Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
35 results about "Fuzzy vault" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
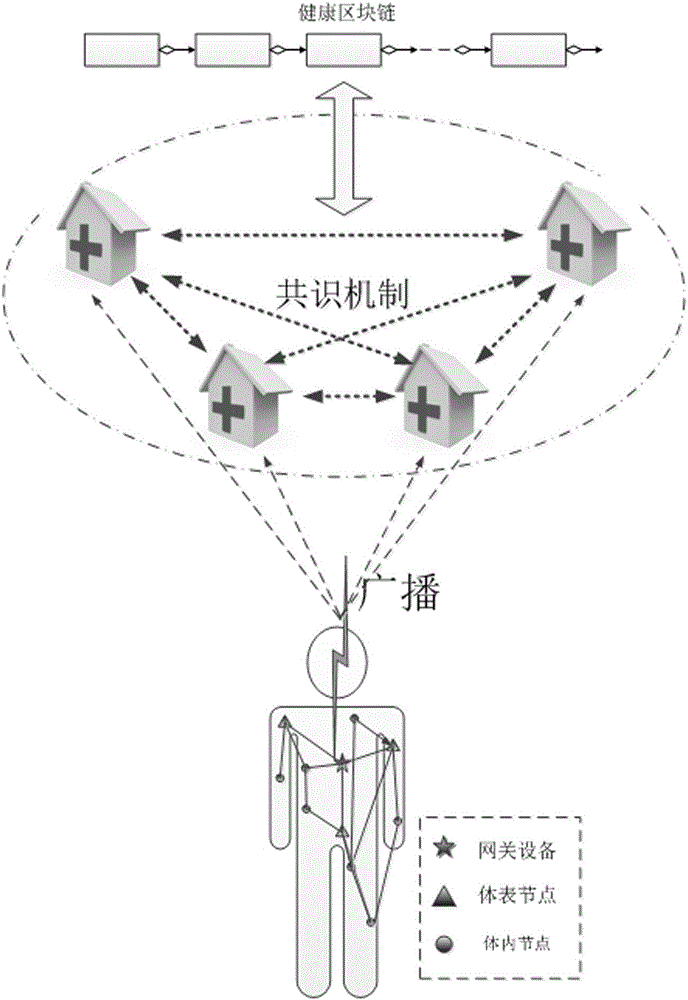
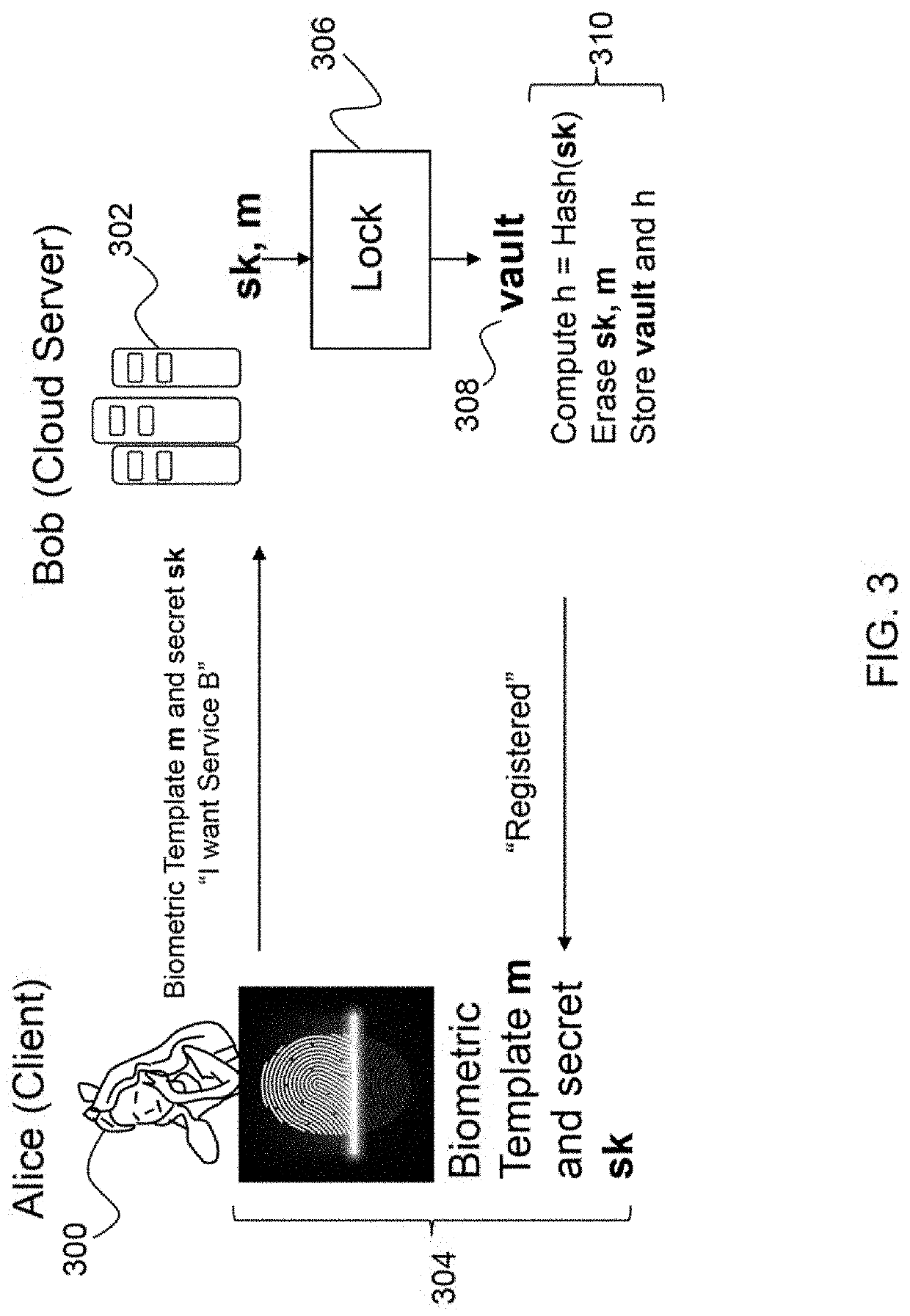
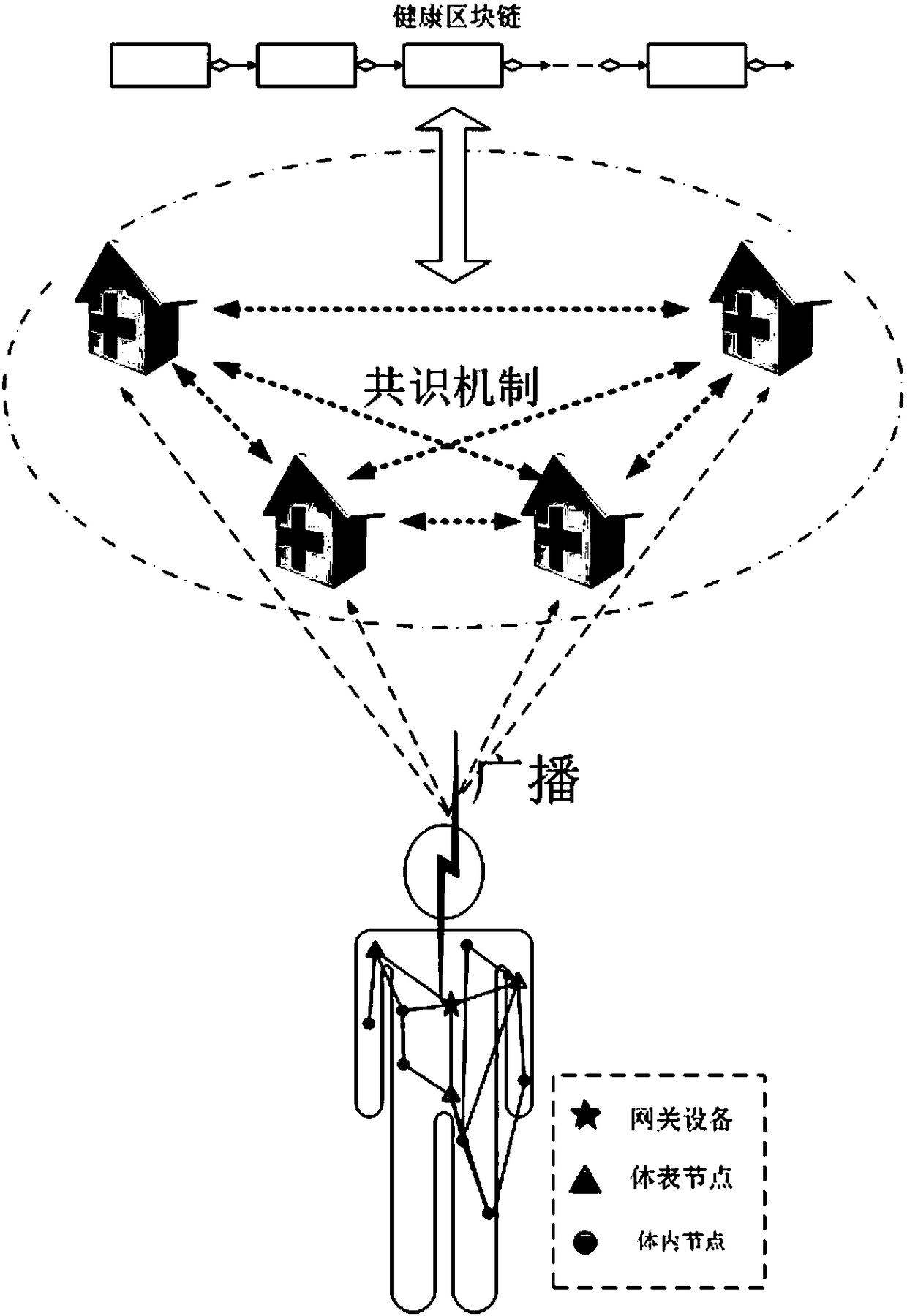
Lightweight back-up and efficient restoration method of health block chain data encryption keys
InactiveCN105812126AReduce management complexityAvoid heavy burdenKey distribution for secure communicationBody area networkRestoration method
The invention provides a lightweight back-up and efficient restoration method of health block chain data encryption keys.Body area networks achieve physiological parameters acquisition of healthy body health, health block chains are produced by a group of credible IT devices appointed by multiple health institutions and used for receiving and storing health data of the body area networks, the health block chain data encryption keys are produced by utilizing a fuzzy technology fuzzy vault and physiological signals acquired by the body area networks, human physiological data acquired in different time periods is encrypted by utilizing different data encryption keys and then is saved in the block chains of the IT devices without storage of historical data encryption keys; historical secret keys are restored by utilizing the health data acquired by the body area networks in real time.The lightweight back-up and efficient restoration method integrates the body area networks with the health block chains, avoids huge burden brought by secret key splitting related in a traditional secret key restoration method and safe storage and retrieval of shadow secret keys and greatly reduces management complexity of the health block chain data encryption keys.
