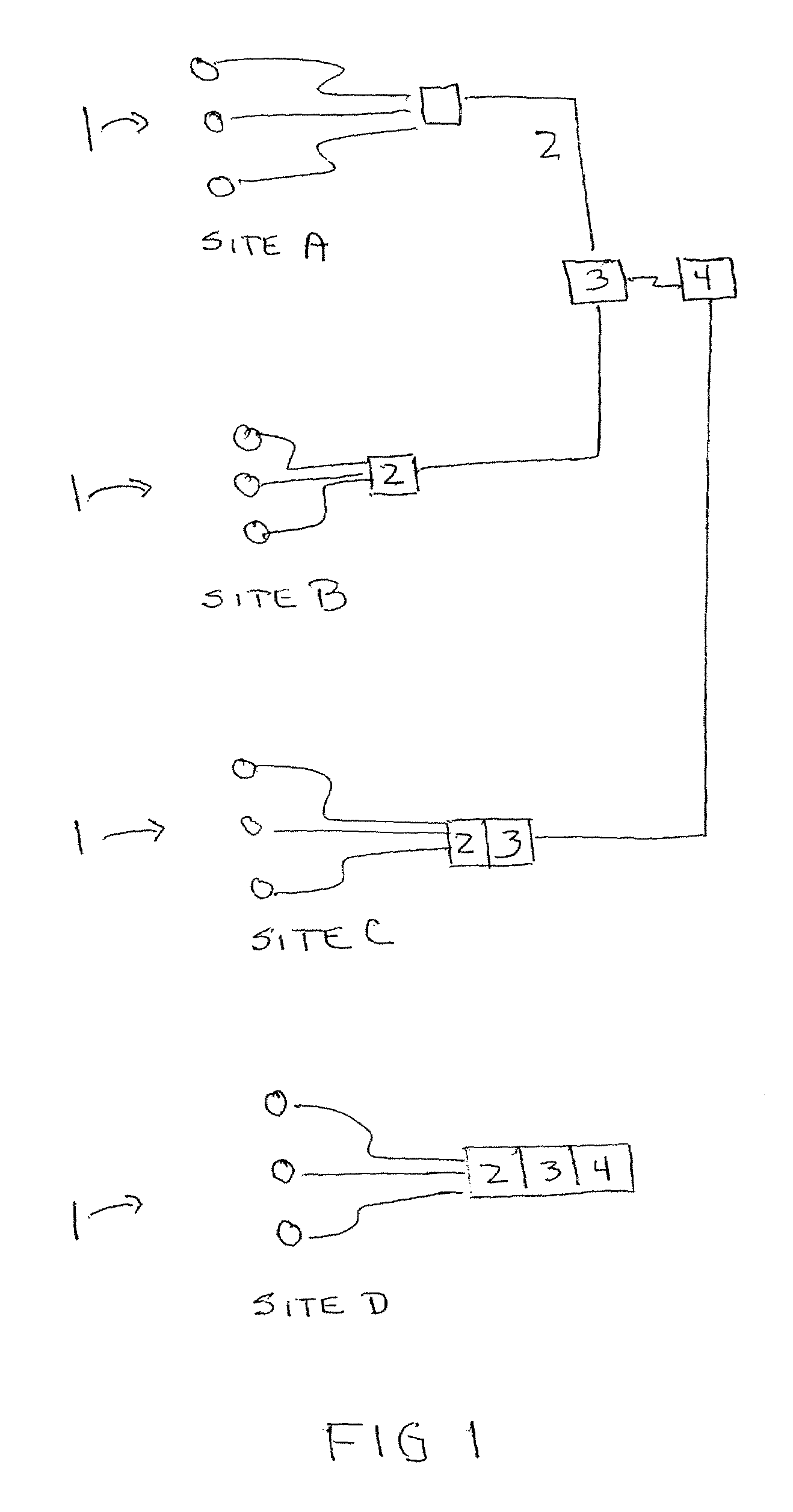
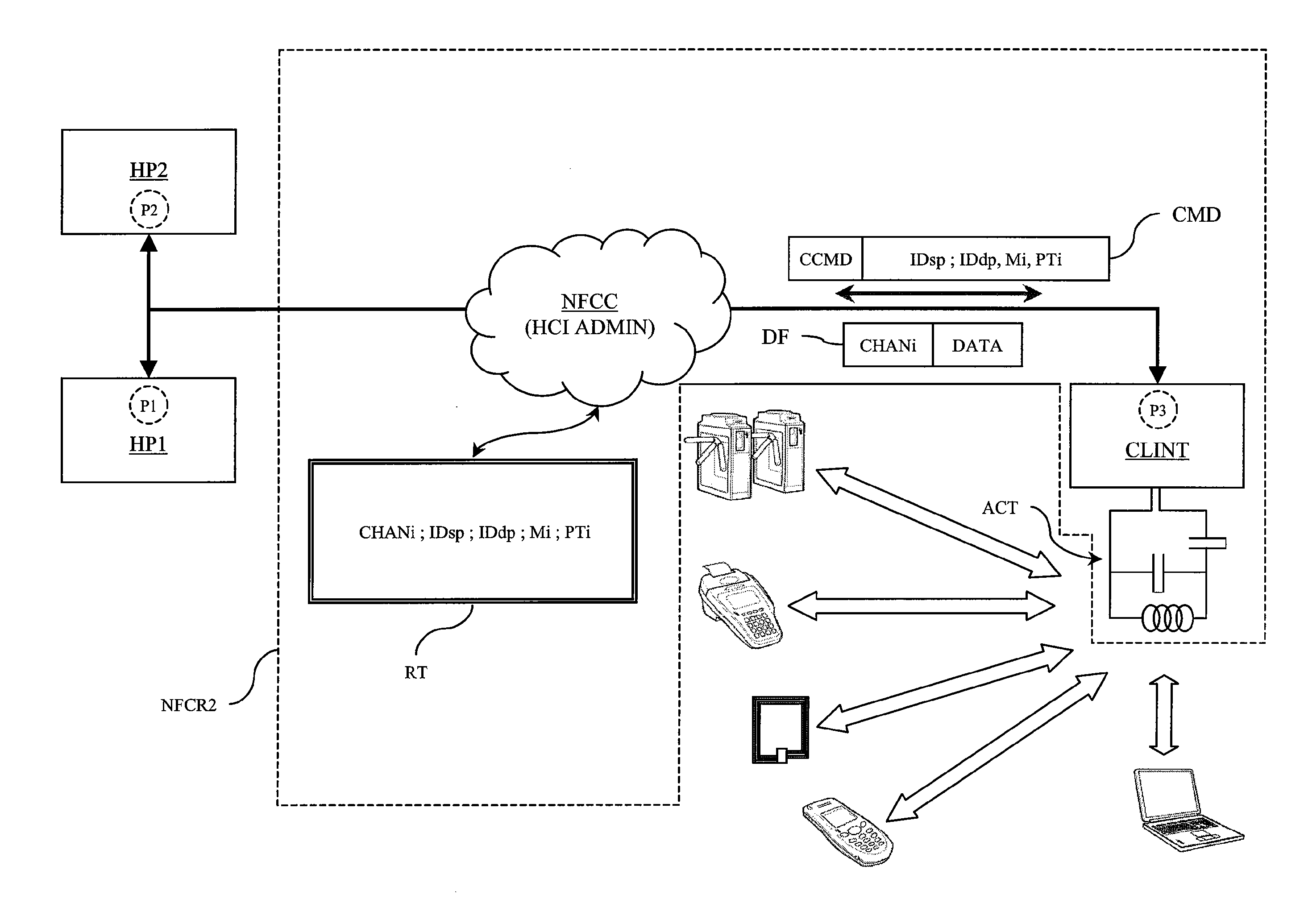
A method for routing data in a chipset comprising at least two host processors and one RFID-type contactless data send / receive interface configurable according to several operating modes and according to several contactless communication protocols includes routing, to at least one of the host processors, data received by the contactless data send / receive interface via a contactless data transmission channel. The method further includes determining a destination point of the data in a host processor using as criteria to determine the destination point the operating mode and the contactless communication protocol used by the contactless data send / receive interface to create the contactless data transmission channel through which the data are received.
