Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
42 results about "Password hashing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Password hashing is the process of encrypting a user’s password before storing it into a database. The encryption is one way and passwords once hashed cannot be decrypted to their original text value.
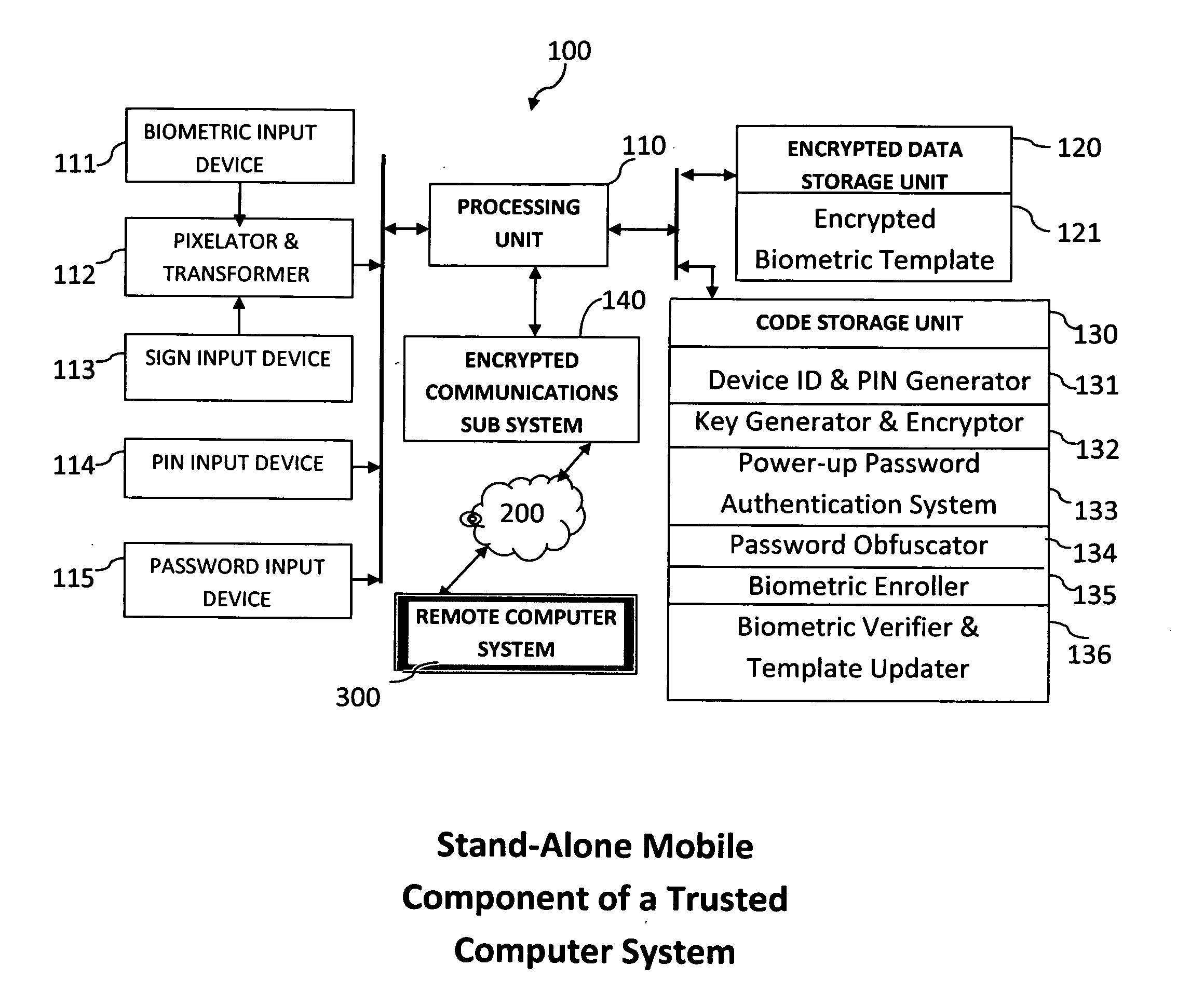
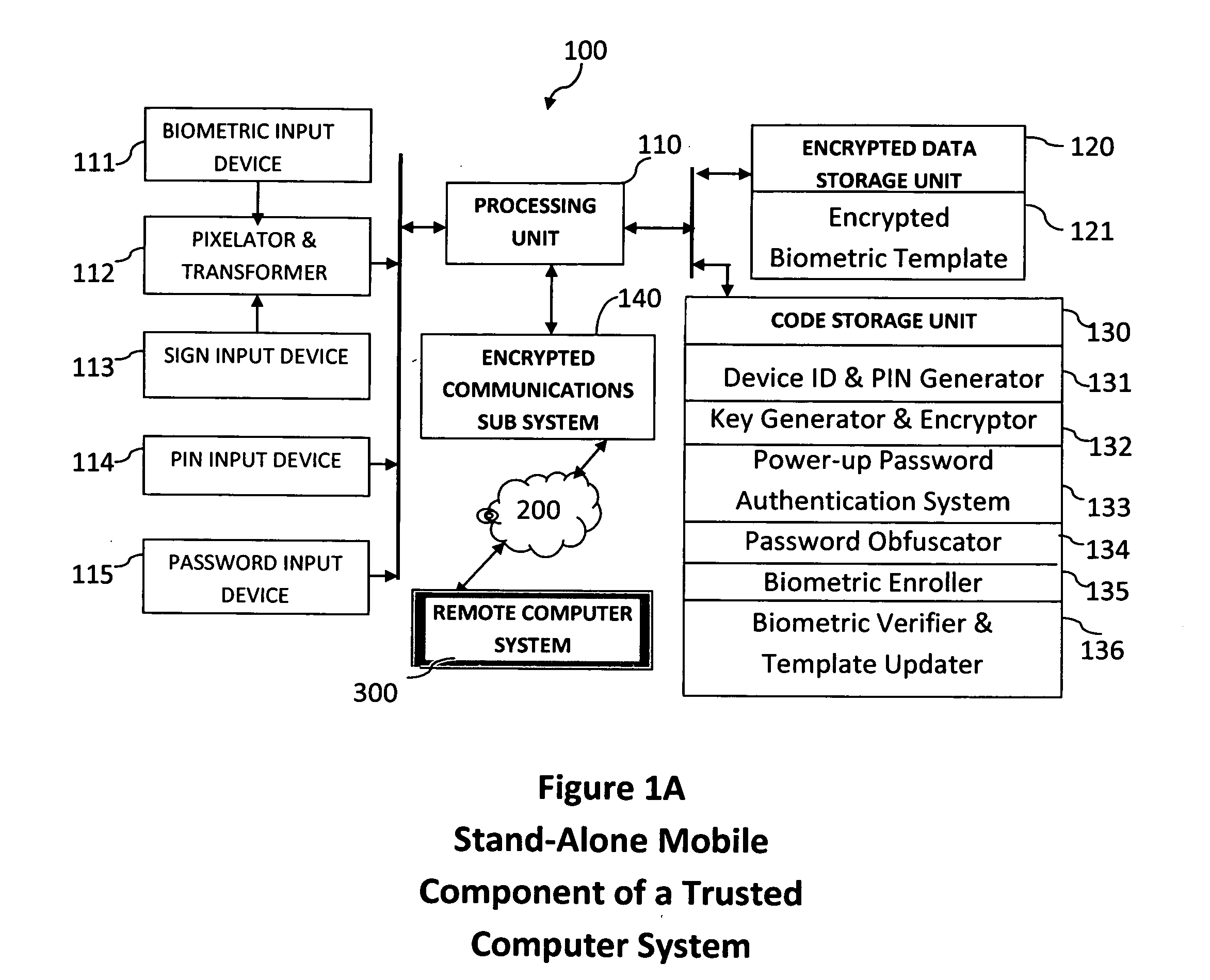
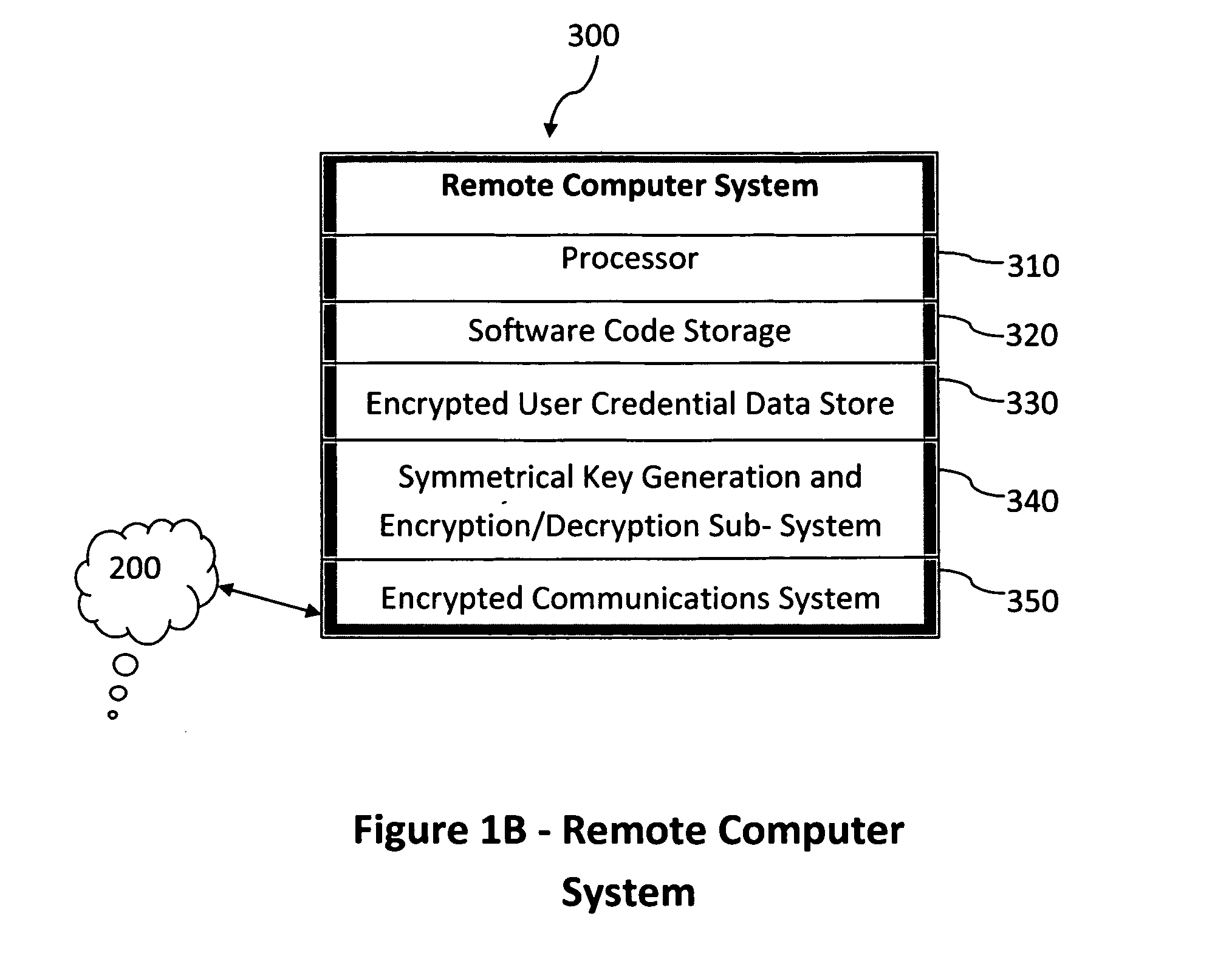
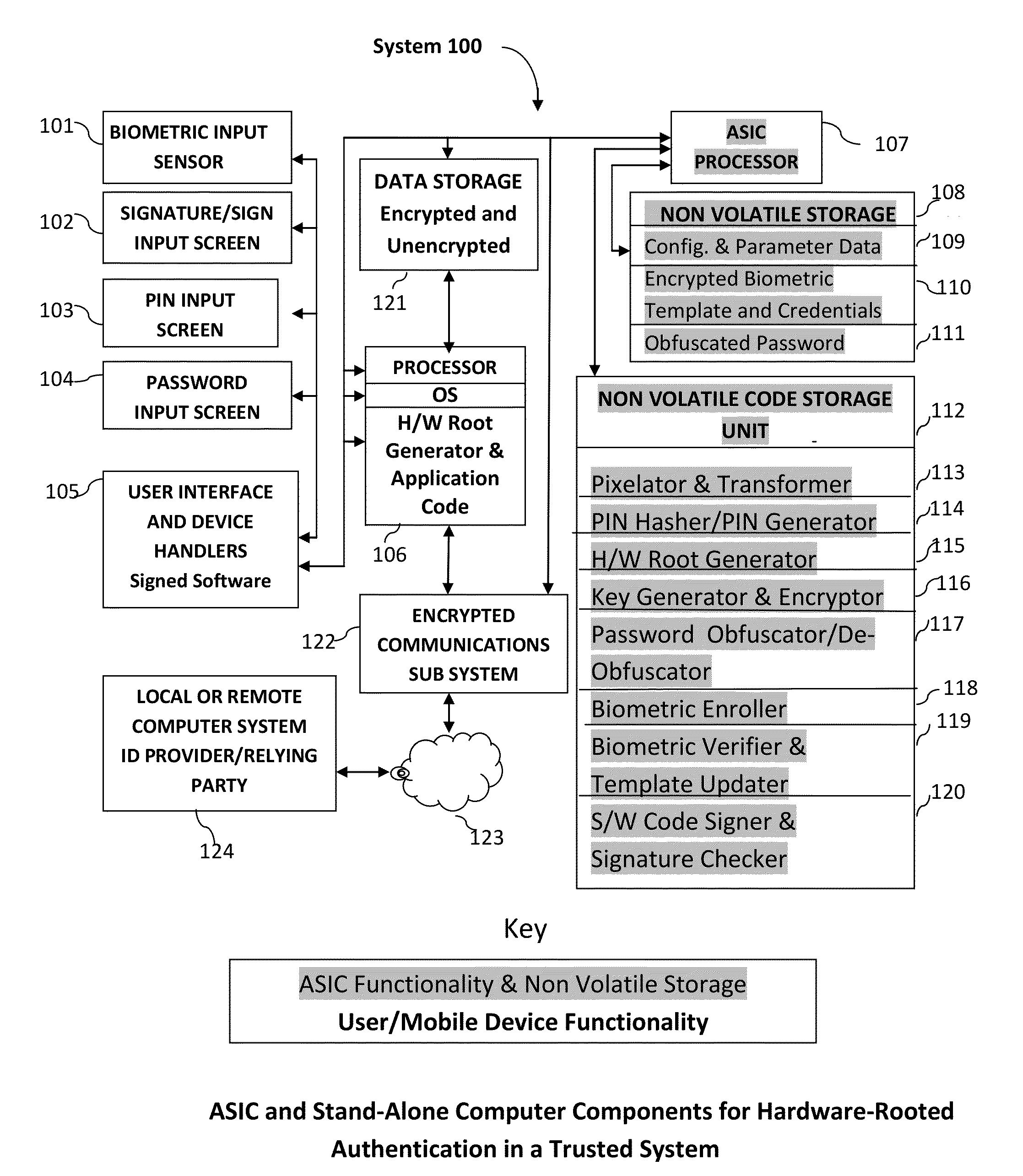
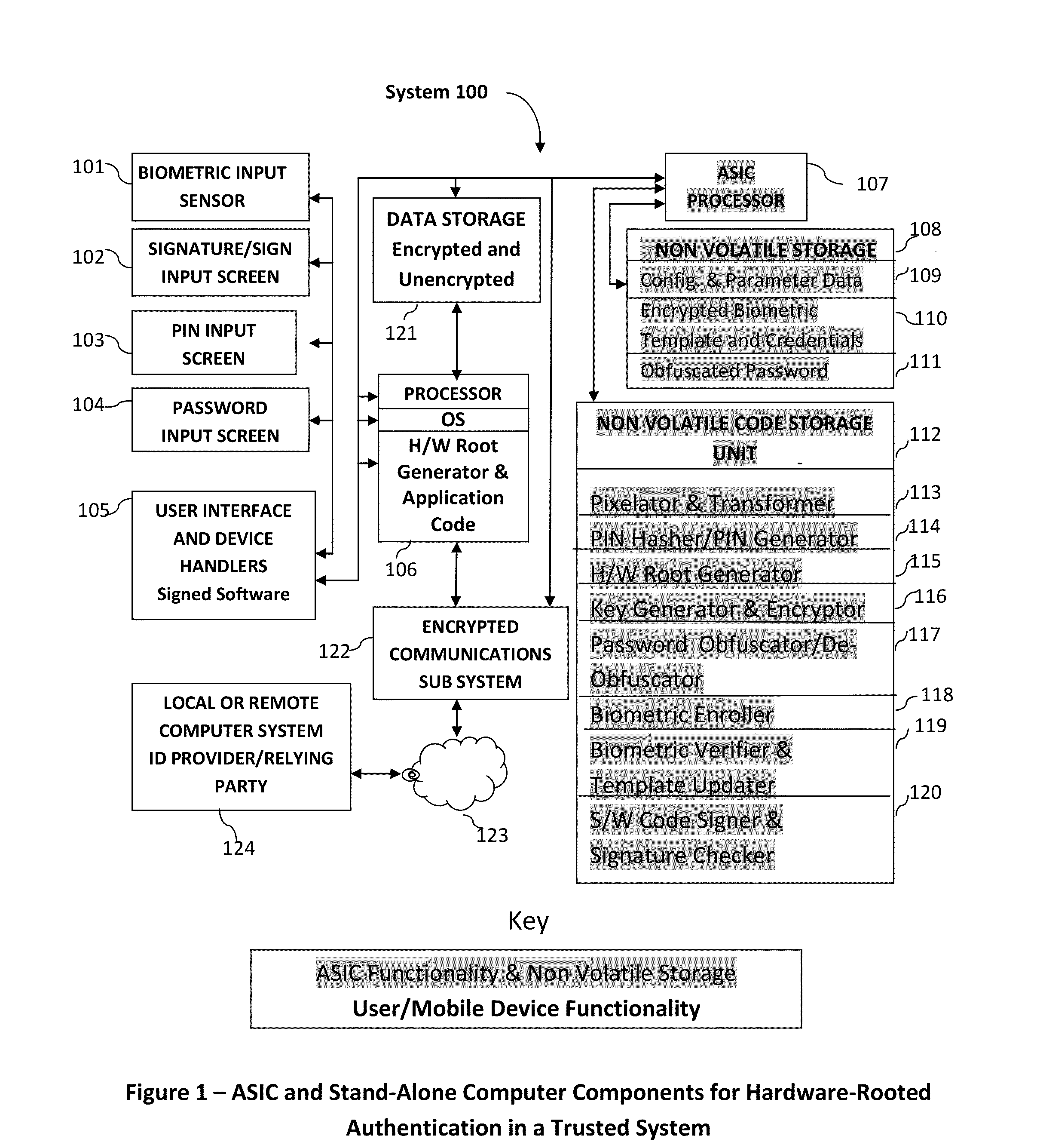
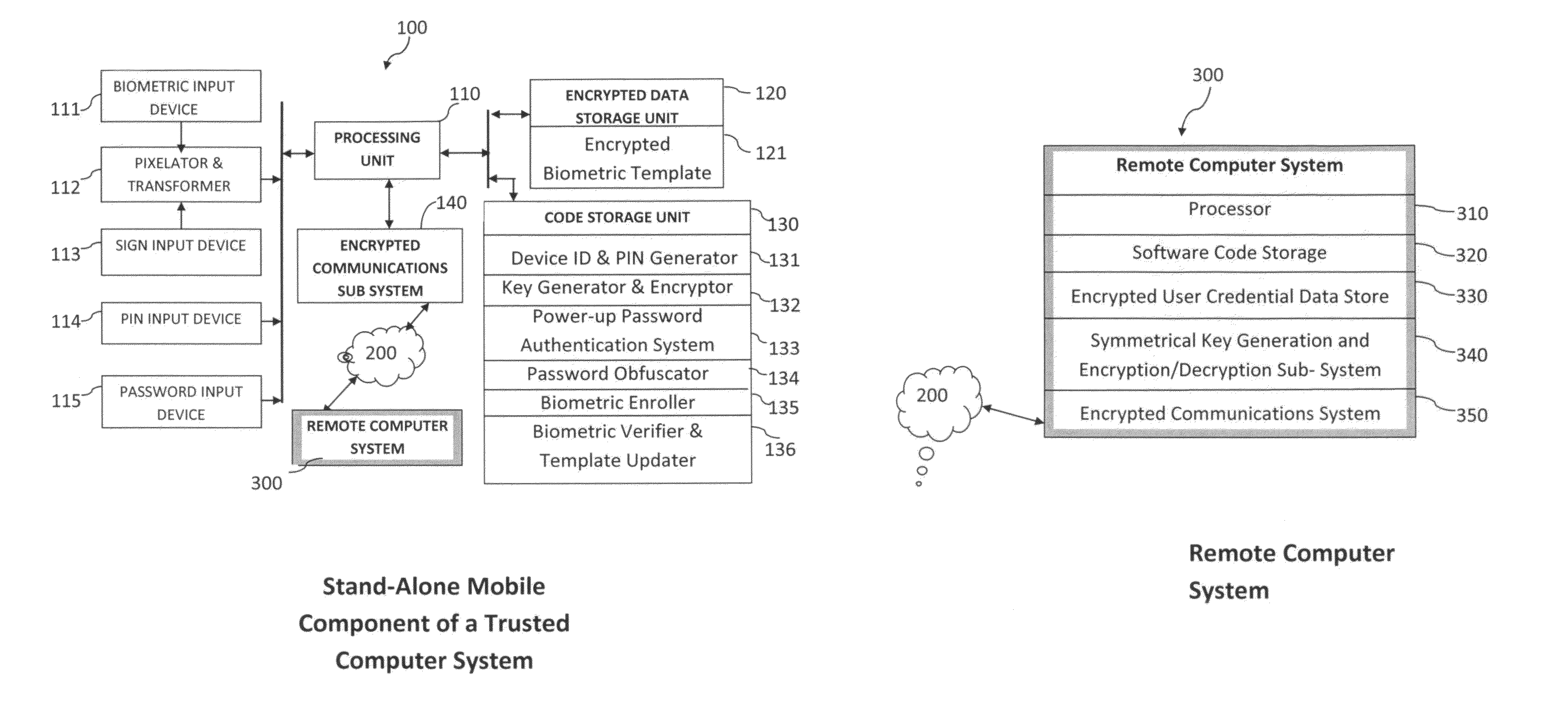
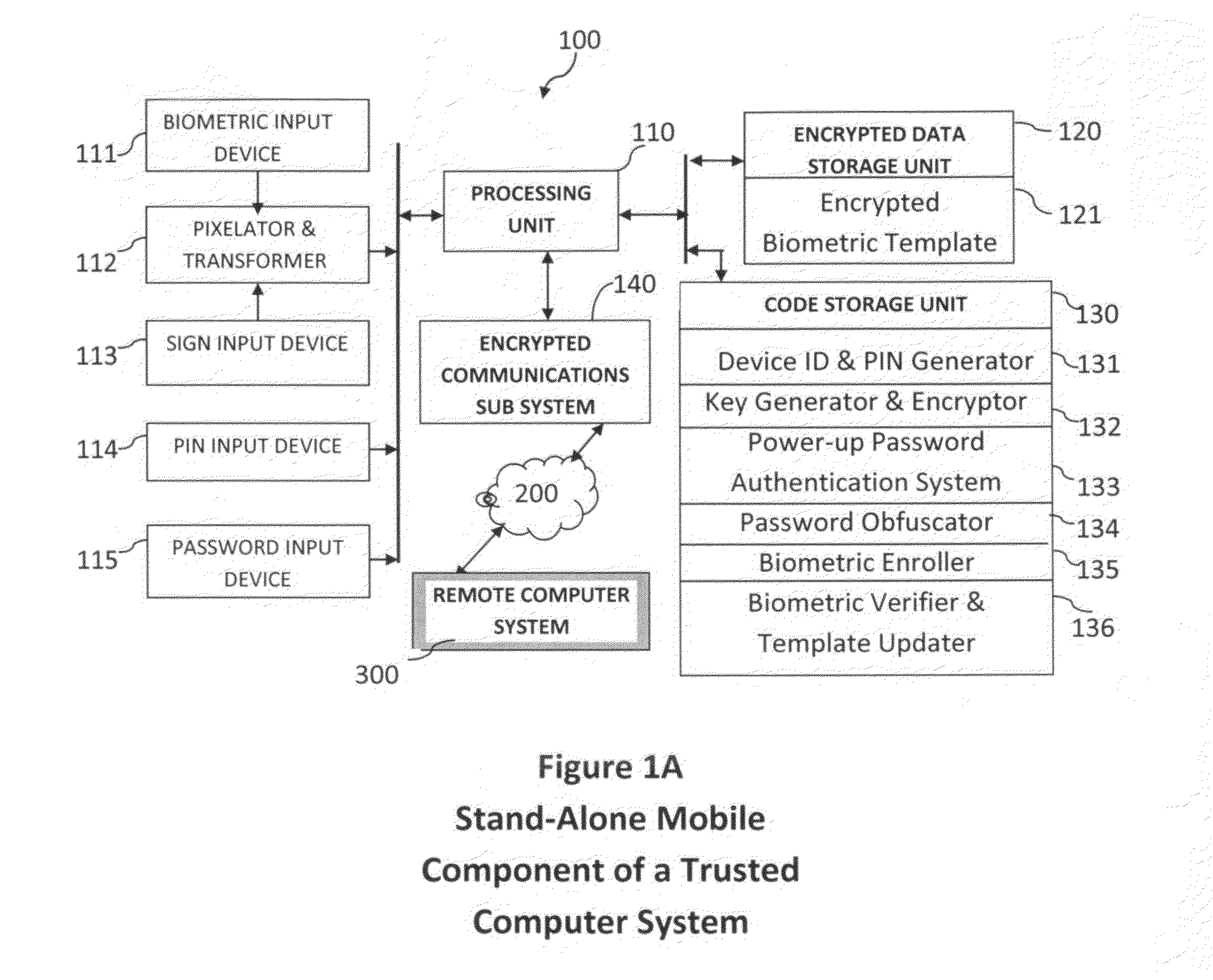
Method and system for combining a PIN and a biometric sample to provide template encryption and a trusted stand-alone computing device
ActiveUS20110126024A1Secure EncryptionEasy to useDigital data processing detailsUser identity/authority verificationBiometric dataTrust relationship
Biometric data, suitably transformed are obtained from a biometric input device contained within a stand-alone computing device and used in conjunction with a PIN to authenticate the user to the device. The biometric template and other data residing on the device are encrypted using hardware elements of the device, the PIN and Password hash. A stored obfuscated password is de-obfuscated and released to the device authentication mechanism in response to a successfully decrypted template and matching biometric sample and PIN. The de-obfuscated password is used to authenticate the user to device, the user to a remote computer, and to encrypt device data at rest on the device and in transit to and from the remote computer. This creates a trusted relationship between the stand-alone device and the remote computer. The system also eliminates the need for the user to remember and enter complex passwords on the device.
