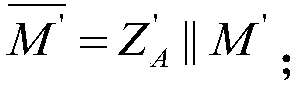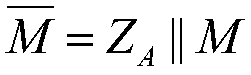Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
272results about How to "Avoid management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
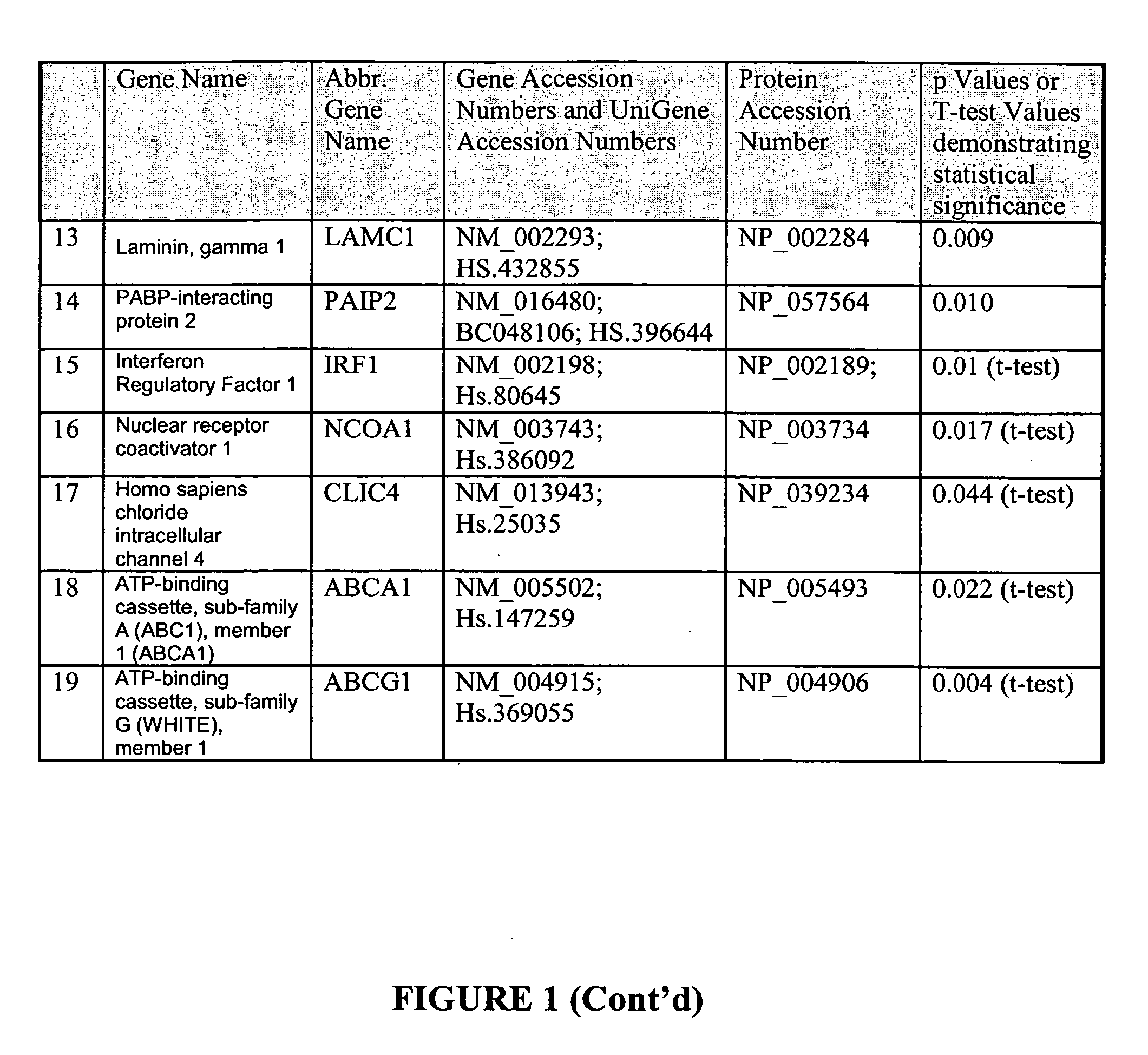
Patent Status
Application Year
Inventor
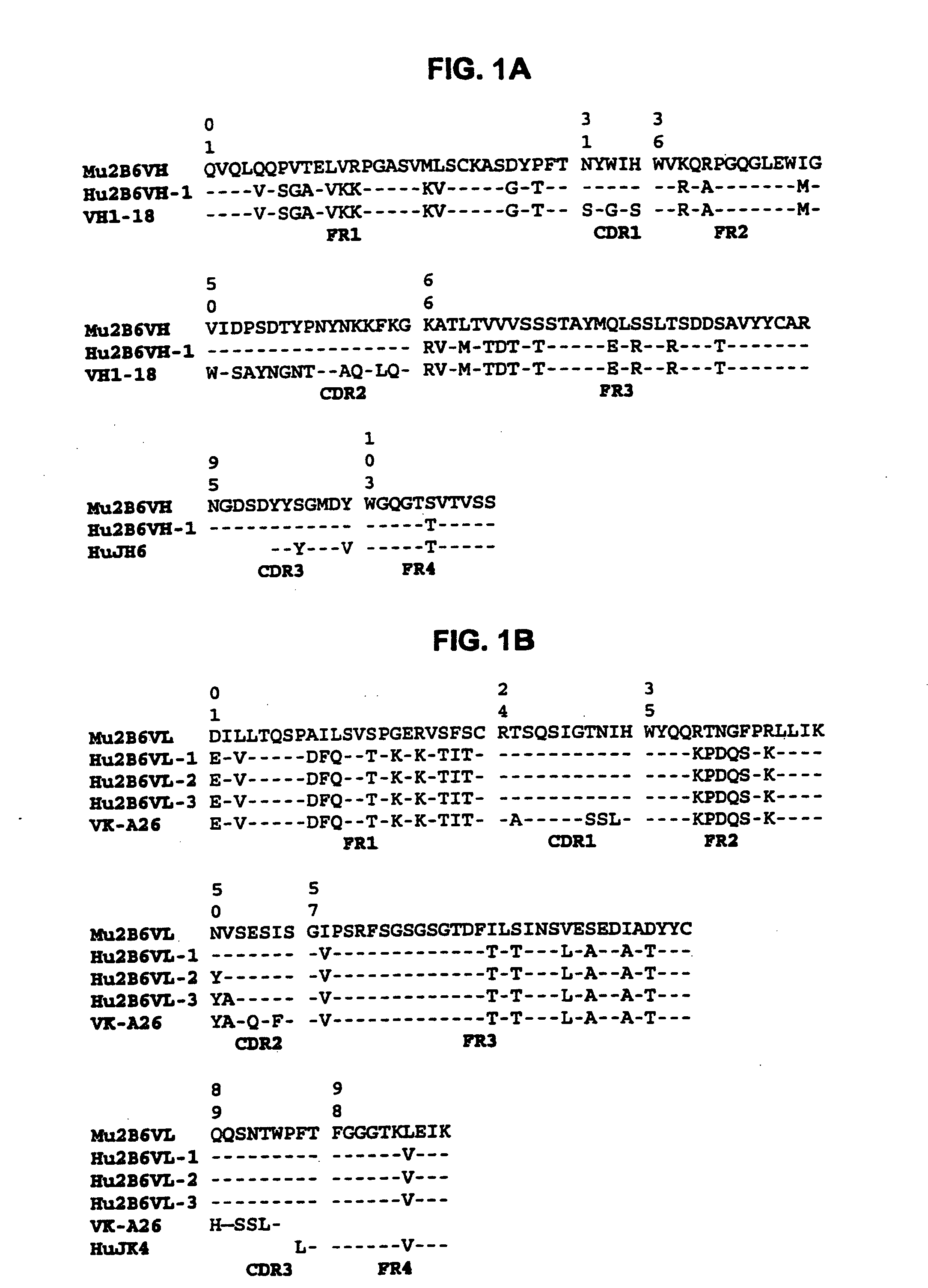
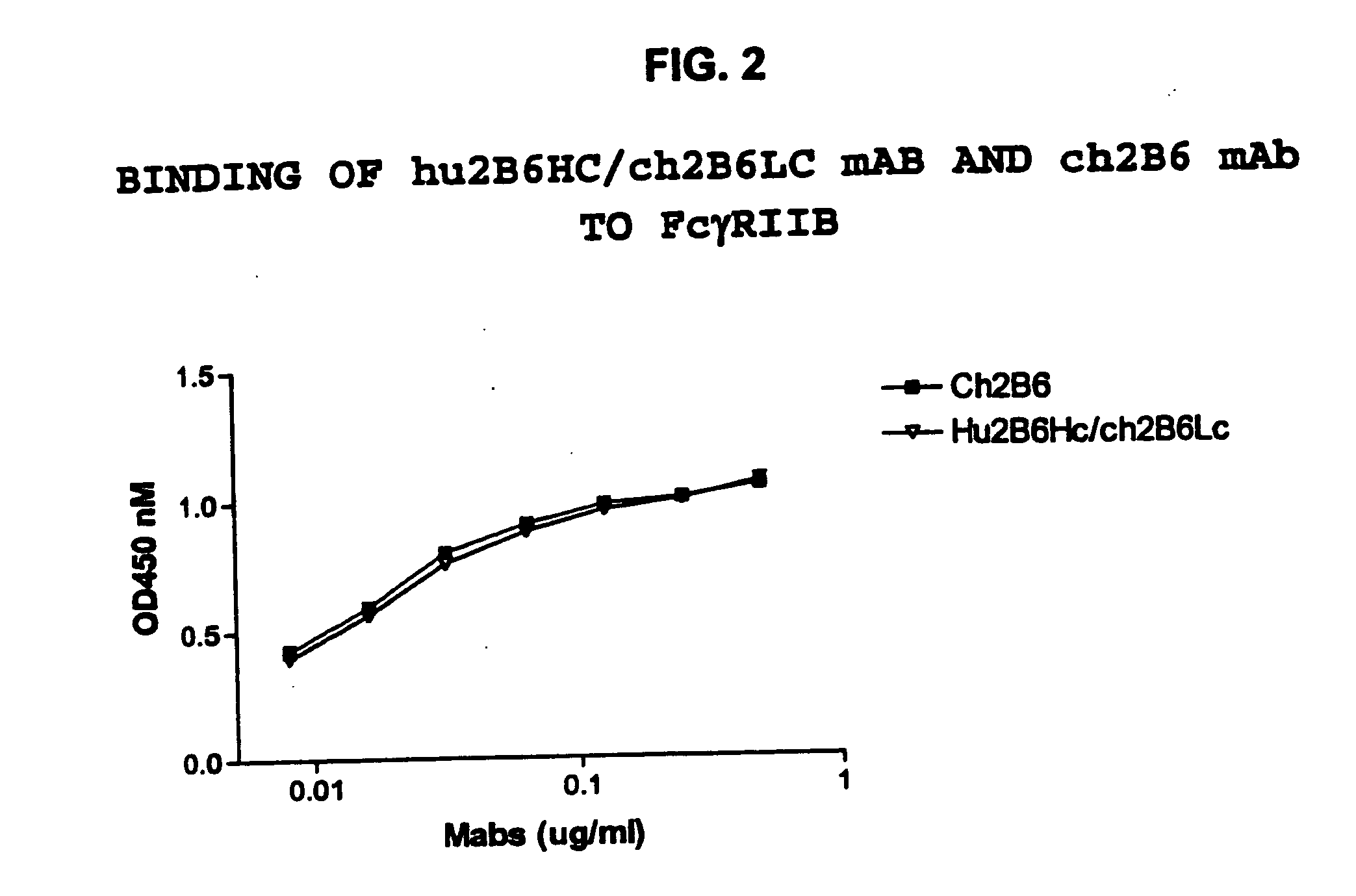
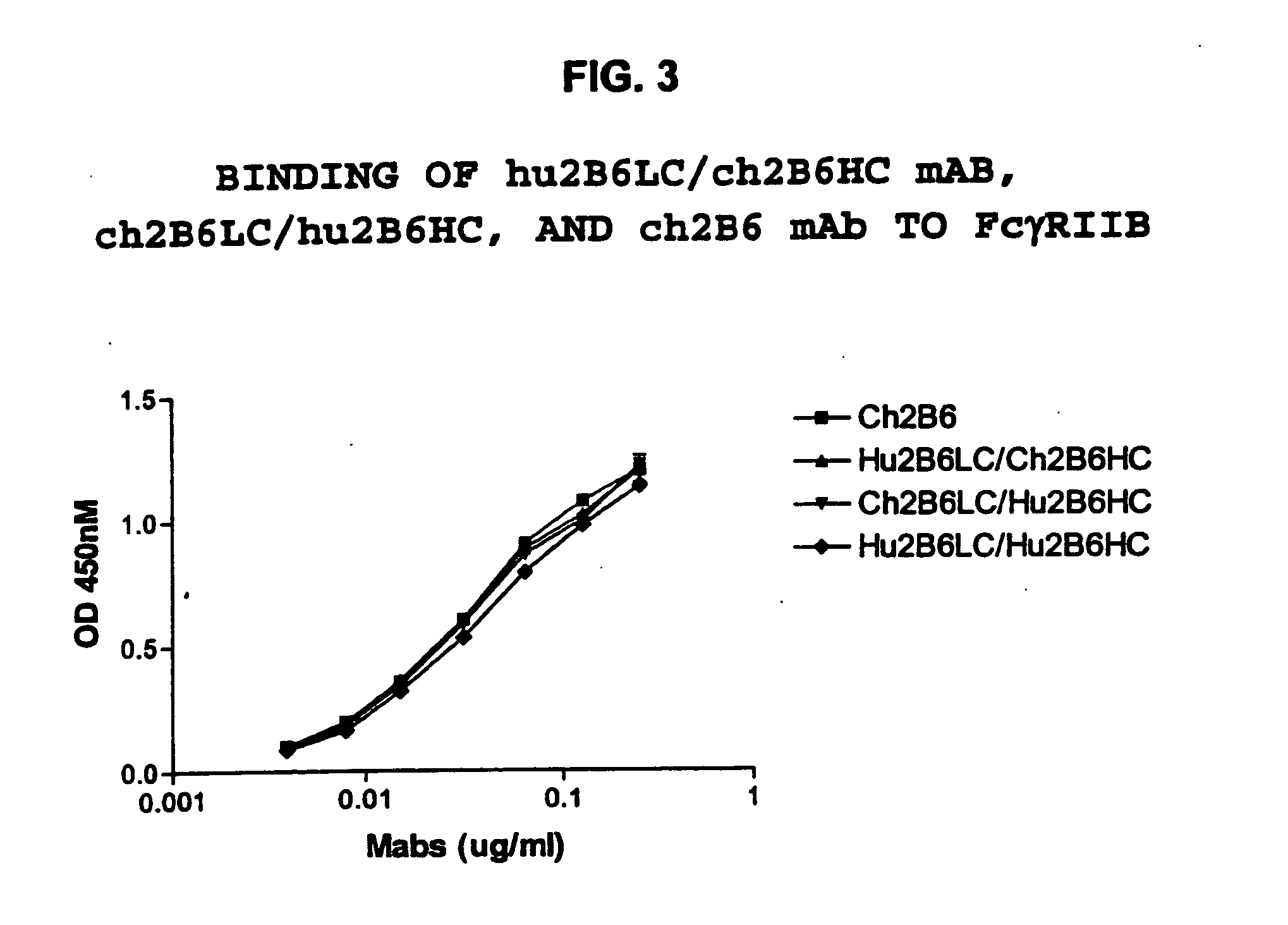
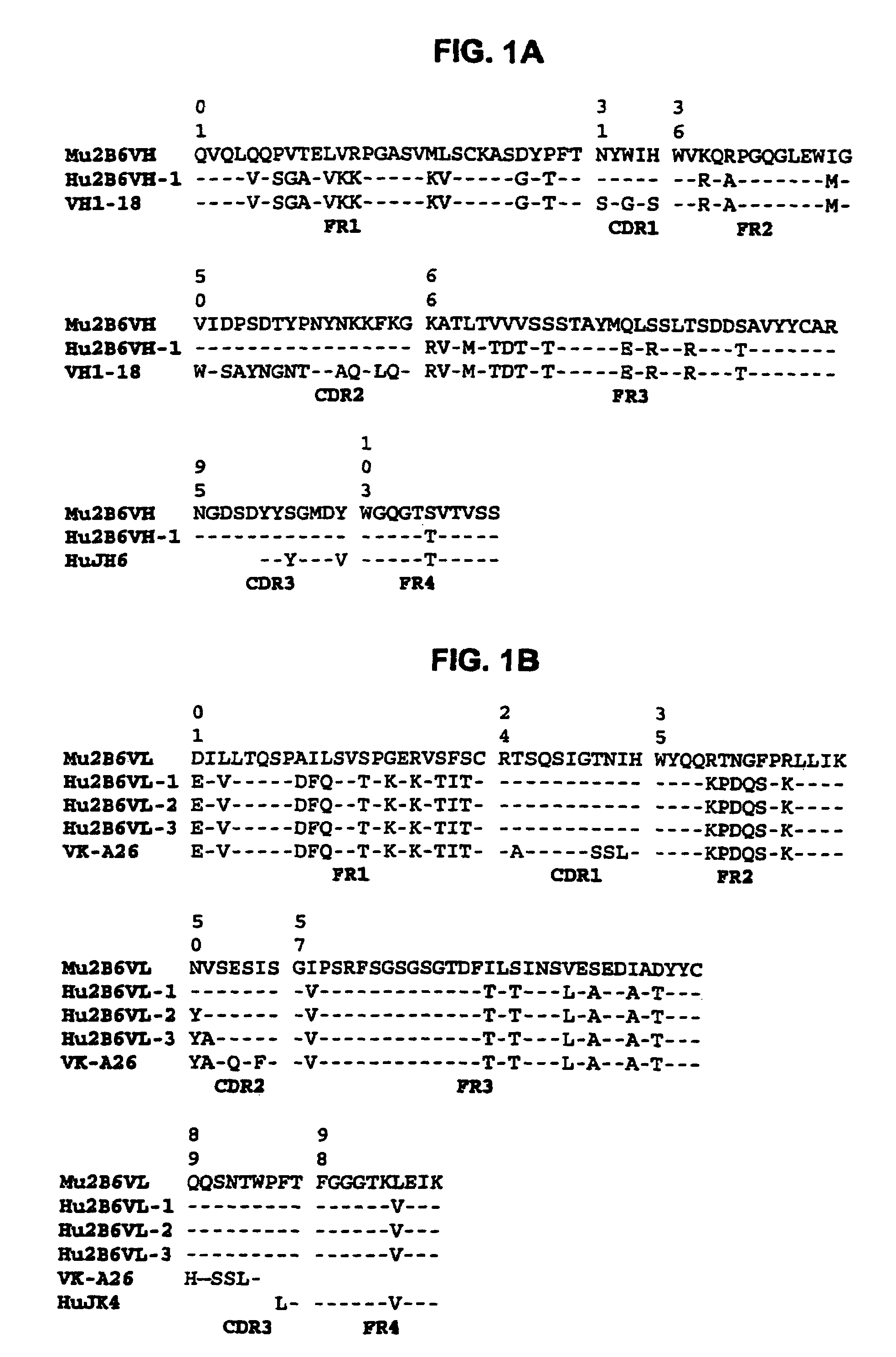
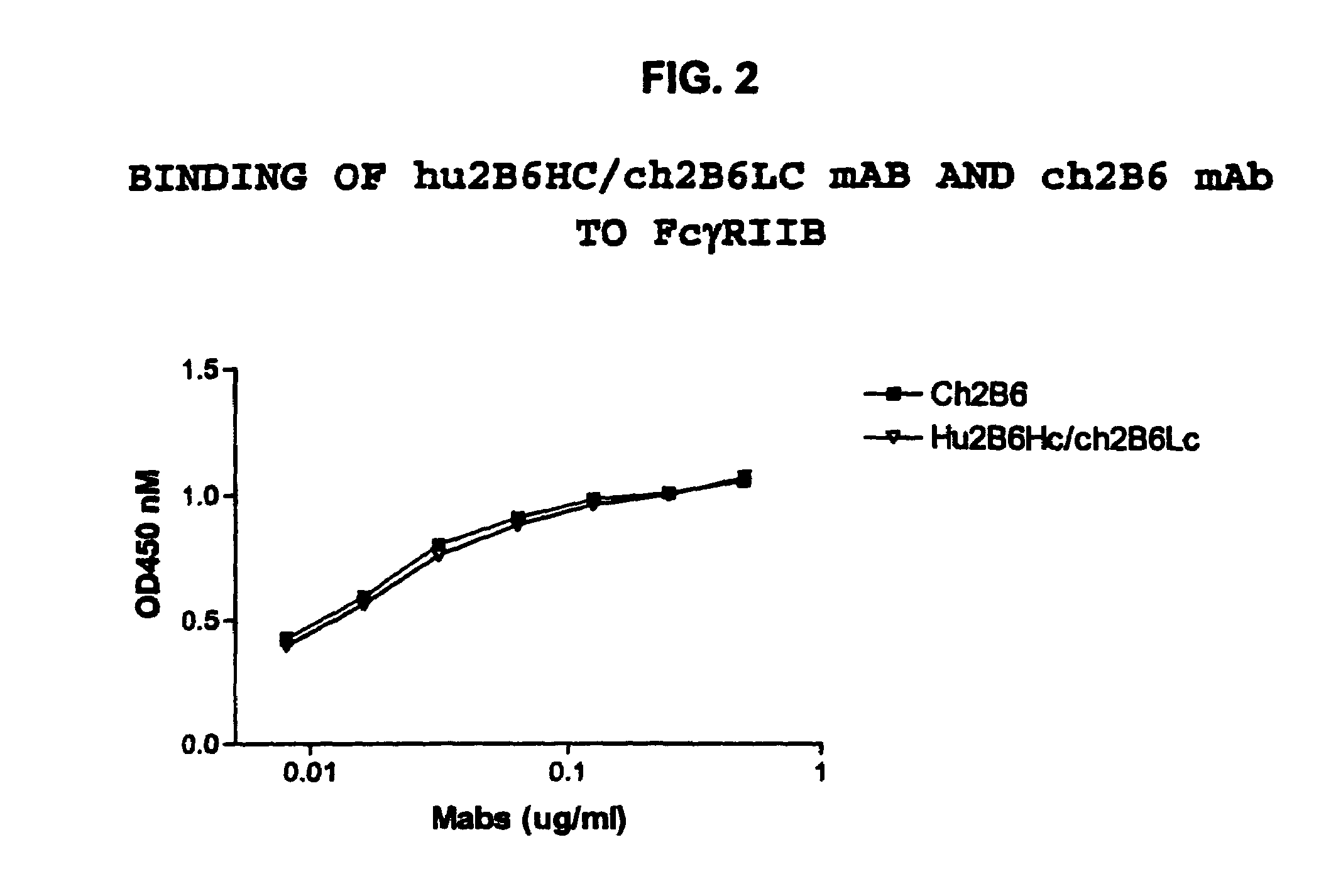
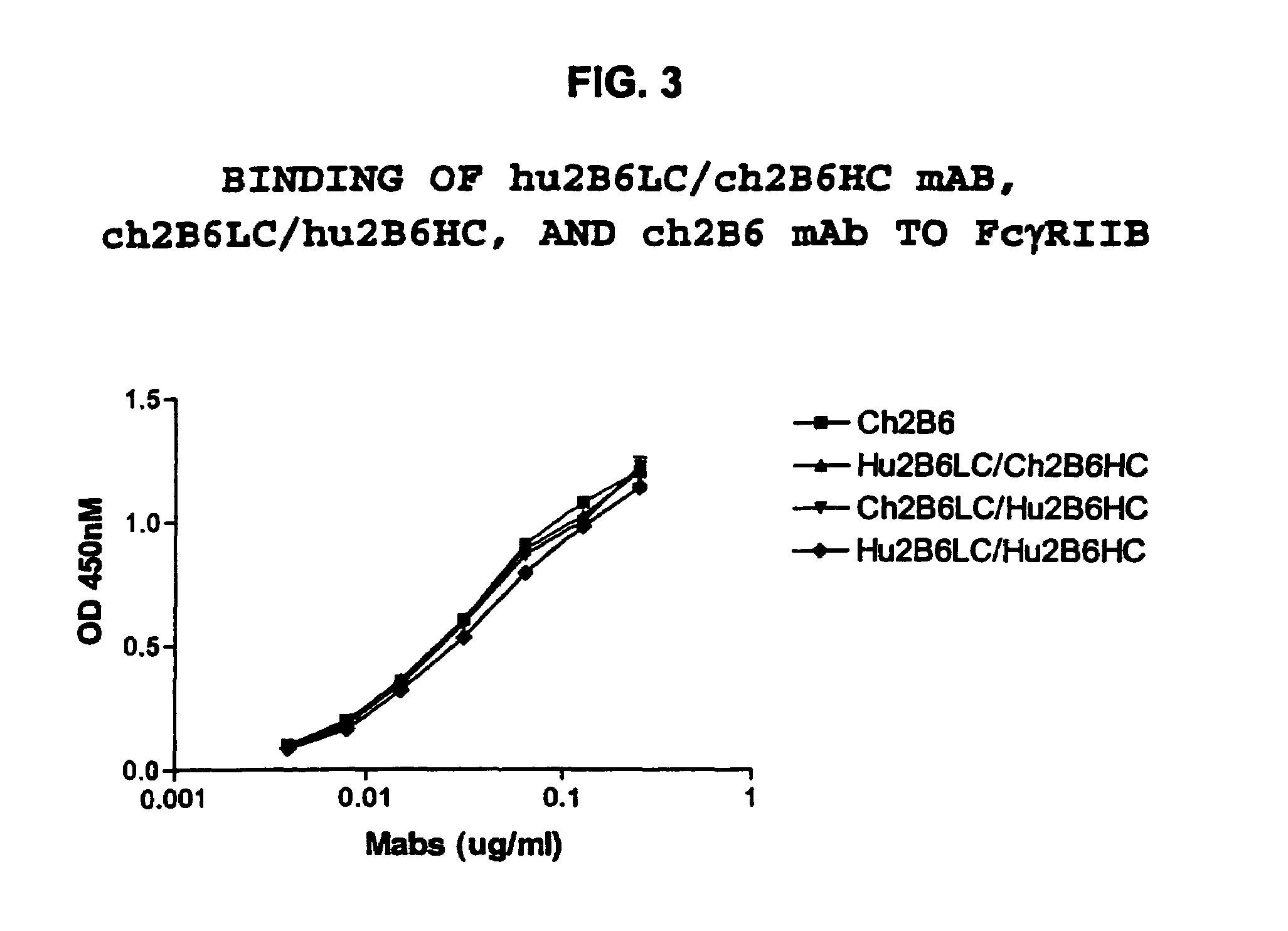
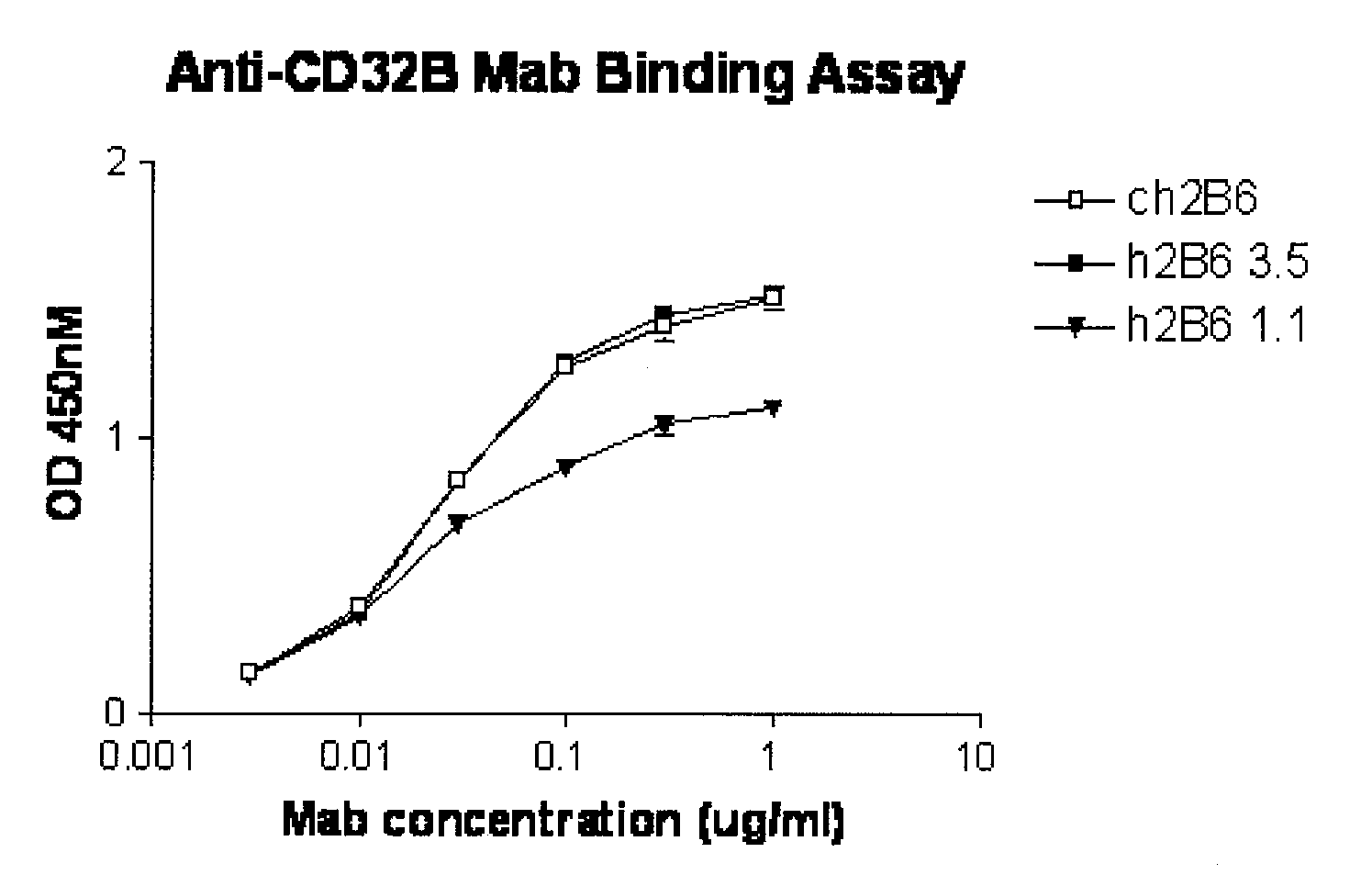
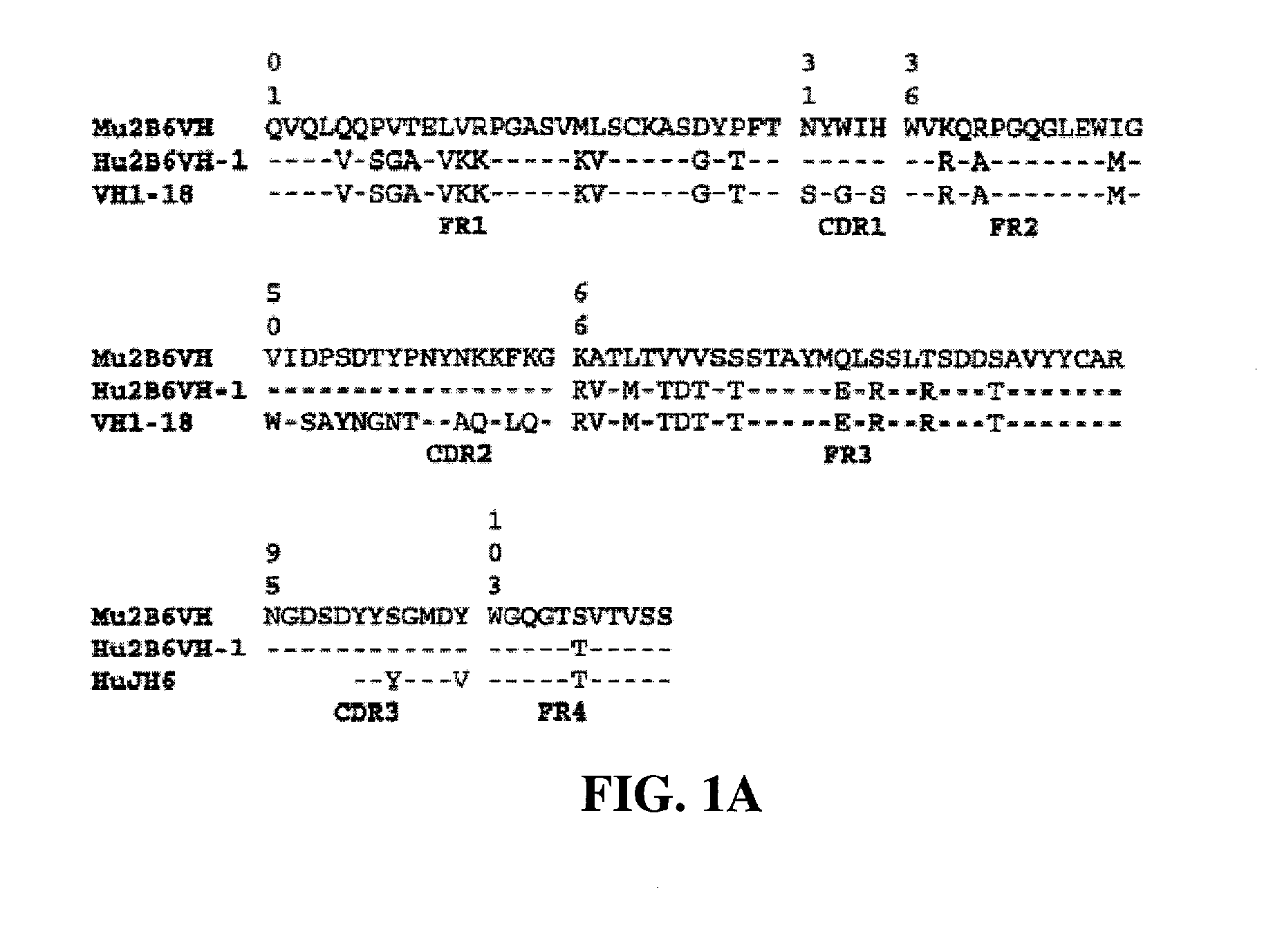
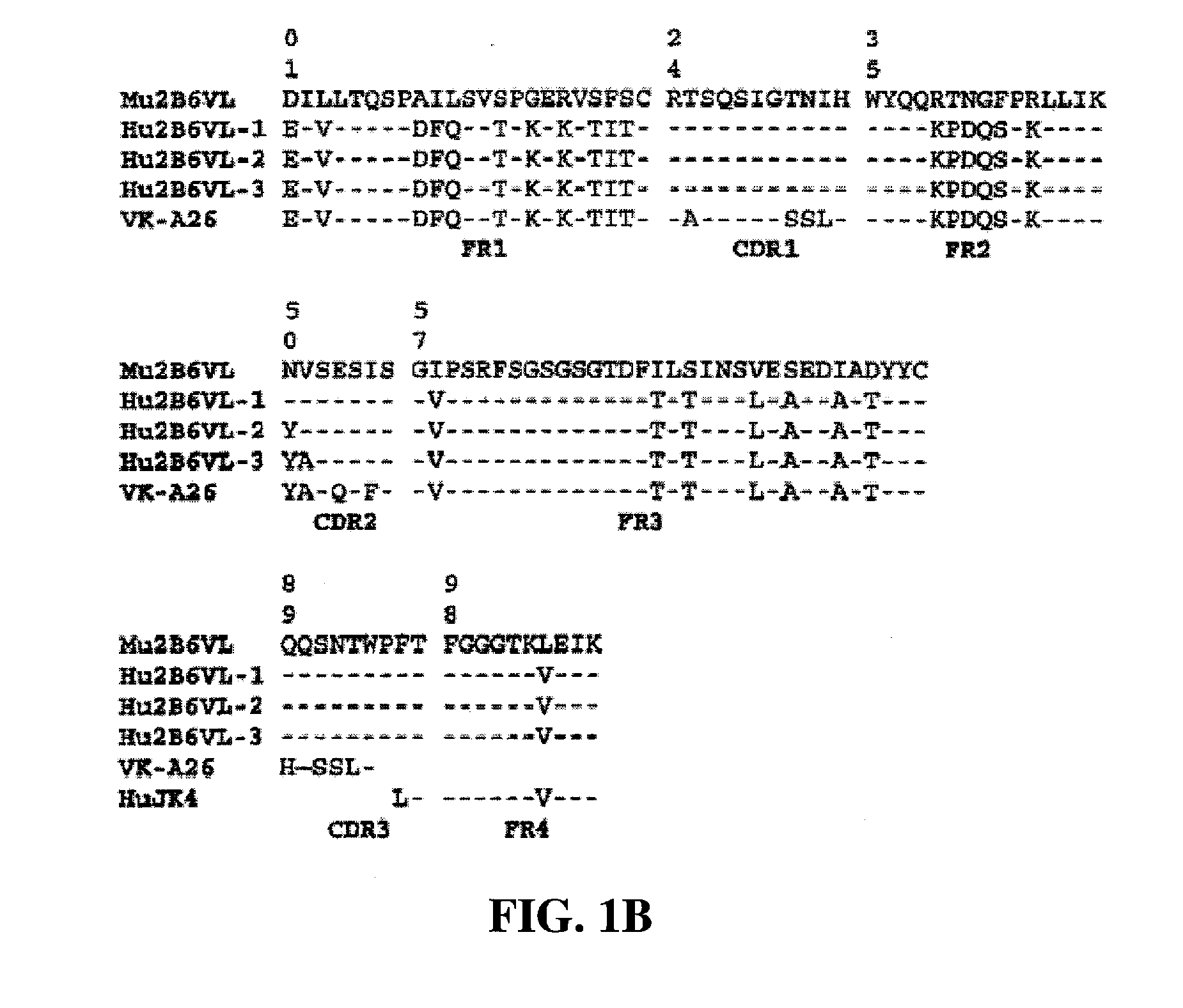
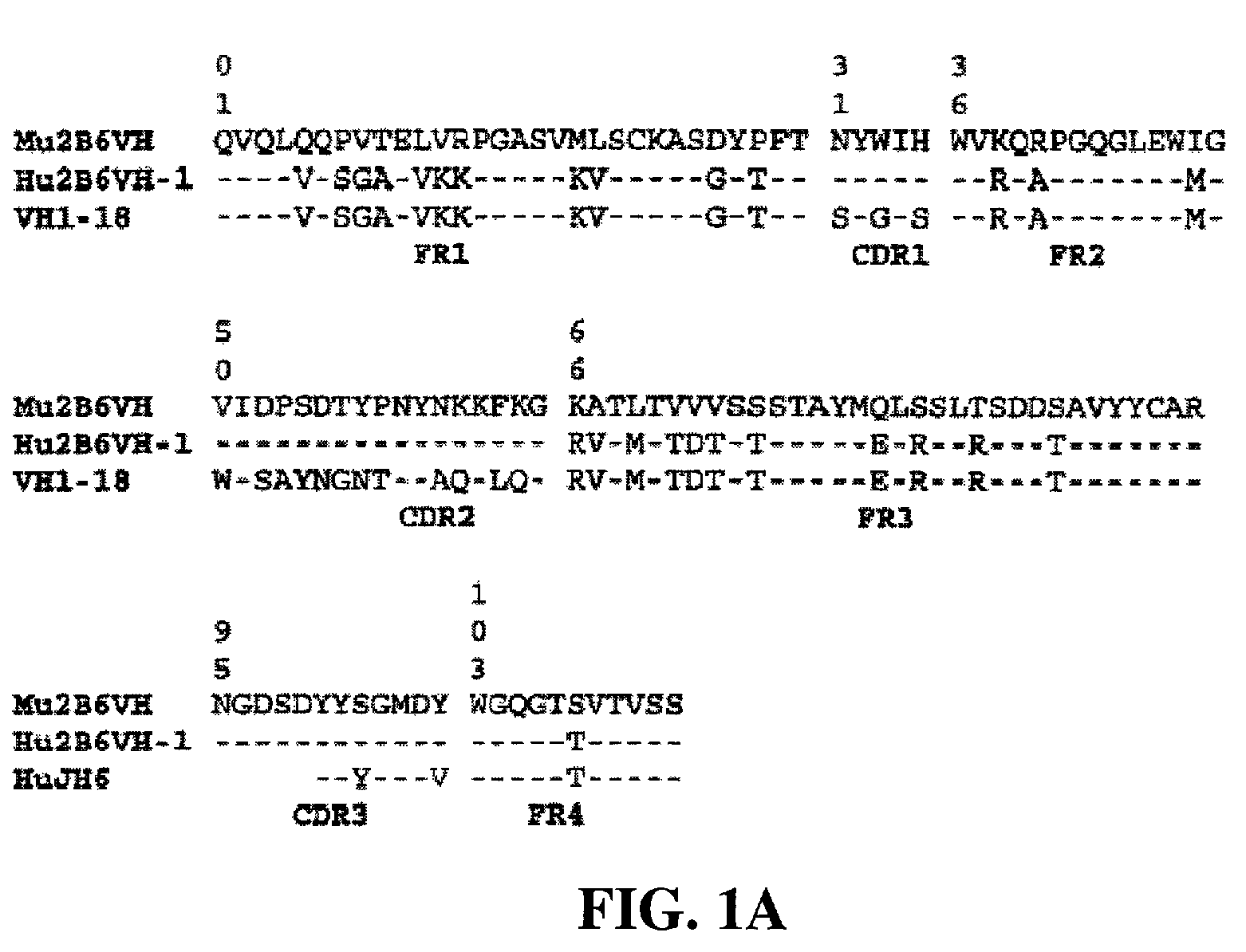
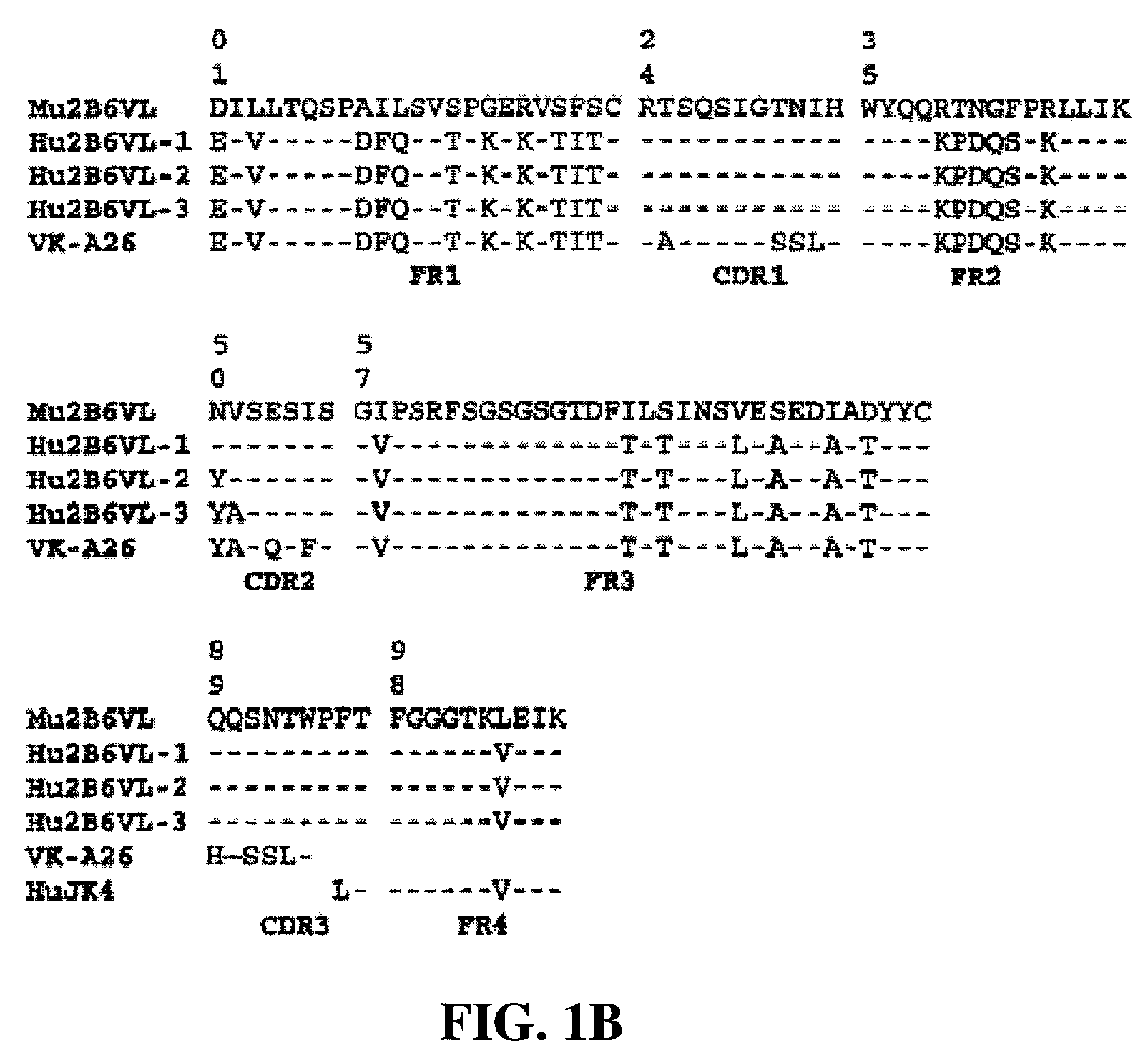
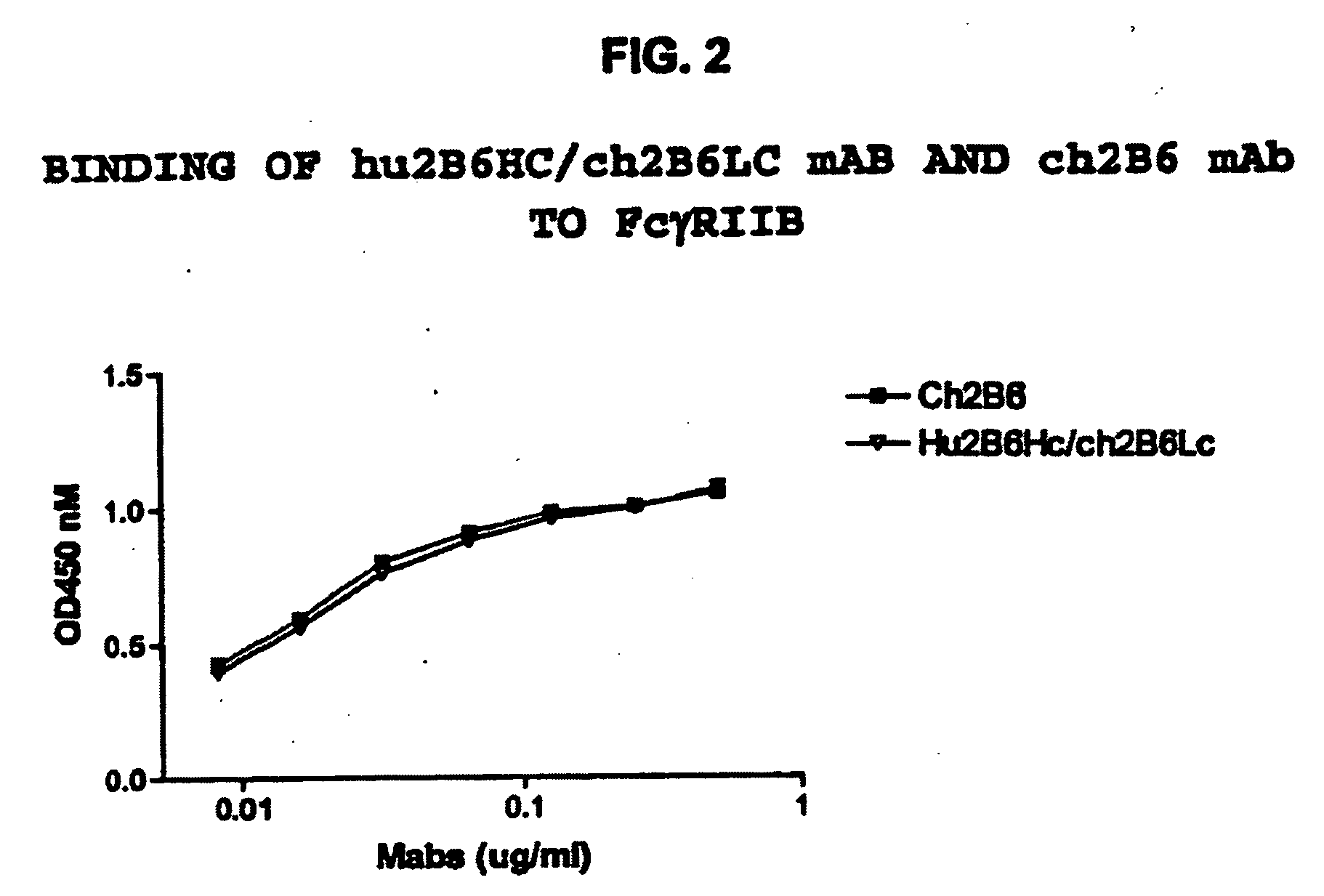
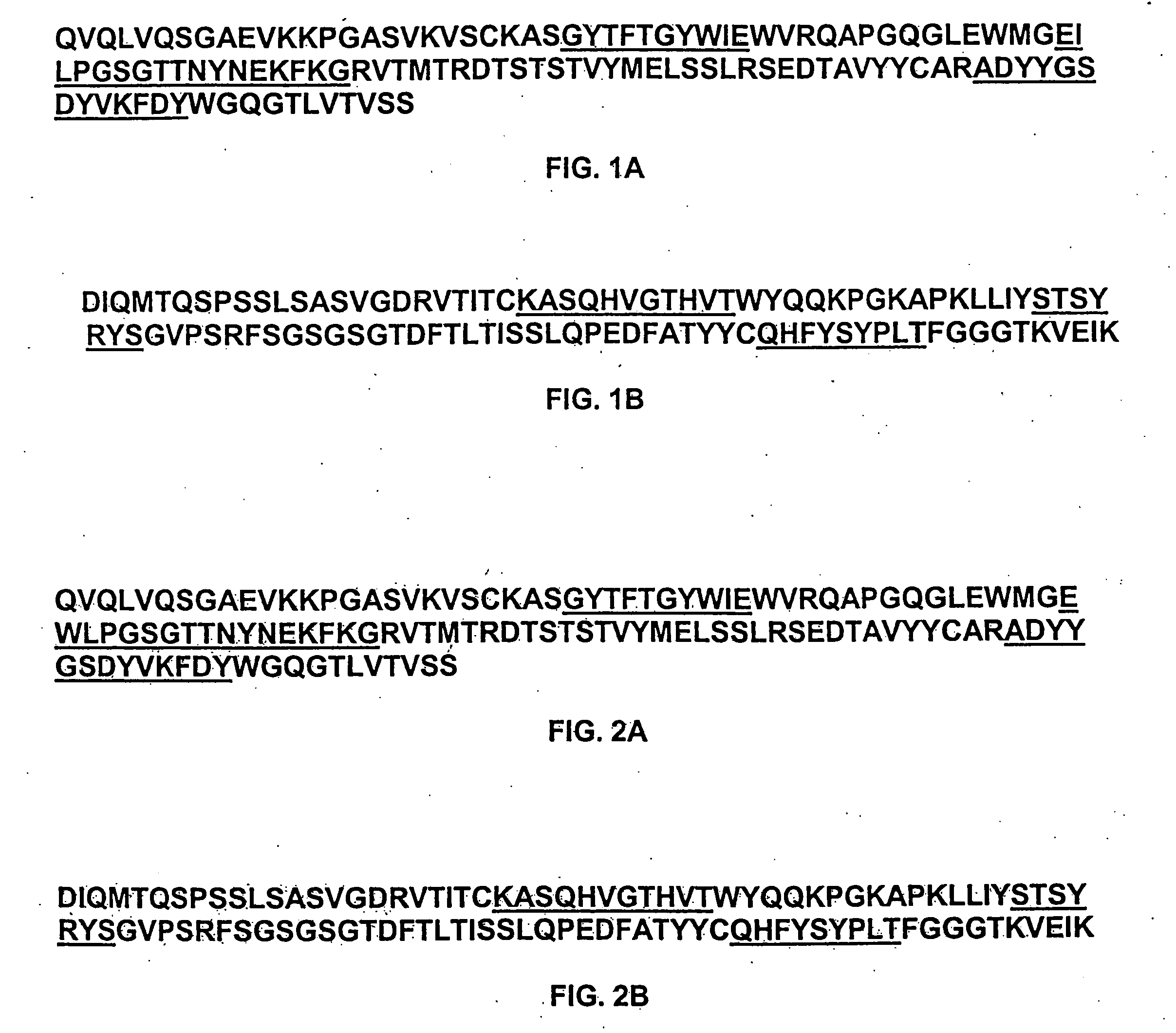
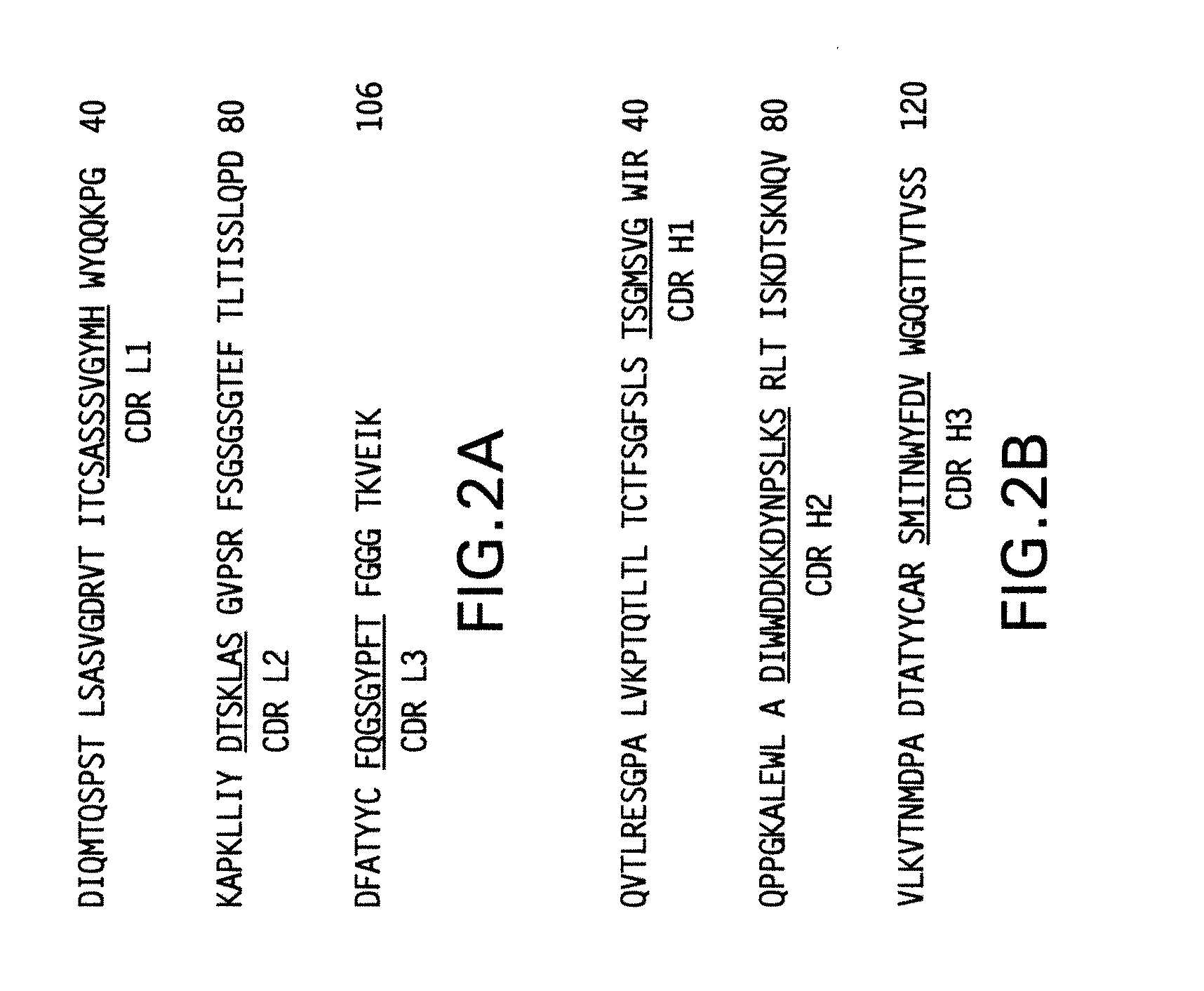
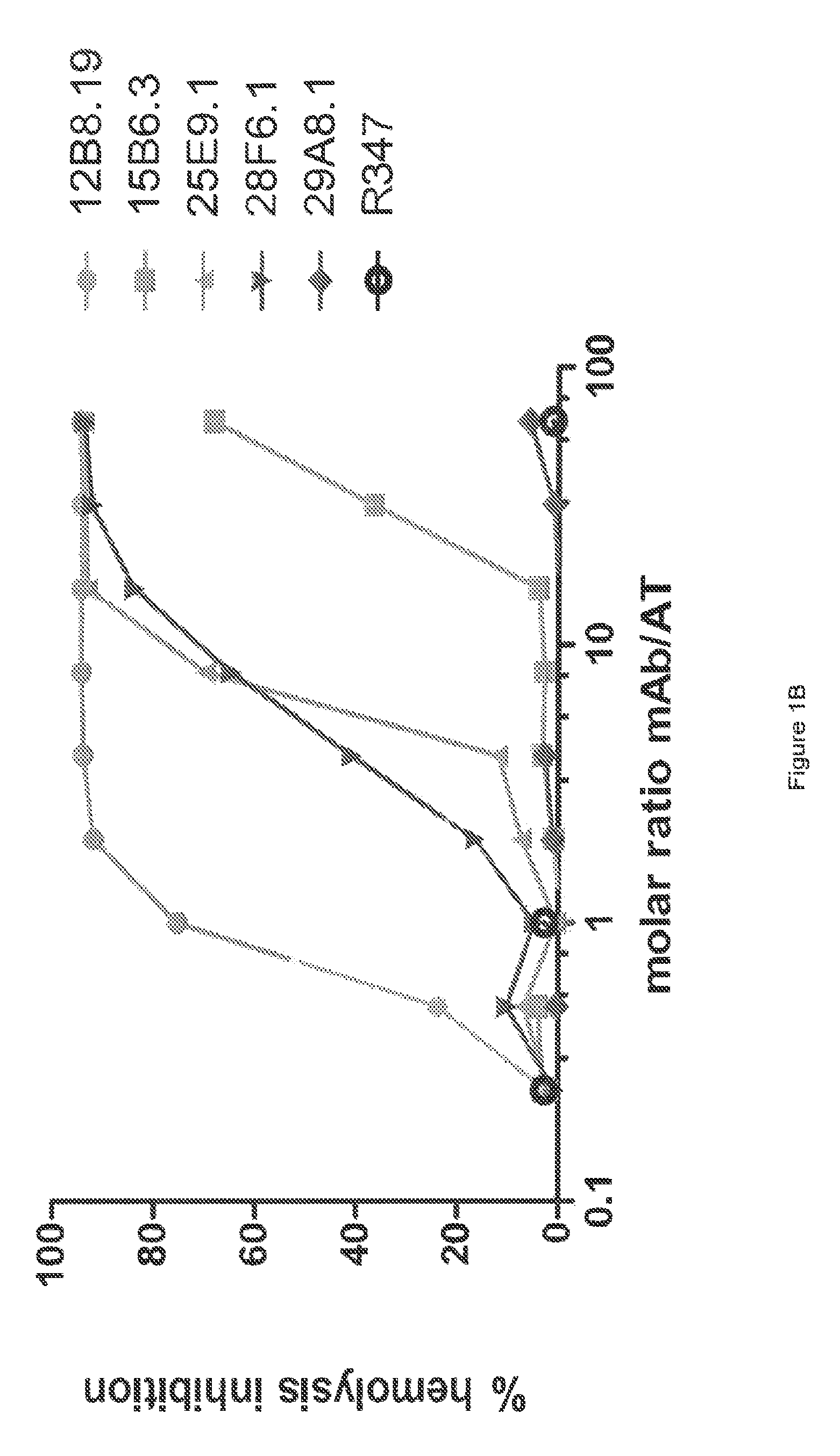
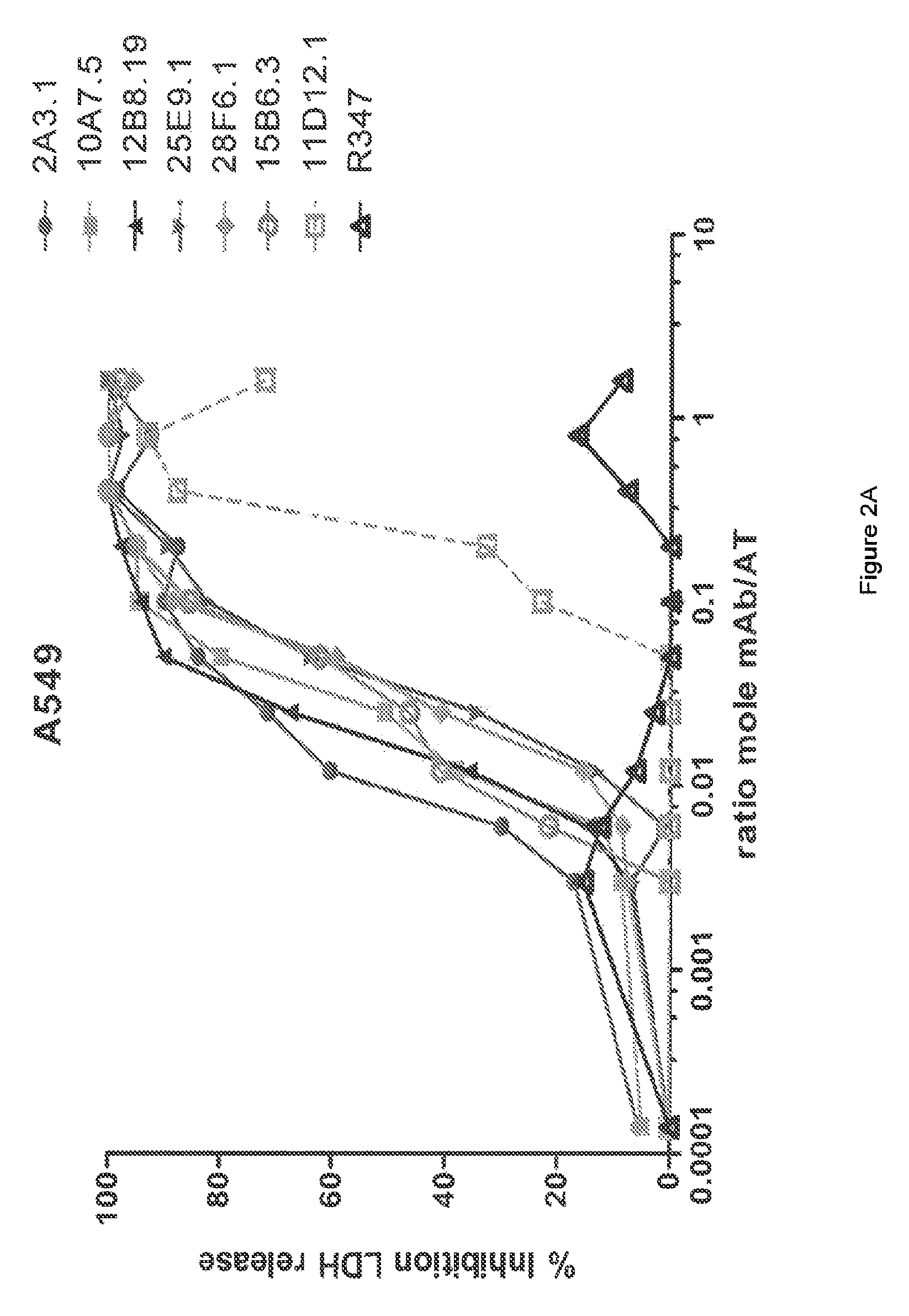
Humanized FcgammaRIIB-specific antibodies and methods of use thereof
ActiveUS20060013810A1Good curative effectConvenient treatmentSenses disorderNervous disorderFc(alpha) receptorDisease
The present invention relates to humanized FcγRIIB antibodies, fragments, and variants thereof that bind human FcγRIIB with a greater affinity than said antibody binds FcγRIIA. The invention encompasses the use of the humanized antibodies of the invention for the treatment of any disease related to loss of balance of Fc receptor mediated signaling, such as cancer, autoimmune and inflammatory disease. The invention provides methods of enhancing the therapeutic effect of therapeutic antibodies by administering the humanized antibodies of the invention to enhance the effector