Owner:VERIMATRIX INC
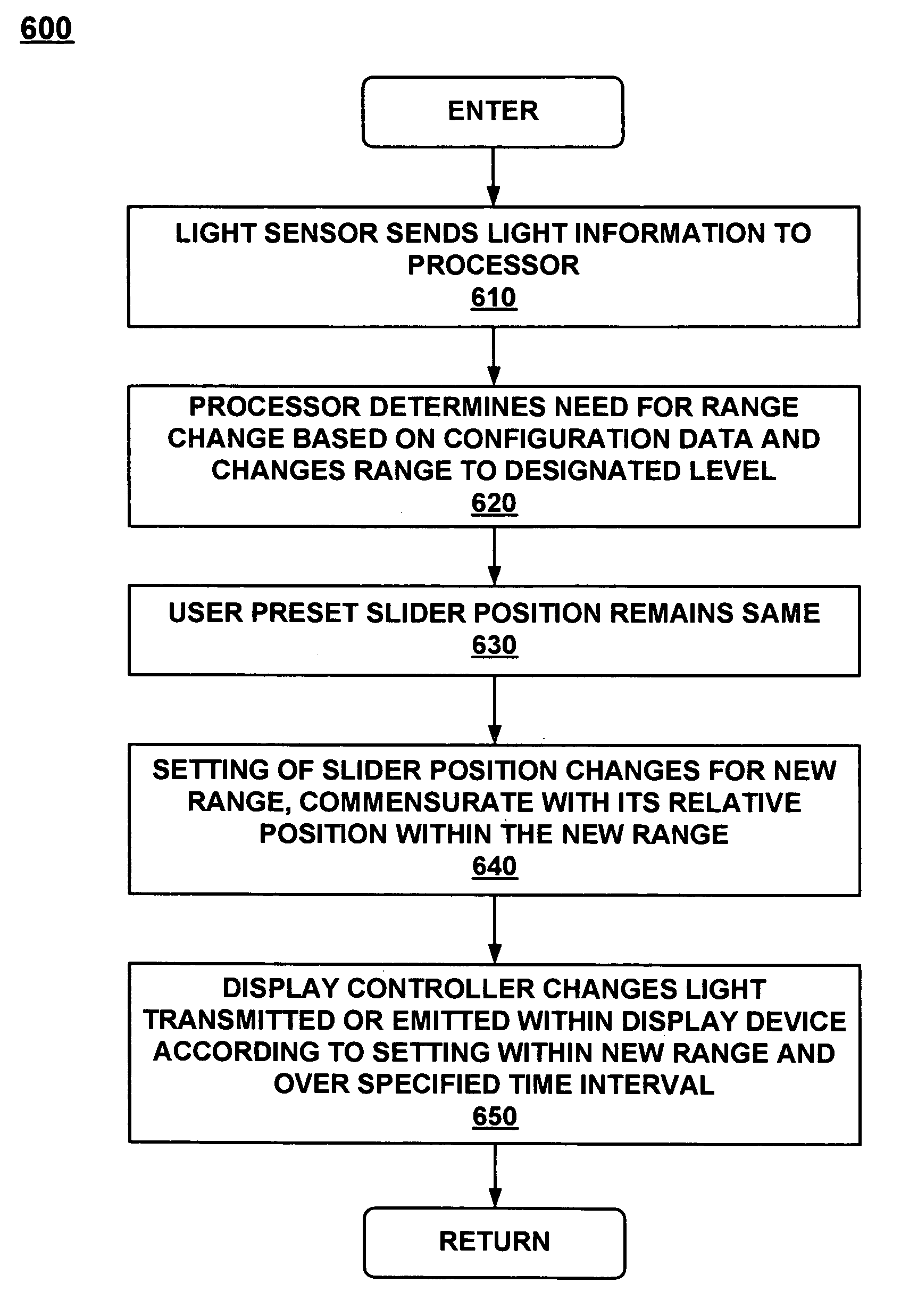
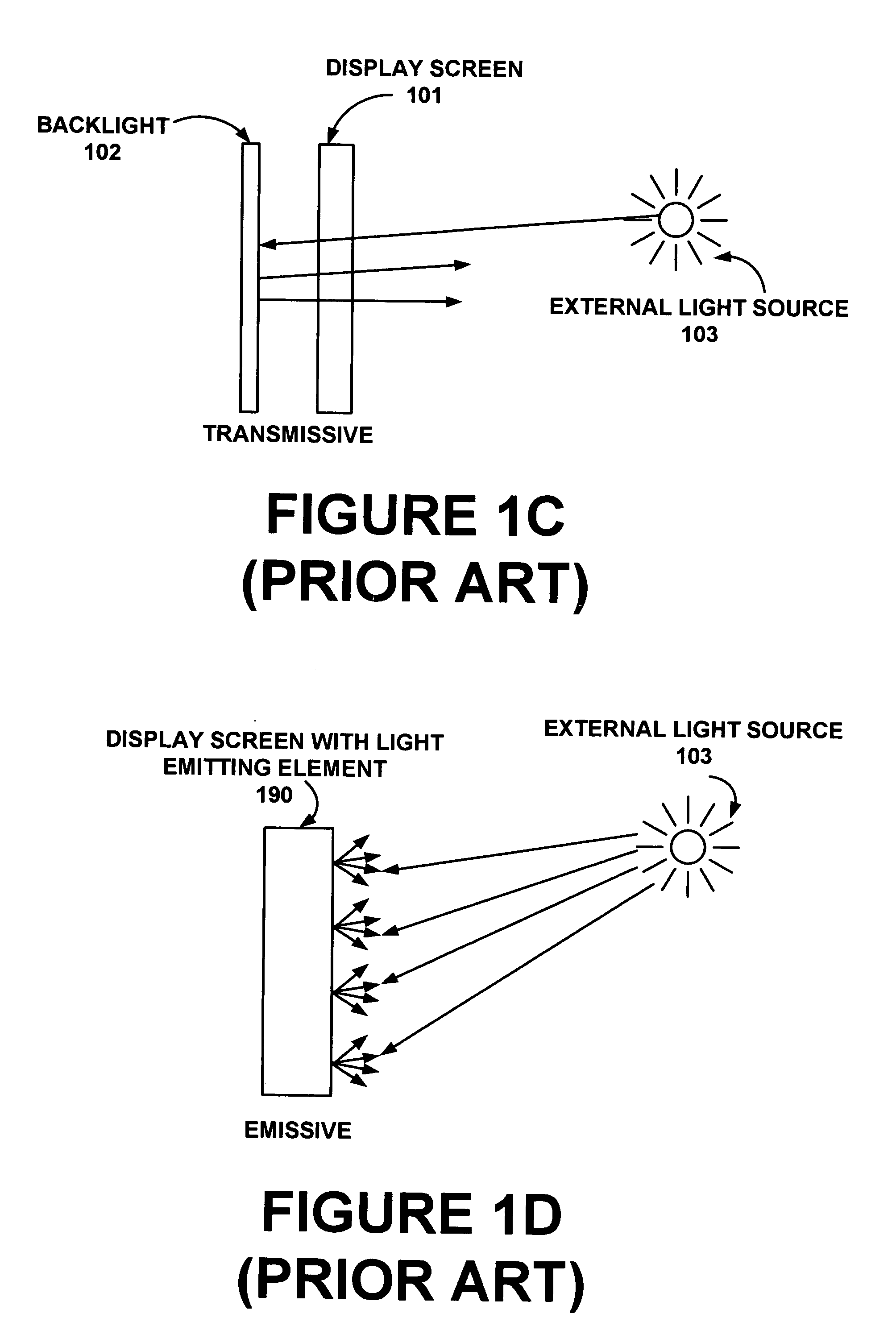
Dynamic brightness range for portable computer displays based on ambient conditions
InactiveUS6947017B1Pleasant battery experienceProlong lifeCathode-ray tube indicatorsInput/output processes for data processingDisplay deviceEmbedded system
A portable computer system that comprises dynamically adjustable brightness range settings and brightness control for providing improved user readability and prolonged component lifetime of the display screen. The main processor can change the range settings based on ambient light conditions or the user can perform the changes. The brightness level of the display changes according to a user selected setting within the range selected. The time required to implement the brightness change can be set to a value which can be configured by the user.
Owner:QUALCOMM INC
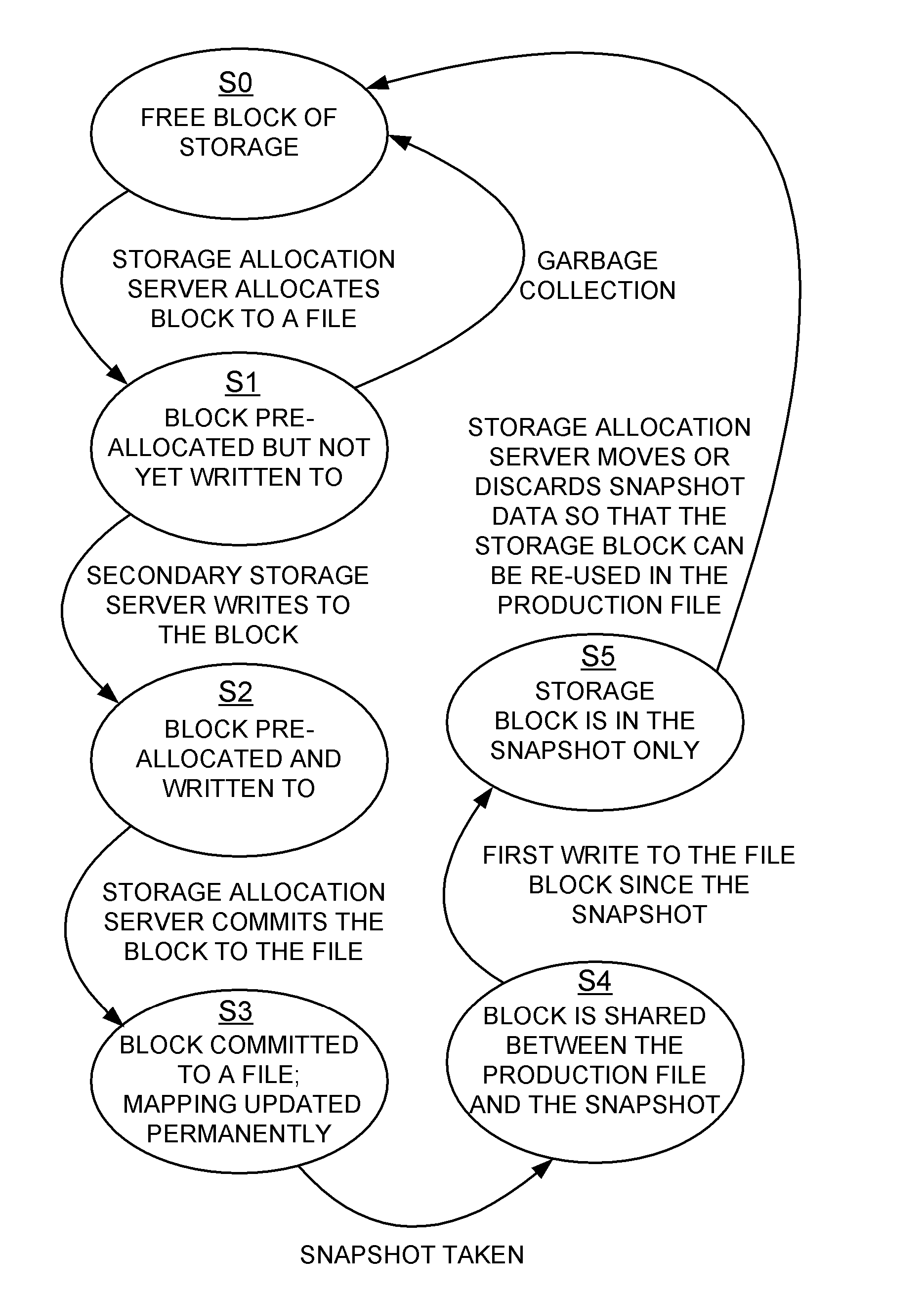
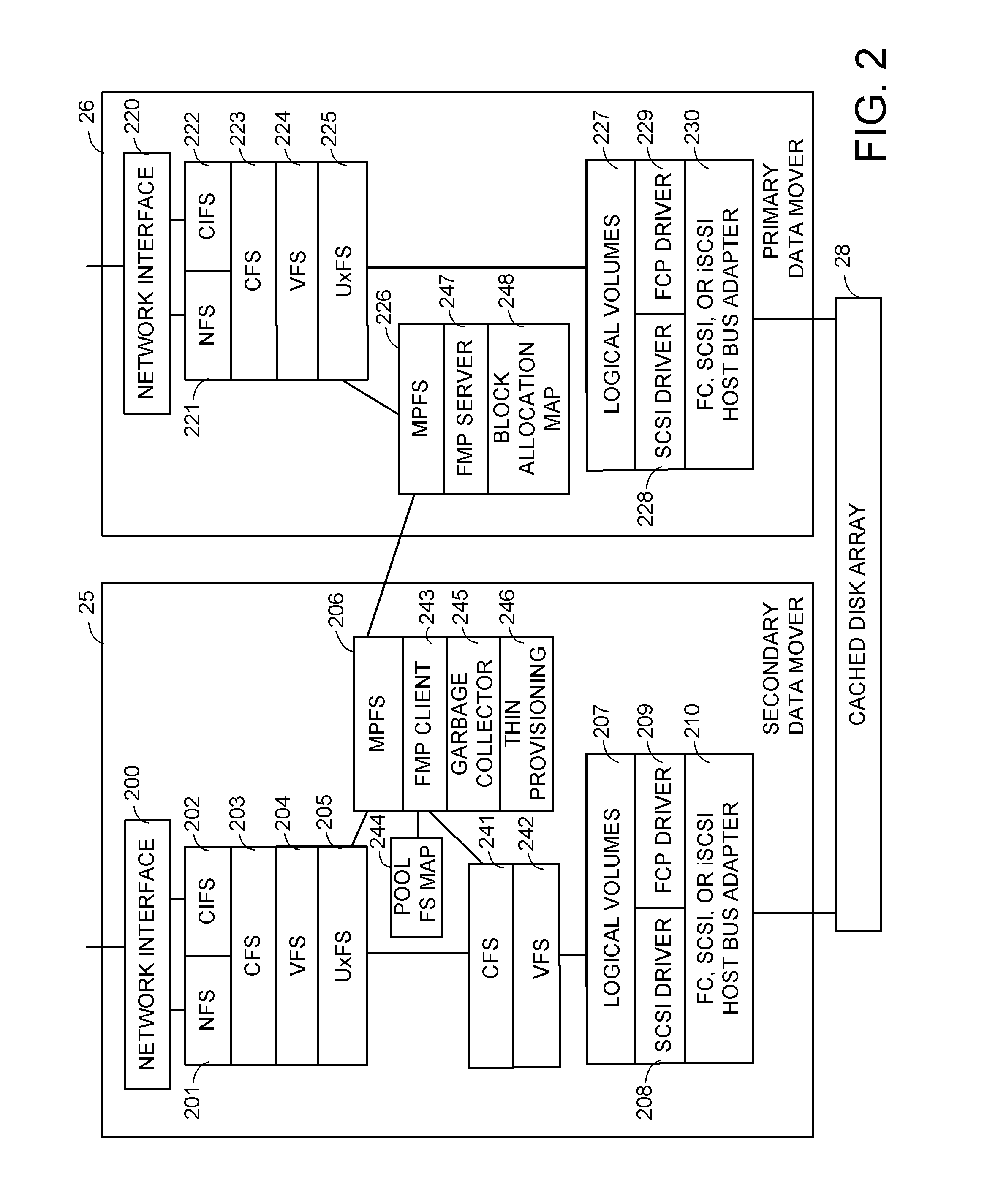
Distributed maintenance of snapshot copies by a primary processor managing metadata and a secondary processor providing read-write access to a production dataset
ActiveUS20070260830A1Degrades I/O performanceImprove I/O performanceMemory loss protectionDigital data processing detailsData setCoprocessor
A primary processor manages metadata of a production dataset and a snapshot copy, while a secondary processor provides concurrent read-write access to the primary dataset. The secondary processor determines when a first write is being made to a data block of the production dataset, and in this case sends a metadata change request to the primary data processor. The primary data processor commits the metadata change to the production dataset and maintains the snapshot copy while the secondary data processor continues to service other read-write requests. The secondary processor logs metadata changes so that the secondary processor may return a “write completed” message before the primary processor commits the metadata change. The primary data processor pre-allocates data storage blocks in such a way that the “write anywhere” method does not result in a gradual degradation in I / O performance.
