Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
81 results about "Trusted operating system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
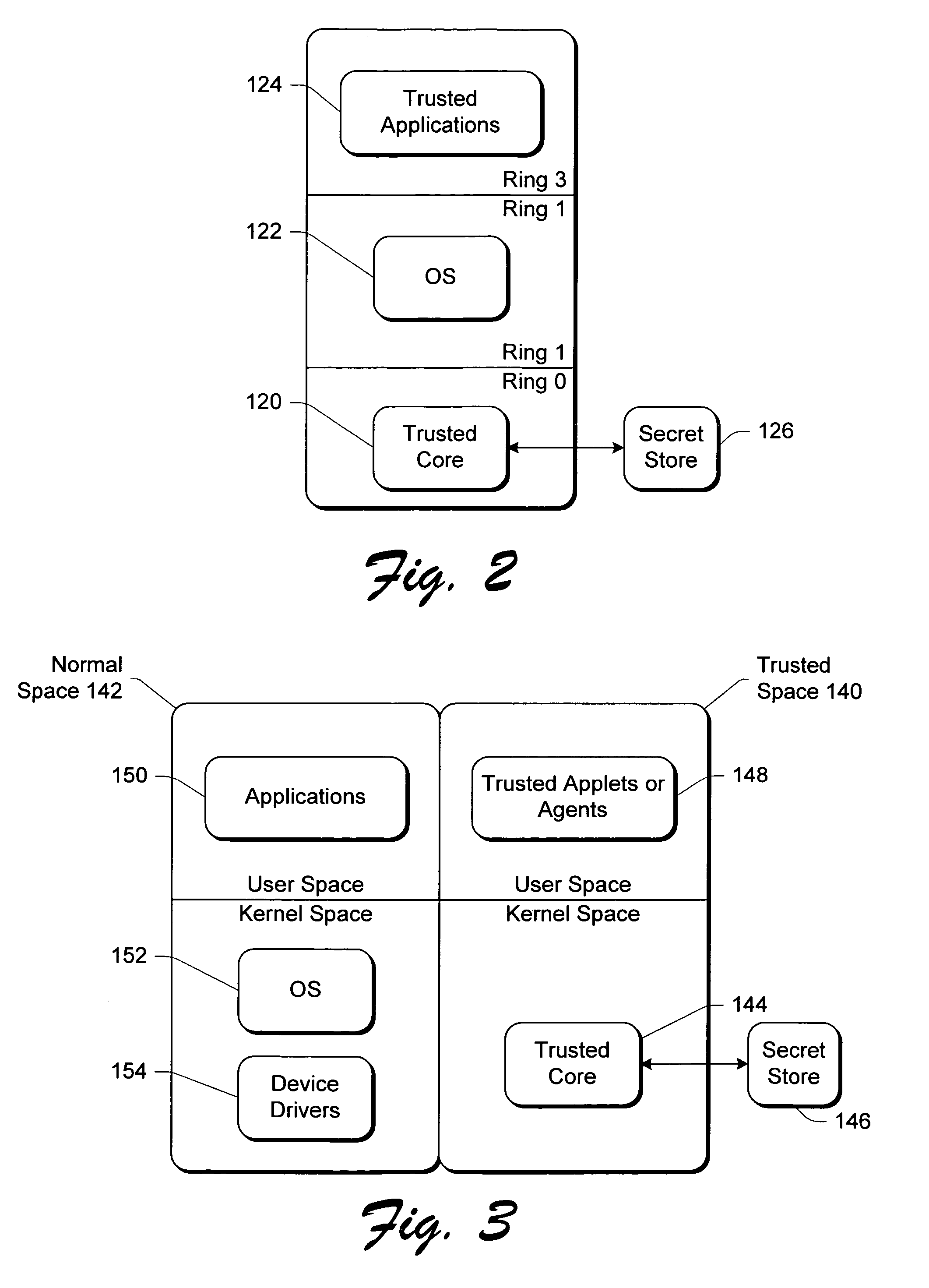
Trusted Operating System (TOS) generally refers to an operating system that provides sufficient support for multilevel security and evidence of correctness to meet a particular set of government requirements.
System and method for the automatic installation and configuration of an operating system
InactiveUS6854112B2Lower deployment costsReduce deployment timeData processing applicationsBootstrappingGeneration processOperational system
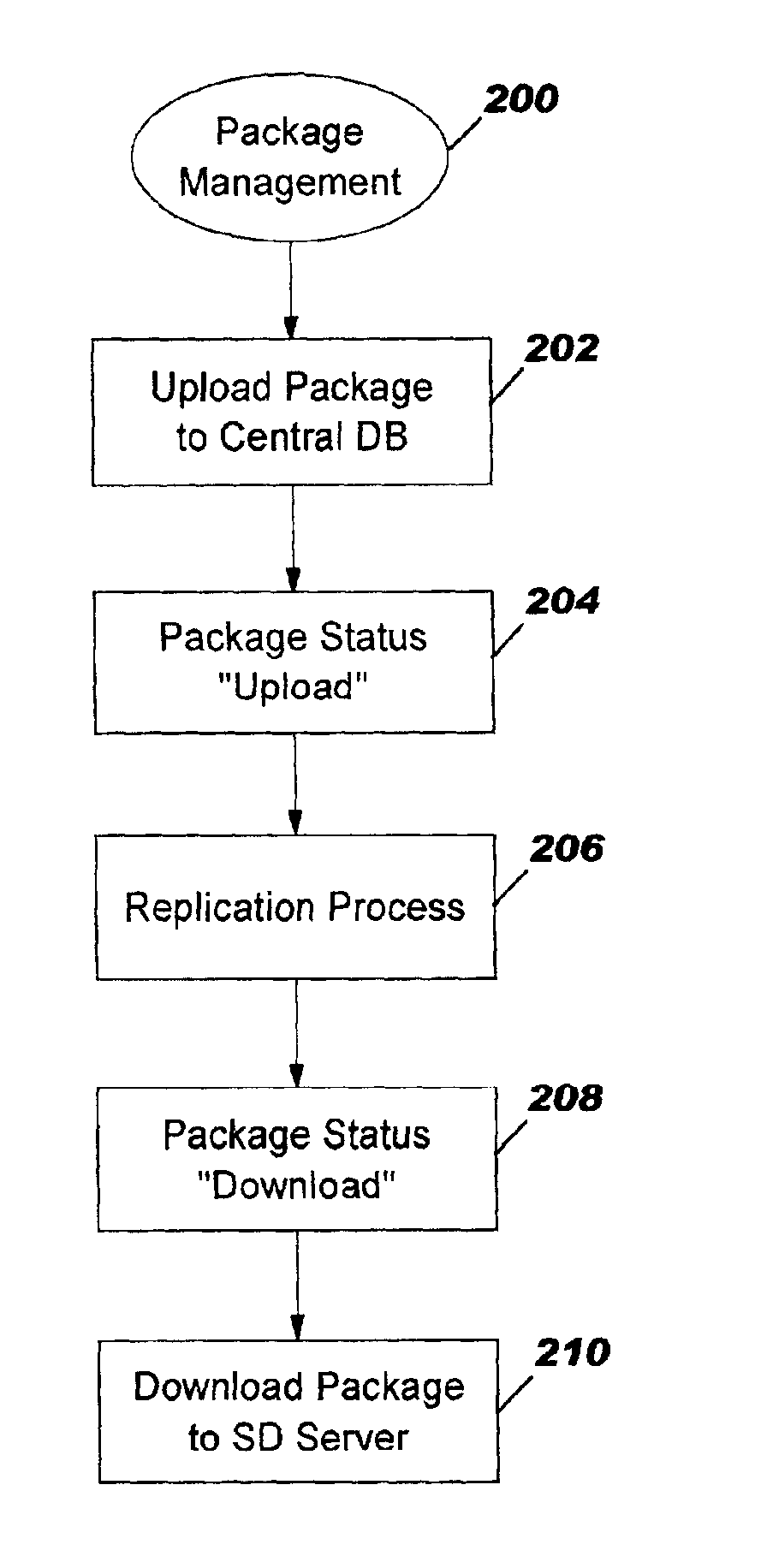
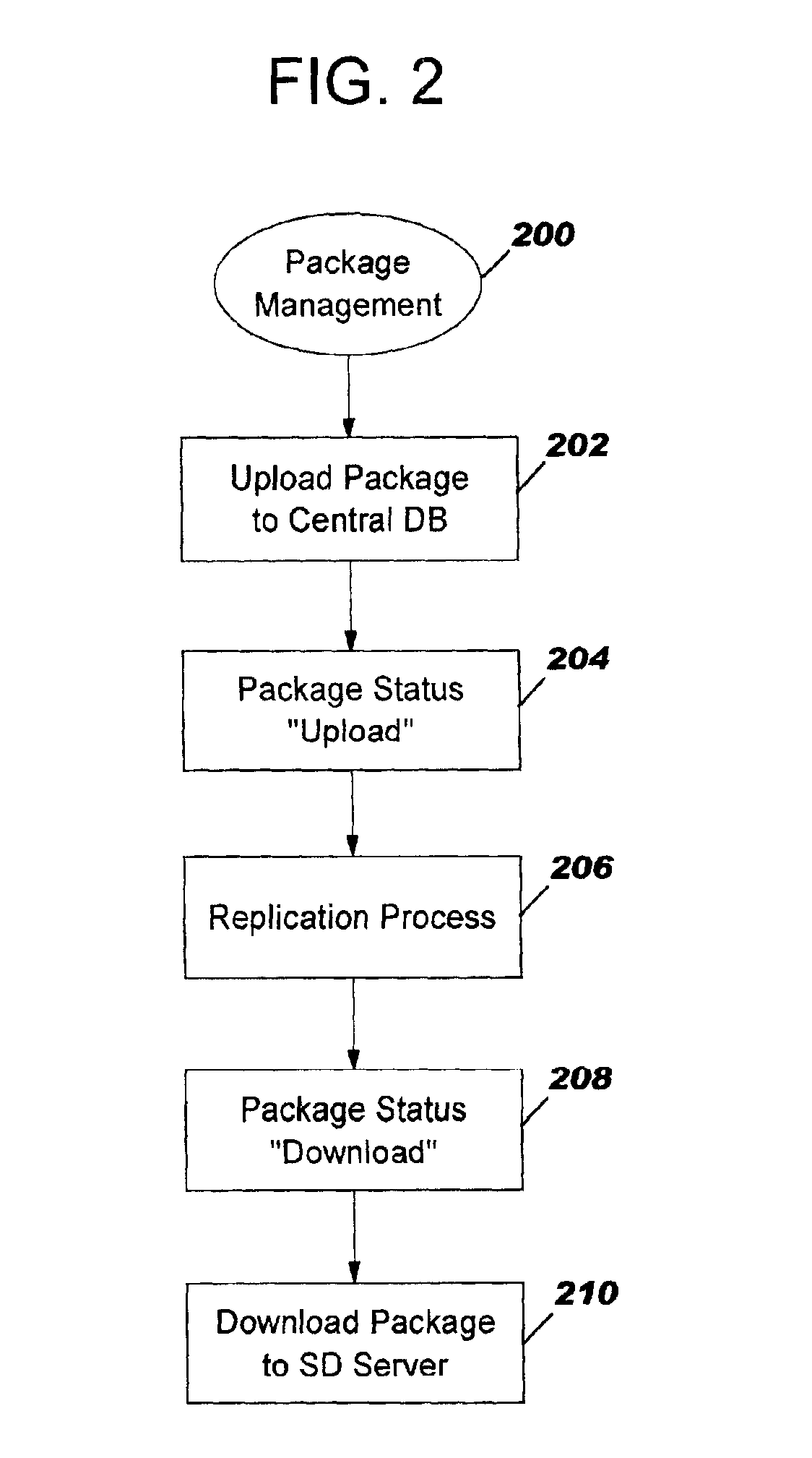
A system and a method for installing and configurating a package including an operating system, software products, and applications on end-user computers connected to server computers in a network. The method is based on a pull deployment model where installation is triggered and performed on site by the end-user, using tools provided by an administrator. Based on a predefined machine function, a generation process generates a source file having required parameters to make the installation, those parameters being stored in a centralized configuration database. Response files needed for the installation are generated in turn. The system allows tracking the installation process and reporting its success or failure to the central database.
Owner:KYNDRYL INC
Managing securely installed applications
ActiveUS20100313196A1Memory loss protectionError detection/correctionOperational systemRandom allocation
Embodiments of the present disclosure provide methods and systems for managing securely installed applications. After installation, an installation framework performs a bind process to correlate the randomly assigned identifier with the unique identifier of the application. The installation framework also manages the execution of the application. When an application is launched, the application framework performs a search for that application's randomly assigned identifier and locates the application's container. The application is then allowed to execute within its container. During execution, the software application may also be restricted in various ways by the installation framework to its dynamic containers. The installer may also work with a trusted operating system component, such as the kernel, to help enforce the container restrictions. In addition, if desired, the use of random identifiers for containers may be used in conjunction with other security mechanisms, such as the use of code signing.
