Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
454results about "Error identification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
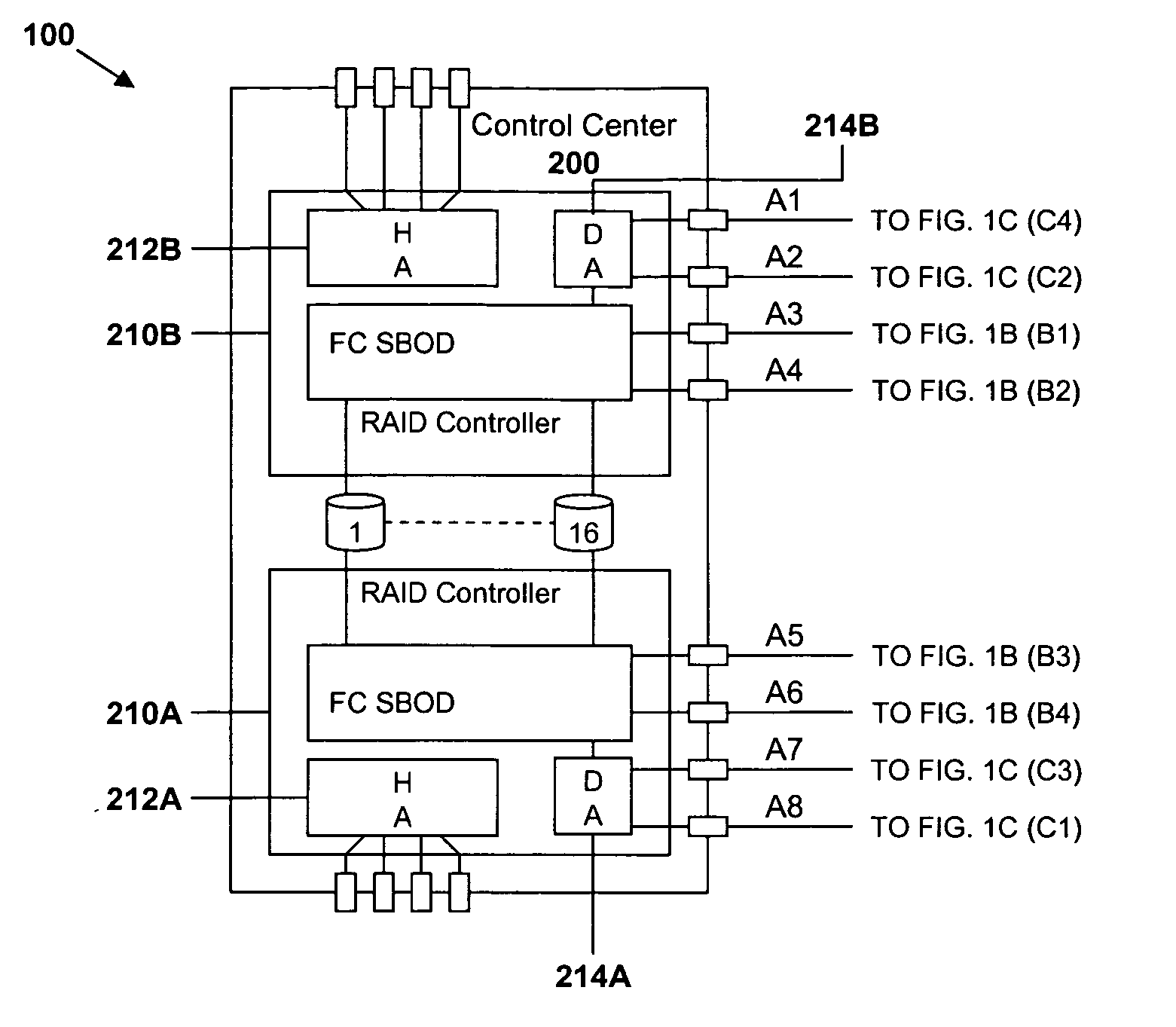
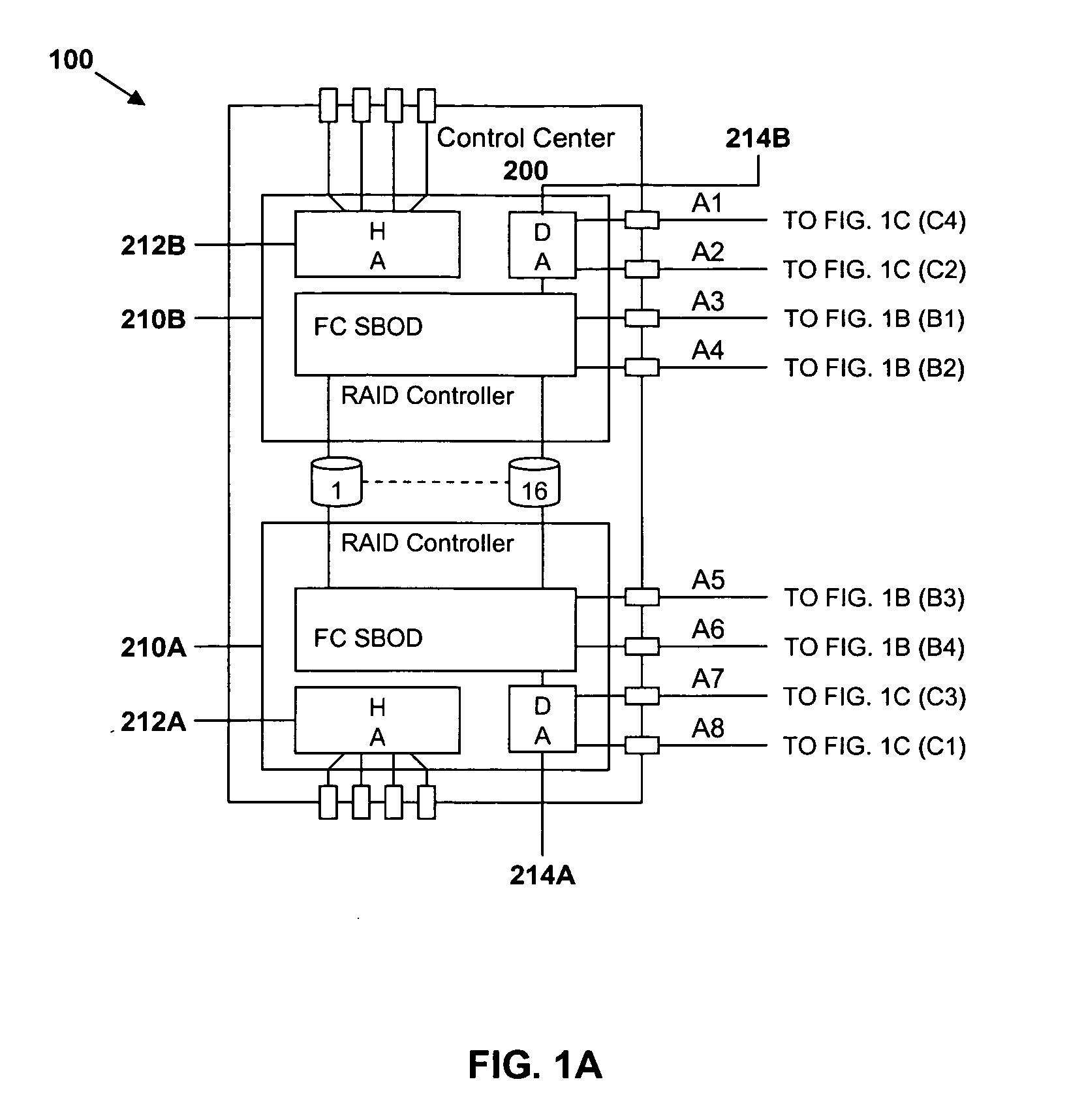
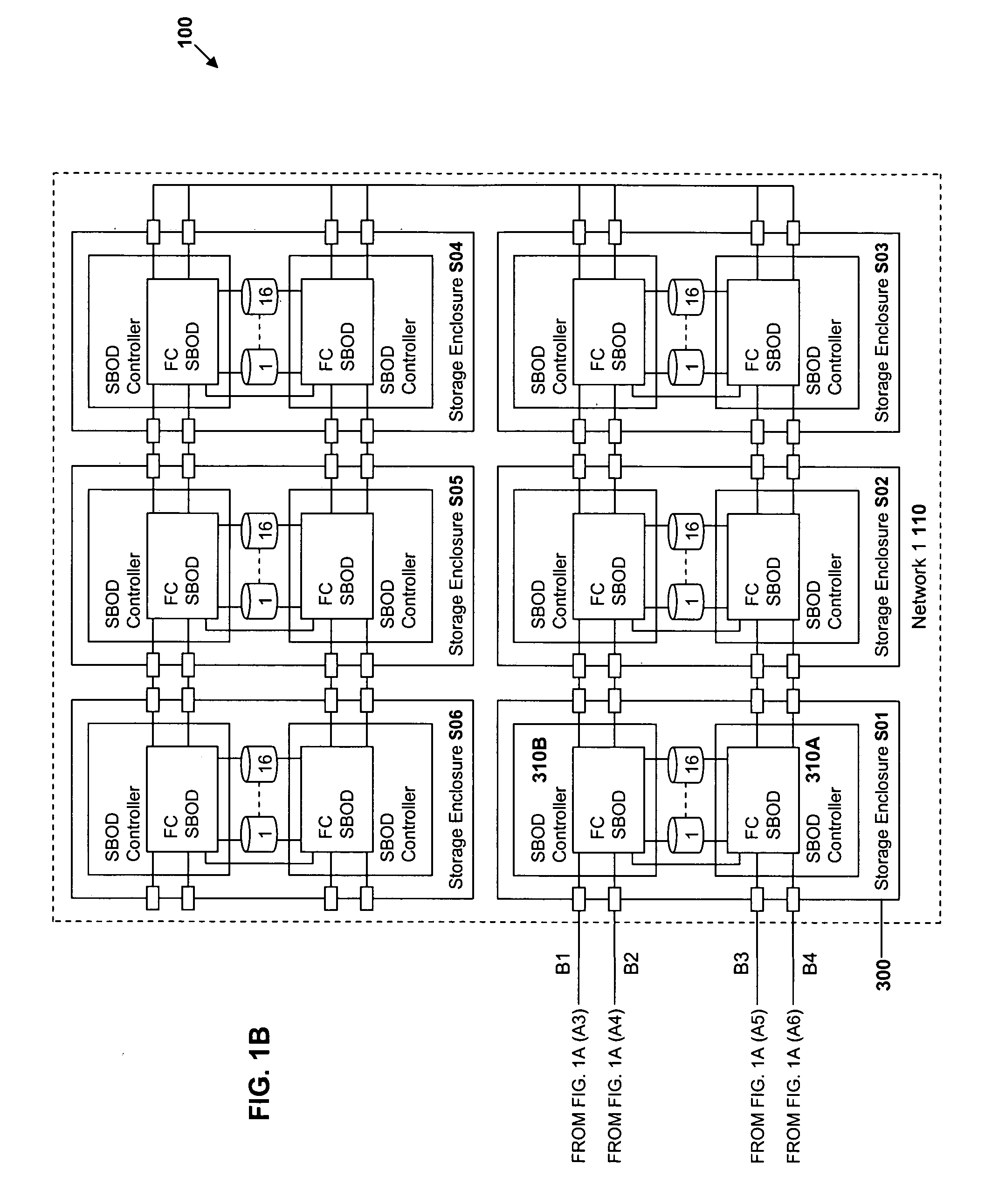
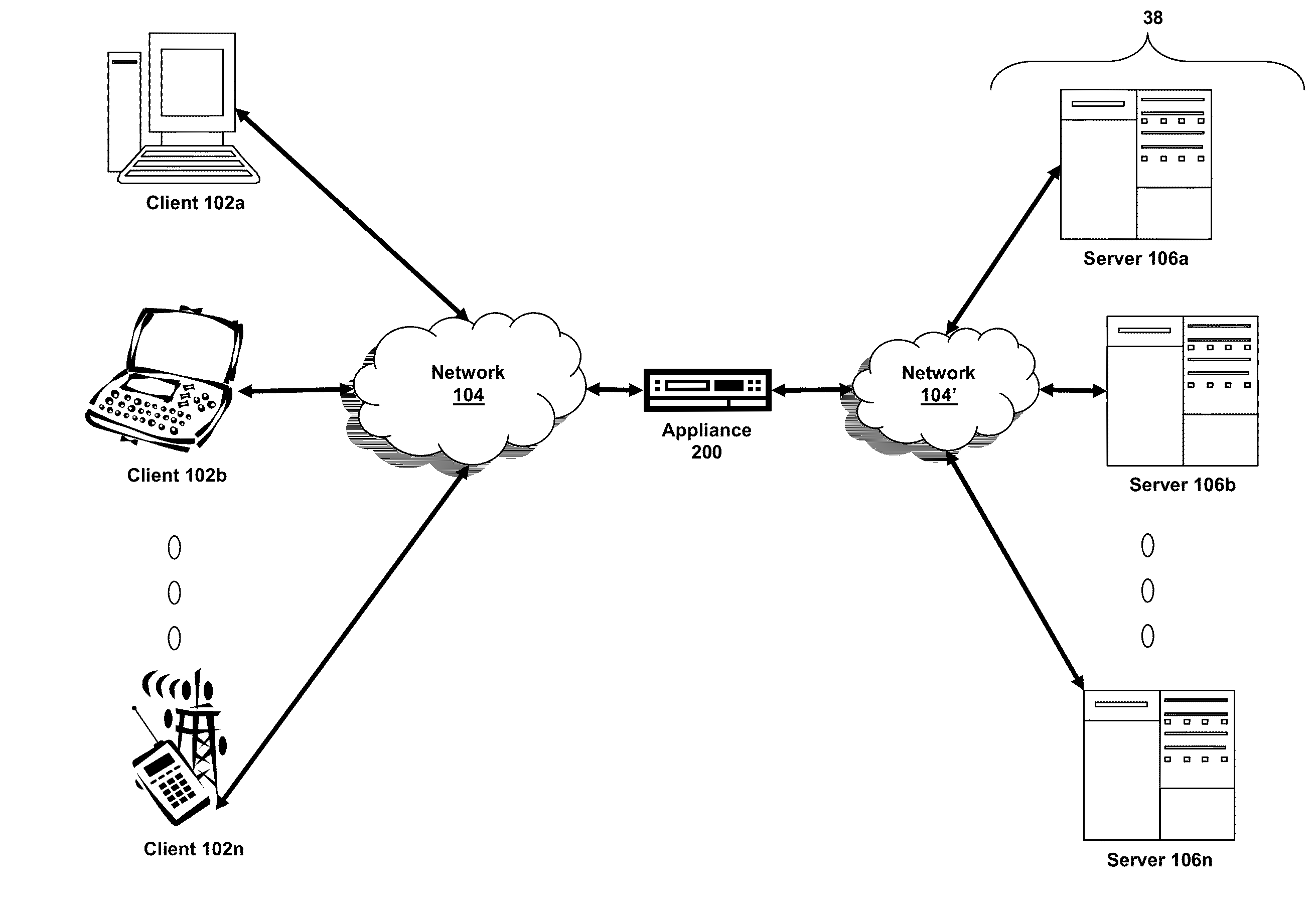
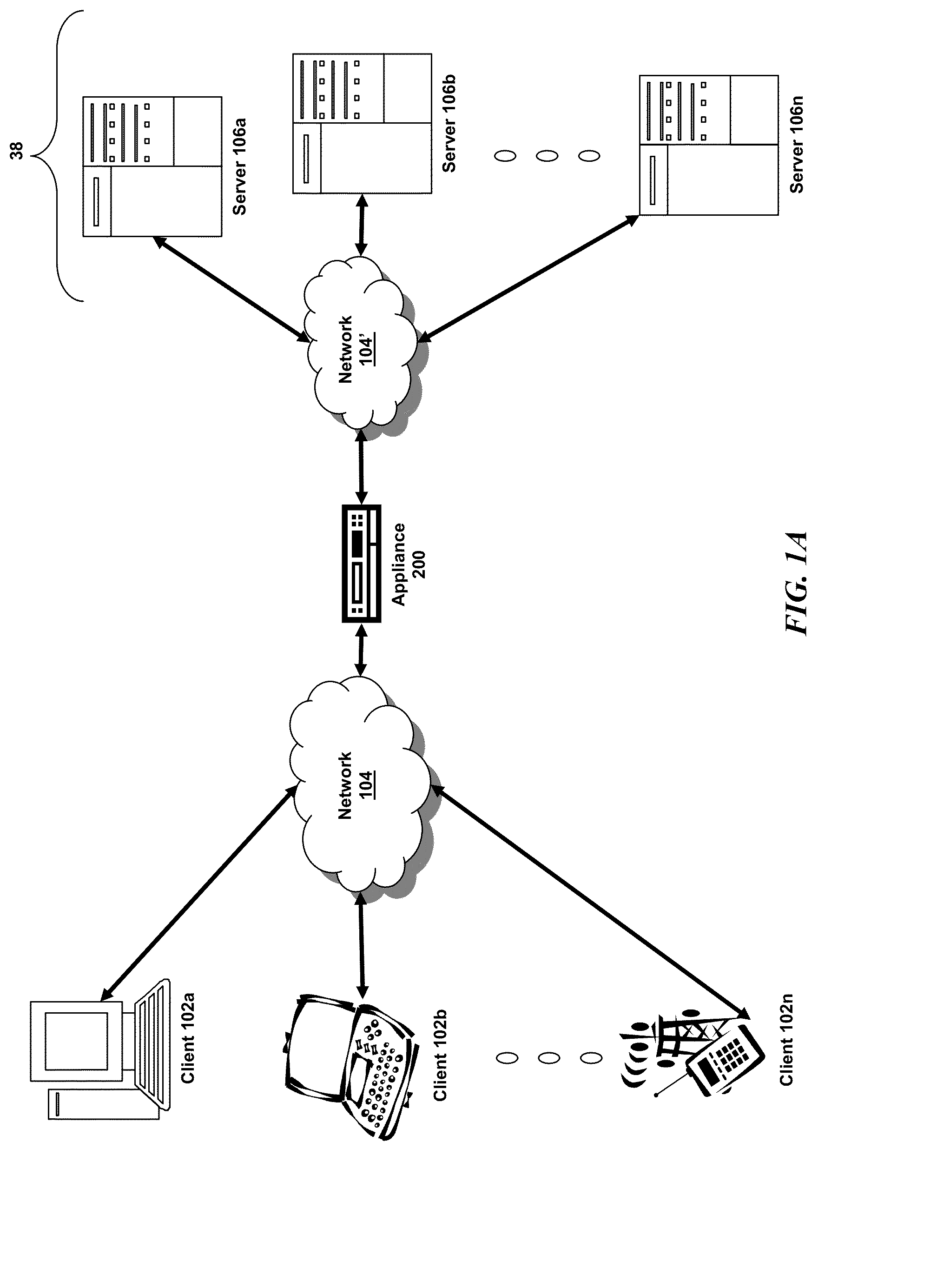
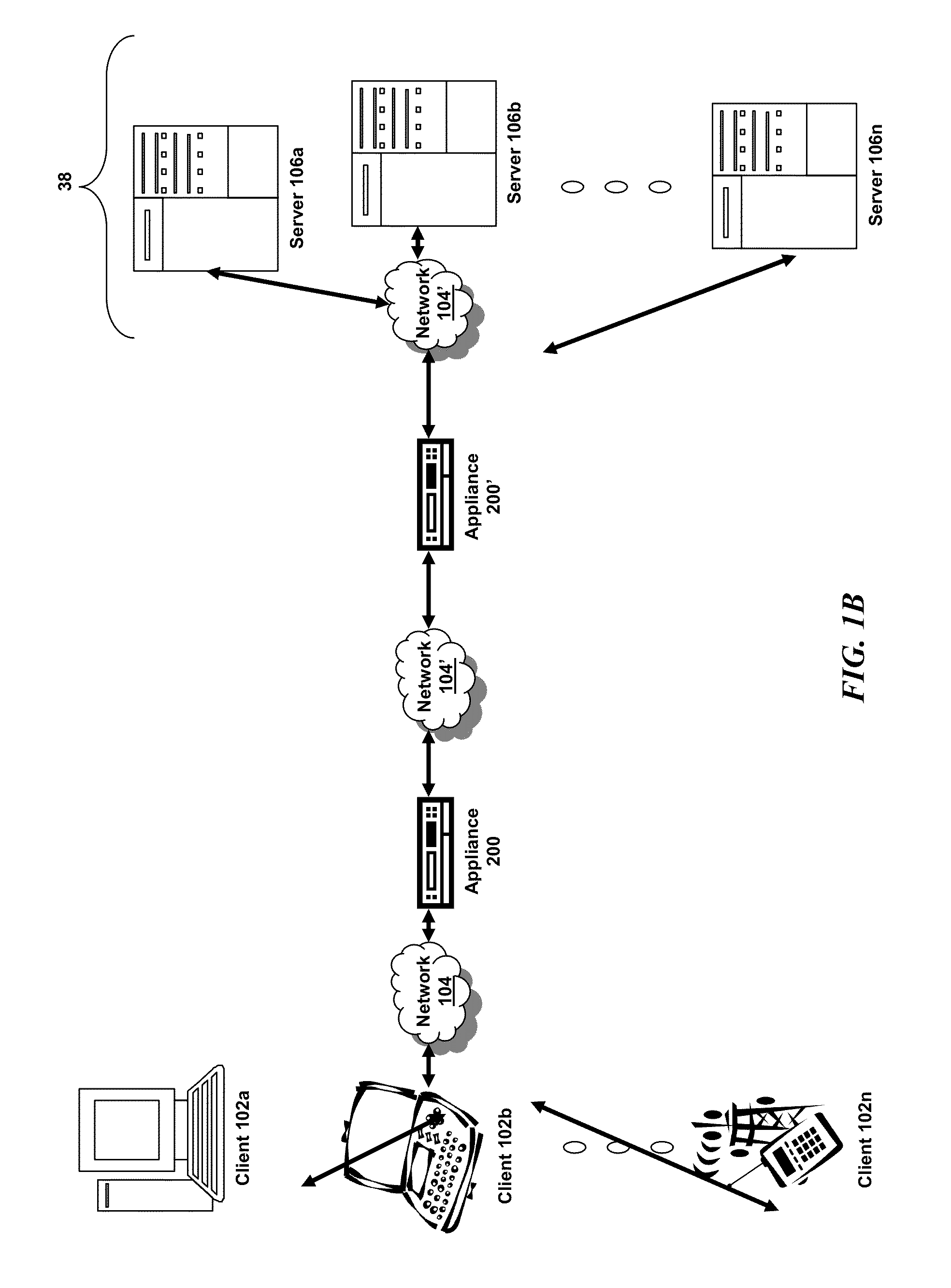
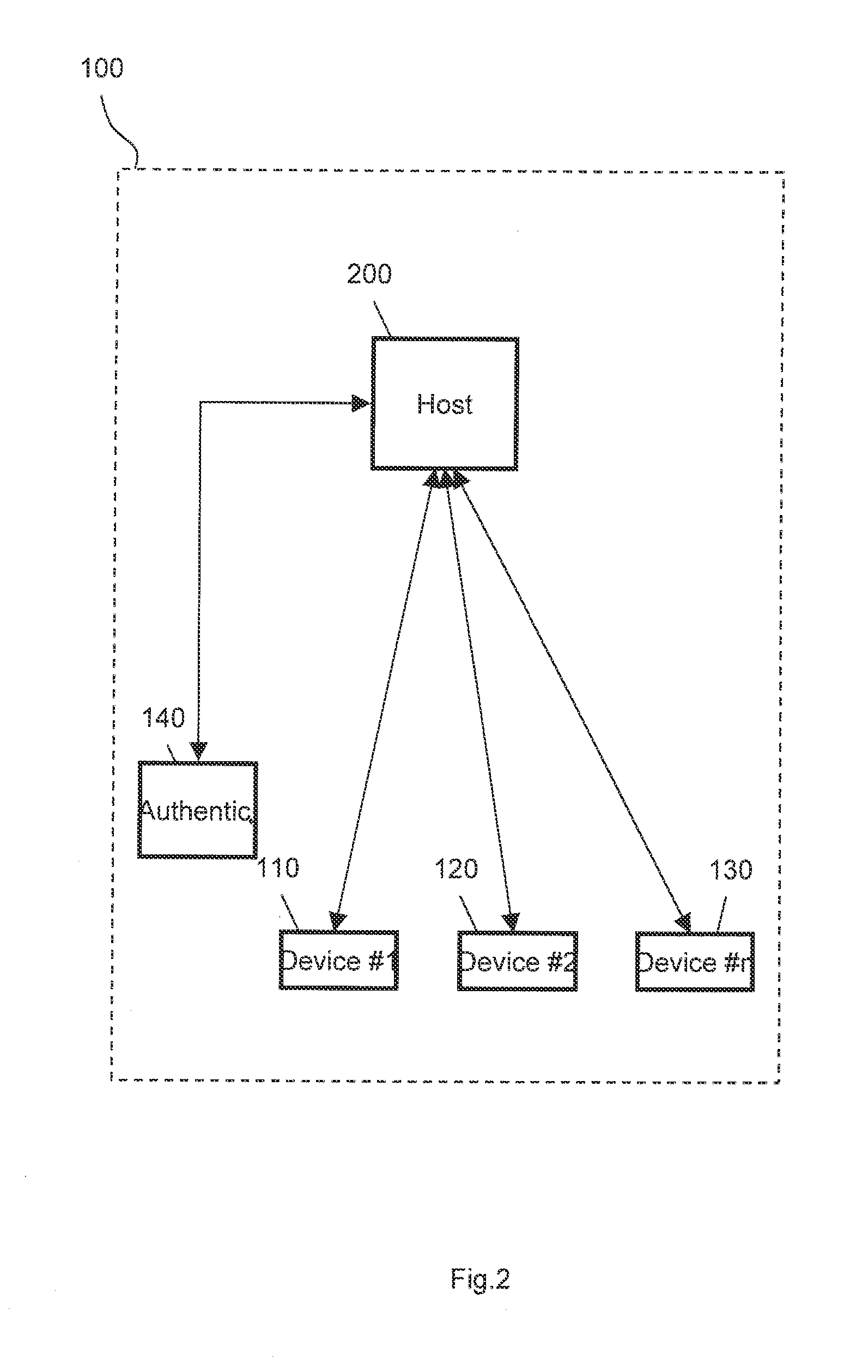
In-band control of indicators to identify devices distributed on the same domain
InactiveUS20060114930A1Additional requirementTime-division multiplexError identificationBiological activationSystems approaches
Systems, methods and a computer program product are provided to permit the identification of all of the devices of a specified domain in a multi-domain environment. All communication among the domain devices is in-band having the advantage that no additional cabling is required. A control center between host devices and the domains receives an in-band command from an initiating device in a specified domain, the command being transmitted in response to the activation of a triggering device on the initiating device. Upon receipt of the command, the control center broadcasts an in-band command to each of the other devices in the domain directing the other devices to activate an indicator on each of the other devices. With the indicators on the devices in the specified domain activated, an administrator is able to identify those devices and thus focus his search for the faulty device only on those devices within the domain.
