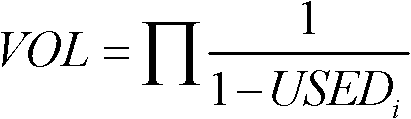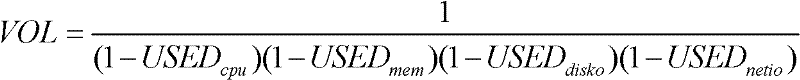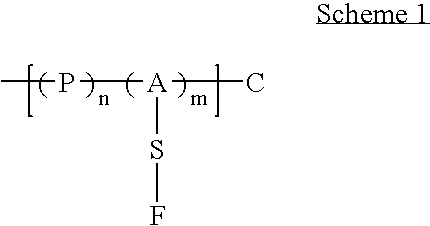Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
121results about How to "Avoid bottlenecks" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
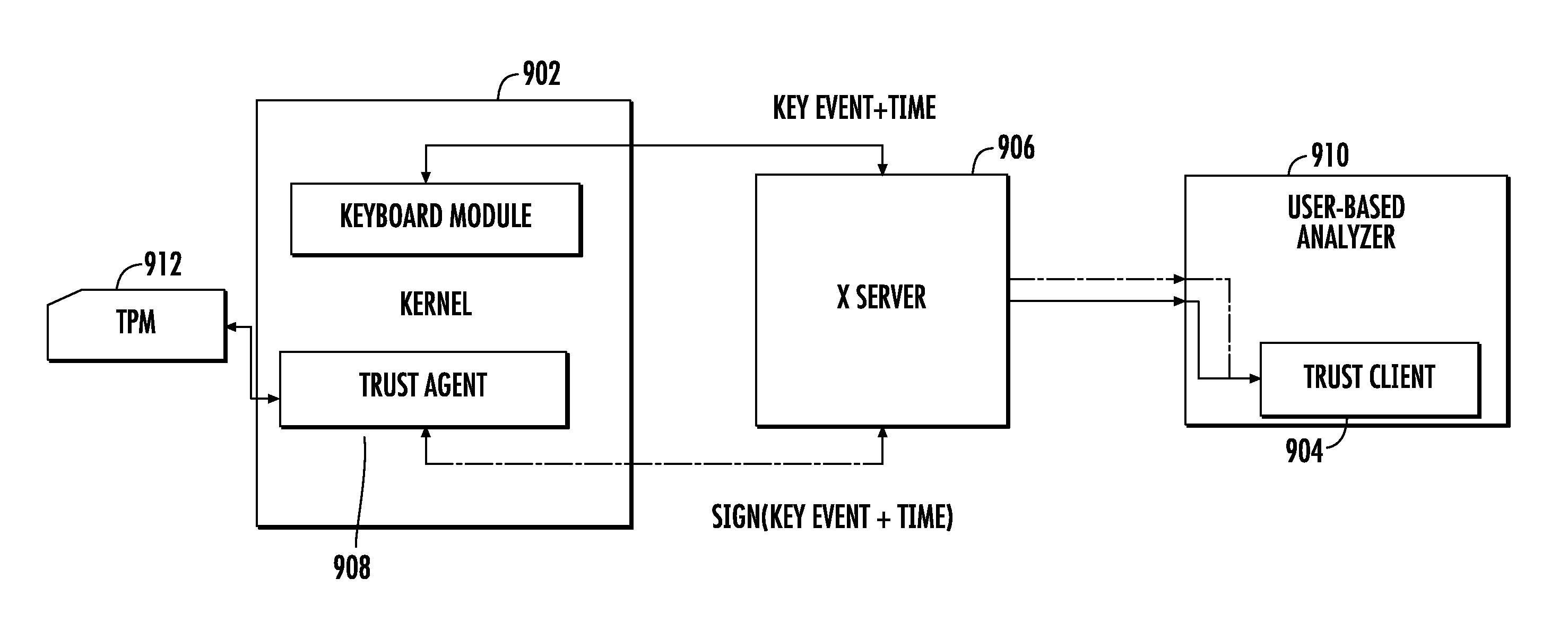
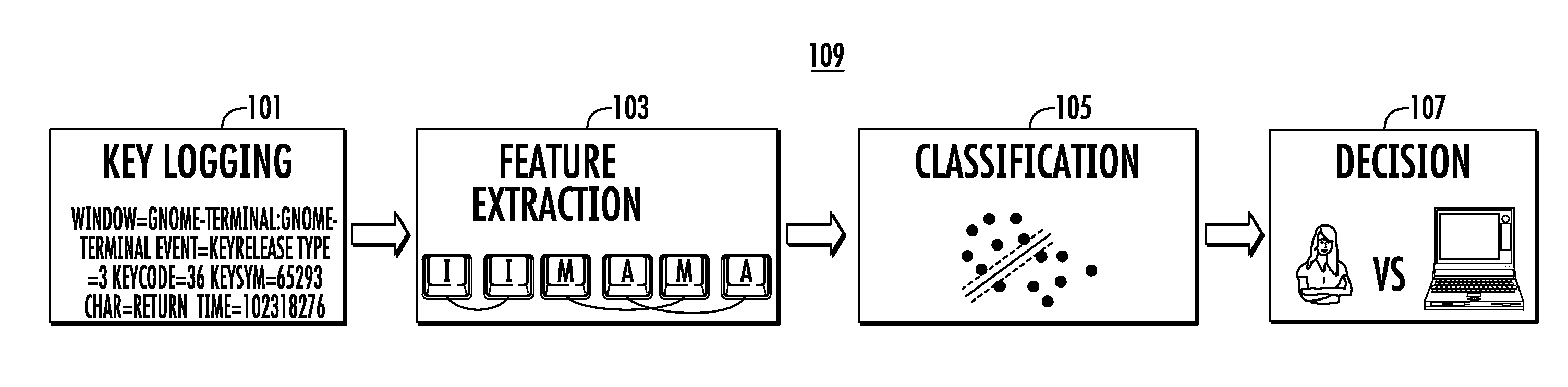
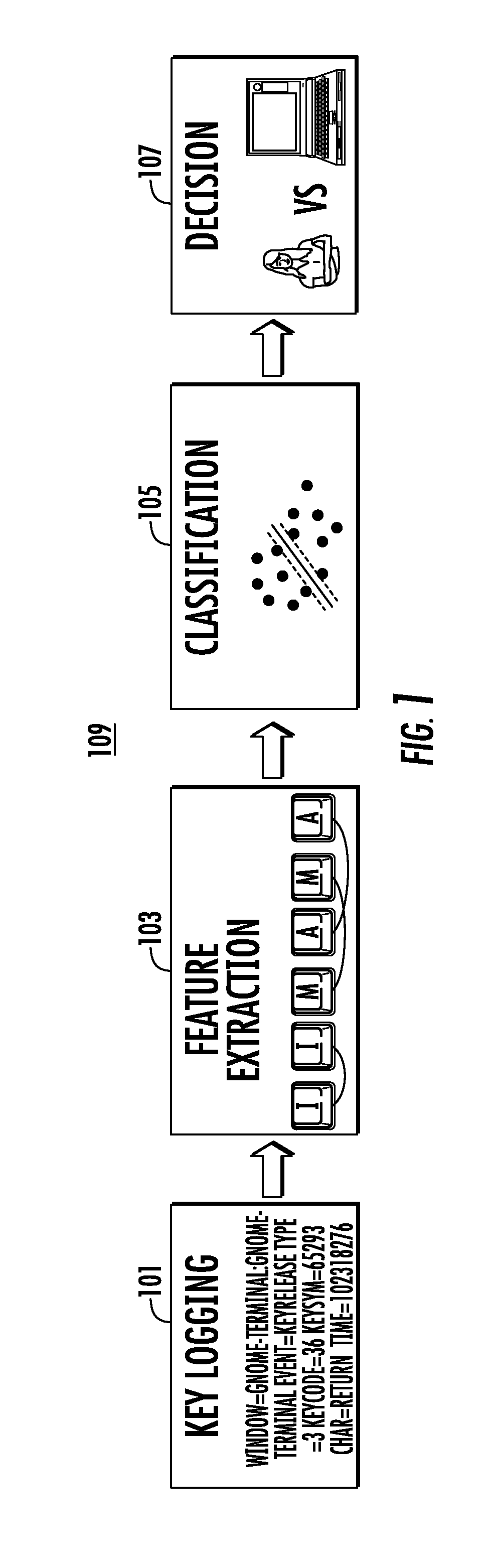
Systems and method for malware detection
ActiveUS20110320816A1Avoid bottlenecksReduce dimensionalityMemory loss protectionDigital data processing detailsFeature vectorSupport vector machine
A system and method for distinguishing human input events from malware-generated events includes one or more central processing units (CPUs), one or more input devices and memory. The memory includes program code that when executed by the CPU causes the CPU to obtain a first set of input events from a user utilizing the input device. The first input events are used to obtain or derive a feature indicative of the user, such as a multi-dimensional feature vector as provided by a support vector machine. Second input events are then obtained, and the second input events are classified against the feature to determine if either the user or malware initiated the second input events.
Owner:RUTGERS THE STATE UNIV
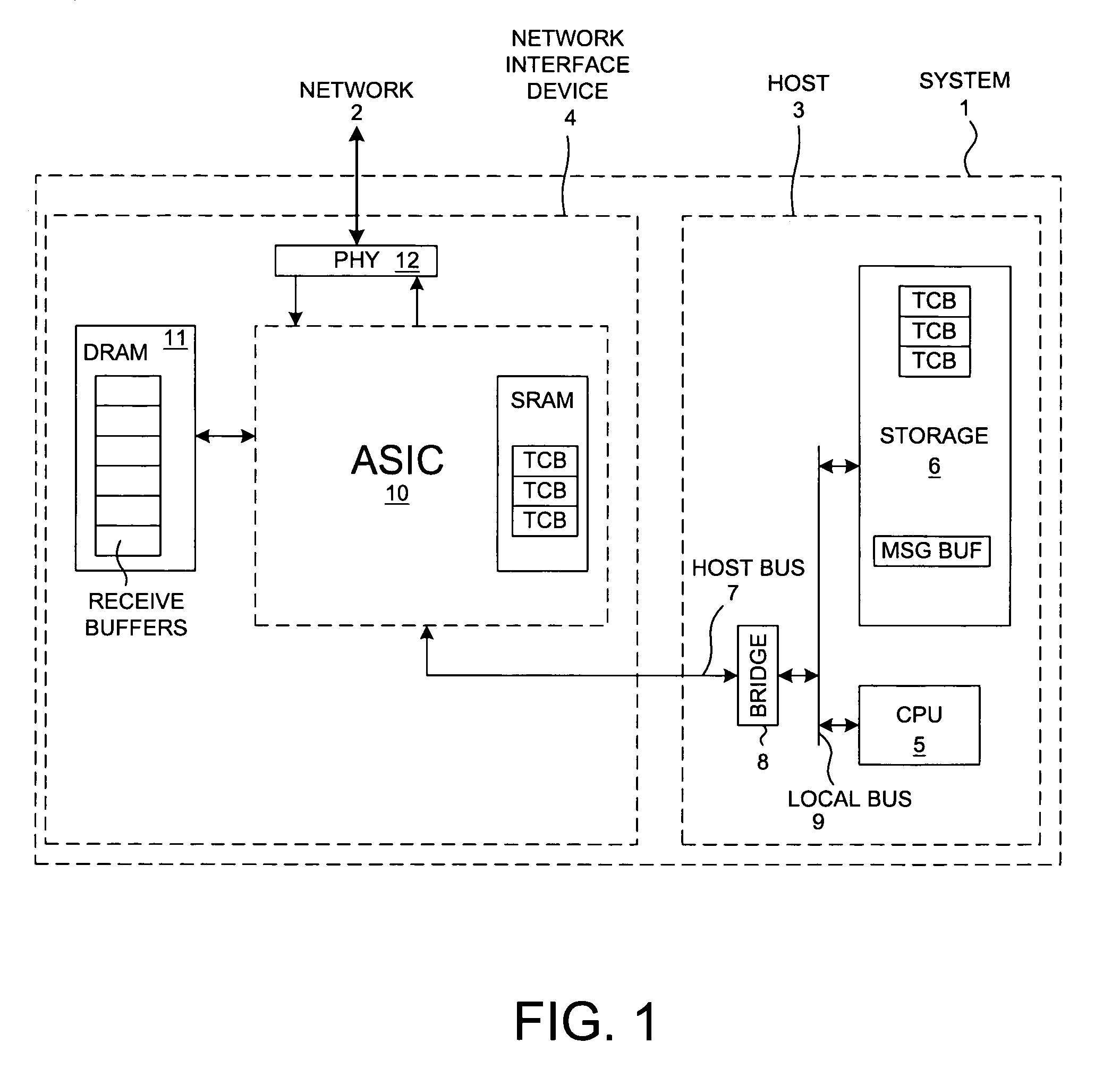
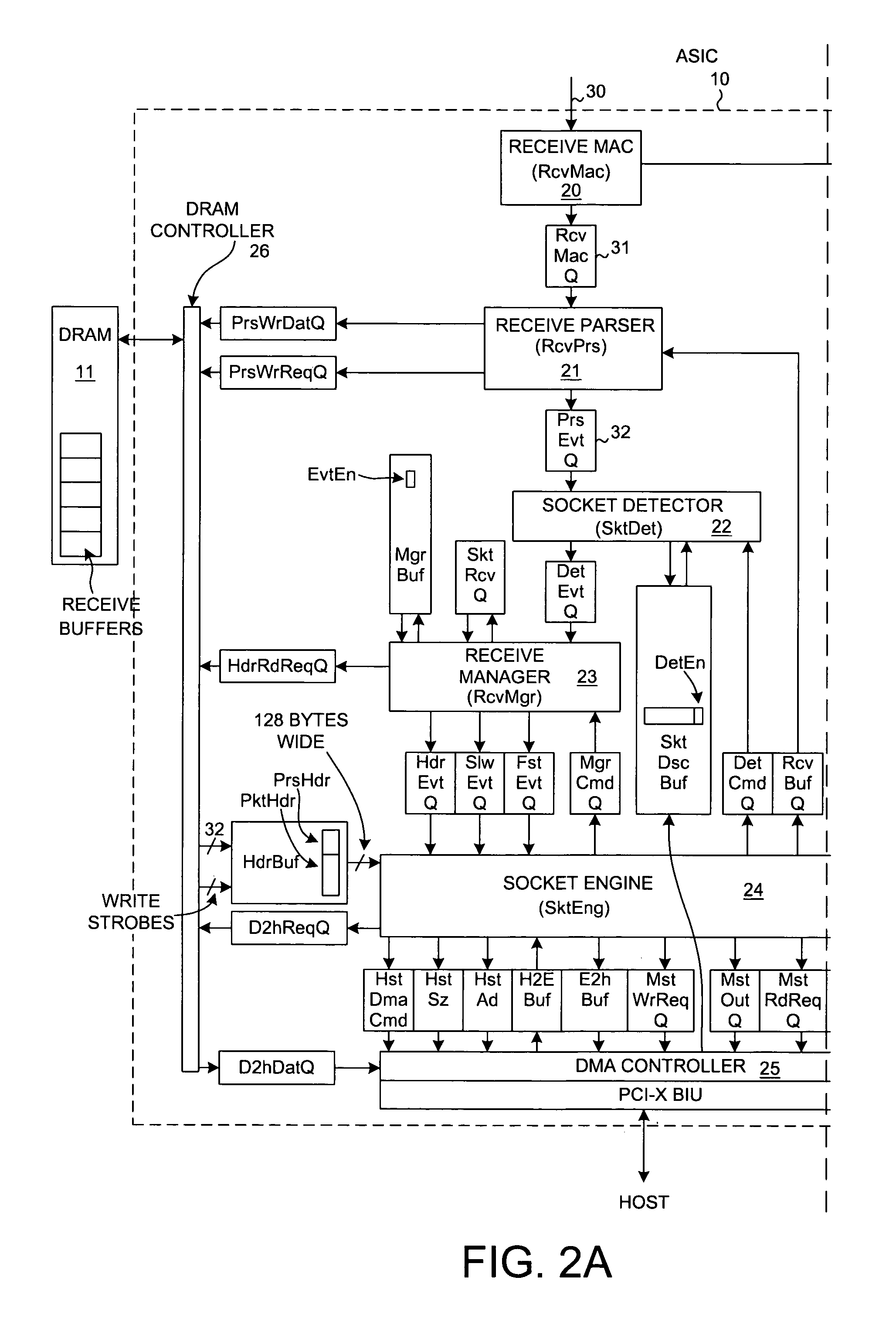
TCP/IP offload device with reduced sequential processing
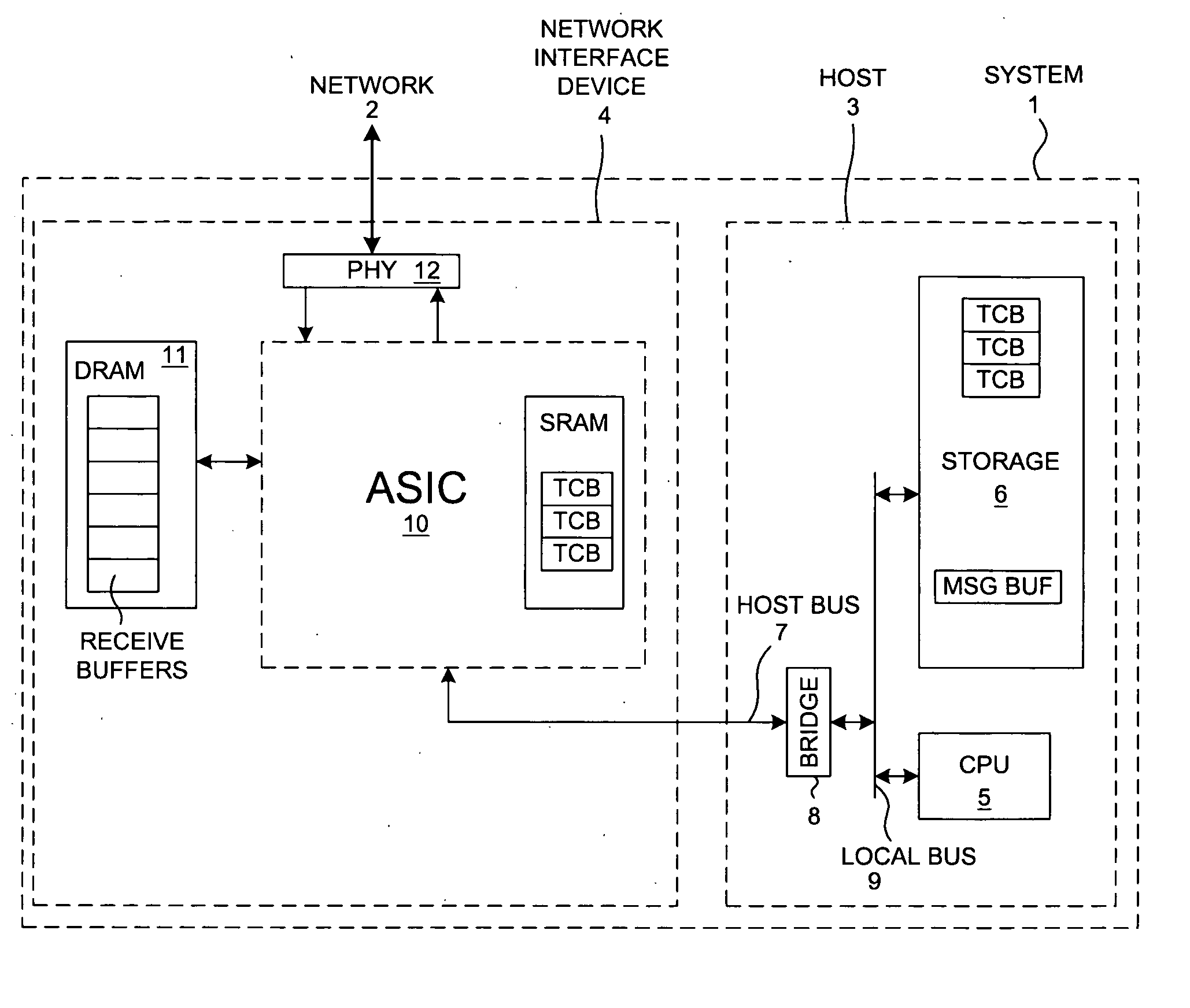
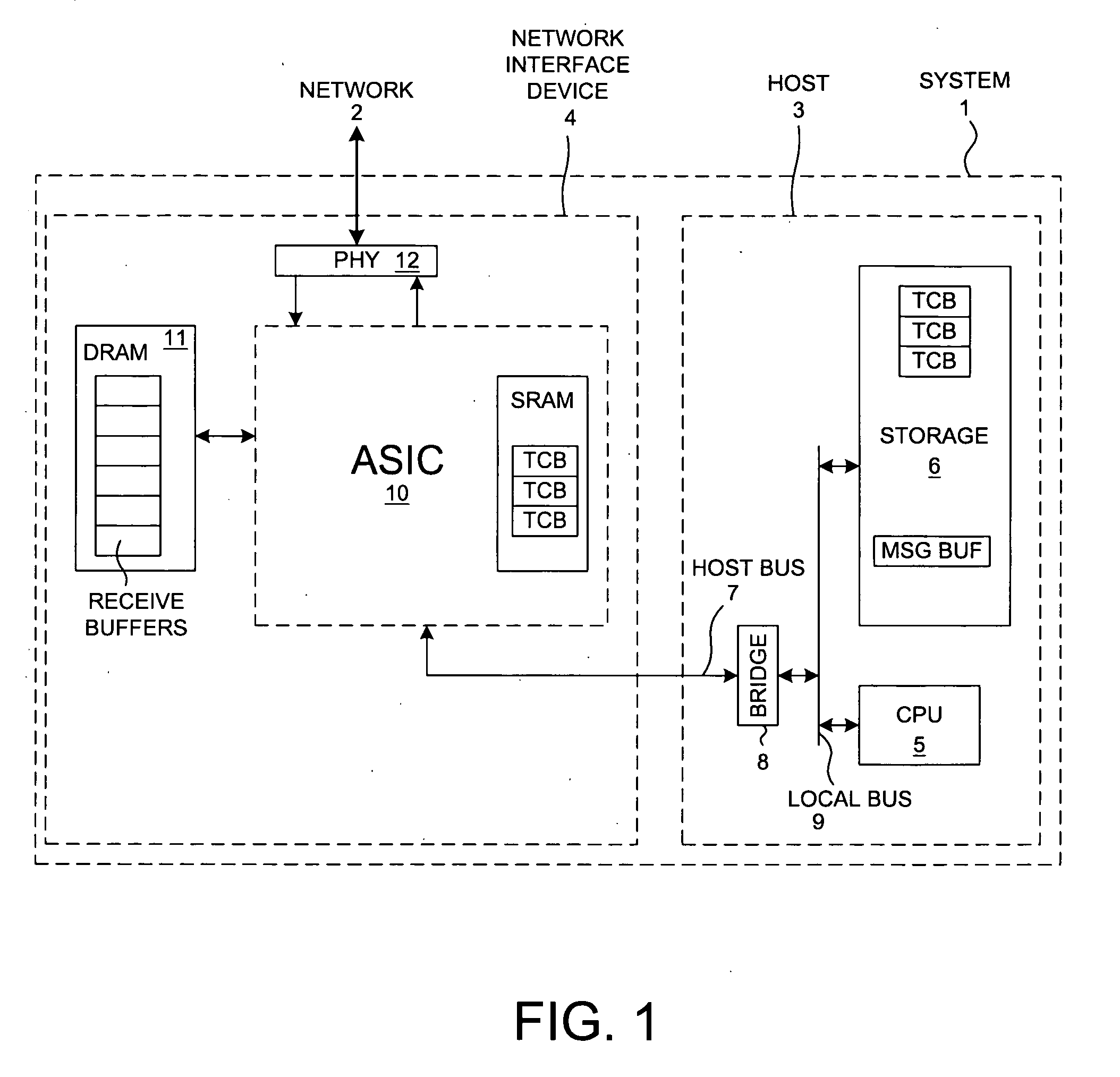
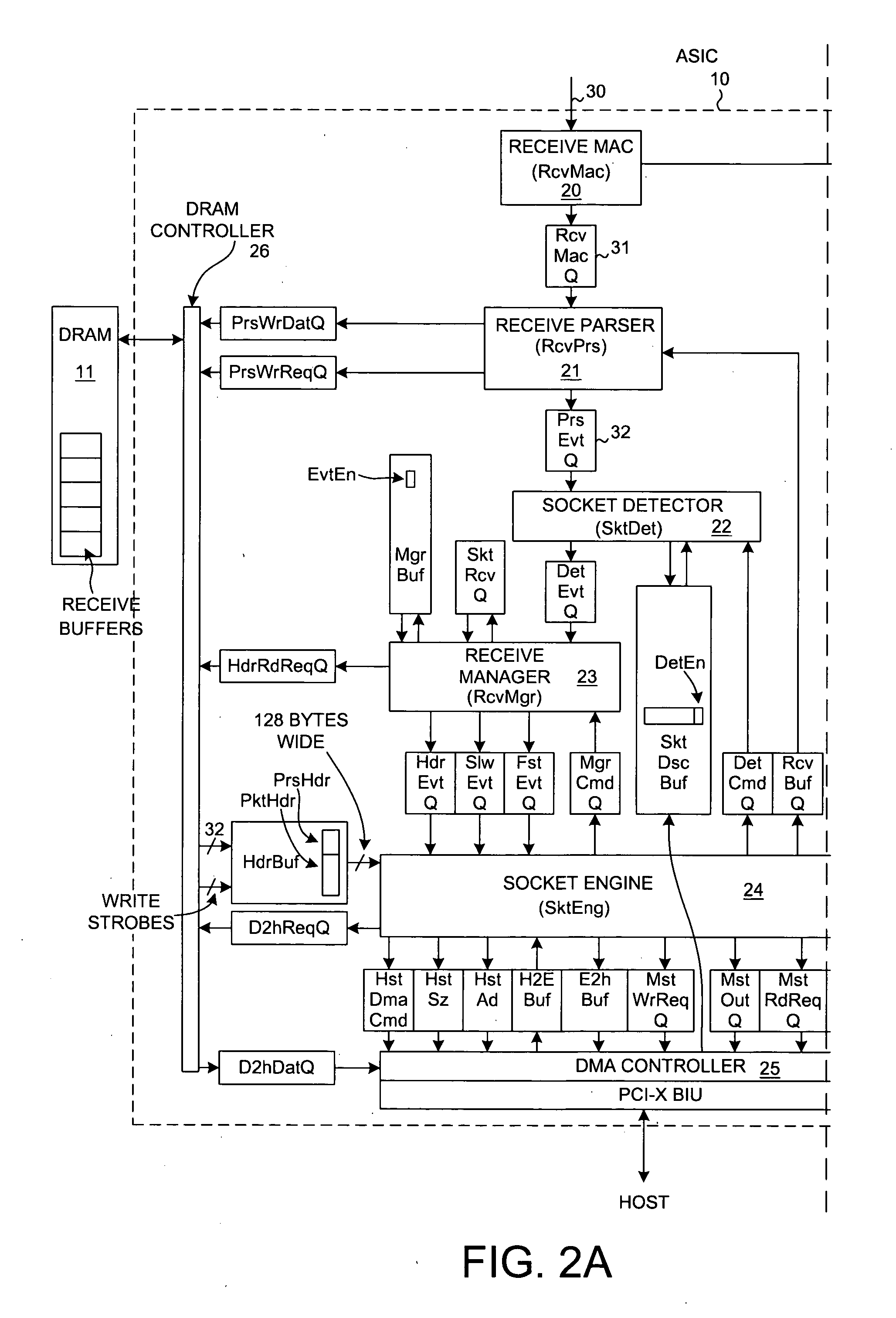
ActiveUS6996070B2Block valueNarrow structureError preventionTransmission systemsProtocol processingState variable
A TCP Offload Engine (TOE) device includes a state machine that performs TCP / IP protocol processing operations in parallel. In a first aspect, the state machine includes a first memory, a second memory, and combinatorial logic. The first memory stores and simultaneously outputs multiple TCP state variables. The second memory stores and simultaneously outputs multiple header values. In contrast to a sequential processor technique, the combinatorial logic generates a flush detect signal from the TCP state variables and header values without performing sequential processor instructions or sequential memory accesses. In a second aspect, a TOE includes a state machine that performs an update of multiple TCP state variables in a TCB buffer all simultaneously, thereby avoiding multiple sequential writes to the TCB buffer memory. In a third aspect, a TOE involves a state machine that sets up a DMA move in a single state machine clock cycle.