Owner:APPLE INC
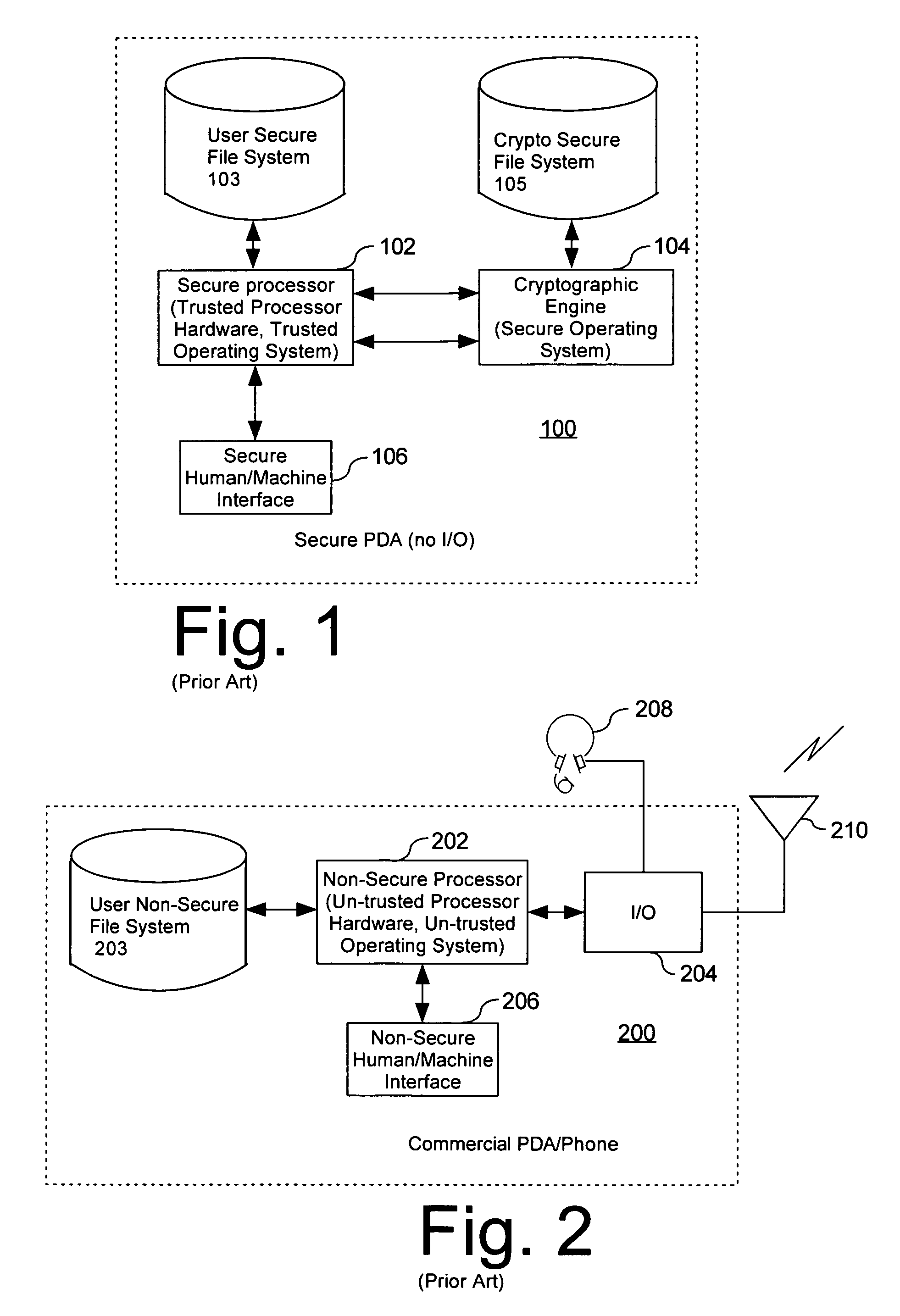
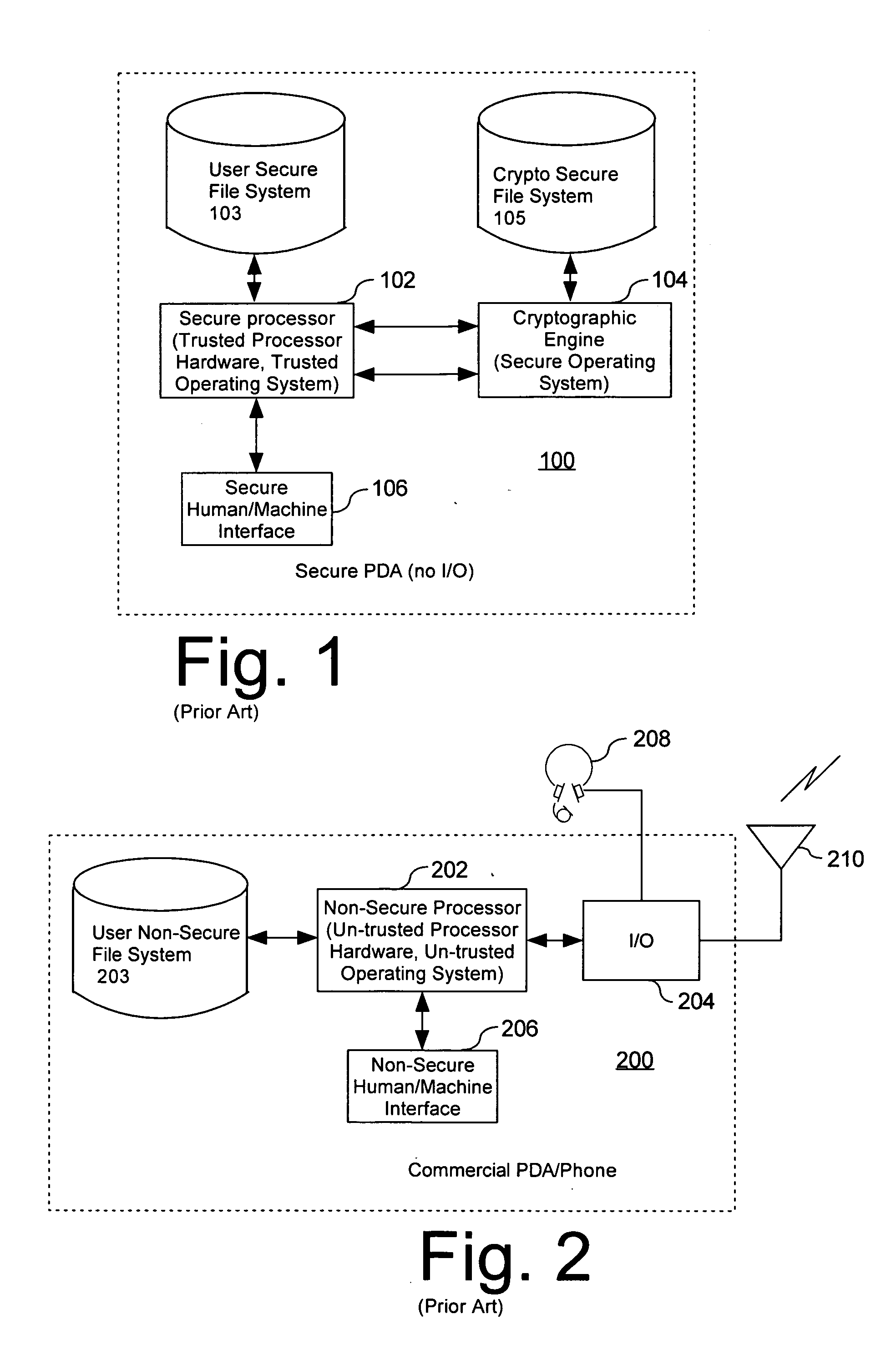
Computer architecture for a handheld electronic device
ActiveUS20070199046A1Digital data processing detailsUser identity/authority verificationTelecommunications linkOperational system
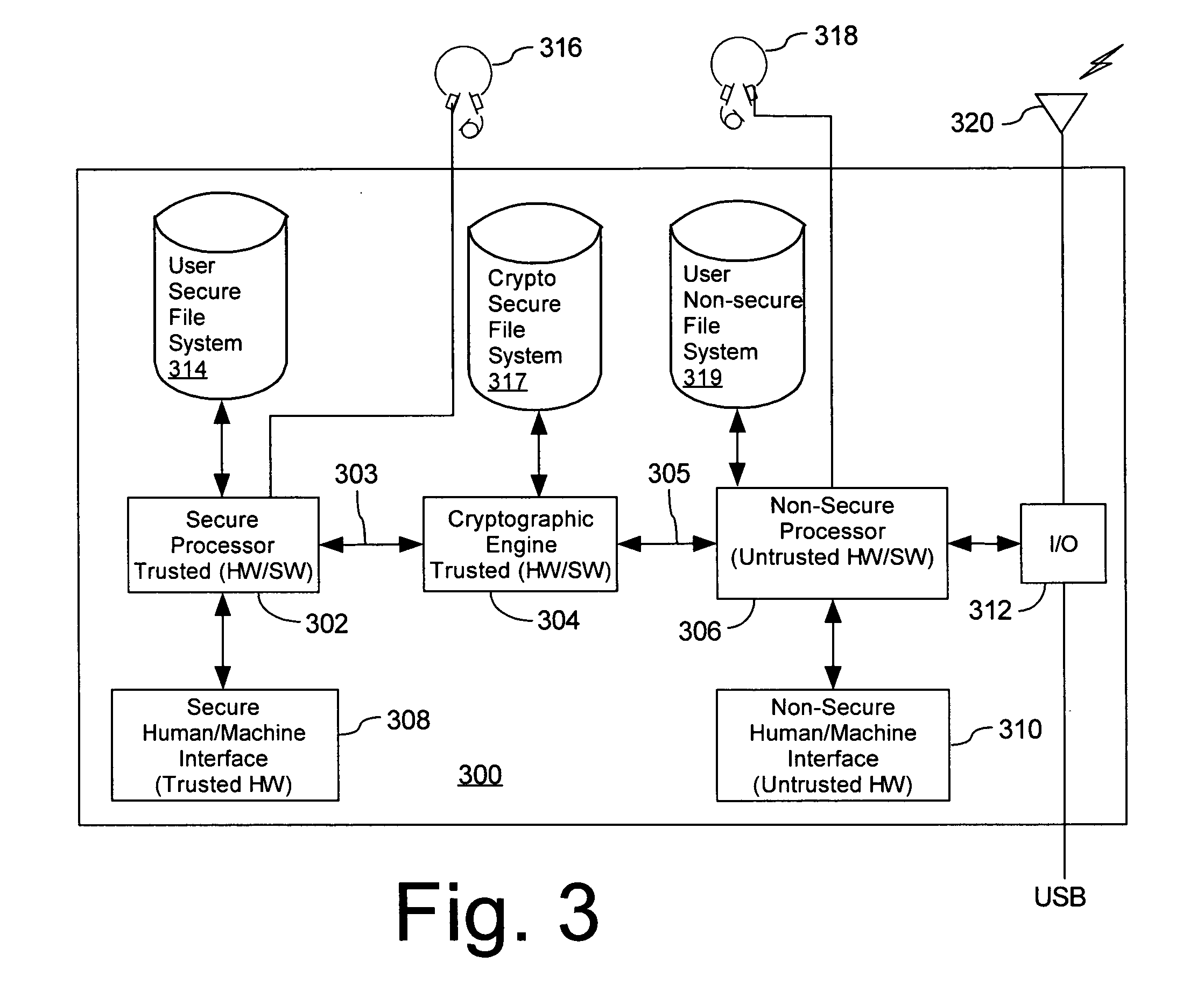
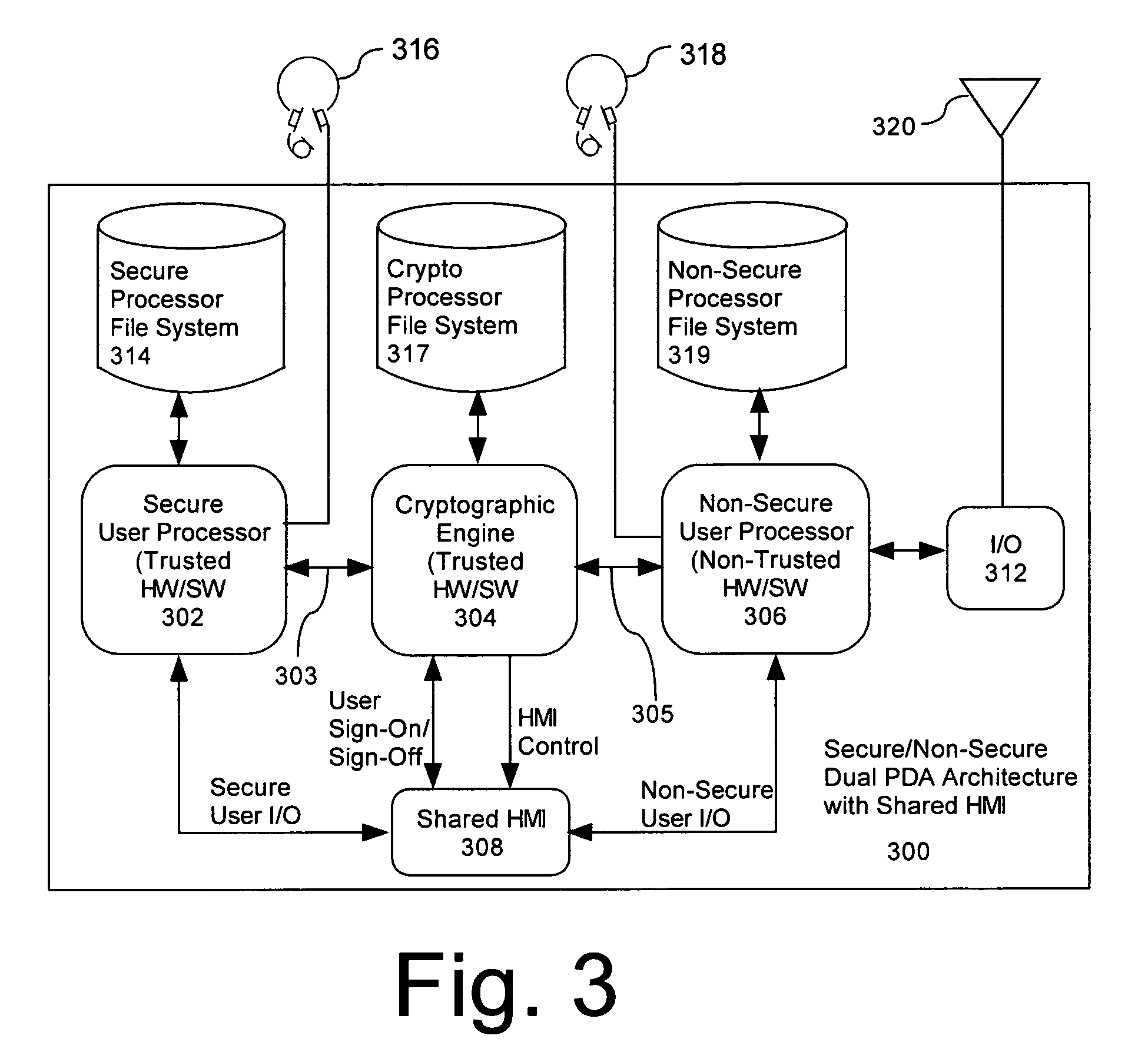
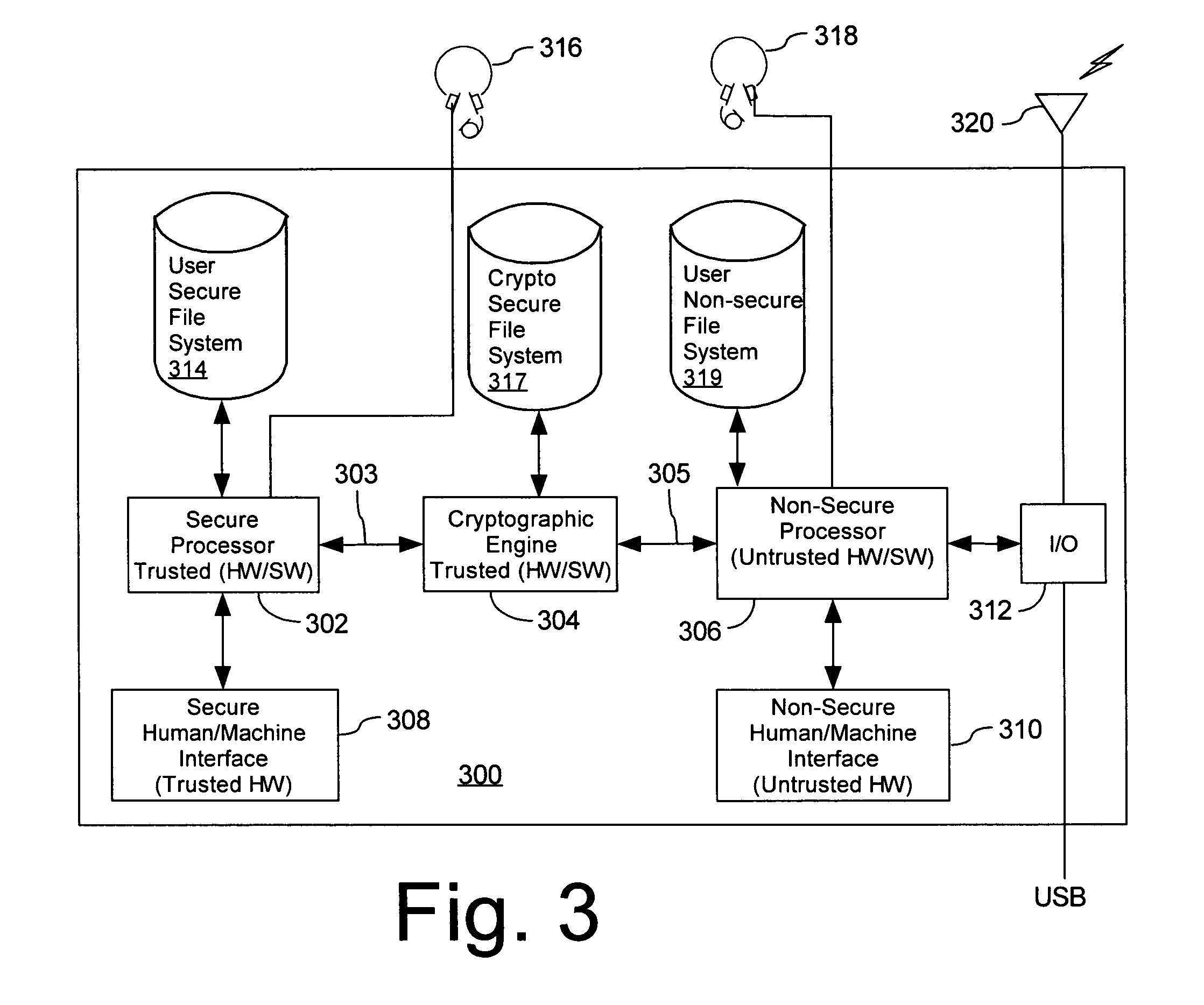
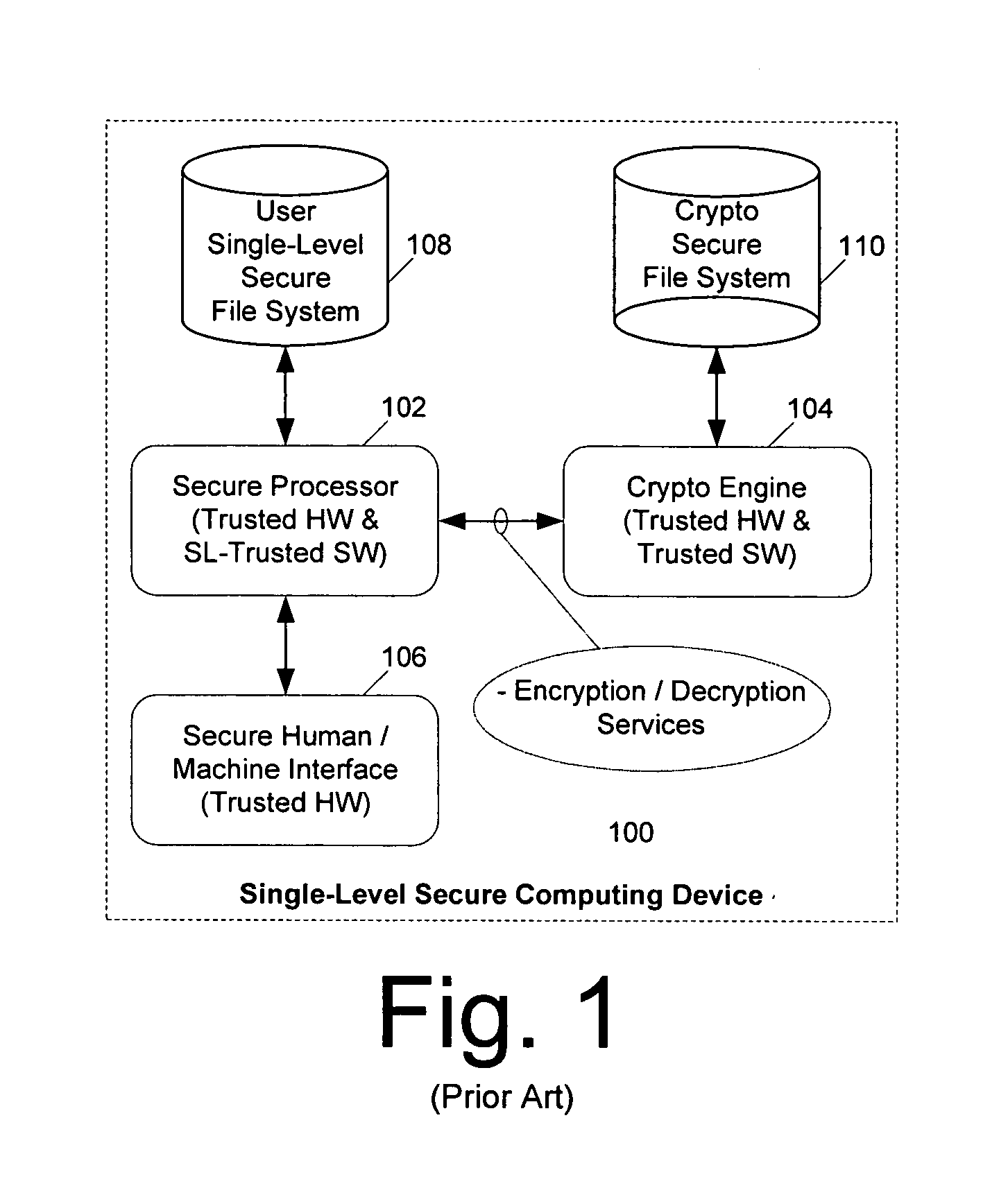
Mobile PDA computer system (300) includes a non-secure processor (306), comprising an untrusted microprocessor and an untrusted operating system executing on the untrusted microprocessor. The system also includes a secure processor (302), comprising a trusted microprocessor and a trusted operating system executing on the trusted microprocessor. A cryptographic engine (304) is provided for encrypting and decrypting data. A first data communication link (303) communicates data between the secure processor and the cryptographic engine. A second data communication link (305) communicates data between the non-secure processor and the cryptographic engine. In this way, the cryptographic engine forms a bridge between the secure user processor and the non-secure user processor.