Owner:EMC IP HLDG CO LLC
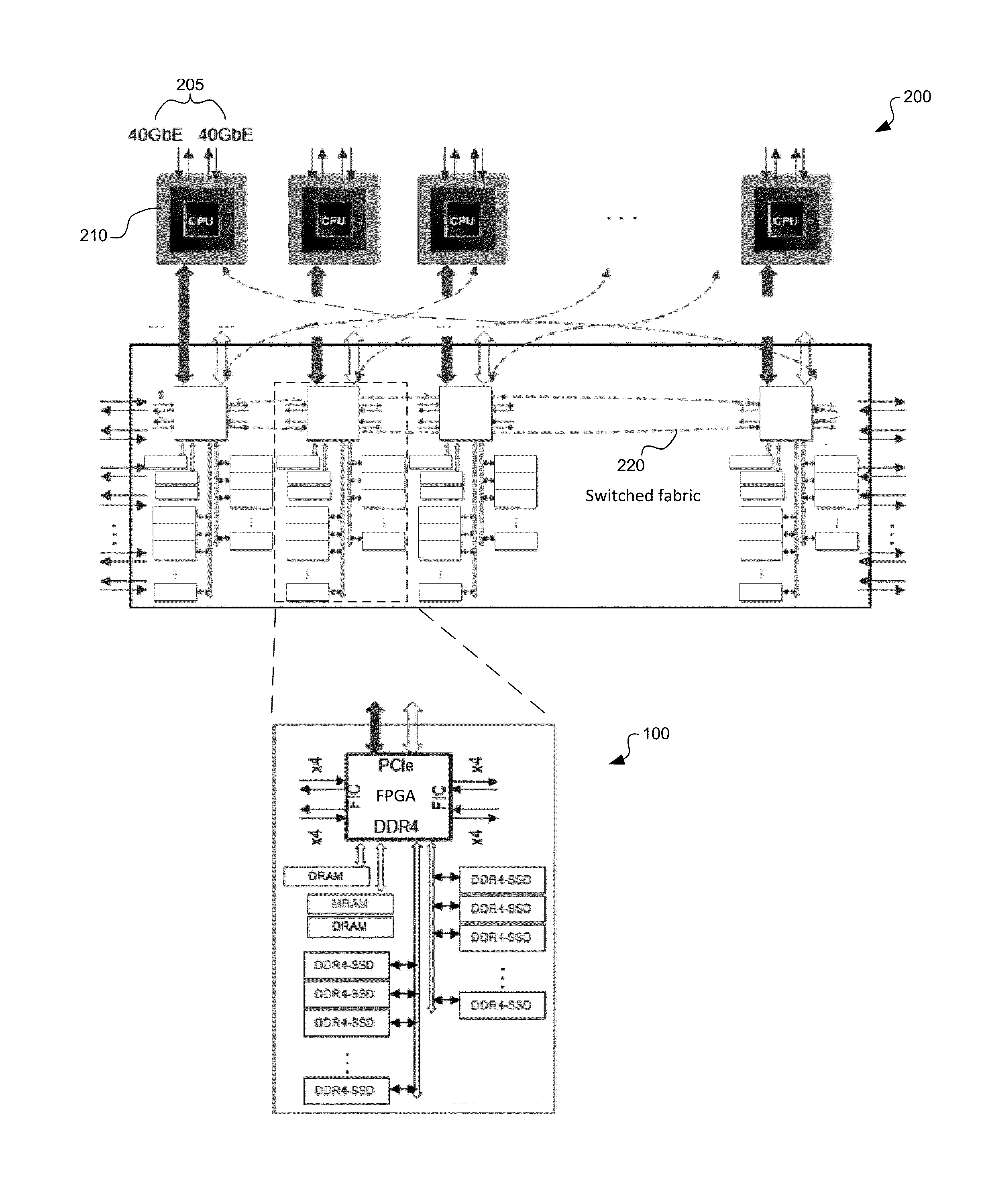
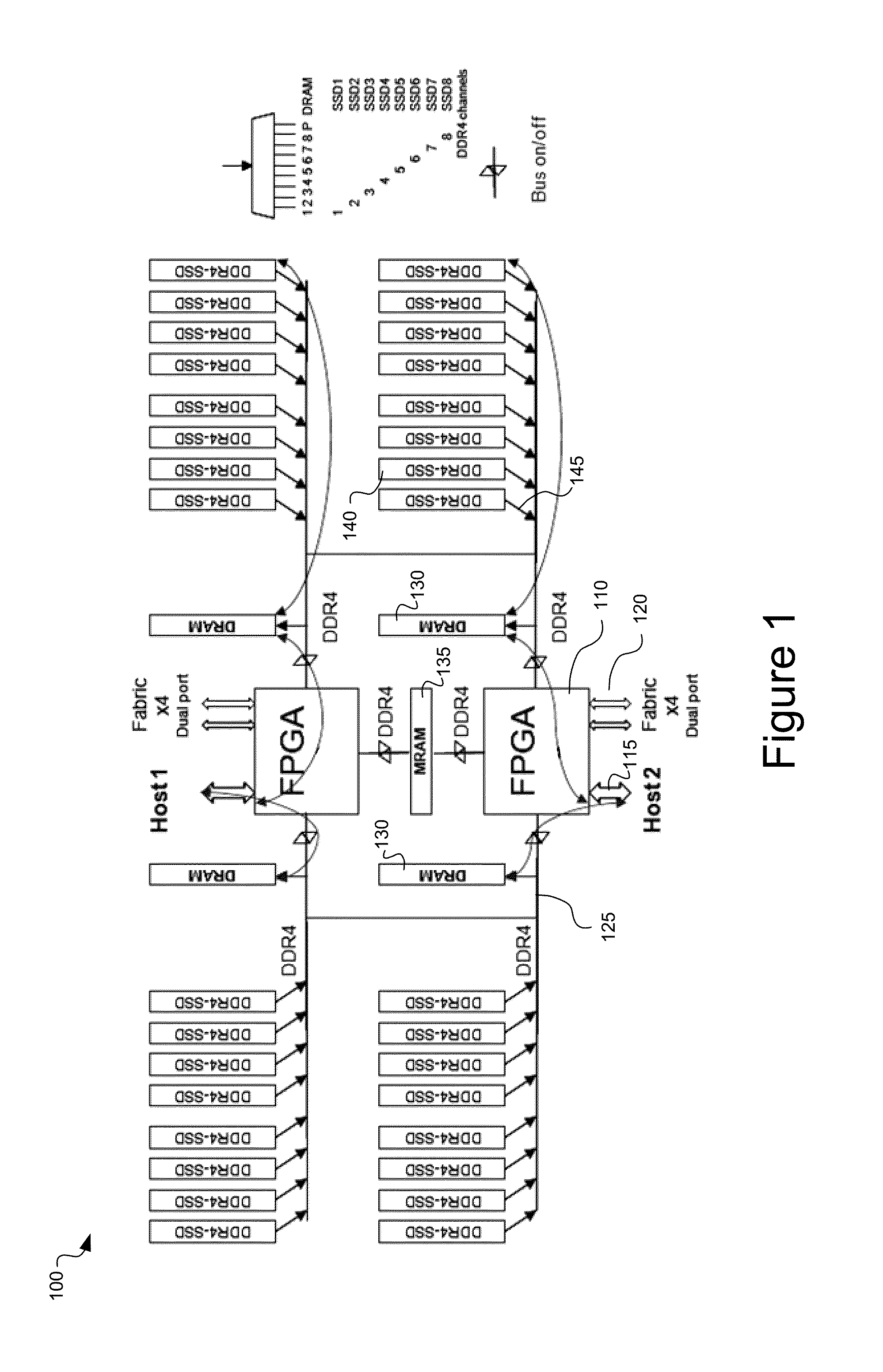
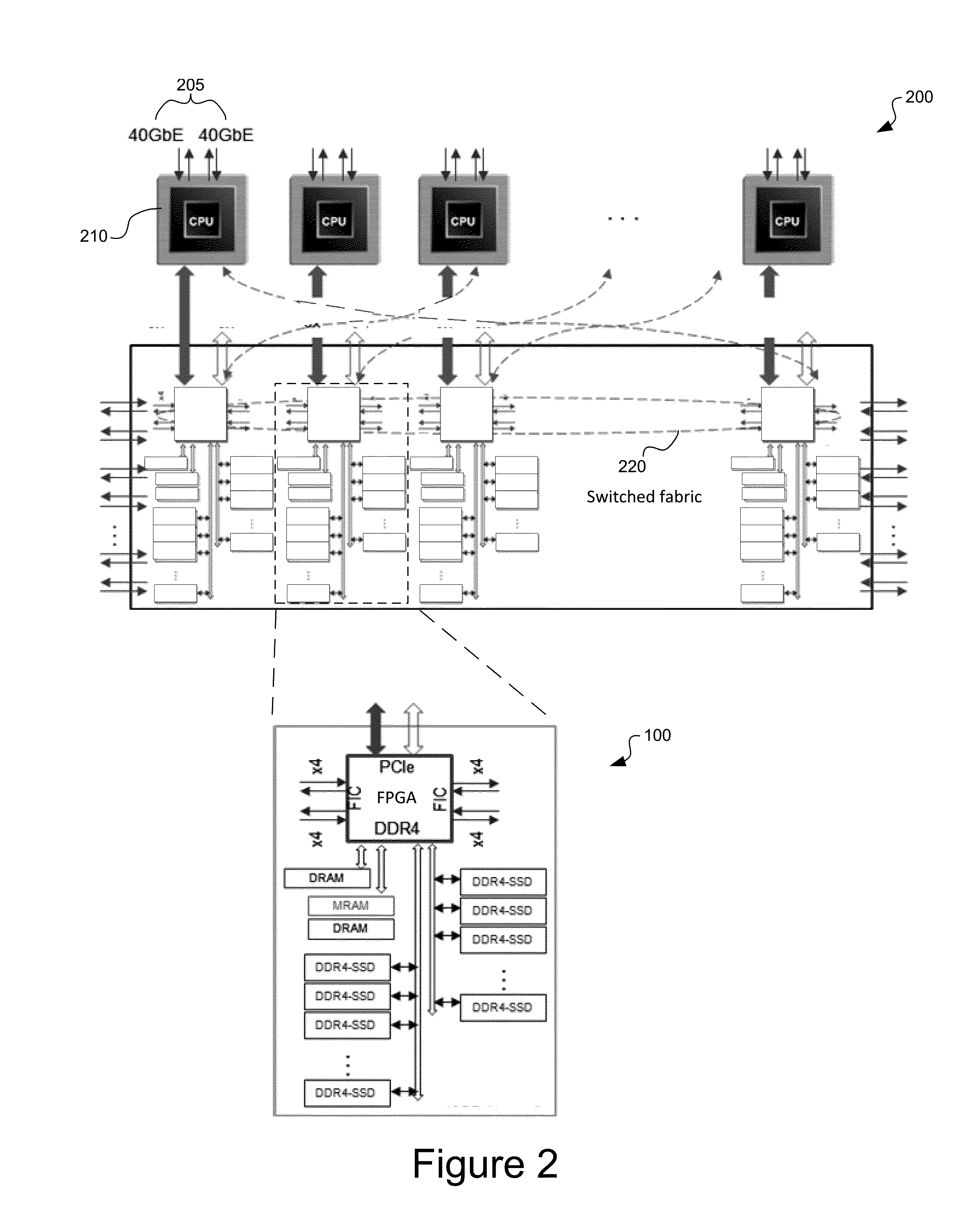
Rdma-ssd dual-port unified memory and network controller
ActiveUS20150254003A1Increase storage capacityLower latencyMemory architecture accessing/allocationInput/output to record carriersMagnetic reluctanceData memory
System and method for a unified memory and network controller for an all-flash array (AFA) storage blade in a distributed flash storage clusters over a fabric network. The unified memory and network controller has 3-way control functions including unified memory buses to cache memories and DDR4-AFA controllers, a dual-port PCIE interconnection to two host processors of gateway clusters, and four switch fabric ports for interconnections with peer controllers (e.g., AFA blades and / or chassis) in the distributed flash storage network. The AFA storage blade includes dynamic random-access memory (DRAM) and magnetoresistive random-access memory (MRAM) configured as data read / write cache buffers, and flash memory DIMM devices as primary storage. Remote data memory access (RDMA) for clients via the data caching buffers is enabled and controlled by the host processor interconnection(s), the switch fabric ports, and a unified memory bus from the unified controller to the data buffer and the flash SSDs.
Owner:FUTUREWEI TECH INC
Method and apparatus for identifying network devices on a storage network
InactiveUS6845395B1Unauthorized memory use protectionDigital data protectionGraphicsGraphical user interface
Owner:EMC IP HLDG CO LLC
Method for BIOS authentication prior to BIOS execution
A cryptographic device is implemented in communication with a host processor to prevent the host processor from performing a standard boot-up procedure until a basic input output system (BIOS) code is authenticated. This is accomplished by a cryptographic device which is addressed by the host processor during execution of a first instruction following a power-up reset. The cryptographic device includes a first integrated circuit (IC) device and a second IC device. The first IC device includes a memory to contain firmware and a root certification key. The second IC device includes logic circuitry to execute a software code to authenticate the BIOS code before permitting execution of the BIOS code by the host processor.
Owner:INTEL CORP
Method and apparatus for correlation of events in a distributed multi-system computing environment
InactiveUS7003781B1Overcome problemsHardware monitoringProgram controlData processing systemApplication software