function of the therapeutic antibodies. The invention also provides methods of enhancing the efficacy of a vaccine composition by administering the humanized antibodies of the invention. The invention encompasses methods for treating an autoimmune disease and methods for elimination of cancer cells that express FcγRIIB.
Owner:MACROGENICS INC
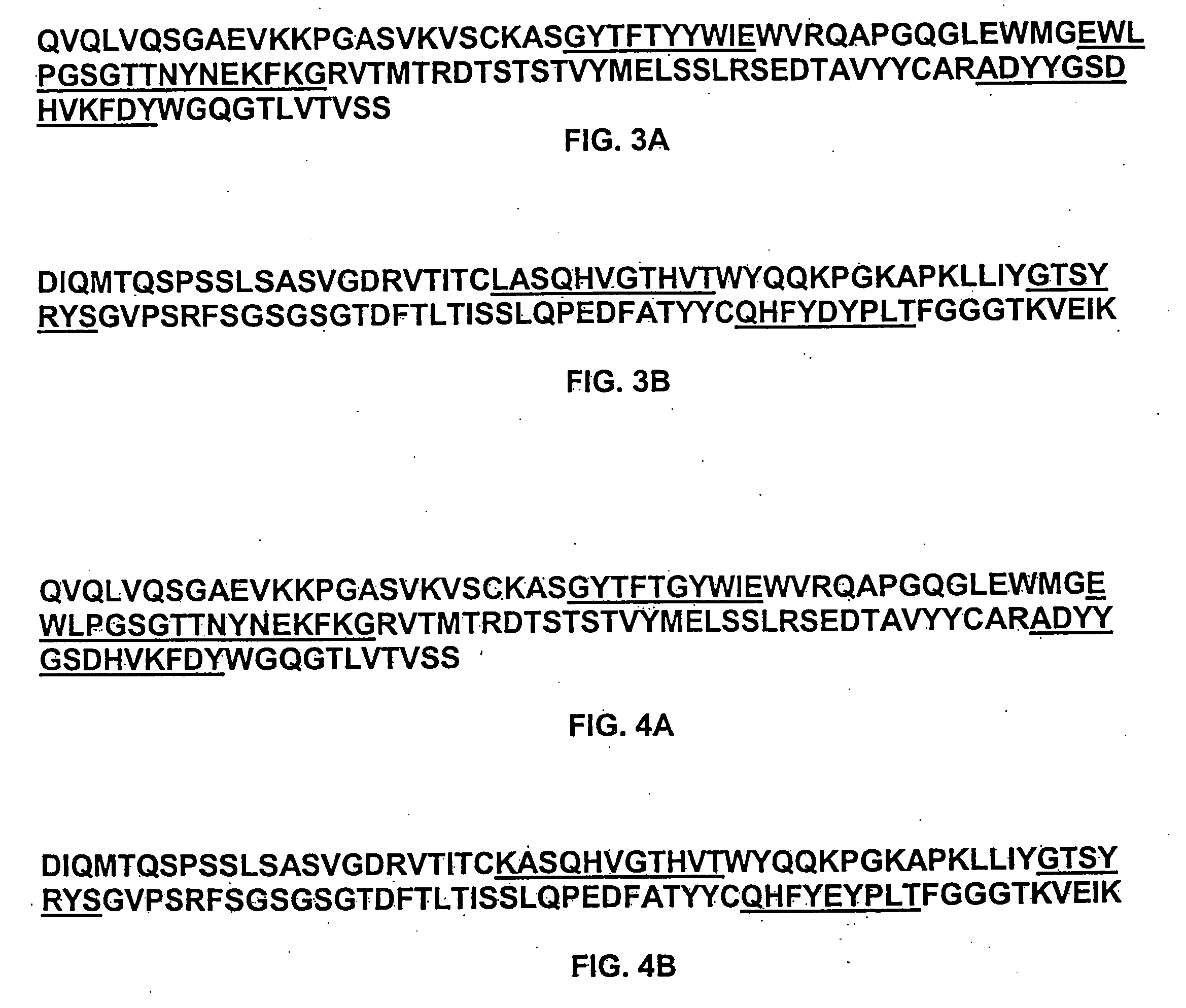
Humanized FcgammaRIIB-specific antibodies and methods of use thereof
ActiveUS7521542B2Immune responseAvoid immune responseSenses disorderNervous disorderFc(alpha) receptorTherapeutic antibody
The present invention relates to humanized FcγRIIB antibodies, fragments, and variants thereof that bind human FcγRIIB with a greater affinity than said antibody binds FcγRIIA. The invention encompasses the use of the humanized antibodies of the invention for the treatment of any disease related to loss of balance of Fc receptor mediated signaling, such as cancer, autoimmune and inflammatory disease. The invention provides methods of enhancing the therapeutic effect of therapeutic antibodies by administering the humanized antibodies of the invention to enhance the effector function of the therapeutic antibodies. The invention also provides methods of enhancing the efficacy of a vaccine composition by administering the humanized antibodies of the invention. The invention encompasses methods for treating an autoimmune disease and methods for elimination of cancer cells that express FcγRIIB.
Owner:MACROGENICS INC
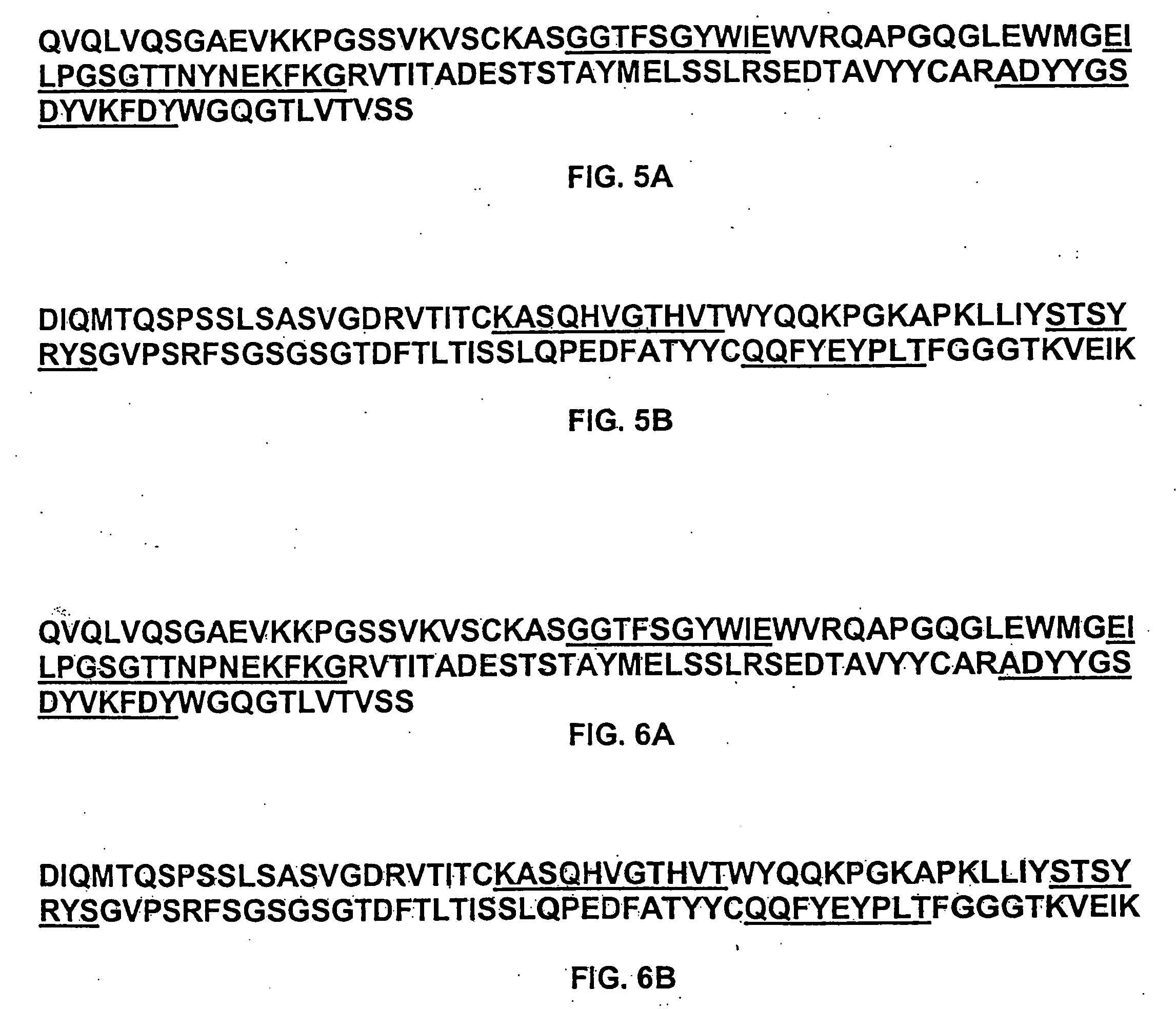
Humanized Fc.gamma.RIIB-Specific Antibodies and Methods of Use Thereof
InactiveUS20080044417A1Good curative effectEnhanced effector functionDisease diagnosisTissue cultureFc(alpha) receptorFc receptor
