Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
551 results about "Binding process" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
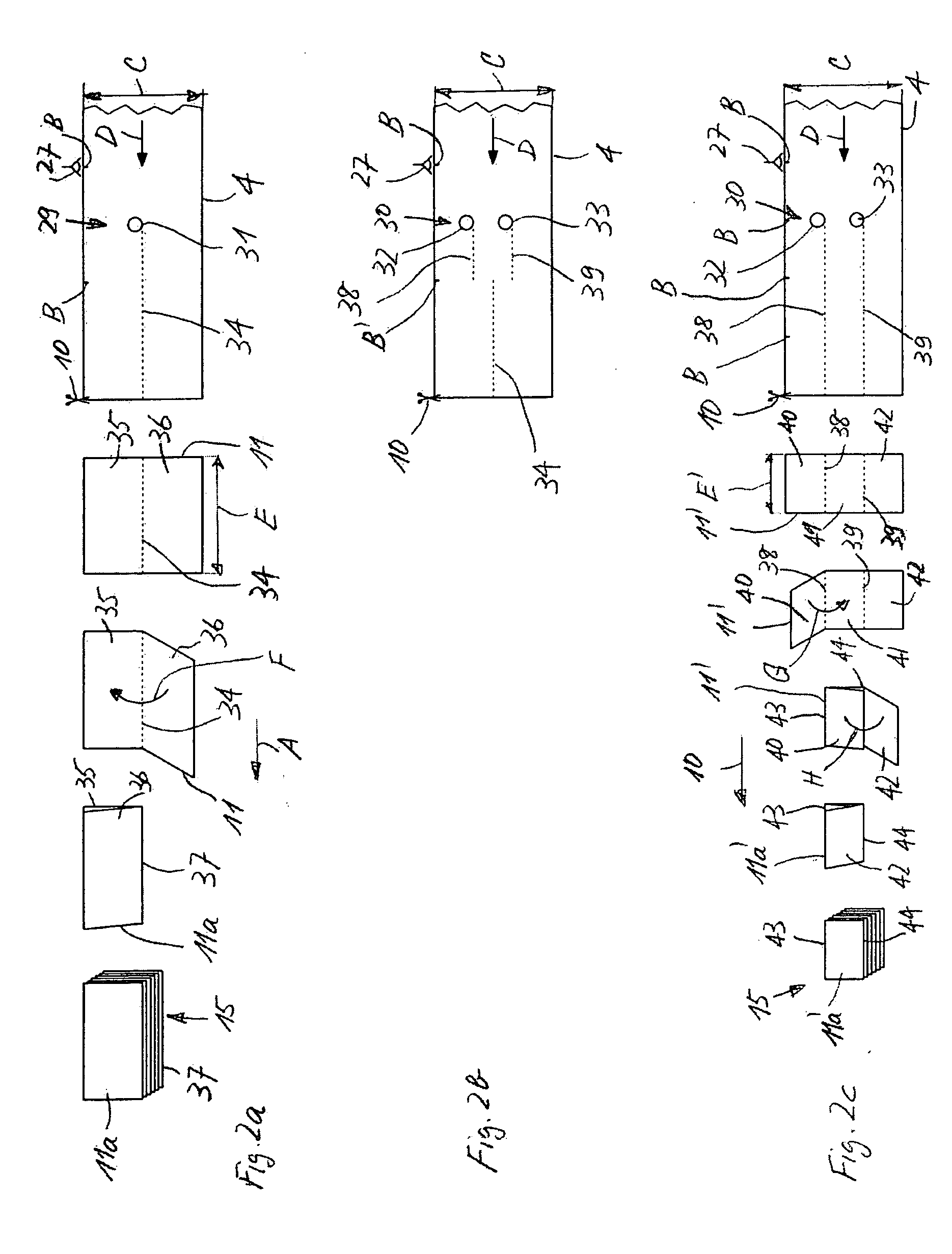
Binding Process. Index. Binding a guitar is the process of cutting a channel along the edge of the body, and gluing in a (typically) plastic strip. The purpose of this is primarily to hide all the end grain of the top and bottom of the guitar.
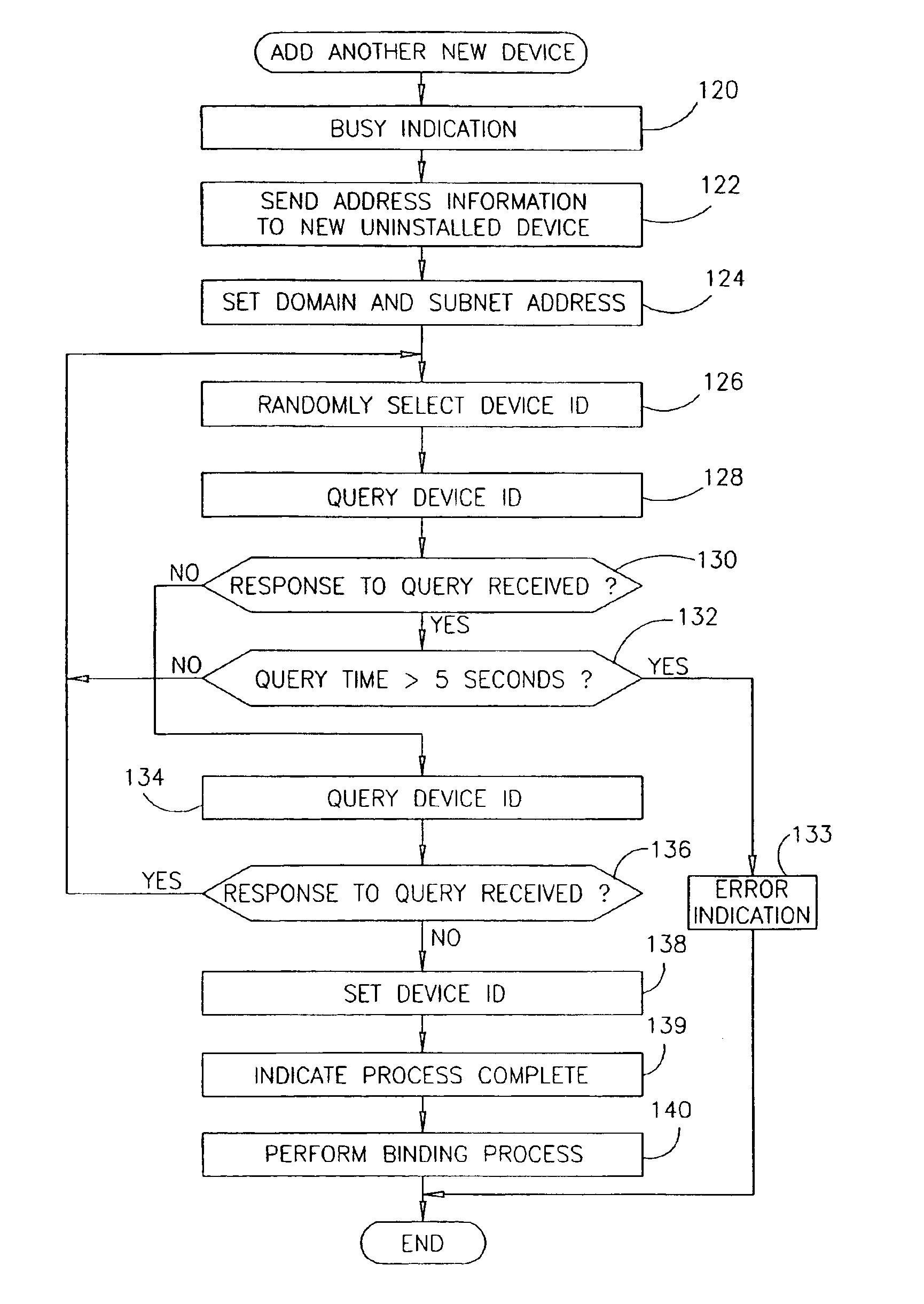
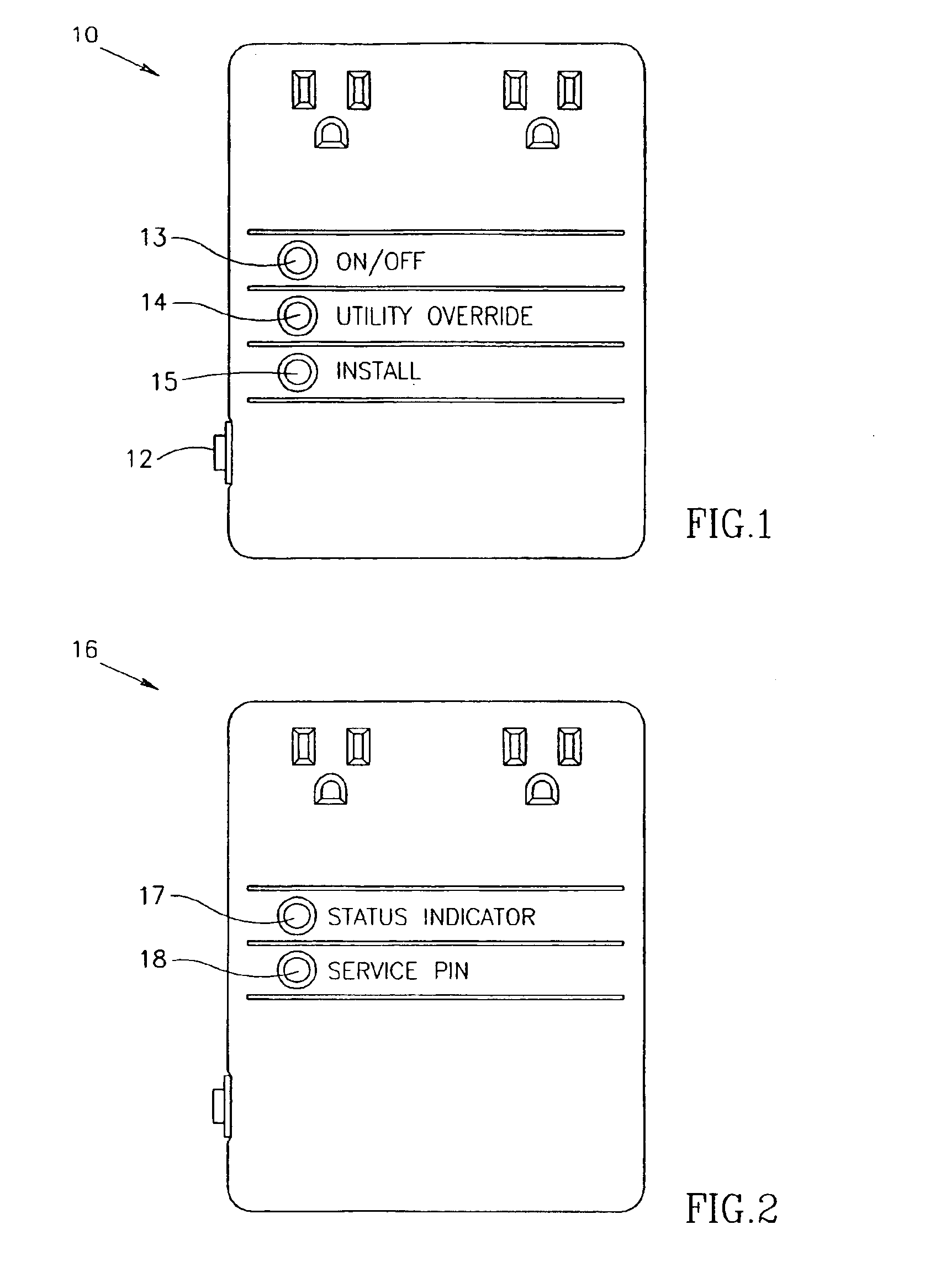
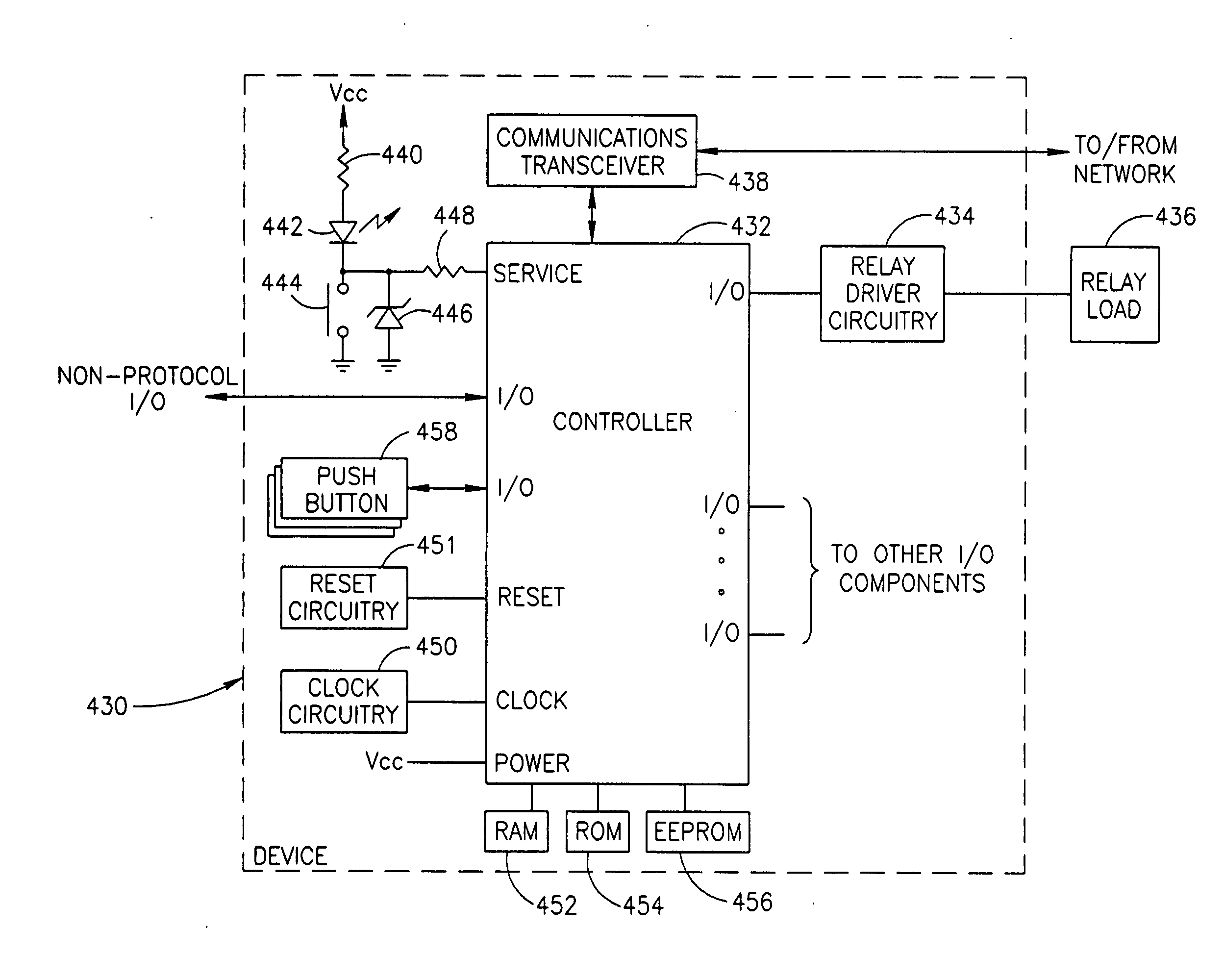
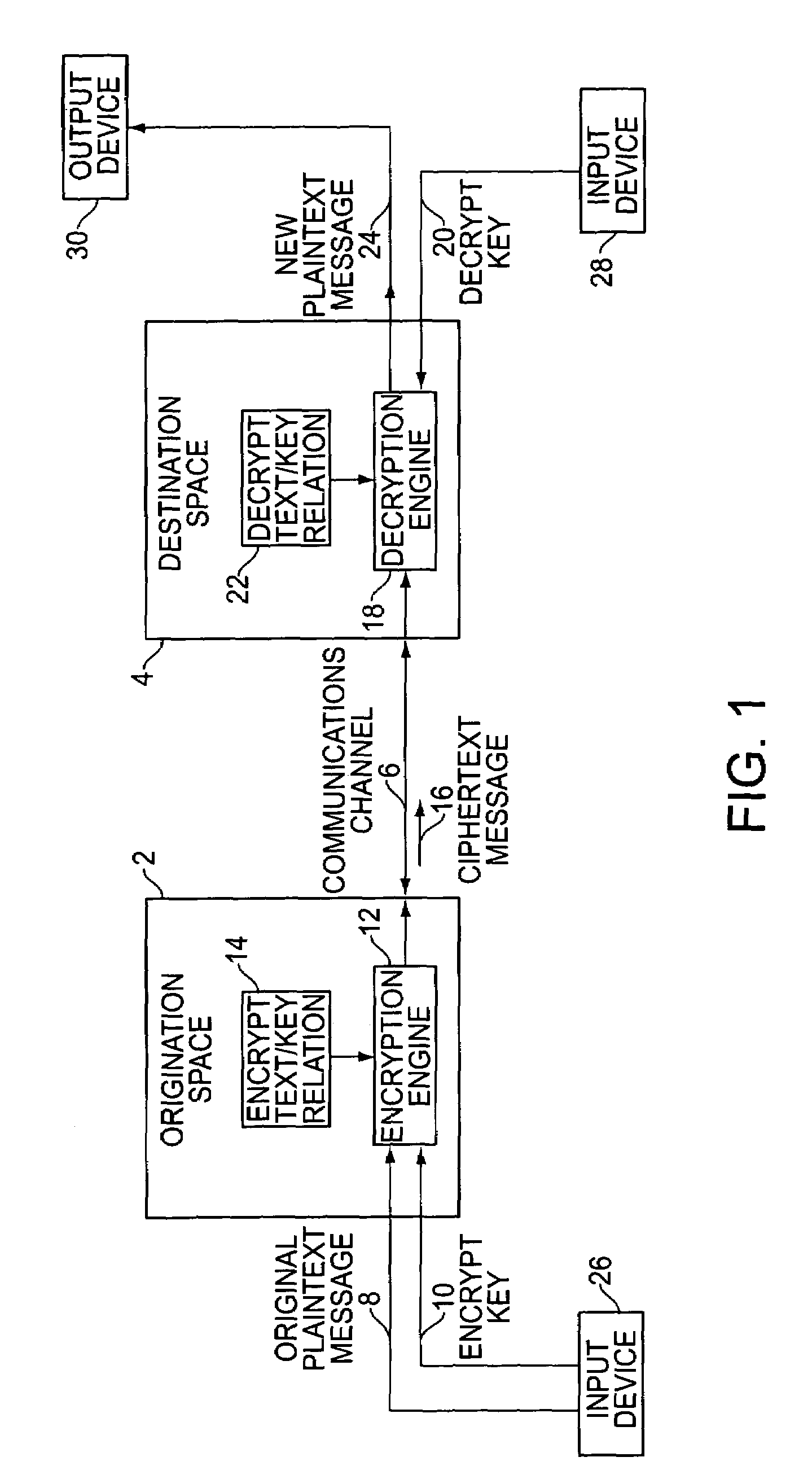
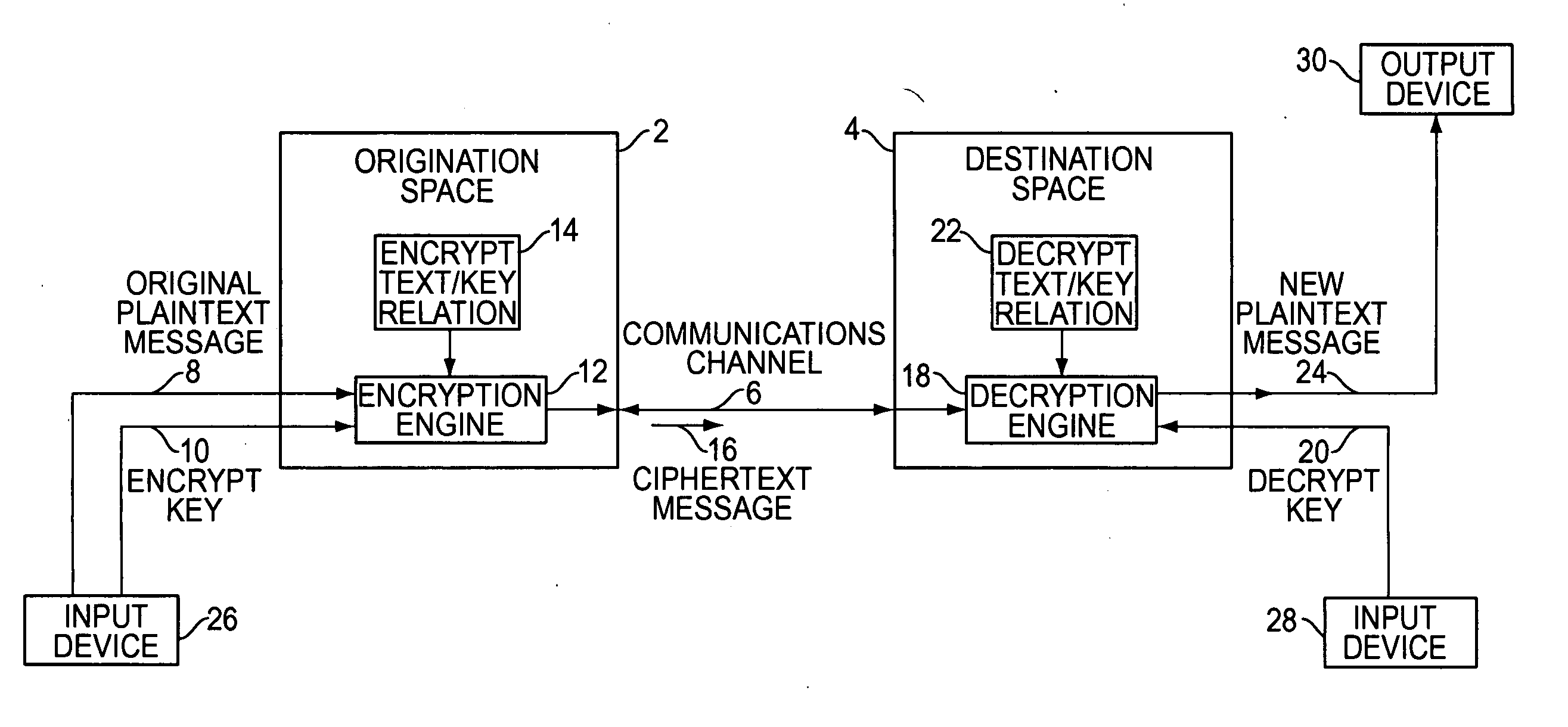
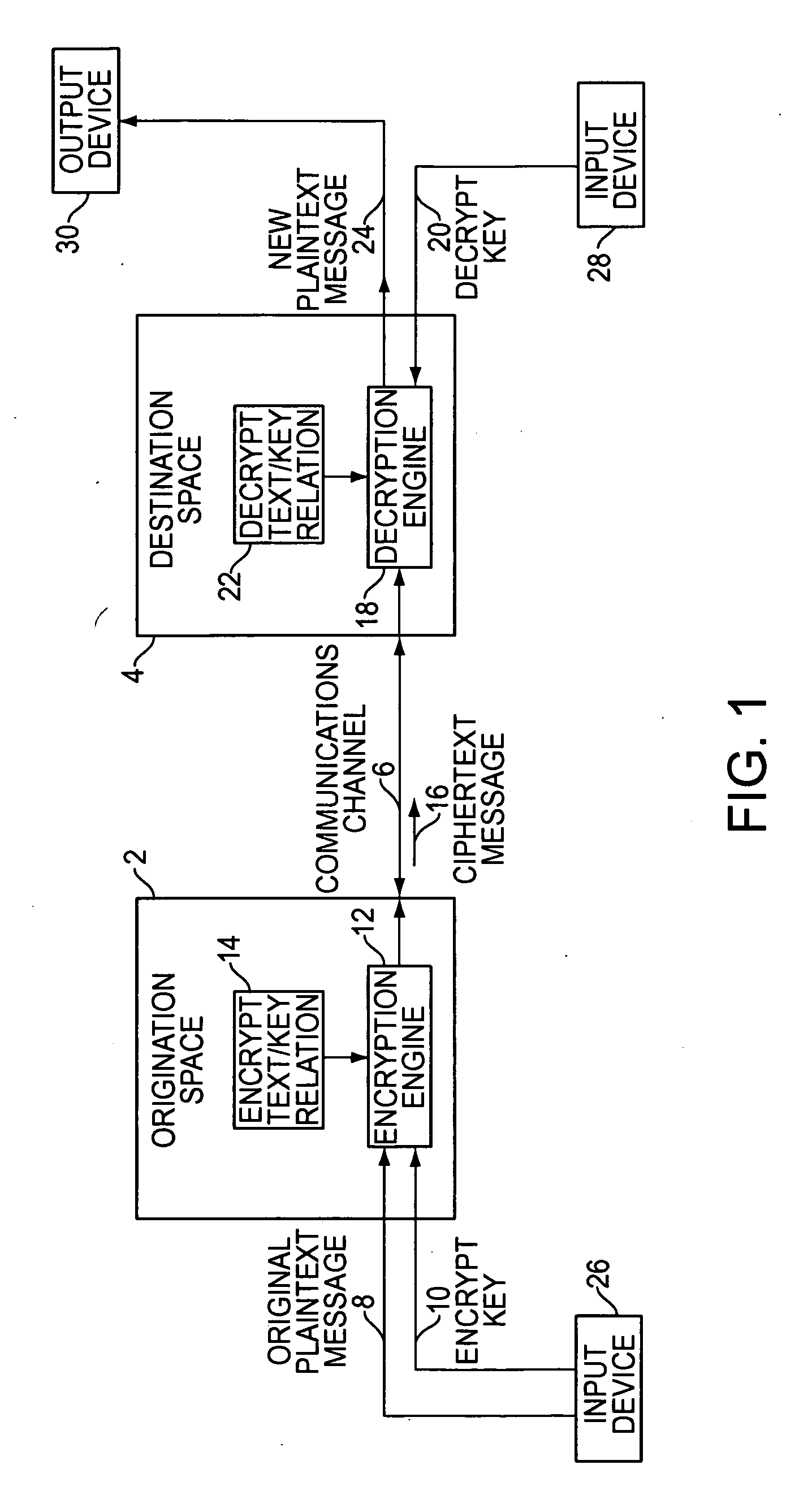
Method of adding a device to a network
InactiveUS6901439B1Low-cost implementationElectric light circuit arrangementMultiple digital computer combinationsHome environmentLonWorks
A method of adding a device to an existing or new electrical or electronic automation or multimedia network. The invention facilitates adding a device to the network that can communicate using various protocols such as LonWorks, CEBus, X-10, etc. over media such as AC power line, IR, RF, twisted pair, optical fiber, etc. The method is a mechanism for adding a device to a system that can be used by an ordinary user of network capable electrical devices. The method comprises the steps an installer would perform including the handshaking that needs to occur between devices to accomplish the binding process. A Functional Profile for LonWorks networks is given as an example. This includes a Home Device profile that employs an automated explicit type messaging for all devices intended for use in a home environment. The invention includes adding to the device an install button and a visual indicator for status such as an LED. Alternatively, existing buttons and LEDs on the device may be used for installed and binding purposes. Other methods of binding can be employed by the use of wired or wireless handheld tools, remote controls, etc. Other interfaces and user feedback can be used such as touch screen, personal computers, cellular phones, PDAs, etc which can offer simple ‘virtual’ binding by the press of an icon versus the physical button on the device. The binding can be performed locally or remotely such as via LAN, WAN, Internet, etc.