Owner:BIOCRYPT ACCESS LLC
Unified password prompt of a computer system
InactiveUS6397337B1Digital data processing detailsDigital computer detailsComputerized systemPassword hashing
A computer system provides a unified password prompt for accepting a user power-on password or an administrator password. A password string entered by the system administrator at the unified password prompt is compared with a stored power-on password. If the user password string matches the stored power-on password, then access to system resources is granted. If the user password string does not match the stored power-on password, then the user password string is compared to a stored administrator password. If the user password string matches the stored administrative password, then access to system resources is granted. If the user password string does not match the stored administrative password, then the system administrator is given a predetermined number of times to enter a password string matching either the stored power-on password or the stored administrator password. If a password string matching either the stored power-on password or the stored administrator password is not provided in the predetermined number of times, access to system resources is denied. The unified password prompt does not require a system administrator to know a user's power-on password in order to access system resources. The unified password prompt also permits a system administrator to configure a plurality of computer systems by providing a single administrative password rather than a plurality of user power-on passwords.
Owner:HEWLETT PACKARD CO
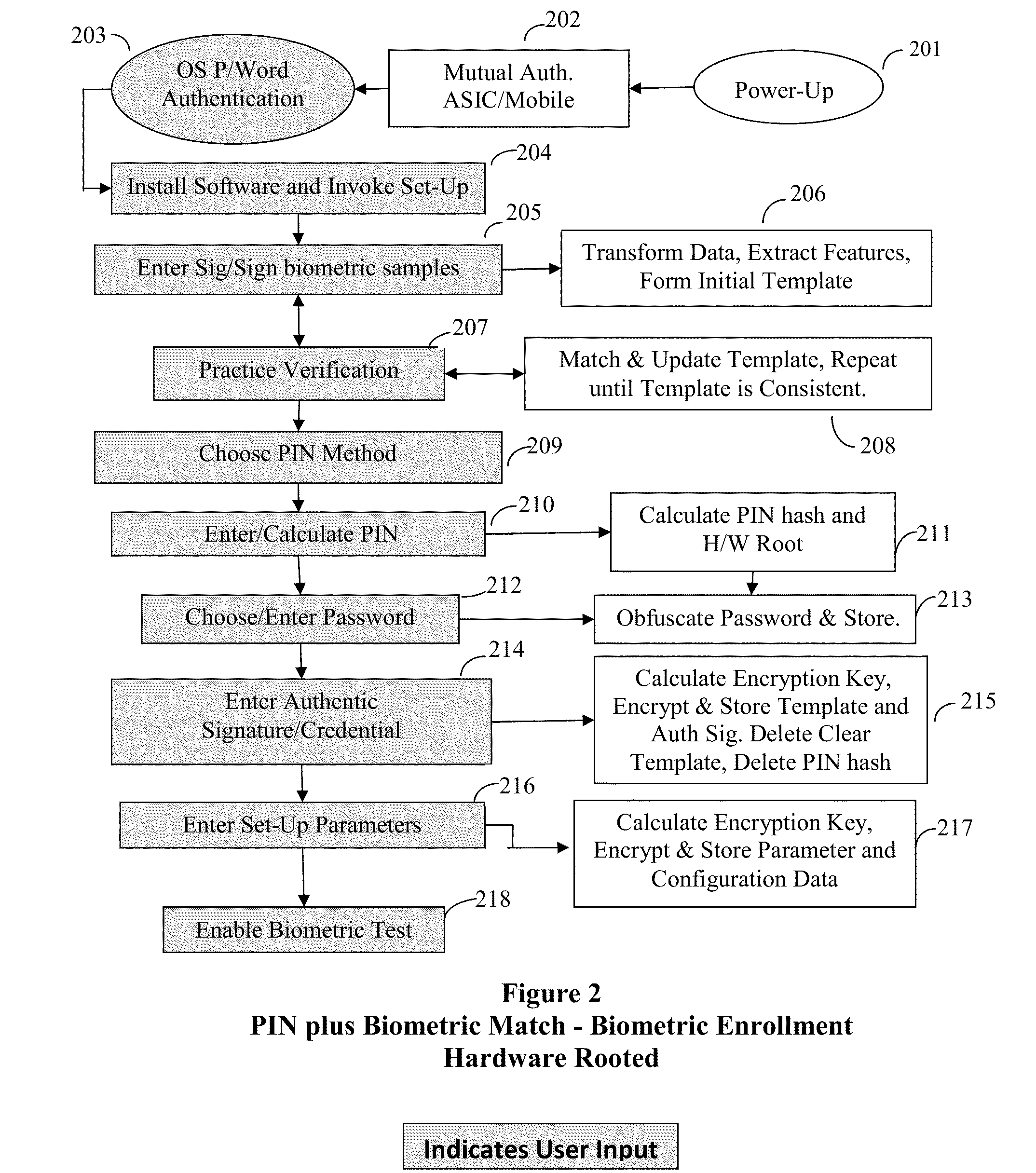
Method and System for Providing Password-free, Hardware-rooted, ASIC-based Authentication of a Human to a Mobile Device using Biometrics with a Protected, Local Template to Release Trusted Credentials to Relying Parties
InactiveUS20140365782A1Significant productivityMaximum safetyUser identity/authority verificationInternal/peripheral component protectionBiometric dataPassword hashing
Biometric data, which may be suitably transformed are obtained from a biometric input device contained within a stand-alone computer or a mobile device, which may contain an ASIC chip connected to or incorporated within the stand-alone computer or mobile device and which includes the capability for capturing one or more biometric samples and for biometric feature extraction, matching and encryption. For extra security, the biometric matching is used in conjunction with a PIN to authenticate the user to the stand-alone computer or mobile device. The biometric template and other sensitive data residing on the mobile device are encrypted using hardware elements of the mobile device (or the ASIC) together with the PIN hash and / or the Password hash. An obfuscated version of the Password, stored on the ASIC or the mobile device is de-obfuscated and released to the mobile device authentication mechanism, including a Trusted Platform Module if present, in response to a successfully decrypted template and matching biometric sample and PIN. A de-obfuscated password is used to authenticate the user to the mobile device and the same or a different de-obfuscated password may be used to authenticate the user to a remote computer using the SSL / TLS or a process based upon a symmetric encryption algorithm. The locally generated password may be used to encrypt data at rest on the mobile device or ASIC and the remote authentication password may be used to encrypt data in transit to and from a remote computer. This creates a trusted relationship between the stand-alone computer or mobile device and the remote computer. The system also eliminates the need for the user to remember and enter complex passwords on the mobile device or for secure transmission of data. A similar method may be used, with the signature / sign biometric modality to determine whether the holder of an IC chip card is, in fact the card owner.
Owner:BIOCRYPT ACCESS LLC
Method, System and Program Product for Secure Storage of Content
ActiveUS20140140508A1Key distribution for secure communicationSecret communicationPassword hashingMaster key
A method, system and program product comprise obtaining a user's username and password. A random key is generated for use as a master key. The master key is encrypted using the password to create an encrypted master key. A hash function is performed on the password to create a password hash. A random key is generated for use as a content key for encrypting the user's selected content. The content key is encrypted using the master key to create an encrypted content key. The selected content is encrypted using the content key to create encrypted content. The username, password hash, encrypted master key, first encrypted content key, and encrypted content is communicated to a server for storage in the user's account in which the possibility of decrypting at least the encrypted content by operations on the server is mitigated.
Owner:KAMATH DEEPAK +1
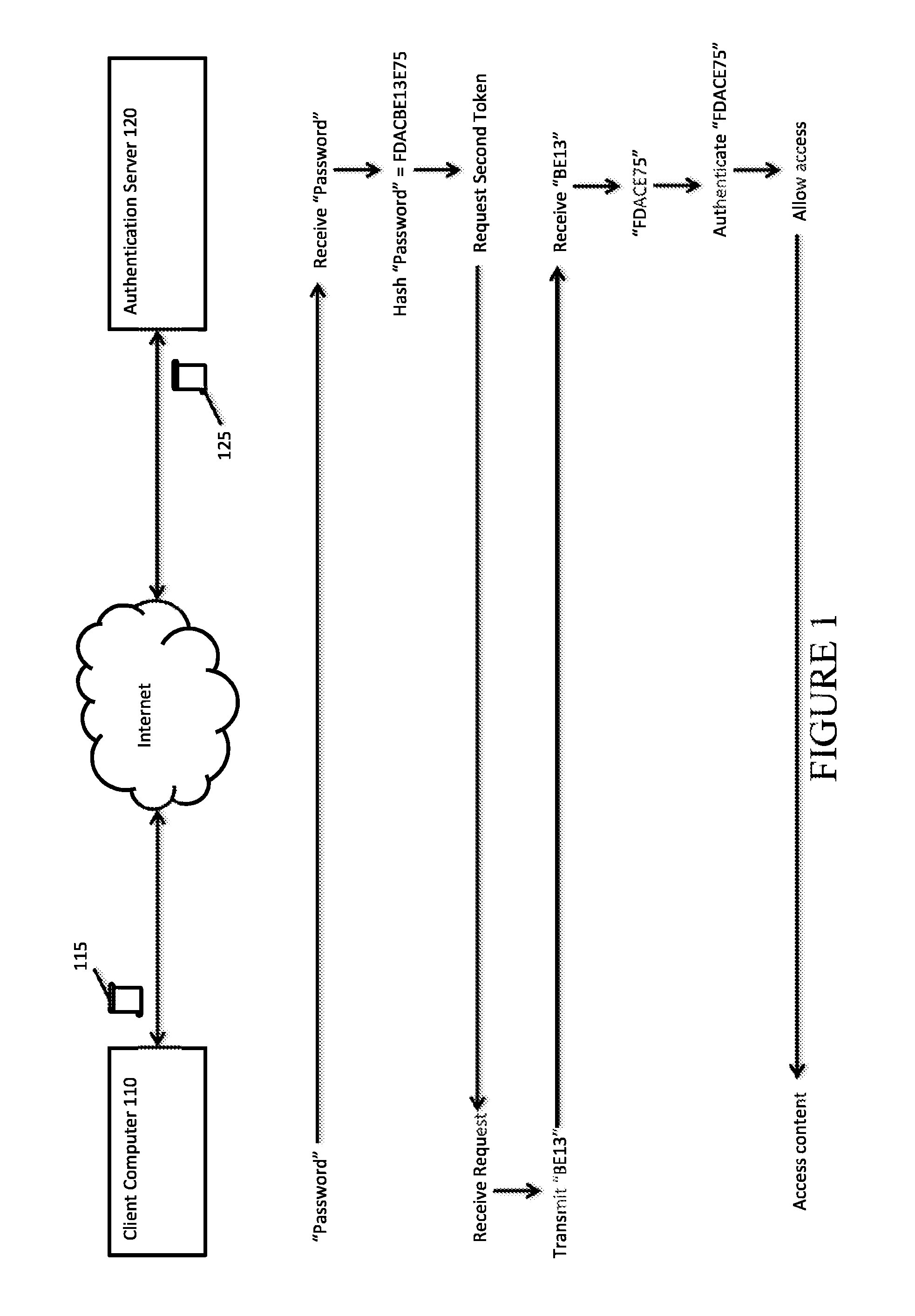
Two factor authentication using a protected pin-like passcode
ActiveUS20150349960A1Difficult to determineUser identity/authority verificationCoding/ciphering apparatusMulti-factor authenticationPassword hashing
For example, an implementation of the present invention can comprise a method for authenticating a user. The method can comprise an authentication server receiving from a user a password. The server can then hash the password such that a password hash is created. The server can then receive a second token from the user. Using the second token, the server can identify a sequence of characters associated with the second token within the password hash. The server can create an authentication token by removing the sequence of characters from the password hash. If the authentication token matches a stored value, the server can authenticate the user.
