Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
169184 results about "Systems engineering" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
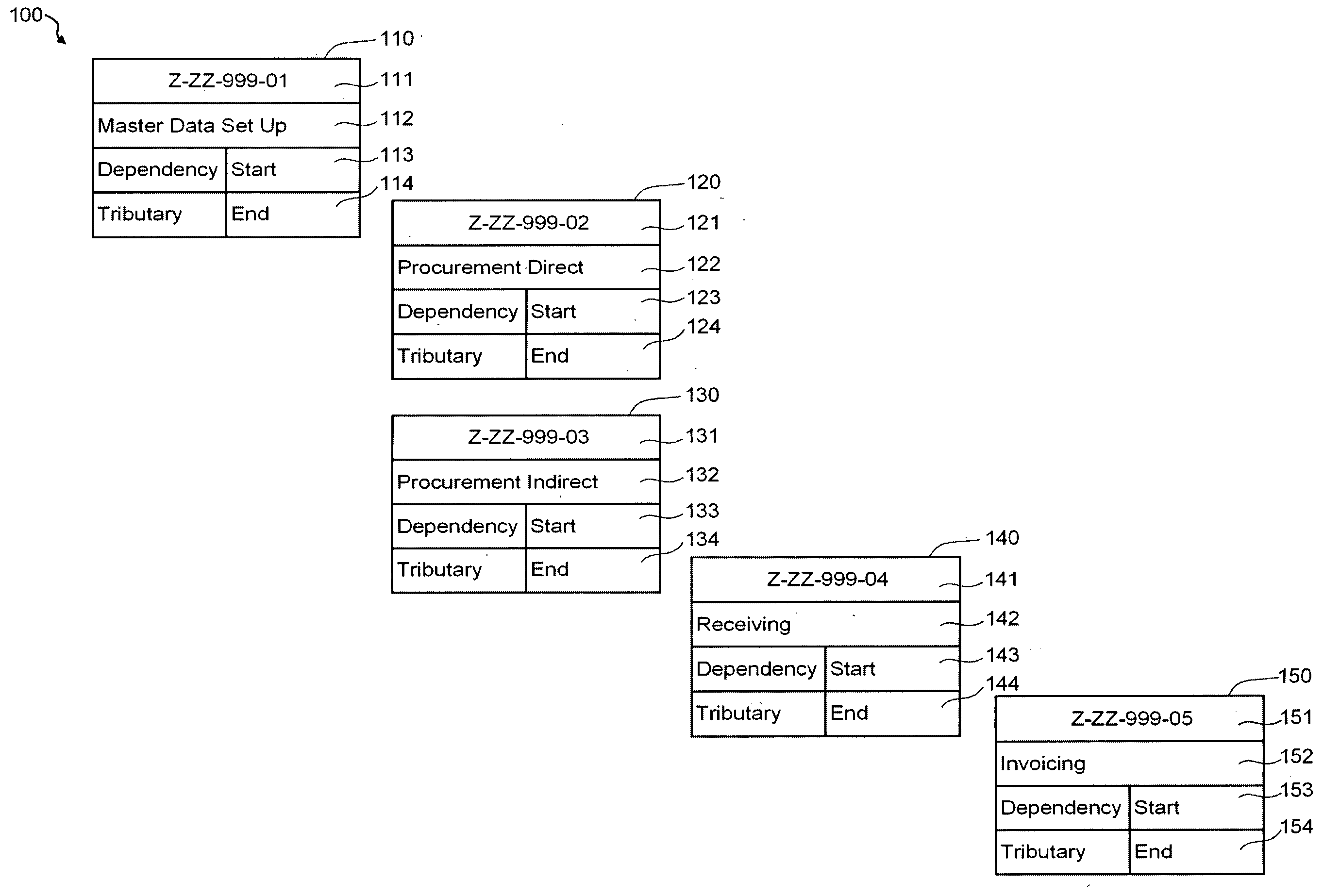
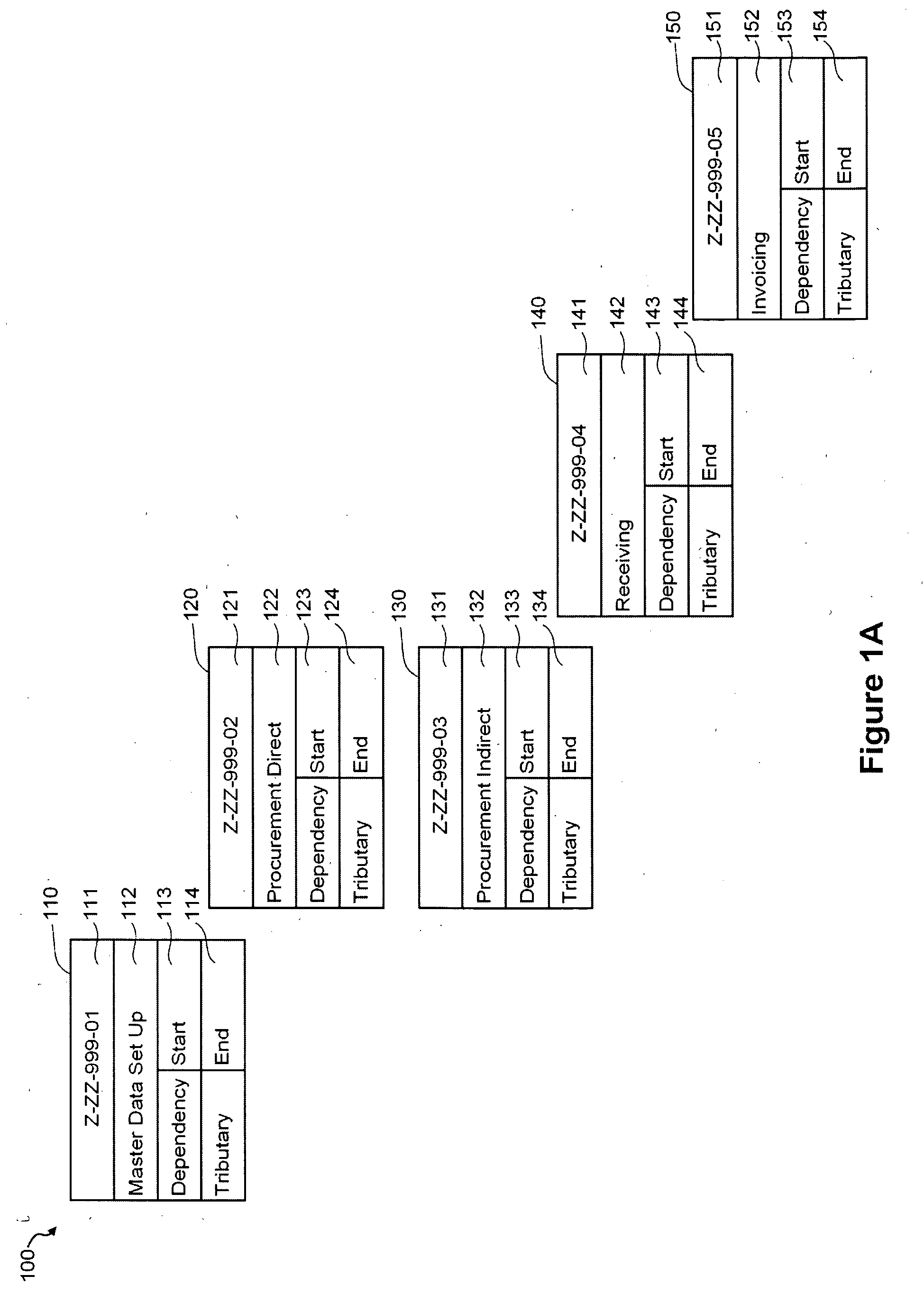
Systems engineering is an interdisciplinary field of engineering and engineering management that focuses on how to design and manage complex systems over their life cycles. At its core, systems engineering utilizes systems thinking principles to organize this body of knowledge. The individual outcome of such efforts, an engineered system, can be defined as a combination of components that work in synergy to collectively perform a useful function.
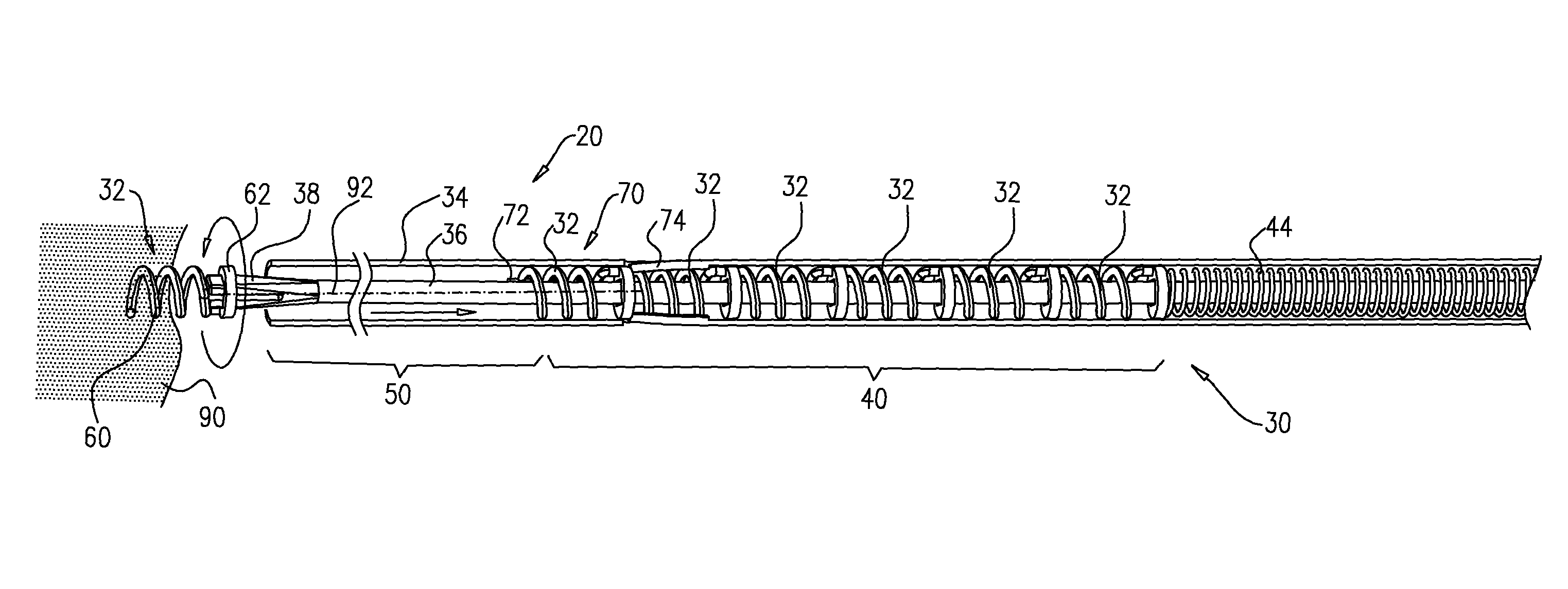
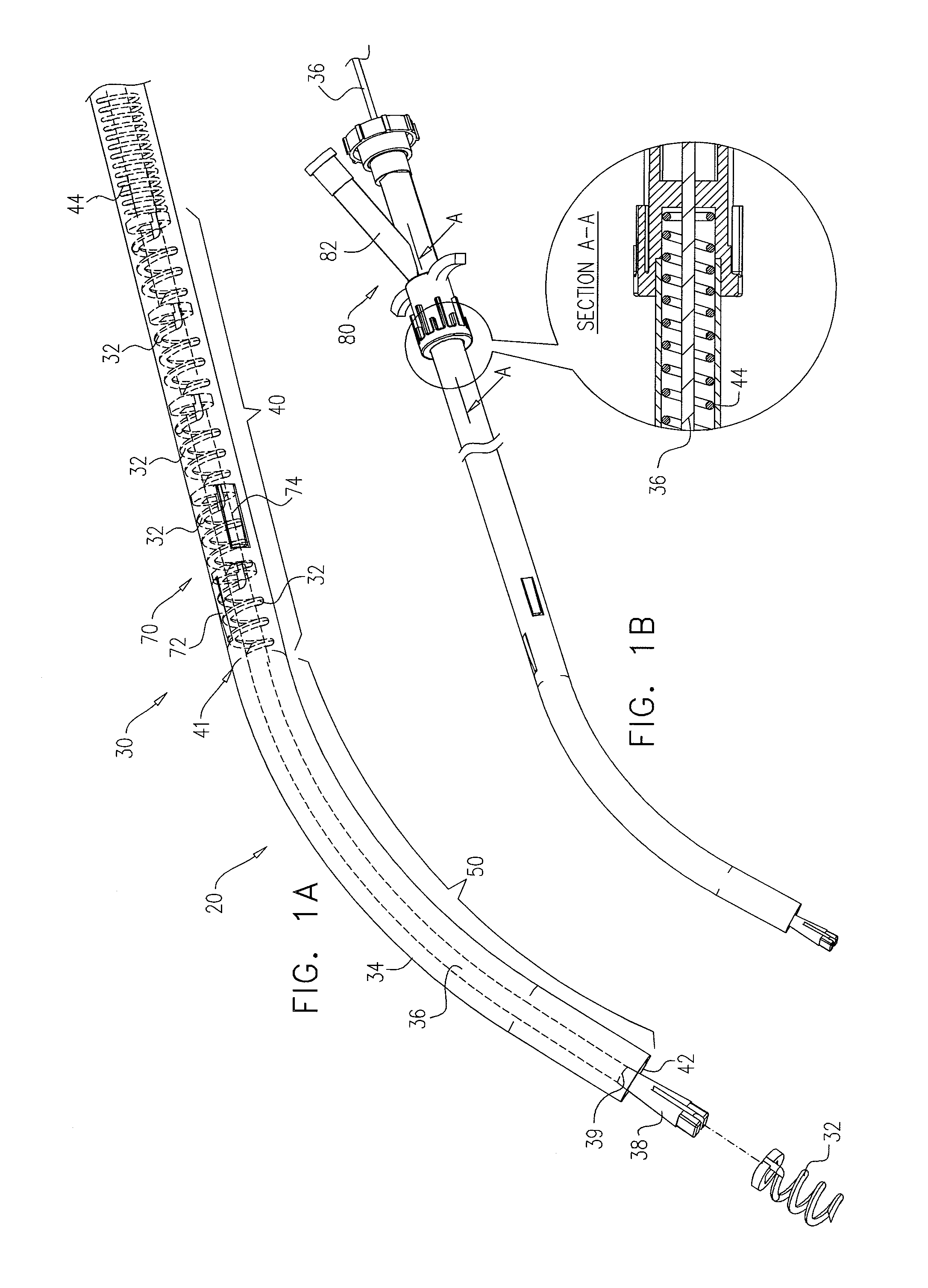
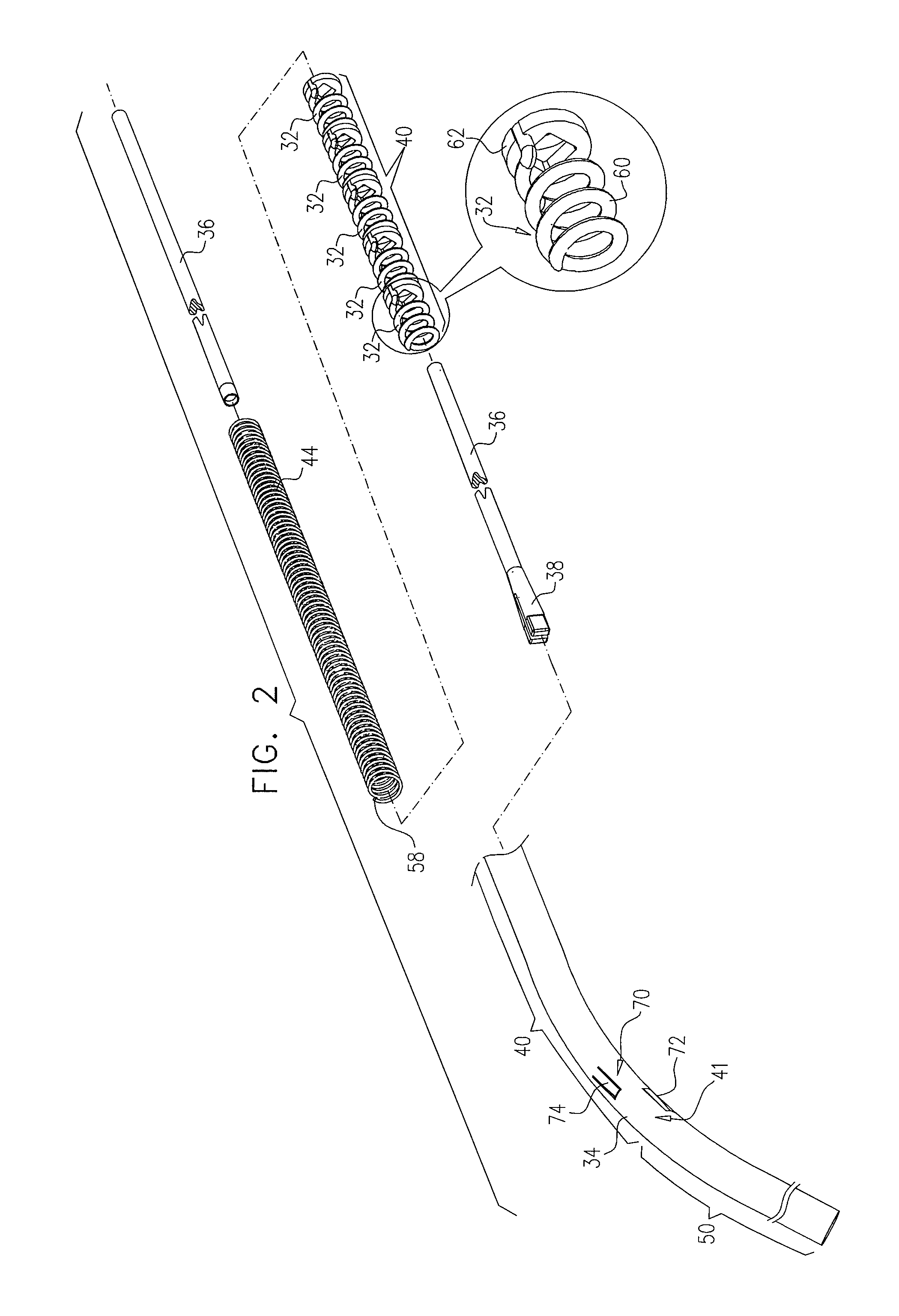
Multiple anchor delivery tool
An anchor deployment tool includes a flexible outer tube, within which is positioned a flexible inner shaft, and a rotating deployment element coupled to a distal end of the shaft. The tool is configured to provide an anchor storage area, which initially stores a plurality of tissue anchors, such that the inner shaft passes through channels of the anchors along entire longitudinal lengths of the anchors, and the anchors are within the outer tube. The rotating deployment element is configured to directly engage the anchors in the anchor storage area one at a time, advance each of the anchors while engaged in a distal direction, and deploy each of the anchors through the distal tube end and into tissue of a subject. Other embodiments are also described.
Owner:VALTECH CARDIO LTD
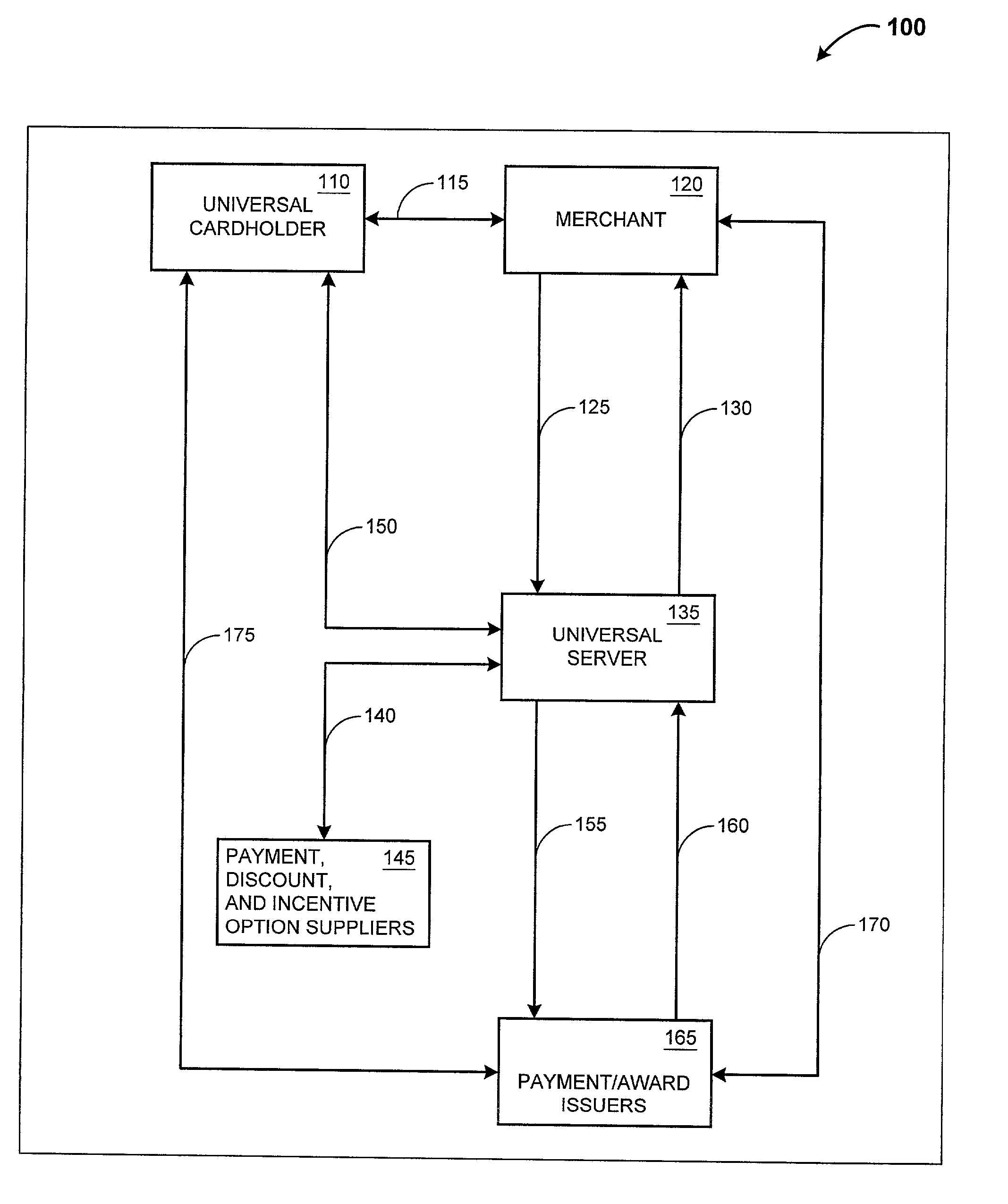
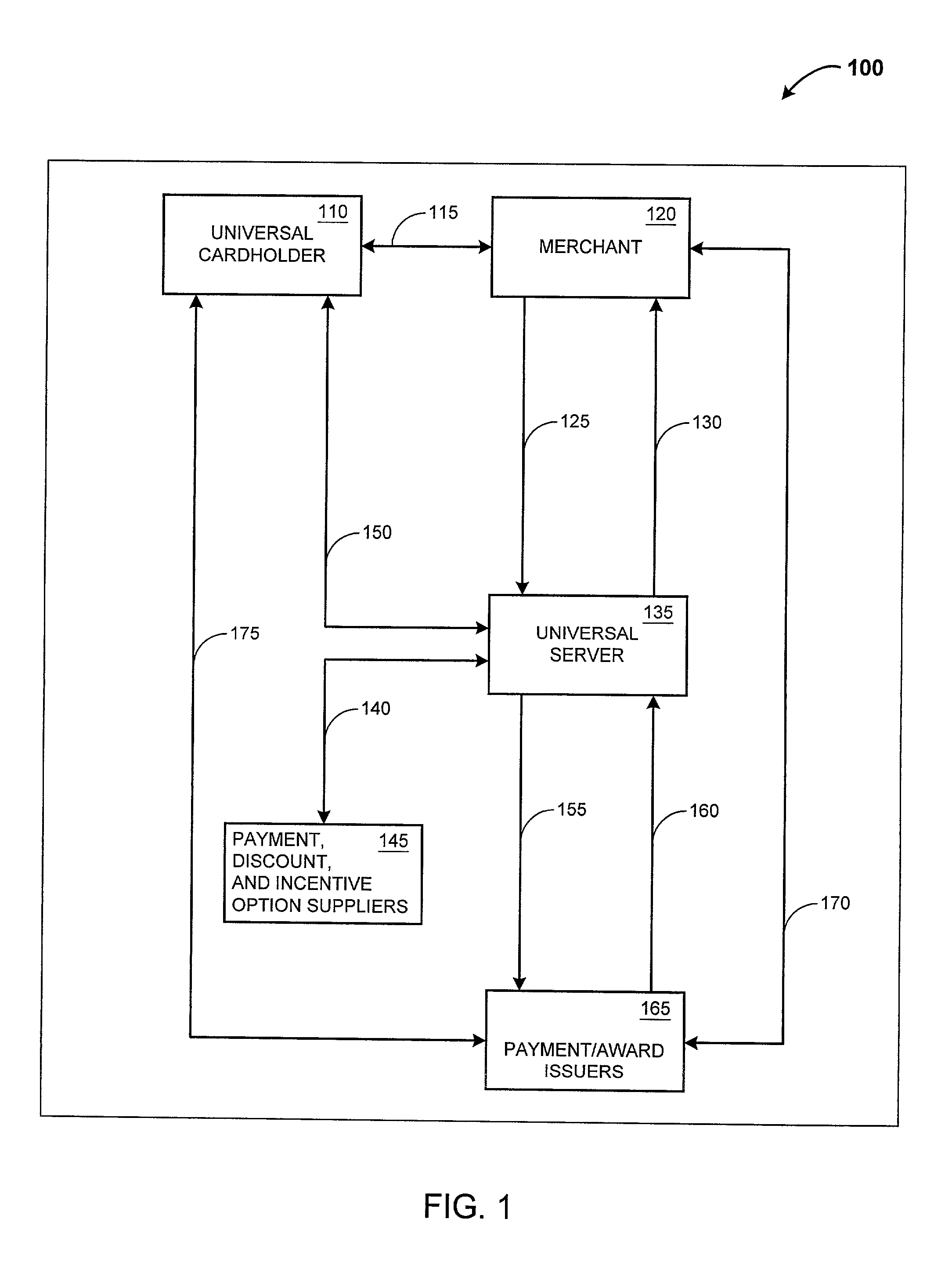
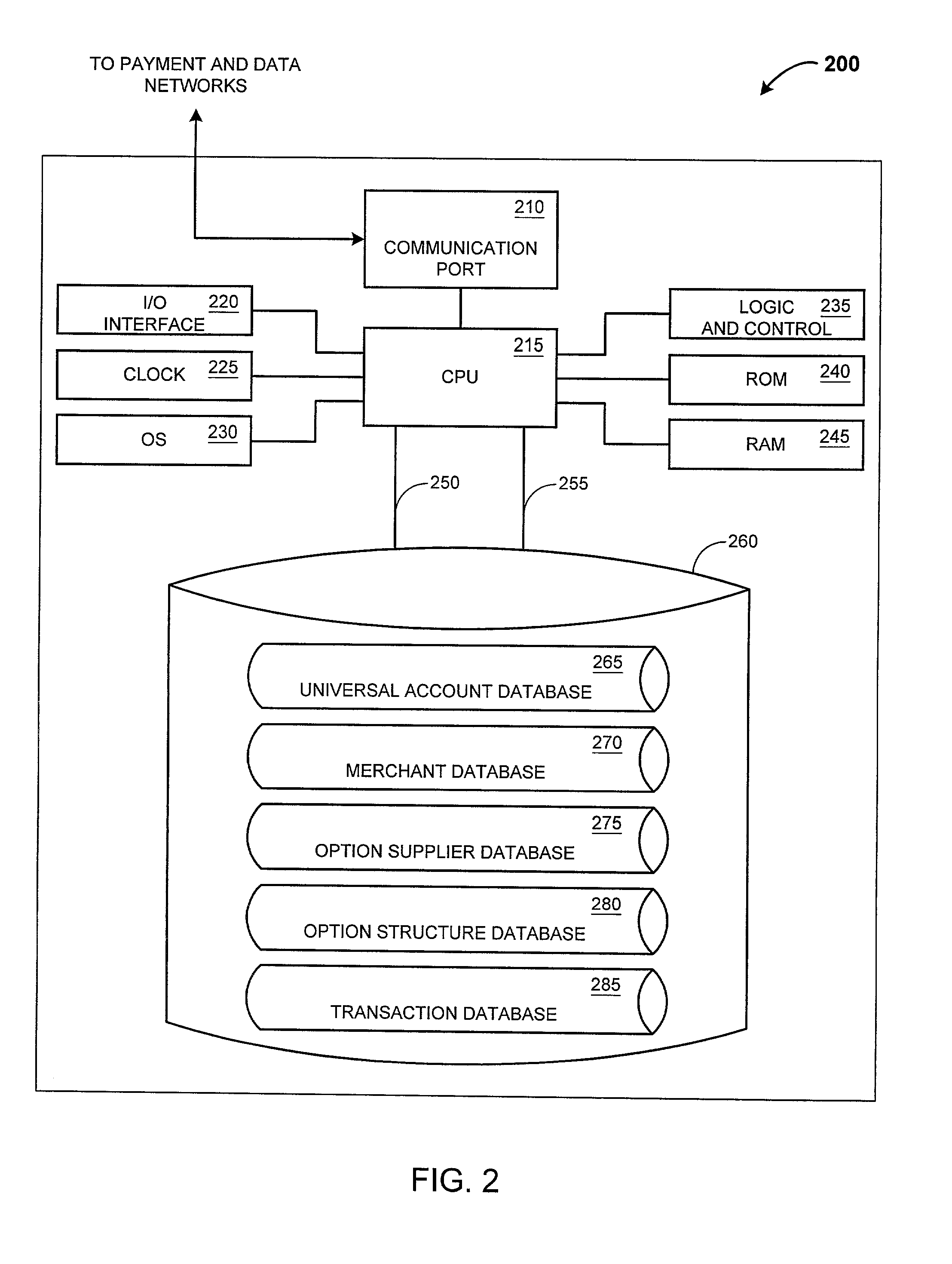
System and method for an automated benefit recognition, acquisition, value exchange, and transaction settlement system using multivariable linear and nonlinear modeling
A system and process that provides an on-line, interactive, and fully integrated benefit-driven value exchange and settlement program that monitors, evaluates, and manages economic and personal benefits and executes functions to produce and acquire the maximum or preferred benefit items for users by guiding and automating appropriate payment and settlement actions. The present invention finds useful patterns in data; produces conclusions based on rules and experience; responds to environmental changes with or without human intervention; and, may evolve through selecting the best results from random mutations all of which are intended to maximise user value.