The present invention relates to humanized FcγRIIB antibodies, fragments, and variants thereof that bind human FcγRIIB with a greater affinity than said antibody binds FcγRIIA. The invention encompasses the use of the humanized antibodies of the invention for the treatment of any disease related to loss of balance of Fc receptor mediated signaling, such as cancer, autoimmune and inflammatory disease. The invention provides methods of enhancing the therapeutic effect of therapeutic antibodies by administering the humanized antibodies of the invention to enhance the effector function of the therapeutic antibodies. The invention also provides methods of enhancing the efficacy of a vaccine composition by administering the humanized antibodies of the invention. The invention encompasses methods for treating an autoimmune disease and methods for elimination of cancer cells that express FcγRIIB.
Owner:MACROGENICS INC
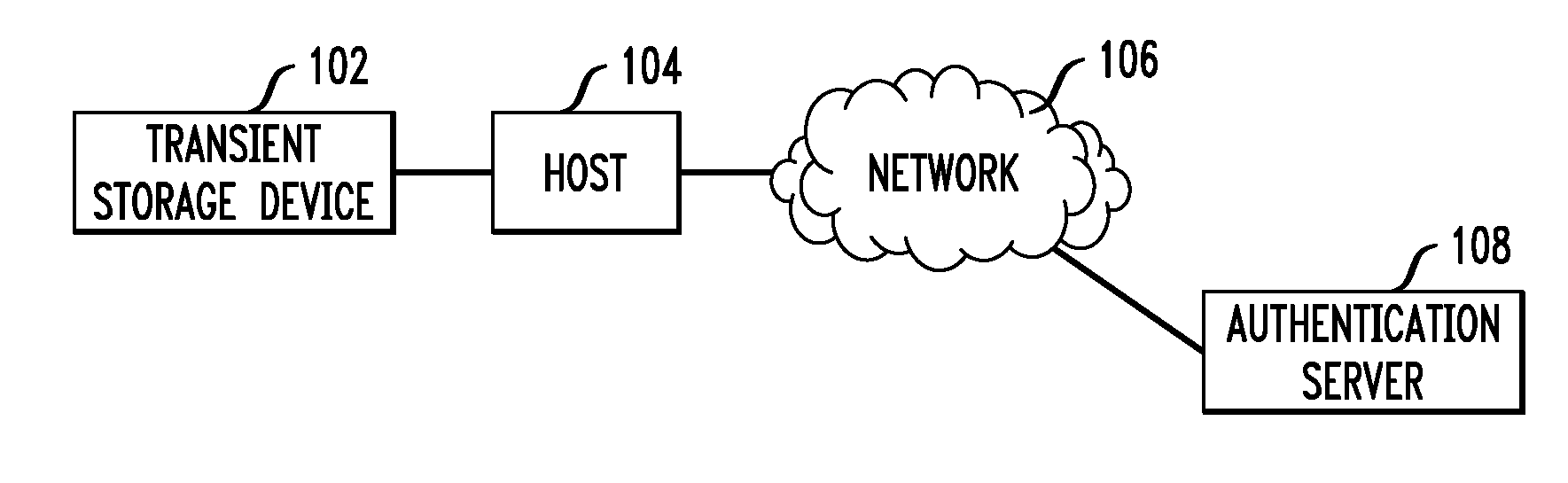
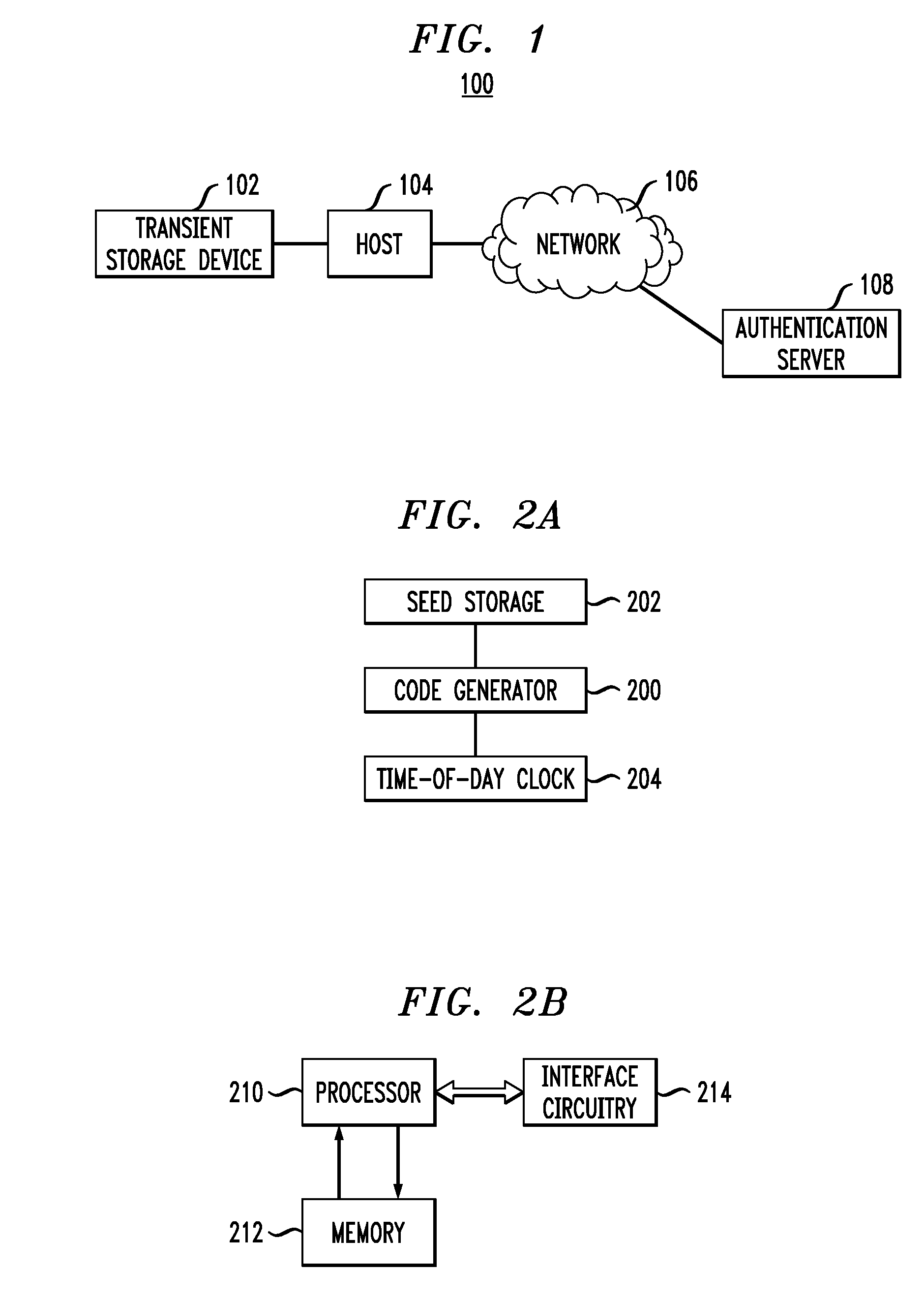
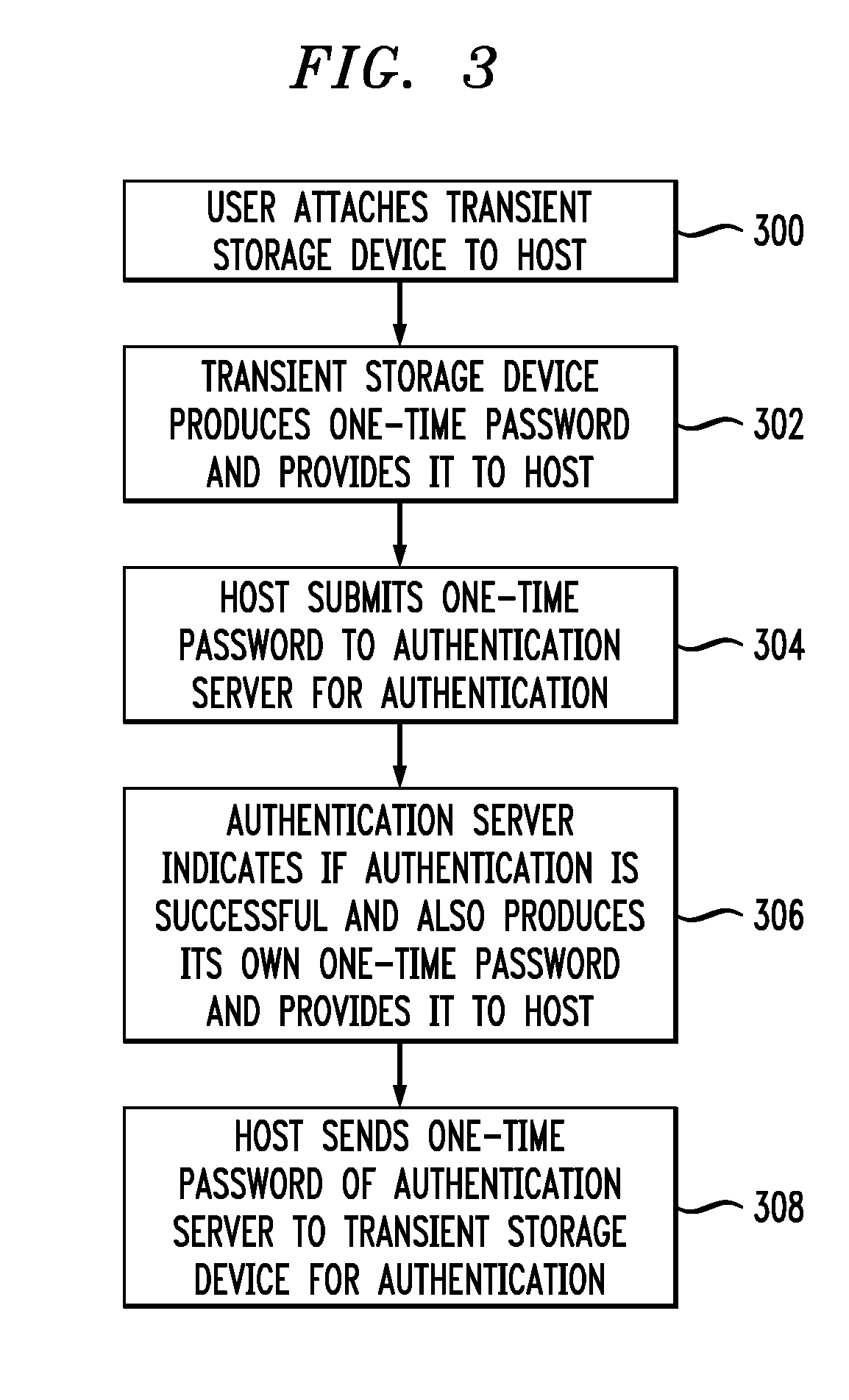
Tokencode Exchanges for Peripheral Authentication
ActiveUS20070061566A1Less bandwidthLess circuit areaUser identity/authority verificationAuthentication serverOne-time password
In a system comprising a transient storage device (TSD) or other type of peripheral configured for communication with a host device, a first one-time password or other type of code is generated in the peripheral and transmitted to the host device. The first code is presented by the host device to an authentication server for authentication. The host device receives a second one-time password or other type of code from the authentication server and transmits it to the peripheral for authentication.