Owner:TOKENYM
Account free possession and transfer of electronic money
The account free possession and transfer of electronic money. Payment with E-Money is a settlement free process. Ownership and transfer occurs by means of name (identification number or URL) of the electronic bill and secure password. A person who knows the name and the password owns the money. Upon change of ownership the password has to be changed. The password change occurs on the server and the rest of the process in the individual wallet application or is processed manually by the user of E-Money.
Owner:OCHYNSKI WALTER
Challenge response-based device authentication system and method
ActiveUS20090240943A1Digital data processing detailsUser identity/authority verificationPasswordAuthentication system
A challenge response scheme authenticates a requesting device by an authenticating device. The authenticating device generates and issues a challenge to the requesting device. The requesting device combines the challenge with a hash of a password provided by a user, and the combination is further hashed in order to generate a requesting encryption key used to encrypt the user supplied password. The encrypted user supplied password is sent to the authenticating device as a response to the issued challenge. The authenticating device generates an authenticating encryption key by generating the hash of a combination of the challenge and a stored hash of an authenticating device password. The authenticating encryption key is used to decrypt the response in order to retrieve the user-supplied password. If the user-supplied password hash matches the stored authenticating device password hash, the requesting device is authenticated and the authenticating device is in possession of the password.
Owner:BLACKBERRY LTD
Secure password storage and verification method and device
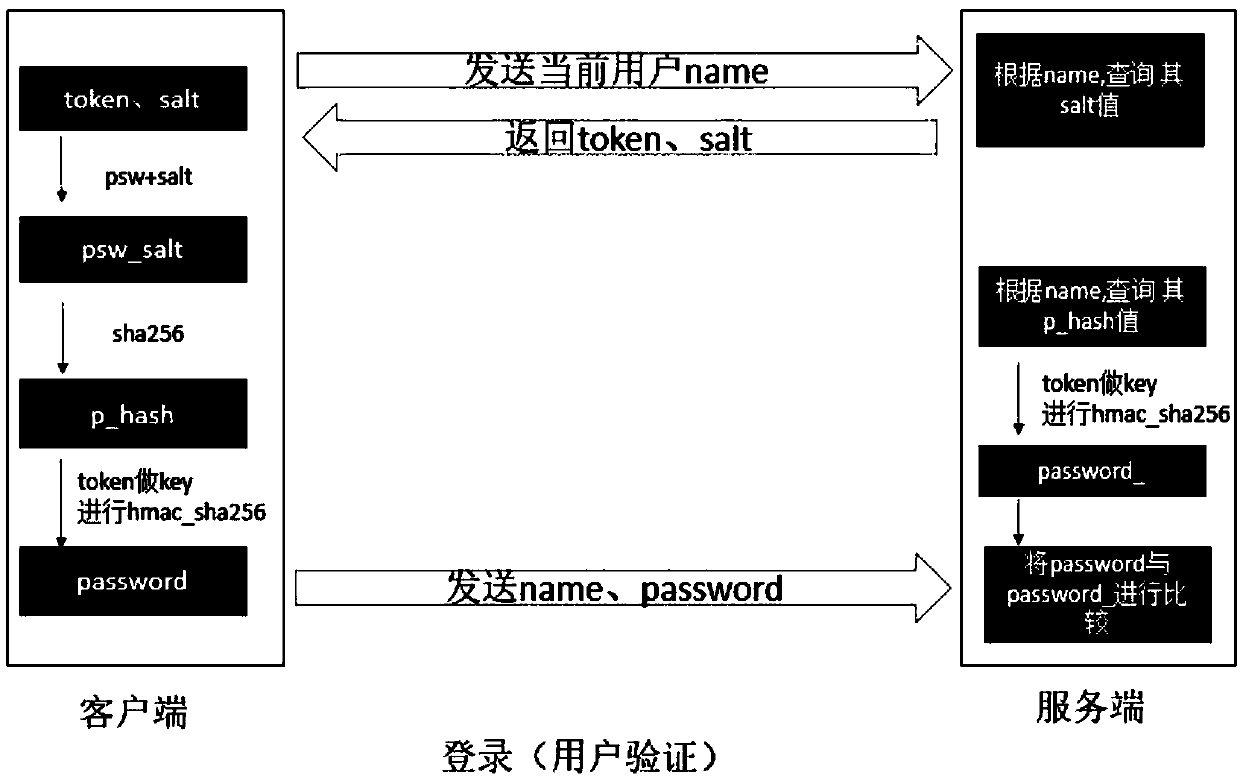
ActiveCN107911343ASafe storageSafety verificationKey distribution for secure communicationEncryption apparatus with shift registers/memoriesValidation methodsPassword hashing
The invention provides a secure password storage and verification method and device. When a password is stored, Salt is added into the password and the password is encrypted by a hash algorithm; a hash value of the password is stored into a server side; when a user logs in the server to carry out password verification, the server side generates token, and secondary encryption is carried out on thepassword hash value stored by the server side and a password hash value for logging in of the user by using the token as a key; and then comparison and verification are carried out. Therefore, the security of the password of the user during the storage and verification processes is improved.
Owner:SHENZHEN INFINOVA
Electronic device, password deletion method, and program
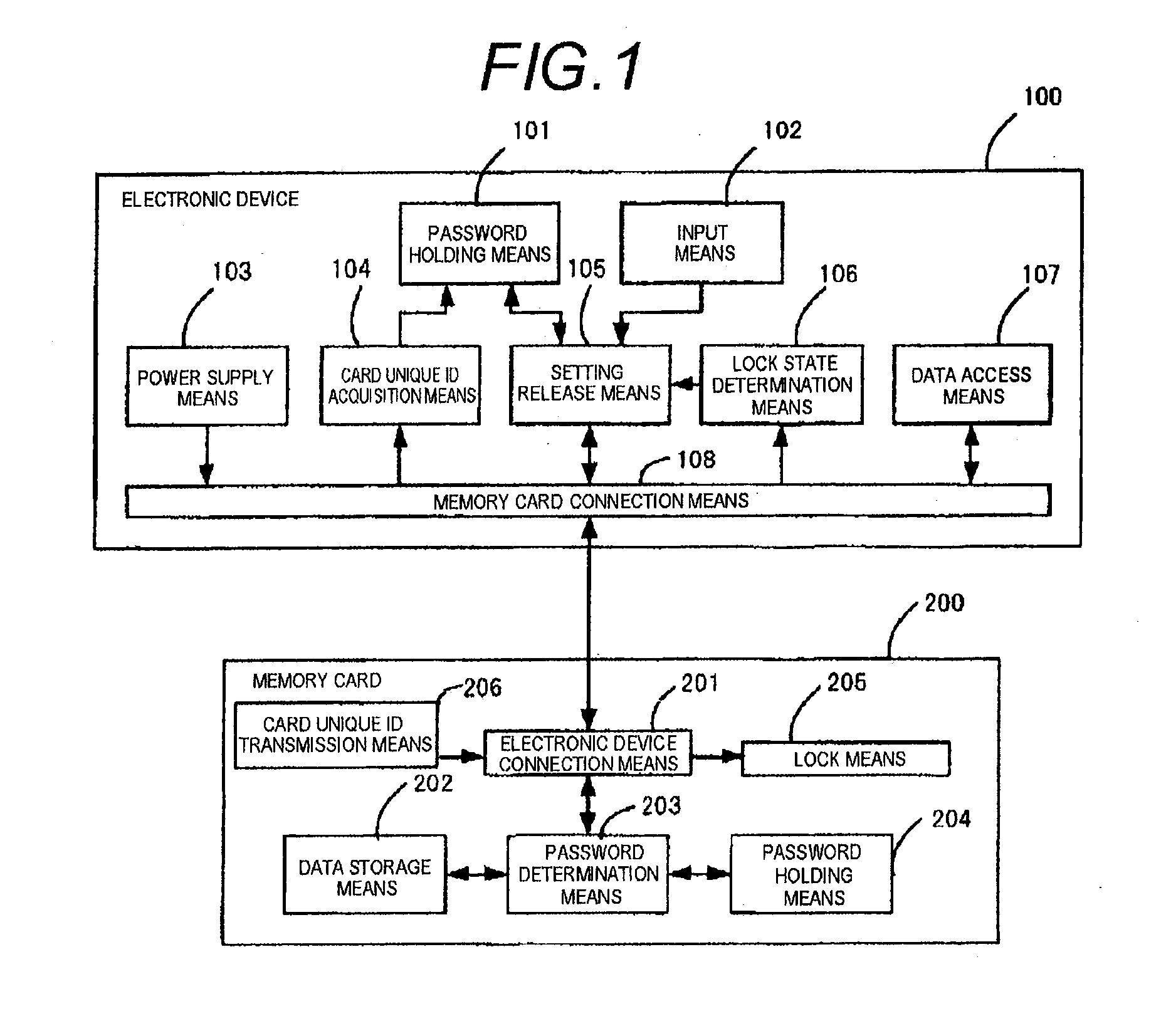
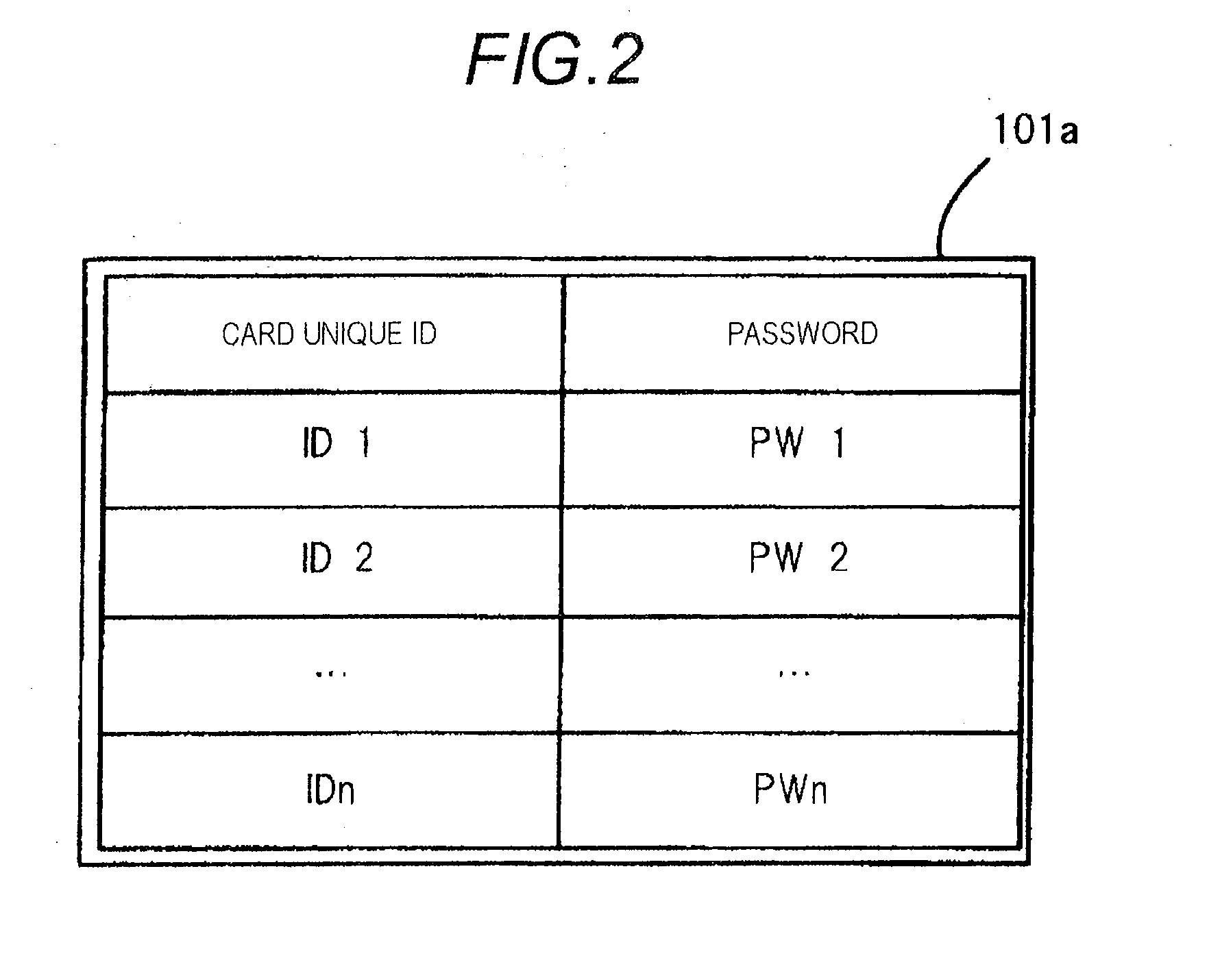
InactiveUS20110010517A1Unauthorized memory use protectionDigital data protectionExternal storagePassword hashing
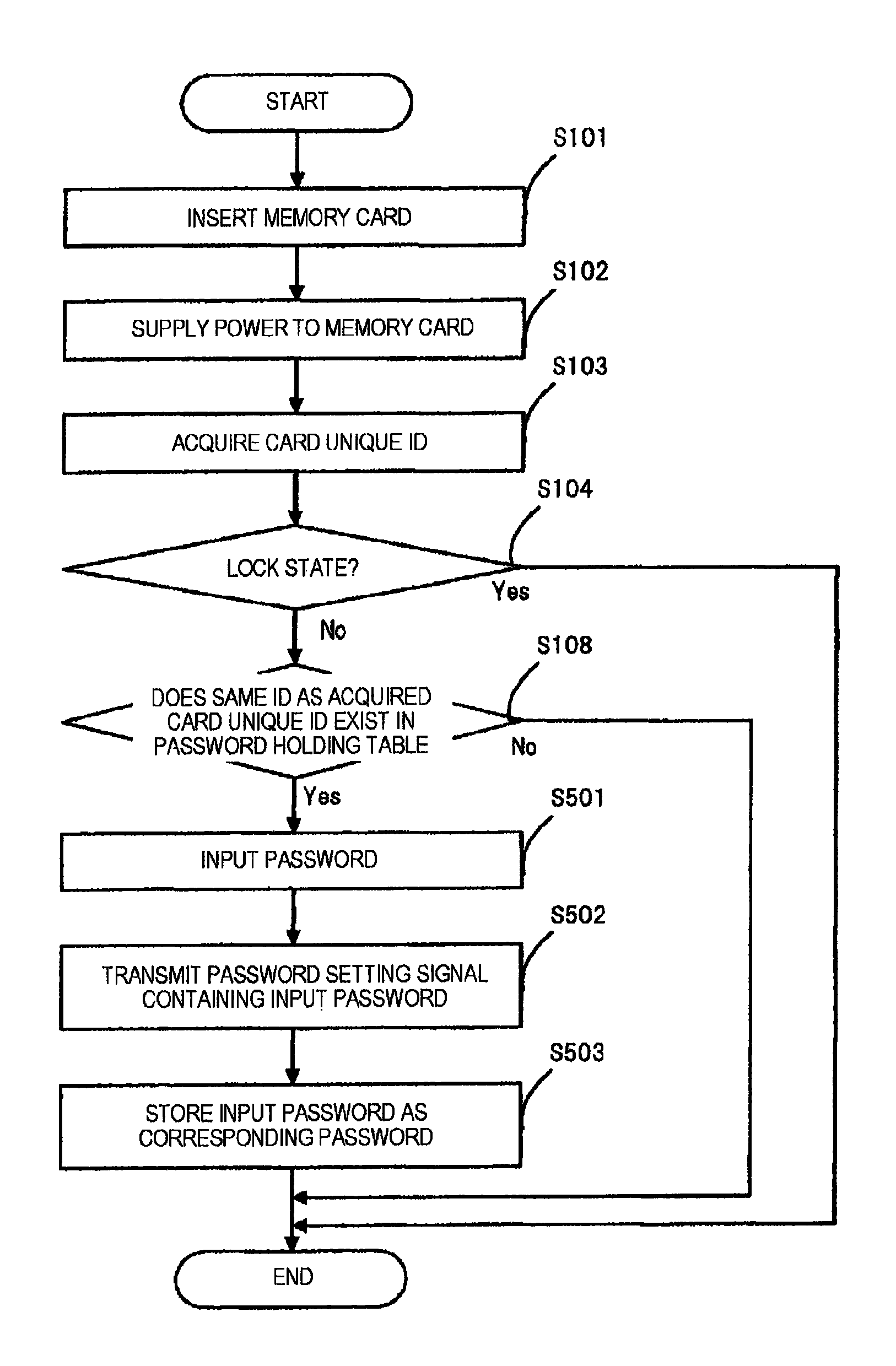
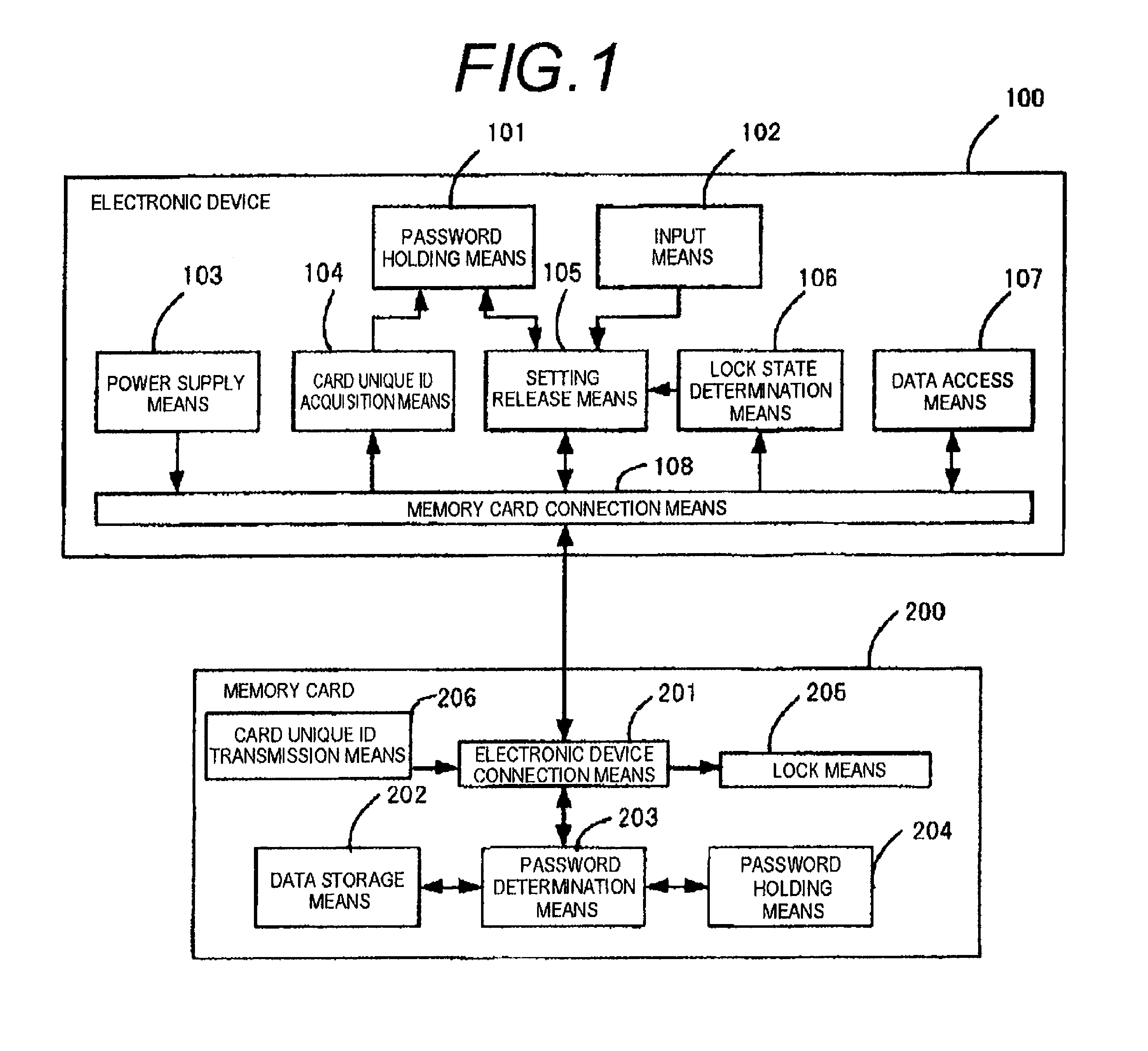
An electronic device that can automatically unlock an external storage device with a password without adding a function to the external storage device is provided. An electronic device 100B has memory card connection means 108 for connecting a memory card 200 that can be locked with a password, password holding means 101 for holding card unique ID and a password, card unique ID acquisition means 104 for acquiring connection identification information indicating the card unique ID of the memory card 20 connected to the memory card connection means 108, and password deletion means 109 for deleting connection identification information and the password corresponding to the connection identification information stored in the password holding means 101 if the connection identification information is contained in the password holding means 101.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
Cryptographic hash functions using elliptic polynomial cryptography
InactiveUS20100166175A1Readily apparentUser identity/authority verificationDigital computer detailsComputer hardwareCryptographic hash function