Owner:IANNACCI GREGORY FX
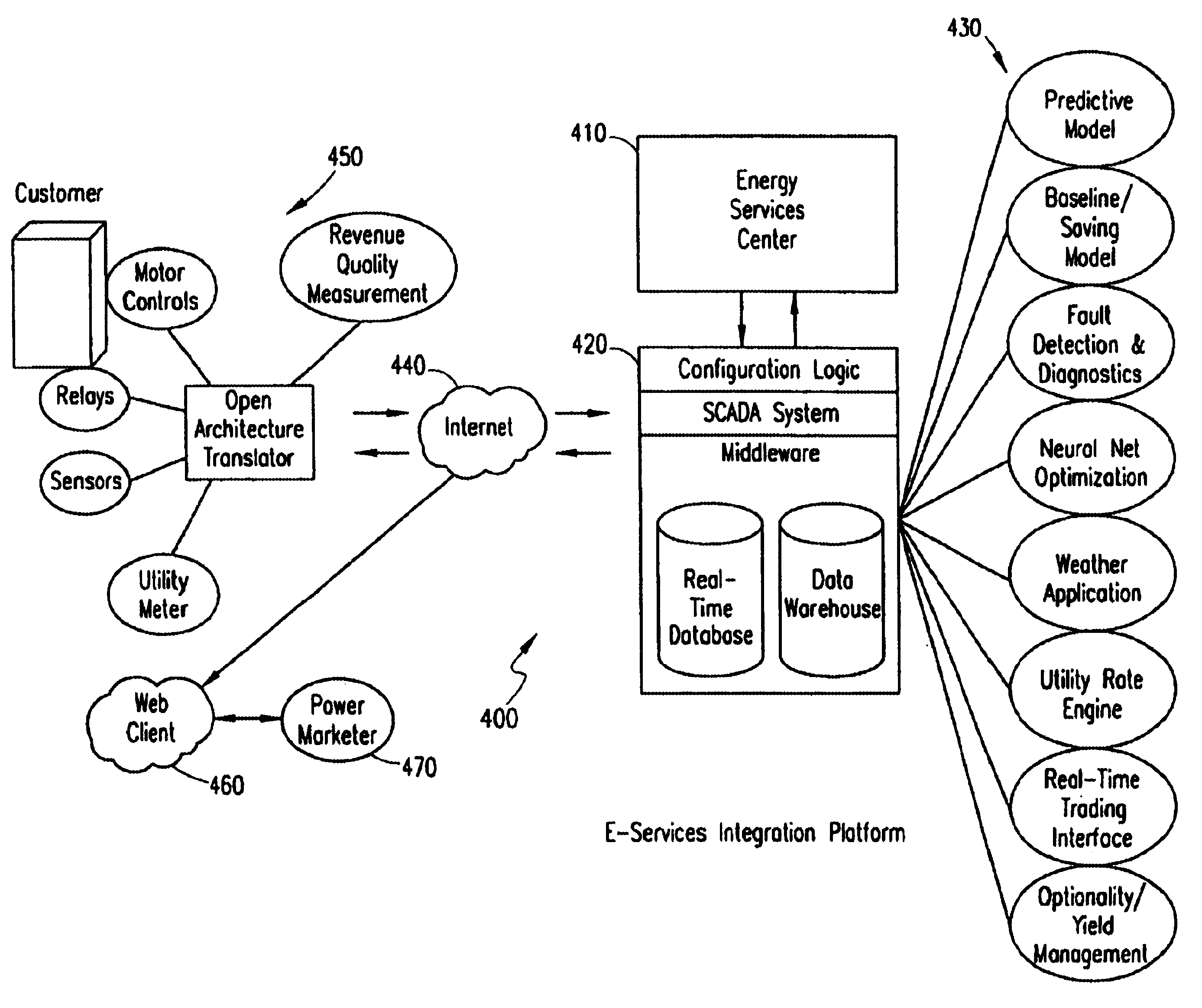
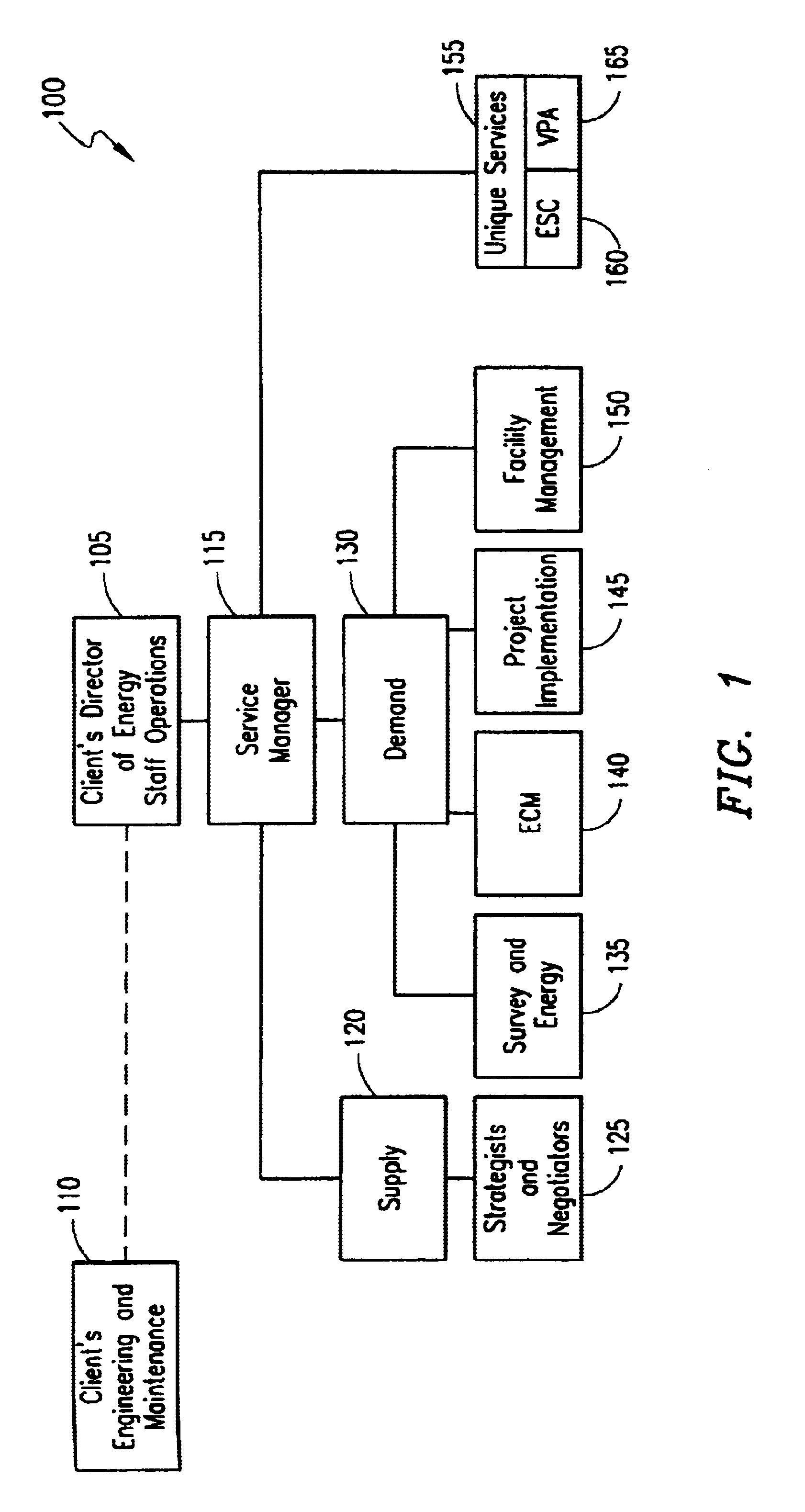
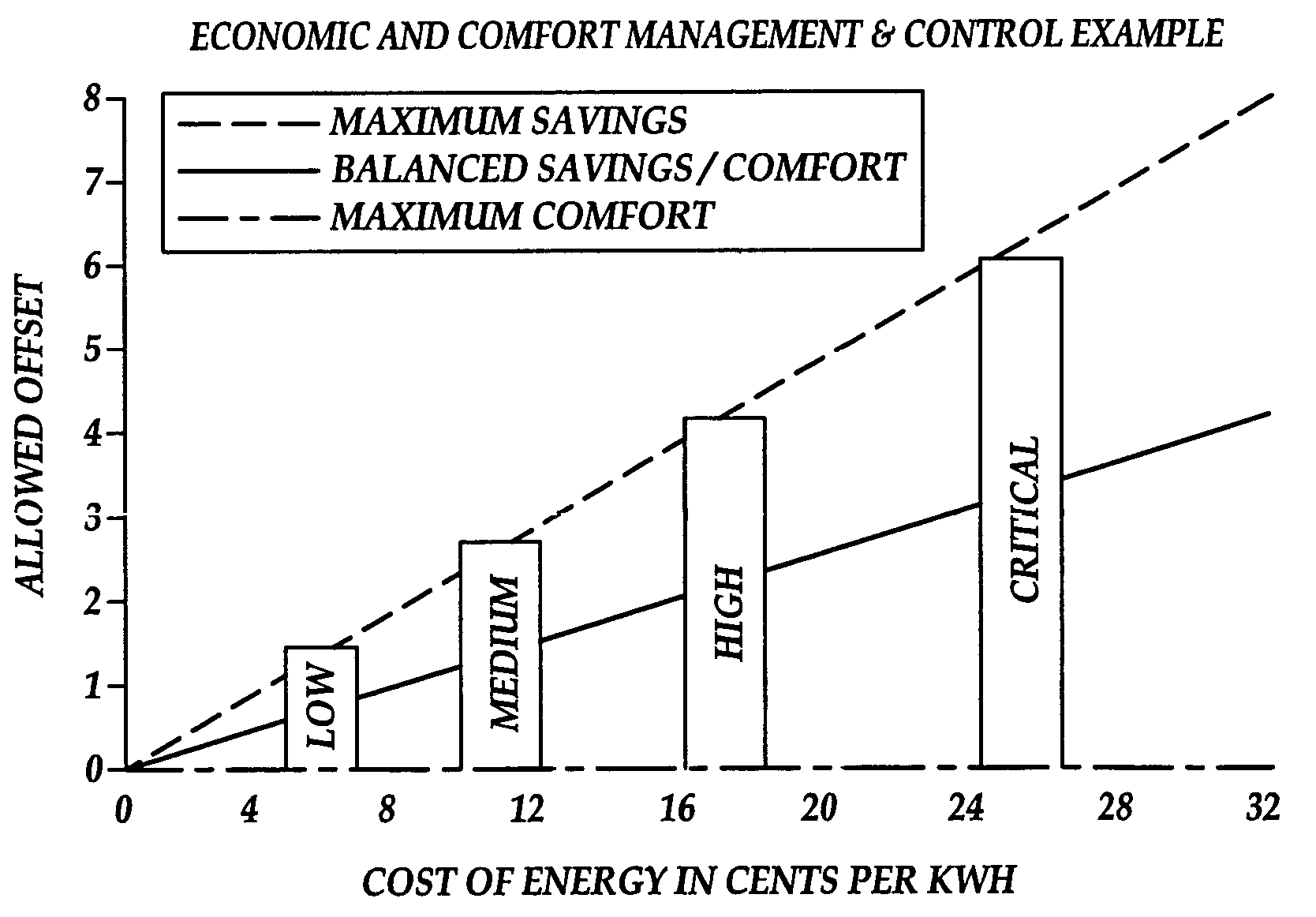
System and method for energy management
InactiveUS6785592B1Economic savingsImprove economyLevel controlSpecial tariff metersConservation energyProcess engineering
A business methodology for optimizing energy procurement energy demand (usage) and energy supply for a facility or complex. After ascertaining a baseline model, energy consumption is monitored and adjusted to reflect dynamic economic factors of operations. With the accumulation of data, contract negotiations with energy suppliers may provide further energy savings. Over time and patterns of usage determined further savings and optimization in energy, equipment, staffing and other operational areas are obtained. Remote access provides efficient monitoring of established systems.
Owner:PEROT SYSTEMS
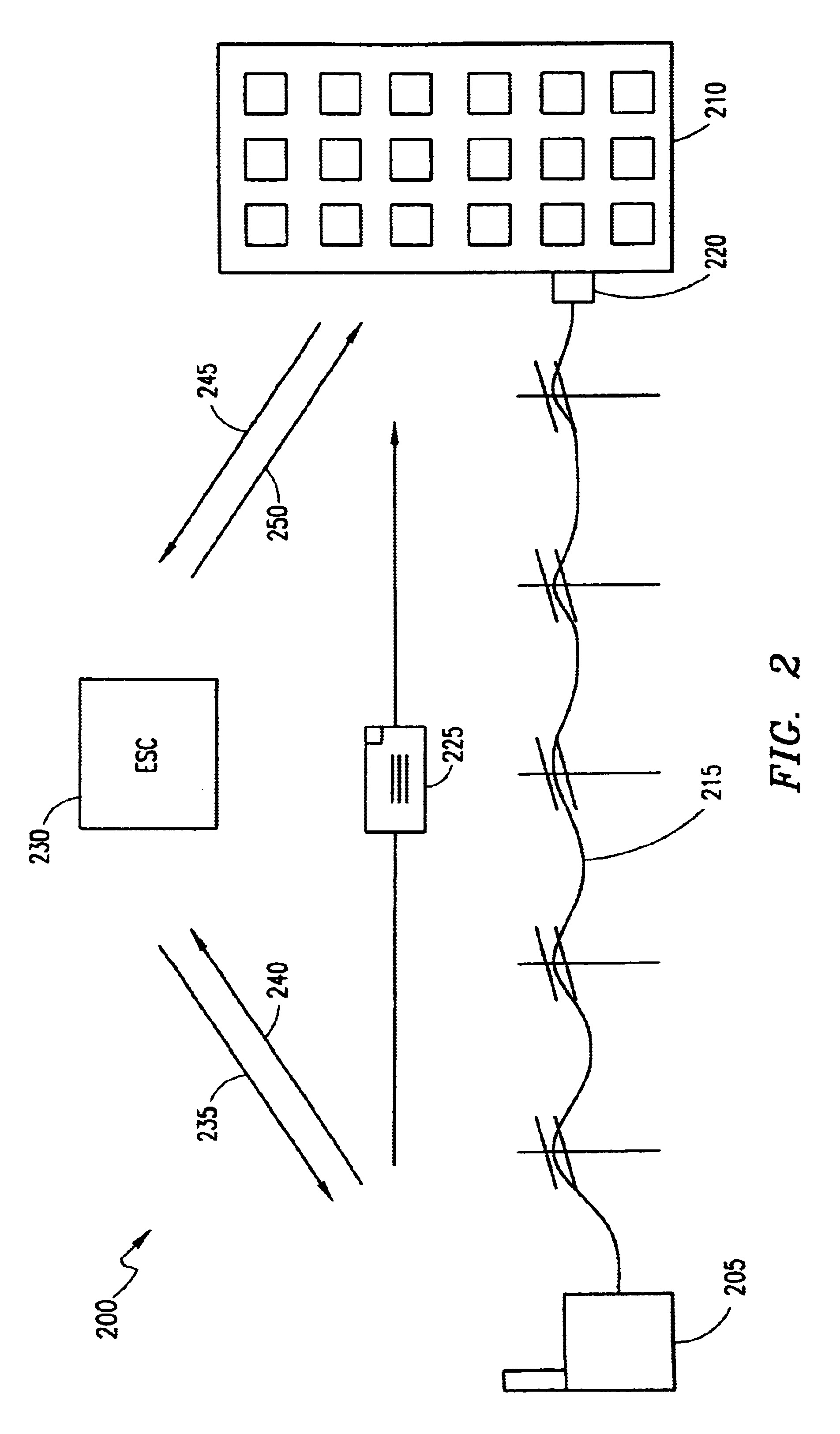
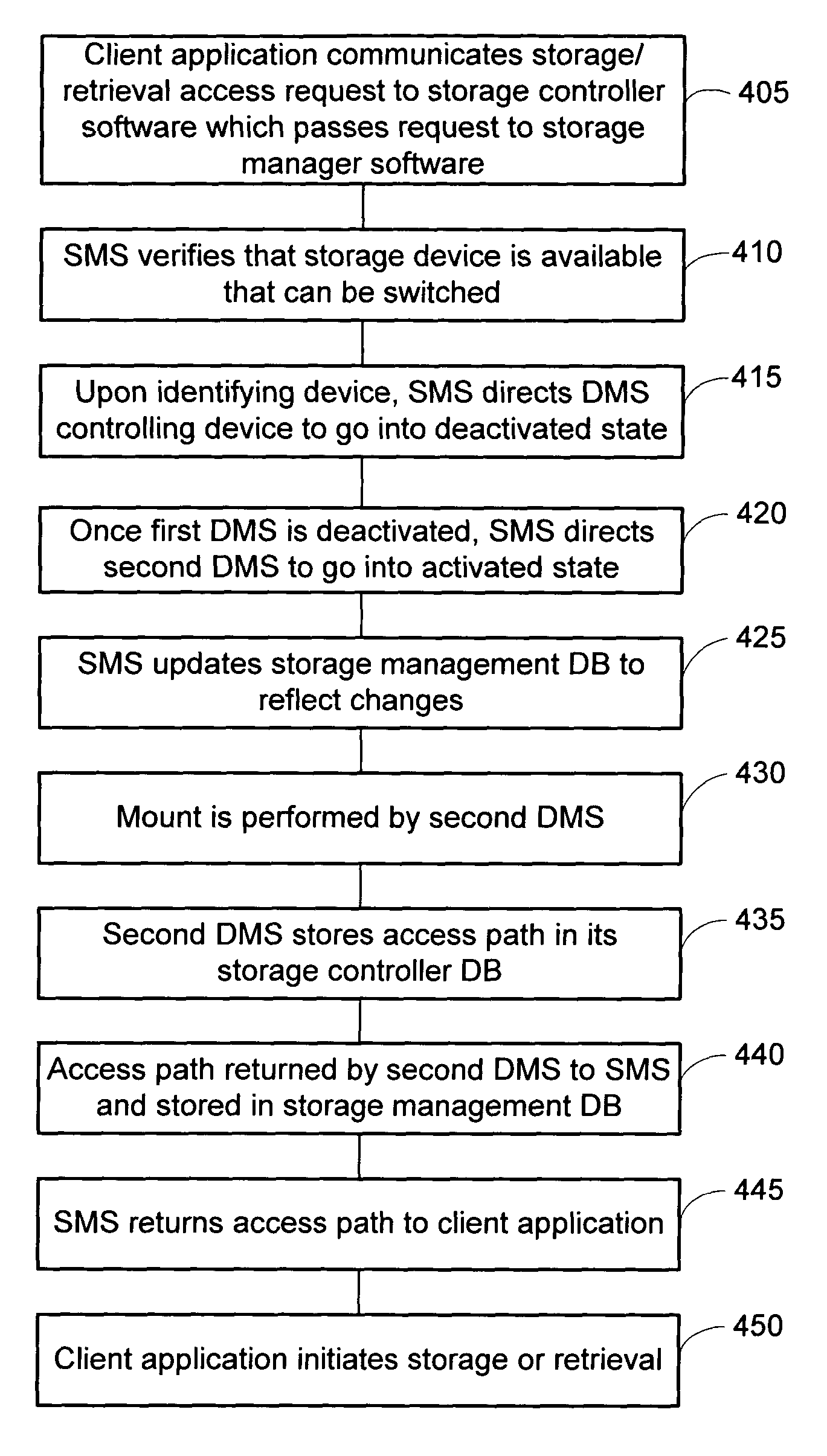
Dynamic storage device pooling in a computer system
ActiveUS7130970B2Not affectInput/output to record carriersMemory loss protectionDynamic storageComputerized system
A method for dynamically allocating control of a storage device, the method comprising receiving an access request from a first computer requesting access to a storage device; directing, based upon the access request, a first storage controller computer to assume an inactive state with respect to control of the storage device; and directing, based upon the access request, a second storage controller computer to assume an active state with respect to control of the storage device.
Owner:COMMVAULT SYST INC
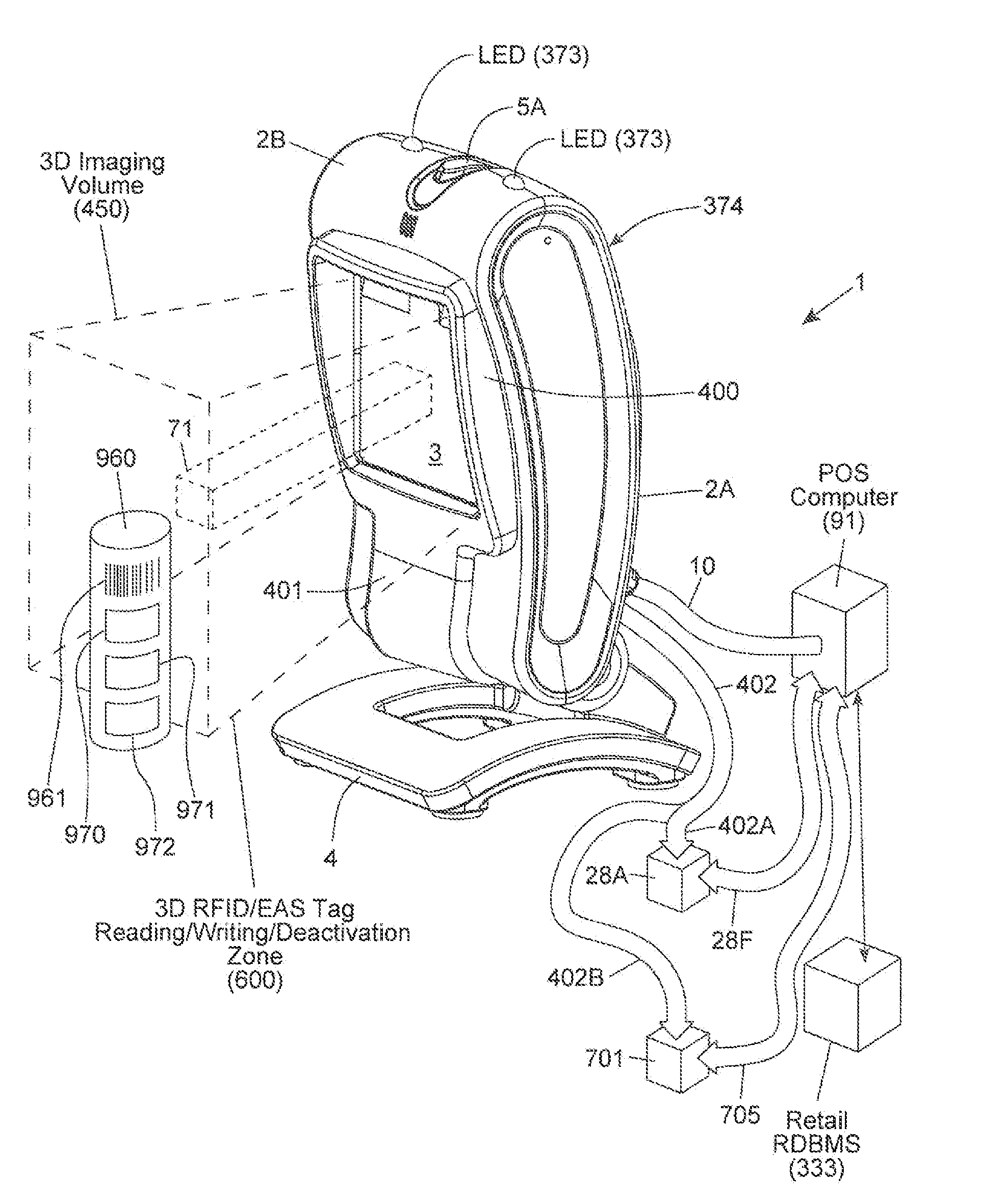
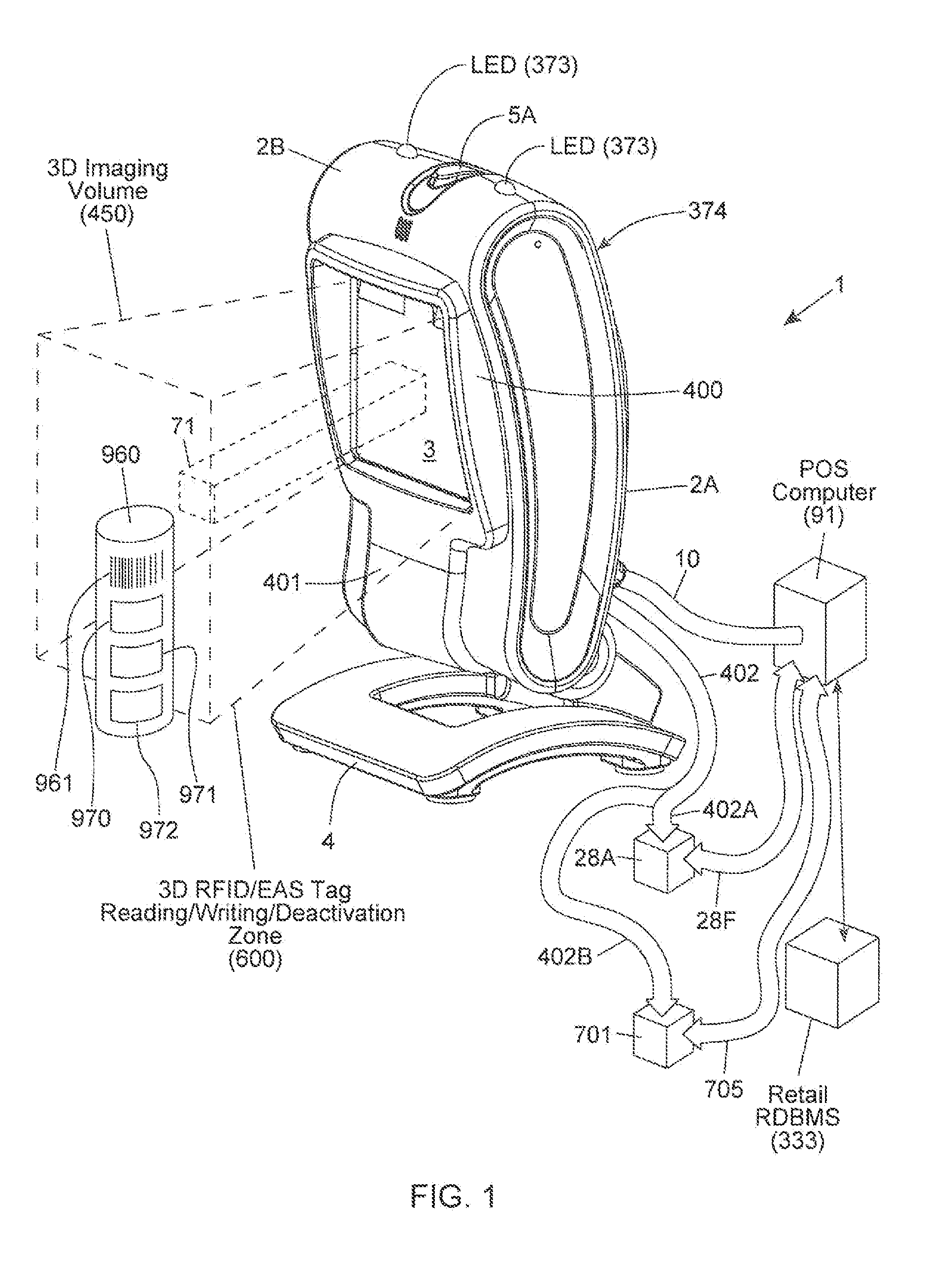
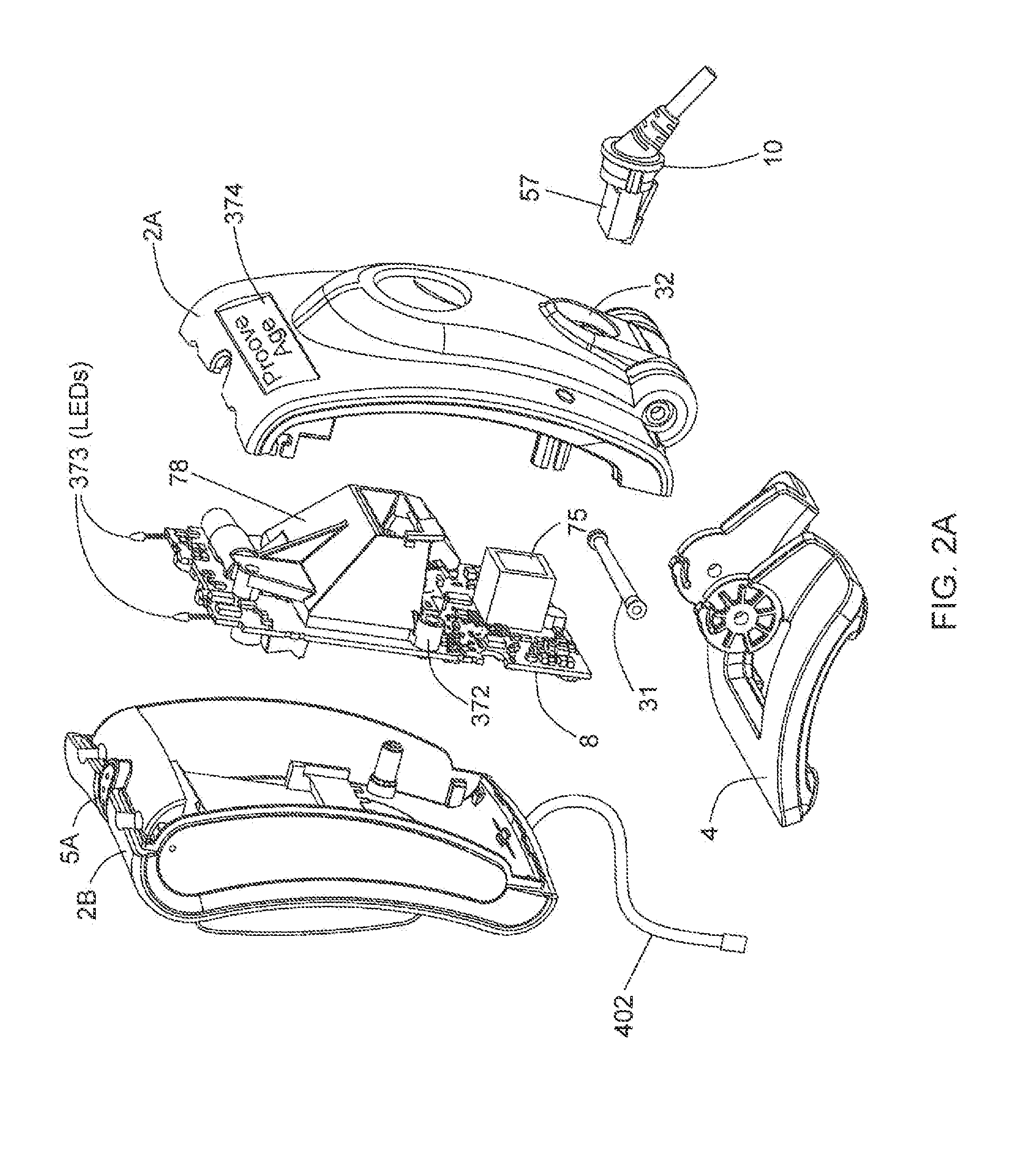
Method of and system for uniquely responding to code data captured from products so as to alert the product handler to carry out exception handling procedures
InactiveUS20120203647A1Avoid disadvantagesEffectively reliably informCash registersPayment architectureLogistics managementSoftware engineering
A code reading system capable of signaling exception handling procedures for products being handled in a work environment, such as, for example, consumer product being purchased in a retail store or a product or package being sorted by a logistics company. The system includes a system housing containing one or more one or more signal sources for generating distinctive visual and / or audible exception handling signals for special classes of products identified in the environment. Such special products may include: EAS tagged products requiring EAS tag deactivation: alcohol and tobacco products requiring proof of age; controlled products requiring additional customer tracking; age restricted products requiring identification; product purchases requiring personnel to show up and approve or assist in a product transaction; and the like.
Owner:METROLOGIC INSTR
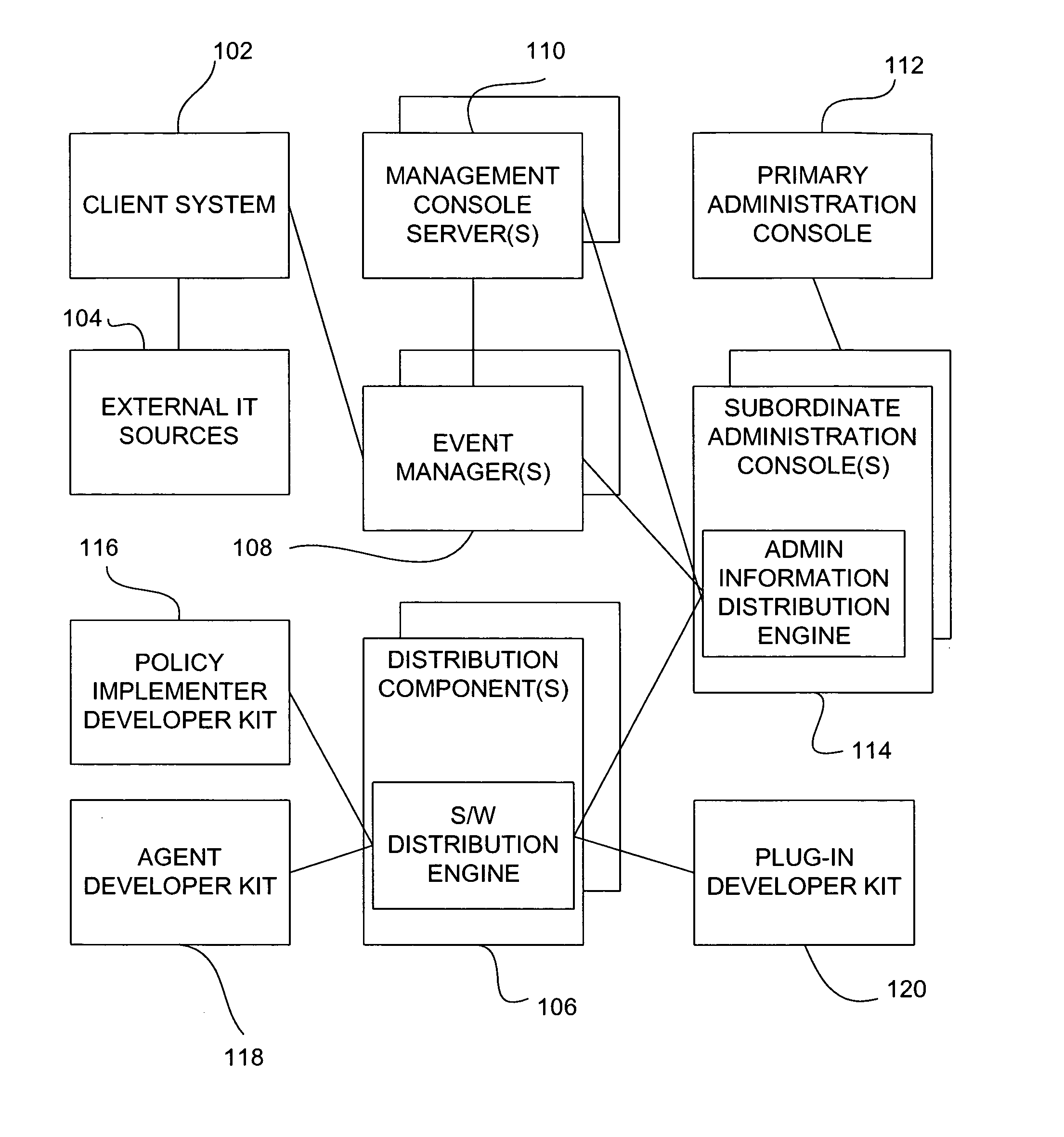
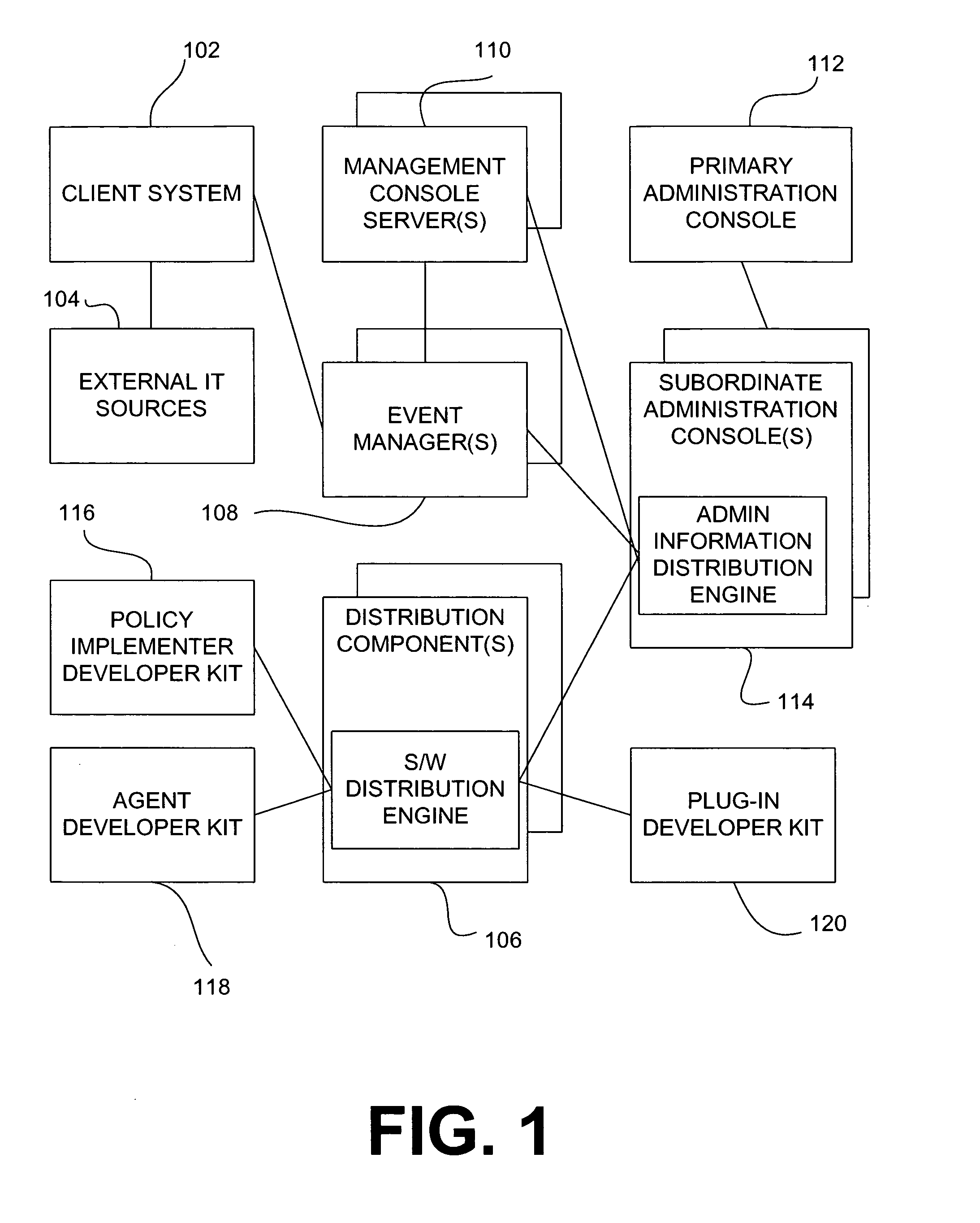
System and method for policy management
InactiveUS20070180490A1Computer security arrangementsSpecial data processing applicationsStrategy makingComputer security
The invention provides a system and method for providing policy-based protection services. As a new threat is understood, one or more protection techniques are considered for protecting the asset, the organization assigns responsibilities to carry out or protect the asset, and a policy is constructed. After the policy is developed a plan is put into action to protect the asset, and a policy implementer is developed and / or purchased, distributed, configured, and managed. Finally, the policy, its enforcement, and its effectiveness, are reviewed to determine any changes needed, and new requirements are discovered, closing the lifecycle.