Owner:SPEIR TECH LTD
Method and apparatus for limiting access to sensitive data
InactiveUS20080091934A1Reduce the possibilityReduced functionalityDigital computer detailsData resettingComputer hardwareOperational system
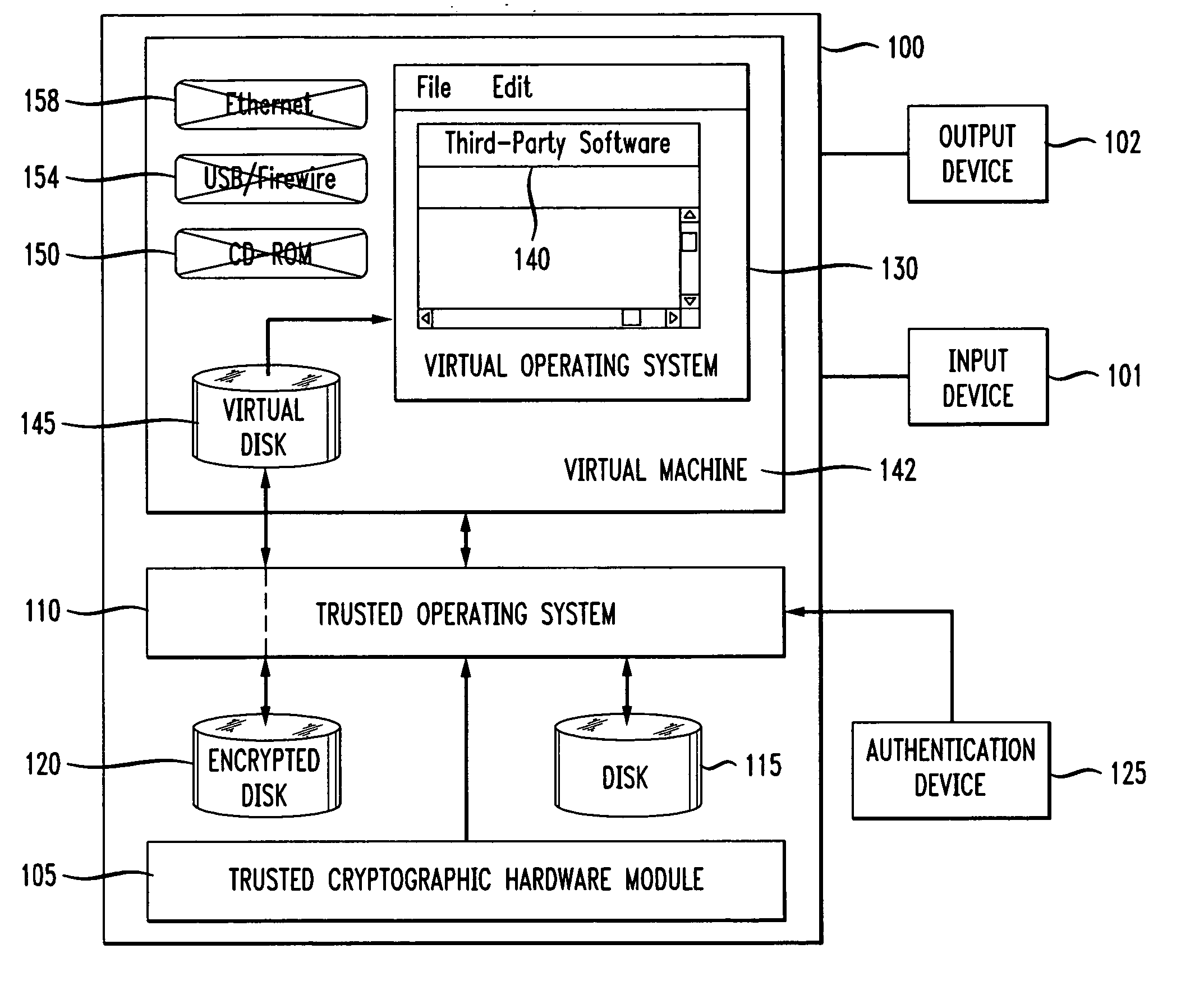
Disclosed is a method and apparatus for sharing sensitive data. A trusted operating system is configured to securely execute boot instructions for one or more hardware component. A virtual operating system in communication with the trusted operating system is configured with one or more security policies defining access rights associated with the one or more hardware component.
Owner:NULLRING
Secure remote management of a TPM
InactiveUS20070192580A1Random number generatorsUser identity/authority verificationTrusted operating systemTrusted Platform Module
A method, system and computer-usable medium are presented for remotely controlling a TPM by loading a trusted operating system into a computer; and in response to the trusted Operating System (OS) being loaded into the computer, authorizing a Trusted Platform Module (TPM) in the computer to execute a command that would otherwise require, for execution of the command, an indication of a physical presence of an operator of the computer.
Owner:LENOVO (SINGAPORE) PTE LTD
Personalized and cryptographically secure access control in trusted execution environment
ActiveUS20200034528A1Reduce eliminateCommunication securityUser identity/authority verificationDigital data protectionOperational systemFile system
An access control system includes a processor configured to provide a trusted execution environment isolated from a rich execution environment. A rich OS operates in the rich execution environment while a trusted OS operates in the trusted execution environment. An access monitoring module operates within the kernel of the rich OS and a trusted application operates in the trusted OS. The access monitoring module intercepts file requests directed at the file systems of the rich OS, and forwards the file requests to the trusted application. The trusted application then evaluates whether the file request is permitted and provides the access monitoring module with a response. The access monitoring module forwards the request to the file system only if the trusted application approves the request.
Owner:BICDROID
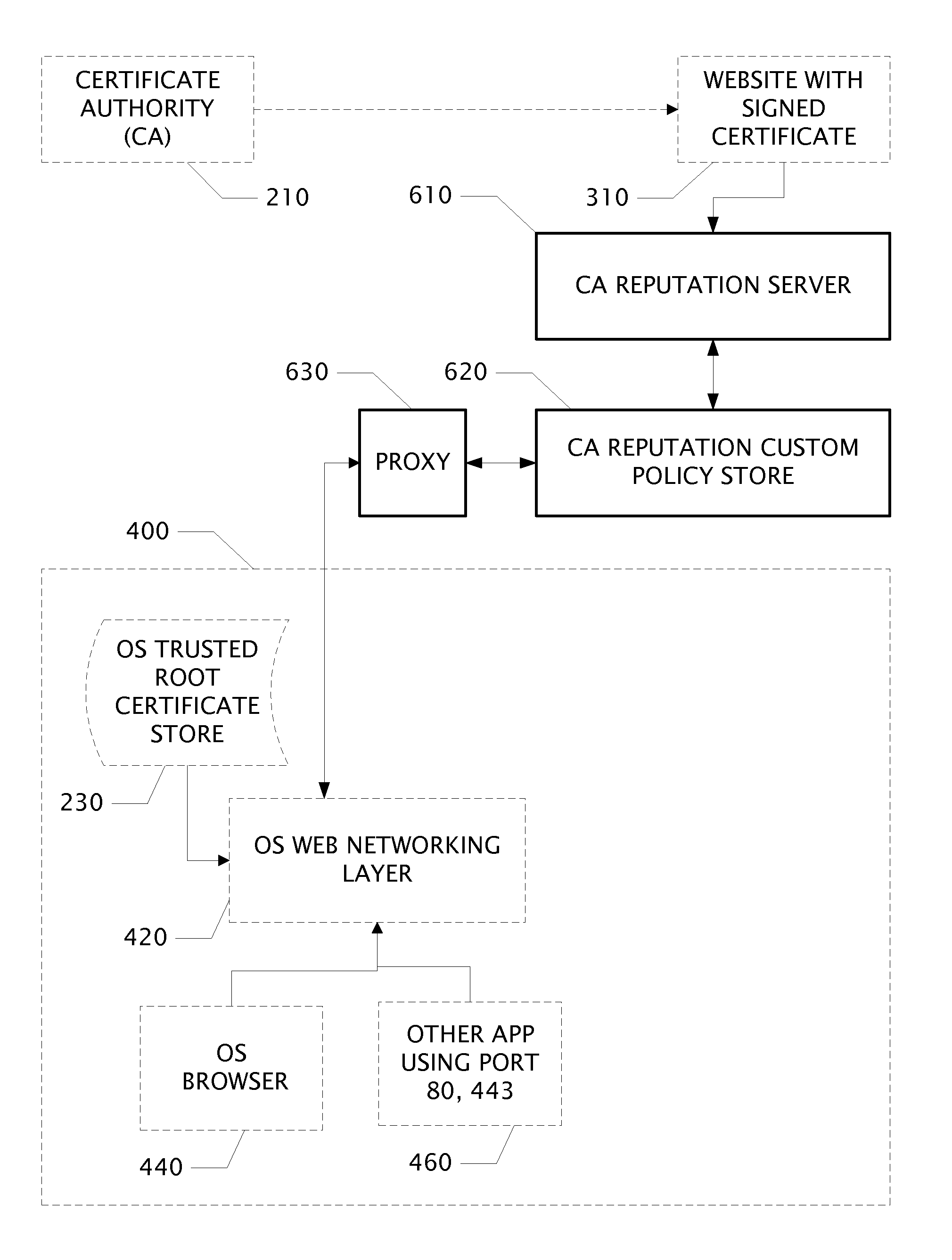
System and Web Security Agent Method for Certificate Authority Reputation Enforcement
InactiveUS20130061281A1Internal/peripheral component protectionDigital data authenticationThird partyRoot certificate
Owner:BARRACUDA NETWORKS
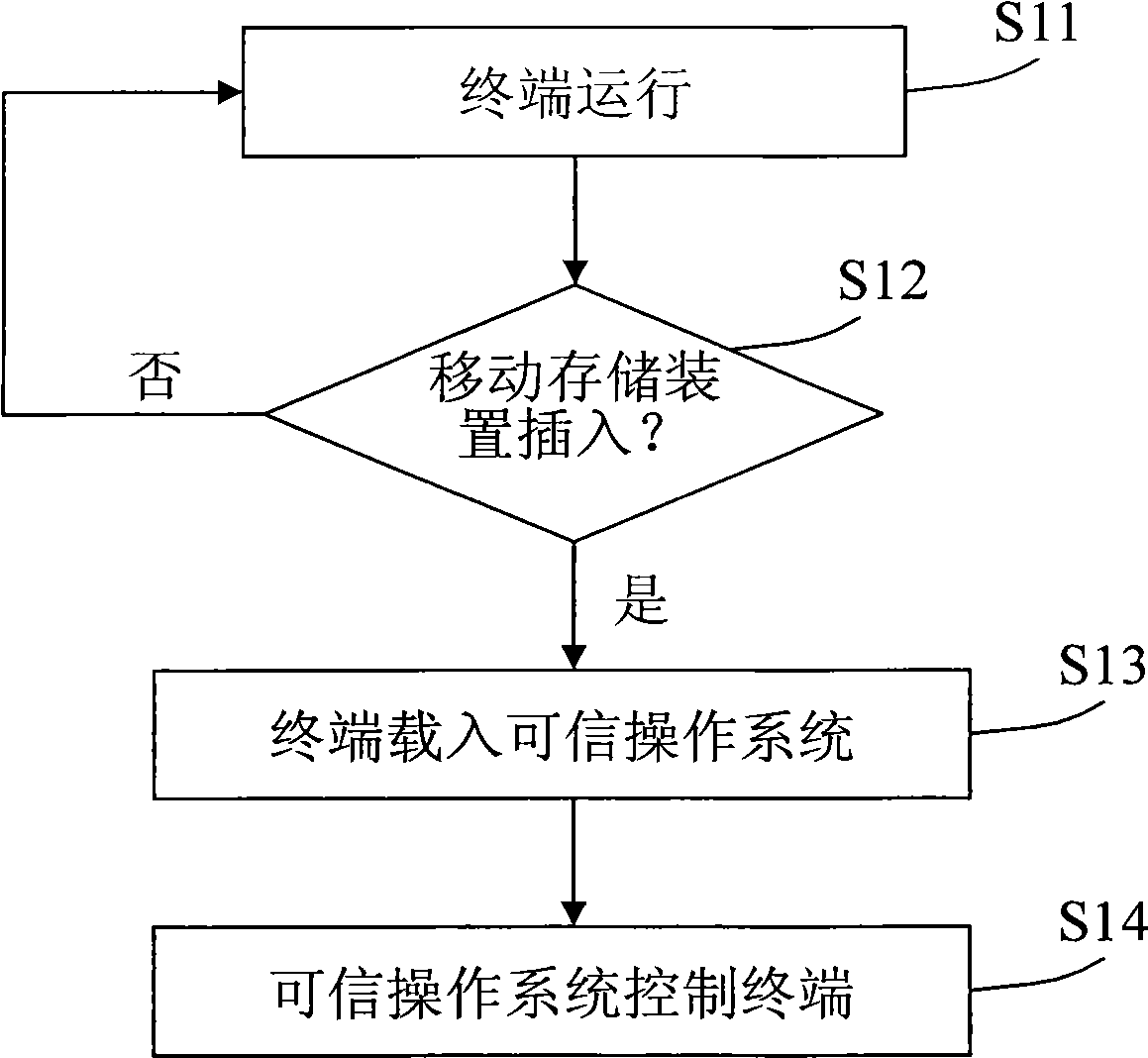
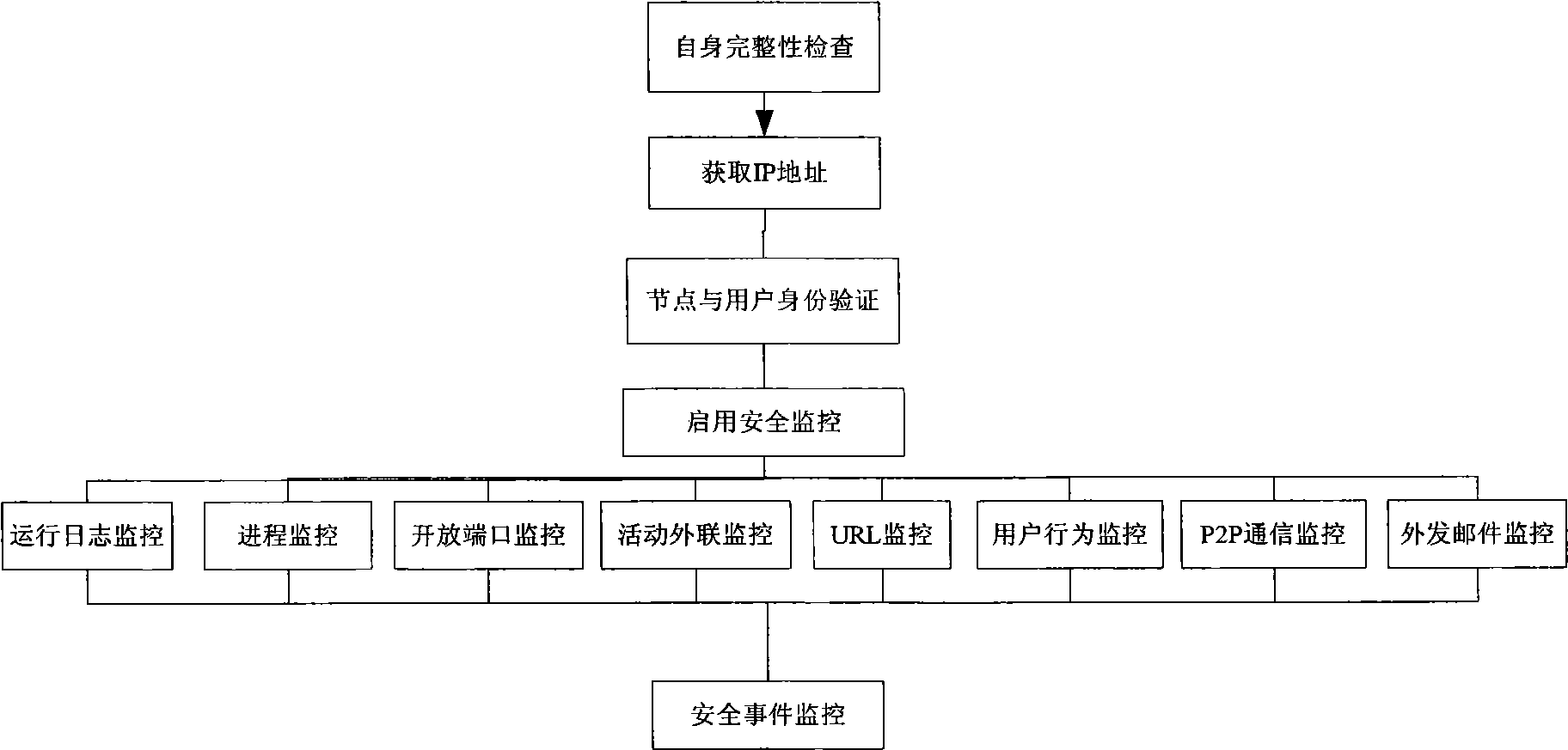
Safe terminal system and terminal safety method
ActiveCN101520831AFulfill security requirementsImprove performanceDigital data protectionTransmissionOperational systemComputer module
The invention relates to a safe terminal system which comprises a terminal and a mobile storage device connected to the terminal through a data interface, wherein the terminal comprises a trusted operating system module and a safe management client-side module which are loaded on the mobile storage device; the trusted operating system module is used for a trusted operating system which controls the operation of the terminal, and the safe management client-side module is used for collecting client identity information and collecting and registering operating procedures. The invention also provides a corresponding terminal safety method. The invention realizes the safety requests and the high property of the terminal in such a way that the trusted operating system loaded on the mobile storage device controls the terminal to thoroughly shield an original system environment of the terminal so as to form a pure safe terminal environment.
