Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1966results about How to "Reduce dimensionality" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
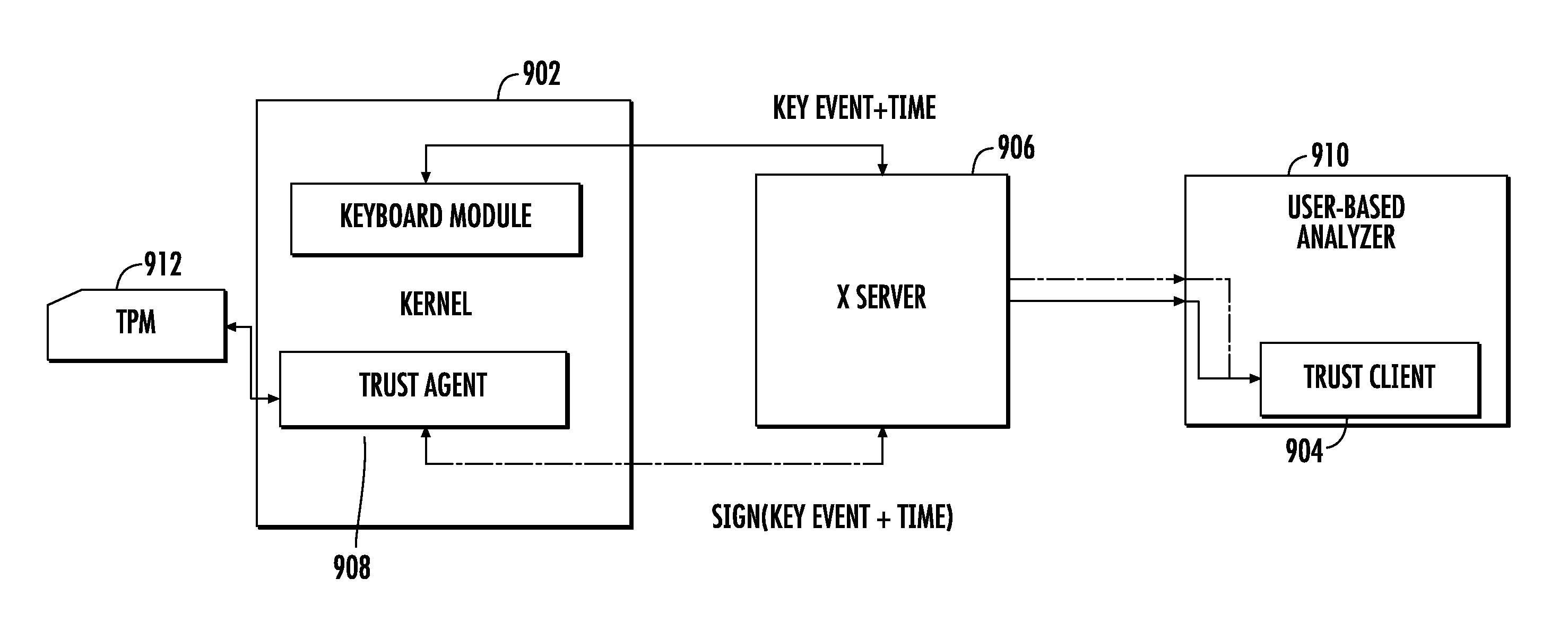
Systems and method for malware detection
ActiveUS20110320816A1Avoid bottlenecksReduce dimensionalityMemory loss protectionDigital data processing detailsFeature vectorSupport vector machine
A system and method for distinguishing human input events from malware-generated events includes one or more central processing units (CPUs), one or more input devices and memory. The memory includes program code that when executed by the CPU causes the CPU to obtain a first set of input events from a user utilizing the input device. The first input events are used to obtain or derive a feature indicative of the user, such as a multi-dimensional feature vector as provided by a support vector machine. Second input events are then obtained, and the second input events are classified against the feature to determine if either the user or malware initiated the second input events.
Owner:RUTGERS THE STATE UNIV
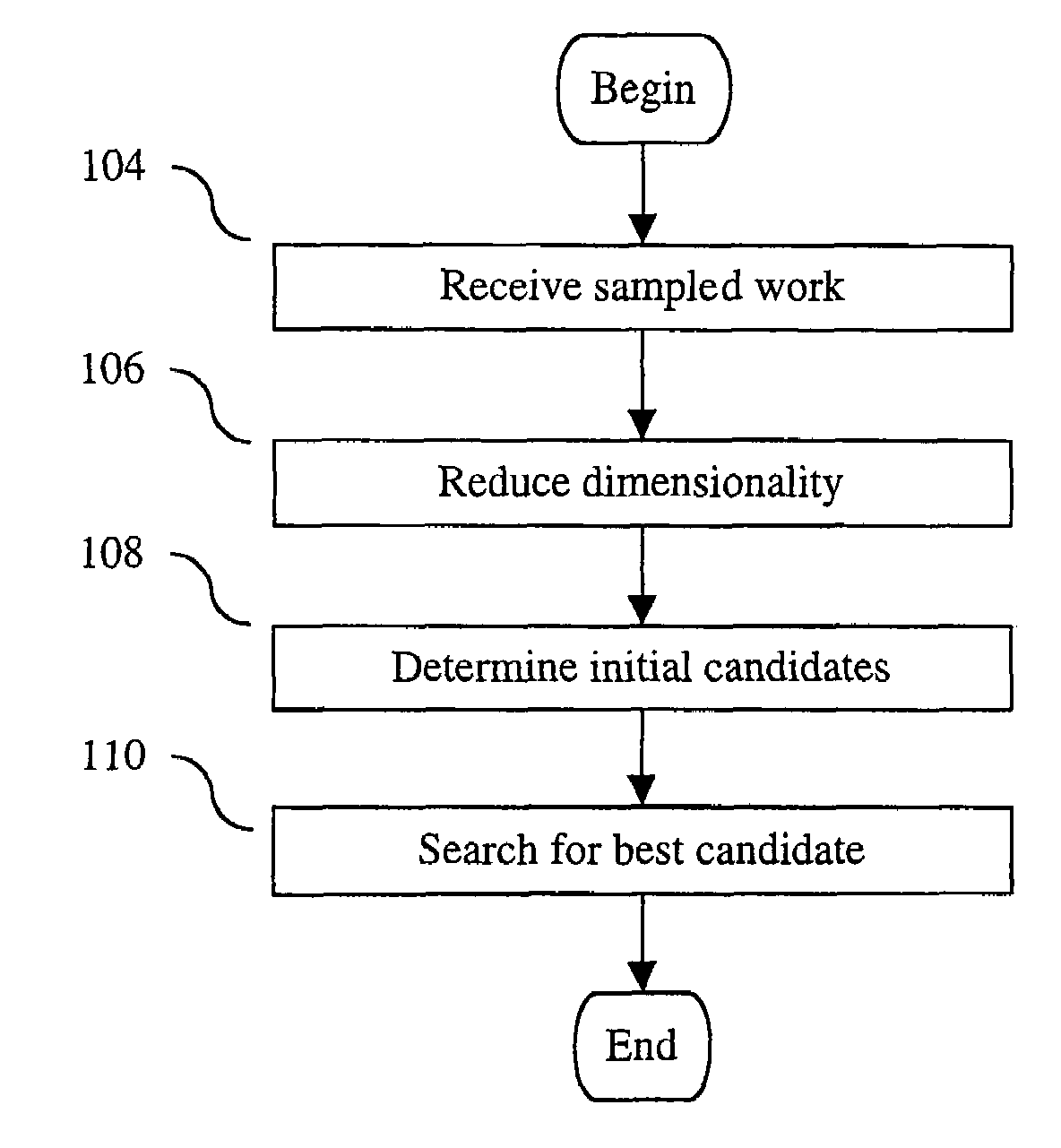
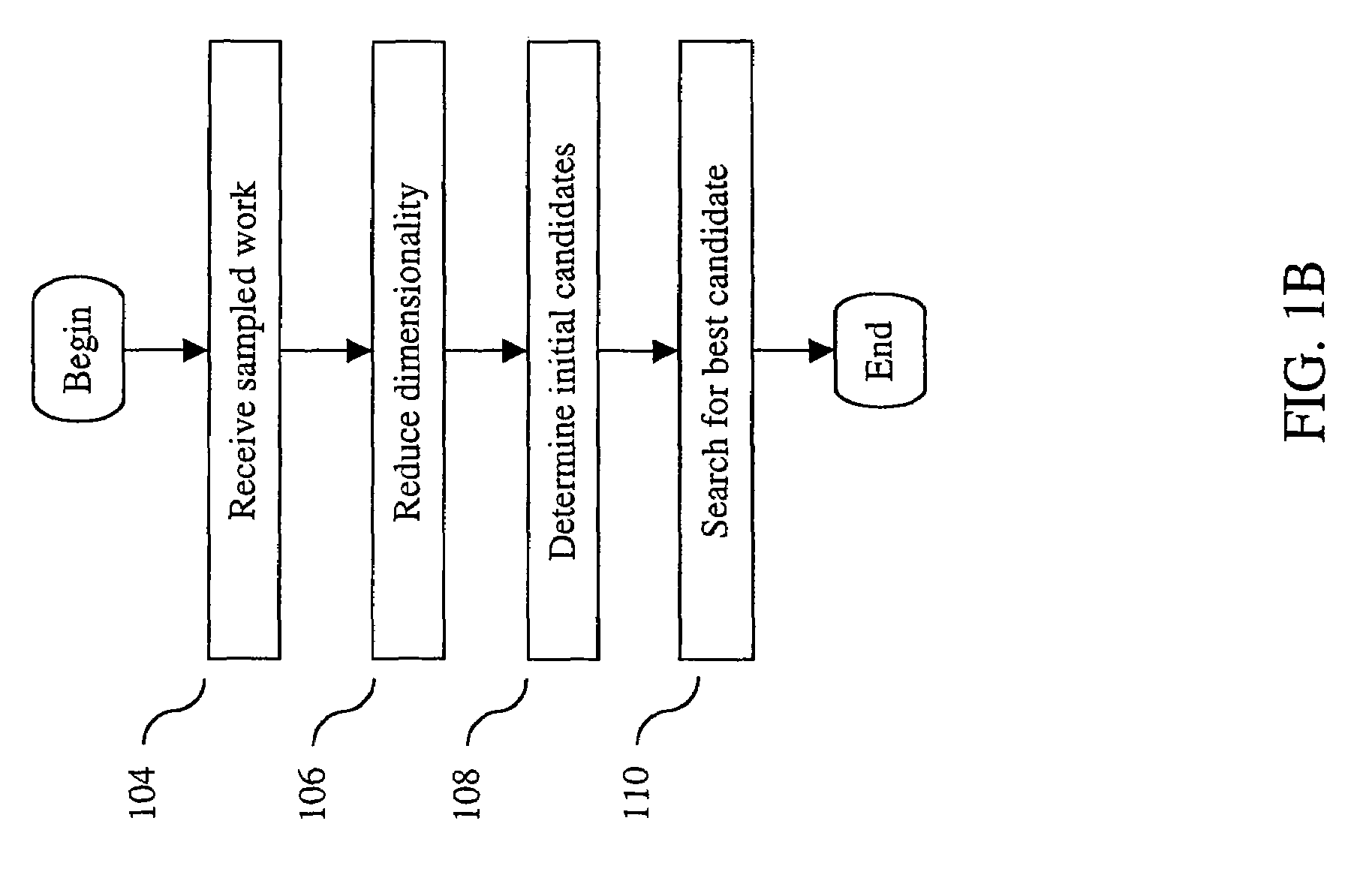
Method and apparatus for identifying an unknown work
InactiveUS6968337B2Reduce dimensionalityData processing applicationsDigital data processing detailsData miningData bank
A system for determining an identity of a received work. The system receives audio data for an unknown work. The audio data is divided into segments. The system generates a signature of the unknown work from each of the segments. Reduced dimension signatures are then generated at least a portion of the signatures. The reduced dimension signatures are then compared to reduced dimensions signatures of known works that are stored in a database. A list of candidates of known works is generated from the comparison. The signatures of the unknown works are then compared to the signatures of the known works in the list of candidates. The unknown work is then identified as the known work having signatures matching within a threshold.
Owner:AUDIBLE MAGIC
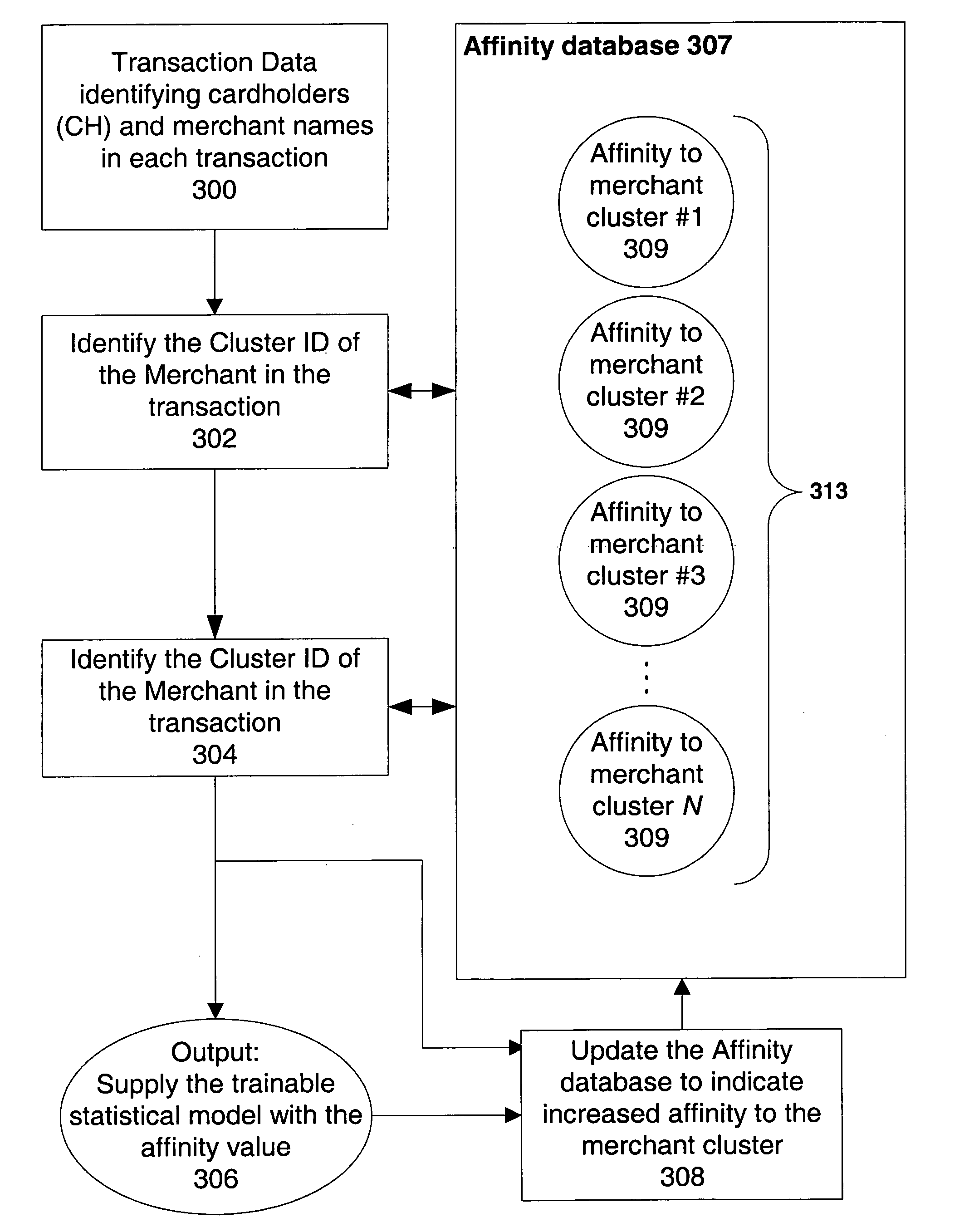
Detecting and measuring risk with predictive models using content mining
InactiveUS7376618B1Reduce dimensionalityEasy to controlFinancePayment architectureData miningStatistical model
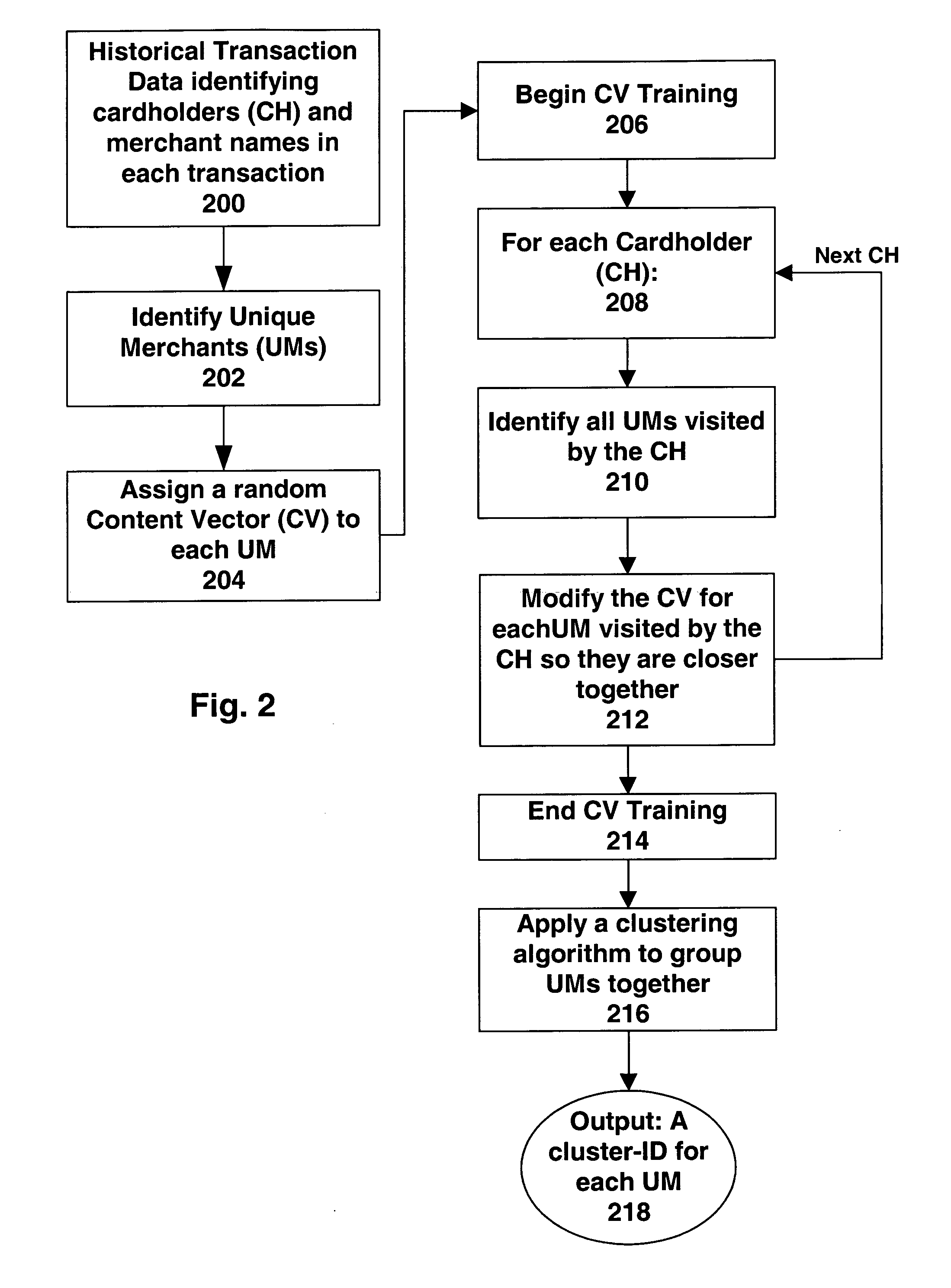
Computer implemented methods and systems of processing transactions to determine the risk of transaction convert high categorical information, such as text data, to low categorical information, such as category or cluster IDs. The text data may be merchant names or other textual content of the transactions, or data related to a consumer, or any other type of entity which engages in the transaction. Content mining techniques are used to provide the conversion from high to low categorical information. In operation, the resulting low categorical information is input, along with other data, into a statistical model. The statistical model provides an output of the level of risk in the transaction. Methods of converting the high categorical information to low categorical clusters, of using such information, and other aspects of the use of such clusters are disclosed.
Owner:FAIR ISAAC & CO INC
Apparatuses and methods for mobile imaging and analysis
ActiveUS20150065803A1Easy to separateReduce dimensionalityBronchoscopesImage enhancementImage analysisDisease
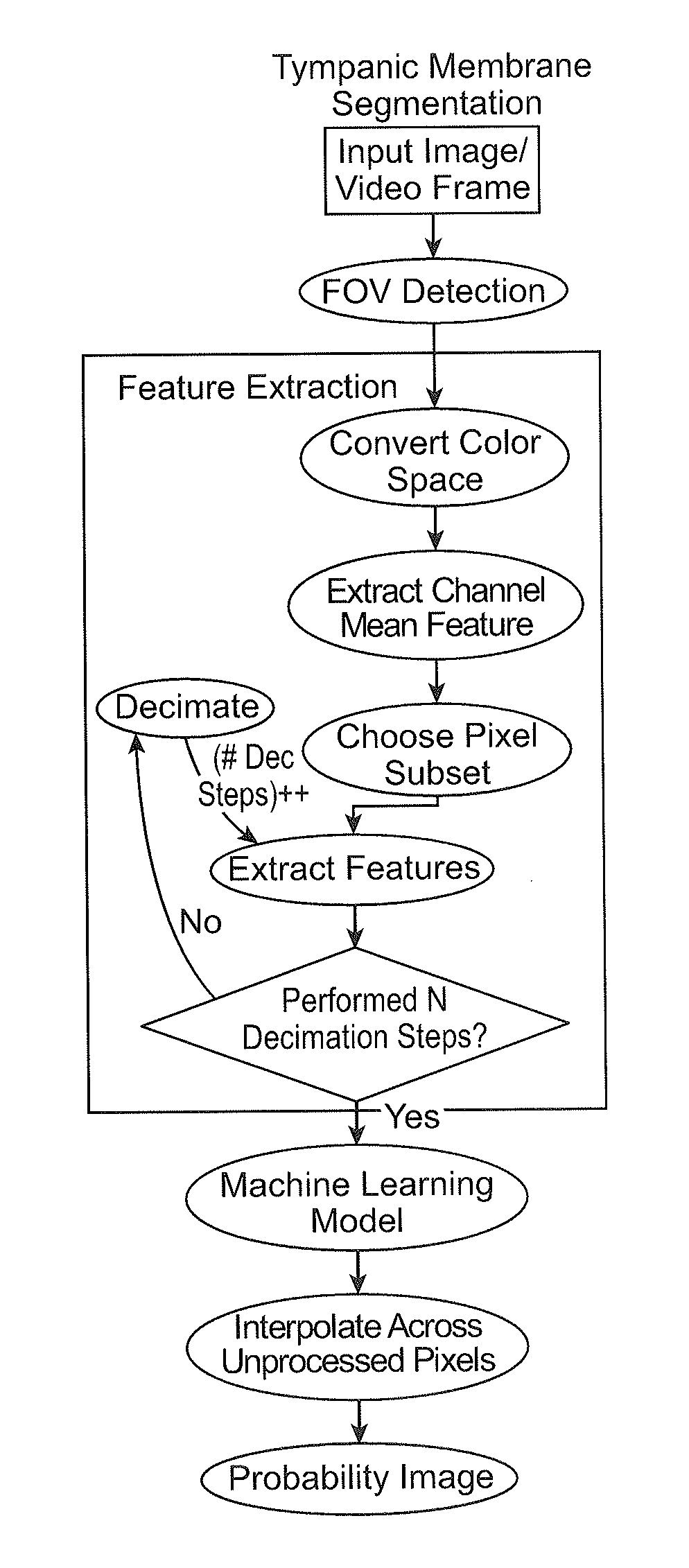
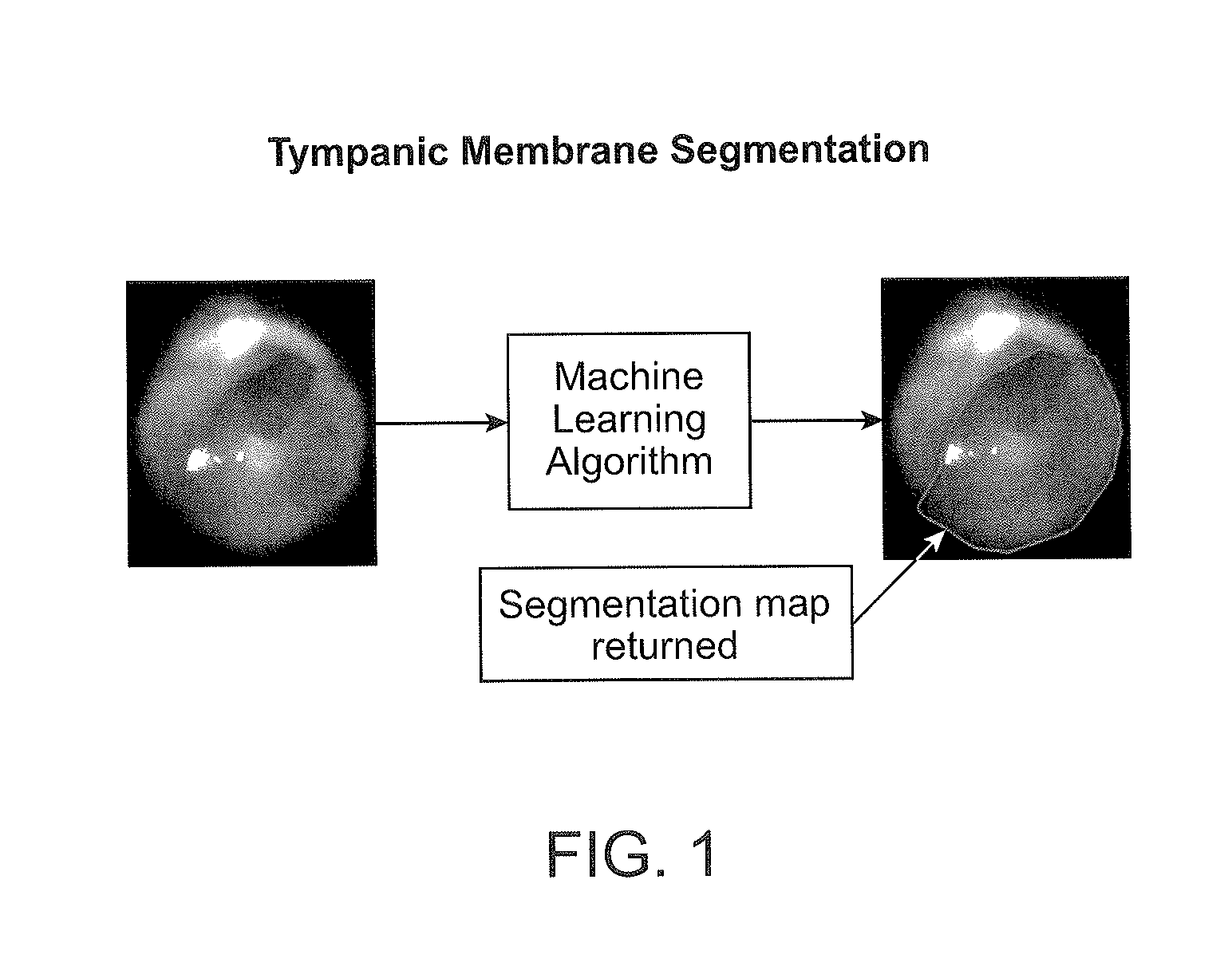
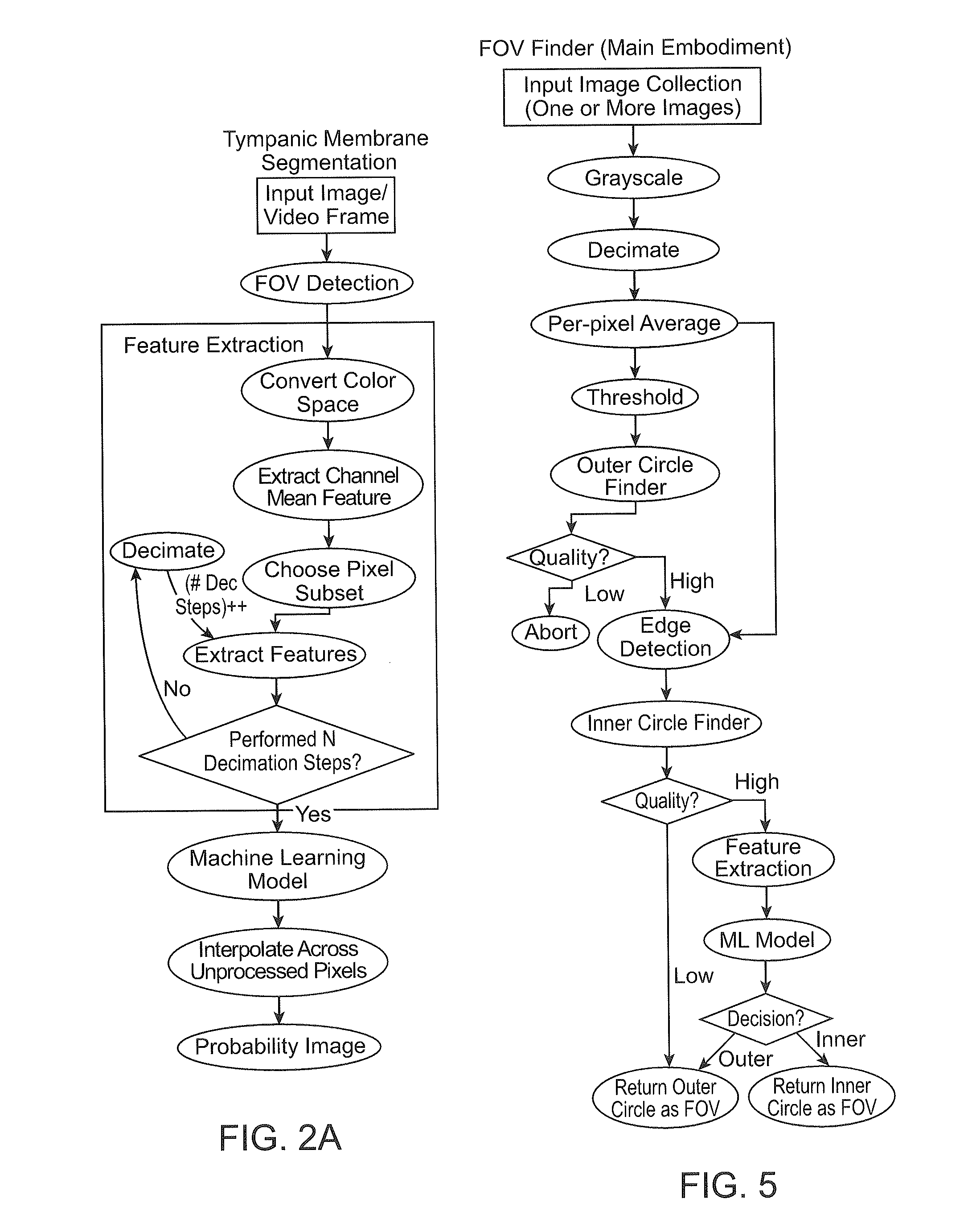
Apparatuses and methods for mobile imaging and image analysis. In particular, described herein are methods and apparatuses for assisting in the acquisition and analysis of images of the tympanic membrane to provide information that may be helpful in the understanding and management of disease, such ear infection (acute otitis media). These apparatuses may guide or direct a subject in taking an image of a tympanic membrane, including automatically detecting which direction to adjust the position of the apparatus to capture an image of the tympanic membrane and automatically indicating when the tympanic membrane has been imaged.