Owner:LEVITON MFG
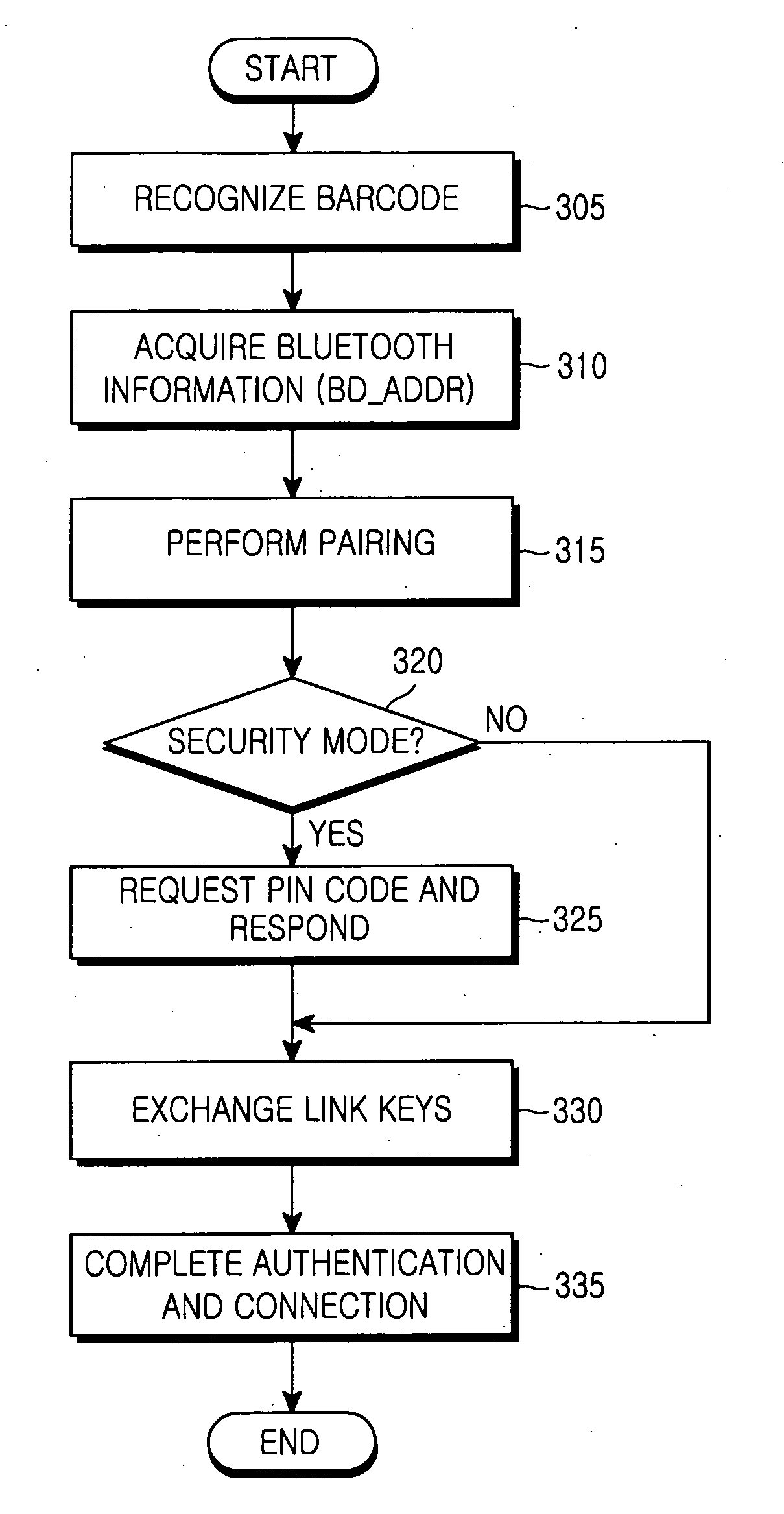
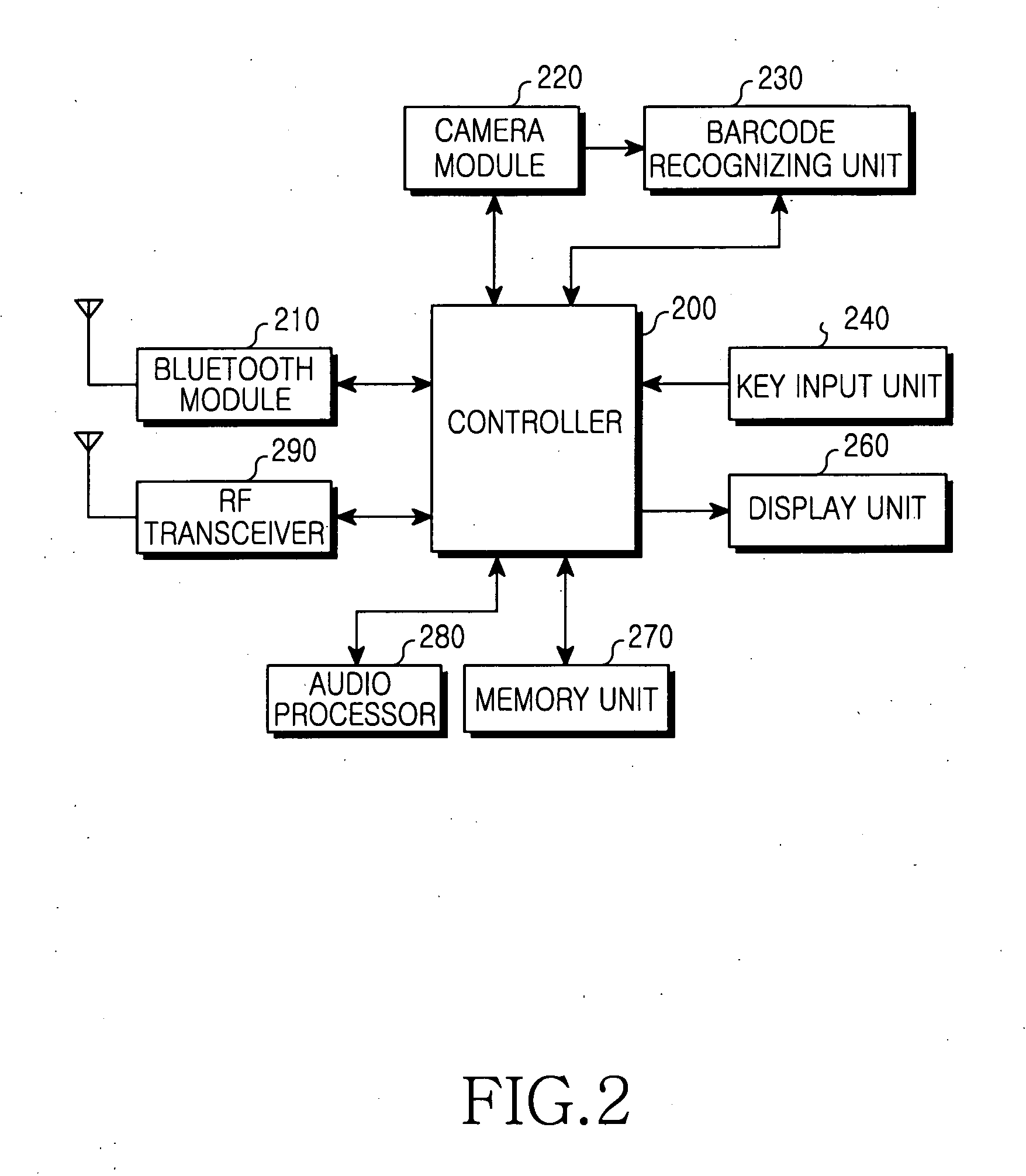
Method and apparatus for bonding process in bluetooth device
InactiveUS20060135064A1Simplify the pairing processEasy to understandNear-field transmissionNetwork topologiesBonding processBarcode
A method and apparatus for a bonding process in a user terminal having a Bluetooth module. The method includes recognizing a barcode of a Bluetooth device to be connected using a camera module, acquiring bonding information of the Bluetooth device from the barcode, performing pairing with the Bluetooth device using the acquired bonding information, and establishing a connection between the user terminal and the Bluetooth device after performing pairing. The bonding information may also be acquired using a secure cable in another embodiment.
Owner:SAMSUNG ELECTRONICS CO LTD
Method of adding a device to a network
InactiveUS20060009861A1Low-cost implementationComputer controlSimulator controlLonWorksHome environment
A method of adding a device to an existing or new electrical or electronic automation or multimedia network. The invention facilitates adding a device to the network that can communicate using various protocols such as LonWorks, CEBus, X-10, etc. over media such as AC power line, IR, RF, twisted pair, optical fiber, etc. The method is a mechanism for adding a device to a system that can be used by an ordinary user of network capable electrical devices. The method comprises the steps an installer would perform including the handshaking that needs to occur between devices to accomplish the binding process. A Functional Profile for LonWorks networks is given as an example. This includes a Home Device profile that employs an automated explicit type messaging for all devices intended for use in a home environment. The invention includes adding to the device an install button and a visual indicator for status such as an LED. Alternatively, existing buttons and LEDs on the device may be used for installed and binding purposes. Other methods of binding can be employed by the use of wired or wireless handheld tools, remote controls, etc. Other interfaces and user feedback can be used such as touch screen, personal computers, cellular phones, PDAs, etc which can offer simple ‘virtual’ binding by the press of an icon versus the physical button on the device. The binding can be performed locally or remotely such as via LAN, WAN, Internet, etc.
Owner:LEVITON MFG
Isolation of proteins
InactiveUS20050176122A1Other chemical processesSolid sorbent liquid separationSpecial classCarboxylic acid
Owner:UPFRONT CHROMATOGRAPHY
Isolation of proteins
InactiveUS6919436B2Other chemical processesSolid sorbent liquid separationSpecial classCarboxylic acid
The present invention relates to a novel method for the isolation or purification of immunoglobulins (a special class of proteins) from a solution containing immunoglobulins, e.g. hybridoma cell culture supernatants, animal plasma or sera, or colostrum. The method includes the use of a minimum of salts, such as lyotropic salts, in the binding process and preferably also the use of small amounts of organic solvents in the elution process. The solid phase matrices, preferably epichlorohydrin activiated agarose matricees, are functionalised with mono- or bicyclic aromatic or heteroaromatic ligands (molecular weight: at the most 500 Dalton) which, preferably, comprises an acidic substituent, e.g. a carboxylic acid. The matrices utilised show excellent properties in a “Standard Immunoglobulin Binding Test” and in a “Monoclonal Antibody Array Binding Test” with respect to binding efficiency and purity, and are stable in 1M NaOH.
Owner:UPFRONT CHROMATOGRAPHY
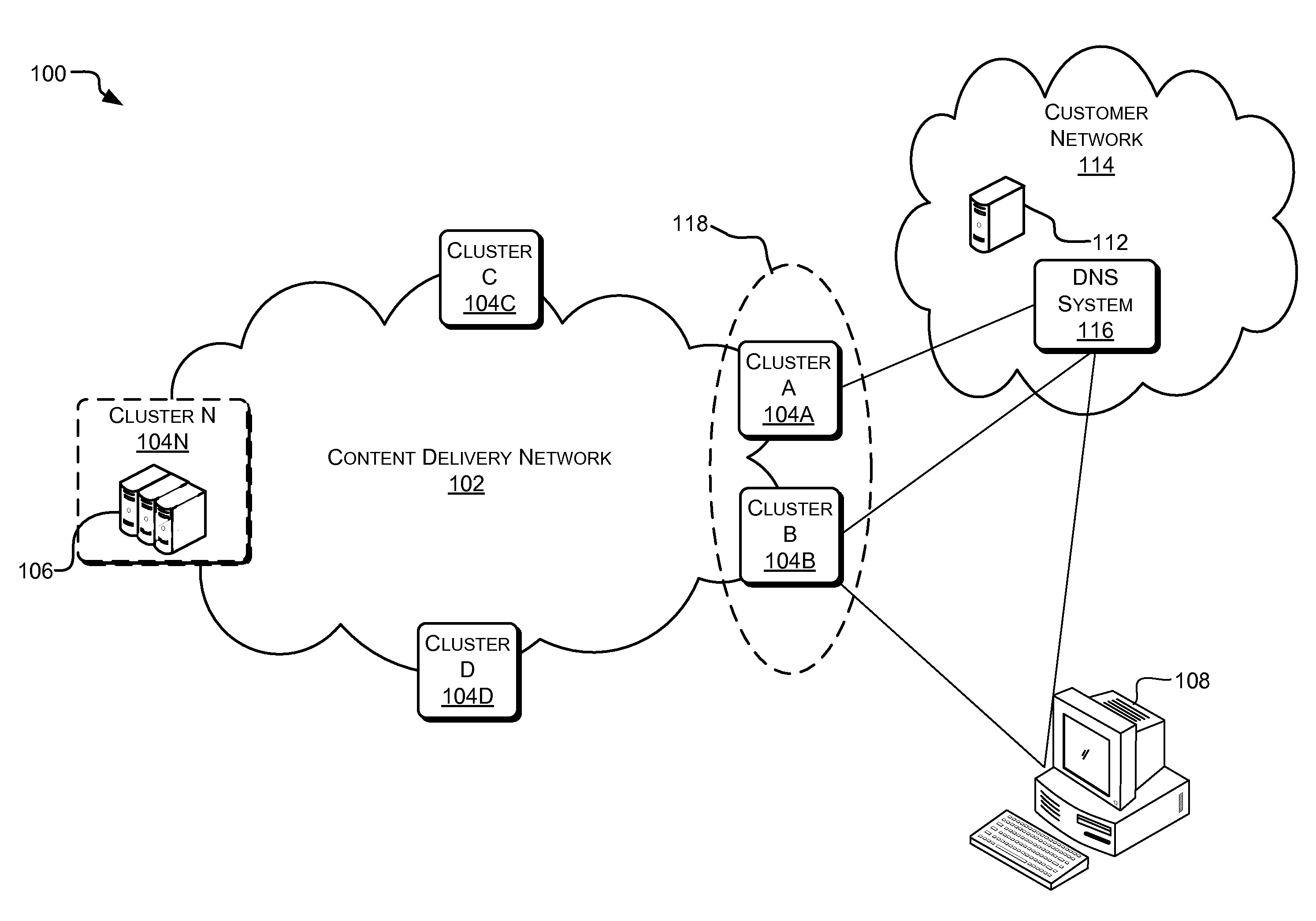
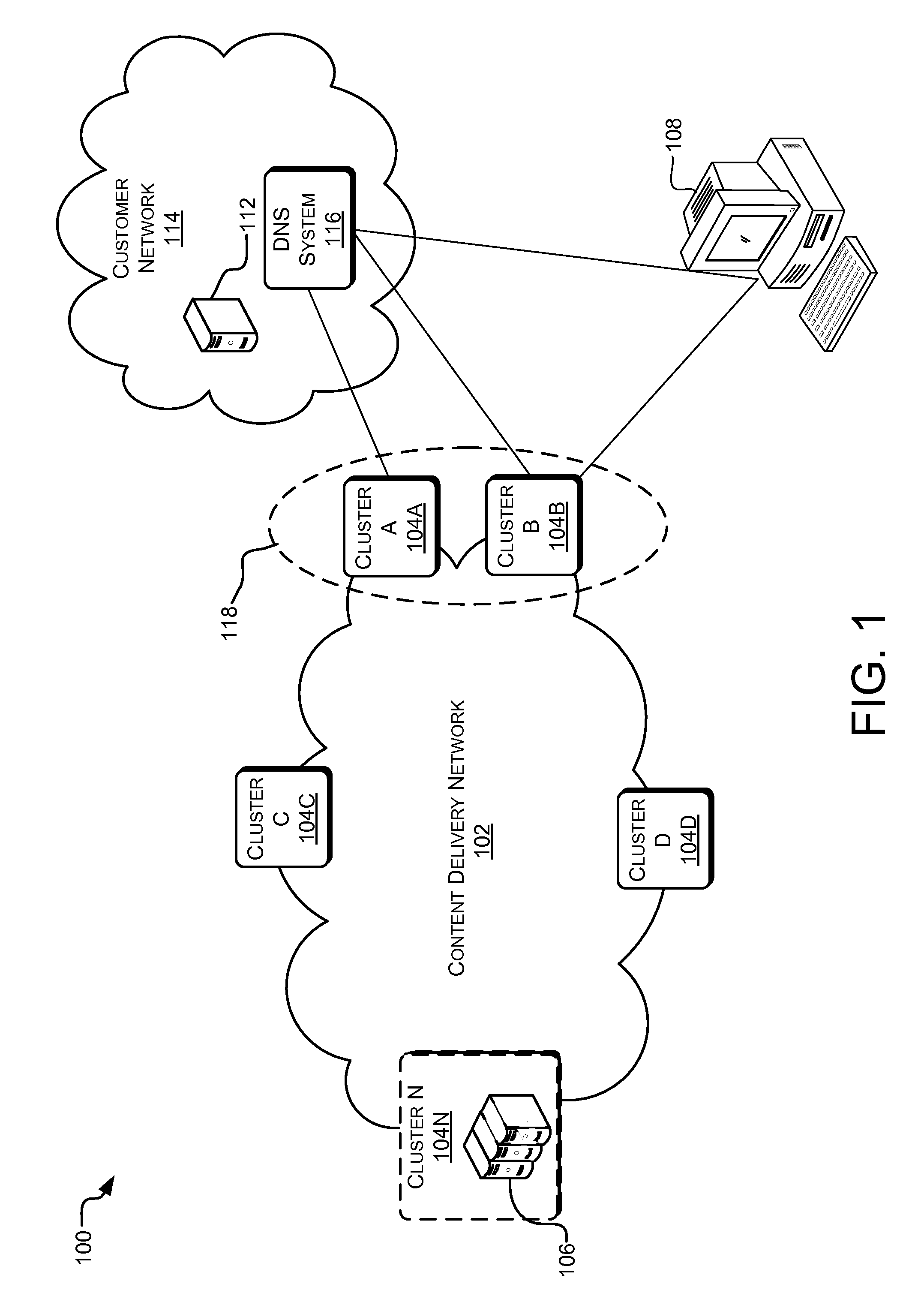
Dynamic binding for use in content distribution
InactiveUS20110276679A1Digital computer detailsTransmissionContent distributionDistributed computing
Provided are methods and systems for dynamic binding in the context of content delivery. For example, the methods and systems may be implemented as a dynamic binding process that maps a content provider to a first set of content servers in a content distribution network. The dynamic binding process may then facilitate the content to be received from the content provider so that the content can be distributed by the first set of content servers in the content distribution network. The dynamic binding process further monitors network traffic associated with the content from the content provider and determines at least one metric associated with the network traffic. Additionally, the dynamic binding process can remap the content provider to a second set of content servers in the content distribution network based on at least one of the metrics.
