Electronic assembly comprising a disabling module
a technology of electronic assembly and disabling module, which is applied in the direction of unauthorized memory use protection, multi-programming arrangement, instruments, etc., can solve the problems of inability to secure the terminal, not being convenient for human users, and no longer guaranteeing the security of terminal data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044]FIG. 1 illustrates an electronic device 1 according to one embodiment of the invention. In this example, the electronic device is a terminal e.g. a touchpad, laptop computer or a mobile telephone.
[0045]As a variant, it could have been a device of machine-to-machine type, such as a computer on-board a vehicle, or a smartcard such as a bank card or an electronic identity document.
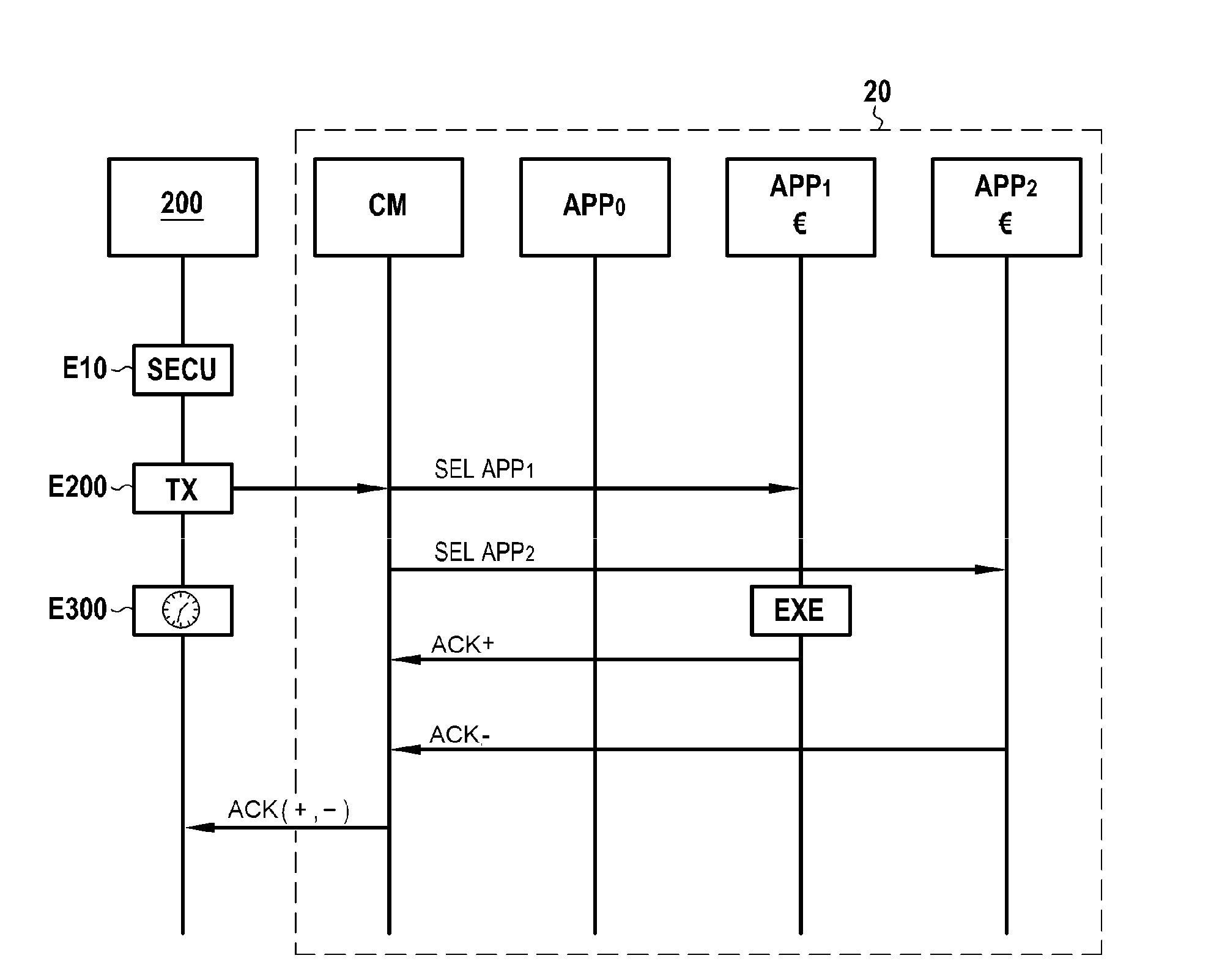
[0046]In the example in FIG. 1, the terminal comprises an electronic assembly 10 conforming to the invention and a secure element 20.
[0047]In this example, the electronic assembly itself 10 comprises a processor 300 and a memory 500 in which in particular the code of two operating systems is stored, namely that of a Rich-OS operating system referenced 100 and that of a trusted operating system referenced 200.
[0048]These two operating systems are jointly started up, on start-up of the terminal 1. As is known to persons skilled in the art, the secure execution environment of the trusted operating system 2...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com