Owner:IBM CORP
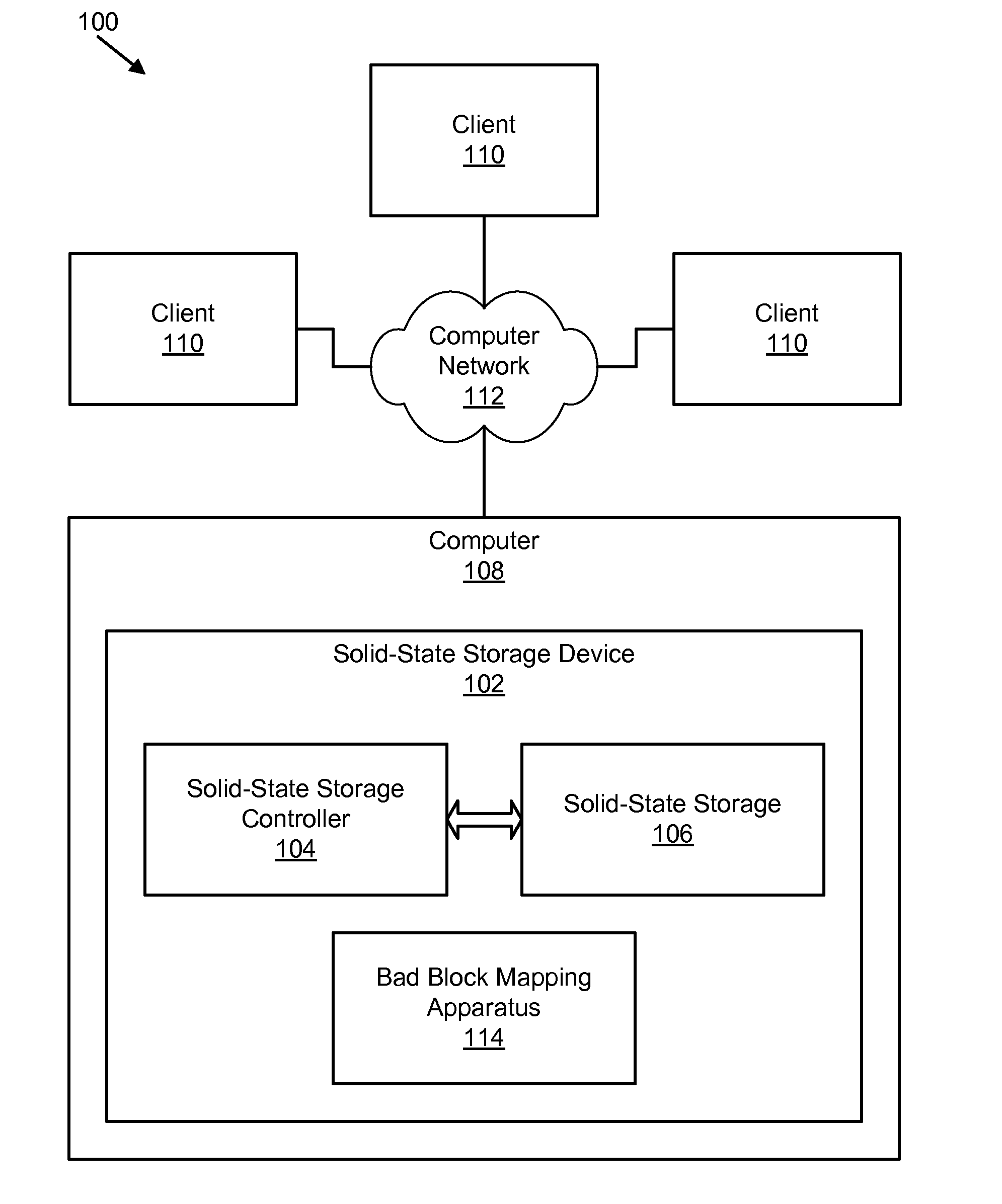
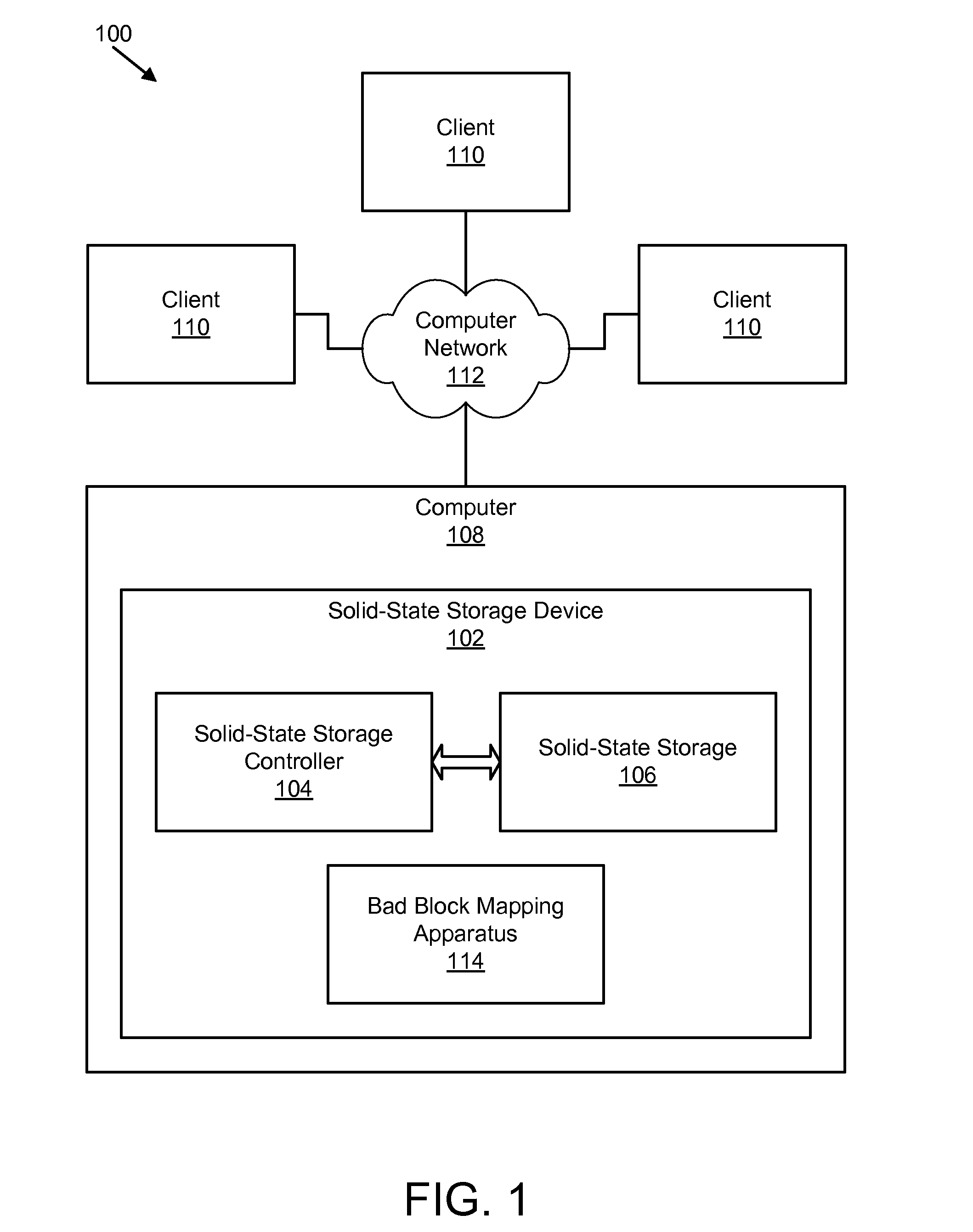
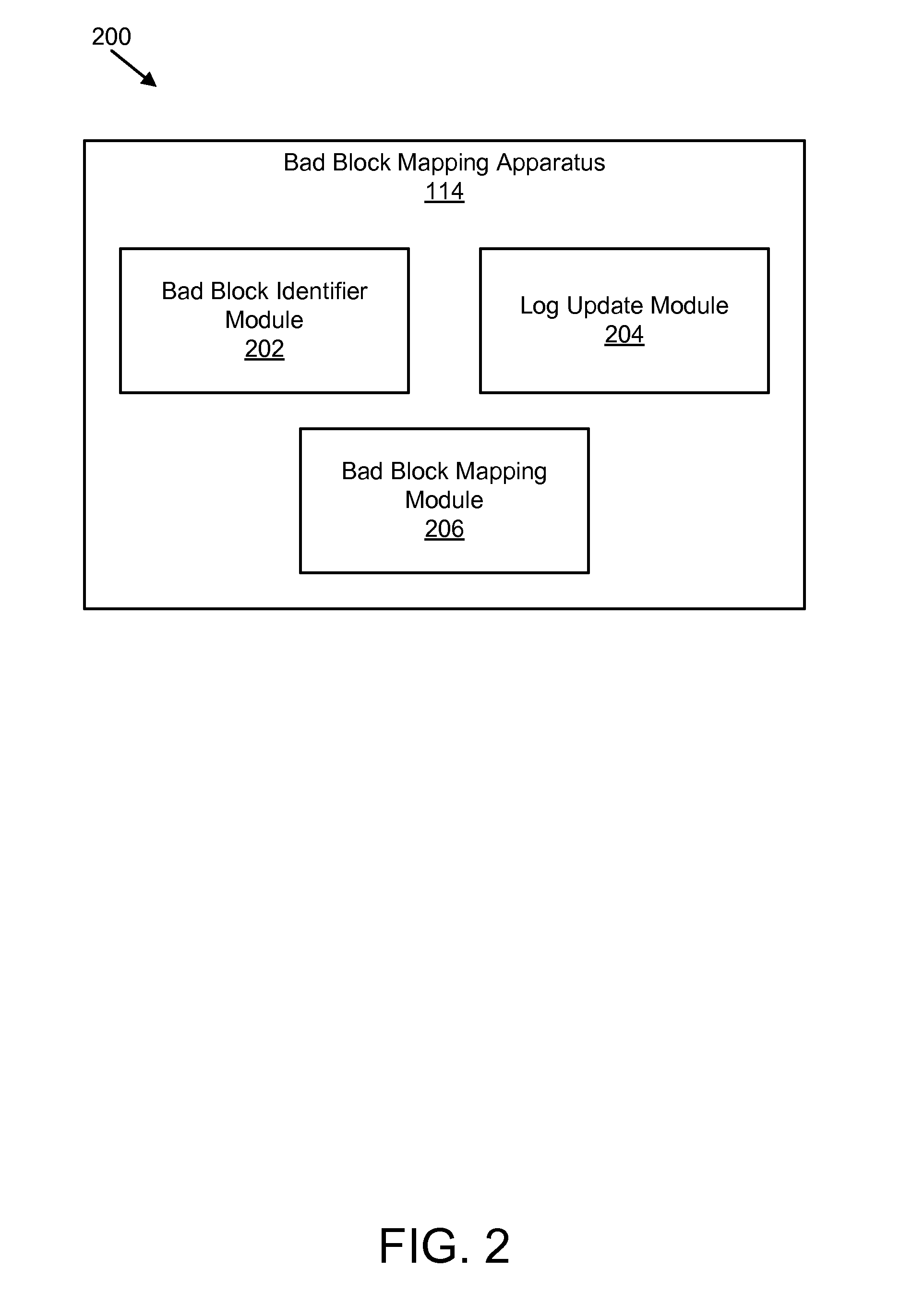
Apparatus, system, and method for bad block remapping
ActiveUS20090282301A1Improve reliabilityAvoid managementMemory architecture accessing/allocationError preventionSolid-state storageParallel computing
An apparatus, system, and method are disclosed for bad block remapping. A bad block identifier module identifies one or more data blocks on a solid-state storage element as bad blocks. A log update module writes at least a location of each bad block identified by the bad block identifier module into each of two or more redundant bad block logs. A bad block mapping module accesses at least one bad block log during a start-up operation to create in memory a bad block map. The bad block map includes a mapping between the bad block locations in the bad block log and a corresponding location of a replacement block for each bad block location. Data is stored in each replacement block instead of the corresponding bad block. The bad block mapping module creates the bad block map using one of a replacement block location and a bad block mapping algorithm.
Owner:SANDISK TECH LLC
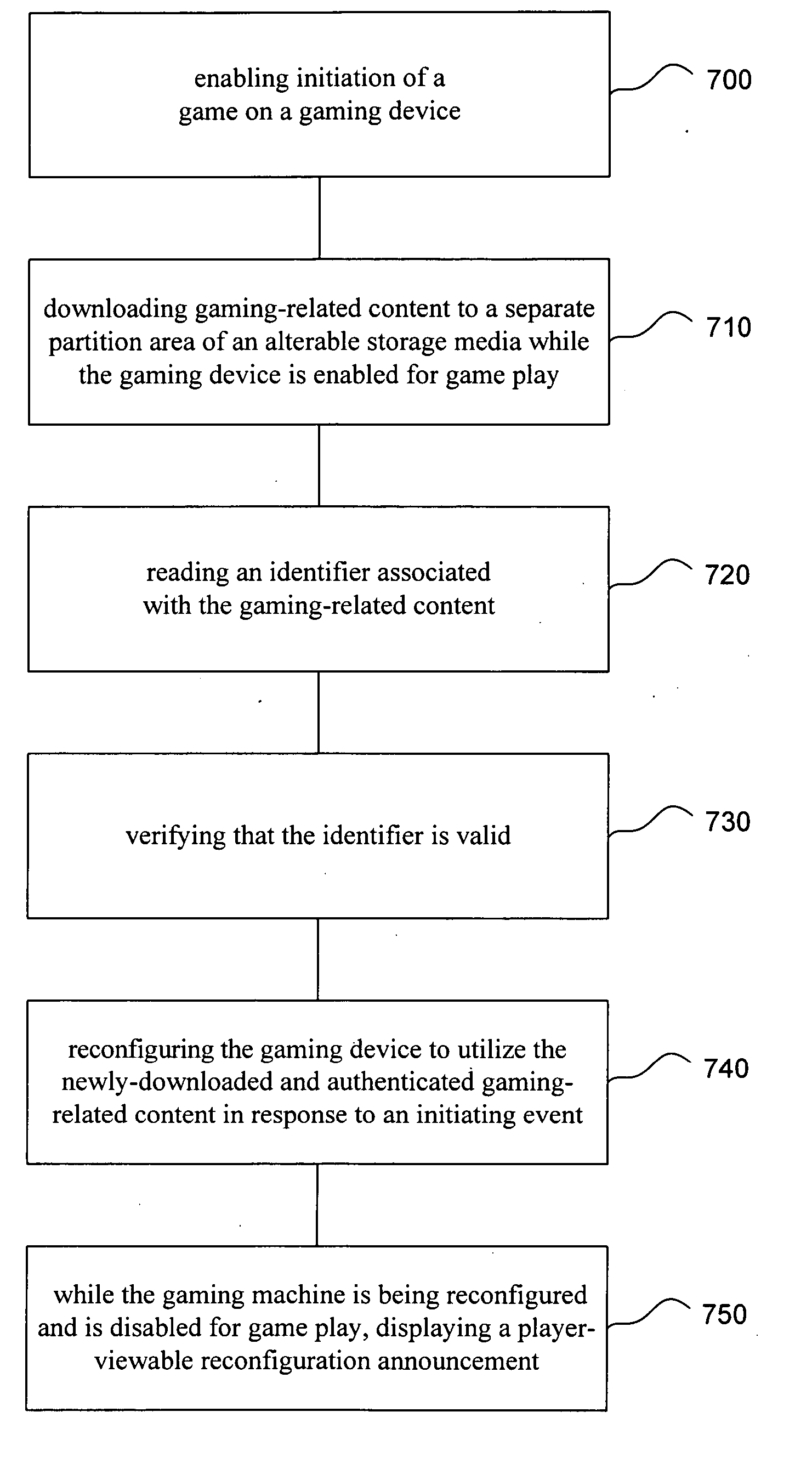
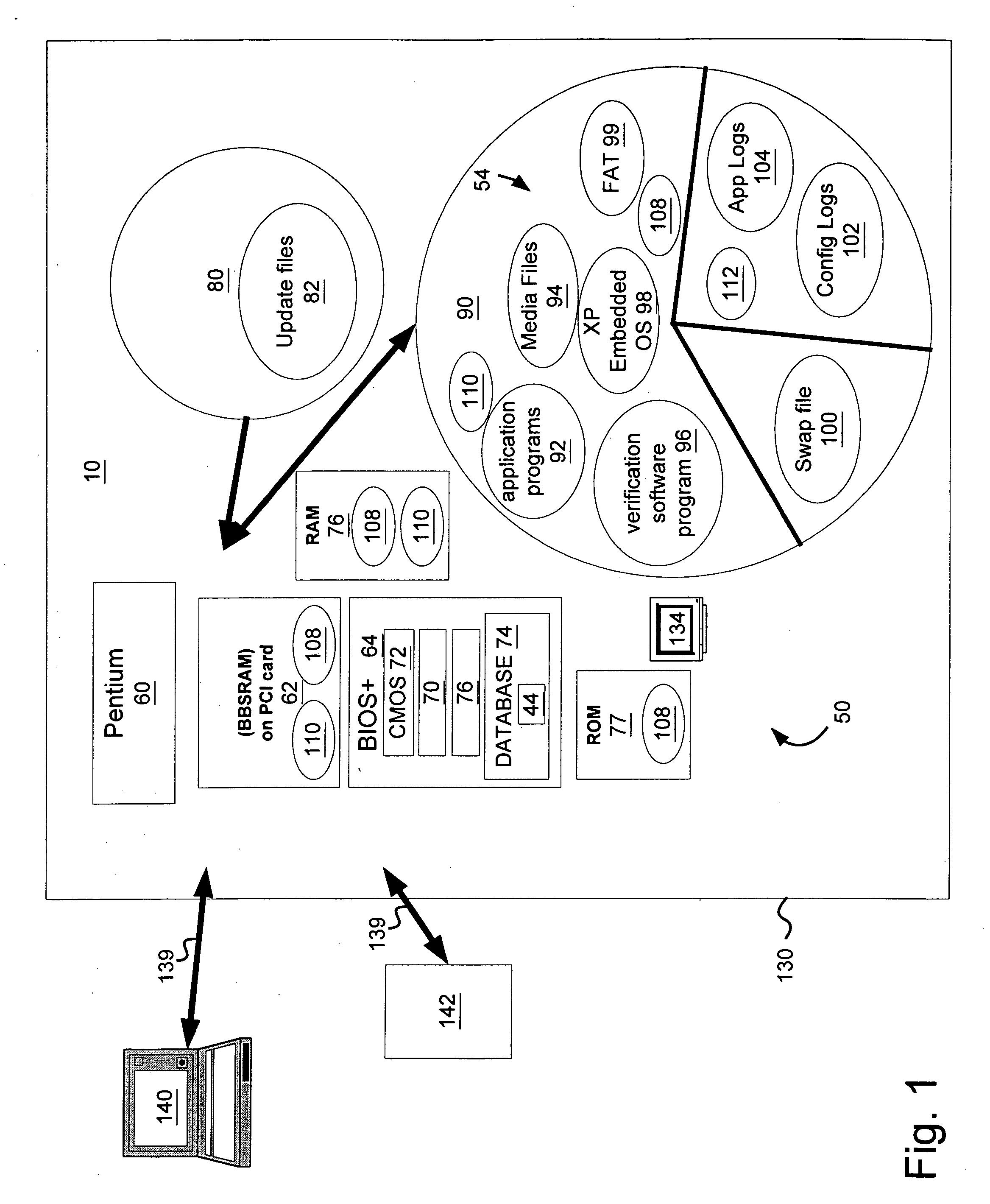
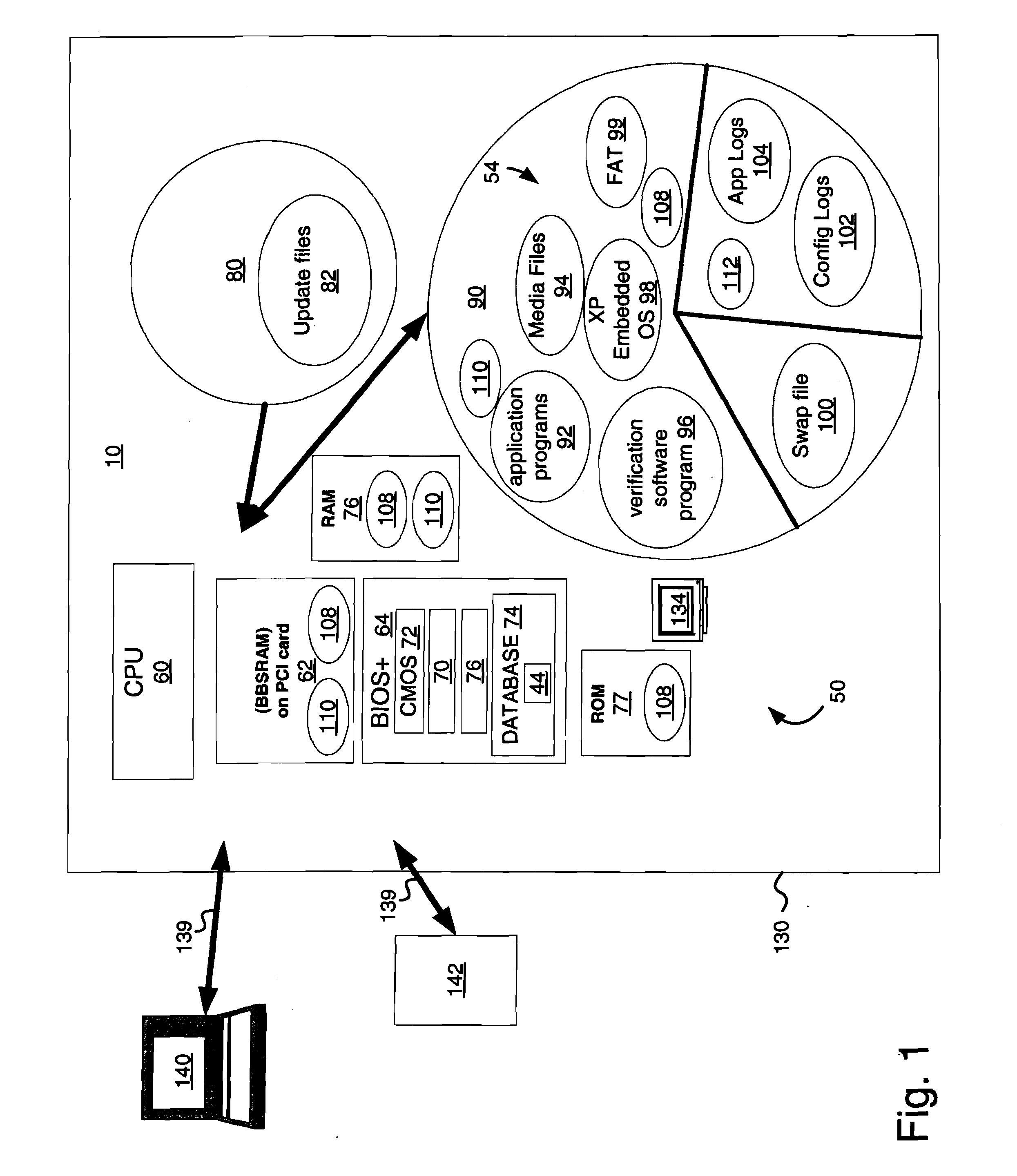
System and method for an alterable storage media in a gaming machine
InactiveUS20060079333A1Easy accessLess instructionDetecting faulty hardware by configuration testDetecting faulty hardware by remote testHard disc driveIdenticon
A system for verifying one or more downloaded components 54 of a gaming device 10 that includes the gaming device, which has an alterable hard drive 80 (or other persistent storage media 90), and the downloaded components that further include gaming-related content 92-96. A related method includes: enabling initiation of a game on the gaming device 10; downloading the gaming-related content 92-96 to the alterable hard drive 80 while the gaming device 10 is enabled for game play; reading an identifier associated with the gaming-related content 92-96; verifying that the identifier is valid (using verification software 70); and reconfiguring the gaming device 10 to utilize the newly-downloaded, gaming-related content 92-96 in response to an initiating event.
Owner:BALLY GAMING INC
Dual clocked synchronous memory device having a delay time register and method of operating same
InactiveUS6035365AFast readWrite quicklyEnergy efficient ICTMemory adressing/allocation/relocationProcessor registerDelay-locked loop
A synchronous memory device having at least one memory section which includes a plurality of memory cells. The memory device comprises a register to store a value which is representative of a delay time after which the memory device responds to a read request and clock receiver circuitry to receive first and second external clock signals. The memory device also includes an output driver(s) to output data on a bus, in response to a read request and in accordance with the delay time, wherein a first portion of the data is output synchronously with respect to the first external clock signal and a second portion of the data is output synchronously with respect to the second external clock signal. The memory device may include a delay locked loop to generate internal clock signal(s) using the external clock signal(s). The output drivers output data on the bus in response to the internal clock signal(s). The memory device may include input receiver circuitry, coupled to the bus, the receive the read request, wherein the read request is sampled from the bus synchronously with respect to the first external clock signal.
Owner:RAMBUS INC
Automatic classification of backup clients
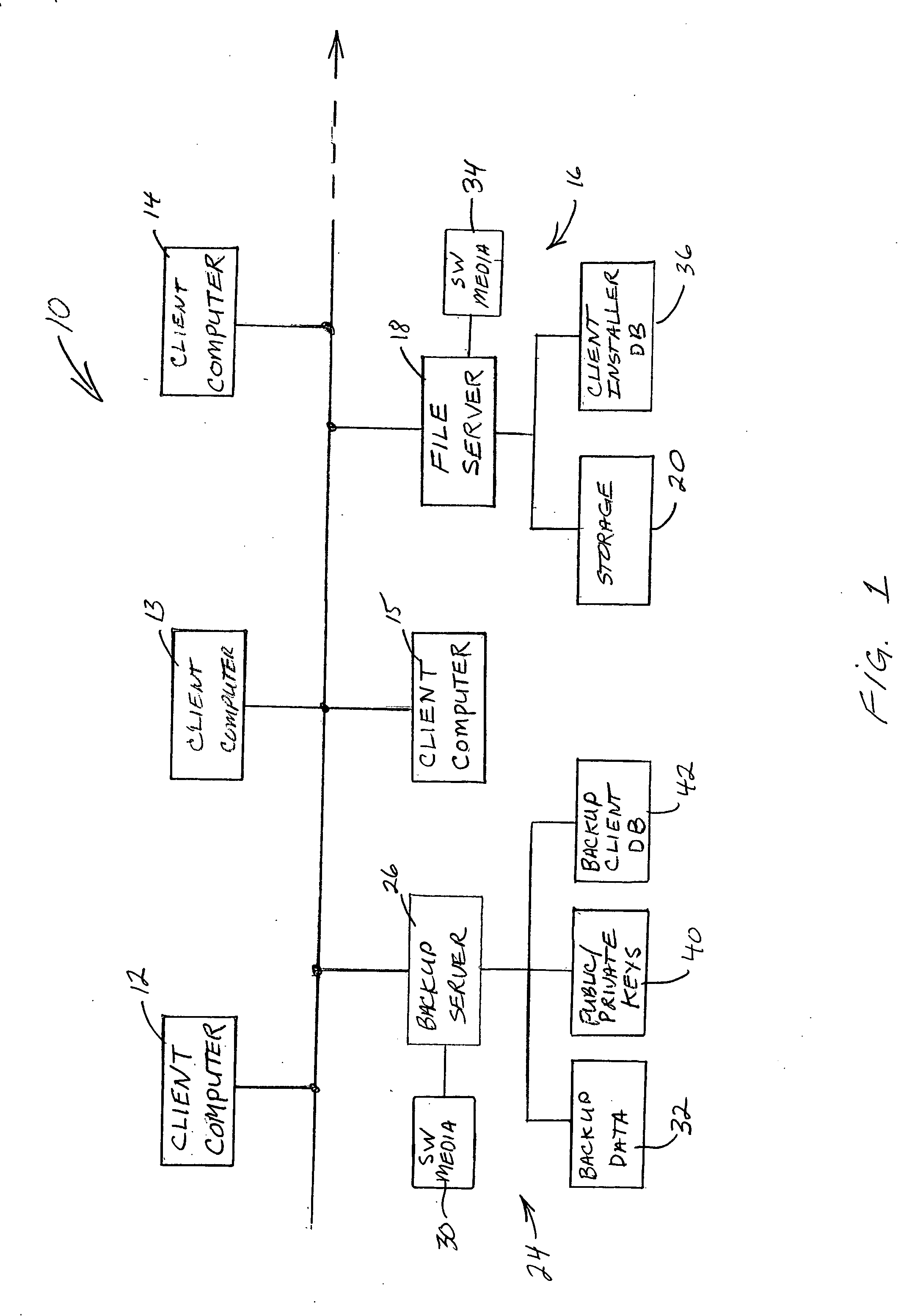
ActiveUS20070220319A1Digital data processing detailsComputer security arrangementsOperational systemClient-side
A method of automatically classifying clients into different backup policy groups according to pre-selected criteria, such as type of client, whether the client is a server, a desktop or a mobile computer, the department or business unit, or even the user. The method uses information obtained from the client itself to classify the client. This information includes the kind of processor platform and operating system in the client, the type and version of software being run, and whether the client has a battery, indicating that it is a mobile computer. Other information that can be used to classify the client for backup may be obtained from information that identifies the user, the department to which the client is assigned, and the location in which it is used. The process enables a mobile client traveling to another site of an enterprise to connect to a local LAN of the enterprise and be authenticated for backup, and to be automatically assigned an appropriate backup classification.
Owner:EMC IP HLDG CO LLC
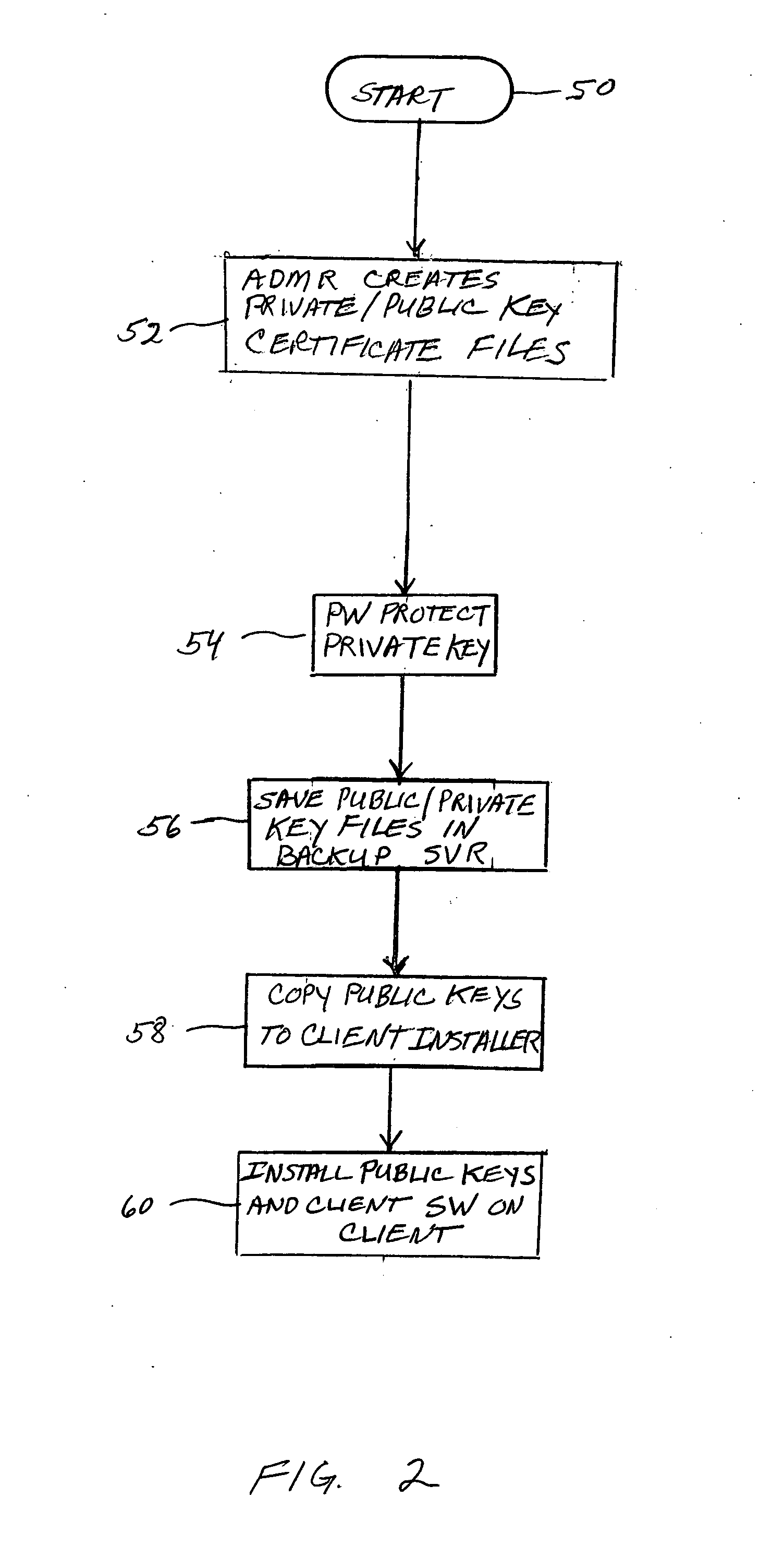
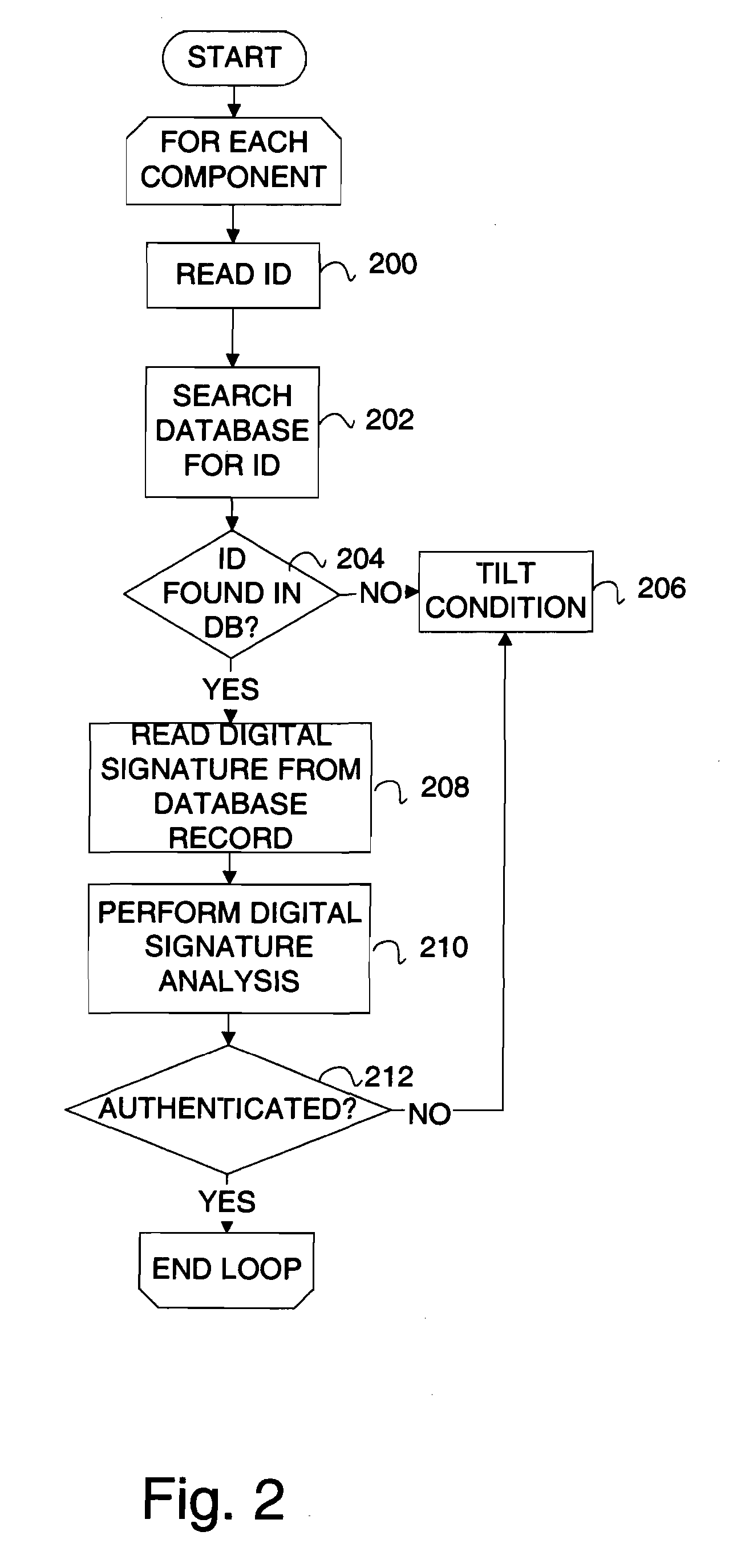
Device verification system and method
InactiveUS20070006329A1Little informationImprove securityDetecting faulty hardware by configuration testDetecting faulty hardware by remote testFile allocationOperational system
There is provided a method and system for verifying a device, having components. Identification numbers of the components are read and then verified. The process of verifying comprises matching each identification number in a database to determine whether each identification number is valid. In one embodiment, the database is remote from the device, wherein verification is performed over a network connecting a database server containing the database with the device. The device transmits the identification numbers for each of the components to the database server for verification. A file allocation structure reader may be located in a basic input / output system of the device for reading and verifying data files from a persistent storage media without loading an operating system. The device may comprise a gaming machine that contains a monitor for monitoring one or more system events being processed by the gaming machine. The monitor monitors routine and non-routine events. A detector is included for detecting selected system events so that they may be recorded.