Owner:ALLEGENT TECH GROUP
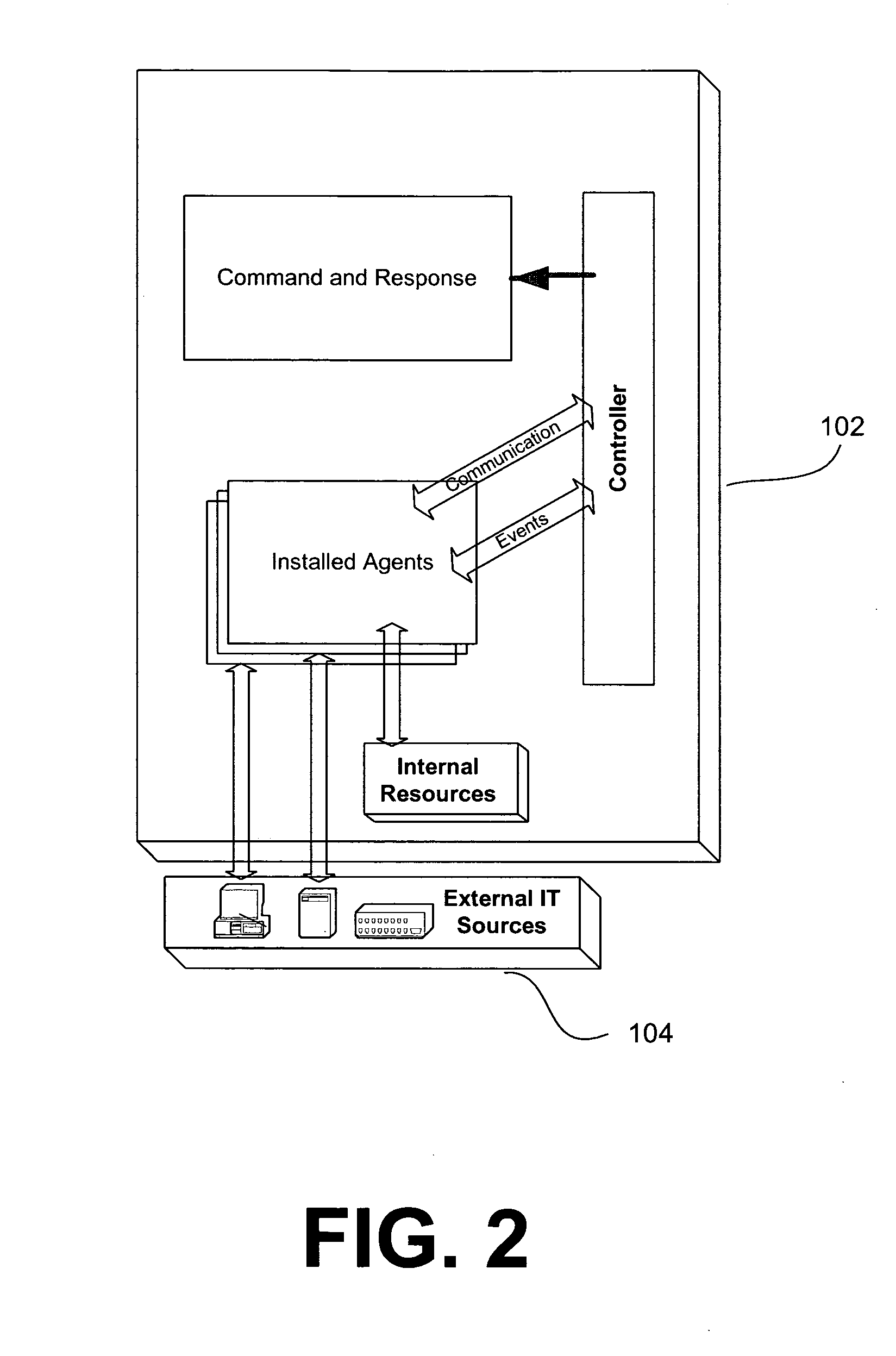
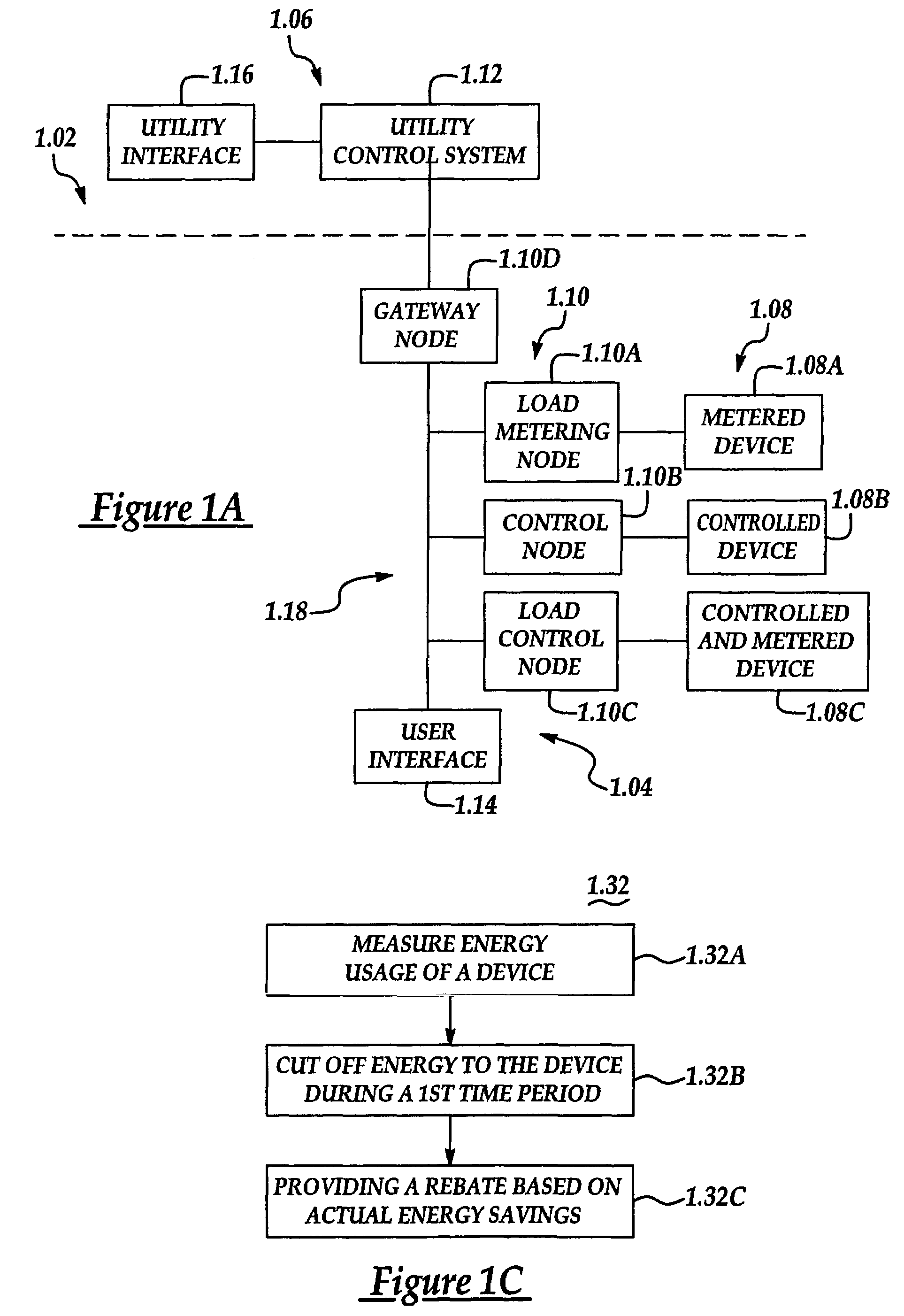
System and method of controlling an HVAC system
A system and method manage delivery of energy from a distribution network to one or more sites. Each site has at least one device coupled to the distribution network. The at least one device controllably consumes energy. The system includes a node and a control system. The node is coupled to the at least one device for sensing and controlling energy delivered to the device. A control system is coupled to the node and distribution network for delivery to the node at least one characteristic of the distribution network. The node controls the supply of energy to the device as a function of the at least one characteristic.
Owner:INVENSYS SYST INC
Multi-object fetch component
InactiveUS6529948B1Digital data processing detailsMultiprogramming arrangementsBusiness objectSoftware engineering
A system, method, and article of manufacture are provided for retrieving multiple business objects across a network in one access operation. A business object and a plurality of remaining objects are provided on a persistent store. Upon receiving a request for the business object, it is established which of the remaining objects are related to the business object. The related objects and the business object are retrieved from the persistent store in one operation and it is determined how the retrieved related objects relate to the business object and each other. A graph of relationships of the business and related objects is instantiated in memory.
Owner:ACCENTURE GLOBAL SERVICES LTD
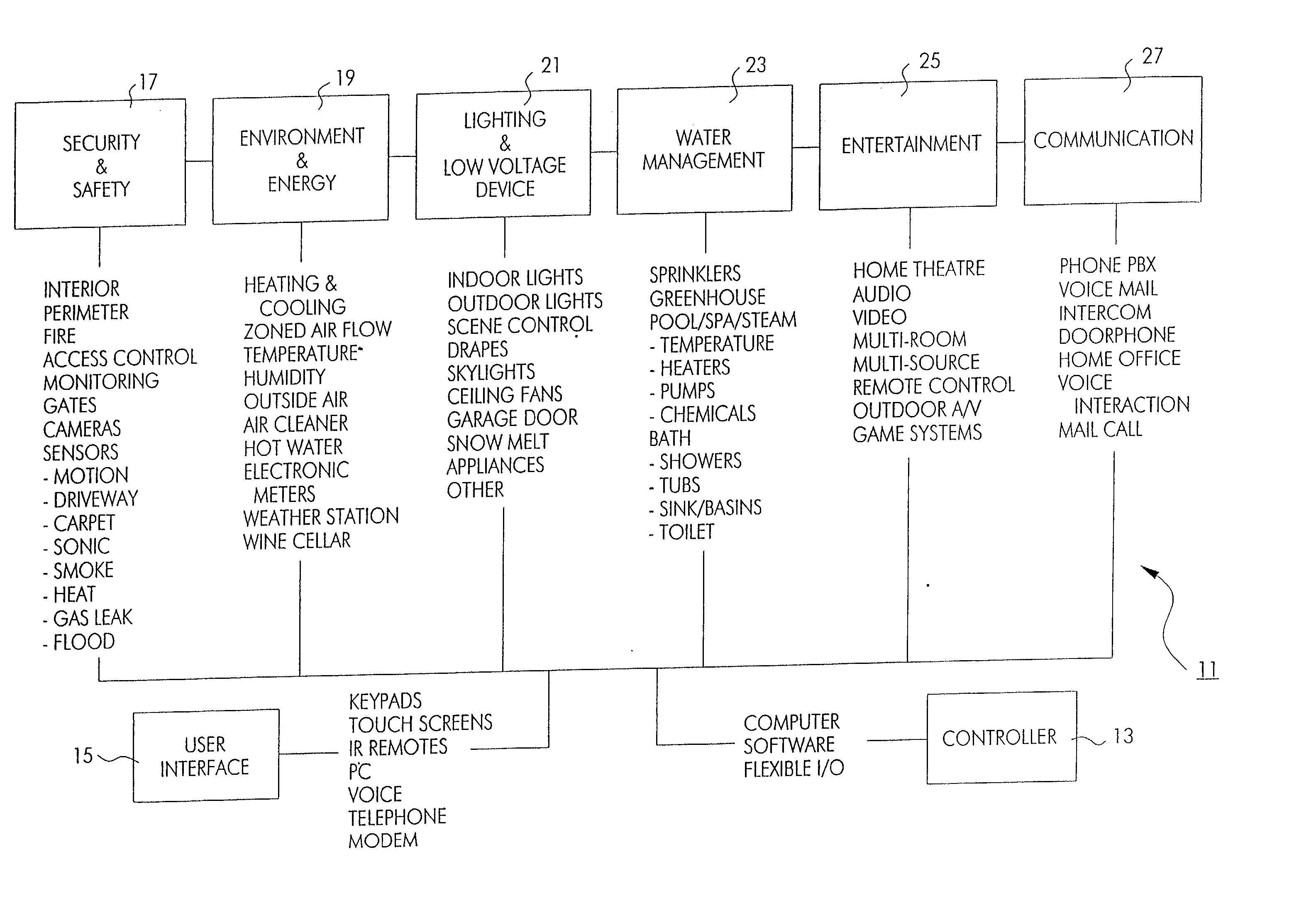
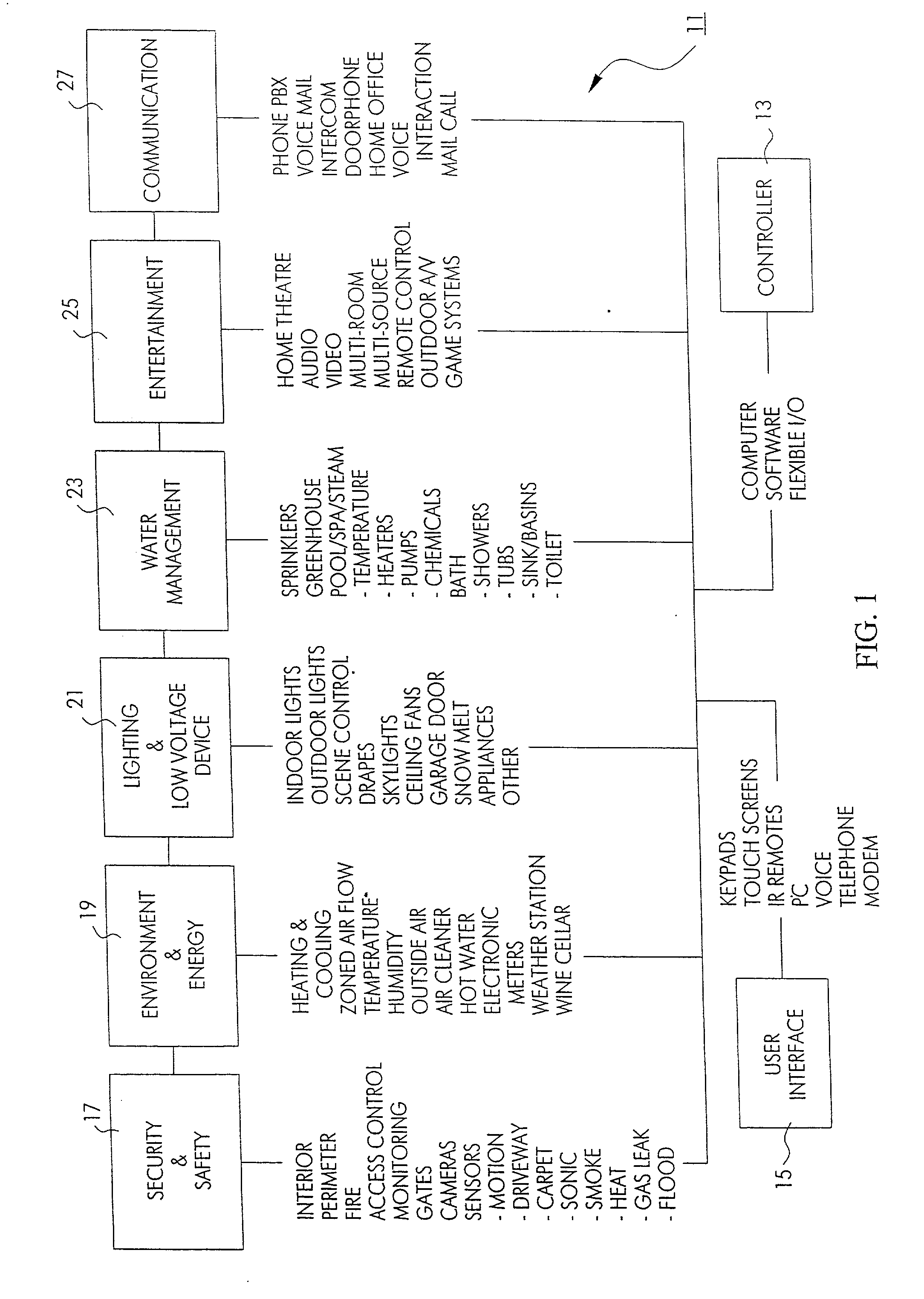
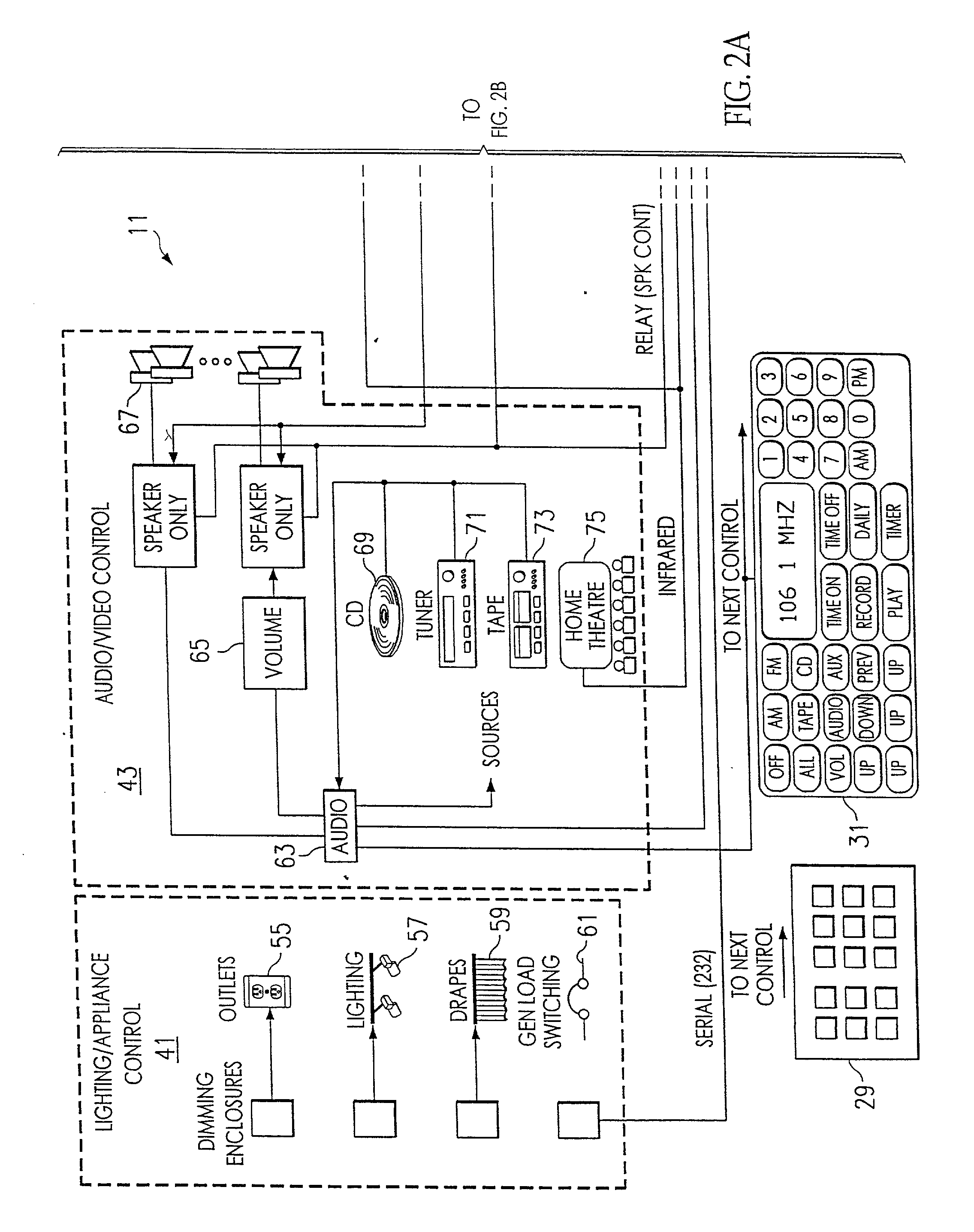
Method and apparatus for improved building automation
InactiveUS20020016639A1Large modularityCommunicationSampled-variable control systemsComputer controlModularityEngineering
The improved building automation system of the present invention is modular in the extreme. This diminishes the amount of custom programming required in order to affect control of a particular building. It allows for a relatively open architecture which can accommodate a variety of unique control applications which are scripted for a particular building. By modularizing many of the common processes utilized in the automation system, the custom programming required to control any particular building is minimized. This modularity in design allows for uniform and coordinated control over a plurality of automation subsystems which may be incompatible with one another at the device or machine level, but which can be controlled utilizing a relatively small and uniform set of "interprocess control commands" which define an interprocess control protocol which is utilized in relatively high level scripts and control applications which may be written for a particular building.
Owner:UNIDEN AMERICA
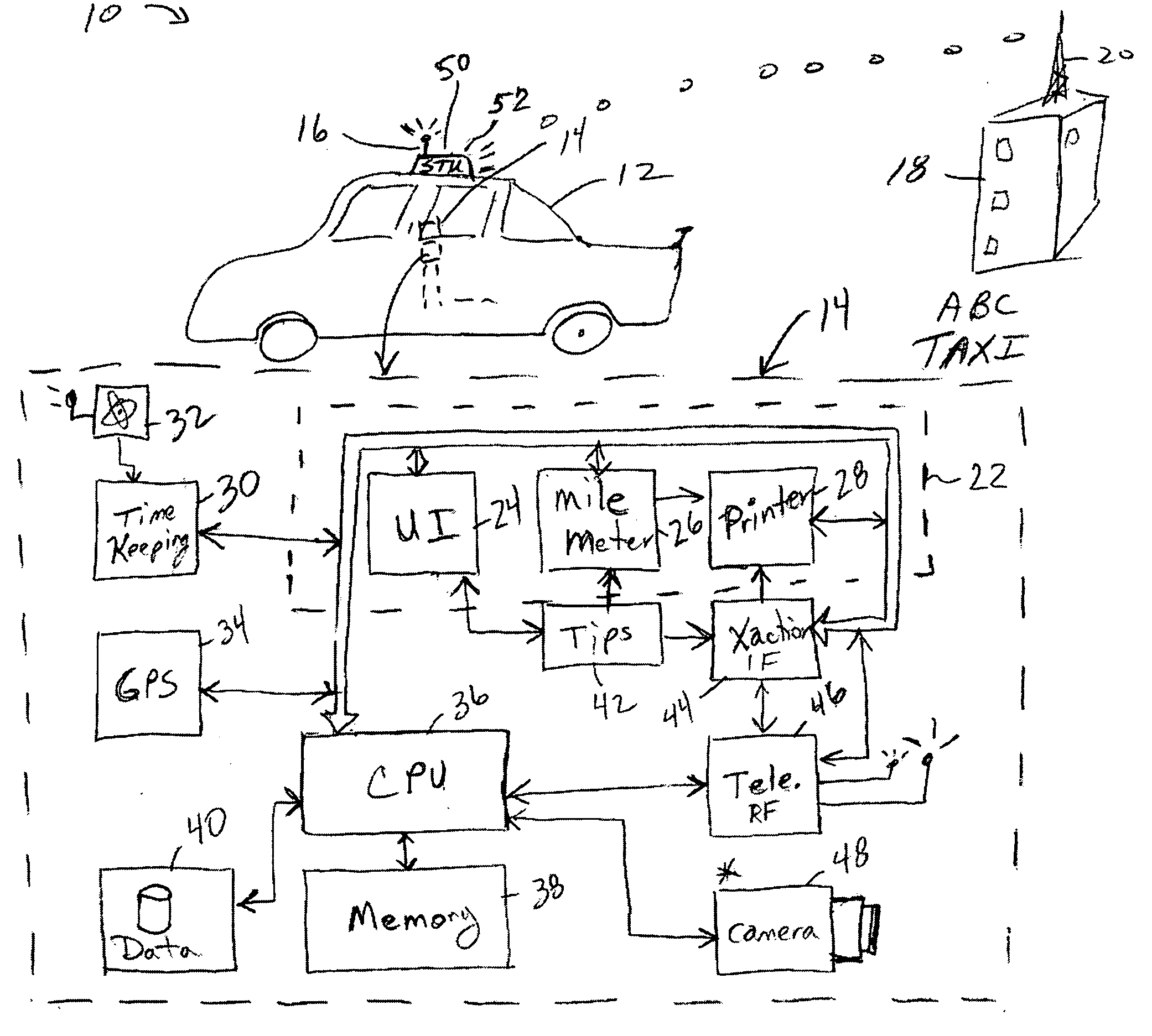
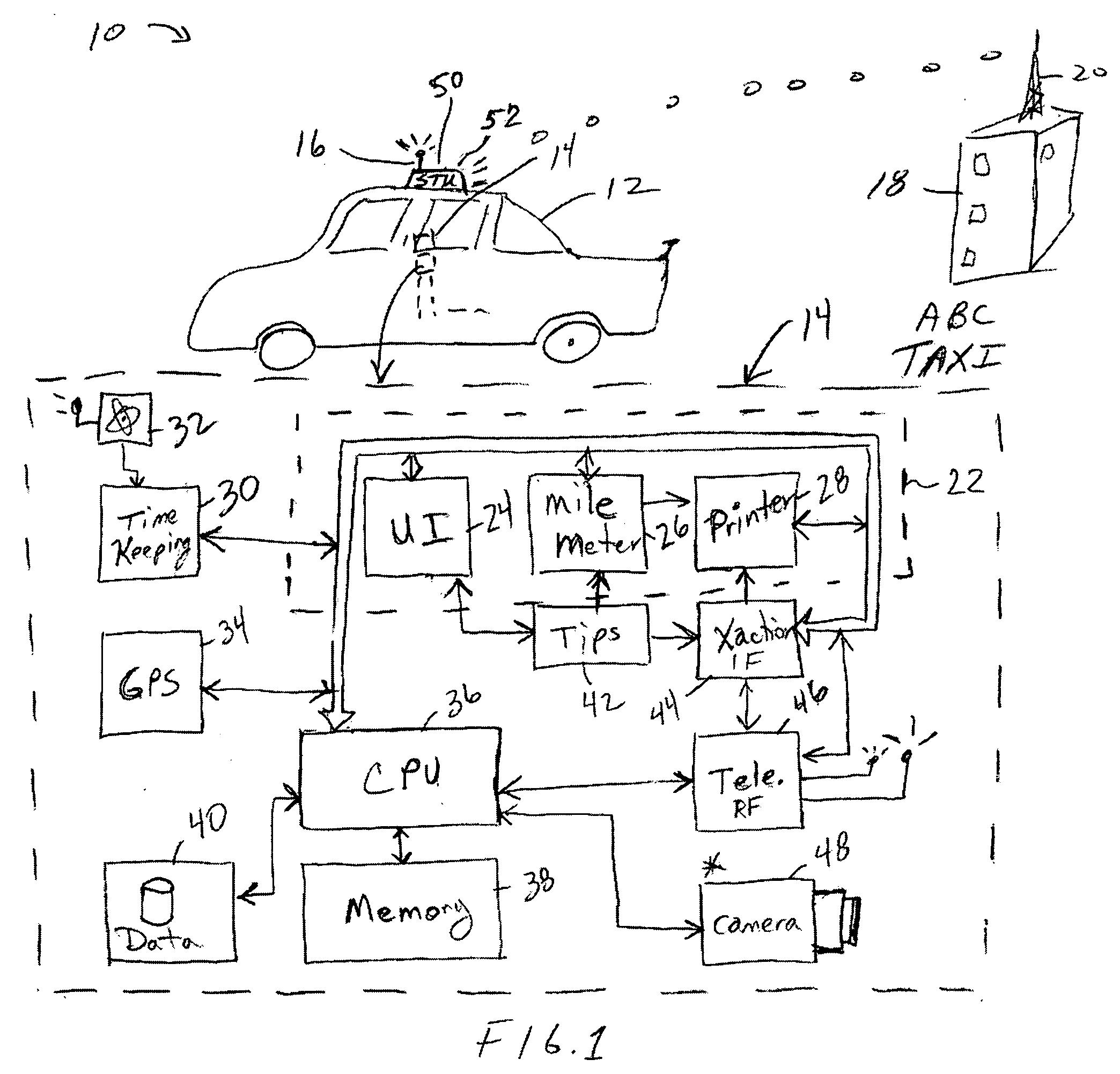
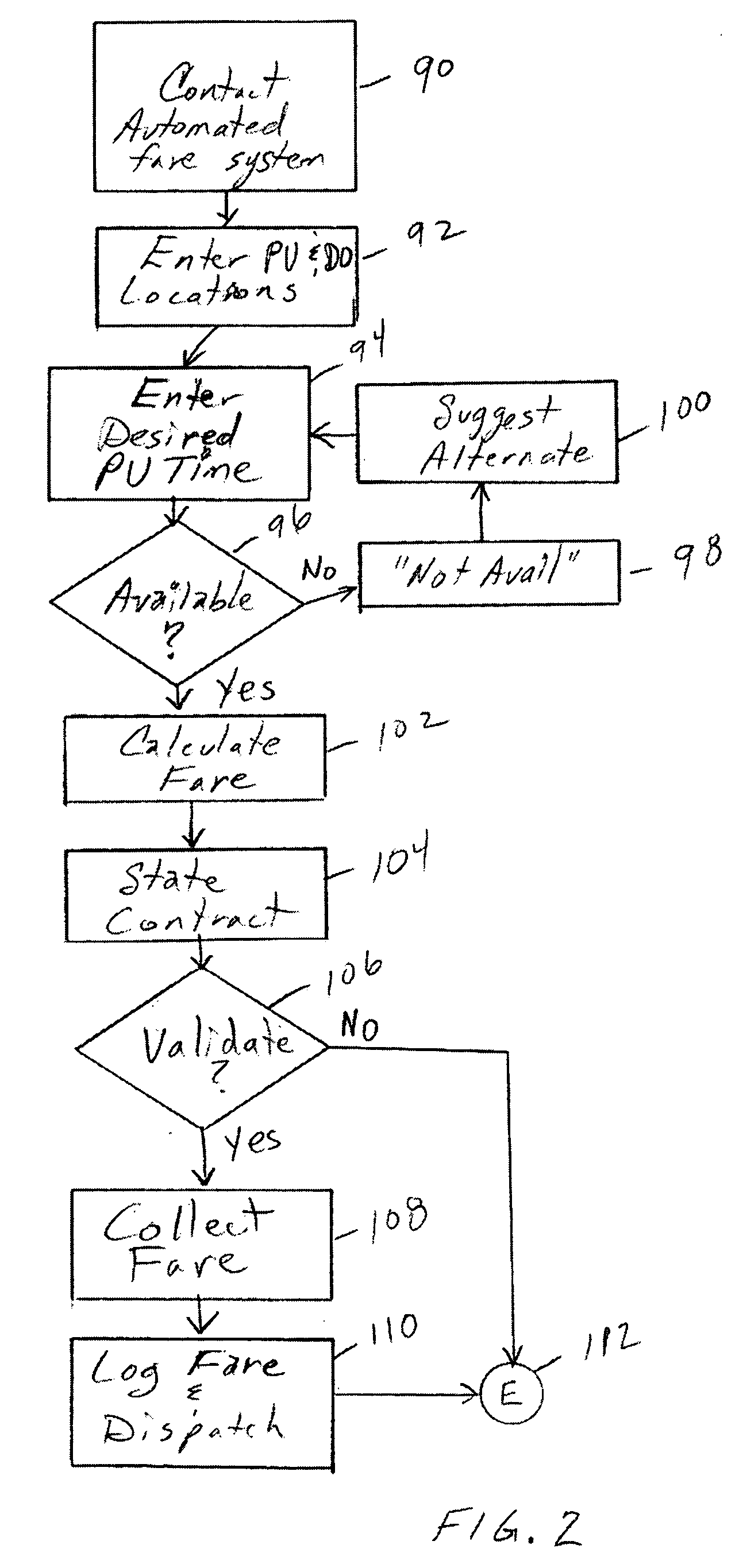
Conveyance scheduling and logistics system
InactiveUS20040260470A1Easy to modifyAvoid narrow scopeRoad vehicles traffic controlResourcesLogistics managementEngineering
An apparatus and method of reserving conveyance, such as taxis and limousines, in which the pickup locations, times, and contract are established and logged electronically. The system is configured to increase the assurance that the conveyance will arrive properly on time and on location, and that the patron will also keep their end of the agreement. The system preferably configured for disincentives for either party to not follow in accord with the contract.