Owner:JOHNSON & JOHNSON CONSUMER COPANIES
Method and apparatus for identifying an unknown work
InactiveUS7529659B2Reduce dimensionalityDigital data information retrievalDigital computer detailsData miningData science
A system for determining an identity of a received work. The system receives audio data for an unknown work. The audio data is divided into segments. The system generates a signature of the unknown work from each of the segments. Reduced dimension signatures are then generated at least a portion of the signatures. The reduced dimension signatures are then compared to reduced dimensions signatures of known works that are stored in a database. A list of candidates of known works is generated from the comparison. The signatures of the unknown works are then compared to the signatures of the known works in the list of candidates. The unknown work is then identified as the known work having signatures matching within a threshold.
Owner:AUDIBLE MAGIC
Method and apparatus for identifying an unknown work
ActiveUS20070074147A1Reduce dimensionalityDigital data information retrievalDigital computer detailsData miningData science
A system for determining an identity of a received work. The system receives audio data for an unknown work. The audio data is divided into segments. The system generates a signature of the unknown work from each of the segments. Reduced dimension signatures are then generated at least a portion of the signatures. The reduced dimension signatures are then compared to reduced dimensions signatures of known works that are stored in a database. A list of candidates of known works is generated from the comparison. The signatures of the unknown works are then compared to the signatures of the known works in the list of candidates. The unknown work is then identified as the known work having signatures matching within a threshold.
Owner:AUDIBLE MAGIC
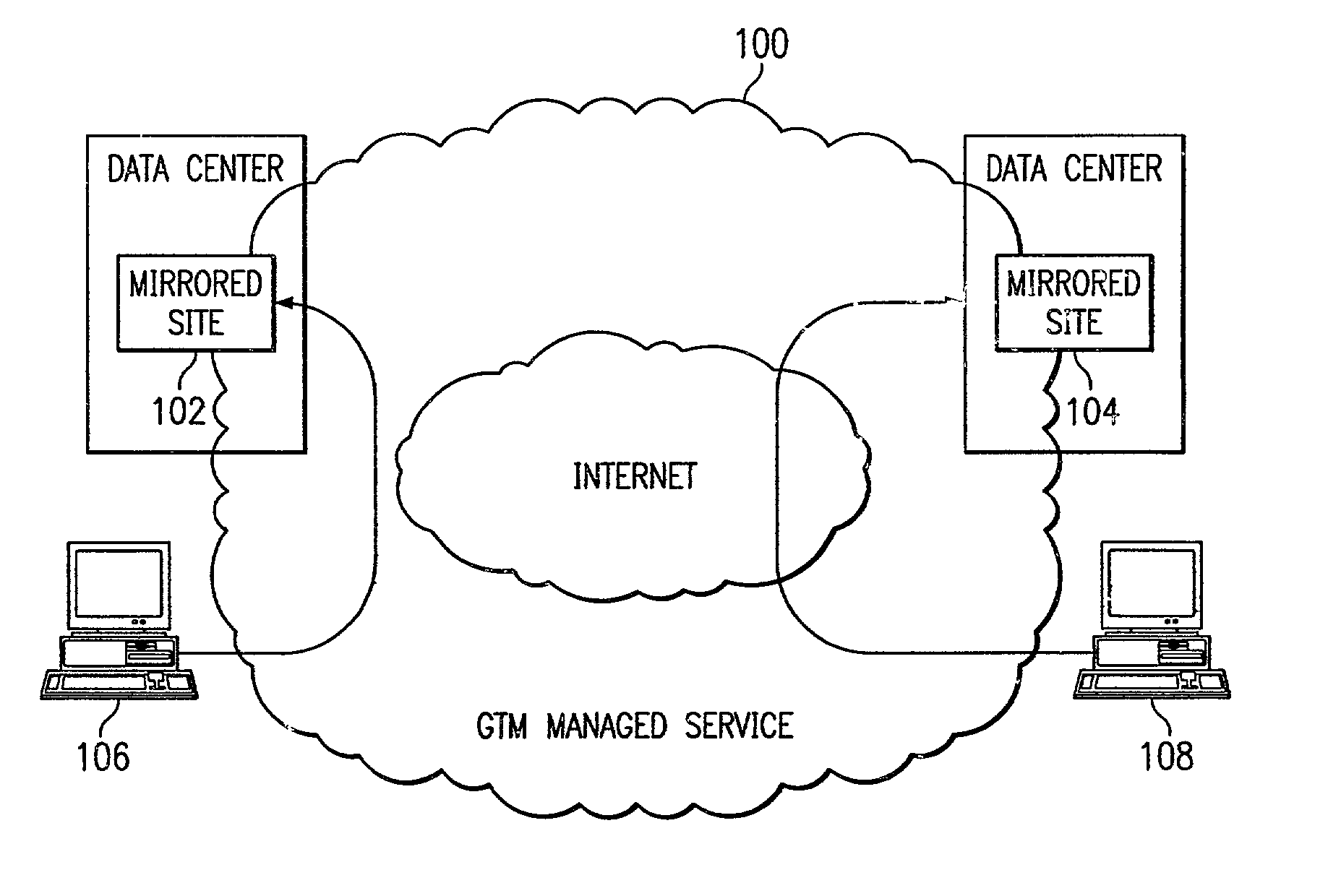
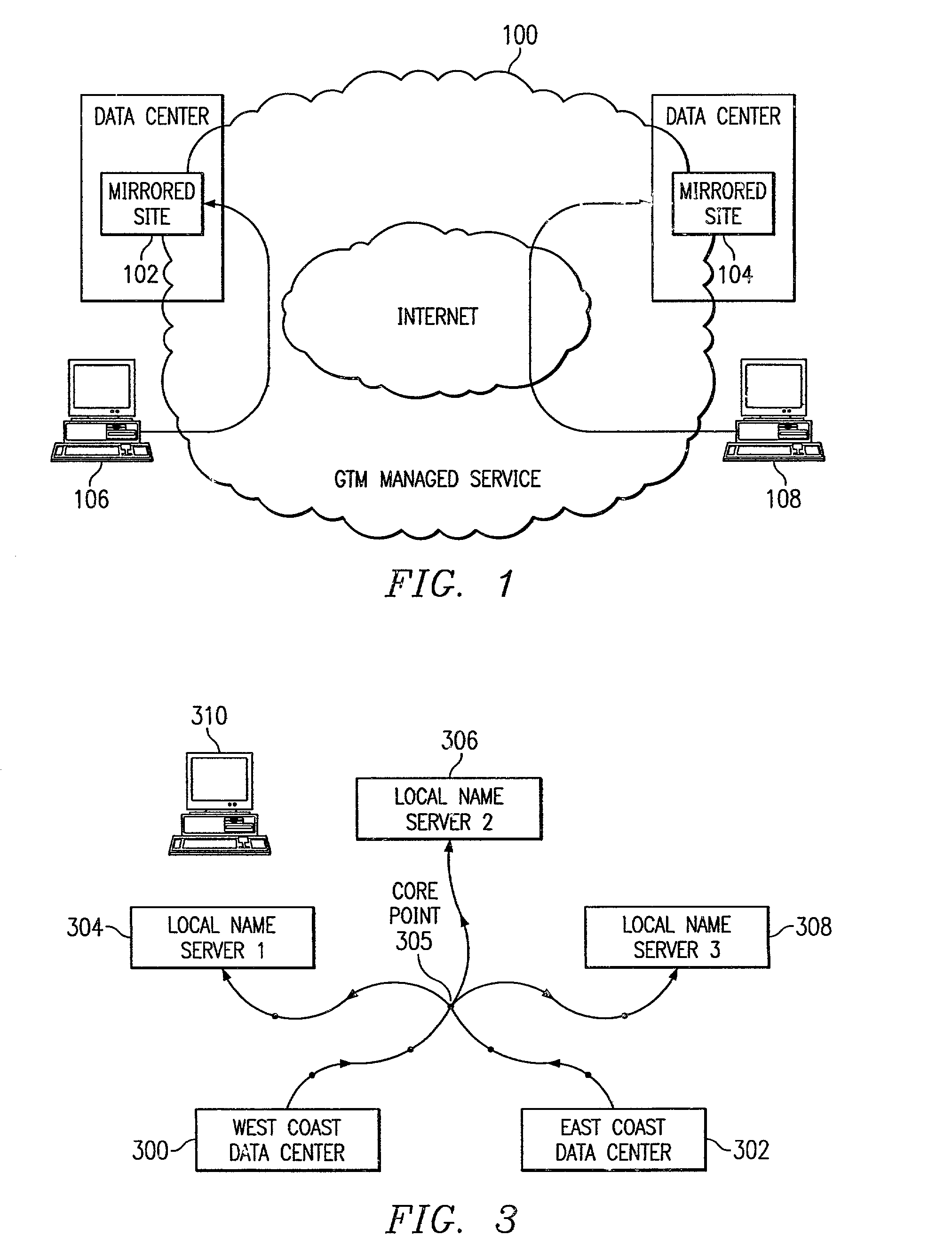
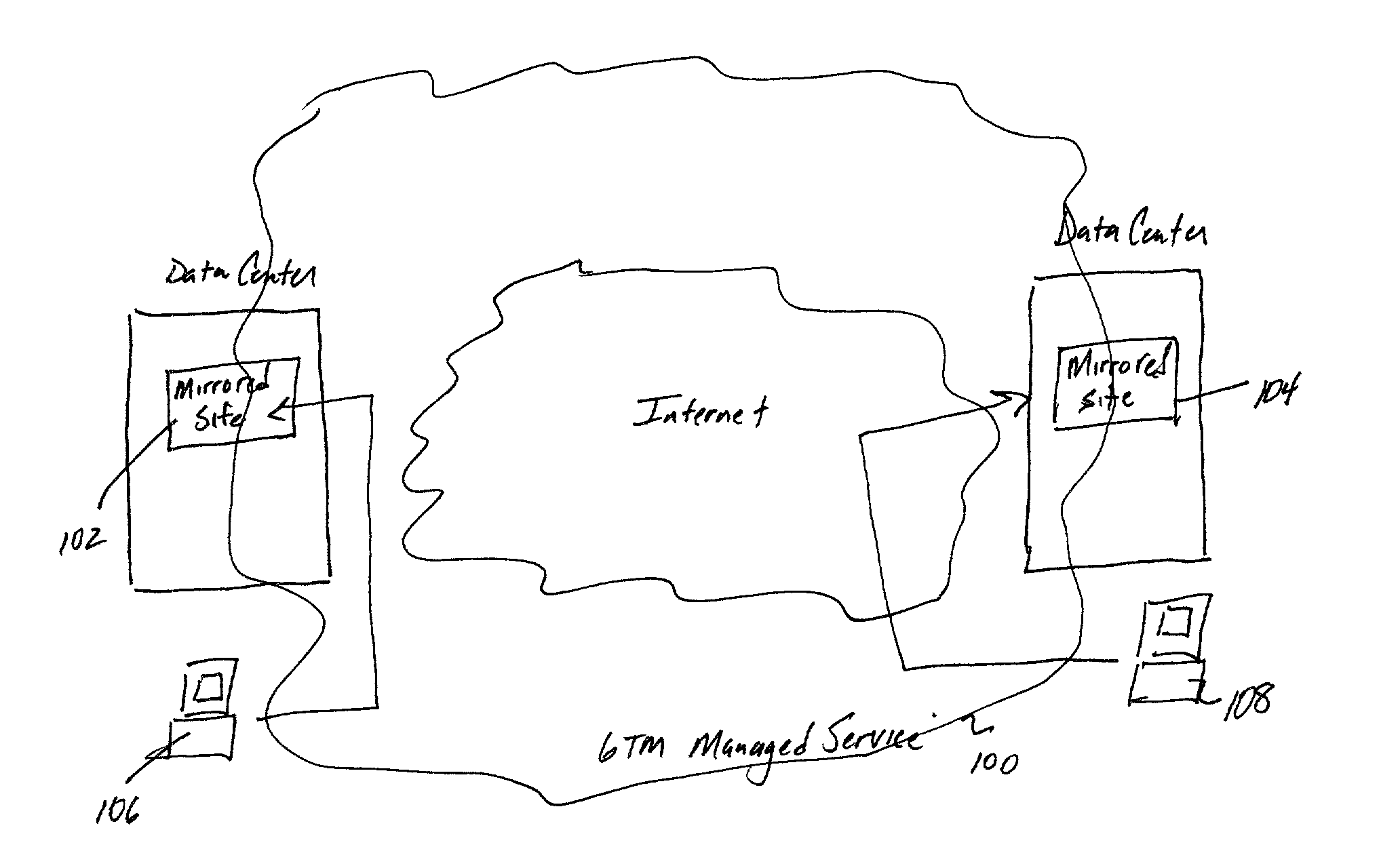
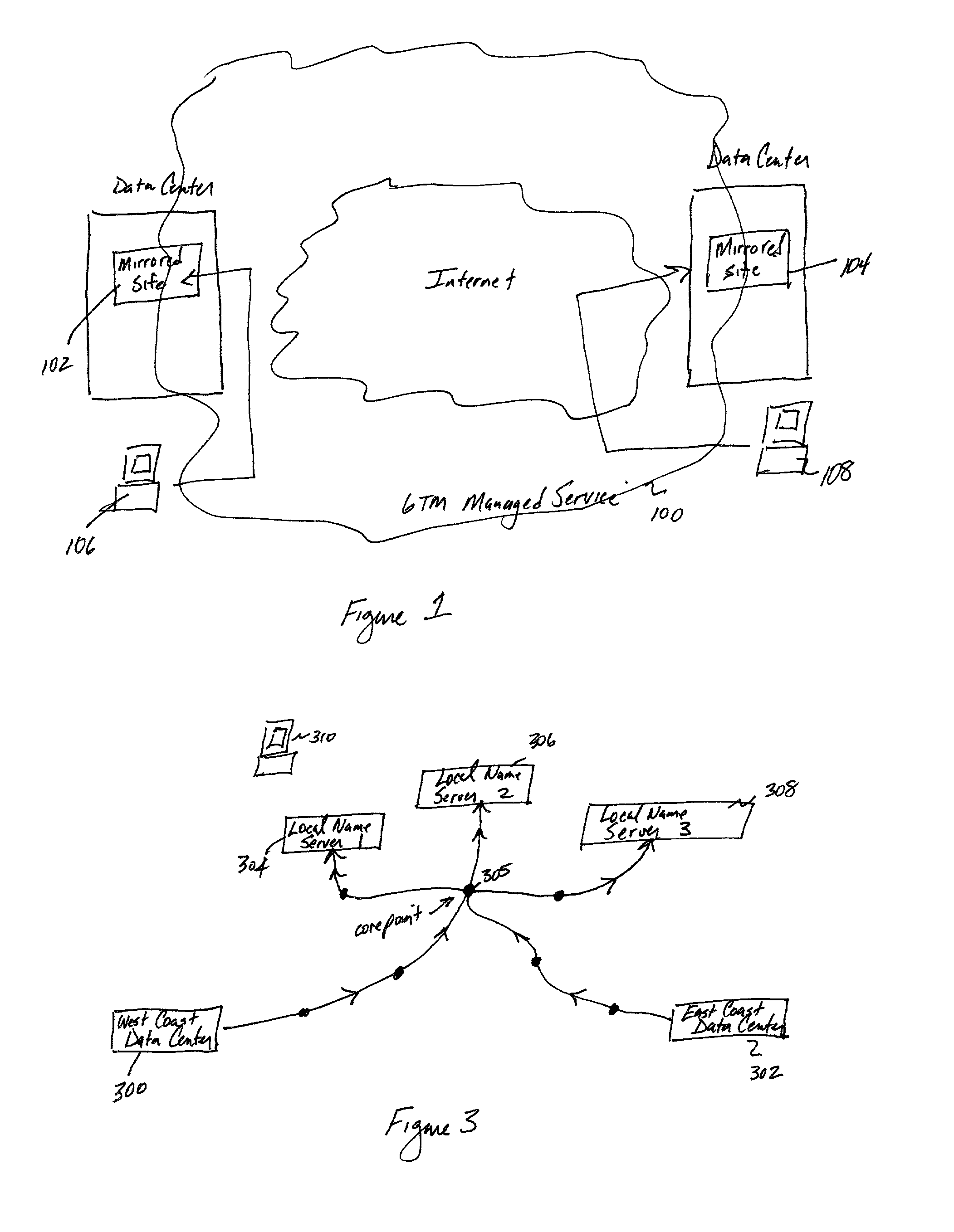
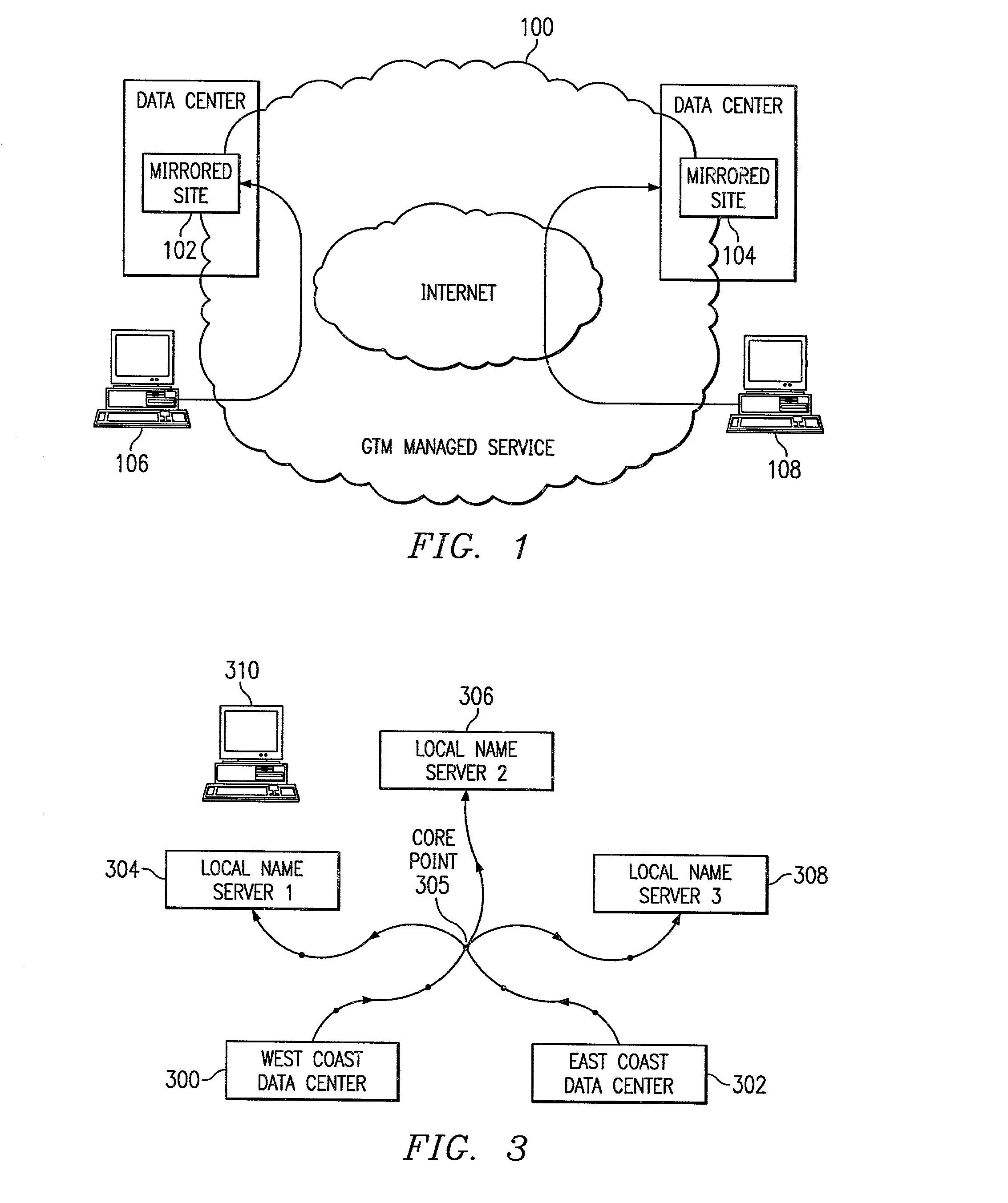
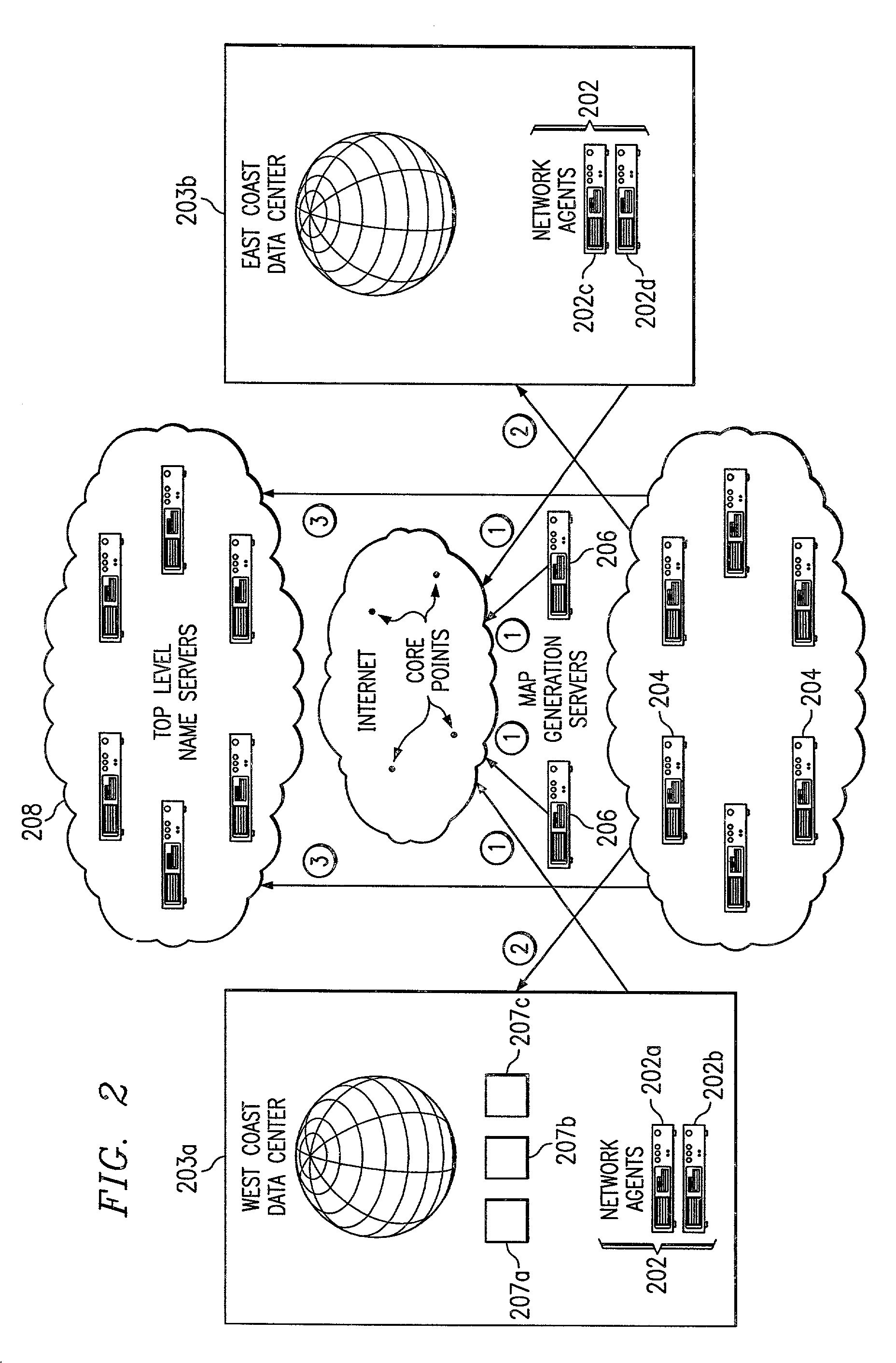
Global load balancing across mirrored data centers
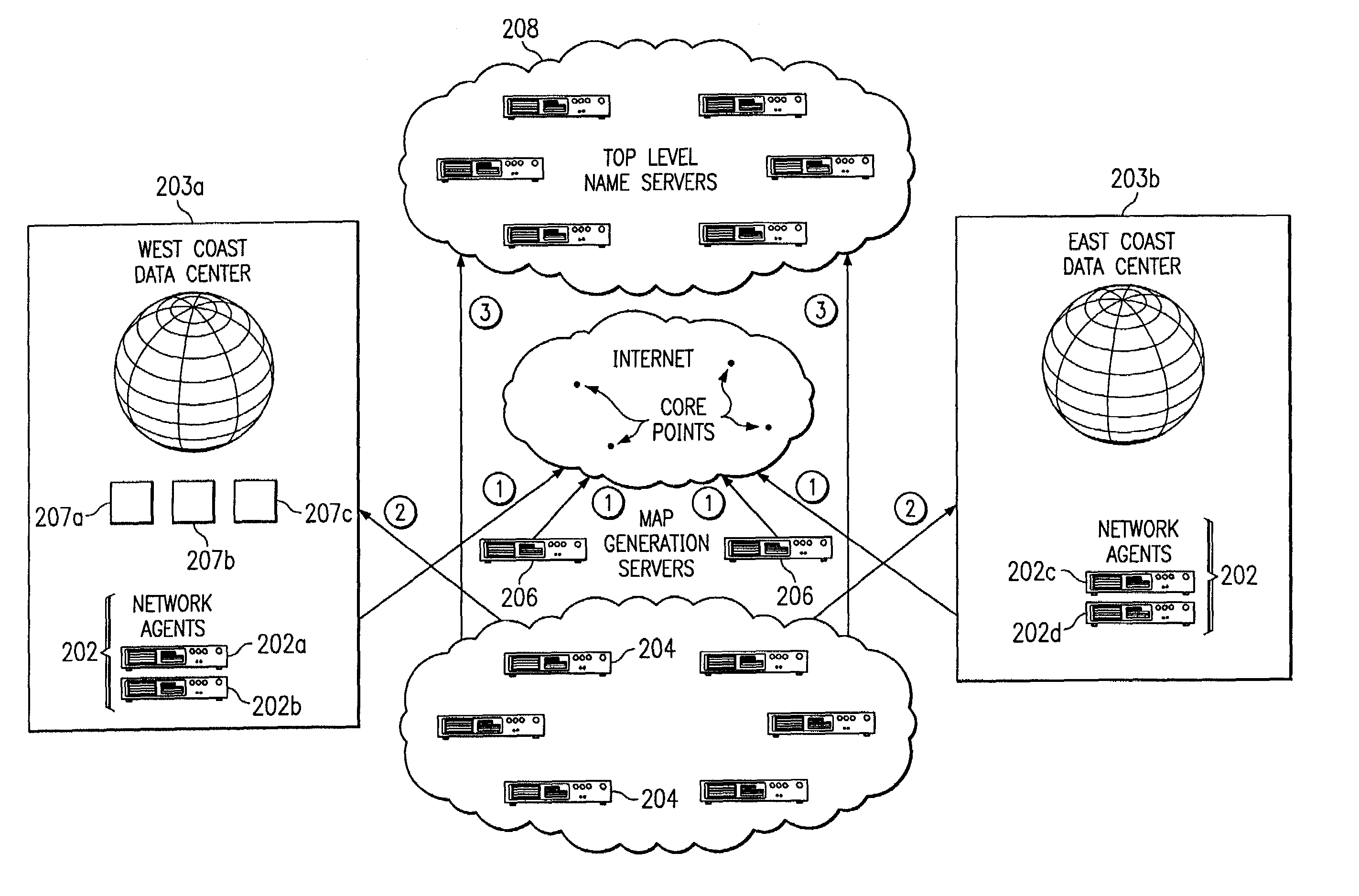
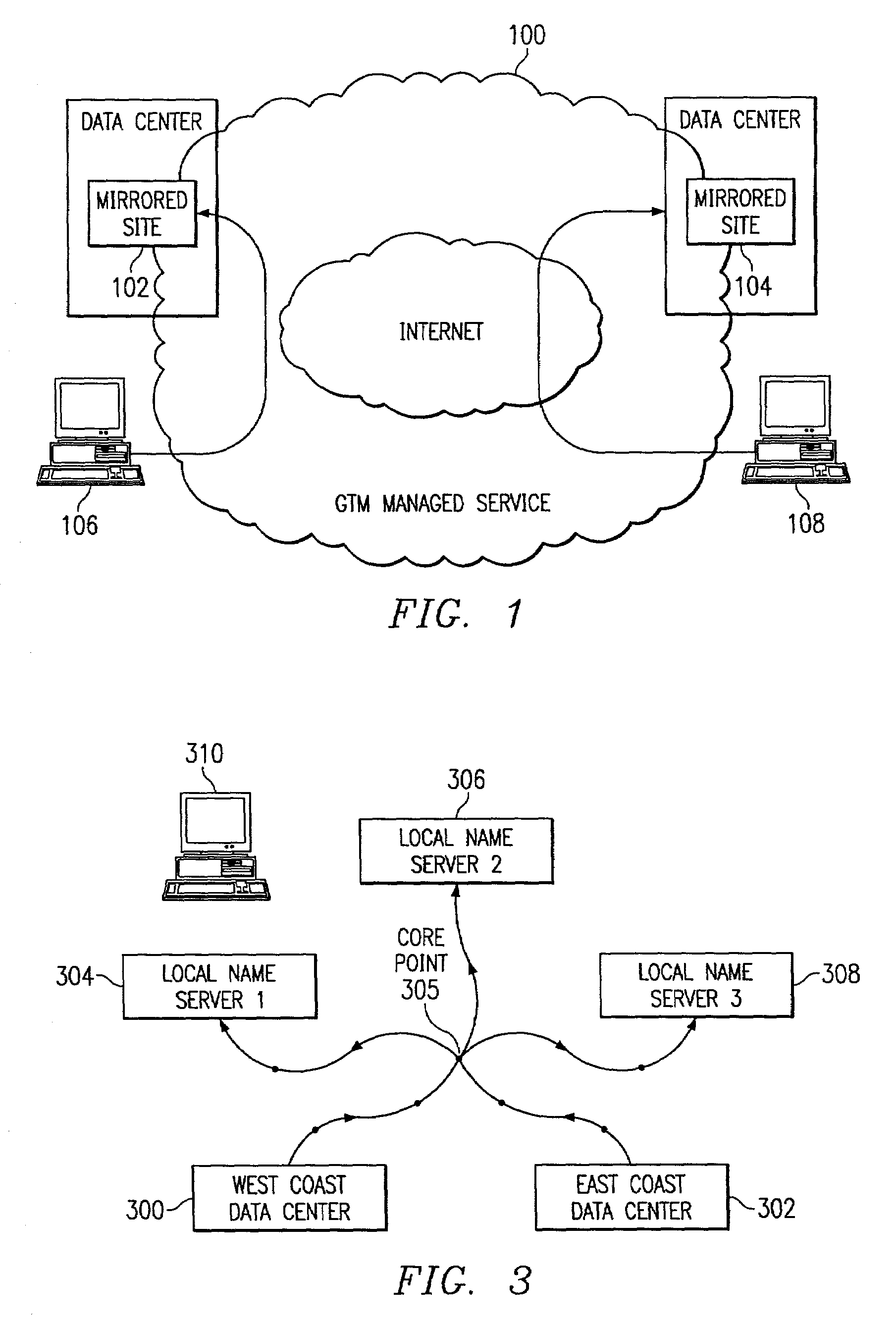
