Fuzzy vault sharing method based on fingerprint characteristic and finite multiplicative group
A technology that blurs the characteristics of vaults and fingerprints, applied in the field of pattern recognition and cryptography, and can solve the problem of loss or theft of storage media.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
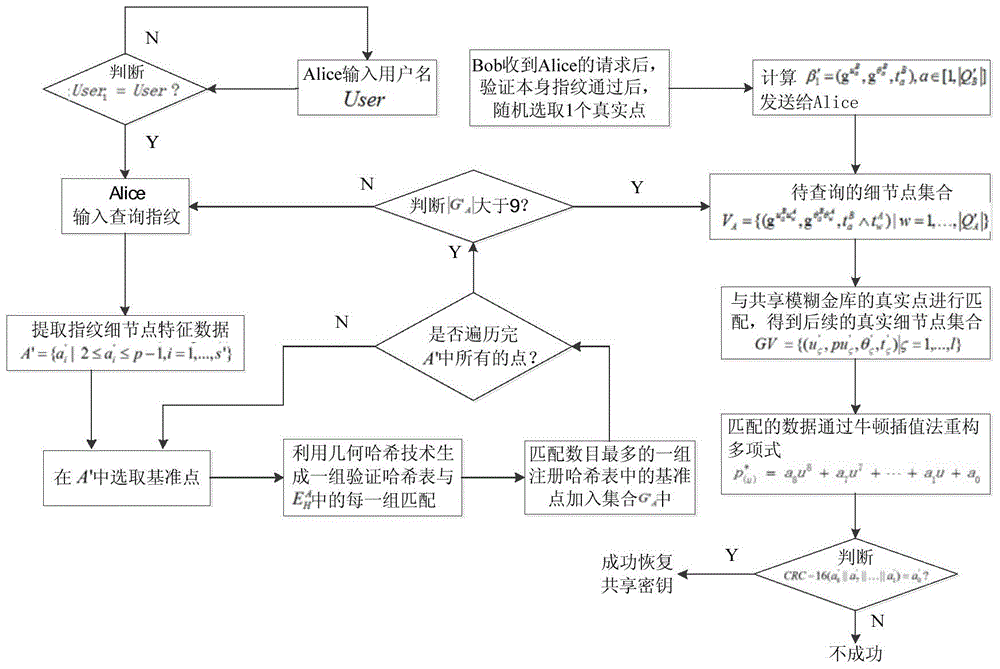
[0050] The present invention will be further described below in conjunction with accompanying drawing.
[0051] 1. The detailed process of binding the shared key to the shared fingerprint fuzzy vault is as follows:
[0052] 1.1. If figure 1 As shown, user 1 Alice and user 2 Bob jointly select a large prime number p, and select g as the multiplicative group A generator in . Alice secretly selects an integer a: 2≤a≤p-1, and calculates g a mod p, sent to Bob. Bob secretly selects an integer b: 2≤b≤p-1, and calculates g b mod p, sent to Alice. Suppose Alice and Bob want to generate a 128-bit shared secret. because (g a ) b =g ab =(g b ) a , so Alice and Bob can calculate H((g b ) a mod p) and H((g a ) b mod p) to obtain the shared key k. Among them, H(·) is selected to generate a 128-bit hash function. At the same time, Alice and Bob respectively enter their personal registered user names, which are recorded as User 1 , User 2 .
[0053] 1.2. From the prev...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com