Owner:LEVEL 3 COMM LLC
Managing securely installed applications
ActiveUS20100313196A1Memory loss protectionError detection/correctionOperational systemRandom allocation
Embodiments of the present disclosure provide methods and systems for managing securely installed applications. After installation, an installation framework performs a bind process to correlate the randomly assigned identifier with the unique identifier of the application. The installation framework also manages the execution of the application. When an application is launched, the application framework performs a search for that application's randomly assigned identifier and locates the application's container. The application is then allowed to execute within its container. During execution, the software application may also be restricted in various ways by the installation framework to its dynamic containers. The installer may also work with a trusted operating system component, such as the kernel, to help enforce the container restrictions. In addition, if desired, the use of random identifiers for containers may be used in conjunction with other security mechanisms, such as the use of code signing.
Owner:APPLE INC
Portable and dynamic distributed transaction management method
InactiveUS6115710AImprove productivityReduce needData processing applicationsProgram control using stored programsComputer resourcesGoal system
A system and method is shown for enabling a plurality of computers and associated computer resources, some or all of which may be of heterogeneous configuration, to cooperatively process various applications such that the execution is transparent to the user regardless of where the application is actually executing. This distributed applications architecture performs an information distribution service between multiple transaction processing systems by working with a transaction processor via communication channels to other hosts within the network and a dialog manager which uses a transaction processor interface to communicate with the transaction processor. The architecture employs a map service which provides an editor to create the maps for the application panels, a compiler to generate the maps into a linkable form, and a linkable interpreter which translates the linkable form into the screen presentation format for that platform. To distribute an application, the source code for the procedures, view and panels are moved as a block to the new system. This is possible because once the application source code is complete, all application logic, user interface control tables, view definitions, and other application-specific tables for one transaction definition are packaged by the present invention in a single load module on the system where the application will reside. The load module is then compiled using the target system's compiler, link editor, and bind process. Thus, all environment-dependent variations of import / export are automatically integrated with the application at load module bind time, requiring no source code changes.
Owner:COMP ASSOC THINK INC
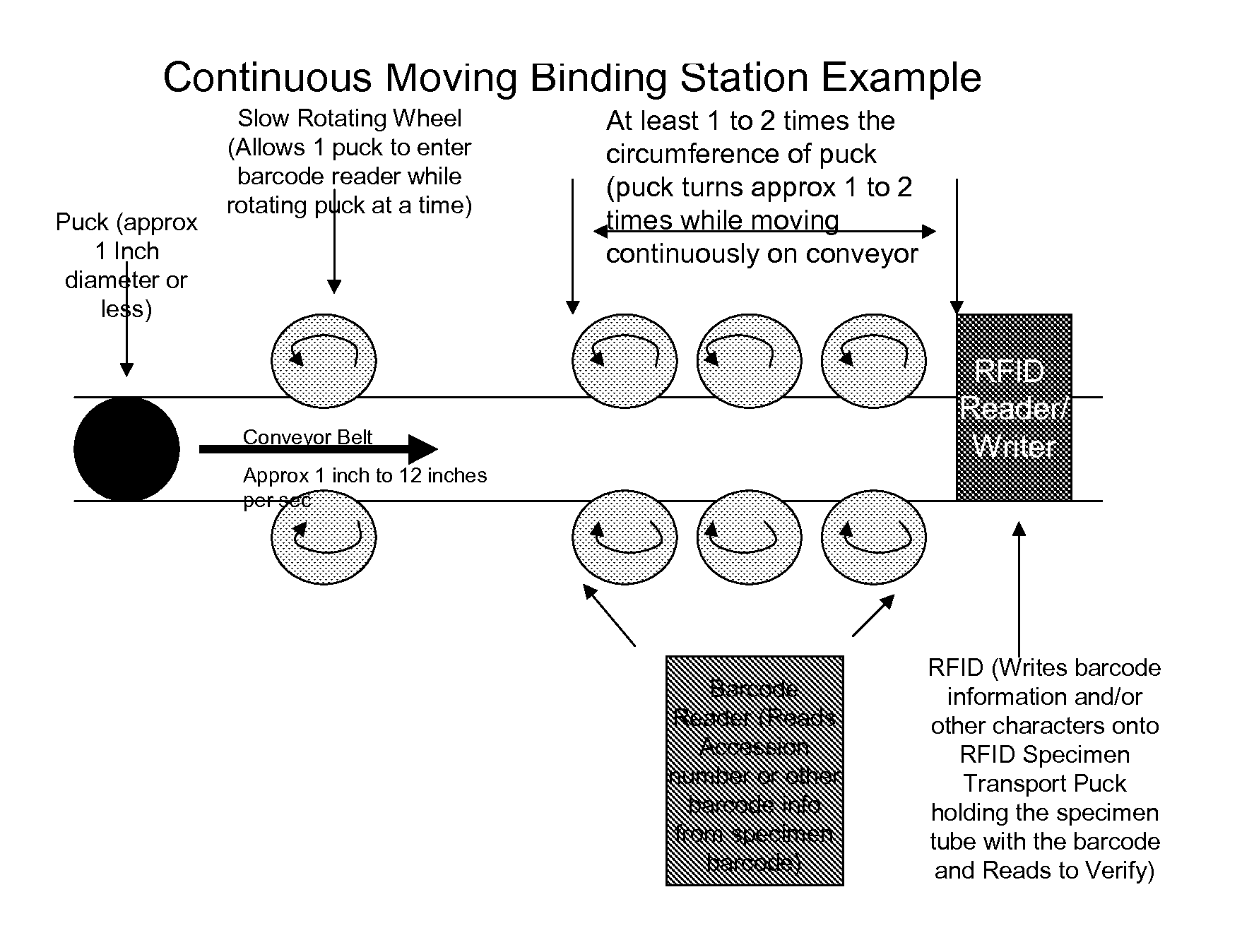
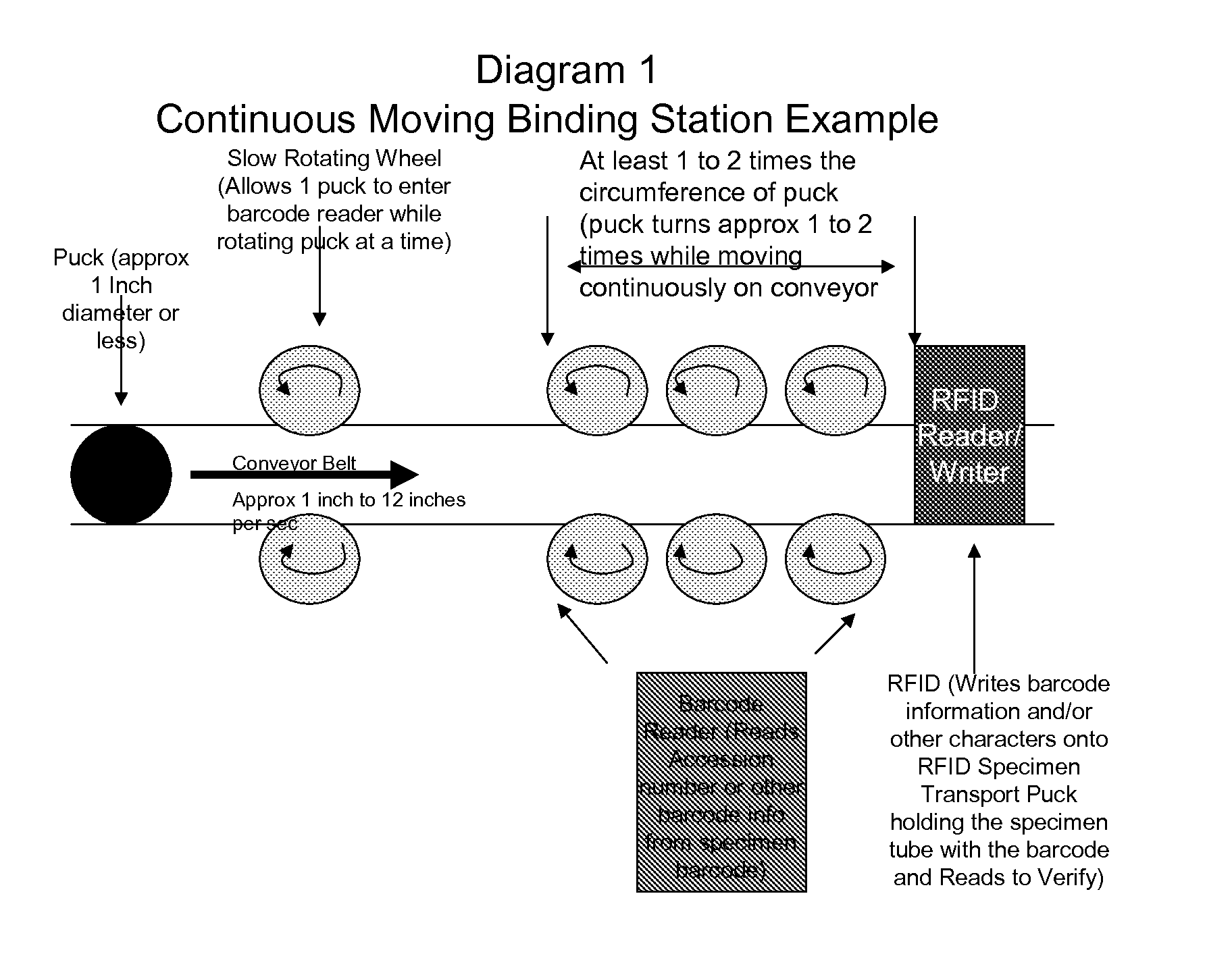
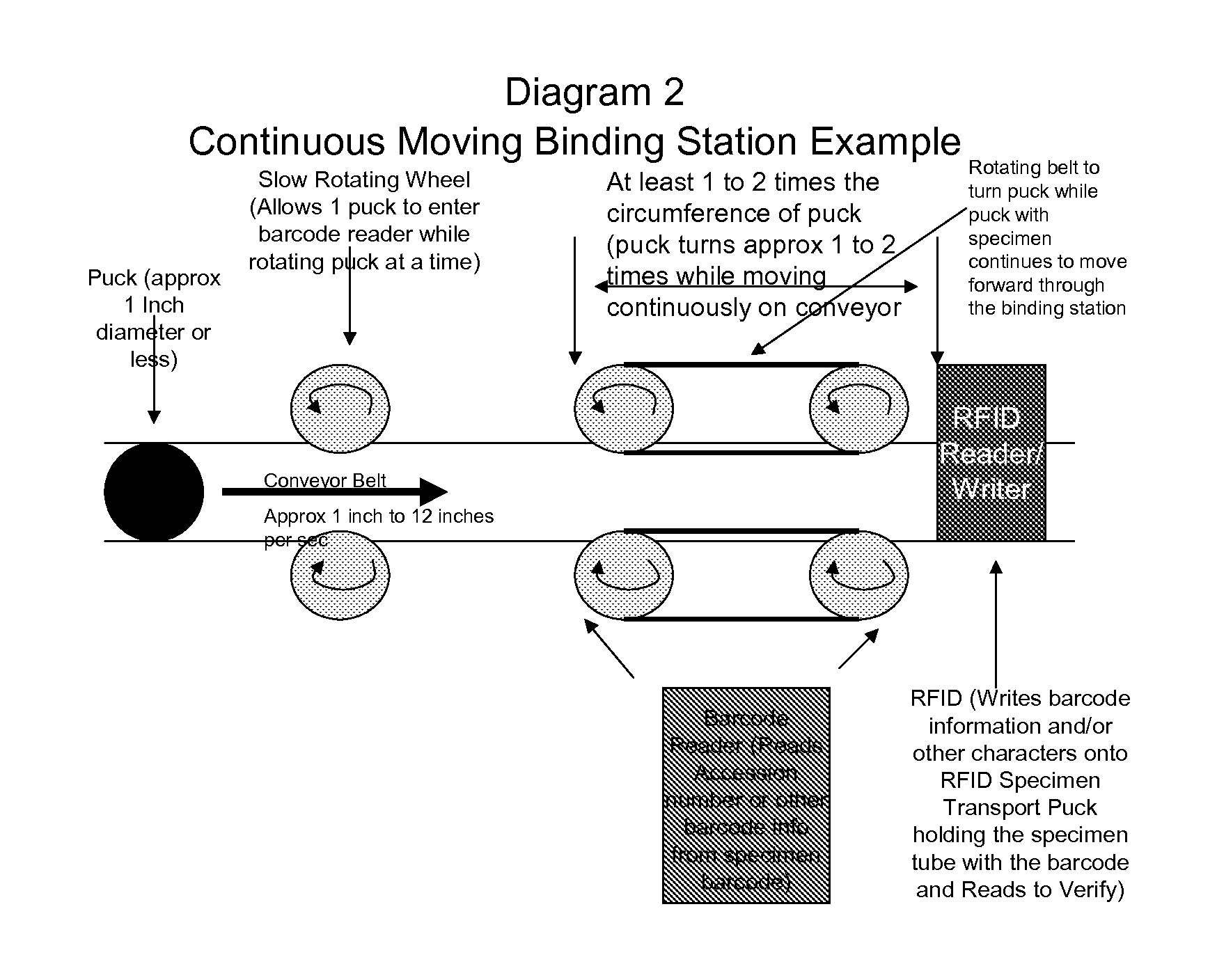
Transfer, Link, Bind, Specimen Tube Barcode Information To RFID Specimen Transport Puck In A Continuous Moving Binding Process Method
ActiveUS20120037696A1Maximize throughputFast and efficientCharacter and pattern recognitionRecord carriers used with machinesDatabase serverBarcode reader
The present invention relates generally to the process method of transferring / linking / binding specimen tube label barcode information (such as unique accession number along with other useful laboratory information such as test code information, testing department, specimen temperature) using an RFID Specimen Transport Puck moving continuously on a continuously moving conveyor belt and an RFID Reader / Writer that writes the information onto the RFID chip on the RFID Specimen Transport Puck. The process method is to space the specimen transport pucks on the conveyor, rotate the specimen transport puck that is holding the specimen tube with the barcode while the specimen is moving continuously forward using rotating wheels on the side of the conveyor belt and using a dispersed barcode reader to read the barcode information from the specimen tube label, and to transfer / link / bind the information from the specimen tube barcode label to the RFID chip on the specimen transport puck holding the specimen tube using an RFID reader / writer beneath the conveyor belt, a PLC and a database server.