Owner:SHENZHEN Y& D ELECTRONICS CO LTD
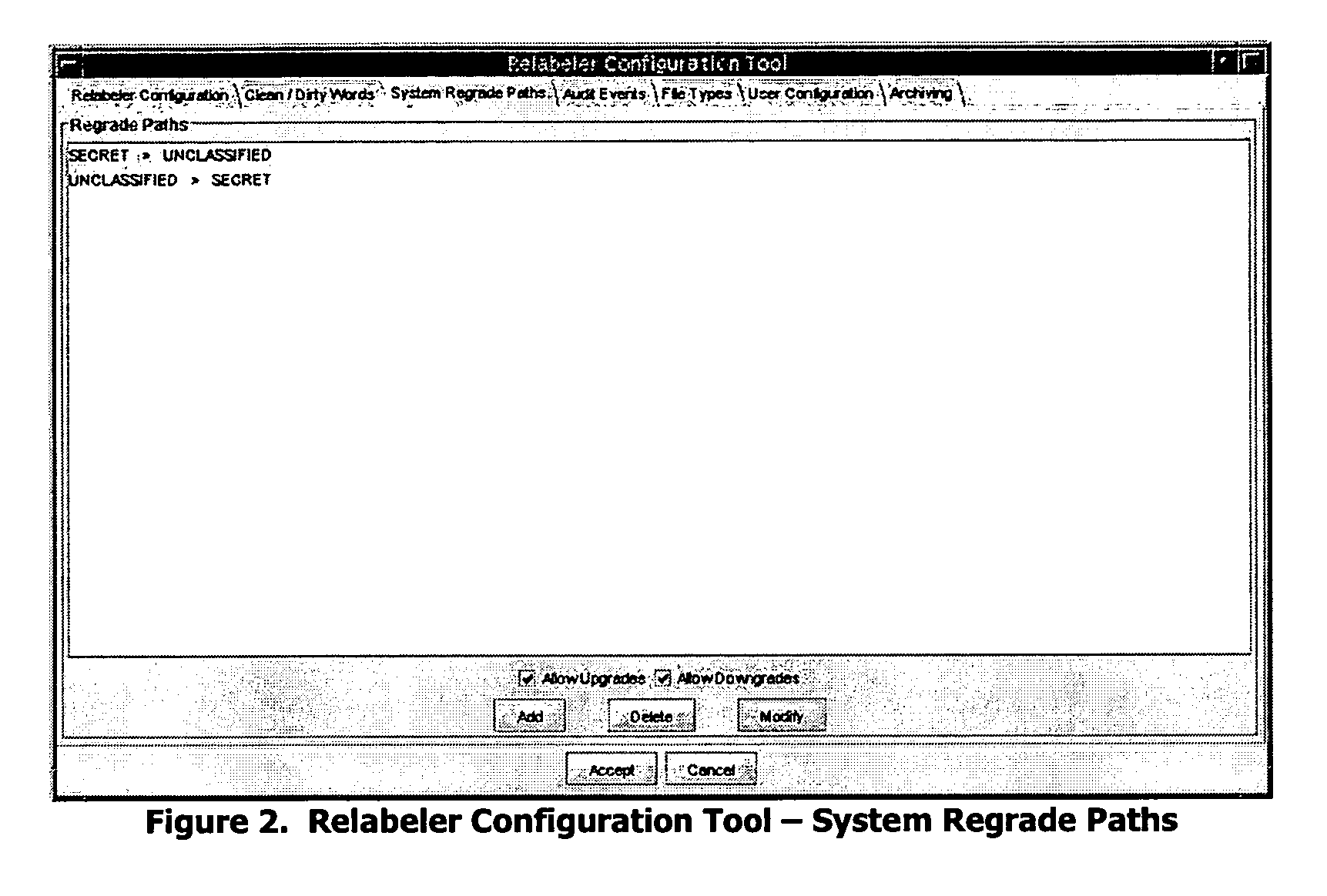
Trusted file relabeler
ActiveUS20060190988A1Shorten the timeSimplified and secure processDigital data processing detailsUser identity/authority verificationOperational systemSpecific function
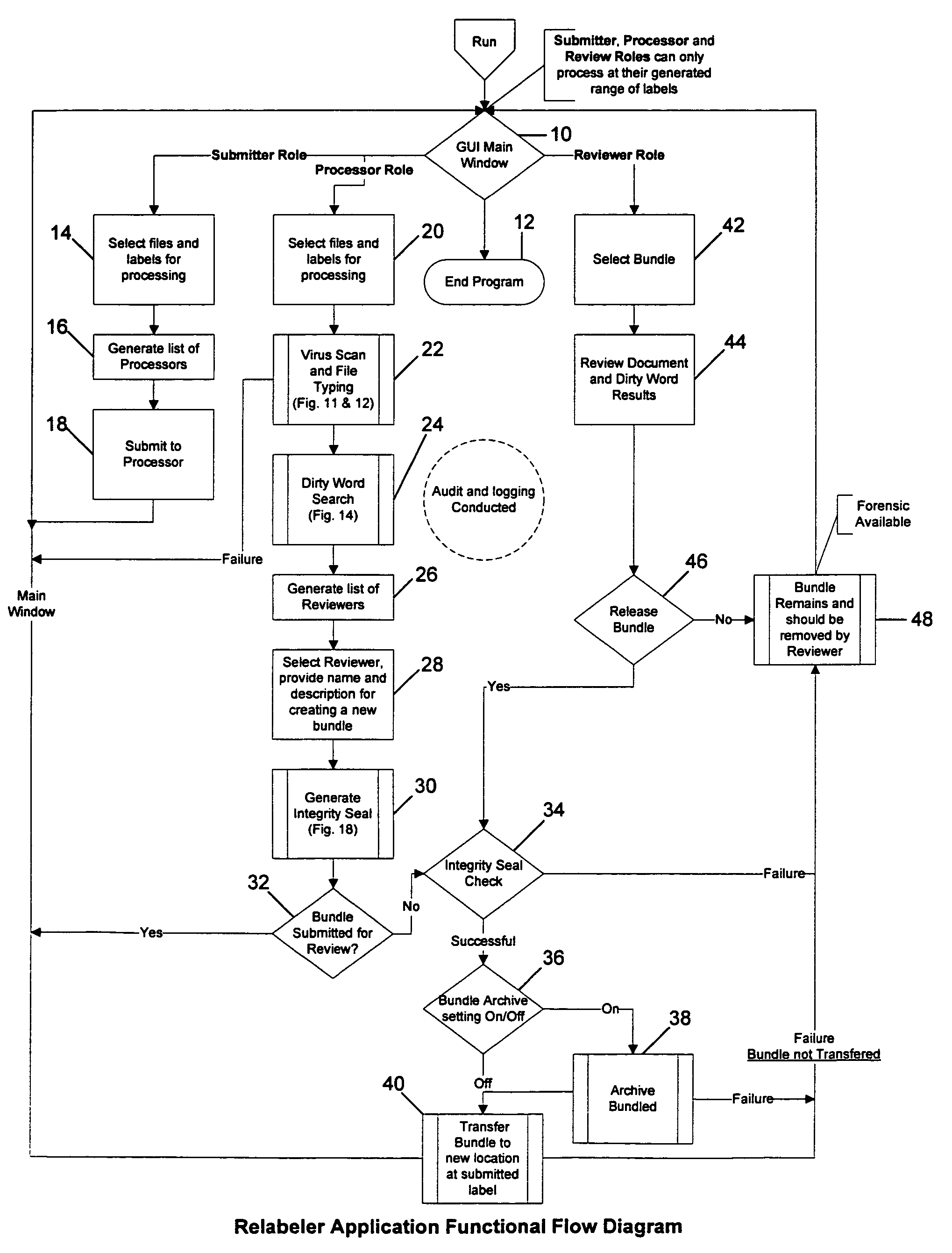
A trusted relabeler system and software is provided that allows for the simultaneous reclassification of multiple files to multiple classification labels (security domains or computer networks) through automation of the multi-person review process. Roles, used to break down the requirements of the multi-person review process, dictate what specific function a user can perform. There are three roles used: Submitter, Processor, and Reviewer. The Submitter is allowed to submit one or more documents for reclassification, while the Processor is allowed to submit one or more documents for reclassification, perform an initial review and acceptance of the document, and assign a specific Reviewer for the document. The Reviewer is allowed to perform final verification and, upon acceptance, allows the document to be reclassified appropriately. Users are assigned one or more roles and a set of source and destination classification labels inside the security policy of a specific user that are bounded (restricted) by the clearance (maximum classification) assigned to a user on the trusted operating system on which the trusted relabeler system is implemented. The bundled documents to be reclassified are virus scanned, file typed, and searched for “dirty words” indicative of a particular classification level. An integrity seal is generated to verify that the files are not tampered with between processing by the Processor and the Reviewer. Files are upgraded or downgraded only if all processes are completed successfully.
Owner:FORCEPOINT FEDERAL
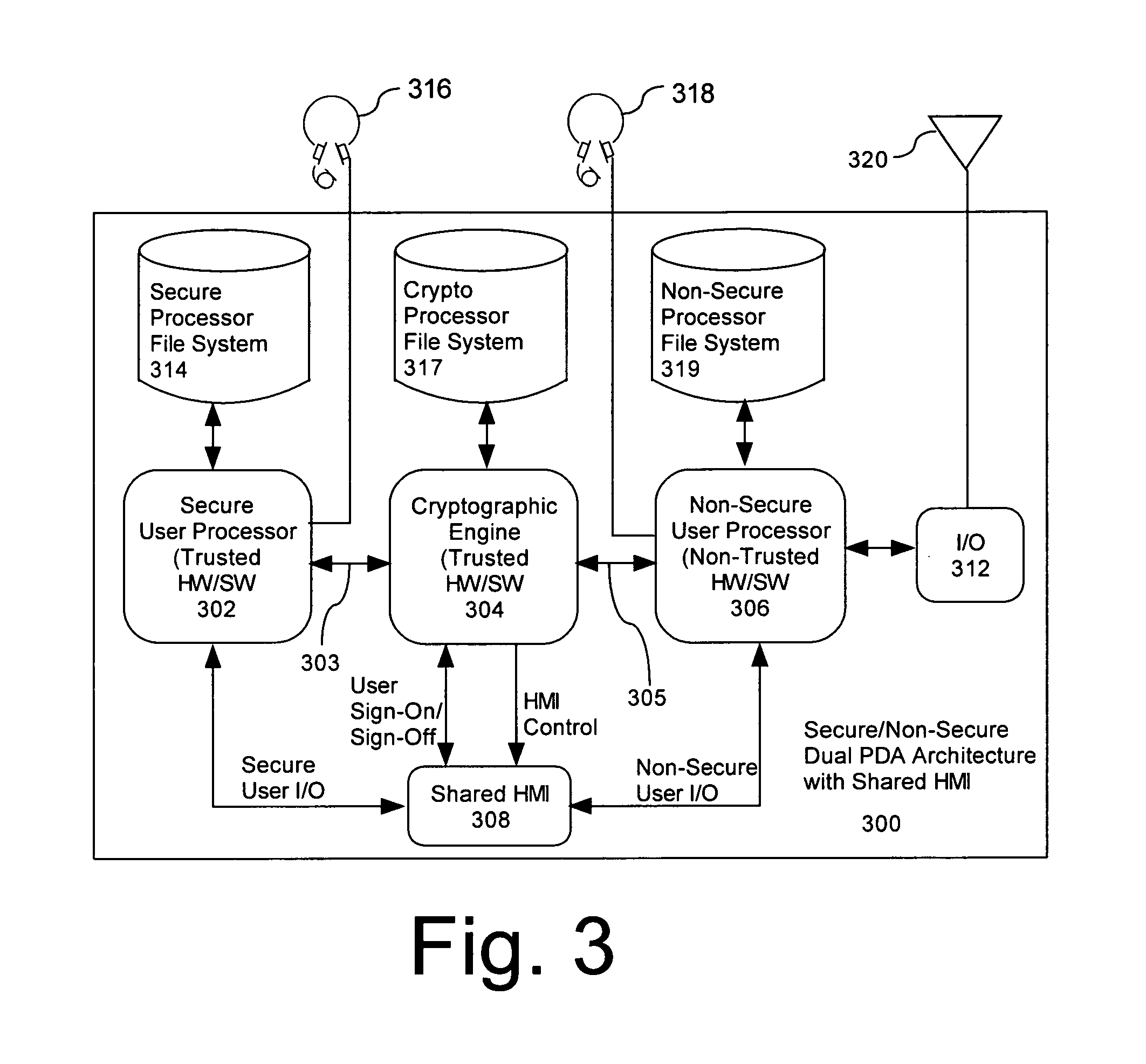
Computer architecture for a handheld electronic device with a shared human-machine interface
ActiveUS7779252B2Public key for secure communicationDigital data processing detailsTelecommunications linkOperational system
Mobile PDA computer system (300) includes a secure user processor (302), a non-secure user processor (306), a cryptographic engine (304), and a shared human / machine interface (HMI) (308). The secure user processor (302) can be comprised of a first trusted microprocessor and a first trusted operating system executing on the first trusted microprocessor. The non-secure user processor (306) can be comprised of a second non-trusted microprocessor and a second non-trusted operating system executing on the second non-trusted microprocessor. A cryptographic engine (304) can be comprised of a third trusted cryptographic processor and a third trusted operating system executing on the third trusted cryptographic processor. The cryptographic engine can be configured for encrypting and decrypting data. A first data communication link (303) communicates data between the secure user processor and the cryptographic engine. A second data communication link (305) communicates data between the cryptographic engine and the non-secure user processor. In this way, the cryptographic engine forms a bridge between the secure user processor and the non-secure user processor. An HMI (308) comprised of trusted hardware for user input and output is time-multiplex-shared among the secure user processor (302), the non-secure user processor (304), and the cryptographic engine (306) in a secure fashion.
Owner:SPEIR TECH LTD
Managing securely installed applications
Embodiments of the present disclosure provide methods and systems for managing securely installed applications. After installation, an installation framework performs a bind process to correlate the randomly assigned identifier with the unique identifier of the application. The installation framework also manages the execution of the application. When an application is launched, the application framework performs a search for that application's randomly assigned identifier and locates the application's container. The application is then allowed to execute within its container. During execution, the software application may also be restricted in various ways by the installation framework to its dynamic containers. The installer may also work with a trusted operating system component, such as the kernel, to help enforce the container restrictions. In addition, if desired, the use of random identifiers for containers may be used in conjunction with other security mechanisms, such as the use of code signing.
Owner:APPLE INC
Method and system for detecting a tamper event in a trusted computing environment
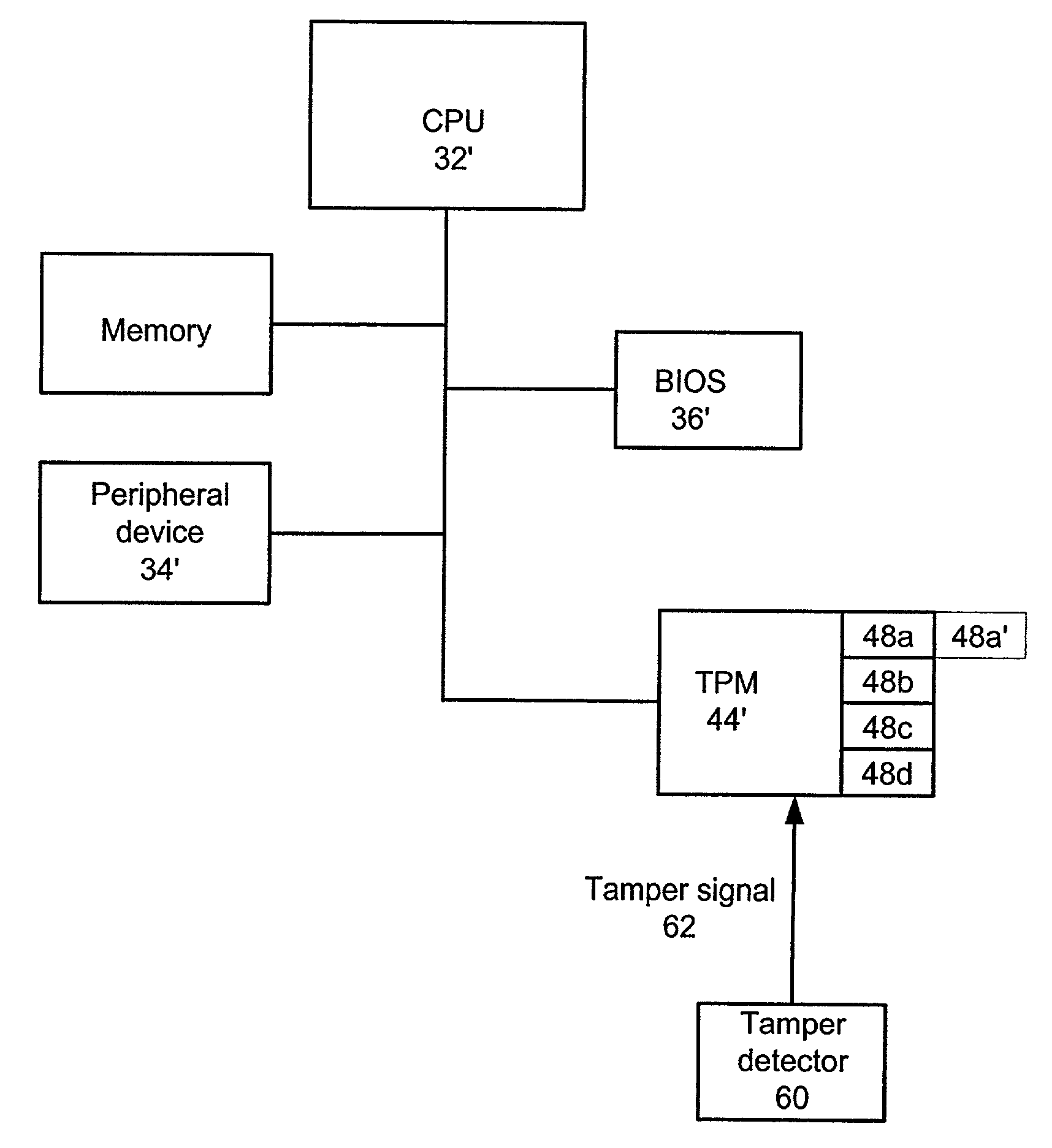
InactiveUS7490250B2Capable of detectUser identity/authority verificationUnauthorized memory use protectionEmbedded securityOperational system
A method, system and computer readable medium containing programming instructions for detecting a tamper event in a computer system having an embedded security system (ESS), a trusted operating system, and a plurality of devices is disclosed. The method, system and computer readable medium of the present invention provide for receiving a tamper signal in the ESS, and locking the tamper signal in the ESS. According to the method, system and computer readable medium of the present invention, the trusted operating system is capable of detecting the tamper signal in the ESS.