A method and system is disclosed for monitoring an operation of a distributed data processing system. The system can include a plurality of applications running on a plurality of host processors and communicating with one another, such as through a message passing technique. The method includes steps executed in individual ones of the plurality of applications, of (a) examining individual ones of generated API calls to determine if a particular API call meets predetermined API call criteria; (b) if a particular API call meets the predetermined API call criteria, storing all or a portion of the content of the API call as a stored event; (c) processing a plurality of the stored events to identify logically correlated events, such as those associated with a business transaction; and (d) displaying all or a portion of the stored API call content data for the logically correlated events.
Owner:MICRO FOCUS LLC
Data security system
InactiveUS7047419B2Easy accessNeed can be addressedDigital data processing detailsInternal/peripheral component protectionComputer usageData access
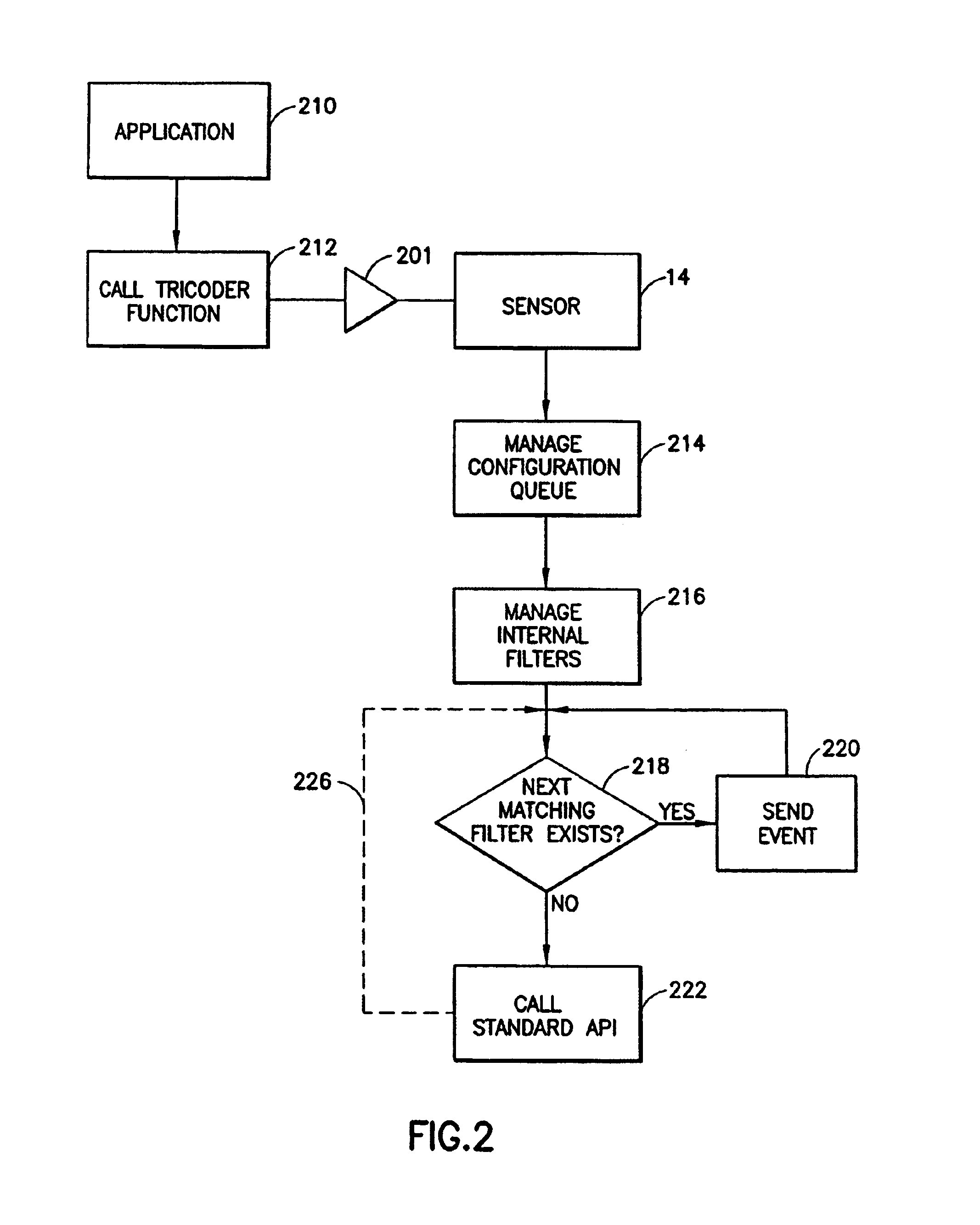
A data security system comprises a host processor, and a plurality of remote computers. Each remote computer provides biometric authentication of a user prior to responding to the user request for data access. The remote computers are handheld when in operational mode. A sensor in the handheld computer captures a biometric image while the remote computer is being used. The biometric sensor is positioned in such a way that the sensor enables the capture of the biometric image continually during computer usage with each request for access to secure data. The biometric authentication occurs in a seamless manner and is incidental to the data request enabling user identity authentication with each request to access secure data.
Owner:UNITED STATES CP LLC
Coprocessor opcode division by data type
InactiveUS6247113B1Easy to scaleReduced hardware coprocessorRegister arrangementsGeneral purpose stored program computerData processing systemCoprocessor
A data processing system having a main processor and a coprocessor. The main processor responsds to coprocessor instructions within its instruction stream by issuing the coprocessor instructions upon a coprocessor bus and detecting if the coprocessor accepts them by returning an accept signal. The coprocessor instructions include a coprocessor number and the coprocessor checks this number to see if it matches its own number(s) to determine whether or not it should accept the coprocessor instruction. A data type field within the coprocessor number in the coprocessor instruction also serves to specify one of multiple data types to be used in the coprocessor operation; particular coprocessors can interpret this part of the coprocessor number to determine data type. If the coprocessor supports multiple data types, then it has multiple coprocessor numbers for which it will issue accept signals and then uses the data type field to control the data type used. If a coprocessor does not support a particular data type then it will not issue an accept signal for coprocessor instructions that specify that data type. The main processor can then use emulation code to provide support for that coprocessor instruction.