Owner:RAST RODGER H
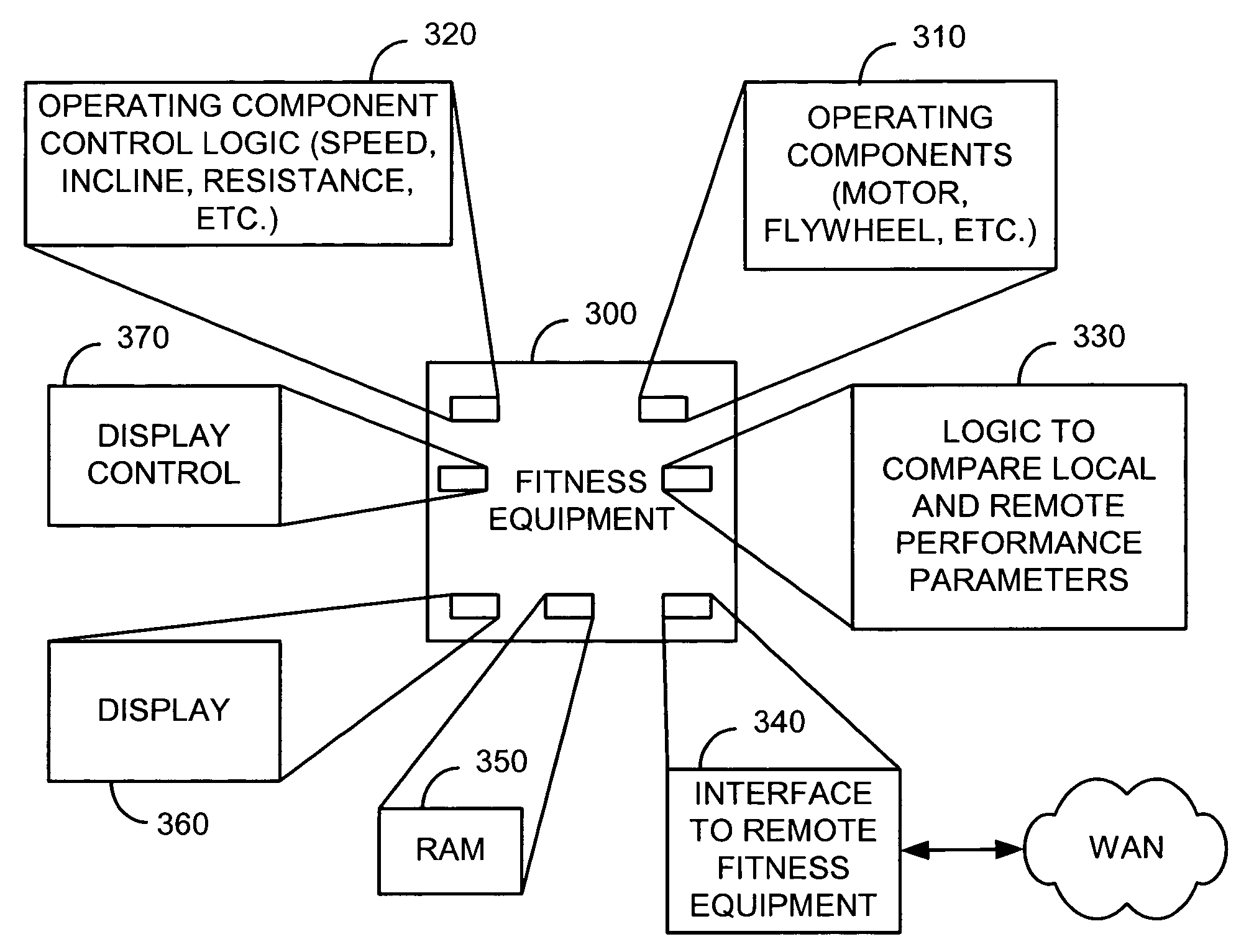
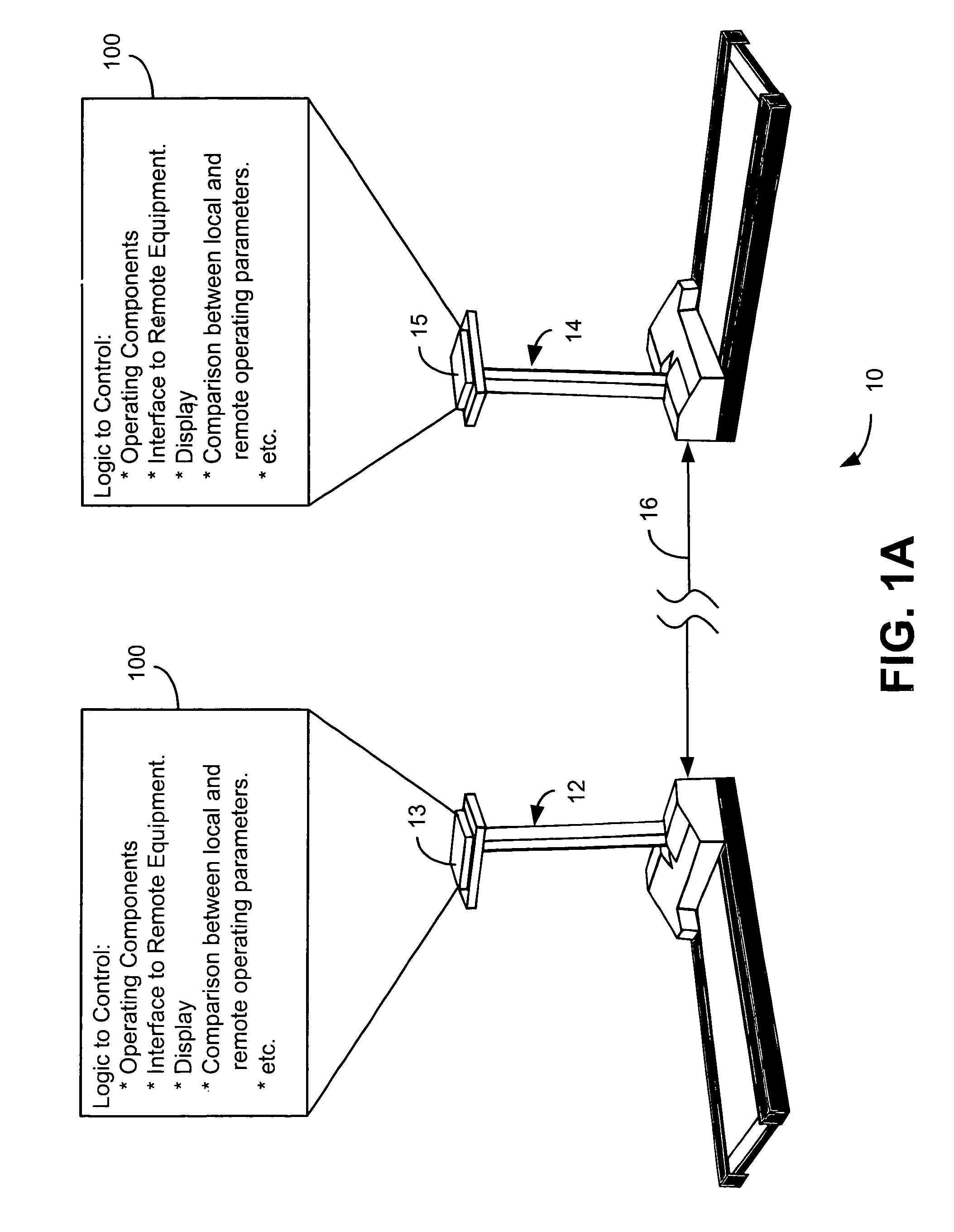
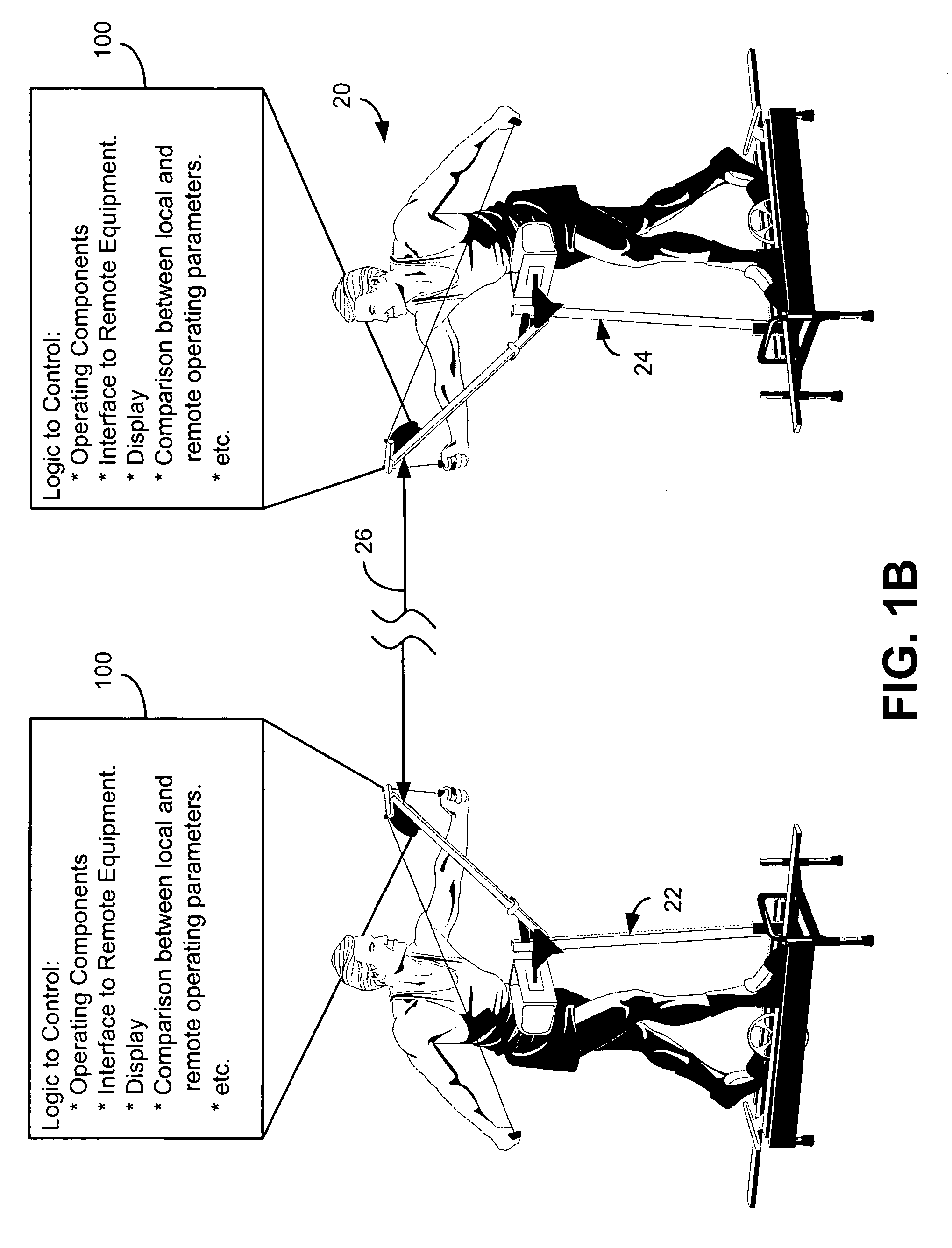
Interactive fitness equipment
InactiveUS6902513B1Therapy exerciseInput/output processes for data processingCommunication interfaceSimulation
The present invention is generally directed to a computerized fitness equipment that is designed to simulate, emulate, or implement actual race conditions with other users. An exemplar fitness equipment includes at least one operating component and sensors to monitor performance parameters of the at least one operating component (such as speed of movement). A display is also provided, along with logic to provide a visual display of a user's performance (as measured through the first performance parameters). In one embodiment, a communication interface is provided to communicate the first performance parameters to at least one remote, similarly-configured, fitness equipment. Performance parameters from the remote fitness equipment are also received through the communication interface. The fitness equipment includes logic to compare the first performance parameters with performance parameters received from remote fitness equipment and display the results in a comparative fashion to the user.
Owner:VR OPTICS LLC
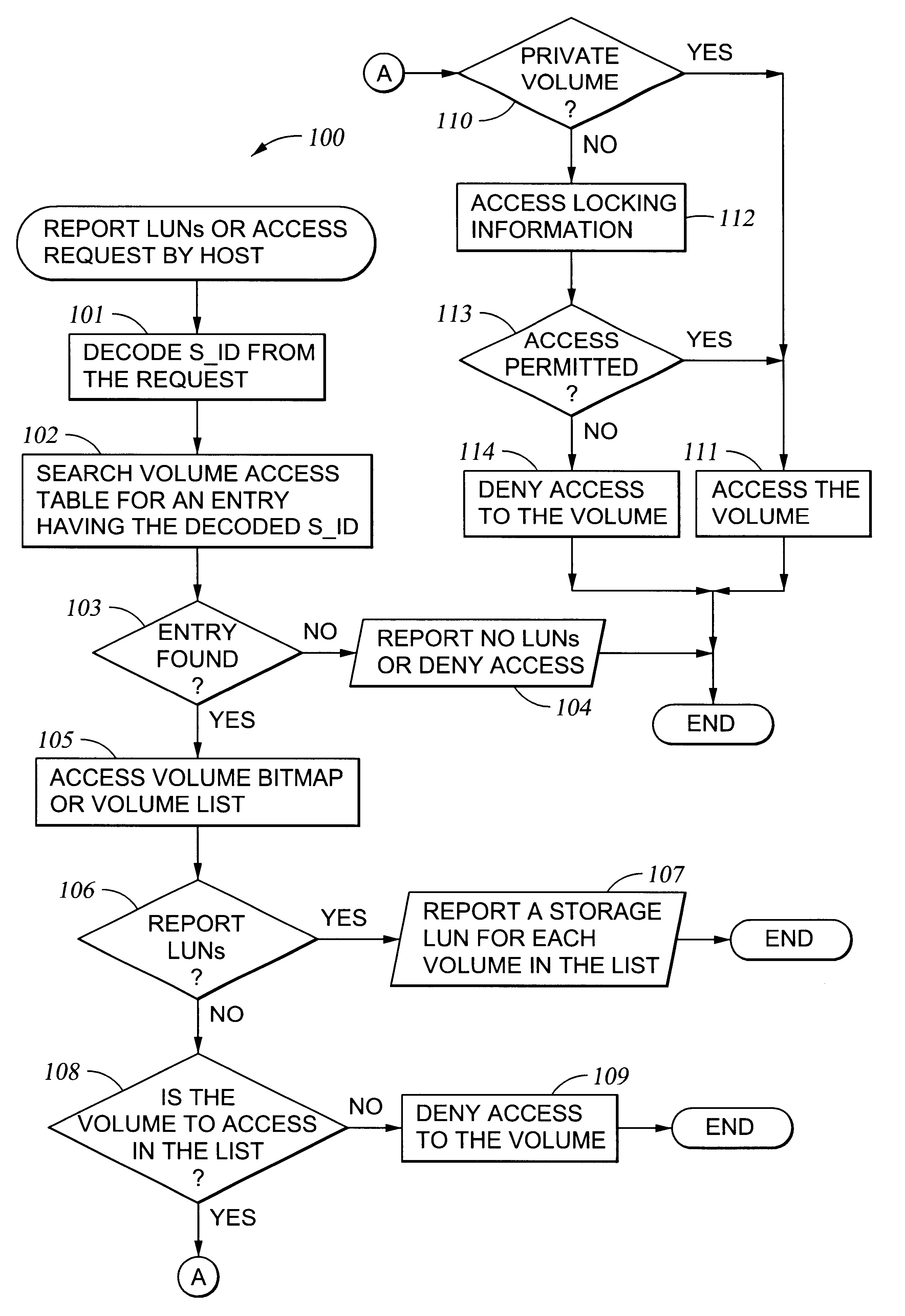
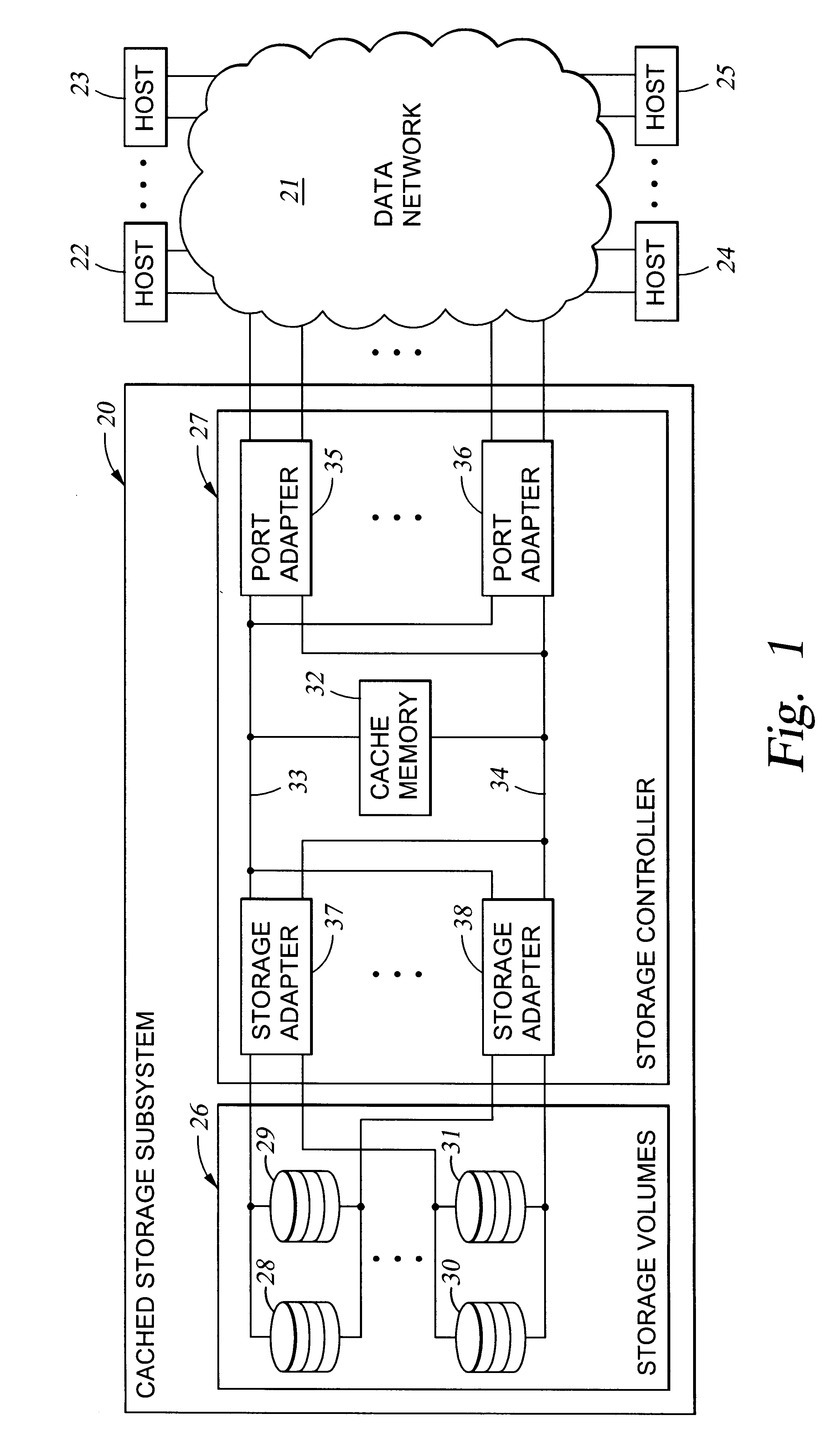
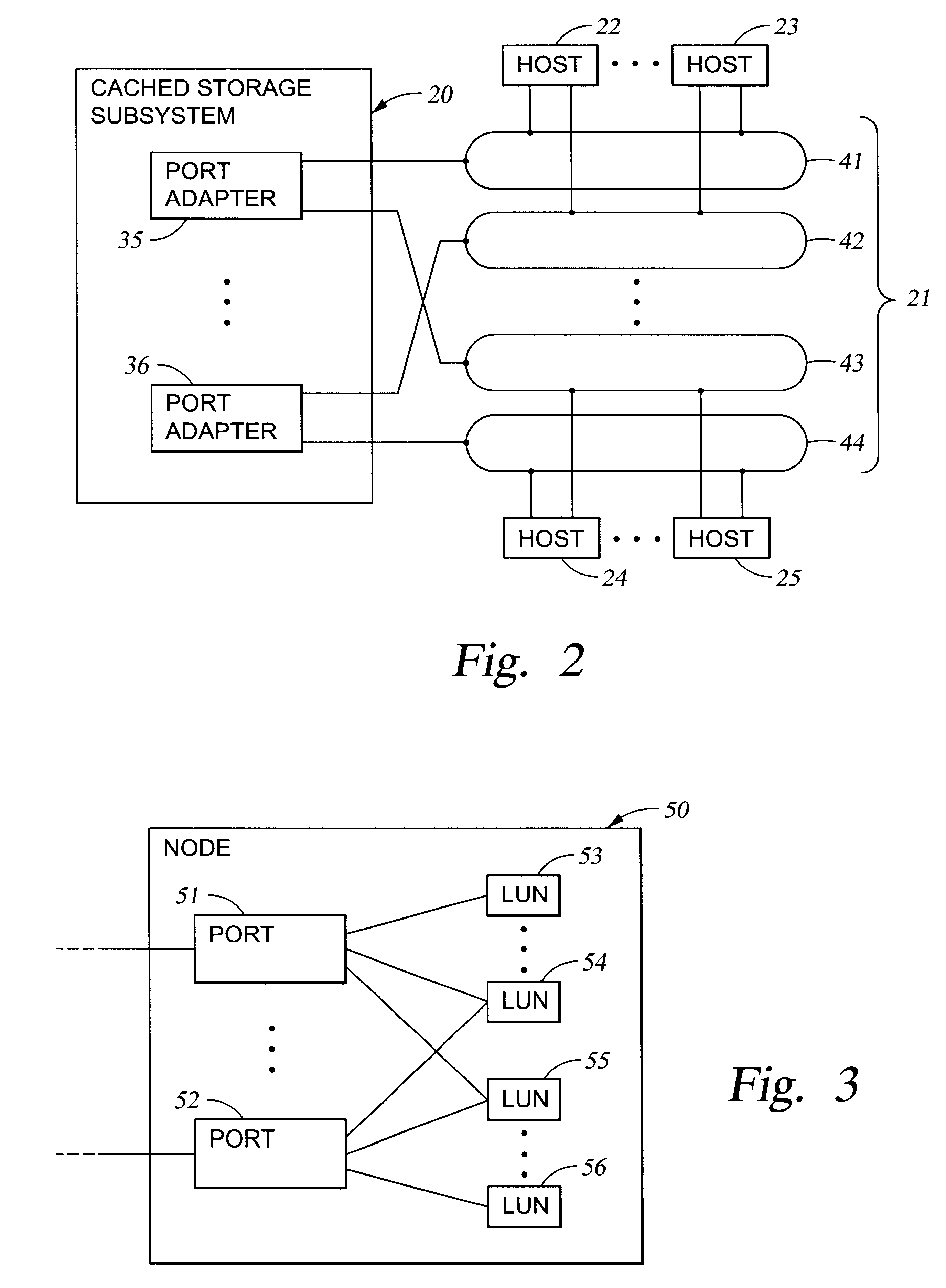
Storage mapping and partitioning among multiple host processors in the presence of login state changes and host controller replacement
InactiveUS6260120B1Input/output to record carriersData processing applicationsData portControl store
A storage controller for controling access to data storage has a memory and at least one data port for a data network including host processors. The memory is programmed to define a respective specification for each host processor of a respective subset of the data storage to which access by the host processor is restricted, and each specification is associated with a host identifier stored in the memory. When the storage controller receives a data access request from a host processor, it decodes a host identifier from the data access request, and searches the memory for a host identifier matching the host identifier decoded from the request. Upon finding a match, the respective specification of the respective subset for the host processor is accessed to determine whether or not storage specified by the storage access request is contained in the respective subset. If so, then storage access can continue, and otherwise, storage access is denied. Preferably the host identifier decoded from the request is a temporary address assigned by the network, and also stored in the memory in association with each respective specification is a relatively permanent identifier for the host processor.
Owner:EMC IP HLDG CO LLC
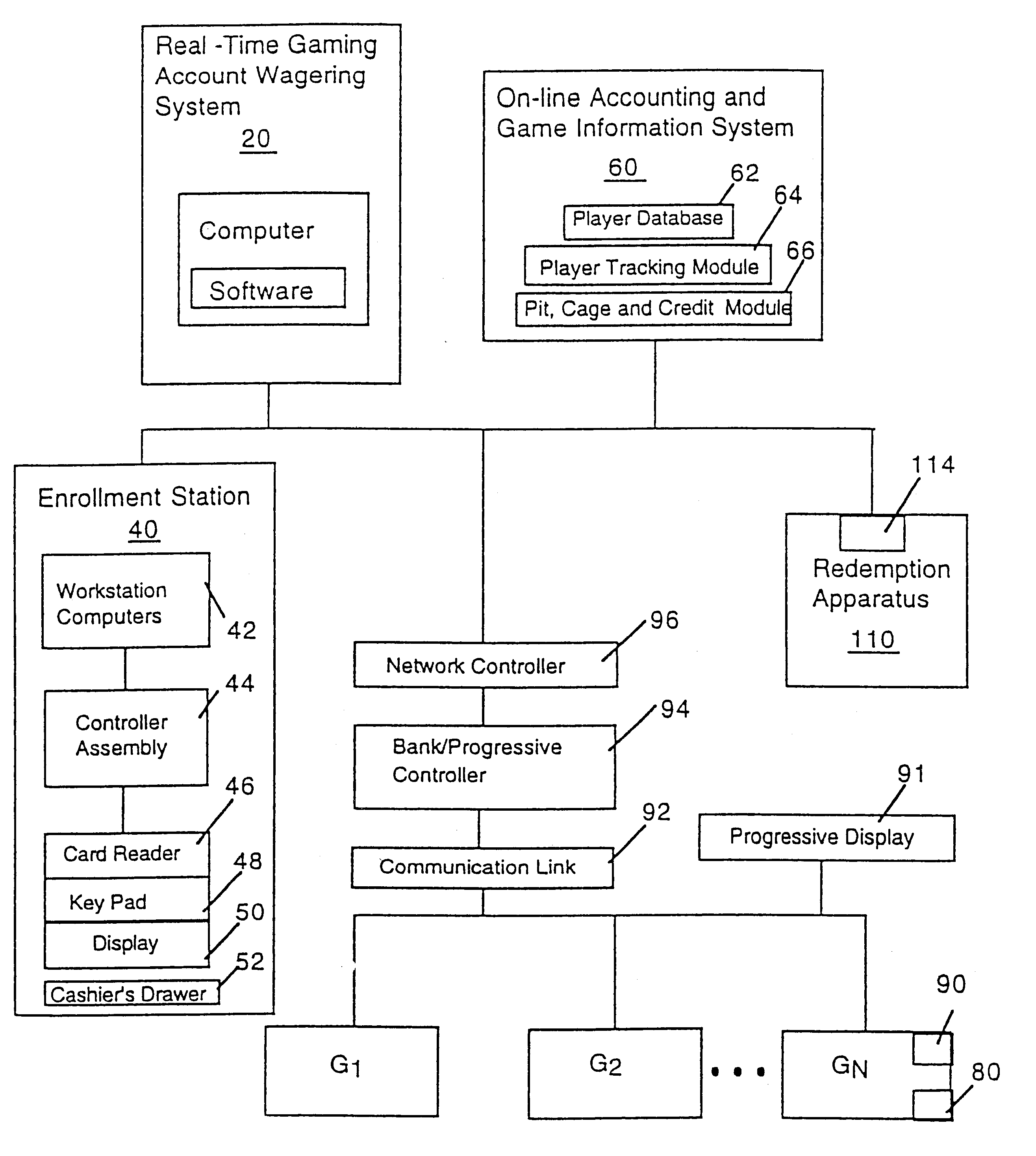
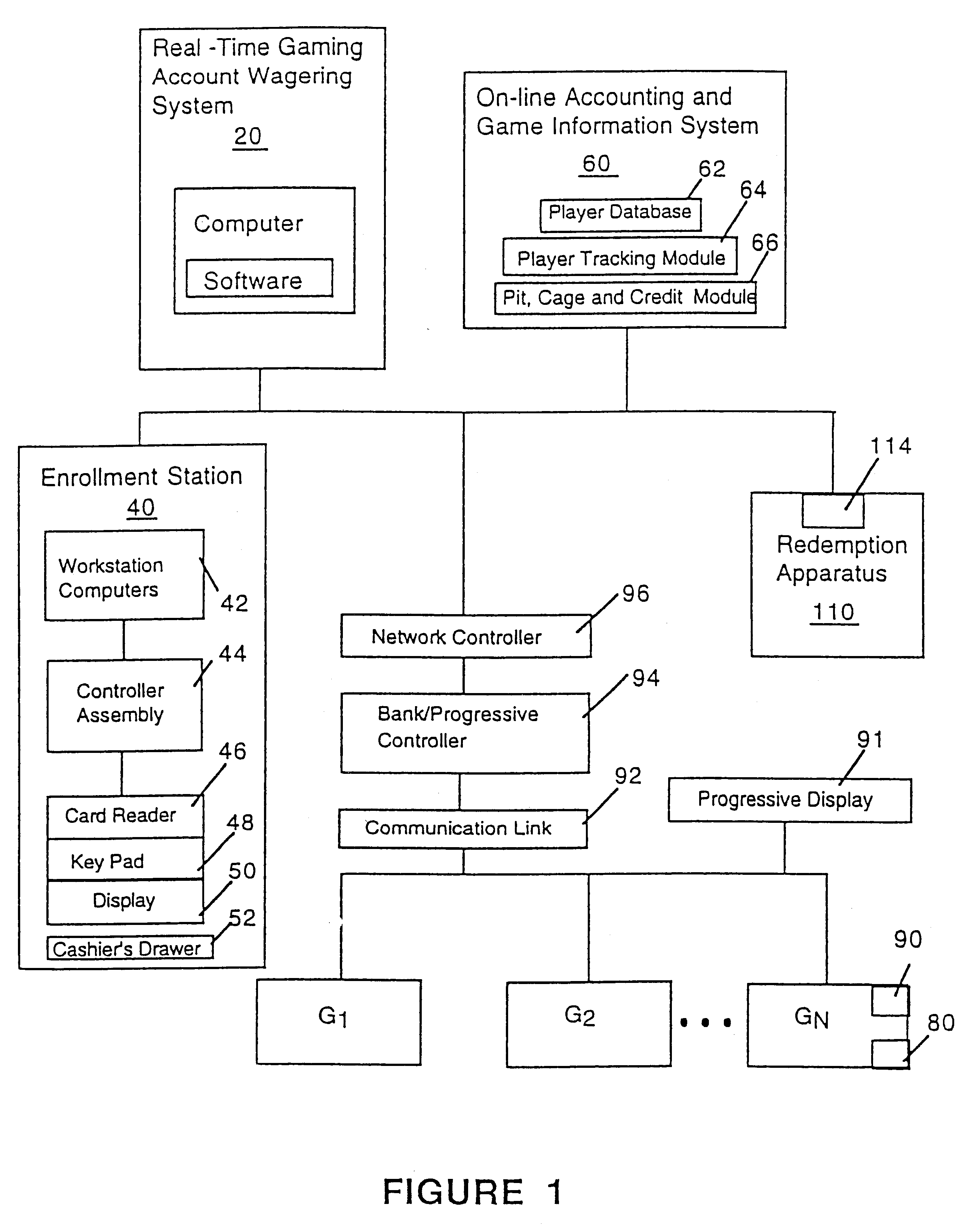
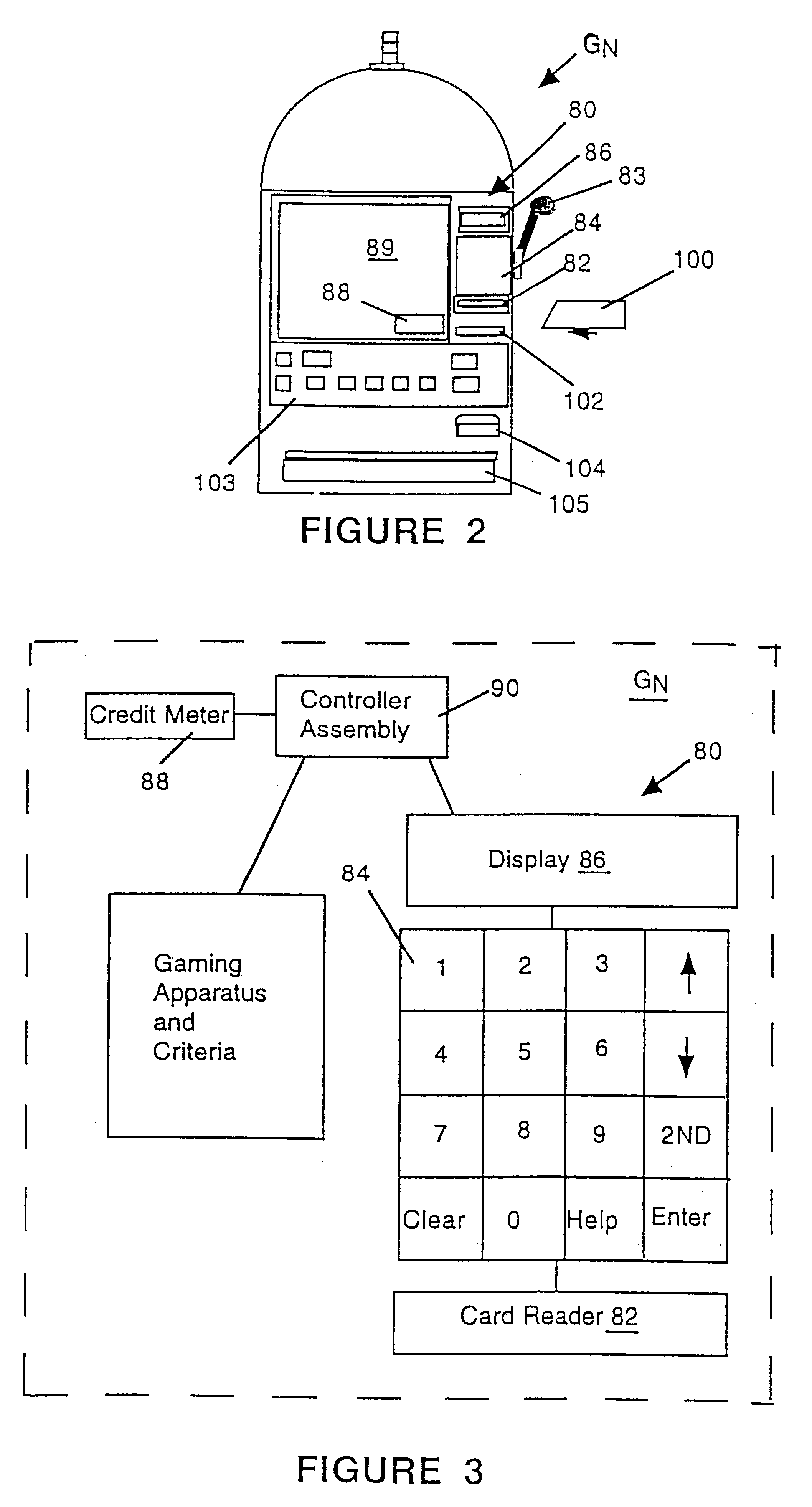
Cashless gaming system: apparatus and method
InactiveUS6511377B1Direct accessTake substantial amountApparatus for meter-controlled dispensingVideo gamesOperating systemComputer engineering
An apparatus and method for cashless gaming wherein a player can access credits via a pin activated keypad located on the gaming machine. Real-time accounting allows the player to redeem credits and secure perquisites as a function of patronage.