Owner:LEAR SIROUS LAVI
Display substrate, display panel, touch display device and manufacturing method thereof
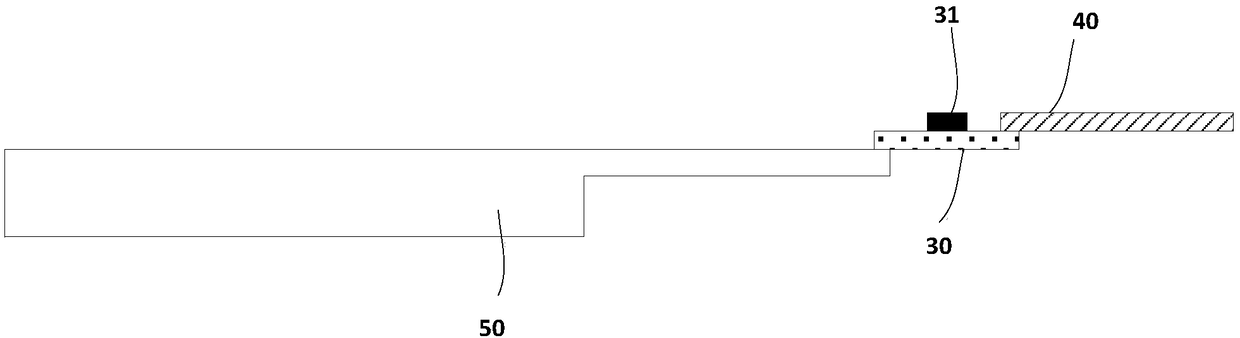
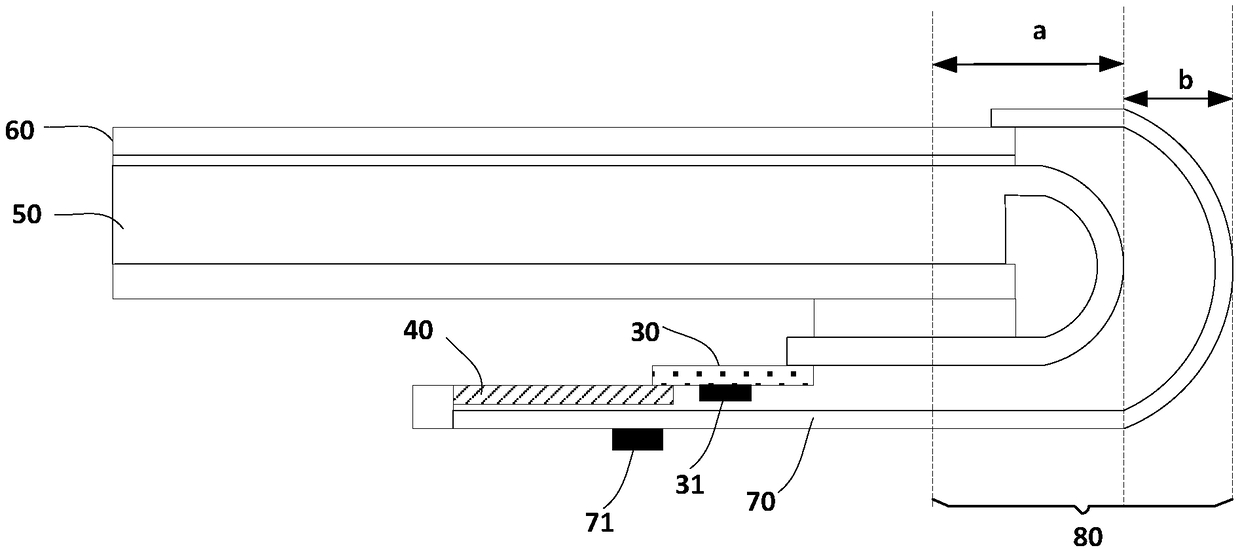
ActiveCN108762562AReduce binding stepsSimplify the bonding processPrinted circuit aspectsNon-linear opticsDisplay deviceEngineering
Owner:BOE TECH GRP CO LTD +1
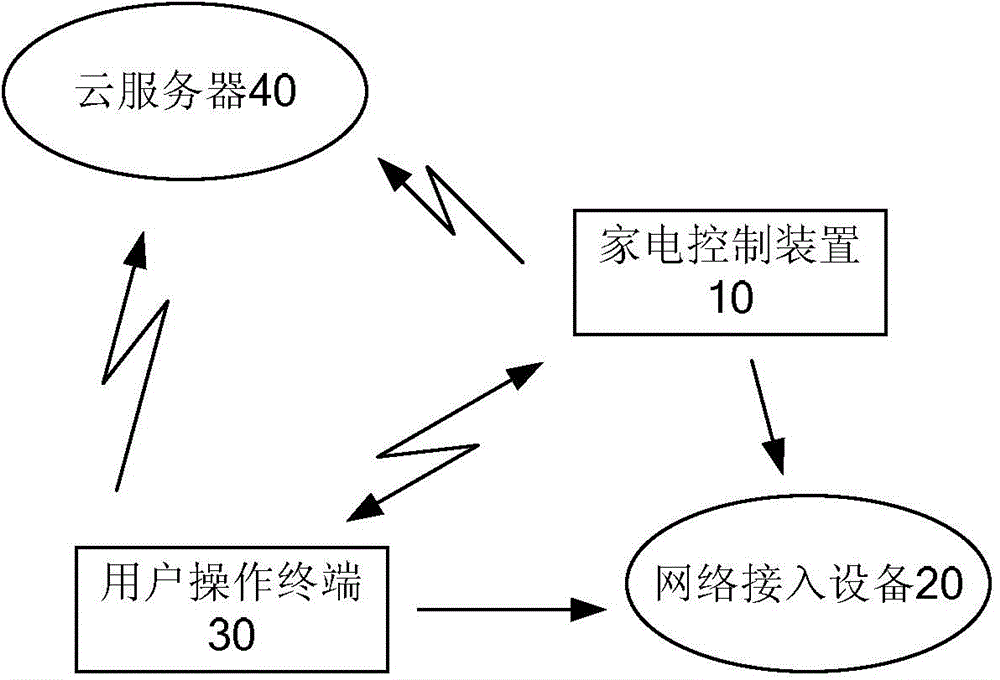
Binding method of user operation terminal and household appliance control device and household appliance control system
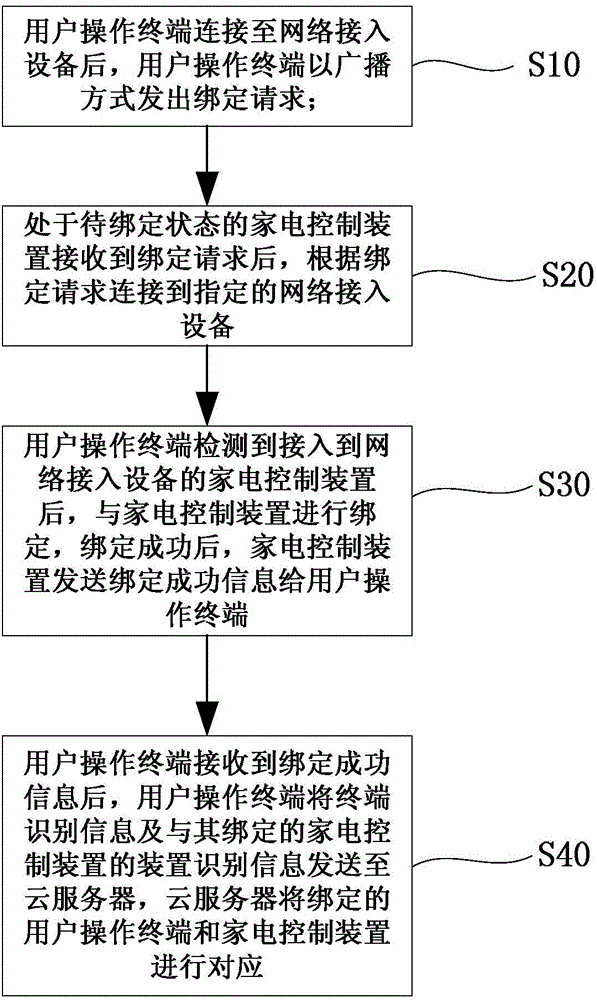
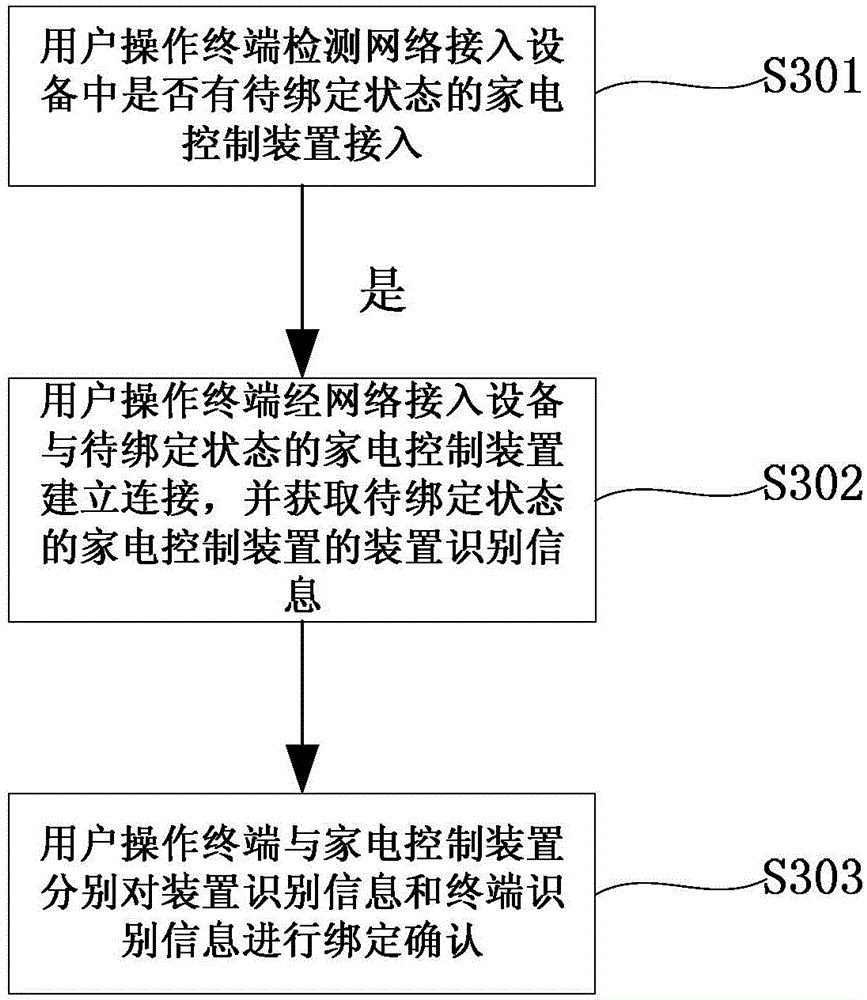
ActiveCN103914041AAvoid the problem of frequent exchangesSimplify binding stepsTransmissionProgramme total factory controlControl systemBinding state
The invention provides a binding method of a user operation terminal and a household appliance control device and a household appliance control system. The binding method of the user operation terminal and the household appliance control device comprises the steps that after being connected to a network access device, the user operation terminal sends a binding request in a broadcasting mode; after receiving the binding request, the household appliance control device in the to-be-bound state is connected to the designed network access device according to the binding request; after detecting the household appliance control device accessed to the network access device, the user operation terminal is bound to the household appliance control device; the user operation terminal sends terminal identifying information and device identifying information of the household appliance control device which is bound to the user operation terminal to a cloud server, and matching of the bound user operation terminal and the bound household appliance control device is conducted by the cloud server. The binding method of the user operation terminal and the household appliance control device effectively solves the problem that the binding process is complicated in the prior art.
Owner:HAIER GRP CORP +1
System and method for establishing a secured connection between an implantable medical device and an external device
ActiveUS20150341785A1Spinal electrodesImplantable neurostimulatorsComputer hardwareTelecommunications link
A system and method are provided for initiating a secured bi-directional communication session with an implantable medical device. The system and method include configuring a pulse generator (PG) device and an external device to establish a communication link there between through a wireless protocol with a defined bonding procedure. The system and method also include transmitting a static identification and dynamic seed from the PG device through a dedicated advertisement channel to the external device and generating a passkey from a pre-defined algorithm based on the dynamic seed and a static identification. Further, the system and method include starting the defined bonding procedure.
Owner:PACESETTER INC
Device binding method and device binding device
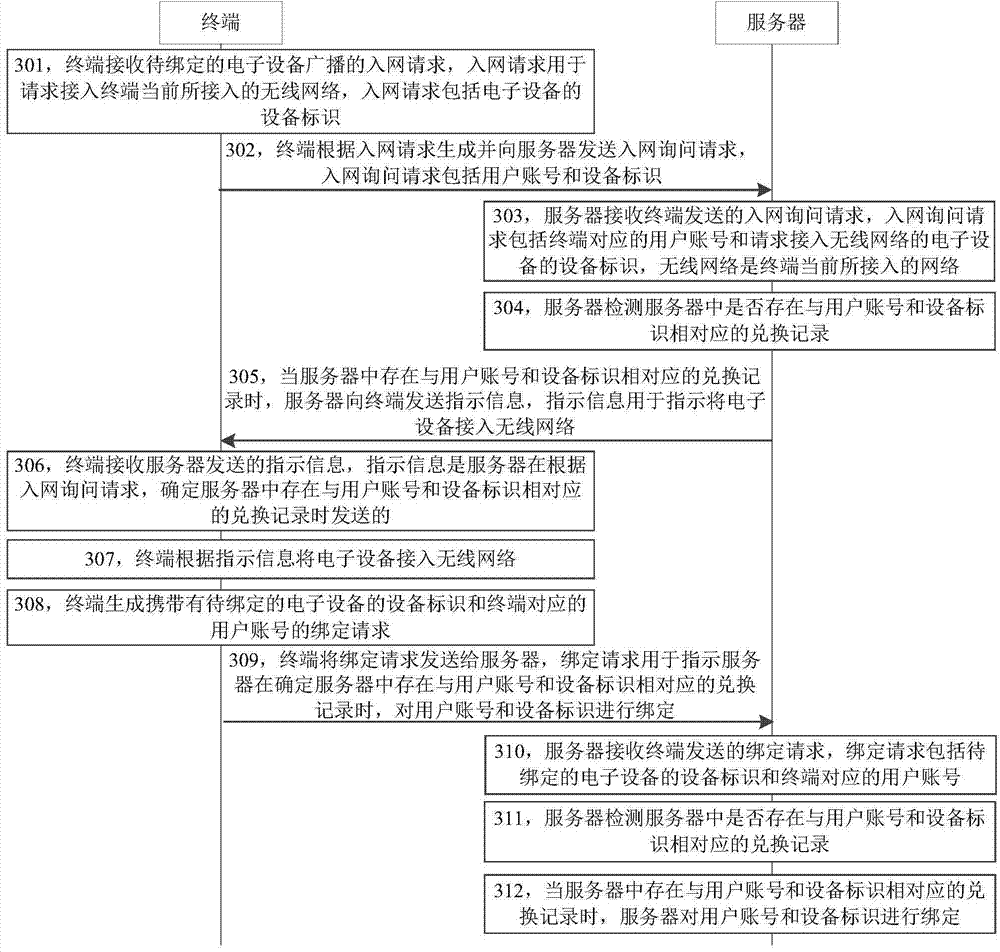
ActiveCN104780154AThe binding process is simpleAvoid wrong bindingSubstation equipmentTransmissionServer-sideBinding process
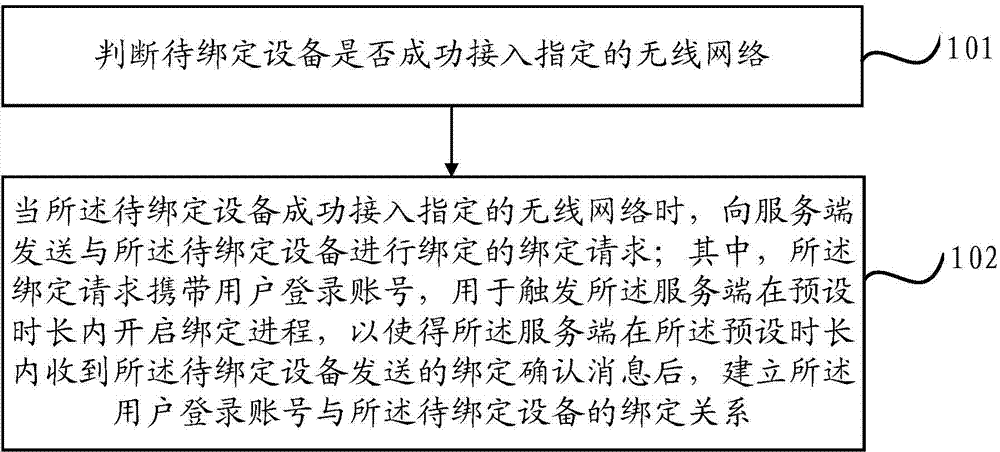
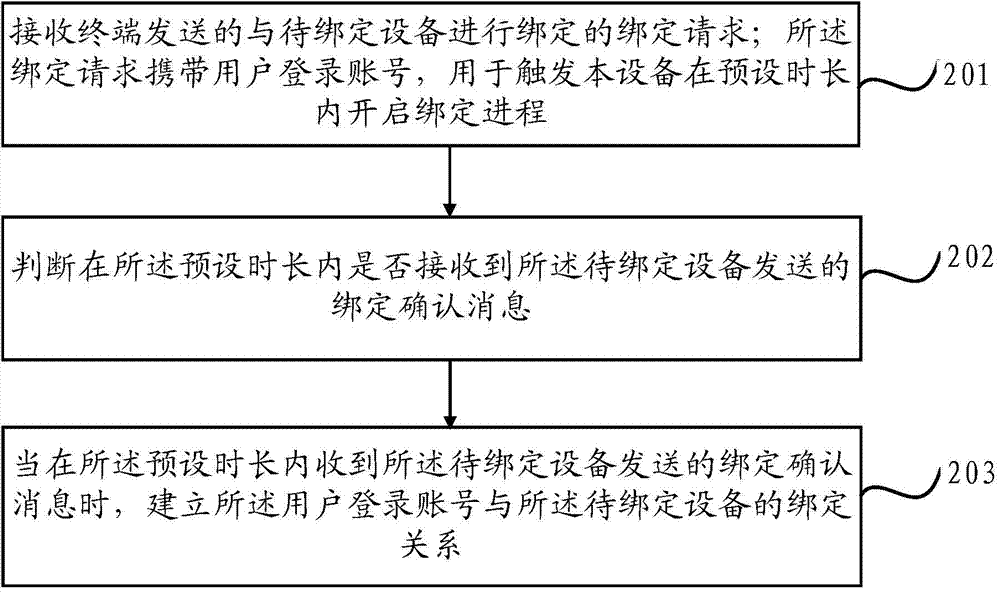
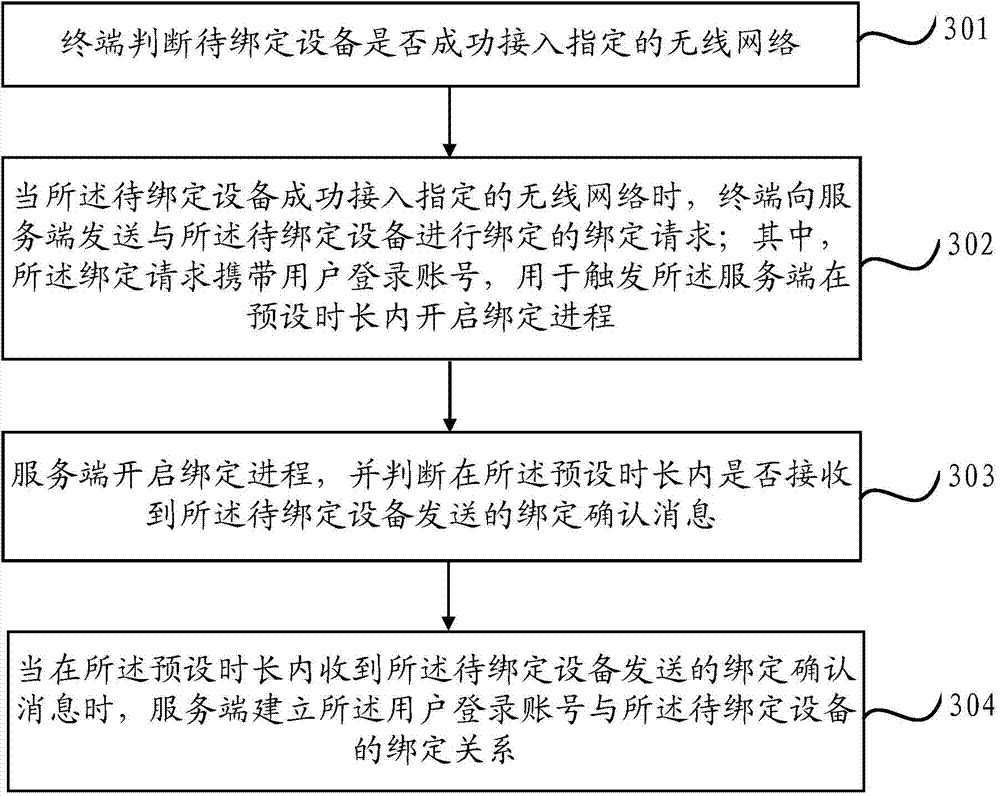
The invention discloses a device binding method. The method comprises the steps of judging whether a to-be-bound device accesses an assigned wireless network successfully; when the to-be-bound device accesses the assigned wireless network successfully, sending a binding request to bind with the to-be-bound device to a server side, wherein the binding request carries a login account of a user, which is used for triggering the server side to start a binding process in a preset time period, so that the server side receives binding acknowledgement information sent by the to-be-bound device in the preset time period, and then establishes a binding relation between the login account of the user and the to-be-bound device. The method can simplify the binding process, and prevents wrong binding so as to improve the safety of the device binding process.