Owner:ARM LTD
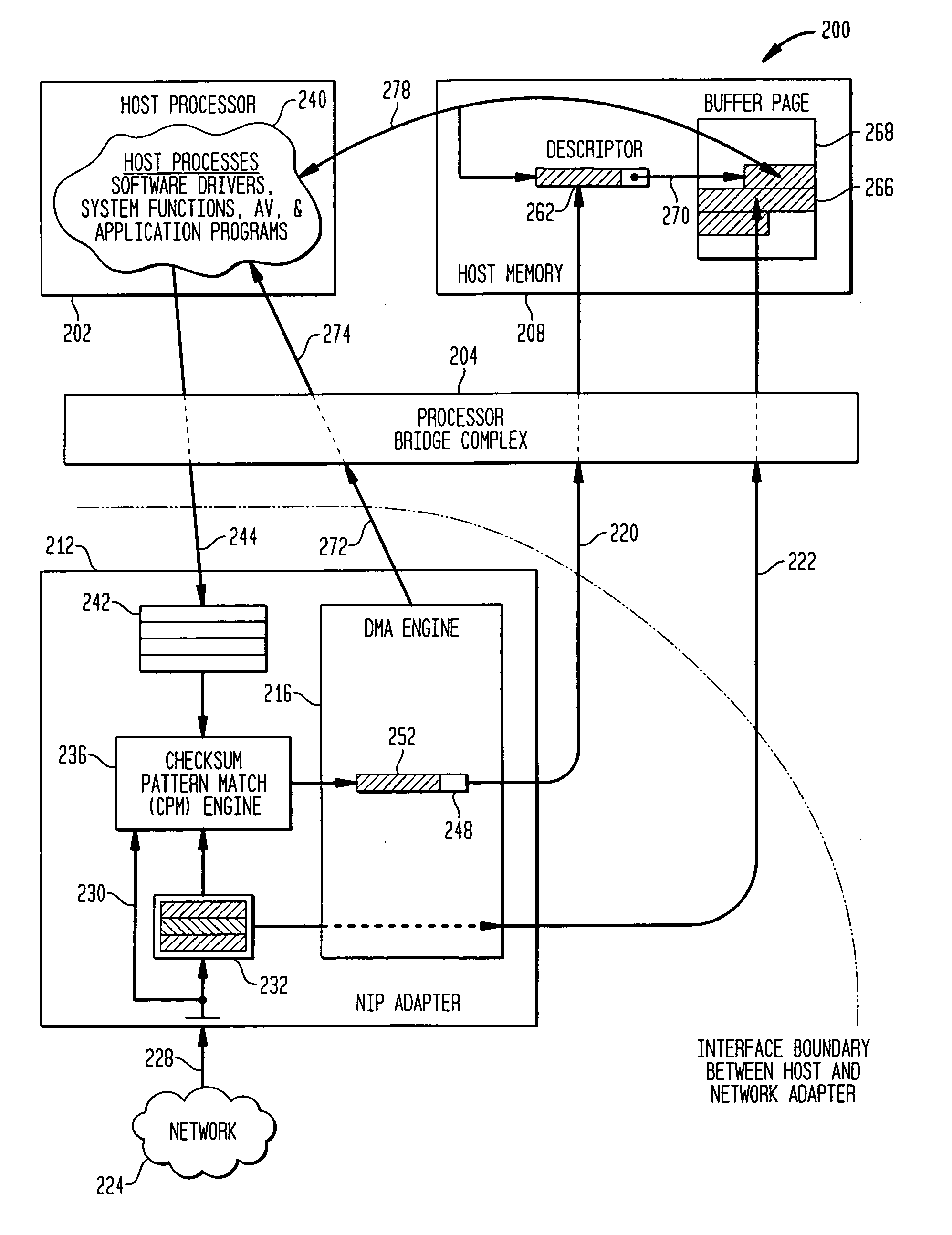
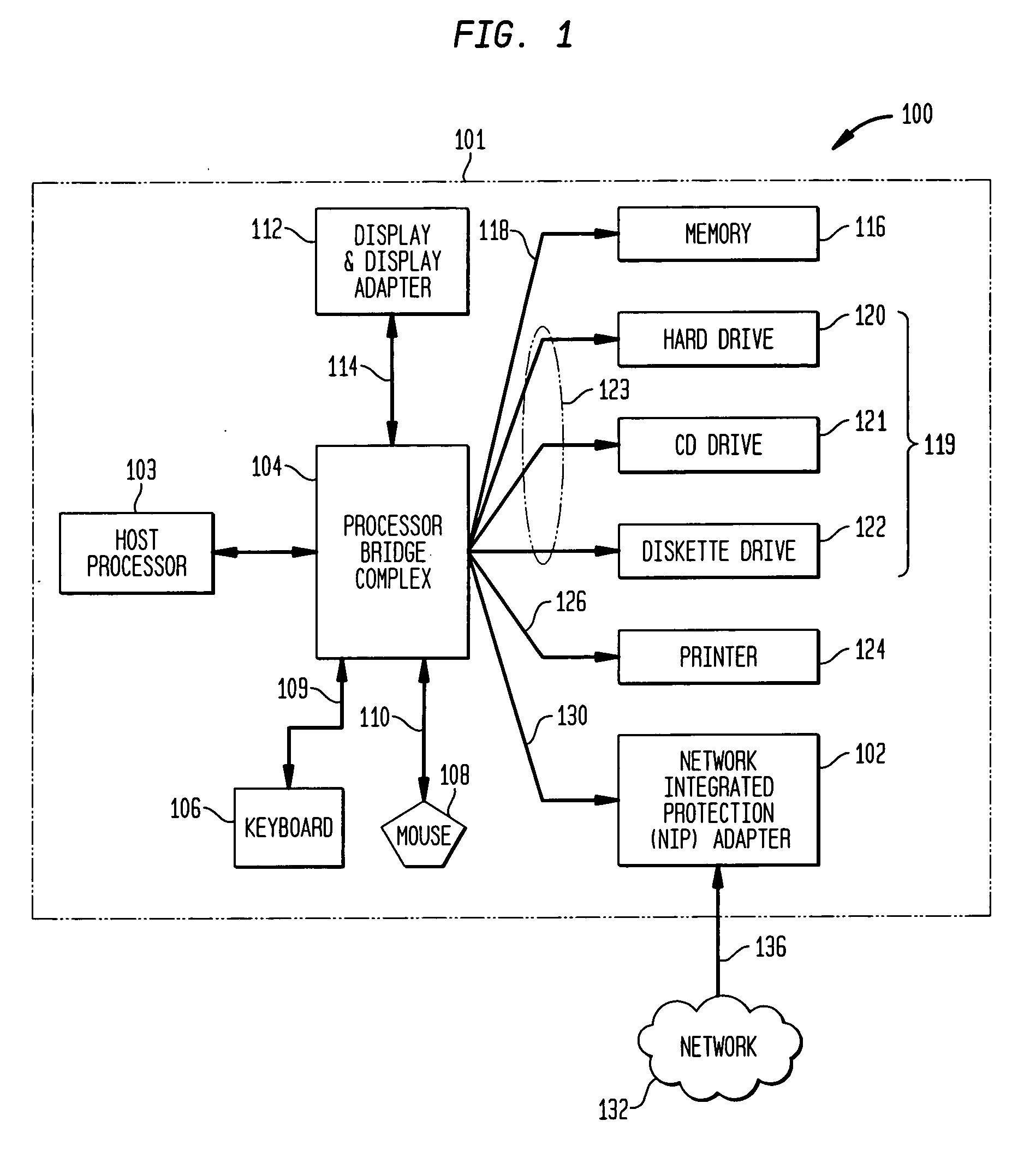
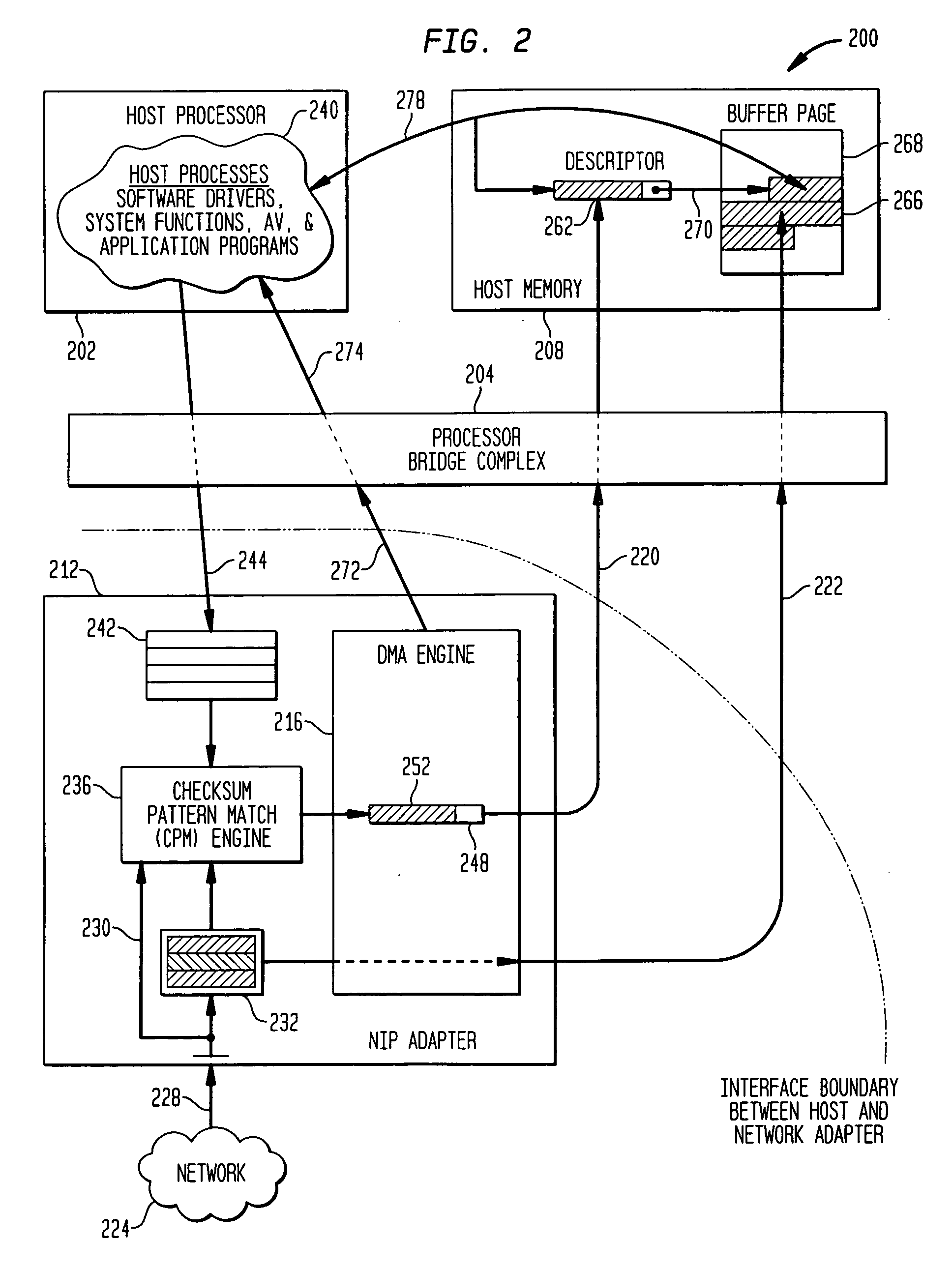
Methods and apparatus for interface adapter integrated virus protection
A virus detection mechanism is described in which virus detection is provided by a network integrated protection (NIP) adapter. The NIP adapter checks incoming media data prior to it being activated by a computing device. The NIP adapter operates independently of a host processor to receive information packets from a network. This attribute of independence allows NIP anti-virus (AV) techniques to be “always on” scanning incoming messages and data transfers. By being independent of but closely coupled to the host processor, complex detection techniques, such as using check summing or pattern matching, can be efficiently implemented on the NIP adapter without involving central processor resources and time consuming mass storage accesses. The NIP adapter may be further enhanced with a unique fading memory (FM) facility to allow for a flexible and economical implementation of polymorphic virus detection.