Owner:ALACRITECH
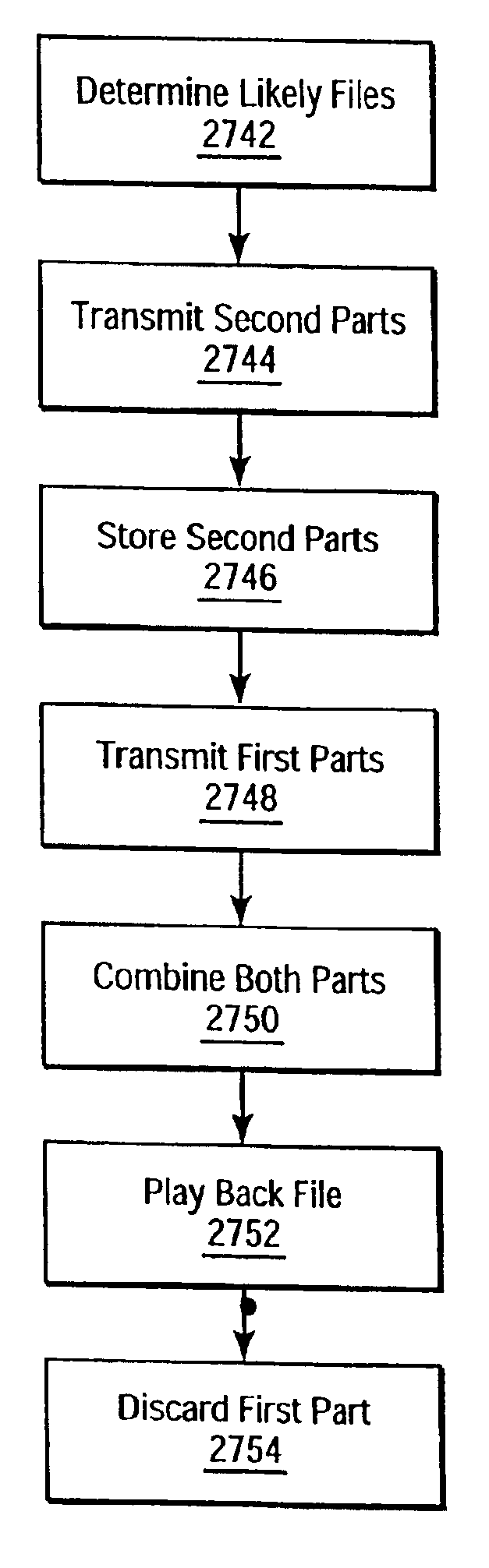
System for controlling and enforcing playback restrictions for a media file by splitting the media file into usable and unusable portions for playback
InactiveUS7024485B2Improved quality and security and efficiencyAvoid bottlenecksMultimedia data retrievalMultiple digital computer combinationsData setQuality level
Files are divided into parts and at least some of the parts are transmitted to a client using a communication channel. At least some of the transmitted parts are cached locally. This allows subsequent streaming playback of the file while using less bandwidth by transmitting the part of the file that hasn't been cached, and combining the cached parts with the transmitted parts. In some embodiments, files may be represented at a low quality level by a first data set, and at higher quality levels with additional data sets. Data sets are cached locally, so that during subsequent streaming playback of the file, the quality level of the playback may be improved by sending additional data sets using bandwidth that would otherwise be dedicated to transmitting the cached data sets.
Owner:R2 SOLUTIONS
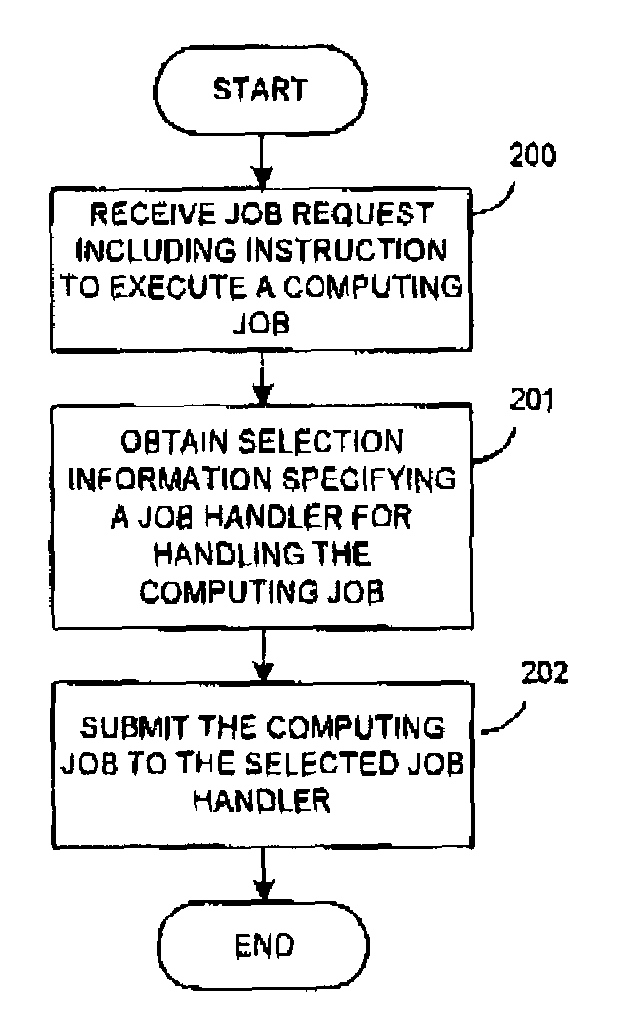
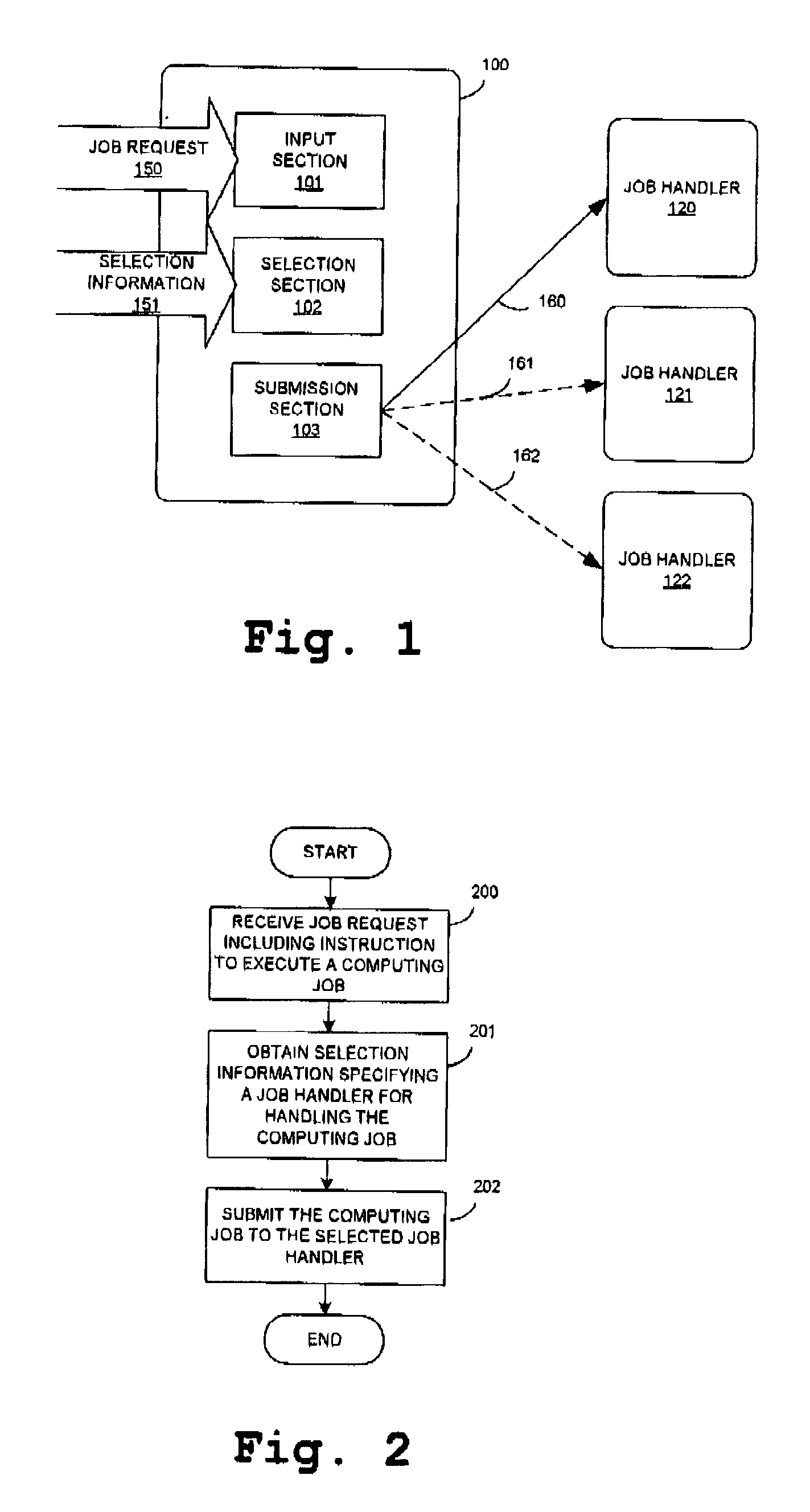
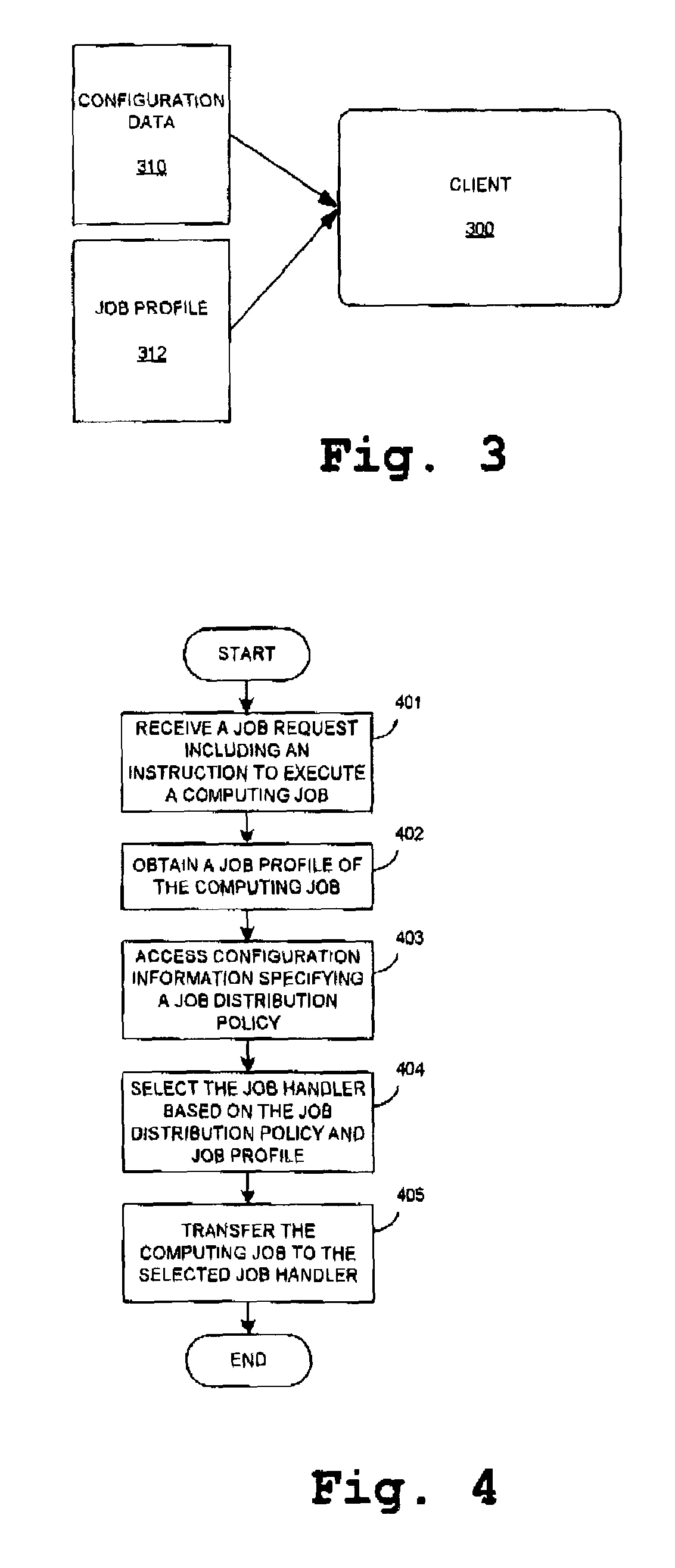
Submitting jobs in a distributed computing environment
ActiveUS7185046B2Improve usabilityAvoid bottlenecksResource allocationInterprogram communicationDistributed Computing EnvironmentClient-side
Method and system for submitting computing jobs in a distributed computing environment including receiving a job request with an instruction to execute a computing job, selecting a job handler for handling the computing job based on selection information and submitting the computing job to the selected job handler. The invention can be embodied in a client unit, thus providing a decentralized distribution of computing jobs and avoiding bottlenecks in the distribution of computing jobs for example in a computing grid.
Owner:ORACLE INT CORP
TCP/IP offload device with reduced sequential processing
ActiveUS20050122986A1Reduce power consumptionLess-expensive memoryError preventionTransmission systemsProtocol processingState variable
A TCP Offload Engine (TOE) device includes a state machine that performs TCP / IP protocol processing operations in parallel. In a first aspect, the state machine includes a first memory, a second memory, and combinatorial logic. The first memory stores and simultaneously outputs multiple TCP state variables. The second memory stores and simultaneously outputs multiple header values. In contrast to a sequential processor technique, the combinatorial logic generates a flush detect signal from the TCP state variables and header values without performing sequential processor instructions or sequential memory accesses. In a second aspect, a TOE includes a state machine that performs an update of multiple TCP state variables in a TCB buffer all simultaneously, thereby avoiding multiple sequential writes to the TCB buffer memory. In a third aspect, a TOE involves a state machine that sets up a DMA move in a single state machine clock cycle.
Owner:ALACRITECH
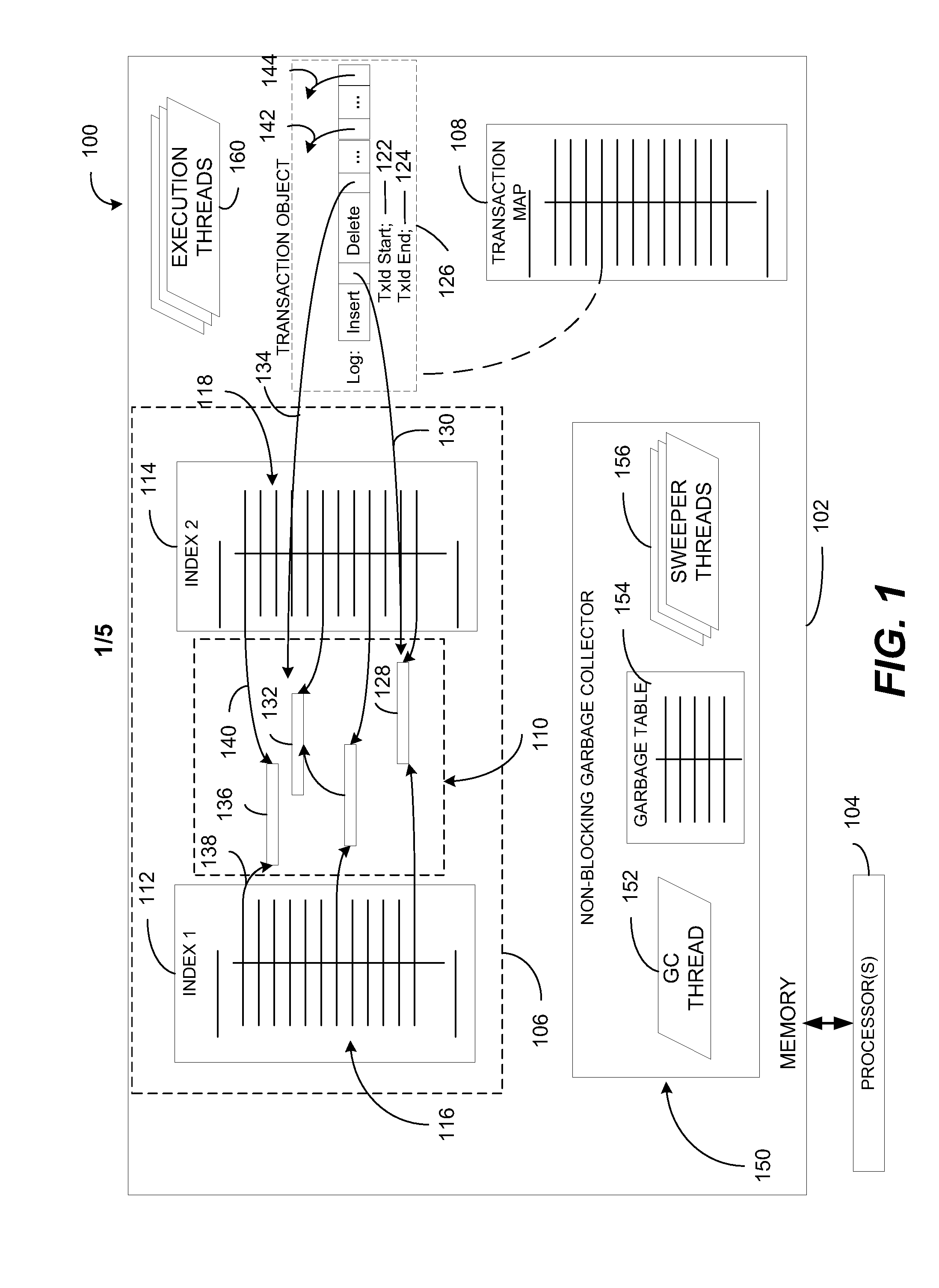
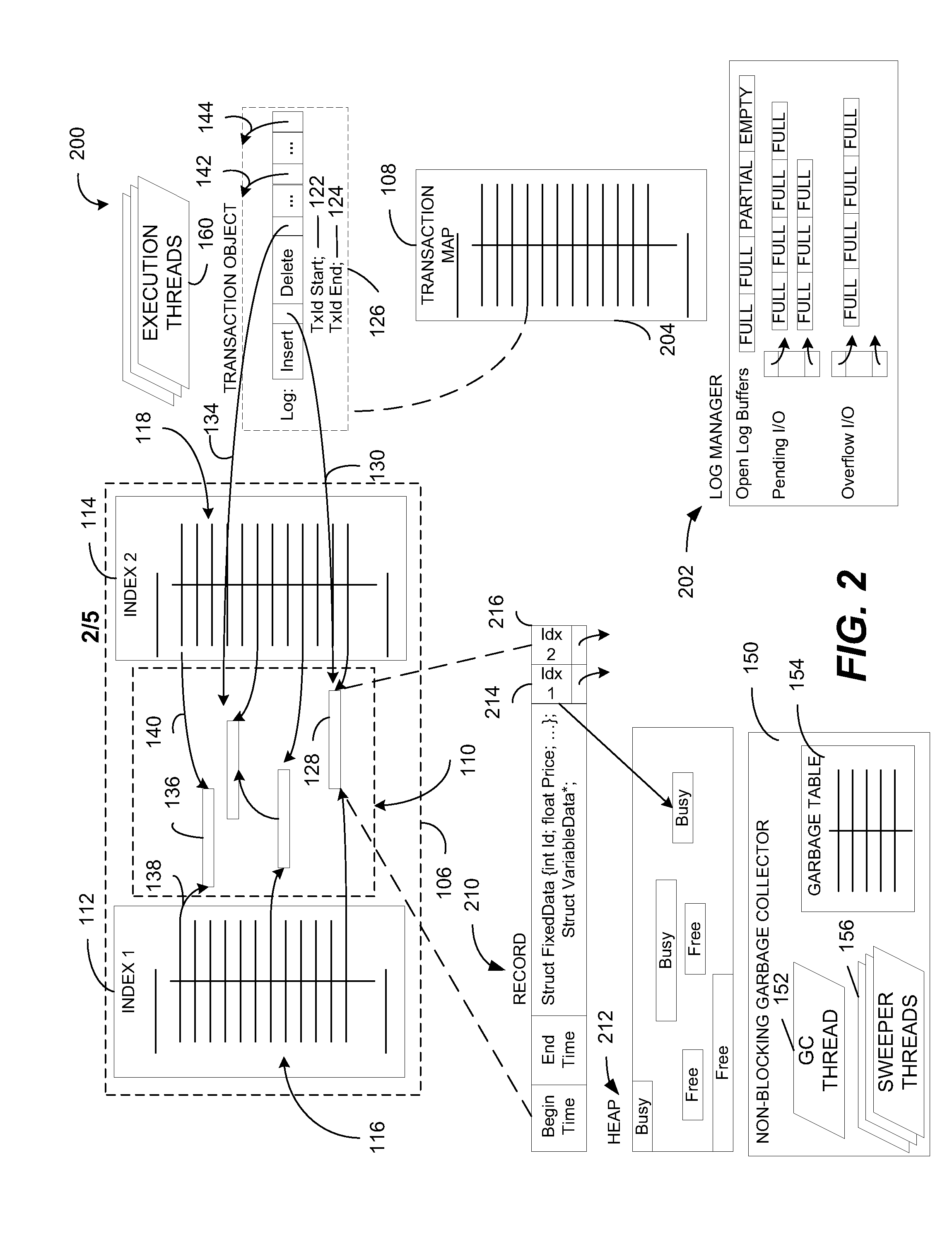
In-memory database system
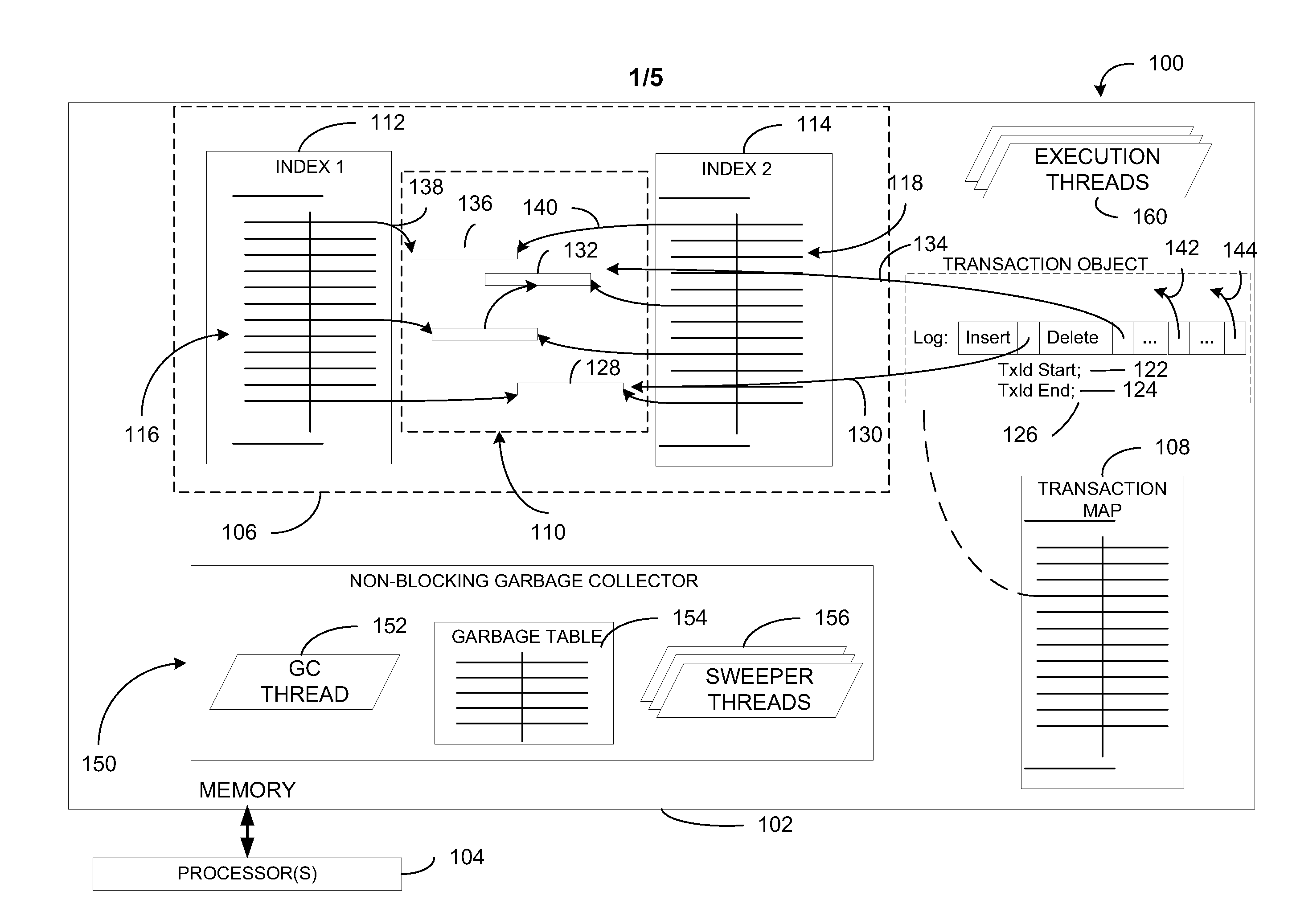
ActiveUS20110252000A1Effectively scaledMeet growth needsMemory architecture accessing/allocationDigital data processing detailsIn-memory databaseComputerized system
A computer system includes a memory and a processor coupled to the memory. The processor is configured to execute instructions that cause execution of an in-memory database system that includes one or more database tables. Each database table includes a plurality of rows, where data representing each row is stored in the memory. The in-memory database system also includes a plurality of indexes associated with the one or more database tables, where each index is implemented by a lock-free data structure. Update logic at the in-memory database system is configured to update a first version of a particular row to create a second version of the particular row. The in-memory database system includes a non-blocking garbage collector configured to identify data representing outdated versions of rows.