Owner:QILU UNIV OF TECH
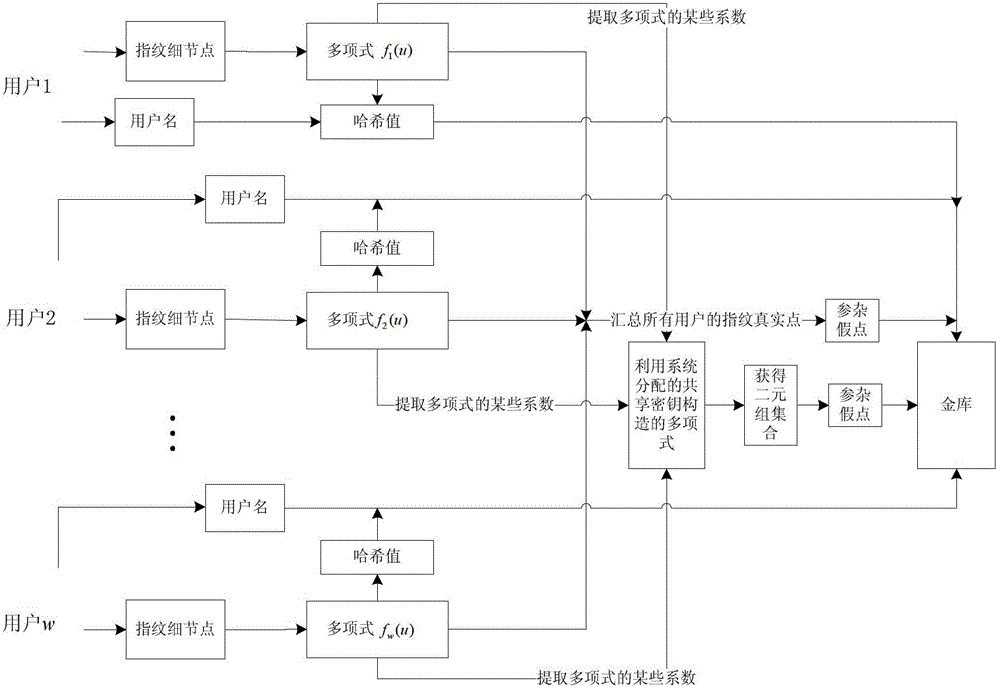
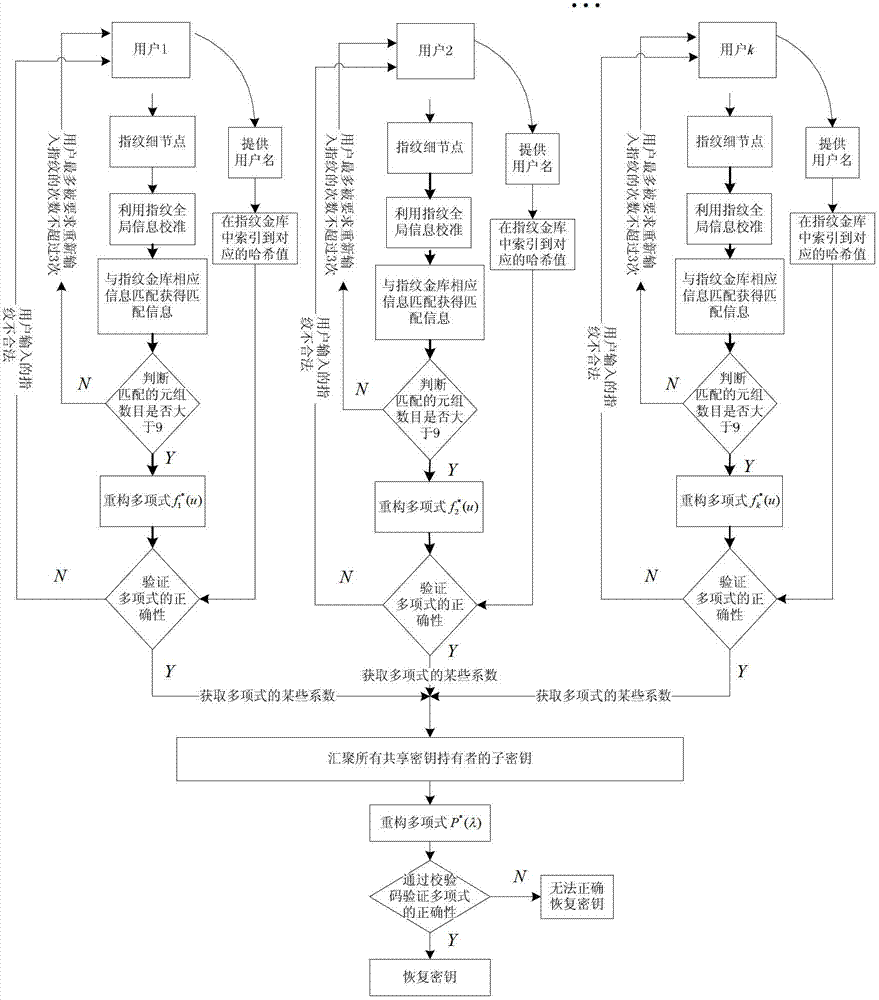
Fingerprint fuzzy vault method based on (k, w) threshold secret sharing scheme
ActiveCN102946310AKey distribution for secure communicationCharacter and pattern recognitionKey distributionKey sharing
The invention relates to a fingerprint fuzzy vault method based on a threshold secret sharing scheme. The method comprises a shared key distribution phase and a shared key reconstruction phase. The shared key distribution phase further comprises a binding process of the fingerprint fuzzy vault and a user subkey, and a shared key binding process. The shared key reconstruction phase further comprises a releasing process of partial user subkeys and a releasing process of the shared key. When the fingerprint fuzzy vault method is used to protect the shared key, the shared key is safely and conveniently released through fingerprint characteristics of the user. The releasing process of the key is very simple, and thus the key sharing scheme is more practical.
Owner:海宁鼎丞智能设备有限公司
Novel fuzzy vault method based on fingerprint characteristic data and matching algorithm
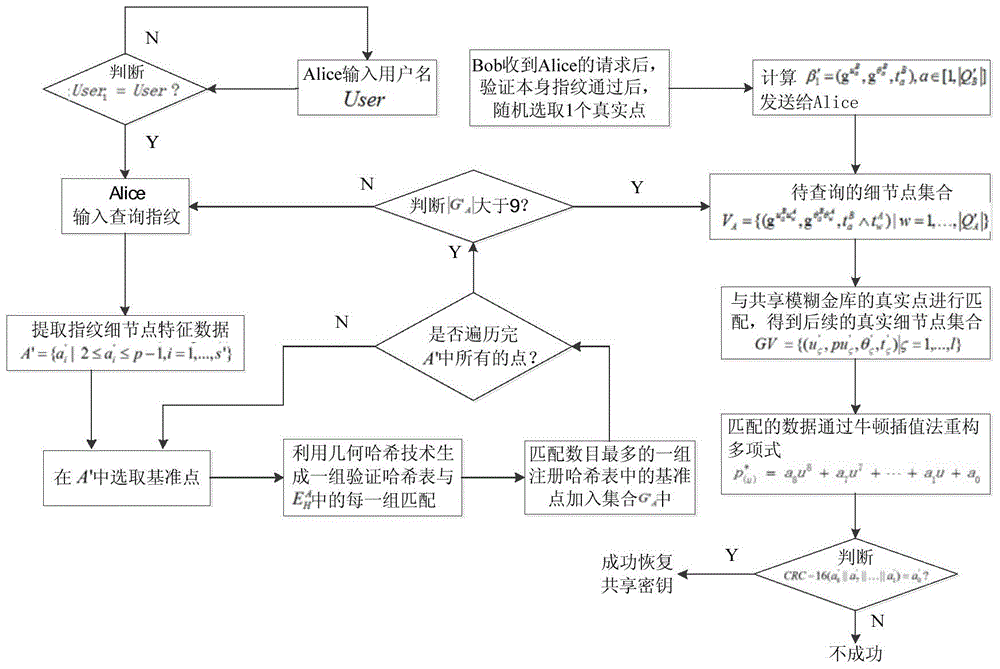
ActiveCN102510330ATroubleshoot calibration issuesProtection securityKey distribution for secure communicationCharacter and pattern recognitionPattern recognitionHash table
The invention relates to a novel fuzzy vault method based on fingerprint characteristic data and a matching algorithm. A locking process in the method comprises the following steps: firstly, carrying out cyclic redundancy check (CRC) coding to random secret key data; then, constructing an associated polynomial; adding a farraginous point; carrying out a characteristic quantization process to each point in an assembly; and disorganizing the sequence of each point in the assembly; and generating a registered Hash table by the assembly. An unlocking process comprises the following steps: firstly, extracting input minutia characteristic data; then, quantizing each minutia characteristics data; generating a verification Hash table; comparing the verification Hash table with the registered Hash table by a matching algorithm to obtain a subset; carrying out a Lagrange interpolation reconstruction polynomial; and finally, carrying out a CRC verification process to the coefficient data of the polynomial obtained by reconstruction. According to the novel fuzzy vault method based on the fingerprint characteristic data and the matching algorithm, the secret key information and the fingerprint characteristic data are organically combined to effectively protect a secret key and simultaneously conceal the fingerprint characteristic template information of a user.
Owner:海宁鼎丞智能设备有限公司
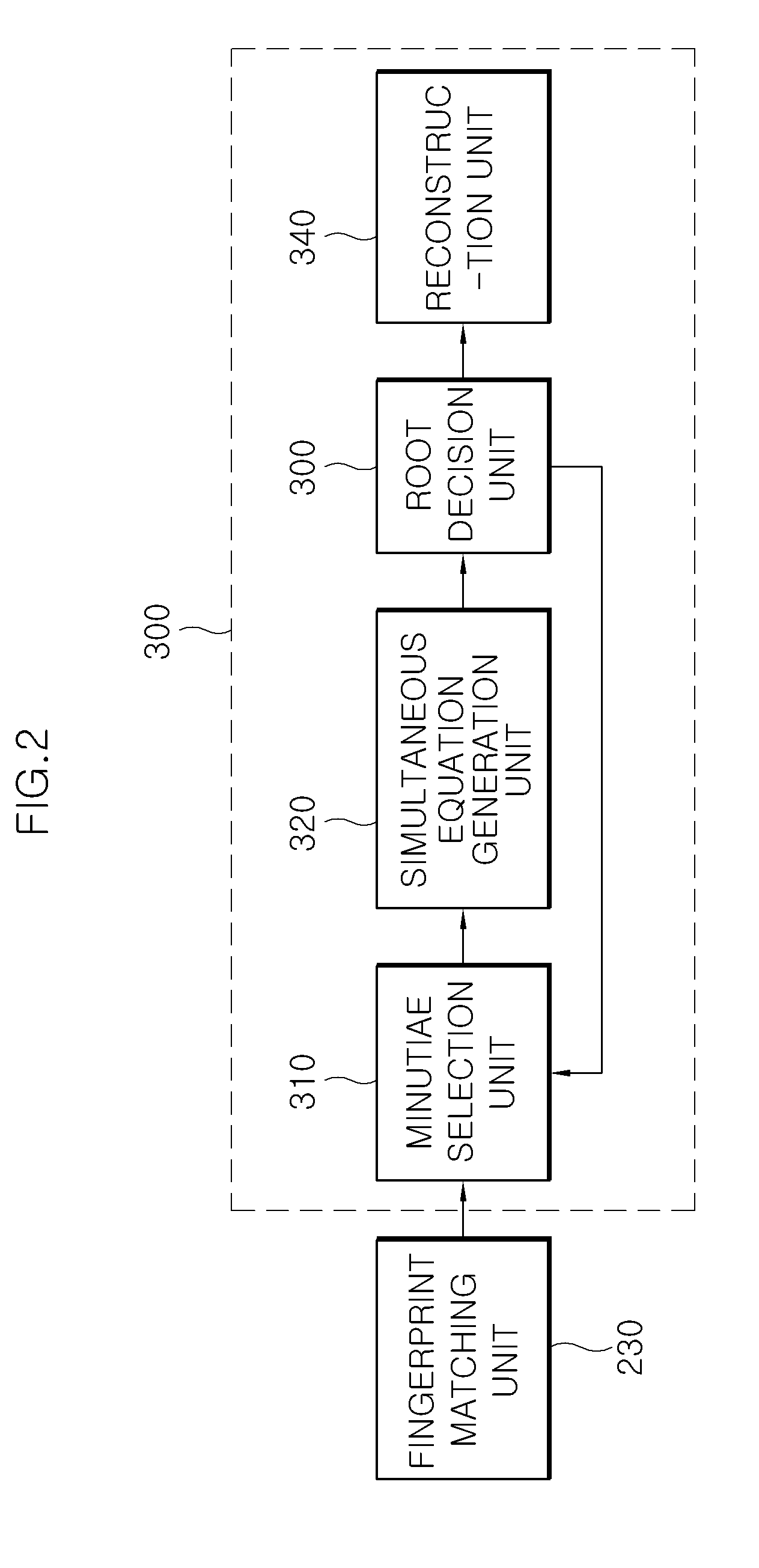
Apparatus and method for polynomial reconstruction in fuzzy vault system
InactiveUS20090262990A1Increase speedIncrease the number ofElectric signal transmission systemsImage analysisPattern recognitionAlgorithm
Provided is a method for polynomial reconstruction in a fuzzy vault system, which includes receiving a set of matching minutiae to select a minutiae combination to be used for the polynomial reconstruction; generating a simultaneous equation using the selected minutiae combination; determining whether a root of the simultaneous equation exists; and reconstructing the polynomial using the selected minutiae combination when the root of the simultaneous equation exists. The high-speed processing polynomial reconstruction method may perform polynomial reconstruction in real time, without using a separate key of a user, and thus may be applicable to various types of fuzzy vault systems.