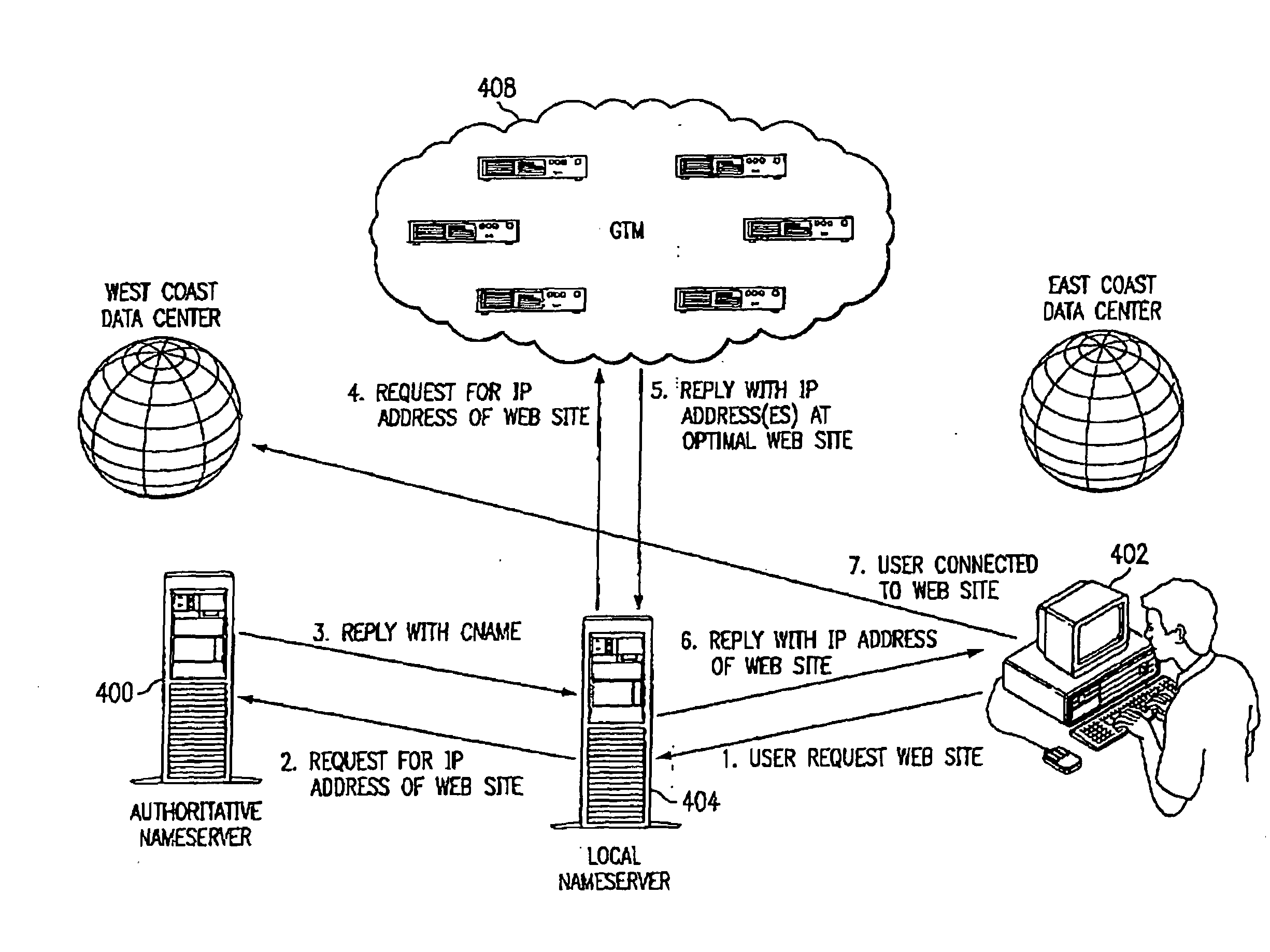
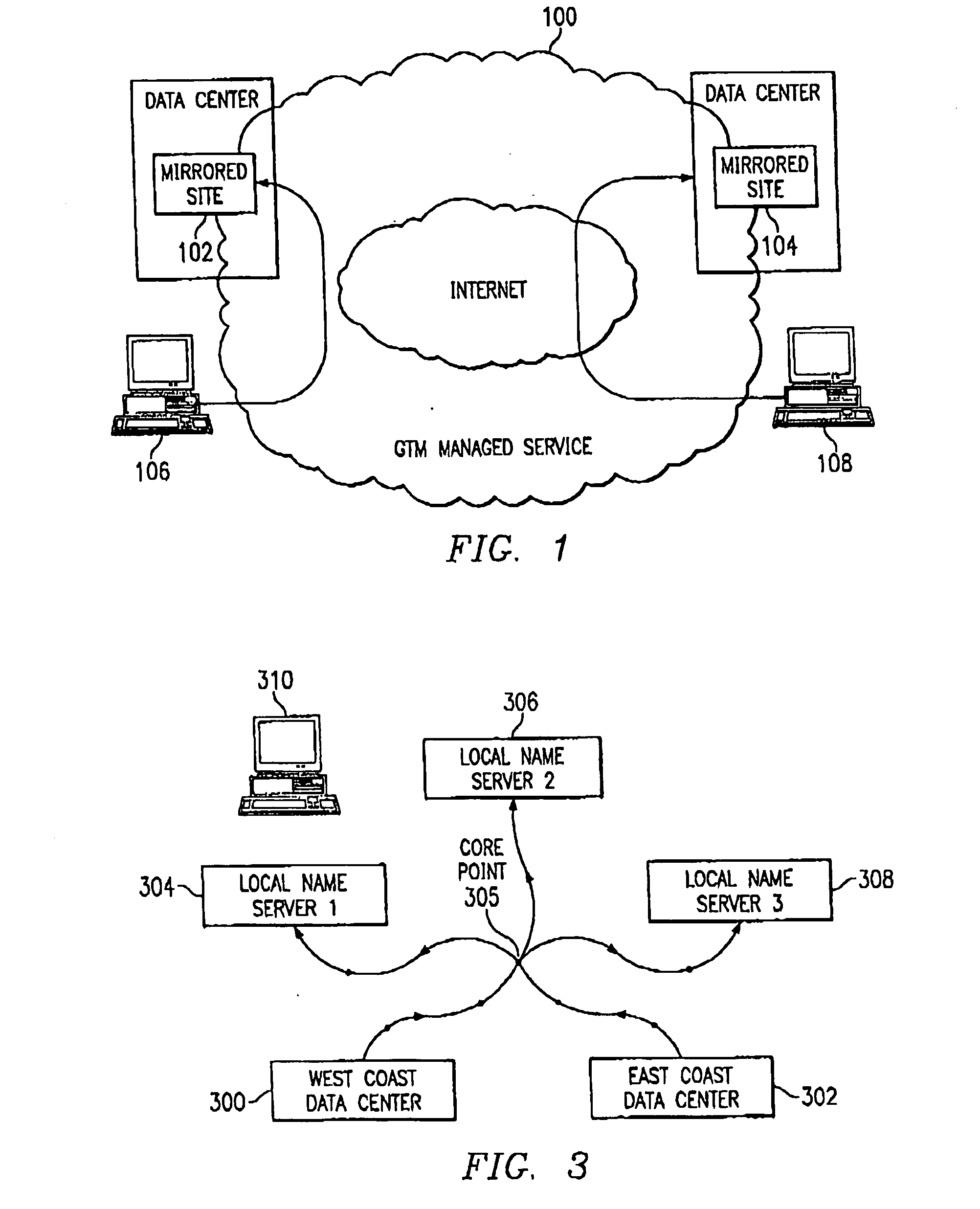
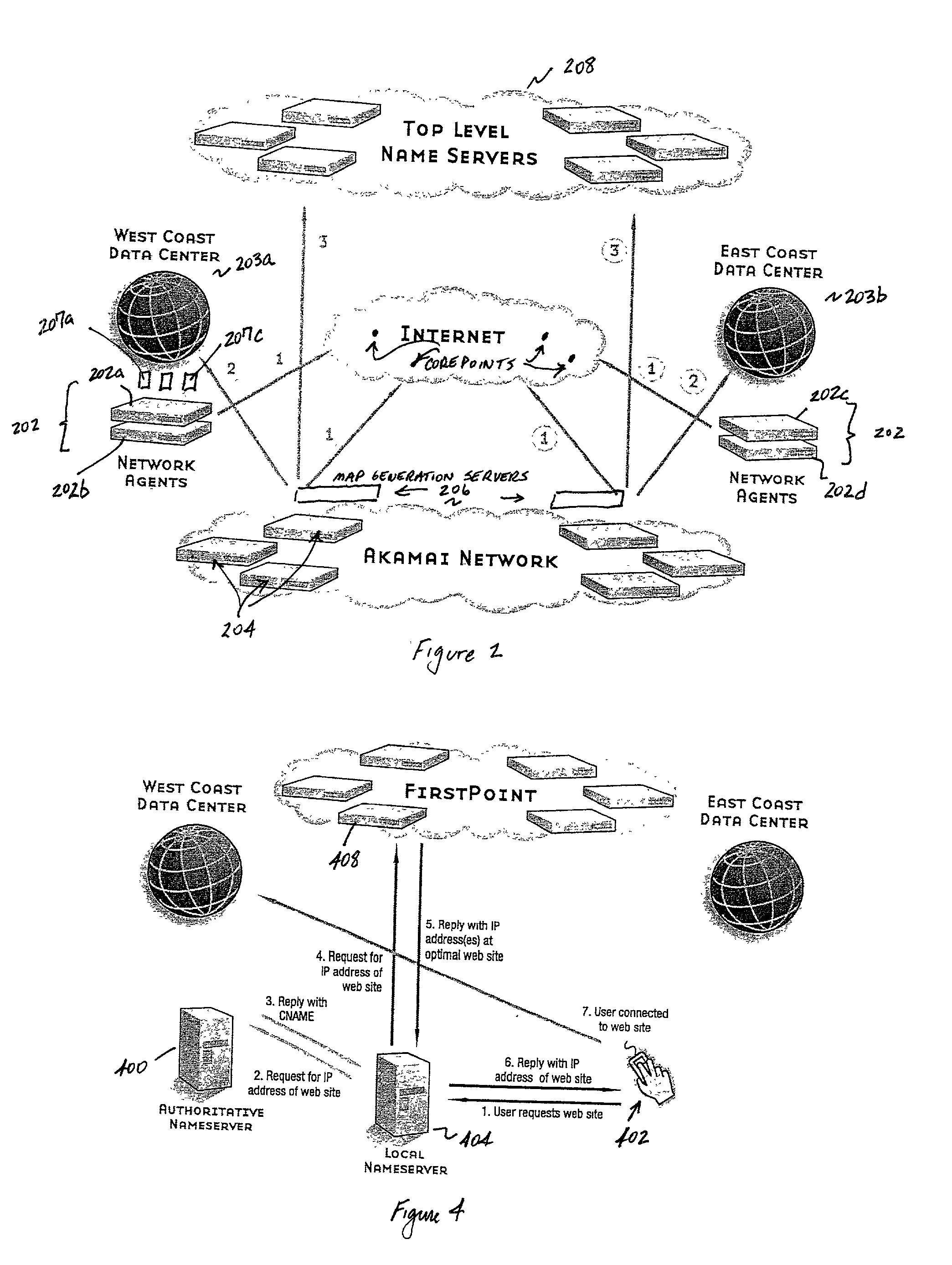
InactiveUS7111061B2Reduce dimensionalityOvercome problemsMultiple digital computer combinationsData switching networksDomain nameTraffic capacity
The invention is an intelligent traffic redirection system that does global load balancing. It can be used in any situation where an end-user requires access to a replicated resource. The method directs end-users to the appropriate replica so that the route to the replica is good from a network standpoint and the replica is not overloaded. The technique preferably uses a Domain Name Service (DNS) to provide IP addresses for the appropriate replica. The most common use is to direct traffic to a mirrored web site.
Owner:AKAMAI TECH INC
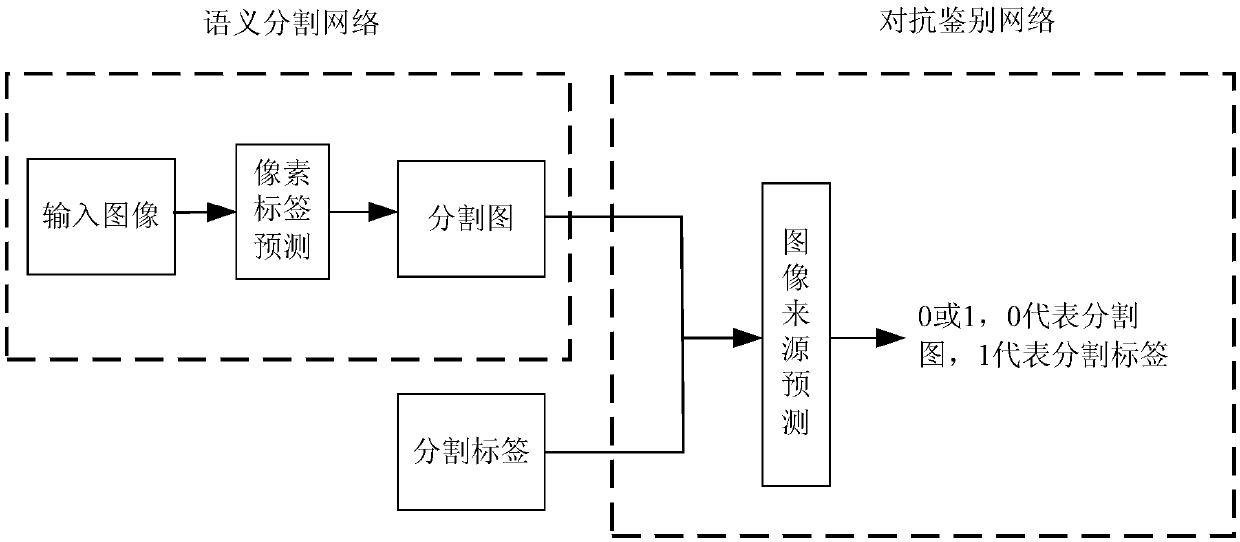
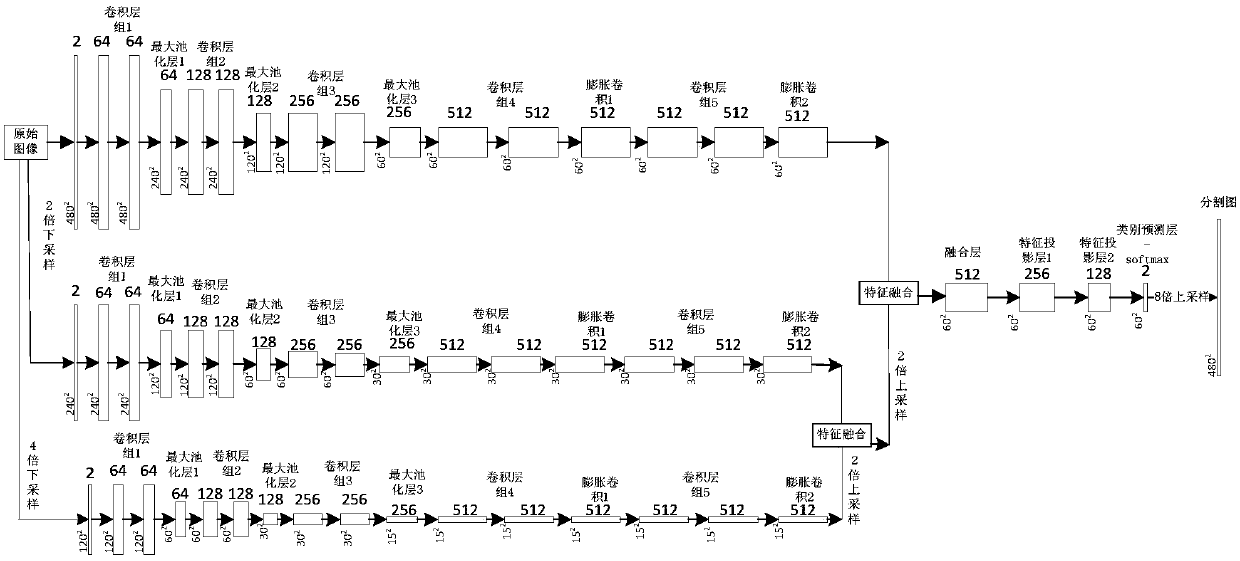
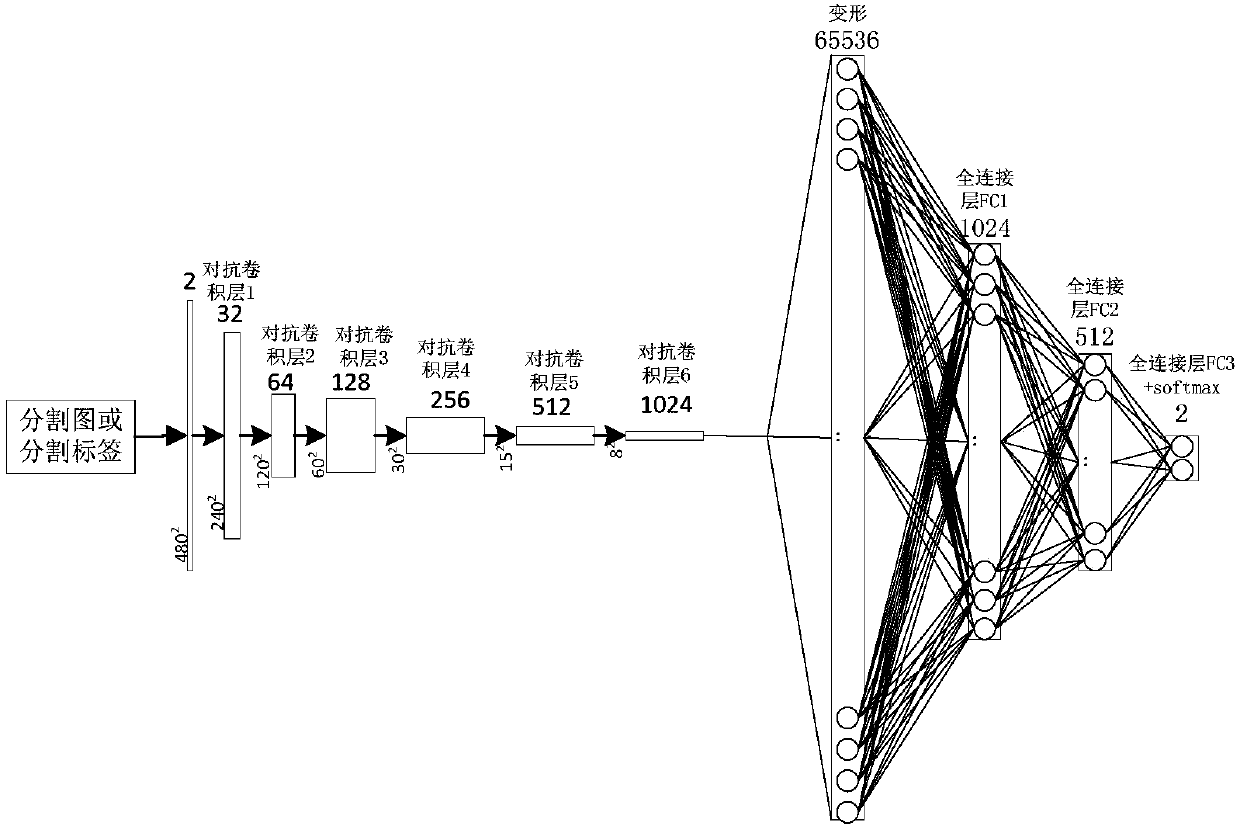
Multi-scale feature fusion ultrasonic image semantic segmentation method based on adversarial learning
ActiveCN108268870AImprove forecast accuracyFew parametersNeural architecturesRecognition of medical/anatomical patternsPattern recognitionAutomatic segmentation
The invention provides a multi-scale feature fusion ultrasonic image semantic segmentation method based on adversarial learning, and the method comprises the following steps: building a multi-scale feature fusion semantic segmentation network model, building an adversarial discrimination network model, carrying out the adversarial training and model parameter learning, and carrying out the automatic segmentation of a breast lesion. The method provided by the invention achieves the prediction of a pixel class through the multi-scale features of input images with different resolutions, improvesthe pixel class label prediction accuracy, employs expanding convolution for replacing partial pooling so as to improve the resolution of a segmented image, enables the segmented image generated by asegmentation network guided by an adversarial discrimination network not to be distinguished from a segmentation label, guarantees the good appearance and spatial continuity of the segmented image, and obtains a more precise high-resolution ultrasonic breast lesion segmented image.