Owner:BALLY GAMING INC
Systems and methods for exporting application details using appflow
ActiveUS20140304393A1Without impairment of administrative processDigital computer detailsError identificationData miningData records
The present disclosure is directed towards systems and methods for lightweight identification of flow information by application. A flow monitor executed by a processor of a device may maintain a counter. The flow monitor may associate an application with the value of the counter and transmit, to a data collector executed by a second device, the counter value and a name of the application. The flow monitor may monitor a data flow associated with the application to generate a data record. The flow monitor may transmit the data record to the data collector, the data record including an identification of the application consisting of the counter value and not including the name of the application. The data collector may then re-associate the data record with the application name based on the previously received counter value.
Owner:CITRIX SYST INC
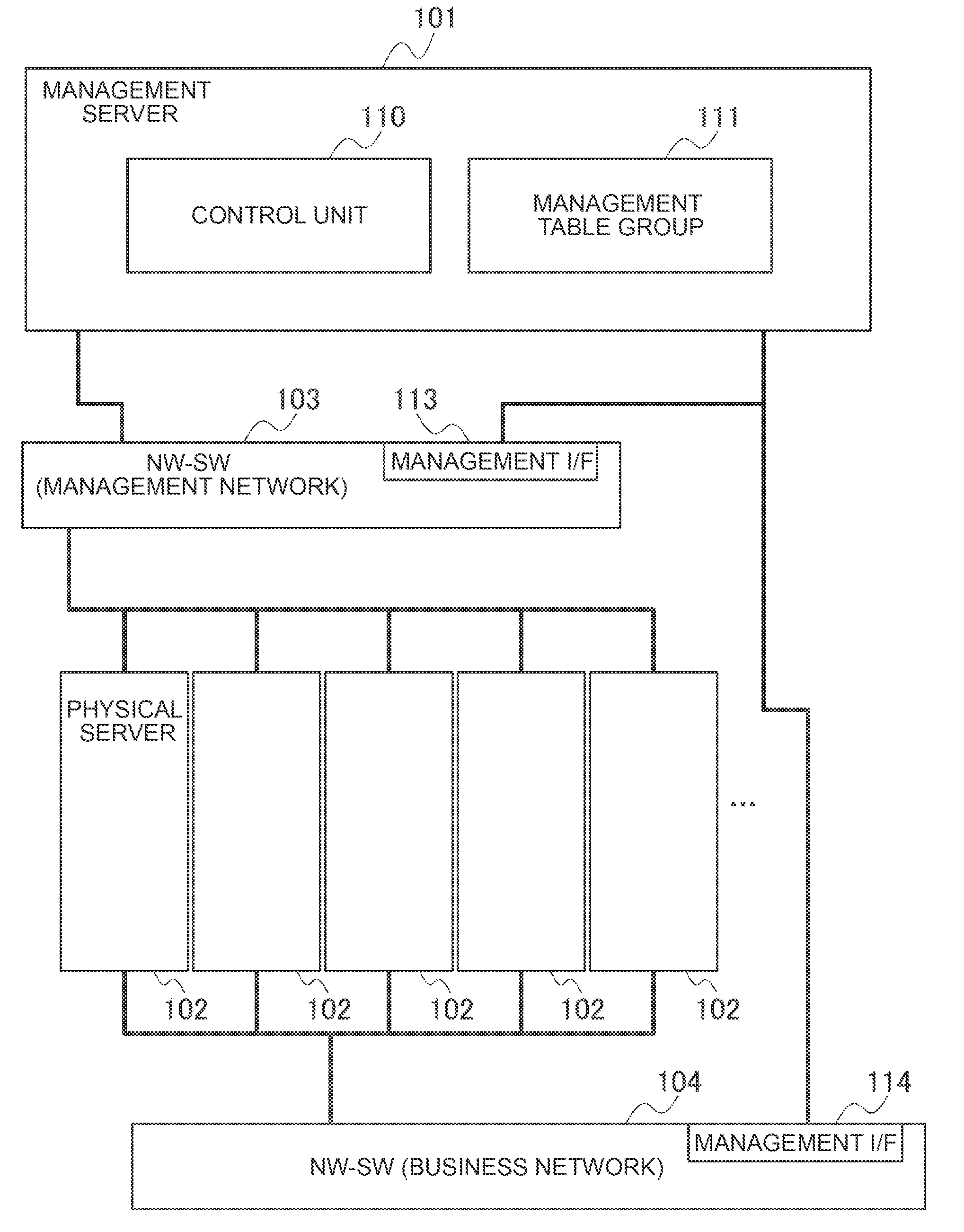
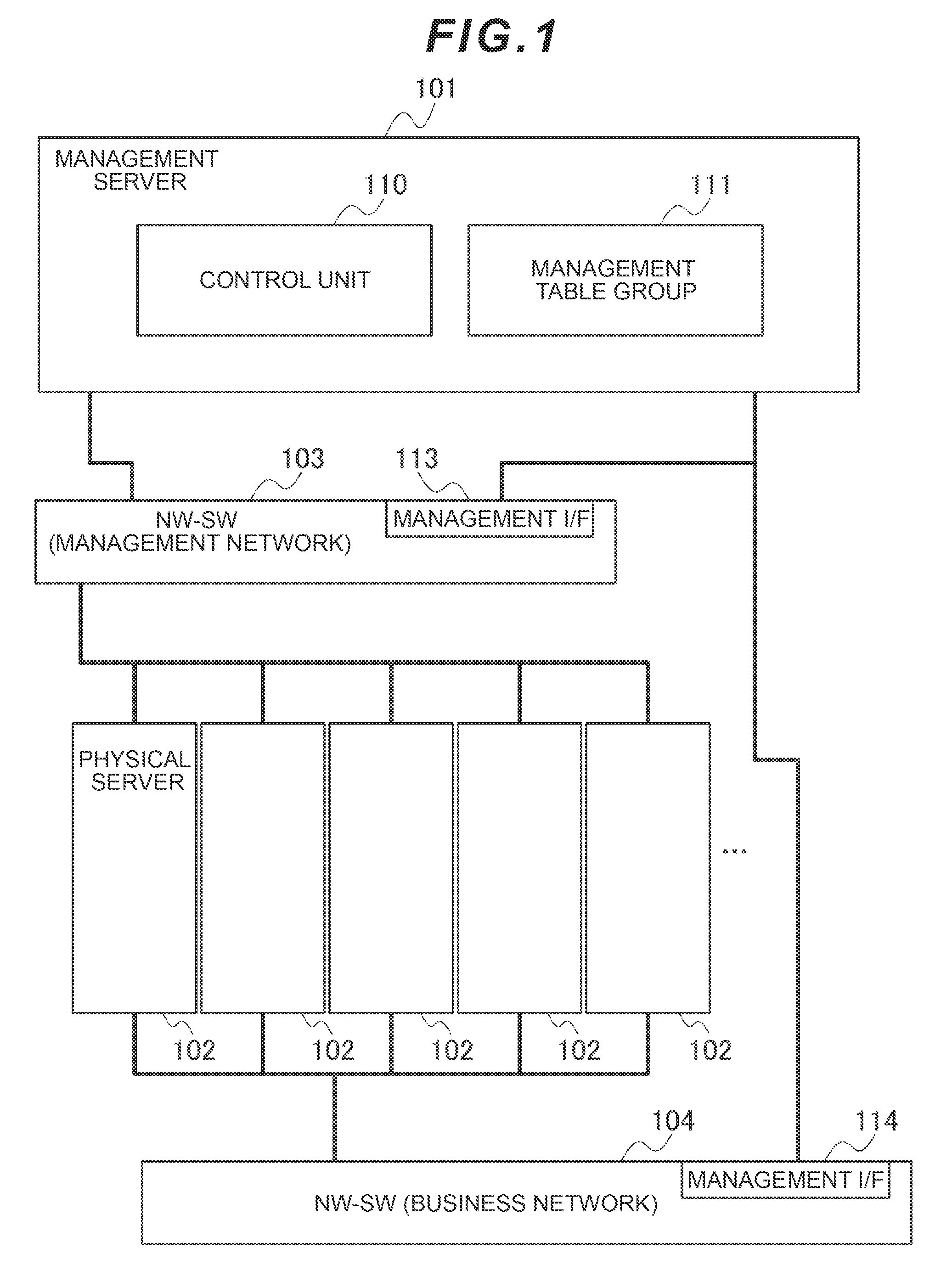
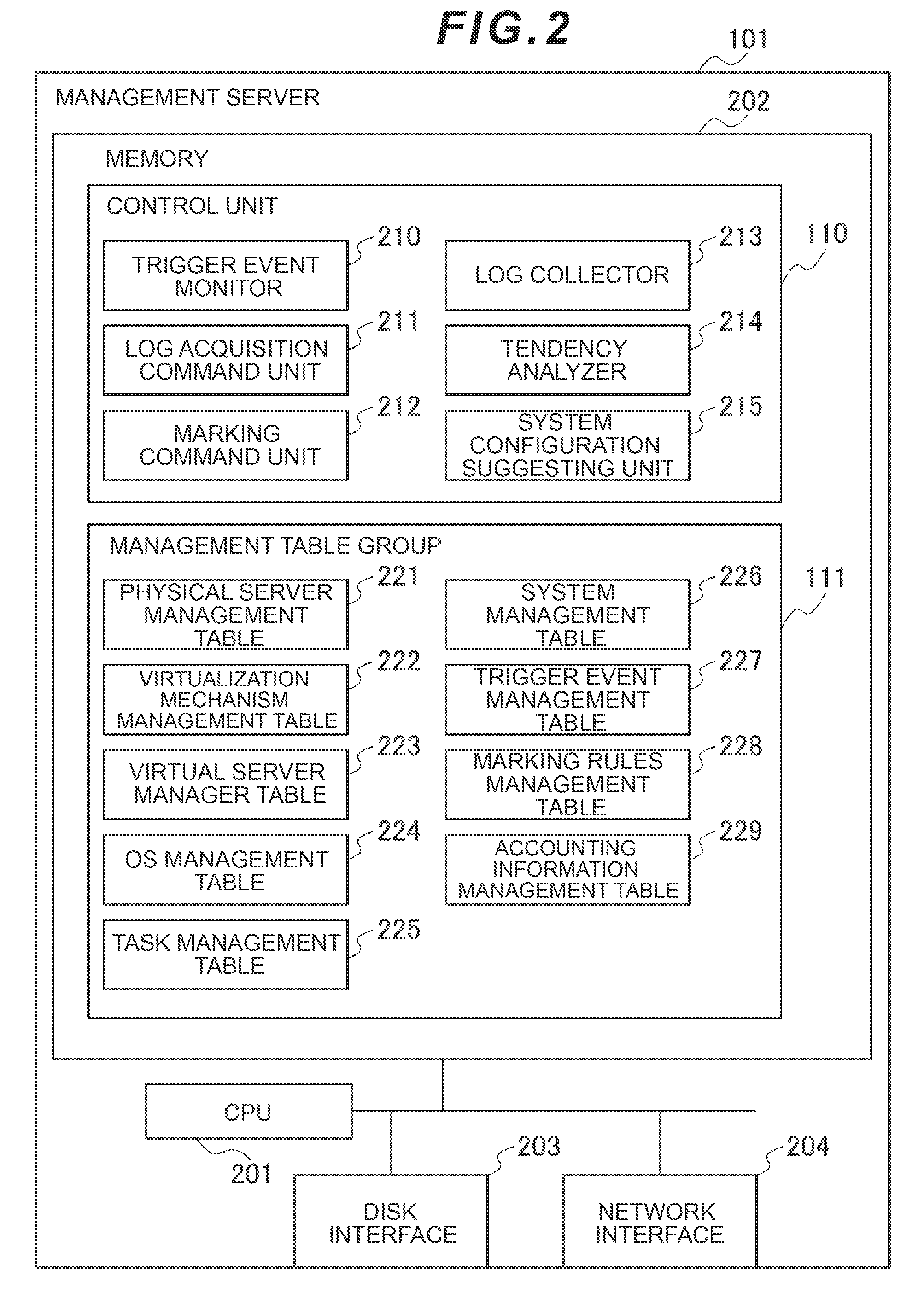
Computer System and Its Operation Information Management Method
InactiveUS20100332661A1Exact matchDigital computer detailsError identificationComputerized systemApplication software
Even if software resources for a physical server are changed, log information about the physical server can be accurately matched against the software resources.If the need arises to migrate business applications in a physical server (migration source), from among a plurality of physical servers, to another physical server (migration destination), a management server collects log information, which has been collected by the migration source physical server, from the migration source physical server, collects identifiers for identifying the business applications at the migration source, and records the collected identifiers in the collected log information. Subsequently, when the business applications are migrated to the migration destination physical server, the management server records the identifiers for identifying the business applications in log information about the migration destination physical server.
Owner:HITACHI LTD
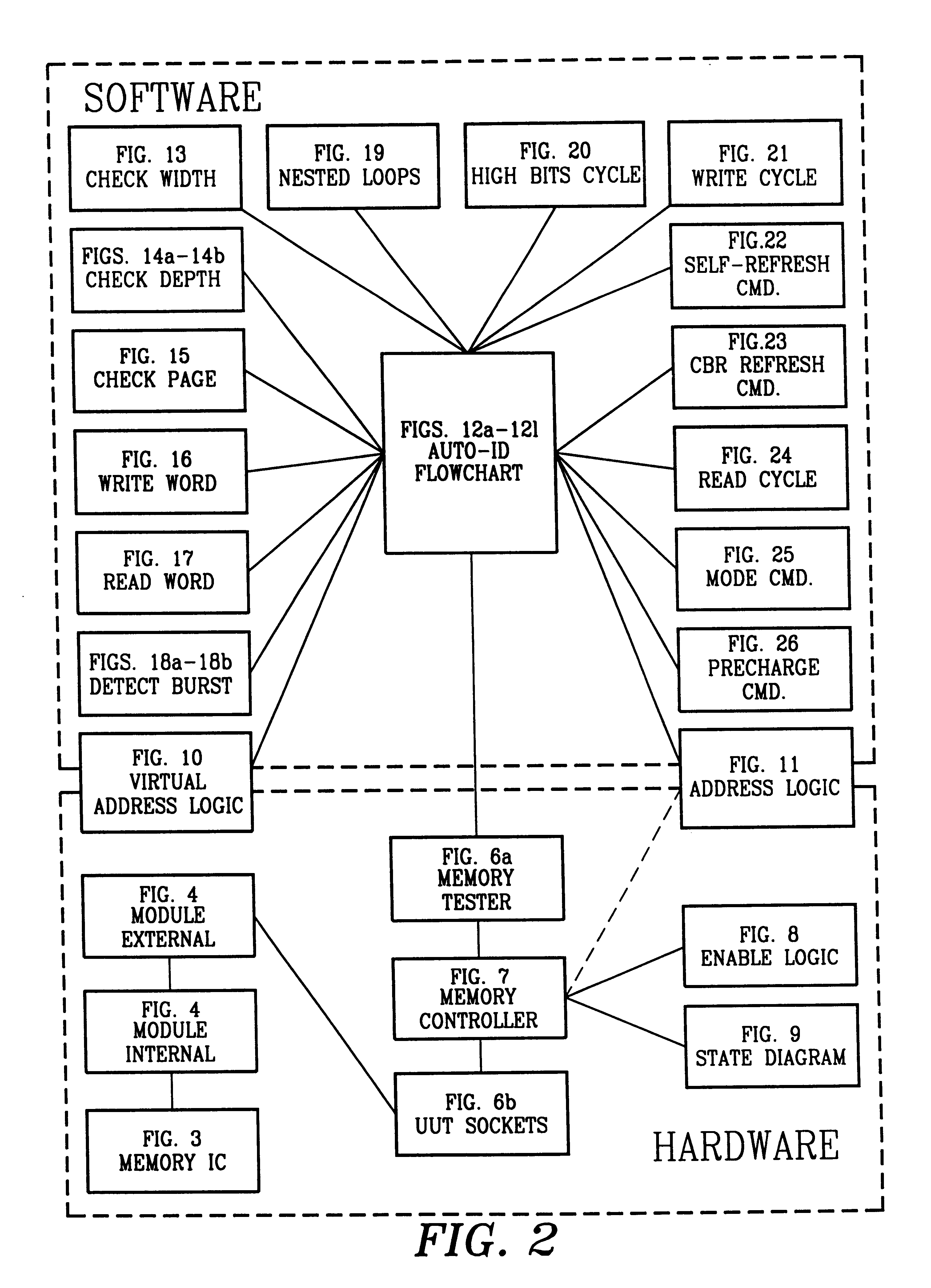
Method and system for automatic synchronous memory identification
A time conserving method of identifying width, depth, access time, control line configurations, and part type of any of a plurality of different synchronous memories. A nested loop process is used to develop, and apply to a synchronous memory being identified, trial control line configurations taken from ordered entries of tables representative of the plurality of synchronous memories. The width, depth, control line configurations, and part type are determined from the responses evoked from the synchronous memory being identified. The delay between a read command issued by the test system CPU and a reading of bit patterns from the synchronous memory is incremented in finite steps in successive write / read iterations until the bit pattern read is identified to the bit pattern written into the synchronous memory, thereby identifying the access time of the synchronous memory.
Owner:TANISYS TECH +1
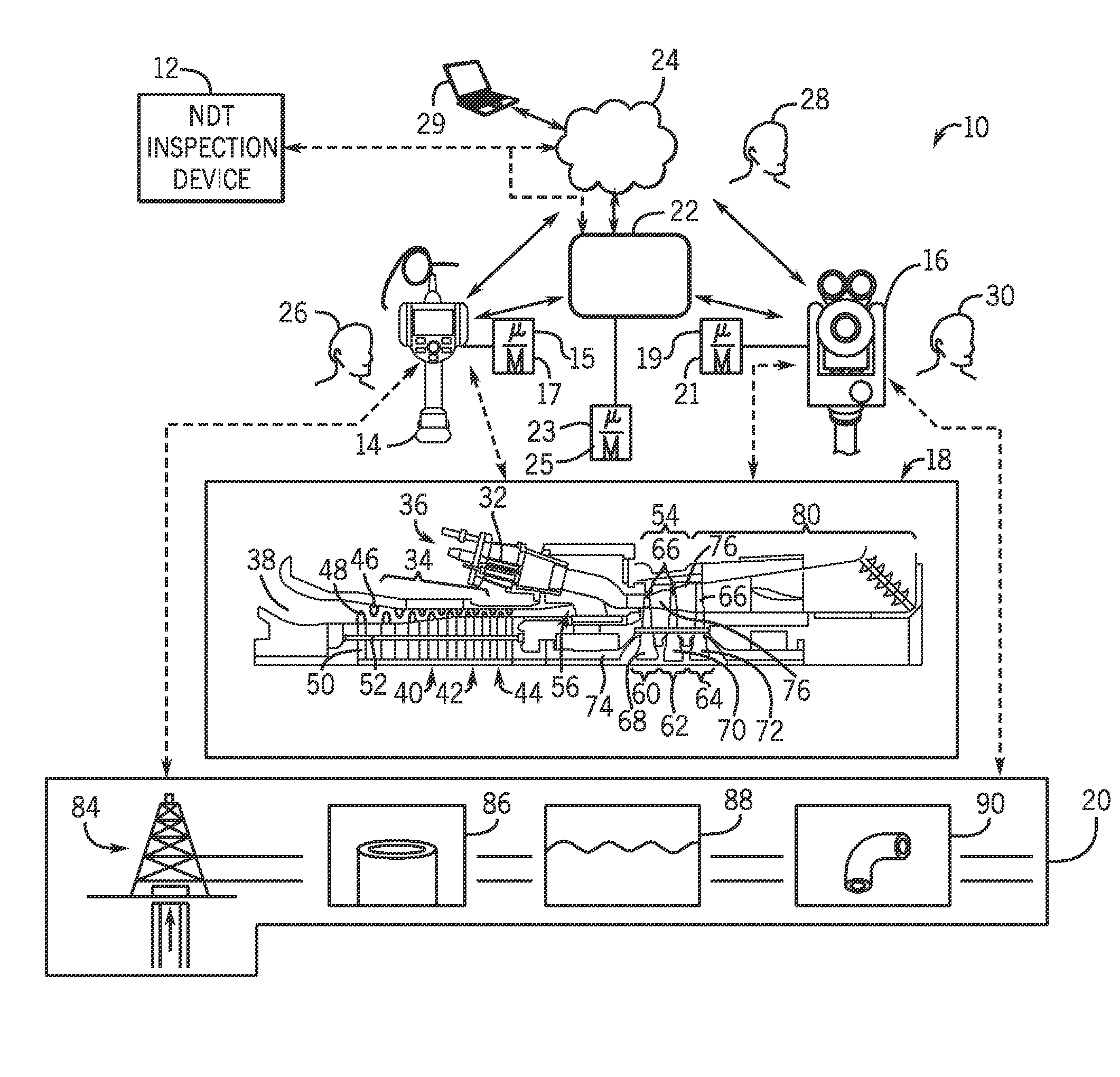
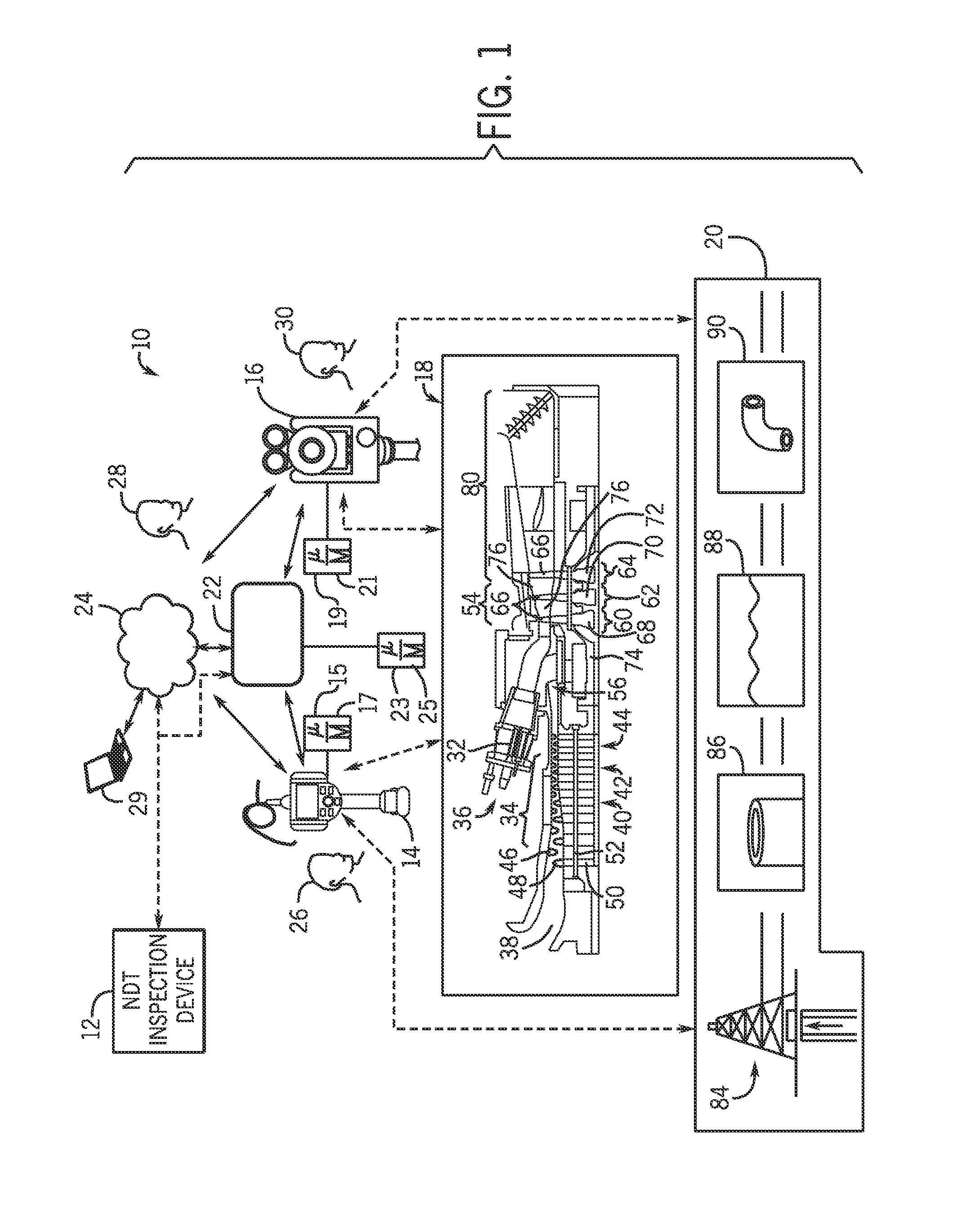
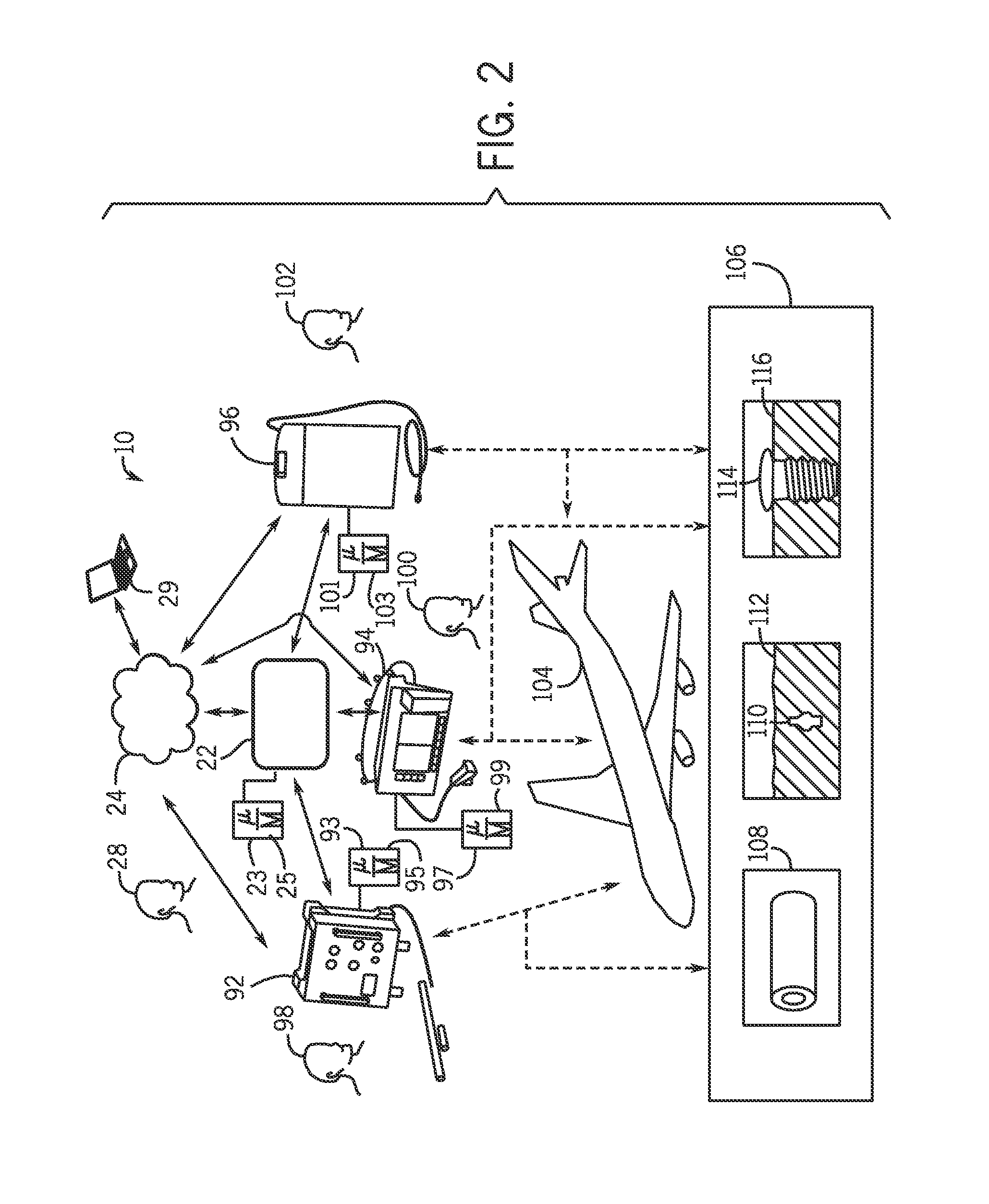
Systems and methods for analyzing data in a non-destructive testing system
ActiveUS20140208163A1Testing/monitoring control systemsError identificationNon destructiveComputer hardware
A collaboration system may include a non-destructive testing (NDT) inspection device that may communicate with at least one other computing device via a computing network. The computing network may communicatively couple a plurality of computing devices and the NDT inspection device may acquire inspection data, establish a communication connection to the at least one other computing device, and send the data to the at least one other computing device. There, the at least one other computing device may analyze the data. After the data is analyzed, the NDT inspection device may receive the analyzed data from the at least one other computing device.