Owner:ELECTRONICS & TELECOMM RES INST
Method for reinforcing fingerprint Fuzzy Vault system security
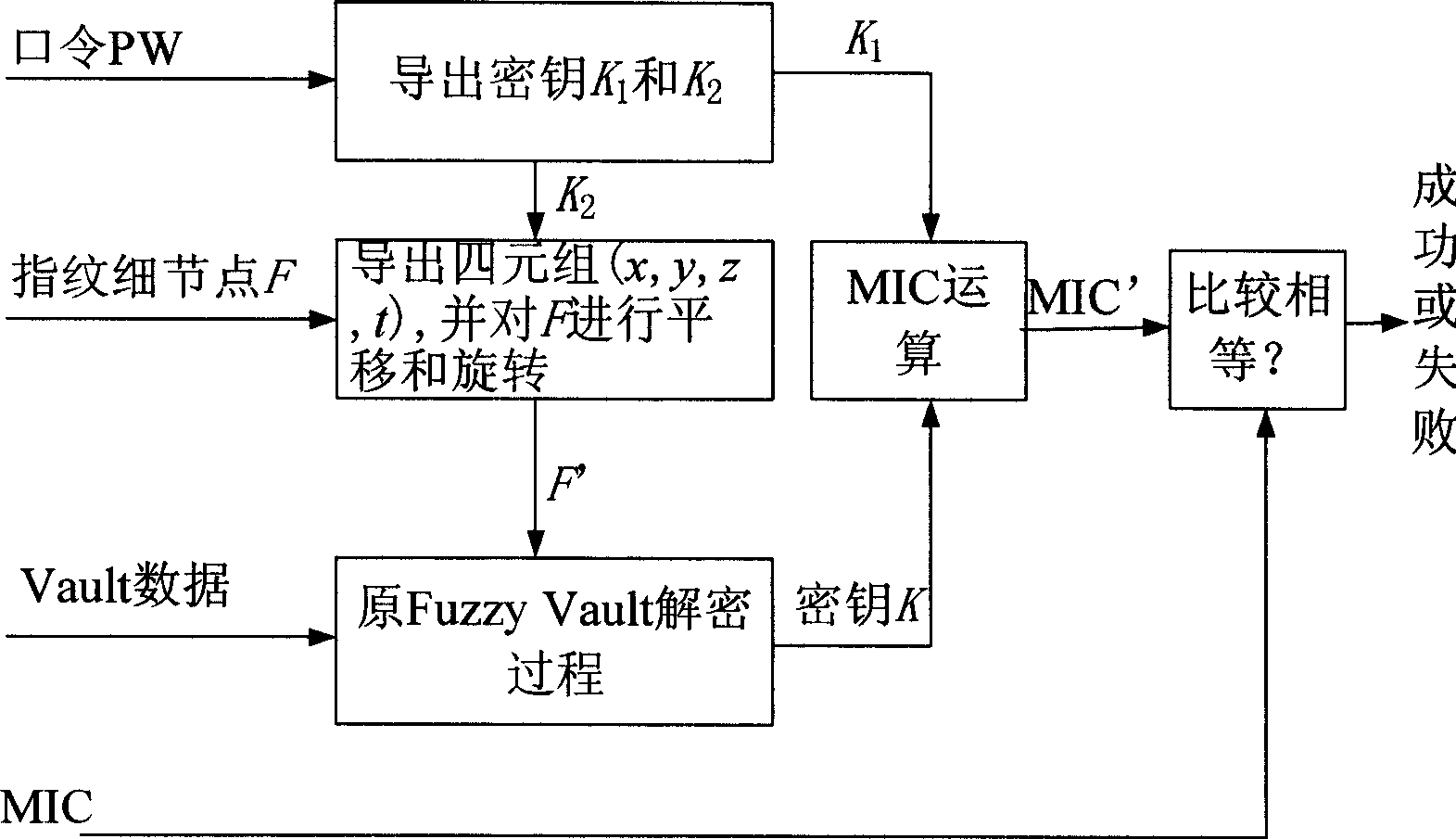
InactiveCN101369892AImprove computing powerMIC EliminationKey distribution for secure communicationUser identity/authority verificationUser needsPassword
The invention provides a method for enhancing safety of a finger print Fuzzy Vault system. The method binds the unique minutia of a finger print, a secret password and a key. When the key is encrypted by the Fuzzy Vault system, the user needs to provide self finger print characteristic information as well as randomly to choose a secret password. The finger print characteristic information is converted through the secret password, thereby the finger print template is protected. When decryption the user also needs to provide self finger print and the chosen secret password, only when the two are all right, the protected key can be correctly calculated, or else the key is not correctly calculated at any conditions. Because the user can choose different passwords to protect the finger print characteristic information under different applications, the encryption and decryption of the Fuzzy Vault operates the finger print information after convention. Thus the method of the invention can effectively prevent the cross-validation security vulnerability inherent in the original Fuzzy Vault system and the safety and application value are improved.
Owner:XIDIAN UNIV
Apparatus and method for polynomial reconstruction in fuzzy vault system
InactiveUS8290221B2Increase speedIncrease the number ofElectric signal transmission systemsImage analysisPattern recognitionAlgorithm
Provided is a method for polynomial reconstruction in a fuzzy vault system, which includes receiving a set of matching minutiae to select a minutiae combination to be used for the polynomial reconstruction; generating simultaneous equations using the selected minutiae combination; determining whether a root of the simultaneous equations exists; and reconstructing the polynomial using the selected minutiae combination when the root of the simultaneous equations exists. The high-speed processing polynomial reconstruction method may perform polynomial reconstruction in real time, without using a separate key of a user, and thus may be applicable to various types of fuzzy vault systems.
Owner:ELECTRONICS & TELECOMM RES INST
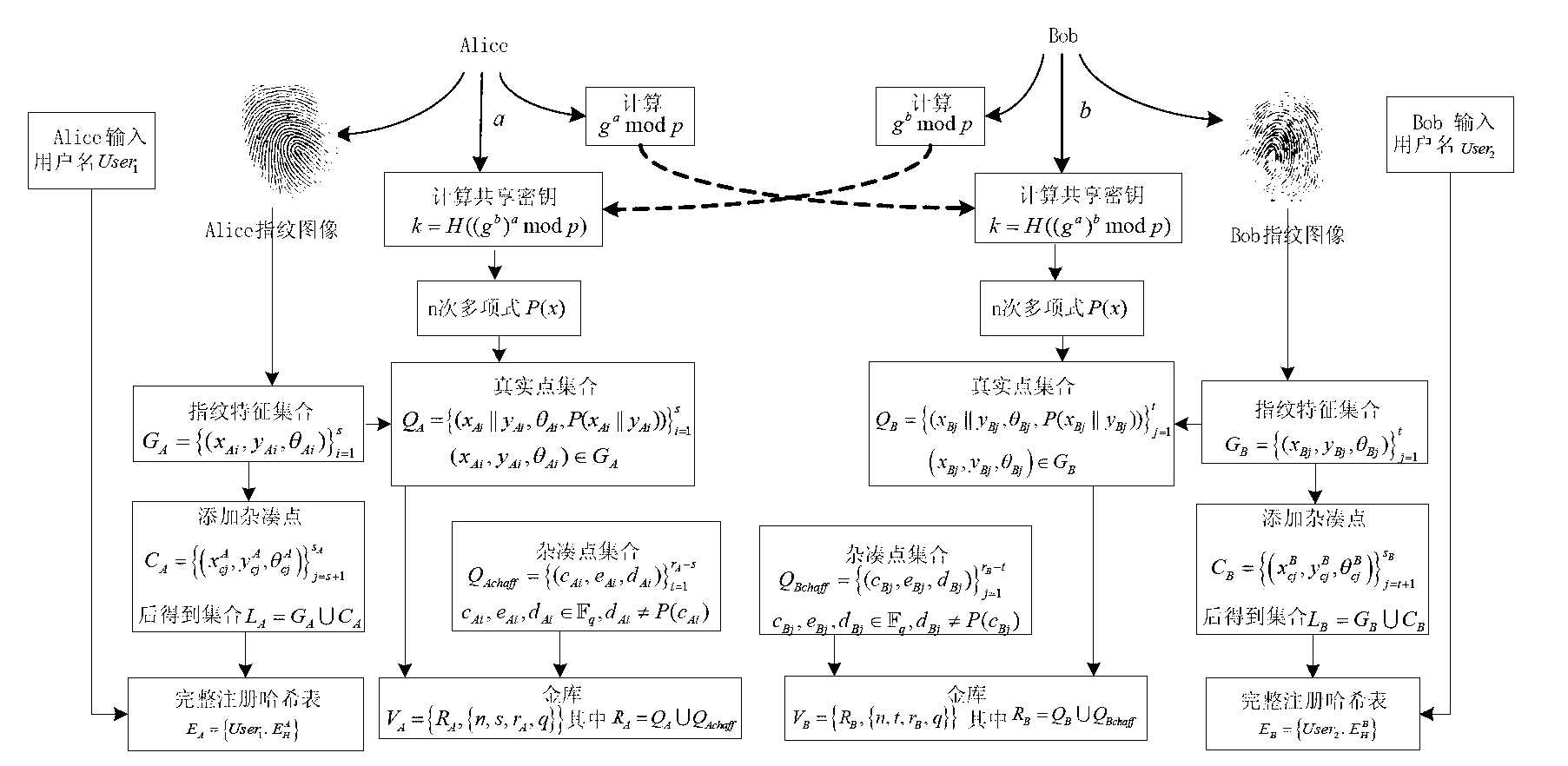
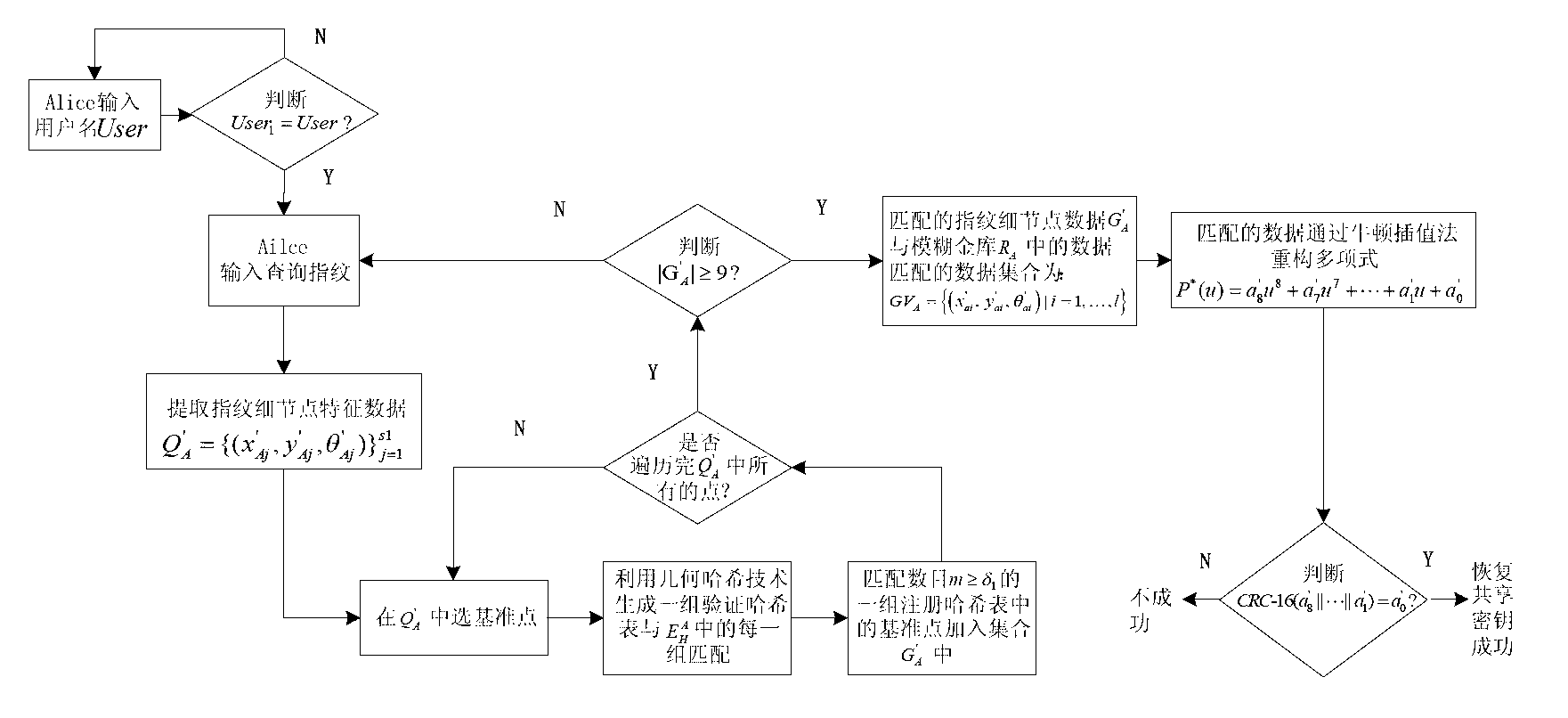
Fuzzy vault method based on fingerprint features and Internet key exchange protocol