Owner:LENOVO PC INT
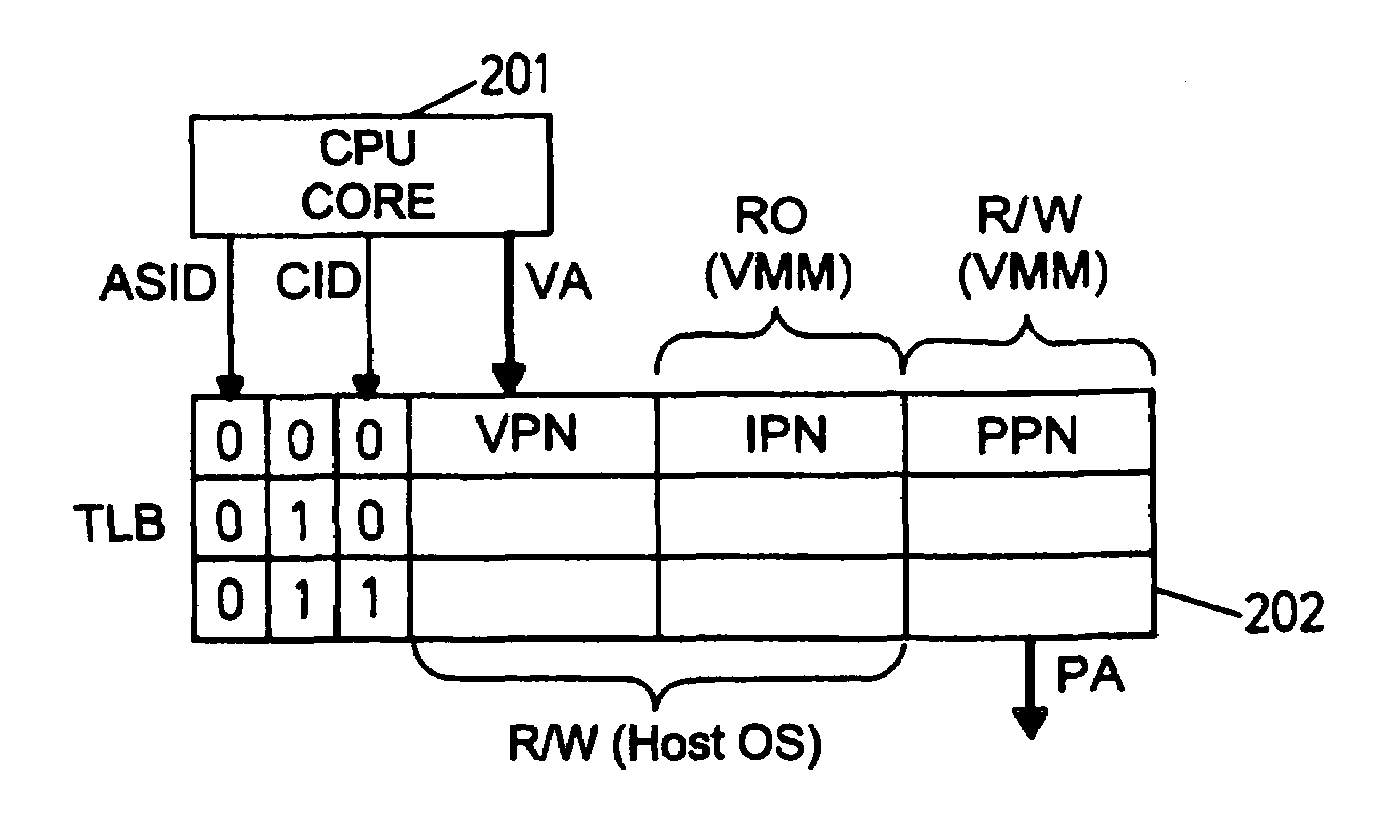
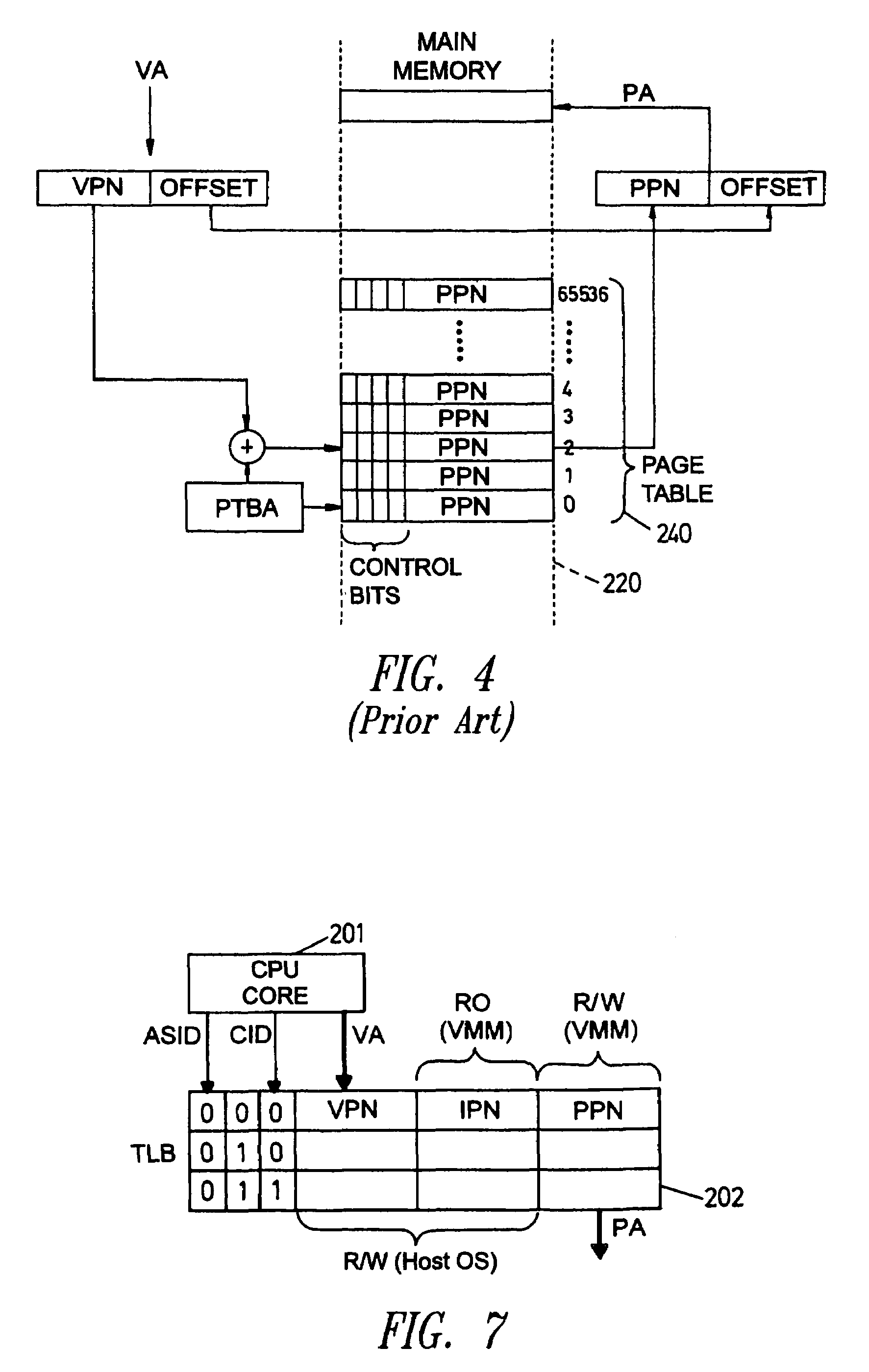
Translation look-aside buffer supporting mutually untrusted operating systems
ActiveUS7461232B2Reduce power levelMemory architecture accessing/allocationEnergy efficient ICTOperational systemOperation mode
Owner:STMICROELECTRONICS SRL
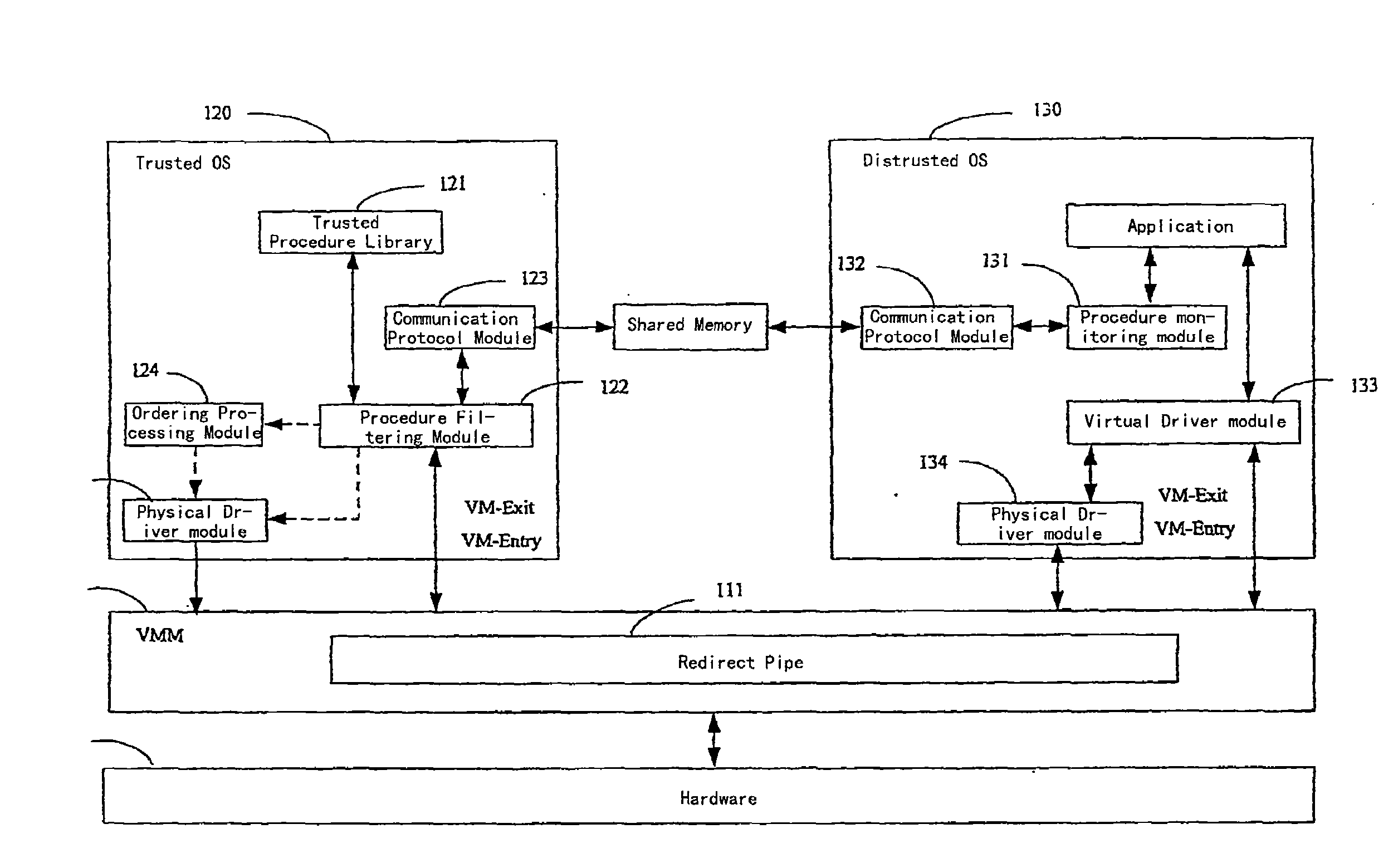
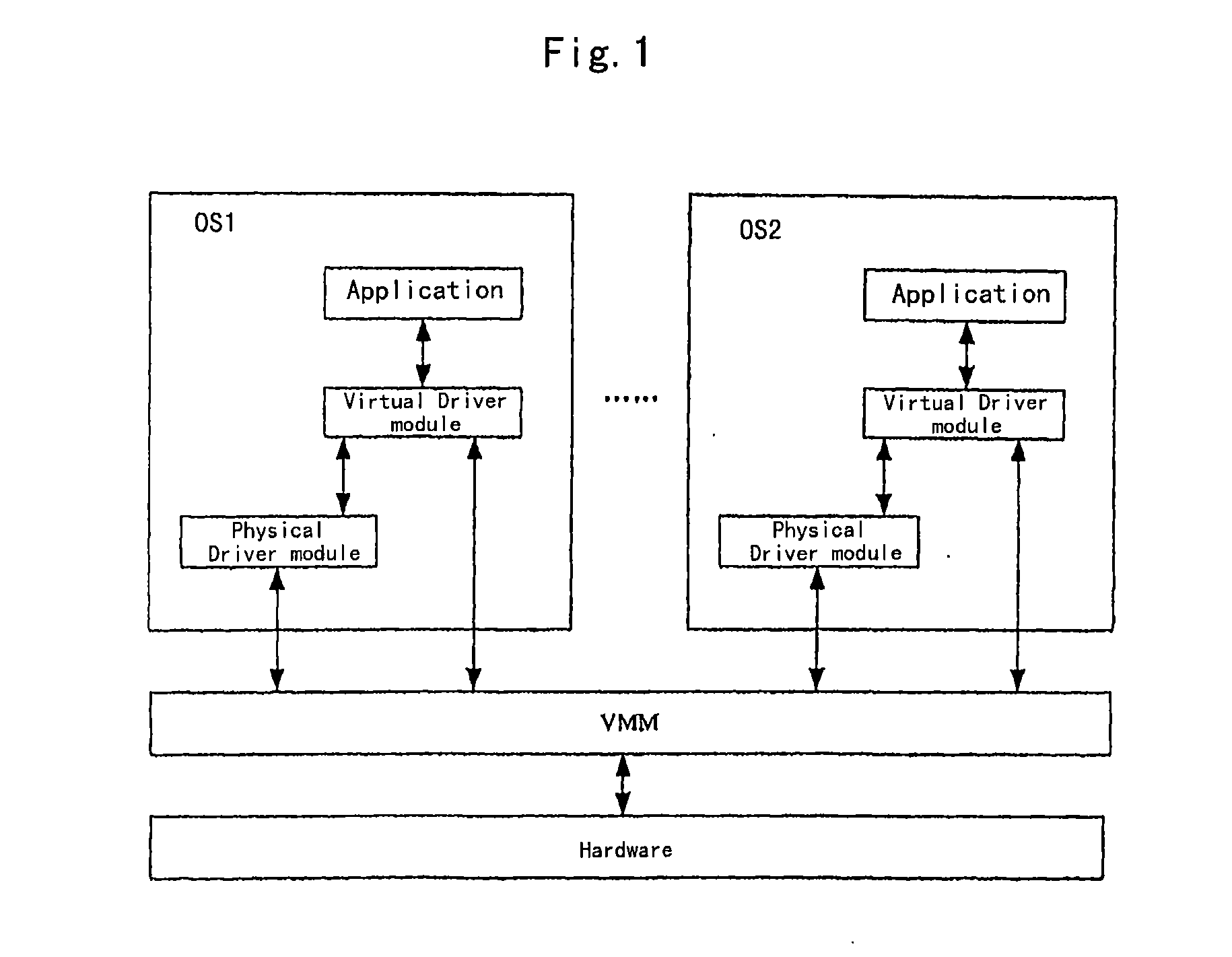
Virtual Computer System Supporting Trusted Computing and Method for Implementing Trusted Computation Thereon
InactiveUS20080216096A1Without additional hardware costEasy to implementMultiprogramming arrangementsPlatform integrity maintainanceOperational systemTrusted Computing
A virtual machine system supporting trusted computing includes a virtual machine monitor, a hardware and multiple operating systems (OSs). Said multiple OSs include at least a trusted OS, and at least a distrusted OS, a redirecting pipe is set in the virtual machine monitor, the redirecting pipe is adapted to redirect an I / O instruction from the distrusted OS to the trusted OS. Wherein, the trusted OS checks the trusted degree of a procedure information of the distrusted OS, and sends to the hardware an I / O instruction that corresponds to trusted procedure information confirmed via the trusted degree check, transferred via the redirecting pipe and came from the distrusted OS, performs an I / O operation by the hardware.