Owner:EMC IP HLDG CO LLC
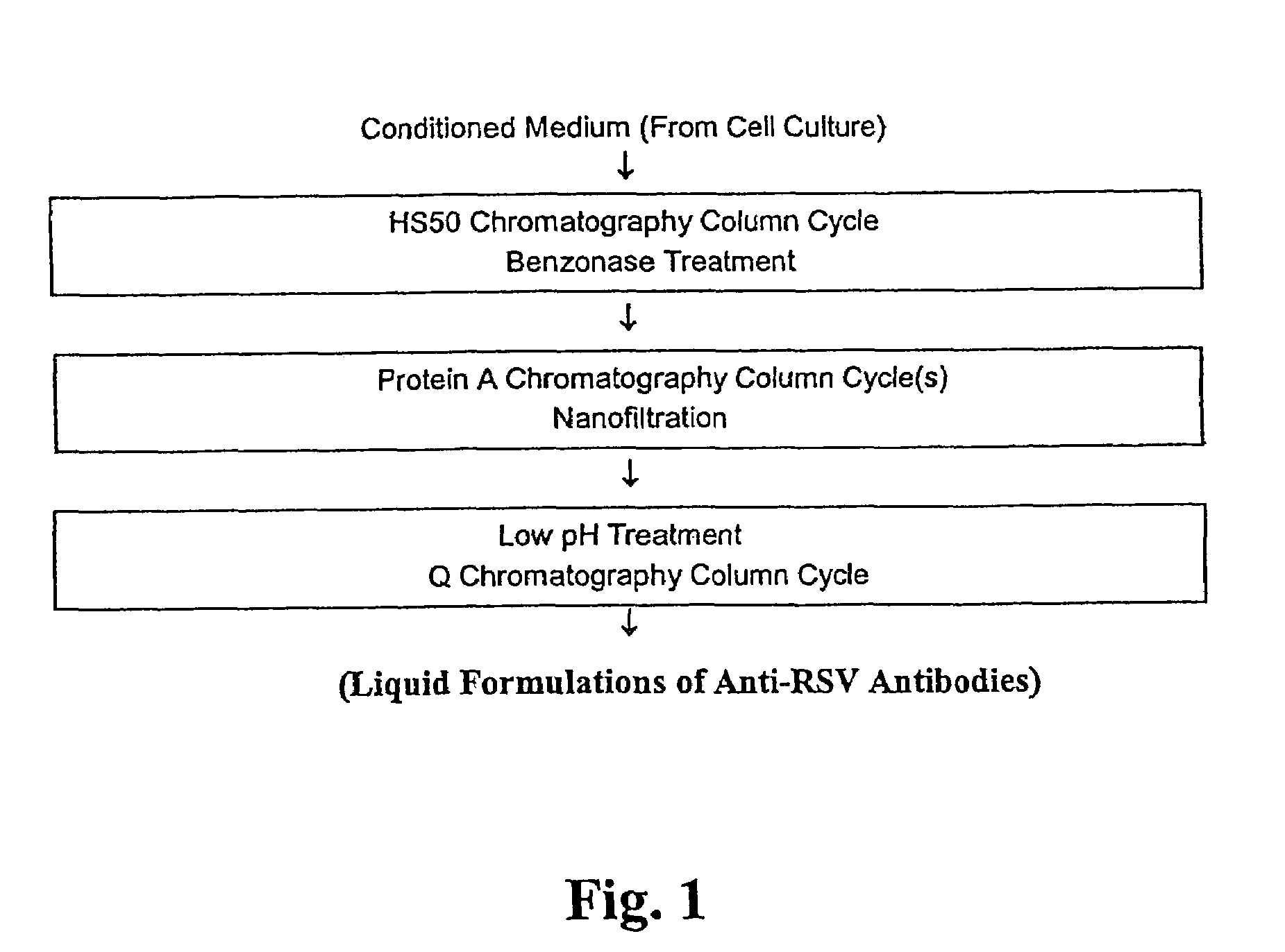
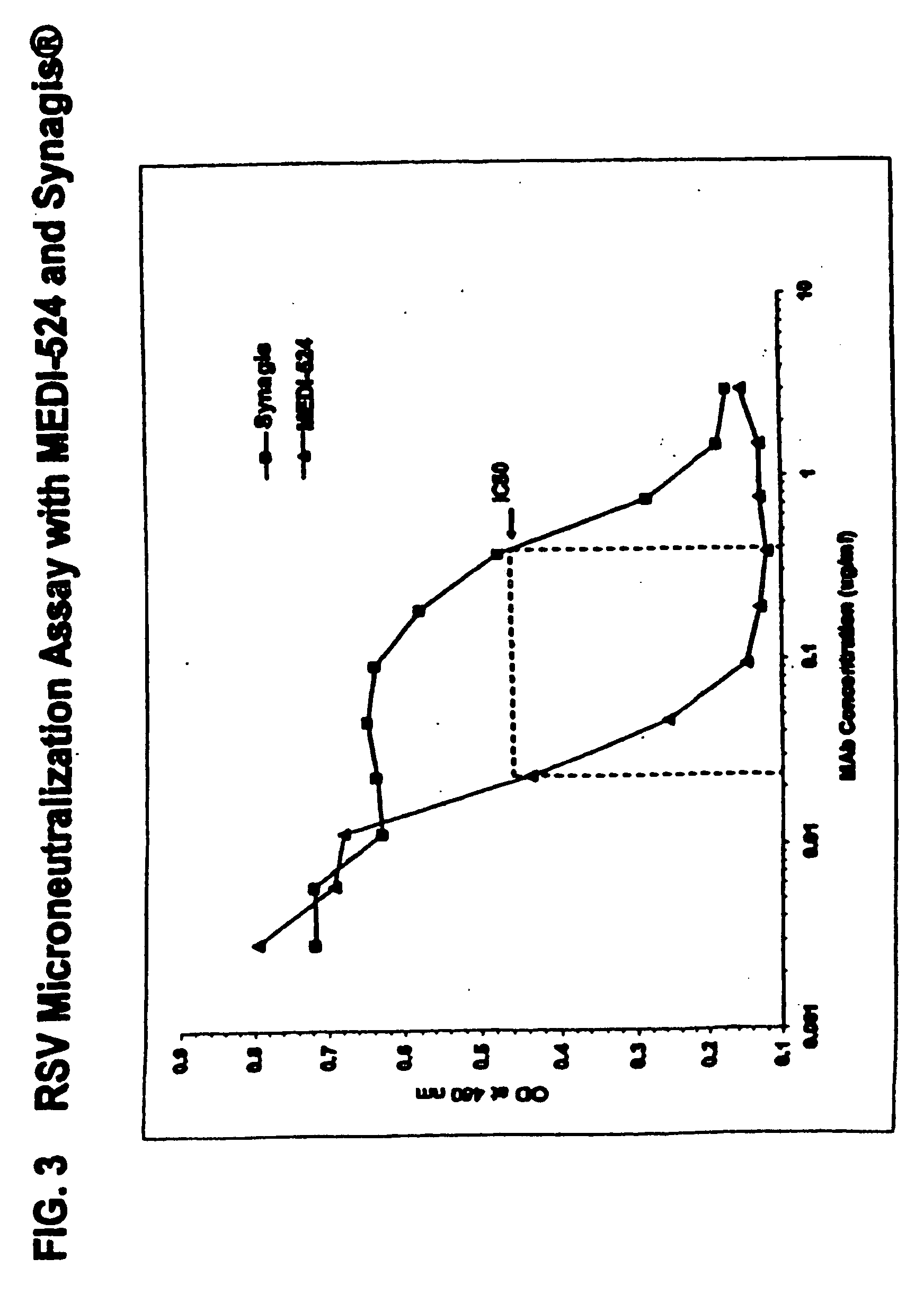
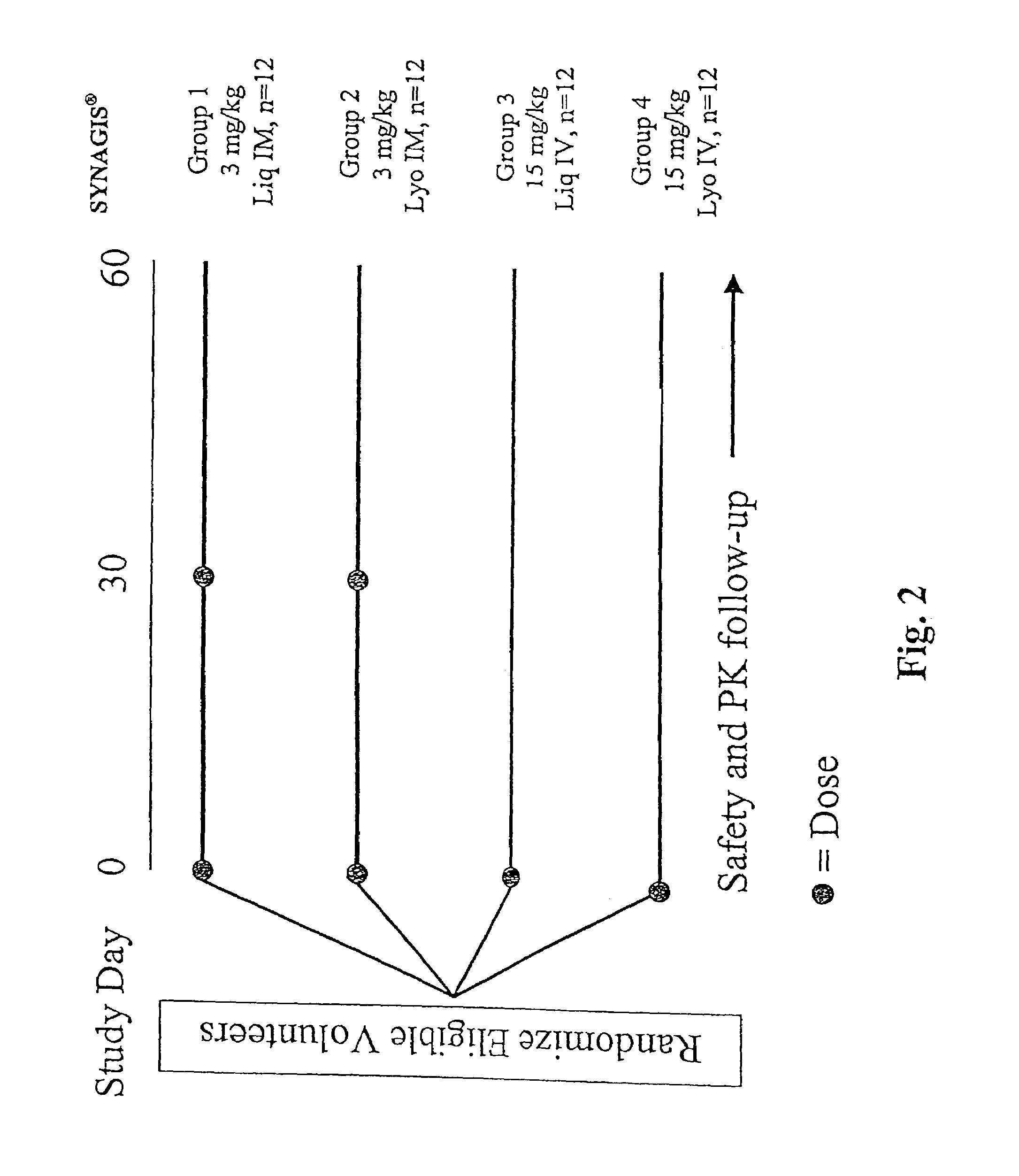
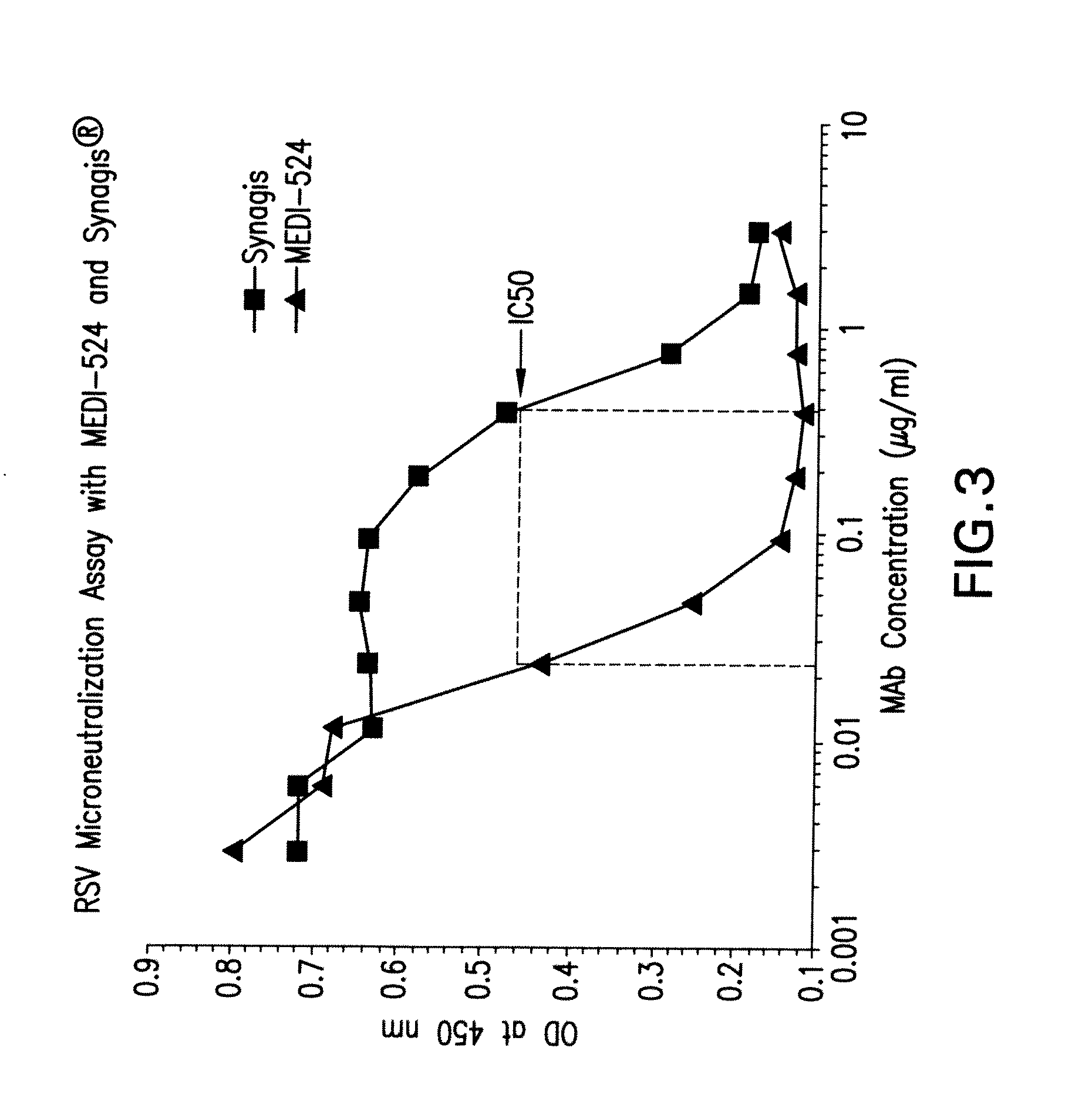
Stabilized anti-respiratory syncytial virus (RSV) antibody formulations
InactiveUS7425618B2Low to undetectable levelEasy to manageImmunoglobulins against virusesPharmaceutical delivery mechanismInorganic saltsAntibody fragments
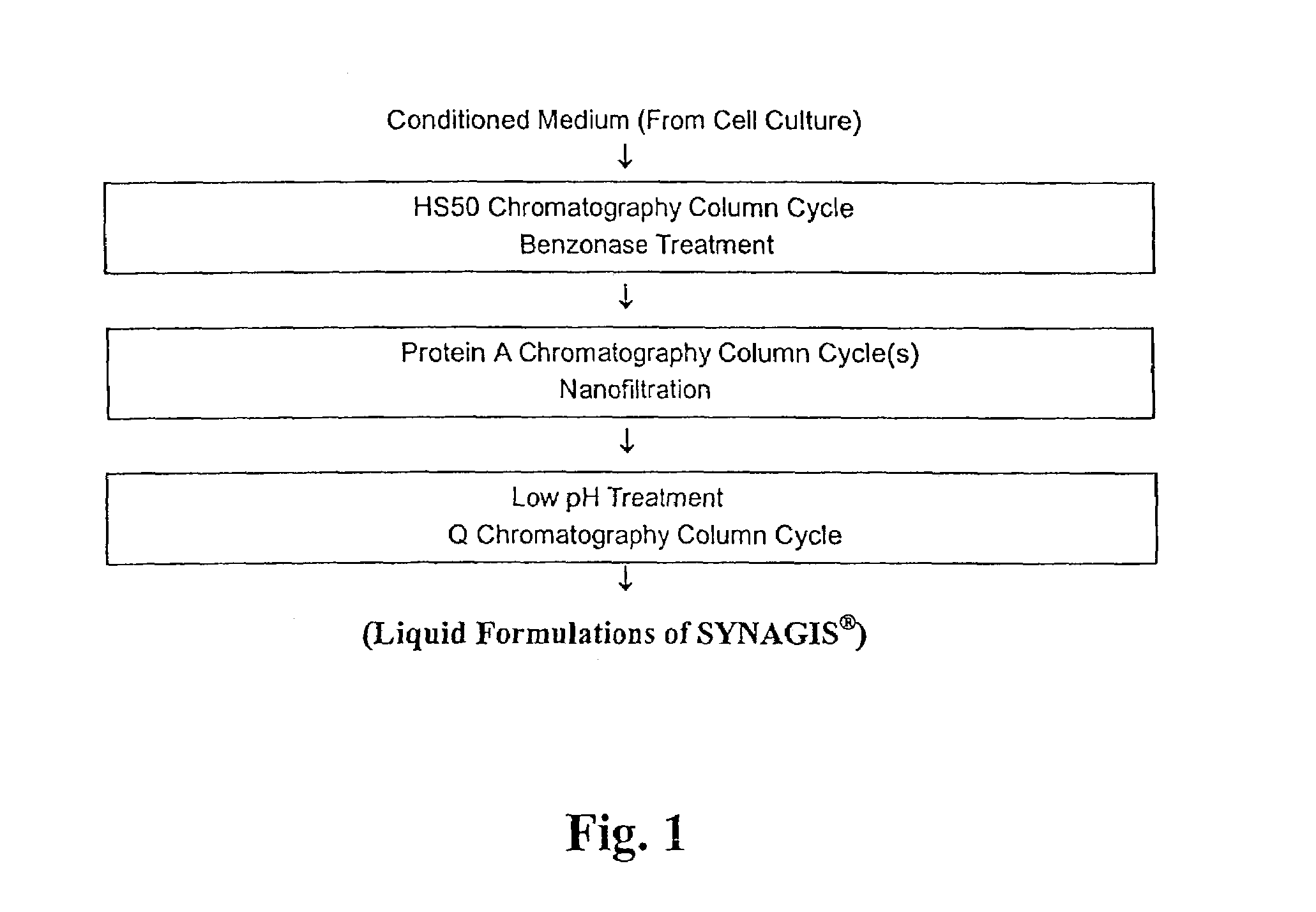
The present invention provides liquid formulations of antibodies or fragments thereof that immunospecifically bind to a respiratory syncytial virus (RSV) antigen, which formulations exhibit stability, low to undetectable levels of aggregation, and very little to no loss of the biological activities of the antibodies or antibody fragments, even during long periods of storage. In particular, the present invention provides liquid formulations of antibodies or fragments thereof that immunospecifically bind to a RSV antigen, which formulations are substantially free of surfactant, inorganic salts, and / or other common excipients. Furthermore, the invention provides methods of preventing, treating or ameliorating one or more symptoms associated with RSV infection utilizing the liquid formulations of the present invention.
Owner:MEDIMMUNE LLC
Humanized FcγRIIB-specific antibodies and methods of use thereof
InactiveUS7786270B2Immune responseAvoid immune responseDisease diagnosisTissue cultureFc(alpha) receptorCancer cell
The present invention relates to humanized FcγRIIB antibodies, fragments, and variants thereof that bind human FcγRIIB with a greater affinity than said antibody binds FcγRIIA. The invention encompasses the use of the humanized antibodies of the invention for the treatment of any disease related to loss of balance of Fc receptor mediated signaling, such as cancer, autoimmune and inflammatory disease. The invention provides methods of enhancing the therapeutic effect of therapeutic antibodies by administering the humanized antibodies of the invention to enhance the effector function of the therapeutic antibodies. The invention also provides methods of enhancing the efficacy of a vaccine composition by administering the humanized antibodies of the invention. The invention encompasses methods for treating an autoimmune disease and methods for elimination of cancer cells that express FcγRIIB.
Owner:MACROGENICS INC
Methods of preventing and treating RSV infections and related conditions
InactiveUS20060115485A1High affinityEfficient reductionAntibacterial agentsSenses disorderAntigenHalf-life
The present invention provides methods for preventing, managing, treating and / or ameliorating a Respiratory Syncytial Virus (RSV) infection (e.g., acute RSV disease, or a RSV upper respiratory tract infection (URI) and / or lower respiratory tract infection (LRI)), otitis media (preferably, stemming from, caused by or associated with a RSV infection, such as a RSV URI and / or LRI), and / or a symptom or respiratory condition relating thereto (e.g., asthma, wheezing, and / or reactive airway disease (RAD)) in a subject, comprising administering to said human an effective amount of one or more antibodies that immunospecifically bind to one or more RSV antigens with a high affinity and / or high avidity. In some embodiments, one or more antibodies comprise a modified IgG constant domain, or FcRn-binding fragment thereof resulting in longer in vivo serum half-life. In particular embodiments the methods of the invention comprising administering to subject an effective amount of one or more modified antibodies that immunospecifically bind to one or more RSV antigens with an association rate (kon) of at least 2×105 M−1s−1 and a dissociation rate (koff) of less than 5×10−4 s−1.