Owner:XIAOMI INC
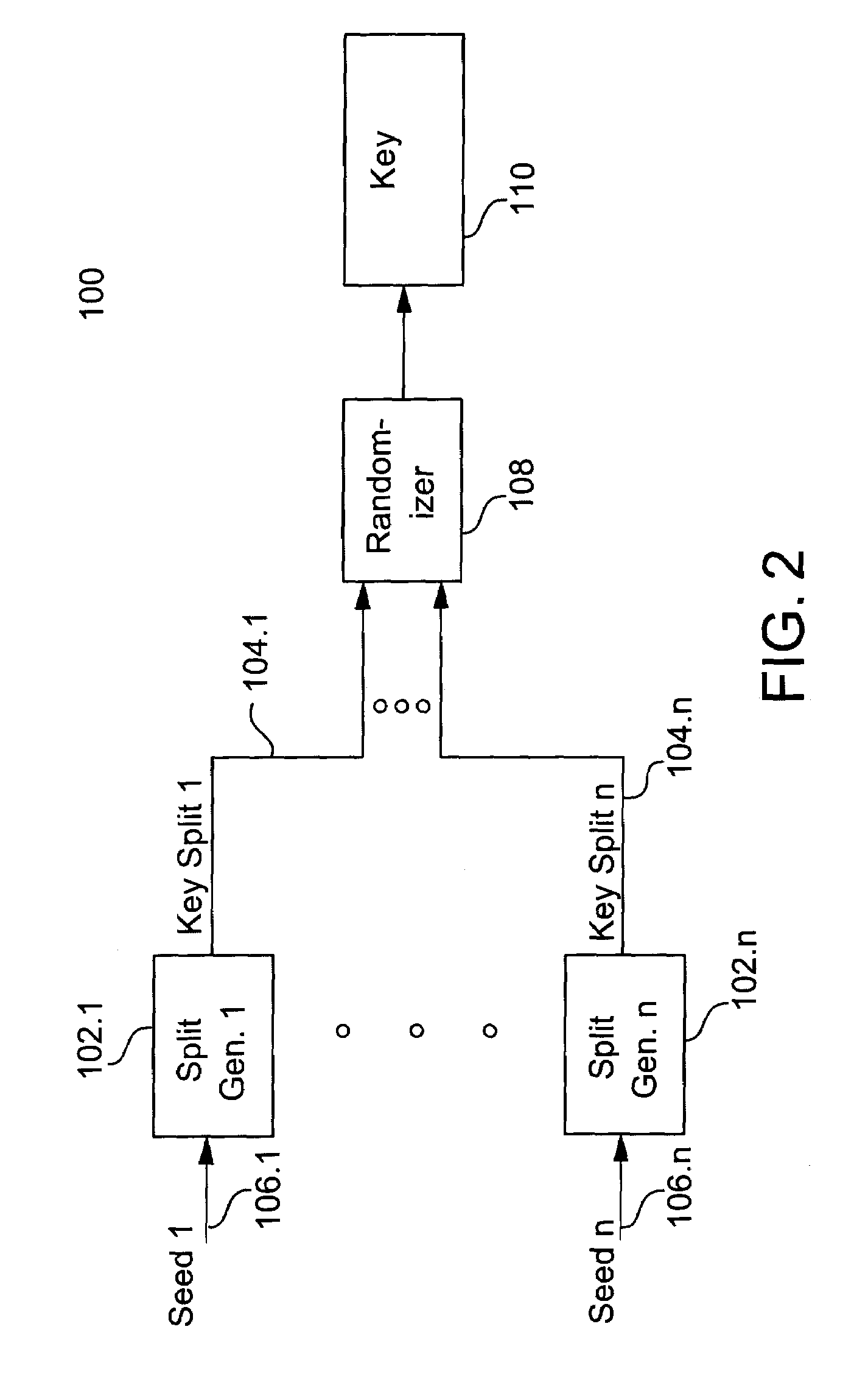
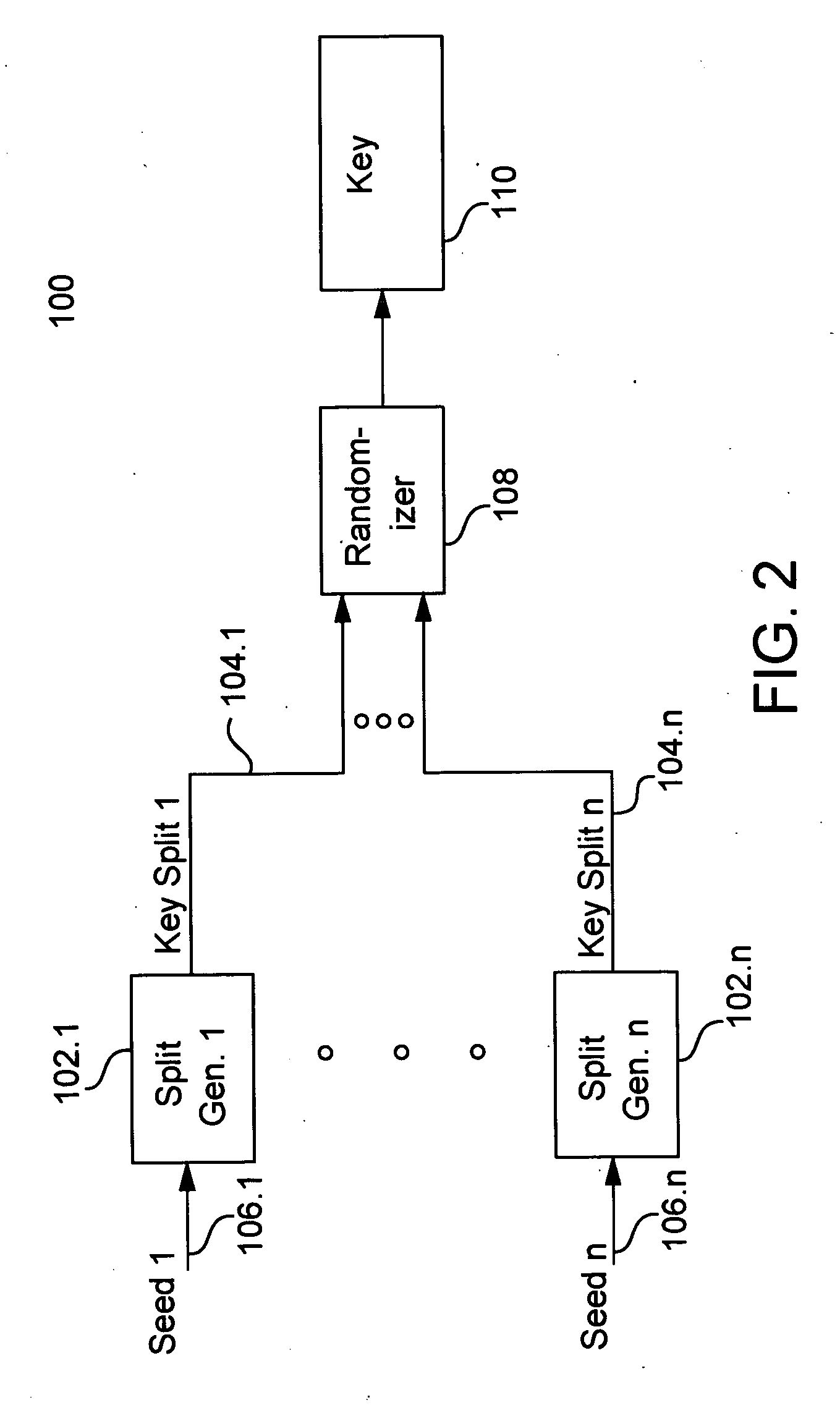
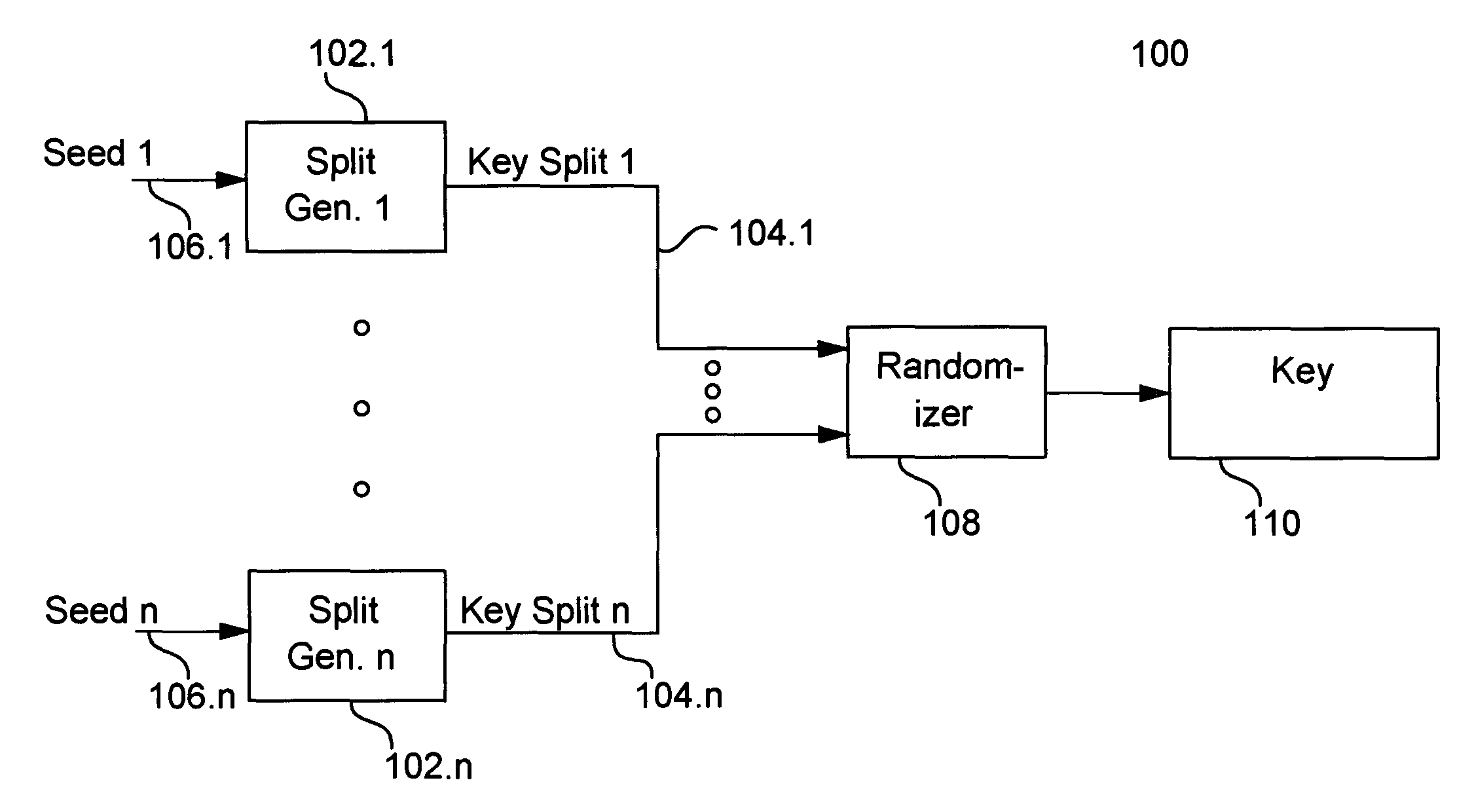
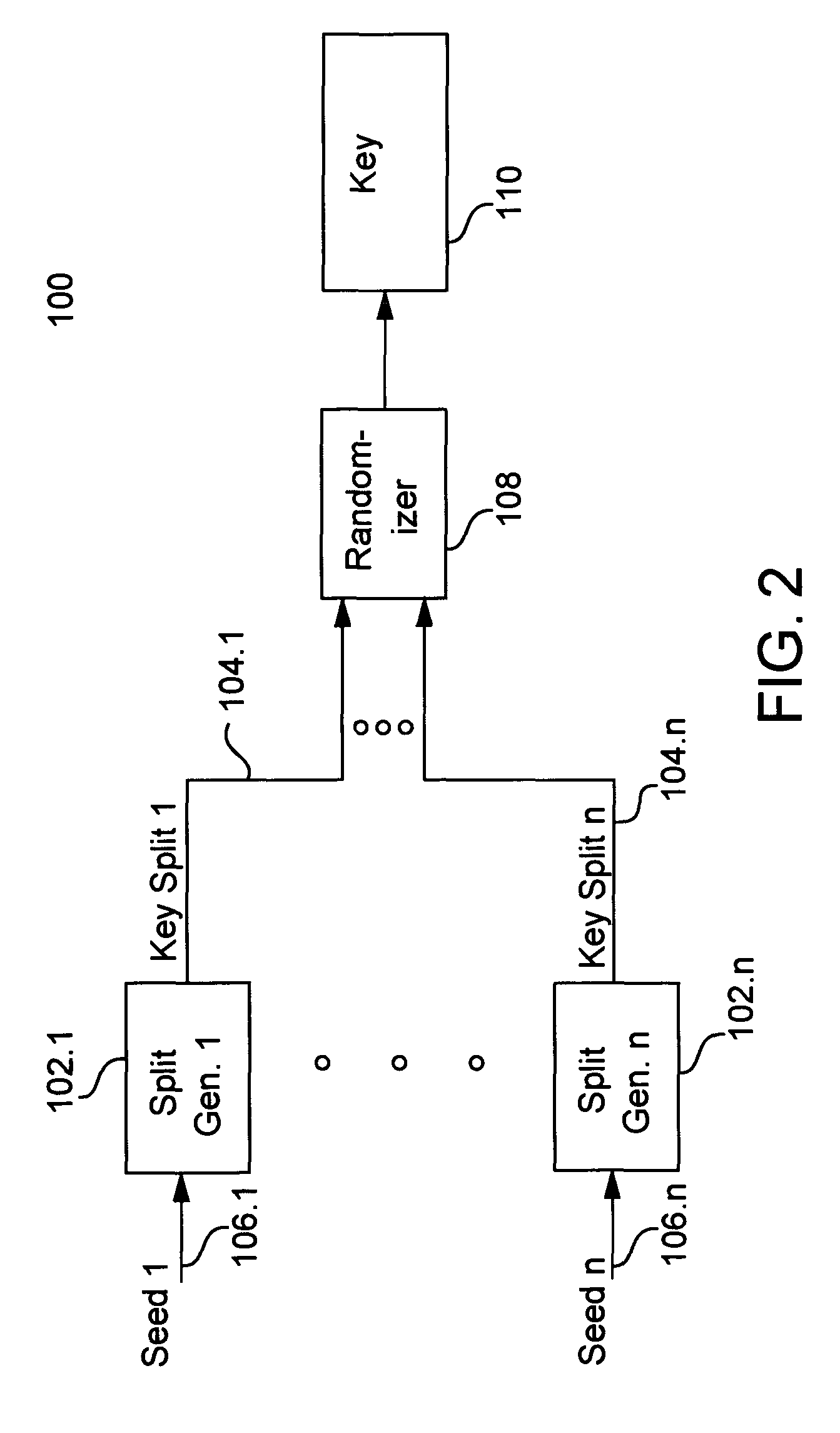
Cryptographic key split binding process and apparatus
InactiveUS7079653B2Key distribution for secure communicationMultiple keys/algorithms usageBiometric dataAuthorization
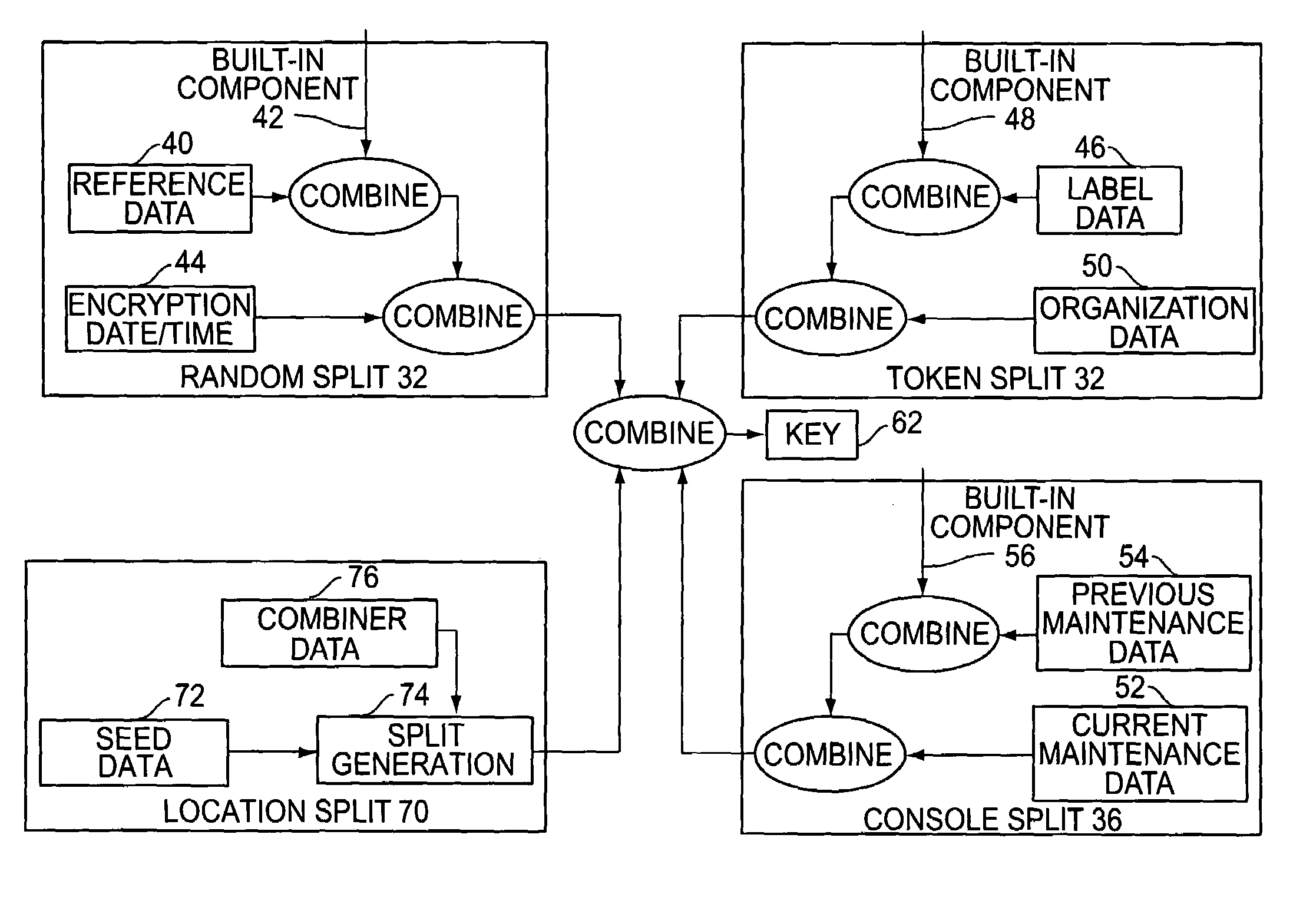
A cryptographic key split combiner includes a number of key split generators for generating cryptographic key splits from seed data, and a key split randomizer for randomizing the key splits to produce a cryptographic key. The key split generators can include a random split generator for generating random key splits, a token split generator for generating token key splits based on label data, a console split generator for generating console key splits based on maintenance data, a biometric split generator for generating biometric key splits based on biometric data, and a location split generator for generating location key splits based on location data. Label data can be read from storage, and can include user authorization data. A process for forming cryptographic keys includes randomizing or otherwise binding the splits to form the key.
Owner:TECSEC
Bidirectional shape memory polymer composite material and preparation method thereof
InactiveCN101164770ALarge deformation rateEasy to useLamination ancillary operationsSynthetic resin layered productsPolymer scienceMemory effect
The present invention relates to a polymer composite material with bidirectional shape memory effect and its preparation method. It is characterized by that said polymer composite material is made up by using polymer material with shape memory function and elastric material which can be actively reverted through a certain superimposing and binding process. Said polymer composite material has bidirectional shape memory effect. The shape memory reversion temperature range of said polymer composite material is large, the different shape memory polymers can be selected and used, the bidirectionalshape memory function with different shape reversion temperature can be obtained. The bidirectional shape memory property also can be obtained by regulating thickness of shape memory polymer and thickness of elastic material. Besides, said polymer composite material has good corrosion resistance, electroinsulating property and heat-insulating effect.
Owner:THE HONG KONG POLYTECHNIC UNIV
Cryptographic key split binding process and apparatus
InactiveUS20070014406A1Key distribution for secure communicationDigital data processing detailsBiometric dataAuthorization
A cryptographic key split combiner includes a number of key split generators for generating cryptographic key splits from seed data, and a key split randomizer for randomizing the key splits to produce a cryptographic key. The key split generators can include a random split generator for generating random key splits, a token split generator for generating token key splits based on label data, a console split generator for generating console key splits based on maintenance data, a biometric split generator for generating biometric key splits based on biometric data, and a location split generator for generating location key splits based on location data. Label data can be read from storage, and can include user authorization data. A process for forming cryptographic keys includes randomizing or otherwise binding the splits to form the key.