Owner:LENOVO (BEIJING) CO LTD
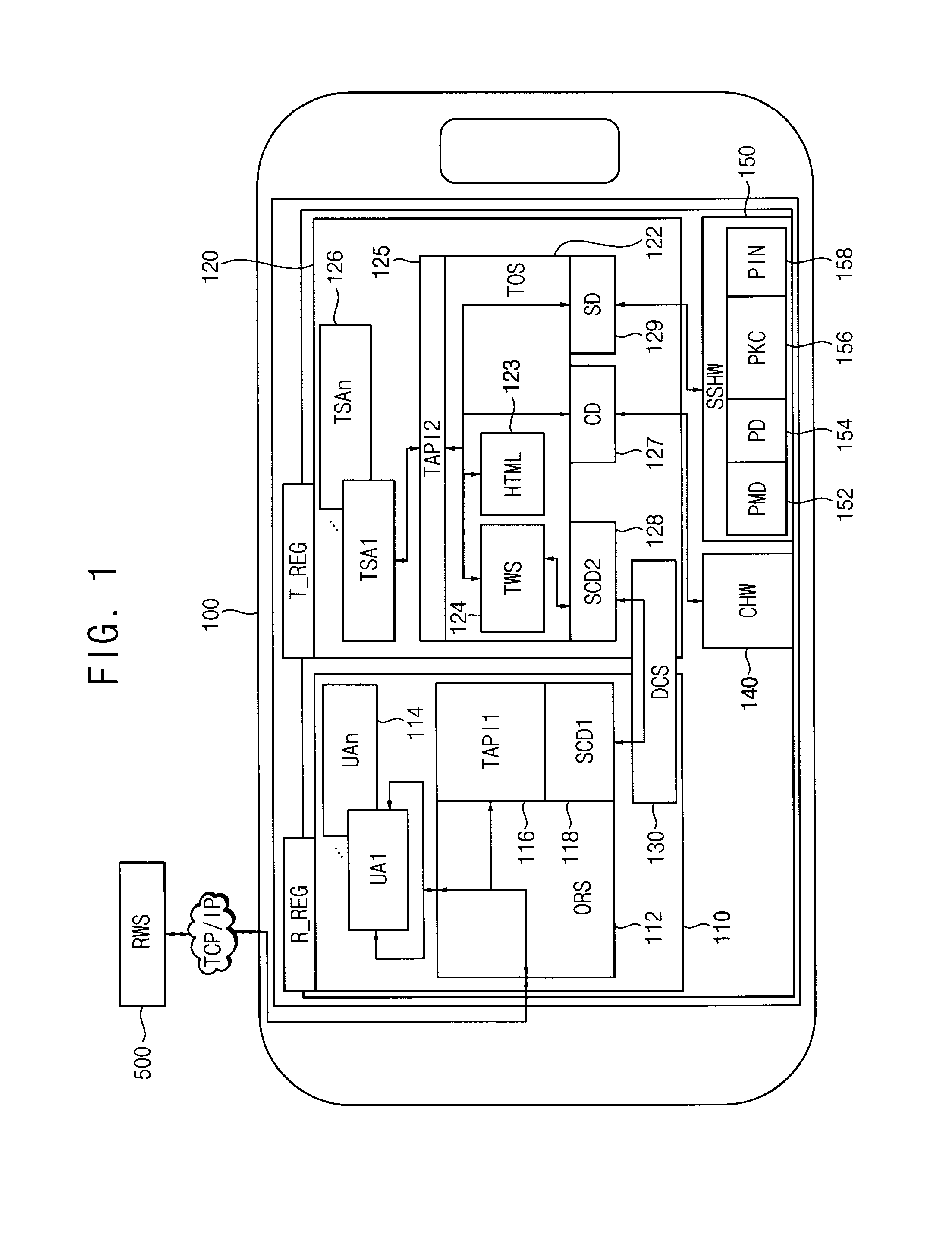
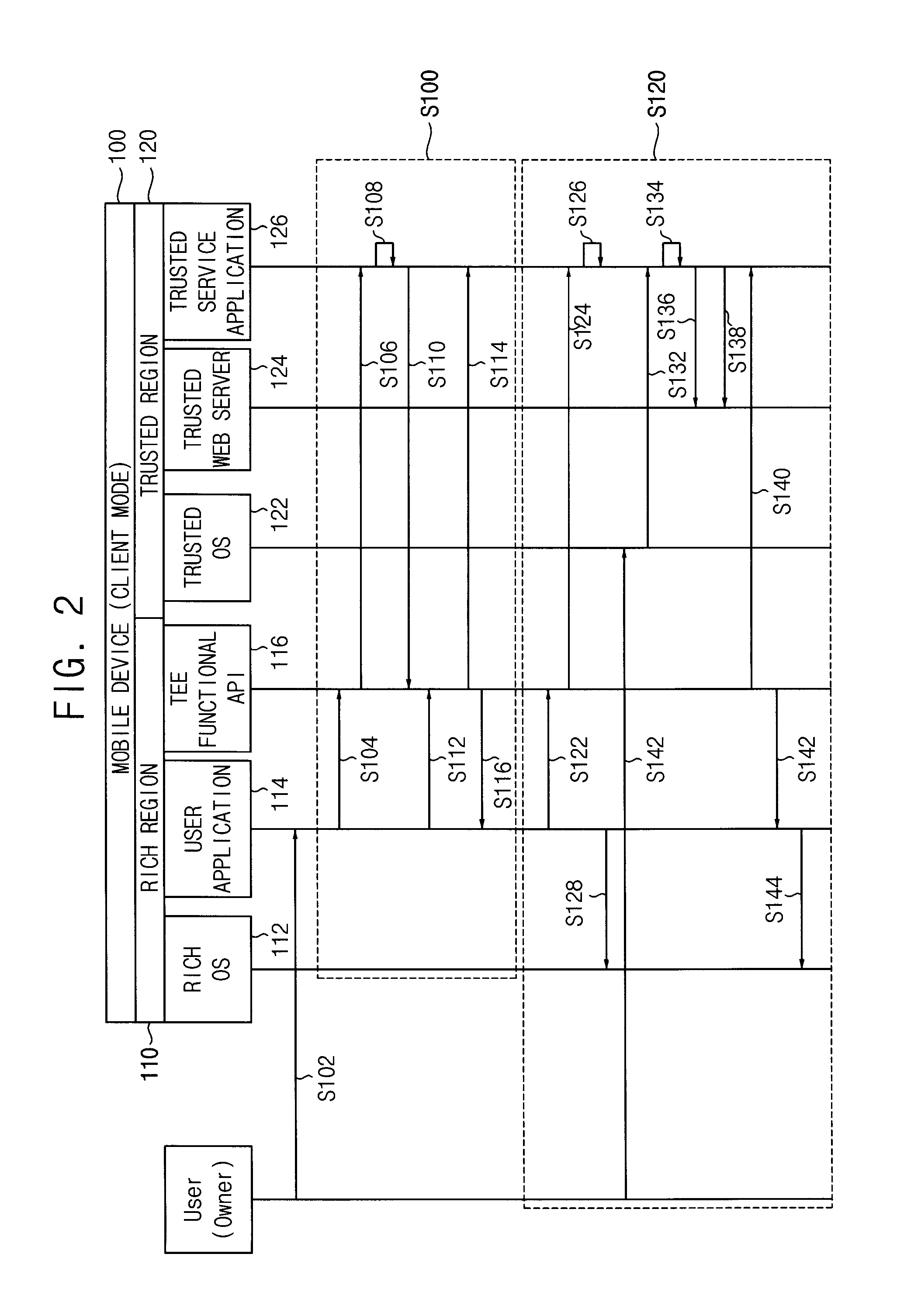
Operation of mobile device as trusted mobile web client or trusted mobile web server
ActiveUS20130254842A1Improve securityReduced compatibilityDigital data processing detailsMultiple digital computer combinationsOperational systemWeb service
A method of operating a mobile device comprises executing a trusted service application in a trusted operating system through secure access, executing a trusted web server module in the trusted operating system, wherein the trusted web server module is configured to transfer information using an internet protocol and the information is generated by execution of the trusted service application, and executing a user application in a rich operating system through normal access, wherein the user application is configured to relay communication between a remote web server and the trusted web server module through a security session.
Owner:SAMSUNG ELECTRONICS CO LTD
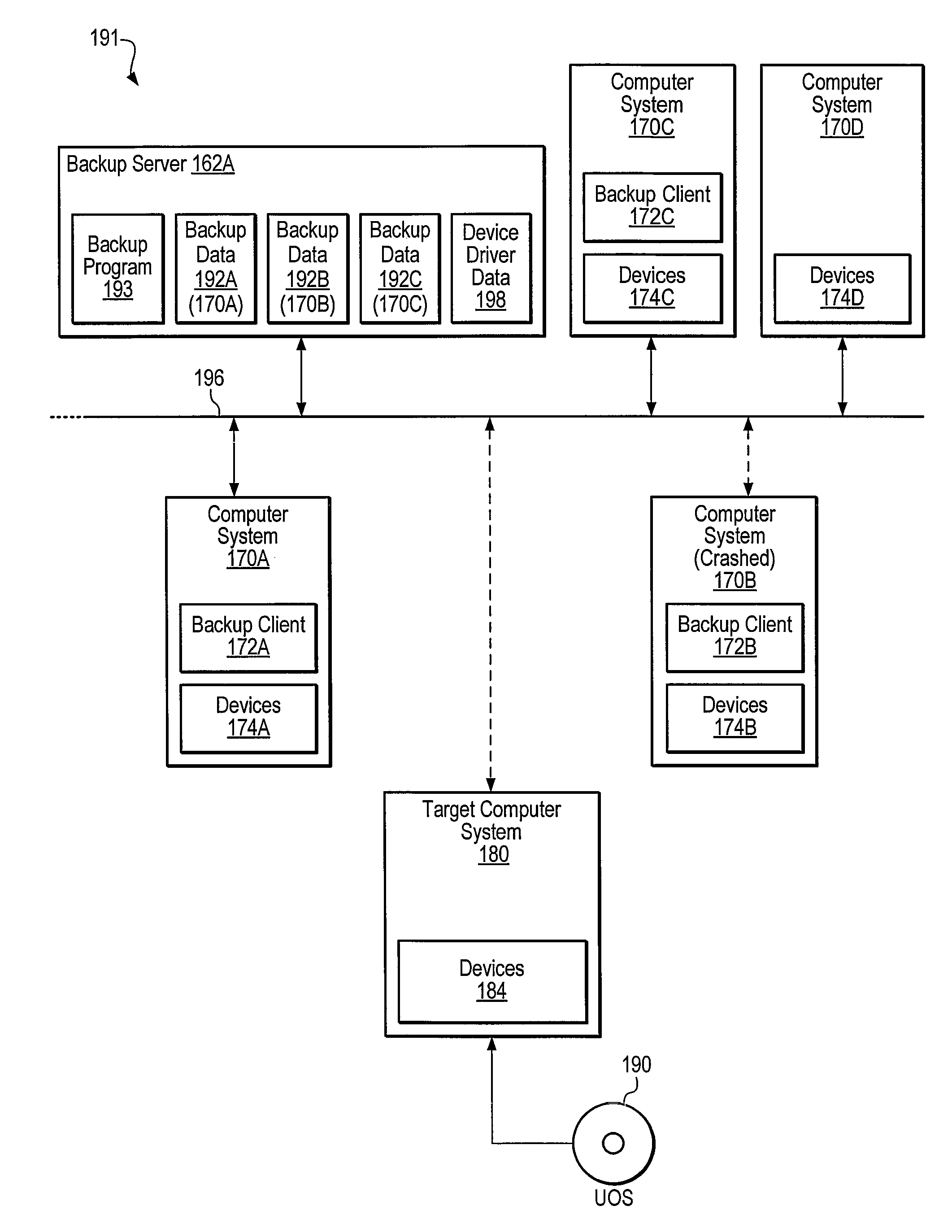
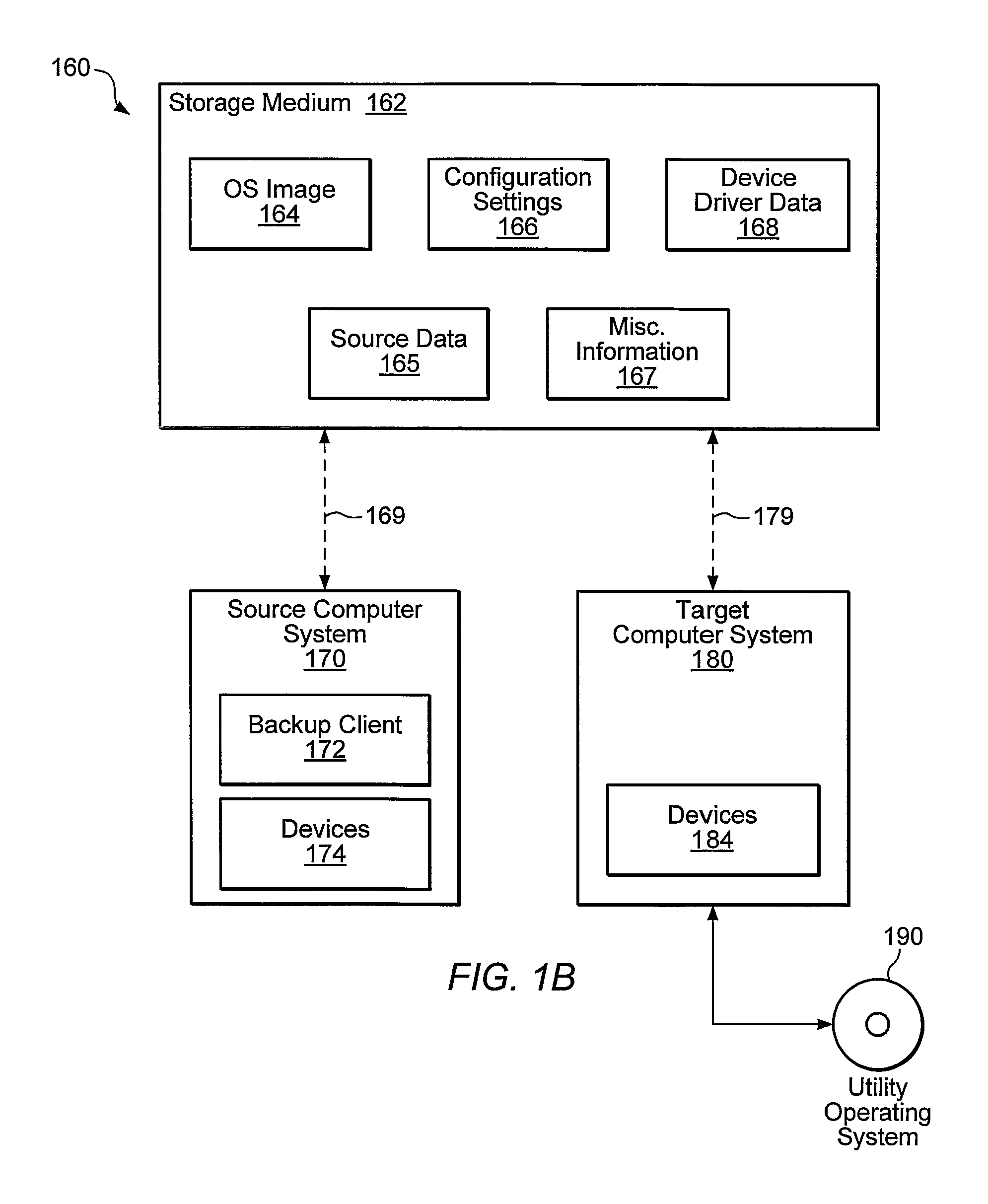
Creation of a device database and synthesis of device driver information during dissimilar system restore
Systems, methods, and computer-readable memory media for performing various computer configuration tasks are disclosed. One such configuration task is dissimilar system restore (DSR). Another such task is software deployment. In various embodiments, these configuration tasks operate on a target computer system using a utility operating system to perform detection of certain target system devices, determination of critical device classes on the source computer system, and updating of target computer configuration settings. Other tasks may be performed upon a computer system such as a backup server. These tasks include locating device drivers for the target operating systems and the installing utility operating system, as well as creating device driver packages that are usable to install device drivers for a plurality of devices.
Owner:VERITAS TECH
Trusted execution method and apparatus for virtual trusted platform module (vTPM)
ActiveCN105389513AEnsure safetyIncrease credibilityPlatform integrity maintainanceComputational securityComputer hardware
The present invention discloses a trusted execution method and apparatus for a virtual trusted platform module (vTPM). An operating system loads an SGX module, and the operating system runs a first vTPM simulator. The method comprises: the first vTPM simulator run by the operating system sending a first creation request to the SGX module, so that the SGX module establishes a first memory protection region enclave according to the first creation request and generates a first communication key, so as to execute program code of the first vTPM simulator in the first enclave to implement a second vTPM simulator; and the second vTPM simulator using the first communication key to decrypt data subsequently forwarded by the SGX module. According to the method and apparatus disclosed by the embodiments of the present invention, security isolation of a vTPM simulator from a non-trusted operating system is realized by using an SGX module and a hardware protection function of an enclave, thereby ensuring computing security of the vTPM simulator.