Owner:CASINO DATA SYST
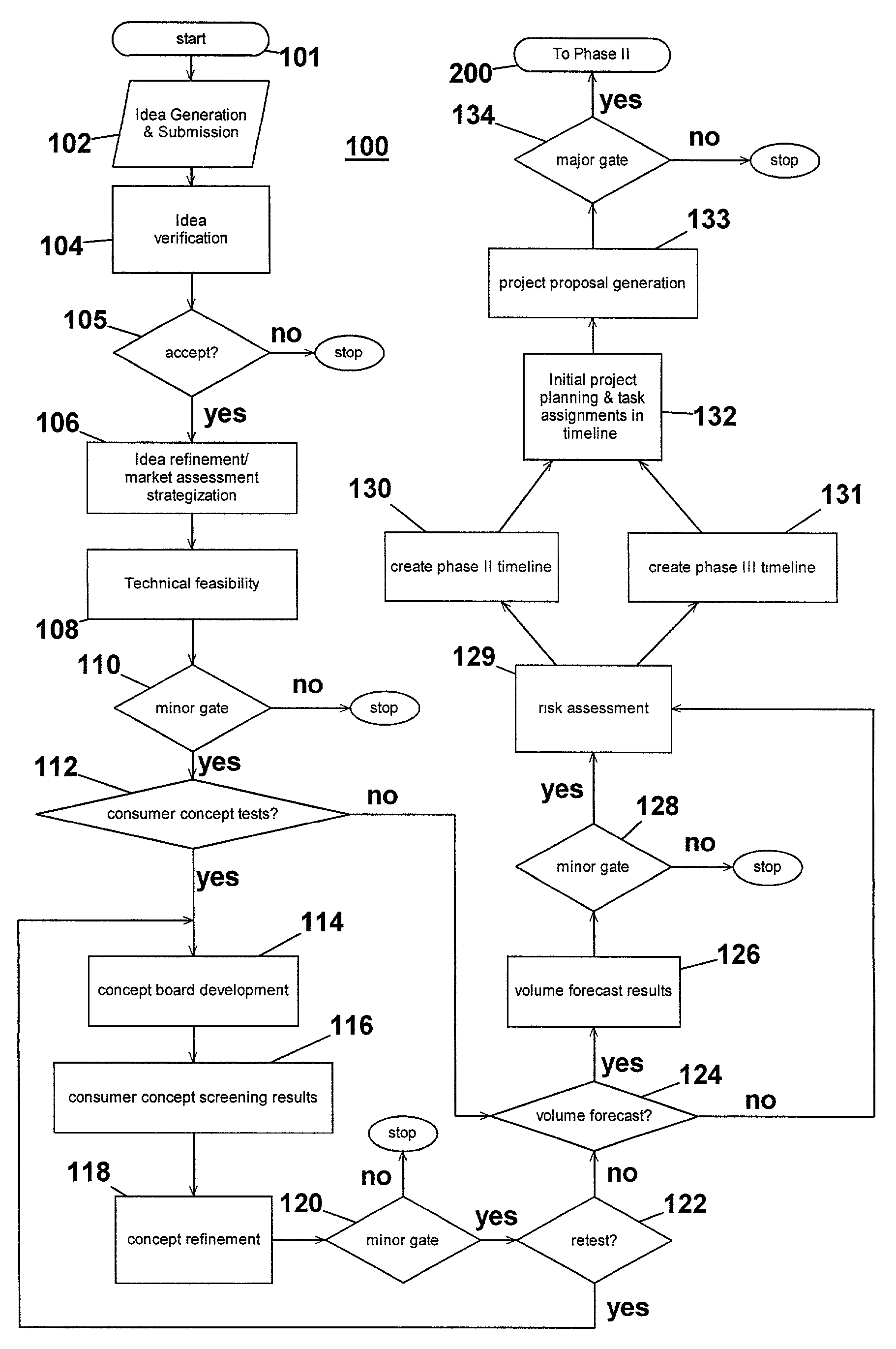
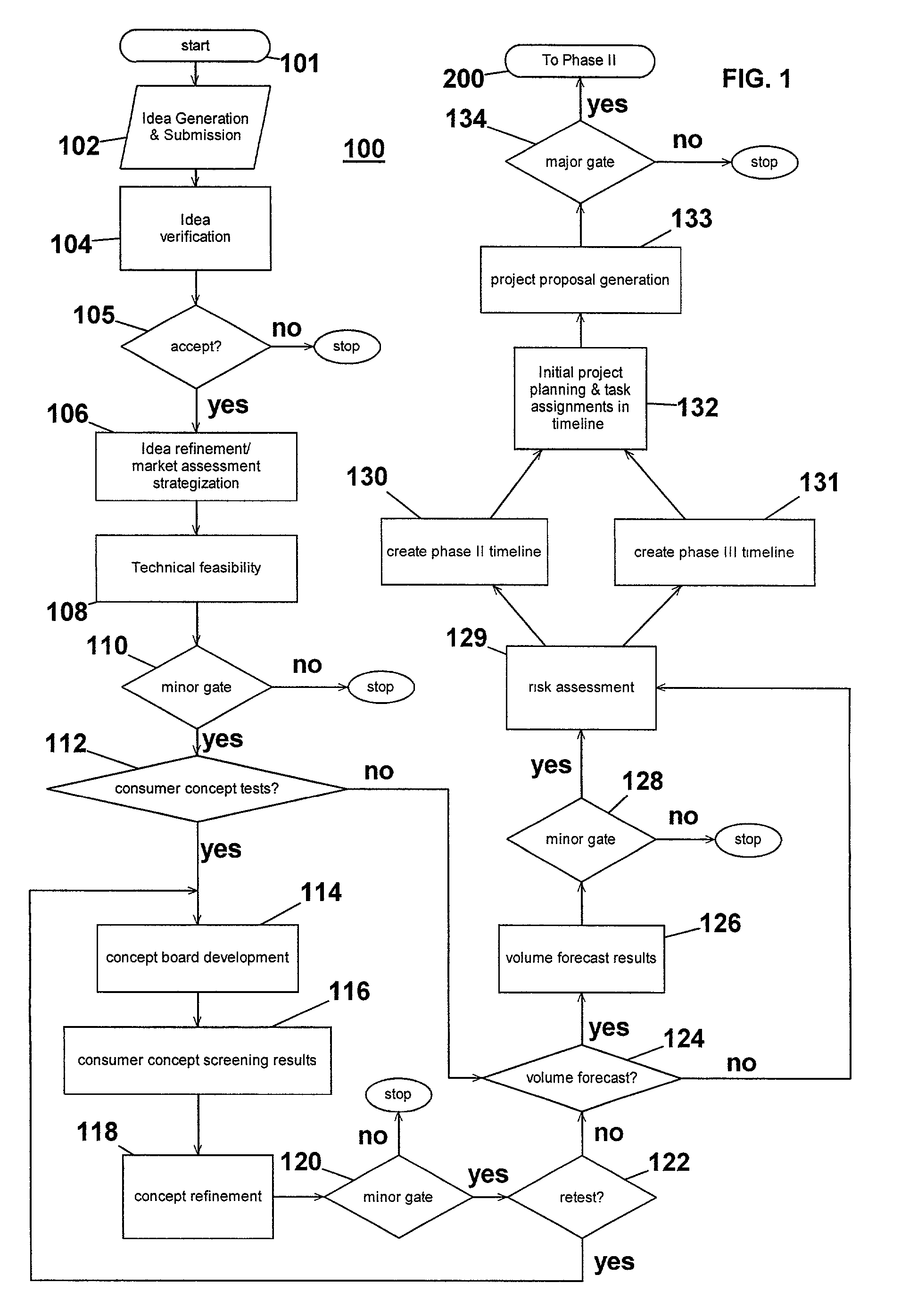
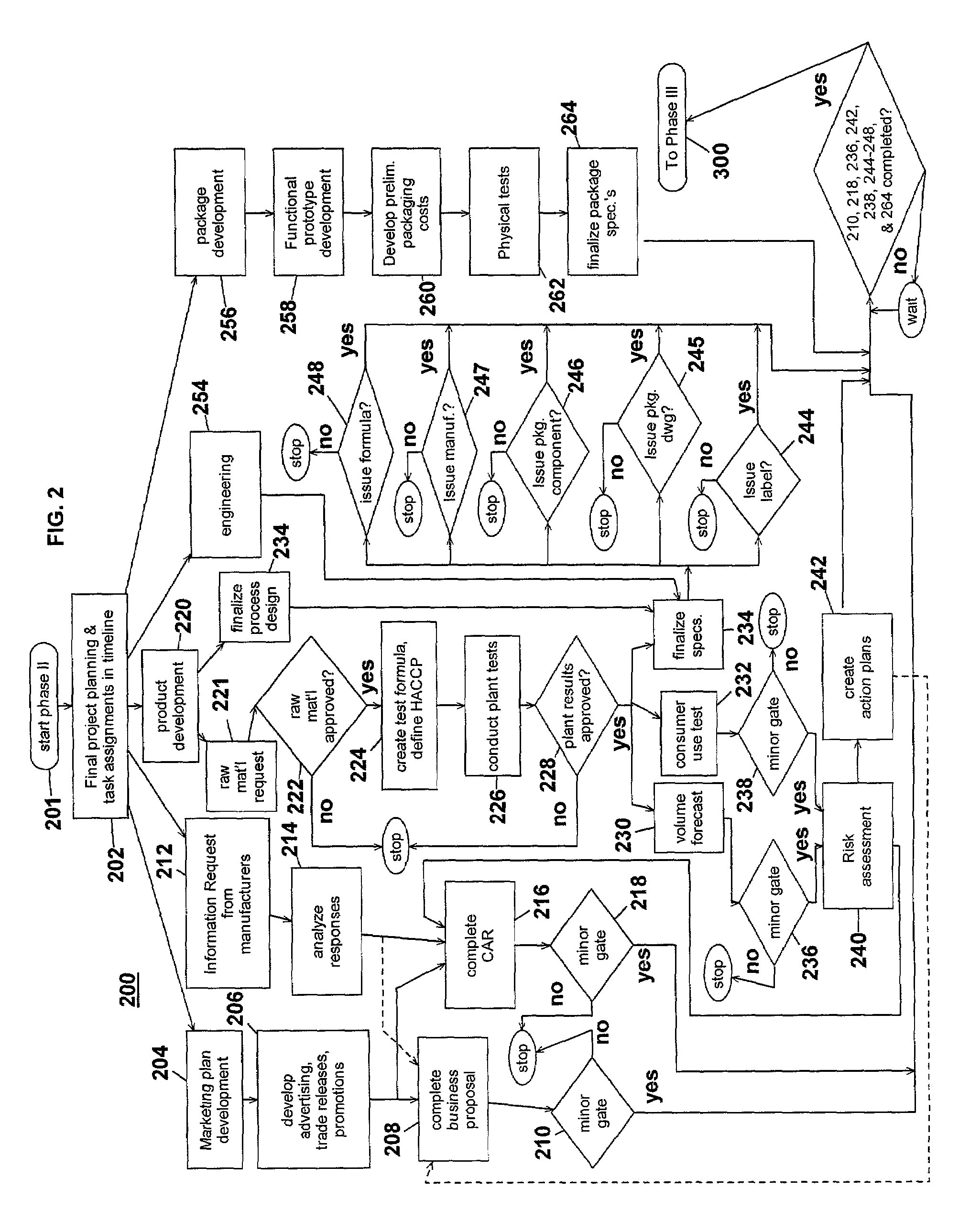
Computer-implemented system and method for project development
InactiveUS7051036B2Avoid repetitionPractical and convenientDigital data processing detailsResourcesProject proposalComputer science
The present invention generally relates to an inventive automated system, and method for its use, including a computer having a computer program defining three development phases including project proposal development, business proposition development, and implementation for market introduction. The project proposal development phase includes a unique idea verification feature by automated reference to an internal knowledge repository and database. The computer is coupled for intercommunication to a plurality of stations or clients from which respective authorized users each have a browser-based interface with the computer.
Owner:KRAFT FOODS GRP BRANDS LLC
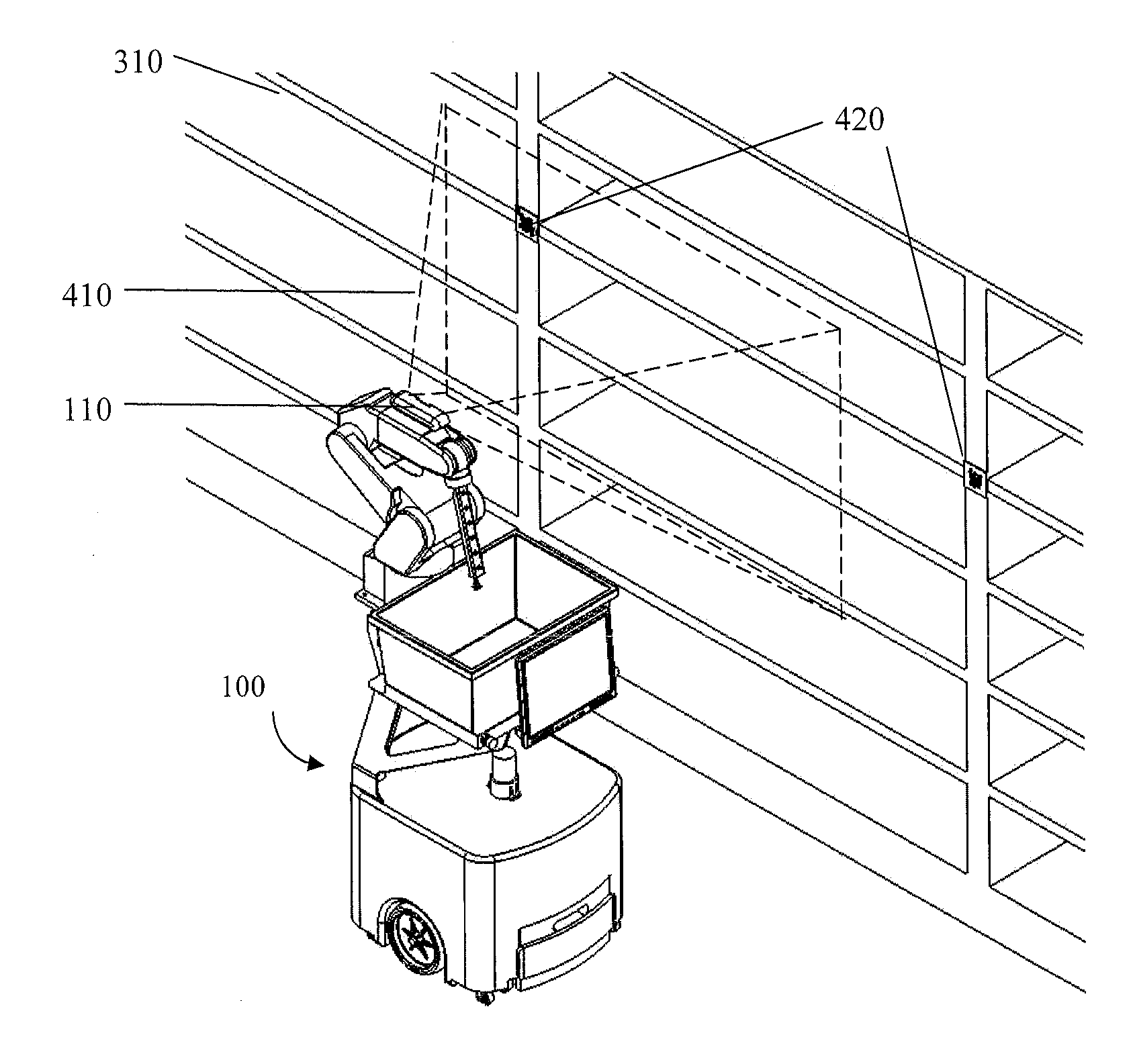
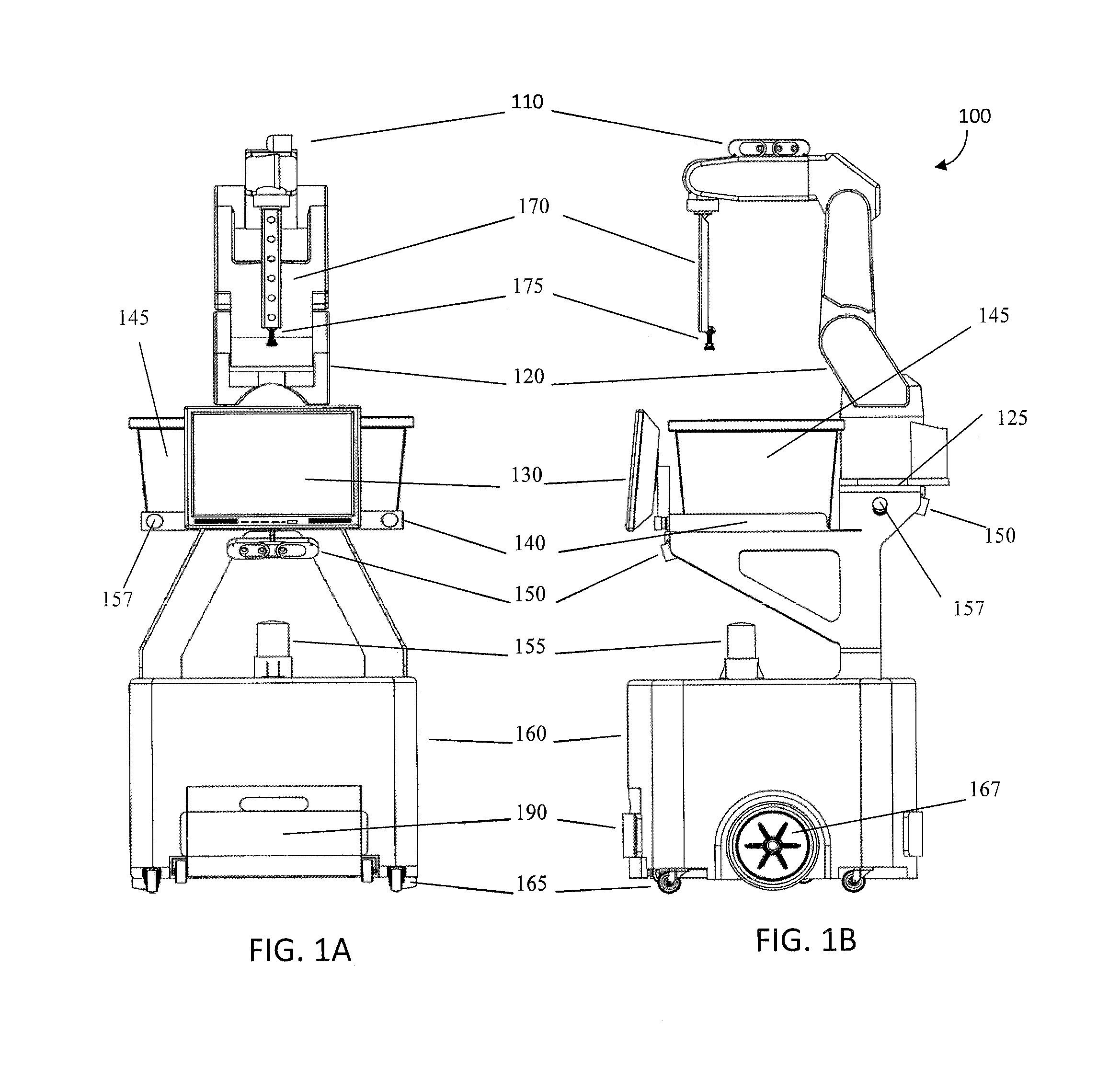
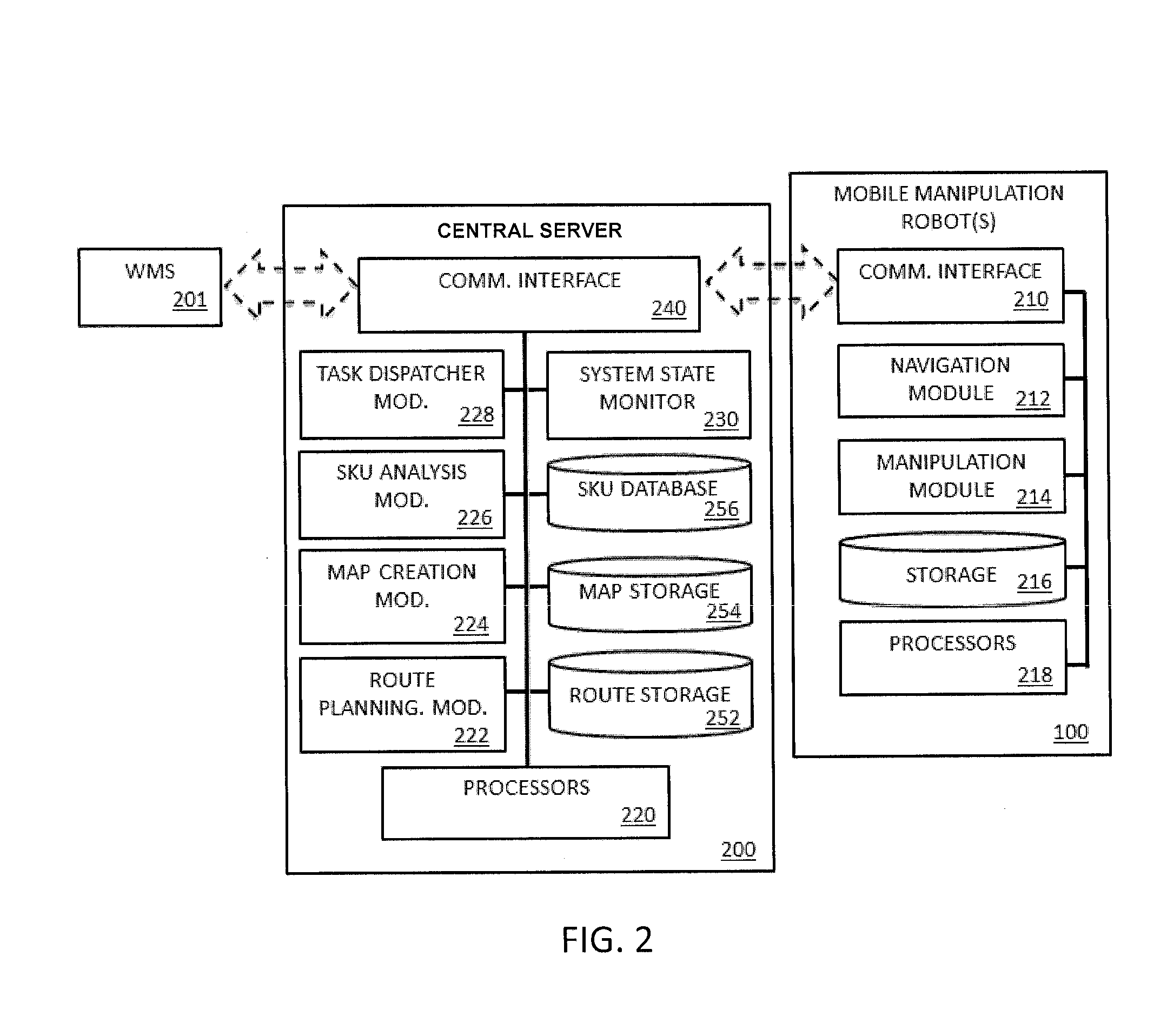
System and method for piece-picking or put-away with a mobile manipulation robot
ActiveUS20150032252A1Overcomes shortcomingReduce complexity and costProgramme-controlled manipulatorAutonomous decision making processLogistics managementPosition dependent
A method and system for piece-picking or piece put-away within a logistics facility. The system includes a central server and at least one mobile manipulation robot. The central server is configured to communicate with the robots to send and receive piece-picking data which includes a unique identification for each piece to be picked, a location within the logistics facility of the pieces to be picked, and a route for the robot to take within the logistics facility. The robots can then autonomously navigate and position themselves within the logistics facility by recognition of landmarks by at least one of a plurality of sensors. The sensors also provide signals related to detection, identification, and location of a piece to be picked or put-away, and processors on the robots analyze the sensor information to generate movements of a unique articulated arm and end effector on the robot to pick or put-away the piece.
Owner:IAM ROBOTICS
Practical platform for high risk applications
InactiveUS20070180509A1Safe and reliable and easy to use practicalIncrease system complexityDigital data processing detailsUser identity/authority verificationSystem integrationComputer hardware
The present invention is a portable device that a computer can boot from, containing a prefabricated independent operating system environment which is engineered from the ground up to prioritize security while maximizing usability, in order to provide a safe, reliable and easy to use practical platform for high risk applications. An embodiment of the present invention may temporarily transform an ordinary computer into a naturally inexpensive logical appliance which encapsulates a turn-key functional solution within the digital equivalent of a military grade security fortress. This allows existing hardware to be conveniently leveraged to provide a self contained system which does not depend on the on-site labor of rare and expensive system integration and security experts.