InactiveCN102710417AKey distribution for secure communicationCharacter and pattern recognitionInternet Key ExchangeDiffie–Hellman key exchange
The invention relates to a fuzzy vault method based on fingerprint features and an Internet key exchange protocol. The existing method has the problems that security storage users share one key. The method comprises the steps of a shared key generation step of a diffie-hellman key exchange protocol and a binding and releasing step of a finger fuzzy vault and the shared key, wherein the shared key generation step is that the shared key is generated on the basis of the Diffie-Hellman protocol. The binding step of the fingerprint fuzzy vault and the shared key is that original fingerprint information is adopted as a polynomial element, and a polynomial is constructed by utilizing the shared key. The releasing step of the fingerprint fuzzy vault and the shared key is that the polynomial is reconstructed by inquiring the fingerprint information, and the shared key is restored. Due to the adoption of the fingerprint fuzzy vault algorithm, while the shared key is protected, the shared key can be safely and conveniently released through the fingerprint features of the user, so that the key sharing scheme has better practicability.
Owner:海宁鼎丞智能设备有限公司
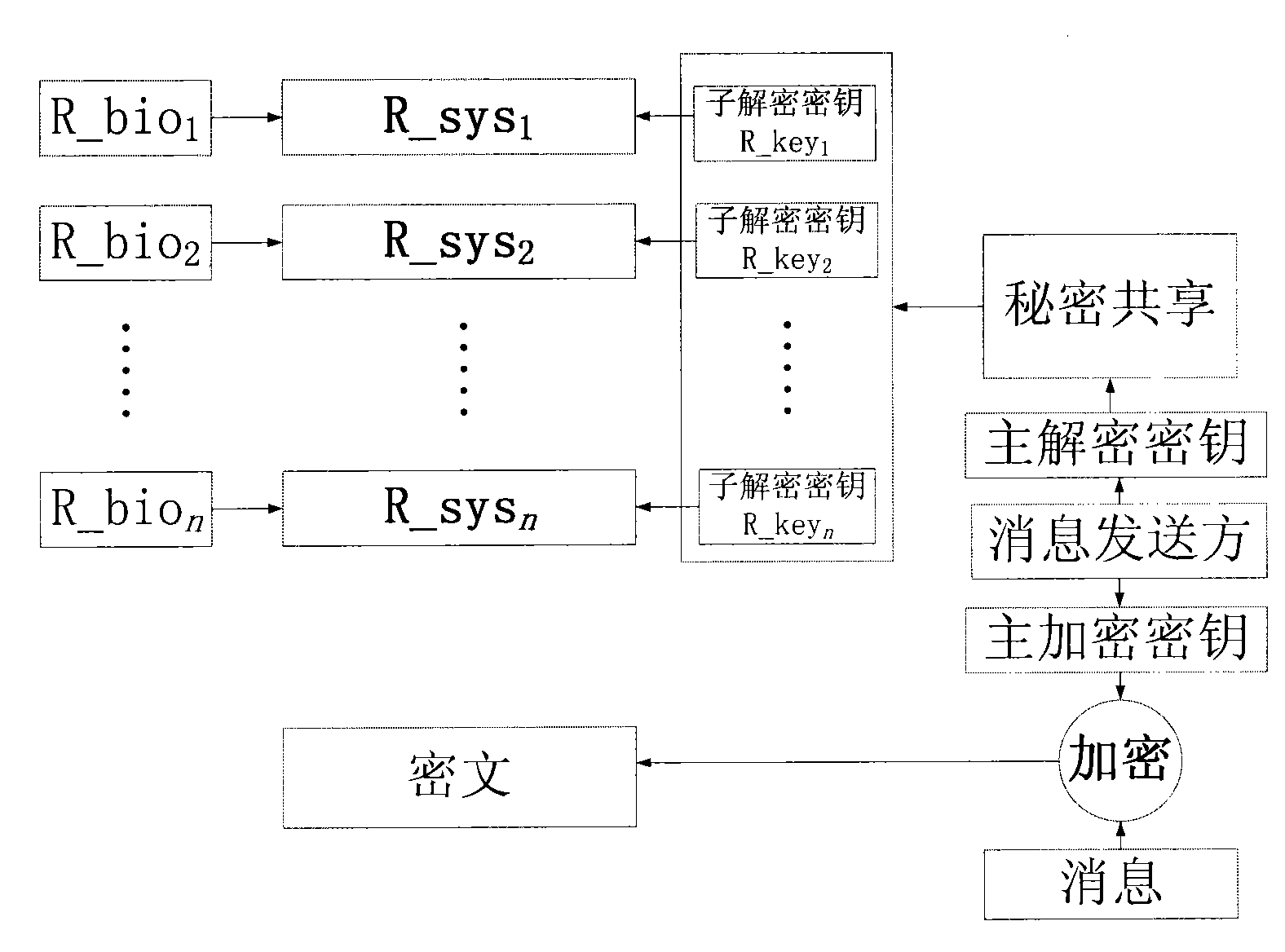
Fuzzy Vault encrypting method based on secrete sharing
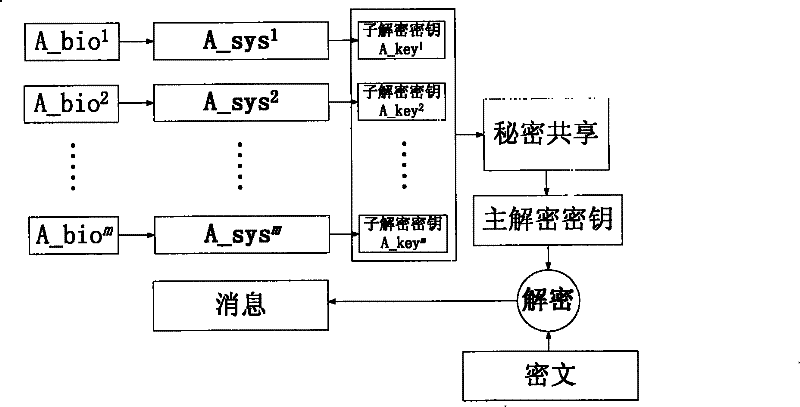
The invention provides a Fuzzy Vault encrypting method based on secrete sharing. The method combines Fuzzy Vault and a secrete-sharing system to protect messages. In the process of encryption, the sender generates a master encryption key and a master decryption key; the master encryption key encrypts a message and makes use of the master decryption key to produce n sub decryption keys via the secrete sharing system; and n receivers sharing messages respectively provide a group of fingerprint minutiae information sets and construct n Fuzzy Vault systems to bind the sub decryption key. In the process of decryption, when m receivers sharing messages provide fingerprint minutiae information sets used in the process of encryption and input the minutiae information sets into the corresponding Fuzzy Vault systems in encryption to decrypt and recover m sub decryption keys, the secrete sharing system uses the m sub decryption keys to recover the master decryption key. The Fuzzy Vault encrypting method solves the problem of message deadlock in Fuzzy Vault systems of single biological trait, realizes the indirect protection over fingerprint minutiae information, and effectively protects the safety of shared information.