Owner:HUAWEI CLOUD COMPUTING TECH CO LTD
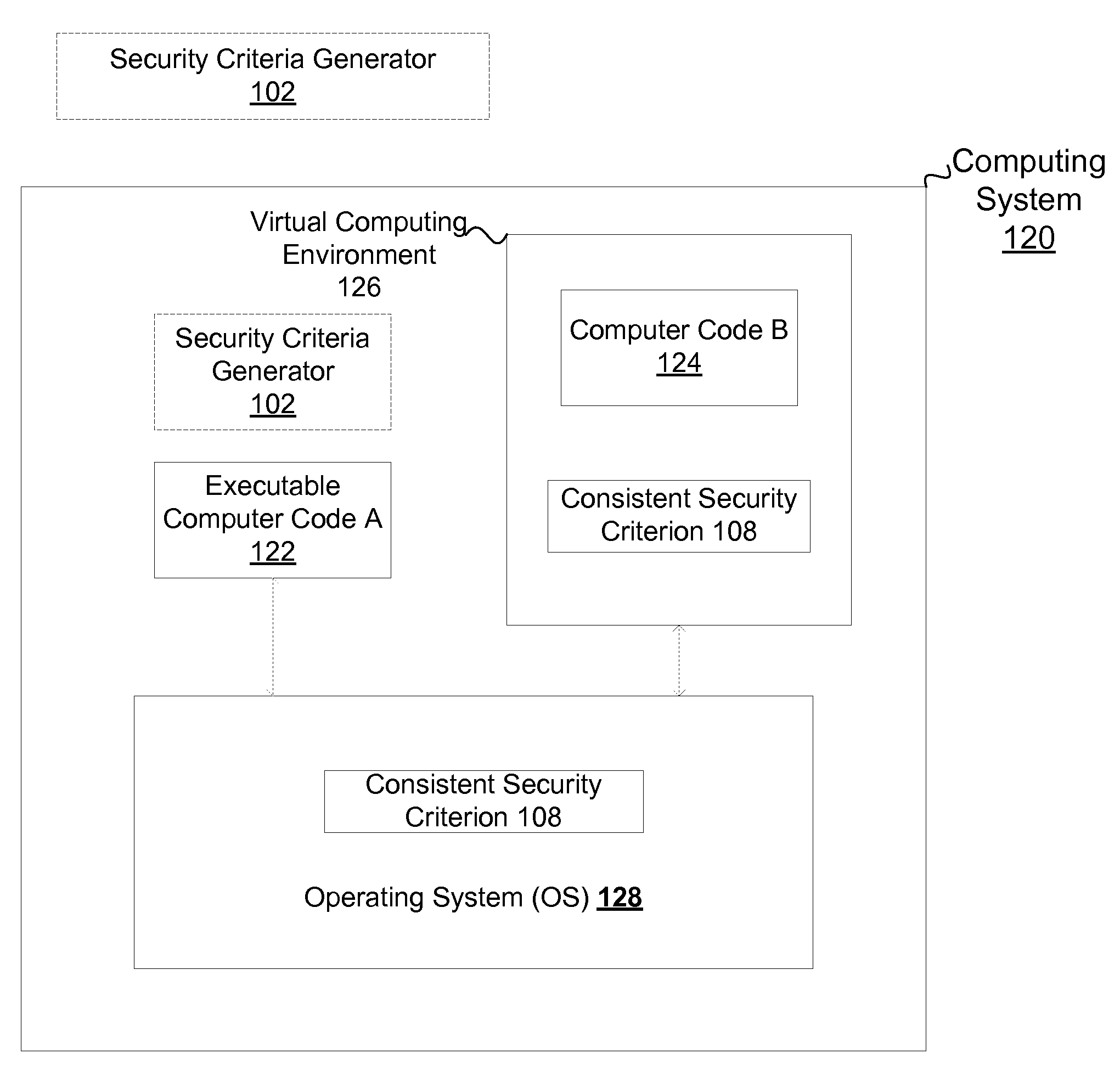
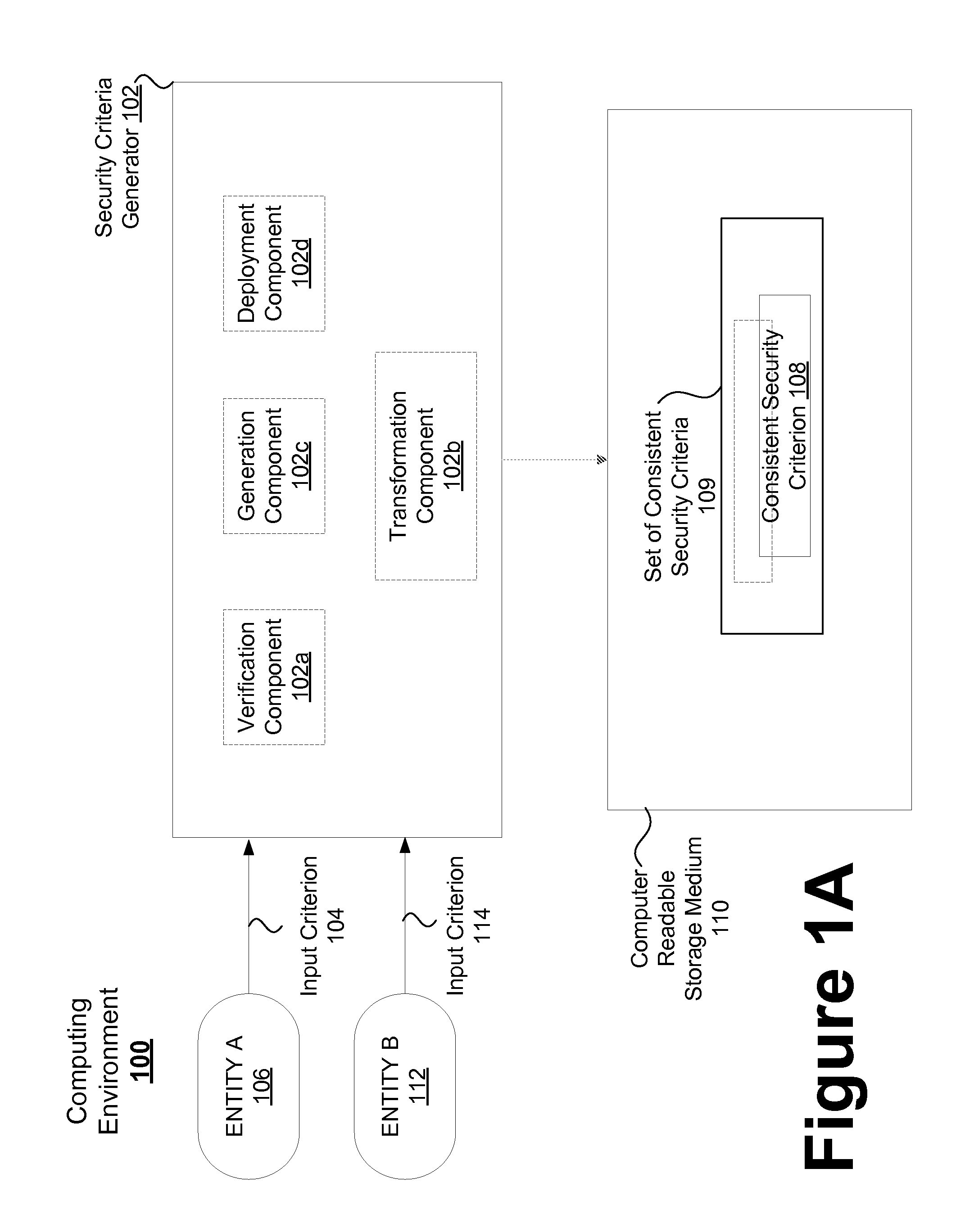
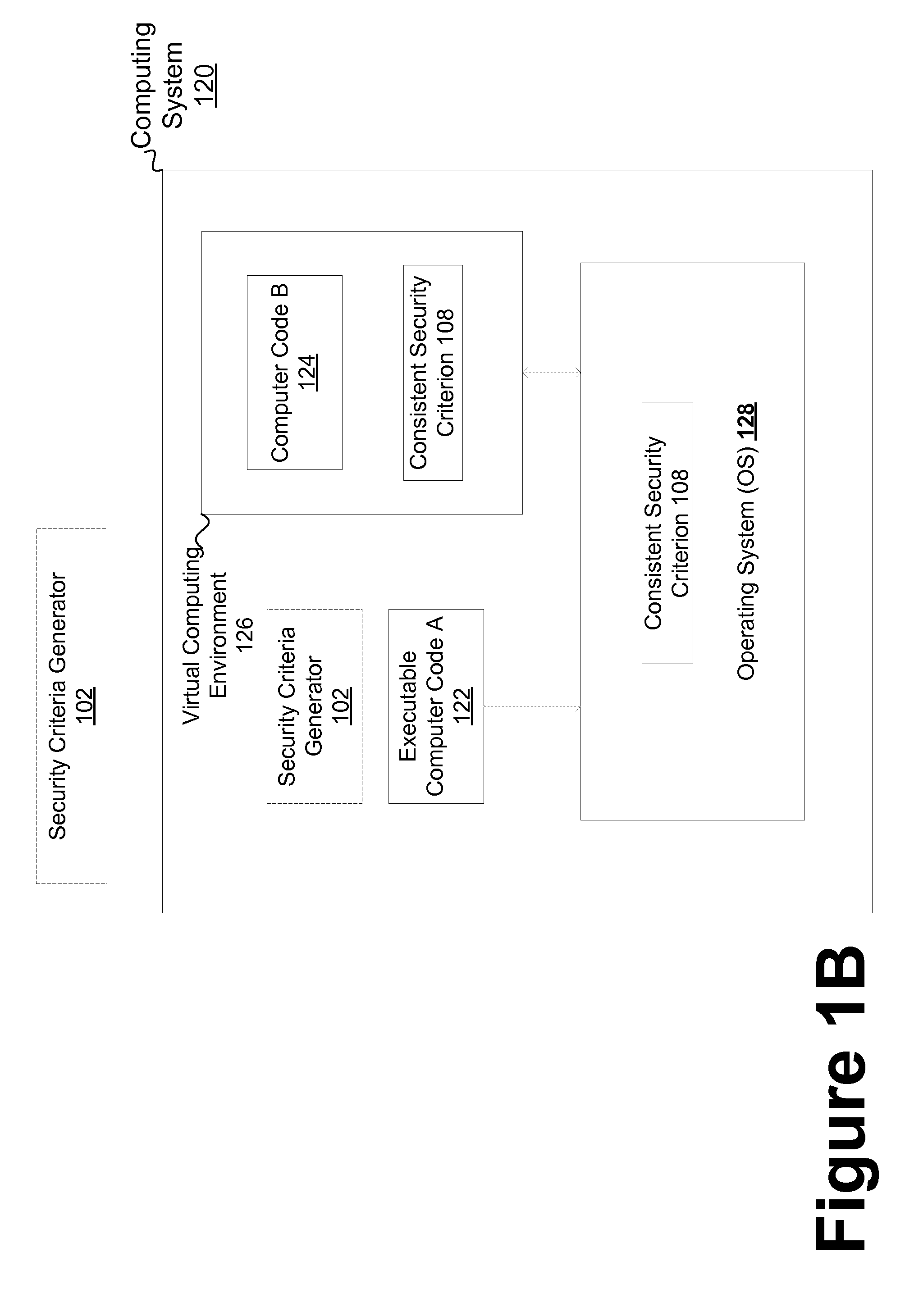
Consistent security enforcement for safer computing systems
InactiveUS20100162240A1Efficiently provideProvide securityComputer security arrangementsSoftware simulation/interpretation/emulationOperational systemTrusted components
Security can be enforced in a consistent manner with respect to various computing environments that may be operable in a computing system. Consistent security criteria can be generated, based on input security criterion, in a computer readable and storable form and stored in a computer readable storage medium, thereby allowing the consistent security criterion to be effectively provided to a computing system for enforcement of the input security criterion in a consistent manner with respect to, for example, (a) a first executable computer code effectively supported by an Operating System (OS), and (b) a second computer code effectively supported by the Virtual Computing Environment (VCE). A Trusted Component (TC) can effectively provide a consistent security criterion as a part and / or form that is suitable for a particular computing environment. The TC can, for example, be an automated tool that performs various functions including: verifying the consistency of security criteria, generation and deployment of consistent security criteria, and transformation of security criteria to parts and / or forms suitable for various computing environments. In addition, a Virtual Computing Environment (VCE) can obtain from the Operating System (OS) one or more security criteria. The Virtual Computing Environment (VCE) can be operable in a Trusted Computing Environment (TCE) and interface with a Trusted Operating System (TOS) that effectively enforces Mandatory Access Control (MAC), thereby allowing the Virtual Computing Environment (VCE) to leverage the security provided by the OS. The OS can, for example, be a Security-Enhanced Linux (SELinux) Operating System operating as a Trusted Component in a Trusted Environment that includes a Trusted Security Agent (TSA) operable to deploy consistent security criteria.
Owner:SAMSUNG ELECTRONICS CO LTD
Computer architecture for a handheld electronic device with a shared human-machine interface
ActiveUS20070223689A1Digital data processing detailsPublic key for secure communicationHuman–machine interfaceTrusted hardware
Mobile PDA computer system (300) includes a secure user processor (302), a non-secure user processor (306), a cryptographic engine (304), and a shared human / machine interface (HMI) (308). The secure user processor (302) can be comprised of a first trusted microprocessor and a first trusted operating system executing on the first trusted microprocessor. The non-secure user processor (306) can be comprised of a second non-trusted microprocessor and a second non-trusted operating system executing on the second non-trusted microprocessor. A cryptographic engine (304) can be comprised of a third trusted cryptographic processor and a third trusted operating system executing on the third trusted cryptographic processor. The cryptographic engine can be configured for encrypting and decrypting data. A first data communication link (303) communicates data between the secure user processor and the cryptographic engine. A second data communication link (305) communicates data between the cryptographic engine and the non-secure user processor. In this way, the cryptographic engine forms a bridge between the secure user processor and the non-secure user processor. An HMI (308) comprised of trusted hardware for user input and output is time-multiplex-shared among the secure user processor (302), the non-secure user processor (304), and the cryptographic engine (306) in a secure fashion.
Owner:SPEIR TECH LTD
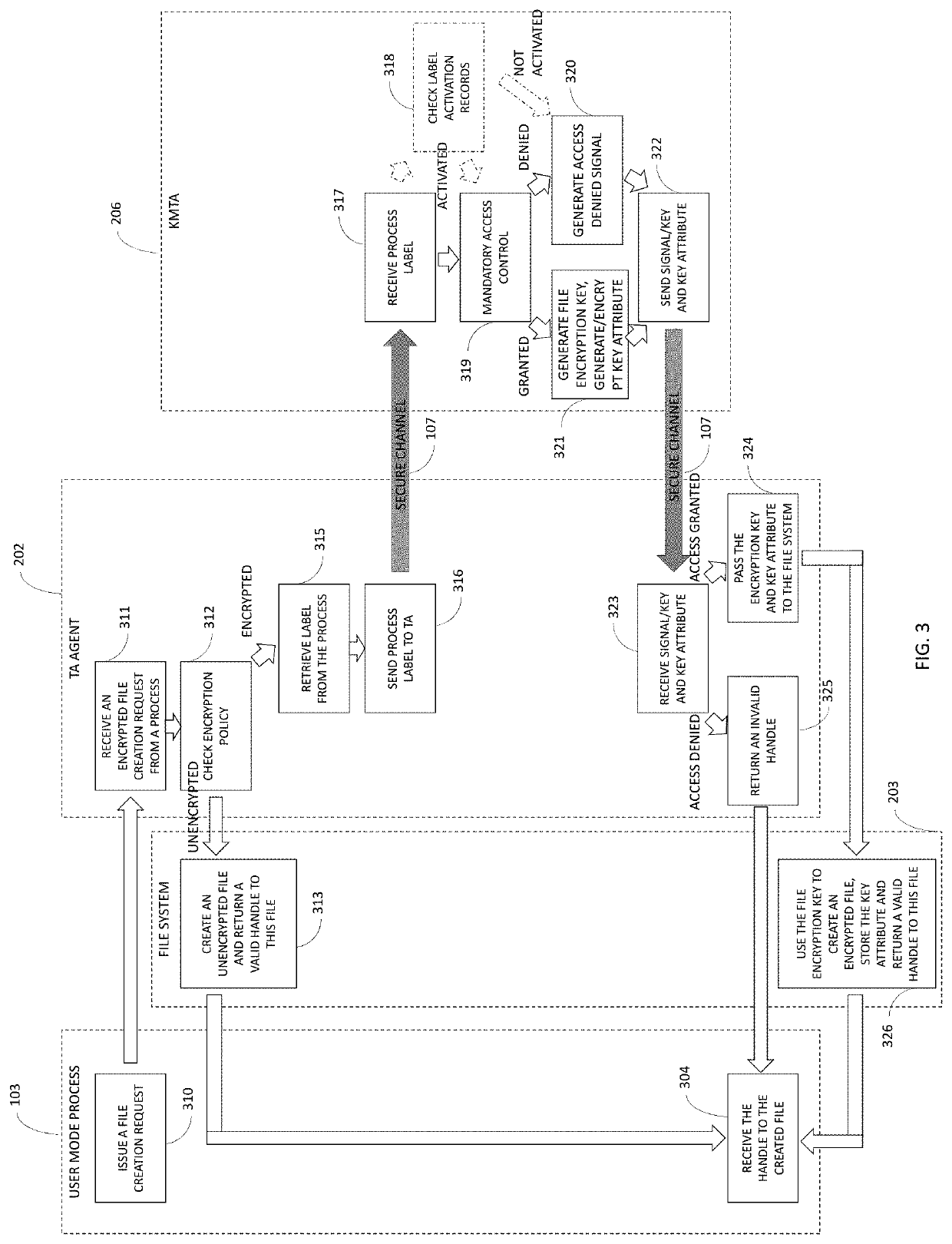
Manifest-based trusted agent management in a trusted operating system environment
InactiveUS7634661B2User identity/authority verificationUnauthorized memory use protectionVirtual memoryOperational system
Manifest-based trusted agent management in a trusted operating system environment includes receiving a request to execute a process is received and setting up a virtual memory space for the process. Additionally, a manifest corresponding to the process is accessed, and which of a plurality of binaries can be executed in the virtual memory space is limited based on indicators, of the binaries, that are included in the manifest.
