Fuzzy Vault encrypting method based on secrete sharing
A technology of secret sharing and encryption method, applied in the field of Fuzzy Vault encryption based on secret sharing, which can solve the problems of message deadlock, tampering and destruction, and expansion of feature space, so as to improve system security performance, avoid message deadlock, and avoid information deadlock. lock effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
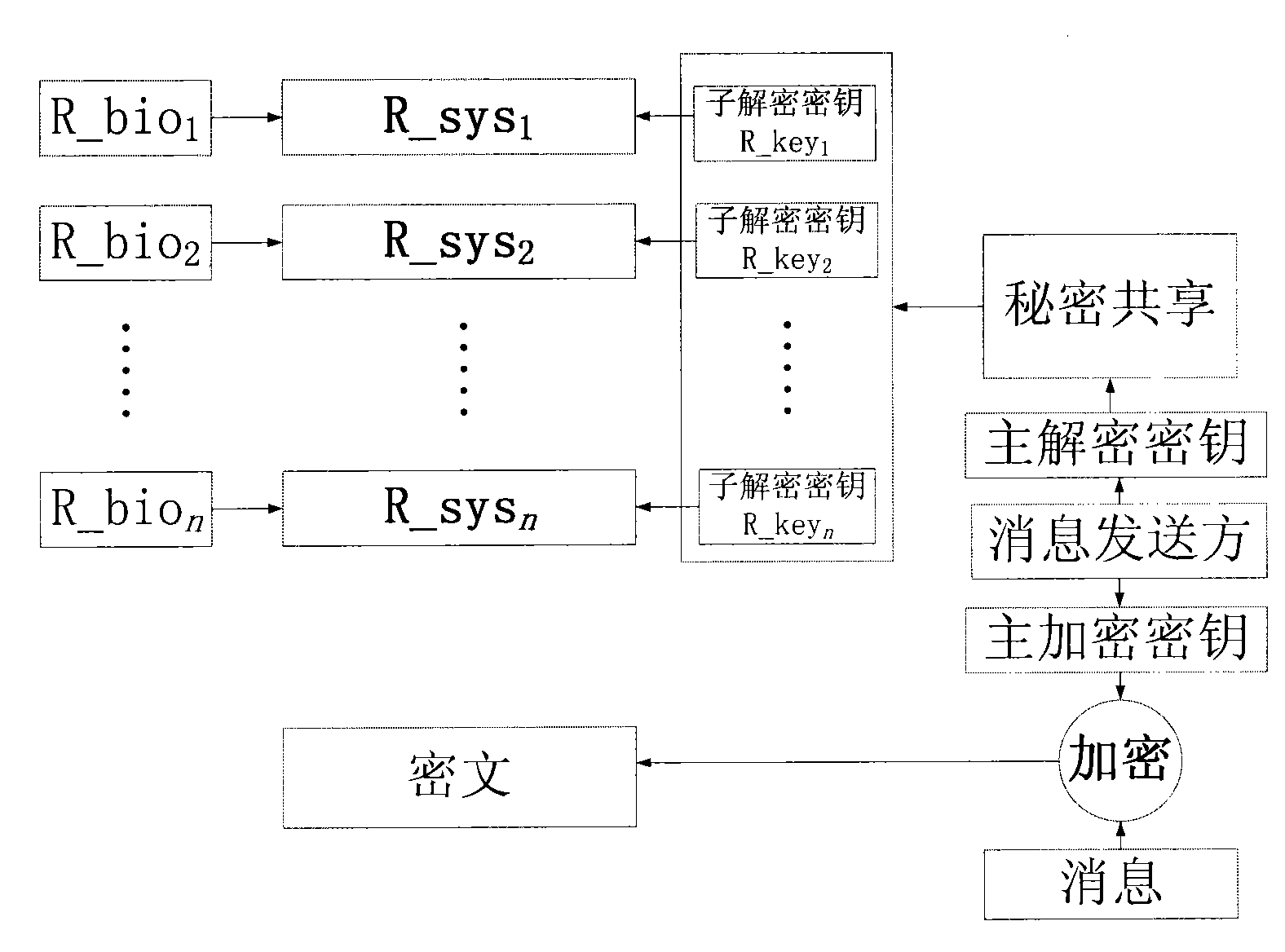
[0034] The flow of the secret sharing-based Fuzzy Vault encryption method of the present invention is divided into two parts: an encryption process and a decryption process. figure 1 It is the process of encrypting messages with the method of the present invention; figure 2 It is the process of encrypting messages with the method of the present invention.
[0035] Such as figure 1 As shown, the message sender of the present invention generates the master encryption key and the master decryption key, encrypts the message with the master encryption key, and each of the n message receivers who share the message provides its fingerprint detail point information combined with the secret sharing method binding sub decryption key. In the encryption process, the input information is the n fingerprint detail point information of the n recipients of the shared message and the message to be encrypted. The steps of the encryption process are as follows:
[0036] 1) The sender of the m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com