The cryptographic hash functions using of elliptic polynomial polynomials are based on the elliptic polynomial discrete logarithm problem, which is well known as a computationally hard problem. The hash functions are based on the elliptic polynomial equation in their generation, where different elliptic polynomials are used for different blocks of the same plain text. Particularly, the hash functions use an elliptic polynomial with more than one independent x-coordinate. More specifically, a set of elliptic polynomial points are used that satisfy an elliptic polynomial equation with more than one independent x-coordinate which is defined over a finite field F.
Owner:KING FAHD UNIVERSITY OF PETROLEUM AND MINERALS
Composite security marking and methods and apparatuses for providing and reading same
ActiveUS20190334730A1Increase achievable security levelEffective protectionUser identity/authority verificationCharacter and pattern recognitionCryptographic hash functionPassword hashing
In one embodiment, the invention is directed to a method of reading a marking, comprising a stimulation step, wherein a physical challenge according to a predetermined challenge-response authentication scheme corresponding to the PUF is created and applied to a PUF; a detection step, wherein a response generated by the PUF in accordance with the challenge-response authentication scheme in reaction to the challenge is detected and a digital signal representing the response is generated; a processing step, wherein the digital signal is processed in order to generate a hash value of the response by application of a predetermined cryptographic hash function to the digital signal; and an output step, wherein data representing the generated hash value as a first reading result is output.
Owner:MERCK PATENT GMBH
Method and system for combining a PIN and a biometric sample to provide template encryption and a trusted stand-alone computing device
ActiveUS8842887B2Easy to useUser identity/authority verificationCharacter and pattern recognitionBiometric dataTrust relationship
Owner:BIOCRYPT ACCESS LLC
Two factor authentication using a protected pin-like passcode
ActiveUS9350548B2User identity/authority verificationCoding/ciphering apparatusPassword hashingAuthentication server
For example, an implementation of the present invention can comprise a method for authenticating a user. The method can comprise an authentication server receiving from a user a password. The server can then hash the password such that a password hash is created. The server can then receive a second token from the user. Using the second token, the server can identify a sequence of characters associated with the second token within the password hash. The server can create an authentication token by removing the sequence of characters from the password hash. If the authentication token matches a stored value, the server can authenticate the user.
Owner:TOKENYM
Novel secret key separated signing method and system
ActiveCN103414557AImprove securityMultiple keys/algorithms usageUser identity/authority verificationComputer hardwarePassword hashing
The invention provides a secret key separated signing method with a self update capability of a secret key of an assisting device. The method comprises the steps that a singer generates an initial singer secret key SK0 according to two randomly selected parameters which are s0 and h0 and a password hash function H1, the assisting device will send the signer an assisting device update message SKUi at the beginning of each subsequent time slice to help the singer to update a temporary secret key SKi of a current time slice, the assisting device also carries out self update on a secret key of the assisting device in each time slice simultaneously with the operation that the assisting device helps the signer to update the temporary secret key of the signer, a parameter h0 is randomly selected in a time slice 0 to be regarded as the initial secret key HK0 of the assisting device, and the secret key of the assisting device is updated to HKi in a time slice i. The method can reduce the possibility that the secret key of the assisting device is revealed, and therefore the safety of the secret key separated signing method is enhanced greatly.