Owner:MICROSOFT TECH LICENSING LLC
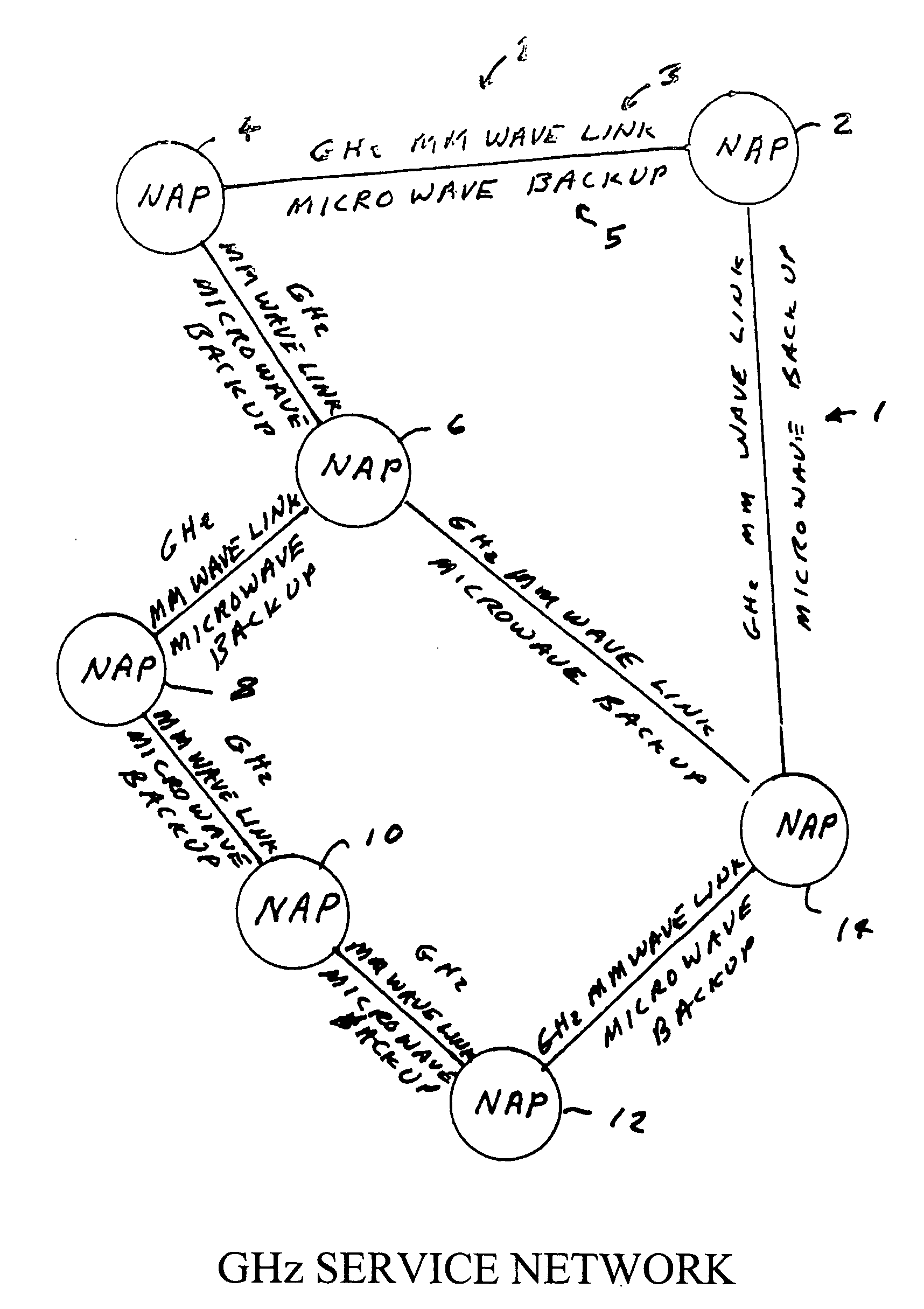
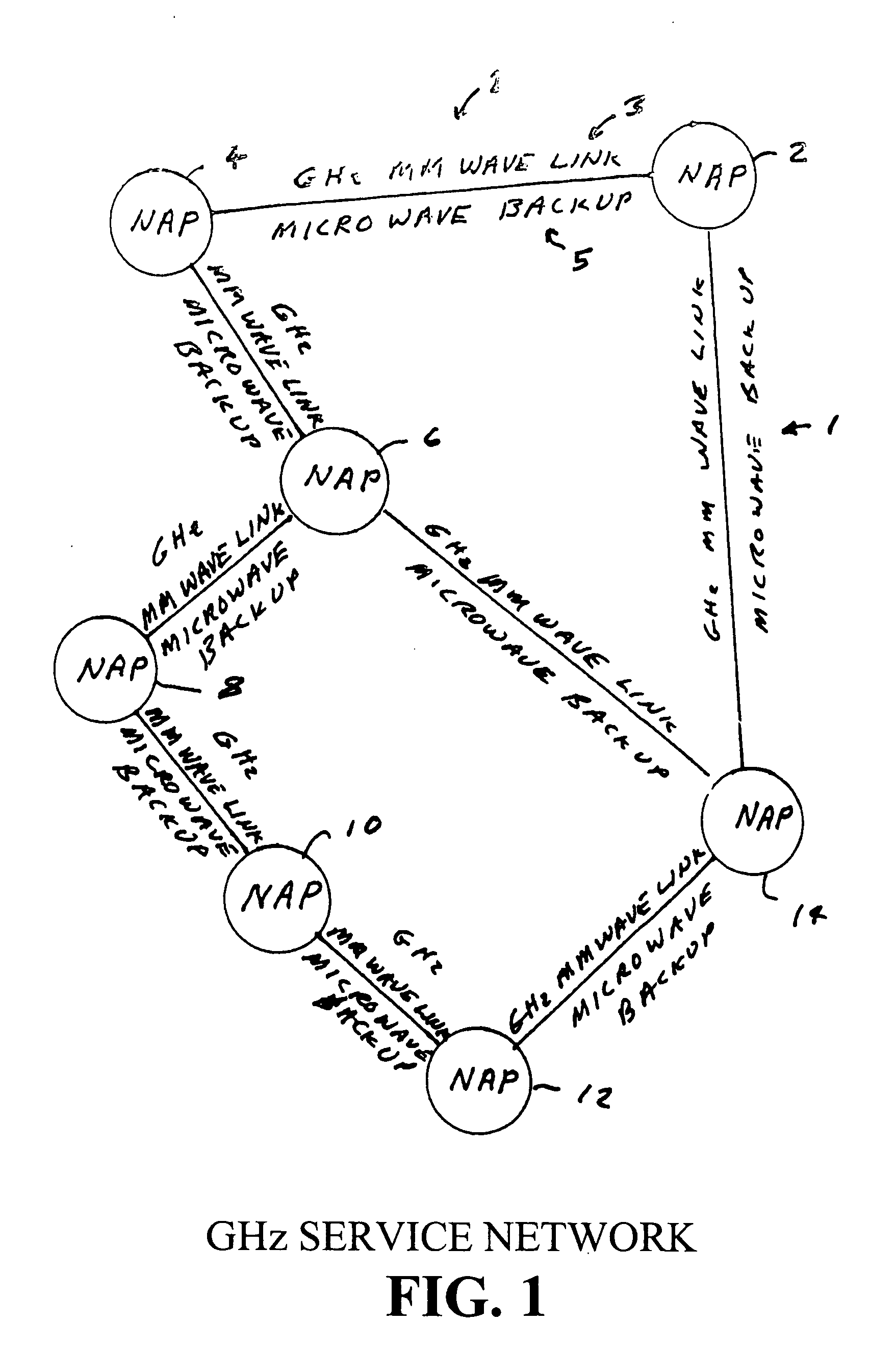
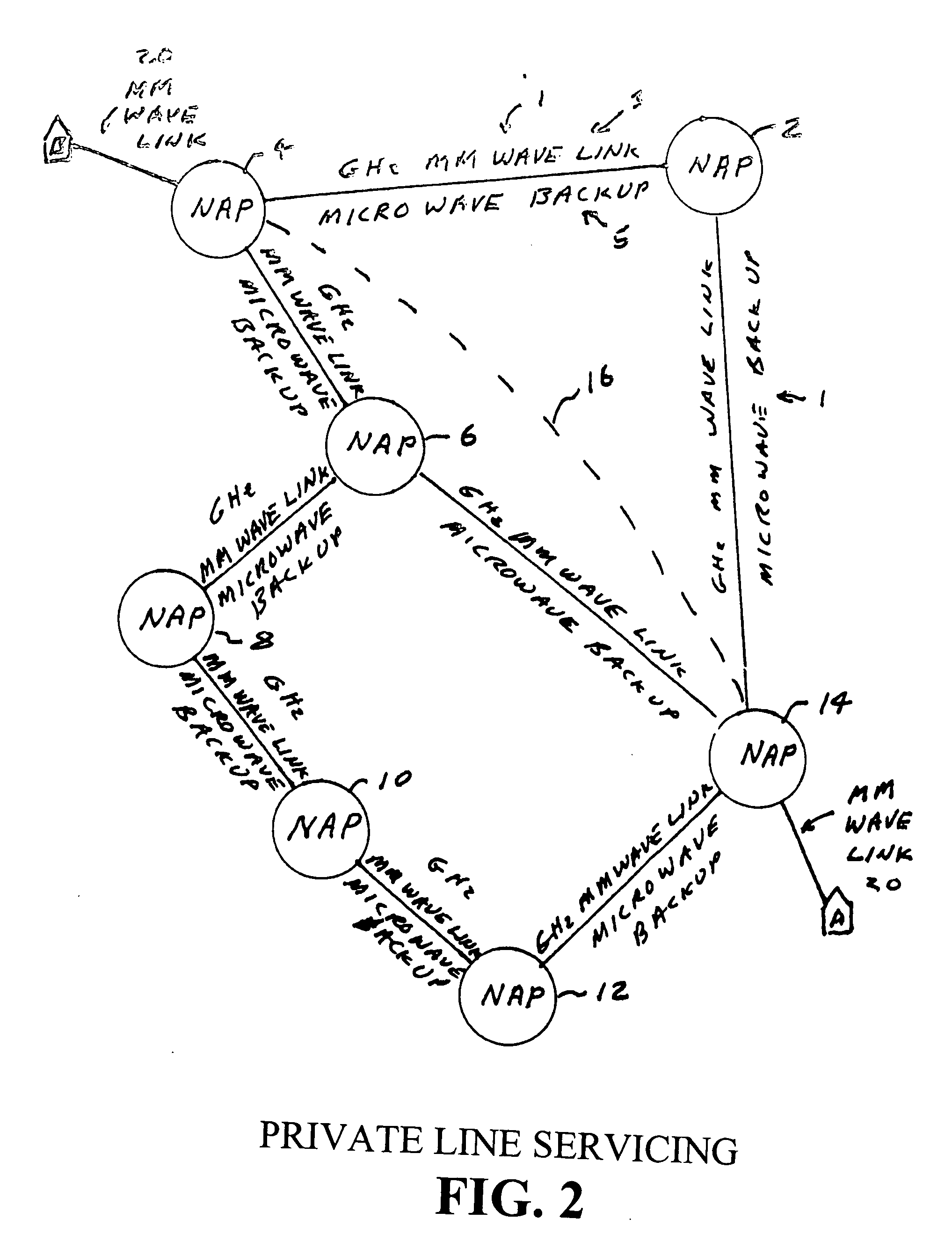
Circuit switched millimeter wave communication network
InactiveUS20120135724A1High bandwidthLower latencyRadio transmissionWireless commuication servicesAntenna designHigh bandwidth
A high bandwidth, low latency middle-mile core communications network providing low-cost and high-speed communications among the users of the network. Embodiments of the invention include a number of network access points located at a number of spaced apart sites. At least some of these network access points in the network are in communication with each other via millimeter radio links with microwave backup links. In preferred embodiments the millimeter radio links include two millimeter radios, one transmitting in the frequency range of 71-76 GHz and receiving in the frequency range if 81 to 86 GHz and the other radio transmitting in the frequency range of 81-86 GHz and receiving in the frequency range if 71 to 76 GHz. In these preferred embodiments each millimeter wave radio is equipped with an antenna designed to produce a millimeter wave beam with an angular spread of less than two degrees. A high-speed switch is located at each network access point. The switches include a plurality of ports through which a plurality of network users transmits information through the network. Preferred embodiments utilize Ethernet switches programmed to encapsulate and tag incoming packets with a special set of tags which allow the tagging switch and other Ethernet switches in the network to direct the packets to one or more output ports of itself and / or one or more of the output ports of other Ethernet switches at one or more distant network access points, without a need for any of the network equipment to read any MAC or IP address information contained in the packets.
Owner:TREX ENTERPRISES CORP
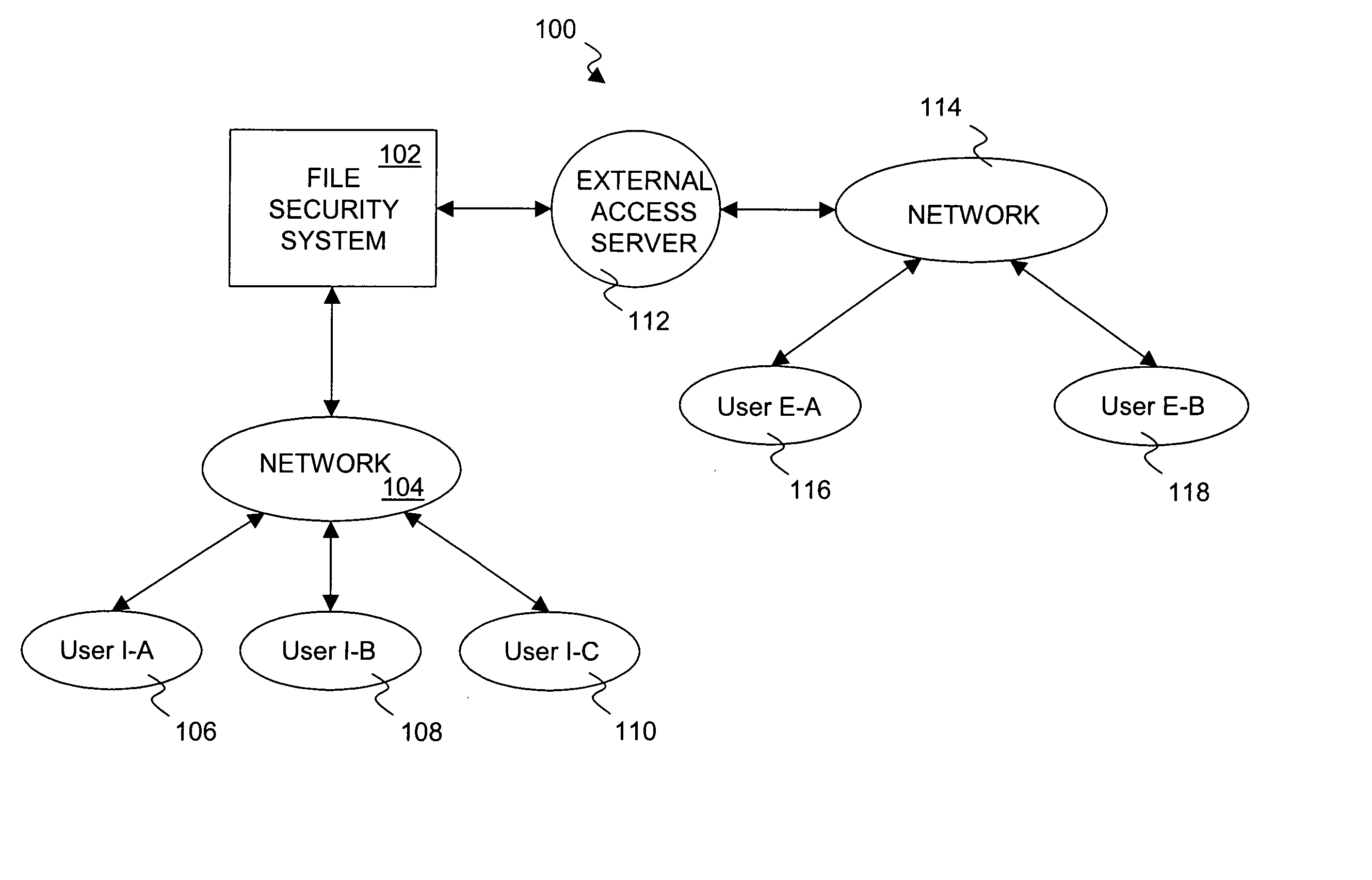
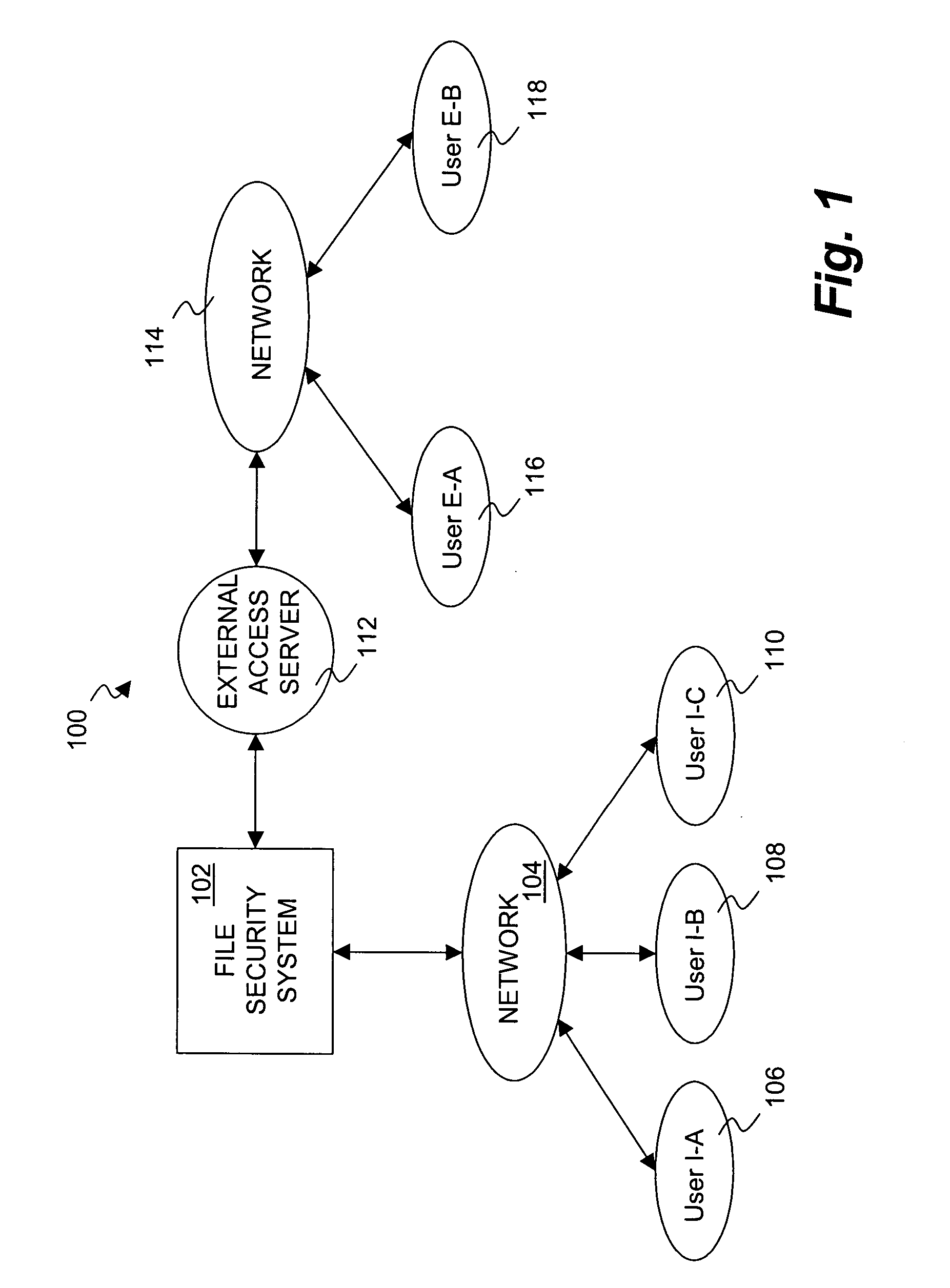
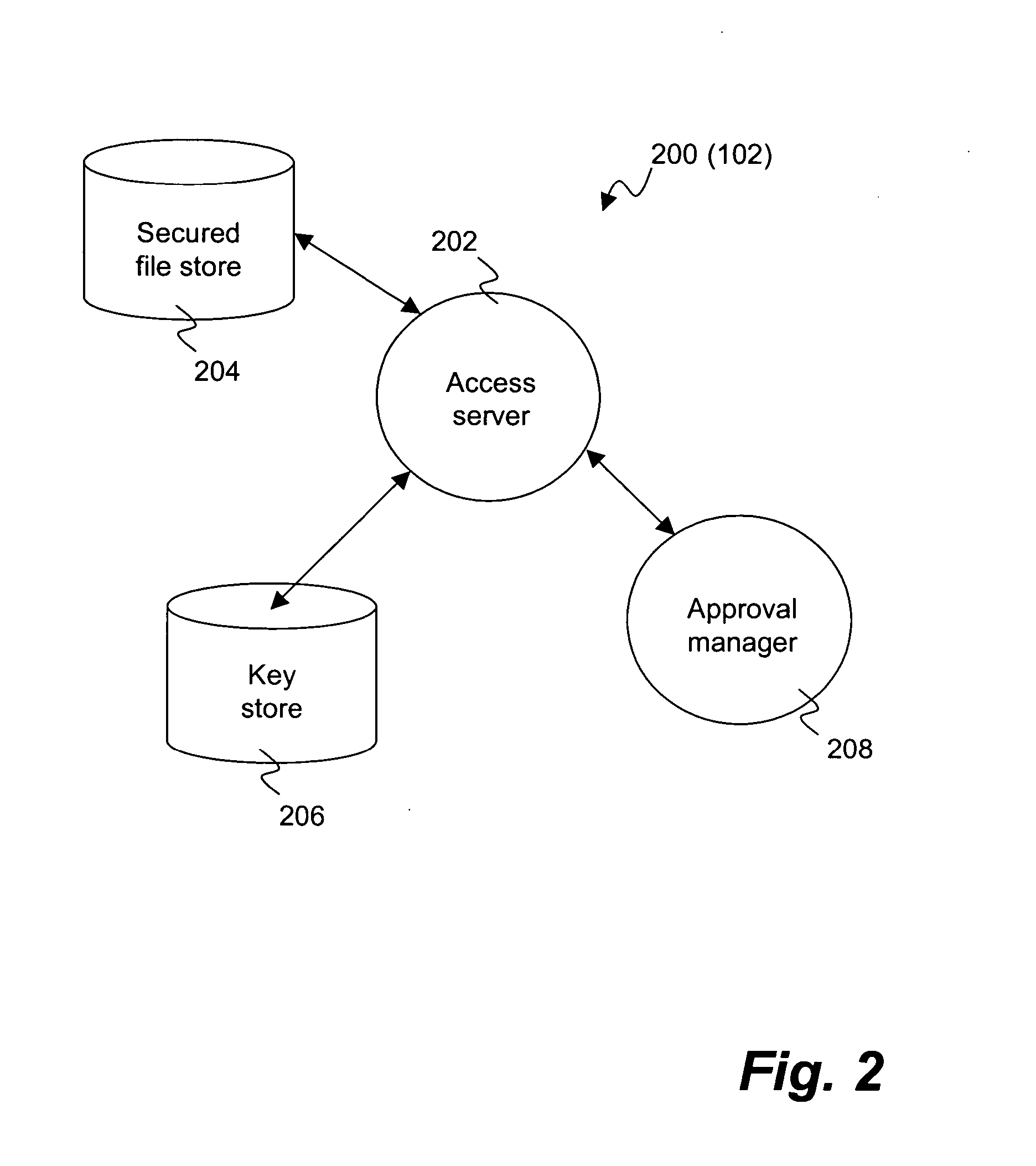
Method and system for proxy approval of security changes for a file security system
InactiveUS20050086531A1Avoid bottlenecksDigital data processing detailsUnauthorized memory use protectionSecurity systemDocument security
A system and method for providing a file security system with an approval process to implement security changes are disclosed. The approval process can be substantially automated as well as configurable and / or flexible. The approval process can make use of a set of approvers that can approve or deny a security change. Different security changes can require the approval of different approvers. The approvers can also be arranged into groups of approvers, and such groups can make use of a hierarchical arrangement.
