Safe terminal system and terminal safety method
A security terminal and terminal security technology, applied in transmission systems, computer security devices, instruments, etc., can solve problems such as single security means and functions, and achieve security requirements and high effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
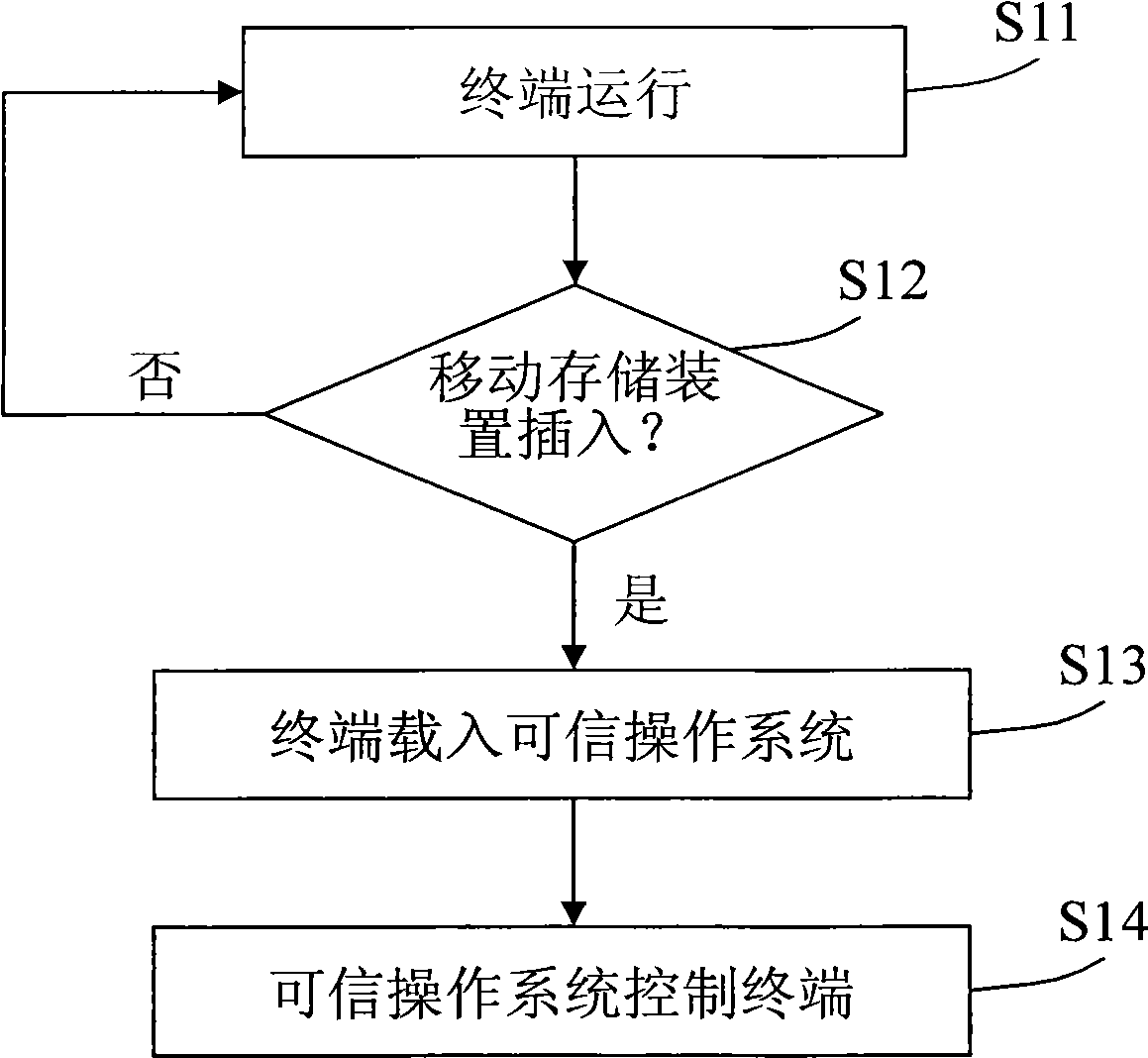
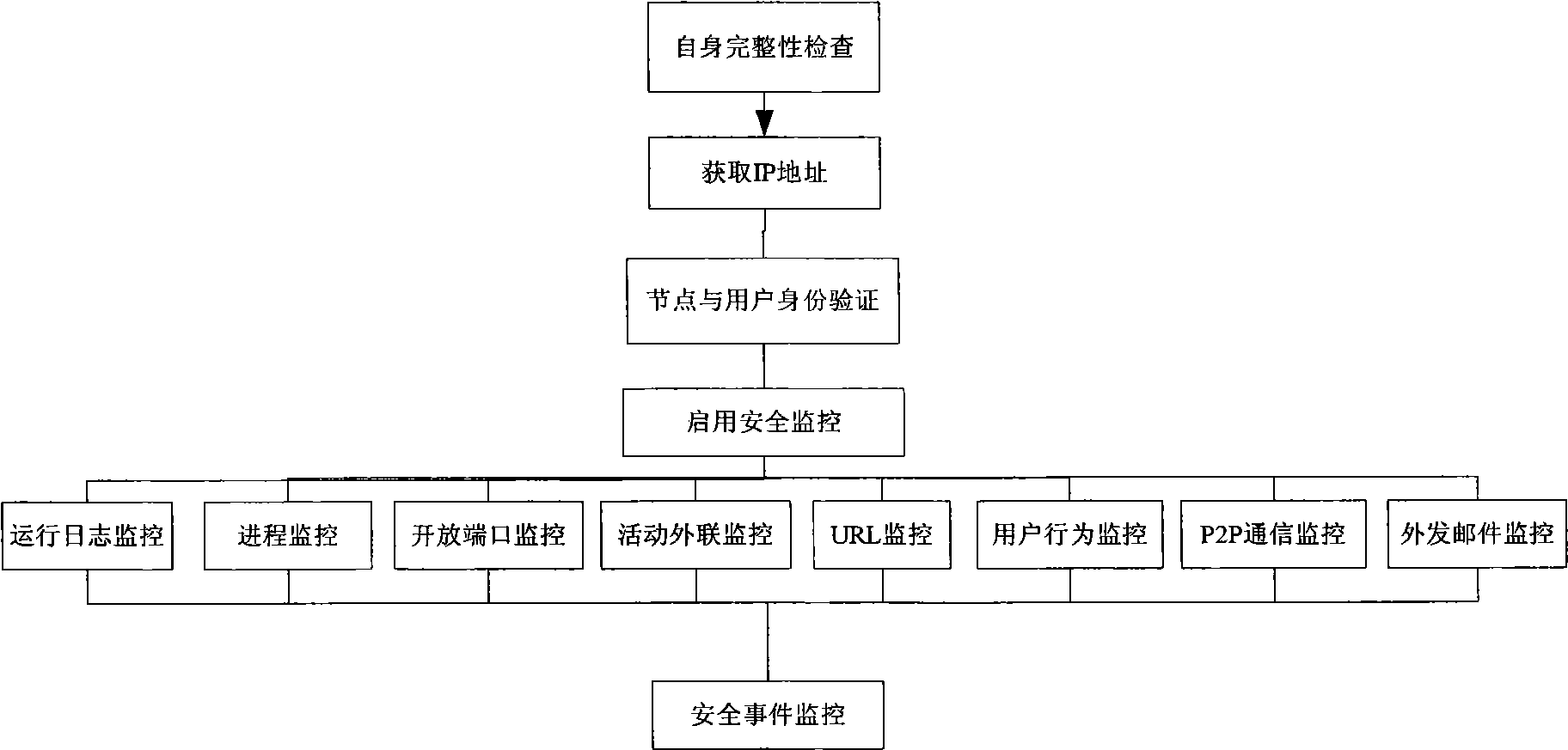
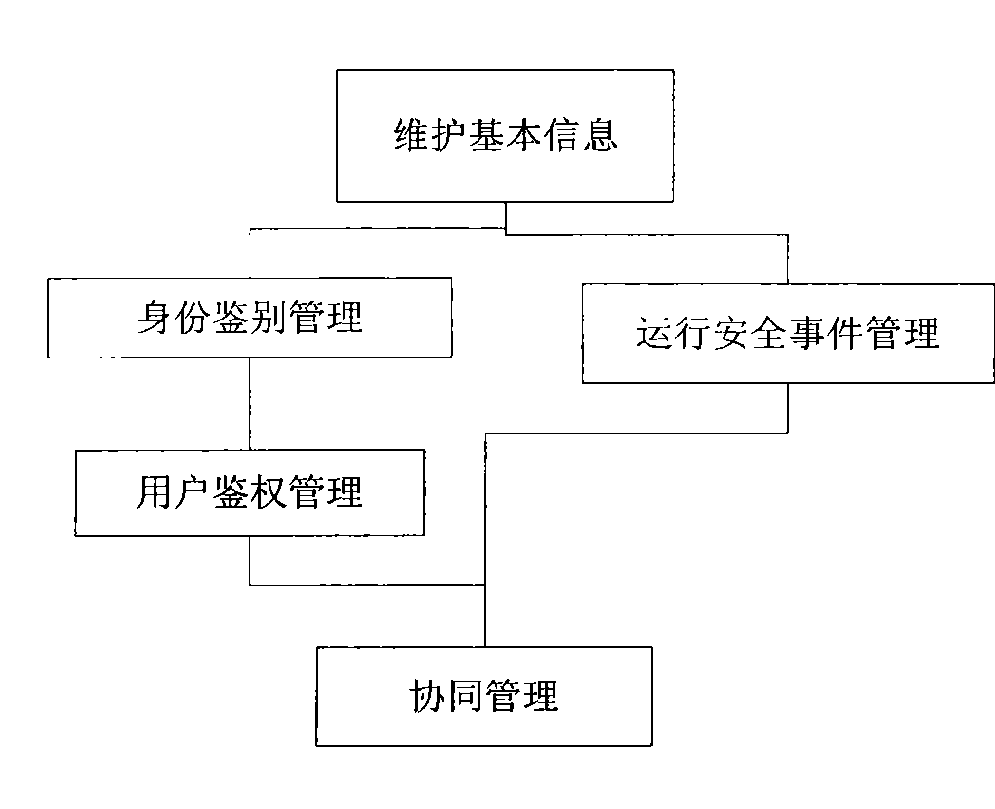
[0035] The present invention provides a new secure terminal system and terminal security method, the core idea of which is: build a security-reinforced trusted operating system (such as a trusted Linux operating system), and maintain a verified list of safe software, The above-mentioned trusted operating system, safety software list and safety software are pre-installed on a mobile storage device (such as a mobile hard disk or a flash drive, etc.), and the mobile storage device is used to start an ordinary terminal, so that the terminal runs the trusted operation on the mobile storage device system, thereby creating a secure endpoint environment. When the terminal is running, the security management client located on the mobile storage device interacts with the security management center located in the protected network inside the organization and / or enterprise to monitor user behavior on the terminal system. After the mobile storage device is unplugged, the terminal will re...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com