Owner:XIDIAN UNIV
Computer system security using a biometric authentication gateway for user service access with a divided and distributed private encryption key
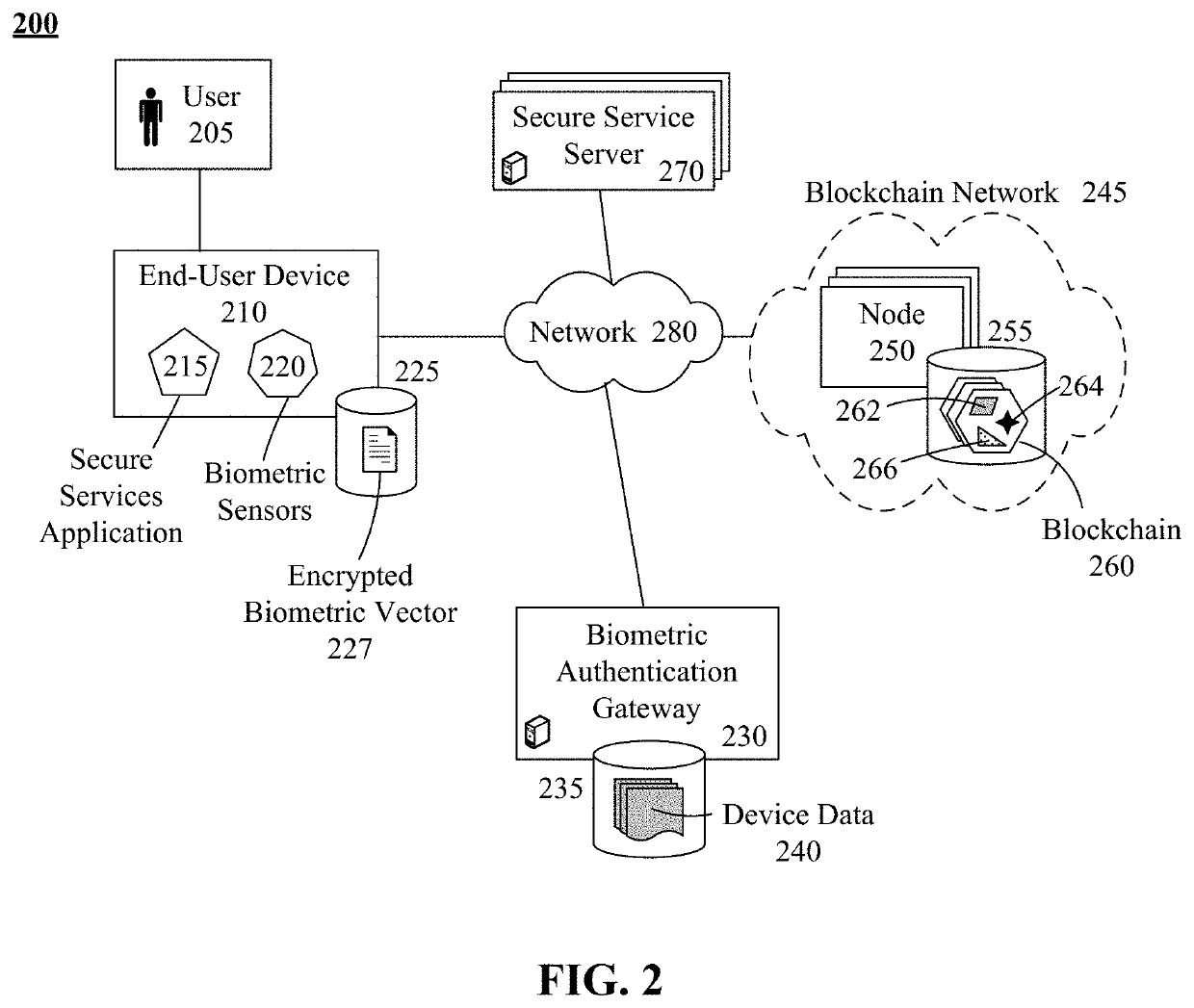
ActiveUS20200296093A1Encryption apparatus with shift registers/memoriesDigital data authenticationUser deviceEngineering
A secure computer system architecture can be comprised of network-enabled end-user devices, services available to the end-user devices, and a biometric authentication gateway. Each service can be provided via one or more appropriately-configured servers meeting a predefined minimum level of computer and network security and / or a blockchain network. The biometric authentication gateway can control access to the services based upon validation of a user's biometric vector against a pre-established biometric vector. The architecture can utilize an improved public key infrastructure (PKI) approach that segments a private encryption key into three parts and distributes the three parts between the end-user device and the biometric authentication gateway. Two of the three parts can be encased within fuzzy vaults based upon the user's biometric vector. Retrieving the key parts from the fuzzy vaults cannot be performed without successful biometric authentication of the user, ensuring that only the user can execute the services.
Owner:HOYOS INTEGRITY CORP
Credibility detection method based on password hash and biometric feature recognition
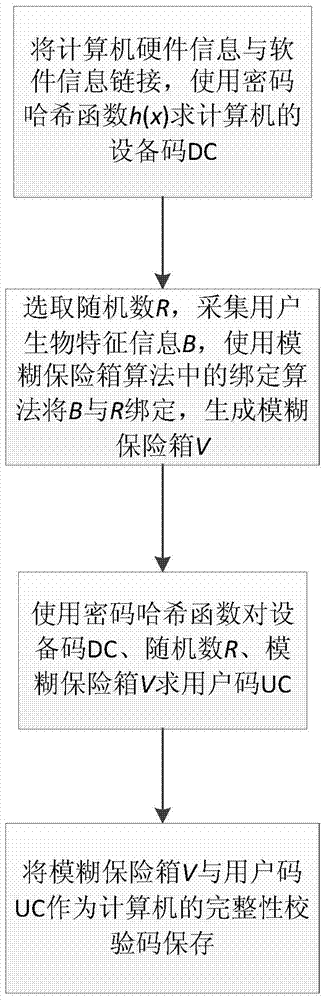
ActiveCN104751042AAvoid the hidden danger of changing and replacingPrivacy protectionDigital data authenticationPassword hashingUser code
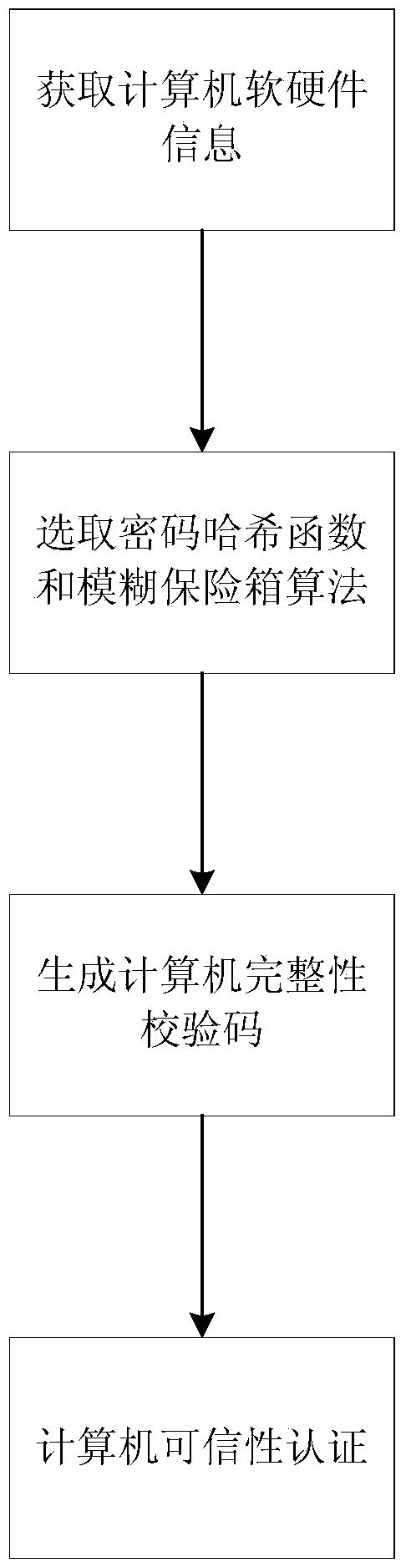
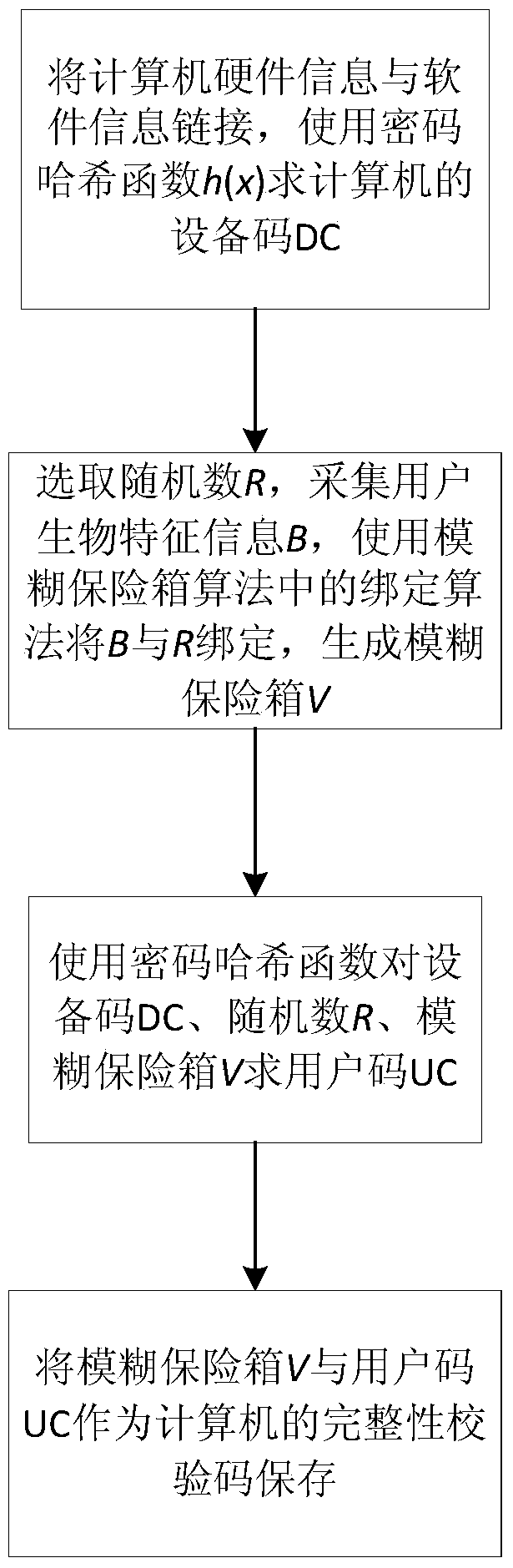
The invention discloses a credibility detection method based on password hash and biometric feature recognition. The method mainly solves the problems that existing computer information detection codes are likely to be reversely calculated and computers cannot recognize physical identities of users. According to the technical scheme, the method includes the steps that 1, software and hardware information of a computer is obtained, and biological feature information of a user is collected; 2, a device code is generated according to the software and hardware information, a fuzzy vault is generated through the biological feature information, and a user code is generated through the device code and the fuzzy vault; 3, the fuzzy vault and the user code serve as computer integrity check codes to be stored; 4, software and hardware information of the computer is obtained again, biological feature information of the user is recollected, and a new user code is generated; 5, the new user code is compared with the stored user code, if the new user code is identical with the stored user code, credibility verification passes, and otherwise, verification fails. The integrity check codes can be prevented from being changed and replaced, the physical identity of the user can be recognized, and the method can be used for protecting computer security.