Owner:CHONGQING NORMAL UNIVERSITY
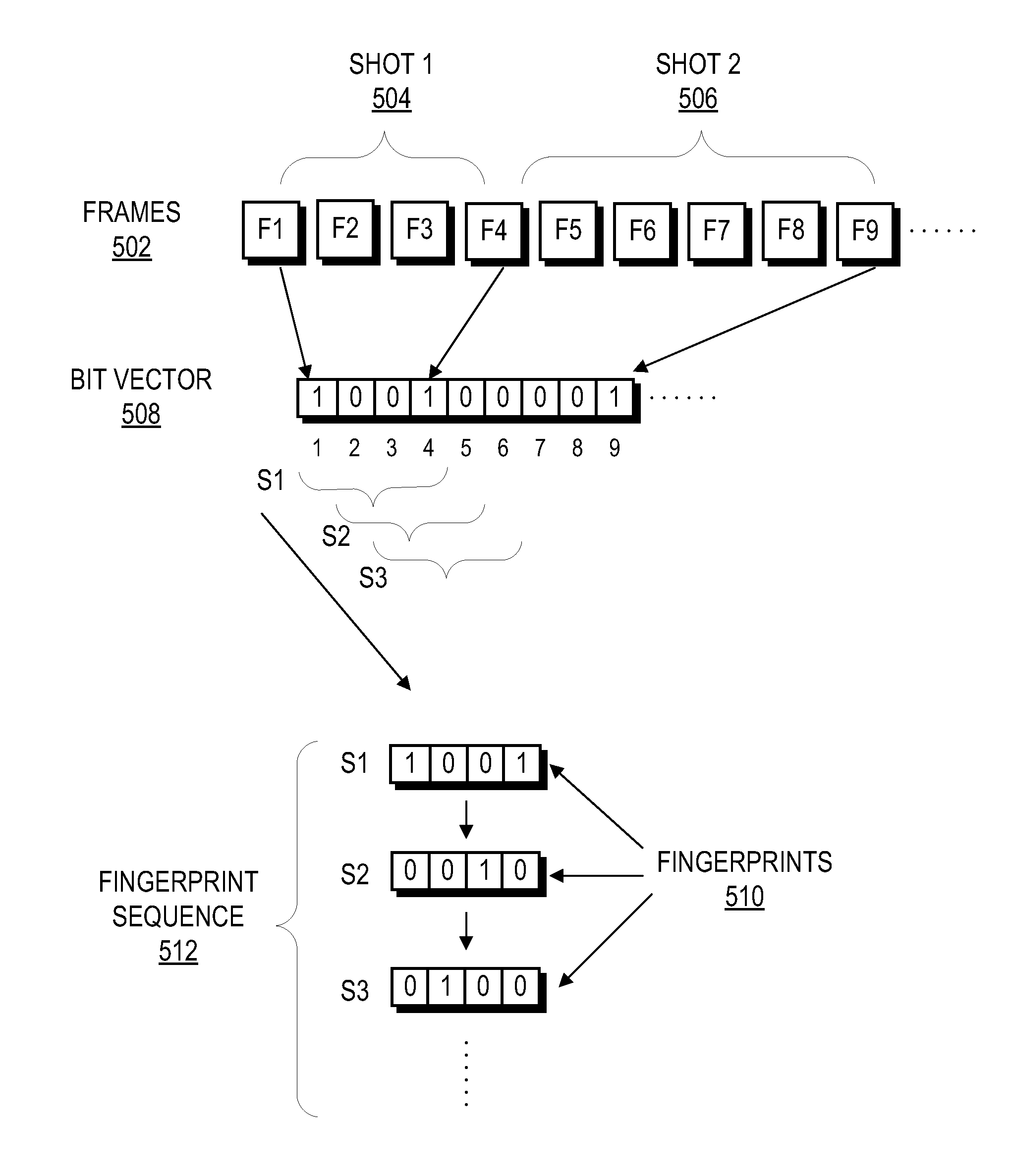
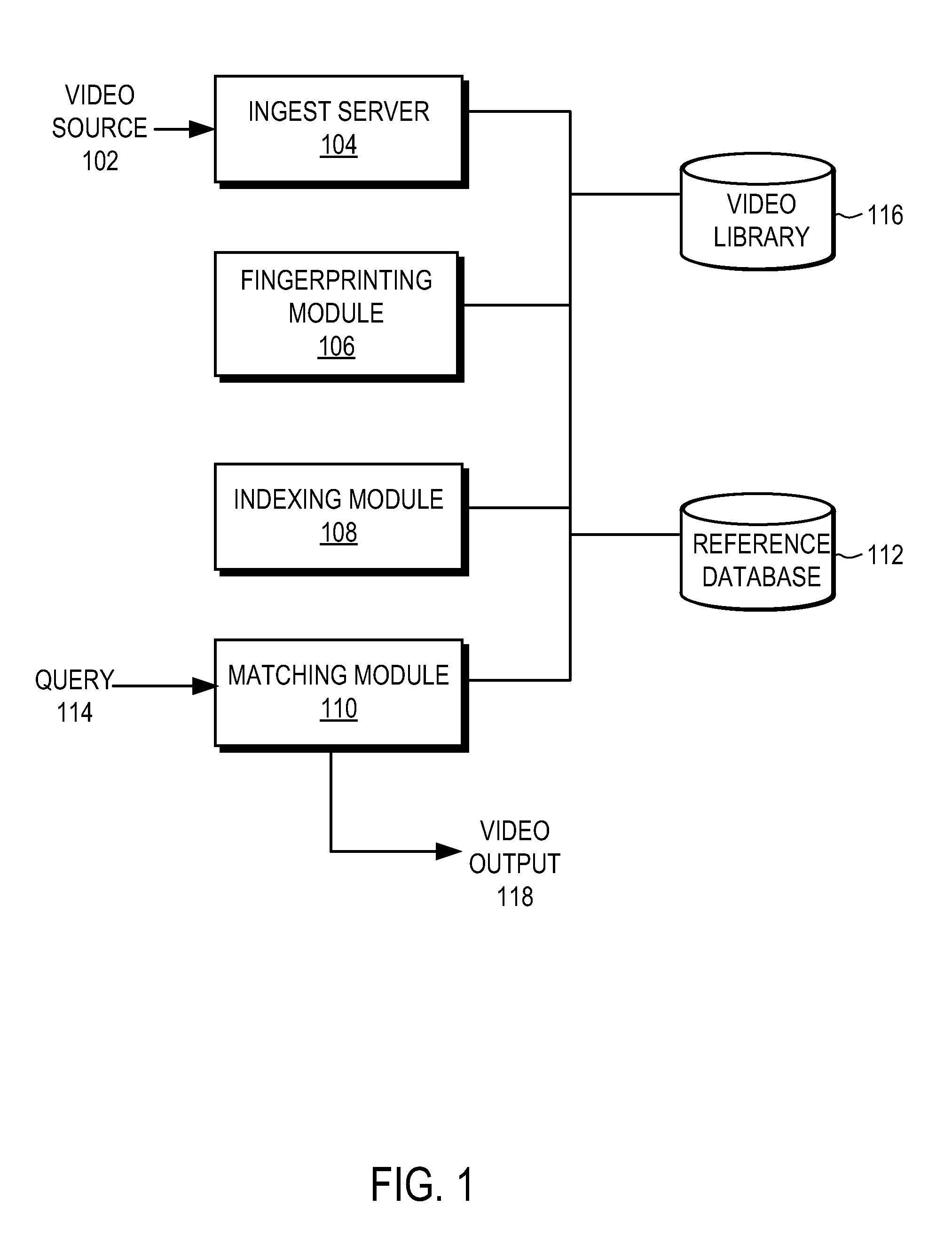
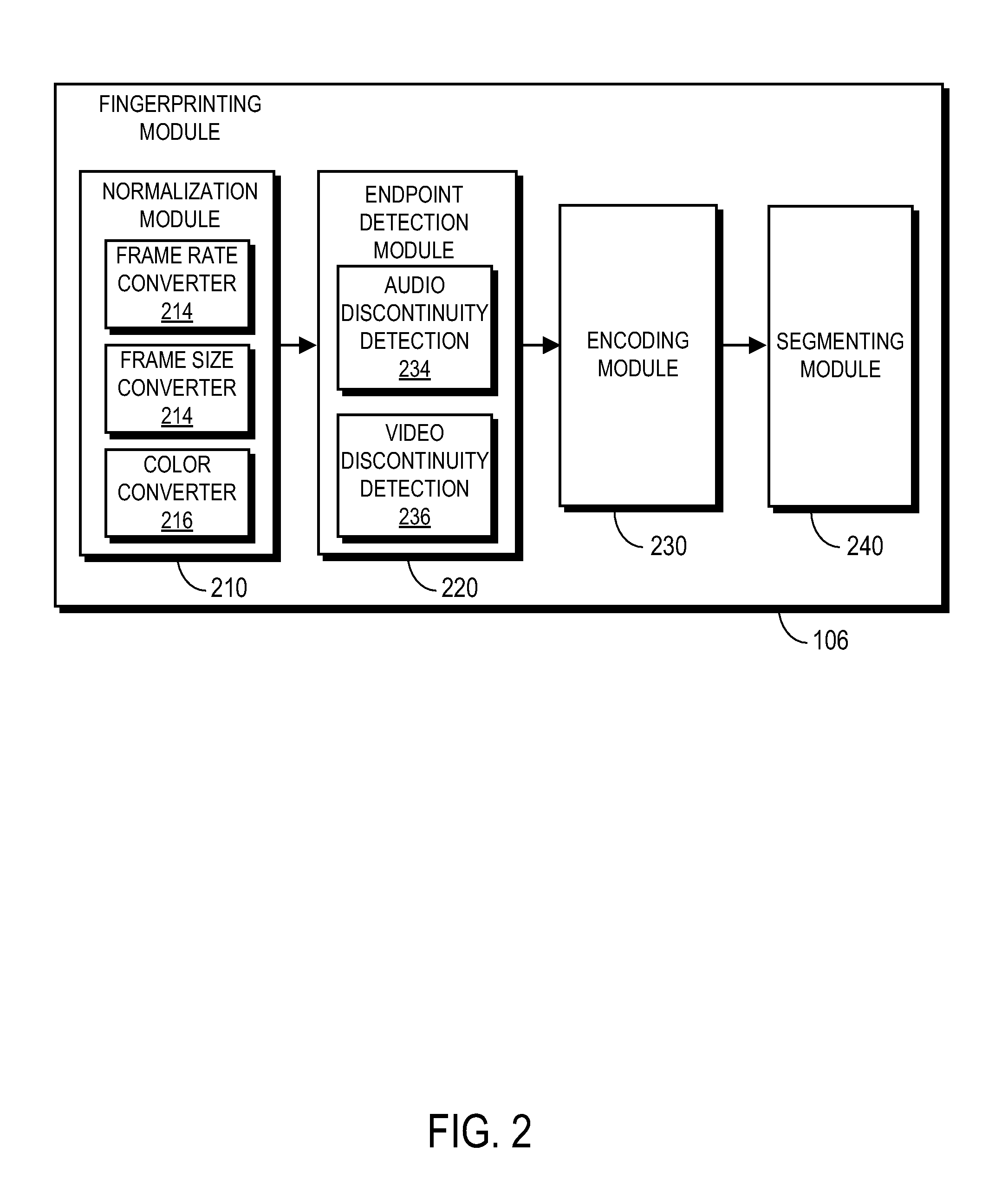
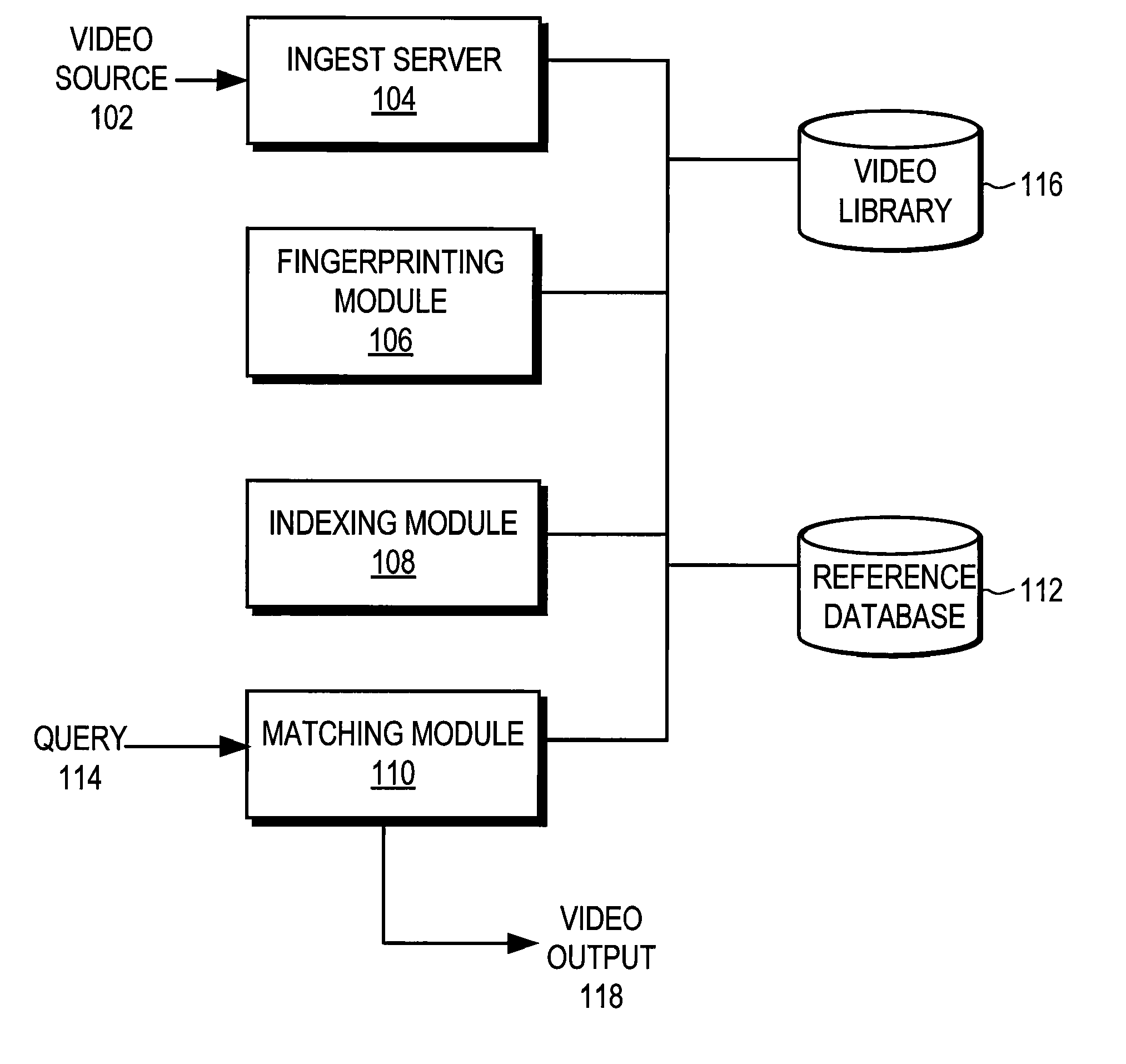
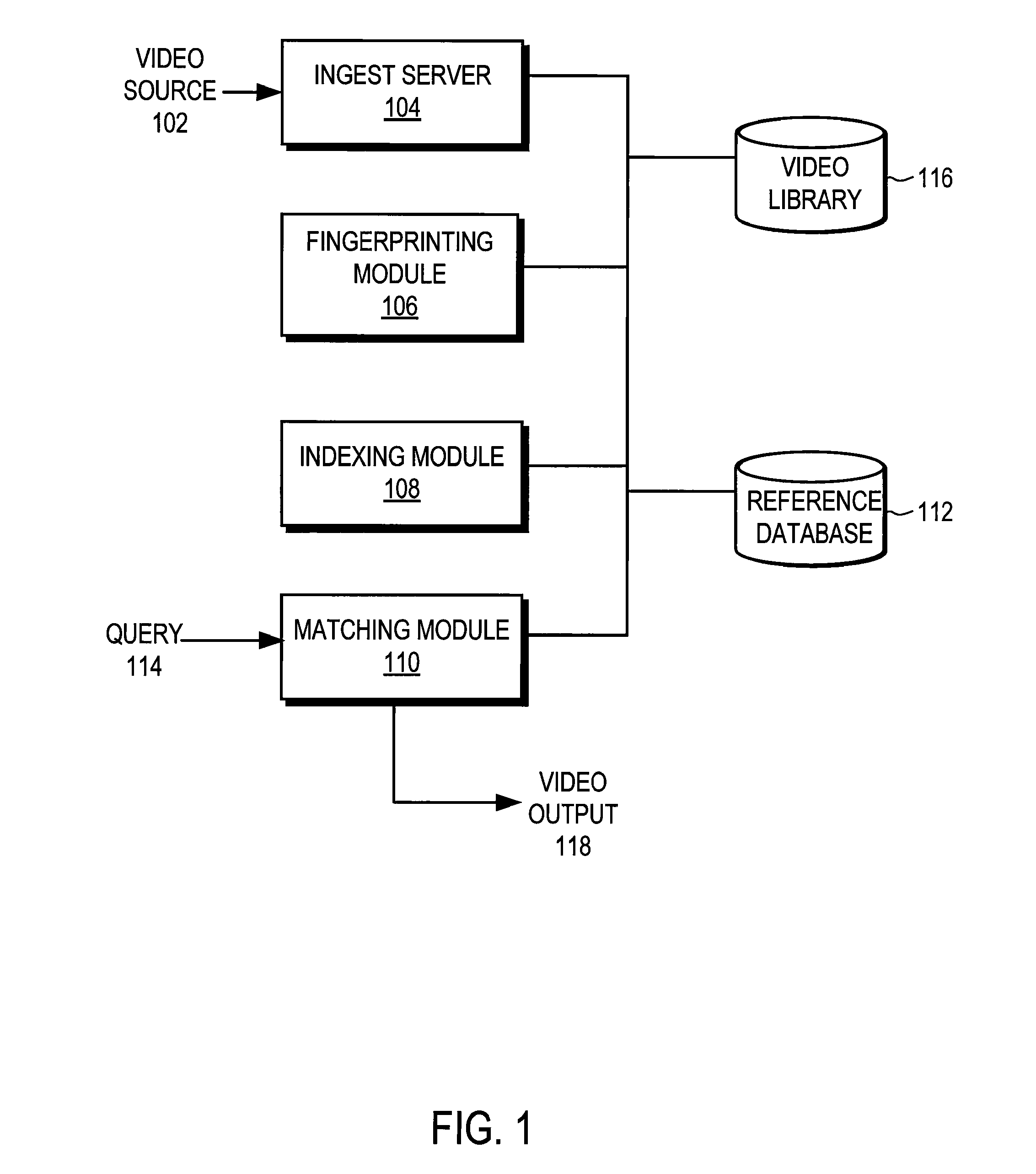
Endpoint based video fingerprinting
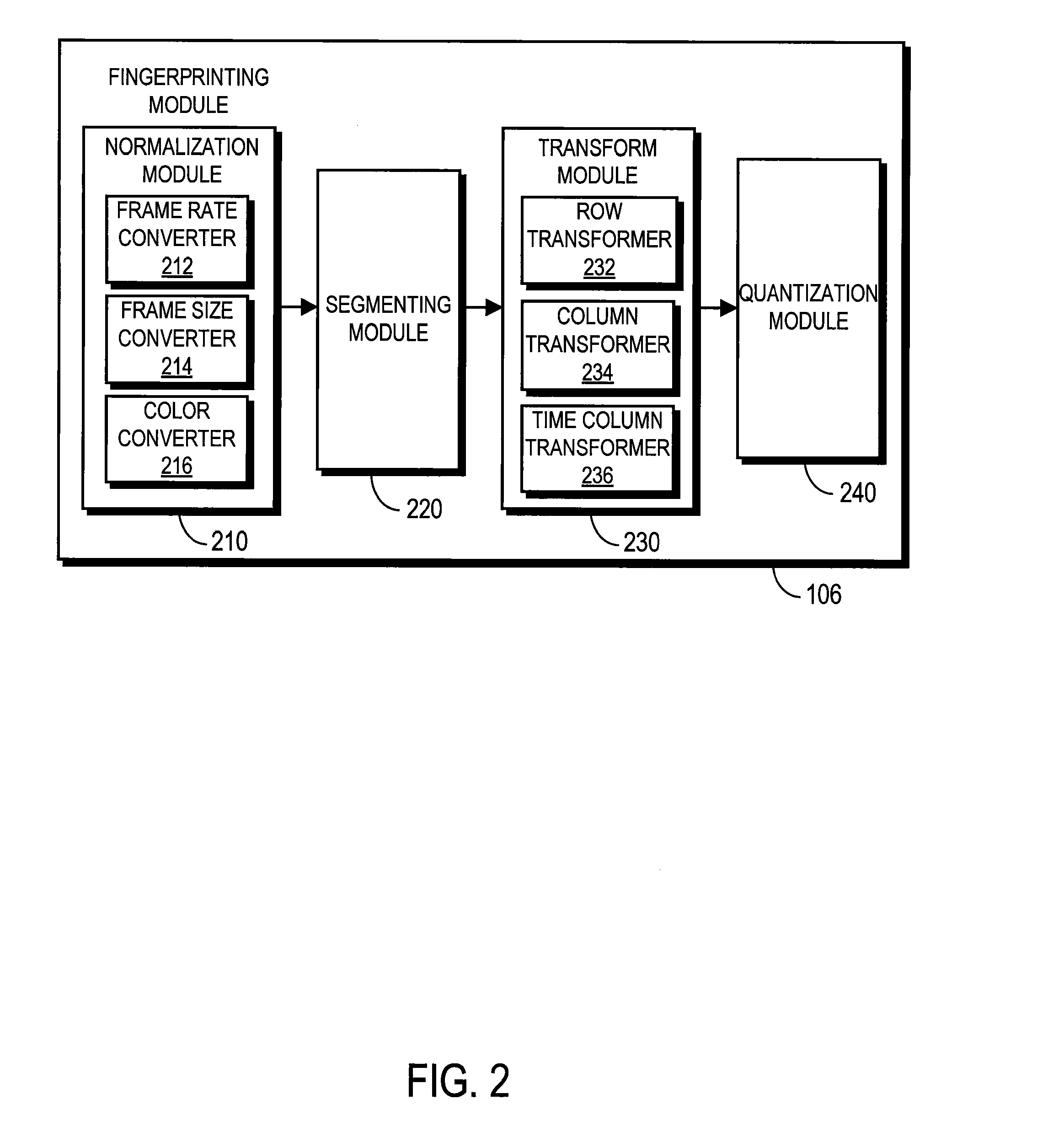
ActiveUS8611422B1Quickly and efficiently identifyImprove the display effectPicture reproducers using cathode ray tubesPicture reproducers with optical-mechanical scanningFrame sequenceComputer graphics (images)
A method and system generates and compares fingerprints for videos in a video library. The video fingerprints provide a compact representation of the temporal locations of discontinuities in the video that can be used to quickly and efficiently identify video content. Discontinuities can be, for example, shot boundaries in the video frame sequence or silent points in the audio stream. Because the fingerprints are based on structural discontinuity characteristics rather than exact bit sequences, visual content of videos can be effectively compared even when there are small differences between the videos in compression factors, source resolutions, start and stop times, frame rates, and so on. Comparison of video fingerprints can be used, for example, to search for and remove copyright protected videos from a video library. Furthermore, duplicate videos can be detected and discarded in order to preserve storage space.
Owner:GOOGLE LLC
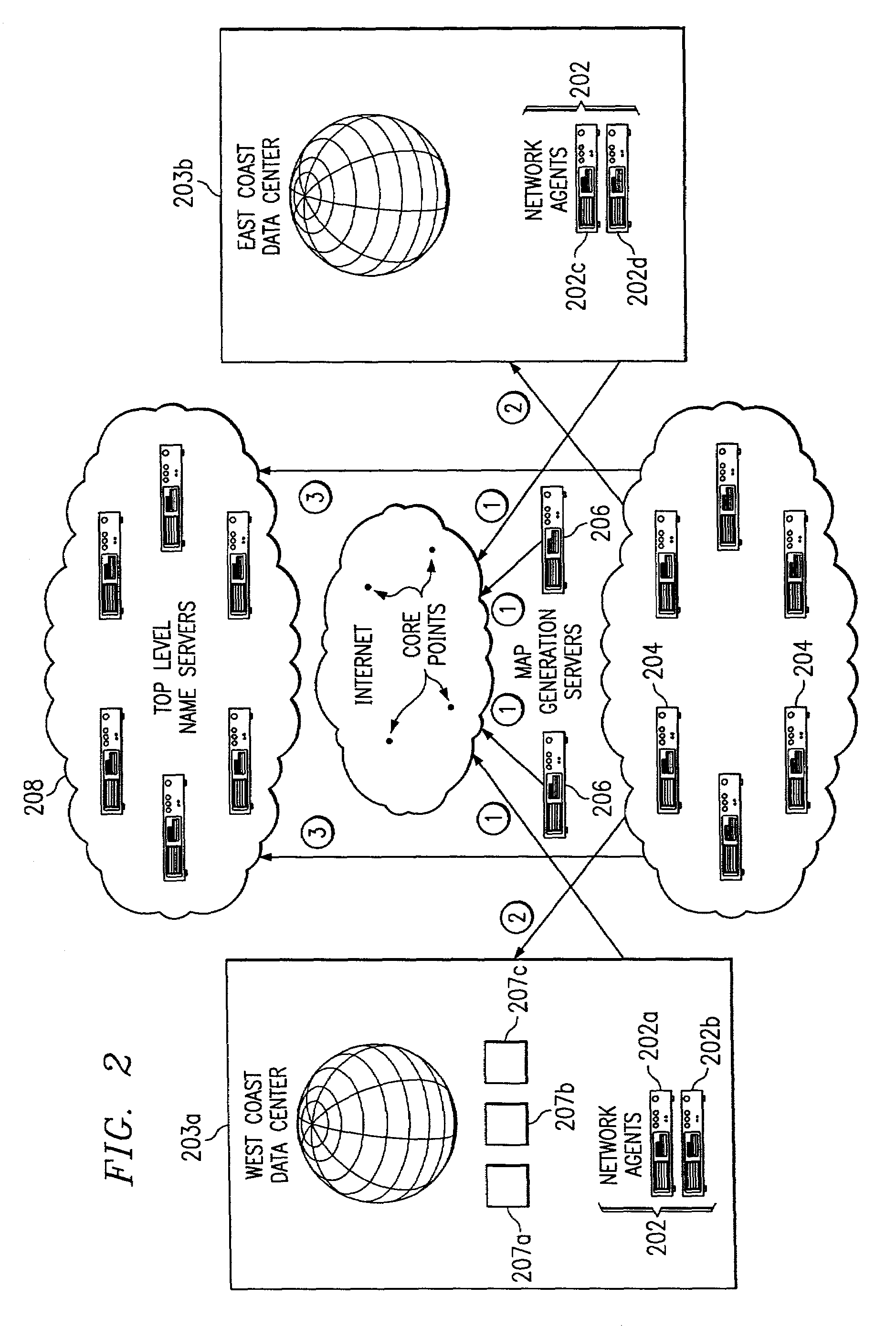
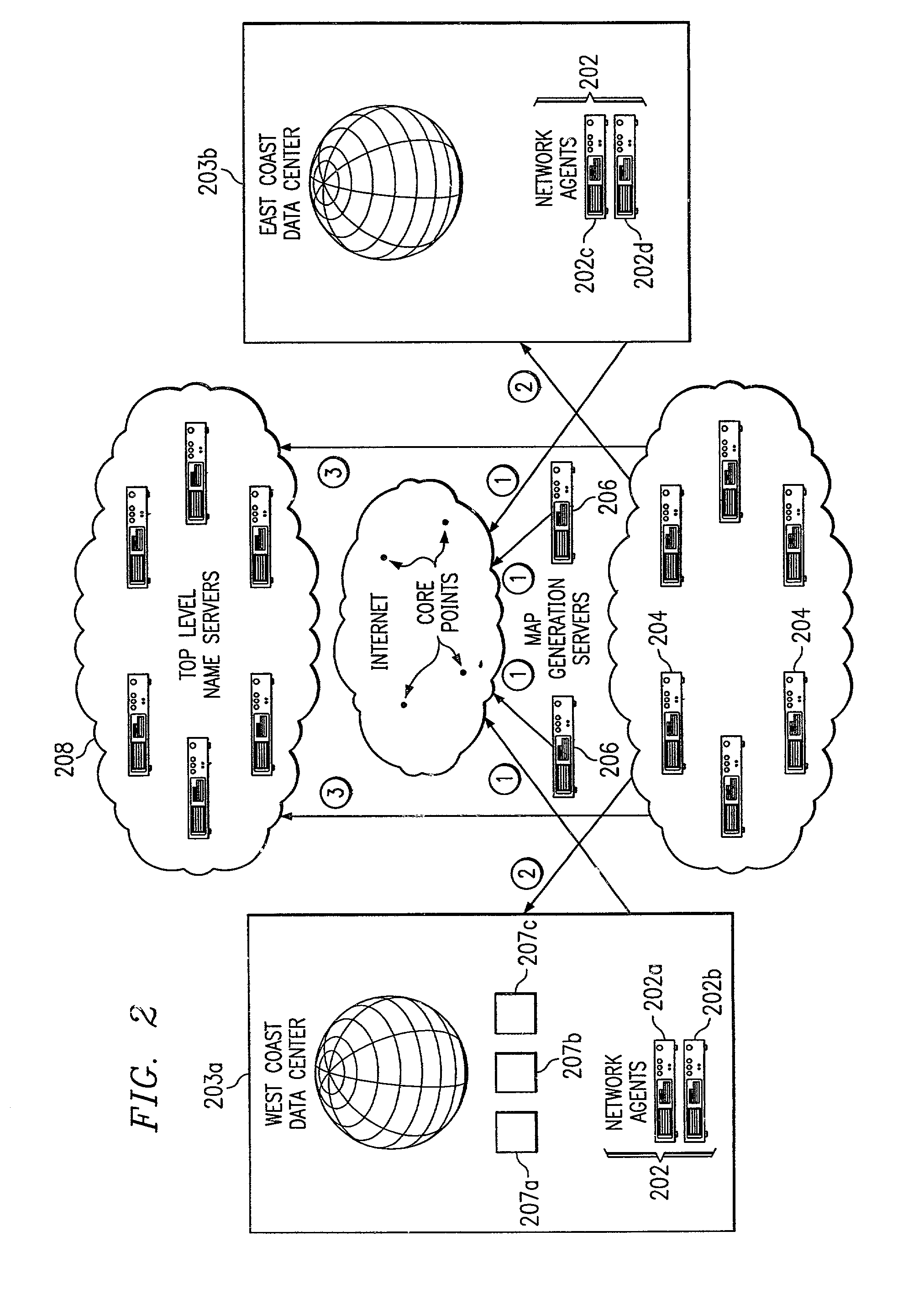
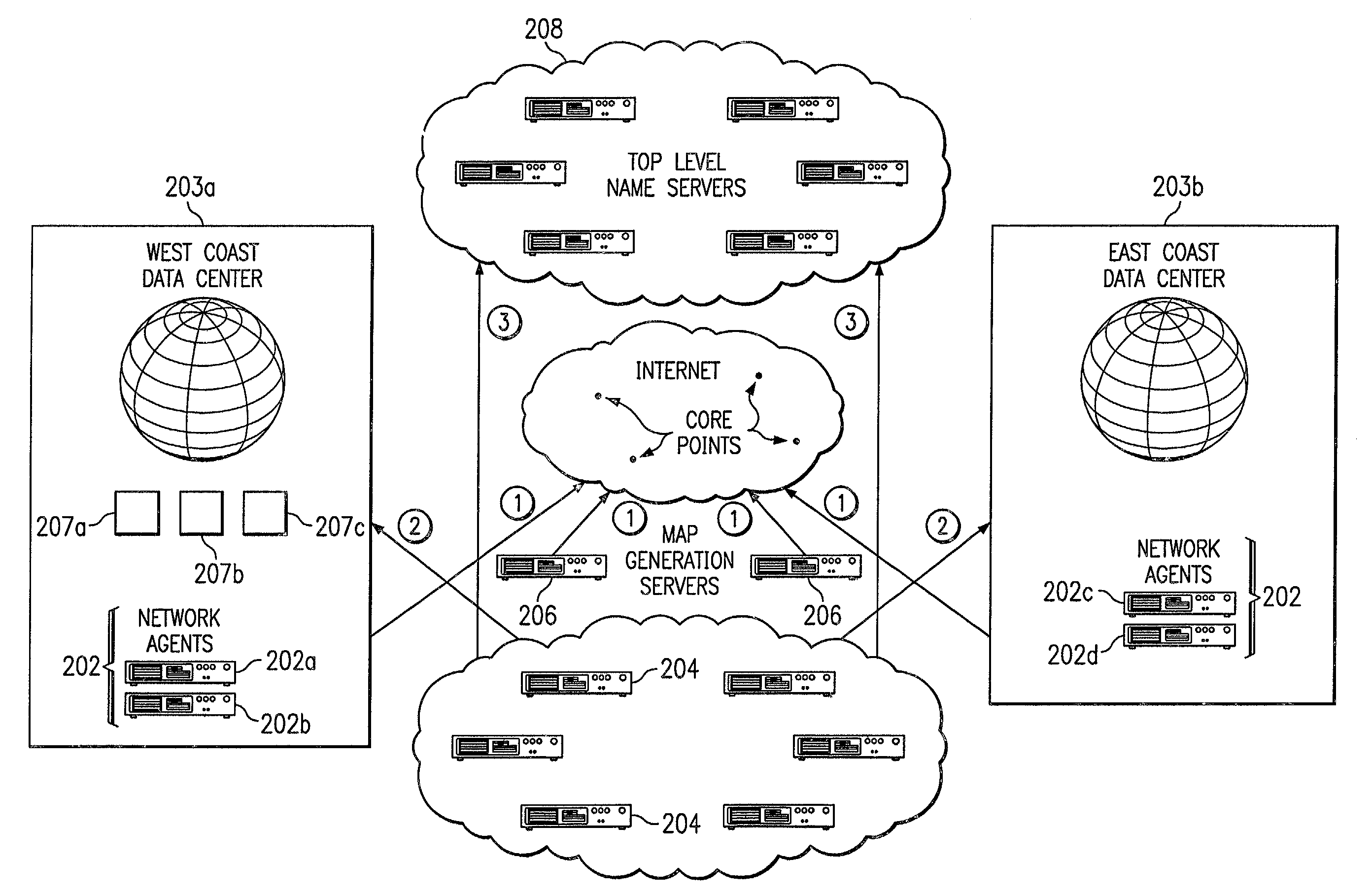
Method for extending a network map
ActiveUS7028083B2Reduce dimensionalityOvercome problemsMultiple digital computer combinationsData switching networksSystem usageIp address
An intelligent traffic redirection system performs global load balancing. The system uses a network map that is generated in part by extending a “sparse” IP address data map. In particular, a method of extending an IP address block map begins by defining a set of one or more upper bound block(s). These upper bound blocks are then used to partition a space of IP addresses into subsets or “territories”, wherein each territory represents a largest set of IP addresses to which a piece of mapping data may be extended. The “piece” of mapping data typically consists of a host (usually a “name server” identified by the core point discovery process) IP address and some data about that host, namely, a “nearest” data center or a flag indicating that either “no data” exists for that host or that the system is “indifferent” as to which of a set of mirrored data centers the host should be mapped. A unification algorithm partitions the territory of each upper bound block into the largest possible sub-blocks in which a given unanimity criterion is satisfied and extends the mapping data in each such sub-block to all of the territory of that sub-block.