Owner:SWARTZ ALON R +1
Method and apparatus for creating and evaluating strategies
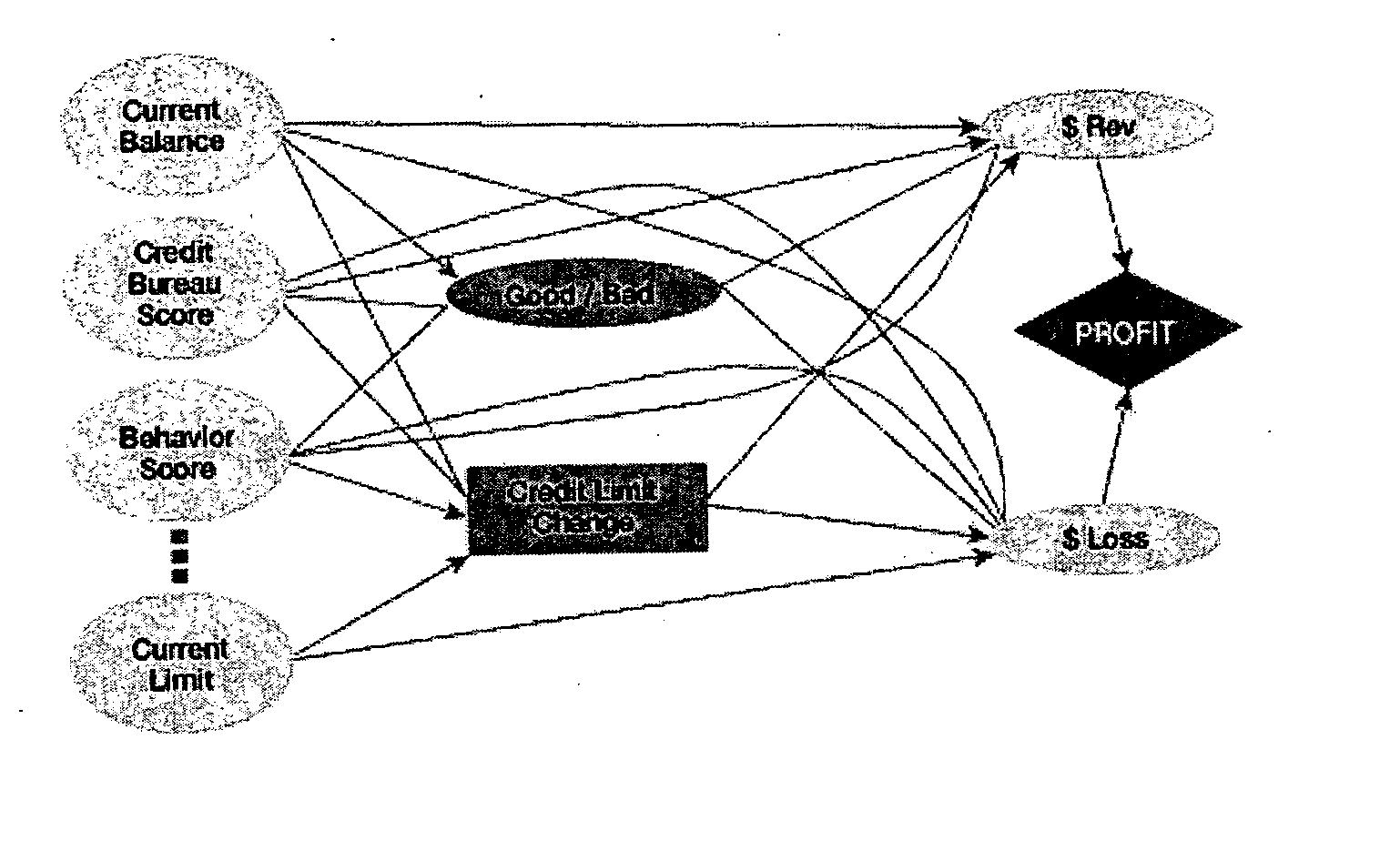
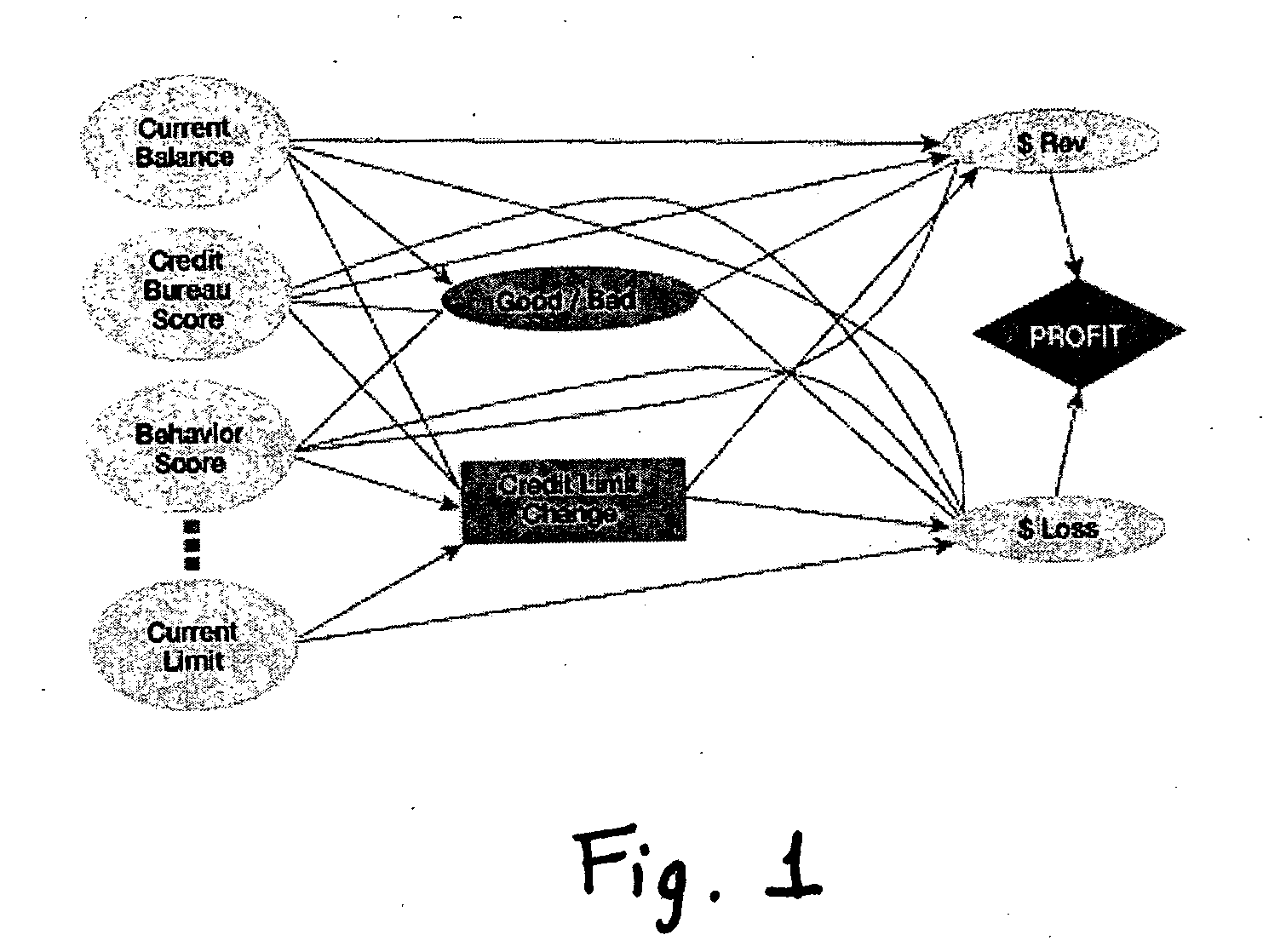
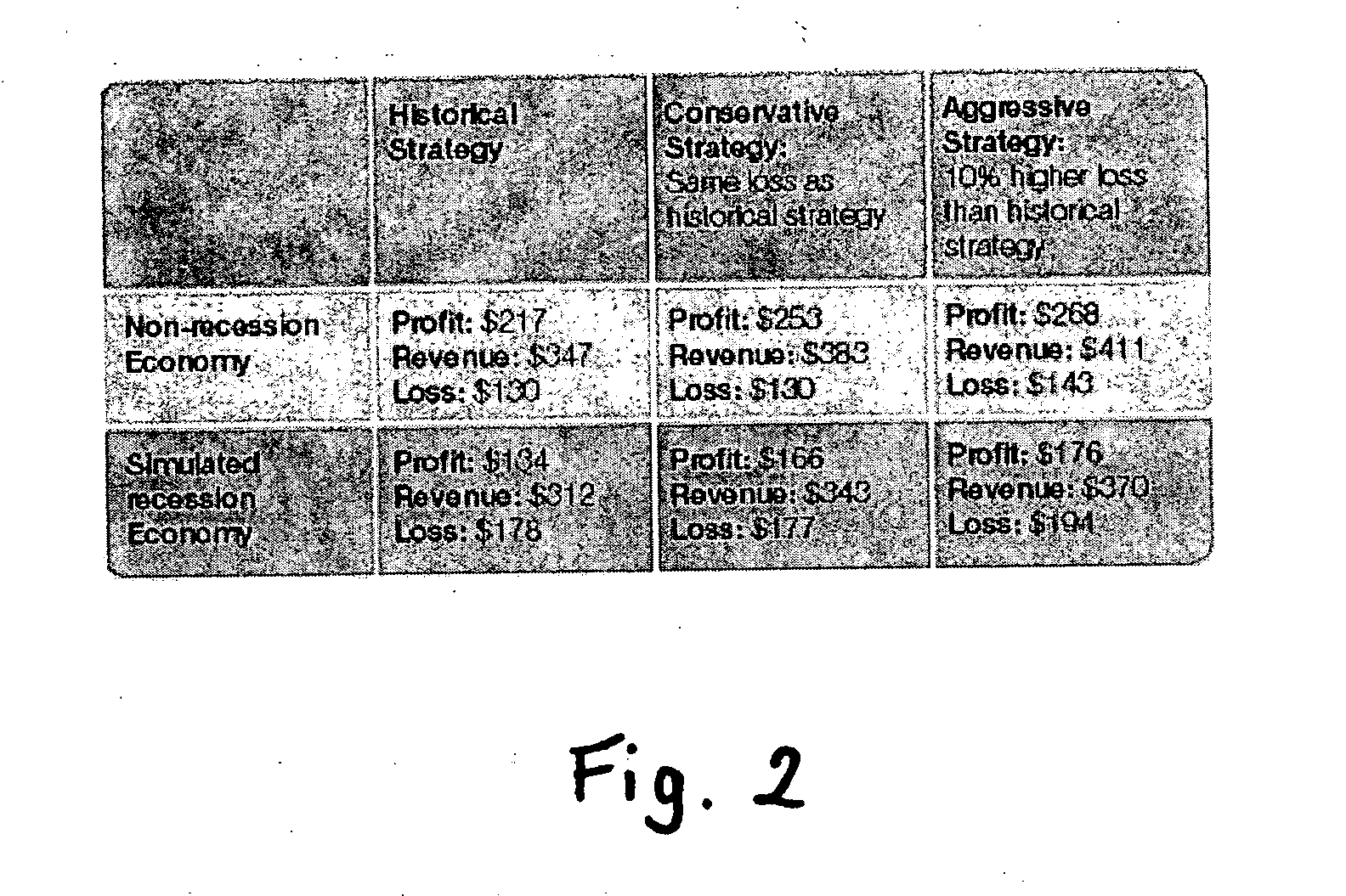
A method and apparatus for strategy science methodology involving computer implementation is provided. The invention includes a well-defined set of procedures for carrying out a full range of projects to develop strategies for clients. One embodiment of the invention produces custom consulting projects that are found at one end of the full range of projects. At the other end of the range are, for example, projects developing strategies from syndicated models. The strategies developed are for single decisions or for sequences of multiple decisions. Some parts of the preferred embodiment of the invention are categorized into the following areas: Team Development, Strategy Situation Analysis, Quantifying the Objective Function, Data Request and Reception, Data Transformation and Cleansing, Decision Key and Intermediate Variable Creation, Data Exploration, Decision Model Structuring, Decision Model Quantification, An Exemplary Score Tuner, Strategy Creation, An Exemplary Strategy Optimizer, An Exemplary Uncertainty Estimator, and Strategy Testing. Each of the sub-categories are described and discussed in detail under sections of the same headings. The invention uses judgment in addition to data for developing strategies for clients.
Owner:FAIR ISAAC & CO INC
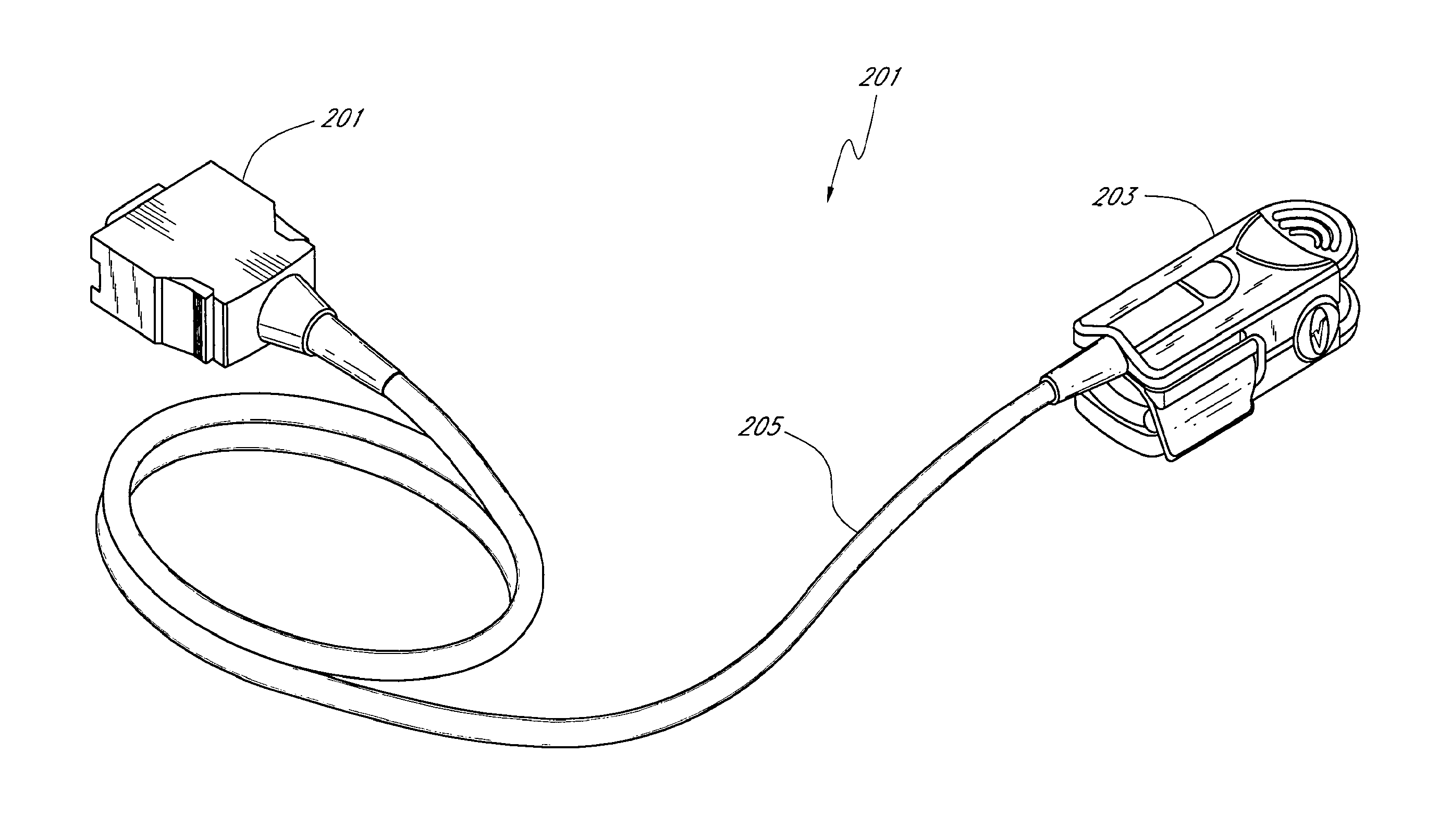
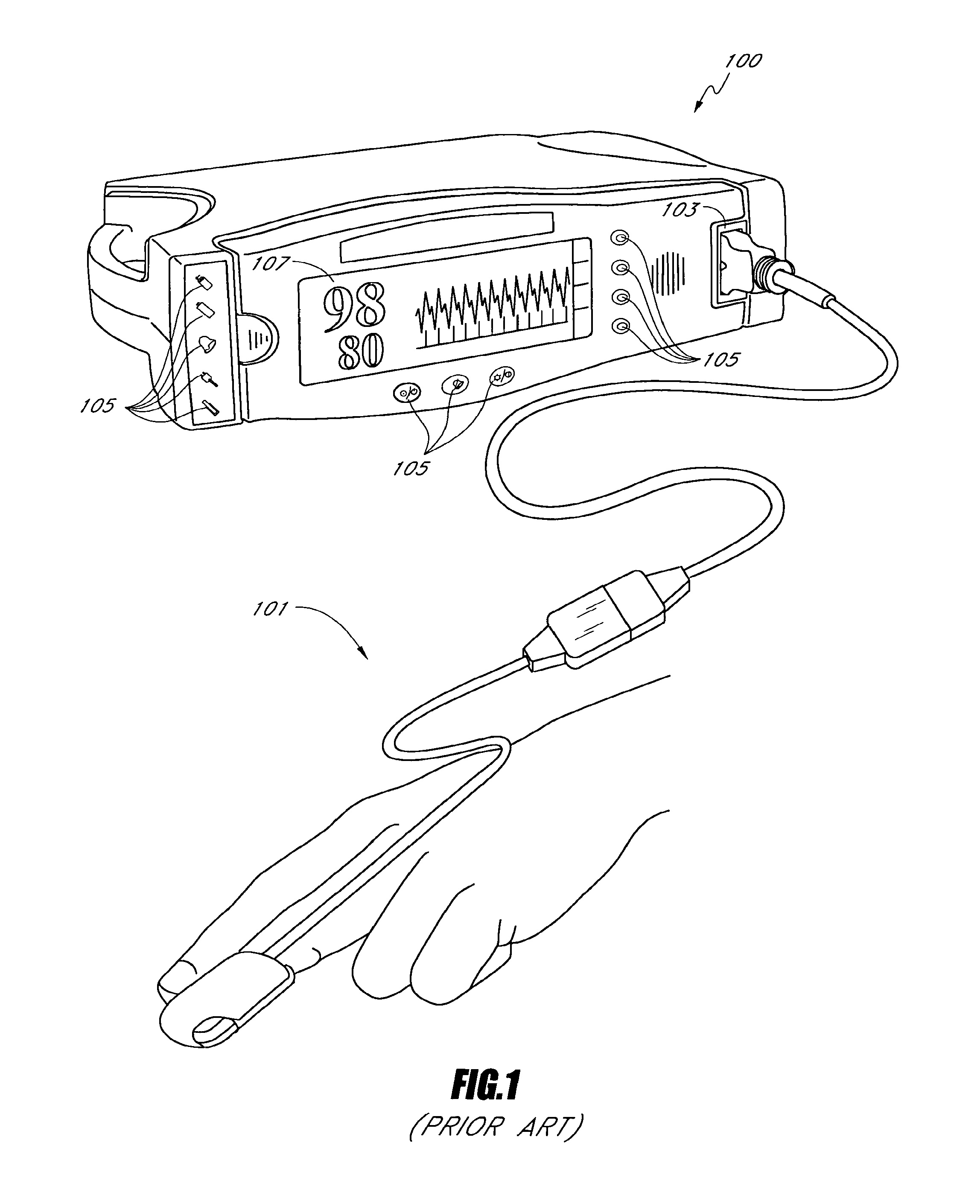
System and method for monitoring the life of a physiological sensor
Owner:JPMORGAN CHASE BANK NA
Testing tool comprising an automated multidimensional traceability matrix for implementing and validating complex software systems
InactiveUS20050166094A1Easy to createSoftware testing/debuggingSpecific program execution arrangementsSoftware systemComputer science
The present invention relates to a testing tool for testing of complex software systems having a plurality of interrelated system components and a suite of test scenarios for testing the performance of the plurality of interrelated system components. The testing tool includes an Automated Multidimensional Traceability Matrix system for determining linkages between interrelated system components, a means for identifying a change in one or more of the interrelated system components, a means for applying the Automated Multidimensional Traceability Matrix, a means for executing all of or a subset of the test scenarios associated with the interrelated system components that may be affected by the change and a means for evaluating the results of the executed test scenarios.
Owner:KIMBERLY-CLARK WORLDWIDE INC
Methods and servers for establishing a connection between a client system and a virtual machine hosting a requested computing environment
InactiveUS20070174429A1Low costReduce difficultyDigital data information retrievalInterprogram communicationClient-sideClient system
A method for providing access to a computing environment includes the step of receiving a request from a client system for an enumeration of available computing environments. Collected data regarding available computing environments are accessed. Accessed data are transmitted to a client system, the accessed data indicating to the client system each computing environment available to a user of the client system. A request is received from the client system to access one of the computing environments. A connection is established between the client system and a virtual machine hosting the requested computing environment.
Owner:CITRIX SYST INC
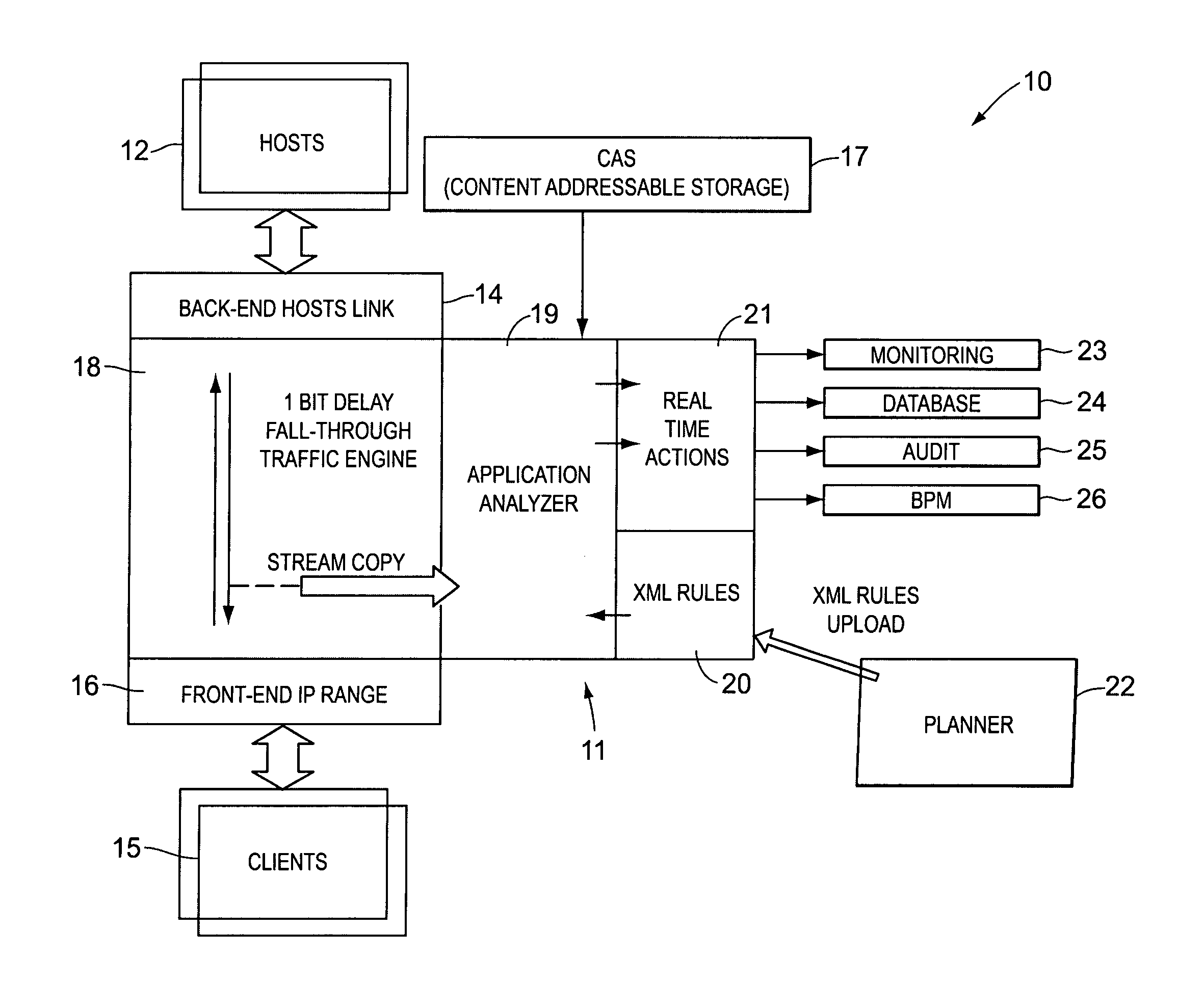
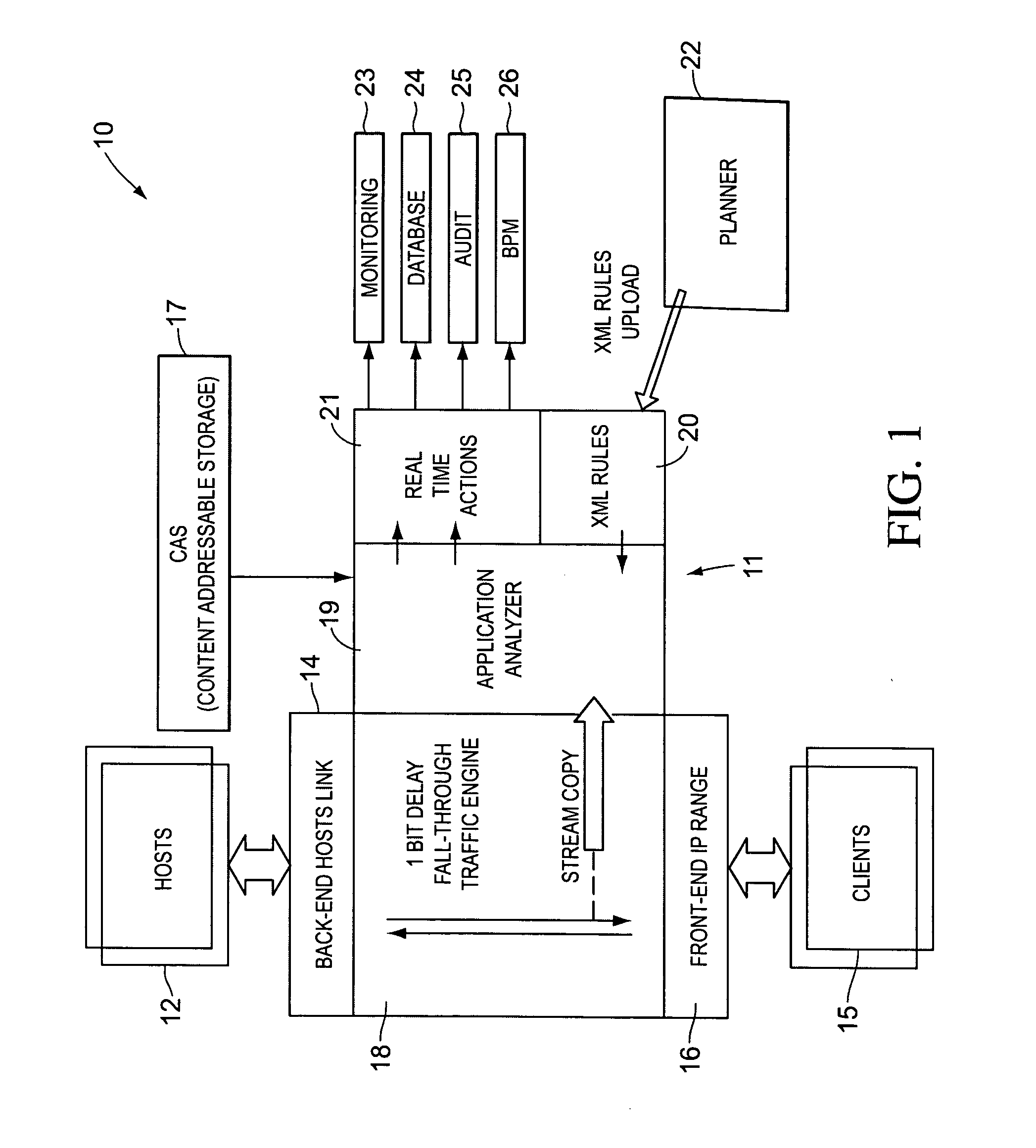
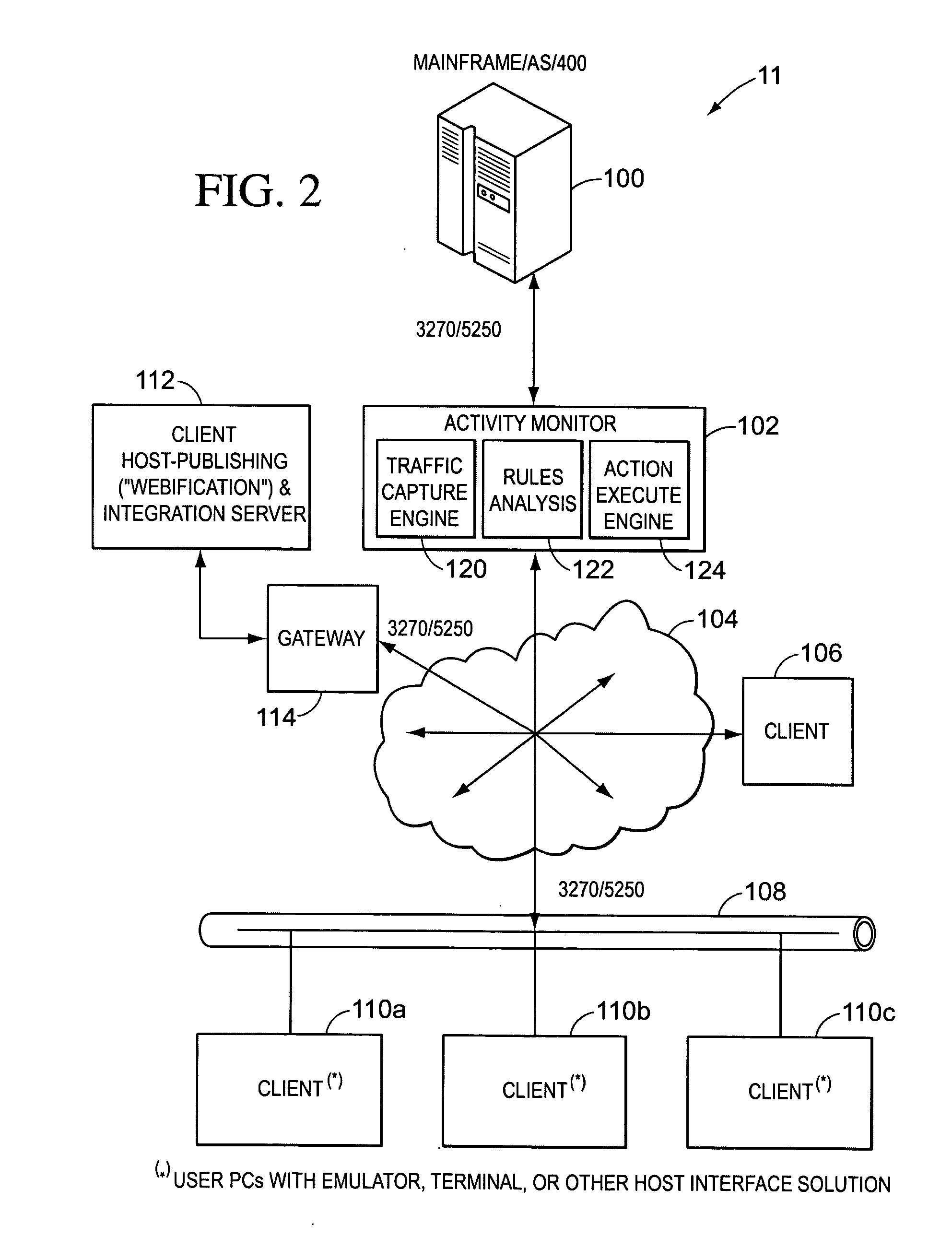
Real-time activity monitoring and reporting
InactiveUS20070039049A1Maintain transparencyNo delayMemory loss protectionError detection/correctionActivity monitorComputerized system
In order to track activities in a computerized system with client-server or other communications, a system configuration is needed which monitors, logs and reports traffic. This is somewhat akin to but not entirely similar a firewall. Thus, the invention contemplates a real-time, platform-independent, rule-based activity monitor for detecting a particular activity of interest as it occurs and for reporting such activity and the user substantially as fast.
Owner:MICRO FOCUS US
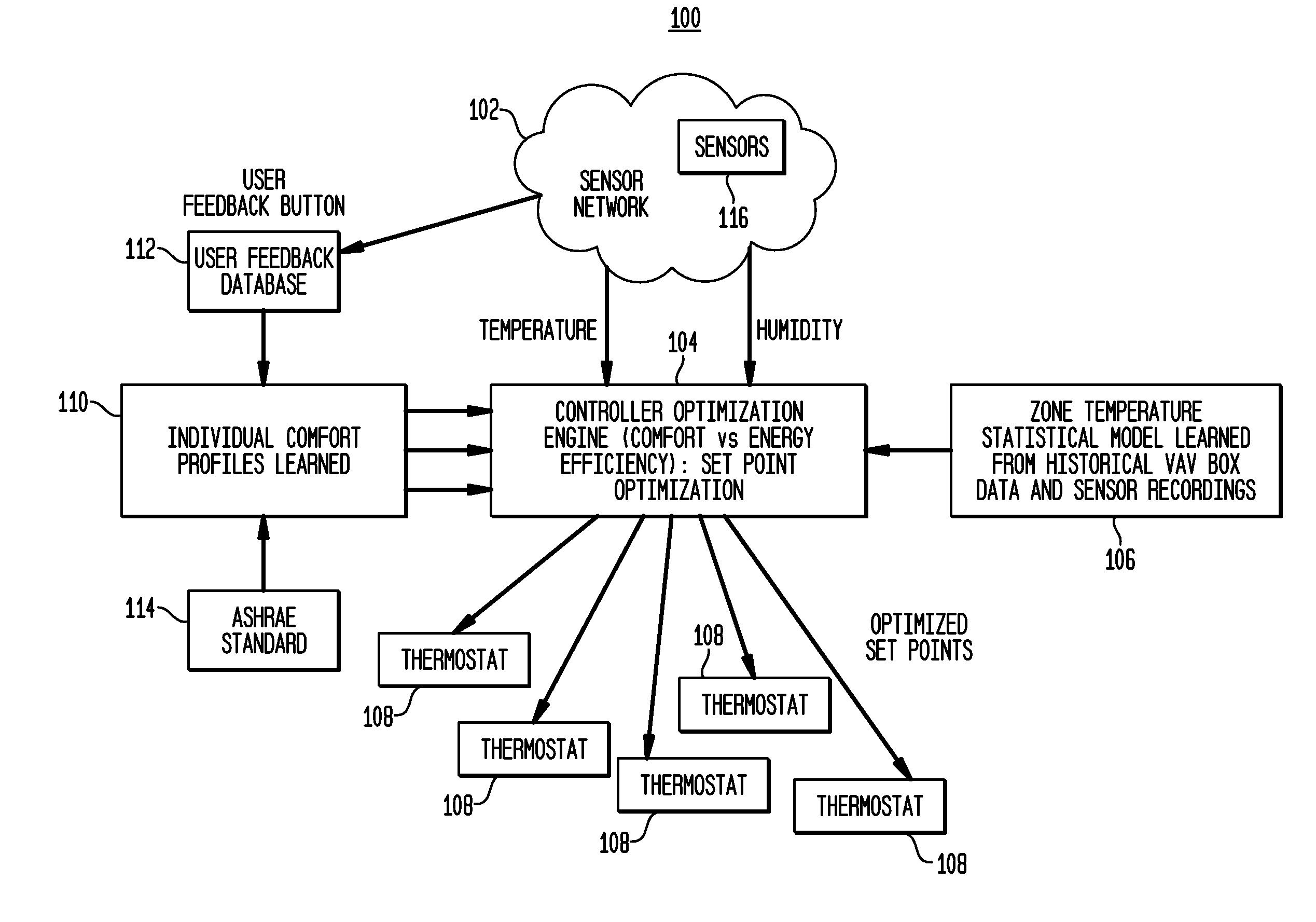
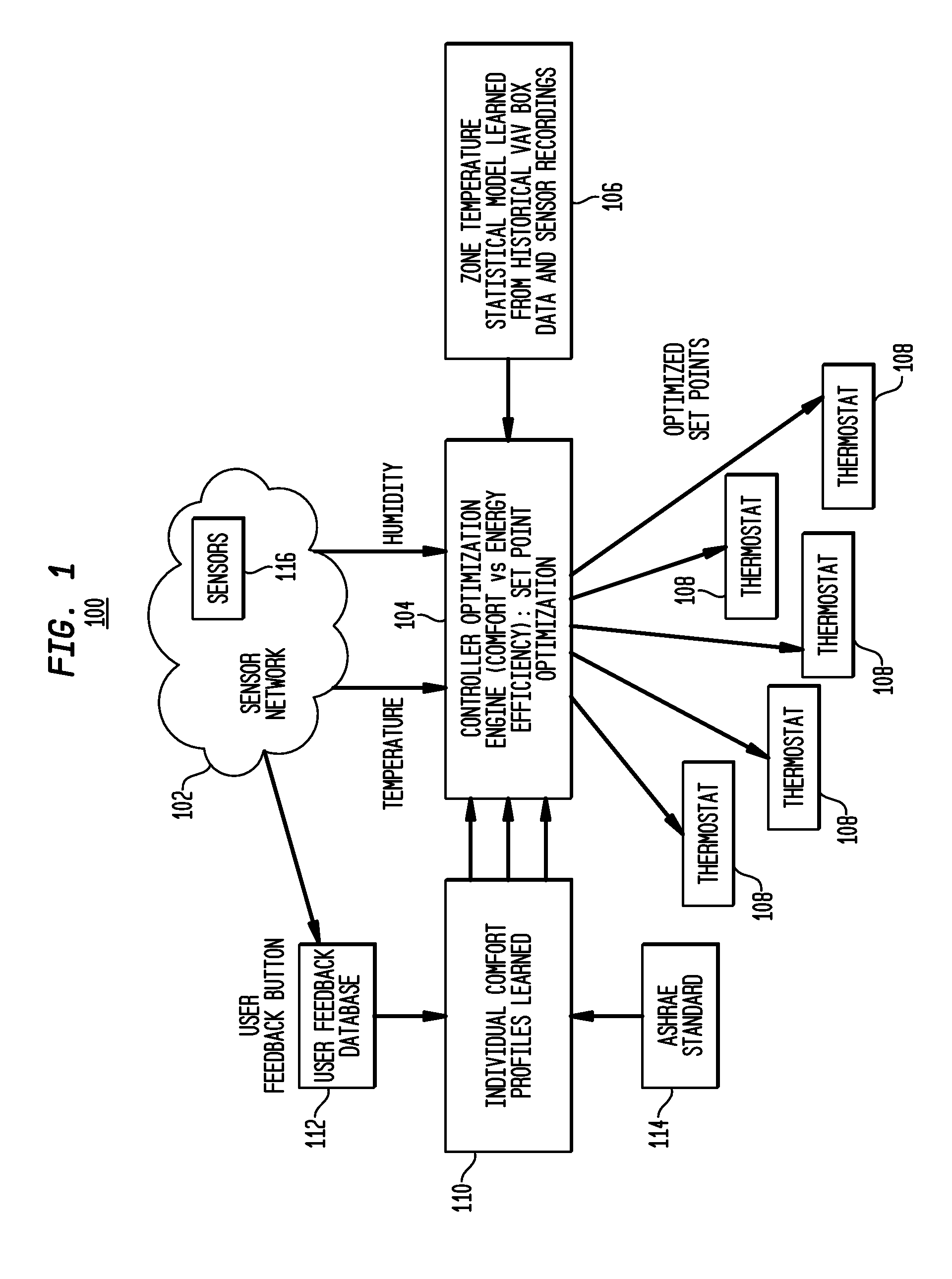
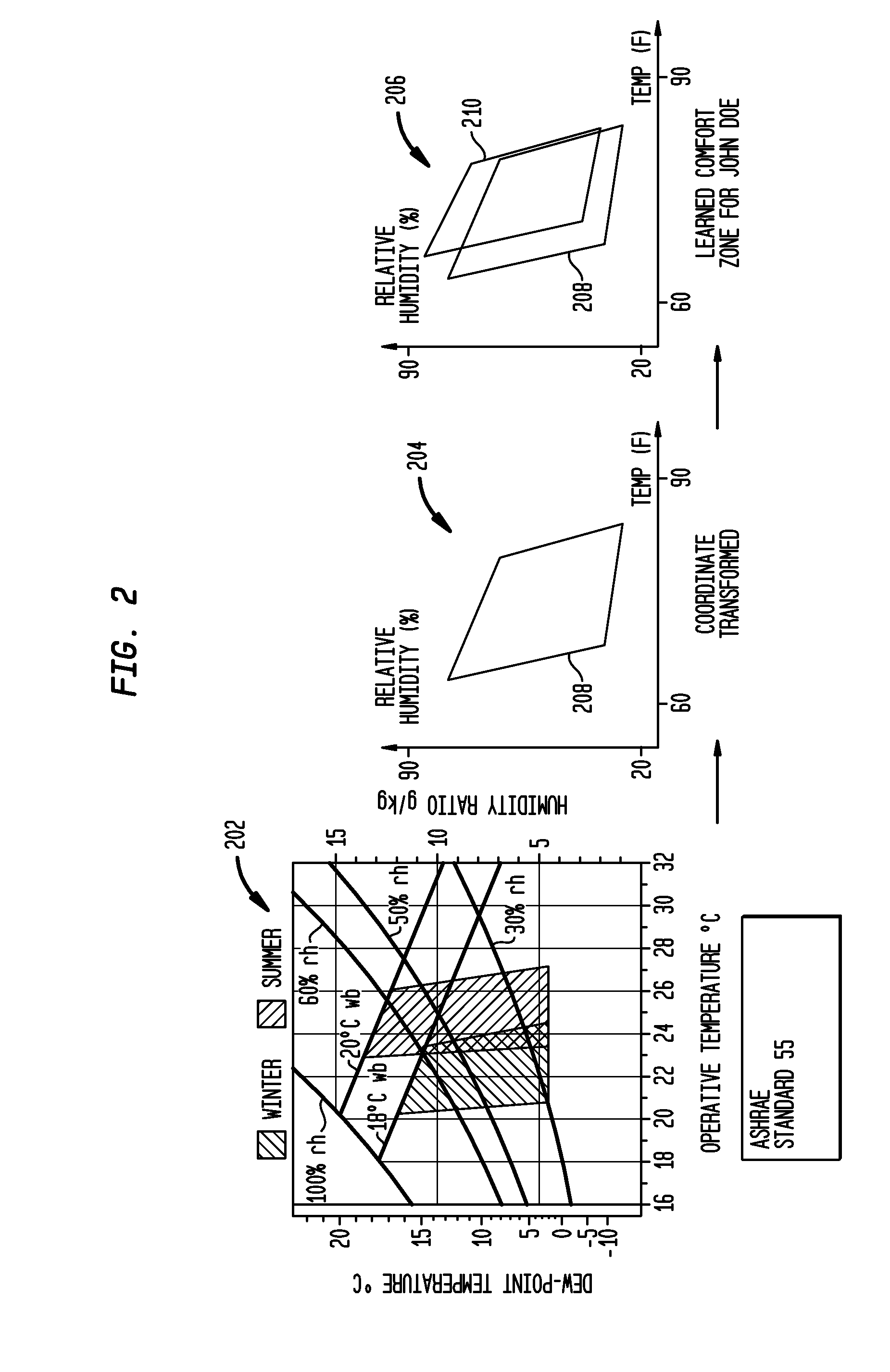
System and Method for Climate Control Set-Point Optimization Based On Individual Comfort
A system and method for calibrating a set-point for climate control includes a sensor network having a plurality of sensors configured to report a climate condition. A database is configured to receive reports from the sensors and generate one or more profiles reflecting at least one of historic climate control information and occupant preferences. A controller is configured to receive information from the profiles to generate a set-point based upon an optimization program. The optimization program is implemented to balance competing goals to generate the set-point for controlling climate control equipment in accordance with the set-point.