Owner:MEDIMMUNE LLC
FcGammaRIIB Specific Antibodies and Methods of Use Thereof
InactiveUS20090202537A1Balanced functionImmune responseSenses disorderNervous disorderFc(alpha) receptorImmunologic disorders
The present invention relates to humanized FcγRIIB antibodies, fragments, and variants thereof that bind human FcγRIIB with a greater affinity than said antibody binds FcγRIIA. The invention encompasses the use of the humanized antibodies of the invention for the treatment of any disease related to loss of balance of Fc receptor mediated signaling, such as cancer (preferably a B-cell malignancy, particularly, B-cell chronic lymphocytic leukemia or non-Hodgkin's lymphoma), autoimmune disease, inflammatory disease or IgE-mediated allergic disorder. The present invention also encompasses the use of a humanized FcγRIIB antibody or an antigen-binding fragment thereof, in combination with other cancer therapies. The invention provides methods of enhancing the therapeutic effect of therapeutic antibodies by administering the humanized antibodies of the invention to enhance the effector function of the therapeutic antibodies. The invention also provides methods of enhancing the efficacy of a vaccine composition by administering the humanized antibodies of the invention with a vaccine composition.
Owner:MACROGENICS INC
Stabilized liquid anti-RSV antibody formulations
InactiveUS7132100B2Low to undetectable levelEasy to managePharmaceutical delivery mechanismImmunoglobulins against virusesAntigenAntigen Binding Fragment
Owner:AREXIS
Digital signature method and system based on SM2-based identity base
ActiveCN108809658AAvoid managementAvoid maintenancePublic key for secure communicationUser identity/authority verificationDigital Signature AlgorithmPublic key certificate
The invention discloses a digital signature method and a digital signature system based on an SM2-based identity base. The method firstly generates system parameters and system master, public, and private keys, and the user sends the identity identifier to the KGC for registration to obtain a signature private key, and then generates and verifies the digital signature of message M by using the signature private key. In the signature process of the invention, since a new type of user private key is generated based on the unchangeable overall architecture of the SM2 signature algorithm, the user's signature private key is generated based on the identity of the user without public key certificate, maintenance and management of the public key certificate as well as time-consuming calculation,thereby ensuring that the signature method of the invention has the characteristics such as low complexity, high security, and easy verification.
Owner:WUHAN UNIV
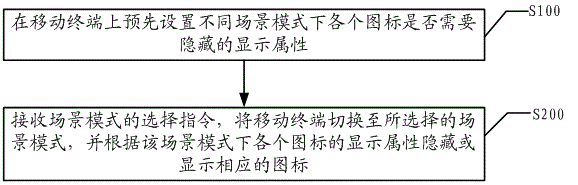
Icon hiding method and system of mobile terminal
InactiveCN104092821AThe interface is clean and refreshingSimplify the mobile terminal interfaceSubstation equipmentUser privacyComputer engineering
The invention discloses an icon hiding method and system of a mobile terminal. According to the method, display attributes, needing hiding or not hiding, of all icons in different scene modes are preset on the mobile terminal; selection instructions of the scene modes are received, the mobile terminal is switched to be in the selected scene modes, and the corresponding icons are hidden or displayed according to the display attributes of all the icons in the scene modes; through hiding or displaying all the icons of the mobile terminal in different scene modes in advance, only the application icons or file icons correspondingly selected for display in different scene modes are displayed in the mobile terminal. In this way, many items of applications and files are effectively managed, besides, an interface of the mobile terminal is cleaner and is simplified, the icons are convenient to search for and use for a user, the privacy of the user is protected from peeping, using is more convenient for the user in a targeted mode, and great convenience is brought to the user.
Owner:HUIZHOU TCL MOBILE COMM CO LTD
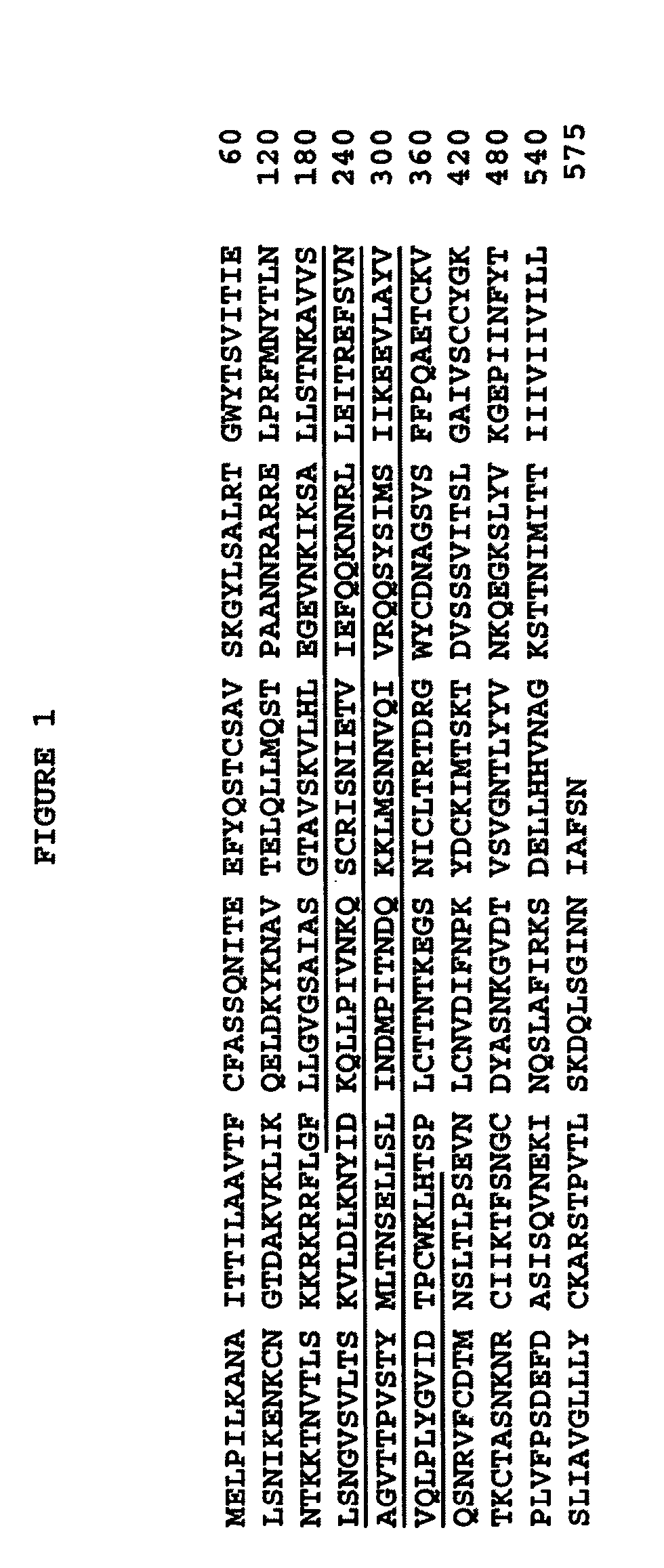
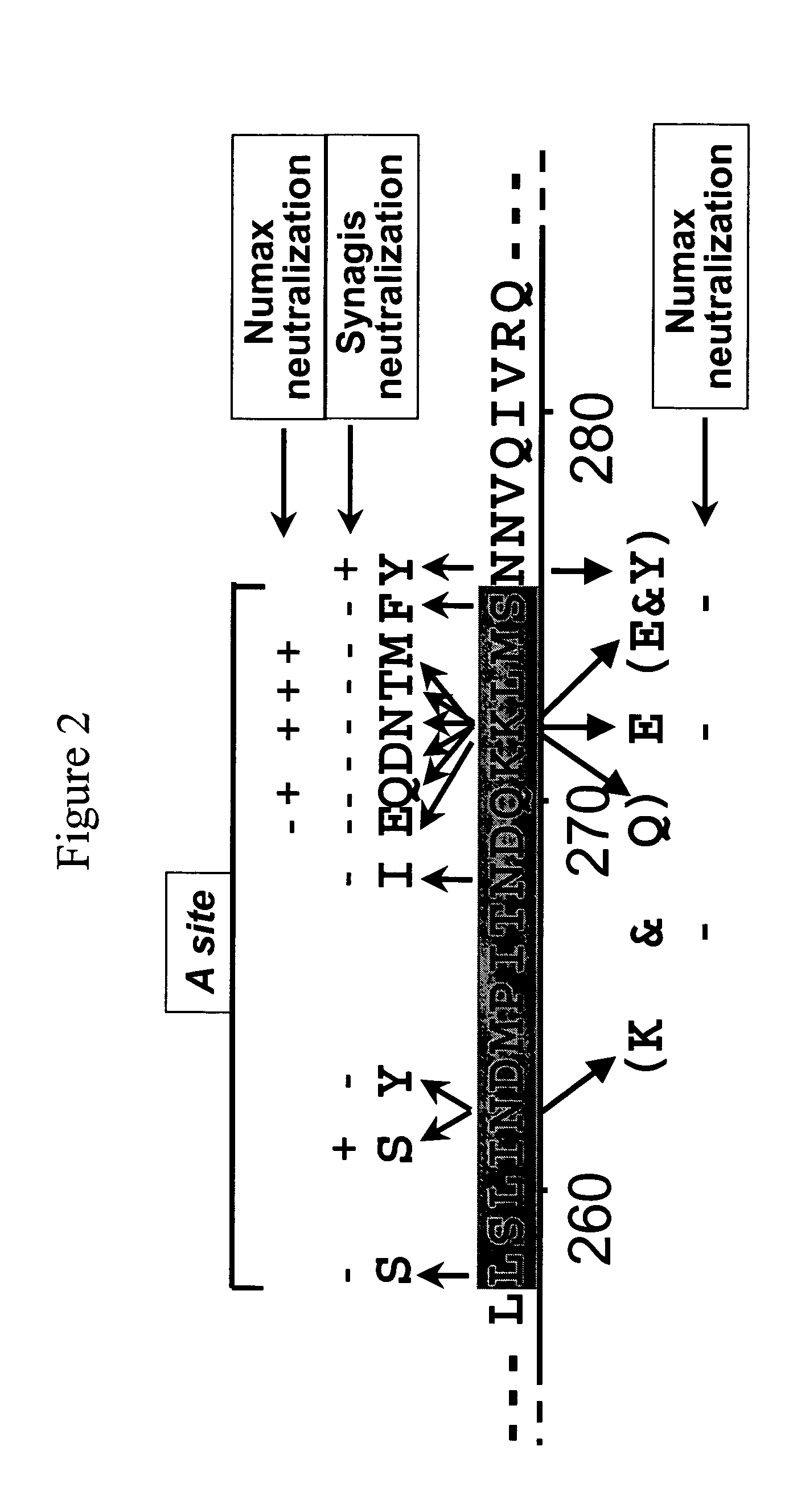
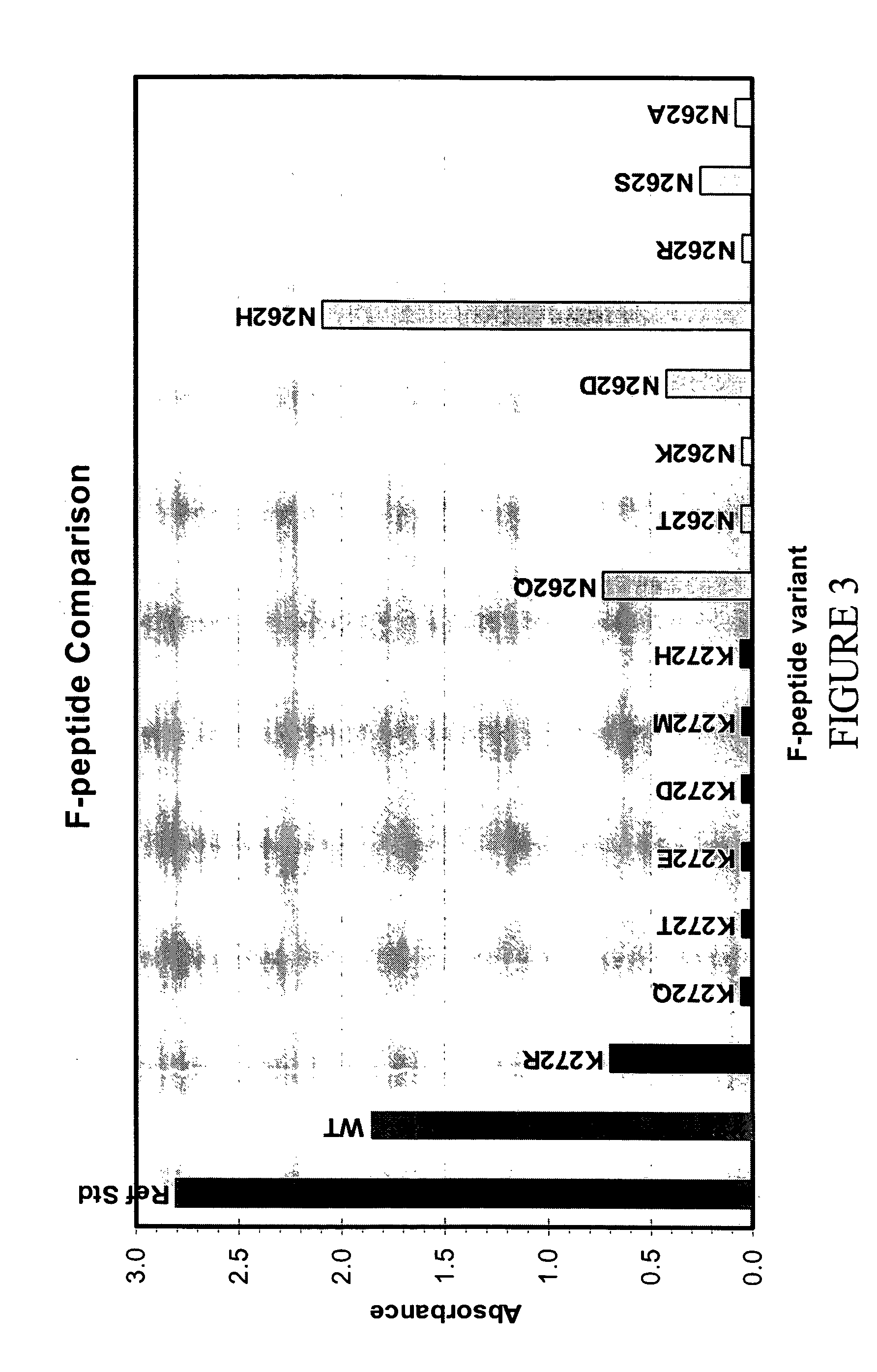
Antibodies against and methods for producing vaccines for respiratory syncytial virus
ActiveUS7700720B2Reduce dosage and frequency of administrationAvoid managementSsRNA viruses negative-sensePeptide/protein ingredientsRSV InfectionsRespiratory syncytial virus (RSV)
The present invention relates to novel respiratory syncytial virus (RSV) F peptides and compositions comprising them. The present invention also relates to methods of evaluating anti-RSV antibody binding to F peptides. The present invention also relates to antibodies that immunospecifically bind to an F peptide of the present invention. The invention further provides methods and protocols for the administration of F peptides and / or antibodies that immunospecifically bind to F peptides for the prevention, neutralization, treatment of RSV infection. Additionally, the methods of the invention may be useful for the treatment, prevention and the amelioration of symptoms associated with RSV infection.
Owner:AREXIS
Methods of preventing or treating respiratory conditions
InactiveUS20050147607A1Reduce development of resistanceAvoid and reduce side effectAntibacterial agentsBiocideIntensive care medicineCombination therapy
The present invention provides prophylactic an tehrapeutic protocols desinged to prevent, manage, treat, or ameliorate a respiratory condition or one or more symptoms thereof. In particular, the present invention provides methods for preventing, managinge, treating, or ameliorating a respiratory condition or one or symptoms caused by environmental factors or a respiratory infection. The present ivnention encompasses combination therapies, pharamceutical compositions, articles of manufacture, and kits.
Owner:MEDIMMUNE LLC
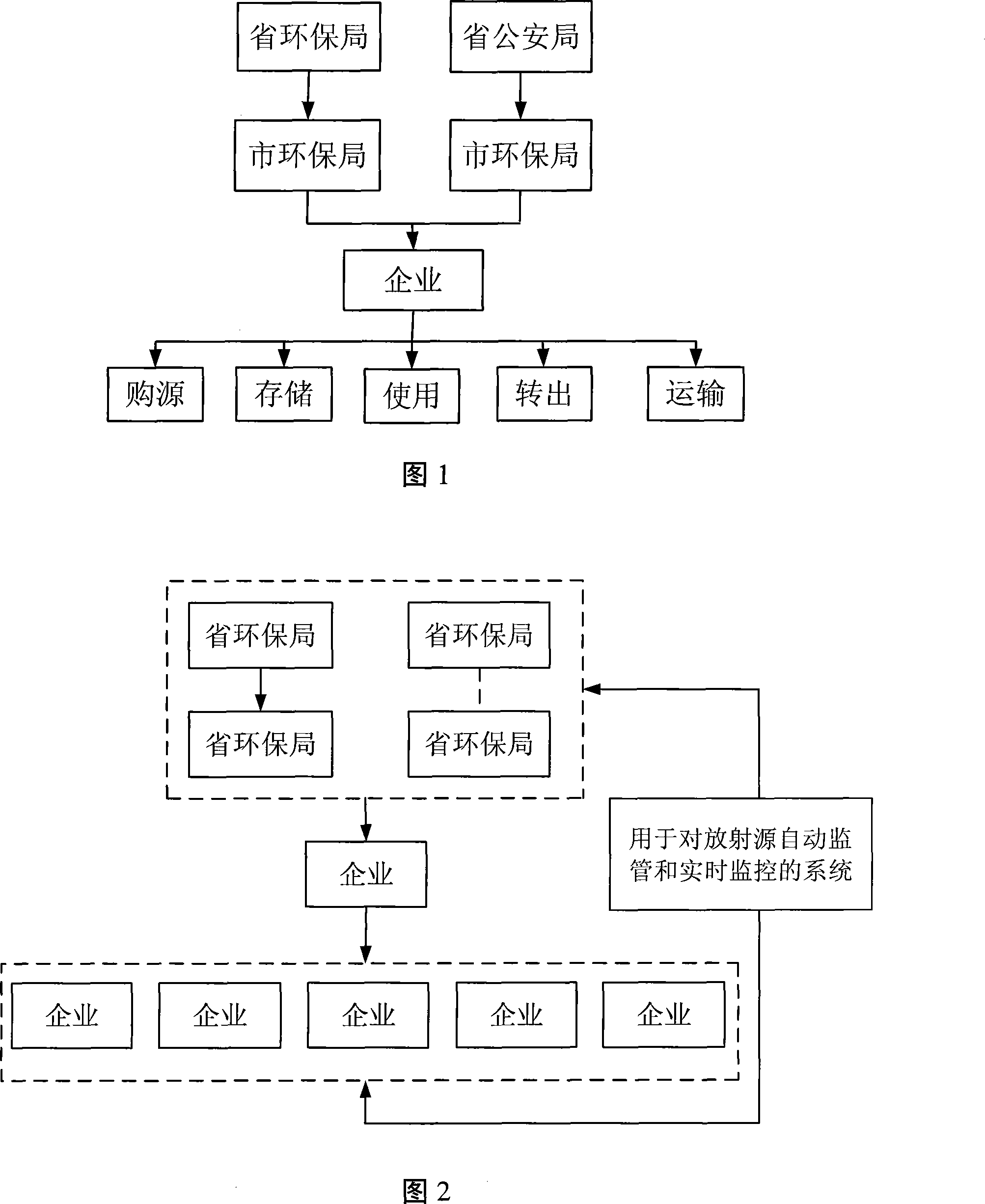
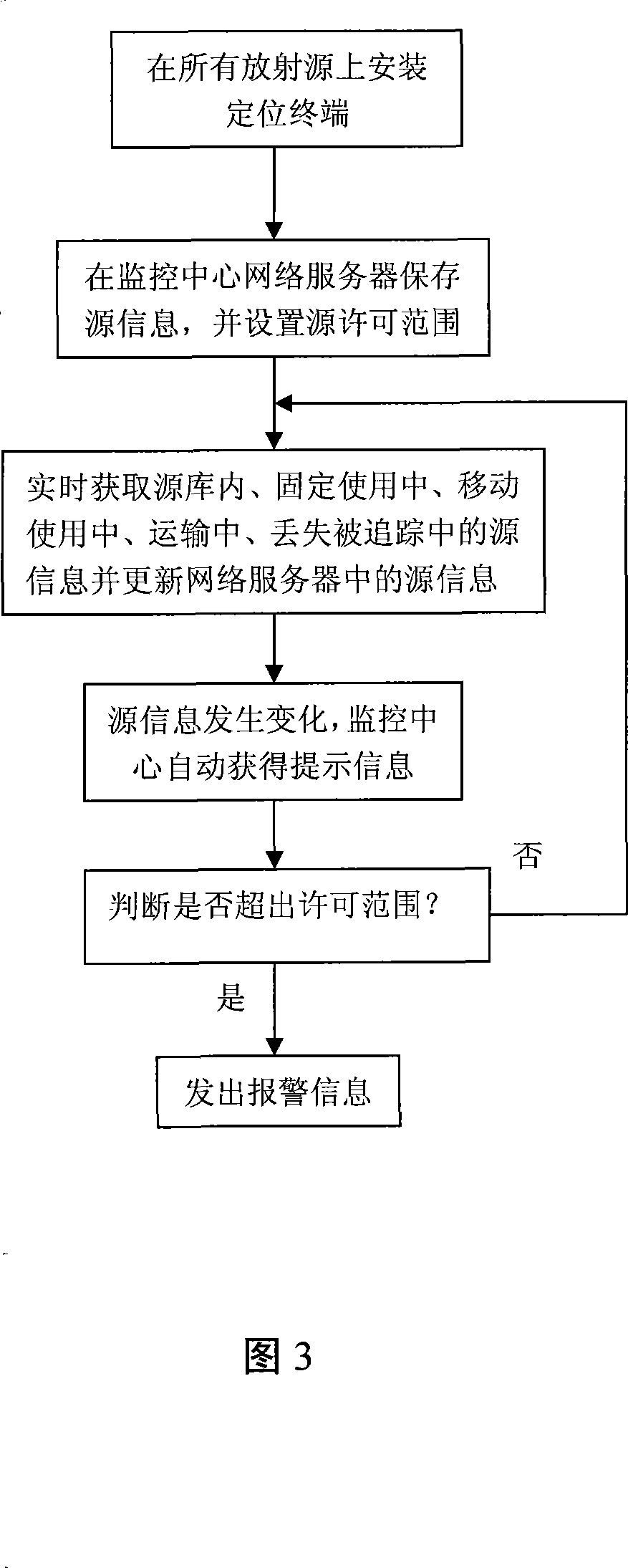
Method and system for automatically monitoring and real time monitoring radioactive source
ActiveCN101221685AAvoid managementAutomate regulationAlarmsTransmissionComputer terminalRadioactive waste
The invention relates to a radioactive source automatic supervision and real-time monitoring method and a system. The method mainly comprises the following steps: a positioning terminal in which a GPS positioning unit and a CDMA network positioning unit are arranged and source file information is solidified is arranged on a radioactive source; the source file information is stored in a network server of a monitoring center and a source admission range is set up; source position information and source file information is acquired at real time and corresponding source information in the network serve is updated at real time; when the source information stored in the network server changes, the monitoring center automatically obtains prompting information and judges whether the change of the source information is beyond the admission range; when the change of the source information exceeds the admission range, automatic alarm is carried out. The system realizing the method comprises a positioning terminal assembly device, a source information storing device, a source information updating device, a source information monitoring device and a real-time alarm device. The method and the system realize automatic supervision and real-time monitoring of all links of the radioactive source, thereby putting an end to severe security accidents like loss of the radioactive source, etc.
Owner:BEIJING HUALIXING SCI TECH DEV
Antibodies against and methods for producing vaccines for respiratory syncytial virus
ActiveUS20060099220A1Reduce fusionPrevents RSV infectionSsRNA viruses negative-sensePeptide/protein ingredientsRSV InfectionsRespiratory syncytial virus (RSV)
The present invention relates to novel respiratory syncytial virus (RSV) F peptides and compositions comprising them. The present invention also relates to methods of evaluating anti-RSV antibody binding to F peptides. The present invention also relates to antibodies that immunospecifically bind to an F peptide of the present invention. The invention further provides methods and protocols for the administration of F peptides and / or antibodies that immunospecifically bind to F peptides for the prevention, neutralization, treatment of RSV infection. Additionally, the methods of the invention may be useful for the treatment, prevention and the amelioration of symptoms associated with RSV infection.