Owner:INTELLECTUAL VENTURES I LLC
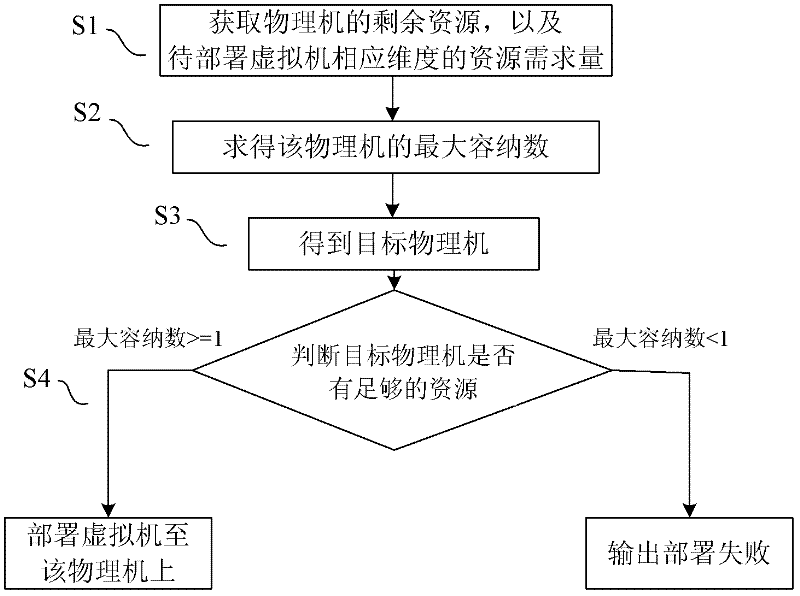
Dynamic deployment method for virtual machines
ActiveCN102446115AEasy to operateWide range of applicationsResource allocationSoftware simulation/interpretation/emulationVirtual machineResource utilization
The invention relates to a dynamic deployment method for virtual machines. The method comprises the following steps: dividing residual resources of each dimension on a physical machine by demanded resource quantity of a corresponding dimension of a to-be-deployed physical machine so as to obtain a ratio sequence, screening out the minimum value of ratios in the sequence and taking the minimum value as the maximum accommodating number of the physical machine to a to-be-deployed virtual machine; selecting a physical machine with the largest maximum accommodating number, and judging whether the physical machine has enough resources to accommodate the to-be-deployed virtual machine; if the value of the maximum accommodating number of the target physical machine is greater than or equal to 1, deploying the virtual machine to the physical machine; and if the maximum accommodating number of the target physical machine is less than 1, outputting that the deployment of the virtual machine fails. By using the method disclosed by the invention, a 'short board' phenomenon, namely, resources of other dimensions are wasted because of the lack of resources of some dimension of a physical machine in a cluster, can be avoided, and the resource utilization ratio of the physical machine can be increased.
Owner:ZHEJIANG UNIV
Method, system, and program for managing client access to a shared resource
InactiveUS20020099843A1Easy to solveReduce rateMultiple digital computer combinationsSpecial data processing applicationsClient-sideShared resource
Provided is a method, system, and program for managing client transactions requesting access to a shared resource. Client transactions are logged in a log file from multiple clients. A determination is made of one client transmitting data at a transmission rate less than a threshold transmission rate. Subsequent transactions from the determined client accessing the shared resource are denied to provide additional space in the log file for new transactions from additional clients requesting access to the resource.
Owner:TWITTER INC
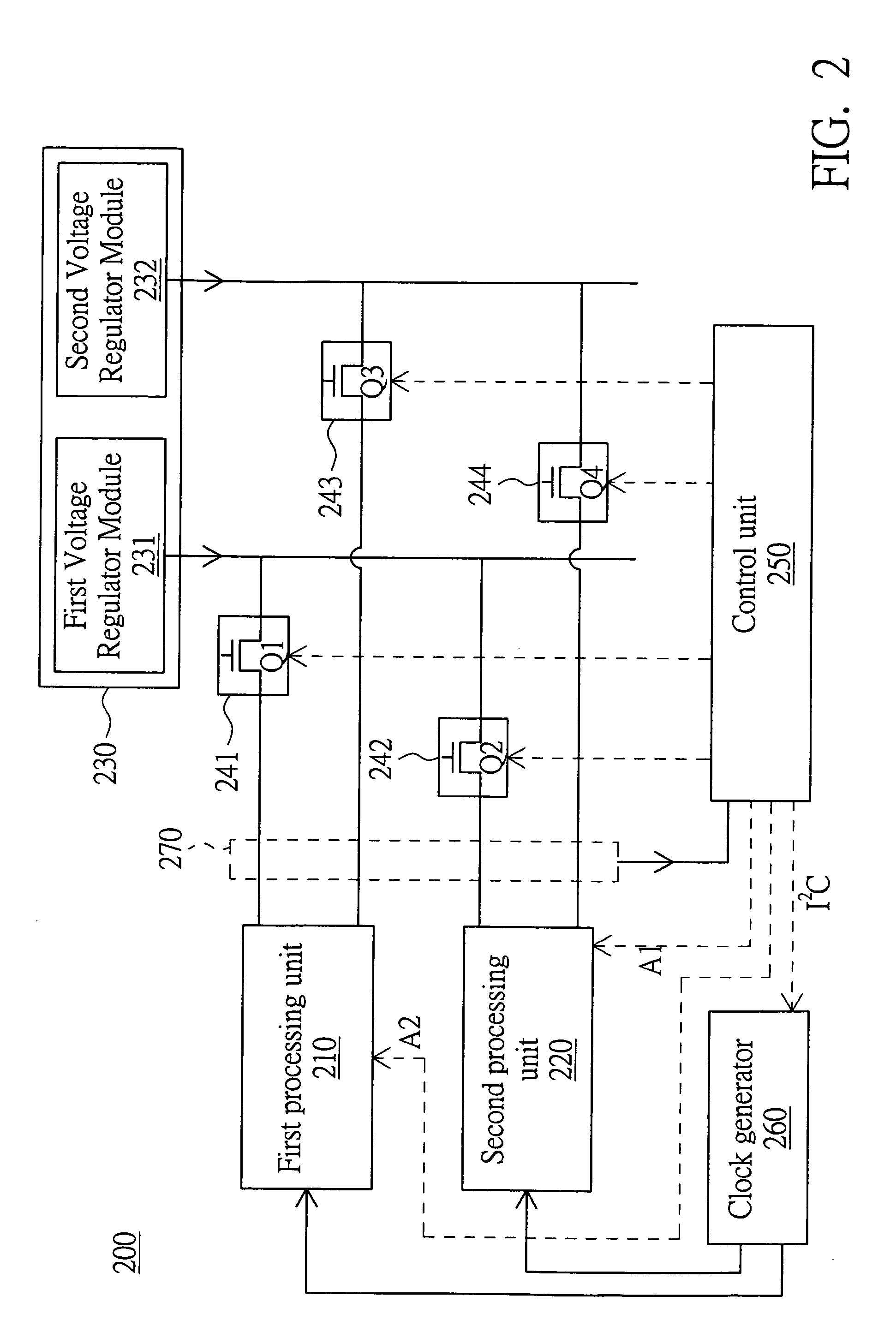
Multi-processor system and performance adjustment method thereof
ActiveUS20080172565A1Avoid bottlenecksImprove system throughputEnergy efficient ICTVolume/mass flow measurementMulti processorParallel computing
A multi-processor system and a performance adjustment method thereof are disclosed. The multi-processor system includes a first processing unit and a second processing unit, the performance adjustment method includes: first, detecting the load of each processing unit to obtain corresponding detected data; then, determining whether one of the processing units has the most load; finally, if the first processing unit has the most load, increasing the power supply to the first processing unit.
Owner:ASUSTEK COMPUTER INC
Systems and method for malware detection
ActiveUS8763127B2Reduce dimensionalityImprove processing speedMemory loss protectionError detection/correctionFeature vectorSupport vector machine
A system and method for distinguishing human input events from malware-generated events includes one or more central processing units (CPUs), one or more input devices and memory. The memory includes program code that when executed by the CPU causes the CPU to obtain a first set of input events from a user utilizing the input device. The first input events are used to obtain or derive a feature indicative of the user, such as a multi-dimensional feature vector as provided by a support vector machine. Second input events are then obtained, and the second input events are classified against the feature to determine if either the user or malware initiated the second input events.
Owner:RUTGERS THE STATE UNIV
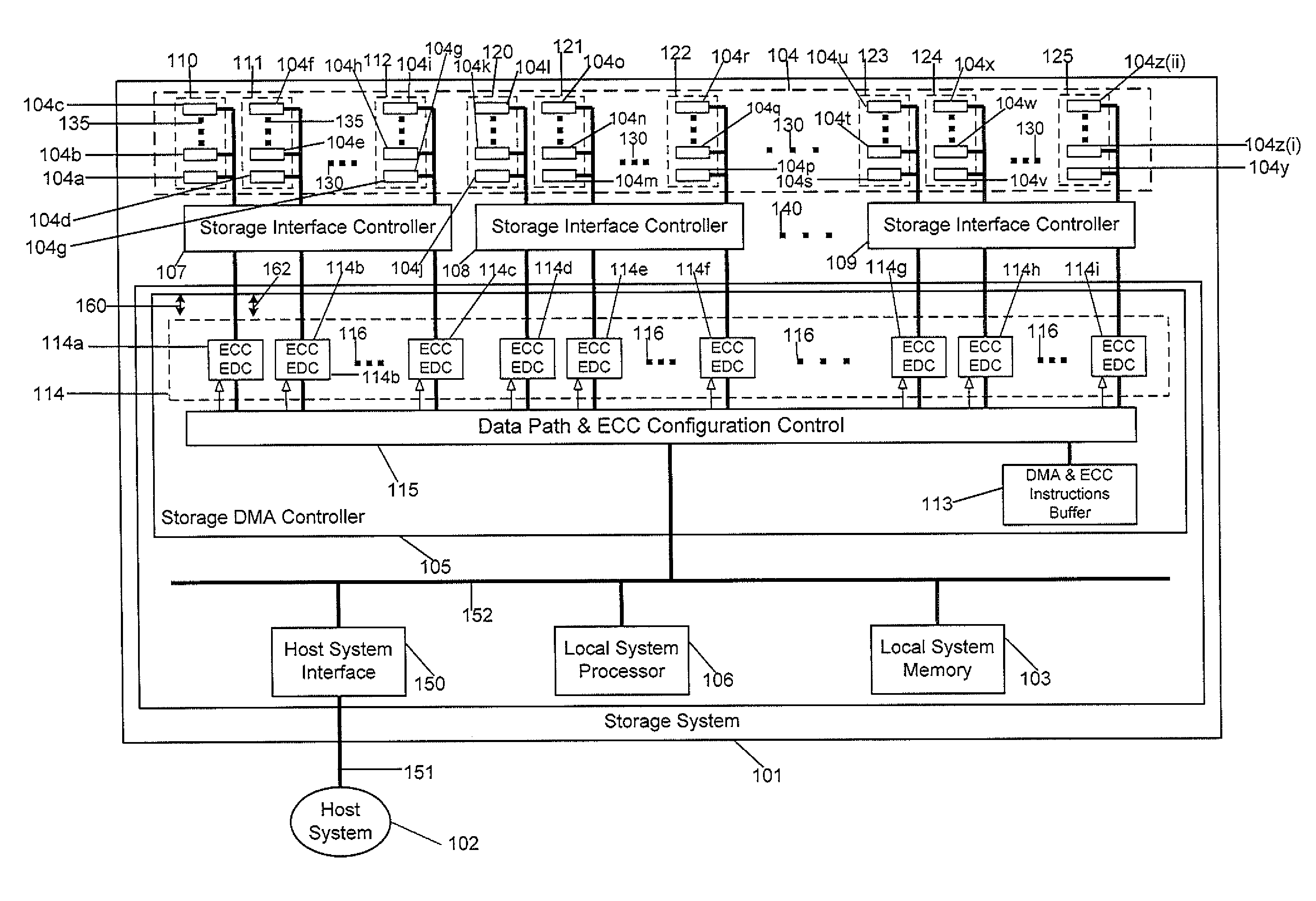
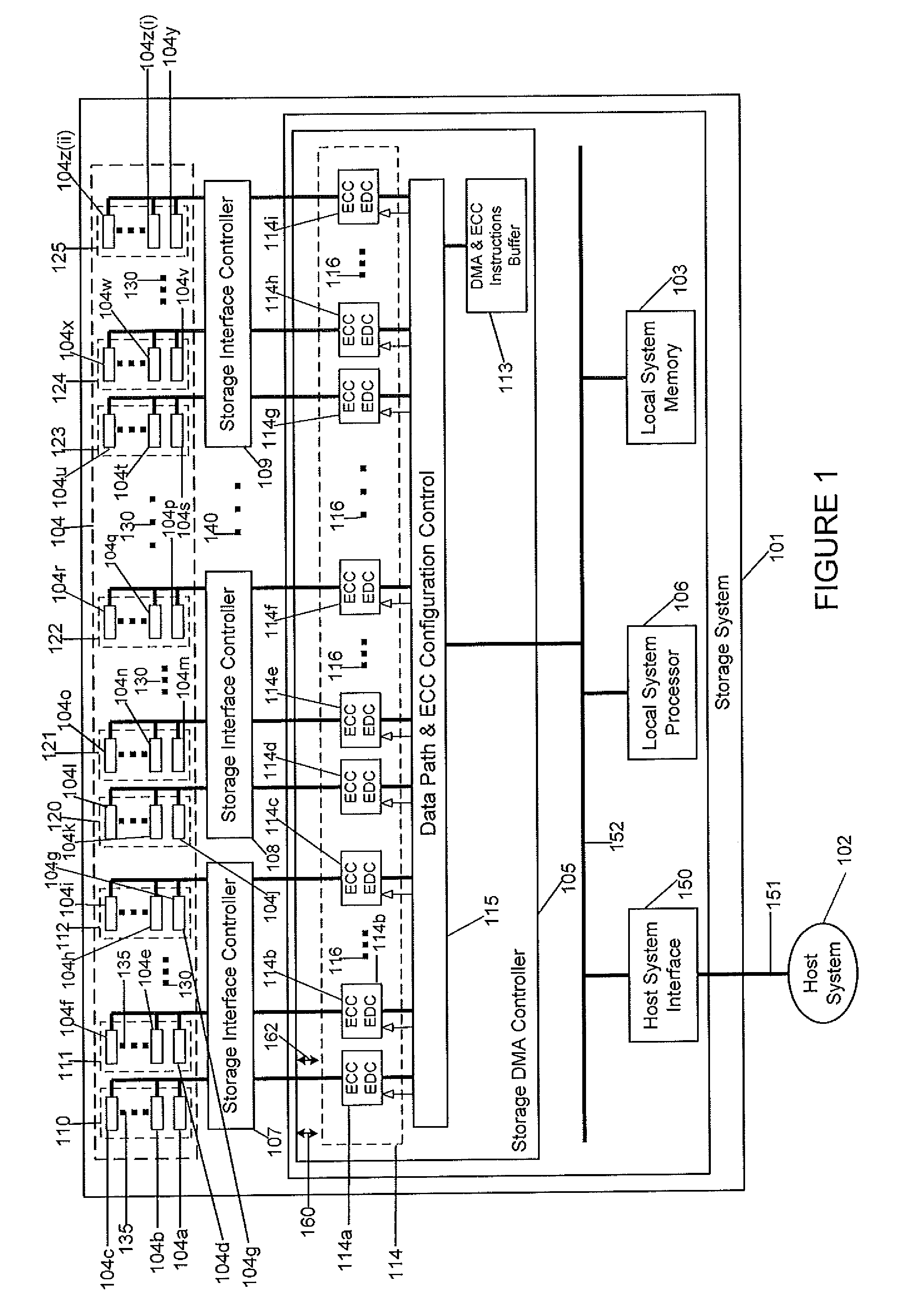
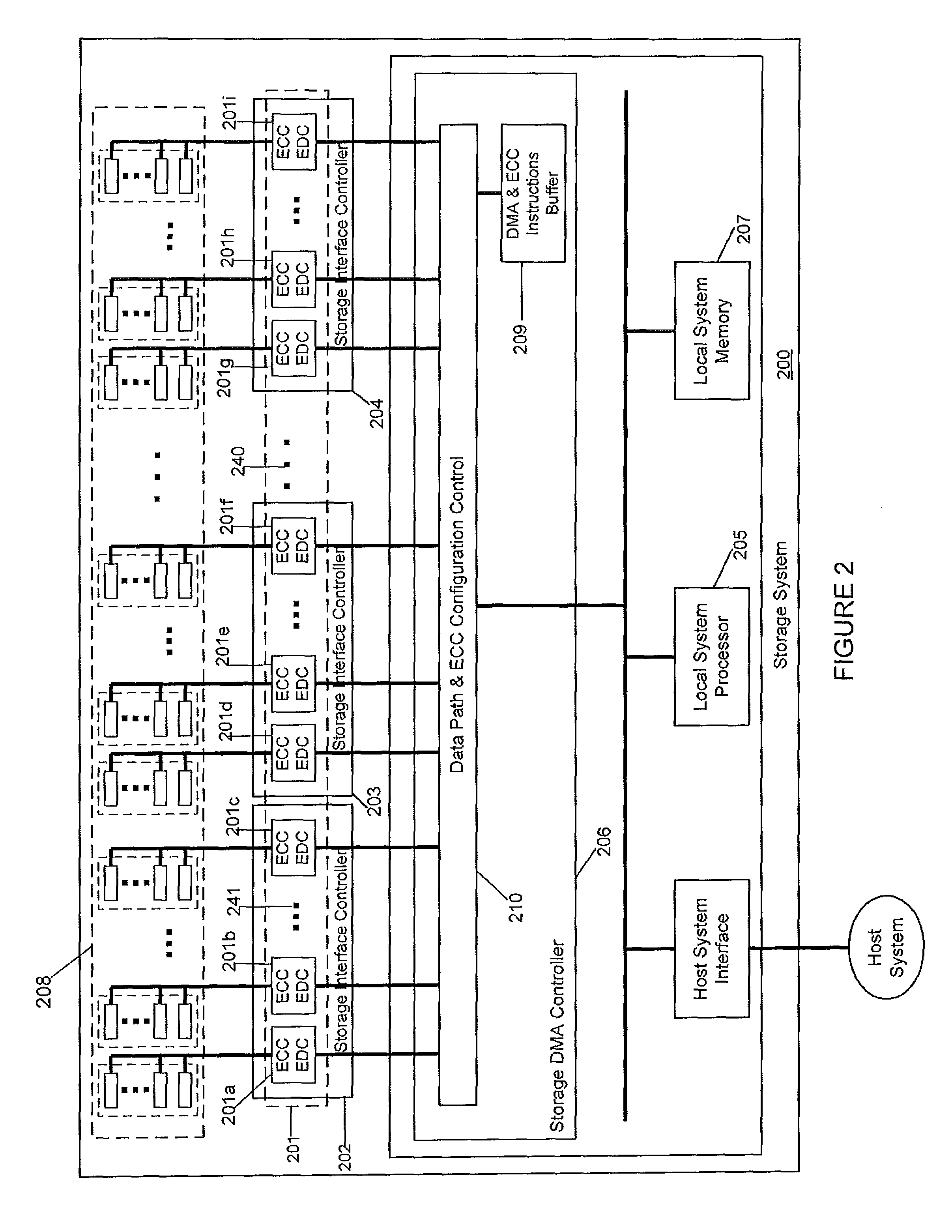
Distributed ECC engine for storage media
ActiveUS9043669B1Bottleneck is avoidedAvoid bottlenecksCode conversionError correction/detection using interleaving techniquesByteDistributed computing
Embodiments of the present invention relate to an apparatus, method, and / or sequence for a distributed ECC that may be used in a storage system. In another embodiment of the invention, an apparatus for handling distributed error correction code (ECC) operations, includes: a plurality of ECC engines configured to perform ECC operations in parallel on multiple data parts; the plurality of ECC engines distributed in parallel to receive some of the multiple data parts that are read from storage media devices and to receive some of the other multiple data parts that are to be written to the storage media devices; and the plurality of ECC engines configured to use respective ECC bytes corresponding to respective ones of the multiple data parts.