Owner:BAKER HUGHES INC
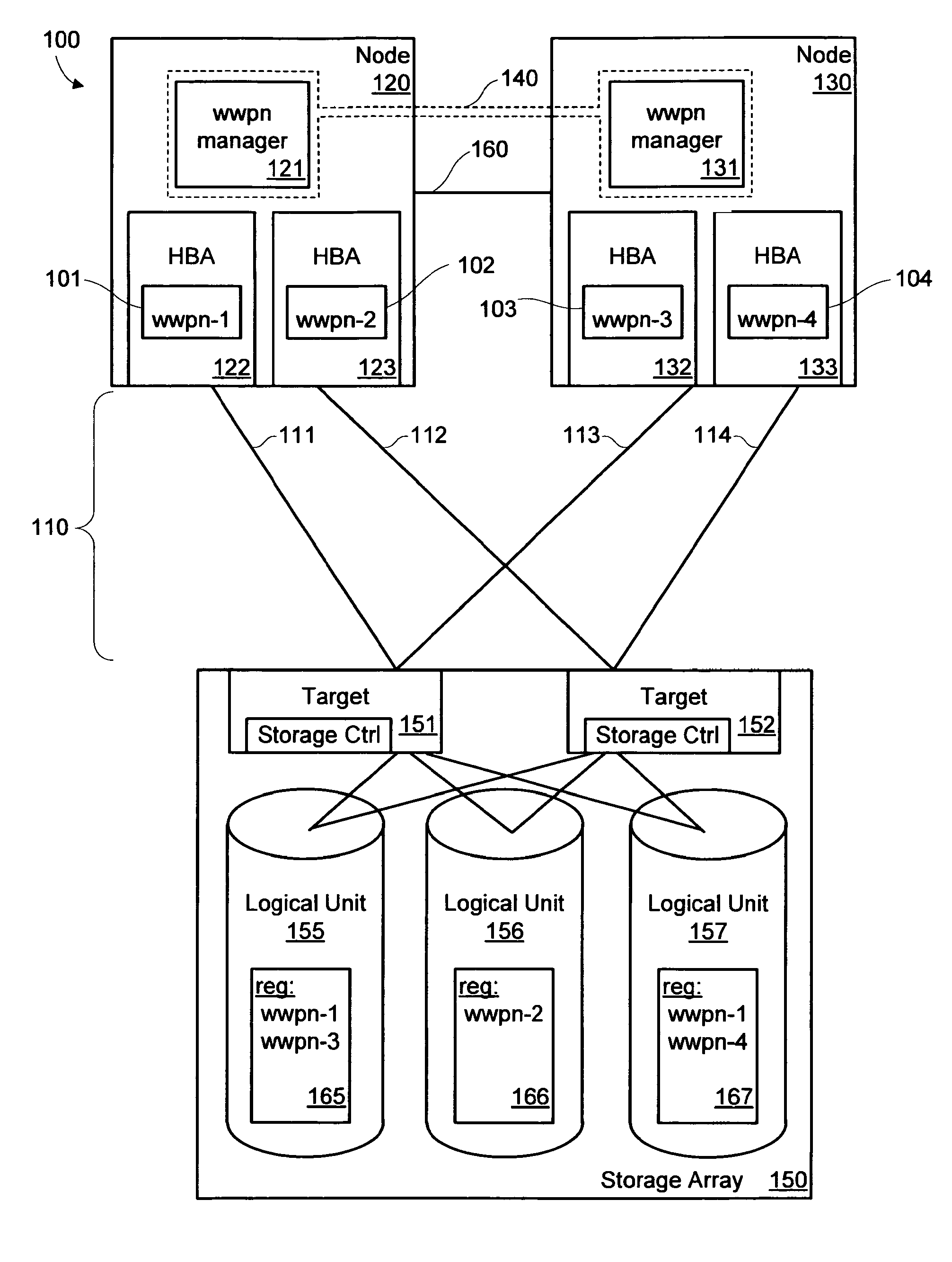
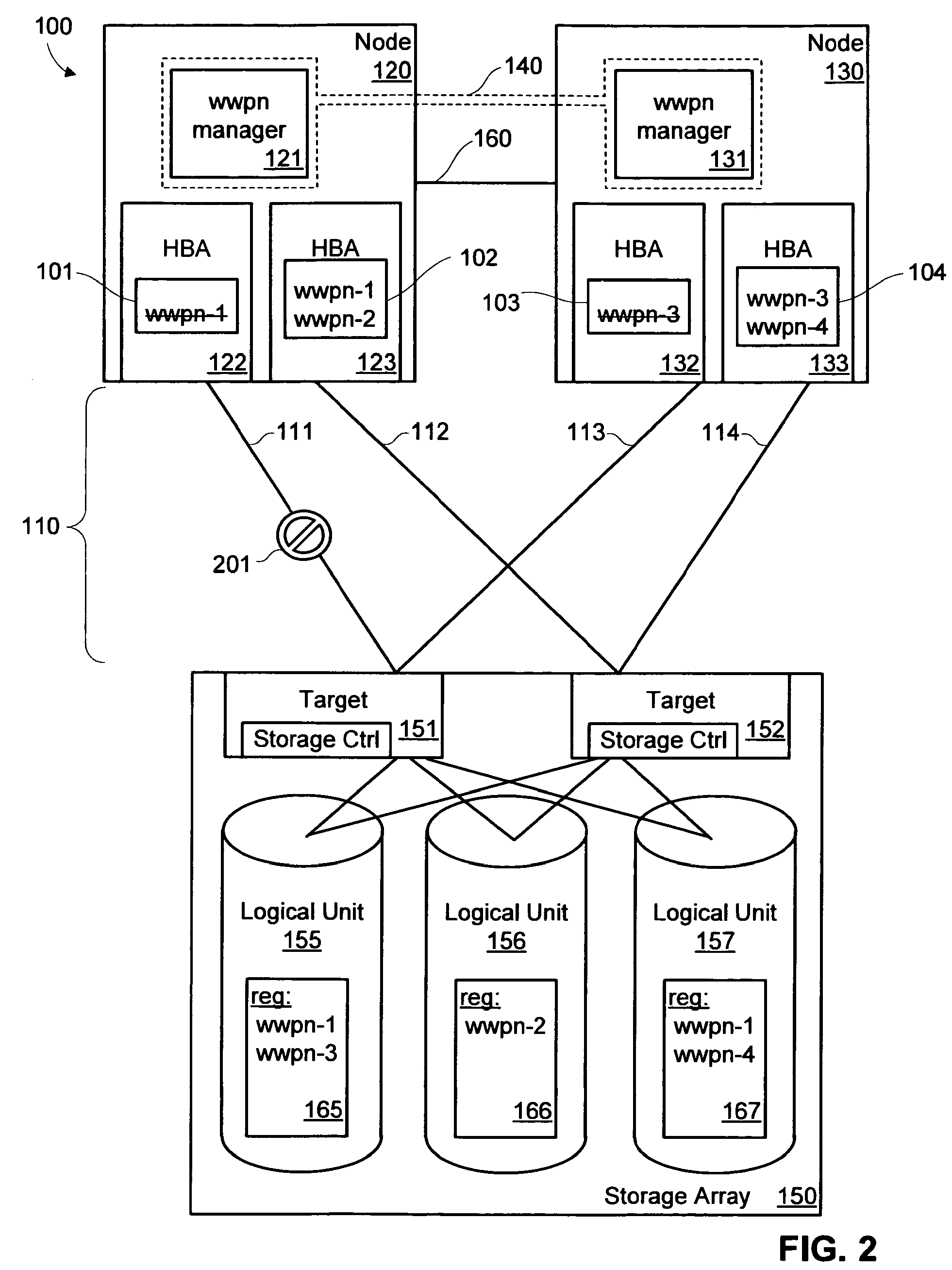
Port identifier management for path failover in cluster environments
A method includes assigning a port identifier to a first port on a node and communicating data on a first path between the first port and a logical unit on an active / passive storage array. The port identifier is registered in a persistent reservation scheme for the logical unit. The method also includes detecting a failure of the first path, de-assigning the port identifier from the first port, assigning the port identifier to a second port on the first node, and resuming communications between the node and the logical unit. One implementation of a system includes a first port configured to communicate with a storage device, a second port configured to communicate with the storage device, and an identifier management block. The identifier management block executes a failover with N_Port ID Virtualization commands that transfer a world wide port name from the first port to the second port.
Owner:SYMANTEC OPERATING CORP
Method to disable use of selected applications based on proximity or user identification
ActiveUS7490763B2Service provisioningDigital data processing detailsApplication softwareMultiple applications
An application for disabling the use of selected applications is provided. A server receives identification information from a user. The location of the user is determined. If the user is determined to be in a reserved location, the use of one or more applications is disabled, for the user.
Owner:GOOGLE LLC
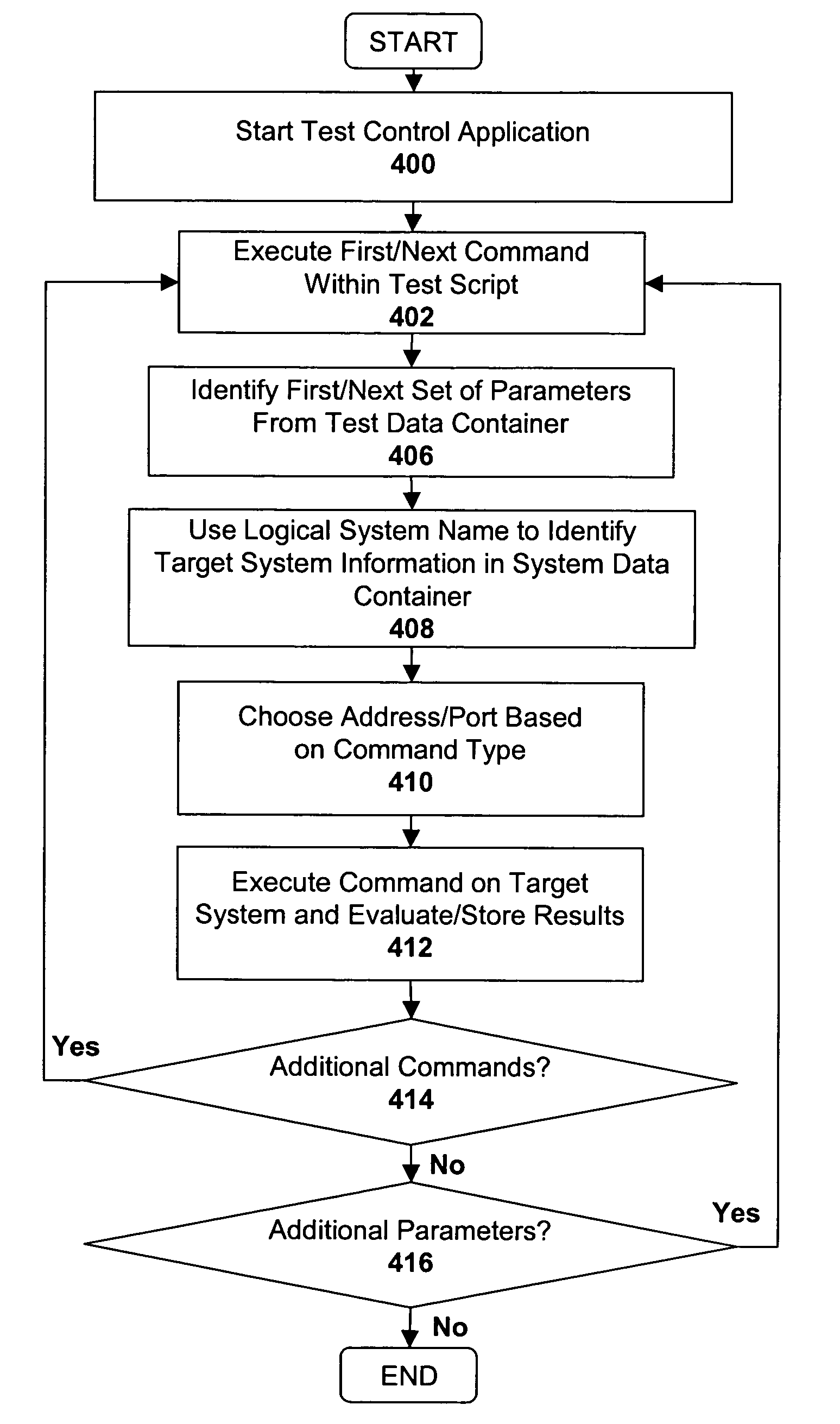
Apparatus and method for identifying a system under test
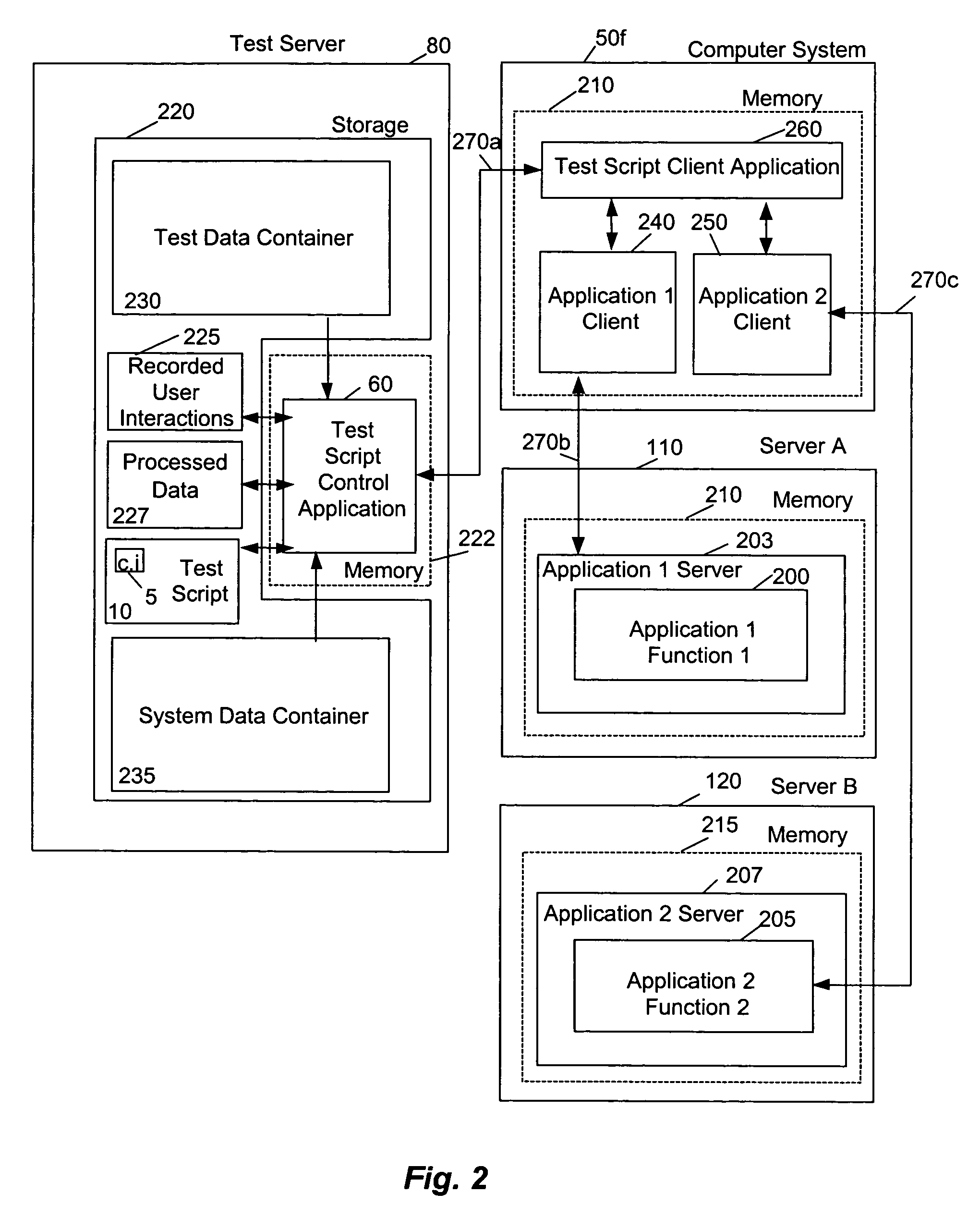
InactiveUS7552424B1Error identificationSpecific program execution arrangementsComputer hardwareRemote function call
A system and method for testing an application on a target system are described. The target system is assigned a logical name which is used by within a test script to reference the target system. The logical name is associated with a plurality of different communication channels within a system data container (e.g., remote function call (“RFC”) channels, HyperText Transport Protocol (“HTTP”) channels, . . . etc). During replay of the test script, a particular communication channel is selected from the plurality of communication channels based on the type of command within the test script that references the target system using the logical name.
Owner:SAP AG
Method, system, and apparatus for providing a single diagnostics module on-demand
ActiveUS6988055B1Detecting faulty hardware by remote testDigital computer detailsComputer hardwareComputerized system
A method, system, and apparatus are provided for retrieving and executing one or more diagnostics modules together capable of testing a single hardware component within a computer system in direct response to a user request. A request is received to perform a diagnostics test on the component. In response to the request, one or more diagnostics modules necessary to test the component are identified. Once the modules have been identified, the modules are retrieved from a remote server computer and installed at the computer system upon which they are to be executed. The modules are then executed, thereby testing the single hardware component. The retrieved diagnostics modules may contain only program code necessary to test the identified component.
Owner:AMERICAN MEGATRENDS
Managing system components
ActiveUS20070234130A1Conserve costFault diagnosis be improvedError identificationFailure rateComputer science
System components are managed. Based on a first communication path to a component, first identification information for the component is determined. Based on a second communication path to the component, second identification information for the component is determined. Based on the first identification information and the second identification information, an identity for the component is determined. Based on the identity, a set of tests is performed on the component. Based on the failure rate of the set of tests, it is concluded that another component on the first communication path is faulty.
Owner:EMC IP HLDG CO LLC
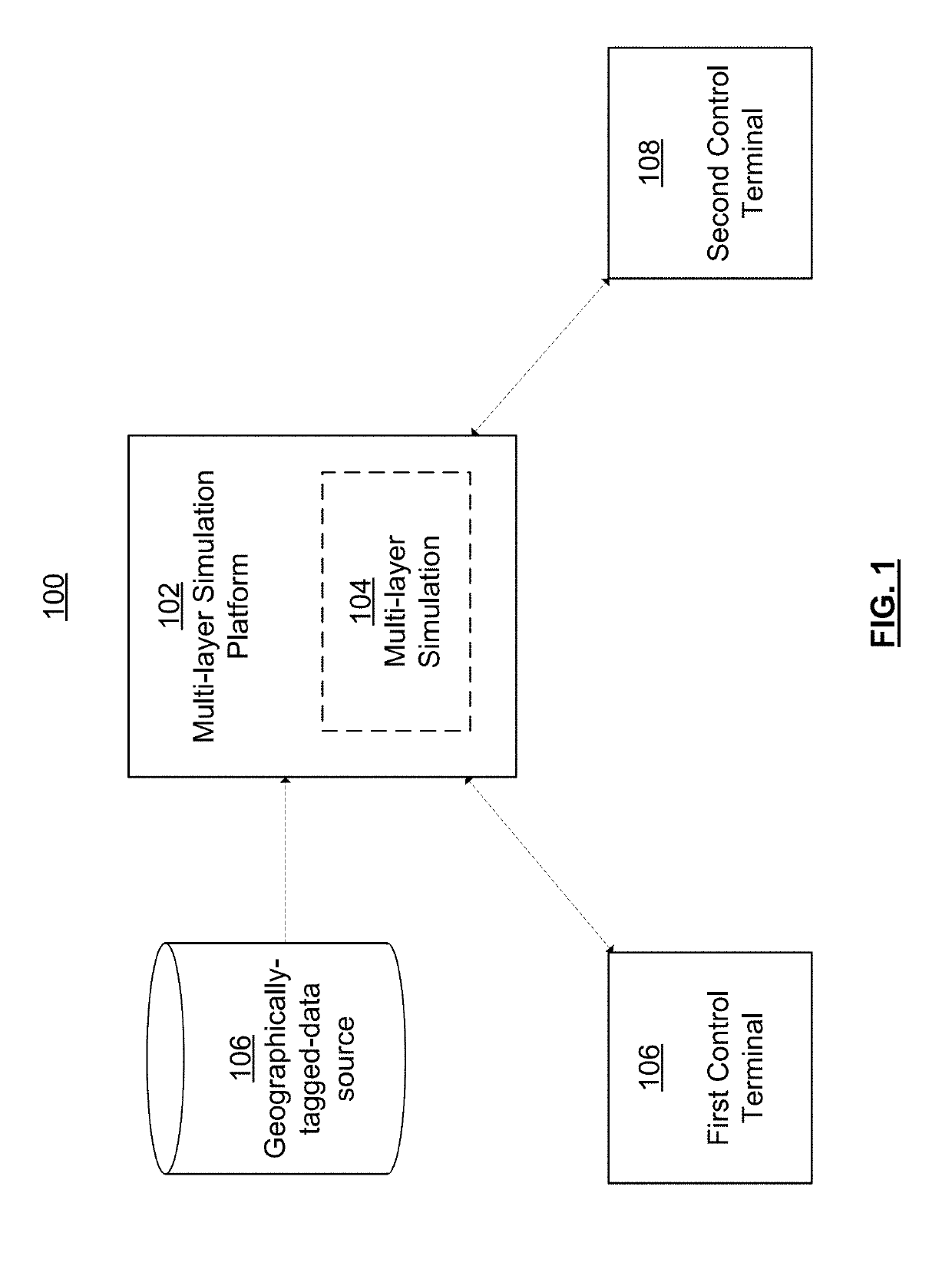
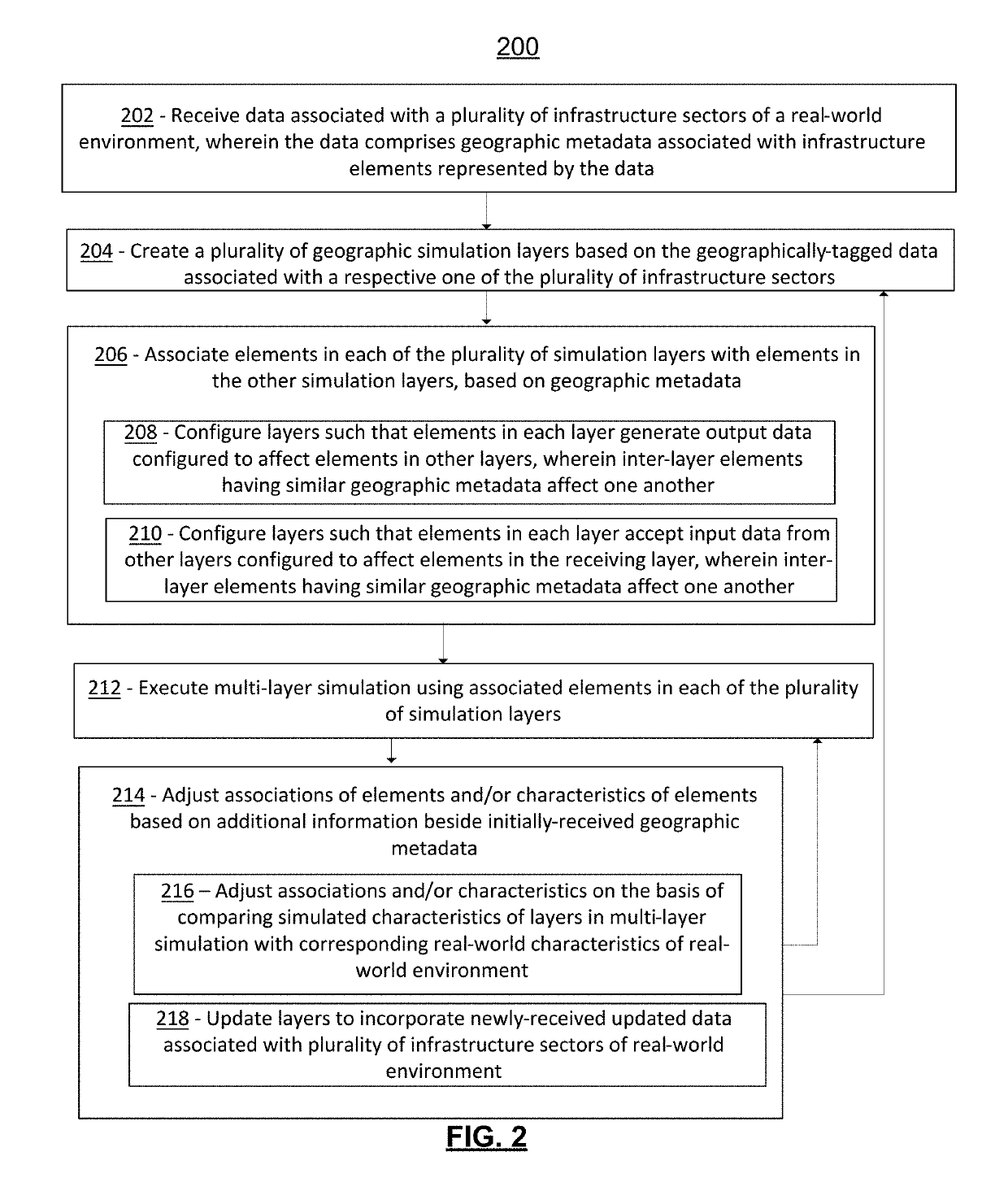
Multi-layer cyber-physical systems simulation platform
ActiveUS20190266297A1Increase the itineraryRapid identification and responseData processing applicationsTesting/monitoring control systemsPhysical systemSystems simulation
Systems and methods for simulating cyber-physical systems are disclosed. A plurality of geographic simulation layers representing respective infrastructure sectors of a real-world environment may be generated, and the layers may be linked together with one another to create a multi-layer simulation. The associations between the layers of the simulation may be adjusted, and characteristics of the simulation layers themselves may be adjusted, to ensure that the simulation conforms to characteristics of the real-world environment being simulated. In some embodiments, a multi-user simulation system allows users at separate terminals to execute attack inputs and defense inputs against the simulation to try to destabilize and stabilize the simulation, respectively. Results of the attack inputs and defense inputs may be simultaneously displayed on a plurality of terminals.
Owner:NOBLIS
Managing disk drive replacements on mulitidisk headless appliances
InactiveUS20020053047A1Input/output to record carriersError preventionComputer hardwareOperational system
A headless computer entity having a plurality of disk drives operates to self restore to a known state, upon failure of either a system disk drive containing an operating system of the computer entity, or failure of a data disk drive containing application data. Depending upon whether the system disk and / or the data disk are replaced by a replacement disk, the computer entity configures itself with either deletion of application data on the data disk, or with deletion of application data on both the system disk and the data disk. The computer entity determines whether a new replacement disk has been installed by comparing a signature of the system disk with a signature of the data disk. If a replacement disk is detected, then the digital signatures are set by the computer entity such that the system disk and data disk have a self consistent set of hardware specific digital signatures. Application data is returned to a known good state after deletion.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
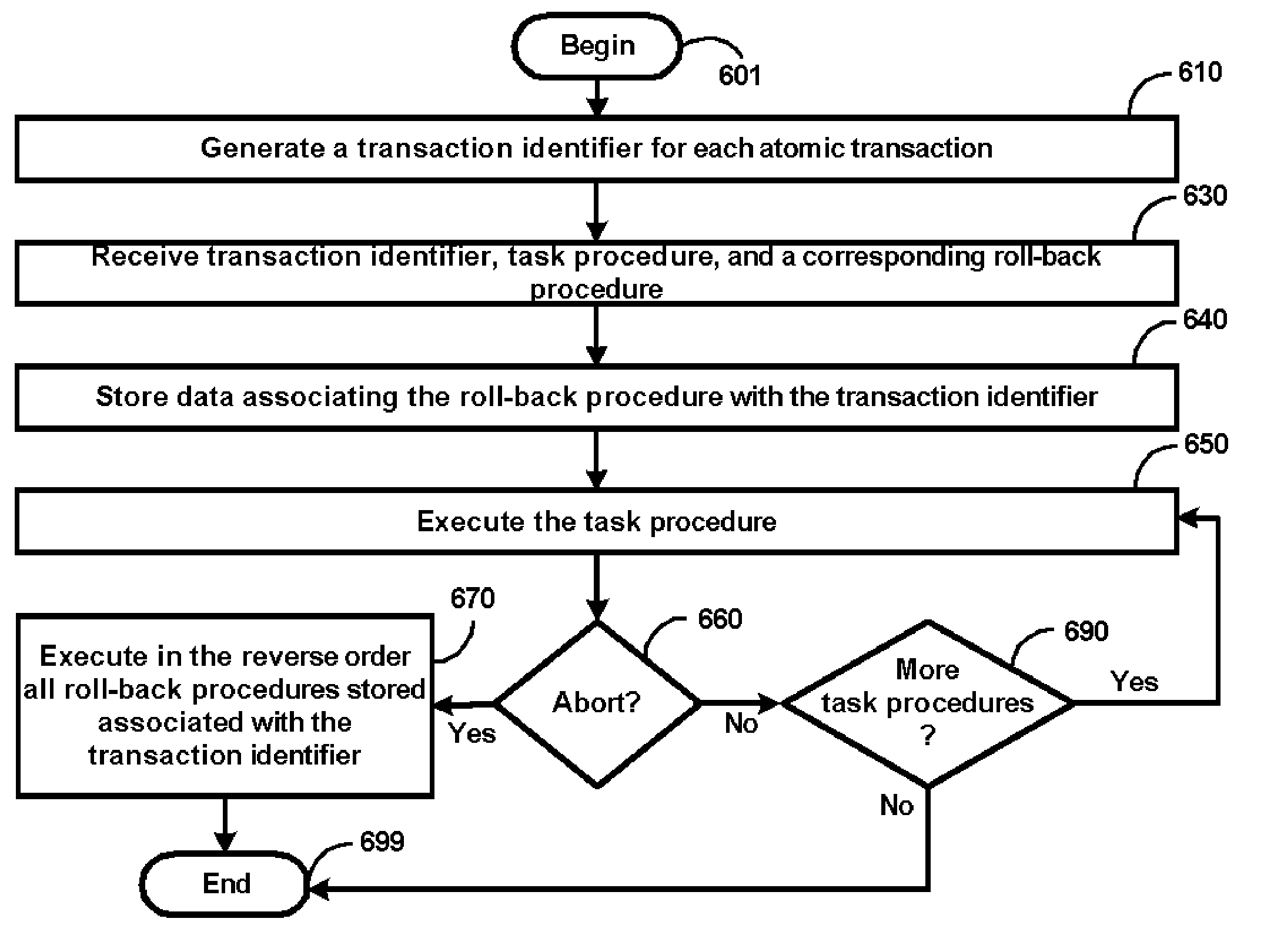
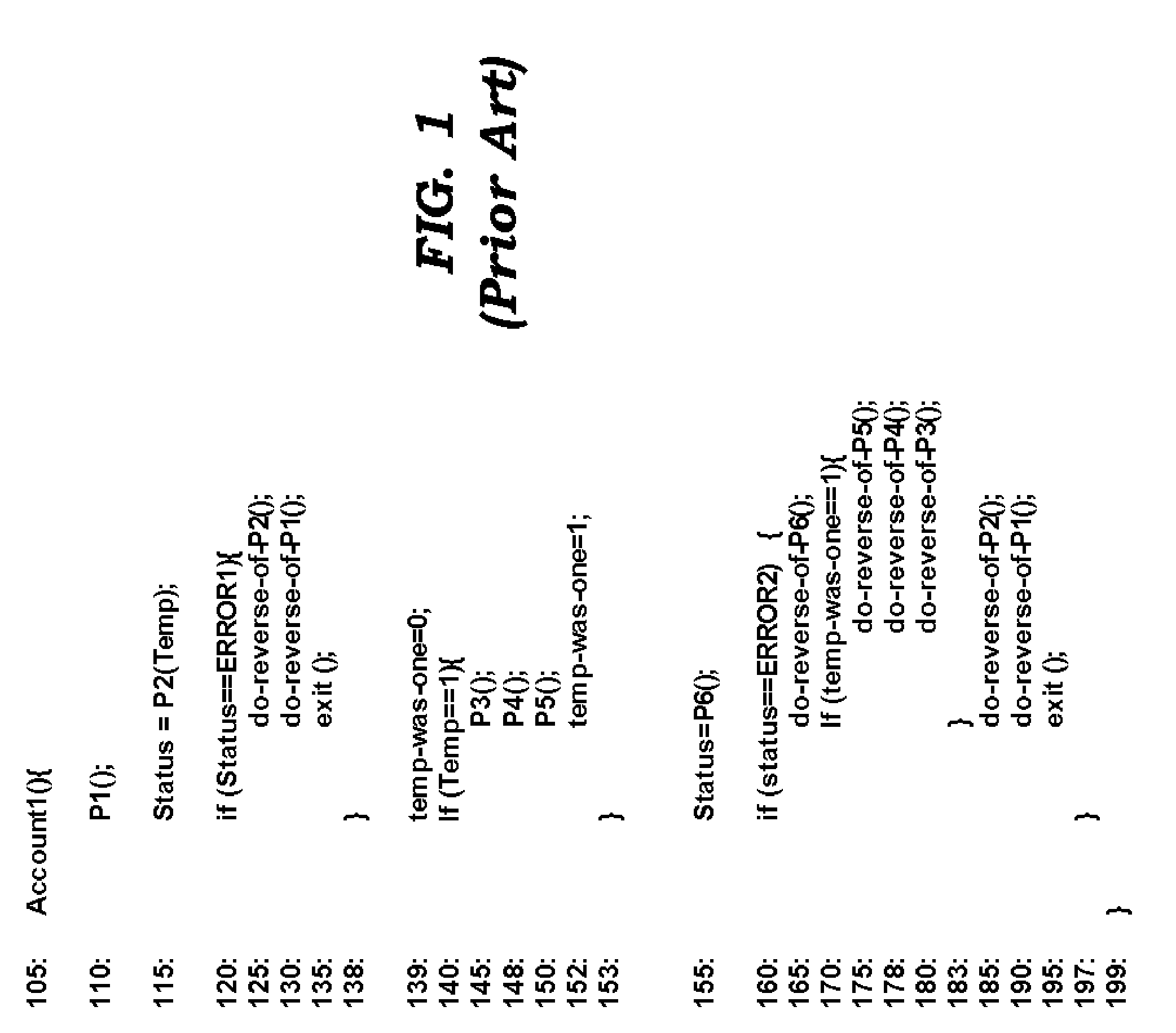
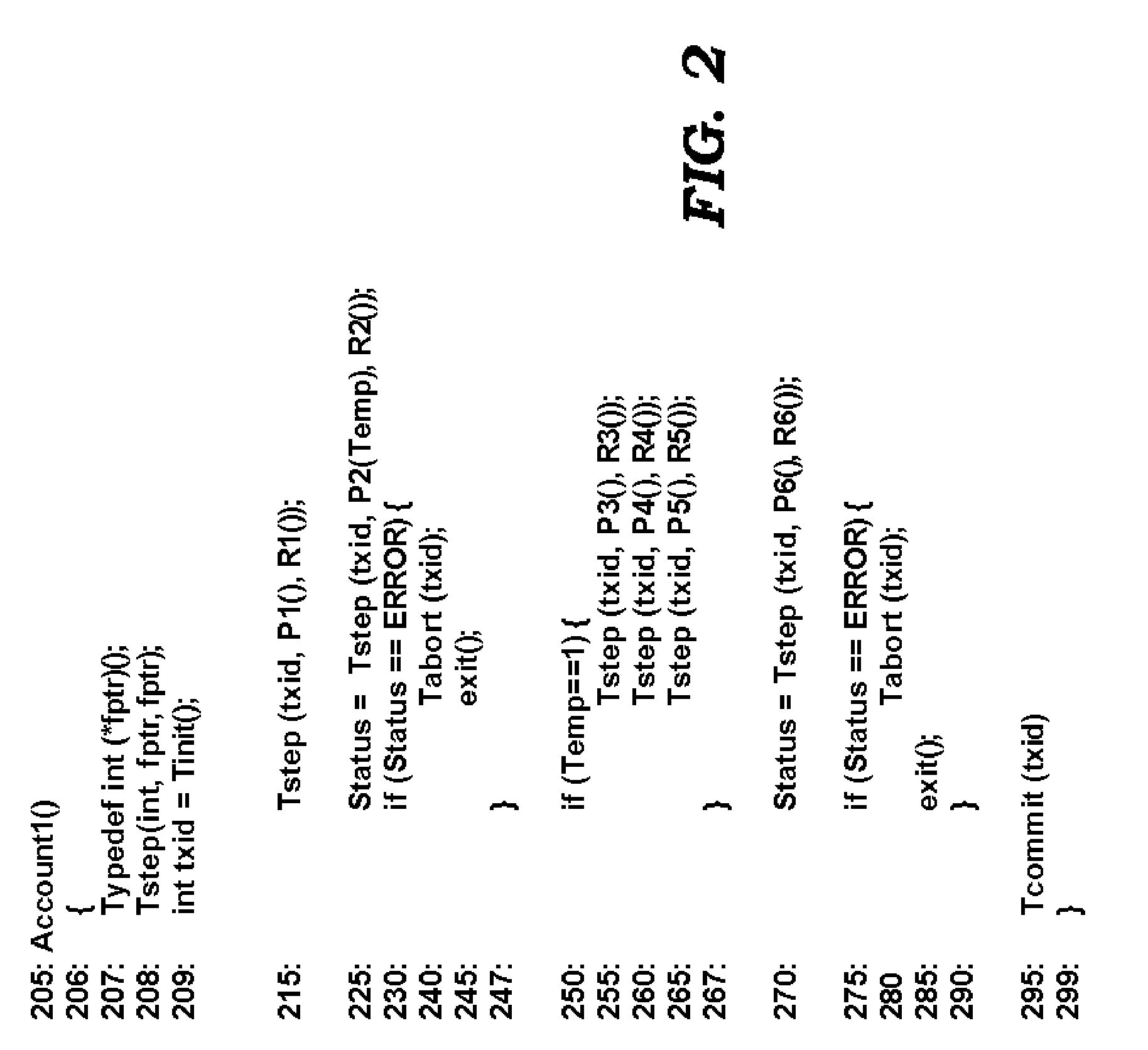
Custom Atomic Transactions in Programming Environments
ActiveUS20060004882A1Error identificationSpecial data processing applicationsProgram logicBack procedures
An aspect of the present invention simplifies the implementation of custom atomic transactions. A program logic (implementing a custom atomic transaction) may request a unique transaction identifier from a programming environment. The program logic may then specify a task procedure, corresponding roll-back procedures, and the transaction identifier using an interface provided by the programming environment. The programming environment keeps track of the specified roll-back procedures. The information maintained by the programming environment may be used to execute the roll-back procedures if the atomic transaction is to be aborted. As the programming environment keeps track of the roll-back procedures to be executed, the implementation of atomic transactions may be simplified.