Owner:AREXIS
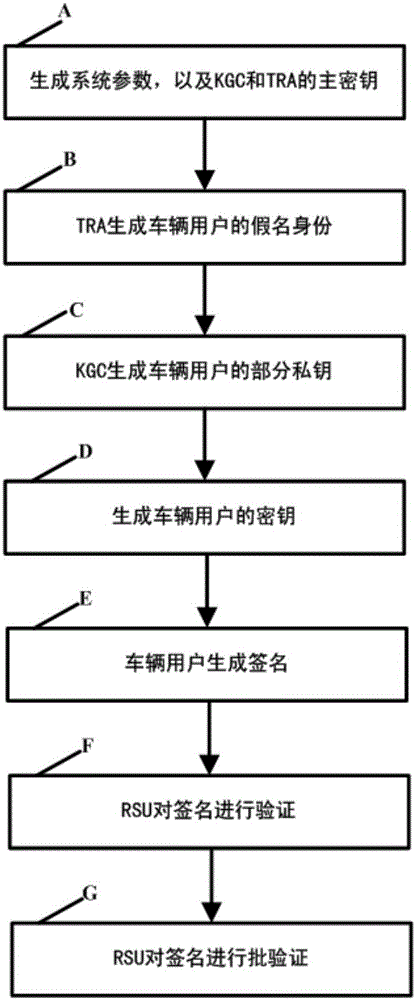
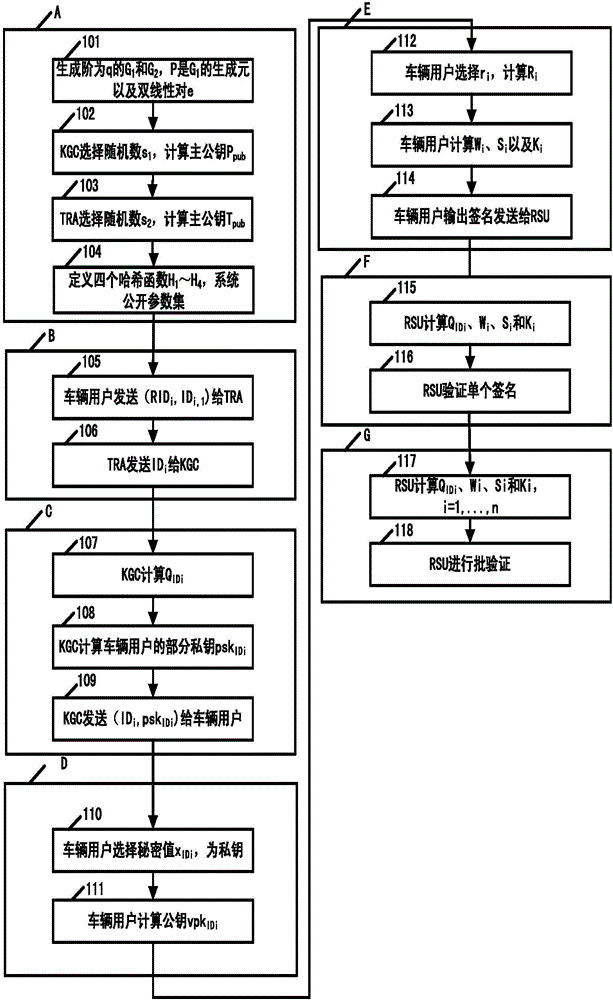
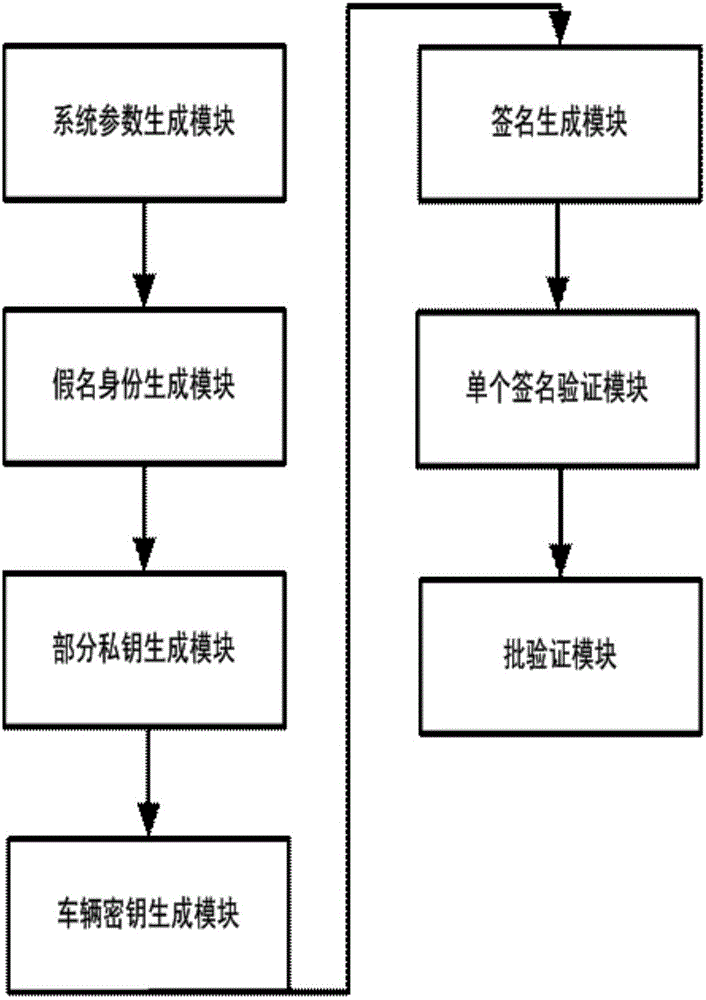
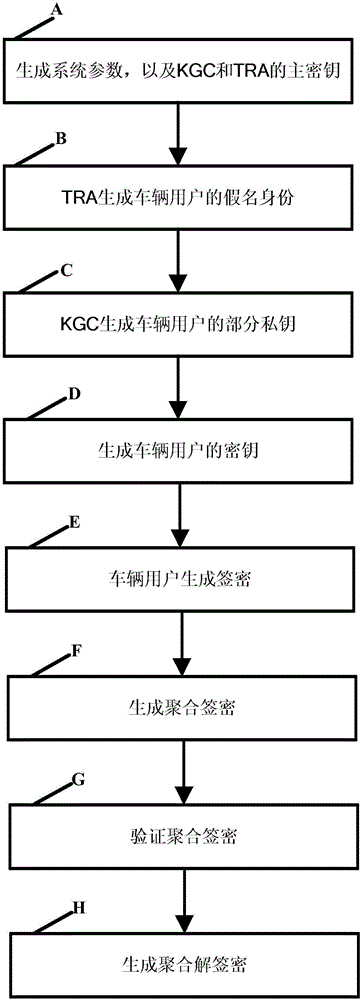
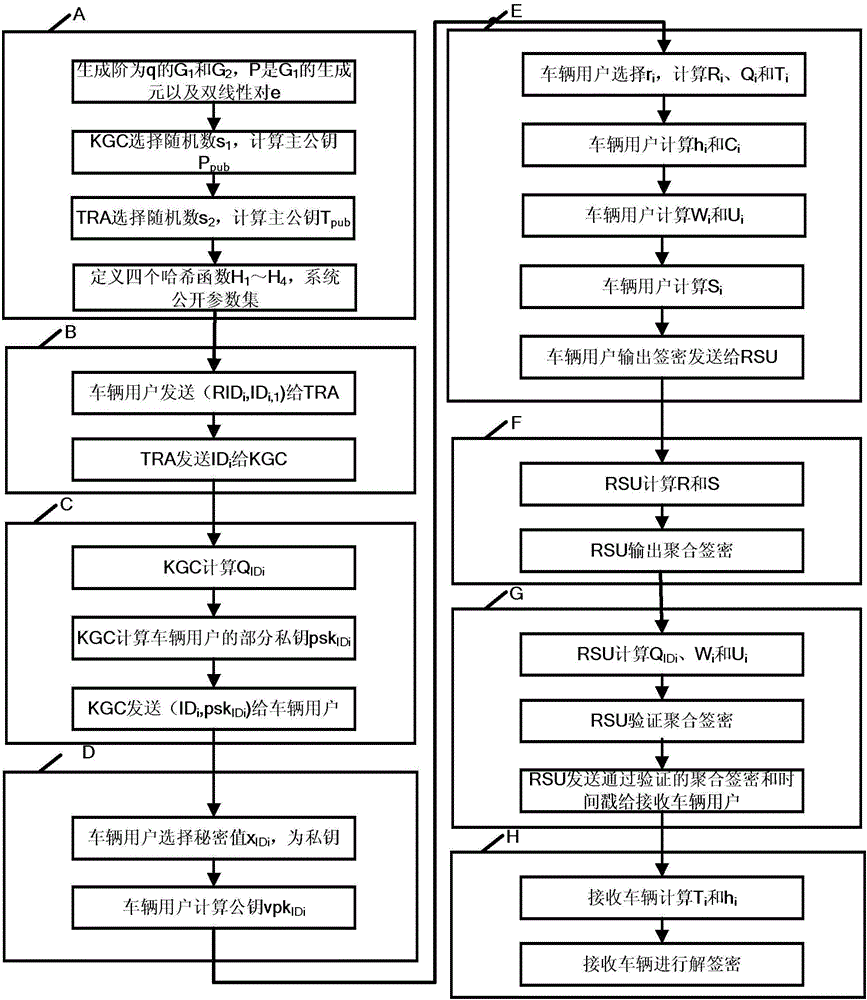
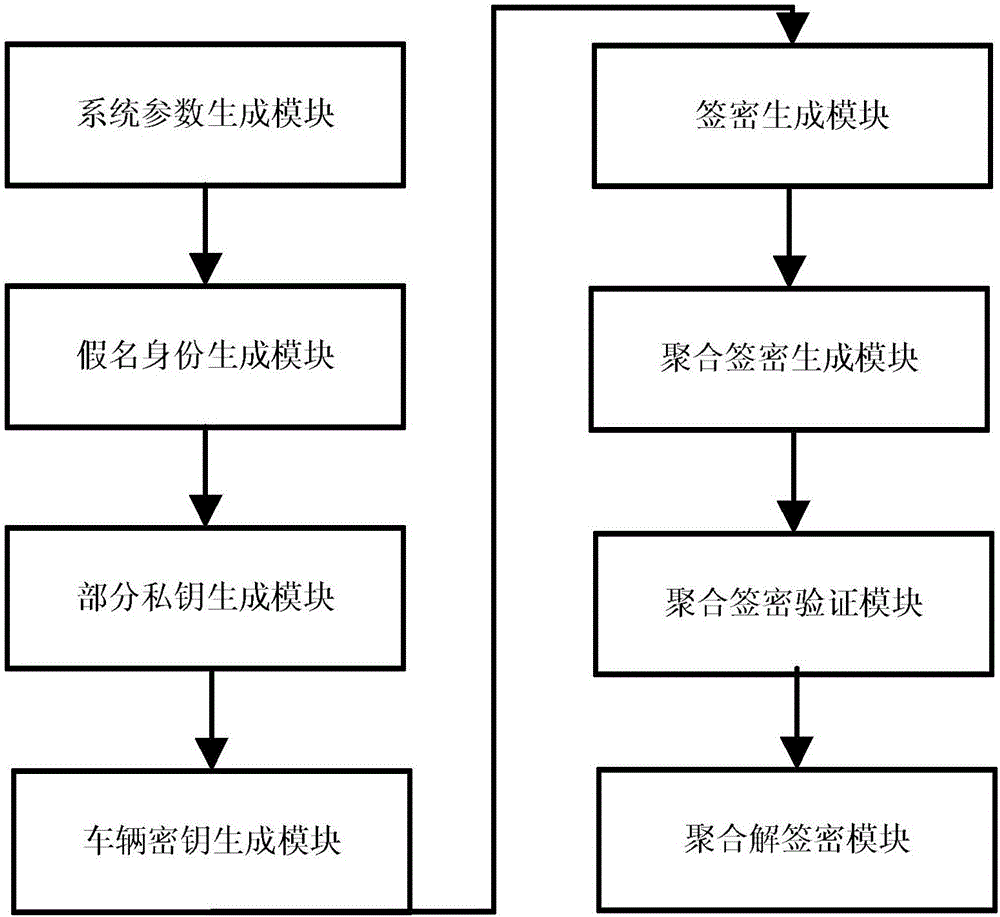
Method and system for protecting condition privacy of internet of vehicles based on certificateless batch verification
ActiveCN106059766AAvoid managementAvoid key escrow issuesKey distribution for secure communicationUser identity/authority verificationCertificateless cryptographyThe Internet
The invention discloses a method and a system for protecting a condition privacy of an internet of vehicles based on certificateless batch verification. The method comprises the following steps: a key generation center KGA and a track authentication center TRA jointly generate a master key and a system parameter of the internet of vehicles; according to the system parameter and vehicle user real identity information, the TRA generates a pseudonym identity of a vehicle user; the KGC generates a partial private key of the vehicle user; the vehicle user generates an own key; the vehicle user signs a message; an RSU carries out verification on a signature; and the RSU carries out the batch verification on the signature. According to the method and the system disclosed by the invention, by adopting a certificateless cryptography system, the unsolvable inherent certificate management problem and the certificate maintenance problem in the traditional public key cryptography system are effectively solved; and meanwhile, the key escrow problem caused by an identity-based cryptography system is also avoided; by adopting a batch verification technology, the signature verification efficiency in the internet of vehicles is improved; and in the internet of vehicles, the key generation center KGA and the track authentication center TRA are adopted to realize the condition privacy protection on the internet of vehicles.
Owner:HOHAI UNIV
Methods of preventing and treating rsv infections and related conditions
Owner:MEDIMMUNE LLC
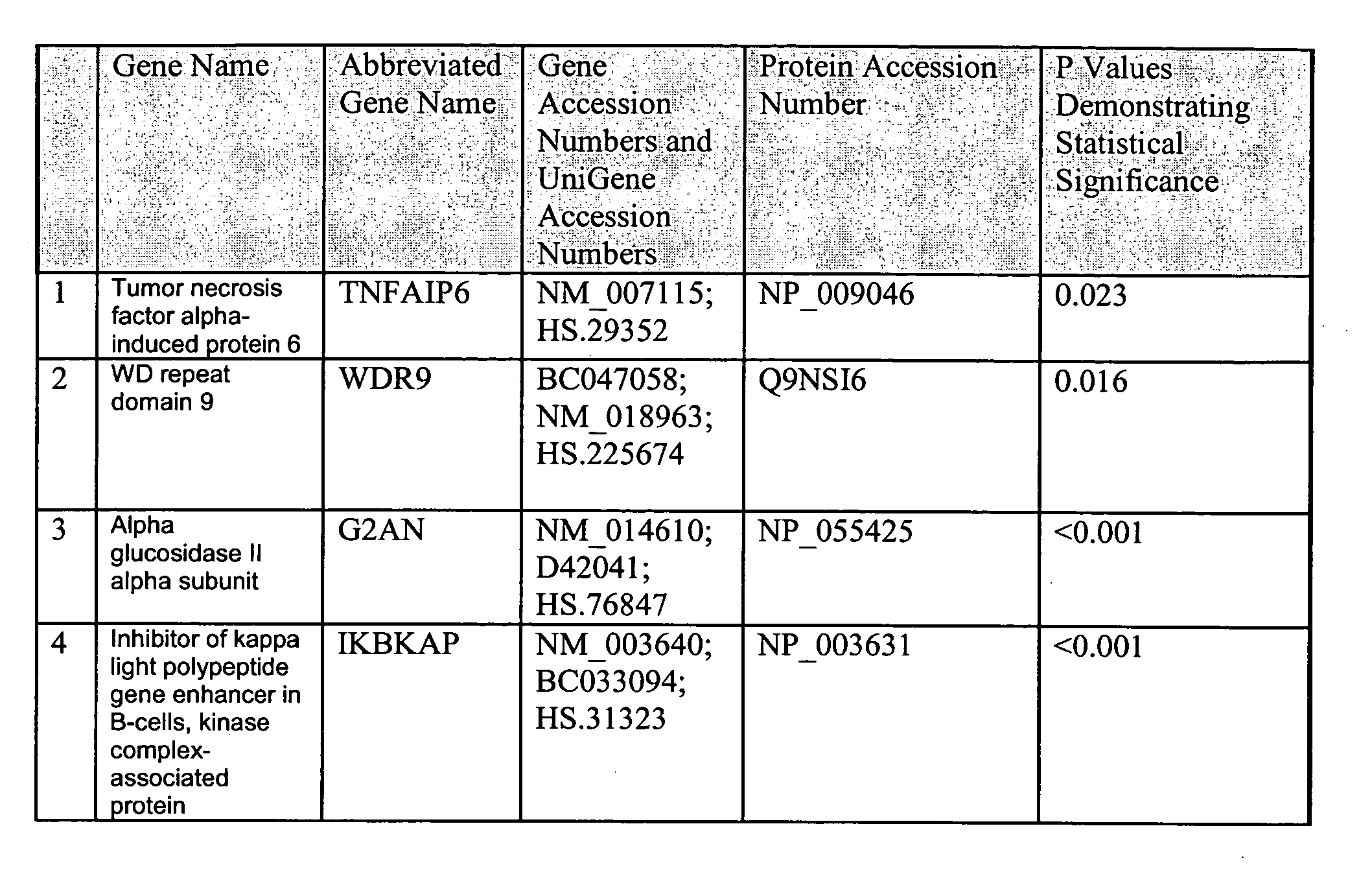
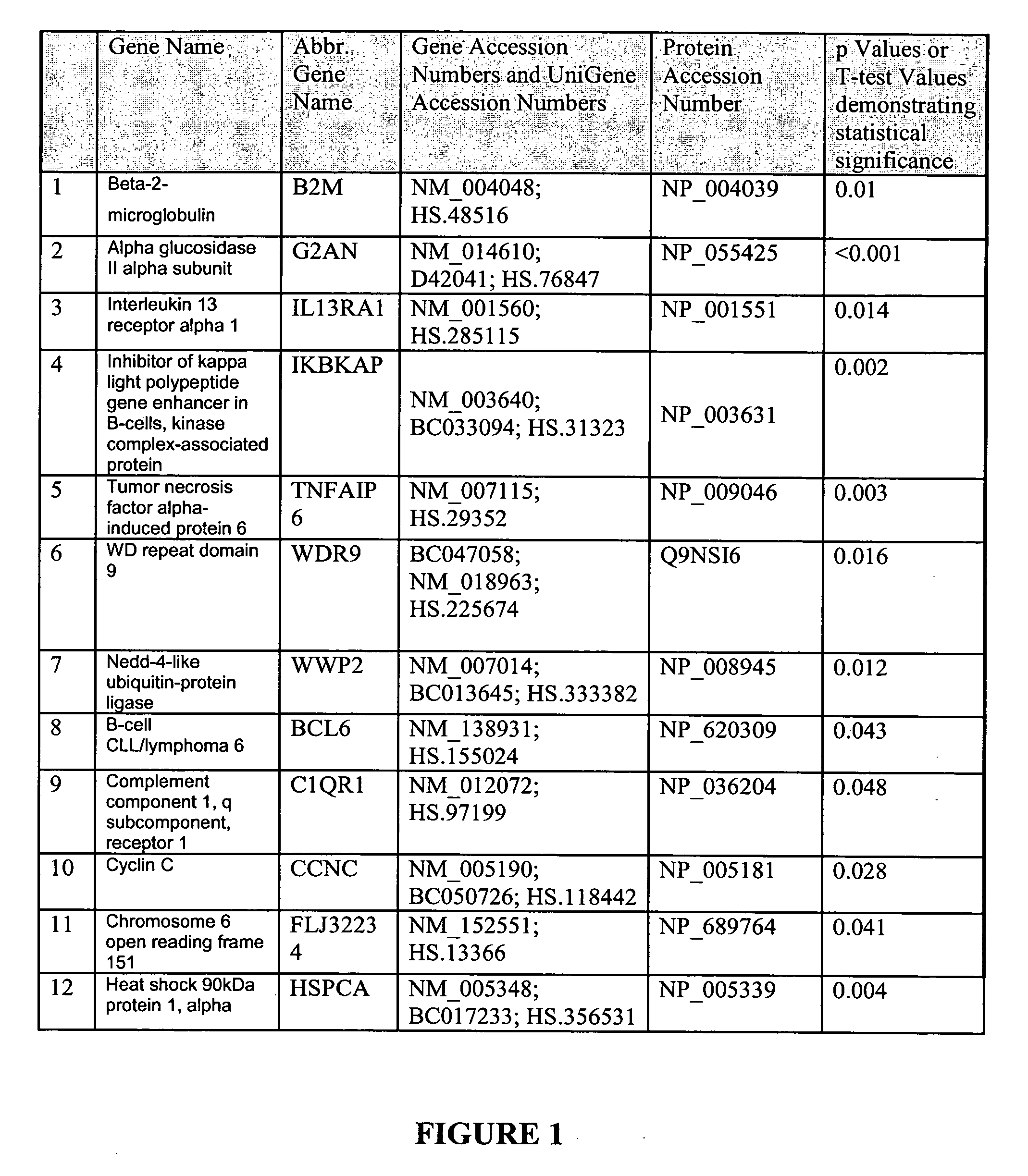
Osteoarthritis biomarkers and uses thereof
InactiveUS20050221383A1Shorten the progressEnhance and improve prophylactic and therapeutic effect(s)Microbiological testing/measurementImmunoglobulins against cell receptors/antigens/surface-determinantsRegimenArthritis
The invention relates to the identification and selection of novel biomarkers and the identification and selection of novel biomarker combinations which are differentially expressed in osteoarthritis and / or in a particular stage of osteoarthritis, as well as a means of selecting the novel biomarker combinations. The biomarkers of the invention may be utilized to diagnose arthritis, differentiate between two stages of osteoarthritis and diagnose a particular stage of osteoarthritis. The invention provides kits comprising polynucleotides and / or proteins which specifically and / or selectively hybridize to the products of the biomarkers of the invention. Such kits are useful in diagnosing arthritis, differentiating between two stages of osteoarthritis, diagnosing a particular stage of osteoarthritis monitoring disease progression, and monitoring the efficacy of therapeutic regimens. The invention also provides for methods of using the products of the biomarkers of the invention in the identification of novel therapeutic targets for osteoarthritis.
Owner:GENENEWS
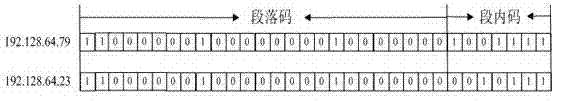
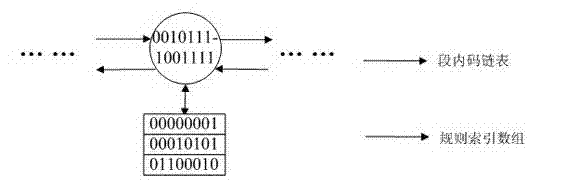
Administration mechanism for standard way access control list (ACL) rule under internet protocol security (IPsec) protocol
InactiveCN102811227AAvoid managementSimple structureTransmissionSpecial data processing applicationsArray data structureBinary tree
The invention discloses an administration mechanism for a standard way access control list (ACL) under an IPsec (internet protocol security) protocol, which belongs to the data communication field. The method is characterized in that address information in the standard way ACL rule is divided into a paragraph code and a segment code, a rule index of the standard way ACL rule is defined, administration of the standard way ACL rule is divided into two independent parts, i.e., source address range rule index and destination address range rule index, and the administration of the standard way ACL rule is performed in the same binary tree data structure. A data structure involved by the method comprises three parts including a binary tree, a segment code link table and a rule index digit group. The administration mechanism has the remarkable characteristics that for the standard way ACL rule with any address range, overlapped address range and multilevel address range, convenience and rapidness in operations of addition, searching and deletion can be realized, and the system expenditure is small.
Owner:CHONGQING UNIV
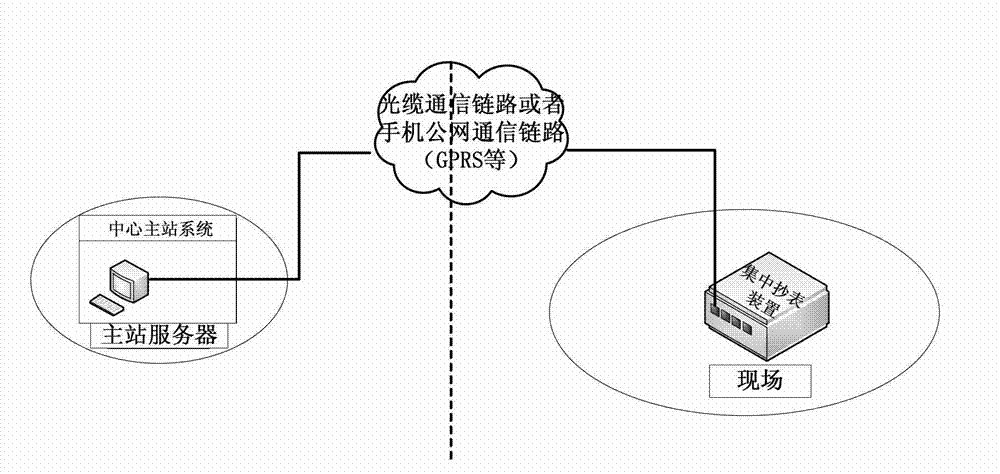
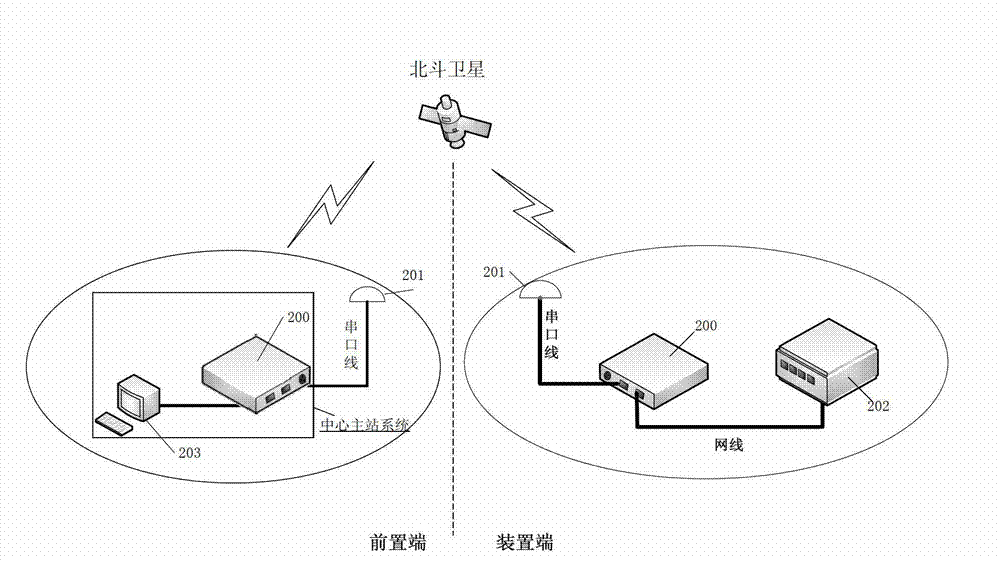
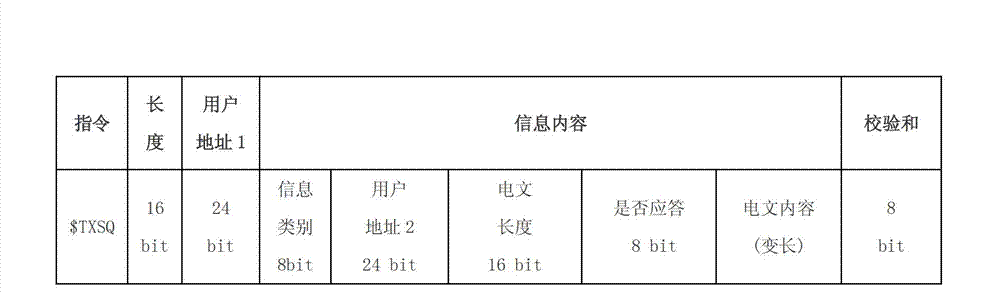
Power utilization information collection method and system based on technology of Beidou satellite navigation system
ActiveCN102810243AAvoid managementAccurate and efficient transmissionTransmission systemsRadio transmissionTelecommunications linkCommunication link
The invention provides a power utilization information collection method and a system based on a technology of a Beidou satellite navigation system. The technical scheme comprises the following steps of: obtaining a meter reading data message of collected power utilization information, also generating a Beidou communication message by the data conversion of the meter reading data message and transmitting the Beidou communication message to a prepositive end by a Beidou communication link; and reducing the Beidou communication message to the original format of the meter reading data message by the prepositive end and also transmitting to an application server of a central master station for carrying out united managing and monitoring. By adopting the method and the system which are provided by the invention, the power utilization information of residents in a site can be connected to a master station of a power utilization information management system in a seamless way by utilizing the two-way communication function of a Beidou satellite navigation system under the condition that traditional operation equipment is not reconstructed so as to realize the process from the collection of data in the site to the connection of a Beidou communication channel. The power utilization information of regions with undeveloped communication can be effectively and reliably obtained at real time.