Owner:BITMICRO LLC
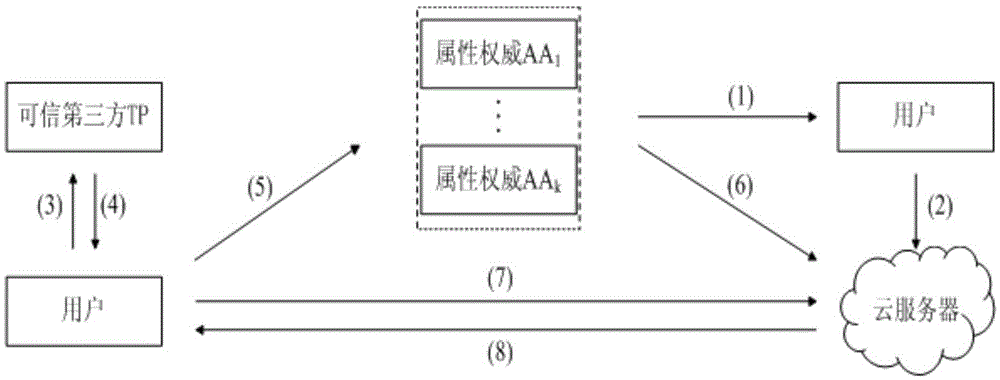
Distributed access control method for attribute-based encryption
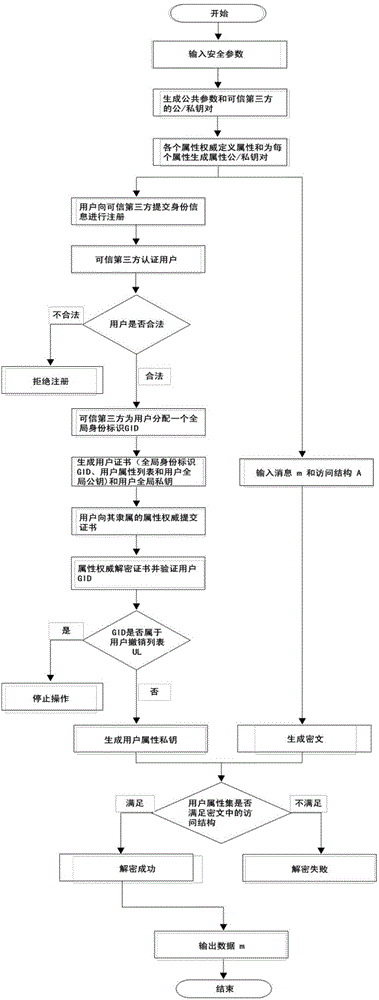
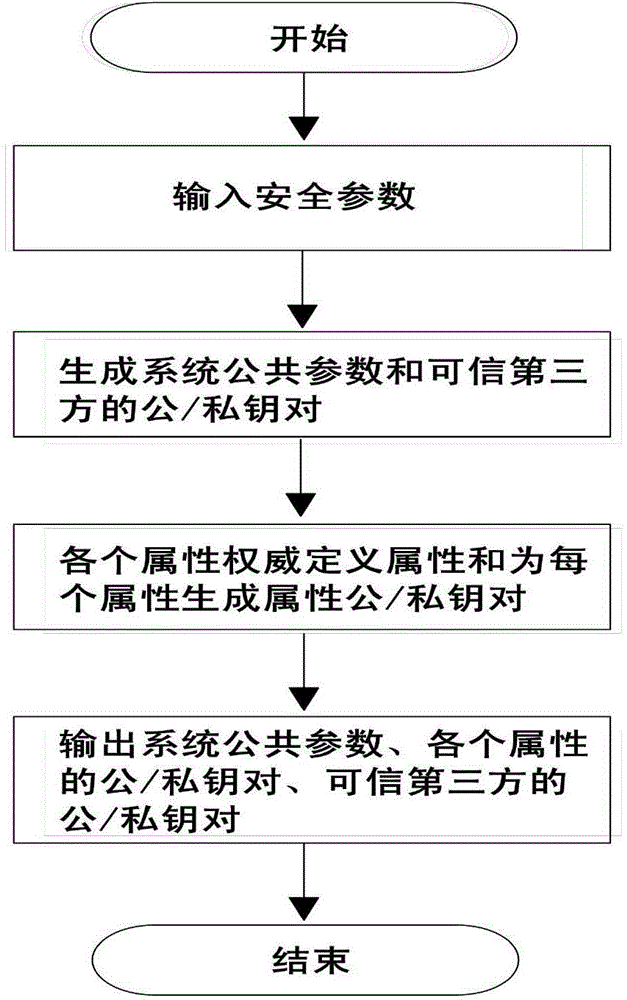
ActiveCN104901942AAvoid collusionAbility to decrypt all system ciphertextsKey distribution for secure communicationUser identity/authority verificationPrivacy protectionEngineering
The invention provides a distributed access control method for attribute-based encryption, and mainly aims to solve the problems of security and privacy protection of massive data in a cloud environment. A multi-authority ciphertext-policy attribute-based encryption (CP-ABE) mechanism is provided on the basis of CP-ABE. According to the mechanism, the workload of a single authority is shared with a plurality of authorities, and efficient outsourcing decryption, user revocation and dynamic join and exit supporting attribute authority (AA) can be realized. Through adoption of an access control mechanism provided by the invention, efficient, distributed, extensible and fine-granularity access control can be realized while the security and privacy of the massive data are protected.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Apparatus and method for performing rearrangement and arithmetic operations on data
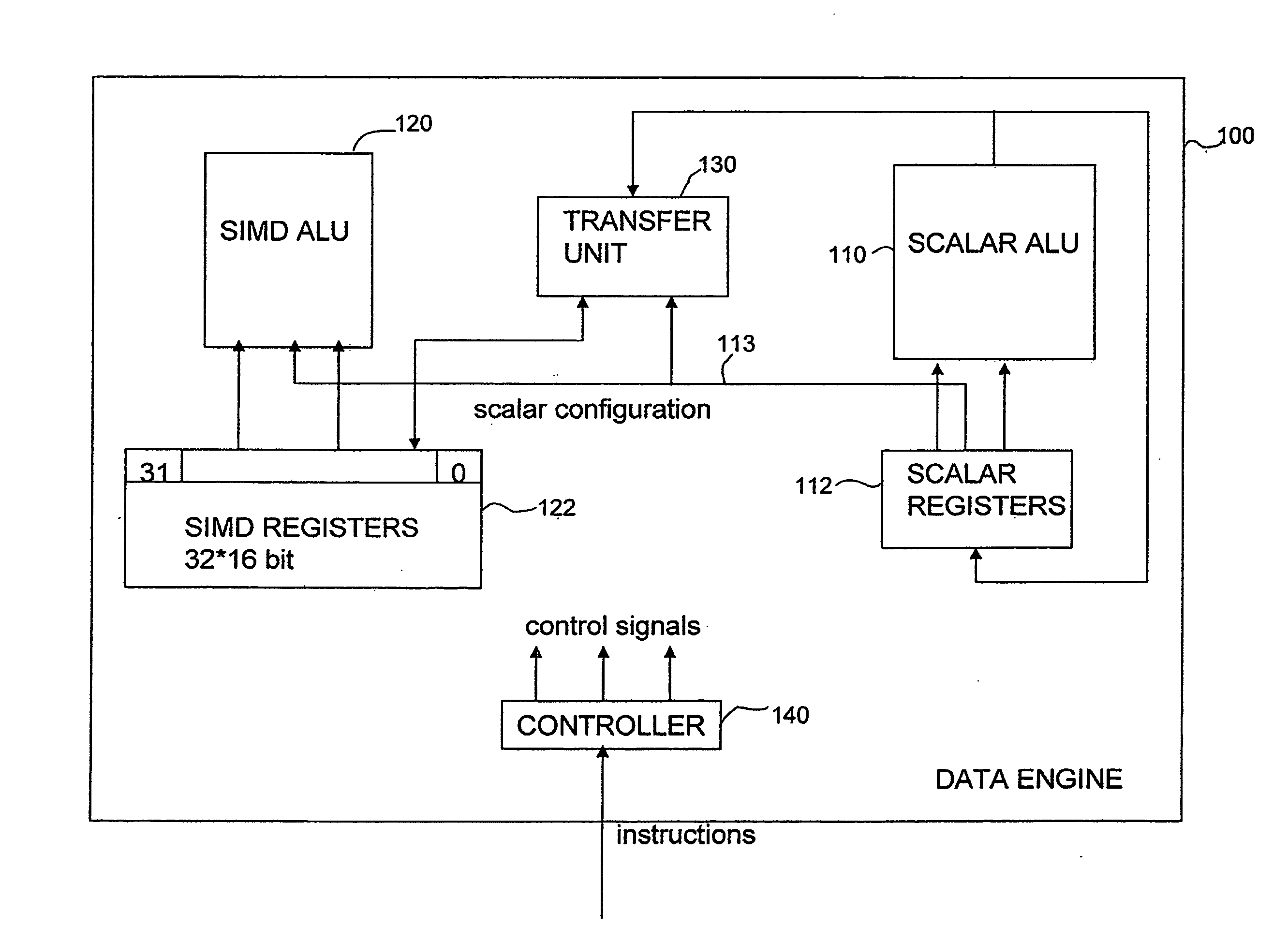
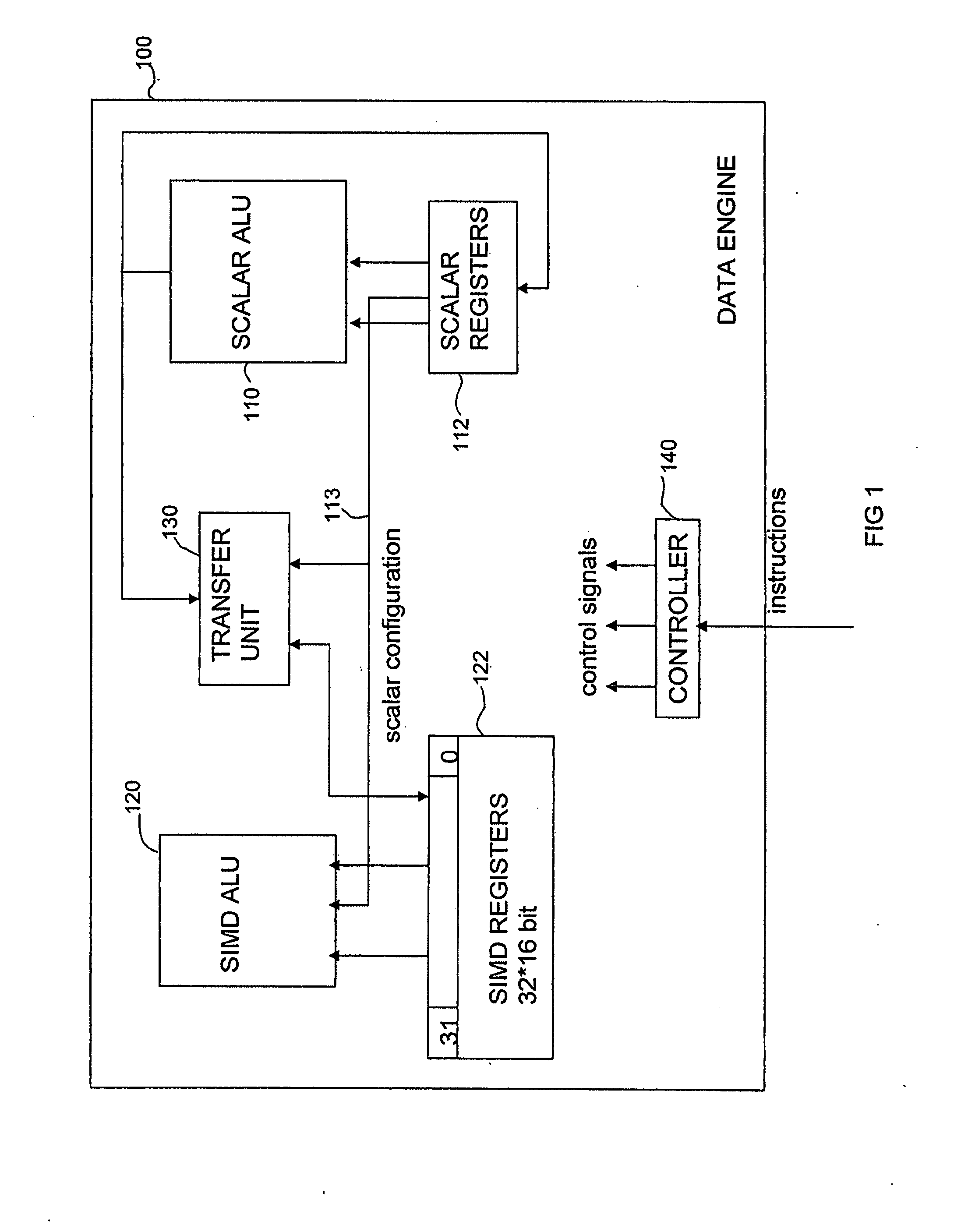
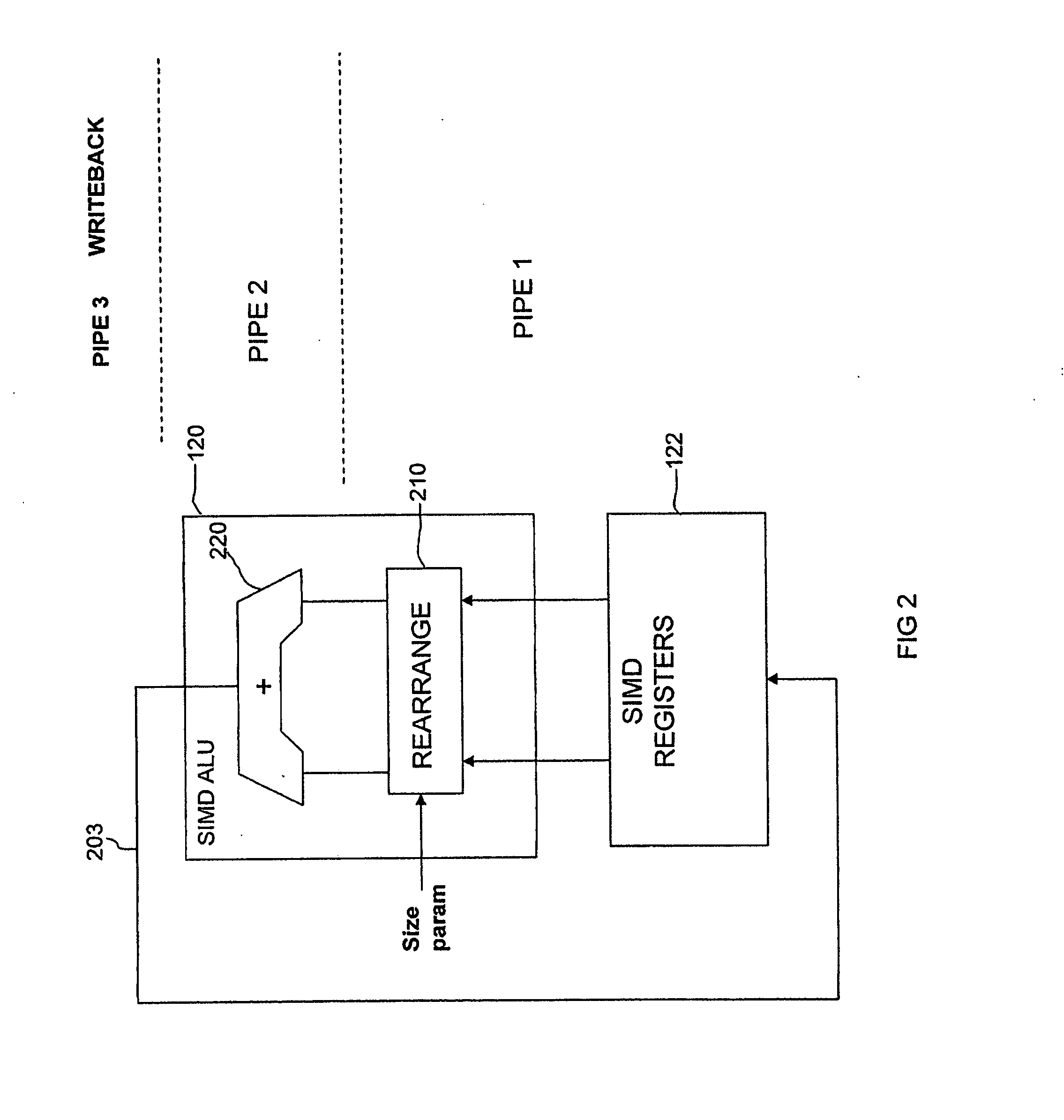
ActiveUS20080140750A1Flexible configurationFacilitates rearrangement operationRegister arrangementsComputation using non-contact making devicesProgram instructionData element
An apparatus and method are provided for performing rearrangement operations and arithmetic operations on data. The data processing apparatus has processing circuitry for performing SIMD processing operations and scalar processing operations, a register bank for storing data and control circuitry responsive to program instructions to control the processing circuitry to perform data processing operations. The control circuitry is arranged to responsive to a combined rearrangement arithmetic instruction to control the processing circuitry to perform a rearrangement operation and at least one SIMD arithmetic operation on a plurality of data elements stored in the register bank. The rearrangement operation is configurable by a size parameter derived at least in part from the register bank. The size parameter provides an indication of a number of data elements forming a rearrangement element for the purposes of the rearrangement operation. The associated method involves controlling processing circuitry to perform a rearrangement operation and at least one SIMD arithmetic operation in response to a combined rearrangement arithmetic instruction and providing the scalar logic size parameter to configure the rearrangement operation. Computer program product is also provided comprising at least one combined rearrangement arithmetic instruction.
Owner:ARM LTD
Server load sharing system
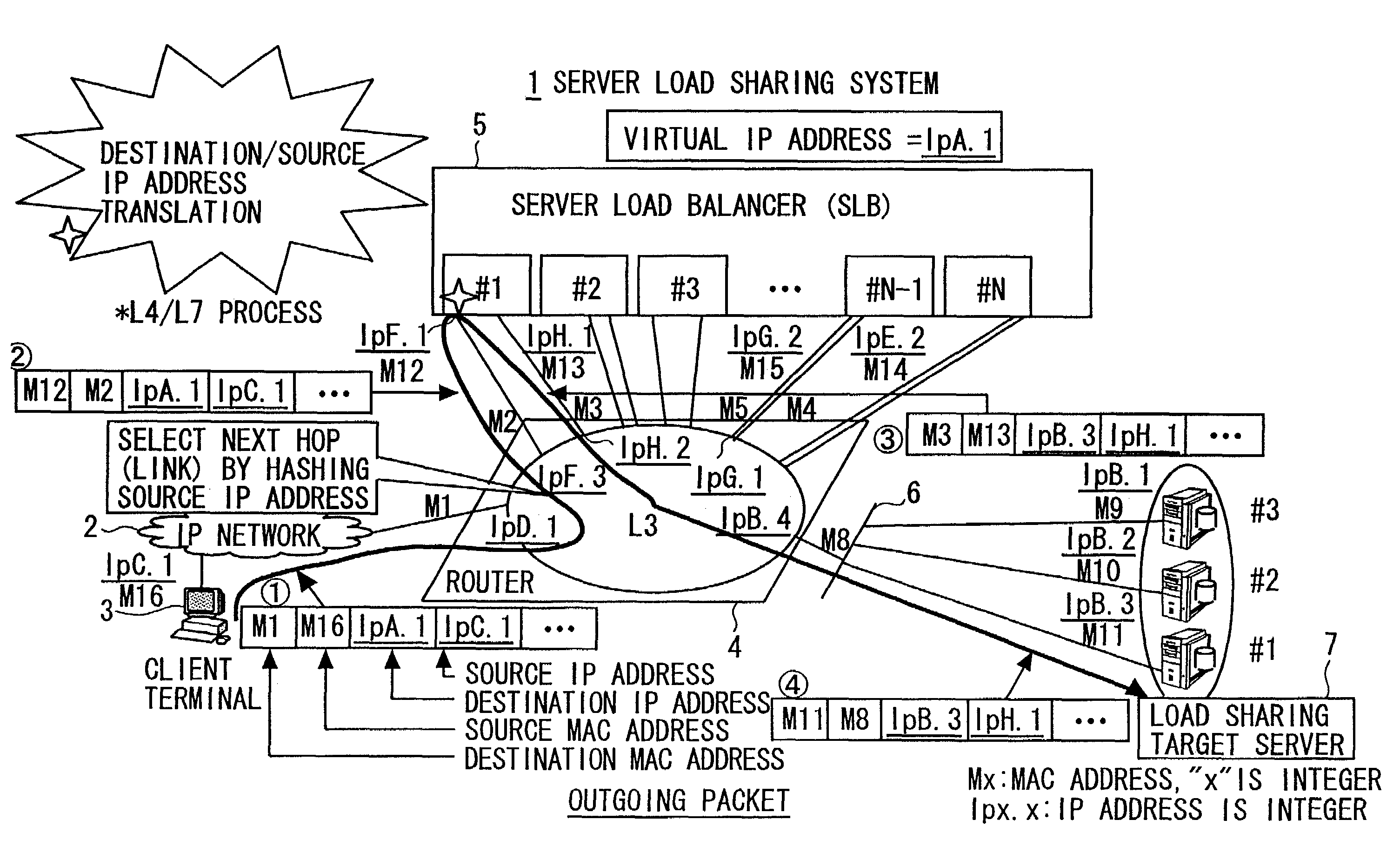
InactiveUS7379458B2Evenly distributedAvoid bottlenecksResource allocationDigital computer detailsDistributed computingVirtual IP address
A server load sharing system having a plurality of server load balancers and a relay device. Each balancer includes a module selecting, any one of a plurality of load sharing target servers specified in their group on the basis of the virtual IP address and each allocated a unique IP address, and a module rewriting a virtual IP address of the received forwarding target packet addressed to the virtual IP address into the unique IP address of the selected server, and rewriting a source IP address of the received packet addressed to the virtual IP address into an IP address capable of specifying the other of the first and second links.