Owner:AVAGO TECH INT SALES PTE LTD
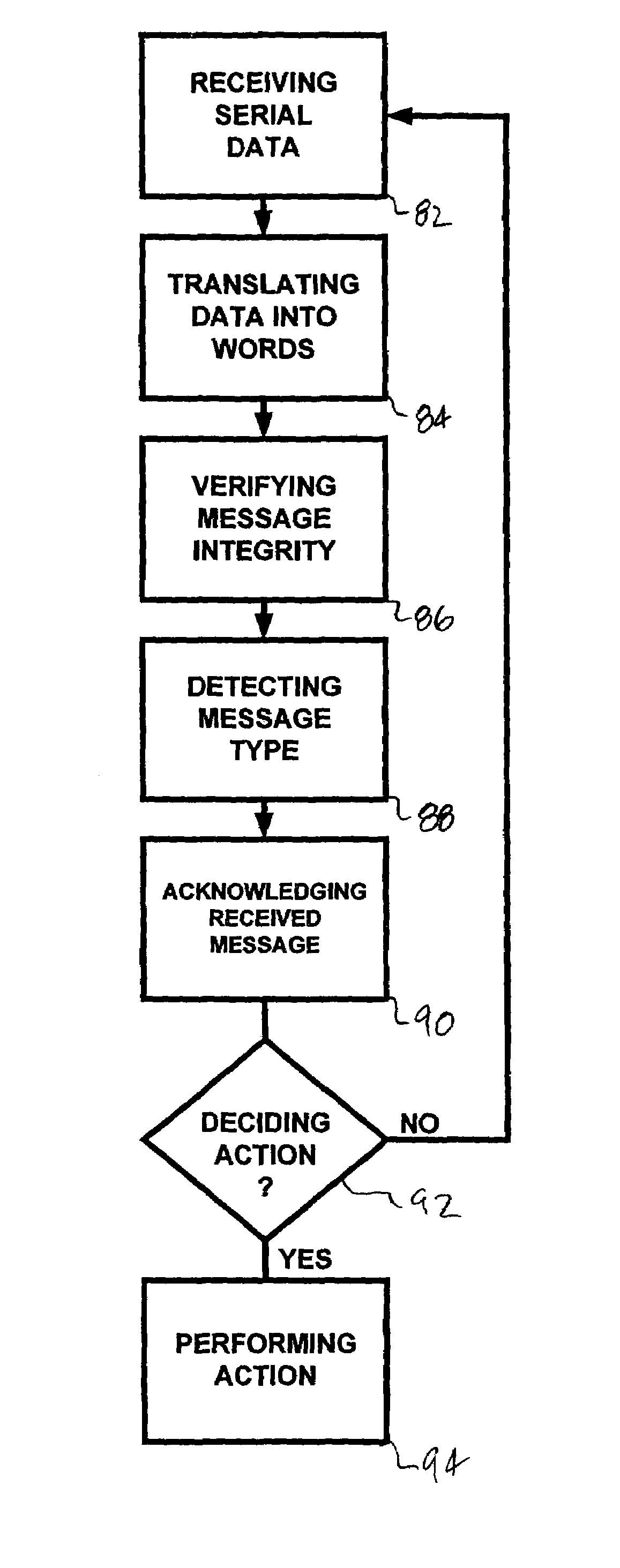
Method of operating an implantable medical device telemetry processor
An implantable medical device with a main processor also has a telemetry processor to perform some telemetry processing functions resulting under some circumstances in reducing demands on the main processor, conserving energy, increasing telemetry processing speed, and many other advantages. A wide variety of implantable medical devices can be configured with a telemetry processor including neuro stimulators, pacemakers, defibrillators, drug delivery pumps, diagnostic recorders, and cochlear implants. The telemetry processor includes control logic, a data decoder, a receive buffer, a data encoder, and a transmit buffer. Methods of receiving messages and transmitting messages with a telemetry processor are also disclosed.
Owner:MEDTRONIC INC
Method and apparatus for a redundancy approach in a processor based controller design
InactiveUS20060174051A1Low costProgramme controlElectric digital data processingLow speedMaster processor
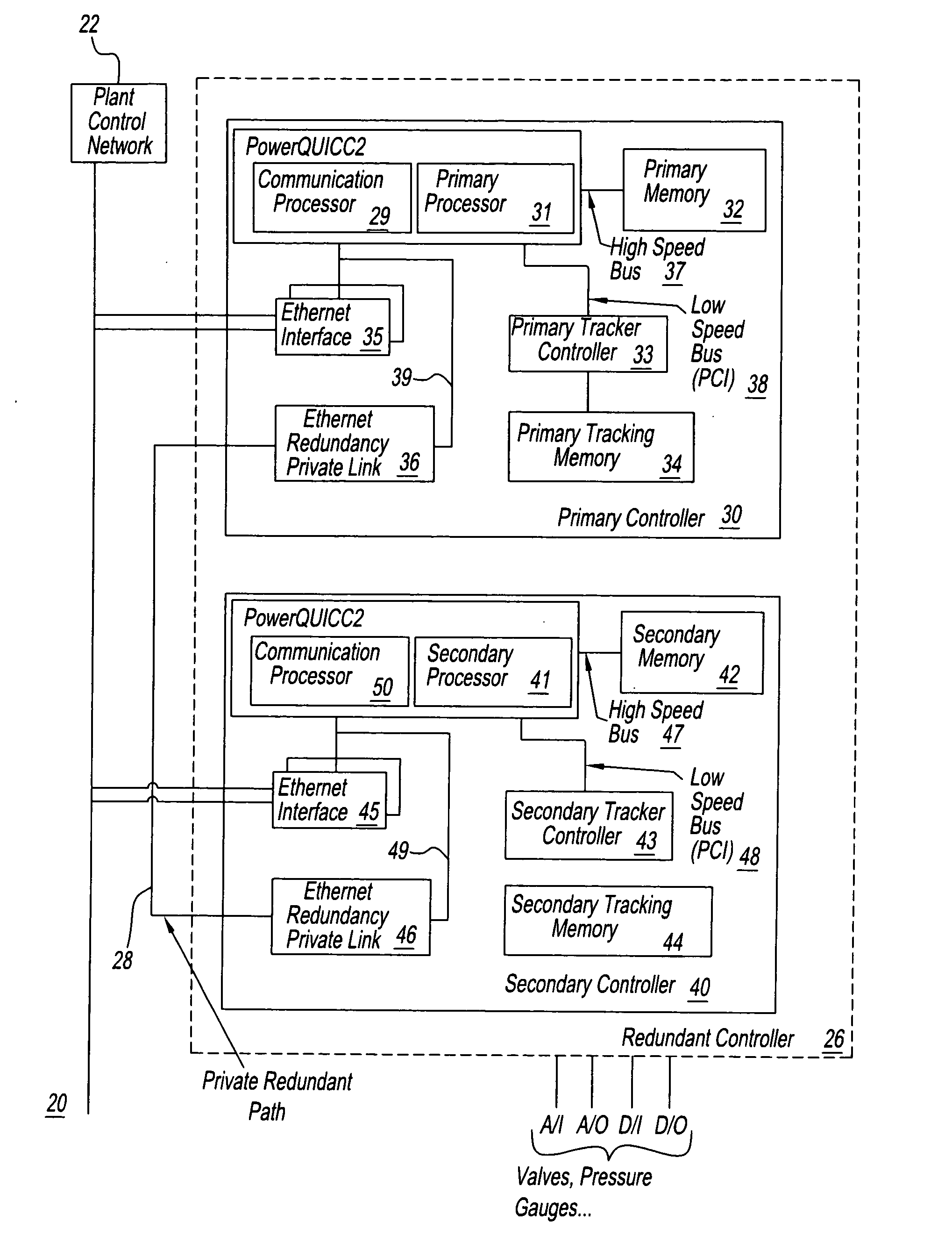
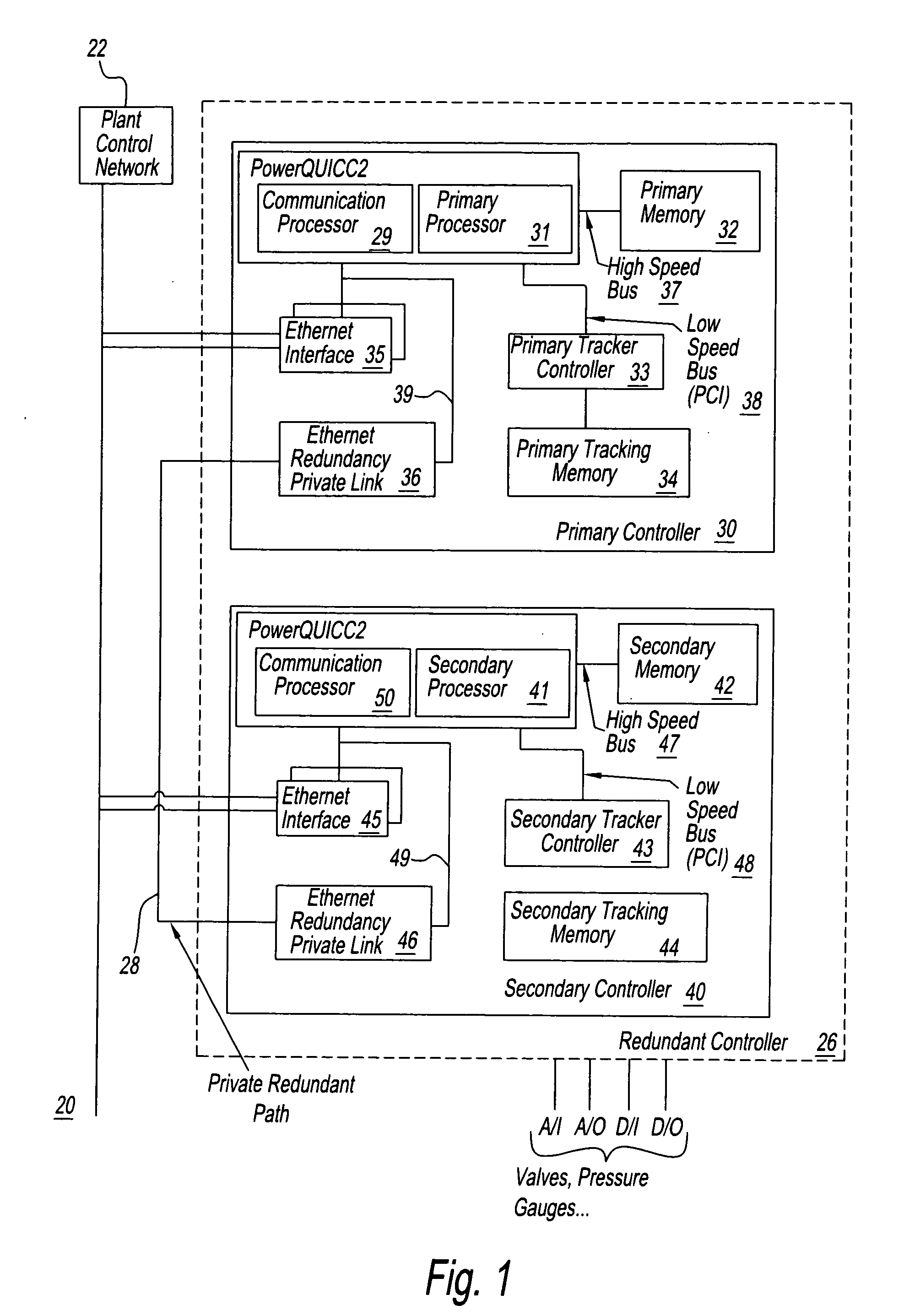
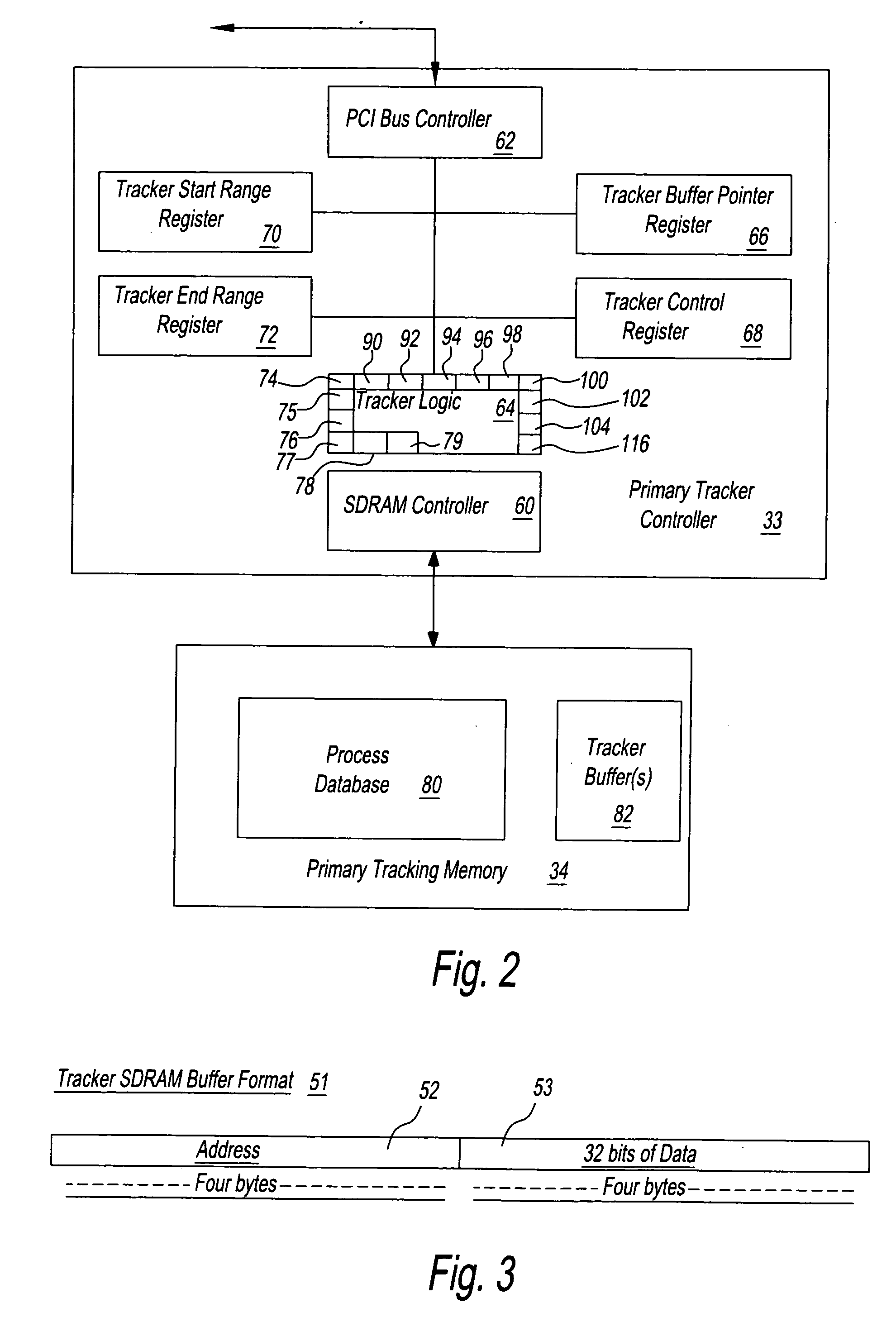
A system for handling data of a process with a primary controller and a redundant controller. The primary controller includes a primary processor that is operable to perform tracking data tasks by using a low speed bus to cooperate with a tracker controller for storage of tracking data in a tracker memory. The primary processor is further operable to perform other tasks by using a high speed bus in cooperation with a primary memory. The second bus has an operating rate considerably higher (for example, a factor of two or more) than that of the first bus.
Owner:HONEYWELL INT INC