Owner:GZH BEIDOU TECH GRP
Performance monitoring and fault positioning method based on service
InactiveCN106656627AAvoid managementImprove efficiencyData switching networksReal-time computingCorrelation analysis
The invention discloses a performance monitoring and fault positioning method based on a service. The method is characterized by comprising the steps of a, defining a service parameter; b, acquiring network data; c, performing data statistics; d, performing data storage; e, performing correlation analysis; and f, displaying a result. The performance monitoring and fault positioning method has advantages of directly obtaining the parameter or the result of various states in an information flow or data flow which is transmitted in a network, realizing definite acquisition of interested service state, state appearance position and state appearance time by operation maintenance personnel, settling defects in prior art, performing automatic retrieval on the whole system according to a preset instruction, finding out data flow abnormity in the network system for performing automatic alarming, performing tracking and backtracking and / or positioning on the state in the network system, realizing management, operation and maintenance of a service-related system of an enterprise, and realizing integral efficiency improvement and safety improvement of the enterprise.
Owner:周向军
Compositions and methods for the prevention and treatment of conditions associated with inflamation
The present invention provides methods for preventing, treating, managing and / or ameliorating a condition associated with inflammation (e.g., an inflammatory disorder) or a symptom thereof, the methods comprising administering to a subject in need thereof an effective amount of a theaflavin composition and an effective amount of one or more therapies other than such a theaflavin composition. In particular, the present invention provides methods for preventing, treating, managing and / or ameliorating a condition associated with inflammation (e.g., an inflammatory disorder) or a symptom thereof, the methods comprising administering to a subject in need thereof an effective amount of a theaflavin composition, an effective amount of a glucosamine composition, and optionally one or more other therapies.
Owner:DUSHENKOV SLAVIK +4
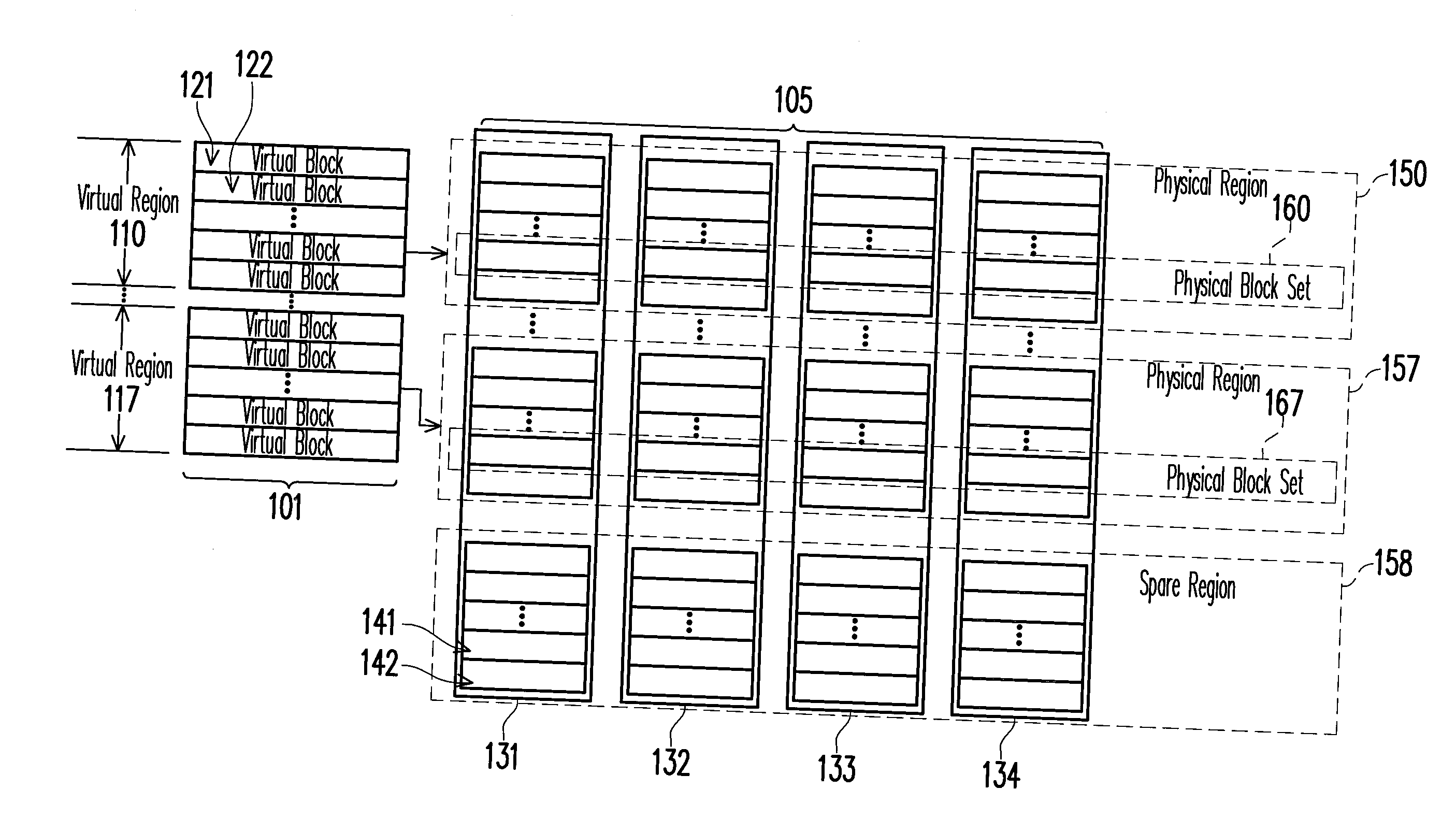
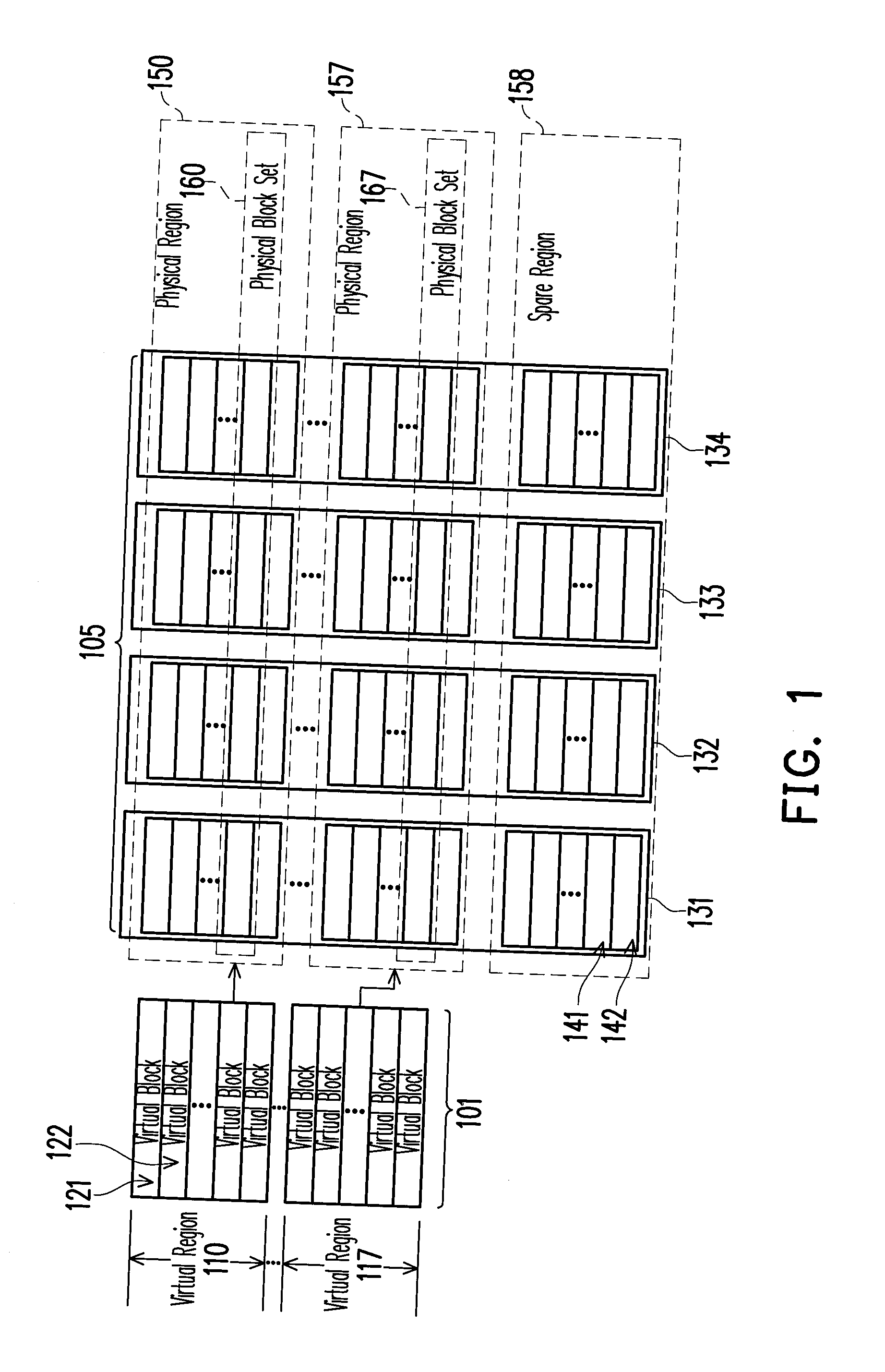
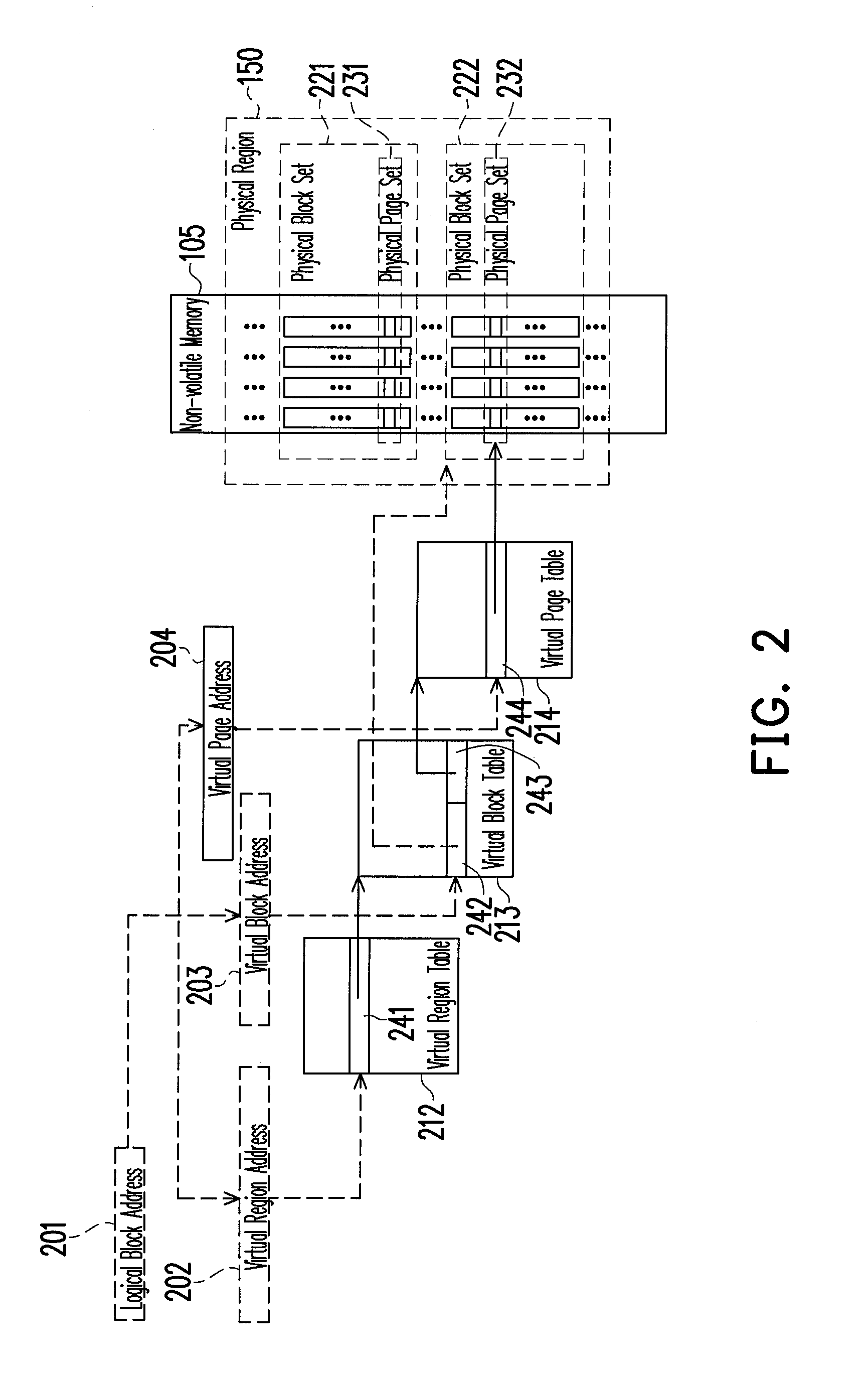
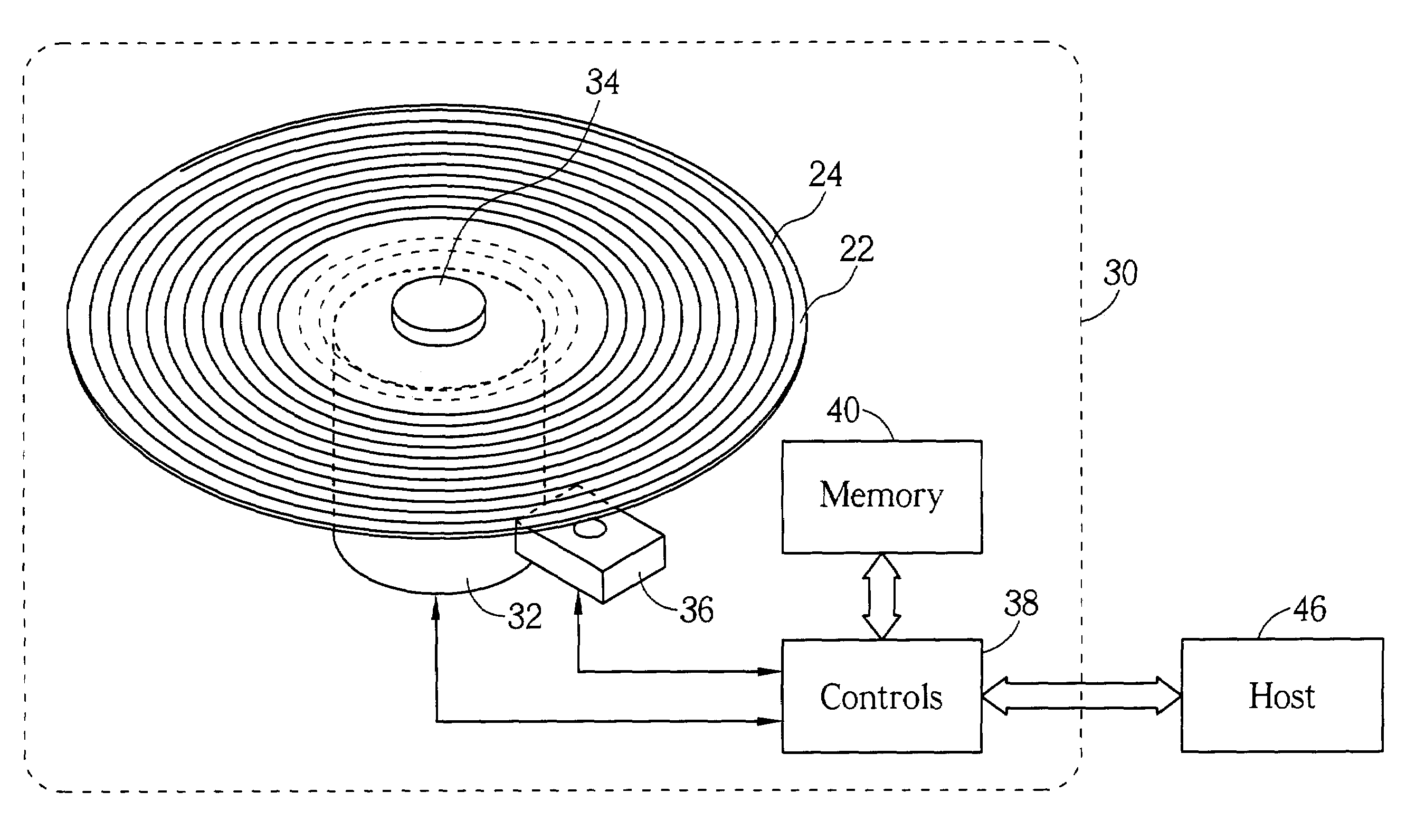
Region-based management method of non-volatile memory
ActiveUS20110161562A1Improve access efficiencyImprove reliabilityMemory architecture accessing/allocationError detection/correctionThree levelLogical block addressing
A region-based management method of a non-volatile memory is provided. In the region-based management method, the storage space of all chips in the non-volatile memory is divided into physical regions, physical block sets, and physical page sets, and a logical space is divided into virtual regions, virtual blocks, and virtual pages. In the non-volatile memory, each physical block set is the smallest unit of space allocation and garbage collection, and each physical page set is the smallest unit of data access. The region-based management method includes a three-level address translation architecture for converting logical block addresses into physical block addresses.
Owner:NAT TAIWAN UNIV
Internet of vehicle condition privacy protection method based on certificateless aggregate signcryption and system
ActiveCN106302406APublicly verifiableAvoid managementUser identity/authority verificationPasswordSigncryption
The invention discloses an Internet of vehicle condition privacy protection method based on certificateless aggregate signcryption and a system, wherein the method and the system have excellent performance based on a certificateless password system. According to the method, problems of certificate management and secret key escrow can be avoided, calculation efficiency of the Internet of vehicle during aggregate signcryption verification and aggregate signcryption efficiency during network transmission are improved, condition privacy protection of Internet-of-vehicle users is realized, and the method and the system can be safely utilized in the open Internet of vehicle.
Owner:HOHAI UNIV
Methods of treating gastro-esophogeal reflux disease using (-) norcisapride in combination with proton pump inhibitors or H2 receptor antagonists
InactiveUS6548518B2Prevent and alleviate symptomReducing and avoiding adverse effectBiocideDigestive systemNorcisapride5-HT3 receptor
Owner:SEPACOR INC
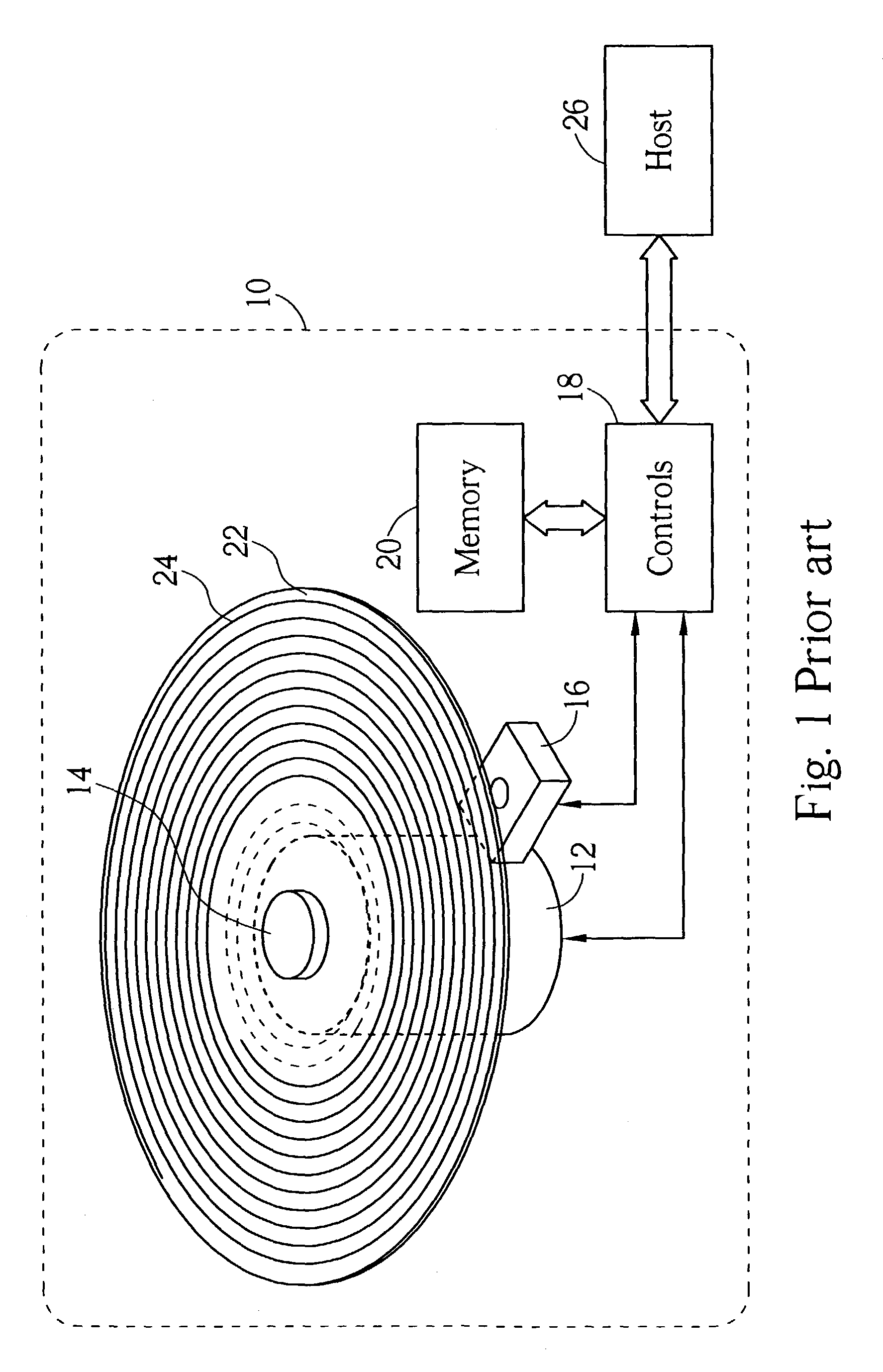
Method for managing spare blocks of an optical disc
InactiveUS7020056B2Efficient managementReadily availableCombination recordingDisc-shaped record carriersComputer hardwareComputer engineering
A method for defect management of an optical disc. The optical disc includes a plurality of data blocks and a plurality of spare blocks, each data block is for recording data, each spare block is for replacing a defect data block to record a data. The method includes recording a status of the spare blocks in a status table according to a location order of the spare blocks, such that the statuses of neighboring spare blocks with different statuses are recording in neighboring items of the status table.
Owner:MEDIATEK INC
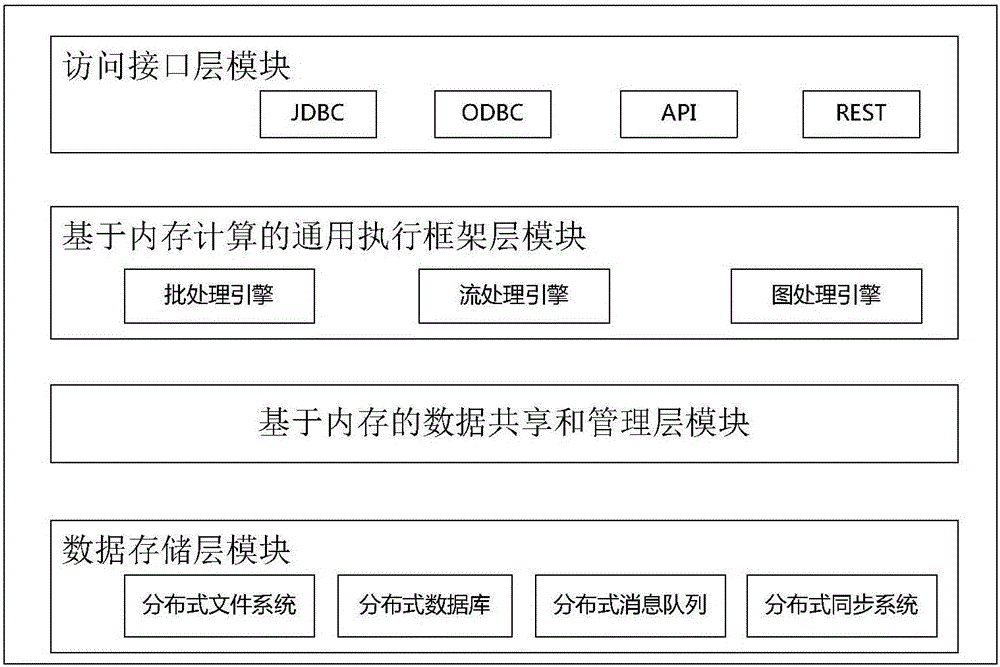
Memory computing-based customizable multimode big data processing system
InactiveCN106021484ATransparent hierarchical storageEfficient hierarchical storageDatabase management systemsSpecial data processing applicationsConcurrent computingData stream
The invention provides a memory computing-based customizable multimode big data processing system. The system comprises a data storage layer module, a memory-based data sharing and management layer module, a memory computing-based universal execution framework layer module and an access interface layer module, wherein a distributed memory abstraction mechanism, a position-sensing scheduling mechanism and a distributed hybrid column storage mechanism of data are adopted. According to the system, massive data storage is constructed; a cluster concurrent computing-oriented memory data management and sharing framework is provided, and an efficient and customized big data multimode universal processing framework is provided; batch processing and real-time data stream computing are supported; and the support is provided for flexible analysis and deep utilization of the data.