Owner:西安电子科技大学工程技术研究院有限公司
Unified account information management method based on biological characteristic encryption
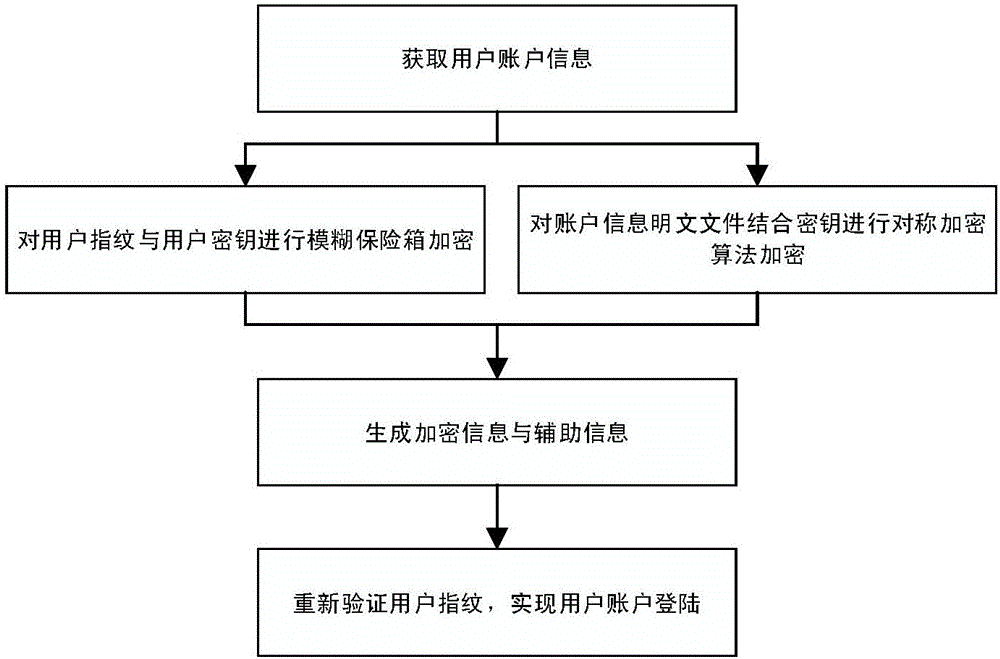
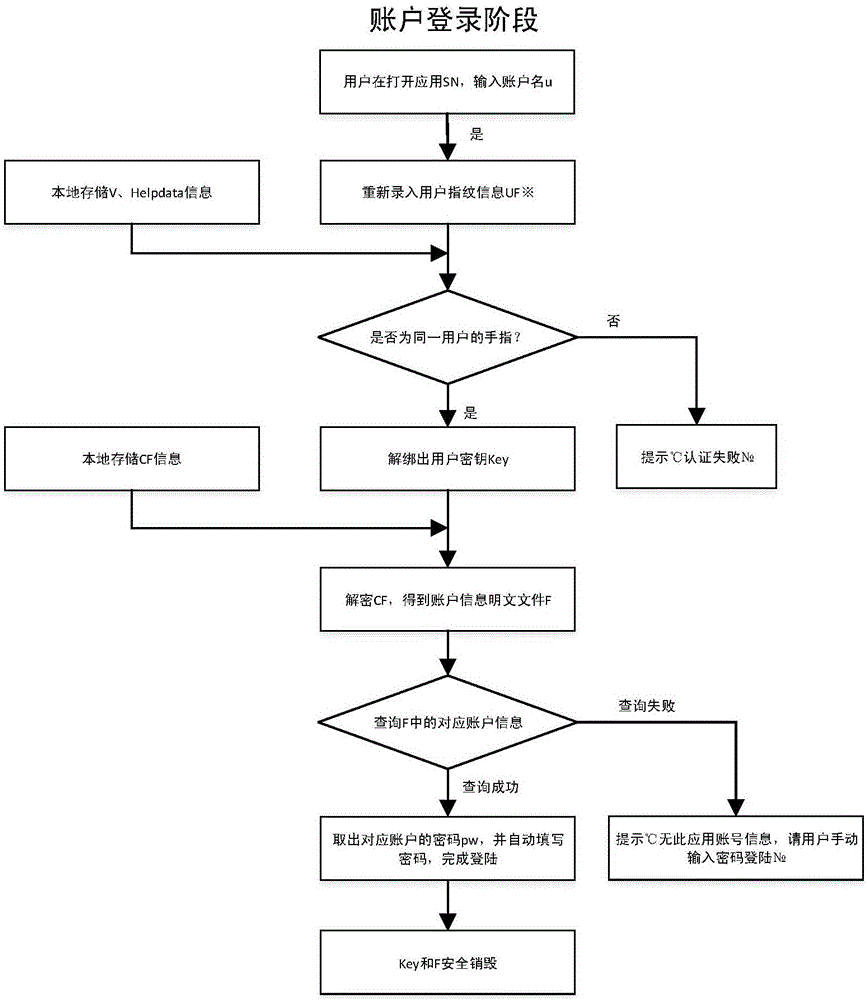
InactiveCN106789017AImprove convenienceImprove work efficiencyKey distribution for secure communicationUser identity/authority verificationPlaintextProtection mechanism
The invention discloses a unified account information management method based on biological characteristic encryption. The management method particularly includes the steps: 1 acquiring user account information; 2 performing crypto-binding on biologic characteristic information and secret keys by the aid of a fuzzy vault algorithm; 3 encrypting plain text files of the account information by the aid of a symmetric encryption algorithm; 4 generating encryption data and auxiliary information; 5 logging user accounts. According to the management method, user fingerprint characteristics and user secret keys are bound by the aid of fuzzy vault technology, the user secret keys and fingerprint security are greatly protected, the plain text files of the account information are encrypted by the aid of the symmetric encryption algorithm, and the security of the user account information is effectively ensured by the aid of a dual-protection mechanism. By the management method, user account information is integrally managed, and user convenience is achieved while security of the account information is ensured.
Owner:XIDIAN UNIV
Finger vein fusion fuzzy vault realization method
ActiveCN106169062AIncrease the number of intersectionsEasy extractionSubcutaneous biometric featuresBlood vessel patternsConfidentialitySafe storage
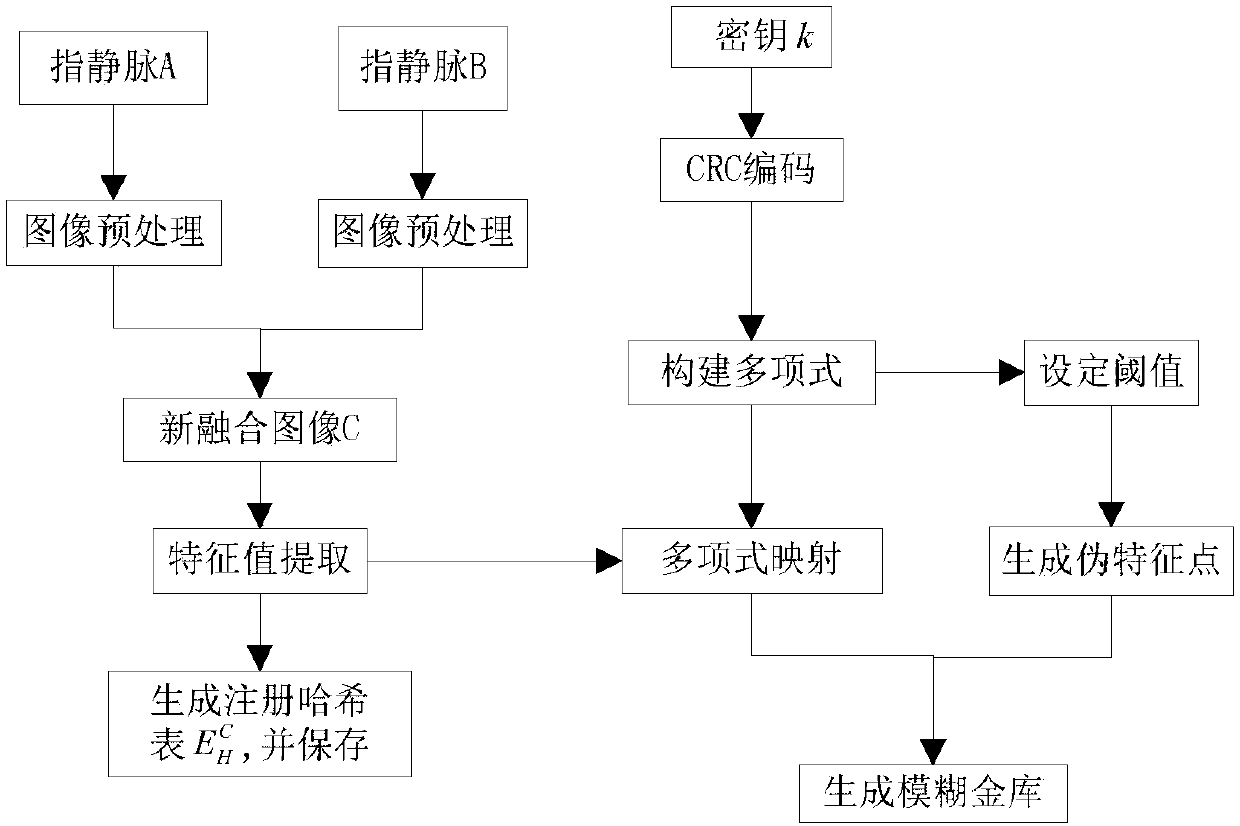
The invention discloses a finger vein fusion fuzzy vault realization method. The finger vein fusion fuzzy vault realization method comprises following steps: step 1, finger vein skeleton information of an image of a finger vein A and finger vein skeleton information of an image of a finger vein B are fused to acquire a vein skeleton image C, and characteristic points are extracted to acquire a characteristic information set, and the characteristic information set is extracted; step 2, by adopting a locking algorithm, a cipher key required to be protected is bound up with the characteristic information set of the step 1, and then a finger vein fusion fuzzy vault is generated; step 3, finger vein skeleton information of a verified query finger vein A' and finger vein skeleton information of a verified query finger vein B' are fused to acquire a vein skeleton image C', and characteristic information is extracted, and the cipher key is extracted from the finger vein fusion fuzzy vault by adopting an unlocking algorithm. The fuzzy vault generated by using the finger vein image fusion is used to realize cipher key protection, and therefore safety performance is strong, realization efficiency is high; only a valid user is capable of extracting the cipher key having a CRC verification function by using a valid finger vein, and therefore confidentiality, integrity, and availability of cipher key safe storage are guaranteed.
Owner:HANGZHOU DIANZI UNIV
Method, device and system for PBOC transaction based on biometric encryption
InactiveCN106709716AResolve UncertaintyAddress decipherable flawsProtocol authorisationPasswordUser input
The invention relates to a method, a device and a system for PBOC transaction based on biometric encryption. The method comprises steps: biometrics of a user are acquired, and effective biometrics are extracted; based on a password inputted by the user, a private key of the user is generated; a fuzzy vault algorithm is adopted to combine the effective biometrics and the private key to generate a biometric template for marking the user identity information; the biometric template is stored to a backstage database, and is located to a financial IC card; and the biometric template in the financial IC card and the password inputted by the user are submitted to the backstage server for verification, and after the verification is passed, the financial IC card is allowed to perform PBOC transaction. The defect that when the financial IC card is adopted to perform PBOC transaction, an asymmetric algorithm is overly dependent and can be decoded can be solved, and the biometric encryption technology is introduced to solve the uncertainty generated as a process with many human factors exists in the PBOC transaction.