Systems and methods for synchronizing the internal clocks of a plurality of processor modules
ActiveUS20060047989A1Promote recoveryData storage is convenientMechanical clocksSynchronous motors for clocksComputer architectureMulti processor
In a multiprocessor system that includes a plurality of processor modules, each one of which includes its own internal clock, one of the plurality of processor modules is designated as a master processor module having a master internal clock. Each other processor module is designated as a slave processor module having a slave processor module internal clock. Each slave processor module synchronizes its internal clock with the master internal clock.
Owner:SYMANTEC OPERATING CORP
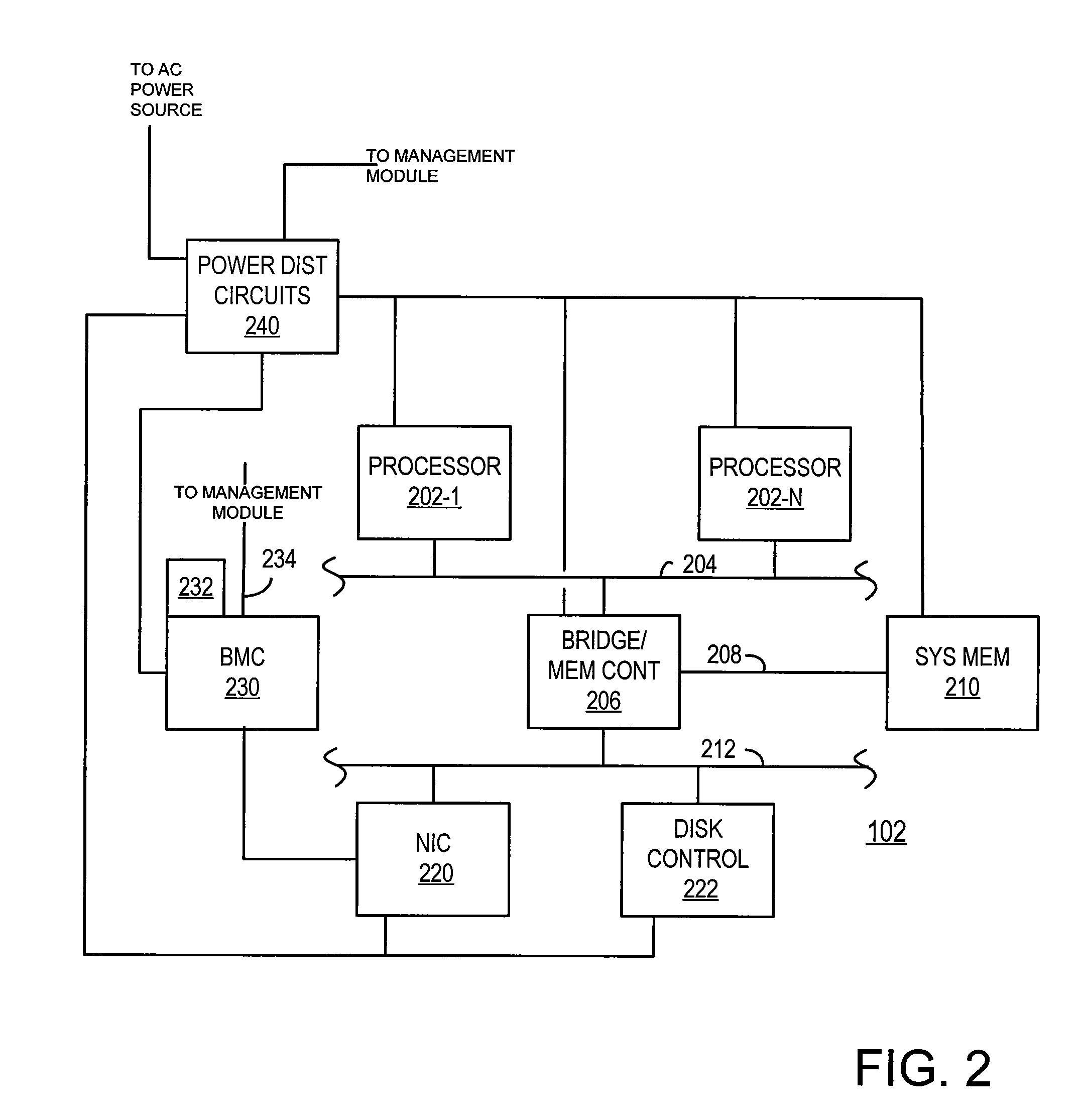
Power allocation management in an information handling system
ActiveUS20070260897A1Effective distributionVolume/mass flow measurementHardware monitoringInformation processingModularity
An information handling system includes modular processing resources, each having a main processor, system memory, and preferably a service processor resource. A management resource coupled to a service processor resource evaluates a system power budget and allocates power to a processing resource by indicating a critical power level. The processing resource determines a warning power level based on the critical power level and monitor its actual power consumption. If actual power consumption exceeds the critical power level, the processing resource is powered down. If actual power consumption exceeds the warning power level, the processing resource throttles its performance to conserve power and requests a power allocation increase. If actual power consumption is below the warning power level, the processing resource may request a reduction in allocated power.