Owner:ORACLE INT CORP
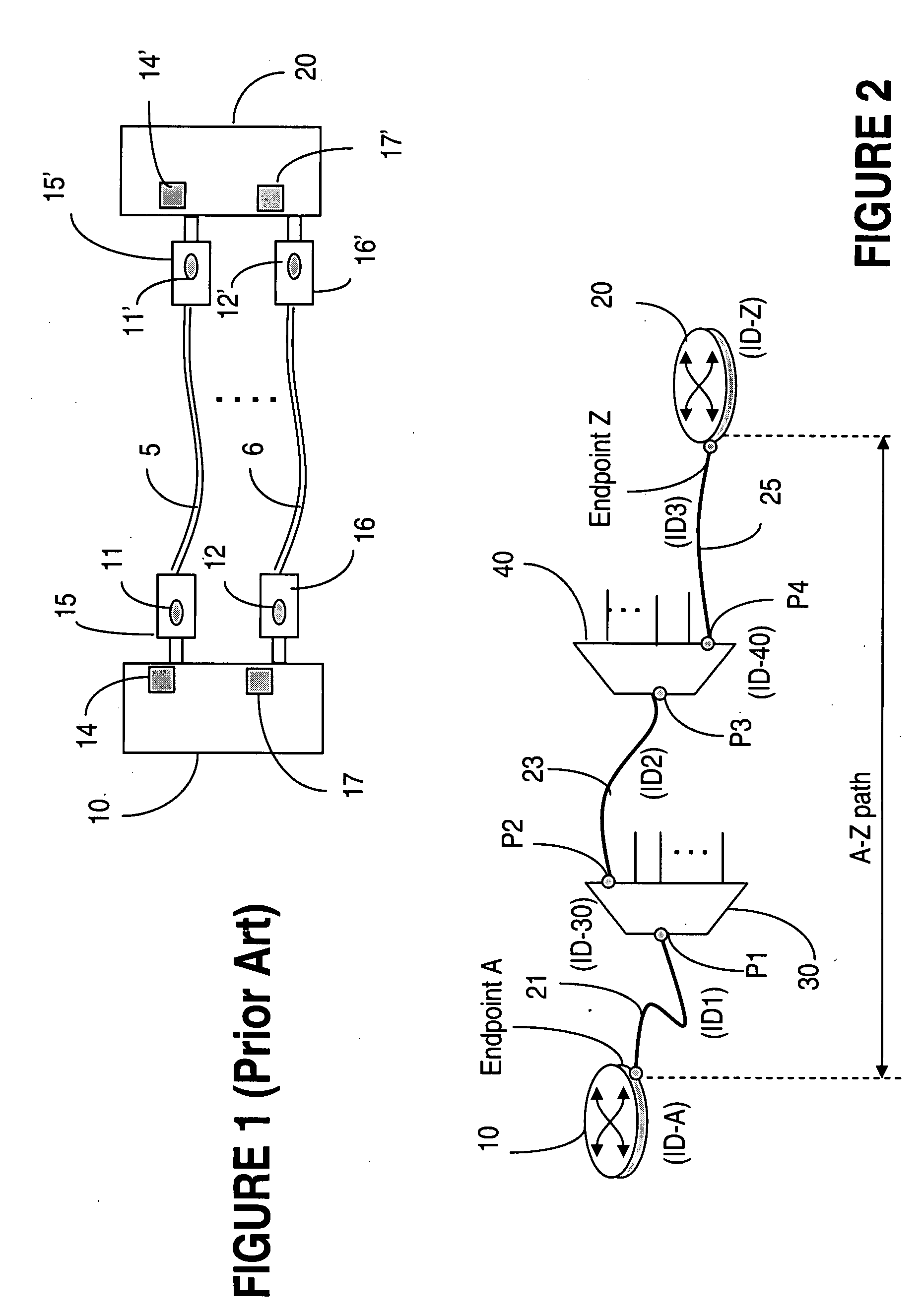
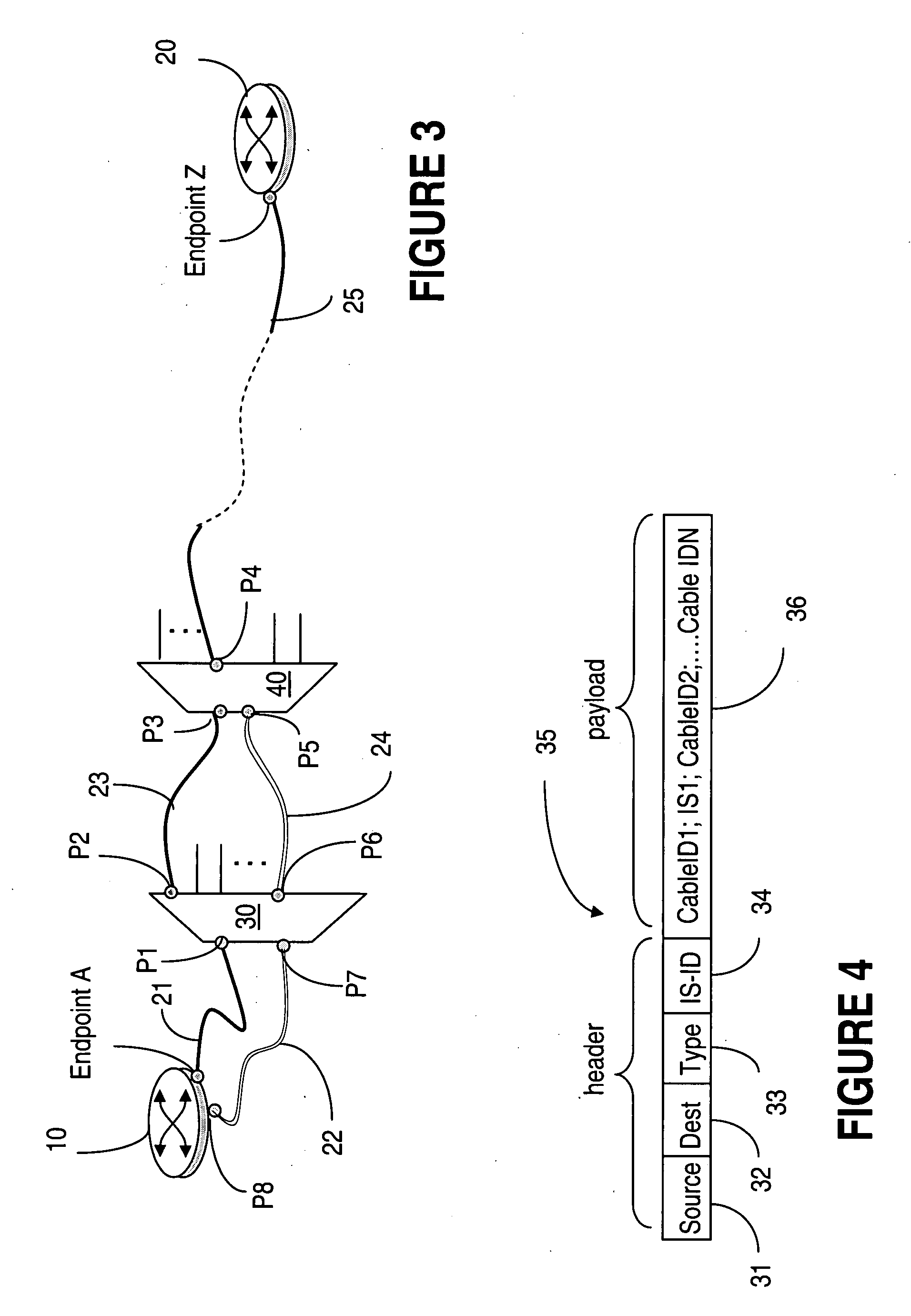
System and method for tracing cable interconnections between multiple systems
ActiveUS20090100298A1Shorten the timeMultiple digital computer combinationsError identificationElectronic systemsEngineering
Techniques to ascertain physical cabling connections of electronic systems are provided for situations where there are numerous systems interconnected by a very large number of electrical or optical cables. A cable identifying code is inserted into a message sent from a local endpoint system to remote endpoint system over the identified cable. Each intermediate system that is in the interconnection path between the two endpoint systems of interest appends its code for the cable connected to the I / O port from which the message will egress that system and be sent to the next system along the path. The remote endpoint system receives the message which now contains codes for all the cables transited along the path, extract the codes, and thereby determines the exact cabling used in the interconnection of the two endpoint systems.
Owner:ALCATEL LUCENT SAS
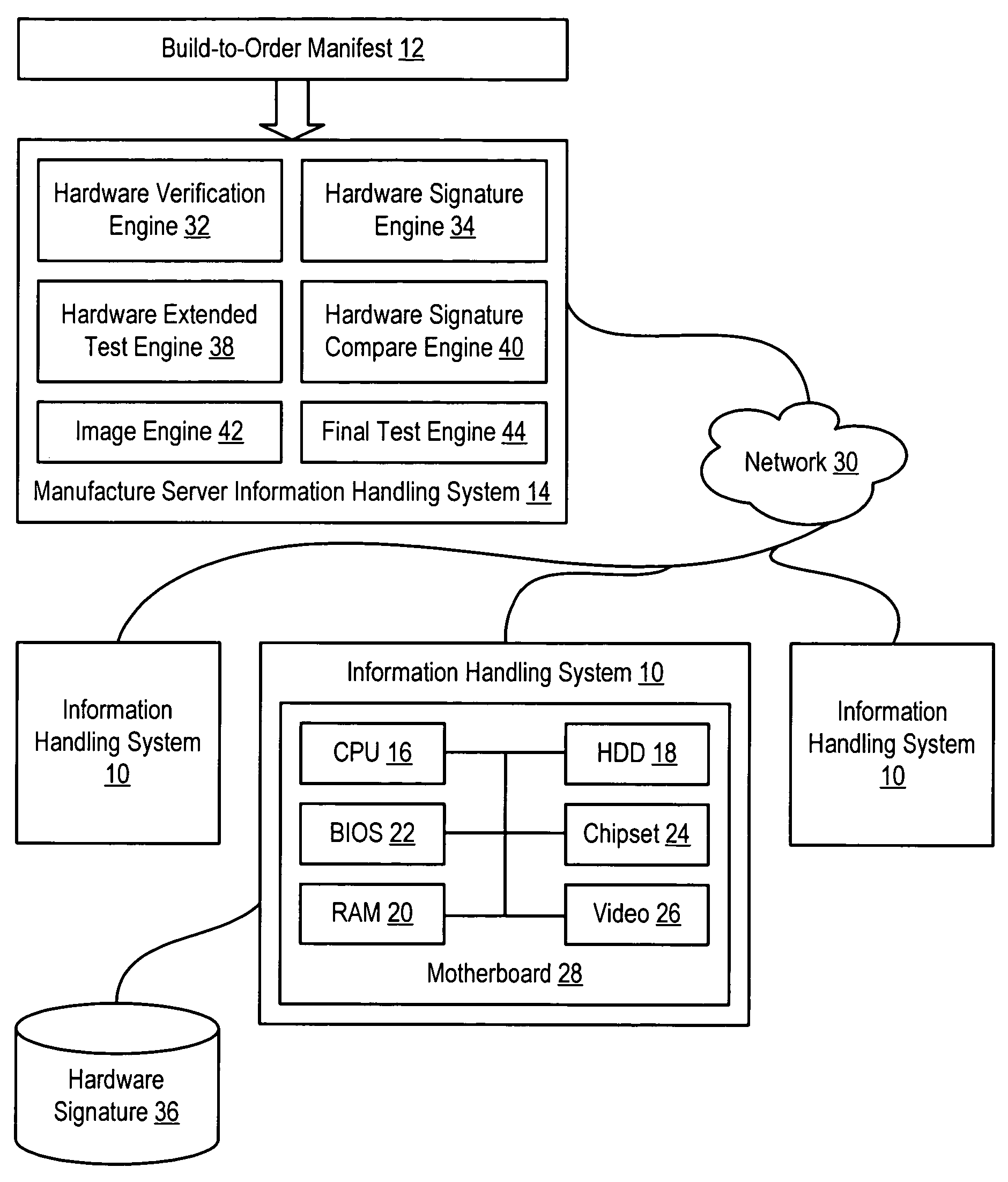
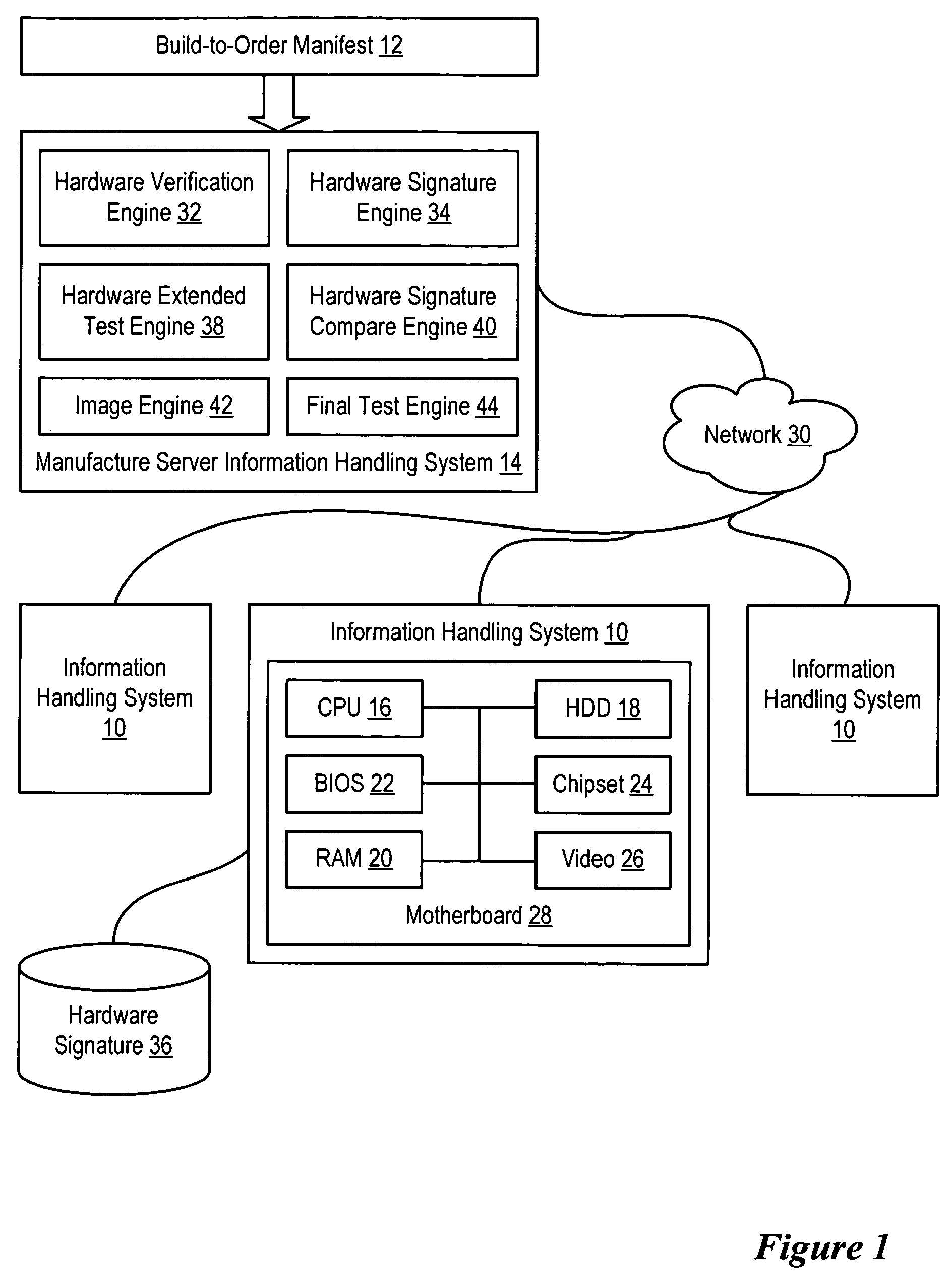
System and method for information handling system manufacture with verified hardware configuration
ActiveUS7577828B2Reduce disadvantagesReduce problemsDigital computer detailsData resettingHandling systemInformation handling system
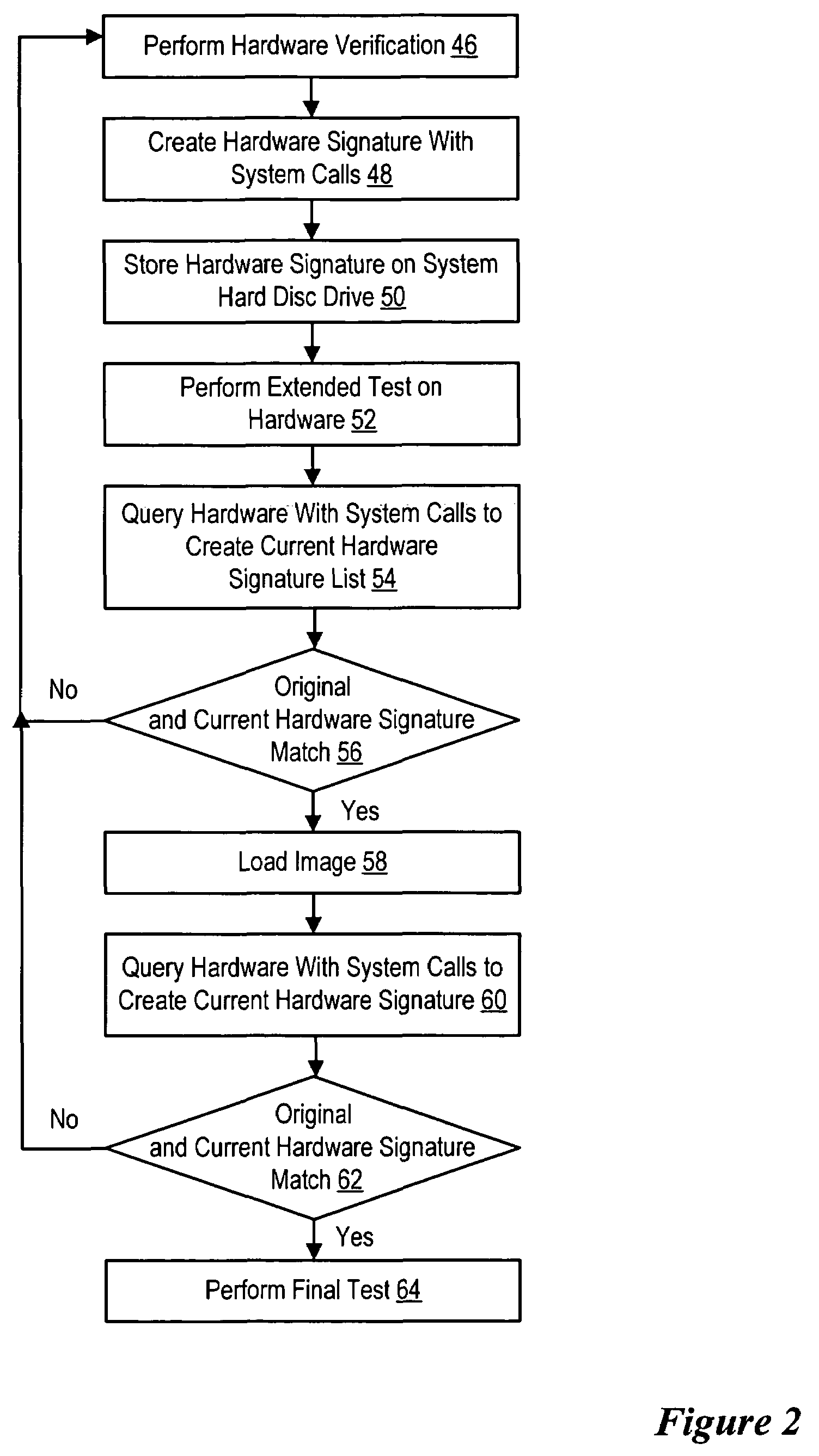
An information handling system hardware signature based on a verified hardware configuration for the information handling system serves as a reference to confirm the hardware configuration of the information handling system through a manufacture process. For instance, after hardware component testing, the hardware components of the information handling system are queried and compared against the hardware signature to ensure continued compliance with the verified configuration. Similarly, the hardware configuration is confirmed against the hardware signature after loading an image and prior to final test of the assembled information handling system. Comparison of current hardware with the hardware signature throughout the manufacture process ensures compliance with a predetermined hardware configuration without requiring multiple hardware verifications.