Owner:AEROSPACE INFORMATION
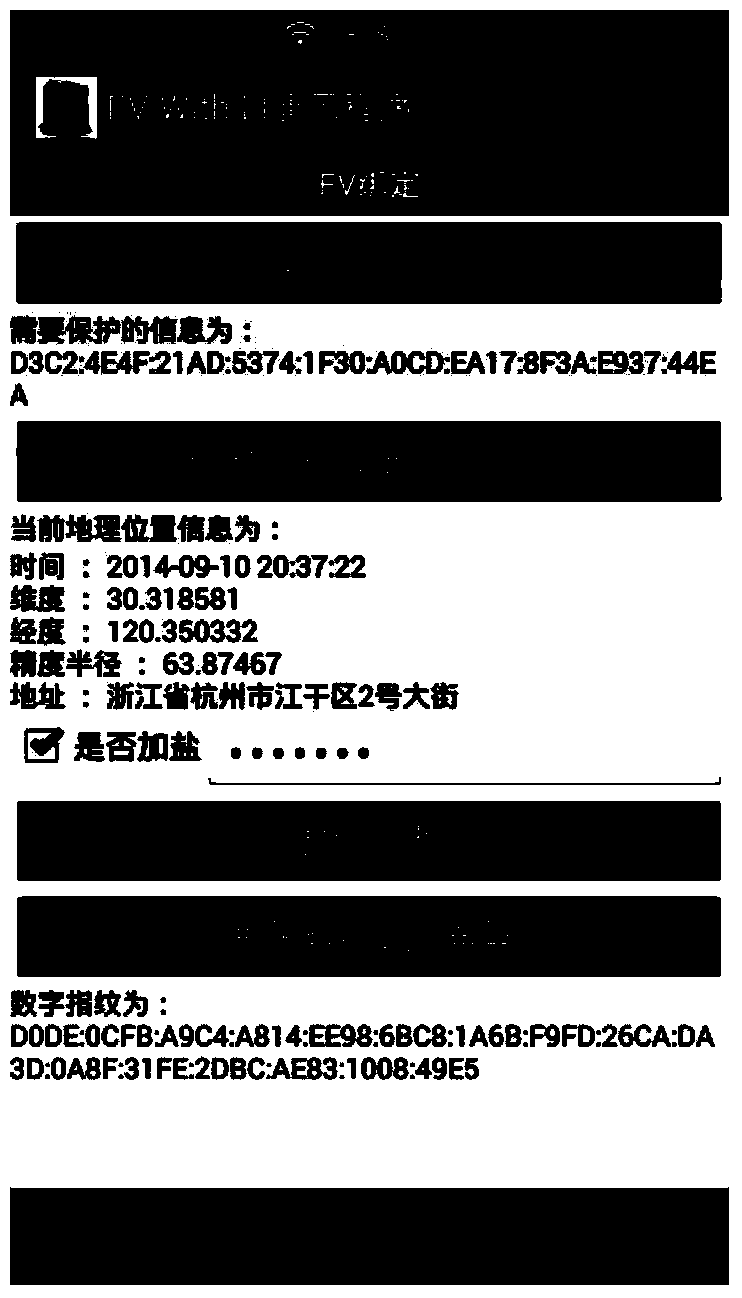
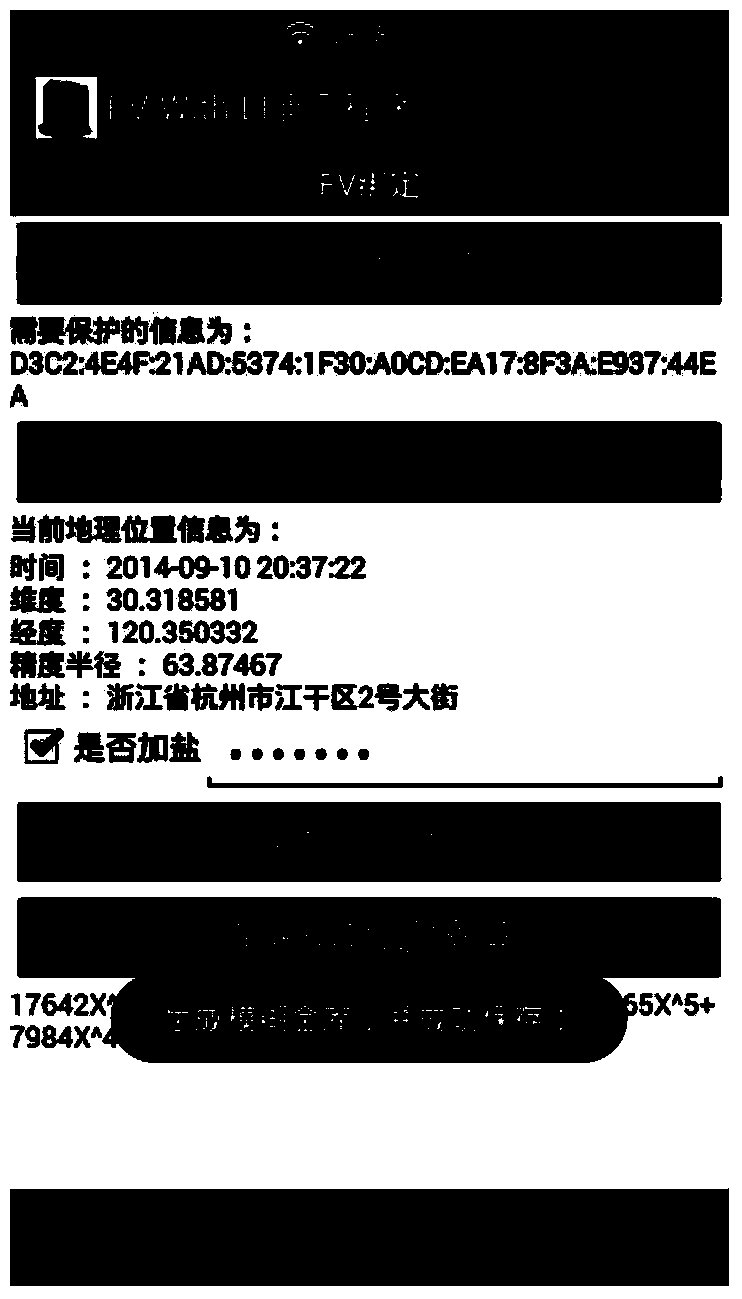
Method for realizing fuzzy vault on the basis of geographical location information
ActiveCN104363089APrevent comparison attacksGuaranteed confidentialityKey distribution for secure communicationCharacter and pattern recognitionConfidentialityGeolocation
The invention relates to a method for realizing a fuzzy vault on the basis of geographical location information. The method can be implemented on various mobile terminals with positioning functions. The method includes generating digital fingerprints on the basis of the geographical location information, binding the fuzzy vault with secret information and extracting the secret information from the fuzzy vault. The step of generating the digital fingerprints on the basis of the geographical location information refers to acquiring the current geographical location information and subjecting the same to treatment such as quantifying and salting to generate the digital fingerprints. The salting process aims to enhance non-duplicability and reliability of the digital fingerprints. The method has the advantages that the fuzzy vault is realized by the aid of the geographical location information, so that confidentiality and integrity of the secret information and system usability are guaranteed; the method can be applied to the all mobile equipment with a positioning function, thereby having high generalizability.
Owner:杭州珞珈数据科技有限公司
Apparatus and method for biometric registration and authentication
InactiveUS8472680B2Electric signal transmission systemsImage analysisFeature extractionRotation matrix
Owner:ELECTRONICS & TELECOMM RES INST
Reusable fuzzy vault system
ActiveUS10826686B1Encryption apparatus with shift registers/memoriesDigital data authenticationAlgorithmTheoretical computer science
Described is a system for biometric based security. The system applies a reusable fuzzy vault (RFV) process to protect secret information. The RFV process comprises a locking algorithm and an unlocking algorithm. The locking algorithm takes as input a fuzzy string m generated from readings of biometrics and secret information sk to be protected, The locking algorithm outputs a public string vault and a hash value h of sk. The unlocking algorithm takes as input a public string vault and a fuzzy string m′, and outputs a string sk′ if fuzzy string m′ is sufficiently close to fuzzy string m. The unlocking algorithm further computes a hash value h′ of sk′ and compares it with h. The system allows access to the secret information sk when h′ is equivalent to h.
Owner:HRL LAB
Key extraction method of palm print-palm vein double-source fuzzy vault
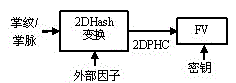
ActiveCN105141424AGood precisionMore real pointsUser identity/authority verificationPalm printTheoretical computer science
The invention discloses a key extraction method of a palm print-palm vein double-source fuzzy vault. The method comprises: segmenting a set key and a cyclic redundancy code thereof and converting into integers and constructing an n-order multinomial coefficient; during registration, converting the row vectors of 2DPHCs (2D Palm Hash Code) of the palm print and the palm veins into an integer as a horizontal ordinate and mapping the horizontal coordinate on the multinomial coefficient to calculate a longitudinal coordinate, constructing a true point using the horizontal coordinate and the longitudinal coordinate, and then adding randomly generated chaff points to construct two independent FVs; during authentication, searching for candidate points in the two corresponding FVs by use of the row vectors of 2DPHCs of the palm print and the palm veins, respectively; and if the candidate points contain more than (n+1) true points, correctly reconstructing an original polynomial and extracting a key. Due to the double-source mode of the method obviously, the accuracy of authentication is improved enough to resist brute-force attack, multi-database attack and heterogeneity analysis attack, and furthermore, the privacy of original characteristics is further effectively protected.
Owner:NANCHANG HANGKONG UNIVERSITY
Fuzzy vault sharing method based on fingerprint characteristic and finite multiplicative group
InactiveCN104104501AImprove securityPerformance against spoofing attacksKey distribution for secure communicationComputer hardwareKey exchange
The invention relates to a fuzzy vault sharing method based on a fingerprint characteristic and a finite multiplicative group. Existing methods have a problem that two parties need to store different fuzzy vaults. According to the fuzzy vault sharing method, the shared information generation stage is that the shared information is obtained by utilizing a designated exchange method via conversion of fingerprint information of the two parties; the shared secret key binding stage is that the shared information generated by conversion and then exchange of the fingerprint information is bound with a shared secret key generated via a Diffie-Hellman secret key exchange protocol so that a shared fuzzy vault is generated; and the shared secret key releasing stage is that the shared information is constructed again via conversion of the fingerprint information of the two parties, the fuzzy vault is unlocked and the shared secret key is recovered. The shared secret key is protected by utilizing a fingerprint fuzzy vault algorithm, the number of the fuzzy vaults is reduced to one, and the shared secret key bound in the shared fingerprint fuzzy vault can only be released via verification of the two parties so that the fuzzy vault sharing method has better security.
Owner:HANGZHOU DIANZI UNIV
Authentication method and device for subscriber identity module card
InactiveCN106851638AImprove securityPrevent theftSecurity arrangementMinutiaeSubscriber identity module
Embodiments of the invention disclose an authentication method for a subscriber identity module card. The method comprises the following steps of collecting biological characteristic information of a user and extracting minutiae of biological characteristics from the biological characteristic information; carrying out binding calculation on the minutiae and a generated authentication key to obtain a fuzzy vault; and writing the fuzzy vault and an international mobile subscriber identification number (IMSI) into an SIM card. The embodiments of the invention disclose an authentication device for the subscriber identity module card.