Owner:FUJITSU LTD
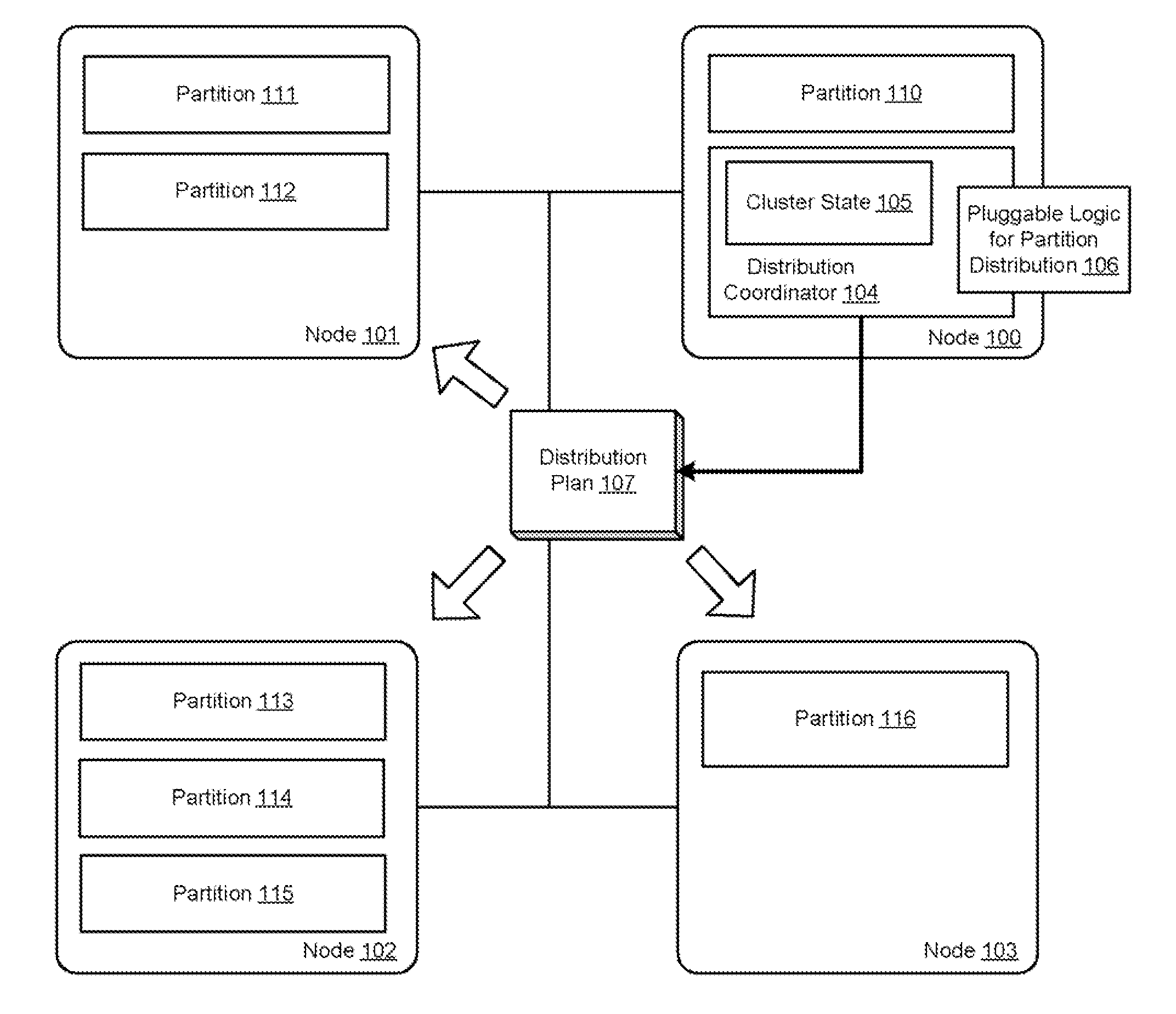
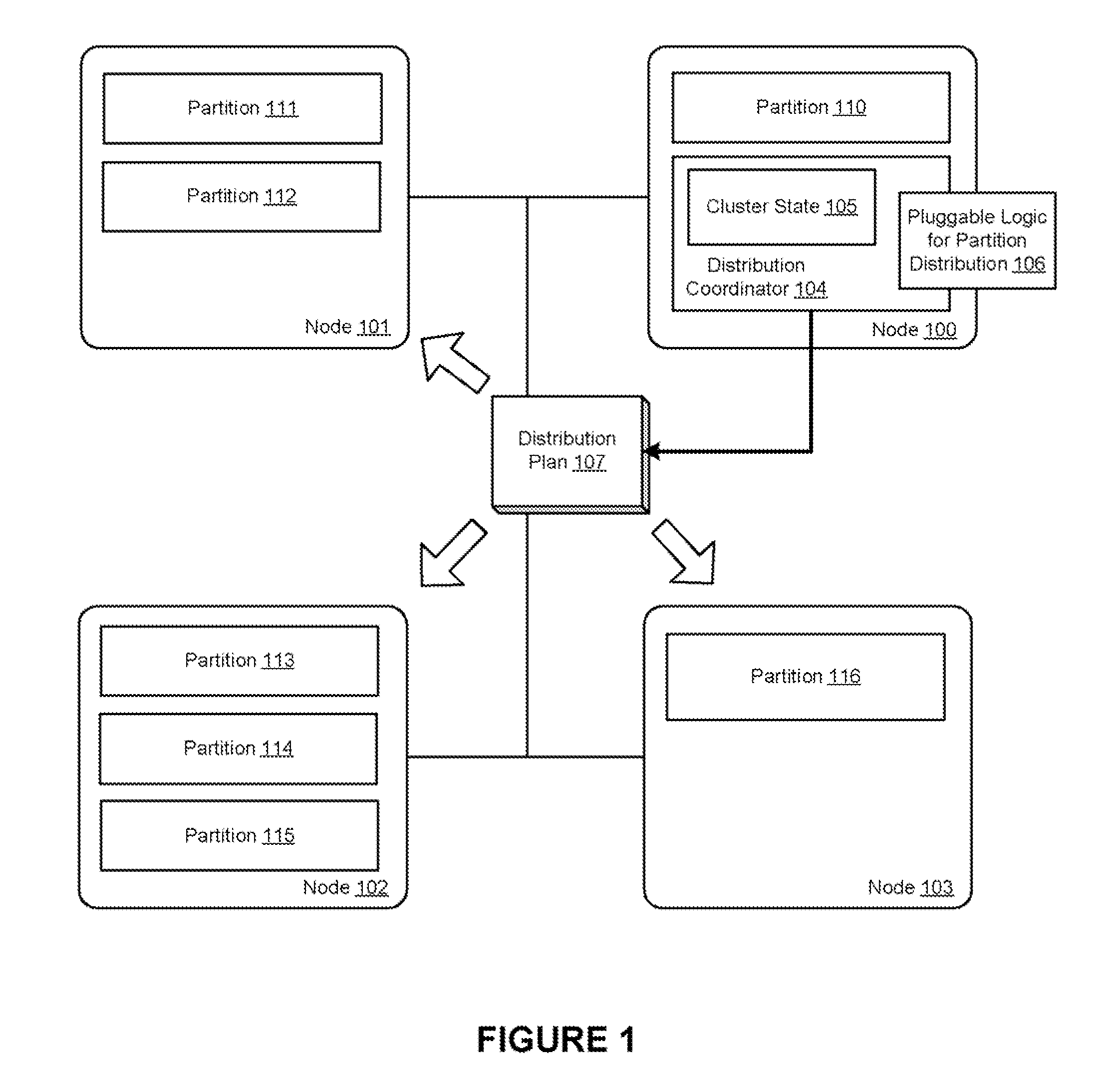
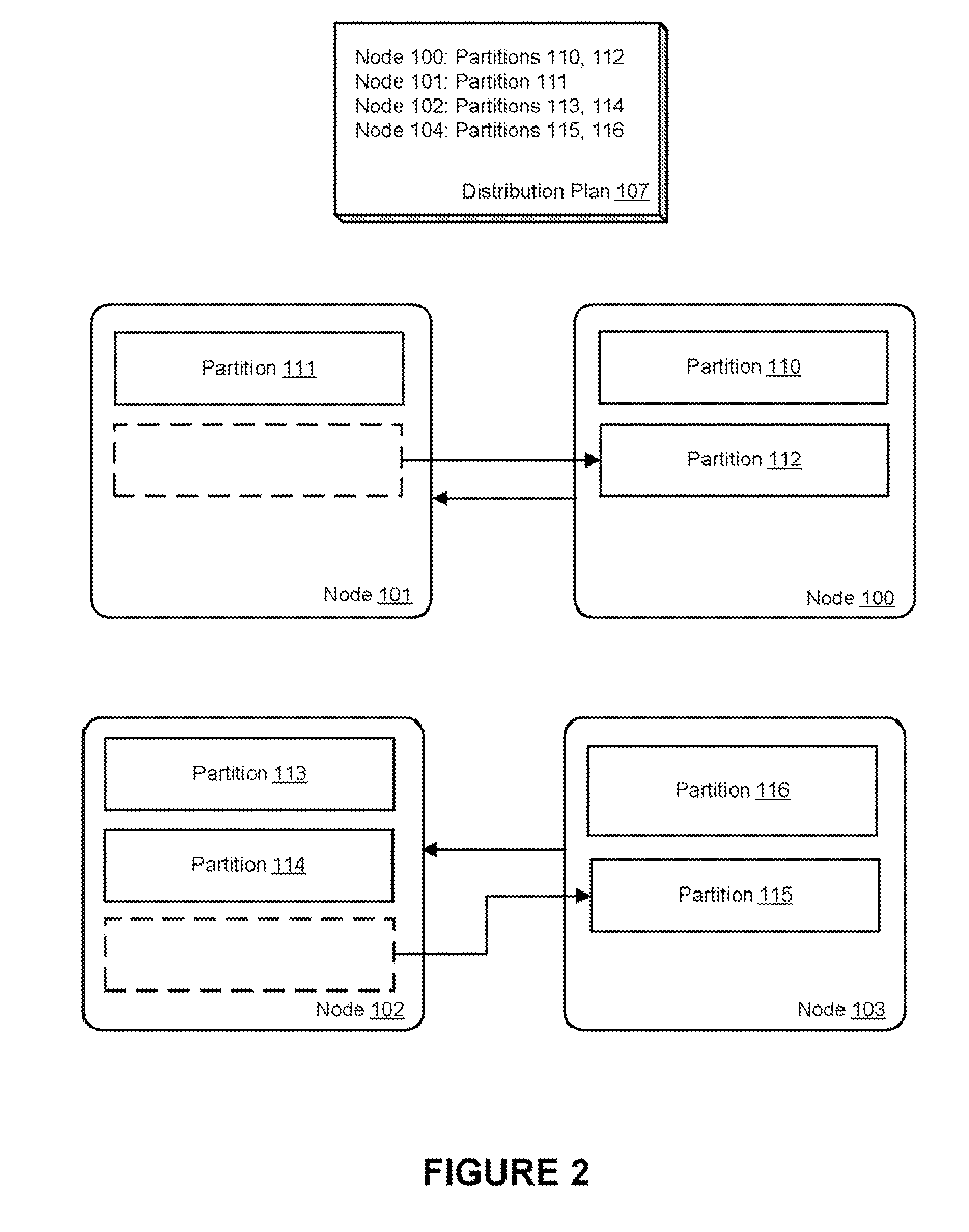
Extensible centralized dynamic resource distribution in a clustered data grid
ActiveUS20120297056A1Avoid bottlenecksBottlenecks caused by a single point of coordination can be preventedDigital computer detailsDatabase distribution/replicationClustered dataDynamic resource
A centralized resource distribution is described where the decision portion of partitioning data among cluster nodes is made centralized while the actual mechanics to implement the partitioning remain a distributed algorithm. A central distribution coordinator is used to create an extensible central strategy that controls how the data will be partitioned across the cluster. The work to implement this strategy is performed by all of the members individually and asynchronously, in accordance with a distributed algorithm. The central strategy can be communicated to all cluster members and each member can perform the partitioning as it relates to itself. For example, in accordance with the distributed algorithm, one node may decide that it needs to obtain a particular partition in light of the central strategy and carry out the necessary steps to obtain that data, while other nodes may be asynchronously performing other individual partition transfers relevant to those particular nodes.
Owner:ORACLE INT CORP
Peer-to-peer (P2P) network system and method and related device for establishing the same
ActiveCN102065112AAvoid the problem of poor scalabilityAvoid bottlenecksData switching networksSpecial data processing applicationsExtensibilityDistributed computing
The invention discloses a peer-to-peer (P2P) network system and a method and a related device for establishing the same, which is used for solving the problem of the existing peer-to-peer network such as low expandability. The system comprises master super nodes and common nodes, wherein, each master super node comprises a unit for acquiring the routing information of a second common node when the second common node which stores corresponding resource exists in the cluster where the super node is located, a unit for sending a search request to other master super nodes and taking the routing information of a third common node fed back by other master super nodes as the acquired routing information when the common node which stores the corresponding resource does not exist in the cluster where the node is located, and a unit for sending the acquired routing information to the first common node which sends the search request or other master super nodes; and the common nodes are used for sending the search request to the master super nodes in the cluster and acquiring the resource to be searched from the common node corresponding to the routing information sent by a master hyperterminal in the cluster.
Owner:CHINA MOBILE COMM GRP CO LTD
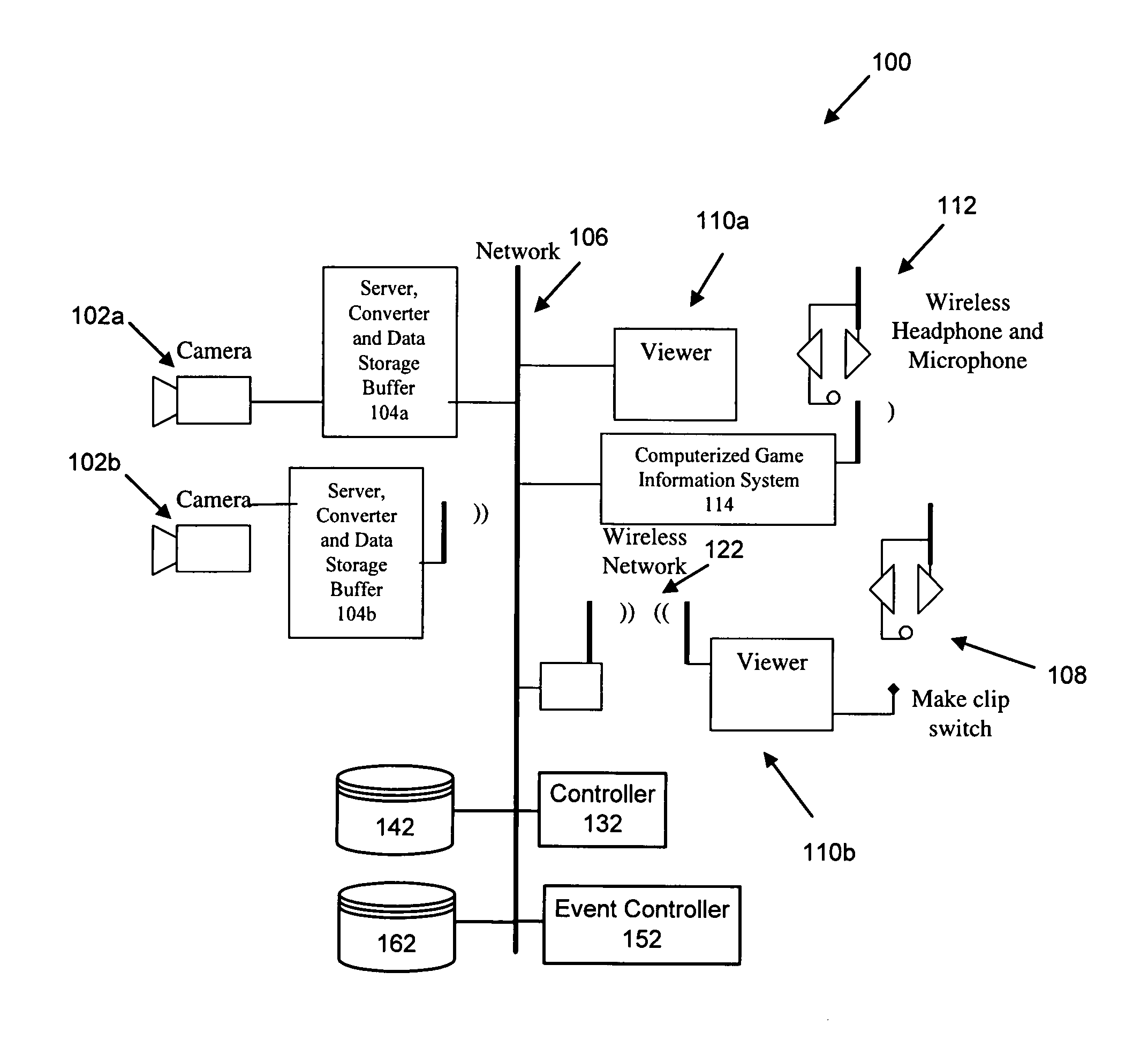
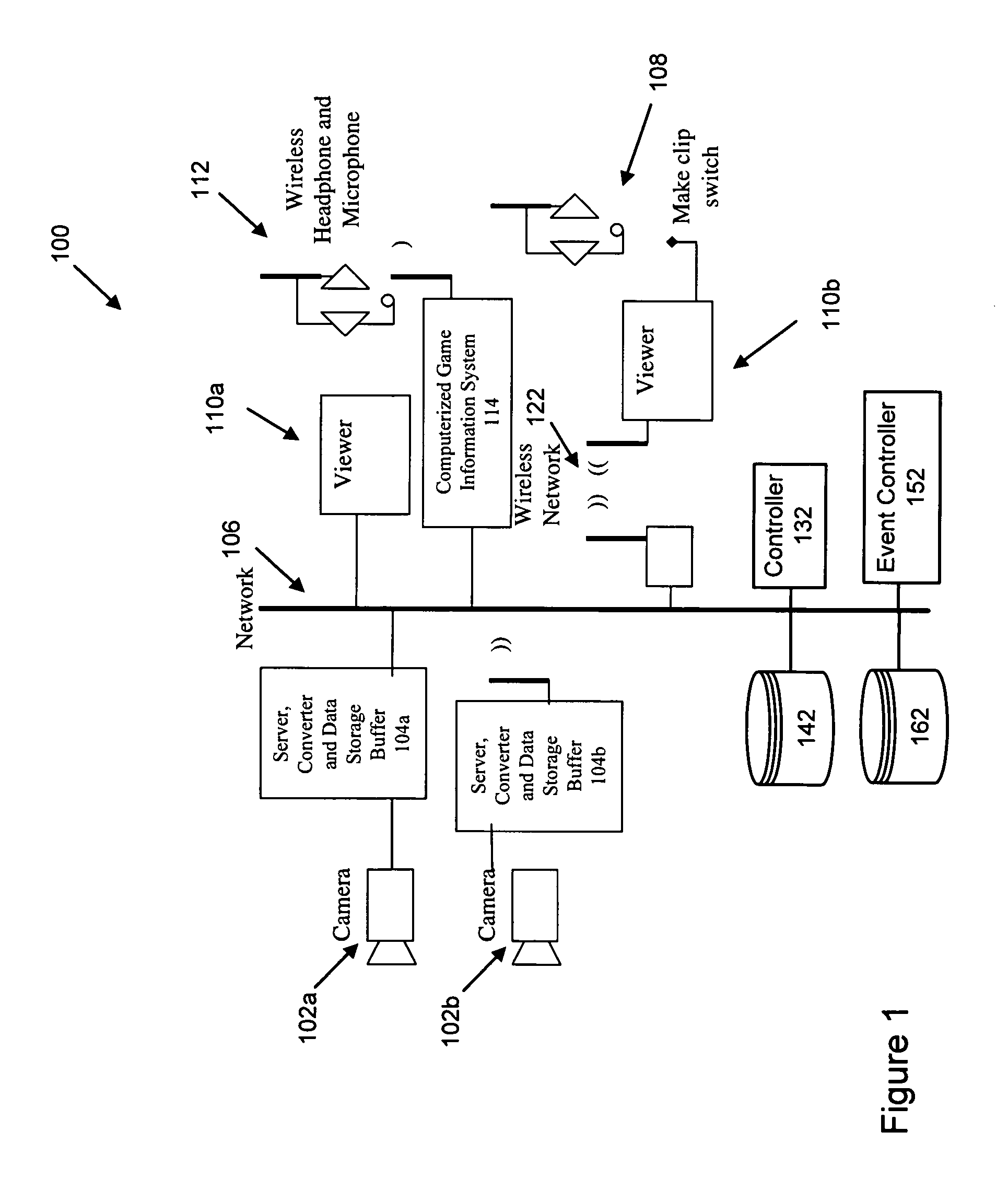
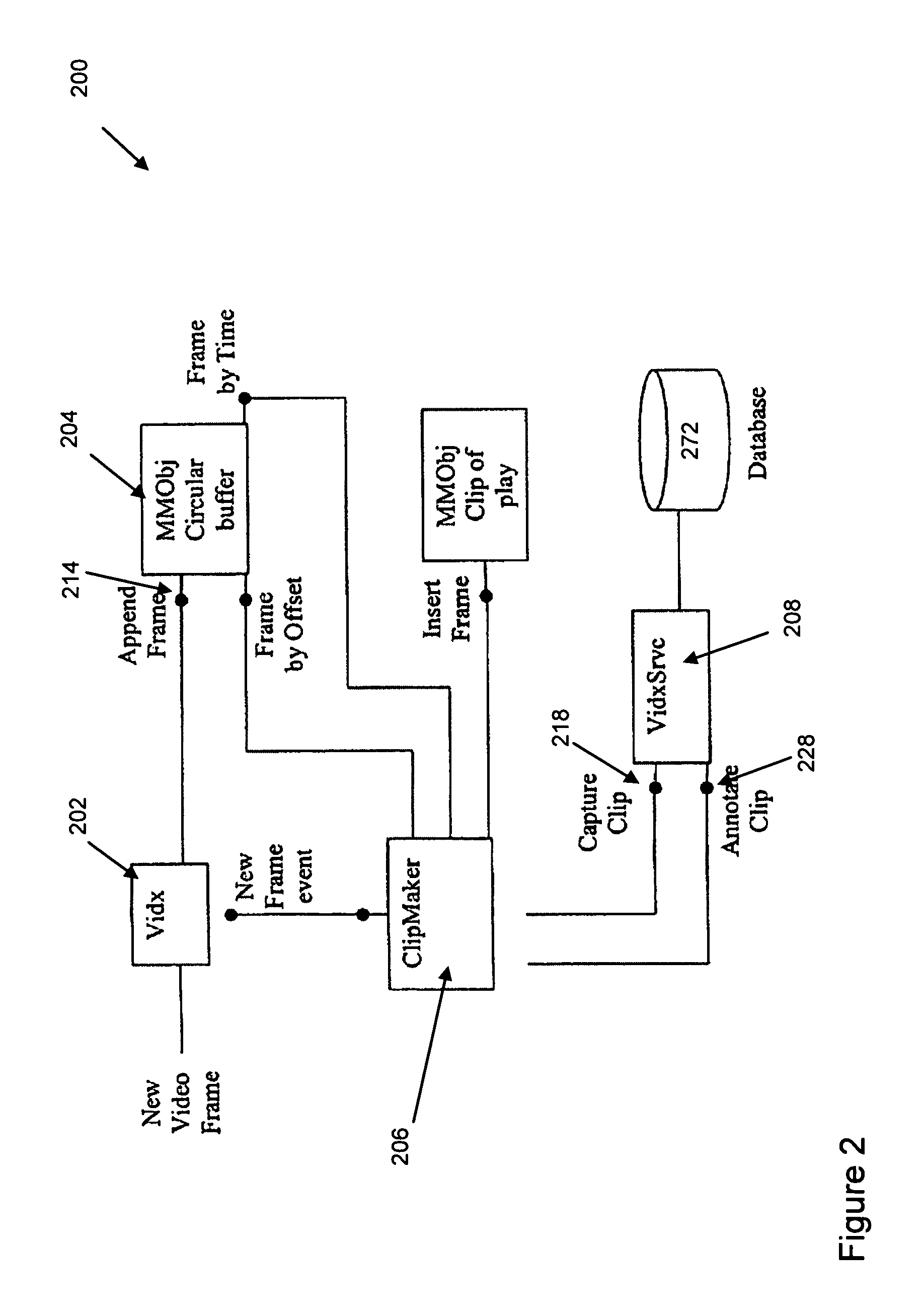
System and method of video capture for sports applications
ActiveUS8358345B1Increase capacityAvoid problemsTelevision system detailsColor burst signal generation/insertionData bufferMonitoring data
A system for monitoring a sporting event includes devices for monitoring characteristics of the event and collecting monitored data. Devices address different aspects of the event and monitor and collect real-time data. The devices process the data into digitized frames, and a digital storage device receives and stores the frames in a random access storage buffer as time-stamped digitized data frames with unique addresses. The storage device is capable of both time-shifting and relational association. The system includes a controller and devices for monitoring and extracting a digitized data frame according to a predetermined criterion. A viewer communicates with the storage device and controller and selects, manipulates, and extracts the digitized data frame. The system records and plays back the monitored data using a circular storage buffer with a memory mapped file and allows playback of stored data without interrupting simultaneous recording of new input data.
Owner:IM52
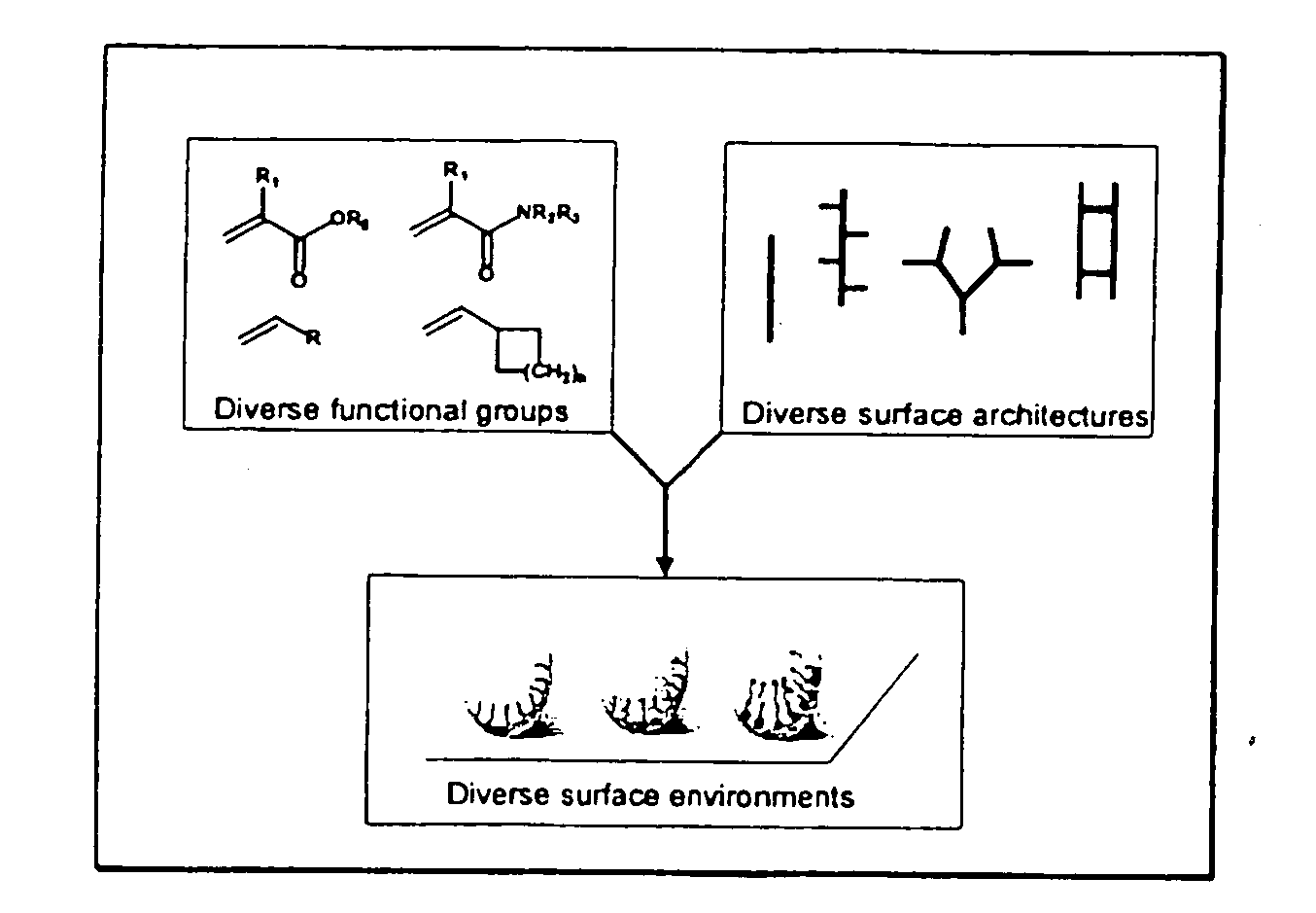
Generation of surface coating diversity
InactiveUS20060083858A1Generation of surfaceControl generationMembranesSequential/parallel process reactionsChemical compositionSynthon
The present invention relates to a surface discovery system comprising chemical compositions and high-throughput combinatorial synthesis methods for generating large numbers of diverse surface coatings on solid substrates. This surface discovery platform is built upon a fundamental chemical unit refereed to as a synthon. Each synthon comprises at least three elements: a chemical backbone coating on the solid substrate that comprises a passive (P) constituent and an active (A) constituent; a spacer unit (S) separating the backbone from a functional group; and a functional group (F). Variation of these synthon elements allows generation of large libraries surface coatings with a broad range of molecular and macroscopic properties. Further the spectrum of surfaces provided by the invention permits optimization of the wide range of solid-phase applications that involve surface immobilization of molecules.
Owner:ANTEO TECH
Virtual network access method and system
InactiveCN103685026AAchieve accessAvoid bottlenecksNetworks interconnectionWide area networksAccess methodTTEthernet
The invention discloses a virtual network (VN) access method and system. The method comprises the following steps: BN-NVE accepts access of VN in a data center by a wide-band subscriber terminal and generates a forwarding table of the VN and corresponding table items; the BN-NVE is in forwarding table information interaction with the NVE (Network Virtualization Edge) of the accessed VN to form the information synchronization of the VN forwarding table; looking up the VN forwarding table by the BN-NVE according to the destination address of the massage of the wide-band subscriber terminal, transmitting the message to a destination NVE in the VN after the massage is encapsulated through a tunnel, and then transmitting the message to a destination VM through the destination NVE, so that the NV access of the wide-band subscriber terminal is completed. Another method comprises the following steps: a VN business development and management entity in the data center accepts an access request of the wide-band subscriber terminal on the VN in the data center and selects one NVE of the VN as the accessed NVE of the VN; a security tunnel is established between the accessed NVE of the VN and the wide-band subscriber terminal, and the VN access of the wide-band subscriber terminal is completed through the security tunnel. The method solves the problem that the gateway of the data center becomes a bottleneck because an internet user accesses the VN in the data center.