Owner:NO 32 RES INST OF CHINA ELECTRONICS TECH GRP
Helmet omnidirectional energy management system
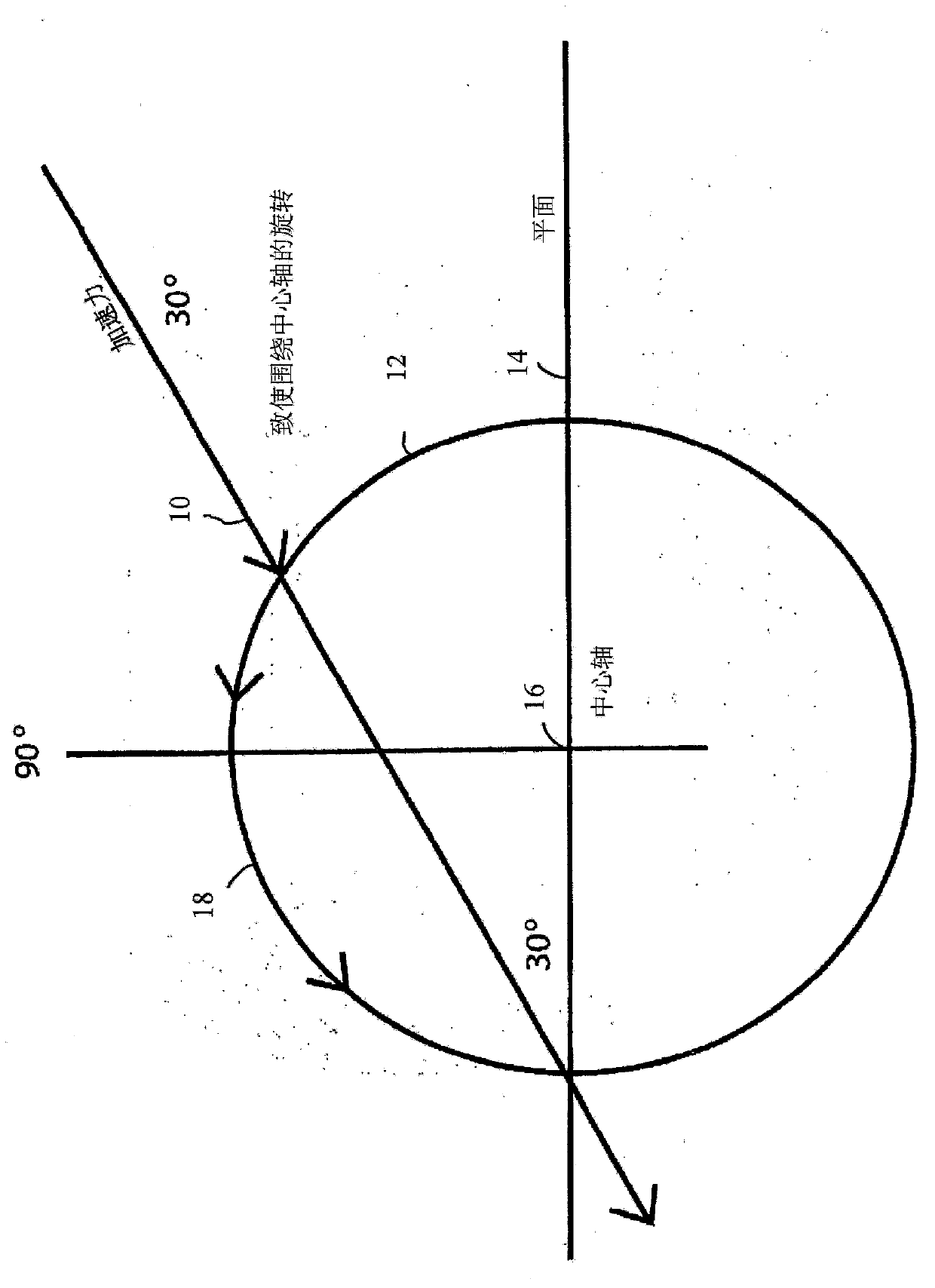
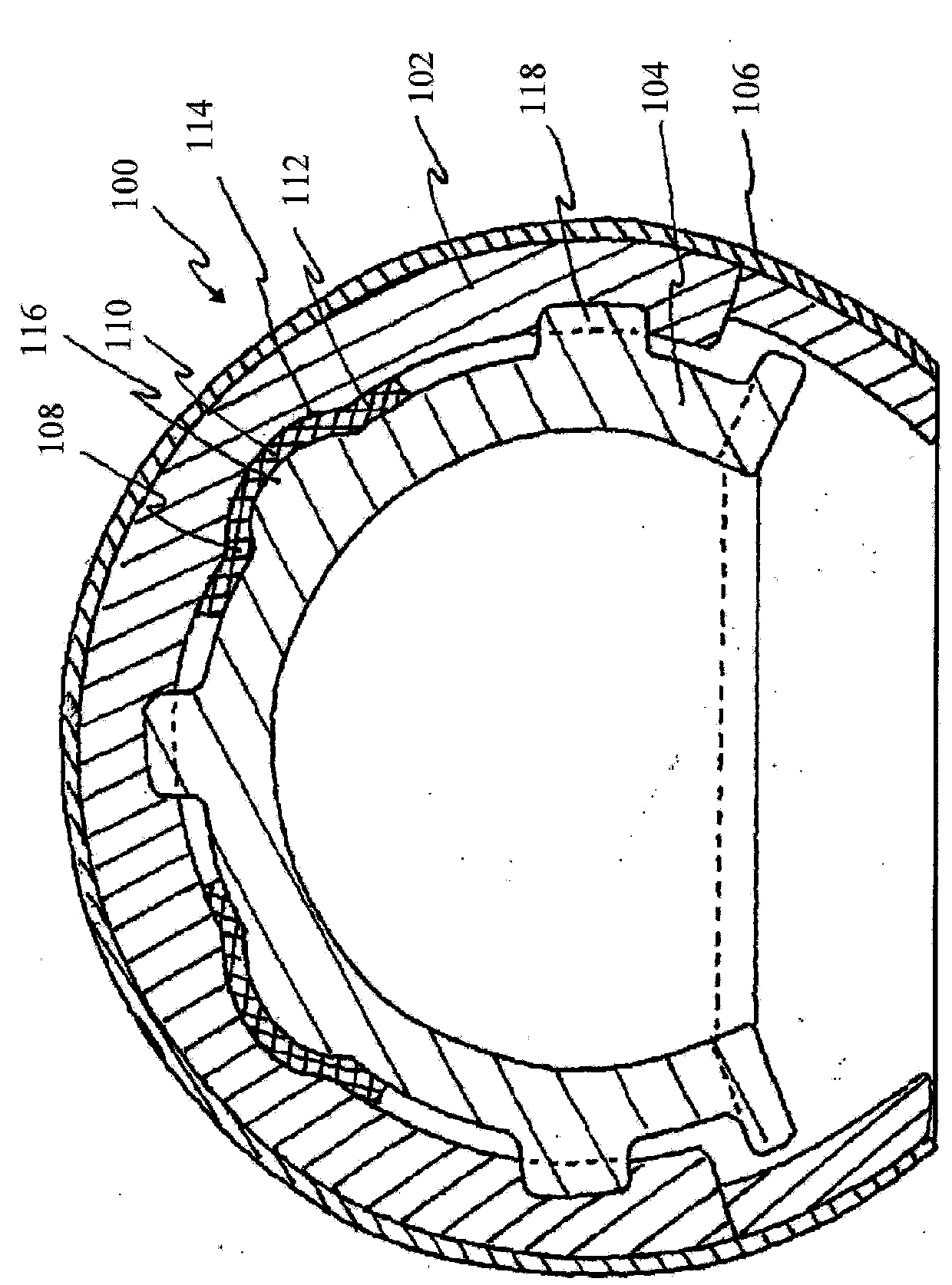
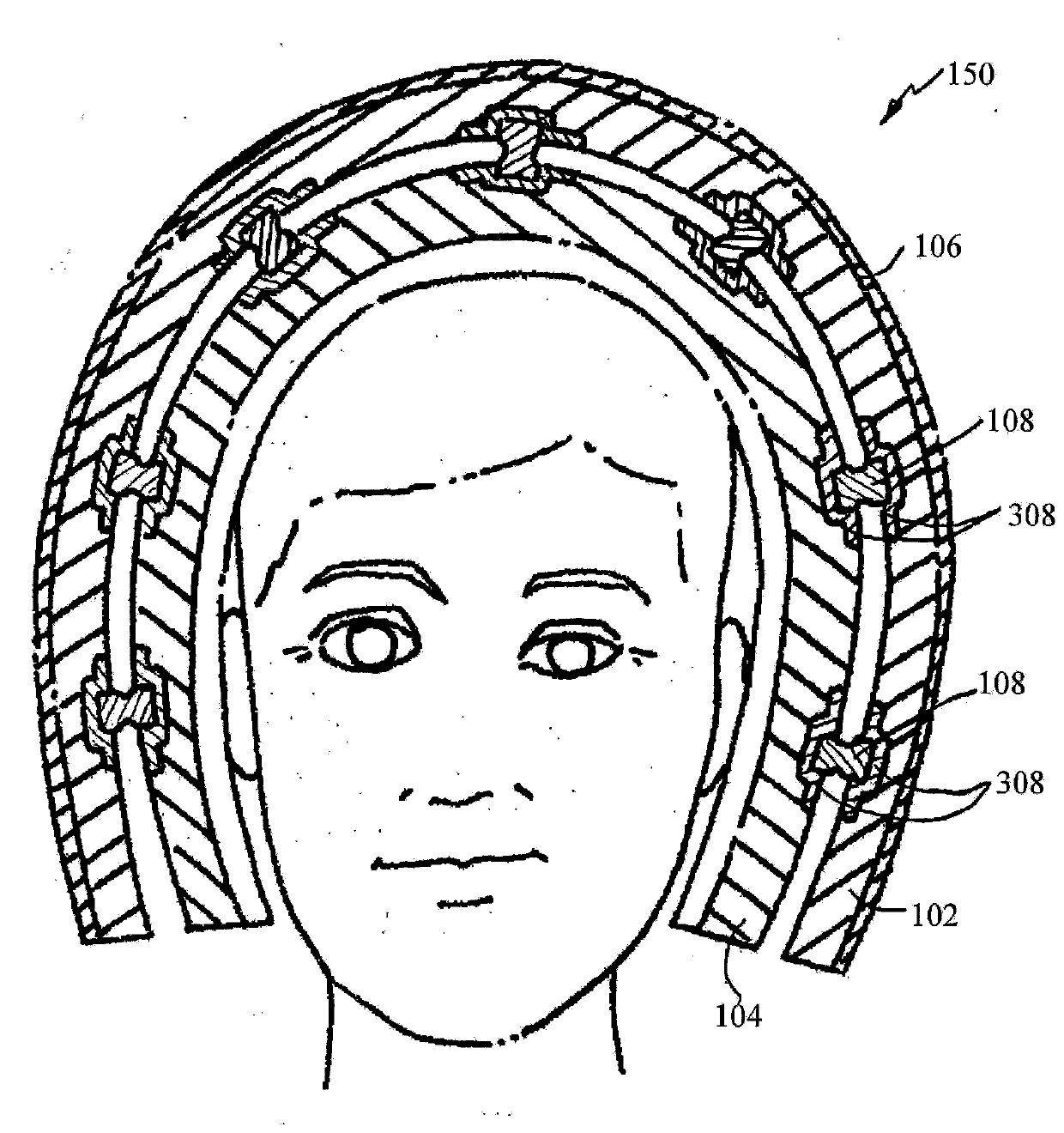
ActiveCN103635112AReduce linear impactAvoid managementHelmetsHelmet coversThumb oppositionEngineering
An embodiment of a safety helmet ( 100 ) for protecting the human head against repetitive impacts, moderate impacts and severe impacts so as to significantly reduce the likelihood of both translational and rotational brain injury and concussions includes an outer shell ( 106 ), an outer liner ( 102 ) disposed within and coupled to the outer shell, and an inner liner ( 104 ) disposed within and coupled in spaced opposition to the outer liner by a plurality of isolation dampers ( 108 ) for omnidirectional movement of the inner liner relative to the outer liner and the outer shell.
Owner:6D HELMETS LLC
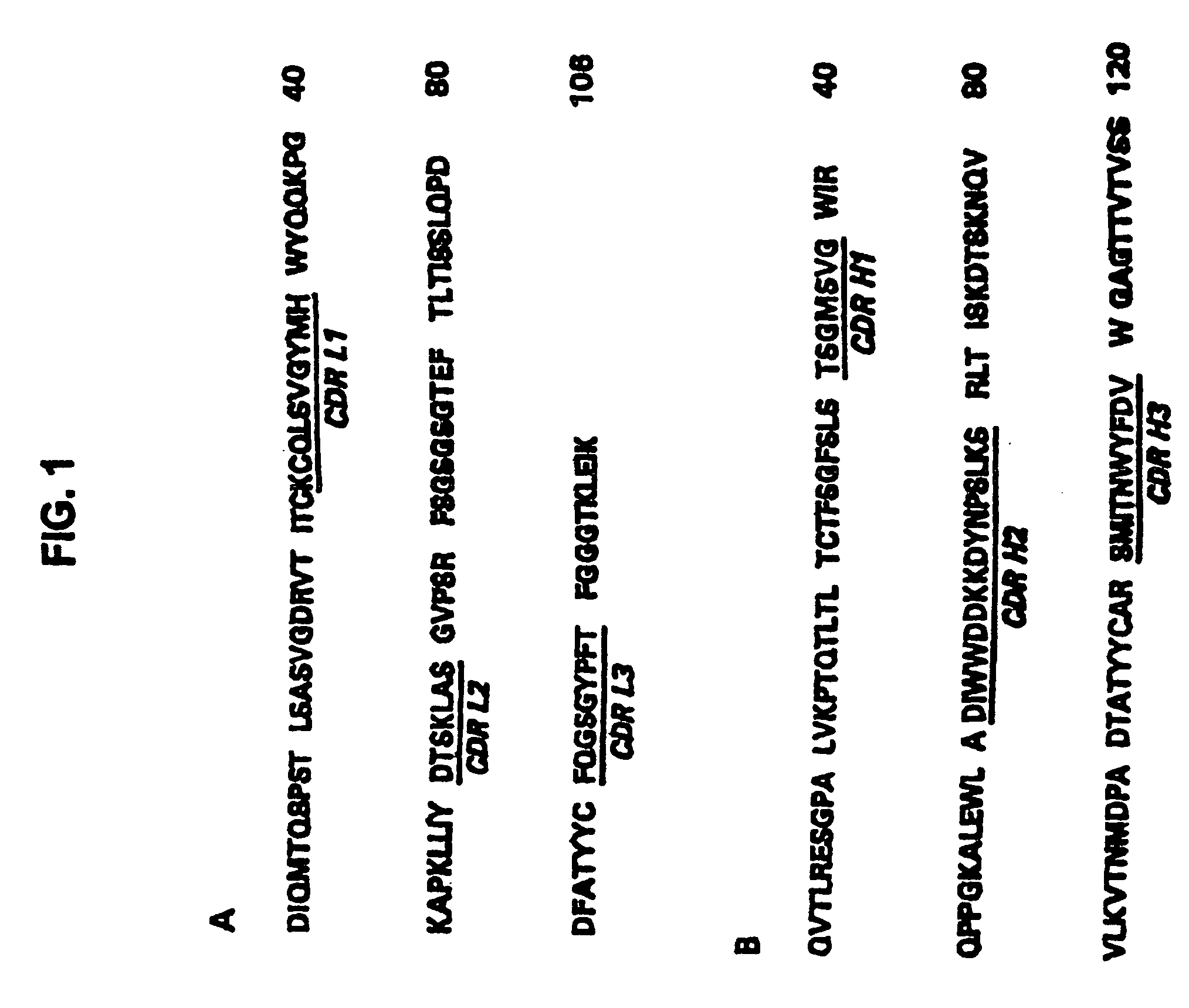
Antibodies that specifically bind Staphylococcus aureus alpha toxin and methods of use
ActiveUS9527905B2Avoid managementAvoid adjustmentAntibacterial agentsAntipyreticStaphylococcus cohniiAlpha-toxin
Herein provided are compositions, methods of manufacture and methods of use pertaining to anti-alpha toxin antibodies and fragments.
Owner:MEDIMMUNE LLC
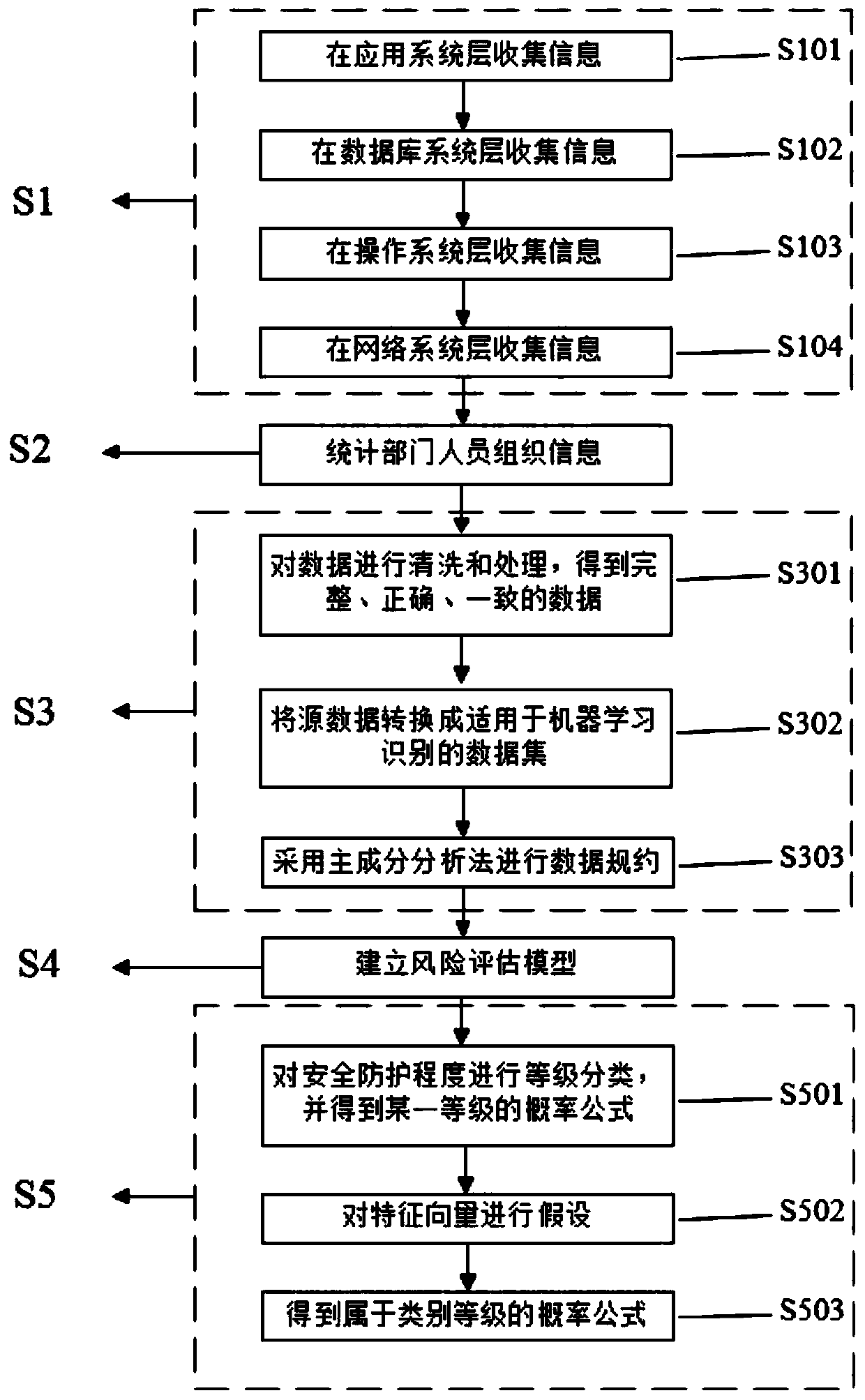
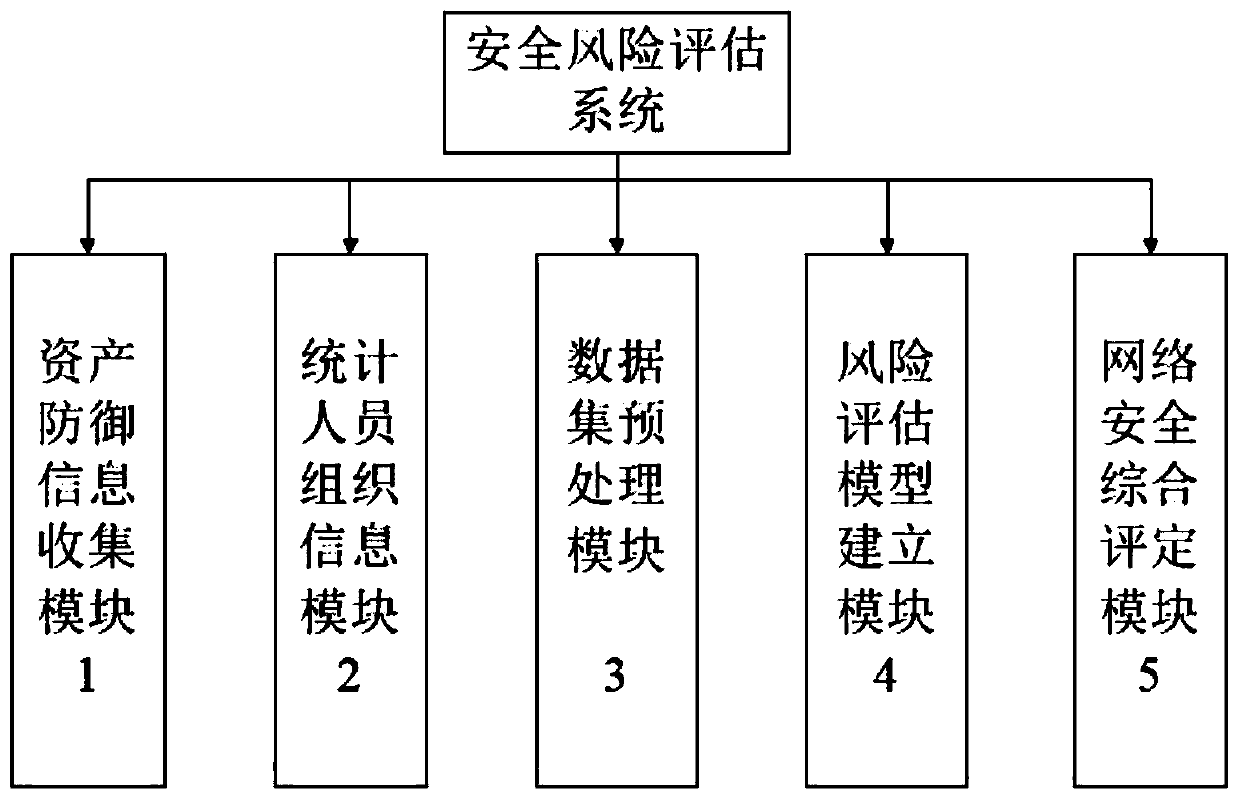
Information security risk assessment method and system based on situation awareness learning
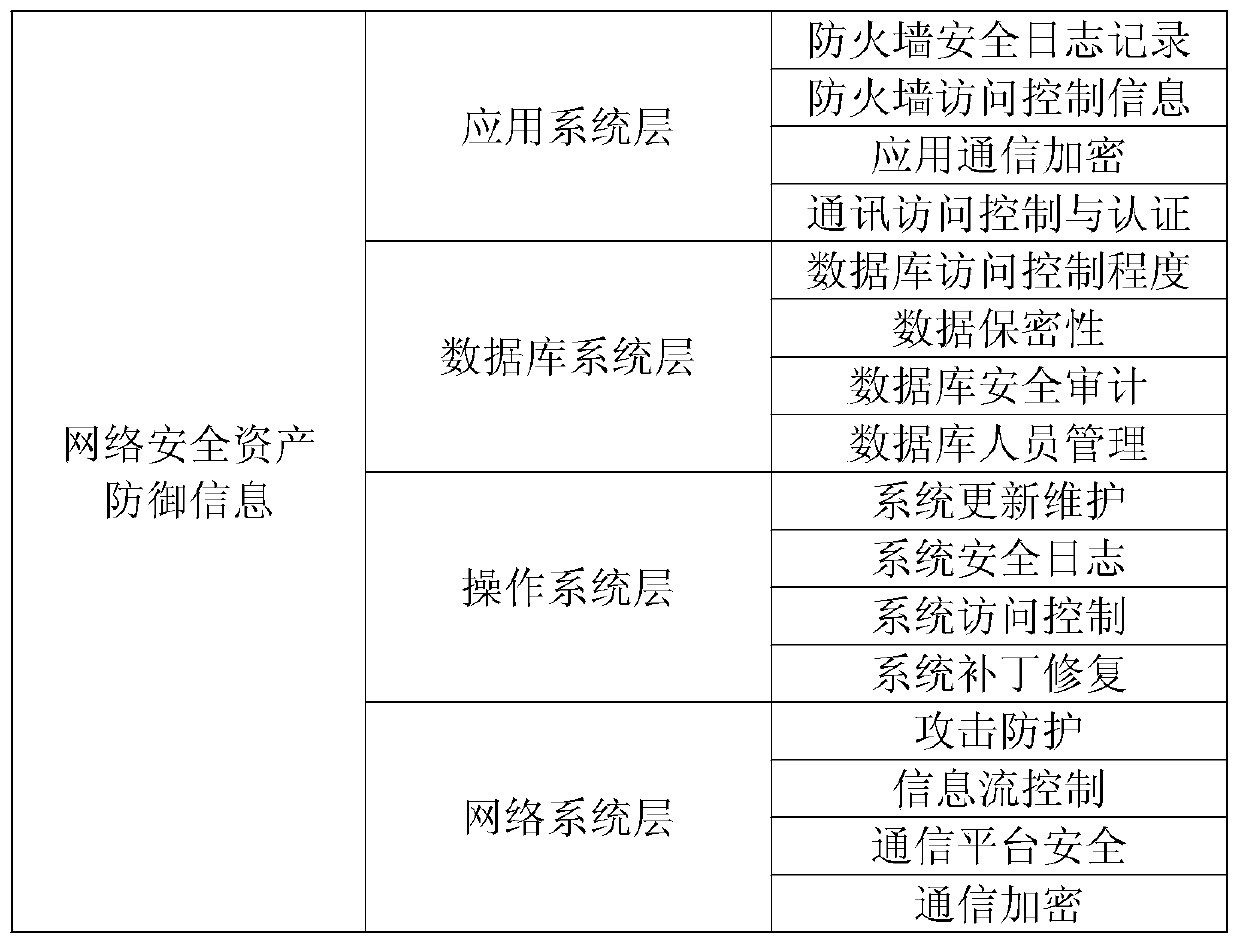
InactiveCN110401649AEase of evaluationReduce sizeMathematical modelsPlatform integrity maintainanceInformation security risk managementData set
The invention discloses an information security risk assessment method and system based on situation awareness learning. The method comprises the following steps: firstly, collecting network securityasset defense information and department personnel organization information; then, preprocessing the collected information; performing format unification, useless data filtering, repeated data mergingand the like on the data; then, in combination with an existing information security risk assessment standard and an existing information security risk assessment model, systematically establishing entry information of the risk assessment model, and finally, grading network security according to the collected information by utilizing a Bayesian network machine learning algorithm. The system comprises an asset defense information collection module, a statistical personnel organization information module, a data set preprocessing module, a risk assessment model establishment module and a network security comprehensive assessment module. According to the invention, a set of more complete risk assessment system is constructed in multiple aspects and multiple ways, and security assessment grading is carried out, so that risk measures are selected in a targeted manner to reduce and control risks.
Owner:湖北央中巨石信息技术有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com