Owner:CHINA MOBILEHANGZHOUINFORMATION TECH CO LTD +1
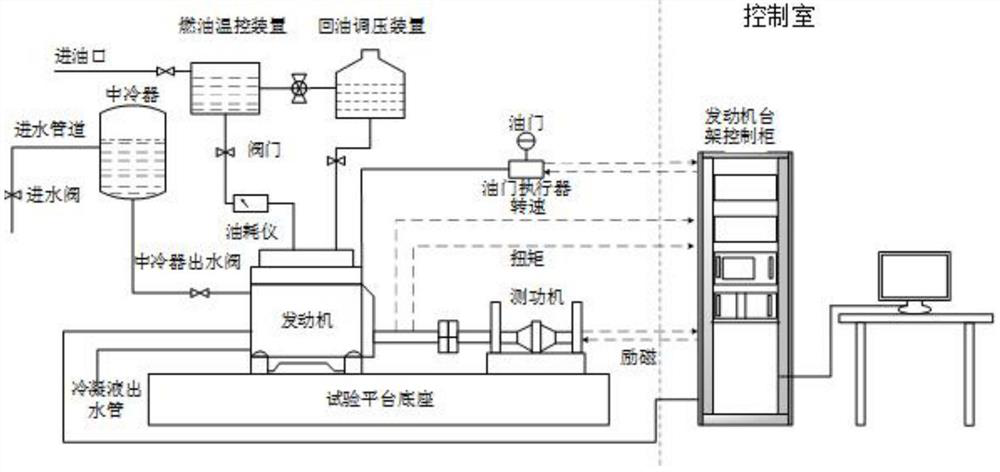
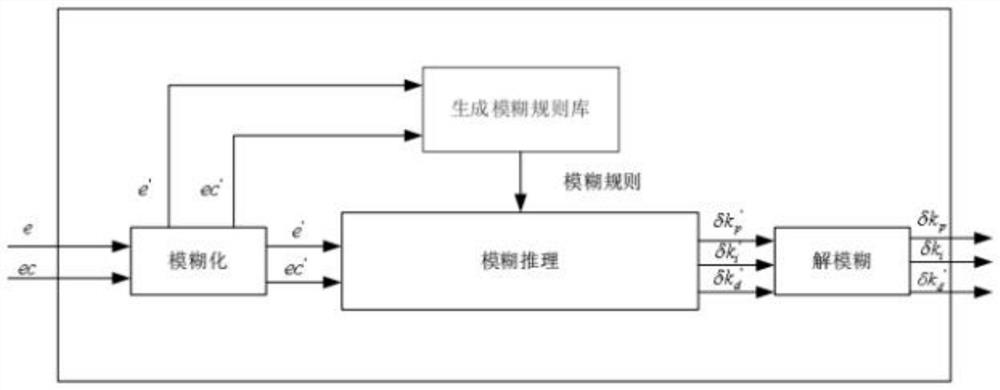
Fuzzy control method of bench control system, storage medium and equipment
ActiveCN113049259AImprove adaptabilityImprove controlInternal-combustion engine testingAdaptive controlData setSelf-tuning
The invention relates to a fuzzy control method of a bench control system, a storage medium and computer equipment. The fuzzy control method mainly comprises the following steps: acquiring a historical data set; clustering the historical data set by using an FCM algorithm, obtaining a value of a data densest region in a clustered historical data subset as a maximum value of a membership function, and dividing the historical data subset into a fuzzy set by using the membership function; constructing a fuzzy control model based on a Wang-Mendel algorithm; acquiring expert experience data as training data, and training the fuzzy control model by adopting a supervised learning method; inputting the fuzzy set into the trained fuzzy control model to obtain a fuzzy rule set; defining fuzzy rules with different conditions in the fuzzy rule set as proximity rules, and complementing incomplete fuzzy rules in the fuzzy library by using the proximity rules to obtain a new fuzzy rule set; and inputting the new fuzzy rule set to the rack control system to carry out PID parameter self-tuning.
Owner:CHINA UNIV OF GEOSCIENCES (WUHAN)
Fingerprint fuzzy vault method based on (k, w) threshold secret sharing scheme
InactiveCN102946310BKey distribution for secure communicationCharacter and pattern recognitionKey distributionKey sharing
The invention relates to a fingerprint fuzzy vault method based on a threshold secret sharing scheme. The method comprises a shared key distribution phase and a shared key reconstruction phase. The shared key distribution phase further comprises a binding process of the fingerprint fuzzy vault and a user subkey, and a shared key binding process. The shared key reconstruction phase further comprises a releasing process of partial user subkeys and a releasing process of the shared key. When the fingerprint fuzzy vault method is used to protect the shared key, the shared key is safely and conveniently released through fingerprint characteristics of the user. The releasing process of the key is very simple, and thus the key sharing scheme is more practical.
Owner:海宁鼎丞智能设备有限公司
A Lightweight Backup and Efficient Recovery Method for Healthy Blockchain Data Encryption Keys
InactiveCN105812126BReduce management complexityAvoid heavy burdenKey distribution for secure communicationRecovery methodBody area network
The invention provides a lightweight back-up and efficient restoration method of health block chain data encryption keys.Body area networks achieve physiological parameters acquisition of healthy body health, health block chains are produced by a group of credible IT devices appointed by multiple health institutions and used for receiving and storing health data of the body area networks, the health block chain data encryption keys are produced by utilizing a fuzzy technology fuzzy vault and physiological signals acquired by the body area networks, human physiological data acquired in different time periods is encrypted by utilizing different data encryption keys and then is saved in the block chains of the IT devices without storage of historical data encryption keys; historical secret keys are restored by utilizing the health data acquired by the body area networks in real time.The lightweight back-up and efficient restoration method integrates the body area networks with the health block chains, avoids huge burden brought by secret key splitting related in a traditional secret key restoration method and safe storage and retrieval of shadow secret keys and greatly reduces management complexity of the health block chain data encryption keys.
Owner:QILU UNIV OF TECH
Biometrics-based remote login
ActiveCN110300971AKey distribution for secure communicationUser identity/authority verificationSecure communicationBiometric data
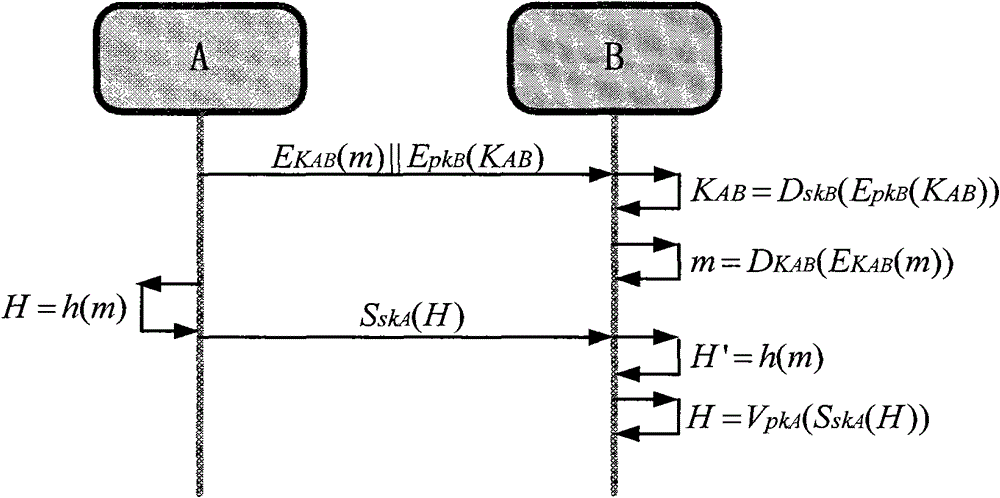
The invention relates to methods and devices for enabling authentication of a user based on biometric data. In an aspect of the invention, a method performed by a client device (100) of enabling authentication of user (200) of the client device (100) with a network node over a secure communication channel based on biometric data is provided. Further, an enrollment set is provided by the client device, which is used for the authentication, where said enrollment set comprises a fuzzy vault, which contains registered biometric data and a first secret key. The enrollment set also comprises transformed non-invertible biometric data, a second secret key and a secret random number.
Owner:FINGERPRINT CARDS ANACATUM IP AB
A Fuzzy Vault Encryption Method Based on Secret Sharing
The invention provides a Fuzzy Vault encryption method based on secret sharing. This method combines Fuzzy Vault and secret sharing system to protect messages. In the encryption process, the sender generates a pair of master encryption key and master decryption key, the master encryption key encrypts the message, and then uses the master decryption key to generate n sub-decryption keys through the secret sharing system, and the n sub-decryption keys shared by the message Each receiver provides a set of its fingerprint detail point information set and constructs n Fuzzy Vault system binding sub-decryption keys. During the decryption process, when the recipients of m shared messages provide the fingerprint minutiae information sets used in the encryption process, and input the respective minutiae information sets into the corresponding Fuzzy Vault system for encryption, m sub-decryption keys are decrypted by The secret sharing system uses m sub-decryption keys to recover the master decryption key. The invention overcomes the message deadlock problem of the Fuzzy Vault system of a single biometric feature; realizes the indirect protection of fingerprint minutiae information; and effectively protects the safety of shared information.
Owner:XIDIAN UNIV
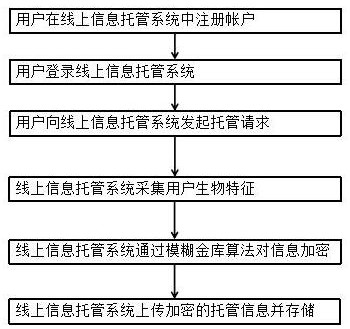
A method and system for online information trusteeship integrating biometric encryption technology
ActiveCN109039650BPrevent theftLarge capacityKey distribution for secure communicationUser identity/authority verificationSoftware systemEngineering
Owner:朱俊
Identity authentication method based on fuzzy vault and digital certificate
InactiveCN101945114BImprove securityIncrease credibilityUser identity/authority verificationDigital identitySmart card
Owner:XIDIAN UNIV +1
Authenticity detection method based on password hash and biometric identification
ActiveCN104751042BAvoid the hidden danger of changing and replacingPrivacy protectionDigital data authenticationCryptographic hash functionPassword hashing
The invention discloses a credibility detection method based on password hash and biometric feature recognition. The method mainly solves the problems that existing computer information detection codes are likely to be reversely calculated and computers cannot recognize physical identities of users. According to the technical scheme, the method includes the steps that 1, software and hardware information of a computer is obtained, and biological feature information of a user is collected; 2, a device code is generated according to the software and hardware information, a fuzzy vault is generated through the biological feature information, and a user code is generated through the device code and the fuzzy vault; 3, the fuzzy vault and the user code serve as computer integrity check codes to be stored; 4, software and hardware information of the computer is obtained again, biological feature information of the user is recollected, and a new user code is generated; 5, the new user code is compared with the stored user code, if the new user code is identical with the stored user code, credibility verification passes, and otherwise, verification fails. The integrity check codes can be prevented from being changed and replaced, the physical identity of the user can be recognized, and the method can be used for protecting computer security.
Owner:西安电子科技大学工程技术研究院有限公司
A realization method of finger vein fusion fuzzy treasury
ActiveCN106169062BIncrease the number of intersectionsEasy extractionSubcutaneous biometric featuresBlood vessel patternsVeinConfidentiality
Owner:HANGZHOU DIANZI UNIV
Fuzzy control method, storage medium and equipment of bench control system
ActiveCN113049259BImprove adaptabilityImprove controlInternal-combustion engine testingAdaptive controlData setSelf-tuning
The present invention relates to a fuzzy control method, a storage medium and a computer device of a bench control system, mainly comprising: collecting historical data sets; clustering the historical data sets by using the FCM algorithm, and obtaining the data-intensive areas in the clustered historical data subsets value as the maximum value of the membership function, and use the membership function to divide the subset of historical data into fuzzy sets; construct a fuzzy control model based on Wang-Mendel algorithm; obtain expert experience data as training data, and use supervised learning methods to train fuzzy control model; input the fuzzy set into the trained fuzzy control model to obtain the fuzzy rule set; define the fuzzy rules with different conditions in the fuzzy rule set as adjacent rules, use the adjacent rules to complement the incomplete fuzzy rules in the fuzzy library, and obtain new Fuzzy rule set; input a new fuzzy rule set to the bench control system for PID parameter self-tuning.
Owner:CHINA UNIV OF GEOSCIENCES (WUHAN)
Privacy protection biological authentication method and device and electronic equipment
ActiveCN114065169AWill not expose privacyReduce storageDigital data protectionDigital data authenticationUser verificationKey (cryptography)
The invention discloses a privacy protection biological authentication method and device and electronic equipment, and the method comprises the steps: constructing a corresponding biological data template according to a biological information data set inputted by a user during registration; generating a public key and private key pair by using an asymmetric cryptography technology; according to the biological data template and a private key, generating encrypted biological data by using a secret sharing scheme and an OKVS technology; sending a public key and the encrypted biological data to a server; recovering the private key by using an OKVS technology according to biological data input during user verification and the encrypted biological data; constructing a signature according to the recovered private key and the corresponding public key; and sending the signature to a server, so that the server verifies the user according to the public key and the signature. The technical problems that in the prior art, the data storage amount is large, and two systems of which the biological information of the same person is encrypted by using a fuzzy vault technology can be mutually unlocked are solved.
Owner:ZHEJIANG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com