Owner:ZTE CORP
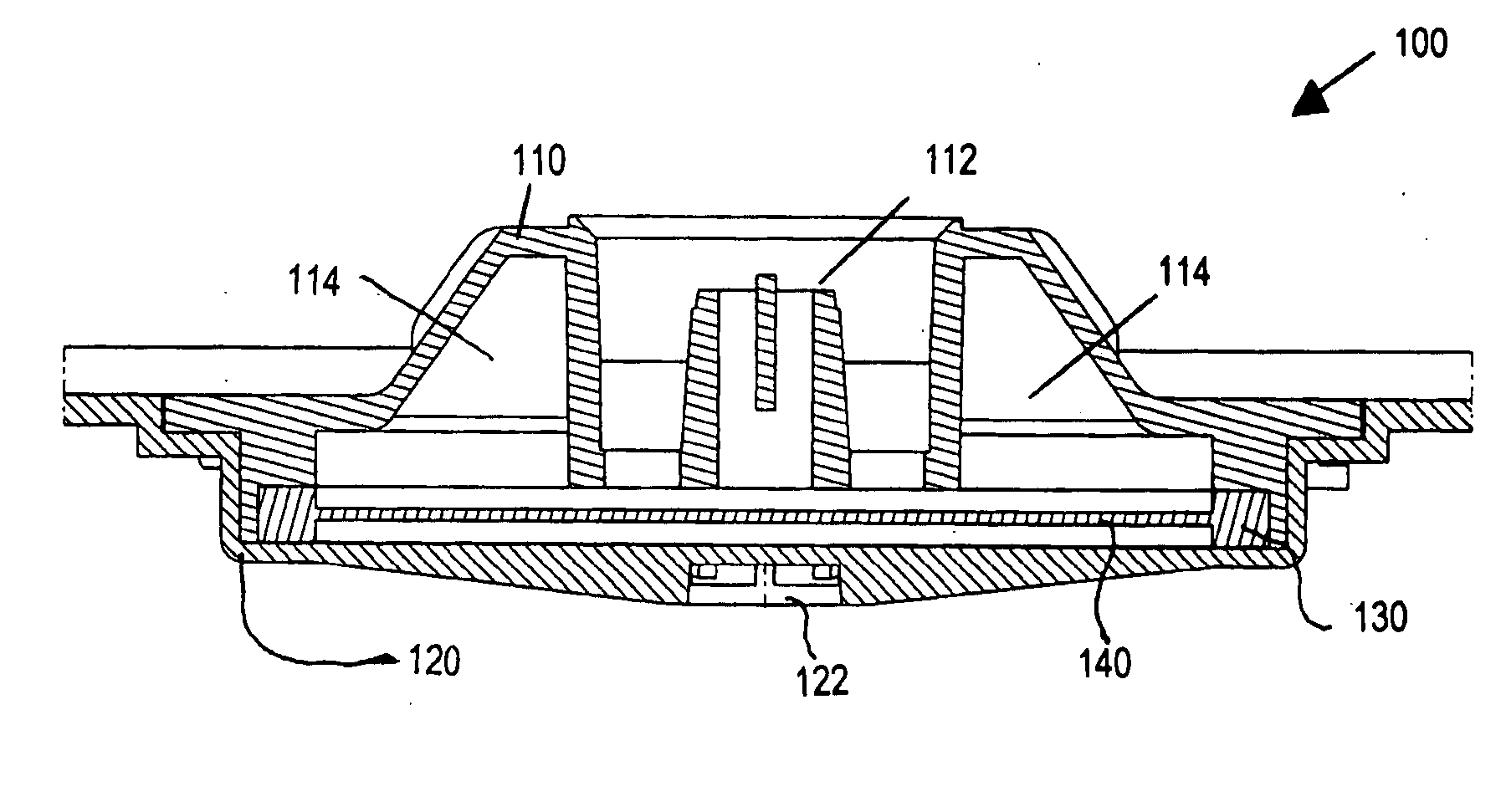
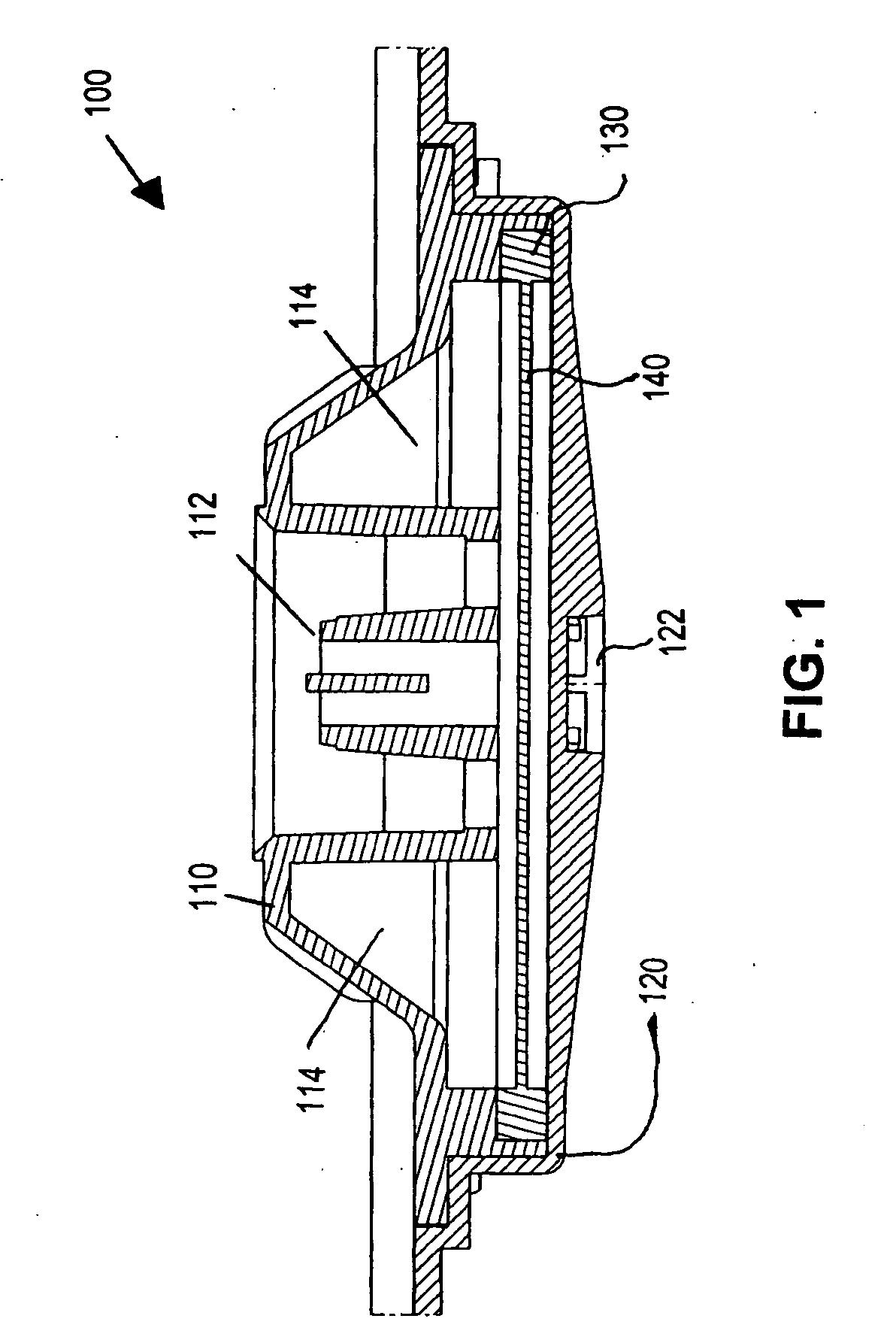
Cooling device for an electronic component
InactiveUS8037927B2Uniform areaAvoid bottlenecksSemiconductor/solid-state device detailsHeat exhanger conduitsEngineeringElectronic component
A cooling device for cooling an electronic component. The device has an enclosure adapted to contain a liquid coolant. The enclosure has an internal channel system comprising a cavity adjacent the electronic component, a first group of arborizing channels adapted to carry the liquid coolant away from the cavity, a second group of arborizing channels adapted to carry the liquid coolant to the cavity, and a plenum fluidically connecting the first and seconds groups of arborizing channels. Each group of arborizing channels has a parent branch and multiple successive sets of daughter branches with successively smaller cross-sectional areas, wherein the sum of the cross-sectional areas of the daughter branches of any set is approximately the same as that of its parent branch. Distal sets of the daughter branches are most distant from the cavity, fluidically connected to the plenum, and have the smallest cross-sectional areas of the daughter branches.
Owner:NYTELL SOFTWARE LLC
Method for the Distribution of a Network Traffic According to Sla and Qos Parameters
InactiveUS20070237078A1Improve reliabilityIncrease flexibilityError preventionTransmission systemsTraffic capacityEdge node
The invention relates to a method, a bandwidth broker and an edge node for providing a predefined quality of service between two communication partners, wherein the quality of service is provided by means of a plurality of connections and a decentralised admission control.
Owner:TELEFON AB LM ERICSSON (PUBL)
Cooling device for an electronic component
InactiveUS20080115916A1UniformAvoid bottlenecksSemiconductor/solid-state device detailsHeat exhanger conduitsEngineeringElectronic component
A cooling device for cooling an electronic component. The device has an enclosure adapted to contain a liquid coolant. The enclosure has an internal channel system comprising a cavity adjacent the electronic component, a first group of arborizing channels adapted to carry the liquid coolant away from the cavity, a second group of arborizing channels adapted to carry the liquid coolant to the cavity, and a plenum fluidically connecting the first and seconds groups of arborizing channels. Each group of arborizing channels has a parent branch and multiple successive sets of daughter branches with successively smaller cross-sectional areas, wherein the sum of the cross-sectional areas of the daughter branches of any set is approximately the same as that of its parent branch. Distal sets of the daughter branches are most distant from the cavity, fluidically connected to the plenum, and have the smallest cross-sectional areas of the daughter branches.
Owner:NYTELL SOFTWARE LLC
Filter housing for a drinking water pitcher
InactiveUS20060163148A1Reduce disadvantagesIncrease ratingsTreatment involving filtrationWater treatment locationWater flowFilter media
A filter housing for a drinking water pitcher is provided. The filter housing includes an upper housing portion and a lower housing portion. A filter media can be housed in between the upper and lower housing portions. The upper and lower housing portions co-operate to provide increased water flow through rate. The filter housing includes a necked down inlet port. Chambers in the upper housing are filled with air. Preferably, an angle of the lower housing preferably extends to the exit port to create a consistent surface tension across the entire surface of the filter media. The filter housing is preferably placed between an upper reservoir and a lower reservoir of the drinking water pitcher, and can be removably attached to, or seated within, the lower reservoir.
Owner:TERSANO INC
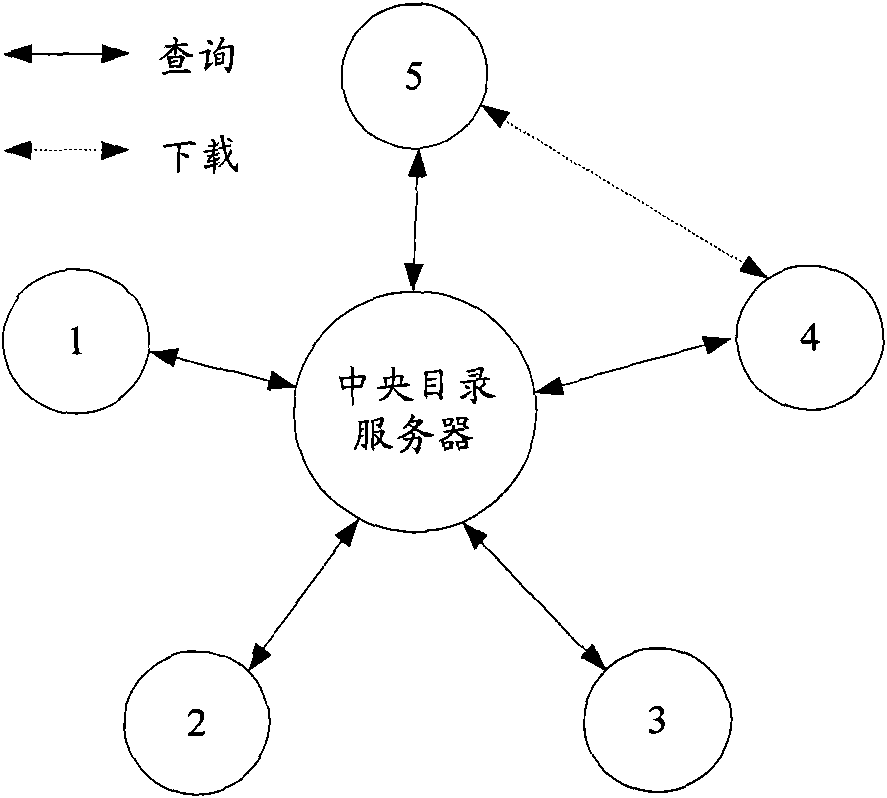
Method and system for storing distributed graph data
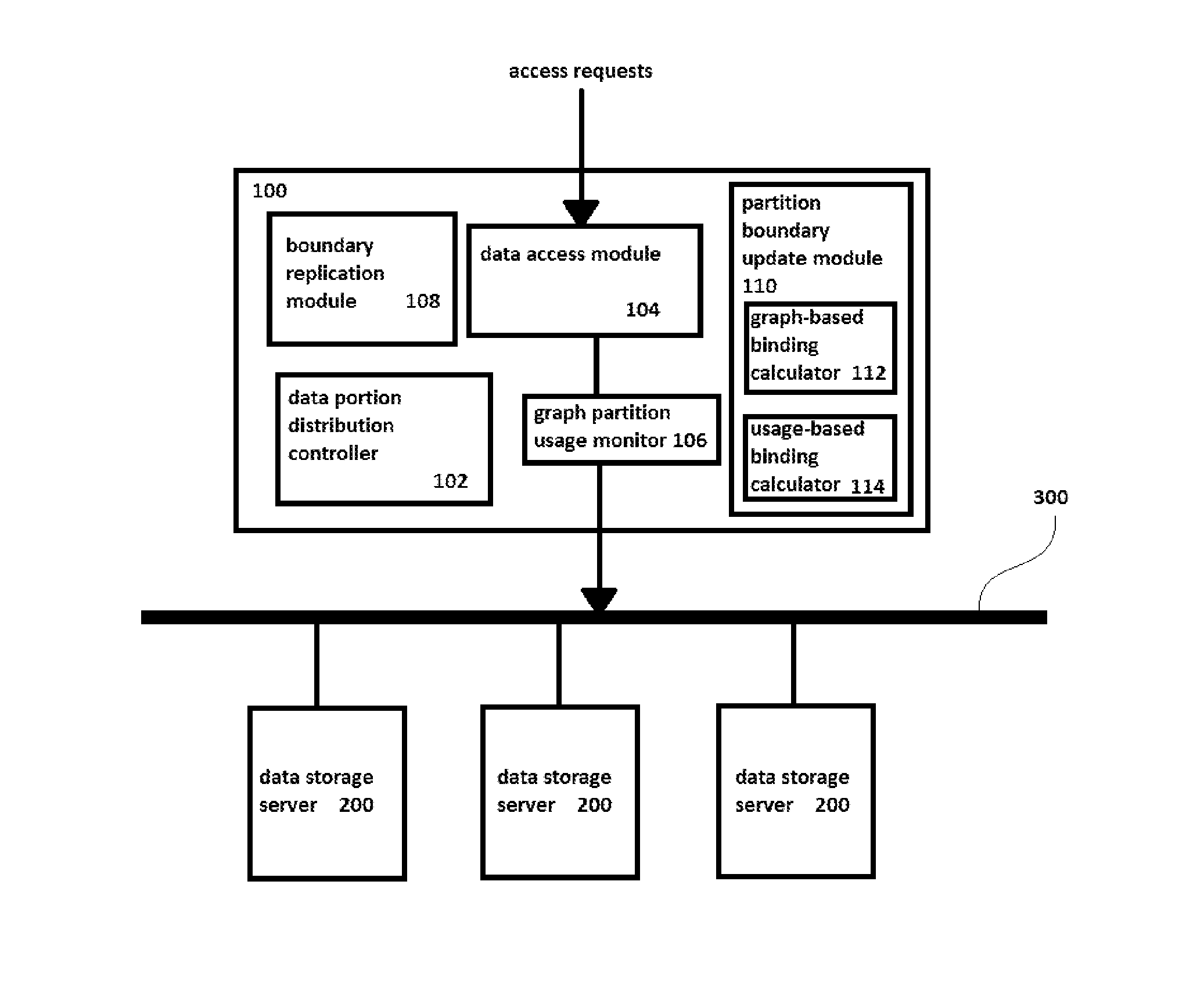
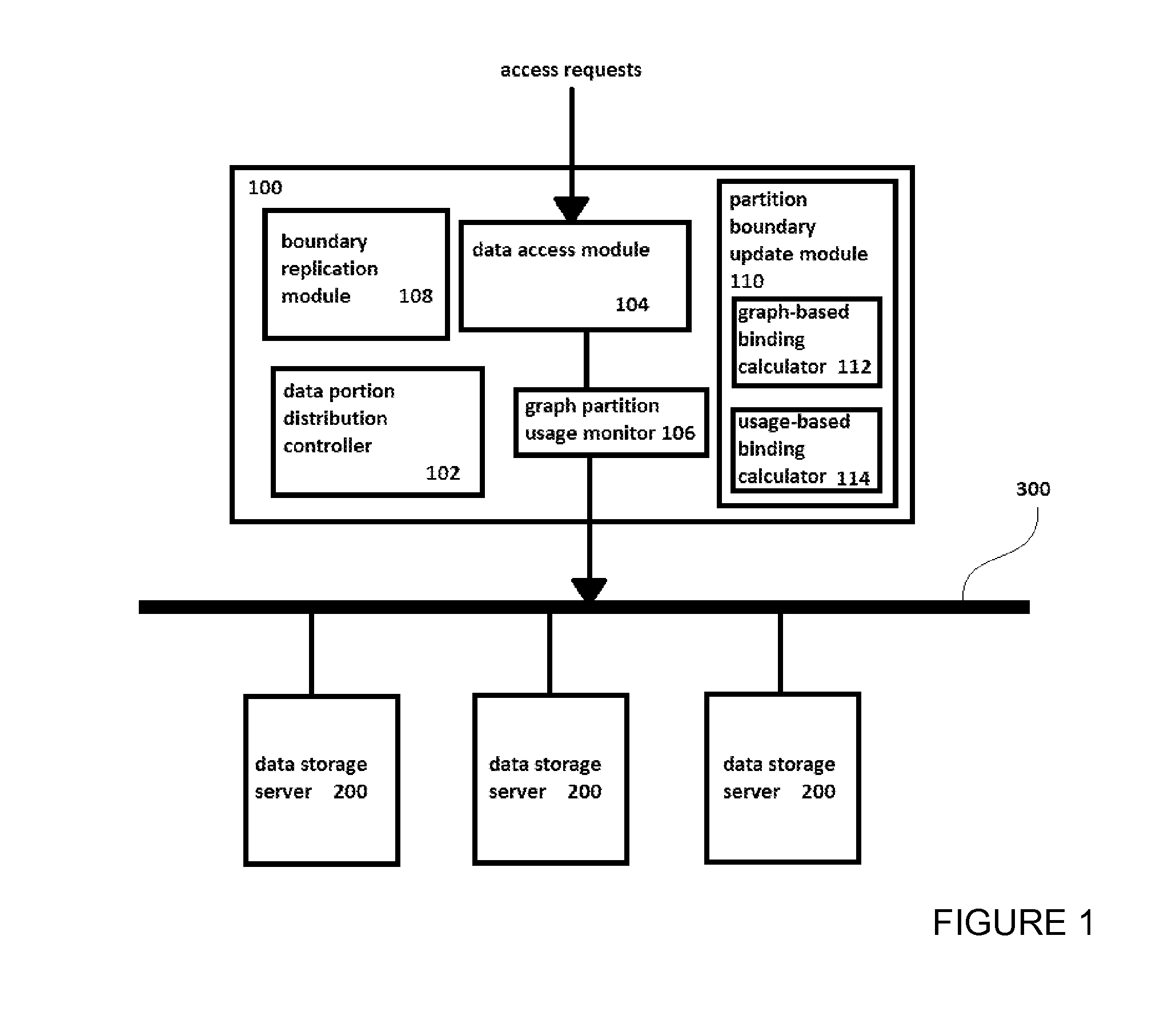
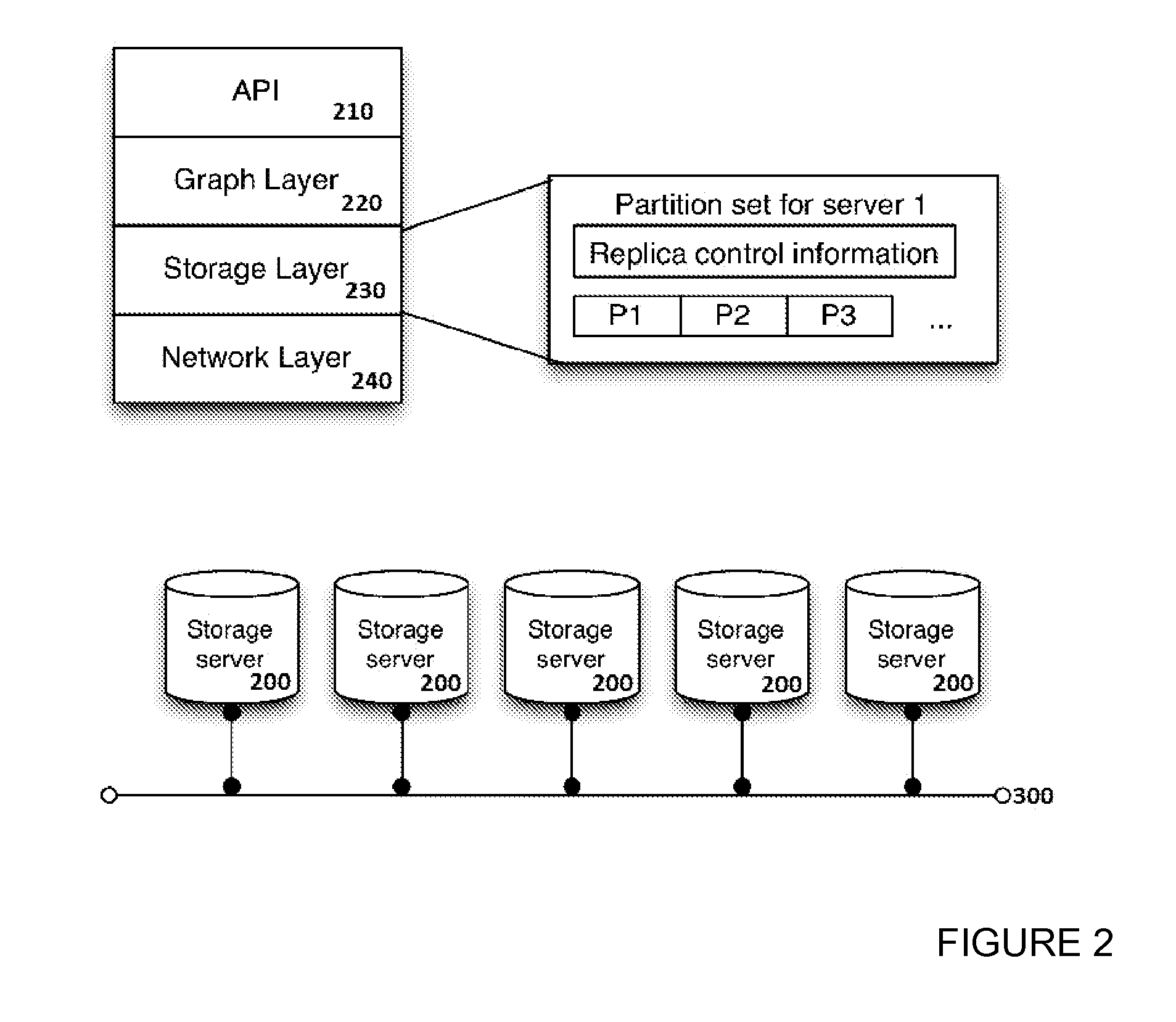
InactiveUS20150350324A1Save spaceAvoid bottlenecksDigital data information retrievalHardware monitoringGraphicsDistribution control
A distributed data graph storage system, to store a data graph representing information as vertices interconnected by edges denoting relationships between connected vertices, the data graph being a plurality of graph partitions. The data graph storage system includes data storage servers to store data portions, each portion encodes a graph partition; a data portion distribution controller, when the data portions each encode a same graph partition, to allocate the portions to different data storage servers; a data access module to receive access requests for the data graph and to distribute the access requests among the servers; a graph partition usage monitor to record statistics representing the distribution of data access events caused by the access requests; where the data portion distribution controller is configured to increase or decrease the number of portions in dependence upon the recorded statistics.