Owner:DELL PROD LP
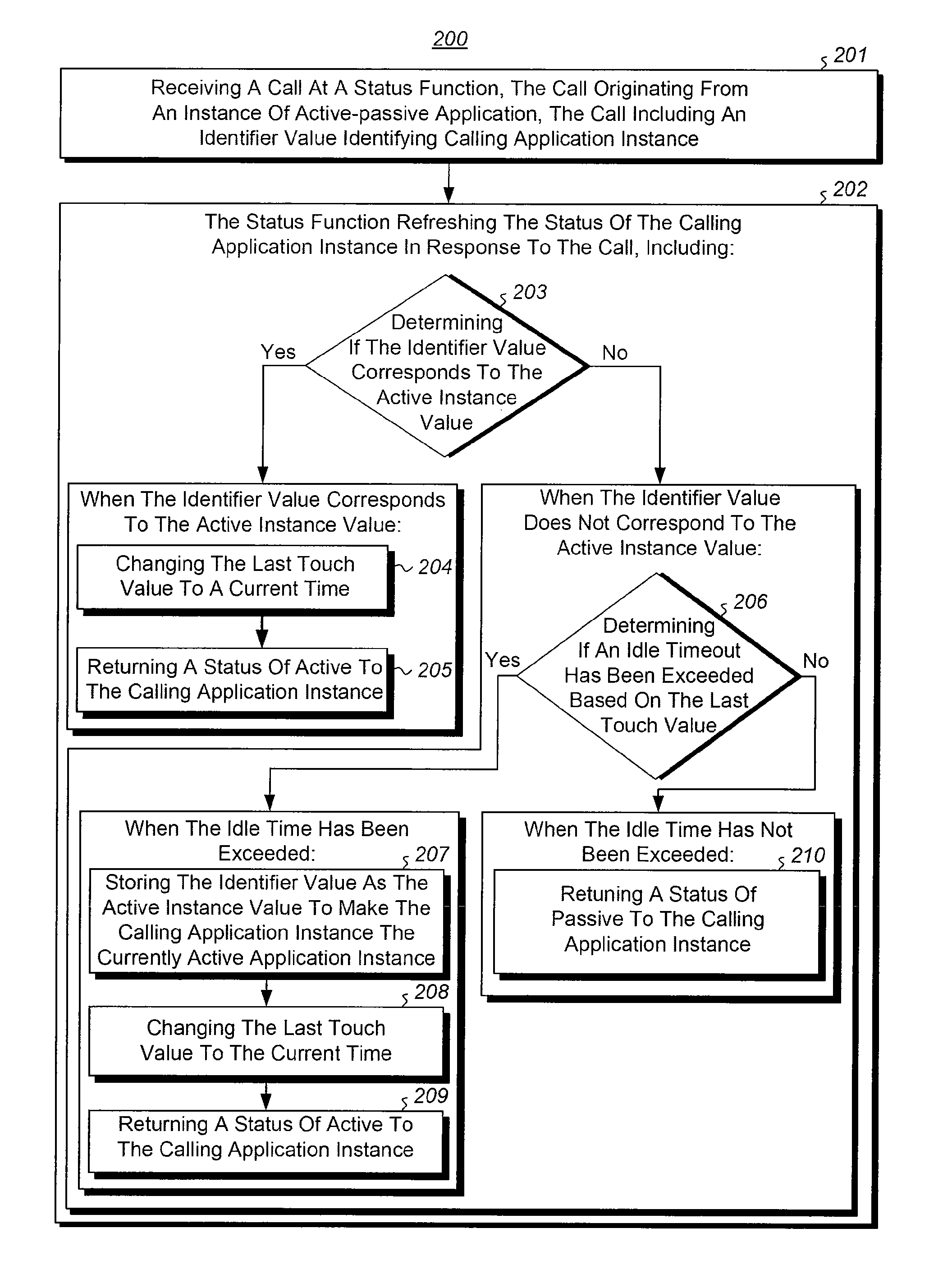
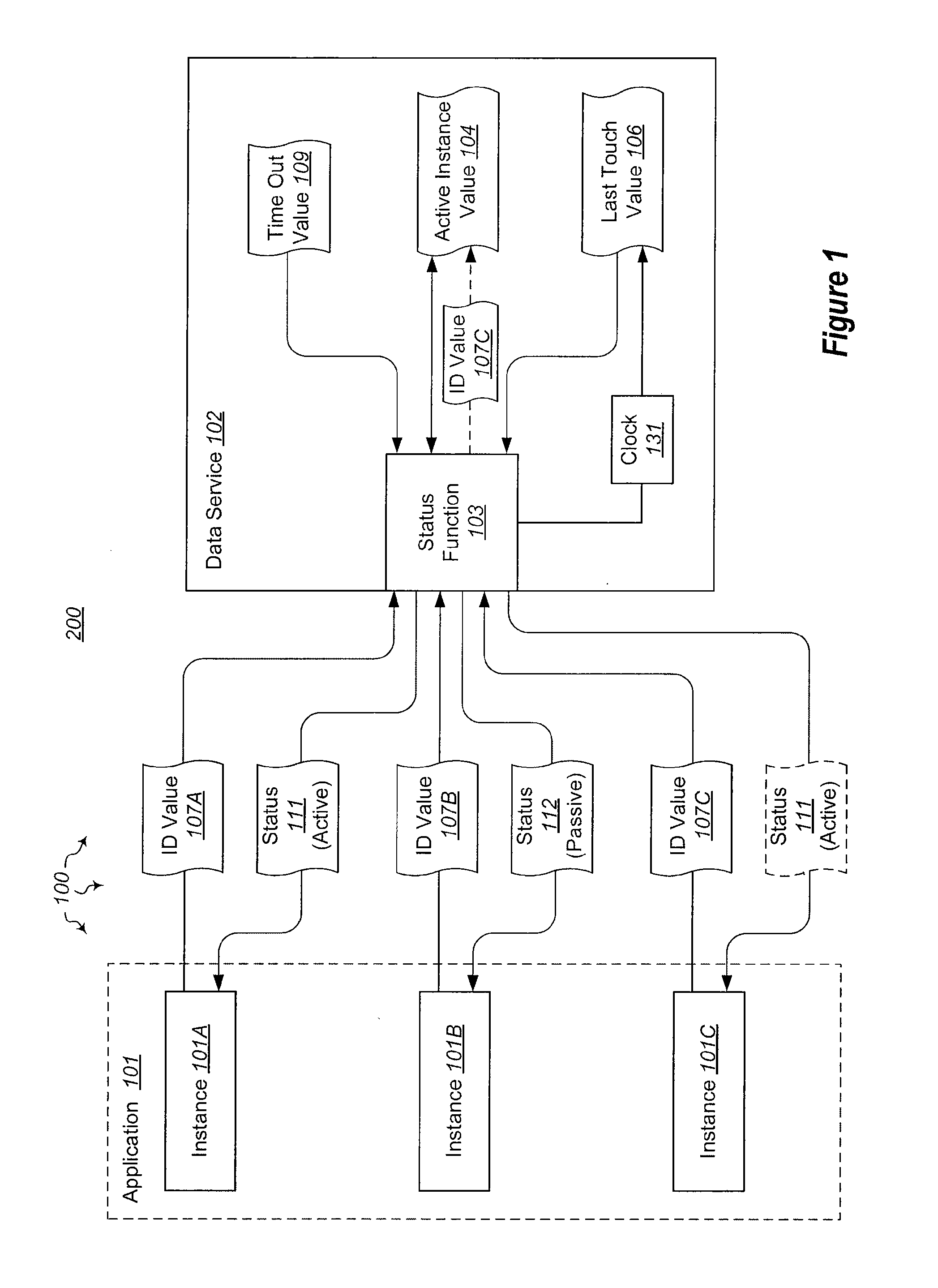
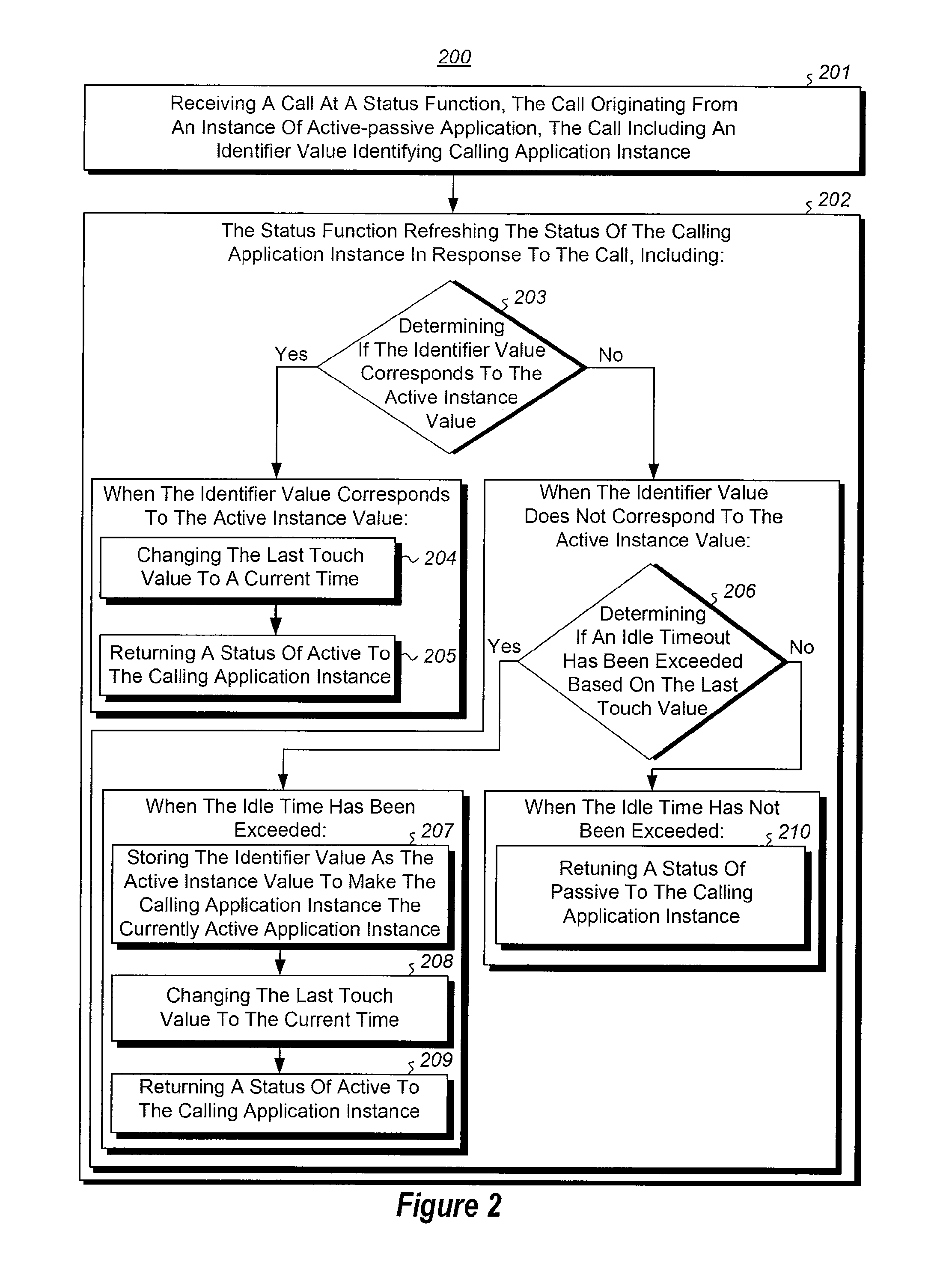
Synchronized failover for active-passive applications
The present invention extends to methods, systems, and computer program products for synchronized active-passive application failover. A data connection to a single data source can be used as a synchronizations point. Interoperating instance side and data source side algorithms coordinate to transition a passive instance to an active instance within a specified period of time when a prior active instance fails. An active-passive controller can operate as an active-active module within an active-active environment to provide active-passive failover to active-passive modules. Application virtual names can be mapped to application instance electronic addresses to assist external modules in establishing application connections to active-passive applications.
Owner:MICROSOFT TECH LICENSING LLC
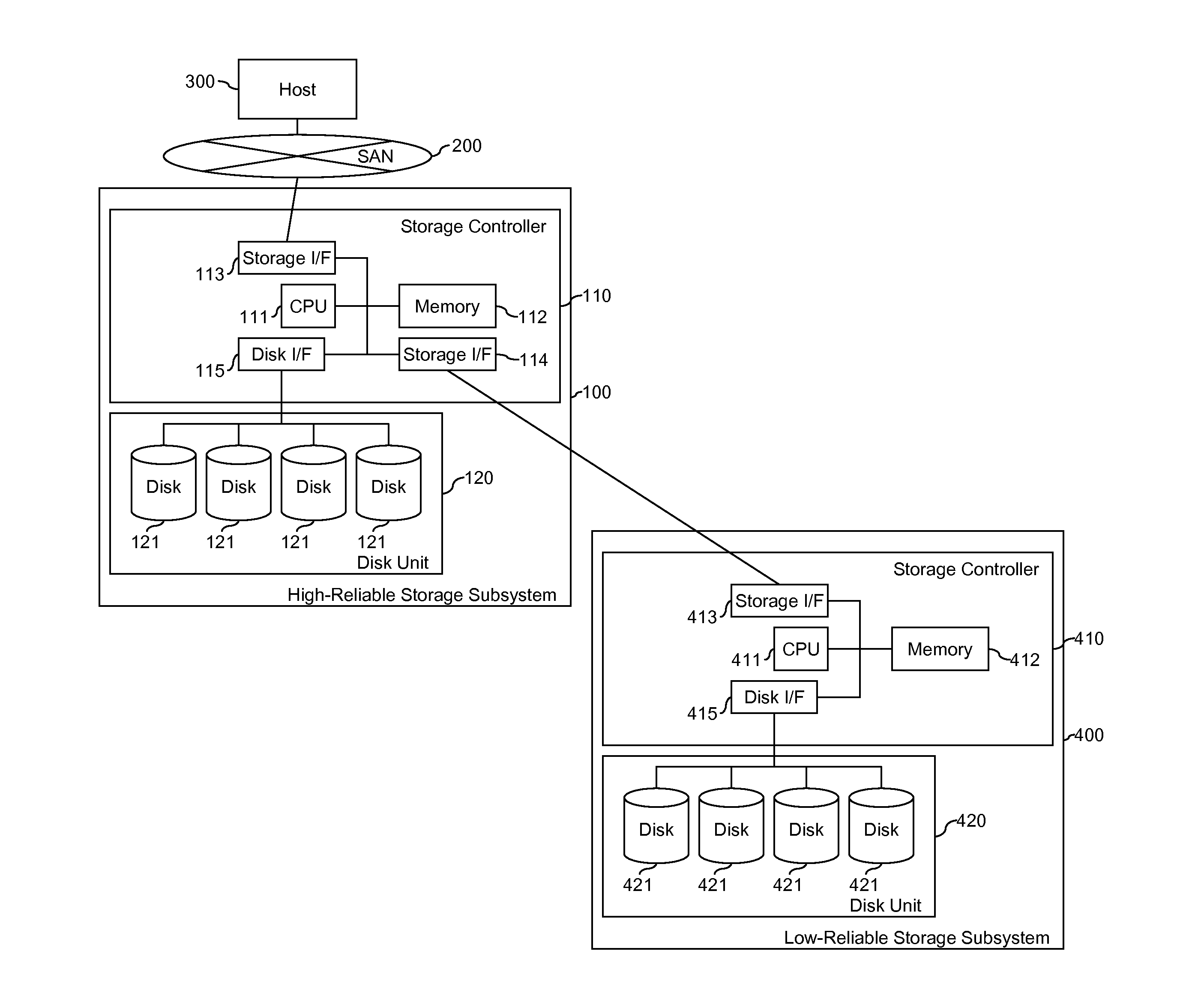
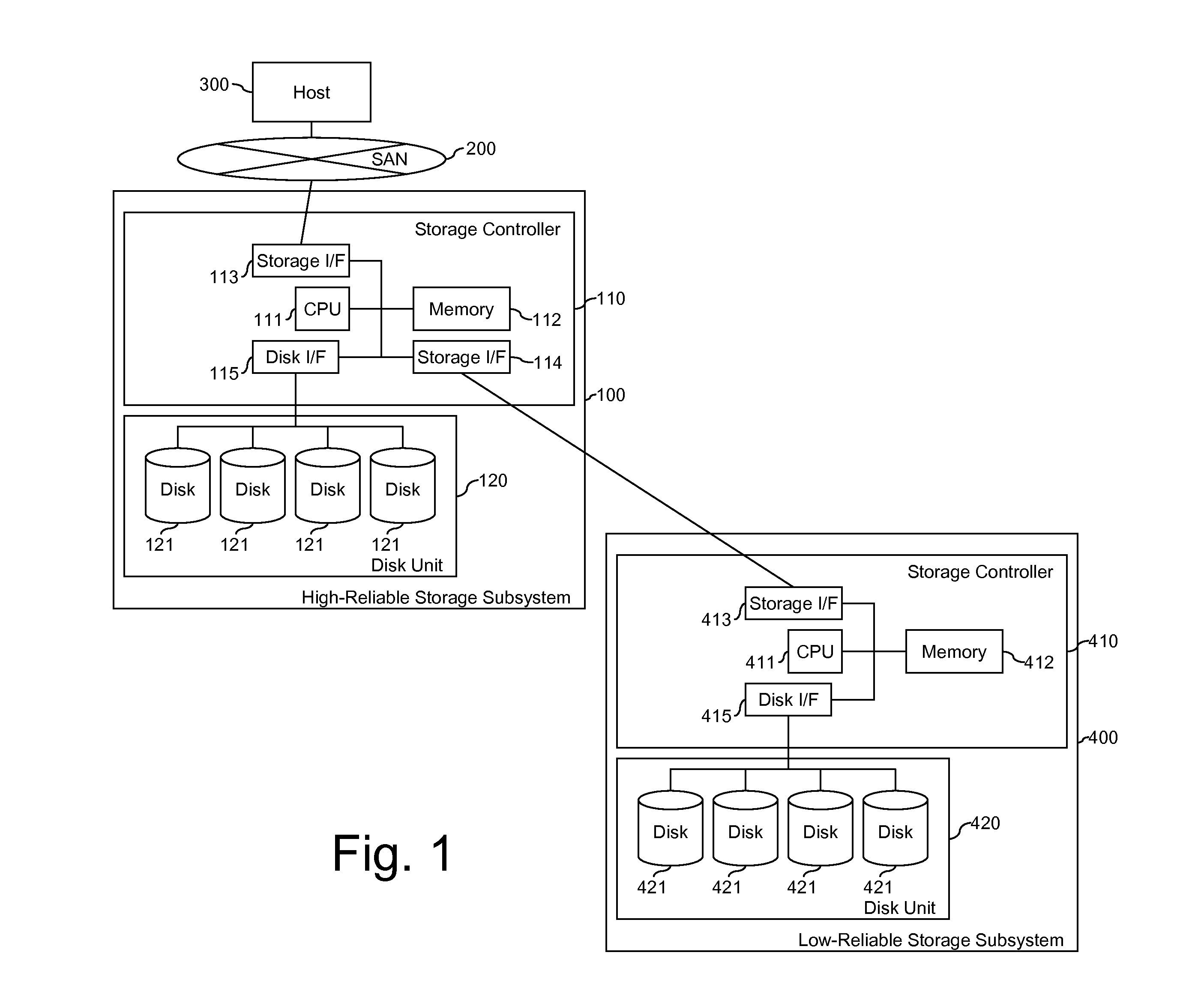
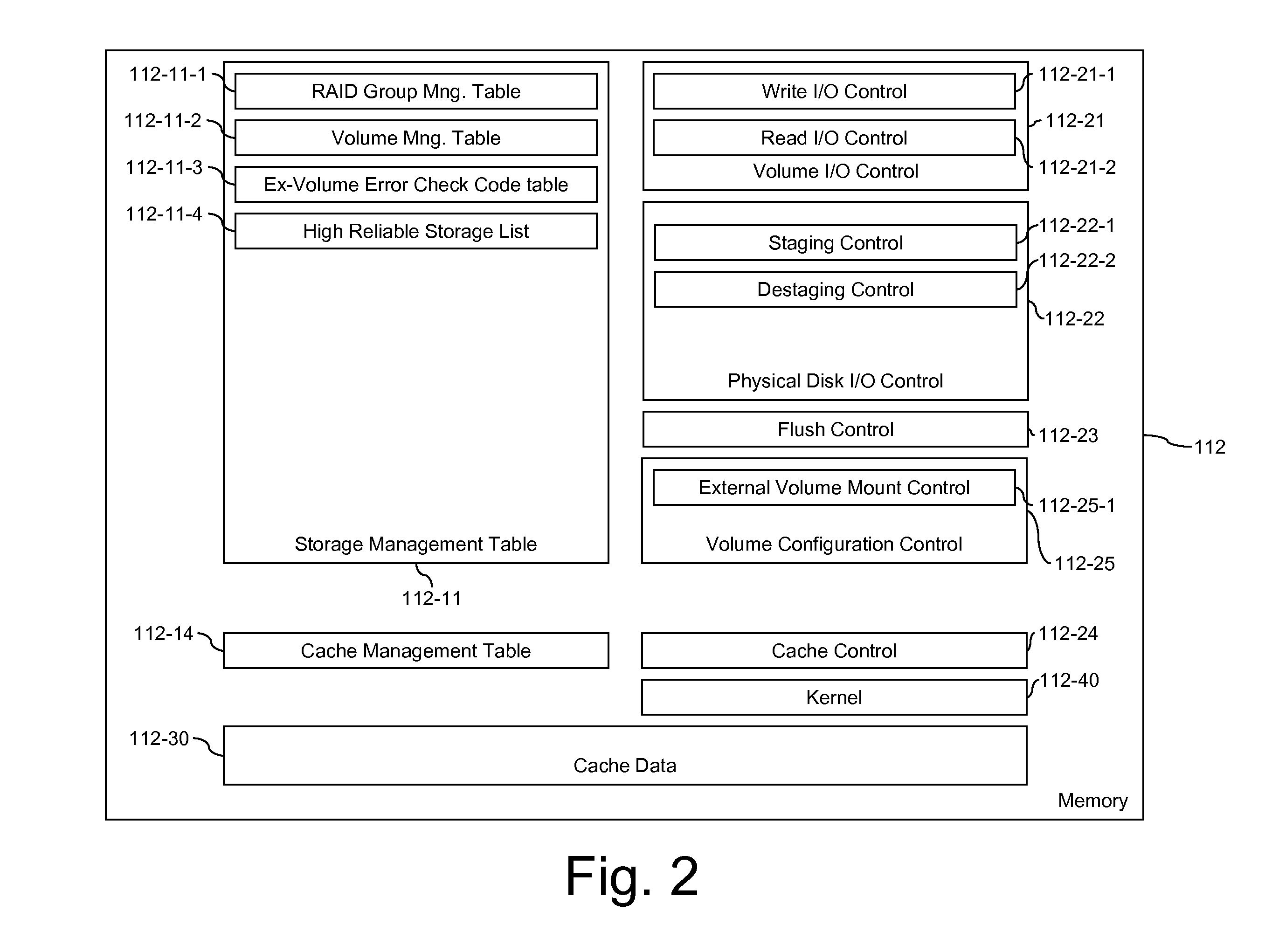
Methods and Apparatus for Managing Error Codes for Storage Systems Coupled with External Storage Systems
ActiveUS20110252274A1Improve reliabilityError identificationRedundant data error correctionExternal storageHash function
A system comprising a plurality of storage systems, which uses storage devices of multiple levels of reliability. The reliability as a whole system is increased by keeping the error code for the relatively low reliability storage disks in the relatively high reliability storage system. The error code is calculated using hash functions and the value is used to compare with the hash value of the data read from the relatively low reliability storage disks.
Owner:HUAWEI TECH CO LTD
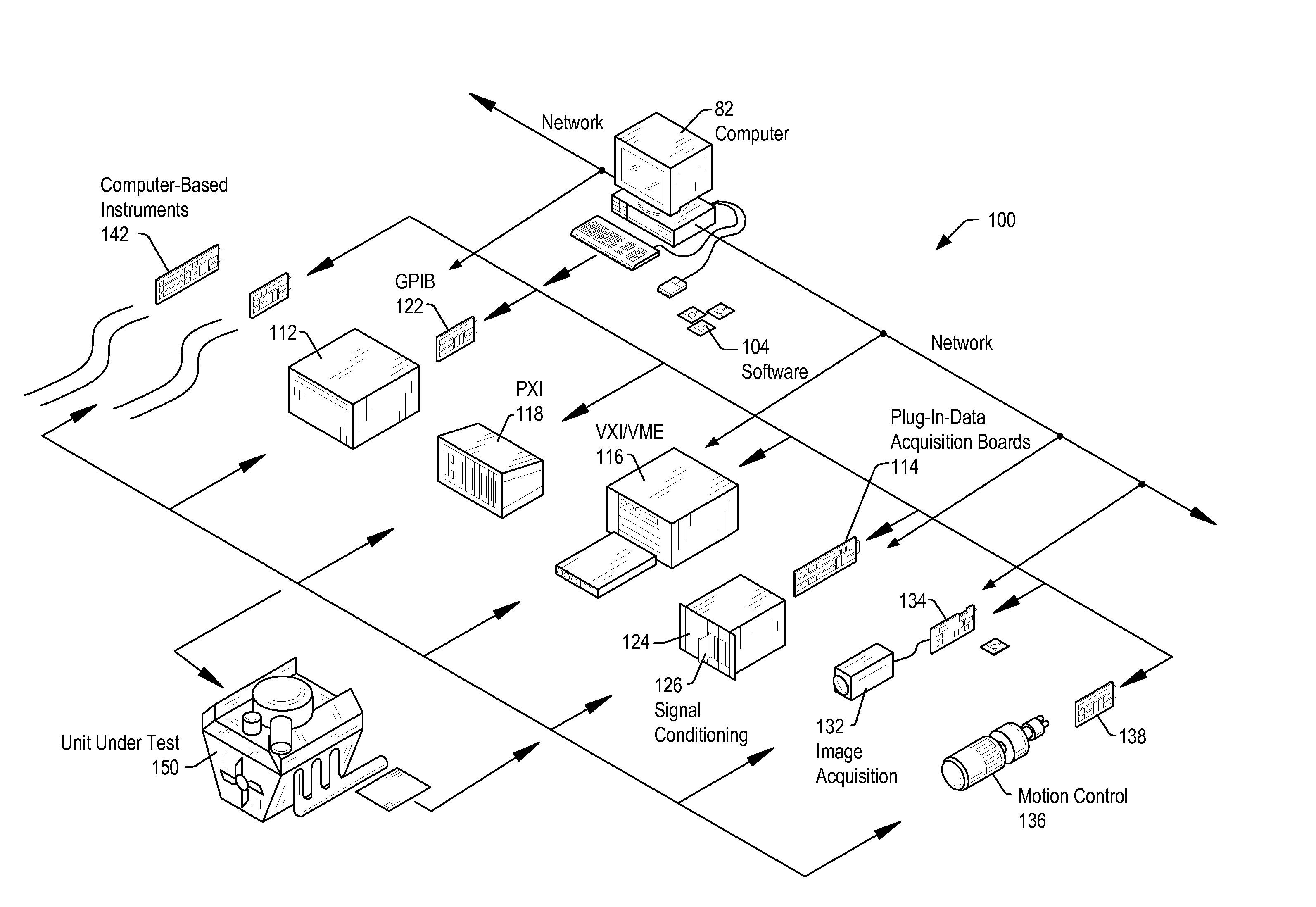
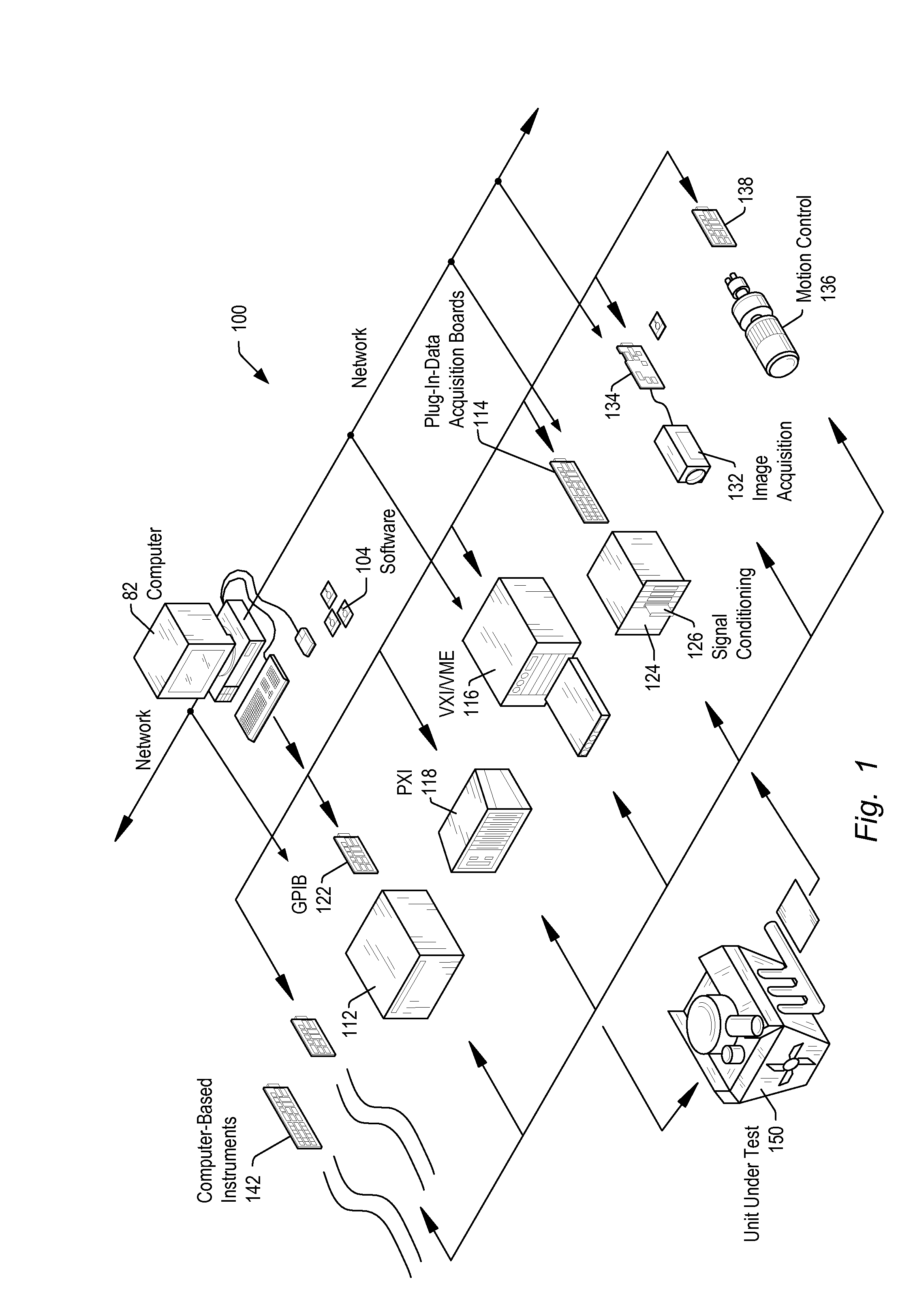
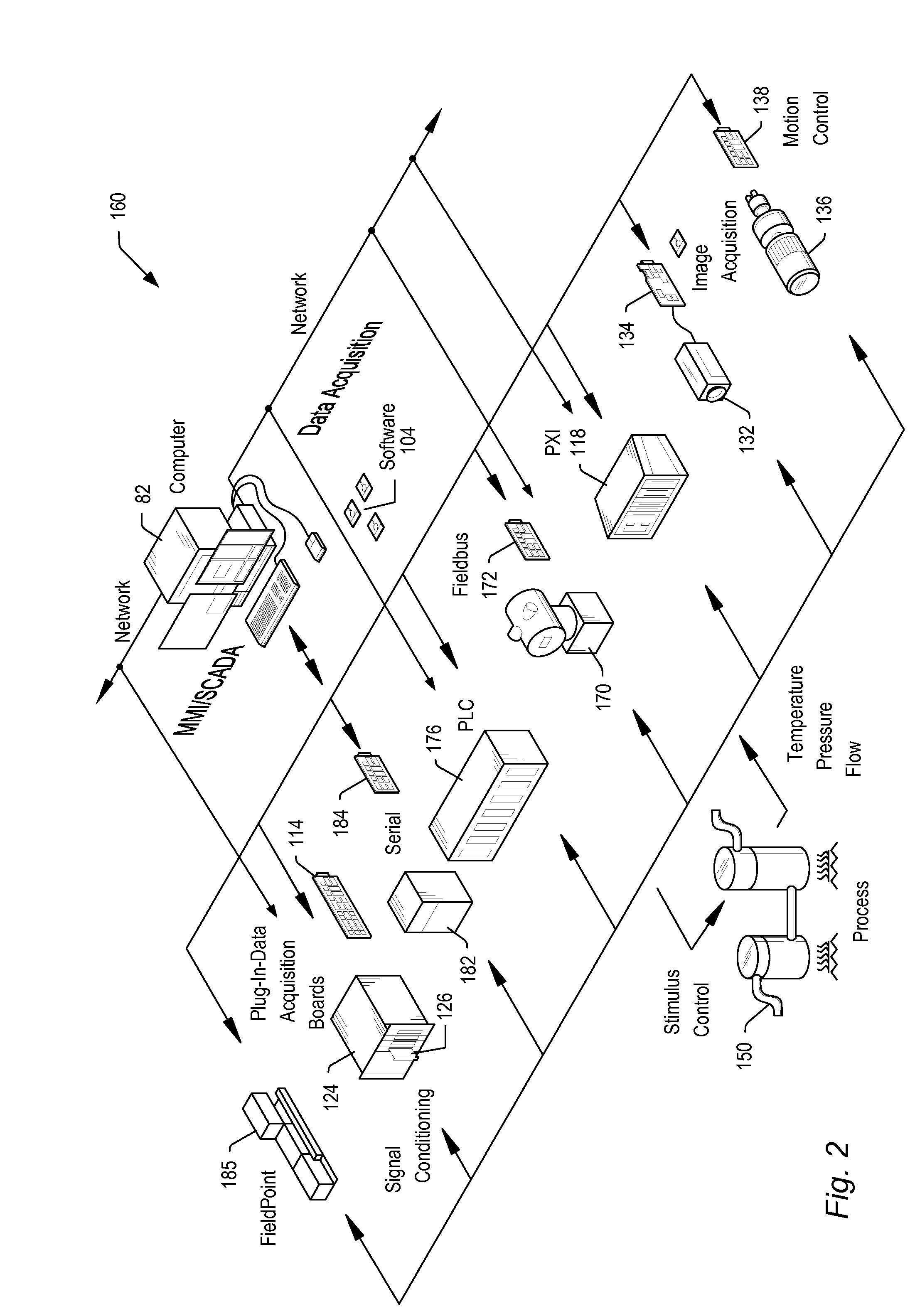
Methods for Data Acquisition Systems in Real Time Applications
ActiveUS20110029101A1Programme controlSampled-variable control systemsProgram instructionControl signal
A system may include a processing unit executing program instructions (SW), a data acquisition (DAQ) hardware device for acquiring sample data and / or generating control signals, and host memory configured to store data samples and various data associated with the DAQ and processor operations. The DAQ device may push HW status information to host memory upon being triggered by predetermined events taking place in the DAQ device, e.g. timing events or interrupts, to avoid or reduce SW reads to the DAQ device. The DAQ device may update dedicated buffers in host memory with status data on any of these events. The status information pushed to memory may be read in a manner that allows detection of race conditions. Interrupts generated by the DAQ device may be similarly handled. Upon generating an interrupt, the DAQ device may gather information required to handle the interrupt, and push the information into system memory, along with information identifying the interrupt. SW may read system memory for this information, and handle the interrupts as required without having to query the DAQ device.