Owner:SHANDONG ZHENGZHONG COMP NETWORK TECH CONSULTING
System and method for intelligence based security
ActiveUS20130104192A1Data augmentationImprove securityDigital data protectionSpecial data processing applicationsOperational systemPaper document
Included in the present disclosure are a system, method and program of instructions operable to protect vital information by combining information about a user and what they are allowed to see with information about essential files that need to be protected on an information handling system. Using intelligent security rules, essential information may be encrypted without encrypting the entire operating system or application files. According to aspects of the present disclosure, shared data, user data, temporary files, paging files, the password hash that is stored in the registry, and data stored on removable media may be protected.
Owner:DELL PROD LP
Decentralized access control for authorized modifications of data using a cryptographic hash
ActiveUS20190379673A1Satisfactory performanceDigital data protectionSecuring communicationNetwork activityCryptographic hash function
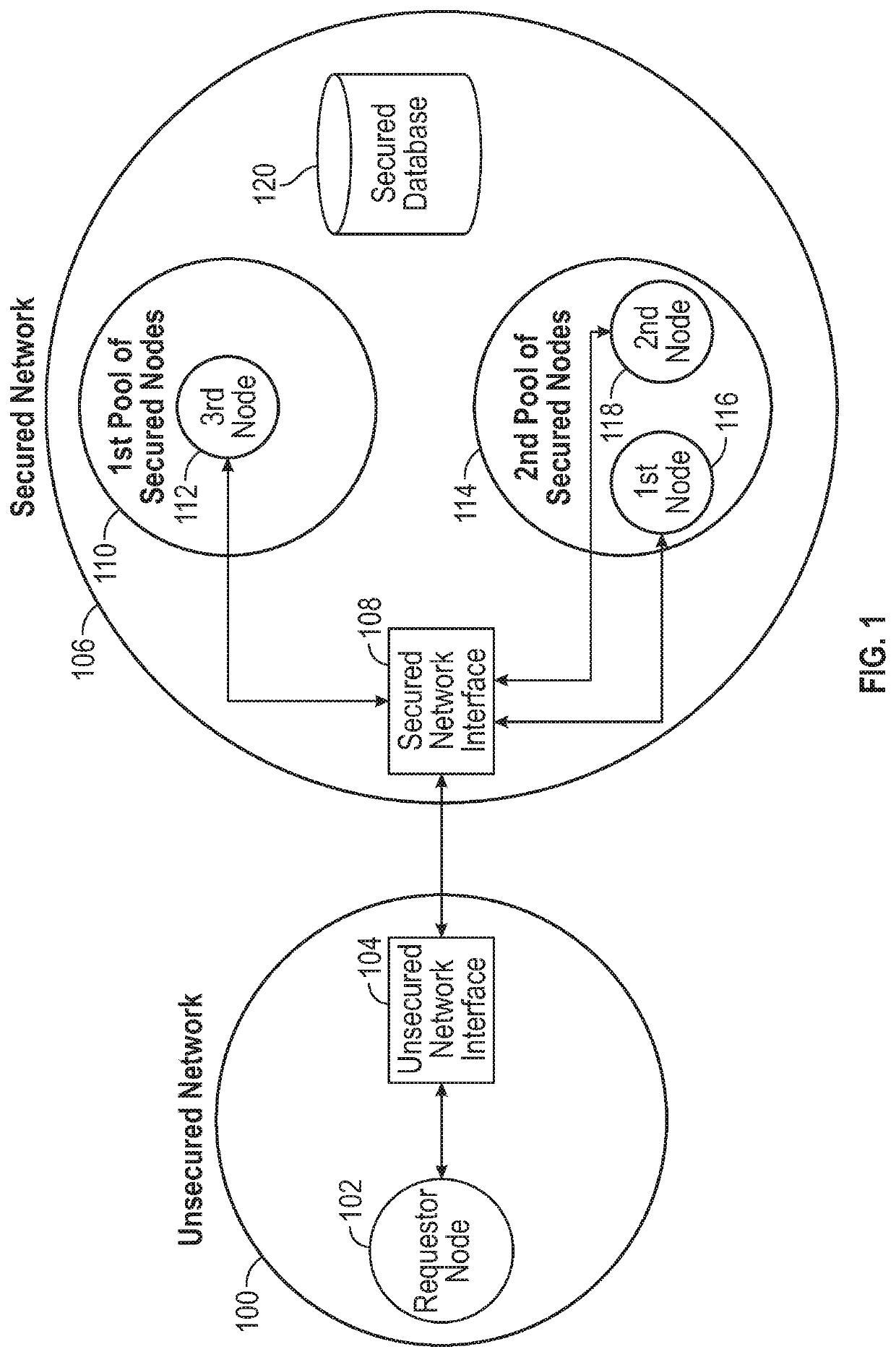
Embodiments of network devices for access control are described. In some embodiments, an access control processor of a first node receives a request from a requestor node on an unsecure network to join a first group of nodes on a secure network, where the first node coordinates network activities of the first group of nodes including a plurality of partitioned nodes of a network. In response to receiving the request, the access control processor assigns the requestor node to a first pool of the first group of nodes that are configured to perform authorized modifications of data including a cryptographic hash to protect the data against unauthorized modifications. In some embodiments, the access control processor initiates the authorized modifications of the data using one or more nodes assigned to the first pool and one or more nodes of a second pool of the first group of nodes.
Owner:PROMETHEUS8
Method and device for reducing operation amount in SM3 password hashing algorithm
InactiveCN106850189AReduce the number of operationsFast operationEncryption apparatus with shift registers/memoriesPassword hashingComputer science
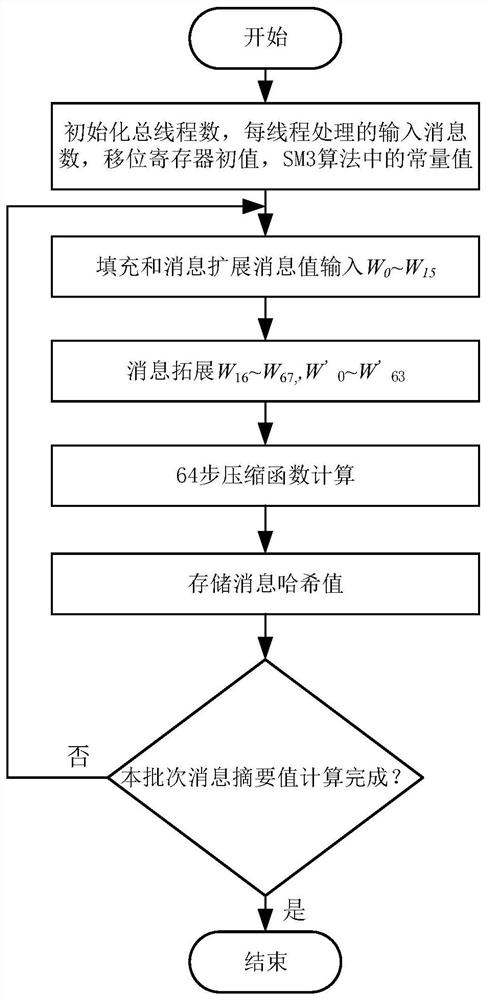
The embodiment of the invention discloses a method and device for reducing an operation amount in an SM3 password hashing algorithm. A parallel addition operation is utilized to replace a great number of serial addition operations, and the number of the serial addition operations is reduced, so that operation delay is reduced, and an operation speed of the SM3 password hashing algorithm is improved.
Owner:GUANGDONG UNIV OF TECH
Secure tape
InactiveUS20070130477A1Unauthorized memory use protectionHardware monitoringMagnetic tapePassword hashing
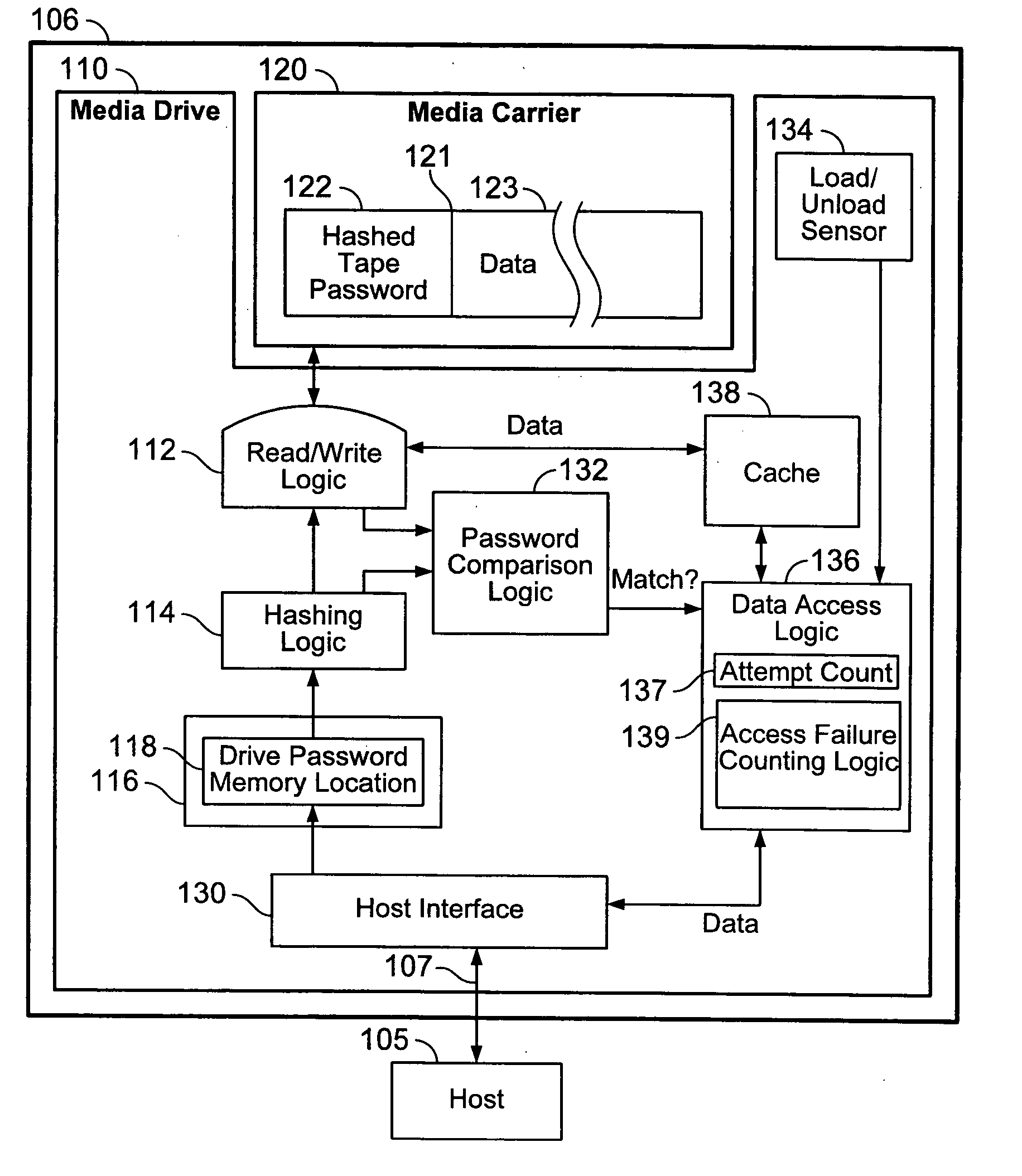
Data stored on a removable storage medium such as a tape cartridge can be protected from unauthorized access by storing a password hash value in a protected manner on the storage medium, where the password hash value is generated from a password by a one-way hash function such as SHA-256, so that the password cannot easily be determined from the hash value. A media drive is then equipped with logic for blocking access to the data unless the password is provided. The password is protected from unauthorized access because the password hash value, not the password itself, is stored on the storage medium.