Owner:AKAMAI TECH INC
Three-dimensional wavelet based video fingerprinting
ActiveUS8094872B1Quickly and efficiently identifyImprove the display effectUser identity/authority verificationCharacter and pattern recognitionComputer graphics (images)Stop time
A method and system generates and compares fingerprints for videos in a video library. The video fingerprints provide a compact representation of the spatial and sequential characteristics of the video that can be used to quickly and efficiently identify video content. Because the fingerprints are based on spatial and sequential characteristics rather than exact bit sequences, visual content of videos can be effectively compared even when there are small differences between the videos in compression factors, source resolutions, start and stop times, frame rates, and so on. Comparison of video fingerprints can be used, for example, to search for and remove copyright protected videos from a video library. Further, duplicate videos can be detected and discarded in order to preserve storage space.
Owner:GOOGLE LLC
Global load balancing across mirrored data centers
InactiveUS20080071925A1Reduce dimensionalityOvercome problemsDigital computer detailsTransmissionTraffic capacityWeb site
The invention is an intelligent traffic redirection system that does global load balancing. It can be used in any situation where an end-user requires access to a replicated resource. The method directs end-users to the appropriate replica so that the route to the replica is good from a network standpoint and the replica is not overloaded. The technique preferably uses a Domain Name Service (DNS) to provide IP addresses for the appropriate replica. The most common use is to direct traffic to a mirrored web site.
Owner:AKAMAI TECH INC
Robust interest point detector and descriptor
ActiveUS20090238460A1Fast computerNot sacrificing performanceImage analysisCharacter and pattern recognitionPattern recognitionInterest point detection
Methods and apparatus for operating on images are described, in particular methods and apparatus for interest point detection and / or description working under different scales and with different rotations, e.g. for scale-invariant and rotation-invariant interest point detection and / or description. The present invention can provide improved or alternative apparatus and methods for matching interest points either in the same image or in a different image. The present invention can provide alternative or improved software for implementing any of the methods of the invention. The present invention can provide alternative or improved data structures created by multiple filtering operations to generate a plurality of filtered images as well as data structures for storing the filtered images themselves, e.g. as stored in memory or transmitted through a network. The present invention can provide alternative or improved data structures including descriptors of interest points in images, e.g. as stored in memory or transmitted through a network as well as datastructures associating such descriptors with an original copy of the image or an image derived therefrom, e.g. a thumbnail image.
Owner:K U LEUVEN RES & DEV +2
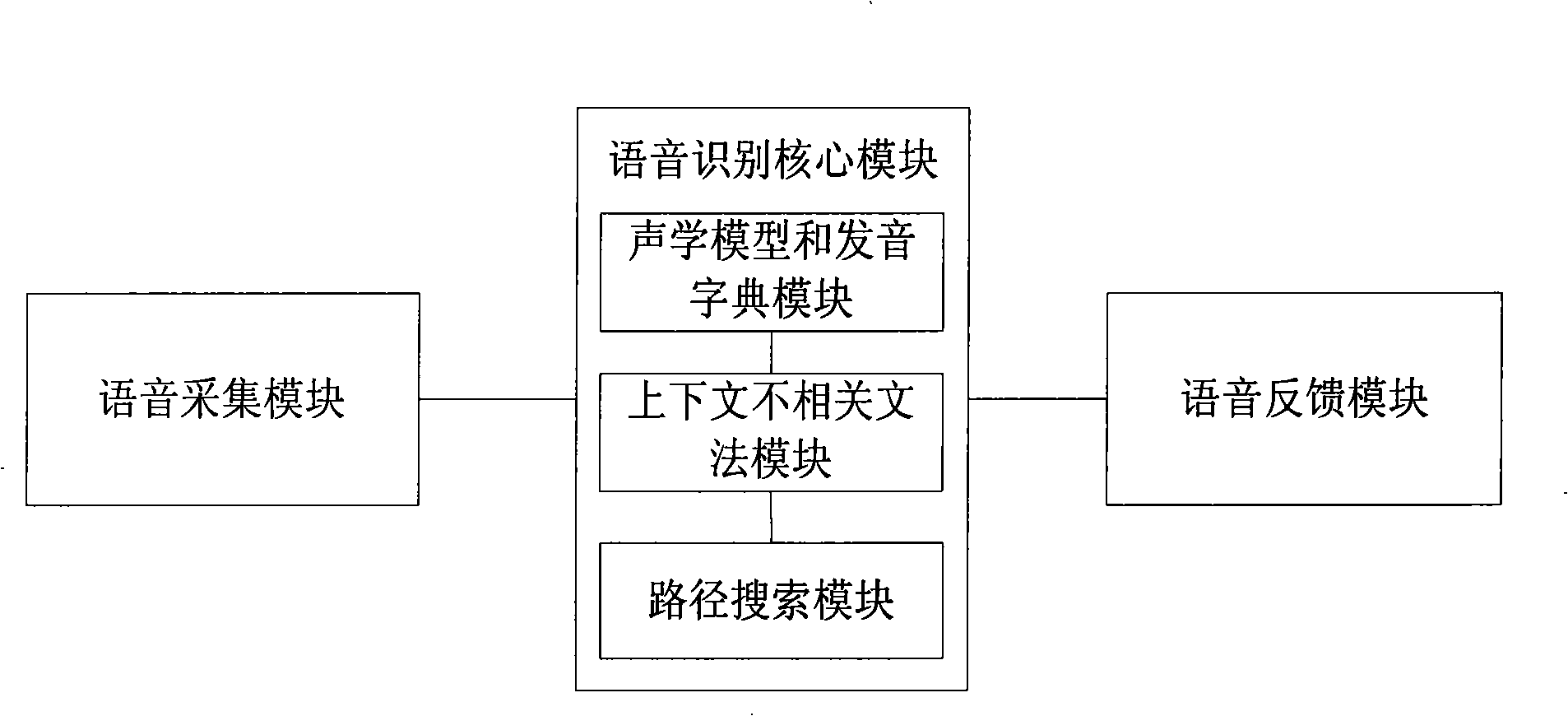
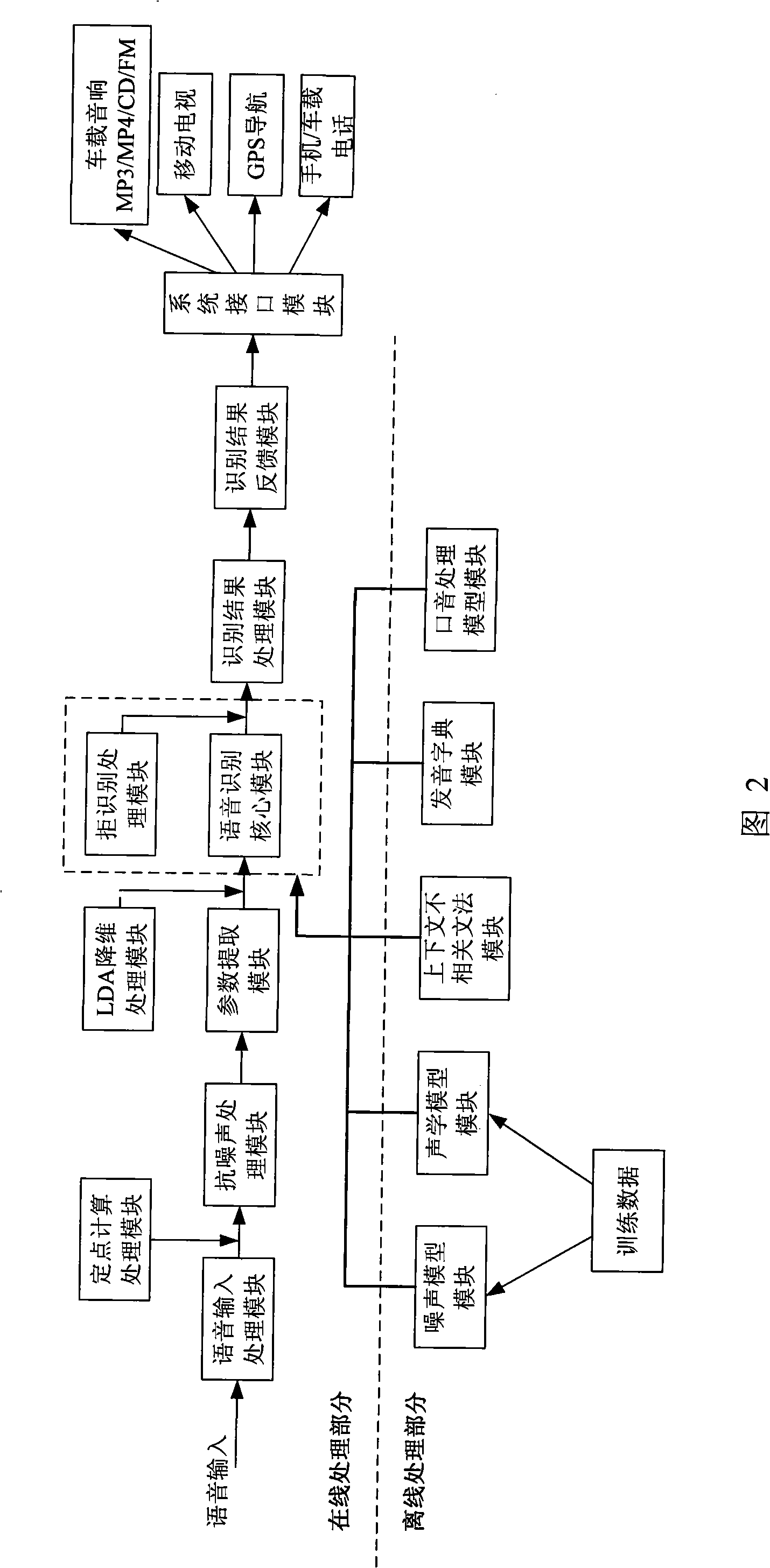
Interactive system for vehicle-mounted voice
InactiveCN101281745AReduce dimensionalityEasy to controlNavigation instrumentsSpeech recognitionDriving safetySpeech identification
The present invention discloses an onboard speech interactive system, which comprises a speech acquisition module, a core speech recognition module, and a speech feedback module, wherein, the core speech recognition module comprises an acoustic model and pronunciation dictionary module, a context irrelevant syntax module, and a path searching module; the acoustic model and pronunciation dictionary module is designed to establish a mapping table related to accent variation characteristic with a statistical algorithm; the context irrelevant syntax module is designed to construct a syntax and rule structure for the natural continuous speech to be recognized; the path searching module is designed to carry out approximate simplification for the observed probability calculation part with the highest amount of calculation. The present invention implements control and operation of the onboard information system by means of natural speech (including command phrases, conjunctions, and continuous speech that follows certain rules), and thereby can enhance driving safety, and implements intelligent man-machine interaction in the onboard information system, independent of driving safety and dynamic performance of the automobile.
Owner:SHENZHEN RAISOUND TECH +1
Global load balancing across mirrored data centers
InactiveUS20020129134A1Small sizeReduce dimensionalityMultiple digital computer combinationsData switching networksWeb siteDomain name
The invention is an intelligent traffic redirection system that does global load balancing. It can be used in any situation where an end-user requires access to a replicated resource. The method directs end-users to the appropriate replica so that the route to the replica is good from a network standpoint and the replica is not overloaded. The technique preferably uses a Domain Name Service (DNS) to provide IP addresses for the appropriate replica. The most common use is to direct traffic to a mirrored web site.
Owner:AKAMAI TECH INC
Face detection and recognition method based on skin color segmentation and template matching
InactiveCN103632132AImprove accuracyReduce dimensionalityCharacter and pattern recognitionTemplate matchingFace detection
The invention discloses a face detection and recognition method based on skin color segmentation and template matching. A face is segmented with the use of a face skin mixing Gauss model according to the clustering characteristics of face skin color in an YCbCr color space and a region of which the color is close to face skin color is separated from an image so as to achieve the purpose of quickly detecting the outer face of a face. A light compensation technology is used to overcome the influence of brightness on face detection and recognition. Adaptive template matching is used to overcome the influence of a skin-color-alike background on face detection and recognition. A secondary matching algorithm is adopted to reduce the amount of computation during the matching process, and singular value features of a face image are extracted to recognize a face and achieve the purpose of reducing the number of dimensions of a characteristic value matrix in the process of face feature extraction. The face detection and recognition method can quickly detect a face, improves the accuracy of face detection and recognition, is strong in practicability and has strong popularization and application values.
Owner:GUANGXI UNIVERSITY OF TECHNOLOGY
Method and appartus for controlling ultrasound system display
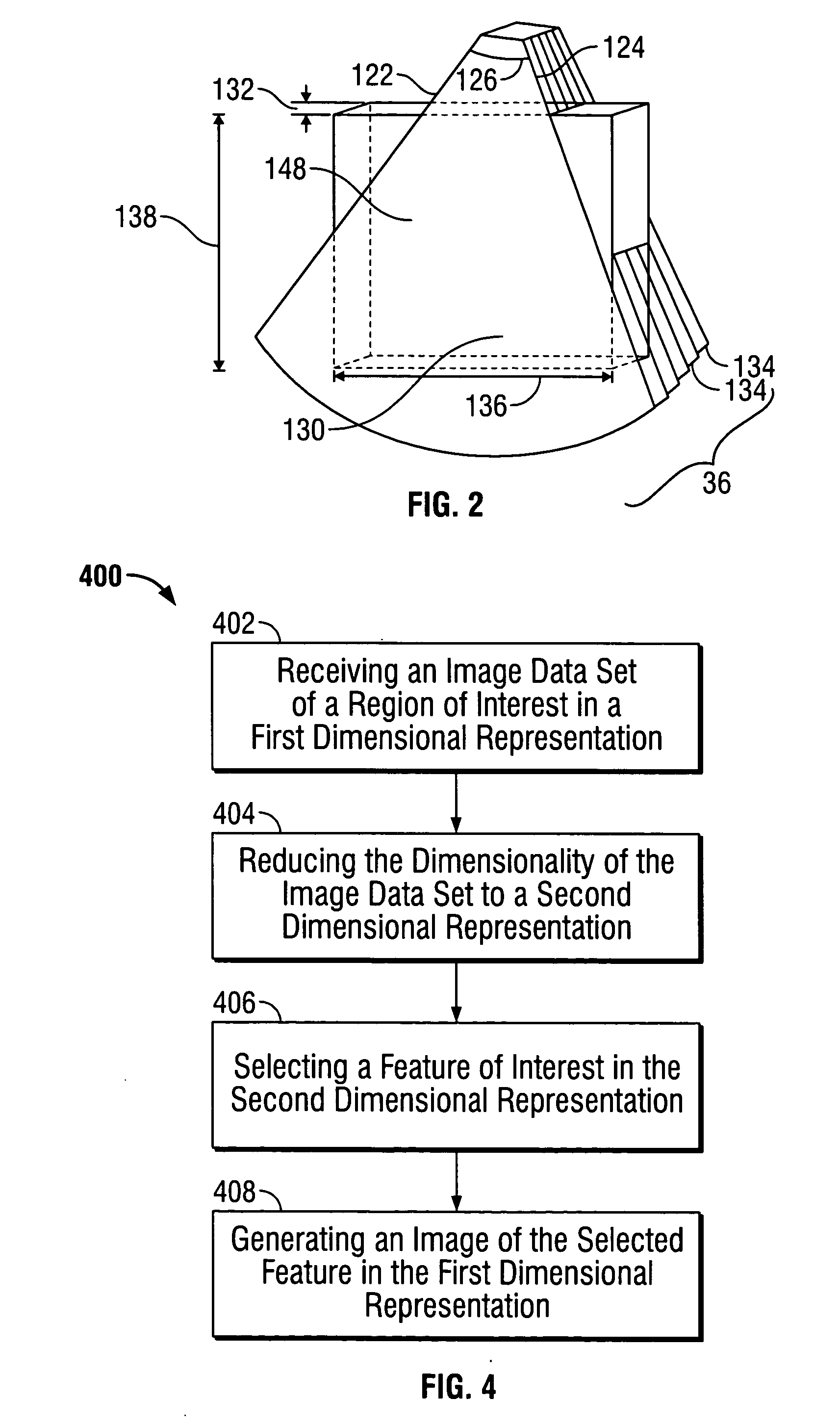
ActiveUS20060020202A1Reduce dimensionalityUltrasonic/sonic/infrasonic diagnosticsCharacter and pattern recognitionMedical imagingRegion of interest
A method for operating a medical imaging system is provided. The method includes receiving an image data set of a region of interest in a first dimensional representation, reducing the dimensionality of the image data set to a second dimensional representation, selecting a feature of interest in the second dimensional representation, and generating an image of the selected feature in the first dimensional representation.
Owner:GENERAL ELECTRIC CO
User configurable multivariate time series reduction tool control method
InactiveUS6442445B1Reduce dimensionalityProgramme controlSemiconductor/solid-state device testing/measurementIntermediate variableTime series
Owner:GLOBALFOUNDRIES INC
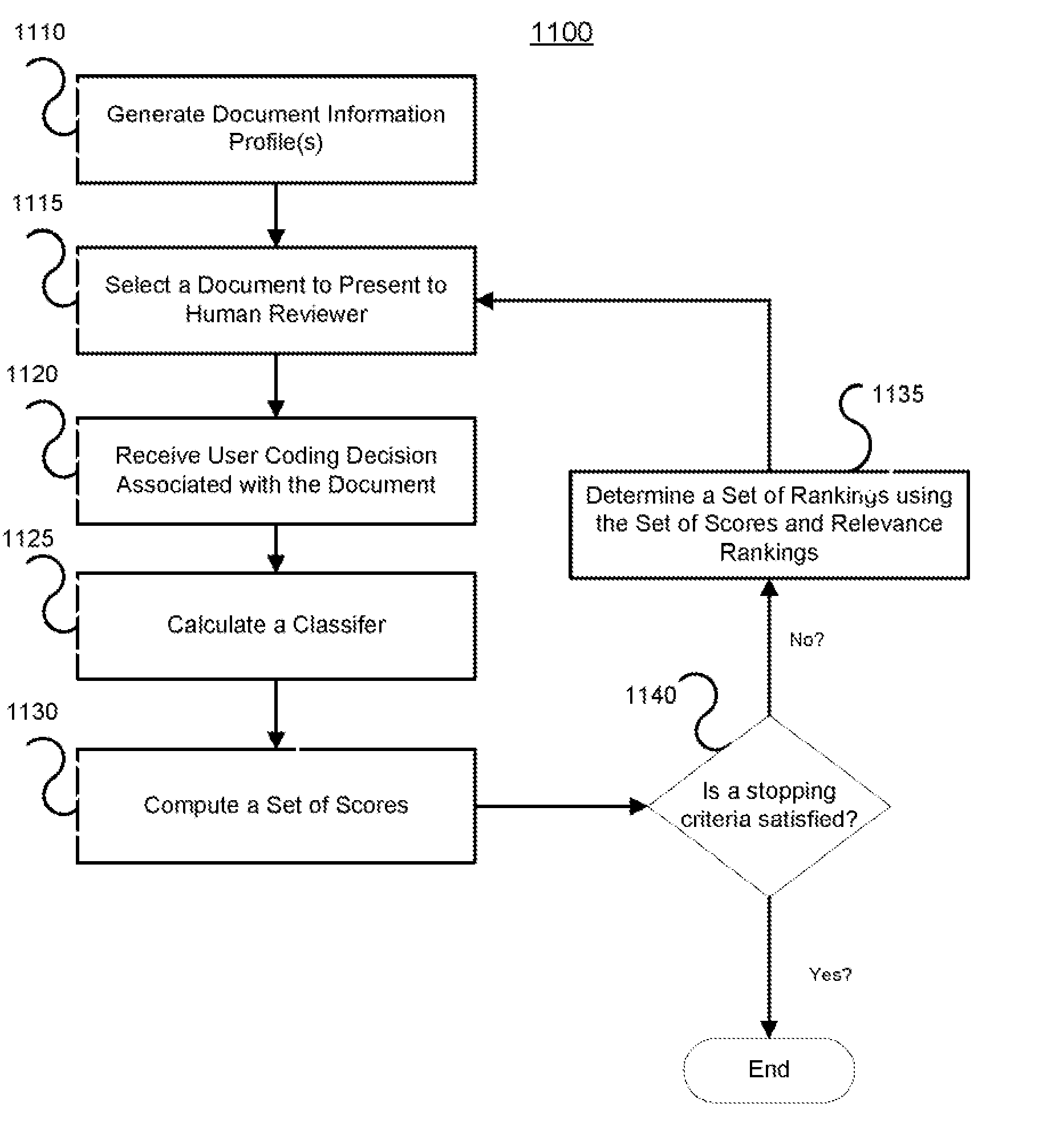
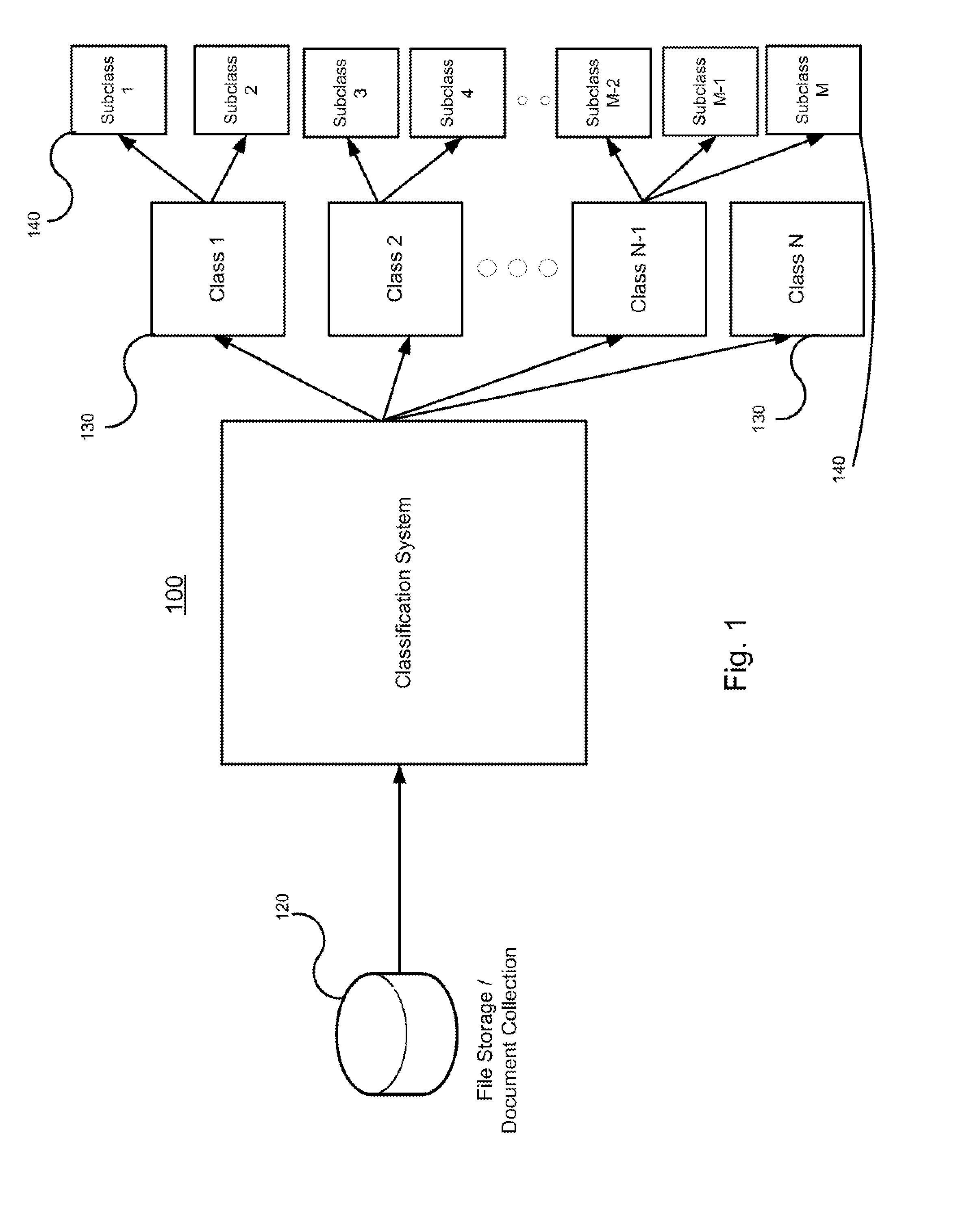
Systems and methods for classifying electronic information using advanced active learning techniques
ActiveUS8620842B1Easy to transportReduce complexityDigital computer detailsRelational databasesElectronic informationData mining
Systems and methods for classifying electronic information or documents into a number of classes and subclasses are provided through an active learning algorithm. In certain embodiments, the active learning algorithm forks a number of classification paths corresponding to predicted user coding decisions for a selected document. The active learning algorithm determines an order in which the documents of the collection may be processed and scored by the forked classification paths. Such document classification systems are easily scalable for large document collections, require less manpower and can be employed on a single computer, thus requiring fewer resources. Furthermore, the classification systems and methods described can be used for any pattern recognition or classification effort in a wide variety of fields.