Owner:SIEMENS IND INC
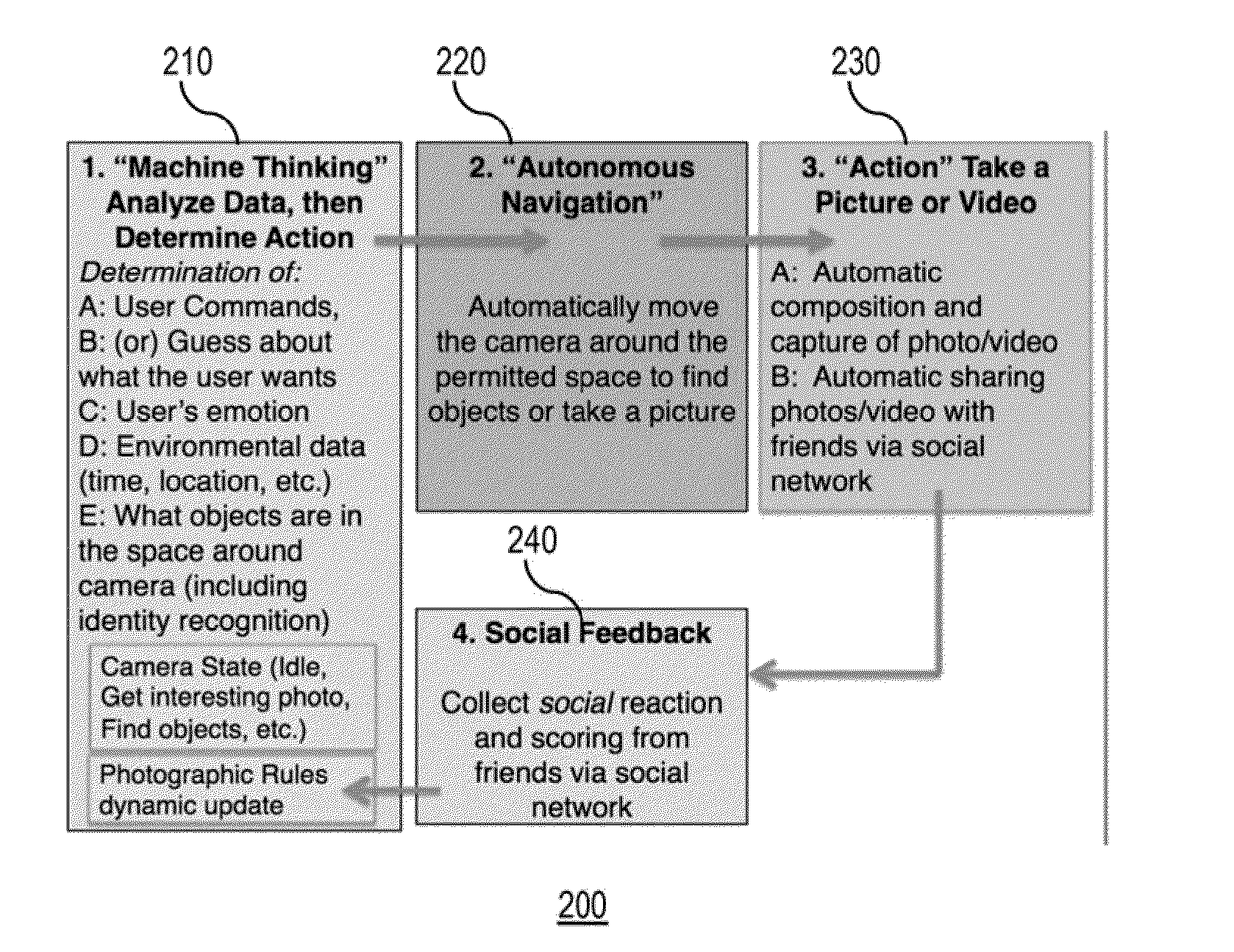
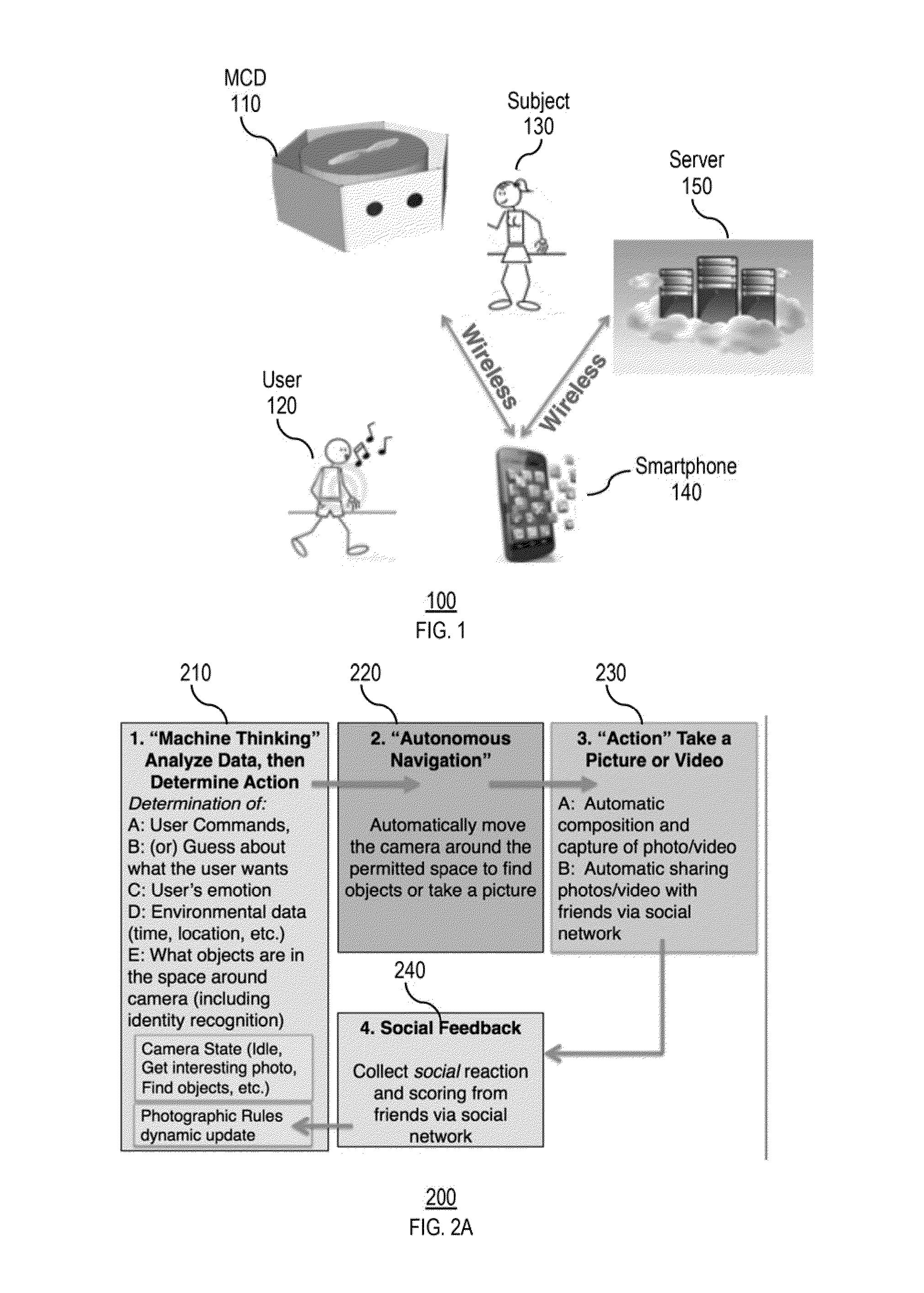
Autonomous media capturing
ActiveUS20160127641A1Simple processGood photoInput/output for user-computer interactionTelevision system detailsSocial circleSkill sets
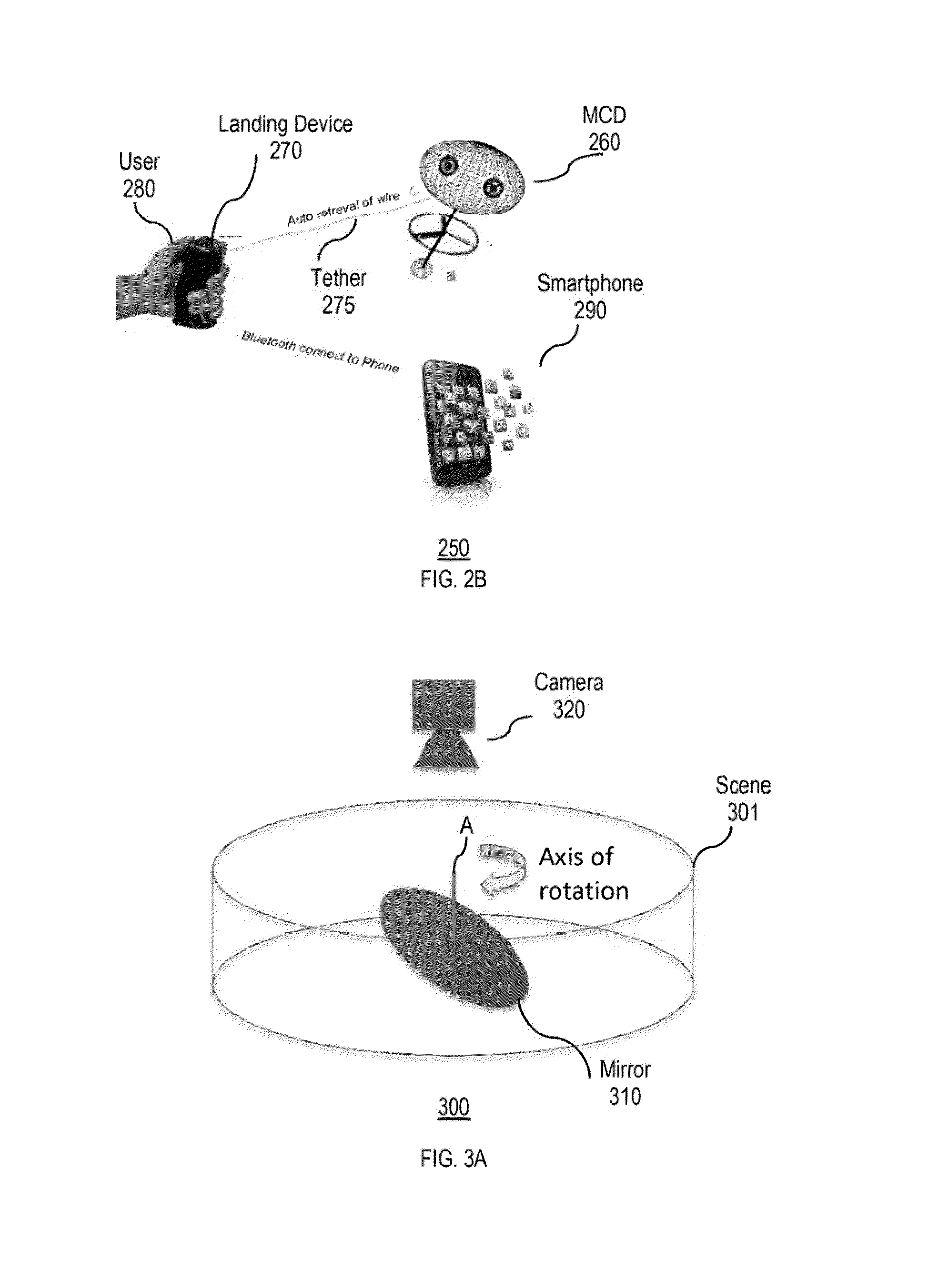
A media capture device (MCD) that provides a multi-sensor, free flight camera platform with advanced learning technology to replicate the desires and skills of the purchaser / owner is provided. Advanced algorithms may uniquely enable many functions for autonomous and revolutionary photography. The device may learn about the user, the environment, and / or how to optimize a photographic experience so that compelling events may be captured and composed into efficient and emotional sharing. The device may capture better photos and videos as perceived by one's social circle of friends, and / or may greatly simplify the process of using a camera to the ultimate convenience of full autonomous operation.
Owner:GOVE ROBERT JOHN
System and method for allocating server resources
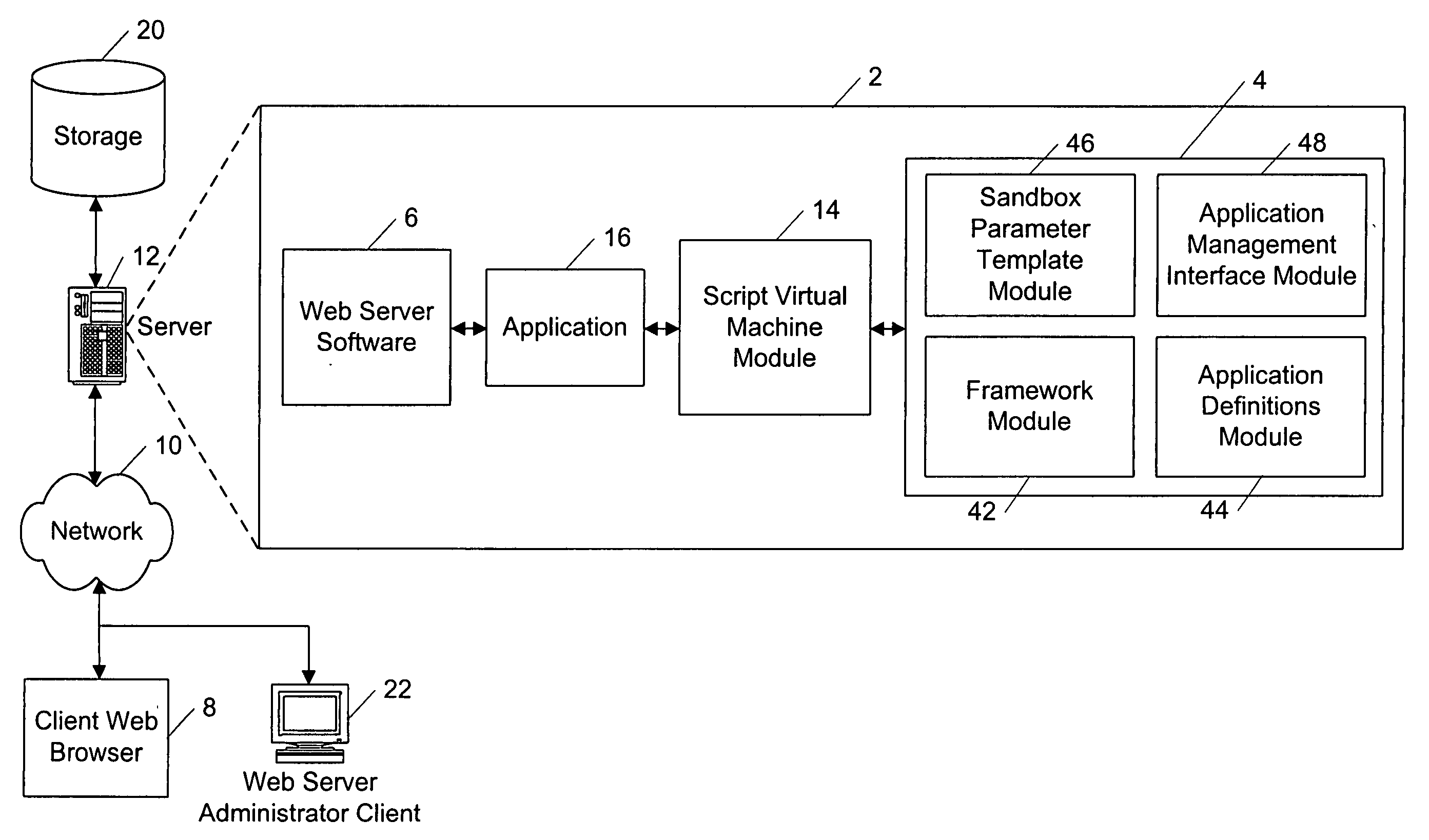
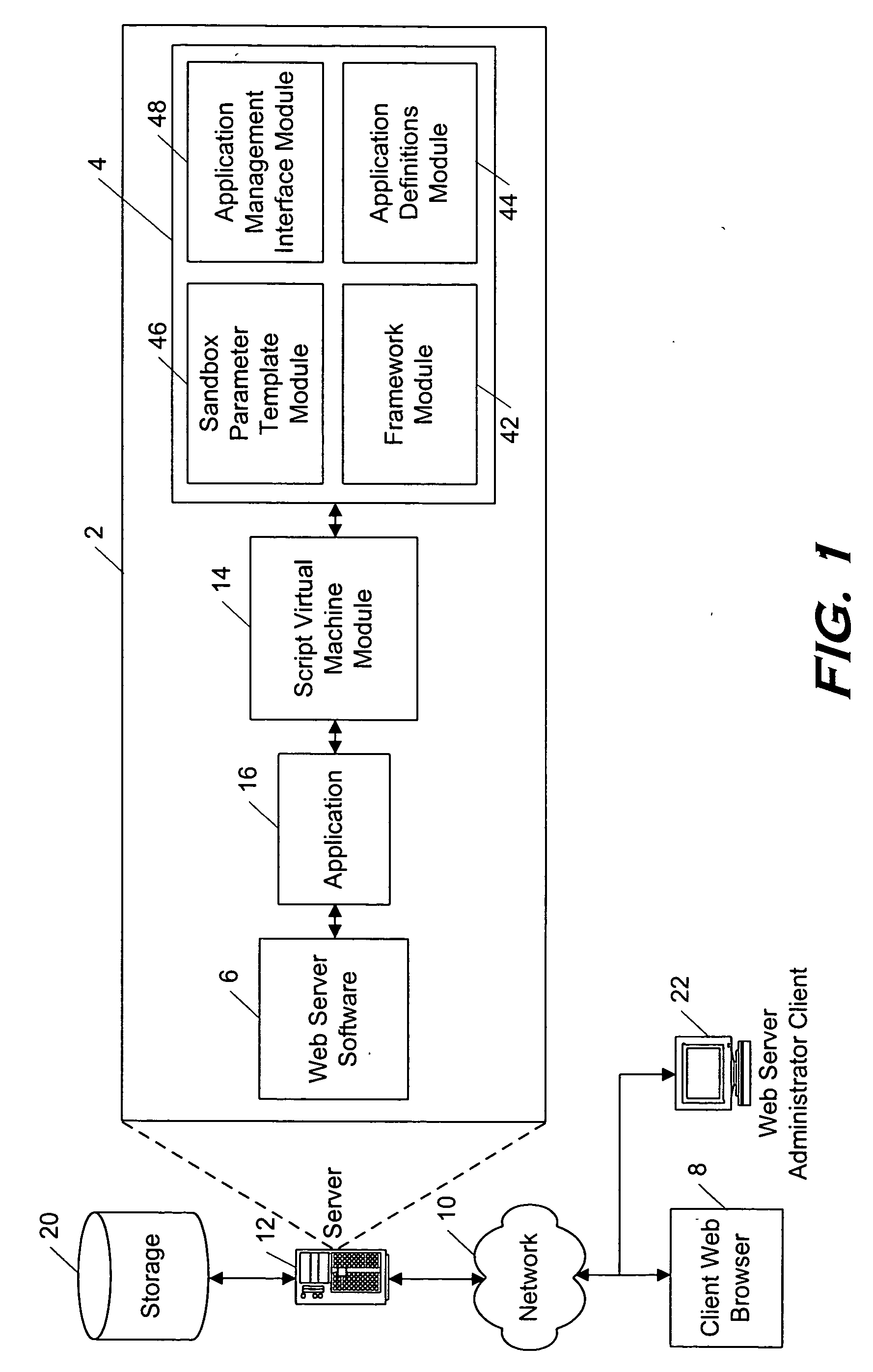
InactiveUS20050177635A1Program synchronisationDigital computer detailsControlling environmentWeb server
A system and method for allowing web-based applications to run in a controlled environment. In particular, a method allocates server resources among applications running in a sandbox environment on a web server. Applications which attempt to exceed limits specified in templates associated with the application may be denied access to a resource.
Owner:CONTEC INNOVATIONS INC
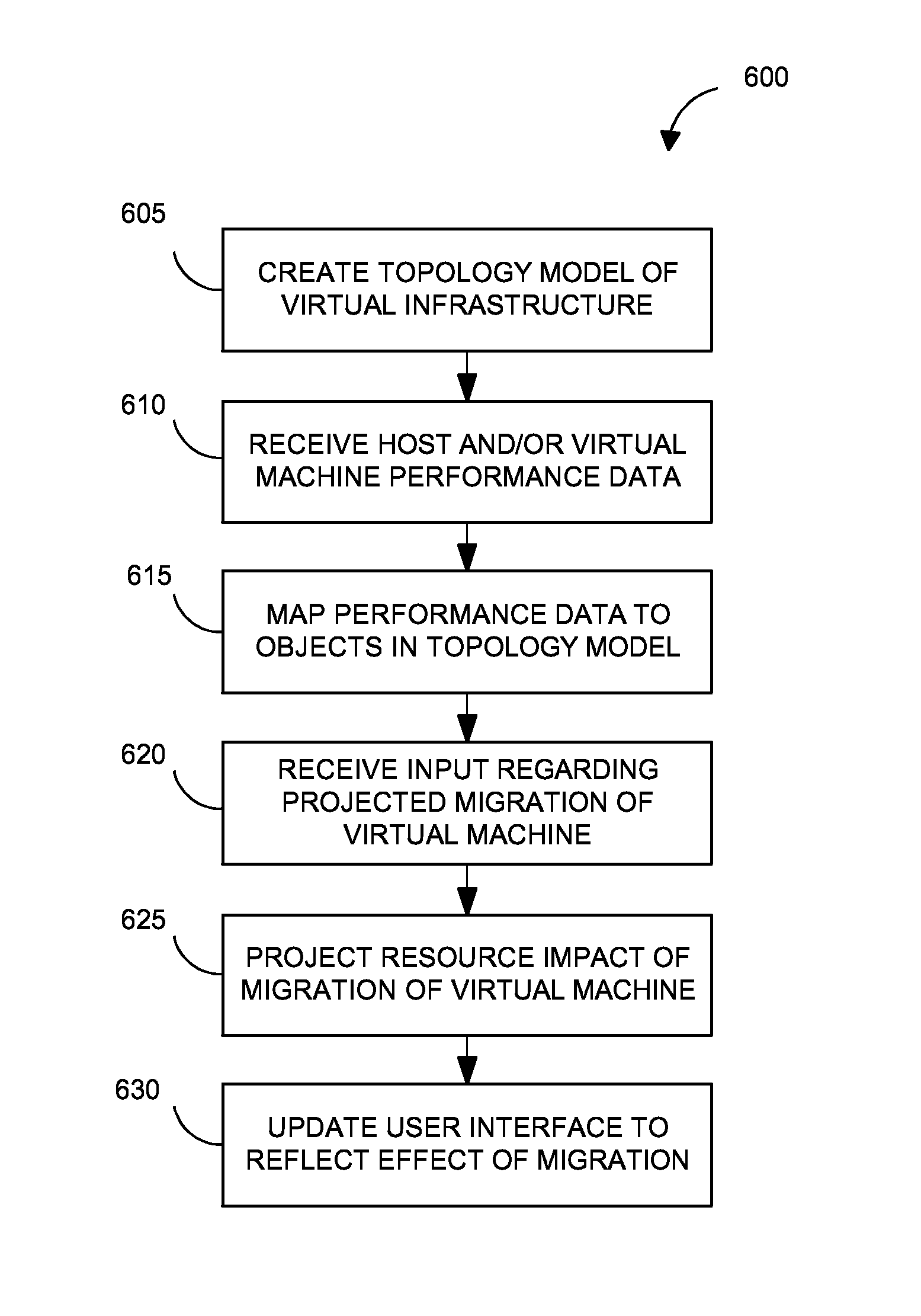
Systems and methods for analyzing performance of virtual environments
InactiveUS8175863B1Effective and efficient diagnosisResource allocationError detection/correctionMonitoring systemSmart surveillance
Intelligent monitoring systems and methods for virtual environments are disclosed that understand various components of a virtual infrastructure and how the components interact to provide improved performance analysis to users. In certain examples, a monitoring system assesses the performance of virtual machine(s) in the context of the overall performance of the physical server(s) and the environment in which the virtual machine(s) are running. For instance, the monitoring system can track performance metrics over a determined period of time to view changes to the allocation of resources to virtual machines and their location(s) on physical platforms. Moreover, monitoring systems can utilize past performance information from separate virtual environments to project a performance impact resulting from the migration of a virtual machine from one physical platform to another.