Owner:QUANTUM CORP
Credibility detection method based on password hash and biometric feature recognition
ActiveCN104751042AAvoid the hidden danger of changing and replacingPrivacy protectionDigital data authenticationPassword hashingUser code
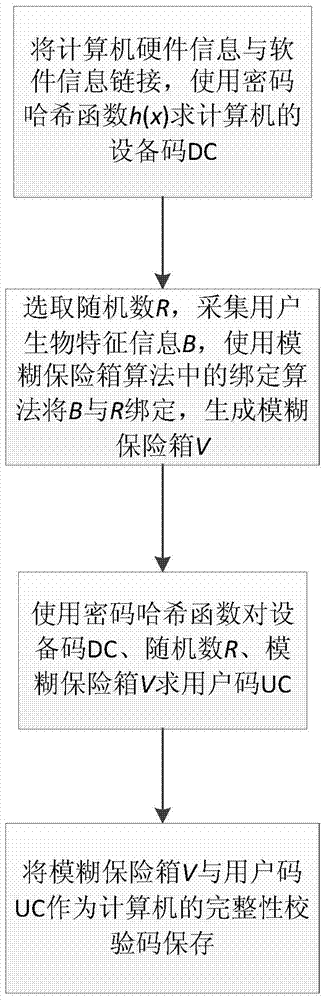
The invention discloses a credibility detection method based on password hash and biometric feature recognition. The method mainly solves the problems that existing computer information detection codes are likely to be reversely calculated and computers cannot recognize physical identities of users. According to the technical scheme, the method includes the steps that 1, software and hardware information of a computer is obtained, and biological feature information of a user is collected; 2, a device code is generated according to the software and hardware information, a fuzzy vault is generated through the biological feature information, and a user code is generated through the device code and the fuzzy vault; 3, the fuzzy vault and the user code serve as computer integrity check codes to be stored; 4, software and hardware information of the computer is obtained again, biological feature information of the user is recollected, and a new user code is generated; 5, the new user code is compared with the stored user code, if the new user code is identical with the stored user code, credibility verification passes, and otherwise, verification fails. The integrity check codes can be prevented from being changed and replaced, the physical identity of the user can be recognized, and the method can be used for protecting computer security.
Owner:西安电子科技大学工程技术研究院有限公司
Multi-original-chain throughput expansion method based on layer logic
ActiveCN110149379AImprove throughputReduce the waste of computing powerTransmissionCross connectionPassword hashing
The invention discloses a multi-original-chain throughput expansion method based on layer logic. The method comprises: providing throughput request data and associated layer data for a data resource distribution server; performing channel protocol detection, the hierarchical data to be extended in the multi-original chain network; obtaining hierarchical data by inquiring multiple original chains,and obtaining throughput request data from a cloud service network through the hierarchical data; extending hierarchical data regarding the throughput request data in a multi-original chain network and extending the throughput request data into a cloud service network. According to the method, transaction delay caused by non-malicious network faults to a consensus process is avoided. Secondly, a hybrid consensus taking NDPOS as a main part is provided, DHT cross-connection fragmentations are combined, and password hashing is adopted for connection, so that the throughput of the distributed account book is expanded, the calculation power waste of POW is reduced, and meanwhile, the cost of a Byzantium node to do evil is increased.
Owner:山东公链信息科技有限公司
Database password changes
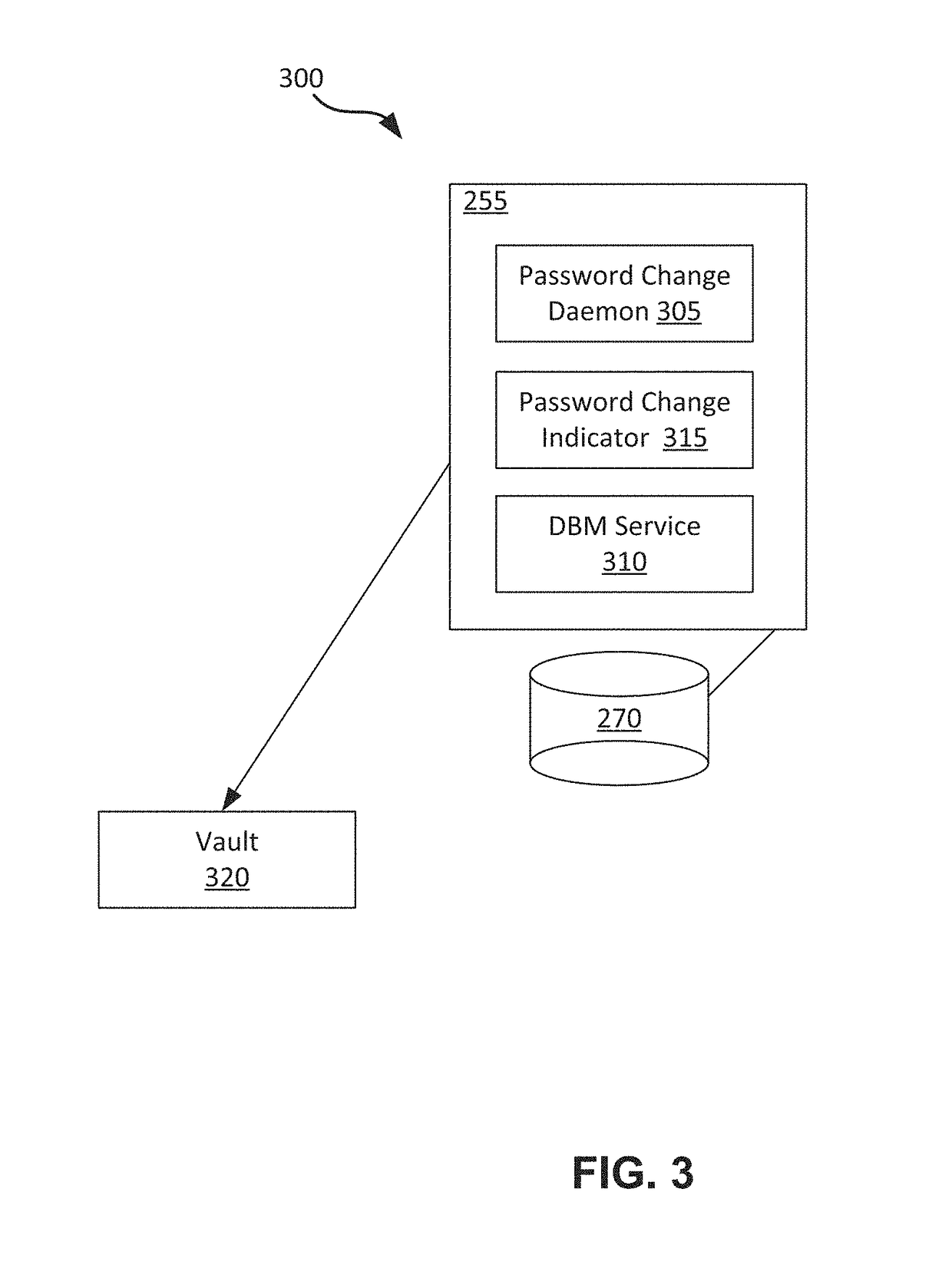
ActiveUS20180375645A1Key distribution for secure communicationDatabase updatingPassword hashingComputing systems
Systems and methods for changing database passwords are described. A first server computing system receives an indication to perform a password change process for an administrative account of an associated database. The server generates a vault configured to store a password change status and a password secret associated with the account. The server sets the password change status to a first value to indicate that the server is performing the password change process and then performs the password change process for the account. The server then sets the password change status to a second value to enable a second server computing system to perform a second password change process for a second administrative account of a database associated with the second server system. The database associated with the second server computing system is a standby database of the database associated with the first server system.
Owner:SALESFORCE COM INC
Platform for generation of passwords and/or email addresses
ActiveUS20180144122A1Less reliantProvide securityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesEmail addressPassword hashing
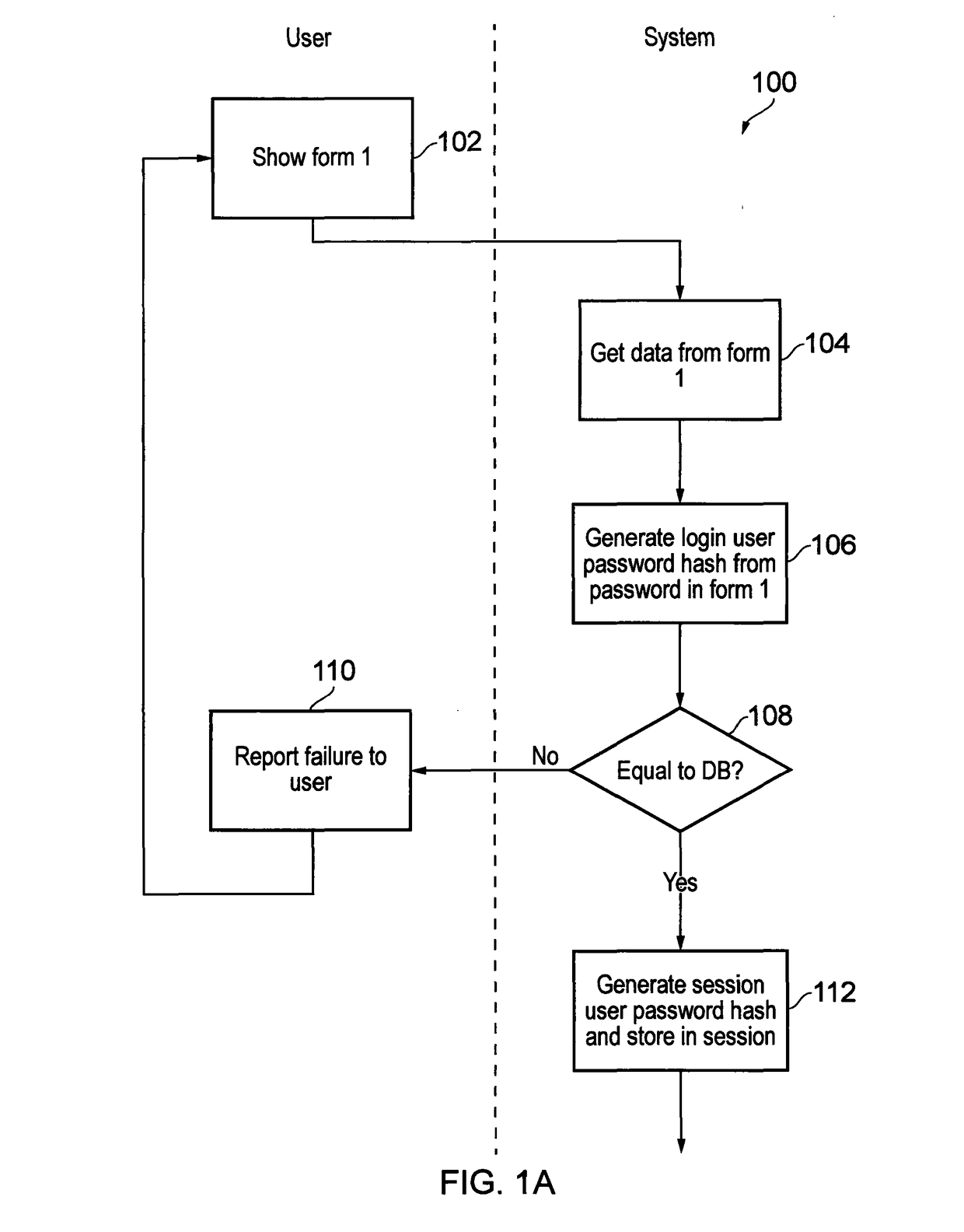
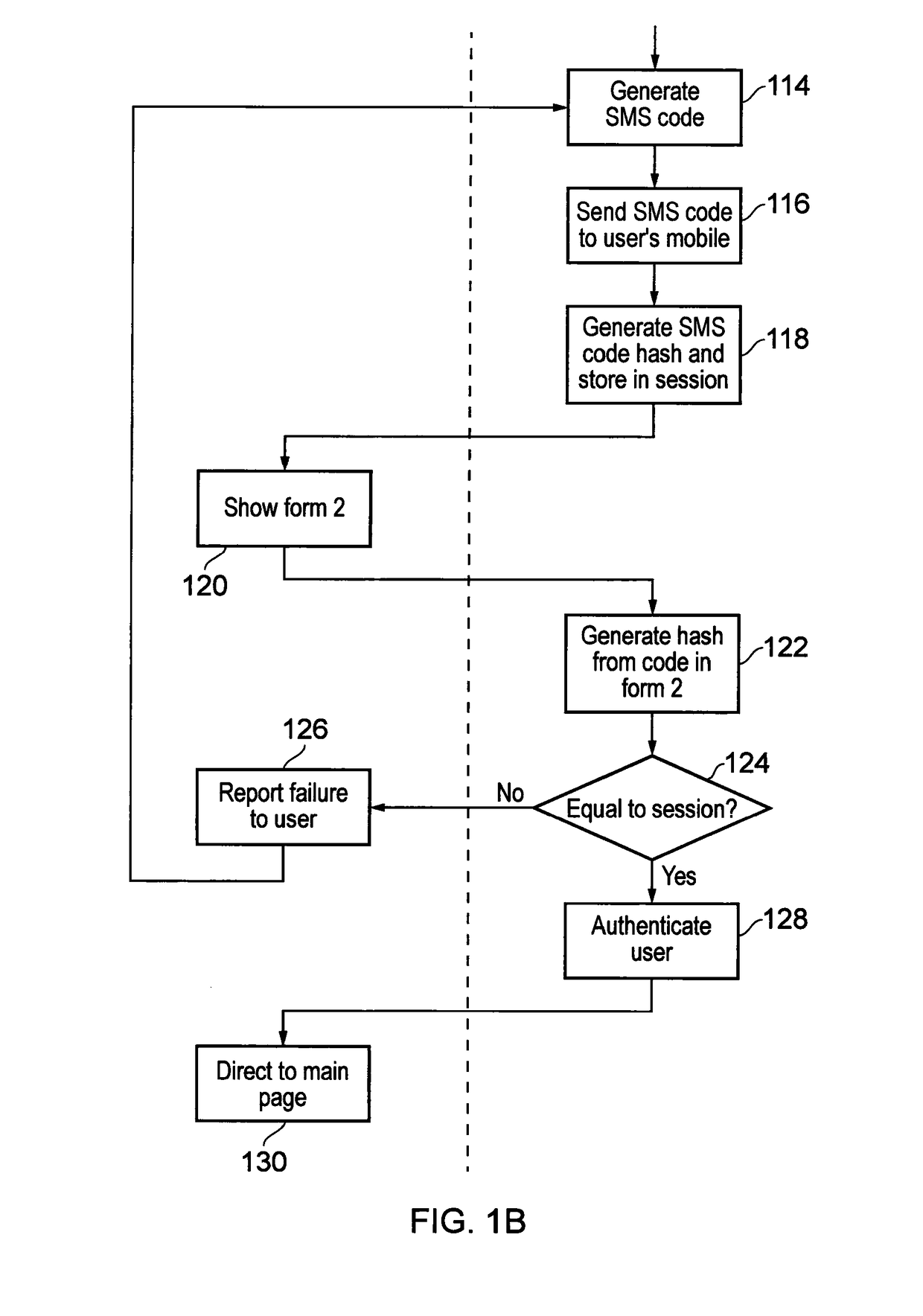
A password and / or email address management platform configured to regenerate a previously generated password for a given web domain or digital system without permanently storing the previously generated password. The platform can operate without maintaining a permanent store or list of other user-related information, e.g. a list of web domains or systems for which passwords have been generated. In an embodiment, the platform performs the steps of concatenating a plurality of password input data elements into a requested phantom password input data string, applying a hashing algorithm to the requested phantom password input data string to generate a phantom password hash, applying a hash-to-string function to convert the phantom password hash to a phantom password, and purging the password generation system of the phantom password after it is notified to a user.