Owner:CORMACK GORDON VILLY
Method for recognizing road traffic sign for unmanned vehicle
InactiveCN102542260AFast extractionFast matchingDetection of traffic movementCharacter and pattern recognitionClassification methodsNear neighbor
The invention discloses a method for recognizing a road traffic sign for an unmanned vehicle, comprising the following steps of: (1) changing the RGB (Red, Green and Blue) pixel value of an image to strengthen a traffic sign feature color region, and cutting the image by using a threshold; (2) carrying out edge detection and connection on a gray level image to reconstruct an interested region; (3) extracting a labeled graph of the interested region as a shape feature of the interested region, classifying the shape of the region by using a nearest neighbor classification method, and removing a non-traffic sign region; and (4) graying and normalizing the image of the interested region of the traffic sign, carrying out dual-tree complex wavelet transform on the image to form a feature vector of the image, reducing the dimension of the feature vector by using a two-dimension independent component analysis method, and sending the feature vector into a support vector machine of a radial basis function to judge the type of the traffic sign of the interested region. By using the method, various types of traffic signs in a running environment of the unmanned vehicle can be stably and efficiently detected and recognized.
Owner:CENT SOUTH UNIV
Methods and systems for identifying and localizing objects based on features of the objects that are mapped to a vector
InactiveUS20080082468A1Improve accuracyEasy to detectDigital computer detailsCharacter and pattern recognitionPattern recognitionObject based
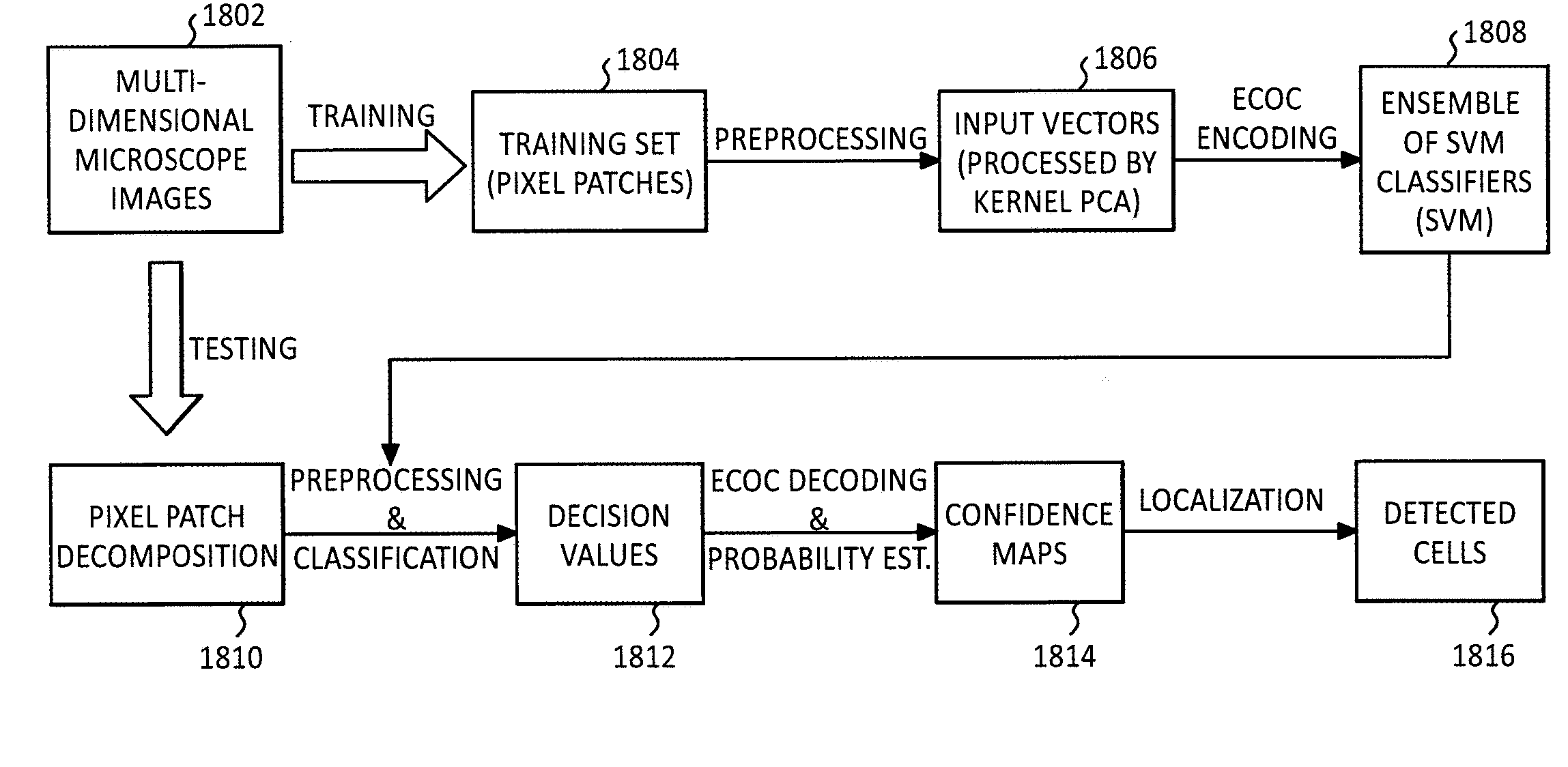
A method of identifying and localizing objects belonging to one of three or more classes, includes deriving vectors, each being mapped to one of the objects, where each of the vectors is an element of an N-dimensional space. The method includes training an ensemble of binary classifiers with a CISS technique, using an ECOC technique. For each object corresponding to a class, the method includes calculating a probability that the associated vector belongs to a particular class, using an ECOC probability estimation technique. In another embodiment, increased detection accuracy is achieved by using images obtained with different contrast methods. A nonlinear dimensional reduction technique, Kernel PCA, was employed to extract features from the multi-contrast composite image. The Kernel PCA preprocessing shows improvements over traditional linear PCA preprocessing possibly due to its ability to capture high-order, nonlinear correlations in the high dimensional image space.
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
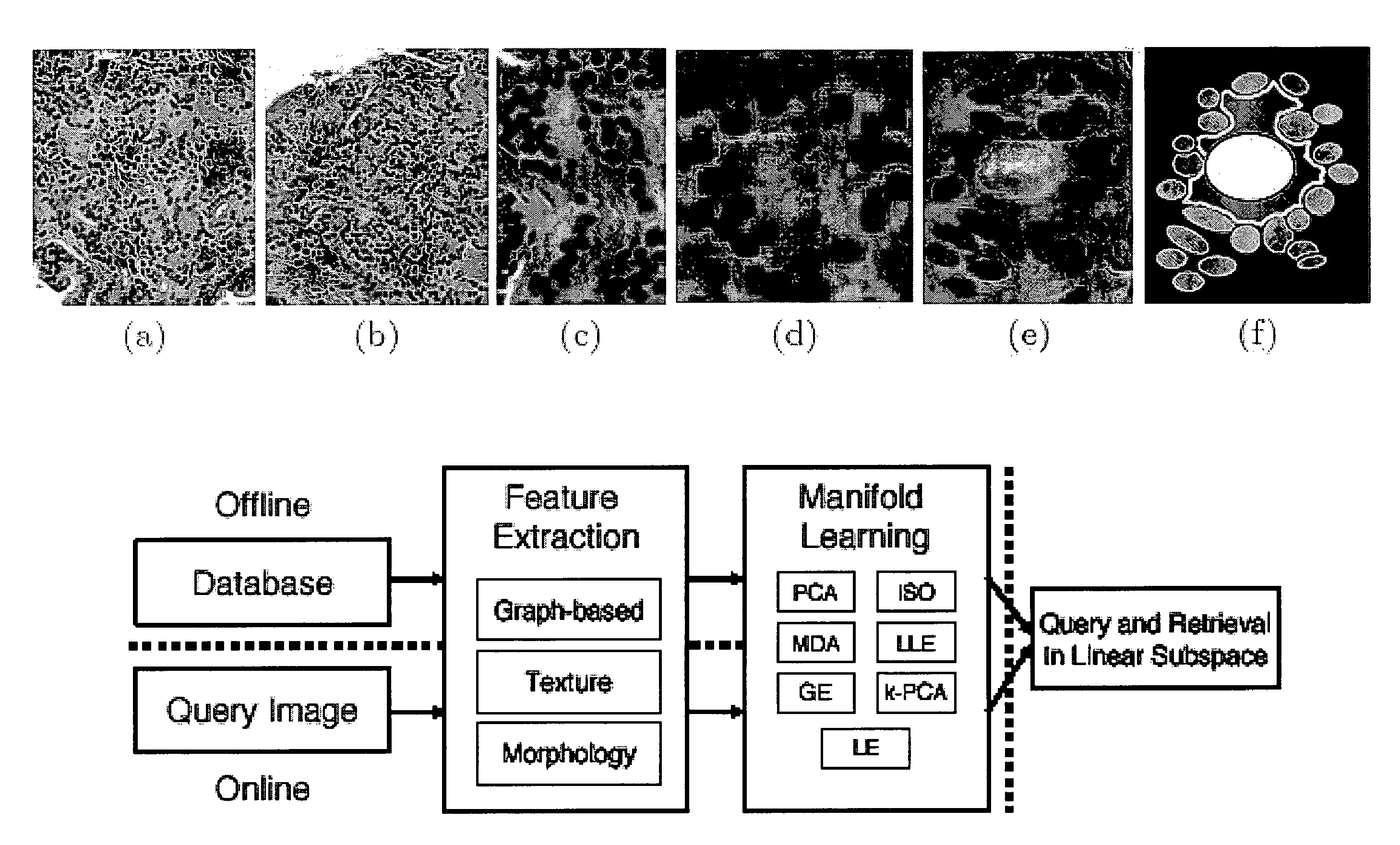
Malignancy diagnosis using content - based image retreival of tissue histopathology
ActiveUS20100098306A1Reduce dimensionalityHigh magnificationImage enhancementImage analysisComputer aided diagnosticsImaging Feature
This invention relates to computer-aided diagnostics using content-based retrieval of histopathological image features. Specifically, the invention relates to the extraction of image features from a histopathological image based on predetermined criteria and their analysis for malignancy determination.
Owner:THE TRUSTEES OF THE UNIV OF PENNSYLVANIA +1
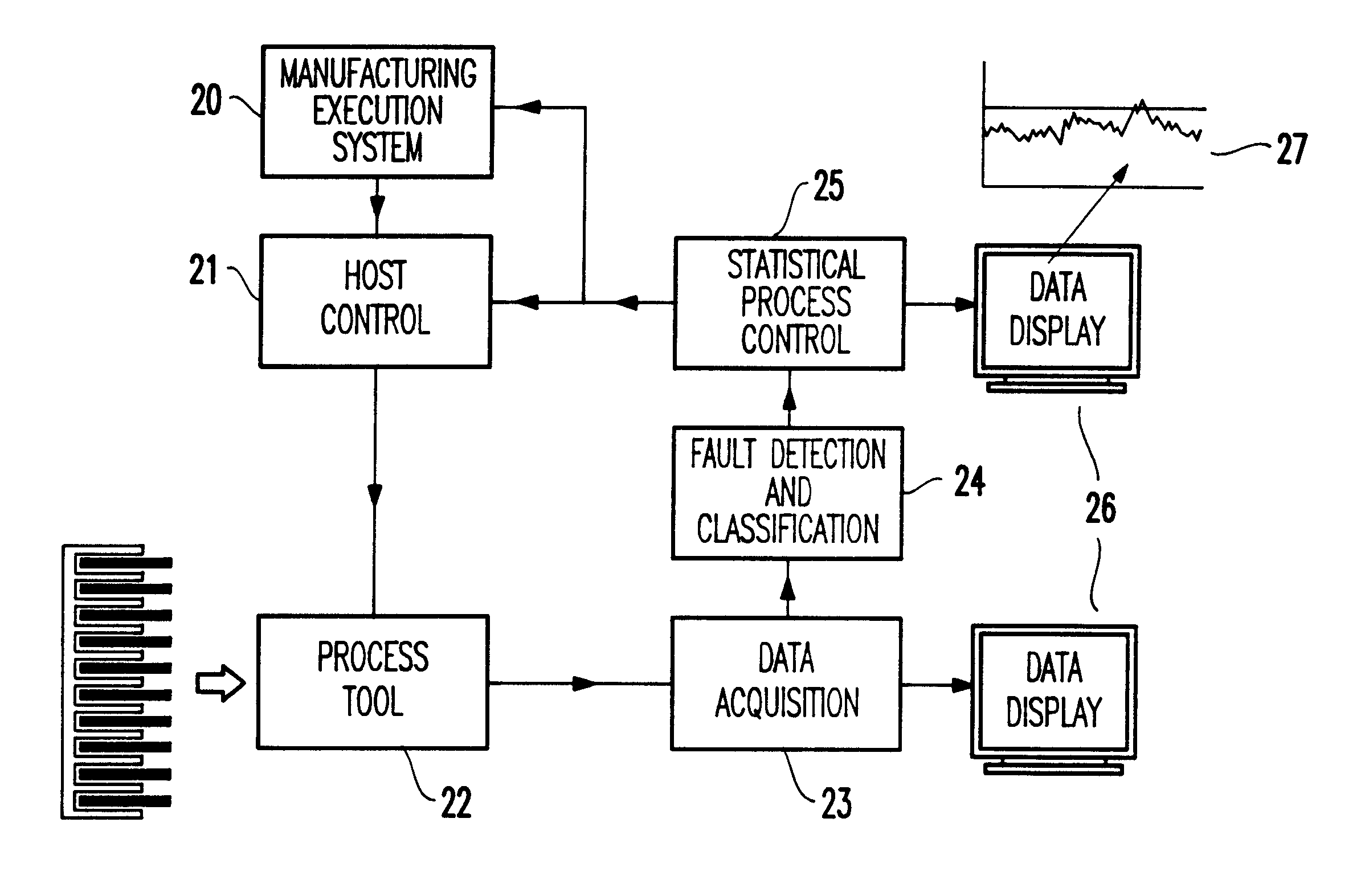
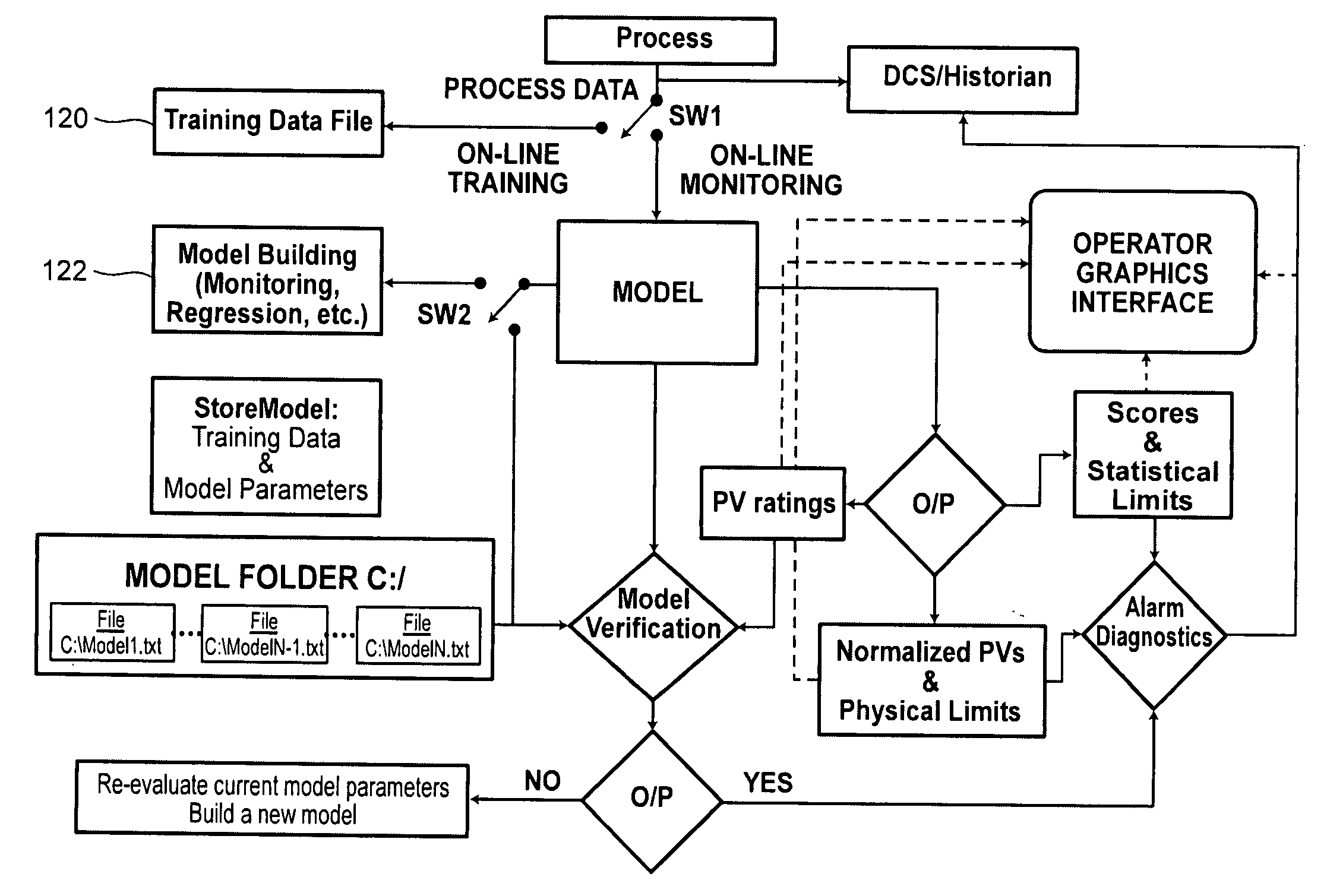
Statistical signatures used with multivariate analysis for steady-state detection in a process
ActiveUS20080082181A1Easy to detectReduce dimensionalityData processing applicationsTesting/monitoring control systemsSteady state detectionPrincipal component analysis
Methods and systems to detect steady-state operations in a process of a process plant include collecting process data. The collected process data is generated from a plurality of process variables of the process. A multivariate statistical model of the operation of the process is generated using the process data. The multivariate statistical model may be generated from a principal component analysis. The model is executed to generate outputs corresponding to the most significant variations in the process. Statistical measures of the outputs are generated and used to determine whether a steady-state or unsteady-state is related to the process.
Owner:FISHER-ROSEMOUNT SYST INC
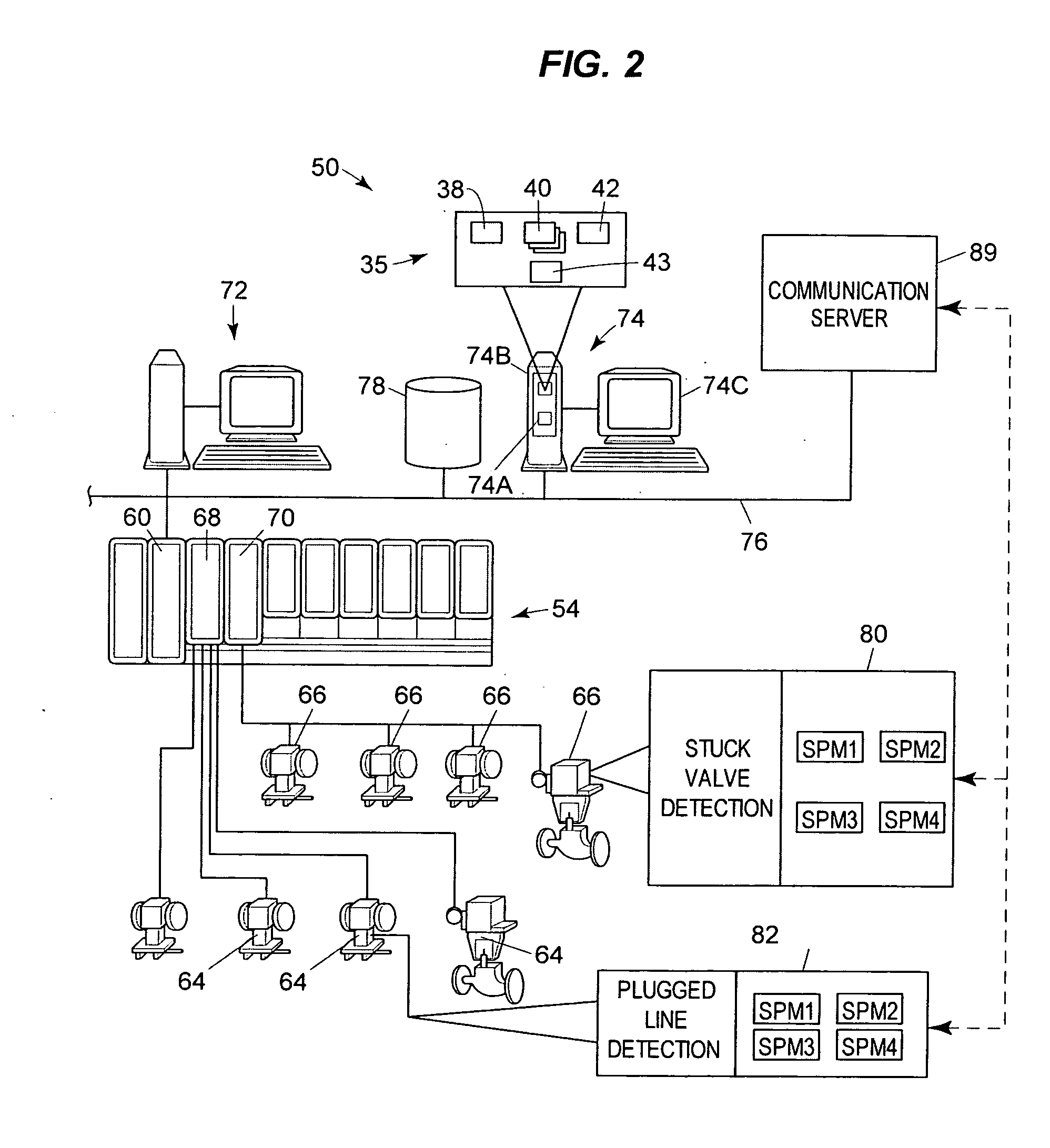
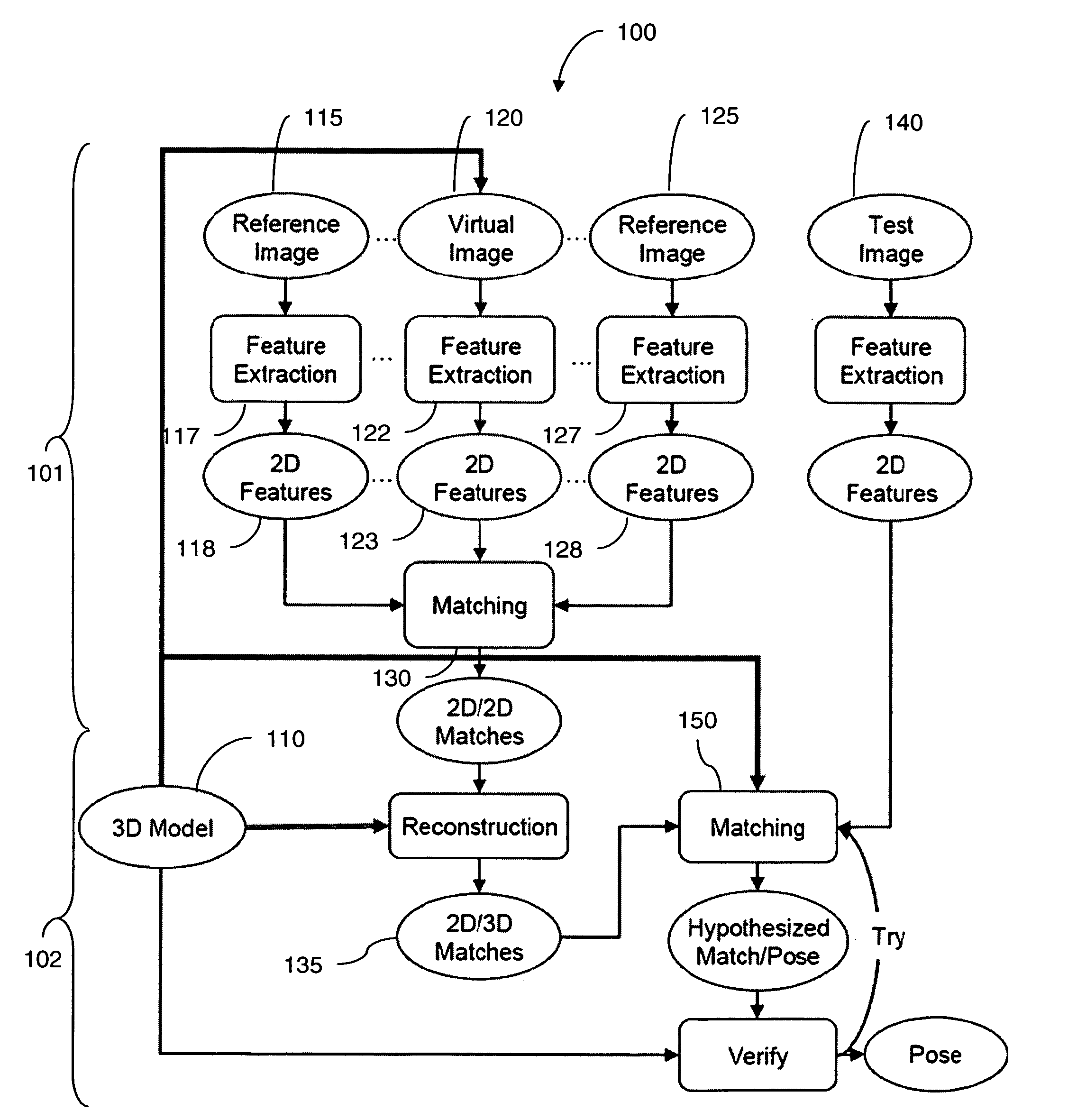
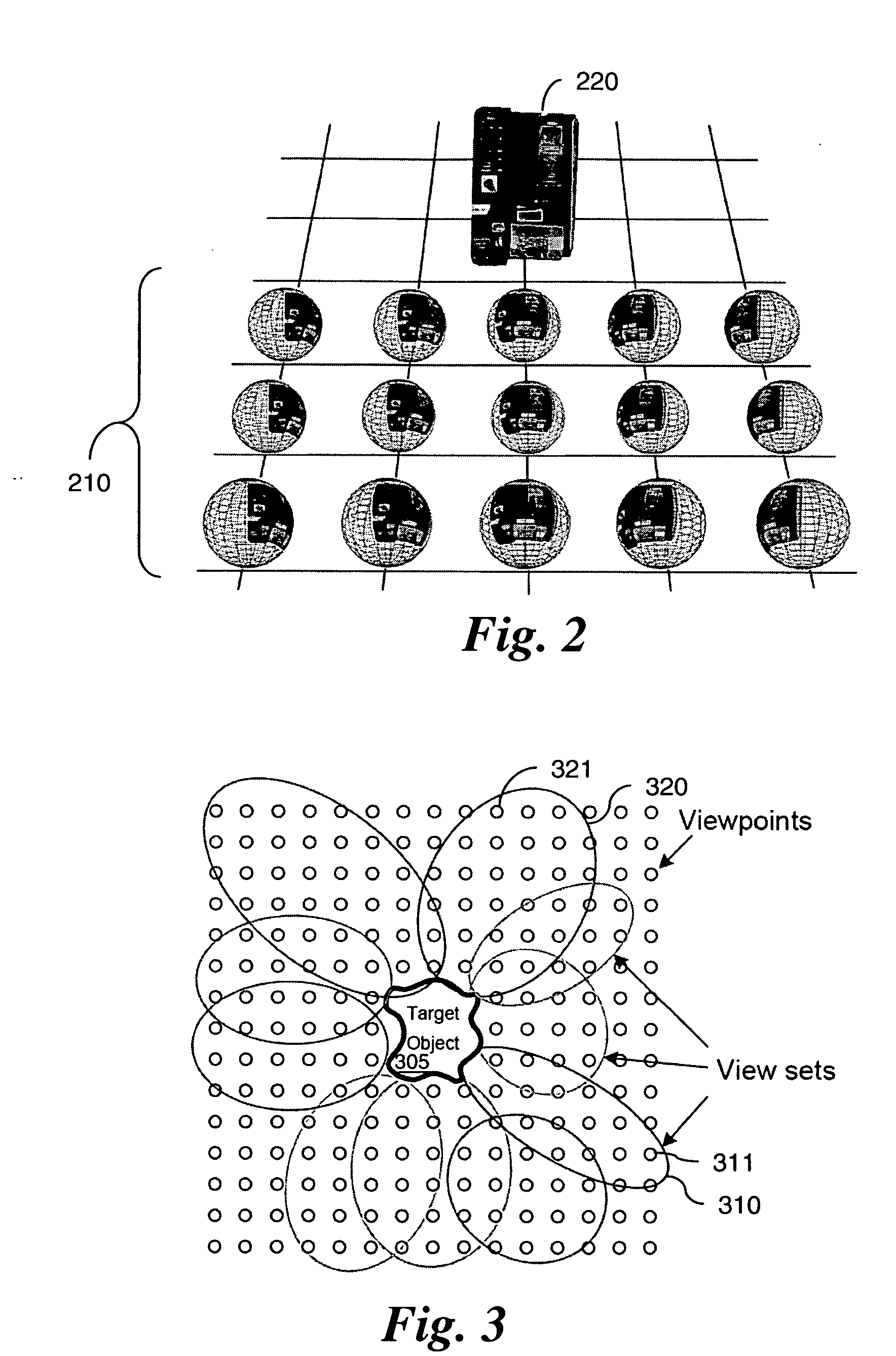
Fast object detection for augmented reality systems
InactiveUS20060233423A1Reduce dimensionalityMinimize impactImage analysisCharacter and pattern recognitionVisibilityViewpoints
A detection method is based on a statistical analysis of the appearance of model patches from all possible viewpoints in the scene, and incorporates 3D geometry during both matching and pose estimation processes. By analyzing the computed probability distribution of the visibility of each patch from different viewpoints, a reliability measure for each patch is estimated. That reliability measure is useful for developing industrial augmented reality applications. Using the method, the pose of complex objects can be estimated efficiently given a single test image. In a fast method to detect objects in a given image or video sequence, a series of hierarchical feature descriptors permit balancing between the complexity of feature extraction and cost of combinatorial matching. The feature descriptors are derived from the 3D model of the object of interest along with the available calibrated real-life images or videos. The variability of the real-life images defines the granularity of the feature descriptors.