Owner:FUJITSU LTD
Loading device for ISO containers
InactiveUS20020044854A1Avoid bottlenecksEffective maneuveringCargo handling apparatusBase supporting structuresOverhead craneVertical axis
A loading device for ISO containers in a container terminal with a container bridge for the loading and unloading of ships and with automatic incoming and outgoing transfer of the containers by means of automatic guided vehicles, with at least one container load suspension device in the form of a spreader and devices for the intermediate positioning of the container within the loading device to allow the installation or removal of the twistlocks, and with platforms for the workers performing this task. The loading device consists of a polar bridge crane, which can rotate around its center vertical axis, and which is designed as a bridge crane with a trolley capable of traveling on a crane bridge supported on a circular track located in the rear area of the land-side rail of the container bridge.
Owner:ROCKWELL SOFTWARE +1
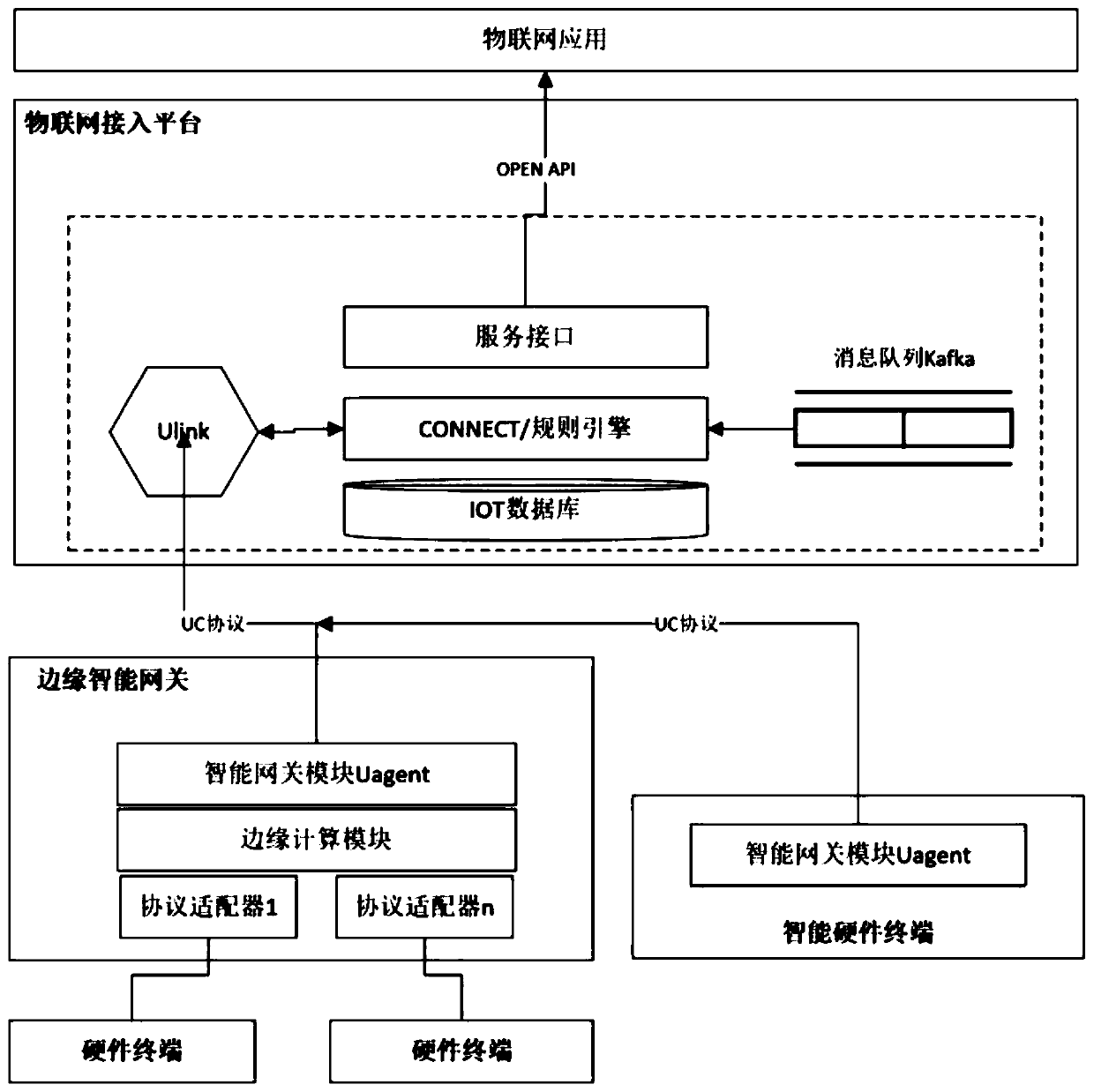
Protocol self-adaptive Internet of Things gateway system
InactiveCN110365758AAvoid bottlenecksPossess edge computing capabilityNetwork connectionsGateway systemSelf adaptive
The invention relates to the technical field of Internet of Things gateways, in particular to a protocol self-adaptive Internet of Things gateway system. The system comprises a hardware terminal, an edge intelligent gateway, an Internet of Things access platform and an Internet of Things application system. The hardware terminal is in communication connection with the edge intelligent gateway. Theedge intelligent gateway is in data communication with the Internet of Things access platform. The internet of things access platform and the internet of things application system are in data communication, the internet of things access platform is further in communication connection with an intelligent hardware terminal. The problems of difference management, autonomous cooperative management and equipment resource sharing of various kinds of equipment are solved, meanwhile, the data computing and processing capacity of the edge side is integrated, and internet platform construction is achieved.
Owner:绿漫科技有限公司
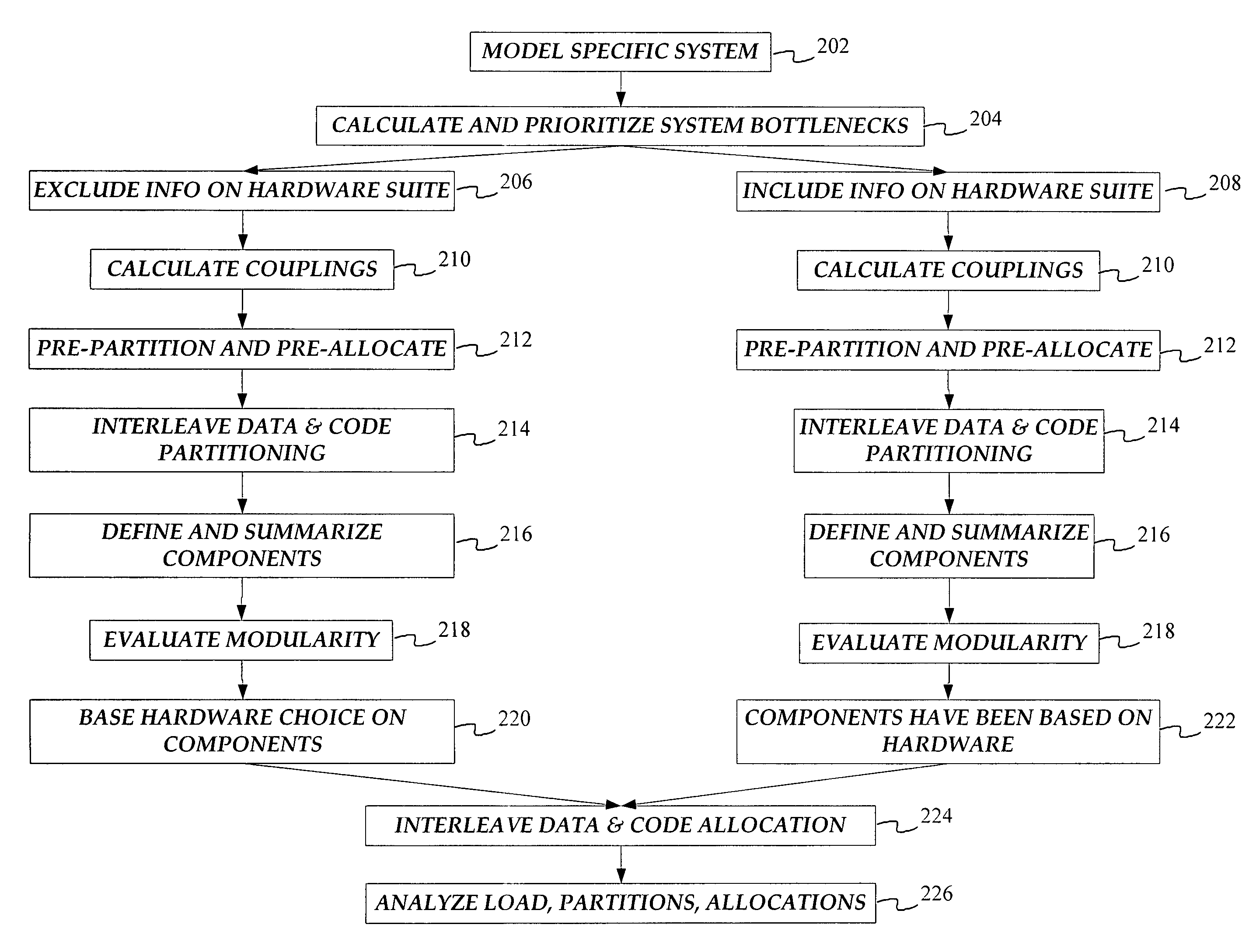
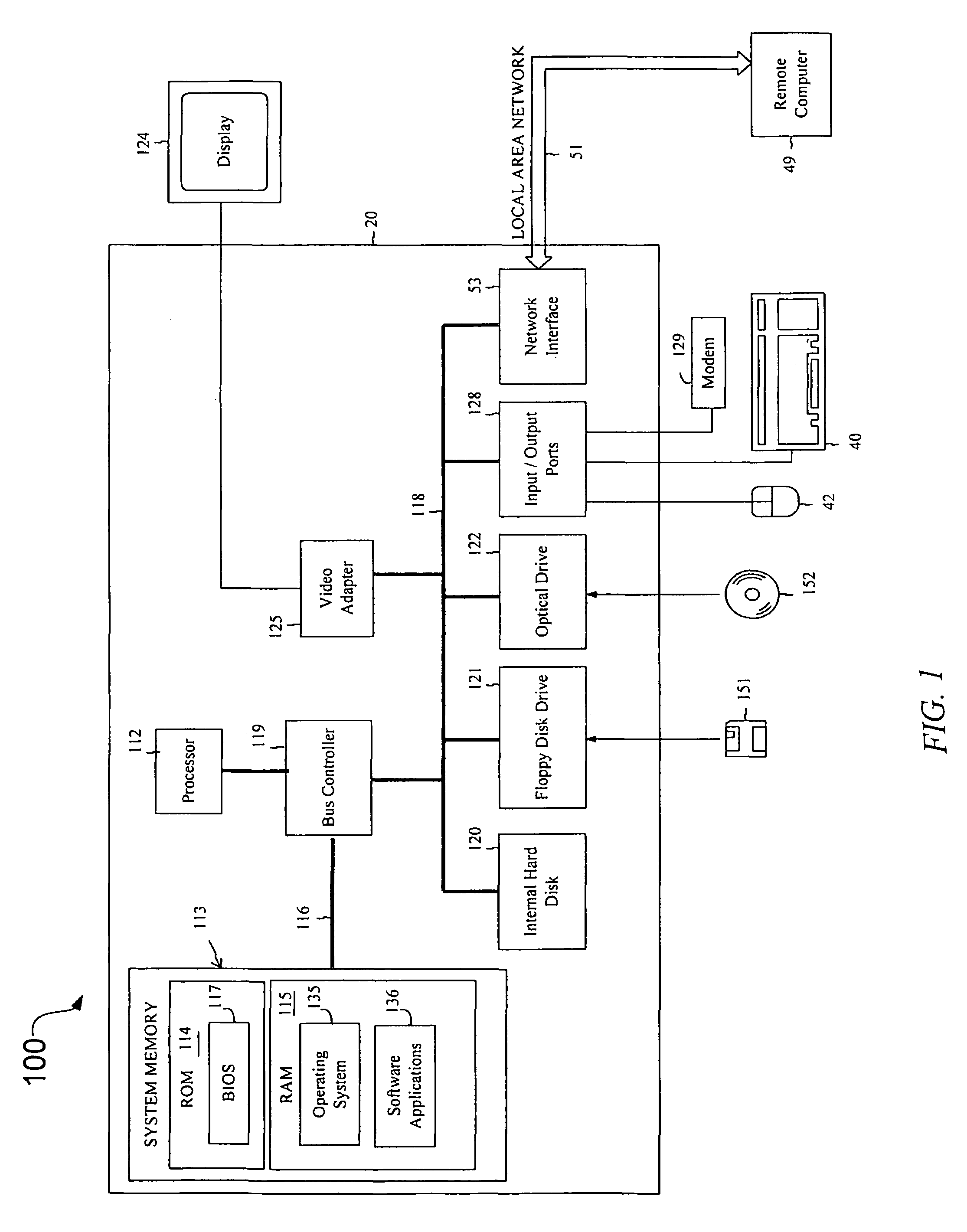
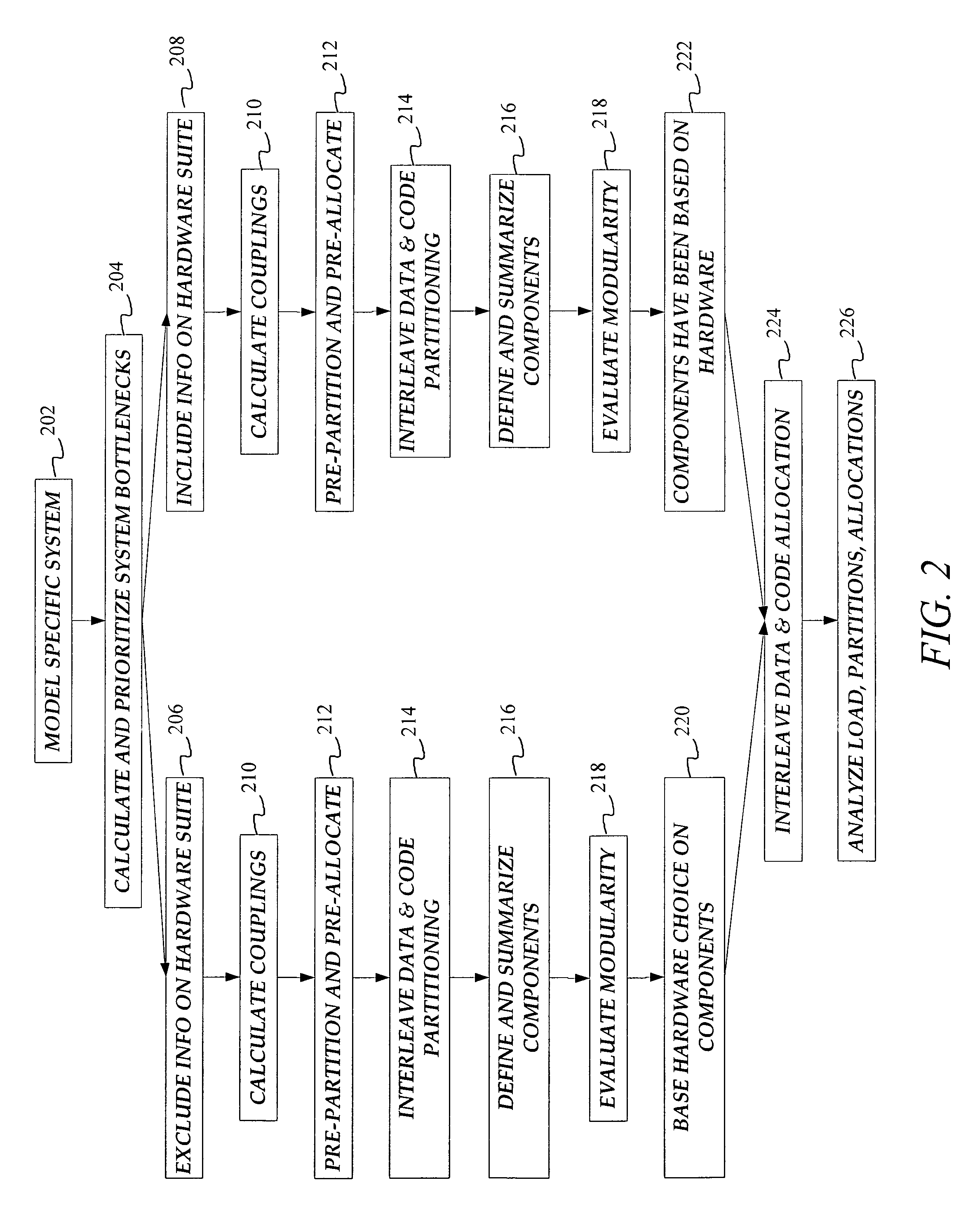
Using constraint-based heuristics to satisfice static software partitioning and allocation of heterogeneous distributed systems
InactiveUS7747422B1Avoid bottlenecksFine granularityAnalogue computers for electric apparatusMultiprogramming arrangementsSoftware distributionCoupling
Systems and methods automatically design a system's architecture by modeling the architectural complexity of large-scale distributed systems to drive a partitioning and allocation algorithm. The result is a configuration based on the structure of the software tasks and data access, and the capacities of the hardware. Coupling and cohesion are relative, dependent on the ratio of load to capacity, and not independent software characteristics. The partitioning and allocation algorithm includes tradeoffs between processor utilization, memory utilization, inter-processor communication, and peripheral contention. The systems and methods take into account both precedence constraints and the directional flow of data. Further aspects include interleaving the decisions of database segmentation and software distribution. This approach is demonstrated with a simplified example of a real distributed system.
Owner:SISLEY ELIZABETH
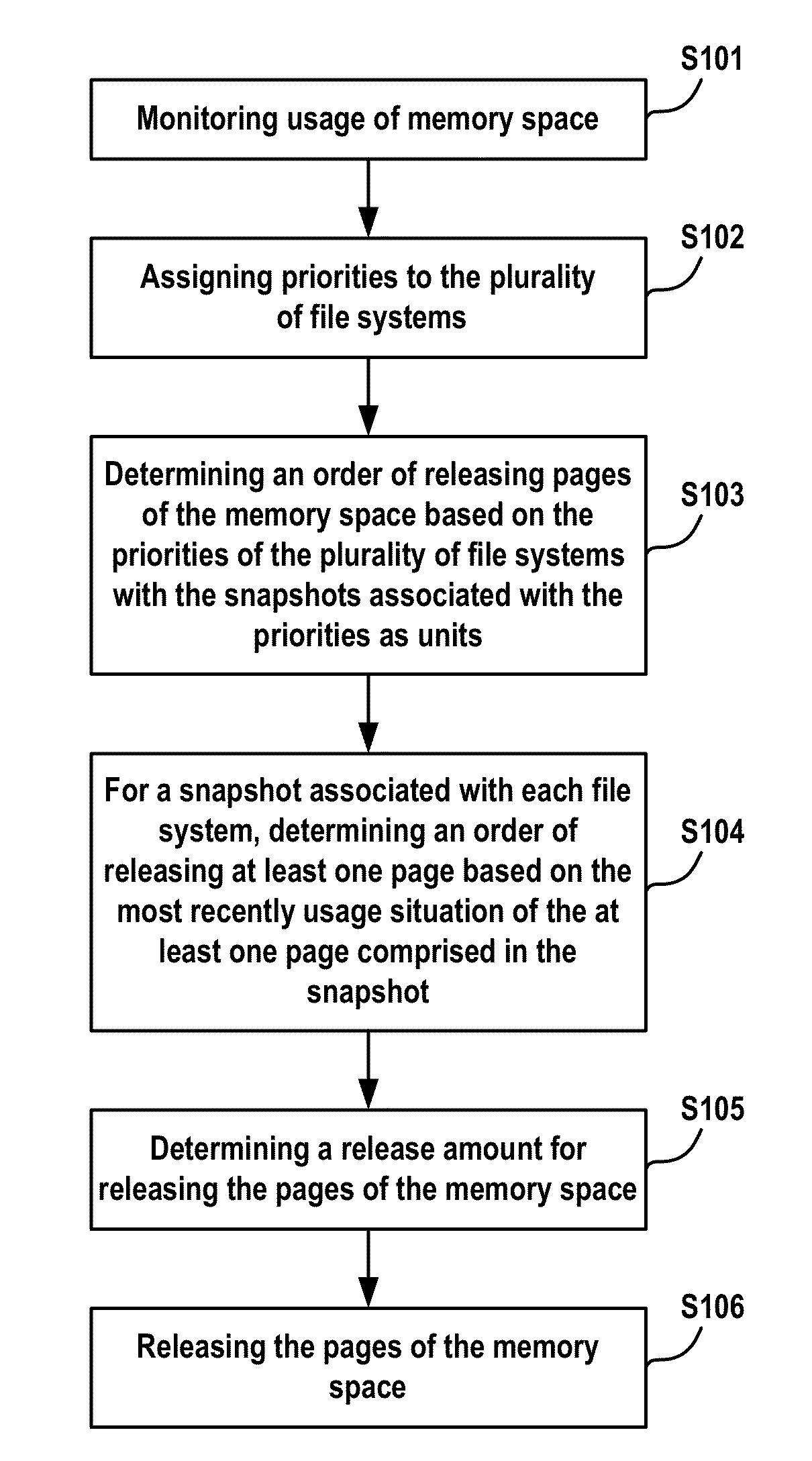
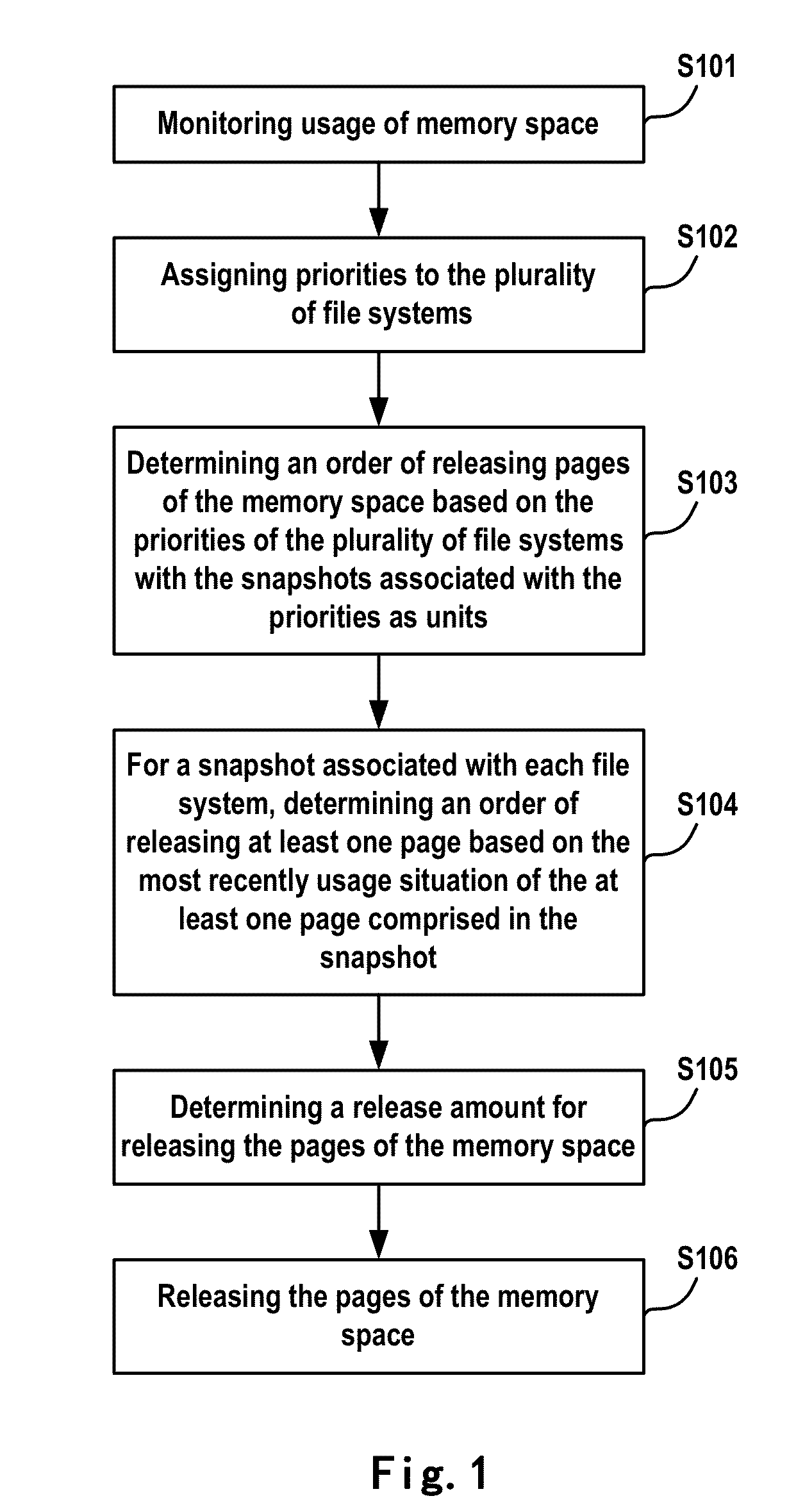
Method and apparatus for managing memory space
ActiveUS20140189267A1Improve scalabilityAvoiding bottleneckMemory adressing/allocation/relocationSpecial data processing applicationsDatabaseTheoretical computer science
Owner:EMC IP HLDG CO LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com