Owner:TECSEC
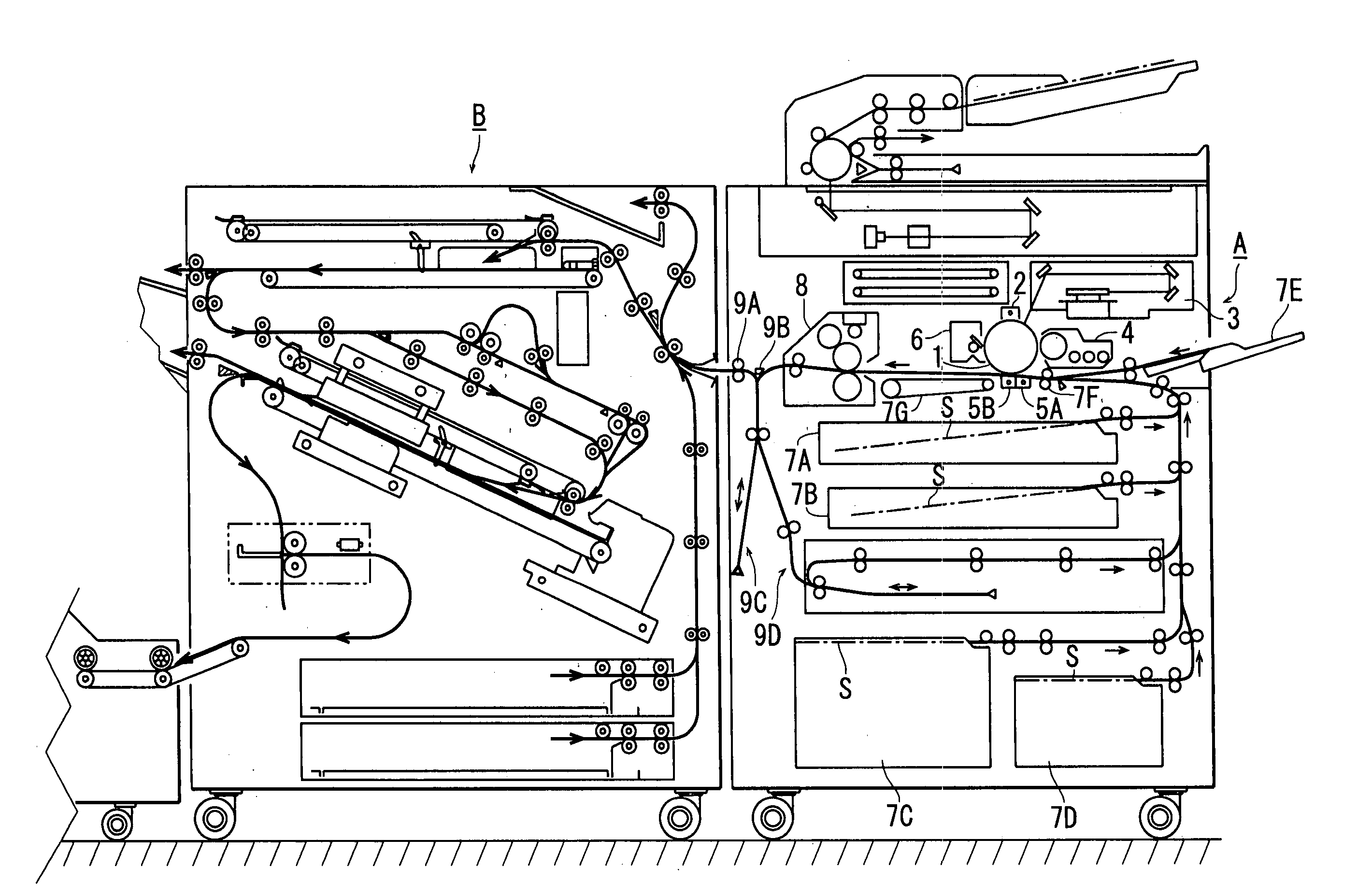
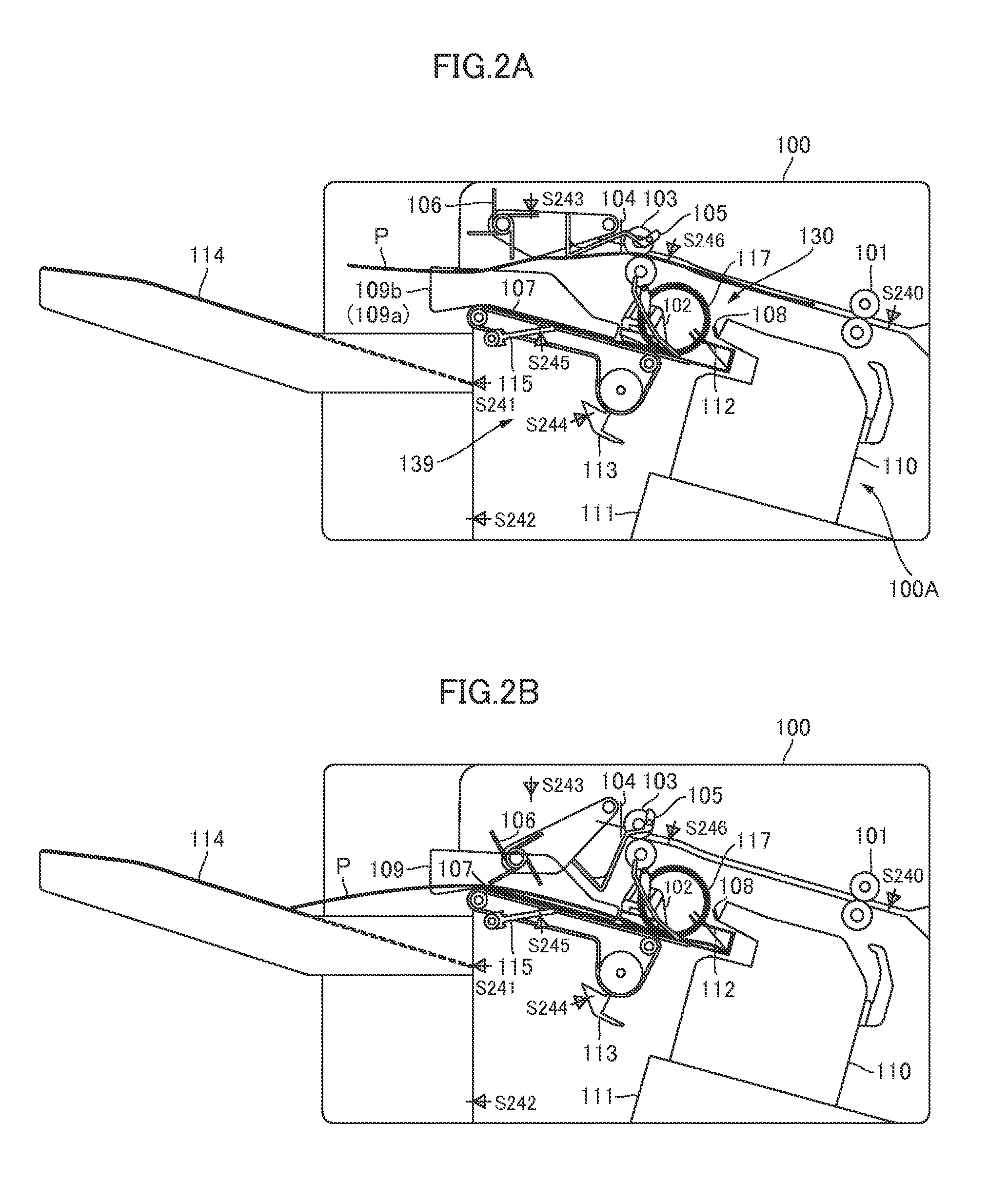
Sheet postprocessing apparatus for use with image forming apparatus and folding method
ActiveUS7052005B2Avoid damageImprove fold qualityMechanical working/deformationFolding thin materialsPunchingImage transfer
This invention relates to a sheet postprocessing apparatus for executing postprocessing including a punching process, folding process, binding process, and the like, midway along a sheet convey path, for sheets discharged from an image forming apparatus, and a folding method. This sheet postprocessing apparatus includes a sheet folding section having the first and second folding sections which are arranged in series in a sheet convey direction to execute folding processes for sheets. The sheet folding section is configured such that the first folding section performs the first folding process in a Z-fold process, the first folding process in an internal three-fold process, and a center folding process with an image-transferred surface facing outside, and the second folding section performs the second folding process in the Z-fold process, the second folding process in the internal three-fold process, and a center folding process with an image-transferred surface facing inside.
Owner:KONICA CORP
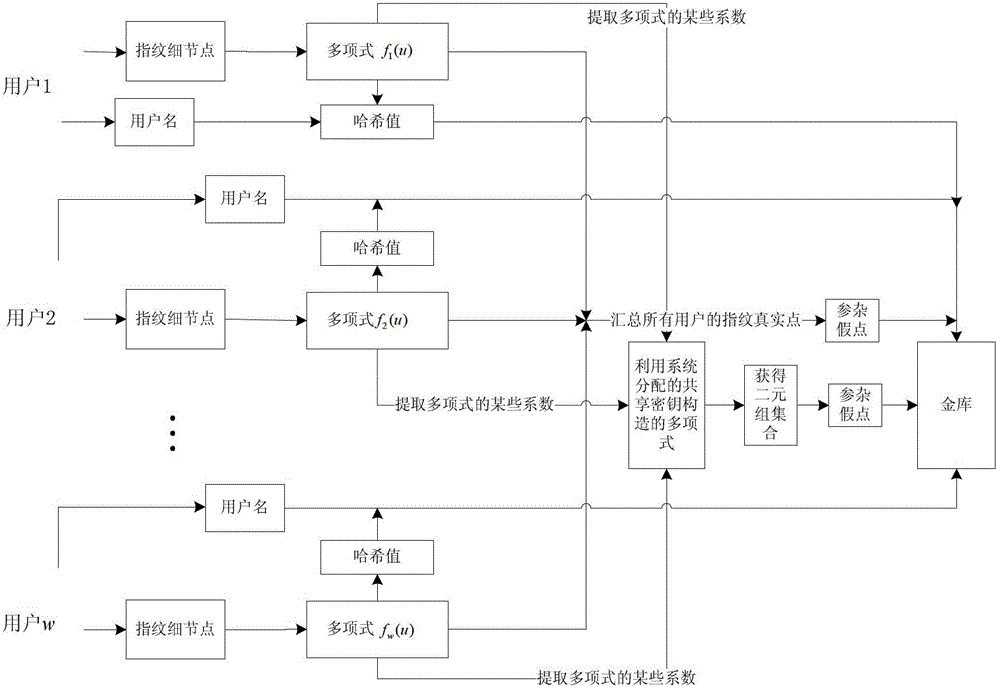
Fingerprint fuzzy vault method based on (k, w) threshold secret sharing scheme
ActiveCN102946310AKey distribution for secure communicationCharacter and pattern recognitionKey distributionKey sharing
The invention relates to a fingerprint fuzzy vault method based on a threshold secret sharing scheme. The method comprises a shared key distribution phase and a shared key reconstruction phase. The shared key distribution phase further comprises a binding process of the fingerprint fuzzy vault and a user subkey, and a shared key binding process. The shared key reconstruction phase further comprises a releasing process of partial user subkeys and a releasing process of the shared key. When the fingerprint fuzzy vault method is used to protect the shared key, the shared key is safely and conveniently released through fingerprint characteristics of the user. The releasing process of the key is very simple, and thus the key sharing scheme is more practical.
Owner:海宁鼎丞智能设备有限公司
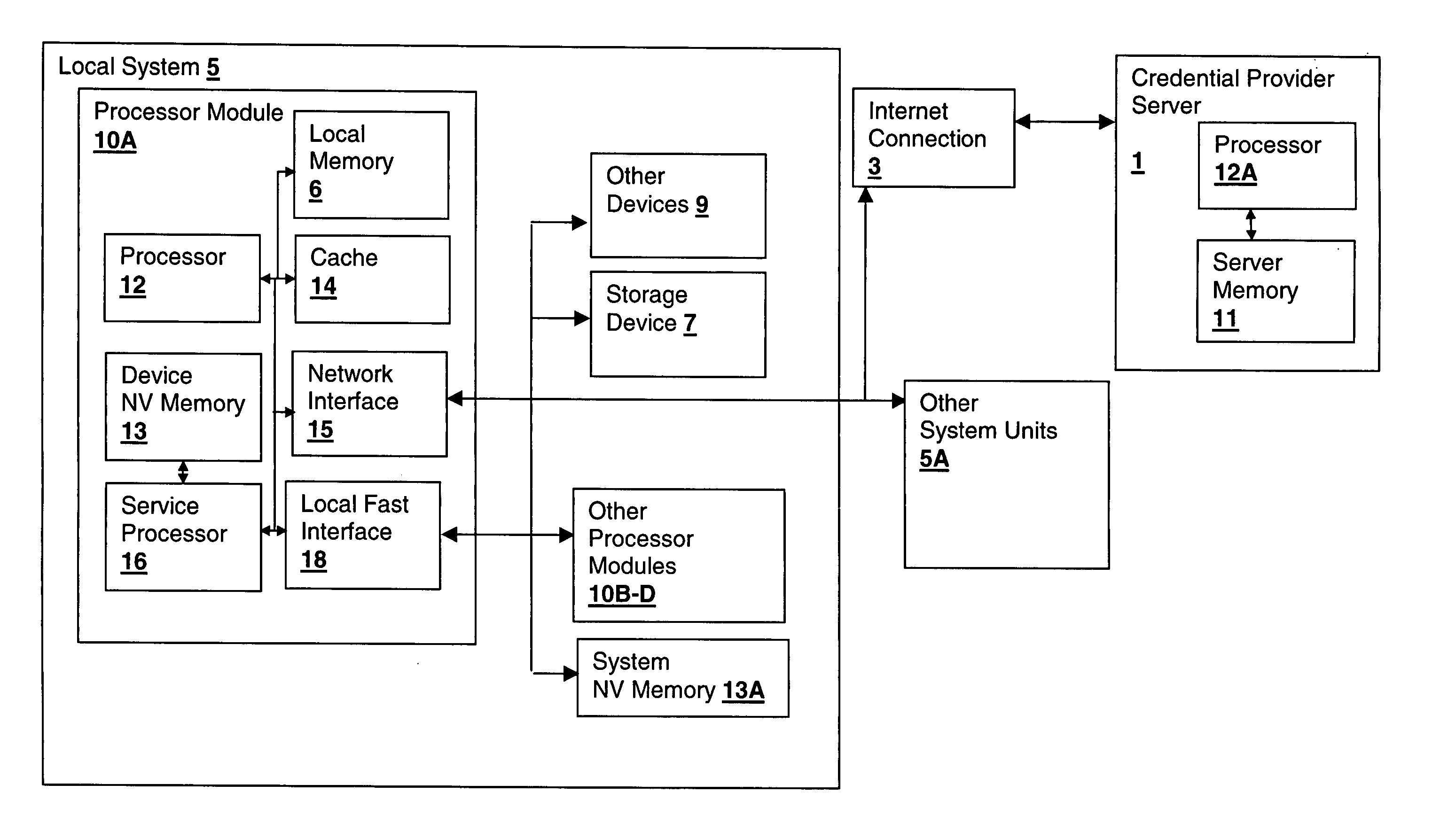
Method and system for verifying binding of an initial trusted device to a secured processing system
ActiveUS20060090070A1User identity/authority verificationPlatform integrity maintainanceOperational systemSystem identification
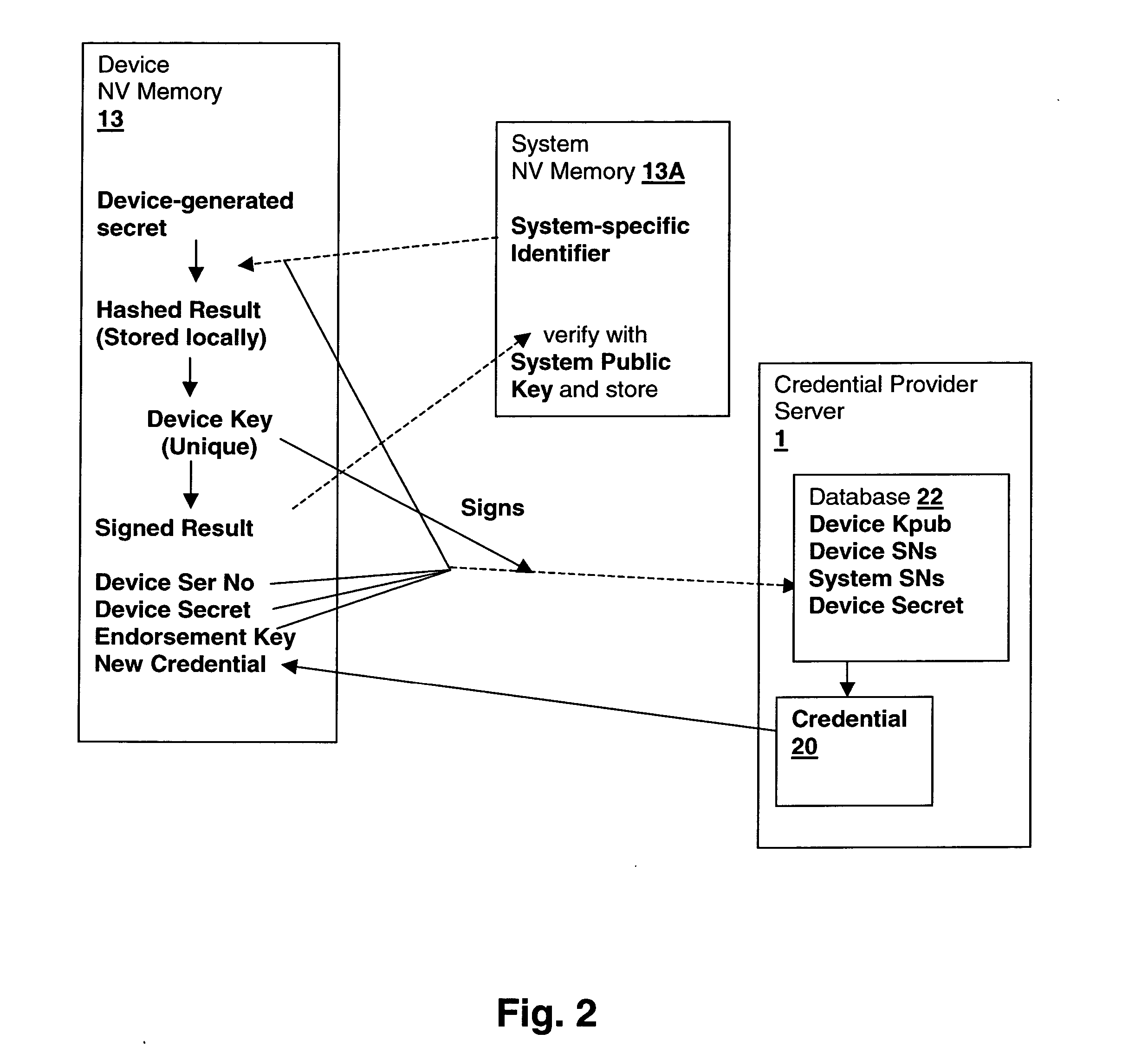
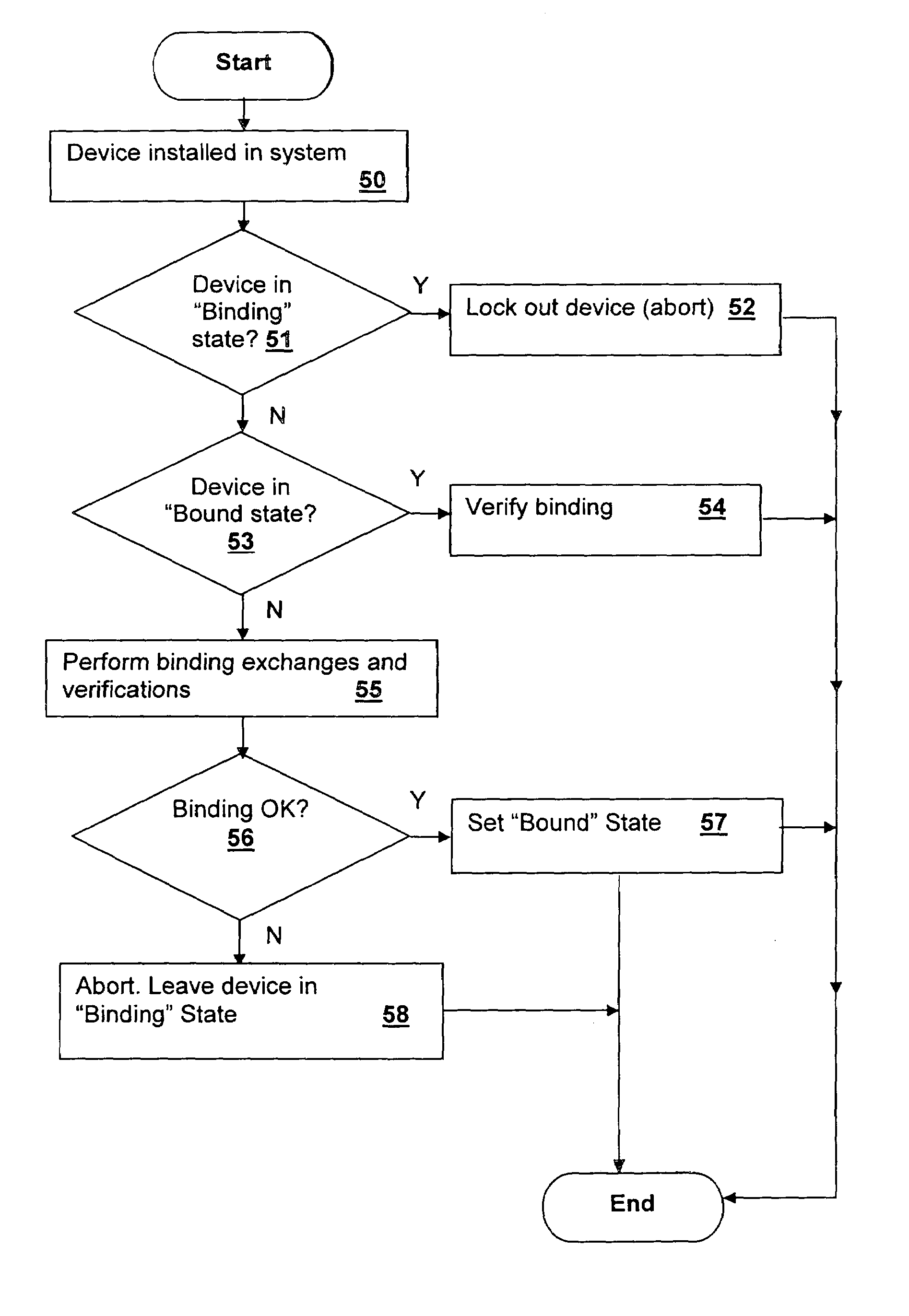
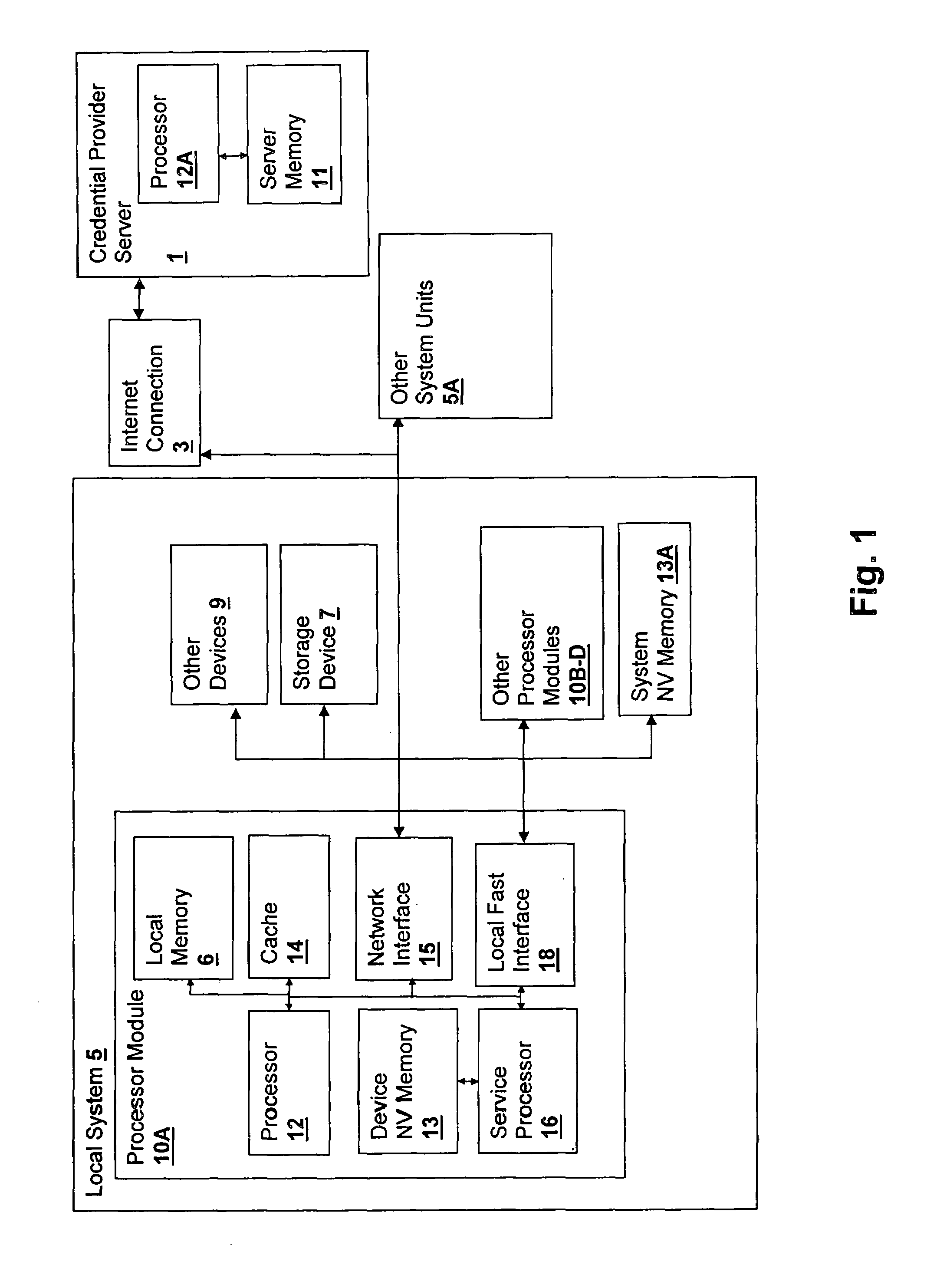
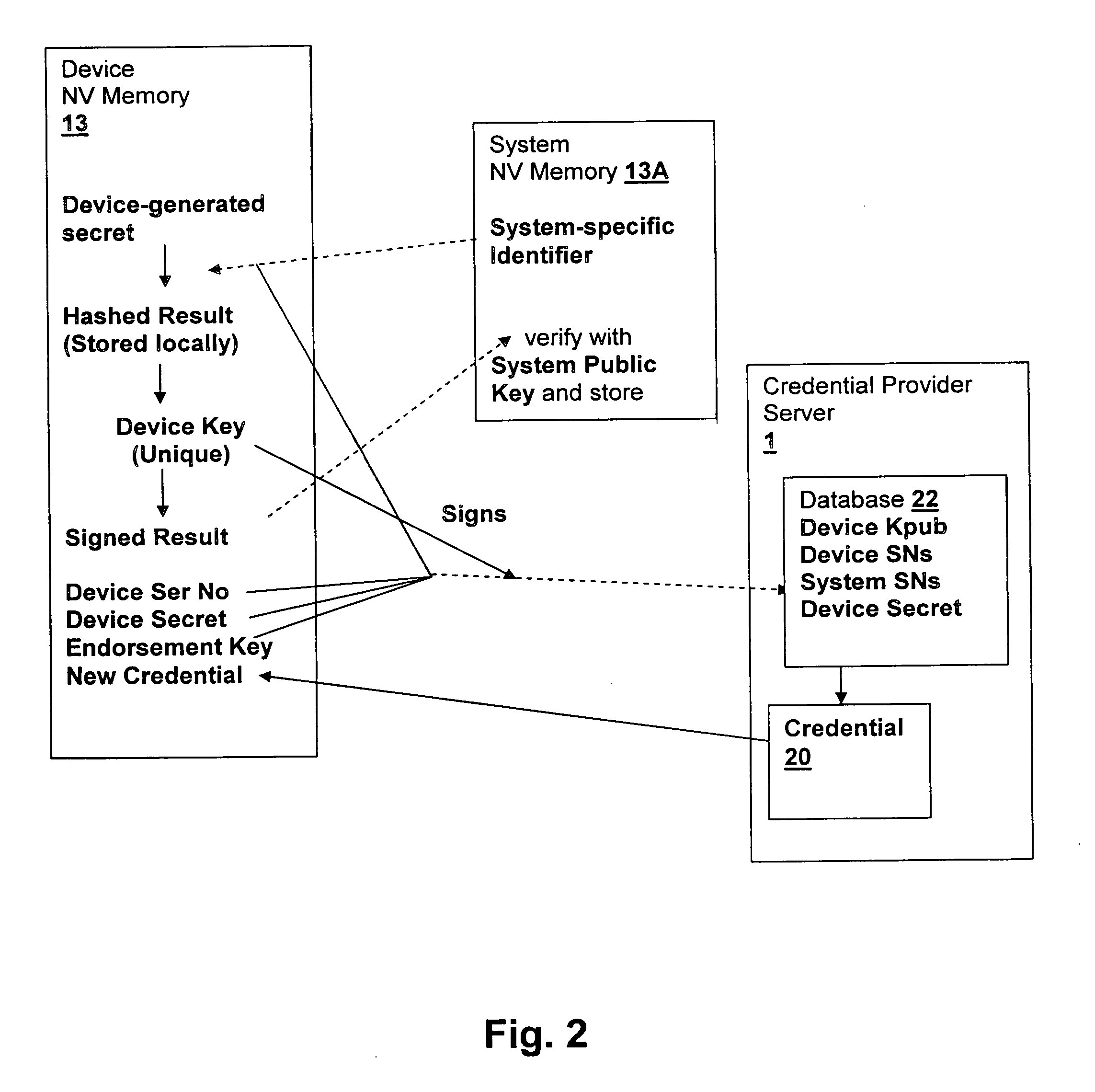
A method and system for verifying binding of an initial trusted device to a secured processing system binds an initial device or replacement when no binding information is available from another device in the system. A platform credential is issued only when a valid binding is verified, by sending a proof of binding to a credential provider, such as the manufacturer. The method secures against security breaches that can occur when a device is removed from the system during the binding process. The binding information is generated in the device upon installation and includes system identification information so that at each initialization, upon return of binding information from the system to the device, the device can ensure that it is installed in the proper system and abort operation if the system does not match.
Owner:LENOVO GLOBAL TECH INT LTD
Intelligent refrigerator netting-in method and system, intelligent refrigerator, intelligent terminal and server
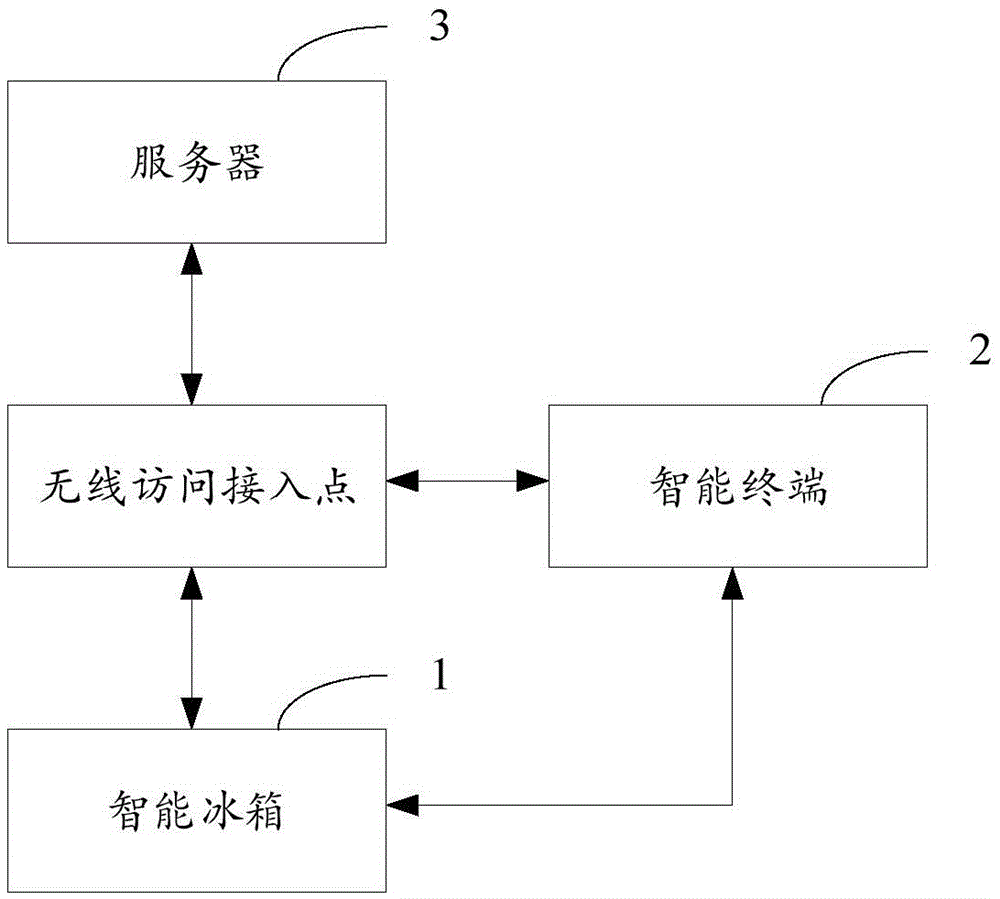
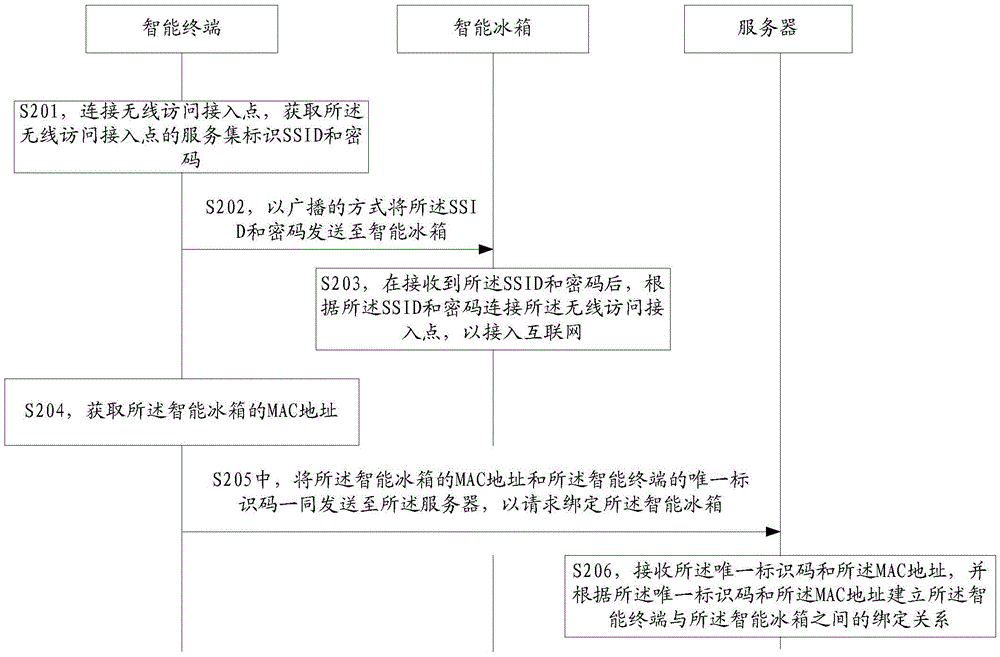
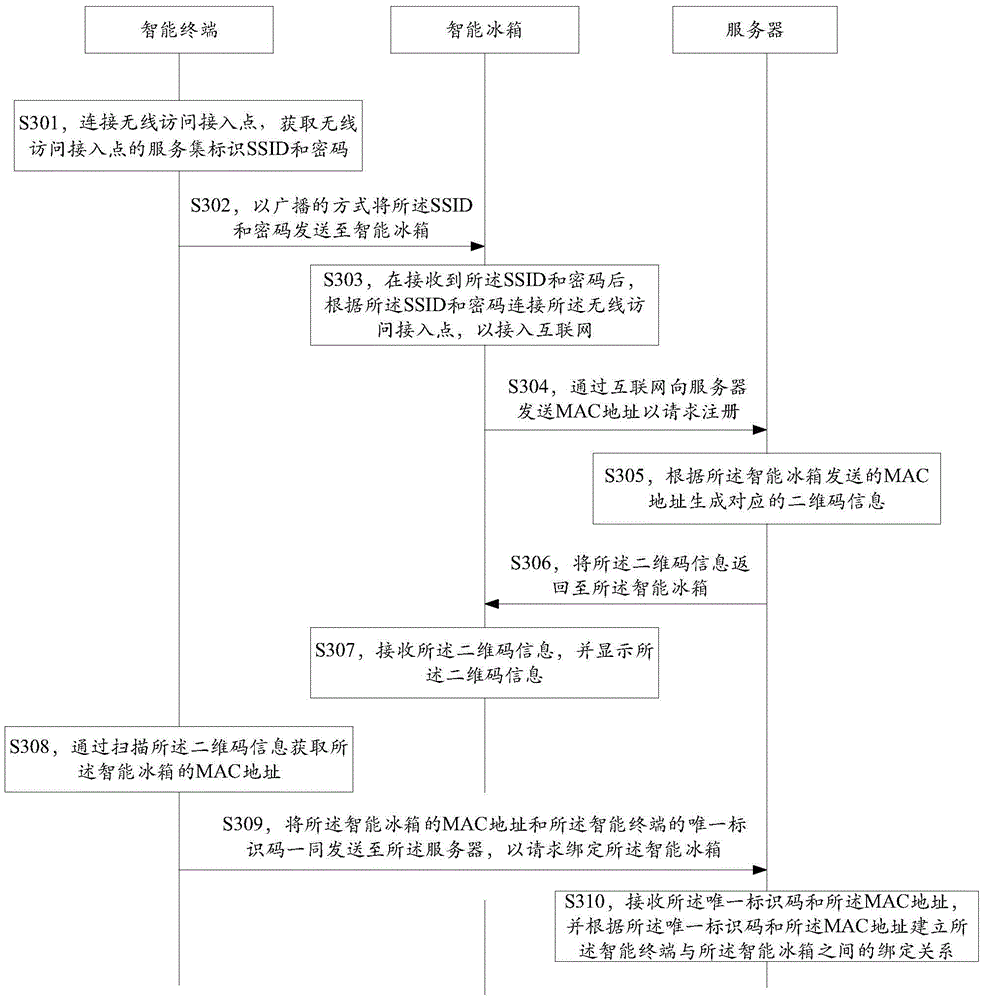
InactiveCN105546931AQuick registrationFast bindingDomestic cooling apparatusLighting and heating apparatusPasswordThe Internet