Owner:SIEMENS CORP
Method for generating a network map
InactiveUS7251688B2Reduce dimensionalityOvercome problemsDigital computer detailsData switching networksWeb siteName server
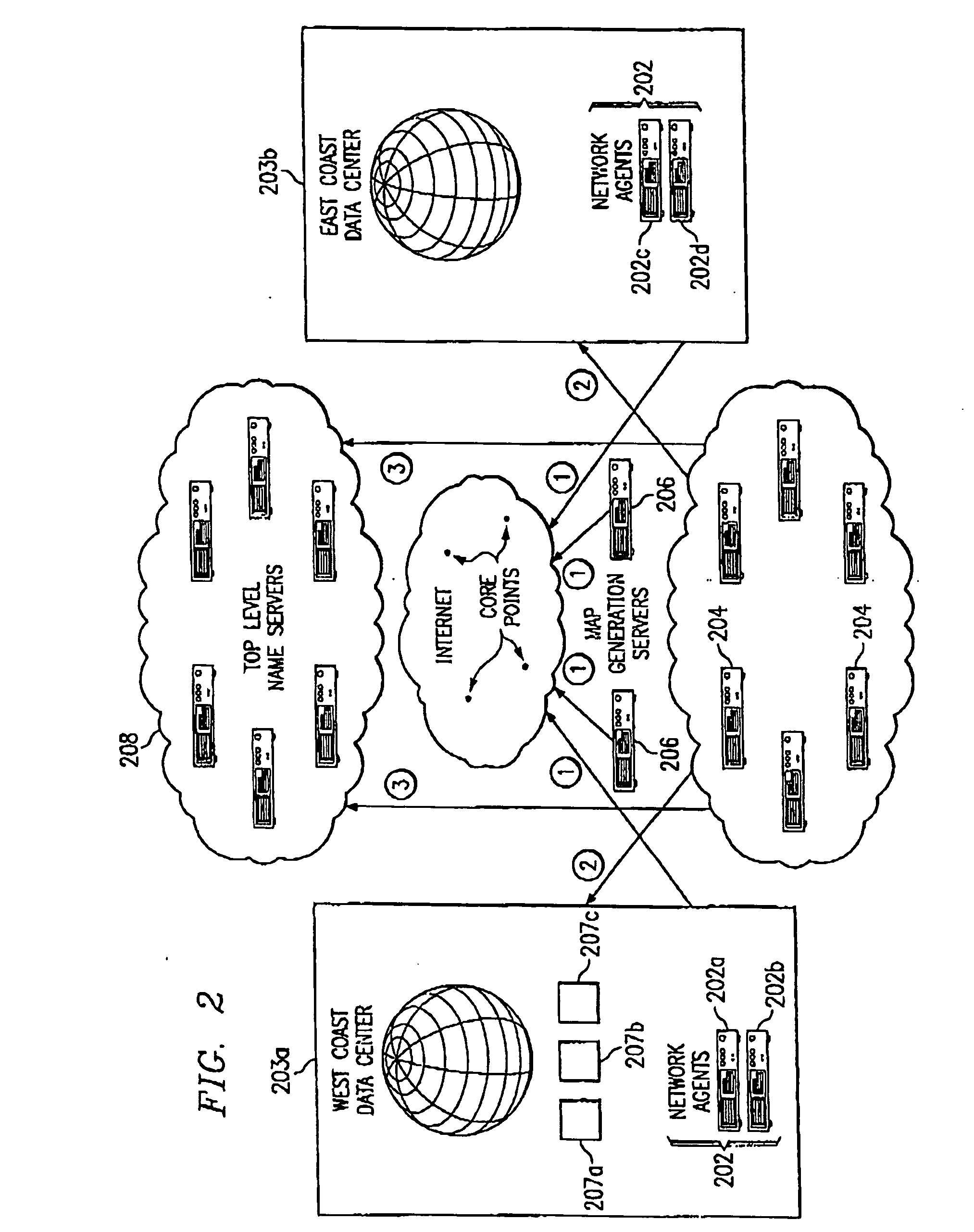
An intelligent traffic redirection system performs global load balancing for Web sites located at mirrored data centers. The system relies on a network map that is generated continuously, preferably for the user-base of the entire Internet. Instead of probing each local name server (or other host) that is connectable to the mirrored data centers, the network map identifies connectivity with respect to a much smaller set of proxy points, called “core” (or “common”) points. A core point is representative of a set of local name servers (or other hosts) that, from a data center's perspective, share the point. To discover a core point, an incremental trace route is executed from each of the set of mirrored data centers to a local name server that may be used by client to resolve a request for a replica stored at the data centers. An intersection of the trace routes at a common routing point is then identified. Thus, for example, the common routing point may be the first common point for the trace routes when viewed from the perspective of the data centers (or the last common point for the trace routes when viewed from the perspective of the local name server). The common routing point is then identified as the core point for the local name server.
Owner:AKAMAI TECH INC
Electric power telecommunication network device fault prediction method based on improved LSTM
ActiveCN107769972AEasy to learnPan-China ability is goodData switching networksTelecommunications networkAlgorithm
The invention relates to an electric power telecommunication network device fault prediction method based on improved LSTM. The invention provides a data preprocessing and time sequence input construction method for the first time. Compared with the simple recurrent neural network, the LSTM is more likely to learn long-term dependence and can solve the prediction problems related to sequences. Because of the strong association between device alerts, the independence of variables can be ensured through PCA. The target replication strategy is also used for improving the LSTM, which can bring local error information in every step. Compared with a simple target output only in the last step, the strategy can improve the accuracy of the model and reduce the risk of over fitting. In combination with dropout, the invention proposes a prediction model of LSTM, which can achieve better prediction precision by deep learning. At the same time, the LSTM is usd for modeling electric power telecommunication network alarm data for the first time and identifying the timing sequence mode therein.
Owner:WUHAN UNIV
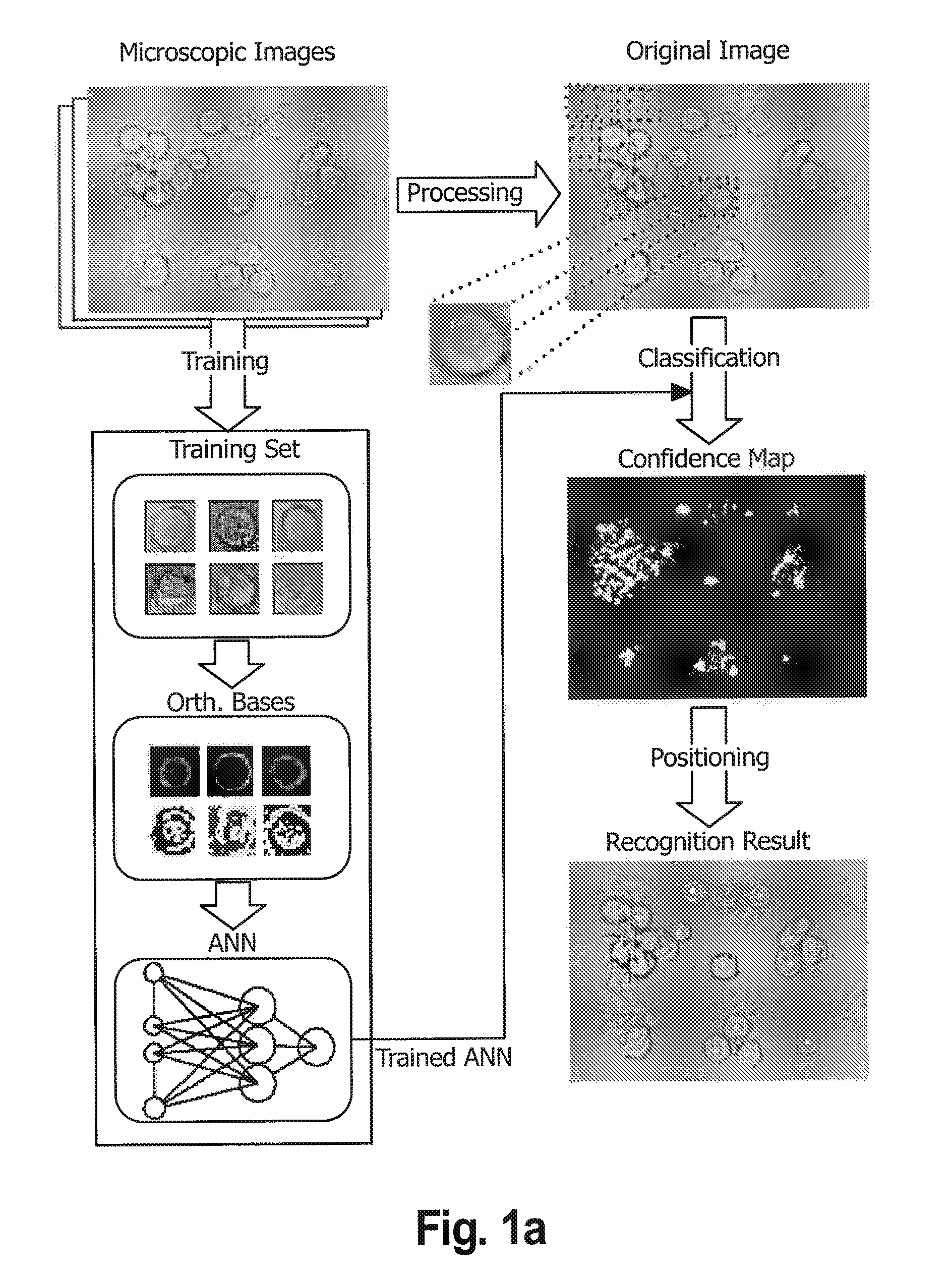
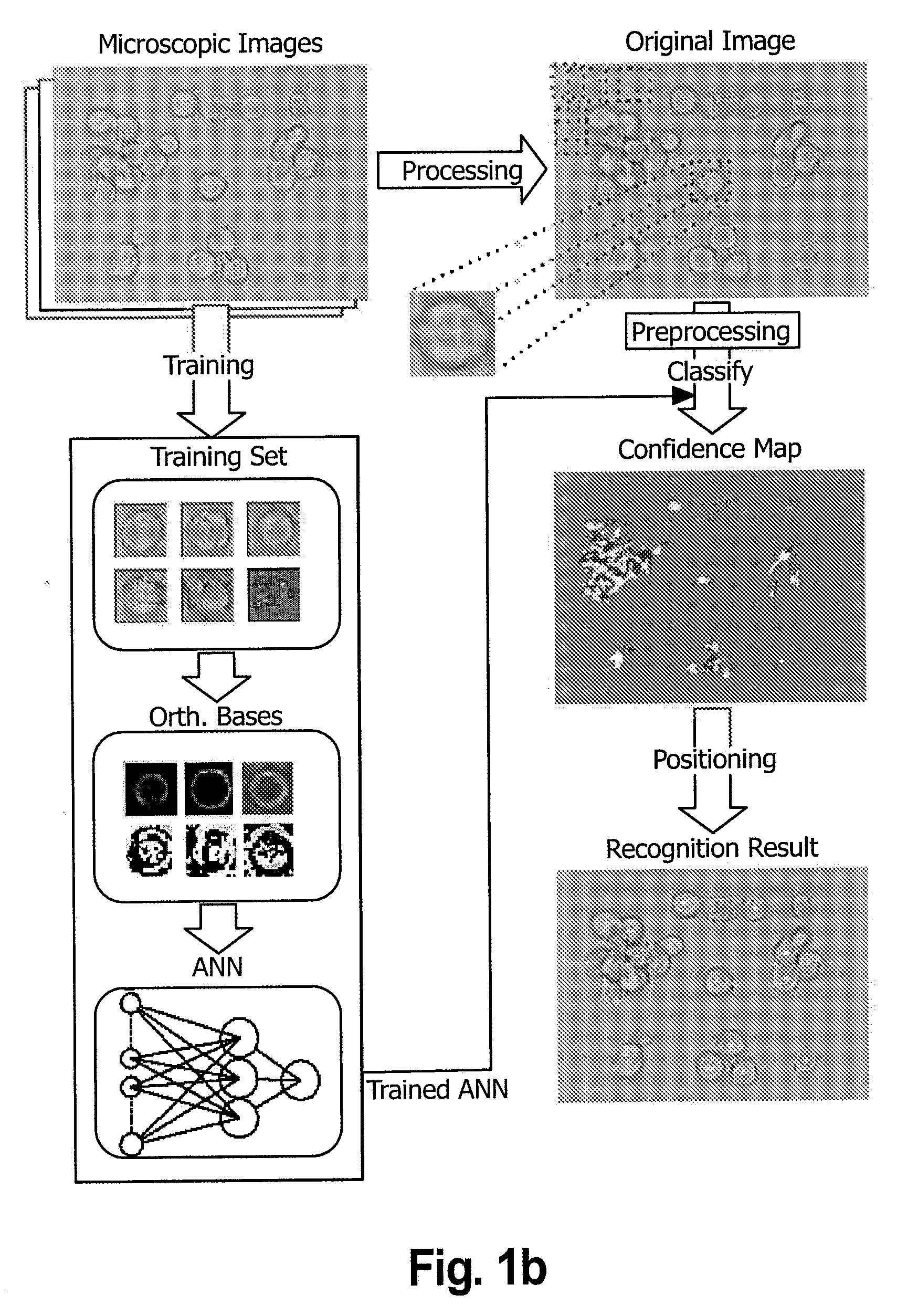
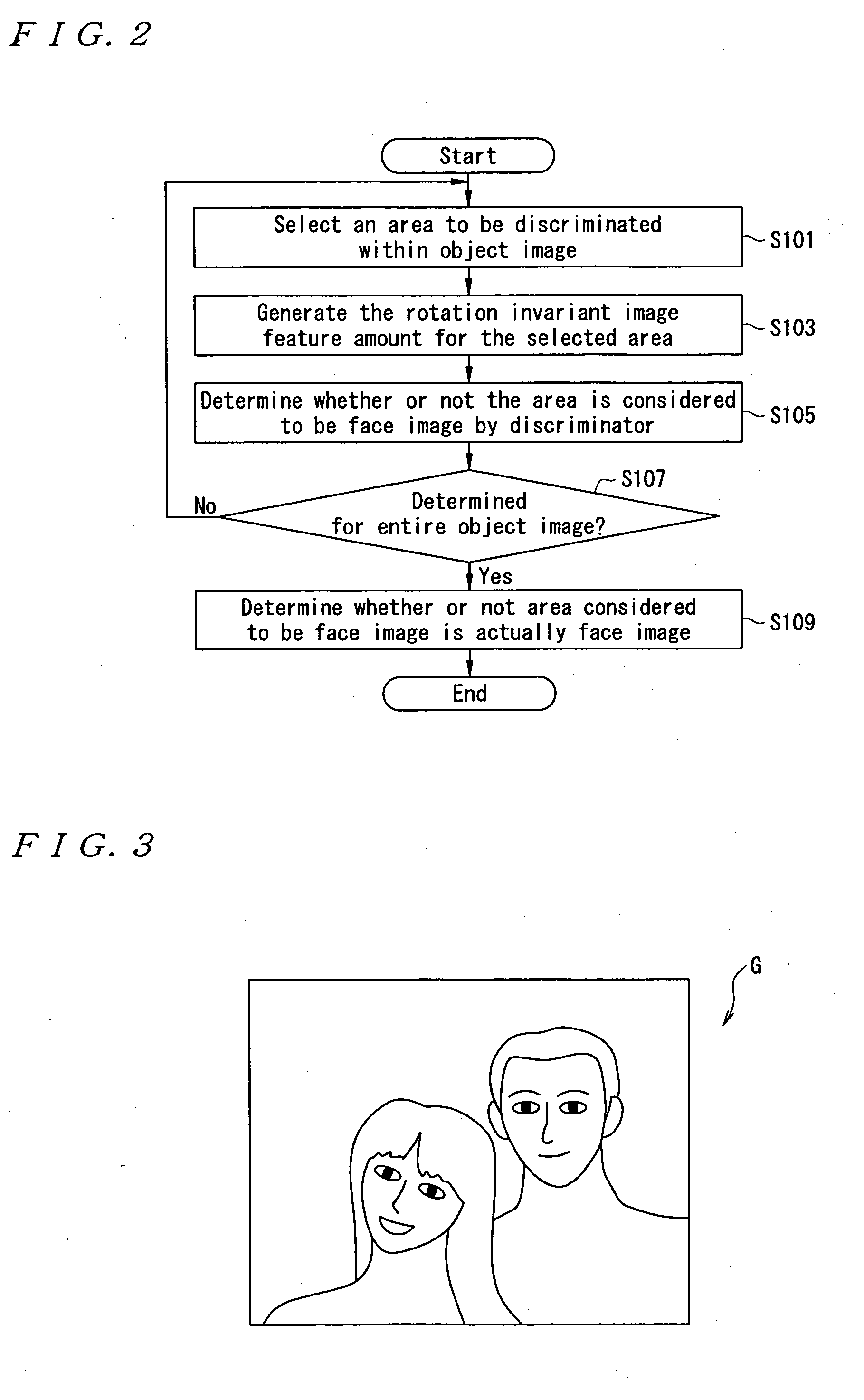
Method, system and program for searching area considered to be face image
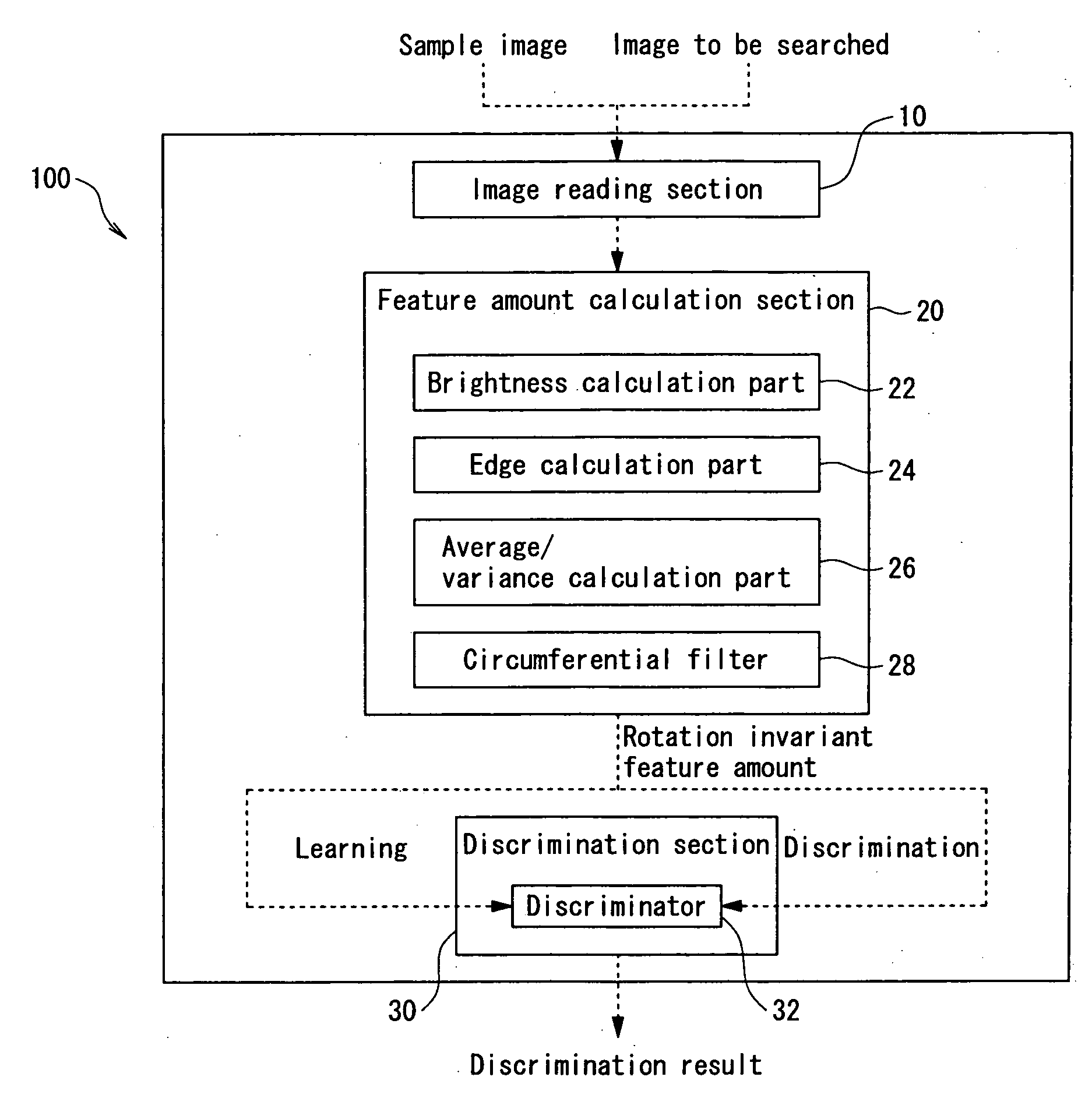
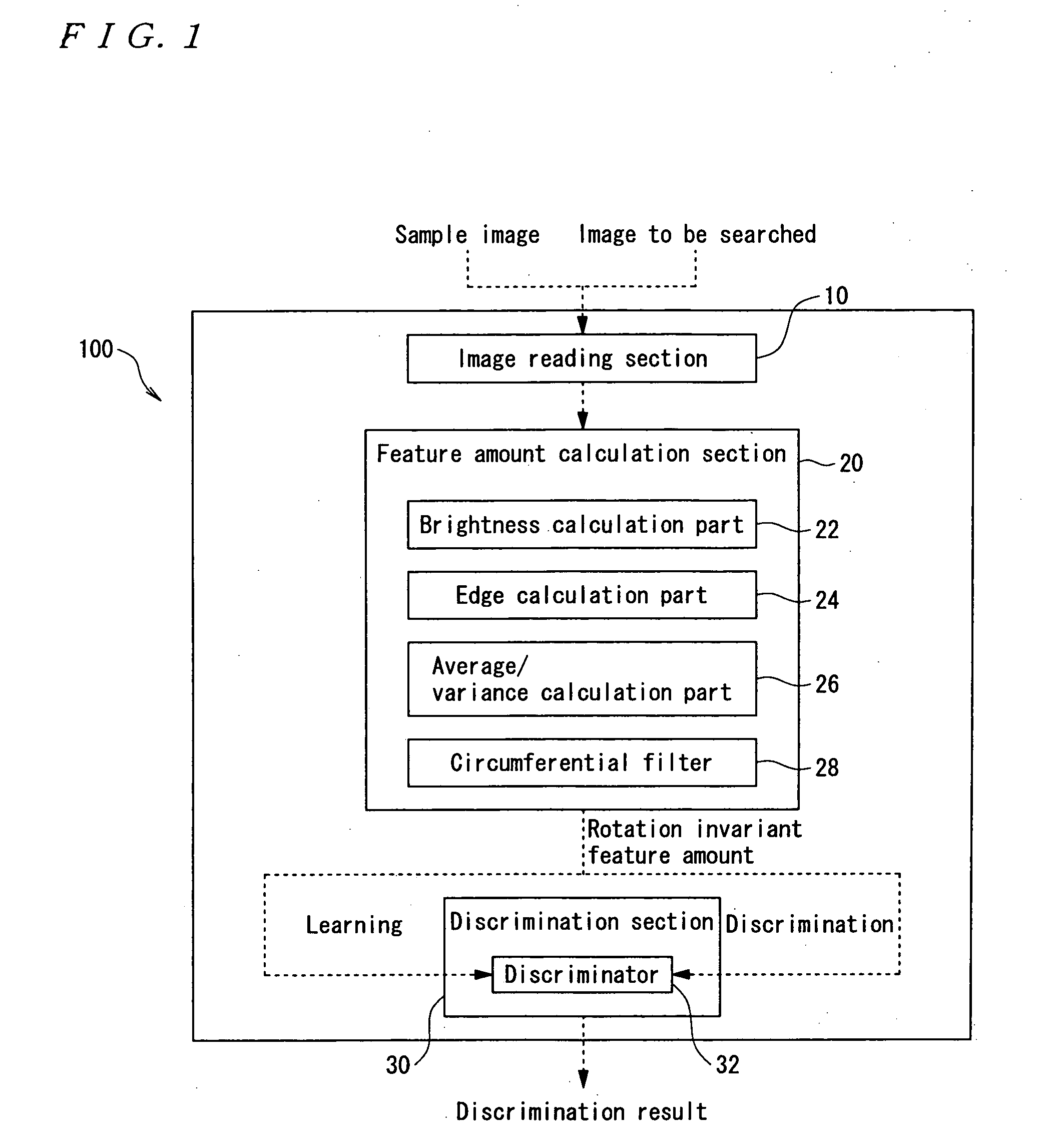
InactiveUS20050141766A1Produced economically and easilyFunction increaseImage enhancementImage analysisSample imageImaging Feature
A sample image is filtered through a circumferential filter 28, an image feature amount is learned in a discrimination section 30, an image G to be searched is filtered through the circumferential filter 28 to detect a rotation invariant image feature amount for each filtered area, and each detected image feature amount is inputted into the discrimination section 30. Thereby, it is discriminated whether or not a filtering area is considered to be face image at high speed. And the dimensional number of image feature amounts is greatly reduced, so that not only the discrimination work but also the learning time of the sample image are greatly reduced.