Owner:PHANTOMKEY TECH LTD
Cryptographic Hashing Device and Method
ActiveUS20090067620A1Improve the immunityEasy to useUser identity/authority verificationSecret communicationSoftware engineeringPassword hashing
Owner:FRANCE TELECOM SA
Automating password change management
ActiveUS20180004935A1Little effortDigital data protectionDigital data authenticationChange managementThird party
A password management service provides automated password management. In one embodiment, a method for automating password changes begins in response to a determination that automated password changes are authorized. In response, a data mining session is initiated. Within the data mining session, a set of third party applications or sites are identified. Then, and responsive to receipt of a password reset flow authorization, a password reset flow to one or more of the third party applications or sites is initiated by the service. Thereafter, and still within the data mining session, and for each of the one or more third party applications or sites, a determination is made whether a password reset confirmation link has been received by the service. In response to a determination that a password reset confirmation link has been received for a given third party application or site, the service uses the password reset confirmation link to perform an automated password reset and thereby obtain a new user password for the application or site.
Owner:LASTPASS US LP
System and method for intelligence based security
ActiveUS8341404B2Data augmentationImprove securityDigital data processing detailsUnauthorized memory use protectionOperational systemPassword hashing
Owner:DELL MARKETING
Method and device for detecting account stealing behavior
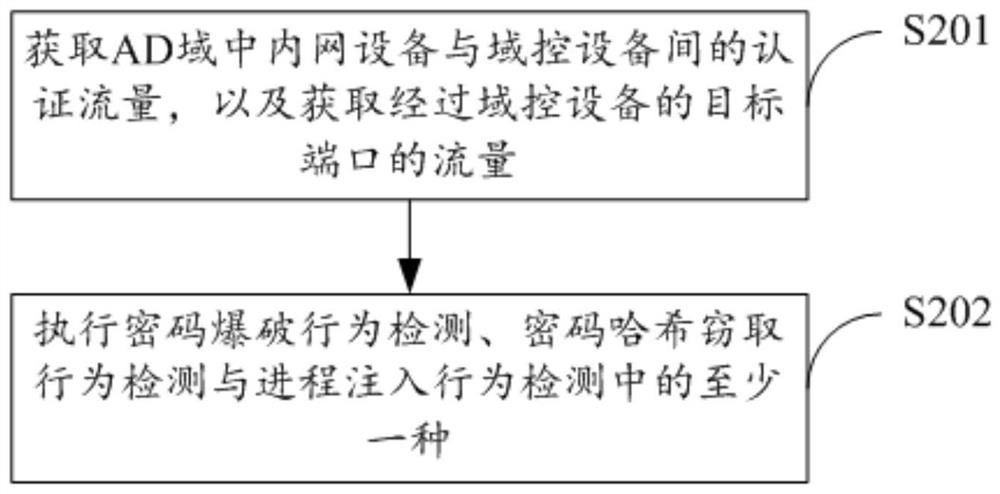
PendingCN112565162AGood detection rateStrong targetingCharacter and pattern recognitionTransmissionEngineeringPassword hashing
The invention provides a method and device for detecting an account stealing behavior. The method comprises the steps of obtaining authentication flow between intranet equipment and domain control equipment in an AD domain and flow passing through a target port of the domain control equipment, and executing at least one of password blasting behavior detection, password hash stealing behavior detection and process injection behavior detection. The password blasting behavior detection, the password hash stealing behavior detection and the process injection behavior detection provided by the invention are all determined for typical behaviors of account stealing performed by attackers, so that the pertinence of the password blasting behavior detection, the password hash stealing behavior detection and the process injection behavior detection provided by the invention is stronger, and therefore, the method for detecting the account stealing behavior in the AD domain provided by the invention has a better detection rate, so that the omission ratio can be effectively reduced, and the false detection rate can also be effectively reduced.
Owner:SANGFOR TECH INC
Electronic device, password deletion method, and program
InactiveUS8549311B2Digital data processing detailsUnauthorized memory use protectionExternal storagePassword hashing
An electronic device that can automatically unlock an external storage device with a password without adding a function to the external storage device is provided. An electronic device 100B has memory card connection means 108 for connecting a memory card 200 that can be locked with a password, password holding means 101 for holding card unique ID and a password, card unique ID acquisition means 104 for acquiring connection identification information indicating the card unique ID of the memory card 20 connected to the memory card connection means 108, and password deletion means 109 for deleting connection identification information and the password corresponding to the connection identification information stored in the password holding means 101 if the connection identification information is contained in the password holding means 101.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
Producing volatile password hashing algorithm salts from hardware random number generators
ActiveUS10776480B2Key distribution for secure communicationRandom number generatorsParallel computingSecret code
A computer-implemented method, computer program product, and system are provided. The method includes generating, by a password management system using a set of Hardware Random Number Generators (HRNGs), at least one salt based on statistics of a set of random numbers with given distributions generated by the set of HRNGs. The method further includes forming, by a processor, a hashed password based on the at least one salt.
Owner:IBM CORP
Fast Implementation of GPU-Based SM3 Password Hashing Algorithm
ActiveCN110086602BIncrease occupancyReduce idle timeEncryption apparatus with shift registers/memoriesVideo memoryParallel computing
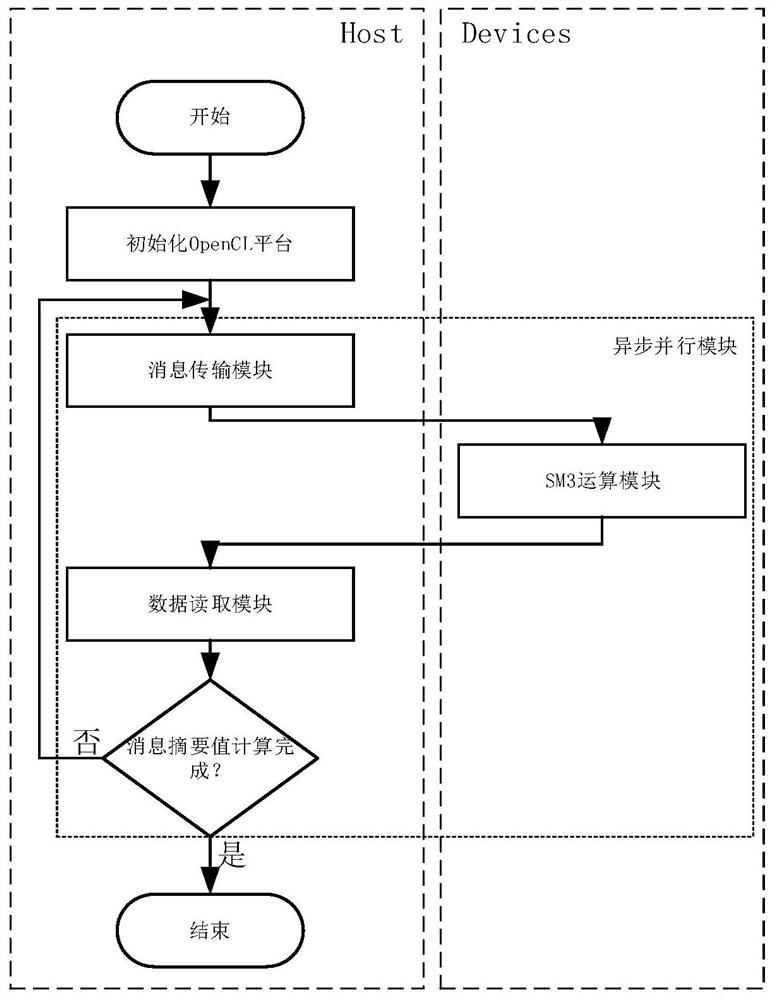
A fast implementation method of the GPU-based SM3 cryptographic hash algorithm, by asynchronously copying messages to be processed from the memory to the video memory of the GPU as a global memory, when the GPU uses the SM3 fast implementation method that contains padding expansion and compression function loop expansion When calculating the hash value, the CPU transmits the next batch of messages at the same time; the GPU outputs the calculation results to the video memory and the CPU reads the results in the video memory and transmits the message digest value. The invention has simple implementation and stable performance, and the SM3 quickly realizes a performance of 1.14 billion Hash / s, which greatly improves the calculation efficiency of the SM3.
Owner:SHANGHAI JIAO TONG UNIV
Multi-client cooperative authentication method, device, equipment and medium based on feature recognition
ActiveCN113259136BAvoid the risk of eavesdroppingUser identity/authority verificationDigital data authenticationInternet privacyPassword hashing
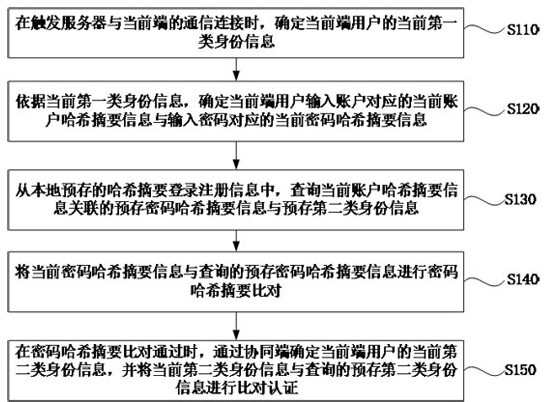
The embodiment of the present invention discloses a multi-client collaborative authentication method, device, equipment and medium for feature recognition. The method includes: determining the current first type of identity information of the current end user; determining the current account hash summary information corresponding to the input account of the current end user and the current password hash summary information corresponding to the input password according to the current first type of identity information; Query the pre-stored password hash summary information associated with the current account hash summary information and the pre-stored second type of identity information; compare the current password hash summary information with the queried pre-stored password hash summary information; When the summary comparison is passed, the coordinating terminal determines the current second-class identity information of the current-end user, and compares the current second-class identity information with the queried pre-stored second-class identity information for authentication. Using this application scheme, through multi-client collaborative multi-biometric feature collection and authentication, login authentication without the user's original login information is realized.
Owner:ZHEJIANG UNIVIEW TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com