Owner:DELL PROD LP
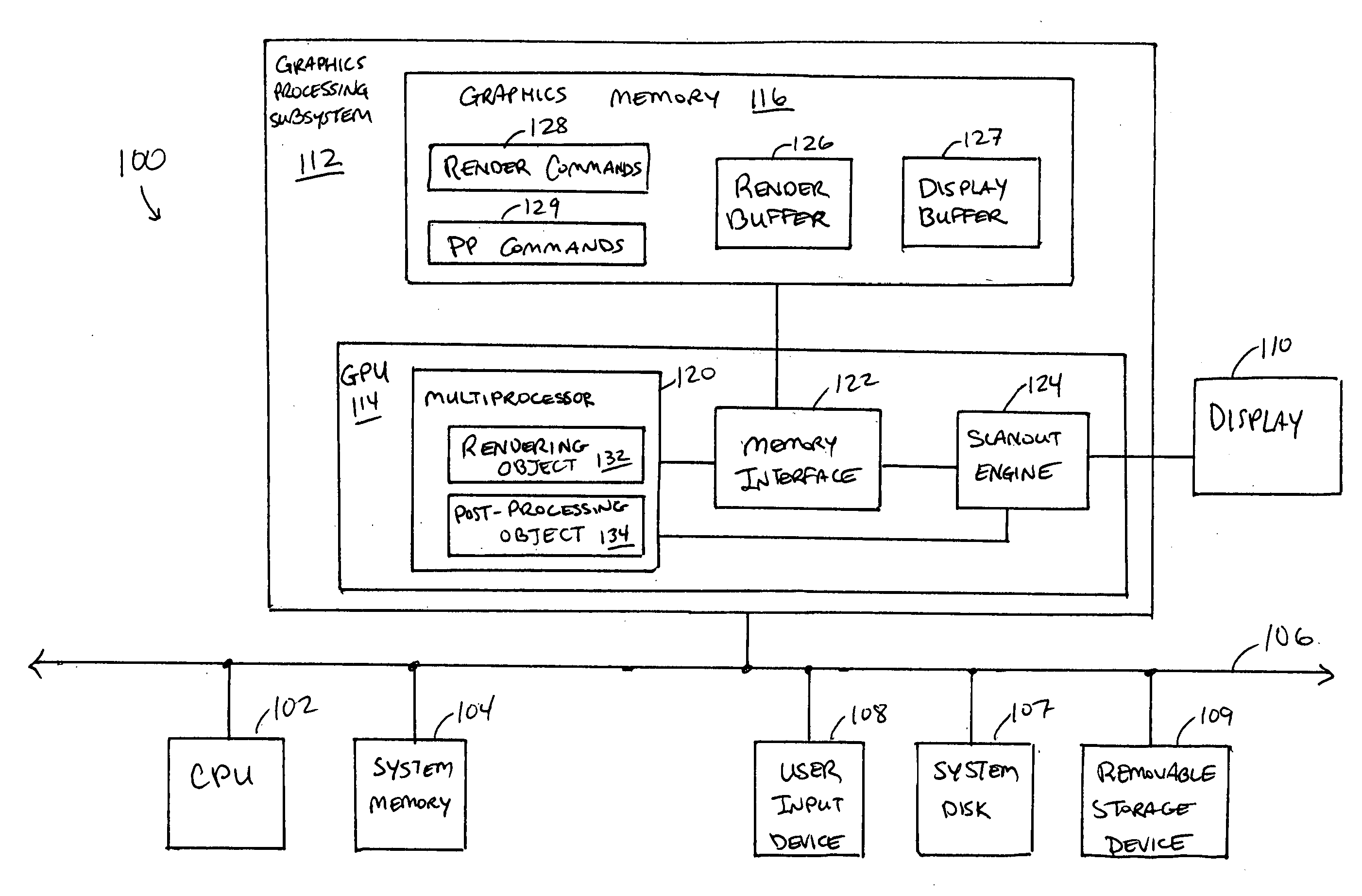
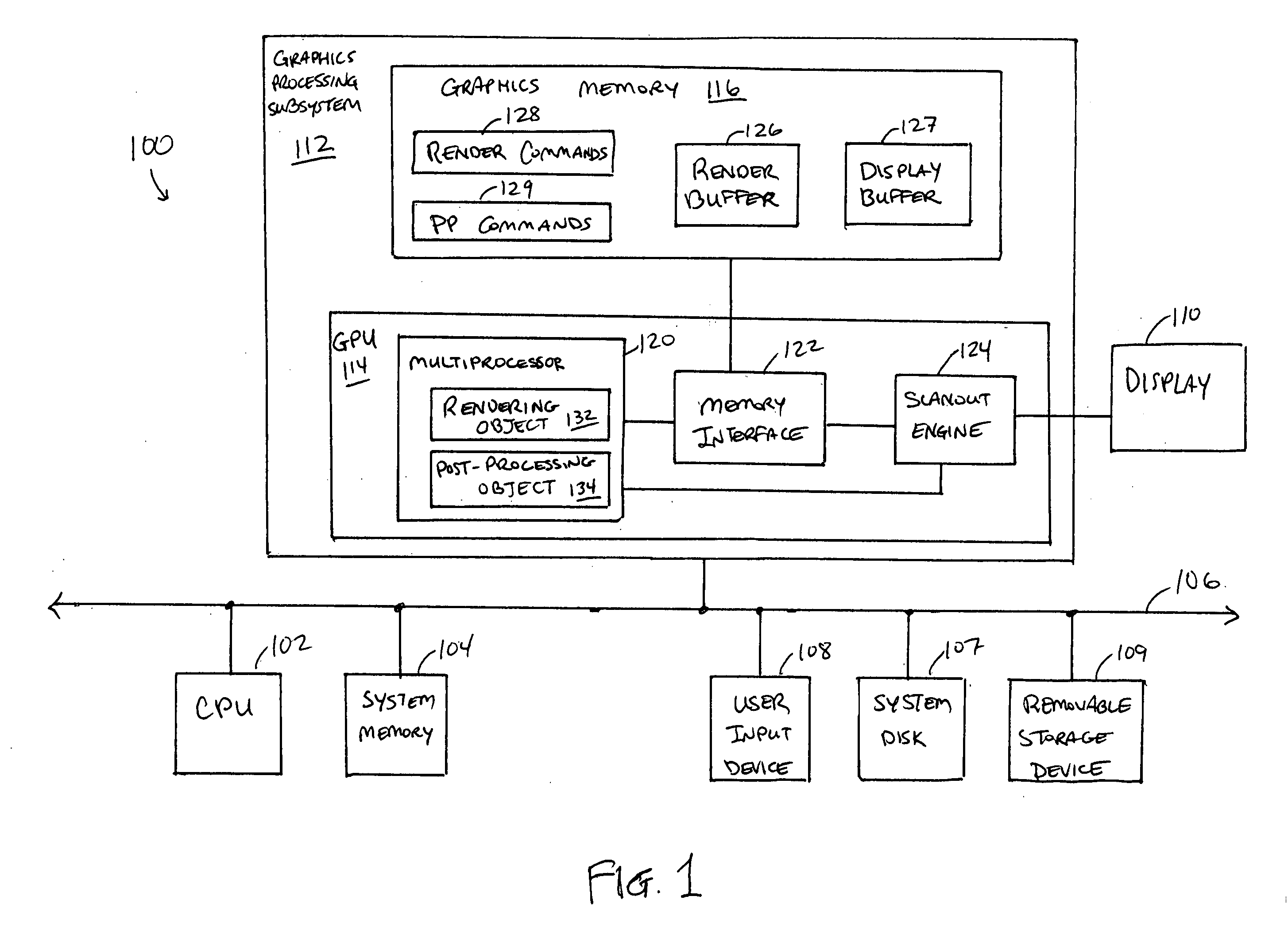
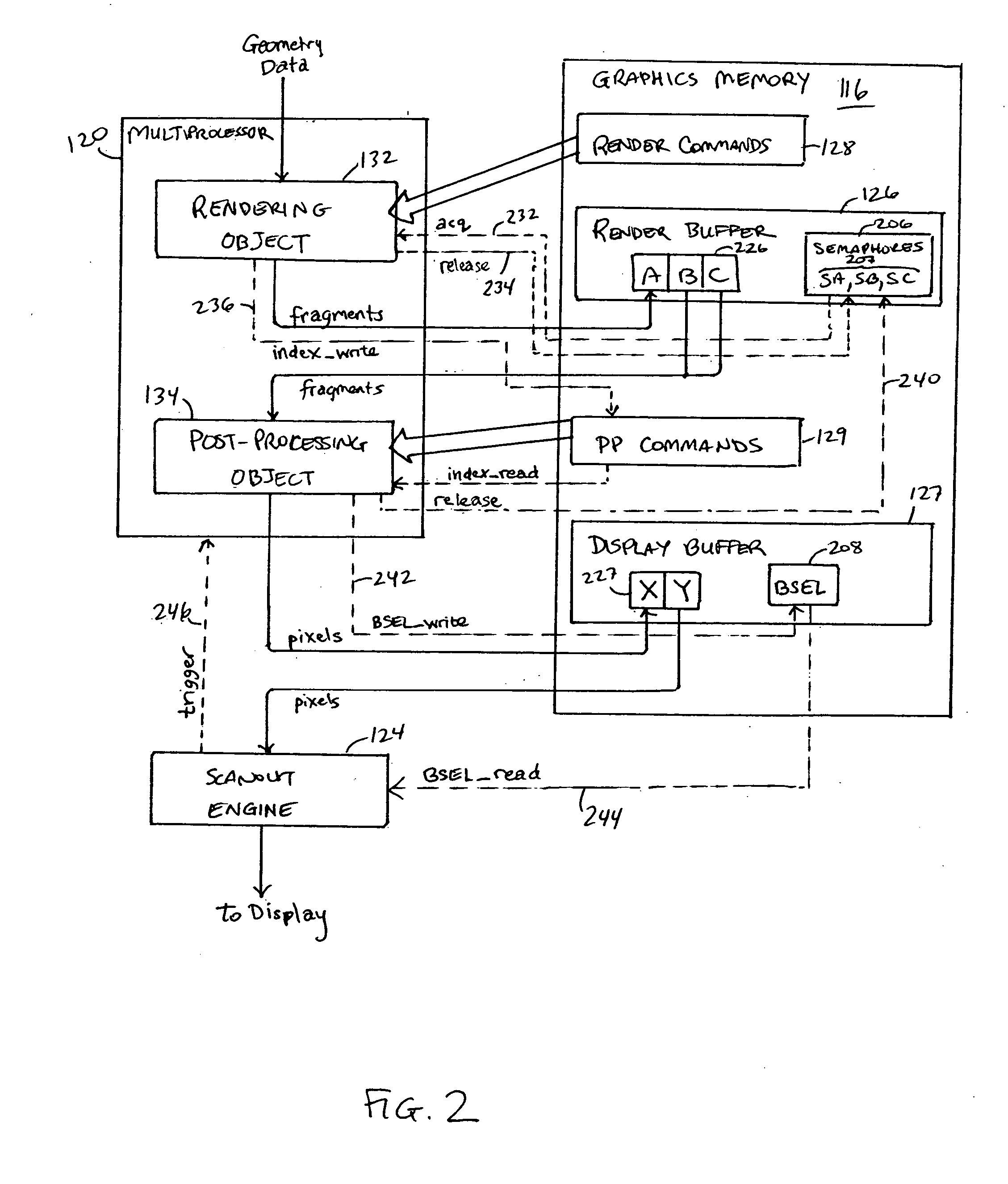
Real-time display post-processing using programmable hardware
ActiveUS20060132491A1Image memory managementMultiprogramming arrangementsDisplay deviceProgrammable hardware
In a graphics processor, a rendering object and a post-processing object share access to a host processor with a programmable execution core. The rendering object generates fragment data for an image from geometry data. The post-processing object operates to generate a frame of pixel data from the fragment data and to store the pixel data in a frame buffer. In parallel with operations of the host processor, a scanout engine reads pixel data for a previously generated frame and supplies the pixel data to a display device. The scanout engine periodically triggers the host processor to operate the post-processing object to generate the next frame. Timing between the scanout engine and the post-processing object can be controlled such that the next frame to be displayed is ready in a frame buffer when the scanout engine finishes reading a current frame.
Owner:NVIDIA CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com