The invention is suitable for the technical field of communication, and provides an intelligent refrigerator netting-in method and system, an intelligent refrigerator, an intelligent terminal and a server. The netting-in method includes the steps that the intelligent terminal is connected with a wireless access point to obtain service set identifiers and passwords of the wireless access point and transmit the service set identifiers and the passwords to the intelligent refrigerator in a broadcast manner; after receiving the service set identifiers and the passwords, the intelligent refrigerator is connected with the wireless access point according to the service set identifiers and the passwords so as to be connected into the internet; the intelligent terminal obtains an MAC address of the intelligent refrigerator and jointly transmits the MAC address of the intelligent refrigerator and a unique identification code of the intelligent terminal to the server so as to request for binding with the intelligent refrigerator; and the server builds the binding relationship between the intelligent terminal and the intelligent refrigerator according to the unique identification code and the MAC address. Rapid netting-in, registering and binding of the intelligent refrigerator are achieved, and the netting-in and binding processes of the intelligent refrigerator are simplified.
Owner:TCL CORPORATION
High temperature TFT (Thin Film Transistor) composite flexible substrate, preparation method of the high temperature TFT composite flexible substrate and flexible display device preparation method
InactiveCN105789242ASmall coefficient of thermal expansionHigh modulus of elasticitySolid-state devicesSemiconductor/solid-state device manufacturingDisplay deviceThermal expansion
The invention discloses a high temperature TFT (Thin Film Transistor) composite flexible substrate. The flexible substrate comprises a flexible substrate layer and reinforcement skeletons. Groove parts are arranged in the surface of the flexible substrate layer for preparing a display device, wherein the groove parts fit with reinforcement skeletons; the reinforcement skeletons are embedded in the flexible substrate layer through the groove parts; and a surface flat layer is also arranged on the surface of the flexible substrate layer for preparing the display device. According to the high temperature TFT composite flexible substrate, through increasing a skeleton support structure in the flexible substrate layer, the coefficient of thermal expansion of the flexible substrate can be reduced, the elastic modulus of the substrate can be increased, and the problems that the substrate made of a high-molecular polymer material deforms and warps in a high temperature technological condition can be effectively solved. Through coating the surface flat layer on the surface of the flexible substrate layer equipped with the reinforcement skeletons, the surface flat precisions of the flexible substrate in preparation of the flexible device tend to be consistent, the processing precision of the TFT on the flexible substrate is improved, and the alignment errors resulting from the deformation of the flexible substrate in an IC binding process are reduced.
Owner:SHENZHEN TCL IND RES INST
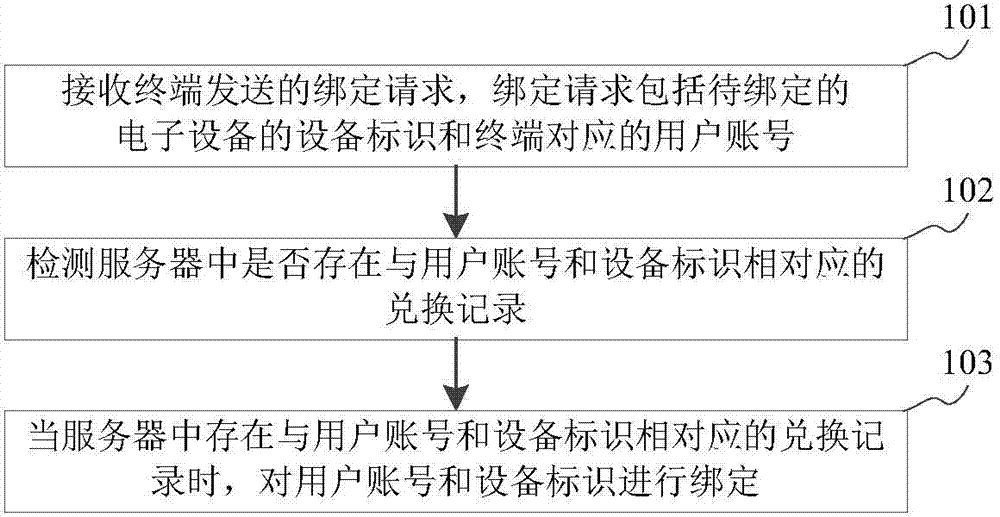
Method and device for binding equipment
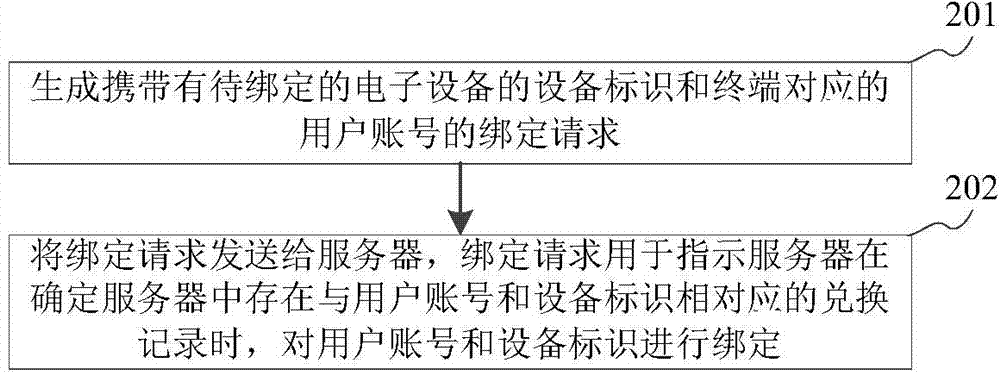
ActiveCN104780155ASolve efficiency problemsImprove binding efficiencyTransmissionSecurity arrangementComputer terminalComputer science
The present disclosure relates to a method and a device for binding equipment, belonging to the technical field of computer, wherein the method comprises the steps as follows: receiving a binding request transmitted by a terminal, wherein the binding request comprises a device identification of electronic equipment to be bound and a user account corresponding to the terminal; detecting whether there is conversion record corresponding to the user account and the device identification in a server; and binding the user account and the device identification when there is conversion record corresponding to the user account and the device identification in the server. The method and the device solve the problem that the binding process is complicated and inefficient because the electronic equipment only can be determined as the electronic equipment owned by the user according to the operation of the user to the electronic equipment and improves the binding efficiency of the equipment.