Owner:NATIONAL INSTRUMENTS
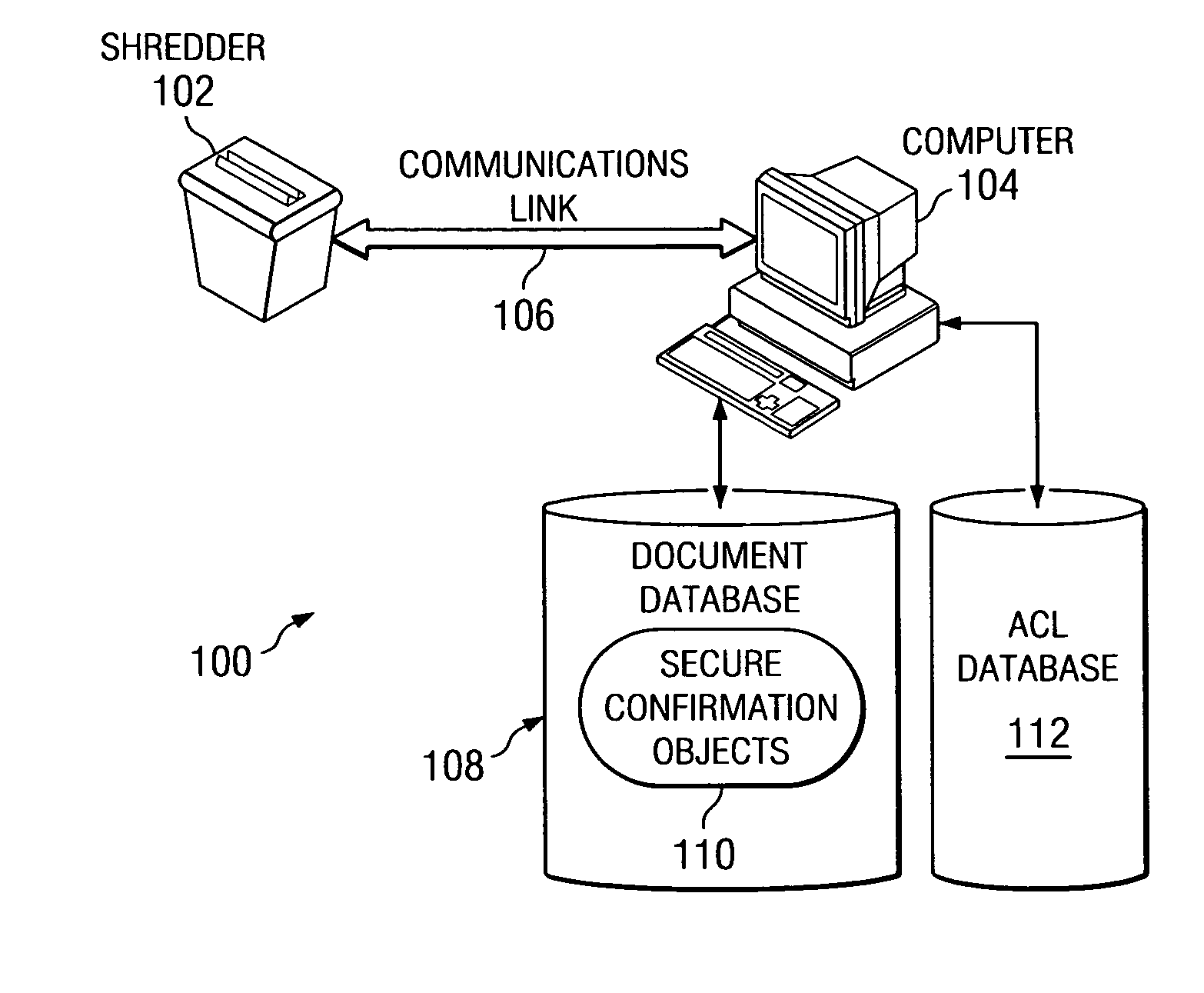
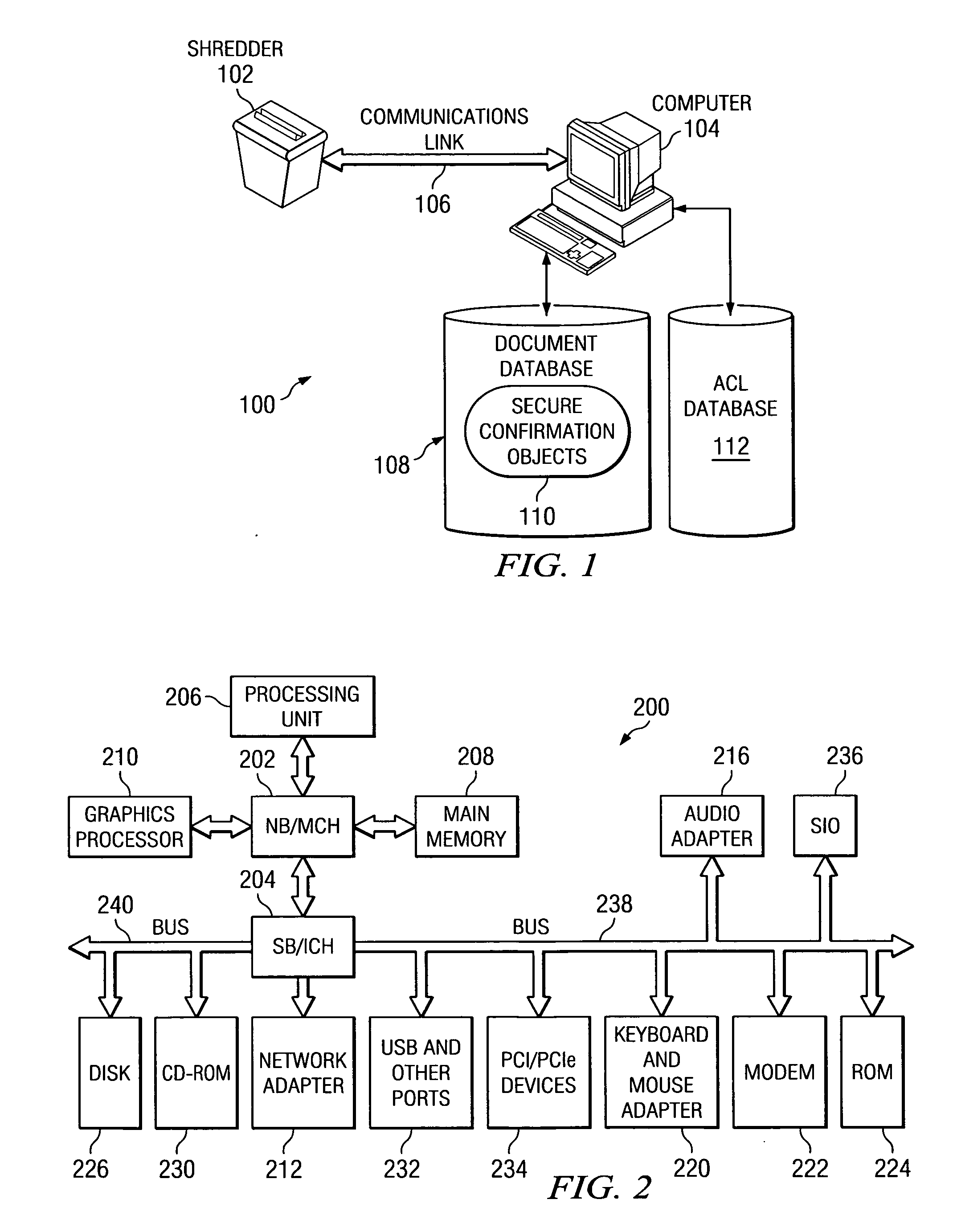
Method and apparatus for document destruction
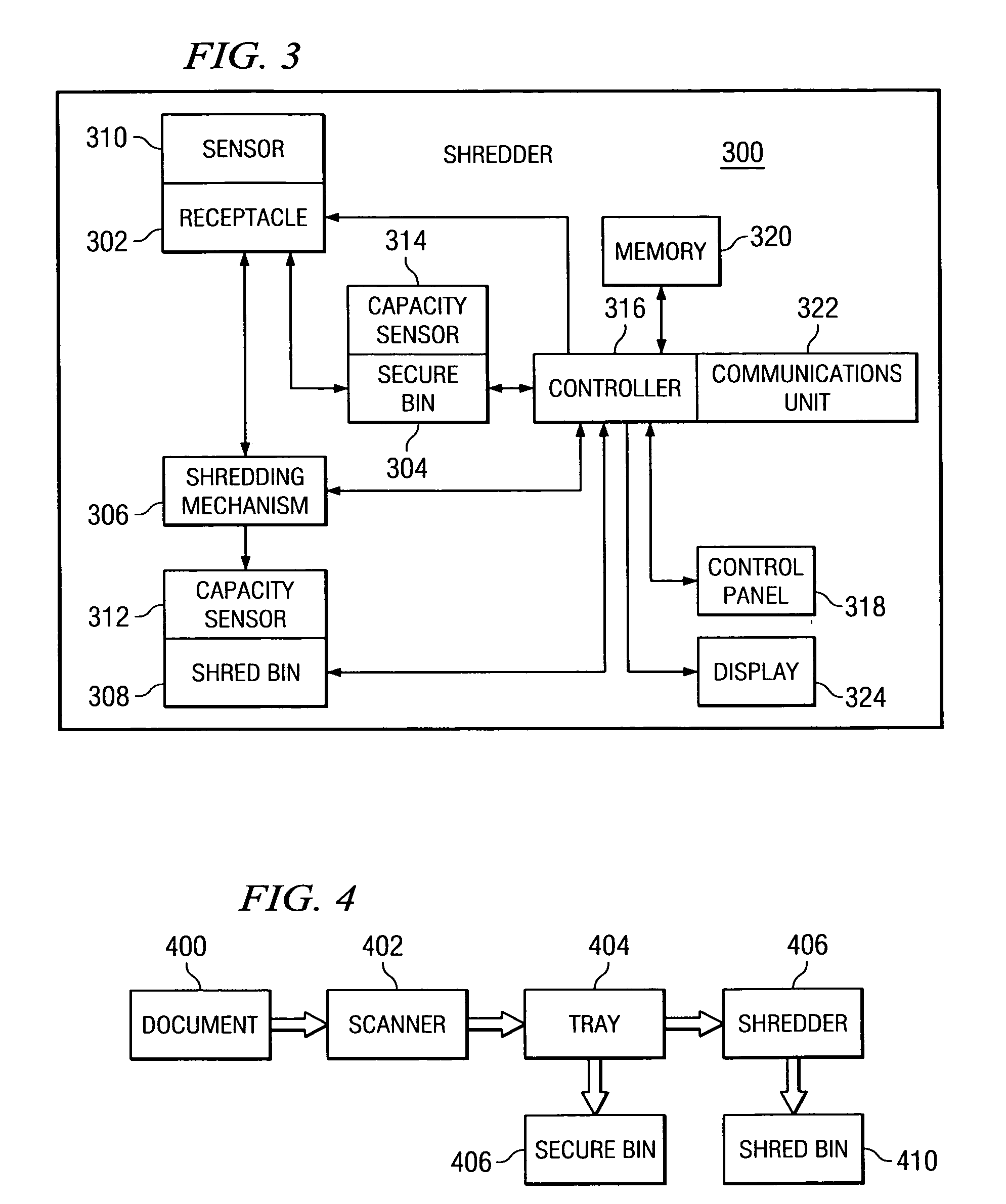
InactiveUS20070075168A1Digital data processing detailsTemperatue controlData processing systemTelecommunications link
A computer implemented method, apparatus, and computer usable code for shredding objects. The apparatus has a number of components including a receptacle that is configured to receive objects. A shredding unit is connected to the receptacle, wherein the shredding unit selectively destroys the objects placed into the receptacle. An object detector is used to detect the presence of an object in the receptacle. An object identifier identifies objects placed into the receptacle. The apparatus also has a memory and a connector. The connector is used to establish a communications link with a data processing system. A controller in the apparatus stores identifications of objects identified by the object identifier in the memory and sends a signal to the shredding unit to control shredding of the objects.
Owner:IBM CORP
Fault tolerant multi-node computing system using periodically fetched configuration status data to detect an abnormal node
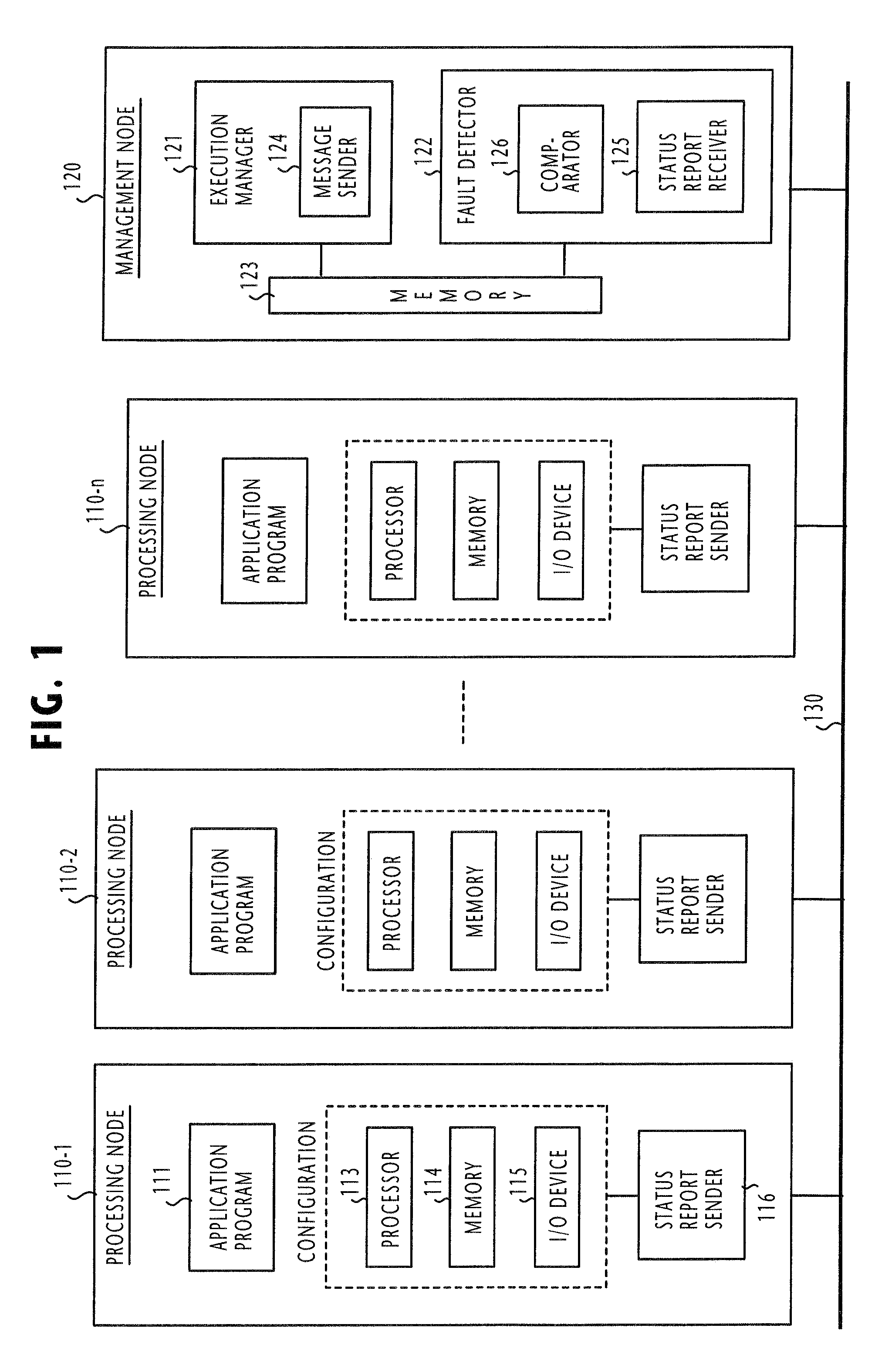
InactiveUS7870439B2Less-costly to developLess costly to develop application programsDigital computer detailsEmergency protective arrangements for automatic disconnectionSoftware faultCommunications media
A fault tolerant computing system comprises a plurality of processing nodes interconnected by a communication medium for parallel-running identical application programs. A fault detector is connected to the processing nodes via the communication medium for periodically collecting configuration status data from the processing nodes and mutually verifying the collected configuration status data for detecting an abnormal node. In one preferred embodiment of this invention, the system operates in a version diversity mode in which the processing nodes are configured in a substantially equal configuration and the application programs are identical programs of uniquely different software versions. In a second preferred embodiment, the system operates in a configuration diversity mode in which the processing nodes are respectively configured in uniquely different configurations. The configurations of the processing nodes are sufficiently different from each other that a software fault is not simultaneously activated by the processing nodes.
Owner:NEC CORP
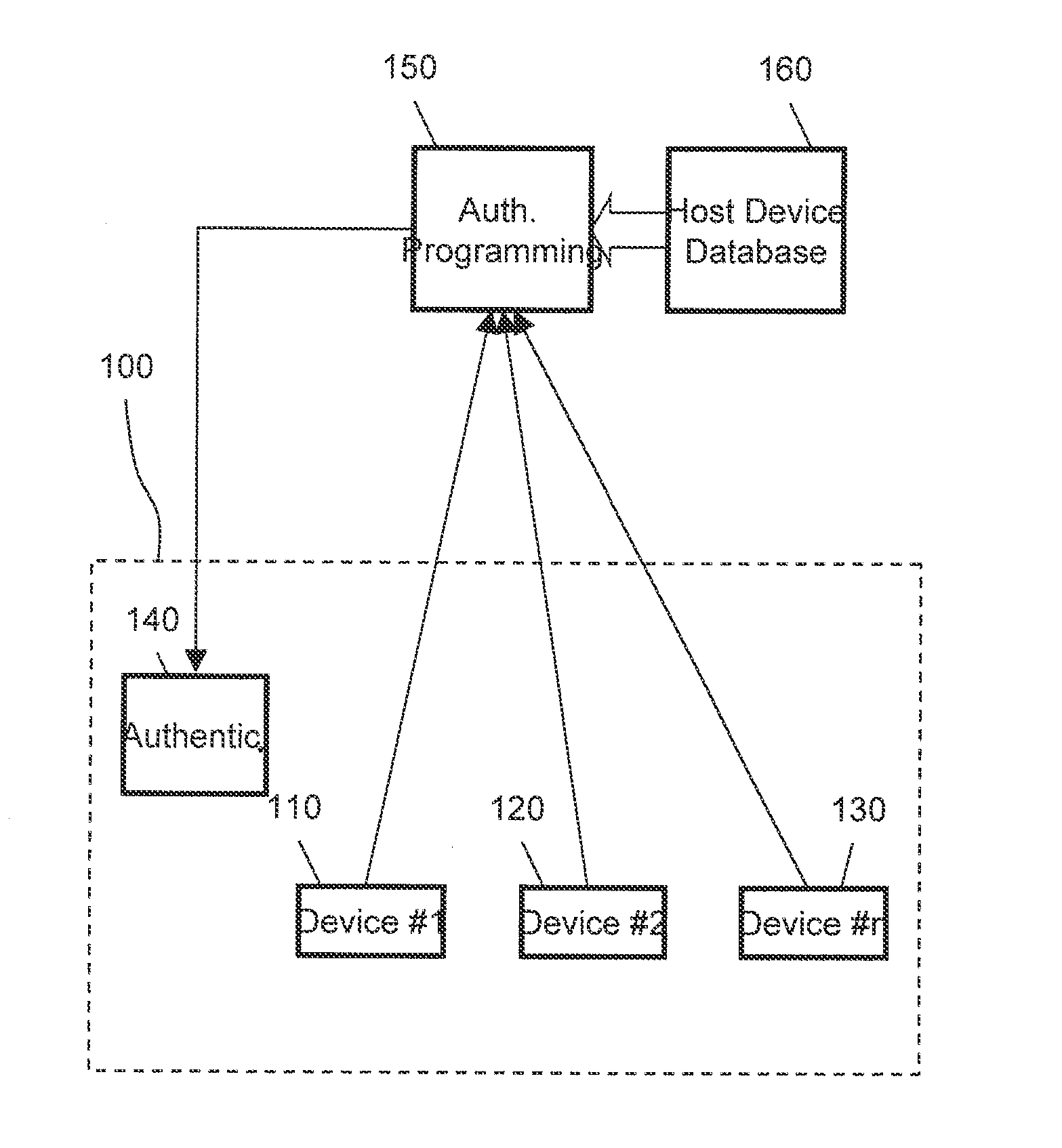
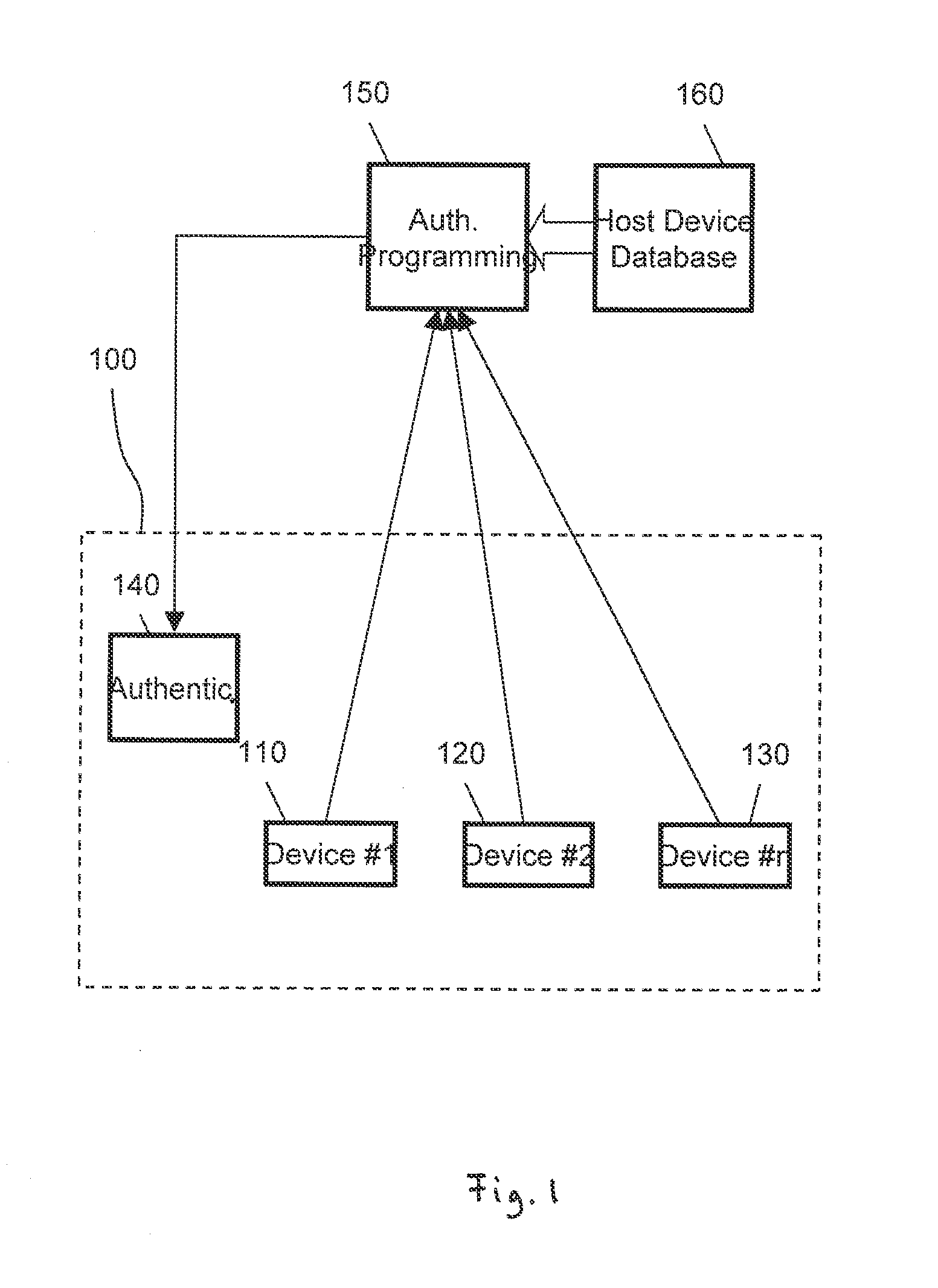
System-Level Chip Identify Verification (Locking) Method with Authentication Chip
ActiveUS20130222109A1Programme controlElectric signal transmission systemsComputer hardwareSystem level
A system for authenticating electronic devices, particularly chips or integrated circuits is described. This allows authenticating that the devices are authorized by the original manufacturer for operation in critical applications.
Owner:INFINEON TECH AG
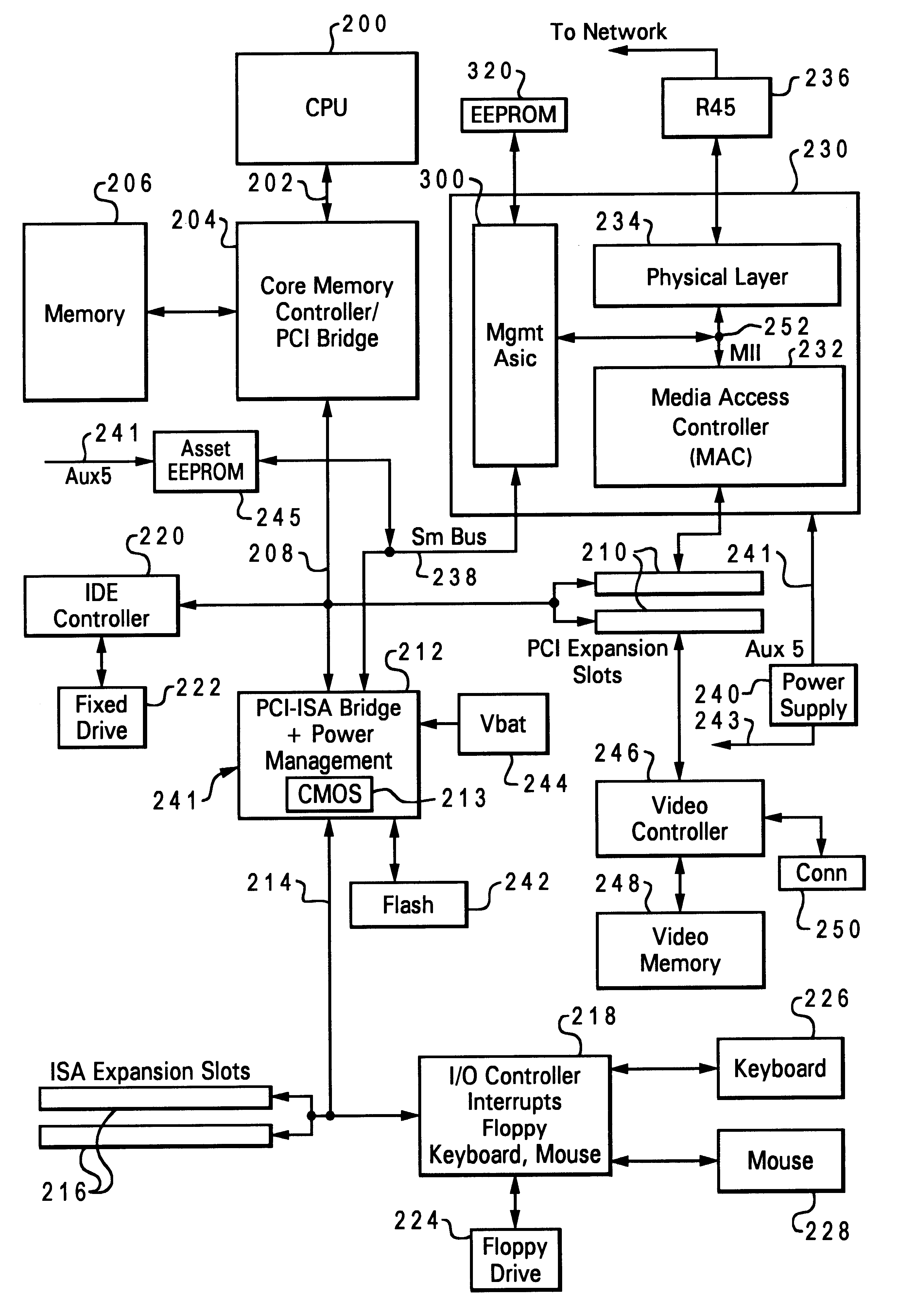
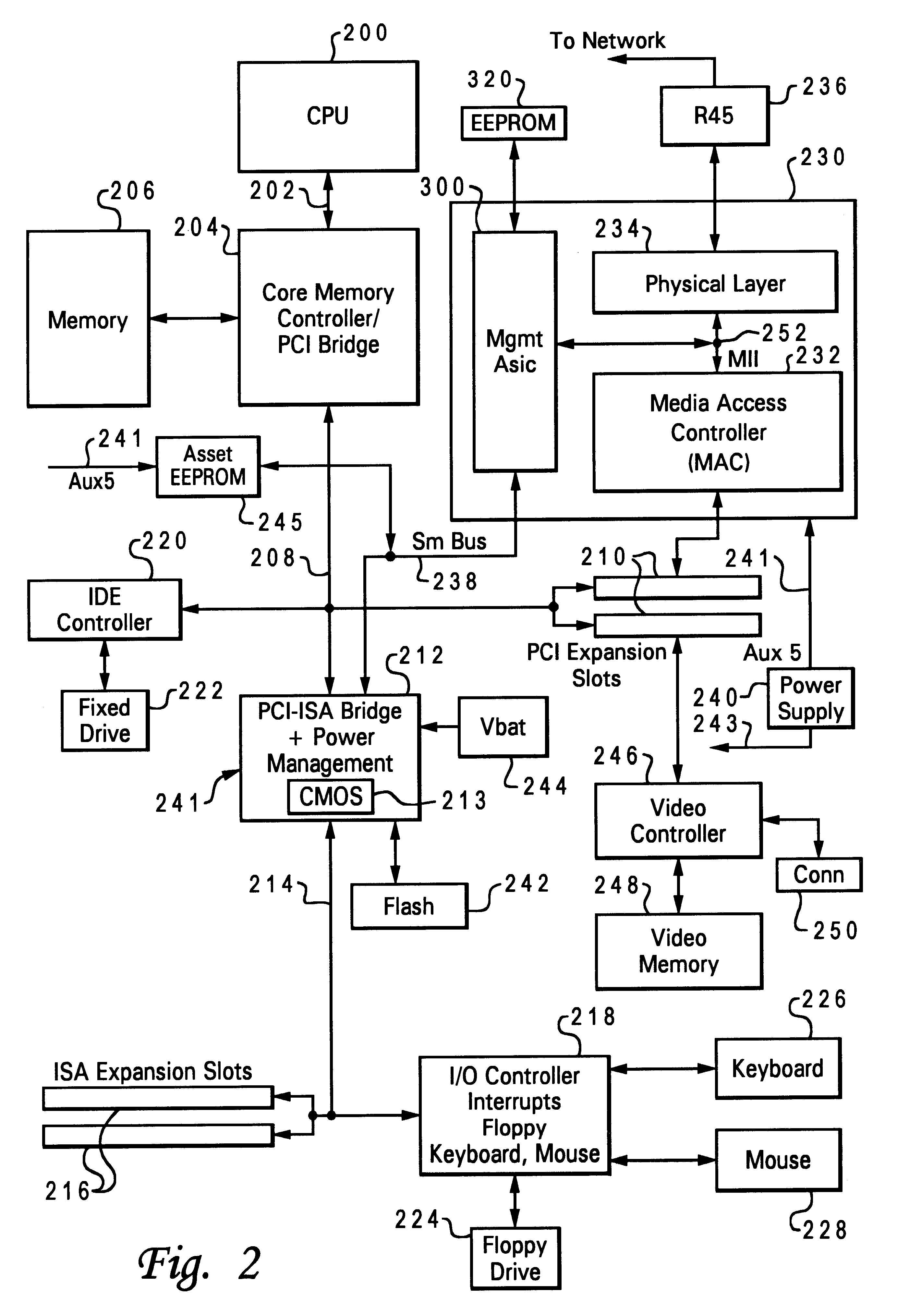
Data processing system and method for permitting a server to remotely access a powered-off client computer system's asset information
InactiveUS6381636B1Input/output to record carriersVolume/mass flow measurementData processing systemComputerized system
A data processing system and method are described for permitting a server computer system to remotely access asset information stored within one of a plurality of client computer systems. The client computer systems are coupled to the server computer system utilizing a network. Asset information is stored in a storage device within the particular client computer system. The asset information includes information identifying a plurality of components of the client computer system. The server computer system transmits a message to the client computer system while the client computer system is powered-off. A network adapter is included within the client computer system. The network adapter accesses the storage device to obtain the asset information while the client computer system is powered-off.