Owner:SEIKO EPSON CORP
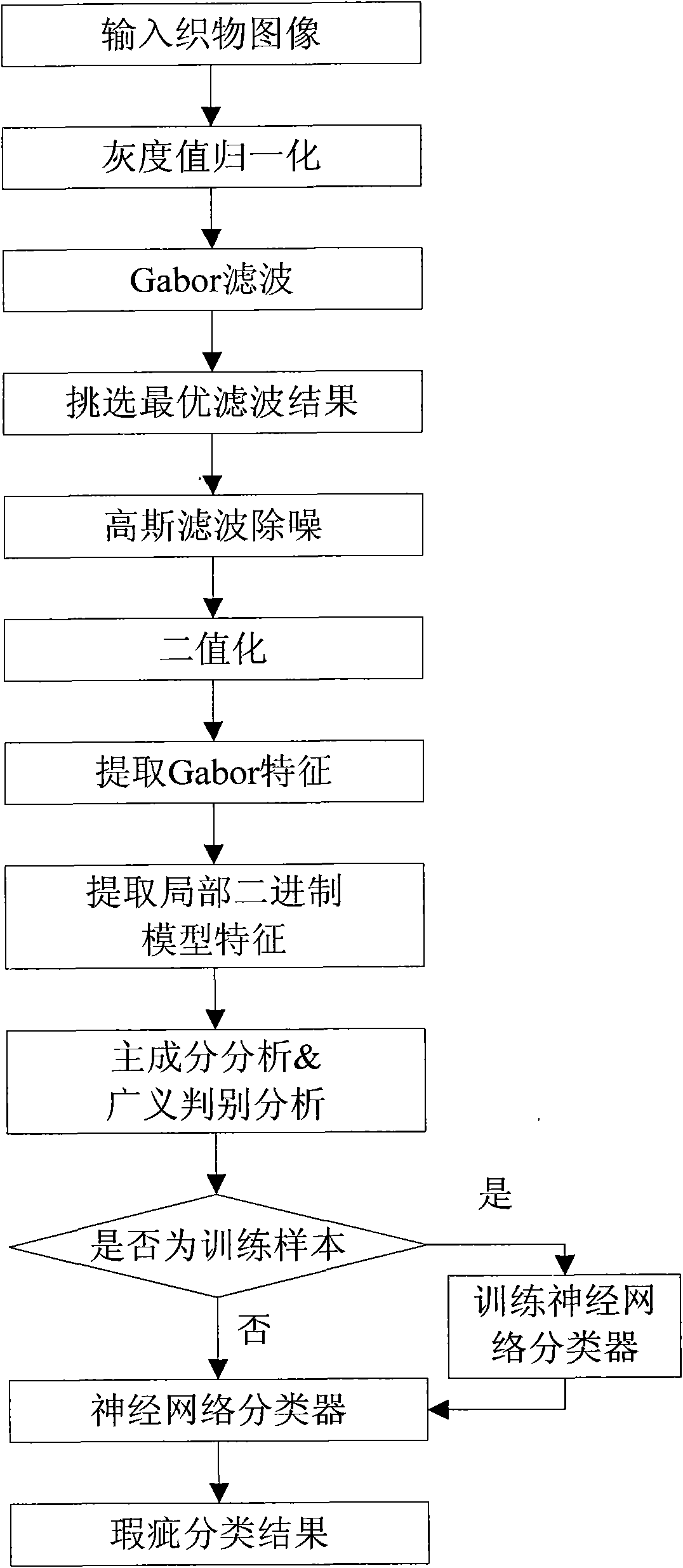
Method for detecting and classifying fabric defects
InactiveCN101866427APrecise positioningFully reflect the difference of flawsCharacter and pattern recognitionTextile millPrincipal component analysis
The invention discloses a method for detecting and classifying fabric defects and mainly aims to solve the problem of automatic detection and classification of fabric defects. The method comprises the following steps of: firstly, detecting a picture of the fabric defects, filtering the picture by using a Gabor filter group, selecting an optimal filtering result and performing binaryzation on the optimal filtering result by using a reference picture so as to position the positions of the defects in the picture; secondly, extracting a compound characteristic consisting of a Gabor characteristic and a partial binary model characteristic according to the positions of the defects; thirdly, performing pre-treatment on the compound characteristic by main constituent analysis and generalized discriminant analysis algorithm; fourthly, training a neural network classifier by using a pre-treated defect characteristic; and lastly, realizing accurate classification of a fabric defect characteristic by using a trained classifier. The method has the advantages of accurate defect positioning and high classification accuracy and can be used for detecting and classifying the fabric defects in a textile mill.
Owner:XIDIAN UNIV
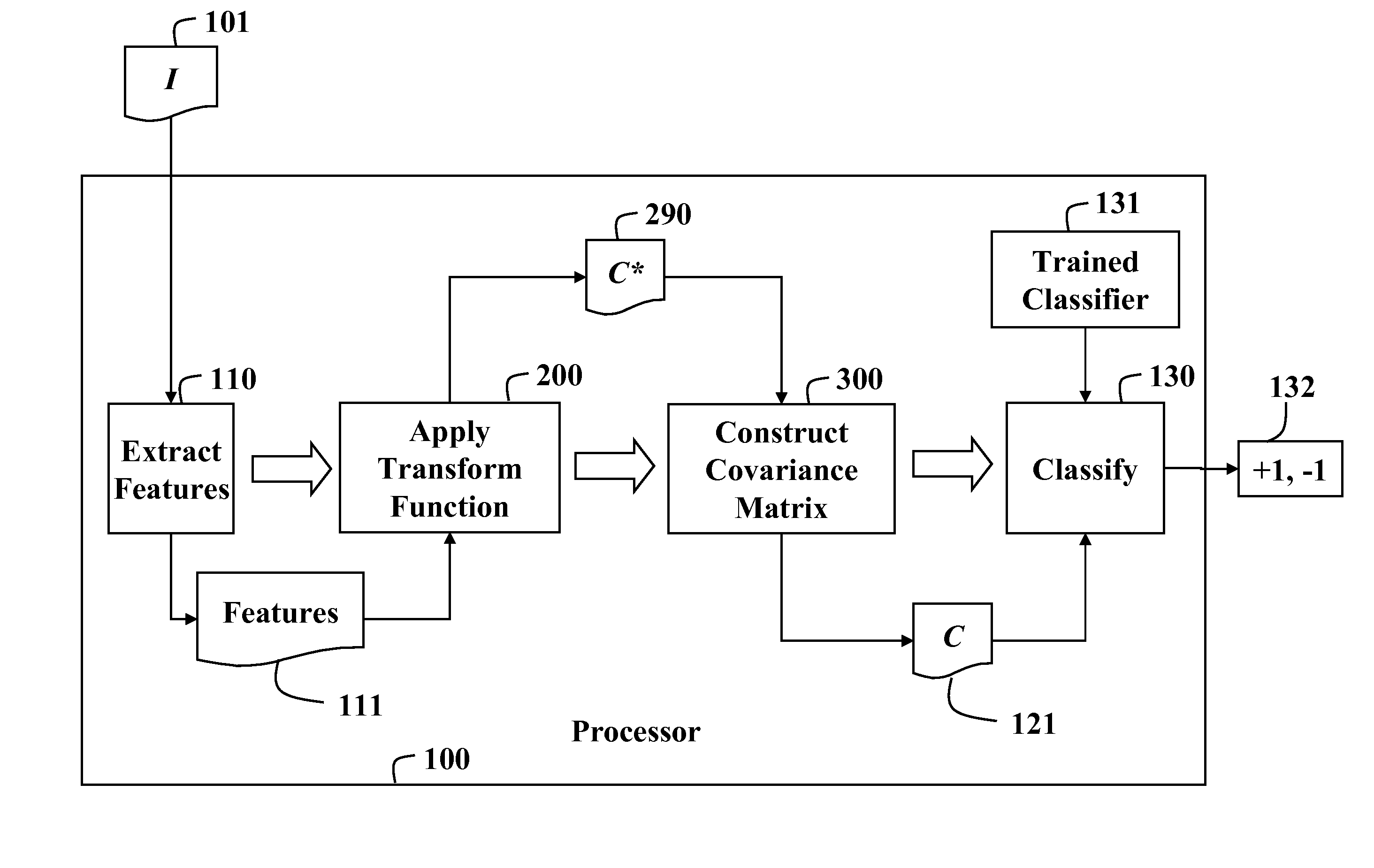
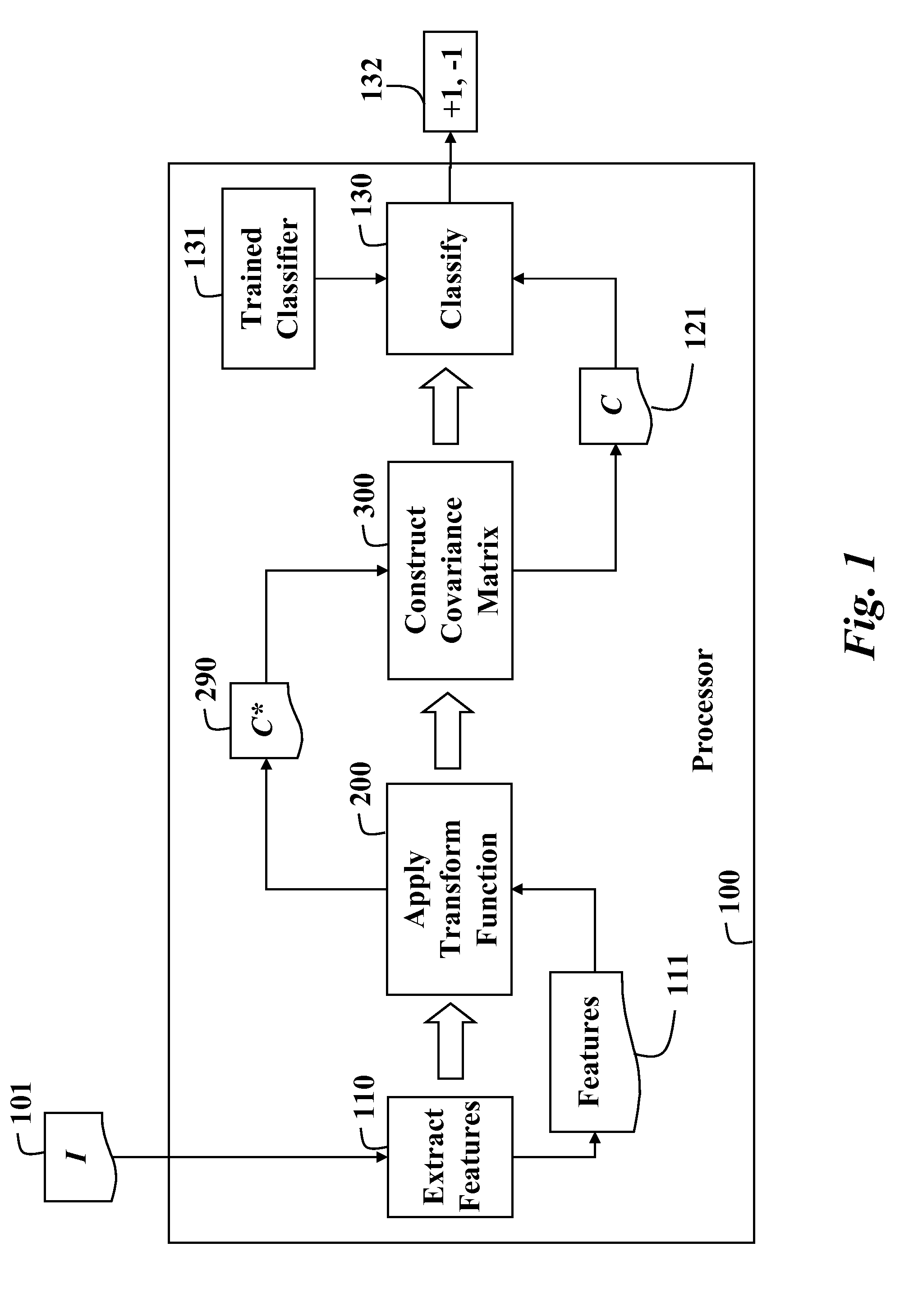
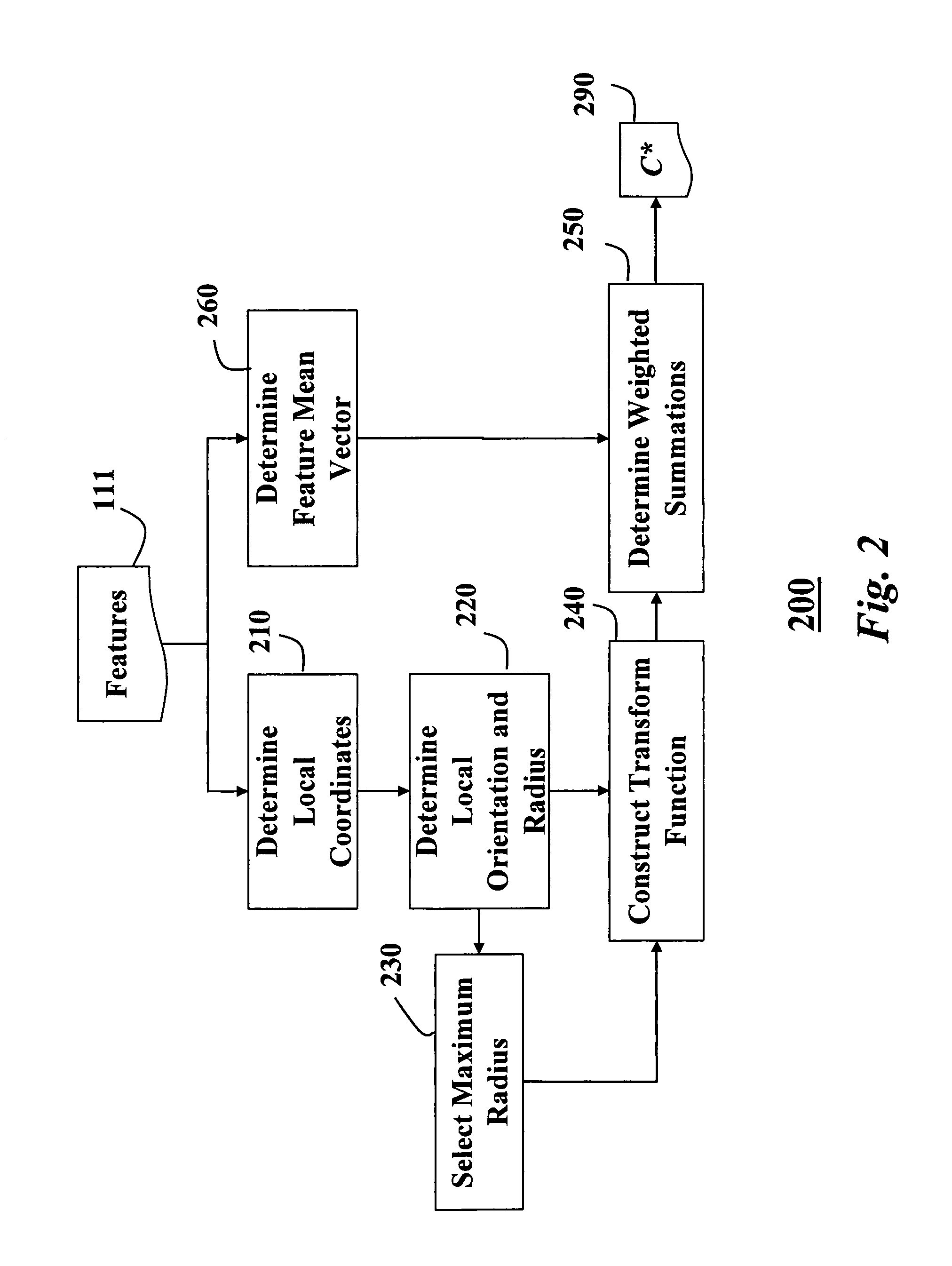
Detecting objects in images with covariance matrices
InactiveUS7734097B1Accurately capture statistical and appearance propertyAccurately captures statistical and appearance property of regionCharacter and pattern recognitionCovariancePattern recognition
A method detects objects in an image. First, features are extracted from the image. A frequency transform is applied to the features to generate transformed features. A covariance matrix is constructed from the transformed features, and the covariance matrix is classified to determine whether the image includes the object, or not.
Owner:MITSUBISHI ELECTRIC RES LAB INC
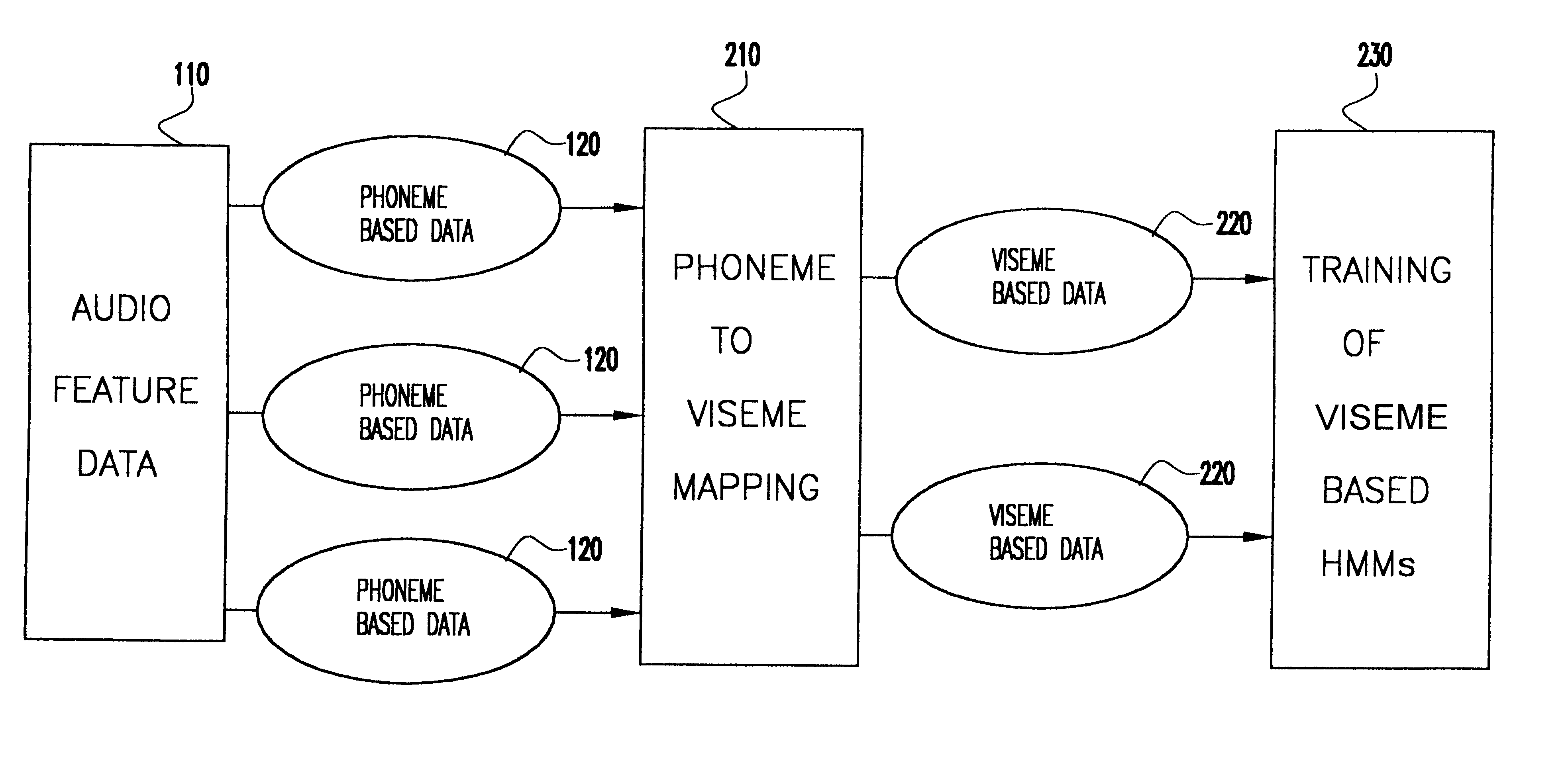
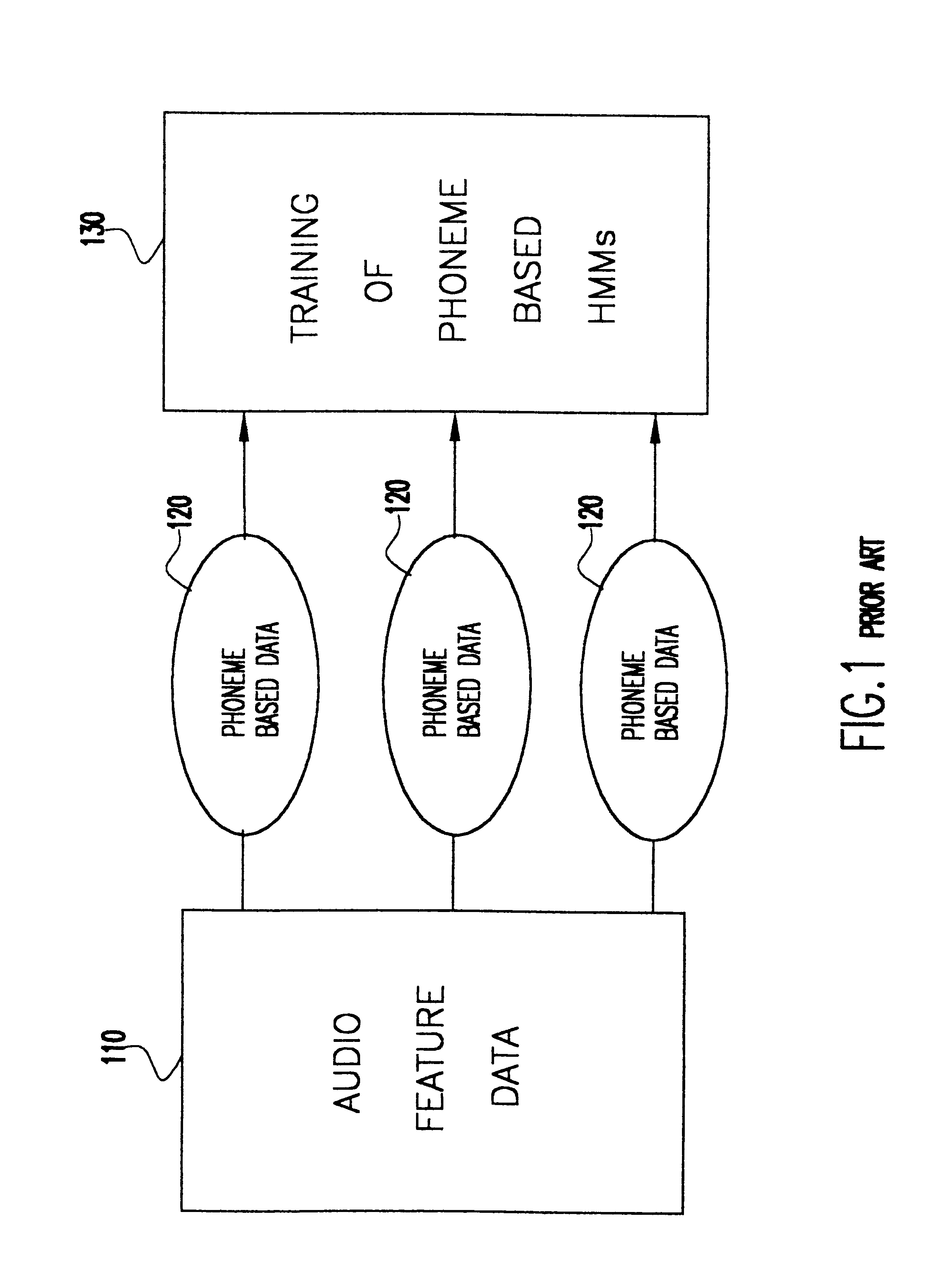
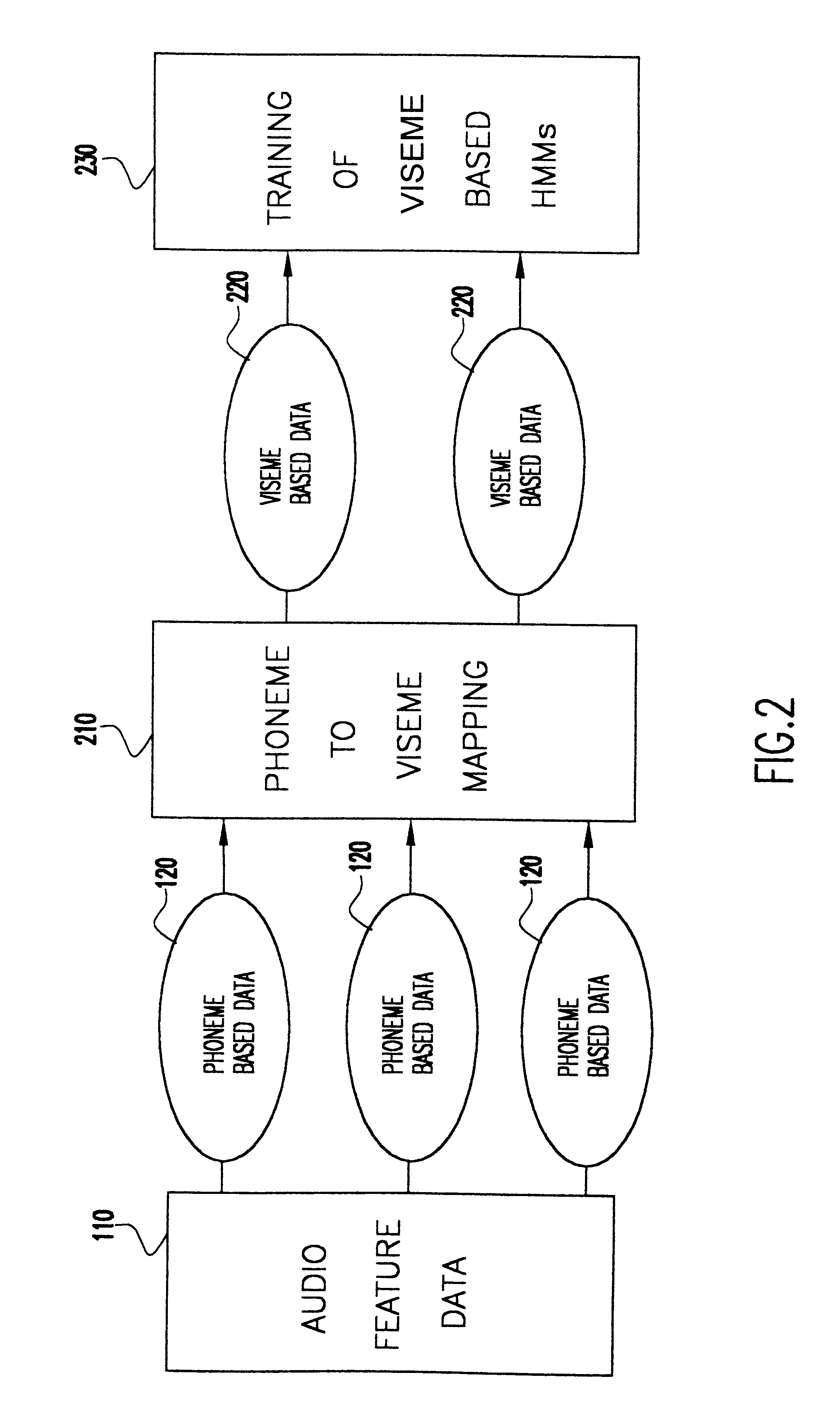
Speech driven lip synthesis using viseme based hidden markov models
InactiveUS6366885B1Shorten the timeSmall sizeElectronic editing digitised analogue information signalsRecord information storageNODALTraining phase
A method of speech driven lip synthesis which applies viseme based training models to units of visual speech. The audio data is grouped into a smaller number of visually distinct visemes rather than the larger number of phonemes. These visemes then form the basis for a Hidden Markov Model (HMM) state sequence or the output nodes of a neural network. During the training phase, audio and visual features are extracted from input speech, which is then aligned according to the apparent viseme sequence with the corresponding audio features being used to calculate the HMM state output probabilities or the output of the neutral network. During the synthesis phase, the acoustic input is aligned with the most likely viseme HMM sequence (in the case of an HMM based model) or with the nodes of the network (in the case of a neural network based system), which is then used for animation.
Owner:UNILOC 2017 LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com