Owner:QUEST SOFTWARE INC
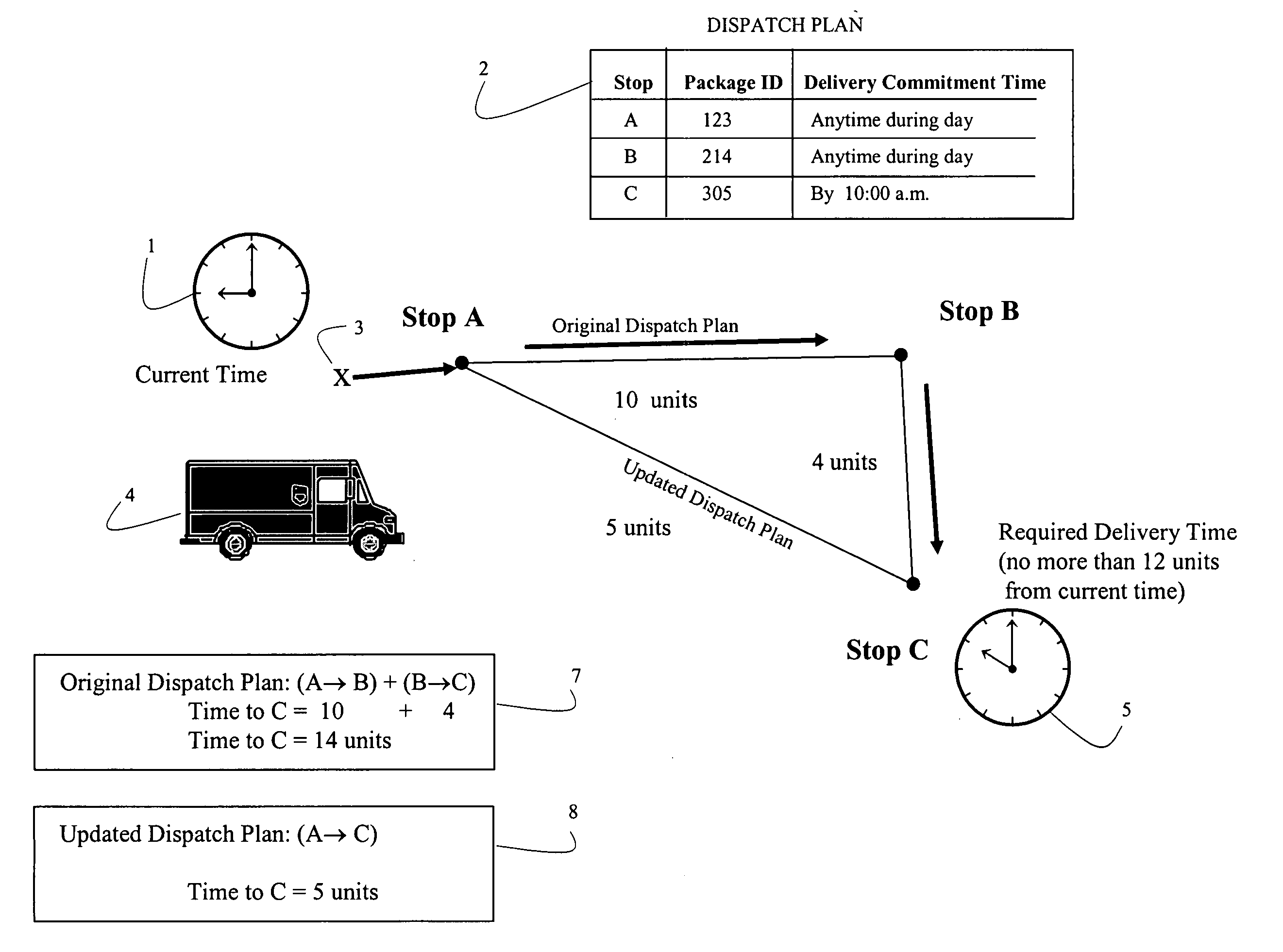
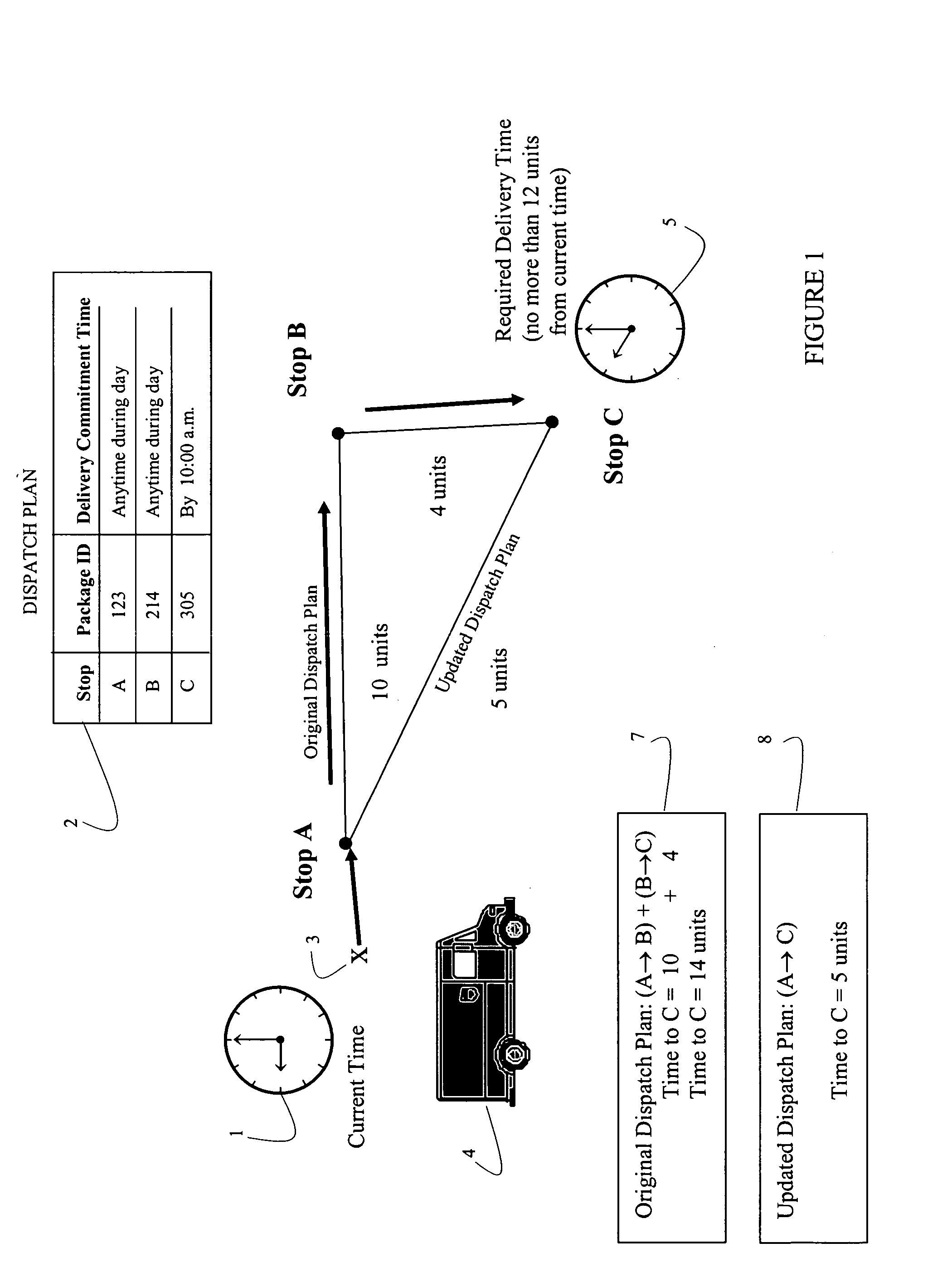
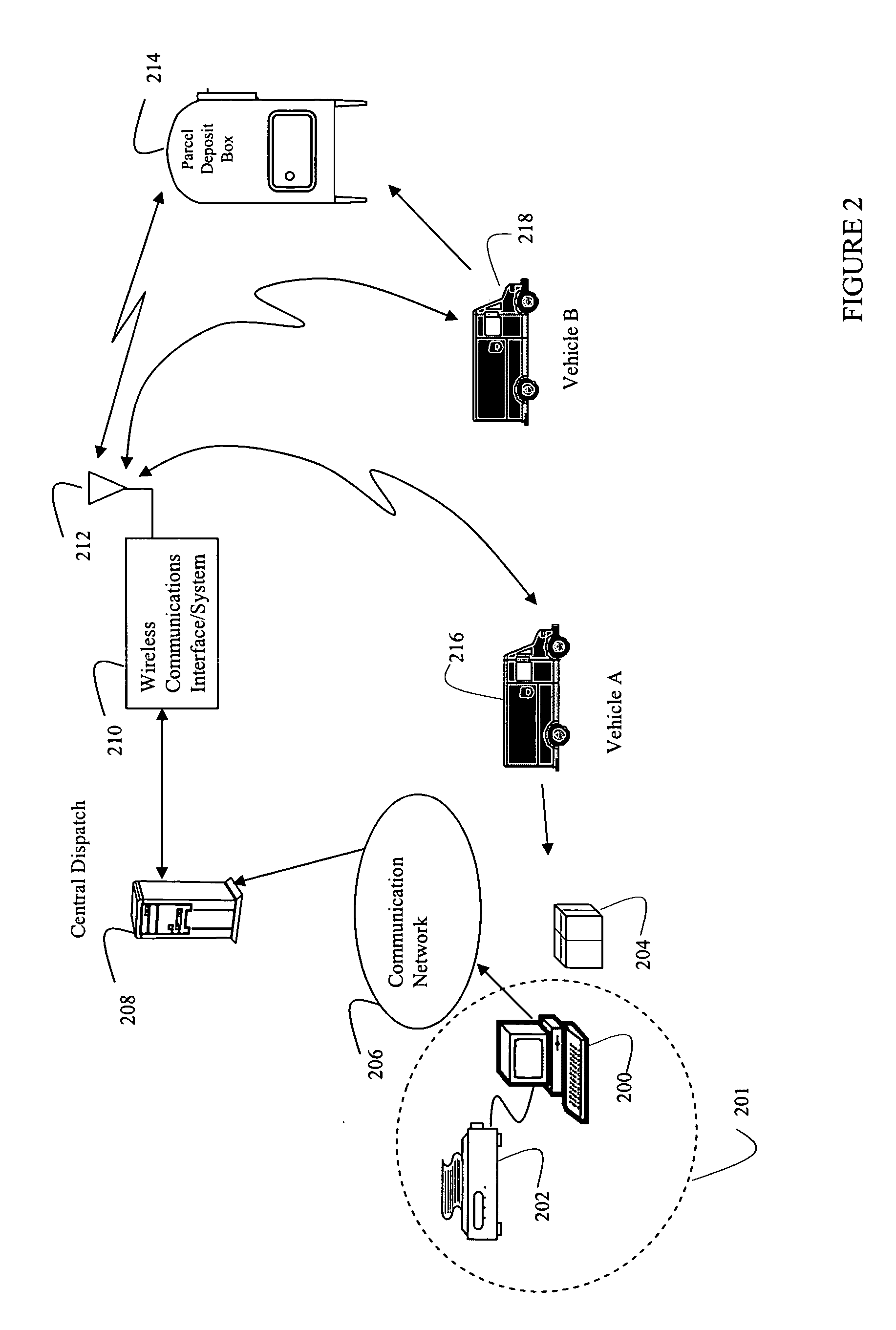
Systems and methods for dynamically updating a dispatch plan
Systems and methods are disclosed for receiving inputs at a portable computer used by personal typically operating a delivery vehicle providing delivery services, where the inputs potentially impact completion of a pre-established dispatch plan according to certain delivery criteria. The inputs include modifications to the manifest, updates regarding weather or traffic conditions, or other factors impacting the remaining deliveries. The inputs are examined to determine if modification of the original dispatch plan are warranted, and if so, a signal is generated triggering the processing of the original dispatch plan to produce an updated dispatch plan meeting the certain delivery criteria. The certain delivery criteria may involve commitments for completing deliveries by certain time frames.
Owner:UNITED PARCEL SERVICE OF AMERICAN INC
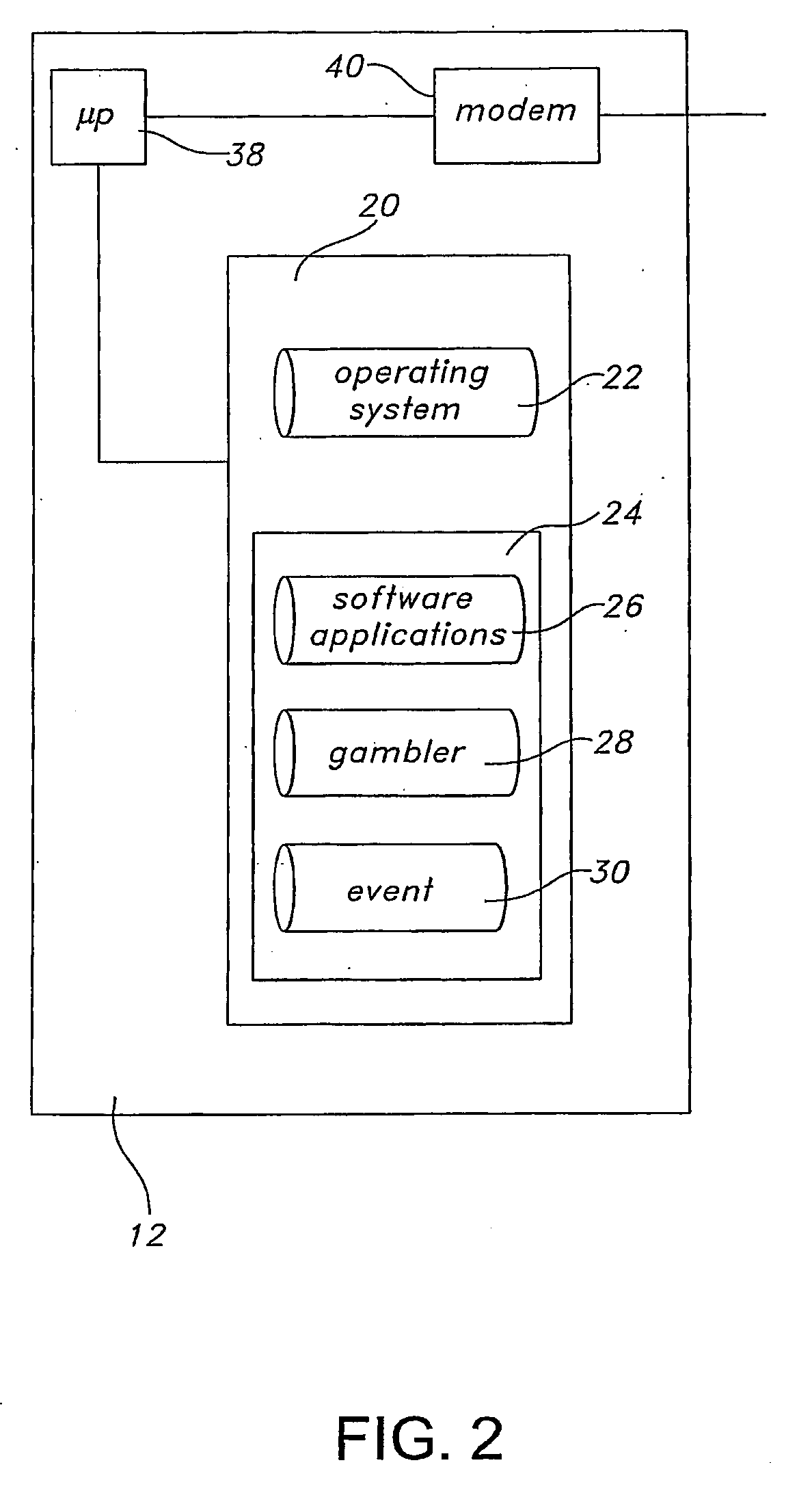
Methods and systems for betting with pari-mutuel payouts
InactiveUS20080113816A1Improved initial payoutQuick buildCard gamesApparatus for meter-controlled dispensingOperational systemEvent data
A server for facilitating real-time betting, wherein the server communicates with clients via a distributed computing network. The server includes a memory storing an operating system, an instruction set, event data related to a sporting event, gambler data related to gamblers participating in a competition based upon the sporting event and site data related to electronic pages associated with the real-time para-mutuel betting. A processor runs the instruction set and communicates with the memory and the distributed computing network. The processor is operative to enroll the gamblers by presenting betting rules associated with the sporting event, collect wagering from the gamblers, accept predictions for discrete events within the sporting event from each gambler and determine a first winner of the competition based upon the predictions. Applications include lotteries with entries received from mobile devices.
Owner:HF SCI INC
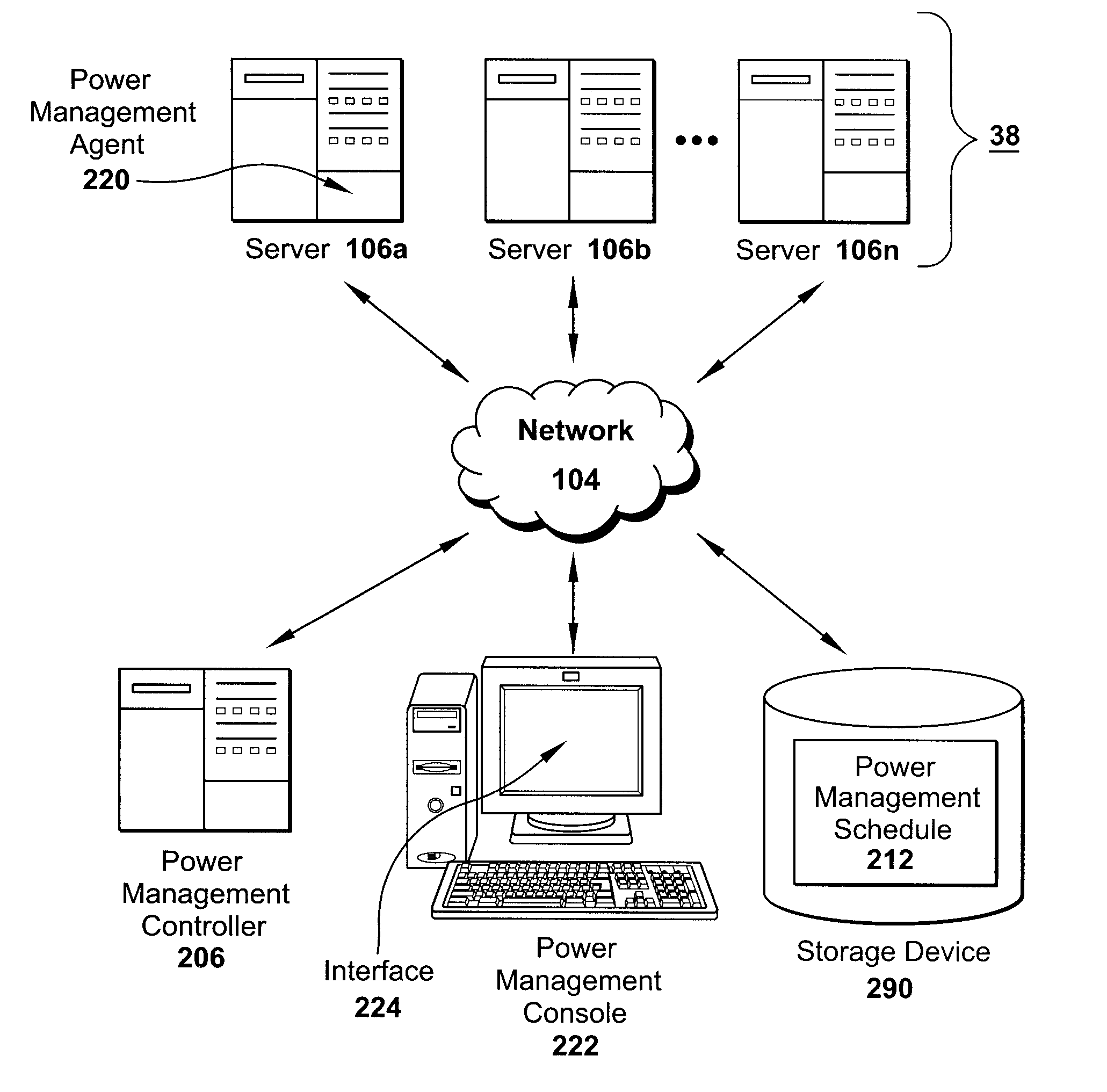
Systems and Methods to Adaptively Load Balance User Sessions to Reduce Energy Consumption
InactiveUS20090106571A1Energy efficient ICTDigital data processing detailsPower modeProgram planning
A method for adaptively load balancing user sessions to reduce energy consumption includes identifying a session type for each of a plurality of user sessions. A server group is defined, providing access to a subset of the user sessions having a common session type. A power management schedule is also defined for the server group. The method includes consolidating, onto at least one server in the server group, the subset of user sessions. In still another aspect, a method for reducing energy consumption by dynamically managing power modes for a plurality of servers, includes monitoring, via a power monitoring agent, a level of load on one of the servers. A power management console generates a power management schedule for a server, responsive to the monitored level of load. Responsive to the power management schedule, a power management controller dynamically controls a level of power for the server.
Owner:CITRIX SYST INC
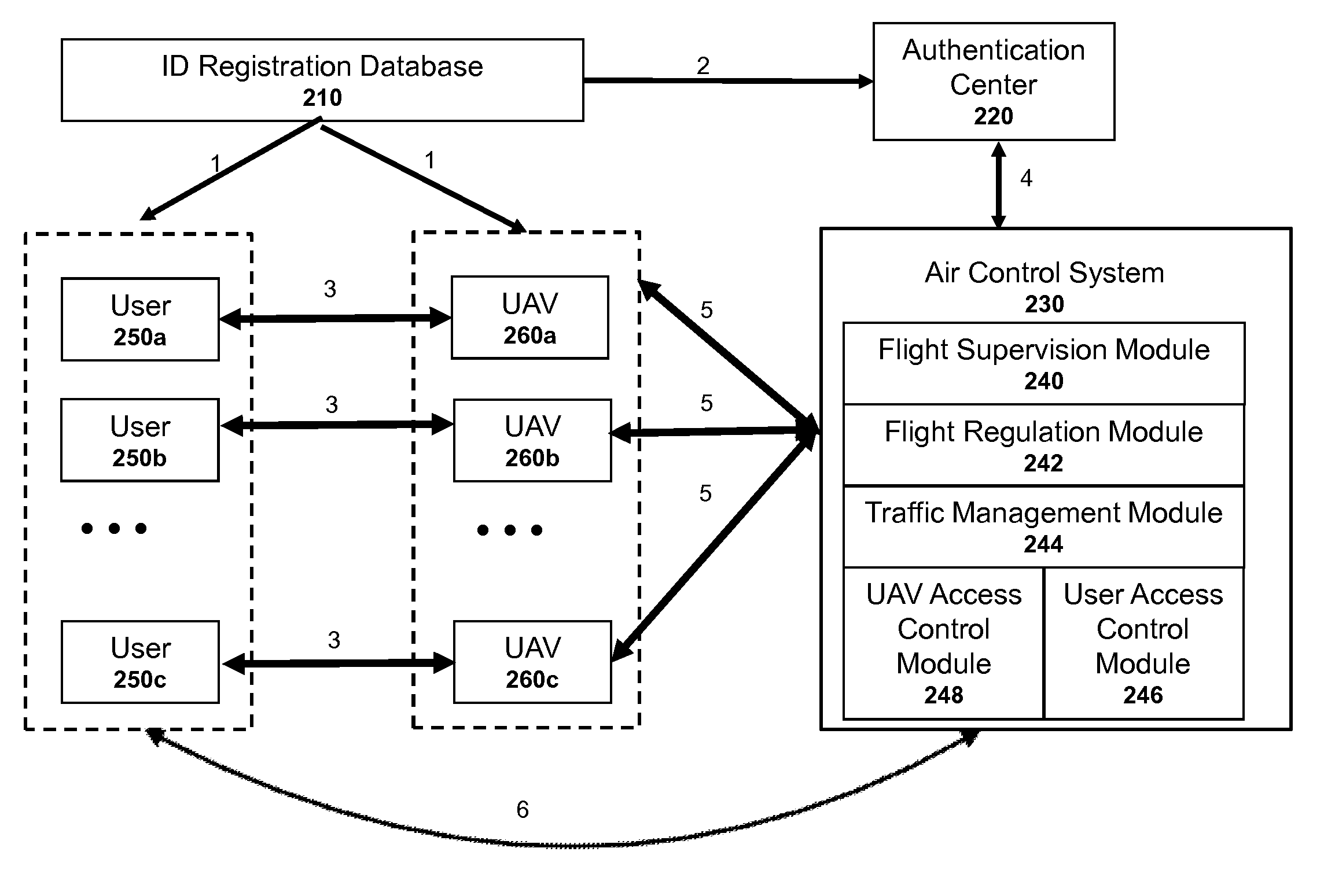
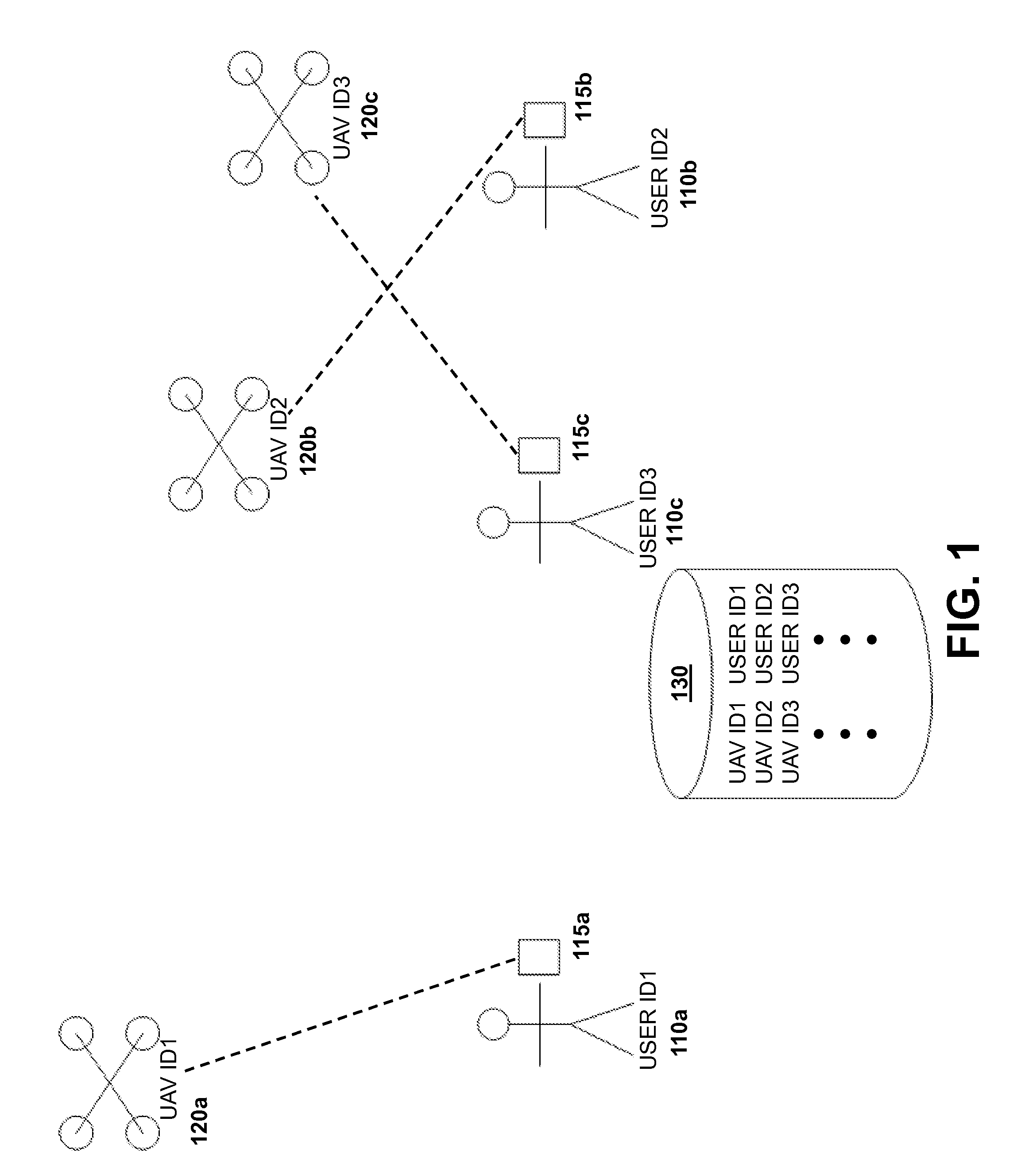
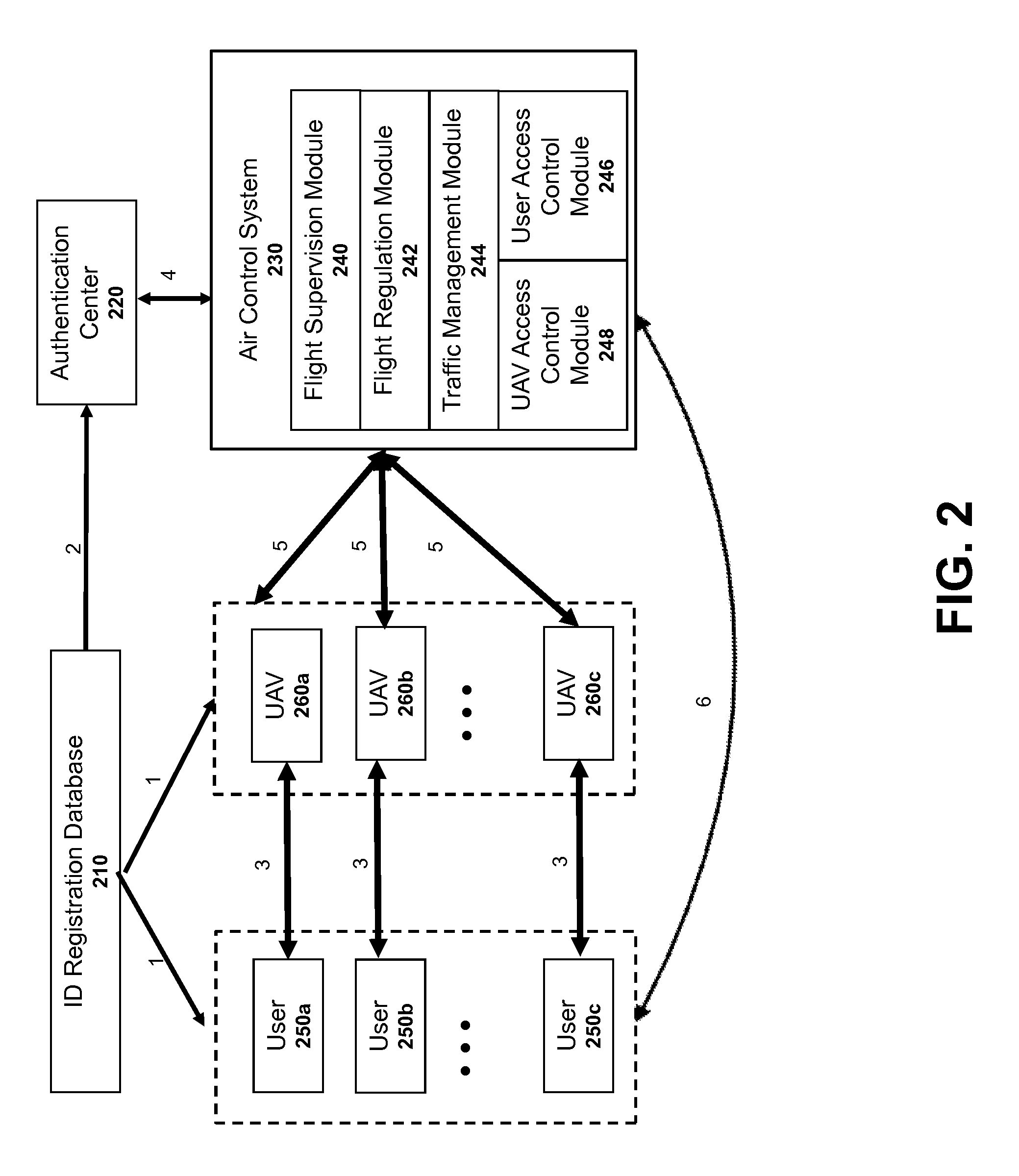
Authentication systems and methods for generating flight regulations
ActiveUS9412278B1Improve flight safetyRemote controlled aircraftDigital data authenticationAuthentication systemComputer science
Systems and methods for UAV safety are provided. An authentication system may be used to confirm UAV and / or user identity and provide secured communications between users and UAVs. The UAVs may operate in accordance with a set of flight regulations. The set of flight regulations may be associated with a geo-fencing device in the vicinity of the UAV.
Owner:SZ DJI TECH CO LTD
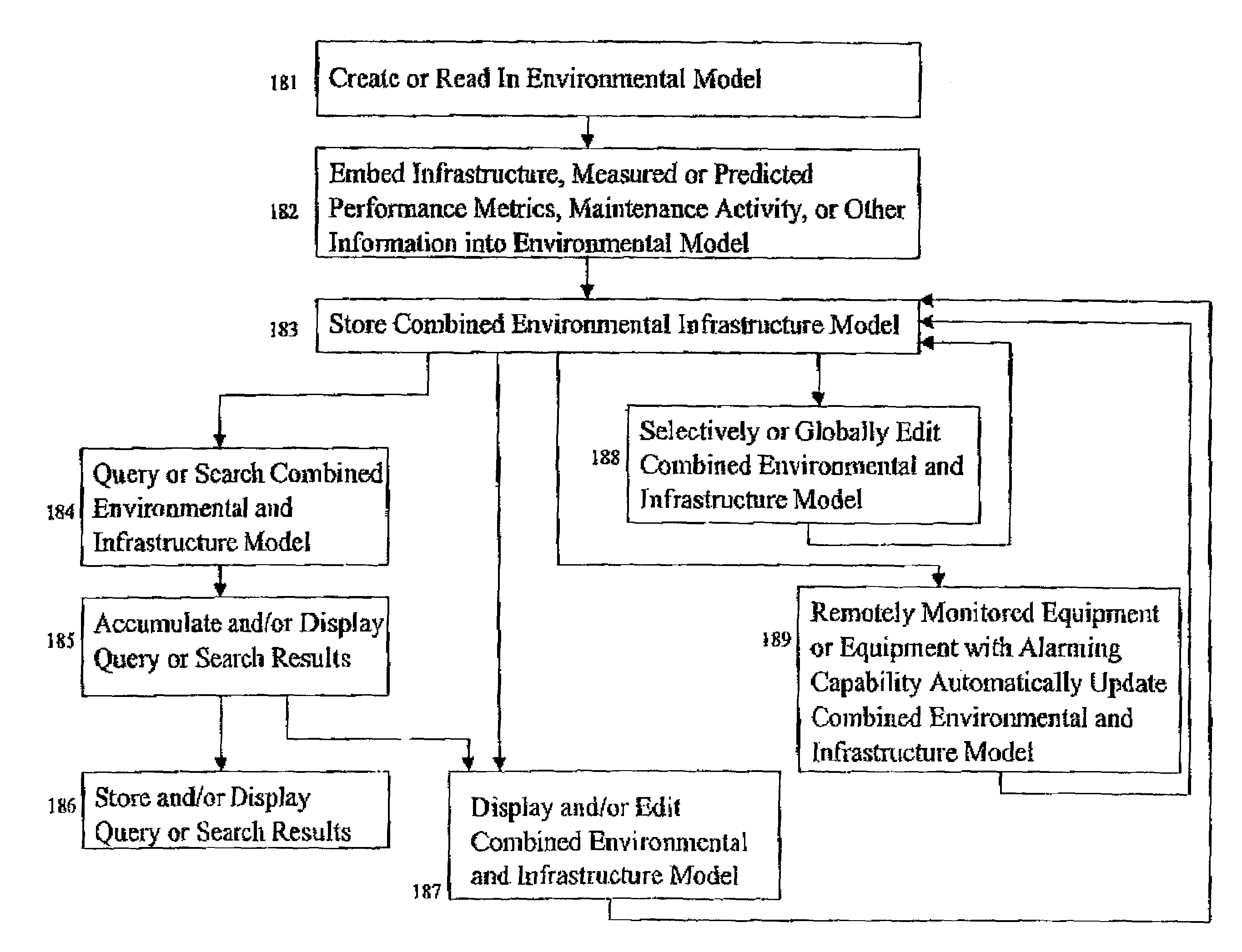
Method and system for modeling and managing terrain, buildings, and infrastructure
ActiveUS7164883B2Enhance on-going managementBroadcast transmission systemsRadio/inductive link selection arrangementsSpecific modelEngineering
A method and system for creating, using, and managing a three-dimensional digital model of the physical environment combines outdoor terrain elevation and land-use information, building placements, heights and geometries of the interior structure of buildings, along with site-specific models of components that are distributed spatially within a physical environment. The present invention separately provides an asset management system that allows the integrated three-dimensional model of the outdoor, indoor, and distributed infrastructure equipment to communicate with and aggregate the information pertaining to actual physical components of the actual network, thereby providing a management system that can track the on-going performance, cost, maintenance history, and depreciation of multiple networks using the site-specific unified digital format.
Owner:EXTREME NETWORKS INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com