Owner:MICROSOFT TECH LICENSING LLC
Data security verification for data transfers between security levels in trusted operating system
InactiveUS20070056037A1Improve robustnessImprove the environmentMemory loss protectionError detection/correctionOperational systemEngineering
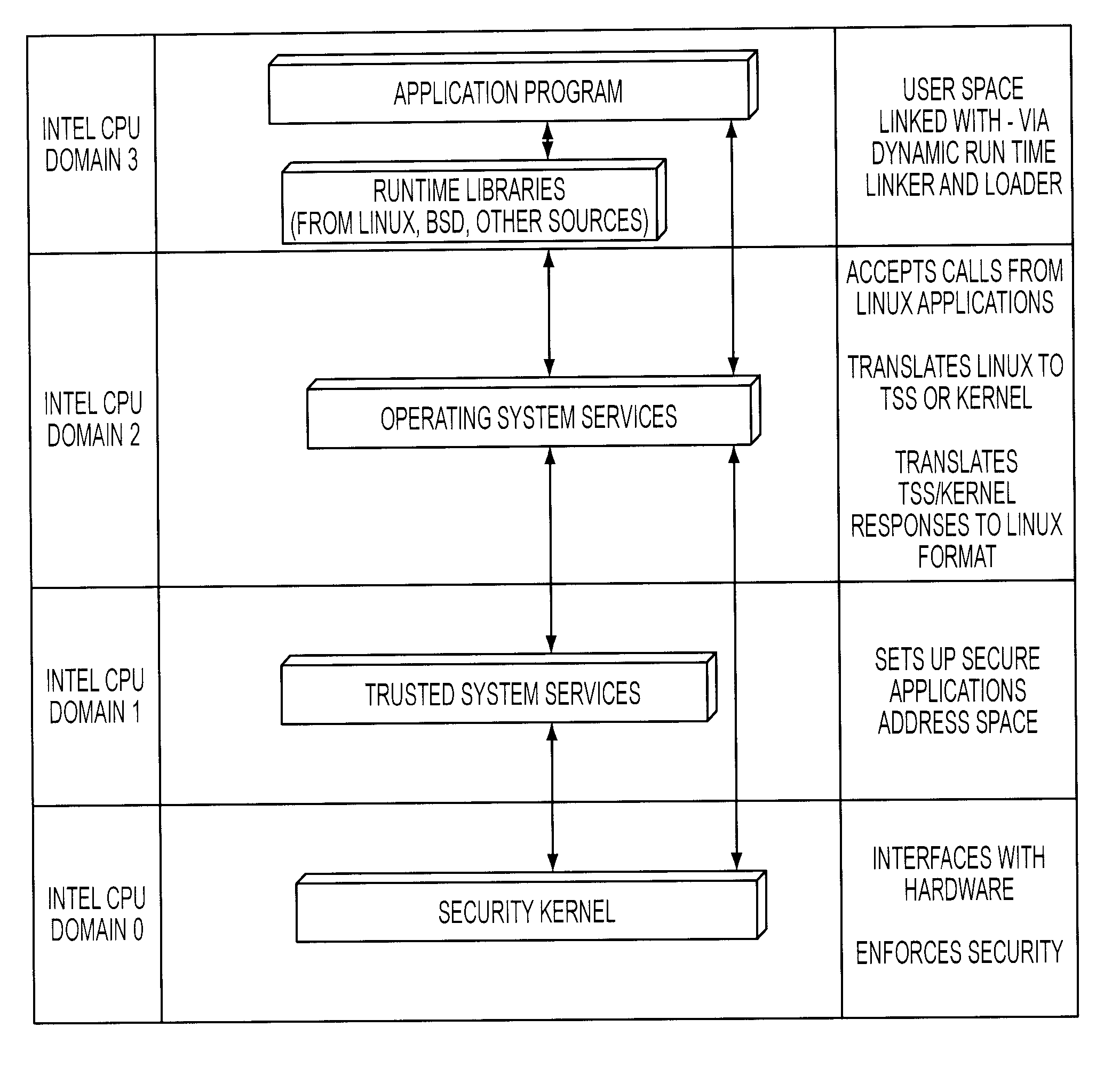
A trusted computer system that offers Linux® compatibility and supports contemporary hardware speeds. It is designed to require no porting of common applications which run on Linux, to be easy to develop for, and to allow the use of a wide variety of modern development tools. The system is further designed to meet or exceed the Common Criteria EAL-5 or higher rating through incorporation of required security features, as well as a very high level of assurance for handling data at a wide range of sensitivity (e.g., classification) levels in a wide range of operational environments. This is achieved through the implementation of a well-layered operating system which has been designed from the ground up to enforce security, but which also supports Linux operating system functions and methods.
Owner:BAE SYST INFORMATION & ELECTRONICS SYST INTERGRATION INC
Computer architecture for a handheld electronic device
ActiveUS7765399B2Digital data processing detailsUnauthorized memory use protectionOperational systemTelecommunications link
Mobile PDA computer system (300) includes a non-secure processor (306), comprising an untrusted microprocessor and an untrusted operating system executing on the untrusted microprocessor. The system also includes a secure processor (302), comprising a trusted microprocessor and a trusted operating system executing on the trusted microprocessor. A cryptographic engine (304) is provided for encrypting and decrypting data. A first data communication link (303) communicates data between the secure processor and the cryptographic engine. A second data communication link (305) communicates data between the non-secure processor and the cryptographic engine. In this way, the cryptographic engine forms a bridge between the secure user processor and the non-secure user processor.
Owner:SPEIR TECH LTD
Computer architecture for an electronic device providing a secure file system
ActiveUS20070226517A1Digital data processing detailsUser identity/authority verificationOperational systemFile system
A secure file service includes a cryptographic processor (302, 602) and a secure file system (301, 601). The cryptographic processor is comprised of a trusted microprocessor and a trusted operating system executing on the trusted cryptographic processor. The cryptographic processor includes hardware and software for accessing at least one classified data file from the secure file system, decrypting the classified data file, and serving the classified data file in decrypted form to a secure user processor (402, 502, 702) that has requested the file. The secure file system can be either a single-level secure file system (301) or a multi-level secure file system (601).
Owner:SPEIR TECH LTD
Method for providing trusted services using trusted execution environment system
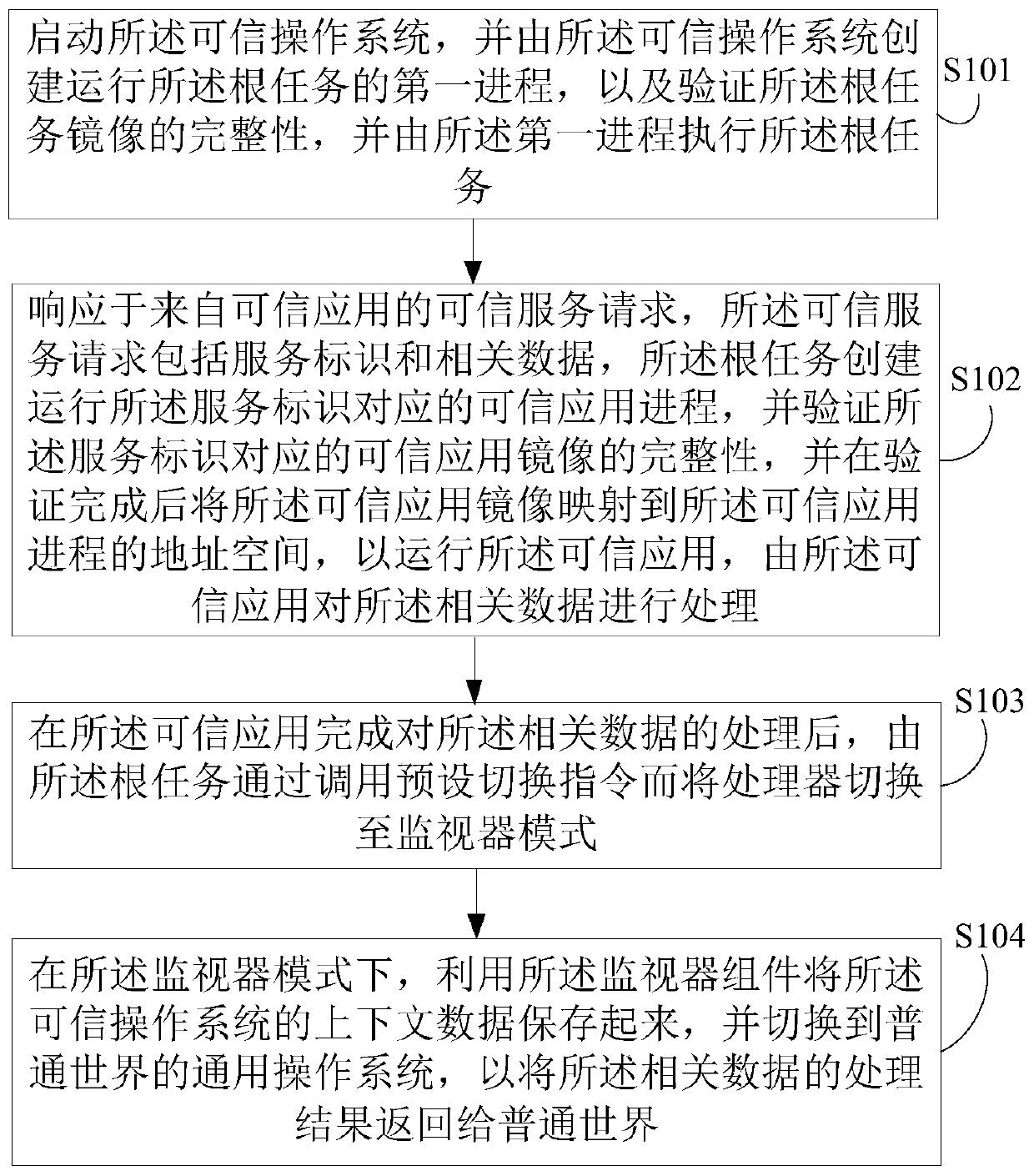
ActiveCN111382445ADoes not compromise securityGuaranteed confidentialityDigital data protectionInternal/peripheral component protectionMonitor modeOperational system
An embodiment of the invention discloses a method for providing trusted services by utilizing a trusted execution environment system based on a microkernel architecture. The method comprises the following steps of: starting a trusted operation system, creating a first process for running a root task by the trusted operation system, verifying the integrity of a mirror image of the root task, and executing the root task by the first process; in response to a service request from the common world, creating and running a trusted application process corresponding to a service identifier by the roottask, verifying the integrity of a trusted application mirror image corresponding to the service identifier, and creating a trusted application process based on the trusted application mirror image after the verification is completed; after the trusted application completes processing of the related data, switching a processor to a monitor mode by calling a preset switching instruction through the root task; and storing context data of the trusted operating system by using the monitor component in the monitor mode, and switching to a general operating system in the common world.
Owner:CAPITAL NORMAL UNIVERSITY
Trusted file relabeler
ActiveUS7840573B2Shorten the timeSimplified and secure processDigital data processing detailsAnalogue secracy/subscription systemsDocumentation procedureOperational system
A trusted relabeler system and software is provided that allows for the simultaneous reclassification of multiple files to multiple classification labels (security domains or computer networks) through automation of the multi-person review process. Roles, used to break down the requirements of the multi-person review process, dictate what specific function a user can perform. There are three roles used: Submitter, Processor, and Reviewer. Users are assigned one or more roles and a set of source and destination classification labels inside the security policy of a specific user that are bounded (restricted) by the clearance (maximum classification) assigned to a user on the trusted operating system on which the trusted relabeler system is implemented. The bundled documents to be reclassified are virus scanned, file typed, and searched for “dirty words” indicative of a particular classification level. Files are upgraded or downgraded only if all processes are completed successfully.
Owner:FORCEPOINT FEDERAL
Secure industrial control platform
ActiveCN110325995AInternal/peripheral component protectionPlatform integrity maintainanceSecure communicationOperational system
According to some embodiments, an overall chain-of-trust may be established for an industrial control system. Secure hardware may be provided, including a hardware security module coupled to or integrated with a processor of the industrial control system to provide a hardware root-of-trust. Similarly, secure firmware associated with a secure boot mechanism such that the processor executes a trusted operating system, wherein the secure boot mechanism includes one or more of a measured boot, a trusted boot, and a protected boot. Objects may be accessed via secure data storage, and data may be exchanged via secure communications in accordance with information stored in the hardware security model.
Owner:GENERAL ELECTRIC CO
A firmware upgrading method of an Android system and a storage device
ActiveCN109240720AAvoid wastingSolve the problem of brickingSoftware deploymentElectricityOperational system
The invention relates to the technical field of embedded development and testing, in particular to a firmware upgrading method of an Android system and a storage device. The firmware upgrading methodof the Android system comprises the following steps: obtaining an upgrading package; writing the upgrade boot information in position 2 of the Boot Communication Partition; restarting the system, if both positions 1 and 2 of Boot Communication Partition are marked with Recovery flag, booting Read Only Trusted Operating System and Read Only Secondary Boot Program, and booting the device into the Recovery system; using the firmware upgrade package to upgrade the device firmware according to the firmware upgrade operation instructions. The above method, if an unexpected interruption occurs duringthe upgrade, when the device is powered up again, because the Recovery flag is present in both positions 1 and 2 of the Boot Communication Partition, the Level 1 Bootstrapper can still successfully boot the Read-Only Trusted Operating System and the Read-Only Level 2 Bootstrapper, and the device firmware can be re-upgraded to avoid device bricking.
Owner:FUZHOU ROCKCHIP SEMICON
System and method for trusted operating system to create trusted process based on trusted chip
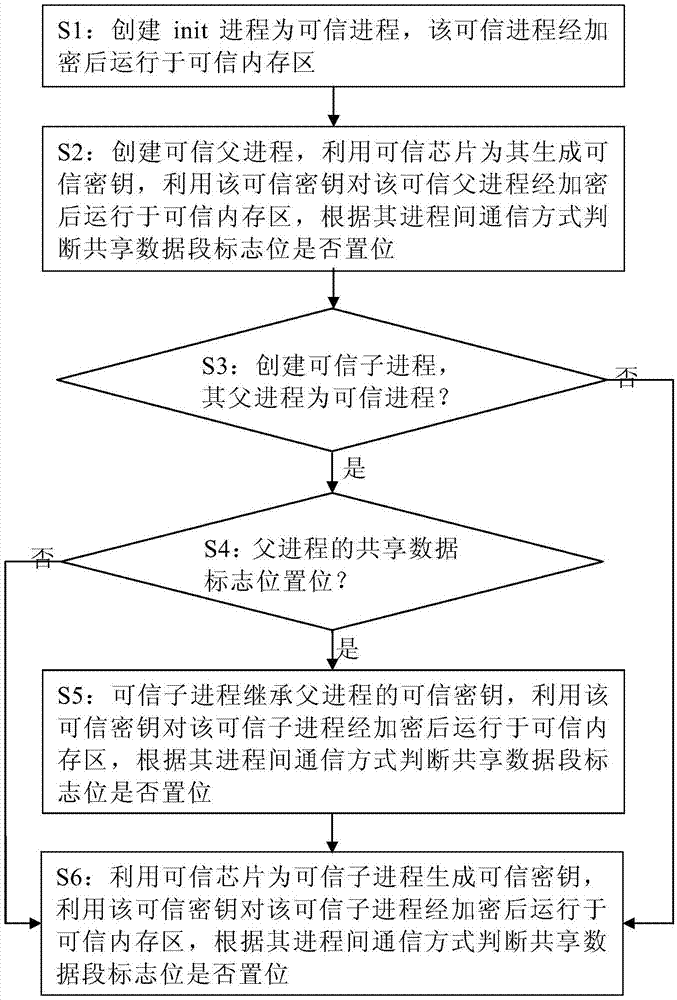
ActiveCN106934303AEnsure safetyAvoid security threatsInternal/peripheral component protectionOperational systemPotential risk
The present invention provides a system and a method for a trusted operating system to create a trusted process based on a trusted chip. The method comprises: installing the trusted operating system on a hardware system based on the trusted chip, creating a trusted process, and after encrypting the trusted process, operating the encrypted trusted process in a trusted memory area of a memory unit. Communication cannot be implemented between the trusted process and the general process, and effective isolation is realized between the trusted process and the general process in the memory space and data communication, so that the potential risk to the trusted process caused by the general process can be effectively avoided, and security of sensitive data can be guaranteed. According to the system and the method provided by the present invention, system security is guaranteed comprehensively from hardware to the operating system and to the application process; and according to the system platform established based on the present invention, not only use requirements of ordinary users can be satisfied, but also specific requirements of institutional users with high requirements for data security can be satisfied.
Owner:DATANG GAOHONG XINAN ZHEJIANG INFORMATION TECH CO LTD
Electronic assembly comprising a disabling module
An electronic assembly for an electronic device may include a detection module to detect a security anomaly of a Rich-OS operating system and a disabling module to disable at least one secure function of the electronic device in response to the detection. The disablement nevertheless allows use of the electronic device in fail-soft mode. The electronic assembly may be implemented such that these two modules are dependent on a trusted operating system, and the trusted operating system and the Rich-OS operating system may be stored in a memory of the electronic assembly and executed on the electronic assembly.
Owner:OBERTHUR TECH SA
Security policies in trusted operating system
InactiveUS20070056036A1Improve robustnessImprove the environmentMemory loss protectionError detection/correctionOperational systemModem device
A trusted computer system that offers Linux® compatibility and supports contemporary hardware speeds. It is designed to require no porting of common applications which run on Linux, to be easy to develop for, and to allow the use of a wide variety of modem development tools. The system is further designed to meet or exceed the Common Criteria EAL-5 or higher rating through incorporation of required security features, as well as a very high level of assurance for handling data at a wide range of sensitivity (e.g., classification) levels in a wide range of operational environments. This is achieved through the implementation of a well-layered operating system which has been designed from the ground up to enforce security, but which also supports Linux operating system functions and methods.
Owner:BAE SYST INFORMATION & ELECTRONICS SYST INTERGRATION INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com