Owner:LENOVO PC INT
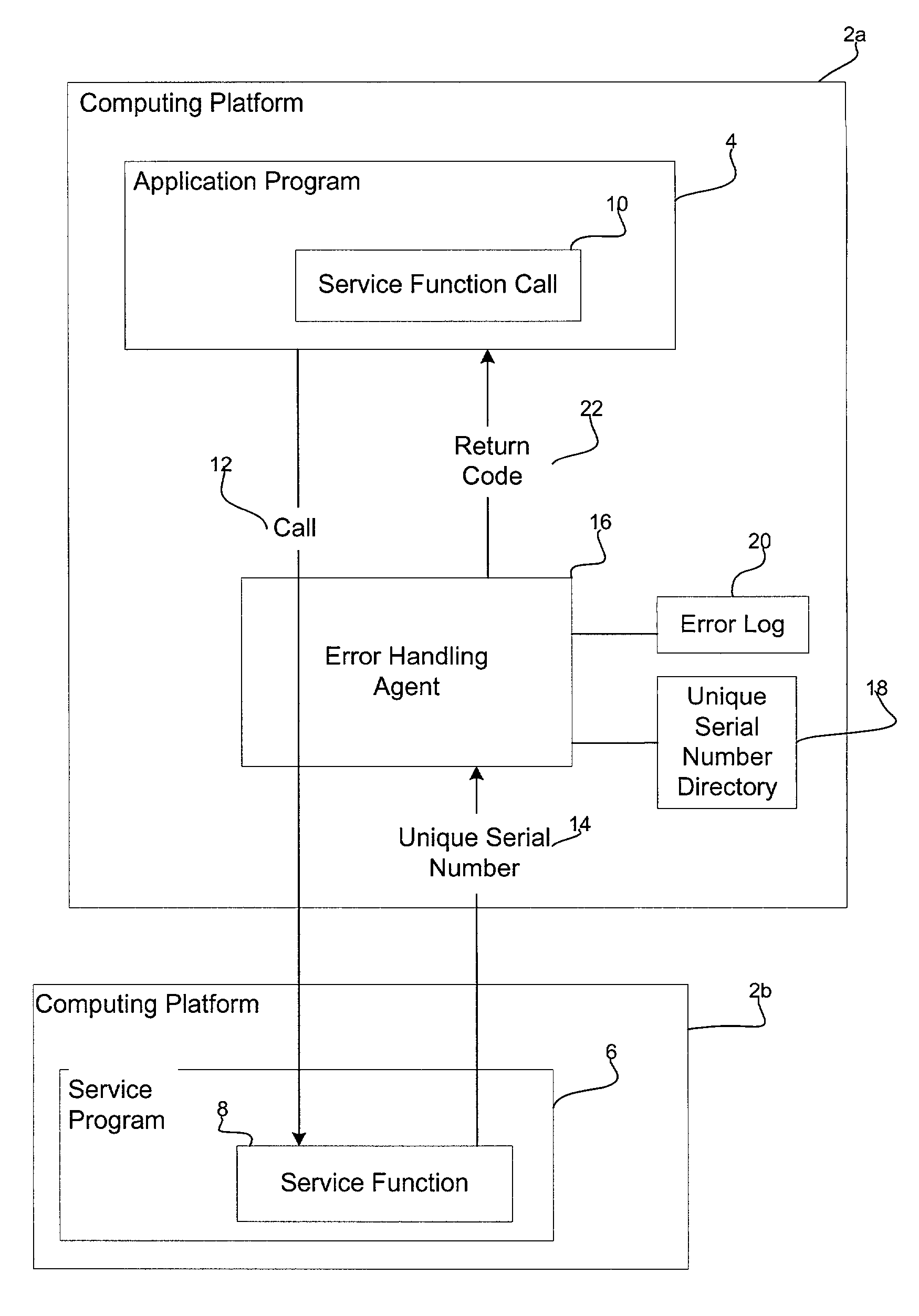
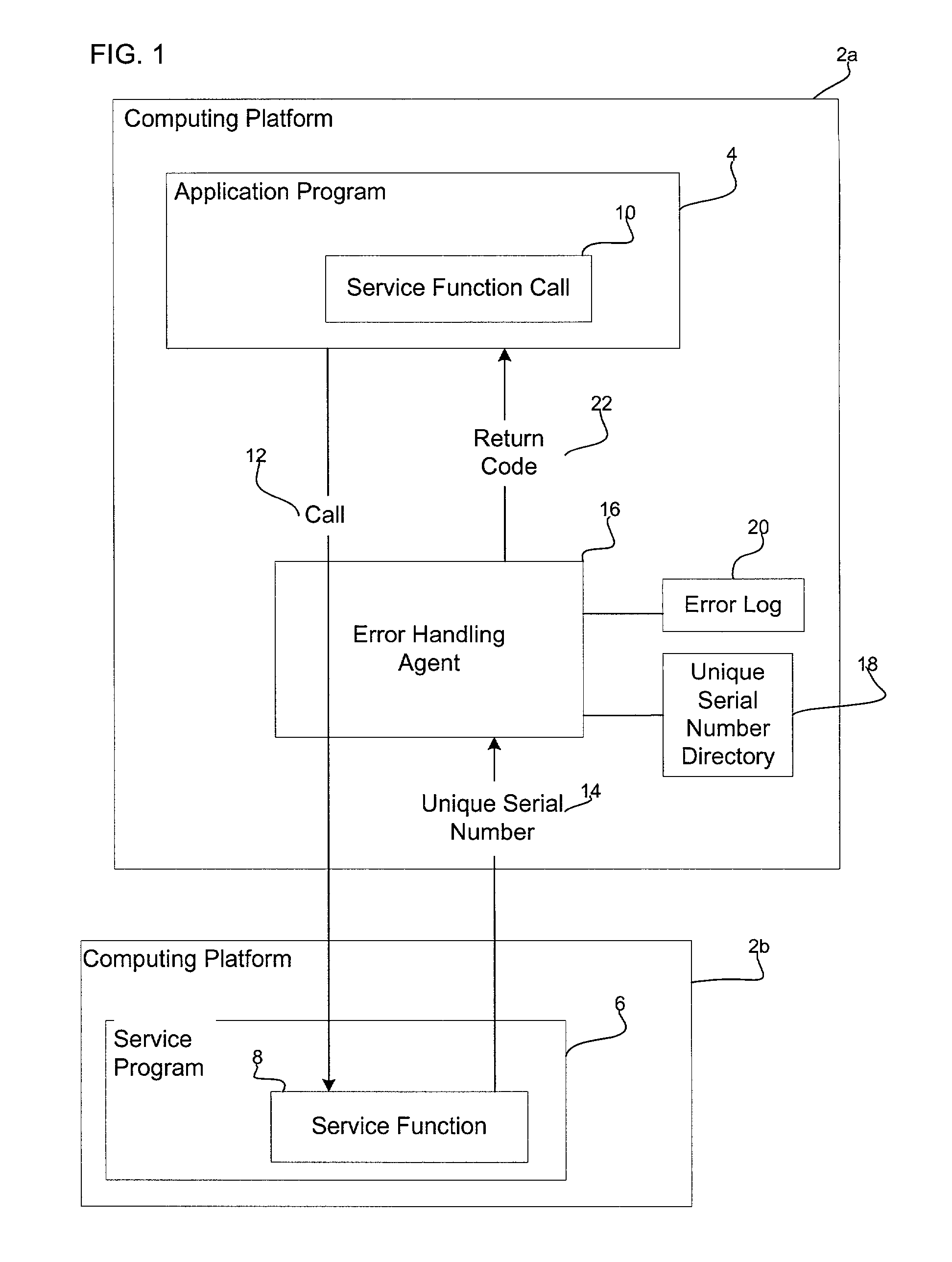
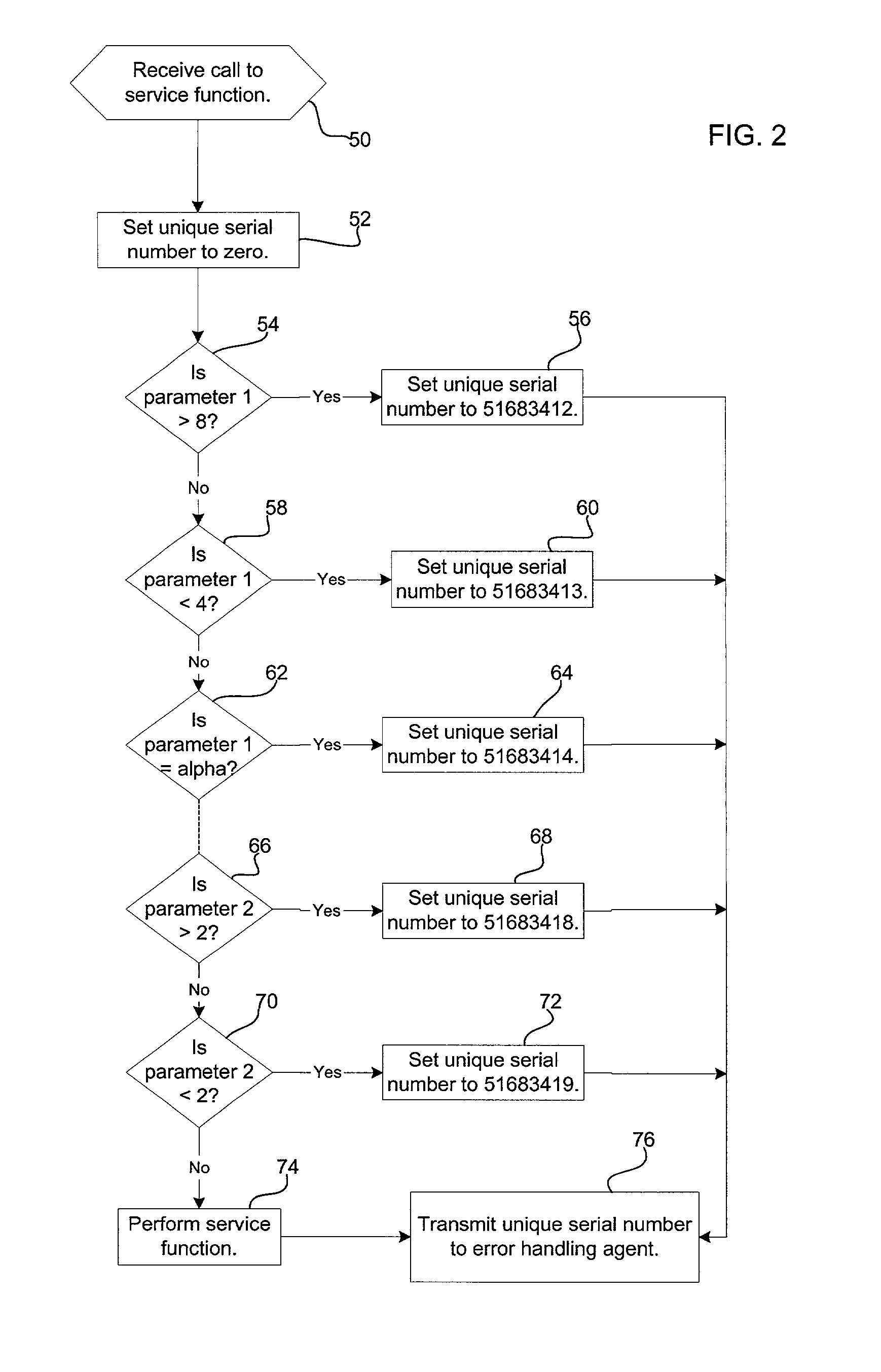
Method, system and program for handling errors occurring in function calls
InactiveUS20030037291A1Efficiently and effectively diagnose and correctReduce handlingFault responseHardware monitoringApplication procedureOperating system
Provided is a method, system, and program for handling errors in a service program including service functions capable of being called from application programs. A call is received for one service function from a service function call within one application program. A series of test operations are performed when executing the service function call. Each test operation returns an identifier if the test operation failed where each identifier is associated with one error state. If one test operation failed, then the identifier for the failed test operation is transferred to an error handling agent, wherein the error handling agent accesses error information associated with the identifier and generates error information describing a specific cause of the error that caused the test operation to fail and then returns to the application program with a generic return code.
Owner:IBM CORP
Verification system and method
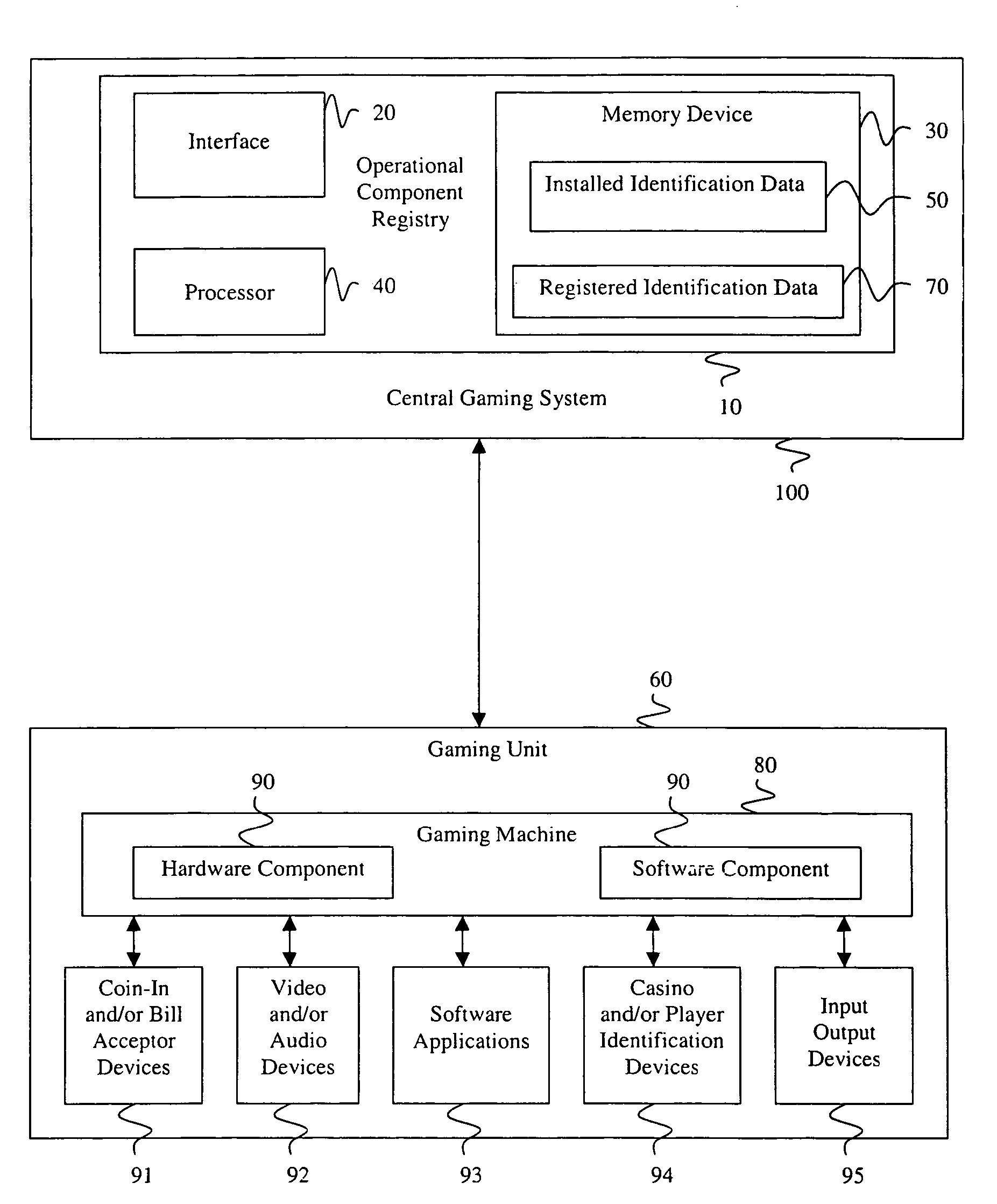
ActiveUS7730325B2Prevent falsification and repudiationPrevents falsification and repudiationDetecting faulty hardware by configuration testDetecting faulty hardware by remote testComputer hardwareVerification system
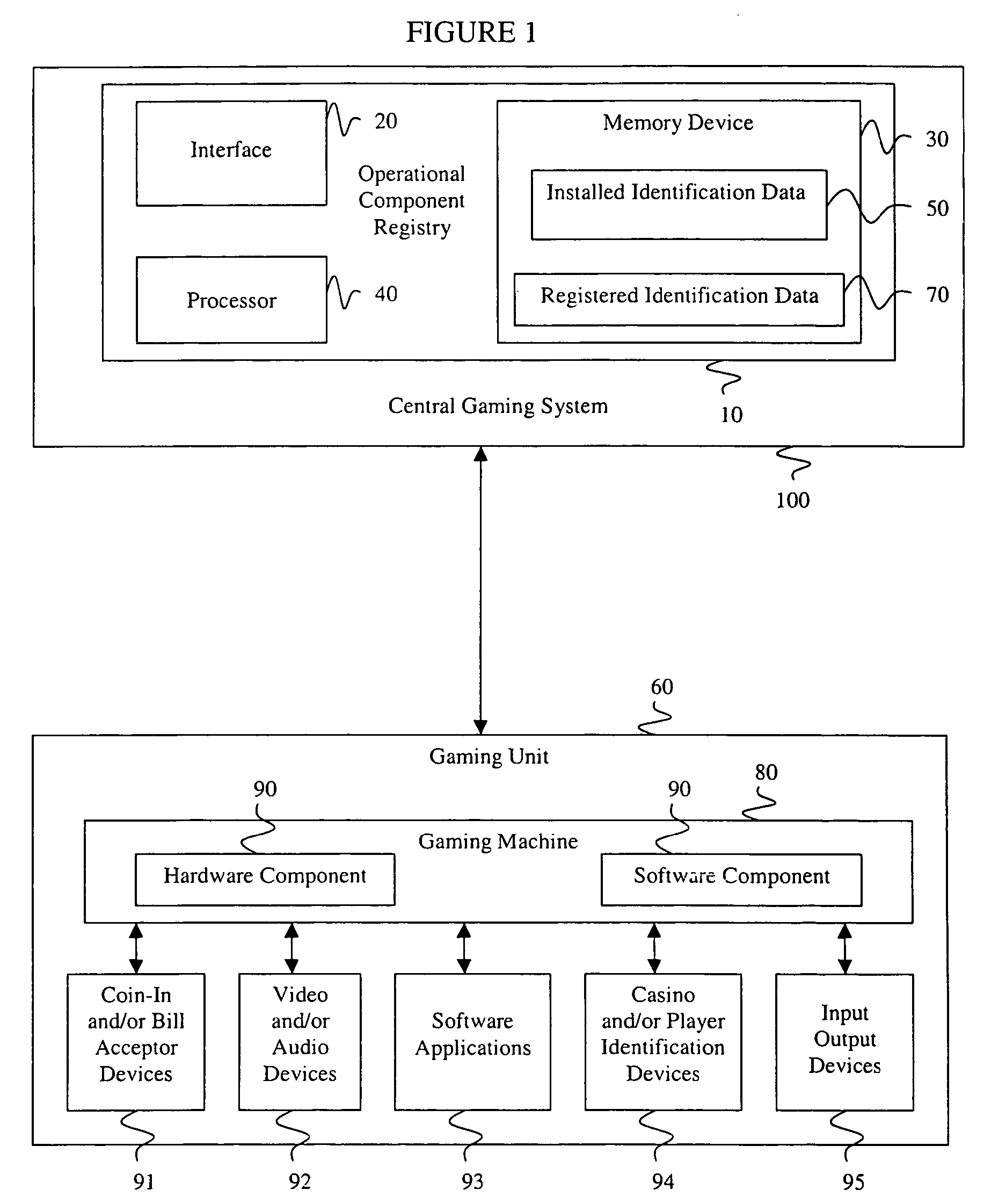
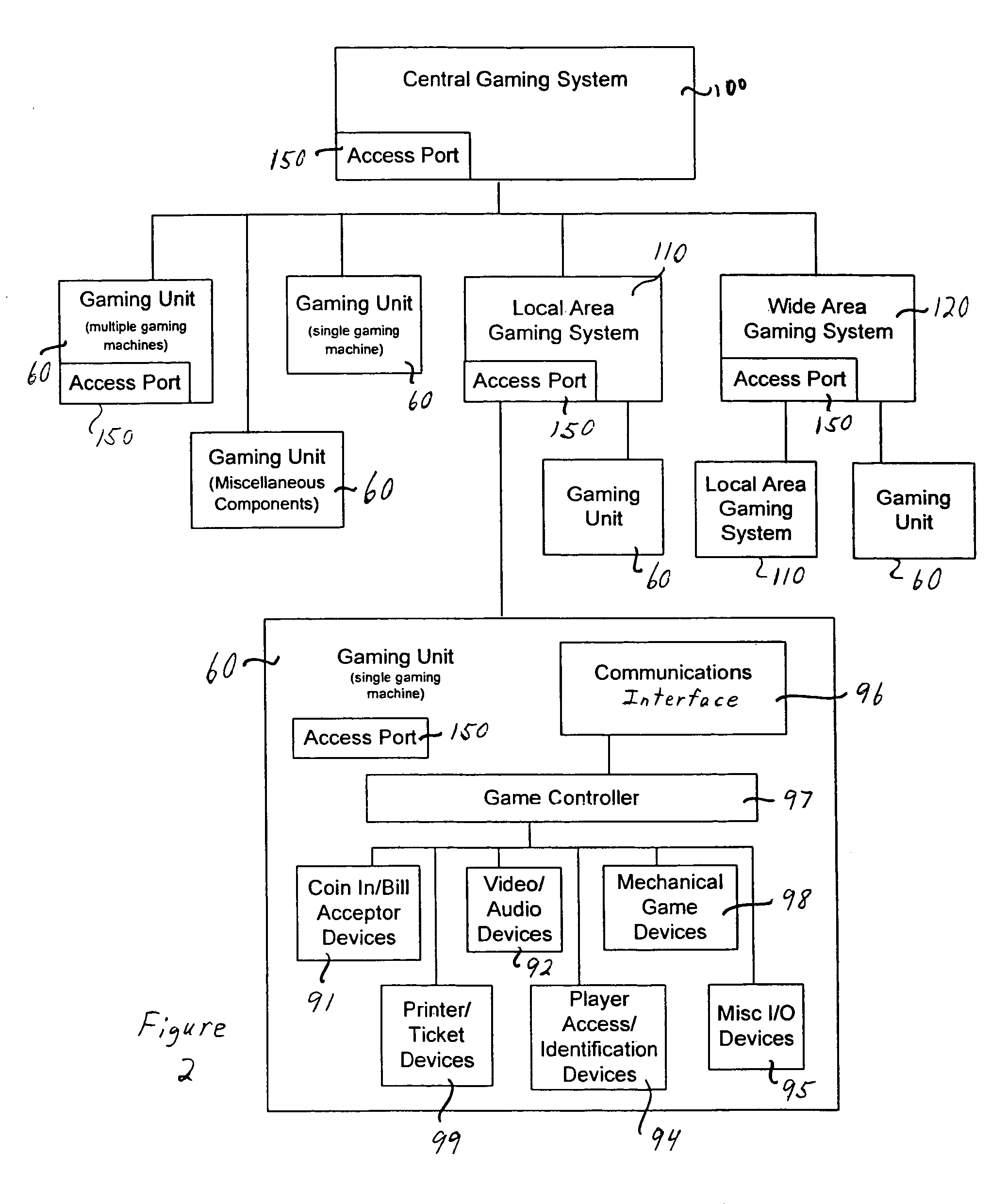
A verification system has an operational component registry 10 that includes an interface 20, a memory device 30, and a processor 40. Preferably, the interface 20 in the operational component registry 10 communicates the installed identification data 50 from the gaming units 60 to the operational component registry. The memory device 30 preferably stores registered identification data 70 for the gaming units 60. Preferably, the processor 40 in the operational component registry 10 then analyzes the registered identification data 70 and the installed identification data 50 from the gaming units 60, after which enablement of the gaming units is determined based upon the examination of the registered identification data and the installed identification data. An operational component registry 10 may also monitor changes, services, requirements, enablement, and productivity of the gaming units or components of the gaming units.
Owner:LNW GAMING INC
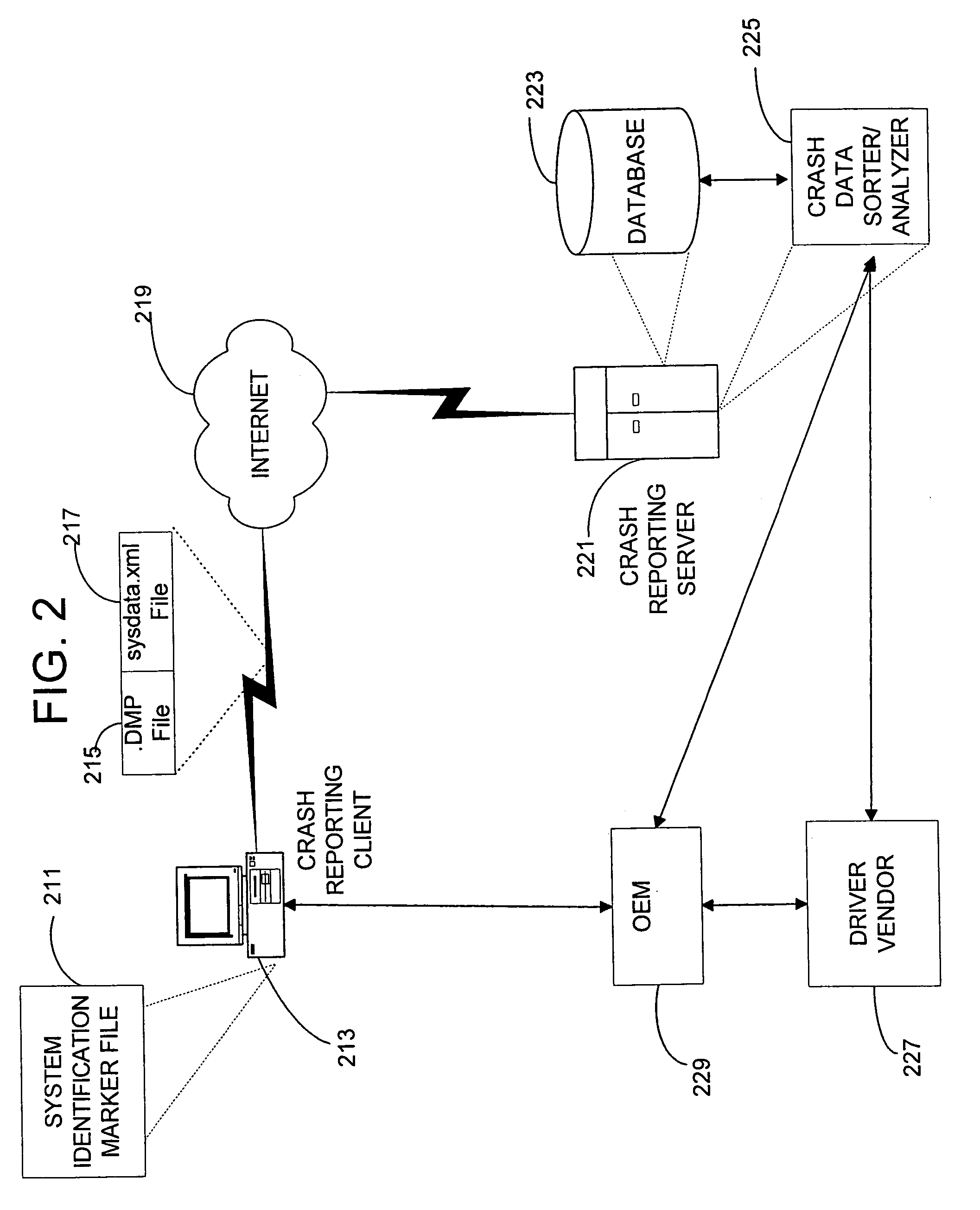
System and method for computer hardware identification
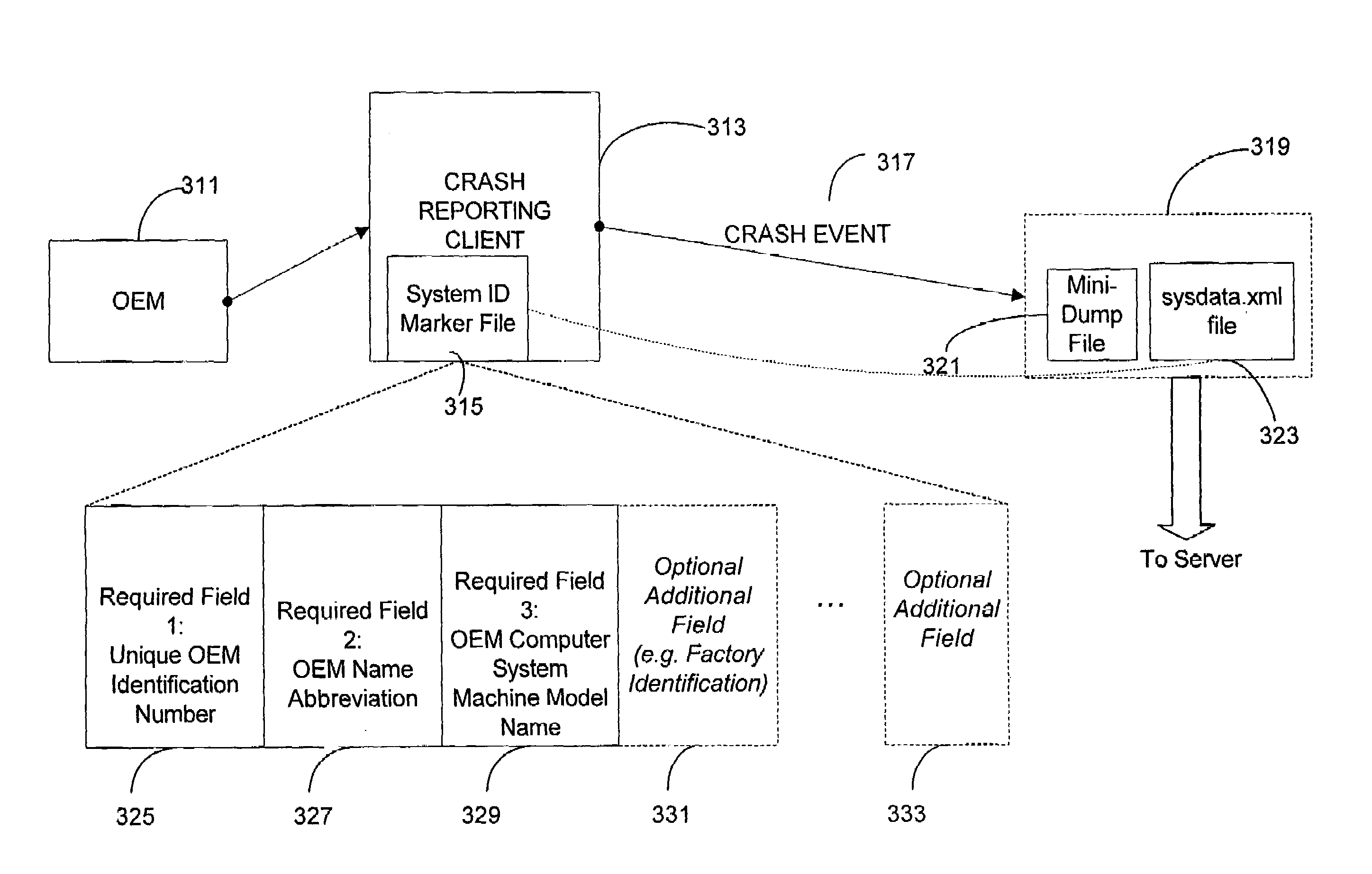
A system for identifying specific information regarding the hardware configuration of a computer system improves resolution of problems via online crash and is usable for other purposes as well. Embodiments of the employ applications directed by remote computers functioning as servers, which use the specific computer system hardware-configuration information provided by the identifying system.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com