Owner:XIAOMI INC
Method and a system for manufacturing printed products
ActiveUS20070179037A1Length of may varyMechanical working/deformationBoxes/cartons making machineryEngineeringDigital printing
For manufacturing books having different sizes and comprising a plurality of text pages constituting a book block, a web of material having a given width is sequentially printed in a digital printing station. The printed web of material is then provided either with one weakening line extending parallel to the longitudinal direction of the web of material or with two weakening lines arranged spaced apart and extending parallel to the longitudinal direction of the web of material. Thereafter the printed web of material is transversely cut to produce individual text sheets which are provided with either one weakening line or two weakening lines. These text sheets are then longitudinally folded along the either one weakening line or in sequence along each of the two weakening lines. The folded text sheets belonging to a particular book block are stacked to a stack. The stacks are either temporarily stored for a later binding process or directly supplied to a binding station.
Owner:EPAC TECH
Credible device with active control function and authentication method thereof
ActiveCN102063593AEnsure safetyAchieve authenticationPlatform integrity maintainanceApplication softwareActive measurement
The invention discloses a credible device with an active control function and an authentication method thereof, relating to the field of information security. A credible platform control module with the active control function and a hardware device are connected to a credible platform of the credible device with the active control function, wherein the hardware device are separated into a credible hardware device and an incredible hardware device by the credible platform control module through the active control function, and the credible platform control module is internally provided with hardware units such as an active measurement engine, a control judgment engine, a work mode customizing engine, a credible control policy configuration engine and the like to realize active check on theworking condition configuration information of the hardware device, control policy configuration information, a firmware code and the working condition of a circuit. Mutual binding between the credible platform and the credible hardware is realized through combing the credible platform control module and a credible pipeline technology, the binding process of the credible platform control module and the credible hardware is completely transparent to an operating system and an application program, and the operating system cannot bypass or intervene the process of binding the credible hardware by the credible platform.
Owner:BEIJING UNIV OF TECH
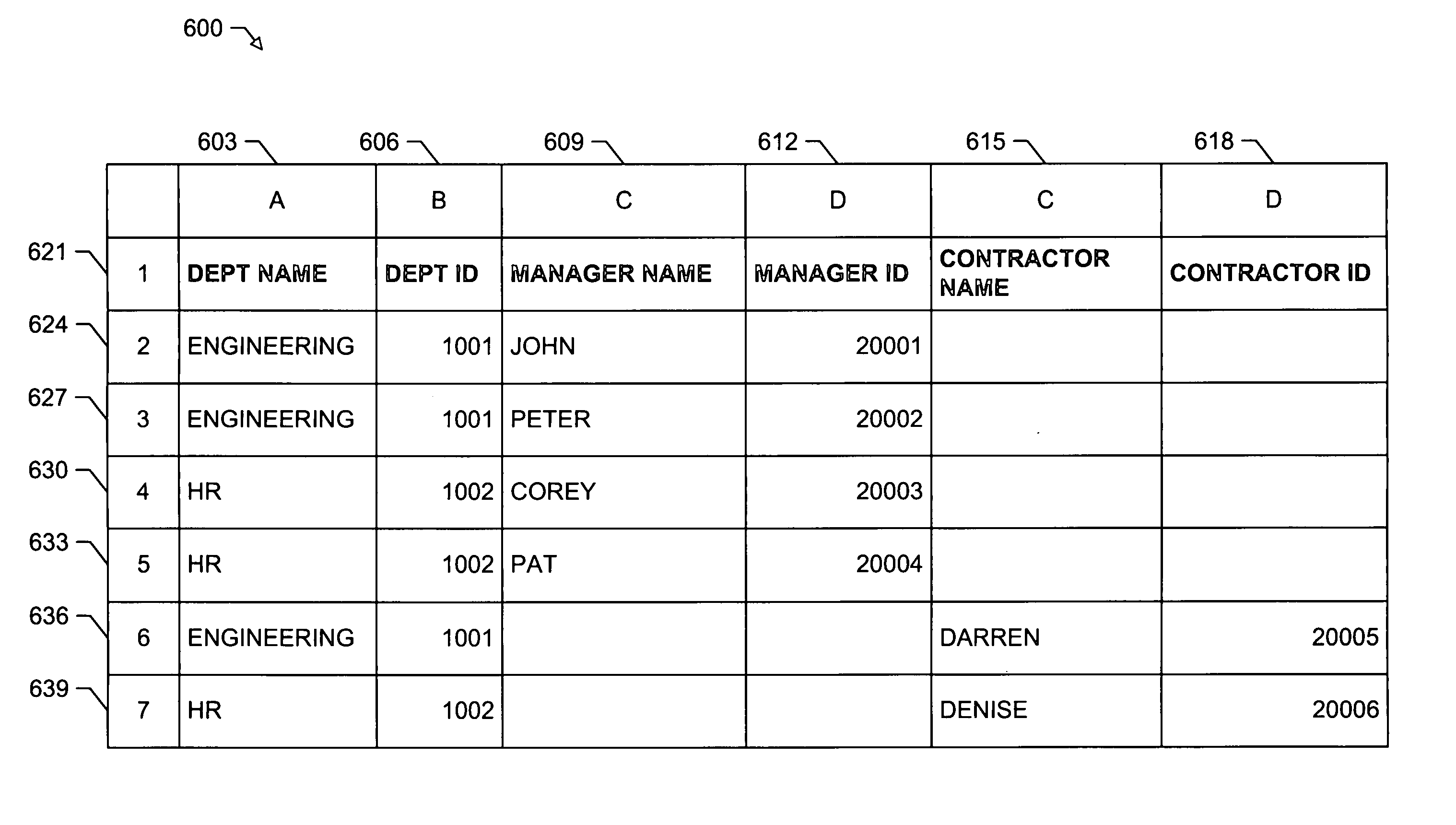
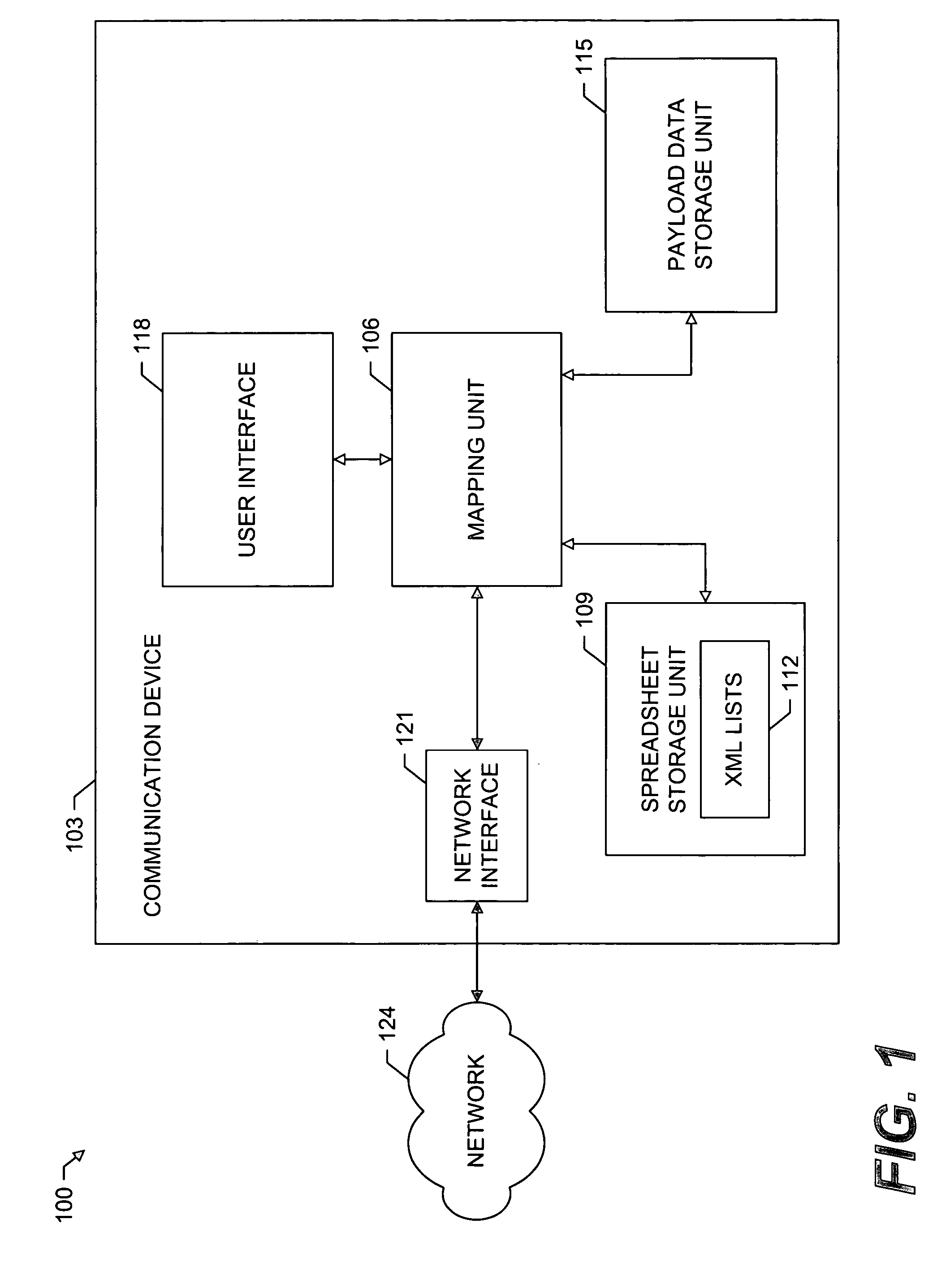
System and method for schemaless data mapping with nested tables
InactiveUS20050172217A1Eliminate dependenciesLower potentialText processingSemi-structured data mapping/conversionElectronic formTheoretical computer science
A system and method for mapping payload data to a spreadsheet list. The present invention comprises a system for mapping payload data to a spreadsheet list while supporting the implementation of nested tables, without the use of a schema. After receiving a spreadsheet list, the present invention generates the parent path of each field path defined in the spreadsheet list. The longest parent path may be used to generate a set of nodes from the payload data. If more than one unique parent path qualifies as the longest parent path, then such parent patents may be designated as branch bottom paths. All other parent paths may then be associated with an appropriate branch bottom path. During the binding process, each branch bottom path may be evaluated to generate result nodes, which may be used to obtain the values of the fields of the spreadsheet list.
Owner:MICROSOFT TECH LICENSING LLC
Sheet processing apparatus and image forming apparatus
A staple-less binding unit including a pair of upper and lower teeth binds a sheet bundle which is discharged to an intermediate processing tray by a sheet discharge portion and whose one edge abuts against a rear edge stopper. A control portion switches a binding mode of the staple-less binding unit that implements the binding process on the sheet bundle in a first binding mode of binding the sheet bundle without any staple such that the pair of upper and lower teeth bite across an edge of the sheet bundle and in a second binding mode of binding the sheet bundle without any staple such that the pair of upper and lower teeth do not bite across any edge of the sheet bundle.
Owner:CANON KK
Method and system for verifying binding of an initial trusted device to a secured processing system
ActiveUS7143287B2User identity/authority verificationPlatform integrity maintainanceSafe handlingSystem identification
Owner:LENOVO GLOBAL TECH INT LTD
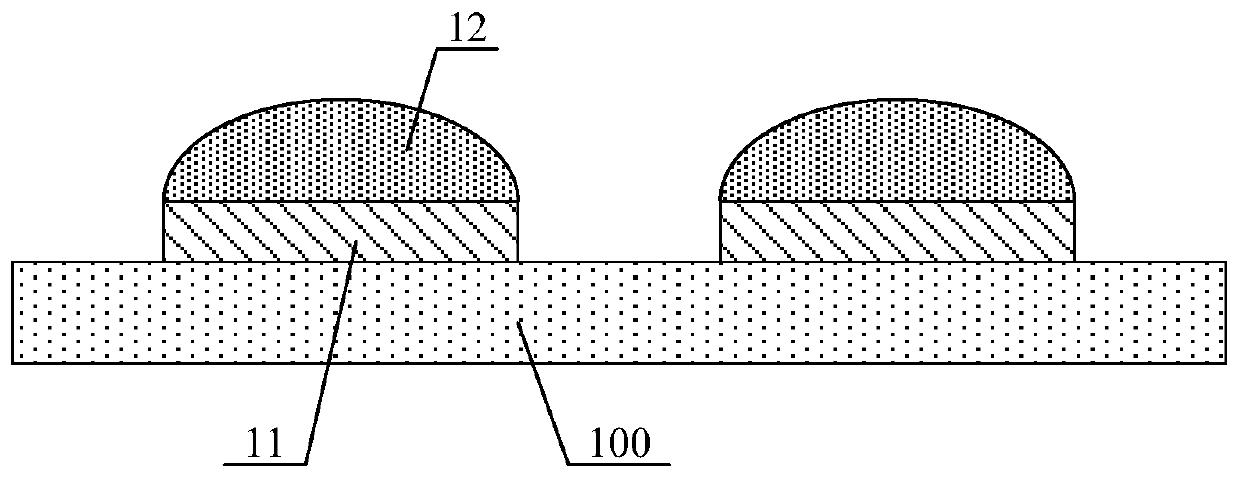
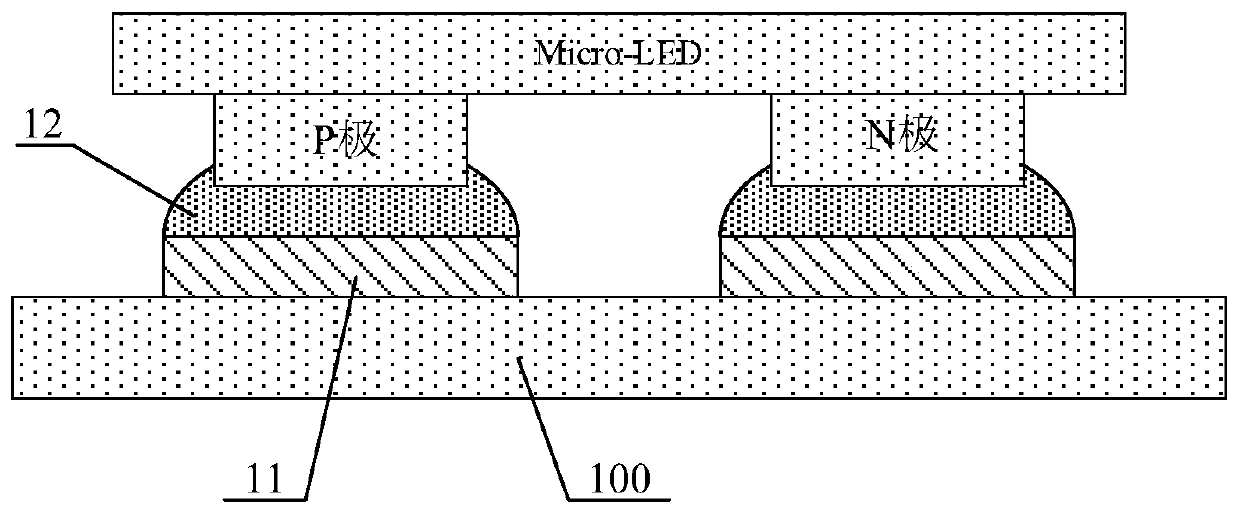
Display substrate, preparation method thereof, and display device
ActiveCN110416248AAvoid short circuitFlow restrictionSolid-state devicesSemiconductor/solid-state device manufacturingDisplay deviceEngineering
The invention discloses a display substrate, a preparation method thereof and a display device. The display substrate includes a driving substrate and a welding pad disposed on the driving substrate.The welding pad is electrically connected to the driving substrate. The display substrate further includes an insulating structural layer disposed on the welding pad, the insulating structural layer is provided with a recess exposing the welding pad, a binding material is received in the recess, and a Micro-LED is electrically connected to the welding pad through the binding material. According tothe display substrate, when the Micro-LED is electrically connected to the display substrate, a dispenser can be controlled to dispense the binding material such as solder paste into the recess, therecess can restrict the binding material from flowing during the binding process, and therefore, the short-circuit of an N-pole and a P-pole of the Micro-LED caused by excessive dispensing can be avoided.
Owner:BOE TECH GRP CO LTD
Cryptographic key split binding process and apparatus
InactiveUS7738660B2Key distribution for secure communicationDigital data processing detailsBiometric dataAuthorization
Owner:TECSEC
Printing apparatus, printing method, and storage medium capable of making quality inspection
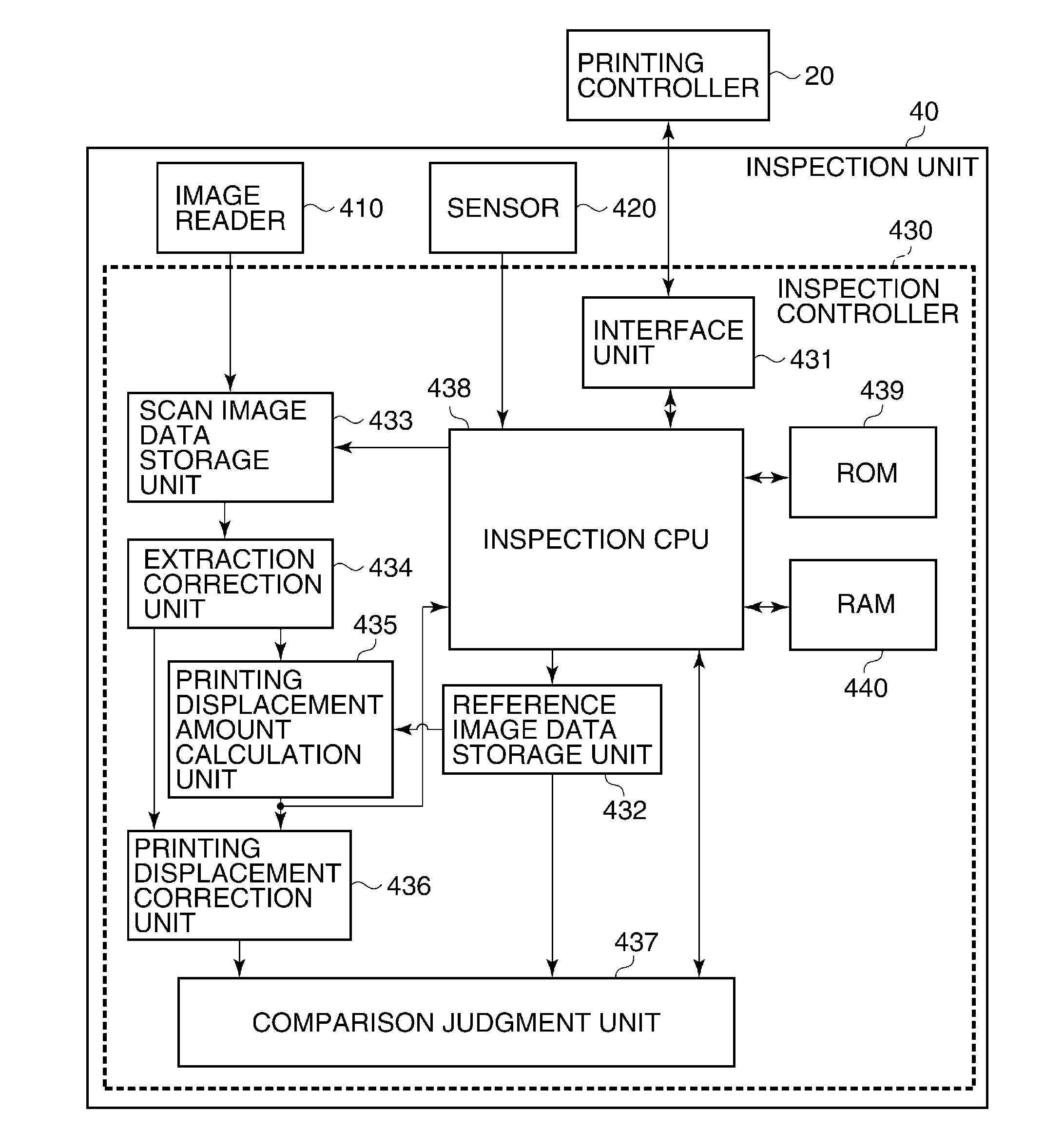
InactiveUS20110179961A1Improve printing qualityReducing printing failure rateInput/output processes for data processingPrinting press partsImaging dataBinding process
A printing apparatus capable of improving the printing quality and at the same time reducing the printing failure occurrence rate. An inspection controller of the printing apparatus causes an image reader to read plural pages, which are printed on a sheet according to first image data from a host computer, and generates second image data based on a result of the reading. The inspection controller detects, based on the first and second image data, an amount of printing displacement on each page printed on the sheet, and determines whether the detected amount of printing displacement on each page falls within an allowable range defined by an allowable value. If a saddle-stitching book-binding process is specified in print settings, the allowable value is changed between particular pages where there is an image in a peripheral area around a folded sheet portion and other pages.
Owner:CANON KK
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com